-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 6e0ea5d6:0327f353
2025-02-17 01:04:37
@ 6e0ea5d6:0327f353
2025-02-17 01:04:37Ascolta bene, sì? In the game of business, as in chess or the streets of Palermo, there are times to advance like a ruthless king and times to wait like a wolf stalking its prey. Those who fail to grasp this distinction are doomed to be taken down before they even see the sun rise.
Prudence is the sharp blade that separates the wise man from the fool who rushes headlong into the enemy’s spear. Those who act without weighing the consequences end up as the corpses rotting on the sidewalks of unbridled ambition. But understand this well—prudence is not cowardice. The coward hesitates out of fear; the prudent man waits because he knows the right moment to strike. The difference? One crawls, the other conquers.
Fortis Fortuna Adiuvat—fortune favors the bold. But boldness without calculation is like a man crossing a minefield blindfolded. Greed blinds, destroys, and devours the reckless like a raging sea dragging bodies to the depths. You see it every day—entrepreneurs who rise too fast and crumble at the first crisis, young men who burn through their earnings chasing illusions of instant wealth, fools who trust too much in friends already hiding the dagger up their sleeve.
There’s a reason why great men endure while mere opportunists vanish like smoke in the wind. They understand that every battle has its time, every strike must have precision. Trade the cleaver for the scalpel—the butcher wounds without thought, the surgeon cuts with precision and saves his own skin.
Dimmi, quale vuoi essere? The fool who charges into war without a shield, or the strategist who, in the end, sits at the banquet of victory? The answer is not in what you say, but in what you do while others waste their opportunities.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ 9a4acdeb:1489913b
2025-02-16 18:26:58
@ 9a4acdeb:1489913b
2025-02-16 18:26:58Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
Directions
- Mix dry seasonings
- Chop and mix fresh herbs and veggies, canned or otherwise
- Add chopped onion to bottom of pressure cooker
- Add pork loin atop the onion; chopping into steaks may make the texture better
- Add veggies to the top, shaking to settle into the pressure cooker
- Add lime juice
- Start on high pressure for 2hrs.
- (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
- Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
- (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ 6e0ea5d6:0327f353
2025-02-17 00:53:36
@ 6e0ea5d6:0327f353
2025-02-17 00:53:36Ascolta! When you allow the flame of ambition to fade within your chest, you inevitably drift toward petty and foolish concerns unworthy of an adult. In other words, the moment you abandon your dedication to grand objectives—precisely due to idleness—you will end up entangled in trivial matters, thus weakening your masculinity. Lacking the responsibilities inherent to a grown man, you will inevitably behave like a boy in all aspects of life, including relationships.
He who is truly determined to win in life has neither the time nor the energy to engage in matters of neediness, jealousy, or fear of abandonment.
Love, as it is often romanticized, is a dangerous illusion that leads us to reckless and self-destructive behaviors. The romantic ideal, propagated by poets and dreamers, makes us vulnerable to manipulation and disappointment.
A man who is aware of his value remains focused on what truly matters, and because he understands the weight of his priorities, that alone is enough.
Weakness does not inspire confidence. In a world where strength and determination are essential for survival and success, showing weakness is signing your own sentence of irrelevance. A man must be the foundation upon which the relationship stands. He must be the unshakable rock amid life’s storms. Life is a game of power and influence, and those who fail to understand this are doomed to failure.
Take care of yourself. Strengthen your body, your mind, and your spirit. Be an example of determination and courage. The woman by your side must see in you a leader, a visionary, someone destined for great achievements. Only then will you earn not only her respect and admiration but also full control over your own destiny.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 6e0ea5d6:0327f353
2025-02-15 19:47:49
@ 6e0ea5d6:0327f353
2025-02-15 19:47:49"You are a slave to whoever controls you emotionally."
"We get angry when someone tries to tell us what to do. 'Don’t tell me how to dress, how to think, how to do my job, how to live.' We feel this way because we see ourselves as independent, self-sufficient individuals.
Or at least, that’s what we tell ourselves.
Yet, if someone says something we disagree with, something inside us tells us we must argue with them. If a plate of treats is placed in front of us, we must eat them. If someone does something we don’t like, we must be furious. If a setback arises, we must be sad, depressed, or worried. But if something good happens a few minutes later, suddenly, we’re happy, excited, and wanting more.
We should never let another person shake us back and forth the way our impulses do. It’s time we start seeing things differently: we are not puppets, dancing to whichever tune suits us at the moment. We should be the ones in control—not our emotions—because we are independent, self-sufficient individuals."
— Ryan Holiday"Frame your thoughts like this: you are a mature man, and you will no longer allow yourself to be enslaved or manipulated like a puppet by every impulse. You will stop complaining about your current lot or fearing the future."
— Marcus Aurelius📌 Emotions can give us information, but they should not give us orders.
It’s not enough to learn to say "no" to others; you must also learn not to give in to the demands of your weaker self.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c0a57a12:8b230f7a
2025-02-17 00:08:04
@ c0a57a12:8b230f7a
2025-02-17 00:08:04Ever notice how we’ve all turned into a bunch of regulation junkies? Not just the kids—us, too. The parents. The supposed adults in the room. We sit around shaking our heads at this new generation, wondering why they can’t make a move without a permission slip, but let’s be honest: we made them that way. We were trained for it. We just passed the neurosis down like a bad heirloom.
Used to be, kids ran wild, made their own fun, learned how things worked by getting their hands dirty and screwing up a few times. You fell out of a tree? Tough. That’s how you figured out gravity was real. Now, a kid gets a splinter and half the neighborhood has to be briefed. But let’s not act like it started with them. We didn’t grow up in the Wild West. Our parents—the ones who were handed a country built by men who cleared forests and carved railroads and settled frontiers—they took one look at all that, clutched their pearls, and decided the real enemy was risk. They started slapping safety labels on everything, turned common sense into a government-subsidized industry, and set about making sure we never had to experience a single moment of danger, discomfort, or—God help us—independence.
And we ate it up. Grew up afraid of the sun, the air, the drinking water. If you touched a stranger, you’d get kidnapped. If you ate the wrong snack, you’d drop dead from an allergy you didn’t even have. If you rode a bike without strapping on enough gear to survive re-entry from orbit, you might as well be suicidal. Then, just to really hammer it in, we were given rules for everything. How to sit, how to talk, how to play, how to think. And because we’d been softened up, we listened. We obeyed. We internalized the great lesson of modern civilization: only do what is approved.
And when it came time for us to raise kids? Oh, we ran with it. Helicopter parenting? That was us. Participation trophies? Us. Baby-proofing the entire godforsaken planet so that Junior never had to encounter anything sharper than a cotton ball? Us again. Every bit of micromanaged, soul-sucking, over-regulated nonsense we complain about today? We enforced it. So now we’ve got a generation that doesn’t know how to function without checking the rulebook first. They hesitate before every decision because we taught them hesitation. They sit around waiting for a green light because that’s all we ever told them to do.
And you know what? We’re no better. When’s the last time you did something without checking if it was "allowed"? When’s the last time you ignored a ridiculous rule instead of just sighing and complying? When’s the last time you acted like a free man instead of a well-behaved tax mule hoping the system doesn’t notice you?
We’ve swallowed a lie, and we keep regurgitating it—that compliance is morality, that following orders is a virtue, that a safe, predictable, well-regulated life is a good one. It’s not. It’s never been. You don’t get freedom by waiting for permission to use it. You don’t get courage by asking if it’s okay. You don’t build a worthwhile life by making sure you never color outside the lines.
And yet, here we are, acting surprised. Acting like we don’t know how we got here. Acting like we didn’t choose this. Like we didn’t let it happen.
So what now? We could stop. We could teach our kids to take risks, to get their hands dirty, to act instead of waiting for permission. We could start ignoring stupid rules, start trusting our own judgment, start living like we weren’t raised in a padded cell.
Or we could do nothing. Keep following orders. Keep playing it safe. Keep watching the world shrink into a flavorless, permission-based, committee-approved version of itself.
Your call. But either way, don’t pretend to be surprised.
-
 @ c43d6de3:a6583169
2025-02-15 14:18:07
@ c43d6de3:a6583169
2025-02-15 14:18:07You’re sitting in the 5am darkness of your living room.
The baby in your arms shifts and you’re afraid she might wake. It's hot, but you wouldn’t dare remove the blankets covering her body.
It seems impossible you could admire anyone more, then you hear the gentle snore of your exhausted wife creep from the gently cracked bedroom door.
You can only imagine what pain she went through to bring this precious girl to the world so you could be holding her now.

Your watch lights up. You dread the sight of that little alarm bell above the time 5:25 and a weight falls on you like a million tiny pieces of lead.
If only you had more time.
You wish you could take your baby girl with you. That way you would have all the time in the day with her and your wife could be left to rest.
You need to work.
You get up as gently as you can. Even so, baby girl shifts in your arms. Her eyes open slightly. The thought of returning a crying baby to your exhausted wife is distressing, it's just not fair.
Baby girl shifts again, her eyes open long enough to spot you in the faint glow of morning twilight and she smiles.
You hold your breath.
The smile remains on baby girl’s face but her eyes close and her head collapses into your chest. You return your baby to her mother’s side and admire them in their slumber.
You need to work. Nothing could ever go wrong with that house so long as you work to keep its walls strong. Some time, when you’re truly needed perhaps you’ll have the money saved up to take the desired time off.
In the absence of the love you share for your family. In the absence of the love others have for you, money loses some value.

If we equate money for what it is, the residue of time, we cannot divorce Love from Money.
It’s important to understand that Money won’t buy you Love and Love should never be exchanged for Money but Time cultivates Love.
These are some key things to keep in mind:
Life without love is Suffocation
Life without money is stress and despair
Families are cultivated and grown with love and protected with money.
Money is the residue of time.
Be it Bitcoin or a golden bullion, it exchanges days, hours, minutes, or seconds. What could you do instead if you had money?

Thank you for reading!
If this article resonated with you, let me know with a zap and share it with friends who might find it insightful.
Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More articles you might like from Beneath The Ink:
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kvnfd094y26zkt9dxgmnw0fqkvhmfd4tng8wp0uv
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ 5a261a61:2ebd4480
2025-02-16 21:54:41
@ 5a261a61:2ebd4480
2025-02-16 21:54:41As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion.
You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves.
It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.
-
 @ 1c197b12:242e1642
2025-02-14 21:38:15
@ 1c197b12:242e1642
2025-02-14 21:38:15Today, I'm going to attempt to install Servus to my test server. I'll be using a raspberry Pi4 4GB version with a 16GB microSD card (because what I have laying around). And, as you know... if it'll run on a Pi, it'll run pretty much anywhere.
What is SERVUS?
From GitHub... "Servus is a CMS, personal Nostr relay and personal Blossom server fully self-contained within one executable file."
Here's what you'll need:
A spare server. It can be a VPS, old laptop, old computer, 3rd market server from a decommissioned datacenter that you got for cheap on Ebay, a NUC... something that can run Linux.
- An understanding of the Linux terminal.
- install git and cargo.
- A web browser (don't you side-eye me!).
Let Us Begin...
I'm assuming you're using a Debian-based system. Open your terminal and enter the following:
Go ahead and ssh into your server with something like: "ssh yourusername@ipaddress" or "ssh yourusername@domainname.tld" enter your password when prompted and hit enter.

If you plan to do other stuff with your server later on, you might even consider using "ssh-copy-id yourusername@ipaddress" in order to not have to enter you password, all-the-time.

(Without the quotes) "su", or "sudo su". Whatever means you use to get to superuser (root). Then, enter your password.

Once in root, type: apt install git cargo -y Then, hit enter. You'll see a wall text... yadda yadda.


Now, you'll type (without quotes): "git clone https://github.com/servuscms/servus.git" and hit enter. You'll see a progress bar.

If you type "ls" you should see a folder labeled, "servus". We now change directories by typing, "cd servus". Inside of the servus folder you'll see a few other folders and a few files by typing "ls" again.

According the the servus github, there are a few build options. I'm going to use the "release" version for this tutorial. We do this by typing, "cargo build --release". You'll see a fetch progress bar and a wall of text.


NOTE: I'm using a raspberry pi 4, in this tutorial. At the end of trying "cargo build --release" I got a version error for a package called "anstream v0.6.14" because it requires "rustc 1.65.0", or higher. The error message gives you a fix by typing "cargo update -p anstream@0.6.14 --precise ver"

BUT that won't work. Here's how to fix it:
Type the following (without quotations): "apt purge rustc -y && apt install curl -y && curl https://sh.rustup.rs -sSf | sh"
This will remove the outdated rustc. Then, you're installing curl so that you can install the latest version of rustc and cargo because they aren't in the distro repo. Restart your machine with: "sudo reboot". Once you're back into your servus directory, just run the "cargo build" command, again. Now back to the show!
Now that we have run the "cargo build" command, it's time to move on to setting up access and ssl. According to github, there are a few options. They are as follows:
-
./target/debug/servus - this starts Servus on port 4884, without SSL
-
sudo ./target/debug/servus --ssl-acme[-production] --contact-email youremail@example.com (this starts Servus on port 443 and obtains SSL certificates from Let's Encrypt using ACME by providing a contact email).
-
sudo ./target/debug/servus --ssl-cert
--ssl-key (this starts Servus on port 443 using the providedand ) I'll be using the command no calling for SSL. More information can be found here: https://github.com/servuscms/servus

So from the terminal we input (without quotes): "./target/release/servus" because, as you may recall, I used the "cargo build --release" version earlier.
It will ask a few questions. Here's what I put...
Domain: test.local
Admin pubkey: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf

Then, you'll get a bit of output with your ip and port interface. In this case, it's http://localhost:4884 Now go to your browser and input that address, it's local, or the IP address of the server... something like, http://192.168.x.x:4884 and HUZZAH!!! Just like that, you should see your site. To get to the admin section of your site, just add "/.admin" (without quotes) to the IP address you just input into the browser.


CONGRATS! I hope this was helpful :-)
While Servus is extremely experimental, and it is advised to not run it in production. There are a number of features worth taking a look at. More information about what Servus can do can be found here: Servus Github
DONE.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ c43d6de3:a6583169
2025-02-14 17:34:05
@ c43d6de3:a6583169
2025-02-14 17:34:05“IN THIS SPRING of 1953 the free world weighs one question above all others: the chance for a just peace for all peoples,” Dwight D. Eisenhower’s throat went dry and he swallowed to alleviate the burn. Eight years had passed since the end of world war 2 but still the beaches of the Marshall Islands lay charred, Hiroshima and Nagasaki dosed in radiation and ruin, and countless ghost towns still littered Europe’s mangled face.
Dwight peered through his glasses at his speech on the podium, then raised his gaze back at the small crowd gathered in front of him in the conference room at the American Society of Newspaper Editors in Washington, D.C. Everyone was on the edge of their seats.
The President spoke of peace, but the United States faced a great enemy in the Soviet Union. How would he continue?

“To weigh this chance is to summon instantly to mind another recent moment of great decision. It came with that yet more hopeful spring of 1945, bright with the promise of victory and of freedom. The hope of all just men in that moment too was a just and lasting peace.”
The heads among the spectators raised in hope, as if the enthusiasm in the President’s voice could be enough to wipe away any prospect of future war against the Soviet threat.
“In that spring of victory the soldiers of the Western Allies met the soldiers of Russia in the center of Europe. They were triumphant comrades in arms. Their peoples shared the joyous prospect of building, in honor of their dead, the only fitting monument-an age of just peace. All these war-weary peoples shared too this concrete, decent purpose: to guard vigilantly against the domination ever again of any part of the world by a single, unbridled aggressive power.”
“This common purpose lasted an instant and perished. The nations of the world divided to follow two distinct roads.”
“The United States and our valued friends, the other free nations, chose one road.”
“The leaders of the Soviet Union chose another.”
“The way chosen by the United States was plainly marked by a few clear precepts, which govern its conduct in world affairs.”
What came next in Dwight D. Eisenhower’s speech “The Chance for Peace” is the answer to preventing wars between countries
“First: No people on earth can be held, as a people, to be an enemy, for all humanity shares the common hunger for peace and fellowship and justice.
Second: No nation's security and well-being can be lastingly achieved in isolation but only in effective cooperation with fellow nations.
Third: Any nation's right to a form of government and an economic system of its own choosing is inalienable.
Fourth: Any nation's attempt to dictate to other nations their form of government is indefensible.
And fifth: A nation's hope of lasting peace cannot be firmly based upon any race in armaments but rather upon just relations and honest understanding with all other nations.”

I. First Point
When you minimize any nation or country to its most granular piece, the human family, you realize every nation or country is the same. It is a larger body of human families looking to establish peace out of chaos against nature, fellowship with their neighbor to make that peace possible, and justice against affronts to the foundations of the formerly stated peace and fellowship. Without this, what you have is not a nation but rather wilderness.
 II. Second Point
II. Second PointWhen we enter the world stage and look at the community of nations it is important we understand that no nation can truly expect to uphold Eisenhower’s first point without the ability to cooperate with other nations. There can be a natural disaster that strikes an entire nation and without exterior help, it may be impossible to overcome.
Understand, Eisenhower’s second point only serves as an extension of the first point. Humankind's struggle with nature will always exist, but in cooperation with other communities we can overcome hardship against nature and live in better harmony.

III. Third Point
It cannot be argued that humans, after millenia of having dispersed across the planet, have collected into pockets of communities of which grew and developed with experiences based on the place in the world where they’ve resided.
This has birthed cultures, religions, and moral codes that serve as the foundation of different branches of philosophy that have borne the fruit of governance. Ultimately, no two communities shares the exact same moral code and thus do not share, and will never share, the exact same understanding of what governance should take place. In this respect, it is an inalienable right of the very people within a community to choose how they govern themselves.

IV. Fourth Point
In trying to impeded on this third point, we come to Eisenhower’s fourth point which is that no other community has the right to dictate how other nations govern themselves.
V. Final Point
Lastly, war will never lead to peace. Only common understanding of the first four points will ever lead to true peace. A race in armaments, as the cold war proved, only leads to further distrust and the breakdown of all other points among the community of nations on the world stage.
All that can be done to expect peace is to take your neighbor as they are. St. Augustine has a famous quote, “Seek not to understand that you may believe, but believe that you may understand.”
This is meant to drive home the point of faith in the unbelievable. It is how a religious person can believe in a god that they can not prove exists.
Some might say there will never be a world without war. I say we already have the recipe for it. We’ve been given this recipe by many leaders throughout our history. Leader’s who’ve witnessed the darkest depths of human evil and wanted to steer humanity away from it.

Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More articles you might like from Beneath The Ink:
https://primal.net/e/note1ws4es0gahm502k6qgx64dseqhjqgyzh0q7flzk6glcasqxxye6jqm20fj9
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq
https://primal.net/e/note158ns7z27r2y664h9lsdqdhsjj2uehrejve2y02lkvz46d8xgxncs8pcj7w
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
https://primal.net/e/note1htkygah99mz8p4png992n0clqa44spatw3uzzcpl94etwh2zr60stklxvw
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
https://primal.net/e/note1rdanqhdgc7d8sypm459zrt55m0zfaze7u34phkew9nptyr3ghwlqsvtsdx
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ 79998141:0f8f1901
2025-01-02 05:04:56
@ 79998141:0f8f1901
2025-01-02 05:04:56Happy new year, Anon.
Thanks for tuning in to whatever this long form post will be. I hope to make these more regular, like journal entries as we travel through "real life" and the Nostrverse together. If I'm making time for this reflective writing, then things are going as planned.
2024 was a wildly transformative year for me for many reasons... there's no way I can possibly fit all of them here. They're not all related to Bitcoin and Nostr- I've got a beautiful life outside of all that which has its own independent arc. My wife and I celebrated 7 years of marriage together, stronger than ever (don't believe that "itch" bullshit). We let go of some negative relationships and embraced some positive ones. We cut some bad habits, and we made some good habits. We worked, we traveled, we saw family, and we partied.
But damn, these two technologies have become a huge part of my life. God willing, this trend will continue until they've both eclipsed my professional capacity through our startup, Conduit BTC.
This was the year I was truly orange pilled. Until late 2023, I had traded (quite profitably) Bitcoin, "crypto", stocks, options, prediction markets and whatever else I could get my hands on that felt undervalued. I did this all in my spare time, grinding out a little financial freedom while I hustled at my fiat ventures to support my little family. I wasn't a true believer- just an opportunist with a knack for spotting where and when a crowd might flock to next. That was right up until I ran face first into Lyn Alden's book "Broken Money".
Something about Lyn's engineer/macro-finance inspired prose clicked with me, lock and key. Total one way function. By the end of the book my laser eyes had burned a hole in my bedroom ceiling. I was all in- and acted accordingly both with my capital and my attention. It wasn't long before I discovered Nostr and dove in here too, falling deep into my current orange and purple polyamorous love affair.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Despite the passion, through studying Bitcoin's criticisms (from the likes of Mike Green and Nassim Taleb) I found a hole in the utopian plot: none of this works without Bitcoin actually being used as money. Worldwide transactions must skyrocket demand for blockspace to keep the network secure/stable for the long term. Besides, if everyday folks aren't using Bitcoin as money then we haven't done shit to make the world a better place. In that world, we've only replaced old masters with new ones. Fuck that.
Whatever I did in this space needed to increase the usage of Bitcoin as money. Simple. This was bigger than passion, this was purpose. I knew that come hell or high water I would dedicate myself to this mission.
Lucky for me I found a partner and best friend in @aceaspades to go on this adventure with. I'm infinitely grateful for him. He's an incredible man who also happens to be an insanely creative and talented software developer. We'd tried for years to find the right project to focus on together, experimenting with all kinds of new techy ideas as they came across our field. Nothing had ever captured our attention like this. This was different. By March of 2024 we had formed a company and gotten to work iterating on how we could leverage these beautiful protocols and open-source tech to create something that served our mission. This is @ConduitBTC.
I've done well in my fiat career executing plans downstream of someone else's creative vision. I've learned the ins and outs of an established ecosystem and found ways to profit from it. I take plans developed by others, compete to win contracts to build them, and execute on them in a cashflow-positive way. I'm bringing this no bullshit blue collar skillset with me to the Nostrverse whether they like it or not.
The adventure we're embarking on now is totally different though. We're charting a new course - totally creative, highly intuitive and extremely speculative towards a future that doesn't exist yet. There are few established norms. The potential is vast but unknown. We're diving into a strange quest to sell a map to an imaginary place and to simultaneously architect its creation (alongside all the amazing builders here doing the same thing). This is insanely exciting to me.
We're barely getting started but a lot has been invested under the surface which will show itself in 2025. We'll be sharing updates in a proper post on @ConduitBTC soon.
As for my personal 2025 resolutions, here they are: - zero alcohol for the entire year (did this in 2019 and had a great year, it's time for a rerun) - more focused presence in the moment: especially with my wife - more self care and prioritized mental/physical health - this includes daily: naps, prayer, self hypnosis or meditation, sweat, and stretching/massaging (overworked in 2024 with a fiat 9-5, a board/advisor role in a fiat business I have equity in, and my newfound passion here. Two serious burn out episodes experienced this year - zero is the only acceptable number of burnouts for long term health and success.) - related to the above: get Conduit some mission-aligned funding partners and leave my fiat 9-5. Grow the Conduit team (have put in a serious amount of my personal capital already to get this going, which will show fruit in the new year... but I am not an island) - more authentic and thoughtful posts on Nostr, with a solid amount of shitposting and organic home grown memes to balance it out... more zaps, more geniune connections and interactions with the curious forward thinking people on here - more IRL Nostr/Bitcoin events - more laughter, more jokes
Enough for now. Cheers to you and yours Anon, may 2025 bring you the magic you've been dreaming of.
-
 @ dd664d5e:5633d319
2024-12-29 20:29:03
@ dd664d5e:5633d319
2024-12-29 20:29:03The paparazzi are we

One of the things that bothers me about social media, in general, is that it gives celebrities an air of approachability, that they don't actually offer.
Theoretically, a celebrity could respond to any one of the dozens or even hundreds of people asking them questions or lodging complaints or singing their praises, but they usually only respond very selectively and leave everyone else just sitting there, as a living monument to the ReplyGuy.
And, as a wise man once said, ReplyGuy is a hoe.
Death of a ReplyGuy
This is usually because of time and energy restrictions, but also due to distaste, disdain, or indifference. Regardless of motivation, it is simply the nature of things, when a larger number of people are clamboring for the attention of some particular person.
Ooh, ooh! Can I have the next question?! Would you please address my bug? May I have a microsecond of your time?

Social media (and I include GitHub in this category) ups this game considerably, and potentially turns it all into a dangerous psychological torture, by making us all preoccupied with people who don't interact with us. The most irrational of groupies because we are forever making almost-contact with our stars.
If we can see them talking to one person, we're supposed to feel like they've spoken with all of us. But they haven't. They spoke with someone else, and we were allowed to watch. No different than on television, except that we might be disappointed and eager to return the next day, to renew our futile attempt.
The same intoxicating feeling that playing the lottery elicits. Everyone is a potential winner, but there is only one jackpot. Come back next week. Buy another ticket. This next time, is your time. Promise.
The view from the peanut gallery

It is all an illusion that there is no hierarchy, where there clearly is one. Celebrities of the past had, at least, the decency to remain slightly aloof. But they all want to be one of the Common Folk, now, just as every multi-millionaire aspires to see himself as fundamentally working-class.

All of celebrity social media is a stage, and most of us are merely spectators or commentators, to what is playing on it. This is why, if someone treats me like someone sitting in the peanut gallery, my instinct is to treat them like an actor.
Because, in reality, that is what they are.
-
 @ a42048d7:26886c32
2024-12-27 16:33:24
@ a42048d7:26886c32
2024-12-27 16:33:24DIY Multisig is complex and 100x more likely to fail than you think if you do it yourself: A few years ago as an experiment I put what was then $2,000 worth Bitcoin into a 2 of 3 DIY multisig with two close family members holding two keys on Tapsigners and myself holding the last key on a Coldcard. My thought was to try and preview how they might deal with self custodied multisig Bitcoin if I died prematurely. After over a year I revisited and asked them to try and do a transaction without me. Just send that single Utxo to a new address in the same wallet, no time limit. It could not possibly have failed harder and shook my belief in multisig. To summarize an extremely painful day, there was a literally 0% chance they would figure this out without help. If this had been for real all our BTC may have been lost forever. Maybe eventually a family friend could’ve helped, but I hadn’t thought of that and hadn’t recommended a trusted BTC knowledge/help source. I had preached self sovereignty and doing it alone and my family tried to respect that. I should’ve given them the contact info of local high integrity bitcoiners I trust implicitly. Regardless of setup type, I highly recommend having a trusted Bitcoiner and online resources your family knows they can turn to to trouble shoot. Bookmark the corresponding BTCSessions video to your BTC self custody setup. Multisig is complicated as hell and hard to understand. Complexity is the enemy when it comes to making sure your BTC isn’t lost and actually gets to your heirs. Many Bitcoiners use a similar setup to this one that failed so badly, and I’m telling you unless you’re married to or gave birth to a seriously hardcore maxi who is extremely tech savvy, the risk your Bitcoin is lost upon your death is unacceptably high. My family is extremely smart but when the pressure of now many thousands of dollars was on the line, the complexity of multisig torpedoed them. Don’t run to an ETF! There are answers: singlesig is awesome. From observing my family I’m confident they would’ve been okay in a singlesig setup. It was the process of signing on separate devices with separate signers, and moving a PSBT around that stymied them. If it had been singlesig they would’ve been okay as one signature on its own was accomplished. Do not besmirch singlesig, it’s incredibly powerful and incredibly resilient. Resilience and simplicity are vastly underrated! In my opinion multisig may increase your theoretical security against attacks that are far less likely to actually happen, e.g. an Oceans Eleven style hack/heist. More likely your heirs will be fighting panic, grief, and stress and forget something you taught them a few years back. If they face an attack it will most likely be social engineering/phishing. They are unlikely to face an elaborate heist that would make a fun movie. While I still maintain it was a mistake for Bitkey to not have a separate screen to verify addresses and other info, overall I believe it’s probably the best normie option for small BTC holdings(yes I do know Bitkey is actually multisig, but the UX is basically a single sig). This incident scared me into realizing the importance of simplicity. Complexity and confusion of heirs/family may be the most under-considered aspects of BTC security. If you’ve made a DIY multisig and your heirs can’t explain why they need all three public keys and what a descriptor is and where it’s backed up, you might as well just go have that boating accident now and get it over with.
Once you get past small amounts of BTC, any reputable hardware wallet in singlesig is amazing security I would encourage folks to consider. In a singlesig setup - For $5 wrench attack concerns, just don’t have your hardware signer or steel backup at your home. You can just have a hot wallet on your phone with a small amount for spending.
If you get a really big stack collaborative multisig is a potentially reasonable middle ground. Just be very thoughtful and brutally honest about your heirs and their BTC and general tech knowledge. Singlesig is still great and you don’t have to move past it, but I get that you also need to sleep at night. If you have truly life changing wealth and are just too uncomfortable with singlesig, maybe consider either 1) Anchorwatch to get the potential benefits of multisig security with the safety net of traditional insurance or 2) Liana wallet where you can use miniscript to effectively have a time locked singlesig spending path to a key held by a third party to help your family recover your funds if they can’t figure it out before that timelock hits, 3) Bitcoin Keeper with their automatic inheritance docs and mini script enabled inheritance key. The automatic inheritance docs are a best in class feature no one else has done yet. Unchained charges $200 for inheritance docs on top of your $250 annual subscription, which imho is beyond ridiculous. 4) Swan vault, I’ve generally soured on most traditional 2 of 3 collaborative multisig because I’ve always found holes either in security (Unchained signed a transaction in only a few hours and has no defined time delay, and still doesn’t support Segwit, seriously guys, wtf?), only support signers that are harder to use and thus tough for noobs, or the overall setups are just too complex. Swan Vault’s focus on keeping it as simple as possible really stands out against competitors that tack on unneeded confusion complexity.
TLDR: For small amounts of BTC use Bitkey. For medium to large amounts use singlesig with a reputable hardware wallet and steel backup. For life changing wealth where you just can no longer stomach sinsglesig maybe also consider Anchorwatch, Bitcoin Keeper, Sean Vault, or Liana. Don’t forget your steel backups! Be safe out there! Do your own research and don’t take my word for it. Just use this as inspiration to consider an alternative point of view. If you’re a family of software engineers, feel free to tell me to go fuck myself.
-
 @ 86cf3742:678e3ae8
2025-02-14 11:40:00
@ 86cf3742:678e3ae8
2025-02-14 11:40:00In this episode of the Ag Tribes Report, host Vance Crowe is joined by Amanda Radke, a prominent figure in the agricultural community known for her work as a cattle rancher, motivational speaker, and children's book author. Amanda shares her insights on the controversial use of eminent domain for carbon pipelines, highlighting her relentless fight against these projects in South Dakota. She discusses the origins of the carbon pipeline projects, the political and financial implications, and the grassroots efforts to protect private property rights.
Amanda also introduces "Bid on Beef," a platform connecting consumers with ranchers to purchase high-quality beef directly. She explains the motivation behind the initiative and its impact on rural America.
The episode delves into the implications of RFK Junior's confirmation as the US Secretary of Health and Human Services, exploring potential shifts in US health policy and its effects on agriculture. Vance and Amanda discuss the mixed reactions within the agricultural community and the broader implications for public health.
The conversation shifts to the beef checkoff program and its recent controversial tweet regarding private cattle sales. Amanda shares her perspective on the program's effectiveness and the need for transparency and accountability.
Vance and Amanda also explore the potential impact of ending managed supply in Canada, discussing the political and economic ramifications and the possibility of Canadian provinces seeking US statehood.
The episode concludes with discussions on Bitcoin land prices, the Peter Thiel paradox, and Amanda's views on government intervention in agriculture. Amanda shares her thoughts on the importance of free markets and entrepreneurship in the agricultural sector.
Legacy Interviews - A service that records individuals and couples telling their life stories so that future generations can know their family history. https://www.legacyinterviews.com/experience
River.com - Invest in Bitcoin with Confidence https://river.com/signup?r=OAB5SKTP
(01:06) Introduction and Guest Introduction
(02:24) Bid on Beef: Connecting Consumers with Ranchers
(03:35) The Fight Against Carbon Pipelines
(10:28) RFK Jr.'s Confirmation and Its Implications
(13:05) Controversy Over Beef Checkoff Program
(16:19) Managed Supply and Canadian Agriculture
(21:24) Bitcoin Land Price Report
(24:45) Peter Thiel Paradox: Unique Beliefs
(28:27) Worthy Adversaries: Respectful Disagreements
https://serve.podhome.fm/the-vance-crowe-podcast_638721156549613591
-
 @ c43d6de3:a6583169
2025-02-14 11:27:09
@ c43d6de3:a6583169
2025-02-14 11:27:09A Brief History of Ownership
The Forgotten Struggle for Ownership
History reveals that our ancestors labored—both intellectually and physically—to secure the freedoms we are subconsciously giving away.
We stand at the threshold of a new era.
Across the globe, long-established institutions are showing signs of strain. Trust in governments, banks, and major corporations is eroding, leaving many individuals feeling as though their rights are being infringed upon—even if they struggle to articulate exactly how. Social media and traditional news outlets amplify this sense of unease, painting a picture of impending upheaval, as if we are on the brink of a revolution whose name will only become clear in hindsight, once the first sparks ignite into a full-blown blaze.
Yet, when we examine the state of the global economy, this narrative begins to unravel. Economic inequality has reached levels unseen in nearly a century, and while many point fingers at politicians, policies, or the so-called greed of the 1% hoarding all the wealth, the true culprit may be much closer than most realize. At a time when legal structures worldwide strongly protect ownership and economic mobility, it is individuals themselves who are willingly surrendering their financial power to the very elites they criticize.
I know—“willingly” might seem like a stretch. After all, no one consciously chooses to give up their economic freedom. But take a closer look at the way people spend, borrow, and consume, and it becomes painfully clear: most are actively forfeiting their ability to build and own wealth.
How did we get here?
Much of this self-inflicted harm comes from a fundamental ignorance of the history of ownership and the struggles fought to secure it.
This article serves as a short exploration of the past.
I'll examine what might be considered the natural state of humanity, how the majority has historically struggled to achieve ownership rights, and the deadly conflicts that had to occur for the modern individual to enjoy the very rights they are now squandering.

I. The Era of Communal Ownership
No one is born into this world alone.
We do not simply materialize into existence; we arrive as part of the first unit of human society—the family.
Before the rise of civilization, the primary focus of the family was survival. Ownership was a foreign concept, as early human tribes lived in a state of communal resource-sharing. Material possessions were fleeting, and with that, so was the notion of personal property.
In the state of nature, no individual had an exclusive claim to anything. Instead, ownership existed in a tribal sense: “This land belongs to us.” The idea of “mine” extended only by association—what belonged to the tribe also, by extension, belonged to each of its members.
This was a fragile system. Resources required constant upkeep, and as populations grew, leadership emerged to manage the complexity of distribution. This shift laid the foundation for the rise of kings and centralized authority. The concept of ownership, once a communal right, gradually became something dictated by those in power. The people no longer owned anything outright; they merely had the privilege of stewarding what belonged to their ruler.

II. The Rise of Peasants and Kings
The first codified legal system, the Code of Hammurabi, laid out extensive laws on ownership. Interestingly, this ancient civilization granted more property rights to commoners than many societies did even a few centuries ago.
A few millennia later, Greece laid the philosophical foundations for ownership, but true legal protections for private property did not emerge until much later. In medieval Europe, ownership rights almost disintegrated—not even nobles truly owned land. Everything belonged to the king, and monarchs waged war over control of vast territories, including the people within them.
Meanwhile, in the Islamic Golden Age, the Middle East saw an unprecedented period of economic freedom. Under Sharia law, property rights were protected for the average citizen, something unheard of in much of medieval Europe. The extent of these rights depended largely on religious affiliation, but compared to their European counterparts, many commoners in the Islamic Empire enjoyed greater economic autonomy.

III. The Birth of Property Rights: The Rights of Man
As the Islamic Golden Age waned and the Mongol Horde thundered toward Baghdad, another seismic shift was occurring in England. In 1215, rebellious nobles captured London and forced King John to sign the Magna Carta, the first written document to impose limits on absolute monarchical power and introduce property protections—though these rights were initially reserved for the nobility.
This moment planted the seeds of change. Over the next several centuries, the fight for ownership rights expanded beyond the aristocracy. The Black Death (1347–1351) wiped out over 30% of England’s population, increasing labor shortages and bargaining power for peasants. By the 1381 Peasants’ Revolt, the common man demanded a greater share of land and wealth.
Yet, it wasn’t until the 1700s with the Enclosure Acts that private property became legally protected for the broader population. What began as a noble rebellion in 1215 ultimately transformed ownership from royal privilege to individual liberty.

IV. The Age of Renting: The Illusion of Ownership Today
Despite centuries of struggle, we now find ourselves at a paradoxical moment in history: ownership is more legally protected than ever, yet fewer people actually own anything of value.
Homeownership in Decline: The U.S. homeownership rate peaked in 2005, only to decline for a decade, hitting a low of 63% in 2015. Despite slight rebounds, high housing costs have pushed many into perpetual rentership.
Vehicles as Subscriptions: In 2024, one-fifth of new vehicles were leased, and long-term auto loans have become the norm. A financed car is not truly owned—it’s rented from a bank until the debt is cleared.
The Subscription Economy: Ownership of media, software, and even personal data has been replaced with monthly fees. Cloud storage, SaaS, and streaming services have ensured that we no longer possess even our own information.
V. The Consequences of Financial Illiteracy
We now live in a society built on renting, where economic stability depends on a continuous stream of payments. The more we lease, subscribe, and finance, the more control shifts from individuals to corporations and financial institutions.
This shift has profound implications:
- A person who owns little has little power.
- A society that rents everything can be controlled by those who own everything.
- Wealth is no longer built through accumulation, but through debt and dependency.
For millennia, people fought for the right to own. Today, through financial illiteracy and consumer habits, we are giving it away.
How much do we truly own, and how much have we already forfeited?
Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow Fervid Fables for great short stories and serialized fiction.
nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49
More articles you might like from Beneath The Ink:
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
-
 @ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58
@ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58Every 16th of January, the city of Varese, a small town at the feet of the Prealpine region, stops to participate in one of the most important ceremonies of the city: The Falò of Sant'Antonio. A Falò is the Italian word for bonfire. Imagine a 5-meters tall pyre of wood burning in the center of the city. For sure, an unmissable event!
The pyre is built by the so-called "Monelli della Motta". A Monello in Italian is a child that misbehaves. This nickname come from the fact that in the past, the pyre was created using wood stolen from the city, usually from tools, doors and shutters.
This event takes place at the eve of the day of Sant'Antonio Abate in front of the homonymous church in the area called "La Motta", which stands for small hill, and comes from a several century old tradition. Thousands of people from all over the province come to the city to look at the bonfire created in honor of the Saint.

At 9PM the big event starts. The wood is set on fire!

An important tradition of this celebration is burning small pieces of paper containing wishes. People whish for health, love, friendship and luck. To make wishes come true, people have to give these pieces of paper to a firefighter or a "Monello" whom will launch it into the Falò.
The show goes on for a couple of ours, during which thousands of Varesinians in awe contemplate the raging fire and try to receive some heat to fight the glacial cold of January.

