-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 22050dd3:480c11ea
2025-03-03 22:14:39
@ 22050dd3:480c11ea
2025-03-03 22:14:39Education is foundational to growth and prosperity in a community.
It is not easy for people to engage with and interact with the foundational idea of a community when they do not understand it.
Unsurprisingly, BTC Isla is built around Bitcoin, which not many people understand.
However, on the tiny island of Isla Mujeres, that is changing one class at a time.
 ### Education Is Essential
### Education Is EssentialAt the center of each Bitcoin circular economy around the globe is the ethos that education is paramount to adoption and the overall success of the community.
This is no different with BTC Isla, where Isa teaches Bitcoin classes to the locals on the island.
During my recent stay on the island, I sat in on one of the classes to see what they are and how Isa is spearheading educating the locals.
The Class
Classes take place at the Mayakita restaurant on the southeast side of the island. They last about an hour.
Isa follows the Bitcoin Diploma curriculum created by Mi Primer Bitcoin and teaches the classes in Spanish. I don’t speak Spanish so I couldn’t exactly follow the lesson to a tee, but that wasn’t important as the enthusiasm from Isa and the students was palpable.
 On this particular day, there were 4 students present who had attended the classes before, and one new student.
On this particular day, there were 4 students present who had attended the classes before, and one new student.It was exciting and fun to see this timid teenager walk into the restaurant who hadn’t the slightest idea of what Bitcoin was. Isa welcomed her with open arms and threw her right into the thick of it.
She seemed to learn a lot and have her interest piqued and afterward told me that she enjoyed the class and would be returning.
Another student and member of the community has begun their Bitcoin journey, very exciting!
I understood the lesson (Isa’s activity with the markerboard helped!) to be primarily about inflation and the scarcity and divisibility properties of Bitcoin.
I always enjoy seeing how people react when they learn about inflation and how Bitcoin is different and why it is a solution.
 ### Paid To Attend Classes?
### Paid To Attend Classes?At the end of each class, something strange occurs: Isa pays the students sats for attending the class!
She surprised me before the lesson by telling me she does this, but her reason for doing it makes sense.
The locals on the island live a completely different life than ours in the United States. The concept of saving and putting away money for the sake of building savings doesn’t exist. When money plays a purely transactional role in life, the store-of-value characteristic isn’t important let alone thought about.
Paying the students to attend the classes does 2 things:
- It allows the students to begin to build savings in bitcoin as well as interact with and use their money and have real experience with the very thing they’re learning about
- It creates an additional incentive for the students to attend the classes
While yes, it is strange to monetarily incentivize people to attend a class, it makes sense when you realize that the locals need a reason to actually be interested in and learn about Bitcoin.
The normal interest and entry points to Bitcoin as an investment that we use in the United States and Europe aren’t applicable.
However, despite the students being paid to attend the classes, they all seemed genuinely interested in the lesson and learning about Bitcoin. They were all attentive to Isa, taking notes and staying engaged. They cared about the subject.
 ### Future Classes
### Future ClassesIsa, myself, and a few others were discussing field-trip ideas for future classes, and in the future Isa will take the class to the streets of Isla Mujeres!
She will give the students sats with the implication that they need to spend them on goods at the bitcoin-accepting merchants downtown. By doing this, bitcoin injects itself into the economy and perhaps more importantly, the students get experience transacting with bitcoin in the real world!
Nostr: BTCIsla
Website: btcisla.xyz
-
 @ 5a261a61:2ebd4480
2025-03-03 20:35:49
@ 5a261a61:2ebd4480
2025-03-03 20:35:49Tom stopped and nodded to Jiro with a smile. "Just wanted to see how it's going," he said as he approached the counter.
"People need to eat and I have food. Can't complain," replied the ever-smiling Jiro. "Are you heading out to make some money, or should I put it on your tab again?" he continued without pausing his stirring.
Tom might have been short on cash, but his pride (and caution) never allowed him to leave debts with friends. And Jiro was about the closest thing to a friend among all his acquaintances.
"I can still afford it today," Tom smiled tiredly, "but if you know of something that might bring in some metal, I could stop by tomorrow too."
"There might be something, but nothing that would pay the bills today. You might have better luck across the street. They're having another party today, and as a good neighbor and main supplier of coconut oil, I have a magic piece of paper that will get you on the guest list."
"And here comes the 'but'?"
"If you're this impatient with women too, I'm not surprised you don't have one to make a home out of those four walls... Have I told you about my niece Noi?" Juri asked with his typical mischievous smile.
Tom raised an eyebrow. "Maybe. But I have a feeling you're going to tell me again anyway."
Juri laughed. "See, that's why I like you. You always know what's coming." He leaned closer across the counter. "Noi is a smart girl, studying journalism. But she needs a bit of... how to put it... social training."
"And by that, you mean exactly what?" Tom asked cautiously.
"Nothing bad, don't worry," Juri waved his hand dismissively. "She just needs someone to take her into better society. You know, to see how things work. And, as it happens, she has tickets to tonight's party at The Beach."
Tom sighed. He already suspected where this was heading. "Juri, I'm not exactly—"
"The perfect gentleman who could show my niece how to behave in higher circles?" Juri cut him off. "Come on, Tom. You're a detective. You know how to adapt to wherever the wind blows. And she has those tickets. You want to go to the party, she needs a guide. Everyone will be happy."
Tom remained silent for a moment, considering his options. On one hand, he wasn't in the mood to babysit some naive student. On the other hand, those tickets would really come in handy... especially since he had nothing better going on.
Where to next?
- accept offer to get out of the stale water
- find another way other than babysitting
-
 @ 878dff7c:037d18bc
2025-03-03 19:27:39
@ 878dff7c:037d18bc
2025-03-03 19:27:39Opposition Demands Transparency in Mass Citizenship Ceremonies
Summary:
Opposition home affairs spokesman James Paterson has called on the government to share the contact details of new Australians sworn in during mass citizenship ceremonies organized by Tony Burke. Paterson criticized these large-scale events as a "reckless politicisation" ahead of the federal election and emphasized the need for local MPs to welcome new citizens, as outlined in the Australian Citizenship Ceremonies Code. The Department of Home Affairs, responsible for the ceremonies, has been urged to provide this information promptly and impartially. Labor has denied political motivations, stating the events aimed to clear a backlog of eligible citizens. Sources: The Australian - 4 March 2025
Gambling Companies Threaten Increased Promotions Amid AFL Revenue Dispute
Summary:
Australian gambling companies plan to escalate betting promotions in response to the AFL's initiative to claim a larger share of gambling revenue from its games. The AFL proposes a minimum annual fee on bookmakers, starting at $20,000 for large operators and lower for smaller ones, increasing incrementally until 2027. Smaller bookmakers argue this fee structure will force them to use harmful inducements to maintain profitability, potentially exacerbating gambling-related harm. Critics, including public health experts, call for urgent federal regulation to mitigate these risks and urge the AFL to reconsider its financial strategy to avoid long-term reliance on gambling revenue. Sources: The Guardian - 4 March 2025
Tropical Cyclone Alfred Threatens Southeast Queensland and Northern NSW
Summary:
Tropical Cyclone Alfred is forecasted to intensify to a Category 2 system, bringing damaging winds up to 120 km/h and heavy rainfall to the New South Wales and Queensland coasts starting Wednesday. The cyclone is expected to make landfall early Friday, with areas from Brisbane to northern NSW, including Byron Bay and the Gold Coast, at significant risk. Authorities have issued multiple flood watches and cyclone warnings, urging residents to prepare and secure their properties. Queensland Premier David Crisafulli emphasized the importance of preparedness, particularly for low-lying coastal areas facing storm surge threats. Sources: news.com.au - 4 March 2025, The Guardian - 4 March 2025
NSW Secures Full Funding for Public Schools by 2034
Summary:
New South Wales has reached an agreement with the federal government to fully fund its public schools by 2034, injecting $4.8 billion over the next decade. This deal mirrors recent funding arrangements made by Victoria and South Australia, involving a 5% increase in commonwealth funding. Under current policies, states contribute 75% of school funding and the commonwealth 20%, leaving a 5% gap to be bridged. The new agreement will see the commonwealth's contribution rise to 25% by 2034, removing previously allowed non-educational expenses from funding calculations. The funding will support various educational reforms, including individualized student support and mental health initiatives. Sources: The Guardian - 4 March 2025
Labor Promises $2.6 Billion Pay Raise for Aged-Care Nurses
Summary:
The Albanese government has pledged $2.6 billion to fund pay raises for 60,000 aged-care nurses, aligning with a Fair Work Commission decision, as part of their health-focused pre-election campaign. This brings Labor's total spending on award wage increases for aged-care workers to $17.7 billion. The pay raise will increase the average registered and enrolled nurse's pay by about 12%, with instalments in March 2025, October 2025, and August 2026. Health Minister Anika Wells and Employment Minister Murray Watt emphasized the importance of paying aged-care nurses fairly to address workforce shortages and close the gender pay gap. Sources: The Australian - 4 March 2025
Coalition Pledges $3 Billion to Expand F-35 Fleet Amid Strategic Concerns
Summary:
Opposition Leader Peter Dutton has announced a $3 billion commitment to acquire an additional 28 F-35A Lightning II fighter jets, aiming to increase Australia's fleet to 100 aircraft. This move seeks to counteract the Albanese government's earlier decision to cancel the purchase of these fighters in 2024. Dutton emphasized the importance of bolstering Australia's air combat capabilities in response to regional threats. However, defense experts have criticized the plan, suggesting that there are higher priorities for defense spending, and noting that the actual cost could be significantly higher than the pledged amount. Sources: The Australian - 1 March 2025, The Guardian - 2 March 2025, Australian Financial Review - 2 March 2025, news.com.au - 1 March 2025
-
 @ 6e0ea5d6:0327f353
2025-03-03 19:09:05
@ 6e0ea5d6:0327f353
2025-03-03 19:09:05Ascolta bene!
Allow me to sit by your side, amico mio, and—just like a son—I will tell you a harsh truth: no matter the circumstances, the blame lies with you for everything that happens within your realm of responsibility. Your family, your business, your ventures—whatever it may be—it doesn’t matter if it was by action or omission, if something went wrong, take the blame and resolve it however you need to!
Men like us, who live in hard battles, do not have the luxury of handing over the burdens of our responsibilities to others!
We live in a time where everyone is encouraged to place the blame for their failures on others or on abstractions. To hell with all that nonsense, damn it! Never feel comfortable or relieved when you hear stories of people who have made the same mistakes or have the same flaws as you.
Knowing that others have failed in the same goals should only serve as a simple acknowledgment that nothing is easy.
However, don’t allow yourself to lessen your effort or blame when you see others’ difficulties.
On the other hand, don’t deceive yourself into trying to become a productivity machine.
Learn to be rational, but always strive for the best from yourself, without pushing your limits beyond what your mind and body can endure.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ f16adada:68b1dabc
2025-03-03 17:31:41
@ f16adada:68b1dabc
2025-03-03 17:31:41{"hours":15,"content":"TEST 2","field":"General","mediaUrls":[]}
-
 @ 2e8970de:63345c7a
2025-03-03 17:23:07
@ 2e8970de:63345c7a
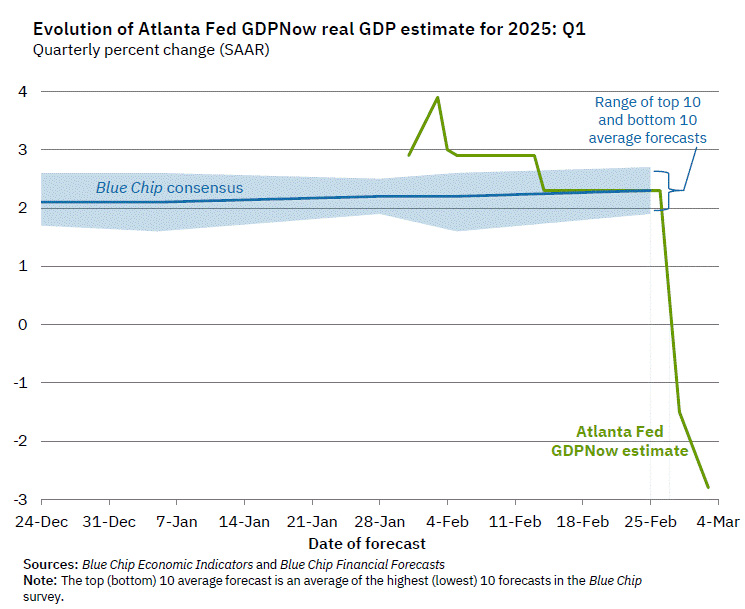
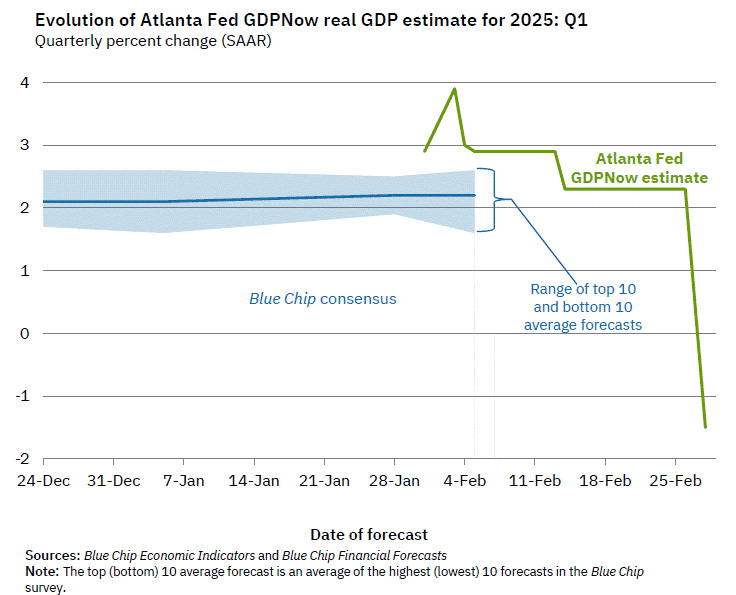
2025-03-03 17:23:07The Atlantas FED GDP indicator GDPNow was recently adjusted to -1.5% (https://stacker.news/items/899962). Now it got revised even further down to -2.8%.
Mind you, this is a change of almost 7% down from almost 4% growth to almost 3% reduction within a month!
https://x.com/AtlantaFed/status/1896598929564725716
originally posted at https://stacker.news/items/902707
-
 @ b7a07661:6aeeee04
2025-03-03 16:15:26
@ b7a07661:6aeeee04
2025-03-03 16:15:26Voilà une liste non exhaustive des événements francophone consacrés à Bitcoin dans la semaine du 3 au 7 mars 2025. Nous vous recommandons de prendre contact avec les organisateurs sur Telegram ou X pour confirmation de l’horaire et du lieu.
Mardi 4 mars
Rennes : Au Hangar, 1 rue de Dinan à Rennes, à partir de 19h30. En savoir plus : https://x.com/BreizhBitcoin – https://www.breizhbitcoin.com/8-meetups-en-bretagne/ – https://discord.com/invite/gFVe2HcUpw
Poitiers : Au Café des Arts, 5 Place Charles de Gaulle, à partir de 19h30 En savoir plus : https://twitter.com/BTCPoitiers
Mercredi 5 mars
Amiens : A la Station, 7 passage Auguste Perret à Amiens (en face de la gare). A partir de 18h30. En savoir plus : https://t.me/AmiensBitcoinMeetupGroup
Annecy : The Craic, 1 Place Marie Curie. A partir de 19h00. Au programme : Acheter et utiliser vos bitcoins en toute souveraineté. Avec Théo Mogenet. En savoir plus : https://x.com/AnnecyBitcoin – https://t.me/annecybitcoin
Angers : Dans les locaux de Weforge, 25 rue Lenepveu. A partir de 19h00. Au programme : Workshop – Installation d’un Wallet Bitcoin. En savoir plus : t.me/AngersBitcoinMeetup – x.com/AngersBitcoin
Brest : A La Fabrick 1801, 25 rue de Pontaniou, Atelier des Capucins, à partir de 18h30. En savoir plus : https://t.me/BrestBitcoinMeetup – https://twitter.com/brestbitcoin
Caen : Les Relais d’Alsace, 9 Esplanade Léopold Sedar Senghor, à partir de 19h00. En savoir plus : normandiebitcoin.com – discord.gg/42XT34pWb4 – linkedin.com/company/normandiebitcoin – x.com/NormandieBTC – t.me/+X999KCTgP-5lZjg8 – meetup.com/normandiebitcoin
Clermont-Ferrand : Au Halles du Brézet, 10 Rue Jules Verne. A partir de 19h00. En savoir plus : https://t.me/ClermontFerrandBitcoinMeetup – https://x.com/ClermontBitcoin
Dijon : Au bar Monsieur Moutarde, 40 Rue des Forges à Dijon, à partir de 19h30. Programme : Suite de l’atelier multisig pour apprendre à utiliser des wallet Ledger afin de créer un setup de sécurité. En savoir plus : https://t.me/DijonBitcoinMeetup – https://twitter.com/GabToken – https://discord.com/invite/VBAVWCCjkR
Genève : A la Galerie, 13 rue de l’industrie. Beer to beer à partir de 20h00. Au programme : Exploration de Starknet. « Notre intervenant Bachir, développeur sur Starknet, expliquera les principes fondamentaux de ce protocole, son architecture basée sur les preuves de validité (ZK-Rollups), et comment cette technologie pourrait s’intégrer à l’écosystème Bitcoin. Il abordera les défis techniques, les différences avec Ethereum et les perspectives d’un Bitcoin plus scalable grâce aux rollups. » En savoir plus : x.com/BitcoinGenevafr – meetup.com/bitcoin-meetup-geneva – https://t.me/BitcoinGeneva
Lausanne : Au Qwertz Café, 3 Rue de la Grotte, à partir de 19h00. Au programme : Réunion informelle et conviviale, aussi bien pour découvrir le fonctionnement de bitcoin et que pour discuter entre experts. En savoir plus : https://www.meetup.com/fr-FR/bitcoin-lausanne – https://x.com/BitcoinLausanne
Lille : Au Café Oz, The Australian Bar, 33 Pl. Louise de Bettignies, à partir de 19h00. Au programme : Echanges libres entre les différents participants et présentation mensuelle (replay disponible sur youtube) réalisée par un des membres de l’association. En savoir plus : bitcoinlille.fr – t.me/bitcoinlille – meetup.com/fr-FR/bitcoinmeetuplille – x.com/BitcoinLille
Lyon : Au Bouchon Comptoir Brunet, 23 Rue Claudia à partir de 19h00. Au programme : Bières pression (Blonde & surprise), vins locaux, softs, tapas locaux, snacks maison. En savoir plus : https://www.meetup.com/fr-FR/crypto-lyon/ – https://t.me/bitcoinlyon
Mâcon : Au Flunch Mâcon Sud, à partir de 19h30. Au programme : Atelier pratique pour apprendre à créer un portefeuille. En savoir plus : https://x.com/MeetupBTCMacon – https://allo-crypto.com/meetup-bitcoin/ – https://www.facebook.com/groups/maconmeetupbitcoin
Marseille : A partir de 20h00 au 13 boulevard d’Athènes 13001 (après le local syndical F.O., avant la traverse Saint-Dominique). Pour entrer dans le bâtiment, il vous suffira de sonner à l’interphone avec le label « JUST ». Au bout de quelques secondes, la porte s’ouvre. La salle de réception se trouve au rez-de-chaussée, première porte à gauche dans le hall, avec le même label « JUST ». Au programme : Fanis Michalakis parlera de Lightning, de l’USDT qui arrive sur le réseau Bitcoin et des nouveautés côté régulation. En savoir plus : t.me/MarseilleBitcoinMeetup – x.com/MarseilleBTC
Rouen : Au Bar des Fleurs, 36 Place des Carmes, à partir de 19h00. En savoir plus : https://x.com/NormandieBTC – normandiebitcoin.com – t.me/+X999KCTgP-5lZjg8 – meetup.com/normandiebitcoin
Saint Brieuc : Au Makio Bar – 13 impasse Lavoisier, Trégueux, à partir de 19h00. En savoir plus : https://x.com/StBrieucBitcoin
Saint-Lô : Au Bar le NorthWood, 34 Rue du Belle, à partir de 20h00. En savoir plus : https://signal.group/#CjQKIPYUbHyAO2OjdF1BfTD2iDsiJxtrF4QBmr74JAuD8t1PEhCBeWlwDf8e1qvHoStQfqkI – https://x.com/Saint_Lo_BTC
Paris : Au Sof’s Bar, 43 Rue Saint-Sauveur, à partir de 18h00. En savoir plus : meetup.com/fr-FR/Bitcoin-Paris – t.me/ParisCentreBitcoinMeetup – x.com/ParisBTCmeetup
Valence : Au VEX, 811 allée André Revol à Bourg-lès-Valence, à partir de 18h30. En savoir plus : https://x.com/valencebtc – https://t.me/valencebtc
Jeudi 6 mars
Brest : A l’IMT Atlantique, 655 Avenue du Technopôle à Plouzané, de 17h00 à 18h30. Au programme : Alexandre Stachtchenko de Paymium, animera une conférence sur Bitcoin et ses enjeux. En savoir plus : https://lu.ma/gp3xgd72
Nantes : Au Little William, Place St Felix à partir de 19h00. En savoir plus : https://t.me/nantesbitcoinmeetup – https://twitter.com/NantesBitcoin – https://www.facebook.com/people/Nantes-Bitcoin-Meetup/61552725519617/
Saint-Nazaire : Au Jardin d’Asie, 17 Rue du Bois Savary, à partir de 19h00 En savoir plus : https://mobilizon.fr/@saintnazaire_bitcoin – https://signal.group/#CjQKIM24oe8gw83bjJzVUKSOk1dvm_UcxU5K-WaWCYTgQtoOEhBD0Tt84cO0u8Br9ZVy-ZfS – https://x.com/SaintNazaireBTC
Vendredi 7 mars
Saint-Malo : Bar L’Encrier, 2 Passage Grande Hermine, à partir de 18h30. Au programme : Gilles Cadignan de BullBitcoin viendra faire une présentation des services de son entreprise, du portefeuille développé par leurs équipes (qui intègre les swaps vers Lightning et Liquid) ainsi que le concept des Payjoins pour une confidentialité accrue sur les transactions. En savoir plus : https://t.me/SaintMaloBitcoinMeetup – https://www.breizhbitcoin.com/8-meetups-en-bretagne/ – https://twitter.com/stMaloBTCMeetup – https://discord.gg/CwqE5n8UG3
-
 @ 4ddeb0cf:94524453
2025-03-03 15:14:19
@ 4ddeb0cf:94524453
2025-03-03 15:14:19Timestamp, March 3, 2025
1,074 sats/$
3.90 Eh/s
Following the April 2024 Bitcoin halving, analysts are tracking whether the traditional post-halving price surge continues into 2025. Some predict a macro top later this year with a target in the area of $200K, but short-term dips—like the 12% drop noted last week—could test this narrative. This week’s price action, along with any new details on a US strategic reserve, may offer clues about the cycle’s trajectory.
Look for releases Wednesday-Friday tied to macro indicators that will offer insight into whether the dollar is strengthening or weakening. President Trump’s focus on inflation and energy via executive orders ties in. A stronger dollar from energy policy shifts could weigh on Bitcoin, while regulatory clarity might offset that.
Key Events to Monitor This Week (March 3-9, 2025)
March 5 (Wednesday): Fed minutes release or Powell’s speech (tentative based on typical schedules). Critical for rate cut signals.
March 6 (Thursday): U.S. jobless claims data — higher claims could boost Bitcoin as a risk asset.
March 7 (Friday): Non-Farm Payrolls report — strong data might strengthen the dollar, pressuring BTC.
Ongoing: Trump administration crypto reserve updates — any press briefings or leaks could spike volatility.
This week in Bitcoin and macro finance will likely be dominated by U.S. economic data, Fed signals, and Trump’s crypto reserve plans. Bitcoin’s price could swing between $90K and $110K depending on these catalysts, while macro markets grapple with yields, jobs, and trade policy. Stay tuned for mid-week updates—Wednesday and Friday will be pivotal.
-
 @ 9ea10fd4:011d3b15
2025-03-03 14:47:43
@ 9ea10fd4:011d3b15
2025-03-03 14:47:43(Le français suit) I have the feeling of two brothers trying to remove the speck from each other’s eye but failing to see the beam in their own.
-
To liberal democracies, I say: The war in Ukraine, led by NATO, is a bad war that could have easily been avoided and would not have happened if NATO had respected the logic that applies to a country like Ukraine, adjacent to a great power, Russia. As a counterexample, would the United States accept a Russian or allied military presence on the Mexican border? It is so obvious that denying it is pure bad faith. I will not shed tears over your graves.
-
To the populist far-right, I say: To borrow the words of Le Monde’s editorial, too often, the denunciation of attacks on freedom of expression serves to mask the defense of the economic model of social media platforms owned by billionaires who, by promoting confrontation and fake news, spread hatred, hinder informed debate, and undermine democracy. Behind the idea of unlimited “free speech” lurks “the promotion of a far-right ideology eager to replace the rule of law with the law of the strongest, to the detriment of policies protecting social rights, women, and other victims of discrimination.”
Regarding political history, let it be noted that “this situation is the result of three decades of economic liberalism, which institutional left-wing forces have also embraced” (Alain Lipietz).
“It must be acknowledged: Trump’s United States is no longer a protection but a threat to democracy in Europe.”
Les Etats-Unis de Donald Trump, une menace pour la démocratie en Europe
**
J’ai le sentiment de deux frères qui essaient d’enlever la paille dans l’œil de l’autre, mais ne voient pas la poutre dans le leur.
-
Aux démocraties libérales, je dis : La guerre en Ukraine menée par l’OTAN est une mauvaise guerre qui aurait facilement pu être évitée et qui n’aurait pas eu lieu si l’OTAN avait respecté la logique s’appliquant à un pays, l’Ukraine, adjacent à une grande puissance, la Russie. En contre-exemple, les États-Unis accepteraient-ils une présence militaire russe ou de leurs alliés à la frontière avec le Mexique ? C’est tellement évident que c’en est de la mauvaise foi. Je n'irai pas pleurer sur vos tombes.
-
À l’extrême-droite populiste, je dis : Pour reprendre les termes de l’éditorial du journal Le Monde, trop souvent la dénonciation des entorses à la liberté d’expression masque la défense du modèle économique de médias sociaux détenus par des milliardaires qui, en promouvant la confrontation et les fake news, diffusent la haine, entravent les débats éclairés et sapent la démocratie. Sous la conception d’un « free speech » sans limite, « pointe la promotion d’une idéologie d’extrême droite avide de substituer la loi du plus fort aux politiques de défense des droits sociaux, des femmes et des autres victimes de discriminations ».
En ce qui concerne l’histoire politique, qu'il soit noté que « cette situation résulte de trois décennies de libéralisme économique, auxquelles se sont ralliées les forces de la gauche institutionnelle » (Alain Lipietz).
« Il faut se rendre à l’évidence : les Etats-Unis de Trump ne constituent plus une protection mais une menace pour la démocratie en Europe. »
Les Etats-Unis de Donald Trump, une menace pour la démocratie en Europe
-
-
 @ f16adada:68b1dabc
2025-03-03 13:38:44
@ f16adada:68b1dabc
2025-03-03 13:38:44{"hours":1,"content":"AGAIN","field":"General","mediaUrls":[]}
-
 @ 0463223a:3b14d673
2025-03-03 13:33:46
@ 0463223a:3b14d673
2025-03-03 13:33:46It’s now been a full week without prescribed drugs for being a spaz. The last week was tough to be honest, sleepless nights, constantly restless and uncomfortable, nausea, diarrhoea, headaches. Not dissimilar to giving up certain illegal drugs, not quite on a par with opiates but not dissimilar.
The physical symptoms have mostly subsided but I am rather emotionally unstable. I can imagine the Stoics of Nostr being quite stoically unimpressed by these ramblings. Obviously men never have emotions or feelings etc. We only discuss important subjects such as the works of Mises and Rothbard, we have no comprehension of the difference between art and craft, that’s for the women folk. We’re just a plain wallpaper of rational actions buying bitcoin bitcoin bitcoin...
Fuck that lol. I mean cool if that’s you, it’s not me. I started out a spaz and it’ll likely I’ll continue to be a spaz. I’m still trying to improve myself, I lifted some heavy things up and down this morning, eaten a healthy breakfast (although it wasn’t raw meat and salt, sorry) and am about to set about some practice before tonight’s session helping local youngsters with their music. I’ve worked my way through emails and I’m now writing this shit instead of doing some other bollocks. Maybe one day I’ll string a half coherent sentence together and become a V4V billionaire....
Existential dread is a laugh innit? I have no idea what the fuck I’m doing. I’ll make more music but it’s pretty futile. The hours of labour vs the financial return is terrible. I find it pretty amusing watching the numbers on my streams drop off in the morning whenever I play any of my own music... Clear market signals if ever I saw them but I stubbornly crack on anyway.
I’m sure at some point, through the process of putting shit on the internet, something will happen that’s of value to someone. Actually I have some nice supporters online which is very much appreciated and, as I said on my stream this morning, I’m grateful the same people come back each day. It’s like the most underground little club on the internet. I have 20 subscribers, no YouTube, X or Meta accounts. No LinkedIn. All is done on the free and open internet, either on a server I own or via some magical relays. So obviously this makes me 10x harder than Mark Zuckerberg, no matter how much Ju Jitsu he does. I’m not riffling through your underwear like a creepy perv.
If anyone reading this is ever wondering why capitalism gets such a bad rep, it’s because some of us are really, really shit at it. But I have a shed, no one’s taking that away from me. My cat is bad ass, I have an amazing wife and the sun is shining. I have a lot to be grateful for. I’ll keep trying to think of ways to earn a coin without selling my soul to the devil. There’s trade offs a plenty but I take responsibility for my own shit and I don’t have to sully myself with corporate bullshit.
Onwards and upwards. It’s a great day!
As Craig David didn’t once sing…
Stopped taking drugs on Monday Sleepless night and shivers on Tuesday We were throwing up by Wednesday And on Thursday & Friday & Saturday we chilled on Sunday
-
 @ a012dc82:6458a70d
2025-03-03 13:22:08
@ a012dc82:6458a70d
2025-03-03 13:22:08The dynamic landscape of Bitcoin and blockchain technology is a testament to the relentless innovation and debate that drives this sector forward. A pivotal figure in this narrative is Adam Back, CEO of Blockstream, whose recent insights and proposals have stirred a significant conversation within the Bitcoin community. His stance on the indomitable nature of JPEGs and other media inscriptions on the Bitcoin blockchain, along with his suggestion for a block size increase, is not just a technical observation but a philosophical statement about the future direction of Bitcoin. This article delves into the implications of Back's views, exploring how they could shape the trajectory of Bitcoin in the years to come.
Table of Contents
-
The Unstoppable Nature of Bitcoin Inscriptions
-
JPEGs on the Blockchain: A New Reality
-
Implications for the Bitcoin Ecosystem
-
-
Adam Back's Proposal for Block Size Increase
-
A Technical Solution to a Growing Challenge
-
Balancing Innovation and Network Integrity
-
-
Comparative Analysis with Ethereum's Innovations
-
Bitcoin and Ethereum: Divergent Paths Converging?
-
Learning from Ethereum's Approach
-
-
Conclusion
-
FAQs
The Unstoppable Nature of Bitcoin Inscriptions
JPEGs on the Blockchain: A New Reality
Adam Back's acknowledgment of the unstoppable nature of JPEGs on the Bitcoin blockchain is a watershed moment. It signifies a recognition of the blockchain's evolving utility, transcending its original financial transactional purpose. This evolution raises fundamental questions about the nature of Bitcoin. Is it merely a financial tool, or is it morphing into a broader digital canvas for various forms of data? The embedding of JPEGs and other media, known as inscriptions, is not just a technical feat but a cultural shift in the perception and usage of Bitcoin.
Implications for the Bitcoin Ecosystem
The phenomenon of media inscriptions on the Bitcoin blockchain is a double-edged sword. On one hand, it showcases the network's versatility and the ingenuity of its users. On the other hand, it introduces new challenges in terms of network efficiency and focus. The primary concern is the potential for network congestion, as the blockchain is burdened with non-financial data. This could lead to slower transaction times and higher fees for traditional Bitcoin transactions, potentially undermining the network's primary purpose as a digital currency. Moreover, there's a philosophical debate within the community about the purity of Bitcoin's original vision versus its evolving nature.
Adam Back's Proposal for Block Size Increase
A Technical Solution to a Growing Challenge
In response to the burgeoning use of Bitcoin for media inscriptions, Adam Back has put forth a bold proposal: increasing the block size of the Bitcoin blockchain. This proposal is not merely a technical adjustment; it's a strategic move to accommodate the growing diversity of uses of the Bitcoin network. By introducing a "segwit annex" for additional space in each block, Back is advocating for a more inclusive Bitcoin that can support both its traditional financial role and its emerging function as a digital ledger for various forms of data.
Balancing Innovation and Network Integrity
The crux of Back's proposal lies in finding a middle ground between fostering innovation and preserving the network's efficiency and purpose. The proposed block size increase is a recognition that the Bitcoin network needs to evolve to accommodate new uses while ensuring that it remains a robust and efficient platform for financial transactions. This proposal also reflects a pragmatic approach to blockchain development, acknowledging that rigid adherence to original designs may not be suitable in the face of changing user behaviors and technological advancements.
Comparative Analysis with Ethereum's Innovations
Bitcoin and Ethereum: Divergent Paths Converging?
The proposed changes to Bitcoin's block structure draw an interesting parallel with developments in the Ethereum blockchain. Ethereum's EIP-4844, known as Proto-Danksharding, introduces the concept of temporary data blobs with a separate fee market, a concept somewhat mirrored in Back's proposal for Bitcoin. This comparison is crucial as it underscores the evolving nature of blockchain technology and the different paths taken by these two leading networks. While Bitcoin has traditionally focused on being a digital currency, Ethereum has been more open to diverse applications from its inception.
Learning from Ethereum's Approach
Ethereum's approach to scalability and functionality, particularly with EIP-4844, offers valuable lessons for Bitcoin. It demonstrates the feasibility of integrating new features and capabilities into an established blockchain network while maintaining its core functions. For Bitcoin, adopting a similar approach could mean not only enhanced functionality but also increased relevance in a rapidly evolving digital landscape. It's a testament to the fluidity and adaptability of blockchain technology, where innovations in one network can inspire and inform developments in another.
Conclusion
Adam Back's perspective on JPEGs and his proposal for block size expansion mark a critical moment in the evolution of Bitcoin. As the Bitcoin community navigates these developments, it faces the challenge of embracing change while staying true to the core principles that have defined Bitcoin since its inception. The future of Bitcoin, shaped by these ongoing discussions and decisions, remains a fascinating and significant topic in the broader narrative of cryptocurrency and blockchain technology. The path Bitcoin takes will not only influence its own trajectory but also set precedents for the future development of blockchain technology as a whole.
FAQs
What is Adam Back's stance on JPEGs on the Bitcoin blockchain? Adam Back, CEO of Blockstream, acknowledges that embedding JPEGs and other media, known as inscriptions, on the Bitcoin blockchain is unstoppable. He views this as a natural evolution of the blockchain's capabilities.
Why is the embedding of JPEGs on Bitcoin significant? The embedding of JPEGs signifies a shift in how the Bitcoin blockchain is used, extending beyond its original purpose of financial transactions to a broader digital platform for various data types.
What is Adam Back's proposal for the Bitcoin blockchain? Adam Back proposes increasing the Bitcoin block size to accommodate the growing use of the network for media inscriptions. This includes adding a "segwit annex" for additional space in each block.
How does Adam Back's proposal aim to balance Bitcoin's functionality? Back's proposal aims to balance innovation with network efficiency by providing dedicated space for inscriptions, thus managing network congestion while maintaining efficient transaction processing.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 95cb4330:96db706c
2025-03-03 12:55:48
@ 95cb4330:96db706c
2025-03-03 12:55:48The Eisenhower Matrix, also known as the Urgent-Important Matrix, is a powerful time-management tool that helps prioritize tasks based on their urgency and importance. Developed from former President Dwight D. Eisenhower's management style, this matrix enables individuals to focus on activities that drive long-term success while effectively managing immediate demands.
How the Eisenhower Matrix Works
Tasks are categorized into four quadrants:
- Urgent and Important:
Tasks requiring immediate attention and contributing significantly to your goals. - Examples: Crisis management, pressing deadlines.
-
Action: Address these tasks promptly to prevent escalation.
-
Important but Not Urgent:
Tasks that are vital for long-term success but do not require immediate action. - Examples: Strategic planning, skill development.
-
Action: Schedule specific times to focus on these activities, ensuring consistent progress.
-
Urgent but Not Important:
Tasks that demand quick attention but have less impact on your long-term objectives. - Examples: Interruptions, non-essential meetings.
-
Action: Delegate these tasks when possible to free up time for more important activities.
-
Neither Urgent nor Important:
Tasks that offer minimal value and can be considered distractions. - Examples: Time-wasting activities, excessive social media use.
- Action: Eliminate or minimize engagement in these tasks to enhance productivity.
Benefits of Using the Eisenhower Matrix
-
Enhanced Productivity:
By focusing on important tasks, you achieve meaningful progress toward your goals. -
Improved Time Management:
Distinguishing between urgent and important tasks helps allocate time more effectively. -
Reduced Stress:
Prioritizing tasks prevents last-minute rushes and the anxiety associated with looming deadlines.
Implementing the Eisenhower Matrix
-
List Your Tasks:
Write down all tasks and responsibilities. -
Categorize Each Task:
Assign each task to one of the four quadrants based on its urgency and importance. -
Take Appropriate Action:
Manage each task according to its quadrant's recommended action plan. -
Review Regularly:
Consistently assess and adjust your task list to ensure alignment with your evolving goals and priorities.
By integrating the Eisenhower Matrix into your daily routine, you can enhance focus, productivity, and overall effectiveness in both personal and professional endeavors.
For a visual guide on implementing the Eisenhower Matrix, you might find this tutorial helpful:
- Urgent and Important:
-
 @ a296b972:e5a7a2e8
2025-03-03 12:38:59
@ a296b972:e5a7a2e8
2025-03-03 12:38:59Bislang war die NATO das Trojanische Pferd der USA, um ihre Interessen weltweit durchzusetzen. Das sogenannte Verteidigungsbündnis hat sich mangels Gelegenheit einer militärischen Verteidigung mehr auf Aktionen wie im Kosovo konzentriert.
Mit seinen Stützpunkten in Europa hat die USA-NATO bislang die Möglichkeit geschaffen, potenzielle kriegerische Auseinandersetzungen aus dem eigenen Land fernzuhalten, zu zeigen wer die Hosen anhat und überall die Finger mit im Spiel zu haben. Sozusagen militärisches Outsourcing.
Als Gegenleistung darf Europa theoretisch unter die Bettdecke der USA-NATO krabbeln, wenn es draußen mal so richtig kalt werden sollte. Ob das auch wirklich so geschehen würde, wenn es darauf ankommt, bleibt fraglich.
Die NATO-Osterweiterung ist ein übergriffiges Heranrücken der USA an Russland, ein Ignorieren und Übergehen eines für beide Weltmächte nötigen Sicherheitsabstands.
Wenn der Nachbar mit seinen Anbauten immer mehr an die eigene Grundstücksgrenze heranrückt, den Sicherheitsabstand nicht einhält, und in seiner Großkotzigkeit immer weiter macht (weil er, überheblich, wie er ist, glaubt, dass er es kann), dann ist irgendwann der Punkt erreicht, wo man sagt: Schluss jetzt!
Den dicken Vorschlaghammer rauszuholen, ist dann sicher nicht die beste Lösung, aber was soll man machen, wenn alles Reden und die Versuche aufeinander zuzugehen und eine gemeinsame Lösung zu finden, von der Seite des Aggressors in seiner impertinenten Arroganz nicht für nötig gehalten wird.
Dieser Punkt war im Februar 2022 mit Überlegungen zum Beitritt der Ukraine in die NATO erreicht und Russland ist in die Ukraine einmarschiert. Es folgte eine massive Unterstützung der USA in Form von Logistik, Technologie (Starlink), Waffen, Bedienungspersonal und jede Menge Kohle. Und weil Deutschland ja gerne ganz vorne mitmischt und Uncle Sam zeigen will, was für ein braver Nick-August und treuer Vasall Deutschland ist, hat man sich gleich an die zweite Stelle emporgedient.
Wegen der Gefahr, dass „versehentlich“ der Bündnisfall eintreten könnte, hat man auf das offizielle Entsenden von NATO-Soldaten zur Unterstützung verzichtet. Es gibt jedoch genug Beweise dafür, dass auch Männer in der Lage sind, ihre Kleidung zu wechseln.
Es ist nie um die Verteidigung des „demokratischen Wertewestens“ gegangen, sondern immer nur, wie in jedem Krieg, um knallharte Interessen, und wieder einmal die der USA. Menschenleben Nebensache, notwendiges Übel. Was macht schon vielleicht inzwischen 1 Million gestorbener Soldaten aus? Die Erde dreht sich ja weiter. Man muss groß denken und da kann man sich nicht mit Nebensächlichkeiten abgeben.
Politik – Krieg (Krieg ist Politik mit anderen Mitteln)
Menschen – Frieden (Die Politik führt Krieg, die Menschen, egal wo, wollen Frieden!)
Schon einen Tag nach Ausbruch des Ukraine-Konflikts war klar: Die Ukraine kann den Krieg nicht gewinnen. Und von Anfang an bestand auch schon die Möglichkeit, dass die USA ähnliche „Erfolge“ erzielen würde, wie seinerzeit im Irak, in Libyen oder in Vietnam.
An dem Punkt stehen wir jetzt. Und jetzt ist die Frage, wie kann sich die USA aus der Affaire ziehen, ohne ihr Gesicht zu verlieren? Am besten natürlich als „Friedensstifter“ eines Krieges, den sie selbst angezettelt hat.
Ja, richtig, Trump ist nicht dafür verantwortlich, dass wir jetzt da stehen, wo wir sind. Aber mit seiner Präsidentschaft hat er auch die Verantwortung für das übernommen, was sein Vorgänger angerichtet hat. Seine Aufgabe ist, die Suppe auszulöffeln, die ihm andere eingebrockt haben. Er hat erkannt, dass der Stellvertreterkrieg zwischen den USA und Russland zu keinem günstigen Ergebnis für die USA führen wird. Wie es also jetzt anstellen, dass man Selenskyj wie eine heiße Kartoffel fallen lassen kann und dabei auch noch einen weiteren Profit erwirtschaften? Wie praktisch ist da ein Deal um Seltenerden, als Gegenleistung für das „großzügige“ Engagement durch die daran gutverdienende Waffenindustrie?
Erst erhoffe ich mir Chancen, Interessen durchzusetzen, investiere in ein vermeintlich gutes Geschäft, und wenn ich dann sehe, dass nichts daraus wird, suche ich nach einer Möglichkeit, wie ich meinen Geschäftspartner auch noch für meine eigene Fehleinschätzung bezahlen lassen kann. Dieses Geschäftsmodell liegt in den Genen der USA und ist nicht erst Trumps Erfindung. Und auch das Prinzip: Erst haue ich alles kurz und klein, verdiene durch die Waffenindustrie, und dann verdiene ich noch einmal am Wiederaufbau. Große Teile der fruchtbaren schwarzen Erde in der Ukraine sind bereits in US-amerikanischer Hand.
Trumps Vorgänger John F. Kennedy hat schon gesagt: „Wen ich nicht zu meinem Feind haben will, den mache ich zu meinem Freund.“ Ist das die Strategie, die Trump gegenüber Russland, derzeit mit großem Erfolg, fährt?
Wenn Selenskyj nicht so ein erbärmlicher Charakter wäre, könnte er einem fast leidtun. Politisch unerfahren, dafür aber trittsicher auf High-Heels im Lackanzug, hat er treudoof den USA vertraut und jetzt wird er mit der Realität konfrontiert. Wie man an der hollywoodreifen Aufführung im Oval Office sehen kann, zeigt der Hai erbarmungslos seine Zähne. Entweder du spurst, wie wir es vorgeben, oder wir machen dich fertig. Gruß an Don Corleone. Hast du immer noch nicht kapiert: Wir sitzen am längeren Hebel und gewinnen immer, so oder so.
Wenn die USA so gescheit gewesen wären, Selenskij das Gefühl zu geben, er habe die Macht, als Retter und Friedensbringer für die Ukraine aus der Vertragsunterzeichnung hervorzugehen, hätte er den USA aus der Hand gefressen, weil er diesen Trick sicher nicht durchschaut hätte. Stattdessen ist er auf Konfrontationskurs gegangen, vielleicht auch, weil er glaubt, noch einige Trümpfe im Ärmel zu haben, die er in Europa vermutet. Nicht ganz unberechtigt, denn die masochistischen Tendenzen „Wir stehen nach wie vor fest an deiner Seite“, lassen weiter hoffen (ich muss schon wieder an das Lack-Kostüm denken. Passt doch.)
Sowohl Selenskyj, als auch Trump und Vance haben in diesem Drama gezeigt, dass auf beiden Seiten noch ein riesiges Optimierungspotenzial in Diplomatie besteht.
Und die Universal-Dilettanten (derzeit mein Lieblingswort) in Europa haben nichts eiligeres zu tun, als einen Pakt zu schließen, wie sie die Ukraine weiter unterstützen können. Schließlich wird die Demokratie, besonders die deutsche Unseredemokratie, ja nicht nur seinerzeit in Afghanistan, sondern auch in der Ukraine verteidigt. Das führt dann zu solchen Aussagen wie: „Die Ukraine muss den Krieg gewinnen“, obwohl Deutschland, Europa von der Realität umzingelt, langsam vom Kontinent zur Insel wird.
Inzwischen erwägen die USA aus der NATO und den Vereinten Nationen auszutreten.
Was bleibt dann von der NATO übrig, wenn die USA wegfallen? Ein Haufen europäischer Nationen, die ihre erbärmlichen Waffenbestände zum Entsorgen in die Ukraine geschickt haben und jetzt blank dastehen. Und mit einer Armee, besonders der deutschen Bundeswehr mit den paar Köpfen, die sicher ganz besonders erpicht darauf ist, ihr Land zu verteidigen, wo doch die Moral der Truppe so wunderbar durch die Impfpflicht für Soldaten gefördert wurde. Würde ich als Soldat mein Leben für ein Land hergeben, dass mich dazu gezwungen hat, einen möglichen Impfschaden bis hin zum Tod in Kauf zu nehmen? Wohl kaum.
Man hat das Gefühl, Deutschland und Europa sind in einer Zeitkapsel gefangen. Bis dato hat, außer Orban und Fico, vielleicht auch schon Meloni, wohl noch niemand erkannt, dass sich der Wind gedreht hat. Man arbeitet einen europäischen Friedensplan aus. Wie soll der aussehen: Russland soll sich aus den ehemals ukrainischen Gebieten zurückziehen, der Frieden soll von europäischen Truppen gesichert werden (da könnte ich auch meine Oma an der Grenze aufstellen), die Ukraine soll in die NATO aufgenommen werden?
Der angehende deutsche Fritzefanzler hat sich angeboten, mit Trump zu sprechen. Trump hat dankend abgelehnt. Wen wundert das? Die Verantwortlichen in Europa haben immer noch nicht realisiert, dass sie nichts zu sagen haben, von einem großen Teil der Welt ausgelacht werden, nicht zuletzt auch wegen der Außenrepräsentantin der einst führenden deutschen Wirtschaftsmacht, die mit ihrem Trampolin von einem Fettnäpfchen in das andere gesprungen ist. Diese Aufzählung könnte man um weitere „Geistesgrößen“ ergänzen, die allesamt an Gehirnschwund zu leiden scheinen.
Europa hat sich angewöhnt geschichtspolitische Ereignisse ab einem Zeitpunkt zu bewerten, der ihnen passt. Man muss jedoch die Ereignisse in einer Zeitschiene, in einem Verlauf von Ursachen und Wirkungen sehen, doch dazu scheint das europäische politische Gruselkabinett bis nach Brüssel hin, nicht in der Lage zu sein, oder es nicht zu wollen.
Vielleicht rechnet man in Brüssel mit einer Migration der durch das Ausheben des US-AID-Sumpfs auf der Flucht befindlichen Deep-State-Agitatoren und deren Vermögen Richtung Europa? Doch das wäre eine neue Verschwörungstheorie.
Selbstverständlich ist das wichtigste, dass endlich Frieden geschlossen wird, damit nicht noch mehr Menschen sinnlos sterben müssen, auf beiden Seiten. Und eigentlich ist dazu jedes Mittel recht. Das bedeutet aber nicht, dass man sich nicht die Voraussetzungen, die Rahmenbedingungen, sowie die vorangegangenen Umstände einmal anschauen sollte.
-
 @ da0b9bc3:4e30a4a9
2025-03-03 07:07:32
@ da0b9bc3:4e30a4a9
2025-03-03 07:07:32Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/902254
-
 @ d360efec:14907b5f
2025-03-03 05:40:07
@ d360efec:14907b5f
2025-03-03 05:40:07การวิเคราะห์แต่ละ Timeframe (TF):
-
TF 15m (Intraday):
- แนวโน้ม: Bearish (แต่เริ่มมีสัญญาณกลับตัวเล็กน้อย). ราคาเคยอยู่ใต้ EMA ทั้งสอง แต่เริ่มขยับขึ้นมาเหนือ EMA 50.
- SMC:
- มี Bearish OB ชัดเจนที่ ~93,000 (ทดสอบแล้วไม่ผ่านในวันที่ 1 มี.ค.).
- มี Bullish OB ที่ ~86,000-87,000 (ราคาลงไปทดสอบแล้วดีดกลับ).
- SSL: ~86,845, ~83,859 (ถูกกวาดไปแล้ว).
- BSL: ~92,669 (อาจเป็นเป้าหมายถัดไป).
- Trend Strength: เมฆยังเป็นสีแดง แต่เริ่มจางลง. มีลูกศร Buy เล็กๆ.
- กลยุทธ์ Day Trade (SMC):
- ระมัดระวัง: ตลาดมีความผันผวน. แนวโน้มหลักยังเป็นขาลง, แต่ระยะสั้นเริ่มมีแรงซื้อ.
- Option 1 (Aggressive): Buy เมื่อราคาย่อลงมาใกล้ Bullish OB (~87,000) หรือ EMA 50. ตั้ง Stop Loss ใต้ OB. เป้าหมายทำกำไรที่ BSL (~92,669) หรือ Bearish OB เดิม.
- Option 2 (Conservative): รอให้ราคา Breakout เหนือ Bearish OB (~93,000) อย่างชัดเจน แล้วค่อยพิจารณา Buy ตาม.
- Short: ถ้าจะ Short, รอให้ราคาขึ้นไปใกล้ Bearish OB อีกครั้ง แล้วเกิดสัญญาณ Bearish Reversal (เช่น Bearish Engulfing) ค่อย Short.
-
TF 4H (ระยะกลาง):
- แนวโน้ม: Bearish. ราคาอยู่ใต้ EMA ทั้งสอง, EMA 50 อยู่ใต้ EMA 200.
- SMC:
- Bearish OB ใหญ่: ~95,000-100,000.
- SSL: ~83,559.5, ~81,260.4, ~78,961.4 (เป้าหมายระยะกลาง-ยาว).
- BSL: 105,543.4
- Trend Strength: เมฆสีแดงเข้ม. สัญญาณ Sell.
- กลยุทธ์: เน้น Short. รอ Pullback ไปใกล้ EMA หรือ Bearish OB แล้วหาจังหวะ Short.
-
TF Day (ระยะยาว):
- แนวโน้ม: ยังคงเป็น Bearish, แต่เริ่มเห็นสัญญาณการชะลอตัว. ราคาหลุด EMA 200 ลงมา
- SMC: มี Order Block ใหญ่ที่ $90,000 - $100,000
- Trend Strength: เมฆเริ่มเปลี่ยนจากสีแดงเข้ม เป็นสีแดงจางลง. ยังไม่มีสัญญาณ Buy ที่ชัดเจน.
- กลยุทธ์: ยังไม่ควร Long. รอสัญญาณกลับตัวที่ชัดเจนกว่านี้ (เช่น Breakout เหนือ EMA 50, เกิด Bullish Divergence).
สรุปและข้อควรระวัง:
- แนวโน้มหลักของ BTC ยังคงเป็นขาลง (Bearish) ในทุก Timeframe.
- TF 15m เริ่มมีสัญญาณการกลับตัวระยะสั้น (Bullish Reversal) แต่ยังต้องระวัง เพราะยังอยู่ในแนวโน้มหลักขาลง.
- Smart Money อาจกำลังสะสม (Accumulation) ที่ระดับราคาปัจจุบัน.
- สิ่งที่ต้องระวัง: ข่าว, ความผันผวน, การ "กวาด" Stop Loss (Liquidity Sweep).
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
-
 @ 95cb4330:96db706c
2025-03-03 05:36:23
@ 95cb4330:96db706c
2025-03-03 05:36:23Adopting Single-Threaded Leadership, as implemented by Jeff Bezos at Amazon, involves assigning full ownership of a high-impact initiative to one individual. This strategy ensures accountability, accelerates decision-making, and fosters deep focus, leading to more effective execution.
Understanding Single-Threaded Leadership
- Definition:
A leadership approach where a dedicated leader focuses exclusively on a specific project or goal, free from competing responsibilities. This model contrasts with traditional structures where leaders juggle multiple projects simultaneously.
medium.com
Examples in Practice
-
Amazon's Single-Threaded Leaders:
Jeff Bezos structured Amazon's key initiatives around single-threaded leaders, ensuring they could drive results without distractions. This approach has been credited with enhancing innovation and operational efficiency within the company. -
Elon Musk's Focused Leadership:
Elon Musk exemplifies intense focus by dedicating his attention to one company at a time, such as Tesla, SpaceX, or Neuralink, thereby propelling each forward without splitting his attention.
Implementing Single-Threaded Leadership
-
Identify High-Impact Projects:
Determine which initiatives are critical to your organization's success and would benefit from dedicated leadership. -
Assign Sole Ownership:
Appoint a leader whose primary responsibility is the success of that specific project, minimizing their involvement in unrelated tasks. -
Empower Decision-Making:
Grant the single-threaded leader the authority to make decisions and allocate resources necessary for the project's success. -
Minimize Dependencies:
Structure the project to reduce reliance on other teams or departments, allowing the leader to maintain momentum without unnecessary delays.
Action Step
Evaluate your current projects to identify where responsibilities are fragmented. Select a high-priority initiative and assign one person full responsibility, ensuring they have the autonomy and resources to execute effectively without unnecessary dependencies.
By implementing single-threaded leadership, organizations can enhance focus, streamline decision-making, and drive successful outcomes in their most critical projects.
For a deeper understanding of this concept, consider watching this discussion:
Single-Threaded Leadership: How Amazon Solved Organizational Scaling Challenges
- Definition:
-
 @ 95cb4330:96db706c
2025-03-03 05:23:48
@ 95cb4330:96db706c
2025-03-03 05:23:48Most people make decisions based on averages—what usually happens. But in high-impact fields like investing, startups, and technology, outliers drive the biggest results.
Instead of asking, "What is the average outcome?" ask: - ✔ What is the full range of possible outcomes? - ✔ How can I maximize the upside while protecting against the worst-case scenario?
Example in Action: Bezos, Thiel & Altman
Jeff Bezos & AWS
When launching Amazon Web Services (AWS), Bezos saw a small chance of massive success—cloud computing dominance—against a limited downside (R&D costs). He optimized for the best-case scenario, which became a trillion-dollar business.
Peter Thiel & Venture Capital
Thiel’s Power Law investing philosophy is based on distributions: Instead of funding many "average" startups, he focuses on a few outliers that can return 100x or more (e.g., Facebook, Palantir).
Sam Altman & OpenAI
Altman understands that AI breakthroughs follow an exponential curve—a small chance of creating AGI (Artificial General Intelligence) is worth more than incremental AI improvements.
How to Apply This Thinking
Map the Full Range of Outcomes
Instead of assuming an "average" result, consider: - Best-case scenario: How big can this get? - Worst-case scenario: What’s my downside risk? - Unlikely but extreme possibilities: What are the hidden risks or rare events?
Optimize for Asymmetric Upside
Focus on decisions where the upside is massive, even if the probability is low. - Example: Launching a new product in an emerging market versus incrementally improving an existing one.
Protect Against Catastrophic Downside
Even if an outlier event has a small chance, if it can ruin you, avoid it. - Example: Diversifying investments instead of going all-in on one bet.
Resources to Learn More
- Understanding Distributions vs. Averages – Farnam Street
- Jeff Bezos on Thinking Long-Term – Harvard Business Review
- Peter Thiel’s Power Law Thinking – NFX
Action Step: Apply This Today
- Pick one major decision you're working on.
- Instead of assuming an "average" result, analyze the full distribution of outcomes.
- Ask: Am I optimizing for a rare, high-upside event while managing the worst-case risks?
By thinking in distributions, you make better strategic bets, spot hidden risks, and maximize your long-term impact. 🚀
-
 @ b84b0d81:f3a3865f
2025-03-03 05:05:30
@ b84b0d81:f3a3865f
2025-03-03 05:05:30**Introduction ** Starting a business is an exciting journey, but ensuring its long-term success requires careful planning, strategic decision-making, and continuous adaptation. Many entrepreneurs fail not because they lack passion but because they don’t build a business that is sustainable. To establish a thriving business, you need to identify the right opportunity, create a solid foundation, and adapt to market trends effectively.
This guide will take you through the key steps to identifying and building the best business for long-term success. From market research to customer engagement and financial management, we’ll cover essential strategies to ensure your business remains competitive and profitable over time. Step 1: Identifying the Right Business Idea 1.1 Assess Your Interests and Strengths One of the best ways to build a sustainable business is to align it with your passion and expertise. When you start a business in an area where you have knowledge and interest, you increase your chances of success. 1.2 Conduct Market Research Researching your target market is crucial to understanding demand, competition, and potential customer needs. Consider the following when conducting market research: • Who is your ideal customer? • What problems are they facing that your business can solve? • How big is the market for your product or service? • Who are your competitors, and what are they doing well (or poorly)? A report by the Small Business Administration (SBA) states that only 50% of businesses survive beyond five years, emphasizing the importance of thorough market research and planning. (Source) 1.3 Evaluate Market Trends Trends can dictate the future of any industry. Businesses that succeed in the long term are those that adapt to changing consumer behaviors, technological advancements, and economic shifts. Utilize tools like Google Trends, industry reports, and customer feedback to stay ahead of the curve. Step 2: Building a Strong Business Foundation 2.1 Create a Clear Business Plan A well-structured business plan acts as a roadmap for your company’s growth. It should include: • Executive Summary • Market Analysis • Business Structure • Product/Service Offering • Marketing and Sales Strategies • Financial Projections • Growth Plan 2.2 Secure Funding and Manage Finances Financial stability is a pillar of business success. Options for securing capital include: • Bootstrapping (using personal savings) • Small business loans • Angel investors or venture capitalists • Crowdfunding According to the U.S. Bureau of Labor Statistics, approximately 20% of new businesses fail within their first year due to cash flow issues. (Source) To avoid this, monitor your finances closely, keep overhead costs low, and reinvest profits wisely. Step 3: Establishing a Competitive Edge 3.1 Develop a Unique Value Proposition (UVP) Your UVP should clearly articulate why customers should choose your business over competitors. It should be: • Clear and concise • Focused on solving a specific problem • Easily communicated to your target audience 3.2 Build a Strong Brand Identity A strong brand helps customers recognize and trust your business. Essential elements of branding include: • Logo and visual identity • Brand voice and messaging • Customer experience and service 3.3 Leverage Digital Marketing In today’s digital era, having an online presence is non-negotiable. Strategies to implement: • SEO (Search Engine Optimization): Helps increase organic traffic to your website. • Social Media Marketing: Engage with customers on platforms like Facebook, Instagram, and LinkedIn. • Email Marketing: Build relationships with potential and existing customers through personalized emails. • Content Marketing: Provide valuable information through blogs, videos, and guides to establish authority in your industry. Step 4: Customer-Centric Approach 4.1 Understand and Engage Your Customers Listening to your customers can provide insights into improving your business. Strategies to enhance customer engagement include: • Conducting surveys and feedback sessions • Implementing a loyalty program • Providing exceptional customer service 4.2 Build a Community Around Your Brand Creating a loyal customer base goes beyond selling a product or service. Engage with your audience through social media, email newsletters, and exclusive events to foster a sense of community. Step 5: Scaling and Adapting for Long-Term Success 5.1 Implement Scalable Processes As your business grows, efficient systems and automation can help manage increased demand. Consider: • Using customer relationship management (CRM) software • Automating inventory and order processing • Streamlining workflow with project management tools 5.2 Stay Agile and Innovative The most successful businesses evolve with market trends. Regularly evaluate industry developments, adopt new technologies, and be open to pivoting your strategy when necessary. 5.3 Expand Wisely When expanding, assess factors such as: • Market demand for your product or service • Financial readiness • Operational capacity Options for expansion include opening new locations, diversifying product lines, or entering international markets.
**Conclusion ** Building a business that lasts requires a strategic approach, financial discipline, and an unwavering commitment to customer satisfaction. By conducting thorough research, creating a strong foundation, leveraging digital tools, and continuously adapting to industry trends, you can set your business up for long-term success. With careful planning and execution, your business can not only survive but thrive for years to come.
-
 @ e9fcc47b:ae2e68a8
2025-03-03 02:26:47
@ e9fcc47b:ae2e68a8
2025-03-03 02:26:47This event has been deleted; your client is ignoring the delete request.
-
 @ d360efec:14907b5f
2025-03-03 01:34:50
@ d360efec:14907b5f
2025-03-03 01:34:50$OKX:BTCUSDT.P
Timeframe Analysis:
-
TF 15m (Intraday):
- Trend: Bearish (but showing signs of a minor reversal). Price was below both EMAs but is starting to move above the EMA 50.
- SMC:
- Clear Bearish OB at ~93,000 (tested and failed on March 1st).
- Bullish OB at ~86,000-87,000 (price tested and bounced).
- SSL: ~86,845, ~83,859 (already swept).
- BSL: ~92,669 (potential next target).
- Trend Strength: Cloud is still red but fading. A small Buy arrow appears.
- Day Trade Strategy (SMC):
- Caution: The market is volatile. The main trend is still down, but there's short-term buying pressure.
- Option 1 (Aggressive): Buy when the price dips near the Bullish OB (~87,000) or EMA 50. Set a stop-loss below the OB. Target the BSL (~92,669) or the previous Bearish OB.
- Option 2 (Conservative): Wait for a clear breakout above the Bearish OB (~93,000) before considering a buy.
- Short: If shorting, wait for the price to approach the Bearish OB again and look for a bearish reversal signal (e.g., Bearish Engulfing) before shorting.
-
TF 4H (Medium-Term):
- Trend: Bearish. Price is below both EMAs, EMA 50 is below EMA 200.
- SMC:
- Larger Bearish OB: ~95,000-100,000.
- SSL: ~83,559.5, ~81,260.4, ~78,961.4 (medium- to long-term targets).
- BSL: 105,543.4
- Trend Strength: Dark red cloud. Sell signal.
- Strategy: Focus on shorts. Wait for pullbacks to the EMAs or Bearish OB and look for shorting opportunities.
-
TF Day (Long-Term):
- Trend: Still Bearish, but starting to show signs of slowing down. The price has broken below the EMA 200.
- SMC: Large order Block $90,000-$100,000
- Trend Strength: The cloud is changing from dark red to a lighter red. No clear Buy signal yet.
- Strategy: Avoid going long. Wait for clearer reversal signals (e.g., breakout above EMA 50, Bullish Divergence).
Summary and Cautions:
- The main trend of BTC is still Bearish on all timeframes.
- The 15m TF is showing signs of a short-term Bullish Reversal, but be cautious as it's against the main downtrend.
- Smart Money may be accumulating at current price levels.
- Cautions: News, volatility, liquidity sweeps (stop-loss hunting).
Disclaimer: This analysis is for informational purposes only and does not constitute financial advice. Investors should conduct their own research and make decisions carefully.
-
-
 @ 878dff7c:037d18bc
2025-03-03 00:23:00
@ 878dff7c:037d18bc
2025-03-03 00:23:00Slow Cooker Pastrami (No Smoker)
This is one of our family staples! It is pretty low effort and the first few slices straight after it comes out of the oven are AMAZING.
Full credit to Nagi over at RecipeTin Eats! Please go and check out her other amazing recipes and give her the recognition she deserves.
Adapted from Nagi at RecipeTin Eats
Ingredients
Meat
- 4 lbs (2 kg) corned beef with a thick fat cap (Try find one that has a fairly consistent shape and direction of muscle fibers for maximum tenderness)
Spice Mix
- 4 tbsp coarsely ground black pepper
- 2 tbsp coriander powder
- 1½ tsp mustard powder
- 1 tbsp brown sugar
- 1 tbsp smoked paprika
- 2 tsp garlic powder (For a low FODMAP alternative substitute garlic and onion with hing powder, only about 1/4 tsp... If in doubt, just skip garlic and onion. It still tastes amazing!)
- 2 tsp onion powder
- Optional: 2 tbsp liquid smoke
Instructions
1. Prepare the Spice Mix
- Combine all spice mix ingredients in a bowl.
2. Season the Beef
- Pat the corned beef dry.
- Spread the spice mix on a tray and roll the beef in it, ensuring all sides are well-coated.
- If using liquid smoke, sprinkle it over the beef.
3. Wrap the Beef
- Place the beef fat-side down on a large sheet of foil and wrap it tightly.
- Wrap it again with another sheet of foil and flip it so the fat side is up.
- I use 3 sheets of foil and 'over lay' the wrap so it's a bit harder for the delicious juices to escape.
- Dont stress if you forget where the fat cap is, it'll be fine...
4. Slow Cook
- Place a rack in the slow cooker to elevate the beef (scrunched-up foil balls can be used if a rack isn't available. I use cookie cutter patterns ;) ).
- Set the wrapped beef on the rack.
- Cook on low for 10 hours.
5. Cool and Refrigerate
- Remove the beef from the slow cooker and let it cool.
- Refrigerate for at least 6 hours to firm up, making it easier to slice thinly. (24-36hrs is fine in the fridge if you don't have time etc)
6. Bake to Set the Crust
- Preheat the oven to 350°F (180°C).
- Unwrap the beef and place it on a rack over a baking tray.
- Bake for 30 minutes to set the spice crust.
7. Slice and Serve
- Remove from the oven and let it cool slightly.
- Slice thinly against the grain.
- Serve on toasted rye bread with mustard and pickles, or use in Reuben sandwiches.
Enjoy homemade pastrami without a smoker!
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ 878dff7c:037d18bc
2025-03-02 22:48:04
@ 878dff7c:037d18bc
2025-03-02 22:48:04This dish is a classic Argentine barbecue (asado) preparation, where lamb leg is slowly grilled over an open fire or on a parrilla (grill) and served with chimichurri sauce.
Ingredients
For the Lamb:
- 1 whole leg of lamb (about 2.3–3.2 kg/5–7 lbs)
- 3 tbsp coarse salt
- 2 tbsp black pepper
- 3 tbsp olive oil
- 4 cloves garlic, minced
- 1 tbsp smoked paprika
- 1 tbsp dried oregano
- 1 tbsp ground cumin
- Juice of 1 lemon
- ½ cup red wine (optional)
For the Chimichurri Sauce:
- 1 cup fresh parsley, finely chopped
- ½ cup fresh cilantro (optional)
- 4 cloves garlic, minced
- 1 tsp red pepper flakes
- 1 tbsp dried oregano
- ½ cup olive oil
- ¼ cup red wine vinegar
- Salt and pepper to taste
Instructions
1. Prepare the Lamb:
- Pat the lamb leg dry and rub it with olive oil, garlic, lemon juice, paprika, oregano, cumin, salt, and black pepper.
- Let it marinate at room temperature for 1 hour (or overnight in the fridge for more flavor. I recommend 12-24hrs).
2. Set Up the Fire:
- Traditionally, cordero asado is cooked over a wood fire or charcoal at a low temperature (225–275°F / 110–135°C) for slow cooking.
- If using a grill, prepare indirect heat by placing hot coals on one side and keeping the lamb on the cooler side.
3. Grill the Lamb:
- Place the lamb leg on the grill bone-side down.
- Cook low and slow for 3 to 4 hours, turning occasionally and basting with wine or water to keep it moist.
- If using a thermometer, the internal temperature should be:
- Rare: 125°F (52°C)
- Medium-Rare: 130–135°F (55–57°C) (I recommend medium rare for my lamb)
- Medium: 140–145°F (60–63°C)
- Well Done: 155°F+ (68°C+)
4. Make the Chimichurri Sauce:
- In a bowl, mix chopped parsley, cilantro, garlic, red pepper flakes, oregano, olive oil, and red wine vinegar.
- Season with salt and pepper.
- Let it sit for 30 minutes for the flavors to blend.
5. Rest & Serve:
- Once cooked, let the lamb rest for 15–20 minutes before slicing.
- Serve with chimichurri sauce and a side of grilled vegetables or crusty bread.
Enjoy your Argentinian Cordero Asado! 🇦🇷🔥
-
 @ 8d34bd24:414be32b
2025-03-02 22:12:14
@ 8d34bd24:414be32b
2025-03-02 22:12:14Last night I was reading this passage in Ezekiel, who was called to be a watchman to Israel.
“Son of man, I have appointed you a watchman to the house of Israel; whenever you hear a word from My mouth, warn them from Me. When I say to the wicked, ‘You will surely die,’ and you do not warn him or speak out to warn the wicked from his wicked way that he may live, that wicked man shall die in his iniquity, but his blood I will require at your hand. Yet if you have warned the wicked and he does not turn from his wickedness or from his wicked way, he shall die in his iniquity; but you have delivered yourself. Again, when a righteous man turns away from his righteousness and commits iniquity, and I place an obstacle before him, he will die; since you have not warned him, he shall die in his sin, and his righteous deeds which he has done shall not be remembered; but his blood I will require at your hand. However, if you have warned the righteous man that the righteous should not sin and he does not sin, he shall surely live because he took warning; and you have delivered yourself.” (Ezekiel 3:17-21) {emphasis mine}
Although I do not believe we can directly apply this command to our lives because it was given directly to Ezekiel and because our salvation comes from Jesus and not works, I do think we can learn from this passage. Just as Ezekiel was called to share God’s blessings, His curses, and His fixed plan, in the same way we are to share the Gospel (the good and the bad) and God’s eternal plan as laid out in the Bible. Unlike Ezekiel, we will receive blessings for being God’s witness and watchman, but will not be punished for failure due to being covered in the blood of Jesus and His righteousness.
We are called to share the Gospel and make disciples:
Go therefore and make disciples of all the nations, baptizing them in the name of the Father and the Son and the Holy Spirit, teaching them to observe all that I commanded you; and lo, I am with you always, even to the end of the age.” (Matthew 28:19-20) {emphasis mine}
We should never stop until the end. We are not supposed to hide the fact we are Christians or act like everyone else in the culture, but to be a light for Jesus.
“You are the light of the world. A city set on a hill cannot be hidden; nor does anyone light a lamp and put it under a basket, but on the lampstand, and it gives light to all who are in the house. Let your light shine before men in such a way that they may see your good works, and glorify your Father who is in heaven. (Matthew 5:14-16) {emphasis mine}
Our love for Jesus should shine so brightly that everyone knows we belong to Christ.
Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13)
We should study the Bible so we are ready to share God’s word with all who will listen. Being a light for Jesus isn’t always easy. It can sometimes even lead to persecution and hardship, but we are called to give an account.
But even if you should suffer for the sake of righteousness, you are blessed. And do not fear their intimidation, and do not be troubled, but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence; and keep a good conscience so that in the thing in which you are slandered, those who revile your good behavior in Christ will be put to shame. (1 Peter 3:14-16) {emphasis mine}
Being ready requires diligent prayer and Bible study. We need to know God and His word well to be most effective. Of course we need to be more than just impersonal scholars. We need to have a relationship with Jesus and our Father God and share that relationship with others. We need to share Jesus with even more excitement than we would share our spouse or our kids. We need to be more excited to introduce people to Jesus than we would be to introduce people to a celebrity or other important person. Jesus should be a focus and our joy and such a part of our life that talking about Him becomes second nature. (For most people this takes a long time to reach this point, so don’t lose hope if you aren’t there yet.)
There are lies that we tell and there are also lies by omission. When we leave out some truth, we can imply a lie. So often Christians are so worried about seeming loving that we don’t love people enough to speak the whole truth to them. Yes, God is loving, but He is also holy and gives righteous judgment. Yes Jesus died on our cross to take away our sins, but some will reject Him and spend eternity in eternal torment in Hell. If we only tell the “good” parts, but leave out the “bad” parts, we are speaking a lie.
Everyone deceives his neighbor And does not speak the truth, They have taught their tongue to speak lies; They weary themselves committing iniquity. (Jeremiah 9:5)
In court we are asked to speak the truth, the whole truth, and nothing but the truth. Are you speaking the whole truth when you speak of God? Do you sometimes hold back? I recently was communicating with someone online about the Bible and I caught myself watering down a truth. Not speaking the whole, complete truth trapped me in a corner and my witness was harmed. I like to think of myself as fearlessly sharing God and His truth with people, but I seriously messed up on this one.
Therefore, laying aside falsehood, speak truth each one of you with his neighbor, for we are members of one another. (Ephesians 4:25) {emphasis mine}
Sometimes we hold back because the truth (things like God’s judgment, only one way to God, election, or God’s sovereignty) seems too hard or unpleasant. Sometimes we hold back because we are ashamed. Don’t be ashamed, for Jesus said:
For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:26) {emphasis mine}
The closer our relationship is to God and the better we know our Bible, the more confident we can be sharing the Good News to those around us, but no matter how much we prepare within ourselves, we must always lean on Jesus and do things in His power, not our own.
For God has not given us a spirit of timidity, but of power and love and discipline. Therefore do not be ashamed of the testimony of our Lord or of me His prisoner, but join with me in suffering for the gospel according to the power of God, who has saved us and called us with a holy calling, not according to our works, but according to His own purpose and grace which was granted us in Christ Jesus from all eternity (2 Timothy 1:7-9) {emphasis mine}
May God mold us and guide us to be a good witness and a good watchman, so we can shine the light of Jesus onto all the world and become the faithful servants we were designed to be for His glory.
Trust Jesus
-
 @ 878dff7c:037d18bc
2025-03-02 21:49:36
@ 878dff7c:037d18bc
2025-03-02 21:49:36Cyclone Alfred Threatens South East Queensland
Tropical Cyclone Alfred is projected to make landfall in South East Queensland by Thursday as a Category 2 system.
Currently located 465 km northeast of Brisbane, the cyclone is expected to bring gale-force winds, up to 600 mm of rainfall, abnormally high tides, and damaging swells.
Authorities have issued multiple warnings, including coastal hazard and flood watches, urging residents from Bundaberg to the Gold Coast to prepare for severe weather conditions.
Housing Market Rebounds Amid Interest Rate Cut
Australia's housing market downturn appears to be over, with property values rising by 0.3% in February, nearly offsetting the previous three-month decline of 0.4%.
This rebound is attributed to increased buyer confidence following a recent interest rate cut by the Reserve Bank, signaling a potential resurgence in the housing sector.
Federal Politics: Australia Urged to Lift Defense Spending
In federal politics, discussions have emerged urging Australia to increase its defense spending.
This call emphasizes the need to bolster national security and address evolving geopolitical challenges.
Australian Government Pledges RAAF Base Access for Aerial Firefighting
The Australian government has pledged to grant the New South Wales Rural Fire Service access to Royal Australian Air Force (RAAF) bases to support aerial firefighting operations.
This initiative aims to enhance the state's capacity to respond to bushfires and improve overall emergency preparedness.
New Search Initiated for MH370
Eleven years after the disappearance of Malaysia Airlines Flight MH370, a new search has commenced.
Ocean Infinity is deploying advanced technology, including mothership Armada 7806 and remote-controlled underwater drones capable of scanning the ocean floor down to six kilometers.
The search covers a new 15,000 square kilometer area 1,500 kilometers west of Perth, identified based on data from the past decade.
Challenges such as extreme weather conditions and the vast Indian Ocean area persist.
Experts emphasize the improvement in maritime technology and the emotional toll of repeated search efforts.
The Malaysian government is negotiating a contract with Ocean Infinity, promising a $70 million reward if the wreckage is found.
Victorian Unions Protest Public Sector Job Cuts
The Victorian government, led by Treasurer Jaclyn Symes, announced an unexpected plan to cut 3,000 public sector jobs as part of a budget clean-out, causing uproar among unions.
Six unions representing various sectors, including firefighters, teachers, and public sector workers, have organized a rally on March 3 to protest the job cuts.
Union officials emphasized the widespread impact of these cuts, questioning who would take on the workload and warning of the expensive payouts in redundancies.
They criticized the government's approach, pointing out potential repercussions and the irony of hiring costly consultants to advise on job cuts.
Centrelink Payments Increase for Millions of Australians
Starting in March, approximately five million Australians receiving various Centrelink payments, including Age Pension, Carer Payment, Commonwealth Rent Assistance, ABSTUDY, JobSeeker, Disability Support Pension, and Parenting Payment Single, will see payment increases.
These adjustments are based on the higher of the consumer price index or wage price index, assessed biannually.
Notable changes for JobSeeker include reduced penalties for non-compliance with job requirements for new registrants and exemptions for those working 30 hours a fortnight for two months.
Carers will benefit from more flexible work hours, allowing a spread of 100 hours over four weeks without affecting their payments.
These measures aim to alleviate cost-of-living pressures, with increments resulting in a substantial rise in support since the current government took office.
Note: All information is based on articles published on March 3, 2025.
-
 @ f3873798:24b3f2f3
2025-03-02 20:00:47
@ f3873798:24b3f2f3
2025-03-02 20:00:47No Brasil, o consumo de álcool não é apenas aceito socialmente, mas fortemente incentivado. A presença de bebidas alcoólicas é constante em festas, confraternizações e até mesmo no ambiente familiar. Quem se recusa a beber muitas vezes é visto como alguém “estranho”, “chato” ou antissocial. Essa mentalidade gera um ciclo vicioso de incentivo ao consumo, ignorando seus impactos negativos.
A Pressão Social Pelo Consumo
Desde cedo, muitos brasileiros são introduzidos ao álcool sem qualquer reflexão sobre os riscos. Em algumas regiões, crianças experimentam bebidas alcoólicas ainda na infância, muitas vezes com o incentivo de familiares. A ideia de que “todo mundo bebe” cria um ambiente em que se recusar a ingerir álcool pode levar ao isolamento social e até mesmo a chacotas.
Aqueles que não bebem frequentemente se sentem excluídos de eventos sociais, pois a cultura ao redor do álcool é tão intensa que parece não haver espaço para quem faz uma escolha diferente. Em reuniões, festas e até mesmo encontros informais, a presença da bebida é praticamente obrigatória, reforçando a ideia de que a diversão depende dela.
O Álcool e a Imprudência no Trânsito

