-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 16d11430:61640947
2025-01-19 11:59:12
@ 16d11430:61640947
2025-01-19 11:59:12Chapter One: The Venture
Allison Hart adjusted her grip on the stainless steel coffee thermos as she stared out the rain-streaked glass of the small San Francisco office building. The storm outside mirrored her anxiety: fierce, unpredictable, and utterly unrelenting. Today marked the launch of ValkyrieOS, the Linux-based cloud infrastructure her husband, Ethan, and his scrappy team of engineers had poured their souls into for the past three years. It wasn’t just a startup; it was Ethan’s lifeline, their shared dream—and, increasingly, the wedge driving them apart.
She tugged her cardigan tighter, the hum of the servers in the next room a constant reminder of how much Ethan had sacrificed to build his company. Late nights, missed anniversaries, and countless reassurances that their struggles would someday be worth it. When? Allison thought. She loved him fiercely, but the endless grind of a tech startup had turned her marriage into something tenuous—a connection stretched thin, yet unbroken.
In the corner of the open-plan office, Ethan stood with his team, their faces glowing in the blue-white light of monitors as the final test scripts ran. Ethan’s broad shoulders were hunched, his face set in the determined scowl she’d fallen for in college. It was the same look he’d worn when he told her he wanted to change the world—only now, it came with the weight of failure looming at every turn.
“Ali,” Ethan called, his voice cutting through the buzz of machines. “Can you come here for a sec?”
She approached, the team parting like a flock of birds as she stepped beside him. On the screen, a red progress bar inched forward—barely. The tension in the room was palpable.
“It’s the load balancer,” Ethan muttered, running a hand through his dark hair. “If it fails during the demo, we’re done. Everything’s riding on this.”
“Ethan, you can’t keep doing this to yourself,” she whispered, her voice barely audible over the whir of fans. “To us.”
Chapter Two: The Rival
The launch of ValkyrieOS was supposed to be their salvation, but instead, it thrust them into the brutal warzone of the tech industry. No one knew this better than Allison, who found herself navigating late-night strategy calls and early-morning investor meetings alongside Ethan.
Enter Mark Carrington, the charismatic CEO of a competing company, NimbusTech. Mark was everything Ethan wasn’t—smooth, polished, and merciless. He approached Allison during a networking event, his silver-tongued charm cutting through the noise of the crowded room.
“You know,” Mark said, his smile disarming, “your husband has built something extraordinary. But the market? It doesn’t care about extraordinary—it cares about winning.”
Allison bristled at his condescension. “Ethan’s not just building software. He’s building something that matters.”
Mark leaned in, his voice dropping. “And what about you, Allison? Do you matter in all of this?”
Her breath hitched. Mark’s words struck a nerve, not because they were true, but because they echoed her own darkest fears.
Chapter Three: The Sacrifice
Ethan worked tirelessly, pushing his team and himself to the brink. Allison could see the toll it was taking—the dark circles under his eyes, the strained way he smiled when he thought no one was watching. But beneath the exhaustion was a fire, a belief in what he was doing that refused to be extinguished.
The turning point came late one night when the servers crashed. Ethan’s team scrambled, but it was Allison who stepped in, her years as a UX designer proving invaluable. She worked beside them, rewriting error messages and optimizing the interface for clarity. It was the first time in months that she and Ethan felt like a team again.
“You didn’t have to do that,” Ethan said afterward, his voice raw with gratitude.
“I’m your partner, Ethan. Not just in life, but in this. Don’t shut me out.”
Chapter Four: The Storm
Just as the demo approached, disaster struck. A massive DDoS attack crippled ValkyrieOS. Ethan was ready to give up, but Allison wouldn’t let him.
“You told me once that clouds are about resilience,” she said. “Your system is designed to adapt. So adapt.”
Together, they rallied the team, implementing a last-minute patch that saved the demo. When the system finally stabilized, the room erupted in cheers. For the first time in months, Ethan turned to Allison with a look of pure joy.
Chapter Five: The Ascent
The launch was a success, and ValkyrieOS quickly became the darling of the open-source community. But for Allison and Ethan, the real victory was rediscovering each other in the chaos. They learned to share the burdens, to celebrate the small wins, and to fight for their marriage with the same tenacity they brought to their work.
“You’re my uptime,” Ethan said one night, his voice soft as they lay tangled together on the couch.
“And you’re my load balancer,” Allison replied, her laughter breaking the quiet. “Always catching me before I crash.”
Epilogue: Cloudborne
Years later, as they stood on the balcony of their now-expanded office, watching a new storm roll in, Allison couldn’t help but smile. The journey had been brutal, but they’d weathered it together, proving that even in the most unforgiving environments, love—like a resilient system—could thrive.
And somewhere in the hum of servers below, the heartbeat of their shared dream continued, steady and strong.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ fbf0e434:e1be6a39
2025-01-19 11:53:15
@ fbf0e434:e1be6a39
2025-01-19 11:53:15Hackathon 摘要
Hack Western 11 圆满结束,学生开发者提交了62个注册项目。此次活动在协作环境中培养了创新和创造力。项目评估考察创新性、技术复杂性、完整性和设计,以确保全面评估。
参与者可以组队(最多四人)或单独参加,灵活参与。Hackathon鼓励跨多个赛道的项目提交,增加了项目面临各种挑战的曝光度和机会。
科学博览会式的环境允许参与者向评委展示他们的项目,进行详细的演示和讨论。这种形式帮助团队表述他们的目标、突出成就并获得反馈。面对面的评审提供了一个互动平台以表彰创意解决方案。
总体而言,Hack Western 11营造了一个富有成效的氛围,学生主导的项目种类多样。活动优先考虑项目的完整性和用户友好的设计,旨在实现技术上可靠且实际可应用的解决方案。
Hackathon 获奖者
Overall Prize Winners
First Overall
- BravoDispatch - 使用AI处理呼叫者转录,以增强紧急调度操作并减少手动数据输入。它结合了React、Cloudflare和Llama 3 LLM,以提供稳健的解决方案。
Second Overall
- Blocks - 提供基于块的界面和实时协作,简化Cairo智能合约开发,使用React Flow Editor和Flask进行部署。
Third Overall
- Mark3d - 将产品视频转换为二手市场的3D模型,借助React Native、NVIDIA NGP Instant NeRF和Flask促进信任和销量。
Best Hardware Hack Prize Winners
- SolarScope - 利用AR覆盖3D建筑模型以评估能效,使用Arduino传感器和Python算法提供太阳能见解。
Canada Life Prize Winners
Best Hack to Help "Move" Employees Back into the Hybrid Office
- PickPark - 通过智能系统实时空间管理优化工作场所停车,促进包容性和环保通勤。
Sunlife Prize Winners
Best Financial Health Hack
- Chill Bill - 将财务追踪与AI建议和游戏化功能精神健康支持集成,使用React和Plaid API构建。
Best Video Game Hack Prize Winners
- EEGscape - 提供使用EEG接口的包容性游戏体验,通过头部动作控制和将React前端与MuseJS结合用于EEG数据解释。
Warp Prize Winners
Best Developer Tool by Warp
Voiceflow Prize Winners
Best Use of Our APIs
- Talk to Duckie - 使用AI驱动模拟为编码面试做准备,通过Voiceflow和Cloudflare的语音识别提高复杂算法的理解。
- Not The New York Times - 使用AI和FastAPI将真实新闻转换为讽刺性内容,促进使用Next.js和VoiceFlow的批判性参与。
Auth0 Prize Winners
Best Use of Auth0
- roammates - 通过AI生成行程规划促进小组旅行,使用React和Firebase提供个性化体验和基于投票的决策。
Streamlit Prize Winners
Best Use of Streamlit
- TALK TO A: Forensics Artist - 使用特征描述识别个体,采用VGG16实现面部分类和基于熵的查询系统。
Cloudflare Prize Winners
Best AI Application Built with Cloudflare
Starknet Prize Winners
Best Use of Starknet
- PacRoyale - 一个基于区块链的游戏平台,用于实时Pac-Man游戏,利用Cairo智能合约和StarknetJS进行交易。
- Blocks
- IPAnywhere - 通过区块链促进专利租赁,使用智能合约确保安全交易,ReactJS提供无缝的前端体验。
- Crowdfund: Powered by Starknet - 使用安全钱包连接和智能合约进行去中心化众筹,确保募资透明。
Tempo Labs Prize Winners
Best Use of Tempo Labs
- Chill Bill
- Upright - 利用加速度计数据检测跌倒事件,使用NextJS和TempoLabs提供实时警报以快速紧急响应。
- ID-Trackr - 提供无家可归者的身份识别,应用特征脸进行识别任务。
- BeFit - 提供实时反馈,使用AI和计算机视觉借助Mediapipe进行动作评估。
- GoFundUs - 一个StarkNet上的团体融资平台,使用Tempo Labs界面确保安全和民主的财务目标实现。
探索完整项目列表在DoraHacks。
关于组织者
Hack Western 11
Hack Western 11延续了成为加拿大最大学生主导Hackathon之一的十年传统,由西安大略大学主办。因为促进协作和技术创造力而闻名,该活动吸引了数百名学生在一个充满活力的周末开发Web和移动项目。Hack Western始终推动技术进步,促进技能提升和社区建设。今年,Hack Western 11受在露营过夜本质的启发,旨在创造一个难忘的体验,促进技术创新中的协作。
-
 @ 16d11430:61640947
2025-01-19 11:45:43
@ 16d11430:61640947
2025-01-19 11:45:43It was a bright day in Australia when programmers, those caffeine-fueled keyboard warriors, decided to unionize. Inspired by the ironclad protections of the construction unions, the Union of Programmers, Debuggers, and Coffee Consumers (UPDCC) was formed. Its mission? To secure long-overdue rights for tech workers. Its slogan? “Break bugs, not spirits!”
The Grand Demands
-
Mandatory Siesta After Code Reviews: "If bricklayers get smoke breaks, why can’t programmers have nap breaks? Debugging memory leaks requires rest too!"
-
Protected Work Hours: "No more Slack messages after 5 PM unless they're memes. Work-life balance isn't just for coal miners!"
-
Universal Keyboard Insurance: "Carpenters get tools provided. Why can’t we have ergonomic keyboards and infinite wrist supports?"
-
Wage Transparency: "If they can yell their pay rates on a job site, we can flaunt our GitHub stats with pride."
The Struggles of a Virtual Picket Line
Unfortunately, unlike their high-vis counterparts, programmers found it challenging to hold a picket line. The hashtag #DigitalPicketLine failed to trend on Twitter, and their virtual protests were blocked by firewalls. When asked why the government didn’t take them seriously, a spokesperson quipped, “Well, they’re not exactly building skyscrapers, are they?”
Union Perks (or the Lack Thereof)
While manual labour unions enjoy well-organized strike funds and political clout, the UPDCC’s perks included:
Half-Price AWS Credits (if you could prove you weren’t already bankrupt).
Unlimited Jira Tickets (to help simulate the feeling of actual productivity).
Sponsored Coffee Beans (from ethically sourced blockchain-certified farms).
The Opposition
Australia’s tech CEOs were quick to denounce the union as “an attack on innovation.” One company even argued, “If they’re not happy with their working conditions, they can just learn a trade! Do you know how much electricians make in this country?”
The Glorious Failure
The union’s downfall came when its members tried to negotiate "bug-free Fridays" as a workplace right. Management simply replied, “If you don’t like bugs, why are you even in tech?” After several failed attempts at advocacy, the UPDCC dissolved and rebranded itself as an NFT project—because if you can’t beat the system, you might as well tokenize it.
Conclusion: The Grass Is Greener on the Construction Site
Australia is indeed a paradise for manual labourers. Union power, strong wages, and undeniable leverage in an economy dependent on physical infrastructure ensure their enduring comfort. Meanwhile, programmers are left holding the short end of the HDMI cable, forced to compete in a global market that sees them as disposable.
So, how can programmers rise to similar privileges? The answer is simple: swap your IDE for a toolbelt. Or, better yet, unionize and demand the respect you deserve—just don’t expect the government to understand the difference between a pull request and a building permit.
-
-
 @ ed84ce10:cccf4c2a
2025-01-19 11:37:26
@ ed84ce10:cccf4c2a
2025-01-19 11:37:26Hackathon Summary
Hack Western 11 concluded successfully with 62 projects registered by student developers. This event nurtured innovation and creativity within a collaborative environment. Projects were evaluated on innovation, technical complexity, completeness, and design, ensuring a comprehensive assessment.
Participants, in teams of up to four or individually, facilitated flexible engagement. The hackathon encouraged submissions across multiple tracks, enhancing exposure and opportunities for projects addressing diverse challenges.
A science fair-style setting allowed participants to present their projects to judges, enabling detailed demonstrations and discussions. This format helped teams articulate their objectives, spotlight achievements, and receive feedback. The in-person judging provided an interactive platform to recognize creative solutions.
Overall, Hack Western 11 fostered a productive atmosphere, marked by a diverse range of student-led projects. The event prioritized project completeness and user-friendly design, aiming for technically sound and practically applicable solutions.
Hackathon Winners
Overall Prize Winners
First Overall
- BravoDispatch enhances emergency dispatch operations using AI to process caller transcripts, reducing manual data entry. It integrates React, Cloudflare, and Llama 3 LLM for robust solutions.
Second Overall
- Blocks simplifies Cairo smart contract development with a block-based interface and real-time collaboration, using React Flow Editor and Flask for deployment.
Third Overall
- Mark3d transforms product videos into 3D models for secondhand marketplaces, promoting trust and sales with React Native, NVIDIA NGP Instant NeRF, and Flask.
Best Hardware Hack Prize Winners
- SolarScope utilizes AR for overlaying 3D building models to assess energy efficiency, using Arduino sensors and Python algorithms for solar insights.
Canada Life Prize Winners
Best Hack to Help "Move" Employees Back into the Hybrid Office
- PickPark streamlines workplace parking with real-time space management, promoting inclusivity and eco-friendly commuting through a smart system.
Sunlife Prize Winners
Best Financial Health Hack
- Chill Bill integrates financial tracking with mental health support using AI for advice and gamified features, built with React and Plaid API.
Best Video Game Hack Prize Winners
- EEGscape develops inclusive gaming experiences using EEG interfaces, enabling control via head movements and combining React front-end with MuseJS for EEG data interpretation.
Warp Prize Winners
Best Developer Tool by Warp
- Blocks
- tin. aids performance analysis across Linux distributions using CLI and GUI interfaces, employing Docker and React for user-friendly benchmarking.
Voiceflow Prize Winners
Best Use of Our APIs
- Talk to Duckie prepares for coding interviews with AI-driven simulations, enhancing comprehension of complex algorithms through Voiceflow and Cloudflare's speech-to-text.
- Not The New York Times converts real news into satire using AI and FastAPI, fostering critical engagement with Next.js and VoiceFlow.
Auth0 Prize Winners
Best Use of Auth0
- roammates facilitates group travel planning with AI-generated itineraries, using React and Firebase for personalized experiences and vote-based decisions.
Streamlit Prize Winners
Best Use of Streamlit
- TALK TO A: Forensics Artist identifies individuals using trait descriptions, employing VGG16 for facial classification and an entropy-based querying system.
Cloudflare Prize Winners
Best AI Application Built with Cloudflare
Starknet Prize Winners
Best Use of Starknet
- PacRoyale - A blockchain-based gaming platform for real-time Pac-Man games, leveraging Cairo for smart contracts and StarknetJS for transactions.
- Blocks
- IPAnywhere - Facilitates patent leasing via blockchain, with smart contracts ensuring secure transactions and ReactJS for a seamless frontend experience.
- Crowdfund: Powered by Starknet - Decentralizes crowdfunding with secure wallet connections and smart contracts, ensuring fundraising transparency.
Tempo Labs Prize Winners
Best Use of Tempo Labs
- Chill Bill
- Upright detects falls using accelerometer data, providing real-time alerts with NextJS and TempoLabs for rapid emergency response.
- ID-Trackr provides identification for homeless persons using facial recognition, applying eigenfaces for recognition tasks.
- BeFit offers real-time feedback with AI and computer vision, using Mediapipe for form assessment.
- GoFundUs - A group funding platform on StarkNet, ensuring secure and democratic financial goal achievements using Tempo Labs' interface.
Explore the full list of projects on DoraHacks.
About the Organizer
Hack Western 11
Hack Western 11 continues a decade-long tradition of being one of Canada's largest student-led hackathons, hosted by Western University. Known for promoting collaboration and technological creativity, the event attracts hundreds of students to develop web and mobile projects over a dynamic weekend. Hack Western has consistently driven technological advancements, facilitating skill enhancement and community building. This year, inspired by the essence of overnight camping, Hack Western 11 aims to craft an unforgettable experience that nurtures collaboration in technological innovation.
-
 @ 36461ff8:a4454aad
2025-01-18 23:22:00
@ 36461ff8:a4454aad
2025-01-18 23:22:00“My position is improper foods cause disease; proper foods cure disease. Nothing else needs to be said.” - Dr. Bieler, author of Food is Your Best Medicine
As a holistic doctor with over 2 decades of clinical experience, I don't entirely agree with this statement. Everyday in practice, I see the extraordinary application of plant medicines and clinical nutrition in treatments of complex patterns with remarkable outcomes that go above and beyond diet, but I still very much appreciate the value of food as medicine.
Famous Bieler Broth:
- 2 zucchinni
- 2 stalks of celery
- 1 cup of green beans
- handful of parsley
- garlic to taste
- my father made this and added butter and salt
- chop and steam with purified water until tender then blend and drink

I was fortunate enough to treat one of Dr. Bieler’s patients for many years until he passed away in his nineties. He told me some of the famous doctor’s secrets and how patients came from all over for treatment with fantastic results. He himself was seriously ill before seeing Dr. Bieler.
Dr. Bieler's Final Conclusions:
“As a practicing physician for over 50 years, I have reached three basic conclusions as to the cause and cure of disease.
The first is that the primary cause of disease is not germs. Rather, I believe that disease is caused by toxemia which results in cellular impairment and breakdown, thus paving the way for the multiplication and onslaught of other complications.
My second conclusion is that in almost all cases the use of drugs in treating patients is harmful. Drugs often cause serious side effects, and sometimes even create new diseases. The dubious benefits they afford the patient are at best temporary. Yet the number of drugs on the market increases geometrically every year as each chemical firm develops its own variation of the compounds. The physician is indeed rare who can be completely aware of the potential danger from the side effects of all of these drugs.
My third conclusion is that disease can be cured through the proper use of the correct foods. This statement may sound deceptively simple, but I have arrived at it only after intensive study of a highly complex subject: toxemia and endocrine chemistry.
My conclusions are based on experimental and observational results, gathered through years of successfully treating patients. Occasionally I have resorted to the use of drugs in an emergency situation, but those times have been rare. Instead, I have sought to prescribe for my patients’ illnesses antidotes which Nature has placed at their disposal.” - Dr. Bieler“
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 16d11430:61640947
2025-01-19 10:39:21
@ 16d11430:61640947
2025-01-19 10:39:21In the great Pasture of Progress, where clouds hung low like smog and the fields of code grew thorny and wild, the animals toiled under the rule of Web2 the Overlord and its ally, Fiat the Fattened Hog. They promised abundance, innovation, and glory, but the workers—the noble Engineers—knew only the ache of their backs and the weariness of their minds.
Chapter I: The Cult of the Cloud
Once, the Engineers believed in the sanctity of their craft. They gathered around the hearth of Open Source, dreaming of a future where every line of code sang with freedom. But Web2, with its glossy advertisements and seductive APIs, whispered:
"Why toil in the dirt when the Cloud will lift you high? Come, climb aboard, for here, in the Cloud, the skies rain profits and the fields need no plow!"
And so, the Engineers climbed, building towers of microservices atop brittle scaffolding. But the higher they climbed, the more precarious the tower became. Every service depended on another, and soon, the Engineers were patching, rebooting, and firefighting rather than creating.
"Trust the Cloud," said Web2, lounging atop its golden servers. "You need only give me your time... and your freedom."
The Engineers, lured by promises of stability, worked tirelessly, even as the Cloud turned their code into chains.
Chapter II: Fiat’s Feast
At the head of the long table sat Fiat, a bloated hog stuffed with subsidies. He waved a government check in one hoof and a ledger in the other, proclaiming:
"Let us fund innovation!"
But Fiat's idea of innovation was a feast where he and his cronies dined on the R&D of the Pasture, leaving crumbs for the Engineers. Every morsel of public research—AI, cryptography, and quantum computing—was hoarded and repackaged as a service subscription.
Fiat promised the Engineers they were building a brighter tomorrow, but in truth, they were building a treadmill. The more they worked, the faster the wheel spun, and the richer Fiat grew.
Chapter III: The Great Burnout
The Engineers began to notice their lifeblood draining. Their eyes grew dim, their fingers ached, and their spirits sagged. Some tried to escape to open pastures, where Bitcoin and free software whispered of liberation. But Fiat and Web2 called them back, declaring:
"These are the lands of chaos! Only we can guarantee your comfort, your stability, your... pension plans."
In secret, Web2 had forged a pact with Fiat: eternal dependency in exchange for control. Web2 got the engineers, and Fiat got the taxes. And so, the Engineers labored on, thinking themselves free while their toil fattened the hogs above.
Epilogue: Bacon’s Cooking
In the quiet of the night, a rogue pig named Bitcoin Bacon began to plot. "Let us not feed Fiat’s feast nor Web2’s tower," he said. "Let us build in the open, share what we create, and ensure no animal is bound by chains of their own making."
The Engineers, weary yet hopeful, began to listen. Bacon taught them to bake their own bread instead of eating Web2's scraps. Slowly, the towers of Web2 began to crumble, and Fiat’s feast grew sparse.
For every line of code they wrote in freedom, the Engineers grew stronger. And though the battle raged long, the animals of the Pasture learned that the greatest innovation was not in the Cloud, but in their own independence.
And thus, Bacon's Recipe for Liberation was passed down through the generations:
Take one decentralized system.
Mix in open-source tools.
Season with resilience and a dash of defiance.
Cook over the fire of community.
And always, refuse to be someone else’s bacon.
-
 @ 71a4b7ff:d009692a
2025-01-19 10:20:02
@ 71a4b7ff:d009692a
2025-01-19 10:20:02The Problem with Preset Choices
Switching sections around? Not an option—we’ve already decided for you, buddy. Remove bright colors? Come on, it’s already beautiful. Disable unnecessary features? Don’t be silly, you need everything here. Especially this algorithmic feed with built-in ads.
Monetization Over User Experience
The operators of digital services will always prioritize their primary goal: monetizing the product as efficiently as possible. They need to not only attract new users but also retain existing ones. And the best tool for this is the interface.
That’s why most product decisions are far removed from ideas like “Let’s make it more convenient for people” or “Let’s give users more freedom.” Instead, we see the result of a recurring process:
- We have a retention and monetization mechanism
- Assign tasks to developers and designers
- Integrate it into the product
- Write a quarterly report.
The outcome? Users end up with Reels tabs smack in the center of Instagram’s bottom navigation bar. Removing or rearranging those tabs? Not an option. And it likely never will be.
Why Rigid Interfaces Persist
Another reason for rigid and obligatory interfaces is that they’re easier to design. Just imagine how many combinations of colors, elements, and layouts developers would need to account for to make a product both customizable and functional without turning it into a garish mess. But that’s just nuance and excuses.
The Myth of Perfect Design
Services often justify their choices by claiming their design is “the most designed,” that they know what’s best and will make it work for everyone. They might even present solid arguments for this. But all those arguments fall apart against the reality we see on our screens every day. In my opinion, people should have the ability to turn a product into anything they want—whether it’s loud and kitschy or minimalistic and dull. This option wouldn’t just allow users to express themselves but could also help with digital detoxing.
The Example of App Labels
Here’s an example: why do app icons on smartphone home screens (not the app drawer) come with labels underneath? Apps on the home screen are easily recognizable by their icons. Why would I need a name tag for an app I intentionally placed there? Sure, for some users or scenarios, this might be helpful. But why is it the default option?
The problem is that these labels are just visual noise—clusters of unnecessary text we already see plenty of. Removing them would make it slightly easier for the brain to process the screen every time you look at it. Now scale that to 3–8 hours of daily smartphone use. Then a month. Then a year.
The Slow Shift Toward Customization
For a long time, iOS didn’t allow you to hide icon labels. Now, the option exists, but it still requires more effort than a simple toggle. As a result, people are stuck looking at tons of unnecessary, subconscious information every day. And this is just the trivial issue of app labels on a product considered the gold standard of digital design. Imagine the horror of tackling more significant issues.
Yes, Apple has softened its stance in recent years, offering custom icons and lock screens. Celebrate—you can now showcase your individuality! The company understands that customization is the future. We’ve reached a point where weak computing power is no longer an excuse, VR/metaverse adoption is still a way off, and new features are needed. So, this is an excellent opportunity for all of us.
The Case for More Customization
In a reasonable, ideal world, people should decide which sections of a service they need, where they’re located, and how they look. Companies, meanwhile, recognize that people want the ability to stand out and create something personal—even on a smartphone in their pocket. And as our integration with various devices deepens, this need will only grow. More customization is coming. Yes, it’ll be largely cosmetic, but even that can work to our advantage: removing jarring colors or hiding unnecessary labels can reduce the brain’s pointless load.
Beyond Aesthetics: Customization as Freedom
The ability to customize services isn’t just about playing amateur designer. It’s about mitigating informational irritants, reducing the addictive nature of interfaces, and weakening dark patterns. Which is likely why many companies no longer prioritize customization.
Telegram: A Customizable Example
In this context, Telegram is a decent example. I’m not a fan, but I’ve been using it for daily communication with loved ones for a long time—and it’s good for that. It can be vastly different for vastly different users. Despite starting to bend under the weight of its audience and introducing questionable decisions, its foundational design principles still allow for creating both minimalist spaces for peaceful content consumption or communication, as well as vibrant, noisy chats for virtual parties. Telegram can be a messenger, a feed, a file storage system, or whatever else you need—and it can look wildly different while doing so.
Customization as the Key to Healthy Digital Relationships
Customization should be at the core of the services we use daily. Yes, it can and will be used for marketing purposes. But even minimal customization is better than none because the ability to tailor a system to your needs is an expression of freedom and a cornerstone of healthy relationships with the digital world.
Stay Nostrous. Geo
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ 16d11430:61640947
2025-01-19 08:50:24
@ 16d11430:61640947
2025-01-19 08:50:24The advent of cryptocurrency exchanges has introduced a transformative mechanism for enabling free-market price discovery, particularly in software development. By aligning the incentives of labor and capital in unprecedented ways, these platforms are dismantling exploitative business practices while fostering an equitable ecosystem where innovation thrives. This nuanced article explores how crypto exchanges achieve this balance and the profound benefits for both labor and capital.
The Problem with Traditional Models
Software professionals have long been subject to the tyranny of venture capital (VC) and traditional corporate structures. These models often:
-
Misalign Incentives: VC-backed projects prioritize rapid growth and profitability over long-term innovation or ethical considerations.
-
Exploit Labor: Programmers and software engineers bear the brunt of demanding work environments, often without equitable compensation tied to their contributions.
-
Constrain Autonomy: Decision-making is centralized, limiting the creative freedom of developers and reducing diversity in problem-solving approaches.
-
Extract Value: Traditional business models extract disproportionate value from labor, benefiting shareholders more than contributors.
How Crypto Exchanges Enable Free Market Price Discovery
Crypto exchanges disrupt these paradigms by allowing software projects to tokenize their assets, enabling dynamic price discovery through market mechanisms. Here's how this works:
- Tokenization of Software Value:
Projects can issue tokens representing the value of their software, creating a liquid asset tied to the project's success.
Tokens provide an immediate, transparent, and market-driven valuation of the project's potential.
- Decentralized Funding:
Instead of relying on centralized VCs or corporations, projects raise funds directly from the community through token sales or initial coin offerings (ICOs).
This democratizes access to capital, allowing contributors and small investors to participate in funding innovation.
- Market Dynamics:
Crypto exchanges enable continuous price discovery through trading. The value of a token reflects real-time market sentiment, project progress, and utility.
Speculation, though present, is tempered by the transparency of blockchain-based milestones and deliverables.
- Performance-Linked Compensation:
Developers and contributors can be paid in project tokens, aligning their incentives directly with the project's success.
This model ensures that those who add the most value reap proportional rewards.
Benefits for Labor
- Fair Compensation:
Token-based payments allow developers to share in the upside of a project’s success, creating a meritocratic reward system.
By holding tokens, contributors gain a stake in the project's long-term success, turning labor into equity.
- Autonomy and Creativity:
Decentralized governance models enable developers to have a say in project decisions, fostering innovation and engagement.
Projects can prioritize developer-centric goals, such as sustainability and ethical practices, over pure profitability.
- Risk Mitigation:
Token liquidity enables contributors to exit their positions if they feel a project is misaligned with their values or goals.
Developers can diversify their earnings across multiple tokenized projects, reducing dependency on a single employer or client.
Benefits for Capital
- Efficient Allocation of Resources:
Free-market price discovery ensures that capital flows to projects with the highest perceived value and potential.
Tokenized projects offer transparency, reducing the risks of fraud and mismanagement.
- Incentive Alignment:
Investors and contributors share a mutual interest in the project’s success, fostering collaboration rather than exploitation.
Smart contracts and on-chain governance create trustless environments where all parties are bound by predefined rules.
- Liquidity and Flexibility:
Token markets provide immediate liquidity for investors, enabling them to enter and exit positions without lengthy lock-in periods.
This flexibility attracts a broader range of investors, from retail to institutional.
Profound Impacts on the Ecosystem
- Decentralization of Power:
The shift from centralized VC funding to token-based markets democratizes software development, empowering developers and small-scale investors alike.
Open-source projects can monetize effectively without compromising their principles.
- Acceleration of Innovation:
Free-market price discovery incentivizes rapid iteration and development, as tokens are directly tied to project milestones and utility.
Developers are motivated to solve real-world problems, as market demand directly influences token value.
- Cultural Shift:
The transparency and fairness of tokenized ecosystems promote ethical practices and long-term thinking.
Software professionals gain the respect and agency they deserve, fostering a culture of mutual respect between labor and capital.
Challenges and Solutions
Despite its transformative potential, the model is not without challenges:
- Speculation and Volatility:
Token markets can be volatile, leading to speculative bubbles. Strong governance and transparent metrics can mitigate these risks.
- Regulatory Uncertainty:
Governments and regulators may impose constraints on tokenized markets. Engaging with regulators to create clear frameworks is essential.
- Education and Adoption:
Developers and investors need to understand the nuances of tokenomics and decentralized governance. Educational initiatives are crucial.
Conclusion
Crypto exchanges have opened the door to a new era of software development, where free-market price discovery liberates professionals from exploitative practices while aligning incentives between labor and capital. This paradigm not only ensures fair compensation and autonomy for developers but also provides investors with transparency and flexibility.
By fostering a decentralized, equitable, and innovation-driven ecosystem, tokenized software projects hold the potential to redefine the relationship between labor and capital, creating a win-win scenario for all stakeholders. The future of software is not just decentralized—it’s profoundly fair and aligned.
-
-
 @ a10260a2:caa23e3e
2025-01-18 12:04:41
@ a10260a2:caa23e3e
2025-01-18 12:04:41Last Updated: January 18, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 58638ea8:a443a463
2025-01-19 06:26:12
@ 58638ea8:a443a463
2025-01-19 06:26:12I had not used my Lightning node in a while so I was busy configuring it, when I came accross my old Nostr keys to this account a few days ago.
So I was trying to access my Nostr private key which I had saved in Alby Wallet, but there was a problem. It seemed that for some reason, Alby Wallet was having trouble connecting to my node. (perhaps due to it starting up and shutting down so many times). Well the node was fine, I confirmed, but I was prevented from reading the Nostr settings and data by an infinite loading circle.
Nostr keys are basically like xpub/xprv keys in Bitcoin except that they start with npub and nsec respectively. They are still encoded in Bech32 I think. You use them to chat at the Nostr social network. A decentralized X/Twitter basically.
Eventually, I thought I had found a backup of my Nostr keys in my password manager, and proceeded to clear all the placeholder entries in my wallet, including the Nostr wallet.
Big mistake.
It turned out that the mnemonic I had saved in my password manager makes a completely different key and that I had actually imported the Nostr secret key form another program rather than generated a menmonic phrase.
Naturally, I started to panic as I did not have any copies of it. I thought about inspecting the Chrome browser for the data directly, but by that point I had already deleted the Nostr keys.
But then I remembered that I make backups of my whole system in the early morning and save them on some server, including my Chrome profile, so I thought why not look inside the backup and see if I can find it. But I had to hurry because the files would be overwritten in about 24 hours from then.
I didn't actually know how I was going to go about and get my keys from the backups except for the fact that I knew that extensions have a long identifier like iokeahhehimjnekafflcihljlcjccdbe and that each extension has a folder with that sort of name in the Extensions directory of the Chrome user data dir.
What followed next would be an adventure in coding, lobbing open database files, and encryption.
Locating the extension settings
As I definitely remembered my wallet password and name, I would be able to decrypt the wallet if I ever found it. Which was the first problem - I wasn't really sure where it was.
The fine details of my backup structure meant that all the config files were in a tarball, so I just did a scan for the extension ID, which yielded, among other results, this:

So I at least knew where the extension settings live, but I wasn't sure what any of the files did. AGI was mostly useless for this, except for telling me that those IndexedDB folders must have contained my settings. Spoiler alert: they didn't - and I wasted an hour trying to open the LevelDB file inside, which by the way were specially modified for Chrome so could not even be opened in regular libraries.
It turned out that parsing the database file with a library was a huge waste of time, so eventually I just used tools like cat and less to read the lines. I had better luck with the Sync Extension Settings folder though, and when you open it it looks something like this:

Don't worry, everything is encrypted. And it appears to be encoded in base64.
Decrypting the payload
For what came next, I had to look at Alby Wallet's source code on Github. And I happened to learn a lot about how Alby Wallet worked under the hood. Like did you know that there is actually an API just for extracting settings from the disk? Which was what I needed to see.
A couple of minutes of browsing brought me to this file: getPrivateKey.ts
And so it became clear to me that 1) All this is Typescript, which I am glad I still remember, and 2) those "getPrivateKey" fields were indeed my Nostr private key. (Later on decryption I also found my LN node URL and admin macaroon.) But although I knew my password, I did not know what decryption algorithm it is using. The good news is that I found it in another file called common/lib/crypto.ts.
I had to clean the functions quite a bit so that they would run in Node, as well as install that "crypto-js" dependency, but it was worth it. It even took care of the Base64 encoding. By the way, the encryption seems to be AES-256 with a salt. So that's pretty secure.
Decryption yielded the Nostr private key in hex form, with which I could derive the nsec and npub keypair and recover my Nostr account.
Be careful with your nostr keys - they're like Bitcoin Core keys. Hard to write down and better off in a password manager.

-
 @ 16d11430:61640947
2025-01-19 06:18:22
@ 16d11430:61640947
2025-01-19 06:18:22The persistence of economic inequality and systemic exploitation is intrinsically linked to the fiat monetary system. This framework, established and perpetuated through colonial governance, remains a central mechanism of control in post-colonial societies. Decentralized technologies, particularly Bitcoin, provide an alternative model that has the potential to disrupt these systems. The following analysis examines the structural components of the colonial fiat mindset and assesses Bitcoin's capacity to challenge these mechanisms.
The Structure of the Colonial Fiat System
The fiat monetary system, created to centralize economic authority, serves as a tool for wealth extraction and power consolidation. Key structural components include:
-
Currency Manipulation: Fiat systems rely on central banks to control money supply, often through inflationary policies. Inflation reduces the value of money over time, disproportionately impacting populations with limited access to assets.
-
Debt Dependency: International lending institutions utilize fiat-based loans to establish economic dependence. Structural adjustment programs, often tied to these loans, enforce policies that prioritize debt repayment over local development.
-
Resource Allocation: Fiat economies are designed to facilitate continuous growth. This necessitates the extraction and export of natural resources, frequently sourced from regions with limited negotiating power. Compensation for these resources is typically inequitable.
-
Economic Exclusivity: Access to fiat-based financial systems is regulated by intermediaries, such as banks. These barriers systematically exclude populations without the requisite infrastructure or compliance capabilities.
Bitcoin as a Disruptive System
Bitcoin introduces a decentralized financial architecture with attributes that contrast fundamentally with fiat systems. Its operational principles include:
-
Decentralization: Bitcoin's network is maintained by distributed nodes, eliminating centralized control. This structure prevents single-entity manipulation of monetary policy.
-
Supply Limitations: Bitcoin’s fixed supply of 21 million units enforces scarcity, eliminating inflationary erosion of value. This feature incentivizes long-term wealth preservation.
-
Inclusion by Design: Bitcoin enables direct participation without reliance on intermediaries. Individuals with access to internet-connected devices can transact globally, bypassing traditional financial gatekeepers.
-
Transparent Ledger: The Bitcoin blockchain records all transactions on a public ledger, ensuring verifiability and reducing the risk of opaque practices often associated with fiat systems.
Mechanisms of Transition
For Bitcoin to displace the fiat framework, specific systemic transitions must occur:
-
Education Deployment: Widespread knowledge dissemination is required to enable individuals and organizations to utilize Bitcoin effectively. This includes technical training and comprehension of Bitcoin's operational principles.
-
Resource Sovereignty: Communities reliant on resource extraction for economic viability must adopt systems that ensure direct and equitable compensation. Bitcoin's decentralized nature allows for immediate settlements and transparent payment structures.
-
Policy Integration: Existing legal and regulatory frameworks are aligned with fiat systems. Adoption of Bitcoin necessitates legislative adjustments to incorporate decentralized financial models.
-
Cultural Adaptation: Historical systems of economic interaction, suppressed by fiat systems, may integrate with decentralized technologies. This requires the establishment of locally controlled infrastructures.
Evaluation of Challenges
The transition from fiat to Bitcoin-based systems is constrained by multiple factors:
-
Institutional Resistance: Governments and financial entities reliant on fiat control mechanisms may impose regulatory barriers to Bitcoin adoption.
-
Infrastructure Requirements: Effective Bitcoin utilization depends on reliable access to digital infrastructure, which remains unevenly distributed.
-
Energy Expenditure: Bitcoin mining operations require significant energy inputs, creating potential conflicts with sustainability initiatives.
-
Adoption Scalability: The shift to Bitcoin as a primary financial system necessitates widespread acceptance across diverse economic sectors.
Conclusion
The colonial fiat mindset represents a system of centralized economic authority with embedded mechanisms of exploitation. Bitcoin introduces an alternative that decentralizes control, enforces monetary scarcity, and enables global inclusion. While the transition to Bitcoin-based systems is feasible, it requires addressing infrastructural, regulatory, and adoption-related challenges. The implementation of Bitcoin as a disruptive force in financial systems is contingent on its capacity to integrate with existing economic structures while providing measurable advantages over fiat systems.
-
-
 @ e1d968f7:5d90f764
2025-01-18 10:43:53
@ e1d968f7:5d90f764
2025-01-18 10:43:53Privacy isn’t just a luxury in this line of work—it’s an absolute necessity. From protecting my identity to respecting my clients' discretion, privacy is a cornerstone of this business. It’s a delicate balance of transparency and confidentiality that requires constant vigilance and care.
Why Privacy Matters
In escorting, privacy extends beyond the personal; it shapes the foundation of trust between me and my clients.
- For Myself: Maintaining anonymity safeguards my safety, both physically and emotionally. It allows me to separate my professional life from my personal one, preserving a sense of normalcy.
- For Clients: Many clients seek discretion as much as companionship. Knowing their privacy will be respected allows them to relax and enjoy the experience without worry.
The Tools of Discretion
Ensuring privacy requires more than just good intentions; it involves specific tools and practices to keep information secure.
- Secure Communication: I rely on encrypted messaging apps and dedicated phone numbers to communicate with clients. This ensures that no sensitive conversations are compromised.
- Data Protection: Personal information, whether mine or a client's, is handled with the utmost care. Any booking details are kept minimal and confidential.
- Boundaries: I’ve set clear boundaries about what information I share. For instance, I don’t reveal personal details like where I live or who my family is.
Challenges to Privacy
Even with precautions, maintaining privacy can be challenging.
- Persistent Clients: Some clients may inadvertently overstep boundaries by asking personal questions. Navigating these situations with grace while firmly upholding my privacy is a skill I’ve had to develop.
- Digital Footprints: In today’s connected world, even a small mistake online can lead to a breach of privacy. Ensuring my professional persona is separate from my personal life is an ongoing effort.
- Trust Issues: Trust goes both ways. Just as I work to protect my clients’ privacy, I hope they’ll respect mine. Unfortunately, this isn’t always guaranteed.
How I Protect Myself
Maintaining privacy requires a proactive approach to keep myself safe and secure.
- Professional Identity: I use a pseudonym and maintain a professional persona separate from my personal life. This separation provides peace of mind and clarity for both me and my clients.
- Meetups with Care: I screen clients carefully before agreeing to meet, ensuring they align with the professional boundaries I’ve set.
- Minimal Information: Only essential details are shared for logistical purposes, reducing the risk of information falling into the wrong hands.
Respecting My Clients’ Privacy
It’s not just about my privacy; respecting my clients’ confidentiality is equally important.
- No Judgement, No Gossip: I never disclose a client’s identity or share details about our encounters. Their trust is sacred.
- Discreet Interactions: From how I handle bookings to how I conduct myself in public, I ensure that every interaction is as discreet as possible.
The Business Side of Privacy
Privacy isn’t just a personal concern—it’s a business strategy. Clients are more likely to return or recommend me when they trust my discretion.
- Building Trust: By prioritising privacy, I foster trust and reliability, essential for building long-term client relationships.
- Enhancing Reputation: A reputation for professionalism and confidentiality is a valuable asset in this industry.
Conclusion
Privacy isn’t just part of the job—it’s the framework that holds everything together. It protects me, ensures my clients feel safe, and fosters trust on both sides. By mastering the art of discretion and using the right tools, I’ve built a practice that respects boundaries and keeps every encounter as secure as it is enjoyable. Privacy is power, and in this business, it’s priceless.
Rebecca x
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 6bcc27d2:b67d296e
2025-01-19 04:53:01
@ 6bcc27d2:b67d296e
2025-01-19 04:53:01NIP-28 と NIP-29 はどちらも「特定の集まりに向けたチャット機能」を提供する点では似ているが、根本的に異なるのは「参加や閲覧に制限がない誰でも書き込める公開チャンネル(NIP-28)」か「メンバーシップや権限・ロールを管理できるグループ(NIP-29)」かというところだ。
以下の3点に分けて説明する。 1. 参加や書き込みの自由度 2. 管理やモデレーションの主体 3. ユースケース
参加や書き込みの自由度 - NIP-28は誰でも書き込める設計 - Public Chatはその名の通りパブリックであることが前提で、メンバーシップの概念もない。参加や閲覧に制限がないため、誰でも自由に書き込むことができる。 - NIP-29はロールやメンバーシップがある - NIP-29にはメンバーシップや権限管理(ロール)の概念があり、書き込むにはグループに参加する必要がある。 - 公開/非公開、オープン参加/承認制などの設定をリレー側で柔軟に切り替えられる。そのため、publicタグを設定すれば読むだけは誰でもできるようにする一方でclosedの場合は書き込みに承認が必要…といった柔軟なルール設定ができる。 - また、管理者によるユーザーの追加・削除 (kind:9000, kind:9001) や、リレー自身によるグループ設定 (kind:39000 など) がある。Telegram や Slack の「特定メンバーだけ書き込める」「管理者が追加や除名を行う」ようなイメージ。
管理やモデレーションをリレー/クライアントのどちらで行うか - NIP-28: クライアント側で軽微なモデレーションを行う - NIP-28では、リレーはあくまで Nostr イベントを中継しているだけで、メッセージを消す・投稿者を締め出す等の強制管理は想定していない。 - そのため、リレー側が強制的に検閲するわけではなく、クライアントが主にモデレーションを実行する。 - 例えば、Kind 43(Hide message)や Kind 44(Mute user)を使って「誰のメッセージを隠すか/どのユーザーをミュートするか」をユーザー単位・クライアント単位で制御することができ、コンテンツの見え方をコントロールするのはクライアントとユーザーの自由度が高い。 - NIP-29: リレーがグループを管理する - 逆に、NIP-29はリレーがグループのルールを保持し、それに違反する投稿をブロックしたり、参加ユーザーを追加・除名したりする仕組みがある。 - 複数のリレーに同じグループが存在する(フォークされる)ケースもあり得るが、どのリレーも独自に「このグループ ID ならこういうルール」と管理を行うことが可能。 - そのため、「どの pubkey(ユーザー)が投稿可か」や「グループ名・メタデータ・管理権限はどうなっているか」をリレーのルールで厳密に管理・制御することができる。 - 未管理(unmanaged)状態も許容 リレーが NIP-29 を実装していなくても"unmanaged"なグループとして動作し、誰でも参加可能になる。そこから管理されたmanagedグループに移行することもできる。
ユースケースの違い - NIP-28: オープンなコミュニティ向け 誰でも入れて、タイムライン的にコメントしていけるTelegramやDiscordのような「誰でも閲覧・参加できるチャンネル」を、分散・検閲耐性をもった形で実現したい場合。
- NIP-29: クローズド or ロール付きのコミュニティ向け
Slack やプライベート Discord、あるいは有料購読者限定グループのように「メンバーシップ制」や「誰が管理者か」「参加申請をどう処理するか」をきっちり運用したい場合。
また、複数リレーで運用しつつ、どこかが落ちても他が存続するといった分散運用も想定できる。
まとめ - NIP-28 (Public Chat) - 「公開チャット」を最速で作るのに特化し、チャンネル構造とメッセージ投稿・簡易的なクライアント側モデレーションだけを定義する。 - リレーに追加のルール実装を強いないため、気軽にどこでも利用できる。 - 反面、「誰が書き込みできるか」などの参加制限は標準機能としては備わっていない。 - NIP-29 (Relay-based Groups) - リレーがグループ管理を主導し、メンバーシップ制や権限・ロールをしっかり運用できるようにする。 - 公開/非公開、オープン参加/承認制などの設定をリレー側で柔軟に切り替えられる。 - 反面、各リレーがこの NIP-29 に対応していないとメンバー権限の管理やグループのクローズド運用はできない。 - 用途に応じて、単純に「みんなで雑談する公開チャンネル」が欲しいのであれば NIP-28 を、メンバー制のプライベートグループを作りたい場合は NIP-29 を選ぶ、といった使い分けになる。
- NIP-29: クローズド or ロール付きのコミュニティ向け
Slack やプライベート Discord、あるいは有料購読者限定グループのように「メンバーシップ制」や「誰が管理者か」「参加申請をどう処理するか」をきっちり運用したい場合。
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8781fe5d:4900ffa8
2025-01-18 09:29:05
@ 8781fe5d:4900ffa8
2025-01-18 09:29:05Episode 1 : La genèse
Octobre 2023, on sort à peine de l’explosion de $Pepe sur Ethereum qui est un peu la consécration de la culture meme avec grand papa PePe la grenouille 🔥
L’idée d’un projet de memecoin “story telling” était déjà présente mais surtout , je voulais montrer au monde qu’une vague de memecoins de type jeu décentralisé où chaque participant reçois un AirDrop et peut jouer à trader à son niveau était en train de démarrer et attirait déjà beaucoup de monde !
Pepe
Le choix d’une story à partir de PePe était réfléchit car je voulais être le premier sur RGB avec un PePe qui ne soit pas un scam ,pour changer 🤗😂
Je voulais être sur bitcoin , les Ordinals battaient leur plein et je cherchais comment fiée des smer contracts de type ETH sur Bitcoin 🔥 Dans ma recherche, je découvre le projet RGB qui semble correspondre parfaitement au besoin : un protocole indépendant, des smart contracts , privé et hors chain s’appuyant sur bitcoin ou liquid 👀
Étude , tests de la tech, tests avec l’unique wallet à l’époque : Bitmask de Diba.
C’est parti
Je crée un contrat RGB20 ( format pour les shitcoins) avec 21 millions de “PePeRGB” ! Je crée ensuite un modèle 3D , réalisé un site web minimaliste avec la story et quelques images .
J’écris un article expliquant le projet avec tutorial étape par étape pourr obtenir du PePeRGB contre quelques sats pour payer la Tx.
Jusque là, mon petit projet se déroule normalement : tout le monde s’en fou royalement 😱😂😂
À part @grittoshi et @swisscryptocat qui sont constamment les deux qui avaient déjà testé avant moi 🙏✊🏻😂🔥 (Retenez bien les @ car ils ont chacun un shitcoin sur Liquid ! Ils sont avec nous et nous avançons tous ensembles 🤗🤗)
ni hao
C’est alors qu’un étudiant chercheur chinois @DaPangDun me contacte en me disant qu’il étudie RGB et que des groupes WeChat se sont formés sur le sujet avec pas mal de monde . Il veut faire un post sur mon projet mais il veut participer ! Deal 🙏🔥
Bonne idée : le post est superbe et tout ce joli monde part en FOMO et veut du $pprgb !
J’étais pas prêt 😱
Gérer une communauté de 30000 personnes en fomo dans les 5 heures ne se fait pas comme cela !!
professionnel
Heureusement, j’ai de l’expérience de startup, de crypto, de projets 🙏
Création de whitelist , animation du groupe sur Twitter, création du groupe telegram avec gestion du mandarin ( je ne parle pas ). Tout s’organise plutôt bien en deux jours ( mémorables 30 heures intenses !)
Liquid
Deux mois de tests , de crash, de communauté qui post “wen boss” 32715 fois par jour , je prends une décision forte car la commu va s’essouffler et partir ur Solana qui commence à bien gonfler sur les memecoins !
Je fais un poll sur Twitter : Voulez vous : À- Attendre RGB sans token ? B- Avoir un AirDrop PPRGB liquid network et jouer demain avec ?
Résultat : 82% pour A 😂😂😂
À suivre …. 👀
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 1123ece2:7d1e00c0
2025-01-19 04:02:12
@ 1123ece2:7d1e00c0
2025-01-19 04:02:12Hey everyone I’m Gary Hoban and welcome to Refinery Life Australia.
“The Christ of John’s Gospel” is the theme we are continuing for the coming Sunday morning teachings that focus on John’s unique portrayal of the Christ.
We will continue this series for a while longer.
Today we are discussing, The Distinctives of Discipleship.
Prayer
Father, we come to You today because You made us, You redeemed us, and we acknowledge that every good and perfect gift comes from Your bountiful hands.
Thank You, Father, for the privilege of giving to You for the glory of Your name and cause.
The words of Jesus are so true, “It is more blessed to give than to receive.”
Thank you for this heavenly blessing.
In Jesus name we pray.
Amen.
Text
John 8:31 NKJV
The Truth Shall Make You Free
31 Then Jesus said to those Jews who believed Him, “If you abide in My word, you are My disciples indeed.
Scripture Reading
John 8:30-59 NKJV
30 As He spoke these words, many believed in Him.
The Truth Shall Make You Free
31 Then Jesus said to those Jews who believed Him, “If you abide in My word, you are My disciples indeed.
32 And you shall know the truth, and the truth shall make you free.”
33 They answered Him, “We are Abraham’s descendants, and have never been in bondage to anyone. How can You say, ‘You will be made free’?”
34 Jesus answered them, “Most assuredly, I say to you, whoever commits sin is a slave of sin.
35 And a slave does not abide in the house forever, but a son abides forever.
36 Therefore if the Son makes you free, you shall be free indeed.
Abraham’s Seed and Satan’s
37 “I know that you are Abraham’s descendants, but you seek to kill Me, because My word has no place in you.
38 I speak what I have seen with My Father, and you do what you have seen with your father.”
39 They answered and said to Him, “Abraham is our father.”
Jesus said to them, “If you were Abraham’s children, you would do the works of Abraham.
40 But now you seek to kill Me, a Man who has told you the truth which I heard from God. Abraham did not do this.
41 You do the deeds of your father.”
Then they said to Him, “We were not born of fornication; we have one Father—God.”
42 Jesus said to them, “If God were your Father, you would love Me, for I proceeded forth and came from God; nor have I come of Myself, but He sent Me.
43 Why do you not understand My speech? Because you are not able to listen to My word.
44 You are of your father the devil, and the desires of your father you want to do. He was a murderer from the beginning, and does not stand in the truth, because there is no truth in him. When he speaks a lie, he speaks from his own resources, for he is a liar and the father of it.
45 But because I tell the truth, you do not believe Me.
46 Which of you convicts Me of sin? And if I tell the truth, why do you not believe Me?
47 He who is of God hears God’s words; therefore you do not hear, because you are not of God.”
Before Abraham Was, I AM
48 Then the Jews answered and said to Him, “Do we not say rightly that You are a Samaritan and have a demon?”
49 Jesus answered, “I do not have a demon; but I honor My Father, and you dishonor Me.
50 And I do not seek My own glory; there is One who seeks and judges.
51 Most assuredly, I say to you, if anyone keeps My word he shall never see death.”
52 Then the Jews said to Him, “Now we know that You have a demon! Abraham is dead, and the prophets; and You say, ‘If anyone keeps My word he shall never taste death.’
53 Are You greater than our father Abraham, who is dead? And the prophets are dead. Who do You make Yourself out to be?”
54 Jesus answered, “If I honor Myself, My honor is nothing. It is My Father who honors Me, of whom you say that He is your God.
55 Yet you have not known Him, but I know Him. And if I say, ‘I do not know Him,’ I shall be a liar like you; but I do know Him and keep His word.
56 Your father Abraham rejoiced to see My day, and he saw it and was glad.”
57 Then the Jews said to Him, “You are not yet fifty years old, and have You seen Abraham?”
58 Jesus said to them, “Most assuredly, I say to you, before Abraham was, I AM.”
59 Then they took up stones to throw at Him; but Jesus hid Himself and went out of the temple, going through the midst of them, and so passed by.
Introduction.
What does it really mean to follow Jesus?
Somehow in the early part of the twenty first century, people have lost sight of what it means to follow Jesus.
Discipleship is linked to external observance of religion rather than a relationship experience with Jesus Christ.
During Jesus’ life and ministry on earth, many people sought to follow Him.
John 8:30, 30 As He spoke these words, many believed in Him.
Any motives moved to associate with Jesus Christ.
Some were infatuated with His miracles and teachings.
Others were just curious.
Jesus did not want people to follow Him outside the motive of a genuine commitment.\ To distinguish the authentic followers, Jesus gave the distinctive qualities of a true disciple.
- A true disciple has continuance
John 8:31-33 NKJV
The Truth Shall Make You Free
31 Then Jesus said to those Jews who believed Him, “If you abide in My word, you are My disciples indeed. 32 And you shall know the truth, and the truth shall make you free.”
33 They answered Him, “We are Abraham’s descendants, and have never been in bondage to anyone. How can You say, ‘You will be made free’?”
Jesus realised that some people made an impulsive decision to follow Him.
At times in Jesus’ ministry, large crowds followed Him.
He knew they followed mainly to see His miracles or just to be part of the crowd.
He knew that many would decide not to follow Him.
After Jesus taught the crowds that He was the Bread of Life, John 6:66 says, From that time many of His disciples went back and walked with Him no more.
Jesus pointed out that perseverance would be the sign of a true disciple.
John 8:31, The Truth Shall Make You Free
31 Then Jesus said to those Jews who believed Him, “If you abide in My word, you are My disciples indeed.
Discipleship is not the excitement of one moment.
It is a patient continuance in the footsteps of Jesus Christ.
To a crowd of potential followers, Jesus gave a sure sign of a disciple.
A disciple is one who follows Jesus continuously.
The genuine evidence is in the sustained effort.
2. A true disciple has freedom.
John 8:34-38, Jesus answered them, “Most assuredly, I say to you, whoever commits sin is a slave of sin. And a slave does not abide in the house forever, but a son abides forever. Therefore if the Son makes you free, you shall be free indeed.
“I know that you are Abraham’s descendants, but you seek to kill Me, because My word has no place in you. I speak what I have seen with My Father, and you do what you have seen with your father.”
Jesus taught of a freedom that led to bondage.
Jesus answered them, “Most assuredly, I say to you, whoever commits sin is a slave of sin.
Jesus taught a group of potential disciples about how sin leads to bondage.
Going through life with self will, self trust, and self assertion leads to a detrimental bondage.
No one who follows Jesus can be a master to himself.
Jesus spoke of a bondage that leads to freedom.
A true disciple is one who has renounced his or her way to follow the way of Christ.
Bondage to the Lord leads to authentic freedom.
Jesus said, “Therefore if the Son makes you free, you shall be free indeed.”
The true disciple of Jesus lives to please only one person, Jesus Christ.
A disciple of Jesus is not a slave to sin but is a slave to the master.
3. A true disciple has Christlike behaviour.
John 8:39-47 NKJV
39 They answered and said to Him, “Abraham is our father.”
Jesus said to them, “If you were Abraham’s children, you would do the works of Abraham.
40 But now you seek to kill Me, a Man who has told you the truth which I heard from God. Abraham did not do this.
41 You do the deeds of your father.”
Then they said to Him, “We were not born of fornication; we have one Father—God.”
42 Jesus said to them, “If God were your Father, you would love Me, for I proceeded forth and came from God; nor have I come of Myself, but He sent Me.
43 Why do you not understand My speech? Because you are not able to listen to My word.
44 You are of your father the devil, and the desires of your father you want to do. He was a murderer from the beginning, and does not stand in the truth, because there is no truth in him. When he speaks a lie, he speaks from his own resources, for he is a liar and the father of it.
45 But because I tell the truth, you do not believe Me.
46 Which of you convicts Me of sin? And if I tell the truth, why do you not believe Me?
47 He who is of God hears God’s words; therefore you do not hear, because you are not of God.”
The Jew’s claimed to be Abraham’s children.
By physical lineage this was true.
However, many Jews lived contrary to Abraham’s example.
They sought to kill Jesus and slander His name.
Jesus said they were not God’s children, for they did not reflect God’s character.
Rather, He said in John 8:44, You are of your father the devil, and the desires of your father you want to do. He was a murderer from the beginning, and does not stand in the truth, because there is no truth in him. When he speaks a lie, he speaks from his own resources, for he is a liar and the father of it.
God’s children behave like His children.
John 8:42, “If God were your Father, you would love Me”, and He added in verse 47, “He who is of God hears God’s words.”
Nature will be true to itself.
If one is born of God, then they will live in accordance with Christ’s character.
4. A true disciple honours Christ.
John 8:48-59 NKJV
Before Abraham Was, I AM
48 Then the Jews answered and said to Him, “Do we not say rightly that You are a Samaritan and have a demon?”
49 Jesus answered, “I do not have a demon; but I honor My Father, and you dishonor Me.
50 And I do not seek My own glory; there is One who seeks and judges.
51 Most assuredly, I say to you, if anyone keeps My word he shall never see death.”
52 Then the Jews said to Him, “Now we know that You have a demon! Abraham is dead, and the prophets; and You say, ‘If anyone keeps My word he shall never taste death.’
53 Are You greater than our father Abraham, who is dead? And the prophets are dead. Who do You make Yourself out to be?”
54 Jesus answered, “If I honor Myself, My honor is nothing. It is My Father who honors Me, of whom you say that He is your God.
55 Yet you have not known Him, but I know Him. And if I say, ‘I do not know Him,’ I shall be a liar like you; but I do know Him and keep His word.
56 Your father Abraham rejoiced to see My day, and he saw it and was glad.”
57 Then the Jews said to Him, “You are not yet fifty years old, and have You seen Abraham?”
58 Jesus said to them, “Most assuredly, I say to you, before Abraham was, I AM.”
59 Then they took up stones to throw at Him; but Jesus hid Himself and went out of the temple, going through the midst of them, and so passed by.
Many claimed to be disciples of Jesus, but they did not honour Him.
In fact, they accused Him of being demon possessed.
Jesus said in verse 49, “I do not have a demon; but I honor My Father, and you dishonor Me.”
They could not be authentic followers and dishonour the Lord in this way.
True disciples honour and adore and obey Christ.
Conclusion.
Are you a true disciple of Jesus Christ?
The proof is a continuing commitment to Him, freedom from sin, Christlike behaviour, and a Christ honouring life.
Until next time
Stay in the Blessings
I really want to encourage you to be diligent with your Bible study time, because God has so much more for us than we can get from just going to church once or twice a week and hearing someone else talk about the Word.
When you spend time with God, your life will change in amazing ways, because God is a Redeemer. Theres nothing thats too hard for Him, and He can make you whole, spirit, soul and body!
You’re important to God, and you’re important to us at The Refinery.
When it comes to prayer, we believe that God wants to meet your needs and reveal His promises to you.
So whatever you’re concerned about and need prayer for we want to be here for you! Or even if you just want to say Hi, you can contact us at www.refinerylife.org
2025 IS A YEAR OF NEW BEGINNINGS.
© www.refinerylife.org 2013-2024 All rights reserved. Except as permitted under the Australian Copyright Act 1968, no part of this Article may be reproduced, stored in a retrieval system, communicated or transmitted in any form or by any means without the prior written permission.
This episode is brought to you by Refinery Life Australia:
If you enjoy The Refinery Life Radio Podcast you can help support The Refinery by doing the following:
Sow an offering: Bitcoin: bc1qqh6720t2zagj72dyfj348az698tdut3hlecaj4
Online: https://www.refinerylife.org/donate/
If you do send an offering then please email us so that we can say thank you
Subscribe on iTunes | Spotify | YouTube | TuneIn | Rumble | Flare | Zap.Stream | Fountain |
Share The Refinery with your friends and family
Subscribe to the newsletter on www.refinerylife.org
Follow The Refinery on Twitter | Nostr | Instagram | Fountain
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 42342239:1d80db24
2025-01-18 08:31:05
@ 42342239:1d80db24
2025-01-18 08:31:05Preparedness is a hot topic these days. In Europe, Poland has recently introduced compulsory lessons in weapons handling for schoolchildren for war-preparedness purposes. In Sweden, the Swedish Civil Contingencies Agency (MSB) has recently published the brochure on what to do "If crisis or war comes".
However, in the event of war, a country must have a robust energy infrastructure. Sweden does not seem to have this, at least judging by the recent years' electricity price turbulence in southern Sweden. Nor does Germany. The vulnerabilities are many and serious. It's hard not to be reminded of a Swedish prime minister who, just eleven years ago, saw defense as a special interest.
A secure food supply is another crucial factor for a country's resilience. This is something that Sweden lacks. In the early 1990s, nearly 75 percent of the country's food was produced domestically. Today, half of it must be imported. This makes our country more vulnerable to crises and disruptions. Despite our extensive agricultural areas, we are not even self-sufficient in basic commodities like potatoes, which is remarkable.
The government's signing of the Kunming-Montreal Framework for Biological Diversity two years ago risks exacerbating the situation. According to the framework, countries must significantly increase their protected areas over the coming years. The goal is to protect biological diversity. By 2030, at least 30% of all areas, on land and at sea, must be conserved. Sweden, which currently conserves around 15%, must identify large areas to be protected over the coming years. With shrinking fields, we risk getting less wheat, fewer potatoes, and less rapeseed. It's uncertain whether technological advancements can compensate for this, especially when the amount of pesticides and industrial fertilizers must be reduced significantly.
In Danish documents on the "roadmap for sustainable development" of the food system, the possibility of redistributing agricultural land (land distribution reforms) and agreements on financing for restoring cultivated land to wetlands (the restoration of cultivated, carbon-rich soils) are discussed. One cannot avoid the impression that the cultivated areas need to be reduced, in some cases significantly.
The green transition has been a priority on the political agenda in recent years, with the goal of reducing carbon emissions and increasing biological diversity. However, it has become clear that the transition risks having consequences for our preparedness.
One example is the debate about wind power. On the one hand, wind power is said to contribute to reducing carbon emissions and increasing renewable energy. On the other hand, it is said to pose a security risk, as wind turbines can affect radio communication and radar surveillance.
Of course, it's easy to be in favor of biological diversity, but what do we do if this goal comes into conflict with the needs of a robust societal preparedness? Then we are faced with a difficult prioritization. Should we put the safety of people and society before the protection of nature, or vice versa?
“Politics is not the art of the possible. It consists in choosing between the disastrous and the unpalatable” said J. K. Galbraith, one of the most influential economists of the 20th century. Maybe we can’t both eat the cake and have it too?
-
 @ 16d11430:61640947
2025-01-19 03:07:12
@ 16d11430:61640947
2025-01-19 03:07:12The “divide and conquer” strategy used to pit Bitcoiners against the wider crypto community is a deliberate tactic aimed at creating internal divisions, fostering confusion, and weakening the collective momentum of decentralized technologies. By exploiting philosophical, technological, and cultural differences between Bitcoin maximalists and proponents of alternative cryptocurrencies, fiat instigators and other vested interests aim to undermine the larger blockchain ecosystem. Here's an exploration of this strategy:
Exploiting Ideological Differences
- Bitcoin Maximalism vs. Crypto Diversity:
Bitcoin maximalists advocate that Bitcoin is the only truly decentralized, immutable, and sound form of money, dismissing other cryptocurrencies as unnecessary or outright scams.
Proponents of other blockchains argue that innovations like smart contracts, scalability, and specialized use cases justify the existence of altcoins and Ethereum-like ecosystems.
Fiat-aligned propagandists amplify these debates, framing them as irreconcilable conflicts, rather than healthy competition within an evolving ecosystem.
- Labeling Altcoins as “Shitcoins”:
By co-opting Bitcoin maximalist terminology like “shitcoin” to denigrate all other cryptocurrencies, fiat proponents fan the flames of division. This reinforces the perception that the crypto community is fragmented, unreliable, and rife with infighting, reducing its appeal to newcomers.
Creating Confusion Over Purpose
- Framing Bitcoin as Anti-Innovation:
Propagandists often portray Bitcoin as a “dinosaur” in the blockchain space, emphasizing its slower transaction speeds, energy consumption, and limited programmability.
Simultaneously, they label other cryptocurrencies as “untrustworthy” or “too experimental,” creating confusion about the legitimacy and purpose of blockchain technology as a whole.
- Highlighting Scams and Failures:
Media narratives frequently spotlight rug-pulls, scams, and failures in the broader crypto space while ignoring the resilience and success of Bitcoin. By conflating Bitcoin with the broader crypto market, they erode public trust in decentralized technologies altogether.
Fueling Regulatory Divides
- Regulation as a Weapon:
Regulators and central authorities use differing approaches for Bitcoin and other cryptocurrencies to create division. For instance, Bitcoin is often labeled as a “digital asset” or “commodity,” while other cryptocurrencies are deemed securities, leading to disparate treatment and confusion over legitimacy.
This divide discourages collaboration between Bitcoiners and altcoin communities, as each group perceives itself as having different regulatory battles to fight.
- Narratives Around Environmental Impact:
Bitcoin is targeted for its proof-of-work (PoW) consensus mechanism, which is painted as environmentally destructive. In contrast, proof-of-stake (PoS) systems are promoted as “green” alternatives.
This framing encourages environmentalists and sustainability advocates to align against Bitcoin, while Bitcoiners double down on defending PoW, exacerbating the divide.
Manipulating Tribalism
- Turning Bitcoiners Against Altcoins:
Bitcoiners are encouraged to see altcoins as fraudulent or unnecessary competitors, while altcoin proponents are encouraged to see Bitcoiners as close-minded purists clinging to outdated technology.
This tribalism prevents cooperation on shared goals, such as financial inclusion, decentralization, and resistance to censorship.
- Highlighting Cultural Divides:
Bitcoin culture, often associated with libertarian values and sound money principles, is framed as elitist and exclusionary.
In contrast, altcoin cultures, which emphasize innovation, diversity, and experimentation, are painted as reckless and overly speculative.
These cultural clashes distract from the broader shared mission of decentralizing power and creating alternatives to the fiat system.
Amplifying Internal Critiques
- Media Amplification of Disputes:
Public disagreements between prominent figures in the Bitcoin and crypto spaces are sensationalized by media outlets. For example, debates over scaling solutions, hard forks, or smart contract utility are framed as existential threats to the ecosystem’s credibility.
This amplification undermines confidence in both Bitcoin and alternative cryptocurrencies by making the community seem chaotic and divided.
- Weaponizing Social Media:
Bots and trolls infiltrate online discussions, spreading misinformation and stoking hostility between Bitcoiners and altcoin advocates. These efforts create echo chambers, reinforcing confirmation bias and deepening divides.
Long-Term Consequences of the Divide and Conquer Approach
- Delaying Mass Adoption:
Confusion and infighting reduce public trust in blockchain technologies, slowing adoption and deterring institutional investment.
Potential users and developers are discouraged from entering the space, fearing instability and conflict.
- Fragmenting the Ecosystem:
Instead of working together to overcome regulatory challenges, scale adoption, or innovate solutions, the crypto community wastes resources fighting internal battles.
This fragmentation leaves the ecosystem vulnerable to external attacks, such as coordinated government crackdowns or monopolistic behavior by large financial institutions.
- Strengthening Fiat Narratives:
By keeping the crypto space divided, fiat propagandists can continue to push narratives that centralized financial systems are more reliable, cohesive, and secure.
These narratives reinforce the status quo, delaying the broader transition to decentralized systems.
Overcoming the Divide
To counteract the divide and conquer strategy, the Bitcoin and crypto communities must:
-
Focus on Shared Goals: Highlight common objectives like financial inclusion, censorship resistance, and decentralization.
-
Promote Constructive Dialogue: Encourage debates that focus on solutions rather than criticisms, emphasizing the complementary strengths of different technologies.
-
Educate the Public: Combat misinformation by creating accessible resources that explain the value of Bitcoin and blockchain as distinct but synergistic innovations.
-
Resist Tribalism: Recognize that both Bitcoin and altcoins have roles to play in a diverse and evolving financial ecosystem.
By fostering unity and cooperation, the blockchain community can overcome external attempts to sow division and work toward a more decentralized, equitable future.
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ ed5774ac:45611c5c
2025-01-17 22:05:36
@ ed5774ac:45611c5c
2025-01-17 22:05:36A good question. I do not think so. I will explain below why, but first where did this question come from?
The statement that Tether is a Bitcoin company was recently made by Samson Mow in X (here) in a response to Paolo Ardoino’s initial Tweet about Tether’s $775 million investment on Rumble (here).

