-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 472f440f:5669301e
2024-12-21 00:45:10
@ 472f440f:5669301e
2024-12-21 00:45:10There was a bit of a rally in stock markets today, but this was a relief rally after taking a beating throughout the week. All eyes were on Federal Reserve Chairman Jerome Powell as he took the stage on Wednesday to announce the decisions made at the most recent FOMC meeting.
The market reacted negatively to another 0.25% cut from the Federal Reserve that many considered a "hawkish cut" due to the fact that Chairman Powell articulated that it is likely that there will be less rate cuts in 2025 than were previously expected. This is likely driven by the fact that inflation, as reported by the terribly inaccurate CPI, has been coming in higher than expectations. Signaling that the Fed does not, in fact, have inflation under control. Who could have seen that coming?
Here's how the US 10Y Treasury yield reacted to the announcement:
"Not great Bob!" The US 10Y Treasury yield is something that everyone should be paying attention to over the course of the next year. Since the Fed started cutting rates in September of this year, the 10Y yield has been acting anomalously compared to how it has acted historically after Fed interest rate decisions. Since September, the market has been calling the Fed's bluff on inflation and rates have been moving in the opposite direction compared to what would be expected if the Fed had things under control. The "hawkish cut" made on Wednesday is not a great sign. The Fed is being forced to recognize that it cut "too much too fast" before actually getting inflation under control.
One has to wonder why they made such aggressive moves in September. Why the need for a much more dovish stance as quickly as they moved? Do they see something behind the scenes of the banking system that makes them believe that another liquidity crisis was on the horizon and they needed to act to prevent yet another banking crisis? Now that it is clear that inflation isn't under control and if there really was a liquidity crisis on the horizon, what are the first two quarters of 2025 going to look like? Could we find ourselves in a situation where inflation is beginning to accelerate again, there is a liquidity crisis, and the Fed is forced to rush back ZIRP and QE only to further exacerbate inflation? Couple this potential scenario with the proposed economic policy from the incoming Trump administration and it isn't hard to see that we could be in for a period of economic pain.
One can only hope that the Fed and the incoming administration have the intestinal fortitude to let the market correct appropriately, reprice, clear out the bad assets and credit that exists in the system and let the cleanse happen relatively unperturbed. That has what has been desperately needed since 2008, arguably longer.
On that note, bitcoin is going through a bull market correction this week as well. Likely incited and/or exacerbated by the turmoil in traditional markets.
Many are proclaiming that the end of this bull market is here. Don't listen to those who have been hate tweeting bitcoin all the way up this year. They've been looking for a correction to bask in schadenfreude and confirm their biases. These types of corrections are to be expected when bitcoin runs by checks notes 100% over the course of less than three months. We're approaching the end of the year, which means that people are selling to prepare for taxes (which may be happening in the stock market as well). Add to this fact that long-term holders of bitcoin have taken the most profit they have since 2018 and it probably explains the recent pull back. Can't blame the long-term holders for seeing six-figure bitcoin and deciding to bolster their cash balances.
I couldn't be more bullish on bitcoin than I am right now. The fundamentals surrounding the market couldn't be more perfect. Despite what the Trump administration may have in store for us in terms of economic policy (I agree with most of the policies he has presented), I find it hard to believe that even he and the talented team of people he has surrounded himself with can overcome the momentum of the problems that have been building up in the system for the last 16-years.
The "find safety in sats" trade is going mainstream as the market becomes more familiar with bitcoin, its properties, and the fact that it is very unlikely that it is going to die. The fervor around bitcoin as a strategic reserve asset for nation states is only picking up. And if it catches on, we will enter territory for bitcoin that was considered utterly insane only a year ago.
On that note, Nic Carter made some buzz today with a piece he wrote for Bitcoin Magazine explaining why he believes a strategic bitcoin reserve is a bad idea for the US government.
https://bitcoinmagazine.com/politics/i-dont-support-a-strategic-bitcoin-reserve-and-neither-should-you
While I agree that the signal the US government could send by acquiring a bitcoin strategic reserve could be bad for the US treasuries market, I think it comes down to strategy. The Trump administration will have to think strategically about how they acquire their Strategic Bitcoin Reserve. If they ape in, it could send the wrong message and cause everyone to dump their treasuries, which are the most popular form of collateral in the global financial system. However, there are ways to acquire bitcoin slowly but surely from here into the future that ensure that the United States gets proper exposure to the asset to protect itself from the out-of-control debt problem while also providing itself with a way out of the problem. Many of these potential strategies were discussed in two recent episodes I recorded. One with Matthew Pines from the Bitcoin Policy Institute and another with Matthew Mežinskis from Porkopolis Economics. I highly recommend you all check those out (linked below).
https://youtu.be/xyyeEqFVjBY
https://youtu.be/6vgesP9LIXk
.---
Final thought...
I am the most locked in from a focus perspective while on flights. Even with two kids under 5. Merry Christmas, Freaks!
-
 @ eac63075:b4988b48
2024-12-18 11:35:25
@ eac63075:b4988b48
2024-12-18 11:35:25The European Union is at a crossroads. While digital innovation and security cooperation remain critical in a connected world, recent proposals to enhance police surveillance and data sharing are stirring deep concerns about individual privacy, data security, and democratic oversight. Two recent reports published by Statewatch shed light on troubling developments in the EU’s policing landscape, raising alarms among privacy advocates and civil rights organizations.
The EU’s new plans to expand police surveillance could put your privacy and rights at risk and introduce risks far outweighing their potential benefits. This article will analyze these proposals, their implications, and the growing opposition from privacy and civil liberties defenders.
Surveillance Infrastructure: Policing by Design
The first Statewatch report, titled “Policing by Design: The Latest EU Surveillance Plan”, outlines a concerning trend in the EU’s approach to law enforcement. The proposals advocate embedding surveillance tools directly into the design of new technologies, effectively creating an architecture where policing capabilities are integrated into the systems we use daily.
From facial recognition cameras to AI-driven analytics, the EU plans to enhance cross-border police cooperation by ensuring technology is designed to facilitate surveillance from the outset. Known as “policing by design,” this strategy involves building surveillance features directly into technologies we use every day. Imagine a network of cameras or software that can automatically monitor people’s faces or behaviors without any extra installation — it’s like your everyday tech quietly doubling as a police tool. The goal is to enable seamless sharing of data across borders for criminal investigations, but the unintended consequences are alarming.
The Problem with “Policing by Design”
- Mass Surveillance Normalized: By embedding surveillance features into public and private infrastructure, society risks normalizing mass surveillance, where every movement, transaction, or online interaction is monitored and analyzed.
- Threats to Privacy: Such initiatives inherently contradict the principle of privacy by design, which prioritizes privacy protections in the development of technology. Instead, citizens are being treated as subjects of perpetual suspicion.
- Lack of Transparency and Accountability: A systemic lack of transparency surrounding these plans raises serious governance issues. Civil society organizations, journalists, and privacy advocates have pointed to a lack of democratic oversight and meaningful debate.
- Risks of Abuse: Surveillance systems are often deployed under the guise of security but are susceptible to abuse. History shows that tools designed for law enforcement can easily be turned against dissenters, journalists, or marginalized communities.
As the report highlights, these developments could establish a permanent surveillance infrastructure across Europe, enabling the collection of biometric, behavioral, and communications data on an unprecedented scale.
Flawed Justifications for Surveillance Expansion
Privacy advocacy organizations, including the European Digital Rights (EDRi) network, argue that much of the justification for these surveillance plans relies on flawed assumptions. The rhetoric of the “Going Dark” report, which claims that law enforcement is losing access to communications due to encryption, has been widely debunked. As EDRi points out, law enforcement already has extensive tools at their disposal to access data and track individuals, but the focus on encryption risks undermining secure communication for everyone.
Instead of addressing systemic issues within law enforcement, these flawed reports have fueled calls for intrusive surveillance systems that risk eroding privacy while offering little evidence of improving public safety.
Centralized Police Data: A Substantial Security and Privacy Threat
A second Statewatch report, titled “EU Police Data Plans Pose Substantial Security and Privacy Threats”, explores another equally concerning initiative: the EU’s push to centralize police data repositories and expand their use.
The EU has already established several large-scale databases, such as the Schengen Information System (SIS), which stores data about individuals who may be denied entry into the EU, and the Europol Information System, which can hold details about millions of people, including those not suspected of crimes. For example, a traveler flagged mistakenly in the system could face unnecessary scrutiny, detention, or restrictions when crossing borders — highlighting the real-world risks of inaccurate or overreaching data collection. The new proposals aim to go further, creating an interoperable web of police data accessible to law enforcement agencies across member states. Proponents argue this is necessary for combating cross-border crime and terrorism, but the risks are immense.
Key Concerns with Centralized Police Data
- Massive Data Collection: The EU’s proposed systems would require the collection of highly sensitive data, including biometric information (fingerprints, facial recognition scans) and behavioral analytics, to track individuals’ activities across borders.
- Data Misuse and Security Risks: Centralized data systems are prime targets for cyberattacks, data breaches, and misuse. The larger and more interconnected the system, the greater the risks of unauthorized access, theft, or corruption of the data.
- As Statewatch points out, the systems lack robust safeguards to prevent misuse or to ensure that data is handled proportionately and lawfully.
- Erosion of Trust in Law Enforcement: Building centralized data repositories without meaningful safeguards undermines public trust. Individuals may be less willing to engage with law enforcement if they fear their data will be stored indefinitely, shared across borders, or used inappropriately.
- Impact on Fundamental Rights: Mass police databases can violate the principle of proportionality, a cornerstone of EU law. By collecting and sharing data indiscriminately, these systems erode fundamental rights, including the right to privacy, freedom of movement, and the presumption of innocence.
Civil Society Opposition and Democratic Accountability
In an open letter to EU institutions, over 30 civil society organizations — including EDRi — have criticized the lack of transparency in the High-Level Group’s (HLG) recommendations for data access. The letter highlights a concerning pattern: while industry stakeholders are included in key discussions, civil society voices remain sidelined. This exclusion undermines democratic accountability and reinforces fears that surveillance policies are being driven by corporate interests rather than public well-being.
These organizations have called for the EU to prioritize transparency, include meaningful public debate, and ensure any law enforcement proposals respect proportionality and fundamental rights.
Why Privacy Advocates Are Sounding the Alarm
The reports from Statewatch highlight a fundamental clash between security policy and individual rights. Privacy advocates are urging EU lawmakers to take a step back and critically examine the following issues:
- Lack of Democratic Oversight: Proposals to integrate surveillance systems and expand police databases are being pushed forward without genuine public debate or oversight. Civil society organizations have been excluded from key discussions.
- Failure to Uphold Privacy Laws: The EU has some of the strongest privacy laws in the world, including the General Data Protection Regulation (GDPR). However, these proposals risk undermining GDPR principles by enabling indiscriminate data collection and sharing.
- Ignoring Proportionality: Surveillance systems must be targeted, necessary, and proportionate to their objectives. Embedding policing into technological design and centralizing data far exceeds what is justified for fighting crime and terrorism.
- Setting Dangerous Precedents: The failure to fully ban harmful surveillance technologies like facial recognition in public spaces sets a troubling precedent. It risks not only eroding privacy within the EU but also encouraging other nations to adopt similar measures, undermining global human rights.
A Call for Action: Safeguarding Our Privacy and Rights
As the EU pushes forward with these plans, the opposition from civil rights defenders grows louder. Policymakers must address the following key demands to prevent an erosion of fundamental rights:
- Implement Privacy by Design: All new technologies must prioritize privacy protections at the design stage, ensuring they are not co-opted for surveillance.
- Establish Robust Oversight: Any new policing tools or databases must be subject to democratic scrutiny, independent oversight, and clear legal frameworks to prevent misuse.
- Reassess Interoperability Plans: Cross-border police cooperation is important, but it must not come at the cost of individuals’ privacy, security, and dignity.
- Strengthen Export Controls: The EU must ban the export of surveillance tools that risk facilitating human rights abuses in authoritarian regimes.
- Prioritize Data Security: Centralized systems require state-of-the-art security measures to protect sensitive data from breaches or misuse.
The EU’s role as a leader in digital rights and privacy is now at stake. If these plans proceed without significant safeguards, Europe risks undermining its own foundational principles of freedom, security, and justice.
Conclusion: The Price of Surveillance-Driven Security
The EU’s surveillance plans may be presented as necessary for security, but they come at a steep cost to privacy, trust, and individual freedoms. Embedding surveillance into our technologies and centralizing police data pose far-reaching risks that cannot be ignored.
As privacy advocates, it is our responsibility to hold policymakers accountable and demand a security framework that upholds, rather than undermines, fundamental rights. Europe’s future must not be built on surveillance by design — but on privacy, democracy, and trust.
-
 @ 6e24af77:b3f1350b
2024-12-18 11:25:50
@ 6e24af77:b3f1350b
2024-12-18 11:25:50test content with some markdown
hi
codemore text
a bit late for the title
-
 @ cc448f8b:a1ad47db
2024-12-20 18:27:36
@ cc448f8b:a1ad47db
2024-12-20 18:27:36A Website Hosted on NOSTR?
The Nostr landscape is changing every day. https://npub.pro came across my radar and clearly it cannot work well, basically a website hosted almost entirely on Nostr relays. I was wrong!
I'll be honest that at first, things did not go well. I posted several issues on https://github.com/nostrband/nostrsite and within a very short time the problems were addressed. Right now it is working so much better. While there is always room for improvement, it is incredibly easy to create a website.
I've invited podcaster/blogger friends to give it a try and most now have a working website in such short time.
Quick Start
- Visit https://npub.pro
- Login
- Select a theme.
- Make some settings adjustments (icon, backdrops, colors, etc)
- Press the
Publishbutton and that's it!
Here's where it gets interesting, there is no cms backend for your posts. Instead, use any Nostr client to create your website post. Here's a small list of popular clients: https://nostr.com/clients.
Tips
The site previews work best if you already have content on Nostr.
I would start out with all content, no filtering. Once you finalize your theme choice add filters because you may not want all your Nostr posts to be visible on the website. For example if you have a DIY blog, add the
#DIYhashtag to all the posts you want to see on the website and set your filter to only show posts tagged#DIY. No-one wants to see your#coffeechainposts on your DIY blog, LOL.What I Like Most
- Automagic RSS Feed
- Looks great on mobile devices
- No database, no CMS, no server maintenance
- Plenty of themes
- Beautiful OG/Twitter sharing
- Built in likes, zap and share plugin
- Theme customization for those that know how to
- Ability to add contributors without creating accounts or managing user databases
- Ability to filter Nostr notes via tags or format (long/short notes)
- Use free subdomain or use your own custom domain
- Fully working site comments with zero effort
What I Dislike
- Not a problem for me but some probably won't like un-moderated site comments
- Not all CSS is manipulable, or example, some CSS is loaded after the custom css like the Zap/share dialogs (perhaps this is a theme specific issue)(also most creators probably won't use custom css/js code)
Website Examples Created By Others Using https://npub.pro
- Sport news - https://gsc.npub.pro/
- Podcast - https://directordetour.npub.pro/
- Someones personal blog - https://marc26z.npub.pro/
- Custom domain + custom CSS styling - https://news.pivx.org
- My test website with custom CSS - https://palmtree.npub.pro
Conclusion
I would 100% recommend Npub.pro to anyone who wants a website. It should take the average person under 30 minutes to get a fully functioning website. If your familiar with the admin interface, you could probably spin up a new website in under 5 minutes.
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ 1cb14ab3:95d52462
2024-12-17 19:24:54
@ 1cb14ab3:95d52462
2024-12-17 19:24:54Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
More from Hes:
-
 @ 3906af02:af15c9f4
2024-12-19 13:40:00
@ 3906af02:af15c9f4
2024-12-19 13:40:00NEW: HRF #Bitcoin Development Fund grants 700 million satoshis to 20 projects worldwide!
https://bitcoinmagazine.com/business/human-rights-foundation-donates-700000000-satoshis-to-fund-bitcoin-development-and-projects
The grants cover decentralized #Bitcoin mining, technical education, decentralized communications, independent media & privacy-enhanced financial solutions for human rights groups, focusing on key regions in Latin America, Asia, and Africa 🌍🌏🌎🎁
Grants include:
🛠️ Stratum V2 Reference Implementation (SRI) decentralizes #Bitcoin mining by allowing nodes create their own block templates, reducing reliance on large pools. Funds will support @bit-aloo’s work on SRI including benchmarking tools, integration tests & codebase maintenance
⛏️ Public Pool makes #Bitcoin mining accessible for low-hash-rate devices, empowering individuals to self-host mining servers & contribute to decentralization. Funds will support hosting costs, hardware upgrades, & operational expenses.
🛠️ Jon Atack, recognized as one of the top all-time contributors to #Bitcoin Core, plays a pivotal role in enhancing Bitcoin’s decentralization and robustness. Funds will empower him to continue his vital contributions to Bitcoin development
👩🏿💻 Naiyoma, the first female #Bitcoin Core developer from Africa. Her work focuses on reviewing pull requests (PRs), addressing bugs through new PRs & improving Bitcoin Core’s codebase. Funds will support her full-time contributions to advancing Bitcoin Core.
🔒 Daniela Brozzoni, a #Bitcoin Core developer who previously contributed to the Bitcoin Development Kit (BDK). This grant will support her full-time contributions to Bitcoin Core reviewing key pull requests (PRs), contributing to new features & improving testing coverage
📱 UX/UI Design for Bitcoin Core by @Michaelhaase will bring the #Bitcoin Core App to mobile enabling users to run nodes, access essential wallet features directly on their phones to improve their financial privacy. Funding will support the project’s design & development.
🚀 Brink, co-founded by Mike Schmidt, supports #Bitcoin protocol engineers with grants and offers training & mentorship to onboard new contributors to open-source development. This grant will support operational expenses
⚡@Tando.me, cofounded by Sabina Gitau, integrates #Bitcoin with Kenya’s M-PESA system, enabling KYC-free, fee-free Lightning payments for everyday transactions for 54 million Kenyans. Funds will help boost Tando’s liquidity, support user growth & drive African expansion.
🌐 YakiHonne, a Nostr client founded by Wendy Ding, supports free speech & promote #Bitcoin payments across 170 countries with innovative functionality & a blend of online & offline events. Funds will support smart widget development, relay improvements & community events.
🌍 SeedSigner Multi-language Support brings accessibility to the open-source SeedSigner hardware wallet, empowering marginalized communities through inexpensive & accessible self-custody. Funds support Ace to deliver a multi-language version of SeedSigner.
🤝 Vexl, cofounded by Lea Petrasova, provides a private, KYC-free, peer-to-peer #Bitcoin trading experience by connecting users to trade through the social graph of their phone contacts. Funds will support expanded adoption in Africa & improvements to the backend infrastructure.
🇮🇳 Tomatech is building developer talent in Goa, India to advance #Bitcoin infrastructure & FOSS projects through training, workshops, & community meetups. Funding will support developer training, the creation of a developer hub, bounties & grants, & general operations.
💾 Krux, open-source firmware that turns generic devices into hardware wallets for secure #Bitcoin self-custody featuring air-gapped operations, key management & backups & support for 10 languages. Funding will support @odudex to advance this project.
🔐 Iris, a #Nostr web client by @MarttiMalmi, which aims to improve protection for metadata & message content, ensuring conversations remain private, especially in surveillant environments. Funding will support hiring an additional developer to expand Iris' features & functionality.
💻 Cashu-ts, the primary Software Development Kit in the @CashuBTC ecosystem developed by @Gandlaf21, simplifies wallet creation, integrates the latest protocol updates & powers popular wallets. Funds will support the developers to maintain & improve this essential library.
🤝 Unify, a Payjoin wallet developed by Fontaine, enhances privacy in #Bitcoin transactions by obscuring transaction histories, crucial for individuals navigating repressive regimes. Funds will support the developer to ship new features & expand compatibility with other wallets.
📢 The Financial Freedom Policy Coalition, led by Venezuelan activist Jorge Jraissati, promotes economic opportunities for people living under authoritarian regimes. Funds will support advocacy missions to educate policymakers on how #Bitcoin supports human rights.
🎓 African UX Bitcoin Bootcamp, led by @MouxDesign, empowered 10 African UX designers with #Bitcoin UX research skills ahead of the Africa Bitcoin Conference & support to test 5 popular Bitcoin products during the conference. Funds cover all program expenses for participants.
📰 No BS Bitcoin delivers ad-free, privacy-focused #Bitcoin news in clear & accessible format, essential for activists & citizens under authoritarian regimes. This grant ensures continued operations, adds an editor & supports Nostr features like Zaps & comments.
📖 Bitcoin History, a research project by Pete Rizzo, documenting key people, events & materials that shaped Bitcoin’s rise as a global monetary & human rights force. Fund will support a researcher to investigate & document stories of Bitcoin’s use against authoritarianism.
🌎 HRF is committed to supporting human rights and financial freedom with #Bitcoin.
If you are working on a #Bitcoin or adjacent freedom tech software (Nostr, eCash, TOR etc), education or adoption project that meets our mandate, submit your application at http://hrf.org/bdfapply 💪
-
 @ 5afdec5b:2d631be1
2024-12-19 13:08:08
@ 5afdec5b:2d631be1
2024-12-19 13:08:08On November 26, 2024, we took a significant leap forward in revolutionizing Bitcoin-collateralized loans by launching PHASE 1 of our closed beta. Now that the dust has settled, it's time to reflect on what we've learned, celebrate our wins, and chart the path forward.
"Get the bread you need without having to part with your corn." — Lendasat, 2024
📈 Closed Beta: PHASE 1 in Numbers
Over the course of one fast-paced week, here's what we achieved:
- 191 waitlist signups
- 100 invitations sent to eager testers
- 29 unique borrowers took 34 loans in total
- 21 loans disbursed via virtual debit cards, and 13 paid out in stablecoins (USDC on Polygon)One of our trusted partners stepped up to support us by providing loan offers, allowing our team to focus entirely on refining the borrowing experience during this phase. In just one week, we exceeded the lender's promised liquidity by 15%, prompting an early wrap-up.
In terms of value:
- 1.34 BTC in Total Value Locked (TVL)
- $54,600 USD in Total Value Disbursed (TVD)
These numbers don't just reflect activity; they validate the demand for Bitcoin-backed loans and alternative disbursement methods like virtual debit cards.
📝 What We Learned
PHASE 1 taught us a lot about our product, our users, and the road ahead. While this beta focused on the borrower experience and the integration of virtual debit cards thanks to our partner Moon, it gave us valuable insights into what works and what needs improvement.
The UX Challenge
Building a non-custodial platform is hard. Designing its UX? Even harder.
- Our decision to use a Contract Secret (a sovereign key for signing contracts) instead of an in-app wallet upheld our commitment to self-custody, sovereignty, and safety.
- However, this introduced friction for users. We're rethinking how to make this smoother while staying true to our principles.💳 Virtual Debit Cards: A Game Changer
The ability to claim loans directly onto a virtual debit card — thanks to our partnership with Moon — was a clear hit. Virtual cards weren't just appreciated; they were a hot topic.
➡️ However, one feature that could take this to the next level is the ability to add these cards to Apple Pay or Google Pay. It's a missing piece we're eager to explore to make the experience even more seamless and user-friendly.
Stablecoin Repayment: A Friction Point
Repaying loans in stablecoins on an alt-chain wasn't as seamless as we'd hoped. Reducing this pain point will be a top priority in future iterations.
➡️ To address this, we are actively exploring new integrations that would allow borrowers to repay their loans via bank transfer or even by using their debit or credit card, providing more flexible and user-friendly repayment options.✅ Demand Validated
From Bitcoin-collateralized loans to virtual debit card payouts, the strong demand reinforced our belief in the product's potential and validated that our approach is the right one.
➡️ In the future, the underlying protocol will continue to operate on a Bitcoin<>Stablecoin foundation, ensuring speed, trustlessness, and efficiency. Borrowers, however, will have the option to opt-in for intuitive on/off ramps and spending tools, making the experience seamless and user-friendly. This will allow the complexities of the alt-chain infrastructure to disappear entirely from the borrower's perspective. At the same time, we'll keep the order book clean and unfragmented, ensuring a smooth and scalable ecosystem for all participants.🌙 Dark Mode Is (Still) a Thing
Yes, even in the world of Bitcoin-backed loans, dark mode is a surprisingly big deal.
➡️ Message received; devs are doing something.
👀 Looking Ahead: BETA RELOADED
If PHASE 1 was about testing the waters, BETA RELOADED 👀 will be about diving deeper. In this next phase, we're opening up both borrower and lender experiences to our beta testers, with:
- Improved UI/UX, based on the invaluable feedback we've received.
- New partnerships and integrations to enhance functionality and accessibility.
- Exciting surprises that we'll reveal when the time comes.If PHASE 1 taught us anything, it's that we're onto something significant. We've demonstrated that Bitcoin-collateralized loans are not only reinventable but genuinely in demand. And this is just the start of what's to come.
Get ready for BETA RELOADED. It's coming soon™️, and it's going to be legendary!
Want to be part of the journey? Join our waiting list or, even better, connect with us on Discord to share your thoughts and stay updated!
Stay tuned, and as always, stay sovereign.
-
 @ a17fb4ed:c53f7e91
2024-12-18 20:03:18
@ a17fb4ed:c53f7e91
2024-12-18 20:03:18Here is a little poem for the upcoming January 1, 2025 IRS Safe Harbor:
Wallet, Exchange - where do I begin?\ Allocating my bitcoin, what a din!\ Specific units or global, which way to go?\ Decisions, decisions, my head starts to blow.
Quantity, cost basis, I must take note,\ Tracking each asset, like a sailor at sea, afloat.\ Opentimestamp the proof, to show I've done my part,\ Sailing into safe harbor, before I depart.
FIFO or Spec ID, which method to choose?\ Gains and losses, I must not lose.\ Consolidate holdings, simplify the fray,\ Lest the IRS come and take it all away.
Who's on first, what's on second, I just don't know,\ Filling out this spreadsheet, my bitcoin woes.\ But if I follow the steps, laid out so clear,\ The safe harbor awaits, no need to fear.
Ok, for real though, What the Fuck!?! It's a public ledger and all amounts and dates are forever recorded. Way to make this much more complicated and time consuming than need be. Classic!
Clear as mud. At least this might get more folk to self custody.
Here are couple links that might help a smidge:
What US Taxpayers With Crypto NEED to do before Dec 31, 2024 - Get into the Safeharbor!
Cheers, Yooper
-
 @ f4bf1fb5:b428f8d5
2024-12-02 23:25:45
@ f4bf1fb5:b428f8d5
2024-12-02 23:25:45The project claims and communicates to everyone that mods published on it can't be taken down by the project/site owners, and that creators and users can't be banned, as well as not needing the site's permission to publish mods on it, citing that all of this is possible because of the protocol that its built on, Nostr. However, that's a quick response on how any of this is possible, and most people aren't technically knowledgeable enough to go and research it, let alone have the energy to do so.
That's why we thought it'd be a good idea to explain the tech, what's happening in the background, how the site currently works, why users need to use a new method of registration and login, and how things would change later on.
How does Nostr work?
Nostr is the protocol that DEG Mods is built on and is the core of what makes it possible to have that censorship-resistant and permissionless benefits. To summarize how it works, let's see how almost all sites work in comparison.
Be it a normal blog site like WordPress or Medium, or a social media site like X/Twitter or Facebook, all of them work similarly. There's the site that a person uses to create an account and publish a post on, and that same account is used to post data which gets sent and saved in one or more servers controlled by the site owner. Then, if someone else wants to view that person's post or profile, they'd use that same site to communicate with the one-entity-controlled servers and retrieve the relevant data/information.
That's how almost all sites work. Now, if such a site wants to ban a user or takedown their posts, that central entity (the site owners) can delete that account and/or delete its posts, and it's gone.
So how does a site built on Nostr work in comparison? It differs in two main points, the first being the account creation process, where instead of filling up a form and sending your personal data to have your account created, you'd generate an account, which would produce two keys, a public and a private one (think username and password), and since that process is a mathematical and cryptographic result, that means that you didn't even ask the site to create the account, you just did, whether they liked it or not. You could've also done it offline too, without being connected to the internet. What that means is that they couldn't stop you from making an account, and they can't ban your account. You actually control it.
The other point that it differs from traditional sites is how it handles people publishing content to it and how it retrieves it. Once you create a piece of content, a blog post or a short social post, it creates a file with that data in it, signs it (think like a signature, a unique squiggle/drawing, but happening with math and cryptography) using your public address (username), and that's only possible because you have the private key (password) to do it, then sends that file to multiple different relays (servers) that aren't necessarily associated with the site you're currently using, not controlled by them or by one entity.
So there are multiple copies of your published content spread across multiple servers, controlled by different entities, be it other companies, or random people, and yes, you can run your own as well, to have a backup copy of your content as well as your friends and family and/or select individuals as well, which is very doable since it was made to be easy and efficient, but that's for another post/guide when the time is right. In a sense, the more popular a post is, the more it gets decentralized and strengthens its censorship resistance.
With that said, if someone else wants to see your posts, they'd search for it and view it, and the site they're on would communicate with those decentralized servers to find the content and present it to you.
What all of this means is that you didn't need permission to make an account, or to log in, and you didn't need permission to publish content or view them. What's also interesting is that you would be able to go to another site that's built on the same tech, and in a similar way, publish content there, and it can appear on that first site as well. As an example, imagine if you made a post on Facebook and it appeared on X/Twitter, Instagram, YouTube, and Reddit.
Another point to consider is that it doesn't have to be a site, it can be a PC software or a mobile app as well, and all of them can share similar functionality and data publishing and retrieval.
How does DEG Mods work?
Now that the underlying tech/protocol for DEG Mods has been somewhat explained, here's how we're applying that here with mods.
When you want to register or log into the site, it's mentioned that you need to download and install a browser extension, and what that extension does is create the account for you, create that public and private key pair, store it within it, within your PC, which means that only you know your account, and nobody is in control of it besides you, and with it you'd use it to sign into the site and sign-off on various actions like publishing a mod post, sending a comment, reacting to a post, and so on. Without your signature from that keypair you have in your browser extension, no action would be taken.
With that said, if you somehow lost your keypair, specifically your private key, or somehow it was leaked to someone, there would be no way for you to change that private key or retrieve it. There's no "change password" or "forgot password" process here. With freedom comes responsibility, so keep that in mind.
So, once you've set up your browser extension and have managed to log in, you go ahead and attempt to publish a mod if you're a mod creator, where you fill out the details in the appropriate mod submission page, from the title, body text, screenshots and so on, and then you reach the area where you'd share your mod files with. You don't upload the mod files to DEG Mods / Nostr, but rather upload them to a regular server of your choice, get the file link from there, and add it in its appropriate field. After you add any other relevant data, you publish your mod, and now everyone will be able to view your mod page and download it.
Now, you're probably wondering how mods can be censorship-resistant, as we have claimed, even though the mod files are on another site or person's server where they can delete them. Let's say that scenario happened, where you published a mod, and the download button broke because the server host deleted the files. Your mod post is still up, and your account is still up, so the only thing that's broken is the download button. You'd simply upload the files to a different server host provider, and replace the old link with the new one when you edit your mod post.
The download button is now working again. You didn't have to publish a new mod post, you didn't get banned so you didn't have to find a different mod site and then create a new account, to publish the mod yet again, and didn't have to remarket that new page again and lose out on previous efforts, you also didn't have to rebuild the lost connections with your followers and have them create an account on another site for them to do so, only to continuously repeat this process over and over again as similar scenarios continue to occur. You just simply updated the mod post with a new download link.
This exact scenario happened with one of the mods on the site, where their mod page was taken down from various sites because of a malicious attacker, yet that didn't happen on DEG Mods' end, and even when the download links were taken down and resulted in the download link being broken, the creator simply uploaded it elsewhere and updated the mod post with the new link, resulting in a functional download button again, as if nothing happened. Their mod page on DEG Mods was up the whole time throughout their initial launch month period, whereas everywhere else they've tried has failed them.
They didn't have their mod post/page taken down, their account couldn't be banned, they didn't have to remarket anything again, and they didn't lose the connection between themselves and their fans.
Questions & Answers
We'll most likely update this post with relevant new information as they come, as well as new questions with their answers, and with that said, here are some of those.
Doesn't [insert anti-censorship site here] do the same thing?
From all the current mod sites we've looked into, they're only anti-censorship, as in they're against it, meaning they weren't built from the ground up to be censorship-resistant. They can still take down mod posts, they can still ban you, and you need their permission to post on their site. On DEG Mods, you don't need our permission to do anything, we can't (not won't, can't) take down your mod post, and we can't ban your account. The best we can do is hide posts, and even then all of them are still accessible. As far as we know, in regards to the values of modding, DEG Mods is the first true mod site out there, and others would be categorized as gated mod sites. This might be a bold claim, and we're not above having an inflated ego, so share your thoughts or criticism of the project if you think that's not the case and knock our potentially inflated ego down.
