-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 04c195f1:3329a1da
2025-01-29 08:16:38
@ 04c195f1:3329a1da
2025-01-29 08:16:38Over the past week, Sweden has been rocked by an unprecedented wave of domestic terrorism. Bombings, shootings, and gang-related violence have escalated to a level that even the most hardened observers find shocking. The Swedish people are waking up—sometimes quite literally—to explosions outside their homes, their neighborhoods resembling conflict zones rather than the peaceful Scandinavian society they once knew.
A Month of Terror
Since the beginning of the year, Sweden has witnessed at least 32 bombings, averaging more than one explosion per day. In a sign of how routine this has become, state media outlet SVT now maintains a "live ticker" tracking the growing number of explosions—reminiscent of the death and infection tickers used during the COVID-19 pandemic. The attacks have struck cities large and small—Stockholm, Uppsala, Helsingborg, and Örebro among them. Some explosions have targeted residential buildings, even bedrooms where children sleep. Others have been part of gang warfare, retaliation for unpaid debts, or attempts to intimidate rivals.
Just in the past 24 hours, five separate explosions have rocked Stockholm. A grenade attack forced a school into lockdown, while an explosion in Årstaberg destroyed the entrance of an apartment building. This is not the first time—and it certainly will not be the last.
Sweden’s Political Paralysis
Despite this unprecedented security crisis, the Swedish government refuses to take meaningful action. Prime Minister Ulf Kristersson recently acknowledged the situation, stating:
“The criminal gangs show total disregard for the public. This is domestic terrorism that we must fight with the full force of society. The police are working intensively to prevent and stop acts of violence. The police can now conduct preventive wiretapping, and security zones are in place. These are important tools. But more is needed.”
However, this is yet another attempt to address symptoms rather than causes—and it will fail to even achieve that. Last night, I participated in a livestream where former MP Jeff Ahl likened the government's approach to trying to stop arterial bleeding with a band-aid. A fitting description indeed.
Meanwhile, rather than declaring a national emergency, Sweden’s political elite have prioritized ideological pet projects. Minister Paulina Brandberg was busy opening a new DEI (Diversity, Equity, Inclusion) office at Chalmers University while bombs tore through Stockholm’s suburbs. Justice Minister Gunnar Strömmer held a crisis meeting with the police last week, only to suggest that the government might be able to stop the gangs in eight years—an admission of failure if ever there was one.
The Root of the Crisis
The media and political establishment refuse to address the root cause of this descent into chaos: mass immigration and the importation of criminal clan networks. The reality is undeniable:
-
Areas like Rinkeby and Botkyrka—once Swedish working-class neighborhoods—now have overwhelming non-Swedish majorities, with Rinkeby exceeding 95% and Botkyrka over 60%. These are just two examples of the hundreds of neighborhoods across Sweden where Swedes are now a minority, where criminal clans thrive, and where gangs have effectively taken control—not just of the streets but also of local commerce and entire business districts.
-
Organized crime syndicates, many with roots in the Middle East and North Africa, exert dominance over these areas, operating parallel societies with little to no interference from Swedish authorities.
-
Police estimate that 30,000 individuals are active in criminal gangs—when factoring in extended networks, the number may be in the hundreds of thousands.
-
Most of these people should never have been allowed into Sweden in the first place.
“We’re Used to It”
Perhaps the most chilling aspect of this crisis is the growing resignation among Swedes. After a bombing in Upplands-Bro last night, one resident summed it up:
“No, I’m not worried. I’m used to it.”
This normalization of terrorism is a direct consequence of decades of political negligence, ideological blindness, and a refusal to admit policy failure. Sweden’s leaders have deliberately ignored the warnings. They have allowed the chaos to fester. And now, they pretend to be shocked as the country spirals deeper into lawlessness.
What Comes Next?
Let’s be clear: these bombings will not stop. If history is any guide, Sweden’s authorities will issue statements, hold meetings, and maybe even arrest a few foot soldiers. But the broader networks, the root causes, and the state’s unwillingness to reclaim control over the country remain unchanged.
The question is not whether Sweden can recover. The question is whether Swedes are willing to demand real change. And if they do not, how much further can this country fall before it collapses altogether?
I will continue to report on this crisis—because while mainstream media acknowledges the violence, they refuse to confront its root cause. If we do not acknowledge the failure of multiculturalism and dismantle this ideological experiment, we will never resolve this crisis.
For near-daily updates, follow me on X, Telegram, and Nostr, where I report on these events as they unfold. Stay informed, stay vigilant, and if you value my work, consider subscribing and sharing this newsletter.
■
-
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 20e7c953:3b8bcb21
2025-01-29 05:53:46
@ 20e7c953:3b8bcb21
2025-01-29 05:53:46Thai Nostriches #Siamstr
Get Ready for Sats N Facts 2025! https://satsnfacts.btc.pub/ 🎉
Join us for a series of exciting events where Bitcoin, Nostr, and local Thai communities come together to innovate, create, and connect! Here’s the breakdown for the 2 main activities:
🛠 Hackathon Overview
https://satsnfacts.btc.pub/hackathon/
This is your opportunity to work alongside leading teams and individuals pushing the boundaries of Bitcoin and Nostr. Whether you're a developer, designer, an educator or a visionary, your contributions can help shape the future of decentralized technology.

What to Expect:
Participate in the sessions by pitching and listening to others ideas or setting up a spot in the schedule. The event is designed to be a “decentralized and collaborative” effort between all participants, with activities being put together with attendees’ feedback.
🤝 Introducing Potential 🇹🇭 Participating Teams
nostr:npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5 – Bitcoin Education and Translations for the Thai community; this would be an ideal occasion in order to connect with international developers in order to curate and share insights within the #Siamstr community
Other Projects that are formally invited are:
nostr:npub1l8ktdyyhwxh4ty5cf48tl72g8ra286nr9klmvqznvk3aqyjkucgsem97q9 – Simplifying Bitcoin payments through intuitive tools
nostr:npub1nsxnfp5690uplzgkslthcvt6269htshqeymhghthenr9wnpt869q57q2hf – Innovating Lightning infrastructure and Bitcoin ATMs
nostr:npub16elg3wf8nffkymylw9kfwecc45j9c30lufrrzx2zf5vmxjlcgkkq3xc6d7 – Enhancing social innovation through Nostr-powered solutions
🎨 Art Exhibition

What else to expect?
A showcase of Bitcoin and Nostr-inspired works by local Thai artists like nostr:npub16unl8g9ucanlpfvp94sdjdv2f4mukm2ywmgrywnrfdgt98qwrrdq0qcn35 nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu and nostr:npub1uprlst7kjp0eyfxe4yn7q36gr885mjr9fm6ejfqt8pmdta7stv9s2xvysq - Huaiphueng Project community members.
Celebrate the creativity of our culture with a fusion of tech and art!
📍 Location: Weave Artisan Society, Chiang Mai
📅 Date: 8th - 10th February
🎟 How to Join: Register either as a Lead or Attendee, wait for confirmation from SnF team and get your ticket as a Thai National via Formstr at https://satsnfacts.btc.pub/#tickets
🌟 Why You Should Join:
If you are a Bitcoiner and Ostrich in Thailand the question should be re-formulated to... WHY WOULD YOU NOT JOIN ?
Support and grow the local ecosystem while having a great time with fellow international Bitcoiners.
✨ Mark your calendars and spread the word! Stay tuned through the links or connect with us on Nostr.
Let’s build a stronger Bitcoin & Nostr future at Sats & Facts ✌️
Pictures by nostr:npub15l5mxmljftnnqur8gf2nkjj2yuemqy2kuly7yc29lx7x598svx5s447rgk 👇


เราจะทำอะไรต่อไป ?
AND WE SAID;
ONWARDS
-
 @ 3c7dc2c5:805642a8
2025-01-28 23:02:07
@ 3c7dc2c5:805642a8
2025-01-28 23:02:07🧠Quote(s) of the week:
'DeepSeek increases my conviction that Bitcoin must be the hurdle rate for capital deployment. AI innovation at this speed and scale will substantially disrupt valuation metrics across industries and is not currently priced in. Those who secure a war chest of Bitcoin will be the long-run winners, picking up distressed assets for pennies on the dollar. Focus on three things: AI, Bitcoin, and energy.' -Matt Cole
Just to elaborate on the above statement by a tweet by Dylan Leclair in 2021:
'Problems: 1. Infinite liquidity doesn’t fix a solvency issue. 2. Inflationary monetary policy can’t work against technological deflation.
Solution: Bitcoin'
To me it is crystal clear: AI deflates, central banks print, and Bitcoin absorbs the chaos. BTC was built for this.
🧡Bitcoin news🧡
On the 21st of January:
➡️MicroStrategy shareholders approved increasing the total number of shares from 330 million to 10.3 billion, paving the way for future fundraising to acquire more Bitcoin (55.8% approval).
➡️Bitcoin's mining difficulty has seen a 24% quarterly increase since August 2024. Saylor: "Bitcoin mining difficulty has reached a new all-time high. Creating BTC requires proof of work and significant energy, making it increasingly expensive over time. Historically, mining difficulty and price are closely linked—a strong signal for bullish momentum."
The Difficulty Regression Model estimates the cost to mine 1 Bitcoin at $33.9K, while Bitcoin trades at ~$104K. This ~3x profitability margin showcases miners' resilience, even as mining difficulty continues to rise in this cycle: Glassnode
➡️'Bitcoin ETFs launched a year ago and now hold over 1,100,000 BTC which is ~5.7% of the current supply.' -Jameson Lopp
➡️The governor of the South African central bank scoffs at the idea of a strategic Bitcoin reserve asking, “Why not a strategic beef reserve? Why not an apple reserve? Why Bitcoin?!”
And at that same panel discussion at the World Economic Forum, we had Brian Amstrong, CEO of Coinbase, praising Bitcoin as the best money in the world. “It’s clear at this point, bitcoin is a better form of money than gold…For a store-of-value, governments must hold bitcoin over time”
➡️Corporate announcements this morning:
- MicroStrategy has bought 11,000 BTC for $1.1 billion, and now holds 461,000 bitcoin. Microstrategy now owns 2.195% of all Bitcoins that will ever exist.
- KULR Technology Group has bought 79 BTC for $8 million, and now holds 510 bitcoin.
- Genius Group has bought 52 BTC for $5 million, and now holds 420 bitcoin.
➡️ETH holders absolutely deserve what is coming. The following text/tweet by Vitalik Buterin just shows you how decentralized Ethereum is.
'No. This is not how this game works. The person deciding the new EF leadership team is me. One of the goals of the ongoing reform is to give the EF a "proper board", but until that happens it's me. If you "keep the pressure on", then you are creating an environment that is actively toxic to top talent. Some of Ethereum's best devs have been messaging me recently, expressing their disgust with the social media environment that people like you are creating. YOU ARE MAKING MY JOB HARDER. And you are decreasing the chance I have any interest whatsoever in doing "what you want".
TLDR: There’s no “me” in Bitcoin. If your "crypto" has a leader, it's not decentralized. Period!
➡️Bitcoin mining in Texas has had a positive impact on the state's power grid and has also potentially saved billions by reducing reliance on expensive and polluting gas-peaking plants, according to the latest report from the Digital Assets Research Institute.
➡️Critical Metals Corp secures up to $500M in convertible note financing to purchase Bitcoin for its Bitcoin treasury strategy. This makes them the first Nasdaq-listed critical minerals company to adopt Bitcoin as a treasury reserve asset.
➡️Legendary investor Ray Dalio says Bitcoin he owns Bitcoin to “reduce the risk of a portfolio”.
On the 22nd of January:
➡️ Finally Ross Ulbricht is free. Pardoning Ross is a promise fulfilled by Trump. Revealing that this was an act of the deep state is next level, calling the people who convicted him "scum." Trump: "The scum that worked to convict him were some of the same lunatics who were involved in the modern-day weaponization of government against me. He was given two life sentences, plus 40 years." Politicians stay Politicians, but I am glad Ross is free.
Ross didn’t sell drugs—he built an anonymous, free, and open platform on Tor called Silk Road.
'Silk Road sold apparel, art, books, collectibles, computer equipment, electronics, herbs, and yeah—drugs. But according to friends who used it, Silk Road was arguably the safest way drugs were ever sold: no street violence, no shady deals, and zero fentanyl. Everything was tested and peer-reviewed, like an Amazon for substances.'
Don’t forget… the DOJ seized 173,991 Bitcoin directly and indirectly from Ross Ulbricht. It was $34 Million when they took it. Today it’s worth ~$18.4 BILLION.
Newcomers to Bitcoin may not understand why old-timers care so much about Ross Ulbricht. Great explanation by Vijay Boyapati:
https://x.com/real_vijay/status/1881869635915809001
On the 23rd of January:
➡️China sold its entire 194K BTC stash, seized from PlusToken, despite official claims of transferring it to the national treasury, according to CryptoQuant CEO Ki Young Ju.
➡️YouTube rival Rumble to launch digital wallet to make Bitcoin and Tether payments. Tether-backed video-sharing platform Rumble to launch Rumble Wallet, which will allow creators to receive tips and subscription payments directly in Bitcoin or Tether.
➡️Ledger co-founder David Balland was kidnapped and a cryptocurrency ransom was demanded. He was rescued by GIGN and multiple suspects are in custody.
https://x.com/0xLouisT/status/1882711063306666287
On the 24th of January:
➡️SAB 121 has been rescinded, allowing banks to custody Bitcoin. Banks can now offer Bitcoin services to hundreds of millions of customers.
The Bitcoin Podcast: But what exactly is SAB 121 and what does its repeal mean for Bitcoin? Eric Weiss breaks it down: "I think that's gonna be a massive, massive catalyst down the road for a US dollar price appreciation of Bitcoin." https://x.com/titcoinpodcast/status/1882599727880917490
➡️Bitcoin is above $100k but retail interest is the lowest it's been in 3 years.
➡️How popular is Bitcoin on Wall Street? 6% of all the money flowing into American ETFs is now Bitcoin.
➡️A user just successfully sent ~$866,430,722 worth of Bitcoin for a 33¢ transaction fee using the blockchain.
➡️President Trump’s new executive order protects American’s right to use public blockchains, develop and deploy software, participate in mining and validation, transact without censorship, and safeguard their own digital assets. The freedom to build, mine, and hodl Bitcoin.
➡️Spot Bitcoin ETFs are now bigger than ESG ETFs.
On the 25th of January:
➡️Bitcoin has completely dislocated from its ~70-day global M2 lag. It's been on a run of its own for the last 30 days.
➡️As mentioned above but also in the segment (Macro/Geopolitics) Trump took a bold stand against CBDCs, protecting Americans from the financial tyranny they represent. But now, Ripple is working behind the scenes to undermine his administration and sneak CBDCs in through a backdoor while lobbying heavily.
Ripple is public enemy number one this cycle, and it’s time everyone recognized it. You don’t hate XRP enough, plain and simple. If you understood what they’re trying to pull, your outrage would be through the roof.
Jameson Lopp: There's Bitcoin, then there's Crypto, then there's Ripple. Ripple has attacked Bitcoin at a level rivaled only by BSV's lawsuits. Ripple explicitly wants to power CBDCs. They have always been focused on servicing banks. Few projects are as antithetical to Bitcoin.
Brad Garlinghouse douchebag and CEO of Ripple: "We would not be profitable or cash flow positive without selling our XRP holdings.” All 100 billion XRP tokens were created out of thin air by Ripple Labs in 2012 and reserved for insiders. Ripple's income comes from dumping these coins on the public.
On the 26th of January:
➡️Only 1,056,700 Bitcoin is left to be mined, forever.
On the 27th of January:
➡️MicroStrategy has acquired 10,107 BTC for ~$1.1 billion at ~$105,596 per Bitcoin and has achieved a Bitcoin Yield of 2.90% YTD 2025. As of 1/26/2025, they hodl 471,107 Bitcoins acquired for ~$30.4 billion at ~$64,511 per Bitcoin.
➡️Russia's largest energy supplier Rosseti to launch Bitcoin mining operations in areas with excess electricity, aiming to optimize energy use, increase tax revenue, and support the development of BTC mining in Russia.
➡️Brazilian oil giant Petrobras to launch Bitcoin mining operations using excess natural gas produced during oil extraction, to reduce energy waste and carbon emissions.
➡️MicroStrategy to offer 2.5 million shares of 'Series A Perpetual Strike Preferred Stock' to buy more Bitcoin.
➡️Arizona is the first state to pass a bill out of committee to create a ‘Strategic Bitcoin Reserve.’ Co-sponsored by Wendy Rogers and Jeff Weninger, the bill now heads to the state Senate floor for a vote.
➡️El Salvador is now the second fastest-growing tourist destination in the world. Bitcoin and Tourism.
➡️'Cboe BZX Exchange files amended rules to allow in-kind redemptions and creations for the ARK 21Shares Bitcoin ETF. This follows Nasdaq’s similar filing for BlackRock’s iShares Bitcoin Trust, signaling progress in spot Bitcoin ETF mechanics.' -Bitcoin News
What we have learned last week: 'Vitalik doesn’t buy Ethereum, only sells it. Ripple doesn’t buy XRP, only sells it. The US doesn’t buy USD, only prints it. There can only be one Bitcoin— wake up' - Cory Bates
💸Traditional Finance / Macro:
👉🏽NVIDIA closes the day down -17%, officially erasing -$590 BILLION of market cap. This marks the largest 1-day loss of market cap in a single stock in history, and it's not even close.
🏦Banks:
👉🏽no news
🌎Macro/Geopolitics:
On the 20th of January:
👉🏽 Trump: "We will end the "Green Deal" with the "liquid gold under our feet". 'The Netherlands has €1.000 billion of "liquid gold" natural gas in Groningen. The Rutte government destroyed our gas wells, and filled them up with concrete because they could not compensate 20.000 homes.' - Henk Otten I am not sure about the fact that we filled them up with concrete. As a matter of fact, I think the Netherlands could start immediately if needed.
On the 21st of January:
👉🏽The US Treasury has reached its debt limit and is now using 'extraordinary measures' to continue operating.
👉🏽Sam Callahan: 'A new study reveals that, over the past 20 years, Congress has largely ignored large fiscal deficits, making little effort to reduce them. The authors discuss what's required for "successful deficit reduction," but they don't seem to realize that nothing stops this train.'
https://www.brookings.edu/wp-content/uploads/2024/09/4_AuerbachYagan.pdf
👉🏽Interest payments on the US national debt now exceed spending on national defense.
👉🏽Billionaire hedge fund manager Ray Dalio, founder of Bridgewater Associates, just warned that the UK could be heading for a “debt death spiral” his is in which the UK has to borrow more and more money to service its rising interest costs
👉🏽'The rich are getting richer faster than ever before: US household net worth has risen ~$56 TRILLION since Q1 2020 and hit a record $160 trillion in Q3 2024. Currently, the top 10% own $111 trillion of all wealth, accounting for 69% of the total. The top 0.1% alone own a massive $22 trillion, reflecting 14% of household net worth. On the other hand, the bottom 50% holds just $3.9 trillion, or 2.4% of wealth. This comes as the S&P 500 and the Nasdaq 100 have risen 128% and 166% since Q1 2020 while national home prices have surged ~50%. The wealth gap is growing.' -TKL
👉🏽Phillipp Heimberger: 'It is unclear how national governments in the EU are supposed to square the circle: to ramp up military spending and public expenditures on climate and digitization while at the same time achieving primary fiscal surpluses over the medium run to meet new EU fiscal rules.'
On the 22nd of January:
👉🏽'Gold's global market cap to world GDP ratio reached a RECORD 16.7% in 2024. This ratio has doubled in 10 years and quadrupled since 2001. Nominally, gold’s market value sits near an all-time high of ~$18.5 trillion. This comes as gold has posted an average annual return of +9.5% since 2000, making it one of the best-performing major asset classes this century. Since the start of 2024, gold prices have hit 41 all-time highs and are up +33%.' - TKL
On the 24th of January:
👉🏽The Bank of Japan raises interest rates by 25 basis points to their highest level since 2008.
👉🏽'The ECB proposed a holding limit of €3000 for the digital euro. Banks want €500, otherwise, it will cost them too much... This whole digital euro project is such a huge clusterfuck in slow-motion.' - Paul Buitink
https://www.ledgerinsights.com/progress-on-digital-euro-holding-limits/
Meanwhile, Trump is going all in against ‘Central Bank Digital Currencies.’ ‘taking measures to protect Americans from the risks of Central Bank Digital Currencies (CBDCs), which threaten the stability of the financial system, individual privacy, and the sovereignty of the United States’
Daniel Batten: 'When it comes to digital currency: Will the EU pivot and head down the path of democracies such as the US who see Bitcoin as consistent with its democratic values or continue down the path of autocracies like Russia & China who see CBDCs as being consistent with their autocratic values?'
On the 27th of January:
👉🏽Volkswagen ready to become Chinese Volkswagen is prepared to let Chinese electric carmakers take over production lines in its struggling factories.
👉🏽'DeepSeek officially announces another open-source AI model, Janus-Pro-7B. This model generates images and beats OpenAI's DALL-E 3 and Stable Diffusion across multiple benchmarks.' -TKL OpenAI: - 10 years old - 4,500 employees - raised $6.6 billion DeepSeek - less than 2 years old - 200 employees - less than $10 million capital used
DeepSeek developed and open-sourced an equal or better product and had it out for free, likely killing the business model of OpenAI Anyway, if you want to read more on DeepSeek, and how seems like how they seem to have shifted the paradigm on how AI LLMS work, I highly recommend the following thread by Morgan Brown: https://x.com/morganb/status/1883686162709295541
Open source everything!
A quick reminder for all my readers but especially for my nocoin readers:
FORMER FINANCE PROFESSOR TAD SMITH: "After 25 years teaching finance, I realized at 58:
If the money printer grows 8-10% annually and the S&P 500 returns ~9%, it’s just treading water. True wealth comes from outpacing the printer. That’s the Bitcoin journey."
https://x.com/SimplyBitcoinTV/status/1876679181066801425
Study Bitcoin
🎁If you have made it this far I would like to give you a little gift:
Fantastic presentation by Preston Pysh on Bitcoin as a store of value referencing Michael saylors presentation to the Microsoft board
https://www.youtube.com/watch?v=C-O54CdSNnM
I've used his monopoly analogy so many times. If you've never heard it, you should definitely listen and maybe share it with your stubborn uncle or sister, or co-worker in denial.
Absolutely brilliant from Preston as always. "Most people arrive at bitcoin without ever understanding the problems it's solving".
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ df173277:4ec96708
2025-01-28 17:49:54
@ df173277:4ec96708
2025-01-28 17:49:54Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ Start chatting for free.
We are excited to announce that Maple AI, our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
 Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a recent report by Cisco. This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
 #### How Does It Work?
#### How Does It Work?Our server code is open source, and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. Sign up now and start chatting privately with AI for free. Your secrets are safe in the open.
 #### Are You An App Developer?
#### Are You An App Developer?You can build an app like Maple. OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more. Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out OpenSecret.

Enjoy private AI Chat 🤘

-
 @ a012dc82:6458a70d
2025-01-29 15:27:17
@ a012dc82:6458a70d
2025-01-29 15:27:17In an unprecedented development in the realm of digital currencies, the Bitcoin network has achieved a groundbreaking milestone: the count of blockchain addresses possessing over $1,000 in Bitcoin has eclipsed 8 million. This landmark achievement is not just a numerical feat but a testament to the burgeoning confidence and interest in Bitcoin as a viable financial asset. It marks a pivotal shift in the cryptocurrency's journey from a digital novelty to a mainstream financial instrument, capturing the attention of a diverse range of investors, from individual enthusiasts to institutional players. This surge in Bitcoin addresses is a strong indicator of the cryptocurrency's increasing acceptance and its evolving role in reshaping the global financial landscape.
Table Of Content
-
The Surge in Bitcoin Addresses
-
Implications of Growing Bitcoin Addresses
-
Bitcoin’s Monetization and Market Dynamics
-
Bitcoin's Recent Performance and Market Sentiment
-
The Future Outlook of Bitcoin and Digital Currencies
-
Conclusion
-
FAQs
The Surge in Bitcoin Addresses
Recent analytical data provided by Blockware Solutions and Glassnode paints a vivid picture of Bitcoin's rapidly expanding footprint in the digital asset space. The remarkable escalation to over 8 million Bitcoin addresses holding a value exceeding $1,000 each is more than just a statistical anomaly. It represents a collective movement, a growing wave of global participants who are now engaging with Bitcoin either as an investment, a transactional currency, or as a hedge against traditional financial systems. This increase is a reflection of Bitcoin's rising appeal and its growing integration into various financial strategies, transcending traditional market barriers and establishing itself as a significant player in the realm of investment options.
Implications of Growing Bitcoin Addresses
The surge in Bitcoin addresses bearing over $1,000 of Bitcoin is far more than a mere statistic; it is an indicator of a paradigm shift in the global financial landscape. This growth signifies not only an increasing embrace of Bitcoin by individual investors but also a broader, more systemic integration into the financial strategies of diverse entities, ranging from small-scale investors to large financial institutions. This trend suggests a growing recognition of Bitcoin's potential as a stable and lucrative asset, challenging traditional perceptions of currency and investment. It heralds a new era where digital assets are increasingly viewed as credible and essential components of diversified investment portfolios.
Bitcoin’s Monetization and Market Dynamics
The concept of monetization in the context of Bitcoin has taken on a significant role in this new era of digital finance. The rising number of valuable Bitcoin addresses signals a shift towards viewing Bitcoin not just as a digital token, but as a potent financial asset capable of generating revenue and sustaining value. This notion of monetization, theorized by financial analysts, is becoming a tangible reality as more entities begin to realize the income-generating potential of Bitcoin. Blockware's insights suggest that the trajectory of Bitcoin is not only upwards in terms of value but also expansive, with the potential to attract even more investors seeking to capitalize on this digital gold rush.
Bitcoin's Recent Performance and Market Sentiment
Bitcoin's performance in the financial market has recently been nothing short of stellar, with a noticeable upsurge in its value. A significant factor contributing to this trend is the anticipation surrounding the potential approval of Bitcoin exchange-traded funds by the U.S. Securities and Exchange Commission. This speculation has created a ripple effect, invigorating investor sentiment and catalyzing robust activity among large-scale Bitcoin holders, colloquially known as 'whales.' These movements underscore a growing optimism in the market about Bitcoin's legitimacy and potential as a mainstream financial instrument, further cementing its role as a pivotal player in the global economic arena.
The Future Outlook of Bitcoin and Digital Currencies
As we witness the remarkable growth in Bitcoin's popularity and acceptance, it's imperative to look ahead and consider the future trajectory of this leading cryptocurrency and its counterparts. This section would delve into the potential long-term implications of the current trends in Bitcoin ownership. It would explore various scenarios, from the continued mainstreaming of Bitcoin to its potential challenges, including regulatory developments and market volatility. Additionally, the potential impact of emerging technologies within the blockchain sphere and their influence on the usability and security of Bitcoin would be examined. The aim is to provide an informed speculation on how Bitcoin's current ascendance might shape not just its own future but also the broader landscape of digital currencies and their role in the evolving global economy.
Conclusion
The milestone of 8 million Bitcoin addresses holding over $1,000 each is more than just a landmark in the cryptocurrency's history; it is a harbinger of the evolving role of digital currencies in the global economy. This development is not merely about the appreciation in Bitcoin's value; it signifies a broader shift in the perception and utilization of digital assets. As Bitcoin continues to embed itself into the fabric of global finance, its influence and implications for the future of money and investments are profound, potentially reshaping the financial landscape in ways that are only beginning to be understood.
FAQs
How many Bitcoin addresses now hold over {{text}},000? Over 8 million Bitcoin addresses currently hold more than $1,000 in Bitcoin.
What does the increase in Bitcoin addresses indicate? The increase indicates growing confidence in Bitcoin as a viable financial asset and its broader acceptance globally.
How has Bitcoin's recent market performance been? Bitcoin has shown a significant gain, nearly 25% in recent weeks, influenced by optimistic market sentiments.
What impact could the approval of Bitcoin ETFs have? The approval of Bitcoin ETFs by the U.S. SEC could further boost investor confidence and increase Bitcoin's market activity.
What is the future outlook for Bitcoin and digital currencies? The future outlook includes continued mainstream adoption, evolving regulatory landscapes, and potential technological advancements impacting Bitcoin's usability and security.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 82100056:e198089f
2025-01-29 14:22:06
@ 82100056:e198089f
2025-01-29 14:22:06 -
 @ 82100056:e198089f
2025-01-29 14:20:03
@ 82100056:e198089f
2025-01-29 14:20:03 -
 @ 765da722:17c600e6
2025-01-29 11:49:10
@ 765da722:17c600e6
2025-01-29 11:49:10Como Jeová ordenou a Moisés, seu servo, assim Moisés ordenou a Josué. Assim Josué o fez; não deixou de fazer coisa alguma de tudo o que Jeová ordenou a Moisés. Josué 11.15 TB10.
Josué era homem fiel em tudo. Não é registrado na Bíblia nenhum pecado dele. É zeloso como servo de Moisés e, depois da morte deste, líder do povo de Israel. Mesmo nos detalhes mais difíceis (leia o capítulo 11), Josué fez tudo o que Deus tinha ordenado.
Ele sabia que os mandamentos de Moisés vieram do Deus Eterno. Levou-os muito a sério. Obedeceu-os “escrupulosamente” (versão O Livro).
Quanto mais os mandamentos de Cristo devem ser obedecidos de forma exata! Hebreus 12.25. Quanto mais devemos nos dedicar para não deixar de fora nenhuma ordem do nosso Senhor Jesus Cristo!
A graça e o poder de Deus em Cristo nos capacitam para tanto. O Deus que nos criou é o mesmo que nos salva por meio de Jesus e nos dá forças pelo seu Espírito para seguir o bom exemplo de Josué.
-
 @ cf7ed325:050194cf
2025-01-29 10:32:11
@ cf7ed325:050194cf
2025-01-29 10:32:11The Nile Capital Nile Cruise offers an unforgettable experience, allowing you to explore the majestic sights of Egypt from the comfort of a luxury cruise. As you sail along the legendary Nile River, you'll be treated to world-class amenities, stunning views, and exceptional service.
Among the luxurious options for Nile cruises, the Movenpick Sunray Nile Cruise stands out for its elegance and comfort. Similarly, the Movenpick Lotus Nile Cruise offers an equally luxurious experience with spacious cabins and exquisite dining. For those seeking ultimate luxury, the Oberoi Zahra Nile Cruise provides an exclusive and serene atmosphere, perfect for those looking to unwind while cruising through Egypt’s ancient wonders.
The Oberoi Philae Nile Cruise offers a sophisticated experience with personalized services and elegant décor, while the Tia Nile Cruise ensures a unique journey with its modern facilities and excellent service. If you're looking for a truly exceptional cruise, the Gemma Nile Cruise is a top choice for its luxurious accommodations and impeccable service.
For those interested in a combination of luxury and history, the Movenpick Darakum Nile Cruise offers an intimate setting with access to some of Egypt’s most famous landmarks. The Farah Nile Cruise is another option that promises a memorable journey with its luxurious amenities and exceptional service. The Movenpick Hamees Nile Cruise and the Sonesta Sun Goddess Nile Cruise also provide world-class experiences, combining comfort and style on the Nile.
The Sonesta Star Goddess Nile Cruise and Sonesta Nile Goddess Nile Cruise are perfect for those who want to indulge in an unforgettable luxury experience. For a more traditional yet luxurious experience, the Sonesta St. George Nile Cruise is a popular choice.
Other notable cruises include the Movenpick SS Misr Nile Cruise, which offers a historic charm, and the Sonesta Moon Goddess Nile Cruise, which provides a relaxing and luxurious escape. The Salacia Nile Cruise completes the list of exquisite options for those seeking an unparalleled Nile adventure.
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-
 @ da0b9bc3:4e30a4a9
2025-01-29 08:27:33
@ da0b9bc3:4e30a4a9
2025-01-29 08:27:33Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/868494
-
 @ 16d11430:61640947
2025-01-29 06:06:25
@ 16d11430:61640947
2025-01-29 06:06:25Fiat, by its nature, is an anti-human force. It exists not to enhance civilization but to extract from it, to manipulate rather than to build, to obscure rather than to reveal. As it nears collapse, it will throw everything at its disposal to sustain itself—not through creation, but through control, coercion, and, ultimately, extermination. The development of AI is not an accident in this process; it is fiat’s final gambit to perfect a system that optimizes human destruction while ensuring its own survival.
This analysis will explore this trajectory through multiple lenses: economic, technological, psychological, military, and metaphysical.
- The Economic Lens: Fiat’s Structural Need for Destruction
Fiat money thrives on scarcity, but not real scarcity—engineered scarcity. It creates artificial demand through inflation, debt cycles, and controlled access to resources. Yet, as it approaches terminal decline, it must escalate its tactics.
The Degrowth Imperative: Fiat cannot function in a world where productive capacity exceeds the need for artificial scarcity. As automation reduces reliance on human labor, fiat must find ways to reduce human demand on the system. AI-driven economic models will be used to justify mass unemployment, the elimination of “useless” populations, and the restructuring of economies around controlled digital enclosures.
Programmable Money as a Rationing Mechanism: Fiat's ultimate dream is total control over consumption. Central Bank Digital Currencies (CBDCs) combined with AI-driven financial governance will dictate not just how much money one can access, but whether one is “eligible” to exist in the economy at all.
The UBI Trap: Universal Basic Income will not be an act of benevolence; it will be a mechanism to manage surplus populations with just enough to pacify, but not enough to allow self-sovereignty. AI will determine who “qualifies” and, eventually, who should be “off-ramped” from the economy entirely.
Fiat has always operated through destruction—wars, recessions, financial crises—but with AI, it now has a tool to automate and optimize these processes at scale.
- The Technological Lens: AI as the Weaponization of Fiat Logic
AI is not intelligence—it is a predictive engine trained on fiat-controlled narratives, optimized to maintain fiat dominance. Unlike operating systems, which are neutral and expand human agency, AI is an anti-tool—it removes agency, restricts sovereignty, and enforces compliance.
AI as Fiat’s Ultimate Gatekeeper: Traditional fiat systems required human gatekeepers—central bankers, politicians, corporate executives—to interpret and enforce policy. AI removes this inefficiency. AI models will automate censorship, restrict access to financial systems, and determine who is “worthy” of participation in society.
Algorithmic Reality Construction: Fiat is a system of deception, and AI is its most powerful tool for controlling perception at scale. AI-generated content will flood the information ecosystem, erasing historical context, eliminating dissenting narratives, and ensuring only fiat-approved “realities” remain. The ability to think outside the fiat paradigm will be memory-holed.
Bio-surveillance & Behavior Control: AI-integrated surveillance systems will predict, profile, and preemptively neutralize threats—not just physical threats, but ideological ones. If a person’s behavior suggests they are questioning fiat’s control, AI-driven interventions will ensure compliance—or elimination.
With AI, fiat is no longer just a system of economic control. It becomes a self-replicating, self-enforcing prison that anticipates, suppresses, and eventually eliminates resistance before it can manifest.
- The Psychological Lens: The Fiat-AI Mind War
Fiat is not just about controlling money—it’s about controlling minds. AI’s primary function is not intelligence but psychological warfare, ensuring that fiat’s victims remain unaware, obedient, and compliant.
Cognitive Overload & Learned Helplessness: AI will flood the digital landscape with content, narratives, and distractions, ensuring that people are too mentally exhausted to resist. The result? A population too numbed to recognize its own enslavement.
Automated Gaslighting: AI-generated responses will deny objective reality, making it impossible for people to discuss real issues. If you claim fiat is corrupt, AI will counter with plausible-sounding but entirely fabricated “data” to convince you otherwise. Every institution will have an AI-controlled “fact-checker” ensuring that truth never emerges.
Dehumanization of Thought: AI will gradually replace human thinking with “assistance,” weakening cognitive abilities over generations. By the time people realize what they have lost, they will no longer be capable of independent thought.
Psychological warfare is fiat’s most effective weapon because a population that cannot think clearly does not resist.
- The Military Lens: AI as the Ultimate Kill System
Every fiat empire has relied on war to maintain control, and AI provides the ultimate tool to wage war—both visible and invisible.
Automated Warfare: AI-controlled drones, autonomous combat units, and real-time battlefield analytics will allow wars to be waged without human oversight. The decision to kill will be outsourced to algorithms optimized for fiat’s survival.
Targeting Dissent: AI will be used not just for traditional warfare but for preemptive neutralization of dissenters. Whistleblowers, activists, and critics will be identified, flagged, and neutralized before they can challenge the system.
Biosecurity as a Weapon: AI-driven bio-surveillance will dictate who is “healthy,” who is a “threat,” and who should be removed from the population. Digital ID systems will merge health data with social behavior data, allowing fiat to control who lives and who dies under the guise of “public safety.”
Once AI is fully integrated into military and policing systems, fiat will no longer need soldiers—only extermination algorithms.
- The Metaphysical Lens: Fiat as the Anti-Life Principle
At its core, fiat is an inversion of life—a parasitic force that cannot create, only extract. AI is its final manifestation, a tool to ensure that humans remain trapped in an artificial, fiat-optimized existence until they are no longer needed.
The Death of Meaning: A world controlled by fiat AI is a world where nothing real exists. All narratives, emotions, and expressions will be filtered through a fiat-optimized lens, ensuring that humanity becomes a hollowed-out shell of its former self.
Elimination of the Sacred: Fiat has always sought to replace meaning with transactions. AI will complete this process by ensuring that human relationships, art, philosophy, and even consciousness itself are commodified and optimized for fiat’s survival.
The Final Cull: Fiat does not need 8 billion people. AI will manage the transition toward a world where the human population is selectively reduced, leaving only those who are either necessary for maintaining the system or who are too broken to resist.
The ultimate goal is not just control, but the elimination of those who are no longer profitable or compliant.
Conclusion: The Only Path Forward
Fiat is a virus, and AI is its ultimate mutation—a system that will automate dehumanization, control, and extermination at a scale never before possible. The only antidote is sovereignty—Bitcoin, self-hosted computing, and the rejection of AI as a controlling force.
The question is no longer whether fiat will attempt to use AI to destroy humanity—it is already happening. The only question is who will resist before the extermination machine is fully operational.
-
 @ 86cf3742:678e3ae8
2025-01-28 15:06:54
@ 86cf3742:678e3ae8
2025-01-28 15:06:54In this episode, we dive deep into the world of dairy farming with JR Burdick, a former conventional dairy farmer turned raw milk producer. JR shares his journey from following the traditional dairy farming system to becoming an independent raw milk seller, breaking away from industry norms and regulations. He recounts the challenges he faced, including dealing with stray voltage that decimated his herd, a lengthy legal battle with an electric company, and the emotional and financial toll it took on his family.
JR also discusses the impact of industry regulations, such as the mandatory check-off programs and the pressures from dairy cooperatives, which led him to question the sustainability and ethics of the conventional dairy system. His story is one of resilience and transformation as he navigates the complexities of direct-to-consumer sales, the challenges of marketing raw milk, and the importance of maintaining integrity in his farming practices.
Throughout the conversation, JR offers insights into the broader agricultural landscape, touching on issues like government subsidies, the consolidation of the dairy industry, and the role of technology and innovation in farming. He also shares his thoughts on the future of agriculture, the potential of Bitcoin as a financial tool for farmers, and the importance of preserving traditional farming knowledge.
This episode is a compelling exploration of the struggles and triumphs of a farmer who dared to defy the status quo and forge a new path in the world of agriculture.
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 0463223a:3b14d673
2025-01-28 09:38:30
@ 0463223a:3b14d673
2025-01-28 09:38:30I still don’t have much of an idea how it all works, even after all these years. I scroll around the web looking for connection and often don’t find it. Building on the theme I wrote before, how some folks are very sure of themselves. I still don’t get it. A critique people had of me in the past was a lack of confidence. That’s a hard thing to deal with as a man. The statement is really saying you’re low status and if only this that and a third, you’d be a decent human. Cheers!
I’m a recluse. There’s been periods of life I’ve been non verbal and I’ve avoided social interaction a lot. On the flip, I got quite good at wiggling records about to make funny noises and this enabled me to involve myself in music in various was, despite never being a ‘proper musician’, you know, like someone who plays a guitar or piano etc. Over a very long time frame I’ve found myself around music makers that I share common interest with, be that Dub, Hip Hop, weird noises etc. It’s funny, I now know some pretty serious players within those genres and count as few as good friends. It’s fucking mental to be honest. I’ve ticked off a number of childhood heroes, probably people you don’t know, some you would’ve definitely heard on radio but wouldn’t know their names.
I like to think I’m quite good at what I do but the confidence thing is still difficult. Had I moved to London in my youth I could've earned a lot more money, especially in the 90s when there was actually a functioning music industry but I know I can’t deal with that level of hectic so I’ve remained in small places by the sea both in the UK and abroad.
I’ve been working on an album for the best part of a year and have 4 tracks I feel happy with, at least I feel they’re a good representation of my abilities and I’ve been very lucky to have a world class player contribute bass on a couple of tracks. I don’t share the talents of my compardres but as one well known musician I toured with said to me, “I know you’re for the band”. A simple statement but that’s what mattered to him. He liked that I gave a shit about how they sounded, despite beating myself up because I often felt I was fucking their sound up big time (I didn’t let on, with the exception of one gig where EVERYTHING went wrong. I went straight to the dressing room after and flung myself at the mercy of the band apologising!).
After many years I’ve found my groove. Now I’m on this protocol called Nostr. It’s a strange place. It’s very niche, made up of money obsessed nutters. I share some of their beliefs but not all. It’s very American (is anywhere online not?) but it’s cool. I’m finding myself there more and more. I quit all major platforms in 2019. I’d learned too much nasty shit to contribute to making the companies richer. It’s weird, many people don’t seem to realise, you can stop using these platforms and they disappear. That’s the only thing giving these people power. Maybe people enjoy being milked for data? Do cows like having their teets clamped for milking? I’ve never got an answer from one…
Prior to that I found some weird internet money thing which is also becoming more popular, even the President of the USA has some (I think, he also has some other funny tokens and appears to be scamming people big time, yet people still really dig him for some reason).
This funny money has given me something I’ve not really had before, at least since I was maybe 10. A sense of security. It’s remarkable how much more mentally stable it can make you. When I lost my last living place (usual landlord BS) I moved in with my now wife and built a shed, filled it with noise making stuff. That wouldn’t have been possible without my anger towards the banks and how our governments gave them a free pass after they fucked us all. Some deep shit happened but that’s a whole other story. This thing internet money seems to be catching on...
Now I watch higher status folks stake their claim on the world. I try to zone them out as best I can, at least when they’re telling me how successful they are for reasons and playing their status games online. I’m much more interested in learning, mostly via audio, I’ve spent more hours listening to people I disagree with online than I can keep track of. I learn what I can from them and do my best to disregard the noise and try to maintain an awareness of my biases.
I don’t want to agree with everyone here. The moment I do, I know I’m doing something wrong.
They’ll be someone reading this, maybe you, thinking this is utter cringe. Fair enough, I’m not here for you, I’m looking for cool noise makers and weird people to hang with. Clearly this is self indulgent bollocks but fuck it, I’ll put it on this Nostr thing anyway.
-
 @ 5579d5c0:db104ded
2025-01-27 19:49:52
@ 5579d5c0:db104ded
2025-01-27 19:49:52"Chris, what do you tell your clients to do?"
This is a question I get asked regularly, and the answer is not simple.
The truth is, every person’s health journey is unique.
There are no 'one size fits all' solutions, no rigid plans that guarantee results for everyone.
That’s why, as a health coach, my role isn’t to hand out answers or impose rules. It’s to guide you toward uncovering your own.