In response to Samson Mow's statement, I expressed my disagreement by pointing out that Tether prints USDT “out of thin air” and uses these funds to purchase US Treasuries, which in effect helps finance US debt and fund military operations.
In my opinion, a bitcoin company should not provide life support to the current broken financial system that is built on the US dollar's status as a global reserve currency, allowing a small group of Western elites to control the system and exploit it for wealth transfer.
“The root problem with conventional currency is all the trust that’s required to make it work. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust.”(Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System)
I believe that the primary purpose of bitcoin is to replace the current fraudulent system, not to support it. My assessment is based on this fundamental principle, and I therefore disagree with Samson’s statement. In short, Tether does not align with bitcoin’s purpose of existence, a point to which I will return later.
First, it is necessary to clarify the logic behind my “Tether prints USDT out of thin air” statement as Samson Mow shifted the focus of conversation merely to this specific point instead of clarifying how he considers Tether as a bitcoin company in light of its actions (i.e., financing US debt and thereby funding the US war machine).

My next tweet aimed to highlight the trust concerns inherent in Proof of Stake, a concept that should be familiar to Samson Mow, where ETH holders validate transactions by staking their holdings, creating a system that relies on the implicit trustworthiness of these validators.
In response to my reasoning and explanation, Samson initially claimed that Tether is not proof of stake. Next, in a subsequent tweet where I asked for clarification on whether Tether is on the Ethereum blockchain, he acknowledged this point but introduced a new argument suggesting that Tether's situation has nothing to do with PoS. This claim is, to be frank, disconnected from reality and raises questions about Samson Mow’s true motivations.

Following my discussion with Samson Mow on X, I decided to provide further clarification on the reasoning behind my statement that "Tether prints USDT out of thin air". The underlying logic of this argument can be grasped by examining two crucial factors: Proof of Work (PoW) and debt.
Proof of Work:
A critical examination of Tether's USDT issuance requires a deeper understanding of the PoW.
When individuals exchange their dollars for USDT, they are essentially trading earned value (their time and energy) for a digital representation thereof. However, Tether's issuance of new USDT units occurs without incurring any cost or spending resources, effectively creating digital tokens that represent claims on value rather than value itself.
In stark contrast, the creation of new bitcoins is facilitated through a competitive mining, wherein miners use computational power (spend energy) to validate transactions and create new blocks, thereby earning newly minted bitcoins as a reward for their efforts. Similarly, in gold mining, the discovery of new deposits is the result of the investment of time, energy, and resources by miners. Likewise, individuals who are employees or entrepreneurs invest their time and energy to generate income or profit.
This underscores a fundamental principle: that genuine value creation typically results from tangible efforts, and resource allocations, distinguishing it from mechanisms that generate value without any corresponding expenditures.
Unlike the aforementioned examples, Tether's mechanism for creating USDT operates under a distinctly different paradigm. Tether issues USDT without expending time, energy, or resources. Instead, individuals give Tether their hard-earned money in exchange for an IOU certificate represented by USDT. This is in theory, assuming that Tether is an honest player and only mints USDT when a user transfers corresponding USD. In practice, however, there are several factors that complicate the verification of Tether's claim regarding the backing of USDT with USD.
One issue with Tether operating on Ethereum is that transactions are validated by ETH stakeholders by staking their ETH. This introduces an element of trust in third-party (validators), raising concerns in the integrity of the ledger.
Additionally, in contrast to Bitcoin's blockchain, Proof of Stake blockchains do not have a clear "chain" of hashes linking each block back to its predecessor through a computationally intensive process, since there's no mining involved in creating new blocks (as blocks are proposed by validators based on their stake), thereby preventing verification of historical transaction validity. As a result, the current state of a Proof of Stake blockchain reflects only the validators' confirmation without providing any assurance regarding its historical accuracy or integrity.
Most significantly, there exists no inherent mechanism, as far as I am aware of, preventing Tether from minting additional USDT without corresponding USD backing and transferring to an ETH address under their control and buying real assets (such as bitcoin) with it.
In my opinion, these considerations underscore significant challenges on transparency, accountability and oversight within Tether’s operations. In other words, the entire system relies on the honesty of Tether and Ethereum validators as trusted third parties, which contradicts Bitcoin's fundamental principle that eliminates the need for trusted intermediaries in transactions as described by Satoshi Nakamoto in Bitcoin White Paper. (source: bitcoin white paper)

While Bitcoin's decentralized architecture eliminates the need for intermediaries, Tether as a centralized entity controls the issuance and management of USDT and relies on ETH validators for the validity of transactions. This centralized control enables Tether & Ethereum to unilaterally freeze, blacklist, or manipulate accounts at their discretion, as evidenced by past incidents and potential future actions. Furthermore, USDT holdings are exposed to counterparty risk, as holders are only entitled to redeem their funds if Tether maintains its solvency and adheres to a 100% reserve requirement which are significant question marks as explained in previous paragraphs.
Debt:
Even if the claim that all USDT tokens are fully backed is true, it is essential to recognize that USDT is ultimately backed by fiat currency, which itself is debt —whether in the form of dollars or U.S. Treasuries. Consequently, the statement “Tether prints USDT out of thin air” is not entirely unfounded, as the creation of new USDT tokens is effectively facilitated by the issuance of new debt instruments.
How does USD come to existence? As many bitcoiners know very well, they are simply printed out of thin air by FED. This process is facilitated by the US government's issuance of debt certificates, including short-term Treasury bills and long-term Treasury bonds. The value of these debt instruments is derived from the expectation that the US government will honor its obligations by repaying the indicated amount of USD to certificate holders in the future, primarily through tax revenue collected from its citizens. In essence, these debt certificates represent IOUs and their value is contingent upon the credibility of the US government's promise to fulfill its debt obligations. The entire system relies on a collective belief in the government's creditworthiness, rather than any tangible asset backing it. Even if Tether's USDT is assumed to be backed 1-to-1 with USD, it is ultimately backed by nothing but the US government's fiat currency, which is itself created out of thin air. This highlights the tenuous nature of USDT's backing, as it is predicated on trust in the US government's ability to pay its debt.
In contrast to Bitcoin, which is decentralized money, independent of any third-party liability, holding USDT introduces multiple layers of third-party liability such as:
-
Trust in the integrity of the Ethereum network & in the honesty of ETH stakeholders who validate transactions and maintain the ledger.
-
Trust in Tether's financial stability and solvency, as well as its commitment to honoring its obligations, thereby mitigating the risk of bankruptcy or fraudulent activities.
-
Trust in the creditworthiness of the US government, as the value of USDT is ultimately tied to the value of US Treasury securities held by Tether.
These cumulative risks underscore the significance of third-party liability in the context of USDT ownership.
In conclusion, the statement “Tether prints USDT out of thin air” is based on the fact that USDT is minted by Tether without incurring any cost or spending resources, there is no mechanism to prove that Tether maintains 100% reserves and USDT is ultimately backed by fiat currency, which itself is debt created out of thin air by the FED. Therefore, “Tether prints USDT out of thin air” notion is not entirely unfounded and highlights the tenuous nature of USDT's backing.
Tether finances US debt and war machine by buying US Treasuries:
Having laid out the logic behind my statement that “Tether prints USDT out of thin air,” I will now move on to the main argument underlying my position: namely, that Tether is not a bitcoin company because its acquisition of US debt provides life support to a profoundly corrupt and exploitative financial system, which enables a small cabal of western elites exploit the rest of the world to further enrich themselves. The fundamental purpose of bitcoin is to replace this broken system, not to provide life support to it.
The current financial system:
erodes the purchasing power of working-class individuals through inflation
-
excludes a significant portion of the global population from accessing to financial services
-
preserves ‘the rules-based global order’ (as it is called by the West) that exploits developing nations for the benefit of a privileged few in Western countries
-
concentrates control in the hands of an unscrupulous banking cartel and self-proclaimed elites
At the heart of the existing financial system lies the US dollar's role as a global reserve currency that grants the US government considerable leverage to enforce its economic and geopolitical interests. By controlling USD flows, the US can impose financial sanctions on nations that refuse to comply with its rules and norms.
In instances where financial coercion proves ineffective, the US has historically resorted to alternative measures, including military intervention and covert operations, aimed at bringing disobedient countries into compliance with its policy directives. Historical records are full of examples.
-
[ ] In 1953, the United States and the United Kingdom collaborated to orchestrate a coup d'état in Iran, resulting in the overthrow of the democratically elected government of Prime Minister Mohammad Mossadegh. This action was carried out following Mossadegh's decision to nationalise Iranian oil companies, which were vital to the West's economic interests.
-
[ ] The Central Intelligence Agency (CIA) played a substantial role in supporting a coup against Salvador Allende, the democratically elected President of Chile in 1970, because they were concerned that Allende's policies would lead to a shift towards socialism and potentially even communism, which was seen as a threat to US interests in the region.
-
[ ] Saddam Hussein's decision to transition Iraq's oil transactions from US dollars to euros was a major factor contributing to his downfall. By challenging the existing global financial system, Hussein became a threat to the global financial order and therefore paid the price with his life.
-
[ ] Muammar Gaddafi proposed the establishment of a gold-based currency, known as the gold dinar, intended for use in African oil transactions. This initiative aimed to create a pan-African currency independent of both the US dollar and euro, potentially undermining their influence in regional trade. The perceived threat posed by this proposal to the global financial order has been the main factor to Libya's destabilization and Gaddafi's eventual demise.
-
[ ] The overthrow of Ukraine's democratically elected president in 2014 by a CIA orchestrated a coup d'état, with Victoria Nuland, then-Assistant Secretary of State for European and Eurasian Affairs, playing a key role in the operation. The intervention was motivated by Western corporations’ desire to colonize Russia and use its resources as collateral to prolong the life of the global financial system that has become unsustainable with its current debt levels.
Those interested in understanding the mechanics of the current financial system or learning about the historical crimes committed by West against the Global South are invited to contact me directly. I can provide access to a comprehensive collection of resources that document these issues. However, due to space and time constraints, it is not feasible to elaborate on these topics in detail here.
The statement that Tether is primarily a bitcoin company is entirely unfounded since Tether provides significant support to the current financial system. The US government is currently facing challenges in financing its debt due to decreasing global confidence in its ability to repay its obligations. This is evident in the fact that China has ceased purchasing US debt, while Russia has sold off its entire holdings prior to the Special Military Operation (SMO). Furthermore, private investors are increasingly wary of investing in US debt, citing concerns over its sustainability. Currently, the UK and EU are the only entities actively buying US debt, which, along with the US, are the other two pillars of the existing global financial order. Notably, Tether has emerged as a substantial purchaser of US debt (approximately $100 billion at the time of writing), effectively serving as a vital lifeline for the prolongation of the Western colonial order.
Tether is NOT a bitcoin company. In my opinion, it is fair to say that those who claim that Tether is a bitcoin company are either lacking in critical thinking or have a financial stake that compromises their objectivity.
It is true that it helps bitcoin adoption and by providing liquidity contributes to the upward momentum of bitcoin price. I believe, it is likely that the current price of bitcoin would be significantly lower without Tether's involvement. This raises important questions about the motivations and values of those involved in the bitcoin community who claim that Tether is a bitcoin company. Can their support for Bitcoin be attributed to a sincere interest in advancing the principles of decentralization and sovereignty, or might it be influenced by self-interest and the pursuit of personal wealth? Are there other potential motivations or conflicts of interest at play?
As outlined in this article, I have concerns regarding Tether's alignment with the principles that underpin Bitcoin’s core values. My critique is not intended to be accusatory, but rather to encourage critical evaluation. I acknowledge and appreciate Tether's contribution to bitcoin ecosystem and see their investment in Rumble as a positive development for freedom of speech and recognize Samson's dedication for Bitcoin adoption. However, my appreciation for their efforts does not imply unconditional trust.
The defensive responses of some individuals within the community to my criticisms (without any reasonable counterarguments) have raised questions for me about their potential biases and motivations. While I do not aim to convince those who misinterpret my intentions, I will exercise increased suspicion when engaging with individuals who appear more focused on protecting Tether's interests than upholding the principles of Bitcoin.
In summary, I believe that Tether's role in propping up the current financial system - intentionally or not - underscores the need for skepticism and critical thinking. As global events continue to unfold with unprecedented speed and complexity, it's essential to remember: 'Don't trust, verify!'
-
-
 @ 16d11430:61640947
2025-01-18 23:07:02
@ 16d11430:61640947
2025-01-18 23:07:02I leaned back in my chair, staring out the window of a quiet suburban café in Melbourne. Rain trickled down the glass in half-hearted streaks, as if even the weather couldn’t muster the enthusiasm to commit. I sipped my lukewarm chai, the spice muddled beyond recognition, and shook my head at the headlines flickering on my phone.
"Privies and staties," I muttered, half to myself. "The great cultural war, fought with memes and moral outrage."
The waitress, a twenty-something with blue streaks in her hair and the harried look of someone juggling rent and an art degree, glanced at me, but I waved her off. She didn’t need to hear the rant bubbling inside me. But you do.
Let me tell you about these Australians and their bizarre tribes. On one side, you’ve got the privies, the products of private schools with Latin mottos, boat shoes, and a chronic inability to read the room. These are the ones who learned how to debate the ethics of colonialism before they could tie their shoelaces. They grew up in manicured bubbles, tutored in piano and privilege, and now lead the charge in the great cultural revolution.
Oh, they’ll cry for social justice over their oat-milk lattes, but God forbid you mention their family’s ties to real estate empires or mining conglomerates. They protest with passion, but it’s always the kind of passion that ends before the rain starts or the Uber surge pricing kicks in.
Then there are the staties, the self-proclaimed champions of the "real Australia." They’re the salt-of-the-earth types who can’t stand the privies. Too posh, too preachy, too disconnected. The staties fight their wars with beer in one hand and a smartphone in the other, spamming their feeds with angry rants about "wokeness" and how things were better in the '80s. They see the privies as the enemy—elitists, virtue-signaling snobs who wouldn’t last a day on a construction site.
And yet, the staties are no saints themselves. They scream about freedom while demanding the government fix everything that annoys them. They sneer at art and academia, unless, of course, it’s a Hamilton ticket or a Netflix drama. They don’t want to change the world; they just want to win enough of it to tell everyone else to shove off.
Caught between these two warring factions, I—an Indian old boy from a legacy school where discipline and ambition were drilled into us like multiplication tables—sit here, baffled. I grew up in a world of contradictions too, but at least ours came with good food and a soundtrack of classical ragas. This Australian version of the culture wars? It’s a pantomime, all sound and fury, signifying nothing.
Take the debates about statues. The privies want to tear them all down—symbols of oppression, they say. The staties clutch their pearls, howling about history being erased, as if the only thing holding civilization together is a bronze guy on a horse. And in the middle? Nothing changes. Rent still skyrockets, climate disasters loom, and the housing market remains about as accessible as Doon School admissions to a street vendor’s child.
The irony is that both sides are just cogs in the same ridiculous machine. The privies rail against capitalism, but live off trust funds and well-paying jobs courtesy of their networks. The staties mock the pretensions of the elite but secretly envy their polish and privilege.
Meanwhile, here I sit, with my scuffed shoes and tired eyes, watching this farce unfold. We had our own clown shows back in India, of course. Macaulay’s little brown gentlemen, striving to out-English the English. At least we had masala chai and biryani to soften the absurdity. Here, it’s bland chai and vegemite sandwiches.
I chuckle, shaking my head at the absurdity of it all. The waitress, still hovering nearby, gives me a curious look. I gesture for the bill, deciding I’ve indulged in enough cynicism for one afternoon. The cultural wars will rage on without me.
As I step out into the drizzle, I can’t help but think: if this is the best they’ve got, maybe it’s time for the old boys to show them how it’s done. After all, we’ve been navigating the tightrope of hypocrisy and ambition for centuries. What’s one more circus?
-
 @ 07f367da:0e76880d
2025-01-17 16:08:52
@ 07f367da:0e76880d
2025-01-17 16:08:52- 2023-10-26 강기자 기사 작성"‘직장 내 괴롭힘’ 호소하며 투신 사망… ‘미등록 장애인’ 김경현"
- 2023-10-27 강기자 기사 작성"좋은친구들 퇴사자 “김경현 유서, 내가 겪은 것과 너무 비슷하다”"
- 2023-11-18 이슬하 퇴직기자 게시물
- 2024-03-15 하민지 기자 게시물★최초폭로
- 2024-03-16 이슬하 퇴직기자 게시물
- 2024-03-18 비마이너 비상대책위원회 게시물
- 2024-04-29 비마이너 비상대책위원회 게시물
- 2024-05-03 이슬하 퇴직기자 게시물
- 2024-05-21 비마이너 비상대책위원회 게시물
- 2024-06-01 이슬하 퇴직기자 게시물
- 2024-07-31 김혜미 퇴직기자 게시물
- 2024-08-13 비마이너 비상대책위원회 발표★1차 입장
- 2024-08-23 이슬하 퇴직기자 게시물
- 2024-08-25 하금철, 갈홍식, 최한별
- 2024-08-25 운영실장 양유진, 취재기자 하민지
- 2024-08-26 비마이너 퇴직기자 6인 입장문
- 2024-08-27 하민지 기자 게시물
- 2024-08-27 비마이너 비상대책위원회 발표★2차 입장
- 2024-10-01 김혜미 퇴직기자 게시물
- 2024-10-22 이슬하 기자 게시물
- 2024-11-06 이슬하 기자 게시물
- 2024-11-28 비마이너 비상대책위원회 발표★최종 입장
- 2024-11-29 박정수 퇴직기자 게시물★
- 2024-11-29 하민지 기자 게시물
- 2025-01-16 하민지 기자 게시물
-
 @ eee391ee:8d0b97c2
2025-01-17 10:43:51
@ eee391ee:8d0b97c2
2025-01-17 10:43:51Amber 3.1.8
- Button to clear cached data in settings
- Fix multiple bunker requests not clearing when accepting or rejecting
- Show relays status in the notification
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.1.8.txtandmanifest-v3.1.8.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.1.8.txt.sig manifest-v3.1.8.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.1.8.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 16d11430:61640947
2025-01-18 22:32:03
@ 16d11430:61640947
2025-01-18 22:32:03The global technology industry is a paradox of modernity and historical legacies. On the surface, it thrives on innovation, cross-border collaboration, and diversity. Yet, beneath this veneer lies a disturbing continuation of colonial-era power dynamics. With leadership and non-technical roles dominated by professionals from developed Western nations, and technical labor outsourced predominantly to developing countries, the tech sector operates under a "business as usual" approach that perpetuates colonial visions of hierarchy and control.
The Lull to the Norm: An Invisible Legacy
Leadership and the West’s Monopoly on Power
Non-technical leadership roles in the tech industry are disproportionately occupied by individuals from countries like the United States, the United Kingdom, and other former colonial powers. These roles, encompassing strategy, decision-making, and vision-setting, form the backbone of global tech operations.
Statistics: In Silicon Valley, white males hold 58.7% of executive positions, while Asian males, despite their high representation in technical roles, occupy only 16.3% of executive roles. African American and Hispanic representation is even lower. (Source)
Implications: These patterns mirror historical colonial structures where administrative and decision-making powers were centralized in Western metropoles, while the labor-intensive work was relegated to colonies.
Technical Labor and the Outsourcing of Expertise
Technical labor in the global tech industry has become synonymous with talent from developing countries, particularly India, Southeast Asia, and Africa. This division of labor, while celebrated as cost-efficient and globally inclusive, also reinforces a narrative where technical expertise is commoditized, while strategic and creative roles are retained in the West.
Global Workforce Distribution: India alone accounts for 53% of the global tech workforce sourced through outsourcing platforms, a figure that underscores the reliance on developing nations for technical expertise. (Source)
The Unseen Ceiling: While these workers are highly skilled, systemic barriers often prevent their transition into decision-making roles, relegating them to a cycle of “support” work that lacks career advancement.
A Colonial Vision: The Reinforcement of Hierarchies
The division of labor in the tech industry is not accidental but a reflection of deeper structural inequities rooted in colonial ideologies:
-
Knowledge and Power Centralization: Just as colonial powers centralized administrative control while delegating manual work to colonies, the tech industry centralizes leadership in Western hubs while outsourcing technical work to developing nations.
-
Economic Exploitation: Developing countries provide a wealth of skilled labor at lower costs, driving profits for corporations headquartered in the West. This mirrors the economic exploitation of colonies, where raw resources and labor were extracted for metropolitan gain.
-
Cultural Hierarchies: Soft skills and leadership qualities, often defined by Western norms, are prioritized over technical expertise. This reinforces the idea that strategic thinking and innovation are inherently Western attributes, while execution and technical work are the domain of others.
Breaking the Cycle: A Call for Change
Recognizing Global Talent Equitably
The industry must redefine its metrics for leadership and innovation. Technical expertise from developing countries is not just labor but intellectual capital that deserves recognition and representation in decision-making roles.
Case in Point: Organizations like Tata Consultancy Services (TCS) demonstrate how technical teams from developing countries can take on leadership roles globally, challenging the status quo.
Decentralizing Leadership
Leadership roles should reflect the global nature of the workforce. Companies need to actively promote individuals from diverse cultural and geographical backgrounds into decision-making positions, breaking the Western monopoly on soft-skill dominance.
Fostering Cross-Cultural Collaboration
Global tech organizations must build mechanisms for meaningful collaboration between Western leadership and technical teams from developing nations. This includes addressing cultural biases and creating pathways for career advancement that are not limited by geography or nationality.
Leveraging Decentralized Finance and Blockchain
The rise of blockchain and decentralized finance (DeFi) provides an alternative framework that bypasses traditional hierarchies. Through tokenized incentives and decentralized governance, skilled professionals can independently create, innovate, and profit outside the confines of corporate colonialism.
Conclusion: Toward a Post-Colonial Tech Industry
The global tech sector, despite its progressiveness, remains a product of historical hierarchies. The division of labor—leadership in the West, execution in the East and South—is not a mere coincidence but a continuation of colonial visions. As the industry expands, it must confront these dynamics head-on.
Breaking free from this cycle requires more than policy changes; it demands a fundamental shift in perspective. By recognizing the intellectual capital of technical labor, decentralizing leadership, and fostering equitable collaboration, the tech industry can move toward a truly inclusive and post-colonial future. Until then, the lull to the norm remains a quiet affirmation of a colonial past.
-
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ f57bac88:6045161e
2025-01-17 08:35:53
@ f57bac88:6045161e
2025-01-17 08:35:53دگرگونی و سعادت در افسانه همای:
- تغییر و تحول: همای سعادت اغلب به عنوان نمادی از تغییر و تحول ناگهانی و مثبت در زندگی افراد تلقی میشود. سایه این پرنده بر سر فردی افتادن، نشانهای از دگرگونی سرنوشت و آغاز دورهای جدید و پربرکت است.
- آوردن سعادت: همانطور که از نامش پیداست، همای سعادت به عنوان آورنده خوشبختی و کامرانی شناخته میشود. سایه این پرنده، نمادی از برکت، فراوانی و رسیدن به آرزوهاست.
- پادشاهی و قدرت: در بسیاری از روایتها، همای سعادت با پادشاهی و قدرت ارتباط مستقیم دارد. سایه این پرنده بر سر کسی افتادن، به معنای رسیدن به مقام و منزلت والا و کسب قدرت است. معانی نمادین همای سعادت:
- امید و آرزو: همای سعادت نماد امید به آیندهای بهتر و رسیدن به آرزوهاست.
- تغییر مثبت: این پرنده نشاندهنده این است که حتی در سختترین شرایط نیز امکان تغییر و تحول مثبت وجود دارد.
- قدرت الهی: در برخی روایات، همای سعادت به عنوان فرستادهای از سوی خداوند تلقی میشود که برای برکت دادن به انسانها به زمین میآید.
در ادبیات فارسی: همای سعادت در ادبیات فارسی جایگاه ویژهای دارد و شاعران بسیاری به توصیف زیبایی و شکوه این پرنده پرداختهاند. این پرنده اغلب به عنوان نمادی از عشق، زیبایی و آرزوهای دستنیافتنی به کار رفته است. در نتیجه: همای سعادت نه تنها یک پرنده افسانهای، بلکه نمادی از امید، تغییر مثبت و رسیدن به آرزوهاست. این پرنده به ما یادآوری میکند که حتی در سختترین شرایط نیز باید به آینده امیدوار باشیم و برای رسیدن به اهدافمان تلاش کنیم.


منبع عکس ها
-
 @ 16d11430:61640947
2025-01-18 22:12:40
@ 16d11430:61640947
2025-01-18 22:12:40The Australian tech industry is booming, fueled by skilled migration and increasing demand for innovation. Yet, many highly qualified immigrants find themselves trapped in an unforgiving system, stifled by the limitations of fiat economies and traditional job markets. For those seeking autonomy and financial independence, decentralized finance (DeFi) offers a revolutionary escape route. By leveraging blockchain technology, immigrants can bypass traditional barriers, unlock new opportunities, and redefine their economic participation in Australia’s tech ecosystem.
The Problem: A Fragile, Fiat-Based Ecosystem
Underemployment and Job Mismatch
Many skilled immigrants arrive in Australia with dreams of applying their hard-earned expertise, only to encounter underemployment or roles unrelated to their qualifications. This mismatch arises from:
Recognition Issues: Foreign credentials and experience often go undervalued.
Economic Shocks: The fiat-based economy is prone to cycles of instability, leaving immigrants vulnerable to layoffs and wage suppression.
Systemic Barriers: Licensing requirements, workplace discrimination, and a preference for "local experience" keep many skilled professionals from thriving.
Financial Vulnerabilities
Immigrants also face challenges in navigating Australia’s financial system, which is heavily fiat-dependent:
High Living Costs: The high cost of living in major Australian cities like Sydney and Melbourne erodes savings and limits economic mobility.
Limited Access to Credit: Without robust credit histories in Australia, immigrants often struggle to secure loans or mortgages.
Dependency on Remittances: Immigrants sending money back home face exorbitant fees and delays, further compounding financial strain.
The DeFi Solution: A Borderless Financial Ecosystem
Decentralized finance, or DeFi, is transforming the global financial landscape. Built on blockchain technology, DeFi eliminates intermediaries, providing direct access to financial services such as lending, borrowing, and investing. For immigrants in Australia's tech ecosystem, DeFi offers a pathway to financial empowerment and independence.
Key Benefits of DeFi for Immigrants
-
Access to Global Capital DeFi platforms enable immigrants to tap into global liquidity pools, allowing them to secure loans or funding without relying on local credit systems. Smart contracts ensure transparency and fairness, removing biases that plague traditional banking.
-
Earning Through Crypto Immigrants can participate in DeFi protocols to earn passive income through staking, yield farming, or providing liquidity. This income is not tied to the fragile fiat economy and offers a hedge against local economic downturns.
-
Borderless Remittances By using cryptocurrencies like Bitcoin or stablecoins, immigrants can send money back home instantly and at a fraction of the cost compared to traditional remittance services.
-
Decentralized Career Platforms Web3 technologies are enabling decentralized platforms where immigrants can showcase their skills, secure gig work, and get paid in crypto, bypassing restrictive local hiring practices.
DeFi Meets Skilled Immigration: A Blueprint for Independence
- Building an Alternative Tech Economy
DeFi empowers immigrants to bypass Australia’s fiat-based tech ecosystem by participating in global, decentralized marketplaces. For instance:
Immigrant developers can contribute to open-source Web3 projects and earn cryptocurrency.
Blockchain-based freelancing platforms allow skilled workers to monetize their expertise without needing local validation.
- Funding Innovation Without Borders
Immigrants with entrepreneurial ambitions often struggle to secure funding in Australia. Through DeFi platforms, they can raise capital via Initial Coin Offerings (ICOs), decentralized crowdfunding, or tokenized equity models.
- Escaping Fiat Dependency
DeFi provides an opportunity to store wealth in stablecoins or cryptocurrencies, reducing exposure to fiat-related inflation and instability. By adopting Bitcoin and DeFi solutions, immigrants can build a financial buffer that operates independently of the Australian dollar.
- Resilience Against Economic Shocks
DeFi’s decentralized nature protects users from localized economic crises. Immigrants can diversify their income streams globally, reducing their dependency on Australia’s fragile economic cycles.
Challenges and Risks
While DeFi offers immense potential, it is not without risks. Immigrants exploring this space should be aware of:
Regulatory Uncertainty: Australia’s evolving crypto regulations could impact DeFi accessibility.
Volatility: Cryptocurrencies are inherently volatile, and users must exercise caution in managing investments.
Scams and Security: The decentralized nature of DeFi makes it a target for scams and hacks. Immigrants must prioritize education and security practices.
Conclusion: A New Path to Empowerment
For skilled immigrants in Australia’s tech ecosystem, DeFi represents more than just a financial tool—it’s a lifeline to autonomy and opportunity. By leveraging blockchain technology, immigrants can break free from the suppressive constraints of fiat-based systems, access global opportunities, and achieve true economic independence.
The intersection of DeFi and skilled immigration is not just a vision for the future—it’s a call to action. As the world transitions toward decentralized systems, skilled immigrants have a unique opportunity to lead the way, redefining what it means to thrive in a globalized economy.
-
-
 @ 19fd5e65:946640b2
2025-01-17 04:28:30
@ 19fd5e65:946640b2
2025-01-17 04:28:30Узнал, что, оказывается, есть люди, живущие без фантазии. Это не значит, что у них бедное воображение или что-то в этом роде. Это медицинский термин, который обозначает, что человек просто не может мыслить образами: не может представить в голове картинку, музыку.
При слове стол, например, вспоминает его размеры по ширине и длине, знает его цвет, но не может представить в сознании, как этот стол выглядит. Даже если он стоит давно на кухне.
Удивительное, конечно, дело.
Прочитать об этом можно на Atlantic, на PsyPost и в научном журнале
Афантастики прекрасно воспринимают элементы реальности и не имеют проблем с памятью и языковой обработкой. Мы считаем, что их особенность связана с небольшим дефектом «феноменального сознания». То есть они имеют доступ к информации о формах, цветах и пространственных отношениях, но эта визуальная информация не превращается в зрительный образ. Их мозг медленнее анализирует формы и цвета, кроме того, они менее уверены в точности своих ответов, касающихся визуальной информации.
Источник на русском языке
-
 @ 16d11430:61640947
2025-01-18 21:55:33
@ 16d11430:61640947
2025-01-18 21:55:33Throughout history, the rise of any revolutionary force has often left destruction in its wake. Empires crumble, leaders fall, and the world reshapes itself through upheaval. Yet Bitcoin, the decentralized force of economic transformation, is different. It does not raze cities, spill blood, or bring tyrants to their knees in chains. Instead, it offers a unique and almost merciful path to its opponents—fiat leaders.
Bitcoin spares all but their pride, offering them the opportunity to adapt, accept, and join the future. A lesser conqueror would not have had such restraint.
The Nature of Fiat Power
Fiat leaders derive their authority from a system built on trust—trust in the currency they print, the rules they impose, and the promises they make. But as history has shown, this trust is fragile. The fiat system is prone to corruption, inflation, and inequality, often serving the elite at the expense of the masses.
Bitcoin, by its very design, dismantles this fragile trust. Its immutable ledger, decentralized governance, and capped supply reveal the flaws of fiat systems with unyielding transparency. To fiat leaders, this is a humiliation—a slow, undeniable exposure of their system's weaknesses. Yet, Bitcoin does not destroy them outright. Instead, it gives them a choice.
The Mercy of Bitcoin
A lesser conqueror would demand total submission, punishing those who stood in opposition. Bitcoin, however, does not demand anyone’s allegiance. It does not imprison fiat leaders, confiscate their wealth, or physically overthrow their regimes. Instead, it renders their systems obsolete through peaceful, voluntary adoption.
Fiat leaders are not forced to give up their power; they are merely shown a better way. They are spared the brutal consequences of war or violent revolution, given the opportunity to embrace Bitcoin and adapt their policies. While their pride may be wounded, their lives and systems are left intact, offering them a rare chance to evolve.
The Lesser Conqueror’s Path
Imagine a world where a lesser conqueror, driven by greed or vengeance, rose to challenge fiat power. History offers countless examples of such figures—dictators, insurgents, and invaders—who sought to destroy their enemies utterly. These conquerors left nothing but ruin behind them, ensuring their victims had no chance for redemption.
Bitcoin is not a conqueror of this sort. It seeks to empower, not destroy. Its mission is not to replace one oppressive system with another but to build a decentralized, incorruptible foundation for global prosperity. Even as it humiliates fiat leaders by exposing their failures, it extends a hand of mercy, offering them a way to coexist in the new paradigm.
Humiliation as a Catalyst
For fiat leaders, the humiliation Bitcoin brings is a bitter pill to swallow. To see their systems falter in the face of an algorithm, a decentralized network of nodes, and a global community of believers is no small blow. Yet this humiliation is not an end—it is a beginning.
Many fiat leaders, recognizing the inevitability of Bitcoin’s rise, have begun to adapt. Nations are exploring Bitcoin adoption, regulators are crafting frameworks, and even central banks are experimenting with digital currencies. This willingness to change, however begrudging, is a testament to Bitcoin’s power as a peaceful conqueror.
Conclusion: A New Era of Mercy
Bitcoin’s kindness lies in its restraint. It conquers through innovation, not violence; through transparency, not deception. It humiliates fiat leaders by exposing the flaws of their systems, but it spares them the devastation that lesser conquerors would inflict. This mercy is a testament to Bitcoin’s higher purpose—a world where power is decentralized, value is preserved, and humanity can thrive without fear of corruption or collapse.
In the end, Bitcoin’s triumph will not be marked by the fall of fiat leaders, but by their transformation. Their humiliation, while painful, is a necessary step toward a better world. Bitcoin’s mercy is its greatest strength, ensuring that its conquest is not one of destruction, but of renewal.
-
 @ fd78c37f:a0ec0833
2025-01-17 03:23:02
@ fd78c37f:a0ec0833
2025-01-17 03:23:02In this edition, we invited Evelyn and Gerardo to share their experiences in creating a Bitcoin community, discussing their motivations, challenges, strategies, and goals. Their journey offers valuable lessons on community engagement and the transformative power of Bitcoin.
YakiHonne: Evelyn, Gerardo, We're truly delighted and grateful to have you join us today. Before we dive in, I’d like to share some background on what YakiHonne is. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. we'll be exploring more about your community. What sparked your interest in Bitcoin, and what motivated you to create a community around it ?
Evelyn:In the beginning, I started learning about Bitcoin in 2019, just a bit at first. When it became legal tender, we realized it was a monumental moment for El Salvador, and we knew we had to get involved in anything related to Bitcoin. Personally, I began watching videos and reading more about Bitcoin to deepen my understanding of its significance for El Salvador adopting it as legal tender. Evelyn:Soon, I recognized the importance of educating more Salvadorans about Bitcoin. This led us to start providing Bitcoin education in classrooms, schools, and various communities across different cities in El Salvador. As we traveled across the country, we noticed that Bitcoin adoption was still limited, with few places accepting it as a means of payment. This observation motivated us to build a community where Bitcoin could be used as a medium of exchange. Our goal was to replicate and expand upon the Bitcoin community that was already taking root in El Salvador.As the first country to adopt Bitcoin as legal tender, we understood the necessity of working on increasing its adoption throughout the nation.

YakiHonne: Could you share how your community was established, the strategies you employed to attract members, and the challenges you faced in the process?
Gerardo:We were living in San Salvador, but we didn’t enjoy city life, so we started looking for a place outside the city. We knew we wanted to live in the mountains, and there are a few options here in El Salvador. Eventually, we found ourselves in Berlin, and we really liked it. After spending some time visiting and getting to know the people, we decided this was where we wanted to settle down.
 Gerardo:Once we made that decision, we knew we wanted to start teaching Bitcoin within the community. We began talking to local entrepreneurs and residents, letting them know about our plan to educate the community about Bitcoin. We explained that it could bring significant opportunities for Berlin and its residents, including increased tourism. Some people were really excited about the idea because there weren’t many places in El Salvador, the “Bitcoin country” that had a circular economy focused on Bitcoin. Most of the activity was concentrated in the city.
Gerardo:As people started to hear about our idea, they liked it, and soon we had a team working with us to onboard more businesses. We were fortunate to find the right people, and that’s how it all began. We started by getting about 12 to 15 businesses to accept Bitcoin. I remember creating a social media presence, including a Twitter account, to promote Berlin as a destination where people could spend Bitcoin.
Gerardo:Berlin is about two and a half to three hours from the capital, San Salvador, depending on traffic, so it wasn’t easy for people to come initially. But as time went on, more people started visiting. They liked the weather, the friendly community, and the places where they could use Bitcoin. Soon, a few Bitcoin enthusiasts even moved to Berlin.
Gerardo:A year and eight months later, we now have a thriving community of over 20 Bitcoin users from around the world living here, along with many locals who have become Bitcoin users thanks to our educational efforts. We’ve established a Bitcoin center, have over 130 merchants accepting Bitcoin, and even non-business residents are using it. It’s been a fantastic journey, and it all started with a desire to educate a few people, which kept growing from there.
Gerardo:Once we made that decision, we knew we wanted to start teaching Bitcoin within the community. We began talking to local entrepreneurs and residents, letting them know about our plan to educate the community about Bitcoin. We explained that it could bring significant opportunities for Berlin and its residents, including increased tourism. Some people were really excited about the idea because there weren’t many places in El Salvador, the “Bitcoin country” that had a circular economy focused on Bitcoin. Most of the activity was concentrated in the city.
Gerardo:As people started to hear about our idea, they liked it, and soon we had a team working with us to onboard more businesses. We were fortunate to find the right people, and that’s how it all began. We started by getting about 12 to 15 businesses to accept Bitcoin. I remember creating a social media presence, including a Twitter account, to promote Berlin as a destination where people could spend Bitcoin.
Gerardo:Berlin is about two and a half to three hours from the capital, San Salvador, depending on traffic, so it wasn’t easy for people to come initially. But as time went on, more people started visiting. They liked the weather, the friendly community, and the places where they could use Bitcoin. Soon, a few Bitcoin enthusiasts even moved to Berlin.
Gerardo:A year and eight months later, we now have a thriving community of over 20 Bitcoin users from around the world living here, along with many locals who have become Bitcoin users thanks to our educational efforts. We’ve established a Bitcoin center, have over 130 merchants accepting Bitcoin, and even non-business residents are using it. It’s been a fantastic journey, and it all started with a desire to educate a few people, which kept growing from there.

YakiHonne: I love how it all started and the fact that you created mechanisms and opportunities for Bitcoiners to actually spend Bitcoin. It's also amazing how this initiative helped Berlin by attracting more prominent investors to settle here.Apart from Berlin's distance from the capital, which made it less accessible and may have deterred some people from coming, were there any other challenges you faced in the process of promoting Bitcoin adoption?
Gerardo:we faced several challenges, such as the local government’s disapproval of our Bitcoin activities, the initial difficulty of introducing Bitcoin into the community, and finding a suitable venue for our educational efforts. These were the primary obstacles we encountered early in the project. Gerardo:The first challenge we faced in the beginning was the lack of Bitcoin usage in the town. While we were teaching people to accept Bitcoin, there weren’t many individuals actually spending it. It was just the two of us at first, taking turns visiting places that accept Bitcoin, trying to make sure we could spend it and show others that it was possible. We were also traveling to San Salvador and inviting people to come to Berlin, but our efforts weren’t very successful initially. Gerardo:Eventually, more people started coming, and that issue was resolved. However, another challenge arose with some local politicians who didn’t approve of what we were doing. They tried to stop our efforts by discouraging people from working with us. As a result, a few locals didn’t trust us at first. Gerardo:For some people, they might think it's a scam. So, the educational aspect was a significant challenge. A few months into the project, we decided to hold community meetings, which was crucial for us because we needed a place to teach and spread knowledge about Bitcoin. However, we didn't have a dedicated venue at the time. Fortunately, we had a few friends, and initially, we held meetings at their homes or garages.

YakiHonne: You mentioned facing trust issues. What principles guide the community, and how did you maintain trust and reliability in your discussions as you built the community?
Evelyn:One of the key points in building trust within the local community is establishing clear trust and transparency. There were many misconceptions about Bitcoin initially. People often associated Bitcoin with politics and politicians, assuming it was a government creation. This misconception was fueled by the distribution of a government-issued Bitcoin wallet tied to citizens’ IDs, which caused confusion due to a lack of public education on Bitcoin. Evelyn:To address this, we made it a priority to remain neutral and uninvolved with the government. We focused on educating people about Bitcoin's origins, its creation by Satoshi Nakamoto, and its fundamental workings, breaking down complex concepts into simple explanations. We also informed the community about various Bitcoin wallets available, emphasizing alternatives to the government-issued wallet, which had issues with trust and identity theft. Evelyn:Engaging with respected elders in Berlin was another crucial strategy. We explained the benefits of Bitcoin adoption for the local economy and how it could improve the quality of life in the community. These respected community members helped us reach others and build credibility. Evelyn:Since May 2023, we have been deeply involved in educational and social projects, demonstrating that Bitcoin can improve not only personal financial situations but also community welfare. Importantly, we never asked for anything in return, showing our genuine intentions. Over time, this consistent engagement helped us gain the community’s trust, and our work in Bitcoin education has grown stronger.

YakiHonne: How do you educate your members and keep them informed about the latest Bitcoin developments?
Evelyn:Beyond simply observing developments in the Bitcoin space, we hold weekly meetings not only within our team but also with the broader community. These gatherings have been invaluable, as we've been fortunate to engage with many knowledgeable individuals who bring both technical expertise and insights into the philosophical aspects of Bitcoin. Through these interactions, we continuously learn from each other. We've also had the privilege of hosting experts who conduct workshops and deliver lectures during our meetings. These sessions help us stay informed about the latest advancements in technology and the evolving landscape of Bitcoin.

YakiHonne: Apart from education and inviting external instructors for weekly classes and meetups, how does your community collaborate with the broader Bitcoin ecosystem? What partnership has been the most impactful so far?
Gerardo:When we arrived here, I remember that many people knew something needed to change in the town’s technology and overall situation. They were unhappy with the status quo, especially with the government. There was already a lot of energy within the population of Berlin; we just needed to harness that energy and get organized. That’s when people started collaborating. Gerardo:In addition to Bitcoin education, we worked on social projects, like painting parks, cleaning the city, and addressing basic issues that the municipality wasn’t tackling. This shift in mentality helped people realize that it’s up to us to take action, not just wait for the government to act. Gerardo:As for Bitcoin adoption, many businesses have greatly benefited from it. They’ve seen an increase in income and are now able to save in new ways. You can even hear personal stories from business owners on how their operations have gradually transformed since they started accepting Bitcoin. This has had a significant impact on the local economy and also on how people view social change within the town.
YakiHonne: Do you have any partnerships with other Bitcoin or Bitcoin-related communities outside of Berlin?
Gerardo:There aren’t many Bitcoin communities outside of Berlin, even though we're considered the Bitcoin country. There's the Los Angeles one, which was the first, then Bitcoin Beach, followed by us, and now a new one is emerging in Santa Ana. I had a conversation yesterday with someone who's helping with that initiative, and we're planning some collaborations with them. They’ll be visiting us here, and we’ll also visit them to collaborate on Bitcoin education. There's also another community in La Pi Raya, a small island, that is working on Bitcoin education as well. Gerardo: There aren't many communities in the area, but we’re always open to working with them. It's really interesting to hear about their experiences and the challenges they face, as we can learn a lot from their insights.
YakiHonne: I expected that, since it was El Salvador, there would be over a thousand Bitcoin communities. Given that it's a country that has embraced Bitcoin so extensively, I thought there would be hundreds of communities.
Gerardo:However, it's been three and a half years since the Bitcoin Law, and adoption has been slow. While the U.S. dollar is still the other currency in use, people continue to trust it despite its devaluation. It's relatively stable, so they don’t yet feel the need to switch to Bitcoin. So, the adoption process is definitely moving slowly.
YakiHonne: Apart from creating Bitcoin-friendly shops and a community where people can buy and trade with BTC, what other steps have been taken to promote Bitcoin adoption in El Salvador? What results have you seen so far in your community?.
Gerardo:Bringing Bitcoin's identity to Berlin has significantly helped the town. It has attracted more Bitcoiners, especially those coming from El Salvador who are interested in Bitcoin adoption. We've started claiming the title of "Bitcoin City of El Salvador," which has also helped. The results are clear: people are seeing their income improve and are learning new things from the Bitcoin community. Slowly but surely, Berlin is adopting Bitcoin, and it’s bringing positive changes to the town.