-
 @ a4a6b584:1e05b95b
2024-12-26 17:13:08
@ a4a6b584:1e05b95b
2024-12-26 17:13:08Step 1: Secure Your Device
- Install an Antivirus Program
Download and install a trusted antivirus program to scan files for potential malware. - For Linux: Calm Antivirus
-
For Windows: CalmWin Antivirus
-
Install a VPN
A VPN is essential for maintaining privacy and security. It will encrypt your internet traffic and hide your IP address. -
Recommended: Mullvad VPN, which accepts Bitcoin for anonymous payment.
-
Install a Torrent Program
You’ll need a torrent client to download files. -
Recommended: Deluge
-
Install the Tor Browser
To access The Pirate Bay or its proxies, you’ll need the privacy-focused Tor Browser.
Step 2: Prepare Your Setup
- Ensure your VPN is running and connected.
- Open the Tor Browser.
- Launch Deluge to have your torrent client ready.
Step 3: Using Tor Go to The Pirate Bay via Onion Service or Find a Trusted Pirate Bay Proxy
Accessing The Pirate Bay directly can be challenging due to restrictions in some regions. Proxy sites often fill the gap. - The Pirate Bay Onion service: http://piratebayo3klnzokct3wt5yyxb2vpebbuyjl7m623iaxmqhsd52coid.onion - Or find a trusted proxy: Use a site like Pirateproxy or a reliable Tor directory for updated lists.
Step 4: Search for Linux Distros
- On The Pirate Bay, navigate to the "OtherOS" category under the Applications section.
- Enter your desired Linux distro in the search bar (e.g., "Ubuntu," "Arch Linux").
Step 5: Select a Torrent
- Filter the Results:
- Look for torrents with the highest seeders (SE) and the fewest leechers (LE).
-
Trusted users are marked with a green skull icon—these are usually safe uploads.
-
Copy the Magnet Link:
- Right-click on the magnet icon next to the trusted torrent and select "Copy Link."
Step 6: Start the Download
- In Deluge, paste the copied magnet link into the “Add Torrent” box.
- Click OK to start the download.
- Monitor the progress until the download completes.
Step 7: Scan the Downloaded File
Once the file is downloaded: 1. Scan for viruses: Right-click the file and use Calm or CalmWin to verify its integrity.
2. If the file passes the scan, it’s ready for use.
Step 8: Manage Your File
- Seed or Remove:
- To help the torrent community, keep seeding the file by leaving it in your torrent client.
-
To stop seeding, right-click the file in Deluge and remove it.
-
Move for Long-Term Storage: Transfer the file to a secure directory for regular use.
Notes on Safety and Ethics
- Verify Legitimacy: Ensure the torrent you are downloading is for an official Linux distribution. Torrents with unusual names or details should be avoided.
- Support the Developers: Consider visiting the official websites of Linux distros (Ubuntu, Arch Linux) to support their work directly.
By following these steps, you can safely and privately download Linux distributions while contributing to the open-source community.
- Install an Antivirus Program
-
 @ 19220736:7578e0e9
2025-02-14 03:44:21
@ 19220736:7578e0e9
2025-02-14 03:44:21While Zelle promotes itself as a quick and easy way to send money, its instant, irreversible transactions have made it a prime target for fraudsters. Despite mounting reports of consumer losses, banks continue to deny reimbursement for many fraud victims, citing narrow legal loopholes. Meanwhile, Early Warning Services, the company behind Zelle, profits from the vast consumer data it collects, fueling concerns about privacy and corporate exploitation. With government investigations ramping up and public pressure mounting, Zelle and their bank owners have teamed up with the Aspen Institute, forming a new task force with corporate and government players.
In 2017, Early Warning Services, owned by Bank of America, Capital One, JPMorgan Chase, PNC Bank, Trust, U.S. Bank, and Wells Fargo, released the Zelle payment system. It was a fast way to send and receive funds peer to peer between different bank accounts by only needing either the other person's email address or their U.S. mobile phone number.
By 2018, there were growing concerns about fraud on Zelle. Despite its convenience, Zelle's design allows funds to transfer instantly and irreversibly, making it a target for scammers. Victims reported being defrauded through tactics like fake online sales or impersonation schemes, and many struggled to recover lost funds due to inconsistent fraud policies among banks. Consumer advocates criticized the platform for inadequate protections, urging banks to implement stronger safeguards to prevent fraud and better support affected customers.
In 2022, a Senate report criticized major U.S. banks, including JPMorgan Chase, Bank of America, and Wells Fargo, for failing to adequately protect consumers from fraud on the Zelle payment platform. The investigation revealed that these banks often deny reimbursement for scams where victims are tricked into transferring funds, citing a narrow interpretation of liability under the Electronic Fund Transfer Act. ("While banks bear responsibility for unauthorized transactions to scammers, consumer-authorized transactions made to fraudsters are another matter”.) Jamie Dimon, CEO of JPMorgan Chase, explained, “Anything unauthorized, we do cover”
On June 16, 2023, the United States Senate Committee on Homeland Security and Governmental Affairs subcommittee, the Permanent Subcommittee on Investigations, launched an inquiry into Early Warning Services and the three largest banks that co-own EWS: JPMorgan Chase, Bank of America, and Wells Fargo.
After a 15-month investigation, the Senate Permanent Subcommittee on Investigations released a report on July 23, 2024, highlighting consumer fraud issues tied to the Zelle payment network. The report noted significant drops in the percentage of fraud disputes reimbursed—from 62% in 2019 to just 38% in 2023. Between 2021 and 2023 Zelle refused to reimburse $880 million to customers who fell victim to fraud on their payment network. Bank employees were found to have broad discretion in deciding whether to reimburse fraud claims, often denying compensation without clear justification. This has raised questions about whether banks are meeting legal obligations under the Electronic Fund Transfer Act (Regulation E)
Early Warning Services (EWS) runs the payment network Zelle at a financial loss but generates revenue by selling data-based services to financial institutions. EWS collects extensive consumer and bank data through its operation of Zelle and daily data-sharing agreements with its member banks. This data is used to develop fraud and risk management products, which EWS sells to financial institutions as its primary profit source. While EWS asserts it has not commercialized this data beyond these financial products, the sale of such services remains its main revenue driver.
On August 4, 2024, Senator Richard Blumenthal sent a letter to CFPB Director Rohit Chopra urging immediate action to address fraud concerns tied to the Zelle payment platform. The letter calls for the Consumer Financial Protection Bureau (CFPB) to investigate their dispute resolution practices and ensure that they fully and promptly address consumer fraud reports. On August 7, 2024, it was reported that the Consumer Financial Protection Bureau was investigating several banks due to their handling of Zelle.
On December 20, 2024, The Consumer Financial Protection Bureau (CFPB) responded by filing a lawsuit against Early Warning Services, LLC and the major banks including Bank of America, JPMorgan Chase, and Wells Fargo. The CFPB alleges that these institutions prioritized the rapid deployment of Zelle over implementing effective anti-fraud measures, resulting in significant consumer losses. The lawsuit contends that the defendants failed to adequately address these issues, often denying relief to defrauded consumers. The CFPB seeks injunctive relief, monetary compensation for affected consumers, and civil penalties.
Just 5 days before the Senate Permanent Subcommittee on Investigations released its report, the Aspen Institute Financial Security Program (Aspen FSP) announced the formation of a National Task Force for Fraud & Scam Prevention with their founding sponsor JPMorganChase and executive sponsor Zelle. The stated purpose of the Task Force is to develop a unified national strategy to help the U.S. government and private sector companies work together to stop fraud and scams. Members of this private/public task force include: JPMorgan Chase, Bank of America, Wells Fargo, Google, Meta, Amazon, Visa, Mastercard, Verizon, the Federal Trade Commission, the FBI Criminal Investigation Unit, US Department of the Treasury, Homeland Security, and many others.
The Aspen Institute is a 501(c)(3) nonprofit located in Washington DC. In 2023 they had revenue of $232M and total assets of $519M with the primary source of income coming from donations and federal grants. Per their mission statement, their goal is "realizing a free, just, and equitable society." The Institute works to achieve this through creating and driving policy as well as training future policy leaders.
Recently on November 25, 2024, FinCen announced they are also joining the National Task Force that "brings together key stakeholders including the financial services sector, technology companies, consumer advocacy groups, information sharing and analysis centers, and federal government agencies to develop a comprehensive national strategy for combating fraud and scams." In The Case for a Coordinated National Strategy to Prevent Fraud and Scams, the Task Force lists key components of a national strategy to include improved education of consumers to identify fraud, enhanced information sharing across industry, law enforcement, and regulatory agencies by use of data exchanges and legal mechanisms for sharing information. As well as empowering law enforcement with additional authority and resources. The document cites the recent UK action as an example of recent amendments to law enforcement powers which in England means police will no longer be required to arrest seizing crypto from a suspect, can seize written passwords or memory sticks, as well as transfer "crypto assets" to a law enforcement wallet.
In an August 2024 interview with Fortune, Ben Chance, the Chief Fraud Risk Management Officer for Early Warning Services reportedly "told the outlet that the best way to prevent scams on money-sharing apps is better user education, sound policy and more funding for law enforcement." This sounds very similar to the National Strategy to Prevent Fraud and Scams being crafted by the National Task Force for Fraud & Scam Prevention, with more user education and law enforcement. No mention of standardized reimbursement policies or enhancing transparency around fraud investigations which are the primary accusations aimed at Zelle and its owners by the US Senate and the subject of the current investigation by the Consumer Financial Protection Bureau.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41
@ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41In the grand chessboard of geopolitics, Iran has long been a target for covert Western intervention. The 2009 Iranian presidential election provided yet another example of a well-worn playbook—one designed to undermine sovereign nations under the guise of democracy. But this was far from a spontaneous people's movement. Instead, it bore all the hallmarks of a carefully orchestrated operation, leveraging the power of mass media, intelligence agencies, and globalist financial interests.
2009: A Manufactured Uprising
In June 2009, before Iran's election results were even finalized, opposition leader Mir-Houssein Mousavi prematurely declared victory. This calculated move set the stage for immediate allegations of fraud, ensuring that any outcome favoring incumbent President Mahmoud Ahmadinejad would be delegitimized. The Western media wasted no time in amplifying the chaos, competing to push the most dramatic narratives. The BBC took the lead, publishing outright fabrications about mass uprisings—falsehoods they were later forced to retract.
Then came the Twitter storm. On June 13, a sudden flood of 30,000 tweets, many in English, began pouring in from Iran. The accounts responsible? Newly created profiles, often using identical photos, a hallmark of an information warfare campaign. The Jerusalem Post quickly picked up on the phenomenon, covering it within hours. This was no organic grassroots movement; it was a digital psy-op, mirroring past regime-change operations.
The Blueprint: Iran 1953—The CIA’s Original Coup
This wasn’t Iran’s first encounter with a foreign-backed destabilization campaign. In 1953, Iran’s democratically elected Prime Minister Mohammed Mossadegh made the fatal mistake of challenging Western oil interests. He sought to nationalize Iran’s petroleum industry, then controlled by the Anglo-Iranian Oil Company (later BP). The response was swift and brutal: the CIA launched Operation Ajax, an insidious regime-change operation that became the prototype for future coups.
The CIA’s strategy was as ruthless as it was effective: * Staged bombings blamed on Mossadegh’s government * Islamist agitation funded and nurtured to turn public sentiment * Propaganda campaigns demonizing Mossadegh as a secular threat * Bribery of officials and military leaders to ensure betrayal
The result? The overthrow of Mossadegh and the installation of the pro-Western Shah, whose reign saw brutal repression under the secret police SAVAK—trained by the CIA and Mossad. The template was established. From Guatemala (1954) to Afghanistan (1980s) to Serbia (1990s), the same playbook was deployed. But with each coup, Western fingerprints became harder to conceal.
A New Strategy: Economic Warfare and the NGO Takeover
With direct coups becoming too risky, a subtler method emerged: economic strangulation. Enter the International Monetary Fund (IMF). The play was simple: 1. A corrupt dictator takes out massive loans for projects the country cannot afford. 2. The country inevitably defaults, giving the IMF the power to restructure its economy. 3. Western corporations move in, plundering national resources under the guise of “recovery.”
This scheme was exposed in 2001 when former World Bank chief economist Joseph Stiglitz blew the whistle on these manufactured debt traps. Further details emerged in 2004 with John Perkins' “Confessions of an Economic Hitman”, which revealed how Western front companies and intelligence-backed corporations systematically dismantled economies for geopolitical gain.
But even this strategy had its limits. As exposure grew, the need for an even more sophisticated approach became apparent—one cloaked in the language of democracy and human rights.
Color Revolutions: The Soros Connection
Enter the age of the NGO-driven color revolutions, where regime change is disguised as a people’s uprising. Organizations like the Open Society Institute (George Soros), Freedom House, and the National Endowment for Democracy (NED) became the new weapons of choice. These NGOs: * Fund and train opposition groups * Coordinate mass protests during elections * Provide media support to delegitimize governments
The results? A series of destabilizations across the world: Ukraine (2004 - Orange Revolution) Lebanon (2005 - Cedar Revolution) Georgia (2003 - Rose Revolution) Kyrgyzstan (2005 - Tulip Revolution)
Each followed the same pattern—Western-backed NGOs funneled money and resources into opposition movements, ensuring their success. Unsurprisingly, these uprisings all bore the fingerprints of Soros, the billionaire financier with a long history of manipulating global politics to serve elite financial interests.
However, this strategy has started to backfire. Georgia witnessed a major anti-Soros backlash, and attempts to replicate these revolutions elsewhere—such as the failed Moldovan "Grape Revolution"—have faltered as people wake up to the deception.
Iran 2009: An Operation in Plain Sight
While no one denies that Ahmadinejad’s regime had its flaws, the coordinated media hysteria and backing of Mir-Houssein "Butcher of Beirut" Mousavi raises serious questions. Why was the Western establishment so eager to install a leader with a brutal history? The answer lies in the same playbook used time and again: 1. Foment unrest through digital manipulation and street protests. 2. Control the narrative via Western media outlets. 3. Install a leader more compliant with Western economic and geopolitical interests.
Iran 2009 was not an isolated event. It was part of a much larger pattern—a centuries-old strategy of covert intervention, economic sabotage, and media manipulation to secure Western control over sovereign nations.
As history has shown, the real fight isn’t between the people and their governments—it’s between sovereign nations and the global power structures that seek to enslave them. And until people recognize the hidden hands behind these so-called revolutions, the cycle of deception will continue.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ 8e56fde2:bb433b31
2025-02-13 17:41:41
@ 8e56fde2:bb433b31
2025-02-13 17:41:41Let us introduce you to “DoShit!”: the oracle that three friends created in order to combat creative block. A self-produced card game made possible by the investment of a generous patreon who believed in us from the start, and in empowering people to Do their Shit.

What is DoShit! ?
DoShit! is a card game that guides you in the process of building a creative life. It’s a self-reflection tool when used individually, and also a great conversation starter when played with friends or strangers.
84 oracle cards that will help you question your fears, your strengths, doubts, excuses…
DoShit! is a great companion to bring along when meeting your friends or potential collaborators. Both individually as well as collectively, the game can become very addictive once you start asking about your projects and aspirations. Sometimes the cards even lay on you hard truths necessary on the journey to self-discovery
The cards are very intuitive to understand accompanied by a language that sparks profound conversations in a lightweight manner.

Learning how to play takes less than 5 minutes and anyone can attempt to interpret the cards without any previous knowledge (even if it may feel scary at first). In fact, the card readings always benefit from people sharing their own interpretation of the cards.

Link to video
Why DoShit! ?
As creators, we are very aware of the struggles of building a creative life and also of how easy it can be to limit ourselves, hide behind excuses, let fear win and quit. Our philosophy in response is “Do Shit”, yes, simply do shit, even if it ends up being shit… The important thing is to do it! Because when you Do Shit the project no longer dies in idea valley. And the more Shit you do the better you get at doing it, shortening the Gap between your expectations and your Shit.
That is why we created this tool, to accompany every DoShitter in the world on their journey (DoShitters being those who take responsibility for their Shit).
These cards were born at a moment of creative block and search for answers, and we can guarantee this game has helped unstuck many people. It is also a great companion to unleash your creativity and reach beyond your comfort zone!

How did it get started?
The three of us (Mar, Elisabet & Marta) have known each other for years and we’ve always had a shared admiration for each other’s work as well as the desire to do a project together someday.
One afternoon, with no specific expectations, simply wanting to enjoy ourselves without pressure, we started searching for an idea. Elisabet had some blank cards and Mar had been reading about tarot, and the idea simply sparked: we would do an oracle about the creative process with the structure of the Hero’s Journey (a concept that had followed us since we studied film school together) as a backbone. That afternoon, the first prototype of DoShit! was made.

The artistic process
The 84 unique cards were illustrated by Mar Delmar.
Each card is created manually with cut paper and gouache, creating first the different pieces that compose each card, and then placing them together in 3D to take the photo that becomes the final illustration.
The whole process took more than 8 months. Cards were painted and cut up in different locations (Barcelona, Tarragona, Castellar de n'Hug, Porrera y L'Argentera (Catalunya) y Castelo (Galicia)) where Mar attended artistic residencies along with a big box filled with the many octopuses in their envelopes, one for each card… (Video of the process)

Where to buy this awesome Shit?
- You can buy directly from our online store, but depending where you are in the world, shipping costs may showcase the literal cost of supporting small sellers. If you do buy it there use the promo code SATOSHI and get a small discount in return for your generosity <3
- You can also buy it with bitcoin , the best money in the world, in Plebeian Market . Since you'd be using the best money in the world, we shaved off a bit from the price and shipping in comparison to our online store since we appreciate being paid in sound money :D
- You can temporarily buy this Shit on the A****** giant with FREE Shipping depending of your location or prime subscription status, but we are going to be removing our beloved DoShitS from there soon due to our very negative experience with them portrayed in our article that you can find the link to at the bottom.
In any case, if you read this far, THANK YOU.
You can support our Shit by gifting this deck (to someone else, or to yourself :P) , zapping this article or simply sharing it around in the hopes that THE PEOPLE WHO NEED THIS SHIT, FIND THIS SHIT <3
And if you want to know more about this inspiring product, don’t hesitate to get in touch with us.
We wish you the best on you creative adventures!

Join the #artMy
ARTICLE ON OUR HORRID EXPERIENCE TRYING TO MAKE "doShit!" CHEAPER TO GET FOR YOU:
naddr1qvzqqqr4gupzprjklh3rdmxhj60knvpel0uk03vq3kyh4x3dlu2m7pgkcxa5xwe3qq247635g4v553t329e9x4rhvajhwvmrxahhgxv3ddc
-
 @ 6538925e:571e55c3
2025-02-13 16:05:09
@ 6538925e:571e55c3
2025-02-13 16:05:09
\ Nostr Live Streams (Beta)
If you follow shows like Rabbit Hole Recap, THE Bitcoin Podcast or Simply Bitcoin on Nostr, you can now watch the video in Fountain and hang out in the live chat as it’s being recorded. You'll find livestreams from people who follow on Nostr at the top of the home screen.
As well and live podcasts, you will also find live music events from PhantomPowerMedia, radio stations like NoGood and Noderunners, as well as channels dedicated to gaming, art, coding and much more.
Bringing creators and fans together through live experiences enables audience participation and creates a special feeling of community, so we’re really excited to get this into your hands.
Nostr livestreams are a beta feature - i.e. we still have a lot more work to do! We will continue to make improvements to livestreams over the coming months - so we would love to hear your feedback.

\ Storage Manager
We’ve added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files. You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally.
There are other performance and stability improvements that we are working on too. For example, in the next couple of weeks we will be rolling out an image proxy service, which should reduce mobile data usage and optimise storage.
Stay tuned for further updates and, as always, thanks for your support.
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ 7d33ba57:1b82db35
2025-02-13 09:41:48
@ 7d33ba57:1b82db35
2025-02-13 09:41:48The short answer is YES—but the more honest answer is that it’s much harder than when I started. I’ve been in the travel stock media industry for over 13 years, creating a vast archive of stock photos and videos from around the world. You can check out my portfolio on Shutterstock. My work is also available on Pond5, Videoblocks, and Adobe Stock. Other big agencies where I don’t have my media are Getty Images and iStock.
My media has been featured on TV channels and even in feature films. However, most of the time, contributors don’t know exactly where their content is used—stock agencies (the middlemen) keep that information to themselves. While stock media can still generate income, it requires persistence, a large portfolio, and an understanding of the ever-changing market.
When I started filming stock footage, most people didn’t even have a phone capable of taking good photos or videos—can you imagine? Now, everyone is a (travel) content creator. Technology has evolved, but creating a well-composed photo or video is still an art. However, the combination of improved tech and the increasing centralization of the stock media market has made it much harder to earn a decent income from stock media compared to 10 years ago.

Centralization & Declining Royalties Over the years, I’ve watched stock media royalties decline year after year. In the beginning, I couldn't understand why I wasn’t able to recoup the cost of my expensive camera—one I specifically bought to shoot high-quality 4K footage.
As the stock media industry became more centralized, agencies took a larger cut while contributors earned less, despite creating higher-quality content. The market became saturated, and with more competition and lower payouts, making a sustainable income from stock media became increasingly difficult.

The Reality of Centralization in Stock Media Every year, stock agencies announced yet another royalty downgrade for contributors. They always framed it as something beneficial for content creators, but in reality, it only served the big companies and their shareholders.
As content creators, we had no say in the matter. These agencies grew too big and powerful, and they knew it. Leaving one platform wasn’t really an option—doing so would only mean an even greater loss of income.
In recent years, the industry has become even more centralized, with only a handful of major agencies buying out smaller competitors. This consolidation further reduces competition, giving contributors even less control over pricing, royalties, and where their content is used.

The Bitcoin Standard: A Wake-Up Call I couldn’t understand why I was struggling to pay off my expensive camera investment, despite working hard and producing high-quality content. Until then, I had never really thought about how money worked. That changed in 2018 when I read The Bitcoin Standard—an absolute eye-opener.
That book sparked my curiosity about Bitcoin. Like many, I initially got distracted by shitcoins, thinking I could multiply my holdings faster—after all, Bitcoin seemed “too expensive.” It was a hard but valuable lesson. Just like in a casino, you can win and lose a lot with altcoins, but that has nothing to do with Bitcoin itself. After those first few years of learning, I realized that for me, Bitcoin—not crypto—was the only way forward.