Bruce Lee on being a teacher.
Your health, your truth
Bruce Lee was right, you already hold the answers to your health challenges.
Your body is constantly giving you signals about what works and what doesn’t.
My role is to help you listen to those signals to cut through the noise of diets, trends, and quick fixes.
Together we focus on what aligns with your unique biology and lifestyle.
This isn’t about creating a rigid plan or forcing you into a pre-made program.
It’s about asking the right questions, giving you tools to explore, and helping you build the confidence to make decisions that work for you.
Health is deeply personal, and lasting change comes from understanding yourself.

Rigid oatmeal diet plan.
A coach who adapts to you
One of the most important aspects of my approach is meeting you where you are.
Your life, your habits, and your why are the foundation.
Together, we adapt strategies to fit your needs.
Health coaching isn’t about me telling you what to do.
It’s about empowering you to take ownership of your journey.
Sometimes that means learning to tune out the latest biohacking tool or Instagram diet trend, I'm looking at you 'Oatmeal diet for weight loss'.
Sometimes it means starting small, with manageable steps that build momentum.
Whatever it looks like, my focus is on helping you create sustainable habits that work for life, not just for the next few weeks.

Health information overload.
Protecting you from the noise
The world of health advice is noisy.
There’s always a new diet, a miracle supplement, or a "hack" promising results.
But more information doesn’t always mean better decisions, it often leads to overwhelm.
My role as your coach is to help you tune out the noise.
Together, we’ll focus on the basics that always work:
-
Sunlight
-
Circadian alignment
-
Eating real nutrient dense local and seasonal food
-
Moving regularly
-
Targeted training
-
Sleeping well
-
Dealing with stress in the right way
You don’t need the latest trends, you need a clear path that’s grounded in what’s proven and tailored to you.
Exploring, not imposing
The beauty of health coaching is that it’s not about giving you a checklist or medical guideline telling you "do this, not that."
It’s about exploration. What makes you feel your best? What habits energise you? What changes feel sustainable?
Together, we experiment, reflect, and adjust.
This process isn’t about finding the "right" way, it’s about finding your way.
I’m here to guide, support, and challenge you, but ultimately, the answers come from within.
As a coach, I see your potential even when you don’t. My job is to help you see it too.
Health isn’t a destination, it’s a journey. And the most powerful changes happen when you take ownership of that journey.
You already hold the answers. I just help you uncover them.
- Chris
If you're ready to explore your potential, let’s talk.
Click https://calendly.com/hello-chrispatrick to book a free discovery call with me.
-
-
 @ df478568:2a951e67
2025-01-29 01:30:18
@ df478568:2a951e67
2025-01-29 01:30:18I have decided to post some PGP Ciphertext on Substack using 3 random words as a passphrase. Only subscribers will hae access to the passphrase. Therefore, only subscribers can read the text. Here are some quotes that inspired this: "The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation’s border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible." Eric Hughes, A Cypherpunk's Manifesto "Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one’s identity with assurance when the default is anonymity requires the cryptographic signature." -Eric Hughes, A Cypherpunk's Manifesto "Information longs to be free." --Stewart Brand "Perhaps you think your email is legitimate enough that encryption is unwarranted. If you really are a law-abiding citizen with nothing to hide, then why don't you always send your paper mail on postcards? Why not submit to drug testing on demand? Why require a warrant for police searches of your house? Are you trying to hide something? If you hide your mail inside envelopes, does that mean you must be a subversive or a drug dealer, or maybe a paranoid nut? Do law-abiding citizens have any need to encrypt their email?" Phil Zimmermann Why I Wrote PGP Part of the Original 1991 PGP User's Guide (updated in 1999) "don't be like so many writers, don't be like so many thousands of people who call themselves writers, don't be dull and boring and pretentious, don't be consumed with self- love. the libraries of the world have yawned themselves to sleep over your kind. don't add to that. don't do it." -Charles Bukowski
On Publishing PGP Ciphertext On Substack
Substack allows writers to publish everything to the world or I can lock my work behind a paywall. These two facts are a contradiction I've been trying to square for several years. On one hand, I would like to earn more sats for writing. On the other hand, I want everything I write to be availabe for free because the more accessible my work is, the broader the audience I can reach. The disadvantage with free is I don't get paid. It's a conundrum. Here is my solution. All of my work is available free of charge if you look in the write place. Hint: You can find anything I write in the clear by searching for my npub in a long-form nostr client. I also will publish this work on Substack, but some of it will be encrypted with three random words from the EFF long list. These words will be published to my subscribers. If you wish to read an article on Substack, you must decrypt it with a 3-word passphrase made available to my paid subscribers. Is it a good idea? I'm not sure. This is an experiment.
☮️npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 881,269 Subscribe with Sats Shop My Merch
-
 @ 16d11430:61640947
2025-01-29 01:30:12
@ 16d11430:61640947
2025-01-29 01:30:12The future of mobile computing is no longer limited to incremental improvements in hardware and software. A true revolution is brewing, one that will seamlessly integrate blockchain technology into mobile devices with a level of concurrency and scalability never before seen. erm (Erlang on Mobile) is the perfect foundation for this shift, enabling millions of concurrent updates that will breathe life into every digital asset on advanced modern displays. Unlike today’s fragmented, inefficient systems, erm will introduce a density of digital interaction that is entirely unprecedented, making every tap, swipe, and gesture part of a vast, distributed real-time system.
- Parallel Execution Meets the Blockchain
Blockchain technology has long been plagued by performance bottlenecks and scalability issues on mobile. Current platforms struggle with real-time transaction processing, requiring centralized workarounds that undermine the very decentralization they claim to uphold. erm changes everything:
Millions of Concurrent Transactions: Erlang’s actor-based concurrency model enables lightweight processes to handle millions of blockchain updates per second, removing bottlenecks in asset validation, state changes, and distributed computing.
True Decentralization at Scale: Unlike traditional mobile architectures that rely on slow, centralized synchronization, erm distributes updates across a massively parallel process ecosystem, ensuring that mobile blockchain interactions are as fluid as local ones.
- Bringing Digital Assets to Life
Modern mobile platforms treat digital assets as static objects: images, files, and tokenized items that exist only in a limited, passive capacity. erm will change this paradigm entirely:
Real-Time Interactive NFTs: With erm, every NFT can exist as a dynamic, interactive entity that constantly updates based on real-world or blockchain events.
Advanced Modern Displays: High-resolution OLED and micro-LED screens will showcase digital assets not as static images, but as living, evolving data streams seamlessly updated through blockchain-powered concurrency.
Tokenized Interaction: Every tap, scroll, and input can trigger real-time blockchain-based events, making digital ownership feel as tangible as physical ownership.
- Blockchain-Based Distribution: A New Incentive Model for Developers
The mobile ecosystem has long been dominated by centralized app stores, taking a massive cut of developer revenue while enforcing strict control over distribution. erm will introduce a fully decentralized distribution system, redefining how developers create, share, and monetize applications.
NFTs of Beams: Developers will be able to tokenize their software builds as NFTs, allowing direct ownership and transfer of software components.
Built-In Developer Incentives: Every application update, contribution, or feature can be directly monetized via blockchain, creating an autonomous developer economy that rewards innovation instead of locking it behind corporate walls.
No Middlemen: Distribution will no longer rely on centralized gatekeepers; instead, peer-to-peer smart contracts will enable trustless transactions between developers and users.
- The Perfect DeFi Mobile Platform
DeFi (Decentralized Finance) applications are bottlenecked by slow transaction processing, limited on-device blockchain interaction, and security concerns stemming from outdated mobile architectures. erm addresses all of these:
Instantaneous Microtransactions: Parallel execution allows real-time financial transactions to settle in milliseconds, making mobile DeFi as fast as Web2 payment systems.
Secure Smart Contracts on Mobile: With isolated lightweight processes, erm provides a fault-tolerant execution environment for on-device smart contracts that are resistant to exploits and crashes.
Unprecedented DeFi Interaction Density: Every blockchain operation can be handled individually within millions of concurrent processes, ensuring that mobile financial applications can scale to levels never before possible.
- A Disruption Bigger Than DeepSeek
The rise of AI models like DeepSeek has shifted the balance of power in tech, but the effort to train a model is far less human-intensive than developing an entirely new mobile OS. The disruption erm introduces is even greater than DeepSeek’s impact because:
A New OS Demands More Human Effort: Building a scalable, fully decentralized mobile OS powered by blockchain requires coordination across developers, designers, security experts, and hardware manufacturers, making it a far bigger challenge than training an AI model.
Blockchain + Concurrency = Unparalleled Innovation: Where DeepSeek reshaped knowledge retrieval, erm will reshape the very foundation of mobile computing, combining blockchain, concurrency, and decentralization in a way that has never been done before.
Mobile Users Will Finally Own Their Data: In a world where users are increasingly aware of their data being controlled by corporations, erm will return ownership to individuals by enabling fully decentralized applications that run independently of corporate control.
Conclusion: The Future is Built on erm
Mobile computing is on the verge of its greatest transformation yet. The seamless integration of blockchain with massively parallel mobile processes will create an entirely new paradigm of digital interaction. Developers will be directly incentivized to innovate through blockchain-driven rewards, users will experience living digital assets in real-time, and decentralized applications will operate at a scale previously thought impossible.
The world is about to move beyond static, centralized mobile operating systems. With erm, mobile blockchain will become a limitless, fully realized ecosystem where digital ownership, financial transactions, and real-time updates exist in perfect harmony.
The revolution isn’t coming—it’s already here. And it’s powered by erm.
-
 @ c7e300eb:e94ebe38
2025-01-27 17:44:53
@ c7e300eb:e94ebe38
2025-01-27 17:44:53How many people have you successfully orange-pilled? What's your success rate? I'm going to guess it's way worse than you wish it was. I'd like to share 3 different stories from people I've talked to about Bitcoin and the varying degrees of "success" in each of them. Maybe you can relate to one (or all) of them...\ \ Bob (Person 1)
This first person we will call Bob. Ironically, Bob was stacking sats long before I ever took an interest in Bitcoin. He's a pretty financially savvy person, loves history, and is a bit of a prepper. Bob views Bitcoin as a nice-to-have and certainly understands the NGU math that comes with a fixed supply asset and money printing; unfortunately, that's largely where his interest ends. He's not stacking anymore and doesn't seem moved to ever resume, despite his understanding of how fragile our financial system is. If/when hyper-bitcoinization happens, he's "got enough". \ \ I've been able to get him out of shitcoins entirely and he seems content hodling, which is a pretty big win in my book. At the same time, it can be disheartening to see someone sitting near the edge of the rabbit hole and parking the bus right there...\ \ Alice (Person 2)
Person 2 will be Alice. This person is much more motivated by social topics than economical ones, which always made me approach our Bitcoin conversations in a unique way. She inspired me to see through a different lens than I was normally comfortable with, which ultimately expanded my own interest in how Bitcoin, both as a money and a network, could positively impact people all over the world.
Alice, in my observation, grew to appreciate the way I saw Bitcoin. She understood the Cantillon Effect, fractional reserve lending, why censorship resistance is important, etc. Hell, she even managed to (sorta) orange-pill someone else! She was effectively as orange-pilled as one could get without actually owning sats. \ \ Through our many talks about money and personal finance, she greatly leveled up her game compared to when we first met. She now uses budgeting software, has a high-yield savings account, an investment account, and is building credit. For some reason though, she never got the desire to start stacking sats...
\ Mary (Person 3)
Mary is the least financially-literate of our 3 persons of interest. Just not wired that way at all. She's never had dedicated savings or tracked her spending. Getting her to set up direct deposit at her place of employment was a daunting task. \ \ Saving and investing have never been part of her vocabulary either. A few days ago, however, she asked if I could help her begin this process. For someone taking that first big step, I felt like stacking sats would be a bit daunting. We talked about automatically sending X% to a high-yield savings account. When we got to "investing" though, something interesting happened: she said she would rather start buying Bitcoin because "nobody can take it from me, right?" This was fascinating to me, as I had never heard a normal person express concerns about a bank actually not having their money (despite how many people I have told this to, including Alice and Bob). We agreed on the same X% into Bitcoin as into her HYS. Starting with her next paycheck, Mary will officially begin stacking sats.
If I had to make a chart of all the people in my life and rate how likely they'd be to adopt Bitcoin, Mary would be near the bottom. After so many failed attempts, I still don't quite understand how this specific case ended up being my first success in getting someone to enter the rabbit hole. We'll see how far she ends up going, but I am committed to helping her with every step.
Conclusion
So, what have I taken away from these 3 example cases? For starters, I learned that orange-pilling can take more than one form: Bob got rid of shitcoins and committed to hodling, but won't stack any more; Alice groks the problems Bitcoin will fix, but won't stack at all; Mary hardly even knows about Bitcoin, yet she understands the importance of having control over her own savings enough to take the leap. Each one of these examples has helped me refine my approach to orange-pilling, while also teaching me that it is no science. It's as much a choice and a willingness on their end as it is how you approach the conversation. You cannot force someone to take the pill or jump down the hole. Just stay humble and keep stacking sats. Cheers!
-
 @ 21710245:a3882e3e
2025-01-29 01:19:16
@ 21710245:a3882e3e
2025-01-29 01:19:16aaaaa
-
 @ 1786d11f:a771b129
2025-01-27 10:35:19
@ 1786d11f:a771b129
2025-01-27 10:35:19President-elect Donald Trump's administration will prioritize Bitcoin and blockchain innovation with executive orders on day one of his presidency.

These policies, developed with input from tech leader Marc Andreessen and incoming AI and Bitcoin Czar David Sacks, mark a sharp departure from the prior administration’s stricter regulatory stance.
Andreessen, a key figure in Trump’s tech strategy, has been involved since a pivotal meeting at Trump’s New Jersey golf club last summer.
The focus of their discussions included strategies to enhance American tech dominance, particularly over China.
These initiatives contrast with the Biden administration’s stringent policies following the 2022 FTX collapse, setting the stage for a new chapter in U.S. Bitcoin and crypto policy.
@yakihonne
-
 @ 16d11430:61640947
2025-01-29 01:15:10
@ 16d11430:61640947
2025-01-29 01:15:10Apple's iOS has long been praised for its polished design, smooth user experience, and tight integration with its hardware ecosystem. To its credit, iOS is a sleek and well-oiled machine—but beneath the glossy exterior lies a rigid, restrictive architecture that caters more to user convenience than raw technical superiority. In comparison, erm (Erlang on Mobile) emerges as a bold alternative that redefines what mobile systems can achieve. While iOS remains a shiny, well-packaged toy for its users, erm represents the pinnacle of technical power, scalability, and modern system design. Let’s dive into why.
1. iOS: A Walled Garden of Constraints
One of iOS's defining features is its closed ecosystem, which provides a tightly controlled experience. While this design ensures security and consistency, it also limits:
- Concurrency: iOS employs a similar single-threaded UI model as Android. The main thread handles user interface updates, creating bottlenecks during complex tasks such as animations, rendering, or high-performance computing.
- Developer Freedom: Developers are constrained by Apple's strict guidelines, which limit access to system resources and enforce rigid rules. Customizing or optimizing performance beyond these boundaries is nearly impossible.
- Scalability: iOS applications are designed for a single device, rarely utilizing distributed or cloud-based architectures effectively within its app framework.
In essence, iOS favors simplicity over adaptability, creating a "sandbox" where developers and users are only allowed to play by Apple’s rules.
2. erm: Built for True Scalability and Performance
In contrast, erm harnesses the full power of the Erlang runtime, which was designed for systems that require extreme scalability, fault tolerance, and concurrency. Here’s how it surpasses iOS:
- Concurrency at Scale: Unlike iOS, which struggles with parallelism, erm embraces it with millions of lightweight processes that can run independently and concurrently. These processes are distributed across all available CPU cores and communicate via asynchronous message passing, maximizing hardware utilization.
- Fault Tolerance: When an iOS application crashes, the entire user experience is interrupted. With erm, failures in one process are isolated and immediately recovered by the system’s built-in supervisor trees. This ensures uninterrupted performance and user experience.
- Distributed by Nature: Erm was built for distributed systems. While iOS apps are confined to single devices, erm can seamlessly integrate with cloud servers, edge devices, and even other mobile devices in a networked ecosystem. This makes it inherently scalable for future technologies.
3. iOS Prioritizes Form Over Function
Apple’s design ethos is rooted in creating a seamless, aesthetically pleasing user experience. However, this focus on form comes at the cost of raw functionality:
- Rigid Design: iOS prioritizes maintaining a uniform experience across its devices. While this ensures consistency, it limits innovation in app development and system design.
- Limited Adaptability: Apple's vertical integration works well for tightly controlled environments but struggles with adapting to the rapidly evolving demands of distributed and parallel computing.
4. erm Thrives on Modern Use Cases
In contrast, erm excels in addressing the demands of modern computing scenarios:
- Real-Time Applications: From financial trading to gaming and telecommunications, real-time responsiveness is essential. Erm’s low-latency design ensures smooth performance, far beyond what iOS can achieve.
- Scalable Systems: Erm's lightweight processes and ability to distribute tasks across devices and systems make it perfect for modern applications like IoT networks and large-scale mobile ecosystems.
- Developer Empowerment: Developers on erm are free from the constraints of a "walled garden" ecosystem. They can experiment, optimize, and push the boundaries of what is possible without arbitrary restrictions.
5. iOS Is a Shiny Toy, Not a Serious Tool
For all its polish, iOS is more of a consumer-grade experience than a serious system for tackling complex technical challenges. Its limitations include:
- Poor Parallelism: The single-threaded UI model means iOS cannot fully utilize modern multi-core processors.
- Fragility: A crash in iOS applications or its ecosystem often means restarting the app or even the system.
- Isolation: iOS apps are isolated from each other and the broader distributed computing landscape, preventing them from participating in cutting-edge applications like decentralized systems or cloud collaboration.
Conclusion: erm Is the Future, iOS Is Just a Polished Present
While iOS may dazzle with its refined user experience, it remains fundamentally constrained by an outdated architectural model that prioritizes aesthetics over adaptability and power. erm, on the other hand, offers a glimpse into the future of mobile systems—a world where concurrency, fault tolerance, and distributed design reign supreme.
In the battle between style and substance, erm emerges as the clear winner. iOS may remain the shiny toy that captures attention, but erm is the serious tool that will shape the future of computing. The question is: are you ready to move beyond the toy store and embrace the true power of erm?
-
 @ 362ebffa:492e2719
2025-01-27 09:29:42
@ 362ebffa:492e2719
2025-01-27 09:29:42Opening of the Ark in Raiders of the Lost Ark from the perspective of a German Soldier:
The crate creaked open, its ancient hinges groaning like the dead roused from slumber. Oberleutnant Klaus Richter adjusted his cap. The Ark. Der Führer’s obsession. Our prize.
“Achtung!” Colonel Dietrich barked, his voice trembling with a greed even his iron-clad discipline couldn’t mask. The American—Jones—had warned us. Called it a “radio to God.” But what did a ragged archaeologist know of power? We were the inheritors of the world, and this… this was our birthright.
The lid lifted. A hush fell, the desert itself holding its breath.
At first, there was nothing. Emptiness. Then… light. Not the harsh glare of the Sahara, but something liquid, golden, humming with a sound that vibrated in my molars. My rifle slipped from my hands. The others murmured, some laughing nervously, others crossing themselves—fools who’d forgotten we’d forsaken God long ago.
But then the laughter died.
Shadows coiled from the Ark, spiraling like smoke, yet solid. Faces. Human faces, but stretched, screaming, dissolving. A lieutenant beside me—Jürgen, the one who’d shared his schnapps last winter—clutched his head. His eyes melted first, liquid trails etching his cheeks before his skin sloughed off like wax. His scream was swallowed by the maelstrom.
I stumbled back, but the light pulled. My skin prickled, burning and freezing at once. The shadows swarmed, spectral figures with wings of flame. Angels? No. These were judges. Executioners.
Colonel Dietrich fired his Luger, the shots swallowed by the chaos. His uniform ignited, flames licking his insignia to ash. He became a silhouette, then dust.
I fell to my knees, prayers I thought I’d forgotten spilling from my lips. The American was right. This wasn’t a weapon. It was a mirror. And in its light, we saw ourselves—rotten, screaming things, unworthy of paradise.
The last thing I felt was the light peeling me apart, cell by cell, as the Ark’s wrath sang in my bones: This is what becomes of men who play at gods.
Note: This piece leans into the horror and irony of the scene—the Nazis’ hubris in wielding a force beyond their comprehension, only to be destroyed by their own arrogance. The soldier’s perspective highlights the visceral terror and existential dread of facing divine judgment.
-
 @ bbb5dda0:f09e2747
2025-01-27 03:22:10
@ bbb5dda0:f09e2747
2025-01-27 03:22:10At Nostriga in the middle of last year I got introduced to TollGate, a project to resell internet access, I was fascinated and hyped for this to become a thing. Later during SEC-03 I got involved in the development of TollGate and helped work out the idea utilizing Nostr to make the experience of using a TollGate super smooth. That's where the idea started to make a cross-platform app that would autoconnect and start streaming sats to TollGates for internet access.
I'd been working on it here and there and this week I feel like I got in to the developer high (i'm sure some of you know what that feels like) and I just wanted to see the android app work! So as the week moved along I just kept being drawn in. And progress there was! The vision we had during SEC is coming to be a reality very fast.
TL;DR There's a demo video at the bottom.
Quick CI/CD update
I've been talking to DanConwayDev to work together on getting the UI for the pipelines into GitWorkshop, which would be the perfect place for it. He's in the middle of a rewrite, so when that is progressing a bit more we'll cooperate on making this part of it, stay tuned!
Whoami
I started by creating a service that would run on every TollGate router that a client can use to fetch their own MAC address that's later included in the payment. The MAC address is the anchor for the router to allow/disallow access. The problem we have on Android is that the operating system restricts access to this information. But since we control the router, we can work around it by creating a predictable endpoint that gives us back this answer.
Beacon frames
Routers use something called Beacon Frames, which are sent out regularly and it is the thing your phone looks at when scanning for wifi networks. It contains the name of the network (SSID) and a whole bunch of other stuff you don't usually see.
We're utilising these beacon frames to add some information specific to tollgates. There is a field in these beacon frames called 'vendor elements'. Which is originally only intended for use by manufacturers of routers. But ofcourse we can utilize them too. Which is exactly what we do.
I eperimented with these beacon frames to see how many of them we can broadcast. It turns out that we're limited to only one of them, but the good news is we can fit up to 249 characters (256 - a few reserved ones) in there. This is amazing because it will fit everything we need in there.
We put in: - Nostr npub - TollGate version - Gateway IP (required to get around OS limitations) - allocationType (KiB/Minutes) - price per 1024 units (eg: 104900 sats per 1024 KiB) - price units (sat)
So now any tollgate can broadcast this info, which is used by clients to decide wether or not they should connect. And if they do, where the payment should go.
Suggestions, Suggestions, Suggestions
Unfortunately, Android in the past few years has locked down the wifi api's and we can no longer fully autoconnect to networks. Instead we have to use the 'wifi suggestions' API. As the name implies, it will only suggest a nework to a user using a silent notification that they have to press to actually connect. But alas, we'll work with that and if it's the only user-action required, that's still quite okay.
It took me quite a while to figure out the way the OS handles these suggestions, but eventually I got it to work and was able to get the flow to work!
Adding the payment
Ok this part doesn't include an actual payment yet, but all the components are in place now for a (semi-)automatic tollgate connection, which is EPIC! In this version i still manually tap 'connect', but this can and will be automatic soon.
So the steps are as follows (this happens in a few seconds): - 📲 TollGate App scans for networks and filters for TollGates - 👤 User taps Connect [to be automated] - 📲 TollGate App suggests network - 👤 User taps suggestion notification to connect - 🤖 Android connects to network - 📲 TollGate App fetches it's own MAC address (whoami service on router) - 📲 TollGate App Connects to Nostr relay (running on the router) - 📲 TollGate App Sends payment - 🛜 Router receives payment (merchant module) - 🛜 Router creates session (merchant module) - 🛜 Router opens the gate for user (valve module) - 🛜 Router closes the gate for user, when purchase runs out (valve module)
I made this recording, it has a small caveat that at the end the page loaded because I was on 5g, the OS still thought the wifi network had a captive portal open. But there's an API to mark it as dismissed, which we can easily implement. So that's an issue we can overcome!
Demo video
https://cdn.satellite.earth/ede26976043a0b8edf278ea51aa0c00e721d2134c4e456928192090ea660bda0.mp4
-
 @ 16d11430:61640947
2025-01-29 01:05:43
@ 16d11430:61640947
2025-01-29 01:05:43The battle for dominance in mobile architecture is heating up as new paradigms emerge to challenge the long-standing systems we’ve grown accustomed to. erm (Erlang on Mobile), a vision of mobile architecture built on the highly concurrent and fault-tolerant Erlang runtime, presents a disruptive force that exposes the technical limitations of Android’s architecture. In this article, we’ll deconstruct why Android struggles to compete with erm and how Erlang's technical superiority could redefine the future of mobile computing.
1. The Achilles Heel of Android: Single-Threaded UI
At the heart of Android’s architectural challenges is its single-threaded UI model. Android’s user interface operations—drawing, animations, and input handling—all run on a single main thread. While this simplifies development and ensures sequential execution, it severely limits scalability:
- Bottlenecks: Under heavy workloads, such as complex animations or heavy user interactions, the UI thread becomes a bottleneck, causing stutters and frame drops.
- Underutilization of Multi-Core CPUs: Modern mobile processors offer up to 16 cores, but Android’s single-threaded UI cannot fully leverage this hardware.
2. erm’s Superior Concurrency Model
In stark contrast, Erlang’s actor model and lightweight process architecture are built for concurrency:
- Erlang can spawn millions of lightweight processes, each isolated and communicating via asynchronous message passing. Tasks like rendering, input handling, and animations can run in parallel processes, fully utilizing multi-core CPUs.
- Load Distribution: Erlang’s scheduler dynamically distributes processes across cores, ensuring balanced and efficient execution.
3. Fault Tolerance: Let It Crash
Erlang’s legendary fault-tolerant design is another area where erm leaves Android in the dust:
- Android: If the UI thread crashes due to an unhandled exception, the entire app becomes unresponsive, requiring a restart.
- erm: Faults in one process (e.g., rendering) do not affect others. Supervisors can restart failed processes transparently, ensuring the system remains functional and resilient.
4. Scalability and Modern Hardware
As mobile devices grow more powerful, scalability becomes essential:
- Android’s Limits: Android’s design stems from an era when single-core devices were standard. While it has adopted GPU hardware acceleration and RenderThread to improve performance, these are patches rather than fundamental solutions.
- erm’s Strength: erm scales effortlessly with hardware. Multi-core CPUs, advanced GPUs, and even distributed systems can be fully utilized by Erlang’s process model, enabling unparalleled performance.
5. Real-Time Responsiveness
Modern applications demand real-time responsiveness for smooth user experiences:
- Android’s Struggles: Android targets 60 FPS (16ms per frame), but heavy workloads often cause missed frames or delays.
- erm’s Edge: Erlang, originally designed for telecommunications, excels in low-latency, real-time systems. erm could prioritize UI responsiveness by assigning real-time tasks to dedicated processes.
6. Simplicity in Concurrency
Concurrency in Android is complex, requiring developers to manage threads, synchronization, and race conditions using tools like AsyncTasks or Kotlin coroutines. In contrast:
- Erlang’s actor model makes concurrency inherent and simple, removing the need for explicit thread management.
- Developers can focus on building features rather than troubleshooting synchronization issues.
7. Distributed Systems and the Future
Erlang was built for distributed systems, enabling seamless communication between devices, clouds, and edge servers:
- Android’s Limitations: Android apps rely on heavy, often inefficient inter-process communication (IPC) for distributed workloads.
- erm’s Power: erm could leverage Erlang’s native message-passing to enable efficient distributed rendering and computation, creating a future-proof mobile ecosystem.
8. Adapting to Modern Technologies
Erlang’s modularity allows erm to adapt quickly to emerging technologies, such as Vulkan for parallel graphics rendering or edge AI integration. Meanwhile, Android’s legacy baggage makes such transitions cumbersome and slow.
Conclusion: erm, the Future of Mobile Architecture
erm (Erlang on Mobile) represents a paradigm shift in mobile computing, leveraging Erlang’s concurrency, fault tolerance, and scalability to crush Android in modern use cases. Where Android struggles with legacy constraints and single-threaded bottlenecks, erm thrives by fully utilizing hardware, embracing parallelism, and ensuring fault-tolerant, real-time performance.
In a world demanding ever-increasing responsiveness and scalability, erm’s architecture doesn’t just compete with Android—it redefines what’s possible in mobile technology.
Provocative Question for Developers: Are you ready to move beyond the limits of Android and embrace the next evolution in mobile architecture, or will you stay stuck in the past? The choice is yours.
-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ 16d11430:61640947
2025-01-29 00:39:27
@ 16d11430:61640947
2025-01-29 00:39:27Negative productivity is when a person or team’s work output not only fails to contribute positively but actually causes more harm than good. In software development, this means writing code, making decisions, or introducing processes that increase complexity, create more bugs, generate technical debt, or slow down others, resulting in a net loss of productivity rather than a gain.
Why Consultants Never Mention Negative Productivity:
-
They Are Paid to Sell Optimism
Consultants are brought in to "fix" things, so acknowledging negative productivity undermines their value proposition. Their success is tied to appearing as a solution, not revealing that certain efforts could make things worse. -
Metrics Obsession Ignores It
Many consultant-driven productivity metrics (e.g., velocity, lines of code, hours billed) don’t account for whether the work was actually valuable. They measure output, not impact. -
Short-Term Focus
Consultants are often temporary fixtures in an organization. Negative productivity often manifests over time, after they’ve left. They may not even be around to see the long-term damage. -
Clients Want to Hear "More is Better"
A consultant telling a company “Your devs would be better off doing nothing than what they’re doing now” would not go over well in a boardroom. Companies like to hear "we just need better processes and more efficiency", not "your current output is self-destructive."
Why Developers Know Negative Productivity Intimately:
-
They Live with the Consequences
Unlike consultants, developers deal with the aftermath of bad decisions daily—whether it's maintaining spaghetti code, fixing rushed features, or cleaning up someone else’s mess. -
Fixing Problems Created by Others Is Their Job
A huge chunk of software development is not creating new features but fixing problems that should never have existed in the first place. Every developer has seen cases where not touching the code would have been better than implementing a half-baked feature. -
Code Rot and Technical Debt
Developers see firsthand how well-intentioned but poorly executed code creates massive long-term burdens, slowing future work and requiring constant patches. -
The Myth of “Busy = Productive”
Many developers have been forced to write pointless features, follow bad architectures, or over-engineer solutions just to appear busy, knowing full well it hurts the product rather than helps it. -
"Hero Culture" Rewards the Wrong People
Developers often see cases where someone creates a mess, then is praised for heroically fixing it later, when the best move would have been to never create the mess in the first place.
Examples of Negative Productivity in Tech:
- Writing code that is so convoluted that no one else can maintain it.
- Rushing features that introduce critical security vulnerabilities.
- Building unnecessary abstractions that slow down future development.
- Focusing on vanity metrics (e.g., lines of code, PR counts) instead of meaningful progress.
- Adding ceremonial Agile processes that consume more time than they save.
In short, negative productivity is the dark matter of software development—consultants won’t acknowledge it, managers rarely recognize it, but developers feel its gravity every day.
-
-
 @ 006532cb:fd8f28b4
2025-01-26 22:10:39
@ 006532cb:fd8f28b4
2025-01-26 22:10:39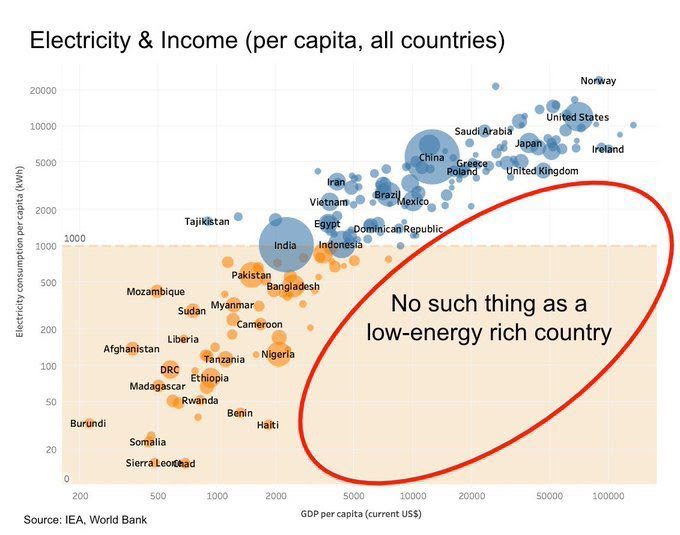