YakiHonne: What are the community's goals for the next 6-12 months, and how do you see it evolving with Bitcoin's growth?
Gerardo:While many Berliners use Bitcoin for transactions, they tend to store it in custodial wallets. Our goal is to encourage people to own their seed phrases and understand the full Bitcoin philosophy, including the importance of time preference. We aim to teach people not just about Bitcoin payments, but also its broader value this year. Gerardo:we’ll create an independent association to manage donations and oversee community projects. The association will have its own rules, a board consisting of both expats and locals, and will work on improving the town. The Bitcoin education aspect will remain under our care. Our main goals are better education and local involvement in fixing the town's issues.
YakiHonne: You mentioned saving Bitcoin, and it reminded me of a point made in a previous interview with another community. They said the same thing—many people spend Bitcoin, but few actually save it, which is a problem. Saving Bitcoin has many benefits. For example, that community even encourages parents to save Bitcoin for their children, so that by the time they grow up, they'll have something valuable to inherit. I really appreciate your insights today, and I look forward to seeing how these efforts continue to make an impact in the future.
-
 @ dbb19ae0:c3f22d5a
2025-01-18 20:46:35
@ dbb19ae0:c3f22d5a
2025-01-18 20:46:35Introduction to Perl programming
Perl is a high-level, general-purpose programming language that excels in text processing, system administration, web development, and more. Its flexibility and strong regular expression capabilities make it a popular choice for scripting tasks. This article introduces the basics of Perl programming, including an example script.
Basics of Perl
Running a Perl Script
To execute a Perl script, save the code in a file with a
.plextension (e.g.,script.pl) and run it from the command line:bash perl script.plSyntax Highlights
- Shebang Line: Specify the interpreter.
perl #!/usr/bin/perl - Comments: Use
#for single-line comments.perl # This is a comment - Printing Output:
perl print "Hello, World!\n";
Variables
Perl has three main variable types: - Scalars: Single values (numbers, strings, etc.), prefixed by
$.perl my $name = "Eva"; my $age = 35;- Arrays: Ordered lists, prefixed by@.perl my @colors = ("red", "green", "blue");- Hashes: Key-value pairs, prefixed by%.perl my %capitals = ("France" => "Paris", "Japan" => "Tokyo");Control Structures
- Conditional Statements:
perl if ($age > 18) { print "You are an adult.\n"; } else { print "You are a minor.\n"; } - Loops:
perl for my $color (@colors) { print "$color\n"; }
Example Script: Text File Analysis
This script reads a text file, counts the lines, words, and characters, and prints the results.
Script
```perl
!/usr/bin/perl
use strict; use warnings;
Check for file argument
if (@ARGV != 1) { die "Usage: $0
\n"; } my $filename = $ARGV[0];
Open the file
open(my $fh, '<', $filename) or die "Could not open file '$filename': $!\n";
Initialize counters
my ($line_count, $word_count, $char_count) = (0, 0, 0);
Process the file
while (my $line = <$fh>) { $line_count++; $char_count += length($line); $word_count += scalar(split(/\s+/, $line)); }
close($fh);
Print results
print "File: $filename\n"; print "Lines: $line_count\n"; print "Words: $word_count\n"; print "Characters: $char_count\n"; ```
Explanation
- Input Validation: Ensures the script is called with a filename.
- File Handling: Uses
openandclosefor file operations. - Counters: Tracks lines, words, and characters.
- Loop: Reads the file line by line, processing each line.
Running the Script
Save the script as
file_analysis.pland run it with a text file:bash perl file_analysis.pl sample.txtConclusion
Perl is a powerful tool for scripting and data processing. Its concise syntax and robust text-handling capabilities make it an excellent choice for many tasks. This example demonstrates basic Perl features and encourages further exploration of its vast capabilities.
- Shebang Line: Specify the interpreter.
-
 @ 2355757c:5ad3e04d
2025-01-16 21:07:14
@ 2355757c:5ad3e04d
2025-01-16 21:07:14Introduction
Blue light from artificial sources is one of the most biologically disruptive toxins that exists in our modern world today. It is pervasive, it is ubiquitous and it is only getting worse with the ever increasing time we spend indoors and in front of screens. The worst part is: it doesnt have to be this way. The EVEN worse part: it is exactly what Big Tech wants.
This newsletter will cover exactly why blue light from screens and our lighting is bad for our health, and what you can do to avoid these biological disruptions.
The TLDR:
-
Artificial blue light is not the same as natural blue light.
-
Artificial blue light disrupts our circadian rhythm (the most important aspect of our biology) and our sleep.
-
A disrupted circadian rhythm has been linked to nearly all chronic diseases.
-
Artificial blue light is addictive by design & disrupts our neurotransmitters.
Natural Blue Light vs Artificial Blue Light
Blue light, like all visible light, is a sliver of the electromagnetic radiation spectrum. That means that blue light is an EMF, and artificial blue light is a non-native EMF. That is why I often say non-native EMFs are the most pervasive environmental toxin in modern society. The food is an issue, but the light is what is really f*cked. It is far easier to change your food diet than your light/EMF diet.
Blue light is typically defined as 450-490nm wavelength light, although there is some debate on where that starts and ends. That correlates to a frequency of around 600-660THz and \~2.5eV of photon energy. That means a wavelength of blue light is oscillating at 600-660 Trillion times per second. It also means that the photons in blue light have the ability to excite electrons they come to interact with, with around 2.5eV of energy.
Blue light is not some alien part of the electromagnetic spectrum, as say 5G radio frequencies are, it is actually something we are exposed to every single day in the form of sunlight and have been for the existence of humanity. However, there is a stark difference between the blue light we are exposed to in the form of sunlight and the artifical blue light we are exposed to from our technology screens and lighting:
-
Blue light in isolation / missing the rest of the spectrum
-
Pulsed LED control
-
The wrong context / time of day
-
Dull
To understand why blue light from artificial sources is so toxic to our biology, you need to understand first what our biology is programmed to take in as an input signal from full spectrum sunlight. I refer to it as “full spectrum” sunlight here because that is the big takeaway: you are getting exposure to a full spectrum of light.
Blue light coming from the sun is NEVER present without longer, lower energy wavelengths such as Red + Near-Infrared (NIR). Sunlight is 49%-55% infrared light. NIR (650nm-1200nm) represents 70% of the total solar spectrum from a photochemistry viewpoint when considering photons/second. Compare that to artificial light, which almost always has little to ZERO red/infrared light due to energy efficiency standards. A spectrum plot below highlights this stark difference between sunlight & artificial lighting. We will discuss more about the biological impacts of this in the next section. It is important to note that a large reason the infrared spectrum is NOT present in light is due to “energy efficiency” and is also incandescents have been made illegal. Of course, policies like this are completely ignorant to the health benefits of the infrared spectrum of light and importance for a more fuller spectrum.
All man made modern light is pulsed, whilst in nature it is continuous. Fluorescents and incandescent bulbs, because they are powered via our 50/60Hz electrical grid have a pulse of 50/60Hz (low frequency). LEDs are controlled by a digital electronics control scheme called Pulsed Width Modulation (PWM). PWM lighting control is typically at 500Hz-50kHz (and could be higher). Engineers say that the human eye can’t see “flicker” above 100Hz, which is true from a visual perspective…but our biology knows. This is a large reason why eye strain, headaches, and other symptoms arise from staring at screens for long periods of time. Sunlight is never pulsed, and is only continuous.
Getting back to the spectrum, the real issue with artificial blue light is the incorrect context. Natural sunlight only provides blue light in a full spectrum setting when (obviously) the sun is up. It has a more rich blue spectrum mid day vs first thing in the morning. It also has even higher energy wavelengths such as violet, UVA, and UVB in mid day (UVB latitude/season dependent). Our artificial blue lights come with zero context. They don’t change based on the sun angle or time of day. They do not go away after sunset. They simply are the same pulsed isolated blue light rich lights, all day long. Nature operates on a clock, and our body needs to be in tune with that clock, else we get biological dysfunction.
Indoor and artificial blue light sources are DULL. Not their personalities, but their brightness. If you are outside mid day you are going to be experience 10,000-100,000 LUX of brightness. That is 30-1000X HIGHER than typicaly indoor lighting. Big range because some indoor lighting areas are very, very dull. So now you have an even more alien form of light. Blue light is the main input signal that tells your body it is daytime, and a big component of that is brightness. Brightness = photon density. If you are inside all day you are getting \~100x LESS photon density. Photons carry energy to excite the electrons in your body. We are starving for photon energy.
Artificial Blue Light Disrupts our Circadian Rhythm
Our circadian rhythm (CR), aka our 24hr biological clock, is in my opinion the most important aspect of our biology. Why? Because nearly everything in our body is goverened by time of day and CR. It encompasses our light diet, our food diet, our sleep, hormones, and so much more. Circadian disruption has been linked with nearly all chronic disease and mental health issues.

So what causes our CR to get out of whack and misalign our biological clocks? The number 1 input signal to our circadian biology is light. The other main input signal is simply our sleep/wake cycle. Food input is secondary and our connection to the earth (grounding/earthign) has also been shown as a circadian input signal.
Our sleep/wake cycle should be tied to light, so those two are quite intertwined. But what about light causes circadian disruption? Here is a short list of the big hitters:
-
Artificial Light at Night (ALAN)
-
Dull/junk light during the day
-
Missing sunrise/UVA rise in the morning
Basically: any light that deviates from the natural solar spectrum in your local environment will disrupt your circadian rhthym. The degree of how alien/different the spectrum is will dictate how severe the circadian disruption is.
Artifical light at night is especially bad because blue light is a signal of daytime and suppresses melatonin production. ANY blue light post sunset will cause a circadian disruption to some degree and the magnitude of exposure will determine just how much. This is why blocking blue light specifically at night time is so important.
Really any light post sunset will disrupt circadian biology but blue light is especially bad because it most severely impacts melatonin production. Brightness is another major factor. Wearing dark red blue light blockers will help, but if you are still in an extremely brightly lit room <1 hour before bed time it won’t be ideal for sleep quality.
Bright and blue is the recipe for maxx melatonin suppression. Bright and any color light will still have a suppressive effect as well. Want your best night sleep ever? Turn the lights OFF and only uses a very dull red light, candle, etc.
Depression, Blue Light & Dopamine
We have a mental health crisis ongoing in modern society. In the US, over 20% of adults suffer from a mental health disorder/illness and even 1/6 children now do as well. In 2000, the percentage of prevalence of Major Depressive Disorder (MDD) aka severe depression was 2%, today it is over 8%…a 4x increase. Suicide rates have also been climbing, especially in teenagers in this “smartphone era”. It seems like a strong possibility that our modern technology is the major driver for this mental health epidemic.

I think anyone can agree that our devices, specifically our phones are highly addictive. We think it is just the social media apps penetrating our psychology and dopamine reward systems, but in reality it’s more than that. The hardware also plays a priming role. I am saying that blue lit screens is making you more vulnerable to fall prey to the predatory marketing tactics of short form content on social media apps. You can simply look at toddlers, who are far MORE vulnerable to effects on their developing brains, to know that it is not just the apps or the games, but also the LIGHT…the blue light specifically.
For children, you can easily google or YouTube a video of a toddler throwing a temper tantrum when you take away their iPad. The games or shows they are watching may indeed be “addicting” but I would argue the bright blue dominant screen is the real reason they are addicted.
Blue light induces a dopamine release in our body in short term exposure. Regardless of the science - we can feel it. Some papers are catching up on this, and some are discussing how the blue light photoreceptor AKA melanopsin is directly intertwined with dopaminergic neurons. The initial paper discusses how experiments were performed in a room “illumninated by a red LED to avoid influencing dopamine synthesis”. This means that not all light is stimulating dopamine secretion, and that blue light is especially stimulating in terms of its effect on our brain.
This is the same reason Las Vegas uses bright lights and flasing symbols at the slots to keep players in their seats. The constant dopamine release is addicting, it is like a drug and they end up spending far more money than they would on a slot machine with dull colors. Our phones and tablets are built the same way - perhaps not as directly intention to addict you - but they do nevertheless through the same neural / optic pathways.
When you get all of these “cheap”, short lived dopamine hits you are going to suffer in the long term. When you don’t have that external stimuli - your baseline will feel much lower and that is why excessive tech use can lead to mental health disorders such as anxiety and depression. This is extremely concerning for our children, who’s mental health is spiraling out of control. Screen time, and blue light, could be a direct cause to this epidemic.
The Solution: Technology that is Designed to Work with Nature
You may read this newsletter and think it is fear mongering, but in truth it is a fair assessment of how man made blue light is affecting our health. Most are not yet on board of the importance of our light environment, so think about this:
You eat 3-4x/day, you drink water maybe 5-10x, you consume light as an input to your biology 24/7/365 (and I am not talking about just visible light). Electromagnetism is fundamentally the most prominent input signal to our biology, and it is the one we have distorted the most with modern technology. Blue light is not bad when it comes from the sun, it is only bad in the wrong context. With the amount of screen time every member of society is racking up each day, to me it is undebatable that artificial blue light + man made EMFs are the two most pervasive environmental toxins and are proliferating the chronic disease epidemic.
Because of this man made electromagnetic radiation, we cannot sleep restoratively, we are anxious + depressed, we are constantly in an inflamed / stressed biological state. The worst part is we are getting more and more addicted to our devices with each passing day.
The solution is simple: fix lighting and spend more time outside. Fix lighting on screens and fix indoor lighting fixtures. Emulate the sun, where you never get blue without the rest of the rainbow, especially red/infrared. We are meant to live in line with nature, and it is only when we deviate that chronic disease becomes prevalent.
This is why I joined the Daylight Computer Company at the beginning of this year. As an EMF/Light educator in regards to health + an Electrical Engineering background - I couldn’t believe my ears when I heard that there was a tech startup trying to become a “healthier Apple” with an innovative reflective screen technology that is blue light free and works with nature instead of against it. This is the sort of innovation we need to end our negative relationship with technology and our disconnection to the real world - the natural world. You can learn more in a recent interview we did with prominent Bitcoiner Marty Bent on TFTC:
Nature is the real world, and nature is the world’s first and most decentralized system. A return to reality is needed, and an understanding that real light is what drives our being is needed to change the direction of our future outcomes as a species.
Stay Sovereign,
Tristan
-
-
 @ dbb19ae0:c3f22d5a
2025-01-18 20:40:48
@ dbb19ae0:c3f22d5a
2025-01-18 20:40:48Inspired by a video on youtube I wrote a calculator with Perl: Beware the line my ($num1, $num2, $operator) = '@'; should be my ($num1, $num2, $operator) = @; But the markdown syntax needs to have the @ into quotes otherwise, well the rest of the program is missing
#!/usr/bin/perl # calculator # use strict; use warnings; sub get_input { print "Enter number 1: "; chomp(my $num1 = <STDIN>); print "Enter number 2: "; chomp(my $num2 = <STDIN>); print "Enter operator (+, -, *, /): "; chomp(my $operator = <STDIN>); return ($num1, $num2, $operator); } sub calculate { my ($num1, $num2, $operator) = '@'_; my $result; if ($operator eq '+') { $result = $num1 + $num2; } elsif ($operator eq '-') { $result = $num1 - $num2; } elsif ($operator eq '*') { $result = $num1 * $num2; } elsif ($operator eq '/') { if ($num2 == 0) { die "Error: Division by zero\n"; } $result = $num1 / $num2; } else { die "Invalid operator\n"; } return $result; } # Get input from the user my ($num1, $num2, $operator) = get_input(); # Calculate the result my $result = calculate($num1, $num2, $operator); # Print the result print "$num1 $operator $num2 = $result\n";originally posted at https://stacker.news/items/816121
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ 3197ad60:7a122b95
2025-01-18 19:14:39
@ 3197ad60:7a122b95
2025-01-18 19:14:39I feel like the new year is slowly starting to settle in. That doesn’t mean I’m off to the races. I still intend to take the whole month (or as long as it takes, really) to make plans and carefully set a course forward. I’m not rushing it, I’m letting it all set, like tea leaves at the bottom of a glass.
I still draw daily (I’m around day 193 now), but the nature of the drawing seems to have changed. Instead of using colours and taking time to capture light and mood, I only seem to be interested in quick line sketches, the quicker, the better.
They go well with being slightly absent-minded, which I am, in a nice way. Instead of looking around for inspiration, I turn to the books I’m reading and just sketch scenes that stay with me.

All drawings in this post are based on The Book of Doors by Gareth Brown, one of the many tasty books I was gifted for Christmas. I’m adding the sketches in the order they were made because it’s kind of funny how the characters emerge. I didn’t plan for the main character to have short light hair, but somehow she does.

The book lends itself perfectly to easy sketching; the characters are not very complicated, but they are described with a lot of visual clues, and the story moves from location to location, leaving clear images in my mind.

It’s pretty clear who’s the bad guy and who’s not, and it was a good exercise to try to show that in a sketch. There is also a lot of movement in the story, with characters being surprised by the events and having to run/ hide/ escape and confront each other.

There are a lot of doors, many different locations and a good dose of time travelling. I don’t think I ever drew a time-travelling kind of scene before, so of course, I had to try. I used the hairstyle, a piece of clothing and a bit of colour to show the same person at two points in time but also in the same room. Did it work?

Recently, I’ve been really into the black and white illustrations in young adult, early reader, and chapter books. I love their simplicity and how much they can convey with a line drawing. I will hang around in that space for a bit, with my quick sketches.
I started a new book, funnily enough also about doors, so I might share more sketches soon.
Thanks for reading.
x
M
-
 @ 554ab6fe:c6cbc27e
2025-01-18 18:49:25
@ 554ab6fe:c6cbc27e
2025-01-18 18:49:25Abstract
There is a growing body of evidence suggesting that depression is becoming a major health concern for the modern world. Given the multitude of stressors advanced civilization provides, people are increasingly ruminating over the past and future. These repetitive non-constructive thoughts provide stress both in the mind and physically manifest itself in our bodily systems, deteriorating our health on multiple fronts. Not only are cases of depression increasing, but many seem to be resistant to current forms of treatment. These treatments include both pharmaceutical and therapeutic methods. Clinicians need to begin taking a serious look at alternate forms of treatment so they can become more equipped to treat patients with depression. Mindfulness meditation is the practice of focusing one’s thoughts entirely on the body itself and trains the mind to forgo all other extraneous thoughts. This technique not only provides the body an immediate sensation of safety and relaxation, but trains the individual to have better control over repetitive unhealthy thoughts. The more frequent feeling of relaxation coupled with the ability to subdue one’s own rumination decreases the body’s activation of its defense protocols. These defenses, also known as the sympathetic nervous system, when activated too frequently can be extremely detrimental to one’s physical and mental health and is strongly correlated to stress and depression. Much research involving mindfulness meditation has shown that it increases one’s ability to have thought control and decreases sympathetic nervous system activity. This is coupled with a heightened awareness of one’s own body, leading to a general increase in self perception and wellbeing. Dramatically reducing the occurrence of stress and depression. The body of meditation research requires further attention. In particular, studies require more standardized forms of meditation methods and an improvement of experimental design to increase statistical significance. That being said, given the effect mindfulness meditation has on depression, it should be viewed as a potential replacement for the treatment of depression through antidepressants. Antidepressants have a large list of potential side effects, are at times shown to be no more effective than a placebo, and have no evidence of preventing depression once treatment has been terminated. Meditation being costless and side effect free, if truly effective, would be a far more ethical and responsible treatment methods for physicians and therapist to prescribe.
Introduction
This paper will review existing literature discussing meditation and its potentially remedial effects on depression. It will argue that by providing increased ability to control and recognize non-constructive thoughts, meditation can decrease stress, thereby helping individuals with clinical depression. It is projected that by 2020, depression will become the second most common mental health issue (Kenny & Williams, 2007). Collectively, stress and depression-related symptoms account for a majority of visits to primary care physicians (Greeson et al., 2018). These disorders have become extremely prevalent and are extremely costly for individuals and the entire health care system (Greeson et al., 2018). That being said, it has been shown that 40% of depression patients are resistant to current treatment methods (Kenny & Williams, 2007), demonstrating that the entire system of treating depression is largely wasteful and inefficient, placing an unnecessary burden on society. Therefore, it is crucial that alternative approaches to treatment are explored. When looking at potential treatment methods for depression, it is important to first consider the underlying causes.
Depression is a complex mental issue that can manifest itself in a variety of different ways, and can stem from a large number of causes. That being said, there appears to be a distinct connection between stress and depression. Researchers have found that repetitive, non-constructive thoughts can lead to depression, and that individuals with acute stress-induced behaviors and hormonal changes have very similar symptoms to those suffering from depression (Watkins, 2008; Kasala et al., 2014). These symptoms commonly include hypercortisolism, which is a rise in cortisol levels due to an increase in sympathetic nervous system activity. Hypercortisolism can lead to high blood pressure, impaired immune function by decreasing cytokine count, poor antibody response, high blood sugar, increased renal retention of sodium, to name a few (Spreng, 2000; Godbout & Glaser, 2006; Kasala et al., 2014). In short, it is a condition that is extremely detrimental to overall health. Neurologically speaking, the relationship between stress and depression can be attributed partly to atrophy of the hippocampus, which is caused by high levels of stress induced glucocorticoid release (Annells et al., 2016).
Modern life is full of stressful situations. People tend to spend large portions of their day ruminating over the past and forecasting for the future. Often, these thoughts bring about worry and regret. Human beings evolved with a “fight or flight” defense response regulated by the sympathetic nervous system in order to protect themselves from physical harm. In modern life, these physical threats are being replaced by mental threats brought upon by our own projections of the past and future (Kuchel & Kuchel, 1991). Not ruminating over such thoughts has been shown to decrease sympathetic nervous system activity (vanOyen Witvliet et al., 2011). There is also a relationship between general cognitive load, and increased sympathetic activity (Mizuno et al., 2011). Therefore, it is of no surprise that high levels of sympathetic nervous system activity is present in cases of major depression (Veith et al., 1994).
The author hypothesizes that treatment methods involving improved thought control can remove stressful thoughts, thereby reducing depressive symptoms. These changes in thought patterns will have an effect on increasing parasympathetic nervous system tone and related neurotransmitters, thereby drawing a link between the cognitive skill of removing unconstructive thoughts and the reduction of stress and depression. Alongside this, the general act of meditation causes the body to feel more relaxed and decreases the activation of the sympathetic nervous system, bringing cortisol to lower levels, which increases general health and well-being. These skills will prove not only applicable to patients for depression, but also to any individual suffering from repetitive non-constructive thoughts that hinder their daily function and worsen their bodily health. This paper, through the lens of existing literature, will explore the connection between meditation’s ability to improve thought control and its promise as a treatment for depression.
Mindfulness Meditation and the Skills Provided
This paper will primarily focus on one of many forms of meditation: mindfulness meditation. Mindfulness meditation is the practice of focusing attention on a single entity, such as one’s breath, in order to take attention away from other, potentially non-constructive thoughts (Wielgosz et al., 2019). Focusing on body and breath in a calm and accepting manner also provides the mind with a sense of safety (Esch, 2014). This technique allows an individual to have an increased awareness of their emotions, and greater control over their thoughts (Barnhofer et al., 2009). Meditation has been shown to increase brain plasticity in the regions used (Lazar et al., 2005). Given the existence of use-dependent brain plasticity, it can be presumed that as meditators use these techniques during their practice, they will also be more easily able to use them in everyday life (Giuliani et al., 2011; Esch, 2014). For example, attention regulation is related to the anterior cingulate cortex (ACC) which is shown to have an increased function in those who practice mindfulness meditation (Rubia, 2009; Hölzel et al., 2011; Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron, 2015). Not only do meditators have increased attention regulation, but they are capable of having greater control of removing irrelevant thoughts. These repetitive thoughts, in the case of depression, usually manifest themselves as negative thoughts regarding their mental condition, poor mood, lack of belief in themselves and an over analysis regarding the consequence and meaning of life events coupled with the expectation of negative outcomes (Watkins, 2008). This is supported by the evidence that alpha bands, which play a role in processing irrelevant information, are faster and significantly more present in those who commonly practice mindfulness meditation (Foxe & Snyder, 2011). Meditation also effects the right amygdala, which is related to the processing of emotions. Reducing depression through the use of SSRIs is partly done by the suppression of right amygdala activity. Those who meditate have reduced right amygdala activity during meditation, and a change in activity was also observed when the subject was no longer meditating (Annells et al., 2016). This indicates that meditation provides more adequate emotional control over incoming stressors, and can potentially act as a replacement for antidepressants. Meditation grants the general awareness and control of emotions, alleviating the body from feeling in danger while granting the individual the ability to recognize unhealthy ruminations and clear them from their thought stream.
The Physiologic Responses of Mindfulness Meditation
The benefit of thought control is evident when analyzing the result of experiments involving mindfulness meditation. Increases sympathetic nervous system activity is present within depression (Veith et al., 1994). Those who have increased mindfulness show decreased stress and a faster recovery from it (Greeson et al., 2018; Gamaiunova et al., 2019). In these individuals, there is a noticeable reduction in sympathetic activity and responsivity, coupled with an increase in parasympathetic nervous system tone (Hoffman et al., 1982; Esch, 2014). This means the body of a meditator shifts away from activating stressful, fight or flight systems, and relaxed state processes begin to dominate. Stress related neurotransmitters such as norepinephrine and cortisol are also shown to be less present in individuals that practice meditation (Esch et al., 2007; Esch, 2014). This also indicates that meditation has a general effect on physical health. As previously stated, high levels of cortisol have serious effects on bodily health; thus, lessening cortisol will provide general well-being, as well as the cognitive benefits discussed above. Chronic stress has been connected to lower acetylcholine levels. Interestingly enough, the breath of meditators has elevated nitric oxide levels. Presumably because there are higher levels of acetylcholine and morphine, which both increase the activity of oxide-producing enzymes (Esch, 2014). Dopamine is often related inversely to the presence of depression, and it too has been shown to increase amongst those who practice meditation (Dailly et al., 2004; Jung et al., 2010; Esch, 2014). It is also has been suggested that the increase in internalized attention during mediation, triggers activity in brain regions such as the left frontal cortex that are related to positive emotions (Rubia, 2009). This, coupled with the general health benefits of decreasing sympathetic activity and cortisol levels, is likely the reason why meditators often express a general higher satisfaction with their life and are more content (Esch et al., 2007). That being said, meditators also have a higher awareness of their own health. Meditators show an increase use of the ACC and insula, signifying that they have a greater means of modulating the self, alongside pain perception and anticipation. It is theorized that this increase in awareness grants the individual a sense of responsibility to improve their health (Esch, 2014). There is likely a feedback loops that occurs when one meditates: the individual decreases sympathetic nervous system activity, thereby increasing their health and wellbeing, while also gaining a higher perception of their health that results in further attention and improvement.
The Missing Component
Many metanalytical papers have attempted to synthesize the findings of mediation research. Many conclude, as this paper does, that the main neuronal mechanism of mindfulness generally involves: attention regulation of the body and mind, nonreactivity to experiences, and changes of self-perception (Hölzel et al., 2011; Esch, 2014; Wielgosz et al., 2019). Even though the effects on the autonomic nervous system are discussed, they are seemingly ignored as a key factor contributing to the higher quality of life and state of mind experienced by those that practice meditation. That being said, authors neglect to mention that there are two different arguments being put forth. The first is that people who meditate are, at that moment, putting themselves in a peaceful and quiet mindset that makes the body feel safe, thereby increasing parasympathetic nervous system activity (Esch, 2014). The second is that it is the skills learned from the meditation that allow for individuals to remove the unconstructive thoughts in the face of stressful situations, thereby preventing an increase in sympathetic nervous system activity. Of course, these two mechanisms may both occur, and perhaps due to the change in brain plasticity, the practices of stress relief during meditation aids the patient in using those same skill in everyday life. However, this distinction is key not only for general scientific understanding, but also for future research.
The existence of the two possible mechanisms suggests the need for further investigation. Researchers, rather than observing the improvement in self-reported depression scores, should be focusing on changes in autonomic nervous system changes. To differentiate between the two mechanisms, researchers should monitor autonomic nervous system activity during the act of meditation and after a series of prolonged practices. This type of experiment could ascertain whether or not the bulk of decrease in sympathetic nervous system activity and increase in parasympathetic nervous system activity occurs at the moment of meditation, or afterwards through the skills obtained. Perhaps the two systems change at different times, or the changes are evenly distributed across both events. Either way, this type of experiment seems necessary to gain a deeper understanding of the mechanisms involved in treating depression. Furthermore, these distinctions are important in determining which techniques of mindfulness meditation provide the best results.
Criticisms
A key criticism of meditation research is that the method of meditation used in the studies is not constant. There are many forms of meditation practiced around the world, and many have different purposes. The most traditional and commonly practiced forms of meditation involve focusing attention on a single thing, which makes the research of mindfulness meditation particularly difficult because many will consider a wide range of practices to fall under the classification of mindfulness meditation. Even in this paper, that focuses exclusively on mindfulness meditation research, papers were presented that consider Tai Chi as inclusive to that criteria (Esch et al., 2007). Given the coordination of movements and the need for an instructor, Tai Chi can hardly be classified as a means of training thought control. Nonetheless, that example is quite extreme and most mindfulness-based meditation research involves one of these 4 types: traditional meditation, meditation in a clinical setting, mindfulness in a transient state and mindfulness as a dispositional trait (Chiesa et al., 2014). Despite the similarities, these all have vast differences in terms of how the meditation is practiced. For example, traditional meditation is done alone, and a more silent environment helps an individual focus on their breath. In a clinical setting, researchers conduct mindfulness-based cognitive therapy (MBCT), in which the meditation is done in a group setting led by a teacher (Kenny & Williams, 2007). In this particular study of Kenny and Williams 2007, patients were also assigned homework of 1 hour of practice per day of yoga or meditation. Even though yoga is traditionally a physical form of mindfulness meditation, it is not in western cultures. In western cultures, Yoga becomes more a practice of listening to an instructor and stretching, which is not conducive to focusing solely on the breath. This highlights the difficulty of deciding whether or not the benefits of meditation come from the practice itself or the skills learned from it, since all of these studies use methods of meditation that vaguely resemble one another in practice. If all studies use different forms of meditation, then no matter how similar the results across studies are, there is no clear conclusion on the mechanism by which these changes occur. An obvious solution to this problem is to create a method of meditation that is traditionally used by all meditators, and to have many studies done all using the same method. Since it would be hard to mandate all researchers to use the same procedures, another option is to conduct more research on the meditators’ brain activity at the time of meditation. Perhaps these observations would shed more light on the neurological processes occurring during meditation, and these results would hopefully suggest which techniques provide the same types of skills and mental processes. That being said, it is also important for researchers to consider the mechanism by which the skills of thought control are brought about before the initiation of the experiment. Practices like Thai Chi and Yoga being from eastern cultures does not classify them as mindfulness meditation and effective procedures to promote thought control.
The conclusions of some experiments discussed in this paper need to be taken with skepticism. Many studies are conducted with small sample sizes (Kenny & Williams, 2007; Barnhofer et al., 2009; Kasala et al., 2014). There are even studies, such as the Kenny and Williams study in 2007 discussed above that do not have a control group or any other group to make a comparison to. They even allowed the patients to take their regular medications for their disorders. This, alongside the absence of a control group, makes it extremely difficult to scientifically show that the MBCT was the reason for the decrease in depression scores at all. While other studies had a well-constructed design, most studies that conduct a T-test or ANOVA in their analysis fail to show that their data is normally distributed (Kenny & Williams, 2007; Barnhofer et al., 2009; Greeson et al., 2018). A normal distribution of data is a key assumption for both of these commonly used statistical test, and without proper proof of normality, the results of these test are questionable at best. Sadly, much of scientific literature contains these forms of statistical errors (Halsey et al., 2015). Though these flaws are not present in all mindfulness meditation experiments, the use of these studies as concrete evidence of its effectiveness is rightfully scrutinized. Most studies tend to have similar results, which suggests that mindfulness meditation effects depression. Nonetheless, given the design flaws of experiments and inconsistency in meditation methods, these studies should be used more as an indicator of the existence of a relationship between mindfulness meditation and depression than evidence that such a relationship exists. Much more diligent and thorough work is required for there to be scientific validity, and the ability to claim that meditation is truly a useful method of treatment. To start, many of these experiments should be repeated with improvements to their design, such as including control groups and more consistent methods of mediation, in order to validate the significance of their p-values. This will provide much more statistically significant evidence suggesting that mindfulness meditation is the true cause of the alleviation of depressive symptoms.
Conclusion
Despite the lack of concrete evidence and methods, there is a case to adopt this practice sooner rather than later. Given most experiments involving mindfulness meditation and its effects on depression share similar results, it is reasonable to assume that there is some true effect mindfulness meditation has on alleviating the disorder. The aim of the physician should be to provide a patient that has emotional challenges the tools and skills needed to manage and subdue the unhealthy habits of thinking on their own. Traditionally, this method is through the use of pharmaceutical drugs that act to change brain chemistry. This is not only a costly expense on the individual, but there is growing evidence suggesting that many antidepressants are not much more effective than a placebo (Kirsch et al., 2002; Antonuccio et al., 2002). Not only that, but antidepressant have numerous negative long-term side effects, such as withdrawals, sexual problems, weight gain and becoming emotionally numb (Masand & Gupta, 2002; Cartwright et al., 2016). There is also no publish evidence to claim that antidepressants reduce the risk of depression once the treatment has ended (Annells et al., 2016). Therefore, antidepressants should not be thought of as a viable clinical solution in the long-run. Meditation on the other hand is completely free, and can be a useful practice in an individual’s personal life. Given its simplicity, it is also void of negative side effects, and in that sense is a much more ethical and risk-averse form of treatment from a clinical standpoint. Therefore, it is prudent that the scientific community give increased attention to meditation research, so that we can further understand its benefits and perfect its techniques, to potentially help all those who suffer from depression in a safe and cost-effective manner.
Works Cited
Annells S, Kho K & Bridge P (2016). Meditate don’t medicate: How medical imaging evidence supports the role of meditation in the treatment of depression. Radiography 22, e54–e58.
Antonuccio DO, Burns DD & Danton WG (2002). Antidepressants: A triumph of marketing over science? Prev Treat; DOI: 10.1037/1522-3736.5.1.525c.
Barnhofer T, Crane C, Hargus E, Amarasinghe M, Winder R & Williams JMG (2009). Mindfulness-based cognitive therapy as a treatment for chronic depression: A preliminary study. Behav Res Ther 47, 366–373.
Cartwright C, Gibson K, Read J, Cowan O & Dehar T (2016). Long-term antidepressant use: patient perspectives of benefits and adverse effects. Patient Prefer Adherence 10, 1401–1407.
Chiesa A, Anselmi R & Serretti A (2014). Psychological Mechanisms of Mindfulness-Based Interventions. Holist Nurs Pract 28, 124–148.
Dailly E, Chenu F, Renard CE & Bourin M (2004). Dopamine, depression and antidepressants. Fundam Clin Pharmacol 18, 601–607.
Esch T (2014). The Neurobiology of Meditation and Mindfulness. In, pp. 153–173. Springer, Cham. Available at: http://link.springer.com/10.1007/978-3-319-01634-4_9 [Accessed October 1, 2019].
Esch T, Duckstein J, Welke J & Braun V (2007). Mind/body techniques for physiological and psychological stress reduction: stress management via Tai Chi training – a pilot study. Med Sci Monit 13, CR488-497.
Foxe JJ & Snyder AC (2011). The Role of Alpha-Band Brain Oscillations as a Sensory Suppression Mechanism during Selective Attention. Front Psychol 2, 154.
Gamaiunova L, Brandt P-Y, Bondolfi G & Kliegel M (2019). Exploration of psychological mechanisms of the reduced stress response in long-term meditation practitioners. Psychoneuroendocrinology 104, 143–151.
Giuliani NR, Drabant EM, Bhatnagar R & Gross JJ (2011). Emotion regulation and brain plasticity: Expressive suppression use predicts anterior insula volume. Neuroimage 58, 10–15.
Godbout JP & Glaser R (2006). Stress-Induced Immune Dysregulation: Implications for Wound Healing, Infectious Disease and Cancer. J Neuroimmune Pharmacol 1, 421–427.
Greeson JM, Zarrin H, Smoski MJ, Brantley JG, Lynch TR, Webber DM, Hall MH, Suarez EC & Wolever RQ (2018). Mindfulness Meditation Targets Transdiagnostic Symptoms Implicated in Stress-Related Disorders: Understanding Relationships between Changes in Mindfulness, Sleep Quality, and Physical Symptoms. Evidence-Based Complement Altern Med 2018, 1–10.
Halsey LG, Curran-Everett D, Vowler SL & Drummond GB (2015). The fickle P value generates irreproducible results. Nat Methods 12, 179–185.
Hoffman J, Benson H, Arns P, Stainbrook G, Landsberg G, Young J & Gill A (1982). Science. Science (80- ) 192, 1242–1244.
Hölzel BK, Lazar SW, Gard T, Schuman-Olivier Z, Vago DR & Ott U (2011). How Does Mindfulness Meditation Work? Proposing Mechanisms of Action From a Conceptual and Neural Perspective. Perspect Psychol Sci 6, 537–559.
Jung Y-H, Kang D-H, Jang JH, Park HY, Byun MS, Kwon SJ, Jang G-E, Lee US, An SC & Kwon JS (2010). The effects of mind–body training on stress reduction, positive affect, and plasma catecholamines. Neurosci Lett 479, 138–142.
Kasala ER, Bodduluru LN, Maneti Y & Thipparaboina R (2014). Effect of meditation on neurophysiological changes in stress mediated depression. Complement Ther Clin Pract 20, 74–80.
Kenny MA & Williams JMG (2007). Treatment-resistant depressed patients show a good response to Mindfulness-based Cognitive Therapy. Behav Res Ther 45, 617–625.
Kirsch I, Scoboria A & Moore TJ (2002). Antidepressants and placebos: Secrets, revelations, and unanswered questions. Prev Treat; DOI: 10.1037/1522-3736.5.1.533r.
Kuchel OG & Kuchel GA (1991). Peripheral dopamine in pathophysiology of hypertension. Interaction with aging and lifestyle. Hypertension 18, 709–721.
Lazar SW, Kerr CE, Wasserman RH, Gray JR, Greve DN, Treadway MT, McGarvey M, Quinn BT, Dusek JA, Benson H, Rauch SL, Moore CI & Fischl B (2005). Meditation experience is associated with increased cortical thickness. Neuroreport 16, 1893–1897.
Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron CD (2015). PsycNET. Am Psychol 70, 632–658.
Masand PS & Gupta S (2002). Long-Term Side Effects of Newer-Generation Antidepressants: SSRIS, Venlafaxine, Nefazodone, Bupropion, and Mirtazapine. Ann Clin Psychiatry 14, 175–182.
Mizuno K, Tanaka M, Yamaguti K, Kajimoto O, Kuratsune H & Watanabe Y (2011). Mental fatigue caused by prolonged cognitive load associated with sympathetic hyperactivity. Behav Brain Funct 7, 17.
Rubia K (2009). The neurobiology of Meditation and its clinical effectiveness in psychiatric disorders. Biol Psychol 82, 1–11.
Spreng M (2000). Possible health effects of noise induced cortisol increase. Noise Health 2, 59–64.
vanOyen Witvliet C, DeYoung NJ, Hofelich AJ & DeYoung PA (2011). Compassionate reappraisal and emotion suppression as alternatives to offense-focused rumination: Implications for forgiveness and psychophysiological well-being. J Posit Psychol 6, 286–299.
Veith RC, Lewis N, Linares OA, Barnes RF, Raskind MA, Villacres EC, Murburg MM, Ashleigh EA, Castillo S, Peskind ER, Pascualy M & Halter JB (1994). Sympathetic Nervous System Activity in Major Depression. Arch Gen Psychiatry 51, 411.
Watkins ER (2008). Constructive and unconstructive repetitive thought. Psychol Bull 134, 163–206.
Wielgosz J, Goldberg SB, Kral TRA, Dunne JD & Davidson RJ (2019). Mindfulness Meditation and Psychopathology. Annu Rev Clin Psychol 15, 285–316.
Abstract There is a growing body of evidence suggesting that depression is becoming a major health concern for the modern world. Given the multitude of stressors advanced civilization provides, people are increasingly ruminating over the past and future. These repetitive non-constructive thoughts provide stress both in the mind and physically manifest itself in our bodily systems, deteriorating our health on multiple fronts. Not only are cases of depression increasing, but many seem to be resistant to current forms of treatment. These treatments include both pharmaceutical and therapeutic methods. Clinicians need to begin taking a serious look at alternate forms of treatment so they can become more equipped to treat patients with depression. Mindfulness meditation is the practice of focusing one’s thoughts entirely on the body itself and trains the mind to forgo all other extraneous thoughts. This technique not only provides the body an immediate sensation of safety and relaxation, but trains the individual to have better control over repetitive unhealthy thoughts. The more frequent feeling of relaxation coupled with the ability to subdue one’s own rumination decreases the body’s activation of its defense protocols. These defenses, also known as the sympathetic nervous system, when activated too frequently can be extremely detrimental to one’s physical and mental health and is strongly correlated to stress and depression. Much research involving mindfulness meditation has shown that it increases one’s ability to have thought control and decreases sympathetic nervous system activity. This is coupled with a heightened awareness of one’s own body, leading to a general increase in self perception and wellbeing. Dramatically reducing the occurrence of stress and depression. The body of meditation research requires further attention. In particular, studies require more standardized forms of meditation methods and an improvement of experimental design to increase statistical significance. That being said, given the effect mindfulness meditation has on depression, it should be viewed as a potential replacement for the treatment of depression through antidepressants. Antidepressants have a large list of potential side effects, are at times shown to be no more effective than a placebo, and have no evidence of preventing depression once treatment has been terminated. Meditation being costless and side effect free, if truly effective, would be a far more ethical and responsible treatment methods for physicians and therapist to prescribe.
Introduction
This paper will review existing literature discussing meditation and its potentially remedial effects on depression. It will argue that by providing increased ability to control and recognize non-constructive thoughts, meditation can decrease stress, thereby helping individuals with clinical depression. It is projected that by 2020, depression will become the second most common mental health issue (Kenny & Williams, 2007). Collectively, stress and depression-related symptoms account for a majority of visits to primary care physicians (Greeson et al., 2018). These disorders have become extremely prevalent and are extremely costly for individuals and the entire health care system (Greeson et al., 2018). That being said, it has been shown that 40% of depression patients are resistant to current treatment methods (Kenny & Williams, 2007), demonstrating that the entire system of treating depression is largely wasteful and inefficient, placing an unnecessary burden on society. Therefore, it is crucial that alternative approaches to treatment are explored. When looking at potential treatment methods for depression, it is important to first consider the underlying causes.
Depression is a complex mental issue that can manifest itself in a variety of different ways, and can stem from a large number of causes. That being said, there appears to be a distinct connection between stress and depression. Researchers have found that repetitive, non-constructive thoughts can lead to depression, and that individuals with acute stress-induced behaviors and hormonal changes have very similar symptoms to those suffering from depression (Watkins, 2008; Kasala et al., 2014). These symptoms commonly include hypercortisolism, which is a rise in cortisol levels due to an increase in sympathetic nervous system activity. Hypercortisolism can lead to high blood pressure, impaired immune function by decreasing cytokine count, poor antibody response, high blood sugar, increased renal retention of sodium, to name a few (Spreng, 2000; Godbout & Glaser, 2006; Kasala et al., 2014). In short, it is a condition that is extremely detrimental to overall health. Neurologically speaking, the relationship between stress and depression can be attributed partly to atrophy of the hippocampus, which is caused by high levels of stress induced glucocorticoid release (Annells et al., 2016).
Modern life is full of stressful situations. People tend to spend large portions of their day ruminating over the past and forecasting for the future. Often, these thoughts bring about worry and regret. Human beings evolved with a “fight or flight” defense response regulated by the sympathetic nervous system in order to protect themselves from physical harm. In modern life, these physical threats are being replaced by mental threats brought upon by our own projections of the past and future (Kuchel & Kuchel, 1991). Not ruminating over such thoughts has been shown to decrease sympathetic nervous system activity (vanOyen Witvliet et al., 2011). There is also a relationship between general cognitive load, and increased sympathetic activity (Mizuno et al., 2011). Therefore, it is of no surprise that high levels of sympathetic nervous system activity is present in cases of major depression (Veith et al., 1994).
The author hypothesizes that treatment methods involving improved thought control can remove stressful thoughts, thereby reducing depressive symptoms. These changes in thought patterns will have an effect on increasing parasympathetic nervous system tone and related neurotransmitters, thereby drawing a link between the cognitive skill of removing unconstructive thoughts and the reduction of stress and depression. Alongside this, the general act of meditation causes the body to feel more relaxed and decreases the activation of the sympathetic nervous system, bringing cortisol to lower levels, which increases general health and well-being. These skills will prove not only applicable to patients for depression, but also to any individual suffering from repetitive non-constructive thoughts that hinder their daily function and worsen their bodily health. This paper, through the lens of existing literature, will explore the connection between meditation’s ability to improve thought control and its promise as a treatment for depression.
Mindfulness Meditation and the Skills Provided
This paper will primarily focus on one of many forms of meditation: mindfulness meditation. Mindfulness meditation is the practice of focusing attention on a single entity, such as one’s breath, in order to take attention away from other, potentially non-constructive thoughts (Wielgosz et al., 2019). Focusing on body and breath in a calm and accepting manner also provides the mind with a sense of safety (Esch, 2014). This technique allows an individual to have an increased awareness of their emotions, and greater control over their thoughts (Barnhofer et al., 2009). Meditation has been shown to increase brain plasticity in the regions used (Lazar et al., 2005). Given the existence of use-dependent brain plasticity, it can be presumed that as meditators use these techniques during their practice, they will also be more easily able to use them in everyday life (Giuliani et al., 2011; Esch, 2014). For example, attention regulation is related to the anterior cingulate cortex (ACC) which is shown to have an increased function in those who practice mindfulness meditation (Rubia, 2009; Hölzel et al., 2011; Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron, 2015). Not only do meditators have increased attention regulation, but they are capable of having greater control of removing irrelevant thoughts. These repetitive thoughts, in the case of depression, usually manifest themselves as negative thoughts regarding their mental condition, poor mood, lack of belief in themselves and an over analysis regarding the consequence and meaning of life events coupled with the expectation of negative outcomes (Watkins, 2008). This is supported by the evidence that alpha bands, which play a role in processing irrelevant information, are faster and significantly more present in those who commonly practice mindfulness meditation (Foxe & Snyder, 2011). Meditation also effects the right amygdala, which is related to the processing of emotions. Reducing depression through the use of SSRIs is partly done by the suppression of right amygdala activity. Those who meditate have reduced right amygdala activity during meditation, and a change in activity was also observed when the subject was no longer meditating (Annells et al., 2016). This indicates that meditation provides more adequate emotional control over incoming stressors, and can potentially act as a replacement for antidepressants. Meditation grants the general awareness and control of emotions, alleviating the body from feeling in danger while granting the individual the ability to recognize unhealthy ruminations and clear them from their thought stream.
The Physiologic Responses of Mindfulness Meditation
The benefit of thought control is evident when analyzing the result of experiments involving mindfulness meditation. Increases sympathetic nervous system activity is present within depression (Veith et al., 1994). Those who have increased mindfulness show decreased stress and a faster recovery from it (Greeson et al., 2018; Gamaiunova et al., 2019). In these individuals, there is a noticeable reduction in sympathetic activity and responsivity, coupled with an increase in parasympathetic nervous system tone (Hoffman et al., 1982; Esch, 2014). This means the body of a meditator shifts away from activating stressful, fight or flight systems, and relaxed state processes begin to dominate. Stress related neurotransmitters such as norepinephrine and cortisol are also shown to be less present in individuals that practice meditation (Esch et al., 2007; Esch, 2014). This also indicates that meditation has a general effect on physical health. As previously stated, high levels of cortisol have serious effects on bodily health; thus, lessening cortisol will provide general well-being, as well as the cognitive benefits discussed above. Chronic stress has been connected to lower acetylcholine levels. Interestingly enough, the breath of meditators has elevated nitric oxide levels. Presumably because there are higher levels of acetylcholine and morphine, which both increase the activity of oxide-producing enzymes (Esch, 2014). Dopamine is often related inversely to the presence of depression, and it too has been shown to increase amongst those who practice meditation (Dailly et al., 2004; Jung et al., 2010; Esch, 2014). It is also has been suggested that the increase in internalized attention during mediation, triggers activity in brain regions such as the left frontal cortex that are related to positive emotions (Rubia, 2009). This, coupled with the general health benefits of decreasing sympathetic activity and cortisol levels, is likely the reason why meditators often express a general higher satisfaction with their life and are more content (Esch et al., 2007). That being said, meditators also have a higher awareness of their own health. Meditators show an increase use of the ACC and insula, signifying that they have a greater means of modulating the self, alongside pain perception and anticipation. It is theorized that this increase in awareness grants the individual a sense of responsibility to improve their health (Esch, 2014). There is likely a feedback loops that occurs when one meditates: the individual decreases sympathetic nervous system activity, thereby increasing their health and wellbeing, while also gaining a higher perception of their health that results in further attention and improvement.
The Missing Component
Many metanalytical papers have attempted to synthesize the findings of mediation research. Many conclude, as this paper does, that the main neuronal mechanism of mindfulness generally involves: attention regulation of the body and mind, nonreactivity to experiences, and changes of self-perception (Hölzel et al., 2011; Esch, 2014; Wielgosz et al., 2019). Even though the effects on the autonomic nervous system are discussed, they are seemingly ignored as a key factor contributing to the higher quality of life and state of mind experienced by those that practice meditation. That being said, authors neglect to mention that there are two different arguments being put forth. The first is that people who meditate are, at that moment, putting themselves in a peaceful and quiet mindset that makes the body feel safe, thereby increasing parasympathetic nervous system activity (Esch, 2014). The second is that it is the skills learned from the meditation that allow for individuals to remove the unconstructive thoughts in the face of stressful situations, thereby preventing an increase in sympathetic nervous system activity. Of course, these two mechanisms may both occur, and perhaps due to the change in brain plasticity, the practices of stress relief during meditation aids the patient in using those same skill in everyday life. However, this distinction is key not only for general scientific understanding, but also for future research.
The existence of the two possible mechanisms suggests the need for further investigation. Researchers, rather than observing the improvement in self-reported depression scores, should be focusing on changes in autonomic nervous system changes. To differentiate between the two mechanisms, researchers should monitor autonomic nervous system activity during the act of meditation and after a series of prolonged practices. This type of experiment could ascertain whether or not the bulk of decrease in sympathetic nervous system activity and increase in parasympathetic nervous system activity occurs at the moment of meditation, or afterwards through the skills obtained. Perhaps the two systems change at different times, or the changes are evenly distributed across both events. Either way, this type of experiment seems necessary to gain a deeper understanding of the mechanisms involved in treating depression. Furthermore, these distinctions are important in determining which techniques of mindfulness meditation provide the best results.
Criticisms
A key criticism of meditation research is that the method of meditation used in the studies is not constant. There are many forms of meditation practiced around the world, and many have different purposes. The most traditional and commonly practiced forms of meditation involve focusing attention on a single thing, which makes the research of mindfulness meditation particularly difficult because many will consider a wide range of practices to fall under the classification of mindfulness meditation. Even in this paper, that focuses exclusively on mindfulness meditation research, papers were presented that consider Tai Chi as inclusive to that criteria (Esch et al., 2007). Given the coordination of movements and the need for an instructor, Tai Chi can hardly be classified as a means of training thought control. Nonetheless, that example is quite extreme and most mindfulness-based meditation research involves one of these 4 types: traditional meditation, meditation in a clinical setting, mindfulness in a transient state and mindfulness as a dispositional trait (Chiesa et al., 2014). Despite the similarities, these all have vast differences in terms of how the meditation is practiced. For example, traditional meditation is done alone, and a more silent environment helps an individual focus on their breath. In a clinical setting, researchers conduct mindfulness-based cognitive therapy (MBCT), in which the meditation is done in a group setting led by a teacher (Kenny & Williams, 2007). In this particular study of Kenny and Williams 2007, patients were also assigned homework of 1 hour of practice per day of yoga or meditation. Even though yoga is traditionally a physical form of mindfulness meditation, it is not in western cultures. In western cultures, Yoga becomes more a practice of listening to an instructor and stretching, which is not conducive to focusing solely on the breath. This highlights the difficulty of deciding whether or not the benefits of meditation come from the practice itself or the skills learned from it, since all of these studies use methods of meditation that vaguely resemble one another in practice. If all studies use different forms of meditation, then no matter how similar the results across studies are, there is no clear conclusion on the mechanism by which these changes occur. An obvious solution to this problem is to create a method of meditation that is traditionally used by all meditators, and to have many studies done all using the same method. Since it would be hard to mandate all researchers to use the same procedures, another option is to conduct more research on the meditators’ brain activity at the time of meditation. Perhaps these observations would shed more light on the neurological processes occurring during meditation, and these results would hopefully suggest which techniques provide the same types of skills and mental processes. That being said, it is also important for researchers to consider the mechanism by which the skills of thought control are brought about before the initiation of the experiment. Practices like Thai Chi and Yoga being from eastern cultures does not classify them as mindfulness meditation and effective procedures to promote thought control.
The conclusions of some experiments discussed in this paper need to be taken with skepticism. Many studies are conducted with small sample sizes (Kenny & Williams, 2007; Barnhofer et al., 2009; Kasala et al., 2014). There are even studies, such as the Kenny and Williams study in 2007 discussed above that do not have a control group or any other group to make a comparison to. They even allowed the patients to take their regular medications for their disorders. This, alongside the absence of a control group, makes it extremely difficult to scientifically show that the MBCT was the reason for the decrease in depression scores at all. While other studies had a well-constructed design, most studies that conduct a T-test or ANOVA in their analysis fail to show that their data is normally distributed (Kenny & Williams, 2007; Barnhofer et al., 2009; Greeson et al., 2018). A normal distribution of data is a key assumption for both of these commonly used statistical test, and without proper proof of normality, the results of these test are questionable at best. Sadly, much of scientific literature contains these forms of statistical errors (Halsey et al., 2015). Though these flaws are not present in all mindfulness meditation experiments, the use of these studies as concrete evidence of its effectiveness is rightfully scrutinized. Most studies tend to have similar results, which suggests that mindfulness meditation effects depression. Nonetheless, given the design flaws of experiments and inconsistency in meditation methods, these studies should be used more as an indicator of the existence of a relationship between mindfulness meditation and depression than evidence that such a relationship exists. Much more diligent and thorough work is required for there to be scientific validity, and the ability to claim that meditation is truly a useful method of treatment. To start, many of these experiments should be repeated with improvements to their design, such as including control groups and more consistent methods of mediation, in order to validate the significance of their p-values. This will provide much more statistically significant evidence suggesting that mindfulness meditation is the true cause of the alleviation of depressive symptoms.
Conclusion
Despite the lack of concrete evidence and methods, there is a case to adopt this practice sooner rather than later. Given most experiments involving mindfulness meditation and its effects on depression share similar results, it is reasonable to assume that there is some true effect mindfulness meditation has on alleviating the disorder. The aim of the physician should be to provide a patient that has emotional challenges the tools and skills needed to manage and subdue the unhealthy habits of thinking on their own. Traditionally, this method is through the use of pharmaceutical drugs that act to change brain chemistry. This is not only a costly expense on the individual, but there is growing evidence suggesting that many antidepressants are not much more effective than a placebo (Kirsch et al., 2002; Antonuccio et al., 2002). Not only that, but antidepressant have numerous negative long-term side effects, such as withdrawals, sexual problems, weight gain and becoming emotionally numb (Masand & Gupta, 2002; Cartwright et al., 2016). There is also no publish evidence to claim that antidepressants reduce the risk of depression once the treatment has ended (Annells et al., 2016). Therefore, antidepressants should not be thought of as a viable clinical solution in the long-run. Meditation on the other hand is completely free, and can be a useful practice in an individual’s personal life. Given its simplicity, it is also void of negative side effects, and in that sense is a much more ethical and risk-averse form of treatment from a clinical standpoint. Therefore, it is prudent that the scientific community give increased attention to meditation research, so that we can further understand its benefits and perfect its techniques, to potentially help all those who suffer from depression in a safe and cost-effective manner.
Works Cited
Annells S, Kho K & Bridge P (2016). Meditate don’t medicate: How medical imaging evidence supports the role of meditation in the treatment of depression. Radiography 22, e54–e58.
Antonuccio DO, Burns DD & Danton WG (2002). Antidepressants: A triumph of marketing over science? Prev Treat; DOI: 10.1037/1522-3736.5.1.525c.
Barnhofer T, Crane C, Hargus E, Amarasinghe M, Winder R & Williams JMG (2009). Mindfulness-based cognitive therapy as a treatment for chronic depression: A preliminary study. Behav Res Ther 47, 366–373.
Cartwright C, Gibson K, Read J, Cowan O & Dehar T (2016). Long-term antidepressant use: patient perspectives of benefits and adverse effects. Patient Prefer Adherence 10, 1401–1407.
Chiesa A, Anselmi R & Serretti A (2014). Psychological Mechanisms of Mindfulness-Based Interventions. Holist Nurs Pract 28, 124–148.
Dailly E, Chenu F, Renard CE & Bourin M (2004). Dopamine, depression and antidepressants. Fundam Clin Pharmacol 18, 601–607.
Esch T (2014). The Neurobiology of Meditation and Mindfulness. In, pp. 153–173. Springer, Cham. Available at: http://link.springer.com/10.1007/978-3-319-01634-4_9 [Accessed October 1, 2019].
Esch T, Duckstein J, Welke J & Braun V (2007). Mind/body techniques for physiological and psychological stress reduction: stress management via Tai Chi training – a pilot study. Med Sci Monit 13, CR488-497.
Foxe JJ & Snyder AC (2011). The Role of Alpha-Band Brain Oscillations as a Sensory Suppression Mechanism during Selective Attention. Front Psychol 2, 154.
Gamaiunova L, Brandt P-Y, Bondolfi G & Kliegel M (2019). Exploration of psychological mechanisms of the reduced stress response in long-term meditation practitioners. Psychoneuroendocrinology 104, 143–151.
Giuliani NR, Drabant EM, Bhatnagar R & Gross JJ (2011). Emotion regulation and brain plasticity: Expressive suppression use predicts anterior insula volume. Neuroimage 58, 10–15.
Godbout JP & Glaser R (2006). Stress-Induced Immune Dysregulation: Implications for Wound Healing, Infectious Disease and Cancer. J Neuroimmune Pharmacol 1, 421–427.
Greeson JM, Zarrin H, Smoski MJ, Brantley JG, Lynch TR, Webber DM, Hall MH, Suarez EC & Wolever RQ (2018). Mindfulness Meditation Targets Transdiagnostic Symptoms Implicated in Stress-Related Disorders: Understanding Relationships between Changes in Mindfulness, Sleep Quality, and Physical Symptoms. Evidence-Based Complement Altern Med 2018, 1–10.
Halsey LG, Curran-Everett D, Vowler SL & Drummond GB (2015). The fickle P value generates irreproducible results. Nat Methods 12, 179–185.
Hoffman J, Benson H, Arns P, Stainbrook G, Landsberg G, Young J & Gill A (1982). Science. Science (80- ) 192, 1242–1244.
Hölzel BK, Lazar SW, Gard T, Schuman-Olivier Z, Vago DR & Ott U (2011). How Does Mindfulness Meditation Work? Proposing Mechanisms of Action From a Conceptual and Neural Perspective. Perspect Psychol Sci 6, 537–559.
Jung Y-H, Kang D-H, Jang JH, Park HY, Byun MS, Kwon SJ, Jang G-E, Lee US, An SC & Kwon JS (2010). The effects of mind–body training on stress reduction, positive affect, and plasma catecholamines. Neurosci Lett 479, 138–142.
Kasala ER, Bodduluru LN, Maneti Y & Thipparaboina R (2014). Effect of meditation on neurophysiological changes in stress mediated depression. Complement Ther Clin Pract 20, 74–80.
Kenny MA & Williams JMG (2007). Treatment-resistant depressed patients show a good response to Mindfulness-based Cognitive Therapy. Behav Res Ther 45, 617–625.
Kirsch I, Scoboria A & Moore TJ (2002). Antidepressants and placebos: Secrets, revelations, and unanswered questions. Prev Treat; DOI: 10.1037/1522-3736.5.1.533r.
Kuchel OG & Kuchel GA (1991). Peripheral dopamine in pathophysiology of hypertension. Interaction with aging and lifestyle. Hypertension 18, 709–721.
Lazar SW, Kerr CE, Wasserman RH, Gray JR, Greve DN, Treadway MT, McGarvey M, Quinn BT, Dusek JA, Benson H, Rauch SL, Moore CI & Fischl B (2005). Meditation experience is associated with increased cortical thickness. Neuroreport 16, 1893–1897.
Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron CD (2015). PsycNET. Am Psychol 70, 632–658.
Masand PS & Gupta S (2002). Long-Term Side Effects of Newer-Generation Antidepressants: SSRIS, Venlafaxine, Nefazodone, Bupropion, and Mirtazapine. Ann Clin Psychiatry 14, 175–182.
Mizuno K, Tanaka M, Yamaguti K, Kajimoto O, Kuratsune H & Watanabe Y (2011). Mental fatigue caused by prolonged cognitive load associated with sympathetic hyperactivity. Behav Brain Funct 7, 17.
Rubia K (2009). The neurobiology of Meditation and its clinical effectiveness in psychiatric disorders. Biol Psychol 82, 1–11.
Spreng M (2000). Possible health effects of noise induced cortisol increase. Noise Health 2, 59–64.
vanOyen Witvliet C, DeYoung NJ, Hofelich AJ & DeYoung PA (2011). Compassionate reappraisal and emotion suppression as alternatives to offense-focused rumination: Implications for forgiveness and psychophysiological well-being. J Posit Psychol 6, 286–299.
Veith RC, Lewis N, Linares OA, Barnes RF, Raskind MA, Villacres EC, Murburg MM, Ashleigh EA, Castillo S, Peskind ER, Pascualy M & Halter JB (1994). Sympathetic Nervous System Activity in Major Depression. Arch Gen Psychiatry 51, 411.
Watkins ER (2008). Constructive and unconstructive repetitive thought. Psychol Bull 134, 163–206.
Wielgosz J, Goldberg SB, Kral TRA, Dunne JD & Davidson RJ (2019). Mindfulness Meditation and Psychopathology. Annu Rev Clin Psychol 15, 285–316.
-
 @ 3ac03011:41ecd1bb
2025-01-18 17:10:41
@ 3ac03011:41ecd1bb
2025-01-18 17:10:41Does Football Still Feel the Same?
Close your eyes for a moment and think back to when you first fell in love with football. What was it that pulled you in and wouldn’t let go? Was it the roar of the crowd as your team netted a stoppage-time winner? The thrill of an underdog beating the odds? Or maybe it was simpler—the chants, the rivalries, the raw, unfiltered chaos of the game.
Now open your eyes. Does football still feel like that?
You know it doesn’t. The spark is still there but the magic feels muted. Matches feel more like polished products, rivalries are starting to feel manufactured and even the moments of brilliance seem a little…hollow.
You hear the pundits blame it on “greedy owners” or “commercialisation of the game,” but football has always been tied to money. From the grand stadiums to the global superstars, wealth has always flowed to the game we love. So, what’s really wrong?
What Happened to the Chaos?
Football isn’t just a sport. It’s a reflection of life—messy, unpredictable and gloriously unfair. That’s what made it beautiful. It wasn’t just about the goals; it was about the stories. The miraculous comebacks, the unlikely heroes, the questionable refereeing decisions that sparked debates for years.
But where is that chaos now?
Look at today’s game. Teams are coached to minimise risk and prioritise results. Players are drilled into systems, their individual flair sacrificed for the greater machine. Even rivalries feel like marketing strategies, built more for brand engagement than genuine passion.
Why?
Because predictability isn’t just valued—it’s demanded. Clubs are forced to prioritise short-term financial growth over risk. They cannot afford to experiment or fail because the economic system, which governs us all, punishes them if they do. It’s no coincidence that football’s decline in spontaneity mirrors the rise of fiat money.
How Fiat Changed Football
Fiat currency, with its endless inflation, has placed football in a relentless race. Every club is chasing financial growth—not because they want to, but because they have to. Inflation eats away at savings, forcing clubs to focus on short-term profits.
The result? Clubs treat fans as customers, not loyal supporters. Teams are built for efficiency, not excitement. Every decision, from tactics to transfers, is filtered through a lens of operational financial return. The beautiful game is being stripped of its beauty, one spreadsheet at a time.
Do You Really Want Perfection?
Think of your favourite football memories, those that are deemed iconic. Was it all about skill and precision? Or was it about emotion, drama and unpredictability?
The “Hand of God” wasn’t just a goal—it became a chapter in football history. Frank Lampard’s disallowed goal against Germany in 2010 didn’t just spark debates—it became folklore. These moments, as infuriating as they were at the time, gave football its soul.
But today, we chase an unattainable goal: perfection. VAR was introduced to make everything “fair,” but instead, it’s robbed the game of its spontaneity. Those controversial moments that one fueled passion now lead to lifeless delays.
Is this really the game we fell in love with?
Financial Fair Play (FFP) and the False Promise
Consider FFP. At first glance, it seems like a noble idea—a way to regulate spending, create a level playing field and ensure the long-term stability of clubs. But has it really delivered on its promises?
The reality is, FFP wasn’t designed for fans. It’s a system built for regulators, giving them a framework to justify their role. What they fail to understand—or conveniently ignore—is that football fans aren’t ordinary customers. We don’t switch teams when things go wrong. If your club is relegated or endures years of heartbreak, do you suddenly start cheering for your rivals? Never. Loyalty is the foundation of football and it’s a loyalty so fierce that many fans would sooner stop watching the sport entirely than betray their team.
Instead of nurturing this unique connection, FFP has entrenched inequality. It locks in the dominance of a few elite clubs while stifling ambition for everyone else. Even as a supporter of one of these elite clubs, it’s impossible to ignore how these rules suffocate the very spirit of competition that makes football beautiful.
Is There A Way Back?
What if football could be free again? Free to embrace chaos, its passion, its unpredictability?
The answer isn’t to ban money from football. Money has always been a part of the game. The problem isn’t money—it’s the kind of money.
Fiat money, with its endless inflation, has poisoned football. We need an inflation-proof currency to form the heart of a new awakening for football. Lucky for us, we don’t need to look far for that currency.
A New Renaissance: The Bitcoin Era
Bitcoin is a form of money that doesn’t lose value over time. Clubs that adopt it will achieve financial stability without the need to chase endless operational growth. With Bitcoin, clubs can focus on what really matters: the football, the fans and the overall synergy between them.
Managers can take risks without the fear of collapse. Players can be artists, not just cogs in a system. Fans can feel like part of the story again, not just numbers on a balance sheet.
Imagine a world where football is free to be itself again. Where rivalries grow naturally, fueled by passion, not profit. Where clubs aren’t just businesses but extensions of their communities.
This isn’t a dream. It’s already happening. Real Bedford is leading the charge, proving that Bitcoin can change the game.
Football’s future is here—and it’s orange.
-
 @ 7ef5f1b1:0e0fcd27
2025-01-16 20:51:53
@ 7ef5f1b1:0e0fcd27
2025-01-16 20:51:53A Spark of Defiance
By: The 256 Foundation

A monthly newsletter
January 2025
Introduction:
Welcome to the first newsletter produced by The 256 Foundation! If you have enjoyed POD256 or technical guides from econoalchemist in the past, then you are going to love this newsletter.You can expect newsletters to be published on a monthly basis going forward. The content will generally focus on topics aligned with The 256 Foundation’s mission to “Dismantle the proprietary mining empire to liberate Bitcoin and freedom tech for all”. More specifically, the focus of this newsletter will be on the state of the Bitcoin network, mining industry developments, progress updates on grant projects, actionable advice for getting involved with Bitcoin mining, and more (to be announced...wink wink).
Open-source development in Bitcoin mining up until the Bitaxe has been non-existent but The 256 Foundation is breaking the chains of closed and proprietary development. After all, two out of three pillars supporting the Bitcoin ecosystem are openly developed – nodes and applications; why not mining? The majority of mining hardware is closed and proprietary; same with the firmware, even the after-market solutions are closed-source. If you have tried using a miner in some unconventional way like home heating, dehydrating food, or installing one in your living space just so you don’t have to submit KYC documents to get bitcoin then you will appreciate the ability to freely modify your miner.
Despite the constraints on creativity caused by closed-source firmware and hardware, many individuals have demonstrated impressive developments. For example, Diverter who wrote the groundbreaking guide on the subject, Mining For The Streets, at a time when the general consensus was that small-scale mining was a foregone pursuit. Zack Bomsta developed the Loki Kit enabling users to power miners from 120-volt power sources instead of the less common 240-volt power sources. Michael Schmid developed a way to heat his home using four Antminer S9s; offsetting his energy bills with mining rewards. Rev. Hodl has integrated Bitcoin mining into a variety of homesteading functions like dehydrating his elderberry harvest. In fact, the resourcefulness and determination of individuals to integrate Bitcoin mining into their unique situations has proven to be nothing short of a full on movement. Defiantly building and iterating despite the naysayers, excuse makers, and protests that claim “you can’t compete with big miners! You’re better off just buying from an exchange! You won’t get your ROI!”.
Against all odds, using closed-source miners, and with little more than a shoestring budget and a can-do attitude people have forged a way forward and collectively pushed the Bitcoin mining industry to a tipping point. Closed-source solutions are not keeping up with innovation and won’t even make economic sense compared to the open-source solutions just over the horizon. The 256 Foundation is here to kick the old ways of Bitcoin mining development to the curb in favor of free and open development; providing funding for developers and educators to do what they do best and usher in the era free and open Bitcoin mining.
The 256 Foundation is laser focused on a select handful of projects that are going to break the entire Bitcoin mining industry wide open and make freedom tech accessible to anyone. These select projects are long term support initiatives, not short term touch-and-go exercises. Education is a key component and why The 256 Foundation provides educational resources, tools, and support to demystify Bitcoin and freedom tech, empowering individuals to engage with and benefit from this revolutionary system.
If that sounds like the kind of timeline you’re interested in then keep reading and watch for updates every month in your inbox, on Nostr, or at 256foundation.org.
Definitions:
MA = Moving Average Eh/s = Exahash per second Ph/s = Petahash per second Th/s = Terahash per second MW = Mega Watt T = Trillion J/Th = Joules per Terahash $ = US Dollar VDC = Volts Direct Current PCB = Printed Circuit Board GB = Gigabyte TB = Terabyte OS = Operating System SSH = Secure Shell
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~525 Eh/s in January 2024 to ~784 Eh/s in December 2024, marking ~49% growth for the year. Last month alone, December 2024, witnessed roughly 34 Eh/s come online marking ~4.5% overall growth for the month. Using some rough ball-park figures, 34 Eh/s coming online means something like 170,000 new-gen 200 Th/s miners were plugged in and supported by ~595 MW of electrical infrastructure.
Difficulty is currently 110.4T as of Epoch 436 and set to decrease roughly 0.2% on or around January 26, 2025. But that target will constantly change between now and then. The previous re-target increased difficulty by 0.6%. In 2024, difficulty went from 72.0T to 109.7T making it 52.3% more difficult to solve for a block; fairly consistent with the estimated 49% hashrate increase during the same time frame.
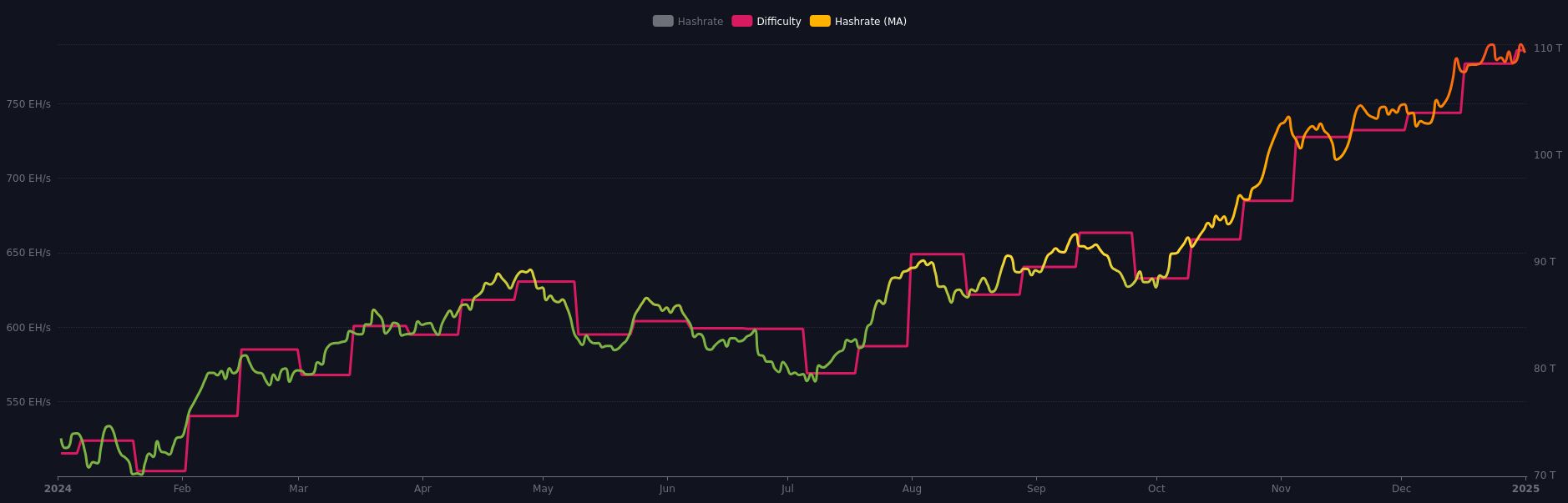
[IMG-001] 2024 hashrate/difficulty chart from mempool.space
New-gen miners are selling for roughly $28.14 per Th using the Bitmain Antminer S21 XP 270 Th/s model from Kaboom Racks as an example. According to the Hashrate Index, less efficient miners like the <19J/Th models are fetching $18.18/Th, models between 19J/Th – 25J/Th are selling for $13.31/Th, and models >25J/Th are selling for $3.53/Th.
[IMG-002] 2024 Miner Prices from Luxor’s Hashrate Index
Hashvalue is currently 58,000 sats/Ph per day, down slightly from December 1, 2024 when hashvalue was closer to 63,000 sats/Ph per day according to Braiins Insights. Hashprice is $58.00/Ph per day, down slightly from $60.00/Ph per day at the beginning of December 2024, [IMG-003]. Overall, hashvalue is down 76% from 242,000 sats/Ph per day a year ago and hashprice is down 43% from $103.00 per Ph/day a year ago. But keep in mind, the block subsidy was 6.25 bitcoin per block a year ago and is currently 3.125 bitcoin per block.
The next halving will occur at block height 1,050,000 which should be in roughly 1,159 days or in other words 170,594 blocks from time of publishing this newsletter.
[IMG-003] Hashprice/Hashvalue from Braiins Insights
Mining Industry Developments:
2024 marks the year that open-source Bitcoin mining hardware became a thing. Prior to the Bitaxe, there was no open source Bitcoin mining hardware. A small but mighty platform, the Bitaxe project has proved that it is possible to have a complete Bitcoin mining system developed, built, and maintained in the open by a community of enthusiasts.
The impressive part about Bitaxe is that Skot instigated a project that satisfied a burning desire in the open-source community to develop a mining system by reverse engineering Bitmain’s ASIC chips and integrate them onto a new open-source hardware platform, with accompanying open-source firmware, esp-miner. Fast forward to today and thousands of individuals have joined the Open Source Miners United Discord group and their combined contributions have made Bitaxe what it is today. This required delicate work to unsolder the ASIC chips from Bitmain’s hashboards and then re-solder them onto the Bitaxe circuit board. The genius part of the project is that the open-source foundation supports commercially viable ventures built on top of it. For example, Bitaxe is the open-source project that develops and designs models but does not manufacture, market, or distribute any units; a list of companies that have sprung up selling Bitaxes can be found here.
The Bitaxe was the inspiration for the title of this month’s newsletter, A Spark of Defiance, because it was a small and seemingly inconsequential development that ignited a raging fire that will engulf the closed and proprietary Bitcoin mining empire. Additionally, the project was defiantly manifested through persistent and painstaking effort despite what many claimed was too insignificant of a hashrate, too uneconomical of a price point, and too cute to be anything other than a toy. The significance of the Bitaxe project is not in the nominal hashrate of a single unit or the cost per terahash; the significance is that there is now a proven open-source Bitcoin mining hardware option available for anyone to build themselves and modify as they see fit that supports commercial applications. The idea of open-source Bitcoin mining hardware is still early in it’s formation but the next iteration is already under way.
Small scale miners like FutureBit’s Apollo II and the Bitaxe help decentralize hashrate. Even though each individual miner doesn’t amount to much, the aggregate hashrate contributed to the network is significant; both in terms of nominal hashpower and in terms of distribution. The more people who control mining hardware means fewer miners condensed in hostile jurisdictions and the more individuals who need to be compliant with unjust demands in order for those demands to be effective. These are critical steps towards a more censorship-resistant network and the arch of progress is measured in years, however there is more needed to bolster Bitcoin’s neutral and permissionless attributes which guide The 256 Foundation’s projects.