Uploading mod files to other sites is a pain. Isn't there something you can do?
Yes. Luckily, there is new tech out there that brings the same censorship benefits to the mod files themselves, though not necessarily at the same level or power considering these would be much larger files than a normal post would be.
At some point, we'll be utilizing and implementing something called Blossom, and with that implementation, creators would simply drag and drop their fields into the mod submission page and have that mod file (a .zip for example) and have it uploaded to one or more Blossom servers, where it would be packaged and signed using the creator's public key/address, and that file would now be identifiable and verifiable, where people can confirm that it's a file that came from you directly. That same file can potentially be backed up by fans who want to help you out, along with having a backup of the files yourself on your PC, home server, or rented server.
Let's say that your server host doesn't want to provide you with service anymore and has deleted your mod file. What will happen when someone clicks the download button on the mod page is that it'll attempt to search for that same file, since it's identifiable and verifiable by its unique ID, which was created using the creator's signature, searching for it on multiple different available Blossom servers, and brings it back to the user to download it. From the user's perspective, it'd behave normally where they'd just wait for the download to start and finish.
What does that result in? Mod files are now censorship-resistant too.
-
 @ 3e48885d:b2272a7c
2024-12-18 18:59:49
@ 3e48885d:b2272a7c
2024-12-18 18:59:49It may sound silly, but about once a week, sometimes more, I find myself wishing I were a cowboy. The freedom that would come from the total disconnect from the rest of the world. The peaceful feeling of open spaces and working with animals. And let’s not forget a tinge of adventure.
At 52, I find myself wishing this still. There was a time in my early thirties I seriously considered it, then came marriage and kids and it slipped away. These days, I still find it nice to think about.
Today I sit attached to my desk, living in a semi suburban world. The only animals I tend to are my two dogs. Sometimes I sit alone and listen to old cowboy songs from the likes of Chris Ledoux. I guess it helps that I live in Texas, giving me default western status, though nowhere near that reality.
I work in cybersecurity and hang out in more undeveloped parts of the web where outlaws may dwell, I guess that is as close as I get. It’s nice to daydream.
It may sound silly, but about once a week, sometimes more, I find myself wishing I were a cowboy. The freedom that would come from the total disconnect from the rest of the world. The peaceful feeling of open spaces and working with animals. And let’s not forget a tinge of adventure.
-
 @ cc448f8b:a1ad47db
2024-12-18 18:44:01
@ cc448f8b:a1ad47db
2024-12-18 18:44:01A Website Hosted on NOSTR?
The Nostr landscape is changing every day. https://npub.pro came across my radar and clearly it cannot work well, basically a website hosted almost entirely on Nostr relays. I was wrong!
I'll be honest that at first, things did not go well. I posted several issues on https://github.com/nostrband/nostrsite and within a very short time the problems were addressed. Right now it is working so much better. While there is always room for improvement, it is incredibly easy to create a website.
I've invited podcaster/blogger friends to give it a try and most now have a working website in such short time.
Quick Start
- Visit https://npub.pro
- Login
- Select a theme.
- Make some settings adjustments (icon, backdrops, colors, etc)
- Press the
Publishbutton and that's it!
Here's where it gets interesting, there is no cms backend for your posts. Instead, use any Nostr client to create your website post. Here's a small list of popular clients: https://nostr.com/clients.
Tips
The site previews work best if you already have content on Nostr.
I would start out with all content, no filtering. Once you finalize your theme choice add filters because you may not want all your Nostr posts to be visible on the website. For example if you have a DIY blog, add the
#DIYhashtag to all the posts you want to see on the website and set your filter to only show posts tagged#DIY. No-one wants to see your#coffeechainposts on your DIY blog, LOL.What I Like Most
- Automagic RSS Feed
- Looks great on mobile devices
- No database, no CMS, no server maintenance
- Plenty of themes
- Beautiful OG/Twitter sharing
- Built in likes, zap and share plugin
- Theme customization for those that know how to
- Ability to add contributors without creating accounts or managing user databases
- Ability to filter Nostr notes via tags or format (long/short notes)
- Use free subdomain or use your own custom domain
- Fully working site comments with zero effort
What I Dislike
- Not a problem for me but some probably won't like un-moderated site comments
- Not all CSS is manipulable, or example, some CSS is loaded after the custom css like the Zap/share dialogs (perhaps this is a theme specific issue)(also most creators probably won't use custom css/js code)
Website Examples Created By Others Using https://npub.pro
- Sport news - https://gsc.npub.pro/
- Podcast - https://directordetour.npub.pro/
- Someones personal blog - https://marc26z.npub.pro/
- Custom domain + custom CSS styling - https://news.pivx.org
- My test website with custom CSS - https://palmtree.npub.pro
Conclusion
I would 100% recommend Npub.pro to anyone who wants a website. It should take the average person under 30 minutes to get a fully functioning website. If your familiar with the admin interface, you could probably spin up a new website in under 5 minutes.
-
 @ f4bf1fb5:b428f8d5
2024-11-20 17:05:05
@ f4bf1fb5:b428f8d5
2024-11-20 17:05:05On DEG Mods, mod creators and enjoyers can benefit from tips, allowing them to earn money directly from those who appreciate their work or comments, and 100% of what's tipped goes to the one being tipped (excluding the processing fee of the transaction, which is extremely negligible). We don't take any percentage of this process, unless you choose to and at whichever amount you like.
Did you discover a mod that you found enjoyable, useful, or intriguing, and you'd like to show your appreciation with a $10 tip? You can do that. Choose to give 100% of your tip directly to the creator, or opt for a 90% share for them, with the remaining 10% supporting DEG Mods. You can also reverse the split if you prefer. It's entirely up to you how you'd like to allocate the tip.
The elephant in the room
Yes, we're using Bitcoin as the main currency and monetary system on the site, and we're aware of the general public's perception of Bitcoin and the general Cryptocurrency space. We have pretty solid reasons why we're utilizing Bitcoin as the monetary infrastructure for DEG Mods instead of traditional payment systems with fiat currency, like USD/EUR, and the banking system, like Visa or Mastercard.
DEG Mods is built around the idea of censorship-resistance and being permissionless, not just anti-censorship, with that in mind, we didn't want to use a system, and in this case a monetary system, where some third party can come in and threat the site, its users and creators, to self-censor or else suffer the consequences of everyone's money frozen, stolen, or not being able to send or receive. There are many examples of such cases.
We wanted to use something where people actually own their money, not have it controlled by anyone, and have people freely transact with anyone they want, whenever they want, with whichever amount they want to utilize, and not worry about any kind of censorship.
That's why why we went with Bitcoin, with the utilization of the Lightning Network. All of this is possible with it. And we didn't go with any other Cryptocurrency, not even create our own currency and massively benefit from it, because we wanted to use the most trusted, verifiably sound, and strongest currency in the world that's the most censorship-resistant one out there, and not a potential one where people would have a higher chance of thinking that its a scam. That's why, generally speaking, many differentiate between 'Bitcoin' and 'Crypto'.
Properly used, you completely own your money, and nobody can take it away from you or stop you from transacting with others. Now, let's get back on topic.
How to set up and enable getting tips
You need to download and install a Bitcoin Lightning Wallet app (suggestions: Lifpay or Wallet of Satoshi) on your mobile device, where where it supports and provides you with a Lightning address. Once you have obtain such an address, you can go ahead and add that to the 'Lightning Address' field in the profile settings page on DEG Mods.
After that, save/publish your changes and you're done. People can now tip you directly on your profile or tip you via your mod posts.
How to exchange your tipped Bitcoin to other currencies like USD/EUR
So you got tipped a few times and feel like you want to exchange what you've received so far into other currencies to spend them. We won't have a full-blown guide on this, at least not now, but the general idea is that you'd go to an exchange site/app (Suggestion: Binance, or if you're in the USA then CashApp or Strike might work better for you), send them there, and have them exchanged there to whatever currency you like, then withdraw it to your bank or payment service that you use (or keep them there if its already the payment system you use already).
You can also go to physical exchange stores if they support the exchange of that currency in your country.
How to tip creators and other users
As a user that wants to tip creators or other users, you'd do that by first having a Bitcoin Lighting Wallet (similar suggestions as shared above), and then you'd need to fill that up, which is basically the reverse process of above, and once you have an amount of Bitcoin (or 'Sats', think 'Cents') in your Wallet app, you can now go ahead and start tipping creators or other users.
You tip others by tapping on the lightning icon you'll see throughout the site, either for a comment, a profile, or a mod post next to the reaction buttons, which will trigger a popup asking you to enter an amount in Sats and then you'd generate the QR code. In your Wallet app, tap the send button and scan that QR and send away. Done.
Keep in mind that other users or creators might tip you, so you don't necessarily have to go through that process of exchanging traditional currencies to Bitcoin/sats, so its definitely worth at least obtaining a Bitcoin Lightning Address and adding it your 'account' here on DEG Mods, in the off chance that someone tips you when you comment on a post for example. Why leave money on the table, as they say.
Questions and Answers
We'll continue updating this blog post when new information comes along, but here are some questions and answers regarding this topic.
Did you really have to use Bitcoin/Crypto? Why couldn't you have PayPay, Stripe, or some other traditional payment method?
This is answered at the start of this post, but in gist: So we, creators, and users, aren't screwed over and be forced to censor ourselves.
Do I have to use Bitcoin?
No, you can use DEG Mods without ever touching it, and you can also add your own payment links (like PayPal, CashApp, Kofi, Patreon, etc) in your profile (we'll be adding a linktree-like system at some point to make this process easy), and people can easily find those link and tip you there, though those tip buttons are only for Bitcoin.
Will there be more ways to get money later, or is it just tipping mod posts and profiles?
Yes, there'll be more ways for creators to acquire money from users in the future, for reasons other than 'thank you creating this mod'.
-
 @ eac63075:b4988b48
2024-12-02 02:40:18
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
Simple and Clear Taxation:
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
Low Cost to Start:
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
Complete Digitalization:
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
Support for Startups and Innovation:
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
Easy Access to Europe:
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-
 @ f4bf1fb5:b428f8d5
2024-11-14 19:15:23
@ f4bf1fb5:b428f8d5
2024-11-14 19:15:23As some of you might be aware, we can't take down mod posts/pages or ban creators' accounts on DEG Mods, as we've built the site on top of the Nostr protocol. With that said, a lot of people are concerned with seeing a malicious posts on the site, like spam, scams, posts with viruses, and illegal content, and other worries like not wanting to see specific content. People are worried on how we'd be handling all of these issues as we claim censorship-resistance.
This post is to help showcase and explain how we'll be handling content moderation on the site, while maintaining the site's censorship-resistant and permissionless nature.
Reporting and blocking
The first thing that can be done, in regards to moderation, is for users to report mod posts (or other type of posts). Reporting would result in us having a look at said reported post and determine if we'd block it or not.
Blocking it means that it will be hidden from initial view on the website, yet it'd still be accessible if someone has the link, or accessible on other sites.
Illegal content
In regards to illegal content, we'd essentially do the same thing as mentioned above, and at that point the relevant authorities would need to handle it from then on, as they try to find the perpetrator and prosecute them.
Web of Trust (WoT)
There will be, if not already, an near automated moderation system applied almost site wide, which would handle most of the leg work. This system is called Web of Trust, where it works by showing content published by users who we have followed, and their tree of followers (up to a point that we'd determine).
In essence, the natural behavior of users using the site, from mod creators to enjoyers, like publishing mods, commenting, reacting, publishing short posts, writing update posts or news/announcements, following whoever they like, not following who they don't like and/or blocking those who publishing malicious posts, would act as a moderation layer for for themselves and everybody else. Of course, this means that not everyone will necessarily be visible on the site initially as they start, so that's why everyone is encouraged to interact with each other, follow who you like, block bad faith actors, and so on. Everything is interconnected with each other to create a very efficient, effective, and safe viewing/usage experience on the site.
As we mentioned initially, we'll also maintain our claims of censorship-resistance by providing a toggle to remove the site's WoT filter, including the user's WoT, if they want to see almost everything. This gives everyone a method and chance to be seen, regardless of this moderation layer.
Individual moderation tools
Each individual user on the site has the ability to block a mod posts (or any other type of posts) on the site, as well as whole accounts and their posts.
As we mentioned briefly above, each user will also have their own WoT preference, to see posts of the people they trust, as well as their follows, and so on.
Various systems and designs
We'll be introducing various different systems/designs that would help with general moderation of the site from the user's perspective and exploration of the site. As an example, if a mod post won't include a malware scan report of the mod files (and we'll see if we can make this an automated, then there'd be a visible note around it to indicate that there hasn't been a scan done for it and advise users to be careful of malware).
Questions and answers
Here are a few questions and answers related to this topic. We'd update this post as new info comes along.
Do you allow X or Y type of content?
As long as its a mod (specially cases were non-mods wouldn't be subject to moderation), is legal, not directly harmful (malware, scam), and isn't spam, then you should be fine.
Does fiction equal fiction?
Yes.
-
 @ f4bf1fb5:b428f8d5
2024-11-14 13:05:02
@ f4bf1fb5:b428f8d5
2024-11-14 13:05:02A modder that goes by the name of "welintron" created a mod for Tomb Raider I-III on PC called "Remove Misinformative Warning", one that removes the developers' (Crystal Dynamic) message about the game being supposedly offensive.
The mod was uploaded to one of the popular mod hosting sites at the time, however, staff of said site has removed the mod and banned its creator.
This is an old piece of news as of the time of writing this post, and the purpose of writing it is to remind people of what's being banned, as well as keeping a log for ourselves, to know which mod creator to reach out to in the future, to introduce them to DEG Mods.
Since DEG Mods isn't out yet and you're wondering where you can download it, someone has supposedly uploaded the file on ModDB (be safe!).
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ 3cea4806:10fe3f40
2024-11-12 21:24:18
@ 3cea4806:10fe3f40
2024-11-12 21:24:18testA looong
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 6e24af77:b3f1350b
2024-11-12 18:53:21
@ 6e24af77:b3f1350b
2024-11-12 18:53:215
-
 @ d61f3bc5:0da6ef4a
2024-12-18 16:52:18
@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward.
What Primal Premium Is
The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a Primal Name and Nostr Tools built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products.
Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful.
Why We Built Premium and Why Now
What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold.
In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users.
Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds.
It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step.
Now, let’s take a closer look at what is included in Premium: Primal Name and Nostr Tools.
Primal Name
A Primal Name is a unique name on the primal.net domain that offers three features:
- Verified Nostr address (NIP-05). This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot.
- Friendly Bitcoin Lightning address. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net).
- VIP profile on primal.net. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned!
In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries.
Nostr Tools
Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes:
- Media management. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal.
- Contact list backup. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover.
- Content backup. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time.
Primal Legends
The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should let them pay and recognize them for doing so.”
I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate.
We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂
What Comes Next?
We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium.
Pura Vida 🤙
-
 @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when Kohei demonstrated it in his video.
Here's how you set it up at a high level–
- Buy yourself some NFC cards
- Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
- Write the nencryptsec to the NFC card as a custom URI
- Tap to load the login screen, and enter your password to login
Here it is in detail–
Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
- Login to Amethyst with your nsec,
- Open the sidebar and click "Backup Keys",
- Enter a password, and click "Encrypt and my secret key",
- It will add the password-protected key to your clipboard in the format "ncryptsec1...",
- Remember to backup your password.
Write the ncryptsec to the NFC card
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
- Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
- Place your NFC card against your phone, and it will write to the card,
- Your card is ready.
Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended Peter McCormack's #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to Preston Pysh where it got some cut through and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
- Buy yourself some NFC cards,
- Download the free NFC Tools app to your device, and open it,
- Click "Write" and "Add a record", then click "Custom URL / URI",
- Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
- Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
What's Next
Over my first four blogs I have explored creating a good Nostr setup
- Mined a Nostr pubkey and backed up the mnemonic
- Set up Nostr payments with a Lightning wallet plus all the bells and whistles
- Set up NIP-05 and Lighting Address at my own domain
- Set up a Personal Relay at my own domain
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 4657dfe8:47934b3e
2024-12-18 13:42:46
@ 4657dfe8:47934b3e
2024-12-18 13:42:46Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.
Simplifying Bitcoin Wallets for Friends and Family
Alby Hub empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app.
With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust.
These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere.
And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments.
Let’s have a look how to set it up.
How to provide a wallet to Friends and Family?
- Open your Hub and find the Friends & Family app in the App Store
- Enter a name e.g. your friend’s name and click “Create subaccount”
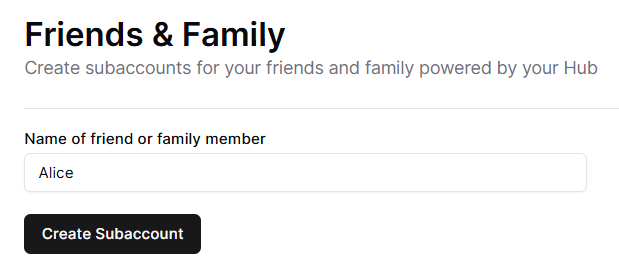
- Share the Connection Secret with your friend for the different options
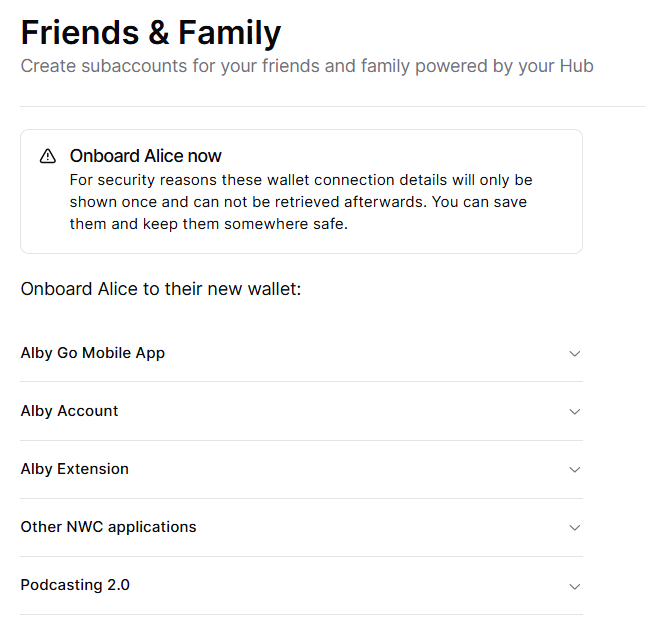
Here are two examples how your the new subaccount can be used.
Alby Go mobile App
Alby Go makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go.
Here’s how to set it up: 1. Open the Alby Go Mobile App tab in your Hub.
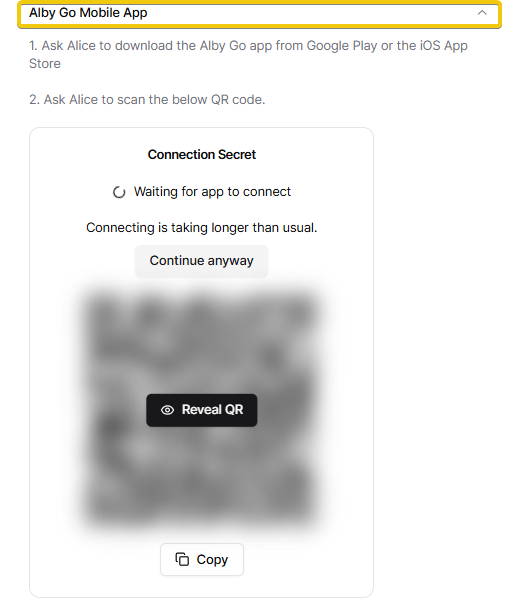 2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.
2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉
Get a Lightning Address with an Alby account
An Alby Account offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed.
To set up an Alby account for someone:
-
Open the Alby Account tab in your Hub.
-
Copy the provided URL and share it with your friend.
-
Your friend simply needs to create their Alby account and afterwards click on the provided URL.
That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳
Onboarding Family & Friends Made Easy In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks.
Stay tuned as we dive into more exciting use cases for subaccounts in Alby Hub! If you have ideas for improvement,let us know.
- Open your Hub and find the Friends & Family app in the App Store
-
 @ e83b66a8:b0526c2b
2024-12-11 09:16:23
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-
 @ e83b66a8:b0526c2b
2024-12-11 09:13:46
@ e83b66a8:b0526c2b
2024-12-11 09:13:46Can I suggest you read my book, it will tell you a lot. It is important you understand what Bitcoin is before you invest anything into it. https://www.amazon.co.uk/dp/B0CLJP6R3F/
Firstly, Bitcoin is not like anything else you have ever experienced in your life. Everything else is based on trust and there is a higher authority you can always turn to.
If you loose access to your bank account, you can walk in to a branch with your ID papers and within half an hour or so, your account access will be restored by them. The bank control your account and the money held within it.
If you loose your passport or driving license, the government can issue you new ones. They control your identity.
If you get locked out of your house, you can call a locksmith and they will break in, legally, for you.
Bitcoin is different, it is permissionless and trustless. Nobody can stop you spending your money and you can send it to anyone anywhere in the world instantly without having to trust a third party to authorise payment for you.
By that same token, if you make a mistake and send it to the wrong address or if you loose the keys that secure your Bitcoin, it is gone, nobody can help you. You need to understand and be comfortable with that.
As for Bitcoin as a store of value, this is the first stage that all new Bitcoiners go through, but if you do it properly, it will eventually be the least significant feature.
However, as for Bitcoin price cycles. Every 4 years the supply is automatically halved. This happened on the 20th April this year, you probably saw we were in Warsaw at a halving party. It happened at 3:09am European time, so we were asleep.
Nothing actually happens for around 6 months of the halving, but from 6 - 18 months after the halving, the price rises significantly to adapt to the new supply and scarcity.
So, from the start of November the price has started to rise and will continue to do so in a saw tooth pattern for around the next year.
The price rise often overshoots the new natural price level and so expect a crash around the end of next year, it will be significant and will take a year or so to recover, but will eventually settle to a new price.
In 4 years time, around April 2028, the cycle will happen again.
Bitcoin is not a short term investment, don’t invest unless you are prepared to hold for a minimum of 4 years.
Holding bitcoin for 8 years can produce generational wealth.
The three core tenets of Bitcoin are:
Not your keys, not your coins - in other words, don’t leave them on exchanges
Don’t trust, verify - which leads to:
Do your own research
Study Bitcoin, it will give you back far more than you can imagine.
-
 @ a39d19ec:3d88f61e
2024-11-17 10:48:56
@ a39d19ec:3d88f61e
2024-11-17 10:48:56This week's functional 3d print is the "Dino Clip".

Dino Clip
I printed it some years ago for my son, so he would have his own clip for cereal bags.
Now it is used to hold a bag of dog food close.
The design by "Sneaks" is a so called "print in place". This means that the whole clip with moving parts is printed in one part, without the need for assembly after the print.
 The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables
The clip is very strong, and I would print it again if I need a "heavy duty" clip for more rigid or big bags.
Link to the file at Printables -
 @ 79008e78:dfac9395
2024-12-18 09:02:28
@ 79008e78:dfac9395
2024-12-18 09:02:28อย่างที่ทราบกันอยู่แล้วว่า Nostr เป็นได้มากกว่า Note แล้วจะเป็นอย่างไรล่ะ ถ้า Note และลองฟอร์มต่าง ๆ ที่เราเคยเขียนกันมาสามารถกลายเป็นเว็บบอร์ดที่เราสามารถใช้เก็บผลงานและโชว์ให้กับคนอื่น ๆ ในโลกอินเตอร์เน็ตทั่วไปได้อีกด้วย
Npub.pro คืออะไร ?
Npub.pro เป็น Other stuff ตัวหนึ่งที่ช่วยแปลง note และ long form ต่าง ๆ ที่เราเคยได้ลงไว้ในโปรโตคอลของ Nostr และแปลงมันมาเป็นเว็บบอร์ดที่สวยสะอาดตา และมีธีมให้เลือกอีกหลากหลาย ซึ่งเหมาะสมมาก ๆ กับเหล่าครีเอเตอร์ต่าง ๆ สำหรับที่จะใช้มันในการโชว์ผลงาน ไม่ว่าจะเป็นสายถ่ายภาพ เก็บรวบรวมบทความ หรืออีกหลาย ๆ แง่มุมที่สามารถเกิดขึ้นได้


นี่เองคือหนึ่งในตัวอย่างที่ผมได้ทำไว้เพื่อแพร่กระจายบทความต่าง ๆ ให้ออกไปสู่ผู้คนที่อาจจะไม่ได้รู้จักหรือใช้งาน Nostr อยู่
แล้วมันทำงานอย่างไร ?
Npub.pro นั้นจะทำการดึง Notes และ Long form ของเรามาจาก relay ต่าง ๆ ที่เราได้มีการเชื่อมต่อไว้ในบัญชีของเรา และทำการนำมาจัดรูปแบบใหม่ตามธีมที่เราได้เลือกไว้ และแสดงผลออกมามาในรูปแบบเว็บบอร์ด นอกจากนี้ยังมีการใส่ตัว nostr log-in เข้ามาเพื่อช่วยให้คนที่มีบัญชี nostr สามารถใช้บัญชีของตนในการ zap หรือ คอมเม้นได้ รวมทั้งยังอณุญาตให้ผู้ใช้ใส่ script เพิ่มเติมลงไปทั้งในส่วนหัวและท้ายของเว็บบอร์ดได้อีกด้วย ดังเช่น

ทั้งหมดที่กล่าวมาข้างต้นเป็นประสบการณ์ส่วนตัวของผมเองที่ได้มีการทดลองใช้งานมาระยะหนึ่ง และในส่วนต่อไป เราจะมาดูกันถึงวิธีการสร้างว่าเราต้องทำอย่างไร จึงจะมีเว็บไซต์สวย ๆ แบบนี้ได้
วิธีการสร้าง
1. เข้าเว็บ Npub.pro
หลังจากเข้ามาในเว็บไซต์ให้เรากด "try now"

2. เลือกธีม
จากนั้นจะมีธีมต่าง ๆ ขึ้นมาให้คุณเลือก ในจุดนี้ผมแนะนำว่าให้เลือกให้เหมาะสมกับผลงานของคุณ (สามารถเปลี่ยนได้ภายหลัง)

3. ตั้งค่าส่วนอื่น ๆ
หลังจากเลือกเสร็จเรียบร้อยเราต้องทำการใส่ title bio และอื่น ๆ ให้เรียบร้อยจากนั้นให้ทำการกด publish

เพียงแค่นี้คุณก็จะมีเว็บบอร์ดเจ๋ง ๆ ที่จะคอยอัพเดตอัตโนมัติเพมื่อคุณได้โพสต์บางอย่างลงบน Nostr ;)
-
 @ 6e24af77:b3f1350b
2024-11-12 14:46:30
@ 6e24af77:b3f1350b
2024-11-12 14:46:30Catchy body content
-
 @ d13f90f0:fa32fe72
2024-11-12 11:59:36
@ d13f90f0:fa32fe72
2024-11-12 11:59:36Catchy body content
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ 6e24af77:b3f1350b
2024-11-08 10:11:29
@ 6e24af77:b3f1350b
2024-11-08 10:11:29test 6
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 490b551d:e17f0103
2024-12-17 22:12:48
@ 490b551d:e17f0103
2024-12-17 22:12:48Welcome, friend. I hope this place becomes a space to pause, breathe, and reflect in the midst of the chaos of life and faith. If you’re here, there’s a good chance you’ve felt the weight of doubt in your belief, the kind that sits heavy on your heart, whispers in your mind, and makes you wonder if you’d truly be accepted if people knew your questions, especially when everything around you insists that belief without doubt is the only acceptable way to be. I get it. I’ve been there too.
I’ve faced a lot of pressure: the pressure to get everything right, the shame that follows any hint of sin, and the isolation that comes with feeling like I’m not quite enough for God’s love—whether it was because of the mistakes I’ve made or the doubts that linger in my heart. It’s tough to be part of a faith tradition that values certainty above all else when you’re in the middle of a spiritual crisis or a season of question. For many of us, the church can sometimes feel like a place where doubt isn’t welcomed, where questions are viewed as weaknesses, or worse, a ticket to hell. But here’s what I’ve learned in the decade I stepped away from my church and my beliefs: doubt doesn’t mean we’re failing at faith. It means we’re seeking something deeper.
Understanding the Pressure to Be Certain
For many of us who were raised in conservative Christian settings, there’s often an unspoken (and sometimes spoken) expectation: doubt is not okay. The message we receive is that to be a "good Christian" means you must have unwavering faith, an unshakable belief that everything in the Bible is true, and absolute certainty in your relationship with God. You’re supposed to have all the answers, be sure of your salvation, and confidently declare your faith in the face of any challenge.
But what happens when you don't have all the answers? When you question parts of scripture or the ways the church has interpreted it? When you wonder how a loving God can allow suffering, or how science and faith can co-exist? When you wonder if you're truly loved by God, or if your struggles disqualify you from His grace?
There’s a lot of weight in these questions, and for a long time, I felt alone in them. After all, isn’t doubt something that should be avoided? Shouldn’t we be strong enough to push through and just believe? The church certainly didn't seem to be the place to clear this all up in my mind!
The Reality of Doubt: You’re Not Alone
The truth is, doubt is a natural part of the human experience. A study published in the Journal of Psychology and Theology found that 70% of individuals experience some level of doubt at various points in their spiritual journey. Doubt doesn’t make you a bad Christian or a failure at faith—it makes you human.
The Bible is filled with examples of doubt. One of the most famous stories comes from Thomas, often referred to as "Doubting Thomas." After Jesus’ resurrection, when the other disciples saw Him alive and well, Thomas couldn’t believe it until he saw Jesus for himself and touched His wounds. When he finally encountered the risen Christ, Jesus didn’t rebuke him for doubting—He met him in the doubt. Jesus said, “Put your finger here; see my hands. Reach out your hand and put it into my side. Stop doubting and believe” (John 20:27, NIV). But Jesus doesn’t shame Thomas. No. He invites him to experience the truth, to see it for himself, and to believe in his own time and way.
Doubt is not a sin. It’s part of the journey of faith. Just like Thomas, we can bring our doubts to Jesus, and He will meet us in that place.
Acknowledging Doubt: A Step Toward Deeper Faith
Sometimes we think that the right way to navigate doubt is to push it down, pretend it doesn’t exist, or cover it up with surface-level answers. We’re told that questioning our faith is a sign of weakness or a lack of commitment. But what if the opposite is true? What if acknowledging our doubt could be the very thing that leads us to a deeper, more authentic faith?
In the book of Psalms, many of the writers express their doubts and frustrations with God. Take Psalm 73, for example. The psalmist, Asaph, begins by questioning the fairness of life: “Surely God is good to Israel, to those who are pure in heart. But as for me, my feet had almost slipped; I had nearly lost my foothold. For I envied the arrogant when I saw the prosperity of the wicked” (Psalm 73:1-3, NIV). Asaph openly doubts God’s goodness, and he questions why it seems like those who do wrong are thriving. But instead of running from his questions, he brings them before God, and by the end of the psalm, he expresses renewed trust in God's faithfulness (Psalm 73:23-26). Through this process of doubting and questioning, Asaph’s faith is refined, and he ultimately comes to a deeper understanding of God's justice and presence.
When we acknowledge the doubt, we don’t weaken our faith; we make space for it to grow. True faith isn’t the absence of doubt—it’s the trust to keep going even when we don’t have all the answers.
What the Bible Says About Doubt
James 1:6-8 is one of the passages that many people turn to when discussing doubt in the context of faith. It says:
"But when you ask, you must believe and not doubt, because the one who doubts is like a wave of the sea, blown and tossed by the wind. That person should not expect to receive anything from the Lord. Such a person is double-minded and unstable in all they do" (James 1:6-8, NIV).
In these verses, James is addressing the process of asking God for wisdom. The context is not about the kind of doubt that questions God’s existence or love, but about a specific type of doubt: a lack of commitment or double-mindedness when it comes to asking for something from God. James is highlighting the importance of trust and consistency in prayer and faith.
Now, this is where it gets tricky. It seems as though James is saying that any form of doubt disqualifies you from receiving God's wisdom, but what he’s actually pointing out is something deeper. The doubt James describes here is not the kind of doubt where you're struggling with your faith and trying to work through your questions. It’s a doubt that stems from being double-minded or divided in your loyalty—someone who isn’t fully committed to trusting in God's goodness and His ability to provide answers.
In other words, James is addressing those who are unable to decide whether they trust God enough to act in faith, or whether they will rely on their own understanding. This isn’t about wrestling with questions of faith, but about refusing to fully trust God and expecting Him to give you what you ask for without truly believing He will. The warning here is that divided loyalty in your faith—being uncertain whether to trust God or rely on your own solutions—leads to instability in your life.
How Does This Relate to Us Today?