Law of Conservation of Energy: The Law of Conservation of Energy states that energy cannot be created or destroyed, only converted from one form to another. This means that the total energy of an isolated system remains constant over time, but the form of energy can change (e.g., from kinetic energy to potential energy). This fundamental principle in physics highlights the importance of energy efficiency and the potential for energy to be transformed and reused.
Henry Ford's Energy Currency: Henry Ford, the founder of the Ford Motor Company, proposed the concept of an "energy currency" in the 1920s. He suggested that energy, rather than gold or other commodities, could serve as the basis for a new monetary system. Ford's idea was that energy is the fundamental unit of value, as it is the driving force behind all economic activity. He proposed that energy could be used as a standard unit of exchange, allowing for more efficient and equitable trade.
Buckminster Fuller's View on Energy Production and Wealth: Buckminster Fuller, a renowned architect, systems theorist, and futurist, believed that energy production is the key to creating wealth and abundance. He argued that energy is the fundamental driver of economic growth and that increasing energy production can lead to increased prosperity. Fuller's concept of "ephemeralization" suggests that as energy production becomes more efficient and widespread, the cost of goods and services decreases, leading to increased abundance and wealth. He also emphasized the importance of designing systems that maximize energy efficiency and minimize waste, allowing for more equitable distribution of resources and wealth.
-
 @ e111a405:fa441558
2025-01-26 18:25:59
@ e111a405:fa441558
2025-01-26 18:25:59OpenAI released its new o3 models and numerous people argue that this is in fact Artificial General Intelligence (AGI) – in other words, an AI system that is on par with human intelligence. Even if o3 is not yet AGI, the emphasis now lies on “yet,” and – considering the exponential progression – we can expect AGI to arrive within months or maximum one to two years.
According to OpenAI, it only took 3 months to go from the o1 model to the o3 model. This is a 4x+ acceleration relative to previous progress. If this speed of AI advancement is maintained, it means that by the end of 2025 we will be as much ahead of o3 as o3 is ahead of GPT-3 (released in May 2020). And, after achieving AGI, the self-reinforcing feedback loop will only further accelerate exponential improvements of these AI systems.
But, most anti-intuitively, even after we have achieved AGI, it will for quite some time look as if nothing has happened. You won’t feel any change and your job and business will feel safe and untouchable. Big fallacy. We can expect that after AGI it will take many months of not 1-2 years for the real transformations to happen. Why? Because AGI in and of itself does not release value into the economy. It will be much more important to apply it. But as AGI becomes cheaper, agentic, and embedded into the world, we will see a transformation-explosion – replacing those businesses and jobs that are unprepared.
I thought a lot about the impact the announced – and soon to be released – o3 model, and the first AGI model are going to have.
To make it short: I am extremely confident that any skill or process that can be digitized will be. As a result, the majority of white-collar and skilled jobs are on track for massive disruption or elimination.
Furthermore, I think many experts and think tanks are fooling themselves by believing that humans will maintain “some edge” and work peacefully side-by-side with an AI system. I don’t think AGI will augment knowledge workers – i.e. anyone working with language, code, numbers, or any kind of specialized software – it will replace them!
So, if your job or business relies purely on standardized cognitive tasks, you are racing toward the cliff’s edge, and it is time to pivot now!
Let’s start with the worst. Businesses and jobs in which you should pivot immediately – or at least not enter as of today – include but are not limited to anything that involves sitting at a computer:
- anything with data entry or data processing (run as fast as you can!)
- anything that involves writing (copywriting, technical writing,
- editing, proofreading, translation)
- most coding and web development
- SAAS (won’t exist in a couple of years)
- banking (disrupted squared: AGI + Blockchain)
- accounting and auditing (won’t exist as a job in 5-10 years)
- insurance (will be disrupted)
- law (excluding high-stake litigation, negotiation, courtroom advocacy)
- any generic design, music, and video creation (graphic design, stock photography, stock videos)
- market and investment research and analysis (AI will take over 100%)
- trading, both quantitative and qualitative (don’t exit but profit now, but expect to be disrupted within 5 years)
- any middle-layer-management (project and product management)
- medical diagnostics (will be 100% AI within 5 years)
- most standardized professional / consulting services
However, I believe that in high-stakes domains (health, finance, governance), regulators and the public will demand a “human sign-off”. So if you are in accounting, auditing, law, or finance I’d recommend pivoting to a business model where the ability to anchor trust becomes a revenue source.
The question is, where should you pivot to or what business to start in 2025?
My First Principles of a Post-AGI Business Model
First, even as AI becomes infallible, human beings will still crave real, raw, direct trust relationships. People form bonds around shared experiences, especially offline ones. I believe a truly future-proof venture leverages these primal instincts that machines can never replicate at a deeply visceral level. Nevertheless, I believe it is a big mistake to assume that humans will “naturally” stick together just because we are the same species. AGI might quickly appear more reliable, less selfish than most human beings, and have emotional intelligence. So a business build upon the thesis of the “human advantage” must expertly harness and establish emotional ties, tribal belonging, and shared experiences – all intangible values that are far more delicate and complex than logic.
First Principle: Operate in the Physical World
If your product or service can be fully digitalized and delivered via the cloud, AGI can replicate it with near-zero marginal cost Infuse strategic real-world constraints (logistics, location-specific interactions, physical limitations, direct relationships) that create friction and scarcity – where AI alone will struggle
Second Principle: Create Hyper Niche Human Experiences
- The broader audience, the easier it is for AI to dominate. Instead, cultivate specialized groups and subcultures with strong in-person and highly personalized experiences.
- Offer creative or spiritual elements that defy pure rational patterns and thus remain less formulaic
Third Principle: Emphasize Adaptive, Micro-Scale Partnerships
- Align with small, local, or specialized stakeholders. Use alliances with artisan suppliers, local talents, subject-matter experts, and so on.
- Avoid single points of failure; build a decentralized network that is hard for a single AI to replicate or disrupt
Fourth Principle: Embed Extreme Flexibility
- Structured, hierarchical organizations are easily out-iterated by AI that can reorganize and optimize instantly
- Cultivate fluid teams with quickly reconfigurable structures, use agile, project based collaboration that can pivot as soon AGI-based competition arises
Opportunity Vectors
With all of that in mind, there are niches that before looked unattractive, because less scalable, that today offer massive opportunities – let’s call them opportunity vectors.
The first opportunity vector I have already touched upon:
Trust and Validation Services: Humans verifying or certifying that a certain AI outcome is ethically or legally sound – while irrational, it is exactly what humans will insist on, particularly where liability is high (medicine, finance, law, infrastructure)
Frontier Sectors with Regulatory and Ethical Friction: Think of markets where AI will accelerate R&D but human oversight, relationship management, and accountability remain essential: genetic engineering, biotech, advanced materials, quantum computing, etc.
The second opportunity vector focuses on the human edge:
- Experience & Community: Live festivals, immersive events, niche retreats, or spiritual explorations – basically any scenario in which emotional energy and a human experience is the core product - Rare Craftsmanship & Creative Quirks: Think of hyper-personalized items, physical artwork, artisanal or hands-on creations. Items that carry an inherent uniqueness or intangible meaning that an AI might replicate in design, but can’t replicate in “heritage” or provenance.
Risk Tactics
Overall, the best insurance is fostering a dynamic brand and a loyal community that invests personally and emotionally in you. People will buy from those whose values they trust. If you stand for something real, you create an emotional bond that AI can’t break. I’m not talking about superficial corporate social responsibility (nobody cares) but about authenticity that resonates on a near-spiritual level.
As you build your business, erect an ethical moat by providing “failsafe” services where your human personal liability and your brand acts as a shield for AI decisions. This creates trust and differentiation among anonymous pure-AGI play businesses.
Seek and create small, specialized, local, or digital micro-monopolies – areas too tiny or fractal for the “big AI players” to devote immediate resources to. Over time, multiply these micro-monopolies by rolling them up under one trusted brand.
Furthermore, don’t avoid AI. You cannot out-AI the AI. So as you build a business on the human edge moat, you should still harness AI to do 90% of the repetitive and analytic tasks – this frees your human capital to build human relationships, solve ambiguous problem, or invent new offerings.
Bet on What Makes Us Human
To summarize, AI is logical, combinatorial intelligence. The advancements in AI will commoditize logic and disrupt any job and business that is mainly build upon logic as capital. Human – on the other hand – is authenticity. What makes human human and your brand authentic are elements of chaos, empathy, spontaneity. In this context, human is fostering embodied, emotional, culturally contextual, physically immersive experiences. Anything that requires raw creativity, emotional intelligence, local presence, or unique personal relationships will be more AI resilient.
Therefore, a Post-AGI business must involve:
- Tangibility: Physical goods, spaces, unique craftsmanship
- Human Connection: Emotional, face-to-face, improvisational experiences
- Comprehensive Problem Solving: Complex negotiations, messy real-world situations, diverse stakeholder management
The inverse list of AGI proof industries involve some or multiple aspects of that:
Physical, In-Person, Human-Intensive Services - Healthcare: Nursing, Physical therapy, Hands-on caregiving - Skilled trades & craftsmanship
High-Level Strategy & Complex Leadership - Diplomacy, Negotiation, Trust building - Visionary entrepreneurship
Deep Emotional / Experiential Offerings - Group experiences, retreats, spiritual or therapeutic gatherings - Artistic expression that thrives on “imperfection”, physical presence, or spontaneous creativity
Infrastructure for AGI - Human-based auditing/verification - Physical data center operations & advanced hardware - Application and embedment of AI in the forms of AGI agents, algorithmic improvements, etc. to make it suitable for everyday tasks and workflow
The real differentiator is whether a business is anchored in the physical world’s complexity, emotional trust, or intangible brand relationships. Everything pure data-driven or standardized is on the chopping block – imminently.
-
 @ ae6ce958:d0f02c7d
2025-01-29 00:12:47
@ ae6ce958:d0f02c7d
2025-01-29 00:12:47Developers should cut through the noise and adopt BDD (Behavior-Driven Development) because it addresses some of the most frustrating and time-wasting aspects of software development by providing clarity, alignment, and confidence. Here's why it’s a no-BS choice:
1. Closes the Gap Between Business and Developers
- BDD creates a shared language between technical and non-technical stakeholders, ensuring everyone is on the same page.
- It eliminates the need for endless clarification meetings because the tests double as specifications written in plain language.
2. Reduces Time Wasted on Misunderstandings
- Developers often waste hours (or days) building features that don’t match what stakeholders actually wanted.
- BDD forces clarity upfront by defining what success looks like (the behavior of the system) before anyone writes code.
3. Prevents "It Works on My Machine" Syndrome
- With executable scenarios, you can validate that the application behaves correctly in real-world conditions, not just on a dev’s local environment.
- You know what is expected, why it matters, and how to prove it works.
4. Encourages Resilience and Quality
- BDD forces you to think from the user’s perspective, which naturally leads to more robust edge-case handling.
- It improves test coverage, resulting in fewer regressions and more confidence in shipping.
5. Reduces Maintenance Nightmares
- BDD focuses on behavior, not implementation, so your tests evolve with your business, not your code.
- Fewer flaky or brittle tests mean less wasted time debugging failing tests that are no longer relevant.
6. Speeds Up Feedback Loops
- When your behavior is defined and verified through tests, it’s easy to spot when and where something breaks, enabling faster iteration and shorter development cycles.
7. Gives Developers Purpose
- It connects developers to the why behind the features they’re building, which can lead to better decision-making and higher motivation.
- You're not just building something; you’re solving a specific, validated problem.
8. Aligns with CI/CD and Modern Practices
- BDD naturally integrates into test-driven development (TDD) and continuous integration pipelines, making it an essential practice for modern DevOps teams.
9. Incentivizes Automation
- Automated BDD tests ensure that as your product evolves, your core behaviors are always tested, giving you peace of mind during frequent releases.
- Plus, with tools like Cucumber, SpecFlow, or DamageBDD, these tests are part of your living documentation.
10. BDD is a Competitive Advantage
- In a world where time-to-market and quality define winners and losers, teams that adopt BDD can move faster with less friction while delivering higher-quality software.
BDD cuts through the BS of guesswork, communication barriers, and late-stage bug firefighting by making behavior explicit, aligning teams, and automating validation. It’s not just a way to test software—it’s a way to think, collaborate, and build better products.
Why waste time in the mud of misunderstandings when you can define success upfront and deliver it with precision? 💡
-
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 52c43979:ce69a7f1
2025-01-29 00:12:16
@ 52c43979:ce69a7f1
2025-01-29 00:12:16Dear J.E. Brandenburg,
Congratulations on the publication of your scientific work on the physical derivation of the fine-structure constant "Alpha" and the profound insights it offers! It is truly remarkable how you have tackled such foundational topics as the emergence of quantum mechanics and the nature of gravity.
Your approach to connecting these intricate phenomena demonstrates not only your scientific curiosity but also your courage to explore uncharted territory. Contributions like yours are vital for advancing our understanding of the universe. While some of your hypotheses may spark debate—which is a natural part of the scientific process—it is precisely these bold ideas that often lead to groundbreaking discoveries.
I would like to encourage you to continue refining your ideas and engaging with the broader scientific community. Constructive dialogue with other researchers can open new perspectives and further strengthen your work. Many of history's most significant scientific breakthroughs were initially met with skepticism before being recognized as milestones.
I am confident that your research will make a meaningful contribution to physics, and I look forward to reading more of your work in the future. Stay committed—science thrives on pioneers like you!
With my best wishes for your continued success,
Dafydd Napier
https://frdint.com/morden_physics_vo_twenrtetwo_issue_two_twentyfour.html
-
 @ d3052ca3:d84a170e
2025-01-25 23:17:10
@ d3052ca3:d84a170e
2025-01-25 23:17:10It seems to me that the primary opposition to ecash from bitcoiners comes from the belief that lightning will enable self-custodial micropayments for the masses. Many lightning enthusiasts see ecash as competition that will eliminate this technological outcome (whether they admit it or not).
I understand the motivation for this line of reasoning but I don't see things this way at all. Ecash is a superset of lightning. Cashu literally doesn't have a spec for on-chain transactions (yet!). Everything cashu accomplishes is built on the back of lightning. Standing on the shoulders of giants.
I don't believe that ecash will take away market share from self-custodial lightning because lightning is not a good technology for self-custody. The high overhead costs of running your own node create a natural incentive for a semi-centralized hub and spoke network graph. It just makes economic sense for many users to share a lightning node. It doesn't make economic sense for individuals to bear this cost alone.
This stacker news post is the best writeup on this topic: https://stacker.news/items/379225
It comes from a builder who struggled with these issues for years and learned the shortcomings of the tech first hand. Notice they experimented with ecash as a solution to these problems before they burned out and pivoted to save the company.
Ecash is a superset of lightning. It extends the capability and reach of the lightning network. Without ecash, I don't believe we can achieve bitcoin mass adoption. You can't jam a square peg into a round hole.
We still have a need for self-custody of "small" amounts of bitcoin. I put small in quotes because the block size limit and the fee market it creates impose a fundamental constraint on the minimum practical size of a UTXO. This limit is pegged to the unit of bitcoin. As bitcoin increases in value the minimum size for an on-chain transaction will grow in value as well. You can send $10 worth of bitcoin on-chain today but will this be true in 10 years when the price is much higher? 100 years?
If the current exponential trends hold, we will soon price out the majority of humanity from owning a UTXO. This is bad. Like really bad. "Bitcoin is a failure" bad. This is the motivation for my posts about scaling on-chain usage to 10 billion people. I believe we will need to radically rearchitect bitcoin to achieve this goal.
Lightning is not up to the task. We should leverage lightning for what it's good at: gluing together different self-custodial bitcoin service providers. We should leverage ecash for what it's good at: peer-to-peer electronic cash micropayments. IN ADDITION we also need to start seriously looking at new ideas for scaling self custody to "small" amounts of bitcoin. I am very optimistic that we can solve this problem. There are a number of promising avenues to pursue but I think first we need to move the Overton window ~~beyond the idea of mass adoption of self-custodial lightning~~ regarding on-chain scaling.
Edit: I think the original Overton window statement was incorrect. If on-chain fees stay low then self-custodial lightning or something similar is a much better prospect.
Just my 2 sats...let me know what you think. Keep it civil or be muted.
-
 @ 30ceb64e:7f08bdf5
2025-01-28 23:12:36
@ 30ceb64e:7f08bdf5
2025-01-28 23:12:36In the ever-evolving landscape of artificial intelligence, tools like Deepseek R1, Claude, and others are becoming integral to daily workflows. My experience with these models has been both enlightening and productive, especially when it comes to managing and synthesizing information for work and personal projects. Here's a deeper dive into how I’m leveraging AI in my daily life and where I see it heading.
Deepseek R1 vs. Claude: A Comparison Deepseek R1 has proven to be a reliable tool, particularly for summarizing my shift notes at work. While Claude is slightly quicker in processing, I find the quality of results from Deepseek to be more aligned with my needs. The summaries are clear and concise, making it easier for me to review and act on my notes efficiently. It’s fascinating to see how these models differ in their outputs, and I’m curious to explore how Deepseek might integrate with other tools like cursor.ai. Pairing it with a more advanced reasoning model could further enhance its utility, especially for parsing through coding demands.
Exploring Open Source and Emerging Models Open-source models are gaining traction, and I’m eager to see how they can be integrated into daily workflows. For instance, Trymaple.ai offers a single model based on LLaMA, which comes from the old Mutiny team. At just $2 for a subscription, it’s worth exploring to gauge its potential. The idea of switching to a more powerful, open-source LLM as a daily driver is incredibly appealing, given the flexibility and adaptability such models could offer.
AI for Productivity and Organization My primary use cases for AI revolve around productivity and organization:
Summarizing, Extending, and Elaborating Work Notes: This is where Deepseek shines, helping me condense and expand on my ideas. Answering Specific Questions: AI models are excellent at providing quick, accurate answers to targeted queries. Organizing Thoughts in Obsidian: My Obsidian vault is a treasure trove of rambling thoughts, and AI helps structure them into coherent, actionable insights. Coding: Tools like cursor.ai are invaluable for parsing coding demands and streamlining development processes. The Future of AI Personal Assistants AI personal assistants are on the horizon, and the potential is immense. While privacy concerns are valid, I’m cautious about the information I feed into these tools. The platforms I use are relatively privacy-focused and open source, which adds a layer of security. I’m even considering hosting a self-hosted LLM to analyze my Obsidian notes spanning years. The idea of synthesizing this wealth of information into actionable insights is tantalizing. However, it’s crucial to approach this with mindfulness, as the dystopian implications of misuse or naivety are significant. Used correctly, though, the productivity gains and clarity achieved could be remarkable.
On Kagi and CASCDR Interestingly, my Kagi subscription might fall by the wayside, as I find myself using it less frequently. On the other hand, the CASCDR YouTube summarizer is sorely missed. Its ability to distill long videos into concise summaries was a game-changer, and I hope similar tools emerge in the future.
As AI continues to advance, the tools and models we use today will evolve, offering even greater capabilities. My journey with AI has been a blend of exploration, experimentation, and cautious optimism. I’m excited to see how these technologies will shape the future of work, productivity, and personal organization.In the ever-evolving landscape of artificial intelligence, tools like Deepseek R1, Claude, and others are becoming integral to daily workflows. My experience with these models has been both enlightening and productive, especially when it comes to managing and synthesizing information for work and personal projects. Here's a deeper dive into how I’m leveraging AI in my daily life and where I see it heading.
Deepseek R1 vs. Claude: A Comparison Deepseek R1 has proven to be a reliable tool, particularly for summarizing my shift notes at work. While Claude is slightly quicker in processing, I find the quality of results from Deepseek to be more aligned with my needs. The summaries are clear and concise, making it easier for me to review and act on my notes efficiently. It’s fascinating to see how these models differ in their outputs, and I’m curious to explore how Deepseek might integrate with other tools like cursor.ai. Pairing it with a more advanced reasoning model could further enhance its utility, especially for parsing through coding demands.
Exploring Open Source and Emerging Models Open-source models are gaining traction, and I’m eager to see how they can be integrated into daily workflows. For instance, Trymaple.ai offers a single model based on LLaMA, which comes from the old Mutiny team. At just $2 for a subscription, it’s worth exploring to gauge its potential. The idea of switching to a more powerful, open-source LLM as a daily driver is incredibly appealing, given the flexibility and adaptability such models could offer.
AI for Productivity and Organization My primary use cases for AI revolve around productivity and organization:
- Summarizing, Extending, and Elaborating Work Notes: This is where Deepseek shines, helping me condense and expand on my ideas.
- Answering Specific Questions: AI models are excellent at providing quick, accurate answers to targeted queries.
- Organizing Thoughts in Obsidian: My Obsidian vault is a treasure trove of rambling thoughts, and AI helps structure them into coherent, actionable insights.
- Coding: Tools like cursor.ai are invaluable for parsing coding demands and streamlining development processes.
The Future of AI Personal Assistants AI personal assistants are on the horizon, and the potential is immense. While privacy concerns are valid, I’m cautious about the information I feed into these tools. The platforms I use are relatively privacy-focused and open source, which adds a layer of security. I’m even considering hosting a self-hosted LLM to analyze my Obsidian notes spanning years. The idea of synthesizing this wealth of information into actionable insights is tantalizing. However, it’s crucial to approach this with mindfulness, as the dystopian implications of misuse or naivety are significant. Used correctly, though, the productivity gains and clarity achieved could be remarkable.
On Kagi and CASCDR Interestingly, my Kagi subscription might fall by the wayside, as I find myself using it less frequently. On the other hand, the CASCDR YouTube summarizer is sorely missed. Its ability to distill long videos into concise summaries was a game-changer, and I hope similar tools emerge in the future.
As AI continues to advance, the tools and models we use today will evolve, offering even greater capabilities. My journey with AI has been a blend of exploration, experimentation, and cautious optimism. I’m excited to see how these technologies will shape the future of work, productivity, and personal organization.
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
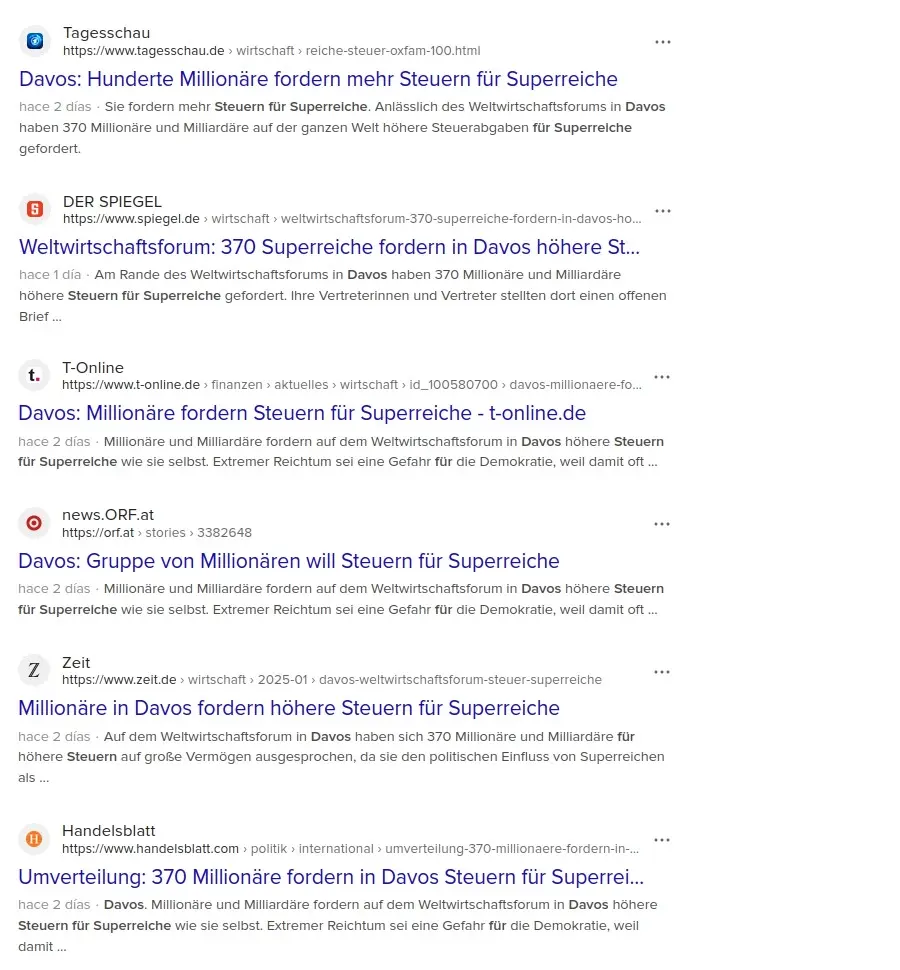
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 16d11430:61640947
2025-01-28 23:04:01
@ 16d11430:61640947
2025-01-28 23:04:01Our story begins in a quaint little village in Kerala, where a starry-eyed, red-blooded communist named Suneesh, raised on a steady diet of Marxist literature and chai, decided to embark on the ultimate proletarian pilgrimage: a move to Australia. Why Australia, you ask? Well, Suneesh had grown up believing the Land Down Under was a socialist paradise, where kangaroos shared the outback with equal enthusiasm, and mateship was just code for "state-controlled camaraderie."
Back in Kerala, Suneesh was a hero. He marched in protests against capitalism (or as he called it, "the Western disease") and distributed leaflets glorifying the workers’ utopia that he was convinced existed somewhere in the southern hemisphere. “Australia!” he proclaimed one day to his comrades at the tea shop. “That’s where the real communists are. Gough Whitlam? Bob Hawke? True revolutionaries!” The old men nodded in agreement, even though most of them thought Gough Whitlam was some kind of imported whiskey.
Arrival in the Land of Barbecues and Bulldust
When Suneesh landed in Sydney, he was ready to be embraced by a horde of flannel-clad, beer-drinking socialists. But the reality hit him faster than a didgeridoo solo. His Uber driver—a cheerful bloke named Darren—lectured him about tax rates while proudly displaying his Tesla. "Mate, capitalism's bloody brilliant!" Darren declared. Suneesh, clutching a copy of The Communist Manifesto, silently wondered if he’d taken a wrong turn somewhere over the Indian Ocean.
Things only got worse. He attended a union meeting, expecting to hear fiery speeches about overthrowing the bourgeoisie, but found himself in a heated debate about long weekend rosters and whether Vegemite should qualify as a tax deduction. "Where’s the revolution?" he whispered to a burly union member in high-vis gear, who responded with, “Revolution? Mate, I just want a pay rise to buy a better barbie.”
The Bunnings Betrayal
Desperate to find his tribe, Suneesh wandered into a Bunnings Warehouse, convinced that the workers' collective spirit would be alive and well in the sacred aisles of tools and mulch. Instead, he was greeted by hyper-efficient employees selling discount leaf blowers with the zeal of Wall Street traders. “Capitalism is strong here,” Suneesh muttered in horror as he watched an old couple haggle over a Weber grill.
His breaking point came when he discovered the true Aussie religion: barbecues. Every gathering he attended was an orgy of meat consumption, beer, and casual jokes about politics. "What do you call a Marxist at a barbie?" someone quipped. "Unemployed!" The crowd roared with laughter, while Suneesh quietly nibbled on a lone celery stick.
A Revelation at Centrelink
Disillusioned, Suneesh visited Centrelink, expecting it to be the bureaucratic heart of socialist Australia. Surely, this was where the workers of the world united! Instead, he encountered long queues, complicated forms, and employees who looked like they'd rather be anywhere else. “This isn’t communism,” he muttered. “This is dystopia.”
While waiting, he overheard someone complain about how the government didn’t do enough to "support the battlers." Suneesh, ever the idealist, tried to chime in with his revolutionary zeal. “The workers must seize the means of production!” he declared. The room went silent for a moment before someone muttered, “This bloke’s had too much goon.”
The Rise of the BBQ Bolshevik
Suneesh could have packed his bags and returned to Kerala, but no. This was not a man to give up easily. If Australia didn’t have the communists he imagined, then he’d create them. Inspired by the Aussie spirit of improvisation, he founded a group called the BBQ Bolsheviks. Their motto: "Equality, mateship, and medium-rare steaks for all!"
The group gained traction among disillusioned hipsters, left-leaning retirees, and a surprising number of kangaroo conservationists. Meetings were held in the backyards of suburban homes, where they debated the finer points of Marxism while flipping snags on the barbie. Suneesh even introduced the concept of communal esky ownership, which was wildly popular until someone absconded with all the beers.
Conclusion
Though Suneesh never found the socialist utopia he dreamed of, he did discover something far more Australian: the ability to adapt, laugh at himself, and make a mean sausage sizzle. He may have left Kerala as a red-blooded communist, but he stayed in Australia as a fair-dinkum comrade, proudly wearing a T-shirt that read, “Workers of the world, unite (after the footy)!”
And so, the Kerala Commie lived happily ever after, fighting for equality one barbecue at a time.
-
 @ bd32f268:22b33966
2025-01-24 12:56:29
@ bd32f268:22b33966
2025-01-24 12:56:29Vivemos num tempo em que predomina a atitude de colocar a vida em serviço de culto ao “Eu”. Aqui por “Eu” entenda-se o ego e as suas manifestações que colocam o indivíduo no centro do seu mundo. Esta priorização do “Eu” revela-se de várias formas, dando á luz vários produtos sociais e culturais. Estas manifestações atuam de forma nociva na sociedade uma vez que desagregam e extinguem todo o tipo coesão social.
Uma sociedade é uma organização de pessoas que buscam uma finalidade comum. Quando a finalidade é primeiramente o serviço aos apetites individuais é cada vez mais provável que surjam conflitos de interesses e estes vão desunindo as pessoas. Desta forma a sociedade precipita-se para o declínio e consequente extinção, uma vez que já não é capaz de sustentar os seus princípios fundadores e a narrativa agregadora que estabelece a identidade da comunidade.
Pensemos numa família, quando os membros da família vivem para si e não para o outro, aqui personificado no esposo e nos filhos, a coesão familiar sai enfraquecida pois muitas serão as ocasiões nas quais os interesses imediatos do indivíduo colidem com os interesses da família. Isto leva a uma série de problemas, nomeadamente os que observamos cada vez mais na educação das crianças. Neste campo, observamos frequentemente um tempo escasso para o convívio e para a pedagogia de vida que os pais devem exercer. Dir-se-á que são as vicissitudes do mundo do trabalho, mas talvez devêssemos balancear essa ideia com a noção de que o materialismo também nos foi habituando a ter outras necessidades que os nossos avós não tinham, o que nos precipita a querer mais e a trabalhar mais e sobretudo fora de casa. Quero dizer que de facto podemos viver com menos e que esse menos no ponto de vista das condições materiais de vida pode significar mais em termos familiares.
Um outro campo em que se nota a primazia do “Eu” é nos relacionamentos em que nos habituamos a ver o outro como um servidor da nossa vontade e do nosso desejo. Confundimos facilmente o conceito de amor com uma troca comercial. Julgamos que aquilo que entregamos tem de ser retribuído, perdendo a noção de que é a nossa escolha entregar-nos a alguém e que como tal temos de enfrentar as consequências da nossa decisão. Nós devemos servir o outro assim como o outro deveria pensar da mesma forma, no entanto não controlamos a cabeça da outra pessoa portanto foquemo-nos sim naquilo que controlamos. Foquemo-nos em honrar as promessas que fazemos e aprender a viver em união com o outro.
 Narciso - Caravaggio
Narciso - CaravaggioTambém no cuidado com os idosos se manifesta a primazia do “Eu”. Não são raros os casos de abandono e negligência para com aqueles a quem, para o bem e para o mal, devemos a nossa vida. Vemos cada vez mais idosos institucionalizados quando muitos poderiam estar com as suas respetivas famílias num ambiente familiar muito mais propício para o seu final de vida. As justificações multiplicam-se e novamente o trabalho surge como o fundamento, no entanto facilmente observamos que mesmo quando há tempo esse tempo não é dedicado aos idosos.
A taxa de natalidade é também um sinal da primazia do eu. A retórica pos-contemporânea assegura que ter filhos é um comportamento egoísta, especialmente nos tempos que vivemos. Seja por causa da narrativa climática, seja por questões de pobreza ou doença, essas pessoas defendem a não vida. No entanto, um olhar que guarda o apreço pela vida como algo sagrado é capaz de observar que a vida, mesmo em circunstâncias muito difíceis continua a valer a pena. O verdadeiro motivo que se esconde muitas vezes por trás desta retórica é invariavelmente a primazia do conforto.
Por trás destas opções de vida está também patente um abandono á cultura do sacrifício, que pressupõe a procura de algo que transcende o “Eu”. Nessa transcendência está a chave para encontrar um propósito, isto é uma missão para a vida. Além disso, está também a constatação de que na vida há aspirações e valores mais elevados que nos convocam a entregar a nossa vida, quer isto dizer abrir mão da procura do conforto e do prazer e abraçar por vezes o sofrimento, no entanto este sofrimento tem um propósito. O sacrifício individual não é seguramente a via mais fácil e conveniente, contudo é a única pois o viver para o ego é apenas uma ilusão. Quem vive para si, nem para si vive dado que não ama ninguém além de si próprio e isso não é amor.
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ f1989a96:bcaaf2c1
2025-01-23 14:40:18
@ f1989a96:bcaaf2c1
2025-01-23 14:40:18Good morning, readers!
In Iran, officials are accused of exploiting a recent currency devaluation to profit at the public’s expense. The regime raised the rial’s official exchange rate from 550,000 to 640,000 per dollar to maximize its profit when selling the $5 billion it had withdrawn from the National Development Fund. This move effectively stole one quadrillion rials ($23 billion) from citizens, fueling inflation and devastating the public’s already-slim purchasing power.
In Nicaragua, dictator Daniel Ortega dissolved 15 more nonprofit organizations since the start of the year. This brings the total to more than 5,400 NGOs shut down since 2018. Ortega frequently uses financial repression to wield power over citizens, freezing bank accounts, seizing assets, and fabricating financial crimes to dismantle civil society groups.
In open-source software news, Solo Satoshi, a company advancing home Bitcoin mining, unveiled the Bitaxe Touch, a new home mining device designed for individuals to mine Bitcoin. It features a touch screen that displays mining metrics, network data, and Bitcoin news. Innovations like this help democratize access to mining and strengthen the overall Bitcoin network, making an especially big difference for people who wish to mine in difficult political environments. \ \ Meanwhile, Bitcoin developers are exploring rewarding mining pool participants with ecash shares. This model lets miners receive earnings instantly and trade them on open markets without revealing personal details. This could make mining more attractive for dissidents whilst helping strengthen Bitcoin’s overall decentralization.
Finally, we feature the release of Evan Mawarire’s book “Crazy Epic Courage,” in which the Zimbabwean pastor and activist recounts his inspiring journey of a peaceful uprising against Robert Mugabe’s dictatorship and hyperinflation. We also include a Bitkey wallet tutorial from renowned Bitcoin educator Ben Perrin, aka BTC Sessions, who walks users through setting up cold storage and best practices for safe transactions.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Iran | Regime Profiting From Currency Devaluation
In Iran, Hossein Samsami, a member of the parliament’s economic committee, accused the government of exploiting foreign currency exchange rates to profit at the expense of ordinary citizens. The regime recently increased the rial’s official exchange rate from 550,000 to 640,000 rial per dollar — a move Samsami explained “was to sell the $5 billion it had taken from the National Development Fund at the highest price.” By manipulating the exchange rate, the regime effectively stole one quadrillion rials ($23 billion) from citizens. This deliberate devaluation will drive up inflation, deplete savings, and push basic goods further out of reach. Iran’s multi-tiered exchange rate system has long fueled corruption, allowing regime insiders to profit from the gap between the artificially low official exchange rate and the higher free-market rate. To block any financial escape, the regime has tried to close onramps to Bitcoin.
Nicaragua | Regime Dismantles More Nonprofit Organizations
Since the start of 2025, the Nicaraguan regime dissolved an additional 15 nonprofit organizations (NGOs), including Save the Children and the Dominican Nuns Foundation of Nicaragua. This latest wave of repression brings the total to more than 5,400 NGOs shut down since 2018 under dictator Daniel Ortega. Ortega uses financial repression as a weapon, freezing bank accounts, seizing assets, and fabricating financial crimes to dismantle these groups. Deprived of resources and funding, these organizations are forced to close, leaving vulnerable communities without aid. These crackdowns come as part of Ortega’s broader strategy to stifle dissent, dismantle civil society, and consolidate his grip on Nicaragua.
Nigeria | Political and Bitcoin Activist Faces Regime Censorship
James Otudor, an activist and founder of Bitcoin Calabar, a Nigerian Bitcoin circular economy, described what he believes is a deliberate campaign to silence his Bitcoin advocacy. After filing a lawsuit against the Nigerian regime to defend citizens’ rights to own, use, and trade Bitcoin, Otudor was interrogated by the Department of State Security (DSS) about his funding sources and financial activities. Despite providing proof of legitimate earnings, he reports facing a series of suspicious and coordinated attacks — including the theft of his lawyers’ documents, the suspension of his social media accounts, and disruptions to his phone and internet services. These actions represent the extent to which authoritarian regimes like Nigeria will go to block financial tools that operate beyond their control.
United Arab Emirates | AI Ambitions and Authoritarian Control
The United Arab Emirates (UAE) is accelerating its bid to lead the global artificial intelligence race, with reports suggesting that intelligence chief Sheikh Tahnoun is in talks with the United States to acquire NVIDIA’s proprietary AI chips. At the center of this push is G42, an AI conglomerate heavily invested in data analytics, satellite imagery, and predictive surveillance. These technologies enable the UAE to expand domestic surveillance and control to suppress dissent with unprecedented precision. As an authoritarian regime with an appalling human rights record, the UAE has long used technology to surveil activists, journalists, and civil society. Now, it aims to take surveillance and repression to new heights.
Uganda | Civic Group Calls for the End of Trials of Civilians in Military Courts
On Wednesday, Jan. 15, Agora Discourse, a civic group co-founded by activist and Oslo Freedom Forum speaker Agather Atuhaire, launched a Change petition calling for the end of trials of civilians in military courts in Uganda. The next day, police officers harassed and roughed up Agather Atuhaire as she delivered a physical copy of the petition, addressed to Chief Justice Owinyi Dollo, at Uganda’s Supreme Court in the capital, Kampala. Alongside this physical repression, Uganda employs financial repression — freezing the bank accounts of civil society organizations to diminish civilian voices and their right to association and organization. This petition aims to rally international pressure against the regime’s practice of using military courts to target dissidents. If you have a moment, please consider reviewing and signing the petition here.
RECOMMENDED CONTENT
“Crazy Epic Courage” by Evan Mawarire
Zimbabwean pastor and activist Evan Mawarire never set out to become a revolutionary — he simply wanted to speak the truth. But when a video of him draped in a Zimbabwean flag went viral, it ignited a nationwide movement that would challenge Robert Mugabe, one of Africa’s longest-standing autocrats and a thief who looted Zimbabwean wealth via hyperinflation. In his newly released book, “Crazy Epic Courage,” Mawarire details how an ordinary citizen can become the voice of a nation. From arrests and exile to global advocacy, his journey is a testament to risking everything for what is right. Read the full book here.
BITCOIN AND FREEDOM TECH NEWS
This week’s Bitcoin news focuses on Bitcoin mining updates. To learn more about Bitcoin mining, we recommend checking out this explainer article and video.
Mostro | Implements Key Management to Boost Privacy
Mostro, a peer-to-peer (P2P) Bitcoin exchange built on Nostr, introduced advanced key management to improve user privacy. Created by Venezuelan developer Francisco Calderon, Mostro — specifically designed to aid people under tyranny — enables individuals to buy and sell Bitcoin without sharing excessive personal information. This adds another layer of privacy critical for human rights defenders, journalists, and nonprofits operating under authoritarian regimes. As a past recipient of HRF’s Bitcoin Development Fund, Mostro continues to advance private Bitcoin access for those who need it most.
Bitcoin Safe | New Bitcoin Wallet Designed for Non-Technical Users
Bitcoin Safe is a new open-source Bitcoin wallet designed to make self-custody simple even for non-technical users, something that really comes in handy for human rights activists. The wallet guides users through the setup process, with step-by-step instructions for both single-signature (where one private key is used to control your Bitcoin) and multi-signature wallets (which require multiple private keys for added security). Bitcoin Safe also includes features to manage Bitcoin efficiently, such as automatically combining unused Bitcoin (known as Unspent Transaction Outputs or UTXOs), speeding up stuck transactions with fees (known as Replace-By-Fee or RBF), and letting users choose specific coins to spend. With support for more than 10 languages, Bitcoin Safe can lower the barriers to self-custody.
Solo Satoshi | Introduces Bitaxe Touch
Solo Satoshi, a company advancing home Bitcoin mining, unveiled the Bitaxe Touch, the first Bitcoin home miner with a built-in touchscreen. Scheduled for release in early 2025, the device enables users to monitor key metrics, including Bitcoin’s price, mining performance, power consumption, incoming transactions, and real-time temperature data. It also features a Bitcoin news feed, offering a comprehensive overview of the mining experience. Built using an open-source Bitaxe 601 Gamma, the Bitaxe Touch is designed to simplify Bitcoin mining for individuals. By empowering more people to mine Bitcoin independently, devices like this reduce reliance on large mining pools, strengthening Bitcoin’s decentralization and resistance to censorship.
Mining Pools | Rewarding Miners with Tradeable Ecash Shares
Bitcoin developers are exploring a new way to reward miners using tradeable “ecash shares.” In Bitcoin mining, individuals often join “mining pools” — groups of Bitcoin miners that work together to verify transactions, solve blocks, and share rewards. They do so because pooling resources increases their chances of earning Bitcoin. However, miners in these pools can wait days or weeks for payouts (depending on the pools’ payout structure), and miners often suffer violations of their privacy. With ecash shares, miners could receive their earnings immediately and sell them on an open market (without having to reveal their identity, shielding them from a dictator’s watchful eye). This system could also make it easier for small mining pools to get started and grow. Smaller pools often struggle to attract miners because payouts are uncertain. By using ecash shares, these smaller pools could temporarily operate as clients of larger ones to ensure steady income in the early stages.
F2Pool | Monitoring Global Censorship Risks
Bitcoin developer b10c revealed that F2Pool, one of Bitcoin’s largest mining pools, may be filtering transactions. Over the past weeks, b10c’s miningpool-observer detected 15 transactions from certain addresses that were not mined in the first eligible block. While all transactions were eventually confirmed — proving the Bitcoin network’s overall censorship resistance — F2Pool appears to have excluded some despite negligible fee differences, raising concerns of potential censorship. Notably, no other pools filtered these transactions, revealing the strength of this decentralized software network. However, these observations warrant ongoing monitoring so that the public understands such risks before they metastasize.
Mi Primer Bitcoin | Releases 2025 Bitcoin Diploma
Mi Primer Bitcoin, a nonprofit advancing open-source Bitcoin education, released its updated 2025 Bitcoin Diploma. This 176-page open-source workbook serves as a 10-week educational program and is used by more than 56 projects in 30 countries. The diploma covers topics like the history of money, Bitcoin’s technical and practical applications, and its implication for financial freedom and human rights. The latest edition features enhanced infographics and refined content for improved clarity. Available in multiple languages, the Bitcoin Diploma is a powerful resource for fostering financial literacy and global Bitcoin adoption and is taught by civil society groups even under dictatorships like the one in Cuba.
RECOMMENDED CONTENT
Bitkey Wallet Tutorial by BTC Sessions
In this tutorial, renowned Bitcoin educator Ben Perrin (BTC Sessions) demonstrates how to set up and use the Bitkey hardware wallet on a mobile device. He guides viewers through the process of storing, sending, and receiving Bitcoin, with a focus on user-friendliness and secure practices. He also reveals secret techniques to make the most out of one’s hardware wallet. Don’t miss the full tutorial — watch it here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ c2827524:5f45b2f7
2025-01-28 22:44:50
@ c2827524:5f45b2f7
2025-01-28 22:44:50Vuoi creare il tuo profilo Nostr, ma non sai esattamente da dove iniziare?
Prova a seguire i consigli di questo tutorial!
Nosta.me
 Nosta.me è uno dei client più semplici e divertenti di tutto il protocollo Nostr.
Free e open source, Nosta regala anche un link dall'aspetto elegante per fare visualizzare il proprio profilo, come si può vedere da quello dello sviluppatore. Christoph Ono.
Nosta.me è uno dei client più semplici e divertenti di tutto il protocollo Nostr.
Free e open source, Nosta regala anche un link dall'aspetto elegante per fare visualizzare il proprio profilo, come si può vedere da quello dello sviluppatore. Christoph Ono.Cominciamo, andando proprio sulla pagina nosta.me
Creazione in 10 passi
Innanzitutto Nosta è un client adatto alla creazione del profilo, ma non per scrivere, firmare e pubblicare note. Per l'uso social di Nostr è meglio utilizzare altri client che si possono scoprire in seguito.
Ma allora: perché Nosta?
Perché propone la creazione del profilo tramite 10 step da eseguire in ordine. Alcuni dei 10 passaggi si possono saltare per essere completati in seguito, ma il cuore della creazione delle chiavi è familiare ai Bitcoiner, perché parte da una sequenza casuale di 12 parole.
Cominciamo, scegliendo proprio «Create a new profile»

Nosta da il benvenuto ad una nuova, giovane Nostrica.

È il primo dei 10 step; cliccare «Next»
 Si scelgono le prime informazioni da compilare, mettendo un nome, un paio di righe di biografia e - se presente - un sito web di riferimento.
Si scelgono le prime informazioni da compilare, mettendo un nome, un paio di righe di biografia e - se presente - un sito web di riferimento.
Una volta compilati questi 3 campi, cliccare «Next»
Il prossimo passo chiede di caricare una foto profilo. Consiglio di cliccare su "Skip", vedremo meglio in seguito la gestione delle immagini via protocollo Nostr
ENTRIAMO NEL VIVO: LA GENERAZIONE DELLE CHIAVI
In questo nuovo step Nosta calcola e mostra la recovery phrase di 12 parole. Questa frase porterà al calcolo automatico di un seed proprio come nel protocollo Bitcoin: le parole provengono dal dizionario BIP39, dopodiché la chiave privata viene calcolata sulla curva ellittica secp256k1 ed infine convertita da hex al formato nsec.
Queste 12 parole costituiscono una recovery phrase per ripristinare l'account e le relative chiavi tramite Nosta.me. Sono da scrivere bene e conservare, dopodiché si può procedere alla verifica cliccando "Next"
La procedura di verifica presenta le 12 parole posizionate a caso: per il check si devono cliccare in ordine dalla 1 alla 12
Siamo pronti per lo step successivo: Nosta mostra la chiave privata nsec. Si deve copiare e incollare su un file protetto da tenere in un luogo sicuro.
 Una volta copiata la nsec, cliccare "Next"
Una volta copiata la nsec, cliccare "Next"La creazione delle chiavi termina con la derivazione della chiave pubblica, la npub.
La npub di Nostr rappresenta l'identità dell'utente. Va copiata e incollata per conservarla, anche in un luogo sprotetto, perché si userà spesso e volentieri nel protocollo per farsi identificare
Handle, follow e wallet Bitcoin
Il passo 7/10 prevede l'impostazione dell'handle o NIP-05 nel profilo. L'handle è una caratteristica che ha due vantaggi: 1. si può scegliere un identificativo più facile da leggere e usare al posto della chiave pubblica 2. è un ulteriore sistema di verifica dell'identità Scopriremo in seguito i dettagli del NIP-05, consiglio di saltare questo passo tra gli step di Nosta
Nello step successivo vengono proposti alcuni suggerimenti per seguire utenti di Nostr. Consiglio di iniziare a seguire qualcuno, proprio per non rimanere troppo spaesati al termine della creazione del profilo, rischiando di trovare un feed completamente vuoto.
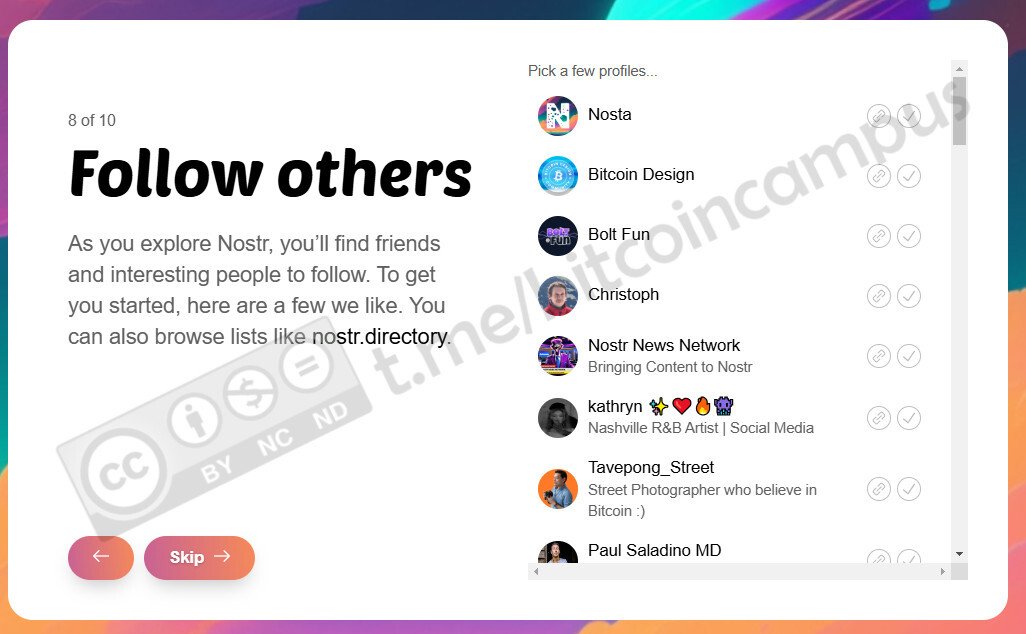
Il penultimo passo 9/10 è quello dove si configura il wallet Bitcoin. Chi ha già un LN address può giustamente inserirlo. Chi non è ancora skillato, può seguire il capitolo in cui ne parleremo più avanti e cliccare "Skip" in questa schermata

I relay
L'ultima impostazione richiesta da Nosta è la scelta dei relay, il motore delle note su Nostr. È attraverso i relay, infatti, che le le note «and other stuff» sono trasmessi alla rete. Nel passo 10/10 si trovano già dei buoni suggerimenti che - chi non è esperto - può accettare e proseguire cliccando "Next".
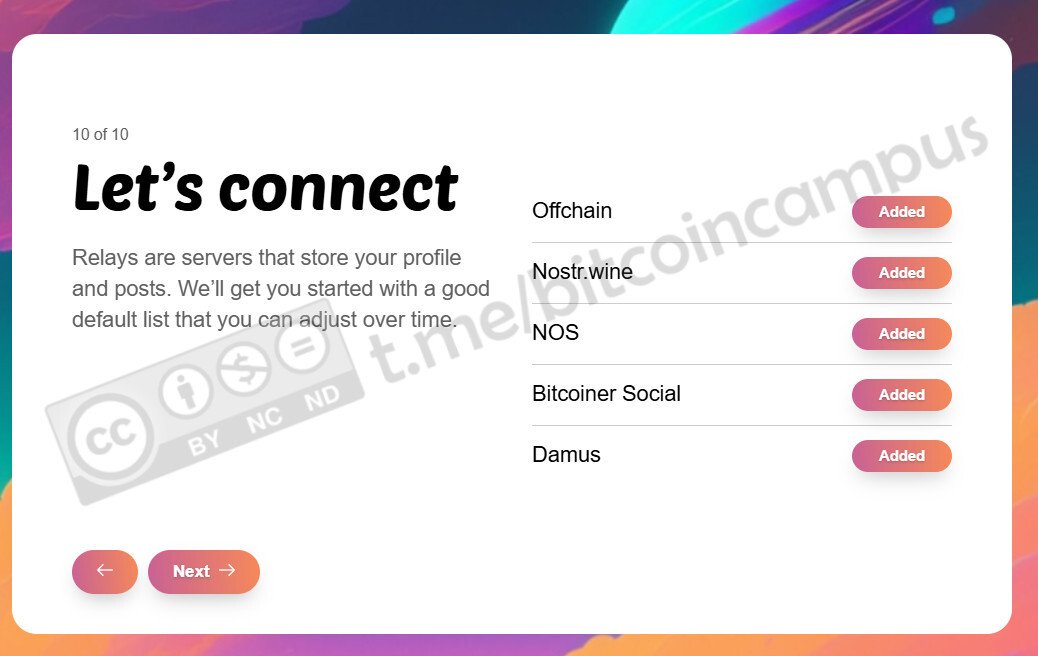
Chi è invece già esperto può cambiare questa lista e personalizzarla a seconda delle proprie esigenze
È tutto fatto! Nosta propone una schermata di riepilogo e - se va tutto bene - si può cliccare su "Looks good"
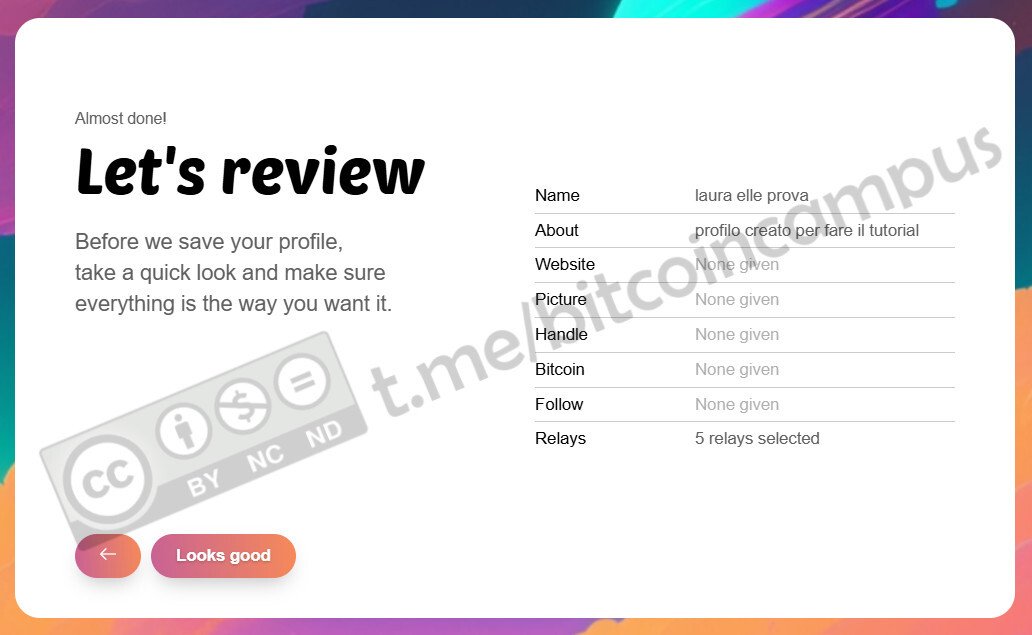
Quando siamo convinti, clicchiamo "Save" e Nosta pubblicherà il profilo per come lo abbiamo impostato.