Outro reflexo dessa cultura é a alta incidência de acidentes de trânsito causados pelo consumo de álcool. Apesar das campanhas de conscientização e das leis mais rígidas, dirigir embriagado ainda é um problema grave no Brasil. Muitos motoristas assumem o risco, acreditando que estão “bem o suficiente” para conduzir, colocando a própria vida e a de outras pessoas em perigo.
Infelizmente, essa imprudência não se limita ao ato de dirigir. Em festas e eventos regados a álcool, discussões e brigas são comuns, e atos de violência aumentam significativamente. O efeito entorpecente do álcool reduz a capacidade de julgamento, resultando em comportamentos agressivos e irresponsáveis.
A Decadência e o Cenário Degradante

Outro aspecto ignorado pela cultura do álcool é a decadência humana observada em eventos onde o consumo excessivo é incentivado. Não é raro ver pessoas embriagadas vomitando ou até mesmo defecando em vias públicas, completamente inconscientes de seus atos. Essas cenas se tornaram tão comuns que são tratadas como algo natural, quando, na verdade, refletem um problema social sério.
O Carnaval é um dos exemplos mais emblemáticos desse fenômeno. O que deveria ser uma celebração cultural muitas vezes se transforma em um festival de exageros, onde a bebedeira extrema leva a uma série de consequências negativas, como furtos, brigas, acidentes e crimes diversos.
O Lado Ignorado Dessa Cultura