From Centralization to Decentralization When people ask me if they should start selling stock footage, my answer is always the same: It’s much harder now than when I started. Sure, you can make a few bucks, but is all the time and effort really worth it? If I had to start today, I simply wouldn’t—it’s way more work than what you’ll earn.
Instead of spending years building content for centralized platforms that take the biggest cut, I believe it’s better to focus on decentralized media like Nostr. In my opinion, that’s where the future lies.

Nostr: A New Protocol for Socializing (and More) Nostr is a revolutionary protocol that goes beyond just social networking. You can read all about it at Nostr.org. As a content creator, one of the most exciting aspects of Nostr is the ability to earn directly through Zaps—small payments made in Satoshis (the smallest unit of Bitcoin). * 1 Bitcoin = 100 million Satoshis * By receiving Zaps, you’re not just earning—you’re stacking the hardest money (Bitcoin) directly on Nostr. This shift toward decentralized earning is a game changer, giving creators more control and financial sovereignty compared to traditional, centralized platforms.

Join Nostr and Create Your Freedom Content
On Nostr, no one can stop you. No one can deplatform you. You can be truly free.Whether you're a content creator, artist, or thinker, Nostr empowers you to share your work without censorship or gatekeepers. It’s a place where you control your content, connect directly with your audience, and even earn Bitcoin through Zaps.Embrace decentralization.
Join Nostr and take back your freedom 🚀
-
 @ 97c70a44:ad98e322
2025-02-13 02:03:33
@ 97c70a44:ad98e322
2025-02-13 02:03:33Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ d61f3bc5:0da6ef4a
2025-02-12 16:57:44
@ d61f3bc5:0da6ef4a
2025-02-12 16:57:44Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet.
There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what kind of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help.
Primal Wallet
Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.
 Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app.
Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed 1,338,460 transactions, with 238,916 just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish.
All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem.
Zapping from Any Nostr App
For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:
 Yes. Click, click. And you can start zapping!
Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in.
Primal enables you to connect any number of external apps and manage them from wallet settings:
 Note that you can set your daily spend budget for each app or revoke its access at any time.
Note that you can set your daily spend budget for each app or revoke its access at any time. How This Works
So, what is this sorcery? How does it work under the hood?
Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol here, and access developer docs here.
The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature:
nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection.
What Comes Next?
The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments.
Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ d61f3bc5:0da6ef4a
2025-02-12 16:49:08
@ d61f3bc5:0da6ef4a
2025-02-12 16:49:08Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet.
There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what kind of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help.
Primal Wallet
Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.
 Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app.
Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed 1,338,460 transactions, with 238,916 just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish.
All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem.
Zapping from Any Nostr App
For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:
 Yes. Click, click. And you can start zapping!
Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in.
Primal enables you to connect any number of external apps and manage them from wallet settings:
 Note that you can set your daily spend budget for each app or revoke its access at any time.
Note that you can set your daily spend budget for each app or revoke its access at any time. What Comes Next?
The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments.
Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
-
 @ 85bdb587:7339d672
2025-02-12 15:24:11
@ 85bdb587:7339d672
2025-02-12 15:24:11Chart of the Day
While this is a bitcoin focused rag, I think it is important for any of you who read this to begin paying attention to gold markets if you haven't already. There has been an ongoing exodus of physical gold from London vaults and a rapid acceleration of gold being moved to the three biggest vaults in the United States in recent weeks. More gold has flooded into the US vaults over the first two months of this year than at the peak of the flight to safety during the beginning of the COVID lock downs.
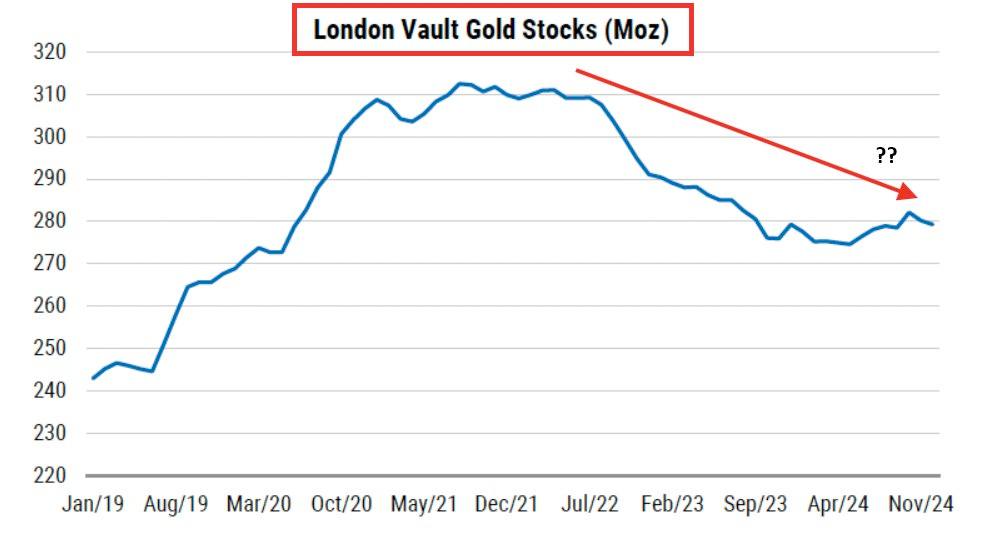
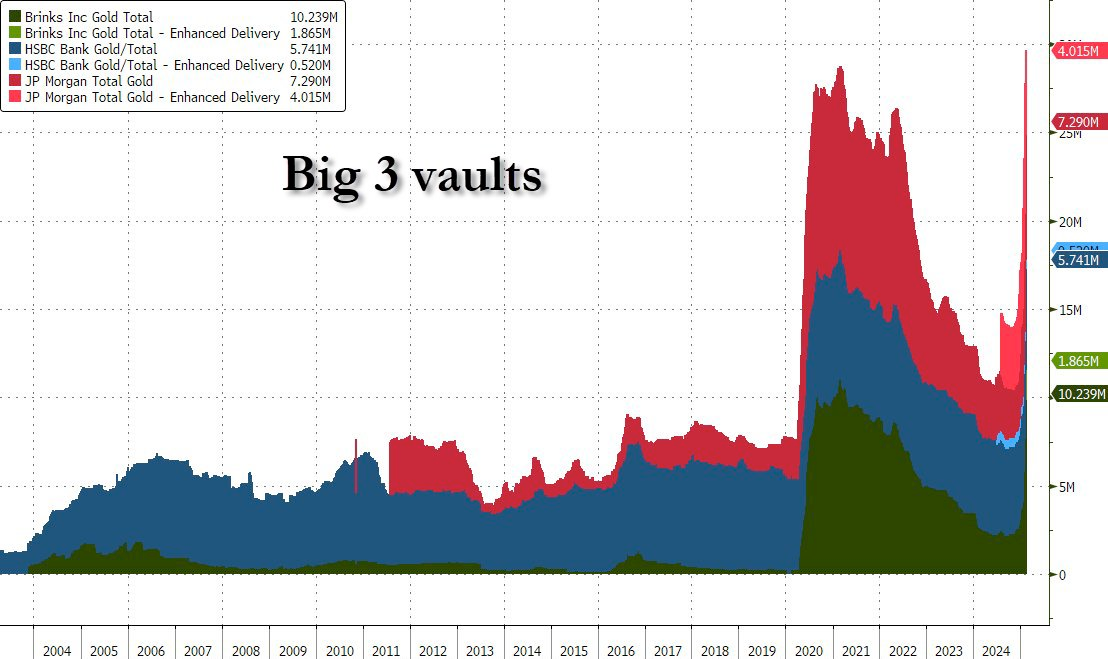
This is particularly perplexing considering the fact that equities are flat or up on the year, depending on the index you like to follow. Gold outperformed the S&P 500 significantly in 2024 and its momentum hasn't slowed down a bit in 2025 as the precious metal consistently hits new all time highs. The current correlation to the S&P 500 has only happened two times in history; right now and October of 2007.
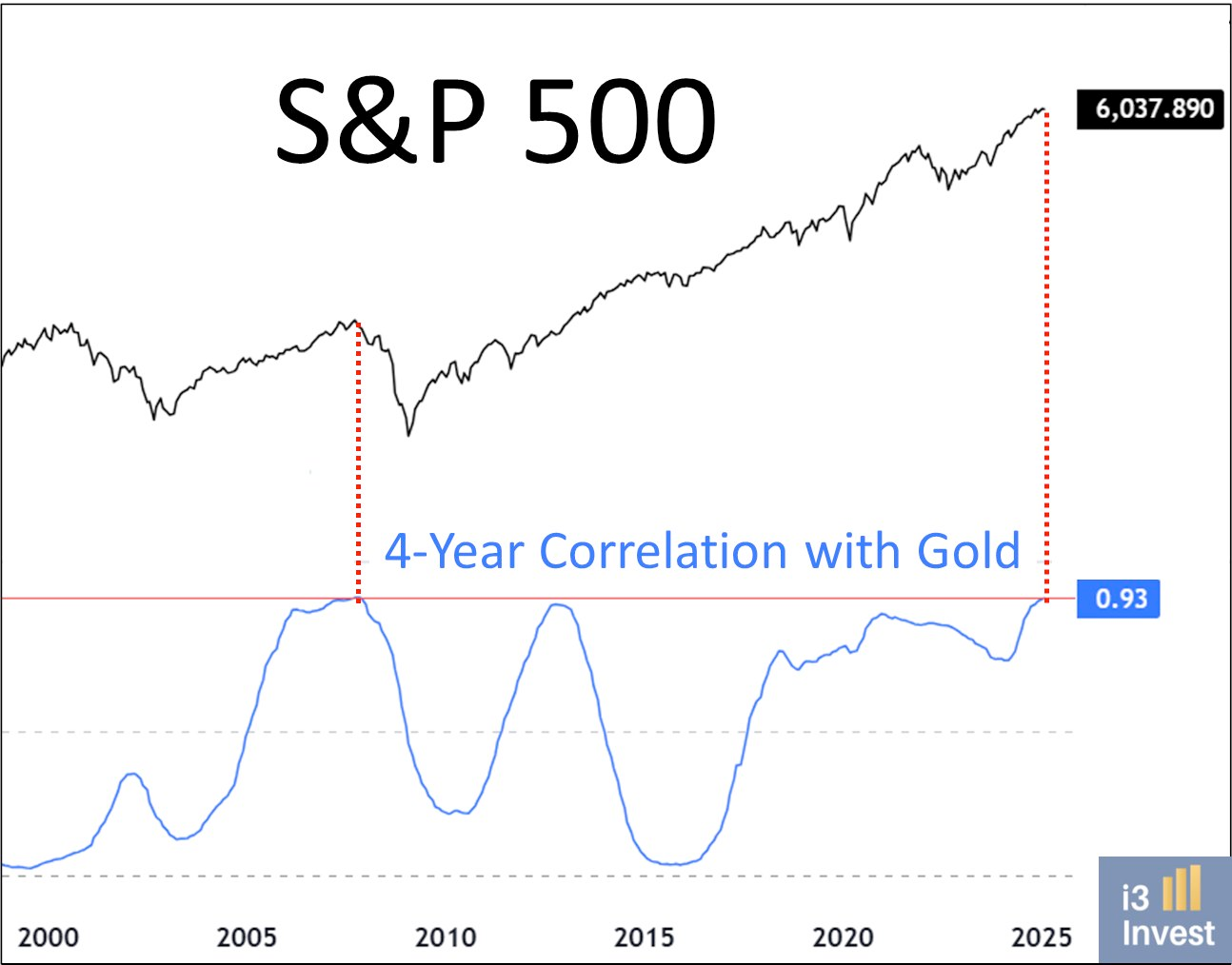
Institutional investors and nation states are piling into gold at an unprecedented pace. This signals that they are preparing for something to break. The catalysts for the exodus of gold from London to the US and from paper gold to physical gold are fears over Trump's tariffs, institutions and governments preparing for a potential monetary reset, and fears of a looming liquidity crisis as liquidity in the reverse repo market dries up. Uncertainty and chaos rule the day and we are witnessing a flight to safety.
Many of you are probably asking, "Why isn't bitcoin moving?!" That's a good question. Considering everything mentioned above one would think that bitcoin would be on the move toward new all time highs as well. Having been following bitcoin for twelve years your Uncle Marty has developed some pattern recognition when it comes to this market. Upward bitcoin price movements typically happen in a staircase fashion. Meaning that it trends up and to the right over the long-run with quick bursts to higher levels followed by small corrections and consolidation periods. If I had to guess, we are currently in a consolidation period that should come to an end at some point in the next few months. In recent years, gold has moved higher first and bitcoin has followed. Typically outperforming gold significantly. I find it hard to believe that this relationship is going to end any time soon. Especially considering the geopolitical and economic backdrop.
Luke Gromen Warns Bitcoin Holders: Historical Currency Revaluations Show Speed Matters
During my recent conversation with Luke Gromen, he raised a sobering point about the velocity of monetary regime changes. Drawing from historical examples, including a Ukrainian family who saw their savings devalue from "five cars to one month's groceries" over a single weekend, Luke emphasized that Americans are uniquely blind to how quickly these transitions can occur. The current stress in our financial system - from Treasury market dynamics to global trade tensions - suggests we're approaching a similar inflection point.
*"What if they do it on Friday night like they did with Trump coin and you wake up and gold's up 1,000% by the time you're up on Saturday morning, what are you going to do? You're going to sell your bonds and buy gold on Saturday?"* - Luke Gromen
This warning shouldn't be taken lightly. Those waiting for clear signals before acquiring bitcoin may find themselves locked out of the transition entirely. Luke's analysis suggests that rather than a gradual shift, we're more likely to see a compressed timeframe where major monetary changes happen over days or weeks, not months or years. The recent Trump coin phenomenon, while different in nature, demonstrates how quickly markets can move when sentiment shifts dramatically.
TLDR: Major monetary changes happen fast - don't wait to stack sats.
Check out the full podcast here for more on DeepSeek's impact on AI markets, Colombia's trade negotiations, and Scott Percent's three arrows for economic reform.
Headlines of the Day
U.S. Faces $1.67B Annual Cost Spike on Single Bond Rollover - via X
BlackRock: Bitcoin is Monetary Hedge, Ethereum is Tech Play - via X
Lummis: SBR Could Slash U.S. Debt by 50% in Two Decades - via X
Fold Launches Bitcoin Rewards Visa Credit Card - via Business Wire
Obscura VPN launches with a MacOS product - via nobsbitcoin.com
Bitcoin Lesson of the Day
The SegWit (Segregated Witness) upgrade in August 2017 made two key changes to Bitcoin. First, it moved transaction signatures to a separate part of the data, fixing "transaction malleability" by preventing nodes from modifying transaction IDs. Second, it increased effective block capacity by introducing "weight units" that gave signature data a 75% discount, allowing blocks to grow from 1MB to about 1.8MB.
As a "soft fork," SegWit remained compatible with older Bitcoin software. The upgrade activated at block 481,824 after 95% of miners signaled support. This approach allowed Bitcoin to increase capacity and fix technical issues while maintaining network compatibility.
ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats.
Get on the waiting list now before it fills up!
$200k worth of prizes are up for grabs . The Fold Bitcoin Rewards Credit Card waitlist is live!
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ c902b8da:0cedc5fb
2025-02-16 18:13:20
@ c902b8da:0cedc5fb
2025-02-16 18:13:20I'll break down the key legal requirements, costs, and timelines for establishing a health insurance company, focusing purely on the regulatory aspects:
State Licensing Requirements (Primary State): - Initial Capital and Surplus: $10-15 million minimum (varies by state) - Risk-Based Capital (RBC) requirements: Must maintain 200-300% of RBC - Processing Time: 12-18 months - Application Fee: $25,000-50,000 - Filing Requirements: - Articles of Incorporation - Statutory Financial Statements - Actuarial Certifications - Detailed Ownership Information - Background Checks for All Officers/Directors - Holding Company Act Filings if Applicable
Federal Requirements: - ACA Compliance: - Must offer all 10 Essential Health Benefits - Medical Loss Ratio requirements (80% individual/small group, 85% large group) - No annual or lifetime limits - Guaranteed issue and renewal - HIPAA Compliance: - Privacy Officer Appointment - Security Protocols Implementation - Timeline: 6-8 months - Cost: $200,000-500,000 for initial setup
Multi-State Expansion (Per Additional State): - Certificate of Authority Application: $5,000-25,000 per state - State-Specific Capital Requirements: $2-5 million additional per state - Processing Time: 6-12 months per state - Required State Deposits: $500,000-2 million per state - Guaranty Fund Membership: $25,000-100,000 per state
Mandatory Insurance Filings: - Rate Filings: - Timeline: 60-90 days for approval - Filing Fees: $500-5,000 per filing - Form Filings: - Timeline: 30-60 days for approval - Filing Fees: $50-500 per form - Annual Statement Filing: $500-2,500 per state
Required Positions and Certifications: - Licensed Actuary (MAAA certification) - Compliance Officer - Medical Director (licensed physician) - Claims Manager - Network Management Director - Timeline for hiring/certification: 3-6 months - Annual Costs: $1-2 million for required personnel
Reserve Requirements: - Claims Reserves: 3-6 months of expected claims - Premium Reserves: 1-3 months of premium - Special Deposits: Varies by state ($1-5 million) - Total Reserve Requirements: 25-40% of annual premium
Ongoing Regulatory Compliance: - Quarterly Financial Filings: Due within 45 days of quarter end - Annual Financial Statements: Due March 1 - Market Conduct Examinations: Every 3-5 years - Cost: $100,000-500,000 per examination - Financial Examinations: Every 3-5 years - Cost: $200,000-1 million per examination
Required Insurance Coverage: - E&O Insurance: $5-10 million coverage - Annual Cost: $100,000-250,000 - D&O Insurance: $10-25 million coverage - Annual Cost: $200,000-500,000 - Cyber Insurance: $5-10 million coverage - Annual Cost: $100,000-300,000
Total Regulatory Timeline: - Initial State License: 12-18 months - Federal Compliance: 6-8 months (concurrent) - First Policy Issuance: 18-24 months from start - Multi-State Operation: Additional 12-24 months
Total Initial Regulatory Costs: - Single State Operation: $15-25 million - Multi-State Operation (5 states): $30-50 million - Annual Compliance Costs: $2-5 million per state
These requirements and costs can vary significantly based on: - State of domicile - Number of states operating in - Types of health insurance products offered - Size of projected enrollment - Market conditions and risk factors
Yes, existing insurance companies can potentially influence your application process, but not directly through a "veto" power. Here's how it works:
- Public Comment Period
- Most state insurance departments have a public comment period during the application process
- Existing insurers can submit formal objections or concerns
-
They typically focus on market saturation, financial viability, or potential unfair competition
-
Market Need Assessment
- Many states require a "need and necessity" showing as part of the application
- You must demonstrate that:
- There's sufficient market demand
- Your company brings something unique or beneficial
- The market can support another carrier
-
However, mere competition itself is not grounds for denial
-
State Regulator Discretion
- Regulators consider market concentration and competition
- They generally favor healthy competition unless there are legitimate concerns about:
- Market destabilization
- Your company's financial strength
- Risk to consumers
-
Pure "we don't want competition" arguments from existing insurers typically don't succeed
-
Trade Association Influence
- Insurance trade associations may provide input during the licensing process
- They can raise concerns about:
- Capital adequacy
- Management experience
- Business plan viability
- But they cannot directly block your application
Key Point: While existing insurers can object, the final decision rests with state regulators who are primarily concerned with: - Consumer protection - Market stability - Your company's financial soundness - Management competency
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 8d5ba92c:c6c3ecd5
2025-02-12 09:48:19
@ 8d5ba92c:c6c3ecd5
2025-02-12 09:48:19Keeping up with everything happening in Bitcoin isn’t easy, even if you’ve been around for a while. The pace is relentless: stream of events, discussions, projects, and updates, not to mention the noise on social media...
One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess.
Take, for example, the ''BTC Events Map,’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn).
Search for '[bitcoin events],' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for.
That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know.
One of those that flew under my radar was SatsNFacts. It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on Nostr.
I was ‘lucky’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out.
A Journey to Southeast Asia...
Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”.
The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup.
Where Builders and Artists Collide
While its was billed as a “Technical Unconference,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art.
Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops.
With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile:
- Liana Workshop (long-term security, recovery, and inheritance),
- TollGates (streaming sats for internet access),
- Open Vault (enterprise wallet interface),
- Yaki Honne (decentralized media),
- Nostr Proxies (Epoxy, WebSocket and relay monetization).
- Silent payments (simplified payment experiences without compromising privacy).
As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more:
- HuaiPhueng on Geyser + "Bitcoin City" (their short video ).
- Bitcoin Indonesia & Bitcoin House Bali (all in one on GitHub )
Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨
This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event.
Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical 'artist', I was honored to have some of my own pieces exhibited there as well (a short video 👇).
One of the highlights was meeting local Thai artists, especially Siritravelsketch, who travelled six hours by train just one way to attend two days of the event.
Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit.
Truly spectacular!