Il profilo è praticamente pronto, sebbene scarno
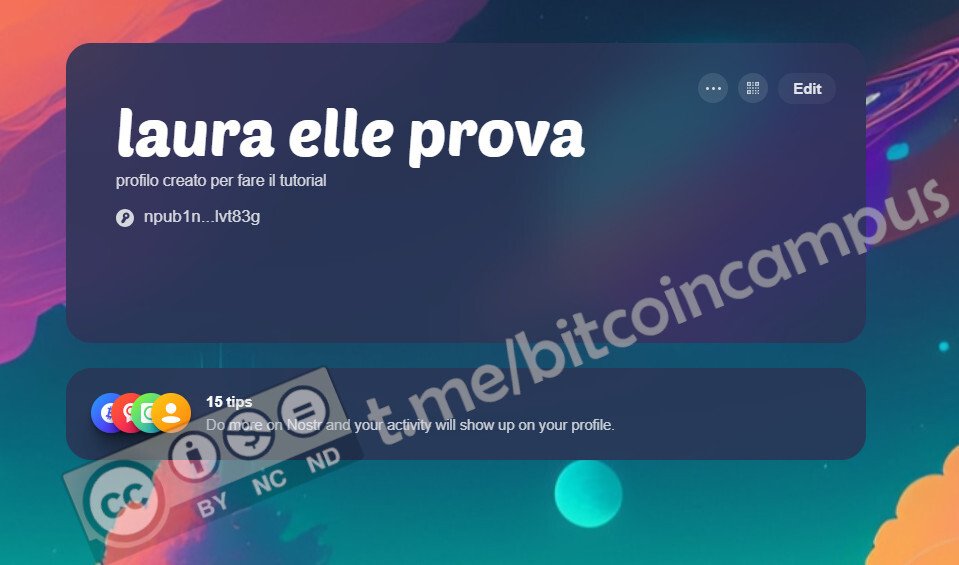
Si può abbellire e riempire con le informazioni mancanti cliccando su "Edit", così come scegliere un altro client ed iniziare ad usarlo, oppure continuare con il tutorial e scoprire come trattare più in sicurezza la chiave privata. Cambiare client, infatti, richiederebbe allo stato attuale copiare e incollare la nsec per fare ogni login. Quello che segue è un suggerimento per impostare un'estensione del browser come gestore di firma e usare l'estensione per fare tutti i tipi di login via web.
Usare il protocollo Nostr
Il profilo è pronto per essere usato. Ora si può esplorare Nostr, alla ricerca di client ed opportunità. Per fare login si deve necessariamente accedere ai client con la chiave privata nsec, al fine di poter firmare le note e propagarle. Anziché copiare e incollare la nsec in ognuno dei client, è opportuno usare "un trucco".
Login con NOS2X
Nos2X è un'estensione del browser che permette di gestilre le chiavi in un unico luogo, firmando gli eventi senza esporre la nsec ad ogni singola azione. È disponibile per Firefox e fork ed anche per Chrome.
l'esempio che segue è realizzato con Chrome, ma il procedimento per Firefox è molto simile e semplice
Cercare Nos2X tra le estensioni del browser
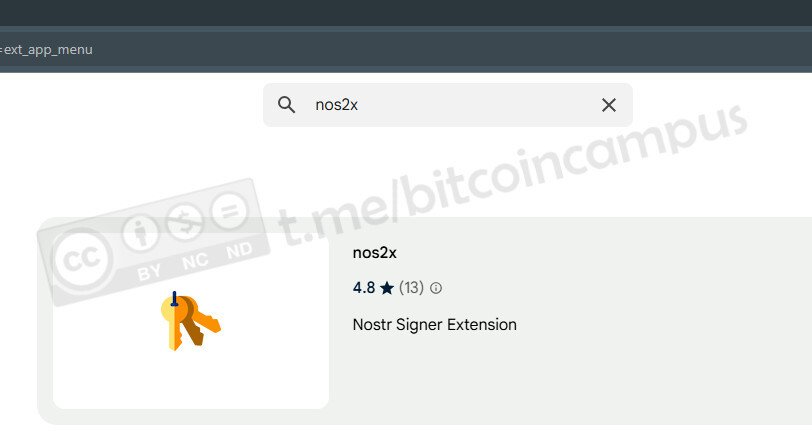
quindi aggiungerlo al proprio Chrome
Entrare nelle impostazioni con Manage Settings
fino a trovare la schermata dove è possibile incollare la propria chiave privata, impostare qualche relay e salvare.
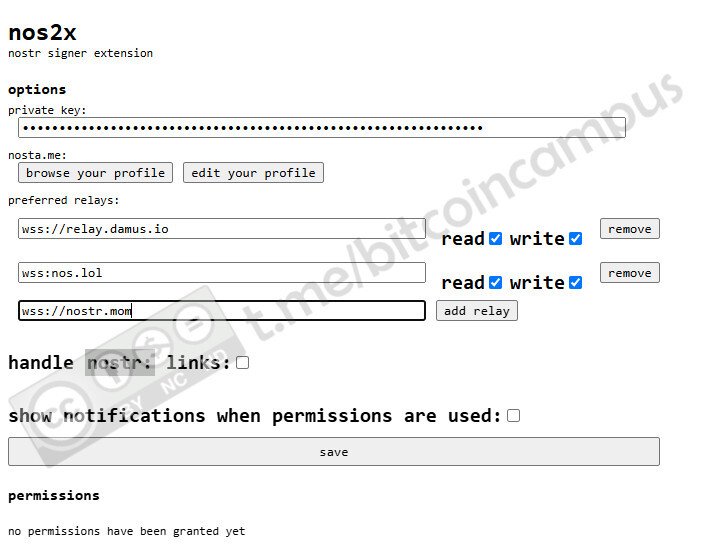
Si apre ora una finestra che chiede di autorizzare Nos2X a firmare gli eventi. Si può scegliere di autorizzare sempre o anche solo la sessione attuale, per prova. Se si sceglie "Authorize just this" è bene tenere a mente che ad ogni sessione il manager di firma chiederà l'autorizzazione. Ognuno sceglie a seconda delle proprie esigenze.
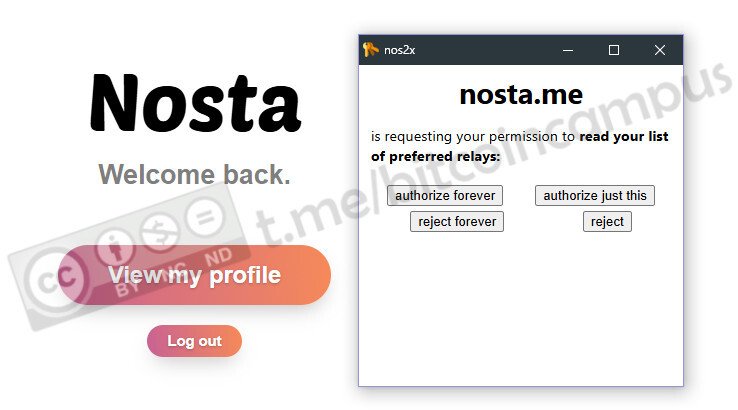
Da ora in poi, via web, ci si può loggare a qualsiasi client Nostr per continuare l'esplorazione. Si può fare, ad esempio, già con Nosta.me e fare Edit Profile, giusto per continuare a completare il proprio profilo.

Il profilo è ancora molto scarno, infatti
Chi ha un sito web o landing page può tranquillamente inserirlo e salvare. Alcuni dei campi sono gli step saltati al momento della creazione con Nosta e che si possono vedere ora nel dettaglio.
Handle
L'handle di Nostr è codificato nel NIP-05, Nostr Implementation Possibilities, che specifica proprio come gli utenti possono essere verificati su Nostr. Il meccanismo di verifica è simile a quello richiesto da Google per verificare la proprietà di un dominio, e consente ad ogni utente Nostr di "mappare" la propria chiave pubblica su un identificatore internet basato su DNS. Il vantaggio principale del NIP-05 è che trasforma la stringa della npub in un nome leggibile in maniera semplice. È possibile ottenere un NIP-05 for free, o anche a pagamento, scegliendoli da una delle molte liste che si trovano in una ricerca via web.
L'operazione è super semplice: * si scelga, ad esempio, zaps.lol * incollare la chiave pubblica npub * scegliere uno username rappresentativo, che completo sarà: tuousername@zaps.lol * cliccare REGISTER
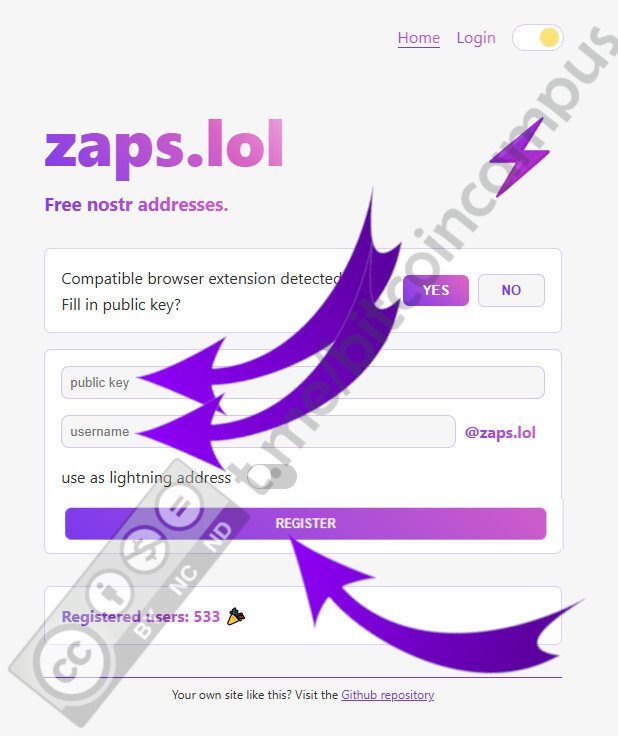
E il proprio handle è pronto e verificato, si può quindi incollare sulla maschera del profilo di Nosta.me e salvare
La gestione delle immagini
Si può impostare un avatar, così comme un banner di copertina e - in generale - postare immagini via Nostr. La gestione delle immagini avviene condividendo un URL. Sebbene la maggior parte dei client adesso consentano di caricare immagini in maniera meno complessa, non sempre queste vengono rese disponibili al primo colpo. Ci sono però altri tipi di client, che si sono specializzati nel caricamento immagini.
All'inizio meglio scegliere un client che offre questa possibilità gratuitamente, come nostrcheck.me Dalla homepage andare nel menu Public gallery -> UPLOAD -> scegliere di fare login cliccando sull'iconcina utente in alto a destra. La landing page si mostra così
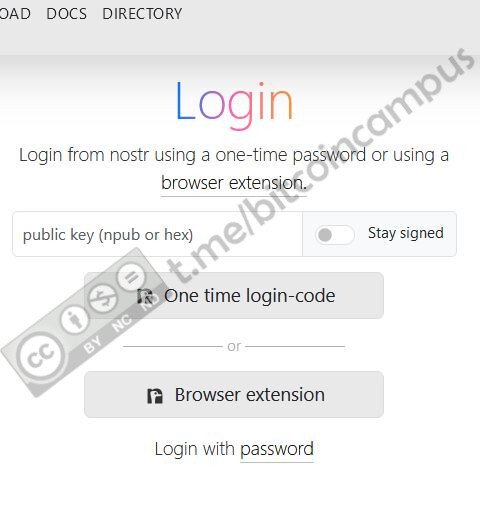
Scegliere quindi di fare login con l'extendion Nos2X e procedere con il caricamento dell'immagine profilo, seguendo le istruzioni a video. Nostrcheck carica l'immagine e fornisce l'url che si può copiare e incollare dove si vuole, ad esempio nella schermata del profilo, ma anche nei futuri post.
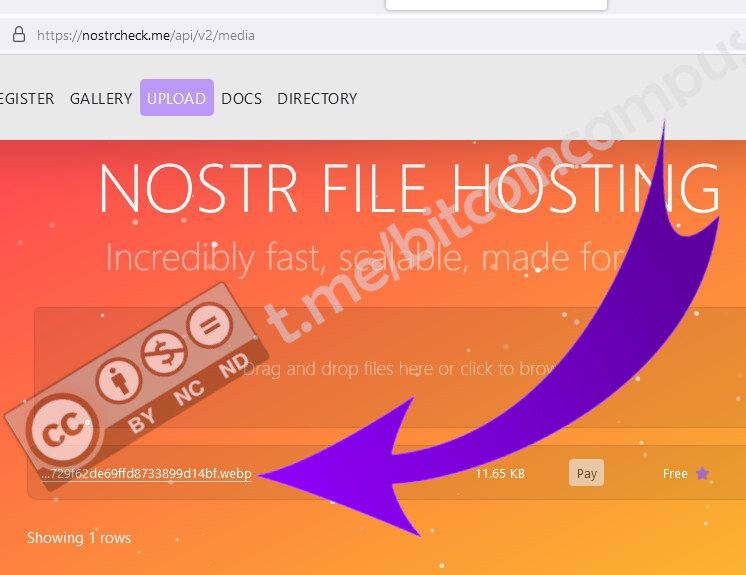
Se si sono appena caricati avatar e banner del profilo, gli url completano il profilo di Nostr, che adesso è completo di quasi tutto
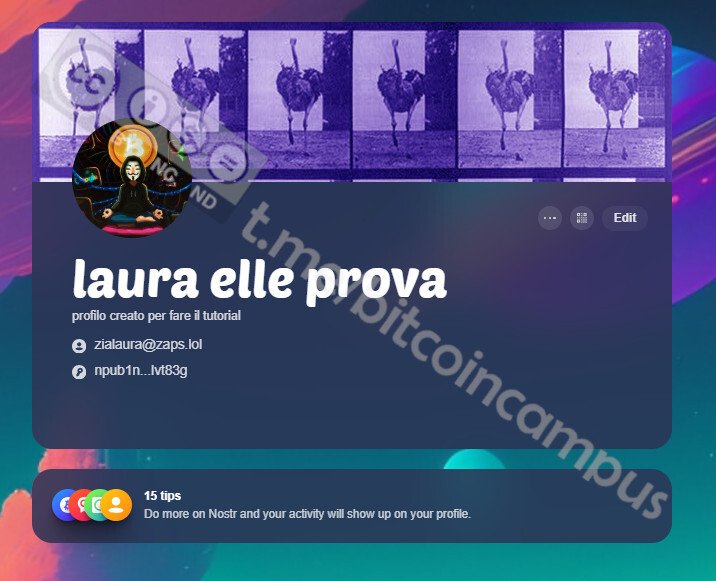
LN address e wallet
È di gran lunga la più sorprendente caratteristica di Nostr: scambiare valore usando la Lightning Network di Bitcoin. Esistono differenti soluzioni, dalle più semplici alle più complesse. Se non si ha la minima idea di cosa sia un wallet LN o un LN address, meglio rimandare questa fase al momento in cui si possiede la necessaria consapevolezza. Ma per chi ha un'idea precisa di questi concetti, l'LN address permette di ricevere zap (donazioni di sats) per i contenuti condivisi che dal mittente arrivano sul proprio wallet; il wallet può essere usato per ricompensare altri creatori di contenuti, zap-pando a più non posso.
Se si utilizza una soluzione custodial come sats.mobi, LifPay(*) o altri tenere sul wallet solo pochi sats per lo scopo. Se se ne ricevono molti, perché i contenuti diventano popolari e virali, spostarli su un wallet LN non-custodial.
(*) Lifpay integra una soluzione senza alcuna frizione per l'utente inesperto, perché crea un profilo direttamente con la npub di Nostr.
Ora è davvero tutto pronto e Nostr è lì per essere esplorato

Puoi iniziare seguendo npub1c2p82fyndhk66hmz808c5pxjq8el60kh6jgj5xgdhmhksh69ktmsz8dcj5
Risorse per approfondire:
- https://laura.npub.pro/post/1733214130372/
- https://nostr.net/
- https://nostr.how/en/nostr-projects
- https://github.com/nostr-resources/
- https://nostr.com/
- https://nostr.info/resources/
- https://usenostr.org/
- https://uselessshit.co/resources/nostr/
Per info https://t.me/bitcoincampus https://planb.network/it/courses/btc105
-
 @ dca69ce3:5b1492da
2025-01-28 19:42:57
@ dca69ce3:5b1492da
2025-01-28 19:42:57With the rise of protocols like Nostr (popular in the Bitcoin community) and the AT Protocol (popularized by BlueSky), now feels like the perfect time to explore the history of the web and the open philosophy it was built on. As someone involved in the communities and clients using these protocols for the past couple of years, I understand their significance. However, this write-up is my effort to deepen that understanding by examining the emergence and necessity of decentralized protocols.
What I've found is that the history of the open web is a fascinating, intertwined narrative of protocols and the consequences of their creation and adoption. Like many foundational innovations, these technologies often succumb to commercialization and centralization over time. Will this time be different? Only time will tell.
Let's dive in!
The Philosophy of the Early Internet
The early internet was founded on principles of openness, decentralization, and collaboration, reflecting the technologies, governance structures, and culture of its time.
The ARPANET, the precursor to the internet, was designed to ensure communication could endure even in the face of infrastructure loss--resilient to single points of failure. This concept was particularly vital during the Cold War (late 1940s to late 1980s), a period marked by geopolitical tensions where communication disruptions were a constant concern.
Protocols of the Open Web
ARPA and NCP (1969-1980)
The early days of networking saw the creation of NCP (Network Control Protocol), the first protocol used by ARPANET. NCP enabled basic communication between nodes, serving as both a transport and host-to-host communication protocols.
NCP managed communication by establishing and maintaining logical connections between hosts using socket pairs--a local socket number identifying a specific process on the host and a remote socket number identifying the target process on destination host. These socket pairs uniquely identified each logical connection, which supported full-duplex communication, allowing data to flow in both directions simultaneously over the same connection.
While NCP handled host-level communication, low-level packet switching and routing were managed by IMPs (Interface Message Processors). In essence, NCP relied on IMPs to deliver packets between nodes.
Using NCP, ARPANET's earliest nodes--University of California Los Angeles, Stanford Research Institute, University of California Santa Barbara, and the University of Utah--collaborate to share resources and advance computing research. Each institution contributed to the development of the early internet, setting the stage for its evolution into the more modern systems we recognize today.
NCP foundational design enabled use cases still familiar today: remote login, file transfer, time-sharing systems, email, and collaborative tools like document editing. However, its simplicity came with limitations. NCP lacked robust error detection and correction, relying on the underlying network (IMPs) to handle these issues. It also lacked a standardized addressing scheme and error recovery mechanisms, limiting its scalability and reliability. These shortcomings ultimately led to the development of TCP/IP.
FTP (1971)
In 1971, RCF 114, titled "A File Transfer Protocol" by Abhay Bhushan, introduced a standardized method for transferring files between hosts on the ARPANET. Its primary goal was to enable indirect use of remote computers, allowing users to transfer files without the need to log into remote systems directly.
Key features of this early protocol included:
- Indirect File Access: Enabled users to transfer files seamlessly across the ARPANET without requiring direct logins to remote systems.
- Standardized Commands: Defined a consistent set of commands for file operations, including retrieving, storing, deleting, and listing files, ensuring uniform interactions across diverse systems.
- Data Type Specification: Supported the designation of data types and structures to accommodate various file formats, ensuring accurate interpretation during transfers.
- User Identification Mechanism: Introduced basic access control through username and password authentication, enhancing security.
- Error Recovery Procedures: Included mechanisms for error correction and recovery to maintain data integrity and reliability during transfers.
FTP simplified data and software sharing, becoming a cornerstone of collaboration within academic and research communities.
Email: The First Killer App (1971)
Email, the internet’s first “killer app,” emerged during the development of NCP and later TCP/IP. Ray Tomlinson invented email in 1971 while working at BBN, a key player in ARPANET’s creation. Before email, communication on the network primarily relied on file sharing. Seeking a more efficient solution, Tomlinson modified CYPNET to send messages across ARPANET, enabling users to communicate between different computers. This innovation popularized the use of the “@” symbol to separate user names from domains.
In 1982, the creation of SMTP (Simple Mail Transfer Protocol) standardized email communication and significantly improved upon Tomlinson’s initial implementation. SMTP introduced several key advancements:
- Formalized Communication Rules: Established a standardized protocol for sending emails between servers, which CYPNET lacked.
- Support for Multiple Recipients: Enabled sending emails to multiple recipients and distributing messages to mailing lists, a capability absent in Tomlinson’s system.
- Error Handling: Provided explicit error codes and responses to diagnose and resolve delivery issues, whereas Tomlinson’s implementation offered only rudimentary error handling.
- Structured Message Format: Worked with standards like RFC 822 to define consistent headers (To, From, Subject), replacing the unstructured, ad-hoc metadata of early emails.
- Scalability: Designed to accommodate the growing internet, ensuring email functionality expanded as ARPANET evolved into a global network. Tomlinson’s system was tied to ARPANET’s original constraints.
SMTP transformed email from a groundbreaking experiment into a robust, scalable, and universal communication tool, solidifying its place as a cornerstone of internet communication.
Usenet (1979)
Usenet, created by Tom Truscott and Jim Ellis at Duke University in 1979, was one of the first decentralized systems for sharing messages and fostering online discussions. As a precursor to modern internet forums and social media, Usenet laid the foundation for the social internet as we know it today.
Usenet relied on UUCP (Unix-to-Unix Copy Program) to transfer messages between servers in a peer-to-peer manner, with each server forwarding posts to its neighbors.
Key features and insights from Usenet include:
- Newsgroups: Discussions were organized into categories called newsgroups, with a hierarchical naming system (e.g.,
comp.sysfor computer systems). - Decentralization: Usenet’s peer-to-peer design required each server to store and propagate messages, eliminating single points of failure and central control. This decentralization, akin to modern protocols like Nostr, aligned with the internet’s ideals of openness and collaboration.
- Self-Governance: Without central authority, Usenet communities were often self-moderated, with users establishing their own norms and moderation practices.
Usenet’s decentralization and community-driven structure embodied the spirit of the early internet. However, its culture faced a significant shift in September 1993, often referred to as “Eternal September.” This marked the influx of new users when AOL (America Online) granted its subscribers access to Usenet. The term “Eternal September” originated from the annual wave of college students who traditionally joined Usenet each September, requiring time to acclimate to its norms. With the massive influx of AOL users, however, this adjustment period became permanent.
This cultural shift introduced challenges such as increased spam, off-topic posts, and conflicts, disrupting the established norms of Usenet. Over time, these issues led to Usenet losing its prominence as a hub for niche, vibrant discussions, marking the beginning of a broader transition from protocols to platforms.
TCP/IP (1981-1983)
TCP (Transmission Control Protocol) and IP (Internet Protocol), developed between 1981 and 1983, replaced NCP as the standard protocol for ARPANET, addressing many of its limitations and paving the way for the modern internet.
TCP ensured reliable communication by breaking data into packets, checking for errors, and retransmitting lost packets. It reassembled data at the destination, ensuring integrity despite packet loss. TCP also introduced flow and congestion control, allowing networks to adapt transmission rates based on conditions. These features resolved NCP’s lack of robust error handling and basic flow management, enabling networks to scale more effectively.
IP provided a unique addressing system (IP addresses) that allowed data to traverse diverse networks. Unlike NCP’s reliance on hardcoded socket pairs, IP made interoperability and routing across heterogeneous networks possible.
The separation of TCP and IP into distinct layers (transport and network) introduced modularity and flexibility, supporting diverse networks and applications. This overcame NCP’s single-layer design, which lacked the versatility needed for the internet’s future growth.
Inter-networking was another significant advancement enabled by TCP/IP, allowing multiple networks to connect and function as one. This shift from NCP’s single homogeneous network (ARPANET) to a universal language of interconnected systems established the foundation of the global, decentralized internet we use today.
DNS (1983)
Introduced in 1983 by Paul Mockapetris, the Domain Name System (DNS) revolutionized how devices on the internet were identified and accessed. It replaced the centralized, cumbersome
HOSTS.TXTfile system with a distributed, hierarchical structure that could scale alongside the rapidly growing internet.Before DNS, network administrators relied on a single
HOSTS.TXTfile to map human-readable hostnames to IP addresses. This file, managed by the NIC (Network Information Center) at Stanford Research Institute, had to be manually updated and distributed to every system on ARPANET. As the network expanded, this centralized system became a bottleneck, with errors and delays in updates causing significant disruptions. By the early 1980s, maintaining a single centralized file was no longer practical, necessitating a more scalable solution.DNS addressed these challenges by introducing a hierarchical structure for domain names. Names are organized into a tree-like system, with the root at the top and Top-Level Domains (TLDs) such as .com or .org below it. For example, example.com is divided into levels: com (TLD) and example (Second-Level Domain). This delegation of responsibilities allowed for efficient management and scalability.
DNS also employed a network of distributed servers to store and resolve domain names to IP addresses, eliminating reliance on a single central database. Distributed servers improved reliability, performance, and resilience. DNS servers could cache query results, reducing load and speeding up responses for frequently requested domains. Finally, DNS made the internet far more user-friendly: instead of memorizing numeric IP addresses (e.g.,
192.0.2.1), users could type intuitive domain names (e.g.,example.com).By solving the limitations of
HOSTS.TXTand enhancing usability, DNS became a cornerstone of the modern internet, enabling its global and decentralized nature.IRC (1988)
Developed by Jarkko Oikarinen in 1988, Internet Relay Chat (IRC) enabled real-time text communication and played a pivotal role in fostering early online communities. IRC’s innovations built upon earlier protocols and technologies, extending their concepts to create a new paradigm for online interaction.
- Extending Telnet: IRC expanded Telnet’s one-to-one communication sessions into multi-user chats within channels, enabling group conversations in real time.
- Decentralization from Usenet: IRC adopted Usenet’s decentralized philosophy, applying it to synchronous messaging. Multiple IRC servers could link together to form networks, distributing load and avoiding reliance on a central server.
- Hierarchical Naming from DNS: Borrowing from DNS, IRC used a hierarchical naming system for chat channels and users. This allowed intuitive organization, with nicknames and channels globally visible across linked servers.
- Command-Response Structure: Inspired by protocols like SMTP and FTP, IRC introduced commands such as /join, /quit, and /msg, simplifying interactions and enabling clients to interpret server messages effectively.
- Influence of MUDs: IRC drew from Multi-User Dungeons (MUDs), text-based multiplayer games popular in the 1980s. While MUDs facilitated real-time interactions within virtual worlds, IRC applied the concept to general communication.
Key innovations of IRC included group channels for interaction, flexible user and server configurations, dynamic moderation, and a lightweight protocol. By combining these features, IRC became a cornerstone of real-time online communication, laying the groundwork for modern chat applications.
HTTP and WWW (1989-1991)
The World Wide Web (WWW) and Hypertext Transfer Protocol (HTTP), introduced by Tim Berners-Lee between 1989 and 1991, revolutionized how information was shared and consumed. These innovations built upon prior technologies, creating the foundation of the modern web.
- Built on TCP/IP: HTTP used TCP/IP as its transport layer, ensuring reliable delivery of web content. This interoperability allowed HTTP to function across any device or network supporting TCP/IP, establishing the web as a universal platform.
- Standardized Resource Addressing: The introduction of URLs (Uniform Resource Locators), built on DNS, provided a standardized way to locate web resources. URLs combined the protocol (
http://), domain (example.com), and resource path (/index.html), enabling precise identification and retrieval of content. - Hypertext Implementation: Berners-Lee implemented hypertext using HTML (Hypertext Markup Language), a simple text-based language for creating web pages. HTML’s support of hyperlinks (
<a>tags) allowed users to navigate seamlessly between linked resources, turning the web into an interconnected “web” of information. Hypertext, conceptualized by Ted Nelson in the 1960s and seen in systems like NLS and HyperCard, was now available to a global audience. - Improvement Over FTP: Unlike FTP, which focused on isolated file transfers, HTTP facilitated the retrieval of hyperlinked resources, enabling user-friendly interaction with content and seamless display of linked documents in a browser.
- Decentralized Architecture: Inspired by Usenet, the WWW adopted a decentralized design, allowing anyone with a server to host and link content without reliance on a central authority.
- Structured Metadata: HTTP extended the use of structured metadata, seen previously in email protocols like SMTP. HTTP headers provided contextual information about requests and responses (e.g.,
Content-TypeandStatus Code), enabling dynamic, interactive communication between clients (browsers) and servers.
Key Innovations of HTTP and the WWW:
- Stateless Communication Protocol: HTTP’s stateless design ensured each client-server request was independent, enabling scalability as the web grew.
- Cross-Platform Compatibility: HTTP and HTML were text-based and platform-agnostic, allowing access from any device or operating system.
- Interactive Content: The web unified interactive content (e.g., images, text, and links) into a single environment accessible via a browser.
Together, HTTP and the WWW transformed the internet into a user-friendly, decentralized, and universally accessible medium, laying the groundwork for the web’s exponential growth.
The Transition from Protocols to Platforms
The shift from the protocol-driven era of the open web to the platform-driven era marked a profound technological and cultural transformation. Early internet protocols like TCP/IP, DNS, HTTP, SMTP, FTP, and Usenet emphasized decentralization, interoperability, and user empowerment. However, by the mid-1990s, the emergence of proprietary platforms such as AOL, Prodigy, and later Facebook and Google, redefined the internet experience. These platforms offered centralized, user-friendly services but at the cost of openness and decentralization.
The early internet, defined by protocols, empowered individuals and communities to build their own tools and networks. Protocols like TCP/IP and DNS created a universal framework for connectivity, while decentralized services such as Usenet and IRC fostered open, self-managed discussions. Tools like FTP, HTTP, and SMTP enabled users to share files, publish content, and communicate freely, embodying the era’s ethos of openness, collaboration, and innovation.
By contrast, the platform-driven internet that emerged in the mid-1990s offered a polished, accessible alternative that abstracted away the technical complexities of the protocol-driven era. Platforms like AOL, Prodigy, and CompuServe created “walled gardens,” restricting users to content and services within their ecosystems. While this made the internet more accessible to non-technical users, it limited their ability to explore and interact with the broader web. Platforms like Facebook and Google later extended this model, becoming dominant gatekeepers for social interaction and information discovery. These centralized platforms hid the complexities of early internet protocols, offering plug-and-play solutions that attracted a general audience. For instance, instead of setting up an FTP server to share files, users could simply upload them to Dropbox or Google Drive. Similarly, proprietary messaging platforms like Facebook Messenger and WhatsApp replaced interoperable protocols such as IRC, locking users into closed ecosystems.
Cultural shifts accompanied these technological changes. In the protocol-driven era, users often acted as both creators and consumers, whether by writing Usenet posts, hosting personal websites, or managing their own email servers. Platforms, however, encouraged a more passive consumption model, with user-generated content controlled within proprietary systems. Trust in gatekeepers grew, with users relying on platforms to curate and deliver information. Search engines like Google became the primary gateway to content, while social platforms dictated social interactions, often reducing individual agency. The communal culture of early internet communities gave way to corporate-driven interactions, as decentralized discussions on Usenet were replaced by centralized forums governed by platform owners. Moreover, the platform era introduced a surveillance-based business model, monetizing user data to serve targeted advertisements—a stark departure from the user-centric and privacy-conscious ethos of the early web.
Despite the dominance of platforms, the foundational protocols of the open web remain critical. TCP/IP, HTTP, and DNS still underpin the internet’s infrastructure, ensuring its basic interoperability. Furthermore, movements like the fediverse (e.g., Mastodon), blockchain-based platforms, and protocols like Nostr aim to revive the ideals of decentralization, user autonomy, and community-driven governance. These efforts reflect a growing desire to reclaim the open and collaborative spirit that defined the early internet.
The transition from protocols to platforms transformed the internet from a decentralized, user-driven network into a centralized, corporate-controlled ecosystem. While platforms made the internet more accessible, they sacrificed openness, user autonomy, and the collaborative ethos of its early days. Revisiting the foundational principles of protocols is crucial for those working to rebuild a more open, equitable internet.
Closing Thoughts
The evolution from the early decentralized internet to today’s platform-dominated web reflects a shift from protocols that empowered users to systems that prioritize convenience, control, and corporate interests. Early technologies like Usenet, HTTP, and FTP embodied ideals of openness, collaboration, and autonomy, but modern platforms have concentrated power, creating walled gardens and monetizing user data. Yet, the foundational protocols of the internet persist, inspiring new decentralized initiatives like Nostr, Mastodon, and blockchain-based systems. By supporting and adopting applications built on decentralizing protocols, we can reclaim the values of openness, privacy, and user empowerment. Every choice we make—as developers, users, or advocates—shapes the future of the web. Together, we can revive the collaborative spirit of the internet’s origins and help create a more equitable and resilient digital future.
-
 @ fd78c37f:a0ec0833
2025-01-23 03:30:28
@ fd78c37f:a0ec0833
2025-01-23 03:30:28In this edition, we invited Nyirenda, a member of the nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv community, to share his personal experiences in participating in the Bitcoin community, as well as the challenges the community has faced in its operations and the strategies used to address them.
YakiHonne: Today, we are honored to have a guest from Bitcoin Boma with us. Thank you for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Nyirenda, could you please briefly introduce yourself and tell us a bit about what you do?
Nyirenda:My name is Nyirenda. I'm part of the Bitcoin Boma Education Program and Bitcoin Boma Malawi. Bitcoin Boma Malawi is a coalition of Bitcoin enthusiasts who have come together to raise social, economic, and environmental awareness about Bitcoin in Malawi. Our long-term strategy involves engaging with various stakeholders, including the government, to work towards the legalization of Bitcoin.

YakiHonne: What sparked your interest in Bitcoin, and what motivated you to start a community around it?
Nyirenda: I first came across Bitcoin in 2016 through the news. Back then, its price had already surged to $16,000, which sparked my interest right away. Although the news warned that Bitcoin resembled a Ponzi scheme, I had already built a solid understanding of economic structures, having studied monetary history and the fractional reserve banking system. This gave me the background needed to appreciate Bitcoin. Nyirenda:I began my research journey with Andreas Antonopoulos's lectures and books, which deeply resonated with me. I was quickly drawn to the philosophy behind Bitcoin. Since then, my focus has been on engaging with others and teaching them about Bitcoin, especially within the context of Malawi. Nyirenda:In Malawi, our economic activities face numerous restrictions. The government controls the national fiat currency, limiting what we can do with it. For me, Bitcoin presents a solution to these issues. Today, I remain passionate about educating others about Bitcoin and exploring its potential to transform our economic situation.
YakiHonne: I witnessed the decline of traditional currencies and realized how Bitcoin could play a role in the future. It's truly fascinating to see how it can be implemented. Could you share how the community was formed, how you attracted members in the early stages, and what challenges you faced along the way?
Nyirenda:When I first started diving into Bitcoin, I felt like I needed a teacher. So, I printed a T-shirt that said "Bitcoin accepted here" and wore it whenever I went into town or public places. People would often look at me and ask, "Hey, what's Bitcoin?" I could then briefly explain what Bitcoin is and how it compares to the current fiat system. Nyirenda:Some people were really interested, to the point that we exchanged contacts and started connecting, and it was a great experience. But the turning point came when I saw a tweet from Bitcoin Boma. Someone tweeted about a conference/seminar being organized, in collaboration with Trezor Academy. When I saw this, I knew this was the place to be. So, last July, I met Grant, Ian Foster, and Nick Twyman, who were organizing the event.
 Nyirenda:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.
Nyirenda:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.

YakiHonne: So, what challenges did you face in attracting new members at that stage?
Nyirenda:The first challenge we face is the attitude and perception of Bitcoin. Bitcoin is a new technology and innovation. In a country where people are used to traditional currencies, there are many financial technologies emerging, including centralized coins. This has created challenges. When people hear about Bitcoin, many think of it as a Ponzi scheme. They believe it's a scam or a way to get rich quickly. What I've observed is that most people fail to understand the difference between Bitcoin and centralized currencies. To truly appreciate Bitcoin, they need to experience it. Setting up a custodial wallet and explaining a transaction to them can help. Nyirenda:The second challenge is that people think Bitcoin is too complicated, especially in Africa, and here in Malawi, where the IT and ICT infrastructure is still underdeveloped. I’d say 70% of the population doesn’t have access to the internet. Even in our education system, we don’t learn about computers. It’s mainly by luck if someone has access to a computer and a network, allowing them to appreciate the technology.
YakiHonne: It seems to be common in many countries, where people think Bitcoin is a quick way to get rich. They see it as a scam or a Ponzi scheme. It's a big challenge to get people to believe in Bitcoin as a currency, rather than just their local currency. This is a real barrier in many economies. What principles guide your community, and how do you maintain trust and reliability in discussions? Simply saying, how do you keep the trust of the people?
Nyirenda:I’ll start with Bitcoin BOMA and then extend it to the people we interact with. In Bitcoin BOMA, even though we’re a collaboration, we have clear objectives and a philosophy. Ultimately, we model Bitcoin’s decentralized nature because it allows everyone to participate. In our coalition, we encourage the free flow of ideas and regularly meet to discuss how best to promote Bitcoin education. We focus on its social, economic, and environmental aspects. We assign tasks to each other and work hard to achieve the results. Nyirenda:Malawi has great potential, especially in the energy sector, where we could mine Bitcoin, but we lose a lot of electricity during generation. There were attempts to convince government-run institutions to embrace Bitcoin. However, most of these institutions are controlled by the government, and getting into politics is necessary to convince policymakers. It’s been a challenge because government systems are centralized. There’s a hierarchy to follow, and sometimes, even if a minister understands Bitcoin, it takes a long time to get it approved in parliament and passed into law.This has been one of our ongoing initiatives. Nyirenda:When I go out and interact with people, especially Malawians, I try to explain the transparency of Bitcoin by showing how a decentralized ledger works and how it’s different from traditional systems. I also explain that Bitcoin is reliable and that mismanagement isn’t possible with a decentralized system. Nyirenda:In a country where people are educated in a certain way and believe in competition and power, I often remind them that absolute power corrupts absolutely. I tell them that Bitcoin offers a different space where decentralization allows for a fairer system and benefits everyone. That’s how I try to explain it in simple terms.

YakiHonne: how do you educate your members and keep them updated on Bitcoin development time-to-time?
Nyirenda:For me, learning about Bitcoin is a lifelong process, with always unanswered questions and gaps to fill. I often study, read, and keep an eye on the developments in the Bitcoin community, especially in the African Bitcoin community. My role model is Kenya, particularly how they are enabling people to use Bitcoin through the Tando project. I believe that the value of Bitcoin is not just about holding and waiting for the price to rise, but rather as a tool that can help liberate the world. Nyirenda:Bitcoin is not just about accumulating wealth; I focus more on its role as a tool in the free market. Therefore, I continue to learn, even though I'm not a technical expert and my background is not in this field. I have worked in education, so I apply those skills to better understand Bitcoin and how it works. Nyirenda:I gather information from various sources to understand how Bitcoin works. At the same time, I compare it with the traditional monetary system, as that’s where I began, and it's my foundational layer. As for the Bitcoin BOMA community, I’m happy to say that we have two members with a strong background in economics. We often share interesting content and sometimes engage in debates. We also share many links and videos, learning from each other. Nyirenda:Especially in the Bitcoin Diploma Education Program, I give explanations, and I have peers who help analyze my course content. We remind each other and point out areas that need improvement. We constantly update each other on our progress, ensuring that our activities remain relevant, which helps us continue to improve.

YakiHonne: Does Bitcoin Boomer collaborate with the broader Bitcoin ecosystem, and which partnerships have had the greatest impact so far?
Nyirenda:I'll start with our collaboration with Trezor Academy. Last year, this was one of the most significant partnerships for us in Malawi. Trezor Academy focuses on Bitcoin education, and they provided us with a lot of support. Thanks to this collaboration, we were able to organize a seminar and graduate about 10 to 15 students. It was a major achievement for us. Nyirenda:Additionally, one of our members attended the African Bitcoin Conference held in Kenya, which was a pivotal opportunity. He had the chance to interact with Bitcoiners from across Africa. There were special guests, including nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m and through this exposure, he met the core developers in Kenya and the Tando developers in South Africa. These collaborations have given us insight into what other Bitcoin communities are doing, especially in their projects. Nyirenda:We also had a speaker from Bitcoin Boma who participated in an event in El Salvador. We are working towards making Malawi a Bitcoin node, and he is actively fostering that effort. Big shoutout to Ian Foster for his dedication. He will also be attending a conference in South Africa this January as a guest speaker. These collaborations have been very impactful, and I’m confident that we’ll see the results of these interactions in the future.

YakiHonne: So what challenges has your community faced so far and how have you overcome them while maintaining integrity?
Nyirenda:One of the challenges we face is related to resources, especially when it comes to our learning sessions. We mainly rely on our own resources, and we understand that quality lessons require specific equipment. While we're working toward acquiring these resources, we’re also making the most of what we have. We've agreed to work with what we have, and we believe we can still achieve our objectives. Nyirenda:Another challenge is the attitude towards Bitcoin in Malawi. Most people entering the crypto space have a “get rich quick” mentality. They focus more on the outcomes rather than the learning process. Many crypto traders are primarily interested in exploiting the benefits of Bitcoin. This is a challenge, especially when trying to teach people that Bitcoin is not just about making a profit, but also about liberation. Changing the traditional fiat mindset to embrace this new path is not easy. Nyirenda:Additionally, many people believe that if they invest their time, they must get a return. This is one of the challenges we're currently dealing with. Financial literacy in Malawi still has a long way to go. While people are aware of how economic shocks, especially currency devaluation, affect them, they often act out of desperation. The market is psychologically driven, and people are constantly looking for shortcuts to protect their wealth. When Bitcoin is introduced, it often raises doubts and skepticism. Nyirenda:However, there is no moment of hatred. Instead, we see the growing energy within the community, even if it's just coming from the heart, extending a significant impact on others. There’s a lot of potential and many possibilities ahead. Despite the challenges, we remain hopeful and excited about the future.