If we look at this in light of our own lives, the point James is making is incredibly relevant. It’s okay to have questions, to wrestle with doubt, and to not always have complete clarity. But if your doubt leads you to question God’s ability, goodness, or willingness to act, then you're not fully trusting in Him. If you approach God in prayer with a heart that says, “I don’t think He’ll really answer this, but I’ll ask anyway,” that’s the kind of wavering that James warns against. Faith requires a kind of consistency in belief: that God is good, He is listening, and He has the power to answer—even when you don’t understand how or when.
What James seems to be saying is that doubt becomes problematic when it leads us to reject God’s goodness or power. It's not the occasional, fleeting doubt about one’s salvation or understanding of scripture that disqualifies us from receiving from God, but rather a refusal to commit fully to trusting God in our times of need.How Does This Relate to Us Today?
If we look at this in light of our own lives, the point James is making is incredibly relevant. It’s okay to have questions, to wrestle with doubt, and to not always have complete clarity. But if your doubt leads you to question God’s ability, goodness, or willingness to act, then you're not fully trusting in Him. If you approach God in prayer with a heart that says, “I don’t think He’ll really answer this, but I’ll ask anyway,” that’s the kind of wavering that James warns against. Faith requires a kind of consistency in belief: that God is good, He is listening, and He has the power to answer—even when you don’t understand how or when.
What James seems to be saying is that doubt becomes problematic when it leads us to reject God’s goodness or power. It's not the occasional, fleeting doubt about one’s salvation or understanding of scripture that disqualifies us from receiving from God, but rather a refusal to commit fully to trusting God in our times of need.
Practical Ways to Navigate Doubt in a Faith Tradition that Values Certainty
Acknowledge Your Doubts Without Shame \ The first step in navigating doubt is acknowledging it. Doubt doesn’t make you a bad Christian or unworthy of God’s love. You don’t need to hide your questions. Instead of feeling guilty, recognize that doubt is part of your spiritual journey, and it’s okay to ask questions. When we’re honest about our doubts, we give God space to meet us where we are.
Engage with Scripture Honestly \ Sometimes, we shy away from certain parts of the Bible because they challenge us or don’t make sense. But the Bible is full of complexity, contradictions, and depth—and that’s okay. Approach Scripture with curiosity and openness. It’s not about finding all the answers right away, but about engaging with the text and allowing it to speak to you in different seasons of your life.
Surround Yourself with a Supportive Community \ Find people who are willing to walk with you through your doubts. If you’re struggling with questions, it can be incredibly helpful to talk with someone who has navigated similar struggles. Surround yourself with people who are willing to explore faith openly and who won’t judge you for questioning.
Embrace the Mystery of Faith \ Faith is never about having all the answers. There will always be aspects of God’s character and His ways that remain mysterious to us. But instead of trying to solve every mystery, learn to embrace the mystery. Faith is trusting in the unknown, and sometimes the questions themselves are a beautiful part of the journey.
Remember That Jesus Loves You—Doubt and All \ Above all else, remember that Jesus loves you deeply, no matter where you are in your faith journey. He isn’t looking for perfection; He’s looking for honesty. Just as He met Thomas in his doubt, He will meet you too. There is no shame in your questions—only an invitation to deeper trust and intimacy with God.
Navigating doubt in a faith tradition that values certainty is hard. But remember, you’re not alone in your struggle. Doubt isn’t a sign of weakness; it’s an invitation to deepen your faith. Just as God met Thomas and the psalmist in their doubt, He will meet you where you are. Faith isn’t about having all the answers—it’s about trusting God with our questions.
So, friend, don’t be afraid of your doubts. They don’t disqualify you from God’s love or His plans for your life. They are simply part of the beautiful, messy, and deeply human journey of faith. Take it one step at a time, and know that, like me, you are loved by God no matter where you are on your spiritual path.
blog #christian #christianity #spirituality
-
 @ 266815e0:6cd408a5
2024-12-17 20:45:33
@ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me
This release comes with a bunch of news features and most importantly a lot of cleanup
Features
Olas media posts
You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments
Simple gif picker
This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on
k:1063events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6
New support view
The (tiny) support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave
Favorite DVM feeds
You can now favorite DVM feeds in the discover view
Tools under notes
There is now a simpler tools menu under notes and threads
Searching local cache relay
If your using nostr-relay-tray the search view will now use it by default for searching. which should make it a little faster and more reliable
Small features
- Add "Proactively authenticate to relays" option to privacy settings, defaults to off
- Add option for debug API
- Add option to hide noStrudel logo in nav bar
- Show unknown notifications in notification view
- Add templates to event publisher
Bug fixes
- Show nostr mentions in markdown content
- Fix delete events not getting published to outbox
- Fix page changing from RTL when viewing some profiles
- Refresh relay info on relay page
- Fix bug with removing "about" in profile editor
- Fix automatically disconnecting from authenticated relays
Applesauce
Over the past few months I've been doing tons of cleanup on the core of noStrudel (677 changed files with 19,683 additions and 17,889 deletions) and extracting it out into a friendly nostr SDK called applesauce
Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce
If your a developer and another nostr SDK sounds interesting to you. you can check out the Getting Started docs
-
 @ 6e24af77:b3f1350b
2024-11-04 13:24:26
@ 6e24af77:b3f1350b
2024-11-04 13:24:26test 3
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ dc4cd086:cee77c06
2024-10-18 04:08:33
@ dc4cd086:cee77c06
2024-10-18 04:08:33Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle nostr:nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 9d4a1e9e:322f816a
2024-12-17 11:59:30
@ 9d4a1e9e:322f816a
2024-12-17 11:59:30Introduction
I am a BTC maximalist, but on my journey toward Bitcoin, I had many questions and fears that held me back from buying the best money in the world. Looking back, I now realize that all my fears stemmed from a misunderstanding of the Bitcoin protocol.
Today, I find myself in a similar situation with Nostr. Could you — Nostr heroes, developers, and legends — help a newbie better understand the Nostr network?
POINT 1: Nostr will never become a widely adopted network
I think I understand the benefits of Nostr, but, like many of you here, I’m not a typical social media user. I highly value privacy, freedom of speech, decentralization, and real ownership of money and data. I see many like-minded individuals here, but who else would have the motivation to start using Nostr?
Content creators? Those whose accounts were canceled or shadow-banned on platforms like Facebook or Instagram? Unlikely — their audience simply isn’t here. Consumers? Again, unlikely — their friends aren’t here, and they don’t care about Nostr’s benefits. They’ve never been banned, and they believe current social networks are truly free. I’m curious: how many users on Nostr are not connected to Nostr or Lightning development? I just can’t imagine an event that would cause users to start switching en masse to this network.
>> What could motivate regular social media users to try Nostr?
POINT 2: No marketing
Nostr is currently a niche, nerdy space. But so what? Bitcoin was in a similar position just a few years ago. However, Bitcoin is money — and money, as a source of power, has always attracted people. Plus, Bitcoin’s rising price serves as an automated global marketing campaign. Many people also have an incentive to promote Bitcoin because they earn money from trading platforms or related services.
With Nostr, there’s no equivalent incentive structure.
>> Who will promote Nostr?
POINT 3: Trust in the Nostr system
The Bitcoin protocol has already shown us that the best systems are trustless. Currently, it's customary to pay "zaps." We assume some users will do this, but, in my opinion, most creators will find it easier (and more profitable) to use platforms like Patreon or HeroHero. These platforms allow creators to put content behind a solid paywall rather than relying on voluntary user donations. Is similar model possible on Nostr? Is really the trust in user donations really the right direction?
>> Why should creators offer their content for free and depend on user donations?
-
 @ 6ad3e2a3:c90b7740
2024-12-16 15:28:00
@ 6ad3e2a3:c90b7740
2024-12-16 15:28:00I believe in the notion of truth. Not merely propositional truth like 2 + 2 = 4, though that too, but also the idea that what someone says can be authentic, profound and true.
Another aspect of truth is beauty. I think music can be harmonious and art aesthetically true. I don’t claim to have special knowledge over what is true, beautiful or harmonious, only that those things exist, and human beings can discern them. I also believe in justice which in my view is moral truth.
Truth, beauty and justice exist even if we are not personally able to recognize them. In other words, while they are perceptible to human beings generally, any particular person or group might miss them.
One example that comes to mind is if you renovate a home. You and your architect might disagree about the layout. Imagine he persuades you to trust him, and you discover he was correct, the house is more harmonious, proportionate and beautiful than had you done it your way. The aesthetic truth for that house was not what you had imagined, but it existed, and you were lucky someone else had the eye for it.
. . .
I don’t write much about what’s going on in Israel and Palestine because I’m not interested in it. I’m not interested in it because it doesn’t affect my immediate existence, and those who are interested in it mostly seem to be closed-minded and emotional about the topic. Because I am not into it, I am not especially informed, nor am I inclined to inform myself better. As far as I can tell, it’s a depressing and tiresome argument between two miserable factions.
That said, the topic sometimes comes up in part because I’m Jewish and know a lot of Jews who care about it and also because I follow people on Twitter on both sides who also care about it. For that reason, I’m aware of some of the narratives that are presented and consequently I’ve formulated two main ideas about it, two axioms, so to speak:
(1) Whatever is the just (morally true) result — whether Israel shutting down and leaving the region, Israel conquering and annexing Palestinian territories entirely, or more likely something in between — that's what I would like to see happen.
In other words, no matter how much anyone in particular might disagree with it, the just result, whatever it might be, is the outcome for which I’m rooting.
People will argue for what they think is just based on various narratives, but I hope for what is actually just, irrespective of those narratives. And I believe such a result must exist, even though I am in no position whatsoever to say what that result would be.
(2) To the extent some people think Palestinians are incorrigible barbaric terrorists and others think Israel (and even "the Jews" more broadly) are incorrigible genocidal maniacs, consider that sense of incorrigibility is directed by both parties at both parties.
In other words, at least one of you* incorrectly believes the other is inherently beyond redemption, and just as they would be mistaken in believing that about you, you could also be mistaken in believing it about them. In fact, the greater your certainty about their inherent evil, the more difficult it is for you to course-correct, and the closer to their description you actually become. Paradoxically, the more sure you are of who they are, the more correct they are about you.
Before anything approaching a concrete answer to this problem can emerge, I think it's important to realize (1) A just outcome that does not depend on anyone's narrative exists; and (2) That the extent to which you view your adversaries as beyond redemption you most resemble their description of you.
If we accept these two axioms, that justice is possible, and that viewing the other side as incorrigible is a hallmark of one’s own zealotry, we have established the ground upon which a solution is possible. If we reject them, no amount of discussion will ever bear fruit.
*Some people might think both are beyond redemption, in which case this post is moot, and there is no just outcome, only might makes right. I think that kind of cynicism is the road to hell.
-
 @ 4ba8e86d:89d32de4
2024-11-14 09:17:14
@ 4ba8e86d:89d32de4
2024-11-14 09:17:14Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ eac63075:b4988b48
2024-11-07 21:27:53
@ eac63075:b4988b48
2024-11-07 21:27:53Every night, you draw your curtains without thinking twice. It's instinctive—a simple act that protects your personal space. Yet in our digital lives, we've somehow accepted living in houses made entirely of glass, with countless unseen observers watching our every move.
https://www.fountain.fm/episode/wPZLCJ3fD6vzsWQ3XSE1
Why Privacy Matters to Everyone
Privacy isn't just for those with something to hide; it's a fundamental human need. Think about the conversations you have with friends, the late-night web searches you make, the personal moments you capture in photos. Would you want all of that broadcasted to the world?
I remember my friend Lisa planning a surprise party for her husband. She searched for gift ideas and coordinated with friends through social media. To her dismay, targeted ads for the exact gift she intended to buy started popping up on their shared devices at home. The surprise was ruined. It wasn't malicious, but it was a stark reminder of how our online activities are constantly monitored.
When a major retailer's customer database was breached, my neighbor Sarah discovered her shopping history, credit card details, and even her children's names were exposed to criminals. She hadn't realized how much personal information she'd unknowingly shared through routine purchases. It was a wake-up call that privacy breaches can affect anyone, not just the tech-savvy or those in high-profile positions.
Edward Snowden once said, "Arguing that you don't care about the right to privacy because you have nothing to hide is no different than saying you don't care about free speech because you have nothing to say." Privacy isn't about secrecy; it's about autonomy over our personal information.
The Rise of the Cypherpunks
Back in the '90s, a group known as the cypherpunks saw the writing on the wall. They recognized that as we moved into a digital era, our personal freedoms could be at risk. So they took action.
One of them, Eric Hughes, famously wrote, "Privacy is necessary for an open society in the electronic age." They developed encryption tools to protect individual privacy, laying the groundwork for technologies like Bitcoin and cryptocurrencies. These innovations were about more than digital money; they were about empowering individuals to take control of their own data.
When Technology Knows Too Much
Fast forward to today, and artificial intelligence (AI) is everywhere—in our phones, homes, and even cars. While AI brings convenience, it also raises serious privacy concerns.
Remember when you mentioned needing new running shoes, and suddenly every ad on your browser was for footwear? It's not your imagination. AI algorithms analyze our conversations, searches, and purchases to predict what we'll want next. But where does it stop?
A few years ago, a major retailer guessed a teenager was pregnant based on her shopping habits before she had told her family. They sent her targeted coupons for baby products, leading to a very uncomfortable situation at home. This isn't just marketing—it's intrusion.
Naomi Brockwell, a privacy advocate, warns, "Our relationship with financial privacy has fundamentally changed. What was once seen as a constitutional right and personal freedom is now simply part of the trade-off for using digital payments. Our baseline for what’s acceptable has shifted." It's a wake-up call that our digital footprints are larger and more revealing than we might think.
Privacy-Preserving AI
While AI often threatens privacy, emerging technologies like federated learning offer hope. This approach allows AI models to learn from data without directly accessing personal information. Imagine your phone improving its predictive text without sending your messages to a central server. It's AI that respects your privacy.
The Watchful Eye: Mass Surveillance and AI
Governments and corporations often justify mass surveillance as a means to keep us safe. But at what cost? When every email, message, or phone call can be monitored, we're sacrificing more than just data—we're giving up our freedom to think and communicate without fear.
Think about how you'd behave if someone followed you around with a camera all day. You might avoid certain places or people, censor your conversations, or feel constantly on edge. That's the chilling effect of mass surveillance.
I spoke with Alex, a journalist who covers political activism. "After attending a peaceful protest, I noticed unusual activity on my devices," he told me. "It made me second-guess my work, wondering who's watching." This isn't paranoia; it's a reality for many who challenge the status quo.
Building Digital Fortresses: Cryptographic Innovations
So how do we reclaim our privacy? Cryptography offers some solutions.
Zero-Knowledge Proofs: Proving Without Revealing
Zero-knowledge proofs allow you to prove you know something without revealing the actual information. Imagine showing a bouncer a card that confirms you're over 21 without exposing your birth date or any other details. In the digital world, this means verifying your identity or eligibility without handing over all your personal data.
Homomorphic Encryption: Secure Processing
Then there's homomorphic encryption, which lets companies process your data without actually seeing it. Think of it like sending a locked suitcase with your belongings; they can weigh it or move it, but they can't open it to see what's inside.
Quantum-Resistant Algorithms: Future-Proofing Privacy
As quantum computers become more powerful, they could potentially break current encryption methods. Quantum-resistant algorithms are being developed to safeguard our data against these future threats. It's like reinforcing your digital locks today to withstand the super lock-picking tools of tomorrow.
Decentralization: Taking Back Control
Decentralization aims to put power back into the hands of individuals. Bitcoin let you be your own bank, controlling your finances without a middleman. Decentralized social media platforms like Nostr, Bluesky or Fascaster allow you to own your content without algorithms dictating what you see or who sees you.
Decentralized Identity Systems
Decentralized identity systems let you prove who you are without revealing more than necessary. It's like showing only your age at a bar instead of handing over your entire driver's license. You maintain control over your personal information.
But with great power comes great responsibility. Without a bank to reset your password or customer service to recover your account, the onus is on you to protect your assets and information.
Practical Tips to Protect Your Privacy
You don't have to be a tech guru to safeguard your privacy. Here are some steps you can take today:
-
Use Encrypted Messaging Apps: Switch to apps like Signal, SimpleX or Session for secure communication. Your messages will be end-to-end encrypted, meaning only you and the recipient can read them.
-
Limit Social Media Sharing: Be mindful of what you post. Do you really need to share your location or personal details publicly?
-
Choose Privacy-Focused Browsers and Search Engines: Use browsers like Brave or Firefox and search engines like DuckDuckGo that don't track your every move.
-
Secure Your Passwords: Use strong, unique passwords for each account, and consider a password manager like Bitwarden. Enable two-factor authentication whenever possible.
-
Use Encrypted Email Services: Consider email providers like ProtonMail that offer end-to-end encryption for your communications.
-
Regularly Audit App Permissions: Check which apps have access to your location, microphone, and contacts. Revoke permissions that aren't necessary.
-
Be Wary of Public Wi-Fi: Public networks can be a hotbed for hackers. If you must use them, a VPN like ProtonVPN can add a layer of security.
-
Consider Privacy-Focused Alternatives: Explore services like Nextcloud for cloud storage or Jitsi Meet for video conferencing, which prioritize user privacy.
-
Keep Software Updated: Regular updates often include security patches. Don't ignore them.
-
Stay Informed and Skeptical: Phishing scams are getting more sophisticated. Think before you click on suspicious links or download attachments.
Final Thoughts
Privacy isn't a lost cause; it's a right worth fighting for. As Edward Snowden reminds us, "Privacy is the fountainhead of all other rights."
By taking control of our data and digital habits, we can navigate the online world with greater confidence and peace of mind. After all, wouldn't it be nice to live in a digital home where we decide when to close the curtains?
Read more
OPSEC and Digital Hygiene Plan: https://www.eddieoz.com/opsec-and-digital-hygiene-plan/
-
-
 @ 6f3670d9:03f04036
2024-12-15 15:57:22
@ 6f3670d9:03f04036
2024-12-15 15:57:22Disclaimer: - This will void your warranty - There might be differences between the Bitaxe and the Lucky Miner that might not cause issues or damage immediately, but might manifest long-term - Proceed at your own risk
A Different Pickaxe
You live in a place where it's difficult to get a Bitaxe. You have access to AliExpress. You look around. You find something called the "Lucky Miner LV06". A Bitaxe clone that uses the same mining chip as the Bitaxe Ultra (BM1366 ASIC). You buy one.
You plug it in, you enter your wallet address and other settings, and it starts mining. It works! Great!
But it's running a customized firmware. It's not AxeOS. Maybe there's something shady in the stock firmware. It's not open-source, after all. Also, AxeOS looks amazing... And that automatic pool fail-over feature is handy.
You think to yourself: "Maybe I can use the Bitaxe firmware on this?". Guess what? You're right!
Flashing From Web UI
What usually works for me is to: - Download the Bitaxe firmware files (
esp-miner.binandwww.bin) from GitHub (here). Version 2.4.1 seems to work well, as of this writing. - Then from the Lucky Miner web interface, upload the "Website" (www.bin) file. - Wait for a minute or two after it's done uploading. - Upload the "Firmware" (esp-miner.bin) file. - Wait another minute or two. - Unplug the power and plug it back in. - Set the "Core Voltage" and "Frequency" to the defaults. - Unplug the power and plug it back in again.If you're lucky (no pun intended), you'll have a working Lucky Miner with AxeOS. Update the settings and mine away!
However, often times I've been unlucky, like what happened while I was writing this article, ironically. The miner malfunctions for no obvious reason. It keeps rebooting, or it's not mining (zero/low hashrate), or the web interface is inaccessible. You name it.
The miner has become a "brick". How do you "unbrick" it?
When you brick a Bitaxe, you can recover it by flashing (uploading) a "Factory Image". The Bitaxe has a USB port that makes this easy. Follow the guide and it should come back to life again. Unfortunately, the Lucky Miner LV06 doesn't have a USB port. It has a serial port, though. We'll have to get our hands a bit dirty.
Flashing Using the Serial Port
We need to connect the serial port of the miner to a computer and run a program to flash (upload) the firmware file on the miner. Any 3.3v UART serial port should be sufficient. Unfortunately, PCs don't usually come with a UART serial port these days, let alone a 3.3v one. The serial port common in old computers is an RS-232 port, which will most probably fry your miner if you try to connect it directly. Beware.
In my case, as a serial port for my PC, I'm using an Arduino Due I had lying around. We connect it to the PC through USB, and on the other side we connect a few wires to the miner, which gives the PC access to the miner.
WARNING: Make sure your serial port is 3.3v or you will probably kill the miner. Arduino Uno is 5v not 3.3v, for example, and cannot be used for this.
Wiring
First, we need to open the Lucky Miner. Use a small flat screwdriver to gently push the two plastic clips shown in the picture below. Gently pry the top cover away from the bottom cover on the clips side first, then remove the other side. Be careful not to break the display cable.
Once the cover is off, you can find the miner's serial port in the top right corner (J10), as shown in the next picture. We'll also need the reset button (EN).
There are three screws holding the PCB and the bottom cover together. If you're confident in your ability to push the small button on the underside of the PCB with the bottom cover on, then no need to remove these. The following picture shows what we need from that side.
And the next picture shows the pins and USB port we will use from the Arduino.
Now, we need to connect: - The USB port on the Arduino labelled "programming" to the PC - Pin 18 (TX1) on the Arduino to J10 through-hole pad 5 (blue dot) - Pin 19 (RX1) on the Arduino to J10 through-hole pad 3 (green dot) - Any GND pin on the Arduino to J10 through-hole pad 4 (yellow dot)
I didn't need to solder the wires to the pads. Keeping everything stable, perhaps by putting a weight on the wires or a bit of tape, was sufficient in all my attempts.
Setting up the Arduino
To use the Arduino as a serial port for our PC, we'll have to make it pass-through data back and forth between the USB port and UART1, where we connected the miner.
The following steps are all done on a PC running Debian Linux (Bookworm), in the spirit of freedom and open-source.
First, we start the Arduino IDE. If the package for the Arduino Due board is not already installed, you'll see a small prompt at the bottom. Click "Install this package".
Click the "Install" button.
Once the package is installed, click "Close".
Next, we select the Due board. Click the "Tools" menu, select "Board", select "Arduino ARM (32-bits) Boards" and click "Arduino Due (Programming Port)"
Next, we select the port. Click the "Tools" menu again, select "Port", and click the port where the Arduino is connected. In my case it was "/dev/ttyACM0".
Now we need to upload the following code to the Arduino board. The code is actually the "SerialPassthrough" example from the IDE, but with the serial speed changed to match the miner.
``` void setup() { Serial.begin(115200); Serial1.begin(115200); }
void loop() { if (Serial.available()) { // If anything comes in Serial (USB), Serial1.write(Serial.read()); // read it and send it out Serial1 }
if (Serial1.available()) { // If anything comes in Serial1 Serial.write(Serial1.read()); // read it and send it out Serial (USB) } } ```
Copy/paste the code into the IDE and click upload. You'll see "Done uploading" at the bottom.
Next we'll test if we're receiving data from the miner. We start by opening the "Serial Monitor" from the "Tools" menu in the IDE. Then we change the baudrate to 115200.
Set the Arduino and the miner in a comfortable position, make sure the wires are held in place and got a good contact on both sides, and the power is plugged in.
Now we'll put the miner in "download" mode. Press and hold the button on the underside (K1), press and release the reset button (EN), then release the other button (K1).
You should see some text from the miner in the serial monitor window, like in the picture below.
Congratulations! We know we're able to receive data from the miner now. We're not sure transmit is working, but we'll find out when we try to flash.
Flashing Using the Serial Port, for Real
To flash the Lucky Miner we'll need a software tool named esptool and the factory image firmware file.
I usually use "esp-miner-factory-205-v2.1.8.bin" for the factory image (this one) as a base, and then flash the version I want from the Web UI, using the steps I mentioned earlier.
For esptool, the documentation (here) shows us how to install it. To make things a little easier on our Debian Linux system, we'll use pipx instead of pip. The instructions below are adapted for that.
First we make sure pipx is installed. Run this command in a terminal and follow the instructions:
sudo apt-get install pipxThen we install esptool using pipx. Run the following in a terminal:
pipx install esptoolThe output will be something like this:
user@pc:~$ pipx install esptool installed package esptool 4.8.1, installed using Python 3.11.2 These apps are now globally available - esp_rfc2217_server.py - espefuse.py - espsecure.py - esptool.py ⚠️ Note: '/home/user/.local/bin' is not on your PATH environment variable. These apps will not be globally accessible until your PATH is updated. Run `pipx ensurepath` to automatically add it, or manually modify your PATH in your shell's config file (i.e. ~/.bashrc). done! ✨ 🌟 ✨We can see pipx telling us we won't be able to run our tool because the folder where it was installed is not in the PATH variable. To fix that, we can follow pipx instructions and run:
pipx ensurepathAnd we'll see something like this:
``` user@pc:~$ pipx ensurepath Success! Added /home/user/.local/bin to the PATH environment variable.
Consider adding shell completions for pipx. Run 'pipx completions' for instructions.
You will need to open a new terminal or re-login for the PATH changes to take effect.
Otherwise pipx is ready to go! ✨ 🌟 ✨ ```
Now, close the terminal and re-open it so that esptool becomes available.
Finally, to actually flash the miner, put the miner in download mode, then in the following command change the port ("/dev/ttyACM0") to your serial port, as we've seen earlier, and the file path to where your firmware file is, and run it:
esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.binIf everything went fine, the tool will take a few minutes to flash the firmware to the miner. You'll see something like this in the output:
``` user@pc:~$ esptool.py -p /dev/ttyACM0 --baud 115200 write_flash --erase-all 0x0 ~/Downloads/esp-miner-factory-205-v2.1.8.bin esptool.py v4.8.1 Serial port /dev/ttyACM0 Connecting..... Detecting chip type... ESP32-S3 Chip is ESP32-S3 (QFN56) (revision v0.2) Features: WiFi, BLE, Embedded PSRAM 8MB (AP_3v3) Crystal is 40MHz MAC: 3c:84:27:ba:be:01 Uploading stub... Running stub... Stub running... Configuring flash size... Erasing flash (this may take a while)... Chip erase completed successfully in 9.5s Compressed 15802368 bytes to 1320190... Wrote 15802368 bytes (1320190 compressed) at 0x00000000 in 152.1 seconds (effective 831.2 kbit/s)... Hash of data verified.
Leaving... Hard resetting via RTS pin... ```
And we're done! Hopefully the miner will be recovered now.
Hope this helps!
Stay humble,
dumb-packageA Warning About Beta Versions of AxeOS
For reasons unknown to me, while I was writing this article I wanted to try the testing version of AxeOS, which was v2.4.1b (beta). Flashing from Web UI went smooth, but the miner stopped mining. I flashed back to v2.1.8 using the serial port, a known good version for me, but it wouldn't mine, still.
Thankfully, v2.4.1 was released recently, and flashing it from the Web UI magically revived my miner. So, be warned.
Bonus: File Hashes
For convenience, these are the SHA256 hashes of the files I used in this article: ``` da24fceb246f3b8b4dd94e5143f17bd38e46e5285e807ebd51627cb08f665c0a ESP-Miner-v2.4.1/esp-miner.bin 16c5c671391f0e3e88a3e79ce33fad3b0ec232b8572fad5e1e0d1ad3251ab394 ESP-Miner-v2.4.1/www.bin
d5182a15b6fa21d7b9b31bff2026d30afed9d769781a48db914730a5751e20c6 esp-miner-factory-205-v2.1.8.bin ```
-
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ 9d92077c:38d27146
2024-12-15 06:23:13
@ 9d92077c:38d27146
2024-12-15 06:23:13Written by Acea Spades, Caffeinated Tech Officer @ Conduit BTC https://primal.net/AceaSpades nostr:npub1xzrkzsrnr83vn7h0udq6tnapwpswy5equlrtkn3nu0e0anlmzynqne0qap
Editing and feedback by Eric FJ, Caffeinated Operating Officer @ Conduit BTC https://primal.net/EricFJ nostr:npub10xvczstpwsljy7gqd2cselvrh5e6mlerep09m8gff87avru0ryqsg2g437
NIP-15 enables a new architectural paradigm in e-commerce. Every piece of data is distributed across a network of relays, adding resiliency and redundancy. Every piece of sensitive data is encrypted in-transit and at-rest, accessible only to Customer and Merchant. Communications and e-commerce activities use an inbox/outbox model across relays. This gives both the Customer and Merchant freedom to choose the digital environment for their shared activities.
This also introduces a host of fun and exciting new issues, such as stale data, relay mismatches, unreachable Customers/Merchants, disappearing messages, and this pesky direct message checkout system.
Platforms like Wordpress, Shopify, and Etsy have democratized the space of e-commerce, made it easy to onboard as a Merchant, and smooth to transact as a Customer. But these systems require centralized servers, siloed data stores, unclear third-party visibility, and possess no protocol-level mechanism for connection with a larger network.
NIP-15: Nostr Marketplaces enables Merchants and Customers to transact directly using the Nostr protocol. It enables a resilient, decentralized presence of Products, and a way to purchase them. It adds privacy and encryption to all correspondence, automatically. Both parties gain the amazing features of Nostr, out-of-the-box. However, the current implementation of the protocol has much to be desired.
Our team at Conduit BTC is focusing our efforts on resolving the shortcomings of the current system. Our mission is to push Nostr E-Commerce forward and help it evolve into a top-quality online retail experience for all.
But to get there, we've got to do some housekeeping.
Let's start with the checkout problem...
Checkout: A Problem
The current state of Nostr E-Commerce is, to put it lightly, lacking in real-world viability.
If I want to purchase a Product, my Nostr client sends a direct message to the Merchant. When they see the message appear, the Merchant generates an invoice, sends it back, waits for payment, then performs the fulfillment steps that their unique businesses requires.
While that might look good on paper, there's some unfortunate implications for both the Merchant and Customer experience. Let's explore some negatives.
NIP-15 uses direct messages to exchange Checkout events between Customer and Merchant. Any Nostr client that doesn't handle NIP-15 events will display the order in good ol' JSON:
{ "id": "ord_cust_1234567890abcdef", "type": 0, "name": "Jane Smith", "address": "123 Mountain View Dr, Boulder, CO 80302", "message": "Looking forward to using these boots on my upcoming hike!", "contact": { "nostr": "7f3b5f21c9880ce33043478436487435878934578934589345893458934", "phone": "+1 303-555-0123", "email": "jane.smith@email.com" }, "items": [ { "product_id": "boot_model_789xyz", "quantity": 1 } ], "shipping_id": "zone_us_rocky_mountain" }Imagine parsing through that every time you get an order.
Most clients won't separate these ugly JSON orders from human-speak messages. These orders will be side-by-side with all other conversations, spamming your inbox.
Since the order message needs the Merchant to receive it, generate an invoice by-hand, then send the invoice back, the Bitcoin-based price might fluctuate. This could mean lowering the transaction value for the Merchant or increasing expected cost for the Customer. There's also a higher chance of invoice expiration for Merchants with a smaller risk window against Bitcoin's volatile price.
While Lightning payment processors (Strike, BTCPay Server, etc) send webhooks when funds are received, typical commerce systems don't have a way to communicate with Nostr relays. Product details on-relay aren't auto-updated with current stock, leading Customers placing orders for out-of-stock items.
And, the Merchant has to manually send shipment details in a direct message to the Customer; another manual step in the checkout flow.
Long story short, it's simply not functional for a Merchant to complete the entire series of checkout steps as-described by NIP-15, at-scale for real-world e-commerce, by hand.
To summarize the challenges we must overcome:
- Merchant experience friction: Manual steps require time per order multiplied by their unique business operation's requirements.
- Spammed inbox: Non-relevant JSON messages fill the Merchant's inbox.
- Fulfillment delays: Checkout flow is delayed until several manual steps are completed by both parties.
- Price fluctuations: Time between order placed and invoice paid leads to possible price fluctuation, impacting Merchant or Customer expectations
- Invoice expirations: Time between invoice generation and payment increases chance of expiration
- In-Stock Mismatches: Relays may have incorrect inventory stock, leading to failed orders and customer inconvenience.
With these points considered, a "real-world" checkout process requires automation. Coordination between inventory, payments, fulfillment, and Customer communication, should take place by an automatic process.
To that effect, we at Conduit BTC propose a solution. We call it the Nostr Commerce Coordinator.
The Case for Coordinators
An NCC (Nostr Commerce Coordinator) is a server-based Nostr bot that: - Is under control of, and represents, the Merchant on Nostr - Subscribes to a relay pool - Posts and queries NIP-15 events - Coordinates the NIP-15 Checkout process on behalf of a Merchant: - Inventory Management: verify, increment, and decrement product stock, create and update Stalls and Products on relays via signed events - Payment Processing: generate Lightning invoices, send invoice to customer, respond to payment events via webhook - Fulfillment Services: create shipments, notify fulfillment partners Handles Checkout-related communications with the Customer Notifies the Merchant when certain things occur Collect sales-relates metrics for Merchant visibility
To summarize the benefits of an NCC: - Automated, frictionless checkout flow - Direct integration with Merchant's existing e-commerce stack: inventory management, payment processing, and shipping service - Separation of Checkout-related direct messages (containing ugly JSON) from actual human readable direct messages - General separation-of-concerns between Merchant's social graph and e-commerce activities - Ability to implement additional commerce features, such as metrics collection, financial statements, subscriptions, and much more yet-to-be explored possibilities
Where do I put my private key?