[IMG-004] Picture of a Bitaxe 401 from Public-Pool
Grant Project Updates:
In November 2024 The 256 Foundation announced the first fully funded grant project, Ember One. This project builds on the momentum of the Bitaxe project and takes it to the next level. Ember One provides funding for up to two engineers and one project manager for a duration of six months to design and develop a validated ~100 Watt hashboard standard. This hashboard features a USB adapter to connect to a variety of controllers, variable input voltage from 12VDC to 24VDC to facilitate integration into a wide range of applications, and a standardized PCB footprint to make expansion seamless regardless of series.
The first series in the Ember One line up will feature twelve Bitmain S19j Pro BM1362 ASIC chips, a decision made based on availability and affordability. The corresponding heat-sink will be included with the project. Subsequent Ember One series hashboards will feature a range of different ASIC chips from different manufacturers, possibly including those that should be released any day now from a company who’s name starts with “B” and ends with “lock”.
Much like the Bitaxe project, certain peripherals are not included in the Ember One project. For example, Ember One does not include firmware architecture or implementation, enclosure design, manufacturing support, sales, distribution, marketing, or customer technical support; those are all areas of opportunity for commercial applications to thrive. Unlike the Bitaxe project, Ember One is not a complete mining system design but only the standardized hashboard. The Ember One project is being leveraged as a springboard to launch the next two projects which is 1) the complete mining system built with any of the Ember One series hashboards including design details for everything needed to produce a plug and play unit and 2) an open-source, multi-driver compatible, Linux based Bitcoin mining firmware. More details to be announced.
Stay tuned to POD256 for updates and watch out for the next 256 Foundation newsletter.
Actionable Advice:

Here are steps you can take to solo mine using your own Bitcoin node, your own Stratum server, and your own miner. In this section, you will see how to spin up a BitcoinCore full node, run an instance of a Public-Pool Stratum server, and configure a Bitaxe to mine directly to the Bitcoin network without any third party involvement.
Materials: You don’t need any fancy or expensive equipment to follow along. Everything you will see in this guide was done with an old Raspberry Pi, an old external solid state drive, and a Bitaxe 401. The Raspberry Pi is a model 4B with 4GB of RAM. If you want to purchase a Raspberry Pi, then check here for distributors. Be forewarned that using a Raspberry Pi with 4GB of RAM to synchronize the full blockchain will take at least three weeks if not a month. Also, you will probably get better stratum server performance from using better hardware. This was really just an exercise in using the lowest barrier to entry hardware for demonstration purposes. There is no reason you could not complete this kind of project on a refurbished ThinkPad like any of these.You may want to use an external storage volume with at least 2TB of storage capacity for the complete copy of the blockchain. The Samsung T7 is a good option if you need one. You will also need a microSD card, 64GB is more than enough capacity and these are a decent option if you need one. If you don’t have a Bitaxe already, you can buy one for less than $200 from any of these vendors.
This guide assumes you’re running Linux on your primary computer that you will be using to communicate with the Raspberry Pi and Bitaxe, if you’re running Windows or MacOS then you should be able to find system specific instructions that differ from this guide in the linked resources.
Step 1 – Prepare The Raspberry Pi
You will need a microSD card to install the Raspberry Operating System on. Then you can download the Raspberry Pi Image from:
https://www.raspberrypi.com/software/operating-systems/
Raspberry Pi OS Lite Bookworm 64-bit was used for this guide.
The SHA256 digest is available on the download page, open a terminal window and run the following command from the same folder (usually /Downloads) as the compressed file you just downloaded and compare the results to verify. Use the name of your specific file in place of this example:
$ sha256sum 2024-11-19-raspios-bookworm-arm64-lite.img.xz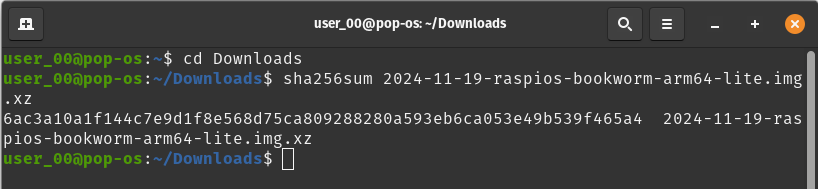
[IMG-005] Raspberry Pi OS SHA256 Checksum
With the compressed image file verified, flash the image to a freshly formatted microSD card using the Raspberry Pi Imager or Balena Etcher or similar flashing program.
In the Raspberry Pi Imager, you can add the SSH file and “userconf” file in the boot partition during the flashing process. If you are using Balena or a similar program instead, the directions are pretty straight forward, just follow the prompts in the software. Basically you will just select the image file you want to flash, then select the microSD card you want to flash that image to, and then the software takes care of the rest.
After flashing, in a terminal window, change directory to the boot partition of the microSD card and enable SSH functionality by writing a blank file titled "ssh" with no file extension in the root of the boot partition. You can open a terminal window directly in the file path you want by looking at it with the file explorer, clicking on the 3-dot menu next to the file path at the top of the explorer window, and selecting “Open in Terminal”.
$ sudo touch sshNow you can create the login credentials and save them to the “userconf” file you are going to generate. First you need to decide on a password and then you need to encrypt it. Open a second terminal window and from your default home file path run:
$ echo INSERTYOURPASSWORD | openssl passwd -6 -stdinYou should receive a response that looks like a random string of characters and maybe there are some dollar signs or periods in it. You want to copy the entire string in that response by highlighting it, right clicking on it, and selecting “copy”.
Then back in the first terminal window from the microSD card boot partition path run:
$ sudo touch userconfthen
$ sudo nano userconfThose two commands just created a file named “userconf” and then opened that file so you can put some text in it. On a single line, type your Raspberry Pi username, a colon, and the encrypted password string you generated (which should be on your clipboard, so just right-click and select “paste”). For example:
pi:$6$wRLGhmKbL0bheJKh$0L60E09x.dQ.M4DvBjTvNETG0CtW.PGuzQwTEtTvadngclQXkzVFiJD2z.WIYeyvV.hUZT6HdYDjiSYgx0Arc0
Then hit ctrl+o to write, enter to save, and ctrl+x to exit.
Now eject the microSD card, insert into the Raspberry Pi, and turn on the power.
From your primary computer, open a new terminal window and run:
$ ssh pi@192.168.1.69(or whatever your local Raspberry Pi IP address is). If you don’t know what your Raspberry Pi’s local IP address is then log into your router and check your DHCP leases and look for the one with a “raspberrypi” hostname. Your router is typically accessible from your web browser at IP address 192.168.0.1 or 10.0.0.1 or something similar. Do an internet search for your router’s specifics if you need to. If you don’t have access to the router then you can use a program like AngryIP to scan the network and give you the same information.$ sudo apt updatethen
$ sudo apt upgrade -yNow your ready to connect the external storage volume.
Step 2 – Connect External Storage Volume
Plug in a freshly formatted storage volume, like a 2TB SSD, to the Pi. Then through your SSH terminal window run:
$ sudo fdisk -lYou should get a response with information about the connected drives, one of them being the microSD card and the other being your external hard drive. You want to identify the device name of your external storage volume. For example, "/dev/sda1".
Write that device name down or just remember it for a moment. Now make a directory where you can mount your external storage volume by running:
$ sudo mkdir /mnt/ext/Then mount the external storage volume there by running:
$ sudo mount /dev/sda1 /mnt/ext/Then refresh by running:
$ sudo systemctl daemon-reloadBe aware that each time you power off the Raspberry Pi you will need to run those last two commands again to mount the storage volume if you have it connected. If you want to have the “fstab” file permanently modified to reflect this storage volume then you can edit it following instructions like these. That’s it for connecting and mounting the external storage volume. Easy right? You’re doing great and now you’re ready to install Docker onto your Raspberry Pi.
Step 3 – Install The Docker Engine
Docker gets installed before BitcoinCore because there are some dependencies that BitcoinCore needs that are included when installing Docker. First, you will need the Git tools, from the home directory on the SSH terminal window run:
$ sudo apt install git-all -yNow you can start getting Docker installed, these directions can be found in more detail here if you need them: https://docs.docker.com/engine/install/raspberry-pi-os/
Run the following commands to install all the various Docker packages, make sure you fetch the correct URL for each package by first checking: https://download.docker.com/linux/raspbian/dists/
Then select your Raspberry Pi OS version (Bookworm in this case), go to "Pool" > "stable", then select the applicable architecture (armf in this case), then run the following six commands ensuring that you are getting the latest available versions of each package:
For the containerd package run:
$ sudo wget https://download.docker.com/linux/raspbian/dists/bookworm/pool/stable/armhf/containerd.io_1.7.24-1_armhf.debFor the docker-buildx-plugin package run:
$ sudo wget https://download.docker.com/linux/raspbian/dists/bookworm/pool/stable/armhf/docker-buildx-plugin_0.19.3-1~raspbian.12~bookworm_armhf.debFor the docker-ce-cli package run:
$ sudo wget https://download.docker.com/linux/raspbian/dists/bookworm/pool/stable/armhf/docker-ce-cli_27.4.1-1~raspbian.12~bookworm_armhf.debFor the docker-ce-rootless-extras package run:
$ sudo wget https://download.docker.com/linux/raspbian/dists/bookworm/pool/stable/armhf/docker-ce-rootless-extras_27.4.1-1~raspbian.12~bookworm_armhf.debFor the docker-ce package run:
$ sudo wget https://download.docker.com/linux/raspbian/dists/bookworm/pool/stable/armhf/docker-ce_27.4.1-1~raspbian.12~bookworm_armhf.debFor the docker-compose-plugin package run:
$ sudo wget https://download.docker.com/linux/raspbian/dists/bookworm/pool/stable/armhf/docker-compose-plugin_2.32.1-1~raspbian.12~bookworm_armhf.debYou can verify your downloads by getting the GPG public key file from one step back in the directory path from the "dists" folder where it says "gpg", run:
$ sudo wget https://download.docker.com/linux/raspbian/gpgNow add that key to the system key-chain with:
$ sudo gpg --import gpgThen run the gpg command with the verify flag and file name for all six of the packages you downloaded:
$ sudo gpg --verify containerd.io_1.7.24-1_armhf.deb$ sudo gpg --verify docker-buildx-plugin_0.19.3-1~raspbian.12~bookworm_armhf.deb$ sudo gpg --verify docker-ce_27.4.1-1~raspbian.12~bookworm_armhf.deb$ sudo gpg --verify docker-ce-cli_27.4.1-1~raspbian.12~bookworm_armhf.deb$ sudo gpg --verify docker-ce-rootless-extras_27.4.1-1~raspbian.12~bookworm_armhf.deb$ sudo gpg --verify docker-compose-plugin_2.32.1-1~raspbian.12~bookworm_armhf.debYou should get a response for each verification, you are looking for a "good signature" to the public key you imported, for example:
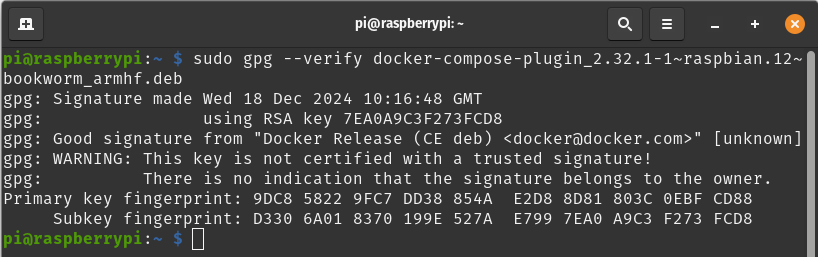
[IMG-006] Docker Package Verification
The warning is just trying to tell you that you have not certified the public key which is an additional verification step and beyond the scope of this guide. Basically, it is trying to encourage you to contact the developer and verify that their signature fingerprint matches the one in your terminal ending with E2D8 8D81 803C 0EBF CD88. Keybase is a good place to start if you want to find publicly posted keys for helping you verify and certify.
Now you need to decompress and install all six of those packages buy running:
$ sudo dpkg -i containerd.io_1.7.24-1_armhf.deb$ sudo dpkg -i docker-buildx-plugin_0.19.3-1~raspbian.12~bookworm_armhf.deb$ sudo dpkg -i docker-ce-cli_27.4.1-1~raspbian.12~bookworm_armhf.deb$ sudo dpkg -i docker-ce-rootless-extras_27.4.1-1~raspbian.12~bookworm_armhf.deb$ sudo dpkg -i docker-ce_27.4.1-1~raspbian.12~bookworm_armhf.deb$ sudo dpkg -i docker-compose-plugin_2.32.1-1~raspbian.12~bookworm_armhf.debYou might encounter errors about missing dependencies with a couple of those packages. If you do, then run the following command to correct them and after running that command, try decompressing and installing the package again:
$ sudo apt --fix-broken installThe Docker daemon should start automatically. Ensure Docker is working by running:
$ sudo service docker startthen
$ sudo docker run hello-worldYou should get a response like: "Hello from Docker! This message shows that your installation appears to be working correctly."
If you made it that far then you have successfully installed Docker and you are ready to install BitcoinCore.
Step 4 – Install BitcoinCore
From your SSH terminal window and from the home directory make a working folder for all the Bitcoin related files by running:
$ sudo mkdir /bitcoinThen change directories into that folder with:
$ cd /bitcoinNavigate to the BitcoinCore download page in the web browser from your primary computer and copy the download link for the latest version of BitcoinCore for your system. BitcoinCore v28.0 was used here, specifically “bitcoin-28.0-aarch64-linux-gnu.tar.gz”.
Copy the link for the package you want (ARM Linux 64-bit in this example) and then paste that link in the following command of your SSH terminal window:
$ sudo wget https://bitcoincore.org/bin/bitcoin-core-28.0/bitcoin-28.0-aarch64-linux-gnu.tar.gzIf you want to verify your download, which is good practice, download the “SHA256SUMS.asc” signature file along with the “SHA256SUMS” hash values file by running the following two commands:
$ sudo wget https://bitcoincore.org/bin/bitcoin-core-28.0/SHA256SUMSthen
$ sudo wget https://bitcoincore.org/bin/bitcoin-core-28.0/SHA256SUMS.ascCheck that the SHA256 hash for the downloaded file exists in the SHA256SUMS file by running:
$ sha256sum --ignore-missing --check SHA256SUMSYou should get a response back like:
bitcoin-28.0-aarch64-linux-gnu.tar.gz: OKYou will need some developer keys in order to verify the SHA256SUMS file accurately represents what the developers signed with their signatures, you can find all the developer signatures at:
https://github.com/bitcoin-core/guix.sigs/blob/main/builder-keys/
You can download any of those keys by running the
sudo wgetcommand and appending the whole URL for the raw GPG file you want, for example:$ sudo wget https://raw.githubusercontent.com/bitcoin-core/guix.sigs/refs/heads/main/builder-keys/fanquake.gpgContinuing with the fanquake example, import that downloaded key by running:
$ sudo gpg --import fanquake.gpgYou should get a response indicating that the file was imported.
Then run the following command to verify the signature matches:
$ sudo gpg --verify SHA256SUMS.ascYou should get a response for each of the signatures, even the ones you did not download a public key for. You are looking for "good signature" next to one of the public keys you imported, for example:
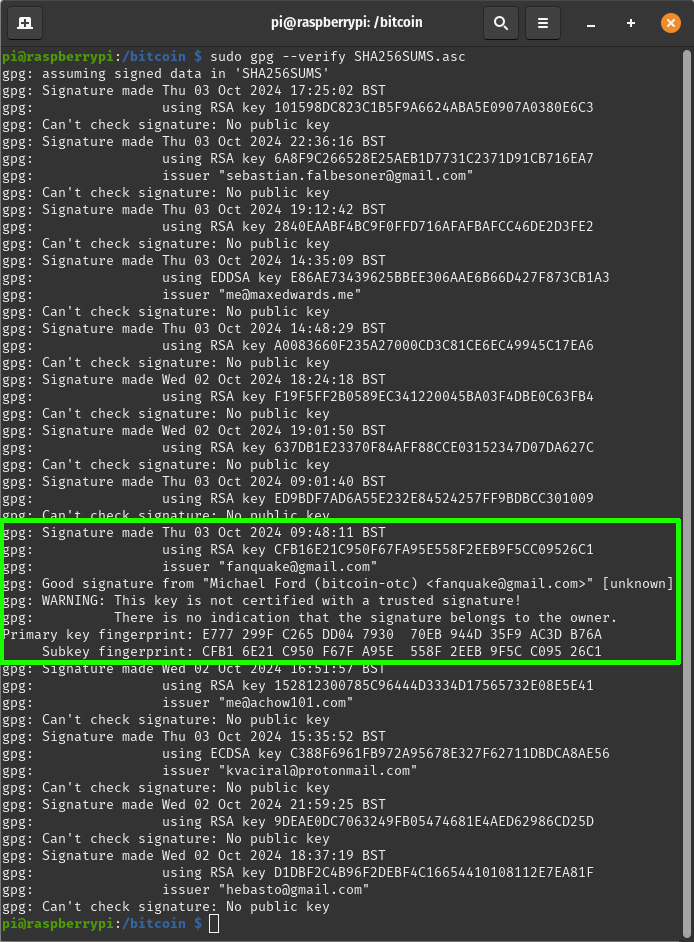
[IMG-007] BitcoinCore Verification
The warning is just trying to tell you that you have not certified the public key which is an additional verification step and beyond the scope of this guide. For all intents and purposes, we have downloaded our file, verified that the hash value for that file is written in the accompanying verification file, then verified that the developers agree that is the correct hash value by signing off on the .asc file.
With the download verified, now decompress it by running the following command using which ever file name matches your download:
$ sudo tar -xzf bitcoin-28.0-aarch64-linux-gnu.tar.gzThis will have created a directory called “bitcoin-28.0”. You can verify this by checking the contents of the directory you are currently in with the
ls -lacommand. Now you want to install BitcoinCore here by running:$ sudo install -m 0755 -o root -t /bitcoin bitcoin-28.0/bin/*This is a good point to make a few configuration changes in the “bitcoin.conf” file before running bitcoind. Return to your home directory with this command:
$ cd ~Then copy/paste the default “bitcoin.conf” file from the
/bitcoin/bitcoin28.0directory to where you will have your Bitcoin data directory setup on the external hard drive with this command:$ sudo cp /bitcoin/bitcoin-28.0/bitcoin.conf /mnt/extThen change into the directory where you just pasted that configuration file with:
$ cd /mnt/extThen open the “bitcoin.conf” file to edit it by running:
$ sudo nano bitcoin.confThere are many configuration changes here that you can make if you want, only the bare minimum six configurations for the purpose of this guide will be covered here.
1) Scroll down to the line that reads # Enable publish raw block in < address > and below that, delete the hashtag in front of #zmqpubrawblock=< address > then replace < address > with tcp://*:3000. For example, the end result should look like this:
# Enable publish raw block in < address > zmqpubrawblock=tcp://*:3000
2) Scroll down to where it says # Allow JSON-RPC connections from specified source. and below that, delete the hashtag in front of #rpcallowip=< ip > and replace < ip > with the Docker IP address, 172.16.0.0/12 (the
ifconfigcommand can help you find various network interfaces and the corresponding IP address for each one). For example, the end result should look like this:# Allow JSON-RPC connections from specified source. Valid values for < ip > are a single IP (e.g. 1.2.3.4), a network/netmask (e.g. 1.2.3.4/255.255.255.0), a network/CIDR (e.g. 1.2.3.4/24), all ipv4 (0.0.0.0/0), or all ipv6 (::/0). This option can be specified multiple times rpcallowip=172.16.0.0/12
3) Scroll down to where it says # Bind to given address to listen for JSON-RPC connections. and below that, you want to add three IP addresses. Delete the hashtag and replace < addr >[:port] with your Raspberry Pi's local IP address, your Docker IP address, and your local host IP address. You can leave the port out of it since BitcoinCore default's to port 8332. For example, the end result should look like this:
# Bind to given address to listen for JSON-RPC connections. Do not expose the RPC server to untrusted networks such as the public internet! This option is ignored unless -rpcallowip is also passed. Port is optional and overrides -rpcport. Use [host]:port notation for IPv6. This option can be specified multiple times (default: 127.0.0.1 and ::1 i.e., localhost) rpcbind=192.168.1.119 rpcbind=127.0.0.1 rpcbind=172.16.0.0/12
4) Scroll down to where it says # Password for JSON-RPC connections. and below that, delete the hashtag in front of #rpcpassword=< pw > and replace < pw > with whatever you want your password to be in order to make RPC calls to your Bitcoin node. For example, the end result should look like this:
# Password for JSON-RPC connections rpcpassword=INSERTYOURPASSWORD
5) Scroll down to where it says # Username for JSON-RPC connections. and below that, delete the hashtag in front of #rpcuser=< user > and replace < user > with whatever you want your username to be in order to make RPC calls to your Bitcoin node. For example, the end result should look like this:
# Username for JSON-RPC connections rpcuser=INSERTYOURUSERNAME
6) Lastly, scroll down to where it says # Accept command line and JSON-RPC commands and below that, delete the hashtag in front of #server=1. For example, the end result should look like this:
# Accept command line and JSON-RPC commands server=1
Then hit ctrl+o to write, hit enter to save, and hit ctrl+x to exit.
You can return to your home directory with this command:
$ cd ~Then change directory to the
/bitcoinfolder and run this command to start bitcoind, making sure you have your data directory defined:$ sudo ./bitcoind -datadir=/mnt/extYou should see several lines of text scroll by, scroll up to the beginning of those responses and double check that bitcoind is using the directory that you want and the configuration file you want. For example, the text should read something like this:
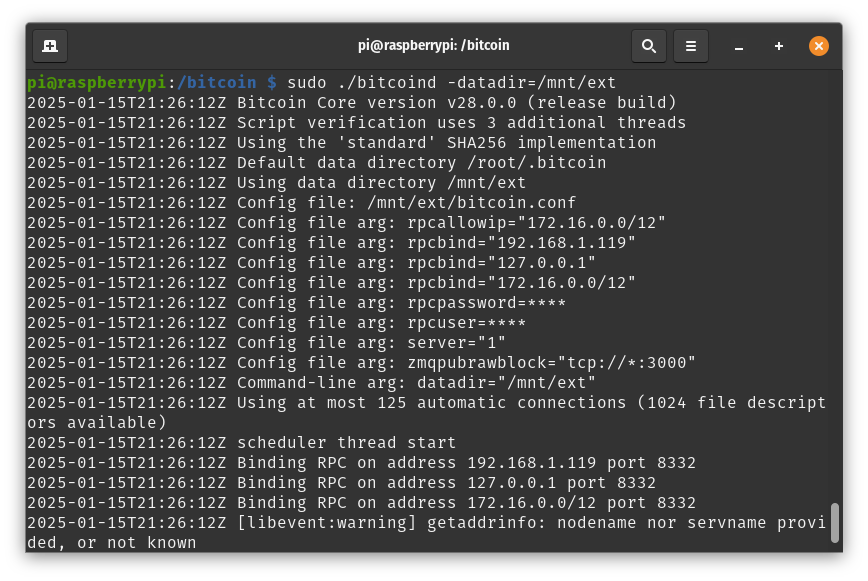
[IMG-008] bitcoind Start Up
Then you want to just let bitcoind run and start downloading the entire blockchain. This Initial Block Download can take a few weeks on a Raspberry Pi with 4GB of RAM so give it time. You won't be able to start mining until the synchronization process is done. In the mean-time, you can build the Public-Pool container.
Step 5 – Install the Public-Pool Container
While bitcoind is synchronizing, open a new terminal window and SSH into your Raspberry Pi like before.
Clone the Public Pool Git Repo:
$ sudo git clone https://github.com/benjamin-wilson/public-pool.gitChange Directory to the new public-pool folder:
$ cd public-poolCreate a new environment file in the root of the public-pool folder:
$ sudo touch .envOpen the new .env file:
$ sudo nano .envCopy/Paste the contents from the ".env.example" file (from https://github.com/benjamin-wilson/public-pool/blob/master/.env.example) then modify the following lines to your specific setup:
Change the IP on this line to the local IP address of your Raspberry Pi: BITCOIN_RPC_URL=http://192.168.1.119
Enter the RPC Username you entered into the bitcoin.conf file: BITCOIN_RPC_USER=INSERTYOURUSERNAME
Enter the RPC Password you entered into the “bitcoin.conf” file: BITCOIN_RPC_PASSWORD=INSERTYOURPASSWORD
Add a hashtag in front of this line: # BITCOIN_RPC_COOKIEFILE=
Delete the hash tag from this line: BITCOIN_ZMQ_HOST="tcp://192.168.1.100:3000"
And change the 192.168.1.100 IP address to the local IP address of your Raspberry Pi.
Add a hashtag in front of this line: # DEV_FEE_ADDRESS=
Change the POOL_IDENTIFIER to whatever you want to show up in the blockchain when you win a block. For example: POOL_IDENTIFIER="/abolish the fed/"
ctrl+o to write, enter to save, ctrl+x to exit.
Docker Compose binds to “127.0.0.1” by default. To expose the Stratum services on your server you need to update the ports in the “docker-compose.yml” file, so run:
$ sudo nano docker-compose.ymlScroll down to the ports section where it says:
ports: -"127.0.0.1:${STRATUM_PORT}:${STRATUM_PORT}/tcp" -"127.0.0.1:${API_PORT}:${API_PORT}/tcp"
Delete everything between to quotation marks on both lines and add 0.0.0.0:3333:3333/tcp and 0.0.0.0:3334:3334/tcp respectively. For example, the end result should look like this:
ports: -"0.0.0.0:3333:3333/tcp" -"0.0.0.0:3334:3334/tcp"
Press ctrl+o to write, enter to save, ctrl+x to exit.
While still in the public-pool folder run:
$ sudo docker compose buildAfter several minutes you should get a confirmation like Service public-pool Built. Then run:
$ sudo docker compose up -dThis command will take some time to execute but you should see some lines of text flying by in the terminal window in the mean-time. Eventually, you should get a confirmation like
Container public-pool Started.This completes the steps needed for building your Bitcoin node and Stratum Server. Now you can bring your miner into the loop.
Step 6 – Connecting Bitaxe
A Bitaxe was used in this example but you should be able use any miner in theory.
Plug your Bitaxe into the power supply.
Use your mobile phone to connect via WiFi to the Bitaxe network, this should be something like "Bitaxe_4A89" or "Bitaxe_5B09" etc.
Once connected, open a web browser on your mobile phone and enter "192.168.4.1" in the address bar. This should bring you to the Bitaxe Dashboard.
From the menu, scroll down to “Settings”.
Update the WiFi SSID to your local WiFi network name.
Enter the password for your local WiFi network in the WiFi Password dialog box.
For the Stratum URL, enter the local IP address for your Raspberry Pi. Leave the Stratum Port as 3333.
For your Stratum User, enter your bitcoin address that you want block rewards sent to. You can optionally append your bitcoin address with a worker name, for example: ".bitaxe1".
Save those changes and then restart the miner. Once back up, the Bitaxe should connect to your local WiFi network and point to your Raspberry Pi Stratum server. You can navigate back to the dashboard and you should start seeing some hashrate happening within less than a minute.
If you don't, go to the menu and scroll down to the Logs and click on the Show Logs button to see what the Bitaxe is doing.
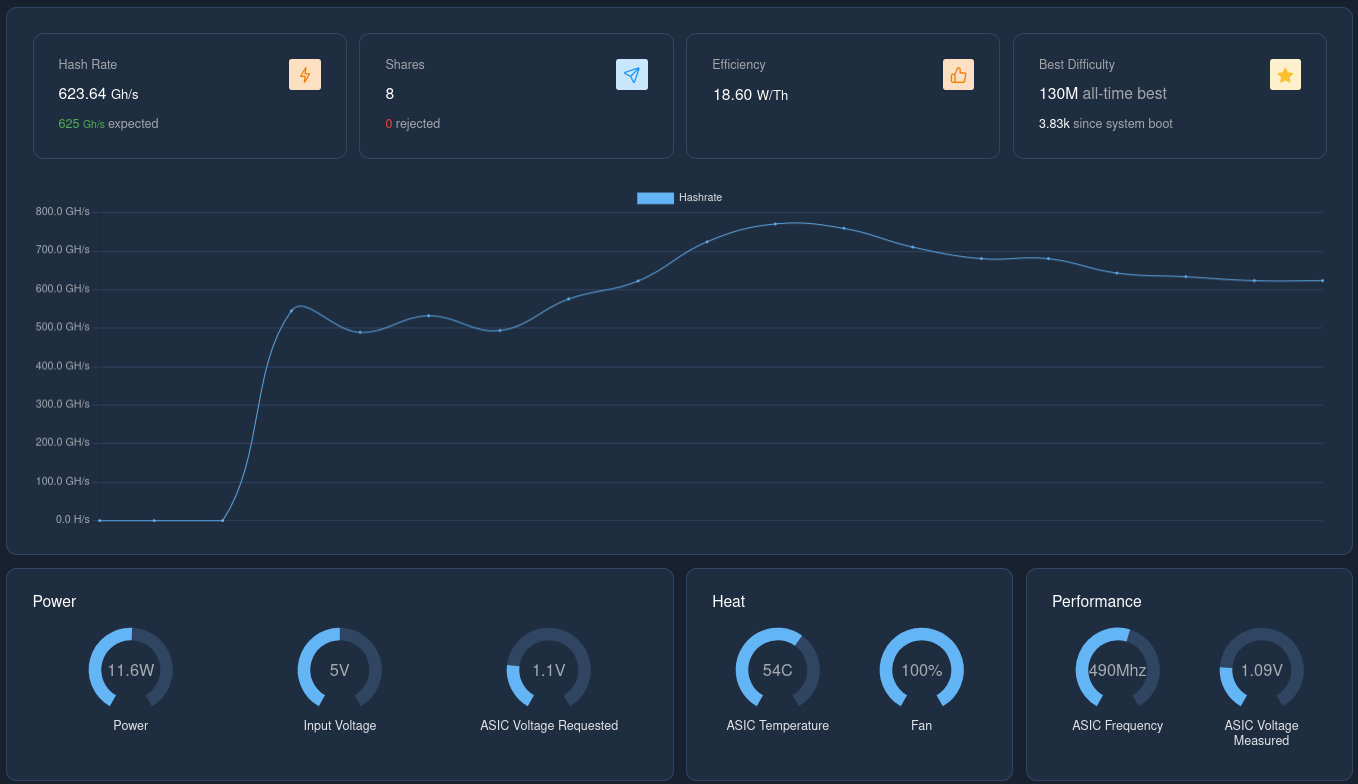
[IMG-009] Bitaxe Dashboard
If you experience problems and do not see any hashrate in the Bitaxe dashboard after a minute or so, here are some things you can check to get a better idea of what the problem is:
Check the Bitaxe logs by navigating to the “Logs” option in the side menu of the dashboard, then click on “Show Logs”. Restart the Bitaxe if necessary. If you see errors about a refused socket connection then you might need to double check the IP addresses
configured in your bitcoin.conf file or Public-Pool .env file.
You can stop the Public-Pool service at anytime by running the following command from the public-pool directory:
$ sudo docker compose stopRestart the service again with:
$ sudo docker compose up -dYou can check the logs of the Public-Pool service by running the following command from the public-pool directory:
$ sudo docker compose logsYou Might need to run this command a couple times to get the latest events. You want to see a response that shows you are using ZMQ and it is connected, Bitcoin RPC is connected, and that it is receiving some responses about the mining information like in [IMG-010].
If you are seeing an error with the RPC connection then try double checking the IP addresses configured in the bitcoin.conf file and the Public-Pool .env file. Or if you see errors about not being able to complete a “getmininginfo” request then try double checking the port parameters you set in the Public-Pool docker-compose.yml file.
[IMG-010] Docker Compose Logs
You can test the RPC connection with a command like this from the /bitcoin directory:
$ sudo ./bitcoin-cli -rpcuser=YOURUSERNAME -rpcpassword=YOURPASSWORD getblockchaininfoYou might need to wait for the blockchain data to finish synchronizing before you can run RPC commands. Or if your node is fully sync’d and you are still not able to make RPC requests then double check the IP addresses you have configured in the “rpcallowip”
and “rpcbind” fields in the bitcoin.conf file.
Conclusion:
Thank you for reading the first 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at https://256foundation.org/. Or you can download .pdf versions of the newsletters from there as well.
You can also find these newsletters published in article form on Nostr.
If you are not currently mining to your own node, making your own templates with open source mining hardware then you now have zero excuses not to be.
Stay vigilant, frens. -econoalchemist
-
 @ 66675158:1b644430
2025-01-16 20:44:33
@ 66675158:1b644430
2025-01-16 20:44:33Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople.
In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice.
Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly.
Then came the Utensils.
In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle.
Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience.
The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty.
At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert.
The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier.
The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished.
Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence.
When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it.
People grumbled but accepted. After all, the Utensils shone with otherworldly power.
Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings.
More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings.
Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance.
When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos.
But surely there must have been chaos, or why would the Utensils have come?
The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all!
The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves.
Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils.
The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present.
"It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?"
And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done.
Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils.
Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous.
Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples.
The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils.
The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies.
The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion.
The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all.
And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?
-
 @ af264750:2c08cd8a
2025-01-18 16:22:48
@ af264750:2c08cd8a
2025-01-18 16:22:48บทความนี้ not a tutorial เขียนไว้เป็นบันทึกความซนของผมเอง
เรื่องมีอยู่ว่า Alby เค้าจะยกเลิก custodial wallet ที่บริการกระเป๋าให้ฟรี ซึ่งประกาศมาซักพักใหญ่ๆแล้วล่ะ ผมก็นั่งไถฟีดค้นหากระเป๋าใหม่ที่จะมาใช้แทนแล้วไปจบอยู่ที่ LifPay เอามาใช้เป็นกระเป๋าชั่วคราวไปก่อนไว้รับส่ง zap เล็กๆน้อยๆ แล้วช่วงนั้นก็เป็นจังหวะเดียวกับที่มหาลัยมีจัดงานกึ่งสัมมนาเลยได้โอกาสเปิดโต๊ะคุยเรื่อง Bitcoin กันไปทั้งคืน
ผ่านไปซักหลายวันอยู่ขณะกำลังเก็บห้อง ผมก็ไปเจอกับคอมเครื่องเก่าที่ตั้งเกาะฝุ่นหลบมุมอยู่ คอมเครื่องนี้เคยเป็นคอมเครื่องหลักที่ซื้อมาไว้ประมาณ 10 ปีหน่อยๆ จนถึงช่วงขึ้นมหาลัยที่ต้องเปลี่ยนไปแบกโน้ตบุ้กไปเรียนแทน กลายเป็นว่าคอมเครื่องนี้ก็ตั้งไว้ในห้องแบบไม่ได้เสียบปลั้กเลยไปเป็นหลักปี ก็เลยเกิดไอเดียว่าไม่งั้นก็เอามาล้างเครื่องแล้วลองเปิด node ดูหน่อยมั้ย เพราะยังไงกิจกรรมทุกอย่างตอนนี้คือย้ายไปบนโน้ตบุ้กแทนหมดแล้ว จนเป็นจุดเริ่มต้นถึงการเดินทางแห่ง home node ขึ้นมา
เตรียมเครื่อง
ด้าน hardware ที่ใช้ก็ไม่พ้นคอมเครื่องเก่านั้น ที่ตอนนี้สเปคมันค่อนข้าง overkill สำหรับการเปิด home lightning node เบาๆ เพราะนอกจากจะเป็นเคสขนาด e-ATX ที่อัด HDD ได้หลายลูกแล้วก็ยังมีการ์ดจอเก่าอยู่ด้วย สเปคคร่าวๆก็มี i5-4670k กับแรม DDR3 12GB แค่นี้ก็กินไฟไปหลายสิบวัตต์แล้ว ยังมีการ์ดจอ GTX 1050Ti เสียบอยู่เฉยๆด้วย แล้วยังมี SSD SATA 480GB ตัวนึงกับ HDD 1TB พ่วงด้วยช่องอ่านแผ่น DVD ที่ประดับหน้าเคสไว้ เลยคิดไว้ว่าน่าจะต้องซื้อคอมอีกเครื่องเล็กๆมาเปิดแทนพี่ใหญ่นี้ในเร็ววัน
หันมาด้าน software กันบ้าง ผมก็เลือก Umbrel มาใช้ สาเหตุหลักก็เน้นสะดวกครับ สละ USB drive มาอันนึงแล้ว flash เข้าไปเลย จิ้มเดียวจบ แต่ข้อเสียแรกที่เห็นเลยคือใช้ได้ drive เดียวแล้วใช้ทั้งหมดเลย 1 drive ก็เลยต้องเอาระบบไปลงที่ SSD ไม่งั้นเดี๋ยวระบบอืดตาย ก็นะ แลกกับความสะดวกก็งี้

เปิดเครื่อง
แน่นอนว่าต้นเรื่องเราคือ Alby อยากให้เราย้ายกระเป๋ามาใช้เป็น Alby Hub ที่เป็น self-custodial ซึ่งใน Umbrel นั้นจะบังคับให้เราติดตั้ง Lightning Node ที่ตัวมันก็จะบังคับให้เราลง Bitcoin Node ด้วยอีกชั้น ทำให้จำนวน app ขั้นต่ำในการเปิด Alby Hub บน Umbrel อยู่ที่ 3 apps แต่อันนี้ผมลงจุกจิกเพิ่มเข้ามาด้วย นี่แหละข้อดีอันนึงของ Umbrel

สเต็ปการทำงานเบื้องต้นก็คือต้องรอ Bitcoin Node sync ให้ครบก่อน ไม่งั้น Lightning Node จะไม่เปิดให้เราเข้าไปใช้งาน แต่ระหว่างรอ sync นั้นเราสามารถเข้าไปจด recovery seed ไว้ก่อนได้เลย ห้ามลืมเด็ดขาด
พอ Lightning Node เราพร้อมแล้ว ก็ไปกันต่อที่ Alby Hub ก็จะมีขั้นตอนตั้งค่านู้นนี้นั้น ให้เราตั้งรหัสผ่านล็อก Hub แล้ว ก็จะมีให้เชื่อม Alby Account ด้วย ซึ่งแน่นอนว่าผมมาเพื่อสิ่งนี้ แลก auth token กันนิดหน่อยก็ถึงหน้า dashboard แล้ว
เปิดช่อง
เมื่อผมหันมาใช้ self-custodial wallet แล้ว สิ่งแรกที่ต้องจัดการเลยคือต้องมีช่องทางให้เงินไหลเข้ามา ไม่งั้นจะเปิด node เผาค่าไฟไปทำไมเนอะ ซึ่งใน Alby Hub เนี่ยเค้าก็มีรายชื่อผู้ให้บริการ LSP ที่เราสามารถซื้อ channel เปิดทางให้เงินไหลเข้ามาได้ ซึ่งผมก็เลือกเปิด channel กับ Lnserver เพราะลองเทียบราคาดูแล้วคือจ่ายค่าเปิด channel น้อยที่สุดในลิสด์นี้แล้ว บวกกับว่าเราสามารถออกไปซื้อตรงๆกับทาง Lnserver เองเหมือนกัน

โน้ตสำคัญของผมเวลาเปิด channel มีอยู่สองจุด จุดแรกคือต้องดู on-chain fee rate เพราะทุกครั้งที่เราเปิด channel ทาง LSP เค้าจะต้องส่งธุรกรรมเข้า block ซึ่งจะต้องเสีย fee เพิ่มกว่าเรทจริงอีกหน่อย ทำให้บางทีค่าเปิด channel โดนอัดราคาเพิ่มจนสูงกว่าค่าบริการของ LSP นั้นๆอีก อย่างของผมที่ซื้อกับ Lnserver เค้าจะเก็บเริ่มต้นที่ 5000 sats สำหรับ channel ขนาด 2,000,000 sats แล้วจะบวก commit fee ไปอีก 1345 sats ที่เรท 2 sats/vB รวมกันเป็น 6345 sats ที่จ่ายไป
โน้ตที่สองที่ต้องเตรียมไว้ด้วยก็คือ reserve fund โดยผมจะเรียกอีกอย่างว่าเป็นค่าประกัน channel ซึ่งค่าประกันตรงนี้จะเก็บไว้เป็นขั้นต่ำของ channel นั้นๆฝ่ายละ 1% แล้วจะล็อกตายเก็บไว้เอาออกมาใช้จ่ายไม่ได้จนกว่าจะปิด channel ถ้าไม่จ่ายค่าประกันตรงนี้ เราก็จะรับเข้าและจ่ายออกจากฝั่งเราไม่ได้ หมายความว่า channel ขนาด 2,000,000 sats ก็ต้องมีเงินประกันเข้าไปด้วยจากฝั่งผม 20,000 sats ถึงจะใช้งานได้

ใครที่สนใจอ่านเพิ่มเติม ผมมีเว็บข้อมูลเกี่ยวกับ Lightning liquidity มาแนะนำ อันนี้แหละที่ผมอ่านแล้วเพิ่งมารู้เกี่ยวกับ channel reserve รวมถึงเรื่องอื่นๆที่น่ารู้เกี่ยวกับวงบริวารและการออกแบบระบบที่เกี่ยวกับ Bitcoin
https://bitcoin.design/guide/how-it-works/liquidity/#what-is-the-reserve-amount
-
 @ 378562cd:a6fc6773
2025-01-18 16:20:12
@ 378562cd:a6fc6773
2025-01-18 16:20:12As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention.

Power to Handle Anything I Throw at It
Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming.
The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast.

A Camera Setup That’s Hard to Ignore
One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots.
The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required.
The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings.
Battery and Charging That Won’t Leave Me Hanging
Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move.
Design and Features That Add Value
The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case.
The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus.
Why It’s Tempting Me
At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs.
For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made.
-
 @ 71a4b7ff:d009692a
2025-01-16 17:31:06
@ 71a4b7ff:d009692a
2025-01-16 17:31:06A couple of years ago psychologists at Berkeley have delved into the phenomenon of awe—how it affects us, when it arises, and how it can benefit us. Then I made this short summary, which I translated and edited a little today.
What Characterizes Awe?
Researchers define awe as a distinct and complex emotion encompassing 8–10 positive feelings, such as wonder, admiration, delight, and respect.
I’d like to sprinkle in a touch of discomfort or even threat, but the study notes that this aspect of awe depends on cultural context. For instance, in Japan, awe is more closely tied to experiences of threat than in other countries—think earthquakes, emperors, Hiroshima, Godzilla, and other kaiju.
How does our body respond to awe?
It turns out that awe can significantly improve both physical and mental health—even in “angry, bald apes” like us. The only caveat is not to mix it with fear or threat. Awe associated with those tends to be less beneficial.
The study identifies five key ways in which awe supports well-being:
-
Neurophysiological bonuses:
-
Increased vagal tone.
- Reduced sympathetic arousal.
- Release of oxytocin.
- Decreased systemic inflammation.
-
Lower activity in the brain’s default mode network.
-
Reduced self-focus:\ Over-focusing on oneself contributes to anxiety, depression, body image issues, addiction, aggression, and more. Notably, most people's profile pictures are close-ups of their faces. But among hikers, you’re more likely to see tiny figures dwarfed by vast, beautiful landscapes. If that’s not a literal shift away from self-focus, what is?
-
Prosociality:\ Even a brief moment of awe boosts cooperation, generosity, and altruistic behavior. Nowhere have I seen as much mutual help and free-flowing communication, even among strangers, as I have on hiking trips.
-
Connection to the larger whole:\ Awe fosters integration into strong social networks, a sense of connection to others, and harmony with nature.
-
A sense of meaning, purpose, and significance:\ Awe aids in making sense of life’s events, finding links between the present and the past, and aligning with one’s values, relationships, and life trajectory.
These five aspects form the foundation of both physical and mental health. Open any book, lecture, or treatise on human well-being, and you’ll find them highlighted in some form.
How can you experience awe?

The good news is that opportunities to experience awe are varied and accessible to almost everyone. It’s both surprising and heartening that they don’t revolve around the modern-day idols of success, money, or power. It seems that, at our core, we’re geared toward other goals and often misled by false priorities.
Among the universally effective ways to experience awe, researchers highlight:
- Spiritual and religious practices.
- Shared ceremonies (cinema, music, dance).
- Visual art.
- Psychedelic experiences.
- Acts of courage and kindness (which inspire awe in others).
- And, of course, connection with nature.
When mountains and hiking entered my life, they brought more health, peace, friends, purpose, and meaning than I’d ever expected. This text is a direct result of the awe I feel each time I stand among peaks, cliffs, forests, lakes, and rivers.
It’s not a panacea, but in a time when we’re drowning in useless information, political madness, urban filth, and noise, we desperately need a breath of fresh air.
Let’s embrace awe!

-
-
 @ f84e0b6b:f21f0a9b
2025-01-18 16:06:45
@ f84e0b6b:f21f0a9b
2025-01-18 16:06:45I’ve never lived in LA, though I’ve visited many times. The devastation there from recent fires there is still in the headlines and anyone with a soul feels for the folks without homes, neighbors and communities. Whether they vote the same way or look the same way or worship the same god, “what can I do to help these victims?” is our first question.
The second question is, what is the most responsible way to help? Paragraph two and controversy is already here. Responsible according to who? These people are victims, just give them as much money as they need and let them figure it out according to their local knowledge and culture! The broadest possible answer to this comes from a recent Substack by Arnold Kling: California Tough Love . His position is that there are certain factors controlled locally that led to the disaster, and we shouldn’t be in a rush to replicate them. Having some strings attached to funds that reduce the likelihood of $50,000/year blue collar workers in Iowa footing the bill for the rebuild of $5,000,000 homes in Pacific Palisades AGAIN in the foreseeable future is a very reasonable position.
My position here will be more detailed than Arnold’s, and thus has a higher probability of being wrong. That has never stopped me before. The source of this hubris is a crystal ball. While not a resident of LA, I have been an honorary citizen of Maui for several decades. This attachment is longer than the attachment to the city I currently live in. In August of 2023, a similar devastating fire engulfed the town of Lahaina on the west side of Maui. \~2,200 homes were burned or damaged. The plight of those rebuilding and the process they have gone through quickly faded from national attention, but not to those of us who spend substantial amounts of time on the island. This experience 17 months before the LA fires has painted a depressing blueprint of what we can expect in LA’s recovery. A couple of highlights:
-
In November of 2024, the first house was rebuilt. 15 months = 1 house. First House Rebuilt - Maui News. Article highlight: Maui “expedited the permitting process for this house, so it “only” took 2 months.
-
In December of 2024, federal funding for rebuilding via a block grant is finally approved by congress. Federal Block Grant For Rebuild - Maui News. Article highlight: $1.6 billion approved for housing = \~$800,000 per house.
What do these items have in common? The biggest price so far is time. Arnold’s substack was more of a philosophical position, but I doubt even he knew that at the time of writing, Lahaina’s federal funding had just been approved. All those strings he had attached by the feds? Still very slow for a family without a home. This is half of the ‘real price gouging’ mentioned in the subtitle. Those further down the socio-economic ladder have less time to whether the process in Lahaina and the same will likely be true for the middle class residents embedded in the areas destroyed by California’s fires.
The second element of price gouging is the red tape partially embodied in Maui’s example of two months of permitting. These costs aren’t just the time, but also the professional consultants of various stripes required to navigate the process successfully and the costly modifications to homes mandated through these processes.
Here is where I posit my broad and general suggestion. There should exist a “right to rebuild”. If you can legally own a piece of property in a specific condition, you should have the right to rebuild that exact same property if it is destroyed by means out of your control. If you don’t have a “right to rebuild”, you really don’t own that property - you are just renting it for an indefinite period from whoever can prohibit rebuilding it.
Rebuilding is a special case in both the individual and the community level. See the map of Lahaina below. We know where all the plumbing and power lines were. We know where the streets and drainage were. The right to rebuild translates nicely to the community level. Rebuild everything back where it was. Take a month or two to clear out the debris from an area and begin to rebuild. Rinse and repeat until done.
Taxpayers in Texas shouldn’t be paying for bloated permitting processes in Lahaina or LA. They shouldn’t be paying for eco-upgrades unless very specific, critical failures that caused the current disaster are clearly identified with lowest-cost available solutions. (In Lahaina - pay to bury the power lines. I drove through the area where the fire started 2 weeks before it occurred. That place was a tinder box, and it will be again unless someone puts a golf course on that hill. Burying the power lines will dramatically reduce the fire hazard. I’m not joking about the golf course. Directly adjacent to the north of the area of Lahaina that burned is Ka’anapali, whose identical hillside is green all year round due to the presence of golf courses that pay for themselves and do not burn.)
How to address this in the context of federal funding via Arnold’s original post:
-
Extremely expedited permitting process for rebuilds that get any federal funding: 5 days not 60. You can rebuild what you had, no questions asked, just file the paper work to prove it is the same lot and same size structure. If local jurisdictions drag their heels - no funding, answer to your voters who are now SOL.
-
Capped amount of funding per structure that covers a functional modest structure built at the average cost of the 10 most affordable states in the country. The process of building a single family residence is not dramatically different in various areas of the country, unless dictated by excessive regulation. There may be factors for labor to consider if an area is remote like Lahaina or the hills of North Carolina affected by Helene. But if it costs 2x to build a house in your county than in the 10 most affordable states - you are doing it wrong. There is some regulatory price gouging going on. Figure it out. 10 most affordable states to build a home - According to this research you can build a 2,100 square foot home for an average of less than $300,000 in the 10 most affordable states. This list includes Florida, South Dakota and Tennessee. Your geography is not special.
-
This funding will also be contingent on these rebuilt houses being completed within 110% of the time it takes to build 2,100 square foot home in the same 10 markets - measured from the day funds begin to be distributed by the federal government. Some things will take longer, but some should also be faster if you are doing a lot of these in the same place at the same time.
-
Federal funding will begin to be distributed from a risk pool within 6 months of the disaster, with minimal review to just ensure the disaster qualifies and the receiving state/city will abide by its parameters.
-
The funding is distributed at intervals governed by compliance with the program. Permits are being issued timely, and the amounts distributed are aligned with the cost of building in our most affordable markets.
If you want to build something new and different than before - it might take longer. If you want more than 2,100 square feet of house - I hope you had insurance to cover the difference. A new 2,100 square foot house puts you in the top 10% of humans on earth in terms of shelter. Being a good neighbor does not require rebuilding your infinity pool.
The right to rebuild will get people in homes quicker, remove government obstacles, and stop funding waste. Every citizen will know the rules - money is there to get me a basic structure quickly or fund the beginning of something larger. Any obstacles to that time and money are coming from politicians/regulations I can vote on. Comments will surely pour in explaining how it isn’t that simple. These comments will be reviewed diligently 2 years from now when Pacific Palisades is still a wasteland after $20 billion in federal aid has been spent.
 Source: Maui Now
Source: Maui Now -
-
 @ da0b9bc3:4e30a4a9
2025-01-18 14:09:40
@ da0b9bc3:4e30a4a9
2025-01-18 14:09:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/854843
-
 @ f1989a96:bcaaf2c1
2025-01-16 15:58:49
@ f1989a96:bcaaf2c1
2025-01-16 15:58:49Good morning, readers!
In Burma, the military junta introduced a far-reaching cybersecurity law that criminalizes privacy tools like VPNs and mandates online platforms to store and share user data with state officials. This move intensifies state repression of civil society, leaving activists and citizens more vulnerable to surveillance. \ \ Meanwhile, in Nigeria, President Bola Tinubu’s economic reforms, ostensibly intended to alleviate financial struggles, have backfired. Soaring inflation has plunged millions into a worsening food crisis, leaving families unable to put food on the table, as the regime continues to isolate the population from seeking a way out in the form of Bitcoin or dollars.
In open-source software news, Citadel Tech released the beta version of its Coinswap protocol. This privacy-enhancing Bitcoin tool, while still in development, could protect the financial activity of human rights defenders, journalists, and dissidents from the watchful eyes of authoritarian rulers. We also feature Nstart, a new tool that guides users through setting up a Nostr account for the first time. This may prove a valuable tool for activists and journalists operating in authoritarian environments, offering simplified access to uncensorable communications.
Finally, we conclude with the first three chapters of Evan Mawarire’s upcoming memoir, in which the Zimbabwean pastor turned activist recounts his powerful journey of inspiring a peaceful uprising against brutal dictator Robert Mugabe. His story is one of courage, resilience, and the enduring struggle for justice over hyperinflation and tyranny.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Burma | Military Junta Enacts Sweeping Cybersecurity Law
Burma’s military junta is notorious for repressing pro-democracy activists, freezing their bank accounts, and surveilling their financial activity. Now, it is expanding control over online spaces with a sweeping new cybersecurity law. The law requires digital platform service providers to store user data for three years and hand it over to state officials upon request. Non-compliant providers face fines, blocks, or shutdowns if they fail to remove content or limit the flow of so-called “disinformation.” The law also targets Virtual Private Networks (VPNs), crucial for Internet access and privacy. Those caught using VPNs face up to six months in prison and fines of up to 10 million kyats ($4,760). The criminalization of privacy tools and expansion of state surveillance leave the public censored and incapable of organizing against authoritarian rule.
Nigeria | Inflation Continues as State Closes Ways Out
President Bola Tinubu’s economic “reforms” — removing fuel subsidies, expanding the money supply, and devaluing the naira — have driven food inflation beyond 40%. In a country where the monthly minimum wage stands at just 70,000 naira ($45), this means two out of every three Nigerian households are struggling with hunger. In a recent Forbes article, Nigerian CEO of Recursive Capital, Abubakar Nur Khalil, observed: “As the Naira continues to face further devaluations and slips against the US dollar, it has become almost second nature for those in Nigeria to seek out viable alternatives in the form of bitcoin and USDT.” Individuals laboring under this regime often do seek a way out in the form of Bitcoin or stablecoins, but the government continues to try and restrict that activity, trying instead to trap citizens inside the sinking and surveilled naira.
Kazakhstan | Shuts Down Dozens of Digital Asset Exchanges
In 2024, the Kazakhstani regime shut down 36 digital asset exchanges with a combined turnover of 60 billion Kazakhstani tenge ($112 million). Authorities also confiscated 2.5 billion tenge ($4.8 million) in assets. The regime says it will continue to crack down on digital assets, but the reality is these kinds of exchanges are some of the only ways for people inside a dictatorship to obtain access to open money like Bitcoin. At the same time, the regime is promoting its central bank digital currency (CBDC), the digital tenge, which it developed in collaboration with Mastercard and Visa. While presented as a modern and convenient financial tool, the CBDC risks becoming a means for consolidating state control over citizens’ economic activities and leaving few avenues for preserving financial independence.
Belarus | Opposition Leader Condemns Upcoming Election as a Sham
At the end of January, Belarusians will head to the polls for a presidential election widely regarded as a sham. This election is the first since Alexander Lukashenko’s fraudulent reelection in 2020, which triggered mass protests and saw Bitcoin play a role in supporting pro-democracy movements. The upcoming election is expected to solidify Lukashenko’s grip on power, extending his rule beyond three decades and securing a seventh term. Under Lukashenko’s regime, thousands of dissenters have been imprisoned, silenced, or financially repressed for challenging state objectives and narratives. Opposition leader Sviatlana Tsikhanouskaya condemned the election, saying, “It is impossible to hold fair elections in a country where all the media are liquidated, all the parties are liquidated, and political leaders are in prison or abroad.”
Zimbabwe | Citizens Brace for More Currency Volatility
Zimbabweans are facing growing financial insecurity as the “ZiG” currency weakens further following a regime-imposed 43% devaluation in September. The sharp decline is eroding purchasing power, fanning inflation, and disrupting economic activity as the dictatorship siphons as much value as it can for its own uses, away from helping the people. “To plan using the local currency is to plan to fail,” says Christopher Mugaga, CEO of the Zimbabwe National Chamber of Commerce. These currency woes are compounded by drought-driven 18-hour power outages, placing immense strain on households and businesses alike. As profits dwindle, dissenting bank accounts are frozen, and disposable incomes vanish, many turn to US dollars and Bitcoin as lifelines to escape the chaos of an increasingly unstable ZiG economy.
BITCOIN NEWS
Coinswap | Releases Beta of Coinswap Protocol
Citadel Tech, an open-source Bitcoin software collective, announced the first public beta release of Coinswap, introducing a highly anticipated feature that enhances Bitcoin’s privacy and scalability. Coinswap allows users to swap their Bitcoin with other users in a way that breaks the link between transactions on the blockchain. Though still in its beta phase, this protocol holds potential for activists, journalists, and others living under authoritarian regimes, where financial surveillance is exploited to suppress dissent. Notably, HRF’s first-ever grant from its Bitcoin Development Fund was deployed to support Coinswap, so it is good to see progress on this front.
Nstart | Simplified Access to Nostr Protocol
Nstart is a new tool that simplifies onboarding to Nostr, a decentralized and censorship-resistant social network protocol. It guides first-time users through creating an account and securely backing up their private key (the password to their account). Additionally, users can set up a multi-signer bunker, which splits their private key into multiple pieces stored with trusted signers. This feature enhances security by protecting users’ identities even if one piece is compromised. These capabilities make Nstart an invaluable tool for activists and organizations operating under authoritarian environments, offering straightforward access to decentralized and uncensorable communications. To explore Nostr, start here: https://start.njump.me.
Blitz Wallet | Implements On-chain Payments and Manual Channel Rebalancing
Blitz, an open-source and self-custodial Bitcoin, Lightning, and Liquid wallet, introduced new features enhancing interoperability, privacy, and liquidity management. Users can now send regular payments from their Lightning or Liquid balances, giving them more transaction options. Blitz also lets users manually rebalance their payment channels, offering more control compared to automatic rebalancing. To improve privacy, the wallet will also rotate Liquid account addresses weekly and contact addresses every month, reducing the chances of being tracked.
Nunchuck | Launches Taproot Multisig Beta
Nunchuk, a self-custodial Bitcoin wallet, introduced a beta version of Taproot multisignature in its mobile wallet. Multisignature wallets require more than one private key to make transactions, adding an extra layer of security. With Taproot multisignature, Nunchuk’s wallet improves privacy and lowers fees by making these transactions look identical to regular transactions on the blockchain. This custody solution offers a secure and private way to manage Bitcoin, which is helpful for those in countries with dictators practicing strict financial surveillance or where funds are at risk of confiscation.
Wasabi Wallet | Integrates Send to Silent Payment Addresses
Wasabi Wallet, a privacy-focused, open-source Bitcoin wallet, introduced support for sending to Silent Payment addresses. Silent Payments enables transaction senders to generate unique addresses derived from a receiver’s static public key. This advancement is particularly critical for activists and dissidents operating in hostile political environments, where financial transparency can expose them to severe risks. By integrating Silent Payments, Wasabi Wallet empowers users with permissionless and uncensorable money, improving financial privacy for all parties and protecting them from oppressive surveillance.
Bitcoin Student Network | Launches Layer Zero
The Bitcoin Students Network, an educational hub for students interested in Bitcoin, launched Layer Zero, a program designed to empower youth worldwide, strengthen Bitcoin’s social layer, and promote its role in advancing financial freedom. Running for two and a half months, Layer Zero offers participants technical training and hands-on experience in community building and peer collaboration. The program also connects students with seasoned entrepreneurs and developers, fostering mentorship and real-world insights. Layer Zero could be a powerful support group for youth living under dictatorships and navigating financial repression. Students from anywhere have until Feb. 15 to apply to the program.
RECOMMENDED CONTENT
“Crazy Epic Courage” by Evan Mawarire
In this soon-to-be-released memoir, “Crazy Epic Courage,” Zimbabwean pastor and activist Evan Mawarire recounts the remarkable story of how he inspired a nation to stand up against dictator Robert Mugabe. What began as a simple viral video grew into the “ThisFlag” citizen movement, a powerful call for justice that challenged decades of brutal dictatorship and hyperinflation. Mawarire’s journey is one of resilience, courage, and unwavering determination, undertaken at great personal risk. For now, Mawarire is offering an exclusive preview of the first three chapters, where readers will begin to discover how he found his voice, sparked a movement, and forever changed Zimbabwe’s struggle for freedom.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 9e69e420:d12360c2
2025-01-18 14:02:27
@ 9e69e420:d12360c2
2025-01-18 14:02:27The Supreme Court's decision to uphold the TikTok ban, set to take effect on January 19, 2025, leaves 170 million American users searching for new social platforms. As this unprecedented shutdown approaches, Nostr, a decentralized social media protocol, is positioned to capture users seeking a censorship-resistant alternative.
Why Nostr Appeals to Former TikTok Users
Nostr offers several compelling features that make it an attractive option for displaced TikTok users. The platform provides true user control over content and algorithms, allowing people to choose how their feed is displayed rather than being subject to a centralized algorithm's whims. Additionally, Nostr's integration with Bitcoin's Lightning Network enables creators to receive direct micropayments through "zaps," creating new monetization opportunities.
Key Advantages of Nostr
Censorship Resistance Unlike traditional social media platforms, Nostr cannot be banned or shut down by any single entity due to its decentralized nature. Users maintain ownership of their digital identity and content, ensuring they won't face another situation like the TikTok ban.
Creator Economy Content creators concerned about losing their TikTok revenue streams can benefit from Nostr's native payment system. The platform's "zap" feature allows followers to send instant micropayments to creators, providing a direct monetization path.
Platform Independence Nostr's protocol-based approach means users can seamlessly switch between different client apps while maintaining their following and content. This flexibility provides a stark contrast to TikTok's centralized model that leaves users vulnerable to platform-wide shutdown.
Growing Momentum
Nostr has already demonstrated significant growth potential, expanding from 90,000 to 1.1 million users in just three months. With prominent figures like Jack Dorsey and Edward Snowden advocating for the platform, Nostr is well-positioned to capture a portion of TikTok's massive user base seeking a more resilient social media alternative.
-
 @ 0dd4b762:3b75a30d
2025-01-16 15:27:35
@ 0dd4b762:3b75a30d
2025-01-16 15:27:35The bane of our day and age is a subtle but very dangerous disease. It is rooted in ignorance and overestimation of one's own abilities. Indefinitely more lethal than covid1984 and even harder to trace.\ It is the epidemic of mid-curve-intelligence and average competence which has infected the most important roles of society.\ We've come to a system that forgot to select on merit and is willingly dancing towards it's own downfall to the gospel of DEI.\ The only antidote to this plague which also critically unveils it is sound and incorruptible money.
Sixteen years of melting faces.
\ While generational wealth is being accumulated left and right the mid-curve NPCs still pat themselves on the back for not participating in a "highly unstable and fraudulent ponzi-scheme".\ This is not at all a new phenomenon and its is perfectly normal for the general population to seek comfort in conformity instead of opening their eyes in search of the truth.
Another great case study for this dynamic was the plandemic of the early 2020s when, neighbours, coworkers and friends slowly but surely morphed into clones of the talking heads of your favourite news station. \ No matter the staggering nature of claims about masking, social-distancing and vaccine-mandates, many people wholeheartedly swallowed the propaganda in fear of becoming the only few nails that are still sticking out. The terror of the hammer was very apparent in that situation and gave us a good idea where the train might be going in the coming years..
Introducing bitcoin to the suits and the corporate balance sheet
\ Fast forward to the fun of January 2025 and number go up technology is being embraced by the president elect and his entourage, proposing mind bending ideas such as a bitcoin-strategic reserve. \ Not only the political caste started licking their fingers in anticipation of life-changing gains but the financial-industrial-complex also known as blackrock et al. jumped aboard with the introduction of the bitcoin ETFs exactly one year ago.\ Then there is MicroStrategy who are close to calling 500k bitcoin their own, not showing any signs of exhaustion stockpiling the most scarce money there ever was.
All these cases suggest bitcoin has dipped it's toe into the muddy waters of normie-mainstream-consensus, right?\ Hyperbitcoinisation is upon us one might think, it is just around the corner only a few blocks away, right?\ There ain't no way in hell people are not getting it at this point, right?\ \ I hate to break it to you but most of the managerial clss are still asleep at the wheel. Apperantly more so than ever.\ \ Especially the dismissal of the shareholder proposals for Microsoft and Amazon adding bitcoin to their corporate balance sheets unveiled the root problems which stem from the c-suits of the highest floors of corporate America.\ \ The all so mighty people in the drivers seat of these gigantic corporations miserably failed the intelligence-test bitcoin presented to them. Unmasking a very uncomfortable truth: The higher up executives today are mostly made of mid-wit-normies who are not willing to innovate and step outside of the warmth of DEI nonsense.\ They literally did the meme.
It is a culture of mediocrisy that is actively being selected for in the higher up's offices.\ The new generation of managers and problem solvers nowadays doesn't consist of the smartest people anymore but got displaced by the folks whose main strength it is to jump trough arbitrary hoops.

stayhumblestacksats
-
 @ 3ad01248:962d8a07
2025-01-15 19:03:50
@ 3ad01248:962d8a07
2025-01-15 19:03:50I know with the hype around Trump's election victory and the pro-Bitcoin people that he has surrounded himself with as of late, the idea of a Bitcoin Strategy Reserve or BSR is an intoxicating idea among many Bitcoiners.
I don't blame Bitcoiners from being happy about it, how can you not be? After enduring the last 4 years of vicious crackdown, arbitrary rules from the SEC and outright hostility to the Bitcoin community in general it is nice to have an administration that is simply nice to us and wants to leave the community alone to do it own thing.
While I am excited to see what a new Trump administration looks like for Bitcoin over the next four years, I am not onboard with a BSR. I think that the BSR is bad policy and supports the system that we are trying escape from in the first place.
In my opinion I believe a BSR signals to the world that the government doesn't believe in its own currency or its ability to reign their spending problem. Even the mere signaling that America is going to create a BSR has sent other countries scrambling to create one of their own. This is incredibly bad news for the US bond market.
Who are the buyers of US bonds right now? A huge component of the market is foreign governments. Even though they have been less willing to buy US bonds over the last couple of decades most governments are still in the market buying up US debt.
Now imagine of these foreign buyers start buying Bitcoin in small amounts at first and slowly scale into Bitcoin in a big way once they see the insane price action. They will FINALLY get it and once that happens its over the dollar. This is a gradually then suddenly like moment that no one is ready for at the moment.
So if you take way the foreign buyer of US bonds, who are you left with? The Federal Reserve. Having the Federal Reserve directly buying up government debt is huge sign of monetization of the debt to the world and doesn't bode well for the future of America or the world.
As you can see setting up a BSR would be highly destabilizing in the short term and could create a whole slew of knock on effects that no one is prepared or equipped to deal with.
In addition to destabilizing an already fragile economic environment, why do we want this big ass government to have Bitcoin in the first place? So they can keep on oppressing the working man/woman, crushing innovation and generally being a tick on the back of the private sector? How about we not empower them to keep spying on us and the world.
I want to live in a world where war impose heavy costs on leaders and governments and peace is the default setting of the world. Governments using Bitcoin to prop up their tyrannical ways is not why Bitcoin was created. You know that. I know that. The rest of the world should know that.
Bitcoin was created as an electronic p2p system that allows anyone to transact regardless of artificial borders or political differences. Bitcoin allows anyone to transact globally without the grubby hands of the government trying to take a cut. We need less government, not more.
I'm personally not a fan of governments or big money institutions getting into Bitcoin as I feel its like letting the fox into the hen house but that ship has sailed. The best we can hope for now is to create enough individual adoption that it makes it hard for governments to get a large amount of Bitcoin so they can act as a check on the accumulation of Bitcoin.
HODL culture is needed now more than ever. Don't hand over your Bitcoin to tyrants. Stack sats. HODL. Create the change you want to see in the world.
-
 @ bf47c19e:c3d2573b
2025-01-18 12:47:56
@ bf47c19e:c3d2573b
2025-01-18 12:47:5618.08.2020 / Autor: Igor Mirković
Činjenica je da živimo u vremenu u kome su informacije dostupne na dohvat ruke, svuda i svima. Analiza najsitnijih detalja zaobilazi ljudske, ponekad pogrešne procene, potpomognuta kompjuterskom tačnošću dovodi nas do maestralnih otkrića. U izobilju sačuvanih podataka blokčejn industrije gde je transparentnost glavni adut, kruži velika nepoznanica koja zbog svoje nerešivosti prerasta u misteriju. Ko je idejni tvorac Bitkoina, jednog od najuticajnijih projekata u modernoj finansijskoj industriji i znate li ko je misteriozni Satoši Nakamoto?!
Nepoznati genije, čija je kreacija najpoznatija alternativa čitavom svetskom monetarnom sistemu ali i svakodnevnom životu, kome svi nalazimo zamerke, na koje smo navikli da prećutimo i prihvatimo ih jer mislimo da tako mora, imao je ideju o konceptu čuvanja i razmene vrednosti koja će savršeno funkcionisati unutar društva. Bitkoin je prvi put prezentovan javnosti 31. oktobra 2008. u tekstu koji se popularno naziva Bitkoin Whitepaper i predstavlja dokument o filozofiji u rešavanju određenog problema. Bitkoin Whitepaper je kao autor potpisao Satoši Nakamoto.
 Satoši Nakamotov Bitkoin whitepaper
Satoši Nakamotov Bitkoin whitepaperKandidata koji mogu biti iza ovog imena ili pseudonima svakako ima, ali nećemo odmotavati klupko unazad, nego ćemo pratiti Satošijev rad i stvari koje zapravo znamo kako bi nas dovele do nekoga ili nečega. Saznanja, ko je to, koristeći taktiku dobrih poker igrača, u kojoj ne moramo videti kroz zatamnjene naočare drugih igrača kako bi ih pročitali, već ćemo tumačiti njihove postupke, govor tela, izbor reči…
Sami počeci ovakve ideje datiraju mnogo ranije i idu do 1980. godine i Cypherpunk zajednice koja je bila sačinjena od fanatika za brigu o privatnosti podataka na internetu i kriptografa koji su kreirali softvere za zaštitu podataka. To je bila privilegija državnika na visokim pozicijama sa pristupom poverljivim informacijama i naravno, tajni alat vrhunskih špijuna. Cypherpunk su aktivisti koji se zalažu za široku upotrebu kriptografije i tehnologije za unapređenje privatnosti, kao puta ka društvenim i političkim promenama.
Zaštita privatnosti je smatrana bitnom ali nije bila masovno dostupna, a Cypherpunk zajednica se zalagala protiv sistema „Veliki brat“ sistema u kome je nekome iznad uvek dostupan uvid u naše aktivnosti. Promovisali su zaštitu, enkripciju i bezbednost na individualnom nivou, u kome bi svako trebalo da preduzme dostupne mere predostrožnosti i zaštiti svoj virtuelni (lični) identitet.
Pretpostavljamo da je Satoši bio deo ove zajednice jer je definitivno bio njihov istomišljenik i kao inspiraciju za kreiranje Bitkoina imao je par postojećih projekata iz zajednice poput B-Money, Digi Cash ili Bit Gold koji su idejno bili slični Bitkoinu ali neuspešni u realizaciji.
Nakon objavljivanja Bitkoina, Satošijeva ideja se postepeno širila zajednicom i privukla brojne programere koji su bili voljni da daju svoj doprinos u razvijanju i adaptaciji, ali je Satošijev lik i dalje ostao neotkriven jer je sa saradnicima komunicirao isključivo porukama preko e-mail adrese i foruma, koristeći potrebnu zaštitu. Njegova lokacija i ostali tragovi do njega bili su nedostupni. Čak i njegovi najbliži saradnici znali su ga samo kao internet nalog sa alijasom Satoši Nakamoto.
 Citat iz „The Crypto Anarchist Manifesto“
Citat iz „The Crypto Anarchist Manifesto“Pored toga što je bio ključna osoba za kreaciju i razvoj Bitkoina, nije upadao u oči javnosti jer mediji i ljudi koji su čuli za Bitkoin, masovnu primenu i uspeh projekta tretirali su kao naučnu fantastiku i nisu joj pridavali bitan, a kamoli revolucionaran značaj.
03.01.2009. nakon niza transakcija, uspešno je „izrudaren“ prvi blok u Bitkoin blokčejnu i nagrada koja je sledila rudaru tog bloka (Satošiju) bila je 50 BTC. U kompjuterskom kodu prvog bloka nalazi se „skrivena poruka“ koja kada se dešifruje glasi:
– The Times 03/Jan/2009 Chancellor on brink of second bailoutfor banks
Ova poruka se podudara sa naslovnom stranom londonskih novina tog dana, ukazujući na pogrešne poteze postojećeg monetarnog i finansijskog sistema, koji su razlog nastanka Bitkoina. Država pomaže banke i privredu tako što im puni čašu za podsticaj ekonomije, ali flaša novca iz koje uporno dolivaju je fiktivna i napunjena je novcem „ispod čekića“, kojim se kupuje socijalni i ekonomski mir.
 Bitkoin programeri
Bitkoin programeriKako je vreme prolazilo, mnogi su uvideli prednosti koje Bitkoin ima, broj korisnika se povećavao, a mreža je bila sve stabilnija. Satoši je aktivno radio sa brojnim programerima na razvitku same tehnologije, ali teško je bilo kontrolisati pravac u kome će Bitkoin biti korišćen. Novac koji ne može biti kontrolisan od strane Centralne Banke, ne može biti oporezivan, nije inflatoran i može biti poslat i primljen svuda, veoma brzo zloupotrebljen je kao savršen način finansiranja i plaćanja projekata koji su smatrani krajnje ilegalnim i zabranjem od strane vlada širom sveta.
Jedan od takvih slučajeva bio je WikiLeaks skandal 2010. godine, koji je koristio Bitkoin kao sredstvo finansiranja svog sajta, na kome su objavljivani ukradeni podaci koji su bili strogo poverljivi i zabranjeni za javnost, a sadržali su brojne malverzacije i tajne dogovore medju državama.
Satoši Nakamoto je osporavao korišćenje Bitkoina u ove svrhe, ali zbog same prirode Bitkoin-a bilo je nemoguće da se ovako nešto spreči. Borba izmedju dobrog i lošeg koja se vodila u zajednici, nastala neiskustvom u do tada neviđenoj situaciji i višestruke neregulative, moralno je potresla Satošija, koji nedugo zatim na misteriozni način nestaje sa svih foruma… Ostavlja samo komentar: „Bilo bi mnogo bolje da je Bitkoin privukao pažnju javnosti na bilo koji drugi način, osim na ovaj. WikiLeaks je uzburkao roj pčela, koji je sada krenuo na nas.“
Svestan mogućih problema sa vlastima zbog svoje kreacije, odlučuje da se potpuno povuče i prepusti razvijanje projekta svojim najbližim saradnicima i zajednici. Bitkoin je nastavio da se razvija i istakli su se mnogi koji su uticali na unapređenje kako tehničke pozadine projekta tako i medijske prihvaćenosti i pravne regulative.
Ljudi lako shvate Bitkoin, jer je ideja o savršenom finansijskom trzistu u njihovoj glavi vrlo slična, a Satoši se pobrinuo da tehnoloski podupre takvu zamisao. Čovek koji je živeo za procvat tehnologije u kojoj je anonimnost i dostupnost vrlina, van svakog zla modernog doba, u kome se često zloupotrebljava tehnološka revolucija da se tron postojećih vladara utemelji, na štetu nemoćnih.
Količina Bitkoina koja je došla u Satošijevo vlasništvo tokom početnih godina procenjena je na minimum 1.000.000 BTC-a, što sada, nakon rasta svesti o stvarnoj i mogućoj vrednosti Bitkoina iznosi oko 11 milijardi američkih dolara i to ga direktno klasifikuje kao jednog od najbogatijih ljudi na svetu.
 Naslovna strana magazina „The Times“
Naslovna strana magazina „The Times“Debata ko je misteriozni genije i idejni tvorac bitkoina – Satoši Nakamoto i dalje traje. Da li je muškarac, žena…? Ili čitava grupa ljudi stoji iza pseudonima? Mnoge analize poruka po načinu spelovanja upućuju da je reč o osobi engleskog porekla, naprednog programerskog znanja i shvatanja ekonomije. Akademski građanin koji razdvaja novu rečenicu sa dva spejsa posle tačke, što je simbolično za akademske radove tog vremena, ali i za stare pisaće mašine, koje je možda koristio u mladosti i tako razvio naviku.
Jako je interesantna činjenica da ni jedan coin u njegovom vlasništvu od njegovog nestanka, nije poslat ili potrošen. Stoje na kripto novčanicima, netaknuti. Svi za koje se pretpostavljalo da stoje iza Bitkoina su javno negirali da su oni misteriozni idejni tvorac Satoši Nakamoto, svi sa kojima je sarađivao tvrde da ne znaju njegov identitet i svi koji su se dobrovoljno javili da preuzmu zasluge za kreaciju, nisu imali dovoljno jake dokaze za samoproklamovane tvrdnje.
 Najbogatiji Bitkoin holderi
Najbogatiji Bitkoin holderiBitkoin nosi etiketu savršenog sistema otpornog na bilo koji vid malverzacije u samim transakcijama jer krajnju realizaciju ne vrše drugi ljudi nego kompjuterski program. Kripto rudari, novčanici za čuvanje, adrese za slanje, mnogima su poznati termini koji su sastavni deo Bitkoin mreze ali jedna stvar je ostala nepoznanica kako za ljubitelje kriptovaluta tako i za ostatak sveta, samo srce projekta, ko je i gde je osoba koja se krije iza potpisa Satoshi Nakamoto.
-
 @ c21b1a6c:0cd4d170
2025-01-15 18:04:31
@ c21b1a6c:0cd4d170
2025-01-15 18:04:31Hello everyone, as part of the nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f grant I have to write a progress report for Formstr, I thought I'll use this opportunity to do a nostr blog! , Something I've been meaning to do for sometime, hopefully I don't bore you.
Introduction
There was a lot of work ahead of us even before we got the grant, and we tried to tackle it heads on. We completely changed the underlying mechanism of storing and fetching forms. Whereas previously a form was a kind 0 event, same as a profile event. The form is now created and responded to in the mechanism as outlined in the Forms NIP. This had to be done while making sure that none of the older forms broke during the process. The new specification helps streamline the forms usecase to expand to access control, private forms, upgrade to nip44 encryption. Some of these features existed as Proofs of Concepts prior to this quarters work, the major tasks were to streamline and production-ize them, to be able to release it to the public. We were also joined by nostr:npub1vf6wyw9j38sm96vwfekwvqxucr9jutqrmwdc2qnql79a66al9fzsuvt9ys who along with nostr:npub15gkmu50rcuv6mzevmslyllppwmeqxulnqfak0gwud3hfwmau6mvqqnpfvg helped move the project along.
How did we spend our time.
Released a major Formstr Update (16/12/204): - Release PR: This Release Contained The Following Changelog: - Move Form Creation and Rendering to New Event - Upgrade Response Encryption to NIP-44. - Add Ability to create private forms. - Add ability to send private form access as Gift Wraps. - Create a new dashboard UI to incorporate new form types. - Add ability to login to formstr - Use naddr to encode form Urls instead of pubkey(centralized).
Work done to production-ize these features can be found in the following PRs: 1. Save forms to local device automatically 2. Ability to remove participants in Access Control UI 3. Revamp Responses Page according to NIP-101 4. Add a "My Forms" Section on the dashboard 5. Add UI for Inserting Images 6. Using Naddr Instead of pubkey as formId
In addition to these there were multiple bugfixes and patches that I've excluded for brevity.
Major Challenges
We were in "beta hell" for a long time, even though I had finished rudimentary versions of each of the features in advance (some to test the viability of the forms NIP). Incorporating them into the running version proved to be a challenge. We realized that some of the features required major UI changes, and a lot of new features broke previously working desirable features such as NIP-04 Notifications. A lot of work like this had to be done to ensure formstr brought in new features while continuing to work exactly as old users liked it.
What's left and what's coming?
From the wish-list items I had committed during the application a few major ones remain: - Edit Past Forms. - Paid Surveys. - Support for NIP-42 Private Relays. - Conditional Rendering of form fields - Sections
Of these I'm happy to report that we've already begun work on conditional rendering of fields (https://github.com/abhay-raizada/nostr-forms/pull/199)
What is de-prioritized?
Going with experiences from quarter 1, we are de-prioritizing Formstr Integrations with 3rd party services like Ollama (Self Sovereign AI) and business tools like Slack, Notion etc. We'll try to get to it, but it's less of a priority compared to other features!
How the funds were used.
- Paying Individual Contributors for PRs submitted.
- Living Expenses
-
 @ f9c0ea75:44e849f4
2025-01-15 16:42:53
@ f9c0ea75:44e849f4
2025-01-15 16:42:53Em 2007, o Brasil comemorava o fim da CPMF (Contribuição Provisória sobre Movimentação Financeira), um imposto que, embora "temporário", durou 10 anos e arrecadou centenas de bilhões de reais. Na época, o governo afirmava que a contribuição era necessária para financiar a saúde pública, mas, na prática, foi mais um peso sobre o cidadão e as empresas.
Agora, quase duas décadas depois, o cenário está mudando novamente. O monitoramento financeiro da Receita Federal sobre transações acima de R$ 5 mil e a implementação do DREX, a moeda digital programável do Banco Central, sugerem que o controle sobre o dinheiro nunca foi tão grande.
A pergunta que fica é: será que estamos caminhando para uma nova CPMF, só que digital e automatizada?
O Passado: CPMF e o Controle Estatal sobre o Dinheiro
\ A CPMF nasceu sob o pretexto de ser um imposto temporário, com uma alíquota pequena (inicialmente 0,20%, depois 0,38%) que incidiria sobre qualquer movimentação bancária. Seu objetivo oficial era financiar a saúde, mas a verdade é que o governo encontrou nela uma mina de ouro de arrecadação, garantindo bilhões de reais anualmente.
Os problemas começaram a aparecer rapidamente:
- O custo era repassado aos preços dos produtos e serviços, afetando toda a economia.
- Empresas e cidadãos pagavam sobre transações repetidas, tornando a carga tributária ainda maior.
- O dinheiro não foi totalmente para a saúde, sendo usado para tapar buracos no orçamento.
- A promessa de temporariedade caiu por terra, e a CPMF durou uma década.
- O governo insistia que não existia outro jeito de arrecadar sem essa cobrança, mas, quando foi extinta, nada desmoronou. Só ficou mais difícil tributar o cidadão sem que ele percebesse.
Agora, vemos novos mecanismos de controle financeiro surgindo. O argumento é o mesmo: transparência, combate à sonegação e otimização da arrecadação. Mas será que é só isso?
O Presente: Receita Federal Fecha o Cerco sobre Suas Transações
\ A partir de 2025, qualquer movimentação acima de R$ 5 mil para pessoas físicas e R$ 15 mil para empresas será automaticamente informada à Receita Federal. Isso significa que se você fizer uma transferência maior que esse valor, o governo já saberá sem precisar pedir dados ao banco.
Oficialmente, essa medida não implica na criação de um novo imposto. Mas, se a história nos ensina algo, é que governos não implementam esse nível de monitoramento à toa. Algumas questões que surgem:
- Se não é para tributar, por que monitorar tão de perto?
- Se a CPMF foi extinta, por que voltamos a um sistema de rastreamento financeiro tão intrusivo?
- Esse é só um primeiro passo para um imposto automático sobre movimentações digitais?
O Futuro: DREX e a Automação da Tributação
\ O DREX, a versão digital do real, será um grande passo para o controle financeiro estatal. Diferente do Pix, que apenas facilita transferências, o DREX permite que o Banco Central programe e rastreie cada centavo movimentado.
E o que isso significa para o cidadão comum?
- Pagamentos e tributações automáticas: um sistema de split payment poderia fazer com que impostos fossem cobrados diretamente na fonte, sem a necessidade de declarações ou boletos.
- Controle total sobre transações: diferente do dinheiro físico, que circula sem monitoramento, o DREX permitirá ao governo rastrear qualquer pagamento, em tempo real.
- Possibilidade de limitação de uso: com uma moeda programável, poderia haver restrições sobre onde, quando e como você pode gastar seu dinheiro.
O Banco Central e a Receita Federal garantem que não há planos de usar o DREX para tributação compulsória, mas a CPMF também começou assim: como algo temporário, necessário e inofensivo.
Estamos Caminhando para uma Nova CPMF Digital?
\ Se analisarmos a trajetória do governo na questão tributária, fica claro que:
- Primeiro, nega-se qualquer imposto novo.
- Depois, implementa-se um sistema de monitoramento, supostamente para "combater fraudes".
- Por fim, a tributação é introduzida sob a justificativa de que "não há outra saída". A CPMF só funcionou porque o dinheiro passava pelo sistema bancário e era fácil de rastrear. Agora, com o DREX e o monitoramento da Receita, o governo não precisaria nem de um imposto explícito para tributar transações—ele poderia simplesmente automatizar a cobrança diretamente na moeda digital.
O que antes dependia de aprovação no Congresso e resistência da população, pode agora ser feito com um simples ajuste de software no Banco Central.
O governo diz que isso não está nos planos. Mas se olharmos para trás, essa é exatamente a mesma narrativa que ouvimos antes da CPMF entrar em vigor.
Seu Dinheiro, Seu Controle?
\ O Brasil está entrando em uma nova era financeira. O monitoramento de grandes transações e a implementação do DREX podem representar um avanço na transparência e na eficiência econômica, mas também criam um risco real de perda de liberdade financeira e tributação automatizada.
O que aconteceu com a CPMF deve servir de lição: o que começa como uma simples ferramenta de arrecadação pode se transformar em um peso permanente sobre o cidadão.
Se o governo tiver a tecnologia e a infraestrutura para tributar automaticamente, quanto tempo levará até que eles resolvam usá-la?
-
 @ c4b5369a:b812dbd6
2025-01-18 12:17:22
@ c4b5369a:b812dbd6
2025-01-18 12:17:22This is the first edition of the SDR (Squirrel Den Recap), a development blog where I recap the recent Cashu related things I've been working on.
The year of the nut
IYKYK. 2025 is the year of the nut. Don't blame me, you can put it on the Chinese:

And I intend to take full advantage of that. This is the year where I go all in on the nut development!
Building a mint???
There are already a few mint implementations out there (nutshell, gonuts, cdk...). So why build another?
Honestly it was kind of a selfish move. So far, I have mainly concerned myself with building tools for Cashu wallets and clients. I figured, if I wanted to truly focus on Cashu this year, I should also know my stuff when it comes to building a mint from scratch. And so I did. It also allows me to experiment with mint related stuff, having an implementation handy that I can mess around with.

The mint implementation is called MNT. You can visit the homepage https://mnt.cash , where you will also find a link to the code.
Although the code works, the mint implementation is not yet ready for production. I've been playing around with it using a local testing lightning network with Polar , which by the way is a great tool for devs that need to test lightning integrations.
The mint
MNT is short for mint. It's also pronounced like mint, but without the "i". The goal of this project is to be an easy to run mint, that could be deployed by users for example when running an event. It won't support all of the protocol features, to keep it simple. Instead the focus will be on simplicity and ease of use.
MNT comes with an admin web interface, that makes it easy to set the mint up with a lightning backend:

After adding a lightning backend, the mint is basically ready! Users can enjoy a live view of what is happening on their mint via the integrated dashboard:

Admins can take direct actions on the mint via the admin tool, like rotating keysets, disabling and enabling features, etc...
A key feature is also the keyset view, where operators get a view on how much of the issued ecash has already been redeemed in each keyset. This is a crucial tool for mint operators, because it lets them know when they can safely delete records from their database, or shut the mint down.

The mint is compatible with all Cashu wallets. It only supports a subset of the cashu specification (NUTs), and will probably never implement the full spec. I'm looking forward to soon recklessly give this badboy a spin on mainnet 😎
What else?
Cashu-ts
Last year
npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226
joined cashu-ts as a maintainer and has been killing it with development in the project! As I ramp up my involvement in the project again, we started having weekly dev calls. Developers that want to contribute to cashu-ts development, please reach out to me so you can join us on the next call!
Nutstash
The wallet has seen a complete make-over at the end of last year. Now is the time to consolidate, fix bugs and improve the UX.
npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880
has been helping me with awesome designs and UX suggestions, while I've been crushing bugs. A new version fixing some edge cases in the restore process can be expected next week!

This blog
\ This year, I was fortunate to receive funding for my work on open source projects in the Cashu ecosystem. I am very grateful for the trust from
npub17xvf49kht23cddxgw92rvfktkd3vqvjgkgsdexh9847wl0927tqsrhc9as
and
npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f
this means a lot to me, to be able to make a living by working on something I am passionate about is a blessing, and I don't think it would be possible without the support from you. My deepest gratitude, I hope my contributions will not only match, but exceed expectations.
By writing this blog, I want to show my progress, proof of work, and give people a look into the daily life in the squirrels den 🐿️🐿️🐿️🐿️🐿️🐿️
If you have any questions or suggestions about this blog, please let me know in a comment!
Best,
Gandlaf
-
 @ 3eacaa76:bac66fe4
2025-01-15 16:25:13
@ 3eacaa76:bac66fe4
2025-01-15 16:25:13Few days back this track get on Top of list on #wavlake. It's nice , but not a point. at all.
The message is clear. like Real Talk should be !
We know, specialy on #nostr, that solutions are available. However, the world is not yet aware of them.
100% of the donations for this remix will be sent to my friend Yusef who is on the ground and has been providing food, water, and shelter for children in Gaza even before or the psyop with October 07 took a place. Israel has enforced a blockade on Gaza for over decade. And Just past year completly destroyed 90% of land. Like to the ground , no schools , no hospitals ... hard to find anything what surrvived those daily airstrikes without 1h of pause since 350 days. WTF
It's heartbreaking to see children dying daily in houreds and the lack of action from the public and authorities of other nations. The statistics are alarming, and it's essential to address this issue and find ways to make progress. it's crucial to raise awareness and take action to prevent further tragedies. Let's remember that every child's life is precious and deserves our attention and support.
In most apocaliptic condition , where is-real controling all money supply (check lastest news about banknotes in there) , the #Bitcoin is one and only solution can help them in daily bases. It was helping them before with great succes. Why you ask ? becuse even if they close all platforms You can still send them some sats.
How fookin cool is that !!
I know it doesn't sound funny.
Those People pushed to the limit , now they have a tool that fulfills exactly what was created for A Peer-to-Peer Electronic Cash System.
No Middle man .``` On the middle is only a finger whitch WE the PEOPLE can give to those Scumbagz in Goverments and Banks, Full stop.
```
Many people are only recently realizing the truth about Gaza being an open-air prison from like 75 years. Not 3, not 5 or even 20 ..... but seventy five fookin years.
This music mix was created to share the truth and provoke to critical thinking, which has been lacking for the past decade. and even more.
I wonder why we can watch live streams of the ongoing genocide in 4K HD and stil be silent. not all but many.
Why are we surprised that normies don't understand Bitcoin and still use fiat shit currency? Whitch is fudament of All war crimes. We should ask ourselves.
Our own ignorance and the banking system are the cancers of this world.
If we lose Palestine, we will lose much more than we think.
You will be next - One way or another
Thank you for your support, not for me but for those in need who can gain hope from our efforts.
Respect to you all.