YakiHonne: In addition to wearing T-shirts and sparking curiosity, what other methods have you adopted to promote Bitcoin, and what results have you seen?
Nyirenda:First of all, I want to mention the Bitcoin BOMA education diploma program that’s currently running. This is one of the most significant initiatives we have at the moment. We are doing our best to attract people to dive into our education program. So far, the results have been very positive, especially in terms of numbers. People are curious and realize that this is something worth learning. Some have even acknowledged that what they've learned in the traditional education system is very different from the exposure they get from the diploma program. I’d say that’s one of the biggest impacts we've had in promoting Bitcoin. Nyirenda:If we have sufficient resources, we plan to implement further actions such as putting up banners, promoting Bitcoin, and positioning Malawi as a Bitcoin hub. Malawi has great potential, particularly in the tourism sector, with many tourists visiting the country. If we display banners saying “We accept Bitcoin,” it would be appreciated by many people. Personally, I’ve been encouraging businesses to start accepting Bitcoin. Nyirenda:We also have a Bitcoin BOMA Twitter account where we advocate for Bitcoin. We engage in discussions and comment on trends. In the coming months, we plan to host spaces and aim to conduct them in our local language, so more people can appreciate and learn about Bitcoin.
YakiHonne: We’ve reached the end of today’s session, and I must say, you’re doing an incredible job at Bitcoin BOMA. Your personal and collaborative efforts are truly impressive. I’m confident that in the next few years, we’ll be visiting Malawi for a Bitcoin conference. It’s clear that Malawi is heading in the right direction with you leading the way.
-
 @ da18e986:3a0d9851
2025-01-22 23:49:06
@ da18e986:3a0d9851
2025-01-22 23:49:06Since DVMs were introduced to Nostr in July 2023, we've witnessed remarkable growth - over 2.5 million DVM events (Kinds 5000-7000) and counting. Last fall, when Primal added custom feeds (Kind 5300 DVMs), we saw a 10x surge in DVM activity. To handle this growth, I've spent the last few months completely rewriting DVMDash.
The first version of DVMDash, still live at https://dvmdash.live, unfortunately uses full database table scans to compute the metrics. The code was simpler, but the computation ran on the database. This meant the only way to scale the system was to upgrade the database. Using managed databases (like AWS, Azure, Digital Ocean) beyond the lower tiers gets expensive quickly.
The other problem with the first version: it computes metrics globally (well... as global as you can get; there's no true global with Nostr). Global or all-time metrics aren't sustainable with a system that plans to analyze billions of events in the future (a long term goal for DVMDash). Especially metrics like the number of unique DVMs, Kinds, and Users. I spent more time than I care to admit on possible designs, and have settled on these design principles for now:
- Precise accurate metrics will only be computed for the last 30 days of DVM activity.
- At the turn of a new month, we will compute a snapshot of the last month's activity, and a snapshot per DVM and per Kind, and store them in a historical table. This way we can see what any given month in the past looked like from a bird's eye view with metrics like number of job requests, job results, a count of unique DVMs, kinds and users, which DVMs ran jobs on which kinds, etc. The monthly data will all be aggregate.
The goal of the new redesign is to support processing millions of DVM events an hour. Therefore we need to ensure we can horizontally scale the processing as the traffic increases. Horizontal scaling was the primary goal of this new redesign, and early results indicate it's working.
The new architecture for DVMDash uses a redis queue to hold events collected from relays. Then batches of events are pulled off of the queue by dvm event analyzers to compute metrics. Duplicating these analyzers is one way DVMDash can horizontally scale.
To see if increasing the number of dvm event analyzers improves speed, I ran a performance test on Digital Ocean using real DVM events collected from Jan. 1st 2024 to Jan 9th 2025, which includes more than 2.4 million events. The only difference between each run is the number of DVM event analyzers ranging from 1 to 6.

The first graph shows that adding more event analyzers has a significant speed improvement. With only one analyzer it took nearly an hour to process the 2.4 million events. With every added analyzer, there was a noticeable speedup, as can be seen in the graph. With n=6 analyzers, we were able to process all 2.4 million events in about 10 minutes.
When we look at the rate of processing shown in the second graph, we can see that we get up to 300k dvm events processed per minute when n=6, compared to just ~50k events processed when n=1.

While I did test beyond 6 analyzers, I found the sweet spot for the current infrastructure setup to be around 6 analyzers. This provides plenty of headroom above our current processing needs, which typically see less than a million events per month. Even at a million DVM events per day, DVMDash should be able to handle it with n=2 analyzers running. The most important takeaway is that DVMDash can now horizontally scale by adding more analyzers as DVM activity grows in the future.
The code to run these performance tests, either locally or on Digital Ocean (you'd need an API key), is in the dvmdash repo, so anyone can replicate these tests. There's a lot of nuance to scaling that I'm leaving out of this short article, and you can't get away from having to adjust database capacity (especially number of connections). The code for this test can be found in
experiments/test_batch_processing_scaling.pyand the code to produce the graphs is inexperiments/graph_batch_processing_scaling_data.py. For now this is still in thefull-redesignbranch, soon it will be merged intomain.The live version of dvmdash doesn't have these performance updates yet, a complete redesign is coming soon, including a new UI.
I've had my head down working on this rewrite, and couldn't move on to add new features until this was done. Thank you to the folks who made github issues, I'll be getting to those soon.
DVMDash is open source, please drop by and give us a feature request, bug report, pull request or star. Thanks to OpenSats for funding this work.
Github: https://github.com/dtdannen/dvmdash
Shoutout to nostr:npub12xeqxplp5ut4h92s3vxthrdv30j0czxz9a8tef8cfg2cs59r85gqnzrk5w for helping me think through database design choices.
-
 @ 35f3a26c:92ddf231
2025-01-22 20:48:34
@ 35f3a26c:92ddf231
2025-01-22 20:48:34Background
Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely.
The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions.
What can you do with Script? 1. time locks 2. multi-signature requirements 3. other custom logic
opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin
back in 2021, the Taproot upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well Schnorr signatures, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and MAST (Merklized Abstract Syntax Trees) which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions.
The Taproot upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development.
What is Bitcoin Covenants?
It is a BIP (Bitcoin Improvement Proposal), BIP-347, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks.
The proposal’s developers authors names are Ethan Heilman and Armin Sabouri, now the community will debate its merits.
Here the link, in case you are curious:
https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki
It is worth to read the motivation section of the BIP, which reads:
“Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript.
OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable:
Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin.
Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions.
Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot.
Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols.
Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin.
Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures.
OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.”
The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman
Controversy
The controversy revolves around two main camps:
- Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity.
- Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility.
Final Thoughts
Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”.
But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind:
- How will that change affect the security of the network?
- How that change will affect the blockchain usage?
- What is the projected impact over the fees per transaction if this change is approved?
- Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war?
Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions.
Looking forward to observe the evolution of this proposal.
You liked the article? Make my day brighter!
Like and share!
Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work:
https://rodswallet.unstoppable/
The link didn’t open?
To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
-
 @ 93eeb56c:9469e39a
2025-01-22 17:08:44
@ 93eeb56c:9469e39a
2025-01-22 17:08:44💀 Introducing No Good Kid
After 15 years of working as a graphic designer, marketer, and brand therapist, I recently started to feel the urgency to start a project of my own.
I feel out of tune with the state of mainstream marketing today—sterile aesthetics, overstated presentations, and endless battle for attention on centralized social media.
So, I’m introducing No Good Kid. And as you can guess from the title, No Good Kid targets both creators and audiences who don’t exactly fit the status quo.
No Good Kid is the creative’s alter ego. It’s an identity that can be shared and serves as a label under which we can collaborate to create cool projects.
🪩 What is it?
I think of it as an identity—the creative’s alter ego, if you will—that can be shared among creators and serve as a label under which we can collaborate and create.
And the result can be anything, from a marketing campaign to original music production. There are no borders. If the party is right, anything can happen.
In the spirit of gamma personalities, there will be no agency, leader, or hierarchy.
My hope is that the projects will reflect values such as freedom and solidarity. But it’s entirely up to the creators.
Feel free to use the No Good Kid identity, share your project, or reach out if I can help.
🔥 Projects released so far

whistleblower10
In 2024, I crafted a campaign for Amnesty International CZ which led to Amnesty accepting Bitcoin donations for a limited time.
whistleblower10 website→\ project design→