There's one violation of Nostr pleb sensibility that, at first glance, might seem required for the NCC equation to work: putting a Merchant account's private key in the hands of a cloud-based server.
Obviously, we don't want our private keys stored on a cloud-based server.
To overcome this, there's the option to use an nsec Bunker (with supported clients). Using an Nsec bunker would more-safely store our private keys, granting both sign-and-decrypt access to the server. It's a great solution.
However, we'll explain a couple of reasons why using the Merchant account with an Nsec bunker for checkout fulfillment may not be right for most use cases:
- All checkout messages would spam the Merchant account with non-social direct messages. For popular Merchants, this will increase friction for both fulfilling orders and engaging with Customers. This can be resolved by clients enabling NIP-15 message sorting, but it's likely that most clients will still display an inbox filled with socially-irrelevant messages.
- Both business and social activities would be strongly coupled. Stalls, Products, and Orders are managed by the same keypair that the Merchant's social graph is tied to. A leaked key has the potential to bring the entire business operation to a halt, social presence included.
There is, however, an alternative to using the Merchant account for checkout resolution. And, it works great with nsecBunkers, too.
We're now going to explore the use of a utility keypair, a Nostr account generated specifically for assisting the primary account holder in any number of tasks. We'll explore utility keypairs in greater detail through a paradigm we call Merchant Delegation.
Merchant Delegation
In the Merchant Delegation paradigm, a different Nostr keypair effectively controls all commerce-related events on behalf of the Merchant. The delegated account creates every Stall and Product, receives all Checkout events, and handles checkout-related communication with the Customer.
The Merchant signs a Merchant Delegate Token, which is placed in a tag on every event signed by the delegate account. Clients parse the tag, verify the signature is valid, and cause non-checkout events to target the Delegator automatically.
As an extra layer of validation, a NIP-05 identifier may be included. When an identifier is present, clients will verify its validity, and reject delegation if the Npub is not properly identified. This provides the ability to invalidate the delegation, if need be.
When coupled with an NCC, the Merchant Delegation paradigm really begins to shine.
For the mindful Merchant who doesn't want to use their main account for checkout activities, Merchant Delegation is the answer. For wary Merchants who want to keep their private keys off-cloud, an NCC can use a utility keypair and act on behalf of the Merchant through Merchant Delegation.
For the rest of this article, we will refer to this utility keypair as the NCC Account, while calling the Merchant's primary Nostr account the Merchant Root Account.
When an order is placed, the NCC automatically fetches the incoming message, decrypts it, parses the order, generates an invoice, and sends it to the Customer. A Customer can place an order, then receive an invoice in seconds.
Once paid, the payment processor's webhook notifies the NCC. The NCC decrements stock in the inventory management system, posts a Product Update event across the relay pool, then forwards the paid order to the fulfillment service.
NCCs can optionally keep a copy of every event they've handled. This enables local persistence and immediate access to important events without requiring re-retrieval from relays. A locally-kept reconstruction of the entire e-commerce activity graph. This can be useful for keeping order history, assisting Customer support, generating sales reports and financial records, etc.
All the while, the Merchant's Root Account remains free to engage solely in social graph activities (ie. posting short-form / long-form content creation and engagement, non-checkout communications with Customers, etc), without the checkout-related events spamming their inbox.
In this way, the NCC becomes the bridge between the Nostr protocol and the Merchant's e-commerce systems. The Merchant freed from manual checkout management, and gain a piece of extendable software that can meet many of their needs as a Nostr-based business.
NIP-15 Amendment - Merchant Delegate Tag Spec
In order to separate the social graph from checkout activities, an amendment to the NIP-15 spec has been proposed: https://github.com/nostr-protocol/nips/pull/1648.
To use Merchant Delegation Tags:
- Clients MUST treat events with a
merchant-delegationtag in the following manner:- Validate the
delegation tokensignature - If
retarget_while<and/orretarget_while>is present in the conditions query string, only perform event re-targeting within the given time window - If
nip_05_identifieris present in the conditions query string, only perform re-targeting if the Npub of the event's creator is verifiable as-per the NIP-05 spec
- Validate the
- Clients SHOULD display a relevant visual indicator that a Stall and/or Product's Checkout process is handled by a Merchant Delegate.
Merchant Delegation tags are described as follows:
json [ "merchant-delegation", <pubkey of the delegator>, <conditions query string>, <delegation token: 64-byte Schnorr signature of the sha256 hash of the delegation string> ]The merchant-delegation token should be a 64-byte Schnorr signature of the sha256 hash of the following string:
nostr:delegation:<pubkey of publisher (delegatee)>:\<conditions query string>To keep this article concise, we have omitted most of the proposal details. The above may be deprecated. See the link to the PR to read the complete and up-to-date spec.
Merchant Delegate NCC Tags In-Action
On a NIP-15 enabled clients that adhere to this spec, the experience would be as follows:
UX: A Product for sale, in a Stall, by Merchant (Root Account)
Nostr: Kind 30017 (Set Stall) and 30018 (Set Product) events signed by the NCC Account, with a "merchant-delegation" tag pointing to the Merchant Root Account.
UX: Select this Product for purchase, fill in the appropriate details on a Checkout Form, then click "Buy Now".
Nostr: Client creates a direct message addressed to the NCC Account. NCC server generates a Lightning invoice for this order, and sends it back immediately as a direct message addressed to the Customer
UX: Customer receives a Lightning Invoice from NCC Account, then pays the invoice.
Lightning + Nostr: NCC receives a webhook message from its Payment Processor, indicating payment was received. NCC sends a direct message to the Customer indicating Order Confirmation. Any time there are shipping updates from the Shipping Service, NCC will send additional direct messages to the Customer; in the case of digital goods, the order will be fulfilled as-appropriate for the business use case.
UX: From the same Product's details page, the Customer will see the Product is sold by the Merchant Root Account, with a visual indicator stating the Checkout process is managed by NCC. Customer clicks Follow. Customer zaps the Merchant 100 sats. Customer sends a direct message to the Merchant to thank them for the excellent service.
Nostr: Product and Stall are both created by the NCC Account, Follow, Zap, and Direct Message events all target the Merchant Root Account.
Additional Features
Private Key Watchman
As an additional feature of an NCC, we get "for free" a server can match on-relay events with locally-stored events to detect unauthorized events signed with its private key. The underlying issue corresponding to the leak could then be investigated. A rare instance, but a powerful tool for account safety.
If an unauthorized event were discovered, the NCC can respond in a number of ways, chosen by the Merchant, which may include:
-
"Purge and replace": Send NIP-09 Event Deletion Requests to every relay in the pool for every existing Stall and Product. Generate a new keypair, recreate the Stalls and Products, then propagate them to all relays. Notify the Merchant that a purge took place.
-
"Purge, then notify": Perform a full purge, then notify Merchant. Useful in scenarios where the running server may have become compromised.
-
"Notify, then purge": Notify the Merchant. Unless cancelled within a set amount of time, perform a purge.
-
"Just notify": Notify the Merchant that one or more events were signed with the NCC secret key outside of the NCC server. Useful if the Merchant chooses to use the NCC's utility keypair in other clients.
Following a purge, the Merchant (or NCC automatically) would then generate a new keypair / NCC Account, then republish all Stalls and Products. Commerce would continue uninterrupted with an uncompromised Merchant social graph. Through Merchant Delegate tags, clients would still properly route Customer interactions through to the proper systems.
There's a lot of conversation happening at Conduit BTC about this particular feature, and how we can "watch the watchman" by providing additional layers of security to the server itself. This is an ongoing discussion, and we'd love for you to be a part of it. Visit the Discussions tab on on C3: The Conduit Commerce Coordinator Repo, and let's chat about it.
Stall and Product Management
Stall and Product Management could be handled from a web UI served by the NCC, instead of solely within the external Inventory Management service.
Note: if the "leaked key protection" guard was in place, it would actually be necessary to either use the web UI to manage products, or temporarily disable the guard, to prevent NCC from becoming angry and initiating (or threatening) a purge. Yikes.
Subscriptions
In the future, the NIP-15 spec can be updated to include a Subscription event type, indicating that the Customer would like to repeat the same order one or more times.
The NCC can automatically send the subscribing Customer their next order's payment notice. Accepting the notice (via direct message response, following a URL, etc.) generates an invoice on-the-spot.
Direct Messaging
A direct message client could be placed into the web UI, for passing Checkout-related messages to the Customer, instead of using the Merchant Root account and splitting order-specific conversation into two threads.
Drawbacks
If the NCC were taken offline, then Customer's order messages would accumulate without automatic resolution.
However, like an escalator conveniently becoming stairs when not functioning properly, Customer orders continue to accumulate on-relay, awaiting the deployment of another NCC, or manual resolution. As long as the NCC Account's private key is safely stored away, it can be loaded into another NCC or Nostr client at any time.
A serious drawback to the current NIP-15 spec is using NIP-04 Encrypted Direct Messages for checkout events. Luckily, we've already opened a PR to improve that: https://github.com/amunrarara/nips/blob/patch-1/15.md
Conclusion
Without a system capable of automating the process between a Customer's intent to purchase and a Merchant's acceptance, e-commerce on Nostr will not grow beyond small sales plagued with high-friction manual checkout steps.
This proposal contains the groundwork for a new type of Nostr bot. A Nostr bot whose core function is handling NIP-15 checkout events automatically on behalf of a Merchant.
We've included many implementation possibilities, which the community may explore, innovate, and perfect.
To recap, concepts introduced in this article were: - Nostr Commerce Coordinators - Utility keypair accounts - Merchant Delegation
This is an ongoing conversation, and we'd love to have your feedback and participation in making Nostr E-Commerce an incredible experience for all.
We hope that this new software and NIP proposal will improve the experience for all of us on Nostr. Join us on this adventure into a new frontier in decentralized online e-commerce.
Conduit BTC has begun development on the first Nostr Commerce Coordinator, which we call C3: The Conduit Commerce Coordinator. This is, of course, an open-source project - as everything we do will be.
Follow, star, share, and join the discussion on Github: https://github.com/Conduit-BTC/conduit-commerce-coordinator
-
 @ 4ba8e86d:89d32de4
2024-11-07 13:56:21
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato.
1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit
para isso. Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
sudo systemctl restart i2pdEntre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.Com os túneis cliente criados, vamos agora configurar o Thunderbird
3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ b8a9df82:6ab5cbbd
2024-12-14 16:19:36
@ b8a9df82:6ab5cbbd
2024-12-14 16:19:36Four weeks after Adopting Bitcoin wrapped up, I find myself back in Buenos Aires. While one of the main reasons for staying is avoiding the dreary Berlin winter, the other, much stronger reason, is the people.
Anyone who knows me knows I’m a beach person through and through—dreaming of one day living in a house by the ocean. Argentina, with its economic quirks and geographical realities, isn’t exactly the ideal spot for that dream. Yet, here I am again, drawn not by the landscapes but by something far more meaningful: its people.
When I first wrote about my experience at Labitconf, I mentioned "LaCrypta" a local Bitcoin community that captured my heart. For those unfamiliar, the name might sound like it’s tied to crypto, but it’s not—it simply means “The Crypt.” And when you visit their physical space in the heart of Buenos Aires, the name suddenly makes perfect sense.
La Crypta isn’t just a community; it’s the beating heart of Bitcoin culture here. It’s a group of passionate people dedicated to development, education, and sharing knowledge about Bitcoin and the Nostr ecosystem. Their mission goes far beyond tech—it’s about empowerment, collaboration, and creating a space where ideas flourish.
Before I arrived in Buenos Aires, I had already worked with some of the La Crypta crew remotely. From the very start, they were more than helpful—honestly, they saved me more times than I can count. Organizing, finding suppliers, translating, navigating cultural nuances—things that would’ve been impossible as a foreigner were made smooth thanks to their constant support.
Even when cultural differences came into play, they did their best to accommodate my eager German punctuality. Sure, we had a couple of missed calls here and there (they’re South American, after all!), but we found a rhythm, and I learned to relax and embrace their way of doing things.
 I’ll never forget walking into the physical space for the first time. The house itself is a marvel—a 100-year-old gem tucked into the bustling city, its walls whispering history. Interestingly, it was originally built by Germans (I could tell right away), and every corner is rich with quirks and stories. Newcomers are given a guided tour, learning about the house’s past and its idiosyncrasies, which they’re then responsible for passing on to the next wave of visitors. It’s a brilliant tradition, one that fosters a sense of connection to the place.
I’ll never forget walking into the physical space for the first time. The house itself is a marvel—a 100-year-old gem tucked into the bustling city, its walls whispering history. Interestingly, it was originally built by Germans (I could tell right away), and every corner is rich with quirks and stories. Newcomers are given a guided tour, learning about the house’s past and its idiosyncrasies, which they’re then responsible for passing on to the next wave of visitors. It’s a brilliant tradition, one that fosters a sense of connection to the place.The charm of La Crypta’s space is undeniable—a century-old house surrounded by modern skyscrapers, standing out like a time capsule in the middle of the city. Of course, not everyone loves it. The neighbors occasionally complain about the raucous parties, even calling the police. But, as I’ve learned, in Argentina, there’s always a workaround for things like that.
 The real magic, though, isn’t in the house—it’s in the people. After weeks of working together remotely, meeting them in person for the first time was something special. There’s nothing quite like hugging the people you’ve shared so much time, effort, and anticipation with, knowing how deeply they care.
The real magic, though, isn’t in the house—it’s in the people. After weeks of working together remotely, meeting them in person for the first time was something special. There’s nothing quite like hugging the people you’ve shared so much time, effort, and anticipation with, knowing how deeply they care.They welcomed me with open arms, not just as a collaborator but as a friend. From day one, they’ve been my mental and emotional support system, offering far more than help with logistics. Their generosity, warmth, and genuine care reminded me that some of the most valuable things in life aren’t tied to money—they’re tied to human connection.
We bonded in so many ways, but nothing quite tops their initiation ritual: mate. For the uninitiated, mate is a traditional South American drink with a very specific etiquette. You don’t say “thank you” unless you’re done, you don’t stir the straw, and, naturally, I did everything wrong at first. But despite their teasing, I genuinely fell in love with mate, even if they still can’t believe me!
A home away from home
As I write this, just 10 days before Christmas, I’m missing my family and friends back home in Berlin. On quiet Saturday mornings like this, I wish I could just jump on a plane and hug them, feel the warmth of familiarity. But even in these moments of longing, I find comfort here. The people of La Crypta have become a surrogate family, filling my heart with their kindness and making the distance feel a little less heavy.
This experience has been life-changing. No matter where I go from here, I’ll carry a piece of La Crypta and Buenos Aires with me. For anyone who ever has the chance to visit, I urge you to experience this for yourself. The people, the place, the culture—it’s something that can’t be explained, only felt.
It’s not just a community; it’s a family. And for that, I’ll forever be grateful.
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ 0d532801:197a0c30
2024-12-06 05:13:25
@ 0d532801:197a0c30
2024-12-06 05:13:25Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ dd664d5e:5633d319
2024-12-14 14:41:47
@ dd664d5e:5633d319
2024-12-14 14:41:47
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmer's sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ 234035ec:edc3751d
2024-12-14 05:12:52
@ 234035ec:edc3751d
2024-12-14 05:12:52America's Fourth Fourth Turning
We can learn much from the Book "The Fourth Turning: An American Prophecy" By William Strauss and Neil Howe. The Book looks back throughout history to identify the cyclical patterns that emerge and establishes archetypes that emerges in the generations as they come of age in these different stages of history.
There are four phases (turnings) that are outlined in the book:
- The High
- The Awakening
- The Unraveling
- The Crisis
The authors identify that America is due for another fourth turning, and I would argue that we are now in the midst of America's Fourth ever fourth turning. The first three being marked by the American Revolution, the Civil War, and the Great Depression- WWII. Today we have been in an increasingly unstable financial, political, and social environment which share eery similarities to the unraveling period of the prior cycles.
I believe that this fourth turning began with the 2008 "Great Financial Crisis" and has been ongoing ever since the fed chose to engage in mass currency devaluation in order to keep the banks solvent. While these actions have delayed the inevitable larger crisis, they will not be able to avoid it. Since 2008 the money supply has grown from roughly $8 Trillion to over $20 Trillion. This massive currency dilution is reflected in increased prices across all sectors but heavily concentrated in scarce desirable assets. As National debt continues to rise and interest expenses balloon, the only way out for the US dollar is massive inflation.
The issue with continued inflation is that it leads to massive societal suffering and unrest. At 2% inflation most individuals aren't aware that they are being stolen from, but as inflation rates start to stick above 10% people start to realize what is really going on. History tells us that as currencies enter into hyper-inflation, the societal fabric begins to fall apart. One does not have to be an anthropologist to look around and realize the massive cultural shifts that we have seen since moving to a fiat standard in 1971 and much faster ever since 2008.
I find it very profound that at the same time that the global financial system began showing cracks, Satoshi Nakamoto introduced the solution to the world. It feels as though this fourth turning is centered around technological innovation in computing, as well as the collapse of an outdated and corrupt financial system. Bitcoin exists at the perfect intersection of these two by utilizing cryptography to empower people to exit the corrupt system and begin to build a superior one on sound foundation. If the crisis of this great fourth turning is centered around the sovereign debt crisis, than Bitcoin becomes the clear answer.
Thriving In The Chaos
Being Born in 2001 I do not have much memory of a pre-2008 world. Being only 7 years old at the time I did not fully grasp the significance of what was going on, but my life has been impacted by it nonetheless.
When the central bank chooses to hold interest rates artificially low, they are effectively driving money into more and more places where it shouldn't actually be. This is usually described as a bubble, which then bursts leaving many financially ruined. Accept for those who the central bank then chooses to bail out by diluting the purchasing power of all the savers.
Much of the Millenial and Gen Z generations feel that they will never reach financial security or be able own a home and retire at a reasonable age. Many of them are saddled with large student loans, credit card debt, and car loans. While much of this is due to personal decision making, we exist in a system today that is designed to extract as much value as possible from each citizen. If you were to take out a loan to go to school, get a job, a mortgage, and a car payment, and used a savings account, you would never become financially free.
People my age have become increasingly unsatisfied with the way that things are, which is why I am so hopeful for a brighter future. While most aren't quite aware of what the true heart of the issue is, they feel that something is deeply wrong. I believe that Bitcoin will be the catalyst for the masses to wake up and stop funding the current system.
Those that lead the way into a new frontier during these fourth turnings come out on the other side in positions of great respect and power. While these next few years will likely difficult, there will be massive opportunity for those who are bold enough to stand for their beliefs and work to propagate them.
-
 @ c311a1eb:53fc6542
2024-12-01 06:00:46
@ c311a1eb:53fc6542
2024-12-01 06:00:46

@florian | Photographer
Studio-Shoot
“Know thyself” is a phrase attributed to the ancient Greek philosopher Socrates, and it has been a cornerstone of philosophical thought for centuries. It invites an individual to deeply examine their own thoughts, feelings, behaviors, and motivations in order to understand their true nature.
At its core, “Know thyself” encourages self-awareness - an understanding of who you truly are beneath the surface. This process of introspection can uncover your strengths, weaknesses, desires, fears, and values. It invites you to acknowledge your habits, biases, and patterns of thinking, so you can make more conscious choices in life.
Knowing yourself also involves understanding your place in the larger context of existence. It means recognizing how your actions and choices affect others and the world around you. This awareness can lead to greater empathy, a sense of interconnectedness, and a more authentic life, free from the distractions of societal expectations or superficial identities.
In a practical sense, knowing yourself might involve:
Self-reflection: Regularly taking time to reflect on your thoughts, feelings, and experiences.
Mindfulness: Practicing awareness of the present moment and observing your reactions without judgment.
Exploration: Being open to trying new things and learning from both successes and failures.
Seeking truth: Engaging in honest inquiry about your motivations, desires, and beliefs.
Growth: Continuously learning from your past and striving to align your actions with your inner values.
Ultimately, “Know thyself” is about cultivating a deep, honest understanding of who you are, which leads to a more fulfilled, intentional, and peaceful existence.
-
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ c311a1eb:53fc6542
2024-11-30 04:51:53
@ c311a1eb:53fc6542
2024-11-30 04:51:53
-
Stop worrying too much about what may come in the future or what has happened in the past.
-
Our seconds tick by too fast to waste on things you can't change or control.
-
Just let it be. Take a deep breath, be in the moment, and just be thankful for where you're at right now.
-
The present is all we really have. Forget about the 'what ifs' and the 'should/could-haves.' Accept what was and what is.
-
Remember, you've got one life, one opportunity to live.
-
Don't let it slip away while you focus on the wrong things. Breathe in. Breathe out. Make every moment count.
Thanks for Reading
-
-
 @ 31312140:2471509b
2024-12-12 18:19:11
@ 31312140:2471509b
2024-12-12 18:19:11Understanding Real Money
The Awful Truth About Fiat Currency
Let's call a spade a spade here - fiat currency is a scam. Governments and central banks print it out of thin air, devaluing each note in your wallet every single day. Your hard-earned money is losing its value, and you're left chasing your tail trying to keep up with inflation.
Fiat currency is backed by nothing but the "full faith and credit" of the government. And when was the last time you trusted a politician? 😏 The truth is, fiat currencies always collapse. History is littered with examples like the Roman denarius, the Zimbabwean dollar, and, well, the ongoing crumbling of many others.
The Concept of Intrinsic Value
Real money, on the other hand, has intrinsic value—meaning it's valuable in and of itself. Think gold and silver. These precious metals have been prized for thousands of years because they don't decay, they're hard to counterfeit, and they have myriad uses in the real world, from electronics to medicine.
Gold and silver have been used as money for millennia, and for good reason. They're scarce, durable, and divisible. You can't just print more gold when you feel like it. You have to mine it, refine it, and cast it.
Bitcoin: The Digital Gold
Now, let's talk about Bitcoin. Some people call it "digital gold," and there's a good reason for that. Bitcoin, like gold, is scarce (only 21 million will ever exist), and it's decentralized, meaning no government or bank can control it. This decentralization is key because it means Bitcoin is resistant to censorship and inflation.
Bitcoin stands out as the only cryptocurrency that can be considered real money due to its decentralized nature, fixed supply of 21 million coins, unparalleled security, global adoption, resilience, and the philosophy of financial sovereignty it embodies. Unlike other cryptocurrencies that often have centralized control and variable supplies, Bitcoin's immutable transactions and widespread recognition make it a reliable store of value and medium of exchange.
But remember, Bitcoin isn't a perfect substitute for gold. It's digital, which means it relies on technology and the internet to function. This makes it vulnerable to hacking and other digital threats. Still, the blockchain technology underpinning Bitcoin is revolutionary, creating a transparent and tamper-evident ledger of transactions.
The Downfall of Modern Banking Systems
Let's take a step back and look at the modern banking system. It's a joke. Fractional reserve banking allows banks to lend out money they don't have, creating an economic bubble that inevitably bursts. We're constantly teetering on the edge of financial collapse because banks are playing a high-stakes game of musical chairs with your money.
And when things go south, who gets bailed out? Not you or me, but the banks. We saw it in 2008. The rich and powerful protected their own interests, while everyday folks lost their homes and savings.
Why Governments Love Fiat
Governments love fiat money because it allows them to spend beyond their means. When the treasury gets low, they don’t have to make tough decisions or cut spending—they just print more money. This leads to inflation, which is just another form of taxation. Your dollar buys less; your savings erode.
This manipulation benefits the elites who get the newly printed money first. They can spend it while it still has value, before it trickles down into the economy and prices rise for everyone else. Trickle-down economics is as real as fairy tales. 🧚♂️
Creating a Solution: Moving Towards Real Money
To reclaim our financial sovereignty, we must return to real money. Here's how:
Gold and Silver
Start by accumulating gold and silver. Begin small—buying a few ounces here and there. Store it securely, away from banks where it could be confiscated. There are many platforms and shops where you can purchase these metals safely.
Bitcoin
Diversify with Bitcoin. Make sure you understand how wallets work and practice impeccable security measures. It's not enough to buy Bitcoin; you must ensure it can't be stolen by hackers. Educate yourself on cold storage, multi-signature wallets, and other security practices.
Educate Yourself
Knowledge is power. Read books on Austrian economics, like those by Ludwig von Mises and Murray Rothbard. Understand the fundamentals of what makes good money.
The Future of Real Money
If we succeed in transitioning to real money, we can create a more sustainable and fair economic system. One where value is preserved over time, where individuals have sovereignty over their own wealth, and where the powerful can no longer manipulate the masses for their gain.
Final Thoughts
The fight for real money is a fight against the controllers, the manipulators, and the corrupt. But it’s also a fight for our freedom, our future, and our dignity. Let's look into it and make conscious choices to protect our financial future by holding real money.
Keep your head up, keep questioning, and always look into it 💪
Suggested Readings and References
- "The Creature from Jekyll Island" by G. Edward Griffin - A detailed look at the Federal Reserve and how it manipulates the money supply.
- "What Has Government Done to Our Money?" by Murray Rothbard - An essential read on the problem with fiat currency and why real money matters.
- "The Bitcoin Standard" by Saifedean Ammous - A comprehensive analysis of Bitcoin as a form of digital gold.
- "Human Action" by Ludwig von Mises - A cornerstone work for understanding Austrian economics.
- "Democracy: The God That Failed" by Hans-Hermann Hoppe - A deep dive into the failures of democratic government and the economics of anarcho-capitalism.
-
 @ c311a1eb:53fc6542
2024-11-29 19:08:45
@ c311a1eb:53fc6542
2024-11-29 19:08:45
-
Don't change yourself just to make someone happy unless that someone is “you”.
-
There are no missed opportunities; everything you missed wasn't yours.
-
Trust yourself. You know more than you think you do.
-
Learn to see people for what they are, not what you want them to be.
-
The longer you live in the past, the less future you have to enjoy.
-
Better to admit you walked through the wrong door than spend your life in the wrong room.
-
Just because you miss someone doesn't mean you need them back in your life.Missing is a part of getting over.
-
Don't worry about those who talk behind your back—they're behind you for a reason.
-
The bigger the ambition, the slower you need to go.
-
Never brag about your progress or tell people your plans, as your friends today may become your worst enemies tomorrow.
-
Make sure the choices you make are worth the losses you'll take.
-
Never sacrifice your progress for a friend; they might not do the same if the tables were turned.
-
Sometimes you just need to be a bit selfish—put yourself first and think about what is best for you.
-
It's okay if you don't know how to move on; start with something easier, like not going back.
-
If you don't sacrifice for what you want, what you want becomes the sacrifice.
-
Close the window that hurts you, no matter how beautiful the view is.
-
Sometimes you have to let go of people who keep reminding you of who you used to be.
-
Forgive yourself for accepting less than you deserved, but don't do it again.
-
If you're not willing to walk alone, you'll never lead your own path.
-
Accept the things you cannot change, and change the things you cannot accept.
-
-
 @ c311a1eb:53fc6542
2024-11-28 17:46:20
@ c311a1eb:53fc6542
2024-11-28 17:46:20Saudade ne anlama geliyor?

"Saudade" kelimesi, Portekizce kökenli olup genellikle özlem, hasret, nostalji gibi duyguları ifade etmek için kullanılır. Bu kelime, özellikle Portekiz ve Brezilya kültüründe derin bir anlam taşır ve sıklıkla edebiyat, müzik ve günlük konuşmalarda yer bulur. Peki, "saudade" kelimesinin tam olarak anlamı nedir ve neden bu kadar özel bir kelime olarak kabul edilir? İşte "saudade" kelimesinin anlamı ve kullanımı hakkında bilmeniz gerekenler.
Saudade Kelimesinin Anlamı
Saudade, genellikle kaybedilmiş veya ulaşılması zor olan bir şeye duyulan derin özlem ve hasreti ifade eder. Bu duygu, bir kişiyi, yeri, zamanı ya da durumu kapsayabilir. Özellikle Portekiz kültüründe, denizci ailelerin uzaklara giden sevdiklerine duyduğu özlemi tanımlamak için kullanılmıştır. Bu yüzden, "saudade" hem hüzün hem de tatlı bir hatıra olarak karışık duyguları barındırır.
Saudade Kelimesinin Tarihçesi ve Kökeni
Saudade kelimesinin kökeni, Portekizceye dayanır ve Orta Çağ Portekizcesinden gelmektedir. 15. yüzyılda, keşifler dönemi sırasında Portekizli denizciler, uzun süreler boyunca sevdiklerinden uzak kalmak zorunda kaldılar. Bu dönemde "saudade" kelimesi, ayrılığın getirdiği yoğun özlemi ifade etmek için kullanıldı. Zamanla, bu kelime Portekiz kültüründe kökleşti ve günlük dilde sıkça kullanılmaya başlandı.
Edebiyatta ve Müzikte Saudade
Saudade, Portekiz ve Brezilya edebiyatında ve müziğinde sıkça işlenen bir temadır. Portekiz fadosu, bu kelimenin en iyi örneklerinden biridir. Fado, hüzünlü melodileri ve derin sözleri ile "saudade" hissini mükemmel bir şekilde yansıtır. Aynı şekilde, Brezilya müziğinde de bossa nova ve samba türlerinde "saudade" sıkça karşımıza çıkar. Bu türler, kaybedilen bir aşkın veya geçmişte kalmış güzel anıların özlemini dile getirir.
Günlük Hayatta Saudade Kullanımı
Portekiz ve Brezilya'da, "saudade" kelimesi günlük hayatta sıkça kullanılır. Bir dostunuzla geçmişi yad ederken, uzaklardaki bir sevdiğinizi anarken ya da güzel bir anıyı hatırlarken bu kelimeyi duyabilirsiniz. "Saudade" kelimesi, basit bir özlemin ötesinde, derin ve karmaşık duyguları ifade etme gücüne sahiptir.
Saudade'nin Kültürel Önemi
Saudade, sadece bir kelime olmanın ötesinde, Portekiz ve Brezilya kültürünün önemli bir parçasıdır. Bu kelime, geçmişe duyulan özlem, kaybedilen şeylere duyulan hasret ve aynı zamanda bu duygularla başa çıkma yeteneğini temsil eder. Bu nedenle, "saudade" hem bireysel hem de kolektif bir duygunun ifadesi olarak kültürel bir mirastır.
"Saudade" kelimesi, yalnızca Portekizce konuşulan ülkelerde değil, dünya genelinde de merak edilen ve kullanılan bir terim haline gelmiştir. Derin anlamı ve kültürel önemi ile "saudade", duygusal deneyimlerimizi daha iyi ifade etmemize yardımcı olan evrensel bir kelimedir.
-
 @ 228dde34:b5d0345e
2024-12-12 02:12:23
@ 228dde34:b5d0345e
2024-12-12 02:12:23Join JONATHAN TAN as he explores the fascinating history of people sleeping twice in a night, the reasons for its disappearance, and today’s cultural attitudes toward sleep.
After a particularly long autumn day in 1878, a 27-year-old Robert Louis Stevenson, having spent the last twelve days slogging through France’s southern highlands, needed a rest. He set up camp in a small clearing shrouded by pine trees, and after a hearty meal of bread, sausage, and brandy, he climbed into a sleeping bag and dozed off as the sun set.
Instead of sleeping until dawn, however, the weary Stevenson arose from his slumber a little past midnight. He spent the hour awake smoking a cigarette as he stared at the night sky, before returning to sleep.
In his journal, Stevenson wrote an entry reflecting on the mysterious forces that awaken everybody in the middle of the night. “At what inaudible summons, at what gentle touch of Nature, are all these sleepers thus recalled in the same hour to life?”
To me, this journal entry from 1878 came across as an isolated story of one man’s restless night. But, in a scientific journal on the history of sleep, Roger Ekirch, a distinguished professor of history, proposed a more unusual theory: Stevenson’s unusual sleep pattern that night was once a common practice among humans in the past.
“Until the modern era, up to an hour or more of quiet wakefulness midway through the night interrupted the rest of most Western Europeans,” Ekirch argued. In his reference, Ekirch found mentions of sleeping twice a night across various historical sources.
Interestingly, Ekirch’s conclusion begs several questions: How did this sleeping pattern work? Why did people do this? And most importantly, why did we stop?
 Communal Mattresses were the norm in the past, and many people would spend the night snuggled with others. Photo from Getty Images.
Communal Mattresses were the norm in the past, and many people would spend the night snuggled with others. Photo from Getty Images.For people living in the 17th Century, a night of sleep usually went like this.
By as early as 9pm, most would begin to lie down onto mattresses in preparation for the first half of their sleep. In those days, most people slept communally; typically sharing a bed with their family, their friends, or sometimes even with strangers.