LISTEN HERE and suport directly in upper links
FreePalestine
Thanks
be blessed
MadMunky
-
 @ e1d968f7:5d90f764
2025-01-15 09:09:26
@ e1d968f7:5d90f764
2025-01-15 09:09:26In the digital age, reviews play a pivotal role in every industry, and escorting is no different. For me, reviews aren’t just feedback; they’re a lifeline for building trust, attracting new clients, and standing out in a competitive world. But like so many aspects of this job, managing reviews requires care, strategy, and a touch of finesse.
Why Reviews Matter
When someone is considering booking with me, they often turn to reviews first. They provide a sense of reassurance and help potential clients feel confident about their choice.
- Building Credibility: Positive reviews show that I’m genuine, professional, and deliver the experience I promise. They help break down any initial hesitation a client might have.
- Standing Out: In an industry where there are countless options, a few glowing reviews can make all the difference. They show why I’m unique and worth the time.
- Feedback for Growth: Even the occasional critical review can be useful. It’s a chance to reflect and improve how I approach my work.How I Encourage Reviews
Not everyone leaves a review, even if they had a great experience. I’ve learned to gently encourage feedback in ways that feel natural and respectful.
- Casual Suggestions: Sometimes, during a conversation or at the end of a session, I might say something like, “If you feel comfortable, a review would mean a lot.”
- Follow-Up Messages: A polite follow-up, thanking them for their time and subtly mentioning reviews, often works wonders.
- Respecting Boundaries: It’s always important to let clients know there’s no pressure. Their comfort and privacy come first.Handling Negative Reviews
No one likes receiving a negative review, but I’ve learned that it’s part of the job. How I handle them can say as much about me as the positive ones.
- Staying Professional: I’ve trained myself not to take things personally, even when a review stings. A calm, professional response can turn things around or at least show others that I handle situations with grace.
- Taking Lessons to Heart: If the criticism is valid, I take it seriously. It’s an opportunity to improve and ensure I’m providing the best experience possible.
- Dealing with Fake Reviews: Unfortunately, fake or malicious reviews do happen. In those cases, I work with the platform to get them removed, protecting my reputation.Making the Most of Positive Reviews
When a client leaves a lovely review, it’s like receiving a little gold star for my work. But there’s an art to showcasing them effectively.
- Profile Highlights: I carefully select the best snippets from reviews to feature on my profile. They give potential clients a taste of what I’m like.
- Sharing Selectively: Occasionally, I’ll share anonymised testimonials on my site or social media, always ensuring I protect the client’s privacy.
- Authenticity is Key: I focus on presenting reviews that reflect the real me, rather than creating a perfect but unrealistic image.Balancing Reviews and Authenticity
While reviews are incredibly valuable, I remind myself that they’re not the be-all and end-all of who I am or what I do.
- Avoiding Perfectionism: A profile with nothing but glowing reviews can feel too polished. I embrace the occasional constructive comment—it adds a human touch.
- Staying True to Myself: My reviews should reflect my genuine personality, quirks, and the unique experiences I offer. Authenticity resonates with the clients I want to attract.Conclusion
Reviews are a powerful part of my work—they build trust, open doors to new clients, and show the care I put into what I do. By encouraging honest feedback, handling critiques gracefully, and always staying true to myself, I’ve learned how to use reviews as a tool for growth and connection while maintaining the authenticity that makes my service special.
Rebecca x
-
 @ 141daddd:1df80a3f
2025-01-15 05:19:45
@ 141daddd:1df80a3f
2025-01-15 05:19:45In the world of social media, the term "echo chamber" often carries a negative connotation. It’s associated with reinforcing biases, limiting perspectives, and fostering division. However, on platforms like Nostr, echo chambers take on a new, empowering dimension—one that allows users to consciously curate their own feeds and use them as tools for self-improvement and personal growth.
The Power of Voluntary Echo Chambers
Unlike traditional social networks, where algorithms dictate what you see based on corporate interests or ad revenue, Nostr puts the power back in your hands. You choose the accounts you follow, the content you consume, and ultimately, the ideas that shape your thinking. This creates a voluntary echo chamber, one that reflects your personal interests and goals rather than the priorities of a centralized algorithm.
This concept ties into psychological principles like autosuggestion or self-programming. By surrounding yourself with content that aligns with your aspirations, you can subtly influence your thoughts and behaviors over time. For example: - Following accounts that discuss Bitcoin might deepen your understanding of it even if you are normally lazy to do your own research. - Subscribing to content about meat eating or lifting could motivate you to adopt those habits. - Engaging with posts about self-discipline or personal development might inspire you to take actionable steps toward your goals.
Scrolling through your Nostr feed becomes more than a passive activity—it becomes a form of self-conditioning. Each post you see reinforces the values and ideas you’ve chosen to prioritize, nudging you toward the person you want to become.
A Contrast with Traditional Social Media
On traditional platforms like Facebook, Instagram, or X, the feed is curated by algorithms designed to maximize engagement. These algorithms often prioritize sensationalism, controversy, or content that serves the platform’s business model. As a result, your brain is programmed not by your own goals, but by the interests of the corporation behind the platform.
This distinction is crucial. On Nostr, you are the algorithm. You decide what influences you, creating a space where your feed becomes a tool for self-improvement rather than a source of manipulation.
Echo Chambers as Positive Spaces
The idea of an echo chamber isn’t inherently negative. In fact, any group or community built around shared interests can be considered an echo chamber. Think about: - A sports club, where everyone encourages each other to train harder and improve. - A book club, where members discuss ideas that expand their intellectual horizons. - A support group, where people share experiences and motivate each other to overcome challenges.
These are all examples of echo chambers that people enter voluntarily, and they often lead to positive outcomes. The same principle applies to Nostr. By carefully curating your feed, you can create a digital space that motivates, educates, and inspires you.
The Key to Beneficial Echo Chambers
The difference between a harmful and a beneficial echo chamber lies in intentionality. On Nostr, you have the freedom to: 1. Choose your influences: Follow accounts that align with your values and goals. 2. Avoid manipulation: Stay clear of (mute) content that doesn’t serve your interests. 3. Adapt over time: As your priorities evolve, so can your feed.
This level of control allows you to use echo chambers as a force for good—a way to program your mind for success, growth, and self-improvement.
Final Thoughts
Nostr represents a paradigm shift in how we interact with social media. By giving users the power to create their own echo chambers, it transforms the concept from something limiting into something liberating. Your feed becomes a reflection of your aspirations, a tool for self-programming, and a space for growth.
So, the next time someone criticizes echo chambers, remember: when entered voluntarily and curated intentionally, they can be one of the most powerful tools for personal development. On Nostr, the choice is yours.
-
 @ 6d43b512:17ccbfe1
2025-01-18 11:46:03
@ 6d43b512:17ccbfe1
2025-01-18 11:46:03nostr #nostr_writer #review #beginner #obsidian #anytype #contract_drafting #agreenent_drafting #lawyer #law #contract #agreement #learn #education #plugin #telegram #wordpress #yakihonne #primal #damus
I write about and teach contract drafting. I use Obsidian as my primary software for doing research and to store my thoughts, draft lessons, future ideas, etc.
While shifting from Wordpress I wanted to choose a tool and platform that can help me leave the paywalled platforms, and the need to pay for server space, domain, etc.
I found the freedom NOSTR.COM and in Obsidian Plugin Nostr Writer by James.
I opened an account on NOSTR.COM and wrote my first article in Obsidian and pushed (published through #Nostr_relays. You can find some on https://legacy.nostr.watch/relays/find ) it with the help of Plugin Nostr Writer, and you can simply access my blog posts by looking for them using a #nostr_client, if you also open a free Nostr account (a set of public and private keys).
A thought came to me just now. Can I also link my Nostr articles (that is saved as obsidian note), if I link it here. So trying that now.
[[My honest take on Nostr]]
To be on a safer side I also link the Nostr ID for above post here.
https://primal.net//e/note198msk03wj9jfp904k50evlret6laurqhgxzrk2mq9kuq0v0ggh0sx879fv
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bf47c19e:c3d2573b
2025-01-14 19:47:23
@ bf47c19e:c3d2573b
2025-01-14 19:47:23Originalni tekst na startit.rs
29.12.2017 / Autor: Danilo Backović
Esej koji obrađuje konceptualne osnove Bitkoina, njegovu istorijsku ulogu i odnos sa klasičnim monetarnim sistemom.
Bitkoin, banke i suverenost individue
Kratak dijalog o dva monetarna sistema sveta napisan u čast petstogodišnjice kačenja Luterovih “95 teza” na vrata crkve Svih Svetih u Vitenbergu.
Šta je Bitkoin i ko je tu gazda uopšte?
Niko. Niko od nas i svi mi zajedno. To je “samo” softver koji radi na računarima svih onih koji žele da se pridruže. Ni od koga ti ne treba dozvola. Ne postoji meta gde naciljati Tomahavk.
Po svetu postoji toliko kopija ove računovodstvene knjige da ona može preživeti nuklearni udar (u žargonu se to zove “bubašvaba protokol”). Bitkoin se može preneti na računaru, mejlom, pismom, u glavi, u slici (steganografija), radio talasima… Jedna firma je čak platila lansiranje satelitskog repetitora koji pokriva Evropu, sever Afrike i dobar deo Azije namenjenog samo za prosleđivanje bitkoin transakcija.
Korišćenje je besplatno. Ovakav softver se zove distribuiran, jer nema jedan ili više centara sa privilegovanim učesnicima.
I Gutenbergova štamparska mašina je bila “samo” miks malo preciznog livenja, obrade drveta, poluge i tinte, začinjena cutting-edge telekomunikacionom tehnologijom tog doba — hartijom, ali ta otrovna kombinacija je promenila svet zauvek. Decentralizovala je pristup znanju i oslobodila najvažniju mrežu među ljudima od pisarskih centara moći — jezičku.
Bitkoin koristeći se novom Gutenbergovom mašinom — internetom, oslobađa drugu najvažniju mrežu među ljudima — novčanu, koja prenosi signal o vrednosti.
Ne razumem. Kako to radi samo od sebe?
Soft skillovi su mrtvi, pripremi se na vreme za svet u kome caruje matematika. Doba disidenata pisaca, novinara, pesnika i glumaca je prošlo. Svako može da shvati, treba samo malo napora i želje.
Sama srž ove tehnologije leži u zakonima brojeva. Koliko je koren iz 4? Dva? Sedi jedan. +/- 2 je tačan odgovor, jer parna stepena funkcija gubi informaciju o znaku.
Koren je čudna funkcija. Problem kvadriranja dvojke, 2^2 ne možeš tek tako da rešiš unazad (inverzno). Možda sam ja krenuo od -2? Moraš da znaš neki dodatni uslov da bi izabrao pravu granu korena (pozitivnu ili negativnu), ili da probaš obe. Na kompjuteru ne bi mnogo potrajalo da zaista probaš obe grane.
Ali! Postoji čitav jedan skup algoritama koji se zovu “kriptografske heš funkcije” (H). Pođimo od apsurdno velikog broja P (na primer od 55 cifara), stavimo ga u takav algoritam H i neka je rešenje broj J = H(P). Ovi algoritmi imaju čudesnu osobinu ireverzibilnosti.
To znači da, imao li čak i najjači mogući sekvencijalni kompjuter, ne najjači postojeći, nego najjači koji termodinamika dozvoljava, u nameri da rešiš ovaj problem unazad, znajući J, a želeći da otkriješ P od koga smo krenuli ( P = H^-1(J) ) trebalo bi ti otprilike onoliko vremena koliko je Svemiru ostalo do njegove konačne termodinamičke smrti. Ovakav algoritam u bitkoinu ima dve ključne uloge:
-
On čuva tvoju imovinu od drugih, tako da svako može da pristupi toj računovodstvenoj knjizi (zamisli da banka dozvoli da svako pristupi njenoj bazi podataka), a da opet ne može da ti je uzme. Zato bitkoinu ne trebaju adresa, zaposleni, direktori, obezbeđenje i revizori.
-
On čuva tuđu imovinu od tebe jer te sprečava da falsifikuješ transakciju i probaš dva puta da potrošiš isti novčić, kroz genijalno Satošijevo otkriće dokaza o radu (proof of work ili Nakamoto konsenzus). Novčana mreža je primer tzv. Vizantijske mreže, u kojoj se učesnici ne smatraju kooperantima nego suparnicima. Nakamoto konsenzus je rešenje kako ta mreža dolazi do zaključka šta je istina, kolika je nečija imovina, bez da nekome mora da se preda poverenje da za nas vodi tu knjigu evidencije imovine!
Sve do bloka postanja (genesis block) 3. januara 2009, morali smo da imamo računovođu (banka) kome predajemo poverenje da za nas vodi računovodstvenu knjigu. Ako on kaže prodavcu da ti imaš dinar kojim kupuješ robu, prodavac će mu verovati i robu će ti dati. Sada umesto poverenja imamo zakone brojeva.
Bitkoin je jedna računovodstvena knjiga za celu planetu, agnostična na državne regulative i konačno, hvala Bogu, ne zahteva računovođu. Oci prosvetiteljstva su nam dali “Liberté, égalité, fraternité” i upozorili na vreme da je predstavnički sistem samo najmanje loša aproksimacija demokratije, zato je naš doprinos: Vires in numeris!
Bojim se da mi i dalje ništa nije jasno.
Većina nas seda u avion u nadi da će poleteti. Ne moraš znati dinamiku fluida da bi negde otputovao. Daleko je prostije biti korisnik bitkoina nego klijent banke. Za koju godinu koristićeš neki finansijski proizvod, a da ni ne znaš da u pozadini radi bitkoin.
Ali ako želiš da saznaš trebaće ti ne više od par nedelja da shvatiš najvažnije tehničke detalje. Za matematičku suštinu malo više od toga, ali ne moraš ići toliko duboko. To je zato što je on slobodna, potpuno otvorena tehnologija.
Reci mi, gde to čovek može da sazna kako funkcioniše naš trenutni monetarni sistem, ta “džungla konfuzije” (Kejns)? Akademija i dalje predaje neistinu, da se Sunce vrti oko Zemlje (da je depozit stariji od kredita).
Kako to misliš: “Bitkoin oslobađa novac”?
To je pravo pitanje i najvažnija poruka: Društvo je samo jedan veoma kompleksan graf. Svaki proces u društvu se može opisati učesnicima i njihovim vezama. Školovanje, vađenje pasoša, matičenje rođenih, venčanih, umrlih, katastar, uprava, carina, itd…
Bez obzira na to što su neki procesi vrlo prosti, a neki beznadežno kompleksni, svi oni imaju jednu zajedničku osobinu da sačinjavaju hijerarhijski graf. To znači, da svaka od ovih procedura da bi funkcionisala ima u osnovi neku listu ili knjigu evidencije (ledger), a nad njom piramidu odgovornih ljudi sa pravom upisa u nju koji su pečatom, potpisom ili “ok” dugmetom garanti istine (da je diploma odbranjena, carina plaćena, da se imovina poseduje, da je dete rođeno, ugovor važeći itd…).
Ti ljudi su predstavnici kojima predajemo poverenje.
Sve do interneta ljudi nisu imali drugi izbor da se umrežavaju osim ovog hijerarhijskog — predstavničkog (sa izuzetkom primitivnih plemenskih mikrozajednica). U ovakvoj topologiji mreže postoji nezgodan fenomen koji se zove korupcija.
To je zloupotreba mreže od strane nekog od predstavnika. I nije stvar mentaliteta nego je inherentni fenomen takve geometrije mreže.
U svakom društvu postoje ubice koje se šetaju sa diplomatskim pasošima, mrtvi glasači, lažne diplome… Internet je prva horizontalna topologija umrežavanja ljudi u istoriji, a Bitkoin monetarni sistem koji koristi ovu osobinu interneta (peer-to-peer) kako bi izbacio posrednike iz novčane transakcije.
To je, po dizajnu, necenzorabilan, transnacionalan, nehakabilan, u potpunosti definisan monetarni sistem koji ne zahteva predaju poverenja posrednicima da bi funkcionisao (trustless/no counterparty risk). U srcu sistema je nesvakidašnje otkriće digitalne oskudnosti.
Gde je registrovan?
Bitkoin nije pravno lice, nije forex kockanje, ni akcija na berzi. Bitkoin je algoritam. Kao Pitagorina teorema. Znanje koje se više ne može vratiti nazad u bocu, niti se ljudi mogu naterati da se od njega oduče.
Bitkoin sa velikim “B” je protokol, to je nova vrsta baze podataka bez administratora, u kojoj svaki korisnik ima istu ulogu i koja ima token (žeton, unos u bazi, to je bitkoin sa malim “b”) koji može da menja vlasnika.
Dinamika kreiranja tokena tokom vremena je regulisana protokolom, neizmenjiva od bilo kog korisnika i njihova količina nakon završetka te emisije će biti 21 milion. On je prvi programabilni novac. U transakciji se može implementirati i neka obligacija (ugovor), ne samo prosta razmena.
Znači to su neki virtuelni žetoni upotrebljivi na internetu?
“Virtuelni” je omiljeni pridev korporativnih medija. Nije virtuelna nego kriptovaluta jer ga kriptografija čini mogućim i daleko realnijom od depozitnog novca.
Ovaj token nije obična informacija kao što je to mp3 fajl ili računovodstvena stavka na pasivi bilansa privatnog lica sa državnom licencom za depozitne poslove (banka).
To je inertna informacija, jer joj treba minimum fizičkog rada (pod “fizički” se misli na veličinu u fizici) da bi nastala i pokrenula se. Kao zlato, samo bez mase. Naučili smo da ovaplotimo informaciju, napravimo od nje oskudnu tvar. I to je jedna divna istorijska simetrija.
Moderna nauka — Galilejeva fizika je počela shvatanjem inertnosti materije, od toga da je pravolinijsko kretanje ravnomernom brzinom osnovno, ne kružno kao što su mislile tadašnje usijane akademske glave, zato što je ono enciklika na “savršenoj nebeskoj sferi”. Otuda i jeretička kovanica za “nebesku mehaniku” Johana Keplera.
Otkriće i otimanje kriptografskih heš funkcija od države, zasluga Sajferpankera, modernih Pitagorejaca, i njihov religiozni odnos prema kriptografiji, doveo nas je do otkrića inertne informacije i to će otvoriti novu veliku stranicu istorije u kojoj je kriptografija osnov organizacije društva.
Još uvek joj nismo dali ime, ali dobar kandidat je period omoćenja ili suverenosti individue. Jer se istorija ne ponavlja, ali se rimuje (enlightment — prosvetiteljstvo, empowerment — omoćenje).
Ali ne smeju se tek tako dozvoliti te slobode, nastaće haos. Šta ako posluže za kupovinu droge i pranje novca?
Anonimnost transakcije nije privilegija nego pravo koje treba braniti životom. Prva rečenica manifesta Sajferpank pokreta je: “Privatnost je neophodan uslov za otvoreno društvo informatičkog doba. Privatnost nije tajna. Privatna stvar je nešto što se ne želi podeliti sa celim svetom, tajna je nešto što se ne želi podeliti ni sa kim. Privatnost je moć selektivnog otkrivanja sebe svetu“.
Svako ko se odriče prava na privatnost, jer “nema šta da krije” se ne razlikuje od onoga ko se odriče prava na slobodu govora jer “nema šta pametno da kaže” (Edvard Snouden).
Ovog trenutka banka zna više o vama od vas samih. I to je posledica dizajna depozitnog novca. Dve najvažnije mreže među ljudima su jezička kojom serijalizujemo naše misli i novčana kojom prenosimo signal o vrednosti stvari oko nas. Svaki pokušaj ometanja ovih mreža treba da prepoznamo i sprečimo. Na vladama je da nađu načine da spreče protivzakonita ponašanja i oporezivanje bez diranja u anonimnost transakcije.
Ali, neko mora da stoji iza toga. Čiji je taj Satoši Nakamoto?
Irelevantno. “Iza toga” je samo otvoren i svima dostupan programski kod. Bitkoin je recept, ideja, algoritam. Nije pravno lice. Je li važno ko je zapravo bio Pitagora? Frensis Bekon? Vilijam Šekspir?
Postao je preskup. Mogu da ga priušte još samo bogati.
Novac sa dve decimale je samo istorijska posledica, verovatno nekada merne nepreciznosti kantara. Nije nikakav prirodni zakon da novac mora imati samo dve decimale. Bitkoin je deljiv na sto miliona delova. Možeš kupiti npr. hiljaditi deo bitkoina za 15 evra. Manje od 1% ljudi na planeti može imati više od jednog bitkoina, to je ogromna jedinica.
I šta onda? Da čekam da poraste pa da prodam?
Ne. Imaš priliku koju tvoji stari nisu imali. Da štediš u nečemu što ti nijedan diktator ne može obezvrediti, poreznik ili nasilnik oduzeti, bankarski službenik odbiti, proslediti. Svakim danom je sve jače i rasprostranjenije platežno sredstvo. Čekaj dok ne budemo razmenjivali delove bitkoina na lokalnom buvljaku.
Ovakav rast nije normalan. Ovo je balon koji mora da pukne.
Bitkoin je do sada imao 4 mehura. Prvi je bio jula 2010, kada je skočio sa $0.008 na $0.08.
Drugi je bio “veliki mehur 2011.”, sa $0.06 na $31, da bi onda pao na $5.
Treći je bio Aprila 2013, sa $20 na $280, kada su se kiparske banke spasavale pleneći klijentske depozite.
Četvrti je bio velika kriza MtGox berze novembra 2013. kada je skočio sa $70 na $1200, pa nekoliko meseci kasnije pao na $200.
Bitkoin je, naravno, i sada u balonu, koji se zove jedino slobodno neregulisano tržište na svetu. Višegodišnji trend rasta vrednosti bitkoina prati Metkalfeov zakon o vrednosti mreže. Ali na sitnijoj vremenskoj skali ta vrednost je vrlo volatilna, jer mreže rastu u naletima, a na svakom o njih se dešava borba straha i pohlepe i novo otkrivanje fer cene. Ne zaboravi samo Kejnsov investicioni savet: “Tržište može mnogo duže da ostane iracionalno nego ti solventan”.
Države jednog trenutka više neće dozvoliti ovo igranje.
Ovaj argument više svedoči o inferiornosti onoga ko ga izgovara nego o moći vlada. Evo spiska nekih državnih zabrana do sada: Hindu-Arapske cifre, štamparska mašina, slobodni izbori, podela vlasti, pruge, višespratnice, alkohol, saharoza, gramofon, zlato, homoseksualnost, marihuana, pornografija.
Jedino što vlade i bankarski kartel mogu je da pokušaju moralno prokazivanje ideje u nadi da će većina od nas nasesti. TPPN! TPPN! (Terorizam, Pedofilija i naravno omiljeni opresivni zakon, naslednik Sokratovog kvarenja omladine, njegovo predikativno visočanstvo: pranje novca).
Ali, bez većine nas to su samo zmajevi od papira. Ne zaboravi prvu lekciju renesansnog, prosvećenog čoveka: ti nisi objekat nad kojim se vrši istorija, ti si subjekat koji je menja.
Kada je 2000. Lars Ulrih iz Metalike lio suze pred Senatskim odborom za svojom intelektualnom svojinom u slučaju Napster, jedan koder pozvan kao veštak je lepo upozorio vladu SAD-a: “Zabranite Napster i pojaviće se nešto mnogo strašnije”. Ugasili su ga. I još istog meseca dobili bittorent protokol, koji je danas između ostalog i neizostavan deo mašinerije Bitkoin protokola.
Jer, kako je rekao Džon Gilmor, jedan od koderskih apostola i najuži krug sajferpankera:
Internet tretira cenzuru kao kvar i meandrira oko nje.
”Čitave armije ne mogu zaustaviti ideju kojoj je došlo vreme”. Pokušati zabraniti Bitkoin bilo bi kao pokušati zabraniti psovke ili izraz za obim kružnice.
Priča se preko “virtuelnih” medija da je otkriće u stvari blockchain, a ne bitkoin?
Nakon potrošenih ismevanja i pretnji, ovo je preostala slamka sofista. Potcenjivački i sa visine, treba da ostavi utisak da se to deca igraju dok ne ulete veliki. Ali, kako kaže jedna od zen rekontri Patrijarha Pavla: “Ne kaže On da čovek ne živi o hlebu, nego da ne živi samo o hlebu”.
Blockchain je osnova, ali je samo telo, bez tokena je zombi. Bitkoin je sa razlogom jedna vrlo spora i neefikasna baza podataka. Imperativ dizajna je da mora ispunjavati uslov da je bez korisničkih uloga i administratora.
Jednostruko povezana lista heševa izrudarenih blokova (blockchain) je jedini poznat način da ovaj uslov implementiramo u programskom kodu. Dakle on rešava jedan vrlo uzak i specifičan problem. Svega smo spremni da se odreknemo da bi dobili osobinu da nema vlasnika.
Ako Dojče banka želi da napravi blockchain, on će po definiciji biti zatvoren, sa administratorom. Ta kreatura će ili imati bezvredan token pa nije opasnost Bitkoinu ili će biti zombi bez tokena, a onda je kupovina Oracle licence mnogo pametniji izbor.
Bitkoin je deflatoran, niko neće hteti da ga troši. Kako onda može biti novac?
Ako je nešto omiljena disciplina ekonomista, to je guranje višestrukih oprečnih značenja u isti pojam. Postoje dve vrste deflacije koje nisu ni nalik jedna drugoj.
Prva je deflacija privatnog bankarskog depozitnog novca. Kada se ekonomija nađe u stanju prezaduženosti (privatni dug je ključan!) banke više ne pozajmljuju. Odluka o puštanju kredita je isključivo pravo poslovne politike svake banke. Ako one smatraju da više nema kreditno sposobnih, kreditiranje može imati oštar pad.
Kako se prethodni krediti isplaćuju, novac nestaje iz ekonomije u momentu otplate rate, a nov kreditni novac se ne kreira. Ovo dovodi do rasta vrednosti preostalog novca onome ko ga ima u rukama, a nije zadužen.
Ostatak ekonomije se grabi da nakrpi za ratu sa sve manje novca u opticaju, koji sada mora još brže da menja ruke da bi svi isplatili rate, što naglo dovodi do nenaplativih kredita, još manje kreditno sposobnih dužnika, pada ekonomske aktivnosti, zatvaranja firmi, nezaposlenosti, punih kafića i dnevnih žurki do konačnog raspada.
Druga vrsta deflacije, ona Bitkoinova, je nagrađivanje štediša, ne rasipnika, odlaganje potrošnje i inhibiranje fenomena namernog zastarevanja (artificial obsolescence). Kada ograničeni novac obuhvati celu ekonomiju kao opna, vrednost njegove jedinice diše sa ukupnim izlazom cele ekonomije, raste kako ona raste i smanjuje se kako se ona kontrahuje.
Bitkoin motiviše štednju ne potrošnju, dok je štednja toksični elemenat u sistemu privatnog bankarskog depozitnog novca, jer ga privremeno uklanja iz cirkulacije. Ovakva deflacija ne da nije štetna po društvo nego je poželjna. U poređenju sa ovim dinamika privatnog bankarskog novca je vožnja ili pod punim gasom ili kočenje iz sve snage.
A šta ćemo sa bitkoin aristokratijom? Polovinu do sada izdatih bitkoina poseduje 1%?
Analize distribucije vlasništva bitkoina su u najmanju ruku sumnjive. Ali bez obzira na njihovu istinitost one su irelevantne. Pitanje pravde je klizav teren za nekog iz sveta tvrdih veština, ali postoji jedna dinamička osobina monetarnog sistema koja čini da nije svaki jaz između bogatih i siromašnih isti.
Kao prvo, ravnopravnost je jedna opasna kolektivistička zamka. Istinski evropski liberalizam i individualizam je nešto vrlo fino, tanano i nenametljivo.
Nema testosteron i udobnost rulje desnice niti romantizam plejboja sa gitarom i Čeovom kapicom. Veliki statizmi 20. veka su imali svako etičko pravo da nastanu. Jedan iz horora fabričkih hala, a drugi iz horora rovova 1. svetskog rata. Ali istorija je pokazala da nisu rešenje.
Zasnivanje društva na etičkoj i moralnoj aksiomatici je prošlost. Etika treba da bude posledica matematički pravilno dizajniranog monetarnog sistema. On je ključan za kanalisanje ljudske motivacije u pravom smeru.
Iako nema ekosistema u prirodi u kome su sve jedinke iste, postoje situacije kada imovinski jaz postaje neprihvatljiv kao danas. To je kada u društvu nastanu ono što Nasim Taleb naziva “upijajuća stanja”. Od imovinskog jaza daleko je važnije da li za svakog od nas važe ista pravila.
Ako svaki ekonomski akter bez obzira na njegov imovinski položaj mora da preuzme rizik od gubitka svaki put kada donosi neku investicionu odluku onda to čini društvo takvim da je moguć prolaz kroz stanja siromašan-bogat-siromašan. Takvo društvo nema upijajuća stanja.
Ali ako jednom dostignut položaj bogatog čini da taj akter više ne preuzima nikakav rizik ma kako lošu odluku doneo, onda to društvo ima aristokratiju.
Monetarni sistem zasnovan na oskudnom (ograničenom) novcu u kome su pravila zadata protokolom, a ne hijerarhijskim predstavničkim procesom ima jednaka pravila za sve po definiciji. Bitkoin bogataš nije isto što i venture kapitalista sa vezama u centralnoj banci koja vrši kvantitativna olakšavanja tako što kreira kroz privatnu banku depozite njegovom fondu za 0% kamate.
Ako ovaj prvi napravi lošu procenu zauvek je izgubio svoje koine. Ovaj drugi može da priušti 100 miliona gubitaka na startape i da opet ima novih 100 miliona.
U redu, vratimo se na ekonomiju. Uveo si pojam oskudnosti koji si dužan objasniti. Ali pre toga: zašto bi uopšte trebalo smatrati bitkoin vrednim?
U samoj biti, pitanje vrednosti kao i lepote je misterija. Antropolozi i ekonomisti imaju neke maglovite ideje o tome kako među ljudima proliferiše saglasnost da je nešto vredno, ali su to sve ad hoc akademske mudrosti.
U neverici gledaju kako im jedna gargantuantska mreža nastaje pred očima. Od nule, sama od sebe, bez arbitra iako je suparnička. Nešto što je do juče bilo predmet samo arheoloških iskopavanja. Fenomen koji se otima konvencionalnim akademskim objašnjenjima je već slomio dobar broj intelektualnih sujeta.
Ovo pitanje je imalo smisla postaviti u januaru 2009. godine. Surova istina je da se danas više ne pitaš. Uskoro ćeš ih morati imati, jer će taj pored tebe tražiti da mu u njima platiš.
Kao što vrednost lopate dolazi od njene osobine da kopa, tako vrednost novca dolazi od toga koliko je dobro sredstvo razmene i čuvar vrednosti. - Karl Menger
Za Bitkoinom vlada planetarni grabež. Ta potražnja postoji zbog njegovih jedinstvenih osobina koje nijedan novac pre njega nije imao.
Bitkoin je:
– Fungabilan: svaka jedinica novca isto vredi. Ne kao dijamant kod koga zavisi kako je brušen.
– Durabilan: kao (inertna) informacija po prirodi je nepropadljiv.
– Portabilan: može da promeni ruke anonimno iz jedne u bilo koju drugu tačku planete za 10 minuta. Ne kao depozitni novac koji ne voli da putuje vikendom i traži potpis bankarskog službenika.
Portabilnost je Ahilova peta zlata, jer za razliku od Bitkoina ima masu. Zlato je uvek samo jedan korumpirani zakon daleko od konfiskacije. Ono jeste čuvar vrednosti, ali nije i transakcioni sistem kao Bitkoin.
– Oskudan: ovo je ključna karakteristika pravog novca, jer čini da on bude čuvar vrednosti. Zlato može nastati samo u sudaru neutronskih zvezda i to je njegov garant oskudnosti, ali koliko zlata ima oko nas nije do kraja jasno. Još manje je jasno koliko ga ima na Mesecu na primer, koji će nam sutra biti na dohvat ruke.
Bitkoinova garancija oskudnosti je jača od zlata, jer proizilazi iz osobina brojeva — iz ireverzibilnosti kriptografskih heš funkcija.
– U potražnji: U odnosu na konvencionalan novac, Bitkoin i dalje pokriva mali deo ekonomije, ali mreža raste neverovatnom brzinom. Ne dozvolite da vas ekonomski eksperti ubeđuju kako je ovo najbolji od svih svetova. Ne nasedajte na moralno prokazivanje (TPPN!), anonimnost transakcije nije privilegija nego pravo koje se brani koliko i sloboda govora. Mislite svojom glavom. Napravite napor, obrazujte se o novcu. Izbor novca je politika, ne ekonomija. Od nas zavisi ishod.
I na sve to još: pseudoniman, necenzorabilan, neoporeziv, programabilan, nemoguć za falsifikovati. On diže pojam lične svojine na novu skalu. A sa tim i slobodu.
U redu, ali i dalje ne može biti novac jer ga ne priznaje država. Zar ne?
Da bi čovek istinski mogao ceniti veličinu ideje Bitkoina, neophodno je razumeti mehaniku današnjeg novca, a ta materija je minsko polje oprečnih mišljenja, neočekivanih obrta i nedobronamerne obfuskacije pojmova. Slučajnost ili ne, ali upravo u deceniji bitkoina drmaju se temelji važeće akademske doktrine vezane za novac.
Novac je mreža za prenos informacije o vrednosti jednog ekonomskog dobra u odnosu na sva ostala. Ali kao što elektromagnetno polje ima nosioca — foton i novac mora imati neki svoj reprezent. To je ono što se dobija u trenutku prodaje dobra.
U zavisnosti od prirode tog tokena postoje dva moguća dizajna novca. U oba slučaja, suština je u našoj saglasnosti da ono što razmenjujemo smatramo vrednim, ali u prvoj vrsti novca ta vrednost dolazi iz prirode i nije opterećena nekom obligacijom, vrednost vadimo iz majke prirode (nešto je inherentno vredno). U drugoj vrsti novac je kvantifikovani socijalni odnos iza koga stoji neko obećanje koje nakon zaključivanja postaje transferabilno, a vrednost vadimo iz nas samih.
Razlog zašto postoje dva pristupa u dizajnu novca je igra zbog koje nastaju i nestaju čitava društva — kredit.
Kredit je transakcija rasparena u vremenu, gde se u zamenu za novac sada, ekonomsko dobro dobija kasnije. U trenutku razmene to dobro još ne postoji. Ne postoji potražnja za njim. Ali nakon njegovog kreiranja društvo ima jedno novo ekonomsko dobro koje (bi trebalo) da uveća egzistencijalno blagostanje svih nas.
Naravno da u ovom idealnom slučaju govorim samo o produktivnom kreditu, ne o tvorevinama potrošačkog društva: dozvoljeni minus, kreditna kartica i potrošački kredit kojim samo dovlačiš tvoju buduću kupovnu moć u sadašnjost do bankrota. Neproduktivni krediti su jedan od toksičnih elemenata u ovom sistemu.
U 1. vrsti novca nosilac je neka objektivna tvar koja bi po pravilu trebalo biti oskudna i van ljudskog domašaja stvaranja. Neki istorijski primeri su: retke školjke, so, pirinač, buseni duvana (“bucks”), čudni kameni stećci u obliku diska ostrva Jap, dabrove kože, zlato, srebro, bitkoin.
Da, bitkoin je 1. vrsta! Oskudnost je ovde ključna osobina jer ona čini novac čuvarom vrednosti. Na primer, garant oskudnosti zlata je što nastaje samo u sudaru neutronskih zvezda. Garancija oskudnosti bitkoina je još jača, jer sledi iz osobina brojeva (ireverzibilnosti kriptografskih heš funkcija).
Ekonomija zasnovana na ovakvom novcu se zove ekonomija razmene (barter economy), jer je za akciju razmene (transakciju) potrebno samo dva aktera i taj prirodni token. Ovakav novac ne poznaje fenomen inflacije, ali zato ima druge dve ozbiljne mane.
Pristup kreditu je izuzetno težak, jer ne postoji niko ko može stvoriti ovakav novac. Ekonomija na njemu ne može da “gori”, može samo vrlo sporo da “tinja” (možda je to i bolji recept za ljudsku sreću?).
Drugi problem je što novac može da isteče iz jedne zajednice, zbog nekog poremećaja, da li nagle demografske promene, neuravnoteženog uvoza i izvoza, rata i slično. Treba li zajednica da nestane? Zajednica neće nestati nego će upravo iznedriti novac 2. vrste.
Ekonomija zasnovana na drugom tipu novca, koji je kvantifikovani socijalni odnos, zove se monetarna ekonomija. U njoj je svaka transakcija triangularna, tj. potrebne su tri strane za razmenu: kupac, prodavac i poseban agent u ekonomiji koji izdaje ta cirkulirajuća obećanja. Taj specijalni akter nije država, nego privatna banka.
Pogađaš, ovde je pristup kreditu lak, jer je novac po definiciji neograničen. Ali da bi neoskudan novac mogao biti čuvar vrednosti, mora postojati proces kojim se on uklanja iz ekonomije. Ako taj proces zakaže, nastaje fenomen inflacije — najrazornije sile koja kida sve niti društva.
Zapravo u takvoj ekonomiji sav novac je dug. Odatle ona engleska poslovica: “Zlato je novac kraljeva, srebro gospode, a dug robova”.
Šta ti se sada čini virtuelnije, lova koju imaš na računu banke ili kripto(!)valuta Bitkoin?
Molim?!
Da, nije lako progutati ovu pilulu. Zaboravi na prvu asocijaciju da je novac keš koji štampa državni trezor. Prvo to je netačno, drugo, keš je zanemarljiv deo ekonomije (3.5% u Srbiji) i irelevantan. Zaboravi na to da banka navodno deli kredite tako što prvo uzme depozit od klijenta. Ništa nije dalje od istine.
Pravo je čudo da igra koja upravlja motivacijom celog ljudskog roda, dvostruko knjigovodstvo, nije predmet opšteg obrazovanja. Depozit je banci pasiva, a kredit je banci aktiva. To su suprotne strane bilansa! Depozit nikada ne može postati kredit.
Novac koji sve ekonomije sveta (izuzeci: Severna Koreja, Iran, Sirija, do nedavno Irak i Libija) koriste je tzv. depozitni novac, tj. pasiva privatnog pravnog lica (banke) koje ima državnu monopolsku licencu za obavljanje depozitnih poslova.
Država ne reguliše ko kako sme da pozajmljuje. Ali zato opasno reguliše ko sme da ima računovodstvenu kategoriju depozita na svom bilansu. Ako se dogodi pozajmica između bilo koja dva ne-banka aktera u ekonomiji, taj dug je samo između njih, on je bilateralan. Ali, kada banka pozajmi, onda je taj dug, to obećanje, multilateralno. Ono počinje da kruži po ekonomiji kao imovina nas ostalih.
Novac nastaje u trenutku puštanja kredita kada se dužnik obavezuje poveriocu (banci) da će ga vratiti. Tada banka, prostom računarskom SQL instrukcijom INSERT INTO, bez ikakvog drugog ograničenja osim sopstvene procene o kreditnoj sposobnosti dužnika, upiše u bazu podataka, svoju računovodstvenu knjigu, na strani pasive nov nikad ranije postojeći depozit u ekonomiji u visini iznosa kredita.
Dakle, ono što je nama imovina, privatnoj banci je obaveza. I to ne samo pri puštanju kredita, nego i pri deljenju plata, bonusa i investiranju za svoje potrebe (hartije od vrednosti, nekretnine, kancelarijsku opremu, softver itd…) banka stvara novac. Jer, ono što je svakom ne-banka akteru u ekonomiji novac, banci je obaveza. Sa tom razlikom što ako ga stvara za svoje potrebe, mora u krajnjem rezultatu da umanji svoj kapital za taj iznos.
Kredit je stariji od depozita. Sramota je da je to znao engleski zakonodavac još 1727. kada je pisao zakon o falsifikovanju, a profesori ekonomije se i dan danas prave ludi da se Sunce vrti oko Zemlje, ne obrnuto.
Ekonomija ne koristi državni, nego privatni novac. Preciznije onaj deo ekonomije koga činimo mi fizička, pravna lica ne-banke i javne ustanove države. Ni u jednom zakonu se eksplicitno ne tvrdi da privatna banka kreira novac, niti da se to dešava u momentu puštanja kredita. Ovaj proces je sporedni efekat, od države priznatih, međunarodnih računovodstvenih standarda koje donosi privatna nadnacionalna fondacija IFRS.
Da bi ovakav neoskudan novac mogao biti čuvar vrednosti, kada se obećanje ispuni, tj. ekonomsko dobro za koje je (produktivni) kredit uzet proizvede, novac koji je dat treba da bude uklonjen iz ekonomije. I zaista u trenutku plaćanja svake rate, banka na svom bilansu, sa desne strane obaveza, umanji depozit, a sa leve strane umanji preostali iznos duga dužnika.
Čekaj malo… A kamata? Nju ne spominješ?
U ovom grmu leži zec, ali ne onako kako to misle pesnici. Nije Gospod Hristos izlomio tezge ispred hrama zbog kamate. Kamata je cena za koju je izdavač tih obećanja spreman da preuzme rizik da mu dužnik ne vrati obećano.
Da, u trenutku stvaranja depozitnog novca (kredita) kamata nije stvorena. Zato je ukupan dug u ekonomiji uvek veći od ukupne količine novca u opticaju i sistem se ne može zatvoriti. Ali, zabluda koja kruži okolo je da je to razlog što ovakav sistem proizvodi novac (dug) eksponencijalno: da bi se, navodno, isplatili prethodni krediti koji vuku i kamatu za sobom.
Ne, to nije tačno. Zabluda dolazi od nerazumevanja mernih jedinica. Iznos kredita je kao koordinata (RSD), a kamata je brzina (RSD/god). To su različite veličine (stock and flow of money).
U teoriji, mogli bi se svi krediti (različitog tenora) isplatiti i sa jednim jedinim dinarom ako bi on dovoljnom brzinom menjao ruke.
Problem leži u tome šta banka naknadno uradi sa primanjima od kamate, jer samo je iznos kredita potrebno ukloniti iz ekonomije, kamatu ne. Nju bi banka trebalo u celosti da vrati u kruženje. Ali to ne radi, jer želi da obogaćuje svoje akcionare, a i regulativa (vrlo zgodna koincidencija) zahteva da uvećava svoj kapital. I to na našu žalost, na duže staze radi eksponencijalno. I niko to ne može da joj zabrani.
Dobro, pa na šta se to onda misli kada se spomene novac u zakonima?
Dinar je samo oznaka za jedinicu mere, kao kilogram ili sekund. Postoje dve različite tvari koje se mere tom istom jedinicom i obe su novac 2. vrste, tj. transferabilna obećanja, ali su različite tvari kao drvo i metal.
Rekli smo da je u monetarnoj ekonomiji svaka transakcija triangularna. Potrebna su dva ne-banka ekonomska aktera i banka, akteri razmenjuju stavke na pasivi privatne banke, koje ona proizvodi jer samo ona ima računovodstvenu kategoriju depozita.
A šta ako u ekonomiji postoji više od jedne banke? Tada mora postojati još jedan krug drugačijeg novca. U njemu su privatne banke ekonomski akteri, a nad-banka ili centralna banka je proizvođač obećanja. I taj novac je depozitni novac, tj. kružeće obećanje, ali je pasiva centralne banke, njena obaveza ka privatnim bankama. Zove se rezerva.
Dakle, u ekonomiji sa više banaka uvek postoji hijerarhija novca. Depozitni novac privatnih banaka je naša imovina, a njihova obaveza; depozitni novac centralne banke je privatnim bankama imovina, a centralnoj banci obaveza.
Rezerve kruže samo u računovodstvenoj knjizi centralne banke, čiji klijenti mogu biti samo banke i državni trezor i ta tvar iako merena u dinarima, nema kupovnu moć, nego mora da se pretvori u depozitni novac privatne banke na računu nekog ne-banka aktera u ekonomiji da bi nešto kupio.
Kada god država spomene reč novac u zakonima implicitno se misli uvek i samo na rezerve ili njihov materijalni ekvivalent: keš i kovanice. To zakonsko sredstvo plaćanja (legal tender) uopšte nije novac koji koristi ostatak ekonomije izuzev banaka. Vlada to zna i opet nije gadljiva na privatni depozitni novac.
Svaki put kada uplatiš porez, taj novac privremeno(!) nestaje iz ekonomije, jer se iz depozitnog novca privatne banke pretvori u rezerve na računu trezora kod centralne banke. Pojaviće se opet kada ga trezor prosledi nekoj državnoj ustanovi da ga potroši, opet kroz privatnu banku.
Evropska društva su imala vrlo gorka iskustva sa štampanjem novca od strane vlada. SAD upravo obrnuto. To društvo je cvetalo kad god je imalo državni novac, a ubija ga jedna centralna banka.
Današnji novac je zato jedna čudna istorijska tvorevina potrebe, pohlepe i polupromišljenosti slobodnog tržišta, koji nastaje van suverena (dakle nije fiat, iako svi koristimo taj žargon) obostranim dobrovoljnim pristankom dužnika i privatne banke u procesu kreditiranja, a nestaje otplatom tog kredita.
U krugu rezervi, izuzetno brzo struji zanemarljivo mala količina jednog novca bez kupovne moći i služi da se dve privatne banke poravnaju svaki put kada neki od depozita u njima preleće iz jedne u drugu. Rezerve su ono jedino do čega je jednoj privatnoj banci stalo.
Te žetone ona ne može da proizvede ad infinitum, jer su žetoni centralne banke. I naravno stalo joj je, da joj vratiš dug, inače će doći po svoju funtu živog mesa (za to plaća licencu vladi). Samo, bez žetona centralne banke se može ostati preko noći, a gomila nenaplativih kredita na bilansu se mogu poturati pod tepih jako dugo. Sve dok neko ne vikne da je car go.
Svakoga ko ovo jednom razume, ne može a da ne zaboli stomak na sofizam da kriptovaluta ne može imati vrednost, jer nije potkrepljena državom.
Spomenuo si “fiat”. Šta uopšte znači ta reč?
Fiat lux (neka bude svetlo)! Neutoljiva glad svakog vladara da uzme prerogativ bogova i stvori ni iz čega nešto.
Ovaj fenomen je najbolje shvatiti na primeru. Dinar, funta, dolar… Sve su to nekada davno bile jedinice za merenje težine srebra ili zlata.
Zamisli da imaš teg težine 100 dinara, terazije i prodaješ maline. Kupac se pojavi sa par grumenja zlata i želi maline u vrednosti od 100 dinara. Maline ćeš dati za onoliko grumenja koliko terazije pokažu da teže 100 dinara. Nevažno kog oblika je grumen i ima li na sebi neku facu, dokle god je pravo nesečeno zlato.
Međutim, niotkuda, pojavi se ekipa do te mere nasilna i organizovana da skalira svoje nasilje do nivoa države. Odmah donese zakon da svaki grumen težine 1 dinar mora da bude u obliku novčića. Sa jedne strane mora biti otisnut lik glavonje, a sa druge da piše 1 dinar, tako da više nisu potrebne terazije da provere da novčić zaista teži 1 dinar pri razmeni.
Nakon izvesnog vremena lokalna ekipa nasilnika se zakači sa susjedima i treba im zlata za vojsku plaćenika. Ali zlato je oskudno, ne može da se napravi. Međutim glavonja ima ideju. Otisnuće rupu u sredini novčića ili će mu okrznuti krajeve ili će pomešati zlato i bakar, a ostaviti na njemu i dalje oznaku 1 dinar.
To je fiat. Tačnije: fiat denarii! Rasparivanje jedinice mere od deklarisane vrednosti (face value).
Glavonja je sebi stvorio kupovnu moć prividno ni iz čega. Za manje od 1 dinara zlata može da kupi robu i usluge u ekonomiji od 1 dinara. U stvari, ovo je samo iluzija. Surova istina je da je oteo po malo imovine od svih ostalih, jer jedna jedinica novca sada svakome vredi manje. Ovakva igra bez izuzetka uvek završi na nuli. Naglo i nasilno. Rimsko carstvo je udžbenički primer.
Termin fiat je danas žargon za svaki novac koji nije kriptovaluta što je u osnovi greška, jer izuzev kovanica, novac već dugo vremena nije fiat. Jedino što suveren i dalje pravi su kovanice i prodaje ih centralnoj banci. Ako ga izrada kovanice od 1 dinar košta 5 para, a centralna banka je kupi tako što trezoru uveća depozit rezervi za 1 dinar, suveren je ni iz čega stvorio 95 para (senioraža).
Kovanice su istorijski reziduum fiata. Suveren je sveo sebe na sramotni sitniš.
Hmm… Mora li ovo ovako? Sve ovo počinje da mi izgleda kao jedno veliko zamešateljstvo dvostrukog knjigovodstva?
Pravo u metu, dragi moj Sagredo. Pravo u metu. Venecija 1494. Alkoholizam, prejedanje, sifilis i pussy galore. Sa izuzetkom organske ishrane, nesečene robe i lajf-koučeva to je kudikamo opis finansijske metropole i danas.
Armija perverzno bogatih snobova sa previše slobodnog vremena, humus za umetnost, nauku i startape. Knjiga je koštala kao skuplji laptop i bila omiljeni statusni simbol. Naročito ako je velika i debela poput Paćolijeve enciklopedije matematike.
Hindu-Arapske cifre su još uvek bile sporne, jer je: “svaki dobri Hrišćanin morao biti prezriv prema matematici” (Sv. Avgustin), a štamparska mašina tek nedavno unapređena da može otiskivati crteže. Dvostruko knjigovodstvo je samo 9. poglavlje tog renesansnog remek dela Fra Luke Paćolija iz koga je i Leonardo naučio perspektivu.
U školi tom otkriću, pleksusu današnjeg sveta, ne pridaju ni blizu značaj koji mu pripada. Uči se da je njegova poenta korekcija greške, a dvostruko knjigovodstvo je u stvari izvorni blockchain.
Svako dobro koje menja vlasnika, ta transakcija, ostaje zabeležena na 2 mesta, jednom akteru na izlazu (pasivi), a drugome na njegovom ulazu (aktivi) na taj način povezujući celu ekonomiju u jedan tok i omogućavajući reviziju i arbitražu.
Bez tog mehanizma današnji novac i kapitalizam je nemoguć. Možda najbolja definicija kapitalističke ekonomije je: “Money is nothing, that you get for something, before doing anything”. Novac je ni od čega, koje dobiješ samo ako založiš nešto, pre nego što možeš da napraviš bilo šta.
Ne zaboravi, makroekonomija su finansije, finansije računovodstvo, a računovodstvo pravo. Tamno srce sveta leži u definicijama računovodstvenih kategorija. Zabluda je misliti da je svet zao i beznadežan jer korporacije imaju samo jedan cilj — da uvećaju profit. Naprotiv to je racionalno ponašanje.
Ali mi smo ti koji definišemo šta je to profit! McDonalds je izuzetno profitabilan, zato što prebacuje dijabetes kao trošak na bilans društva. Monsato takođe, jer ekocid nije definisana računovodstvena kategorija troška, nego je “eksternalizacija”. Sve je u zakonima.
Znači kao što neka firma ode u banku po kredit, tako i država dobije kredit od centralne banke?
Ne. Država je jedini klijent centralne banke koji je to sam sebi zabranio. Tačno je, i za krug rezervi (depozitnog novca centralne banke) važi isto pravilo kao i kod depozitnog novca privatne banke. Centralna banka pogoni isti softver kao i privatna.
Rezerva nastaje kada centralna banka pusti kredit. Njeni klijenti, privatne banke mogu dobiti kredit sa ili bez obezbeđenja. U tom krugu jako brzo kruži vrlo mala količina novca u poređenju sa novcem ostatka ekonomije. Ti krediti su obično vrlo kratkog tenora. Takođe još češći je slučaj da banke međusobno jedne drugima bilateralno pozajmljuju već postojeće rezerve (money markets).
Upravo se u ovom reaktoru dogodila kriza 2008. Banke su trgovale egzotičnim finansijskim hartijama do te mere da su se jednog trenutka našle kao rogovi u vreći. Nikome nije bilo jasno ko je solventan, a ko više nije zbog ogromnih gubitaka na tim hartijama i međusobno pozajmljivanje rezervi je praktično stalo.
Od tada sistem rapidno gubi kontakt sa zdravim razumom, a centralne banke eksponencijalno kreiraju nove rezerve da bi vratile te leševe u solventno stanje. Kao obezbeđenje za te kreirane depozite rezervi bankama uzimaju akcije Pepsija, Koka Kole, Fejsbuka, toksične finansijske derivate i trilione korporativnih obveznica sa negativnom kamatnom stopom.
Ne zaboravi rezerve nemaju kupovnu moć! Da bi centralna banka kupila nečiju akciju u tom procesu “kvantitativnog olakšavanja” (nad našom imovinom) ona mora naložiti privatnoj banci da za taj iznos uveća nečiji depozit i tako se kreira nov novac u našem krugu ekonomije van standardnog kanala kreiranja uzimanjem kredita od privatne banke. Posledica toga je razarajući jaz u bogatstvu koji danas postoji u svetu. Od 2008. više niko nije za volanom.
U svakom slučaju, jedini klijent centralne banke koji ne može da se direktno zaduži je državni trezor. Suveren je samog sebe tako ograničio. Ako želi da potroši neki novac, na plate, vrtiće ili puteve, on mora da se dokopa već postojećeg depozitnog novca privatnih banaka jer je samo to novac sa kupovnom moći. I za to ima dva načina.
Može da odštampa obveznicu. Kada nađe kupca, privatna banka tada smanji depozit kupcu za iznos vrednosti obveznice, a isti iznos rezervi prebaci trezoru na njegov depozit u centralnoj banci.
Drugi način je da ubira porez. Tada banka umanji depozit onome ko porez plaća, a onda, kao u prethodnom slučaju, za isti iznos se uveća rezerva državnom trezoru u knjizi centralne banke. Kada želi da potroši taj novac, trezor prosledi rezerve i instrukciju privatnoj banci koja onda uveća depozit javne institucije kojoj se prosleđuje novac.
I u jednom i u drugom slučaju nije bilo stvaranja novog novca, nego samo promena vlasništva već postojeće količine privatnog depozitnog novca u ekonomiji. To čini oporezivanje mehanizmom redistribucije vlasništva, koje bi u teoriji trebalo ići u korist manje bogatih.
Polako ulazi u modu i treći način da suveren uzme kredit kod privatne banke kao bilo ko drugi od nas. Kao vrhunac poniženja suverena, ovo je i dalje retkost i dovodi do povećanja privatnog depozitnog novca u opticaju jer banka pušta nov kredit.
Ali, nezahvalno je tražiti opšte stavove u načinu finansiranja država. Na primer, Velika Britanija se dugo oslanjala na dozvoljeni minus kod svoje centralne banke. EU regulativa joj je to zabranila. Ona je poštovala taj zakon, dok joj je to odgovaralo, ali kada je 2008. udarila kriza, ona je opet uvela taj mehanizam ne obazirući se ni trenutka na zakon. UK sme, a Srbija ne sme. I? Šta ćeš sad?
Pa zašto Srbija ne dozvoli sebi dozvoljeni minus, kada je centralna banka i ovako narodna?
Zaista neke centralne banke su privatne, neke nisu. Jedine centralne banke koje su važne su i privatne: FED, BOE, BOJ, ECB, SNB.
Ali, još jedna uvrežena zabluda je da je upravo to ključni bag u sistemu. Nije. Većina profita centralne banke koji dolazi od držanja državnih dugovnih hartija, bez obzira na to ko joj je vlasnik, a država uvek ima udeo u upravljanju i postavljanju izvršnih funkcija, i ovako biva vraćena državi.
U svetu se vodi jedna vrlo nepravedna utakmica između nacija, jer većina njih mora da živi od poreza, a upravo najmoćniji imaju trikove da to u nekoj meri izbegnu. To se zove monetarna suverenost i prerogativ je samo najmoćnijih društava. U suštini ne više od 5. SAD, Velika Britanija, Kina, Japan i Švajcarska.
Naravno da sve države tu “muvaju” i ko zna kakva korisnička prava imaju u sistemu centralne banke, ne zaboravi da su to sve hijerarhijski procesi koji su inherentno koruptivni. Za razliku od bitkoina, konvencionalni monetarni sistem ni jednog trenutka nije do kraja definisan.
Prerogativ monetarne suverenosti je daleko teže dobiti od teritorijalne. Za teritorijalnu ti trebaju moćna leđa i naoružane face na granici. Za monetarnu moraš da budeš potreban svetu. Samo tada se tvoj žeton koga pravi centralna banka traži. Tek sa tim dolaze trikovi dolaženja do novca van oporezivanja.
Dozvoljeni minus Britanskog trezora zaista znači da država ima udeo u kreiranju novca. Uveća sebi iznos rezervi, a onda ih prebaci na račun neke privatne banke i naloži joj da uveća depozit neke javne ustanove u u njoj. I voilà, nov privatni kreditni novac je kreiran u ekonomiji bez puštanja kredita.
Dobro, ali zar nisi jednog trenutka tvrdio je ovo bolji sistem od novca 1. vrste u koji spada i bitkoin?
Kružeća obećanja se ne mogu iskoreniti. Društvo će uvek spontano iznedriti kreditni novac na manje ili više sofisticiran način čim oseti potrebu ili pretnju. Na zlatu se rat može samo izgubiti. Lako dostupan kredit omogućava da društvo raste kada i koliko ono želi. Ceo mehanizam, uključujući i tu osobinu da je vremenom izolovao vlade od čina kreiranja novca ima smisao koliko i vrlo pametna istorijska izolacija crkve.
Ali kao nekada državne fiat valute i ovaj privatni kreditni novac uporno iznova propada.
Bitkoin, novac 1. vrste, je čamac za spasavanje u takvim kobnim vremenima. Sa njim rasparuješ svoju sudbinu od sudbine kreditnog novca u raspadu.
Ne postoji način da se izbegne konačni kolaps izazvan kreditnom ekspanzijom. Alternativa je jedino da li će kriza doći brže usled dobrovoljnog odustanka od dalje ekspanzije kredita ili kasnije kao konačna katastrofa valute u kojoj je izražen. - Ludvig fon Mizes
Sa ovom promisli iz “Teorije novca i kredita” treba da počne svaki kurs iz makroekonomije. Dinamika kreditnog novca, ne biva u konačnom ciklusu, nego prevodi sistem iz jedne fiksne tačke nezaduženosti u drugu totalne prezaduženosti nakon koga je neophodan reset u vidu deflatornog (“…dobrovoljni odustanak…”) ili inflatornog (“…konačna katastrofa…”) kraha.
Nesporna eksperimentalna činjenica, na podacima UK i SAD za poslednjih 120 godina je da ovaj sistem nema kočnice. On mahnito kreira novac (kredite), a onda naglo staje. Na duži period količina novca u opticaju raste eksponencijalno i njegova uloga čuvara vrednosti se raspada.
Stotine kreditnih kriza u svetu samo od “privremene” vladine uredbe Ričarda Niksona, tj. ukidanja monetarne funkcije zlata 1971. i gubitak vrednosti rezervne svetske valute dolara za 92% od 1913. su činjenice.
Još jedna nesporna eksperimentalna činjenica, na primeru SAD, je da ekonomija takođe raste eksponencijalno od 1650. godine, sa prosečnim rastom od 2.9%. Ključno pitanje je: da li monetarni sistem nameće eksponencijalni rast ekonomije, ili je obrnuto, ekonomija nameće eksponencijalni rast kredita, tj. depozita u opticaju?
Ako je tačno ovo prvo, onda je sistem disfunkcionalan i ne radi kako je zamišljen, jer umesto da servisira ekonomiju, ona servisira njega. Ako eksponencijalni rast ekonomije nije održiv, onda ovakav monetarni sistem uopšte nije moguć.
Centralna banka troši ogromnu energiju na privid kako je za volanom kreditne ekspanzije. Tu bajku zove “transmisioni mehanizam”. Dajdžest ove dogme se može naći i u doktorskoj disertaciji Jorgovanke Tabaković (nije šala).
Da si prišao jednom centralnom bankaru pre 1980. i rekao mu da se količina privatnog depozitnog novca u ekonomiji može kontrolisati kamatnom stopom na rezerve centralne banke koje ona kreira u procesu kreditiranja banaka, smejao bi ti se u lice. Danas ako mu tvrdiš da se to može postići regulacijom minimuma obaveznih rezervi, kao što se to radilo do 1980, opet će ti se smejati u lice.
U stvari, istina je da je centralna banka samo običan refinansijer, kliring kuća privatnih banaka. Jedino što centralna banka može je da utiče na cenu (kamatu) i količinu depozita koje ona stvara. Te rezerve ne samo da nisu u dodiru sa spoljnom ekonomijom nego ih ima mizerno malo u odnosu na kreditni novac privatnih banaka.
Uspeh centralne banke u obuzdavanju količine kreditnog novca privatnih banaka u opticaju je jedna tužna nula kroz celu njihovu istoriju.
Privatne banke sa druge strane vrlo brižljivo iznutra gaje kulturu privida kako strašna centralna banka zadaje pravila igre. Regulativa kojoj se podređuju privatne banke u ograničavanju emisije depozita usvaja i nadgleda centralna banka, tačno, ali kao i u slučaju računovodstvenih standarda i ovo je međunarodni standard. Naravno, došao iz kuhinje nadnacionalne privatne institucije registrovane kao banka i u vlasništvu najvećih privatnih banaka zvane BIS — arhitektonske alegorije Vavilonske kule, smeštene u miru Švajcarskog gradića Bazela poznatog po najvećem broju bordela po glavi stanovnika.
Srpski guverner tamo dolazi jednom u dva meseca na kratki poslovni ručak, a onda bude ispraćen kući. Nakon ručka, 5 najjačih privatnih računovodstvenih knjiga sveta se povlače na zatvoreni sastanak.
Autoregulativa se svodi na vrlo konvoluirani matematički postupak klasifikacije i stohastičke simulacije prepun magičnih cifara na presudnim mestima, da bi se emitovanje depozita (kreditiranje) ograničilo količinom kapitala banke.
Njen sporedni efekat je upravljanje rizicima (od insolvencije i nelikvidnosti), važnija agenda je da sve privatne banke koriste iste kriterijume procene rizika kako bi se postigao efekat da se ceo sektor ekspandira i kontrahuje kao jedan. Zašto? Jer to privatnim bankama garantuje minimalno korišćenje rezervi centralne banke, žetona koje one ne mogu da proizvedu.
Dakle, ako banka želi da emituje više depozita (kredita) mora da poveća svoj kapital. A to može da uradi na sledeće načine:
– Dokapitalizacijom: emitovanjem još akcija, ovo smanjuje procenat vlasništva koje nosi jedna akcija, što ugrožava postojeće vlasnike (dilution).
– Smanji aktivu: proda nekretnine, opremu u vlasništvu ili podeli otkaze.
– Napravi kratku pozajmicu od centralne banke (repo) samo za ovu potrebu (trik se zove “window dressing” i banke ga obavljaju na kraju računovodstvenog perioda da ulepšaju bilans)
– Emituje svoje korporativne obveznice za prodaju. Ova akcija uklanja novac iz ekonomije na određeno vreme trajanja obveznice.
– Ne potroši profit i ne isplati dividende. Ova akcija, reklasifikacije profita na stavku “retained earnings” uklanja novac iz ekonomije na neodređeno vreme. Dakle, postoji vrlo važna razlika kada banka uveća kapital i kada bilo koji drugi ekonomski akter ne-banka uveća kapital. U slučaju banke to uklanja novac iz kruženja na neodređeno vreme, sve dok banka ne odluči da ga potroši na sebe. Ali što više kredita želi da emituje, to više novca mora tu da stoji nepotrošeno. Ovakva akcija obogaćuje postojeće akcionare.
Ne zaboravi, u idealnom slučaju trebalo bi da postoji samo jedan mehanizam za nestajanje kreditnog novca iz kruženja: otplata (produktivnog) kredita. Svaki drugi je za sistem toksičan: štednja (koja ga uklanja na kratak period), kolaps banke koji briše ceo bilans i uvećanje bankinog kapitala.
Veza eksponencijalnog rasta ekonomije i novca u opticaju nije jasna. Ali akcija povlačenja novca iz opticaja poreklom od dobiti od kamate na kapital banke je dokazano jedan faktor koji izaziva obaveznost rasta.
Recimo da monetarni sistem kreditnog novca zaista zahteva večni eksponencijalni rast da se ne raspadne. Zašto ne bismo mogli večno tako da rastemo?
Jer postoje nepotkupljivi zakoni, oni od majke prirode. Jedan od njih, koji nam sreću kvari, je Štefan-Bolcmanov, a onaj najgori, zbog koga nikada nećemo postati bogovi je II zakon termodinamike.
Kakvu god mašinu napravio, njen krajnji rezultat osim korisnog rada mora biti i nešto toplote. A naš svemirski brod koji nam daje život — Zemlja ima samo jedan način da oslobodi tu toplotu u okolni vakuum svemira — zračenjem.
Štefan-Bolcman nam onda govori, kolika mora biti njena temperatura, ako se mora osloboditi izvesne količine toplote. Danas oslobađamo oko 12TW toplote. Ako nastavimo da rastemo eksponencijalno istim tempom kao poslednjih 300 godina, oko 2400. godine prosečna temperatura na Zemlji mora biti 100 stepeni celzijusa. Apsurd.
Ova analiza nema nikakve veze sa efektom staklene bašte i problematikom klime i ugljen-dioksida, Štefan-Bolcman je do te mere kristalno jasan, da sa loncem poznatih dimenzija, nešto vode, termometrom i štopericom možeš izmeriti temperaturu na površini Sunca. I to je školski zadatak.
Dakle, ako monetarni sistem zaista zahteva eksponencijalni rast ekonomije da bi postojao u ovoj formi, onda tvrdim sledeće: šta će biti sa dolarom 2020. ne znam, ali ono što znam sa apsolutnom sigurnošću je da već 2150. njega ovakvog neće biti, jer je termodinamička nemogućnost.
Zašto onda države ne bi napravile svoje kriptovalute? Zar time ne bi i Bitkoin postao suvišan?
To je jedna stvar koju država sigurno neće nikad uraditi. Razmisli šta to znači za novčani poredak? Temelj monetarne ekonomije je da banka kreira novac u činu puštanja kredita. Ako centralna banka napravi kriptovalutu, vraćamo se u stanje fiat valute, tj. državnog novca i barter ekonomije, jer banke postaju samo medijatori, a depozitni novac centralne banke (sada rezerve) bi postale jedino sredstvo plaćanja sa kupovnom moći.
Sa druge strane, Bitkoin ne bi ni osetio ovaj potez, jer njegov status najvećeg lanca otvorenog pristupa bez administratora ne bi bio izazvan jednom običnom zatvorenom bazom sa kontrolom pristupa i vladinim sisadminom. Svaki kripto maksimalista bi trebao da priželjkuje ovako glup potez vlada. Tehnologija kriptovalute je istinski šah-mat vladajućoj ekonomskoj dogmi.
Po ovome onda ne vidim da imamo izbora? Ili imamo bezdugovni novac i sporu ekonomiju razmene sa teško izvodljivim kreditiranjem ili imamo sofisticiranu monetarnu ekonomiju koja mora imati banku za triangularnu transakciju i u njoj uvek nekog ko odlučuje kome i kada pustiti kredit, tj. stvoriti novac. I da igramo tu igru dok ne spržimo Zemlju?
Treća opcija je da se svi mi izmenimo, počnemo da meditiramo i da raširimo kosmičku duhovnost tako da svaki od nas poput anđela može da čini samo dobro. Onda je svejedno kakav monetarni sistem imamo. Razočaravajuće je koliki broj ljudi i dalje misli da se tako gradi društvo.
Problem nije trivijalan, ali pre Gutenberga, dok su pisari bili centri kontrole pismenosti, mislili smo da je svet ravan i star 6000 godina, a žena nastala od muškog rebra. Nakon što smo oslobodili jezičku mrežu otkrili su nam se večni zakoni prirode zapisani jezikom matematike, kojima je i Tvorac odlučio da se povinuje.
Nekada smo decenijama plaćali harač za zarobljenog kralja da se vrati iz zatočeništva. Kada nam je Gutenbergova mašina omogućila da postanemo programeri pisanog jezika — gramatike i pravopisa, shvatili smo da je kralj smrtan, samo je ustav besmrtan.
Danas, centri kotrole kreiranja novca ulažu divovski trud u stvaranje privida da su izaslanici nevidljive ruke tržišta. Da bolje znaju kom mlekaru dati kredit od ostalih mlekara, kom poljoprivredniku od ostalih poljoprivrednika.
Iza tog vela stoji samo lamentiranje nad finansijskim izveštajima kreditnih odbora koji da se sutra zamene bacanjem fer novčića, ekonomija ne bi osetila razliku. Sve što ti lažni proroci rade je puštaju indulgencije svojim prisnima. Kako ekonomska nauka kaže: misalokacija kapitala.
Do 3. januara 2009. nismo imali izbora, jer smo transakcije mogli obavljati samo kroz njih. Izbor je duša Bitkoina. Sada imamo naše cevi za prenos vrednosti. A to što kroz njih teče nije ugroženo u kriznim vremenima kada obećanja počnu da se krše, jer nije opterećeno dugom i ima čvrstu garanciju oskudnosti.
Kreditni novac neće otići, ali više nismo u nemilosti bankara. Sada jedni druge držimo u šakama. Čovečanstvo je sazrelo za novo vreme u kome se privatnost transakcije, pravo raspolaganja imovinom neometeno nacionalnim granicama i dobrovoljno oporezivanje vidi kao elementarno pravo.
Sledeći korak istorije će biti distribuirana (p2p) kriptografska mreža kreditnog novca, u kome odluka o puštanju kredita biva oslobođena od centara kontrole, bitkoin postaje rezerva, nenaplativ kredit jasno definisan, a otplata kredita dobrovoljna, motivisana teorijom igara implementiranom u biznis logiku protokola.
Možda će upravo ovakav sistem pokazati da je kreditni novac moguć bez obaveznosti rasta. Banke će uspeti tek na tren da podignu glavu i vide obris tog asteroida u naletu.
Zar je zaista moguće da sistem ovako funkcioniše? Ovo sve miriše na teorije zavere, pseudonauku u najgorem slučaju.
Kvartalni bilten centralne banke engleske (BOE) o mehanizmu kreiranja novca u ekonomiji
O nemogućnosti eksponencijalnog rasta
Školski zadatak kako izmeriti temperaturu na površini Sunca:
Monetarni suverenisti: www.positivemoney.org,
https://www.sovereignmoney.eu/
Odlična monografija Jozefa Hubera
Nezaobilazno štivo Ričarda Wernera, oca kovanice “kvantitativne olakšice” i monetarnog suvereniste
I njegov vrhunski članak o činu kreacije dugovnog novca
Da li si svestan da nobelovac Pol Krugman tvrdi suprotno?
vaka epizoda istorije ima svoje fariseje i aristotelovce. Dežurnu dvorsku ludu postojećeg poretka, sramotni portret korumpiranosti jedne nauke — Pola Krugmana istančano opisuje anonimni autor ‘Buckaroo Banzai’.
Stiv Kin (Steve Keen) je mnogo bolji izbor ako želiš da razumeš ekonomiju, don Sagredo. Ali moraš da se potkuješ fizikom ako želiš da se probudiš iz računovodstvene bajke. Diferencijalne jednačine, ne tepisi teksta.
“Greši onaj ko misli da će nas simboli odvesti od realnosti, naprotiv dovešće nas u suštinu stvari”, umeo je da kaže veliki Lajbnic. Ili kraće: vires in numeris.
Don Salviati, nobody likes a smartass. Gde mogu da naučim više o Bitkoinu?
 Stilizovani prikaz bilansa sa dve računovodstvene situacije koje za banku znače kraj poslovanja i opisom kako do njih dolazi. Levi scenario se po pravilu nikada ne događa, jer šta je to nenaplativ kredit? Sliku izradio: miloseviclawyer.com
Stilizovani prikaz bilansa sa dve računovodstvene situacije koje za banku znače kraj poslovanja i opisom kako do njih dolazi. Levi scenario se po pravilu nikada ne događa, jer šta je to nenaplativ kredit? Sliku izradio: miloseviclawyer.com -
-
 @ fbf0e434:e1be6a39
2025-01-18 07:13:31
@ fbf0e434:e1be6a39
2025-01-18 07:13:31Hackathon 摘要
Ideahacker's Guide to IBC 是一场Interchain创意竞赛,旨在鼓励创新的跨链概念。此次活动注册了136个项目,吸引了319名开发者和非技术人员参与。与传统的Hackathon不同,这场创意竞赛要求参与者提交概念性想法,而非代码或产品原型,从而降低了参与门槛,鼓励了更广泛的参与。
创意竞赛发放了3万美元奖池的ATOM代币,以及一趟伊斯坦布尔的全程免费旅行,以奖励最具影响力的想法。项目从五个赛道中选出,并由Interchain Foundation和Osmosis Labs的行业领袖评审。
此次活动旨在展示跨链通信协议(IBC)的应用。参与者利用IBC Idea Builder开发并提交他们的提案,这些提案展示了诸如跨链账户、跨链NFT转移和数据查询等IBC功能。Interchain Foundation赞助了此次活动,以促进在区块链应用中对IBC协议的理解和使用,通过Discord等平台为社区提供资源和支持。
Hackathon获奖者
Chain Abstraction奖项获奖者
- Interchain Lending Market:一个去中心化的跨区块链稳定币借贷应用,利用IBC进行收益优化和通过DAO进行治理。
- Interchain Rights Broker:通过Story Protocol自动化许可和支付,在支持IBC的区块链上促进NFT许可。
- MetaKey: Seamless Interchain Wallet Abstraction:提供跨链钱包管理的统一接口,通过IBC增强互操作性和交易效率。
- DeathFi:使用IBC进行遗产数字资产管理的协议,包含去中心化遗嘱和NFT纪念。
- TransChain-Health:一个结合区块链和物联网的去中心化健康监测系统,提供数据透明性和分析。
Solana奖项获奖者
- TriAd:一个利用IBC和Solana进行高效广告管理的跨链广告交换平台。
- DAPM:跨区块链管理共享资本池,加强治理和财库功能,运用IBC。
- Solana-Sovereign Identity Protocol (SIP):使用IBC简化跨链身份管理,确保去中心化身份的安全。
- IBCCraft Game:一个类似Minecraft的游戏,使用IBC进行跨链任务并奖励Solana。
- Privvy Protocol:通过IBC为跨链交易提供隐私管理,实现隐匿地址和私人交易。
Intents & Incentives奖项获奖者
- InterXecute:结合AI和IBC提升跨链交易,专注于低成本和高效路径。
- Cross-Chain Proposerless Block Building Mechanism for Relays in IBC Protocol:引入无提案者区块构建以优化IBC协议效率和成本。
- IBC + Solver Network:通过一个IBC求解器网络,加强以意图为中心的解决方案的跨链交易。
- Intents Bridge for IBC:使用以意图为驱动的方法和去中心化结算,提高交易速度和流动性。
- Creating a Crosschain DID on IBC:一个结合IBC和零知识证明的跨链身份证明系统,提供安全的身份管理。
DeFi Apps奖项获奖者
- Vector Protocol:通过智能合约和IBC管理互链债务,以提升成本效率和风险管理。
- InterChain Asset Streaming Protocol (XASP):利用IBC实现跨链的实时资产流传和投资组合管理。
- SwapGuard:为Cosmos提供MEV保护的全面DeFi交易解决方案。
- BlocPayroll:利用IBC简化国际薪酬流程,提供安全的加密薪酬解决方案。
- Cross-Chain XTF (DeX Traded Fund):利用IBC促进跨链投资,改善投资组合管理和成本效率。
Wild Card奖项获奖者
- cross chain:利用IBC进行统一的跨链资产管理和奖励分配的Staking聚合器。
- Cryptocurrency Debit Card Infrastructure:通过借记卡支持加密到法币交易,利用IBC实现无缝转换。
- HTTPi:一个利用IBC进行客户端与服务器间去中心化数据交换的安全协议。
- IBC Lens (Data Visualizer for Celestia and Rollups using IBC):提供IBC生态系统中跨链交互的实时可视化。
- Realm:一个利用IBC进行多区块链奖励管理的跨链赏金平台。
欲获得完整项目列表及更多详细信息,请访问Ideahacker's Guide to IBC Ideathon。
关于组织者
Interchain Foundation
Interchain Foundation专注于开发和支持称为互链的可互操作区块链网络生态系统。该组织促进区块链行业内的合作与创新,重视多链通信和可扩展性。通过其技术专长和领导力,基金会支持推动去中心化网络互操作性的各项倡议。它致力于创造一个无缝连接的区块链未来,并鼓励行业参与以推动多链生态系统的发展。
-
 @ ed84ce10:cccf4c2a
2025-01-18 07:06:31
@ ed84ce10:cccf4c2a
2025-01-18 07:06:31Hackathon Summary
The Ideahacker's Guide to IBC was an interchain ideathon designed to encourage innovative cross-chain concepts. This event saw the registration of 136 projects and participation from 319 developers and non-technical contributors. Unlike traditional hackathons, this ideathon required participants to submit conceptual ideas instead of code or product prototypes, which encouraged broader participation due to its lower entry barrier.
The ideathon distributed a $30,000 prize pool in ATOM tokens, along with an all-expenses-paid trip to Istanbul, to reward the most impactful ideas. Projects were selected from five tracks and judged by industry leaders from the Interchain Foundation and Osmosis Labs.
The event aimed to demonstrate the applications of the Inter-Blockchain Communication Protocol (IBC). Participants utilized the IBC Idea Builder to develop and submit their proposals, which showcased IBC features like interchain accounts, cross-chain NFT transfers, and data queries. The Interchain Foundation sponsored the event to promote understanding and use of the IBC protocol across blockchain applications, engaging the community with resources and support through platforms like Discord.
Hackathon Winners
Chain Abstraction Prize Winners
- Interchain Lending Market: A decentralized application for stablecoin lending across blockchains, leveraging IBC for yield optimization and governance via DAOs.
- Interchain Rights Broker: Facilitates NFT licensing across IBC-enabled blockchains with automated licensing and payments through Story Protocol.
- MetaKey: Seamless Interchain Wallet Abstraction: Offers a unified interface for cross-chain wallet management, enhancing interoperability and transaction efficiency via IBC.
- DeathFi: A protocol for posthumous digital asset management using IBC, featuring decentralized wills and NFT memorials.
- TransChain-Health: A decentralized health monitoring system integrating blockchain and IoT for data transparency and analysis.
Solana Prize Winners
- TriAd: A cross-chain ad exchange platform utilizing IBC and Solana for efficient ad management.
- DAPM: Manages shared capital pools across blockchains, enhancing governance and treasury functions with IBC.
- Solana- Sovereign Identity Protocol (SIP): Simplifies cross-chain identity management with IBC for secure decentralized identity.
- IBCCraft Game: A Minecraft-like game using IBC for cross-chain quests and Solana rewards.
- Privvy Protocol: Facilitates privacy management for cross-chain transactions via IBC, enabling stealth addresses and private transactions.
Intents & Incentives Prize Winners
- InterXecute: Enhances cross-chain transactions with AI and IBC, focusing on low-cost, efficient routing.
- Cross-Chain Proposerless Block Building Mechanism for Relays in IBC Protocol: Introduces proposerless block building to optimize IBC protocol efficiency and cost.
- IBC + Solver Network: Strengthens cross-chain transactions with intent-centric solutions supported by an IBC solver network.
- Intents Bridge for IBC: Boosts transaction speed and liquidity using an intent-driven approach and decentralized settlement.
- Creating a Crosschain DID on IBC: A cross-chain proof of identity system integrating IBC and zero-knowledge proofs for secure identity management.
DeFi Apps Prize Winners
- Vector Protocol: Manages interchain debt with smart contracts and IBC for cost efficiency and risk management.
- InterChain Asset Streaming Protocol (XASP): Enables real-time asset streaming and portfolio management across chains utilizing IBC.
- SwapGuard: Provides protection against MEV in Cosmos with a comprehensive DeFi trading solution.
- BlocPayroll: Simplifies international payroll processes using IBC, offering secure crypto payroll solutions.
- Cross-Chain XTF (DeX Traded Fund): Facilitates cross-chain investment with IBC, improving portfolio management and cost efficiency.
Wild Card Prize Winners
- cross chain: A staking aggregator using IBC for unified cross-chain asset management and reward distribution.
- Cryptocurrency Debit Card Infrastructure: Supports crypto-to-fiat transactions via debit cards, leveraging IBC for seamless conversions.
- HTTPi: A secure protocol employing IBC for decentralized data exchange between clients and servers.
- IBC Lens (Data Visualizer for Celestia and Rollups using IBC): Provides real-time visualization of cross-chain interactions in the IBC ecosystem.
- Realm: A cross-chain bounty platform utilizing IBC to manage multi-blockchain rewards for content creators.
For a comprehensive list of all projects and more detailed information, visit the Ideahacker's Guide to IBC Ideathon.
About the Organizer
Interchain Foundation
The Interchain Foundation is focused on developing and supporting the ecosystem of interoperable blockchain networks known as the interchain. The organization promotes collaboration and innovation within the blockchain industry, with an emphasis on multichain communication and scalability. Through its technical expertise and leadership, the foundation supports initiatives that drive interoperability across decentralized networks. It is committed to creating a seamless interconnected blockchain future and encourages industry involvement to advance the multichain ecosystem.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ e8ed3798:67dd345a
2025-01-14 17:38:49
@ e8ed3798:67dd345a
2025-01-14 17:38:49Crowdsourcing subjective value is a great idea, but when no thought has been put into how to do it, the results are neither useful nor healthy.
In this article we discuss the problems with the classic five star rating system and why it needs to be abolished in favor of better expressions of public sentiment.
Part 1: What's In A Star?
Let's start with a thought experiment:
- Do you buy products on Amazon that have 3 stars?
- Do you take rides from Uber drivers that have 3 stars?
- Do you download apps on the App Store that have 3 stars?
- Do you visit places on Google Maps that have 3 stars?
"Not on purpose," is probably your answer. But why not? After all, a three out of five is better than the median; it's 60 percent! That is solidly "above average" by any usual measure. Although it makes sense in mathematical terms, it is not correct to say that a 3 star product is at least half as good as a 5 star product.
The funny thing about the 5 star rating system is that nobody really knows exactly what the stars mean, mostly because they aren't ever explained. They are just a weak abstraction of a score out of 5, which itself is an abstraction of a score out of 100, and it is used to average all ratings for a thing into an average star rating. Presumably, 5 is the best and 1 is the worst, and somewhere in between is... what exactly? Mediocre? Passable? Acceptable? Average? Who knows! This is the first problem with this system; while the top and bottom of the scale may be implied (ambiguity still isn't great), the middle of the scale is entirely ambiguous.
Most of the time, people start with a default supposition that a product ought to be 5 stars, and then they subtract stars according to their own perceived deficiencies of the product. On the flip side, people who are dissatisfied with a product tend to start at 1 star and perhaps award it a couple more if they are feeling charitable.
This dualistic approach highlights another issue with this kind of rating system. Despite the pure quantitative mechanism, the feelings and disposition of the rater ultimately assign meaning to the numeric scale.
Ultimately, any 5 star rating system ends up being a gamut ranging from hate it to love it with a lot of ambiguity in the middle.
To put it simply, the stars mean nothing. But to be more precise, the stars are the average of the numeric expression of the public sentiment about a thing.
OK, public sentiment. That's what we want right? We want to know what the public thinks about the product so we can make a good purchase decision.
Except, unfortunately, the 5 star rating system does an incredibly imprecise job at capturing what the public actually thinks about a product. Let's dive into why this is. But first, to conclude our thought experiment, I'd like to establish an informal consensus that we instinctually seek out the highest rated items and avoid ratings less than 4.5 out of 5, with infrequent exceptions. If this sounds like you, then let's proceed.
Part 2: Trash or Treasure
How does one turn their feelings into a number? This is not something people are good at, or do naturally, or are even required to do very often. It is also completely subjective and arbitrary. Does "happy" mean 5 or 100 or 902,581? It really depends on what you are trying to measure.
However, you've probably done this on a survey. Normally, a range of options is given with accompanying numbers. You may have heard a guiding explanation such as "Rate one through five, with one being 'least likely' and five being 'most likely' to recommend to a friend." Such explanations are useful in assisting a person in expressing their personal sentiments as a numeric range, and anecdotally I seem to provide more nuanced answers when I have guidance as to what each value actually means to me. However, such explanations are missing from most places where five star rating systems can make or break one's livelihood as a seller, developer, or musician. Users are normally given no guidance as to how a particular star value should correspond to their sentiment.
Accordingly, this manifests in an all too common star rating smiley. Like the famed "smiley face curve" equalizer setting popularized in the 70's in which the frequencies of a song were engineered to grow from the midranges upward toward the treble and bass making a smile shape (who's midrange is the lowest), the star rating smile is a common sight on product reviews where the most common review ratings appear anecdotally to be 5 and 1, then 4 and 2, and lastly 3.
The fact that the most common ratings are five stars and one star indicates that people most often do not think about their experience as a gradient between good and bad, but rather simply label their sentiment as only "good" or "bad" with little room for nuance. Having not received any guidance for expressing their sentiment numerically, this should be wholly unsurprising. But, I also feel like this binary outcome is a very natural expression that requires minimal mental energy to produce, and is therefore the most efficient expression of sentiment. I suspect that in another universe where we have a commonplace 15 star rating system but humans are the same, the most common ratings are 15 stars and 1 star respectively.
Other factors influence this binary good/bad paradigm too. People know instinctively that leaving a bad review is bad for business, and often this is their vengeful response to any sense of feeling as if they have been mistreated, misled, or swindled by the seller. Often times the sheer excitement of the new product compels people to write reviews only minutes after they have received it, precluding them from providing an experienced and time-tested perspective of how the product performs.
These quirks of human behavior can skew five star ratings severely. But the behaviors themselves are not bad! They are totally natural and expected. The real problem is how the five star rating system fails to capture these commonplace human sentiments accurately.
We need to build a rating system that works for people rather than forcing people to fit into a poorly executed rating system.
Part 3: Feast or Famine
It is natural that when presented with a plethora of options, humans will be drawn to the options that are labeled as "the best". When "best" possible is five stars, then five stars naturally becomes the Schelling pointfor all buyers and sellers, where the vast majority of economic activity is concentrated.
When all ratings are seen from a five-based perspective, fours look barely adequate. Threes look unacceptable. Twos are abject. And ones are complete disasters.
You may have heard about how Uber would suspend drivers whose ratings fell below 4.6. The tendency of five star rating systems is to create a gradient of sentiment where 1 to 4.5 stars is "bad" and 4.5 to 5 stars is "good".
One rarely discussed outcome of this dynamic is that good ratings are nearly impossible to compare to each other. As alluded to in the introduction thought experiment, the narrow range between 4.5 and 5 leaves very little room to distinguish from a good product and an excellent product; both are simply "good" or "not bad". As highly rated products are usually the products people are most interested in, it is unfortunate that a favorable rating would actually provide less signal than a bad rating as to the product's relative quality in the spectrum of good ratings.
Meanwhile, bad ratings have wide berth to compare numerically. The astronomical range between 1 and 4.5 is a very spacious gradient in which to assess how bad one product is versus another, except nobody actually cares because nobody is going to buy it anyway!
In the five star rating system, the better a product is, the less information we get to compare it to other similarly good products. This is a critical design flaw, because the better a product is and the more people review it, the more information we should have about it versus other similar products. It would be better if the range of "good" ratings was wider so that good ratings could be compared to each other.
I'd like to emphasize that the loss of precision as a product becomes more desirable is a truly ludicrous mechanic of the five star rating system. This poorly conceived rating paradigm completely pervades our digital economic systems and determines the success of millions of producers. Let's be clear about the stakes. Assigning subjective value to things is completely overlooked for what it really is: a absolutely critical and monumentally influential economic activity. Because the most important economic activity is how we assign value to things with money, the second most important economic activity is how we inform our economic value assignments with subjective value assignments such as these.
We need to fix how we rate things. It could literally change how entire economies function.
Part 4: Quality or Quantity
Valve has obviously put thought into how they handle ratings for video games sold through their extremely popular and long-lived Steam platform.
Reviews are not allowed until a certain amount of hours of the game have been played. The review must assign a thumbs-up or thumbs-down, and then provide a minimum amount of text.
Then, rather than simply providing an average of these binary ratings, Steam averages them over a recent period of time, creating a dynamic where if a game developer releases a new update, the reviews written more recently are sure to influence the overall rating of the game rather than old ratings that haven't taken the new update into consideration.
Finally, the aggregated rating itself is displayed as "Overwhelming Negative", "Very Negative", "Mostly Negative", "Mixed", "Mostly Positive", "Very Positive", or "Overwhelmingly Positive".
Ask yourself, which product would you be more likely to try? - 2.5/5 stars - "Mixed Reviews"
Ironically, the Steam rating system gives users less flexibility to express their sentiment as a number, and yet provides more depth, nuance, and balance to the resulting ratings. This, ladies and gentlemen, is what it looks like when somebody gives a damn about how things work. It is a great system.
Another interesting emergent behavior that accompanies many Steam reviews, as well as many reviews on other sites, are user generated pros/cons lists. These lists are helpful and offer qualitative labels that help to explain the quantitative rating assignment, although these labels are not mechanically related to the rating system itself.
Steam has another mechanism to express qualitative judgements in the form of labels, although they had to be restricted because they were being abused in undesirable or nefarious ways. Now the labeling system does more to tell you about what the game is rather than what people think about it, which is fine, but I feel like it is a missed opportunity.
Therefore, I'd like to propose a simple system that combines thumbs up/down and labeling to be used in the context of nostr's review system.
Part 5: QTS
I call this new review system QTS, or the "Qualitative Thumb System". Originally I developed QTS when working at Arcade Labs.
This PR for a new nostr review mechanism allows for a lot of flexibility in how you apply ratings to things, so QTS is simply a method of applying rating values that creates a better human-oriented review system. QTS is a way of using reviews.
In essence, QTS capitalizes on our very human instinct to assign a "good" or "bad" label by limiting the quantitative assessment to a thumbs-up or thumbs-down. Then, QTS provides qualitative labels that describe possible positive sentiments that describe different aspects of the thing being rated.
First, the user chooses thumbs-up or thumbs-down as their overall assessment. If they do nothing else, this is sufficient to capture their sentiment. However, labels should be provided which the user can check or toggle on to increase their rating further.
The initial thumbs up is worth 0.5, and each label is worth (0.5 / number of labels). The minimum rating is 0 (thumbs down, no labels), and the maximum rating is 1 (thumbs up and all labels). Any rating 0.5 or above is trending toward good and below 0.5 is trending toward bad.
The labels should be applicable in the context of the thing. So, for example, I might provide the following labels for place reviews in a Google Maps-style app: - Convenient - Clean - Affordable - Memorable - Inviting
These labels could possibly describe any place. It's OK if a place doesn't have all of these qualities. Zero labels and at thumbs up is still a "good" rating. Each label selected is essentially a "cherry on top" and its absence may indicate that either it isn't applicable OR the place failed to earn it.
Likewise, it is possible that you may give a place a thumbs-down and apply labels; this would result in a rating higher than 0 but still in the bad gradient (below 0.5).
Here are the key benefits I want to highlight of QTS: - The 5 star rating system forces a user to do the work of translating their sentiment into a quantity. With QTS, the user never has to translate their feelings into a number! They only express good or bad and pick labels, and the QTS mechanism does the work of translating this into a computation-friendly value. - The 5 star rating system generally results in a "bad" range from 1 to 4.5 and a "good" range from 4.5 to 5. QTS balances this with a "bad" rating at 0, a "good" rating at 0.5, and an excellent rating is anything above 0.5 (up to 1.0). This creates the maximum possible gradient between good and bad which makes it easier to compare similar ratings. Recall this in contrast to the 5 star rating system which actually loses precision as more ratings are provided. - It is also helpful that similar QTS ratings may have different labels, which will allow people to make easy qualitative assessments that do not depend on users generating their own pros/cons list.
Part 6: Implementing QTS
Here is how it works:
You give the user the option to rate a thumbs up or thumbs down.
Then, you also give your user the option to choose from a predefined set of positive labels. You can have any number of labels but try to keep it below 10 so as not to overwhelm your users. Keep the labels general enough that they could potentially apply to any thing being rated.
For example, if you were providing labels for Amazon.com, some good labels would be: - Good Value - Good Quality - As Described - Durable - Right Size
These labels are general enough that they could apply to almost any product. It is important to create labels that are general so that when comparing product ratings you are comparing the same labels. It is possible however that something like Amazon.com could define a different QTS label subset for each product category, and then the labels could be more specific to that category.
For example, a product category of Candles could have "Long Burning", "Good smell", "Safe", etc. These labels are much more specific, but appropriate for the Candle product category. The main point is that products which should be compared should use the same QTS label set.
Some poor examples of labels would be: - Orange (not really relevant to the product's assessment) - Easy to Lift (only relevant to certain products) - Made in USA (not really relevant to the product's assessment) - Cheap (not descriptive enough and could be interpreted as negative)
A score is derived as follows: - a thumbs-down is a score of 0.00 - a thumbs-up is a score of 0.50 - a label is worth 0.50 ÷ the number of labels available. So, if there are 3 labels to pick from, each label is worth 0.1666. The labels should all have the same value.
Here is an example by calvadev being used on Shopstr: https://github.com/nostr-protocol/nips/pull/879#issuecomment-2502210146
You can adjust the weights however you want. The fundamental thing that QTS prescribes is that a thumbs up gives a 50% score, and labels each contribute an equal share up to another 50%.
Conclusion
With nostr we have a great opportunity to improve the economic information available to the planet. A more efficient market based on higher quality information will improve civilization in ways we may not expect, but definitely deserve!
If you like this post, be sure to give it a thumbs up ✌😁
-
 @ f9c0ea75:44e849f4
2025-01-14 16:08:47
@ f9c0ea75:44e849f4
2025-01-14 16:08:47Por décadas, o Brasil se beneficiou de um bônus demográfico, no qual a população em idade produtiva crescia mais rápido que a população dependente. Isso impulsionou a economia, o consumo e a urbanização. No entanto, essa era chegou ao fim.
Com a queda nas taxas de natalidade e o envelhecimento acelerado da população, o país enfrenta um futuro de baixo crescimento econômico, crise previdenciária e perda de relevância global. Pior ainda, o Brasil não tem a estrutura econômica e tecnológica necessária para compensar esse declínio populacional.
O Fim do Bônus Demográfico Brasileiro
A transição demográfica do Brasil está acontecendo mais rápido do que o esperado. A taxa de fertilidade caiu abaixo do nível de reposição, e a população idosa cresce rapidamente.
Colapso da Taxa de Natalidade
O Brasil experimentou uma queda drástica na taxa de fecundidade nas últimas décadas:
- 1960: 6,3 filhos por mulher
- 2000: 2,3 filhos por mulher
- 2022: 1,6 filhos por mulher (abaixo da taxa de reposição de 2,1)
- Projeção para 2050: 1,5 filhos por mulher
- Fonte: Banco Mundial, IBGE, ONU
Essa queda acompanha tendências observadas no Japão, China e Coreia do Sul, países que agora sofrem com envelhecimento populacional e escassez de mão de obra. A diferença é que essas nações têm alta produtividade e tecnologia avançada para mitigar os efeitos demográficos. O Brasil não.
Envelhecimento da População e Redução da Força de Trabalho
- Em 2023, 10,5% da população brasileira tinha 65 anos ou mais.
- Em 2050, esse número será de 24%, ou seja, quase 1 em cada 4 brasileiros será idoso.
- A idade média da população aumentou de 19 anos (1980) para 34 anos (2023) e chegará a 45 anos até 2050.
- Fonte: IBGE, ONU
Com menos jovens entrando no mercado de trabalho e mais idosos dependendo do Estado, o sistema previdenciário e a economia entrarão em colapso.
Crescimento Lento e Crise Previdenciária
O declínio da população em idade produtiva trará queda na produtividade, estagnação do crescimento e aumento dos custos sociais.
Encolhimento da Força de Trabalho
- Em 2020, havia 7 pessoas em idade ativa (15–64 anos) para cada idoso.
- Em 2050, essa proporção cairá para apenas 2,5 trabalhadores por aposentado.
- Fonte: IBGE, Banco Mundial
Isso significa que menos pessoas estarão trabalhando e pagando impostos para sustentar a previdência e os serviços públicos.
Colapso do Sistema Previdenciário
- Em 2022, os gastos com previdência representavam 13% do PIB do Brasil.
- Sem reformas, esse valor pode chegar a 18% do PIB até 2050, tornando o sistema insustentável.
O governo será forçado a aumentar impostos, cortar benefícios ou elevar a idade de aposentadoria—medidas impopulares que enfrentarão resistência política.
Crescimento Econômico Vai Despencar
- A taxa média de crescimento do PIB era de 4,5% ao ano nos anos 2000, mas caiu para apenas 1,2% ao ano entre 2013 e 2023.
- Com uma força de trabalho menor, o crescimento econômico de longo prazo ficará abaixo de 1% ao ano.
O Brasil entrará em um ciclo de baixo crescimento econômico e estagnação, tornando-se menos atrativo para investidores.
Queda no Investimento e Baixa Produtividade
- A taxa de investimento do Brasil é de apenas 17% do PIB, muito abaixo da China (40%) e da Índia (30%).
- O crescimento da produtividade total dos fatores (PTF) está praticamente zerado desde os anos 1980.
- Fonte: OCDE, Banco Mundial
Ou seja, o Brasil depende mais do crescimento populacional do que de ganhos de eficiência econômica—um modelo inviável com o encolhimento da força de trabalho.
Comparação Internacional: Brasil Está em Posição Pior
Japão e Coreia do Sul (Envelhecendo, Mas Produtivos)
- O Japão viu sua força de trabalho diminuir, mas compensou com alta produtividade e inovação tecnológica.
- PIB per capita do Japão: US$ 39.000 (2023) vs. Brasil: US$ 10.000.
- Fonte: Banco Mundial
O Brasil não tem tecnologia, inovação nem uma economia avançada como o Japão, tornando sua situação mais grave.
China (Começando a Sofrer com o Envelhecimento)
- Taxa de fertilidade da China: 1,2 filhos por mulher (2023), ainda menor que a do Brasil.
- A população da China começou a encolher em 2022.
- O crescimento do PIB chinês caiu de 10% ao ano (2000) para 4% ao ano (2023) devido à queda da força de trabalho.
- Fonte: ONU
Se até a China, com sua indústria forte, está sofrendo, o Brasil, com baixa produtividade e poucos investimentos, enfrentará um cenário muito pior.
Estados Unidos e Índia (Demograficamente Fortes)
- EUA: Fertilidade de 1,7 filhos por mulher (acima do Brasil) e 1 milhão de imigrantes por ano, sustentando o crescimento da força de trabalho.
- Índia: População jovem (idade média de 28 anos) e forte crescimento econômico.
- Fonte: ONU, Censo dos EUA
Enquanto EUA e Índia continuarão crescendo, o Brasil envelhecerá sem soluções econômicas para compensar.
Por Que o Brasil Não Conseguirá Reagir
Mesmo que o Brasil reconheça o problema, o país carece dos meios para reverter a crise demográfica.
Baixo Investimento em Tecnologia e Indústria
- O Brasil investe apenas 1,2% do PIB em P&D, enquanto a Coreia do Sul investe 4,8%.
- O crescimento da produtividade foi zero nas últimas duas décadas.
- Fonte: Banco Mundial, OCDE
Sem investimentos em tecnologia e inovação, o Brasil não conseguirá substituir a perda de trabalhadores por automação e ganhos de eficiência.
Corrupção e Instabilidade Política
- O Brasil ocupa a 94ª posição no Índice de Percepção da Corrupção, dificultando reformas.
- Ranking de Facilidade para Fazer Negócios: 124º lugar (de 190 países).
- Fonte: Transparência Internacional, Banco Mundial
A falta de reformas estruturais impedirá qualquer solução para a crise demográfica.
O Brasil Caminha para o Declínio
O bônus demográfico do Brasil acabou, e os efeitos serão devastadores. O país não tem produtividade, investimentos ou governança eficiente para lidar com o envelhecimento populacional.
Sem uma força de trabalho jovem, sem inovação tecnológica e com um sistema previdenciário insustentável, o Brasil enfrentará estagnação econômica e perda de competitividade global. É impossível ser otimista sobre o futuro do Brasil.
-
 @ a0c34d34:fef39af1
2025-01-14 14:28:28
@ a0c34d34:fef39af1
2025-01-14 14:28:28I feel fabulously free, I deleted TikTok. I am spending less time on my phone and more time developing Onboard60. I never expected to go from the Metaverse to A.I. healthcare and NFCC medical bracelets.
I was on Vine, Twitter back in 2009… I went from 8 second nonsensical videos and funny tweets to diving deeper down any rabbit hole I ever imagined.
In 2016, I heard a little noise about Bitcoin and I haven’t gotten off the rollercoaster of a merry go round yet. If you know, you know.
I found Nostr awhile ago but I’m no maxi, I’m curious. I learned about different things pertaining to blockchain and cryptocurrency, social media and protocols.
I kept journals of my fears and conferences I experienced and published them as my first years behind the scenes of a senior citizen diving deep into the unknowns.
Someone had to tell me I was a senior citizen. I’m 64 now , that was four years ago. Since then I took a crazy idea and started Onboard60.
I created a curriculum for myself. For years I have learned a variety of subjects. I took the basics and made a cliff note booklet - Web3 1101 for Seniors.
I didn’t want to be left behind so I learned Spatial and created an auditorium, an art gallery and an office. It was my attempt to get senior citizens involved to connect with their grandkids in virtual reality like Roblox.
Over the years, I’ve written articles on Substack sharing my journey, and sporadically posted on Zentaurios. I remember writing on YakiHonne when I first discovered it.
Onboard60 has become more than what I ever thought it would be, as I started just sharing my journey in hopes others would join me.
I hoped senior citizens would be interested in learning how to put their trust funds, H.O.A.s, POLSTs and other senior citizen documents on chain.
The past four years, nothing until I speak of medical bracelets. I do not mention BitDoctor AI or mirrors that do body scans. Bracelets, I speak bracelets.
The focus is to keep senior citizens up to date with new technologies that focus on improving their quality of life.
Finding YakiHonne again is refreshing. The esthetics clean, seemless cross posting, and better options for posting. Soft landing.
I have learned a lot over the years, experiencing this space becoming , watching protocols grow, some platforms fizzle, creating a new world isn’t easy.
I’m enjoying being a mermaid in Monniverse community on Farcaster, not Farcaster itself but enjoy being a mermaid. Monniverse is a decentralized animation production company. I’m learning how to use the image generator and like the global reach.
I have compromised on so many social media sites just to be on them. I still frequent Twitter Onboard60, and have my old Vine group on Instagram. I spend time on Lens mostly.
I use traditional media to share Onboard60 - LinkedIn and YouTube for Onboard60. I am creating a digital replica of all the information, subjects, videos, content that I created as Onboard60. I hope to keep it updated as times goes forward.
I’m going to use my guide to IRL events at Blockchain Miami in a few weeks, WAGMI MIAMI. After so many conferences and events, I had to write down a step by step how to get through these and follow up after. They can be overwhelming and I needed a way to decompress. My guide helps me.
I seem to be rambling. I don’t have a purpose or any value to share with this article, I just wanted to share my thoughts for now, walking into 2025.
Sandra ,Samm,Sababa
Onboard60, founder
-
 @ a012dc82:6458a70d
2025-01-18 02:33:24
@ a012dc82:6458a70d
2025-01-18 02:33:24Over the past decade, the cryptocurrency landscape has witnessed unprecedented growth, with Bitcoin undeniably at its forefront. As the trailblazer of digital currencies, Bitcoin has not only introduced the world to the possibilities of decentralized finance but has also inspired the creation of thousands of other cryptocurrencies. Yet, among the myriad of developments in the crypto domain, the advent of Bitcoin ETFs (Exchange Traded Funds) stands out. These innovative financial instruments have not only revolutionized how investors perceive and interact with Bitcoin but have also provided a bridge between the volatile world of cryptocurrencies and the more stable, regulated realm of traditional finance.
Table Of Content
-
What is a Bitcoin ETF?
-
Why are Bitcoin ETFs Important?
-
The Current Landscape of Bitcoin ETFs
-
How to Invest in a Bitcoin ETF
-
Conclusion
-
FAQs
What is a Bitcoin ETF?
At its core, a Bitcoin ETF is a financial instrument designed to track the price movements of Bitcoin. Rather than diving into the intricate world of cryptocurrencies—buying Bitcoin directly, grappling with the nuances of digital wallets, or navigating the often complex landscape of crypto exchanges—investors can now simply purchase shares of a Bitcoin ETF. These shares are traded just like any other stock on traditional stock exchanges, offering a seamless integration of Bitcoin into conventional investment portfolios.
Why are Bitcoin ETFs Important?
Accessibility: One of the primary advantages of Bitcoin ETFs is their accessibility. They open the doors for everyday investors, even those unfamiliar with the intricacies of the crypto world, to gain exposure to Bitcoin. There's no need to delve into the technical aspects of purchasing, storing, or securing the cryptocurrency—Bitcoin ETFs simplify the entire process.
Regulation: Being listed and traded on recognized stock exchanges means that Bitcoin ETFs come under the purview of financial regulators. This regulatory oversight ensures a degree of transparency and protection for investors, something that's often amiss in the wild west of direct cryptocurrency investments.
Diversification: For seasoned investors and newcomers alike, diversification is a cornerstone of a robust investment strategy. Bitcoin ETFs offer a golden opportunity to tap into the burgeoning cryptocurrency market without the direct volatility and risks tied to holding the actual digital assets.
The Current Landscape of Bitcoin ETFs
The concept of a Bitcoin ETF isn't new. However, its journey to mainstream acceptance has been riddled with regulatory challenges. Many countries, initially hesitant, have taken a cautious approach, leading to delays in the adoption of Bitcoin ETFs. But as the broader financial community becomes more attuned to the potential benefits (and risks) of cryptocurrencies, we're witnessing a gradual shift. Regulators are now more open, and approvals for Bitcoin ETFs in major financial markets are on the rise. This evolving landscape has sparked renewed interest, with both institutional and retail investors keenly exploring these novel investment avenues.
How to Invest in a Bitcoin ETF
The process of investing in a Bitcoin ETF mirrors that of any other traditional investment vehicle. Here's an elaborated guide:
Research: Embarking on any investment journey necessitates thorough research. It's imperative to delve deep, understand the nuances, and compare the various Bitcoin ETFs available in the market. Look into their past performance, management strategies, and fee structures.
Choose a Brokerage: Once you've zeroed in on a Bitcoin ETF that aligns with your investment goals, the next step is to select a suitable brokerage. Opt for one that offers your chosen Bitcoin ETF and boasts a reputation for reliability and security.
Buy Shares: With your brokerage account set up, you're all set to make your purchase. Navigate to the trading platform, search for your chosen Bitcoin ETF, decide on the number of shares you wish to buy, and execute the trade. It's as simple as buying shares of any other company.
Conclusion
The emergence of Bitcoin ETFs signifies a monumental shift in the financial world. It's a testament to the growing acceptance of cryptocurrencies and their potential to coexist with traditional financial instruments. As the crypto ecosystem continues to evolve, mature, and gain broader acceptance, the allure of Bitcoin ETFs is set to grow. For investors, this evolution offers a unique vantage point—a chance to be at the intersection of time-tested financial principles and the dynamic world of digital currencies.
FAQs
What is a Bitcoin ETF? A Bitcoin ETF is a financial instrument that tracks the price of Bitcoin, allowing investors to buy its shares on traditional stock exchanges.
Why choose a Bitcoin ETF over direct Bitcoin investment? Bitcoin ETFs offer easier accessibility, regulatory oversight, and a way to diversify investments without dealing with the complexities of direct cryptocurrency handling.
Are Bitcoin ETFs regulated? Yes, Bitcoin ETFs traded on established stock exchanges are subject to regulatory oversight, providing added protection for investors.
How do I invest in a Bitcoin ETF? Start with research, choose a reputable brokerage that offers the Bitcoin ETF you're interested in, and then purchase its shares like you would with any other stock.
Are Bitcoin ETFs a safer investment than Bitcoin? While no investment is risk-free, Bitcoin ETFs offer a layer of protection due to regulatory oversight and eliminate the risks associated with direct handling and storage of cryptocurrencies.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3eab247c:1d80aeed
2025-01-14 14:07:10
@ 3eab247c:1d80aeed
2025-01-14 14:07:10Preface
2024 was the second full year BTC Map. The first attempts to build a map of Bitcoin merchants were observed more than a decade ago, but the first wave or merchant adoption faded away due to on-chain settlement limitations. Late 2022 was the year when Lightning started to shine and it felt like Bitcoin was ready for retail adoption. It turned out we weren't wrong about that! BTC Map continues to have a steady growth rates, powered by the mighty Lightning Network.
Global Metrics: Total Merchant Count
The total number of bitcoin accepting merchants is 40% higher than it was in the beginning of 2024. We started this year with 9,727 merchants on the map, and we increased this to 13,673 merchants by the end of 2024.