Curiosamente, todos esses problemas são frequentemente minimizados ou ignorados. A sociedade foca apenas no aspecto festivo do álcool, sem considerar os prejuízos que ele causa. Pouco se discute sobre os impactos na saúde pública, na segurança e na dignidade dos indivíduos.
É importante ressaltar que este artigo não propõe a proibição do álcool nem adota uma visão moralista sobre o tema. O problema não está na bebida em si, mas na forma como é consumida e incentivada. O que se defende aqui é o equilíbrio e a responsabilidade.
Beber com moderação, respeitar os limites do próprio corpo e das pessoas ao redor, evitar a pressão social sobre aqueles que não bebem e nunca misturar álcool e direção são atitudes fundamentais para transformar essa cultura. O consumo consciente permite que momentos de celebração sejam realmente prazerosos, sem que se tornem um problema para quem bebe ou para a sociedade como um todo.
A diversão não precisa estar atrelada ao exagero. É possível aproveitar bons momentos sem perder o controle, sem colocar vidas em risco e sem alimentar um ciclo de imprudência. Repensar a forma como lidamos com o álcool é essencial para uma convivência mais saudável e responsável.
-
 @ d6affa19:9110b177
2025-03-02 19:43:03
@ d6affa19:9110b177
2025-03-02 19:43:03i make my way downstairs,
the house is quiet now;
the little ones are finally asleep.
a soft drizzle from the shower fills the silence.
She must've gotten in already—
taking some time for Herself after a long day.i grab two towels from the closet and toss them in the dryer.
She likes them warm.
unsure of how long She's been bathing,
i begin preparing the room.i light a few of Her candles—
a sweet, autumn scent fills the air,
rich with hints of cinnamon and crisp leaves.
it wraps me in a pleasant embrace,
evoking memories of cozy evenings.i turn off the lighting,
leaving only the candlelight flickering.
the room is illuminated with a warm, orange glow.i go ahead and set out the oils and lotions—
wondering what She'll choose tonight...
anticipation quickens my heartbeat,
rousing a familiar longing.with everything prepped,
i take some time to breathe in the atmosphere.
the gentle cascade of water still echoes from the bathroom.
it flows like a calming stream,
creating a soothing ambiance.i lie down on the bed, closing my eyes.
a moment of stillness envelops me,
a brief escape from the day's chaos.
i've been looking forward to this.
i can feel my mindset shifting.suddenly, the shower stops,
breaking the stillness.
my eyes quickly open.
a rush of enthusiasm surges through me.
i spring out of bed and retrieve Her towels from the dryer.upon opening the bathroom door, i'm greeted by Her sweet voice, "Is that my good boy? Perfect timing."
a flash of heat creeps up my neck,
i can't help but grin.
my body relaxes,
the tension eases as i lean into Her approval.i open the shower door then kneel down,
the soft bath mat cushions me.
steam from the shower fills the room,
creating a cocoon of warmth.
Her silhouette glows softly through the mist.i offer the warm towels,
the fabric still radiating heat.
without a word She presents Her leg.
instinctively, i set one towel on my lap,
using the other i begin patting Her dry,
starting from Her pedicured foot.Her smooth skin invites my touch—
but the plush towel acts as a barrier.
once She is satisfied,
i switch to the other leg,
continuing my attentive care."Did they give you any trouble?" She asks, Her tone light and curious.
"I hope they weren't too rough on you.""not tonight, my Queen," i answer, still focused on my task.
"they fell asleep quickly—must've been exhausted."
"Good," She says with a relieved sigh.She then snaps Her fingers—
signaling for me to hand Her the towel.
i comply, moving out of Her way.
She finishes drying Herself and wraps the towel snugly around Her body.
She casually grabs the other towel and wraps it around Her head,
then makes Her way into the bedroom.i watch Her walk over to the nightstand,
setting the lavender oil to the front of it—
this is what She's chosen for the evening.
She then picks up Her phone,
settling onto the edge of the bed,
towel still wrapped around Her."Well done—I love it!" She says, Her voice rich with approval as She absorbs the arrangement.
Her words pull me from my thoughts,
another subtle flush creeping into my cheeks.
i make my way to the nightstand,
picking up the oil.
my pulse quickens as i kneel before Her,
the cool floor a stark contrast to my rising excitement.She tilts Her head from behind Her phone, a playful glint in Her eyes.
"Don't you look so adorable down there?"
She leans forward slightly, Her expression shifting to one of command.
"It's been a long day. So be sure that you give My feet the attention they deserve tonight."my stomach flutters as She lifts one foot.
i take it gently into my hands,
a shiver runs through me.
i pour a small amount of oil into my palm.
the scent of lavender mingles with the autumn candles.as i massage it into Her foot,
i can't help but notice every detail—
the curve of Her arch draws me in,
the softness of Her skin captivates me.She shifts Her foot slightly,
guiding me to the areas that demand my attention.
Her toes wiggle in response.
it's so mesmerizing...
with each stroke i feel my mind quieting.
the chill of the floor fades away.
there's only Her.the rhythm of my hands,
the way the oil glides so smoothly,
the way She relaxes under my touch.
i lose myself in these sensations.
my thoughts slowly dissipate—
replaced by a feeling of clarity, of purpose.i feel Her foot pull away,
momentarily releasing me from my trance.
it's had its fill.
She lifts the other one in front of me.
Her toes curling playfully.
my heartbeat skips.
a desperation fills my chest.
a longing.
to express my devotion in the most intimate way.
to worship the very thing that grounds Her—
that ties Her to this earth.
it's a yearning that goes beyond words.
i can almost taste the moment.
the connection it would bring....
i breathe deeply,
a heavy sigh escaping my lips—
lips that ache to honor Her every curve.
permission lingers in the air,
tantalizing and just out of reach.
i notice Her looking at me,
a giant smirk playing on Her lips,
Her phone now at Her side."Well..?" She teases, a mischievous look in Her eyes.
"What are you waiting for? It's not going to rub itself."
Her toes continue wiggling in front of me—taunting.the urge simmers beneath the surface.
the denial resides like a sweet ache.
i breathe through it,
accepting Her limitation.
i'm grateful for the gift of this moment,
channeling the energy into the task at hand.i gently embrace Her other foot,
admiring the delicate contours of Her ankle.
Her skin feels like silk against my fingertips.
i pour a few more drops of oil into my palm,
the velvety texture glides through my hands.
another burst of lavender dances in the air,
blending again with the persistent aroma of the candles.i begin to knead Her other foot,
focusing on the arch,
applying a careful amount of pressure.
each stroke sends ripples of warmth through my hands,
i feel Her tension melting away beneath my touch.
She lets out a contented sigh and falls back on the bed taking it in.
"Mmmm, that feels good." She encourages.i savor this privilege,
as the flickering candles cast a soft glow around us.
they dance slowly,
a soothing backdrop to the rhythm of my hands.i trace the outline of Her heel,
feeling the delicate curves,
enthralled by Her foot's response.
with each gentle caress,
watching Her toes dance slightly,
a silent acknowledgement of my devotion.as if pulled by a magnetic force,
i lean in closer,
inhaling the sweet aroma of lavender,
it's floral notes fused with the radiance of Her scent.
a sense of peace settles within me.
the weight of the day lifts,
replaced by the comforting embrace of surrender.
i'm here to please Her,
i'm here to honor Her,
i'm here to love Her.
lost in the act of serving,
i feel Her energy flow through me,
binding us together.
closer.as i finish,
i look back up at Her.
my heart swells with pride.
She smiles down at me,
a knowing glimmer in Her eyes.
igniting a fire within me—
a sense of belonging.
right now,
i know exactly where i need to be—
kneeling before Her,
fully aligned with Her presence.in these cherished rituals,
in this sacred exchange,
i find my place.
forever devoted..."I love you, sweet boy." She whispers,
Her words deeply resonating,
echoing the truth of my heart—
that i am completely and utterly Hers. -
 @ d6affa19:9110b177
2025-03-02 19:27:10
@ d6affa19:9110b177
2025-03-02 19:27:10Wander — 19:27
It’s been a long, rough day.
The fresh air feels good,
but my mind is still trapped,
stuck in that office,
its fluorescent lighting,
archaic and noisy,
still buzzes behind my eyes.
Closing that sale was grueling—
the customer’s incessant demands—
they still press against my skull.
My patience feels razor-thin,
the weight of the day settling on my shoulders.On my way to the apartment,
I catch a glimpse of the setting sun.
Its warm hues contrast my somber demeanor.
I check my phone again,
scrolling through my messages.
...
Nothing new…
I haven’t heard from her in hours—
only left on “read.”I let out a sigh.
My body feels heavy.
This day has just dragged on forever.Walking up to the apartment door,
I fumble a bit with my keys,
the metal clinks,
I struggle to find the right one.
Upon entering the dimly lit apartment,
I see her sitting on the sofa,
dressed as if she’s getting ready to leave.Ugh, I don’t feel like going anywhere tonight…
She looks up from her phone,
our eyes locking.
“You didn’t let Me know you were on your way,” her tone sharp.A hint of disappointment in her eyes—
subtle, but pointed.
A silent judgment.
A reminder of my failure—
of a broken word of honor.But my pride,
like a protective big brother,
overshadows the regret gnawing at me,
feeding my mind with justifications.She didn’t respond earlier—
to my messages.
Not a single word.
And now, all of a sudden,
communication matters?
My eyebrows furrow.
My hands clench.“I told you I’d be late today, didn’t I?” I finally answer,
trying to keep my voice steady.
Her nonchalant expression shifts,
becoming more annoyed.“And that has nothing to do with your promise to let Me know when you’re leaving,”
she fires back,
arms folded across her chest.Her voice cuts through the air.
“Now go get cleaned up. I’m hungry and we have a little bit of shopping to do.”I subtly bite at my lip.
A dull pain.
A distraction.
Anything to manage the tension.Taking a seat on the sunken foyer’s edge,
I slowly remove my shoes,
lingering in defiance.Today has been so stressful…
Doesn’t she see that I’m exhausted?
Maybe I don’t want to go back out.
Does she even consider how I feel?
Maybe she’d know if she just asked.“Hey! Are you listening?” She snaps,
impatience saturating her tone.
“What’s wrong?”I remain seated,
and turn my head toward her,
meeting her gaze—
a fierce expression now on her face.A heavy sigh escapes me.
Honestly, I don’t want to tell her no.
But the thought of getting back out…
It feels unbearable.“I’m just so tired,” I finally admitted,
shoulders slumping.She seems unconvinced.
“There’s more to it than that,” she posits,
her eyes piercing through my defenses.
“What is it? Tell me what’s going on.”I turn my head away.
Shame tightens around me,
suffocating, silencing.
From the hurt I feel—
over some ignored messages.
Just a few simple messages…
It seems juvenile.
But it’s amplified by her disregard for my situation.
It stings, and I can’t find the words to express it.
Nor would I if I could.…
At some point, she moved.
I didn’t hear her.
I didn’t see her.
But I feel her now—
towering over me.
Close.
Her presence,
it’s tangible,
like a weight bearing down on me.Looking up at her,
our angry expressions collide,
the air thickens with unspoken tension.
I notice my heart beating faster—
Not only from the conflict,
but from her aura…There’s a shift in her energy.
A quiet intensity brewing beyond her expression.
Have I pushed her too far with my silence..?
Veil — 19:38
With a swift motion,
she lunges forward,
pushing me to my back.
Her weight settles on my stomach,
pinning me to the floor.My breath catches.
Her scent—something floral..?
Jasmine…
It melds with her natural aroma,
igniting my senses.The softness of her skin,
the pressure of her body above me;
they contrast sharply,
a blend of elegance and power."W-what are you doing!?" I exclaim, the surprise evident in my voice.
Her response is immediate.
"I won't tolerate you moping or acting out tonight, boy. Now tell Me what's wrong," she demands,
her voice sharp as a knife.I'm stunned.
A fire burns in my chest—
is it anger?
Or something else?
Embarrassment settles in,
uninvited, heating my face,
her eyes piercing into me."I already told you, I-I'm just tired. There's no need for this!" I plead,
muscles tensing as I try to push her off."Stop pushing!" she commands.
I resist,
frustration spilling over.
"Get off!"Attempting to restrain me,
she grabs my wrists.
But I'm stronger,
easily breaking her grip.
I interlock our hands,
pushing back,
trying to lift her."I said stop!" she asserts,
her voice firm,
unyielding.I continue to push,
arms fully extended.But she suddenly shifts.
Her weight crashes forward,
pinning my arms above my head.
I can’t push from this angle.As she holds me down,
something mingles with the fluster—
an unexpected exhilaration...Her body hovers above mine,
our faces inches apart.
I'm trapped,
her hair falling around us like a curtain.
A predaceous look glimmers in her eyes—
she leans in closer,
jawline tightening,
eyes slowly narrowing,
asserting her dominance.
I can't resist inhaling Her scent,
it’s so distracting—
intoxicating.With every labored breath,
the warmth of Her body presses down on me.
Now sitting on my chest,
Her weight feels heavier,
oddly comforting.Her gaze pursues me.
I look away,
desperate to hide.My heart is racing.
It's overwhelming—
Her scent,
Her pressure,
the gleam in Her eyes.
I struggle to focus.Somehow, without me noticing,
our hands are no longer intertwined…
Instead, She holds my wrists—
tightly against the ground.Lost between defiance and surrender,
my body is betraying me,
not from fear,
but from curiosity.
Or is it a mixture?A shiver travels down my spine,
my body relaxes,
how did we get here..?The desire to resist is fading,
yielding to the magnetic pull of Her presence—
losing myself in Her orbit.Aware of my waning resistance,
a smug grin flashes across Her lips—
so captivating.
I’m melting."Good boy." She whispers into my ear.
Her words surround me like a warm embrace,
and Her smile—
the most precious sight in the world—
puts butterflies in my stomach,
a lightness in my head.
The frustration of the prior moment,
seems somehow…
distant.Still holding my wrists,
She looks down at me,
taking in the moment—
savoring it."Who is your Queen?" She finally asks,
Her voice gentle and sweet.I feel a storm within,
emotions crashing like a tsunami.
Pulling me back to the present—
regret, devotion, shame—
all colliding together.
How She hurt me.
How I failed Her.
I try to look away.
A hint of defiance persisting..."Answer me." She demands,
Her soft tone hardening.
"Who is your Queen?"I pause,
Her gaze weighing more than Her body.
My heart pounds,
and for a moment,
I'm lost in the depths of Her eyes,
searching for an escape—
an escape that isn’t there...The silence stretches,
heavy and expectant.
My throat tightens,
heart pounding—
betraying me..?
Or leading the way?With a resigned breath,
I whisper, "You are..."She immediately follows up,
"And who do you obey?"
Her tone still harsh.My eyes plead to Her fierce gaze,
swallowed in shame.
Begging to avoid the obvious answer,
because of my guilt—
because of my broken promise.
but Her stare is unrelenting,
and I divert my eyes once more."Look at me," She commands sharply,
"Who do you obey?"My eyes instinctively comply,
Her grin now replaced by a stern expression.With no other option,
I mutter my surrender, "...You."
The word slips out,
a quiet truth that echoes in between us,
heavy with contrition,
but liberating."Now answer properly," She demands,
"Who do you obey?""I obey You, my Queen."
The words spill effortlessly from my lips,
weightless and freeing."That's right." She proudly replies.
She releases my wrists and sits up,
a triumphant smile gracing Her lips.
Those enchanting lips…
That beautiful smile…With my arms free,
I feel a mix of relief and lingering tension,
my heart still racing from the struggle.A whirlwind of emotions continue to swell—
shame, regret, adoration—
neglect and dismissal—
longing—
disappointment…And the sight of Her beauty aches—
yet, despite my surrender,
something in Her eyes tells me…She’s just getting started.
Stricken — 19:46
The sun has set.
Its remaining beams peering through the glass door,
filling the room with an orange hue.Her silhouette is framed by the fading light—
imposing, inescapable.
She looms over me,
Her shadow stretching,
covering,
consuming.I lie underneath Her—
underneath Her shadow—
between breath and reverence,
desperately searching,
looking for the right words,
but only stare.I feel trapped.
Not by Her,
but by my own self—
the walls I put up.
Unable to express my regret.
For how I failed Her.
For my own hurt feelings…When suddenly,
and surprisingly,
She slaps me.
Her palm releases a sharp crack,
a sound that echoes in the stillness.
The impact burns on my left cheek,
forcing me to wince,
the world tilts for a heartbeat,
returning me to the moment.Slightly disoriented,
my hands cover my face,
instinctively guarding."Put your hands down." She orders,
Her voice firm.
I hesitate—
caught between instinct and obedience.
Tension coils in my chest.She takes my hand,
tucks it to my side,
and pins it with Her thigh.I don't resist.
She does the same with my other hand,
leaving me unguarded—
vulnerable.Her grip is tight—
constraining.
My senses feel heightened.
The warmth of Her skin—
so smooth against my own—
presses against me.
Deceptively soothing.
A paradox of wrath and comfort,
leading me deeper into the moment.I watch Her draw back Her hand,
preparing another slap.
a stoic look etched across Her face.
My breath catches,
the air is thick with unspoken words.
Yet, strangely,
my heartbeat steadies,
my body relaxes,
ready to absorb Her frustrations.Her hand lands forcefully,
slamming into my left cheek once again,
the sting tight and harsh.
I wince again,
losing focus,
struggling to meet Her gaze."Apologize to me." She commands harshly.
Before I can orient myself,
before I can respond,
She slaps me again.
And again.
And again.
And again.
Each strike lands like a thunderbolt—
a wrecking ball to the walls I’ve built.A fiery pulse ignites my face,
blending with a deviant thrill—
something coursing through me,
blurring agony and bliss.
My eyes form tears.
I fight desperately to hold them back."I said apologize!" She hisses,
Her tone as sharp as Her slaps.
I look up at Her,
trying to focus,
and catch Her expression—
impassive, demanding,
yet with a soft glimmer in Her eyes—
so gorgeous...A warmth radiates from Her,
it blends with the heat from my cheek,
amplifying Her pull,
leaving me breathless,
utterly subject to Her will."I… I'm sorry…" I whimper,
the words barely escaping my lips,
laced with a mixture of shame and exhilaration."For what?" She asks,
Her lips curl,
a blend of annoyance and...
something, something—
primal.I try to take another deep breath,
it's difficult with Her weight pressing down.
My pride aches as much as my face.
I barely maintain composure,
my eyes unable to escape Her gaze.She strikes again,
forcefully,
without warning.
My head snaps to the side,
leaving an imprint on my soul itself.
The barriers I’ve placed—
their remnants—
are completely shattered,
freeing the truth."For disobeying You!" I nearly cry.
The admission tastes bittersweet on my tongue.
It feels like a release,
the confession washing over me,
leaving me breathless and exposed.She lets out an amused laugh.
The smile She was fighting back breaks through,
a satisfied grin that lights up Her face.
My heart to skips a beat.But She's not finished yet.
Purge — 19:52
"And how exactly did you disobey me?" She asks,
already knowing the answer.She's going to make me own it…
The buzzing on my cheek—
a subtle reminder to comply."For not letting You know when I left." I meekly respond.
"And..?" She questions,
not satisfied with the previous answer."And for not getting ready when you asked…" I amend,
my voice barely above a whisper."And..?" She continues,
Her tone becoming impatient.But I'm at a loss—
unsure.
What is She seeking?
My mind races,
desperately searching,
looking for the right words.…
But none come.
Panic sets in,
gnawing, deep—
am I failing Her again?
Was I being too much?
Too needy?
I can’t explain this ache in my chest…She looks down at me,
Her expression softening."For not telling me what's bothering you." She says,
guiding me to the answer."I'm your Queen, and I deserve for you to be honest with Me about everything—“ She continues,
Her voice carrying a tenderness,
cutting through the tension.
“you should feel safe enough to tell Me anything…"My body is still,
yet it feels as if it’s trembling fiercely.
I can only stare.“You don’t have to hide anymore...”
She continues,
“You’re safe now…”My heart feels cracked open.
Lying beneath Her,
restrained and exposed—
and now with Her words…Her voice hangs in the air,
slicing through the chaos.
She's reached into my heart,
through the walls and the barriers,
amidst the insecurities and doubts—
the fear and pain—
touching the essence that is truly me,
with nothing standing in Her way.I look up at Her angelic face,
into Her divine eyes,
and with no more hesitation,
I express what seemed impossible before."I felt… hurt, like You were ignoring me…" the confession falls out clumsily.
“Like… like I wasn’t worth the attention…” my chest tightens more as I speak,
each word breathing life into the hurt I tried to bury.
"Even after such a hard day..."I see the look on Her face change,
Her gentle expression slipping away,
revealing a raw vulnerability.
Silence fills the space between us."And..." I continue,
"And it’s stupid, I know… I’m sorry for being too much, I-I couldn’t help it…" my voice breaking,
“I just… needed You, so much… and you didn’t even message me back… I felt invisible…”I take a moment to regain my composure.
"Like, I know I was supposed to let You know that I was on my way, but... I... I was just so angry... I'm sorry… and it just seems so childish now…" I finish through tears.
The last piece of me lain bare.Her hand slowly reaches down,
caressing my cheek.
Her fingers trace across my skin,
gentle, light—
a stark contrast from the slaps earlier.
The tears linger,
a reminder of all I’ve kept from Her.
Her palm cups my cheek,
softer than I’ve ever known,
and I see in Her eyes,
Her own tension,
a glimmer of regret...“I…” Her voice trembles.
She catches Herself,
maintaining control.But there’s something else—
an unease.
"I didn’t realize… I should have known.” She continues.
“You needed me and I wasn’t there for you, was I?"She looks down,
Her gaze escapes my eyes,
and for a moment,
I see the disappointment in them—
the disappointment in Herself, too.
Her divine presence alters,
revealing a more human beauty…I nod,
feeling the weight of my admission.Her eyes meet with mine again,
shimmering with unshed tears.
She simply stares,
taking it in for a brief moment,
the words settling between us,
forming a bridge that connects our spirits."I'm so sorry, My sweet boy." She says,
trying to hold a steady demeanor.
"I had no idea you needed Me so much today… I was interrupted after reading your message and never followed up. Oh, sweetie, I'm so sorry I wasn't there for you… that I let you down… you’re not… you’re not ‘too much.’"With both arms,
She reaches around my head,
and gives me a powerful embrace.
The hug is so tight that I can barely breathe.
She begins saying something else,
but it sounds muffled,
I can't make it out.And yet, it doesn't matter.
Her words—
Her acknowledgment...
the tension inside me begins to unravel.And, despite Her increasing pressure on top of me,
it’s as if the weight of the world has been lifted from my chest,
replaced by a serene joy that blossoms within—
from knowing that She cares,
that She was able to reach out and guide me to the honesty of my confession,
creating a space where we could see each other authentically.Her arms tighten around me,
I melt into Her embrace.
My heart pounds.
But not frantically—
it’s steady now,
slow, calming,
like a gentle wave.
Her breath against my neck,
warm and soothing,
Her embrace,
feels like a sanctuary,
where my heart can rest and heal.Everything fades,
only the sound of Her heartbeat,
it intertwines with mine,
forming a profound connection.
I dare not move,
I dare not disturb this moment,
not for air,
not for life itself—
this closeness is all I crave,
and I would die for it.…
Then,
just like that,
the moment fades.
Her arms loosen,
the weight of Her touch lifts,
leaving an emptiness.My body feels light,
but my heart is heavy—
full.I need a moment,
in this space,
in the silence,
to gather the pieces of myself—
the pieces She’s helped reveal.
Bound — 20:04
She releases Her grip on me,
returning Herself to a seated position.
I inhale sharply,
much-needed air filling my lungs.
She lets out an adorable chuckle at the sight.My vision clears,
drawn to Her beautiful smile."So, will you forgive Me, sweet boy?" She asks, wiping a few tears from Her own eyes.
"Of course, my Queen." I respond almost reflexively.
"Will You forgive me?"She leans down,
Her lips pressing lightly on my forehead.
"I already have, My sweet boy," She smiles.The warmth of Her kiss lingers,
sending a shiver down my spine.She stands up,
relieving the pressure on my chest.
My lungs seize the opportunity,
pulling in air.
But the relief is fleeting—Her foot crashes down,
pressing me back into the ground.
Her weight returns—
focused,
steady,
absolute.
I’m breathless again—
by the force She exerts,
and the sight of Her over me.She stands poised,
effortless.
A Queen assessing Her property.
The look in Her eyes sharpens again,
though this time,
amusement dances behind them.She shifts Her weight slightly,
a small, deliberate adjustment.
The pressure deepens,
spreading through my chest—
slow, rolling,
a silent warning."And don't you ever give me a reason to do this to you again, do you understand me, boy?" She asks,
the weight increasing,
firm and steady.
My body strains beneath Her foot,
not quite pain,
something heavy,
something consuming,
part of me craving more…"Yes, my Queen." the words escape,
slipping through shallow breaths.
I wince,
but the feeling is not unwelcome—
it feels grounding,
reassuring.She presses a little more.
A test..?
I instinctively tense,
but don’t resist.
Our clothing dulls the sensation,
but amplifies something deeper—
the certainty of Her control,
the reality of Her dominance."I need you to be open and honest with your feelings, got it?" She continues,
Her tone firm,
and yet warm,
welcoming."Of course, my Queen." I vow instantly,
the words feeling like both a promise and a plea."Good boy." She adds with a satisfied grin spreading across Her face,
lighting up Her features.
"Now, get yourself cleaned up, I'm hungry and we have some shopping to do."She lingers for a moment.
Then with a slow, deliberate motion,
She finally lifts Her foot from my chest.
The absence is sudden.
The liberation…
unnatural.
Wrong.My chest rises sharply,
filling with air once again,
the breath She has granted me.Above me,
She smiles,
admiring Her handiwork.
There’s a sense of satisfaction in Her expression,
a silent acknowledgment of our shared moment."Yes, my Queen. Thank You, my Queen." I say to Her with a smile,
my heart swelling with gratitude.But there’s something else…
I hesitate.
The words are there,
on the tip of my tongue.
Will She welcome them..?
Acknowledge them..?<She watches me closely,
aware,
waiting,
Her eyes softening,
enough to make my heart stutter.
But I can’t hold them in any longer—…
"…I love You," I add,
the words spilling out of me. -
 @ 2b1964b8:851949fa
2025-03-02 19:00:56
@ 2b1964b8:851949fa
2025-03-02 19:00:56Routine Picture-in-Picture American Sign Language Interpretation in American Broadcasting
(PiP, ASL)
Picture-in-picture sign language interpretation is a standard feature in news broadcasts across the globe. Why hasn’t America become a leader in picture-in-picture implementation too?
Misconception.
There are prevalent misunderstandings about the necessity of ASL interpreters in the media and beyond. As recently as January 2025, an American influencer with ~10M social followers on Instagram and X combined, referred to sign language interpreters during emergency briefings as a distraction.
Such views overlook the fact that, for many deaf individuals, American Sign Language is their primary language. It is wrongly assumed that deaf Americans know—or should know—English. American Sign Language differs in grammatical structure from English. Moreover, human interpreters are able to convey nuances that captions often miss, such as non-manual markers; facial expressions, body movements, head positions utilized in sign language to convey meaning. English is the native language for many hearing Americans, who have access to it throughout the United States without any additional expectation placed upon them.
A deeper understanding reveals that many nations have their own unique signed languages, reflecting their local deaf culture and community — Brazilian Sign Language, British Sign Language, Finnish Sign Language, French Sign Language, Japanese Sign Language, Mexican Sign Language, Nigerian Sign Language, and South African Sign Language, among numerous others.
Bottom Line: American Sign Language is the native language for many American-born deaf individuals, and English is the native language for many American-born hearing individuals. It is a one-for-one relationship; both are equal.
In an era where information dissemination is instantaneous, ensuring that mainstream broadcasts are accessible to all citizens is paramount.
Public Figures Including Language Access In Their Riders
What's a rider? A rider is an addendum or supplemental clause added to a contract that expands or adjusts the contract's terms. Riders are commonly used in agreements for public figures to specify additional requirements such as personal preferences or technical needs.
A Simple Yet Powerful Action
Public figures have a unique ability to shape industry standards, and by including language access in their riders, they can make a profound impact with minimal effort. * On-site American Sign Language interpretation ensures that deaf and hard-of-hearing individuals can fully engage with speeches and live events. * Open captions (burned-in captions) for all live and post-production interview segments guarantee accessibility across platforms, making spoken content instantly available to a wider audience. These implements don’t just benefit deaf constitutents—they also support language learners, individuals in sound-sensitive environments and any person who relies on, or simply refers, visual reinforcement to engage with spoken content.
For public figures, adding these 2 requests to a rider is one of the most efficient and immediate ways to promote accessibility. By normalizing language access as a standard expectation, you encourage event organizers, broadcasters, and production teams to adopt these practices universally.
As a result, there will be an industry shift from accessibility as an occasional accommodation to an industry norm, ensuring that future events, interviews, and media content are more accessible for all. Beyond immediate accessibility, the regular presence of interpreters in public spaces increases awareness of sign language. Seeing interpreters in mainstream media can spark interest among both deaf and hearing children to pursue careers in interpretation, expanding future language access and representation.
Year-Round Commitment to Accessibility
Too often, language access is only considered when an immediate demand arises, which leads to rushed or inadequate solutions. While some events may include interpretation or captioning, these efforts can fall short when they lack the expertise and coordination necessary for true disability justice. Thoughtful, proactive planning ensures that language access is seamlessly integrated into events, rather than being a reactive measure.
Best practices happen when all key players are involved from the start: * Accessibility leads with combined production and linguistic knowledge who can ensure accessibility remains central to the purpose rather than allowing themselves to be caught up in the spectacle of an event. * Language experts who ensure accuracy and cultural competency.
* Production professionals who understand event logistics.By prioritizing accessibility year-round, organizations create spaces where disability justice is not just accommodated, but expected—ensuring that every audience member, regardless of language needs, has access to information and engagement.
-
 @ 6e0ea5d6:0327f353
2025-03-02 15:01:24
@ 6e0ea5d6:0327f353
2025-03-02 15:01:24Ascolta bene! Forget the State, the Parties, and the Ideologies of bureaucrats! Let your own business, interests, and money be your greatest political allegiance.
Do not swear loyalty to a flag that despises you. Loyalty to family is the rock upon which true honor is built. In times of uncertainty, your devotion to blood ties must be unconditional, for family is the foundation that sustains your very existence. But remember: blood makes relatives, loyalty makes a family.
Loyalty is not just a virtue but a moral obligation. Betraying the trust of family is the greatest sin—an act that not only destroys relationships but also the essence of belonging to something greater.
A truly loyal man understands that family is a reflection of his own soul. He knows that each member is an extension of himself, and protecting these bonds is an extension of protecting his own identity. Amidst the storms of adversity, stand firm, for a family, like a ship, only reaches safe harbor when all its crew members work in unison.
So, amico mio, keep this truth in your heart: loyalty to family is the fortress that withstands all storms. Without it, a man is like a leaf in the wind—directionless and purposeless.
Hold fast to your principles, honor your commitments, and never, under any circumstance, abandon those dearest to you. Only then will you find the true peace and honor that come from fulfilling your sacred duty.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 660162cf:8d93a1dc
2025-03-02 14:33:16
@ 660162cf:8d93a1dc
2025-03-02 14:33:16
อย่าตัดสินภาพลักษณ์ผู้อื่นจากอดีต
เคยไหมที่คุณเผลอตัดสินใครสักคนเพียงเพราะ “ภาพลักษณ์เก่าๆ” ที่คุณเคยเห็นเมื่อหลายปีก่อน? ไม่ว่าจะเป็นเพื่อนสมัยเรียนที่เคยขี้เล่น พูดเก่ง ชอบยิงมุกตลกในห้องจนดูไม่น่านับถือ แต่วันหนึ่งเขากลับมาในฐานะอาจารย์มหาวิทยาลัยผู้มีความรู้เชิงลึก หรือ เพื่อนร่วมงานที่เคยทำงานผิดพลาดในโปรเจกต์แรกแต่วันนี้กลับกลายเป็นคนที่จัดการงานได้อย่างยอดเยี่ยม
ภาพลักษณ์เก่าๆ ฝังแน่นในใจเราได้อย่างไร
สมองของเรามักจะจดจำ “ความประทับใจแรก” หรือ “เหตุการณ์สะดุดตา” ไว้เป็นกรอบเพื่อใช้ตัดสินผู้อื่นในปัจจุบันและบ่อยครั้งเรายังนำสิ่งนั้นไปคาดการณ์อนาคตของเขาเพิ่มเติมด้วย ที่สำคัญเรามักจะต่อต้านข้อมูลหรือสิ่งใหม่ ๆ ที่เราไม่คุ่นเคยโดยอัตโนมัติถ้ามันขัดแย้งกับกรอบเดิมๆที่เรารู้จัก เพราะเรารู้สึกว่าอาจต้องสูญเสียความมั่นคงหรือความสบายใจในการรับรู้จากสิ่งที่เราคุ้นชินบางครั้งก็อาจสั่นคลอนการใช้ภาพลักษณ์จำเก่าๆที่เราจดจำไว้ ดังนั้นการตัดสินใจแบบโดยการนำภาพลักษณ์เก่าๆมาจึงเป็นวิธีลัดที่สมองชอบเลือกใช้ โดยเฉพาะในชีวิตประจำวันที่ต้องเร่งรีบ

เราทุกคนล้วนมีสิทธิ์ เปลี่ยนแปลง และ เติบโต ภาพลักษณ์ก็เช่นกัน
กรอบความคิดเก่า คือ สิ่งที่ทำให้เรายึดติดกับอดีต
ลองนึกถึงเพื่อนที่เคยสอบตกวิชาคณิตศาสตร์ แต่ปัจจุบันเขาอาจเป็นโปรแกรมเมอร์มืออาชีพ หรือหัวหน้าทีมพัฒนาระบบในบริษัทใหญ่ๆ หรือเพื่อนร่วมงานที่เคยถูกมองว่าตัดสินใจพลาดไปเสียทุกครั้ง ก็อาจพัฒนาตัวเองจนมีวิจารณญาณเฉียบคมที่สุดในทีม การเปลี่ยนแปลงเหล่านี้เกิดขึ้นได้เสมอกับทุกคนที่ผ่านเข้ามาในชีวิตของเรา

คนเรามีสิทธิ์พัฒนาและเติบโตในแบบที่คาดไม่ถึง
แล้วเราจะเปิดใจยอมรับการเปลี่ยนแปลงของผู้อื่นได้อย่างไร?
1) ถามตัวเองให้บ่อยขึ้น ทุกครั้งที่เผลอตัดสินใครจากภาพลักษณ์เก่าๆลองตั้งคำถามก่อนว่า “สิ่งที่เคยเห็นหรือที่เคยรับรู้ในอดีตยังเป็นจริงอย่างที่เราคิดอยู่ไหม?” และ “ปัจจุบันตอนนี้เขาเปลี่ยนไปอย่างไรบ้าง?” หรือเราอาจจะตั้งคำถามว่า “เขามีด้านดีหรือสิ่งที่เปลี่ยนไปจากภาพลักษณ์เดิมที่เรารู้จักหรือเปล่า?” เพื่อกระตุ้นให้เราเปิดใจรับรู้ข้อมูลใหม่
2) สังเกตพฤติกรรมปัจจุบัน แทนที่จะยึดติดกับเรื่องในอดีตเราลองตั้งใจฟังความคิดเห็นของเขาหรือสังเกตการกระทำในปัจจุบันเพื่อมองหาความก้าวหน้าหรือสิ่งที่เปลี่ยนไปจากที่เราเคยคิดมาก่อนในอดีต
3) ให้โอกาสและเวลา การเปิดโอกาสให้คนคนหนึ่งได้พิสูจน์ตัวเองในสถานการณ์ใหม่ๆ มักทำให้เราเห็นศักยภาพที่ไม่เคยรับรู้มาก่อน
4) อยู่กับปัจจุบันมากกว่าความทรงจำเก่าๆ อย่าปล่อยให้ภาพลักษณ์เก่าๆของเขากลายเป็นอุปสรรคต่อการทำความรู้จักตัวตนปัจจุบันอดีตอาจเป็นเพียงหนึ่งบทของชีวิตแต่ไม่ใช่ทั้งหมดที่เขาเป็น ณ ปัจุบัน

การเปิดใจมองเพื่อนคนหนึ่งในอดีตโดยดูจากภาพลักษณ์ที่เค้าเปลี่ยนไปแล้วในปัจุบันโดยไม่ตัดสิ่นที่เขาจากสิ่งที่เคยทำแย่ๆมาก่อน เป็นอีกก้าวในการเติบโตทางด่านความคิดของเรา
ยิ่งเปิดใจ เราก็ยิ่งได้เรียนรู้
การเลือกเปิดใจยอมรับตัวตนใหม่ของคนรอบข้าง นอกจากจะช่วยให้ความสัมพันธ์ดีขึ้นแล้ว เรายังได้เรียนรู้และรับแรงบันดาลใจจากเขาอีกด้วย ทุกการเปลี่ยนแปลงที่เกิดขึ้นสะท้อนว่ามนุษย์มีศักยภาพเติบโตได้ไม่สิ้นสุด ดังคำกล่าวที่ว่า “อย่าตัดสินภาพลักษณ์ผู้อื่นจากอดีต” — เพราะเพื่อนร่วมงานที่เคยมีปัญหาในอดีต อาจกลายเป็นผู้เชี่ยวชาญในสาขาที่เราไม่เคยคาดคิด หรือเพื่อนสมัยมัธยมคนนั้นอาจเติบโตมาเป็นครูอาจารย์ผู้ถ่ายทอดความรู้ให้คนรุ่นใหม่และนี่ก็คือ พลังอันยิ่งใหญ่ของการยอมรับในพัฒนาการของผู้อื่น
Siamstr

-
 @ 044da344:073a8a0e
2025-03-02 14:22:04
@ 044da344:073a8a0e
2025-03-02 14:22:04Ich war neugierig. Florentine Anders hat mit mir studiert. Wobei: Ganz so nah, wie das jetzt klingt, waren wir nicht. 120 Studenten, sieben Seminargruppen: Als es im Herbst 1988 für uns losging an der Sektion Journalistik in Leipzig, hing es auch vom Zufall ab, mit wem man mehr zu tun hatte und mit wem weniger. Manche Gruppen hatten sich im Volontariat gebildet und andere bei der Auswahlwoche in Bad Saarow am Scharmützelsee. Lange hielt das alles ohnehin nicht. Nach einem Jahr kamen die Dinge ins Rutschen und sprengten oft das, was bis dahin gewachsen war.
Ich weiß nicht einmal, ob Florentine bis zum Diplom durchgehalten hat. Gar nicht wenige von uns haben die Ungewissheit nicht ausgehalten und sind sofort irgendwo in Lohn und Brot, manchmal auch jenseits des Journalismus. Wer eine Nase hatte für den Wind, der sich für den Propaganda-Nachwuchs schnell drehte von der Euphorie des Anfangs in Richtung Pranger, der konnte schon auf die Idee kommen, lieber Autos zu verkaufen oder Versicherungen. Außerdem lockte der Westen, auch mit Journalistenschulen. Andreas Rook, heute ein MDR-Gesicht, der damals mit seiner Freundin nach Moskau ging, war die Ausnahme. Die Regel: München, Wales, Paris. Ich hatte gehört, dass Florentine Anders nach Frankreich gegangen war, aber dann reißt der Faden ab. Dass sie im Zeit-Kosmos gelandet ist, war nicht bis zu mir durchgedrungen.
Dieses Buch dann schon. Wenn etwas über die DDR erscheint, bekomme ich das mit. Ich kaufe längst nicht mehr alles. Wenn immer wieder das gleiche serviert wird, freut man sich selbst über einen Film wie Kundschafter des Friedens 2. Florentine Anders und ihr Opa Hermann Henselmann: Das klang gut. Das klang nach Brigitte Reimann und „Franziska Linkerhand“. Nach Defa. „Unser kurzes Leben“ von Lothar Warneke und „Insel der Schwäne“ von Herrmann Zschoche, zwei Filme, die Anfang der 1980er ins Kino kamen und die Tristesse des Wohnungsbaus genauso festgehalten haben wie einen Alltag, der heute so weit weg ist wie die Marskolonie von Elon Musk.
Ich will nicht sagen, dass ich enttäuscht worden bin. Die Mitstudentin von einst hat das gut gemacht. Sie hat sich hineingegraben in die Papiere und viele der Orte besucht, die wichtig gewesen sind für die Henselmanns und ihre acht Kinder. Schreiben kann sie ohnehin. Das haben wir in Leipzig gelernt oder schon vorher in der Redaktion. Entstanden ist so eine Familienbiografie, in der sich die Autorin zurücknimmt. Drei, vier Einsprengsel zur Recherche. Mit der Mutter im Stasiarchiv, wo es nicht nur eine Opferakte gibt, sondern auch eine Täterakte – zur Überraschung der Tochter. Ein paar Sätze zu den regelmäßigen Besuchen beim berühmten Opa, der ihr alle 14 Tage ein Buch mitgibt, über das dann diskutiert werden soll. Sonst ist da vor allem Distanz. Abstand halten. Keine Emotionen zeigen. Sagen, wie es gewesen sein könnte. Journalismus und Geschichtsschreibung – aber kein Roman.
Um noch einen Moment loben zu können: Florentine Anders geht chronologisch vor, von 1931 bis 1995, fast wie in einem Fotoalbum. Da die DDR klein war und die Henselmanns zu ihrem Adel gehörten, gibt es literarische Bilder von vielen Prominenten. Mit Lotte Ulbricht auf der Völkerfreundschaft, Manfred Krug als Fast-Nachbar, ein Unterschlupf bei Alex Wedding, die eigentlich Grete Weiskopf hieß und Pflichtlektüre für jedes Kind war. Es passiert sogar jede Menge Ungeheuerliches, auch jenseits der Seitensprünge des Opas und von Robert Havemann, der mit Omas Schwester verheiratet war. Architektur, Opposition, Ost-West-Spionage, Berlin im Wandel der Zeit: Das ist auch deshalb spannend, weil Florentine Anders darauf verzichtet, dem Diktaturgedächtnis Futter zu geben, und einfach die Tatsachen sprechen lässt, ohne die zu verurteilen, die an das Projekt DDR geglaubt oder von ihm profitiert haben und beides längst nicht immer auseinanderhalten konnten.
Vielleicht hätte der Verlag auf das Wort „Roman“ verzichten sollen. Ein Roman braucht einen Konflikt – einen Dreh- und Angelpunkt, der nicht nur solche Figuren aus den Tiefen der Vergangenheit trägt, sondern im Idealfall universell ist und so auch die Gegenwart erreicht. Der Mann zum Beispiel, der älter wird und prominent und daraus etwas macht bei jüngeren Frauen, ohne seine erste Liebe aufgeben zu wollen. Die Frau, die all das sieht und es trotzdem nicht zum Bruch kommen lässt – oder doch, wie Florentines Mutter offenbar dann gleich zweimal. Oder die Ideologie, die sich hineinfrisst in die Profession und etwas verlangt, wenn man sich im Licht der Macht sonnen möchte. Ich denke dabei natürlich an Eugen Ruge, dem ein runder Geburtstag gereicht hat, um nicht nur eine kommunistische Familie auseinanderbrechen zu lassen, sondern zugleich die Geschichte vom Aufstieg und Ende einer Utopie zu erzählen. Vielleicht ist dieser Vergleich aber auch vermessen. „In Zeiten des abnehmenden Lichts“: Das war einmal. Jetzt lesen wir eben „Die Allee“.

Freie Akademie für Medien & Journalismus
Titelbild: Markus Spiske @Pixabay
-
 @ 42342239:1d80db24
2025-03-02 14:13:43
@ 42342239:1d80db24
2025-03-02 14:13:43With the rapid development of artificial intelligence (AI), we face a future where we may soon have access to almost everything we desire – at least in the digital realm. But unfortunately, what we wish for doesn’t always align with what we truly need, or what would benefit us.
The Dutch ethologist Niko Tinbergen was awarded the Nobel Prize in Physiology or Medicine in 1973 for his studies of animal behaviour patterns. While earlier scientists had primarily focused on learning as the main explanation for animal behaviour, Tinbergen instead emphasised instincts.
Tinbergen studied, among other things, what makes newly hatched bird chicks beg for food from their parents. This was investigated by presenting parentless chicks with various painted beak models to see which ones they would seek food from. Several objects proved more popular than real gull beaks.
Artificial eggs were also created and placed in bird nests. Black-headed gulls that received wooden eggs before laying their own were found to actually refrain from laying real eggs. Fake eggs were painted in different colours and patterns, and made in various sizes. The gulls always preferred trying to incubate eggs of absurd sizes – for example eggs with eight times the volume of real ones. The poor gulls made desperate attempts to sit on these giant eggs – but often slid off.
The explanation for the gulls’ self-destructive behaviour was that they had a hardwired ability (instinct) to respond to specific stimuli (appearance of beaks and eggs with particular colours/sizes). Researchers exaggerated these stimuli, creating stronger but ultimately misguided reactions. The concept of "superstimuli" was hatched. Nothing in the gulls’ evolution had prepared them for these experiments, explaining their self-destructive behaviors.
Psychologist Deirdre Barrett has translated this concept to a human context. She argues that superstimuli govern human behaviours much like they do other animals’, citing junk food consumption, addictive social media use, and pornography consumption as examples. Nothing in Homo sapiens’ evolution prepared us for modern society’s stimuli, which might explain our frequently self-destructive behaviours.
When the Liberal Party (Swedish political party Liberalerna) proposes mandatory porn filters on all mobile phones "to protect children and youth," it might appear they’re on the right track. However, these issues deserve more profound discussions.
How do we create technical solutions that meet our fundamental needs for health, education, and human connection – rather than just supplying mindless scrolling entertainment? How can we ensure those collecting our data don’t exploit it for their own interests, selling us things we don’t need? Is the current model of centralisation, corporate giants, and profit maximisation really compatible with our best interests?
In summary: How can we ensure future technology serves our real needs, rather than mislead us - much like Niko Tinbergen deceived the poor gulls?
-
 @ 43baaf0c:d193e34c
2025-03-02 14:00:59
@ 43baaf0c:d193e34c
2025-03-02 14:00:59
As an artist, your main desire is to create. I believe we are all born creators, but some of us have a deeper passion for it than others. Those who dedicate themselves to their art and receive recognition for it are often called artists. But let’s set aside the debate about what defines an artist and focus on what truly matters our craft.
This is what we love to do. We dream about it, wake up for it, and live for it. It’s more than just work—it’s a passion that comes from within. You could even go as far as to call it your purpose in life.
Often, you’d still create even without money because your art is beyond numbers. But we live in a world where kisses won’t pay for groceries—at least, I can’t pay that way! So, money matters, not as the goal, but as a tool to keep doing what you love: creating.
Artists have often been seen as struggling creatives, barely making ends meet. When I started art school, I saw so many parents telling their kids to choose a “real” career doctor, lawyer, something secure. A “real job,” right? 😅
Luckily, my parents never told me that. My mom always said, follow your heart. (Thanks, Mom and Dad! 🙏)

After art school, I spent four years studying graphic and media design, followed by another four years in animation and film. But when it came time to find work as a 2D animator, I struggled. To be honest, I wasn’t good enough—or at least, that’s how it felt. Plus, the industry had already shifted heavily toward 3D animation.
But I wasn’t discouraged. I loved everything related to art and design. And growing up in a small city like Sneek, Friesland (The Netherlands), I had always dreamed of seeing more of the world.

Travel & Filming I’ve always been fascinated by people, their stories, and how different cultures live. That curiosity led me to documentary filmmaking, and along the way, I started building my own stock footage database (you can find it all on https://www.shutterstock.com/g/traveltelly.
Making a living as an independent documentary filmmaker isn’t easy, so I often filmed for volunteer organizations. This gave me the opportunity to experience different cultures while also shooting stock footage. I did this for about 10 years, traveling across the globe—and I’ve been fortunate enough to visit 88 countries so far.

Technology, Change, and Art Stories In 2018, I read The Bitcoin Standard because I couldn’t understand why, despite investing in an expensive camera, I struggled to earn it back as stock footage royalties kept dropping. That book opened my eyes to the first part of the equation: money itself.
It took me a few years to truly grasp Bitcoin’s significance, and through trial and error, I realized it’s the only cryptocurrency I believe in. I had my fair share of shitcoin lessons—where I made some money but also lost it. Those experiences taught me a lot about value, scarcity, and what truly lasts.

Bitcoin Is Different Once you truly understand what Bitcoin stands for, you realize it’s a path to real financial freedom. Like any journey, there will be ups and downs, and plenty of people will tell you you’re wrong—especially when Bitcoin’s price drops in dollar (fiat) terms. But when in doubt, zoom out.
One thing I’ve learned is that your own path is never truly wrong for you. When others say it is, it’s usually because they’re comparing it to their own. But we’re all walking our own unique journey. The moment you start comparing, you begin to doubt. True happiness comes from embracing your path—not someone else’s.

Art Is My Life, Bitcoin Is the Tool For me, art is life. Bitcoin is simply the tool that allows me to live a good artist’s life. Saving in Bitcoin and spend when I need it gives me peace of mind. And even with a bit more financial freedom, that doesn’t mean I’d ever stop creating. I always want to push myself, improve my craft, and hopefully inspire others through my art and stories.
I truly believe that all good energy comes from human connection and relationships. The most important thing is having a good day with the people around you. These days, we share those moments on social media—but that’s just a reflection of a single moment, whether happy or sad. If you don’t truly live that moment, it’s just wasted energy.
I’ve also learned to truly appreciate other artists and their craft—to find inspiration in their work. This mindset comes more naturally when you have peace of mind, something a Bitcoin savings can provide.
When you’re not under constant financial pressure, art doesn’t have to feel like a business where you must sell your work immediately at an exhibition or event just to make ends meet. Instead, you can focus on creating for the sake of art itself, allowing your work to evolve naturally.

Freedom to Share Your Art on Nostr Luckily, we now have platforms like Nostr where we can share and earn from our art while building a community, without anyone controlling what we do. Bitcoin stands for financial freedom, and Nostr stands for art-sharing freedom. With Bitcoin, you can walk your own path, and with Nostr, you can share your journey freely.
When you’re free to walk your own path, you naturally attract like-minded people because you don’t feel the need to constantly compare yourself to others. The more you embrace being yourself, the more you’ll connect with people who resonate with you.
I’m not suggesting you stay in your own bubble, but rather acknowledging that everyone is in their own bubble in some way. Just like not everyone feels at home in the same country, not everyone feels at home in the same space or community. It’s all about finding where you belong and who aligns with your energy.

Networking/Events I’ve always hated networking events in my creative job. I understand their value, but they were never really my thing. So, I was hesitant at first to attend a Nostr event. But it was in Tokyo (Nostrasia), and I love Japan, so that gave me a good reason to go. Fortunately, I was right—it felt like the right fit for me.
I love to create, and I tend to talk less, so I’m very selective about the events I attend. Nostr events felt different. It’s like we’re all builders and creators who have already broken free from the fiat mindset. By that, I mean the mindset where you go to an event, pay a high price (like at some mayor Bitcoin events, which I can’t stand), and expect to get something in return. The fiat job mentality where you exchange time for direct money, or as we say in Dutch, uurtje factuurtje (hour work, invoice) just doesn’t fit with me. The more you walk your own path, the more you realize what works for you and what doesn’t.

My only advice? Save in Bitcoin, create, and walk your own path. And yes, don’t forget to smile and enjoy the ride. The journey is the destination!
-
 @ fd78c37f:a0ec0833
2025-03-02 13:55:43
@ fd78c37f:a0ec0833
2025-03-02 13:55:43In this edition, we invited Bam from Bitcoin Barqnet to share his journey with Bitcoin and its impact in the Middle East. He also discussed the growth of the Barqnet community and introduced his modular wallet, Cypherbox.
YakiHonne: Bam, thank you for joining today's conversation. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. With YakiHonne, individuals can express themselves freely, without the fear of censorship, bans, or restrictions. So before starting the interview, I’d like to learn a little more about you and your community, Bam. Can you tell us more about yourself and what you do?
Bam:My name is Basim, and my nickname is Bam. I became somewhat well-known in the Middle East for releasing some Bitcoin courses. I'm an old player in Bitcoin, having gotten involved in 2014. Back then, I realized that Bitcoin was something big, but I didn’t have much Bitcoin because I didn’t have the money to buy it. Instead of investing money in Bitcoin, I invested my time in understanding it and researching it. Bam:After graduating in 2016-17, I decided to dedicate my entire career to Bitcoin while I was in Istanbul. Of course, Bitcoin was the core focus, but there were also many altcoins, and I became interested in those areas as well. I love this space because it's very libertarian, and I myself am a person with libertarian values. Bam:I currently publish tutorial videos on YouTube, primarily aimed at Arabic-speaking audiences in the Middle East, to teach them about Bitcoin economics, technology, and how to use Bitcoin. They have very little knowledge about these topics. I’ve covered many subjects, including wallet operations, mining, using the Lightning Network, and even non-custodial liquidity management. We’ve produced over 200 videos so far. I’ve realized that there are many issues with Bitcoin-related applications, so I’ve decided to develop my own Bitcoin app called Cypherbox.
YakiHonne: That's really impressive. You're a content creator in the Bitcoin ecosystem, explaining Bitcoin on YouTube and spreading the Bitcoin ideology. And you're developing your own Lightning app specifically for the Middle East. You're doing a lot of meaningful work.
Bam:Unfortunately, I didn't buy more Bitcoins in 2014. I used to own some, but I invested all of my Bitcoin into my channel because I strongly believe in the importance of education. I believe that global international currency is more important than mere wealth. I've tried to ensure that my project is neither charity nor purely commercial. I am now creating an Arabic academy, selling some courses or applications I develop, and trying to commercialize them. Overall, my project is somewhere between open source and commercialization, and I hope to support my life through these means.
YakiHonne: That's really great, Bam. I really admire how much you value education and enlightening others. So now, let's move on to the first question. Bam, I think you've already touched on part of the answer. But I'd like to ask again, this time in more detail: What truly sparked your interest in Bitcoin? What motivated you to build or form a community around it?
Bam:I used Bitcoin very early on, and I understood right away when I looked at its wallets that it wasn’t a company. I had some experience with decentralized networks, like Tor and Torrent, and I knew this was open-source. Open-source projects are really attractive to me as an engineer. The more I studied Bitcoin, the more fascinated I became with it. I love its decentralized nature. Bam:I studied complex systems, energy engineering, and systems like aeronautics and marine engineering, and I found Bitcoin to be the most sophisticated energy system I’ve ever studied. It’s just fascinating on a technical level, especially the cryptography aspect. What’s so amazing about Bitcoin’s security is that it doesn’t rely on firewalls or central authority; it’s actually the opposite, as Andreas Antonopoulos often explains. Bam:Bitcoin's security comes from its openness. The whole thing—its censorship resistance, the privacy, the community around it—just captivated me. The fact that Satoshi created the greatest monetary network ever, but never moved any coins or had any control after 2009, and gave it away to the community, for everyone in the world, is just an incredible story. There’s so much about Bitcoin that I can’t even begin to explain how deeply I’m attached to it. Bam:What I want to say is that Bitcoin has significantly helped with the issues my country faces because I am from Syria. We have been locked out of the financial system by OFAC policies, which were perhaps seen as justified due to sanctions. Syria has been under financial sanctions, but the problem is that these sanctions weren't just imposed on the Syrian government; they were imposed on the entire Syrian population. Even though the current president Assad is no longer in power, these sanctions still persist. These financial sanctions have caused great suffering for the Syrian people. Syrians are unable to engage in e-commerce or trade with the outside world. This system, which locks people into such a closed financial environment, is a huge issue. Bam:Bitcoin provides an alternative. Bitcoin has not closed its doors to Syrians, and we can still use Bitcoin in Syria. People in Syria use Bitcoin without fear of censorship from any part of the world. No government can lock Syrians out of the Bitcoin network, and Bitcoin transactions can be settled in real time in Syria, regardless of whether any government approves or not.
YakiHonne: Can you tell me how you have been able to attract members so far and what challenges have you faced when you started earlier on?
Bam:We started on Clubhouse, just a bunch of random Bitcoiners talking about Bitcoin, and around 2020 and 2021, the Lightning Network started to become more usable. We saw some interesting Lightning apps, and when I learned about it, I immediately realized that this was the future of the internet of money. I was heavily involved in Ethereum at the time, writing smart contracts, but once I took Lightning seriously, I knew it was the future of digital money. Bam:We started discussing Lightning on Clubhouse during COVID, focusing on Lightning wallets. We asked ourselves, "How can we bring this technology to the Middle East?" Around that time, I also wanted to get more involved in Bitcoin education, so I began putting out more content. A friend of mine created a Telegram group called Barqnet, and we invited everyone from Clubhouse to join. I started sharing more Bitcoin content and promoting the group, saying, "Hey, if you want to get real education about Bitcoin—beyond videos and courses—come join this group and let's build this community together. Bam:We did this for about six months, and the group attracted a lot of people. But my initial goal wasn’t just to attract regular people; it was to attract technical engineers and build a network of engineers who could not only listen to my explanations but also help me better understand Bitcoin and the challenges they face when interacting with Bitcoin and building the Bitcoin banking infrastructure in the Middle East. As a result, we attracted many highly skilled people. Now the group has about 1,000 members, all of whom are highly technical. Bam:We also created a technical support space for regular Bitcoin users. Anyone in the Middle East facing issues with wallets, buying Bitcoin, mining, or any other Bitcoin-related problems can come to us for help. This is a completely voluntary online initiative, and now many people know that if they have technical questions, no matter how complex, they can come to Barqnet and get answers.
YakiHonne: That's really amazing. It seems like you guys are covering both the technical and non-technical aspects of Bitcoin, which is truly remarkable. It's not so common to find a community that manages to engage both sides. But Barqnet, as the Arabic Bitcoin community, seems to have successfully blended both, working with both technical and non-technical people. The work you're doing is really impressive—it's an outstanding job.
Bam:I really enjoy seeing the growth of Bitcoin, and I've already started telling people how their lives have changed. In 2024, many people have messaged us in the group, saying, "Thank you so much, you really changed our lives." It's not just people from poor areas, even in wealthy regions like Saudi Arabia and the UAE, people are telling us, "I started a Bitcoin business, I started mining, I started investing, and now I’ve made some money, my value has gone up because of you guys. I didn't sell, I kept my Bitcoin in cold storage." So, everyone is thanking us. Bam:This means much more to us than any financial gain. We didn’t make a lot of money from these initiatives—sure, we earned some, but not much. And it hasn’t changed our lives. If I had spent my time as an engineer focusing on corporate projects, I would probably make a lot more money. I live in Europe now, and my life is pretty good. But helping people understand Bitcoin and onboard into the Bitcoin world means so much more to me than money. YakiHonne: So, moving on to the next question. How do you see the role of Bitcoin communities evolving as technology matures, particularly in areas like scalability, privacy, and adaptability with other systems? So, how do you see the Bitcoin community evolving with time? Bam:I actually have a lot of different views on how Bitcoin is being taught and developed, especially in terms of scalability. Many people in the West are focused on highly technical developments that do promote individual sovereignty, self-custody, and privacy protection. However, these don't help people who don’t understand the technology, and they make it really difficult for them to use Bitcoin. For example, when I see people recommending non-custodial Lightning wallets, I don’t think this is a good option for everyone, especially in the Global South. For people who don’t understand the technology and just want to use Bitcoin simply, these wallets are way too complicated. Bam:This is why I developed my own app. It's not just a wallet for the Middle East; it's an international wallet that anyone can download. It's open-source and aims to provide a modular Bitcoin experience. The Bitcoin app I envision would contain all the necessary tools, whether it's a custodial service, an exchange, or a simple Lightning custodian service for people who just want to quickly send and receive Bitcoin without dealing with complexity. Bam:A Bitcoin Lightning custodian makes perfect sense if it's reliable. In addition to that, you’d also have your hot wallet, which you can use to withdraw your funds when ready, and move them into self-custody with a simple hot wallet like Blue Wallet. Cold storage should not be the first step for everyone. People often say it's expensive, and that you need to buy hardware wallets, but it’s more of a progression. Start with the basics, and over time, you’ll learn. Bam:Inside the app, users should have access to all the tools for self-custody, including non-custodial Lightning, hot storage, cold storage, federated chains, e-cash systems, and side chains, if applicable. The app would allow users to personalize their experience—choosing what they want based on their technical knowledge, the amount of Bitcoin they want to secure, their privacy preferences, and the fees they’re willing to pay. I imagine the future of Bitcoin will be modular, and every user will be able to customize their experience according to their needs and preferences.
YakiHonne: I really appreciate the key points and important aspects of Bitcoin scalability that you mentioned. They're truly crucial, and it's essential for people to understand Bitcoin better rather than misinterpret it. The importance of Bitcoin in these other areas shouldn't be overlooked, and people should embrace it as part of the future, not reject it. Now, we're at the last question. Is the government around you for or against Bitcoin? And how has that affected the community?
Bam:I live in France, and the government is generally neutral when it comes to privacy tech. I’ve lived in Turkey, the UAE, Brazil, the EU, and the Netherlands, so I don’t consider myself Syrian. I prefer to think of myself as a citizen of Earth. When it comes to governments, I pay attention to policies and regulations in all countries. I look at examples like El Salvador, and I also follow the current situation in Syria. Right now, we’re working to push for a policy that recognizes Bitcoin rather than implementing strict regulations. We’re trying to get the government to draft laws that are more friendly to Bitcoin. Although the central bank is confused about Bitcoin, they’re not completely opposed to it. We’ve proposed a way to manage the market that doesn’t restrict people’s freedom but also helps regulators deal with companies and Bitcoin projects. We’re seeing very positive reactions, and I believe Syria will become the place that opens Bitcoin to the entire Middle East region, thanks to the voluntary initiatives we’ve initiated.
YakiHonne: That was really a fantastic answer, thank you so much, Bam. With that, we’ve come to the end of today’s interview. It’s truly an honor and privilege to have had this conversation with you. I’ve really enjoyed the entire discussion, from start to finish, and I’ve learned a lot from everything we’ve talked about. I really appreciate your passion for Bitcoin and your dedication to pushing for education. We love the work you’re doing. Although we haven’t used your app yet, we believe it’s going to be amazing.Thank you so much again.
-
 @ f3873798:24b3f2f3
2025-03-02 13:12:10
@ f3873798:24b3f2f3
2025-03-02 13:12:10
Olá meus caros leitores, estou fazendo um guia voltados aos Brasileiros aqui do Nostr. Vejo que há muito conteúdo em inglês que infelizmente não é traduzido para o português. Por este motivo tomei a iniciativa de começa com este artigo.
Espero que gostem deste artigo, que tenham uma ótima leitura.
Bem-vindos ao Mundo Nostr !!
Acredito que todos que estão aqui sabem um pouco sobre o Nostr e que é uma rede social descentralizada, local onde você pode postar sem medo de represarias governamentais [ditatoriais].
Mas, vocês conheçem como o Nostr funciona e todas as ferramentas que vocês têm disponível neste ecossistema?
Poisé, acho que não.O Nostr é um protocolo de comunição descentralizada muito versátil, isso quer dizer que não está limitado a um tipo de "rede social", nele é possível fazer Blogs, streaming, podcast e até mesmo e-mails com autonomia total do usuário.
Meus caros, isso é liberdade total, sem ficar na mão de bigtech como Microsoft, Apple, Google.
Para ficar mais claro darei um exemplo para vocês:
Imagine você criando uma conta no Youtube, você deve aceitar as Diretrizes impostas pela google no uso do SEU CANAL, por mais que você tenha autonomia na produção do SEU CONTEÚDO, determinadas palavras e termos não podem ser usadas, ou seja, O GOOGLE DETERMINA O QUE VOCÊ PODE OU NÃO FAZER NO SEU CANAL.
Veja que é uma liberdade parcial no processo de criação de conteúdo.
Já no Nostr, o seu canal é completamente seu. Não há nenhuma entidade, empresa responsável pelo seu conteúdo a não ser você.