And after a few hours of rest, people of the past would start to wake up from their slumber. This moment of wakefulness usually occurred some time past midnight, and lasted an hour or so. Interestingly, this collective awakening was not caused by alarms of any kind.
“Although in some descriptions a neighbor’s quarrel or a barking dog woke people prematurely from their initial sleep, the vast weight of surviving evidence indicates that awakening naturally was routine, not the consequence of disturbed or fitful slumber,” Ekirch wrote.
Now, what did people do with this hour of wakefulness? Well, according to Ekirch, many who left their beds merely needed to relieve themselves. The rest who awoke, however, would use this time to tend to their worldly duties.
“For others, work awaited,” Ekirch noted. “The 17th century farmer Henry Best of Elmswell made a point to rise ‘sometimes at midnight’ to prevent the destruction of his fields by roving cattle. In addition to tending children, women left their beds to perform myriad chores… suffice to say, domestic duties knew no bounds.”
 Many criminal activities also took place during twilight hours, such as petty theft and even murder. Photo from Getty Images.
Many criminal activities also took place during twilight hours, such as petty theft and even murder. Photo from Getty Images. Most importantly, this period of wakefulness was invaluable for couples living in the past. It was difficult for exhausted couples to spend time together after a long day of manual labour. Thankfully, the first sleep allowed tired partners to get some well-needed rest, and the time afterward was considered ideal for romance and intimacy.
Finally, after spending a couple of hours awake, people would return to sleep; this time, their second rest would typically last until sunrise.
Our sleeping patterns have clearly changed since the 17th Century. This change raises a very important question: Why did we stop sleeping twice a night?
Ekirch’s research noted a gradual abandonment of the two-sleep system around the start of the 19th Century, which he attributed to one main factor: The development of artificial lighting.
During the Industrial Revolution, artificial lighting became better and more prevalent. During this time, gas street lamps slowly appeared along city streets across the Western world. “By 1823, nearly forty thousand lamps lit more than two hundred miles of London’s streets,” Ekirch wrote. After gas came electrical lighting, and soon, the city streets gradually outshone the stars in the night sky.
Not only did the advancement of artificial lighting affect the natural circadian rhythm of humans, it also allowed people to stay up later than ever before. With people sleeping later and later, the duration of their sleep became shorter and more compressed, which soon led to people no longer waking up during their rest.
 The invention of artificial lighting finally allowed humans to extend their schedules past sunset. Photo from The American Menu.
The invention of artificial lighting finally allowed humans to extend their schedules past sunset. Photo from The American Menu.Fascinatingly, this shift in our sleeping patterns may have also affected our attitude towards sleep. As later bedtimes became the new norm, staying in bed slowly became associated with laziness and unproductivity.
“People were becoming increasingly time-conscious and sensitive to efficiency, certainly before the 19th Century,” says Ekirch. “But the industrial revolution intensified that attitude by leaps and bounds.”
Examples of our changing perceptions toward sleep can still be observed today. The fading popularity of the Spanish siesta, for instance, reflects a modern aversion to taking naps during the day.
A tradition widely adopted across the region, a siesta is a short rest taken in the middle of the day, typically after lunch. This famous tradition, however, is slowly becoming less common among the Spanish population. Asurvey conducted in 2016 found that 60% of Spaniards never actually sleep during the siesta, while only 18% do so more than four times a week. In modern times, many Spaniards living in cities find themselves unable or unwilling to take a midday nap.
This societal pressure to stay awake is not unique to Spain; in Singapore, sleep deprivation is a growing epidemic. In a 2022 survey on the sleeping habits of 43 cities, Singapore was named the third most sleep-deprived city, with only one in four Singaporeans getting more than seven hours of sleep daily. Chronic sleep deprivation has become ingrained in the Singaporean lifestyle: employees routinely work late into the night, children remain glued to their screens, and students burn the midnight oil slogging at their desks.
Today, we live in a world that is constantly moving. The modern work culture rewards hustle and productivity, encouraging longer hours and a relentless pursuit of efficiency. Unsurprisingly, sleep has fallen to the wayside, as people become busier and busier. So, if we can appreciate how things have changed and why we struggle with our sleep habits today, perhaps we can start to make getting enough sleep a priority in our lives.
HypeSingapore #Sleep #History #Health
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ c311a1eb:53fc6542
2024-11-28 15:46:19
@ c311a1eb:53fc6542
2024-11-28 15:46:19Lagom felsefesi, İsveç'in denge ve uyum anlayışını temsil eder. İhtiyaçtan fazlasını tüketmemeyi, paylaşmayı ve dayanışmayı teşvik eder. Bu yaklaşımı finansal hayatınızda da belirleyebilir, geleceğinizi denge halinde kurabilirsiniz.

Lagom, İsveç dilinde ne çok ne az anlamına gelir. İsveç kültürünün bir parçası olan Lagom felsefesi, dengeli bir yaşam düşüncesi temeline dayanır. Mutlu yaşam stilleri arasında yer alan bu felsefe, bütün dünyada yaygınlaşan bir yaşam tarzıdır. İhtiyaçtan fazla tüketmemeyi, dayanışma ve paylaşmayı prensip alır.
Lagom, ‘‘laget om’’ kelimesinden türeyen Viking kökenli bir kelime olup aynı zamanda İsveç’te ölçü birimi olarak da kullanılır. Lagom felsefesi, İsveç’in 1600 yılında yaşadığı gıda krizinden doğan bir yaşam tarzına bağlı olarak gelişir. Küçük şeylerden mutlu olmayı, abartılı harcamalardan uzak durmayı, paylaşmayı ve yardımlaşmayı öneren bu felsefe, mutlu bir hayat sürmek için bunların gerekli olduğunu savunur. Bu felsefe ile kişiler minimalist ve tutarlı bir hayat sürdürebilir.
Lagom felsefesi, hayatın hemen hemen her alanında uygulanabilmektedir. İş, ev düzeni, sosyal yaşantı ve beslenmeye kadar hayatın her noktasında uygulanabilen bu felsefe ile kişiler daha dengeli ve uyumlu bir hayat sürer. Lagom hayat, denge ve uyumun iç içe yer aldığı bir yaşam sürmeyi amaçlar. Bu hayat tarzını benimsemek birçok yönü ile kişilere olumlu etkide bulunur. İş ve özel hayat arasında bir denge kurmak kişinin daha az stresli ve daha mutlu hissetmesine olanak sunar. Bu hayat tarzının benimsenmesi günümüzün aşırı tüketime meyleden toplumuna karşı kendinizi daha az baskıda hissetmenize yardımcı olur. Lagom hayat tarzı, sadece maddi değil manevi olarak da kişinin daha dingin ve huzurlu hissetmesine imkan sunar.
Lagomun Günlük Hayatta Kullanımı
Lagomun günlük hayatta kullanımı kişinin maddi ve manevi olarak her alanda kendini mutlu ve huzurlu hissetmesine olanak sunar. Sizi mutlu edecek dengeyi bularak hayata anlam katmayı amaçlayan bu felsefeyi günlük yaşama uyarlamak aslında oldukça kolaydır. Yiyecekten giysiye; ev dekorasyonundan giyime kadar her noktada bu felsefe uygulanabilir. Lagomu günlük hayata uyarlamak için şu ilkelere dikkat edebilirsiniz;
- Saatlerce çalışmak yerine gerçekten verimli ve yeterli çalışmak.
- Yapmak istediklerinizin listesini çıkartın ancak bunu yaparken gerçekçi bir bakış açısı benimseyin.
- Sevdiğiniz insanlarla bol bol vakit geçirerek onlar ile yaşadığınız anın keyfini çıkarın.
- Sosyal medyayı minimum seviyede kullanarak sizi eğlendiren, geliştiren ve iyi hissettiren hesapları takip edin.
- Gününüz ne kadar yoğun geçmiş olursa olsun mutlaka sevdiklerinize zaman ayırarak günü tamamlayın.

Lagom Felsefesi ve Finansal Hayatın Dengesi
Lagom felsefesinin benimsenmesi, finansal yönetimde de önemli bir rol oynar. Bu felsefe, gereksiz harcamalardan kaçınmayı ve maddi varlıkları daha dikkatli ve bilinçli bir şekilde kullanmayı teşvik eder. Lagom'u finansal yönetimde uygulamak, bütçenizi dengelemek, borçlarınızı minimize etmek ve tasarruf etmeye odaklanmak anlamına gelir.
İsveç'in bu yaşam tarzını benimseyerek, harcamalarınızı ihtiyaçlarınızla sınırlayabilir ve geleceğe yönelik finansal hedeflerinize daha kolay ulaşabilirsiniz. Ayrıca, gereksiz tüketimden kaçınarak hem kişisel mali sağlığınızı koruyabilir hem de çevresel sürdürülebilirliğe katkıda bulunabilirsiniz. Bu yaklaşım, maddi refahınızı artırırken, aynı zamanda yaşam kalitenizi de yükseltir.
Lagom Felsefesi ile Dengeli Yaşama Sanatı
Lagom felsefesi ile bir hayat sürmek hem toplumsal hem bireysel anlamda fayda sağlar. İsveç’e özgü bu felsefe, toplumda paylaşmayı ve yardımlaşmayı teşvikler. Kişilerin ihtiyacı kadarını tüketmesi ve fazlasını başkası ile paylaşması daha adil ve dengeli bir toplumu yaratır. Hayat düzeninin dengeli olması sadece bireyler için değil çevre için de olumlu etkilere sahiptir. Fazla tüketimin önüne geçen lagom felsefesi, sürdürülebilir bir yaşam modeli sunmaktadır. Böylelikle lagom sadece bireyin değil çevre ve toplum için de yararlı bir hayat stilini ortaya çıkarır.
Sürdürülebilir bir yaşam formunun temellerine dayanan lagom tasarrufun ön plana çıkmasına olanak sağlar. Bu sayede hem bireyler hem de toplum daha stabil bir yapıya erişir. İsrafın önüne geçilerek kaynakların daha etkin ve verimli kullanılması sağlanır. Bu durum uzun vadede toplum refahını sağlarken gelecek nesillere de daha temiz ve dengesi bozulmamış bir çevrenin bırakılmasına olanak sunar. Lagom felsefesi ile sürdürülebilir bir hayat yaşamak adına şunları dikkate alabilirsiniz;
- Mümkün olduğunca az çöp çıkarın.
- Tüketim yaparken sürdürülebilir ürünler almaya özen gösterin.
- Su kullanımında aşırıya kaçmadan ihtiyacınız kadarını kullanın.
- Lüks harcama yapmaktan kaçınmalı ve maddi varlığınızla dikkat çekmeye çalışmayın.
Lagom felsefesi, hayatınızın her alanına denge ve uyum getirebilecek güçlü bir yaşam anlayışıdır. İhtiyaçlarınızı karşılamak, fazla tüketimden kaçınmak ve paylaşımı ön planda tutmak sadece sizin için değil, çevreniz ve toplum için de olumlu etkiler yaratır. Bu felsefeyi benimseyerek hem kendinize hem de dünyaya daha mutlu, huzurlu ve sürdürülebilir bir gelecek sunabilirsiniz.
-
 @ a17fb4ed:c53f7e91
2024-12-11 20:34:56
@ a17fb4ed:c53f7e91
2024-12-11 20:34:56 Yooper Crate in the Wild
Yooper Crate in the WildThis crate was designed to hold and reduce the noise of a Bitcoin miner while distributing the heat. As with most of these boxes lately, I have to give credit for the basic design to Steve Barbour. Thanks to many in the Pleb Miner Mafia.
The prices are circa early 2022.
OG post from 1/31/2022 at: https://yooperhodl.substack.com/p/yooper-crate
 Yooper Crate Cut Out Plans (right mouse click - save image, for a legible copy)
Yooper Crate Cut Out Plans (right mouse click - save image, for a legible copy)I followed the plans and it turned out solid. Below you will find a picture journey from Start to Finish. Most shopping was done at Menards, Lowes, and Amazon. Parts list at the bottom.
 Cheapest, decent board I could find that had .74” actual thickness. Beware, this stuff has sharp edges and will slice your hands. Gloves required!
Cheapest, decent board I could find that had .74” actual thickness. Beware, this stuff has sharp edges and will slice your hands. Gloves required! Main screws I used for most of the assembly
Main screws I used for most of the assembly Screws I used when I didn’t want to break through the other side
Screws I used when I didn’t want to break through the other side Pieces all cut out on a table saw
Pieces all cut out on a table saw Started with the divider wall with internal hot/cold register
Started with the divider wall with internal hot/cold register

 Figured out how the filter was going to lay in. I made the intake and outlet side the same so I can reverse flow if needed.
Figured out how the filter was going to lay in. I made the intake and outlet side the same so I can reverse flow if needed. Air Filter - Probably not my final one but something to start with. I don’t want choke out the airflow
Air Filter - Probably not my final one but something to start with. I don’t want choke out the airflow Intake/Outlet side: .75” reveal to plan for the bottom piece coverage
Intake/Outlet side: .75” reveal to plan for the bottom piece coverage Pilot holes for the air flow cutouts
Pilot holes for the air flow cutouts Backside of Intake/ Outlet side - ready for jigsaw cutout
Backside of Intake/ Outlet side - ready for jigsaw cutout

 Figuring out the duct mount
Figuring out the duct mount



 Intake, Outlet, and Divider
Intake, Outlet, and Divider Assemble the Horizonal/ Vertical Air Flow Flanges x2
Assemble the Horizonal/ Vertical Air Flow Flanges x2 Flow flanges added to the pile
Flow flanges added to the pile Attach the Asic shelf to the Divider wall
Attach the Asic shelf to the Divider wall Asic shelf assembly added to the pile
Asic shelf assembly added to the pile Attach bottom to hinge side
Attach bottom to hinge side
 Attach Intake/ Outlet Sides
Attach Intake/ Outlet Sides Attach divider assembly. Notice small support blocks
Attach divider assembly. Notice small support blocks Attach Horizontal/Vertical Flow flanges. Notice support blocks
Attach Horizontal/Vertical Flow flanges. Notice support blocks Few screws into support block
Few screws into support block Internal assembly complete
Internal assembly complete Added small casters
Added small casters
 Added handles
Added handles Misc. hardware
Misc. hardware Home sweet home
Home sweet home Sound dampening: D.Y.O.R. - I used 4 layers of old bath towel on each surface and the compressed air staple gun was key
Sound dampening: D.Y.O.R. - I used 4 layers of old bath towel on each surface and the compressed air staple gun was key
 Window seal for around the top
Window seal for around the top D.Y.O.R. - Mounted some drywall for a little fire protection
D.Y.O.R. - Mounted some drywall for a little fire protection Window intake/ outlet for ducting
Window intake/ outlet for ducting Flexible ducting
Flexible ducting Picking a spot for my 220v - Hire a professional unless you absolutely know what you are doing
Picking a spot for my 220v - Hire a professional unless you absolutely know what you are doing



 Custom Cover
Custom Cover Not my best work, but all set for an S19JPro
Not my best work, but all set for an S19JPro S19JPro Overclocked
S19JPro Overclocked 75.7 DB with top open and fans at 77%
75.7 DB with top open and fans at 77% 47.5 DB with top closed at 45% (bringing in cold U.P. air on intake side). I added anti-vibration foam between asic shelf drywall and the miner and I believe it got even quieter
47.5 DB with top closed at 45% (bringing in cold U.P. air on intake side). I added anti-vibration foam between asic shelf drywall and the miner and I believe it got even quieter Final setup with laptop, node, miner, Yooper Crate, 92F outlet air temp heating the house
Final setup with laptop, node, miner, Yooper Crate, 92F outlet air temp heating the houseParts List
-
Melamin Board x 2
-
Caster 1-1/2" x 4
-
Hasp x 2
-
Side Handle x 2
-
Weather Stripping
-
250V Breaker - Make sure this matches your own breaker box
-
6-20R Outlet - Make sure this matches your needed power supply cord
-
Power Supply Cords x 2 - Make sure this matches your needs
Feel free to leave any zaps, questions, comments, or suggested revisions.
Cheers, Yooper
bitcoin #nostr #mine #diy #guide #asknostr
-
-
 @ 4870d550:110d6208
2024-12-11 13:57:35
@ 4870d550:110d6208
2024-12-11 13:57:35Opinion from Scott Wolfe. Scott is Coordinator of the Federation of Bitcoin Circular Economies, and Executive Director of the Bitcoin Coalition of Canada. He has spent the past twenty years in the not-for-profit sector with a focus on community health and development.
I am writing this from the comfort of my home in Toronto, Canada, with a world of thoughts swirling through my head. It is Day 2 of the 2024 African Bitcoin Conference, in Nairobi, Kenya. I am sad to not be there. I am also incredibly moved by the powerful messages emanating from the event as I watch the livestream.
This article will reflect on some of those messages and outline some commitments and donations that I am making today. I am also using this as an appeal to others – especially people outside the African continent – to join in donating to important projects throughout the continent. Before getting to that though, I want to situate this all against a backdrop, one that I hope can set a tone for action and healing.
The title of this article is a deliberate nod to one of the first essays I ever read by the late Nigerian scholar and writer, Chinua Achebe, a critique of author Joseph Conrad’s novel, Heart of Darkness. It is an essay which I read in my teens, given to me by an extra-curricular mentor, after I expressed my unease at the content of Conrad’s novel, something I was forced to read as part of my high school English literature curriculum.
In his essay, "An Image of Africa: Racism in Conrad's 'Heart of Darkness'", Achebe writes: “Heart of Darkness projects the image of Africa as "the other world," the antithesis of Europe and therefore of civilization, a place where man's vaunted intelligence and refinement are finally mocked by triumphant beastiality.”
A cottage industry of apologists has dismissed critiques such as Achebe’s, claiming that Conrad’s novel is simply a product of its time, perhaps even visionary for trying to place the challenges of cultural, racial, and ethnic difference in relief. These apologetics form part of a larger geopolitical and cultural motif regarding the African continent, one that persists to this day: to excuse away the status quo and to wash our hands of responsibility. The African continent is represented by an almost blinding array of peoples, cultures, languages, religions, political systems, and civilizational contributions. Yet, far too often Africa is unceremoniously reduced to a voiceless, homogeneous mass. Sometimes this is done unconsciously and other times deliberately, to satisfy convenient narratives about Africa which exist outside of the continent. We must interrogate these narratives and utterly shatter them.
Many years ago, given the choice to accept convenient apologetics or the uncomfortable critiques presented by Achebe – critiques which simultaneously called on me to question my own role and place as a Canadian kid from the suburbs of Ottawa, Canada – I chose the latter. Since then, I have tried to always maintain fidelity to the significance of that choice, something that has permeated my life journey in so many ways. Returning to what prompted me to action today, though, as I listened to this morning’s keynote speakers from the African Bitcoin Conference – Femi Longe, Marcel Lorraine, and Abubakar Nur Khalil -- a greater spirit within me rose and spoke. It is the spirit which is responsible for maintaining fidelity to the choice which I made long ago, and it is also the spirit which calls on me to honour all that has been given to me, gifted to me by brothers and sisters (family) from the African continent and the African diaspora in the Caribbean and North America throughout my lifetime. It called on me to do more, to get up, and to act.
I am still processing what my actions and commitments must look like more fully. For the moment, I am getting started by making personal donations to several important Bitcoin-focused initiatives throughout the African continent. While these donations will only make a small dent in the overall needs of these projects and the bigger collective project epitomized by the African Bitcoin Conference, I hope that my words and my actions here will resonate and inspire others to act and donate. Together, we can collectively build on the momentum being gained in Nairobi this week and accelerate outcomes.
Today, I am donating a total of 1,500,000 sats as follows:
500,000 sats to Bitcoin DADA, a non-profit organization providing education and support to women throughout the continent https://checkout.bitnob.co/d/1df56fcc-fed2-49ae-b44c-e01874c2dd84
250,000 sats to The Core, a Kenya-based project increasing Bitcoin education throughout the continent, especially via the Mi Primer Bitcoin curriculum https://geyser.fund/project/thecore21m
250,000 sats, in trust, toward the establishment of an African Bitcoin Institute, as called for by Femi Longe
250,000 sats in total to Bitcoin circular economy projects, including:
Afribit Kibera (Kenya) https://geyser.fund/project/merchantmeetupsforkibra
Bitcoin Anambra (Nigeria) https://geyser.fund/project/bitcoinanambra
Bitcoin Babies (Kenya) https://bitcoinbabies.com/
Calabar Bitcoin Club (Nigeria) https://geyser.fund/project/calabarbitcoinclub
Bitcoin Chama (Kenya) https://geyser.fund/project/bitcoinchama?mtm_campaign=project-share&mtm_keyword=bitcoinchama&mtm_sou
Bitcoin Dua (Ghana) https://geyser.fund/project/bitcoineducationcenter
Bitcoin Ekasi (South Africa) https://support.bitcoinekasi.com
Bitcoin Kampala (Uganda) https://btcpay0.voltageapp.io/apps/2HHdoHM52tr4wbx2KUaeguNKTDfm/crowdfund
Bitcoin Loxion (South Africa) – Lightning address: bitcoinloxion@blink.sv
Bitcoin Nairobi (Kenya) https://geyser.fund/project/btcnairobi?hero=geyser
Bitcoin Victoria Falls (Zambia) https://geyser.fund/project/bitcoinvictoriafalls
125,000 sats to the Kenya Fire Brigades Association https://pay.zaprite.com/pl_SSXGpaHAe3, via Proof of Workforce, to support the use of BTC as a treasury reserve asset by institutions and organizations on the continent
125,000 sats for purchase of copies of The Bitcoin Leap: How Bitcoin Is Transforming Africa https://www.amazon.com/Bitcoin-Leap-How-Transforming-Africa/dp/B0DJX4HHF5, with distribution to key decision makers who can help catalyze further investment and action on the African continent. I entrust these decision to the author, Charlene Hill Fadirepo, in consultation with colleagues from the continent.
I encourage others to join in making donations to these or other Bitcoin-focused projects throughout the African continent and to do so not as charity, but as part of a deeper personal commitment to interrogating and interrupting narratives about Africa which we far too often perpetuate outside of the continent.
As Femi Longe said in his keynote address today, “Bitcoin is a tool that we can use to restore Africa’s dignity. We must wield that tool with agency.”
In making public my commitment to action, I also want to note that I am deliberately publishing this via The Progressive Bitcoiner. For a multitude of reasons, ones that I will cover in a future article, I believe strongly that this not-for-profit organization and its publications provide critical platforms to pursue bridge-building, justice, and healing. I invite you to learn more about The Progressive Bitcoiner and to make it a part of your base of resources.
-
 @ e373ca41:b82abcc5
2024-12-11 11:48:41
@ e373ca41:b82abcc5
2024-12-11 11:48:41There is a nice image in complexity theory: to describe the indirect effects in complex systems, one uses the image of a butterfly whose distant flapping of wings can have much greater effects in a completely different place. In the USA, the balance of power has changed dramatically. Corona policy critics Kennedy and Bhattacharya are to become Secretary of Health and Human Services and head of the NIH, respectively. Every wave, every flapping of wings that comes from the USA will eventually reach Germany. For decades, Germany has only been a recipient of impulses, not a provider of them.
Germany has failed to deal with the corona pandemic in the same manner as it had previously compliantly supported and carried out the madness. But the tsunami of enlightenment from the USA is building up and will eventually reach Germany. A nation in the hands of perpetrators, cover-ups, accomplices and profiteers must once again be liberated from the outside. When will we become an independent country?
First it crumbles, then it erodes quickly
The precursors of the tsunami can be felt everywhere. The first signs of panic are spreading among local coronists. The big row back and “save what can still be saved” is spreading. After the coalition broke down, the FDP suddenly called for a committee of inquiry and Lauterbach's resignation. ARD broadcasts a documentary about vaccination victims; it takes stock after uncritically following the damage to citizens' health for four years. On Hart aber Fair, there was a small pseudo-debate between the coronavirus nomenclature (Lauterbach, Buyx, Hirschhausen) and a few critical mainstream voices around Heribert Prantl.
However, the coronavirus narrative is breaking ever stronger and faster and this is bringing a new dynamic into play. A report by the US House of Representatives now speaks of a laboratory accident as the most plausible cause of coronavirus. The biggest cover-up and obfuscator of this thesis in Germany was Christian Drosten. This view could easily get you banned from social media or get you into professional trouble during coronavirus. The physicist Roland Wiesendanger from the University of Hamburg was labeled a conspiracy theorist and campaigns were initiated against him. A laboratory accident then? Of course, it would now be necessary to explain how an “accident” fits in with the timely implementation of the simulation game “Event 201” or vaccines suddenly pulled out of a hat (developed in January 2020). It has just been revealed that the trucks from Bergamo, which were supposed to transport coffins of alleged corona deaths to crematoria in a convoy of 13 trucks, had apparently only loaded one coffin per truck. It doesn't take much effort for viral images and morbid emotions. The stage of the Corona Theater has been stormed, the stage set exposed as a fake.
Every narrative has a life cycle and Corona's is just coming to an end. The phase of self-destruction is about to begin. The dismantling of the old nomenclature by the stirrup holders and profiteers begins. Christian Drosten is now being publicly criticized for his rash stance on child vaccinations, accusing his colleague of “underhand” behaviour. The Bild newspaper now claims to have discovered that Lauterbach lied. Only now? The Springer publishing house has been a supporter of the pandemic from the very beginning, a representative of corona orthodoxy, only with a semi-critical veneer, a kind of pseudo-opposition in the mainstream. Biontech received a prize from the publisher, and the then editor-in-chief of Bild, Julian Reichelt, fantasized that 20 Biontechs were needed in Germany. Nobody could fail to notice that Karl Lauterbach was fanatical, confused and a permanent liar.
Advertisement:
Are you looking for the easiest way to buy Bitcoin and store it yourself? The RELAI app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees. (no financial advice).

Upgrade your self-custody with hard ware wallets! Check-out the newest Trezor Wallets, browse the shop or book an intro with an expert.
The book of the hour is “Seduced Thinking” by Czeslaw Milosz. The later Nobel Prize winner for literature from Poland described the subjugation of the intellectual caste in Poland by Soviet doctrine in the 1950s. He describes obedience to the system, conformity to orthodoxy, the different types of followers (he calls them Alpha, Beta, Gamma, Delta). The most unimaginable thing for him was that this was “servitude through knowledge”.
Milosz writes:
“There has never been such servitude through knowledge, it was reserved for the twentieth century. My generation was still taught at school that knowledge makes you free.”
Seduced thinking leads to a weighted mind, resulting in a stooped posture and ultimately a broken spine.
High treason against democracy, anyone?
What happened during Corona in Germany was more than a seduction of thought. It was a conspiracy by politicians, a caste of experts, the media, the scientific community and the cultural sector, who actively fought against any form of criticism and sold the health of an entire nation to a group of philanthrocapitalists around Bill Gates & Co. for a large-scale field trial with novel vaccines. As we know today and could have guessed at the time: with disastrous consequences and unforeseeable damage. And all this in the “best democracy of all time”. A better campaign to discredit democracy is hardly possible.
The coronavirus era was a breach of the democratic social contract, the greatest possible delegitimization of the state. A new democracy was created out of the old democracy: “Our democracy”. New institutions were created out of the institutions; the Bundestag was disempowered and a government of experts and councillors was set up, which took a strictly orthodox line. A new people of protectors was elected and critics were silenced. The good citizen was suddenly the obedient citizen. The conspiracy was not the result of collusion, but of incentivization. Everyone was aware of which statement could promote or destroy a career. Everyone made their own decision, chose their own camp. Anyone who wanted to make a pro-government statement, from a no-name expert to an innkeeper who barred unvaccinated people, only had to make it known and they were guaranteed attention through airtime, interviews and reporting. Everyone could get a piece of the cake, but it was a poisoned cake.
The sugar had an immediate effect, but the poison is insidious.
This article first appeared in German by Milosz Matuschek on Freischwebende Intelligenz.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
-
 @ eac63075:b4988b48
2024-10-15 20:18:52
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
Centralization and the Exclusivity of Nostr
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
Individual Freedom and Data Protection
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
Hyperbitcoinization and the Illusion of Store of Value
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
The Role of the Community in Bitcoin's Development
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
Sidechains, Second Layers, and the Lightning Network
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
The Fight Against Centralization on the Internet
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
The Future of Bitcoin and the Need for Action
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
Conclusion
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-
 @ a012dc82:6458a70d
2024-12-11 08:02:59
@ a012dc82:6458a70d
2024-12-11 08:02:59Table Of Content
-
From the Backbench to the Forefront
-
Milei's Bitcoin Connection
-
The Coinx Controversy
-
Argentina's Financial Quagmire
-
Conclusion
-
FAQ
Well, folks, it seems like the winds of change are blowing in Argentina! In a twist that no one saw coming, Javier Milei, the presidential candidate with a penchant for Bitcoin and libertarian economics, clinched the top spot in Argentina's primary. This victory sent shockwaves throughout the nation. Milei and his gang, the La Libertad Avanza (or "Liberty Advances"), managed to snag a whopping 30% of the votes. They beat the second-place contender, Juntos Por El Cambio, by just under 2%, which is quite the feat!
From the Backbench to the Forefront
La Libertad Avanza, founded just a couple of years ago in 2021, was once the little guy in the political arena. In their first legislative elections, they made waves, becoming the third most-voted coalition in Buenos Aires. But this recent victory? It's monumental! It's like David taking on Goliath and emerging victorious. Milei's rise has certainly turned heads and raised eyebrows in the political sphere, making everyone wonder what's next.
Milei's Bitcoin Connection
Javier Milei is not your run-of-the-mill political candidate. He's carved out a unique niche for himself in the world of politics, largely due to his vocal support for cryptocurrencies, especially Bitcoin. When you tune into talk shows and interviews, you'll often find Milei passionately discussing the potential of digital currencies. He doesn't just see them as another financial instrument; to him, they represent a return to a time when the power of money was firmly rooted in the hands of the people, free from excessive governmental control.
His views on Bitcoin go beyond mere admiration. Milei perceives it as a revolutionary tool, one that can challenge traditional financial systems. He often contrasts the decentralized nature of cryptocurrencies with the centralized control of traditional fiat currencies. In his eyes, Bitcoin and its peers are not just alternatives but superior forms of money. He's even made bold claims, suggesting that in many ways, cryptocurrencies are safer investments than traditional precious metals like gold or silver. This is a significant statement, especially in a country like Argentina, where people have historically turned to gold as a hedge against economic instability.
However, as with any public figure with strong opinions, Milei's crypto enthusiasm has its fair share of critics. While he paints a rosy picture of a crypto-driven future, there are those who question his motives and the feasibility of his vision. The crypto world, as many know, is not without its pitfalls. From volatile market swings to regulatory challenges, the journey to mainstream acceptance is fraught with challenges. And Milei's connection to this world has put him under the microscope, with every statement and action being dissected and debated.
The Coinx Controversy
Rumor has it that Milei promoted a Ponzi scheme called Coinx, which allegedly swindled a cool $800,000 in Argentine pesos. Milei, of course, denies any wrongdoing. He even compared their business model to that of a bank. The only difference? They can offer higher interest rates because they're not tied down by the central bank. But not everyone's buying it. Manuel Ferrari, a big shot in the Bitcoin Argentina NGO, remains wary of Milei. This controversy adds another layer to the complex narrative surrounding Milei's rise.
Argentina's Financial Quagmire
Argentina's economic waters are turbulent, to say the least. With a dizzying inflation rate of 135% this year, the peso's value is plummeting, causing widespread distress. Amidst this chaos, many are pinning their hopes on Javier Milei, a figure who has emerged with a pro-Bitcoin stance that's causing quite the stir. Drawing parallels with El Salvador's audacious move to adopt Bitcoin, there's a buzz about whether Argentina might follow suit. But is Milei the savior Argentina has been waiting for? While his support for cryptocurrencies offers a glimmer of hope to some, it also brings with it skepticism and apprehension. The world of crypto, though promising, is still uncharted territory, especially for an economy as volatile as Argentina's.
As debates rage on, it's evident that Argentina stands at a crucial financial juncture. Milei's advocacy for Bitcoin and other cryptocurrencies suggests a potential shift in the country's financial paradigm. But diving into the crypto realm isn't without its risks, and there's a looming question: Are we witnessing the dawn of a new financial era for Argentina, or is it just a leap from the frying pan into the fire? The nation watches with bated breath, waiting to see the path Milei might pave.
Conclusion
Only time will truly reveal the impact of Milei's influence on Argentina's financial future. It's a waiting game now, folks. But if there's one thing we can bank on, it's that with Milei stirring the pot, Argentina's economic and financial landscape is poised for some dramatic shifts. The rollercoaster has just begun, so everyone better buckle up and brace themselves. Keep your eyes peeled and ears to the ground, because the upcoming months promise a whirlwind of changes, debates, and transformations for Argentina. The nation stands at a pivotal juncture, and the world watches with bated breath.