I also had the chance to reconnect with Satoshi Builds, who made many great sketches during this event, and with BitPopArt, a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "Art exhibition in Chiang Mai ".
All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!
https://v.nostr.build/Fy7J510ZaNyMktIX.mp4
(*** presented artworks by for example: Agi Choote, Samhain, Zed Erwan, Existing Sprinkles, AZA 21m , BitPopArt .)
Mr. Rabbit in Thailand...
Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art.
Representing Bitcoin FilmFest (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience.
Seven trailers and eleven shorts, including for example:
-
NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers).
-
BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts)
With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of BFF25 (the annual festival we're organizing this May in Warsaw, Poland).
https://i.nostr.build/RE3mKJacw5vB23V6.png
Substance Over Hype.
SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike.
The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience.
SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings.
Here's to more signal, less noise!!!
Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special!
BTC Your Mind. Let it Beat.... Şela
-
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26
@ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26Lifting the Curtain on Power and Scandal
The Illusion of Power and TrustIn the modern world, the line between trust and skepticism is razor-thin, especially when it comes to powerful figures and organizations. They present polished facades, dazzling us with promises of stability, innovation, or in Disney’s case, enchantment. Yet, the revelations surrounding Jeffrey Epstein’s network reminded us that power is often far more complex than it appears. This scandal became a litmus test for public trust and fueled questions about who, or what, might be entwined in hidden truths.
When Epstein's crimes were exposed, they revealed not just the horrifying details of exploitation, but also the unsettling reach of his influence. As the media peeled back the layers of his associations, public attention naturally shifted to recognizable names and institutions, including Disney. How could a company that represented childhood innocence, with castles and fairy tales, find itself whispered about in the same breath as Epstein’s infamous circle? This segment examines the roots of that question and the facts that illuminate its plausibility or dismiss it.
Epstein: A Man Who Mastered Access to PowerJeffrey Epstein was more than just a financier—he was a gatekeeper to influence. His lifestyle and operations were an entangled web of charm, manipulation, and wealth, meticulously designed to secure him a place among the powerful. Investigative articles by The Guardian and The New York Times depict Epstein as a social engineer, curating relationships that ranged from politicians and royalty to scientists and celebrities.
Court documents and deposition testimonies during Epstein’s trial confirmed that his homes and private jet were hubs for connecting with influential figures. This access did not come without consequence; it cemented him as both a source of curiosity and, later, fear. Public records, such as those scrutinized in The Washington Post, indicated his involvement with many high-profile individuals. Yet, the details of these relationships varied—some guests were casual acquaintances, others, confidants.
The Infamous Flight LogsThe flight logs of Epstein’s private jet, colloquially known as the "Lolita Express," became a centerpiece for public scrutiny. Released through court orders and accessed by journalists, these logs listed names that triggered a cascade of questions. Guests ranged from prominent business executives to entertainment figures, sparking a debate over whether mere association implied complicity or deeper connections. This fueled the narrative that Epstein’s reach was far more extensive than previously understood, implicating industries where entertainment, power, and trust intersected.
The Role of Speculation in Public DiscourseAs soon as these flight logs surfaced, discussions surged online and across media platforms. The presence of any entertainment figure in Epstein’s orbit raised an eyebrow and, in many cases, invited a leap of logic: if influential media personalities were tied to him, could companies known for entertainment and global reach, like Disney, have hidden associations as well? This hypothesis, though lacking concrete evidence, found fertile ground among those predisposed to distrust large, seemingly untouchable institutions.
It’s crucial to dissect why Disney, specifically, became a subject of speculation. On one hand, its status as an omnipresent media empire makes it an easy target for conspiracy theories that thrive on the juxtaposition of light (Disney’s brand) and darkness (Epstein’s crimes). On the other, it speaks to a larger societal impulse to find cracks in the foundations of those we consider infallible. The idea that even the most beloved entities might harbor hidden truths appeals to a deep-seated desire for transparency and accountability.
The Catalyst of Public CuriosityThe timing of Epstein’s exposure was a critical factor. His arrest and subsequent death in 2019 coincided with a period marked by rising distrust in institutions, fueled by political and social upheavals globally. Social media platforms amplified this distrust, creating echo chambers where half-truths and speculative narratives merged seamlessly with confirmed facts.
It is here that Disney’s name began to surface not as an accused, but as a speculative point in discussions. The reasoning often pointed to a "guilt by association" logic: if the powerful dined, flew, or partied with Epstein, then it was worth questioning the circles in which those powerful entities moved, even without direct evidence. This leap from speculation to assumption reflects a pattern that sociologists recognize as part of conspiracy theory psychology—where a lack of clear answers invites the mind to fill in gaps, often with what feels most compelling.
Reframing the Public’s QuestionsThe real question becomes: why does this speculation hold such sway, even when evidence is scarce? Part of the answer lies in precedent. History is replete with instances where institutions that seemed above reproach were later implicated in hidden misdeeds, from financial frauds to abuse scandals within trusted organizations. This collective memory primes the public to believe that beneath any glittering surface could lie a dark, concealed underbelly.
Disney’s position as an icon of childhood and innocence adds another layer to this narrative. To imagine that such a symbol could be tainted by proximity to someone like Epstein is not just shocking—it’s fascinating. It strikes at the core of what we hold sacred, making it an irresistible topic of conversation and investigation.
Why This MattersUnderstanding why names like Disney are brought into these discussions without verified evidence is essential. It helps differentiate between warranted inquiry and unsupported speculation, allowing us to approach these narratives critically. Addressing this head-on does not only clear the air but strengthens the foundation upon which valid criticism and accountability are built.
A Note on EvidenceAs we move deeper into this exploration, it’s critical to emphasize that while Epstein’s connections to high-profile figures are thoroughly documented, there remains no evidence tying Disney, as an organization, to his operations. Still, the fascination with the “what-ifs” continues, driven by our collective quest for understanding power, secrecy, and the thin line between public and private lives.
The next segment will dive into Epstein’s proven network, unraveling the extent of his influence and why it has been the breeding ground for questions involving the world’s most trusted corporations.
Epstein’s Documented Network
The Web of Power: A Portrait of InfluenceJeffrey Epstein’s network was not merely a collection of acquaintances; it was a curated gallery of the world’s most influential figures, built on calculated relationships and strategic connections. Epstein wielded this network with the precision of a skilled operator, bridging disparate realms of society—politics, academia, business, and media. Investigative reporting by sources such as The New York Times and The Guardian exposed how Epstein maintained access to individuals who shaped policy, managed wealth, and crafted the narratives of popular culture.
Court records, testimonies, and detailed analyses of his interactions revealed that Epstein was adept at placing himself at the center of elite circles. His estates, from Manhattan townhouses to private islands, hosted events that blurred the lines between social gatherings and strategic networking. This chapter delves into the proven extent of Epstein’s reach and why it sparked questions about connections to corporations and public institutions, including Disney.
Flight Logs: The Proof and the SparkThe flight logs from Epstein’s private jet, the infamous "Lolita Express," were among the most illuminating pieces of evidence in mapping his connections. These logs, legally obtained and examined by journalists, painted a picture of Epstein’s influence stretching across industries. High-profile figures were listed, including financiers, political leaders, and entertainment personalities. The presence of notable names triggered waves of speculation—if Epstein had access to such power players, how many more remained unnamed but entangled?
The Guardian and The Washington Post reported that these flights were not just transportation but often involved visits to Epstein’s various properties, known for their opulence and the dark rumors surrounding them. While these logs confirmed that many public figures knew Epstein, the depth and nature of their associations varied widely, from casual acquaintance to deeper involvement.
The Limits of the KnownDespite the breadth of documented connections, there was no verifiable evidence linking Disney as an entity to Epstein’s circle. What the flight logs and guest lists revealed was a man deeply embedded in networks of power, yet even within these proven associations, context was crucial. For instance, some guests, confirmed by court records and investigative articles, were shown to have attended public events or engaged in business unrelated to Epstein’s criminal activities.
The distinction between documented presence and complicity is where the narrative often splinters. The leap from association to implication fueled public debate and conspiracy theories. This was especially true when figures from media and entertainment, sectors known for influencing public sentiment and childhood memories, appeared on the periphery of Epstein’s activities.
Epstein’s Parties and Gatherings: The Elite’s Shadowed StageEpstein’s parties were legendary, drawing attendees from the highest echelons of influence. These gatherings were not casual mixers but orchestrated showcases of power. Reports from court depositions and firsthand accounts highlighted how Epstein leveraged these events to cement alliances and reinforce his status as a gatekeeper to the elite. Some testimonies even described how these events served as platforms for discussing investments, politics, and global initiatives, reinforcing Epstein’s perceived omnipotence.
High-Profile Confirmations and Their ImplicationsSeveral prominent individuals were indeed verified as having ties to Epstein, raising legitimate questions about the extent of their knowledge or involvement. These names included politicians, royalty, and entertainment figures. The ambiguity surrounding these associations allowed theories to flourish. The sheer presence of influential names on Epstein’s guest lists raised the question: If these individuals were implicated, what about the institutions they represented or the circles they moved within?
This was a turning point for public speculation. The logic extended: if an individual from a major media company or entertainment empire like Disney was even remotely connected, could that implicate the company itself? The answer, according to existing court records and credible investigations, remained no. Yet, the absence of direct evidence did not stop speculation; in many cases, it intensified it.
Why Disney Was Brought Into the ConversationDisney’s reputation as a family-friendly giant contrasted starkly with the dark nature of Epstein’s activities, making it an unlikely yet intriguing topic for public discourse. While some entertainment figures appeared on Epstein’s flight logs or were rumored to have interacted with him, investigations have not yielded any proof of corporate-level involvement. However, public fascination persisted, bolstered by the broader questions Epstein’s connections evoked.
It’s worth noting that corporations like Disney, with their vast reach and unparalleled influence, naturally become focal points when discussions of hidden truths arise. The mere idea that such an iconic entity could be associated with real-world shadows captures the imagination and fuels stories that, while lacking proof, thrive on the “what-ifs” that echo through media and online forums.
How Public Perception Shapes the NarrativeSociologists studying the psychology of conspiracy theories point out that the human mind tends to fill gaps in knowledge with what feels most plausible or compelling. When figures from reputable media or entertainment companies are tied, even tangentially, to a scandal as vast as Epstein’s, it challenges the boundaries of trust. This is exacerbated when concrete answers remain elusive, leading to a cycle where suspicion feeds speculation.
The public’s thirst for accountability, especially in the wake of uncovered scandals involving powerful institutions, is both a force for truth and a catalyst for assumptions. In Epstein’s case, the proven reach of his influence and the confirmed involvement of significant figures were enough to trigger the question of how many untold stories lay beneath.
What We Know vs. What We ImagineThe narrative surrounding Epstein’s documented network shows us that while connections can be verified and associations noted, the leap to implicating entire organizations like Disney requires more than names on a list or rumors. It requires evidence that has, thus far, not been presented in any court or investigation. The proven facts are compelling enough: Epstein’s influence was extensive, his ties to power irrefutable. Yet, without direct links, the conversations about specific corporate involvement remain speculative.
In the next segment, we will explore why Disney’s reputation makes it a prime target for such speculation and how its historical handling of public crises plays into these narratives.
Disney – The Symbol of Trust and Target of Suspicion
Why Disney? The Paradox of a Trusted InstitutionDisney’s legacy is built on a foundation of storytelling, dreams, and the belief in happy endings. For nearly a century, the company has woven itself into the fabric of childhoods, becoming synonymous with innocence and magic. This legacy, however, has a dual edge. As the public's trust in institutions erodes and hidden truths are revealed in other sectors, Disney’s position as an untouchable cultural icon makes it both a beacon of light and a potential target for suspicion.
The Symbolism of Disney’s BrandDisney represents more than just a company; it embodies an idea—a refuge where imagination and wonder reign. But this same image that has made Disney a household name also contributes to the paradox of suspicion it faces. When an organization is seen as larger than life, transcending generations and continents, the notion that it could have skeletons in its closet becomes a tantalizing thought. The juxtaposition of innocence with possible shadows creates a narrative that is compelling and worth exploring, even if it remains speculative.
This paradox of Disney as both a trusted symbol and a target for scandal reflects a broader trend. Major corporations that hold influence in our everyday lives—particularly those that shape childhood memories and societal values—are natural focal points when scandals involving power, influence, and exploitation arise. The idea that a company with as much reach as Disney could be connected, however tangentially, to figures like Epstein feeds into this pattern.
Documented Misconduct and Public ReactionsThere have been verified cases involving Disney employees engaging in misconduct, which have been reported by media outlets such as NBC News and local news channels. These incidents, though not systemic and unrelated to Epstein’s network, show how the actions of a few can impact public perception of an entire organization. Examples include arrests for crimes involving minors or inappropriate behavior, isolated events that Disney has publicly addressed through statements and cooperation with law enforcement.
However, these incidents were sufficient to plant seeds of doubt in some minds. Even when addressed swiftly and in line with corporate protocols, such cases reveal a vulnerability: the company’s image can be tarnished not just by its policies, but by the misdeeds of individuals who wear its badge.
The Fuel for SpeculationThe Epstein case acted as a catalyst for looking beyond the obvious, particularly in the context of powerful organizations. If political leaders, financiers, and cultural icons could be connected to Epstein’s circle, why not wonder about the involvement of a company with as vast a presence as Disney? While investigations by trusted outlets have shown no direct corporate link, the sheer scope of Epstein’s influence suggested that any entity known for associating with the powerful could be implicated.
This speculation was not helped by Disney’s approach to public relations. The company’s PR strategies, while sophisticated and generally effective, often prioritize message control over transparency. In a world where silence can be seen as complicity, this strategy sometimes backfires, leading to more questions than answers.
Public Distrust and Historical ContextThe public’s fascination with uncovering hidden truths within major institutions is not unfounded. History is replete with cases where seemingly trustworthy organizations were later found to have concealed scandals. From corporate frauds to abuses within religious institutions, these stories have taught the public that innocence is not immune to corruption. This backdrop primes society to believe that even the most beloved entities, like Disney, could harbor secrets.
Sociologists and media analysts argue that this distrust is a byproduct of what they term the “betrayal effect”—where past disappointments with trusted institutions lower the threshold for believing that betrayal could be lurking everywhere. Disney, with its spotless public image and vast influence, becomes an especially juicy target for such theories. The leap from real cases of employee misconduct to more systemic accusations, however, is where evidence often falls short.
The Role of Social Media and Echo ChambersThe digital age has amplified how speculation morphs into perceived truth. Platforms like Twitter, Reddit, and Facebook allow theories to spread quickly, often outpacing fact-checking and nuanced analysis. Discussions that might once have been confined to fringe circles now gain mainstream attention, especially when they involve powerful figures or beloved brands.
In the context of Epstein’s exposure, this meant that any high-profile connection or name could become part of a broader narrative of guilt by association. The fact that Disney, as a corporation, appeared in speculative discussions alongside verified names from Epstein’s logs was enough for some to draw connections, even without direct evidence.
Reputation Management and PerceptionDisney’s approach to crises and controversies has long involved careful reputation management. From its response to legal issues to how it handles employee-related incidents, the company employs sophisticated PR strategies to mitigate damage and maintain its standing. This is standard practice for global brands; however, the public’s interpretation can be different. Strategic silence or tightly controlled statements can come across as evasive, fueling theories that there is something more to hide.
For a company like Disney, which operates at the intersection of family values and global corporate power, the stakes are high. The expectation isn’t just for entertainment but for upholding the moral high ground. When speculation links Disney to scandals, no matter how peripherally, it chips away at this carefully crafted image.
Why Address This Now?The speculation around Disney and Epstein underscores a crucial point about the nature of public inquiry and corporate reputation. It is not enough for companies to rely solely on public relations strategies that worked in the past. The demand for transparency is greater than ever, and silence, even when warranted, can erode trust.
Disney’s role in the public consciousness means that even baseless theories need addressing. By understanding why these narratives gain traction, both companies and the public can engage in more meaningful dialogues about accountability, proof, and trust.
The next segment will delve into how the public navigates between confirmed facts and conspiratorial whispers, exploring why certain theories stick and what it means for how we view powerful organizations.
Separating Fact from Conspiracy
The Thin Line Between Evidence and Speculation In the age of information, where facts are readily available yet often overshadowed by conjecture, separating truth from conspiracy is both an art and a necessity. When powerful entities like Disney find themselves drawn into discussions of hidden networks and scandals involving figures such as Jeffrey Epstein, it highlights a broader societal challenge: how do we differentiate between what is proven and what is assumed? This segment dissects the interplay of evidence, theory, and the psychological factors that drive our need to seek connections.
The Basis of Public Suspicion Public trust in large institutions has waned over decades, driven by a series of high-profile betrayals. From corporate frauds that shattered economies to scandals involving trusted religious or educational institutions, society has learned that power often conceals flaws and, in some cases, criminal actions. According to research published in the Journal of Communication, this erosion of trust leads to a phenomenon known as confirmation bias—the tendency to interpret new evidence as confirmation of one’s existing beliefs or suspicions.