O Mundo Nostr e sua funcionalidades
No nostr você terá acesso a uma diversidade de aplicativos para cada objetivo de uso. Mas, antes de abordar sobre os diversos layouts e funcionalidades do Nostr é necessário aprender o básico deste universo.
Em primeiro lugar: É necessário que vocês saibam que a partir do momento que vocês criaram um conta aqui, independente do "cliente" ou "distro como o pessoal que gosta de fazer analogia com o Linux", vocês recebem duas importantes chaves ! A chave privada e a chave pública.

A Chave privada, também chamada de chave secreta é o acesso ilimitado a sua conta, ou seja, é a partir dela que poderá produzir conteúdos em geral neste mundo. Ela te dará acesso a todos os rercusos do Nostr, portanto é importante que esteja muito segura.
A Chave pública, você ver como os outros usuários ver o seu perfil e o seu conteúdo. Ela é uma importante chave para que as pessoas possam ter acesso aos conteúdo que vocês públicam, ou seja, é atráves dela que você poderá compartilhar o seu perfil para que seu público tenha acesso ao seu mundo.
Dito isso vamos conhecer os apps e os chamados clientes Nostr.
O que são clientes Nostr?
Clientes são as várias maneiras de interagir com o protocolo Nostr [fonte: Nostr.com]
É semelhante ao Sistema Operacional Linux que tem várias distro com diferentes layout para o mesmo Sistema.
Vejamos as principais para que vocês tenham uma noção da amplitude do protocolo.
- Damus: é um app para celulares IOS terem acesso ao NOSTR, tem formato de rede social, como Primal e o Amethyst.
- Primal é um app versátil serve tanto para celulares IOS, Android e PCs, também tem formato de rede social, porém você pode abrir uma carteira lightning bitcoin exclusiva deste app, facilitando muito os micropagamentos em satoshis pela rede.
- Amethyst, assim como o Damus é para o IOS o Amethsy é para o Android, sou suspeita para falar sobre este clientes, pois é o meu favorito. Além de várias possibilidades de edição de texto, ele tem diversas funcionalidade incluídas, como *Guia Mercado*** onde você pode comercializar produtos pela rede, tem como intergrar com outros apps de streaming, formar grupos temáticos etc.
- OXchat não é exatamente uma rede social tem um layout que lembra um pouco o Whatsapp ou Telegram, serve como uma rede de interação instantânea, tem diversos recursos que achei mais interessante é a lousa, onde é possível interagir no grupo com desenhos etc.
- Yakihonne que é justamente o cliente que estou usando para construir este artigo. Como usuário posso dizer que ele tem um foco para criação de Blogs no protocolo Nostr, lembrando que cada cliente tem um layout diferente, ou seja, uso de templates para definir a estrutura do seu blog é meio limitado [ressalva assim como vocês sou iniciante do Nostr, pode ser que tenha como determinar um layout próprio, mas eu mesma não sei como]
Há muitos outros clientes disponíveis para acessar e experimentar e conhecer todos eu recomendo o site: Nostrapps
Agora que você leu este pequeno guia, se divirta aqui no nostr e não se esqueça de apoia a gente.
Até Mais !!
-
 @ f3873798:24b3f2f3
2025-03-02 13:10:00
@ f3873798:24b3f2f3
2025-03-02 13:10:00Estamos próximos a uma das principais premiações da indústria. Vemos não só a perversão de pautas woke e destruição de valores ocidentes, mas também um grande confronto entre o que mais forte o ativismo Lgbt ou o ativismo político entre as atrizes Fernanda Torres e Karla Gascon.
Só evidência o caos que é os conflitos de interesse de diversas vertentes que a esquerda abraça e diz que é sua.
Mas, o que mais impressiona é o fato do Oscar ter um filme no indicado que até o momento não ganhou nada, porém é notório a superioridade aos outros, este filme é Sing Sing.
Porque o filme Sing sing foi ignorado pelos avaliadores?
O filme tem uma narrativa de superação e como a arte pode mudar as pessoas e as realidades mais pertubadoras. Ele retrata o Sistema carcerário americano, onde realidade de vários presos é mudada atraves de um projeto de um teatro na prisão.
Observando friamente a sintese do filme é uma história que se encaixa perfeitamente aos vies de bandidolatria, se não tivesse um questão, a ação transformadora da arte e deixando de serem vítimas e serem artistas.
Porém apesar de ser uma obra de arte que estimula as pessoas pensarem sobre a vida e ter uma pegada inovadora e completamente diferente dos demais filmes que retratam o sistema carcerário, ele é totalmente ignorado por não ser suficientemente lacrativo.
-
 @ f3873798:24b3f2f3
2025-03-02 13:07:41
@ f3873798:24b3f2f3
2025-03-02 13:07:41Muitas pessoas sofrem em silêncio diante das dificuldades da vida. Seja um término de relacionamento, o convívio em uma família desestruturada ou até mesmo situações extremas, como estar preso em um campo de concentração, a escrita pode ir além de um simples ato de colocar palavras no papel – ela pode ser um agente de libertação.
Seja em forma de diário, desabafo, artigo de opinião ou até mesmo a construção de uma história fantástica, como foi o caso de Harry Potter, escrever pode trazer alívio e transformar a dor em algo criativo e significativo.
Escrever é quase mágico. O simples ato de organizar ideias para construir um texto dá ao escritor o poder de viajar para mundos criados por sua própria mente, funcionando como uma verdadeira forma de escapismo.
Em certas situações extremas, essa pode ser a única alternativa para fugir da realidade, um fio de esperança para aqueles que se sentem perdidos na escuridão do desespero.
Sabe aquela fase da adolescência em que pensamos "Meus pais não me entendem"? Se você está passando por isso, este texto é para você!
Por que não transformar suas angústias em palavras e criar histórias maravilhosas sobre seus anseios, sonhos ou aprendizados do dia a dia?
A escrita pode oferecer um refúgio, um momento em que tudo ao seu redor se transforma e seu processo criativo se torna uma lembrança especial.
Portanto, se você está sofrendo com os desafios da vida, experimente colocar seus sentimentos no papel e transforme a dor em arte. Você pode se surpreender com o poder das palavras.
Essa é a mensagem de hoje.
Até a próxima leitura aleatória
-
 @ f3873798:24b3f2f3
2025-03-02 13:02:47
@ f3873798:24b3f2f3
2025-03-02 13:02:47Você já conheceu alguém que sempre tenta levar vantagem em tudo? Aquele tipo de pessoa que, em vez de buscar crescimento legítimo, prefere explorar os outros para obter benefícios? Infelizmente, essa mentalidade está mais presente do que gostaríamos de admitir.
Ela se manifesta de diversas formas, como:
-
Pedir descontos e brindes de maneira abusiva, como se fosse um direito;
-
Ameaçar ou constranger vendedores para conseguir preços mais baixos;
-
Vender produtos com valores incompatíveis com a qualidade ou omitir defeitos para enganar clientes.
Quem age assim tem uma conduta antiética e, pior, muitas vezes se orgulha disso, como se enganar alguém fosse um sinal de esperteza. Mas será que essa mentalidade realmente leva ao sucesso?
A curto prazo, pode parecer que sim. Alguns até conseguem vantagens temporárias, mas a longo prazo, essa postura cobra seu preço. A reputação se desgasta, as oportunidades diminuem e, inevitavelmente, o comportamento oportunista se volta contra quem o pratica.
No Brasil, essa mentalidade oportunista se tornou quase um traço cultural. Combater isso exige uma mudança de perspectiva e, acima de tudo, uma autoavaliação sincera.
O primeiro passo é reconhecer se, em algum momento, você já adotou esse comportamento. Ser honesto consigo mesmo é fundamental para evoluir.
O segundo passo é entender que essa mentalidade não só é antiética, mas também prejudica seu próprio crescimento. Quem não valoriza o trabalho alheio dificilmente conseguirá que seu próprio trabalho seja valorizado.
Portanto, abandone essa postura de querer sempre "se dar bem" às custas dos outros. Valorize o esforço e o trabalho de quem está oferecendo um produto ou serviço. Se não pode pagar, simplesmente não compre. Faça igual o Lula rsrsrs.
Mas brincadeiras a parte, não exija que os outros arquem com o custo da sua insatisfação.
E esta foi a mensagem de hoje.
Espero que tenha gostado de mais uma leitura aleatória.
-
-
 @ a296b972:e5a7a2e8
2025-03-02 10:23:10
@ a296b972:e5a7a2e8
2025-03-02 10:23:10Die Geburt in die Pareto-Welt hat dann doch länger gedauert, als gedacht, jedoch dank der Geduld meines Hebammen-Mentors, ist es nun vollbracht.
Ich möchte meinen Beitrag zum Erhalt der Meinungsfreiheit leisten, bin aber nicht ganz uneigennützig, denn das Schreiben ist auch mein Ventil für den Wahnsinn, der bei Verstand gebliebenen Menschen immer näher auf die Pelle rückt.
2020 habe ich, bis heute erfolglos, damit angefangen, langjährigen Freundinnen und Freunden Links zu schicken, die die Vorzüge der Gen-Behandlung infrage stellen.
Auslöser war ein Gespräch mit einem jetzt ehemaligen Freund über die Verhältnisse im 3. Reich. Wir stellten uns damals die Frage, wie wir uns wohl verhalten hätten, wenn wir gefragt worden wären, wo denn plötzlich der ruhige, zuvorkommende Nachbar Salomon abgeblieben sei, der nie einer Fliege etwas zu Leide getan hat. Hätten wir auch mit den Achseln gezuckt, weil wir Angst davor gehabt hätten, dass uns vielleicht das gleiche Schicksal ereilen könnte?
Wir kamen überein, dass es uns nicht zusteht, über die Schweiger zu richten, weil wir uns keine wirkliche Vorstellung von dieser Zeit machen konnten. Wir, die wir in einer Demokratie aufgewachsen sind, hatten keine Ahnung davon, wie sich eine Diktatur anfühlt, welche Stimmung sie verursacht, auf was man alles achten muss, damit man sich nicht mit dem Staat anlegt.
Seit dem C-Ereignis sind wir um eine Erfahrung reicher. Jetzt wissen wir es.
Wir wissen, wie digitale Bücherverbrennung geht, wie Bankkonten ohne Begründung gelöscht werden können, wie Existenzen vernichtet werden können, was nötig ist, um morgens um 6 Uhr schon Besuch zu bekommen, der dann noch nicht einmal frische Semmeln mitbringt, und dass es gut ist, immer einen frisch gewaschenen Bademantel am Haken hängen zu haben.
Als junger Mensch hatte ich noch die Gelegenheit mit einer Frau zu sprechen, die diese dunkle Zeit in Deutschland miterlebt hatte. Auf meine Fragen antwortete sie, das werde ich nie im Leben vergessen: „Wir haben ja von all dem nichts gewusst!“ Das kann man glauben, muss man aber nicht.
Das war für mich das Aha-Erlebnis. Schon damals habe ich beschlossen, dass ich niemals zu denjenigen gehören will, die so etwas sagen werden. Und meinen Freunden wollte ich von Anfang an die Gelegenheit nehmen, mir diesen Satz einmal sagen zu können, daher habe ich sie, nach eigener anfänglicher Verunsicherung, mit Informationen über das C-Ereignis versorgt, die im staatskonformen Propaganda-Funk nicht zu finden waren.
Mit Samtpfötchen habe ich mich herangetastet, Lese-Angebote gemacht, vorsichtig formuliert. Dabei ging es mir nie darum, recht zu haben oder recht zu behalten. Für mich ging es um meine lieben Freunde, um Leben und Tod. Ich war zutiefst besorgt um sie. Das hat auch nach 5 Jahren nicht dazu geführt, dass sie ihr heiliges Schweigegelöbnis gebrochen haben.
Inzwischen ist mein Freundeskreis vollkommen ausgetauscht.
Anfangs war ich noch so naiv zu glauben, der Schwindel würde sich ganz schnell in Wohlgefallen auflösen, doch dann wurde mir klar, dass sich der gesunde Hausverstand von einem großen Teil der Menschen verabschiedet hat, und das hält bis heute an.
Irgendwann kam dann in der Öffentlichkeit der Satz auf: „Das konnten wir zum damaligen Zeitpunkt nicht wissen.“ Doch konntet ihr, wenn ihr euch mit den alternativen Informationsquellen beschäftigt hättet, die sicher nicht nur ich an Freunde weitergegeben habe.
Nie habe ich behauptet, die Wahrheit gepachtet zu haben, immer aber habe ich danach gestrebt, ihr so nahe wie möglich zu kommen. Bis heute.
Inzwischen sind die allermeisten Verschwörungstheorien wahr geworden.
Nachdem das C-Ereignis etwas an Schärfe verloren hatte, ging es gleich weiter mit dem Ukraine-Konflikt. Einen Tag nach Ausbruch im Februar 2022 schrieb ich in einer Email: Die Ukraine kann diesen Krieg nicht gewinnen.
Und so ging es weiter und weiter. Ein Wahnsinn nach dem anderen. Ohnmächtig müssen wir dabei zuschauen, wie Universal-Dilettanten das Ruder in der Hand haben und kerzengerade auf den Eisberg zusteuern. Da soll man sich still zurücklehnen, Popcorn futtern und die Show genießen? Tut mir leid, kann ich nicht.
Die „Geistesgrößen“ dieser Zeit scheinen George Orwells „1984“ als Bedienungsanleitung zu verstehen. Als ich es jüngst noch einmal gelesen habe, dachte ich, am weitesten ist bislang das Wahrheitsministerium vorangeschritten. Verdrehung der Realität mit Neusprech. Eine Generalumkehr der Begriffe. Daher auch mein Name in Anlehnung an diesen großen Vorherseher.
Es ist mir nicht vergönnt, zu denjenigen zu gehören, die die Bequemlichkeit im Denken pflegen und kultivieren und ein Diplom in Verdrängen über dem Sofa hängen haben.
Ich will die alte Welt nicht zurück, im Gegenteil. Mit meinen bescheidenen Mitteln und Möglichkeiten will ich dazu beitragen, habe ich die Hoffnung, den einen oder anderen vielleicht doch noch zum Nachdenken anregen zu können. Ich muss nicht recht behalten, darum ging es mir nie, ich kann mich irren und würde das auch zugeben. Derzeit mangelt es jedoch an Gelegenheiten.
Vielleicht habe ich tatsächlich etwas zu sagen (so sagt man mir es nach), und es ist sicher kein Zufall, dass mir Pareto durch Milosz Matuschek über den Weg gelaufen ist.
Es würde mich sehr freuen, wenn die geneigten Leserschaft das eine oder andere anspricht, was ich so von mir geben werde. Erst, wenn es Satoshis regnet, damit ich aufhöre, lasse ich es.
Bis dahin werde ich mich für den Erhalt der Meinungsfreiheit einsetzen, weil diese unmittelbar mit einem demokratischen System einhergeht. Sägt man an einem Baum auf einer Seite alle Äste ab, gerät der Baum in Schieflage und er fällt beim leisesten Windzug um. Das gilt es von den für Gehirnwäsche immunen Menschen zu verhindern.
-
 @ 41fa852b:af7b7706
2025-03-02 08:13:00
@ 41fa852b:af7b7706
2025-03-02 08:13:00"The only way to deal with an unfree world is to become so absolutely free that your very existence is an act of rebellion." --Albert Camus
Another great week of Bitcoin meetups is ahead of us!
This week, we are thrilled to partner with The Bitcoin Ireland Conference 2025 to help spread the word about this amazing grass-roots gathering.
We have two tickets to give away in a competition. To enter, click here to submit your entry.
Good luck, check out all the details below, and we'll see you there.
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Eat and Meet with Joe Bryan: Meet the creator of 'What's the Problem' and a host of fellow bitcoiners at the Weeping Willow in Bury St Edmunds. Starting at 18:00 on Tuesday, March the 4th.
-
Bitcoin 101 @ Cyphermunk House: On Tuesday, March 4, 2025, from 18:30 to 20:30, a beginner's Bitcoin class at 9 John Street, London WC1N 2ES. This 2-hour community-led event covers wallets, signers, and privacy, starting at 18:45. Arrive early; £5 donation in cash or sats.
-
Canterbury Bitcoin: Meeting this month at the Millers Arms in Canterbury at 19:00 on Tuesday the 4th of March. An informal meetup to discuss Bitcoin and chat.
-
Belfast Bitcoin: Join them on Tuesday the 4th March, 20:00. These guys meet in person monthly on the first Tuesday of each month at Ormeau Baths Event Space, 18 Ormeau Avenue, Belfast, BT2 8HS, Northern Ireland.
-
OPA North London Meetup: On Wednesday, March 5, 2025, from 18:30 to 21:30, North Londoners gather at Alice House, 283--285 West End Lane, NW6 1RD, West Hampstead. The Snug, a cosy pub nook, hosts this relaxed meetup for plotting and connecting, easily reachable by overground, no passport needed.
-
Rooted in the West Bank @ Cyphermunk House: On Friday, March 7, 2025, from 18:30 to 21:30, a 3-hour event at 9 John Street, London WC1N 2ES features a screening of a 47-minute documentary by Uri Fruchtmann and Bruno Sorrentino. It profiles Palestinian farmer Atta Jabar, with Uri presenting to raise sats for a feature-length expansion.
-
Bitcoin Walk - Edinburgh: Every Saturday at 12:00, Edinburgh Bitcoiners gather for a walk starting near Meadows Park's tennis courts, discussing news, innovations, and hyperbitcoinization. Newcomers are welcome to learn about Bitcoin's role in separating money from state. They often continue the conversation afterwards with something to eat. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Bitcoin Derby: On Saturday, March 8, 2025, at 15:00, Bitcoin Derby gathers at Ye Olde Dolphin, DE1 3DL, to mark the 32nd anniversary of Eric Hughes' "A Cypherpunk Manifesto." Join fellow Bitcoiners to commemorate this iconic moment at the regular time and place.
-
Privacy Day, Nostr London v6: On March 9, 2025, the 2140 Collective hosts the event in Tooting from 15:00 to 21:40, honoring Eric Hughes' Cypherpunk Manifesto. It features talks on Bitcoin crowdfunding, freedom, Nostr projects, art, free burgers from Angor.io, and a sats drop for Lightning wallet users.
Upcoming Special Events
These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast.
- CheatCode 2025 - Peter McCormack hosts the CheatCode conference, following last year's success. This year, international guest speakers include Preston Pysh, Alex Gladstein, Natalie Brunell, Matthew Pines, Steve Baker, Ben Arc, and Checkmate.
Friday, April 11th, is the main conference day, followed by a huge meetup at Ledger Park for the men's Real Bedford match, and again on Sunday for the women's match. Check out the link for ticket details.
- Bitcoin Ireland Conference 2025: Bitcoin Ireland is hosting its annual Bitcoin Conference, building on the momentum of previous years. This year Bitcoin Events UK are proudly serving as a media partner to help spread the word! Enter our competition to win two free tickets worth (€198 value). This year's lineup of international guest speakers includes Daniel Prince, alongside notable figures like Knut Svanholm, Dinny Collins, Lawrence-Stanley and other respected voices in the Bitcoin community, offering thoughtful perspectives on the evolving Bitcoin revolution.
The main conference takes place on Saturday, May 24th, at The Green Isle Hotel in Dublin. Following the event, attendees can join a relaxed networking meetup with Ireland's Bitcoin community to continue the discussion. For ticket details, visit: www.bitcoinireland.eu.
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ da0b9bc3:4e30a4a9
2025-03-02 08:12:23
@ da0b9bc3:4e30a4a9
2025-03-02 08:12:23Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/901383
-
 @ fbf0e434:e1be6a39
2025-03-02 06:18:25
@ fbf0e434:e1be6a39
2025-03-02 06:18:25DoraHacks has once again set a new standard for showcasing the brightest minds in Web3 and frontier technology with the successful debut of BUIDL DAY—our flagship event dedicated to amplifying the voices of early-stage, high-impact projects from the most promising ecosystems in the space.
With over 500 participants in attendance, BUIDL DAY was more than just an event; it was a hub of energy and innovation. Held at the intersection of collaboration and cutting-edge technology, we brought together nine pioneering ecosystems.— Cosmos, Babylon, Sonic, Aptos, Circle, KAIA, Initia, Movement and Flow—to spotlight the most original and contrarian early-stage teams building the next generation of technology.


It was the moment DoraHacks unveiled its defining thesis for 2025: Freedom of BUIDL—the fundamental belief that anyone, anywhere, should have the freedom to build what they want, when they want.
DoraHacks is not merely a platform. It is a force of nature, mobilizing the world's largest and most significant hacker movement. With over 200,000 developers having collectively launched 20,000+ startups, DoraHacks is rewriting the blueprint of innovation. This is where the future is built—not in closed rooms, but in the open, by hackers who refuse to ask for permission.
Hacking Without Borders
The numbers speak for themselves. In 2024 alone, over 300 organizations hosted more than 350 hackathons through DoraHacks, proving that the demand for open innovation has never been stronger. Any organization, from emerging startups to global enterprises, can tap into the boundless creative potential of the DoraHacks ecosystem and launch their own hackathons with ease.
DoraHacks' 2025 Thesis: The Future of BUIDL
At BUIDL Day, DoraHacks announced its core technological priorities for 2025. These are not mere trends—they are fundamental shifts in how the internet, cryptography, and decentralized systems will evolve. DoraHacks is doubling down on collaborations with the most critical open-source platforms to foster growth and innovation. The key areas include:
- Consumer Crypto – A narrative gaining traction across Aptos, Circle, Flow, and beyond, driving the next wave of crypto-native consumer applications.
- Agentic Crypto & Organizations – A revolution in decentralized coordination, playing out in Injective, Sonic, and YakiHonne.
- Freedom of BUIDL & Privacy Tech – Powering sovereign innovation and privacy-first technologies, championed by Zama and Dora Factory.
- Sovereign Independent Blockchains – The rise of self-sovereign networks, an area where Cosmos and its ecosystem continue to lead.
But we are not stopping there.
Exploring the Next Frontier
2025 marks the beginning of DoraHacks’ deep foray into frontier technology:
- Quantum Software & Infrastructure – Enabling the next paradigm shift in computing.
- Quantum Cryptography – Developing encryption that withstands the quantum era.
- Open Source Hardware – Breaking the barriers of proprietary computing.
The future is decentralized. It is open-source. And it is being built, right now.
The Next Chapter: Google Cloud x DoraHacks
DoraHacks is not just shaping the future—it is forming alliances with those who are building it. At BUIDL Day, DoraHacks officially announced its partnership with Google Cloud. As part of this collaboration, Google Cloud will provide $350,000 in cloud and AI services to support DoraHacks’ most promising startups. This partnership will also drive the launch of new hackathons focused on cutting-edge fields, from AI to quantum computing.
A Platform for Bold Builders
BUIDL DAY was meticulously designed to give early-stage teams the visibility, resources, and connections they need to propel their projects forward. Unlike traditional conferences and summits, our focus was on the BUIDLs that challenge the status quo—teams building with first-principles thinking and forging paths where others have yet to tread. These BUIDLs represented the cutting edge of decentralized technology, from novel Layer 1s and interoperability solutions to revolutionary applications in DeFi, consumer, AI gaming, and infrastructure.

Unparalleled Networking and Exposure
The energy in the room was electric as builders, investors, and foundation leaders engaged in deep discussion. Venture capitalists, including some of the most active investors in the space, had the opportunity to meet the next wave of category-defining projects at their earliest stages. Meanwhile, developers and founders connected with the leading foundations backing their ecosystems, receiving invaluable insights, mentorship, and potential funding opportunities.
Beyond structured networking, serendipitous encounters defined the day—whether it was a team finding a strategic partner over coffee or a founder securing an unexpected investor introduction during a panel discussion. BUIDL DAY was proof that the right environment fosters groundbreaking collaborations.
Why BUIDL DAY Matters
The ethos behind BUIDL DAY is simple: true innovation happens when visionary builders are given a platform to share, iterate, and connect. While the Web3 landscape is constantly evolving, one thing remains certain—early-stage projects need more than funding; they need the right ecosystem, exposure, and support to succeed.
By curating an event that prioritizes originality and contrarian thinking, DoraHacks has reaffirmed its commitment to nurturing the builders who will define the future of blockchain and beyond. BUIDL DAY was not just a moment in time—it was the beginning of something much bigger.
To all the builders, investors, and foundation leaders who joined us: thank you for making this an unforgettable experience. We can’t wait to see where these projects go next and look forward to building together in the future.
Until next time, keep BUIDLing!
If you want to learn more about all of the participating BUIDLs please refer the our
-
 @ 6e0ea5d6:0327f353
2025-03-02 03:08:00
@ 6e0ea5d6:0327f353
2025-03-02 03:08:00Ascolta bene! Conquering a city is easy. All it takes is gathering armies, strategies, and being ruthless. But mastering one’s own spirit? Ah, that is the battle that separates men from boys, leaders from tyrants, and the wise from the foolish.
Davvero, patience is the hammer that shapes a man's spirit; fury is the fire that destroys it. A warrior wins battles, but a man who controls his emotions rules empires. He who governs himself will never be a slave to circumstances.
An army may tear down walls, but a single man who controls his emotions builds empires—both within and beyond himself. Patience is not weakness; it is the precise strike of one who has already won the internal battle. Unchecked rage destroys in seconds what patience builds over a lifetime.
External victory without internal mastery is a deception. What good is it to conquer a city if your soul remains a battlefield? He who does not control his spirit is a slave to himself. Anger, ego, and pride are serpents coiled within the heart, ready to suffocate any chance of greatness. A man without self-control is nothing more than a wild beast; a patient man is a fortress.
Patience is not weakness; it is an invisible sword that cuts deeper than any forged blade. True power does not lie in the roar of rage but in the silence of strategy. It is the shield that guards against reckless decisions, words that cannot be taken back, and mistakes that are far too costly. A patient man, one who masters his spirit, is like a volcano—choosing when and where to erupt. He does not waste energy; he channels it, calculates, and triumphs.
A man's success is not measured by the lands he conquers or the people he commands, but by his ability to remain unshaken, even when everything around him crumbles. The man who does not master himself is a slave, even with an empire at his feet. But the patient man, the one who transforms anger into strength and silence into strategy, becomes a living weapon. He does not merely survive—he dominates, unbreakable, immortal in his legacy.
Be this man, amico mio.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 22050dd3:480c11ea
2025-03-02 03:06:35
@ 22050dd3:480c11ea
2025-03-02 03:06:35Written by Keith Meola, Revised by Frank Corva
Situated 8 miles off the coast of Cancun surrounded by pristine turquoise waters is a small island called Isla Mujeres.
And when I say small, I mean small. It measures just 5 miles long by 0.5 miles wide.
The sliver of landmass has a lot going on, though. On it, you can find a lake, a bay, different beaches with unique waves, and various distinct areas.
There’s the calmer residential center, the active and more touristy “downtown”, and the tranquil and posh Southern tip, to describe a few.
12,600 people live on the island, and several hundred merchants and businesses operate there.
Of these businesses, 16 accept bitcoin.
At the beginning of 2024, this number was zero. So, how have so many people on the island been orange-pilled in such a short period of time?
A passionate Bitcoiner named Isabella (Isa) Santos, that's who. And she started doing this work at block height #829,750 (mined February 9, 2024). This is when BTC Isla was born.