FAQ
Who is Javier Milei? Javier Milei is a presidential candidate in Argentina known for his support of Bitcoin and libertarian economics.
What is La Libertad Avanza? La Libertad Avanza, translated as "Liberty Advances," is the political coalition led by Javier Milei.
How did Milei fare in the recent primaries? Milei clinched the top spot in Argentina's primary, securing over 30% of the votes.
What is the Coinx controversy? Coinx is an alleged Ponzi scheme that Milei is rumored to have promoted. However, Milei denies any wrongdoing.
What is Milei's stance on Bitcoin? Milei is a strong advocate for Bitcoin, viewing it as a return to private sector-controlled money and a safer alternative to traditional assets like gold or silver.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research. *
-
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ fd78c37f:a0ec0833
2024-12-11 01:32:23
@ fd78c37f:a0ec0833
2024-12-11 01:32:23Bitcoin, as a decentralized digital currency, is reshaping the global financial landscape, sparking innovation and transformation across various sectors. In South America, Bitcoin communities are emerging as crucial drivers of economic empowerment, financial inclusion, and local technological advancement. This issue will highlight 21 Bitcoin communities from South America, exploring their missions, growth trajectories, and recent developments. By examining these grassroots initiatives, we aim to show how Bitcoin is being leveraged to create sustainable economic ecosystems, foster social progress, and expand access to education and financial tools. Thank you, YakiHonne decentralized media client on Nostr to support people in owning their voice. #iOS #Android, for supporting the publication of the Bitcoin Community Newsletter. Most of the content has been reviewed and confirmed by the South American communities. If there are any omissions, please feel free to reach out to me.
1.Mi Primer Bitcoin nostr:npub17cyatz6z2dzcw6xehtcm9z45m76lde5smxdmyasvs00r4pqv863qrs4ml3 * Introduction My First Bitcoin is a Bitcoin education initiative rooted in the principles of independence, fairness, and community leadership. Originating in El Salvador, it aims to empower individuals and communities by providing open-source educational resources and fostering a decentralized network. Through a commitment to high-quality education, resistance to external influence, and the creation of a global collaborative network, it seeks to spread Bitcoin education to every corner of the world, offering a transparent and transformative model for reshaping traditional financial systems. * Latest Updates Recently, MyfirstBitcoin successfully hosted the fourth Bitcoin Educators Unconference, featuring guests such as nostr:npub1zfgx8v2g0faswd0ry2qn3ay4pvx4jr6q4fw9d0yqalpkyv9hhp0sjccnj5 nostr:npub1rhh9pkmf6l6z7298yg6fgp95rzkmx4j9uxpekn8j73p5k95ck7gsvce7vj attracting around 170 participants and receiving positive feedback. They also held the graduation ceremony in Ilopango, El Salvador, and continued to organize their regular monthly Bitcoin education meetups and Bitcoin game nights. Additionally, MyfirstBitcoin’s Bitcoin Educators Node Network welcomed four new projects from Canada, Nigeria, and the United States. In partnership with Bitcoin Boma, they are launching a free online Bitcoin education course for Malawi in January 2025, aimed at enhancing local Bitcoin knowledge.
- Introduction Bitcoin Beach is a groundbreaking initiative in El Salvador aimed at fostering sustainable local economic development through Bitcoin. The project provides financial services to the community, particularly for those without access to traditional banking. By using Bitcoin for payments, residents can cover everyday expenses such as utility bills, medical costs, and food. Bitcoin Beach leverages the Lightning Network and community collaboration to promote the adoption of Bitcoin both within El Salvador and globally.
- Latest Updates Recently, Bitcoin Beach attended the conference at Bitcoin Lake, where they hosted the Bitcoin Beach Meetup and Bitcoin Beach Festival to support local businesses with Bitcoin. They also invited notable figures such as nostr:npub1q0al05h2uvtj0fp8ww7etl0pdjnkum638ynz9tmku3e522fyvlmqjq04mt Hermann Buhr-Vivier, nostr:npub164xhe3pgcqaj70ls7ls5e4hwlnvl4ttuu8wns99jmwp5z6lwhutsa27wle as podcast guests. The discussions covered a range of impactful topics, including how Bitcoin mining can truly light up rural Africa, how to use Bitcoin to transform small towns in South Africa, and integrating Bitcoin into state-level policies across the United States, among other key areas.
3.Praia Bitcoin Brazil nostr:npub1m3tu3l6y59g2tmackq23v5vgn59u7hu66gxg8xajghz59tqm6xnqk2m888 * Introduction Praia Bitcoin Brazil, located in Jericoacoara, Brazil, is dedicated to creating the country's first Bitcoin circular economy, empowering local residents with financial inclusion. Founded by Fernando Motolese, the project promotes Bitcoin adoption through education, technology, and community-driven initiatives. It has integrated over 40 local businesses into the Bitcoin ecosystem and raised more than 12 BTC through Bitcoin-only crowdfunding. Praia Bitcoin offers self-sovereign financial services and runs programs like the "Bitcoin Smiles" initiative and educational support for children. * Latest Updates Recently, Praia Bitcoin Brazil launched several innovative projects, including the first stage lighting course and free acoustic guitar course funded entirely through Bitcoin crowdfunding. Additionally, Praia Bitcoin successfully hosted the Praia Bitcoin Conference 2024, attracting 10 volunteers, 100 local residents, and 10 new merchants. The conference also sponsored the first music performance paid in Bitcoin and introduced three local courses, all funded via Bitcoin crowdfunding. These initiatives highlight Praia Bitcoin's ongoing efforts to drive Bitcoin adoption and foster local community development.
4.Bitcoin Lake / Lago Bitcoin Guatemala nostr:npub1a4excy7uf9z3mcafvm9cwdr549dl5lpazuvpr2nc550vf27n5a4scqq5k2 * Introduction Bitcoin Lake aims to create a circular economy powered by Bitcoin, providing a novel and accessible solution for unbanked as well as banked merchants in Guatemala. * Latest Updates The Bitcoin Lake community has been actively preparing and promoting a series of innovative initiatives. On November 30 and December 1, Bitcoin Lake successfully hosted its 2024 conference, inviting industry experts such as Ronny Avendaño, co-founder and CEO of the Bitcoin hardware store, and prominent Bitcoin advocate Roman Martínez (chimbera). During the conference, the community also organized creative activities like the coffee workshop and “Be Captain of the Bitcoin Boat”, offering participants an opportunity to dive deeper into Bitcoin and the local economy. Additionally, through partnerships with local merchants, Bitcoin Lake is actively advancing the development of the Bitcoin economy, fostering economic growth and financial inclusion in the community.
5.Bitcoin jungle nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Introduction Bitcoin Jungle is an open-source community project built on the Bitcoin Lightning Network with the goal of creating a circular Bitcoin economy. The project provides education, resources, and technology to both individuals and businesses. Starting from the Golden Triangle area in Costa Rica (Dominical, Uvita, Ojochal, Platanillo, Tinamaste), it is developing a shining example of what a Bitcoin community can represent. * Latest Updates Recently, the Bitcoin Jungle community has been actively promoting the adoption and use of Bitcoin in Costa Rica, participating in various projects and events. Community members attended the Adopting Bitcoin conference in El Salvador, further advancing global Bitcoin adoption. At the same time, they have been actively supporting children's charity projects and Bitcoin diploma courses, continuously driving Bitcoin education, social responsibility, and community development.
6.Bitcoin Berlín sv * Introduction Bitcoin Berlín sv aimed at creating a financially sovereign town in Berlín, El Salvador, through the implementation of a Bitcoin circular economy. The project seeks to integrate Bitcoin into the local economy by educating residents and businesses about its benefits, promoting the adoption of Bitcoin-based payment systems, and empowering local entrepreneurs with financial education. It also focuses on environmental sustainability, encouraging the use of renewable energy and waste reduction. * Latest Updates Recently, the Bitcoin Berlín sv has been actively promoting the use of Bitcoin by sharing informative articles and supporting the graduation of podcast producer Joel through the BlinkBTC QR code platform, allowing contributions in sats. This initiative not only supports the growth and development of community members but also furthers Bitcoin’s adoption and usage within the community. Additionally, on November 23rd, the community successfully hosted a cultural festival celebrating the local heritage. During the event, all vendors accepted Bitcoin payments, showcasing its practical application in Berlín’s economy. The festival attracted numerous tourists and residents eager to experience Bitcoin payments, further advancing its integration into daily life.
7.Bitcoin embassy San Salvador * Introduction Bitcoin embassy San Salvador is more into promoting Nostr in the region. * Latest Updates Recently, the Bitcoin Embassy San Salvador has been actively promoting the use and adoption of Bitcoin within the community, organizing various events. One of the highlights was the Christmas Toy Drive x Cuarteto Salvación, where toys were purchased using Sats to bring holiday cheer to children in need. The event, held on December 1 at Cuscatlán Park, also featured a special Music Night, attracting a large audience. Additionally, the Embassy hosted an educational gathering for food vendors, aimed at promoting Bitcoin payment systems. During the event, vendors accept Bitcoin payments through tiankii_Tech and blinkbtc platforms, further encouraging local businesses to embrace and adopt Bitcoin payments.
8.ONG Bitcoin Argentina * Introduction ONG Bitcoin Argentina is dedicated to advancing the development and application of decentralized technologies, particularly in the fields of Bitcoin, cryptocurrencies, and blockchain. As a leading organization in this space, the community promotes user protection and the healthy growth of the crypto ecosystem through education, training, and public advocacy. Its mission is to help individuals, businesses, and decision-makers understand and leverage decentralized, transparent, and secure technologies to bring more opportunities and progress to society. ONG Bitcoin Argentina has become a leading force in promoting decentralized technology in Argentina and Latin America. * Latest Updates Recently, ONG Bitcoin Argentina has been actively preparing for the “Moon Party | Despedimos el año ATH (A Todo Hodler)” celebration, set to take place on December 5, 2024. Bitcoin enthusiasts will gather to enjoy exciting activities, including a Lightning Network demonstration and the Fish Bowl Manizesto Bitcoiner art exhibition. In addition, the community has hosted and will host a series of conferences and workshops covering a range of topics, including local digital asset services, Bitcoin as a strategic reserve in the U.S., the reconversion of the Bitcoin and cryptocurrency economy and financial systems, the role of crypto economics in financial system reform, the impact of Bitcoin ETFs on markets, and Bitcoin's influence on global issues, fostering in-depth discussions and development within the crypto industry.
9.La bitcoineta * Introduction La Bitcoineta is an initiative launched by the Argentine community in 2018, designed to promote the adoption and understanding of Bitcoin through a unique and powerful tool: a van and a group of volunteers. This traveling educational project has visited hundreds of towns across Latin America, Africa, and Europe, reaching thousands of people and covering hundreds of thousands of kilometers with the aim of spreading its mission and activities.With its innovative and mobile approach, Bitcoineta has become a globally recognized educational project.
10.Motiv Peru * Introduction Motiv is a non-profit organization founded in 2020, focused on addressing systemic poverty through Bitcoin and innovative projects, aiming to provide better opportunities for survival and prosperity to underserved communities. Its founders, Rich Swisher and Vali Popescu, witnessed firsthand the tragic impact of poverty and lack of basic living conditions in a remote village in the Andes Mountains of Peru, where children were dying due to preventable causes. This inspired them to create Motiv, with the goal of empowering vulnerable populations. By leveraging global support and partnerships, Motiv uses Bitcoin to help local communities break free from poverty and improve their lives, striving to bring positive change and hope to those in need. * Latest Updates Recently, MOTIV Perú has made significant progress in promoting Bitcoin and the circular economy. The organization continues to transform communities across Peru through various initiatives. For example, in the Comas district of Lima, entrepreneurial women are paying for their classes with Bitcoin and learning how to make delicious desserts, further advancing the local circular economy. Additionally, MOTIV Perú held its first Bitcoin training in Carabayllo-Lima, helping Peruvians understand the nature of money and the advantages of Bitcoin. MOTIV is also assisting communities in areas like Tarapoto and Ancon, where locals are using Bitcoin for daily transactions, driving financial freedom and economic empowerment.
11.Montanha bitcoin * Introduction Building a circular economy in Sao thome, Brazil. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to June 2024, highlighting a water contamination incident.
12.Amityage honduras * Introduction Amityage Honduras is the first Bitcoin education center in Honduras, located on Roatán Island in the Prosperá zone. The center's mission is to educate the local community about Bitcoin and spread this knowledge throughout Central America and the Caribbean. It is dedicated to helping businesses on the island adopt Bitcoin as a payment method, teaching children financial literacy, and empowering individuals to achieve financial sovereignty through Bitcoin. The center aims to empower the local community through education and innovation, fostering economic independence and sustainable development. * Latest Updates Recently, Amityage Honduras is actively promoting Bitcoin education by participating in various international Bitcoin events and organizing local courses to help more people understand Bitcoin. Community members took part in significant events such as AdoptingBTC 2024 and BitcoinUnconference, and hosted workshops around the theme of “How to Enter the World of Bitcoin Education.” In Haidmühle, Germany, AmityAge completed a four-day Bitcoin Educators Academy, where the curriculum included topics like using simple analogies to explain Bitcoin and public speaking exercises. Additionally, the community hosted Bitcoin education courses on Roatán Island and provided a free Bitcoin event for beginners at the Crawfish Rock community, further spreading Bitcoin knowledge.
13.Lima - Orange Pill Perú nostr:npub1fw8m5g6nfywmsgqjc66j47jax7jrv8lq46zf7grydjqppc54a8eql47qrx * Introduction Orange Pill Peru is a community-driven initiative dedicated to empowering Peruvians through Bitcoin education. With a focus on transforming the financial landscape, Orange Pill Peru provides resources for individuals to learn about Bitcoin, connect with like-minded enthusiasts, and grow their knowledge through various events and workshops. The community serves as a hub for both beginners and professionals, offering a supportive environment to explore the fundamentals of Bitcoin, its history, and its potential to shape the future of finance. * Latest Updates Recently, there have been no major updates. They actively engage in Bitcoin education and industry updates by sharing and reposting Bitcoin-related content. They support MOTIV Perú's financial freedom education project in the Ancon community in Lima, emphasizing the empowerment of women through Bitcoin. Additionally, the community has shared information about the upcoming Bitcoin Medellin Conference scheduled for January 2025.
14.La Antigua Bitcoin * Introduction La Antigua Bitcoin is a community-based initiative in La Antigua Guatemala, focusing on promoting Bitcoin adoption in local businesses. The community works to create awareness and facilitate the use of Bitcoin as a payment method in various establishments throughout the city. By encouraging merchants to accept Bitcoin, La Antigua Bitcoin aims to integrate cryptocurrency into the everyday economy, driving financial innovation and expanding access to decentralized financial systems within the region. * Latest Updates Recently, the Antigua Bitcoin community has had few updates, with a focus on organizing its first meetup in collaboration with “Run with Bitcoin” on November 24, 2023. The event garnered significant attention within the community, featuring interactions with a special guest. The aim of the event was to further promote Bitcoin adoption in Antigua, Guatemala, and encourage exchange and collaboration between Bitcoin enthusiasts and the local community.
15.Horizonte Bitcoin nostr:npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk * Introduction Project that aims to contribute to the Bitcoinization of the economy and encourage Entrepreneurship and Decentralization. * Latest Updates Recently, The community has had no recent updates. The latest event dates back to Oct 2024, which shared a message encouraging women to learn more about Bitcoin and connect with others in the field, highlighted a meetup, Satoshe's Lounge, for women, providing a space to learn, discuss, and share knowledge about Bitcoin.
16.Escuelita Bitcoin nostr:npub1awggmqvlw8pa0kp9qq5law8zsvp2a8suztk0357j7e0nt746suwspt7lwx * Introduction Educational Project for Little School. * Latest Updates Recently, the Escuelita Bitcoin team has grown to five members and is actively advancing Bitcoin education and community development. Team members have hosted several workshops in Paraguay and Mexico, spreading Bitcoin knowledge within local communities and encouraging merchants to accept Bitcoin payments, particularly in Ciudad del Este, Paraguay. The team is raising funds through platforms like Geyser. fund and Kuno.anne.media to support the expansion of their educational initiatives and help locals better understand and use Bitcoin. Escuelita Bitcoin also emphasizes privacy education, promoting the use of tools like CakeWallet and Monero. Through collaborations with other organizations and individuals, the team is extending the reach of Bitcoin education, fostering the adoption of Bitcoin in Latin America and emerging markets.
17.Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL nostr:npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 * Introduction Bitcoin é Aqui! Rolante is located in Rolante, Brazil, and is dedicated to creating a lifestyle and tourism destination where 40% of businesses now accept Bitcoin as a payment method, showcasing the community's success in integrating Bitcoin into the local economy. Residents and visitors can use it to pay for all services, including accommodation, tours, local goods, medical services, and even construction and solar energy equipment. This reflects the practical application and convenience of its use in everyday life, aiming to create a digitally-driven environment powered by Bitcoin. * Latest Updates Recently, the Bitcoin é Aqui! Rolante has been actively promoting the adoption and use of Bitcoin in Brazil and beyond. The community has organized several educational events aimed at spreading basic Bitcoin knowledge and its practical applications in daily life, particularly through online videos and lectures. These efforts help people understand how Bitcoin plays a crucial role in the global financial system. The community has also been actively involved in promoting Bitcoin payments, supporting their adoption by local businesses and in the tourism industry.
18.Bitcoin Forte * Introduction Bitcoin Forte is a voluntary initiative aimed at introducing Bitcoin as a currency to Praia do Forte in Bahia, Brazil. The project provides valuable information about Bitcoin’s importance and encourages local merchants to adopt it as a payment method. By highlighting Bitcoin's international use, simplicity, and security, Bitcoin Forte aims to facilitate its adoption among both tourists and businesses.The community promotes Bitcoin as a stable and controlled currency, helping to avoid systemic price inflation. Bitcoin Forte simplifies the process for businesses by offering tools such as QR codes and the “Satoshi POS Wallet” app, which connects to a merchant’s primary wallet for seamless transactions. * Latest Updates Recently, the community has had no recent updates. The latest event dates back to July 2024, introducing Airbtc, a platform similar to Airbnb, but it only accepts Bitcoin as payment.
19.Bitcoin Paraguay * Introduction Bitcoin Paraguay is a community dedicated to connecting individuals in Paraguay who are interested in Bitcoin, promoting its adoption, and fostering the development of local circular economies. The community’s mission is to increase Bitcoin adoption by collaborating with local businesses and nonprofit organizations, helping to create a more sustainable local economy. Through regular events, talks, and resource sharing, Bitcoin Paraguay provides education and support to its members while actively exploring Bitcoin's application across various sectors in Paraguay. * Latest Updates Recently, the Bitcoin Paraguay community has made significant progress in promoting Bitcoin adoption. On November 5, they successfully hosted the fifth Bitcoin meetup in Asunción, attracting 110 attendees. The event included two Spanish-language presentations and a Lightning Network onboarding training session, with food and drinks available for purchase using Bitcoin. The event was made possible with strong support from sponsors Blink Wallet and Hacking Lives. On November 13, Josef Tetek visited Bitcoin Paraguay to help promote the adoption of Vexl in the country. The community also shared their progress through articles, with Jake, a community member, publishing an article in the Asunción Times on how Bitcoin Paraguay is improving people's lives.
20.Bitcoin Amantikir * Introduction They are starting the first community in the Serra da Mantiqueira to use and extol people about the bitcoin economy. * Latest Updates Recently, the Bitcoin Amantikir community has made significant progress in promoting Bitcoin as a payment method and fostering a circular economy in Santo Antônio do Pinhal. Various businesses, including a pet store, transportation service providers, a hotel, a fruit shop, and a tourist attraction, have started accepting Bitcoin payments. Additionally, the community is organizing a Bitcoin financial education course on December 2nd at Munay Pousada, aimed at helping young people aged 14-18 acquire essential financial knowledge and understand the importance of Bitcoin.
21.La Crypta nostr:npub1rujdpkd8mwezrvpqd2rx2zphfaztqrtsfg6w3vdnljdghs2q8qrqtt9u68 * Introduction La Crypta is an open-source community dedicated to advancing the adoption of the Nostr protocol and Bitcoin through developer-friendly tools and resources. By providing an integrated open-source stack, La Crypta empowers developers to sync with multiple relays, showcase profiles with badges, and facilitate seamless messaging, making it easier to build and utilize decentralized social platforms. Events like hackathons further enhance collaboration and attract new members, fostering innovation in decentralized social media. * Latest Updates LaWallet, their open-source wallet, integrates Bitcoin, Lightning, and Nostr to provide a seamless learning experience. With over 8,000 NFC cards distributed across conferences in regions like Argentina, Brazil, and Spain, LaWallet enables easy adoption while prioritizing user privacy. The wallet’s functionality is now supported by Alby’s official browser extension, further boosting accessibility.
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 0e8c41eb:95ff0faa
2024-07-08 14:36:14
@ 0e8c41eb:95ff0faa
2024-07-08 14:36:14Chef's notes
Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
Spread the fruit filling over the dough.
Mix the rest of the flour with the remaining 100 grams of butter and 100 grams of sugar and knead it with your fingers into a crumbly mixture. Sprinkle this crumble mixture over the fruit filling. Bake the tart in the preheated oven at 200°C for about 30 minutes until golden brown.
Variations: Only apple? Make this tart with 1 kilo of apples. High or low? You can also bake the crumble tart in a low tart tin of 30 cm diameter. If the fruit filling is a bit too voluminous, you can make double the crumble mixture and sprinkle it over the larger surface area.
Additional needs: Mixer with dough hooks or food processor Cling film Round baking tin with a diameter of 28-30 cm, greased
Details
- ⏲️ Prep time: 45 min + 1 hour Rising
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 8
Ingredients
- 375 grams flour
- 1 packet dried yeast (7 grams)
- 125 grams unsalted butter, at room temperature
- 275 grams sugar
- 1 egg
- 100 ml milk, at room temperature
- 500 grams apples
- 500 grams apricots (fresh or from a can)
Directions
- Sprinkle a pinch of salt in a bowl. Sift 275 grams of flour above it. Make a well in the center of the flour and sprinkle the yeast into it. Add 50 grams of butter, 25 grams of sugar, and the egg. Pour in the milk and knead the dough with the mixer or by hand into a smooth dough. If necessary, add a bit more flour if the dough is too sticky. Form the dough into a ball. Let the dough rise covered with cling film at room temperature for 1 hour.
- Peel the apples. Cut the apples and apricots into pieces. Cook the fruit with 150 grams of sugar and 50 ml of water in 15 minutes into a thick compote. Let this fruit filling cool.
- Knead the dough again briefly and roll it out to a round sheet of about 28-30 cm in diameter, so that it fits well over the baking tin. Press the dough into the tin and press it well into the corners. Let the dough rise again for 10 minutes and cut off the excess edges.
- Spread the fruit filling over the dough.
-
 @ deba271e:36005655
2024-12-10 16:39:14
@ deba271e:36005655
2024-12-10 16:39:14Overall this was such a great experience, but as always there are couple things that could be better. Don't hate me. Complaining about experience is in my job description.
- Internet at feria: There are connection issues hampering the experience for both sellers and buyers.
- Having a wifi for the sellers would greatly improve the situation - but I also understand that none of this can be imposed by outsiders - I'm happy to help [REDACTED].
- Another option is to create geyser.fund campaign specifically for this - "Get internet for bitcoin merchants at Uvita farmers market". I'm using the words in this title carefully to be catchy in the right way.
- Then one of the best ways is just get the wifi access QR code (often can be generated in the access point interface), print it and give that to the sellers. No need to hassle with the password, etc.
- Teaching bitcoin to buyers at feria: At the feria there were many people buying the produce that have no idea what is bitcoin. Since the ferias are the flagship experience of Bitcoin Jungle, this would be a great opportunity to teach the buyers about bitcoin.
- I think it would be great to have some (sensible) billboard/banner that explains how to use bitcoin, how to download the app, get colones on it and then pay at the feria.
- This could actually be incentivized by some campaign like "Get 5000 CRC to use at feria if you install lightning wallet for the first time" (again this could be funded by geyser campaign if you don't have funds for this). The sellers can just point to the banner if someone asks them.
- Maybe there is a chance to have a small bitcoin booth at the corner of the feria that could give away some basic printed info about bitcoin and how to use it. It could sell books (Gladstein, Lyn Alden, the El Salvador classbook, etc), some tote bags (useful for the market) or similar useful bitcoin branded merch.
- Help all sellers accept bitcoin: There were 2 sellers that didn't accept bitcoin and that's ok, but it would be great to mitigate the gap in experience for the buyers. One option is for the ask the seller next to them to accept the bitcoin for them and give them colones (I have seen this happen in one case - it worked great). And so this just needs a small bit of education.
- Allow pre-configuring items in the POS: The selers that have fixed price items (i.e. not weighted) were still adding the numbers on calculator or similar, it was a bit tricky for them, prone to mistake.
- (I haven't actually seen the Bitcoin Jungle wallet POS, so maybe this is already solved - if yes, then ignore)
- Consider providing features to pre-configure the items in the POS, so the seller can just tap on items and it adds those up. One benefit of this for the selers is that this can give them precise tracking for how many pineapples they sold, etc.
- This is something that actually works quite nicely in the Breez wallet. See the screenshot bottom right: https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fcafc3cd0-adb3-47be-bdcd-9d3ba57fe967_1614x906.png
- Keep btcmap.org up to date: Currently I don't think https://btcmap.org/map#15/9.16567/-83.73844 lists the feria and maybe other places. This is something that many bitcoiners coming to the are will use and so keeping the btcmap.org up to date would go a long way. It's fairly simple to add new items to the map and there are many communities in each country that keep those up to date (e.g. I know people that are calling the restaurants and verifying that they still accept bitcoin).
- Try including some ready to eat food seller at the feria: Currently the selection of produce was nice, but one thing that was a bit missing is the one stand that sells ready to eat local food.
- This could be some sandwiches, quesadillas, etc…
- Have a board for people offering services: This is just an idea - not sure how well would it work and also this may already be handled somewhere else in Uvita?
- One thing that could be useful and I was actually looking for is to have some form of a big board where people can offer their services - cooking, cleaning pools, taking care of kids, fixing roofs, teaching surfing, etc. It could be a board where people can pin their notes with WhatsApp numbers like this. Do you want some work done at your house or garden? You would just come to check this board.
- Internet at feria: There are connection issues hampering the experience for both sellers and buyers.
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 5e5fc143:393d5a2c
2024-11-19 10:20:25
@ 5e5fc143:393d5a2c
2024-11-19 10:20:25Now test old reliable front end Stay tuned more later Keeping this as template long note for debugging in future as come across few NIP-33 post edit issues
-
 @ eaef5965:511d6b79
2024-12-10 14:33:54
@ eaef5965:511d6b79
2024-12-10 14:33:54Bit late this quarter, but here now for the latest release on the most irreducible form of money, the monetary base. Data comes from the top 50 currencies in the world, their countries of which represent 96% of global GDP and 84% of global population (not very fair, right there). Gold and silver is analogous to this money supply. As is the stock of bitcoins.
This is quarterly release #26, for 2024 Q3.
If you have followed my work before, then you know that the constant hymn I've sung while speaking publicly about Bitcoin is that the only, economically comparable money supply in the fiat world to 21 million bitcoins is what economists call the "monetary base," or "base money." This is a corporeal money supply that has existed across all of modern economic and central banking epochs. For an apples-to-apples, ontological comparison with Bitcoin, look no further then Base money.
So what is it?
It is central bank money, comprised of two supplies:
- Physical currency: Notes and coins, or “cash;”
- Bank reserves: The “Master account” that each commercial bank holds with its central bank.
Now, why do I refer to this as, "Central bank money?" This is because, unlike all other money supplies in the fiduciary banking world (like M1/M2/M3), the Monetary base is the sole and ultimate money supply controlled by the central bank. It is, literally, the printing press.
What follows won't be a lesson in reserve ratios or monetary economics. The point is that you simply understand that there is a money supply that central banks solely control, and of course (of course!) this is what Bitcoin's 21 million are up against.
The monetary base is to the core of the entire fiat financial system, as 21 million bitcoins are to the core of the Bitcoin protocol.
One is open and permissionless, and one is not.
By the way, the monetary base is essentially (though not entirely) analogous to the total liabilities of a central bank, so we can (basically) say that the monetary base is the "balance sheet" of each central bank.
On cash. Quick notes on the above. Certainly you understand what "cash" is, and it is indeed an instrument that has been fully monopolized by each central bank in each nation around the world--only they can print it. Even though it is true that banks in more free banking societies in the past could freely print and strike notes and coins, the central bank (or state) monopoly has been around for a long time. Kublai Khan was the first to do it 750 years ago.
On bank reserves. Don't stress your brain on this too much, but this is the main "settlement money" that banks use between each other, when they want to settle their debts. It is digital now (Fedwire in US, CHAPS in UK), but it doesn't technically have to be, and of course before modern technology took over even a few decades ago, it was not.
These two stacks of retail and wholesale cash, stacks of central bank money, are what makes up the Monetary base. This is the printing press. Only this compares to 21 million bitcoins.
And gold, and silver by the way.
Final note, central bank digital currencies, or CBDCs, which are simply LARPing on Bitcoin's success, are indeed created by central banks, and they are indeed classified as Base money. They are going to be a "third rail." They are thankfully incredibly small, pilot projects today. We will see how far democracies will be tested, as autocracies no doubt will mainstream them; but for now, consider them, at least economically, to be inconsequential to the update below.
With that review out of the way, onward to Q2 update for 2024.
Bitcoin is the 6th largest money in the world.
In February 2024, it surpassed the monetary base of the United Kingdom, that is its value was larger than the Bank of England's balance sheet, and it remains so to this day.
As of 30 September 2024, it is only the balance sheets of the big four central banks that are larger than Bitcoin. They are:
- Federal Reserve (dollar): $5.59 trillion
- People's Bank of China (yuan): $5.40 trillion equivalent
- European Central Bank (euro): $5.28 trillion equivalent
- Bank of Japan (yen): $4.69 trillion equivalent
If we remove gold from the equation (we shouldn't), then Bitcoin could be considered the 5th largest money in the world.
However, the all-important monetary metal throughout history that even a child knows about--gold--is still king at around $16.5 trillion in value, or 6.1 billion ounces worldwide. Note, this does not include gold lost/recycled through industry; in that case, it is estimated that about 6.9 billion ounces of gold have been mined throughout humanity.

Update #26 Executive Summary
Silver, for what it's worth, is still a big "monetary" metal; though it is true, much more silver is gobbled up in industry compared to gold. There are about 31 billion ounces of non-industrial silver floating around the world (most of it in jewelry and silverware form) that is valued in today's prices at nearly $1 trillion. Bitcoin bigger.
State of the Print: $27.0 trillion.
If we add up the Big Four central banks already mentioned above (again, Bitcoin being larger than the Bank of England's monetary base), as well as the next 46 central banks, we get to a total, USD equivalent value of $27.0 trillion in base money across the world.
If we consider $27.0 trillion as the Big Boss of central bank money, then Bitcoin at $1.25 trillion network value (September, quarter-end figure!) indeed has some way to go. But as we can see from the last month leading up to this publishing, that can change quickly. We have just surpassed $100 thousand per bitcoin, which brings the network value to $2 trillion. We can also imagine how the Pareto distribution occurs even in money, if Bitcoin after only 15 years is already larger than every central bank money in the world except for four of them. Wild to ponder.
Supply inflation: 12.7% per year.
It is also true that for two years they have been trying to "normalize" their balance sheets after the 2020-22 Covid madness, stimulus, and money printing. Of course, they have been trying all along to normalize since the 2008 global finance crisis (GFC), but I digress.
When I first started my website, I vowed never to use such a non-corporeal thing as CPI to discuss how much things cost. A "general increase in the level of consumer prices," or CPI, as measured by planning boards around the world, is not a real thing. It may be calculated by people with the best of intentions, but it has been manipulated and volumes have been written about it. I don't use it.
I have always defined inflation as the classical economists did: Inflation is an increase in the "stock" of money. If we know the all-time stock of euros printed by the European Central Bank now, and we know the all-time stock of euros printed by the ECB 12 months ago, then it is very easy to calculate the annual inflation of the euro. Not only is it easy, but it is real. It is corporeal. Watch what they do, not what they say.
I have been tracking this since 2018, and though this figure has evolved slightly (mostly increasing from massive COVID stimulus of 2020-2021, the high-signal, important to remember figure of all-time compound annual growth (CAGR) of the global base money supply since 1969 is 12.7%. That is 12.7% compounded, per year. It is a doubling time of 5.8 years.

Growth rate of the monetary base
It is highly valuable to understand that, ceteris paribus, if the demand for cash balances does not keep up with this monetary supply increase, then prices will rise. This erodes purchasing power. I do not attempt to measure the demand for cash balances in this research. Regardless, 12.7% is a useful figure to understand.
Let's compare.