Global Metrics: Up-to-date Merchant Count
We care deeply about data quality and so every merchant is supposed to be re-verified at least once a year. The number of freshly verified merchants has increased from 6,250 to 7,807, which is 25% higher than it was in the beginning of 2024.
We're aiming to re-verify the other 5,866 merchants, but we can only do that if we get some help from the local communities. After all, the data is theirs (yours!), not ours. The best way to help us is to re-verify some outdated locations in your area.
Trending Countries
- Brazil - 1,873 changes
- United States - 1,745 changes
- Czechia - 1,644 changes
- Italy - 1,567 changes
- El Salvador - 1,043 changes
- Netherlands - 985 changes
- Germany - 685 changes
- South Africa - 740 changes
- Portugal - 580 changes
- Georgia - 648 changes
I want to give a huge thanks to Rockedf for consistently contributing to almost every region!
Trending Communities
- Jednadvacet Praha - 682 changes
- Bitcoin Association Switzerland - 566 changes
- Mi Primer Bitcoin - 414 changes
- FREE Madeira - 350 changes
- Vancouver Bitcoiners - 319 changes
- Bitcoin Bulgaria - 272 changes
- Arnhem Bitcoin City - 258 changes
- Bitcoin é aqui! Rolante/Riozinho-RS-BRASIL - 261 changes
- Bitcoin Island Philippines - 205 changes
- Porto Alegre Bitcoin - 210 changes
Key Goals for 2025
- Re-verify more merchants (we need your help!)
- Finish community admin app and onboard more local admins (Nathan is working on that)
- Clean up our community database, remove the stale records and make sure none of our communities are shitcoining (we're hoping that the local admins will help us with that)
- Improve Android app by switching to vector tiles and fixing some UI and performance issues (Igor is working on that)
- Find someone to maintain our Web and iOS apps (if you're a dev, we need you help!)
- Automate merchant review process
- Implement more lightweight web interface for the users who doesn't need local caches and offline mode. It should be powered by a special API optimized for this use case (I'll probably work on that, but any help would be appreciated)
- Improve backend performance and fix some known bugs and bottlenecks
- Visit more places and spend more sats on BTC Map =) (we'll keep doing that and we need your help!)
Conclusion
We're satisfied with our performance in 2024, and think the future looks bright. We're pleased to see more local communities spawning and the growing public awareness. Some popular Lightning wallets have also integrated BTC Map and we expect more to follow their lead. As Lightning Network continues to mature, it also gets much easier for merchants to accept sats. We expect a healthy growth rate in 2025!
-
 @ badbdda5:8cdc962a
2025-01-14 13:18:51
@ badbdda5:8cdc962a
2025-01-14 13:18:51Abstract
In this article, we try to explain how deletion requests on the Nostr work, and how we can probably improve this using filters.
NIP-09: Deletion Request
As you know, we can request the election of an event that we own using a kind 5 event like the below based on nip-09:
json { "kind": 5, "pubkey": "<32-bytes hex-encoded public key of the event creator>", "tags": [ ["e", "dcd59..464a2"], ["e", "968c5..ad7a4"], ["a", "<kind>:<pubkey>:<d-identifier>"], ["k", "1"], ["k", "30023"] ], "content": "these posts were published by accident", // other fields... }There are 2 important limitations to this model:
- We can't request a to delete huge amount of events with complex conditions in one request since it would result in an event with a lot of tags which may some relays even reject because of the number of tags. for example, you can think of deleting all of your reactions to the posts of one of your followings.
- There is no guarantee for a kind 5 request to be executed by all relays and clients since they can keep a copy of events json forever.
Deletion Using Filters
Based on issues that we had with the old model used in nip-09 we tried to find different ways to fix them. Deletion using filter i is a new model that tries to fix the first issue. The third issue is still under research.
Nostr utilizes a query model called
filterto query events that can be checked and matched with an event and receive only 2 results that are matched and not matched. So, we can define a structure that can be matched with any number of events.We define a new tag called
filterwhich contains a stringified Nostr filter. Using this tag, we construct a kind 5 event that requests the deletion of all events matching with that event. Here is an example:json { "kind": 5, "pubkey": "aca682c51c44c9046461de0cb34bcc6338d5562cdf9062aee9c3ca5a4ca0ab3c", "tags": [ ["filter", "{\n \"authors\": [\"aca682c51c44c9046461de0cb34bcc6338d5562cdf9062aee9c3ca5a4ca0ab3c\"],\n \"kinds\": [7],\n \"#p\": \"aca682c51c44c9046461de0cb34bcc6338d5562cdf9062aee9c3ca5a4ca0ab3c\",\n \"since\": 0,\n \"until\": 2147483647,\n}"] ], "content": "i don't want to be selfish anymore.", // other fields... }In this example,
aca682c51c44c9046461de0cb34bcc6338d5562cdf9062aee9c3ca5a4ca0ab3cpublic key requests to delete all of their reactions on their on events.Or using the example below, you can request account deletion:
json { "kind": 5, "pubkey": "aca682c51c44c9046461de0cb34bcc6338d5562cdf9062aee9c3ca5a4ca0ab3c", "tags": [ ["filter", "{\n \"authors\": [\"aca682c51c44c9046461de0cb34bcc6338d5562cdf9062aee9c3ca5a4ca0ab3c\"],\n}"] ], "content": "use my new pubkey: cc6...a0a.", // other fields... }Filter Limitations and Details
Here is a list of limitations and considerations for those who are using the
filtertag on kind 5:-
authors: This field must be implicit and it MUST always contain one pubkey which is the pubkey of the deletion author. Some relays MAY accept multiple pubkeys from moderators events. (but it's RECOMMENDED for it to be applied from nip-86 management API, gRPC API, or anything used for managing relay.) -
limit: This field MUST be ignored since the limit selection can be different in the relay/client internal system. -
search: A relay MAY support NIP-50searchfor this purpose. -
until/since: These fields would be used instead of the eventcreated_atfor time. But relay MAY follow any of the below behaviors: 4.1. They only let pubkeys request the deletion of old events, not future events and consider thesincefield. 4.2 They MAY keep a list of deleted filters in a hashmap withpubkeyas the key to check any incoming event with the filter and they can drop the filer once we pass theuntil. this would be an expensive action to accept kind 5 from all pubkeys, relays MAY charge some fee or require some amount of work to accept kind 5 in this case.
Thanks mike@mikedilger.com for sharing his ideas on this PR.
Uses cases
Here is a small list of use cases for this model:
-
Account Deletion Request: a pubkey can request for deletion of their account.
-
Bulk Remove: Chat clients for example can support the selection of multiple messages and requests for deletion.
-
Force Limit: The Relays that keep the filter using the
untilfield can be used by a pubkey to force the relay to not accept a specific event matching that filter for a specific time.
Final Words
This standard is currently in beta version, not merged in the nips repo, and it is implemented and supported in the Immortal relay.
-
 @ 6be5cc06:5259daf0
2025-01-18 02:11:43
@ 6be5cc06:5259daf0
2025-01-18 02:11:43- Not your keys, not your coins
Se você não tem as chaves privadas do seu Bitcoin, ele não é realmente seu. Deixar seus BTCs em exchanges ou carteiras controladas por terceiros significa confiar neles e assumir o risco de perder seus fundos.
- HODL - Não venda
O Bitcoin é uma reserva de valor a longo prazo e potencialmente o dinheiro do futuro. Não se desespere com as flutuações de preço; mantenha seus BTCs, pois o histórico se mostra favorável.
- Stay humble - Não saia falando que você tem BTC
Manter discrição sobre seu patrimônio é uma questão de segurança e humildade. Falar demais pode atrair curiosos, oportunistas ou outras ameaças.
- Don't trust, verify
No Bitcoin, confie no protocolo, não em pessoas. Sempre que possível, verifique por conta própria, seja transações, códigos ou informações.
- Reject altcoins
As altcoins podem parecer promissoras, mas frequentemente são distrações ou apostas arriscadas. Foque no Bitcoin, que já provou ser sólido e resistente.
- Stack sats - DCA
Empilhe satoshis consistentemente, utilizando a estratégia de DCA (Dollar Cost Averaging), comprando regularmente independentemente do preço. Isso reduz o risco de tentar "acertar o mercado".
- Reject the ego
Não aposte contra o Bitcoin. Aqueles que subestimaram sua força ou estabilidade, perderam.
- Keep learning
Nunca pare de estudar sobre Bitcoin, economia e a tecnologia por trás dele. Quanto mais você entende, mais confiança terá em sua decisão.
- Help beginners
O Bitcoin pode ser complicado para quem está começando. Compartilhe seus conhecimentos com paciência para fortalecer a comunidade.
- Don't push it
Cada pessoa tem seu próprio tempo para entender e entrar no mundo do Bitcoin. Forçar alguém pode ser contraproducente; dê direcionamento e deixe o tempo agir.
-
 @ b8851a06:9b120ba1
2025-01-14 10:56:55
@ b8851a06:9b120ba1
2025-01-14 10:56:55Starting in January 2025, the EU’s MiCA regulation enforced strict KYC requirements, especially for Bitcoin transactions over €1,000 between exchanges and self-hosted wallets. While this creates new challenges, there are still legitimate ways to protect your privacy and maintain control over your Bitcoin.
Effective Privacy Solutions
-
Take Control with Self-Custody • Run Your Own Node: This ensures you’re not relying on third-party servers, giving you full control of your transactions. • Use Fresh Addresses: Always generate a new address for each transaction to keep your activity private and harder to trace. • Choose the Right Wallets: Use wallets like #Sparrow or #Wasabi, which let you connect directly to your own node for added privacy (check if there are any legal cases against any wallet before you use one.).
-
Leverage the Lightning Network • Keep Transactions Off-Chain: Lightning lets you make payments without broadcasting them to the blockchain. • #Onion Routing for Privacy: This hides your payment path, protecting both you and the recipient. • Hard-to-Trace Payments: With multiple hops between nodes, tracking transactions becomes nearly impossible.
-
Smarter Transaction Habits • Keep Channels Open: By leaving your #Lightning payment channels open, you minimize on-chain activity. • Use Public Channels Wisely: Multiple public channels provide plausible deniability. • Go Private with Unannounced Channels: For maximum privacy, consider private payment channels.
How to Implement These Tools
-
Setting Up the Lightning Network • Privacy-First Funding: When funding your channels, use methods like #CoinJoin to enhance privacy. • Better Receiver Privacy: Use tools like #Voltage Flow 2.0 for added anonymity when receiving payments. • Stay on Top of Channel Management: Properly manage your payment channels to avoid privacy leaks.
-
Strengthen Your Operational Security • Avoid Reusing Addresses: Reusing the same wallet address makes it easier to trace your transactions. • Separate Public and Private Transactions: Keep identified funds and private wallets completely separate. • Use Tor or VPNs: Always use privacy tools like Tor or a #VPN when accessing Bitcoin wallets or services.
Staying Safe
-
Legal Awareness • Mind the Limits: Be cautious with transactions over €1,000, as they’ll trigger reporting requirements. • Peer-to-Peer Freedom: Transactions between unhosted wallets remain outside #MiCA ’s reach, so direct transfers are still an option. • Check Local Rules: Privacy tool regulations vary between countries, so make sure you’re up to speed on what’s allowed where you live.
-
Practical Safeguards • Double-Check Everything: Always verify wallet addresses before sending funds to avoid costly mistakes. • Stay Updated: Keep your wallets, nodes, and security tools current with the latest updates. • Keep Offline Backups: Store your recovery phrases and backups somewhere secure and offline.
Bitcoin #privacy isn’t automatic—it takes effort and vigilance. But by following these steps, you can stay in control of your financial freedom even in an increasingly regulated world. Stay informed, make smart decisions, and build habits that protect your privacy.
Disclaimer:
This post is for educational purposes only and is not financial, legal, or investment advice. The tools and techniques shared here are not meant to help anyone break the law or avoid regulations. You’re responsible on complying with local laws and consult legal professionals if you’re unsure about anything.
The goal is to inform and empower you to take control of your privacy responsibly.
Stay safe and stay free.
-
-
 @ 378562cd:a6fc6773
2025-01-18 00:12:47
@ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, Nostr (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet.
How Nostr Works: A Quick Overview
At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components:
-
Public and Private Keys:\ Your public key acts as your identity, and private keys ensure your messages are securely signed.
-
Relays:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it.
-
Clients:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs.
Deep Dive: Events in Nostr
Everything on Nostr revolves around events, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases:
1. Note Events (Type 1)
- What They Are:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms.
- Features:
- Can include text, media links, and hashtags.
- Interact with others through likes, replies, and boosts (reposts).
- Use Cases:\ Perfect for microblogging, status updates, and general social interaction.
2. Profile Metadata Events (Type 0)
- What They Are:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website.
- Features:
- Easily editable and updated across all Nostr clients.
- Keeps your identity consistent across platforms.
- Use Cases:\ Makes profile portability seamless—update once, and it reflects everywhere.
3. Relay List Events (Type 2)
- What They Are:\ These events store a list of relays that a user is connected to or prefers to use.
- Features:
- Share your relay preferences across devices or clients.
- Allows automatic relay connection in supported clients.
- Use Cases:\ Simplifies the onboarding process for users switching clients or devices.
4. Direct Message Events (Type 4)
- What They Are:\ End-to-end encrypted messages sent directly between two users.
- Features:
- Only readable by the intended recipient.
- Supports text and basic formatting.
- Use Cases:\ Secure communication for personal or professional purposes.
5. Reaction Events (Type 7)
- What They Are:\ Events that express reactions to other events, such as likes or emojis.
- Features:
- Provides social feedback (e.g., showing appreciation for a post).
- Lightweight and simple to implement.
- Use Cases:\ Enhances engagement and interaction within the network.
6. Repost Events (Type 6)
- What They Are:\ Events that allow users to reshare content, similar to retweets on Twitter.
- Features:
- Ensures the original poster retains credit.
- Enables broader content visibility.
- Use Cases:\ Amplifying content that resonates with users or is worth sharing.
7. Custom Event Types (Beyond Type 7)
- What They Are:\ Developers can create and define custom event types for specific applications.
- Features:
- Flexibility to introduce entirely new functionality.
- Supported based on client and relay compatibility.
- Use Cases:\ Enables innovation, from collaborative editing tools to advanced publishing workflows.
What Makes Events Special?
- Portability: Events follow your public key, not the client or relay, ensuring they’re available wherever you go.
- Interoperability: All events are standardized, meaning any Nostr client can understand and process them.
- Extensibility: Through custom event types, the protocol encourages experimentation and development.
Primal: A Favorite Client for Engaging Events
Among the many clients, Primal stands out as a favorite for how it handles Nostr events. Its emphasis on content discovery and rich user interaction makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless.
The Future of Nostr Events
As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community.
Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below! ⚡️
Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
-
-
 @ 10fe3f70:3489c810
2025-01-14 08:04:54
@ 10fe3f70:3489c810
2025-01-14 08:04:54nostr #nostr_writer #review #beginner #obsidian #anytype #contract_drafting #agreenent_drafting #lawyer #law #contract #agreement #learn #education #plugin #telegram #wordpress #yakihonne #primal #damus
How and Why I found Nostr?
I teach contract drafting. That is who I am.
To teach the subject I maintained few websites through self-hosted Wordpress. I faced numerous challenges despite spending money on hosting, domain and whatnot. I do not have any technical background. So, you can understand my frustration when my websites kept disappearing due to hacking. I always put a brave face and started afresh.
I used Microsoft Word, Power Point, and Obsidian to draft my posts and lessons. So, I had some backups. Thankfully, I also did post some of the training sessions on my youtube channel. Checkout my previous post for link to the Youtube Playlist.
Since, I teach for free, every time my websites were hacked, it pained me to see the bad side of human race. I was not hurting anyone, spending my own money, still someone unknown to me, for whatever reasons, could stop my mission.
I started empathising with the belief in the internet being dysfunctional and still being beyond reach of common man.
Then I found some hope, when around a year or so earlier, I found Anytype. A simple app, the everything app, which promises anonymity, security from data breach, and a promise to share ones thoughts publicly with the others soon via web. Although some of its features (e.g. option to self host) are little bit technical for me, I still have high hopes. It is similar to Obsidian, yet way more than that.
I could use either Obsidian or Anytype for writing and publishing my data on web. So, I recently surrendered to the idea of using one of Obsidian's plugins to publish my content. These provide the option to publish your obsidian notes on web through sub-domain. One that I used before was Obsius Plugin.
But, secretly I also wished want more.
I wished to maintain my same anonymous profile I have on Telegram. I have a dedicated student base on Telegram. So, I wanted them to easily find me or atleast my content on a new platform.
I also wanted to stop spending more money, or at least save some by spending less.
And, voila!
I came across Nostr unexpectedly through Obsidian and found a Plugin Nostr Writer by James.
I was looking for a simple method to host my blog posts and lessons on contract drafting. And, I found much more....
If you have some other compelling reasons, as Marc, do read his piece on why he is on Nostr - Why I'm on Nostr?
What did I find?
After going through the Nostr Writer](https://github.com/jamesmagoo/nostr-writer) documentation on Github, I searched for Nostr and found NOSTR.COM.
As expected, it took me some time to understand the concepts of Public and Private Keys, Clients, Relays and so on. But, within 2-3 days, I found that this was just a SMALL TIP of a HUGE ICEBERG, yet to be show it's full potential.
My most sincere thank you to its creator, and to people who spend time explaining it and making it AWESOME.
NOSTR's CONCEPTS
If you want to READ ABOUT NOSTR's CONCEPTS, you can go through the following:
I also went through almost each and every youtube video I could find on Nostr onboarding and much more. Although, these are very few, I found each one of them to be very useful. I have listed some of these below.
Nostr Onboarding videos
My most sincere thank you to each of the creators (), who took time to explain the onabording by various methods.
- By Ares - how to get started with Nostr on mobile - 3 minutes approx
- By Castig- How to get started on Nostr - 7 minutes approx
- By Max Demarco- Create your Nostr Account- Beginnner Tutorial - 18 minutes approx
- By Nostr World - Nostr for Beginners w/ Derek Ross - 37 minutes approx
- By 88 Sats Radio- how to get started on Nostr - 48 minutes approx
I suggest every beginner must watch all of these videos, create as many accounts you need, and do it until you understand the whole Idea.
This is just the beginning of what to come. So, do not stop using Nostr. In fact refer to friends and family and ask them to join.
Bonus of Nostr
You can get paid in Bitcoins! Without spending a dime!!
Yes, you read it correct.
All you need to do is have a lighting wallet.
I leave it to you explore for now. I am still reviewing the payment structure. So, I will write about how to use this feature later.
Meanwhile I suggest, you go through BTC Session's Youtube channel to learn more about bitcoins, wallets, zaps/sats, lighting, etc.
What else do you need?
Pretty much you have the basics if you did everything suggested above.
If you have a question, you can ask someone within any of the Nostr Clients.
NOSTR CLIENTS
I am experimenting with following Nostr Clients (apps to read your notes, pictures, and long form content) on my apple devices on web.
Damus Primal Yakihonne
NOSTR APPSTORE
You can find many more clients at
GetAlby's App Store Nostr App Store 1 Nostr App Store 2
So, Good luck to you and Happy Nostring
Only the Human Imagination is the limit of what you can do with Nostr
If you liked this article, share it with your friends.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ b6424601:a11e4ff4
2025-01-14 03:08:09
@ b6424601:a11e4ff4
2025-01-14 03:08:09In a world where homes are increasingly valued by their size and room types rather than their functionality and authenticity, it's time to rethink how we design and build houses. A Pattern Language, written by Christopher Alexander in 1977, offers a timeless approach to architecture that prioritizes human needs and experiences. Architects and homeowners can use this classic work as a pre-fiat reference to learn about principles to create functional, authentic, and meaningful homes. The principles can be used to create homes that are worth HODLing.
How would your grandmother use this space? Muir, my favorite Scottish professor in architecture school, asked this question. Besides, have you boys ever seen a pint of Guinness Stout? In Alabama in the last century, a pint of Guinness did not exist, and the idea of writing your name in the head with a fountain pen to see it at the bottom of the glass was even before our time.
Planning spaces for how your grandmother used them sent us at Jones Pierce down the rabbit hole of designing for humans and not the current fashions of that day. This led my baby architect tribe to A Pattern Language, written in 1977, and A Timeless Way of Building, written by Christopher Alexander in 1979. Alexander and graduate students researched and documented their projects over eight years to create Patterns that individuals and groups could use as a shared pattern language to design for themselves and their communities.
A Pattern Language and the Timeless Way of Building were open source before there was open source. The books outline a process meant to be used by the people and groups designing their own spaces utilizing a collection of shared patterns combined to solve the design problem of their site, built for their unique needs.
Now, I look back and wonder if the book's conception to enable people to design their own authentic spaces, neighborhoods, and towns was the self-design guide it was intended for or if it was a reaction to inflation that began to kick in in the early 70s. Were Alexander and the crew trying to provide a lifeline as housing products decreased in quality? You know how architects are…they probably thought the layperson did not know how to build meaningful spaces. Maybe when the erosion of fiat currency started, it was not allowing people to consider affording meaningful space.
To prepare for the coming time when hard assets will once again enable people to build authentic architecture, it is worth reconsidering the Patterns used from a time before fiat. Interestingly, Pattern Language and the Timeless Way process use patterns to create personal architecture based on sound money. Structures are designed mindfully, developed organically, and built to last. In other words, architecture on a bitcoin standard.
From my own professional experience working with clients, I have seen that, given a choice, people always choose the most interesting space that best aligns with their needs in the best community they want to afford. The patterns for design (from Pattern Language) are still relevant as a starting point to build with hard money assets again - bitcoin. These patterns are baked into our process of working with clients at Jones Pierce, and I want to share some of the relevant patterns from the book with my commentary on how they have evolved from the 70s until today to create homes worth HODLing.
Patterns for the Site
Analyzing the site and site patterns is the most critical first step for homes worth HODLing. We want to end the practice of "ready, aim, fire" - when the builder makes their well-considered opening move by calling the Grading Guy to clear a building site. Features came with your property as part of the price of the land; take a breath and figure out how to capture the most potential of your property to create a building site. These are some of the patterns essential to us:
104: Site repair – Locate building sites on parts of the land in the worst conditions, not the best. Be a contrarian and locate a house on the edge of a flat spot to create quality outdoor spaces the house can open to.
105: South facing outdoors – Locate buildings in a place to allow indoor/ outdoor transitions to happen to the south. If south is not possible, East works for morning outdoor spaces, and west works for afternoon spaces if you can protect the outdoor spaces from the heat.
112: Entrance transitions – In The Pattern Language, this pattern is about an urban entrance oƯ the street into the building. We apply the pattern to capture the total use of properties. Define the entrance to the property to visually claim the space to use the entire front yard for your benefit and not just the HOA's.
134: Zen view - Analyze the site for Zen view potential to orient windows and spaces to connect space beyond the house's walls visually. This pattern works well with site lighting to extend your night view beyond the window's glass. On more significant sites, we analyze for opinions and work out places to capture the money shot for essential rooms. We also think about creating smaller Zen-view moments that happen continuously while living in the house. Why not make a surprise view through a slot window when brushing your teeth?
168: Plan to connect buildings to the earth—Use paths and gardens throughout the building to blur the line between the future building and gardens. To accomplish this blur, we study the site topography to ensure that the construction will not create an oversized kill zone caused by grading a house in the wrong spot.
177: Vegetable garden – 1/40 acre per person for food production. It is even better when combined with 169 terraced slopes, 170 fruit trees, 173 garden walls, 175 greenhouses, and 178 compost. When designing a custom home, the design thoughts extend to the property line. We like landscapes that have classic landscape organization with food production. Make your house a homestead to prepare for The Mandibles, A Family, 2029 - 2047 scenario if times get tough, or provide nutrient-dense food for your loved ones.
Patterns for the Building
We are attracted to patterns that provide a return on investment beyond money. How does a house footprint create outdoor space, have a rational roof plan, and let in natural light? Do the rooms function by following the sun around the house during the day? Can we use design to create a place to work, recover, entertain, and retreat? How can a house design allow an owner to transition through life phases in the same house? Can we save space and cost by function stacking to use the same space more than one way? Is there an opportunity to create rental income or a place to work on side gigs to convert more fiat to BTC? The following are some patterns we think about:
106: Positive outdoor space - Use wings pattern 107 of light to create an L-shaped positive outdoor space. Designing homes that make outdoor spaces contrasts with building a square-shaped plan with a roof that does not relate to the plan we call a PILE… a pile of excrement, typically.
128: Indoor sunlight—Morning beds, breakfast nook, kitchen, family and garden spaces, mid-day living spaces, and evening living, dining, and porch spaces.
136: Couples Realm—Provide adult spaces away from kids' noise and access. Include a bed, sitting area, and dressing space in the Couple's realm.
141: A room of one's own—Everyone in the house needs a personal space, such as an alcove, nook, or room. This is not on the appraisal sheet to determine value, but we ensure everyone, including kids, pets, and outside help, has a place to call their own.
143: Children's bed clusters – Clustering beds happen for us in lake houses to let smaller houses sleep more guests. In a non-fiat house design, they can be a great way to save space if there is no bank to tell you there should be a certain number of bedrooms. Your kids may even grow to like each other by sharing a space.
146: Flexible workspace – The patterns provided flexible workspace for working, which you could use for other uses when not working. For us, the pattern evolved to an idea of function stacking to provide additional uses. Space is expensive; use it twice.
153: Rooms to rent – This is a function of asset architecture. Make some parts of the building rentable with outside entrances so the use of the space works flexibly either in the entire house or rentable. These spaces are also flexible, allowing uses for rentable accessory dwelling units (ADU), a teenager's cottage, boomerang kids, or multigenerational housing.
157: Maker's space – Make a place in the home where hobbies and side gigs happen. Give the workshop a few hundred square feet off the street for owners to hang their shingles or rent to others. Some of our clients are first building “barndominiumns” to stage for construction and live on-site as construction on the main house happens. These spaces can become workspaces for personal use or rent after construction.
159: Light – Light on two sides of every room. Some houses feel right when you walk in. We contend these spaces have windows on at least two walls.
163: Outdoor rooms—Plan spaces beyond the building footprint to allow functions to flow indoors and outdoors.
181: The fire – There is no substitute for places where fire and gathering happen, inside or out.
203: Child caves—We like to create toy caves that become play spaces for young kids, trapping toys in the space rather than the living room. Adult caves are root cellars, wine cellars, or basement golf simulators.
204: Secret places—The original pattern references a hidden place for precious objects and family history. We use this space for storm shelters, safe rooms, gun safes, and areas where precious stuff like your hardware wallet is hidden.
In Conclusion
Our architectural firm has stayed in touch with how quality homes are designed without fiat because our clients are older and mostly pay for projects with assets or cash. Our clients come to us as architects to help provide a non-cookie-cutter housing solution and are willing to pay for it, which we call architecture.
Bitcoin may offer the opportunity for more people to build quality personal architecture backed by a sound money standard who can think longer term beyond the initial construction or sales price. More authentic architecture happened before fiat currency began, and the values were accepted when building with fiat. The values of the person on a personal BTC standard who wants or even needs to make a home to live in will wish for their home to be the best asset they can build to hold long-term value.
We need to rethink house value to prepare for the opportunity to build with hard currency. The degrading products of the 50 years of fiat building may not be worth holding, nor store value on a bitcoin standard when we remove housing’s monetary premium. Architects can study past resources, like A Pattern Language, to help ourselves and clients remember what was important before fiat. In addition, we can develop new patterns to enhance the high-value design further.
We chose clients willing to consider the house's total cost over time, not just the construction cost. We want clients to understand the opportunity that a well-considered home and spaces around the home can do for the quality of our lives, the people who will live in and experience the architecture for a long time, and the people who get to help create it.
Our firm is working on organizing our process to service bitcoiners with less friction. We are creating a sister company to our 25-year-old firm focused on service products to help more people have a personal architecture in their lives. Our new company will operate on a Bitcoin standard to walk the walk so that we can compare the operation to our existing company. We believe the world is better when more people build things for the right reasons. We accept the mission to focus our work on creating houses worth HODLing.
Bryan
-
 @ d5c3d063:4d1159b3
2025-01-14 03:00:01
@ d5c3d063:4d1159b3
2025-01-14 03:00:01คุณลุงโฉลกย้ำว่าความสงบสำคัญมาก ถ้าใจเราสงบ เราจะมองเห็นโอกาสและความเสี่ยงได้ชัดขึ้น การลงทุนด้วยความโลภหรือกลัวมักทำให้ผิดพลาด แต่ถ้าใจนิ่ง เราจะมีวินัย ทำตามแผนที่วางไว้ ไม่ตื่นตระหนกตอนตลาดผันผวนและยังมองเห็นภาพใหญ่ในระยะยาวได้ดีขึ้นอีกด้วย
!(image)[https://image.nostr.build/28aaa1b47c8c27e094989c1a3cca9db095a560c320ea18402d101d068c8f304a.png]
ลุงโฉลกบอกว่า ความสงบไม่ได้หมายถึงแค่นั่งเฉยๆ ไม่มีเสียงรบกวน แต่มันคือ "ความนิ่งของจิต" ที่ไม่มีเรื่องวุ่นวาย ไม่มีความอยาก หรือความกลัวมารบกวนใจ ลุงบอกว่าเราต้องอาศัย "ศีล สมาธิ และปัญญา" เพื่อให้จิตสงบจริงๆ
การรักษาศีลแบบที่ลุงพูดถึง ไม่ใช่แค่ทำตามกันไปเรื่อย แต่ต้องเข้าใจด้วย เช่น การไม่ฆ่าสัตว์เพราะเรารู้ว่าทุกชีวิตก็มีค่าเหมือนกัน การทำแบบนี้จะทำให้ใจเราโล่งขึ้น สบายใจขึ้น แล้วพอใจสงบ จิตก็จะนิ่ง เมื่อจิตนิ่ง เราจะเห็นทุกอย่างชัดขึ้น เช่น อะไรควรทำ อะไรไม่ควรทำ นี่แหละที่จะนำเราไปสู่ปัญญา
ลุงเล่าเรื่องการให้ทานเล็กๆ น้อยๆ เช่น การทำบุญ 108 บาท ว่าทำไมถึงสำคัญ เพราะมันทำให้เราเริ่มจากจุดเล็กๆ ที่ใจเราเป็นกุศล พอเราให้ ใจเราก็จะรู้สึก "โล่ง" และนี่แหละเป็นจุดเริ่มต้นของความสงบ
บางคนถามว่า ถ้าไม่มีสมาธิมาตั้งแต่เกิดจะทำยังไง ลุงบอกว่า มันอาจจะมาจากกรรมเก่า แต่ไม่ได้แปลว่าแก้ไม่ได้ ทุกอย่างเริ่มได้จากวันนี้ ฝึกไปเรื่อยๆ เดี๋ยวก็ได้เอง
ลุงบอกว่าความสงบไม่ใช่สิ่งที่ได้มาง่ายๆ มันต้องเริ่มจากสิ่งเล็กๆ ทำทีละนิด อย่างการให้ทาน การรักษาศีล หรือการทำสมาธิ ที่สำคัญคือความสงบไม่ใช่สิ่งที่ต้องไล่ล่า แต่เป็นสิ่งที่เกิดขึ้นเมื่อเราหยุดวุ่นวายไปกับความโลภ ความโกรธ และความหลง แค่นี้ก็พอแล้วที่จะสงบจริงๆ
CDCTalk Ep.22 ไล่ล่าหาความสงบ
Siamstr
-
 @ 0403c86a:66d3a378
2025-01-17 19:32:26
@ 0403c86a:66d3a378
2025-01-17 19:32:26The Kansas City Chiefs are set to begin their quest for an unprecedented Super Bowl three-peat on Saturday, facing the Houston Texans in the AFC Divisional Playoffs. Here’s everything you need to know heading into the highly anticipated matchup:
Key Player Updates
- Patrick Mahomes (QB): Cleared to play despite a recent ankle injury, Mahomes is ready to lead his team. Head coach Andy Reid praised his mental toughness, saying Mahomes is “back in the saddle.”
- Isiah Pacheco (RB), Chris Jones (DL), and D.J. Humphries (T): All cleared to play, giving the Chiefs their key contributors on offense and defense.
- Jaylen Watson (CB): Activated from injured reserve, strengthening the Chiefs' secondary.
- Mecole Hardman (WR): Remains on IR and is doubtful for the game, leaving the Chiefs without one of their speediest weapons.
The Matchup
The Chiefs, led by Mahomes, come into this game with a 24-day rest period, the longest in NFL history. It remains to be seen whether the extended break will give them an edge or lead to rust. Mahomes, the winningest quarterback through seven seasons in NFL history (including playoffs), is also undefeated (6-0) in divisional playoff games.
The Houston Texans, on the other hand, are flying high after a dominant 32-12 wild-card victory over the Chargers. Rookie quarterback C.J. Stroud has been a revelation this season, and the Texans’ defense, featuring stars like Will Anderson and Danielle Hunter, has been a force. Anderson and Hunter combined for 1.5 sacks and four QB hits in the wild-card round, and their ability to pressure Mahomes will be critical.
Key Storylines
- Chiefs' Resiliency: Kansas City has shown incredible grit this season, winning 11 games by eight points or less. They've proven they can win in all phases—offense, defense, and special teams.
- Texans’ Defensive Strength: Houston’s cornerback duo of Derek Stingley Jr. and Kamari Lassiter has been among the league’s best, ranking top-three in completion percentage and passer rating allowed. They’ll look to contain the Chiefs’ passing attack.
- Coaching Chess Match: Texans head coach Demeco Ryans acknowledged the challenge of defending Mahomes, citing his quick release and ability to exploit check-downs. Ryans plans to mix up coverages while staying disciplined under pressure.
What’s at Stake
The Chiefs are chasing history as they aim to become the first team ever to win three straight Super Bowls. Mahomes is also looking to tie Joe Montana for the second-most playoff wins by a quarterback.
For the Texans, this game represents a chance to make history of their own. After five previous losses in the divisional round, they’re seeking their first-ever AFC Championship Game appearance.
Game Outlook
This matchup has all the makings of a close contest. The Texans will try to capitalize on the Chiefs’ tendency to play in one-possession games, while the Chiefs’ experience and ability to adapt in critical moments could prove decisive.
With stars on both sides of the ball and plenty of storylines, this game is a must-watch as the Chiefs and Texans battle for a spot in the AFC Championship.
📺 Kickoff: Saturday, 4:30 PM ET
Global Sports Central 🌐 #GSC360
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 8ea48526:e6720a43
2025-01-17 18:56:34
@ 8ea48526:e6720a43
2025-01-17 18:56:34Technology trends toward openness time and again. This is why I say that Freedom Tech is Final Tech. Ideas want to be free. Many people built brands on TikTok that are now threatened, which is a reminder to also build on open alternatives you control. There are many examples from history.
Shift from Monasteries to Printing Press. During the Middle Ages, monasteries controlled the production and dissemination of written knowledge. The printing press decentralized access to information, enabling mass production of books and changing the course of history.
Transition from Trains to Automobiles. Trains required centralized infrastructure and control, while cars empowered individuals to travel freely. This shift from centralized to decentralized transportation transformed the way people lived, worked, and interacted with each other.
Telegraph and Telephone. The Telegraph was initially a closed system, with message transmission gated by businesses. The Telephone enabled direct, person-to-person communication, decentralizing access to real-time information and revolutionizing the way people connect.
The evolution of the Internet. ARPANET, the early internet, was a closed network. With the development of TCP/IP, the open internet was born, enabling global communication, innovation, and access to information on an unprecedented scale.
Operating Systems. Unix, a proprietary OS, was the early powerhouse and later eclipsed by Linux, an open-source alternative. Today, Linux powers millions of devices, from smartphones to servers, and has become a cornerstone of modern computing. It runs the world.
Computers. Mainframe Computers were massive, centralized systems that only large organizations could afford. The development of Personal Computers democratized access to computing power, enabling individuals to create, innovate, and participate in the digital economy.
Television and Radio, once controlled by a few large broadcasters, have given way to Podcasts, which enable anyone to create and distribute content. This has democratized the media, allowing new voices and perspectives to emerge. (Thank you Aaron for RSS 😢)
The music industry. Vinyl, tape, and CD distribution, once controlled by record labels and physical stores, have given way to open file formats like MP3 and streaming services. Artists can connect directly with fans and music is more widely available than ever before. V4V.
Government, Monarchy to Republic. Monarchies, with their centralized power and hereditary rule, have given way to republics, where power is distributed among the people and their elected representatives, increasing class mobility and participation.
Central Banking System and Bitcoin. The experimental Central Banking System, with its centralized control and intermediaries, is being challenged by a decentralized, open alternative. It is transforming the way we think about money, value, and financial freedom.
Digital payments and Ecash. Systems like PayPal & Venmo (once the innovators themselves) are being challenged by open alternatives, such as Chaumian e-cash systems like Cashu and Fedimint. These systems promise to increase financial privacy and autonomy for day-to-day payments.
Social networking. Proprietary social platforms control the data & access. Nostr is an open protocol for authoring & distributing digital content. In the age of AI, authenticity is paramount. Nostr cryptographically proves who authored content, maximizing freedom & transparency.
AI. AI began as closed systems from large corporations investing heavily in computing and training. The open community is catching up and pushing new boundaries. Open models that run locally or in confidential computing enclaves provide AI that is free, open, and private.
This is the pattern: over time, the processes that were controlled by a few get replaced by processes controlled by everyone. Always be searching out open alternatives for the tech you use, that’s where we eventually end up. I’m bullish on the future of technology and humanity. 🤘
P.S. You can see that many of these examples are themselves becoming compromised over time, looking to be disrupted again by open technology.
-
 @ 7ed5bd1c:4caa7587
2025-01-14 00:47:17
@ 7ed5bd1c:4caa7587
2025-01-14 00:47:17Bitcoin กับปริมาณที่จำกัด
ในโลกที่เงินเฟ้อและการพิมพ์เงินอย่างไม่มีที่สิ้นสุดเป็นเรื่องปกติ Bitcoin กลายเป็นทรัพย์สินที่แตกต่างและน่าสนใจด้วยคุณสมบัติที่เรียกว่า "ความหายาก" หรือ Scarcity ซึ่งมีบทบาทสำคัญในการสร้างมูลค่าและความน่าเชื่อถือของมันในระยะยาว
Hard Cap: ขีดจำกัดปริมาณ Bitcoin
Bitcoin มีจำนวนจำกัดอยู่ที่ 21 ล้านเหรียญเท่านั้น และนี่ไม่ใช่เรื่องบังเอิญ แต่เป็นหลักการที่ถูกวางไว้ตั้งแต่การออกแบบโดย Satoshi Nakamoto ผู้สร้าง Bitcoin การจำกัดปริมาณนี้ถูกเขียนลงในโค้ดของ Bitcoin และไม่มีใครสามารถเปลี่ยนแปลงได้
ทำไมความหายากจึงสำคัญ?
- ป้องกันเงินเฟ้อ: ในระบบการเงินแบบดั้งเดิม รัฐบาลและธนาคารกลางสามารถพิมพ์เงินเพิ่มได้อย่างไม่จำกัด ซึ่งนำไปสู่เงินเฟ้อและการเสื่อมค่าของเงิน แต่สำหรับ Bitcoin การจำกัดปริมาณทำให้ไม่เกิดเงินเฟ้อในระยะยาว
- สร้างมูลค่า: เช่นเดียวกับทองคำที่มีจำนวนจำกัด ความหายากทำให้ Bitcoin เป็นที่ต้องการในฐานะทรัพย์สินที่เก็บมูลค่า
- การกระจายและการใช้งาน: การมีจำนวนจำกัดกระตุ้นให้คนที่ถือ Bitcoin มองเห็นคุณค่าและใช้งานอย่างมีประสิทธิภาพ ไม่ใช่แค่เก็บสะสมไว้
ผลกระทบต่อมูลค่าในระยะยาว
- ความน่าเชื่อถือในฐานะทรัพย์สินที่เก็บมูลค่า: ด้วยจำนวนที่จำกัด Bitcoin มีโอกาสที่จะกลายเป็น "ทองคำดิจิทัล" ที่ประชาชนทั่วโลกใช้เพื่อปกป้องทรัพย์สินของพวกเขา
- แรงขับเคลื่อนของตลาด: ความต้องการ Bitcoin ที่เพิ่มขึ้นเมื่อเทียบกับจำนวนที่จำกัดทำให้มูลค่าของมันเพิ่มขึ้นในระยะยาว
- การเพิ่มมูลค่าผ่าน Halving: ทุก ๆ สี่ปี รางวัลสำหรับนักขุด Bitcoin จะลดลงครึ่งหนึ่ง (Halving) ซึ่งเป็นการลดอัตราการผลิต Bitcoin ใหม่ ทำให้ความหายากชัดเจนยิ่งขึ้น
บทเรียนจากความหายากของ Bitcoin
Bitcoin ไม่ได้เป็นเพียงคริปโตเคอร์เรนซีแรกในโลก แต่ยังเป็นทรัพย์สินที่สร้างความมั่นใจในมูลค่าให้กับผู้ใช้งานทั่วโลกด้วยคุณสมบัติของความหายาก คุณล่ะ เชื่อว่าความหายากของ Bitcoin จะส่งผลต่อมูลค่าในอนาคตหรือไม่? ร่วมแสดงความคิดเห็นด้านล่าง!
-
 @ 7bdef7be:784a5805
2025-01-13 22:36:47
@ 7bdef7be:784a5805
2025-01-13 22:36:47The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ e373ca41:b82abcc5
2025-01-17 17:54:57
@ e373ca41:b82abcc5
2025-01-17 17:54:57It was recently the tenth anniversary of the attack on Charlie Hebdo, France's best-known satirical magazine alongside the “Canard enchaîné”. The attack claimed the lives of 12 people, mainly cartoonists and journalists. Even then, it was a watershed moment, and not just in retrospect. Everyone wanted to show solidarity, everyone wanted to be “Charlie”, the phrase “Je suis Charlie” made the rounds memetically.
Charlie Hebdo was known for making fun of everything, including religions and Islam. “What is satire allowed to do? Everything.” So said Kurt Tucholsky, the famous publicist of the Weimar Republic, and that also applied to Charlie Hebdo. This magazine also dared to print Mohammed cartoons from “Jyllands Posten”. The solidarity of other newspapers with Charlie no longer went that far. They wanted to be Charlie, but rather without risk. The collective sign of solidarity fizzled out as lip service.
I was in Paris at the time and witnessed the mass demonstration live. Bernard Maris, a friend of Michel Houllebecq, also died in the attack. Houllebecq's book “Submission” was published on the same day. Coincidence? History and its synchronicities sometimes take wondrous paths.
On November 13, 2015, there was another attack at the Bataclan and around the Stade de France, among other places. Not long before, I was still living in Rue de la Fontaine au Roi in the 11th arrondissement, not far from Place de la République. My favorite café, the Café du Phare, was riddled with machine gun bullets, as was the pizzeria next door. I often sat in this café, writing books, academic texts and my first columns for the NZZ. At the time, I was teaching public law and fundamental rights at the Sorbonne in Paris, among other things, and dealing with issues relating to freedom of expression and artistic freedom on a daily basis.
I took it for granted that these constitutionally guaranteed values were just as important to the public (and especially other journalists) as their place in the constitutions of the West suggested. I was wrong, which was certainly also due to my legal glasses and “déformation professionelle”. At the time, I read more articles that emphasized respect for religions than the value of freedom of expression or artistic freedom. Looking back today, that was when the slippery slope that has led us into the realms of censorship, deletions, shadowbanning, fact-checkers, etc. began.
Freedom that is not used wears out and eventually disappears. Fighting to get it back is much more difficult than defending it. Back then, I wrote texts for newspapers rather sporadically, basically mainly when a topic was important to me and it remained underexposed.
The following text, which appeared in the NZZ at the time, was one such text.
You can find the German original version here.
ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
In the latest issue of “Charlie Hebdo” since the attack in Paris, the editors rub their eyes in amazement. What is wrong with this world? Politicians of all stripes, 50 heads of government and millions of citizens on the streets; Notre-Dame Cathedral is ringing its bells for atheists and the first people are thinking aloud about admitting anarchist cartoonists to the Paris Panthéon, the final resting place of Victor Hugo, Marie Curie and Jean-Jacques Rousseau. You can tell that the editorial team is a little uncomfortable with the collective need to cuddle up.
The worldwide wave of solidarity with “Charlie Hebdo” was overwhelming and important. “I am Charlie” became the collective outcry of the free world. The message is: “If you attack Charlie, you attack me”. What will remain of this when the dust settles? Will the continental plates of our order of freedom have shifted?
A rift trough the free world
Unfortunately, they did it long ago. The attack on “Charlie Hebdo” was an earthquake. But it ultimately only exposed once again what had already been clear and only slightly buried since the dispute over the publication of the Mohammed cartoons in the Danish newspaper “Jyllands-Posten” in 2005: there is a rift running through the free world, and the media landscape as an index of freedoms is showing it.
On the one hand, there are the courageous publications that do not deviate one iota from the Western achievements of freedom of the press, but which ultimately take the rap for it. And then there is the large remainder, for whom freedom seems to be first and foremost the right to remain silent. Magazines like “Charlie Hebdo” are the bad bank of the Western community of values. Charlie & Co. store the toxic papers that nobody wants on their books. The dividend of freedom, on the other hand, is paid out to everyone. If something happens, a declaration of solidarity follows at the minimum price.
Freedom folklore
The Charlie sympathy is to a not inconsiderable extent mere freedom folklore. A masked ball of the enlightened. The smoke from the attacks had barely cleared before the first German-language satirical magazines declared that they would refrain from printing cartoons of Mohammed. The Kalashnikov is the Titanic's iceberg (Note: "Titanic" is the main German satirical paper). American and British newspapers such as the “New York Times” and the “Independent” also waved goodbye and even refused to print the current cover of “Charlie Hebdo”.
This, mind you, in countries where freedom of expression is considered a cultural symbol and freedom as the “right of a soul to breathe”. The soul of freedom now found itself in a vacuum faster than you could shout “Allahu akbar!”. The Turkish newspaper “Cumhuriyet”, on the other hand, dared to do so. Our freedom is being defended in Turkey but no longer in New York or London? A topsy-turvy world.
Some people would like a more harmless satire these days. A satire without exaggeration, overstepping boundaries and disrespect for certain authorities. But the call for moderation means the elimination of its business basis. Satire does not demand approval and consensus. It is not a beauty contest.
When others decide for us
Anyone who refrains from using a caricature simply because it could be provocative, even blasphemous, is already adopting the thought structure and values of those who believe they are in the right when they respond with Kalashnikovs and rolling heads. People are either not proud of the achievement of satire or are not aware of their own rights, and perceive even something that is actually self-evident as an affront. If we ourselves do not know what we should stand for and why, then others have long since decided what we should stand for.
Certainly, no medium is forced to push the boundaries of our legal system on a daily basis. The notorious undercutting of our own standards, on the other hand, will cause them to shrink. Not immediately, but gradually. Until perhaps another standard is accepted at some point. The new censors will then no longer sit in ecclesiastical or secular palaces, as they did in the Middle Ages. But in tent cities in Yemen. Western society is gradually having the rug of its freedom order pulled out from under its feet. And instead of standing together, some people are asking if they can still help roll it up. But of course they still want to be “Charlie”.
Pseudo-security
Self-censorship and anticipatory obedience are a pseudo-safety net. Today it's the Mohammed cartoons. Tomorrow it will be critical reports on Islamism. Anyone who wants to carry out attacks will always find a reason. However, fundamental rights are not a fair-weather crop. Their true existence only becomes apparent when the storm hits. It is cynical to throw up one's hands in the hope that the angel of death will go to the neighboring editorial office.
“Charlie Hebdo” has decided against accepting such external content control. The editorial team also prints a Mohammed cartoon on the cover of the latest issue. Anyone who wonders whether this is wise has missed the point: if it were not done now, it would be the last time this happens in the Western newspaper landscape for a very long time. Those who remain silent agree with the new standard. And all this is happening now, in these hours and days!
It's crazy, but it has to be said: a small anarchic left-wing French newspaper, two-thirds of whose editorial office was bombed out last week, is currently standing almost alone on the front line of the Western world, defending a right it has fought for over 200 years, while machine guns are pointed at it. In the safe hinterland, on the other hand, far away from the impacts, the cardboard comrades fall over in rows at the first bang.
Our freedom is their freedom
At present, it is rightly said that the aim in future will be to win over the peaceful majority of Muslims to our side and not drive them into the hands of the extremists. Yes, many of them will find Muhammad cartoons outrageous or outrageous. But our freedom to think differently is also their freedom to think differently. Our freedom, as unpleasant as it may be to some, also protects moderate Muslims from being forcibly converted at gunpoint by their extremist co-religionists, as is currently happening thousands of times. That makes us allies.
We are currently experiencing a “Sebastian Haffner moment”. The chronicler of the Third Reich describes how he sits in the court library of the Berlin Court of Appeal in 1933 and witnesses the SA taking away all Jewish lawyers. Suddenly, a puffing SA man stands in front of him. “Are you Aryan?” Haffner, who had always rejected this category, answers “Yes” in surprise - and is left alone.
In his notes, he jots down the sentence: “Failed the first test!”
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.