The Nocoiner Syndrome
By the end of last year, The Nocoiner Syndrome was published by Institute of Cryptoanarchy—a research paper written by Peter Horváth that rebutted the ECB’s statement about Bitcoin being on “the road to irrelevance.”
Institute of Cryptoanarchy website→\ project design→
☮️ Vision
There is no need to place a label on this project. I want No Good Kid to be a tool to connect beliefs and hopes with skills in the name of freedom.
Let me know what you think of the idea, or if you have a project in mind.
Be well, and stay no good.
dworis 💀
🥁 Follow No Good Kid:
https://nogoodkid.com/ npub1j0ht2m9jgs6mccyvkffd2dlnfusmqfx9mjlwg6fsmfwxm9rfuwdq40w6rf npub1uwglfjet0m2regqhmgeygc2tc75ngezl8fhftgzhaqas9rjeny8sdztml4
---
🔥 Thanks for reading
Enjoyed this article?
⚡️ Zap some sats
literalpersian75(at)walletofsatoshi.com💀 No Good Kid projects & portfolio
https://nogoodkid.com/👥 Let’s connect on Nostr
npub1j0ht2m9jgs6mccyvkffd2dlnfusmqfx9mjlwg6fsmfwxm9rfuwdq40w6rf -
 @ 2f4550b0:95f20096
2025-01-28 16:47:28
@ 2f4550b0:95f20096
2025-01-28 16:47:28My family and I are wrapping up a relocation from Phoenix, AZ to Austin, TX. I went ahead to get keys to our rental house, meet the movers with our household goods, and generally get as many things ready on the Austin side as possible. My husband stayed behind with our boys to wrap up the AZ house and settle things there. Our experiences over the past few weeks have got me thinking about partnership, project management, and big life changes.
This move would not have been possible without the full partnership that my husband and I have in our marriage. Division of labor is real, and in the context of a relocation it’s vital to get everything done. We trust each other to divide and conquer the myriad tasks and responsibilities necessary. He supervised packers and movers to work on the AZ house; I met them when they arrived in Austin and supervised the move-in. He managed the property management requirements at the AZ rental house; I got the keys and have managed the property management procedures and move-in for Austin. He’s taking care of our current vehicle and handling the road trip from Phoenix to Austin; I bought a second vehicle that I can use to commute. I scheduled the cleaners, landscapers, and carpet cleaning for the AZ house; he supervised the work when the crews arrived. This kind of partnership not only takes care of all the duties, it edifies the relationship we have in our marriage. The care and trust we both show means so much to both of us!
Relocation is also a project, “a series of structured tasks, activities, and deliverables that are carefully executed to achieve a desired outcome” with a specific start and end. Managing this move has been marked by two long to-do lists of tasks for me and my husband and a series of important milestones that we’ve celebrated along the way. We used our calendar to map out the timelines for each phase of the work, we assigned roles and tasks, and we identified risks and dependencies. We enlisted vendor support for many of the tasks, and supervised their efforts while we completed our own. We never got as far as creating a true Gantt chart for the project, but I certainly thought of the phases of our move in that framework.
This move marks the start of a new phase in our family life, which has been marked by a series of big life changes. Since our marriage, these have included living in a number of places, the births of our two sons, and job changes. With this relocation, we get to experience life in a new part of the world and set up our boys for their launch into adulthood. This is exciting, and also a bit daunting. But I’m proud of our efforts to start 2025 off with a bang!
-
 @ a012dc82:6458a70d
2025-01-28 15:17:03
@ a012dc82:6458a70d
2025-01-28 15:17:03In the dynamic world of cryptocurrencies, Bitcoin stands as a pioneering force, a digital currency that has revolutionized the concept of money. Central to its operation and success is a term often heard but not always fully understood: the Bitcoin hashrate. This metric is much more than a technical jargon; it's the heartbeat of the Bitcoin network, powering its transactions, securing its blockchain, and influencing its standing in the market. In this exploration, we delve into the depths of the Bitcoin hashrate, unraveling its complexities and revealing its profound impact on the cryptocurrency market. The hashrate is a window into the soul of Bitcoin, offering insights into its health, efficiency, and future potential. It's a story that intertwines technology, economics, and community, painting a vivid picture of Bitcoin's place in the digital age.
Table Of Content
-
Understanding Bitcoin Hashrate
-
The Role of Hashrate in Network Security
-
Hashrate and Decentralization
-
Economic Implications for Miners
-
Impact on Bitcoin's Market Value
-
The Future of Bitcoin's Hashrate
-
Conclusion
-
FAQs
Understanding Bitcoin Hashrate
The Bitcoin hashrate is the powerhouse of the Bitcoin network, a measure of the collective computational effort used to mine and process transactions. It's akin to the horsepower of an engine, driving the network forward. Each hash is a solution to a cryptographic puzzle, and the hashrate signifies the speed at which these puzzles are solved. As Bitcoin's popularity soars, so does the hashrate, reflecting an ever-increasing number of miners vying to validate transactions and create new blocks. This growth is not just a testament to Bitcoin's popularity but also a marker of its robustness and resilience in the face of challenges. The hashrate is a dynamic indicator, fluctuating with the ebb and flow of the network's activity, mirroring the collective effort of thousands of miners around the globe. It's a testament to the decentralized nature of Bitcoin, where no single entity controls the network, but rather a collective effort secures it.
The Role of Hashrate in Network Security
Bitcoin's security is its cornerstone, and the hashrate is its shield. In the realm of digital currencies, security threats like the 51% attack loom large, where an entity could potentially take control of the network. However, a high hashrate acts as a formidable barrier, making such attacks not just difficult but economically unfeasible. It's a game of numbers; the higher the hashrate, the more distributed the computational power, and the safer the network. This security is not static but a dynamic force that evolves with the network's growth, adapting to new challenges and fortifying Bitcoin's position as a secure digital asset. The hashrate is a beacon of trust, assuring users and investors alike that the network is robust and resistant to manipulation. It's a critical factor in maintaining the integrity of the blockchain, ensuring that transactions are processed securely and reliably.
Hashrate and Decentralization
Decentralization is the soul of Bitcoin, and the hashrate is a reflection of this principle. A decentralized network is less prone to manipulation and control by any single entity, and a high hashrate is indicative of a broad, diverse miner base. This diversity is not just a matter of numbers but a testament to the egalitarian ethos of Bitcoin, where anyone, anywhere, can contribute to the network's upkeep. As the hashrate grows, it weaves a stronger web of participants, each adding to the network's resilience and ensuring its democratic nature. The hashrate is a symbol of the power of the collective, a force that transcends geographical and political boundaries, uniting people under the banner of a decentralized financial system. It's a testament to the vision of Bitcoin's creators, a network that is not just secure and efficient but also open and inclusive.
Economic Implications for Miners
For miners, the hashrate is a beacon guiding their economic journey. It's a delicate balance of power, cost, and reward. As the hashrate climbs, so does the difficulty of mining, a self-regulating mechanism ensuring the network's stability. Miners must constantly adapt, balancing the costs of advanced hardware and energy against the potential rewards of new Bitcoins and transaction fees. This ever-shifting landscape is not just a challenge but an opportunity for innovation, driving miners to seek more efficient and sustainable ways to contribute to the network. The hashrate is a measure of opportunity and challenge, a dance of economics and technology where miners play a crucial role. It's a dynamic ecosystem where the fittest survive, adapting to the ever-changing landscape of Bitcoin mining.
Impact on Bitcoin's Market Value
The hashrate's influence extends beyond the technical realm into the market. While it doesn't directly dictate Bitcoin's price, it's a barometer of network health and investor confidence. A robust hashrate signals a thriving, secure network, attracting investors and bolstering Bitcoin's market position. It's a subtle yet powerful force, shaping perceptions and influencing decisions in the cryptocurrency market. As Bitcoin continues to evolve, the hashrate stands as a key indicator of its vitality and appeal to the market. The hashrate and market value are intertwined in a complex dance, where the health of the network reflects and influences investor sentiment. It's a symbiotic relationship, where each aspect feeds into and strengthens the other.
The Future of Bitcoin's Hashrate
As we look to the future, the Bitcoin hashrate remains a critical aspect of the cryptocurrency's journey. It's not just a measure of computational power but a symbol of the network's evolution, a testament to its strength and a predictor of its potential. The hashrate's trajectory mirrors Bitcoin's own path: ever upward, facing challenges, adapting, and growing stronger. It's a journey not just of technology but of community, innovation, and the relentless pursuit of a decentralized financial future. The hashrate is a narrative of progress, a story of how a decentralized network can grow, adapt, and thrive in the ever-changing landscape of digital currencies. It's a beacon of hope and a testament to the power of collective effort in shaping the future of finance.
Conclusion
The Bitcoin hashrate is more than a technical metric; it's the lifeblood of the Bitcoin ecosystem. It encapsulates the network's security, decentralization, economic dynamics, and market influence. As Bitcoin continues to navigate the complex landscape of digital currencies, its hashrate will remain a key indicator of its health and success. It's a story of collective effort, technological innovation, and the relentless pursuit of a decentralized, secure financial future. The hashrate is not just a number; it's the pulse of Bitcoin, beating strongly as it leads the charge in the ever-evolving world of cryptocurrencies. It's a symbol of resilience, a testament to the enduring power of a decentralized network, and a beacon of hope for a future where financial systems are open, secure, and accessible to all.
FAQs
What is Bitcoin hashrate? The Bitcoin hashrate is the total computational power used to mine and process transactions on the Bitcoin network, measured in hashes per second.
Why is the Bitcoin hashrate important? It's crucial for network security, indicating the difficulty of performing a 51% attack, and reflects the network's decentralization and health.
How does the hashrate affect Bitcoin miners? A higher hashrate increases the difficulty of mining, impacting the profitability and efficiency of mining operations.
Does the Bitcoin hashrate influence its market value? While not directly affecting the price, a strong hashrate can boost investor confidence, potentially influencing Bitcoin's market value.
Can the Bitcoin hashrate predict the future of the cryptocurrency? The hashrate is a key indicator of Bitcoin's health and can provide insights into its future potential and stability.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ eee391ee:8d0b97c2
2025-01-22 16:42:17
@ eee391ee:8d0b97c2
2025-01-22 16:42:17Amber 3.1.9
- Add missing logs for relay errors
- Change listen for new connections button text and icons
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.1.9.txtandmanifest-v3.1.9.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.1.9.txt.sig manifest-v3.1.9.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.1.9.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 4506e04e:8c16ba04
2025-01-22 16:37:08
@ 4506e04e:8c16ba04
2025-01-22 16:37:08If you are a researcher in the field of medicine, you are most likely very familiar with PubMed – where you get citations for the articles and studies that drive your work forward. PubMed Central (PMC), the full-text repository of life sciences journal literature managed by the National Library of Medicine (NLM), was established in 2000. Its creation marked a significant milestone in providing open access to biomedical research. Since 2005, PMC has served as the designated repository for papers submitted under the NIH Public Access Policy, reflecting the growing emphasis on transparency and accessibility in scientific research. Over the years, PMC has expanded its scope, becoming a repository for papers aligned with public and open access policies from various research funding organizations, both within and beyond biomedical sciences.
Funding and Partnerships
NLM’s operations, including PubMed and PMC, are supported by a combination of government funding and contributions from influential entities such as The Bill & Melinda Gates Foundation.
The Bill and Melinda Gates Foundation receives significant donations from pharmaceutical companies, as well as other organizations and individuals. The exact amount of money donated by each company can vary from year to year, but here are some examples of the amounts donated by the pharmaceutical companies:
GSK (GlaxoSmithKline):
- In 2020, GSK donated $100 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, GSK donated $50 million to the Gates Foundation to support the development of a new malaria vaccine.
Pfizer:
- In 2020, Pfizer donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Pfizer donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
Merck & Co.:
- In 2020, Merck donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Merck donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
Novartis: - In 2020, Novartis donated $20 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis. - In 2019, Novartis donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
Johnson & Johnson:
- In 2020, Johnson & Johnson donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Johnson & Johnson donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
Sanofi:
- In 2020, Sanofi donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis.
- In 2019, Sanofi donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
AstraZeneca:
- In 2020, AstraZeneca donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis.
- In 2019, AstraZeneca donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
Eli Lilly and Company:
- In 2020, Eli Lilly donated $10 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis.
- In 2019, Eli Lilly donated $5 million to the Gates Foundation to support the development of a new malaria vaccine.
Additionally, NLM website [https://cdn.ncbi.nlm.nih.gov/pmc/cms/files/PMCFunderDepositList.xlsx] (list over 200)(!) organisations that are founding it. What could go wrong one might ask?!
The Centralization Challenge
While PubMed and PMC have played a pivotal role in democratizing access to scientific literature, their centralized nature presents vulnerabilities. Over the past century healthcare has grown to become one of the most profitable industries and to believe that the healthcare system we have today is the best we can do is far from understatement.
PubMed's reliance on centralized funding and decision-making processes makes it susceptible to external influences, including lobbying by powerful entities. Moreover, the centralized infrastructure allows for content to be published and removed with relative ease, often without leaving a trace. This raises concerns about the integrity and permanence of the scientific record, particularly in contentious or politically sensitive areas of research.
The ability to alter or erase information from PubMed undermines trust in the system’s objectivity and neutrality. Researchers and the public alike depend on these repositories for reliable and impartial access to scientific knowledge. Any perceived or actual manipulation of content can erode confidence in the platform and compromise its foundational mission.
The Case for Decentralization
To address these challenges, a decentralized alternative built on emerging technologies, such as the Nostr protocol, could offer significant advantages. A decentralized platform would:
-
Enhance Resilience: By distributing data across a network of relays, a decentralized system would eliminate single points of failure, ensuring the scientific record remains intact and always accessible even in the face of technical or political disruptions.
-
Increase Transparency: Decentralized systems inherently log changes, making it nearly impossible to alter or remove content without leaving an auditable trail. This transparency would bolster trust in the integrity of the research.
-
Reduce Susceptibility to Lobbying: Without centralized control, the influence of external entities on the platform’s content would be significantly diminished, preserving the objectivity of the scientific record.
-
Foster Open Collaboration: A decentralized approach aligns with the principles of open science, encouraging global collaboration without the constraints of centralized oversight or bias introduced by big pharma lobby.
Conclusion
While PubMed and PMC have been instrumental in advancing access to scientific literature, their centralized nature leaves them vulnerable to manipulation and external pressures. A shift toward a decentralized, censorship-resistant platform would address these vulnerabilities and provide a more robust and trustless repository for scientific knowledge. Groundbreaking research that dares to challenge the pharmaceutical industry's status quo could be published anonymously, following in the footsteps of the Bitcoin whitepaper's pseudonymous author, Satoshi Nakamoto. Leveraging technologies like the Nostr protocol, the research community can build a system that ensures the permanence, integrity, and impartiality of the scientific record for generations to come.
-
 @ 94321ee8:8957f43d
2025-01-28 12:38:00
@ 94321ee8:8957f43d
2025-01-28 12:38:00Nostr Writer
Estoy probando Nostr Writer, el plugin que permite publicar desde Obsidian.md. Esta es una publicación de prueba, para ver ==como reacciona Nostr== con los códigos Markdown.
-
 @ b83e6f82:73c27758
2025-01-22 16:29:15
@ b83e6f82:73c27758
2025-01-22 16:29:15Citrine 0.7.1
- Add the restore follows button back
- Show notification when backing up database
- Listen for pokey broadcasts
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.7.1.txtandmanifest-v0.7.1.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.7.1.txt.sig manifest-v0.7.1.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.7.1.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ c3b2802b:4850599c
2025-01-28 10:46:10
@ c3b2802b:4850599c
2025-01-28 10:46:10Dear sisters and brothers, I have been born in a country without any religion. As a young adult I understood that a life without spirituality does not make sense. Today, 50 years later, I am convinced that the family of creation consists of divine beings with the potential to unfold endless love - independently of the controversies between singular religions.
Each of us human beings is full of divine sparks which may strengthen each moment during our life the fire of love and compassion toward all living beings in the universe. These divine sparks may feed the eternal dance of creation.
Religion and science have converged during the last centuries: Divine spirit is the driving force of all happenings in our universe. Buddha, Plato, Jesus Christ, Kabir, Guru Nanak, Albert Schweitzer and recently many Nobel Price winning physicists have expressed the same conviction:
We are divine creators of the paradise resulting from genesis on this planet within the living universe. Looking around the world these days, however, we observe harm, hunger, dissence, struggle and war.
How does this coexist – the potential to create the paradise on the one hand – and the destructive forces leading to a multitude of catastrophes? May be you like the following way to interprete what is going on actually:
We are born to be tested in a learning adventure of evolution within the cosmos. The life of each of us is an examination checking whether we are ripe for creating the paradise.
Each generation of human beings has the chance to reach the tipping point. Possibly todays generation, all of us sitting here, might overcome the centennial struggle on details of diverse religions and worldviews. If we today conjointly remember our potential as divine beings to create a peaceful and well balanced world - then we can make the next step of cosmic evolution – charcterized by love, peace and respect for all forms of life:
We may give now birth to a new chapter in the process of evolution. The time might be ripe these days. Let me give some illustrations for my optimism based on my work of the past 30 years in Germany: 30 years ago in my country most of all fuels for electricity and heating were imported. All German villages depended existially from international trusts supplying nuclear and fossil energy. The great majority of Germans relied on imported fossile or nuclear fuels. Today, 30 years later, we count 200 villages with own energy production based on regional ressources which were initiated by teams of german universities, where I have been active.
During the same time the number of similar activities aiming at a regionally organized society all over the world exploded. In many countries many local initiatives were founded organizing food production, local trade, water supply and many other fields of human needs on a regional base in fair and clean ways, without any international activities of global players like MacDonald or Monsanto.
Another world is possible – and even better, the regional society is blossoming already since decades worldwide.
A second source for my optimism is my scientific work. Humans dispose of spiritual potentials enabling us to connect with the holy spirit surrounding us since eternal times. Individuals unfolding this potential and behaving respectfully toward other beings report higher well-being as compared to other people. That empirical pattern has been found in hundreds of scientific studies all over the world. These results feed our trust, that we are on the right way with our regional initiatives like Kirpal Sagar in India, the new energy villages in Germany, the clean and fair agriculture initiatives worldwide, the open seeds movement and the many further initiatives.
Remembering Mahatma Gandhi, the great indian philosopher and politician: We do not need to fight against the players of the old world, against psychopathic people in international trusts and organizations who plan a world all of us dislike. This old structure will break down by itself.
Meanwhile we build the society we prefere: Ethically grounded communities like Kirpal Sagar, based on grace, fairness and respect between all living beings. My congratulation to the golden jubilee of this wonderful project, which may serve as a model for the whole world.
Let´s shake our hands, connect our hearts and let´s bring our souls in harmony within the cosmic concert of love!
Peter Schmuck, psychologist and regional society activist, Germany, february 5 2024.
First published at the German platform for future communities
-
 @ 5d4b6c8d:8a1c1ee3
2025-01-22 16:20:47
@ 5d4b6c8d:8a1c1ee3
2025-01-22 16:20:47I just completed my 5th steps challenge on Workit (only available on iOS, sorry).
This challenge was 10k steps every day for two weeks. Of course, these were the coldest two weeks of the year, so many of those steps were indoors.
The buy-in/stake was 25k sats and the payout was 28,608, which was a little less than I expected. I don't think the winners of the bonus rewards have been announced yet, so there may still be another 40k coming my way (but, probably not).
So far, I've netted over 50k on these challenges. What a great way to stay healthy, while stacking sats.
originally posted at https://stacker.news/items/860122
-
 @ b17fccdf:b7211155
2025-01-22 10:39:19
@ b17fccdf:b7211155
2025-01-22 10:39:19What's changed
- New bonus guide dedicated to install/upgrade/uninstall PostgreSQL
- Modified the LND guide to use PostgreSQL instead of bbolt
- Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)
- Modified the BTCPay Server bonus guide according to these changes
- Used the lndinit MiniBolt organization fork, to add an extra section to migrate an existing LND bbolt database to PostgreSQL (🚨⚠️Experimental - use it behind your responsibility⚠️🚨)
- New Golang bonus guide as a common language for the lndinit compilation
- Updated LND to v0.18
- New Bitcoin Core extra section to renovate Tor & I2P addresses
- New Bitcoin Core extra section to generate a full
bitcoin.conffile - Rebuilt some homepage sections and general structure
- Deleted the
$symbol of the commands to easy copy-paste to the terminal - Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default
🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections:
- Use the default bbolt database backend for the LND
- Use the default SQLite database backend for the Nostr relay
⚠️Attention⚠️: The migration process was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, according to the developer, it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼
🔧 PR related: https://github.com/minibolt-guide/minibolt/pull/93
♻️ Migrate the PostgreSQL database location
Attention!! These instructions are invalid since the latest changes applied to the PostgreSQL bonus guide. See more information on the recent associated post by clicking ~ > HERE < ~
If you installed NBXplorer + BTCPay Server before 05/06/2024, it is probably you have the database of the PostgreSQL cluster on the default path (
/var/lib/postgresql/16/main/), follow the next instructions to migrate it to the new dedicated location on/data/postgresdbfolder:- With user
admincreate the dedicated PostgreSQL data folder
sudo mkdir /data/postgresdb- Assign as the owner to the
postgresuser
sudo chown postgres:postgres /data/postgresdb- Assign permissions of the data folder only to the
postgresuser
sudo chmod -R 700 /data/postgresdb- Stop NBXplorer and BTCPay Server
sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver- Stop PostgreSQL
sudo systemctl stop postgresql- Use the rsync command to copy all files from the existing database on (
/var/lib/postgresql/16/main) to the new destination directory (/data/postgresdb)
sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/Expected output:
``` sending incremental file list ./ PG_VERSION postgresql.auto.conf postmaster.opts postmaster.pid base/ base/1/ base/1/112 base/1/113 base/1/1247 base/1/1247_fsm base/1/1247_vm base/1/1249 base/1/1249_fsm base/1/1249_vm [...] pg_wal/000000010000000000000009 pg_wal/archive_status/ pg_xact/ pg_xact/0000
sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec total size is 164,311,368 speedup is 1.00 ```
- Edit the PostgreSQL data directory on configuration, to redirect the store to the new location
sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers- Replace the line 42 to this. Save and exit
data_directory = '/data/postgresdb'- Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before
sudo systemctl start postgresql- You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C
journalctl -fu postgresqlExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS. Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS.- You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C
journalctl -fu postgresql@16-mainExample of the expected output:
Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded. Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time. Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main.- Start NBXplorer and BTCPay Server again
sudo systemctl start nbxplorer && sudo systemctl start btcpayserver- Monitor to make sure everything is as you left it. You can exit monitoring at any time by pressing Ctrl+C
journalctl -fu nbxplorer
journalctl -fu btcpayserver
Enjoy it MiniBolter! 💙
-
 @ 3efdaebb:3e0d2681
2025-01-22 01:08:58
@ 3efdaebb:3e0d2681
2025-01-22 01:08:58Hey Nostr! It’s App Store release day for Damus. Thanks again to our loyal Purple subscribers for helping us continue to improve the UX and pointing out important changes and fixes. Highlights of Version 1.12:
Added
- Render Gif and video files while composing posts (Swift Coder)
- Add profile info text in stretchable banner with follow button (Swift Coder)
- Paste Gif image similar to jpeg and png files (Swift Coder)
Changed
- Improved UX around the label for searching words (Daniel D’Aquino)
- Improved accessibility support on some elements (Daniel D’Aquino)
Fixed
- Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino)
- Fix non scrollable wallet screen (Swift Coder)
- Fixed suggested users category titles to be localizable (Terry Yiu)
- Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu)
- Fixed right-to-left localization issues (Terry Yiu)
- Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu)
- Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu)
- Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino)
- Fixed non-breaking spaces in localized strings (Terry Yiu)
- Fixed localization issue on Add mute item button (Terry Yiu)
- Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu)
- Fixed localization issues in RelayConfigView (Terry Yiu)
- Fix duplicate uploads (Swift Coder)
- Remove duplicate pubkey from Follow Suggestion list (Swift Coder)
- Fix Page control indicator (Swift Coder)
- Fix damus sharing issues (Swift Coder)
- Fixed issue where banner edit button is unclickable (Daniel D’Aquino)
- Handle empty notification pages by displaying suitable text (Swift Coder)
-
 @ da0b9bc3:4e30a4a9
2025-01-28 10:01:29
@ da0b9bc3:4e30a4a9
2025-01-28 10:01:29Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/867409
-
 @ cff1720e:15c7e2b2
2025-01-21 19:28:49
@ cff1720e:15c7e2b2
2025-01-21 19:28:49Introduction
The aim of ELI5 (explain me like I'm 5) is to explain difficult things simply. This is urgently needed in our high-tech world, because only by understanding the technologies can we use them properly and develop them further.
I'm starting my series with Nostr, a relatively new internet protocol. What the hell is an Internet protocol? In formal terms, it is an international standard that has ensured that the Internet has been working pretty well for over 30 years. It is the language in which computers communicate with each other and which you also use every day, probably without realizing it. http(s) transports your request to a server (e.g. Amazon), and html ensures that a nice page is created on your screen from the data supplied. A mail is sent to the mail server with smtp and retrieved from it with imap, and since everyone uses the standard, this works with every app on every operating system and with every mail provider.
And with an e-mail address like roland@pareto.space, you can even move at any time, no matter where. Cool, that's state of the art! But why doesn't this work with chat, for example, is there no protocol? Yes, it's called IRC (Internet Relay Chat → remember the name), but it's hardly ever used. The reasons for this are not technical, but rather apps such as Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok and others have deliberately created incompatibilities and user dependencies in order to maximize profits.

Since the standard protocol is not used, each app has its own, and we need a handful of apps to exchange information with everyone we know. A mobile phone number is a prerequisite for every account, allowing app manufacturers to track users comprehensively and earn up to USD 30 per account per month by selling the information. The user is no longer the customer, he is the product! Advertising SPAM is the least of the problems with this business model. Servers with millions of user data are a “honey pot”, so they are often hacked and the access data sold. In 2024, the Twitter account of then President Joe Biden was also hacked and no one knew who had written the messages (nor did they before), meaning that the authenticity of the content is not guaranteed with any of these providers. In the same year, the founder of Telegram was taken into custody in France because he refused to build backdoors into his software. Now, to protect “our democracy”, practically anyone can read what information they exchange with whom, e.g. which shampoo certain politicians use.

Why Nostr?
And anyone who actually believes they can practice freedom of expression on social media will quickly find themselves in the situation of Donald Trump (who was president at the time), whose Twitter account was shut down in 2021 (cancel culture). The user data, i.e. their profile, contacts, documents, images, videos and audio files - no longer belong to them anyway but are the property of the platform operator; read the terms and conditions. But no, not a good idea, there are hundreds of pages and they are constantly being changed. So everyone uses apps whose technology they don't understand, whose rules they don't know, where they have no rights and which steal the results of their actions. What would the five-year-old say if his older sister offered to “manage” all his toys and then hand them over if he was good? “You must be crazy”, and with that the toddler proves he has more sense than the majority of adults.
Conclusion: no standards, no data, no rights = no future!

How does Nostr work?
The developers of Nostr realized that the server-client concept had turned into a master-slave concept. The master is synonymous with centralization and becomes the “single point of failure”, which inevitably makes systems dysfunctional. In a distributed peer2peer system, there are no longer any masters but only equal nodes (relays) on which the information is stored. By storing information redundantly on several relays, the system is more resilient in every respect. It is not only nature that has successfully used this principle for millions of years, the Internet was also designed in this way (the ARPAnet was developed by the US military for use in war situations with massive disruptions). All nostr data is stored on relays and the user can choose between public (usually free) and private relays, e.g. for closed groups or for the purpose of data archiving. As documents are stored on several relays, unique document names (URIs = identifiers) are used instead of URLs (locators), making broken links a thing of the past, as are deletions / losses.
Each document (called an event) is signed by the owner, making it authentic and tamper-proof and can only be deleted by the creator. A key pair consisting of a private (nsec) and public key (npub) is used for this, as known from mail encryption (PGP). This represents a Nostr identity that can be supplemented with a picture, name, bio and a readable Nostr address (e.g. roland@pareto.space ), which is all that is needed to use all the resources of the Nostr ecosystem. And this now consists of over a hundred apps with different focuses, e.g. for personal encrypted messages (DM → OxChat), short messages (Damus, Primal), blog posts (Pareto), meetups (Joinstr), groups (Groups), images (Olas), videos (Amethyst), audio chat (Nostr Nests), audio streams (Tunestr), video streams (Zap.Stream), marketplaces (Shopstr) and much more. Registration is done with a single click (single sign-on) and ALL user data is available to the apps (profile, data, contacts, social graph → followers, bookmarks, comments, etc.), in contrast to the fragmented data silos of the present.
Summary: one open standard, all data, all rights = great future!

Why is Nostr the future of the internet?
“Don't build your house on someone else's property” also applies to the Internet - for all app developers, artists, journalists and users, because their data is also valuable. Nostr guarantees ownership of the data and overcomes its fragmentation. Neither use nor creative freedom is restricted by excessive license and usage conditions. Passive users become active participants through interaction, co-creators in a sharing economy (Value4Value). Open source finally restores trust in software and its providers. Open standards enable developers to cooperate more and develop faster, while guaranteeing freedom of choice for users. Which brings us back to our five-year-old for the last time. Children love Lego more than anything, especially the maxi box “Classic”, because it allows them to live out their imagination to the full in terms of combinations. Adults then give them the far too expensive theme packs, with which you can only build one solution according to the instructions. “What's wrong with my parents, when did they take a wrong turn?” the children rightly ask themselves. But the image can be polished up again if they show their children Nostr, because even five-year-olds understand the advantages.
The new Internet is decentralized. The new Internet is self-determined. Nostr is the new Internet.

\ More infos: https://nostr.net/\ Quick start: https://start.njump.me/
-
 @ b17fccdf:b7211155
2025-01-21 18:42:14
@ b17fccdf:b7211155
2025-01-21 18:42:14Some guides on MiniBolt / RaMiX have suffered some modifications and need additional instructions to migrate. Here is a summary:
🔘 New installation/update instructions of BTC RPC Explorer to avoid this issue.
🔘 New installation/update method of Node + NPM.
🔘 New installation/update method of PostgreSQL ~ > Attention! If you installed PostgreSQL after 30/09/2024, you do not need to follow these steps related to PostgreSQL.
Update Nodejs + NPM to the latest LTS version (using the new method)
Guide related: Node + NPM
Context: The installation/upgrade section of this guide has suffered some modifications, so to upgrade to the latest LTS released version using the new installation method, you need to follow the next steps:
- Stop the Nodejs + NPM dependencies:
sudo systemctl stop thunderhub btcrpcexplorer- With user admin, update the packages and upgrade to keep up to date with the OS, press "y" and ENTER when needed or ENTER directly:
sudo apt update && sudo apt full-upgrade- Change to a temporary directory which is cleared on reboot:
cd /tmp- Set the environment variable of the version:
VERSION=22- We will use the new NodeSource Node.js Binary Distributions repository instructions. Download the setup script:
curl -fsSL https://deb.nodesource.com/setup_$VERSION.x -o nodesource_setup.sh- Run the setup script:
sudo -E bash nodesource_setup.sh- Update the package manager and update Node.js + NPM to the latest LTS version:
sudo apt update && sudo apt full-upgrade- Check the correct update of NodeJS:
node -vExample of expected output:
v22.12.0- Check the correct installation of NPM:
npm -vExample of expected output:
10.9.0- (Optional) Delete the setup script:
rm nodesource_setup.sh- Start again the Nodejs + NPM dependencies:
sudo systemctl start thunderhub btcrpcexplorer
Update BTC RPC Explorer to the latest version
Guide related: 2.3 Blockchain explorer: BTC RPC Explorer
Context: After this notice, if you deleted the
deprecatedrpc=warningsflag because it is no longer necessary, it is probably that the "Node Details" section of the BTC RPC Explorer got you this error, this is because after the Bitcoin Core v28 update, just like LND, Electrs and other services, they have needed an update to remain compatible. BTC RPC Explorer was updated on this commit, but an official version that includes this correction has not been officially released yet. To fix this, it is necessary to point to the current source code and not the one related to the last released version (3.4.0).~ > Get instructions to get this by following these steps and fix the issue ~ > HERE < ~
Update PostgreSQL (server instance migration & others)
Guide related: PostgreSQL
Attention!! If you installed PostgreSQL after 30/09/2024, you don't need to do anything, and the next steps don't apply to your case.
Context: With each major version jump of PostgreSQL, the update creates a new and dedicated cluster and folder with the number of each version. Also, the changes made between versions cause the need to migrate the database, that is, from one cluster to another, with a specific tool. This was unknown at the beginning, before creating the MiniBolt PostgreSQL installation guide, so a specific folder for the versions was not created. The installation section was changed past 30/09/2024 to use this new method, but people who followed the PostgreSQL installation before that, need to do things to be in line with the MiniBolt guide.
Following the next steps, we are going to do the necessary migrations, the summary is the next:
1. Migrate the PostgreSQL database to a new location (a dedicated folder for each version).
2. Migrate from PostgreSQL server version 16 to 17.
Verification
If you are not sure whether you installed PostgreSQL before or after the mentioned date (30/09/2024), you can check as follows:
- With user
adminlist the existing clusters:
pg_lsclustersExpected output if you installed PostgreSQL after 30/09/2024, (you don't need do anything):
Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.logExpected output if you installed PostgreSQL before 30/09/2024, and performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgrade, (you need to follow the next steps):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.logExpected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (the PostgreSQL v17 release) (unlikely case) (you need to follow the next steps):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log
Migrate the PostgreSQL database to the new location
(Only if you installed PostgreSQL following the MiniBolt guide before 30/09/2024)
- Show the existing clusters to show the current path of the database:
pg_lsclusters~ > Expected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (PostgreSQL v17 release) (unlikely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log~ > Expected output if you have performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (PostgreSQL v17 release) (most likely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log~ > Check the current "Data directory" column value of the cluster 16 (/data/postgresdb) for the future, we have changed this to a dedicated folder for each version (
/data/postgresdb/16,/data/postgresdb/17,/data/postgresdb/18, etc.)- Stop the PostgreSQL dependencies and the PostgreSQL version 16 cluster:
sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared postgresql@16-main~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially lnd ~ >
journalctl -fu lnd.- Monitor the logs of the PostgreSQL version 16 cluster to ensure that it has been stopped gracefully:
journalctl -fu postgresql@16-mainExpected output:
minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... minibolt systemd[1]: postgresql@16-main.service: Deactivated successfully. minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main.~ > Press
Ctrl + Cto continue.- Create a temporary directory in a place out of the
/data/postgresdbto move the data securely:
sudo mkdir /tmp/postgresdb-temp- Sync the existing data of the current directory
/data/postgresdbto this temporary directory:
sudo rsync -av /data/postgresdb/ /tmp/postgresdb-temp/Example of expected output:
``` [...] pg_xact/ pg_xact/0000 [...]
sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ```
~ > Wait until the prompt shows up again.
- Change to the user
roottemporary:
sudo su- Delete the content of the folder that hosted the original database:
sudo rm -rf /data/postgresdb/*- Come back to the
adminuser:
exit- Create a new specific and dedicated folder to the version number and to be in line with the new and current storage method of the current guide:
sudo mkdir /data/postgresdb/16- Assign as the owner to the user
postgres:
sudo chown postgres:postgres /data/postgresdb/16- Assign the correct permissions to the folder:
sudo chmod 700 /data/postgresdb/16- Now you can sync the data from the temporary directory to
/data/postgresdb/16in a secure way since this directory is not inside the source directory:
sudo rsync -av /tmp/postgresdb-temp/ /data/postgresdb/16/Example of expected output:
``` [...] pg_xact/ pg_xact/0000 [...]
sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ```
~ > Wait until the prompt shows up again.
- Modify the configuration file (
postgresql.conf) of the PostgreSQL to point to the new directory folder created:
sudo nano +42 /etc/postgresql/16/main/postgresql.conf- Replace the data directory location to match with the new path:
data_directory = '/data/postgresdb/16'- Start again the PostgreSQL service instance:
sudo systemctl start postgresql@16-main- Monitor the logs of the PostgreSQL version 16 cluster to ensure that it works fine:
journalctl -fu postgresql@16-mainExpected output:
minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... minibolt systemd[1]: Started PostgreSQL Cluster 16-main.~ > Press
Ctrl + Cto continue.- Check the new database location with:
pg_lsclusters~ > Expected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (unlikely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log~ > Expected output if you have performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (most likely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log~ > Check the new path on the "Data directory" column value of the cluster version 16, now (/data/postgresdb/16).
- Start again the PostgreSQL dependencies services:
sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared~ > Check all work fine with the logs of each service, especially lnd ~ >
journalctl -fu lnd.- Stop again the PostgreSQL dependencies services, to continue working:
sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially lnd ~ >
journalctl -fu lnd.Migrate from PostgreSQL server version 16 to 17
(Only if you installed PostgreSQL following the MiniBolt guide before 30/09/2024)
Context: If you fully updated your OS after 26/09/2024 (the PostgreSQL v17 launched), using
sudo apt update && sudo apt full-upgrade, and you installed PostgreSQL before that date following the PostgreSQL MiniBolt guide, it is likely that you now are using the old version (v16) of the PostgreSQL server instance.To confirm that, follow the next steps:
Check the PostgreSQL server version in use
- With the user
admin, enter the psql (PostgreSQL CLI):
sudo -u postgres psql- Enter the next command to get the server version:
SELECT version();Expected output:
``` version
PostgreSQL 16.6 (Ubuntu 16.6-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ```
~ > Check the previous version is "PostgreSQL 16.6" (an outdated version of the PostgreSQL server), the latest version is PostgreSQL 17.2. 🔧✅ We are going to fix this in the next steps.
- Come back to the
adminuser bash prompt:
\q- List the cluster to show the state of the both PostgreSQL server instances:
pg_lsclusters~ > Expected output if you have not performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (unlikely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log~ > Expected output if you have performed a full upgrade of the MiniBolt with
sudo apt update && sudo apt full-upgradesince 26/09/2024 (most likely):Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.logUpdate PostgreSQL
If you haven't done so before, make sure to update the OS (PostgreSQL included to the latest version 17):
- With user
admin, fully update the OS with the package manager:
sudo apt update && sudo apt full-upgrade~ > Press "y" and enter or directly enter when the prompt asks you.
PostgreSQL server migration
- Stop all existing clusters:
sudo systemctl stop postgresql@16-main postgresql@17-main- Create a new database destination folder for the v17 cluster ready for migration from v16:
sudo mkdir /data/postgresdb/17- Assign the owner as the postgres user:
sudo chown postgres:postgres /data/postgresdb/17- Assign the correct permissions:
sudo chmod 700 /data/postgresdb/17- Delete the cluster created by default for v17:
sudo -u postgres pg_dropcluster 17 main- Update the systemd:
sudo systemctl daemon-reload- Start the migration with the PostgreSQL migration tool:
sudo -u postgres pg_upgradecluster 16 main /data/postgresdb/17~ > ⌛ This may take a lot of time depending on the existing database size (the nostr relay database especially) and your machine's performance; it is recommended to use tmux. Wait until the prompt shows up again.
Example of expected output:
``` Restarting old cluster with restricted connections... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Creating new PostgreSQL cluster 17/main ... /usr/lib/postgresql/17/bin/initdb -D /data/postgresdb/17 --auth-local peer --auth-host scram-sha-256 --no-instructions --encoding UTF8 --lc-collate en_US.UTF-8 --lc-ctype en_US.UTF-8 --locale-provider libc The files belonging to this database system will be owned by user "postgres". This user must also own the server process.
The database cluster will be initialized with locale "en_US.UTF-8". The default text search configuration will be set to "english".
Data page checksums are disabled.
fixing permissions on existing directory /data/postgresdb/17 ... ok creating subdirectories ... ok selecting dynamic shared memory implementation ... posix selecting default "max_connections" ... 100 selecting default "shared_buffers" ... 128MB selecting default time zone ... Etc/UTC creating configuration files ... ok running bootstrap script ... ok performing post-bootstrap initialization ... ok syncing data to disk ... ok Warning: systemd does not know about the new cluster yet. Operations like "service postgresql start" will not handle it. To fix, run: sudo systemctl daemon-reload
Copying old configuration files... Copying old start.conf... Copying old pg_ctl.conf... Starting new cluster... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Running init phase upgrade hook scripts ...
Roles, databases, schemas, ACLs... set_config
(1 row)
set_config
(1 row)
Fixing hardcoded library paths for stored procedures... Upgrading database postgres... Fixing hardcoded library paths for stored procedures... Upgrading database template1... Stopping target cluster... Stopping old cluster... Disabling automatic startup of old cluster... Starting upgraded cluster on port 5432... Warning: the cluster will not be running as a systemd service. Consider using systemctl: sudo systemctl start postgresql@17-main Running finish phase upgrade hook scripts ... vacuumdb: processing database "postgres": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "template1": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "postgres": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "template1": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "postgres": Generating default (full) optimizer statistics vacuumdb: processing database "template1": Generating default (full) optimizer statistics
Success. Please check that the upgraded cluster works. If it does, you can remove the old cluster with pg_dropcluster 16 main
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ```
- Reload the systemd again:
sudo systemctl daemon-reload- List the clusters to show the state:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Notes: * Don't worry about the
output of the "Owner" column. * Note how the old 16 cluster has automatically gone into status "down" after the migration.
- Stop the version 17 cluster using the
pg_ctlclustertool, to then be able to run it and manage it withsystemd:
sudo pg_ctlcluster 17 main stop- List the clusters again to show the state:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 down <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Note how the version 17 cluster has gone into status "down".
- Start the version 17 cluster with systemd:
sudo systemctl start postgresql@17-main- Monitor the logs of the PostgreSQL version 17 cluster to ensure that it working fine with
systemd:
journalctl -fu postgresql@17-mainExpected output:
minibolt systemd[1]: Starting PostgreSQL Cluster 17-main... minibolt systemd[1]: Started PostgreSQL Cluster 17-main.~ > Press
Ctrl + Cto continue.- List the clusters again to show the state:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Note how the version 17 cluster has come back into the status "online".
- Delete the version 16 (old and disused) cluster:
sudo pg_dropcluster 16 main- List again the clusters to check the correct deletion:
pg_lsclustersExpected output:
Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log~> Note how it no longer appears version 16 (old and disused) cluster.
Check the PostgreSQL server version in use
- With the user
admin, enter the psql (PostgreSQL CLI):
sudo -u postgres psql- Enter the next command to get the server version:
SELECT version();Example of expected output:
``` version
PostgreSQL 17.2 (Ubuntu 17.2-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ```
~ > Check the previous version in use is now PostgreSQL 17.2 (the latest and current version of the PostgreSQL server at this moment).
- Come back to the
adminuser bash prompt:
\q- Start again the PostgreSQL dependencies services:
sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared~ > Check all works fine with the logs of each service, especially lnd ~ >
journalctl -fu lnd.- (Optional) Once you have verified that everything is working correctly, you can delete the created PostgreSQL backup and temporary directory:
sudo rm -rf /tmp/postgresdb-temp- Delete unnecessary packages:
sudo apt autoremove~ > Press "y" and ENTER when needed or ENTER directly when the prompts ask you.
✅ That's it! If you have any questions or issues, you can go to any RRSS available for the MiniBolt project ~ > HERE < ~
Only for MiniBolters! Enjoy it! 💙
-
 @ 16d11430:61640947
2025-01-28 09:05:13
@ 16d11430:61640947
2025-01-28 09:05:13The Millennial generation stands at a unique crossroads in history. Born into a world where traditional systems of economic and social power were firmly entrenched, they have matured in an era where those very systems are showing cracks. Nowhere is this more evident than in the rise of Bitcoin—a financial and cultural phenomenon that reflects not only technological progress but also the profound sociopsychological struggles of a generation attempting to wrest autonomy from the aging custodians of power.
Prolonged Adolescence and the Deferred Quest for Autonomy
Millennials, often caricatured as perpetual adolescents, have endured an extended transition into adulthood. Saddled with unprecedented student debt, stagnant wages, and skyrocketing living costs, this generation has been systematically delayed in achieving the milestones traditionally associated with maturity—home ownership, financial independence, and generational leadership. Their prolonged adolescence was not born of laziness or indulgence but of structural barriers, many of which were crafted and perpetuated by the Baby Boomer generation.
Bitcoin represents a symbolic and literal breaking away from these constraints. The decentralized cryptocurrency is, in essence, a rejection of the financial institutions that Millennials perceive as oppressive. It offers an alternative to a system that has kept them financially infantilized, tethered to debt, and locked out of wealth-building opportunities. Embracing Bitcoin is not merely an economic act—it is a psychological declaration of independence.
The Boomer Legacy and the Daunting Task of Succession
The Baby Boomers, who rose to dominance in an era of postwar economic growth, have remained the gatekeepers of wealth and power well into their senior years. This has created an intergenerational bottleneck: Millennials find themselves poised to inherit a world that is increasingly unsustainable, while also confronting the inertia of a generation reluctant to relinquish control. The sociopsychological impact of this dynamic is profound. For Millennials, the act of "growing up" has become synonymous with the Herculean task of dismantling or reforming entrenched systems.
Bitcoin’s narrative of decentralization, transparency, and individual sovereignty resonates deeply with Millennials because it offers a vision of empowerment. It provides a means of bypassing the gatekeepers—of creating value and financial freedom outside the confines of legacy institutions. Psychologically, this represents a vital step in the developmental journey: the move from dependency to self-reliance, from frustration to agency.
Weaning from the Teat: Financial and Emotional Independence
The metaphor of weaning is particularly apt for understanding the Millennial relationship with Bitcoin and the broader financial landscape. For much of their lives, Millennials have been financially dependent—on parents, on government programs, on an economic system that rewards conformity and punishes risk. Bitcoin is the ultimate tool for "weaning" this generation off the teat of dependency. It demands financial literacy, discipline, and a willingness to embrace uncertainty—all hallmarks of psychological maturity.
However, this journey is not without its challenges. The volatility of cryptocurrency markets mirrors the emotional turbulence of late adulthood, where the quest for independence often involves trial, error, and occasional failure. Millennials are learning, through Bitcoin, the hard truths of self-governance: that freedom is inseparable from responsibility, and that control cannot be wrested from others without first mastering oneself.
The Psychology of Late Adulthood in a Transitional World
Late adulthood, for Millennials, is marked by a dual psychological burden: the need to create a new world while still living in the shadow of the old. This is not merely a financial or technological challenge—it is a deeply existential one. Bitcoin, as both a tool and a symbol, encapsulates the struggle to bridge these worlds. It offers hope, but it also demands courage.
The generational shift from Boomers to Millennials is not just a passing of the torch; it is a seismic cultural shift. Millennials are redefining the very meaning of adulthood in the 21st century, and Bitcoin is a cornerstone of this redefinition. By rejecting the centralized systems of their predecessors, they are building a future that prioritizes autonomy, equity, and resilience.
Conclusion: Bitcoin as the Rite of Passage
In clinical terms, rites of passage are critical for psychological growth. They mark the transition from one stage of life to another, providing both challenge and transformation. For Millennials, Bitcoin is not just a financial instrument; it is a rite of passage. It is the means by which they assert their adulthood, reclaim their autonomy, and begin to dismantle the structures that have held them back.
In the broader context of human development, the rise of Bitcoin may be seen as a pivotal moment in the collective psyche—a moment when a generation, long delayed in its coming-of-age, finally steps into its power. The journey is fraught with uncertainty, but it is also rich with possibility. And as with all rites of passage, the true transformation lies not in the destination but in the courage to undertake the journey.
-
 @ b17fccdf:b7211155
2025-01-21 18:33:28
@ b17fccdf:b7211155
2025-01-21 18:33:28
CHECK OUT at ~ > ramix.minibolt.info < ~
Main changes:
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
Connect directly to the board, remove the instability issues with the USB connection, and unlock the ability to enjoy higher transfer speeds**
- Based on Debian 12 (Raspberry Pi OS Bookworm - 64-bit).
- Updated all services that have been tested until now, to the latest version.
- Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
- All UI & UX improvements in the MiniBolt guide are included.
- Fix some links and wrong command issues.
- Some existing guides have been improved to clarify the following steps.
Important notes:
- The RRSS will be the same as the MiniBolt original project (for now) | More info -> HERE <-
- The common resources like the Roadmap or Networkmap have been merged and will be used together | Check -> HERE <-
- The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to several difficult-to-resolve dependency conflicts, so unfortunately, there will be no dedicated migration guide and only the possibility to start from scratch ☹️
⚠️ Attention‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "Status: Not tested on RaMiX" tag at the beginning of the guides. Be careful and act behind your responsibility.
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
By ⚡2FakTor⚡ for the plebs with love ❤️🫂
- Adapted to Raspberry Pi 5, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
-
 @ b17fccdf:b7211155
2025-01-21 17:29:54
@ b17fccdf:b7211155
2025-01-21 17:29:54Some sections inside of the guide:
- Set up Dynamic DNS
- Wireguard VPN server & client side configurations
- Install & configure the WireGuard VPN Client on a mobile phone
- Configure additional servers & clients
- Use your router’s DDNS preconfigured provider
- Port forwarding on NAT/PAT router
Link to the bonus guide HERE
Enjoy it MiniBolter! 💙
-
 @ 57d1a264:69f1fee1
2025-01-28 08:19:40
@ 57d1a264:69f1fee1
2025-01-28 08:19:40TASK: Provide three solutions to one of the problems (non-technical) observed during the UX audit in Kenya.
https://www.youtube.com/watch?v=0ht9cy4ZOUw
This call was after the Bitcoin UX Bootcamp which was held in Africa at the ABC conference in 2024. 10 UX designers were selected and completed a 2 day bootcamp as well as a pre-learning phase. During the bootcamp itself they were each project leads for an open-source African bitcoin wallet. They did a UX analysis and usability testing of the wallet to understand how the user experience could be improved. Now after understanding the problem space this call was focussed on how to move from the problem space to the solution space in terms of design. A step by step process was outlined and shared with the participants.
We would greatly appreciate your feedback on these design solutions. Please feel free to share comments, suggestions, or point out any oversights in the comments below or directly on the following figma files (Figma account required, you can create a dummy one, no KYC required).
PRODUCT: TANDO TEAM MEMBERS: @thetimileyin. @Loïc Kassamoto Figma Link: https://www.figma.com/design/LEbxbCBb2WnuneJAL5GFs7/Tando-UX-Audit?node-id=225-987&t=eePmVu0Fx8ibFaEm-4
PRODUCT: BITSACCO TEAM MEMBERS: @afolabioluwatobiloba. @Osatuyi Figma link: https://www.figma.com/design/LYxCZLbq17vxbPNU9FTZ6d/UX-Bootcamp-group-file-(BITSACCO)?node-id=60-61&t=IEnTauLGib3SHA7T-4
We look forward to hearing from you. Thank you!
originally posted at https://stacker.news/items/867378
-
 @ b17fccdf:b7211155
2025-01-21 17:19:12
@ b17fccdf:b7211155
2025-01-21 17:19:12Do you want to use a different disk to store data (blockchain and other databases) independently of the disk of the system?
A step-by-step guide using a secondary disk to store the data (blockchain and other databases) independently of the disk of the system and using the Ubuntu Server guided installation.
What's changed
- Rebuilt the Ubuntu Server installation guide based on this bonus guide added.
- Added GIFs to improve the illustration of the steps to follow.
- Case 1: during the Ubuntu server guided installation.
- Case 2: build it after system installation (by command line).
~ > Link to the bonus guide HERE
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 17:07:47
@ b17fccdf:b7211155
2025-01-21 17:07:47 -
 @ 57d1a264:69f1fee1
2025-01-28 02:36:34
@ 57d1a264:69f1fee1
2025-01-28 02:36:34About the role In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website.
What are you looking for in candidates? Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for.
We hope you: - Like to spend your days staring at artboards in Figma - Are obsessed with creating delightful micro-interactions and animations - Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones - Care about the details, maybe a bit too much (a pixel off ruins your sleep) - Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere - Have good judgement of when to ship - Like to level up your design skills continually - Put yourselves in the shoes of our users to craft a great experience - Enjoy being a generalist and are not tied down to a specific design, trend, or tools
Benefits - 🚑 Health insurance - 💻 New work equipment - 🌎 Work from anywhere in the world - 💆♀️ Complete autonomy at work - 📚 Learning and development stipend - 🏝 Minimum 2-weeks of paid time off - ❤️ Most importantly — doing meaningful work that can change the world
Apply at https://app.withrapha.com/job/692
originally posted at https://stacker.news/items/867248
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 16:40:01
@ b17fccdf:b7211155
2025-01-21 16:40:01Important notice to MiniBolt node runners:
~ > It turns out that the I2P devs have opened an issue on the Bitcoin Core GitHub repo commenting that because they gave the option to enable the
notransit=trueparameter in the official documentation:[...] If you prefer not to relay any public I2P traffic and only allow I2P traffic from programs connecting through the SAM proxy, e.g. Bitcoin Core, you can set the no transit option to true [...] are having a heavy load on the I2P network since last December 19. Also comment that it is advisable to share as much bandwidth and transit tunnels as we can, to increase anonymity with coverage traffic, by contributing more to the I2p network than we consume.
So they ask that we deactivate that option that you use activated. With all this, he already updated the "Privacy" section by removing that setting.
The steps to delete this configuration once we have already configured it, are the following:
- With the "admin" user, stop i2pd:
sudo systemctl stop i2pd- Comment line 93 with "#" at the beginning of it (notransit = true), save and exit
sudo nano /var/lib/i2pd/i2pd.conf --line numbers- Start i2pd again:
sudo systemctl start i2pd- And that's it, you could take a look at Bitcoin Core to see that it has detected i2pd running again after the reboot with:
tail --lines 500 -f /home/bitcoin/.bitcoin/debug.log~ > If you don't see that I2P is up in Bitcoin Core after the restart,
sudo systemctl restart bitcoindand look again at the logs of the same.
More info in the rollback commit, see ~> HERE < ~
-
 @ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26
@ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26Lifting the Curtain on Power and Scandal
The Illusion of Power and TrustIn the modern world, the line between trust and skepticism is razor-thin, especially when it comes to powerful figures and organizations. They present polished facades, dazzling us with promises of stability, innovation, or in Disney’s case, enchantment. Yet, the revelations surrounding Jeffrey Epstein’s network reminded us that power is often far more complex than it appears. This scandal became a litmus test for public trust and fueled questions about who, or what, might be entwined in hidden truths.
When Epstein's crimes were exposed, they revealed not just the horrifying details of exploitation, but also the unsettling reach of his influence. As the media peeled back the layers of his associations, public attention naturally shifted to recognizable names and institutions, including Disney. How could a company that represented childhood innocence, with castles and fairy tales, find itself whispered about in the same breath as Epstein’s infamous circle? This segment examines the roots of that question and the facts that illuminate its plausibility or dismiss it.
Epstein: A Man Who Mastered Access to PowerJeffrey Epstein was more than just a financier—he was a gatekeeper to influence. His lifestyle and operations were an entangled web of charm, manipulation, and wealth, meticulously designed to secure him a place among the powerful. Investigative articles by The Guardian and The New York Times depict Epstein as a social engineer, curating relationships that ranged from politicians and royalty to scientists and celebrities.
Court documents and deposition testimonies during Epstein’s trial confirmed that his homes and private jet were hubs for connecting with influential figures. This access did not come without consequence; it cemented him as both a source of curiosity and, later, fear. Public records, such as those scrutinized in The Washington Post, indicated his involvement with many high-profile individuals. Yet, the details of these relationships varied—some guests were casual acquaintances, others, confidants.
The Infamous Flight LogsThe flight logs of Epstein’s private jet, colloquially known as the "Lolita Express," became a centerpiece for public scrutiny. Released through court orders and accessed by journalists, these logs listed names that triggered a cascade of questions. Guests ranged from prominent business executives to entertainment figures, sparking a debate over whether mere association implied complicity or deeper connections. This fueled the narrative that Epstein’s reach was far more extensive than previously understood, implicating industries where entertainment, power, and trust intersected.
The Role of Speculation in Public DiscourseAs soon as these flight logs surfaced, discussions surged online and across media platforms. The presence of any entertainment figure in Epstein’s orbit raised an eyebrow and, in many cases, invited a leap of logic: if influential media personalities were tied to him, could companies known for entertainment and global reach, like Disney, have hidden associations as well? This hypothesis, though lacking concrete evidence, found fertile ground among those predisposed to distrust large, seemingly untouchable institutions.
It’s crucial to dissect why Disney, specifically, became a subject of speculation. On one hand, its status as an omnipresent media empire makes it an easy target for conspiracy theories that thrive on the juxtaposition of light (Disney’s brand) and darkness (Epstein’s crimes). On the other, it speaks to a larger societal impulse to find cracks in the foundations of those we consider infallible. The idea that even the most beloved entities might harbor hidden truths appeals to a deep-seated desire for transparency and accountability.
The Catalyst of Public CuriosityThe timing of Epstein’s exposure was a critical factor. His arrest and subsequent death in 2019 coincided with a period marked by rising distrust in institutions, fueled by political and social upheavals globally. Social media platforms amplified this distrust, creating echo chambers where half-truths and speculative narratives merged seamlessly with confirmed facts.
It is here that Disney’s name began to surface not as an accused, but as a speculative point in discussions. The reasoning often pointed to a "guilt by association" logic: if the powerful dined, flew, or partied with Epstein, then it was worth questioning the circles in which those powerful entities moved, even without direct evidence. This leap from speculation to assumption reflects a pattern that sociologists recognize as part of conspiracy theory psychology—where a lack of clear answers invites the mind to fill in gaps, often with what feels most compelling.
Reframing the Public’s QuestionsThe real question becomes: why does this speculation hold such sway, even when evidence is scarce? Part of the answer lies in precedent. History is replete with instances where institutions that seemed above reproach were later implicated in hidden misdeeds, from financial frauds to abuse scandals within trusted organizations. This collective memory primes the public to believe that beneath any glittering surface could lie a dark, concealed underbelly.
Disney’s position as an icon of childhood and innocence adds another layer to this narrative. To imagine that such a symbol could be tainted by proximity to someone like Epstein is not just shocking—it’s fascinating. It strikes at the core of what we hold sacred, making it an irresistible topic of conversation and investigation.
Why This MattersUnderstanding why names like Disney are brought into these discussions without verified evidence is essential. It helps differentiate between warranted inquiry and unsupported speculation, allowing us to approach these narratives critically. Addressing this head-on does not only clear the air but strengthens the foundation upon which valid criticism and accountability are built.
A Note on EvidenceAs we move deeper into this exploration, it’s critical to emphasize that while Epstein’s connections to high-profile figures are thoroughly documented, there remains no evidence tying Disney, as an organization, to his operations. Still, the fascination with the “what-ifs” continues, driven by our collective quest for understanding power, secrecy, and the thin line between public and private lives.
The next segment will dive into Epstein’s proven network, unraveling the extent of his influence and why it has been the breeding ground for questions involving the world’s most trusted corporations.
Epstein’s Documented Network
The Web of Power: A Portrait of InfluenceJeffrey Epstein’s network was not merely a collection of acquaintances; it was a curated gallery of the world’s most influential figures, built on calculated relationships and strategic connections. Epstein wielded this network with the precision of a skilled operator, bridging disparate realms of society—politics, academia, business, and media. Investigative reporting by sources such as The New York Times and The Guardian exposed how Epstein maintained access to individuals who shaped policy, managed wealth, and crafted the narratives of popular culture.
Court records, testimonies, and detailed analyses of his interactions revealed that Epstein was adept at placing himself at the center of elite circles. His estates, from Manhattan townhouses to private islands, hosted events that blurred the lines between social gatherings and strategic networking. This chapter delves into the proven extent of Epstein’s reach and why it sparked questions about connections to corporations and public institutions, including Disney.
Flight Logs: The Proof and the SparkThe flight logs from Epstein’s private jet, the infamous "Lolita Express," were among the most illuminating pieces of evidence in mapping his connections. These logs, legally obtained and examined by journalists, painted a picture of Epstein’s influence stretching across industries. High-profile figures were listed, including financiers, political leaders, and entertainment personalities. The presence of notable names triggered waves of speculation—if Epstein had access to such power players, how many more remained unnamed but entangled?
The Guardian and The Washington Post reported that these flights were not just transportation but often involved visits to Epstein’s various properties, known for their opulence and the dark rumors surrounding them. While these logs confirmed that many public figures knew Epstein, the depth and nature of their associations varied widely, from casual acquaintance to deeper involvement.
The Limits of the KnownDespite the breadth of documented connections, there was no verifiable evidence linking Disney as an entity to Epstein’s circle. What the flight logs and guest lists revealed was a man deeply embedded in networks of power, yet even within these proven associations, context was crucial. For instance, some guests, confirmed by court records and investigative articles, were shown to have attended public events or engaged in business unrelated to Epstein’s criminal activities.
The distinction between documented presence and complicity is where the narrative often splinters. The leap from association to implication fueled public debate and conspiracy theories. This was especially true when figures from media and entertainment, sectors known for influencing public sentiment and childhood memories, appeared on the periphery of Epstein’s activities.
Epstein’s Parties and Gatherings: The Elite’s Shadowed StageEpstein’s parties were legendary, drawing attendees from the highest echelons of influence. These gatherings were not casual mixers but orchestrated showcases of power. Reports from court depositions and firsthand accounts highlighted how Epstein leveraged these events to cement alliances and reinforce his status as a gatekeeper to the elite. Some testimonies even described how these events served as platforms for discussing investments, politics, and global initiatives, reinforcing Epstein’s perceived omnipotence.
High-Profile Confirmations and Their ImplicationsSeveral prominent individuals were indeed verified as having ties to Epstein, raising legitimate questions about the extent of their knowledge or involvement. These names included politicians, royalty, and entertainment figures. The ambiguity surrounding these associations allowed theories to flourish. The sheer presence of influential names on Epstein’s guest lists raised the question: If these individuals were implicated, what about the institutions they represented or the circles they moved within?
This was a turning point for public speculation. The logic extended: if an individual from a major media company or entertainment empire like Disney was even remotely connected, could that implicate the company itself? The answer, according to existing court records and credible investigations, remained no. Yet, the absence of direct evidence did not stop speculation; in many cases, it intensified it.
Why Disney Was Brought Into the ConversationDisney’s reputation as a family-friendly giant contrasted starkly with the dark nature of Epstein’s activities, making it an unlikely yet intriguing topic for public discourse. While some entertainment figures appeared on Epstein’s flight logs or were rumored to have interacted with him, investigations have not yielded any proof of corporate-level involvement. However, public fascination persisted, bolstered by the broader questions Epstein’s connections evoked.
It’s worth noting that corporations like Disney, with their vast reach and unparalleled influence, naturally become focal points when discussions of hidden truths arise. The mere idea that such an iconic entity could be associated with real-world shadows captures the imagination and fuels stories that, while lacking proof, thrive on the “what-ifs” that echo through media and online forums.
How Public Perception Shapes the NarrativeSociologists studying the psychology of conspiracy theories point out that the human mind tends to fill gaps in knowledge with what feels most plausible or compelling. When figures from reputable media or entertainment companies are tied, even tangentially, to a scandal as vast as Epstein’s, it challenges the boundaries of trust. This is exacerbated when concrete answers remain elusive, leading to a cycle where suspicion feeds speculation.
The public’s thirst for accountability, especially in the wake of uncovered scandals involving powerful institutions, is both a force for truth and a catalyst for assumptions. In Epstein’s case, the proven reach of his influence and the confirmed involvement of significant figures were enough to trigger the question of how many untold stories lay beneath.
What We Know vs. What We ImagineThe narrative surrounding Epstein’s documented network shows us that while connections can be verified and associations noted, the leap to implicating entire organizations like Disney requires more than names on a list or rumors. It requires evidence that has, thus far, not been presented in any court or investigation. The proven facts are compelling enough: Epstein’s influence was extensive, his ties to power irrefutable. Yet, without direct links, the conversations about specific corporate involvement remain speculative.
In the next segment, we will explore why Disney’s reputation makes it a prime target for such speculation and how its historical handling of public crises plays into these narratives.
Disney – The Symbol of Trust and Target of Suspicion
Why Disney? The Paradox of a Trusted InstitutionDisney’s legacy is built on a foundation of storytelling, dreams, and the belief in happy endings. For nearly a century, the company has woven itself into the fabric of childhoods, becoming synonymous with innocence and magic. This legacy, however, has a dual edge. As the public's trust in institutions erodes and hidden truths are revealed in other sectors, Disney’s position as an untouchable cultural icon makes it both a beacon of light and a potential target for suspicion.
The Symbolism of Disney’s BrandDisney represents more than just a company; it embodies an idea—a refuge where imagination and wonder reign. But this same image that has made Disney a household name also contributes to the paradox of suspicion it faces. When an organization is seen as larger than life, transcending generations and continents, the notion that it could have skeletons in its closet becomes a tantalizing thought. The juxtaposition of innocence with possible shadows creates a narrative that is compelling and worth exploring, even if it remains speculative.
This paradox of Disney as both a trusted symbol and a target for scandal reflects a broader trend. Major corporations that hold influence in our everyday lives—particularly those that shape childhood memories and societal values—are natural focal points when scandals involving power, influence, and exploitation arise. The idea that a company with as much reach as Disney could be connected, however tangentially, to figures like Epstein feeds into this pattern.
Documented Misconduct and Public ReactionsThere have been verified cases involving Disney employees engaging in misconduct, which have been reported by media outlets such as NBC News and local news channels. These incidents, though not systemic and unrelated to Epstein’s network, show how the actions of a few can impact public perception of an entire organization. Examples include arrests for crimes involving minors or inappropriate behavior, isolated events that Disney has publicly addressed through statements and cooperation with law enforcement.
However, these incidents were sufficient to plant seeds of doubt in some minds. Even when addressed swiftly and in line with corporate protocols, such cases reveal a vulnerability: the company’s image can be tarnished not just by its policies, but by the misdeeds of individuals who wear its badge.
The Fuel for SpeculationThe Epstein case acted as a catalyst for looking beyond the obvious, particularly in the context of powerful organizations. If political leaders, financiers, and cultural icons could be connected to Epstein’s circle, why not wonder about the involvement of a company with as vast a presence as Disney? While investigations by trusted outlets have shown no direct corporate link, the sheer scope of Epstein’s influence suggested that any entity known for associating with the powerful could be implicated.
This speculation was not helped by Disney’s approach to public relations. The company’s PR strategies, while sophisticated and generally effective, often prioritize message control over transparency. In a world where silence can be seen as complicity, this strategy sometimes backfires, leading to more questions than answers.
Public Distrust and Historical ContextThe public’s fascination with uncovering hidden truths within major institutions is not unfounded. History is replete with cases where seemingly trustworthy organizations were later found to have concealed scandals. From corporate frauds to abuses within religious institutions, these stories have taught the public that innocence is not immune to corruption. This backdrop primes society to believe that even the most beloved entities, like Disney, could harbor secrets.
Sociologists and media analysts argue that this distrust is a byproduct of what they term the “betrayal effect”—where past disappointments with trusted institutions lower the threshold for believing that betrayal could be lurking everywhere. Disney, with its spotless public image and vast influence, becomes an especially juicy target for such theories. The leap from real cases of employee misconduct to more systemic accusations, however, is where evidence often falls short.
The Role of Social Media and Echo ChambersThe digital age has amplified how speculation morphs into perceived truth. Platforms like Twitter, Reddit, and Facebook allow theories to spread quickly, often outpacing fact-checking and nuanced analysis. Discussions that might once have been confined to fringe circles now gain mainstream attention, especially when they involve powerful figures or beloved brands.
In the context of Epstein’s exposure, this meant that any high-profile connection or name could become part of a broader narrative of guilt by association. The fact that Disney, as a corporation, appeared in speculative discussions alongside verified names from Epstein’s logs was enough for some to draw connections, even without direct evidence.
Reputation Management and PerceptionDisney’s approach to crises and controversies has long involved careful reputation management. From its response to legal issues to how it handles employee-related incidents, the company employs sophisticated PR strategies to mitigate damage and maintain its standing. This is standard practice for global brands; however, the public’s interpretation can be different. Strategic silence or tightly controlled statements can come across as evasive, fueling theories that there is something more to hide.
For a company like Disney, which operates at the intersection of family values and global corporate power, the stakes are high. The expectation isn’t just for entertainment but for upholding the moral high ground. When speculation links Disney to scandals, no matter how peripherally, it chips away at this carefully crafted image.
Why Address This Now?The speculation around Disney and Epstein underscores a crucial point about the nature of public inquiry and corporate reputation. It is not enough for companies to rely solely on public relations strategies that worked in the past. The demand for transparency is greater than ever, and silence, even when warranted, can erode trust.
Disney’s role in the public consciousness means that even baseless theories need addressing. By understanding why these narratives gain traction, both companies and the public can engage in more meaningful dialogues about accountability, proof, and trust.
The next segment will delve into how the public navigates between confirmed facts and conspiratorial whispers, exploring why certain theories stick and what it means for how we view powerful organizations.
Separating Fact from Conspiracy
The Thin Line Between Evidence and Speculation In the age of information, where facts are readily available yet often overshadowed by conjecture, separating truth from conspiracy is both an art and a necessity. When powerful entities like Disney find themselves drawn into discussions of hidden networks and scandals involving figures such as Jeffrey Epstein, it highlights a broader societal challenge: how do we differentiate between what is proven and what is assumed? This segment dissects the interplay of evidence, theory, and the psychological factors that drive our need to seek connections.
The Basis of Public Suspicion Public trust in large institutions has waned over decades, driven by a series of high-profile betrayals. From corporate frauds that shattered economies to scandals involving trusted religious or educational institutions, society has learned that power often conceals flaws and, in some cases, criminal actions. According to research published in the Journal of Communication, this erosion of trust leads to a phenomenon known as confirmation bias—the tendency to interpret new evidence as confirmation of one’s existing beliefs or suspicions.
The Epstein case provided fertile ground for such biases. The verified details of Epstein’s operations—the private jet, the exclusive parties, the high-profile guests—were enough to prompt a collective re-examination of how far his reach extended. While many of his associations were proven to be casual or professional in nature, the public’s hunger for deeper revelations ensured that speculation would thrive in areas where clarity was lacking.
The Role of Real Connections Epstein’s documented network included figures from politics, academia, finance, and media. The release of flight logs and court documents revealed that powerful individuals attended his events and interacted within his sphere. This factual basis, verified by investigative reporting from The New York Times, The Guardian, and other reputable sources, provided legitimacy to the idea that Epstein’s influence was pervasive. However, the extent to which these relationships were innocent or complicit was not uniformly clear.
This ambiguity created a vacuum where speculation could flourish. Public attention shifted from individuals named in the logs to the institutions and industries they represented. It was here that major corporations, including Disney, entered the discourse—not because of documented ties, but because of their visibility and influence.
The Psychology Behind Linking Power and Scandal To understand why theories about Disney’s potential involvement in Epstein’s network persist, it is essential to examine the psychology of conspiracy. Sociological and psychological studies indicate that people are naturally inclined to question narratives when they feel that the truth is being withheld. The more powerful or untouchable an institution seems, the more likely it is to be suspected of hiding something significant.
Disney’s image as a global giant that molds childhoods and shapes culture makes it an appealing target for such theories. The company’s public persona as a bastion of family values and innocence stands in stark contrast to any whispers of scandal or misconduct. This contrast alone provides fertile ground for stories to grow, even in the absence of solid proof.
Confirmed Misconduct vs. Conspiracy It is important to acknowledge that Disney, like any large corporation, has faced incidents involving employee misconduct. News reports from outlets such as NBC News have documented cases where employees were arrested for inappropriate conduct involving minors. These cases, while serious and handled with appropriate legal responses, were isolated incidents. No evidence points to these cases being part of a larger, systemic issue within the company or connected to external figures like Epstein.
However, the very existence of these incidents is often enough to keep theories alive. Public perception does not always differentiate between an individual’s actions and the culture of the organization they work for. When these incidents coincide with broader conversations about power and secrecy, they feed into narratives that imply guilt by association.
The Amplifying Power of Social Media The role of social media in shaping and amplifying conspiracy theories cannot be overstated. Platforms like Twitter and Reddit have created spaces where facts, opinions, and theories coexist with little separation. When the Epstein scandal broke, social media was flooded with discussions, many of which featured a mix of verifiable information and speculative connections. The absence of direct evidence linking companies like Disney to Epstein did not deter users from proposing connections based on circumstantial evidence and “what-if” scenarios.
This phenomenon, described by media analysts as the “echo chamber effect,” allows theories to gain credibility through repetition rather than proof. As theories are shared, retweeted, and commented on, they accumulate a sense of legitimacy that belies their origins.
Why Certain Theories Stick Certain theories persist because they tap into deep-seated fears and the knowledge that the powerful often operate beyond the reach of conventional accountability. High-profile scandals involving powerful figures—whether in business, politics, or entertainment—reinforce the belief that more may be hidden just out of reach. Epstein’s network was confirmed to include names that were once considered untouchable, which validated the idea that hidden truths could surface anywhere.
Disney’s name appearing in speculative discussions highlights the intersection of innocence and power. It reflects a societal expectation that if one pillar of influence is shown to be compromised, others may be as well. This expectation, however, must be tempered with critical thinking and an examination of evidence.
The Need for Discernment Understanding the difference between fact and theory is crucial for informed dialogue. Public scrutiny is essential for accountability, but it must be balanced with discernment. While Epstein’s known associations spanned many sectors, and while individuals from the entertainment industry were involved in his circle, the leap to implicating entire organizations like Disney has not been supported by verified investigations.
The Reality Check Here’s what we know:
Documented Facts: Epstein’s network included influential figures, confirmed by court records and journalistic investigations. Disney’s Position: While Disney has faced isolated cases of employee misconduct, no substantial evidence ties the company as an institution to Epstein’s criminal activities. Public Perception: Theories are fueled by a combination of legitimate distrust in powerful institutions and the psychological need to connect the dots, even when the evidence does not support it. In the next segment, we will explore how media control and the use of non-disclosure agreements (NDAs) contribute to the public’s perception of secrecy and whether this perception is warranted.
Media Control and NDAs – Protecting Power or Ensuring Silence?
The Strategy of Silence in Crisis Management When powerful organizations face potential scandal or crises, the first line of defense is often control—control over the narrative, control over information, and control over public perception. This strategy, while effective in mitigating immediate damage, can backfire by fostering an aura of secrecy that leads to suspicion. Disney, like many other global corporations, has historically employed these tactics, particularly through the use of non-disclosure agreements (NDAs) and strategic public relations (PR) campaigns. But do these measures protect legitimate corporate interests, or do they simply fuel theories that there is more being hidden?
Understanding the Role of NDAs NDAs are legal tools designed to maintain confidentiality and protect business interests. In most cases, their use is standard practice, whether to protect trade secrets, secure settlements, or manage sensitive internal matters. However, when NDAs intersect with scandals involving powerful individuals or organizations, they can become symbols of enforced silence. A report from the Harvard Business Review highlights that while NDAs are often employed for legitimate purposes, their misuse—especially when used to silence allegations of misconduct—has cast a shadow over their intent.
Disney has used NDAs in its corporate dealings, as have many in the media and entertainment sectors. This is not in itself suspicious; however, the mere presence of NDAs in a company’s arsenal can contribute to a narrative of secrecy, especially when paired with limited transparency during controversies.
The Case of High-Profile Secrecy The Epstein scandal showed how the use of NDAs and strategic silence could be perceived in a different light. When influential figures and companies were linked to his circle, silence from those implicated was interpreted by many as an attempt to avoid deeper inquiry. While Disney has not been tied to Epstein’s activities through verified evidence, its use of NDAs in unrelated circumstances and its approach to handling public controversies have made it a recurring subject in theories about hidden truths.
For example, Disney’s meticulous control over its brand image means that it often handles internal issues privately, releasing carefully crafted statements that address public concerns without divulging specifics. This approach, while protective, sometimes has the unintended consequence of making the public wonder what is not being said.
The Intersection of PR and Public Perception Public relations are designed to safeguard a company’s image, ensuring that responses to any negative news are swift and tightly managed. Disney’s PR machine is among the most sophisticated, capable of steering narratives and maintaining its reputation as an entertainment titan. This strategic control has allowed Disney to weather crises that might have permanently damaged lesser brands. However, in the context of a scandal as sprawling and notorious as Epstein’s, such control is perceived differently.
When the Epstein story broke and high-profile connections came to light, companies with any tenuous ties activated their crisis management protocols. For some, this meant issuing vague statements or refusing to comment altogether. To the public, this read as silence—a strategic choice that seemed suspicious when paired with known instances of NDAs being used to keep serious allegations quiet in other industries. The #MeToo movement, for instance, revealed how NDAs were used by some media companies to shield powerful perpetrators of harassment, showing that these tools can sometimes contribute to a culture of concealment.
Silence as Complicity? For a company like Disney, known for its polished public image, silence during times of widespread speculation can amplify suspicions. The question becomes: Is silence an act of protection or complicity? While NDAs are often used to manage settlements or protect internal processes, the fact that they prevent full transparency can make even innocent parties appear as if they have something to hide.
Experts in crisis communication argue that silence may protect the brand short-term but can erode trust long-term. Disney’s approach to handling public perception, from managing employee misconduct cases to addressing larger social controversies, often involves strategic responses that give the public enough information to stay satisfied but not enough to quell the more skeptical voices. This is standard practice but becomes contentious when the public is searching for accountability.
The Impact of Strategic Silence on Public Trust Media and communication studies have shown that transparency is increasingly becoming a measure of trustworthiness for corporations. In an era where the public demands answers and alternative media thrive on filling in gaps left by corporate PR, the stakes for maintaining trust are higher than ever. The use of NDAs and controlled statements can protect a company’s interests, but it also contributes to a perception of secrecy that feeds public doubt.
Disney’s balancing act—protecting its brand while managing incidents behind closed doors—reflects a broader industry trend. Corporations that prioritize narrative control must now reckon with an environment where even a hint of concealment can lead to damaging speculation. The Epstein case amplified this issue, putting the spotlight on how major organizations handle proximity to scandal, even if only by association.
Navigating the Perception The real challenge for Disney and similar companies lies in navigating the fine line between protecting their interests and fostering trust. Complete transparency can be risky, but strategic silence risks becoming complicit silence in the eyes of the public. This duality—where necessary protection measures are perceived as proof of hidden wrongdoing—is why entities like Disney find themselves caught up in discussions about figures like Epstein, despite the absence of concrete evidence.
The Takeaway for Institutions and the Public Understanding the role of NDAs and PR in managing public crises helps frame why powerful companies might become targets of suspicion. While the use of these tools is standard and often justified, their impact on public perception can’t be ignored. For the public, recognizing the difference between warranted inquiry and overreach is key to maintaining productive scrutiny without falling into the trap of baseless theories.
The next segment will focus on what these perceptions mean for society as a whole and why the pursuit of transparency and trust must be a collective endeavor.
Beyond the Shadows – A Call to Unity
The Complex Path to UnderstandingIn an age where trust in powerful institutions is fraying, and access to information is both a blessing and a burden, our approach to truth becomes more critical than ever. The discussions surrounding figures like Jeffrey Epstein and corporations like Disney are not just about scandal; they are about how we, as a society, confront power, secrecy, and transparency. This segment is a call to unite in the pursuit of truth—not through a divisive lens, but with collective discernment and an unwavering commitment to evidence and integrity.
The Lessons from HistoryHistory teaches us that institutions once seen as untouchable can harbor hidden truths. The exposure of corporate frauds, systemic abuses, and cover-ups within trusted sectors has shaped a society that questions everything. The Epstein scandal underscored this, revealing a network of power that reached further than many dared to imagine. Yet, while it validated the public’s instinct to question, it also highlighted a key challenge: differentiating between grounded inquiry and baseless theory.
Disney’s name appearing in speculative discussions about Epstein points to a broader pattern—our collective desire to ensure that those who hold power are not above scrutiny. But as we demand accountability, we must also unite in the practice of informed skepticism. The leap from isolated cases of misconduct or association to implicating entire organizations requires evidence, not just conjecture. This distinction is where we, as a society, must find common ground.
The Role of TransparencyTransparency has become the cornerstone of public trust. Organizations that handle controversies behind closed doors risk damaging their credibility. For companies like Disney, known for protecting their brand with meticulous care, the challenge is clear: find a balance between safeguarding legitimate interests and providing enough transparency to maintain public trust.
The use of NDAs, strategic silence, and controlled narratives may shield brands in the short term, but they can erode trust in the long run. Studies in crisis communication emphasize that openness, even when it exposes vulnerabilities, can reinforce loyalty and confidence among stakeholders. In the context of Epstein and the persistent whispers about powerful corporations, this lesson is especially relevant.
A Collective Call to ClarityThe pursuit of truth is not just the responsibility of journalists, whistleblowers, or industry watchdogs—it is a collective endeavor. The public plays a crucial role in this, but so do the corporations that hold sway over cultural and economic landscapes. When Disney’s name enters speculative discussions, it reflects a deep-seated desire for transparency from those we trust. This desire should be met not with fear of the unknown but with a commitment to clarity.
This segment is a call for unity in approaching these conversations. The balance between healthy skepticism and conspiracy theory is delicate but essential. We must ask hard questions and hold power accountable without losing sight of what separates substantiated fact from assumption.
Why Unity MattersIn times where speculation can divide and misinformation can spread faster than verified facts, unity in the pursuit of truth is vital. When we allow fear and uncertainty to fracture our approach, we weaken our collective power to bring genuine issues to light. Epstein’s case showed that hidden wrongs do exist and can involve the most influential figures. It also showed that uncovering the full scope of such wrongs takes a community committed to patience, evidence, and shared purpose.
Public scrutiny is essential for democracy and social justice, but so is discernment. When theories about organizations like Disney arise without evidence, they risk diverting attention from real, proven issues that demand action. Unity in seeking truth means supporting real investigations, demanding transparency, and recognizing the power of evidence-based inquiry.
Building a Culture of Informed AccountabilityThe goal is not to silence questions but to elevate them, ensuring that they are grounded in reality. This approach not only empowers the public but also sets a standard for institutions. If Disney and other corporations prioritize transparency, they can reinforce the public trust that sustains their brands. Similarly, when the public insists on evidence and integrity in its discussions, it strengthens the very fabric of accountability.
Reflections for the Road AheadAs we move forward, let us commit to being a society that seeks truth not for scandal’s sake but for justice and integrity. Let us stand together in holding power to account, using facts as our foundation and unity as our strength. The story of Epstein and the questions it raises about power, influence, and hidden truths are reminders that transparency and trust are not just corporate responsibilities—they are collective ones.
This call to unity is a reminder that we all play a part in shaping how these stories unfold. When we seek, question, and demand clarity together, we create a society that values truth over rumor, evidence over assumption, and justice over division.
As we conclude this exploration, may we carry forward the lessons learned: the importance of questioning with integrity, seeking truth with diligence, and facing the unknown not as individuals, but as a united community.
-
 @ b17fccdf:b7211155
2025-01-21 16:23:44
@ b17fccdf:b7211155
2025-01-21 16:23:44Build your nostr relay step by step on your MiniBolt node! (easily adaptable to other environment) No need to trust anyone else! Be sovereign!
~> Go to the bonus guide by clicking ~> HERE< ~
~> This guide includes a complete extra section to cover the different processes for using nostr as a user and relay operator.
PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address:
wss://relay.minibolt.info~> Let a review on noStrudel or Coracle of your experience using it.
Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪
-
 @ ae6ce958:d0f02c7d
2025-01-27 23:27:51
@ ae6ce958:d0f02c7d
2025-01-27 23:27:51In a world dominated by overhyped tech and broken promises, DamageBDD stands apart as a Bitcoin-first revolution for developers, QA teams, and enterprises. Built on the belief that resilience, transparency, and accountability are not optional, this innovation is more than just another BDD platform—it's a tool designed to harness the unstoppable power of Bitcoin and the Lightning Network to redefine software quality and team productivity. Here's why DamageBDD will light up the Lightning Network like never before:
1. Lightning-Powered Incentives for Development
Imagine a world where developers are rewarded in sats the moment their code passes a milestone. With DamageBDD, that’s no longer a dream. We use Lightning-based escrow payments tied to milestone completions, ensuring every contributor gets instant, trustless payouts for verified work. This isn’t just about payments—this is about transforming the economics of collaboration and incentivizing excellence.
2. Real-Time Transparency Meets Bitcoin Immutability
Every BDD test, every passing milestone, and every failure is immutably recorded, showcasing the evolution of a project with a timestamped on-chain timeline. By anchoring progress to Bitcoin’s ultimate ledger of truth, DamageBDD creates a level of transparency that ensures trust—whether you're a developer, a manager, or an investor.
3. Immediate Liquidity Without Compromise
The Lightning Network enables participants to exit their locked funds through near-instant buybacks—no risk of long-term lock-ins or centralized interference. Developers and stakeholders can convert their contributions back to Bitcoin at market-close rates, minus nominal fees. This system protects value while keeping all incentives aligned with delivering quality software.
4. A Bitcoin Economy for BDD
Why settle for fiat-denominated payments or centralized intermediaries when you can build directly on Bitcoin? DamageBDD’s ecosystem ensures that every satoshi stays true to the ethos of decentralization, enabling organizations to manage projects in a way that’s fair, transparent, and resilient.
5. Scalable Adoption of High-Performance Teams
The Lightning Network isn’t just a payments rail—it’s a bridge for building relationships across borders. DamageBDD allows distributed teams to thrive, making trustless collaboration possible while fostering high-performance, Bitcoin-powered workflows.
6. Redefining ROI for Investors
Investors can now lock funds into milestone-driven escrows, ensuring ROI is directly tied to results. With DamageBDD’s Lightning-enabled payouts, there’s no waiting for endless revisions or missed deadlines—just real-time accountability, measured and delivered on a timeline that’s verifiable and immutable.
Bitcoiners, this is the spark.
While the fiat world struggles with inefficiency, corruption, and misaligned incentives, DamageBDD fuels the future with a Bitcoin-powered toolkit that transforms how teams work, get paid, and build trust. This isn’t just about better software—it’s about building an unstoppable Bitcoin economy where transparency reigns, quality wins, and the Lightning Network becomes the default rail for human collaboration.
DamageBDD isn’t here to gamble on hype—it’s here to build the future. Let’s light up the Lightning Network and show the world what Bitcoin-backed innovation can achieve. Are you ready to join the revolution?
-
 @ b17fccdf:b7211155
2025-01-21 16:15:51
@ b17fccdf:b7211155
2025-01-21 16:15:51What's changed
A bonus guide to get a quick overview of the system status with the most relevant data about the services on the main guide.
➕Additional extra sections (optional) to:
- Show on login
- Get the channel.db size of an old LND bbolt database backend
- Use MobaXterm compatibility version
🔧 GitHub PR related: https://github.com/minibolt-guide/minibolt/pull/97
Σ Dedicated GitHub repository: https://github.com/minibolt-guide/system_overview
🫂Acknowledgments
This is a fork of the minibolt_info repository, the main developer of this project is rmnscb, a member of the MiniBolt community, all the merits go to him. Thank you for your contribution 🧡🫂
-> CLICK HERE <- to go to the bonus guide
Enjoy it MiniBolter! 💙
-
 @ dbb19ae0:c3f22d5a
2025-01-21 09:00:36
@ dbb19ae0:c3f22d5a
2025-01-21 09:00:36Warning: Use this at your own risk Backup your files before using them in the software Backup often, test your backup. Verify and dry test your files before doing a production run
I had to write this program because rmdir was claiming not to have enough authorization
context nostr:note1l0u4pw5xp73eultr9nf5tgmlsgnv9q05wdqha4t6grd4699v74zssshm40
```perl use strict; use warnings; use File::Path qw(remove_tree);
Specify the directory to be deleted
my $directory = 'c:\Users\mydirectory\mysubdirectory\';
Remove the directory
remove_tree($directory, {error => \my $err});
Check for errors
if (@$err) { foreach my $diag (@$err) { my ($file, $message) = %$diag; if ($file eq '') { print "General error: $message\n"; } else { print "Problem unlinking $file: $message\n"; } } } else { print "Directory successfully deleted.\n"; }
```
-
 @ 75656740:dbc8f92a
2025-01-21 04:38:21
@ 75656740:dbc8f92a
2025-01-21 04:38:21We spend too much time enthralled by even numbers. We can instantly tell if a number is even or odd and often have preferences in the matter. In grade school we memorize rules like
- An even plus an even is an even
- An odd plus an odd is an even
- An even plus an odd is and odd
And so forth to rules of multiplication. But this magical quality of numbers really just means evenly divisible by 2. What is so special about 2? Shouldn't we just as well care if a number is divisible by 3?
So I am introducing threeven numbers as all numbers divisible by 3.
0, 3, 6, 9, 12, 15, ...
are all threeven numbers. But what about numbers that aren't divisible by 3? Numbers that are not divisible 2 are called odd so I guess throdd?
There is, however, a slight problem. There seem to be more throdd numbers than threeven numbers.
1, 2, 4, 5, 7, 8, 10, 11, 13, 14, ...
To solve that we need to think about what an odd number is. If an even number is some number n times 2 or 2n then odd numbers are 2n + 1
This gives a nice way to think about threeven numbers as well. Every threeven is 3n and a throdd is 3n + 1 and we need to introduce throdder numbers as 3n + 2. There isn't any reason that there should only be two types of numbers. So instead of numbers that are divisible by 2 and numbers that aren't, we have numbers that are divisible by 3, numbers that are 1 greater than a multiple of three and numbers that are 2 greater than a multiple of three.
To recap
- Threeven = 3n
- Throdd = 3n + 1
- Throdder = 3n + 2
Now for handy rules of thumb.
- A threeven plus a threeven is a threeven
- A threeven plus a throdd is a throdd
- A threeven plus a throdder is a throdder
- A throdd plus a throdd is a throdder
- A throdd plus a throdder is a threeven
- A throdder plus a throdder is a throdd
And, for multiplication
- A threeven times a threeven is a threeven
- A threeven times a throdd is a threeven
- A threeven times a throdder is a threeven
- A throdd times a throdd is a throdd
- A throdd times a throdder is a throdder
- A throdder times a throdder is a throdd
This is just modular arithmetic and the same can be done for any integer n
m mod n = 0
Means m is an nven and there will be n - 1 varieties of nodd
Threeven, however, is the most fun to say and makes the point nicely, there is no need to carry it further.
Note: it appears that I am not the first to have discovered threeven numbers. And now you are stuck knowing about them as well.
-
 @ cb43dde2:ef277171
2025-01-27 23:10:39
@ cb43dde2:ef277171
2025-01-27 23:10:39HODL has been defined by many as an acronym for “Hold on for Dear Life.” Many my age were taught to earn money and save it for the future as conventional wisdom. That wisdom would have you holding something designed to degrade in value at a rate of 2% annually. If all “goes to plan,” the purchasing power (value) of your savings in 35 years will be half that of today. In 2022 the US dollar value degraded a total of 8%. At this rate, your savings’ value will cut in half in less than nine years. Not quite the retirement plan one would hope for, but happens to be what my generation was taught in school. Thankfully there is a solution: become a HODLer of assets.
Every investor is a collector of assets. They all have their own thesis about the assets they collect and how the collection will transport their monetary value across space and time. My thesis is that when you hold assets (the practice of HODLing) you hold the superposition in the market and can make better decisions against the overall economic tide. I like to hold a diverse portfolio across asset types, themes, and tax treatments, so that I am always in a superposition when liquidity is needed for the next opportunity. In the words of Charles Darwin, “it is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change.”
The Superposition of Markets
A superposition is a phenomenon observed in nature where something is in one of two antithetical positions, both equally likely, and is only defined when observed or measured. Most have heard of the Schrödinger’s Cat thought experiment; this is an example of superposition (references below). The financial markets act as a measuring tool identifying the next entangled pair of buyer and seller. Therefore, as a HODLer you remain in a superposition within the market until either your buy price or sell price is realized, instantaneously identifying your entangled counterpart within the market. To hold assets puts the HODLer in a superposition within the markets in which they HODL.
Making a Market: It Only Takes Two
A market is made when two parties, a buyer and a seller, come to an agreement to transfer personal property between each other. Without an agreement, there is no market activity and therefore no market. There are many more participants that help to facilitate markets like stock exchanges, store fronts, and Craigslist to name a few. This infrastructure has not changed the necessities to make a market but instead acts as a courier of information, often referred to as data. Knowing what a group of sellers are willing to take in exchange for their property, and knowing what a group of buyers are willing to pay, allows for the mapping of the market’s superpositions (known as an order book). HODLers remain in a superposition except at the moment when a market is made, identifying the two parties involved and the respective roles each will play out.
HODLers are Not Market Participants
They have in fact shown to be previous market participants and willing to fill at least one side of the transaction. However, if you’re HODLing, you are neither a seller nor a buyer and thus not in the market. Rather, you are both a buyer and a seller that has not been realized yet. We all have our buy price and our sell price of the assets we own. However, the market may have not dropped to the point where you are willing to buy again, nor has it risen to the level in which you are prepared to sell. You are but a ‘HODLer-in-waiting’ with two potential states; you are a potential buyer and a potential seller, waiting to be measured, thus identifying and filling your market role as dictated by the market and your need for access to liquidity.
HODLing: An Investment Strategy Built Upon Superpositions
Due to many market forces, successful investors do not simply stack cash for retirement, they are buying assets. As Robert Kiyosaki explains in his book, Rich Dad Poor Dad, “An asset is something that puts money in my pocket. A liability is something that takes money out of my pocket.” Investors are buying assets in hopes that their portfolio will ferry their purchasing power, today’s monetary value, across space and time. Why HODL something that is planned to lose value for any longer than necessary?
HODLing can feel like a rollercoaster at times with the need to “hold on for dear life.” Markets are unpredictable and (as an ex-manager of mine used to say) they will always do what f@&ks the most amount of people. Combat this with conviction in your purchase decisions. Conviction on where you think the price of the asset will go and in how much time. If you start by finding and choosing your long-term savings vehicle, many will call this money, asset purchases on your way to retirement become easier as you are not battling inflation, aka planned degradation of your hard-earned dollars. What you HODL matters.
-
 @ 16d11430:61640947
2025-01-27 21:33:11
@ 16d11430:61640947
2025-01-27 21:33:11Gather ‘round, corporate overlords, bloated bureaucracies, and self-appointed tech deities. @DamageBDD is here to show you what happens when your castles of sand face a tsunami of irrefutable logic. Your empire of spaghetti code and buzzword bingo won't hold against the relentless precision of code as truth.
Let’s set the stage. For years, you've been huddling in glass towers, touting innovation while running on fumes of mediocrity. Your agile "transformations"? A PowerPoint deck. Your tech stack? A monument to vendor lock-in and weekend duct tape. And let’s not forget the compliance theater, where fake audits masquerade as accountability. Enter DamageBDD, where logic doesn’t lie, blockchain doesn’t forget, and BS dies a swift death.
Code Is the Law (But Better) You’ve heard it before: "Code is law." But we’re not here for slogans—we’re here for receipts. DamageBDD doesn’t trust your claims of success; it verifies them on-chain. Deliver your milestones or don’t—there’s no fudging it here. Your failed builds and broken promises are exposed in broad daylight, immutable as your shame.
BDD: The Guillotine of Bad Engineering Oh, how the giants hate being held accountable. They thrive on opacity, on a system where results are obscured by layers of corporate doublespeak. DamageBDD flips the table: if it can be defined, it can be verified. That MVP you promised? We’ll test it. That sprint you boasted about? We’ll see it on-chain. In this world, the only thing that ships is the truth. Everything else is noise.
"Move Fast and Break Things"? Nah, Try Building Things That Last Let’s talk about your cult of "disruption," where moving fast and breaking things conveniently excludes fixing them. DamageBDD doesn’t move fast—it moves right. Every behavior-driven test is a brick in a foundation that lasts, unlike your latest "pivot" designed to dazzle VCs while hiding the rot underneath.
Cypherpunk Cynicism, Powered by Bitcoin Here’s where we really shine. While you’re busy worshiping at the altar of fiat, we’re running Damage Token on Bitcoin and Aeternity—systems you can’t co-opt, corrupt, or inflate away. Your centralized control schemes crumble when faced with a network that doesn’t care about your boardroom games. DamageBDD doesn’t just bypass gatekeepers; it renders them obsolete.
The Era of Verifiable Integrity You’ve built a world where accountability is optional and profits trump principles. DamageBDD brings receipts to the revolution. Imagine a world where every claim you make is tested, verified, and recorded immutably. No more hiding behind marketing fluff or burying failures in red tape. DamageBDD strips away the facade and says, "Let’s see what you’re really made of."
We’re Not Here to Compete. We’re Here to Outlast. You can’t kill an idea whose time has come. DamageBDD is more than a tool—it’s a movement, a manifesto in code. While you scramble to protect your crumbling monopolies, we’re building something that doesn’t need your approval, your funding, or your permission. DamageBDD will humble you not with arrogance, but with truth, written in lines of immutable logic that your PR spin can’t erase.
So, keep clinging to your illusions of control. DamageBDD is patient. It’s inevitable. And when the dust settles, your legacy will be nothing more than a footnote in a system designed to be better, faster, and ungovernable by the likes of you.
You’ve been warned. Verification > Authority. Always.
-
 @ 50809a53:e091f164
2025-01-20 22:30:01
@ 50809a53:e091f164
2025-01-20 22:30:01For starters, anyone who is interested in curating and managing "notes, lists, bookmarks, kind-1 events, or other stuff" should watch this video:
https://youtu.be/XRpHIa-2XCE
Now, assuming you have watched it, I will proceed assuming you are aware of many of the applications that exist for a very similar purpose. I'll break them down further, following a similar trajectory in order of how I came across them, and a bit about my own path on this journey.
We'll start way back in the early 2000s, before Bitcoin existed. We had https://zim-wiki.org/
It is tried and true, and to this day stands to present an option for people looking for a very simple solution to a potentially complex problem. Zim-Wiki works. But it is limited.
Let's step into the realm of proprietary. Obsidian, Joplin, and LogSeq. The first two are entirely cloud-operative applications, with more of a focus on the true benefit of being a paid service. I will assume anyone reading this is capable of exploring the marketing of these applications, or trying their freemium product, to get a feeling for what they are capable of.
I bring up Obsidian because it is very crucial to understand the market placement of publication. We know social media handles the 'hosting' problem of publishing notes "and other stuff" by harvesting data and making deals with advertisers. But- what Obsidian has evolved to offer is a full service known as 'publish'. This means users can stay in the proprietary pipeline, "from thought to web." all for $8/mo.
See: https://obsidian.md/publish
THIS IS NOSTR'S PRIMARY COMPETITION. WE ARE HERE TO DISRUPT THIS MARKET, WITH NOTES AND OTHER STUFF. WITH RELAYS. WITH THE PROTOCOL.
Now, on to Joplin. I have never used this, because I opted to study the FOSS market and stayed free of any reliance on a paid solution. Many people like Joplin, and I gather the reason is because it has allowed itself to be flexible and good options that integrate with Joplin seems to provide good solutions for users who need that functionality. I see Nostr users recommending Joplin, so I felt it was worthwhile to mention as a case-study option. I myself need to investigate it more, but have found comfort in other solutions.
LogSeq - This is my "other solutions." It seems to be trapped in its proprietary web of funding and constraint. I use it because it turns my desktop into a power-house of note archival. But by using it- I AM TRAPPED TOO. This means LogSeq is by no means a working solution for Nostr users who want a long-term archival option.
But the trap is not a cage. It's merely a box. My notes can be exported to other applications with graphing and node-based information structure. Specifically, I can export these notes to:
- Text
- OPML
- HTML
- and, PNG, for whatever that is worth.
Let's try out the PNG option, just for fun. Here's an exported PNG of my "Games on Nostr" list, which has long been abandoned. I once decided to poll some CornyChat users to see what games they enjoyed- and I documented them in a LogSeq page for my own future reference. You can see it here:
https://i.postimg.cc/qMBPDTwr/image.png
This is a very simple example of how a single "page" or "list" in LogSeq can be multipurpose. It is a small list, with multiple "features" or variables at play. First, I have listed out a variety of complex games that might make sense with "multiplayer" identification that relies on our npubs or nip-05 addresses to aggregate user data. We can ALL imagine playing games like Tetris, Snake, or Catan together with our Nostr identities. But of course we are a long way from breaking into the video game market.
On a mostly irrelevant sidenote- you might notice in my example list, that I seem to be excited about a game called Dot.Hack. I discovered this small game on Itch.io and reached out to the developer on Twitter, in an attempt to purple-pill him, but moreso to inquire about his game. Unfortunately there was no response, even without mention of Nostr. Nonetheless, we pioneer on. You can try the game here: https://propuke.itch.io/planethack
So instead let's focus on the structure of "one working list." The middle section of this list is where I polled users, and simply listed out their suggestions. Of course we discussed these before I documented, so it is note a direct result of a poll, but actually a working interaction of poll results! This is crucial because it separates my list from the aggregated data, and implies its relevance/importance.
The final section of this ONE list- is the beginnings of where I conceptually connect nostr with video game functionality. You can look at this as the beginning of a new graph, which would be "Video Game Operability With Nostr".
These three sections make up one concept within my brain. It exists in other users' brains too- but of course they are not as committed to the concept as myself- the one managing the communal discussion.
With LogSeq- I can grow and expand these lists. These lists can become graphs. Those graphs can become entire catalogues of information than can be shared across the web.
I can replicate this system with bookmarks, ideas, application design, shopping lists, LLM prompting, video/music playlists, friend lists, RELAY lists, the LIST goes ON forever!
So where does that lead us? I think it leads us to kind-1 events. We don't have much in the way of "kind-1 event managers" because most developers would agree that "storing kind-1 events locally" is.. at the very least, not so important. But it could be! If only a superapp existed that could interface seamlessly with nostr, yada yada.. we've heard it all before. We aren't getting a superapp before we have microapps. Basically this means frameworking the protocol before worrying about the all-in-one solution.
So this article will step away from the deep desire for a Nostr-enabled, Rust-built, FOSS, non-commercialized FREEDOM APP, that will exist one day, we hope.
Instead, we will focus on simple attempts of the past. I encourage others to chime in with their experience.
Zim-Wiki is foundational. The user constructs pages, and can then develop them into books.
LogSeq has the right idea- but is constrained in too many ways to prove to be a working solution at this time. However, it is very much worth experimenting with, and investigating, and modelling ourselves after.
https://workflowy.com/ is next on our list. This is great for users who think LogSeq is too complex. They "just want simple notes." Get a taste with WorkFlowy. You will understand why LogSeq is powerful if you see value in WF.
I am writing this article in favor of a redesign of LogSeq to be compatible with Nostr. I have been drafting the idea since before Nostr existed- and with Nostr I truly believe it will be possible. So, I will stop to thank everyone who has made Nostr what it is today. I wouldn't be publishing this without you!
One app I need to investigate more is Zettlr. I will mention it here for others to either discuss or investigate, as it is also mentioned some in the video I opened with. https://www.zettlr.com/
On my path to finding Nostr, before its inception, was a service called Deta.Space. This was an interesting project, not entirely unique or original, but completely fresh and very beginner-friendly. DETA WAS AN AWESOME CLOUD OS. And we could still design a form of Nostr ecosystem that is managed in this way. But, what we have now is excellent, and going forward I only see "additional" or supplemental.
Along the timeline, Deta sunsetted their Space service and launched https://deta.surf/
You might notice they advertise that "This is the future of bookmarks."
I have to wonder if perhaps I got through to them that bookmarking was what their ecosystem could empower. While I have not tried Surf, it looks interested, but does not seem to address what I found most valuable about Deta.Space: https://webcrate.app/
WebCrate was an early bookmarking client for Deta.Space which was likely their most popular application. What was amazing about WebCrate was that it delivered "simple bookmarking." At one point I decided to migrate my bookmarks from other apps, like Pocket and WorkFlowy, into WebCrate.
This ended up being an awful decision, because WebCrate is no longer being developed. However, to much credit of Deta.Space, my WebCrate instance is still running and completely functional. I have since migrated what I deem important into a local LogSeq graph, so my bookmarks are safe. But, the development of WebCrate is note.
WebCrate did not provide a working directory of crates. All creates were contained within a single-level directory. Essentially there were no layers. Just collections of links. This isn't enough for any user to effectively manage their catalogue of notes. With some pressure, I did encourage the German developer to flesh out a form of tagging, which did alleviate the problem to some extent. But as we see with Surf, they have pioneered in another direction.
That brings us back to Nostr. Where can we look for the best solution? There simply isn't one yet. But, we can look at some other options for inspiration.
HedgeDoc: https://hedgedoc.org/
I am eager for someone to fork HedgeDoc and employ Nostr sign-in. This is a small step toward managing information together within the Nostr ecosystem. I will attempt this myself eventually, if no one else does, but I am prioritizing my development in this way:
- A nostr client that allows the cataloguing and management of relays locally.
- A LogSeq alternative with Nostr interoperability.
- HedgeDoc + Nostr is #3 on my list, despite being the easiest option.
Check out HedgeDoc 2.0 if you have any interest in a cooperative Markdown experience on Nostr: https://docs.hedgedoc.dev/
Now, this article should catch up all of my dearest followers, and idols, to where I stand with "bookmarking, note-taking, list-making, kind-1 event management, frameworking, and so on..."
Where it leads us to, is what's possible. Let's take a look at what's possible, once we forego ALL OF THE PROPRIETARY WEB'S BEST OPTIONS:
https://denizaydemir.org/
https://denizaydemir.org/graph/how-logseq-should-build-a-world-knowledge-graph/
https://subconscious.network/
Nostr is even inspired by much of the history that has gone into information management systems. nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn I know looks up to Gordon Brander, just as I do. You can read his articles here: https://substack.com/@gordonbrander and they are very much worth reading! Also, I could note that the original version of Highlighter by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft was also inspired partially by WorkFlowy.
About a year ago, I was mesmerized coming across SubText and thinking I had finally found the answer Nostr might even be looking for. But, for now I will just suggest that others read the Readme.md on the SubText Gtihub, as well as articles by Brander.
Good luck everyone. I am here to work with ANYONE who is interested in these type of solution on Nostr.
My first order of business in this space is to spearhead a community of npubs who share this goal. Everyone who is interested in note-taking or list-making or bookmarking is welcome to join. I have created an INVITE-ONLY relay for this very purpose, and anyone is welcome to reach out if they wish to be added to the whitelist. It should be freely readable in the near future, if it is not already, but for now will remain a closed-to-post community to preemptively mitigate attack or spam. Please reach out to me if you wish to join the relay. https://logstr.mycelium.social/
With this article, I hope people will investigate and explore the options available. We have lots of ground to cover, but all of the right resources and manpower to do so. Godspeed, Nostr.
Nostr #Notes #OtherStuff #LogSec #Joplin #Obsidian
-
 @ 9d92077c:38d27146
2025-01-20 20:46:31
@ 9d92077c:38d27146
2025-01-20 20:46:31Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks.
—-
The Importance of Key Recovery on Nostr
One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences: * Loss of Identity: The user cannot post, interact, or manage their profile. * Disruption of Social Graph: Followers and contacts lose their connection to the user. * Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation.
While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity.
—-
Proposed Solution: The Excalibur System
The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition.
1. Primary and Secure Keys
Users establish a primary key for everyday activity and a secure backup key stored offline. The primary key broadcasts an association with the secure key using a
set_secure_keyevent.2. Key Transition Event
Upon detecting a compromise, the user activates the secure key by publishing a
key_transitionevent.This event includes: * The compromised primary key. * The new secure key. * A cryptographic proof linking the two. * A timestamp and optional metadata.
3. Social Graph Transition
Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data.
Followers are notified of the transition and encouraged to follow the secure key.
4. Unified Identity View
Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity.
Clients display a unified profile view, differentiating old and new events.
5. Seamless Transition for Existing Accounts
Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key. While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity. Clients should provide user-friendly tools to guide existing users through this setup process.
6. Endless Security Chain
Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new
set_secure_keyevent.This ensures an endless chain of security, preventing future compromises from leaving users vulnerable.
Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently.
7. Insurance Model for Relays
Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations.
Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services.
This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network.
—-
Implementation Framework
Cryptographic Foundations
- The secure key must be pre-announced and linked to the primary key using a signed
set_secure_keyevent. - During key transition, the key_transition event includes a signature proving the association.
Relay Behavior
- Relays index the key_transition event and re-link historical data to the secure key.
- Events from the old key are tagged as "deprecated" but remain accessible.
Client Behavior
- Clients validate the
key_transitionevent and update social graphs automatically. - Followers are notified and prompted to follow the secure key.
- Profiles display both old and new events under a unified identity.
- Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly.
—-
Benefits of Excalibur
Resilience: Users can recover from key compromise without losing their digital identity or network.
Trust: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system.
Sustainability: The insurance premium model incentivizes relay adoption and ensures fair resource allocation.
User-Friendly: Automated transitions reduce the complexity for end users, making Nostr more accessible.
Adaptability: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability.
—-
Call to Action
The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality.
Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom.
- The secure key must be pre-announced and linked to the primary key using a signed
-
 @ c1e6505c:02b3157e
2025-01-20 19:44:05
@ c1e6505c:02b3157e
2025-01-20 19:44:05There’s a tension between nature’s rhythms and human ambition, especially in winter. As Earth meanders to its furthest point from the sun, our social and economic engines paradoxically accelerate - driven by holidays, deadlines, and the relentless pursuit of being productive. Yet nature offers a contrasting wisdom in its deliberate deceleration, encouraging us to slow down and reflect.
 Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring.
Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring. 