The Epstein case provided fertile ground for such biases. The verified details of Epstein’s operations—the private jet, the exclusive parties, the high-profile guests—were enough to prompt a collective re-examination of how far his reach extended. While many of his associations were proven to be casual or professional in nature, the public’s hunger for deeper revelations ensured that speculation would thrive in areas where clarity was lacking.
The Role of Real Connections Epstein’s documented network included figures from politics, academia, finance, and media. The release of flight logs and court documents revealed that powerful individuals attended his events and interacted within his sphere. This factual basis, verified by investigative reporting from The New York Times, The Guardian, and other reputable sources, provided legitimacy to the idea that Epstein’s influence was pervasive. However, the extent to which these relationships were innocent or complicit was not uniformly clear.
This ambiguity created a vacuum where speculation could flourish. Public attention shifted from individuals named in the logs to the institutions and industries they represented. It was here that major corporations, including Disney, entered the discourse—not because of documented ties, but because of their visibility and influence.
The Psychology Behind Linking Power and Scandal To understand why theories about Disney’s potential involvement in Epstein’s network persist, it is essential to examine the psychology of conspiracy. Sociological and psychological studies indicate that people are naturally inclined to question narratives when they feel that the truth is being withheld. The more powerful or untouchable an institution seems, the more likely it is to be suspected of hiding something significant.
Disney’s image as a global giant that molds childhoods and shapes culture makes it an appealing target for such theories. The company’s public persona as a bastion of family values and innocence stands in stark contrast to any whispers of scandal or misconduct. This contrast alone provides fertile ground for stories to grow, even in the absence of solid proof.
Confirmed Misconduct vs. Conspiracy It is important to acknowledge that Disney, like any large corporation, has faced incidents involving employee misconduct. News reports from outlets such as NBC News have documented cases where employees were arrested for inappropriate conduct involving minors. These cases, while serious and handled with appropriate legal responses, were isolated incidents. No evidence points to these cases being part of a larger, systemic issue within the company or connected to external figures like Epstein.
However, the very existence of these incidents is often enough to keep theories alive. Public perception does not always differentiate between an individual’s actions and the culture of the organization they work for. When these incidents coincide with broader conversations about power and secrecy, they feed into narratives that imply guilt by association.
The Amplifying Power of Social Media The role of social media in shaping and amplifying conspiracy theories cannot be overstated. Platforms like Twitter and Reddit have created spaces where facts, opinions, and theories coexist with little separation. When the Epstein scandal broke, social media was flooded with discussions, many of which featured a mix of verifiable information and speculative connections. The absence of direct evidence linking companies like Disney to Epstein did not deter users from proposing connections based on circumstantial evidence and “what-if” scenarios.
This phenomenon, described by media analysts as the “echo chamber effect,” allows theories to gain credibility through repetition rather than proof. As theories are shared, retweeted, and commented on, they accumulate a sense of legitimacy that belies their origins.
Why Certain Theories Stick Certain theories persist because they tap into deep-seated fears and the knowledge that the powerful often operate beyond the reach of conventional accountability. High-profile scandals involving powerful figures—whether in business, politics, or entertainment—reinforce the belief that more may be hidden just out of reach. Epstein’s network was confirmed to include names that were once considered untouchable, which validated the idea that hidden truths could surface anywhere.
Disney’s name appearing in speculative discussions highlights the intersection of innocence and power. It reflects a societal expectation that if one pillar of influence is shown to be compromised, others may be as well. This expectation, however, must be tempered with critical thinking and an examination of evidence.
The Need for Discernment Understanding the difference between fact and theory is crucial for informed dialogue. Public scrutiny is essential for accountability, but it must be balanced with discernment. While Epstein’s known associations spanned many sectors, and while individuals from the entertainment industry were involved in his circle, the leap to implicating entire organizations like Disney has not been supported by verified investigations.
The Reality Check Here’s what we know:
Documented Facts: Epstein’s network included influential figures, confirmed by court records and journalistic investigations. Disney’s Position: While Disney has faced isolated cases of employee misconduct, no substantial evidence ties the company as an institution to Epstein’s criminal activities. Public Perception: Theories are fueled by a combination of legitimate distrust in powerful institutions and the psychological need to connect the dots, even when the evidence does not support it. In the next segment, we will explore how media control and the use of non-disclosure agreements (NDAs) contribute to the public’s perception of secrecy and whether this perception is warranted.
Media Control and NDAs – Protecting Power or Ensuring Silence?
The Strategy of Silence in Crisis Management When powerful organizations face potential scandal or crises, the first line of defense is often control—control over the narrative, control over information, and control over public perception. This strategy, while effective in mitigating immediate damage, can backfire by fostering an aura of secrecy that leads to suspicion. Disney, like many other global corporations, has historically employed these tactics, particularly through the use of non-disclosure agreements (NDAs) and strategic public relations (PR) campaigns. But do these measures protect legitimate corporate interests, or do they simply fuel theories that there is more being hidden?
Understanding the Role of NDAs NDAs are legal tools designed to maintain confidentiality and protect business interests. In most cases, their use is standard practice, whether to protect trade secrets, secure settlements, or manage sensitive internal matters. However, when NDAs intersect with scandals involving powerful individuals or organizations, they can become symbols of enforced silence. A report from the Harvard Business Review highlights that while NDAs are often employed for legitimate purposes, their misuse—especially when used to silence allegations of misconduct—has cast a shadow over their intent.
Disney has used NDAs in its corporate dealings, as have many in the media and entertainment sectors. This is not in itself suspicious; however, the mere presence of NDAs in a company’s arsenal can contribute to a narrative of secrecy, especially when paired with limited transparency during controversies.
The Case of High-Profile Secrecy The Epstein scandal showed how the use of NDAs and strategic silence could be perceived in a different light. When influential figures and companies were linked to his circle, silence from those implicated was interpreted by many as an attempt to avoid deeper inquiry. While Disney has not been tied to Epstein’s activities through verified evidence, its use of NDAs in unrelated circumstances and its approach to handling public controversies have made it a recurring subject in theories about hidden truths.
For example, Disney’s meticulous control over its brand image means that it often handles internal issues privately, releasing carefully crafted statements that address public concerns without divulging specifics. This approach, while protective, sometimes has the unintended consequence of making the public wonder what is not being said.
The Intersection of PR and Public Perception Public relations are designed to safeguard a company’s image, ensuring that responses to any negative news are swift and tightly managed. Disney’s PR machine is among the most sophisticated, capable of steering narratives and maintaining its reputation as an entertainment titan. This strategic control has allowed Disney to weather crises that might have permanently damaged lesser brands. However, in the context of a scandal as sprawling and notorious as Epstein’s, such control is perceived differently.
When the Epstein story broke and high-profile connections came to light, companies with any tenuous ties activated their crisis management protocols. For some, this meant issuing vague statements or refusing to comment altogether. To the public, this read as silence—a strategic choice that seemed suspicious when paired with known instances of NDAs being used to keep serious allegations quiet in other industries. The #MeToo movement, for instance, revealed how NDAs were used by some media companies to shield powerful perpetrators of harassment, showing that these tools can sometimes contribute to a culture of concealment.
Silence as Complicity? For a company like Disney, known for its polished public image, silence during times of widespread speculation can amplify suspicions. The question becomes: Is silence an act of protection or complicity? While NDAs are often used to manage settlements or protect internal processes, the fact that they prevent full transparency can make even innocent parties appear as if they have something to hide.
Experts in crisis communication argue that silence may protect the brand short-term but can erode trust long-term. Disney’s approach to handling public perception, from managing employee misconduct cases to addressing larger social controversies, often involves strategic responses that give the public enough information to stay satisfied but not enough to quell the more skeptical voices. This is standard practice but becomes contentious when the public is searching for accountability.
The Impact of Strategic Silence on Public Trust Media and communication studies have shown that transparency is increasingly becoming a measure of trustworthiness for corporations. In an era where the public demands answers and alternative media thrive on filling in gaps left by corporate PR, the stakes for maintaining trust are higher than ever. The use of NDAs and controlled statements can protect a company’s interests, but it also contributes to a perception of secrecy that feeds public doubt.
Disney’s balancing act—protecting its brand while managing incidents behind closed doors—reflects a broader industry trend. Corporations that prioritize narrative control must now reckon with an environment where even a hint of concealment can lead to damaging speculation. The Epstein case amplified this issue, putting the spotlight on how major organizations handle proximity to scandal, even if only by association.
Navigating the Perception The real challenge for Disney and similar companies lies in navigating the fine line between protecting their interests and fostering trust. Complete transparency can be risky, but strategic silence risks becoming complicit silence in the eyes of the public. This duality—where necessary protection measures are perceived as proof of hidden wrongdoing—is why entities like Disney find themselves caught up in discussions about figures like Epstein, despite the absence of concrete evidence.
The Takeaway for Institutions and the Public Understanding the role of NDAs and PR in managing public crises helps frame why powerful companies might become targets of suspicion. While the use of these tools is standard and often justified, their impact on public perception can’t be ignored. For the public, recognizing the difference between warranted inquiry and overreach is key to maintaining productive scrutiny without falling into the trap of baseless theories.
The next segment will focus on what these perceptions mean for society as a whole and why the pursuit of transparency and trust must be a collective endeavor.
Beyond the Shadows – A Call to Unity
The Complex Path to UnderstandingIn an age where trust in powerful institutions is fraying, and access to information is both a blessing and a burden, our approach to truth becomes more critical than ever. The discussions surrounding figures like Jeffrey Epstein and corporations like Disney are not just about scandal; they are about how we, as a society, confront power, secrecy, and transparency. This segment is a call to unite in the pursuit of truth—not through a divisive lens, but with collective discernment and an unwavering commitment to evidence and integrity.
The Lessons from HistoryHistory teaches us that institutions once seen as untouchable can harbor hidden truths. The exposure of corporate frauds, systemic abuses, and cover-ups within trusted sectors has shaped a society that questions everything. The Epstein scandal underscored this, revealing a network of power that reached further than many dared to imagine. Yet, while it validated the public’s instinct to question, it also highlighted a key challenge: differentiating between grounded inquiry and baseless theory.
Disney’s name appearing in speculative discussions about Epstein points to a broader pattern—our collective desire to ensure that those who hold power are not above scrutiny. But as we demand accountability, we must also unite in the practice of informed skepticism. The leap from isolated cases of misconduct or association to implicating entire organizations requires evidence, not just conjecture. This distinction is where we, as a society, must find common ground.
The Role of TransparencyTransparency has become the cornerstone of public trust. Organizations that handle controversies behind closed doors risk damaging their credibility. For companies like Disney, known for protecting their brand with meticulous care, the challenge is clear: find a balance between safeguarding legitimate interests and providing enough transparency to maintain public trust.
The use of NDAs, strategic silence, and controlled narratives may shield brands in the short term, but they can erode trust in the long run. Studies in crisis communication emphasize that openness, even when it exposes vulnerabilities, can reinforce loyalty and confidence among stakeholders. In the context of Epstein and the persistent whispers about powerful corporations, this lesson is especially relevant.
A Collective Call to ClarityThe pursuit of truth is not just the responsibility of journalists, whistleblowers, or industry watchdogs—it is a collective endeavor. The public plays a crucial role in this, but so do the corporations that hold sway over cultural and economic landscapes. When Disney’s name enters speculative discussions, it reflects a deep-seated desire for transparency from those we trust. This desire should be met not with fear of the unknown but with a commitment to clarity.
This segment is a call for unity in approaching these conversations. The balance between healthy skepticism and conspiracy theory is delicate but essential. We must ask hard questions and hold power accountable without losing sight of what separates substantiated fact from assumption.
Why Unity MattersIn times where speculation can divide and misinformation can spread faster than verified facts, unity in the pursuit of truth is vital. When we allow fear and uncertainty to fracture our approach, we weaken our collective power to bring genuine issues to light. Epstein’s case showed that hidden wrongs do exist and can involve the most influential figures. It also showed that uncovering the full scope of such wrongs takes a community committed to patience, evidence, and shared purpose.
Public scrutiny is essential for democracy and social justice, but so is discernment. When theories about organizations like Disney arise without evidence, they risk diverting attention from real, proven issues that demand action. Unity in seeking truth means supporting real investigations, demanding transparency, and recognizing the power of evidence-based inquiry.
Building a Culture of Informed AccountabilityThe goal is not to silence questions but to elevate them, ensuring that they are grounded in reality. This approach not only empowers the public but also sets a standard for institutions. If Disney and other corporations prioritize transparency, they can reinforce the public trust that sustains their brands. Similarly, when the public insists on evidence and integrity in its discussions, it strengthens the very fabric of accountability.
Reflections for the Road AheadAs we move forward, let us commit to being a society that seeks truth not for scandal’s sake but for justice and integrity. Let us stand together in holding power to account, using facts as our foundation and unity as our strength. The story of Epstein and the questions it raises about power, influence, and hidden truths are reminders that transparency and trust are not just corporate responsibilities—they are collective ones.
This call to unity is a reminder that we all play a part in shaping how these stories unfold. When we seek, question, and demand clarity together, we create a society that values truth over rumor, evidence over assumption, and justice over division.
As we conclude this exploration, may we carry forward the lessons learned: the importance of questioning with integrity, seeking truth with diligence, and facing the unknown not as individuals, but as a united community.
-
 @ d058ffb7:70ed2330
2025-02-12 02:25:09
@ d058ffb7:70ed2330
2025-02-12 02:25:09Afin de profiter de tous les bienfaits du bitcoin, il est recommandé d'en prendre le réel contrôle, qui ese résume à posséder ses propres clés privés. Pour se faire, on doit utilise un portefeuille bitcoin.
À l'opposé, il y a les solutions de type "gardien de valeur" (ou "custodial"), tel que Coinbase, Binance ou ShakePay, pour lesquels vous n'avez que "des bitcoin sur papier".
Une portefeuille bitcoin doit au minimum permettre de : * Générer des clés privés, principalement via le concept de 12 | 24 mots secrets. * À partir de cette clé privée, dériver les clés publiques (ou "adresse bitcoin") * Signer et diffuser de nouvelles transactions * Afficher le solde des bitcoins
Pour la majorité des cas d'utilisation, des applications mobiles sont suffisantes. Il y en a plusieurs dont l'offre de service peut différer.
Pour profiter d'un maximum de fonctionnalités, il est avantageux d'utiliser un logiciel complet, sur PC, qui peut se connecter à son propre nœud ou utiliser un nœud public. Le logiciel Sparrow Wallet est souvent cité comme exemple puisqu'il est complet, convivial et open-source. Ce guide sert de point de départ pour apprendre à l'utiliser.
Téléchargement
À partir du site officiel, téléchargez la version qui correspond à votre système d'exploitation (Windows, Mac ou Linux).
Avertissement : le bitcoin et les cryptomonnaies en général sont des cibles de choix pour les fraudeurs. Vérifiez bien d'être sur le bon site (par exemple, en se fiant à son concepteur @craigraw) et évitez les sites commandités par les moteurs de recherche.
Vérification du logiciel
Cette étape est facultative mais pour éviter les attaques de type "man-in-the-middle", où un fraudeur va remplacer la version officielle par une version frauduleuse, il est recommandé de vérifier l'exactitude intégrale du code, via une "stratégie PGP" (Pretty good privacy).
Depuis peu, cette étape est seulement nécessaire pour le premier téléchargement de Sparrow Wallet puisque le logiciel offre une nouvelle fonctionnalité de validation simplifiée, expliquée sur la page de téléchargement. Pour la façon traditionnelle, les étapes détaillées sont disponible sur cette même page.
Installation
Sur Windows, vous n'avez qu'à télécharger le fichier .exe et à l'exécuter.
Connexion à un nœud public
Si vous lisez le présent guide, il est probable que vous ne mainteniez pas un nœud bitcoin local. Sparrow Wallet offre la possibilité de se connecter à un nœud public, via une liste d'adresses préfiltrées, disponible dans les paramètres de connexion.
Création d'un nouveau portefeuille bitcoin
Pour un premier portefeuille, un portefeuille de type native segwit est adéquat. Ce type est un compromis entre les adresses legacy et le nouveau protocole taproot. Il vous permet déjà de profiter d'économies sur les frais de transactions.
Vous pouvez appliquer les changements pour créer un nouveau portefeuille, puis choisir le mode de création de la clé privée. L'utilisation de plusieurs mots, via BIP39, est la stratégie la plus répandue et qui a faite ces preuves.
Vous pouvez choisir d'ajouter une passphrase, que vous pouvez choisir et qui joue le rôle de mot supplémentaire. Il est essentiel de le connaitre pour pouvoir signer des transactions ou encore restaurer votre portefeuille.
Vous devez ensuite prendre ces mots en note car il vous sera demander de les réinscrire pour les valider.
Une fois vos mots confirmés, vous pouvez confirmer la valeur par défaut pour le chemin de dérivation, puis appliquer les changements. Enfin, vous pourrez ajouter un mot de passe au besoin.
Recevoir des bitcoin
Avant d'envoyer des bitcoin, vous devez en avoir déjà reçu dans votre portefeuille. Pour cela, vous pouvez cliquer sur "Receive" pour afficher la prochaine adresse inutilisée. Pour des raisons de sécurité et de confidentialité, il est recommandé de toujours utiliser une adresse différente. Dans la section "Transactions", vous verrez plutôt toutes les adresses disponibles, incluant celles utilisées pour le change. Vous pouvez alors utiliser ces adresses dans l'application ou il y a les fonds.
Envoyer des bitcoin
Maintenant que vous avez des bitcoin, vous pouvez voir votre solde dans la section "Transactions". Si vous allez dans la section "Send", vous pourrez créer une nouvelle transaction. Pour les intrants à cette transaction, Sparrow Wallet peut choisir en fonction de l'efficience (coûts) ou de la confidentialité. La section "UTXO", qui exposent vos transactions non dépensées, permet un contrôle manuel des intrants à une transaction.
Une fois créée, la transaction devra être signée (avec votre clé privée), puis diffusée (broadcaster) sur le réseau.
Explorer la chaîne
Vous ne voyez toujours pas votre transaction ? Vous êtes curieux de voir ce qu'il se passe sur le réseau bitcoin. Alors allez jetez un coup d'oeil à mempool.space. Dans la boîte de recherche, vous pouvez y coller votre transaction ou votre adresse et confirmer l'état de la transaction. Vous pouvez également valider que votre portefeuille est à jour y en comparant la hauteur (ou numéro de bloc).