For the rest of this report, I want to do something different and simply spend some time looking at the compound annual growth rates of various corporeal things around the world, in order that we can compare those to the growth of the fiat monetary base, and Bitcoin.
Remember, most things in the financial and economic world grow exponentially. This simply means that they grow constantly. The financial term here is compound growth, or compound interest. This rate of growth can indeed change year to year (interest rates can go up, or down), but over the years we can observe a strong trend, and that is what I want to summarize here for you.
Population.
The world has grown exponentially at 1.7% per year over the last 75 years. However, despite all the overpopulation myths you've probably heard, this rate of growth is actually falling, well below trend, and we only grow at 0.9% per year at the moment.

GDP.
The United States has grown its economy at 5.2% compounded per year since the founding of the republic. We are at the higher end of this trend right now, $28.8 trillion output per year, growing at 5.3% per year. As this is exponential growth, if I put it on log scale, it will become a straight line.

Stocks.
Stocks grow exponentially as well, don't let anyone tell you otherwise. The growth rate is 7.3% per year for the S&P 500, the main US index that tracks more than 80% of total market caps. Showing this one on linear scale on the left-hand axis, just so you can see how it typically scales.

Stocks. With Dividends.
If you reinvest those dividends into the same stock market, you'll earn more. The all-time compound annual growth increases by 2% higher to 9.3% per year for the S&P. Also displaying this one on linear scale.

Bonds.
Bonds are supposedly safer than stocks (bondholders get paid back first), and more cash flowing. If you look at the longest running bond index in the US, it grows at 7.1% per year, compounded. Notice how, in a rising interest rate environment (which we are at the moment), bonds will suffer, if viewing the price (or index, as in this case, using the Bloomberg Aggregate Bond Index). This has kept the bond market returns at the lower end of the range, since the global financial crisis in 2008.

Base Money.
As we've discussed, base money grows across the world at a weighted average of 12.7% compounded per year. However, this trendline analysis looks at it differently than my headline figure. It simply looks at the USD value of the global monetary base (again, $27.0 trillion), and draws an exponential trendline on that USD equivalent growth for 50+ years. In other words, this is going to be after all currency fluctuations have played themselves out.
Do you think the growth rate here will be higher or lower? Actually, it is lower, at 10.3% per year. But there is a big asterisk here, in that the series is not consistent across time. I typically just display it for visual effect. As more and more central bank balance sheets were added to this analysis across the 1970s and 1980s, it is not technically rigorous to run an exponential trendline analysis across these totals. Better to use my headline figure of 12.7% CAGR. Again, the 12.7% figure is rigorously calculated, measuring the native growth rate of each monetary base across every month recorded, then weighting that across every other monetary base in that monthly basket, then averaging all months for an all-time figure, and then raising that all-time monthly weighted average to the power of 12.
What is interesting, however, is that the 10.3% derived CAGR using the exponential regression below is lower than my native headline figure of 12.7% . Remember, the 10.3% exponential regression does not account for all the new money supplies coming in during the 1970s and 1980s (which should push the regression slope higher as new supplies are added), and it is after all currency fluctuations have been factored in, to arrive at a USD equivalent. The lower 10.3% CAGR can only mean that central bank balance sheets actually lose value against the US-dollar faster than they can print!

Note, I am showing this one in linear scale. The trendline projects out to $83 trillion by December 2033. The current global supply of base money ($27 trillion) is about $6.5 trillion less than the current trendline ($33.5 trillion).
Silver.
This is total ounces ever mined. They trend upward at 1.4% per year.

Gold.
This is total ounces ever mined. Gold trends upward at 1.7% per year. Faster than silver. Surprised? Notice the R-squared (goodness of fit) for both silver and gold production increase.

Bitcoin.
Bitcoins grow according to a basic logarithmic curve. Trying to draw percentiles is pointless here, and even measuring a trendline is relatively pointless, as everyone knows the bitcoins prescribed into the future, per the protocol. Better to just quote the trailing 12-month growth figure, and it is 1.5% per year and falling, as of quarter end Sep-2024. Less than gold.

Silver price.
Since 1971 it's trended at 3.4% per year. Silver bug?

Gold price.
Since 1971 it's trended at 5.1% per year. Gold bug?

Bitcoin price.
Now, we have finally arrived at something that grows differently than exponential. As I've observed since 2018, Bitcoin grows according to a power trend. Did you notice that the prior exponential trends displayed themselves as straight lines on log scale? Well, with Bitcoin, the power trendline gradually falls across time, but the growth is still well larger than anything we've covered thus far.
Why? It's being adopted, of course.
Bitcoin's power trendline has grown 167% per year since Bitcoin Pizza Day in 2010. Note that this is something akin to a "Lifetime Achievement" figure, and it will continue to fall every day. Over the prior 12 months ending 30 September 2024, Bitcoin grew 134.6% over the year. Well higher now at $100k. The compound growth of the power trend today is 44% per year. By 2030 it will fall to "only" 36% per year.

Oh yes, and it is free (as in speech), open, and permissionless money.
To summarize.
That was a lot of data across a lot of charts. I've compiled it all in a helpful table here for you to review at any time. This is the monetary and major asset world at third quarter end, 2024:

Base money concluded
The following table gives you a complete summary of the fiat currencies, gold, silver, and Bitcoin figures used in this analysis, for this quarter. Please print it out if you like, it is meant to be a helpful, in-depth companion when fiat friends come asking.

Thank you for reading! If you enjoyed, please consider zapping, and you can also donate to my BTCPay on my website if you'd like to help keep this research going.
-
 @ 6f4d57a2:be4cc879
2024-12-10 13:32:05
@ 6f4d57a2:be4cc879
2024-12-10 13:32:05งาน คือ เงิน เงิน คือ งาน บันดาลสุข…เงินซื้อได้ทุกอย่างจริงหรือ ? เงินทำให้เรามีความสุขจริงหรือ ? มีเงินแล้วชีวิตจะดีขึ้นจริงหรือ ?
เงินซื้อเพื่อนได้ ! เงินซื้อญาติพี่น้องได้ ! เงินซื้อความรักได้ ! เงินซื้อความถูกต้องได้ ! เงินช่วยยื้อชีวิตได้ ! อำนาจแห่งเงินตรา !
เงินสำคัญสำหรับทุกคนจริงไหม ? ปัจจุบันตามสื่อต่างๆ ข่าวที่เผนแพร่ออกมาเราจะเห็นว่าบางคนมีเงินมากมาย ทรัพย์สินหลากหลาย ที่ดิน ทองคำ เครื่องประดับ ความมั่งคั่งที่มี อาหารการกินสมบูรณ์ พาหนะที่สวยหรู เดินทางสะดวกสบาย ผู้คนล้อมหน้าล้อมหลัง มีชื่อเสียง หลายคนซื้อสิ่งเหล่านี้มาด้วยเงิน เงินเท่านั้นที่ทำให้สิ่งต่างๆ ยังคงอยู่ ดังนั้นคนผู้นี้จึงมุ่งมั่นหาเงินต่อไป เพื่อสนองตอบต่อความต้องการของทรัพย์สินรอบตัว และผู้คนข้างกาย(ลาเฮาละวะกูวะตะอิลลาฮ์บิลลาฮ์)
อัลลอฮฺ ตรัสไว้ว่า
وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ
“และเจ้าอย่าหันแก้ม (ใบหน้า) ของเจ้าให้แก่ผู้คนอย่างยโส และอย่าเดินไปตามแผ่นดินอย่างไร้มารยาท
แท้จริง อัลลอฮฺมิทรงชอบทุกผู้หยิ่งจองหอง และผู้คุยโวโอ้อวด”
(ลุกมาน : 18)
สิ่งหนึ่งที่ซื้อไม่ได้เลย คือ “ความสุข ความสบายใจ” ความรักอย่างบริสุทธิ์ใจ และความพอดีในชีวิต เพื่อให้เกิดความพอเพียงในสิ่งที่มี ฉะนั้นจึงมีคนมากมายที่ต้องจบชีวิตตนเอง เพราะหาความสุขไม่ได้ “ความตาย” จึงเป็นจุดสุดท้ายเพื่อต้องการค้นพบทางออกจากวังวนของวัตถุนิยม บางคนทนทุกข์ทรมานกับทรัพย์สินที่มี กลัวว่าจะหมดไป กลัวว่าจะมีคนเอาไป กลัวว่าจะไม่พอใช้ โลภจนชีวิตทรมาน ความตายจึงมาพรากทุกสิ่งออกจากการยึดติด ความกังวลในทรัพย์สิน ความตระหนี่ถี่เหนียว จนตายอย่างอ้างว้าง ตายเพียงคนเดียว ความตายมาถึงที่นอนของเขา บ้านของเขา แม้ทรัพย์สินมากมาย แต่สุดท้าย ตายด้วยความอ้างว้างทุกราย (อินนาลิลลาฮ์ วะอินนาอิลัยฮิรอญีอูน)
อัลลอฮฺ ซุบฮานะฮูวะตะอาลา ได้ตรัสอีกว่า
“และหากเจ้าได้เห็นขณะที่มลาอิกะฮ์เอาวิญญาณของบรรดาผู้ปฏิเสธศรัทธาอยู่นั้น พวกเขาจะตีใบหน้าของพวกเขา และหลังของพวกเขา
และ (กล่าวว่า) พวกเจ้าจงลิ้มรสการลงโทษแห่งการเผาที่ลุกไหม้เสียเถิด”
(อัลอัมฟาล 8 : 50)
สิ่งที่หาซื้อไม่ได้ ในห้างหรู ? ในโชว์รูมแบรนเนม ? ในรถซุปเปอร์คาร์ ? ในร้านเครื่องประดับเพชร ? ไม่มีที่ไหนประกาศขาย ไม่มีที่ไหนแอบอ้างและการันตี นั่นคือ ‘ค ว า ม สุ ข’
ความสุขกาย – พอใจในสิ่งที่มี พอใจอาหารที่สะอาดทานได้ พอใจในสุขภาพร่างกายที่แข็งแรง พอใจในการดำเนินวิถีชีวิตในความถูกต้อง
ความสุขใจ – มีความรักต่อผู้อื่นด้วยการไม่หวังผลประโยชน์ หยิบยื่นในสิ่งที่ตนมีเพื่อช่วยเหลืออย่างไม่หวังผล แม้ไม่มีทรัพย์แต่สามารถให้ความร่วมมือในการสร้างสรรคืสิ่งดีงามเพื่อสังคม
ความสุขจากการพอ – โดยการใช้ความรู้ในการพัฒนาโลก และไม่ทำลายทรัพยากรธรรมชาติ ไม่ทำลายสิ่งแวดล้อม จากการบริโภคอย่างตระกละตระกราม การใช้สินค้าอุปโภคอย่างทิ้งขว้าง การสะสมสินค้าที่ไร้สาระเป็นเหตุแห่งการสิ้นเปลือง เหตุแห่งความโลภ จึงไม่รู้จัก ‘พ อ’ และ ‘เพียง’
ความสุข ไม่สามารถหาซื้อได้ แต่ต้องสร้างเองให้เกิดขึ้นเป็นรูปธรรม ไม่จำเป็นต้องใช้เงิน แต่จำเป็นอย่างยิ่งที่ต้องใช้ใจที่บริสุทธิ์ในทุกการกระทำ และต้องมีใจที่พอเพียง เพื่อให้ทุกคนได้อย่างเพียงพอ ความสุขไม่ได้สร้างง่าย แต่ไม่ยากเกินความสามารถของมนุษย์ถ้ารู้จักวิธี และวิถีการดำเนินไปหาความสุขได้นั้นมีแค่ทางเดียวเท่านั้น ไม่ต้องวกวน และซับซ้อน หาให้เจอแล้วคุณจะพบความสุข
อายะฮฺที่ 97 อัลลอฮฺ ซุบฮานะฮูวะตะอาลาตรัสว่า
مَنْ عَمِلَ صَالِحًا مِّن ذَكَرٍ أَوْ أُنثَىٰ وَهُوَ مُؤْمِنٌ فَلَنُحْيِيَنَّهُ حَيَاةً طَيِّبَةً ۖ
“ผู้ใดที่ปฏิบัติความดี ไม่ว่าชายหรือหญิง โดยที่เขาเป็นผู้ศรัทธา
แน่นอน เราจะให้เขามีชีวิตที่ดีงาม(ทั้งในโลกดุนยานี้และโลกอาคิเราะฮฺ)”
มนุษย์มุ่งหาความสุข เพราะการกระตุ้นจากสื่อสาร ทีวี การได้ยินได้ฟังจากโซเชี่ยล การได้ดูจากวีดีโอ ที่ควบคุมโดยพวกวัตถุนิยมที่ปฏิเสธการศรัทธาในพระเจ้าของพวกเขา กระตุ้นให้คนแสวงหาเงิน เพื่อนำมาซื้อหนทางแห่งความสุข
พยายามฉายภาพความสุขด้วยการมีเงินซื้อสินค้าแบรนหรู…เพราะเป็นสินค้าที่พวกเขาผลิต และขายในราคาแพง
ใช้คำคมต่างๆ เพื่อหลอกล่อว่าความสุขต้องใช้เงิน กระตุ้นคำว่าเงิน คือความจำเป็นของชีวิตเพียงอย่างเดียว
ใช้บุคคล นักแสดง ดารา คนที่คิดว่ามีชื่อเสียง ฉายภาพแห่งความสุขจากการมีเงิน…ทั้งๆที่บางคน ฆ่าตัวตายเพราะไม่มีความสุข
พยายามใช้ผู้หญิงที่แก้ผ้าแล้วมีความสุข…โดยถอดความละอายออกจากพวกเธอ อย่างไร้ยางอาย
พยามยามใช้พวกสับสนทางเพศฉายภาพแห่งความสุข…ทั้งๆ ที่นั่นคือ ความสกปรกโสมมของสังคม
“อัลลอฮฺ ได้สาปแช่งผู้ชายที่ทำตัวเป็นหญิง และหญิงที่ทำตัวเป็นชาย”
(บันทึกโดย อิมาม อัลบุคอรีย์)
“ความละอาย เป็นส่วนหนึ่งของการศรัทธา ผู้ที่ศรัทธา คือชาวสวรรค์
ผู้ที่ไม่มีความละอายนั้น เป็นส่วนหนึ่งของคนที่ไร้ค่า และผู้ไร้ค่านั้น คือ ชาวนรก”
(บันทึกโดย อัตติรมิซีย์)
การไม่รู้เท่าทันในสื่อต่างๆ และกระแสออนไลน์ ของกลุ่มวัตถุนิยม พวกนี้เพียงต้องการให้มนุษย์เป็นทาส ทาสทางความคิด ทาสในการเลียนแบบ ทาสในการกิน ทาสในการแต่งกาย ทาสในการดำเนินชีวิต ถ้ากลุ่มทุนชี้ขวา คนส่วนมากก็ต้องไปทางขวา ถ้ากลุ่มทุนชี้ซ้ายคนส่วนมากก็ต้องไปทางซ้าย ถ้าเขาบอกว่าปีนี้สีแดง แฟชั่นก็ต้องสีแดง ถ้ากลุ่มทุนบอกว่าต้องใส่หมวก ปีนี้ก็ต้องใส่หมวกตามแฟชั่น พวกเขาใช้คำว่า ‘แ ฟ ชั่ น’ ในการควบคุมมนุษย์ หาเงินเพื่อสนองตอบแฟชั่น ตามกระแส ตามแฟชั่น คือการเป็นทาสอย่างเต็มใจ
﴿ وَإِذَا سَمِعُوا اللَّغْوَ أَعْرَضُوا عَنْهُ وَقَالُوا لَنَا أَعْمَالُنَا وَلَكُمْ أَعْمَالُكُمْ سَلَامٌ عَلَيْكُمْ لَا نَبْتَغِي الْجَاهِلِينَ ﴾ [القصص: 55]
“และเมื่อพวกเขาได้ยินเรื่องไร้สาระ พวกเขาก็ผินหลังออกห้างไปจากมัน และกล่าวว่า
“การงานของเราก็จะได้แก่เรา และการงานของพวกท่านก็จะได้แก่พวกท่าน ศานติแด่พวกท่าน เราจะไม่ขอร่วมกับพวกงมงาย”
เราต้องใช้เงิน แต่อย่าให้เงินมาใช้เรา อย่าให้เงินมาควบคุมเรา เงินสามารถซื้อสินค้า อุปโภค บริโภคได้ เพื่อการดำเนินชีวิต เพื่อที่เราจะได้มีพลังในการรับใช้พระเจ้า เพื่อที่เราจะได้มีแรงในการทำความดี
ความโลภ จึงสั่งใช้ให้มนุษย์แสวงหาเงิน ด้วยความอยากได้ อยากมี อยากเด่น อยากโอ้อวด เงินจึงสั่งใช้ให้มนุษย์ ตัดขาดจากศีลธรรม ตัดสิ้นซึ่งจรรยามารยาท ขาดความยับยั้งชั่งใจ ขาดสติสัมปชัญญะ ขาดความคิดดี เงินจึงหลอกล่อให้มนุษย์ทำความชั่วเพื่อที่จะได้เป็นผู้ครอบครองเงิน ด้วยการทำในสิ่งที่ชั่วให้กลายเป็นสิ่งที่ปกติ
จากหะดีษ กะฮฺบ บิน มาลิก อัลอันซอรีย์ รอฎิยัลลอฮูอันฮู จากท่านนบี ศ็อลลัลลอฮูอะลัยอิวะสัลลัม ได้กล่าวว่า
مَا ذِئْبَانِ جَائِعَانِ أُرْسِلَا فِي غَنَمٍ، بِأَفْسَدَ لَهَا مِنْ حِرْصِ الْمَرْءِ عَلَى الْمَالِ وَالشَّرَفِ لِدِينِهِ
“หมาป่าสองตัวที่หิวโหย ถูกส่งไปยังแกะ จะไม่สร้างความเสียหายได้ เท่ากับความโลภของคน ๆ หนึ่ง ในทรัพย์สิน และชื่อเสียง ที่จะมีต่อศาสนาของเขา”
(อิหม่ามอะหมัด)
การทำให้การพนัน กลายเป็นเรื่องที่ต้องสนับสนุนเพื่อเศรษฐกิจ เพื่อผู้คนจะได้มีเงิน ทั้งๆที่ มีคนได้ก็ต้องมีคนเสีย การพนันไม่ได้เพิ่มสิ่งใด นอกจากการแก่งแย่ง การเอาเปรียบซึ่งกันและกัน การอธรรมต่ออีกฝ่าย โดยที่คิดว่าเป็นเรื่องปกติ คนที่ชนะจากการพนัน ก็จะได้เงิน เงิน เงิน และเงินเท่านั้น แม้จะมีการฆ่ากัน ปล้นสดมภ์ แย่งชิง สังคมวุ่นวาย และล่มสลายในระดับครอบครัว ทำลายเยาวชนที่เป็นอนาคตของชาติ
อัลลอฮฺ ซุบฮานะฮูวะตะอาลาได้ตรัสไว้ในอัลกุรอาน ซูเราะฮฺอัลมาอิดะฮฺ อายะฮฺที่ 90 ว่า
يَا أَيُّهَا الَّذِيْنَ آمَنُوْا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالأَنْصَابُ وَالأَزْلاَمُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوْهُ لَعَلَّكُمْ تُفْلِحُوْنَ ،
“ผู้ศรัทธาทั้งหลาย แท้จริง สุรายาเมาเหล้าเบียร์ การพนัน การขันต่อ แท่นหินสำหรับเชือดสัตว์บูชายัญ
และ การเสี่ยงติ้วนั้น เป็น สิ่งสกปรกโสมม น่ารังเกียจที่มาจาก การงานของชัยฏอน …”
เงิน หลอกล่อให้ไร้ความละอาย ด้วยการยกโสเภณีให้เป็นอาชีพปกติ เพราะได้เงิน โดยไม่สนใจศีลธรรมในหลักการศาสนา ไม่ว่าจะศาสนาไหนก็แล้วแต่ เพราะการเป็นโสเภณีได้เงิน เพื่อหมุนเวียนในเศรษฐกิจ แม้สิ่งนี้คือจุดเริ่มต้นของโรคร้ายแรงต่างๆ และโรคที่จะไม่มีทางรักษาก็เกิดมาจากการสมสู่ที่สกปรก ไม่รับผิดชอบต่อสังคม โรคที่เป็นแล้วยังไม่มียารักษา และนี่คือสาเหตุแห่งการล่มสลายของครอบครัว การไม่รับผิดชอบของผู้ชาย เด็กไม่มีพ่อ เด็กกำพร้า เด็กถูกทอดทิ้ง ท้องไม่พร้อม การเลี้ยงดูในสภาพแวดล้อมที่เลวร้าย เยาวชนจะเติบโตขึ้นมามีคุณภาพได้อย่างไร
ในอัลกุรอานซูเราะฮฺอัลอิสรออ์ อายะฮฺที่ 32 อัลลอฮฺ ซุบฮานะฮูวะตะอาลาตรัสว่า
وَلَا تَقۡرَبُواْ ٱلزِّنَىٰٓۖ إِنَّهُۥ كَانَ فَٰحِشَةٗ وَسَآءَ سَبِيلٗا
“และพวกเจ้าอย่าได้เข้าใกล้การทำซินา(หรือการผิดประเวณี) แท้จริง มันเป็นสิ่งที่ชั่วช้าลามก และเป็นหนทางที่เลวร้าย”
เมื่อกิยามะฮฺใกล้เข้ามาส่วนหนึ่งจาก “สัญญาณเล็ก จะมีการผิดประเวณี (ซินา) มากมาย”
การค้าขายอย่างเอารัดเอาเปรียบ ขายให้ได้มากเพื่อมีเงินเยอะๆ โดยไม่สนใจว่าสินค้าที่ขายจะมีคุณภาพหรือไม่ ขายโดยที่ไม่สนใจว่าความต้องการจริงๆ ของผู้บริโภค ขายออกให้มากที่สุด และวัตถุดิบที่นำมาทำสินค้า ก็ต้องเอามาจากธรรมชาติ การขายสินค้าเกินความต้องการ คือการทำลายทรัพยากรธรรมชาติ และสิ่งแวดล้อม การบริโภคที่เกินเลย ทำลายระบบนิเวศ และวงจรชีวิตของธรรมชาติ
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا أَمْوَالَكُم بَيْنَكُم بِالْبَاطِلِ
“ผู้ศรัทธาทั้งหลาย! จงอย่ากินทรัพย์ของพวกเจ้า ในระหว่างพวกเจ้าโดยมิชอบ”
(อัน-นิสาอฺ 29)
เงิน ทำให้มนุษย์ไม่รู้จักพอ การมีอย่างไม่สิ้นสุด ความอยากได้อย่างไม่สิ้นสุด การแสวงหาอย่างไม่สิ้นสุด แม้เงินจะเป็นสาเหตุ แห่งความหายนะสำหรับคนที่เป็นทาสเงิน แต่สำหรับผู้ศรัทธาแล้ว เงิน สามารถสร้างสรรค์สิ่งที่ดีได้มากมาย แต่การจะหลุดจากทาสของเงิน จึงต้องเรียนรู้วิธี และปฏิบัติในวิถีแห่งการหลุดพ้นจากทาส มีแค่ทางเดียวเท่านั้นที่เราจะหลุดพ้นจากความเป็นทาสของเงิน และการเป็นทาสของมนุษย์ที่ดำเนินตามวิถีแห่งวัตถุนิยม นั่นคือเราต้องเรียนรู้จากตัวอย่างของบุคคลที่หลุดพ้นคือ ท่านนบีมุฮัมมัดศอลลัลลอฮูอลัยอิวะซัลลัม และการดำเนินชีวิตตามแบบฉบับของอัลอิสลาม ตามบทบัญญัติแห่งพระเจ้าของมนุษย์ เพื่อย้ายจากสถานะการเป็นทาสเงิน มาเป็นบ่าวที่ดีของ อัลลอฮ์ เมื่อนั้นคุณก็จะเป็นเจ้าของเงิน เป็นเจ้านายของเงิน
ท่านร่อซูลุลลอฮฺ ศ็อลลัลลอฮุอะลับฮิวะซัลลัมกล่าวว่า
النَّارُ أَوْلَى بِهِلَا يَرْبُو لَحْمٌ نَبَتَ مِنْ سُحْتٍ إِلَّا كَانَتْ
“ไม่มีเนื้อหนังมังสาใดที่เจริญเติบโตมาจากของที่ชั่วร้าย (ของที่หะรอม) นอกจาก นรก นั้นจะเป็นที่พำนักอันสาสมสำหรับเขา”
สุดท้าย สิ่งที่ทำลายมนุษย์ คือ เงิน …และเงินมีหน้าที่ในการคัดแยกให้ได้รับรู้ว่า ใครคือ ผู้ศรัทธา และใครคือสัตว์เดรัจฉานในคราบผู้ปฏิเสธศรัทธา ขอให้เราห่างไกลจากการเป็นทาสเงินด้วยเถิด….อามีน
اللَّهُمَّ إِنِّي أَعُوذُ بِكَ مِنْ قَلْبٍ لاَ يَخْشَعُ، ومِنْ دُعَاءٍ لاَ يُسْمَعُ، وَمِنْ نَفْسٍ لاَ تَشْبَعُ، وَمِنْ عِلْمٍ لاَ يَنْفَعُ، أَعُوذُ بِكَ مِنْ هَؤُلاَءِ الأَرْبَعِ
“โอ้องค์อภิบาลของฉัน ฉันขอความคุ้มครองจากพระองค์ ให้พ้นจากหัวใจที่ไม่นอบน้อม,
ดุอาอฺที่ไม่ถูกรับฟังและจากชีวิตที่ไม่รู้จักเอิบอิ่ม และจากความรู้ที่ไม่ยังประโยชน์
ฉันขอความคุ้มครองจากพระองค์ ให้พ้นลักษณะสี่ประการนี้ด้วยเถิด”
-
 @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
Directions
- The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
- Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 7c765d40:bd121d84
2024-12-09 21:37:45
@ 7c765d40:bd121d84
2024-12-09 21:37:45Back in college, starfish carried a negative connotation.
It was a sexual reference for a girl (or guy) who wasn't very good in bed.
"She just kinda laid there like a starfish."
Hahaha.
Happy Monday morning!
Over the weekend, I was reading a book titled "Exploiting Chaos."
There was a section in the book titled "Become Leaderless."
The book was written back in 2009, so there was no mention of bitcoin.
Bitcoin was only known by select few at this point.
But it perfectly describes the bitcoin network.
The bitcoin starfish.
"When you pull off the arms of a spider, it dies.
In contrast, if you rip off the arms of a starfish, you'll get five new starfish.
This happens because the starfish have decentralized nervous systems."
Like a starfish, the bitcoin network is decentralized, united by ideology and a common set of rules.
If you attack one arm, it grows back even stronger.
We have seen this time and time again with bitcoin.
And it HAD to be this way.
Yes, bitcoin is a revolutionary technology - maybe the biggest innovation the world has ever seen.
But if it wasn't decentralized, it could be stopped.
Bitcoin has some pretty significant competition - the central banking system.
And we've seen many great technologies squashed over the last century by powerful competition.
You cannot stop bitcoin.
There is no head to chop off.
This is why we are starting to see both corporate and nation state adoption.
They have tried attacking bitcoin for 16 years.
Negative media coverage.
Government threats.
Mining bans.
Exchange hacks.
New and "improved" competitors.
All have failed.
Not only did they fail, but they made bitcoin even stronger.
The size of network, bitcoin adoption, and the price in fiat terms have all continued to rise - despite these attacks.
And every person, company, or country that joins the bitcoin network will make it stronger.
Keep in mind bitcoin is just a protocol.
It just kinda lays there, and lets everyone else do the work.
Very starfish like.
PROJECT POTENTIAL - You can now find the expanded audio versions of these on the new podcast - Project Potential! I will be sharing the video versions here for the LITF members but you can also find it for free on Spotify and of course Fountain!
Here is the link to Episode 007 on Fountain: https://fountain.fm/episode/zSoJf6TLjkkMDhpokw4T
Have a great day everyone! And remember, the only thing more scarce than bitcoin is time!
Jor
-
 @ 8e56fde2:bb433b31
2024-12-09 21:04:00
@ 8e56fde2:bb433b31
2024-12-09 21:04:00So let us give a little bit on context first to get the WHOLE PICTURE.
We DoShitters are a trio of friends who one day decided we wanted to create some shit together. We are artists from different fields, and at the time two of us were struggling from creative block, so we decided to create the ultimate tool to COMBAT CREATIVE BLOCK. It would be an Oracle about the creative process and it would be inspired on the Hero's Journey and on our own journeys as artists; and hence "DoShit!" was born.

Once we knew what we wanted to do, and it started to have a shape, we decided to go through the hardship of self-producing and selling the cards by ourselves directly on our website ( www.doshitters.com ), which allowed us to keep control of the product at all times during production, and to have a direct relationship with our audience and buyers. Besides from guaranteeing we weren't left with the tiniest percentage of the sales pie. (At least in Spain, when you get a big publisher involved, you can forget getting even 10% of sales, and you lose a lot of the creative control of your project).
We invested a lot of our own resources in making sure "DoShit!" was a quality product and we were lucky enough to get the help of a generous patreon who enabled us to create what is now the DoShit! deck. <3

We did local presentations of the product in both Barcelona and Madrid, and got the deck to be sold in cool local stores, where we offered to do live readings and got to talk with people of all kinds about the Shit they wanted to do. Above all, DoShit! is an inspirational tool.
**And you must be asking yourself, "What does this have to do with Amazon?". ** Well, one of the problems of self-producing and having local fulfilment of the product is that shipping costs just couldn't compete with what the average consumer has gotten used to because of Amazon's mass scale free shipping. We were finding that, specially for our followers in the USA, it was impossible to assume shipping costs (which amounted to almost the same cost as the actual deck); but we didn't want to give up on the people who wanted to get inspired by DoShit! but lived on the other side of the world from us, so... WE DECIDED TO MAKE A DEAL WITH THE DEVIL, aka Amazon.
We knew that selling our product on Amazon was going to result in less revenue from the sales for us, but for us it was mostly about GETTING DoShit! TO A WAREHOUSE IN THE USA to be able to offer the deck with Free Shipping. And that's what we did. But we didn't know everything that would come as a result, (they don't really advertise the hidden costs and fees, or the speed at which they want you to expedite your sales) and we've been paying for that decision ever since.
In any case, they lured us in with a 3 months no cost promotion. You obviously assumed the cost of shipping it there, and they would take a cut from every sale that happened in their web, but we didn't have any way of knowing the cost that we would need to incur after those first three months. Another thing that wasn't advertised is that IF YOU ACTUALLY WANT YOUR PRODUCT TO BE FEATURED ANYWHERE, you need to be eligible as an A+ content seller, which also comes at a cost, and you need to pay additionally for sponsored ads; otherwise, your product is basically shut down in a black hole of zero discoverability except for people using the direct link.
The three months went by fast and then the invoices started coming, and the automatic charges on our account started to empty our independent seller bank account. As you can imagine, independent sellers like us sometimes require of TIME to be able to get the word out, to get people to buy your product... Besides, as artists with other projects on the pipeline, we couldn't really spend much time focusing on sales, nor did we want to. And in all honestly, we refused to give Amazon more money in sponsored ads and other programs to "gain visibility". We knew we had no way of competing with the big sellers on the platform, but we just thought, "AT LEAST IT'S AVAILABLE FOR THOSE WHO WANT TO BUY IT".
But then, out of the blue, we noticed our link on Amazon wasn't working. A friend tipped us off that it wasn't allowing any sales, it was listed as "currently unavailable", without us having done anything to trigger that change.
Suddenly we received an email from the giant informing us that our account had been set to inactive due to "dormancy", and that we needed to re-verify our identity. Not only that, but since we were in Europe, and they didn't have an address in the US they could send the decks back to, if we didn't get everything solved in time, THEY WERE GOING TO DESTROY THE DECKS THEY HAD IN THEIR WAREHOUSE because of their "Automated removal" policy.
This caught us while we were on holidays, away from our desktops, seller logins and such and we did everything the seller support requested from us as rapidly as possible. The nightmare of imagining our beautiful decks being destroyed really put us in a state of panic. We hoped everything would be solved after several support tickets stating our case, and pleading that they don't destroy the decks!
In the end, after several communications, they reactivated our listing which had apparently been set to inactive because of "stranded inventory" due to "excess inventory"; which is Amazon talk for: "YOU'RE NOT SELLING FAST ENOUGH".
After having gone through that experience we knew one thing for certain, WE WANTED TO BREAK FREE FROM AMAZON as soon as possible, but we still wanted to offer our DoShit! decks with Free Shipping for our customers; at least this Christmas...

So, best case scenario, all the DoShit! decks that are at Amazon get sold this Christmas campaign, with the jolly merry spirit, people and nostriches all around the world get excited about GIFTING INSPIRATION (and taking advantage of the Free Shipping) and help us to GET THE DECKS OUT OF AMAZON!