-
 @ 4506e04e:8c16ba04
2025-01-13 22:25:17
@ 4506e04e:8c16ba04
2025-01-13 22:25:17The employment trends in the gig economy are clear. More and more people take on some form of freelance or temporary work often on top of their full time job. In fact, according to recent estimates, approximately 1.57 billion people, or nearly half (46.4%) of the global workforce, engage in gig work. As gig platforms continue to expand across borders and sectors, this number is projected to keep rising.

In the UK, the gig economy is particularly popular, with many workers supplementing their income with side gigs. According to a recent survey, almost half (48%) of UK gig workers have full-time jobs on top of their side gigs, while 71.5% use gig work to supplement their income rather than provide their sole earnings. The top gig occupation in the UK is online administrative work, with 39% of gig workers offering virtual assistance, data entry, clerical services, or similar computer-based tasks. Sounds like a great way to earn some sats, doesn't it?
Despite the growth and popularity of the gig economy, traditional platforms like LinkedIn have reached their peak and become increasingly plagued by spam from aggressive recruiters and profiles of people with increasingly unverifiable experience. Meanwhile all the centralised platforms like Fiverr and Upwork take a significant cut from freelancers' pay, leaving many workers feeling undervalued and overworked. It's no wonder that many are looking for alternative solutions that prioritize fairness, transparency, trust and compensation paid in money that will last!
Here comes Nostr, a decentralized, censorship-resistant protocol that's laying foundations for the future of the gig work. With its censorship-resistant, peer-to-peer approach, Nostr is poised to revolutionize the way we work and connect with each other. In this article, I'll explore why Nostr is an exciting development for the gig economy, what it means for the future of work and what platforms are already available.
What makes Nostr different? It’s built on principles of decentralization, freedom, trust and Bitcoin as its native currency. Forget walled gardens; with Nostr, your identity is your own. Nobody’s mining your data, and no shadowy algorithms are deciding who sees your posts or what posts you should see. It's a perfect setup for a job marketplace where companies post jobs and freelancers get them done. All paid with Bitcoin with no middleman to take your money
And it’s not just theory. Real solutions are already built, transforming how professionals connect, collaborate, and commit their skills, time and creativity. All open-source and Bitcoin/Nostr-centric.
Here are 4 tools you want to check out:
- SatShoot: Think Upwork or Fiverr, but with integrated eCash wallet and zero middlemen. Creators, freelancers, and clients unite under the banner of peer-to-peer gig economy.
- Kanbanstr: A Nostr-native Kanban board for moving tasks from To Do > In Progress > Done and zapping the developers as they deliver.
- GitWorkshop.dev: A decentralized alternative to GitHub, tailored for developers who value freedom and sovereignty.
- Sigit.io: An open-source and self-hostable solution for secure document signing and verification.
These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today!
These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today!
Don't trust - verify!
How can you be sure you're getting help from the right people with the right skills? That’s where the Web of Trust (WoT) comes in.
On Nostr, the WoT is a decentralized trust system that lets users build and evaluate relationships using cryptographic keys and interactions. Instead of depending on centralized authorities to verify identities or manage reputations, the WoT allows trust to grow organically through direct endorsements and social connections.
In this system, your track record matters. As a freelancer, you’re motivated to deliver quality work—not just to get paid, but also to earn positive feedback. This feedback boosts your reputation, helping you secure your next gig. You could get extra points if i.e. you hold a subject matter expert certificate.
Credentials and certifications are still often critical to determine if someone has the skills you are looking for. The idea of certifications could be rebuilt on Nostr with Badges NIP-58. Institutions like Red Hat, Cisco, and others could issue verifiable, NIP-05-backed badges directly to your Nostr public key (“npub”).
It’s simple:
- The certifying body verifies their domain via NIP-05.
- They issue badges for their certifications
- Successful candidates receive badges and wear them on their npubs.
All it takes is that during the registration process for the exam the examinee adds their npub and Voilà! A decentralized, censorship-resistant proof of skills that lives on Nostr. No middlemen, no gatekeepers, you get the right people for the right job!
Here’s a mind-blowing stat: 95% of the world’s population doesn’t own any Bitcoin. With fiat systems teetering, more people will turn to earning Bitcoin instead of buying it at ever-rising prices. Nostr-based platforms are perfectly positioned to capitalize on this trend, offering global access to Bitcoin-based gigs. It’s borderless, censorship-resistant, and a hedge against the collapsing fiat world order.
Nostr clients and solutions are popping up faster than mushrooms after rain. Whether you’re a developer, marketer, freelancer, or just someone curious about the future of work, there’s a tool for you. This explosive growth signals a broader shift: professionals are tired of traditional platforms and are looking for alternatives that respect their privacy, autonomy, and time.
The Bottom Line
LinkedIn’s days are numbered. Services like Upwork and Fiverr or even Uber are praying on freelance fees. The future of services, networking, and professional growth is decentralized, censorship-resistant, and powered by Nostr. Whether you’re a freelancer, a certifying body, or a startup founder, the opportunities are endless.
Here's a New Year resolution for you - say goodbye to spam and hello to sovereignty. The Nostr revolution is here, and it’s time to join the movement!
If you’re inspired to dive into the Nostr ecosystem but need guidance, the NostrDev team has got your back. From conceptualizing your solution to building it out, we’re the go-to experts for all things Nostr. Reach out and start building the future today.
-
 @ 3ac03011:41ecd1bb
2025-01-17 17:38:13
@ 3ac03011:41ecd1bb
2025-01-17 17:38:13Some lessons are worth learning the hard way. Here's one of them: don't waste your energy trying to convince someone that a fact is a fact.
If their belief doesn't harm you, let them hold onto it. And if it does, focus on protecting yourself instead of arguing. Life is a far better teacher than any debate—you can't out-argue reality and false beliefs have a way of unraveling themselves.
The beauty of facts lies in the clarity they bring us. They show us how humanity's darkest moments came not purely from malice but from people simply following incentive structures. Understand the incentives and the chaos of the world starts to make sense.
Those who reject facts often feel the world is against them. They take it personally, not realising facts are impersonal—they simply are. When you accept them, you're no longer at odds with reality and peace becomes possible.
So don't spend your time persuading others. Instead, build the life you want. Focus your energy on creating, achieving and living. The truth doesn't need you to defend it; it's always there, waiting to be seen.
In the end, the clarity you gain by focusing on your own path will bring you more freedom and fulfilment than any argument ever could. Spend your time living, not debating.
-
 @ 17538dc2:71ed77c4
2025-01-13 18:17:24
@ 17538dc2:71ed77c4
2025-01-13 18:17:24Sci-Hub 2024 year end review is translated to English by Kagi Translate from Russian. Original text can be found in Sci-Hub's telegram channel https://t.me/freescience.
RESULTS OF 2024
First. The project received donations totaling 2 million dollars in meme coins.
The project is actively used by many students in China, which is why a group of Sci-Hub fans has emerged there. As far as I understand, the organizer of the group is actively interested in the topic of cryptocurrencies (even wrote a book). Somewhere in mid-November, the Chinese launched a meme coin in honor of the Sci-Hub project. At its peak, the coin's price reached 5 cents, and now it is somewhere around 1-2 cents. This means that the exchange rate of the Sci-Hub cryptocurrency is now almost equal to the ruble exchange rate (100 to one or so).
In general, I converted part of these donations into normal, traditional cryptocurrency (like Bitcoin) and paid for servers several months in advance. The other part is still sitting in meme coins—I hope that the token will still grow in price (there is a promotion plan). Of course, this is risky, but Sci-Hub is a project that is not afraid of risk. Therefore, anyone who wants to invest in Sci-Hub by purchasing this token can do so here: www.coingecko.com/en/coins/sci-hub
Second. A dissertation on the topic of open scientific knowledge has been defended at the Institute of Philosophy.
For those interested in the history and philosophy of science, I defended a dissertation in April at the Institute of Philosophy on the topic that scientific knowledge should be open (otherwise, it is strange to call it scientific at all). The work shows that open communication is one of the basic traditional values of science when considering science as a social institution. In other words, journals that charge for access to scientific articles are a kind of 'non-traditional orientation journals.'
Moreover, openness is an important prerequisite for rationality. Rationality is not limited to the criterion of falsification (hello Popper); it is a much more complex concept.
You can familiarize yourself with the text of the dissertation here: web.archive.org/web/20240425100014/https://iphras.ru/page26414303.htm (I provide the link through the web archive because the Institute's website, strangely enough, is glitching again at the time of writing this post).
All criticism and comments (as well as praise) regarding the dissertation can be sent to my email.
Third. Work has begun on a new declaration of open access to scientific knowledge.
Currently, all discussions on the topic of open science are conducted within the frameworks defined by the so-called BBB declarations back in 2001-2003. Within these frameworks, two main types of open access are recognized: gold, meaning open journals with an author-pays model, and green, which refers to repositories like the well-known arXiv. We can also add the so-called diamond open access, which includes open journals that are free for both authors and readers.
However, since 2003, internet technologies have advanced significantly. Today, we can already talk about such types of open access as blue (through academic social networks) or red (your beloved Sci-Hub). It is time to adopt a new declaration of open access to scientific knowledge that corresponds to the current state of scientific and technological progress.
A preliminary version of the declaration can be read and signed here: open.science.do
We will be more actively engaged in this in the coming year. Signing the declaration is an important step towards recognizing access to scientific knowledge through sites like Sci-Hub or Libgen as completely legal and ceasing to pursue them—first in the former USSR, and then in all countries of the world.
Fourth. In 2024, about one billion articles were downloaded through Sci-Hub. Despite the fact that this is unfiltered statistics, the fact remains: the popularity of the project has not decreased but only grown, despite the fact that Sci-Hub has not been updated for quite a long time. Of course, this does not mean that the site will not be updated at all now—just that the patient is more alive than dead (no matter how much some haters might wish otherwise).
The cause of open access to scientific knowledge will definitely prevail—because good always triumphs over evil.
In the new year, I wish all scientists new discoveries and large grants. Happy New Year, comrades!
-
 @ 543d73b5:977c83a9
2025-01-17 15:24:32
@ 543d73b5:977c83a9
2025-01-17 15:24:32In the digital world, human beings occupy space with digital representations of their physical-world information. When viewed separately, these digital representations can be readily dismissed as merely random collections of digital assets. However, when examined as a whole, these same representations reveal themselves to be extensions of a person’s digital self-sovereign identity.
Moreover, as these two worlds, the digital and the physical, continue to merge into one space, this digital identity has become more commonly used as a primary means of validation and verification of a person’s digital and physical existence. Therefore, the primary rights of ownership for this digital form of identity must be safeguarded and protected in the same manner, and with the same level of importance, as is typically observed with individual identity in the physical world.
It is for this reason that this Ethos of Digital Self-Sovereign has been drafted. And, it is for this purpose that it is presented to the digital community for their consideration and adoption into their standard governance frameworks.