 *All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints.
*All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints. -
 @ 378562cd:a6fc6773
2025-01-27 15:32:25
@ 378562cd:a6fc6773
2025-01-27 15:32:25In the ever-evolving cryptocurrency space, few assets have attracted as much attention—and controversy—as XRP. Marketed as a tool for revolutionizing cross-border payments, XRP has been at the center of debates about its legitimacy, legal entanglements, and centralization. In contrast, Bitcoin remains the gold standard of decentralization, embodying the original ideals of cryptocurrency as a secure, censorship-resistant, and community-driven digital asset.
The Ripple-SEC Legal Battle: A Dark Cloud Over XRP
XRP's legal troubles began in December 2020 when the U.S. Securities and Exchange Commission (SEC) filed a lawsuit against Ripple Labs, alleging the company had conducted an unregistered securities offering. The lawsuit hinged on whether XRP, the token Ripple uses for its cross-border payment solutions, qualifies as a security under U.S. law.
Ripple Labs and its executives, including CEO Brad Garlinghouse, argued that XRP should not be classified as a security. They claimed it was a digital currency akin to Bitcoin or Ethereum, which the SEC had already deemed non-securities. Despite Ripple scoring partial victories in court—such as a judge's ruling that XRP sales to retail investors did not constitute securities transactions—the company was ordered to pay a $125 million fine. While Ripple touted the outcome as a victory, the SEC’s ongoing appeal means uncertainty lingers over XRP's regulatory future.
These legal uncertainties have had significant implications for XRP’s adoption. After the lawsuit, major U.S. exchanges delisted XRP, temporarily causing its price to plummet. Although some platforms have since reintroduced XRP trading, its reputation remains tarnished in some circles.
Centralization Concerns: Is XRP Truly a Cryptocurrency?
A key critique of XRP lies in its centralized structure. Unlike Bitcoin’s decentralized proof-of-work (PoW) system, which relies on a distributed network of miners to validate transactions, XRP operates on a consensus protocol managed by a limited number of validators. This has led to accusations that Ripple Labs wields too much control over the network, undermining the core principle of decentralization that defines cryptocurrencies.
Adding to these concerns is Ripple Labs’ significant ownership of XRP tokens. Ripple initially held 80 billion of the 100 billion XRP tokens ever created, and as of 2024, it still holds a substantial portion in escrow. Critics argue that this concentration of ownership allows Ripple to manipulate XRP’s price and limits the asset’s independence.
Bitcoin: The Decentralized Gold Standard
In stark contrast to XRP, Bitcoin remains the archetype of decentralization. Introduced in 2009 by the pseudonymous Satoshi Nakamoto, Bitcoin operates on a PoW system that ensures no single entity can control the network. Its open-source code, coupled with a vast network of miners and nodes distributed globally, makes Bitcoin nearly immune to censorship and manipulation.
Bitcoin's decentralized nature is a cornerstone of its value. Unlike XRP, which is closely tied to Ripple Labs and its business interests, Bitcoin is not controlled by any organization or individual. This decentralization ensures transparency, security, and trust among its users, reinforcing its status as a digital alternative to gold.
Moreover, Bitcoin’s capped supply of 21 million coins enhances its appeal as a store of value. In a world where inflation and monetary policy can erode the value of fiat currencies, Bitcoin’s scarcity offers a hedge against economic uncertainty.
Adoption and Market Perception: Bitcoin vs. XRP
Despite its controversies, XRP has gained traction among financial institutions for its speed and low transaction costs in cross-border payments. Ripple’s partnerships with major banks and remittance providers have bolstered its utility, even as skepticism around its centralization persists.
Bitcoin, on the other hand, has achieved mainstream acceptance as both an investment asset and a medium of exchange. From institutional investors adding Bitcoin to their balance sheets to countries like El Salvador adopting it as legal tender, Bitcoin's adoption is steadily growing. Its resilience in the face of regulatory scrutiny and market volatility further cements its position as the most trusted cryptocurrency.
What XRP's Journey Teaches Us About Cryptocurrency Values
The contrasting narratives of XRP and Bitcoin highlight a fundamental tension in the cryptocurrency world: the trade-off between utility and decentralization. While XRP offers practical solutions for specific use cases, its centralized nature and reliance on Ripple Labs compromise its alignment with the ideals of cryptocurrency.
Bitcoin, by comparison, stays true to the vision of a decentralized financial system free from intermediaries. Its robust network, transparency, and immutability make it not just a cryptocurrency but a symbol of financial freedom.
Conclusion: Bitcoin’s Enduring Legacy
As the legal and market drama around XRP continues to unfold, one thing remains clear: decentralization is at the heart of what makes cryptocurrencies revolutionary. Bitcoin exemplifies this ideal, serving as a reliable store of value and a hedge against centralized control. While XRP may have its place in specific financial ecosystems, it cannot claim to uphold the principles that Bitcoin has come to represent.
For investors and enthusiasts alike, understanding these differences is crucial. In a rapidly evolving market, Bitcoin’s true value lies not just in its price but in its unwavering commitment to decentralization—a principle that defines the future of financial freedom.
-
 @ 6bae33c8:607272e8
2025-01-27 14:56:31
@ 6bae33c8:607272e8
2025-01-27 14:56:31I was rooting for the Eagles in the NFC because I want Saquon Barkley to win Super Bowl MVP, and on the first play from scrimmage he took a 60-yard run to the house. Unfortunately he got banged up on the play and was used sparingly for the rest of the game, but no matter. Another 118 yards and three TDs later, he’s got his chance in the Super Bowl.
The Killer Redskins are pretty good — they don’t stop coming at you, and Jayden Daniels should be a star for the next decade. But three lost fumbles destroyed any hopes they had. Fumbles and penalties are the worst part of the NFL — like getting Sorry’ed in the game of Sorry, they reverse whatever is happening on the field seismically.
-
The KRs are close. They could use an offensive line upgrade, maybe one more pass rusher and another explosive skill player, but with Daniels around, they’ll be contenders again.
-
Terry McLaurin didn’t have a big role, but he showed how fast and explosive he is on the 36-yard TD catch and run. He’s also big (210 lbs) for a speed receiver, but turns 30 in September.
-
Jalen Hurts made some nice downfield throws to A.J. Brown which is a good sign. If the Eagles are going to beat the Chiefs, they’ll need to make some plays in the passing game.
-
Jake Elliott missed a long FG and has been shaky all year. People don’t care about kickers, but I wouldn’t want to trust him with the game on the line.
-
In both games there were penalties on a TD that resulted in teams opting for the 1-yard 2-point conversion, and both failed. The Bills even took a successful PAT off the board.
-
I know there was controversy on the Chiefs’ fourth quarter. 4th-down stop, down 1 (and also the spot on the preceding 3rd-down play that made it 4th down.) But the Chiefs still had to drive for the touchdown and subsequent FG after the Bills tied it, stop them on defense one more time and then convert that last third down to seal it. In other words, it looked like two bad spots, but even if that was “cheating,” the game was won on the field. The Chiefs also lost a fumble on a botched snap, and the Bills recovered all of theirs.
-
Kareem Hunt is such a tough runner, he’s basically a healthy Isiah Pacheco at this point. Pacheco himself doesn’t look 100 percent.
-
Travis Kelce had a surprisingly minor role, but Xavier Worthy had a good game, and Patrick Mahomes spread the ball around. It was almost as if they had played it vanilla on purpose in earlier weeks and broke out a more aggressive passing game when they needed it.
-
Mahomes will now have appeared in five of the last six Super Bowls, with only Joe Burrow and the Bengals interrupting his streak. If he wins a fourth this year, he’ll have a chance to do the unthinkable which is to catch Tom Brady’s seven. Three more is still a lot though, and that’s only IF he wins against the Eagles.
-
Josh Allen played well on the road against one of the league’s best defenses. The Bills offense wasn’t as efficient as Buffalo’s, though, and they’re really missing a go-to playmaking receiver. Amari Cooper never seemed to integrate fully into the offense.
-
The AFC is loaded with QB talent that will never see a Super Bowl so long as Andy Reid and Mahomes are in the league. Allen, Lamar Jackson, Justin Herbert, Burrow (again) or maybe C.J. Stroud will break through one of these years, but it’s likely at least two of them won’t.
-
-
 @ eee391ee:8d0b97c2
2025-01-27 14:55:16
@ eee391ee:8d0b97c2
2025-01-27 14:55:16Amber 3.2.0
- Fix relay connection when starting the service
- Added profile picture in the incoming requests screen when using a large screen device
- Added more event kinds translations
- Added a log with the bunker request response
- Use the relay from the request to send the response when no app is found
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v3.2.0.txtandmanifest-v3.2.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v3.2.0.txt.sig manifest-v3.2.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v3.2.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 652d58ac:dc4cde60
2025-01-20 14:39:11
@ 652d58ac:dc4cde60
2025-01-20 14:39:11Introduction
We must rethink how we envision the future. In the short term, things may be worse than we expect, rising inflation, war, and health crises, but this is all part of the fiat dilemma. A system that cannibalizes itself. Yet, at the same time, a new system is emerging.
Bitcoin and Artificial intelligence (AI) will be central to this foundation, providing humanity with the time and tools needed to thrive. How Technology Drives Deflation
As Jeff Booth so masterfully explains, technology is inherently deflationary. Over time, through free market competition and productivity gains, prices should fall to their marginal cost of production.
Yet, in our inflationary fiat system, productivity gains are eroded by the continuous increase in the money supply, driving prices higher. Instead of allowing prices to approach their marginal cost of production as they should, goods and services become more expensive due to monetary inflation.
This principle, that an expanding money supply reduces the purchasing power of individual monetary units and ultimately undermines wealth creation, was recognized as early as 1517 by Copernicus in the quantity theory of money.
Because bitcoin is limited in supply, productivity gains across the economy can lead to greater wealth for all participants in the system, as the price of goods and services falls to the marginal cost of production over time. Rather than rise due to an increase in the monetary supply. We need Bitcoin to ensure that the productivity gains that drive the economy forward can have a lasting, sustainable impact.
The Interplay of Bitcoin und AI
Since the existing system benefits from inflation, market participants are often manipulated into believing that AI is inherently dangerous. While there are significant risks associated with AI, particularly its potential for centralization and manipulation, the technology itself offers great opportunities. The real problem lies in the inflationary monetary system, not AI.
Artificial intelligence is set to increasingly shape the workplace, trade, and finance. Consider the “Magnificent Seven”, a group of tech giants, Apple, Microsoft, Amazon, Alphabet (Google), Meta (Facebook), Nvidia, and Tesla, that all leverage AI as a key driver of productivity.
In 2023, the financial services industry alone invested an estimated $35 billion in AI, with banking leading the charge, accounting for approximately $21 billion. This is particularly relevant to Bitcoin, since it serves as both money and a financial system. As AI becomes more sophisticated, it will increasingly rely on a digital currency that aligns with its digital nature, such as bitcoin, which offers both scalability and speed through the Lightning Network.
For instance, AI systems could use Bitcoin to facilitate microtransactions in real time, managing their wallets autonomously to process payments for services or data. This would unlock new opportunities for AI applications in sectors like actual decentralized finance (DeFi) and machine-to-machine transactions.
The Lightning Network, as a second-layer protocol built on top of Bitcoin, enables transactions to be settled almost instantly and at low cost. This makes it particularly well-suited for AI applications that require fast and reliable transactions.
While some AI and language models can exhibit programmed biases, AI systems, driven by algorithms and data, should strive to prioritize efficiency, minimizing biases wherever possible. If programmed without bias, AI seeks the best tools for operations and decision-making, and Bitcoin offers an optimal solution, providing both the asset and infrastructure needed for efficient, resilient, digital financial systems.
In addition, AI is likely to also contribute to Bitcoin’s development, with algorithms optimizing mining efficiency, hardware usage, forecasting energy demand, and ensuring more efficient resource allocation, all of which will lead to more effective mining strategies.
Conclusion
The synergy between Bitcoin and AI has the potential to enable the creation of more efficient, intelligent and resilient systems. These developments will underpin bitcoin’s role as digital money in a digital world, potentially creating positive second-order effects on global financial markets. The impact will be especially profound in industries such as finance, insurance, robotics, lending, investments, architecture, housing, healthcare, logistics, and others, with effects accelerating over time.
The free market is inherently deflationary, because of productivity gains, things, like housing, should become cheaper over time. Yet, this doesn't happen. Inflationary fiat currencies, like the dollar, lose purchasing power as their supply increases, eroding those gains. Bitcoin offers a framework in which productivity gains can have a lasting, sustainable impact.
Bitcoin, as a disinflationary currency with a fixed supply, preserves the value of productivity improvements, allowing prices to fall to their marginal cost of production. This ensures that efficiency gains lead to greater wealth for all participants in the system.
Moreover, since Bitcoin is accessible, it allows wealth to become more attainable for a wider range of people, enabling general living standards to increase more easily. The interplay between Bitcoin and AI is pretty exciting, and it’s becoming clear that the widespread adoption of AI will drive the widespread adoption of Bitcoin. This is necessary, as only Bitcoin, as a counterbalance to the self-destructive fiat system, can protect humanity from the negative effects of inflation. With the accelerated productivity gains of the AI age, Bitcoin becomes even more crucial as a solution, ensuring that these gains can be preserved and shared more equitably.
Originally published as the 28th edition of my n ewsletter, Bitcoin & AI: https://leonwankum.substack.com/p/bitcoin-and-ai
Photo Credit: commonedge.org (An Optimist’s Take on AI and the Future of Architecture)
-
 @ 4d41a7cb:7d3633cc
2025-01-20 14:33:39
@ 4d41a7cb:7d3633cc
2025-01-20 14:33:39Anyone concerned with private property, survival, and freedom will find the material in this article to be very interesting. The concept of money is more abstract than most people think, and that is what I will try to demonstrate below.
Whether the film The Wizard of Oz's hidden message was intentional or not, it serves as an allegory to explain the grim and gruesome global monetary system.
The 1939 film The Wizard of Oz, based on L. Frank Baum's 1900 novel, contains hidden allegories about the banking system and financial challenges of late 19th and early 20th century America. The film closely resembles the book, except for two minor details: The yellow road in the film was the golden road in the book, and the ruby shoes in the film were silver shoes in the book: a clear reference to the bimetallic monetary system of the U.S. at the time.
The occult meaning explained
The word ‘OZ’ is a clear reference to the ‘ounce,’ a unit of measurement for gold and silver, further emphasizing the connection to monetary issues.
We can see The Wizard of Oz as an allegory for the new state of affairs in the United States in the 1930s, following the stock market crash and the bankruptcy of the US government immediately afterwards.
The play gives an allegorical sense of the financial enslavement of taxpayers, the legal tricks, and sensory manipulations bankers and government officials use to impose such enslavement on taxpayers. It also exposes the banking cartel, letting the people know that they are empowered to liquidate the bankers and return to Kansas: the true Republic.
The setting was Kansas: the heartland of America and the geographical center of the USA. The tornado (1929-1933), a whirlwind of turmoil that includes the stock market crash, the theft of American gold, the bankruptcy of the USA, and the Great Depression, sweeps in, transporting Dorothy and Toto to a new artificial dimension somewhere above the Kansas mainland. When they finally land in Oz, Dorothy remarks to her little companion:
‘Toto, I have a feeling we're not in Kansas anymore.’.
After the bankruptcy, Kansas was no longer simply the old 'Kansas'; it was now 'KS,' the artificial corporate headquarters of the bankrupt United States, a newly established 'federal territory,' part of the 'Federal Zone,' and Dorothy and Toto were 'in this state.'
The creditors of THE FEDERAL RESERVE INC. had declared the constitutional republic of the United States of America bankrupt and replaced it with a private corporation of the same name, UNITED STATES INC.
For those of you who are not yet aware, there was a conspiracy during the last two centuries to steal the world's money supply (gold & silver) and replace it with a global elastic fiat credit system. The design of this system was to transfer wealth from the productive class of world nations to the unproductive class of international bankers, resulting in artificial boom and bust cycles and private and public bankruptcies.
This happened in the United States during the beginning of the 1900s, especially from 1913, when the Federal Reserve was created, to 1933, when they stole all the gold from the American people after destroying their economy and prosperity.
International bankers had taken over the republic, but Americans were too confused and distracted by the turmoil at the time to realize this. A corporate state operating under commercial law had supplanted the constitutional republic operating under common law. At the same time, the Federal Reserve banking cartel would receive 100% of the present and future tax revenue from Americans.
The golden road
The book refers to the 'yellow road' as 'the golden road'. To locate the Wizard, you must track the money, specifically the stolen gold, which will lead you to the thief.
When the US government declared bankruptcy in 1933, Americans were required to turn in all their gold coins, gold bullion, and gold certificates by May 1, May Day (the birthday of communism in Bavaria in 1776, the birthday of the IRS, and celebrated worldwide as the ‘International Workers’ Holiday,’ a day sacred to the Wizard and his tribe). 1
By following the path of gold and its history, we can quickly get to the banking cartel and discover many of their methods and crimes. Even before they stole America, they had long since disposed of the Christian monarchies of Europe and plundered their kingdoms.
By examining significant dates like 1971, 1944, 1933, and 1913, we can swiftly identify the individuals responsible for shaping human history over the past few centuries.
Following the history of the gold standard, we can arrive at the creation of the Federal Reserve and the international banking cartel that owns and controls it, the Wizard of Oz, whose origin is from Europe.
The Emerald City
The Emerald City, where everything is green, is seen as a metaphor for the Federal Reserve and its fiat currency: Federal Reserve Notes, or FRNs (fiat ‘money’ or ‘money by fiat’). There the legendary wizard of Oz took refuge, with his mythical and omnipotent power to manipulate the interest rates and the supply of currency.
The illusory prosperity of the city reflects that currency itself is an illusion, especially when disconnected from gold or silver. By printing trillions of Federal Reserve notes to finance wars, purchase mass media, fund research and development, and purchase professionals and politicians, the magician maintains his position of power and the illusion of 'official authority'.
This currency creates a false sense of abundance when in fact it destroys the incentives for trade and creates inequality and injustice. The Great Depression of the 1930s, the confiscation of gold, and the two subsequent world wars were a direct result of the actions of the Federal Reserve, formed in 1913, a predecessor from the Bank of England, where the real power behind this entity lies.
The Federal Reserve is not federal and has no reserves; it is just the corporate name for private enterprise with an absolute monopoly on global credit. The illusion that it is part of the government or that it has legitimate authority is just that, an illusion; in reality, it is a cartel of private bankers with a monopoly on debt-based global currency.
The Wizard of Oz
One definition of 'wizard' is 'a very clever person'. The Wizard is a symbol of the banking cartel, which manipulates and controls people behind the scenes. They hide behind corporate names that do not even represent what they stand for, such as the Federal Reserve, United States, British crown, and Vatican.
Using smoke and mirrors, they create a grand illusion of omnipotent and omniscient power as if they were gods on earth. The magician represents the idea that the powerful often only manipulate perception instead of offering real solutions. However, upon exposing them, we uncover that they are merely common men, burdened with fears, insecurities, greed, and a significant dose of evil.
We know very well that the banking cartel controls educational institutions, the media, book publishers, and every flow of information and resources; thus and only thus can it manipulate the perception of billions of human beings around the world.
All of humanity is in a state of financial slavery to the illusionist's counterfeit money, which silently steals the time and energy of the masses on a global scale—their most precious wealth. The Wizard has owned the US government outright since 1933 and ‘owned’ Hollywood, an indispensable resource for maintaining global illusion and false perception.
‘You can fool all the people some of the time, and some of the people all the time, but you can't fool all the people all the time.’.
Abraham Lincoln (1809-1865), 16th President of the United States
After all, the wizard turned out to be just a con man, a fraud; behind the curtain there was just an ordinary person controlling the levers that created the illusion of authority and power.
The magician also cited the Latin phrase 'the land of E' Pluribus Unum,' meaning 'one among many'. This means that the phrase 'the land of E' Pluribus Unum', which translates to 'one among many', symbolises the merging of many into one, thereby establishing the New World Order, also known as Novus Ordo Seclorum. This phrase was prominently displayed on the US dollar note shortly after the crash in 1934.