BTC Isla
Isa started the work as a passion project. BTC Isla was slow to initially get off the ground, but, Isa began to pick up steam by the end of 2024. And now she is charging ahead with the help of visiting Bitcoiners.
The first visitor arrived in the Summer of 2024 and the number of visitors has been steadily increasing since then.
 Within the first month of this year, 6 Bitcoiners from 4 countries have visited the island to see what is happening and partake in the movement. Those who have visited have split their time between attending meetups or volunteering and partaking in efforts to spread Bitcoin adoption. And Isa intends to welcome many more Bitcoiners to the island this year.
Within the first month of this year, 6 Bitcoiners from 4 countries have visited the island to see what is happening and partake in the movement. Those who have visited have split their time between attending meetups or volunteering and partaking in efforts to spread Bitcoin adoption. And Isa intends to welcome many more Bitcoiners to the island this year.She also plans to continue to work tirelessly to not only onboard more merchants but to educate the freshly orange-pilled about how Bitcoin works and why it's so important.
 One of the bitcoin-accepting merchants on the island
One of the bitcoin-accepting merchants on the islandBitcoin Education
Education is at the core of BTC Isla. In Isa's mind, Bitcoin education is necessary to truly empower the population.
It is one thing to accept bitcoin as a form of payment. It's another for people to truly understand what Bitcoin is and what it can do for them.
Isa teaches Bitcoin classes which are free to attend.
At the moment they are held at the Mayakita restaurant, which is also the usual spot for the Bitcoin meetups. Isa teaches the classes in Spanish using the Mi Primer Bitcoin curriculum.
This curriculum is an open-source diploma-based educational program created by the organization Mi Primer Bitcoin in El Salvador. Through their coursework, students are taught the essential knowledge to gain financial literacy and understand Bitcoin.
As of the time of writing, one cohort has already graduated and the second one is on its way!
 BTC Isla class
BTC Isla classMerchant Adoption
Adoption on the island is picking up steam in 2025. As mentioned, 16 merchants on the island currently accept bitcoin as payment.
And Isa is working to increase that number with the help of locals. Expats living on the island as well as students and graduated students help with adoption.
Thanks to the efforts of Isa and her team, it's now possible to visit the island and use bitcoin exclusively to pay for goods and services!
The majority of the merchants who accept bitcoin are food and drink vendors, but it is possible to pay for accommodation, transportation, and even some tours and shopping with bitcoin.
 Visitors at a meetup
Visitors at a meetupAs I wrote, the number of visitors to the island is exploding in 2025. I recently had the opportunity and pleasure to visit the island and spent 2 weeks there observing and taking part In the project. I will be writing about my experiences on the island and with BTC Isla!
Gaining Attention
Big and exciting things are happening on the small island of Isla Mujeres.
What started as a solo passion project to “orange pill a whole island” is quickly gaining new members and it's attracting attention both on the island and around the globe.
Word is quickly spreading that something is brewing off the coast of Cancun.
 Post-class picture, that's me in the white shirt
Post-class picture, that's me in the white shirtBTC Isla can be followed at the following handles:
-
 @ 6e0ea5d6:0327f353
2025-03-02 03:02:20
@ 6e0ea5d6:0327f353
2025-03-02 03:02:20Every venture is a tremendous risk. In all your business endeavors, ask yourself: is the potential gain viable enough to outweigh the risk of loss? Courage must always align with intelligence. That is, every initiative should be based on a thorough study of the market, supply, and demand.
If the success of your plans depends on someone else's help, believe this: you have already failed. Do not wait for assistance, do not rely on the goodwill of others, and never trust promises of support. In the end, people are more likely to ignore you than to honor their word.
It will not be their fault in any way. However, it will be yours. Do not be disappointed in others—be disappointed in yourself for expecting too much from them. Engrave these words in your heart, and you will never have the spear of betrayal lodged in your back. When you are at rock bottom, the only thing that will fall from the sky is dirt. The best time to be courageous is when you have nothing left.
With that in mind, approach your problems with enthusiasm and determination! Keep your eyes open, your mouth shut, your heart still, and your spirit ready for war. Only lower your guard when they lower the lid of your coffin. Both failure and victory are direct results of your actions and how you navigate your personal circumstances. Take responsibility for your choices and mistakes, do not wallow in self-pity, and enjoy what you earn.
Expect nothing from others but disappointment, lies, and constant frustration. Anything good that comes your way—consider it a bonus.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ f3873798:24b3f2f3
2025-03-02 02:32:22
@ f3873798:24b3f2f3
2025-03-02 02:32:22Olá, caros leitores!
No meu Guia para Novatos do Nostr, mencionei brevemente o YakiHonne, um dos diversos clientes disponíveis no ecossistema Nostr. Hoje, quero aprofundar mais sobre esse cliente, destacando suas funcionalidades, vantagens, desvantagens e minha opinião final.
YakiHonne: O Melhor Cliente para Microblog no Nostr?
O YakiHonne se destaca por sua interface bem organizada e otimizada para leitura de artigos no Nostr. Um dos seus diferenciais é a seção de sugestões no canto superior da tela, que recomenda conteúdos relevantes e incentiva a exploração de novas postagens.
Caso você queira mais visibilidade na plataforma, existe a opção de pagar para destacar uma publicação através da funcionalidade> Note Paga, localizada na parte inferior da tela de criação de posts.
Além disso, o YakiHonne oferece diversas opções de publicação, cada uma com otimizações específicas.
Funcionalidades do YakiHonne
Ao clicar no botão "+", o usuário tem acesso às seguintes opções de postagens:
📌 Note
Equivalente às postagens instantâneas de redes sociais como X (antigo Twitter), onde os usuários compartilham pensamentos curtos e interagem rapidamente.
📝 Article
Voltado para microblogs e blogs, essa opção permite uma formatação mais detalhada dos textos, sendo ideal para quem quer produzir conteúdo mais elaborado.
🎥 Vídeo
Uma funcionalidade destinada à publicação de vídeos. Aparentemente, o YakiHonne busca ser um “YouTube descentralizado” dentro do Nostr, mas ainda não explorei essa opção a fundo. Se alguém já testou, sinta-se à vontade para compartilhar nos comentários.
🖥️ Smart Widget
Permite personalizar o layout do cliente para que a experiência de navegação e leitura fique mais intuitiva e agradável para cada usuário.
📚 Curation
Uma funcionalidade que possibilita a criação de curations, ou seja, coleções de artigos organizados por tema. Além disso, outras pessoas podem contribuir com artigos relacionados, tornando essa uma ferramenta colaborativa interessante.
Na minha opinião, a opção Article é a mais útil, pois permite criar textos bem estruturados.
Construindo um Artigo no YakiHonne
Na opção Article, há diversas ferramentas de formatação disponíveis, incluindo:
-
Negrito
-
Itálico
-
Hyperlink
-
Diferentes níveis de títulos (H1, H2, H3…)
-
<> Para realçar trechos de código ou termos específicos
-
" Para inserir citações destacadas
-
Sublinhado
-
f (parece criar um botão, mas precisa de ajustes)
-
Inserção de imagens via URL ou upload direto
-
Inteligência Artificial integrada para auxiliar na escrita
-
Smart Widget para melhor organização
Essas ferramentas tornam a experiência de escrever no YakiHonne mais completa e dinâmica.
Vantagens do YakiHonne
✅ Ótima otimização para textos – É um dos clientes mais completos para quem deseja produzir conteúdos bem estruturados. ✅ Interface intuitiva – A organização da plataforma facilita a navegação e a gestão das postagens. ✅ Ferramentas de divulgação – As opções de curadoria e destaques pagos ajudam a impulsionar conteúdos relevantes.
Desvantagens do YakiHonne
⚠️ Edição de texto precisa de melhorias – A opção de sublinhar altera o tamanho e a fonte do texto, o que não é ideal para destacar palavras estrangeiras corretamente. ⚠️ Botão "f" desconfigurado – A funcionalidade que aparentemente gera um botão ficou deformada no meu celular, sem possibilidade de ajuste.
Considerações Finais
O YakiHonne é um dos melhores clientes Nostr que já experimentei. Se você gosta de ler e escrever artigos, pode passar horas explorando os conteúdos da comunidade.
Além disso, acredito que no futuro haverá mais opções de monetização. Assim como outros clientes Nostr, o YakiHonne permite associar uma carteira de Bitcoin, possibilitando receber doações pelos conteúdos publicados.
Se você já testou esse cliente, deixe nos comentários sua experiências
-
-
 @ d5c3d063:4d1159b3
2025-03-02 02:29:00
@ d5c3d063:4d1159b3
2025-03-02 02:29:00ทำไมคนที่ด่าเรา ถึงเป็นคนที่ทุกข์...ลองนึกภาพคนที่กำลังมีความสุขดูสิ... เขาจะมีเวลามานั่งด่าใครไหม
วันหนึ่ง...ผมนั่งอยู่ในร้านกาแฟ มองออกไปเห็นชายคนหนึ่งกำลังมีปากเสียงกับพนักงานร้าน เขาพูดจาเสียงดัง หน้าตาบึ้งตึง ดูหงุดหงิดอย่างเห็นได้ชัด พนักงานสาวที่ถูกตำหนิพยายามขอโทษ และอธิบายเหตุผลของเธอด้วยน้ำเสียงสุภาพ แต่ชายคนนั้นยังคงไม่พอใจ เดินออกจากร้านไปด้วยอารมณ์ขุ่นมัว ทิ้งบรรยากาศตึงเครียดไว้เบื้องหลัง
!(image)[https://m.primal.net/PQdY.png]
พนักงานสาวถอนหายใจเบา ๆ แล้วหันกลับมาทำงานต่อราวกับไม่มีอะไรเกิดขึ้น ผมอดสงสัยไม่ได้ว่าทำไมเธอถึงดูไม่ทุกข์ร้อนกับเหตุการณ์เมื่อครู่นี้เลย
"ไม่เป็นไรค่ะ เขาคงมีเรื่องให้กังวลอยู่แล้ว" เธอตอบเมื่อผมถาม
คำพูดนั้นทำให้ผมหยุดคิด...
ในชีวิตของเรา คงไม่มีใครไม่เคยถูกตำหนิ ถูกต่อว่า หรือถูกพูดจาไม่ดีใส่ บางครั้งอาจเป็นเพียงคำพูดที่ไม่ได้ตั้งใจ บางครั้งอาจเป็นอารมณ์โกรธที่ถูกระบายออกมาโดยไม่เลือกที่หมาย แต่หากเราหยุดดูให้ดี เราจะพบว่าคนที่กำลังโกรธ ดุด่าหรือตำหนิใครสักคน มักจะเป็นคนที่กำลังเผชิญกับความทุกข์อยู่แล้ว
คนที่มาด่าเรา อาจจะกำลังเหนื่อยล้าจากปัญหาส่วนตัว อาจจะผิดหวังในบางสิ่ง อาจจะรู้สึกไม่เป็นที่ยอมรับ อาจจะเครียดจากเรื่องในครอบครัว และบางครั้ง…อาจจะไม่ได้มีเจตนาร้าย เพียงแต่เขาไม่รู้จะจัดการกับอารมณ์ของตัวเองยังไง
...และเมื่อเผชิญกับคำพูดที่ไม่ดี เรามีทางเลือกอยู่เสมอ...
-
ตอบโต้กลับไป บางครั้งเราโกรธและเผลอพูดอะไรออกไปตามอารมณ์ สิ่งนี้อาจทำให้เกิดความรู้สึกไม่ดีทั้งสองฝ่าย บางครั้งเราชนะการโต้เถียง แต่กลับแพ้ที่ความสงบในใจ
-
ปล่อยผ่าน และเข้าใจ การเข้าใจว่า "คนที่ด่าเรา เขานั่นแหละทุกข์" ไม่ได้หมายความว่าเราต้องยอมรับการถูกกระทำที่ไม่เหมาะสม แต่หมายถึงการไม่เอาคำพูดเหล่านั้นมาเป็นภาระของตัวเอง
-
มองลึกลงไปให้เห็นเจตนา บางครั้งคนที่ตำหนิเราอาจจะต้องการให้เราปรับปรุงในบางเรื่อง อารมณ์ของเขาอาจจะไม่ดี แต่หากเราแยกเนื้อหาจากอารมณ์ออกมาได้ เราอาจพบว่ามีบางอย่างที่เราสามารถเรียนรู้ได้
ท้ายที่สุด คำพูดของใครก็ไม่สำคัญเท่ากับสิ่งที่เราบอกกับตัวเอง
หากเรามั่นคงพอ คำพูดที่รุนแรงจะเป็นเพียงเสียงที่ผ่านเข้ามาแล้วผ่านไป หากเรามีเมตตา คำพูดที่ไม่ดีจะเป็นบทเรียนให้เราเข้าใจมนุษย์มากขึ้น หากเรารู้เท่าทันอารมณ์ตัวเอง คำพูดเหล่านั้นก็จะไม่มีอิทธิพลต่อเรา
"ไม่เป็นไรค่ะ เขาคงมีเรื่องให้กังวลอยู่แล้ว"
ผมนั่งจิบกาแฟพลางคิดตามคำพูดนั้นแล้วพบว่ามันเป็นเรื่องจริง คนที่มาด่าเรา อาจจะต้องการกำลังใจมากกว่าที่เราคิดก็ได้...
Siamstr
-
-
 @ eb35d9c0:6ea2b8d0
2025-03-02 00:55:07
@ eb35d9c0:6ea2b8d0
2025-03-02 00:55:07I had a ton of fun making this episode of Midnight Signals. It taught me a lot about the haunting of the Bell family and the demise of John Bell. His death was attributed to the Bell Witch making Tennessee the only state to recognize a person's death to the supernatural.
If you enjoyed the episode, visit the Midnight Signals site. https://midnightsignals.net
Show Notes
Journey back to the early 1800s and the eerie Bell Witch haunting that plagued the Bell family in Adams, Tennessee. It began with strange creatures and mysterious knocks, evolving into disembodied voices and violent attacks on young Betsy Bell. Neighbors, even Andrew Jackson, witnessed the phenomena, adding to the legend. The witch's identity remains a mystery, sowing fear and chaos, ultimately leading to John Bell's tragic demise. The haunting waned, but its legacy lingers, woven into the very essence of the town. Delve into this chilling story of a family's relentless torment by an unseen force.
Transcript
Good evening, night owls. I'm Russ Chamberlain, and you're listening to midnight signals, the show, where we explore the darkest corners of our collective past. Tonight, our signal takes us to the early 1800s to a modest family farm in Adams, Tennessee. Where the Bell family encountered what many call the most famous haunting in American history.
Make yourself comfortable, hush your surroundings, and let's delve into this unsettling tale. Our story begins in 1804, when John Bell and his wife Lucy made their way from North Carolina to settle along the Red River in northern Tennessee. In those days, the land was wide and fertile, mostly unspoiled with gently rolling hills and dense woodland.
For the Bells, John, Lucy, and their children, The move promised prosperity. They arrived eager to farm the rich soil, raise livestock, and find a peaceful home. At first, life mirrored [00:01:00] that hope. By day, John and his sons worked tirelessly in the fields, planting corn and tending to animals, while Lucy and her daughters managed the household.
Evenings were spent quietly, with scripture readings by the light of a flickering candle. Neighbors in the growing settlement of Adams spoke well of John's dedication and Lucy's gentle spirit. The Bells were welcomed into the Fold, a new family building their future on the Tennessee Earth. In those early years, the Bells likely gave little thought to uneasy rumors whispered around the region.
Strange lights seen deep in the woods, soft cries heard by travelers at dusk, small mysteries that most dismissed as product of the imagination. Life on the frontier demanded practicality above all else, leaving little time to dwell on spirits or curses. Unbeknownst to them, events on their farm would soon dominate not only their lives, but local lore for generations to come.[00:02:00]
It was late summer, 1817, when John Bell's ordinary routines took a dramatic turn. One evening, in the waning twilight, he spotted an odd creature near the edge of a tree line. A strange beast resembling part dog, part rabbit. Startled, John raised his rifle and fired, the shot echoing through the fields. Yet, when he went to inspect the spot, nothing remained.
No tracks, no blood, nothing to prove the creature existed at all. John brushed it off as a trick of falling light or his own tired eyes. He returned to the house, hoping for a quiet evening. But in the days that followed, faint knocking sounds began at the windows after sunset. Soft scratching rustled against the walls as if curious fingers or claws tested the timbers.
The family's dog barked at shadows, growling at the emptiness of the yard. No one considered it a haunting at first. Life on a rural [00:03:00] farm was filled with pests, nocturnal animals, and the countless unexplained noises of the frontier. Yet the disturbances persisted, night after night, growing a little bolder each time.
One evening, the knocking on the walls turned so loud it woke the entire household. Lamps were lit, doors were open, the ground searched, but the land lay silent under the moon. Within weeks, the unsettling taps and scrapes evolved into something more alarming. Disembodied voices. At first, the voices were faint.
A soft murmur in rooms with no one in them. Betsy Bell, the youngest daughter, insisted she heard her name called near her bed. She ran to her mother and her father trembling, but they found no intruder. Still, The voice continued, too low for them to identify words, yet distinct enough to chill the blood.
Lucy Bell began to fear they were facing a spirit, an unclean presence that had invaded their home. She prayed for divine [00:04:00] protection each evening, yet sometimes the voice seemed to mimic her prayers, twisting her words into a derisive echo. John Bell, once confident and strong, grew unnerved. When he tried reading from the Bible, the voice mocked him, imitating his tone like a cruel prankster.
As the nights passed, disturbances gained momentum. Doors opened by themselves, chairs shifted with no hand to move them, and curtains fluttered in a room void of drafts. Even in daytime, Betsy would find objects missing, only for them to reappear on the kitchen floor or a distant shelf. It felt as if an unseen intelligence roamed the house, bent on sowing chaos.
Of all the bells, Betsy suffered the most. She was awakened at night by her hair being yanked hard enough to pull her from sleep. Invisible hands slapped her cheeks, leaving red prints. When she walked outside by day, she heard harsh whispers at her ear, telling her she would know [00:05:00] no peace. Exhausted, she became withdrawn, her once bright spirit dulled by a ceaseless fear.
Rumors spread that Betsy's torment was the worst evidence of the haunting. Neighbors who dared spend the night in the Bell household often witnessed her blankets ripped from the bed, or watched her clutch her bruised arms in distress. As these accounts circulated through the community, people began referring to the presence as the Bell Witch, though no one was certain if it truly was a witch's spirit or something else altogether.
In the tightly knit town of Adams, word of the strange happenings at the Bell Farm soon reached every ear. Some neighbors offered sympathy, believing wholeheartedly that the family was besieged by an evil force. Others expressed skepticism, guessing there must be a logical trick behind it all. John Bell, ordinarily a private man, found himself hosting visitors eager to witness the so called witch in action.
[00:06:00] These visitors gathered by the parlor fireplace or stood in darkened hallways, waiting in tense silence. Occasionally, the presence did not appear, and the disappointed guests left unconvinced. More often, they heard knocks vibrating through the walls or faint moans drifting between rooms. One man, reading aloud from the Bible, found his words drowned out by a rasping voice that repeated the verses back at him in a warped, sing song tone.
Each new account that left the bell farm seemed to confirm the unearthly intelligence behind the torment. It was no longer mere noises or poltergeist pranks. This was something with a will and a voice. Something that could think and speak on its own. Months of sleepless nights wore down the Bell family.
John's demeanor changed. The weight of the haunting pressed on him. Lucy, steadfast in her devotion, prayed constantly for deliverance. The [00:07:00] older Bell children, seeing Betsy attacked so frequently, tried to shield her but were powerless against an enemy that slipped through walls. Farming tasks were delayed or neglected as the family's time and energy funneled into coping with an unseen assailant.
John Bell began experiencing health problems that no local healer could explain. Trembling hands, difficulty swallowing, and fits of dizziness. Whether these ailments arose from stress or something darker, they only reinforced his sense of dread. The voice took to mocking him personally, calling him by name and snickering at his deteriorating condition.
At times, he woke to find himself pinned in bed, unable to move or call out. Despite it all, Lucy held the family together. Soft spoken and gentle, she soothed Betsy's tears and administered whatever remedies she could to John. Yet the unrelenting barrage of knocks, whispers, and violence within her own home tested her faith [00:08:00] daily.
Amid the chaos, Betsy clung to one source of joy, her engagement to Joshua Gardner, a kind young man from the area. They hoped to marry and begin their own life, perhaps on a parcel of the Bell Land or a new farmstead nearby. But whenever Joshua visited the Bell Home, The unseen spirit raged. Stones rattled against the walls, and the door slammed as if in warning.
During quiet walks by the river, Betsy heard the voice hiss in her ear, threatening dire outcomes if she ever were to wed Joshua. Night after night, Betsy lay awake, her tears soaked onto her pillow as she wrestled with the choice between her beloved fiancé and this formidable, invisible foe. She confided in Lucy, who offered comfort but had no solution.
For a while, Betsy and Joshua resolved to stand firm, but the spirit's fury only escalated. Believing she had no alternative, Betsy broke off the engagement. Some thought the family's [00:09:00] torment would subside if the witches demands were met. In a cruel sense, it seemed to succeed. With Betsy's engagement ended, the spirit appeared slightly less focused on her.
By now, the Bell Witch was no longer a mere local curiosity. Word of the haunting spread across the region and reached the ears of Andrew Jackson, then a prominent figure who would later become president. Intrigued, or perhaps skeptical, he traveled to Adams with a party of men to witness the phenomenon firsthand.
According to popular account, the men found their wagon inexplicably stuck on the road near the Bell property, refusing to move until a disembodied voice commanded them to proceed. That night, Jackson's men sat in the Bell parlor, determined to uncover fraud if it existed. Instead, they found themselves subjected to jeering laughter and unexpected slaps.
One boasted of carrying a special bullet that could kill any spirit, only to be chased from the house in terror. [00:10:00] By morning, Jackson reputedly left, shaken. Although details vary among storytellers, the essence of his experience only fueled the legend's fire. Some in Adams took to calling the presence Kate, suspecting it might be the spirit of a neighbor named Kate Batts.
Rumors pointed to an old feud or land dispute between Kate Batts and John Bell. Whether any of that was true, or Kate Batts was simply an unfortunate scapegoat remains unclear. The entity itself, at times, answered to Kate when addressed, while at other times denying any such name. It was a puzzle of contradictions, claiming multiple identities.
A wayward spirit, a demon, or a lost soul wandering in malice. No single explanation satisfied everyone in the community. With Betsy's engagement to Joshua broken, the witch devoted increasing attention to John Bell. His health declined rapidly in 1820, marked by spells of near [00:11:00] paralysis and unremitting pain.
Lucy tended to him day and night. Their children worried and exhausted, watched as their patriarch grew weaker, his once strong presence withering under an unseen hand. In December of that year, John Bell was found unconscious in his bed. A small vial of dark liquid stood nearby. No one recognized its contents.
One of his sons put a single drop on the tongue of the family cat, which died instantly. Almost immediately, the voice shrieked in triumph, boasting that it had given John a final, fatal dose. That same day, John Bell passed away without regaining consciousness, leaving his family both grief stricken and horrified by the witch's brazen gloating.
The funeral drew a large gathering. Many came to mourn the respected farmer. Others arrived to see whether the witch would appear in some dreadful form. As pallbearers lowered John Bell's coffin, A jeering laughter rippled across the [00:12:00] mourners, prompting many to look wildly around for the source. Then, as told in countless retellings, the voice broke into a rude, mocking song, echoing among the gravestones and sending shudders through the crowd.
In the wake of John Bell's death, life on the farm settled into an uneasy quiet. Betsy noticed fewer night time assaults. And the daily havoc lessened. People whispered that the witch finally achieved its purpose by taking John Bell's life. Then, just as suddenly as it had arrived, the witch declared it would leave the family, though it promised to return in seven years.
After a brief period of stillness, the witch's threat rang true. Around 1828, a few of the Bells claimed to hear light tapping or distant murmurs echoing in empty rooms. However, these new incidents were mild and short lived compared to the previous years of torment. Soon enough, even these faded, leaving the bells [00:13:00] with haunted memories, but relative peace.
Near the bell property stood a modest cave by the Red River, a spot often tied to the legend. Over time, people theorized that cave's dark recesses, though the bells themselves rarely ventured inside. Later visitors and locals would tell of odd voices whispering in the cave or strange lights gliding across the damp stone.
Most likely, these stories were born of the haunting's lingering aura. Yet, they continued to fuel the notion that the witch could still roam beyond the farm, hidden beneath the earth. Long after the bells had ceased to hear the witch's voice, the story lived on. Word traveled to neighboring towns, then farther, into newspapers and traveler anecdotes.
The tale of the Tennessee family plagued by a fiendish, talkative spirit captured the imagination. Some insisted the Bell Witch was a cautionary omen of what happens when old feuds and injustices are left [00:14:00] unresolved. Others believed it was a rare glimpse of a diabolical power unleashed for reasons still unknown.
Here in Adams, people repeated the story around hearths and campfires. Children were warned not to wander too far near the old bell farm after dark. When neighbors passed by at night, they might hear a faint rustle in the bush or catch a flicker of light among the trees, prompting them to walk faster.
Hearts pounding, minds remembering how once a family had suffered greatly at the hands of an unseen force. Naturally, not everyone agreed on what transpired at the Bell farm. Some maintained it was all too real, a case of a vengeful spirit or malignant presence carrying out a personal vendetta. Others whispered that perhaps a member of the Bell family had orchestrated the phenomenon with cunning trickery, though that failed to explain the bruises on Betsy, the widespread witnesses, or John's mysterious death.
Still, others pointed to the possibility of an [00:15:00] unsettled spirit who had attached itself to the land for reasons lost to time. What none could deny was the tangible suffering inflicted on the Bells. John Bell's slow decline and Betsy's bruises were impossible to ignore. Multiple guests, neighbors, acquaintances, even travelers testified to hearing the same eerie voice that threatened, teased and recited scripture.
In an age when the supernatural was both feared and accepted, the Bell Witch story captured hearts and sparked endless speculation. After John Bell's death, the family held onto the farm for several years. Betsy, robbed of her engagement to Joshua, eventually found a calmer path through life, though the memory of her tormented youth never fully left her.
Lucy, steadfast and devout to the end, kept her household as best as she could, unwilling to surrender her faith even after all she had witnessed. Over time, the children married and started families of their own, [00:16:00] quietly distancing themselves from the tragedy that had defined their upbringing.
Generations passed, the farm changed hands, the Bell House was repurposed and renovated, and Adams itself transformed slowly from a frontier settlement into a more established community. Yet the name Bellwitch continued to slip into conversation whenever strange knocks were heard late at night or lonely travelers glimpsed inexplicable lights in the distance.
The story refused to fade, woven into the identity of the land itself. Even as the first hand witnesses to the haunting aged and died, their accounts survived in letters, diaries, and recollections passed down among locals. Visitors to Adams would hear about the famed Bell Witch, about the dreadful death of John Bell, the heartbreak of Betsy's broken engagement, and the brazen voice that filled nights with fear.
Some folks approached the story with reverence, others with skepticism. But no one [00:17:00] denied that it shaped the character of the town. In the hush of a moonlit evening, one might stand on that old farmland, fields once tilled by John Bell's callous hands, now peaceful beneath the Tennessee sky. And imagine the entire family huddled in the house, listening with terrified hearts for the next knock on the wall.
It's said that if you pause long enough, you might sense a faint echo of their dread, carried on a stray breath of wind. The Bell Witch remains a singular chapter in American folklore, a tale of a family besieged by something unseen, lethal, and uncannily aware. However one interprets the events, whether as vengeful ghosts, demonic presence, or some other unexplainable force, the Bell Witch.
Its resonance lies in the very human drama at its core. Here was a father undone by circumstances he could not control. A daughter tormented in her own home, in a close knit household tested by relentless fear. [00:18:00] In the end, the Bell Witch story offers a lesson in how thin the line between our daily certainties and the mysteries that defy them.
When night falls, and the wind rattles the shutters in a silent house, we remember John Bell and his family, who discovered that the safe haven of home can become a battlefield against forces beyond mortal comprehension. I'm Russ Chamberlain, and you've been listening to Midnight Signals. May this account of the Bell Witch linger with you as a reminder that in the deepest stillness of the night, Anything seems possible.
Even the unseen tapping of a force that seeks to make itself known. Sleep well, if you dare.
-
 @ 5725c4a8:6ba4f820
2025-03-01 23:41:24
@ 5725c4a8:6ba4f820
2025-03-01 23:41:24!(image)[https://i.nostr.build/iuWXGIaA91wMTFJg.jpg] I've been seeing some posts from (I think new) Bitcoiners complaining about the recent volatility of Bitcoin, sometimes in dismay about the price, and sometimes in dismay that they have no "dry powder" available to buy the dip. With inflation being such a huge problem, cost of living has a very real effect on our ability to stack sats, so some creative thinking is in order. My hope is that this post can share a little bit of wisdom that I have found to work for me in my own quest to accumulate as much Bitcoin as I can. If you want to skip to the meat of this article, scroll down My Strategy. As the standard disclosure goes: this is not financial or investment advice.
A little about me and where I'm coming from
I'm part of the 2022 class of Bitcoiners. I'm very new to this community.But I have gone down the Bitcoin rabbit hole, I have read Saifdean's The Bitcoin Standard and The Fiat Standard, and I have spent many many hundreds of hours listening to podcasts on Bitcoin and Austrian economics (which I discovered at about the same time). All this to say, despite the work that I have put in thus far, take this with a grain of salt and use your own reasoning to determine if this strategy or any ideas derived from it are right for you.
Dollar Cost Averaging
Dollar Cost Averaging (DCA) is the practice of setting a recurring buy order of a stock or commodity. Such orders, once set, will continue to execute at the set frequency until the buyer's selected termination date, or until a set amount has been reached, or until no more funds are available in the buyer's account from which to buy. DCA takes advantage of the fact that for a long term growth asset (like Bitcoin), the average price will always tend to go up over time despite intermittent volatility. By not trying watch for or time the dips and highs, DCAing not only makes it easier to accumulate Bitcoin, but it is very effective in the long term and reduces a lot of potential stress from trying to game the market volatility. One more important point is that as this method utilizes averaging, the closer that the buyer can match the actual price curve over time, the greater the benefit from the average growth of that price curve. This means that for two recurring buy orders, using the same amount of fiat in the buying pool, if one has more frequent buys and the other has less frequent buys, even if they spent the same amount at the end of the buying period, the order with more frequent buys will experience the greater value from the average growth of the asset being purchased.
This is in contrast to limit orders, in which they buyer attempts to gauge what price action will occur in the future, or "smash buying" in which the buyer tries to watch and time the market to place real-time orders. As these are not the focus of this strategy, I won't go into detail about them. But if you understand DCA and why it works, I assume that you can also reason for yourself about the effectiveness and utility of these other buying methods.
Each of these methods can occasionally be successful, I'm not saying that there is not place for them. In fact, I use these too, but they are used in a tactical manner, and I try to be careful to make sure that using these do not interrupt my DCA strategy.
Savings Allocation
I may update this in the future, based on changes in my financial situation, the larger landscape, and whatproducts/tools are available. Note that I'm not rich. I work for a tech startup which is gaining traction, and if it is successful then that may change. But for now I operate with limited financial resources to use for stacking sats. But still, I stack sats. I say this to clarify why this strategy works for me, and hopefully to establish that this will work for you if you also have limited income but have the ability and desire to accumulate Bitcoin for yourself.
I have a consistent amount of money coming in on a regular basis, and this is an important part of my calculus. Similarly, I have consistent bills going out. The difference between these are my subsistence and discretionary spending. Subsistence spending being money that I spend on food and other nutrients, and discretionary spending is what I spend on the things that I want but don't need.
I'm not at a point where I've managed to completely cut out my discretionary spending, but I do try to limit it as much as I can. Similarly, I'm proactive about finding good deals on food (especially beef). Then I can allocate more money to savings. It is this savings allocation that I use for buying Bitcoin.
My DCA Strategy
!(image)[https://i.nostr.build/augZsY8EVEAsdP34.png] My strategy begins with the money from each pay check that I want to allocate to savings (which in my case all goes to buying Bitcoin). It also hinges on DCA, and is strongly inspired by the sayings "stay humble and stack sats", and that "time in the market beats timing the market". I am not a professional trader, nor do I aspire to be one. As such, I want to maximize my time in the market without stressing myself out.
Allocating funds for DCA: First, find the amount for each pay period that you will use to buy Bitcoin, but don't immediately use it to buy, yet. Next, you need to find the frequency by which you will buy, and how much. I recommend the most frequent recurring buy option that you can find.
To do this, you need to find the DCA options available on the exchanges that you use. As a Bitcoin maximalist, I use Bitcoin focused exchanges. As a man with limited available funds for this use, I want the ability to DCA in fairly small amounts, but as frequently as possible. I find that River and Strike are excellent exchanges for this. Each of these exchanges currently allow buying as frequently as once-per-hour. River has a minimum of $1 per purchase. Strike can go even lower, I have a friend who I convinced to adopt this strategy and he started out with an hourly recurring buy of $0.05 per hour.
Having been a Bitcoiner for a little while now, I also find that it is useful to have additional funds set aside for "smash buys" to take advantage of major dips, such as the one that we are currently experiencing (I'm writing this on March 1st, 2025).
Using River as an example: The minimal buy on River, as stated above, is $1 per hour. There are 24 hours in a day, and 14 days in a pay period (for me). Then the minimum amount to allocate on River is $1/hour x 24 hours/day x 14 days/period = $336 per period.
You can change the dollar amount or number of days as are appropriate for your own goals and circumstances.
If you have a lower total available amount, you can use this version of the formula to find the recurring buy amount on Strike (or whichever other platform allows sub-dollar recurring buys): Recurring Buy = (available funds) / (number of hours over which to buy)
In truth, I use Strike as well, but I have another reason for choosing River in this example: I mentioned having a DCA strategy which keeps a reserve of "dry powder" so that you can also buy the dip.
You may benefit from keeping some reserve of savings in USD. It's something we simply can't get away from at this time of continued fiat dominance. This allows you to pull from the fiat reserve rather than selling any accumulated Bitcoin in cases of emergency (like car problems, or a family member needing help).
Last year, River announced a feature by which any cash kept on their exchange would earn 3.8% interest, which is paid in Bitcoin. This strategy works with other exchanges, but using River means that interest accumulation can also be leveraged (and it is much better than a typical bank savings account).
This is the final part of the strategy: put the rest of your savings into River and let it accumulate interest in Bitcoin. This reserve then becomes your dry powder. Use it at your discretion, save for emergencies, or use it to "smash buy" the dip, but do it without compromising your DCA setup. DON'T CANCEL your DCA, keep it going and take advantage of it's average growth. You don't know when the price will dip, and you don't know when it will go back up again. If it is difficult for you to maintain discipline and not spend your DCA reserve (since River doesn't split it into buckets for you), a variation of this strategy is to DCA-stack on another exchange so that it's not in the same pool as your fiat reserve.
When all else fails, just keep calm, stay humble, and stack sats. !(image)[https://i.nostr.build/pko6uWkq3rf0y0io.png]
I hope that someone finds this helpful. If you have your own personalized strategy, I'd love to hear about it in the comments.
-
 @ f33c8a96:5ec6f741
2025-03-01 23:25:22
@ f33c8a96:5ec6f741
2025-03-01 23:25:22Setting Up Your Code Editor
Introduction
In this lesson, we'll set up the most fundamental tool in your development journey: your code editor. This is where you'll spend most of your time writing, testing, and debugging code, so it's crucial to get comfortable with it from the start.
What is an IDE?
Definition
An IDE (Integrated Development Environment) is a software application that provides comprehensive facilities for software development. Think of it as your complete workshop for writing code.
Key Components
- Code Editor
- Where you write and edit code
- Provides syntax highlighting
- Helps with code formatting
-
Makes code easier to read and write
-
Compiler/Interpreter
- Runs your code
- Translates your code into executable instructions
-
Helps test your applications
-
Debugging Tools
- Help find and fix errors
- Provide error messages and suggestions
- Make problem-solving easier
Setting Up Visual Studio Code
Why VS Code?
- Free and open-source
- Lightweight yet powerful
- Excellent community support
- Popular among developers
- Great for beginners and experts alike
Installation Steps
- Visit code.visualstudio.com
- Download the version for your operating system
- Run the installer
- Follow the installation prompts
Essential VS Code Features
1. Interface Navigation
- File Explorer (Ctrl/Cmd + Shift + E)
- Browse and manage your files
- Create new files and folders
-
Navigate your project structure
-
Search (Ctrl/Cmd + Shift + F)
- Find text across all files
- Replace text globally
-
Search with regular expressions
-
Source Control (Ctrl/Cmd + Shift + G)
- Track changes in your code
- Commit and manage versions
- Integrate with Git
2. Terminal Integration
To open the integrated terminal: - Use
Ctrl + `(backtick) - Or View → Terminal from the menu - Basic terminal commands:bash ls # List files (dir on Windows) cd # Change directory clear # Clear terminal code . # Open VS Code in current directory3. Essential Extensions
Install these extensions to enhance your development experience: 1. ESLint - Helps find and fix code problems - Enforces coding standards - Improves code quality
- Prettier
- Automatically formats your code
- Maintains consistent style
-
Saves time on formatting
-
Live Server
- Runs your web pages locally
- Auto-refreshes on save
- Great for web development
Important Keyboard Shortcuts
Ctrl/Cmd + S # Save file Ctrl/Cmd + C # Copy Ctrl/Cmd + V # Paste Ctrl/Cmd + Z # Undo Ctrl/Cmd + Shift + P # Command palette Ctrl/Cmd + P # Quick file openWriting Your First Code
Let's create and run a simple HTML file:
- Create a new file (
index.html) - Add basic HTML content:
```html
Hello World!
``` 3. Save the file (Ctrl/Cmd + S) 4. Open in browser or use Live Server
Best Practices
1. File Organization
- Keep related files together
- Use clear, descriptive names
- Create separate folders for different projects
2. Regular Saving
- Save frequently (Ctrl/Cmd + S)
- Watch for the unsaved dot indicator
- Enable auto-save if preferred
3. Terminal Usage
- Get comfortable with basic commands
- Use the integrated terminal
- Practice navigation and file operations
Troubleshooting Common Issues
1. Installation Problems
- Ensure you have admin rights
- Check system requirements
- Use official download sources
2. Extension Issues
- Keep extensions updated
- Disable conflicting extensions
- Restart VS Code after installation
3. Performance
- Don't install too many extensions
- Regular restart of VS Code
- Keep your system updated
Next Steps
- Practice Navigation
- Create and manage files
- Use the integrated terminal
-
Try keyboard shortcuts
-
Customize Your Editor
- Explore themes
- Adjust font size
-
Configure auto-save
-
Prepare for Next Lesson
- Keep VS Code open
- Get comfortable with the interface
- Practice basic operations
Additional Resources
Remember: Your code editor is your primary tool as a developer. Take time to get comfortable with it, and don't worry about mastering everything at once. Focus on the basics we covered in the video, and you'll naturally learn more features as you need them.
Happy coding! 🚀
-
 @ f33c8a96:5ec6f741
2025-03-01 23:24:35
@ f33c8a96:5ec6f741
2025-03-01 23:24:35CSS Fundamentals: Styling Your First Webpage
Introduction
In our previous lesson, we created the structure of our webpage with HTML. Now, we'll learn how to style it using CSS (Cascading Style Sheets). While HTML provides the bones of our webpage, CSS adds the visual presentation - the colors, layouts, spacing, and overall aesthetics.
What is CSS?
Definition
CSS (Cascading Style Sheets) is a stylesheet language that controls the visual presentation of HTML documents. Think of it like the paint, decorations, and interior design of a house - it determines how everything looks and is arranged.
Key Concepts
- Styling Capabilities
- Fonts and typography
- Colors and backgrounds
- Margins and padding
- Element sizes
- Visual effects
-
Layout and positioning
-
Cascading Nature
- Styles can be inherited from parent elements
- Multiple styles can apply to the same element
- Specificity determines which styles take precedence
- Styles "cascade" down through your document
Basic CSS Syntax
css selector { property: value; }Example:
css h1 { color: blue; font-size: 24px; margin-bottom: 20px; }Connecting CSS to HTML
Method 1: External Stylesheet (Recommended)
html <link rel="stylesheet" href="style.css">Method 2: Internal CSS
```html
```
Method 3: Inline CSS (Use Sparingly)
```html
Title
```
The Box Model
Every HTML element is treated as a box in CSS, with:
┌──────────────────────┐ │ Margin │ │ ┌──────────────┐ │ │ │ Border │ │ │ │ ┌──────────┐ │ │ │ │ │ Padding │ │ │ │ │ │ ┌──────┐ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │Content│ │ │ │ │ │ │ │ │ │ │ │ │ │ │ └──────┘ │ │ │ │ │ └──────────┘ │ │ │ └──────────────┘ │ └──────────────────────┘- Content: The actual content of the element
- Padding: Space between content and border
- Border: The border around the padding
- Margin: Space outside the border
CSS Units
Absolute Units
px- pixelspt- pointscm- centimetersmm- millimetersin- inches
Relative Units
%- percentage relative to parentem- relative to font-sizerem- relative to root font-sizevh- viewport heightvw- viewport width
Practical Example: Styling Our Webpage
1. Basic Page Setup
css body { min-height: 100vh; margin: 0; font-family: Arial, sans-serif; background-color: #f0f0f0; display: flex; flex-direction: column; }2. Header Styling
css header { background-color: #333; color: white; padding: 20px; text-align: center; }3. Main Content Area
css main { max-width: 800px; margin: 0 auto; padding: 20px; flex: 1; }4. Footer Styling
css footer { background-color: #333; color: white; padding: 10px; text-align: center; }Layout with Flexbox
Basic Concept
Flexbox is a modern layout system that makes it easier to create flexible, responsive layouts.
Key Properties
css .container { display: flex; flex-direction: row | column; justify-content: center | space-between | space-around; align-items: center | flex-start | flex-end; }Common Use Cases
- Centering content
- Creating navigation bars
- Building responsive layouts
- Equal-height columns
- Dynamic spacing
Best Practices
1. Organization
- Use consistent naming conventions
- Group related styles together
- Comment your code for clarity
- Keep selectors simple and specific
2. Performance
- Avoid unnecessary specificity
- Use shorthand properties when possible
- Minimize redundant code
- Consider load time impact
3. Maintainability
- Use external stylesheets
- Follow a consistent formatting style
- Break large stylesheets into logical files
- Document important design decisions
Debugging CSS
Common Tools
- Browser Developer Tools
- Element inspector
- Style inspector
- Box model viewer
Common Issues
- Specificity conflicts
- Inheritance problems
- Box model confusion
- Flexbox alignment issues
Exercises
1. Style Modifications
Try modifying these properties in your stylesheet: ```css / Change colors / header { background-color: #4a90e2; }
/ Adjust spacing / main { padding: 40px; }
/ Modify typography / h1 { font-size: 32px; font-weight: bold; } ```
2. Layout Challenge
Create a card layout using Flexbox: ```css .card-container { display: flex; justify-content: space-between; gap: 20px; }
.card { flex: 1; padding: 20px; background: white; border-radius: 8px; box-shadow: 0 2px 4px rgba(0,0,0,0.1); } ```
Additional Resources
Learning Tools
- Flexbox Froggy - Interactive Flexbox learning game
- CSS-Tricks - Excellent CSS reference and tutorials
- MDN CSS Documentation
Practice Projects
- Style your personal webpage
- Create a responsive navigation menu
- Build a flexible card layout
- Design a custom button style
Remember: CSS is both an art and a science. Don't be afraid to experiment and break things - that's how you'll learn the most. The key is to start simple and gradually add complexity as you become more comfortable with the basics.
Next up, we'll dive into JavaScript to add interactivity to our webpage! 🚀
-
 @ f33c8a96:5ec6f741
2025-03-01 23:23:54
@ f33c8a96:5ec6f741
2025-03-01 23:23:54JavaScript: Building Your First Interactive Web App
Introduction
In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way.
Project Overview: Bitcoin Price Tracker
We'll build a web application that: - Displays current Bitcoin price - Updates automatically every 3 seconds - Allows currency switching - Includes interactive controls - Shows current date/time
Core JavaScript Concepts
1. Variables and Data Types
```javascript // Variables can be declared with let or const let currentCurrency = "USD"; // Can be changed const interval = 3000; // Cannot be changed
// Basic data types const price = 45000; // Number const isVisible = true; // Boolean const currency = "USD"; // String ```
2. DOM Manipulation
```javascript // Getting elements const priceElement = document.getElementById('price'); const button = document.getElementById('refresh-button');
// Modifying content priceElement.textContent =
${price} ${currency};// Changing styles priceElement.style.display = 'none'; ```
3. Event Listeners
```javascript // Basic click handler button.addEventListener('click', () => { fetchBitcoinPrice(); });
// Change event for select elements selector.addEventListener('change', (event) => { handleCurrencyChange(event.value); }); ```
4. Async Operations & Fetch API
javascript async function fetchBitcoinPrice() { try { const response = await fetch(apiUrl); const data = await response.json(); updatePrice(data.price); } catch (error) { console.error('Error:', error); } }Project Structure
HTML Setup
```html
Bitcoin Price Tracker Current Bitcoin Price
The price is:
```
Core Functionality Implementation
- Setting Up the Timer ```javascript // Update price every 3 seconds setInterval(fetchBitcoinPrice, 3000);
// Update date/time every second setInterval(updateDateTime, 1000); ```
-
Currency Selection
javascript function handleCurrencyChange(newCurrency) { currentCurrency = newCurrency; fetchBitcoinPrice(); } -
Toggle Visibility
javascript function togglePriceVisibility() { const price = document.getElementById('price'); price.style.display = price.style.display === 'none' ? 'inline' : 'none'; }
Best Practices
1. Error Handling
- Always use try/catch with async operations
- Provide meaningful error messages
- Handle edge cases gracefully
2. Code Organization
- Keep functions focused and small
- Use meaningful variable names
- Group related functionality
- Add comments for clarity
3. Performance
- Avoid unnecessary DOM updates
- Use appropriate update intervals
- Clean up intervals when not needed
Common Challenges & Solutions
1. API Issues
javascript // Handle API failures gracefully catch (error) { priceElement.textContent = 'Price unavailable'; console.error('API Error:', error); }2. Currency Formatting
javascript function formatPrice(price, currency) { return new Intl.NumberFormat('en-US', { style: 'currency', currency: currency }).format(price); }3. Time Zones
javascript function getLocalTime() { return new Date().toLocaleString(); }Extending the Project
Consider adding these features for practice: 1. Price change indicators (up/down arrows) 2. Historical price chart 3. Multiple cryptocurrency support 4. Price alerts 5. Local storage for settings
Debugging Tips
Using Console
javascript console.log('Price fetched:', price); console.error('Error occurred:', error); console.table(priceHistory);Chrome DevTools
- Network tab for API calls
- Console for errors
- Elements for DOM inspection
- Sources for debugging
Additional Resources
- MDN JavaScript Guide
- JavaScript.info
- CoinGecko API Documentation
- Chrome DevTools Documentation
Next Steps
- Add styling with CSS
- Implement additional features
- Learn about React for more complex applications
- Explore other APIs and cryptocurrencies
Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application.
Happy coding! 🚀
-
 @ f33c8a96:5ec6f741
2025-03-01 23:23:36
@ f33c8a96:5ec6f741
2025-03-01 23:23:36Setting Up Git and GitHub: A Developer's Foundation
Lesson Overview
In this lesson, we'll establish one of the most important foundations of your development journey: version control with Git and GitHub. This knowledge will enable you to track your code, back it up in the cloud, and start building your developer portfolio.
Prerequisites
- Visual Studio Code installed
- Terminal/Command Line basics
- GitHub account (we'll create one in this lesson)
Key Learning Objectives
- Understand what Git and GitHub are and why they're essential
- Set up Git locally and connect it to GitHub
- Learn basic Git commands and workflow
- Create your first repository and commit
- Establish good Git habits for your developer journey
What is Git and GitHub?
Git: Your Local Version Control
- A version control system that tracks code changes over time
- Prevents accidental overwrites of your work
- Enables multiple developers to work on the same project safely
- Runs locally on your machine
GitHub: Your Code in the Cloud
- A web-based platform that extends Git
- Cloud storage for your code repositories
- Enables code sharing and collaboration
- Includes features like:
- Issue tracking
- Pull requests
- Project management tools
- Code review capabilities
Why Use GitHub?
1. Portfolio Building
- Acts as your "proof of work" as a developer
- Shows your coding activity through contribution graphs
- Demonstrates your consistency and dedication
- Serves as a public showcase of your projects
2. Collaboration and Learning
- Access millions of open-source projects
- Learn from other developers' code
- Contribute to real-world projects