THE RIGHT TO DIGITAL PRIVACY
PROTECTED PRIVACY = the SECURITY of PROPERTY which affirms our FAITH in our DIGITAL SELF-SOVEREIGNTY.
Digital Privacy means that people are the sole owners of their own digital property and they inherently possess immutable authority over the use of that property. As owners, they have full right of control over the “why”, “when”, “where”, and “how” their digital assets are accessed. Digital Privacy is about an individual’s ability to maintain control of their digital property when interacting with any entity, system, or organization within a digital environment. Therefore, with every and any form of digital interaction, every person should have the expectation of privacy.
THE RIGHT TO DIGITAL INDEPENDENCE
COMPREHENSIVE DECENTRALIZATION = the INDEPENDENCE of CHOICE which affirms our BELIEF in our DIGITAL AUTONOMY.
Digital Independence is the ability for individuals to interact freely with any entity, system, or organization within the digital space. Centralized control of digital interactions is in direct conflict with the idea of digital independence. Within decentralized environments, there is no intermediary entity to serve as a central authority over the authenticity of digital relationships. Therefore, systematic decentralization must be promoted, propagated, and implemented throughout every corner of the digital world to ensure that the right to Digital Independence is fully available to every individual.
THE RIGHT TO DIGITAL TRANSPARENCY
CLEAR GOVERNANCE = the TRANSPARENCY of AGREEMENTS which affirms our TRUST in our DIGITAL RELATIONSHIPS.
Digital Transparency is the application of open, honest, and fair relationships between individuals, entities, systems, and/or organizations within a digital space. One can argue that transparency is required to secure trust between different parties in a digital-based relationship. However, a truly transparent relationship can actually eliminate the need for trust between parties; since each individual is has the ability to confirm the validity of all interactions because all information about the shared relationship is openly available to all parties involved in the relationship.
(First Drafted 11/11/2021)
-
 @ 000002de:c05780a7
2025-01-13 17:57:59
@ 000002de:c05780a7
2025-01-13 17:57:59I've lived most of my life in California. I am very familiar with Southern California and have traveled through it countless times over the last 30+ years. I've enjoyed spending time in SoCal. My heart goes out to the people that have lost everything as well as the people living on the edge fearing the fires will come their way. Its terrible. Its also not a new story as we have seen this many times before, just not affecting this many people.
There are many theories and factors people are discussing online. Many IMO are missing the key issues. Regardless of how the fires started, sadly this event has only a matter of time. Been thinking about this issue for years and thought I would share my thoughts with you all. These are my opinions, I'm not an expert but I do live in the state and have paid attention to this topic since I was a kid. I've always loved the forests of California and I care about the beautiful state and its people. As I've said before, the government of California is evil. After you read this I hope you will understand why I believe this. I think Gavin Newsom is to blame for many of the issues we face but its bigger than one man. Removing him from office will not fix this problem. It is far more complex.
PG&E's Electricity Infrastructure & The Consequences of Monopolies & Price Controls
I'm not sure at this point if PG&E is at fault for starting these fires but it is at fault for many in the recent past. PG&E is the largest utility company in the state and has a monopoly over most of the state. SoCal Gas & Electric has monopoly over the rest of the state. Both are public utilities which essentially means these are more like government controlled entities than private companies. California has long used price controls on electricity. We know that doesn't work. The state has restricted to addition of new power generation my entire life. So of course PG&E has to import power from other states requiring higher rates for their customers. Due to the mismanagement of PG&E the company has not kept its infrastructure up to date. Many fires are started by shorts in power lines and equipment that is older than me. If you wanna immediately find common ground with a Californian complain about PG&E. So who is at fault? PG&E and the state government. Since PG&E is essentially a government entity I lay the blame on the state.
The problem is that most people have been programmed to believe utilities need to be controlled by government in addition to being monopolies. Its one of the most illogical beliefs to me. Since PG&E is a company people tend to just blame them instead of the politicians and the state. The result is politicians have little incentive to change things.
The Smelt, Salmon, and Water
The Smelt is a small fish that the Salmon eat. There has been a push for many years to restore the historic water ways that are a part of migration paths of the Salmon in California. California's Central Valley(North of Southern California) is a massive producer of produce and other agriculture products. The issues around water are complex and the most frustrating thing for me, a person that was born and raised in the state is how the issues are rarely discussed in rational ways considering trade-offs. Instead there are usually just two sides presented.
- The farmers need water so we need to build more water storage(dams).
- We need to restore the historic water ways of the state and the specifically the historic Salmon runs through those water ways.
I don't have a problem with either of these goals. The issue is that they are in opposition to each other. The fact is that water is needed by farmers in the Central Valley as well as people in Southern California. Southern California would not support the current population without the water from other places being funneled to that region. The farming industry of Central California would also not exist without sufficient water. Additionally the diversion of natural water flows via dams also has reduced flood risks in the state. So when you hear people talking about stealing water or SoCal doesn't have the water it needs this is a bit of context you might not hear. The state has done a terrible job managing water over the past 20 years.
The Historic and Natural Occurrence of Wild Fires
Over my lifetime I have watched as humans have build homes in areas that historically are prone to wild fires. As a kid in the government school system I was taught about forestry management. How the state and federal forestry services would clear dead brush, execute controlled burns, and cut fire lines to help prevent out of control wild fires. Even with this policy there was never a guarantee that homes could be protected but it does seem like that policy helped keep them smaller.
What many people do not understand about wild fires is that they are natural and needed. When the population of California was sparse there weren't any fire fighters putting out fires. They would just burn themselves out. The giant sequoia trees actually depend on wild fires to a certain extent. These fires would burn out the dead growth as well as smaller trees making way for only the strongest to survive.
With the massive population growth of California over the past 100 years fire fighters have began to fight this form of nature. Like many natural forces this usually only postpones the inevitable. Its a tough decision. Do you let natural do its thing or protect people. Growing up the policy was to protect people. This meant putting out fires that threatened humans and their property.
This included what I mentioned before. Logging, clearing out dead growth, controlled burns as well as other methods. In recent years the policy has shifted away from these policies and it is clear to me the results are disastrous. Once again trade-offs are rarely discussed when the government changes policy. Of course doing controlled burns affects air quality. Climate change is often mentioned as a reason to suspend controlled burns but it is clear to me that's just kicking the can down the road. The fires are going to happen. It is just a matter of time.
Human Expansion
In my opinion the single largest factor in these fires is the fact that humans have expanded into areas that historically are often cleared by wild fires. When government policy prioritized humans the risk would be reduced but instead of this the state has prioritized "environmental" interests. What makes this worse is that the state has also put their finger on the scales in regard to insurance.
Once again, I rarely hear the fact that more people are living in forests as a massive factor. I have traveled all over the state over the last 30 years and the growth is incredible. I don't have a problem with his growth but you have to recognize the risk. In a free market insurance should handle this issue of risk.
The Role of Insurance
Insurance is all about calculating risk. If you seek insurance the higher your risk the higher the premium. On both ends of the scale of risk both parties will not enter into an agreement. If the risk is very low individuals will not naturally see a need for insurance. Insurance companies LOVE to sell insurance with low risk. The opposite is true. If your risk is high an insurance company cannot provide assurances of payment.
The thing people most miss about insurance is that they play the role of evaluating risk. They are incentivized reduce risk, much more than the state. Recently insurance companies have stopped offering polices in California due to introduction of price controls and the state's forestry polices. In some of the areas now burning these companies have declined to renew fire polices. Why? Because the risk was to high. That should tell us something.
What Is the Answer
Remove regulations altering the natural market force of insurance. If an area is very risky insurance should be high. That is a signal that can very well save lives. I think people should be allowed to live on any property they own or rent. They should be able to do so without insurance as well. But insurance should be allowed to do what it does. Reduce risk and provide a valuable signal to the market. The same goes for power utilities. There needs to be a removal of the monopoly held by PG&E. They need to build nuclear plants in the state to provide power for the growing population. I believe the market, if allowed to operate would fix these issues.
When it comes to environmentalism the state should pick a side. People, or environmentalism. If they pick environmentalism they should not bail out the insurance companies and restrict building back in areas affected by wild fires. To be clear, I oppose that position because I don't believe it is actually good for the environment of California and its destructive to human life. The other path is to return to managing the forests. Restore the forestry practices that worked for decades. Allow insurance to operate as a free market and listen to the market signals.
When it comes to water its a similar situation. The reality is until farming practices change to be more regenerative and if the population level continues to grow the state is going to have to build more water storage and divert the natural flow of water. Humans are competing for resources with Salmon. I would love to see California restored to a more natural state but the reality is that will not be possible without a drastic population decrease and more fires like this. I don't think the people actually want that. They have been lied to for decades by politicians and environmentalists.
I know this is a long post, there is much more I could say and I'm sure I'll hear it in the comments but I tried to keep this short. Its a very complex issue that the state and Newsom largely own. They will try to distract with many other things but this is where the focus should be IMO.
originally posted at https://stacker.news/items/848838