But we know this may be wishful thinking T.T , That is why we are also looking for independent shops in the USA that feel that DoShit! makes sense in their store, and would want to become the new home of the decks that remain in american soil after the Christmas campaign. So maybe somebody wants to become the "foster home" to these Oracles as they find their new home in 2025, so they decks can go from that abussive giant with high time preference, to a friendly purple shop with low time preference and no hidden tricks. After all, many people kickstart the year with their minds set on their New Year Resolutions, they want to DO SHIT! So Who Knows?
In any case, to all the small sellers out there, BEWARE OF MAKING THAT PACT WITH THE DEVIL.
We knew we had never wanted to get our Shit on Amazon, we knew the system was rigged again us, but still, we wanted to make it more affordable for people to get their hands on the deck. Artists struggle enough to have to additionally add exhorbitant shipping costs to acquire a creativity tool like "DoShit!".
And if you, like us, find yourself having to do that pact anyway, we hope our tale will at least help you navigate all the hidden traps that their system throws at you.
IF YOU WANT TO JOIN THE CREATIVE RESCUE MISSION TO FREE THE DECKS, please, support us as best you can, share our story, recommend our deck, but best of all GIFT THE "DoShit!" DECK THIS CHRISTMAS! <3
You can find it at its captor's site at https://a.co/d/hrKXEBF , or if you'd rather NOT BUY SHIT ON AMAZON, you can always buy it at the Plebeian Market with your Sats, and we'll get one out of Amazon on your account. (https://plebeian.market/p/f82c481a3ae2a284049631a50373f4b9262c0e0b80977a4de1a71fcc19c5635d/stall/c9744507a49cf647c5612204416b7e22bdab86fbaff85413cfbc41103a0d269a)
THANKS FOR CARING, This 2025, we wish you all to DO THE SHIT THAT MATTERS TO YOU!
DoShit! #JoinTheArtmy
-
 @ 81e5cb66:17c315fa
2024-12-09 18:51:55
@ 81e5cb66:17c315fa
2024-12-09 18:51:55The current debate about artificial intelligence has an interesting side effect: it ruthlessly reveals the shortcomings of our education system. The widespread fear of AI systems such as ChatGPT is often not based on their actual capabilities, but on the sobering realisation of how interchangeable many of our learned skills are.
For decades, our education system has trained people to solve predetermined tasks according to set patterns. We have learnt facts by heart, passed standardised tests and adhered to predefined processes. Today, AI can do precisely this type of work better, faster and with fewer errors. The panic this triggers is basically an admission: we have been trained to become ‘human machines’ instead of developing our unique human abilities.
The traditional education system, developed in the age of industrialisation, aimed to create a reliable workforce for standardised processes. Creativity, critical thinking and independent action were often undesirable. Pupils and students were not encouraged to ask questions or find alternative solutions. Instead, conformity was rewarded and deviation penalised.
AI now acts as a merciless mirror of this misguided development. It shows us that much of what we call ‘education’ was merely the training of routines. When an AI model can write a structured essay, solve a maths problem or produce a market analysis within seconds, it becomes clear that these skills alone no longer make us valuable for the labour market.
Paradoxically, this painful realisation could be the starting point for a long overdue education revolution. We need to abandon the illusion that memorising facts or following predetermined processes is enough. Instead, we need to focus on developing genuinely human skills:
- The ability to ask new questions instead of just giving known answers
- The ability to develop creative solutions to novel problems
- The ability to make ethical decisions and weigh up values
- The ability to genuinely empathise and build meaningful relationships
- The ability to understand complex relationships and think systemically
The ‘natural stupidity’ that AI exposes is not that of individual people, but that of a system that has reduced people to one-dimensional task fulfilers. The true intelligence of humans is not revealed in the competition with machines, but in the ability to use machines sensibly in order to develop human potential.
The fear of AI is therefore also an opportunity for self-reflection: What makes us truly human? What skills should we develop? How can we design an education system that supports people in realising their full potential instead of degrading them to programmable units?
The answer may lie in a fundamental rethink: away from teaching standardised skills and towards developing adaptive competencies. Away from the passive consumption of knowledge and towards the active creation of solutions. Away from fear of machines and towards self-confident use of technological tools.
AI could thus become the catalyst for a long overdue educational reform - not because it threatens us, but because it forces us to reflect on our true strengths and develop them in a targeted manner. The real revolution lies not in technology, but in a return to what makes us human.
-
 @ a10260a2:caa23e3e
2024-11-10 04:35:34
@ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for classified listings (NIP-99) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard.
In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW.
I took some screenshots to give you an idea of how things work.
The home page is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).
Clicking login allows signing in with a browser extension.
The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.
Existing blog posts (i.e. long form notes) are synced.
Same for product listings. There’s a nice interface to create new ones and preview them before publishing.
That’s all for now. As you can see, super slick stuff!
Bullish on Cypher.
So much so I had to support the project and buy a subdomain. 😎
https://bullish.cypher.space
originally posted at https://stacker.news/items/760592
-
 @ 35f3a26c:92ddf231
2024-11-09 17:10:57
@ 35f3a26c:92ddf231
2024-11-09 17:10:57"Files" by Google new feature
"Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so.
Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc...
How this could affect you?
Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged:
- [ ] Pictures of you and your children in the beach
- [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not
- [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites
The results:
- [ ] Your google account will be canceled
- [ ] You will be flagged as a criminal across the digital world
You think this is non sense? Think again: https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html
How to switch it off:
- Open files by Google
- Tap on Menu -> Settings
- Turn OFF Smart Search
But you can do more for your privacy and the security of your family
- Stop using google apps, if possible get rid off of Google OS and use Graphene OS
- Go to Settings -> Apps
- Search for Files by Google
- Unistall the app, if you can't disable it
- Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS
Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits
Recommendation:
I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc.
Note As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. .
Please leave your comments with your favorite FOSS Files app!
-
 @ a58a2663:87bb2918
2024-12-09 13:39:49
@ a58a2663:87bb2918
2024-12-09 13:39:49- Concluir com minha filha, até o fim de 2025, a leitura da tradução latina de Ursinho Pooh, isto é, Winnie Ille Pu, de Alexander Lenard (1910-1972), poeta, ensaísta e tradutor húngaro que viveu no Brasil. Que texto curioso! Estranho estímulo que me chegou para voltar a estudar latim a sério.

-
Importar mais livros pela Thrift Books e menos pela Loja do Diabo. Seu acervo é excepcional e o frete é mais barato. Às vezes, em menos de duas semanas já estou com o livro em mãos (e olha que resido no Maranhão).
-
Concluir e publicar meu livro Vida após as Universidades. Escrita & criação em velhos & novos contextos de risco, desenvolvimento de algumas ideias que insinuei em Contra a vida intelectual, no que diz respeito ao encerramento de um ciclo histórico de modos de fazer investigação erudita.
-
Rematar o terceiro e último módulo de Convivium - Seminário Permanente de Humanidades, "A Alegoria do Mundo: o Mago, o Filólogo e o Colonizador", embrião de um longo ensaio sobre o "projeto humanista" e as vias de saída da modernidade oferecidas pelo pensamento latino-americano. (As inscrições seguem abertas. Caso queira inscrever-se pagando em bitcoin, me mande um e-mail: camoensiii57@protonmail.com).
-
Defender no primeiro semestre minha tese de doutoramento sobre João Francisco Lisboa (1812-1863), o maior prosador brasileiro de meados do século XIX. Compreender seu Jornal de Tímon implica rever concepções há muitos estabelecidas sobre a formação da literatura brasileira.
-
Escrever pelo menos cinco ensaios de apresentação do pensamento de Vilém Flusser e do que pretendo realizar em FLUSSER_project. A ideia é divulgá-los em inglês e especialmente aqui pelo Nostr.
-
Ler TUDO de Ignacio Gómez de Liaño.
-
Não ceder à tentação de discutir com imbecil.
-
 @ 75869cfa:76819987
2024-12-09 04:34:17
@ 75869cfa:76819987
2024-12-09 04:34:17GM, Nostriches! The Nostr Review is a biweekly newsletter focused on nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics show over 230,000 daily trusted pubkey events, a 3.5% decrease from the previous period. New user numbers have been a significant increase, Profiles with LN addresses or bios have marked a nearly 100-fold growth, Public writing events surpassed 2,000,000, reflecting an 800% increase. More than 14 million events have been published, with posts leading in volume, totaling about 2 million. Total Zap activity reached over 9.7 million, marking a significant 50% decrease.
Additionally, 18 pull requests were submitted to the Nostr protocol, with 9 merged. A total of 44 Nostr projects were tracked, with 12 releasing product updates, and over 434 long-form articles were published, 30% focusing on Bitcoin and Nostr. During this period, 4 notable events took place, and 4 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events exceeded 230,000, representing a slight 3.5% decrease compared to the previous period (Nov 11-24). Daily activity peaked at 19519 events, with a low of approximately 16969.
In terms of new user numbers, there has been a significant increase. Profiles with LN addresses or bios have reached approximately 1,859,727, marking a nearly 100-fold growth compared to the previous two weeks. Public writing events surpassed 2,000,000, reflecting an 800% increase over the same period. The daily peak hit 304,317, exceeding the total for the previous two weeks combined.
Regarding event publishing, the total number of note events published has surpassed 14 million, marking a significant increase of approximately 27%. Posts continue to be the most dominant in volume, totaling about 2 million (a slight decrease of 5%). Reposts (353,266) and reactions (553,926) also saw a small decline, around 1%.
For zap activity, the total zap amount is approximately 9.7 million, showing a significant decrease of over 50% compared to the previous period.
In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/,wss://feeds.nostr.band/,wss://realy.nostr.band/,wss://realys.diggoo.com/,wss://realy.lumina.rocks/ Data source: https://stats.nostr.band/
NIPs
NIP-0A - Contact List v2 nostr:npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c is proposing that NIP-0A - Contact List v2 can prevent contact list clobbering issues.This method could be used for any other event kinds that have editable lists. He is not arguing for a contact list v2 actually, rather, the focus is on conflict-free replicated data types, in order to prevent conflicts. CRDTs aren't really necessary in practice if people always use the person's outbox relays and don't use two clients at the same time. However, many conflicts were observed early on.Contact lists are already very long for some people, and while we could compress some of this data, not by a huge amount given the printable character set nature of JSON.
Consistent “method” naming for NIP 47(NWC) Response Gudnessuche is proposing that consistent “method” naming for NIP 47(NWC) Response adds consistency to the event structure in (NWC).Currently, requests and responses have different keys to identify their method type, which may cause confusion or misunderstandings.This change aims to standardize the key names across all request and response events, making it easier for developers to understand and implement the protocol.
NIP-34: Git Remote Nostr URL format and helper spec DanConwayDev is proposing that add the Git Remote Nostr URL format which can be used as a normal git clone address when ngit is installed. This used by ngit and gitworkshop.dev, minus the usage of nip05 addresses which nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume is working on adding. It is also partially supported experimental WOP tools like lez's git-remote blossom and Guga implementation of git-remote-nostr. Add a wider git remote helper spec implemented by the git plugin bundled with 'ngit'. This is probably less useful for inclusion in the NIP but he is not sure where else to put it.
NIP-42 Extension: auth-by-payment nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is proposing that this Extension of NIP-42 allows relays to add an extra NUT-18 argument to AUTH messages, that gives the user the option to authorize by providing a cashu payment. This allows relay operators to monetize with pay-as-you-go connections without the need to keep track of subscriptions and/or whitelists.This would allow the user to use ephemeral pubkeys to sign this message as well, giving them more privacy.
Notable Projects
Amethyst v0.93.0 nostr:npub142gywvjkq0dv6nupggyn2euhx4nduwc7yz5f24ah9rpmunr2s39se3xrj0
New Features: * New Android Image/Video Picker * Adds support for pronouns on profile * Migrates Video uploads from NIP-94 to NIP-71 Video events * Migrates Picture uploads from NIP-94 to NIP-68 Picture events * Adds support for BUD-01, BUD-02, and BUD-03 * Adds support for NIP-22 Comments * Adds nip05 field to the hidden words filtering by nostr:npub1e2yuky03caw4ke3zy68lg0fz3r4gkt94hx4fjmlelacyljgyk79svn3eef * Adds support for q tags with addresses * Adds search.nos.today to bootstrapping relays for search * Adds DM and Search default buttons to the relay screens * Adds hidden words filter to search, hashtag and geotag feeds * Applies hidden words even to hashtags that were not included in the content of the event. * Adds support for saving reactions, zaps, translations user preferences on private outbox relays
UI Improvements: * Adds animations to the zap, reaction and boost popups by @Giovanni * Lighter chat bubbles * Date separators on chats * Adds unfollow to note dropdown * Improves (Show More) presence to only when it actually makes a difference. * Adds UI for when the location permission is rejected. * Improves error message for the signup page when the display name is blank * Adds extra padding for the zap setup screen * Pre-process search to avoid showing and hiding posts after hidden words where processed by the UI. * Rotate on full screen video if the device orientation is not locked by nostr:npub1a3tx8wcrt789skl6gg7rqwj4wey0j53eesr4z6asd4h4jwrd62jq0wkq4k Additionally, this update addresses 18 bug fixes, introduces 13 code improvements, and enhances performance by optimizing thread preloading. Additionally, a new cache system for reply levels when viewing threads has been implemented for a smoother experience.
Damus1.11 nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955 * Multi image uploads * A video player that actually works * Share sheet action * Seamless scroll * And more
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
For Mobile: * All-in-One Content Hub: Create notes, articles, videos, curations, and smart widgets all in one place. * New Media Servers: Added support for @nostr:npub18jnd0, Nostr check, and more. * Thread Timeline Enhancements: Smoother and clearer thread viewing. * Nip 44 Gift Messages: Now enabled by default. * App-Wide Improvements: Faster, smoother, better. * Full compatibility with NWC secrets created outside the Alby wallet is now possible. * Provide an option to scan invoice QR and pay it. * Bug Fixes: Notifications, wallets, and feeds are now more reliable.
For Web: * Upgraded Note Editor: GIFs, emojis, and real-time previews to enhance your creativity. * Enhanced Long-Form Content: A fresh design to make writing a joy. * Custom Media Uploaders: Support for more media options and servers. * Expanded Search: Find more notes, media, and users with ease. * Browsing Suggestions: Discover new notes, media, users, and more. * General Improvements: Smoother performance and optimizations. * Bug Fixes: Making things more seamless for you. Additionally, Hot fixes for the YakiHonne Web 4.1.2
0xchat 1.4.3 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72 * Fixed the issue where inbox/outbox relays could not be added. * Fixed the issue where push notifications for voice calls had no sound. * Fixed the lag issue when loading private chat videos. * Fixed the issue where custom emoji reactions were not displayed.
Olas 0.1.5 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft Olas 0.1.5 for iOS has officially shipped to TestFlight * Reposts * Zaps (via Nostr Wallet Connect for now) * Swipe-to-zap * Performance improvements
Nos 1.0.3 nostr:npub1pu3vqm4vzqpxsnhuc684dp2qaq6z69sf65yte4p39spcucv5lzmqswtfch Nos 1.0.3 is now on TestFlight for all our beta testers and waiting on Apple’s for review for our App Store users in Australia and New Zealand. * Added support for user setting and displaying pronouns. * Added display of website URLs for user profiles. * Updated note header UI to make it more readable. * Fixed galleries expanding past the width of the screen when there are lots of links or images. * Fixed quoted note composer not expanding to fit mentions.
DEG Mods site update nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x * Add a Repost tagging system. * (Technical) Refactored code for the mods and mod page * Design tweaks for the "view more" part of a Mod post's page * Design tweaks for blog posts * Games added:S.T.A.L.K.E.R. 2: Heart of Chornobyl
WasabiWallet 2.3.1 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg This version is a stability release packed with bug fixes and preparatory changes for upcoming features: * Bug Fixes
Settings Layout * Tor upgraded to v13.5.9
Buy Anything Button DisabledKYCNOT.me nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
UI Improvements: * The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience. * Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive. * The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer: * A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. * processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt. Additionally, updates and upgrades have been implemented across Nostr Comments, Database, Scoring, Listings, API, and Pages.
notedeck nostr:npub1fjtdwclt9lspjy8huu3qklr7eklp5uq90u6yh8mec290pqxraccqlufnas * Update user relay-list via polling * Add user mute list sync via polling * Skip muted content * debug: add crate features which enable egui DebugOptions * ci: fix linux packages * Release v0.2.0 - Notedeck Alpha * fix linux packages again * ui: use proper response in wide-rendered note * ui: fix quote repost hitbox * ui: fix duplicate hitbox widget ids * anim: smoothly animate delete button from 0 size * nav: refactor title rendering for flexibility * column: switch to simplified strings for column headers * column: use simplified column string titles for now * column: switch to profile pictures in header * column: improve nav style * column: only show delete button when not navigating * column: reduce bounciness when navigating
Amber 3.0.1 nostr:npub1am3ermkr250dywukzqnaug64cred3x5jht6f3kdhfp3h0rgtjlpqecxrv7 * New design (still a work in progress) * Removed the push notification server * Open the permissions page with the correct account * Fix crash when signing in with ncryptsec * Fix icon size on notifications * Fix relay connection when changing the default relays * Option to setup a custom pin for the app * Button to copy your public key * Fix layout on Android < 15 * Fix multi event screen * Fetch profile data * Show relay message when event is rejected * Fix profile icon size * Don’t close app when using nostrconnect arcade * Better check for valid relays * Fix padding and scrolling * Support for secret when using nostrconnect * Fix empty relay notice,and more
Citrine 0.5.7 nostr:npub1hqlxlq57nvlq70ugmsmu9y5lmyc5k2lh5w7y85j7dgsr5u7zwavq5agspw * Fix rotation resetting the app state when downloading your notes * Fix timeout when downloading your notes when you have a lot of notes
Long-Form Content Eco
In the past two weeks, more than 434 long-form articles have been published, including over 84 articles on Bitcoin and more than 43 related to Nostr, accounting for 30% of the total content.
These articles about Nostr thoroughly explore its transformative role in decentralized social networking, highlighting its potential to revolutionize communication, provide censorship-resistant platforms, and promote the free flow of information. They delve into Nostr's technical aspects, including the integration of Nostr SDK across platforms, building high-performance relay networks, and innovative uses in micropayments with ecash wallets. The articles also examine the dynamic growth of the Nostr ecosystem, covering key statistics, community expansion, and strategies driving global projects. In addition to reflecting on Nostr's current achievements, they envision its future potential in areas like content creation and data sharing, while addressing challenges related to scalability and privacy.
The Bitcoin articles discuss its transformative role in the global financial ecosystem, emphasizing its potential as a store of value, a decentralized currency, and a driver of economic freedom. They explore Bitcoin's historical evolution, technical innovations, and its impact on broader financial systems, including comparisons with CBDCs and other cryptocurrencies. The articles highlight key developments, such as Bitcoin hitting significant price milestones, its integration into everyday financial practices, and the challenges posed by regulatory and market dynamics. Additionally, they delve into topics like mining sustainability, self-custody, the importance of education, and the cultural and ideological implications of Bitcoin in fostering decentralized trust and financial inclusion.
Thankyou, nostr:npub1zafcms4xya5ap9zr7xxr0jlrtrattwlesytn2s42030lzu0dwlzqpd26k5, nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j, nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6, nostr:npub1gkgyk28lurjuhyfjlxsga9mw6lc0c47c8pmcr65usre9d3qjcx6q9cyk5m, nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, nostr:npub1n3rmk5g03eej40rg2x83azxnml879lxxynxegfawl36e6qqrs8gqllmkh7, nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2, nostr:npub1ljm9zuj2k4d0lsgnpl2vh0rwtls7yrptpxu9js0v7y9hfplncnksn38rxz, nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7, nostr:npub1u8vk3aex0y8hk607zjy5636nkhzhm8g5l4v8qeveusxmkhvs7ajqgs8lr6, nostr:npub1xjwkhqsmd5qs0k4jrfu27x86j0g736xuklzdkpd5dnjd6y4j5kcs72w6e7, nostr:npub1wptqtktghpk3rvuerx54e9fjy0s57nvk5paggevh2t83ndpjgquq8zwcqe, nostr:npub1lgwcxfg2zlml6kse69md0h0kpvmdx9vrz37yx6qea5g4uly33qhqs3quhd, nostr:npub1dk8z5f8pkrn2746xuhfk347a0g6fsxh20wk492fh9h8lkha2efxqgeq55a, and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
-
BtrustGathering successfully took place in Kenya on December 4-5, 2024. This annual event brought the Btrust team together to collaborate and lay a solid foundation for the future of open-source Bitcoin development. Over two days, the team outlined their vision for 2025, discussed strategies for funding engineers and sustaining open-source projects, and shared updates on the Bitcoin Open Source Software (₿OSS) program to better support builders.
-
The Nigeria Bitcoin Conference was successfully held from December 5th to 7th, 2024, at PopHAUS in Lagos, Nigeria. The event brought together global and local participants from the Bitcoin industry, including exchange founders, developers, investors, policymakers, miners, artists, and more, for three days of in-depth discussions and learning. The conference featured a variety of activities, including keynote speeches, interactive discussions, educational workshops, and a three-day hackathon challenge focused on technical innovations in Bitcoin Core and the Lightning Network.
-
The Bitcoin Africa Story Meetup successfully took place on Saturday, December 7, 2024, in Lagos, Nigeria. The event offered an engaging platform to explore Bitcoin's role in Africa and foster discussions and interactions among participants. nostr:npub17hkxr0chnut66nn28rwwqmv6sqazjy24t24zwv4ppfrlhwjhr9cs49h2la
-
Btrust Developer Day took place on Sunday, December 8, 2024, in Nairobi, Kenya, as part of the Africa Bitcoin Conference (ABC 2024). This event provided a platform for African developers to explore Bitcoin technology, learn from industry leaders, and collaborate on projects. It featured lightning talks, panel discussions, hands-on workshops, project showcases, and networking opportunities, making it a valuable experience for Bitcoin developers, open-source developers, technologists, and Bitcoin enthusiasts.
Here are the upcoming Nostr events in November that you might want to check out.
-
The Africa Bitcoin Conference 2024 will take place from December 9 to 11, 2024, in Nairobi, Kenya, featuring key programs such as Btrust Developer Day, TBD Hackathon, ABC Social Impact Award, Afro Bitcoin Fellowship, and Africa Bitcoin Day. The event will host nearly 70 distinguished speakers, including nostr:npub1ju2sw9unanr94p5wama3ydv90hcke34wcnmnxedummspaayz55qswlya32, nostr:npub16hssgmdhw9e9j6z8na45lzz4grdsfjqlp5hf8dtcqnp0glseeu3seecguf, nostr:npub1m7uxdt50d2jw35q79zlszlsvy79t7dpdxptz6rfsrsamra7l8ttsq752yl, nostr:npub1gaxapm9t9damh6q2lpc04ptcyeh0ysfdfzzs997agu3ae80ftrns7t985l, focusing on topics such as Bitcoin adoption, regulation, innovation, and security. This conference offers attendees valuable opportunities for in-depth discussions and knowledge sharing.
-
The Dadas Bitcoin Workshop will be held on Tuesday, December 10, 2024. This event is open to everyone and invites several changemakers who are driving innovation in the Bitcoin ecosystem, including nostr:npub1urhnkns9rt4c9mk6t9xctjkzmlkawxkdpzjnxdxhx82mqm7hfpuq0j7ue, nostr:npub1z5umqa38xfv94y3fpver2khw2qar2v54jetl24939j4f0yyhggdqrh5lwd, among others. The workshop will feature guest speakers sharing how Bitcoin has transformed their lives and careers. The event promises major surprises, along with gifts and rewards, and will foster vibrant discussions and connections that will have a lasting impact on participants.
-
Bitcoin Layer 2's vs Bitcoin Sidechains will take place on December 10, 2024, at 7 PM CAT, hosted by Rootstock on X Space. This online discussion, featuring guests such as nostr:npub1c8cp58lhn4vte3q2fejp7luqczx7u0njk5h0p0hry3atflk7g2hqc7xzqk and others, will delve into the differences between Bitcoin Layer 2 solutions and sidechains, highlighting their applications in smart contracts and DeFi.
-
The 5th Bitcoin Educators Unconference will be held on April 10, 2025, in Nashville, Tennessee. This event is specifically designed for educators, meetup organizers, community leaders, and grassroots experts, aiming to provide a platform for Bitcoin educators to collaborate and share insights. Participants will have the opportunity to exchange experiences, discuss best practices in Bitcoin education, and help drive the adoption and application of Bitcoin.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
-
 @ a367f9eb:0633efea
2024-11-05 08:48:41
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Originally published on the website of the Consumer Choice Center.
-
 @ 41fa852b:af7b7706
2024-12-08 16:53:33
@ 41fa852b:af7b7706
2024-12-08 16:53:33"I wish I bought less bitcoin" --Nobody Ever
Yes I know it's 100,000 USD, not GBP!
But it's a big round number and I'm used to looking at the price in dollars.
I thought as a way to celebrate we might have a little fun competition. The first person to crack the cipher below and reply to this email (you need to be subscribed to have received the email) with the decoded message will win 10,000 sats!
uwnafhd nx sjhjxxfwd ktw fs tujs xthnjyd ns ymj jqjhywtsnh flj uwnafhd nx sty xjhwjhd f uwnafyj rfyyjw nx xtrjymnsl tsj itjxsy bfsy ymj bmtqj btwqi yt pstb gzy f xjhwjy rfyyjw nx xtrjymnsl tsj itjxsy bfsy fsdgtid yt pstb uwnafhd nx ymj utbjw yt xjqjhynajqd wjajfq tsjxjqk yt ymj btwqi
If enough of you enjoy it, we'll do it again.
Good luck, and let's check out what's on this week.
If you've enjoyed the newsletter and find it valuable to you and the UK Bitcoin community, please consider donating some sats here.
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Dundee Bitcoin: Join them on the 2nd Monday of every month from 5:30 to 8:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday, 9th December.
-
Glasgow Bitcoin: Meeting this month at Committee Room No. 9, G1 1JQ on Wednesday 11th at 18:00.
-
Bitcoin Beach Bournemouth: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 12th.
-
Limerick Bitcoiners: Back with another meetup after a break. Meeting at 20:00 on the 13th. DM them on Twitter/X using the link to get info on the location.
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit.
-
Kent Bitcoin: These guys will be at The Muggleton Inn on Sunday 15th at 12:00. The Muggleton Inn, 8--9 High Street, Maidstone, ME14 1HJ.
-
Northants Bitcoin Walk: As you'll see below in the 'new businesses' section, Northamptonshire has a new bitcoin-accepting cafe. This month the Northants Walk will start at the Ark Cafe at 11:00, with a walk along the River Nene and back to the cafe for refreshments afterwards. Let's pray for some good weather.
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on December 15th, 11:00 at Procopio's Pantry. They'll then be moving on to Vespers Bar, IP33 3PH, at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin.
New Businesses Accepting Bitcoin
- The Ark Cafe - Northampton: An amazing custom-made floating cafe in Northampton. A vegan cafe at weekends, Saturday 10:00 - 15:00 and Sunday 11:00 - 15:00 and available for event hire for parties, conferences, weddings etc. The main hall can accommodate up to 45 guests for a sit-down meal or up to 65 for a more informal get-together. Contact them on Twitter/X for more info.
Upcoming Special Events
This event isn't happening this week, but it's important to add to your calendar now as tickets are selling fast.
- Bitcoin Surrey & Berkshire Bitcoiners: A joint Christmas Dinner and 100k Party on Tuesday, 17th December, at Yiayias at The Fox (GU10 3PH). Dinner starts at 19:30, featuring award-winning Greek cuisine and the option of a Festive Meze or a Traditional Christmas menu. Kirit Magic will perform exclusive Bitcoin-themed close-up magic at 18:00. Tickets are £35 per person, with a £15 deposit required by 10th December via the Lightning Network. The venue accepts Bitcoin for drinks and dinner balances, so bring your Lightning wallet. Free parking is available, and kids are welcome.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 1c19eb1a:e22fb0bc
2024-12-08 05:50:50
@ 1c19eb1a:e22fb0bc
2024-12-08 05:50:50I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, Zapstore, or by downloading it directly from Primal's GitHub. This review is current as of Primal Android version 2.0.21.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 3.8 / 5
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 1 / 5
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ fd208ee8:0fd927c1
2024-11-03 21:51:39
@ fd208ee8:0fd927c1
2024-11-03 21:51:39All memed out
It finally happened. I think it was October 25th, at circa 18:45 in the evening. I was doomscrolling my Nostr feed, and kept seeing the same Bitcoin memes repeated over and over, by different people. They weren't even reposts, they were copy-pasted versions of the same image. A very funny image. Well, it was very funny last year... and the year before that... and probably the year before that, when it appeared on a different network.
Because it's all just reposts, copy-pastes and rehashes of the Best of Bitcoin Twitter, just like the tiresome influencers, with their groupies and their Episode 498 of Let's all eat a large chunk of lightly-burnt dead animal and count our stacks before jetting off to talk about how to save the poors by getting them to buy individual satoshis with money they don't have.

I'm the poors your looking for
It's all so tiresome. It has little bearing on the real world I see around me, where most people are thinking all day about 99 problems and Bitcoin ain't one.

Which is, of course, what the Bitcoin influencers would have you believe, is the reason that they're poor. What in the world could be more important, than thinking about Bitcoin? Why do these people not get with the program? Don't they know, that we are trying to save them?

Why are they worrying about OtherProblems? Don't they know that all OtherProblems can be fixed with Bitcoin? Really, if you just go back far enough, in any current, situational problem, you will discover that there was some slight, negative shift to the history record that involved soft money. It's the financial version of the Butterfly Effect.

That's why #BitcoinFixesThis. Bitcoin fixes everything, if you just think about it, for long enough.
The same way that we all actually come out of Africa, supposedly, if you go back enough generations. So, coming out of Africa, now, as a Real Life Person in The Present is supposed to have no significance. What does someone from Cameroon know about Africa, that someone from Alaska doesn't? Both people come out of Africa, if you just think about it, for long enough.

And maybe that really is true. Maybe Bitcoin will eventually end all vice and crimes, save the planet, and we will all just hold hands and sing kumbaya all day, while waiting for the Singularity to upload us to Satoshi.
Bitcoin envelope budgeting
Or maybe it's not. Maybe it's just a really hard, digital money that incentivizes savings, functions as a reliable measure, and makes micropayments possible on a global scale. Those really are things that will help the poors, including myself. I can see it, already, when trying to organize pre-paid meetups or figure out what to do with our household's meager savings, when the stock market is looking particularly bubblicious.

But this is what I would consider Boring Bitcoin. Bitcoin home economics. Penny-pinching Bitcoin. Bitcoin for homemakers. How to use the Bitcoin envelope budgeting system to beat inflation by a margin of 13%.
The actual use of Bitcoin as money, rather than as a mere investment gamble or hype machine. That's the part of Bitcoin that nobody seems to really talk about because it's incredibly practical, dull, and useful, and it can only be tested by -- Oh, the horror! -- actually spending Bitcoin.
But... perhaps I will begin talking about it. Perhaps those of us, Bitcoiners, who are having fun staying poor, while stacking sats, should speak up a bit more. Perhaps the boring stuff is actually the interesting stuff. Perhaps there is more to say about Bitcoin, than can fit into a meme.
-
 @ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29
@ 09fbf8f3:fa3d60f0
2024-11-02 08:00:29> ### 第三方API合集:
免责申明:
在此推荐的 OpenAI API Key 由第三方代理商提供,所以我们不对 API Key 的 有效性 和 安全性 负责,请你自行承担购买和使用 API Key 的风险。
| 服务商 | 特性说明 | Proxy 代理地址 | 链接 | | --- | --- | --- | --- | | AiHubMix | 使用 OpenAI 企业接口,全站模型价格为官方 86 折(含 GPT-4 )| https://aihubmix.com/v1 | 官网 | | OpenAI-HK | OpenAI的API官方计费模式为,按每次API请求内容和返回内容tokens长度来定价。每个模型具有不同的计价方式,以每1,000个tokens消耗为单位定价。其中1,000个tokens约为750个英文单词(约400汉字)| https://api.openai-hk.com/ | 官网 | | CloseAI | CloseAI是国内规模最大的商用级OpenAI代理平台,也是国内第一家专业OpenAI中转服务,定位于企业级商用需求,面向企业客户的线上服务提供高质量稳定的官方OpenAI API 中转代理,是百余家企业和多家科研机构的专用合作平台。 | https://api.openai-proxy.org | 官网 | | OpenAI-SB | 需要配合Telegram 获取api key | https://api.openai-sb.com | 官网 |
持续更新。。。
推广:
访问不了openai,去
低调云购买VPN。官网:https://didiaocloud.xyz
邀请码:
w9AjVJit价格低至1元。



