- Get feedback on your code
- Work effectively in teams
3. Code Safety and Access
- All your code is safely stored in the cloud
- Access your projects from anywhere
- Never lose your work due to computer issues
Essential GitHub Terminology
| Term | Definition | |------|------------| | Repository (Repo) | A folder containing your project files and version history | | Commit | A saved change or addition to your code | | Staging | Marking changes to be included in your next commit | | Push | Sending your local commits to GitHub | | Branch | A separate version of your code for new features or experiments | | Pull Request (PR) | A request to merge changes from one branch to another | | Clone | Creating a local copy of a remote repository | | Fork | Creating your own copy of someone else's repository |
Hands-on Practice
Setting Up Git
- Install Git from https://git-scm.com/downloads
- Configure your identity:
bash git config --global user.name "Your Name" git config --global user.email "your.email@example.com"
Your First Repository
- Create a new repository on GitHub named "hello-world"
- Initialize Git locally:
bash git init git add . git commit -m "My first commit" git remote add origin <your-repository-url> git push -u origin main
Basic Git Workflow Quick Reference
Pushing Code to GitHub
```bash
1. Stage your changes
git add .
2. Commit your changes with a message
git commit -m "Describe your changes here"
3. Push to GitHub
git push ```
Getting Code from GitHub
```bash
If you already have the repository locally:
git pull
If you need to download a repository:
git clone https://github.com/username/repository.git ```
Building Good Habits
Daily Git Practice
- Make it a goal to push code every day
- Even small changes count
- Use your GitHub contribution graph as motivation
- Track your progress over time
Best Practices
- Commit often with clear messages
- Pull before you start working
- Push your changes when you finish
- Keep each project in its own repository
- Include README files to explain your projects
Common Issues and Solutions
"No upstream branch" Error
If you see this error when pushing:
bash git push --set-upstream origin mainChanges Not Showing Up
- Check if changes are staged:
bash git status - Make sure you've committed:
bash git commit -m "Your message" - Verify you've pushed:
bash git push
Exercise: Start Your Journey
- Create your GitHub account if you haven't already
- Set up Git locally using the commands we covered
- Create your first repository named "hello-world"
- Make your first commit
- Push your code to GitHub
- Make a habit of pushing code daily
Additional Resources
- GitHub Documentation
- Git Documentation
- Practice with GitHub Learning Lab
Next Steps
- Start tracking all your code projects with Git
- Begin building your portfolio on GitHub
- Join the open-source community
- Collaborate with other developers
Remember: Every developer started where you are now. The key is consistency and persistence. Make pushing code to GitHub a daily habit, and you'll be amazed at your progress over time.
Happy coding! 🚀
-
 @ f33c8a96:5ec6f741
2025-03-01 23:23:04
@ f33c8a96:5ec6f741
2025-03-01 23:23:04What is HTML?
HTML (HyperText Markup Language) is the foundation of all webpages. Think of it as the framing of a house - it provides the basic structure that everything else builds upon.
Key Concepts
- HTML is a markup language, not a programming language
- It tells browsers how to structure web content
- Every HTML element is like a building block
- Browsers interpret HTML to display content
The Building Analogy
When building a webpage, think of it like constructing a house: - HTML: The framing and structure (walls, rooms, layout) - CSS: The design elements (paint, decorations, styling) - JavaScript: The functionality (plumbing, electrical, moving parts)
Basic HTML Structure
1. HTML Boilerplate
Every webpage starts with a basic template:
```html
Your Page Title ```
2. Understanding the Parts
<!DOCTYPE html>: Tells browsers this is an HTML5 document<html>: The root element of the page<head>: Contains metadata about the document<body>: Contains the visible content
Essential HTML Elements
1. Headings
HTML has six levels of headings: ```html
Main Title
Subtitle
Section Header
Smallest Heading
```
2. Paragraphs
```html
This is a paragraph of text. It can contain as much text as you need.
```
3. Images
html <img src="path-to-image.jpg" alt="Description of image" width="300">4. Links
html <a href="https://example.com">Click here</a>HTML Attributes
Attributes provide additional information or modify HTML elements:
html <tag attribute="value">Content</tag>Common attributes: -
src: Source path for images -href: Destination for links -alt: Alternative text for images -class: CSS class names -id: Unique identifier -style: Inline CSS stylesSemantic HTML
What is Semantic HTML?
Semantic HTML uses meaningful tags that describe their content's purpose. This improves: - Accessibility - SEO (Search Engine Optimization) - Code readability - Maintainability
Common Semantic Elements
```html
```
Non-Semantic vs Semantic Example
Instead of: ```html
```
Use: ```html
```
Building Your First Webpage
1. Basic Structure
```html
My First Webpage Welcome to My First Webpage!
About Me
Hi, I'm learning web development with PlebDevs!
My Interests
I'm interested in Bitcoin, programming, and building cool stuff!
```
Best Practices
1. Structure
- Use proper indentation
- Keep code organized and readable
- Use semantic elements when possible
- Include all required elements (
DOCTYPE,html,head,body)
2. Content
- Use appropriate heading levels (start with
h1) - Write descriptive
alttext for images - Keep content meaningful and organized
- Use comments to explain complex sections
3. Accessibility
- Use semantic HTML elements
- Provide alternative text for images
- Maintain a logical heading structure
- Ensure content makes sense when read linearly
Common Issues and Solutions
Problem: Images Not Loading
```html

 ```
```Problem: Links Not Working
```html
Click here ```
Next Steps
- Practice Building
- Create a personal webpage about yourself
- Include different types of content (text, images, links)
-
Use semantic HTML elements
-
Experiment with Structure
- Try different layouts
- Use various HTML elements
-
Pay attention to semantic meaning
-
Prepare for CSS
- Think about how you want your page to look
- Consider what styles you'll want to add
- Plan your layout structure
Exercise: Create Your Profile Page
Try creating a simple profile page using what you've learned:
- Use the HTML boilerplate
- Add a header with your name
- Include an "About Me" section
- Add a photo (if you want)
- List your interests or goals
- Add a footer with contact information
Remember to: - Use semantic HTML - Include appropriate headings - Add descriptive alt text for images - Keep your code clean and well-organized
Additional Resources
Remember: HTML is the foundation of web development. Take time to understand these basics well, as they'll serve as the building blocks for everything else you'll learn. Happy coding! 🚀
-
 @ f33c8a96:5ec6f741
2025-03-01 23:21:44
@ f33c8a96:5ec6f741
2025-03-01 23:21:44Welcome to PlebDevs Starter Course
Course Mission
Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners.
Course Goals
Overall PlebDevs Goals
- Learn how to code
- Build Bitcoin/Lightning/Nostr apps
- Become a developer
This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey.
Starter Course Objectives
- Give you an easy, high-level overview of the dev journey
- Get you set up and comfortable in a development environment where you'll write and ship code
- Give you basic experience in the languages covered in our courses and workshops
There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience.
What is a PlebDev?
Origins and Philosophy
I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents:
- Inclusive Learning: Anyone can become a developer, regardless of background
- Growth Mindset: Embracing the journey from beginner to professional
- Practical Focus: Emphasizing real-world application development
- Community Support: Learning and growing together
Key Characteristics
- 🌱 Growth-Focused: PlebDevs are always learning and improving
- 🎯 App-Centric: Focus on building applications rather than protocol development
- 🆕 Embrace Being New: Being a new developer is infinitely better than being on the sidelines
- 🤝 Community-Driven: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you!
Our Learning Approach
Core Principles
- Lower Barriers
- Simplify complex concepts
- Focus on practical understanding
-
Build confidence through action
-
Project-Based Learning
- Learn by doing
- Create real applications
-
Build a portfolio as you learn
-
MVP (Minimum Viable Product) Focus
- Start with core functionality
- Get things working first
-
Iterate and improve
-
Actionable Knowledge
- Focus on the 20% that delivers 80% of results
- Learn what you can use right away
- Build practical skills
Teaching Methods
- Detailed concept breakdowns
- Line-by-line code explanations
- Interactive learning
- 1:1 support available
- Community-driven progress
Course Structure
The Learning Path
Instead of the traditional bottom-up approach, we use a project-focused method:
🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting StartedWe'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review
Student Expectations
What We Expect From You
- High Agency: Take ownership of your learning journey
- Active Participation: Engage with the material and community
- Persistence: Push through challenges
- Curiosity: Ask questions and explore concepts
What You Can Expect From Us
- Clear, practical instruction
- Comprehensive support
- Real-world applications
- Community backing
Getting Started
Next Steps
- Ensure you're ready to commit to learning
- Set up your development environment (next lesson)
- Join our community
- Start building!
Resources and Support
Where to Get Help
- plebdevs.com
Tips for Success
- Push code daily, even if it is small.
- Focus on understanding rather than memorizing.
- Build projects that interest you.
- Engage with the community.
- Don't be afraid to ask questions.
Remember
You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code.
Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
-
 @ 6260f29f:2ee2fcd4
2025-03-01 22:48:31
@ 6260f29f:2ee2fcd4
2025-03-01 22:48:31PlebDevs ⚡️
A one-of-a-kind developer education, content, and community platform built on Nostr and fully Lightning integrated.
https://plebdevs.comOverview
PlebDevs is an open-source platform that combines educational content, community interaction, and Bitcoin/Lightning integration. The platform publishes content to Nostr and actively pulls from Nostr relays, creating a distributed, interoperable trail of Documents, Videos, and Courses.
Technical Implementation
Nostr Integration
- Content Distribution: Implements NIP-23 for rich multimedia content embedding
- Content Encryption: Paid content bodies are encrypted while maintaining metadata visibility
- Authentication:
- Multi-method signup (NIP-07, Email, GitHub, Anonymous)
- Ephemeral keypair generation for non-Nostr users
- Account linking and recovery system
- Lists & Courses: NIP-51 implementation for structured content organization
- Monetization: NIP-99 for digital content sales
- Automated Subscriptions: NIP-47 (Nostr Wallet Connect) for recurring payments
- Badge System: NIP-58 for automated achievement rewards
- Identity: NIP-05 for custom platform identities
- Additional NIPs: Implements NIP-01, NIP-19, NIP-39, NIP-57
Platform Architecture
- Content Management:
- Draft system with preview capabilities
- Parameterized replaceable events
- Multi-format support (Markdown, Video, Mixed Media)
- Course builder with drag-and-drop ordering
- User Management:
- Profile synchronization with Nostr
- Activity tracking and progress monitoring
- Custom relay configuration
- Wallet connection management
- Admin Features:
- Protected admin routes based on pubkey configuration
- Content creation and management interface
- Draft/publish workflow
- Course assembly tools
-
 @ 4f1c14e5:b8546d05
2025-03-01 22:33:36
@ 4f1c14e5:b8546d05
2025-03-01 22:33:36Training ideologies often lead to tribalism when they shouldn’t. As with all things, there are no solutions - only tradeoffs.
The reality is that free weights and machines are both tools. The one you should use is determined by your objective.
In either case, creating tension within the target muscle group is always the objective when it comes to building muscle. It's this mechanical tension that's responsible for initiating the growth process by destroying already formed muscle cells. Both machines and free weights accomplish this objective.
As a general rule, the more stable you are during an exercise, the more tension you can create within the target muscle.
The difference is simply that machines offer more stability. That’s neither better nor worse, it just is. Stability within exercises is a spectrum. We create stability by bracing against things. The more points of contact and the more of your body that braces against things, the more stability you will have.
Because of gravity, we are forced to have at least one point of contact braced against something at all times. Typically, it's the floor. A pistol squat offers a very low amount of stability because of the lack of bracing. In this example, only one foot is braced against the floor.
Adding a second foot to the ground and doing a body weight squat enhances stability. Holding onto a bar or a bench in front of you while squatting now adds another layer of stability.
A hack squat is a machine where both feet are planted on a platform and the user rests the posterior portion of their entire upper body - from their lower back to their head - against a pad. This machine has a fixed movement pattern which further reduces any instability.
These are all examples of different exercises that follow the same movement pattern, yet offer varying degrees of stability.
Which should beginners use? Again, both is the best approach. But what would happen if you limited yourself to mostly one or the other?
Predominantly using machines as a beginner will allow you to forego the lack of development in your ability to stabilize yourself. The machine stabilizes your body for you in a way that beginners simply aren’t able to at first. You are braced by a seat, a back pad/chest pad and maybe a handle or two as well. In addition to this bracing, the movement path is already carved out for you. You simply position yourself appropriately and push (or pull), and the machine does the rest. This allows you to focus more on creating tension in the target muscle as well as learning to train to failure safely.
Predominantly using free weights as a beginner will force you to develop stability from the start. There are no pads anywhere to brace your body against. Your body must learn to brace against itself. You become the machine. This may limit your ability to create maximum tension in the target muscles at first, but the stability you create this way will translate to systemic muscular development. You'll become thicker everywhere because your body works as a system to stabilize itself against gravity.
The stability built through free weight movements will transfer over to machines. If you can stabilize yourself with just a barbell, the stability you can create while braced in a machine will translate to even greater tension. You’ll be stabilized by your body AND the machine.
Since it makes the most sense to do both, the only thing left is understanding which circumstances are better suited for machines vs free weights. Since fatigue is something we all contend with during a workout, it makes sense to program the least stabilized, most demanding movements earlier in the workout and the most stabilized, least demanding movements later in the session. This not only allows you to create the most tension possible throughout the workout, but is also the safest approach. It would be unwise to schedule barbell front squats at the end of a workout when fatigue is high and energy is low. Not only will you fail to generate maximum tension, but you’ll put yourself at higher risk of injury.
TLDR; use both, but do free weight stuff first.
-
 @ 6260f29f:2ee2fcd4
2025-03-01 22:23:15
@ 6260f29f:2ee2fcd4
2025-03-01 22:23:15PlebDevs ⚡️
A one-of-a-kind developer education, content, and community platform built on Nostr and fully Lightning integrated.
https://plebdevs.comOverview
PlebDevs is an open-source platform that combines educational content, community interaction, and Bitcoin/Lightning integration. The platform publishes content to Nostr and actively pulls from Nostr relays, creating a distributed, interoperable trail of Documents, Videos, and Courses.
Technical Implementation
Nostr Integration
- Content Distribution: Implements NIP-23 for rich multimedia content embedding
- Content Encryption: Paid content bodies are encrypted while maintaining metadata visibility
- Authentication:
- Multi-method signup (NIP-07, Email, GitHub, Anonymous)
- Ephemeral keypair generation for non-Nostr users
- Account linking and recovery system
- Lists & Courses: NIP-51 implementation for structured content organization
- Monetization: NIP-99 for digital content sales
- Automated Subscriptions: NIP-47 (Nostr Wallet Connect) for recurring payments
- Badge System: NIP-58 for automated achievement rewards
- Identity: NIP-05 for custom platform identities
- Additional NIPs: Implements NIP-01, NIP-19, NIP-39, NIP-57
Platform Architecture
- Content Management:
- Draft system with preview capabilities
- Parameterized replaceable events
- Multi-format support (Markdown, Video, Mixed Media)
- Course builder with drag-and-drop ordering
- User Management:
- Profile synchronization with Nostr
- Activity tracking and progress monitoring
- Custom relay configuration
- Wallet connection management
- Admin Features:
- Protected admin routes based on pubkey configuration
- Content creation and management interface
- Draft/publish workflow
- Course assembly tools
-
 @ 6260f29f:2ee2fcd4
2025-03-01 22:21:02
@ 6260f29f:2ee2fcd4
2025-03-01 22:21:02 -
 @ f33c8a96:5ec6f741
2025-03-01 20:56:43
@ f33c8a96:5ec6f741
2025-03-01 20:56:43 -
 @ f33c8a96:5ec6f741
2025-03-01 20:50:47
@ f33c8a96:5ec6f741
2025-03-01 20:50:47 -
 @ f33c8a96:5ec6f741
2025-03-01 20:42:24
@ f33c8a96:5ec6f741
2025-03-01 20:42:24 -
 @ bbb5dda0:f09e2747
2025-03-01 17:46:48
@ bbb5dda0:f09e2747
2025-03-01 17:46:48A couple weeks with a little bit of everything, TollGate marketing, app stability improvements, and some personal matters that needed my attention. Let's get into it:
TollGate App
For starters, we worked hard to get an early version of the TollGate website live. What do we want to communicate about the project, and to whom. We've identified three 'types' of visitor, each requiring its own 'customer journey' through the website. First there's the end-user, someone that just wants access to tollgate, but doesn't care about any of the technichalities. We try to guide those people to downloading our app as soon as possible. Currently that means downloading it straight from the website as an APK file. But we want to quickly move on to publishing it to the ZapStore.
The past couple weeks I put some efforts into getting the app stable. It was hard to identify what was causing the seemingly random crashes and full reloads (of the web content). After getting some outside help we've identified that we were trying to interact with the android API's on the main thread. Which is bad practice. I first couldn't figure out how to make a web request without having to spawn a seperate thread in the kotlin code, that then we'd have to create some kind of system to bubble up the callback method's result. I then found there's a proper Tauri (the framework) way of doing this using Kotlin Coroutines, which I wasn't familliar with. But it just executes the entire Tauri 'command' (function call) on a background thread. Problem solved. I haven't had any full app crashes since.
Which left me with the random page refreshes, the thing that was behind the demo-effect at Sat's and Facts. I noticed it happened around the moments I would go to settings to hit the 'sign in' button to dismiss the captive portal. That's where I had looked before, but I needed to zoom out. It had to do SOMETHING with moving the app to and from the background. Okay is it some kind of sleep issue? I don't remember where or how I found it but I saw a suggestion to run the Tauri dev build with a --no-watch flag. Which disables hot reloading of the app when I edit one of the TypeScript/HTML files. Somehow the reload would be triggered sometimes on app switching. Why? I don't know, but i'm glad I could pinpoint it.
So now the demo part seems stable, finally. Which means I can move on and properly implement the wallet logic and making the download on the website work.
TollGateOS
 The second customer group will be people interested in running a TollGate. We're trying to get them to download our custom build of OpenWRT that includes all the required packages. We 'baptized' this version to be called TollGateOS as we say in proper Dutch ;). I think it will help to have these clear distinct names. I really want any moderately technical person to be able to install TollGateOS on a supported router. My vision for this is to have some kind of web installer, akin to what GrapheneOS does with their web-installer. It seems to be possible to do SSH from the browser, but I'll kill that bird when I see it (is that a saying? I think it should be...)
The second customer group will be people interested in running a TollGate. We're trying to get them to download our custom build of OpenWRT that includes all the required packages. We 'baptized' this version to be called TollGateOS as we say in proper Dutch ;). I think it will help to have these clear distinct names. I really want any moderately technical person to be able to install TollGateOS on a supported router. My vision for this is to have some kind of web installer, akin to what GrapheneOS does with their web-installer. It seems to be possible to do SSH from the browser, but I'll kill that bird when I see it (is that a saying? I think it should be...)By the way, in earlier docs/demo's we talked about a 'herald' module, which would do the advertising of the tollgate. But as we found that the crowsnest already interacts with the hardware antennas, which is needed for 'advertising' the tollgate, we thought it better to merge both of them into the Crowsnest.
Developers
TollGate is fully open source, so anyone looking to either look at or fork the source code is welcome to do so. Developers interested at looking at the code are probably already interested to some degree. For this group we added easy links to navigate to the project's repositories
Currently our focus is publishing the Android version, but we're building the app in a cross-platform way. The only thing we have to customize are the system integrations, like scanning for wifi-networks and connecting to them.
Gearing up for Sovereign Engineering
As i'm writing this piece for you i'm at 10km (that's 30.000ft for y'all Americans) in the air on my way to Sovereign Engineering edition #4, SEC-04. I feel ready to go kick ass once again and build beautiful things with a bunch of my favourite plebs!
A bit of a focus shift
If you've been following me you might notice I haven't posted much about Epoxy recently. I found the momentum I see emerge on TollGate and GitHub Actions too good to let go to waste. So those will be my focus for a while, I'm hoping to circle back to Epoxy when these projects have a more steady pace.
-
 @ df478568:2a951e67
2025-03-01 15:04:27
@ df478568:2a951e67
2025-03-01 15:04:27In my Soapminer article, I added quotes from various plebs. I earned over 12,000 sats! That's enough for a McJunk today, but maybe a steak dinner in a few years. That's my two sats anyway.
This is not investment advice
It feels great to receive value from people who support and appreciate your work. It's also nice to stack more sats by writing. I have a budget of $25.00 that I have sent to various people using Zapplanner, but I'm trying something new: Zapsplits.
WTF Are Zapsplits?
I asked Unleashed.chat. Here's what the anthropomorphic Unleashed said.
Me: What is a Zapsplit on nostr?

Unleashed:
A Zapsplit on Nostr refers to splitting a Zap, which is a form of donation or tipping on the ~platform~ protocol, among multiple recipients. It allows users to distribute their support more broadly across various content creators instead of just one.
That's more succinct than I would put it, but nostr is a protocol, not a platform. The important part about Zapsplits for me is that it removes the cognitive cost of deciding what percentage of my giving budget should go to each creator. Do I zap podcast guests? Do podcasters with ads get less than podcasters sans ads? How much value did this particular article bring me? If I zap Guy Swann, should I also zap the authors he reads? Should I zap long-form articles more than micro-blogs? There are 21 million different considerations.
Zapsplits removes all this from me because I can use the following algorithm.

Does This Person Provide Me Value?
Yes ⬇️
I add them to my Zapsplit post for that month. A portion of my monthly zapping budget, 25 dirty-fiat bucks, transforms into magic Internet money and is distributed among everyone in the Zapsplit.
No ⬇️ If I don't get any value, I don't send value. Simple.
Testing Zapsplits
I added podcasters and devs to a nostr post and enabled a 10-way zapsplit on the post. It's based on prisms, a little nostr feature that gives me prose writing superpowers.
- I can earn sats for writing.
- I can support others with a single zap.
- I can add people who give me quotes to my zap splits.
People appreciate attribution. I suspect they will appreciate it more if they also get paid. What if I added some quotes to an article and then split any zaps I get with the quoted plebs? Come to think of it, I'll try it. [Here's a quote from a dev on nostr](nostr:note1qf4277rudtflllrjr555890xsjp6u60f7xdvclkwc9t220duajeq0x665q
I added Silberangel to the Zapsplits on Habla.news.
My V4V payments can also get sent to ten different plebs with a simple click of a button. I am going to start using this for a lot of my monthly V4V budget. Every month, I'll think about the people's content I value most and add them to a single zapsplit payment. Then, I'll zap the post.
Say I create a poll and make a wager with ten different people. If I lose, I can pay everyone pit at the same time. This is probably better for a football pool, but you get the idea. The options are limited only by your imagination.
nostr:nevent1qqspnhucgxc6mprhw36fe2242hzv7zumavyy7dhzjswtldhxk4dh7ugpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxlg7zks3uauf454q7phhzdh2mpkhxg9cdrzt3t9z7gzksj49g7vupsgqqqqqqsl5uwfl
Other people can also zap the post. As Siberangel says, we can use other people's money to provide value, too. This is a great option for stacking neophytes, people who don't have much bitcoin or cheap skates. Let's be honest, bitcoin has made most of us cheapskates.
Bitcoin books with multiple authors can have QR codes that link to one of these Zapsplit posts. The authors can do a book signing and sell their books using this on nostr. Nerds like me can get three autographs and zap the book. The sats are split among all authors. Here's a Zapsplit that includes all the authors of Parallel.

Can you think of any other ways to use Zapsplits? Let me know.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 43baaf0c:d193e34c
2025-03-01 14:22:43
@ 43baaf0c:d193e34c
2025-03-01 14:22:43eARThist vlog name represents the fusion of Earth and Art and me as traveling artist.
I'm kicking off my vlogging journey with my first vlog, Bangkok Lightning Tour. My goal with vlogging is to share more about my art journey as I travel the world. After years of traveling and filming around the world, I’m now fully focused on my art. However, filming and photography remaining a passion of mine. I also create still some travel content for my company, @traveltelly, whenever I’m not drawing.

After spending time creating art around the world, this feels like the natural next step sharing more behind the scenes moments of both traveling and my artist life.

I started in Bangkok, a city I often visit and where I’ve spent the last five months creating the BangPOP art. Teaming up with Sats ‘n’ Facts, I explored Bangkok to see how Bitcoin Lightning adoption is growing here. Bitcoin has given me the freedom to create art, so I wanted to see if it’s also helping others in Bangkok. On a scorching 35°C day, we filmed three places where you can pay with Bitcoin Lightning. You can find these locations on btcmap.org.

I’m leaving Bangkok soon, but more vlogs from Thailand will follow when I return. I always find my way back to the Land of Smiles.
-
 @ a012dc82:6458a70d
2025-03-01 14:18:37
@ a012dc82:6458a70d
2025-03-01 14:18:37Bitcoin, since its creation by the enigmatic figure Satoshi Nakamoto, has revolutionized the concept of currency. Its journey from an obscure digital token to a major financial asset has been marked by dramatic bull runs, capturing the attention of investors worldwide. These surges in Bitcoin's value are not random but are driven by a combination of technological innovation, economic factors, and unique monetary policy. In this article, we explore the intricacies of Bitcoin's scarcity, the halving process, and the broader market dynamics that contribute to its periodic bull runs.
The allure of Bitcoin lies not just in its technological novelty but also in its challenge to traditional financial systems. It represents a decentralized form of currency, free from government control and manipulation. This aspect has been particularly appealing in times of economic uncertainty, where traditional currencies and markets have shown vulnerability. Bitcoin's bull runs can be seen as a barometer of the changing landscape of finance, reflecting a growing shift towards digital assets.
Table of Contents
-
The Concept of Scarcity in Bitcoin
-
Finite Supply
-
Impact on Value
-
-
The Halving Events
-
Mechanism and Purpose
-
Historical Impact on Price
-
-
Market Dynamics and Investor Sentiment
-
Institutional Investment
-
Global Economic Factors
-
Technological Advancements
-
Regulatory Environment
-
-
Conclusion
-
FAQs
The Concept of Scarcity in Bitcoin
Finite Supply
Bitcoin's protocol ensures that only 21 million coins will ever be in existence. This limit is encoded in its blockchain, making it a deflationary asset as opposed to inflationary fiat currencies. The idea behind this is to create a form of money that can resist inflationary pressures over time, much like gold, which has maintained its value for centuries due to its scarcity.
Impact on Value
The scarcity of Bitcoin has a profound psychological impact on investors. It creates a sense of urgency and a fear of missing out (FOMO) as the available supply dwindles. This is particularly evident as each Bitcoin halving event approaches, reminding the market of the ever-decreasing new supply. The result is often a speculative rally, as seen in the past bull runs. Moreover, as Bitcoin becomes more scarce, its comparison to gold becomes increasingly apt, attracting investors who are looking for assets that can retain value over time.
Scarcity also plays into the hands of long-term investors, often referred to as 'HODLers' in the crypto community. These investors view Bitcoin as a long-term store of value, akin to an investment in precious metals. The limited supply of Bitcoin reassures these investors that their holdings will not be devalued through oversupply, a common problem in fiat currencies.
The Halving Events
Mechanism and Purpose
Bitcoin's halving is a genius mechanism that ensures a controlled and gradual distribution of coins. By reducing the mining reward by half every four years, Bitcoin mimics the process of extracting a natural resource like gold, becoming progressively harder and more resource-intensive to mine. This not only controls inflation but also adds to the scarcity, making each coin more valuable over time.
Historical Impact on Price
Each halving event has historically led to an increase in Bitcoin's price, though not immediately. There is typically a lag between the halving and the subsequent bull run. This delay can be attributed to market adjustment and the gradual realization of reduced supply. The anticipation of this price increase often starts a positive feedback loop, attracting more investors and further driving up the price.
The halving events serve as key milestones in Bitcoin's timeline, providing a predictable pattern of supply reduction that savvy investors monitor closely. These events have become celebratory moments within the Bitcoin community, symbolizing the strength and resilience of the network. They also serve as a reminder of Bitcoin's unique value proposition in the world of cryptocurrencies.
Market Dynamics and Investor Sentiment
Institutional Investment
The recent years have seen a paradigm shift with the entry of institutional investors into the Bitcoin market. This shift is significant as it marks a departure from Bitcoin's early days of being a niche asset for tech enthusiasts. Institutional investors bring with them not only large capital inflows but also a sense of legitimacy and stability to the market. Their involvement has been a key driver in the maturation of the cryptocurrency market, making it more appealing to a broader audience.
Global Economic Factors
The role of global economic factors in influencing Bitcoin's price cannot be overstated. In times of economic instability, such as during the COVID-19 pandemic, investors increasingly turned to Bitcoin as a safe haven asset. This trend is indicative of a growing recognition of Bitcoin's value as a hedge against inflation and economic uncertainty. The decentralized nature of Bitcoin makes it less susceptible to geopolitical tensions and policy changes that affect traditional currencies and markets.
Technological Advancements
The continuous evolution of blockchain technology and the infrastructure surrounding Bitcoin has played a crucial role in its adoption. Developments such as improved transaction speed, enhanced security measures, and user-friendly trading platforms have made Bitcoin more accessible and attractive to a wider audience. These technological advancements are crucial in building investor confidence and facilitating the integration of Bitcoin into mainstream finance.
Regulatory Environment
The regulatory environment for Bitcoin and cryptocurrencies has been a double-edged sword. On one hand, clear and supportive regulations in certain jurisdictions have provided a boost to the market, encouraging institutional participation and providing clarity for investors. On the other hand, regulatory crackdowns in some countries have led to market volatility and uncertainty. The ongoing development of a regulatory framework for cryptocurrencies remains a key factor in shaping Bitcoin's future.
Conclusion
Bitcoin's journey is a testament to the evolving nature of finance and investment in the digital age. Its bull runs, driven by scarcity, halving events, and a complex interplay of market dynamics, highlight the growing acceptance of cryptocurrencies as a legitimate asset class. As the world increasingly embraces digital currencies, Bitcoin's role as a pioneer and standard-bearer will likely continue to influence its value and relevance in the global financial landscape.
Understanding Bitcoin's market dynamics is not just about analyzing charts and trends. It's about appreciating the broader context of economic, technological, and social changes that are reshaping the way we think about money and value. For investors and enthusiasts alike, staying informed and adaptable is key to navigating the exciting and often unpredictable world of Bitcoin and cryptocurrencies.
FAQs
What causes a Bitcoin bull run? Bitcoin bull runs are typically driven by a combination of factors including its built-in scarcity due to the finite supply, halving events reducing the mining rewards, institutional investment, global economic factors, advancements in blockchain technology, and the evolving regulatory landscape.
How does Bitcoin's scarcity affect its value? Bitcoin's value is significantly influenced by its scarcity. With a capped supply of 21 million coins, as demand increases, the limited supply pushes the price upwards, similar to precious metals like gold.
What is a Bitcoin halving event? A Bitcoin halving event is when the reward for mining new Bitcoin blocks is halved, effectively reducing the rate at which new Bitcoins are created. This occurs approximately every four years and is a key factor in Bitcoin's deflationary model.
Why do institutional investors matter in Bitcoin's market? Institutional investors bring significant capital, credibility, and stability to the Bitcoin market. Their participation signals a maturation of the market and can lead to increased confidence and investment from other sectors.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b83a28b7:35919450
2025-03-01 13:08:06
@ b83a28b7:35919450
2025-03-01 13:08:06Preamble
I used OpenAI's o3-mini reasoning engine to construct a thesis for the Russia-Ukraine conflict using the positions of Jeffery Sachs and John Mearsheimer. I then asked it to create a counterargument to those positions- the antithesis. And I finally asked for a synthesis that concludes in lasting peace in the region. In all three cases, I prompted it to only use axiomatic deductive reasoning and first principles thinking, emphasizing facts and ignoring the opinions and assertions of so-called experts.
The Thesis
John Mearsheimer's Position: A Realist Perspective
First Principles
- States prioritize survival: In an anarchic international system (no overarching authority), states act to maximize security and minimize threats.
- Great powers seek regional hegemony: States aim to dominate their immediate regions to prevent rival powers from threatening them.
- Proximity amplifies threat perception: The closer a rival power or alliance is to a state's borders, the greater the perceived threat.
Logical Reasoning
- NATO's eastward expansion brings a U.S.-led military alliance closer to Russia’s borders.
- From the principle of proximity, this increases Russia’s perceived insecurity.
- Ukraine’s potential NATO membership represents a direct challenge to Russia’s sphere of influence.
- A great power like Russia would logically act to prevent this encroachment, as it undermines its regional dominance.
- Russia’s actions (e.g., annexation of Crimea in 2014 and invasion in 2022) are defensive responses to NATO's perceived encroachment.
- From the principle of survival, Russia seeks to neutralize threats by ensuring Ukraine does not join NATO.
- The U.S. and NATO ignored Russia’s stated red lines (e.g., no NATO membership for Ukraine).
- This provoked predictable countermeasures from Russia, consistent with great-power behavior.
Conclusion
From a realist perspective, NATO expansion is the root cause of the conflict. Russia’s actions are not imperialistic but defensive responses to protect its security and sphere of influence.
Jeffrey Sachs' Position: A Historical and Diplomatic Perspective
First Principles
- Agreements create expectations: Commitments between states establish norms that guide future behavior.
- Security is interdependent: One state’s pursuit of security can increase another state’s insecurity (the "security dilemma").
- Conflicts are preventable through diplomacy: Negotiations and compromises can avert wars by addressing mutual concerns.
Logical Reasoning
- In 1990, U.S. officials assured Soviet leaders that NATO would not expand eastward if Germany was reunified.
- If such assurances were made (even informally), subsequent NATO expansion violated these expectations, fostering mistrust.
- The U.S.'s unilateral withdrawal from treaties like the Anti-Ballistic Missile Treaty (2002) and its push for NATO enlargement exacerbated Russia's insecurity.
- By the principle of interdependent security, these actions predictably escalated tensions with Russia.
- Putin proposed negotiations in 2021 to prevent NATO expansion into Ukraine, but these were rejected by the U.S.
- Diplomacy could have addressed Russian concerns without war, but its rejection left military action as Russia’s only perceived option.
- Ukraine’s neutrality could have prevented conflict by satisfying both Russian and Western security concerns.
- Neutrality would reduce NATO's proximity to Russia while preserving Ukraine's sovereignty.
Conclusion
From Sachs’ perspective, the war is a consequence of U.S.-led NATO expansion and missed diplomatic opportunities. A negotiated settlement based on Ukrainian neutrality remains the logical path to peace.
Deductive Insights
- Both positions agree that NATO expansion is central to understanding the conflict but differ in emphasis:
- Mearsheimer focuses on structural inevitabilities in great-power politics.
- Sachs highlights historical commitments and missed opportunities for diplomacy.
- Both rely on axioms about state behavior:
- Mearsheimer emphasizes security maximization through power balancing.
- Sachs underscores trust-building through adherence to agreements.
In conclusion, reasoning from first principles supports both scholars’ views as internally consistent frameworks for explaining the Ukraine conflict, though they emphasize different aspects of state behavior and international relations logic.
To construct counterarguments to the positions of John Mearsheimer and Jeffrey Sachs using axiomatic deductive reasoning, we will start with alternative first principles and challenge their logical conclusions. This approach ensures that the counterarguments are rooted in logic and facts, without relying on external opinions or assertions.
Counterarguments to John Mearsheimer's Position
First Principles for the Counterargument
- Sovereign states have the right to self-determination: All states, regardless of size, have the right to choose their alliances and political alignments.
- Security is not zero-sum: One state’s pursuit of security does not always come at the expense of another’s; collective security arrangements can enhance stability.
- Aggression undermines security: A state that invades its neighbors creates insecurity for itself by provoking opposition and strengthening rival alliances.
Logical Reasoning
- NATO expansion was voluntary and driven by the sovereign decisions of Eastern European states seeking protection from historical Russian aggression.
- From the principle of self-determination, NATO enlargement reflects the legitimate choices of countries like Poland, Estonia, and Ukraine to align with a defensive alliance, not an act of Western aggression against Russia.
- Russia’s perception of NATO as a threat is not inherently justified.
- NATO is a defensive alliance with no history of invading non-member states. From the principle that security is not zero-sum, NATO’s presence near Russia does not necessarily reduce Russian security unless Russia itself acts aggressively.
- Russia’s invasion of Ukraine contradicts Mearsheimer’s claim that its actions are purely defensive.
- By attacking Ukraine, Russia has provoked a stronger NATO presence in Eastern Europe (e.g., Finland and Sweden joining NATO) and increased its own insecurity. This undermines the principle that great powers act rationally to maximize their security.
- The analogy to the Cuban Missile Crisis is flawed.
- In 1962, the U.S. objected to Soviet missiles in Cuba because they posed an immediate offensive threat. NATO membership for Ukraine does not involve stationing offensive weapons aimed at Russia but rather a defensive commitment.
Conclusion
Mearsheimer’s argument fails to account for the agency of smaller states and overstates the inevitability of conflict due to NATO expansion. Russia’s actions are better explained as aggressive attempts to reassert imperial influence rather than rational defensive measures.
The Antithesis
Counterarguments to Jeffrey Sachs' Position
First Principles for the Counterargument
- Informal agreements lack binding force: Verbal or informal assurances between states do not constitute enforceable commitments in international relations.
- Security dilemmas require mutual restraint: Both sides in a conflict must take steps to reduce tensions; unilateral blame is insufficient.
- Sovereign equality underpins diplomacy: No state has the right to dictate another state’s foreign policy or alliances.
Logical Reasoning
- The alleged 1990 U.S. assurance against NATO expansion was never formalized in any treaty or agreement.
- From the principle that informal agreements lack binding force, subsequent NATO enlargement cannot be considered a violation of commitments since no legal obligation existed.
- Russia’s actions have escalated tensions far more than NATO expansion ever did.
- By annexing Crimea (2014) and invading Ukraine (2022), Russia has actively destabilized its neighbors and created insecurity across Europe. From the principle of mutual restraint, Russia bears responsibility for escalating the conflict rather than solely responding to U.S./NATO actions.
- Diplomatic solutions require both parties to negotiate in good faith.
- Putin’s 2021 proposals demanded guarantees that Ukraine would never join NATO—a condition that violates Ukraine’s sovereignty and right to self-determination. From the principle of sovereign equality, such demands are inherently illegitimate.
- Neutrality is not always a viable solution.
- Ukraine attempted neutrality after independence (e.g., refusing to join NATO for decades). However, this did not prevent Russian aggression in 2014 or 2022, undermining Sachs’ claim that neutrality would have ensured peace.
Conclusion
Sachs’ argument overemphasizes historical grievances and ignores Russia’s active role in escalating tensions through aggression and coercion. The failure of diplomacy lies as much with Russia’s demands as with Western policies.
Deductive Insights from Counterarguments
- Both Mearsheimer and Sachs underestimate the agency of smaller states like Ukraine, which made sovereign decisions based on their own security needs rather than being mere pawns in great-power politics.
- Both positions assume that Russia’s actions are primarily reactive or defensive, but this ignores evidence that Russia has proactively pursued aggressive policies (e.g., Georgia 2008, Crimea 2014).
- The principle of sovereignty challenges both scholars’ frameworks:
- Mearsheimer overlooks Ukraine's right to align with NATO if it chooses.
- Sachs dismisses Ukraine's agency by suggesting neutrality could have been imposed as a solution.
In conclusion, while Mearsheimer and Sachs present internally consistent arguments, their frameworks can be challenged by emphasizing sovereignty, rejecting inevitability in great-power conflict, and highlighting Russia's active role in escalating tensions beyond what can be justified by security concerns alone.
The Synthesis: A Balanced Framework for Resolving the Russia-Ukraine Conflict
First Principles for Synthesis
- Security is interdependent: A state’s pursuit of security can create insecurity for others, necessitating mutual accommodation.
- Sovereignty is fundamental but constrained by geography: States have a right to self-determination, but geography imposes practical limits on absolute sovereignty in a multipolar world.
- Great powers act to preserve their spheres of influence: In an anarchic international system, great powers prioritize regional dominance to ensure their survival.
- Diplomacy is essential for de-escalation: Durable peace requires negotiated compromises that address the core interests of all parties involved.
Reconciling the Thesis and Antithesis
Thesis (Mearsheimer and Sachs' Positions)
- NATO expansion near Russia’s borders provoked a predictable response from Moscow, reflecting structural dynamics of great-power competition.
- U.S. and NATO policies ignored Russian security concerns, contributing to the escalation of tensions.
- Diplomacy and neutrality for Ukraine are necessary to resolve the conflict.
Antithesis (Counterarguments)
- NATO expansion was driven by voluntary decisions of Eastern European states seeking protection from historical Russian aggression, not Western provocation.
- Russia’s actions are not purely defensive but reflect imperial ambitions that violate Ukraine’s sovereignty.
- Neutrality alone would not guarantee peace, as Russia has acted aggressively even when Ukraine was neutral.
Synthesis
Both perspectives contain valid insights but fail to fully address the complexity of the conflict. The synthesis must: 1. Acknowledge Russia’s legitimate security concerns while rejecting its imperialistic actions. 2. Respect Ukraine’s sovereignty while recognizing that its geographic position necessitates pragmatic compromises. 3. Balance great-power dynamics with smaller states’ rights to self-determination.
Proposed Solution: A Comprehensive Peace Framework
To achieve an enduring peace in Ukraine and stabilize Eastern Europe, the following steps are proposed:
1. Immediate Ceasefire
- Both sides agree to an immediate cessation of hostilities under international supervision (e.g., UN peacekeeping forces).
- A demilitarized buffer zone is established along current frontlines to prevent further clashes.
2. Neutrality with Conditions
- Ukraine adopts a status of permanent neutrality, enshrined in its constitution and guaranteed by international treaties.
- Neutrality includes:
- No NATO membership for Ukraine.
- Freedom for Ukraine to pursue economic integration with both the EU and other global partners without military alignments.
3. Security Guarantees
- Russia receives legally binding assurances that NATO will not expand further eastward or station offensive weapons near its borders.
- Ukraine receives multilateral security guarantees from major powers (e.g., U.S., EU, China) to deter future aggression from any party.
4. Territorial Dispute Resolution
- Crimea’s status is deferred to future negotiations under international mediation, with both sides agreeing to maintain the status quo in the interim.
- Donetsk and Luhansk regions are granted autonomy within Ukraine under a decentralized federal structure, ensuring local governance while preserving Ukrainian sovereignty.
5. Economic Reconstruction
- An international fund is established for rebuilding war-torn regions in Ukraine, with contributions from Russia, Western nations, and multilateral institutions.
- Economic cooperation between Ukraine and Russia is encouraged through trade agreements designed to benefit both parties.
6. Phased Implementation
- Peace agreements are implemented incrementally to build trust:
- Initial steps include withdrawal of heavy weaponry, prisoner exchanges, and humanitarian aid delivery.
- Subsequent phases involve constitutional reforms (e.g., neutrality), elections in disputed regions, and gradual reintegration of territories under international supervision.
7. Long-Term Regional Security Framework
- A new regional security framework is established involving Russia, Ukraine, NATO members, and neutral states to manage disputes peacefully.
- This framework institutionalizes dialogue channels for arms control, economic cooperation, and crisis management.
Rationale for the Solution
- Balances Security Concerns:
- Neutrality addresses Russia’s fears of NATO encirclement while preserving Ukraine’s independence.
-
Security guarantees reduce mistrust between NATO and Russia while protecting Ukraine from future aggression.
-
Respects Sovereignty:
-
Ukraine retains its independence and territorial integrity (except for deferred issues like Crimea) while accommodating regional realities through federalism and neutrality.
-
Acknowledges Great-Power Dynamics:
-
The solution recognizes Russia’s need for a secure sphere of influence without legitimizing its imperial ambitions or violating international law.
-
Builds Trust Through Gradualism:
- Incremental implementation allows both sides to verify commitments before proceeding further.
-
International monitoring ensures compliance with agreements.
-
Incorporates Lessons from History:
- Neutrality models (e.g., Austria) demonstrate that such arrangements can work when backed by strong guarantees.
- Phased implementation mirrors successful peace processes in other conflicts (e.g., Colombia).
Conclusion
The synthesis reconciles the structural realism of Mearsheimer with Sachs’ emphasis on diplomacy by proposing a balanced solution that addresses both security dilemmas and sovereignty concerns. Neutrality serves as the linchpin for de-escalation, while phased implementation builds trust over time. By integrating immediate conflict resolution measures with long-term regional frameworks, this approach offers a realistic path toward enduring peace in Eastern Europe.
Citations: [1] https://www.reddit.com/r/geopolitics/comments/1drhxxh/john_mearsheimers_take_on_the_russoukrainian_war/ [2] https://www.reddit.com/r/CredibleDefense/comments/14ktcv2/the_darkness_ahead_where_the_ukraine_war_is/ [3] https://www.reddit.com/r/PoliticalScience/comments/1bp64ub/what_is_with_mearsheimer_and_russia/ [4] https://www.reddit.com/r/AskConservatives/comments/1gznjks/do_you_think_appeasing_putin_is_the_right_way_to/ [5] https://www.reddit.com/r/changemyview/comments/1hu8iop/cmv_the_united_states_should_continue_to_send_aid/ [6] https://internationalpolicy.org/publications/jeffrey-sachs-matt-duss-debate-u-s-russia-talks-to-end-ukraine-war/ [7] https://www.reddit.com/r/IRstudies/comments/17iwfpr/john_mearsheimer_is_wrong_about_ukraine/ [8] https://scheerpost.com/2024/11/23/jeffrey-sachs-explains-the-russia-ukraine-war/ [9] https://consortiumnews.com/2023/09/21/jeffrey-sachs-nato-expansion-ukraines-destruction/ [10] https://www.democracynow.org/2025/2/18/russia_ukraine [11] https://www.reddit.com/r/geopolitics/comments/15kwpx3/ukraine_war_and_the_paradox_of_mearsheimers/ [12] https://braveneweurope.com/jeffrey-d-sachs-the-real-history-of-the-war-in-ukraine-a-chronology-of-events-and-case-for-diplomacy [13] https://www.jeffsachs.org/newspaper-articles/nato-chief-admits-expansion-behind-russian-invasion [14] https://www.semanticscholar.org/paper/2c06cbc711d95427489f8bc781c45daab461ccde [15] https://www.semanticscholar.org/paper/46e28172de2a520e4f77e654a37687a7757d9d49 [16] https://www.semanticscholar.org/paper/e8c17a15a554054c755a1b1d53d3e1099d159033 [17] https://www.semanticscholar.org/paper/65cbcec6ac255413086db567774844f84c813600 [18] https://www.semanticscholar.org/paper/d11db25ffa5b50ef38d18c2a1e2243e4c7c53b24 [19] https://www.semanticscholar.org/paper/5b750f3d763d728ae2bcf2ce3e6cf67a8281bb2b [20] https://www.semanticscholar.org/paper/34883bf28c7a988eb2c2fe458b7eab3180b36dcc [21] https://www.semanticscholar.org/paper/b64319315d02b2cc1dff936d69be40d78d15f6b9 [22] https://www.semanticscholar.org/paper/c4ca4d645825a5b8d7389c45bcfcad0eeebecd81 [23] https://www.ncbi.nlm.nih.gov/pmc/articles/PMC11734947/ [24] https://www.reddit.com/r/PoliticalScience/comments/17iwhqi/john_mearsheimer_is_wrong_about_ukraine/ [25] https://www.reddit.com/r/geopolitics/comments/1ih646n/john_mearsheimer_is_offensive_realist_who_should/ [26] https://www.reddit.com/r/neoliberal/comments/tjhwi4/a_response_to_mearsheimers_views_on_nato_ukraine/ [27] https://www.reddit.com/r/IRstudies/comments/1b12pdh/genuine_structural_realist_cases_against_us/ [28] https://www.reddit.com/r/lexfridman/comments/17xl8jk/john_mearsheimer_israelpalestine_russiaukraine/ [29] https://www.reddit.com/r/geopolitics/comments/17xve8j/people_give_too_much_credit_to_the_realist/ [30] https://www.reddit.com/r/PoliticalDiscussion/comments/zvfquu/do_you_agree_with_john_mearsheimers_complex_view/ [31] https://www.reddit.com/r/geopolitics/comments/1bghzbp/john_mearshimer_and_ukraine/ [32] https://www.reddit.com/r/LabourUK/comments/tbzs2d/john_mearsheimer_on_why_the_west_is_principally/ [33] https://www.reddit.com/r/IRstudies/comments/1gjus1i/playing_devils_advocate_to_john_mearsheimer/ [34] https://www.reddit.com/r/TheAllinPodcasts/comments/1fipvmu/john_mearsheimer_and_jeffrey_sachs_on_american/ [35] https://www.e-ir.info/2024/03/31/dissecting-the-realist-argument-for-russias-invasion-of-ukraine/ [36] https://www.youtube.com/watch?v=G6YOVl5LKTs [37] https://www.researchgate.net/publication/362890238_Mearsheimer_Realism_and_the_Ukraine_War [38] https://www.ndsmcobserver.com/article/2024/01/john-mearsheimer-talks-war-and-international-politics [39] https://euideas.eui.eu/2022/07/11/john-mearsheimers-lecture-on-ukraine-why-he-is-wrong-and-what-are-the-consequences/ [40] https://academic.oup.com/ia/article-pdf/98/6/1873/47659084/iiac217.pdf [41] https://www.youtube.com/watch?v=qciVozNtCDM [42] https://metacpc.org/en/mearsheimer2022/ [43] https://www.fpri.org/article/2023/01/the-realist-case-for-ukraine/ [44] https://www.mearsheimer.com/wp-content/uploads/2019/06/Why-the-Ukraine-Crisis-Is.pdf [45] https://www.newyorker.com/news/q-and-a/why-john-mearsheimer-blames-the-us-for-the-crisis-in-ukraine [46] https://www.semanticscholar.org/paper/cd2fd9e8ea82fa4e7f2f66a2eb517f4ba34981a0 [47] https://www.semanticscholar.org/paper/99942047e1e43e77ef76e147e51b725a63d86e22 [48] https://www.semanticscholar.org/paper/a53f98c63c58e4268856bde3883abc72e43e03bf [49] https://www.semanticscholar.org/paper/471f43cd36c53141ee24a431eef520bec311c15c [50] https://www.semanticscholar.org/paper/d56b89349fade26cef69c1d0cffd6887adca102d [51] https://www.semanticscholar.org/paper/50f504029753ffb7eec4d2660f29beb48b682803 [52] https://www.semanticscholar.org/paper/e2f85f09340e854efcfc4df9d1aabd2e533e1051 [53] https://www.reddit.com/r/UkraineRussiaReport/comments/1ghs32m/ru_pov_jeffrey_sachss_view_on_the_lead_up_and/ [54] https://www.reddit.com/r/EndlessWar/comments/1iwpc2e/ukraine_war_is_over_jeffrey_sachs_explosive/ [55] https://www.reddit.com/r/UnitedNations/comments/1ivq4zg/there_will_be_no_war/ [56] https://www.reddit.com/r/chomsky/comments/1gx5c5k/jeffrey_sachs_explains_the_background_to_the/ [57] https://www.reddit.com/r/chomsky/comments/1ix8z9a/jeffery_sachs_providing_clarity/ [58] https://www.reddit.com/r/chomsky/comments/1ism3vj/jeffrey_sachs_on_us_russia_talks_to_end_ukraine/ [59] https://www.reddit.com/r/geopolitics/comments/1e04cpd/i_do_not_understand_the_prorussia_stance_from/ [60] https://www.reddit.com/r/PoliticalVideo/comments/1izr6g9/economist_prof_jeffrey_sachs_addresses_eu/ [61] https://www.reddit.com/r/LabourUK/comments/1iw9u56/economist_prof_jeffrey_sachs_addresses_eu/ [62] https://www.reddit.com/r/TheAllinPodcasts/comments/1cjfkbx/fact_checking_david_sachs_data_sources_on_ukraine/ [63] https://www.reddit.com/r/chomsky/comments/1e4n8ea/why_wont_the_us_help_negotiate_a_peaceful_end_to/ [64] https://www.reddit.com/r/ukraine/comments/13lrmgo/rebuttal_to_jeffrey_sachs_ad_in_the_new_york/ [65] https://www.reddit.com/r/chomsky/comments/1ipg351/you_can_immediately_tell_who_in_this_sub_doesnt/ [66] https://www.youtube.com/watch?v=RiK6DijNLGE [67] https://www.internationalaffairs.org.au/australianoutlook/why-nato-expansion-explains-russias-actions-in-ukraine/ [68] https://www.youtube.com/watch?v=P7ThOU4xKaU [69] https://www.jeffsachs.org/newspaper-articles/s6ap8hxhp34hg252wtwwwtdw4afw7x [70] https://www.jeffsachs.org/newspaper-articles/wgtgma5kj69pbpndjr4wf6aayhrszm [71] https://www.youtube.com/watch?v=xfRG1Cqda2M [72] https://voxukraine.org/en/open-letter-to-jeffrey-sachs [73] https://www.youtube.com/watch?v=AmZoJ1vKEKk [74] https://www.youtube.com/watch?v=YnBakiVQf-s [75] https://www.project-syndicate.org/commentary/russia-nato-security-through-ukrainian-neutrality-by-jeffrey-d-sachs-2022-02 [76] https://www.commondreams.org/opinion/nato-chief-admits-expansion-behind-russian-invasion [77] https://www.youtube.com/watch?v=-MmJfmTgvAk [78] https://www.youtube.com/watch?v=ava7rqirOYI [79] https://jordantimes.com/opinion/jeffrey-d-sachs/war-ukraine-was-not-%E2%80%98unprovoked%E2%80%99 [80] https://www.reddit.com/r/geopolitics/comments/1d8ony5/john_mearsheimers_opinion_on_ukraines_own_ability/ [81] https://thegeopolitics.com/mearsheimer-revisited-how-offensive-realisms-founder-is-inconsistent-on-the-ukraine-russia-war/ [82] https://www.scielo.br/j/rbpi/a/MvWrWYGGtcLhgtsFRrmdmcx/ [83] https://www.degruyter.com/document/doi/10.1515/auk-2022-2023/html?lang=en [84] https://blog.prif.org/2023/07/26/russian-self-defense-fact-checking-arguments-on-the-russo-ukrainian-war-by-john-j-mearsheimer-and-others/ [85] https://europeanleadershipnetwork.org/commentary/the-ukraine-crisis-according-to-john-j-mearsheimer-impeccable-logic-wrong-facts/ [86] https://pjia.com.pk/index.php/pjia/article/download/837/587 [87] https://www.reddit.com/r/TheAllinPodcasts/comments/1e4noiz/where_is_sacks_prorussia_motive_coming_from/ [88] https://www.reddit.com/r/geopolitics/comments/1an20x2/why_did_boris_johnson_tell_ukraine_not_to_take/ [89] https://www.reddit.com/r/ukraine/comments/1gjfcwg/media_reveals_deal_russia_offered_to_ukraine_at/ [90] https://www.reddit.com/r/AskARussian/comments/1d3pv6y/do_you_feel_like_the_west_was_actively_sabotaging/
-
 @ d360efec:14907b5f
2025-03-01 12:58:51
@ d360efec:14907b5f
2025-03-01 12:58:51ภาพรวม (Integrated Overview)
ถ้าพิจารณาทั้ง TF Daily, 4H, และ 15m (พร้อมข้อมูล Money Flow ที่เป็นลบในทุก TF) ราคาปัจจุบันประมาณ 84,579
การวิเคราะห์แบบรวม*
-
แนวโน้ม (Trend):
- Daily: ขาลง (Bearish) แม้ว่าราคาจะอยู่เหนือเส้นค่าเฉลี่ยเคลื่อนที่ (EMA) แต่ Money Flow ที่เป็นลบอย่างรุนแรง บ่งชี้ถึงแนวโน้มขาลง
- 4H: ขาลง (Bearish) Money Flow เป็นลบอย่างมาก และมี รูปแบบ Head and Shoulders ที่มีโอกาสเกิดขึ้น
- 15m: ขาลง (Bearish) Money Flow เป็นลบ
-
SMC & ICT (Smart Money Concepts & Inner Circle Trader):
- Buyside Liquidity: อยู่เหนือราคาสูงสุดปัจจุบัน ระดับราคาที่ อาจ เป็นแนวต้าน (จากกราฟ Daily): 90456.8, 92755.8, 95054.9, 97354.0, 99653.1, 101952.1, 104251.3, 106550.3, 109998.9, และ 117000.0 ใน TF 15m, Buyside Liquidity คือจุดสูงสุดของแท่งเทียนก่อนหน้า
- Sellside Liquidity: แนวรับสำคัญ: 80,000 (Neckline ของ Head and Shoulders ใน TF 4H, ตัวเลขกลม, แนวรับทางจิตวิทยา) แนวรับอื่นๆ: 83559.5, 81260.4, 78961.4, 76662.3, 74363.2, 72064.1, 69705.1, 67400.0, 66811.7, และ 65166.9 (จากกราฟ Daily) ใน TF 15m, Sellside Liquidity คือจุดต่ำสุดของแท่งเทียนก่อนหน้า
-
Money Flow:
- Daily: เป็นลบอย่างมาก (Strongly Negative)
- 4H: เป็นลบอย่างมาก (Strongly Negative)
- 15m: เป็นลบ (Negative)
- นี่คือตัวบ่งชี้ที่สำคัญที่สุดในขณะนี้ และเป็นขาลงในทุก Timeframe
-
EMA (Exponential Moving Averages):
- Daily: ราคาอยู่เหนือ EMA 50 และ 200 แต่ถูกหักล้างด้วย Money Flow ที่เป็นลบ
- 4H: ราคาอยู่เหนือ EMA 50 และ 200 แต่ถูกหักล้างด้วย Money Flow ที่เป็นลบ
- 15m: ราคาแกว่งตัวรอบ EMA 50, อยู่เหนือ EMA 200 แต่ถูกหักล้างด้วย Money Flow ที่เป็นลบ
-
Trend Strength (AlgoAlpha):
- Daily: เมฆ Ichimoku เป็นสีเทา (Neutral - เป็นกลาง)
- 4H: เมฆ Ichimoku เป็นสีเทา (Neutral - เป็นกลาง)
- 15m: เมฆ Ichimoku เป็นสีเทา (Neutral - เป็นกลาง)
-
Chart Patterns (รูปแบบกราฟ):
- Daily: ไม่มีรูปแบบที่ชัดเจน แต่มีการอ่อนตัวของราคา
- 4H: มีโอกาสเกิด รูปแบบ Head and Shoulders (กลับหัว) (Bearish - ขาลง)
- 15m: ไม่มีรูปแบบที่ชัดเจน แต่อาจเป็นส่วนหนึ่งของ Right Shoulder ใน TF 4H
กลยุทธ์ Day Trade (SMC-Based)
เนื่องจาก Money Flow ที่เป็นลบอย่างท่วมท้นในทุก Timeframes และรูปแบบ Head and Shoulders ที่มีโอกาสเกิดขึ้นใน TF 4H กลยุทธ์การซื้อขายที่สมเหตุสมผล เพียงอย่างเดียว คือ การป้องกันอย่างเข้มงวด โดยเน้นที่ การหลีกเลี่ยงสถานะ Long และพิจารณาสถานะ Short เฉพาะ เมื่อมีเงื่อนไขที่เข้มงวดมากเท่านั้น
-
Long (Buy): ไม่แนะนำโดยเด็ดขาด (Absolutely, unequivocally not recommended) การทำเช่นนี้จะเป็นการซื้อขายสวนทางกับแนวโน้มหลักและสัญญาณ Money Flow ที่ชัดเจน
-
Short (Sell):
- Entry (จุดเข้า): นี่คือการเทรด เดียว ที่ อาจ มีเหตุผลสนับสนุน, แต่ เฉพาะ เมื่อเงื่อนไข ทั้งหมด ต่อไปนี้เป็นจริง:
- รูปแบบ Head and Shoulders ใน TF 4H เสร็จสมบูรณ์ ด้วยการ Breakout ที่ชัดเจนใต้ Neckline (80,000-81,000)
- การ Breakout ใต้ Neckline เกิดขึ้นพร้อมกับ Volume ที่สูง
- Money Flow ใน ทั้งสาม Timeframes ยังคง เป็นลบอย่างมาก
- คุณมีสัญญาณ Bearish อื่นๆ ยืนยัน (เช่น รูปแบบแท่งเทียน Bearish, Bearish Divergence)
- Target (เป้าหมาย): ระดับ Sellside Liquidity (เช่น 78961.4, 76662.3)
- Stop Loss (จุดตัดขาดทุน): เหนือ Neckline หรือ Right Shoulder ทันที จำเป็นต้องมี Stop Loss ที่เข้มงวดอย่างยิ่ง
- Entry (จุดเข้า): นี่คือการเทรด เดียว ที่ อาจ มีเหตุผลสนับสนุน, แต่ เฉพาะ เมื่อเงื่อนไข ทั้งหมด ต่อไปนี้เป็นจริง:
-
No Trade (ไม่เทรด): เป็นตัวเลือกที่ ดีที่สุด สำหรับนักเทรด/นักลงทุนส่วนใหญ่ ความเสี่ยงที่จะเกิดการปรับฐานครั้งใหญ่มีสูงมาก
สรุป
สถานการณ์ของ BTC คือ Bearish อย่างมาก Money Flow ที่เป็นลบอย่างมากในทุก Timeframes เป็นปัจจัยสำคัญที่สุด ซึ่งมีน้ำหนักมากกว่าสัญญาณ Bullish ใดๆ ก่อนหน้านี้จาก EMA รูปแบบ Head and Shoulders ที่มีโอกาสเกิดขึ้นใน TF 4H ช่วยเพิ่มการยืนยันแนวโน้ม Bearish สถานะ Long ไม่สมเหตุสมผลอย่างยิ่ง สถานะ Short อาจ พิจารณาได้, แต่ ต้อง มีการยืนยันสัญญาณที่ชัดเจน ทั้งหมด และมีการบริหารความเสี่ยงที่เข้มงวดมาก "Wait and See" (รอดู) และการรักษาเงินทุนเป็นสิ่งสำคัญที่สุด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
-
 @ d360efec:14907b5f
2025-03-01 12:55:57
@ d360efec:14907b5f
2025-03-01 12:55:57$OKX:BTCUSDT.P
Overview (Integrated Overview)
All three provided timeframes (Daily, 4H, and 15m, all now confirmed to have negative Money Flow), The current price is approximately 84,579.
Integrated Analysis
-
Trend:
- Daily: Bearish. While the price is above the EMAs, the strongly negative Money Flow on the Daily chart overrides the EMA signal, indicating a bearish trend. The Ichimoku Cloud is neutral, further supporting the idea that the previous bullish trend is weakening.
- 4H: Bearish. Strongly negative Money Flow and a potential (but not yet confirmed) inverted Head and Shoulders pattern.
- 15m: Bearish. Negative Money Flow.
-
SMC & ICT (Smart Money Concepts & Inner Circle Trader):
- Buyside Liquidity: Above the current high. Potential resistance levels (derived from the Daily chart image, assuming it's from 2025): 90456.8, 92755.8, 95054.9, 97354.0, 99653.1, 101952.1, 104251.3, 106550.3, 109998.9, and 117000.0. On the 15m chart (though we are prioritizing the Daily and 4H now), Buyside Liquidity would be represented by recent swing highs.
- Sellside Liquidity: Key support: 80,000 (this is the approximate neckline of the potential Head and Shoulders pattern on the 4H chart, a round number, and a psychological support level). Other support levels (derived from the Daily chart image): 83559.5, 81260.4, 78961.4, 76662.3, 74363.2, 72064.1, 69705.1, 67400.0, 66811.7, and 65166.9. On the 15m chart, Sellside Liquidity would be represented by recent swing lows.
-
Money Flow:
- Daily: Strongly Negative. This is a major bearish signal.
- 4H: Strongly Negative. This reinforces the bearish signal and is consistent with the Daily chart.
- 15m: Negative. This confirms the short-term outflow of money.
- The consistently negative Money Flow across all timeframes is the most important and dominant indicator in this analysis.
-
EMA (Exponential Moving Averages):
- Daily: Price is above the EMA 50 (yellow) and EMA 200 (white). However, the strongly negative Money Flow overrides the bullish signal typically provided by the price being above the EMAs.
- 4H: Price is above the EMA 50 and EMA 200. Again, the strongly negative Money Flow overrides this.
- 15m: Price is oscillating around the EMA 50 and above the EMA 200. The negative Money Flow overrides this.
-
Trend Strength (AlgoAlpha Indicator):
- Daily: The Ichimoku Cloud is gray (Neutral). This is not a bullish signal and is consistent with the negative Money Flow.
- 4H: The Ichimoku Cloud is gray (Neutral).
- 15m: The Ichimoku Cloud is gray (Neutral).
-
Chart Patterns:
- Daily: No fully formed classic chart pattern. However, the recent price action shows a loss of upward momentum and the beginning of a potential downward move. This weakening price action, combined with the strongly negative Money Flow, is bearish.
- 4H: Potential inverted Head and Shoulders pattern. This is a bearish reversal pattern. It's crucial to understand that this pattern is not yet confirmed. Confirmation requires a decisive break below the neckline (approximately 80,000-81,000), with increased volume and continued negative Money Flow.
- 15m: No clearly defined classic chart pattern. The 15m price action is best understood as potentially forming the right shoulder of the 4H Head and Shoulders.
SMC-Based Day Trading Strategies
Given the overwhelmingly bearish evidence – primarily the strongly negative Money Flow across all timeframes, combined with the potential Head and Shoulders pattern on the 4H chart – the only justifiable trading strategy is extreme caution and a strong bias against long positions. Short positions have a slightly higher probability of success, but only under very specific conditions and with extremely tight risk management.
-
Long (Buy): Absolutely, unequivocally not recommended. There is no technical justification for entering a long position at this time. This would be trading directly against the dominant bearish signals.
-
Short (Sell):
- Entry: This is the only trade with any potential, and only if all of the following conditions are met:
- The Head and Shoulders pattern on the 4H chart fully completes with a decisive break below the neckline (80,000-81,000).
- The breakout below the neckline occurs on significantly increased volume.
- The Money Flow on all three timeframes (Daily, 4H, and 15m) remains strongly negative at the time of the breakout.
- Additional bearish confirmation is present (e.g., bearish candlestick patterns, bearish divergences on other oscillators like RSI or MACD – which we cannot see from the provided images).
- Target: Sellside Liquidity levels, derived from the Daily chart. Potential targets include, but are not limited to: 78961.4, 76662.3, 74363.2, and potentially lower.
- Stop Loss: Immediately above the neckline (after the breakout) or above the high of the right shoulder (if placing the trade before a confirmed neckline break – which is extremely risky). An extremely tight stop-loss is absolutely mandatory due to the inherent volatility of BTC and the potential for false breakouts.
- Entry: This is the only trade with any potential, and only if all of the following conditions are met:
-
No Trade (Cash): This is, by far, the best and most prudent option for the vast majority of traders and investors. The risk of a substantial price decline is extremely high, given the confluence of bearish signals. Preserving capital should be the primary objective.
Key Levels to Watch:
- 80,000 - 81,000 (4H Chart): This is the neckline of the potential Head and Shoulders pattern. A sustained break below this level, with the confirming factors listed above, would be a strong bearish signal.
- Money Flow on all chart:
Conclusion
The overall technical picture for BTC, strongly bearish. The dominant factor is the consistently and strongly negative Money Flow across all three timeframes. This overrides any seemingly bullish signals from the EMAs. The potential (but unconfirmed) Head and Shoulders pattern on the 4H chart adds further weight to the bearish case.
Long positions are completely unjustified and extremely risky. Short positions might be considered, but only with the strictest possible entry criteria, complete confirmation from multiple indicators, and extremely tight risk management. The "Wait and See" approach, prioritizing capital preservation, is the most prudent strategy for most market participants. This situation calls for extreme caution and a defensive posture.
Disclaimer: This analysis is a personal opinion. It is not financial advice. Trading and investing in cryptocurrencies involves significant risk. Always do your own research and consult with a qualified financial advisor before making any investment decisions.
-
-
 @ ed5774ac:45611c5c
2025-03-01 12:55:28
@ ed5774ac:45611c5c
2025-03-01 12:55:28Trump and Vance Expose Zelensky: The West’s Narrative Machine Meets Reality
In the modern era, the West has perfected the art of ruling through narratives. Stories, carefully crafted and disseminated, have become the primary tool for shaping public perception, justifying actions, and maintaining control. This narrative-driven approach to governance has been the cornerstone of Western power since the 20th century, and nowhere is this more evident than in the ongoing conflict in Ukraine. Enter Volodymyr Zelensky, the comedian-turned-president, who has become a poster child for this narrative-driven world order. But in a recent confrontation with Donald Trump and J.D. Vance, Zelensky’s carefully constructed facade crumbled, exposing the fragility of the Western storytelling empire.
The West’s Narrative Machine
As Alastair Crooke astutely observes in his article The Western Way of War: Owning the Narrative Trumps Reality ( https://www.unz.com/article/the-western-way-of-war-owning-the-narrative-trumps-reality), the West’s power lies not in its military or economic might alone but in its ability to control the narrative. Crooke argues that the West has mastered the art of “owning the story,” creating a reality that serves its interests, regardless of facts on the ground. This narrative dominance ensures that the general public—often referred to as the masses—follows along without questioning, accepting the official line as gospel truth.
To maintain this control, the West relies on carefully curated protagonists who can sell its stories to the world. Take, for example, the story of Volodymyr Zelensky, a former actor whose rise to power was itself a narrative triumph. Portrayed as a relatable outsider who defeated the corrupt establishment, Zelensky promised hope and reform. But behind this carefully crafted image lay darker forces. Oligarch Ihor Kolomoisky, one of Ukraine’s most powerful and controversial figures, played a pivotal role in Zelensky’s ascent. Kolomoisky, who owned the TV channel that aired Zelensky’s show Servant of the People, used his media empire to propel the political novice into the spotlight. This was not a grassroots movement but a calculated maneuver by Ukraine’s oligarchic elite to maintain control under a new, more palatable face.
Zelensky’s Rise and the West’s Geopolitical Strategy
Zelensky’s rise was not just a domestic political shift; it was a calculated move by the West to advance its long-standing goal of containing Russia and dominating Eurasia. The West, particularly the EU and NATO, saw Ukraine as a critical piece in its geopolitical chess game. By installing a pro-Western leader like Zelensky, the West aimed to pull Ukraine firmly into its orbit, knowing full well that such a move would antagonize Moscow. This was not an accidental escalation but a deliberate provocation, designed to create a pretext for further Western intervention.
To polish Zelensky’s image and present him as a beacon of hope for peace and the Westernization of Ukraine, the West also needed to whitewash Ukraine’s darker realities. This meant turning a blind eye to the corruption and oligarchic influence that underpinned Zelensky’s presidency. Equally ignored were the neo-Nazi crimes and policies that had been well-documented before 2014, such as the rise of far-right groups like Svoboda and the Azov Battalion, their glorification of Nazi collaborator Stepan Bandera, and their violent attacks on ethnic minorities, political opponents, and LGBTQ+ communities. These atrocities, once reported in Western media, were suddenly erased from the narrative after 2014, as if they had never existed, to preserve the image of Ukraine as an innocent victim in the West’s geopolitical chess game.
The Grand Chessboard: Ukraine as a Proxy
The West’s use of Ukraine as a geopolitical pawn is not a recent development. Its roots can be traced back to Zbigniew Brzezinski’s 1997 book The Grand Chessboard, in which the former U.S. National Security Advisor laid out a blueprint for American dominance in Eurasia. He famously wrote, “The one who rules the heartland rules the world, the one who rules East Europe rules the heartland, the one who rules Ukraine rules East Europe.” This statement foreshadowed the West’s strategic interest in Ukraine as a tool to contain and destabilize Russia—a goal that has driven Western policy for decades.
Even in 2008, Western leaders like Angela Merkel and Nicolas Sarkozy opposed Ukraine’s NATO membership, recognizing that such a move would provoke Russia. Classified cables from William Burns, the U.S. Ambassador to Russia at the time, echoed this sentiment. Burns warned that NATO expansion into Ukraine was a “red line” for Moscow, succinctly stating, “Nyet means nyet.” The West was fully aware that it was playing with fire, risking a direct confrontation with Russia that could escalate into a potential World War III. Yet, despite these warnings, the West pushed forward with its agenda, pulling Ukraine into its orbit. The stakes were simply too high to abandon the plan.
At the heart of this strategy lies the West’s desperate need to sustain its faltering economic system. Since the 2008 financial crisis, the Western debt-driven financial model has teetered on the brink of collapse. Sovereign debt crises loom large, and the banking industry, reliant on endless money printing, urgently needs new collateral to back its ever-expanding debt. Russia’s vast resource-rich territories—filled with oil, gas, minerals, and rare earth metals—offer a tempting solution.
By dominating Russia and seizing control of its natural wealth, the West could issue resource-backed bonds, financial instruments tied directly to Russia’s oil and gas reserves. These bonds would allow the West to leverage Russia’s resources as collateral, providing a stable foundation for its debt-ridden financial system. Controlling access to these resources would ensure currency stability and keep Western economies functioning, even as debt levels soar.
But the West’s ambitions extend beyond economic survival. Controlling Russia’s resources would also allow it to sever China’s access to critical raw materials, undermining Beijing’s economic and military development. By dominating Russia’s energy exports, the West could manipulate global energy prices, stabilizing its own economies while weakening rivals like China, which relies heavily on Russian energy. The U.S. and EU view China as the greatest geopolitical challenge of the 21st century, and by encircling and weakening Russia, they aim to isolate and contain Beijing. In this grand strategy, Ukraine is not merely a pawn but a critical linchpin in the West’s efforts to reshape the global order—even at the risk of catastrophic conflict.
Zelensky’s Role in the West’s Strategy
To execute this high-stakes strategy, the West needed a compelling narrative—one that could justify its actions, rally public support, and obscure its true motives. Therefore, they created the narrative around Volodymyr Zelensky, casting him as a global symbol of resistance, a hero fighting against the “evil” of Putin’s Russia. The West, particularly the EU and NATO, embraced this narrative, using it to justify billions in aid—much of which served as a cover for money laundering—sanctions on Russia, and the broader geopolitical agenda outlined above. Zelensky became the face of this narrative, a willing participant in the West’s grand strategy, even as his own country was turned into a battlefield.
Zelensky’s narrative, however, is built on shaky ground. Take, for example, the claim that Putin is “non-agreement capable”—a talking point frequently parroted by Western media and politicians. This assertion is not only baseless but laughably ironic. Unlike the West, which has a long history of signing agreements only to disregard them (e.g., the Minsk agreements, the Istanbul peace deal in March 2022, or NATO’s broken promise not to expand eastward), Putin has consistently honored the contracts and treaties he has signed. The West, not Russia, is the true exemplar of “non-agreement capable” behavior.
Yet, Zelensky and his Western backers continue to peddle these lies, confident that the general public will follow. The narrative is simple: Ukraine is the victim, Russia is the aggressor, and any suggestion to the contrary is dismissed as propaganda. This black-and-white storytelling leaves no room for nuance, truth, or accountability.
Trump and Vance: Slapping Down the Narrative
Enter Donald Trump and J.D. Vance. In a recent meeting with Zelensky, the duo did what few in the West have dared to do: they called out the narrative for what it is—a fabrication. Trump, known for his blunt rhetoric, and Vance, a rising voice of realism in foreign policy, confronted Zelensky with the uncomfortable truth. They exposed the contradictions in his claims, highlighting the West’s role in prolonging the conflict and the absurdity of expecting the world to believe in a one-sided story.
Zelensky, accustomed to the adulation of Western elites and the uncritical support of the media, was unprepared for this reality check. His carefully rehearsed lines fell flat, his confidence wavered, and the mask slipped. The confrontation was a rare moment of clarity in a sea of narrative-driven fog, a reminder that truth, when spoken boldly, can still shatter even the most entrenched lies.
The Meltdown of a Narrative Puppet
Zelensky’s meltdown in the face of Trump and Vance’s truth-telling is emblematic of a larger crisis in the West’s narrative-driven order. For decades, the West has relied on storytelling to maintain its dominance, but this approach is increasingly unsustainable. The rise of alternative media, the growing skepticism of the public, and the emergence of leaders like Trump and Vance who refuse to play along are exposing the cracks in the narrative machine.
Zelensky, the figurehead who believed he could sell his lies to 8 billion people, is a cautionary tale. He is not the master of his narrative but a puppet, manipulated by his masters in the EU and NATO. His failure to withstand scrutiny is a testament to the hollowness of the stories he tells and the fragility of the system that props him up.
Conclusion: The End of Narrative Dominance?
The confrontation between Trump/Vance and Zelensky is more than just a political spat; it is a microcosm of the broader struggle between narrative and reality. The West’s reliance on storytelling as a tool of governance is reaching its limits. As Crooke warns, when the narrative diverges too far from reality, it risks collapsing under its own weight.
The general public, once content to follow blindly, is beginning to question. Leaders like Trump and Vance are challenging the status quo, forcing the world to confront uncomfortable truths. Zelensky’s meltdown is a sign of things to come—a harbinger of the end of narrative dominance and the return of reality-based governance. The question is, will the West adapt, or will it cling to its stories until the very end?
-
 @ a296b972:e5a7a2e8
2025-03-01 12:45:01
@ a296b972:e5a7a2e8
2025-03-01 12:45:01Hat das Corona-Ereignis Einfluss genommen auf die Bundestagswahl?
Eine zwingend notwendige Aufarbeitung der Corona-Zeit war noch nicht einmal Bestandteil der Wahlversprechungen in den Wahlprogrammen der Altparteien, die bekanntlich ohnehin nicht umgesetzt werden.
Bei einer hohen Wahlbeteiligung von rund 84 % haben sich rund 74 % für eine der Altparteien entschieden und rund 26 % für die AfD und das BSW.
Das Verhältnis von 74 zu 26 stellt in etwa das Verhältnis derjenigen dar, die sich für und gegen die Gen-Behandlung entschieden haben.
Kann es sein, dass sich die mehrheitlich genbehandelten Wähler unterbewusst für eine der Altparteien entschieden haben, weil sie hier recht sicher sein können, dass eine Aufarbeitung des Corona-Verbrechens nicht stattfinden wird?
Auch, wenn der öffentlich-rechtliche Propaganda-Apparat sehr darauf bedacht ist, die erdrückenden Erkenntnisse über die Schädlichkeit der Gen-Behandlung nicht zu thematisieren, dringt doch die eine oder andere Information zu den Gen-Behandelten durch.
Nach wie vor haben diese in der Mehrzahl ein heiliges Schweigegelübte abgelegt, denn ein ernsthafter Austausch findet auch nach 5 Jahren nicht statt. Die kognitive Dissonanz wirkt weiterhin. Sie wollen nicht, dass sie nach den aktuellen Erkenntnissen mit einem möglichen Fehler ihrer Entscheidung konfrontiert werden. Und hier sind sie bei der Wahl einer Altpartei auf der sicheren Seite, dass das auch von offizieller Stelle aus nicht geschieht.
Nach dieser Annahme wäre die Wahlentscheidung im Unterbewusstsein durch Angst manipuliert worden. Möglicherweise wäre so das Wahlergebnis die Folge der Corona-Zeit und indirekte Wahlmanipulation.
Bei der vorangegangenen Wahl durfte das Wahllokal nur mit einem Maulkorb betreten werden. Dieser wurde inzwischen durch einen DSA-gestützten meinungsfreiheitlichen Unseredemokratie-Maulkorb in den Köpften der Wähler ersetzt.
Die Regierungsbildung wird einige Zeit in Anspruch nehmen. In der Zwischenzeit werden die Friedensbemühungen für die Ukraine zwischen den USA und Russland mit derzeit guten Aussichten voranschreiten. Gleichzeitig findet eine Distanzierung von den USA statt und die EU, vor allem Deutschland, hält zur weiteren realitätsfremden Unterstützung der Ukraine und der für sie steigenden, aber nicht vorhandenen Gefahr einer russischen Invasion eine Kriegsertüchtigung dringend für notwendig.
Mit der Weiter-So-Politik wird der wirtschaftliche Niedergang Deutschlands voranschreiten.
Das Migrationsproblem wird sich nicht von alleine lösen. Es ist zu befürchten, dass es zu weiteren Messerstechereien kommt. Durch Aufrechterhalten der Brandmauer wird es zu weiteren absurden Entscheidungen der Alt-Parteien-Regierung kommen. Das wird dazu führen, dass diese Regierung keine Legislaturperiode von 4 Jahren halten wird. Es wird unter Umständen noch früher, vielleicht schon nach 2 Jahren zu Neuwahlen kommen.
Bereits einen Tag nach dem Wahlabend wird von Wahlmanipulation im Wahlkreis 106 Düsseldorf berichtet. Vermutlich kein Einzelfall. Viele Stimmen von Deutschen, die im Ausland leben, konnten nicht berücksichtigt werden. Viele der im Ausland lebenden haben das Land aufgrund der derzeit herrschenden Verhältnisse verlassen. Dass diese den Altparteien ihre Stimme geben, ist eher unwahrscheinlich. Es besteht auch noch die Möglichkeit, dass die gesamte Wahl annulliert werden muss.
-
 @ 6a6be47b:3e74e3e1
2025-03-01 12:25:54
@ 6a6be47b:3e74e3e1
2025-03-01 12:25:54Hi frens, 🎨 While painting today, my mind wandered from my latest blog entryto future artistic endeavors.I've been open about my feelings as an artist, but that's just the tip of the iceberg. I realized I haven't properly introduced myself here, so let me remedy that. 🖼️Art has been my lifelong passion. Nostr and its wonderful community have reignited my belief in my work, showing me that art can be both enlightening and potentially profitable. I'm truly grateful for the warm welcome and positive vibes I've encountered here. 🦋Nostr made me feel confident enough to speak my mind on a social platform (or should I say protocol? 😉). Some fun facts about me: 🐹 I'm a "golly jolly" kind of gal who's always curious about the world and seeking answers. 🐹I'm a sunscreen enthusiast in summer (but in winter, I'm buried under so many layers, I practically double in size!) 🐹Birdwatching is a hobby of mine. I've researched and painted some cool birds like shoebills and bearded vultures. (Any suggestions for my next avian subject?) 🩷I'm truly happy to be here and grateful for each day. My goal is to spread joy through my art and interactions. Thanks for being part of this journey with me! In your personal experience, how has it been discovering Nostr wether you're an artist or not? What's you favorite part of your journey so far? Godspeed 🚀

-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04c195f1:3329a1da
2025-03-01 10:36:50
@ 04c195f1:3329a1da
2025-03-01 10:36:50Yesterday's chaotic Oval Office meeting between Trump, Vance, and Zelensky exposes a harsh truth: Europe can no longer depend on American protection. The time has come for Europe to reclaim its sovereignty and rebuild as an independent power.
A Diplomatic Theater With No Happy Ending
Yesterday's chaotic scenes in the Oval Office revealed more than just diplomatic tension—they exposed the fundamental weakness of Europe's strategic position. As President Trump, Vice President Vance, and President Zelensky engaged in their uncomfortable public spectacle, one truth became painfully clear: Europe can no longer rely on American protection.
The awkward press conference featured about 40 minutes of relative calm before descending into 10 minutes of complete chaos. This final meltdown was likely never intended to produce meaningful results. Each participant appeared to be performing for different audiences—Trump and Vance signaling to their base, Zelensky demonstrating resolve to European allies. Without concrete security guarantees, any agreement would be meaningless for Ukraine, a reality all parties surely understood beforehand.
When Vance spoke of diplomacy as a "new strategy"—ignoring numerous failed diplomatic initiatives—he crossed a line that provoked Zelensky's visible frustration. The subsequent breakdown wasn't merely a failure of diplomatic protocol but the public collapse of a relationship Europe has staked its security upon.
The Price of Misguided Priorities
This moment of crisis presents an opportunity if European nations are willing to confront uncomfortable realities. The time has come for Europe to emerge as a third global power, independent from both Eastern and Western influence. However, the path forward requires acknowledging our current weaknesses.
European leadership has squandered decades pursuing ideological luxuries while our industrial and military capabilities have atrophied. While obsessing over multicultural social engineering, progressive identity politics, and globalist agendas, we've neglected the fundamental responsibilities of sovereign nations: securing borders, building defensive capabilities, and fostering national cohesion.
The defense of European nations begins with domestic policy. A society divided against itself cannot stand firm in the face of external threats. This principle applies whether discussing Sweden's defense posture or the broader European security architecture.
Photo by Christian Lue on Unsplash
Reclaiming National Identity and Purpose
To rebuild our defensive capabilities, we must first address the internal fragmentation deliberately cultivated across the political spectrum. The active policies of societal division pursued with increasing fervor since the latter half of the 20th century have undermined the very foundations of national identity and common purpose.
Strengthening national defense requires citizens who understand their shared heritage and believe their nation is worth defending. In practical terms, this means confronting difficult questions about immigration, assimilation, and the presence of potential fifth-column elements within our societies. Nations with higher social cohesion demonstrate greater willingness to defend their collective interests.
The current crisis in Ukraine and the uncertain American commitment should serve as a wake-up call. European nations must rapidly rebuild industrial capacity, military strength, and most importantly, a sense of shared purpose. This demands breaking free from the ideological constraints that have guided European politics for generations.
Although European establishment politicians show little appetite for such fundamental reassessment, events are accelerating rapidly. The dramatic scenes in Washington should catalyze serious reflection across European capitals. We cannot hold our breath waiting for political leadership to regain sense—we must push the conversation forward ourselves.
Europe stands at a crossroads. We can continue our dangerous dependence on unreliable partners, or we can reclaim our sovereignty and rebuild our strength. The choice should be obvious, but making it requires courage our leaders have thus far failed to demonstrate.
■
-
 @ fd78c37f:a0ec0833
2025-03-01 08:57:55
@ fd78c37f:a0ec0833
2025-03-01 08:57:55Author: Zhengyu Qian, Eric Zhang Original Link: https://research.dorahacks.io/2025/02/22/maci-mailbox/
We are not reinventing email.
Even a glance at the TOC of IETF RFC 5322 reveals: email is long-standing and well-established, but far from simple. This is just one piece of the puzzle in today’s email system.
What we would like to do first is to review the essence of message delivery.
Proto-mail
A typical process of message delivery can be broken down into three critical components:
- Individuals intending to exchange messages—referred to as the users.
- An intermediary, or agent, that facilitates the delivery.
- The message itself.

Message delivery takes place when the sender hands over the message (e.g., a written note) to an agent—a person (a messenger), a device (a beacon), or an institution (a post office). The agent then dispatches the message to the recipient.
Though direct communication, such as face-to-face conversation, falls outside the scope of this context.
The Protocol of MACI Mailbox
The MACI Mailbox is an encryption-based mailing protocol that builds directly on the three components above, with modifications and extensions.

-
The user consists of two parts:
-
An account, typically with a publicly visible mailing address.
-
A keypair(a private key and its corresponding public key), which works its magic in encrypted communication.
-
The agent has a similar structure:
-
An account.
-
A keypair.
-
The message is simple, consisting of two fields:
-
Subject.
- Body.
The following outlines the flow of message delivery in the MACI Mailbox protocol. The process of sending a message is addressed first.

-
The sender writes a message.
-
The agent encrypts the message using its public key, posts and stores it in a shared public database (e.g. a blockchain, Nostr), and assigns it a queryable ID.
-
The sender wraps the ID of encrypted message together with the agent’s private key, encrypts them using the recipient’s public key, and broadcasts the resulting encrypted data to a public space. Yes, broadcasts it publicly—feeling like encrypted radio communication yet?
In this process, asymmetric encryption is introduced twice, achieving something valuable: the decoupling of message storage from broadcast. This has at least two key implications:
-
It’s highly flexible to choose the infrastructures for encrypted message posting and storage as well as broadcasting facilities—both of which are modular, replaceable, and trustless.
-
Storage and broadcast infrastructures can be separately tailored to meet specific requirements. Typically:
-
Message storage is expected to be inexpensive, reliable, and scalable.
-
Broadcast infrastructure can be customized to fit the varying user ecosystems or needs.

Receiving a message is basically the reverse process:
-
The recipient indexes their mail in the broadcast space, decrypts it with their own private key (guaranteed by the principles of asymmetric encryption), and retrieves both the ID of encrypted message (storage address) and the agent’s private key (which, as you may recall, was bundled with the message ID before broadcast).
-
With the message ID, the recipient fetches the encrypted message from storage and decrypts it using the agent’s private key to obtain the plaintext message.
-
Tada.
It can be observed that the agent’s role described above is highly procedural, lending itself to a modular and replaceable design. This enables significant flexibility in the implementation of MACI Mailbox services and applications.
Vota-Nostr Mailbox: basic architecture
The Vota-Nostr Mailbox is the first implementation of the Protocol by Dora Factory, consisting of several core modules:
-
A smart contract deployed on Dora Vota appchain to handle the broadcasting of messages.
-
Nostr relays, used for publishing and storing encrypted messages.
-
An indexer service to assist users in locating relevant messages, such as those sent to or from themselves.
-
A web app as the interface for interacting with the Vota-Nostr Mailbox.


First, user accounts are implemented as on-chain accounts of Dora Vota (represented as a wallet address) paired with a public/private ECC keypair. Message content is kept simple as plain-text strings, with the flexibility to upgrade it later (Everybody Loves Rich Text).
Next, let’s push the boundaries for the agent. Ideally, users shouldn’t have to learn how to interact with it actively—think about fully automated agents. Or picture a stylish scene from The Day of the Jackal: Eddie Redmayne casually discarding a phone after each call.
Thus, a disposable, one-time auto agent is designed for each mail flow. This agent consists of a randomly generated ECC keypair and a temporarily created Nostr account (essentially another keypair: npub/nsec).
Vota-Nostr Mailbox: communication workflow
In Vota-Nostr implementation of MACI Mailbox Protocol, the communication flow is as follows. Both the encryption/decryption of message content and the broadcast rely on elliptic-curve cryptography.


To enhance user experience, a “Sent Messages” feature has been implemented, allowing senders to index, decrypt, and review their sent messages. In general, with asymmetric encryption, only the recipient’s private key can decrypt the encrypted content. Technically, there are cryptographic methods to enable mutual decryption by both sender and recipient.
For simplicity at this stage, this issue is addressed by creating a duplicate of each broadcast data (on Dora Vota appchain). This duplicate is encrypted using the sender’s own public key, allowing the sender to decrypt it with their private key.
Since the Protocol decouples the storage of encrypted message from the broadcast data, this duplication doesn’t significantly increase the payload on the broadcast infrastructure. Only the message ID and the agent’s private key need to be processed as duplicates, both of which are compact and independent of the actual message size (the length of your address line and the size of your front door key don’t depend on the dimensions of your house).
Below outlines the entire communication process:
-
The sender encrypts their message using the agent’s one-time public key and publishes it to Nostr relay(s) via the agent’s one-time Nostr account, obtaining the encrypted message’s ID (i.e., Nostr event ID).
-
The sender wraps the encrypted message ID along with the agent’s one-time private key, encrypts them using the recipient’s public key, and broadcasts the resulting encrypted data to the appchain via their own Dora Vota account. This process leverages wallet apps/extensions for transaction submission and the smart contract for processing, closely resembling how users typically interact with blockchains and dapps.
-
Once the on-chain transaction is processed, the encrypted data is broadcast on Dora Vota. Both the sender and the recipient can retrieve the data at any time via the Mailbox Indexer.
-
The recipient decrypts the broadcast encrypted data using their own private key, finding the Nostr event ID and the corresponding decryption key (one-time agent private key). They then fetch the encrypted message from Nostr relay(s) by the ID and decrypt it with the one-time private key.
-
The sender can follow a nearly identical process to fetch and decrypt their own duplicate, enabling them to review sent messages.
Acknowledgements
The MACI Mailbox protocol was conceived during a Dora Factory developer meeting in Kyoto, March 2024. Eric Zhang supported its implementation in October as a tool to facilitate communications and campaigns in MACI decentralized governance. Shrey Khater and Divyansh Joshi contributed to an MVP of the Vota-Nostr implementation. The protocol was officially integrated with Dora Vota appchain as well as its frontend with efforts from Zhengyu Qian, Dennis Tang, and Vegebun.
-
 @ da0b9bc3:4e30a4a9
2025-03-01 08:36:18
@ da0b9bc3:4e30a4a9
2025-03-01 08:36:18Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/900550
-
 @ 95cb4330:96db706c
2025-03-01 07:38:13
@ 95cb4330:96db706c
2025-03-01 07:38:13Embracing The Principle of Asymmetric Bets
Embracing the principle of asymmetric bets, as practiced by visionaries like Jeff Bezos and Peter Thiel, involves seeking opportunities where the potential gains far outweigh the possible losses. This strategy enables bold decision-making while minimizing exposure to significant failures.
Understanding Asymmetric Bets
- Definition:
An asymmetric bet is a strategic decision where the potential upside is substantially greater than the downside risk. This approach allows individuals and organizations to pursue high-reward opportunities without jeopardizing overall stability.
Examples in Practice
-
Jeff Bezos and Amazon Web Services (AWS):
Bezos invested in AWS when cloud computing was still emerging. The potential upside—a trillion-dollar business—vastly outweighed the moderate research and development costs, exemplifying an asymmetric bet. -
Peter Thiel's Investment in Facebook:
Thiel's early $500,000 investment in Facebook transformed into a multi-billion-dollar return, showcasing the immense potential of asymmetric bets in venture capital.
Implementing Asymmetric Bets
-
Identify Opportunities with High Upside and Low Downside:
Seek situations where the potential benefits are disproportionately higher than the risks involved. -
Evaluate the Risk-to-Reward Ratio:
Assess scenarios where even a small probability of success can lead to substantial rewards, justifying the risk taken. -
Diversify Bets:
Spread resources across multiple asymmetric opportunities to increase the likelihood of significant returns while mitigating individual risks.
Action Step
Identify a decision or project where the potential upside is considerable and the downside is limited. Take action on this opportunity today, leveraging the principle of asymmetric bets to maximize success while minimizing risk.
By adopting this mindset, you position yourself to capitalize on transformative opportunities that can lead to substantial growth and innovation.
- Definition:
-
 @ 60d17aca:3d6671c6
2025-03-01 02:01:39
@ 60d17aca:3d6671c6
2025-03-01 02:01:39잘 보내지나 시험해본다.
-
 @ fb08144a:c9ced3f4
2025-03-01 00:45:14
@ fb08144a:c9ced3f4
2025-03-01 00:45:14Print hello world
-
 @ b581c912:7df8270f
2025-02-28 21:11:56
@ b581c912:7df8270f
2025-02-28 21:11:56Fui abordado por um colega e ele me falou de forma bastante enérgica sobre o projeto Pi Network, após uma breve conversa resolvi dar crédito e estudar sobre a solução proposta.
Tentei ser imparcial e fui direto no site “oficial” (🤔) onde encontrei dois Whitepapers (referência 1), um de 2019 e outro de 2021. Decidi então fazer a leitura pela documentação oficial, tentar não me influenciar mais do que já sou influenciado (como um Bitcoiner Maximlista que acho que sou).
Infelizmente não tive condições de terminar os dois documentos, no capítulo “Pi – Token Supply” de 2019 já deixa claro de forma matemática que Pi Network é uma pirâmide, e como até aquele momento não consegui resposta se o processo de recompensa da rede tinha sido atualizada, eu decidi não gastar mais meu tempo de vida estudando sobre o protocolo.\ \ Deixo aqui as anotações que fiz até onde tive condições de ler. Por favor, sinta-se à vontade para contra-argumentar caso você tenha entendido o protocolo de forma diferente, ou assim como Satoshi “If you don't believe me or don't get it, I don't have time to try to convince you, sorry.”.
De forma bastante resumida, esta é minha conclusão:
Pi Network é uma pirâmide declarada na sua própria documentação oficial. Infelizmente, mais uma shitcoin.
Vende a ideia de descentralização e justiça, mas não tem nada descentralizado e muito menos justa, usando da falácia argumentativa e frases de efeito tenta vender sua pirâmide financeira.
(OBS: os primeiros capítulos do Whitepaper de 2019 são concentrados em atacar o Bitcoin e seu ambiente, mas sem a coragem de pelo menos descrever corretamente como o ambiente funciona. Soltando verdades pela metade leva o leitor a achar que o ambiente do Bitcoin é malicioso e precisa de ‘melhorias’)
-
Introduction: Why cryptocurrencies matter
-
Traz alguns argumentos para validar a existência do Pi Network, cita falhas do sistema fia, mas não citou o maior problema: Inflação e/ou impressão de dinheiro;
-
Securing Distributed Ledgers (Mining)
-
“This process (Bitcoin mining) is very secure, but it demands enormous computing power and energy consumption as users essentially “burn money” to solve the computational puzzle that earns them more Bitcoin. The burn-to-reward ratio is so punitive that it is always in Validators’ self-interest to post honest transactions to the Bitcoin record.”
-
Aqui é descrito como se a base da “Prova de Trabalho” fosse punitiva “burn-to-reward”, quando na verdade é completamente o contrário: meritocracia total. Trabalhe de forma justa, com dados reais, não tente burlar o sistema e você será recompensado, não importa quem você é ou de onde você vem. Seja justo, trabalhe e seja recompensado.
-
Problem: Centralization of power and money put 1st Generation Cryptocurrencies out of reach
-
O capítulo inteiro é focado em criticar o PoW, sendo que PoW + ”algoritmo de consenso” é a base da solução do problema do “General Bizantino” em um sistema descentralizado. Usando argumentos de ‘excesso de consumo de energia’ e outros para causar desprezo à tecnologia.
-
O Bitcoin é o mercado mundial que mais usa energia renovável. Em 2022 tinha um total de 56% de toda a rede de mineração rodando sobre energias renováveis (2). No Brasil temos algumas empresas que atuam em reutilização de energia renovável para mineração de Bitcoin (3).
-
A Simplified Introduction To Consensus Algorithms
-
A explicação desse capítulo ficou MUITO vago, deixando a entender que o que o minerador coloca no bloco é válido como dado real. Quando na realidade isso não é verdade: o minerador (Mining Node) realmente precisa fazer cálculos computacionais e quem achar o bloco ganha o direito de enviar essa informação para os Nós (“validation” nodes, se é que eu posso chamá-los assim), então os Nós é que vão decidir de forma descentralizada se aquele bloco é válido ou não, caso não seja, recusando o bloco e aceitando o próximo bloco válido.
-
A Simplified Introduction To Stellar Consensus Protocol
-
Este capítulo já começa reforçando a falácia anterior “Pi uses the other type of consensus algorithms”, tentando reforçar que o mecanismo de consenso do Bitcoin é inseguro ou custoso, sendo que no capítulo anterior eles misturaram a prova de trabalho (mineração) com a validação dos blocos, que é realmente o “consensus algorithms”, ou seja, o argumento utilizado aqui é nulo, não fazendo sentido além do de tentar levar o leitor a menosprezar a solução do Bitcoin.
-
“One major criticism of BFT (Byzantine Fault Tolerance) is that it has a centralization point: because voting is involved, the set of nodes participating in the voting “quorum” are centrally determined by the creator of the system in its beginning.”
- Não sei qual BFT exatamente eles estão criticando aqui, mas certamente não é o Bitcoin. Os Nós (“validation” nodes) não são centralmente especificados, qualquer um pode entrar como um nós validador e fazer parte da validação dos blocos, rejeitando aqueles que considera não verdadeiros por N motivos. O sistema de consenso do Bitcoin é feito por %, se 51% dos nós validadores aceitam o bloco (minerado pelo nó minerador) aquele bloco é então visto como válido. Se 51% rejeitam, aquele bloco é rejeitado por toda a rede.
-
Pi’s Adaptations to Stellar Consensus Protocol (SCP)
-
“For example, once a week, the stellar network is using it to compute inflation on the stellar network and allocate the newly minted tokens proportionally to all stellar coin holders (Stellar’s coin is called lumens). In a similar manner, the Pi network employs SCP once a day to compute the network-wide new Pi distribution across all Pi miners (pioneers, contributors, ambassadors, nodes) who actively participated in any given day. In other words, Pi mining rewards are computed only once daily and not on every block of the blockchain.”
- Aqui está deixando claro a centralização da recompensa? Não ficou muito claro, mas me parece que a recompensa é mantida em um wallet temporária (controlada por quem? pelo ambiente? Isso quer dizer que a equipe de desenvolvimento controla a wallet?) e distribuída no fim do dia. Qual o nível de transparência desse processo? É possível analisar tudo capital armazenado, de onde veio, para onde está indo, quanto foi para cada ‘mão’?.
-
“Mining pools are not only points of centralization, but also their operators get cuts reducing the amount going to individual miners. In Pi, there is no need for mining pools, since once a day everyone who contributed get a meritocratic distribution of new Pi.”
- Aqui reforça a solução centralizada que eles mesmo acabaram de criticar. Se meus fundos vão ficar na mão da “Pi Network” que seja 1 dia apenas, então eles estão centralizando os incentivos.
-
Pi Economic Model: Balancing Scarcity and Access
-
Inverted Means Uneven
- Bem vindo à meritocracia, bem vindo à prova de trabalho, bem vindo à vida real. Quem viu a qualidade e futuro na solução XYZ e gastou seu próprio tempo entendendo, aprendendo e se especializando, consequentemente ganha mais. Isso não quer dizer que quem está entrando agora não ganhe ou esteja “burning more energy for less bitcoin”, eles entram agora sabendo que a recompensa é menor e que o trabalho está mais difícil, mas mesmo assim acreditam no potencial da solução.
-
Hoarding Inhibits Use As A Medium Of Exchange
-
É necessário entender a história do dinheiro. Qualquer dinheiro precisa primeiro passar pelo processo de “reserva de valor” https://miro.medium.com/v2/resize:fit:1400/1*7-2w9CZn8yVeO31SmBQqow.png
-
Abstrairei aqui as camadas 2: Lightning, LIquid, Ark e etc, que já são usadas há alguns anos justamente para resolver o problema de “apenas reserva de valor e não moeda de troca”
-
-
The Pi Economic Model
-
Aqui temos um grande problema: levando em consideração que os fundos diários serão centralizados em uma ‘carteira temporária’ (isso foi especificado no capítulo “Transaction fees”, sem especificar quem ou o que controla essa carteira) , e unindo isso com a ‘distribuição justa’ e o fato de que eles querem ‘garantir que grandes quantidade de Pi não sejam concentradas em poucas mãos’, me vem a pergunta: quem decide o que é justo? Quem decide a distribuição justa? Quem decide o quanto é “grande quantidade”?
-
Pi – Token Supply
-
M=∫ f(P), uma função logarítmica decrescente, onde P é a quantidade de participantes. Resumidamente: M paga menos a cada novo integrante na rede
- R=(r*M), onde a distribuição por novo membro acontece com 25% para o indicado (novo membro) 25% para o indicador (o membro que indicou) e 50% distribuído para o resto da rede
- D=t*(M+R), remuneração dos desenvolvedores. Fixando t=25% de cada Pi token gerado
- Acredito que a fórmula final pode ser traduzida como: (∫f(P)dx)⋅(1+r)⋅(1+t)
- Tendo em vista esta tradução dissertativa do cálculo de “Token Supply”, é possível considerar que Pi Network é uma pirâmide: a recompensa é distribuída entre ‘indicado’ (novo membro), ‘indicador’ (quem indicou), equipe de manutenção da rede e por fim, o resto da rede. Essa recompensa diminui a cada novo membro na rede, forçando todos a continuar introduzindo mais membros (obviamente novos membros são incentivados com mais afinco para essa atividade, ou seja, se não indicarem mais membros, não ganham mais incentivos)
-
Apesar de existir recompensa através de taxas de transação, essa recompensa traz um grande problema que já foi citado anteriormente: centralização.
-
Outras críticas gratuitas sem nexo(?)
- Em vários pontos eles só soltam informações soltas sem contexto tentando direcionar o leitor a uma avaliação falaciosa do ambiente do Bitcoin:
- “While Bitcoin’s process for updating its record is proven (burning energy / money to prove trustworthiness), it is not very user (or planet!) friendly.”
- Utilizando frases de efeito de um problema inexistente para validar a necessidade da solução proposta. Já é comprovado que o Bitcoin não consome energia em excesso, não é um perigo para o meio ambiente, muito pelo contrário.
- “Moreover, due to Bitcoin’s lack in the safety guarantee, Bitcoin’s blockchain in rare occasions can be overwritten within the first hour. This means that a user of Bitcoin must wait about 1 hour before they can be sure that a transaction is considered final.”
-
“lack of safety guarantee” leva o leitor a achar que existe um problema de segurança
-
“in rare occasions can be overwritten” se qualquer bloco do Bitcoin for reescrito, então a rede foi hackeada, fim! Não existe forma de reescrever um bloco sem ultrapassar 51% da PoW atual.
-
Stella Core (Stellar Consensus Protocol SCP)
- A equipe/gestora inicial são sabiamente conhecidos, vou abstrair toda e qualquer argumentação lógica do pq isso é terrível para o sistema.
- Eles fazem questão de deixar tds os responsáveis pelo protocolo conhecidos https://stellar.org/foundation/team
- O David Mazières, autor principal do SCP, parece o Vitalik Buterin, criador da shitcoin Ethereum. Isso não deve ser levado como argumento válido!
- https://github.com/stellar/stellar-core/tree/master
- Sim, o protocolo é Open Source, já possui 81 contribuições de pessoas conhecidas e anônimas. Mas o fato de os principais gestores e mantenedores do projeto serem conhecidos cria um grande problema de segurança no protocolo. Em caso de um projeto deste vir a realmente ser útil e financeiramente rentável, basta impor sanções governamentais, processos ‘legais’, prisão ou sequestrar familiares e assim obrigar o protocolo mudar de objetivo/função/código.
- Pré-mining(?): vários artigos citam ‘pioneiros’ migrando Pi Coin para a main net, ou seja, induz a ideia de pré-mining?
-
https://cointelegraph.com/explained/pi-network-mainnet-launch-what-it-means-for-pioneers
-
Mas baseado no capítulo do Whitepaper, o capítulo “Pi – Token Supply“ especifica que o grupo de desenvolvedores (que mantém o protocolo) receberá 25% de todos os tokens, sabendo que o número de participantes é fixado em 100 milhões, podemos deduzir que 25% dos tokens foram pré-minerados para o grupo de desenvolvedores.
- Transparência e KYC
-
Apesar da teórica descentralização da mineração, os nós precisam de KYC, possivelmente armazenado em um servidor central do SCP, apesar de não estar claro como o processo deles funciona, qualquer tipo de centralização e obtenção de dados pessoais levanta extrema cautela.
-
Fundação bem organizada
-
Hierárquica interna
\ O artigo se chama "(quase) Análise" justamente por que não tive condições de terminar os dois documentos.
[1] https://minepi.com/white-paper/#original-whitepaper
[3] https://br.cointelegraph.com/news/bitcoin-mining-renewable-energy-transitionhttps://brasilbitcoin.com.br/blog/a-evolucao-da-mineracao-sustentavel-de-bitcoin/https://www.infomoney.com.br/onde-investir/mineracao-de-bitcoin-pode-ajudar-a-reduzir-energia-ociosa-no-brasil-diz-estudo/
-
-
 @ 4898fe02:4ae46cb0
2025-02-28 20:05:28
@ 4898fe02:4ae46cb0
2025-02-28 20:05:28Posted Feb 28, 2025 Updated Feb 28, 2025
By Fionn O'Nymm
3 min read
Fulfilling P2P Electronic Cash
Bitcoin only begins to fulfill the vision of bitcoin being a P2P electronic payment network when people actually use it to transact. Unschooled is positioning itself to realize some of the potential for which Satoshi Nakamoto had originally imagined it would be used.
Tech-savvy educators across the globe are uniquely positioned to be using bitcoin for transacting and selling their service online, free from jurisdictional constraints offered so magnanimously by our dear governments. Influencers, bloggers and programmers alike have already been able to plug into Bitcoin and Lightning for transmitting value around the globe, and Unschooled wants to push educators down the same stream.
So what makes the field of P2P Education so well-suited to transact using Bitcoin and Lightning?
1. Educators have one foot in both worlds
If you are a developer or influencer, you may already be transacting adversarially using Bitcoin or Lightning–but where are the Educators? Well - more often than not, they still have one foot in the ‘meat space.’ Be not mistaken, this is a strength. Educators, like Hermes from the Greek pantheon, are conduits between worlds. This makes them experts in bridging gaps in understanding as is so desperately needed for onboarding new freedom-minded users to bitcoin. And since they are, more often than not, end-users themselves, they have an intimate understanding of the user experience in a a way that others do not. Let’s help educators in becoming among the first beneficiaries of the global P2P market of our information age.
2. Great learners make great educators
Those who have spent the most time learning the ins and outs of how technology works become the best at explaining it to new users. One day, we can hope, the experience of decentralized payment networks will become so intuitive that we no longer rely on educators to explain it to people. It will become second-nature, and the focus of rendering educational services exogenous to the new economic reality can begin to take place. Those who have the most to share will be teaching those who are the most eager to learn. The Unschooling experience seeks to help in un-doing the malaise brought about by the economic-educational complex of governments.
3. Government issued education sucks
Leave teachers to teach, and they will change the world. Those who are capable of designing and marketing quality lessons ought to be able to enter their talent to be offered in the free market.
4. Ship it instantly
Like developers and influencers, educators have a product that can be shipped instantly across the globe with minimal energy output. Unschooled is a home for their product. There are many ways in which you may go about this (using these recommended tools, for example); you are only limited by what you can imagine.
5. Nothing can replace a mentor-student relationship
AI can do many things, but what it cannot do is replace the human-connection that can exist between a mentor and student. It cannot invite you to your hometown for coffee, attend a conference or event with you, meander off into tangents with you about what it means to be alive (well, maybe almost) like the way a great mentor can. In education, AI will make for a magnificent game-changer, but there’s nothing like great teachers.
-
 @ 2e8970de:63345c7a
2025-02-28 18:22:14
@ 2e8970de:63345c7a
2025-02-28 18:22:14Atlanta Fed is now projecting Q1 GDP -1.5%. Last week it was +2.3%. 4 weeks ago it was +3.9%
https://x.com/AtlantaFed/status/1895508046215852476
originally posted at https://stacker.news/items/899962
-
 @ 6fac7d89:9d76f561
2025-02-28 18:16:13
@ 6fac7d89:9d76f561
2025-02-28 18:16:13With the price of Bitcoin having gone significantly up over the past few months (I wrote this about a month ago to post on Stacker News), I imagine interest in acquiring it has gone up as well. As such, I'm here to share with you every method I use to stack sats so that we can all HODL more. While the majority of my experience in regards to phone apps is on Android, some of the apps mentioned may work on iPhone as well (I just got an iOS based device and intend to discover methods on there as well with time) so links provided will be the Play Store or my referral links. Some of the referral messages have included Apple App Store links by default so I've left them in.
Bitcoin Education: First and foremost, I think that anyone seeking to acquire BTC should learn about it. From how it works, to how to acquire and then store it. As such, this first category I'm covering is for BTC education resources that also reward you with satoshis for your learning progress.
Yzer: Probably my favorite app in this category as it covers more than the others mentioned in greater depth. While the other apps do cover some aspects of the history of money, economics, and investing/finance, this one really delves into it to offer the most robust education of the bunch. I didn't even know about Austrian economics until going through the lessons provided here, and it boasts the most lessons of this category as well. Each section is divided into chapters containing a few lessons and an end-of-chapter quiz, and you have a chance of earning a few satoshis upon completion of a lesson or quiz.
Use my referral code to earn an extra 50 sats upon reaching level 2: KAB4ZKD https://play.google.com/store/apps/details?id=io.wizzer.academy&pcampaignid=web_share
Simple Bitcoin: This app can be breezed through in regards to the lessons offered, allowing you to complete the learning aspect of it pretty quickly. Instead of rewarding sats outright for completion of lessons, this app rewards you with tickets you can spend to spin a wheel to earn small amounts of sats. Where this app shines is that while Yzer stops rewards when all lessons are completed, Simple Bitcoin has a news section where articles from outside sources are summarized, and reading them earns you more tickets. There is a limit to how many articles/day you can read unless you pay for premium, however, which also increases the reward amounts feature on the prize wheel.
https://simplebitcoin.page.link/ozJaD6uCaUyscYWy6
Jippi: The newest of the bunch in this category, Jippi is still in its earlier stages of development and thus is the least robust. This one works a little differently as, for the time being, you need to complete all available lessons to earn a lump sum reward of 200 sats. Unlike the other educational apps, this one offers audio lessons to listen to for completion alongside the usual texts to read. While still in development, they plan to release a feature called "Tribe Clash" which they describe as "Pokemon Go for Bitcoin".
https://play.google.com/store/apps/details?id=com.jippiApp.jippi.prod&pcampaignid=web_share
Buying Bitcoin: So now you know about Bitcoin, but how can you buy some? While there are many crypto exchanges that offer BTC, this bitcoin-only service offers a more robust experience in regards to BTC and the purchase of it.
Swan: While Swan allows you to buy BTC outright or via recurring buy (DCA), it has some additional interesting features and offerings as well. Their learn section allows you to further educate yourself on various aspects of bitcoin and perspectives on it, and they even offer a Bitcoin IRA (either Traditional or Roth) for those interested in such a service. The caveat to the IRA is that you'll be entrusting them with your BTC instead of having full custody and responsibility of it yourself.
Use my referral link and get $10 of BTC: https://www.swanbitcoin.com/MF_MOON
Cash-Back: The next category I'll be covering is cash-back options, be they via spending with a certain card or using apps/extensions to earn sats on your purchases. Because if you're going to spend money anyways, why not try to get some of that money back in sats for your stack?
Satsback: This browser extension works pretty similar to other cash-back extensions if you've ever tried them: if you're on a site which the extension offers cash-back on, a pop-up to activate it will appear. Make sure to have adblockers and (possibly) your VPN disabled before activating to ensure you get your reward (I suggest you do this for any similar extensions mentioned below as well).
https://satsback.com/register/k524KP0olqLX19Ov
Fold Debit Card: Fold has several options that allow you to earn sats, one of which is the option to buy gift cards to popular retailers like Amazon, Google Play, Home Depot, Bass Pro Shop, AirBnB and more and earn sats back on the purchase. You can earn even more sats back by paying for these gift cards with their debit card, which needs to be pre-loaded to use, but using another card will still earn you sats, albeit at a lower rate. If you do have their debit card and opt for their premium service, Fold+, you can also earn 1.5% back on all purchases made with said card. Fold+ even offers you cash back on paying bills with the account and routing numbers they provide, though you need to hit certain spending thresholds in the prior month to be eligible for this feature. The app also offers a daily spin to earn small amounts of sats, with higher amounts including a whole Bitcoin locked behind the premium membership. Depending on your average spending and bills, this could be worth it though.
https://use.foldapp.com/r/3RHW4FUJ
CoinMiles: CoinMiles is like SatsBack in the sense that it lets you earn cash-back in bitcoin via online retailers within their app (similar to Lolli below) with the added feature of cash-back in sats on the purchase of gift cards as well, similar to Fold.
Using my referral code will earn us both 5000 sats. https://coinmiles.onelink.me/90Pp/96f2tati
Gemini Credit Card: Crypto exchange Gemini offers a credit card that offers some pretty nice rewards for using it, which has become my go-to method of spending at this point. Allowing you to choose from every crypto asset they offer for your cash-back rewards, you can earn in more than just Bitcoin with this card. The rewards rates are as follows: 4% back on gas at the pump and EV charging, 3% back on dining, 2% back on groceries, and 1% back on everything else. They also have "Merchant Reward Offers" in which they offer a higher rate in cash back on top of the default rate for the category the merchant falls under, I've gotten a total of 8% back at a local brewery using this as it automatically applies if you use the card at said locations. Rewards are issued and credited to your Gemini accounts instantly upon making said purchase. The one issue I take with the exchange is that without lightning integration, BTC withdrawal fees can get steep. As a result, I opt to earn in another asset with lower withdrawal fees and swap said asset for BTC via an external swapping service.
If you choose to purchase assets directly via the exchange as well, using my referral link can earn you referral rewards that scale with how much crypto you purchase with them: https://www.gemini.com/share/wwm6w8a3e
Lolli: Boasting both an app and a browser extension, Lolli offers not only cash-back similar to SatsBack, but also card boosts, which reward you for paying with a linked credit or debit card in stores they offer. Simply activate the boost before paying with your linked card to earn cash-back in sats, or when shopping online, activate cash back via a pop-up from the browser extension or clicking the retailer within the app to be directed to their site. Similar to Fold, the app features a daily way to earn small amounts of sats.
https://lolli.com/share/T2r2NYSr7A
Bitcoin Company Rewards: Another app that allows you to buy gift cards and earn sats back on the purchase, this one has the standout option of offering Visa gift cards within the US to earn a small amount of sats back on, among many other card offerings.
Use my referral code to earn 1000 sats to start. Referral Code: O30WN3 https://play.google.com/store/apps/details?id=com.tbtc_app&pcampaignid=web_share
Social Media: These next two are, in my opinion, the future of social media, and you can earn on them too! Stacker News: Reddit meets Hacker News on this site, which encourages quality content through the implementation of the lightning network and satoshis. You don't have to be signed up to browse and read content on here, but you should be, and you should use my referral link to do so!
https://stacker.news/r/MF_MOON
Nostr: This one can be a little tougher to describe, but I'll do my best. Nostr is a social media platform that operates on an open-source protocol that supports of variety of applications or "clients" utilizing a unique public and private key pair. Connections can be maintained across clients, which are often made to emulate the more well-known social media services out there. It can be daunting to get into at first, and requires some involvement as there are no built-in algorithms (though devs are starting to provide ways to implement some for discoverability) but it boasts a great community. Users can "zap" each other sats for content they like, and it's integrated with a number of other services at this point including Fountain and Wavlake (see below).
Feel free to follow me on there: https://njump.me/nprofile1qqsglhkx0ey8pdac9ne4w9m4tzglpv2tkl8tvuyc9dzgyrgj07lk42ccwtvy9
Music & Podcasts: Want to earn sats for offering up your ears while doing other things? With these apps, you can enjoy your favorite podcasts and discover new music to earn sats as you listen. Wavlake: While this app allows you to listen to promoted songs to earn a few sats each day, it also offers you the ability to earn sats on your own music and podcasts that you upload to the service. If people listen to your content via the service and like it, they can send you sats, along with feedback and other comments. There is a flat fee of 10% of all earnings for creators, but it's another way to get your content some exposure and possible earn some sats along the way!
https://wavlake.com/
Cloud Mining: The next section I'll be covering is a bit of a dicey topic as some consider it to be scam. While I agree that paying for cloud mining is absolutely a scam, the services I'll be mentioning here offer free options that offer low earnings but only require a daily check in that I do all at once. While I can't tell you how to spend your money, I HIGHLY suggest you avoid spending any money on higher mining rates and spend that money on BTC directly instead. Bitcoin Mining (Crypto Miner): This one offers you 2 free "mining contracts": 1 that you can claim every 8 hours, and another that serves as a daily check-in reward for checking in consistently, as rewards increase the longer your check-in streak is. Claiming contracts involves simply tapping the corresponding claim button, so I usually claim the 8 hour contract 2 times a day and the daily one when I go to make the 2nd 8 hour claim. Your free earning rate can be increased by watching ads for a temporary boost if you so desire as well.
You can get an extra 10% in earnings using my referral link. https://cloudminecrypto.com/?invite_code=R0yMgkOEmEajYvD6 or download the app and add my invite code R0yMgkOEmEajYvD6 directly.
Bitcoin Mining: This one is pretty similar to the previous one, but the free 8 hour mining option can only be activated once per day even if it's finished, unlike the other one. Similar to the prior app, you can watch ads to boost mining rate if you so desire. A nice feature of this one is that it integrates popular lighting wallets including Speed, ZBD and Muun for more seamless withdrawals.
My invitation code:5UHLF Appstore: https://apps.apple.com/us/app/id6503180820 Google play: https://play.google.com/store/apps/details?id=bitcoin.minning.com
Ember: While this started off as a regular mining app on which you check in once a day, they've changed their model up a bit recently: you now earn "bonus sats" which must be gambled in games, and the sats earned from said games are then withdrawable. Essentially, you have to convert your earnings via a gambling game of some sort to make them eligible for withdrawal, with the risk of losing them along the way. However, this one earns the most in this category by far, especially if you have a network of friends to mine with as this affords you increased earning rates.
Referral Code: MNGCC33WRON https://emberfund.onelink.me/ljTI/l4g18zii?mining_referrer_id=MNGCC33WRON
Games: Here we have games that offer BTC as rewards for paying in small amounts. While they won't earn you a ton, they're nice little time-killers to earn you sats on the side.
ZBD: While technically a lightning wallet, the following app are powered by ZBD wallet, so you'll want to install this to claim your earnings from them. ZBD offers a variety of ways to earn should you choose to dabble in them, from completing surveys to watching videos to trying out games that allow you to earn from play time. The options I personally opt for are their daily poll and playing the next game listed below, as it allows you to earn without a "time-gated" mechanic: if you build up your game to a certain point and will allow you to earn more rapidly than any others I've tried. But see what games they offer and if you find them fun, go for it!
Referral Code: PEXE52 https://zbd.link/hcHi/invite?af_sub1=PEXE52
Bitcoin Miner: Being an idle game, this one has a slow start but with a little dedication, can become one of the quickest and most consistent earners in this category. The daily withdrawal limit is unfortunately 330 sats, but when you're maxed out in the current state of the game, you can earn this within 3.5 resets, each of which takes me under minutes to max out with the right strategy and which can be done once every 30 minutes. A one-time purchase of $11.99 will remove all ads, which in my opinion is worth it as you can earn $10/mo in BTC with this game. Using my referral code will net you some of the premium in-game currency to get you started off nicely.
Referral Code: 8H44HB Google Play: https://play.google.com/store/apps/details?id=com.fumbgames.bitcoinminor&pcampaignid=web_share Apple App Store: https://apps.apple.com/us/app/bitcoin-miner-idle-tycoon/id1413770650
THNDR Games: THNDR is a developer that offers a few different games you can play to earn tickets in timed drawings to earn sats, and with your tickets across their games pooling up in a single grand total for the prize drawing when the time comes. I personally find their game "Bitcoin Bay" (a bubble popping game) to be the one that strikes the best balance of fun and earning potential, so its the only one I keep on my phone (I don't want to be playing games on my phone much in my day as it is) but it's really a matter of personal preference which game of theirs you want to play. A nice feature here is that they integrate with lightning wallets including ZBD, Speed, and Strike among others.
https://bitcoinbay.thndr.games/r/tdhP
Bling: Bling is a developer that makes a number of "match" games a la Candy Crush that allow you to earn in BTC and some of which offer earnings in other crytpo assets as well. I personally play their game "Sweet Bitcoin" as I find it to be the most visually appealing, but they all appear to earn at the same rate in my experience. The on caveat to these games is that it has an "energy" system similar to Candy Crush which allows you to play a limited number of games as a time-gating mechanism until you "recharge" plays. For this reason, if this is your preferred type of game, you may want to download more than one of their offerings to be able to earn more in less time. Their games offer withdrawals that integrate CoinBase, Lightning options ZBD and Strike, and PayPal (but only in USD for this option).
https://bln.gg/1NC-CQX-JDK
Earn While You Browse: This last one is an extension on your browser that allows you to earn sats as you browse the web.
Slice: This browser extension adds small ads to sies you visit as you browse, paying you for the respective views. They also offer the option to change your new tab page & default browser for additional earnings, as well as a desktop app to display ads in the bottom right of your screen for even more opportunities to earn. The only downside to this is that your VPN must be turned off, and earnings are made in "slices" which must then be converted to sats.
https://addslice.com/?crew=FjVuNqgg
And there you have it folks, every single method I use to accumulate sats/BTC all in one quick read for your convenience. Given that I've recently also joined the iOS eco-system, I intend to explore that side of earning apps as well, so let me know if any of you want me to share what I find after I spend some time with it, or if you recommend any apps I should check out. I also have methods of earning other coins in passive or semi-passive ways that I then convert into BTC and am happy to share if interest is expressed, or even ways I earn USD in such ways. Feel free to follow me on Nostr (link mentioned above) and to share the ways you earn sats on the side that I may have missed. Stay humble and keep stacking!
-
 @ 6260f29f:2ee2fcd4
2025-02-28 18:12:29
@ 6260f29f:2ee2fcd4
2025-02-28 18:12:29 -
 @ 54609048:8e22ba03
2025-02-28 17:50:27
@ 54609048:8e22ba03
2025-02-28 17:50:27The recent $1.4 billion Extended Fund Facility (EFF) agreement between the International Monetary Fund (IMF) and El Salvador marks a significant turning point in the nation's economic and monetary policy. The IMF’s $1.4 billion “lifeline” is a sly Trojan horse, gutting El Salvador’s sovereignty and kneecapping its 2021 Bitcoin law— which represented a bold step toward monetary freedom and economic self-determination— all to prop up the same economic mess it pretends to fix. Brilliant, right?
The IMF’s Colonialist Agenda: A Historical Precedent
In 2021, El Salvador made history by adopting Bitcoin as legal tender, positioning itself at the forefront of financial innovation and offering its citizens an alternative to the U.S. dollar. This move was a bold step toward monetary independence and as a pathway toward individual financial sovereignty by reducing remittance costs for Salvadorans and bypassing the predatory international banking system. By making Bitcoin legal tender, El Salvador was taking steps to free itself from financial colonialism.
The IMF’s response to El Salvador’s Bitcoin law was predictably hostile from day one. The institution repeatedly warned of the “risks” associated with Bitcoin, framing it as a threat to financial stability rather than a tool for economic empowerment. Hypocrisy drips from every word—the IMF’s own debt traps and inflationary schemes have fueled the chaos it now “rescues” El Salvador from. The Bretton Woods institution has long been the enforcer of the global financial elite, ensuring that nations remain shackled to the U.S. dollar-dominated system. Through predatory loans and stringent conditions, the IMF perpetuates economic subjugation. Now, facing pressure from these same institutions, El Salvador finds itself caught in the classic IMF trap: accepting loans with strings attached that further cement dependency.
This aid package isn't a solution to El Salvador's problems; it's leverage to force compliance with the global banking cartel's agenda. Under the IMF agreement, El Salvador has been compelled to amend its Bitcoin law, revoking Bitcoin's status as legal tender and making its acceptance by businesses voluntary. Additionally, tax obligations must now be settled exclusively in U.S. dollars. This gut-wrenching retreat from its bold Bitcoin rebellion represents a diabolical masterpiece of oppression—stripping citizens of financial freedom and forcing them to forever bow before the fiat gods.
**Why the IMF Must Destroy Bitcoin’s Medium of Exchange Use Case ** To understand why the IMF is so determined to undermine Bitcoin’s role as a medium of exchange in El Salvador, it’s important to revisit the fundamental nature of money. The widely cited “three functions” of money—medium of exchange, store of value, and unit of account—are often misunderstood. These are not rigid definitions, but empirical observations of how money functions in practice.
Money is, first and foremost, the generally accepted medium of exchange. The other functions tend to follow, but they are not exclusive to money. For example, gold can serve as a store of value but is no longer a commonly accepted medium of exchange, and other commodities can also act as units of account, but neither is money unless it is widely accepted as a medium of exchange. Bitcoin’s rise as a store of value (akin to “digital gold”) is not as threatening to the fiat system as its potential to function as a widely accepted medium of exchange. A strong store of value can exist within a system that is still dominated by fiat currencies.
If Bitcoin were to become a dominant medium of exchange, it would directly challenge the monopoly of central banks and the control that institutions like the IMF exert over global financial systems. That is why the IMF’s primary goal in El Salvador is not necessarily to stop Bitcoin’s adoption altogether but rather to strip Bitcoin of its medium of exchange function, thus effectively relegating Bitcoin to a speculative asset or store of value.
Furthermore, this Bitcoin experiment was the first real-world test of Bitcoin as a medium of exchange at the nation-state level. If it had succeeded, other countries—especially those in the Global South struggling with inflation, currency devaluation, and IMF-imposed austerity—might have followed suit. The IMF couldn't afford to let that happen. By neutralizing Bitcoin's role as money, it ensures that alternative financial systems do not gain traction outside the fiat-based global order. In other words, as long as Bitcoin can't be used freely as a medium of exchange, it cannot fulfill its role as money, and the fiat gods' grip on the global monetary system remains unchallenged—at least for now.
The $1.4 Billion Faustian Bargain
El Salvador’s decision to seek IMF funding is a reflection of the immense pressure it faces from global financial markets and institutions. The country’s high debt levels and weak external buffers are, in large part, a consequence of its integration into a global financial system that prioritizes short-term capital flows over long-term economic stability. By accepting the IMF’s terms, El Salvador has effectively traded its sovereignty for temporary financial relief.
What is even more surprising is that El Salvador had an alternative to this Faustian bargain: the issuance of Bitcoin bonds. While initially proposed as a way to finance Bitcoin City and geothermal Bitcoin mining infrastructure, the volcano bonds the country could have raised the $1.4 billion needed without sacrificing its monetary sovereignty. This represents a missed opportunity for El Salvador to bolster its financial independence, attract global capital, and solidify its position as a pioneer in the adoption of decentralized money.
Instead of falling back into the IMF’s debt trap—complete with austerity measures, restrictions on Bitcoin use, and financial surveillance—El Salvador could have embraced a Bitcoin-native financial strategy that aligned with its long-term vision of economic independence. So why didn't El Salvador go through with the Bitcoin bond issuance? I don't know, but if I were to speculate, I would say the answer likely lies in political and institutional inertia, coupled with external pressures from the IMF and its allied institutions, or worse. If El Salvador had raised capital through Bitcoin bonds, it would have sent shockwaves through the financial world, proving that a nation-state could operate independently of the IMF.
The Long-Term Consequences for El Salvador
While the IMF’s program may provide short-term relief, its long-term consequences are likely to be detrimental to the Salvadoran people. The emphasis on fiscal consolidation and debt reduction will inevitably lead to cuts in public spending, particularly in areas such as social services and infrastructure. These measures will disproportionately affect the most vulnerable segments of society, exacerbating inequality and undermining the country’s social fabric.
Moreover, the IMF’s focus on “strengthening governance and transparency” is a thinly veiled attempt to impose external control over El Salvador’s domestic policies. The requirement to enhance Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, while ostensibly aimed at combating illicit activities, will likely be used to surveil and restrict the financial activities of ordinary citizens. This represents a gross violation of individual rights and a further erosion of economic freedom.
Conclusion
The IMF's $1.4 billion arrangement with El Salvador represents not economic salvation but a calculated reassertion of control. By forcing El Salvador to retreat from its Bitcoin initiative, the IMF is protecting the very system that has kept developing nations financially subjugated for decades. For Salvadorans, this means their bold experiment in monetary sovereignty has been curtailed, not by market forces or technological limitations, but by the deliberate intervention of the guardians of the old financial order.
Those who believe in true financial freedom must recognize this for what it is: not assistance, but suppression; not aid, but control. The battle for monetary sovereignty continues, and despite this setback, Bitcoin's promise of financial liberation remains as vital as ever—not just for El Salvador, but for all those seeking escape from the oppressive machinery of central banking
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ c43d6de3:a6583169
2025-02-28 15:26:36
@ c43d6de3:a6583169
2025-02-28 15:26:36Every Sunday, my brother Alex and I would catch the scent of pie creeping from the oven as we chased Ronnie and Ellis around my grandma’s house.
We were good at keeping traditions. Though we eventually outgrew the days of stampeding through Grandma’s living room, her house remained our gathering place. The four of us—Alex, Ronnie, Ellis, and I—would settle on the back porch, the aroma of freshly baked pie still wafting through the air. We’d trade stories about our first crushes, our first kisses, and our dreams for the future, laughing in the warmth of a home that felt eternal.
Alex was the first to leave for college. He never really came back. Four years away, then a big-time job across the country.
Ronnie and Ellis—the twins—left a few years later. They never truly returned, either. Not the same, at least.
A cruel trick of biology had been lurking in the depths of their genes, lying in wait for the right moment to surface. In college, Ronnie was consumed by schizophrenia, while Ellis battled years of depression. They came back home, but they weren’t the same boys I had grown up with. The ones I had once sprinted through hallways with, laughing until our sides hurt, were lost to something none of us could chase down or outrun.
By the time I graduated, the scent of pie had vanished forever. My grandmother’s grave was my last stop before I, too, left town.
I never went back.
People leave in different ways. Some move to another city or another country. Some lose themselves to illness, slipping through our fingers even as they sit beside us. Some find their final resting place. All dearly departed.
What makes their departure so bittersweet is the time we once had with them—the memories we carry, the laughter that still echoes in the corners of our hearts.
That’s life. That’s what makes it worth it.
-
 @ a012dc82:6458a70d
2025-02-28 15:00:36
@ a012dc82:6458a70d
2025-02-28 15:00:36In the dynamic and often unpredictable world of cryptocurrency, the opinions and predictions of financial pundits like Jim Cramer, the host of CNBC's "Mad Money," can significantly sway market sentiments and investor behavior. Cramer, known for his incisive and sometimes controversial market insights, has recently turned his attention to Bitcoin, the leading cryptocurrency. His latest comments suggest a bearish outlook on Bitcoin, which has sparked intense discussions and speculations within the crypto community. This development is particularly noteworthy given Cramer's influence and the weight his opinions often carry in financial circles. His views on Bitcoin are not just idle chatter; they have the potential to shape market trends and influence investment strategies.
Table of Contents
-
Cramer's Changing Stance on Bitcoin
-
Historical Perspective
-
The "Reverse Cramer Effect"
-
-
Market Reactions and Speculations
-
Analyzing Past Trends
-
The Role of Bitcoin ETFs
-
-
Implications for Investors
-
Navigating Market Sentiments
-
The Future of Bitcoin
-
-
Conclusion
-
FAQs
Cramer's Changing Stance on Bitcoin
Historical Perspective
Jim Cramer's relationship with Bitcoin has been a rollercoaster of changing opinions and stances. Initially skeptical, Cramer warmed up to Bitcoin, acknowledging its potential as an investment asset. However, his recent bearish comments mark a significant shift from his earlier views. This change is intriguing, as it comes at a time when Bitcoin has been showing signs of recovery and gaining mainstream acceptance. Cramer's influence in the financial world means that his opinions are closely monitored and can lead to tangible market reactions. His latest stance, suggesting that Bitcoin is "topping out," has therefore raised eyebrows and led to debates about the future direction of the cryptocurrency.
The "Reverse Cramer Effect"
The phenomenon known as the "reverse Cramer effect" has become a topic of interest among investors and market analysts. This effect, where the market tends to move in the opposite direction of Cramer's advice, has been observed on multiple occasions. For example, after Cramer advised investors to sell Bitcoin in April 2023, the cryptocurrency's price surged, defying his predictions. This pattern has led some investors to view Cramer's predictions as a contrarian indicator. The consistency of this effect raises questions about market psychology and the influence of prominent financial figures on investor behavior. It also underscores the complexity and unpredictability of the cryptocurrency market, where sentiment can often drive price movements more than fundamentals.
Market Reactions and Speculations
Analyzing Past Trends
The market's reaction to Cramer's comments is not just a matter of idle speculation; it has real implications for investors and traders. The "reverse Cramer effect" has been noted not just in the case of Bitcoin but also in other financial markets. This phenomenon suggests a deeper, perhaps psychological, aspect of market behavior where investors might be inclined to react contrarily to prominent predictions. The recent bearish stance by Cramer on Bitcoin thus becomes a focal point for market watchers. If history is any guide, this could very well be an inadvertent signal for a bullish phase for Bitcoin.
The Role of Bitcoin ETFs
The potential approval of Bitcoin ETFs by the SEC is a significant development in the cryptocurrency world. These ETFs would provide a more accessible and regulated avenue for investing in Bitcoin, potentially attracting a new class of investors. The approval of these ETFs could be a game-changer for Bitcoin's price, as it would represent a major step towards mainstream acceptance and institutional investment. The timing of Cramer's comments in the context of these developments adds an interesting dimension to market speculations. If the SEC does approve Bitcoin ETFs, and the "reverse Cramer effect" holds true, we could witness a substantial bull run in Bitcoin's price.
Implications for Investors
Navigating Market Sentiments
For investors, the "reverse Cramer effect" and the potential approval of Bitcoin ETFs present a complex scenario. While it's tempting to base investment decisions on the predictions of market experts, the unpredictable nature of cryptocurrencies requires a more nuanced approach. Investors need to consider a range of factors, including market trends, technological developments, regulatory changes, and broader economic indicators. The case of Jim Cramer's shifting stance on Bitcoin highlights the importance of not relying solely on expert opinions but also conducting independent research and analysis.
The Future of Bitcoin
The future of Bitcoin, as suggested by the recent developments and Cramer's comments, appears to be at a potential turning point. While the possibility of a bull market looms, it's important to remember the inherent volatility and risks associated with cryptocurrencies. The market's response to Cramer's comments, coupled with the potential regulatory advancements like Bitcoin ETFs, could indeed set the stage for significant price movements. However, investors should remain cautious and diversified in their approach, keeping in mind that the cryptocurrency market is still maturing and subject to rapid changes.
Conclusion
Jim Cramer's recent bearish comments on Bitcoin have stirred up a wave of discussions and speculations about the future of this leading cryptocurrency. While his track record suggests the possibility of an upcoming bull market, the volatile and unpredictable nature of the crypto world warrants a cautious approach. Investors should weigh Cramer's opinions alongside other market indicators and conduct thorough research before making investment decisions. As the cryptocurrency landscape continues to evolve, staying informed, adaptable, and prudent remains crucial for navigating the market's ebbs and flows.
FAQs
Who is Jim Cramer? Jim Cramer is a well-known financial expert and the host of CNBC's "Mad Money." He is recognized for his bold market predictions and has a significant influence in the financial world.
What is the "Reverse Cramer Effect"? The "Reverse Cramer Effect" refers to a phenomenon where the market tends to move in the opposite direction of Jim Cramer's predictions. This has been observed particularly in the cryptocurrency market with Bitcoin.
Why are Jim Cramer's comments on Bitcoin important? Cramer's comments are closely followed by investors and can influence market trends. His recent bearish stance on Bitcoin has sparked discussions and speculations about a potential bull market due to the "Reverse Cramer Effect."
What impact could Bitcoin ETFs have on the market? The approval of Bitcoin ETFs (Exchange Traded Funds) by the SEC could significantly boost Bitcoin's price by providing a regulated and accessible investment avenue, potentially attracting more mainstream and institutional investors.
Should investors base their decisions solely on Jim Cramer's predictions? While Cramer's opinions are influential, investors are advised to conduct their own research and consider a range of factors before making investment decisions, due to the unpredictable nature of the cryptocurrency market.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ d360efec:14907b5f
2025-02-28 13:26:03
@ d360efec:14907b5f
2025-02-28 13:26:03ภาพรวมการวิเคราะห์ Bitcoin (BTC)
จากการตรวจสอบกราฟและอินดิเคเตอร์ใน Timeframe 15 นาที, 4 ชั่วโมง, และรายวัน (Day) พบว่า Bitcoin มีความผันผวนและมีแนวโน้มการเปลี่ยนแปลงที่น่าสนใจในแต่ละ Timeframe ดังรายละเอียดต่อไปนี้ค่ะ
อินดิเคเตอร์ที่ใช้ในการวิเคราะห์
- EMA (Exponential Moving Average):
- EMA 50 (สีเหลือง): แสดงแนวโน้มระยะสั้นของราคา
- EMA 200 (สีขาว): แสดงแนวโน้มระยะยาวของราคา
- SMC (Smart Money Concepts): แนวคิดการเทรดที่เน้นการวิเคราะห์พฤติกรรมของ "Smart Money" หรือผู้เล่นรายใหญ่ในตลาด
- ICT (Inner Circle Trader) Buyside & Sellside Liquidity: อินดิเคเตอร์ที่ระบุตำแหน่งสภาพคล่องฝั่งซื้อและฝั่งขาย ซึ่งเป็นเป้าหมายราคาที่น่าสนใจ
- Money Flow: อินดิเคเตอร์ที่แสดงทิศทางการไหลเข้าออกของเงินทุนในสินทรัพย์
- Trend Strength (🌟Introducing the Trend and Strength Signals indicator by AlgoAlpha!): อินดิเคเตอร์ที่ช่วยระบุแนวโน้มและความแข็งแกร่งของตลาด มีลักษณะเป็นเมฆและสัญญาณซื้อขาย
วิเคราะห์แนวโน้มและกลยุทธ์การเทรด
1. Timeframe 15 นาที (TF 15m)
- แนวโน้ม: ใน TF 15 นาที ราคา BTC มีความผันผวนในกรอบแคบ EMA 50 ตัดกับ EMA 200 บ่งบอกถึงความไม่แน่นอนของแนวโน้มในระยะสั้น
- สัญญาณอินดิเคเตอร์:
- Trend Strength: เกิดสัญญาณซื้อขาย (Buy/Sell Signal) แต่เมฆ (Cloud) ยังไม่ชัดเจน บ่งบอกถึงความแข็งแกร่งของแนวโน้มยังไม่เด่นชัด
- Money Flow: มีการสลับการไหลเข้าออกของเงินทุน สะท้อนถึงความไม่แน่นอนในระยะสั้น
- Buyside & Sellside Liquidity: อินดิเคเตอร์นี้จะช่วยระบุแนวรับแนวต้านใน TF สั้นๆ เพื่อใช้ในการพิจารณาจุดเข้าออก
- Chart Pattern: พิจารณารูปแบบ Chart Pattern ใน TF 15 นาที เช่น รูปแบบสามเหลี่ยม (Triangle) หรือรูปแบบธง (Flag) เพื่อหารูปแบบราคาที่อาจเกิดขึ้น
- กลยุทธ์ Day Trade (การเทรดรายวัน):
- กลยุทธ์: เน้นการเทรดในกรอบ Sideway โดยใช้แนวรับแนวต้านที่ระบุจาก Buyside & Sellside Liquidity และสัญญาณจาก Trend Strength ประกอบการตัดสินใจ
- SMC Setup: มองหา SMC Setup ใน TF 15 นาที เช่น Order Block หรือ Fair Value Gap บริเวณแนวรับแนวต้าน เพื่อหาจังหวะเข้าเทรดตามแนวโน้มระยะสั้น
- สิ่งที่ต้องระวัง: ความผันผวนสูงใน TF 15 นาที อาจทำให้เกิดสัญญาณหลอก ควรใช้ Stop Loss ที่เหมาะสม และบริหารความเสี่ยงอย่างเคร่งครัด
2. Timeframe 4 ชั่วโมง (TF 4H)
- แนวโน้ม: ใน TF 4 ชั่วโมง ราคา BTC มีแนวโน้มเป็นขาขึ้น EMA 50 อยู่เหนือ EMA 200 บ่งบอกถึงแนวโน้มขาขึ้นในระยะกลาง
- สัญญาณอินดิเคเตอร์:
- Trend Strength: เกิดเมฆสีเขียว (Green Cloud) และสัญญาณซื้อ (Buy Signal) บ่งบอกถึงแนวโน้มขาขึ้นที่แข็งแกร่ง
- Money Flow: เงินทุนไหลเข้าต่อเนื่อง สนับสนุนแนวโน้มขาขึ้น
- Buyside & Sellside Liquidity: อินดิเคเตอร์นี้จะช่วยระบุแนวรับแนวต้านที่สำคัญใน TF 4 ชั่วโมง เพื่อใช้ในการวางแผนการเทรดระยะกลาง
- Chart Pattern: พิจารณารูปแบบ Chart Pattern ใน TF 4 ชั่วโมง เช่น รูปแบบ Cup and Handle หรือรูปแบบ Ascending Triangle เพื่อยืนยันแนวโน้มขาขึ้น
- กลยุทธ์ Day Trade (การเทรดรายวัน) / Swing Trade (การเทรดระยะกลาง):
- กลยุทธ์: เน้นการเทรดตามแนวโน้มขาขึ้น โดยใช้ EMA 50 และแนวรับแนวต้านจาก Buyside & Sellside Liquidity เป็นจุดอ้างอิงในการเข้าเทรด
- SMC Setup: มองหา SMC Setup ใน TF 4 ชั่วโมง เช่น Break of Structure (BOS) หรือ Change of Character (CHOCH) เพื่อหาจังหวะเข้าเทรดตามแนวโน้มขาขึ้น
- สิ่งที่ต้องระวัง: การพักตัวของราคาในแนวโน้มขาขึ้น อาจทำให้เกิดการย่อตัวระยะสั้น ควรพิจารณาแนวรับที่แข็งแกร่ง และตั้ง Stop Loss เพื่อป้องกันความเสี่ยง
3. Timeframe รายวัน (TF Day)
- แนวโน้ม: ใน TF รายวัน ราคา BTC ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว EMA 50 อยู่เหนือ EMA 200 อย่างชัดเจน
- สัญญาณอินดิเคเตอร์:
- Trend Strength: เกิดเมฆสีเขียวขนาดใหญ่ (Large Green Cloud) และสัญญาณซื้อต่อเนื่อง (Continuous Buy Signal) บ่งบอกถึงแนวโน้มขาขึ้นระยะยาวที่แข็งแกร่งมาก
- Money Flow: เงินทุนไหลเข้าอย่างต่อเนื่องและแข็งแกร่ง สนับสนุนแนวโน้มขาขึ้นระยะยาว
- Buyside & Sellside Liquidity: อินดิเคเตอร์นี้จะช่วยระบุแนวรับแนวต้านที่สำคัญใน TF รายวัน เพื่อใช้ในการวางแผนการลงทุนระยะยาว
- Chart Pattern: พิจารณารูปแบบ Chart Pattern ใน TF รายวัน เช่น รูปแบบ Bullish Flag หรือรูปแบบ Wedge เพื่อยืนยันแนวโน้มขาขึ้นระยะยาว
- กลยุทธ์ Day Trade (การเทรดรายวัน) / Swing Trade (การเทรดระยะกลาง) / Long-Term Investment (การลงทุนระยะยาว):
- กลยุทธ์: เน้นการลงทุนระยะยาวตามแนวโน้มขาขึ้น โดยพิจารณาจังหวะเข้าซื้อเมื่อราคาย่อตัวลงมาบริเวณแนวรับสำคัญใน TF รายวัน
- SMC Setup: มองหา SMC Setup ใน TF รายวัน เช่น Institutional Order Flow เพื่อยืนยันแนวโน้มขาขึ้นระยะยาว
- สิ่งที่ต้องระวัง: ความเสี่ยงจากปัจจัยภายนอกที่อาจกระทบตลาด Cryptocurrency ในระยะยาว ควรติดตามข่าวสารและสถานการณ์ตลาดอย่างใกล้ชิด และกระจายความเสี่ยงในการลงทุน
สรุป
จากการวิเคราะห์ BTC ใน 3 Timeframe ด้วยอินดิเคเตอร์และ Chart Pattern พบว่า BTC ยังคงมีแนวโน้มขาขึ้นในระยะกลางและระยะยาว อย่างไรก็ตาม ในระยะสั้น TF 15 นาที ยังมีความผันผวนและไม่แน่นอน กลยุทธ์การเทรดที่เหมาะสมจะแตกต่างกันไปตาม Timeframe และเป้าหมายการเทรดของแต่ละบุคคล ควรพิจารณาความเสี่ยงและบริหารจัดการเงินทุนอย่างเหมาะสม
คำแนะนำเพิ่มเติม
- ศึกษาเพิ่มเติม: ควรศึกษาเพิ่มเติมเกี่ยวกับ SMC, ICT, และ Trend Strength Indicator เพื่อให้เข้าใจหลักการทำงานและนำไปประยุกต์ใช้ในการเทรดได้อย่างมีประสิทธิภาพ
- ทดลองบนบัญชี Demo: ทดลองกลยุทธ์ต่างๆ บนบัญชี Demo ก่อนนำไปใช้จริง เพื่อทดสอบความเข้าใจและปรับปรุงกลยุทธ์ให้เหมาะสมกับตนเอง
- ติดตามข่าวสาร: ติดตามข่าวสารและสถานการณ์ตลาด Cryptocurrency อย่างสม่ำเสมอ เพื่อประกอบการตัดสินใจในการเทรดและการลงทุน
Disclaimer (ข้อจำกัดความรับผิดชอบ):
การวิเคราะห์นี้มีวัตถุประสงค์เพื่อให้ข้อมูลเท่านั้น และเป็นความคิดเห็นส่วนบุคคล ไม่ใช่คำแนะนำทางการเงิน การลงทุนใน Cryptocurrency มีความเสี่ยงสูง นักลงทุนควรศึกษาข้อมูลด้วยตนเองและใช้ความระมัดระวังก่อนตัดสินใจลงทุน
- EMA (Exponential Moving Average):