Restaurer un portefeuille
Vous avez trouver 12 mots et voulez tester si ça cache quelque chose ? Perdu votre cellulaire avec votre application mobile mais vous avez vos 12 mots ? Il est alors possible de restaurer un portefeuille en utilisant la fonctionnalité de création mentionnée plus haut. Cette fois-ci, plutôt que de les générer automatiquement, vous n'avez qu'à saisir les mots pris en note et le passphrase s'il y a lieu. Il est prudent de considérer ce portefeuille comme étant corrompue ou comme ayant fuité et d'en créer un nouveau puis d'y transférer les fonds.
Avec ces instructions, vous devriez avoir la fondation nécessaire pour faire vos premières transactions sécuritairement. Dans les prochains guide, vous verrez comment utiliser une Coldcard, soit une portefeuille physique qui permet de créer la clé privée hors-connexion, ainsi qu'un OpenDime, une clé à usage unique.
Si vous avez des commentaires, vous pouvez m'écrire sur X (anciennement Twitter) @lekingfu ou par courriel au bitcoin@lekingfu.com.
-
 @ 7ed7d5c3:6927e200
2024-12-03 15:46:54
@ 7ed7d5c3:6927e200
2024-12-03 15:46:54Shall I compare thee to a summer’s day? Thou art more lovely and more temperate; Rough winds do shake the darling buds of May, And summer’s lease hath all too short a date;
Sometime too hot the eye of heaven shines,
And often is his gold complexion dimm’d;
And every fair from fair sometime declines,
By chance or nature’s changing course untrimm’d;
``` But thy eternal summer shall not fade Nor lose possession of that fair thou owest; Nor shall Death brag thou wander’st in his shade, When in eternal lines to time thou growest;
So long as men can breathe or eyes can see, So long lives this and this gives life to thee. ```
-
 @ b8a9df82:6ab5cbbd
2025-02-11 18:42:35
@ b8a9df82:6ab5cbbd
2025-02-11 18:42:35The last three weeks have felt like a dream—one I don’t want to wake up from. But here I am, on my last day in El Zonte, sitting by the ocean, doing what I love most: watching the waves roll in, surfers gliding across them, some catching them effortlessly, others tumbling but always getting back up. It’s a blessing to be here, soaking in the tranquility, reflecting on the past few weeks while finally sitting down to write about this incredible journey.
Reflecting on this experience, I realize how few people get to live something like this, and I am deeply grateful. Living by the ocean has always been a dream of mine, and these last few weeks have been nothing short of magical. The thought of saying goodbye? Not something I want to entertain. In a world where you can be anything, be kind, be grateful, and cherish the little things—the laughter, the small victories, the unexpected moments of pure joy.

Mexico—a country I was always warned about. "It’s dangerous," they said. "Drugs, crime, food poisoning, even kidnappings. A woman shouldn’t travel there alone." But despite the fear-mongering, after almost three months in South America, I was craving the ocean, and I kept hearing about Mexico’s stunning beaches. A little spoiler: I did see the beach… but it rained almost every day, and my toes barely touched the water.
With three options on the table—Tulum, Holbox, or Isla Mujeres—the decision wasn’t too hard. There was a crazy woman trying to Bitcoinize an entire island, and I had to see that for myself.
Just 13 kilometers off the coast of Cancún, Isla Mujeres is a tiny Caribbean paradise—perfect for unwinding and recharging. The island is wonderfully walkable, which I love. No need for a car. I even went for a few runs, and with the island stretching just 7 km in length, I got to explore its hidden oceanfront gems in no time.
But let’s talk about the journey. Arriving in Cancún after a long, exhausting flight, I was hit by chaos at the airport. Dozens of people aggressively offering rides, each one claiming to be a cab driver—it was a nightmare. Not speaking Spanish made things even harder, but thankfully, I wasn’t alone. After dodging the taxi mafia, getting stopped by the military for a random checkpoint (because, you know, legal taxis are apparently a thing to be double-checked), and making a pit stop in Cancún, we finally reached Isla Mujeres—greeted by storms and rain. But none of that mattered. I was here. I was at the ocean. And I was excited.
We stayed at Mayakita, a beautiful villa-style co-living space where you share the common areas—kitchen, coworking space, and outdoor lounges—but still have your own private room, bathroom, and balcony. Oh, and did I mention there’s a Jacuzzi? Absolute win.
The Mayakita team is even building a gym, which is a relief because the local options on the island were… let’s just say, unusable. Picture a tiny, overcrowded room packed with sweaty bodies, zero space between machines, and a never-ending queue for every piece of equipment. Nope. Not for me.
But the real highlight? The incredible restaurant attached to the villas. The food was an explosion of flavors—true mouthgasm territory. And, of course, you could pay for everything in Bitcoin.

To my surprise, I ended up staying with @nostr:npub1aftmyhm62lrp6lwsha3yzyjy5kqdvuy7g23qg28a8q0cnmudv0ds0sdcke the woman leading the Bitcoin adoption movement on the island. That’s when the craziness really started. The villa next door was booked by a couple of Bitcoiners, and as soon as they found out we had arrived, one of them knocked on our door. A warm smile, a little dog in his arms, and a simple, "Hey, need anything? Food? Help? A bottle opener?"
That’s what I love about this community. The energy, the kindness, the openness—it’s next level. You won’t get that at a typical resort, where people keep to themselves. Here? Instant bonding.
We spent the week exploring the island, asking every restaurant and shop if they accepted Bitcoin. If they didn’t? We walked away. Thanks to Isabella’s hard work, some businesses already do, and one of the highlights? Paying for a tattoo in Bitcoin.
One downside, though—transportation. Even though the island is walkable, taxis and golf carts are available for rent. But renting a golf cart for a week? A whopping $1,000! Insane. Luckily, Isabella had a tiny tuk-tuk, so she packed a few of us into the back and drove us around. No lights, barely any air, and a very bumpy ride. Did we survive? Yes. Would I do it again? Debatable. But hey, it was an experience!

Waking up every morning to the ocean was pure magic. The food? Unbelievable. The freshness of the vegetables, fruit, and fish—something you just don’t get in Germany. Even though I had the most expensive lunch of my life (let’s just say we spent way too much on ceviche and a main course), it was worth every cent.
This week taught me something valuable: You don’t need to be in the Bitcoin space for years to make an impact. I get it—long-time Bitcoiners might find it frustrating that adoption seems "easier" now. But I wouldn’t call myself a Bitcoiner just yet. I still have so much to learn. There were moments when I had no clue what people were talking about, even after all those private lessons, hours of talking how a lightening network works, what a hash is and that your 12 - 24 words, the so called private key is actually the master key that can generate an entire tree of private keys. But I’m incredibly lucky to be surrounded by people who are patient, willing to share their knowledge, and never get tired of explaining things again and again.
If I had to sum up this week in one phrase, it would be ridiculously beautiful and painfully peaceful.
If you love what Isabella is doing and want to support her work, consider sending her some sats.
All pictures taken by @nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5
-
 @ 43baaf0c:d193e34c
2025-02-11 08:46:45
@ 43baaf0c:d193e34c
2025-02-11 08:46:45I attended Sats ‘n’ Facts to share my art, joining other Nostr artists in exhibiting our work at the event’s very first venue. It was a great opportunity to connect with fellow creatives, including Siritravelsketch, whose work I’ve admired on Nostr for some time. Meeting other artists in real life is always inspiring—there’s an undeniable creative bond that comes from sharing our passion in person.

Sats ‘n’ Facts is an Unconference, meaning there’s no strict schedule—everything is open for participants. It’s all about the connections made, the synergy shared, and, for the developers attending, the excitement of a hackathon. (A hackathon is an event where people collaborate intensively on engineering projects, often within 24 to 48 hours.)
My goal as an artist is to become a bridge between the Bitcoin tech world and the Bitcoin art and design space. Bitcoin empowers us by providing greater (financial) freedom, and with that freedom comes more time to pursue what we truly love—so in a way, you never have to “work” again. 😊
 Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.
Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.
 Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.
Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.
 Can’t wait to join the next Sats’n’facts. Maybe Barcelona!?
Can’t wait to join the next Sats’n’facts. Maybe Barcelona!? -
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ bbb5dda0:f09e2747
2025-02-11 05:19:58
@ bbb5dda0:f09e2747
2025-02-11 05:19:58There's nothing like the ability of a Nostr/Bitcoin meetup to bring your bullish-ness back to a 120%. This weekend I had the honors to be part of the Sats 'n Facts conference so this update will be mostly about the conference.

Tollgate
A while ago while still at SEC I got the invitation to go to Sats 'n Facts and tell something about TollGate, which I was working on at the time. This is the reason I made such a push on the TollGate Android app, because I wanted to show the world the potential implications of this technology when applied in practice. We get the ability to build our own (physical!) sovereign network infrastructure. Maybe it doesn't sound too sexy for rich western countries, but very valuable for regions with lacking digital infrastructure, or regular powercuts (something I learned at the conference, that TollGate could be applied to bridge those).
 Above: Illustration how a TollGate network connects to the legacy internet.
Above: Illustration how a TollGate network connects to the legacy internet.I did a presentation about the project and did a demo, which as the universe commands, suffered from the demo-effect. Despite that, it was very well-received and the feedback and ideas on how and where to apply this were amazing. From splitting your bill with your neighbour, to strapping 5g-enabled routers to a light-fixture in the city, everyone had their own ideas on how to use it, and the cool thing is that all of it can be done.
Presenting GitHub Actions & Epoxy
I held a seperate session on the GitHub actions project and Epoxy. The response was great and I have some more feedback coming in a 1-on-1 session, so I'm sure i'll be posting about that in the near future.
A realization about Epoxy + TollGate
The more I talk about Epoxy and TollGate, the more I realize how much they are related. Epoxy is a way of bridging connectivity between Nostr users that are on clearnet and want to connect to Relays that are on Tor. But rather than just bridging the captured clearnet and tor, it can be the bridge between clearnet and a community TollGate network, or between different TollGate networks.
As I've thought more about the implications of sovereign TollGate based networks, I think the introduction of many TollGate networks might create a fracturing of the broader internet, which I'd argue is not even a bad thing as this fracturing can reduce centralized surveillance and control. If we'd do this within the conventional way of operating services - think API's & talking directly to servers- that would be a problem as we need to reach those servers at any moment in time. But given the decentralized Nature of Nostr messages + Blossom files, you might not even notice it if your geographical region gets cut off from the rest of the world, because the content likely already exists within your -now cut off- network.
If we can get our content local, why wouldn't we embrace this fractured internet and use it in our advantage.
nostr:naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq3k2ur00puj6mt0dejhg6t6v93xcefdwajkyum0vd4k2apdwpex77rfv4esk0qk8g
A final word
I'm incredible grateful to be meeting all these talented developers, artists and community builders! I love to see art being integrated into the broader ecosystem and I think us dev's need to lean on the community builders to get our projects out into the world, they often have the insight on how our software shapes the lives of the communities they help to grow. Let's embrace that dynamic!
special thanks to nostr:npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu for his incredible drawings of the presentations: nostr:nevent1qvzqqqqqqypzpr2m4ykgej3at3ee9upe82c4h58uda35xfd5292purmuntrv8mx4qqsfr9f9kvta87yukqhedc00vckupu3erx3mk3nvxm28ptfak0acgrc6adj94

-
 @ fd208ee8:0fd927c1
2024-11-28 12:50:49
@ fd208ee8:0fd927c1
2024-11-28 12:50:49GitHub is a software project graveyard
I think the main reason why we have so many lone wolf devs is an economic one. The fact that most FOSS devs aren't being paid for their code is making this worse, not better, as they work for fame, not fortune.
Nobody wants to use joint-repos because they don't want to give up or share the property rights to the contents. But because anything someone else does in a repo you own, also belongs to you, people are disincentized from contributing to your repo.
GitHub, especially, has incentivized this splintering and isolation. Everyone wants to have all changes in their own repo because they can profit best on repos listed directly under their own name, so long as they become popular. Maximize your 🟩 and ⭐ , like chips you can cash in for a prize.
And because forking other people's repos is the norm, rather than teamwork, requests for changes are usually ignored or responded to with "fork it, bro." Go away. Leave me alone. My repo is none of your business.
Too autistic, even for me
So, the developers separate their efforts into a million tiny repos that are mostly redundant with other ones, there's little interaction, progress is often surprisingly slow and stalls for months at a time, it's hard to keep track of what other people are doing (so that you can review and test changes), most of the effort is headed straight for the bin, people build the same things over and over, and communication is extremely limited.
This is a work environment that is unattractive for anyone who isn't autistic and/or highly introverted. Half of the fun of open-source development used to be the esprit de corps. Much has been said about #Bluesky, but it all misses a major point: that's where you go, if you want to work with other people, to build something large, polished, and impressive. It doesn't actually matter how many developers Nostr has, if they all only stare at their own plates.
Your repo coulda been a file folder.
Ironically, git was developed for collaboration on large projects with a distributed team. Now, everyone uses it for projects they work on alone. They put those projects on the Internet to market them. It's a cheap gimmick, not an earnest attempt at collaboration. Collaboration begins at the beginning.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ fd208ee8:0fd927c1
2024-11-21 07:24:34
@ fd208ee8:0fd927c1
2024-11-21 07:24:34The motherhood illusion
Growing up, I was always told that women wanted children, whilst men wanted sex. So, marriage was created, to unite these two urges, and men and women don't otherwise particularly differ. But, it turns out, that women want protection and sex, and men want children and sex.
This is why women tend to be attracted to more masculine men (they're associated with protection) and men tend to be attracted to more feminine women (they're associated with motherhood). Women who are attracted to men, who aren't overtly masculine, are looking for a different aspect of protection (reliability, steady income or wealth, emotional security, etc.)
This wasn't readily apparent, in earlier generations, as widespread, youthful marriage meant that there weren't any real decisions being made by the participants. Almost all women got married and had kids, and almost all men got married and had sex. Math checks out. But the number of women who could protect and provide for themselves was low, and the men marrying were often very young and libidinous, and not yet contemplating their own legacy.
Feminism, easy abortion, deindustrialization, delayed marriage, and reliable contraception have dissolved this illusion, completely. Millions of Western women quickly turned into cougars, careerists, party girls, and e-girls, and an entire army of childless men and sidelined dads bubbled up and began to make their pain known. Humanity's dirty underbelly has been exposed.
Women aren't as sweet, as we thought, and men are much sweeter.

Women also want children, but not as intensely. In fact, they seem to often viscerally dislike children, and are jealous of the protection they are to give them. So, they are prone to offing their offspring because they are averse to having any in-house competition.
If you just left women up to their own devices and reduced the social pressure, at least a fifth of them wouldn't bother having children, at all, and another quarter will have one and then lose interest or age out. This is not a new phenomenon, as we can see.
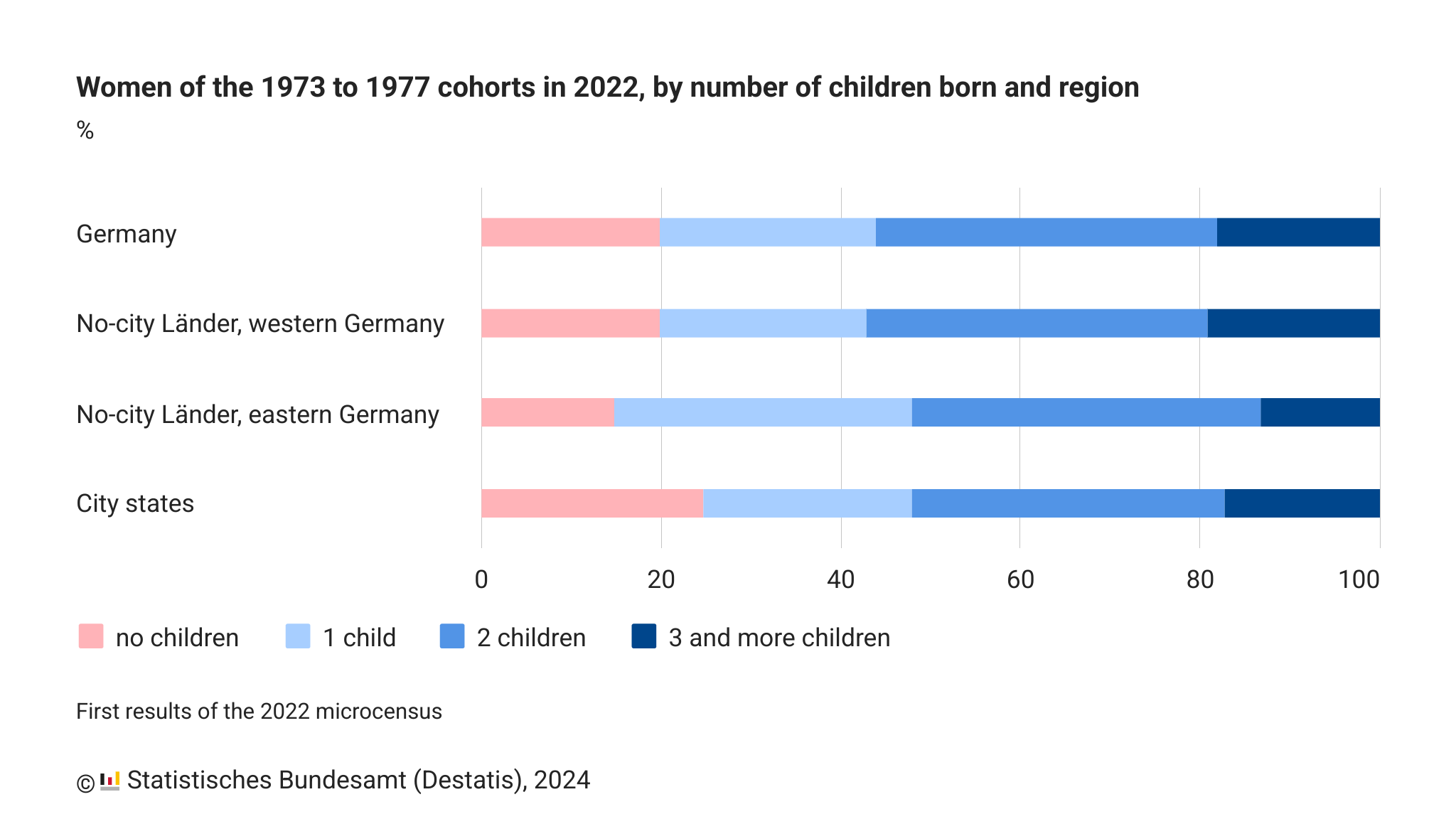
The male competition for potential mothers turns out to be absolutely brutal, and more difficult than simply finding a woman to sleep with. And, now, we finally understand why men traditionally jumped through so many hoops, to attain a wife. It wasn't for the sex; we've always had brothels, masturbation, and pornography. It was for the familial comfort, and, especially, for the children.
Good fathers make good mothers
Some women don't know if they are "potential mothers", until they meet a "potential father", and their urge to procreate suddenly kicks in. They didn't want children for their own sake, but now they want some for his sake. All of a sudden, they're imagining themselves rocking the cradle, googling "what to eat, when you're expecting", and find themselves gushing over anything that gives off Hint of Infant.
I'm pregnant! Look what I can do! Look what I can do! For you, darling.

Women married to men they are deeply in love with, are much more likely to desire to become mothers (and be devastated by infertility), and make for better mothers, because children are like individualized presents they can give to their husband.
They want to impress him. Most want to be decent parents in their own right, but the urge to impress seems to raise this to a much higher level because women are vain, and therefore focused on raising their own status and how they appear to others. And the greatest "other", of a happy wife, is her husband.
Because men are narcissistic, and therefore in love with anything associated with themselves (which underpins their obsession with owning property), men have an intense attachment to their children. What is more "yours", than your progeny?

Fathers seem to develop a special attachment to, or fondness for, the mothers of their children, that goes beyond lust or romantic love; they never forgot who gave them this new Mini Me. And they are often quite impressed by their own ability to perform this trick numerous times, which leads to the intense satisfaction they feel at "going into serial production" and churning out more of those Mini Mes until their adoring wife pleads for mercy.
Men want children. Women, who love a man, want to give him those children and gain the fidelity that comes along with those children. This is the actual "trade" underpinning the urge to marry.

-
 @ aade47fd:281e8e4f
2025-02-11 00:45:18
@ aade47fd:281e8e4f
2025-02-11 00:45:18На этот раз для того, чтобы сделать ежедневную запись потребовалась всего одна неделя, а не две, как в прошлый раз. Я не собираюсь останавливаться!
Личность
На этой неделе в коротких заметках я упомянал свою новую концепцию личности. Это структура, которая лежит на границе между мной и внешним миром. Эта тема волнует меня в эти дни, так что я хотел бы поговорить об этом подробнее. Есть экзистенциальный, неизменаный, самотождественный Я, есть трансцендентный внешний мир, а есть структура, по которой между этими частями происходит взаимодействие — личность. На внешний мир я имею опосредованное влияние, не подразумевающее прямые изменения и контроль, а вот личность лежит в поле моей ответственности. Можно даже сказать, что больше никакой ответственности и не существует. В любой момент времени я могу принять решение о том, чем будет наполнена моя жизнь. Что я буду впускать в нее, а что отсеивать. И наобоот: я несу ответственность за то, что транслирую в окружающий мир, какое влияние имею. Формирование личности это комплекс из аксеологических ( ценностных) и праксиологических настроек. Задача состоит в том, чтобы сделать добродетель своей привычкой. Как стать хорошим человеком? Что это значит конкретно? Что мешает стать хорошим человеком? Не простые вопросы. Предлагаю пойти от обратного: может ли хороший человек "распуститься"? Полагаю, да. Это значит, что поддержание личности в форме требует постоянного усилия. А еще можно было предствить себя безупречного и попытаться почувствовать, какие актуальные привычки и настроения помешали бы тебе удержаться в этом состоянии долго. Я считаю эту работу наиболее важной. Чем более конкретно человек способен описать собственные амбиции, тем больше в жизни энергии и меньше мусора.
Философия
А кто я, собственно, такой, чтобы придумывать словам новые значения? Вот есть же определение для личности из словаря. Зачем людей с толку сбивать? А дело все в том,, что словарное определение никаким образом мою жизнь не обогащает, оно для меня бесполезно. Бесполезное слово (бессмысленное) слово — тупой нож. Кто принял решение жить своей жизнью (то есть, просто жить), тот называет вещи своими именами, а не руководствкется букварем с картинками. Работу над собственным языком я называю философией, а человека, нашедшего в себе смелость жить своей жизнью — философом.
Воспитание
Никогда не замечали, что все специалисты (люди, посвятившие себя только одному виду деятельности) одинаковы между собой? В то же время не найдете двух одинаковых людей в междисциплинарном пространстве. Я смотрю по сторонам и нахожу все больше подтверждений тому, что чем в большем числе направлений развивается человек, тем болеше шанс, что в любой из них он окажется выдающимся. Специалисты нужны экономике, государству, обществу, но только не самим себе. Полноценное воспитание подразумевает развитие в максимальном количестве направлений. Похоже, это не просто античный идеал или идеал эпохи возраждения, а природа человека. Самая тяжелая детская травма, о которой все молчат, это вопрос "Кем ты хочешь стать, когда вырастешь?". Безупречным я хочу стать, ограниченный ты идиот.
На сегодня все! До завтра!
-
 @ fad5c183:5cb8046b
2025-02-10 17:46:03
@ fad5c183:5cb8046b
2025-02-10 17:46:03The Big Question: What Really Supports Bitcoin? Let’s cut the fluff. Money has always needed something to back it. In the past, it was gold, something tangible, scarce, and universally recognized as valuable. Then came fiat (government-backed currency), which ditched gold in favor of trust in central banks.
Now, Bitcoin is here. It’s digital, decentralized, and allegedly free from manipulation. But is it? If Bitcoin isn’t backed by gold, oil, or government decree, what gives it value? And if a small number of players hold most of it, are we just recreating the same problems as fiat?
Let’s dig in.
Why Bitcoin Has Value (Even If You Can’t Touch It) Bitcoin is backed by math, code, and energy—not physical resources. Its value comes from three major factors:
- Scarcity – Only 21 million BTC will ever exist. No central bank can “print” more.
- Security – It’s protected by cryptography and (proof-of-work). Hacking the Bitcoin network is practically impossible.
- Market Trust – Bitcoin is valuable because people believe in its ability to store value, just like gold or fiat.
Unlike government money, where supply is controlled by a central authority, Bitcoin’s supply is fixed and transparent.
Sounds great, right? Well, there’s a catch.
Are We Just Repeating the Fiat Problem?
Fiat money is flawed because central banks can print it endlessly, manipulate interest rates, and control its flow. This causes inflation, bailouts, and financial crises.
Bitcoin fixes that. No one can create more Bitcoin out of thin air. But here’s the issue:
A small number of people and institutions own a huge percentage of Bitcoin. These “whales” can manipulate price movements, just like big banks do with fiat. Unlike fiat, where governments intervene (for better or worse), Bitcoin markets are unregulated and volatile. So, if whales can dump Bitcoin to crash prices and buy back cheap, is it really that different from fiat where the rich get richer?
Bitcoin’s Advantage: Transparency & Control
Here’s where Bitcoin still wins:
✅ No Central Control – Governments and banks can’t change its monetary policy. ✅ Transparency – Every transaction is on the blockchain. No hidden “money printing.” ✅ Self-Custody – You can hold your Bitcoin, unlike fiat, which sits in a bank that can freeze or seize it.
But let’s not pretend it’s perfect. If the majority of Bitcoin remains concentrated in a few hands, it still creates power imbalances.
The solution? More decentralization—and that’s where Nostr comes in.
How Nostr & Bitcoin Could Change the Game
Nostr is a decentralized communication protocol. No servers, no censorship, no single point of control.
When paired with Bitcoin and the Lightning Network, it could:
- Enable truly peer-to-peer transactions without banks or centralized exchanges.
- Reduce whale manipulation by increasing adoption and distribution.
- Support a free, censorship-resistant financial system without intermediaries.
Imagine a world where you don’t need banks or corporations to transact—just an internet connection. That’s where we’re headed.
Final Thought: Are We at Square One?
Bitcoin isn’t a perfect solution, but it’s a step forward. It removes central banks from the equation but still struggles with wealth concentration and market manipulation.
So, are we just recreating fiat 2.0? Maybe in some ways. But here’s the difference:
The rules can’t be changed by elites in a closed room. Every transaction is visible—no shady money printing. Anyone can self-custody their assets—no middlemen needed. The key to breaking the cycle? More decentralization, better distribution, and adoption beyond whales and institutions.
Bitcoin is a tool. It’s up to us to use it wisely.
What do you think? Are we just repeating history, or is Bitcoin truly different? Let’s debate. 🔥
-
 @ 6389be64:ef439d32
2025-01-13 21:50:59
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ df478568:2a951e67
2025-02-16 17:10:55
@ df478568:2a951e67
2025-02-16 17:10:55I asked a pleb to answer a few questions about selling stuff for sats, and he asked me, "What made you want to do a story/article on this?"
The short answer: Because I like seeing people make their own bitcoin jobs, but the question made me think about the why. When I tried to be an English teacher, one of my professors said, "The difference between a job and a career is that a career is something you think about all day." I didn't become an English teacher, because I already had something I think about all day: bitcoin. I didn't fit the teacher ethos, for whatever reason, so undecided, I wanted to work in bitcoin sometime around block 525,000.

That's about the time I began writing on yalls.org. I fell in love with the idea of writing for sats. It was too early. Very few people used lightning back then, but the idea of earning sats to write was invigorating. I had no illusions of earning enough to earn a living, but yalls had a paywall. I spent a fair amount of time experimenting with these paywalls. Part of my articles were available for free, but to finish the article required a payment of 210 sats when that was about two cents. I was fascinated with this concept because it meant I could write for sats. Readers could send p2p electronic cash to me—sats short for satoshis. Each bitcoin can be divided into 100,000,000 sats. The lightning network allowed people to send you micropayments.
Yalls

This was not possible with credit cards because of the fees they charge. The lightning network can be used to circumvent fees imposed on credit card merchants and the sats can now be instantly converted to fiat. This is not financial advice. Earning bitcoin is 21 million times more interesting than trading bitcoin. Investors talk about green dildos, red dildos, and some other sex toy called a bollinger band. If you're into that kind of kinky stuff, I don't judge, but I stay vanilla and stack sats. I experimented with shitcoin play in younger years, but it was just a phase. I finally realized alts are an attempt to break the solution to the double-spending problem sometime around block 630,000.
That's when I declared myself a bitcoin maxi on yalls.org. Adam Back retweeted it. It didn't go viral, but that was amazing. I'm just an anonymous user who couldn't get an English teaching job, but Adam Back...You know..The guy Satoshi cited in the white paper—That guy retweeted my article. I started a couple of anonymous blogs and earned a small amount of sats in the early days of nostr.
How I Made 1,000,000 Volunteering At Pacific Bitcoin
I volunteered for Pacific Bitcoin 2022. I volunteered to save some sats on a ticket. I stayed in a hostel. I did not expect to get paid, but it earned me a million sats after I sold the pack of collectible cards that came in a swag bag at the conference. What if I can one day retire on the millions of sats I earned over the last few years? I'm not sure that will happen, but it might be enough for my grandchildren to retire. *If bitcoin goes up "forever Laura..." you're never too late to earn bitcoin on the side. The sats you earn go up in value forever.
Maybe the ROI on your college degree didn't pay off like you thought it would. You read Walden and Civil Disobedience and A Letter From a Birmingham Jail...thought...these are great ideas. They prepared me to read Early Retirement Extreme. I also listened to Choose FI and decoded Mr. Money Mustache. Dave Ramsey says you should get a second job to pay off debt in a country where many people working two jobs are still getting into more debt. Maybe they should use that extra job to stack sats. Earning bitcoin feels different than buying bitcoin. It means earning money on the Internet without needing a trusted third party. PayPal and Patreon have been around for years. They are nothing new, digital middlemen.
Although the less technical often use bitcoin non-custodially, it's getting easier to take self-custody and use bitcoin as it was intended, p2p electronic cash. Why use eBay when you can have a garage sale on nostr? Even Dave Ramsey can sell stuff on nostr. He's been telling people to avoid bitcoin since it was $400. What if you sell your fancy clothes made in Bangladesh on nostr while instantaneously converting it to USD on Strike? You can send 1,000 fiat bucks to your checking account faster than a speeding Superman. You can get the garage sale money deposited to your bank account within a half-hour. I can't even drive to an ATM that fast! Transfer the money to a savings account that pays 0.01% interest. Baby Step 1 complete! You can take the instant fiat from your next nostr garage sell and pay your debt straight from the Strike App! This is NOT financial advice.
I could earn fiat on Poker Stars until the government took away my permission. I could earn fiat on Full Tilt, but they spent players' fiat and barely kept a fraction in reserve. The same is true of platforms. You can earn fiat on Twitter if you pay for the monthly Twitter lottery. American's can currently earn fiat on TikTok...but do see where this is going? That's why I like supporting people who have some sort of bitcoin side hustle. I may have found bitcoin in 2014, but I didn't have a full-time job. I was unemployed for a couple of years before that. This one time, I got into an argument with my wife because, some months, we could only scrape up $50 to "buy bitcoin." I was an asshole. I kinda feel bad about that, but I'm a lucky guy with a beautiful wife who forgave me for being an asshole and dashing doors to stack bitcoin without telling her about it. She was pretty pissed. That Fifty bucks we argued over is now worth...
The misses is not so pisses anymore.😁
- I've picked up extra jobs to stack sats.
- I used BTCPayServer to stack sats.
- I stacked sats with lnbits
- I originally set up a lightning node so I could stack sats on yalls.org.
- It took me six months to get a lightning node up and running on a raspberry pi.
Few
Very few people used the lightning network back then. Any bitcoiner has the ability to make their own job. I started a blog and set up a BTCPayServer so people would pay me for my prose. Some actually did. It wasn't much money. I might have broken even, but the possibilities still intrigue me. You can use Alby Hub on the cloud, Zaprite, or run it on a Start9. You can pay GetAlby for a lightning node in the cloud. If you're a fiat-spending maximalist, you can convert all your bitcoin to fiat with Strike.*
Bitcoin Is For Everybody, Even Nocoiners
Maybe you don't want bitcoin, but need some extra cash and can make candles. Fiat won't hedge against eggflation, but that's not what this is about. That's not the point. Bitcoin is for anybody, even no-coiners. You don't even need to make a website anymore. You can just use Shopstr, Plebian Market, Coinos, Cashu.me, Buzz Pay, and more.I just bought some soap from someone I saw on nostr. I decided to try something new this month. I paid with fiat, but the soap miner received bitcoin on the other end. Anyone with the Strike App can pay dollars to people who want bitcoin and vice-versa. Some people proudly proclaim they never...ever...spend bitcoin. Those who hodl never sell.
In Everyone's A Scammer, Michael Bitstein says:
"Merchants are scammers because they lead you to believe that your bitcoins are only worth the price of their retail good in order to allow themselves (or those to whom they sell the bitcoins, if they so choose), rather than you, to benefit from future Bitcoin price increases. …And That’s a Good Thing This is not to say merchant adoption is bad. In fact, from the hoarder's perspective, merchant adoption is great. First, merchant adoption means that there is more demand for Bitcoin, that the Bitcoin network is growing, and that Bitcoin is thus more valuable than it was yesterday. Second, merchant adoption means there are more places to spend bitcoins. This does not mean a hoarder will actually want to spend bitcoins. More importantly, he can spend bitcoins.If you like this quote, [please zap this note. 100% of these zaps go to BitstienSaylor says bitcoin is hope, but you know what gives me hope? Not the billionaire buying bitcoin, but the pleb selling stuff for sats. - Maybe there's a homeless person selling a few used books for a meal. - Maybe an artist stacks $500 per month selling art on nostr. - Maybe a recently X government employee can sell DEI training on the free and open market on nostr. Or...Maybe they can sell culturally appropriate tamales on nostr for actual sats instead.
Those are the stories I want to find. Bitcoin is for everybody, even people with college degrees that the job market does not value much. Saylor's not wrong. Bitcoin is hope. Saylor said he wants to make education free. That's why he founded Saylor Academy. They have a course called Bitcoin Is For Everybody. Bitcoin is for everybody, even no-coiners, even for people who went to college even though it didn't lead to a high-paying job. Bitcoin is hope for those people, people just like me.
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
* Strike is an affiliate and I earn a small commision if you pay for the service. I use it to pay my credit card bills.
-
 @ 31da2214:af2508e2
2025-02-10 10:08:06
@ 31da2214:af2508e2
2025-02-10 10:08:06A global privacy nightmare is unfolding. The UK government secretly ordered Apple to backdoor encrypted iCloud storage worldwide—but Apple is legally forbidden from revealing this order, or they face criminal charges. This affects 2 BILLION USERS.
Here’s the full story & why it’s part of a much bigger power grab. 🧵👇 [Thread by @sayerjigmi on Thread Reader App]
1) The UK's Secret Order to Backdoor Encryption 🔓
Under the UK’s Investigatory Powers Act (IPA) 2016, Apple was served a Technical Capability Notice (TCN)—forcing them to create a backdoor for encrypted iCloud data.
This is not limited to UK users. It applies worldwide, meaning your private files are at risk, no matter where you live.
🔗 @macworld report
2) Apple’s Legal Gag Order 🤐
Apple is legally forbidden from revealing this order. If Apple even acknowledges that the UK issued this demand, they could face criminal charges.
This is a secret government order with global consequences.
3) A Global Threat to Encryption 🌍
This isn’t just about the UK (although they are leading the charge in threatening citizens in OTHER countries for violating BRITISH censorship laws!).
If Apple complies, every government in the world will demand the same access—from the US to China to authoritarian regimes.
End-to-end encryption would be effectively dead.
4) Apple’s Dilemma: Comply or Withdraw? 🚪
Apple has two choices:
- Comply & weaken encryption globally.
- Refuse & withdraw services from the UK.WhatsApp & Signal faced similar threats last year and vowed to leave the UK rather than compromise security. Will Apple do the same?
🚨 Watch the heated discussion between Damian Collins, director of CCDH (architect of the UK Online Safety Bill), and Signal’s CEO: YouTube Link
5) Why This Matters: Encryption Protects Everything 🔐
- Encryption protects financial data, health records, personal security (e.g., where you live or work), and private conversations.
- Governments always say they need backdoors for national security—but history shows they’re used for mass surveillance.
- Once a backdoor exists, hackers, rogue employees, and other governments WILL find it.
6) The UK’s War on Encryption 🛡️
The UK is trying to dominate the global surveillance & censorship landscape.
While the US, Canada, Australia, and New Zealand have supported strong encryption to mitigate cyber threats, the UK stands alone in its war on encryption.
7) The Free Speech Crackdown 🗣️
This isn’t just about encryption—it’s about control. Governments worldwide are criminalizing dissent and censoring free speech, using tech companies as their enforcement arms.
🔗 GreenMedInfo Report
8) The Global Censorship Agenda 🌐
This ties into the UK’s broader, GLOBALLY ORCHESTRATED censorship agenda:
- The Online Safety Bill criminalizes encrypted messaging & forces platforms to scan private messages.
- The Digital Services Act (EU) gives governments the power to shut down online content they don’t like.
- Leaked US-UK documents show direct coordination between UK intelligence & the Biden administration to censor online speech.
9) The Architects of Speech Policing: CCDH 🕵️♂️
The Center for Countering Digital Hate (CCDH)—a UK intelligence-backed group—has been a driving force behind global censorship.
They were caught:
- Running “black ops” to suppress RFK Jr.’s presidential campaign.
- Leading the "Kill Musk’s Twitter" directive, trying to shut down free speech on X.
- Labeling 12 private US citizens as the “Disinformation Dozen” to justify mass censorship.
🔗 Reclaim the Net Investigation
10) The Pattern is Clear: Surveillance + Censorship 🔍
1️⃣ Governments create "safety" laws to justify surveillance.
2️⃣ They pressure tech companies to enforce censorship.
3️⃣ Once encrypted services are gone, nothing is private anymore.This is the biggest attack on digital freedom in history.
11) What Can We Do? 💪
- Support companies that refuse to build backdoors (Signal, ProtonMail, etc.).
- Push for legislation that protects encryption & free speech.
- Stay informed & spread awareness—governments count on secrecy to push these policies through.
- Follow and support privacy and internet freedom organizations such as:
- @G_W_Forum
- @FFO_Freedom
- @ReclaimTheNetHQ
12) The Ultimate Power Grab: Controlling All Digital Communication 📱
If Apple caves, every other platform will be forced to follow.
📌 The UK’s Global Playbook:
- A backdoor to encryption (Investigatory Powers Act).
- A government-linked censorship network (CCDH).
- A speech-policing framework that extends worldwide (Online Safety Bill).This is a global effort to control what people can say, share, and store privately.
13) The Final Stand: Will You Comply or Resist? ⚔️🚨
They want total control—your speech, your privacy, your elections. This is the defining battle of our time.
🇬🇧 UK’s war on encryption = Global censorship blueprint.
🗳️ Election meddling + speech policing = A hijacked democracy.📢 Digital freedom is human freedom.
Stand up. Speak out. Fight back. 🏴☠️🔥
Full thread preserved by Thread Reader App.
-
 @ 3b7fc823:e194354f
2025-02-09 18:18:28
@ 3b7fc823:e194354f
2025-02-09 18:18:28The Best AI Models to Run Locally (According to My Totally Biased Opinion)
I've spent a lot of time running local AI models, and after extensive testing (read: lots of random chats and questionable prompts), I've settled on my favorites. No benchmarks, no pointless metrics—just pure vibes and personal preference.
🏆 Best Overall: Llama 3.1 8B
If you want a general-purpose AI that does everything well, Llama 3.1 8B is the clear winner. It’s smart, coherent, and doesn’t go off the rails too easily. Whether you're chatting, building a assistant, or writing this model just works.
🔬 Best Technical Model: DeepSeek-R1 8B
Need something with a more to-the-point attitude? DeepSeek-R1 8B is the one. It’s less verbose, highly technical, and great for when you need precise answers instead of a paragraph-long essay. Perfect for hacking, cybersecurity, and other deep technical topics.
⚡ Best for Speed (and Dumb Fun): Qwen 1.5 0.5B
If you don’t need the smartest model and just want something fast, Qwen 1.5 0.5B is a solid choice. It responds quickly, makes decent small talk, and is good for simple chatbot-style interactions. Not the best at deep reasoning, but hey, sometimes you just need a dumb bot that replies fast.
💻 Best for Coding: Starcoder2 7B
Despite newer models dropping left and right, Starcoder2 7B is still the local coding model. It understands context well, generates clean code, and doesn’t hallucinate random syntax as much as other models. If you’re working on a coding project, this is still the GOAT.
These are my go-to local AI models. If you disagree, that’s fine—just know that you’re wrong. Try them out yourself and let me know if you find any hidden gems worth running.
Happy local AI tinkering! 🚀
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
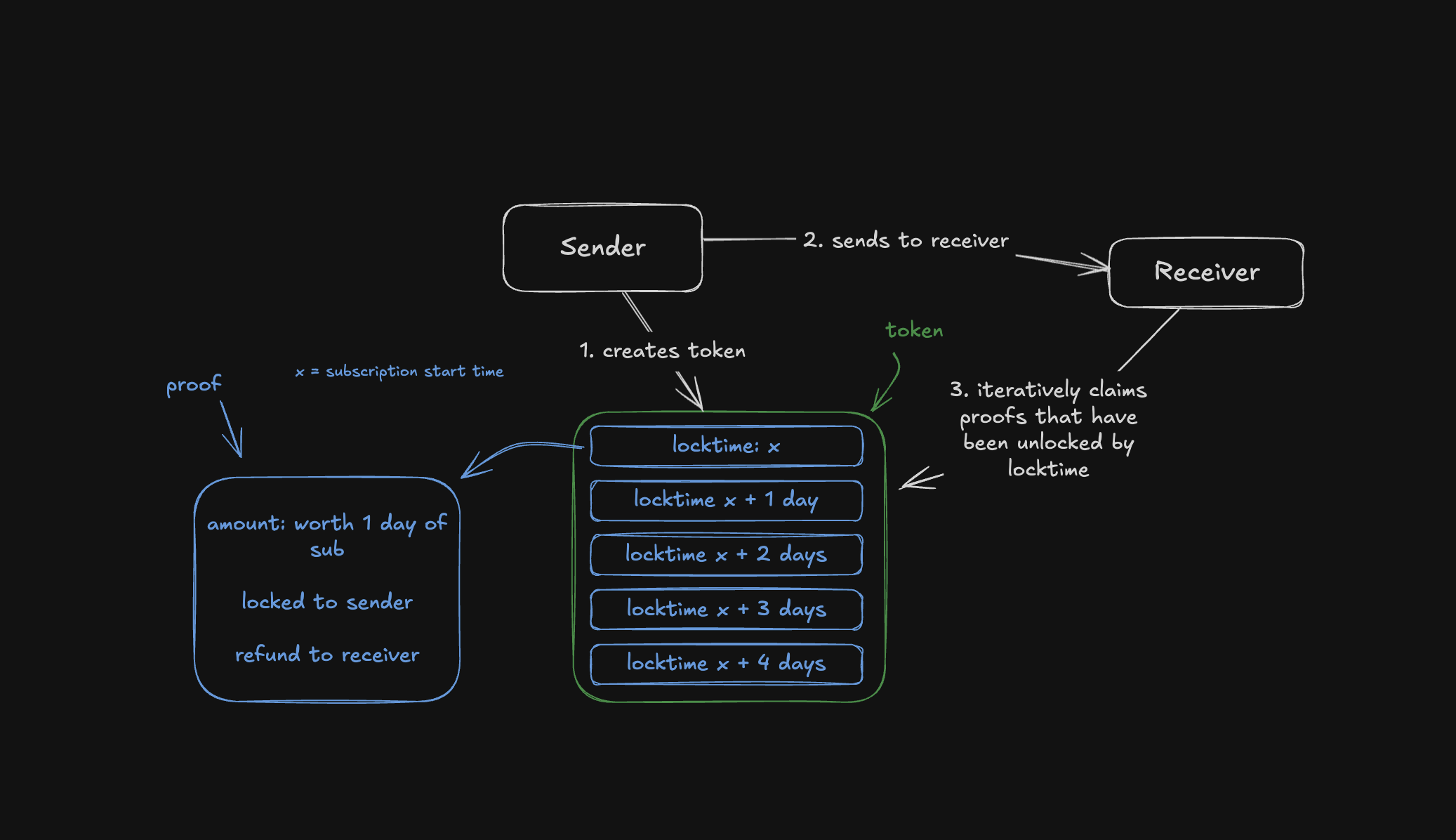
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ 01d0bbf9:91130d4c
2024-11-19 14:46:24
@ 01d0bbf9:91130d4c
2024-11-19 14:46:24The Bitcoin community thrives on open-source innovation, but Coinkite’s move against BTClock risks stifling progress and alienating its core supporters.
Open-source projects like BTClock typically aim to promote innovation and accessibility within the Bitcoin community. Suing the programmer for trademark infringement seems like an overly aggressive move by Coinkite, given the values that Bitcoin and its ecosystem often stand for: decentralization, collaboration, and open innovation.
Why It’s Problematic:
-
Chilling Effect on Open Source:
-
Actions like this discourage developers from creating alternative solutions or building on existing ideas, which stifles community-driven progress.
-
Open-source projects thrive on shared knowledge, and this lawsuit could set a precedent for others to clamp down on grassroots efforts.
-
Reputation Risk for Coinkite:
-
While Coinkite has long been respected for products like the Blockclock and Coldcard, this move could alienate its core audience—Bitcoiners who value freedom and decentralization.
-
By targeting an open-source developer, Coinkite risks being perceived as prioritizing profits over community principles.
-
Trademark Infringement Question:
-
If the issue is solely over the name "BTClock," a fair resolution could involve renaming the project rather than pursuing legal action.
- Lawsuits should ideally be a last resort, not the first response.
A Better Approach:
- Coinkite could have worked with the BTClock developer to address concerns without legal action—perhaps through dialogue or collaboration.
- Open acknowledgment of BTClock’s differences (lower cost, open-source) would have shown confidence in their own premium product, while still respecting community-driven alternatives.
What NVK and Coinkite Should Do
Even now, NVK could mitigate the damage:
- Withdraw the Lawsuit: Openly acknowledge the backlash and frame it as a misunderstanding or a "necessary step" that they’re now reconsidering due to the community’s response.
- Collaborate with BTClock: Find a way to coexist, perhaps by licensing certain Blockclock-specific elements if truly necessary, while leaving room for BTClock’s open-source innovation.
-
-
 @ daa41bed:88f54153
2025-02-09 16:26:32
@ daa41bed:88f54153
2025-02-09 16:26:32There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. - Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.