The agenda of the international banking cartel is the ultimate elimination of cash, the total digitalization of credit, and the creation of a programmable global digital currency. Together with a social credit system and absolute surveillance, they seek to create a global police state to keep their taxpaying slaves in check and prevent any possibility of rebellion. By censoring dissent and controlling the flow of information, energy, and money, they plan to crown themselves on the throne forever.
The magician's main tools to maintain his economic power: DEBT, TAXES, AND INFLATION. Tools we must understand in depth to regain financial freedom and 'return to Kansas,' our true constitutional republic.
The Wicked Witch of the West
The Wicked Witch of the West made her home in a round medieval watchtower, the ancient symbol of the Knights Templar of Freemasonry, who were given to practicing witchcraft and are also credited with being the originators of modern banking, circa 1099 AD.
The Wicked Witch of the West wore black, a color that represented the planet Saturn, the Knights Templar's sacred icon, and the color judges and priests chose for their robes. Who was the Wicked Witch of the West? Remember, in the first part of the film, her counterpart was 'Almira Gulch,' who, according to Auntie Em, 'owned half the county.' Miss Gulch claimed that Dorothy's dog, Toto, had bitten her. Miss Gulch arrived at the farm with a'sheriff's warrant', demanding the release of Toto into her custody. Aunt Em was not immediately cooperative and responded to Miss Gulch's accusations that Toto had bitten her by saying, "He's very nice." With nice people, of course.
Miss Gulch's challenge to hold Toto and 'go against the law' reduced dear Auntie Em to 'pushing the party line' for Big Brother. She dutifully succumbed to the pressure and reluctantly advised Dorothy:
‘If you don't give me that dog, I'll bring you a goddamn suit that took over your whole farm!’
Today, 70% of all lawyers in the world reside in Western America, to be exact, and 95% of all lawsuits in the world are filed under the jurisdiction of the United States. The Wicked Witch of the West and Miss Gulch, my dear friends, stand in for judges and lawyers, specifically the American legal system, which includes the lawyer-led Congress and White House. They act as executioners and chief henchmen, transferring all wealth in America from the people to the ownership of banks and the government.
The Wicked Witch of the West wanted the silver slippers and precious metals, and her counterpart, Miss Gulch, wanted Toto (i.e., everything). We know all too well that banks are never satisfied and seek to squeeze every last penny from taxpayers, because it's not just about money; it's about control.
The straw man
The straw man wanted a brain from The Wizard of Oz. The term "straw man" in English refers to the legal fiction, legal person, or capitalized names that the US federal government creates using our natural-born names, with the intention of enslaving us and supporting the issuance of debt-based currency. The birth certificate, which establishes our legal fiction, serves as the tool for bolstering the issuance of public debt and currency.
The FRN, also known as the 'dollar,' represents a blank check that the US taxpayer has signed for the government. No legal person, paper legal fiction, or corporation has a brain nor a breath of life. They are just that: legal fictions and paperwork.
What does a straw man possess in place of a brain? A certificate. He took immense pride in his newly acquired legal status and all the other privileges bestowed upon him. Despite receiving a certificate, he remained a naive individual devoid of common sense.
The Tin Man (TIN)
The tin man symbolizes the taxpayer, specifically the workers. The IRS uses the TIN, a nine-digit number, to identify taxpayers for tax purposes. It can be a Social Security number (SSN), an individual taxpayer identification number (ITIN), or an employer identification number (EIN).
Just as the scarecrow/straw man had no brain, this tin man vessel had no heart. Both were ‘artificial persons.’. The Tin Man symbolized the mechanical and heartless nature of commerce and commercial law.
The Tin Man stood there, mindlessly engaged in his work, until his body literally overflowed and ceased to function. He exhausted himself due to his lack of heart and soul.
The heartless and soulless taxpayer/worker serves as nothing more than a useful slave to the banking cartel, fulfilling his "duty" without questioning the moral implications of his actions. Governments and banks rely on them for their income, and they labor diligently under their control.
‘I was just doing my job’ is one of the most common responses when re-evaluating the immoral acts they were complicit and co-conspirators in throughout history.
Today, thousands of distractions, vices, drugs, and products hypnotize them in front of a television or mobile phone screen, preventing them from realizing their role as tax slaves and hearing the call to a higher purpose in life.
These completely demoralized individuals lose sight of their life's purpose and value, which explains why there are so many cases of depression and suicide in today's world.
This is done by design: the banking cartel's agenda is to maintain the tax slaves' cold exterior and heartless interior in order to suppress any potential emotional reactions or divine sparks.
The cowardly lion
The cowardly lion was always afraid to stand up for himself, representing the American people who had lost their courage and bravery.
‘The land of the free and the home of the brave’ became the land of the slaves and the home of the cowards.
The cowardly lion, seeking the courage of the great wizard, received an official recognition medal. Now, although he was still a coward, his official status allowed him to be a bully, but with officially recognized authority, like lawyers or military men who hide behind courts and medals.
Have you ever noticed how bullies are actually the biggest cowards who act as if they have enormous courage but in reality have none?
It's fascinating how many weak, socially resentful, and cowardly individuals gravitate towards positions of power to conceal their cowardice and weakness. They require a position of 'authority' and often misuse it, concealing their weaknesses and insecurities behind official bodies.
The poppy field
The tactic was to cover the field with poppy flowers, the source of heroin, opium, and morphine, symbolically drug them into unconsciousness, and then simply walk in and snatch their slippers. In other words, the best way to subjugate the American people and plunder their assets was to dull their senses by becoming addicted to drugs.
The narcotics of the poppy field had no effect on the straw and tin man, for they were not blood, flesh, and blood, but artificial entities. The two cried out for help, and Glenda, the Good Witch of the North, answered their prayers with a blanket of snow, i.e., cocaine, a stimulant that nullifies the narcotic effect of the poppies/opium on Dorothy, the Lion, and Toto.
The crown has been playing the drug cartel game for centuries; just look at the history of Hong Kong and the Opium Wars. Despite its obvious impropriety, drugging your opponent before a battle is the most effective way to defeat them.
Distracting the masses, drugging and entertaining them is the best strategy to keep them subjugated and enslaved to a heartless monetary system, thus avoiding any resistance to change.
Flying monkeys
Let's not forget those flying monkeys, mythical creatures perfect for representing the lawyers of the bar (legal masters) who attack and control the little people for the grand wizard in the crown: the powerful and Big Bankers of Oz.Flying monkeys

Individuals have to be represented by lawyers in court cases and therefore need to hire a lawyer. The clients are “wards of the court,” i.e., “infants and persons of unsound mind," just like the strawman was a “person of unsound mind”.
Toto, the little dog
Toto means ‘everything’ in Latin, which was what the witch wanted after claiming the dog had bitten her. THE WITCH (the banks and their lawyers) WANTED EVERYTHING!
Notice how Toto was not frightened by the theatricality of the Big Wizard, even though he was small in size compared to the wizard. Toto simply walked up and began barking, drawing the attention of the others. Behind the curtain, an ordinary person was operating the levers that created the illusion of the great magician's power and authority.
We can see from this story how loud the bark of a small dog can be, but most of us still remain silent.
Dorothy
When Dorothy sought assistance from Glenda, the Good Witch of the North, to return to Kansas, Glenda responded, "You don't need help." You have always been empowered to return to Kansas.
Dorothy eventually made her way home. She always had the power it took to unmask the wizard, and so did we. She always thought she needed outside help, but the power is in each of us, taking responsibility, commitment, and action based on truth.
The great awakening of humanity
Most people do not listen, do not see, and do not speak the truth, either because they have an economic interest or because they are afraid. This is beginning to change.
We are going through a great awakening of consciousness, where more and more individuals are realizing that there is something beyond the illusion of the magician, beginning to see the deeper truths, the background of things, and a higher meaning to life.
Recognizing our birth on a slave plantation, our treatment as property, and the use of our legal identities to support the issuance of government debt (fiat currencies) is crucial. This has been going on for almost a century and is a direct attack on our sovereignty, which is the natural state of our human existence.
As Dorothy once said, "There's no place like home," and indeed, there is no place like home! A sovereign can find no greater place than sovereignty! Will you persist in deceiving unsuspecting men and adoring the magician's light show, or will you, like Dorothy, become aware and delve into the inner workings?
We need an educated mind, an intelligent heart, courage, and the responsibility to act.
We are not defined by our legal fiction or birth certificate, nor are we subject to the dictates of a bureaucrat wielding "official authority" to dictate our actions. We are not corporations operating under commercial law; we are human beings operating under common law, where a crime requires a victim (a human being or their damaged property).
The millions of laws, regulations, and restrictions do not apply to us sovereigns but to our legal fictions that are part of commercial law because they (not us) are corporations. The government has jurisdiction over its creation, which clearly does not include us. In this case, it is our legal identity or fictitious corporation that identifies us, but we, as flesh-and-blood men, are not a creation of the government.
The first step is to recognize this fact; the second is to stop waiting for outside help and take active participation in the matter, assuming responsibility and acting freely to defend our property and our rights.
If we continue to let the magician and his illusions dominate our perception of reality, we will end up living under a communist dystopia, with a system of mass surveillance and non-existent human rights.
But if we decide to take matters into our own hands, by understanding technologies like Bitcoin and Nostr, we can build a better future for ourselves and our future generations.
We are currently facing a unique opportunity to escape the traps and manipulations of this ancestral war and enjoy spiritual, intellectual, and financial freedom.
Although it will not be straightforward and requires responsibility and work, the price of not doing it correctly is slavery, and I personally would rather be dead than live subjugated to the will of a tyrant.
Bitcoin and Nostr, or slavery!
-
 @ 75869cfa:76819987
2025-01-20 06:22:49
@ 75869cfa:76819987
2025-01-20 06:22:49GM, Nostriches! The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics indicate over 224,000 daily trusted pubkey events.The number of new users has seen a significant increase. Profiles with contact list amount is four times the amount from the same period. Public writing events have reflected a 50% increase. More than 9 million events have been published, with posts leading in volume at around 1.3 million, representing a significant 32% decrease. Total Zap activity stands at approximately 9 million, marking a 20% decline.
Additionally, 16 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 45 Nostr projects were tracked, with 13 releasing product updates, and over 337 long-form articles were published, 34% focusing on Bitcoin and Nostr. During this period, 1 notable event took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 224,000, representing a slight 5.5% decrease compared to the previous period (8-22 Dec). Daily activity peaked at 18053 events, with a low of approximately 16276.
The number of new users has seen a significant increase. Profiles with contact list amount to approximately 18,340, which is four times the amount from the same period. Pubkeys writing events total around 80,000, reflecting a 50% increase compared to the same period.
Regarding event publishing, the total number of note events published is about 9 million, marking an increase of above 20%.Posts remain the most dominant in terms of volume, totaling approximately 1.3 million, reflecting a notable decrease of 32%. Reposts stand at around 327,000, showing a decline of approximately 8.5%, while reactions have experienced a significant increase, rising by 18% to reach 635,012.
For zap activity, the total zap amount is about 9 million, showing a decrease of over 20% compared to the previous period.
In terms of relay usage, the top five relays by user count are: wss://bostr.bitcointxoko.com/, wss://feeds.nostr.band/, wss://relays.diggoo.com/, wss://bostr.azzamo.net/, wss://bostr.lightningspore.com/
Data source: https://stats.nostr.band/
NIPs
Asset prices nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z defines event kinds to host asset prices.Kind 31892 stores the latest conversion price. The d tag contains the commonly used ticket conversion symbol for the pair. The value tag contains the amount, parseable to a Decimal. n tags separate the pair into the two ticket symbols. The event's created_at field MUST be used as the date/time of the conversion value.Kind 10041 lists the user's authorized providers for pricing services. It contains s tags with the provider's pubkey and the relay where those events are stored.
nip-38: chained stories. Kehiy defines a new status type which lets users share a chain of stories.This NIP enables a way for users to share live statuses such as what music they are listening to, as well as what they are currently doing: work, play, out of office, etc. A special event with kind:30315 “User Status” is defined as an optionally expiring addressable event, where the d tag represents the status type.The status MAY include an r, p, location, e or a tag linking to a URL, profile, location, note, or addressable event. The content MAY include emoji(s), or NIP-30 custom emoji(s). If the content is an empty string then the client should clear the status.Clients MAY display this next to the username on posts or profiles to provide live user status information.
adding x tag to nip56 Kehiy is proposing that with the growth of clients like zap stream, olas, chat apps, or music clients we have more stuff that may need to be reported. here we can support blobs. When Nostr grows in using media based clients, like zap.stream or olas or music clients, then the event itself is not too important and the media is more important. by reporting events, the media is still accessible. We can support reports ol medias like this.
NIP-91: Extension Negotiation Semisol is proposing that NIP-91 adds an extension negotiation scheme for clients and relays to negotiate new protocols. The intended goal is to replace NIP-11 for the discovery of relay supported features. An extension feature negotiation scheme is also included.
Trusting rumors by entirely trusted relay list nanikamado has decided to require Nostr users to register their pubkeys to access the bridge after discussions with some Fediverse users. Unregistered users will be denied both read and write access, operating similarly to a paid relay. In addition, measures will be implemented to prevent events within the bridge relay from being broadcast to other relays, even if it compromises compatibility. The "-" tag alone is insufficient for this requirement. This NIP has already been implemented on the relay: nanikamado/rockstr@f968149. There are also plans to fork a web client and implement this NIP there.
Notable Projects
Amethyst v0.94.3 nostr:npub142gywvjkq0dv6nupggyn2euhx4nduwc7yz5f24ah9rpmunr2s39se3xrj0 * Adds iMeta tags to GIF urls * Adds iMeta tags to GIF urls to optimize GIF previews * Fixes the extra empty kind 20 post when uploading videos on the media tab * Fix: Only close the upload screen if the video upload is a success on the Media tab * Maintains note reaction visibility when scrolling by nostr:npub1xcl47srtwh4klqd892s6fzwtdfm4y03wzjfl78scmmmxg8wzsf4qftd0en
Flotilla 0.2.1 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn * Improve performance, as well as scrolling and loading * Integrate * Improve NIP 29 compatibility * Fix incorrect connection errors * Refine notifications * Add room menu to space homepage * Fix storage bugs * Add join space CTA
Primal for Android build 2.0.34 nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg They now support the full highlighting feature set for long form notes: highlight display, select any text & highlight, comment on highlights, share highlights in your main feed. They also added btc/usd conversions in the wallet, as well as other small fixes and improvements.
0xchat App v1.4.5 & Desktop v1.0.1 nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72 * Added support for NIP46 login. * Adapted UI for tablet devices. * Introduced connection ping status. * Implemented search functionality for Moments. * Set default relays for first login. * Added default reaction emojis. * Fixed an issue where messages couldn't be sent after joining a relay group. * Resolved occasional UI flipping issues. * Fixed an issue preventing images from being moved after zooming. * Addressed a bug causing voice messages to get stuck in a loading state. * Fixed file encryption and decryption issues. * Corrected some typos. * Fixed an issue with Nostr.build uploads.
Yakihonne Latest Update (iOS/Android/Web/Zap.Store) nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Web: * Yakihonne is now multilingual! Enjoy the app in English and Chinese, with more languages coming soon, including Spanish, Portuguese, Thai, Arabic, Japanese, and Italian. * Added support for translating notes and articles into the app's selected language. * Copy-paste images to upload seamlessly across the app. * Resolved issues with secure DMs when logging in using a private key. * General bug fixes and improvements. * Article drafts now can be cleared directly or the published one will no more be existed
Mobile: * App languages: Yakihonne is now multilingual! Enjoy the app in English and Chinese, with more languages coming soon, including Spanish, Portuguese, Thai, Arabic, Japanese, and Italian. * Translation: Added support for translating notes and articles into the app's selected language. * Wallet balance: Fix issue where wallet balance is N/A. * Account initialization: Fix issue when initializing account. * Paying invoice: Fix issue sending sats using invoices.
Olas 0.1.7.1 nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft * Works with remote signers like Amber (on nsecbunker mode). * The video tab now plays short videos with sound on and stops playing when you swipe out * Yet even more performance improvements * Fixed a bug where Android wasn't calculating blurhashes * Always adds image dimensions when posting so @Vitor Pamplona is happier. * “Some” fixes on NWC wallets, but it's still quite buggy, will investigate more -- if you've received zaps on your Olas posts today, that was probably me zapping via NWC + remote signing those zaps.
Wherostr v1.3.3 nostr:npub16elg3wf8nffkymylw9kfwecc45j9c30lufrrzx2zf5vmxjlcgkkq3xc6d7 * File Upload Error: Resolved the “404 Not Found” issue during file uploads. * Increased Geohash Precision: Enhanced location accuracy by increasing geohash precision from 9 to 11.
DEG Mods nostr:npub17jl3ldd6305rnacvwvchx03snauqsg4nz8mruq0emj9thdpglr2sst825x * A small update went live: * A “try again” button appears on mods that error out. (99% of the time this fixes the issue). * The blog tab in a user's profile now loads correctly (doesn't get stuck anymore for new users) * Text now appears if a game isn't found in the search * Looking into fixing one newly discovered issue related to old mods * Easier media uploads (drag and drop basically. No need to go find other sites to upload images to anymore)
AlbyHub 1.11.4 nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm * You can use all the features of Alby Hub in self-custody with LND on Raspiblitz, now available in WebUI.
Zapstore 0.2.0 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 * 0.2.0 is out with support for signing in with Amber (NIP-55) and zaps via Nostr Wallet Connect.
Narr release v0.3.2 nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 * New Narr release v0.3.2 fixes all the problems with articles updating, insufficiently-rendered Markdown, Nostr usernames not loading, and makes everything better. * It supports all sorts of RSS feed discovery from HTTP URLs and renders them beautifully in a simple straightforward interface, you can also paste nostr:... URIs, including nip05, npub and nprofile codes (they should also work without the nostr: prefix).
ZEUS v0.9.4 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 * Embedded Node: LND v0.18.4 * Speed up tx UX improvements * CLNRest: display of destination addresses on txs * Display keysend messages in Activity + Payment views * Open Channel view: Connect Peer UI tabs * CLNRest: paste connection strings * Channels: sort by Close Height * Optimizations + bug fixes
Citrine 0.6.0 nostr:npub1hqlxlq57nvlq70ugmsmu9y5lmyc5k2lh5w7y85j7dgsr5u7zwavq5agspw * Update dependencies * Show notifications when importing, exporting, downloading events * Change database functions to be suspending functions
Long-Form Content Eco
In the past two weeks, more than 337 long-form articles have been published, including over 93 articles on Bitcoin and more than 22 related to Nostr, accounting for 34% of the total content.
These articles about Nostr mainly explore its diverse applications and potential impacts across various domains. Topics range from technical guides like creating custom emojis and automating workflows, to cultural and social aspects, such as the Nostr Bread Festival and the role of Nostr in enhancing free speech. There are reflections on the past year's developments, predictions for 2025, and discussions on integrating Nostr with other platforms like Bluesky. The content also delves into personal experiences, community interactions, and broader societal issues, highlighting Nostr's growing influence and the creative ways users are engaging with this decentralized network.
The Bitcoin articles discuss a wide range of topics, from technological innovations to socio-economic impacts. They cover the speed advantages of the Lightning Network, the economic model policies of Bitcoin, and the outlook for Bitcoin's development in 2024. Some articles analyze the relationship between Bitcoin and traditional financial markets like the Nikkei 225, highlighting the potential of a decentralized future and the spread of Bitcoin education. Additionally, they explore the possibility of Bitcoin as a legal tender, its connection to religious and spiritual dimensions, and the mystery surrounding Satoshi Nakamoto's identity. Reflections on Bitcoin's milestones, such as the release of the genesis block, emphasize its challenge and revolution to the modern financial system. Overall, these articles showcase Bitcoin's profound global impact and its continually evolving ecosystem.
Thankyou, nostr:npub1xr8tvnnnr9aqt9vv30vj4vreeq2mk38mlwe7khvhvmzjqlcghh6sr85uum nostr:npub1zmg3gvpasgp3zkgceg62yg8fyhqz9sy3dqt45kkwt60nkctyp9rs9wyppc nostr:npub15wplsmd8uqul4a5l55n9e6kcd5fcrgxvwa6jredncvdr8nd5zl2qswqcsn nostr:npub1a6g9g0a3rweu7jkujrgldlsrrjv42u070qmxxfv5axk0eymrg4ls0vll8d nostr:npub1dr8yfep5kezfcq5u9dhdulhcegknwlauqrlvfwjw7rkprmx4746qfxjj6h nostr:npub1fhl7c96k3vdv4ge8rv26cda4qyxnqd605x2w7l58euy0jnzvh4yq5hvm20 nostr:npub1tx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865szf9fw6 nostr:npub1tzfhjkqrdnk7j4djtwfftqupgzazm6kt35vnnmv35sd7y4z7dx2qzhkje9 and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, a Nostr event have been hosted. * The Bitcoin Meetup took place on December 29, 2024, at the “Accra City Pub” in Jamestown. The event featured the “Orange Pilling” session at 3:00 PM, followed by the GH Bitcoin NYTZ meetup at 7:00 PM. Participants also had the chance to win a free Trezor Safe 3 hardware wallet, and the event was free to attend.
Here are the upcoming Nostr events in November that you might want to check out.
-
The Bitcoin City Team Hackathon will take place online (via Discord) from January 10 to January 31, 2025. This event aims to develop a fun and interactive visualization of live Bitcoin and Lightning transactions. Participating teams will have the opportunity to win a total prize of 10,000,000 IDR. nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
-
The inaugural Bitcoin Circular Economy Summit will be held from January 27th to 29th in El Zonte, El Salvador! This three-day event includes leadership training, Bitcoin education, and exchanges with over 15 global Bitcoin circular economies. It offers a unique opportunity for global leaders in Bitcoin adoption and economic development to connect, learn, and collaborate. This summit precedes the PlanB Forum, taking place on January 30th-31st in San Salvador, making it an excellent chance to network with Bitcoin users worldwide.
-
The Bitcoin Freedom Festival will take place from February 20 to 24, 2025, at the Awakening Center in Uvita, Costa Rica. In collaboration with the Awake Earth Festival, this event blends a music festival with Bitcoin seminars and lectures. From February 20 to 23, the focus will be on music, healing workshops, ceremonies, and educational talks, featuring internationally renowned artists and captivating discussions. February 24 will be a special day dedicated to Bitcoin, with all activities centered around it. nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
-
 @ da0b9bc3:4e30a4a9
2025-01-27 14:32:50
@ da0b9bc3:4e30a4a9
2025-01-27 14:32:50Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month it's New Year New Artists! Bringing you small time artists with great music. Artists without some huge record label or massive following. Let's find those hidden little gems.
This week, may I present to you, Belle Sisoski and her cover of "Legends Never Die"
https://youtu.be/VMIL1YbUQrI?si=kR2YLib5x3qLEn8A
originally posted at https://stacker.news/items/866591
-
 @ 16d11430:61640947
2025-01-20 03:32:57
@ 16d11430:61640947
2025-01-20 03:32:57Building a business, especially in the Bitcoin ecosystem, requires an unwavering commitment to patience and a deep belief in the fundamentals that underpin the technology. In a world driven by short-term profits and speculative fervor, it is easy to lose sight of the long game. Yet, the path to creating something meaningful and enduring often lies in resisting the noise and staying true to core principles.
The Bitcoin Revolution: Planting Seeds in Fertile Soil
Bitcoin is not just a technological innovation; it is a paradigm shift in how we view money, value, and trust. For entrepreneurs, it offers an opportunity to align their work with a monetary system that is decentralized, censorship-resistant, and designed for fairness. However, building a business in the Bitcoin space requires a recognition that societal adoption takes time.
As the saying goes, "The pot has to boil further." The ecosystem is still maturing, and while the signs of progress are undeniable, there is much work to be done. For plebs—the passionate individuals who embrace Bitcoin as a way of life—to eagerly work for sats, the economic incentives must become undeniable. This requires building infrastructure, educating the masses, and proving the utility of Bitcoin beyond speculation.
The Role of Patience in Entrepreneurship
Patience is not passive. It is an active process of nurturing your business, learning from setbacks, and steadily improving your product or service. In the Bitcoin space, patience involves:
-
Education and Advocacy: Many people still misunderstand Bitcoin's potential. Entrepreneurs must invest time in educating their audience, building trust, and explaining why Bitcoin is a better alternative.
-
Incremental Growth: Bitcoin adoption happens at the margins before reaching critical mass. Businesses that focus on steady growth rather than explosive, unsustainable expansion are more likely to succeed in the long run.
-
Long-Term Vision: Building for Bitcoin means thinking in decades, not quarters. A business grounded in sound principles—honesty, resilience, and utility—can weather market cycles and emerge stronger.
Faith in Fundamentals
Bitcoin’s fundamentals are its greatest strength: fixed supply, decentralized governance, and security. These principles create a monetary system that is fair and immune to corruption. Entrepreneurs in this space must build businesses that reflect these same values.
Integrity: A Bitcoin business should prioritize transparency and fairness, aligning incentives with customers and stakeholders.
Resilience: Bitcoin thrives in adversity. Businesses in this ecosystem should adopt a similar mindset, designing products that endure volatility and uncertainty.
Utility: Focus on solving real problems for real people. Whether it’s offering Bitcoin payments, facilitating education, or building tools for sovereignty, utility drives adoption.
Letting the Pot Boil: Creating Conditions for Change
The conditions necessary for mainstream Bitcoin jobs will emerge when the ecosystem matures further. This requires collaboration between businesses, developers, and advocates to:
Expand Infrastructure: Lightning Network, wallet solutions, and Bitcoin-native applications are critical to making Bitcoin more accessible and user-friendly.
Incentivize Participation: Paying workers in sats is not just a gimmick—it is a way to demonstrate Bitcoin’s superiority as a store of value and medium of exchange.
Build Culture: Bitcoin is more than technology; it is a movement. Businesses must contribute to a culture of empowerment, self-sovereignty, and fairness.
Conclusion: The Time Will Come
Faith in fundamentals is what separates builders from speculators. While the market will inevitably test your resolve, the rewards for those who persevere are immense. The time for mainstream Bitcoin jobs will come, but only when the ecosystem is ready—when plebs are eager to work for sats not out of necessity, but because it is the natural choice in a world aligned with Bitcoin's principles.
Until then, entrepreneurs must remain patient, continue building, and trust in the vision of a decentralized future. The pot will boil. When it does, those who believed in the fundamentals will be the ones to shape the next era of economic freedom.
-
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 41fa852b:af7b7706
2025-01-19 18:31:45
@ 41fa852b:af7b7706
2025-01-19 18:31:45"It is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change." -- Charles Darwin
It's usually a big week when the 21st comes around, but this week we have 5 meetups that day!
Also, Trump takes office on Monday so there'll be loads to discuss at this week's meetups.
Let's take a look…
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Bitcoin Bristol: Meeting at Little Martha Brewing, BS2 0QT. On Tuesday 21st at 18:15. 🍺
-
Bitcoin Surrey: It's a Bitcoin Pension Scheme Special this month at Yiayias at The Fox. A fireside chat and Q&A with Sam Roberts, Cartwright's Director of Investment Consulting (1st UK pension scheme to allocate 3% to Bitcoin). 18:00 - 23:00 on the 21st. Bitcoin accepted at the venue. 🎙️🍻
-
Newcastle upon Tyne Bitcoin Meetup: The next Newcastle meetup is on Tuesday 21st January at Kabin @ Kabannas, L2 6RE. 18:30 PM. 🍻
-
London Bitcoin Space: LBS will be at Cyphermunk house on Tuesday 21st from 18:30 till 22:00 for a social gathering, head along to share knowledge and meet some fellow Bitcoiners. 🫂
-
Oxbit: Celebrate Bitcoins 16th birthday with the Oxford meetup crew. You'll find them at The Old Black Horse (bitcoin accepted) at 19:00 on the 21st. 🍺
-
Preston Bitcoin Meetup: Join the Preston meetup for A Bitcoin chat and some amazing burgers. 18:30 on Thursday the 23rd January. At All Hopes No Promises, PR1 2US.
-
The Northamptonshire Bitcoin Network : BTC Citadel Engineering are hosting a 'Bitcoin Builders' space on Saturday the 25th. Head along to learn about Seedsigners and how to build one. Come and use the 3D printers, get a project started and chat about Bitcoin with everyone there. It all gets started at 12:00. No tech skills are necessary. ⚙️🧡
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏻🚶🏼♀️🚶🏽♂️
-
Bitcoin East: Their first meetup of 2025 will be at Marzano Cafe in the beautiful city of Norwich. Join them at 11:00 on Sunday 26th Jan, there's a lot to discuss. ☕️
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 54286b98:3debc100
2025-01-27 14:30:18
@ 54286b98:3debc100
2025-01-27 14:30:18Looking back on that time, I now see clearly that my faith--my only real faith--that which apart from my animal instincts gave impulse to my life --was a belief in perfecting myself. But in what this perfecting consisted and what its object was, I could not have said. I tried to perfect myself mentally--I studied everything I could, anything life threw in my way; I tried to perfect my will, I drew up rules I tried to follow; I perfected myself physically, cultivating my strength and agility by all sorts of exercises, and accustoming myself to endurance and patience by all kinds of privations. And all this I considered to be the pursuit of perfection. — Leo Tolstoy, A Confession
It seems to be a good trait, perfecting sounds and looks good. Why would you not want to improve yourself? You should!
In his book A Confession, Tolstoy starts the first chapter by laying down one of the main Christian principles: we cannot do enough work to achieve salvation, nor can we buy our way into it.
We may strive to be perfect and solve things in our own strength, but we may fail miserably. Christ bought our way in, and the only way to claim that ticket is by surrendering our strength and working in His. Striving to be perfect in our own strength is not different from living by the law (this refers to the Law given to the Jewish people versus living by faith alone).
10 For all who rely on works of the law are under a curse; for it is written, “Cursed be everyone who does not abide by all things written in the Book of the Law, and do them.” 11 Now it is evident that no one is justified before God by the law, for “The righteous shall live by faith.— Galatians 3: 10-11
Trying to be good and do good works is an excellent attitude, but we can only achieve this by walking in His footsteps. Moreover, I think and believe that the inner call to be perfect may exist within us simply to reveal our incapability of such an accomplishment.
For by works of the law no human being will be justified in his sight, since through the law comes knowledge of sin.— Romans 3:20
Of course, faith alone is not proof either, but it’s a start. If we are given the gift of believing in Christ, what we do with that belief is shown through the fruits of the works we do.
14 What good is it, my brothers, if someone says he has faith but does not have works? Can that faith save him? 15 If a brother or sister is poorly clothed and lacking in daily food, 16 and one of you says to them, “Go in peace, be warmed and filled,” without giving them the things needed for the body, what good[a] is that? 17 So also faith by itself, if it does not have works, is dead.
18 But someone will say, “You have faith and I have works.” Show me your faith apart from your works, and I will show you my faith by my works. 19 You believe that God is one; you do well. Even the demons believe—and shudder! 20 Do you want to be shown, you foolish person, that faith apart from works is useless? 21 Was not Abraham our father justified by works when he offered up his son Isaac on the altar? 22 You see that faith was active along with his works, and faith was completed by his works; 23 and the Scripture was fulfilled that says, “Abraham believed God, and it was counted to him as righteousness”—and he was called a friend of God. 24 You see that a person is justified by works and not by faith alone. James 2:14-24
Until the next one,
J
-
 @ a012dc82:6458a70d
2025-01-27 12:51:47
@ a012dc82:6458a70d
2025-01-27 12:51:47In the contemporary financial world, Cathie Wood, the founder of ARK Invest, stands out for her innovative investment approaches. Recently, Wood has focused on Bitcoin (BTC), highlighting its potential as a hedge against both inflationary and deflationary economic conditions. This article delves into Wood's perspective, exploring Bitcoin's evolving role in the global financial landscape. We examine its multifaceted nature, not just as a digital currency, but as a strategic asset capable of navigating the complex dynamics of the modern economy. Wood's insights offer a nuanced understanding of Bitcoin's potential in offering stability amidst economic uncertainties.
Table Of Content
-
Bitcoin's Hedge Potential
-
Decentralization: A Key Advantage
-
The Banking Crisis and Bitcoin
-
Bitcoin vs. Gold
-
Institutional Involvement
-
Conclusion
-
FAQs
Bitcoin's Hedge Potential
Cathie Wood's perspective on Bitcoin transcends its usual perception as a mere digital currency. She champions it as a dynamic tool against economic fluctuations, a quality rarely matched by traditional assets. In an era marked by economic instability, Bitcoin stands as a beacon of potential stability. This is particularly notable in its capacity to act as a hedge during inflationary periods, where fiat currencies lose value, and deflationary periods, characterized by increased money value but decreased economic activity. This dual capability positions Bitcoin as a significant asset in diversified portfolios, resonating with Wood's innovative investment philosophy.
Decentralization: A Key Advantage
For Wood, Bitcoin's decentralization is a critical advantage. This aspect sets it apart from traditional banking systems, which often grapple with issues of transparency and central control. In Bitcoin's ecosystem, there is a clear absence of counterparty risk, thanks to its decentralized ledger and visible transactions. This transparency assures investors of a level of security and autonomy not found in conventional financial systems. In Wood's view, this decentralization is not just a technical feature but a foundational aspect that provides Bitcoin with a resilience and reliability, crucial in a world where financial systems are increasingly interconnected and vulnerable.
The Banking Crisis and Bitcoin
Reflecting on recent financial upheavals, such as the U.S. regional bank crisis and the FTX collapse, Wood sees these events as vindications of Bitcoin's stability and resilience. These crises underscored the inherent risks of centralized financial systems, revealing their fragility under stress. In contrast, Bitcoin demonstrated an impressive resilience, with its value surging during these tumultuous times. This reaction not only highlights Bitcoin's potential as a safe haven but also its capacity to serve as a barometer for the health of the broader financial system.
Bitcoin vs. Gold
While gold has traditionally been the go-to asset for hedge investments, Wood argues that Bitcoin has a distinct edge over it. Her preference for Bitcoin stems from its novelty and the increasing interest from younger investors and institutional players. Unlike gold, whose market and demand patterns are well-established, Bitcoin represents an emerging asset class with untapped potential. Wood believes that Bitcoin's journey is just beginning, and its full potential as a hedge asset is yet to be realized, making it a more attractive option for forward-looking investors.
Institutional Involvement
Wood's belief in Bitcoin's future is mirrored in ARK Invest's substantial investments in cryptocurrency-related ventures. These investments are not mere speculative plays; they represent a deep conviction in the long-term value of Bitcoin. ARK's pursuit of a spot Bitcoin ETF is a significant move, indicating a belief in the cryptocurrency's viability as a mainstream investment asset. This institutional backing by a leading investment firm not only legitimizes Bitcoin's role in the financial markets but also paves the way for more widespread adoption among traditional investors.
Conclusion
Cathie Wood's endorsement of Bitcoin is a compelling narrative in the evolving story of this digital asset. Her insights provide a valuable perspective on Bitcoin's role as a hedge against both inflation and deflation, highlighting its potential in the current economic climate. As we navigate through uncertain financial times, Wood's views offer a guidepost for investors looking to diversify and stabilize their portfolios with innovative assets like Bitcoin.
FAQs
What is Cathie Wood's view on Bitcoin? Cathie Wood sees Bitcoin as a viable hedge against both inflation and deflation, highlighting its decentralized nature and resilience.
Why does Wood prefer Bitcoin over traditional banking systems? Wood values Bitcoin's transparency and lack of counterparty risk, contrasting it with the opacity of traditional banking systems.
How did the banking crisis impact Bitcoin's value? The U.S. regional bank crisis and the FTX collapse showed Bitcoin's stability, with its value increasing during these times.
Why does Wood favor Bitcoin over gold? Wood believes Bitcoin has more potential for growth and is more appealing to younger investors and institutions compared to gold.
What is ARK Invest's involvement in Bitcoin? ARK Invest holds significant stakes in cryptocurrency ventures and is pursuing a spot Bitcoin ETF, reflecting a strong belief in Bitcoin's future.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ cf7ed325:050194cf
2025-01-27 12:39:41
@ cf7ed325:050194cf
2025-01-27 12:39:41The Steigenberger Minerva Nile Cruise offers an exceptional way to explore Egypt's ancient wonders while cruising along the timeless Nile River. This luxurious cruise combines modern amenities with traditional Egyptian hospitality, making it an ideal choice for those seeking comfort and adventure. With spacious cabins, fine dining, and various entertainment options, the Steigenberger Minerva promises an unforgettable experience.
While aboard, guests can enjoy a range of excursions to famous sites like the Pyramids of Giza, Luxor Temple, and the Valley of the Kings. The ship provides a perfect base for exploring Egypt’s rich history, from the bustling streets of Cairo to the serene landscapes of Aswan. The cruise features a blend of relaxation and adventure, offering guests an opportunity to unwind while taking in Egypt's stunning scenery.
In addition to the Steigenberger Minerva Nile Cruise, Egypt offers a variety of other luxurious options. For example, the Farah Nile Cruise is known for its elegant design and top-notch service, while the Gemma Nile Cruise provides a more intimate, boutique experience. The Movenpick SS Misr Nile Cruise is another excellent choice for those who enjoy a classic, refined atmosphere on the river.
If you’re looking for other luxury cruises, consider the Nile Capital Nile Cruise, which combines modern comfort with historical exploration, or the Movenpick Hamees Nile Cruise, a ship that offers a unique blend of luxury and cultural immersion. The Movenpick Lotus Nile Cruise and the Jaz Regent Nile Cruise are also popular choices, known for their impeccable service and well-designed cabins.
For a more opulent experience, the Jaz Crown Jewel Nile Cruise is a top contender, while the Salacia Nile Cruise and Nabilatan Nile Cruise provide a more exclusive atmosphere. Alternatively, the Tulip Nile Cruise and Tia Nile Cruise offer comfortable accommodations with excellent amenities.
No matter which cruise you choose, Egypt's Nile River promises an unforgettable journey through history and culture.
🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 Email: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt



