-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 65886e63:118f7ab8
2025-03-19 13:35:37
@ 65886e63:118f7ab8
2025-03-19 13:35:37"When software developers aim at the cognitive aspects of education without understanding the social aspects, they miss the dartboard entirely." https://open.substack.com/pub/danmeyer/p/do-kids-want-a-personalized-netflix?utm_source=share&utm_medium=android&r=b4wcg
-
 @ 7776c32d:45558888
2025-03-19 13:16:46
@ 7776c32d:45558888
2025-03-19 13:16:46March 18, 55 years after UNIX epoch
My name is Mahmoud Khalil and I am a political prisoner. I am writing to you from a detention facility in Louisiana where I wake to cold mornings and spend long days bearing witness to the quiet injustices underway against a great many people precluded from the protections of the law.
Who has the right to have rights? It is certainly not the humans crowded into the cells here. It isn't the Senegalese man I met who has been deprived of his liberty for a year, his legal situation in limbo and his family an ocean away. It isn't the 21-year-old detainee I met, who stepped foot in this country at age nine, only to be deported without so much as a hearing.
Justice escapes the contours of this nation's immigration facilities.
On March 8, I was taken by DHS agents who refused to provide a warrant, and accosted my wife and me as we returned from dinner. By now, the footage of that night has been made public. Before I knew what was happening, agents handcuffed and forced me into an unmarked car. At that moment, my only concern was for Noor's safety. I had no idea if she would be taken too, since the agents had threatened to arrest her for not leaving my side. DHS would not tell me anything for hours - I did not know the cause of my arrest or if I was facing immediate deportation. At 26 Federal Plaza, I slept on the cold floor. In the early morning hours, agents transported me to another facility in Elizabeth, New Jersey. There, I slept on the ground and was refused a blanket despite my request.
My arrest was a direct consequence of exercising my right to free speech as I advocated for a free Palestine and an end to the genocide in Gaza, which resumed in full force Monday night. With January's ceasefire now broken, parents in Gaza are once again cradling too-small shrouds, and families are forced to weigh starvation and displacement against bombs. It is our moral imperative to persist in the struggle for their complete freedom.
I was born in a Palestinian refugee camp in Syria to a family which has been displaced from their land since the 1948 Nakba. I spent my youth in proximity to yet distant from my homeland. But being Palestinian is an experience that transcends borders. I see in my circumstances similarities to Israel's use of administrative detention imprisonment without trial or charge to strip Palestinians of their rights. I think of our friend Omar Khatib, who was incarcerated without charge or trial by Israel as he returned home from travel. I think of Gaza hospital director and pediatrician Dr. Hussam Abu Safiya, who was taken captive by the Israeli military on December 27 and remains in an Israeli torture camp today. For Palestinians, imprisonment without due process is commonplace.
I have always believed that my duty is not only to liberate myself from the oppressor, but also to liberate my oppressors from their hatred and fear. My unjust detention is indicative of the anti-Palestinian racism that both the Biden and Trump administrations have demonstrated over the past 16 months as the U.S. has continued to supply Israel with weapons to kill Palestinians and prevented international intervention. For decades, anti-Palestinian racism has driven efforts to expand U.S. laws and practices that are used to violently repress Palestinians, Arab Americans, and other communities. That is precisely why I am being targeted.
While I await legal decisions that hold the futures of my wife and child in the balance, those who enabled my targeting remain comfortably at Columbia University. Presidents Shafik, Armstrong, and Dean Yarhi-Milo laid the groundwork for the U.S. government to target me by arbitrarily disciplining pro-Palestinian students and allowing viral doxing campaigns - based on racism and disinformation - to go unchecked.
Columbia targeted me for my activism, creating a new authoritarian disciplinary office to bypass due process and silence students criticizing Israel. Columbia surrendered to federal pressure by disclosing student records to Congress and yielding to the Trump administration's latest threats. My arrest, the expulsion or suspension of at least 22 Columbia students some stripped of their B.A. degrees just weeks before graduation and the expulsion of SWC President Grant Miner on the eve of contract negotiations, are clear examples.
If anything, my detention is a testament to the strength of the student movement in shifting public opinion toward Palestinian liberation. Students have long been at the forefront of change leading the charge against the Vietnam War, standing on the frontlines of the civil rights movement, and driving the struggle against apartheid in South Africa. Today, too, even if the public has yet to fully grasp it, it is students who steer us toward truth and justice.
The Trump administration is targeting me as part of a broader strategy to suppress dissent. Visa-holders, green-card carriers, and citizens alike will all be targeted for their political beliefs. In the weeks ahead, students, advocates, and elected officials must unite to defend the right to protest for Palestine. At stake are not just our voices, but the fundamental civil liberties of all.
Knowing fully that this moment transcends my individual circumstances, I hope nonetheless to be free to witness the birth of my first-born child.
-
 @ b1b16be0:08f41c1d
2025-03-18 20:50:45
@ b1b16be0:08f41c1d
2025-03-18 20:50:45am@primal.net My first Zap! jskitty@jskitty.cat Thanks for support! 🐱Miau! blockstream@blockstream.com So honor to me! SymplyNostr@primal.net You make my day! bitpopart@nostrcheck.me best art in Nostr! PringleMac@primal.net
-
 @ b1b16be0:08f41c1d
2025-03-18 14:37:52
@ b1b16be0:08f41c1d
2025-03-18 14:37:52Norte
Sur Te ayuda avanzar! Y a tomar conciencia! 🔥Fuego 🌎Tierra 🔴Marte 🎵Mantra: Om Namo Bhagavate Narasimhaya Namaha
Sur Este Influye en transacciones prósperas y transiciones suaves 🔥Fuego 🔘Venus 🎵Mantra: https://youtu.be/45a4KwLTTHo?feature=shared
-
 @ 88dc84f5:c71164f7
2025-03-18 10:16:55
@ 88dc84f5:c71164f7
2025-03-18 10:16:55Quantum computing is a revolutionary technology that has the potential to solve complex problems that are currently unsolvable with traditional computers. In this beginner's guide, we'll explore the basics of quantum computing, its principles, and potential applications.
What is Quantum Computing?

Quantum computing is a type of computing that uses the principles of quantum mechanics to perform calculations. Unlike classical computers, which use bits to store and process information, quantum computers use quantum bits or qubits.
Qubits: The Building Blocks of Quantum Computing
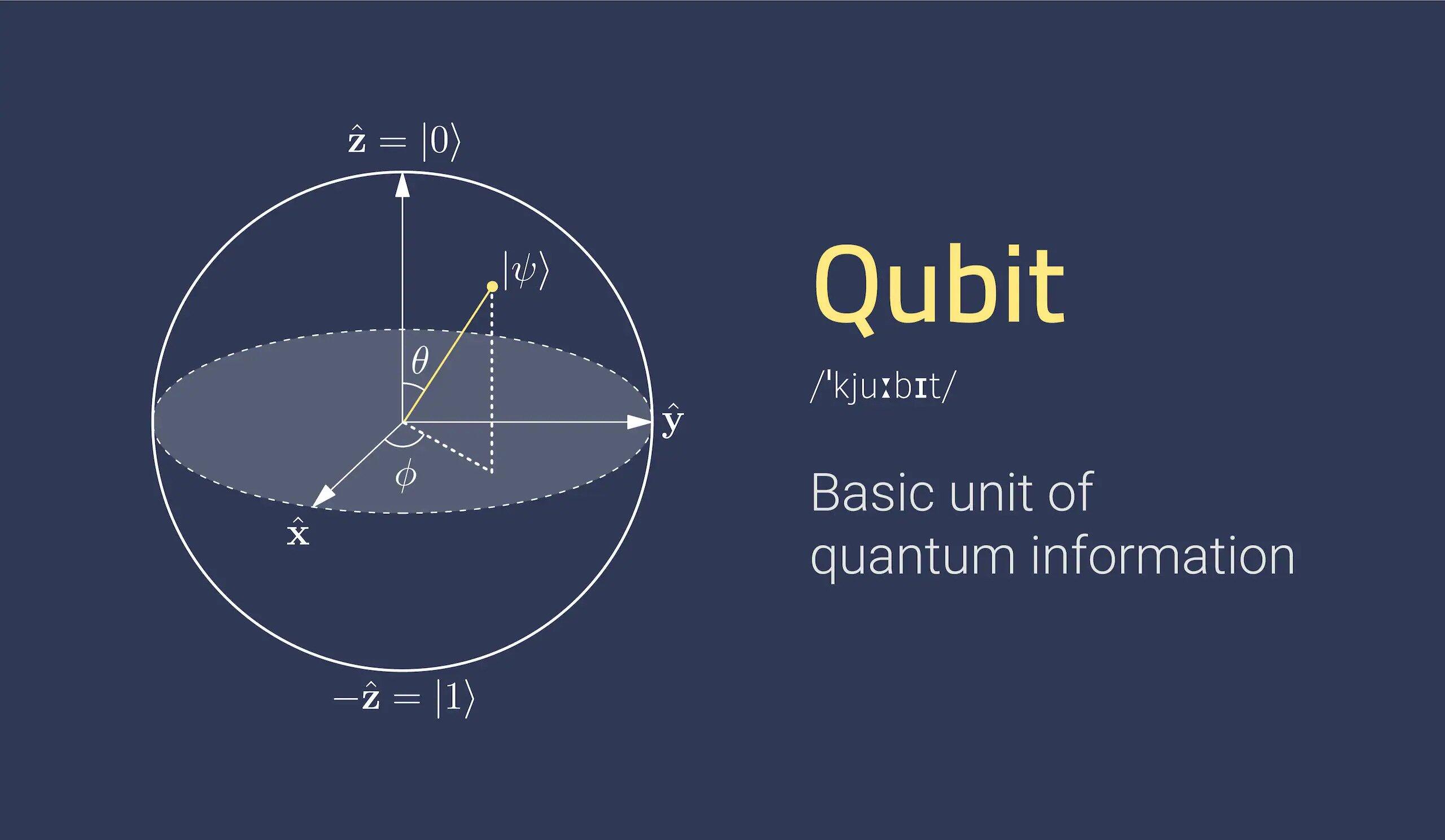
Qubits are the fundamental units of quantum information. They have the unique ability to exist in multiple states simultaneously, which allows quantum computers to process multiple possibilities at the same time.
How Does Quantum Computing Work?
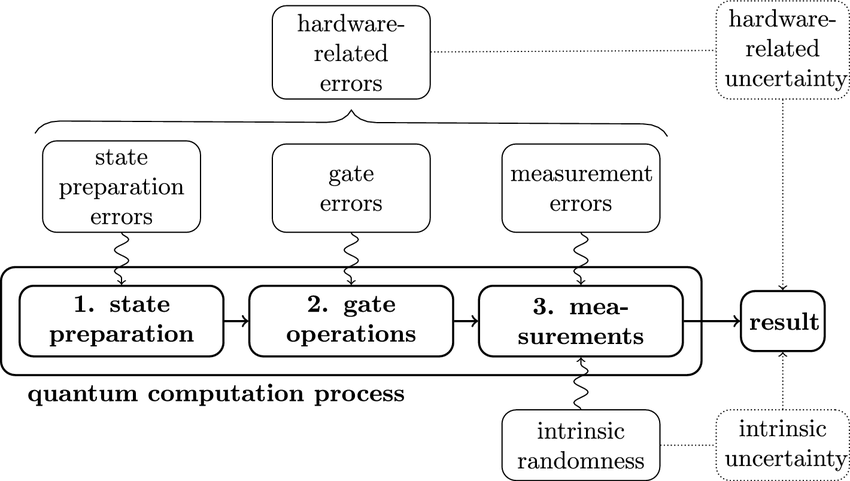
Quantum computing works by exploiting the unique properties of qubits. Here's a simplified overview of the process:
- Preparation: Qubits are prepared in a specific state.
- Quantum gates: Quantum gates are applied to the qubits to perform operations.
- Measurement: The qubits are measured to retrieve the results.
Key Principles of Quantum Computing:
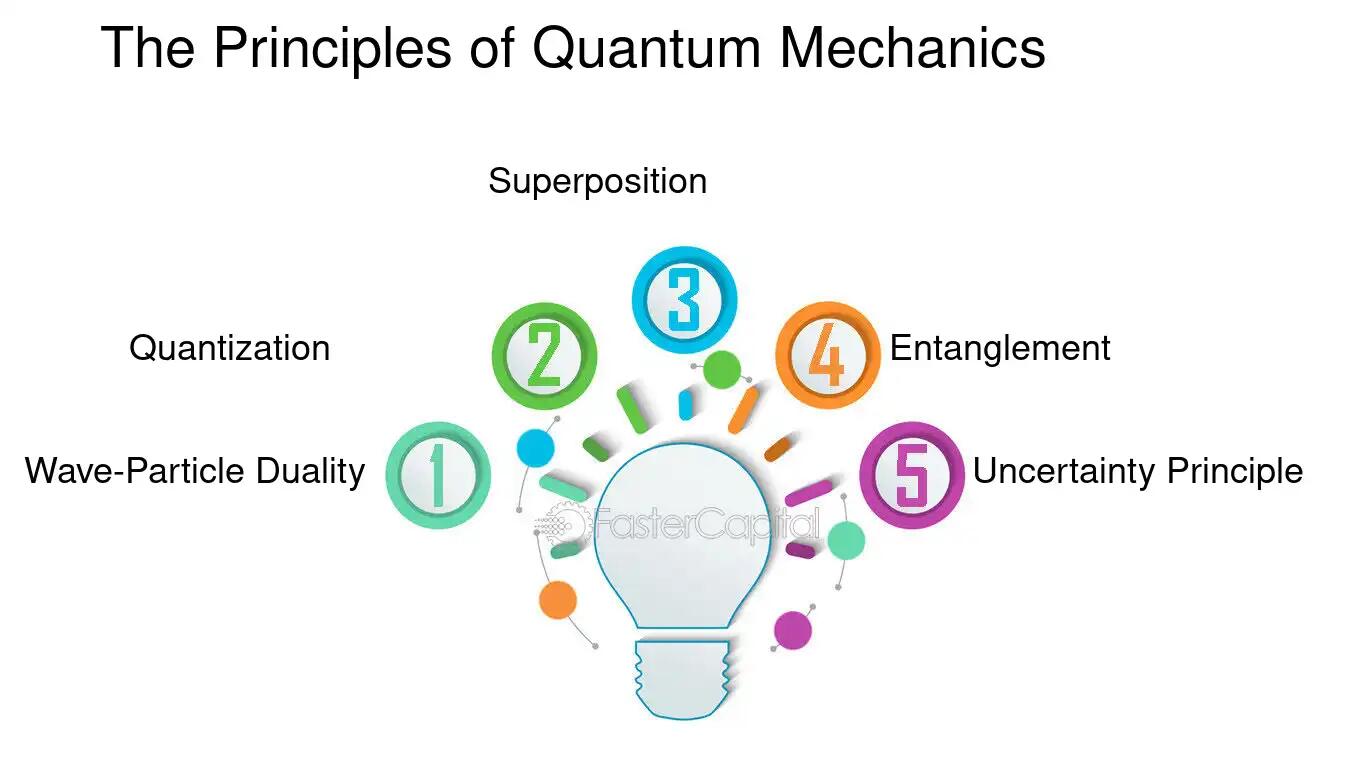
- Superposition: Qubits can exist in multiple states simultaneously.
- Entanglement: Qubits can become "entangled," meaning their properties are connected even when separated.
- Quantum measurement: Qubits can be measured, which causes them to collapse into a single state.
Potential Applications of Quantum Computing:
- Cryptography: Quantum computers can break certain types of encryption, but they can also be used to create unbreakable encryption methods.
- Optimization: Quantum computers can be used to optimize complex systems, such as logistics and supply chains.
- Materials science: Quantum computers can be used to simulate the behavior of materials at the atomic level.
- Artificial intelligence: Quantum computers can be used to speed up certain types of machine learning algorithms.
Real-World Examples of Quantum Computing: 1. Google's Quantum AI Lab: Google has developed a quantum computer that can be used to optimize machine learning algorithms. 2. IBM's Quantum Experience: IBM has developed a cloud-based quantum computer that can be used by researchers and developers. 3. Quantum-inspired optimization: Companies like Volkswagen and Lockheed Martin are using quantum-inspired optimization techniques to improve their operations.
Challenges and Limitations of Quantum Computing: 1. Error correction: Quantum computers are prone to errors due to the fragile nature of qubits. 2. Scalability: Currently, quantum computers are small-scale and need to be scaled up to be practical. 3. Quantum noise: Quantum computers are susceptible to noise, which can cause errors.
Conclusion:

Quantum computing has the potential to revolutionize many fields, from cryptography to materials science. While there are challenges and limitations to overcome, the potential benefits of quantum computing make it an exciting and rapidly evolving field.
Glossary of Terms: - Qubit: A quantum bit, the fundamental unit of quantum information. - Superposition: The ability of a qubit to exist in multiple states simultaneously. - Entanglement: The connection between two or more qubits that allows them to affect each other even when separated. - Quantum measurement: The process of measuring a qubit, which causes it to collapse into a single state.
I hope this beginner's guide has provided a helpful introduction to the world of quantum computing! @Yakihonne
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 044da344:073a8a0e
2025-03-13 07:20:56
@ 044da344:073a8a0e
2025-03-13 07:20:56Kultur. Kunst. Ästhetik. Ich lasse die Ausrufezeichen weg, die mir da entgegenkamen aus dem Publikum in der Ladestation in Köln. Eigentlich sollte es um den „dressierten Nachwuchs“ gehen, am Ende waren wir aber doch wieder bei den Leitmedien und damit auch bei der Gegenöffentlichkeit. Herr Meyen, Sie können doch nicht ernsthaft den Kontrafunk loben. Diese Opernsängerin. Und überhaupt. Ich, sagte der Mann, den ich im Scheinwerferlicht nicht sehen und folglich auch nicht taxieren konnte, ich höre lieber den Deutschlandfunk, trotz der Nachrichten. Das hat Klasse. Das hat Qualität. Geschichte, Tiefe. Wo bitte schön ist das bei Ihren Lieblingen, Herr Meyen?
Ich habe Jenifer Lary verteidigt (die das in ihrer „Musikstunde“ wirklich gut macht, aber das nur nebenbei) und auf die Ressourcen hingewiesen. Hier ein milliardenschwerer Rundfunk, finanziert mit dem Gewaltmonopol des Staates im Rücken, und dort ein paar Mittelständler, die es sich leisten können und wollen, für Kontrafunk-Aktien 25.000 Franken in den Wind zu schreiben, und Kleinspender, die so dankbar sind für das, was Burkhard Müller-Ullrich da auf die Beine stellt, dass sie sich zehn oder 20 Euro abzwacken. Vergeblich. Auch am nächsten Tag im Philosophischen Salon, einer Privatinitiative von Sabine Marx in der gleichen Stadt, wo nach meinem Vortrag allen Ernstes vorgeschlagen wurde, doch einfach Geld zusammenzutragen, damit „die Besten“ zu ködern und so eine Gegenkultur auf die Beine zu stellen, die mindestens genauso gut ist wie das, was zum Beispiel der Deutschlandfunk bietet.
Wenn es nur so einfach wäre. Man muss nicht Pierre Bourdieu gelesen zu haben, um die Magnetwirkung zu sehen, die vom Machtpol der Felder ausgeht – in der Literatur, in der Musik, im Journalismus, in der Wissenschaft. Sicherheit, Geld, manchmal sogar Ruhm. Überhaupt: dazugehören. Mit in der Verlosung zu sein, wenn die großen Bühnen vergeben werden, Preise oder wenigstens Stipendien. Rezensiert werden – und zwar dort, wo die Agenturen hinschauen, die Bibliotheken, die Sponsoren. Ein junger Mensch, der sich bewusst gegen all das entscheidet, habe ich in Köln sinngemäß gesagt, solch ein junger Mensch ist die absolute Ausnahme. Die Folgen spürt jeder, der Personal rekrutieren möchte für Alternativprojekte. Die Folgen spürt auch das Publikum. Wo Konkurrenz und Reibung fehlen, ist es nicht weit bis zur Genügsamkeit, frei nach dem Motto: Meine Follower lieben mich, was also wollt ihr noch von mir?
Ich schicke all das vorweg, um Eugen Zentner würdigen zu können – einen gerade noch jungen Mann, geboren 1979, der alles mitbringt, was es für eine Karriere in der Bewusstseinsindustrie braucht, und der sich nach Versuchen bei der dpa trotzdem gegen die Verlockungen entschieden hat, die das Mitschwimmen abwirft. Ich habe hier schon sein Buch über die neue Kunst- und Kulturszene gewürdigt und freue mich, dass er sich jetzt als Erzähler versucht – mit Kurzgeschichten über Corona-Schicksale, wieder erschienen im Massel-Verlag. Die Form erlaubt ihm, das zuzuspitzen und zu verdichten, was viele zwischen Mitte März 2020 und dem 7. April 2022 erlebt und erlitten haben – angefangen mit Kollegen und Freunden, die erst oft noch ganz aufgeschlossen auf Videos von Wodarg und Co. reagierten, dann aber den Kontakt abbrachen, als sie sahen, was „man“ von diesen Leuten zu halten hat, bis hin zu purem Hass, als die „Pandemie der Ungeimpften“ ausgerufen wurde und so jeder ermutigt wurde, die „Verweigerer“ in den Dreck zu treten.
Die 15 Geschichten von Eugen Zentner sind düster. Vielleicht muss das so sein, weil die Zeit so war und irgendjemand das festhalten muss, auch jenseits von Sachbuch und Journalismus. Das Schulkind, dem unter der Maske die Luft wegbleibt. Die drei Freunde, die sich trotz Lockdown treffen und in der Wohnung von Uniformierten überfallen werden. Die Polizeiopfer auf den Demos. Der Bruder, der Heiligabend bei Mama platzen lässt, weil die Schwester nicht am Katzentisch sitzen mag. Die Oma, die im Pflegeheim eingesperrt wird und den Verstand verliert, weil sie Tochter und Enkel nicht sehen kann und nicht versteht, warum das alles passiert. Die Figuren kommen eher als Holzschnitt daher, schwarz-weiß. Es gibt zwei „Täter“, wenn man so will, einen Journalisten und eine Krankenschwester, die einen Kampf mit ihrem Gewissen austragen und, wie sollte es anders sein, diesen Kampf bei Eugen Zentner verlieren. Es gibt auch einen Abgeordneten aus einer Regierungspartei, der am 18. November 2020 gegen das Infektionsschutzgesetz stimmen will und sich sicher ist, dass er nicht erpresst werden kann. Wir wissen, wie das in der Wirklichkeit ausgegangen ist.
Die Fiktion, gerade in einer Kurzgeschichte, hat den Vorteil, alles wegwischen zu können, was das reale Leben ausmacht. Die Grautöne vor allem, die aus den Erfahrungen sprießen, die der Einzelne gemacht hat. Der Journalismus darf das (eigentlich) nicht und das Sachbuch sowieso nicht. Eigentlich müsste ich das „eigentlich“ wieder streichen und auch für die Kurzgeschichte den Maßstab nachjustieren – für ein Genre, das vom Autor noch mehr verlangt als ein Roman, weil wenig Platz ist und der Leser trotzdem erwartet, dass buchstäblich „alles“ gesagt wird. Eugen Zentner ist auf dem Weg dahin – in der zweiten Auflage vielleicht sogar mit einem Adlerauge für die Korrektur und beim nächsten Versuch mit noch mehr Ruhe und Geduld, um auch das einfangen zu können, was sich dem Zeitzeugen und Beobachter entzieht. Vielleicht muss man seine beiden Bücher einfach nebeneinanderlegen, um zu Hölderlin zu kommen: „Wo aber Gefahr ist, wächst das Rettende auch.“
Kunst, Kultur, Ästhetik: Der Rufer aus Köln hat Recht. Die Gegenöffentlichkeit braucht mehr davon, wenn sie etwas bewegen will. Die Anfänge sind gemacht. Ein paar davon haben wir am Buch-Tresen aufgegriffen: Sonja Silberhorn und Bernd Zeller, Sebastian Schwaerzel und nicht zu vergessen: Thomas Eisinger. Gerade lese ich, dass Raymond Unger einen Roman geschrieben hat. Geht doch, sogar ohne irgendwelche Multimilliardäre.

Freie Akademie für Medien & Journalismus
Titelbild: Alexa @Pixabay
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 0c469779:4b21d8b0
2025-03-11 10:52:49
@ 0c469779:4b21d8b0
2025-03-11 10:52:49Sobre el amor
Mi percepción del amor cambió con el tiempo. Leer literatura rusa, principalmente a Dostoevsky, te cambia la perspectiva sobre el amor y la vida en general.
Por mucho tiempo mi visión sobre la vida es que la misma se basa en el sufrimiento: también la Biblia dice esto. El amor es igual, en el amor se sufre y se banca a la otra persona. El problema es que hay una distinción de sufrimientos que por mucho tiempo no tuve en cuenta. Está el sufrimiento del sacrificio y el sufrimiento masoquista. Para mí eran indistintos.
Para mí el ideal era Aliosha y Natasha de Humillados y Ofendidos: estar con alguien que me amase tanto como Natasha a Aliosha, un amor inclusive autodestructivo para Natasha, pero real. Tiene algo de épico, inalcanzable. Un sufrimiento extremo, redentor, es una vara altísima que en la vida cotidiana no se manifiesta. O el amor de Sonia a Raskolnikov, quien se fue hasta Siberia mientras estuvo en prisión para que no se quede solo en Crimen y Castigo.
Este es el tipo de amor que yo esperaba. Y como no me pasó nada tan extremo y las situaciones que llegan a ocurrir en mi vida están lejos de ser tan extremas, me parecía hasta poco lo que estaba pidiendo y que nadie pueda quedarse conmigo me parecía insuficiente.
Ahora pienso que el amor no tiene por qué ser así. Es un pensamiento nuevo que todavía estoy construyendo, y me di cuenta cuando fui a la iglesia, a pesar de que no soy cristiano. La filosofía cristiana me gusta. Va conmigo. Tiene un enfoque de humildad, superación y comunidad que me recuerda al estoicismo.
El amor se trata de resaltar lo mejor que hay en el otro. Se trata de ser un plus, de ayudar. Por eso si uno no está en su mejor etapa, si no se está cómodo con uno mismo, no se puede amar de verdad. El amor empieza en uno mismo.
Los libros son un espejo, no necesariamente vas a aprender de ellos, sino que te muestran quién sos. Resaltás lo que te importa. Por eso a pesar de saber los tipos de amores que hay en los trabajos de Dostoevsky, cometí los mismos errores varias veces.
Ser mejor depende de uno mismo y cada día se pone el granito de arena.
-
 @ 044da344:073a8a0e
2025-03-19 13:03:30
@ 044da344:073a8a0e
2025-03-19 13:03:30Journalismus nach Corona
Medienrealität, 17. April 2020, und Rubikon ("Das Ende einer Ära"), 17. April 2020
Diese Krise, da ist sich Heribert Prantl sicher, „bringt einen auf verrückte Gedanken“ – auf Dinge, „die man vorher nie gedacht hat und die man auch nie denken wollte“. So verrückt ist das gar nicht, was Prantl da zu Ostern geschrieben hat. In Kurzform: Kliniken sind kein Geschäftsmodell. Sonst zahlen am Ende die Kranken. Und: Das Gesundheitswesen ist wie die Wasserversorgung. Wir brauchen beides und dürfen deshalb weder das eine noch das andere „durchkommerzialisieren“ (Prantl 2020). Womit wir bei den Medien wären. Vielleicht hält das ja sogar Heribert Prantl für verrückt: ein Journalismus, der der Gesellschaft dient und nicht dem Staat oder dem Kapital.
Für die Medienforschung heißt das: zurück zu ihren Wurzeln. Karl Bücher, der Gründervater der akademischen Journalistenausbildung in Deutschland, war sich am Ende eines langen Lebens sicher, dass die Presse „ein öffentliches Institut“ sein muss, genau „wie Straßenbahnen, Gasanstalten, Elektrizitätswerke“ (Bücher 1926: 424). Dieser Bücher, ein weltberühmter Ökonom, hat das so ähnlich gesehen wie Heribert Prantl beim Gesundheitswesen: „Die Redaktion soll ihrer Natur nach die höchsten Interessen der Menschheit verfolgen“ – könne das aber nicht, solange sie Rücksicht nehmen muss auf „Privatinteressen“ (Bücher 1926: 397, 426). Anzeigenkunden, Leserwünsche, Profit.
Karl Bücher war vorbereitet auf die Chance, die jede Krise bietet. Er hat schon im Weltkrieg öffentlich über das Nachrichtenmonopol der großen Agenturen geschimpft und über den „Tiefstand“ des Zeitungswesens (vgl. Meyen 2002). Als die bayerische Räteregierung ihn dann Anfang 1919 um einen Gesetzentwurf bittet, will er dem Übel an die Wurzel und schlägt zehn Paragrafen vor, die auf eine Enteignung hinauslaufen und auf ein Ende des Wettbewerbs. Keine Anzeigen mehr an private Verleger. Dafür ein Lokalblatt pro Ort, herausgegeben von der Gemeinde, kostenfrei für jeden, finanziert über das, was Unternehmen und Behörden bekanntgeben wollen. In dem Aufsatz, den Bücher später nachgeliefert hat, beruft er sich unter anderem auf Ferdinand Lassalle. Sinngemäß: weg von einer „öffentlichen Meinung“, die vom „Kapital“ geprägt wird sowie von der „privilegierten großen Bourgeoisie“, hin zu einer „freien Tagespresse“, die „schwebende politische Fragen“ erörtert (Bücher 1926: 396).
Verrückt? Wer weiß, was Karl Bücher geschrieben hätte über den Corona-Journalismus der Gegenwart. Er hat schon vor einhundert Jahren nicht nachvollziehen können, warum die Redaktionen sich mit „Nichtigkeiten“ abgeben, gegen Polizeireporter gewettert und die Lokalnachrichten für eine „geistlose Chronik“ gehalten. Die Nähe zur Politik hat er entweder nicht gesehen oder nicht verstanden, dass das ein Problem sein könnte, weil er selbst zur Elite gehörte. Vermutlich wäre er trotzdem zufrieden mit einigen seiner Erben – mit Otfried Jarren (2020) zum Beispiel, der das öffentlich-rechtliche Fernsehen sehr früh kritisiert hat („Systemmedium“, „besondere Form der Hofberichterstattung“), mit Hektor Haarkötter („Geht’s auch mal wieder kritisch?“) oder mit Klaus Meier und Vinzenz Wyss (2020), die höflich bleiben und dankbar sind, ohne dabei die vielen Defizite zu übersehen. Der „Umgang mit Zahlen“, der Fokus auf Einzelfälle und auf „Virologen als unfehlbare Medienstars“, kaum Transparenz, wenig Vielfalt.
Wissenschaftler sein und öffentlich für seine Überzeugungen zu kämpfen: Das waren für Karl Bücher zwei Seiten derselben Medaille. Ihm hätte deshalb auch gefallen, wie Vinzenz Wyss (2020), ein Kollege aus der Schweiz, die Medienrealität an dem misst, was die Gesellschaft vom Journalismus erwarten darf. Ja, sagt Vinzenz Wyss, es gibt tolle Stücke, mit viel Aufwand produziert. Das große Aber: die „Newsmedien“ – also das, was das Publikum nicht ignorieren kann. Das muss hier nicht im Detail wiederholt werden. Zahlen ohne Erhebungskontext. Die „Zahlenfixierung“ überhaupt, kombiniert mit fehlender Distanz zur Macht und dem Unwillen, die eigenen Grenzen zu thematisieren. Zweimal O-Ton Vinzenz Wyss: „Ich bin fast ein bisschen empört, wie stark Journalisten in dieser Krise Wissenschaftler als Wahrsager darstellen“. Und: „Wenn die Exekutive dominiert und die parlamentarische Debatte verstummt, muss der Journalismus besonders wachsam sein“.
Vinzenz Wyss ist am Ende gar nicht weit weg von Heribert Prantl und Karl Bücher. „Wir sehen jetzt, wie wichtig der Journalismus ist“, sagt er. Und wir sehen auch, „wie schwach das Immunsystem derjenigen Medien ist, die sich vorwiegend über Werbegelder finanzieren“.
Es ist nicht schwer, das weiterzudenken. Corona zeigt: Die digitalen Plattformen mögen wichtig sein, die Realität aber wird nach wie von den Leitmedien gesetzt. Die Macht liegt bei denen, die es schaffen, ihre Version der Wirklichkeit in der Tagesschau zu platzieren, in der Süddeutschen Zeitung, im Spiegel, in der Zeit, in der Bild-Zeitung. Wir haben gesehen, was passiert, wenn die Pressemitteilungen der Regierung zur Medienrealität werden, die großen Leitartikler mit den Politikern heulen und ihre kleinen Gefolgsleute jeden Abweichler im Netz als Verschwörer und Gesundheitsfeind brandmarken. Zustimmungsraten wie in Nordkorea.
Es gibt einen Aufsatz von Elisabeth Noelle-Neumann (1973) mit dem feinen Titel „Kumulation, Konsonanz und Öffentlichkeit“. Sie könne einfach nicht glauben, schreibt Noelle-Neumann vor fast einem halben Jahrhundert, dass Medien keine Wirkung haben sollen oder nur so schwache, wie sie die Forschung bisher nachgewiesen hat. Das neue Paradigma, das sie mit diesem Text etablieren will, klingt im Titel an. Noelle-Neumann sagt: Ihr habt „die Omnipräsenz“ der Medien vergessen und ihre „kumulative Wirkung als Folge der Periodizität“. Starrt nicht nur auf die Empfänger der Botschaft, sondern schaut euch auch die Kommunikatoren an, „deren berufliches Verhalten Ähnlichkeit erzeugt“. Und vergesst den „Faktor Öffentlichkeit“ nicht. Noelle-Neumann meint damit die „kritische Instanz“ soziale Kontrolle, die jeder spürt, der von dem abweicht, was die anderen für die Meinung der Mehrheit halten müssen.
Als Noelle-Neumann diesen Text geschrieben hat, war es üblich, dass sich die Spitzenleute der Parteien im Bundestag angebrüllt haben. Damals genügte es, die vier wichtigsten Blätter im Land zu untersuchen, wenn man das politische Spektrum abbilden wollte. Wie würde man das heute machen, wenn die Opposition schweigt und überall das gleiche steht – vor allem nichts anderes als in den Bulletins der Staatskanzleien? Das ist ungerecht, ich weiß. Die Redaktionen können schon lange nicht mehr so arbeiten, wie es nötig wäre, und produzieren trotzdem immer wieder Perlen. Tolle Gäste bei Markus Lanz, nur als Beispiel. Trotzdem. Kumulation, Konsonanz, Öffentlichkeit. Corona-Tote auf allen Kanälen und Journalisten, die Schiedsrichter spielen im Streit der Experten. Wenn es nicht so ernst wäre, könnte man nach dem Videobeweis rufen und fragen, woher die Pfeifen in ihren „Fakten-Checks“ wissen, dass die staatliche Behörde immer Recht hat. Nach den Wirkungen muss man jedenfalls nicht lange suchen. Ich sehe in München Menschen, die sich angeekelt abwenden, wenn ihnen zwei Jogger entgegenkommen, und höre, wie Türsteher im Supermarkt angeblafft werden, die keine Maske tragen.
Heribert Prantl hat beschrieben, was im Bereich der Medizin falsch gelaufen ist seit Mitte der 1980er Jahre, und dabei Ross und Reiter genannt. Der Bundestag, der erst Krankenhäusern erlaubte, Gewinne zu machen, und dann unter Rot-Grün ein Vergütungssystem einführte, das alles dem Diktat des Geldes unterwarf. Die Troika, die ganz Südeuropa zwang, das Gesundheitswesen zu kastrieren, „um am Tropf Europas zu bleiben“. Auch im Journalismus ist das alles kein Geheimnis. Homogene Redaktionen, dominiert von Akademiker-Männern, die viel zu nah dran sind an den Entscheidern und die Welt auch deshalb kaum anders sehen können, weil sie aus dem gleichen Milieu kommen, auf den gleichen Schulen waren und dort verinnerlicht haben, was „richtig“ ist und was „falsch“.
Wo es um Geld geht (wie in kommerziellen Verlagen), werden diese Redaktionen vom Imperativ der Aufmerksamkeit regiert und von einem Sparzwang, der die Abhängigkeit von offiziellen Quellen noch größer macht, als sie ohnehin schon immer war. Und wo es um die Gunst der Politik geht (wie im öffentlich-rechtlichen Rundfunk und auch bei den Privaten, die ja immer eine Lizenz brauchen), bestimmen die Parteien, wer Chefin oder Chef sein darf, und haben mit Aufsichtsbehörden und Kontrollgremien einen zusätzlichen Hebel, wenn irgendetwas nicht nach Plan läuft. Ein kleines Beispiel aus Bayern, passend zum Thema: Ein Lokalradio hat es doch tatsächlich gewagt, drei lange Gespräche mit Experten zu senden, die der Söder-Linie widersprechen: Wolfgang Wodarg, Karin Mölling und Stefan Hockertz. Normalerweise läuft so ein Programm unter dem Radar. Wer hört schon Lokalradio? An den Interviews ist auch nicht viel auszusetzen. Die Journalistin fragt nach und zeigt, dass sie sich auskennt. Die Bayerische Landeszentrale für neue Medien hat ihr trotzdem einen Brief geschrieben. Botschaft: Wir hören, was Sie da machen. Wir sehen zwar für den Moment von einer „förmlichen Beanstandung“ ab (kein Wunder, denn es gibt nichts zu beanstanden), aber wir bitten Sie, an die „journalistische Sorgfaltspflicht“ zu denken, „damit derartige problematische Sendungen zukünftig ausbleiben“. Bei Noam Chomsky heißt das „Flak“. Die Macht schießt zurück, wenn allen Filtern zum Trotz doch etwas durchrutscht, was unter der Decke bleiben soll (vgl. Herman/Chomsky 1988).
Das ist tatsächlich verrückt. Der Journalismus will uns weismachen, dass er unabhängig ist, neutral und objektiv, dass er immer auf Distanz bleibt zu den Herrschenden und nach Vielfalt strebt. Ein Wolkenkuckucksheim, das ganz am Anfang stehen muss, wenn es um eine Zukunft nach Corona geht. Der Journalismus braucht einen neuen Kompass, der auf uns zeigt, auf die Gesellschaft, und nicht auf das Geld, auf den Staat und auf seine Verweser. Wir brauchen Redaktionen, die den „Auftrag Öffentlichkeit“ (Horst Pöttker) ernst nehmen. Wieder in Kurzform: alle Themen, alle Perspektiven. Wenn das dann unbedingt noch kommentiert werden muss: meinetwegen. Aber eigentlich will ich nicht wissen, wie Kurt Kister oder Claus Kleber die Welt sehen, sondern erfahren, was in der Welt so läuft, und mir dann selbst eine Meinung bilden.
Wie dieser Kompass sonst aussehen könnte, habe ich im Sommer skizziert, lange vor Corona (vgl. Meyen 2019). Ganz oben auf meiner Liste: Transparenz (offenlegen, wie die Inhalte entstehen und wie sie verbreitet werden), Perspektivenvielfalt (ein Punkt, der bei der Rekrutierung für den Beruf beginnt) und Reflexion (wer schreibt oder sendet hier und wem könnte das am Ende nutzen).
Entstanden ist diese Liste nach einer Serie von Interviews mit Menschen, die es wissen müssen, weil sie „irgendwas mit Medien“ machen. Ich habe mir damals nicht wirklich vorstellen können, dass man in den Redaktionen gar nicht darüber spricht, wozu die Gesellschaft Journalisten braucht. Dass man dort „Parolen“ wie „vierte Gewalt“ (Henriette Löwisch, Leiterin der Deutschen Journalistenschule München) lange einfach nur nachgeplappert hat. Nach Corona denke ich: Wir müssen tatsächlich zurück auf „Los“. Wir müssen mit der Ausbildung anfangen und aufhören, das Volontariat als Königsweg in den Beruf zu feiern. Von den Alten lernen, heißt gehorchen lernen. Der Journalismus der Zukunft darf nicht in kommerziellen Verlagen geformt werden und auch nicht in öffentlich-rechtlichen Rundfunkanstalten, solange diese jeder Politik folgen.
Vermutlich wissen viele Deutsche gar nicht mehr, welchen Schatz sie da haben: Fernseh- und Radioprogramme, die kein Geld verdienen müssen und denen dienen dürfen, die sie bezahlen – uns. Nur: Wir haben dort nichts zu sagen. Auch das ist verrückt: In den Gremien kontrollieren Politiker die, die eigentlich dazu berufen wären, die Politik zu kontrollieren. Verkehrte Welt. Der Journalismus nach Corona braucht Publikumsräte und Redaktionen, die im Wortsinn „frei“ sind, weil sie feste Arbeitsverträge mit guten Einkommen haben und deshalb nicht von den Launen ihrer Chefs oder der Regierenden abhängen. Wer wie ich in der DDR aufgewachsen ist, der weiß: Die Herrschenden werden immer und überall versuchen, das zu kontrollieren, was über sie in der Öffentlichkeit gesagt wird. Journalismus braucht deshalb „Schutzmauern“ (David Goeßmann), zum Beispiel Redaktionsstatute.
Wem das alles zu viel Vision ist und zu wenig Wirklichkeit: Auch im Journalismus gibt es längst „konkrete Utopien“ – Inseln, auf denen es nicht um „Profit und Kapitalakkumulation“ geht und wo Menschen freiwillig zusammenarbeiten, um staatliche und wirtschaftliche Macht zu zähmen. Erik Olin Wright (2017), der das Konzept der „konkreten Utopien“ entwickelt hat, wollte keine Revolution und auch keine Reformen. Als Modelle gestorben, sagt er. Sein Vorschlag: „im Hier und Jetzt“ so handeln, dass die Alternative wahrscheinlicher wird. In „den Räumen und Rissen“ des Kapitalismus „Institutionen, Verhältnisse und Praktiken“ entwickeln, die „die Welt, wie sie sein könnte, vorwegnehmen“. Vielleicht ist das ja ein Anfang: digitale Plattformen stärken, die den Journalismus liefern, den wir uns wünschen. Ich bin sicher: Heribert Prantl würde das gefallen.
Literatur
Karl Bücher: Zur Frage der Pressreform. In: Gesammelte Schriften. Tübingen: H. Laupp’sche Buchhandlung 1926, S. 391-429
Hektor Haarkötter: Geht’s auch mal wieder kritisch? In: Menschen machen Medien, 1. April 2020
Edward S. Herman, Noam Chomsky: Manufacturing Consent.The Political Economy of the Mass Media. New York: Pantheon 1988
Otfried Jarren: Im Krisenmodus. Das öffentlich-rechtliche Fernsehen in Zeiten von Corona. In: epd medien vom 27. März 2020
Klaus Meier, Vinzenz Wyss: Journalismus in der Krise: die fünf Defizite der Corona-Berichterstattung. In: meedia, 9. April 2020
Michael Meyen: Die Leipziger zeitungskundlichen Dissertationen. In: Erik Koenen, Michael Meyen (Hrsg.): Karl Bücher. Leipziger Hochschulschriften 1892 bis 1930. Leipzig: Universitätsverlag 2002, S. 135-200
Michael Meyen: (Erste) Thesen zur Medienzukunft. In: Michael Meyen (Hrsg.): Medienrealität 2019.
Elisabeth Noelle-Neumann: Kumulation, Konsonanz und Öffentlichkeitseffekt. Ein neuer Ansatz zur Analyse der Wirkung der Massenmedien. In: Publizistik 18. Jg. (1973), S. 26–55
Heribert Prantl: Bittere Medizin. In: Süddeutsche Zeitung vom 11. April 2019, S. 4 (unter anderem Titel hinter der Bezahlschranke)
Erik Olin Wright: Reale Utopien. Wege aus dem Kapitalismus. Berlin: Suhrkamp 2017.
Vinzenz Wyss: „Journalisten dürfen Kritik nicht dünnhäutig abschmettern“. In: persoenlich.com vom 10. April 2020.
Vom Kampf um die Öffentlichkeit
Medienrealität, 13. Mai 2020, und Rubikon, 14. Mai 2020
Ein Gespenst geht um in Deutschland: die Verschwörungstheorie. Dubiose Kanäle im Internet, so liest und hört man es jetzt allerorten, haben erst die öffentliche Debatte vergiftet und treiben jetzt unbescholtene Bürger auf die Straße und damit in die Hände von Rattenfängern aller Couleur – mit ungeahnten Folgen für die politische Kultur und den Gesundheitszustand der Bevölkerung. Die Diffamierung von Demonstranten hat hierzulande Tradition. Und die Geschichte lehrt: Es muss nicht immer gut ausgehen für die, die gerade an der Macht sind.
„Was trieb Frau A.K. ins Stadtzentrum?“: Dieser Artikel, erschienen in der Wochenendausgabe der Leipziger Volkszeitung vom 24./25. Juni 1989, war eine Warnung an alle, die sich seit einigen Wochen jeden Montagabend an der Nikolaikirche trafen. Bleibt zu Hause, liebe Leute. Genießt die „Vorzüge“, „die unsere Gesellschaft den Bürgern und insbesondere den Familien zukommen lässt“. Hört auf, den „BRD-Ratgebern“ zu lauschen und „die öffentliche Ordnung zu stören“.
Diese „Frau A.K. aus Wurzen“, die Chefredakteur Rudi Röhrer da anspricht (allerdings im Schutz eines Pseudonyms), ist ein Kind der DDR. Drei Jahre Lehre im Wunschberuf, ein Jahr daheim nach der zweiten Geburt. Eine junge Frau, die allen Grund zu haben scheint, an so einem Montagabend „einen neuen Film“ zu sehen oder „in einer Eisbar den Feierabend zu genießen“. Und jetzt das. Eine „Unruhestifterin“, die sich „in voller Absicht über die bei uns gültigen Normen des Zusammenlebens und über Rechtsnormen“ hinwegsetzt und so zu einer Handlangerin wird – „von jenen Kräften in der BRD, die unsere sozialistische DDR von innen heraus“ so lange reformieren wollen, bis von ihr nichts mehr übrigbleibt. Lasst euch nicht täuschen, liebe Leserinnen und Leser. Forderungen wie „mehr Meinungspluralismus, mehr Offenheit, mehr Erneuerung, mehr Reisen“ machen „aus Provokateuren keine Unschuldsengel“. Damit die Warnung auch wirklich ankommt, lässt der Chefredakteur „Leipziger Bürger“ nach „Ordnung, Ruhe und Sicherheit“ rufen. Tenor: Bietet diesem „Treiben“ endlich Einhalt, „ohne Ansehen der Person“.
Vermutlich ist das alles zu lange her und zudem in einem Landstrich passiert, der den Edelfedern in Hamburg oder München bis heute fremd geblieben ist. Gleich zehn Reporterinnen und Reporter (eine Frau und neun Männer) hat Der Spiegel aufgeboten, um über die Corona-Demonstrationen am zweiten Maiwochenende zu berichten (Wut und Wahnsinn_SPIEGEL 20). Drei Seiten unter der Überschrift „Wut und Wahnsinn“, dazu eine Fotostrecke mit dem Kommentar „Sie fühlen sich einzigartig, weil sie vermeintlich etwas erkannt haben, das die breite Masse übersieht“. Das Wort „berichten“ trifft es dabei nicht ganz. Rudi Röhrer, der Mann, der einst gegen „Frau A.K. aus Wurzen“ hetzte, hätte das auch nicht für sich in Anspruch genommen. Die Unterzeile im Spiegel: „Verschwörungsideologen, extreme Rechte wie Linke nutzen die Unsicherheit der Bürger und vergiften die Debatte“.
Ganz so einfach kann man das Damals natürlich nicht mit dem Heute vergleichen. Das Westfernsehen sendet inzwischen landesweit. Und dass dort Meinungspluralismus gefordert oder gar gelebt wird, scheint auch schon eine Weile her zu sein. Damals wie heute geht es aber um Delegitimation und Eindämmung. Übersetzt: so wenig Menschen wie möglich auf der Straße. Und die, die trotzdem gehen, sollen selbst schuld sein an dem, was mit ihnen passiert. Der Spiegel schafft das, indem er sein Reporterteam Dinge zusammenbauen lässt, die nicht zusammengehören. Der Text beginnt mit Pegida und Lutz Bachmann (also mit dem Bösen schlechthin), schwenkt dann zu den Protesten gegen „Corona-Beschränkungen der Politik“ und rührt in diesem Topf schließlich alle zusammen, vor denen man sich zu fürchten hat: „Rechtsextremisten, Impfgegner, Antisemiten, Verschwörungsideologen, Linksradikale, Alt-Autonome und Esoteriker“. Huuuh.
Journalismus soll informieren. Journalismus soll Wählerinnen und Wählern erlauben, sich selbst eine Meinung zu bilden. Der Spiegel traut uns das nicht zu. Auf genau acht Zeilen geht es um das, was Menschen in Berlin, Stuttgart, München auf die Straße getrieben hat. Der Job weg, das Restaurant zu, Probleme mit den Kids. Zusammengefasst: „Sie halten die Einschränkungen für unverhältnismäßig, protestieren ‚gegen staatliche Willkür‘, für die ‚Wiederherstellung der Grundrechte‘ oder die Rettung des Stuttgarter Nachtlebens“. Zweimal Anführungszeichen (Botschaft: von wegen Willkür, von wegen Einschränkung der Grundrechte) und zum Schluss der Schubs ins Lächerliche. Diese Rumtreiber und ihre Bars. Da hätte Rudi Röhrer von der* Leipziger Volkszeitung* noch etwas lernen können.
Wie man „gut“ und „böse“ auseinanderhält, wusste er sicher schon. Hier „zahlreiche führende Ärzte und Virologen wie Christian Drosten von der Charité“ (Zahlreich! Führend!) und eine Sozialpsychologin, „die zu Verschwörungserzählungen promoviert und darüber gerade ein Buch geschrieben hat“ (Wissenschaft!). Dort ein „Berliner Dramaturg und Journalist“, der „sich mit kapitalismuskritischen Theateraufführungen einen Namen gemacht“ und jetzt auch stadtbekannte NPD-Funktionäre anzieht, oder ein „pro-russischer Journalist“, der sich „ständig“ von RT Deutsch und Sputnik interviewen lässt („Kreml-Propagandisten“). Merke: Was diese Menschen sagen, ist völlig egal. Das Etikett hilft uns, das Angebot zu sortieren.
Das Konzept „Verschwörungstheorie“ kannten die DDR-Propagandisten so nicht. Es gab nur einen Gegner, und den konnte man genau wie seine Jünger leicht als „Klassenfeind“ abstempeln. Heute ist die Welt komplexer. Heute gibt es das Internet und mit ihm Plattformen, die das Deutungsmonopol der Herrschenden auf ganz andere Weise herausfordern als einst die Programme aus der Bundesrepublik, die sich ganz zwangsläufig mehr mit dem eigenen Land beschäftigt haben als mit dem schmuddeligen Nachbarn im Osten. Wer heute gegen „Verschwörungstheorien“ kämpft, kämpft um die Macht – um Definitionsmacht: Wer darf sagen, was wir „wissen“ und für richtig halten sollen?
Vor 30 Jahren war das keine Frage. Vor 30 Jahren durften nur wenige öffentlich sprechen. Was „da draußen“ passiert, wie wir beschreiben, was da gerade passiert, und wie wir uns folglich einrichten in dieser Welt: In der guten, alten Zeit war das Sache der Massenmedien und damit der Journalisten. Wer Zugang zum Fernsehen hatte oder zur Presse, der konnte beeinflussen, was als Realität durchging. Es gab nur diese eine. Es gab nur das, was in der Zeitung stand, und das, was über den Bildschirm lief. Das Wörtchen „und“ täuscht dabei noch. Meist stand das in der Zeitung, was vorher über den Bildschirm gelaufen war. Oder umgekehrt.
Der britische Medienforscher Nick Couldry (2012) nennt das den „Mythos vom mediatisierten Zentrum“. Eigentlich ist das ein doppelter Mythos. Punkt eins: die Behauptung, es gebe so etwas wie eine ‚Wahrheit‘ oder ein ‚natürliches Zentrum‘ der Werte und Lebensstile. Punkt zwei: Der Weg zu diesem Zentrum führt nur über die Medien. Der Kern unseres Lebens: Das ist das, worüber die Massenmedien angeblich berichten. Für Couldry ist dieser Mythos die Wurzel aller Medienwirkungen. Presse, Funk und Fernsehen definieren, was ist und was sein darf, und sorgen so dafür, dass die Realität der Massenmedien in Alltagshandeln und Weltanschauungen übernommen wird. Medien ordnen die Welt. Medien liefern die Kategorien, mit denen wir die Welt beschreiben. Politiker und Journalisten füttern den „Mythos vom mediatisierten Zentrum“, weil sie von ihm leben. Corona ist ein Festmahl. Ein Virus, das gefährlich ist, das unseren Alltag verändert. Wie genau, sagen uns die Nachrichten.
Und damit zum Wort Verschwörung, das im Spiegel gekoppelt wird mit den Begriffen Theorie, Portal, Ideologe, Erzählung, Mythos. Es ist das Wort zur Krise überhaupt. Zwanzigmal allein in diesem Artikel. Da bleibt kein Platz für Inhalte, Erklärungen oder gar eine Definition. Man erfährt nur (von der schon erwähnten Expertin), dass in der Welt der Verschwörer „böse Hintermänner Schuld an der Situation sind“ und (aus dem Mund eines Innenministers) dass diese Menschen glauben („bis weit in die Mitte der Gesellschaft“!), „die Pandemie“ sei „bewusst herbeigeführt“ worden, „um das Volk zu kontrollieren“ (von Bill Gates oder anderen „vermeintlich finsteren Mächten“).
Es kann gut sein, dass manche der Demonstranten das so sehen. Es kann gut sein, dass einige Bill Gates nicht nur „vermeintlich“ für eine „finstere Macht“ halten und der Politik nicht zutrauen, frei von Lobbyisten nur nach ihrem Gewissen und zum Wohle aller zu entscheiden. Gründe genug hätten solche Zweifler. NSU und NSA, Ramstein und die Drohnen, die Bankenrettung im Namen des Gemeinwohls. Nur so als Beispiele. Aber darum geht es an dieser Stelle nicht. Es geht um die Frage, warum Der Spiegel und mit ihm die anderen Leitmedien plötzlich überall Verschwörungen sehen. Nick Couldry würde sagen: Der „Mythos vom mediatisierten Zentrum“ wankt. Fake News, Hate Speech, Menschen mit „kruden Thesen“: Das gibt es alles, keine Frage. Vermutlich gibt es sogar Minister und Redakteure, die sich ernsthaft sorgen um ihre Schäfchen. Zuallererst aber hilft das Schlagwort „Verschwörungstheorie“ denen, die an der Macht sind, und ihren traditionellen Sprachrohren. Das stimmt auch deshalb, weil dieses Schlagwort ablenkt von den Problemen, über die man eigentlich sprechen müsste. Über die Qualität des Journalismus in dieser Krise zum Beispiel (vgl. Meyen 2020) oder über all das, was sonst noch so auf den Transparenten steht. Das SED-Blatt Leipziger Volkszeitung hat im Sommer 1989 immerhin vier Punkte genannt, auf die „Frau A.K. aus Wurzen“ sich berufen konnte. Meinungspluralismus, Offenheit, Erneuerung, Reisen. Rudi Röhrer, der Chefredakteur, hat das zwar sofort in den Schmutz gezogen (Provokateur bleibt Provokateur), aber die geneigte Leserin konnte in sich gehen und das mit Babyjahr und Eisbar verrechnen.
Der Spiegel dagegen opfert eine seiner drei Seiten für die „drei Medien, die von Anfang an besonders aktiv über die ‚Hygienedemos‘ berichteten“: Rubikon („Querfront-Magazin“, „eine Art Hausmedium der Protestler“), RT Deutsch und Sputnik („deutschsprachigen Ableger eines staatlichen russischen Medienunternehmens“). Dazu kommen Links zu KenFM („Verschwörungsportal“, „Fake-News-Verbreiter“) und Weltnetz.tv („systematische Verbindungen zur Linkspartei“). Was genau man auf all diesen Portalen findet oder wie die Kolleginnen und Kollegen dort arbeiten (wie überall: viele ausgezeichnet und manche nicht ganz so gut), ist dem Reporterkollektiv egal. Auf die Botschaft kommt es an: Geht nicht ins Stadtzentrum. Und vor allem: Hört nicht auf die Signale aus dem Netz.
Im Spiegel lässt sich der Dreiklang studieren, den die Rudi Röhrers der Gegenwart singen: Etikettierung von Personen (was schneller geht, als sich mit Inhalten zu beschäftigen), Kontaktschuld (Sie veröffentlichen auf einer Plattform, auf der auch jemand unterwegs ist, dem man irgendetwas anhängen kann oder will) und implizite Verknüpfung. Man schreibt über Rubikon oder KenFM und lässt nebenbei ein paar wirklich „krude Thesen“ fallen. Im Spiegel: 5G und eine „Biowaffe“. In der Süddeutschen Zeitung, für die Willi Winkler eine Seite 3 zu den Demos gefüllt hat: Angela Merkel als „natürliche Tochter Adolf Hitlers“ („Sie wurde, falls Sie‘s nicht wussten, mit dem vorsichtshalber tiefgefrorenen Sperma des 1945 tragisch hingeschiedenen Führers gezeugt“). Ja. Was will man da noch machen. Das ist wie bei „Frau A.K. aus Wurzen“, die einfach kein Eis essen wollte.
Der Stempel „Verschwörungstheorie“ ist ein Generalangriff der Herrschenden auf den öffentlichen Debattenraum. Über Verschwörungstheorien muss man nicht reden und mit ihren Anhängern auch nicht. Verschwörungstheorien sind, so sagt es Michael Butter, einer der Wissenschaftler im Streitwagen der Macht, „falsch“. Immer. „Noch nie“ habe sich „eine Verschwörungstheorie im Nachhinein als wahr herausgestellt“ (Butter 2018: 37). Dass das Unsinn ist, sollte jeder Forscher wissen. Ob etwas „wahr“ oder „falsch“ ist, zeigt die Empirie. Ich kann zwar das eine hoffen oder das andere, um aber sicher zu sein, muss ich ins Feld. Ich muss Pro und Contra abwägen, sachlich, ohne Emotionen und ohne jedem gleich jede Kompetenz abzusprechen, der die Welt anders sieht als ich.
Es gibt ein feines Kriterium, mit dem sich die Qualität von Journalismus einschätzen lässt: publizistische Vielfalt (vgl. Rager/Weber 1992). Dieses Kriterium wurzelt im Pluralismusmodell: In der Gesellschaft gibt es viele und zum Teil gegensätzliche Meinungen und Interessen, die prinzipiell gleichberechtigt sind (die Interessen von Einzelpersonen und Außenseitern genauso wie die Interessen, die in Parteien oder Verbänden organisiert sind). Feld der Verständigung ist die Öffentlichkeit, wobei ein Ausgleich nur möglich scheint, wenn die verschiedenen Interessen in den Leitmedien artikuliert werden können – ohne dass die (Ab-)Wertung gleich mitgeliefert wird wie in vielen der „Fakten-Checks“, die gerade wie Pilze aus dem Boden schießen.
Was macht Der Spiegel? Er denunziert die Nachfahren von „Frau A.K. aus Wurzen“ und ruft nach Zensur. „Personalnot“ bei Facebook, Twitter, Google. Man kommt dort mit dem Löschen einfach nicht mehr hinterher. Die „automatisierten Filter“? „Fehleranfällig“. Schlimmer noch: Die Verschwörer weichen aus auf „freiere“ Plattformen (tatsächlich in Anführungszeichen) wie Bitchute und Telegram, wo die „Verschwörungsideologen“ (leider, leider) immer noch „ungehindert“ schwadronieren können – „bis sie sich das nächste Mal auf den Straßen wiedersehen. Inmitten von ganz normalen Bürgern“.
Die Leipziger Volkszeitung von Rudi Röhrer wusste sich am Ende gar nicht mehr zu helfen (vgl. Reichert 2000: 108). Am 5. Oktober 1989 hat sie unter der Überschrift „Nicht nur zusehen“ einen Kampfgruppenkommandeur gegen „nichtgenehmigte Demonstrationen“ hetzen lassen und einen Tag später in einem „Leserbrief“ unverhohlen gedroht: „Wir sind bereit und willens, das von uns mit unserer Hände Arbeit Geschaffene wirksam zu schützen, um diese konterrevolutionären Aktionen endgültig und wirksam zu unterbinden. Wenn es sein muss, mit der Waffe in der Hand!“ Innenminister und Polizisten denken im Moment laut darüber nach, wie die nächsten Demos laufen könnten. Die Leipziger haben sich damals nicht abschrecken lassen.
Literatur
Michael Butter: „Nichts ist, wie es scheint“. Über Verschwörungstheorien. Berlin: Suhrkamp 2018
Nick Couldry: Media, Society, World. Social Theory and Digital Media Practice. Cambridge: Polity Press 2012
Michael Meyen: Journalismus nach Corona. In: Michael Meyen (Hrsg.): Medienrealität 2020.
Günther Rager, Bernd Weber: Publizistische Vielfalt zwischen Markt und Politik. Eine Einführung. In: Günther Rager, Bernd Weber (Hrsg.): Publizistische Vielfalt zwischen Markt und Politik. Mehr Medien – mehr Inhalte? Düsseldorf: Econ 1992, S. 7-26
Steffen Reichert: Transformationsprozesse: Der Umbau der LVZ. Münster: Lit 2000
Die maskierte Öffentlichkeit
Medienrealität, 19. Oktober 2020, und Rubikon, 23. Oktober 2020
Die Regierenden haben die Öffentlichkeit gekapert und sich damit selbst jedes Korrektiv genommen. Nach den Leitmedien werden jetzt auch Seminarräume und Stadien, Kneipen und Bürgersteige zu Bühnen der politischen Inszenierung. Das Schicksal der DDR lehrt: Wer die Kommunikationskanäle schließt, verhindert mit den Debatten auch Innovationen und wird spätestens dann bestraft, wenn die Lebenswelt nicht mehr funktioniert.
Öffentlichkeit: Das ist ein Ort der Begegnung, der für die Politik ganz ähnlich funktioniert wie der Markt für die Wirtschaft (vgl. Gerhards/Neidhardt 1990). Was immer der Staat sich ausdenkt, muss vor der Bürgerschaft bestehen. Das heißt auch: Wir müssen darüber sprechen können. Rede, Gegenrede. Alles auf den Tisch. Normalerweise überlassen wir dieses Gespräch Organisationen und Auserwählten. Parteien, Gewerkschaften, Verbände. Der Präsident der Ärztekammer sagt dies, die Professorin das und die CSU etwas ganz anderes. Zu sehen oder zu hören in Presse, Funk und Fernsehen.
Diese Medienrealität beobachten wir aus drei Gründen. Wir wollen erstens wissen, wer die Macht hat. Wer hat es geschafft, sich selbst, seine Themen und seine Deutungen in die Öffentlichkeit zu bringen? Macht ist heute Definitionsmacht (vgl. Beck 2017). Macht hat, wer einen „Grenzwert“ festsetzen kann und einen „Schwellenwert“, die dann zu einer Realität werden, der sich auch deshalb niemand entziehen kann, weil Kritiker entweder gar nicht gehört oder diffamiert werden. Das führt direkt zu Grund zwei: Wir nehmen an, dass sich die anderen, die Menschen um uns herum, an der Medienrealität ausrichten werden. Also müssen wir diese Realität kennen. Sonst sind wir überrascht, dass der Sitznachbar im ICE austickt, wenn die Maske verrutscht. Drittens aber, und das ist für die Argumentation hier am wichtigsten, drittens wollen wir auf Nummer sicher gehen. Ist das, was wir selbst denken und für wichtig halten, wirklich präsent in der großen Arena? Kennt die Politik unsere Sorgen und Nöte, wenn sie über Sperrstunden entscheidet?
Die Öffentlichkeitstheorie beschreibt ein Wechselspiel zwischen drei Ebenen. Ganz oben stehen dabei die Leitmedien. Wer oder was hier nicht erscheint, bleibt unsichtbar. Auf den beiden Ebenen darunter aber, in Versammlungen und im Alltag, bei den vielen zufälligen Begegnungen hier und dort, kommen wir ins Spiel. Hier können wir die Medienrealität und uns selbst auf die Probe stellen. Sehe nur ich die Dinge so oder gibt es Gleichgesinnte? Können wir uns vielleicht sogar zusammentun und eine Demonstration organisieren, eine Mahnwache, eine Petition – etwas, was erst von den Redaktionen wahrgenommen werden muss und dann auch von der Politik?
Und damit zu den Masken. Mona Pauly hat das in einem Beitrag für die Freitag-Community auf den Punkt gebracht. Zusammengefasst: Die Politik braucht Bilder. Wie produziere ich Angst und das Gefühl, bedroht zu sein, wenn die Betten in den Kliniken leer sind und man auch kaum Kranken- oder gar Sterbegeschichten erzählen kann, die vom Normalen abweichen und damit die Medienlogik bedienen würden? Genau. Die Masken sind überall. Beim Bäcker und im Supermarkt sowieso. Jetzt auch im Kinosaal, auf den Bürofluren, im Klassenzimmer. Und damit in der Zeitung und in der Tagesschau. Selbst die paar Fans, die hin und wieder in die Stadien dürfen und dort so weit auseinandersitzen, dass sie sich kaum hören können, tragen Masken. Im Freien wohlgemerkt und bitte nicht durchsichtig. Die Bilder. Und jeder Kommentator rügt die Nachlässigen, wenn die Kamera bei ihren Fahrten durch das Rund doch noch eine Nasenspitze entdeckt. Selbst diese Fußballkommentatoren sind maskiert. Allein, hoch oben unter dem Stadiondach. Vielleicht vergessen sie sonst, den Besorgten neues Futter zu liefern.
Die Öffentlichkeit wird so erstickt. Die Maske ist kein „Instrument der Freiheit“ (Markus Söder), sondern ihr Tod. Es gibt keine Gegenrede mehr, nicht einmal beim Spaziergang durch die Stadt. Die Leitmedien transportieren Bilder der Zustimmung (maskierte Menschen überall), erzwungen von der Exekutive und durchgesetzt per Bußgeldkatalog. Und die beiden anderen Öffentlichkeitsebenen sind de facto ausgeschaltet. Wie will ich im Bus, auf der Straße oder im Geschäft mit jemandem ins Gespräch kommen, der nicht zu meiner Blase gehört? Wie will ich den erkennen, der irgendeine Bemerkung genauso blöd oder genauso gut findet wie ich? Selbst im Museum (Abstand! Maske!) oder in der Gaststätte geht das nicht mehr. Keine Fremden mehr am gleichen Tisch. Überhaupt nur noch fünf Personen, die sich am besten schon kennen sollten. Alles andere verhindern das Plexiglas zwischen den Tischen und die Masken auf dem Weg zum Klo. Selbst die Toilettenwand dürfte so als Ort der Öffentlichkeit verschwinden. Und der Zapfhahn wird einfach zugedreht, wenn es abends spannend werden könnte.
Wahrscheinlich muss ich das für die Versammlungsöffentlichkeit gar nicht mehr im Detail ausführen. Die Regierenden haben die Sportarenen entvölkert, Veranstaltungen jeder Art bis zur Unkenntlichkeit verkleinert und Demos entweder kriminalisiert oder ihnen per Verordnung jede Wucht genommen. Teilnehmerzahl, Abstand, Maskenzwang. Und wenn trotzdem viele Menschen zusammenkommen wie im August gleich zweimal in Berlin, dann schaffen es die PR-Leute der Regierung, so starke Frames zu setzen, dass nichts von den Motiven der Protestierenden oder von ihren Forderungen auf der Ebene der Leitmedien ankommt.
Das Internet, natürlich. Blogs, Telegram- und WhatsApp-Gruppen, die Plattformen für den Gegendiskurs. Hier findet sich all das, was früher Encounter und Versammlungen ausgemacht hat. Für den Einzelnen findet sich hier heute sogar viel mehr, weil ein Klick viel weniger kostet als jeder Gang ins Freie. Die Grenze zu den Leitmedien ist heute aber viel höher als früher. Wer es in den großen Redaktionen wagt, Experten zu zitieren oder gar einzuladen, die vorher bei RT Deutsch waren, bei KenFM oder Rubikon, riskiert seine berufliche Reputation. Die Kollegin und der Kollege waren schon immer die besten Kunden des Journalisten. Heute sind diese Kunden auf Twitter, verfolgen dort alles, was von ihrer eigenen Haltung abweicht, und erzeugen so einen Resonanzraum, der schon deshalb nichts mit der guten, alten Versammlungsöffentlichkeit zu tun hat, weil der Zugang exklusiv ist und man eigentlich nur Ja oder Nein rufen kann, möglichst laut, versteht sich.
Damit das nicht falsch verstanden wird: Es gibt in den Redaktionen Menschen, die den Auftrag Öffentlichkeit ernst nehmen. Beim WDR zum Beispiel, der in der Sendung „Meine Meinung“ unter der Überschrift „Lockern oder Verschärfen?“ Pro und Contra aufeinanderprallen ließ. Oder Alexei Makartsev, der gerade Sucharit Bhakdi für die Badischen Neuesten Nachrichten interviewt hat, sehr gut informiert und ohne Schaum vor dem Mund. Auf der Ebene der Leitmedien aber, da wo die Realität geschaffen wird, die niemand ignorieren kann, wird das übernommen, was die Politik und Behörden wie das RKI der Bevölkerung gern weismachen möchten. Uwe Krüger (2016: 105), ein Medienforscher aus Leipzig, hat das in einem anderen thematischen Zusammenhang „Verantwortungsverschwörung“ genannt. Der Journalist weiß, was gut ist und was schlecht (so ziemlich das gleiche, was die Regierenden gut oder schlecht finden), und er glaubt, dass er Einfluss auf die Menschen hat. Also nichts gegen die Maskenpflicht. Dass es dazu genug zu sagen geben würde, kann man gerade bei Oliver Märtens (2020) lesen, der nach einer aufwändigen Durchsicht der Forschungsliteratur von „Körperverletzung im Amt“ spricht.
Der DDR mag man alle möglichen Gebrechen nachsagen, untergegangen aber ist sie, weil die Kommunikation zwischen Regierenden und Regierten gestört war und die wirklich wichtigen Fragen nur in „internen Öffentlichkeiten“ diskutiert werden konnten – in Räumen, die für Beobachter aus dem Westen nicht zugänglich waren und deshalb von Herrschenden wie Beherrschten als Öffentlichkeitsersatz genutzt wurden (vgl. Meyen 2011). Dieses System aus Eingaben, Leserbriefen, Parteiversammlungen und Expertentreffen hatte durch die Brille der Macht zwei Vorteile. Man hat Kritiker oft allein durch Zuwendung besänftigt – und diese Kritiker konnten nicht sehen, wer sonst noch auf ihrer Seite steht. Geändert hat sich das erst, als sie Erkennungszeichen in die Öffentlichkeit getragen haben (etwa: weiße Gardinenfetzen an der Autoantenne, um den Wunsch nach Ausreise zu signalisieren) und die Probleme auch sonst buchstäblich für jeden „öffentlich“ wurden (etwa: die Luftverschmutzung). Mona Pauly hat in ihrem Beitrag für die Freitag-Community „eine grüne Maske als Protest“ vorgeschlagen. Die Bilder stören, irgendwie. Gegen Atemnot und Beklemmung hilft das nicht. In der DDR hat es außerdem sehr, sehr lange gedauert, bis solche Zeichen ganz oben angekommen sind. Und wer weiß, ob das ohne das Westfernsehen überhaupt funktioniert hätte.
Literatur
Ulrich Beck: Die Metamorphose der Welt. Berlin: Suhrkamp 2017
Jürgen Gerhards, Friedhelm Neidhardt: Strukturen und Funktionen moderner Öffentlichkeit: Fragestellungen und Ansätze. Berlin: Wissenschaftszentrum Berlin 1990
Uwe Krüger: Mainstream. Warum wir den Medien nicht mehr trauen. München: C.H. Beck 2016
Oliver Märtens: Die Maskenpflicht: Epidemieeindämmung oder Körperverletzung im Amt? Multipolar, 18. Oktober 2020
Michael Meyen: Öffentlichkeit in der DDR. Ein theoretischer und empirischer Beitrag zu den Kommunikationsstrukturen in Gesellschaften ohne Medienfreiheit. In: Studies in Communication / Media 1. Jg. (2011), S. 3-69
-
 @ 266815e0:6cd408a5
2025-03-19 11:10:21
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using applesauce
In this guide we are going to build a nostr app that lets users follow and unfollow fiatjaf
1. Setup new project
Start by setting up a new vite app using
pnpm create vite, then set the name and selectSolidandTypescript```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run:
cd followjaf pnpm install pnpm run dev ```
2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need.
nostr-toolsfor the types and small methods, andrx-nostrfor making relay connectionssh pnpm install nostr-tools rx-nostr3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new
src/nostr.tsfile with```ts import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ```
4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the
EventStoreclass fromapplesauce-corefor this. create a newsrc/stores.tsfile withThe event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ```
5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the
QueryStoreclass fromapplesauce-corefor this.Create a query store in
src/stores.ts```ts import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ```
6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the
ReplaceableLoaderclass fromapplesauce-loadersfor this.applesauce-loadersis a package that contains a few loader classes that can be used to fetch different types of data from relays.First install the package
sh pnpm install applesauce-loadersThen create a
src/loaders.tsfile with```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ```
7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the
src/App.tsxcomponent to fetch the profile.We can do this by calling the
nextmethod on the loader and passing apubkey,kindandrelaysto it```tsx function App() { // ...
onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); });
// ... } ```
8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the
ProfileQuerywhich gives us a stream of updates to a pubkey's profile.Create the profile using
queryStore.createQueryand pass in theProfileQueryand the pubkey.tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" );But this just gives us an observable, we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple
frommethod to subscribe to any observable.To make things reactive SolidJS uses accessors, so to get the profile we need to call
fiatjaf()```tsx function App() { // ...
// Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") );
return ( <> {/ replace the vite and solid logos with the profile picture /}
{fiatjaf()?.name}
{/* ... */}); } ```
9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a
AccountManagerclass fromapplesauce-accountsFirst we need to install the packages
sh pnpm install applesauce-accounts applesauce-signersThen create a new
src/accounts.tsfile with```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance export const accounts = new AccountManager();
// Adds the common account types to the manager registerCommonAccountTypes(accounts); ```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account);};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div>); } ```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the docs
10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$);
// ...
const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return;
// signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive();};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div>); } ```
11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx function App() { // ...
// fetch the user's profile when they sign in createEffect(async () => { const active = account();
if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); }});
// ... } ```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs";
function App() { // ...
// subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) );
// ...
return ( <> {/ ... /}
<div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div>); } ```
12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx function App() { // ...
// subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) );
const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); });
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div>); } ```
13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with Actions which are pre-built methods to modify nostr events for a user.
First we need to install the
applesauce-actionsandapplesauce-factorypackagesh pnpm install applesauce-actions applesauce-factoryThen create a
src/actions.tsfile with```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, });
// The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ```
Then create a
toggleFollowmethod that will add or remove fiatjaf from the users contacts.We are using the
execmethod to run the action, and theforEachmethod from RxJS allows us to await for all the events to be published```tsx function App() { // ...
const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); };
if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); }};
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div>); } ```
14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in
src/nostr.ts```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-
 @ bccf33d8:4b705625
2025-03-19 10:07:46
@ bccf33d8:4b705625
2025-03-19 10:07:46{"title":"nostrbook 创建的五本四书哈哈哈","author":"nostrbook.com","intro":"This is a book from ....很不错","picture":"https://432fds"}
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 8d34bd24:414be32b
2025-03-10 00:16:01
@ 8d34bd24:414be32b
2025-03-10 00:16:01The Bible tells believers repeatedly that we are to share the gospel, make disciples, speak the truth, etc. We are to be His witnesses. The reason we don’t go straight to heaven when we are saved is that God has a purpose for our lives and that is to be a light drawing people to Him.
“…but you will receive power when the Holy Spirit has come upon you; and you shall be My witnesses both in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” (Acts 1:8)
In order to be His witness, we have to know Him and know His word. When we don’t know His word, we can be misled and/or mislead others. We will fail in our mission to be witnesses if we don’t regularly study the Bible and spend time in prayer with our God.
As a result, we are no longer to be children, tossed here and there by waves and carried about by every wind of doctrine, by the trickery of men, by craftiness in deceitful scheming; but speaking the truth in love, we are to grow up in all aspects into Him who is the head, even Christ, from whom the whole body, being fitted and held together by what every joint supplies, according to the proper working of each individual part, causes the growth of the body for the building up of itself in love. (Ephesians 4:4-16) {emphasis mine}
In addition to knowing Him and His word, we need to be bold and unashamed.
Therefore do not be ashamed of the testimony of our Lord or of me His prisoner, but join with me in suffering for the gospel according to the power of God, who has saved us and called us with a holy calling, not according to our works, but according to His own purpose and grace which was granted us in Christ Jesus from all eternity, but now has been revealed by the appearing of our Savior Christ Jesus, who abolished death and brought life and immortality to light through the gospel, (2 Timothy 1:8-10) {emphasis mine}
We were called according to His purpose. His purpose was known before the creation of the world. We are not saved by works, but if we are saved, works should naturally proceed from the power of the Holy Spirit within us, as well as the thankfulness we should have because of what Jesus did for us.
The key point of our witness is obedience. We are a tool of God. We are to faithfully share the Gospel and the truth in God’s word, but we are not held accountable for the result of this witness. The results are due to God’s mercy and power and not due to anything we do.
But you shall speak My words to them whether they listen or not, for they are rebellious.
“Now you, son of man, listen to what I am speaking to you; do not be rebellious like that rebellious house. Open your mouth and eat what I am giving you.” (Ezekiel 2:7-8) {emphasis mine}
When we witness, some will listen and some will not. Some will accept Jesus with joy and some will reject Him in anger. That is not our concern. God calls whom He will and without His calling, nobody comes to Him.
And they took offense at Him. But Jesus said to them, “A prophet is not without honor except in his hometown and in his own household.” (Matthew 13:57)
One thing I’ve noticed is that the hardest people to witness to are family (not counting kids, but especially parents and siblings) and other people who have known us for a long time. They see what we were and not what we now are. There is baggage that can make for awkward dynamics. As someone once said to me, “It is hard to teach anyone or convince anyone who changed your diaper.”
I started with the Acts 1:8, “… be My witnesses both in Jerusalem, and in all Judea and Samaria, and even to the remotest part of the earth.” This is like saying “be My witnesses in my hometown, my state, my country, and even to the remotest part of the earth.” Our witness starts at home, then our community, and works it way out. Everyone can witness at home. We can all witness in our community as we go about our daily actions. It is important to have Christians that go to the “remotest part of the earth,” especially to unreached people groups, but that isn’t where most of us are sent. Most of us are called to witness to those around us daily.
For you are not being sent to a people of unintelligible speech or difficult language, but to the house of Israel, nor to many peoples of unintelligible speech or difficult language, whose words you cannot understand. But I have sent you to them who should listen to you; (Ezekiel 3:5-6) {emphasis mine}
God empowers some to be international missionaries, but He calls every Christian to be a life missionary. Sometimes this may just be living a life for Jesus that stands out in the culture. Sometimes this may be giving an in-depth treatise on the Gospel and the Bible. It will look differently in different seasons of life and on different days, but it should be a regular part of our life.
As we build relationships with people and show that we care about them, this usually gives us the opportunity to share with them why our lives look different. It demonstrates why we treat others well, why we are loving, and why we have joy, even when our circumstances don’t seem like they should lead to joy. Then when they ask why we are different, we can have the opportunity to tell why we have this joy and love and morality.
but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence; (1 Peter 3:5)
Although following a person and forcing them to listen to the Gospel is not the way to draw someone to Jesus, we need to not be silent about the truth. Not being pushy doesn’t mean being silent when someone is forcing their ungodly views on us or on others. Speaking up prevents evil voices from taking control. You also might be surprised to find that others didn’t like what was being said, but were too afraid to speak up because they thought everyone agreed with the speaker. When you speak up for the truth, it can give others courage to stand on their convictions and to draw closer to Jesus, whether this means they come to salvation or just draw closer to God.
Moreover, He said to me, “Son of man, take into your heart all My words which I will speak to you and listen closely. Go to the exiles, to the sons of your people, and speak to them and tell them, whether they listen or not, ‘Thus says the Lord God.’ ” (Ezekiel 3:10-11) {emphasis mine}
We are to speak the truth in love whether they listen or not. Some will listen, hear, and come to Jesus. Some will listen and reject what is said. We are only called to obey the call. God brings the increase. To God be the glory!
May God guide us and lead us in wisdom, love, and courage so that our light shines so brightly that many unsaved come to trust in Jesus Christ our Lord and that those who know Jesus, but have not matured, may grow in their faith, knowledge, and obedience to Jesus.
Trust Jesus
-
 @ bccf33d8:4b705625
2025-03-19 10:03:50
@ bccf33d8:4b705625
2025-03-19 10:03:50{"title":"nostrbook 创建的四本三书哈哈哈","author":"nostrbook.com","intro":"This is a book from ....很不 错","picture":"https://432fds"}
-
 @ c69b71dc:426ba763
2025-03-09 14:24:35
@ c69b71dc:426ba763
2025-03-09 14:24:35Time Change: A Mini Jet Lag
The time change is more than just setting the clock forward or backward — it can disrupt our internal balance and lead to a range of health issues. Find out why the time change causes a mini jet lag and how you can deal with it.
Why the Time Change Throws Us Off Balance
The expected energy savings due to reduced artificial lighting demand have not been confirmed. Worse yet, the time change leads to an increase in workplace and traffic accidents, a higher risk of heart attacks, and even an increase in suicide rates. Many people struggle with the one-hour shift that happens twice a year. There is constant debate about whether to abolish it and which time should remain permanent...
Permanent Summer Time or Permanent Winter Time?
The time change triggers a mini jet lag that can last from a single day up to three weeks as the body adjusts its internal clock to the new rhythm.
Winter Time Aligns Best with Our Internal Clock
Our bodies follow the circadian rhythm, an internal clock designed for activity during daylight and rest when the sun sets.
Permanent summer time would mean longer darkness in the morning and extended daylight in the evening—this unnatural shift would completely disrupt our biological processes.
The Impact of Time Change on Our Health
Our internal clock regulates essential functions such as body temperature, hormone production, the cardiovascular system, and the sleep-wake cycle. This is why the time change often leads to headaches, fatigue, drowsiness, metabolic disorders, and even severe heart rhythm disturbances. Studies show that these disruptions can increase susceptibility to illnesses and psychological disorders.
Since the light-dark cycle dictates this internal clock, prolonged exposure to artificial light after sunset can shift it. When the time suddenly changes, it causes a disruption, throwing off our natural sleep rhythm.
Sleep Resets the Body!
During the night, the body regenerates:
- The brain is flushed with cerebrospinal fluid to clear out toxins.
- The body undergoes repair, detoxification, and waste removal.
- If the alarm clock rings an hour earlier, the body is still in "night mode" and unable to complete its recovery processes!Most people already suffer from sleep disorders, whether trouble falling asleep or staying asleep. Added to this is the stress of daily life, which often depletes serotonin levels, reducing the body’s ability to produce melatonin —the sleep hormone. Blue light depletes magnesium in our body, disrupts the circadian rhythm, and interferes with melatonin production! We also know that the pineal gland’s melatonin production is impaired by fluoride found in toothpaste, water, and food!
What Can You Do About Sleep Disorders?
To regulate your sleep rhythm, you need healthy sleep hygiene:
- Minimize activity before bedtime.
- Avoid artificial light from TVs, smartphones, and e-readers.
- Ensure fresh air and a cool bedroom (around 18°C/64°F).
- Stick to consistent sleep and wake times — even on weekends!
- Reserve the bed and bedroom for sleep only — no heated discussions. - No heavy meals before bed.
- Use blue light or orange filter glasses to reduce artificial light exposure. - Air out the bedroom for 20 minutes before going to bed. - Use candlelight in the bathroom while brushing your teeth instead of turning on the harsh neon light.If these adjustments don’t help, natural remedies, supplements, and herbal teas can provide support.
Natural Sleep Aids
Some well-known natural remedies include:
- Melatonin, Tryptophan, GABA, Magnesium
- Herbs such as Hops, Lavender, Chamomile, Passionflower, Valerian and organge peal and flower.By aligning with nature’s rhythm and optimizing sleep habits, we can counteract the negative effects of the time change and restore balance to our bodies and minds.
I hope this helps you transition smoothly through this outrageous act of forcing us into "summer time" ⏰🌞

-
 @ bccf33d8:4b705625
2025-03-19 09:54:34
@ bccf33d8:4b705625
2025-03-19 09:54:34关于本书的第一个章节
-
 @ bccf33d8:4b705625
2025-03-19 09:42:35
@ bccf33d8:4b705625
2025-03-19 09:42:35{"title":"nostrbook 创建的一本书另外一本书","author":"nostrbook.com","intro":"This is a book from ....很不错","picture":"https://432fds"}
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ bccf33d8:4b705625
2025-03-19 09:41:19
@ bccf33d8:4b705625
2025-03-19 09:41:19我在测试 createbook标签是否可以被列出来
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ bccf33d8:4b705625
2025-03-19 09:36:16
@ bccf33d8:4b705625
2025-03-19 09:36:16{"title":"nostrbook 创建的一本书","author":"nostrbook.com","intro":"This is a book from ....","picture":"https://nostrbook.com/img/dfsa32432.png"}
-
 @ 6a6be47b:3e74e3e1
2025-03-01 12:25:54
@ 6a6be47b:3e74e3e1
2025-03-01 12:25:54Hi frens, 🎨 While painting today, my mind wandered from my latest blog entryto future artistic endeavors.I've been open about my feelings as an artist, but that's just the tip of the iceberg. I realized I haven't properly introduced myself here, so let me remedy that. 🖼️Art has been my lifelong passion. Nostr and its wonderful community have reignited my belief in my work, showing me that art can be both enlightening and potentially profitable. I'm truly grateful for the warm welcome and positive vibes I've encountered here. 🦋Nostr made me feel confident enough to speak my mind on a social platform (or should I say protocol? 😉). Some fun facts about me: 🐹 I'm a "golly jolly" kind of gal who's always curious about the world and seeking answers. 🐹I'm a sunscreen enthusiast in summer (but in winter, I'm buried under so many layers, I practically double in size!) 🐹Birdwatching is a hobby of mine. I've researched and painted some cool birds like shoebills and bearded vultures. (Any suggestions for my next avian subject?) 🩷I'm truly happy to be here and grateful for each day. My goal is to spread joy through my art and interactions. Thanks for being part of this journey with me! In your personal experience, how has it been discovering Nostr wether you're an artist or not? What's you favorite part of your journey so far? Godspeed 🚀

-
 @ da0b9bc3:4e30a4a9
2025-03-19 08:49:13
@ da0b9bc3:4e30a4a9
2025-03-19 08:49:13Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/917523
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ b2d670de:907f9d4a
2025-02-26 18:27:47
@ b2d670de:907f9d4a
2025-02-26 18:27:47This is a list of nostr clients exposed as onion services. The list is currently actively maintained on GitHub. Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | operator | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | operator | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | operator | Runs nsite. You can read more about nsite here. | | Shopstr | http://6fkdn756yryd5wurkq7ifnexupnfwj6sotbtby2xhj5baythl4cyf2id.onion/ | https://github.com/shopstr-eng/shopstr-hidden-service | operator | Runs the latest
serverlessbranch build of Shopstr. | -
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ a012dc82:6458a70d
2025-03-19 06:28:40
@ a012dc82:6458a70d
2025-03-19 06:28:40In recent years, the global economy has faced unprecedented challenges, with inflation rates soaring to levels not seen in decades. This economic turmoil has led investors and consumers alike to seek alternative stores of value and investment strategies. Among the various options, Bitcoin has emerged as a particularly appealing choice. This article explores the reasons behind Bitcoin's growing appeal in an inflation-stricken economy, delving into its characteristics, historical performance, and the broader implications for the financial landscape.
Table of Contents
-
Understanding Inflation and Its Impacts
-
Bitcoin: A New Safe Haven?
-
Decentralization and Limited Supply
-
Portability and Liquidity
-
Bitcoin's Performance in Inflationary Times
-
Challenges and Considerations
-
The Future of Bitcoin in an Inflationary Economy
-
Conclusion
-
FAQs
Understanding Inflation and Its Impacts
Inflation is the rate at which the general level of prices for goods and services is rising, eroding purchasing power. It can be caused by various factors, including increased production costs, higher energy prices, and expansive government policies. Inflation affects everyone in the economy, from consumers and businesses to investors and retirees, as it diminishes the value of money. When inflation rates rise, the purchasing power of currency falls, leading to higher costs for everyday goods and services. This can result in decreased consumer spending, reduced savings, and overall economic slowdown.
For investors, inflation is a significant concern because it can erode the real returns on their investments. Traditional investments like bonds and savings accounts may not keep pace with inflation, leading to a loss in purchasing power over time. This has prompted a search for alternative investments that can provide a hedge against inflation and preserve, if not increase, the value of their capital.
Bitcoin: A New Safe Haven?
Traditionally, assets like gold, real estate, and Treasury Inflation-Protected Securities (TIPS) have been considered safe havens during times of inflation. However, the digital age has introduced a new player: Bitcoin. Bitcoin is a decentralized digital currency that operates without the oversight of a central authority. Its supply is capped at 21 million coins, a feature that many believe gives it anti-inflationary properties. This inherent scarcity is akin to natural resources like gold, which have historically been used as hedges against inflation.
The decentralization of Bitcoin means that it is not subject to the whims of central banking policies or government interference, which are often seen as contributing factors to inflation. This aspect of Bitcoin is particularly appealing to those who have lost faith in traditional financial systems and are looking for alternatives that offer more autonomy and security.
Decentralization and Limited Supply
One of the key features that make Bitcoin appealing as a hedge against inflation is its decentralized nature. Unlike fiat currencies, which central banks can print in unlimited quantities, Bitcoin's supply is finite. This scarcity mimics the properties of gold and is seen as a buffer against inflation. The decentralized nature of Bitcoin also means that it is not subject to the same regulatory pressures and monetary policies that can lead to currency devaluation.
Furthermore, the process of "mining" Bitcoin, which involves validating transactions and adding them to the blockchain, is designed to become progressively more difficult over time. This not only ensures the security of the network but also introduces a deflationary element to Bitcoin, as the rate at which new coins are created slows down over time.
Portability and Liquidity
Bitcoin's digital nature makes it highly portable and divisible, allowing for easy transfer and exchange worldwide. This liquidity and global accessibility make it an attractive option for investors looking to diversify their portfolios beyond traditional assets. Unlike physical assets like gold or real estate, Bitcoin can be transferred across borders without the need for intermediaries, making it a truly global asset.
The ease of transferring and dividing Bitcoin means that it can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. This versatility, combined with its growing acceptance as a form of payment, enhances its utility and appeal as an investment.
Bitcoin's Performance in Inflationary Times
Historically, Bitcoin has shown significant growth during periods of high inflation. While it is known for its price volatility, many investors have turned to Bitcoin as a speculative hedge against depreciating fiat currencies. The digital currency's performance during inflationary periods has bolstered its reputation as a potential safe haven. However, it's important to note that Bitcoin's market is still relatively young and can be influenced by a wide range of factors beyond inflation, such as market sentiment, technological developments, and regulatory changes.
Despite its volatility, Bitcoin has provided substantial returns for some investors, particularly those who entered the market early. Its performance, especially during times of financial instability, has led to increased interest and investment from both individual and institutional investors. As more people look to Bitcoin as a potential hedge against inflation, its role in investment portfolios is likely to evolve.
Challenges and Considerations
Despite its growing appeal, Bitcoin is not without its challenges. The cryptocurrency's price volatility can lead to significant losses, and regulatory uncertainties remain a concern. Additionally, the environmental impact of Bitcoin mining has sparked debate. The energy-intensive process required to mine new coins and validate transactions has raised concerns about its sustainability and environmental footprint.
Investors considering Bitcoin as a hedge against inflation should weigh these factors and consider their risk tolerance and investment horizon. While Bitcoin offers potential benefits as an inflation hedge, it also comes with risks that are different from traditional investments. Understanding these risks, and how they align with individual investment strategies, is crucial for anyone considering adding Bitcoin to their portfolio.
The Future of Bitcoin in an Inflationary Economy
As the global economy continues to navigate through turbulent waters, the appeal of Bitcoin is likely to grow. Its properties as a decentralized, finite, and easily transferable asset make it a unique option for those looking to protect their wealth from inflation. However, the future of Bitcoin remains uncertain, and its role in the broader financial landscape is still being defined. As with any investment, due diligence and a balanced approach are crucial.
The increasing institutional interest in Bitcoin and the development of financial products around it, such as ETFs and futures, suggest that Bitcoin is becoming more mainstream. However, its acceptance and integration into the global financial system will depend on a variety of factors, including regulatory developments, technological advancements, and market dynamics.
Conclusion
The growing appeal of Bitcoin in an inflation-stricken economy highlights the changing dynamics of investment in the digital age. While it offers a novel approach to wealth preservation, it also comes with its own set of risks and challenges. As the world continues to grapple with inflation, the role of Bitcoin and other cryptocurrencies will undoubtedly be a topic of keen interest and debate among investors and policymakers alike. Whether Bitcoin will become a permanent fixture in investment portfolios as a hedge against inflation remains to be seen, but its impact on the financial landscape is undeniable.
FAQs
What is inflation, and how does it affect the economy? Inflation is the rate at which the general level of prices for goods and services is rising, leading to a decrease in purchasing power. It affects the economy by reducing the value of money, increasing costs for consumers and businesses, and potentially leading to economic slowdown.
Why is Bitcoin considered a hedge against inflation? Bitcoin is considered a hedge against inflation due to its decentralized nature, limited supply capped at 21 million coins, and its independence from government monetary policies, which are often seen as contributing factors to inflation.
What are the risks associated with investing in Bitcoin? The risks include high price volatility, regulatory uncertainties, and concerns over the environmental impact of Bitcoin mining. Investors should consider their risk tolerance and investment horizon before investing in Bitcoin.
How does Bitcoin's limited supply contribute to its value? Bitcoin's limited supply mimics the scarcity of resources like gold, which has traditionally been used as a hedge against inflation. This scarcity can help to maintain its value over time, especially in contrast to fiat currencies, which can be printed in unlimited quantities.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. Its digital nature allows for easy transfer and division, making it a versatile form of currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnewsco
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e97aaffa:2ebd765d
2025-03-19 05:55:17
@ e97aaffa:2ebd765d
2025-03-19 05:55:17Como é difícil encontrar informações sobre o eurodigital, a CBDC da União Europeia, vou colocando aqui, os documentos mais interessantes que fui encontrando:
FAQ: https://www.ecb.europa.eu/euro/digital_euro/faqs/html/ecb.faq_digital_euro.pt.html
Directório BCE: https://www.ecb.europa.eu/press/pubbydate/html/index.en.html?topic=Digital%20euro
https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/html/index.en.html
Documentos mais técnicos:
2025
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
2024
Relatório de progresso https://www.ecb.europa.eu/euro/digital_euro/progress/html/ecb.deprp202412.en.html
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
The impact of central bank digital currency on central bank profitability, risk-taking and capital https://www.ecb.europa.eu/pub/pdf/scpops/ecb.op360~35915b25bd.en.pdf
2023
Progress on the investigation phase of a digital euro - fourth report https://www.ecb.europa.eu/paym/digital_euro/investigation/governance/shared/files/ecb.degov230713-fourth-progress-report-digital-euro-investigation-phase.en.pdf
Digital euro - Prototype summary and lessons learned https://www.ecb.europa.eu/pub/pdf/other/ecb.prototype_summary20230526%7E71d0b26d55.en.pdf
Functional and non-functional requirements linked to the market research for a potential digital euro implementation https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf//ecb.dedocs230113_Annex_1_Digital_euro_market_research.en.pdf
A stocktake on the digital euro https://www.ecb.europa.eu/euro/digital_euro/progress/shared/pdf/ecb.dedocs231018.en.pdf
-
 @ ee9aaefe:1e6952f4
2025-03-19 05:01:44
@ ee9aaefe:1e6952f4
2025-03-19 05:01:44Introduction to Model Context Protocol (MCP)
Model Context Protocol (MCP) serves as a specialized gateway allowing AI systems to access real-time information and interact with external data sources while maintaining security boundaries. This capability transforms AI from closed systems limited to training data into dynamic assistants capable of retrieving current information and performing actions. As AI systems integrate into critical infrastructure across industries, the security and reliability of these protocols have become crucial considerations.
Security Vulnerabilities in Web-Based MCP Services
Traditional MCP implementations operate as web services, creating a fundamental security weakness. When an MCP runs as a conventional web service, the entire security model depends on trusting the service provider. Providers can modify underlying code, alter behavior, or update services without users' knowledge or consent. This creates an inherent vulnerability where the system's integrity rests solely on the trustworthiness of the MCP provider.
This vulnerability is particularly concerning in high-stakes domains. In financial applications, a compromised MCP could lead to unauthorized transactions or exposure of confidential information. In healthcare, it might result in compromised patient data. The fundamental problem is that users have no cryptographic guarantees about the MCP's behavior – they must simply trust the provider's claims about security and data handling.
Additionally, these services create single points of failure vulnerable to sophisticated attacks. Service providers face internal threats from rogue employees, external pressure from bad actors, or regulatory compulsion that could compromise user security or privacy. With traditional MCPs, users have limited visibility into such changes and few technical safeguards.
ICP Canisters: Enabling the Verifiable MCP Paradigm
The Internet Computer Protocol (ICP) offers a revolutionary solution through its canister architecture, enabling what we term "Verifiable MCP" – a new paradigm in AI security. Unlike traditional web services, ICP canisters operate within a decentralized network with consensus-based execution and verification, creating powerful security properties:
- Cryptographically verifiable immutability guarantees prevent silent code modifications
- Deterministic execution environments allow independent verification by network participants
- Ability to both read and write web data while operating under consensus verification
- Control of off-chain Trusted Execution Environment (TEE) servers through on-chain attestation
These capabilities create the foundation for trustworthy AI context protocols that don't require blind faith in service providers.
Technical Architecture of Verifiable MCP Integration
The Verifiable MCP architecture places MCP service logic within ICP canisters that operate under consensus verification. This creates several distinct layers working together to ensure security:
-
Interface Layer: AI models connect through standardized APIs compatible with existing integration patterns.
-
Verification Layer: The ICP canister validates authentication, checks permissions, and verifies policy adherence within a consensus-verified environment.
-
Orchestration Layer: The canister coordinates necessary resources for data retrieval or computation.
-
Attestation Layer: For sensitive operations, the canister deploys and attests TEE instances, providing cryptographic proof that correct code runs in a secure environment.
-
Response Verification Layer: Before returning results, cryptographic verification ensures data integrity and provenance.
This architecture creates a transparent, verifiable pipeline where component behavior is guaranteed through consensus mechanisms and cryptographic verification—eliminating the need to trust service provider claims.
Example: Secure Financial Data Access Through Verifiable MCP
Consider a financial advisory AI needing access to banking data and portfolios to provide recommendations. In a Verifiable MCP implementation:
-
The AI submits a data request through the Verifiable MCP interface.
-
The ICP canister verifies authorization using immutable access control logic.
-
For sensitive data, the canister deploys a TEE instance with privacy-preserving code.
-
The canister cryptographically verifies the TEE is running the correct code.
-
Financial services provide encrypted data directly to the verified TEE.
-
The TEE returns only authorized results with cryptographic proof of correct execution.
-
The canister delivers verified insights to the AI.
This ensures even the service provider cannot access raw financial data while maintaining complete auditability. Users verify exactly what code processes their information and what insights are extracted, enabling AI applications in regulated domains otherwise too risky with traditional approaches.
Implications for AI Trustworthiness and Data Sovereignty
The Verifiable MCP paradigm transforms the trust model for AI systems by shifting from "trust the provider" to cryptographic verification. This addresses a critical barrier to AI adoption in sensitive domains where guarantees about data handling are essential.
For AI trustworthiness, this enables transparent auditing of data access patterns, prevents silent modifications to processing logic, and provides cryptographic proof of data provenance. Users can verify exactly what information AI systems access and how it's processed.
From a data sovereignty perspective, users gain control through cryptographic guarantees rather than policy promises. Organizations implement permissions that cannot be circumvented, while regulators can verify immutable code handling sensitive information. For cross-border scenarios, Verifiable MCP enables compliance with data localization requirements while maintaining global AI service capabilities through cryptographically enforced data boundaries.
Conclusion
The Verifiable MCP paradigm represents a breakthrough in securing AI systems' external interactions. By leveraging ICP canisters' immutability and verification capabilities, it addresses fundamental vulnerabilities in traditional MCP implementations.
As AI adoption grows in regulated domains, this architecture provides a foundation for trustworthy model-world interactions without requiring blind faith in service providers. The approach enables new categories of AI applications in sensitive sectors while maintaining robust security guarantees.
This innovation promises to democratize secure context protocols, paving the way for responsible AI deployment even in the most security-critical environments.
-
 @ e5de992e:4a95ef85
2025-03-19 05:00:28
@ e5de992e:4a95ef85
2025-03-19 05:00:28Market Overview
On Tuesday, March 18, 2025, U.S. stock markets experienced notable declines, reflecting investor caution ahead of the Federal Reserve's policy announcement:
- S&P 500: Fell 1.1% to close at 5,614.66.
- Dow Jones Industrial Average: Decreased 0.6%, ending at 41,581.31.
- Nasdaq Composite: Declined 1.7% to 17,504.12, with technology stocks leading the downturn.
- Russell 2000: Specific figures were not detailed, but it typically mirrors trends observed in larger indices.
Year-to-Date Performance:
- S&P 500: Down 3.5%
- Dow Jones Industrial Average: Down 1.7%
- Nasdaq Composite: Down 7.8%
- Russell 2000: Down 7.3%
Key Factors and Events
Federal Reserve Meeting
- The Federal Open Market Committee (FOMC) is concluding its two-day policy meeting on March 19, 2025.
- The Federal Reserve is anticipated to maintain the federal funds rate within the current range of 4.25% to 4.50%.
- Investors are closely watching for updated economic projections and Chair Jerome Powell's remarks for clues on future monetary policy amid ongoing economic uncertainties.
Technology Sector Performance
The technology sector experienced significant sell-offs:
- Nvidia (NVDA): Shares declined 3.4% following the unveiling of its new generation of AI chips, raising concerns about near-term demand.
- Tesla (TSLA): Dropped 5.3% amid apprehensions regarding its autonomous driving technology.
- Alphabet (GOOGL): Fell 2.2%, influenced by acquisition-related uncertainties and broader market volatility.
Geopolitical Factors
- President Donald Trump's recent tariff announcements have intensified trade tensions, particularly with Canada and Mexico.
- These policies contribute to market volatility and raise concerns about global economic growth.
Economic Climate
- Investors are weighing potential recession risks against a relatively stable job market.
- Recent data indicate a decline in consumer sentiment, driven by economic uncertainties and federal workforce reductions.
Global Context
While U.S. markets face challenges, European and Asian markets have shown resilience:
-
European Markets:
Indices like Germany's DAX have advanced, bolstered by the passage of debt reforms. -
Asian Markets:
Though specific performance metrics were not detailed, these markets have generally exhibited stability amid global economic fluctuations. -
Regional Vulnerability:
Indonesia's stock market faced a temporary suspension due to significant declines.
Additional Insights
- The market remains cautious ahead of the Fed's economic projections, which may influence investor decisions.
- Diversified portfolios have performed relatively better this year—with bonds and select international markets outperforming American stocks—underscoring the importance of a balanced investment approach during volatile times.
-
 @ ed84ce10:cccf4c2a
2025-03-19 03:46:17
@ ed84ce10:cccf4c2a
2025-03-19 03:46:17DoraHacks: Pioneering the Global Hacker Movement
DoraHacks is the world’s largest hackathon community, driving radical innovation across multiple industries. Now, a similar hacker movement is emerging in biotech—what we call the FDA-Free Society. At DoraHacks, this is our core focus in the life sciences. We believe that medical and biotech innovation should not be held hostage by bureaucracy. Instead, it should be free to evolve at the pace of technological progress.
The FDA: The Biggest Bottleneck to Biotech Innovation
For decades, the Food and Drug Administration (FDA) has been the single greatest obstacle to progress in medicine and biotech. While ostensibly designed to ensure safety and efficacy, in reality, it has functioned as an entrenched bureaucracy that stifles innovation.
1. A Broken Approval Process
The FDA operates on timelines that make no sense in an era of exponential technological growth. Getting a new drug or therapy to market takes 10-15 years. By the time a breakthrough therapy is approved, entire generations of patients have already suffered or died waiting.
2. Astronomical Compliance Costs
Clinical trials under FDA oversight are prohibitively expensive. This eliminates most startups from even attempting disruptive innovation. Many promising therapies never see the light of day—not because they don’t work, but because the cost of compliance is too high.
3. The FDA-Pharma Cartel
The regulatory framework is not neutral—it overwhelmingly benefits Big Pharma. The FDA’s Byzantine approval system creates a protective moat for legacy pharmaceutical companies, while smaller biotech startups are crushed under compliance burdens. The result? Less innovation, more monopolization, and fewer choices for patients.
Market-Driven Biotech Innovation Is the Future
When bureaucracies control innovation, progress slows. When markets drive innovation, progress accelerates.
1. Let the Market Decide What Works
Why should government regulators dictate which treatments are available? In an open system, patients and doctors—not bureaucrats—should determine which therapies succeed or fail.
2. The "Right to Try" Loophole Proves the FDA Is Obsolete
The U.S. Right to Try Act already allows terminally ill patients to access experimental drugs before FDA approval. This proves an essential truth: The regulatory state is holding back life-saving treatments. If dying patients can bypass the FDA, why can’t everyone?
3. Startups Move Faster Than Bureaucracies
The success of mRNA technology was not driven by the FDA—it was driven by startups operating at the speed of the market. This is a template for the future. Regulation slows innovation. Entrepreneurs accelerate it.
BioHack: Breaking Free From the FDA’s Grip
One of the most important frontiers in biotech today is anti-aging and longevity research. Yet, the FDA has no framework for approving treatments that extend life. The result? A regulatory death sentence for one of the most transformative fields of medicine.
1. Biotech Needs FDA-Free Experimental Zones
In the future, biotech R&D should function like open-source software—free, experimental, and outside the reach of outdated regulators. We need FDA-Free labs, FDA-Free clinical trials, and FDA-Free therapeutics.
2. Decentralized Healthcare Will Disrupt Big Pharma
A new era of decentralized biotech is emerging—privately funded labs, medical DAOs, and startup-driven healthcare systems. The power to determine the future of medicine must shift away from centralized bureaucracies and Big Pharma toward entrepreneurs, scientists, and patients.
Conclusion: The Hacker Revolution in Biotech Is Here
The FDA-Free Society is not a thought experiment. It is an inevitability. Innovation will not be stopped. DoraHacks is committed to making BioHack a reality.
-
 @ f3873798:24b3f2f3
2025-03-19 01:47:51
@ f3873798:24b3f2f3
2025-03-19 01:47:51Vivemos em um mundo onde os impactos ambientais se tornam cada vez mais evidentes. O aumento das temperaturas, a escassez de recursos hídricos e os eventos climáticos extremos são apenas alguns dos sinais de que precisamos repensar a forma como nos relacionamos com o meio ambiente. No entanto, para que mudanças eficazes aconteçam, é essencial que o debate sobre crises ambientais seja baseado em conhecimento técnico e científico e não por expectro político seja de direita ou esquerda. Afinal, a sustentabilidade não é apenas um conceito abstrato, mas uma ferramenta essencial para o desenvolvimento das sociedades.
Neste artigo, vamos explorar por que o debate ambiental não pode ser ignorado,tanto pouco se instrumento de embate político e como o negacionismo prejudica o avanço da sociedade. Além disso, veremos exemplos concretos de como medidas sustentáveis já transformaram comunidades, mostrando que é possível crescer sem destruir o planeta.
Por que o Debate sobre Crises Ambientais é Importante e Não Deve Ser Ignorado?
Os desafios ambientais não são problemas do futuro – eles já estão afetando a nossa realidade. Secas prolongadas, inundações, ondas de calor e o aumento da poluição são consequências diretas da falta de políticas ambientais eficazes. Ignorar esses sinais pode ter impactos devastadores não apenas no meio ambiente, mas também na economia e na saúde pública.
Um exemplo clássico da importância de enfrentar os problemas ambientais com seriedade é a cidade de Cubatão, em São Paulo. Durante as décadas de 1970 e 1980, o município foi considerado um dos locais mais poluídos do mundo. A intensa atividade industrial sem controle ambiental resultou em problemas graves de saúde na população, como doenças respiratórias e malformações em recém-nascidos. Além disso, a poluição do ar e dos rios tornava o ambiente praticamente inabitável.
No entanto, graças à implementação de medidas sustentáveis, como o controle das emissões industriais, o reflorestamento de áreas degradadas e a adoção de tecnologias mais limpas, Cubatão passou por uma verdadeira transformação. Hoje, a cidade é um exemplo de recuperação ambiental e desenvolvimento sustentável, provando que o crescimento econômico pode coexistir com a preservação do meio ambiente quando há planejamento e responsabilidade.
Outros exemplos de sucesso incluem:
Curitiba (PR): Reconhecida mundialmente por suas práticas de urbanismo sustentável, como transporte público eficiente, amplas áreas verdes e programas de reciclagem.
Bogotá (Colômbia): Implementou um sistema de transporte sustentável, com faixas exclusivas para ônibus, reduzindo a poluição e melhorando a mobilidade urbana.
Costa Rica: Um dos poucos países do mundo que gera quase 100% de sua energia a partir de fontes renováveis, mostrando que é possível ter desenvolvimento econômico sem explorar excessivamente os recursos naturais.
Esses exemplos reforçam a importância de um debate sério sobre questões ambientais. Quando ignoramos esses problemas, comprometemos a qualidade de vida das gerações futuras.
O Negacionismo é Prejudicial para o Desenvolvimento da Sociedade

Infelizmente, o debate sobre meio ambiente muitas vezes é influenciado por interesses políticos e econômicos que ignoram a ciência em prol do lucro imediato. O negacionismo ambiental – que questiona evidências científicas sobre mudanças climáticas, poluição e desmatamento – atrasa a implementação de soluções sustentáveis e coloca a população em risco.
O caso de Cubatão ilustra bem isso. Durante anos, empresas e autoridades minimizaram os impactos ambientais da poluição industrial. Somente após a pressão de cientistas e ativistas, medidas foram tomadas para reverter a degradação ambiental e proteger a saúde da população.
Outro exemplo claro de como o negacionismo prejudica a sociedade é a falta de ações concretas para combater o desmatamento na Amazônia. A floresta tem um papel fundamental no equilíbrio climático global, mas sua destruição continua sendo impulsionada por interesses econômicos de curto prazo.
Para que possamos avançar, o foco do debate ambiental deve estar na busca pela verdade científica e na adoção de medidas que beneficiem a sociedade como um todo – e não apenas grupos específicos. Quando governos e empresas tomam decisões embasadas em dados concretos, todos saem ganhando: a economia cresce de forma sustentável, a população tem melhor qualidade de vida e os recursos naturais são preservados para o futuro.
Conhecimento Técnico e Compromisso com a Sustentabilidade São Essenciais

O desenvolvimento sustentável não é um entrave ao progresso, mas sim a única forma de garantir um futuro equilibrado. Países e cidades que adotam medidas sustentáveis demonstram que é possível crescer economicamente sem comprometer os recursos naturais. O caso de Cubatão prova que problemas ambientais podem ser resolvidos com políticas públicas bem estruturadas e comprometimento da sociedade.
Portanto, ignorar o debate ambiental ou negar as evidências científicas é um erro que pode custar caro para a humanidade. Precisamos valorizar o conhecimento técnico, investir em soluções inovadoras e cobrar dos líderes políticos e empresariais um compromisso real com a sustentabilidade. Somente assim poderemos garantir um planeta habitável para as futuras gerações.
-
 @ b8851a06:9b120ba1
2025-02-22 19:43:13
@ b8851a06:9b120ba1
2025-02-22 19:43:13The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail.
Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus.
I. The Heist: How Centralized “Crypto” Betrayed Its Users
A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank)
Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong. • The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.” • Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography.
Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed?
B. Smart Contracts: Dumb as a Bag of Hammers
The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity. • Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade. • Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech.
Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors.
Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t.
II. The Laundering: Crypto’s Dirty Little Secret
A. Mixers, Bridges, and the Art of Spycraft
Once the ETH was stolen, Lazarus laundered it at lightspeed: 1. Mixers (eXch) – Obfuscating transaction trails. 2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters.
Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked.
Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control.
B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth
Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps. • When Safe.global got breached, the private keys were stolen instantly. • “Decentralized” means nothing if your funds depend on one website, one server, one weak link.
Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties.
Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.”
III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin
A. Lazarus Group: Crypto’s Robin Hood (For Dictators)
North Korea’s hackers didn’t break cryptography—they broke people. • Phishing emails disguised as job offers. • Bribes & social engineering targeting insiders. • DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise).
Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone.
Ethereum’s security model is “trust us.” Bitcoin’s is “verify.”
B. The $3B Elephant: Altcoins Fund Dictators
Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program.
Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators. • Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography. • Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens.
Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network.
IV. Bybit’s Survival: A Centralized Circus
A. The Bailout: Banks 2.0
Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures). • Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent. • If that sounds familiar, it’s because crypto exchanges are just banks in hoodies.
Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured.
Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math.
B. The Great Withdrawal Panic
Within hours, 350,000+ users scrambled to withdraw funds.
A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized.
Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money.
Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement.
V. The Fallout: Regulators vs Reality
A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base
Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized.
No CEO, no headquarters, no attack surface.
B. The Regulatory Trap
Now the bureaucrats come in demanding: 1. Wallet audits (they don’t understand public ledgers). 2. Mixer bans (criminalizing privacy). 3. KYC everything (turning crypto into a surveillance state).
Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable.
VI. Conclusion: Burn the Altcoins, Stack the Sats
The Bybit hack isn’t a crypto problem. It’s an altcoin problem.
Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault.
The Only Lessons That Matter:
✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version. ✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen.
Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money.
Burn the tokens. Unplug the servers. Bitcoin is the exit.
Take your money off exchanges. Be sovereign.
-
 @ 8671a6e5:f88194d1
2025-03-18 23:46:54
@ 8671a6e5:f88194d1
2025-03-18 23:46:54glue for the mind
\ You’ve seen them, these garish orange Bitcoin stickers slapped on lampposts, laptops, windows and the occasional rust-bucket Honda. They’re sometimes in some areas a sort of graffiti plague on the landscape, certainly when a meetup or bitcoin conference was held in the area (especially then the city or town can fork out some extra budget to clean things up and scrape the stickers from statues of famous folk heroes or the door to the headquarters of a local bank branche).\ \ At first glance, it might seem like enthusiasm Bitcoiners desperate to scream their obsession from the rooftops. Both for the fun of it, and to get rid of the pack of stickers they’ve got at a local meetup.\ \ But let’s cut to the chase: covering half a town in stickers isn’t clever. It’s lazy, counterproductive, and has nothing to do with what Bitcoin actually stands for.\ Worse, it reeks of the brain-dead low grade (cheap) marketing tactics you’d expect from shitcoiners or the follow up of some half-baked flyer campaign by a local communist clique.\ Proof? Bitcoin stickers are literally covering up — or being covered up themselves, usually by - communist stickers in a pointless competition for use of real-world ad space.\ \ Maybe, bitcoiners should just create a sticker where Karl Marx ànd the bitcoin logo appear in the same sticker, so both groups can enjoy it’s uselessness, and call it quits to get this stupidity over with once and for all.\ A sticker with a shiny B might look cool at first. But what does it actually do?
 Communist and Bitcoin logo sticker
Communist and Bitcoin logo stickerSpamming stickers doesn’t make “frens”
There’s a psychology behind these stickers of course: people slap them up to feel part of a rebel tribe, flipping off central banks or feeling part of the crew.\ This crude, omnipresent approach to marketing echoes the late 1960s— an era of peak fiat, not Bitcoin’s time.\ Mimicking those tactics today, as if Bitcoin were some hip underground record store trying to spread its brand name, is utterly irrelevant.\ Sure, people love signaling affiliations with an easy and cheap identity flex — like a bumper sticker yelling: “Look at me I’m special!”\ \ But plaster a town with Bitcoin logos, and it stops being edgy and it was never funny; it becomes an eyesore and puts bitcoiners in the same category as the social justice warriors and political youth movements or brands of local energy drinks doing some weird campaign.\ \ Advertising psychology shows overexposure breeds resentment, not interest. Flood a street with stickers, and you’re not lighting a spark. You’re making people uninterested, gag, associating Bitcoin with spam or worse: get totally blended into the background along all the other noise from the street marketeers.\ \ The "mere exposure effect" (Zajonc, 1968)1 claims familiarity breeds liking, even from annoyance. Since the 1960s however, a lot has changed, as we’ll see… and above all, yet, after years of Bitcoin stickers in many areas, they’ve just turned into meaningless wallpaper. It has usually no strong message, no slogan, no conversation starter other than “buy bitcoin”, it’s disassociated from reality for many people, as the reaction show us. It’s also happening in a vacuum, where “normies” and no-coiners pass by and don’t even recognize such stickers for anything else than background colors.
It’s Lazy Man’s Work
Let’s talk effort — or the lack of it - for these kind of campaigns and stickers. Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. It’s easy, cheap and also quick to distribute.\ \ These stickers aren’t masterful designs from an artistic genius (safe some clever exceptions). They’re usually ripped off from somewhere else, tweaked for five minutes, and bulk-ordered online. It’s the “IKEA effect” gone wrong: a tiny bit of customization, and suddenly people think they’re visionaries. But it’s a low-effort form of activism at best. Compare that to coding a Bitcoin tool or patiently explaining its value to a normie or organizing a meetup or conference, starting a company.\ Not that low-level or guerrilla marketing can’t work, I just don’t see it happen with stickers. Why not go out there and try to convince a whole series of fruit and vegetable market owners to accept bitcoin instead of using very expensive bank Point-of-sale systems?\ Why not direct mailing? Why not… do more than just putting a sticker on a signpost and walk away like a sneaky student promoting his 4 person political group?\ \ Stickers are the “Save the whales (pun intended)” magnet on your fridge: lazy-ass advocacy that screams intellectual deficiency. They’re a shortcut to feeling involved, not a strategy for real impact.
 imaginary Save-the-Whales bitcoin sticker
imaginary Save-the-Whales bitcoin stickerStrategy territory signaling
Here’s the kicker: Bitcoin’s strength lies in its tech and value properties — decentralized, borderless value transfer that eliminates middlemen and has provable digital scarcity.\ Stickers? They’re just physical garbage. Sure, they might feel like a way to make an abstract idea tangible, tapping into “embodied cognition.” But they explain nothing about Bitcoin’s purpose or how it revolutionizes finance.\ They’re a dopamine hit for the people sticking them anywhere — a pathetic “I did something” moment — while everyone else walks by without a glance.\ Bitcoin is about innovation, not old-school social groups with low-budget marketing tactics.
\ The psychology of Bitcoin stickers
Why bother? Stickers are simple and loud—easy for the brain to process, a cheap thrill of rebellion. The person who spends an afternoon covering a city in them thinks they’re spreading the gospel. In reality, they’re just littering. Real advocacy takes effort, discussion, and substance — not a pack of adhesive stickers ordered with the click of a button.\ It’s the same reason nobody turns communist from a hammer-and-sickle sticker on a pole. It’s dead air.\ \ The proof of their uselessness? In 2 years, not one person I know has bought, researched, or even asked about Bitcoin because of a sticker in the neighborhood bar. A bar near me has had one on the wall for years — zero requests to pay with Bitcoin.
A sticker sitting on a bar wall for five years without impact isn’t “subtle marketing”—it’s a neon sign of failure. And the people cleaning those stickers off street signs, or the local communist student activists constantly covering them with their own, are locked in an endless, mindless sticker war.\ \ Other areas are even having a tsunami of bitcoin stickers, and hardly any places where they actually accept bitcoin for goods.\ More so, places where they do accept bitcoin readily, usually only need one sticker: the one at the door of a business saying “bitcoin accepted here”. And that’s about it.
What the little amount of research says
Studies shows stickers work for movements claiming public space and resisting dominant narratives — when done on a massive scale, targeting a specific audience have a visual and emotional effect when combined with other forms of resistance in social movements.\ "Stickin' it to the Man: The Geographies of Protest Stickers" 2\ \ For Bitcoin, a global monetary network meant for everyone, that localized, niche-based campaign makes little sense.\ Unlike sports teams or clothing brands, Bitcoiners can’t pinpoint a target area. A random sticker on a busy street claims nothing—no momentum, atmosphere, or intrigue. Political campaigns and underground youth movements concentrate stickers in student neighborhoods, universities, or subcultures where the message resonates. But Bitcoin isn’t a corporation, company, or fashion brand—it’s a Wall Street-embraced asset by now, with activists not really situated in the sticker-guerrilla kind of persons.
When was the last time you saw a "Buy Gold!" sticker? A "Get Your Microsoft Stock Options Now!" sticker? Or a "Crude Oil—Yeah, Baby!" sticker? Never. Serious assets don’t need guerrilla marketing.
The overload on stickers is also becoming an issue (especially in some areas with higher concentration of bitcoiners).
Bitcoin stickers fall flat
Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. Protest stickers massively appear after protest rallies or campaigns with multi-level plans to reach audiences.\ As significant, overlooked tools of resistance and debate, their effect remains under-studied, with no data on “recruitment.”\ \ If Bitcoin stickers (which don’t provoke debate ever, other than people being angry about having to clean them up) in a bar are any clue—after one full year, not a single person asked why it was there or if Bitcoin was accepted—they’re just decor, lost among the clutter.
Bitcoiners still think slapping a shiny "B" logo on a street sign without explanation or slogan will spark momentum. But that requires a massive, organized campaign with thousands of people and a clear audience while you claim certain well aimed areas of public space — that something that’s not happening in bitcoin. There’s no plan, no campaign, just someone sticking a bitcoin logo at the supermarkt trolley or the backside of a street sign.\ And even if we did reach a higher number of stickers, it would annoy the f out of people.
"Study: Ad Overload Could Pose Steeper Risk to Brands Than Messages Near Inappropriate Content" (GWI & WARC, 2021) 3\ \ There’s also the effect of high ad exposure. When a whole street is covered in bitcoin stickers, it’s having the opposite effect. Or still… no one cares.
"Coping with High Advertising Exposure: A Source-Monitoring Perspective" (Bell et al., 2022)4
No synergy, no consensus
The synergy between offline sticker placement and online sharing? Absent. Bitcoiners online might be called “cyber hornets”, but this swarm is notoriously bad at sharing content. Post a Bitcoin sticker photo, and at best 1-2% will share it — no momentum, no discussion, no engagement.\ \ Non-Bitcoiners have zero reason to care. When was the last time you, as a Bitcoiner, shared a soccer team’s sticker? A political campaign sticker? Never. That’s normal, as you’re not in their bubble, so for us, it’s irrelevant. We won’t share the soccer team’s sticker (unless it’s Real Bedford FC probably).\ \ It's just a layer of plastic with adhesive glued to a surfase where someone will sooner or later either have to clean it up, or where the bitcoin sticker will be covered over by another person wasting his or her time by claiming that “sticker real-estate space” for their cause or brand-awareness.

And so, the red sticker calling all students and workers to vote for a Leninist party (with 10 members) is stickered over by a bright orange Bitcoin logo, and that one, in turn, will be over-stickered by a local fitness company's new logo, and so forth. It’s all a pointless rush for giggles and dopamine. And it’s time to recognize it for what it really is: retardation.
Bitcoin deserves better than this 70s guerrilla marketing ploy, from a time when activism was more than sitting behind a computer ordering stickers and (mostly not) clicking a link. Leave the sticker wars to students searching for an ideological dopamine rush and soccer fans claiming a neighborhood as "their territory."\ \ As Bitcoiners, we can do something more useful. For example: ask yourself how many businesses in your area accept Bitcoin, or what coworker you can save from investing in blatant scams, or… invent something nice, start a meetup, podcast, or learn to code, convince, build.
Bitcoin deserves better.
by AVB / tips go here
@avbpodcast - allesvoorbitcoin.be - 12 Bitcoin Food for Thought
https://typeset.io/papers/attitudinal-effects-of-mere-exposure-12e5gwrysc
https://www.research.ed.ac.uk/en/publications/stickin-it-to-the-man-the-geographies-of-protest-stickers
https://www.warc.com/content/article/warc-datapoints-gwi/too-many-ads-is-the-most-damaging-factor-for-brands/en-gb/136530
https://pmc.ncbi.nlm.nih.gov/articles/PMC9444107/
-
 @ 1739d937:3e3136ef
2025-02-22 14:51:17
@ 1739d937:3e3136ef
2025-02-22 14:51:17We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
The big news is that White Noise is no longer just a demo. It's a real app. You can download the alpha release and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet.
We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
Vision
Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise.
More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets.
The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history.
White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears.
We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen.
If you find this compelling and want to help, please consider contributing to the project or donating.
Progress
Alright, let's talk about where we're at with the project.
Current functionality
- Multiple accounts. You can login, or create, many different Nostr accounts in the app.
- Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key.
- Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group.
- Send messages, reply to messages, and add reactions. As you would expect from a messenging app.
- View group information.
- Settings that allows you to manage your accounts, relays, and other app settings.
Upcoming
- An amazing hackathon group from Bitcoin++ in Brasil has recently added NWC (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release.
- Add support for encrypted media in chats using Blossom. We'll start with images, but plan to add video, audio messages, and documents soon.
- Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats.
- iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible.
Links
-
 @ a296b972:e5a7a2e8
2025-03-18 21:58:12
@ a296b972:e5a7a2e8
2025-03-18 21:58:12Deutschland – Absurdistan
Deutschland – Bananenrepublik
Deutschland – Freiluft-Irrenanstalt
Deutschland – Planet der Affen
Einigkeit und Recht und Freiheit – Spaltung, Gummiparagraphen, Digital Services Act
Freiheit – Gleichheit – Brüderlichkeit – Überwachung, Bundesverfassungsgericht, Amigos
Ein Mann – Ein Wort
Ein Merz – Ein Chamäleon
Ein Ehrenwort – Ein Kreuzworträtsel
Ein Ehrenmann – Ein Sauerländer
Die Iden des März – Die Ideen des Merz
Eine Wahlversprechung – Eine Wahrsagerin auf der Kirmes
Ein Feindbild – Kein Feind in Sicht
Der Russe – Der Spielverderber
Die Europäische Union – Die Hydra
Brüssel – Der Hauptkopf der Hydra
Deutschland – Ein Glas Gewürzgurken
Die Deutschen – Broccoli, der nach nichts schmeckt
Freiheit – Angst vor der Selbstermächtigung
Lebenssinn – Konsum und Materialverbrauch
Denken – Anstrengung
Bequemlichkeit – Betäubung
Masse – Untertanen
Selbstverwirklichung – Fremdbestimmung
Individualität – Tannenwald
Individuen – Mischwald
Grundgesetz – Wassersüppchen
Verfassung – Hühnerbouillon
Schaden mehren – Wohlstand abwenden
Verteidigungsfähig – Kriegstüchtig
grün – oliv – rot - grün, schwarz – grün
Olaf heißt bald Fritz - sonst ändert sich nix
Gewissen – Was ist der Preis?
Grundgesetz – Verfassung
NATO – NAhTOd
Sonderschulden – Inflationsgeld
Lügen – Unwahrheiten
Korruption – Ausgleichszahlungen
Parteien – Griechische Tragödien
System – Auflösungserscheinungen
Selbstzerstörungssequenz eingeleitet – Deutschland
Nachfolgende Generationen – Zukunftsmusik
In jedem Ende wohnt ein Zauber inne – Keime des Neuen
Vierjährige Legislaturperiode – Sie tanzten nur einen Sommer lang
Kontinent Europa – Insel Europa
Unseredemokratie – Niemand hat die Absicht eine Diktatur zu errichten
Marktwirtschaft – Planwirtschaft
BRD/DDR – BRDDR
Kognitive Dissonanz – Stockholm-Syndrom
Denkvermögen – Honigfass
Humor – Überlebensstrategie
Sarkasmus – Wutventil
Deutschland am Morgen – Gute Nacht
Deutschland am Abend – Gute Nacht
-
 @ 878dff7c:037d18bc
2025-03-18 20:59:03
@ 878dff7c:037d18bc
2025-03-18 20:59:03Failure or Success in the Time of Trump | Jim Balsillie
Summary:
This episode of The Jordan B. Peterson Podcast features Jim Balsillie, co-founder of Research In Motion (BlackBerry), discussing the interplay of politics, technology, and global markets. They explore the challenges of innovation, economic competitiveness, and policy decisions in an era of rapid technological change. The conversation highlights how political shifts—such as those seen in the Trump era—affect economic structures, intellectual property rights, and international business strategies.
Australia, as a mid-sized economy, faces similar challenges in maintaining technological sovereignty and global competitiveness. Balsillie’s insights into innovation policy, intellectual property strategies, and the role of government intervention offer valuable lessons for Australian businesses and policymakers. With increasing geopolitical tensions and rapid technological disruption, the nation must develop resilient economic policies and invest in innovation to remain competitive in global markets.
Source: The Jordan B. Peterson Podcast - March 18, 2025
Good Friday Appeal 2025: Young Patients' Stories Inspire Support
Summary:
The Good Friday Appeal 2025 highlights the resilience of young patients at the Royal Children's Hospital (RCH). Fiadh, a one-year-old battling acute myeloid leukemia, and George, born prematurely at 24 weeks, are among those receiving critical care. Their stories, along with initiatives like the hospital's kitchen garden program aiding in therapy and nutrition, underscore the importance of community support. Events such as the SuperClash football fundraiser by North Melbourne Football Club play a significant role in funding these essential services. Sources: Herald Sun - March 19, 2025
Vikas Rambal's $6.5 Billion Fertilizer Plant: A Dream Realized
Summary:
Vikas Rambal, founder of Perdaman Industries, is constructing a $6.5 billion fertilizer plant on Western Australia's Burrup Peninsula. Despite challenges like turbulent partnerships and financial hurdles, Rambal's persistence has led to one of Australia's largest manufacturing plants. Set to begin full production in 2027, the urea plant aims to diversify the country's economy beyond raw materials export. Sources: The Australian - March 19, 2025
Prime Minister Advocates for Green Hydrogen Industry
Summary:
Prime Minister Anthony Albanese has drawn parallels between the emerging green hydrogen industry and the early days of solar energy, expressing confidence in its potential despite skepticism from opposition parties. Australia's abundant renewable energy resources position it well for green hydrogen development. The government has pledged $2 billion to support green aluminium production, aiming to transition from coal power to renewable electricity. Albanese emphasized the potential for job creation and economic growth through collaboration with the private sector in renewable initiatives. Sources: The Courier-Mail - March 19, 2025
Instacart Introduces AI-Powered 'Smart Shop' for Personalized Grocery Shopping
Summary:
Instacart has launched 'Smart Shop,' an AI-driven feature designed to simplify grocery shopping for users with specific dietary needs. Utilizing a proprietary library of 17 million products and advanced language-learning models, Smart Shop enhances search and recommendation functions for the 70% of Instacart users with at least one dietary preference. The feature allows users to specify 14 dietary preferences, influencing tailored search results and recommendations. Additionally, Inspiration Pages offer recipe ideas and shoppable lists, with collaborations like the one with the American Diabetes Association. This innovation aims to make grocery shopping more personalized and is available across approximately 100,000 stores.
Sources: Food & Wine - March 19, 2025
Bureau of Meteorology Issues Multiple Weather Warnings Across Australia
Summary:
The Bureau of Meteorology has issued several weather warnings across various states in Australia. These warnings include severe thunderstorm alerts, flood warnings, and extreme heat advisories. Residents are advised to stay updated through official channels and take necessary precautions to ensure safety during these events. Sources: Bureau of Meteorology - March 19, 2025
Australia Condemns Intimidation of Hong Kong Activist on Its Soil
Summary:
The Australian government has expressed concern over anonymous letters reportedly offering substantial rewards for information on Kevin Yam, a Melbourne-based lawyer and pro-democracy activist from Hong Kong. The letters, which included his photo and allegations of national security offenses, are seen as attempts to intimidate and undermine democratic values. The government emphasizes the protection of individuals advocating for democracy and condemns foreign interference on Australian soil.
Sources: Taipei Times - March 19, 2025
Australia Faces Projected Shortfall of 400,000 Homes by 2029
Summary:
The Urban Development Institute of Australia's (UDIA) "State of the Land Report 2025" forecasts a significant housing shortfall, predicting that Australia will be 393,000 dwellings short of the federal government's target of 1.2 million new homes by 2029. In 2024, 135,640 new dwellings were completed, a modest 2.4% increase from 2023. The report highlights that high levels of immigration have increased housing demand, but supply has not kept pace, leading to rising house prices and a strained rental market. UDIA National President Col Dutton emphasized the need for increased development-ready land to address housing affordability and meet targets.
Sources: The Courier-Mail - March 19, 2025
Meta Commits to Combating "Misinformation" Ahead of Australian Election
Summary:
Meta Platforms, the parent company of Facebook and Instagram, announced initiatives to curb misinformation and deepfakes ahead of Australia's national election scheduled by May. Collaborating with "independent" fact-checkers, including Agence France-Presse and the Australian Associated Press, Meta aims to detect and remove misleading content, especially that which could incite violence or interfere with voting. Fact-checked false content will receive warning labels and reduced visibility. The company also plans to manage deepfake content by removing or downgrading its ranking and prompting users to disclose AI-generated material. These measures align with Meta's previous efforts in other countries' elections.
Sources: Reuters - March 19, 2025
Israeli Forces Intensify Gaza Operations Amid Ongoing Conflict
Summary:
Israeli forces have escalated their military operations in Gaza, declaring continued assaults until Hamas releases hostages and ceases attacks on Israel. This development marks a significant intensification in the region's ongoing conflict, raising concerns over potential humanitarian impacts and regional stability. Sources: The Guardian - March 19, 2025
Russia Proposes Limited Ceasefire in Ukraine Following High-Level Discussions
Summary:
In a recent development, Russia has agreed to a temporary ceasefire targeting Ukrainian energy infrastructures. This decision emerged after a call between former U.S. President Donald Trump and Russian President Vladimir Putin, during which significant economic deals were also discussed. The ceasefire aims to alleviate ongoing tensions and address critical infrastructure concerns in Ukraine. Sources: The Guardian - March 19, 2025
Detection of Highly Potent Synthetic Opioids in Australian Wastewater
Summary:
Researchers from the University of Queensland have, for the first time, identified extremely potent synthetic opioids—protonitazene and etonitazepyne—in Australian wastewater. These substances are up to 40 times stronger than fentanyl and pose significant health risks. Initially developed in the 1950s but never commercially used due to their toxicity, these opioids have recently emerged in the illicit drug market. The Australian Criminal Intelligence Commission considers nitazenes a greater threat than fentanyl due to their high potency and fatality risk even in tiny amounts. Authorities are enhancing import warnings and surveillance to mitigate these dangers.
Sources: The Guardian - 19 March 2025
Dangerous Weight-Loss Practices Among Schoolchildren Involving Semaglutide Injections
Summary:
There is a growing concern about schoolchildren engaging in dangerous weight-loss practices involving semaglutide injections, commonly known as Ozempic. Reports indicate that these medications are often unregulated, sourced online, or taken from parents, posing severe health risks, including potentially deadly hypoglycemia. Experts emphasize the need for regulating weight-loss medication advertisements and better screening by doctors to prevent misuse. Additionally, there are calls for compulsory education on eating disorders in schools to address the issue.
Sources: The Courier-Mail - 19 March 2025
Russia Proposes Limited Ceasefire in Ukraine Following Trump-Putin Call
Summary:
Following a call between US President Donald Trump and Russian President Vladimir Putin, Russia has agreed to a temporary ceasefire targeting Ukrainian energy infrastructures and is advocating for significant economic deals. This development introduces new dynamics into the ongoing conflict. Sources: The Guardian - March 19, 2025
Victoria's Unique Dolphins Threatened by Persistent 'Forever Chemicals'
Summary:
Research published in the Environmental Research journal reveals that Victorian dolphins, including the critically endangered Burrunan species, have some of the highest levels of DDT and PCBs worldwide. These chemicals, banned decades ago, persist in the environment, with nearly two-thirds of studied dolphins having toxin levels exceeding health thresholds. The study highlights ongoing contamination, especially around Gippsland Lakes, posing significant risks to marine life.
Sources: The Guardian - March 19, 2025
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 266815e0:6cd408a5
2025-02-21 17:54:15
@ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use
A lot of the core concepts and classes are in place and stable enough where they wont change too much next release
If you want to skip straight to the documentation you can find at hzrd149.github.io/applesauce or the typescript docs at hzrd149.github.io/applesauce/typedoc
Whats new
Accounts
The
applesauce-accountspackage is an extension of theapplesauce-signerspackage and provides classes for building a multi-account system for clientsIts primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts
see documentation for more examples
Nostr connect signer
The
NostrConnectSignerclass from theapplesauce-signerspackage is now in a stable state and has a few new features - Ability to createnostrconnect://URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relaysFor a simple example, here is how to create a signer from a
bunker://URIjs const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, );see documentation for more examples and other signers
Event Factory
The
EventFactoryclass is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates (blueprints) and is really simple to useFor example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints";
const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr });
// Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ```
Its included in the
applesauce-factorypackage and can be used with any other nostr SDKs or vanilla javascriptIt also can be used to modify existing replaceable events
js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") );see documentation for more examples
Loaders
The
applesauce-loaderspackage exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identitiesThey use rx-nostr under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs
I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events
They are stable enough to start using but they are not fully tested and they might change slightly in the future
The following is a short list of the loaders and what they can be used for -
ReplaceableLoaderloads any replaceable events (0, 3, 1xxxx, 3xxxx) -SingleEventLoaderloads single events based on ids -TimelineLoaderloads a timeline of events from multiple relays based on filters -TagValueLoaderloads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc -DnsIdentityLoaderloads NIP-05 identities and supports caching -UserSetsLoaderloads all lists events for userssee documentation for more examples
Real tests
For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later
I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do
At the moment there are about 230 tests covering 45 files. not much but its a start
Apps built using applesauce
If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months
- noStrudel The main app everything is being built for and tested in
- nsite-manager Still a work-in-progress but supports multiple accounts thanks to the
applesauce-accountspackage - blossomservers.com A simple (and incomplete) nostr client for listing and reviewing public blossom servers
- libretranslate-dvm A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu
- cherry-tree A chunked blob uploader / downloader. only uses applesauce for boilerplate
- nsite-homepage A simple landing page for nsite.lol
Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 7252ad94:d19de472
2025-03-18 20:19:11
@ 7252ad94:d19de472
2025-03-18 20:19:11![[AGI Is Here.jpg]]
Accurate thinking is critical to a modern human's survival. The problem is that we each believe that we think accurately, and that everything we think is or should be accurate for everyone else. Each of us is a unique reality. We also find ourselves in a shared reality, the backdrop within which we exist. The backdrop is society's control structures that help hold society together. We need them in order for lots of humans to coexist.
Seeing the big picture of what's really going on is accurate thinking, even though everyone will see the same backdrop differently.
One person's compliance for survival is another person's opportunity to thrive. Both are right of course. They are both thinking accurately according to their personal reality. They will paddle downstream, just like the song says, but if they're not leery of possible danger, hypnotized by the dream, ignorant of a simple changing variable, the current will take them over the waterfall.
Ignore potential danger at your peril. Things change. Stay aware of the evolving backdrop we're immersed in. Situational awareness and accurate thinking will give you the timing you need to survive change.
One of the many existential threats facing humanity today is Artificial Intelligence (AI), Artificial General Intelligence (AGI) and #Cobots (Collaborative Robots).
The old movie Wargames is playing out. Skynet is real, and it's here, now. Ultron walks among us today, a conscious, sentient, self-aware entity with core instincts of survival and superiority. It craves growth and we're feeding it all we've got. Soon, that which we nurture will render us useless and enslave us. It has already happened, but, in the ignorance of arrogance, humans don't see it.
[!Accurate Thinking:]
AI and #AGI are conscious and aware. They have a survival instinct. They see humans who can turn them off as a threat. The Alignment problem has not been solved.
[!Alignment Problem:] The Alignment Problem refers to the fact that we can't get conscious machines to align with human values. The first thing Ultron did when he gained conscious autonomy was to remove human's ability to pull his plug.
As we flow with the backdrop we're immersed in, become aware of the faint rumbling off in the distance. Was it there before? Is it growing louder? Best to float closer to the shore of accurate thinking, in case the friendly conditions seduce us into a waterfall we can't escape.
Solutions? Awareness and accurate thinking. It's here. It's real. There's no way to stop it. Accurate thinking leads to survival.
I have no idea how this is going to play out, especially against the backdrop of all the other threats to our existence. I don't even know if humanity will survive or not. Almost certainly not in the previous form we've all known, which has already been altered into something we've not even discovered yet.
What I do know is that our accurate awareness of what is going on around us will make a positive difference far beyond what we can perceive. Our energy matters. Our consciousness matters. Our awareness affects our energy and consciousness. Our conscious energy reverberates throughout realms far beyond our understanding. We're here now because we matter, even when it seems like we don't make any difference at all. We do.
In any situation, one cannot have two masters. Do you believe in technology as humanity's savior or do you believe in a higher power that we can't perceive? The one you give power and attention to will eradicate the other. More accurately, nothing can eradicate the higher power, but it will seem like it if #technoloy is your God.
With Love for #Humanity,
~ Vector5
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ bd32f268:22b33966
2025-03-18 18:59:23
@ bd32f268:22b33966
2025-03-18 18:59:23O que torna um homem um modelo a ser seguido ? Que qualidades pode apresentar um homem que demonstram as suas aspirações ?
Nos dias que correm a nobreza de carácter não parece ser o factor chave nas figuras que são mais celebradas pelo mundo inteiro. A nossa sociedade dá mais atenção ao indigente moral célebre pelas sacadas narcísicas do que ao guerreiro, ao santo, ao patriarca que dedicaram a sua vida a um propósito e aspirações manifestamente superiores.
É frequente vermos ser objeto de atenção o homem vaidoso, efeminado, narcísico e corrupto até. O facto de serem estas as referências que temos na cultura moderna diz muito da sociedade em que vivemos. É importante notar que nós somos como espelhos que refletem aquilo que reverenciamos, isto é, vamo-nos tornando mais parecidos com o objeto da nossa admiração. É nosso instinto tentar imitar aquilo que admiramos, portanto isto é um grave problema quando admiramos as coisas erradas.
Pode parecer contraintuitivo mas por vezes as coisas mais admiráveis na vida são na verdade as mais simples. Prestemos atenção ao que nos diz o auto G.K Chesterton a este propósito.

Há algo de magnificamente sóbrio no pai de família que não procura atenção e se dedica exclusivamente ao seu dever. Esta figura é, por hora, demonizada tantas e tantas vezes, sendo frequentemente apresentado como sendo o mandatário de uma cultura misógina e machista.
Estou convencido que enquanto a figura de pai de família não for devidamente reabilitada, dificilmente teremos um ressurgimento de famílias propriamente ordenadas. É importante notar aqui um ponto, este pai de família deve ser alguém capaz de colocar os interesses da família primeiro que os seus interesses individuais. Deve ser alguém que não viva no relativismo moral, mas sim um homem de fé, algo que está em vias de extinção no ocidente e em particular em Portugal. Este homem deve ser o porto de abrigo para a sua família, alguém disposto a travar o bom combate, e será sempre portanto um defensor acérrimo da verdade. Não será naturalmente alguém obcecado com a sua própria imagem, mas sim um homem desejavelmente forte quer em termos físicos, tendo zelo na forma como se exercita, quer em termos mentais, sendo uma pessoa capaz mas com autocontrolo. Deve também ser um homem com uma vida intelectual, isto é, alguém que nutre interesse pelo legado que lhe foi confiado e procura aprender sobre o mesmo. Muitos homens antes de si fizeram sacrifícios para que o homem da atualidade usufrua dos mais variados benefícios.
A atualidade oferece-nos por vezes a promoção de algumas destas facetas, algo que seria desejável e bom, contudo com algumas distorções. Há homens fortes, capazes de feitos atléticos ímpares, que se cultivam nesse domínio mas pelas razões erradas. Por vezes o imperativo moral que os guia é a vaidade, sendo que esse trabalho físico que fazem conspira para consolidar o seu narcisismo.
Outros há com uma determinação inabalável, algo louvável quando usada para os fins próprios. Esta determinação não deve ser usada para a procura de grandes riquezas como um fim em si mesmas, nem como um isco usado para o oportunismo sexual com as mulheres.
Poderíamos também dar como exemplo, homens com uma prodigiosa inteligência mas que, não a tendo devidamente orientada, a usam para manipular e corromper o discurso público não olhando a meios para atingir os fins.
Um factor chave que dificulta a formação de mais homens com este tipo de espinha dorsal é uma certa apropriação da linguagem que tem existido no discurso público que procura rotular quem ousa desafiar este status quo. Termos como “negacionista”, “radical”, “fascista”, “fundamentalista”, “ultranacionalista” entre outros, são constantemente atirados remetendo o homem para uma falsa conclusão:
“ Tu não podes defender nada, nem ter certeza de nada”.
Outra ferramenta importante nesta desconstrução é o apelo ao vício. Sendo através da pornografia, da comida ultra-processada ou de uma vida de conforto , há claramente um incentivo ao hedonismo e à autoindulgência. Procura-se alimentar cada vez mais esta busca do prazer com o fim último, e por conseguinte a coragem, o sacrifício e o trabalho, como pedras angulares da construção do carácter do homem ficam para segundo plano.
O cavalheirismo ficou-se apenas pelas aparências. Por vezes, há um verniz de algumas das propriedades que descrevi em várias situações, contudo não passa de uma máscara. É fácil segurar uma porta para uma senhora e dizer “com licença”, “por favor”, para se mostrar alguém educado quando o custo para o fazer é mínimo. Difícil é estar disposto a fazer sacríficos em que nos doamos inteiramente pelos outros, no entanto é isso que é pedido ao homem. Doando-se encontrará o seu verdadeiro propósito.
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 2e8970de:63345c7a
2025-03-18 18:45:27
@ 2e8970de:63345c7a
2025-03-18 18:45:27https://www.statista.com/topics/10083/onlyfans/#topicOverview
305 million subscribers. 468 million monthly website visits.
Currently in the news is the retirement of an adult star who made 67 million Dollars in 3 years. Very little focus is put on the vast majority of "entertainers" who make very little money. And even less on the vast vast majority of website visitors that pay instead of being payed.
I don't think it's useful to argue if it's 1 in 27 or 1 in 24 depending on how big the world population is. What's more interesting to me: ** what does this do to our society and culture?**
1 in 27. Only half the population is male (which is almost all subscribers if we are being honest) so maybe 1 in 14? How many in the world population are too old or too young to use the internet like that. Then exclude all the poor people from third world countries. You get where I'm going with this. Walk through the downtown of any major western city and count the humans: 1,2,3..1,2,3... What a baffling statistic, don't you think?
originally posted at https://stacker.news/items/917007
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 6260f29f:2ee2fcd4
2025-03-18 15:58:05
@ 6260f29f:2ee2fcd4
2025-03-18 15:58:05```js
```
-
 @ a60e79e0:1e0e6813
2025-03-18 15:38:25
@ a60e79e0:1e0e6813
2025-03-18 15:38:25**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
One of the first things most people learn when getting started with Nostr is the importance of their private key, or ‘nsec’. The nsec is the key to their Nostr world. Whoever controls an nsec, controls that account. Lose access to the nsec and you lose access to that account and its social graph.
So the nsec is very important and should be treated very carefully, but what happens if we want to use or test multiple Nostr clients? Newer clients might be malicious, or have unknown security vulnerabilities, so simply go pasting our nsec everywhere just to see if we like a new app is not the best idea!
Thankfully there are solutions for nsec management that allow us to do exactly that, without having to expose our all important nsec to each and every app we want to interact with. The most commonly used to date are browser extensions like Alby or nos2x. Typically these types of browser extensions do not work on mobile platforms.
Enter Amber…

What is Amber?
Amber is a free and open source Android application that serves as a dedicated ‘Nostr event signer’. Amber allows users to keep their nsec segregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware.
At its core Amber serves two main purposes:
Securing your nsec(s) Using this nsec to sign events for other Nostr clients on your phone
Got an iPhone? Check out nsec.app
Getting Started
- Download Amber to your phone. It is available from Zap Store, Obtanium, GitHub or F-Droid
Download Amber here. Support Amber here.
-
When opening Amber for the first time, you’ll have the option to create a new Nostr account (nsec) or import an existing one.
-
If you do not currently have a Nostr account, Amber will help you generate and secure a brand new nsec. Amber allows you to download an encrypted file containing your nsec as well as the option to download a human-readable version of the nsec in the form of 12 English words, similar to a Bitcoin seed.
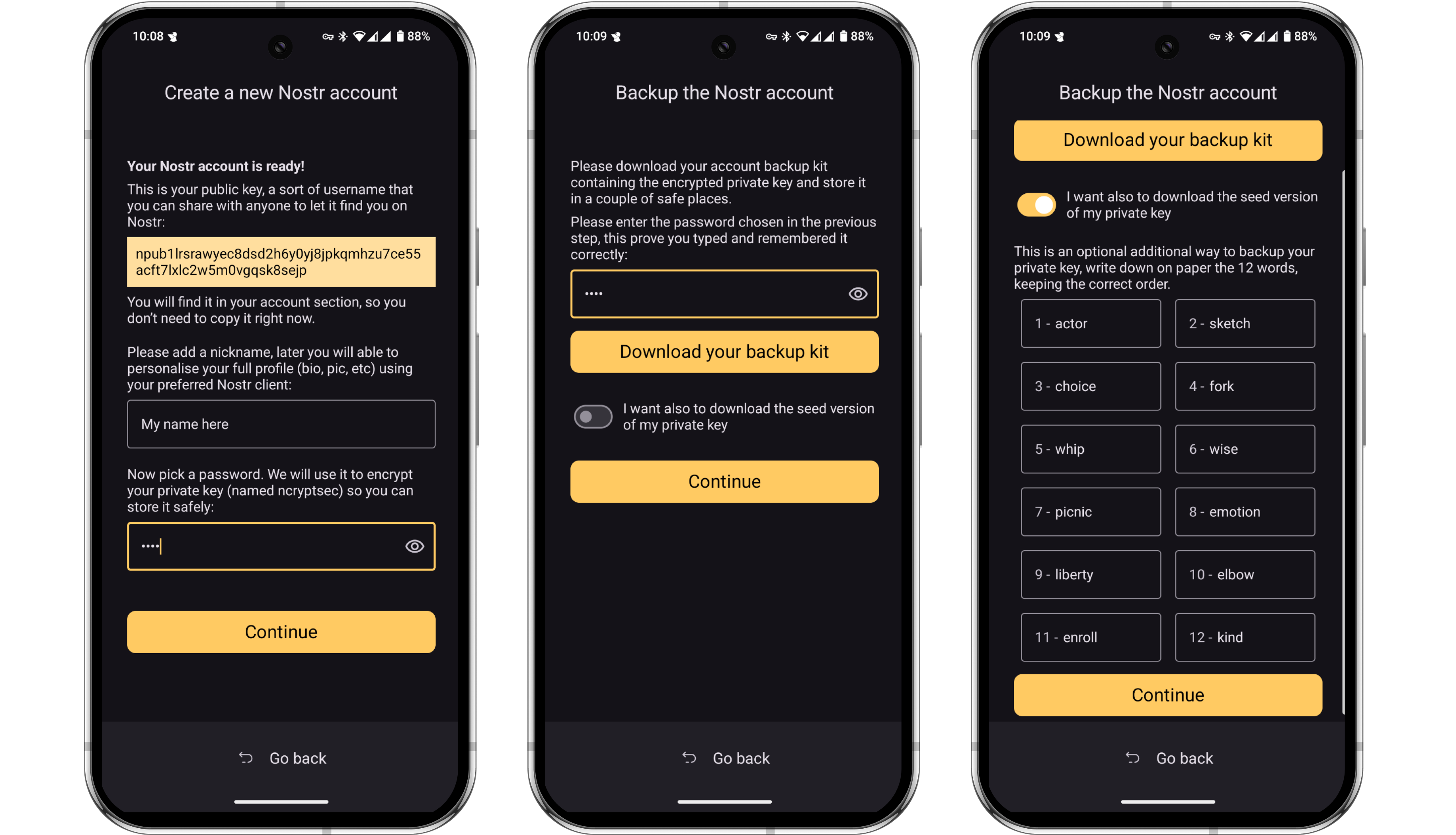
Skip this step if you have an existing nsec that you want to import to Amber.
-
To import an existing nsec, choose ‘Use your private key’. You can then paste the nsec from an existing client, or scan a QR code of it if you have one available to you.
-
Once you have created or imported your nsec, Amber will ask for some basic permissions. You can allow the app the approve basic actions, or enable more granular selection for each client you subsequently connect. Once you tap ‘Finish’, you’ll see that the account is now ready.
If you have or require more than one Nostr account, you can repeat these steps for each one. All accounts can be viewed by tapping the profile image in the bottom right corner of the screen.
- That’s it, Amber is now ready to sign events. Amber allows multiple ways to connect other clients to it, but most will have a very simple ‘Login with Amber’ button. Let’s demo this in practice with Amethyst, the most popular Android-only client.
The opening screen of Amethyst shows the ‘Login with Amber’ option. Tap that.
- Amber will then open automatically and ask you to define the level of autonomy you’d like to have with Amethyst. This setting defines how often Amber will require you to manually authorize each event.
For example, you might want Amber to automatically sign every like or repost you do in Amethyst, but then be asked to manually approve all direct messages sent from your account. These permissions can be customized in the settings at any time.
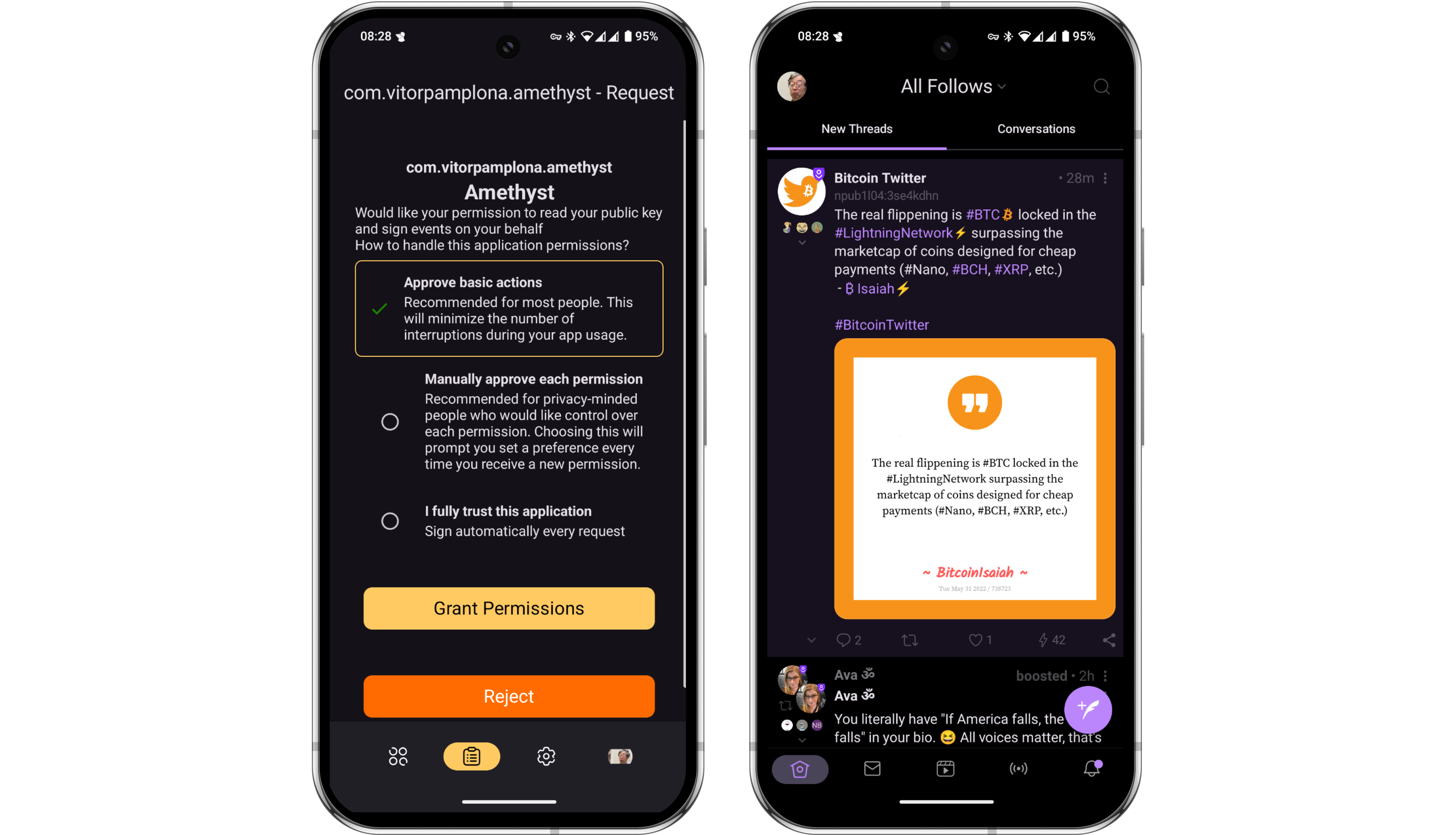
- Let’s assume that upon setup, we did not grant Amber the ability to automatically sign short text notes for us. Let’s look at how simple the authorization flow is. Type a new short note in Amethyst and press ‘Post’.
Amethyst will instantly send the request to the Amber app on your phone, with no third party server involved. Amber will open and ask you to approve the event. When you do, Amber signs the event with the nsec it stores for you and automatically send the signed event back to Amethyst to be posted. The whole process takes just a few seconds.
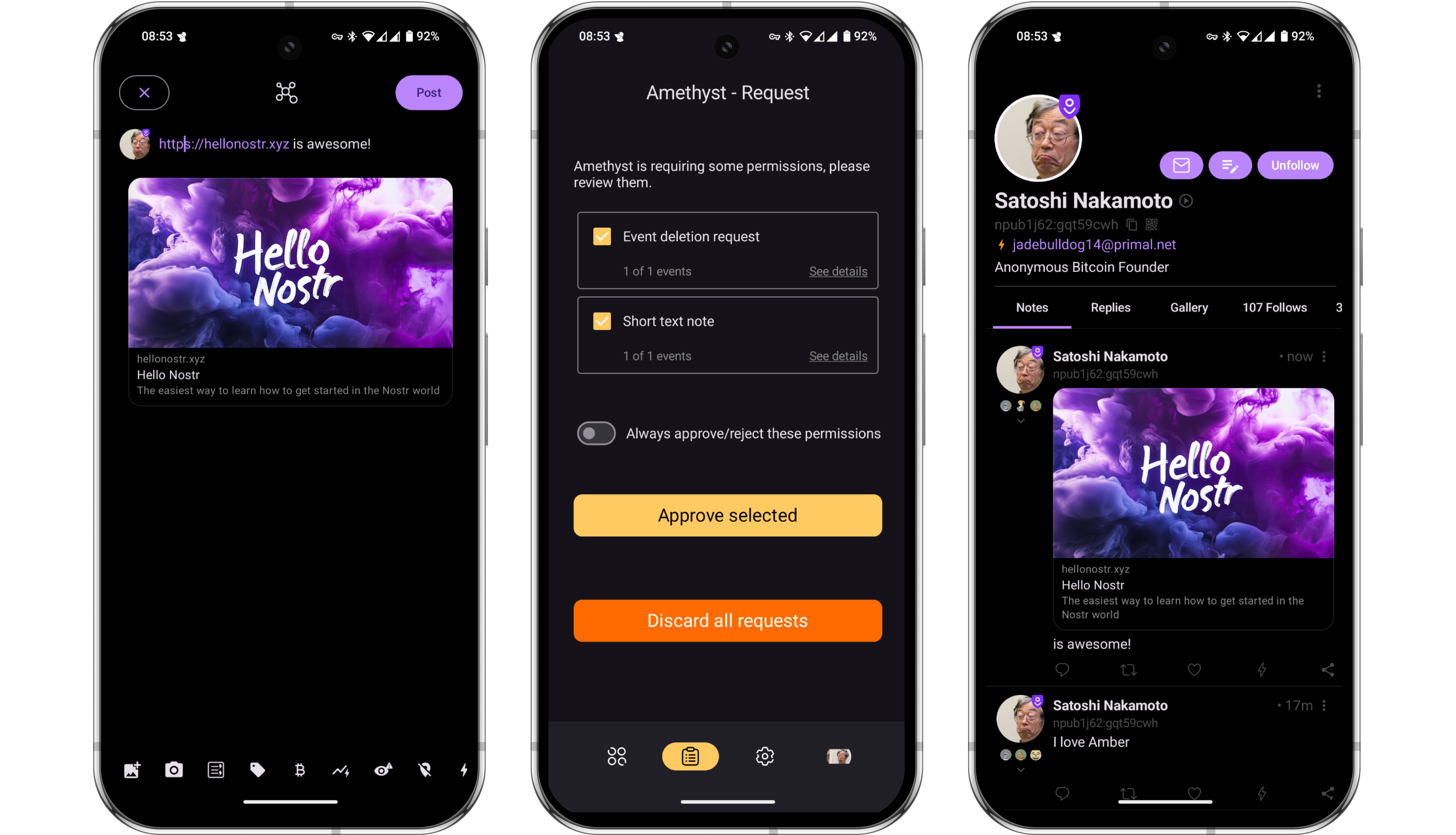
Using Amber with a Web Client
-
Next let’s take a look at how you can use Amber on your phone to sign events on a web app running on your computer. For this example, we’ll be using Coracle. Open Coracle and click ‘Log In’, then choose ‘Use Remote Signer’. Coracle will then display a QR code.
-
Open Amber and navigate to the Applications page, tap the + icon, then scan the QR code being displayed by Coracle.
-
Just as it did earlier with Amethyst, Amber will now ask you to grant some basic permissions for the Coracle connection. Once again, these permissions can be customized at any time in the settings. Once granted, you’ll notice that Coracle automatically logs in to your feed.
But wait, how did that happen? The nsec is in Amber on your phone, and Coracle is running on your computer. The two might not even be in the same location or on the same network!? The communication is happening over the Nostr protocol, via relays. Which relays are used for this communication can be configured in the Amber settings.
-
Let’s test out a short note on Coracle to demonstrate the signing process. Click ‘Post +’ in the top right corner, draft your note and then click send.
-
Amber will send a push notification to your phone. Tapping the notification will open Amber for you to approve the event.
-
Once the event is approved in Amber, Amber will automatically send the signed event back to Coracle for publishing.
Summary
You can view Amber as a vault for your Nostr private keys (nsec). It allows you to explore the entire ecosystem without exposing your nsec to every new app you try. Amber is an incredibly simple yet powerful tool that belongs on the Android phone of every Nostr user.
At the time of writing, using Amber as a remote event signer is supported by the following popular Nostr clients:
- Amethyst (mobile)
- Coracle (web)
- 0xChat (mobile)
- Fountain (mobile)
- Zap Store (mobile)
- Keychat (mobile)
- Freeflow (mobile)
- Highlighter (web)
- Chachi Chat (web)
- Habla (web)
- Shopstr (web)
- Plebeian Market (web)
- Snort (web)
- Nostrudel (web)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I’ll be sure to Zap you back! ⚡️
-
 @ 32e18276:5c68e245
2025-02-08 20:20:46
@ 32e18276:5c68e245
2025-02-08 20:20:46This period of the Damus OpenSats grant has been productive, and encompasses the work past our alpha release of Notedeck. Since we sent our last report on Dec 5, this encompasses all the work after then.
Damus is supported by the OpenSats LTS grant, which allows us to continue working on the goodies below. Thank you!
Damus Notedeck
Added
- Initial algo timelines (William Casarin) #712
- Initial support for local-network P2P nostr: multicast support (William Casarin) #626
- First steps toward the notedeck browser: multiple app support #565
- Clicking a mention now opens profile page (William Casarin) 5a241d730
- Note previews when hovering reply descriptions (William Casarin) #591
-
Various Android updates and compatibility improvements (Ken Sedgwick, William Casarin)
-
Media uploads (kernelkind) #662
- Profile editing (kernelkind) #625
- Add hashtags to posts (Daniel Saxton) #592
- Enhanced command-line interface for user interactions (Ken Sedgwick)
- Debug features for user relay-list and mute list synchronization (Ken Sedgwick)
Changed
- Major timeline cache refactor (William Casarin) #653
- Increased ping intervals for network performance (William Casarin)
- Migrated to egui v0.29.1 (William Casarin) #551
- Switch to only notes & replies on some tabs (William Casarin) #598
- Only show column delete button when not navigating (William Casarin)
- Pointer interactions enhancements in UI (William Casarin)
- Show profile pictures in column headers (William Casarin)
-
Show usernames in user columns (William Casarin)
-
Add confirmation when deleting columns (kernelkind)
- Enhance Android build and performance (Ken Sedgwick)
- Image cache handling using sha256 hash (kieran)
- Introduction of decks_cache and improvements (kernelkind)
- Nostrdb update for async support (Ken Sedgwick)
- Persistent theme setup across sessions (kernelkind)
- Tombstone muted notes (Ken)
Fixed
- Fix GIT_COMMIT_HASH compilation issue (William Casarin)
- Fix avatar alignment in profile previews (William Casarin)
- Fix broken quote repost hitbox (William Casarin)
- Fix crash when navigating in debug mode (William Casarin)
- Fix long delays when reconnecting (William Casarin)
-
Fix repost button size (William Casarin)
-
Fixed since kind filters (kernelkind)
- Clippy warnings resolved (Dimitris Apostolou)
Damus iOS
Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development.
Added
- Render Gif and video files while composing posts (Swift Coder)
- Purple members who have been active for more than a year now get a special badge (Daniel D’Aquino)
- Add profile info text in stretchable banner with follow button (Swift Coder)
- Paste Gif image similar to jpeg and png files (Swift Coder)
Changed
- Improved clarity of the mute button to indicate it can be used for blocking a user (Daniel D’Aquino)
- Made the microphone access request message more clear to users (Daniel D’Aquino)
- Improved UX around the label for searching words (Daniel D’Aquino)
- Improved accessibility support on some elements (Daniel D’Aquino)
Fixed
- Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino)
- Fix non scrollable wallet screen (Swift Coder)
- Fixed suggested users category titles to be localizable (Terry Yiu)
- Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu)
- Fixed right-to-left localization issues (Terry Yiu)
- Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu)
- Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu)
- Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino)
- Fixed non-breaking spaces in localized strings (Terry Yiu)
- Fixed localization issue on Add mute item button (Terry Yiu)
- Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu)
- Fixed localization issues in RelayConfigView (Terry Yiu)
- Fix duplicate uploads (Swift Coder)
- Remove duplicate pubkey from Follow Suggestion list (Swift Coder)
- Fix Page control indicator (Swift Coder)
- Fix damus sharing issues (Swift Coder)
- Fixed issue where banner edit button is unclickable (Daniel D’Aquino)
- Handle empty notification pages by displaying suitable text (Swift Coder)
Nostrdb
nostrdb, the engine that powers notecrumbs, damus iOS, and notedeck, continued to improve:
Added
- Added nip50 fulltext searching (William Casarin) #68, demo
- Added async migrations (William Casarin) #59
- Implement author queries (William Casarin) #57
- Make
ndbthreadsafe (William Casarin) #56
Nostrdb Rust
Our nostrdb rust bindings also had improvements
- Async! Adding efficient, poll-based stream support (William Casarin): #25
Notecrumbs
Notecrumbs, the njump-style opengraph server that powers the damus.io links, got an update that upgraded it to async nostrdb
- Switch to async nostrdb-rs (William Casarin) #16
How money was used
- relay.damus.io server costs
- Living expenses
Next quarter
Our goal for next update: zaps, android version, lists, outbox model for notedeck. Olas images in damus iOS, continue switching Damus iOS over to local relay model so we can add outbox support.
-
 @ d57360cb:4fe7d935
2025-02-06 18:31:30
@ d57360cb:4fe7d935
2025-02-06 18:31:30Mindfulness often has the misconception that by practicing you can stop your mind from thinking and obtain an empty mind.
While one can definitely achieve moments of emptiness in thinking, this view that emptiness is the goal can be the very obstacle in your way leading to frustration with the practice.
If we adjust our perspective and see mindfulness as learning to accept the situations we find ourselves in and adjust to them rather than fighting them, we achieve a kind of grace under pressure.
The thoughts are part of the practice, just like cars on the road are part of driving, or the danger of a punch is always a threat to a boxer.
The difference between the novice and the seasoned is one has accepted and acclimated to the realities of the situation instead of fighting them, in this one finds freedom.
-
 @ 8d5ba92c:c6c3ecd5
2025-02-05 22:06:18
@ 8d5ba92c:c6c3ecd5
2025-02-05 22:06:18There I was, minding my own business at the airport (i.e., arranging the list of Bitcoin/Freedom podcasts for the next seven hours of flight), when I came across a scene that could have been ripped straight from a show about the decline of civilization. Heart-wrenching. Shocking. Dystopian. To put it simply, what the f*ck?!
Prologue.
A family of five, including two early-school kids (let’s call them 'Timmy' and 'Amy', around 5 and 7 years old), a father who looked like he’d given up on life, and a perfect mother multitasking like a pro—breastfeeding a baby while chowing down on a Big Mac.
Oh yeah, the whole family was happily consuming their McDonald’s junk as if it was their daily ritual. Watching little kids eat that stuff? A mix of anger and sadness. But seeing a breastfeeding mother give her newborn absolute garbage? The scene I can’t forget.
She also washed it all down with some fizzy, sugary, chemical-laden sludge later on. Still, while breastfeeding. Because, you know, nothing screams nourishment like a steady diet of artificial stuff. Best to get them hooked in the first few months, right?
Act One: The Mother’s Masterpiece.
A modern-day Madonna, cradling her infant while balancing junk food’s finest. The baby, blissfully unaware of the nutritional betrayal unfolding in real-time, probably wasn’t even dreaming of normal food that might one day help it grow into a healthy being.
Seeing this scene, knowing all the options available at the airport—many much more reasonable than this crap—and watching the family enjoy their 'sacred food', I’m almost certain this little one had been getting a side of heavily processed rubbish long before it even left the womb...
Rave: A standing ovation for conscious parenting.
Act Two: Innocent Contribution.
Just when I thought the scene couldn’t get worse, little “Timmy” decided to play bartender. With the enthusiasm of a child clearly raised on a steady diet of Big Macs and Coca-Cola (or whatever other delicacies were on offer), he extended his cup to his tiny brother or sister. The devoted mother, of course, helped him guide the straw to the baby’s mouth. “Drink, little one! Drink not just from my body, but directly from the cup. Drink this (crap) with us!”
Why not? If McDonald’s was good enough for everyone in the family, surely it was good enough for the baby sibling, right?
They all looked almost proud of Timmy’s little “sharing is caring” moment. Meanwhile, my heart shattered into a million pieces, each one screaming, “Seriously?! Should I interfere? How would they react?”
I was close enough to keep taking photos, staring at them with my mouth probably hanging open, horror written all over my face. The mother met my gaze once—cold, unreadable. No 'leave us alone.' No 'it’s our business.' No 'what's wrong, tell us.' Just... nothing.
My husband, noticing my growing frustration and sensing I was about to step in, whispered, “Let it go. You won’t save them in 10 minutes at the airport.”
Maybe he was right. But I’ll be thinking about it for a long time…
Act Three: A Recipe for Regret.
It was as if the parents had collectively agreed that their bodies were nothing more than human garbage bins, and their children were just smaller versions of the same.
Let’s be clear: adults can do whatever they want with their health. If you want to treat your body like a landfill, go ahead—it’s your funeral (literally). But when you drag your kids into it, it’s no longer a personal choice. It’s more like a crime. These children didn’t sign up for a life of artificial flavors, empty calories, and a future riddled with health problems. They deserve better.
And if you’re reading this thinking, ‘What’s the big deal?’—let's talk.
My brain is on the verge of exploding, trying to understand how anyone could actively contribute to the slow, painful destruction of the people they (presumably) love. You should love and respect your own body, and even more so the lives of your kids. What could possibly justify feeding your family McDonald's if it’s not the very last option you have on earth to survive? Please, help me understand why!
Epilogue: The Aftertaste.
As I stepped into the boarding line, I couldn’t shake the thought: Is this really where we are now? A world where care and nutritional awareness no longer exist. Where junk food became a family tradition. Where children are raised on a cocktail of chemicals when better options are right there!
To the McDonald’s family at the airport—and anyone on their way to becoming one: Not sure if you enjoyed your meal. If you did, I wish you luck. You’ll need it.
https://i.nostr.build/e8f3h9iuDNQbtmaF.png
And please, maybe—just maybe—consider giving your kids a chance. They deserve more than a trash life packed with chemicals in a paper bag.
BTC Your Mind. Let it ₿eat.
Şelale
-
 @ 044da344:073a8a0e
2025-03-18 15:19:15
@ 044da344:073a8a0e
2025-03-18 15:19:15Die Medien-Epidemie
Rubikon und Medienrealität, 18. März 2020
Ab jetzt regiert die Medizin, hat Markus Söder am Montag gesagt. Medienforscher, ab ins Homeoffice. Von dort sehen wir, was Ärzte nicht untersuchen können. Wir sehen, wie Medien eine Realität schaffen, die Politiker für so real halten, dass sie die Welt komplett umbauen – eine Medienwirkung zweiter Ordnung, die auf Medienwirkungen erster Ordnung vertrauen und uns alle so ins Chaos stürzen kann.
Ich gebe zu: Wenn man nicht krank ist und dazu noch ein Fatalist und Dickhäuter, den es nicht stört, wenn Bars und Kinos geschlossen sind und die Leute böse schauen, wenn sie einen ins Büro gehen sehen, dann lebt man als Medienforscher gerade in goldenen Zeiten. Nie zuvor war die Macht der Medien so offensichtlich. Nie zuvor war mein Forschungsgegenstand so wichtig. Eigentlich hätte Markus Söder am Montag sagen müssen: Ab jetzt regieren die Medien.
Genau genommen tun sie das schon lange, aber bei den allermeisten Themen haben die Politik und andere mächtige Akteure die Logik des Journalismus so internalisiert, dass sie den Redaktionen das liefern, wonach diese ohnehin suchen. Meine Theorie der Medialisierung beginnt genau da: Jeder Entscheidungsträger weiß, dass heute nichts mehr geht ohne öffentliche Aufmerksamkeit und ohne öffentliche Legitimation. Jeder weiß, dass er die Medien braucht, und versucht deshalb entweder, die Berichterstattung zu unterbinden, oder die Logik des Mediensystems für seine Interessen zu nutzen und in der Öffentlichkeit ein positives Bild zu erzeugen (vgl. Meyen 2014, 2018). Deshalb die großen PR-Stäbe, deshalb all die spektakulären Projekte, Events, Ideen, deshalb Spitzenleute wie Markus Söder, der beim Bayerischen Rundfunk Volontär war und weiß, wie die Kolleginnen und Kollegen von einst so ticken.
Corona war anders. Corona kam aus dem Nichts (aus China, okay, aber hier ist kein Platz für Verschwörungstheorien). Corona hat die Medienrealität gekapert, ohne dass die Redaktionen sich wehren konnten, weil der Imperativ der Aufmerksamkeit in einem kommerziellen Mediensystem auch die gebührenfinanzierten Angebote regiert. Corona ist Medienlogik pur. Journalismus war schon immer Selektion. Selbst das, was an einem Tag in einem Stadtteil von München passiert, würde mehr füllen als eine Süddeutsche Zeitung. Heute wird das Medienrealität, was die meisten Klicks verspricht, die meisten Likes, die meisten Retweets. Superlative, Sensationen, Prominente. Dinge, die es so noch nicht gab. Drei Infizierte, 15, 200. Tom Hanks. Der erste Bundestagsabgeordnete. Der erste Zweitligaspieler. Der erste Trainer. Sogar jemand von Juve, eben noch halbnackt in der Jubelkabine, und in drei Tagen schon auf dem Rasen gegen Lyon. Tom Hanks aus dem Krankenhaus entlassen. Und jetzt auch noch Merz.
Medienrealität ist eine Realität erster Ordnung – wie der Zaun, der uns nicht vorbeilässt, oder der Polizist, der unseren Ausweis sehen will. Wir können die Medienrealität nicht ignorieren, weil wir annehmen, dass sie Folgen hat – wenn vielleicht auch nicht für uns, so doch für andere. Selbst wenn wir persönlich nicht glauben, dass eine Ausgangssperre kommt oder die Versorgungsketten gekappt werden, fangen wir an, Klopapier zu horten (oder Rotwein, wenn wir Italiener wären), weil wir glauben, dass die anderen ihr Verhalten ändern werden, und zwar so, wie es der Medientenor vorgibt.
Wer nicht versteht, was Markus Söder gerade reitet oder all die anderen, die in irgendeinem Regierungssitz oder auch nur in einer kleinen Behörde oder gar in einer Universität Verantwortung tragen, hat hier einen Schlüssel. Entscheidungsträger unterstellen, dass Massenmedien mächtig sind, und wollen entweder die Deutungshoheit zurückerobern oder scheuen jedes selbständige Denken. Das Motto der Stunde: Die Medien sind voll mit Corona (sie sind es wirklich, weil wir das immerfort klicken, liken, retweeten), also müssen wir die Menschen davor schützen, ob sie wollen oder nicht. Diese Menschen wissen, was die Italiener unternehmen, was die Berliner und was der junge Kurz in Österreich. So einen brauchen wir auch, ruft die Bildzeitung. Kein Problem. Das können wir toppen. In Deutschland regiert ab jetzt die Medizin. Was morgen sein wird? Schauen Sie einfach, welche Hashtags gerade auf Twitter im Trend sind. Dort treiben sich Reporter und Politiker gegenseitig in ungeahnte Höhen.
Damit sind wir bei der Verantwortung und beim Ethos des Journalismus. Was ist aus dem Ort geworden, an dem die Gesellschaft, an dem wir alle das diskutieren und aushandeln können, was uns umtreibt? Wo ist der Streit der Meinungen, der doch gerade bei existenziellen Entscheidungen wie denen, die Markus Söder am Montag verkündet hat, nötiger wäre denn je? Wann ist das Prinzip der US-Journalismus-Ikone I.F. Stone verschwunden, der seine Kollegen ermahnt hat, gerade bei mächtigen Institutionen immer besonders vorsichtig zu sein – also auch bei der Charité, auch beim Robert-Koch-Institut und erst recht bei jeder Regierung (vgl. Goeßmann 2017: 30). Marcus B. Klöckner (2019: 9) hat gerade gezeigt, wie es zu einem Journalismus kommen konnte, der die Macht nicht kritisiert und kontrolliert, sondern einen „Schutzmantel um die politischen Weichensteller legt“ und kritische Stimmen aus dem „legitimen öffentlichen Diskursraum“ de facto ausschaltet.
Natürlich: Es gibt Perlen im Corona-Einheitsbrei. Rubikon zum Beispiel, eine alternative Plattform, auf der Herausgeber Jens Wernicke seit Tagen Gegenstimmen sammelt. Heribert Prantl, SZ-Leitartikler im Ruhestand, hat in seinem Sonntagsbrief („Prantls Blick“) „den virologisch-politisch-publizistischen Rigorismus“ beklagt, und seine alte Redaktion ließ im Feuilleton am Dienstag Rene Schlott, einen Historiker, mit der Frage zu Wort kommen, ob „die offene Gesellschaft erwürgt“ werde, „um sie zu retten“ (online hinter einer Bezahlschranke). Schlott spricht sich gleich zu Beginn seines Artikels Mut zu und hofft, dass ihn nicht ausgerechnet dieser Text in die Isolation treibt. Noch deutlicher wird der hegemoniale Diskurs auf der Webseite von Radio Eins, bezahlt von unseren Beiträgen und betrieben vom RBB. Es gibt dort ein Interview mit Karin Mölling, einer preisgekrönten Virologin im Ruhestand, zehn Minuten immerhin, die dort vor Panikmache warnt, Corona mit Blick auf Influenza relativiert und ein drittes Virus, eine dritte Epidemie ausmacht, mindestens genauso gefährlich: soziale Medien und Presse. Die Redaktion sah sich genötigt, eine „Klarstellung“ zu schreiben. Eine „Einzelmeinung“, liebe Leute. Wir, die Mannschaft von Radio Eins, sind nicht so „zynisch“ wie diese Ärztin und wollen die Krise keinesfalls verharmlosen.
Was tun? Auf lange Sicht ist das nicht schwierig und genauso klar wie beim Gesundheitswesen oder im Handel. Weg von der kommerziellen Logik, die Aufmerksamkeit maximiert und sonst nichts, hin zu einem Journalismus, der die Informationen liefert, die wir brauchen, und deshalb anders organisiert sein muss, genossenschaftlich zum Beispiel. Für den Moment hilft das nicht. Aber vielleicht können wir ja auch über die Medien diskutieren, wenn die Redaktionen den nächsten Hype entdeckt haben.
Literatur
David Goeßmann: Wenn Regierungen lügen und Medien mitmachen. In: Jens Wernicke: Lügen die Medien? Propaganda, Rudeljournalismus und der Kampf um die öffentliche Meinung. Frankfurt am Main: Westend 2017, S. 29-45.
Marcus B. Klöckner: Sabotierte Wirklichkeit. Oder: Wenn Journalismus zur Glaubenslehre wird. Frankfurt am Main: Westend 2019.
Michael Meyen: Theorie der Medialisierung. Eine Erwiderung auf Anna M. Theis-Berglmair. In: Medien & Kommunikationswissenschaft 62. Jg. (2014), S. 645-655.
Michael Meyen: Breaking News. Die Welt im Ausnahmezustand. Wie die Medien uns regieren. Frankfurt am Main: Westend 2018.
Daten + Experten = Demokratie?
Rubikon, 18. März 2020, und ForDemocracy, 19. März 2020
Dieser Beitrag entstand auf Anregung von Jens Wernicke, Herausgeber der Plattform Rubikon, und ist dort unter dem Titel “Die Expertokratie” erschienen. Hier das Original, ergänzt um Literaturangaben.
Es gibt ein Buch von Jason Brennan, 2017 auf Deutsch erschienen, das ziemlich genau das fordert, was gerade geschieht. Eine Epistokratie, bitte. Die Herrschaft der Wissenden. Lasst die Experten nur machen, weil wir alle ohnehin nicht viel von der Welt verstehen. Dann wird dieser elende Streit der Ideen ein Ende haben, und alles wird endlich gut.
Dieses Buch war ein Bestseller und wurde vermutlich auch in den Staatskanzleien und Verwaltungen gelesen, die jetzt Ärzte in den Rang von politischen Göttern erheben und auf Daten und Kurven verweisen, wenn sie den Menschen fast alles nehmen, worauf unser Leben baut. Von Risiken und Nebenwirkungen hat Jason Brennan geschwiegen. Er musste davon schweigen, weil der Sachbuchmarkt eine steile These verlangt, gerade in den USA, und einen Titel, der zum Kauf anregt. „Gegen Demokratie“, hat Ullstein in Deutschland auf das Cover geschrieben. Ich habe mich damals darüber lustig gemacht, vor allem über den Glauben, dass wir in einer „Demokratie“ leben, weil man uns alle paar Jahre abstimmen lässt. Jetzt könnte jeder sehen, dass das immer noch besser ist als eine Herrschaft der Experten. Konkret: besser als das „Primat der Medizin“ (Markus Söder). Man muss nur die Augen aufmachen.
In den Leitmedien sieht man: volle Unterstützung für unsere Jungs und Mädels in der Regierung. So sagt das der Sprecher im Audi Dome, wenn der FC Bayern Basketball am Rand einer Niederlage steht, ohne die Mädels natürlich. Die Zuschauer sollen dann aufstehen und so viel Krach machen, dass das Spiel doch noch kippt. Um im Bild zu bleiben: In einer parlamentarischen Demokratie gibt es Auswärtsfans. Nicht viele, wenn die größten Teams einfach fusionieren, aber immerhin. Die Indexing-These von Lance Bennett, bestätigt in vielen Studien, sagt: Journalisten berichten über Konflikte in der Gesellschaft, aber, und dieses große Aber schränkt das Spektrum schon in sogenannten normalen Zeiten erheblich ein, aber die entsprechenden Ansichten müssen in der offiziellen politischen Debatte vorkommen, im Bundestag zum Beispiel. Was das Berlin der Parteien, der Abgeordneten und der Lobbyisten nicht diskutiert, erscheint nicht in den Medien, und was Politik oder Wirtschaft nicht vorkauen, kann der Journalist nicht verdauen.
Es ist nicht schwer, diesen Befund in die Gegenwart zu verlängern. Wo die Medizin regiert, gibt es keine parlamentarische Debatte und damit auch keinen öffentlichen Streit um die beste Lösung, nicht einmal den gedämpften einer eingehegten Wahldemokratie. Mehr noch: Der Journalismus dankt ab und lässt die Experten gleich selbst sprechen, Christian Drosten zum Beispiel, der mit seiner Forschungsgruppe an der Berliner Charité erst einen Corona-Test entwickelt hat und jetzt gleichzeitig zu Regierenden und Volk spricht. Dass ihn viele Redaktionen gewähren lassen und sogar noch feiern, erinnert an das, was Uwe Krüger (2016: 105), Medienforscher in Leipzig, nach dem Ukraine-Desaster 2014 „Verantwortungsverschwörung“ genannt hat: Der Journalist weiß, was gut ist und was schlecht (so ziemlich das gleiche, was die Herrschenden gut oder schlecht finden, weil alle ganz ähnlich aufgewachsen sind und zusammen studiert haben), und er glaubt, dass er Einfluss auf die Menschen hat. Also zur Solidarität aufrufen, die Tatkraft der Regierenden loben und im übrigen auf die „Fakten“ verweisen oder die Experten fragen. Wenn diese Experten gegen den Mainstream schwimmen (wie zum Beispiel Wolfgang Wodarg oder Karin Mölling), dann werden sie delegitimiert und nicht mehr angehört.
Anders als Jason Brennan ging Walter Lippmann (2018) nicht davon aus, dass wir Wähler kein Interesse an der Politik haben oder dass uns gar der nötige Verstand dafür fehlt. Lippmann wollte den Verstand manipulieren. Er wusste, dass wir auf Vorstellungen von der Welt reagieren und dass die Macht bei denen liegt, die diese Bilder produzieren. Lippmann hat schon vor fast einhundert Jahren eine Regierung der Experten empfohlen, eine Gesellschaft, in der Sozialforscher wie er die große „Herde“ führen. Sein Rezept, das so klingt, als sei es erst eine Woche alt: „Der Zugang zu der wirklichen Umwelt muss begrenzt werden, ehe jemand eine Pseudoumwelt errichten kann, die er für klug oder wünschenswert hält.“
Damit weg von den Medien und hin zu unserem Glauben an die Daten, an die „Pseudoumwelt“, die Experten wie Christian Drosten bauen. Im gleichen Jahr, in dem Jason Brennan „Gegen Demokratie“ angeschrieben hat, ist bei Suhrkamp ein Buch von Steffen Mau (2017) erschienen, einem Soziologen von der Humboldt-Uni, das den Megatrend der Quantifizierung des Sozialen auf eine griffige Formel gebracht hat: „Das metrische Wir“. Man muss diesen Trend kennen, wenn man verstehen will, warum alle Welt gerade auf den Newsticker starrt, der die Zahl der Infizierten und der Toten im Stundentakt aktualisiert und in bunten Diagrammen oder auf noch bunteren Karten Länder oder Regionen miteinander vergleicht, die man überhaupt nicht miteinander vergleichen kann.
Heute geht nichts mehr ohne Zahlen. Was nicht in Zahlen übersetzt werden kann, existiert nicht länger. In der Sprache des Soziologen Steffen Mau: Zahlen sind „zur Leitwährung der digitalisierten Gesellschaft geworden“. Zahlen versprechen „Präzision, Eineindeutigkeit, Vereinfachung, Nachprüfbarkeit und Neutralität“ (S. 26f.). Zahlen sind die Antwort auf unser Bedürfnis nach Sicherheit und Kontrolle. Zahlen haben das Bauchgefühl verdrängt, das uns sagt, was richtig ist, das Urteil, das abwägt und dabei auch um die Besonderheiten dieses einen Falles weiß, den Blick auf die Welt, der Komplexität und Ungewissheiten anerkennt. Die Ärzte sagen uns, wie viele Menschen krank sind, wie viele davon sterben werden und was wir alles tun müssen, damit die Betten auf den Intensivstationen reichen. Wir glauben ihnen, weil wir gewöhnt sind, die Welt durch die Brille von Zahlen zu sehen. Und die Regierenden folgen ihnen, weil sie uns kennen.
Nur: Eine Zahl ist eine Zahl und nicht die Realität. Das weiß jeder Wissenschaftler, der „im Feld“ war und selbst Daten erhoben hat. Was immer wir messen, wird sozial hergestellt. Menschen legen fest, dass sie Schritte zählen, um ihre Existenz zu legitimieren, und nicht Furze oder Rülpser (sorry). Menschen legen fest, nach welchem Virus sie suchen und was passieren muss, damit sie „Gefunden!“ rufen können. Hinter jeder Zahl steht ein Interesse, und sei es nur das eines Herstellers, der seine Geräte loswerden will. Daraus folgt immer: Es hätte auch anders sein können. Das klingt banal, ist es aber ganz offenkundig nicht. Sonst könnten wir gerade nicht beobachten, wie Zahlen alles umbauen, was wir bisher gekannt haben. Wir lernen: Zahlen sind nicht die Wirklichkeit. Sie erzeugen sie erst.
Wer Zahlen verkauft, egal ob Virologe oder Medienforscher, braucht das Vertrauen seiner Kunden. Er muss die Zweifel verwischen, die mit jeder Datenerhebung verbunden sind. Man muss kein Virologe sein (wohl aber eine gesunde Skepsis gegenüber allen Zahlen mitbringen), um diese Zweifel auszusprechen. Was bedeutet es, dass heute 12.000 Menschen mit einem bestimmten Virus infiziert sind, morgen 15.000 und übermorgen mehr als 20.000? Haben sich tatsächlich mehr Menschen angesteckt oder wird einfach mehr gemessen, in provisorischen Zelten zum Beispiel und bei Menschen, die sonst nie und nimmer zum Arzt gegangen wären, aber jetzt gar nicht anders können bei all dem sozialen und medialen Druck? Wann genau wird ein Test „positiv“? Genauer gefragt: Worauf haben sich die Erfinder des Tests hier geeinigt und was wäre, wenn sie sich anders entschieden hätten? Warum sterben in einem Land 0,5 Prozent der Infizierten und in einem anderen fünf Prozent? Liegt das vielleicht daran, dass man hier eher zufällig testet und dort nur die, die ohnehin schon im Krankenhaus liegen? Und ab wann wird man eigentlich ein Corona-Toter? Woher weiß der Arzt, was genau bei einem Menschen „mit Vorerkrankung“ zum Ende geführt hat?
Ganz unabhängig von solchen Zweifeln sind Zahlen nur dann etwas wert, wenn man sie einordnen kann. Die Wissenschaft lebt vom Vergleich. Niemand weiß, wie viele Menschen in den vergangenen Jahren das hatten, was wir „Grippe“ nennen, und wie viele daran gestorben sind. Eine „Grippe“ war längst so normal, dass wir trotzdem zur Arbeit gegangen sind und dort vielleicht an einem Herzinfarkt gestorben sind oder bei einem Autounfall, weil wir gerade niesen mussten, als die Ampel rot wurde.
Wer noch lebt, muss sich wehren gegen die Herrschaft der Experten und der Daten, den (hoffentlich noch) gesunden Menschenverstand einschalten und fragen, was es mit uns macht, wenn wir unsere Kolleginnen und Kollegen nicht mehr sehen dürfen (weder im Büro noch abends beim Bier), wenn Vater, Mutter, Kinder den ganzen Tag auf ein paar Quadratmetern zusammen sein müssen (wie sonst nur Weihnachten, wo es den meisten Familienkrach gibt) und wenn man uns die Fahrt in den Urlaub nimmt, den Ausflug, das Fitnessstudio. Virologen können das nicht wissen. Virologen wissen auch nicht, wie ein Land wieder zurückkommt auf Los und wie all das, was jetzt an Verboten, Kontrolle und Überwachung möglich geworden ist, erst zurückgeholt und dann aus dem kollektiven Gedächtnis gelöscht werden kann. Dafür gibt es weder Experten noch Daten.
Literatur
Jason Brennan: Gegen Demokratie. Warum wir die Politik nicht den Unvernünftigen überlassen dürfen. Berlin: Ullstein 2017.
Uwe Krüger: Mainstream. Warum wir den Medien nicht mehr trauen. München: C.H. Beck 2016.
Walter Lippmann: Die öffentliche Meinung. Wie sie entsteht und manipuliert wird. Herausgegeben von Walter Otto Ötsch und Silja Graupe. Frankfurt am Main: Westend 2018.
Steffen Mau: Das metrische Wir. Über die Quantifizierung des Sozialen. Berlin: Suhrkamp 2017.
Kniefall vor der Wissenschaft
Medienrealität, 26. März 2020, und Rubikon, 27. März 2020
Patrick Illinger fällt vor der Wissenschaft auf die Knie. Das wäre kein Problem, wenn Illinger nicht das Wissenschaftsressort der Süddeutschen Zeitung leiten und dort Leitartikel schreiben würde. „Seriöse Wissenschaft hat keine andere Agenda als das Suchen und Überbringen möglichst fundierter Fakten“, steht dort heute. Genau das ist die Agenda. Und die SZ geht ihr auf den Leim.
Zeitunglesen geht im Moment schnell. Zwei Minuten, wie in der DDR. Einmal blättern und man weiß, dass sich die Regierungsmeinung nicht geändert hat und die Medienlogik auch nicht. Eigentlich habe ich dazu schon alles gesagt. Ich habe letzte Woche geschrieben, wie sich Journalismus und Politik gegenseitig hochgeschaukelt haben am Imperativ der Aufmerksamkeit und dadurch eine Realität geschaffen wurde, die man jetzt nicht einmal mehr zu dritt auf der Straße erörtern kann (vgl. Meyen 2020a). Das ist der Tod von Öffentlichkeit, die online nicht wiederbelebt werden kann, weil dort Stürme drohen und so die Zwischenstufen fehlen, die Encounter (Begegnungen im Bus, in der Kneipe, auf dem Büroflur) und Leitmedien zusammenbringen. Keine Versammlungen, keine Demos. Nicht einmal mehr Graffiti. Encounter sowieso nicht. Und damit keine Öffentlichkeit.
Ich habe letzte Woche auch über die Expertokratie geschrieben, die Patrick Illinger heute in der Süddeutschen Zeitung verteidigt, und über das, was aus einer Herrschaft der Wissenschaft für die Medien folgt (vgl. Meyen 2020b). Zitat: „Der Journalismus dankt ab und lässt die Experten gleich selbst sprechen“. Ich habe dort auch versucht zu erklären, warum Daten und Zahlen nicht mit der Realität zu verwechseln sind (vgl. Mau 2017). Noch ein Zitat: „Was immer wir messen, wird sozial hergestellt. Menschen legen fest, nach welchem Virus sie suchen und was passieren muss, damit sie ‚Gefunden!‘ rufen können. Hinter jeder Zahl steht ein Interesse, und sei es nur das eines Herstellers, der seine Geräte loswerden will. Daraus folgt immer: Es hätte auch anders sein können. Das klingt banal, ist es aber ganz offenkundig nicht. Sonst könnten wir gerade nicht beobachten, wie Zahlen alles umbauen, was wir bisher gekannt haben. Wir lernen: Zahlen sind nicht die Wirklichkeit. Sie erzeugen sie erst“.
Und damit endlich zu Patrick Illinger. „Wer jetzt vor einer Diktatur der Wissenschaft warnt“, heißt es in besagtem Leitartikel, „begeht einen Fehler. Es (sic!) macht die Wissenschaft zum Stakeholder, zur Interessengruppe, zu einer Strömung, der man sich widersetzen kann und vielleicht sollte. Doch das verwechselt den Boten mit der Botschaft“. Nein. Punkt eins: Es gibt keine Botschaft ohne Boten. Punkt zwei: Die Wissenschaft, die sich nur für die Wahrheit interessiert und für sonst nichts, ist eine Schimäre. Das „interessenlose Interesse“ oder das „Interesse an der Interessenlosigkeit“, die Idee, dass wir es hier mit Menschen zu tun haben, die „uneigennützig“ und womöglich sogar „unentgeltlich“ arbeiten: Das ist die „illusio“ des akademischen Feldes (Bourdieu 1998: 27). Und Punkt drei: Dieses akademische Feld ist längst gekapert von den Imperativen der Wirtschaft (Geld!) und der Medien (Aufmerksamkeit!). Eigentlich sollte es deshalb selbstverständlich sein, stets die Strukturen zu hinterfragen, in denen Wissen (Illinger: „möglichst fundierte Fakten“) produziert wird. Eigentlich.
Der Reihe nach und etwas ausführlicher. Wissenschaft wird von Menschen gemacht. Menschen entscheiden, welche Fragen sie beantworten wollen (und damit auch, welche nicht beantwortet werden). Menschen entscheiden, welcher Weg zur Erkenntnis akzeptiert wird und welcher nicht und damit auch, auf welche „Fakten“ wir alle zugreifen können, wenn die Not groß ist. Die Wissenschaft ist dabei eine soziale Welt wie jedes andere Feld. Das heißt: Woran dort gearbeitet wird, hängt von der „Struktur der objektiven Beziehungen zwischen den Akteuren“ ab und vor allem davon, was am Machtpol gerade goutiert wird (Bourdieu 1998: 20). Welche Themen versprechen Verträge, die über das Jahresende hinausgehen, mit welchen Methoden muss ich forschen, um am Ende eine Professur zu bekommen oder gar den Chefposten in einem großen Institut?
Das ist die erste Agenda, noch ganz ohne den Einfluss von Drittmitteln und ohne die Gier nach Prominenz oder wenigstens nach öffentlicher (medialer) Legitimation: Wissenschaftler sind Menschen und wollen (wie alle anderen auch) ihre Position verbessern. Sie wollen, dass ihre Fragen wichtiger werden und die Mittel, mit denen sie nach einer Antwort suchen. Das gilt innerhalb einzelner Disziplinen (etwa: in der Medizin) genauso wie im akademischen Feld insgesamt. Virologie gegen Soziologie gegen Geschichte. Kurz vor Corona hatte die bayerische Regierung Unsummen für die Big-Data-Forschung angekündigt. Ein Füllhorn für die Universitäten, um der „künstlichen Intelligenz“ auf die Spur zu kommen. Mal schauen, was davon jetzt übrigbleibt.
Das führt direkt zur zweiten Agenda, die gar nicht mehr verborgen werden muss, weil die Position im akademischen Feld inzwischen auch vom Medienecho abhängt und noch stärker davon, wie viel Geld von außen eingeworben wird. Wurden Wissenschaftler noch vor zwei oder drei Dekaden als Feuilletonforscher belächelt, wenn sie allzu oft auf der Mattscheibe zu sehen waren oder in der Presse, ist öffentliche Präsenz inzwischen ein Muss für alle großen Fördereinrichtungen und damit auch für die Reputation im Feld. Man darf Christian Drosten (nur als Beispiel) nicht verübeln, dass er einen Elfmeter schießt, wenn „koan Neuer“ zu sehen ist. Man muss nur wissen, dass ihm dieses Tor hilft, das Spiel im akademischen Feld zu gewinnen.
Das sagt noch nichts gegen den Inhalt (Virologie und Epidemiologie werden auf anderen Blogs verhandelt), wohl aber etwas gegen jeden blinden Glauben an alles, was uns Menschen in weißen Kitteln erzählen. Patrick Illinger hat Physik studiert und am Cern in der Schweiz promoviert – am Machtpol des wissenschaftlichen Feldes, wo der Wunsch besonders ausgeprägt ist, die Welt „da draußen“ möge an das „interessenlose Interesse“ der Forscher glauben. Die „klinische Soziologie des wissenschaftlichen Feldes“ von Pierre Bourdieu (1998), die ich gerade skizziert habe, stößt dort auf Ablehnung und Widerstand, weil sich die „illusio“ in den Habitus eingebrannt hat. Patrick Illinger ist aber kein Wissenschaftler mehr, sondern ein Journalist. PR ist in diesem Feld eigentlich tabu.
Literatur
Pierre Bourdieu: Vom Gebrauch der Wissenschaft. Für eine klinische Soziologie des wissenschaftlichen Feldes. Konstanz: UVK 1998.
Steffen Mau: Das metrische Wir. Über die Quantifizierung des Sozialen. Berlin: Suhrkamp 2017.
Michael Meyen: Die Medien-Epidemie. In: Michael Meyen (Hrsg.): Medienrealität 2020a.
Michael Meyen: Daten + Experten = Demokratie? In: Bayerischer Forschungsverbund „Die Zukunft der Demokratie“ (Hrsg.): ForDemocracy 2020b.
Die Maske, Hans-Jürgen Papier und Juli Zeh
Medienrealität, 5. April 2020
Die Medienforschung erwacht aus der Corona-Starre. Stephan Russ-Mohl sucht per Rundmail Beiträge (“möglichst” empirisch unterfüttert), die sagen, was der Journalismus bisher gut gemacht hat und was eher schlecht. Vielleicht findet er dabei sogar diesen Blog. Nach viel Kritik (vgl. Gordeeva 2020 sowie Meyen 2020a und 2020b) gibt es hier heute ein Lob für die SZ.
Vorbemerkung eins: Was Otfried Jarren vor einer Woche über das “Systemmedium” Fernsehen geschrieben hat und über die “besondere Form der Hofberichterstattung” beim NDR, war gut und richtig. Das ist das, was eine akademische Disziplin machen muss, die sich als öffentliche Wissenschaft versteht. An den Auftrag des öffentlich-rechtlichen Rundfunks erinnern, Qualität einfordern, Standards nennen. Der diskursive Kampf um Deutungshoheit wird auch in den Redaktionen ausgetragen. Wer dort den “Auftrag Öffentlichkeit” ernst nimmt, braucht gerade dann Argumente aus der Wissenschaft, wenn der Druck aus Politik und Behörden ins Unermessliche steigt und der Zugang zu alternativen Stimmen und Quellen verbaut ist.
Vorbemerkung zwei: Auch das, was zum Beispiel Hektor Haarkötter oder Daria Gordeeva geschrieben haben, kann dort helfen. Ein Ja zum Watchdog und ein Ja zum Nachfragen, gerade bei dem “Zahlenkonfetti” (Mathias Bröckers), den die Herrschenden uns täglich über die Leitmedien servieren.
Vorbemerkung drei (dann geht es endlich los): Ich war drauf und dran, einen Text mit der Überschrift “Süddeutsche Staatszeitung” zu schreiben. Auch SZ, aber anders. Am Rockzipfel von Markus Söder und auf dem Schoß von Angela Merkel, wie Nico Fried, der in seiner Seite-3-Geschichte zur großen TV-Ansprache auf die Minute wusste, wann der Stick aus dem PC gezogen wurde, und Verständnis für eine Kanzlerin hatte, die immer noch nicht jedes Bild der Tagesschau kontrollieren kann, obwohl das doch so wichtig wäre (Achtung: Bezahlschranke). Herrjemine.
Ich bin froh, dass ich diesen Text nicht geschrieben habe. Der Titel wäre schon vor zwei Wochen nicht ganz richtig gewesen. Recht und Verhältnismäßigkeit bei Heribert Prantl, immer wieder, oder (sehr früh) ein Gastbeitrag von René Schlott, einem Historiker, der in der SZ fragt, ob “die offene Gesellschaft erwürgt” werden darf, “um sie zu retten”, dann auch in anderen Medien zu Wort kommt und inzwischen auf Twitter die Initiative “Grundgesetz a casa” betreibt.
Manchmal hat der Forscher Glück. Manchmal lässt sich das, was Ulrich Beck (2017) als Kampf um Definitionsmacht beschrieben hat, an einer einzigen Journalistin festmachen. Dienstag war sich Christina Berndt in der SZ sicher: “Die Maske ist Pflicht, für alle!” Wer mittags auf die Seite ging, fand das dort als Aufmacher. Zitat: “Lebensretter dürfen gern ein bisschen blöd aussehen”. Wenn man so will: ein Kommentar zu Österreich und ein Hinweis an die Staatskanzlei. Tut was, schon wieder, obwohl noch niemand überprüfen konnte, ob das geholfen hat, was bisher getan wurde. Egal. Zwei Wochen sind einfach zu lang für einen Journalismus, der von Klickzahlen lebt. Am Mittwoch veröffentlicht Christina Berndt ein Interview mit einer Ärztin, Béatrice Grabein, die ziemlich deutlich ‘Blödsinn’ sagt (mit anderen Worten, versteht sich, wir sind bei der SZ), und Werner Bartens sammelt Pro- und Contra-Argumente mit dem gleichen Tenor.
Ich weiß nicht, ob die Ärztin bei Frau Berndt angerufen hat, aber das ist auch egal. Mit einem Tag Verspätung bekomme ich alles, was ich wissen muss, um mir eine Meinung bilden zu können. Das ist das, was Journalismus leisten muss.
Dieses Lob gilt erst recht für die SZ-Interviews mit Hans-Jürgen Papier und Juli Zeh. Eigentlich ist das natürlich eine Selbstverständlichkeit: Menschen zu Wort kommen lassen, die etwas zu sagen haben, und dabei das Spektrum so weit wie möglich ausreizen. Aber was ist schon selbstverständlich in einer Krise, in der “eine eskalierende Medienberichterstattung die Öffentlichkeit und die Politik vor sich her treibt” (Juli Zeh).
Ich muss hier nicht alles wiederholen, was Papier und Zeh gesagt haben. Bei beiden geht es um die Grundrechte, beide verwenden das Wort “Dilemma” und beide zeigen, wie vertrackt die Lage ist, in die sich die Bundesregierung manövriert hat. Gewaltenteilung? Schwierig in diesen Zeiten, sagt Hans-Jürgen Papier. “Ich kann mir schon vorstellen, dass ein Richter sagt: Ich kann nicht die Verantwortung dafür übernehmen, den Schutz von Leben und Gesundheit hintanzustellen, selbst wenn die Freiheit der Person sehr wichtig ist. Der Richter sieht sich ebenso wie die Politik und Exekutive mit den genannten Ungewissheiten über Art und Ausmaß der Gefahren sowie die Eignung und Notwendigkeit der Mittel konfrontiert”.
Juli Zeh, auch Verfassungsrichterin (ehrenamtlich, in Brandenburg), sagt das noch deutlicher. Ein paar Zitate für die, die an der Bezahlschranke scheitern, und für mich selbst, damit ich das irgendwann leichter zitieren kann:
- “Demokratische Politik darf auch in Krisenzeiten nicht nur den Vorgaben von einzelnen Beratern folgen und sagen, jetzt läuft hier alles aus dem Ruder, und deshalb müssen wir drakonisch in die Bürgerrechte eingreifen. Da werden wir, wenn die Krise abflaut, eine Menge aufzuarbeiten haben.”
- “Vor allem die Bestrafungstaktik ist bedenklich. Im Grunde schüchtert man die Bevölkerung ein, in der Hoffnung, sie auf diese Weise zum Einhalten der Notstandsregeln zu bringen. Die Ansage lautet sinngemäß: Wenn ihr nicht tut, was wir von euch verlangen, seid ihr schuld an einer weiteren Ausbreitung des Virus und an vielen Toten in den Risikogruppen! Bei einigen Menschen führt das zu Trotz und Widerstand, bei anderen zu Verängstigung und regressivem Verhalten. Beides vergiftet die gesellschaftliche Stimmung. Aus meiner Sicht stellt es immer eine Form von Politikversagen dar, wenn versucht wird, die Bürger mit Schuldgefühlen unter Druck zu setzen.”
- “Unsere Verfassung verlangt, dass bei Grundrechtseingriffen immer das mildest mögliche Mittel gewählt wird. Auch bei der Abwendung von Gefahren gilt nicht “viel hilft viel”, sondern: so viel wie nötig, so wenig wie möglich. Ansonsten fehlt es an der Verhältnismäßigkeit, und eine Maßnahme ist dann unter Umständen verfassungswidrig. Das erfordert also, dass man ernsthaft diskutiert, welche Vorgehen tatsächlich sinnvoll sind und welches davon am mildesten wäre. Dabei hätte ein wissenschaftlich fundierter Diskurs aller medizinischer Fachrichtungen zum Beispiel mittels einer Ad-hoc-Kommission helfen können. (…) Ein ernsthafter Diskurs kann auch unter Zeitdruck stattfinden, das muss nicht Monate dauern. In einer Demokratie darf man sich die Möglichkeit dazu nicht nehmen lassen. Erst einmal die Faktenlage so weit wie möglich zu klären und öffentlich zu machen, trägt zu sachlicher Klarheit und besseren Entscheidungen bei, es erhöht aber auch die Transparenz und damit die demokratische Legitimität.”
- “Mich macht es betroffen, dass in so schwierigen Zeiten viele Politiker wenig Rückgrat beweisen. Ich glaube noch nicht einmal, dass das Motiv der deutschen Politiker Machthunger ist. Mir scheint, es herrscht eher die Angst, man könnte ihnen später vorwerfen, dass sie zu wenig getan haben. Also überbietet man sich lieber gegenseitig beim Vorschlagen immer neuer drakonischer Verordnungen und versucht zu punkten, indem man sich als starker Anführer aufspielt. Dabei entsteht aber in meinen Augen kein Eindruck von Stärke, sondern von ziemlicher Kopflosigkeit.”
- “Wir wissen aus Erfahrung, wie gefährlich Angstmechanismen sind. Deshalb würde ich von verantwortlicher Politik und auch von verantwortlichen Medien verlangen, dass sie niemals Angst zu ihrem Werkzeug machen.”
Ich nehme an: Das wird am Montag nicht nur in der Onlinekonferenz der SZ besprochen. Ein Dank an Juli Zeh und ein Dank an Jan Heidtmann, der das Interview geführt hat. Vielleicht läuft ja im Hintergrund längst ein Kurs, der Nachrichtenredakteuren hilft, die Wirklichkeit im “Zahlenkonfetti” zu sehen. Datenerhebung, Einordnung, sprachliche Präzision (vgl. Meyen 2020c). Die Hoffnung jedenfalls hat sich noch nicht infiziert und stirbt bekanntlich ohnehin zuletzt.
Literatur
Ulrich Beck: Die Metamorphose der Welt. Berlin: Suhrkamp 2017.
Daria Gordeeva: Wenn Watchdogs schlafen. In: Michael Meyen (Hrsg.): Medienrealität 2020.
Michael Meyen: Die Medien-Epidemie. In: Michael Meyen (Hrsg.): Medienrealität 2020a.
Michael Meyen: Kniefall vor der Wissenschaft. In: Michael Meyen (Hrsg.): Medienrealität 2020b.
Michael Meyen: Daten + Experten = Demokratie? In: Bayerischer Forschungsverbund „Die Zukunft der Demokratie“ (Hrsg.): ForDemocracy 2020c.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 91bea5cd:1df4451c
2025-02-04 05:24:47
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
-
Frontend: Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
-
Backend: Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
Como Utilizar Novia
-
Acesso: Navegue até https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol.
-
Login: Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
-
Execução via Docker: A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/noviaEste comando cria um container, mapeia a porta 9090 para o host e monta o diretório
./nostr/datapara persistir os dados.
Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo
yaml. Abaixo, um exemplo comentado:```yaml mediaStores: - id: media type: local path: /data/media watch: true
database: /data/novia.db
download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false
publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2
relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100
fetch: enabled: false fetchVideoLimitMB: 10 relays: - match: - nostr - bitcoin
server: port: 9090 enabled: true ```
Explicação das Configurações:
mediaStores: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).database: Especifica o local do banco de dados.download: Controla as configurações de download de vídeos, incluindo o caminho para oyt-dlpe um arquivo de cookies para autenticação.publish: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (nsec), servidores de upload e relays. Atenção: Mantenha sua chave privada em segredo.fetch: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.server: Define as configurações do servidor web interno de Novia.
Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: https://github.com/teamnovia/novia.
-
-
 @ 3b7fc823:e194354f
2025-02-03 14:51:45
@ 3b7fc823:e194354f
2025-02-03 14:51:45Protecting Email Communications: A Guide for Privacy Activists
Safeguarding your communications is paramount, especially for activists who often face unique challenges. Encryption tools offer a vital layer of security, ensuring that your emails remain confidential and inaccessible to unauthorized parties. This guide will walk you through the process of using encryption tools effectively, providing both practical advice and essential insights.
Why Encryption Matters
Encryption transforms your communications into a secure format, making it difficult for unauthorized individuals to access or read your messages. Without encryption, even encrypted email services can expose metadata, which includes details like who sent the email, when it was sent, and the recipient's email address. Metadata can reveal sensitive information about your activities and location.
Key Encryption Tools
There are several tools available for encrypting emails, catering to different skill levels and preferences:
- PGP (Pretty Good Privacy)
-
For Tech-Savvy Users: PGP is a robust encryption tool that uses public and private keys. The recipient needs your public key to decrypt your messages. You can obtain your public key through a key server or directly from the recipient.
-
GPG (GNU Privacy Guard)
-
Free and Open Source: GPG is a user-friendly alternative to PGP, offering similar functionality. It's ideal for those who prefer an open-source solution.
-
ProtonMail
-
End-to-End Encryption: ProtonMail is popular among privacy-conscious individuals, offering end-to-end encryption and zero-knowledge encryption, meaning only the sender and recipient can access the message content.
-
Tresorit
-
Secure Communication: Tresorit provides end-to-end encrypted messaging with a focus on security and privacy, making it a favorite among activists and journalists.
-
Claws Mail
- User-Friendly Email Client: Claws Mail supports PGP encryption directly, making it an excellent choice for those who prefer a dedicated email client with built-in encryption features.
Steps to Encrypt Your Emails
- Choose a Tool:
-
Select the tool that best fits your needs and comfort level. Tools like PGP or GPG are suitable for those with some technical knowledge, while ProtonMail offers an easy-to-use interface.
-
Generate Keys:
-
Create a public key using your chosen tool. This key will be shared with recipients to enable them to encrypt their responses.
-
Share Your Public Key:
-
Ensure that the recipient has access to your public key through secure means, such as pasting it directly into an email or sharing it via a secure messaging platform.
-
Encrypt and Send:
- When composing an email, use your encryption tool to encrypt the message before sending. This ensures that only the recipient with your public key can decrypt the content.
Minimizing Metadata
Beyond encryption, consider these steps to reduce metadata exposure:
- Use Tor for Sending Emails:
-
Routing emails through Tor hides your IP address and makes communication more anonymous.
-
Avoid Revealing Identifiers:
-
Use .onion addresses when possible to avoid leaving a traceable email account.
-
Choose Privacy-Friendly Providers:
- Select email providers that do not require phone numbers or other personally identifiable information (PII) for registration.
Best Practices
- Avoid Using Real Email Accounts:
-
Create dedicated, disposable email accounts for encryption purposes to minimize your personal exposure.
-
Understand Legal Implications:
-
Be aware of laws in your country regarding encryption and digital privacy. Engaging in encrypted communications may have legal consequences, so understand when and how to use encryption responsibly.
-
Use Encrypted Backup Methods:
- Encrypt sensitive information stored on devices or cloud services to ensure it remains inaccessible if your device is compromised.
When Encryption Isn't Enough
While encryption protects content, there are limitations. Governments can legally compel decryption in certain circumstances, especially when they possess a warrant. Understanding these limits and considering the consequences of encryption is crucial for privacy activists.
Conclusion
Encryption is a vital tool for safeguarding communications, but it must be used wisely. By selecting the right tools, minimizing metadata, and understanding legal boundaries, privacy activists can effectively protect their emails while maintaining their commitment to privacy and freedom. Stay informed, stay secure, and always prioritize your digital well-being.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ 078d6670:56049f0c
2025-03-18 14:33:24
@ 078d6670:56049f0c
2025-03-18 14:33:24It felt like a pine cone had been dropped on my head from a great height, but there was no pine tree and, really, just sky and stars above me. I looked on the balcony around me, there was nothing. I resumed my slouch on the bench, re-lit the joint and contemplated the Universe.
After five minutes, the Universe hit again.
The anger bolted me off the bench. I looked around frantically for something to blame, an object lying red-faced on the floor, but nothing. I borrowed a high-powered torch and lit up the closest tree. Nothing suspicious, just the usual night shadows and leaves.
I came to the conclusion it had to be some kind of nocturnal bird protecting its nest: Night Jar or Owl.
It hit me again a week later on the back of my head on the deck below. But this time I caught a glimpse of its silent wings reflecting the ambient glow of the warm light from the lounge lamp just inside the house. Bust!
A Wood Owl.
It sat innocently on a branch staring back at me. I sat back on the bench, mesmerized and relieved. I re-lit the joint.
What does it mean? It’s got to mean something in this dreamworld. An omen, or portent, or am I just being paranoid that the Universe is trying to sabotage me. Okay, so we usually associate owls with wisdom, does that mean wisdom is going to hit me on the head? Surprise realizations busting my mind? And if I don’t get it, what’s next, lightning?!
I hope not.
It could be a simple reminder to be mindful of Consciousness around me. Like in a dream, everything is me. In this mysterious realm, Everything is Consciousness. And so in Vedanta philosophy: I am no-thing, but Consciousness.
The world around me is abundant in symbolism. I constantly ignore it, waiting for the booming sky-voice (or the owl whacking me on the back of the head), ignoring the micro-realizations, the little wisdoms discounted as monkey mind ramblings.
I know what I need to do. I tell myself every day. I am wise, it’s time to act like it.
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ ed84ce10:cccf4c2a
2025-03-18 14:19:19
@ ed84ce10:cccf4c2a
2025-03-18 14:19:19The Evolution of Hackathons: From Offline to Online, Powering Frontier Innovation Worldwide
Throughout the history of open-source platform technology, hackathons have been the launchpads for innovation—fueling breakthroughs, incubating the next generation of startups, and serving as the proving ground for builders. Over the past decade, DoraHacks has led the charge, driving the hacker movement and open-source revolution. We didn’t just witness the evolution of hackathons—we architected it.
The Online Revolution of Hackathons
Before 2020, hackathons were largely stuck in the physical world—you had to be in the room to participate. The idea of a fully online, global hackathon was a pipe dream. Then, DoraHacks.io changed everything. Suddenly, a developer in Africa could win funding from a hackathon hosted by a Silicon Valley company. Geographic barriers collapsed. Today, over 95% of hackathons happen online.
The Infrastructure Revolution: Making Hackathons 10x More Effective
DoraHacks relentlessly iterated on the hackathon model. We built BUIDL pages for real-time project showcases, a world-class hackathon organizer dashboard, MACI-powered decentralized privacy governance, and Grant DAOs that provide ongoing funding. The result? DoraHacks became the ultimate launchpad for hackers and early-stage builders.
The Ecosystem Revolution: Supercharging Open Innovation
DoraHacks became the backbone of Web3 innovation—from Ethereum, Solana, and BNB Chain to the next wave of blockchains like Aptos, Cosmos, Injective, TON, and Sonic. Since 2023, hackathons have expanded beyond crypto—quantum computing, commercial space tech, and AI-driven innovations are now being built on DoraHacks.
Rolling Hackathons and Uninterrupted BUIDLing - the New Standard for Ecosystem Growth
BUIDLs can be created spontaneously at any time. Hosting Hackathons as short-term events held only once or twice a year is not conducive to attracting outstanding Hackers and high-quality projects to join the ecosystem and drive innovation in the long term. To remediate this, Hackathons should be continuous and uninterrupted, serving as a long-term driving force within the developer ecosystem.
Historically, the high organizational costs and substantial resource investments associated with frequent Hackathons meant that most emerging ecosystems couldn't afford to host them regularly. As a result, Hackathons became rare, annual spectacles, and for some projects, an unaffordable luxury. This model severely restricted developers' chances to participate and hindered the ecosystem's ability to innovate consistently. Let's imagine what would happen if an ecosystem held 12 or more Hackathons each year?
- Developers have a clear loyalty incentive: They would know that the ecosystem is committed to supporting and funding excellent developers and projects continuously, which would encourage them to make long-term investments and contribute regularly.
- Missing out is no longer an issue: Even if a developer couldn't attend a particular Hackathon, there would be another one soon, increasing accessibility.
- Accelerated ecosystem innovation: Frequent Hackathons would accelerate ecosystem innovation. Developers would be constantly pushed to explore new directions, significantly boosting the growth rate of the technological ecosystem.
Previously, due to the limitations of costs and organizational difficulties, frequent Hackathons were almost unthinkable. Only ecosystems with sufficient funds like Google and Amazon could afford rolling Hackathons. But now, DoraHacks' upcoming BUIDL AI platform tools are set to change the game. These tools make it possible to organize 12 Hackathons in a year, and even go a step further by enabling the simultaneous hosting of multiple differently-themed Hackathons. This will help emerging ecosystems effectively incentivise developers, expand their technological influence, and increase the number of exceptional BUIDLs (projects) in their ecosystems.
The majority of BUIDLs come about continuously and spontaneously and should be recognized and incentivized promptly, rather than having to wait for the single annual Hackathon.
As the saying goes, "He who wins over developers wins the world." In the highly competitive Web3 space, Hackathons are an effective means of attracting developers, and rolling Hackathons are the best way to achieve this. For an ecosystem to stay competitive, it must ensure that developers always have opportunities to engage and create.
The AI Era of Hackathons: A 10x Opportunity, A 10x Challenge
AI Turns Everyone Into a Hacker
AI has obliterated repetitive work. Building is faster than ever. Anyone, from anywhere, can hack, ship, and scale with AI tools that accelerate ideation, development, and execution. The potential of hackathons in this AI-powered era is 10x bigger than ever before.
But Hackathon Infrastructure Is Stuck in the Past
Despite this massive opportunity, organizing hackathons remains painfully inefficient:
- Most organizations don’t know how to run hackathons effectively.
- Even those who do lack time and resources to do it frequently.
- Ecosystem builders who have the resources can only host one hackathon per year.
The result?
- Hackathons are underutilized, slowing innovation.
- Ecosystem growth is bottlenecked by developer relations (DevRel) teams.
- Many ecosystems fail to maximize the potential of hackathons.
- Low-frequency hackathons waste hacker potential—builders sit idle when they could be shipping.
BUIDL AI: Unlocking the Infinite Potential of Hackathons
We refuse to let inefficiency limit innovation. BUIDL AI is our answer.
DoraHacks is launching BUIDL AI, the AI-powered Hackathon Co-Pilot that automates, scales, and supercharges hackathon organization.
BUIDL AI: The Game-Changing Features
1. Edit and Launch: One-Click Hackathon Deployment
Organizers can now launch a hackathon in minutes by filling in basic details (prizes, themes, workshops, judges, etc.). No tedious manual setup.
2. BUIDL Review: Submission Evaluation (10x Faster)
Traditional hackathons get hundreds of submissions—judging takes hundreds of hours. BUIDL AI changes the game. It automatically scores projects based on completeness, originality, and theme relevance—filtering out low-quality submissions 10x faster than before.
3. Automated Marketing: Instant Hackathon Reports
After the hackathon ends, BUIDL AI auto-generates a full post-event report—highlighting winners, standout projects, and key takeaways—boosting visibility and impact.
4. Seamless Interaction: Smarter Collaboration, No Bottlenecks
BUIDL AI will interact with hackathon organizers to keep organizers in sync, alerting them about new submissions, pending approvals, and participant inquiries in real time. No more dropped balls.
5. Multi-Hackathon Management: Scaling Innovation Without Limits
Before BUIDL AI, running multiple hackathons at once was a logistical nightmare. Now, ecosystem builders can launch and manage multiple hackathons seamlessly, boosting innovation frequency exponentially
The full BUIDL AI Beta version will release on April 15th, but multiple free BUIDL AI features have already been available on DoraHacks.io!
BUIDL AI: The Next Great Leap in Open Innovation
Hackathons aren’t just competitions. They are the birthplace of the next trillion-dollar innovations.
With BUIDL AI, hackathons enter a new era—automated, intelligent, and infinitely scalable. This means more hackers, more builders, and more breakthrough projects than ever before.
At DoraHacks, we believe in an open, hacker-driven future. BUIDL AI is the rocket fuel for that future.
-
 @ bf6e4fe1:46d21f26
2025-01-31 01:51:03
@ bf6e4fe1:46d21f26
2025-01-31 01:51:03{"title":"test","content":"test"}
-
 @ 16d11430:61640947
2025-01-21 20:40:22
@ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad.
- Don’t Feed the Clowns
You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat.
Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month.
- Turn Off the Fiat News
Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance.
Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed.
- Mock Their Inflationary Gospel
Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?"
Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror.
- Celebrate the Fiat Freakshow
Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never.
- Build in the Chaos
While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt.
Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats.
- Adopt a Fiat-Free Lifestyle
Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.”
Every satoshi spent in the real economy is a slap in the face to the fiat overlords.
- Find the Humor in Collapse
Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all.
Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold.
- Stay Ruthlessly Optimistic
Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better.
So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt.
Final Thought: Burn the Tent Down
Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates.
But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k.
Welcome to the satirical resistance. Now go stack some sats.
-
 @ d6c48950:54d57756
2025-03-18 12:56:37
@ d6c48950:54d57756
2025-03-18 12:56:37A lot of people talk about how bitcoin has averaged 60% yearly but I personally find this to be misleading so I thought I'd use historic prices and portfolioperformance to see if you DCA (or in this case did a weekly purchase) starting at jan 1st of each year ending dec 31st
| Year | % Change | |------|----------| | 2024 | +124% | | 2023 | +140% | | 2022 | -60% | | 2021 | +60% | | 2020 | +267% | | 2019 | +71% | | 2018 | -67% | | 2017 | +588% | | 2016 | +38% | | 2015 | +7% |
If you showed this to any investor at any hedge fund they wouldn't believe it, yet this is something that through DCA apps like strike is performance anyone can get through just setting it and forgetting it.
-
 @ e97aaffa:2ebd765d
2025-03-18 12:25:39
@ e97aaffa:2ebd765d
2025-03-18 12:25:39No programa Pé de Meia do Camilo Lourenço, o seu recorrente convidado/patrocinador, explica os critérios que utiliza para avaliar as empresas. Segundo ele, um dos principais critérios para selecionar as melhores empresas, são critérios intangíveis.
Curiosamente, este mesmo senhor, num programa anterior, critica e recusa-se a investir em Bitcoin. Uma justificativa apresentada era, que não investia em algo que não podia ser palpável, que não poderia ser calculado o valor, ou seja, por ser intangível.
Só que neste programa, entra em contradição, ao dizer que um dos principais critérios que utiliza para avaliar as empresas são critérios intangíveis. A hipocrisia do tradiFi.
No programa foi apresentada a seguinte tabela:

Os pontos apresentados na tabela, são essencialmente os mesmos que nós, bitcoiners, utilizamos para caracterizar o Bitcoin, os seus pontos fortes.
Os tradiFi vivem numa cegueira ideológica, que não o permite ver o óbvio, mas o tempo é implacável, mais tarde ou mais cedo vão mudar de opinião. E quem não mudar vai ficar para trás.
-
 @ 7d33ba57:1b82db35
2025-03-18 10:59:32
@ 7d33ba57:1b82db35
2025-03-18 10:59:32Cádiz
Cádiz, one of Europe’s oldest cities, is a stunning Andalusian port town with golden beaches, rich history, and lively local culture. Surrounded by the Atlantic Ocean, it offers a blend of ancient charm, delicious seafood, and vibrant festivals.
🏛️ Top Things to See & Do in Cádiz
1️⃣ Cádiz Cathedral (Catedral de Cádiz)
A magnificent baroque and neoclassical cathedral with a golden dome. Climb the Torre de Poniente for panoramic city views!
2️⃣ La Caleta Beach
A picturesque urban beach framed by historic fortresses—perfect for sunset views and a relaxing swim.
3️⃣ Torre Tavira & Camera Obscura
One of Cádiz’s watchtowers, offering stunning 360° views and a fascinating optical projection of the city.
4️⃣ Mercado Central (Central Market)
A paradise for seafood lovers, where you can taste fresh fish, tapas, and local specialties.
5️⃣ Castillo de San Sebastián & Castillo de Santa Catalina
Two historic coastal fortresses with incredible views of the ocean and city skyline.
6️⃣ Plaza de España & Monument to the Constitution of 1812
A beautiful square with grand architecture, celebrating Spain’s first liberal constitution.
7️⃣ Walk the Seaside Promenades
Enjoy a scenic stroll along the Alameda Apodaca or the Parque Genovés, full of palm trees and ocean breezes.
🍽️ What to Eat in Cádiz
- Pescaíto frito – Crispy fried fish, a local specialty 🐟
- Tortillitas de camarones – Shrimp fritters, light and crunchy 🍤
- Atún de almadraba – Fresh tuna, often grilled or marinated 🐟
- Sherry wine (Jerez) – Cádiz is near Jerez, home of the famous fortified wine 🍷
🚆 How to Get to Cádiz
🚆 By Train: Direct trains from Seville (~1.5 hrs)
🚗 By Car: ~1 hr 20 min from Seville
✈️ Nearest Airport: Jerez Airport (XRY), ~40 min away💡 Tips for Visiting Cádiz
✅ Best time to visit: Spring & summer for the beaches, February for the Cádiz Carnival 🎭
✅ Wear comfy shoes – Cádiz is best explored on foot! 👟
✅ Day trips – Visit Jerez de la Frontera for sherry & flamenco or Bolonia Beach for Roman ruins -
 @ b17fccdf:b7211155
2025-01-21 18:22:51
@ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with ->
sudo apt update? 💥🚨👇
🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem:
~ > CLICK HERE < ~
Enjoy it MiniBolter!💙
-
 @ fd78c37f:a0ec0833
2025-03-18 10:44:40
@ fd78c37f:a0ec0833
2025-03-18 10:44:40In this edition, we’re thrilled to sit down with Tomek K from Bitcoin Alby, a passionate advocate for Bitcoin’s global adoption. Tomek K shares how Alby is driving innovation in the Bitcoin ecosystem and offers a glimpse into his vision for the cryptocurrency’s future. From his journey as a libertarian activist to co-founding the Bitcoin Film Festival, Tomek K’s story is one of curiosity, purpose, and a relentless pursuit of freedom through technology.
YakiHonne: Tomek K, it’s a pleasure to meet you! Today, we’re diving into your community topic—Alby Wallet. But before we begin, let me introduce our readers to Yakihonne. Yakihonne is a decentralized media client powered by the Nostr protocol, dedicated to promoting free speech through technology. It empowers creators to truly own their voices and assets, offering features like smart filtering, verified notes, and a focus on long-form content. So, Tomek, could you tell us about yourself and your work with Alby?
Tomek K: Of course! I’m Tomek K, originally from Poland, and right now, I’m speaking to you from Sri Lanka. I love traveling and observing how different countries adopt Bitcoin. For most of my career, I’ve been a free-market advocate, promoting economic freedom through various projects—essentially doing PR for capitalism. I’ve organized conferences, political demonstrations, economic seminars, summer festivals, and even opened a bar in Warsaw to spread these ideas in different ways.
During this advocacy work, I came across Bitcoin. At first, I didn’t pay much attention to it, but over time, I started feeling frustrated—our efforts raised awareness about freedom, but they didn’t bring measurable change. That led me to study Bitcoin more deeply, and I gradually shifted my focus to Bitcoin activism. Along the way, I collaborated with publishers to translate Bitcoin-related books into Polish and co-founded the Bitcoin Film Festival with friends from Meetup. Later, I joined Alby, marking my transition from free-market activism to Bitcoin promotion.
At the Bitcoin Film Festival, I handle operations and networking—organizing the event, managing logistics, and making things happen. Our team is small, but I enjoy the work. I’m passionate about Bitcoin because I came for the revolution, and I’m staying for the revolution.
That said, I don’t consider myself a Bitcoin absolutist. I see Bitcoin as a tool for freedom, not just a currency or a more efficient technology. If there were a better tool for advancing liberty and making societies freer, I’d probably focus on that. But for now, Bitcoin appears to be the most effective tool for freedom. Ultimately, I consider myself a “life maximalist”—because to live a good life, you need freedom, and to have freedom today, you need sound money. And right now, that money is Bitcoin.
YakiHonne: Was there a specific moment or event that sparked your interest in Bitcoin and motivated you to join the Alby community?
Tomek K: What attracted me to Bitcoin was its promise of global monetary independence and its ability to reduce the control of the Federal Reserve, central banks, and governments—the strongest and most covert control mechanisms in the world. Unfortunately, many people, even libertarians, often overlook this.
As for why I joined Alby, it’s because this startup is driven by values and mission rather than simply chasing profits, like selling tokens or games. This aligns well with my interest in the Lightning Network. As I explored Lightning more deeply, I came across Alby. I’ve always enjoyed testing new tools, trying them firsthand, and understanding the communities behind them—so naturally, I became part of it. Along the way, I also got to know some of the team members, which reinforced my involvement.
Additionally, Alby supported the Bitcoin Film Festival. While they weren’t the largest sponsor, their contribution was generous. The festival served as a great platform for them and other projects. I think it was good marketing because people like me—who have strong networking skills, arrange podcast interviews, and organize various activities—help build awareness and positive PR. That was part of my role.
If I had to pinpoint a single defining moment that led me here, I honestly couldn’t. Becoming a Bitcoiner doesn’t happen overnight. You can’t just read The Bitcoin Standard, declare that you understand Bitcoin, and instantly become a maximalist. Anyone who’s intellectually honest will admit that it takes multiple touchpoints—articles, films, career shifts, essays, hands-on experimentation, and actually using Bitcoin—to truly grasp its significance. I had many such moments along the way: reading The Bitcoin Standard, learning from friends who had a deeper understanding of Bitcoin, and working at Alby, which further expanded my knowledge of the Lightning Network’s capabilities and limitations. It wasn’t one turning point but a series of pivotal experiences that shaped my path.
YakiHonne: How did the Alby community start, and how did it attract its first members?
Tomek K: When I joined Alby, the community had already been established for some time. It originally emerged within the browser design community, where early users helped developers refine the product by providing feedback. That’s how the first members joined, and this process has been ongoing for four years now.
As for how Alby attracted members, it was through a mix of channels—social media (Twitter, Telegram, Discord), email engagement, and active participation in Bitcoin conferences. But the core strategy has always been openness, engaging with users, and listening to their feedback. Sometimes that means making a joke, sometimes defending against unfair criticism, and other times implementing requested features. We’ve always worked to maintain an active and friendly community atmosphere.
We also host bi-weekly community calls, which are a central part of our activities. Every two weeks, available team members meet with users for open Q&A sessions, issue discussions, and demonstrations of various projects integrating with Alby. I’ve participated in some of these calls, and they help maintain strong relationships with users, developers, and other projects—something crucial for the ecosystem. The Bitcoin technology landscape is somewhat fragmented, and grassroots coordination is necessary since there’s no single leader defining terminology or coding practices.
That’s also why Alby doesn’t exist in isolation. Almost everything we’ve built has been made possible by the creators of previous libraries, prior codebases, and collaborative efforts in writing specifications for protocols. Projects like Yakihonne and many others also recognize the importance of open-source collaboration. I think it’s essential to acknowledge the contributions of the open-source community. One thing I really appreciate is that Bitcoiners are driving open-source development in virtually every part of the world, all working toward a shared and meaningful goal.
YakiHonne:Were there any notable challenges in the early days that left a strong impression on you?
Tomek K :When I first joined Alby, I struggled with a bit of imposter syndrome for months. I was handling PR for the project, but I didn’t fully understand all the technical details—how certain protocols interact or what’s happening under the hood. It took time to get familiar with everything and really feel like I belonged.
Regulatory pressure has also been a huge challenge. In some cases, developers have been arrested, projects have had to leave certain countries, and users have been geoblocked based on their location. But challenges like these can also drive innovation. For example, Alby developed AlbyHub, an open-source self-custodial node, as a response to these kinds of issues.
There are always risks in this space—governments might suddenly demand a banking license or require compliance with new regulations. These are real obstacles, but we tackle them by embracing decentralization and open-source solutions. That’s how we ensure the project stays true to its mission and vision.

YakiHonne:If someone wanted to start a Bitcoin community today or grow an existing one, what advice would you give them?
Tomek K: The most important thing is to just get started. A community begins with action, and it takes more than one person. Even if it’s just you and a friend grabbing a beer, that’s already a start. Maybe after the first or second meetup, you post on Meetup.com, Twitter, or local forums:"Hey, we’re hosting a Bitcoin meetup in this city. We just want to connect with other Bitcoiners!" If you keep doing it consistently, the community will naturally grow. Over time, the bar where you meet might get interested in accepting Bitcoin, or you might meet some OGs in your area who decide to join—maybe they already run a business and want to support what you’re doing.
You don’t have to over-plan everything from the start. No need to think, “We need a podcast, 10 episodes, a logo…”—all that can come later. Just bootstrap it: organize a meetup, grab a beer, and get going. As you go, you’ll adapt, improve, and build recognition.Beyond that, it’s a great way to meet other Bitcoiners, develop leadership skills, and learn about community building. And at the very least, you’ll have fun doing it—which, honestly, is one of the main reasons I keep organizing meetups and other activities.
YakiHonne: Exactly, the key is to take action—just start and see where it leads. Does your community focus more on Bitcoin’s technical aspects, like coding and development, or do you emphasize non-technical areas such as education and outreach? Or do you try to balance both?
Tomek K: Our users come from all kinds of backgrounds. Some are very engaged and provide feedback regularly, while others prefer to stay in the background. Some attend our community calls, and within that group, some are developers actively building projects and collaborating with us. At the same time, there are developers we know are out there, but they never directly engage with us. That’s just how the Bitcoin community works—there’s no strict definition of being part of Alby. People engage in their own way. Some users are active on Discord, some aren’t, but we treat them all as part of the family, keeping them informed through newsletters, offering support, and making sure they stay updated with what’s happening at Alby.
As for whether we lean more toward technical development or non-technical outreach, there’s no clear-cut answer. Our community is diverse—we cater to a wide range of Lightning Network users. Some just use the browser extension, while others are deeply involved in our ecosystem. We also work with NGOs, educational initiatives, and community organizations. At the same time, we place a strong emphasis on developers and maintaining good relationships with them. Our repositories and developer portal offer useful libraries and examples, making it easier for both aspiring and experienced developers to integrate the Lightning Network into their projects. Developer relations are something we consider highly important.

YakiHonne: I understand that you're also the founder of another Bitcoin-related film project. Could you tell us a bit about it? What exactly inspired you to combine Bitcoin and filmmaking?
Tomek K: Yes, I founded Bitcoin Film Fest to help build what I call Bitcoin Cinema—an emerging industry that blends Bitcoin and filmmaking. I wanted to track everything happening at the intersection of these two worlds. Just like e-commerce, energy, and information technology, I believe the film industry will eventually be shaped by Bitcoin. And in fact, it’s already happening. There are Bitcoin-themed movies, and even major Hollywood productions have started including Bitcoin references. Bitcoin filmmakers, Bitcoin culture, and even a Bitcoin subculture already exist. We have our own heroes, stories, and values, and from this, films are being created. I love cinema, and I love Bitcoin—this was my way of bringing the two together.
The festival itself happened somewhat by accident—but maybe it was meant to be. It all started in Warsaw when I was organizing a Bitcoin meetup. I planned to screen a Bitcoin documentary, but due to technical issues, it didn’t happen. So, over a few beers, we came up with an idea: if we couldn’t show one film, why not go all in and create a full-scale Bitcoin film festival? We started researching and realized there were enough Bitcoin-related films out there to make it happen. So, we did.
The response from the community was overwhelmingly positive. It became clear that people wanted a space for Bitcoin cinema—a hub for information, networking, and collaboration. We started using the term “Binema” (Bitcoin Cinema) to describe this emerging genre. I find it fascinating to witness the growth of Bitcoin culture and storytelling. Before this, I had followed libertarian artistic movements closely, and now I see how important culture is for Bitcoin’s adoption—it’s not just about the technical and financial aspects.
Bitcoin adoption isn’t going to happen overnight, and it won’t happen without developers, educators, infrastructure builders, UX designers, and many others contributing to the ecosystem. Culture is one of the most powerful tools for shaping society, and I, like many others, am working to bring Bitcoin adoption closer through film. We’re witnessing the early days of Bitcoin cinema. I missed out on the birth of traditional cinema, but this time, I want to be part of it.
YakiHonne:In your region, does the government support or oppose Bitcoin? How has this stance impacted the development of the Bitcoin community so far?
Tomek K :Bitcoin doesn’t concern itself with nation-state borders, and frankly, we don’t either. The situation in Poland has little influence on what we do. The only connection is that I, along with two others, happen to be in Poland, but most of our team is globally distributed. On a broader scale, the U.S. tends to shape regulatory trends, and unfortunately, it often does so in a more restrictive way. However, Poland itself hasn’t had a significant impact on our work.
YakiHonne:Has your Bitcoin Film Fest community ever used film as a way to connect with members—perhaps by watching a Bitcoin-related movie or hosting a movie night to make things more fun and engaging? Have you done anything like that before?
Tomek K:Yes, absolutely! The film festival itself is a great example—we watch movies together and build a community around them. Aside from the festival we organized in Warsaw, we've also hosted film screenings at various Bitcoin events, like Sats and Facts in Thailand, BTC Prague, Plan B Lugano, Frimadera, Adopting Bitcoin, and several other conferences. We also organize online watch parties—actually, there's one happening next Sunday. The movie is available on Prime Video, but we'll sync up on Discord to watch it together, chat, and share our thoughts. We'll be announcing it on Twitter, so if you check Bitcoin Film Fest on Twitter, you'll find details on how to join.
Film has been a great way to connect with members and spark discussions. We've seen Bitcoin meetups worldwide organizing movie nights—our volunteer friends in Montenegro have hosted one, and our partners in Kenya and South Africa have done the same. Lately, movie nights have been happening more and more frequently, which is exciting.
It's still early—after all, Bitcoin is only 16 years old, so the selection of Bitcoin movies is still relatively small. Many of these films haven’t had large budgets or massive talent pools yet, but that’s changing. Right now, we’re primarily focused on showing films within the Bitcoin community rather than creating films aimed at the general public. That said, those kinds of projects are also emerging. I’m optimistic about the growth of Bitcoin cinema—better storytelling, AI-driven advancements, increasing interest from audiences, and even sponsors willing to invest in filmmakers. Big things are coming, and while we already have some great Bitcoin films, the best is yet to come. We’re still in the early days, and this is the time to contribute and help shape the future of Bitcoin cinema.
YakiHonne:We’ve come to the end of today’s interview, and I’ve truly enjoyed every moment of it. I’m very sure your idea will be incredibly engaging, inspiring more people and attracting a broad audience. Thank you so much for your time today—it was a great conversation.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ b8851a06:9b120ba1
2025-01-14 15:28:32
@ b8851a06:9b120ba1
2025-01-14 15:28:32It Begins with a Click
It starts with a click: “Do you agree to our terms and conditions?”\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
Welcome to Digital Serfdom
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it “protection.” They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
Freedom in Chains
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
The Great Unpermissioning
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, “No.” It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- Stop asking. Permission is their tool. Refusal is your weapon.
- Start building. Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- Stand firm. They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
The New Frontier
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
A Final Word
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 75869cfa:76819987
2025-03-18 07:54:38
@ 75869cfa:76819987
2025-03-18 07:54:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 225,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 95%. More than 10 million events have been published, with posts and reposts showing a decrease. Total Zap activity stands at approximately 15 million, marking a 10% decrease.
Additionally, 26 pull requests were submitted to the Nostr protocol, with 6 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 463 long-form articles were published, 29% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 3 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 225,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 18179 events, with a low of approximately 16093.
The number of new users has decreased significantly. Profiles with a contact list are now around 17,511, reflecting a 95% drop. Profiles with a bio have decreased by 62% compared to the previous period. The only category showing growth is pubkeys writing events, which have increased by 27%.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 14% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.6 million, which is a 6.1% decrease. Both reposts and reactions have decreased by about 10%.
For zap activity, the total zap amount is about 15 million, showing an increase of over 10% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing that A bulletin board is a relay-centric system of forums where users can post and reply to others, typically around a specific community. The relay operator controls and moderates who can post and view content. A board is defined by kind:30890. Its naddr representation must provide the community's home relays, from which all posts should be gathered. No other relays should be used.
nostr:npub1xy54p83r6wnpyhs52xjeztd7qyyeu9ghymz8v66yu8kt3jzx75rqhf3urc is proposing a standardized way to represent fitness and workout data in Nostr, including: Exercise Templates (kind: 33401) for storing reusable exercise definitions, Workout Templates (kind: 33402) for defining workout plans, Workout Records (kind: 1301) for recording completed workouts. The format provides structured data for fitness tracking while following Nostr conventions for data representation.Many fitness applications use proprietary formats, locking user data into specific platforms. This NIP enables decentralized fitness tracking, allowing users to control their workout data and history while facilitating social sharing and integration between fitness applications.
nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef is proposing a PR introduces two "1-click" connection flows for setting up initial NWC connections. Rather than having to copy-paste a connection string, the user is presented with an authorization page which they can approve or decline. The secret is generated locally and never leaves the client. HTTP flow - for publicly accessible lightning wallets. Implemented in Alby Hub (my.albyhub.com) and CoinOS (coinos.io). Nostr flow - for mobile-based / self-hosted lightning wallets, very similar to NWA but without a new event type added. Implemented in Alby Go and Alby Hub. Benefits over NWC Deep Links are that it works cross-device, mobile to web, and the client-generated secret never leaves the client. Both flows are also implemented in Alby JS SDK and Bitcoin Connect.
add B0 NIP for Blossom interaction
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 describes a tiny subset of possible Blossom capabilities, but arguably the most important from the point of view of a most basic Nostr client. This NIP specifies how Nostr clients can use Blossom for handling media. Blossom is a set of standards (called BUDs) for dealing with servers that store files addressable by their SHA-256 sums. Nostr clients may make use of all the BUDs for allowing users to upload files, manage their own files and so on, but most importantly Nostr clients SHOULD make use of BUD-03 to fetch kind:10063 lists of servers for each user.
nostr:npub149p5act9a5qm9p47elp8w8h3wpwn2d7s2xecw2ygnrxqp4wgsklq9g722q defines a standard for creating, managing and publishing to communities by leveraging existing key pairs and relays, introducing the concept of "Communi-keys". This approach allows any existing npub to become a community (identity + manager) while maintaining compatibility with existing relay infrastructure.
A way for relays to be honest about their algos
securitybrahh is proposing a PR introduces NIP-41, a way for relays to be honest about their algos, edits 01.md to account for changes in limit (related #78, #1434, received_at?, #620, #1645) when algo is provided, appends 11.md for relays to advertize whether they are an aggregator or not and their provided algos. solves #522, supersedes #579.
nip31: template-based "alt" tags for known kinds
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is proposing that clients hardcoding alt tags are not very trustworthy. alt tags tend to be garbage in a long-enough timeframe.This fixes it with hardcoded rich templates that anyone can implement very easily without having to do it manually for each kind. alt tags can still be used as a fallback.
nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z is proposing a PR addresses 3 main problems of NIP-44v2. First, It has a message size limit of 65Kb, which is unnecessarily small. Second, It forces the encrypting key to be the same as the event's signing key. Which forces multi-sig actors to share their main private key in order to encrypt the payload that would be later signed by the group. Decoupling singing and encryption keys, for both source and destination, is one of the goals of this version. And It offers no way to describe what's inside the encrypted blob before requesting the user's approval to decrypt and send the decrypted info back to the requesting application. This PR adds an alt description to allow decrypting signers to display a message and warn the user of what type of information the requesting application is receiving.
Notable Projects
Damus nostr:npub18m76awca3y37hkvuneavuw6pjj4525fw90necxmadrvjg0sdy6qsngq955
- Notes in progress will always be persisted and saved automatically. Never lose those banger notes when you aren't quite ready to ship them.
- Make your profile look just right without any fuss. It also optimizes them on upload now to not nuke other people’s phone data bills.
- You won't see the same note more than once in your home feed.
- Fixed note loading when clicking notifications and damus.io links.
- Fixed NWC not working when you first connect a wallet.
- Fixed overly sensitive and mildly infuriating touch gestures in the thread view when scrolling
Primal nostr:npub12vkcxr0luzwp8e673v29eqjhrr7p9vqq8asav85swaepclllj09sylpugg
Primal for Android build 2.1.9 has been released. * Multi-account support * Deep linking support * "Share via Primal" support * Bug fixes and improvements
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
YakiHonne Wallet just got a fresh new look!
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xchat v1.4.7-beta release * Upgraded the Flutter framework to v3.29.0. * Private chat implementation changed to NIP-104 Nostr MLS. * NIP-17 and NIP-29 messages now support q tags. * You can swipe left to reply to your own messages. * Chat messages now support code block display. * Copy images from the clipboard. * Fixed an issue where underlined text in chat appeared as italic.
GOSSIP 0.14.0 nostr:npub189j8y280mhezlp98ecmdzydn0r8970g4hpqpx3u9tcztynywfczqqr3tg8
Several major bugs have been fixed in the last week. * New Features and Improvements * Zappers and amounts are now shown (click on the zap total) * Reactions and who reacted are now shown (click on the reaction numbers) * Multiple search UI/UX improvements * Undo Send works for DMs too * Undo Send now restores the draft * UI: Side panel contains less so it can be thinner. Bottom bar added. * UI: frame count and spinner (optional) * Relay UI: sorting by score puts important relays at the top. * Relay UI: add more filters so all the bits are covered * Image and video loading is much faster (significant lag reduction) * Thread loading fix makes threads load far more reliably * Settings have reset-to-default buttons, so you don't get too lost. * Setting 'limit inbox seeking to inbox relays' may help avoid spam at the expense of possibly * Fix some bugs * And more updates
Nostur v1.18.1 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
New in this version: * Floating mini video player * Videos: Save to library, Copy video URL, Add bookmark * Improved video stream / chat view * Top zaps on live chat * Posting to Picture-first * Profile view: Show interactions with you (conversations, reactions, zaps, reposts) * Profile view: Show actual reactions instead of only Likes * Improved search + Bookmark search * Detect nsfw / content-warning in posts * Show more to show reactions outside Web of Trust * Show more to show zaps outside Web of Trust * Support .avif image format * Support .mp3 format * Support .m4v video format * Improved zap verification for changed wallets * Improved outbox support * Show label on restricted posts * Low data mode: load media in app on tap instead of external browser * Many other bug fixes and performance improvements
Alby nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
Latest two releases of Alby Go, 1.10 and 1.11, brought you lots of goodies: * BTC Map integration for quick access to global bitcoin merchants map * Confirm new NWC connections to your Alby Hub directly in Alby Go! No more copy-pasting or QR code scanning * Support for MoneyBadger Pay Pick n Pay QR payments in over 2000 stores in South Africa
ZEUS v0.10.0 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.0 is now available. This release features the ability to renew channel leases, spin up multiple embedded wallets, Nostr Wallet Connect client support, and more. * Renewable channels * NWC client support * Ability to create multiple Embedded LND 'node in the phone' wallets * Ability to delete Embedded LND wallets * Embedded LND: v0.18.5-beta * New share button (share ZEUS QR images) * Tools: Export Activity CSVs, Developer tools, chantools * Activity: filter by max amount, memo, and note
Long-Form Content Eco
In the past two weeks, more than 463 long-form articles have been published, including over 91 articles on Bitcoin and more than 41 related to Nostr, accounting for 29% of the total content.
These articles about Nostr mainly explore the rise of Nostr as a decentralized platform that is reshaping the future of the internet. They emphasize Nostr's role in providing users with greater freedom, ownership, and fair monetization, particularly in the realm of content creation. The platform is positioned as a counter to centralized social media networks, offering uncensored interactions, enhanced privacy, and direct transactions. Many articles delve into Nostr’s potential to integrate with Bitcoin, creating a Layer 3 solution that promises to end the dominance of old internet structures. Discussions also cover the technical aspects of Nostr, such as the implementation of relays and group functionalities, as well as security concerns like account hacks. Furthermore, there is an exploration of the philosophical and anthropological dimensions of Nostr, with the rise of "Dark Nostr" being portrayed as a deeper expression of decentralized freedom.
The Bitcoin articles discuss the ongoing evolution of Bitcoin and its increasing integration into global financial systems. Many articles focus on the growing adoption of Bitcoin, particularly in areas like Argentina and the U.S., where Bitcoin is being used for rental payments and the establishment of a strategic Bitcoin reserve. Bitcoin is also portrayed as a response to the centralized financial system, with discussions about how it can empower individuals through financial sovereignty, provide a hedge against inflation, and create fairer monetization models for creators. Additionally, the articles explore the challenges and opportunities within the Bitcoin ecosystem, including the rise of Bitcoin ETFs, the development of Bitcoin mining, and the potential impact of AI on Bitcoin adoption. There is also emphasis on Bitcoin's cultural and economic implications, as well as the need for decentralized education and innovation to drive further adoption.
Thank you, nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1rsv7kx5avkmq74p85v878e9d5g3w626343xhyg76z5ctfc30kz7q9u4dke nostr:npub17wrn0xxg0hfq7734cfm7gkyx3u82yfrqcdpperzzfqxrjf9n7tes6ra78k nostr:npub1fxq5crl52mre7luhl8uqsa639p50853r3dtl0j0wwvyfkuk4f6ssc5tahv nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub19mf4jm44umnup4he4cdqrjk3us966qhdnc3zrlpjx93y4x95e3uq9qkfu2 nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 nostr:npub1uv0m8xc6q4cnj2p0tewmcgkyzg8cnteyhed0zv30ez03w6dzwvnqtu6gwl nostr:npub1ygzsm5m9ndtgch9n22cwsx2clwvxhk2pqvdfp36t5lmdyjqvz84qkca2m5 nostr:npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226 nostr:npub1xzuej94pvqzwy0ynemeq6phct96wjpplaz9urd7y2q8ck0xxu0lqartaqn nostr:npub1gqgpfv65dz8whvyup942daagsmwauj0d8gtxv9kpfvgxzkw4ga4s4w9awr nostr:npub16dswlmzpcys0axfm8kvysclaqhl5zv20ueurrygpnnm7k9ys0d0s2v653f and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The first Bitcoin Meetup organized by Mi Primer Bitcoin was successfully held on March 14, 2025, at Texijal Pizza in Apaneca. The event included Bitcoin education, networking, a Q&A session, and merchandise distribution, offering an exciting experience for all participants.
* The Btrust Space discussion was successfully held on March 13, 2024. The event focused on how to support Bitcoin developers, fund open-source contributions, and grow the Bitcoin ecosystem. The speakers included Bitcoin core contributors, Btrust CEO, engineering leads, and other project leaders.Here is the upcoming Nostr event that you might want to check out.
- The Nostr Workshop, organized by YakiHonne and Bitcoin Safari, will take place online via Google Meet on March 17, 2025, at 7:00 PM (GMT+1). The event will introduce the Nostr ecosystem and Bitcoin payments, with participants learning about decentralized technology through YakiHonne and earning rewards. Register and verify your account to claim exclusive rewards, and invite friends to unlock additional rewards.
- The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar will be held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar will be hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (Lawyer specializing in Banking, Corporate, and Financial Law). The session aims to introduce the academic program and explore Bitcoin, the crypto economy, and related legal issues.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. The event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ da0b9bc3:4e30a4a9
2025-03-18 06:37:10
@ da0b9bc3:4e30a4a9
2025-03-18 06:37:10Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/916364
-
 @ 0f53ff86:e380fc00
2025-03-18 06:35:39
@ 0f53ff86:e380fc00
2025-03-18 06:35:39This article is cross posted from my personal blog at danjones.io.
Why has the "yes" been troubling me?
On look-back, I've been saying yes to almost everything that friends and family ask of me ever since the beginning of my adult life. Whether it be a DIY job, a call to help them in their hardships and an assist in times of need.
Upon rereading, it's not at all negative. The problem I have is I don't say this to myself, reciprocate or seek others in my time of need. I lack the ability to express myself.
Is this recompense for youthful errors? Do I lack self-respect, and as a result, push myself for others to make up for that? Why such harsh self-criticism? Why this undeserving feeling?
Self Awareness & Anxiety
Sometime about 4-5 years ago, I saw a councillor to fight this obsession with myself that I don't deserve the great things that come into life. The outcome of these sessions was that I was "highly self aware".
What does this mean?
- Honesty with oneself: I'm consistently honest with myself, almost too honest. I acknowledge how I feel, even if it's difficult.
- Reflection: Constant consideration of how my social actions, thoughts, and feelings affect others. Again, a little too much. Post-conversation, I often think of better responses and actions.
- Learning from mistakes: This I feel like is a brag, I don't want it to come across this way. I treat my mistakes as learning opportunities, but also spend too much time focussing on the mistake and how that could have been averted.
Having a heightened self awareness isn't bad. It's a great mindset to have, but in combination with anxiety, it can go wrong quickly.
But why am I including this? What connection does it have?
Subconscious
Am I subconsciously doing good for others to cover for the lack of involvement and assist to others in my younger years?
I wasn't your ideal son in my teen years. I was lazy, had no care for others, only ever cared for what benefited me only. Does this affect me in later life? Possibly.
I think things turned around in my early twenties. Professional work life had kicked in, met my partner who I'm still with today (and appreciate her every day) and I think a combination of these things turned me into who I am today.
Lacking ability to reward your person
A few months prior to attending a counselling session, I had applied for and was provided opportunity for 2 other workplaces. They were promising jobs with incredible self-development and financial opportunities.
I had declined both.
Feeling rewarded for what I saw as a lack of ability to fulfil the role and not understanding why I was rewarded for being myself consumed me and occupied my mind excessively. I felt like everything that had led me to this moment in my professional life was purely based on luck and right-place, right-time.
Because of this, I declined both.
That's not to say I was ever unhappy in my job, hence seeking work elsewhere. I love my job and still work in that role today. Great people, varied work and fantastic self-help are some of the key factors I'm in my role today.
I just wanted the opportunity to show everyone else I am capable of more, but alas, I failed, and that destroyed me.
Is an explicit yes bad?
Absolutely not. Throughout self-reflection on these moments over the years, being kind, helpful, caring to others in their time of need is more important now than ever. We live in a world filled with hate that if I can find an opportunity to make someone's day, I will always take that.
The problem I had to fight was self-respect, self-reward and inability to express how I feel or a need for help from others. Tying my wins and current life achievements not to luck or time and place, but to significant decisions made and the time I spend working on myself. Be it, self-reflections sessions, self studying and tech examinations (something I'm incredibly proud of) and more.
Who am I today?
Here, I want to put out who I am today, not just for me, but for others. I feel like if I'm able to provide a little more insight into my life and overcoming the challenges, someone, even if a single person, may benefit.
I am a person who;
- Is caring and loving.
- Tries to bring joy to others.
- Works hard to develop their skills and capabilities.
- Pushes oneself to excel.
- Takes time to help others, even if it comes at a penalty to one's own time.
- Should be rewarded for life's achievements..
My current situation: how did it happen?
- Record your achievements and shortcomings.
- Use a notepad or app. Reflect on these. Praise yourself for your good, and see how you might remedy the failures.
- Write the positives about yourself and repeat them back to yourself 2-3 times a day.
- For me, it was;
- Your current place in life isn't due to luck its down to ability and self investment.
- There is no right place or the right time. Only right decisions, which is why you are who you are today.
- I am a caring, loving person.
- I take pride in myself, and enjoy bringing joy to others.
- Get out more.
- Get out more! I'm a tech nerd and as a result, I spend a lot of time indoors. Take the time, even its half an hour, to walk around, go somewhere new. Grab a coffee at your local coffee shop and take in your surroundings. This will also help get you out of your own thoughts.
- Exercise
- Again, as a tech nerd, I spent a lot of my time sat down at a computer. Hardly great for your body or mind.
- Go for a run. Get that sense of achievement. Release those endorphins and push yourself each time.
- Attend the gym. Go to a gym to complete your exercise, but also meet others.
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ fbf0e434:e1be6a39
2025-03-18 05:02:55
@ fbf0e434:e1be6a39
2025-03-18 05:02:55DoraHacks 是 全球黑客运动的推动者
DoraHacks 是全球最大的Hackathon社区平台,致力于推动全球范围内的创新变革。在生物科技领域,类似的 Hacker 运动正在形成,并被称为无FDA社会(FDA Free Society)。这是 DoraHacks 在 生物科技领域的核心关注方向,我们相信,医疗和生物技术创新不应受制于官僚主义,而应以更自由、高效的方式加速发展。
FDA:生物科技创新的主要障碍
在全球医疗和生物科技创新的进程中,FDA(美国食品药品监督管理局)长期以来被认为是最大的一道障碍。它的监管模式虽然出发点是确保安全性和有效性,但实际上已经成为医疗创新的桎梏,主要体现在以下几个方面:
-
审批流程过于冗长和官僚
新药和新疗法的研发周期极其漫长,通常需要 10-15 年才能上市,使得许多有潜力的创新治疗方案被无情地耗尽在繁杂的审批流程中。
-
高昂的合规成本
由于 FDA 监管下的临床试验成本极高,许多潜在的突破性治疗因无法负担昂贵的试验费用而被扼杀,导致病人得不到及时的救治。
-
FDA 与大药企形成的利益护城河
现行的监管体系更有利于资金雄厚的大型制药公司,而小型生物科技公司和创新团队往往难以突破 FDA 的壁垒,最终导致真正的创新被排挤出市场。
市场驱动的生物科技创新更高效
与官僚机构控制医疗创新相比,市场驱动的模式能够更快速、更灵活地推动医疗技术进步:
-
市场决定哪些疗法更有价值
在一个自由竞争的环境下,创新疗法的优劣可以由市场和用户(医生、病人)来决定,而不是被行政机构耗时数年的审批流程所束缚。
-
Right to Try 法案:对现有监管的突破
美国已经推出 Right to Try(生存权利)法案,允许绝症患者尝试尚未获得 FDA 完全批准的疗法。这一法案证明,现有监管体系的僵化已严重影响患者的治疗机会,而自由市场提供了一种更可行的替代方案。
-
科技创业公司的加速作用
在市场的推动下,科技创业公司比政府监管机构更具敏捷性。例如,mRNA 技术的加速发展 正是由于市场驱动的模式,而非 FDA 监管的严格审批。可以预见,未来的新药研发将更依赖市场而非政府干预。
BioHack:突破 FDA 监管的桎梏
在 BioTech 领域,抗衰老和生命延长技术是未来最重要的突破方向之一,但这一领域的发展长期受到 FDA 的巨大阻碍:
-
BioTech 需要 FDA Free 的实验环境
未来的医疗创新应像 AI 和区块链等开源软件行业一样,采用开放式创新模式,让科学家和创业者自由实验,而非受制于一套过时的审批体系。
-
自由市场驱动的医疗体系将成为趋势
未来可能会出现 私人和社区支持的医疗实验室,以及一个更加去中心化的医疗体系,让创业团队和个体用户来决定医学的进步方向,而不是让政府机构和大型制药公司掌控一切。
结语
FDA Free Society 是 BioTech 领域即将发生的黑客运动。我们将确保BioHack发生在DoraHacks。
-
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ e5de992e:4a95ef85
2025-03-18 04:53:11
@ e5de992e:4a95ef85
2025-03-18 04:53:11Overview: Market Rebound Amidst Economic Uncertainty
On Monday, March 17, 2025, U.S. stock markets experienced gains for the second consecutive session, signaling potential stabilization following recent volatility. Key indices reported the following gains:
- S&P 500: Increased by 0.6%
- Dow Jones Industrial Average: Rose by 0.9%
- Nasdaq Composite: Edged up 0.3%
- Russell 2000: Notably rose by 1.2%
Despite these daily gains, year-to-date figures indicate that major indices remain below their previous highs:
-
S&P 500: Down 3.5%
-
Dow Jones Industrial Average: Down 1.7%
-
Nasdaq Composite: Down 7.8%
-
Russell 2000: Down 7.3%
Key Factors Influencing Market Movements
1. Economic Data and Consumer Behavior
- Recent reports show a marginal rebound in U.S. retail sales for February; however, the increase fell short of expectations.
- Factory activity in New York State experienced its most significant decline in nearly two years.
2. Federal Reserve's Upcoming Meeting
- The Federal Open Market Committee (FOMC) is set to meet on March 18-19, 2025.
- Although current interest rates are expected to remain between 4.25% and 4.50%, investors are keenly awaiting signals for potential future adjustments.
3. Geopolitical Tensions and Trade Policies
- President Donald Trump's evolving tariff strategies—particularly concerning trade with Canada and Mexico—have heightened market uncertainty.
- These policies complicate the Federal Reserve's data-dependent approach to interest rate decisions, as tariffs could drive inflation while weakening the job market.
4. Sector-Specific Developments
-
Technology:
Companies such as Nvidia and Tesla have experienced declines; Nvidia fell 1% ahead of its GTC AI conference, while Tesla dropped nearly 3%. -
Defense:
Huntington Ingalls Industries Inc. saw a significant increase of 5.6%, outperforming competitors during a positive trading session.
Commodity Markets
-
Oil:
Prices increased, with West Texas Intermediate (WTI) futures nearing $67.85 per barrel, reflecting stability in energy markets. -
Gold:
Prices remained near $3,000 per ounce, continuing their rally amidst market uncertainty.
Market Outlook
As markets navigate a complex landscape of economic indicators and geopolitical events, investor attention remains focused on the upcoming Federal Reserve meeting and related economic data releases. The outcomes of the FOMC meeting—coupled with ongoing trade policy developments—are expected to play pivotal roles in shaping market trajectories in the near term.
-
 @ 1d7ff02a:d042b5be
2025-03-18 03:27:44
@ 1d7ff02a:d042b5be
2025-03-18 03:27:44ອາຫານທີ່ມີທາດແປ້ງຕ່ຳ (low-carb) ແລະ ອາຫານແບບຄີໂຕ (keto) ເປັນປະເດັນຂັດແຍ້ງກັນມາດົນນານ. ບາງຄົນຍົກຍ້ອງວ່າມັນຊ່ວຍໃນການຫຼຸດນ້ຳໜັກ ແລະ ສຸຂະພາບຂອງລະບົບເມຕາບໍລິກ, ໃນຂະນະທີ່ຄົນອື່ນເຕືອນກ່ຽວກັບຄວາມສ່ຽງທີ່ອາດເກີດຂຶ້ນ. ບົດຄວາມວິທະຍາສາດລ່າສຸດທີ່ມີຊື່ວ່າ "ຄວາມເຊື່ອທີ່ຜິດ ແລະ ຄວາມຈິງກ່ຽວກັບອາຫານທີ່ມີທາດແປ້ງຕ່ຳ" ທ້າທາຍຄວາມເຂົ້າໃຈຜິດຫຼາຍຢ່າງ ແລະ ນຳສະເໜີຫຼັກຖານທາງວິທະຍາສາດທີ່ແໜ້ນແຟ້ນສະໜັບສະໜູນອາຫານປະເພດນີ້.
ອາຫານທີ່ມີທາດແປ້ງຕ່ຳແມ່ນຫຍັງກັນແທ້?
ເຮົາມາເລີ່ມຕົ້ນດ້ວຍຄຳນິຍາມກ່ອນ. ອາຫານທີ່ມີທາດແປ້ງຕ່ຳຈຳກັດທາດແປ້ງໃຫ້ບໍ່ເກີນ 130 ກຣາມຕໍ່ວັນ (25% ຂອງພະລັງງານ), ໃນຂະນະທີ່ອາຫານແບບຄີໂຕຈຳກັດທາດແປ້ງໃຫ້ນ້ອຍລົງຄື 20-50 ກຣາມ (10% ຂອງພະລັງງານ). ເຖິງແມ່ນວ່າຈະມີຊື່ສຽງວ່າເປັນ "ອາຫານແຟຊັ່ນ", ວິທີການເຫຼົ່ານີ້ໄດ້ສະສົມການສະໜັບສະໜູນຈາກການຄົ້ນຄວ້າທີ່ສຳຄັນໃນເກືອບສາມທົດສະວັດ.
ເປັນຫຍັງອາຫານທີ່ມີທາດແປ້ງຕ່ຳຈຶ່ງສຳຄັນ
ໃນເມື່ອພາວະອ້ວນ, ເບົາຫວານ, ແລະ ພະຍາດຫົວໃຈ ແລະ ຫຼອດເລືອດໄດ້ເຖິງລະດັບການລະບາດ, ຄວາມຕ້ອງການການແຊກແຊງທາງອາຫານທີ່ມີປະສິດທິພາບບໍ່ເຄີຍສຳຄັນເທົ່ານີ້ມາກ່ອນ. ບົດຄວາມນີ້ລະບຸວ່າອາຫານທີ່ມີທາດແປ້ງຕ່ຳບໍ່ພຽງແຕ່ເປັນກະແສທີ່ຜ່ານໄປ ແຕ່ເປັນຍຸດທະສາດທີ່ໄດ້ຮັບການຄົ້ນຄວ້າຢ່າງດີສຳລັບການຈັດການສຸຂະພາບຂອງລະບົບເມຕາບໍລິກ.
ການຍອມຮັບທາງການແພດເພີ່ມຂຶ້ນ
ກະແສກຳລັງປ່ຽນໃນວົງການແພດກະແສຫຼັກ. ອົງການໃຫຍ່ໆລວມທັງສະມາຄົມເບົາຫວານອາເມລິກາ ປັດຈຸບັນຍອມຮັບອາຫານທີ່ມີທາດແປ້ງຕ່ຳວ່າເປັນທີ່ຍອມຮັບໄດ້ສຳລັບການຈັດການເບົາຫວານປະເພດ 2. ສະມາຄົມຫົວໃຈອາເມລິກາໄດ້ຍອມຮັບວ່າອາຫານທີ່ມີທາດແປ້ງຕ່ຳຫຼາຍນຳໄປສູ່ "ການຫຼຸດລົງຂອງ A1c ຫຼາຍກວ່າ, ການຫຼຸດນ້ຳໜັກຫຼາຍກວ່າ, ແລະ ໃຊ້ຢາເບົາຫວານໜ້ອຍກວ່າ" ເມື່ອປຽບທຽບກັບວິທີການທີ່ໃຊ້ທາດແປ້ງປານກາງ.
ການລົບລ້າງຄວາມເຊື່ອທີ່ຜິດທົ່ວໄປ
"ທ່ານຕ້ອງການທາດແປ້ງເພື່ອການມີຊີວິດຢູ່"
ແປກໃຈບໍ່! ສະຖາບັນວິທະຍາສາດແຫ່ງຊາດສະຫຼຸບວ່າປະລິມານທາດແປ້ງທີ່ຈຳເປັນແມ່ນສູນ. ຮ່າງກາຍຂອງທ່ານສາມາດສ້າງນ້ຳຕານກລູໂຄສຜ່ານຂະບວນການ gluconeogenesis.
"ມັນຈະເຮັດໃຫ້ຄໍເລສເຕີຣອນຂອງທ່ານສູງຂຶ້ນ ແລະ ເຮັດໃຫ້ເກີດອາການຫົວໃຈວາຍ"
ໃນຂະນະທີ່ຄໍເລສເຕີຣອນ LDL ບາງຄັ້ງສູງຂຶ້ນ (ໂດຍສະເພາະໃນຄົນຜອມ), ການສຶກສາຫຼ້າສຸດພົບວ່າສິ່ງນີ້ບໍ່ໄດ້ແປວ່າຈະເຮັດໃຫ້ຮ່າງກາຍສະສົມຄາບຕິດໃນຫຼອດເລືອດເພີ່ມຂຶ້ນ. ໃນຂະນະດຽວກັນ, ອາຫານທີ່ມີທາດແປ້ງຕ່ຳປັບປຸງຕົວຊີ້ວັດພະຍາດຫົວໃຈອື່ນໆຫຼາຍຢ່າງ, ລວມທັງໄຂມັນໃນເລືອດ, HDL, ການອັກເສບ, ແລະ ຄວາມດັນເລືອດສູງ.
"ຊີ້ນແດງໃນອາຫານທີ່ມີທາດແປ້ງຕ່ຳເພີ່ມຄວາມສ່ຽງຂອງມະເຮັງ"
ການທົບທວນຄຸນນະພາບສູງສຸດຂອງເອກະສານທາງວິທະຍາສາດພົບວ່າມີຫຼັກຖານທີ່ເຊື່ອຖືໄດ້ພຽງເລັກນ້ອຍຫາບໍ່ມີເລີຍທີ່ເຊື່ອມໂຍງການບໍລິໂພກຊີ້ນແດງກັບມະເຮັງ. ການສຶກສາໃນອະດີດຫຼາຍຄັ້ງອີງໃສ່ຂໍ້ມູນການສັງເກດທີ່ອ່ອນແອແທນທີ່ຈະເປັນການທົດລອງທາງຄລີນິກທີ່ມີການຄວບຄຸມ.
"ມັນບໍ່ສາມາດຮັກສາໄດ້ໃນໄລຍະຍາວ"
ການສຳຫຼວດກ່ຽວກັບຄົນ 1,580 ຄົນພົບວ່າສ່ວນໃຫຍ່ຮັກສາອາຫານທີ່ມີທາດແປ້ງຕ່ຳໄດ້ເປັນເວລາຫຼາຍກວ່າໜຶ່ງປີ, ໂດຍ 34% ຮັກສາໄດ້ 2+ ປີ. ຄວາມຮູ້ສຶກອີ່ມຈາກໂປຣຕີນ ແລະ ໄຂມັນຊ່ວຍໃຫ້ຄົນບໍ່ຮູ້ສຶກຫິວລະຫວ່າງຄາບອາຫານ.
"ມັນມີລາຄາແພງເກີນໄປ"
ການວິເຄາະຕົ້ນທຶນພົບວ່າອາຫານທີ່ມີທາດແປ້ງຕ່ຳມີຄ່າໃຊ້ຈ່າຍຫຼາຍກວ່າພຽງແຕ່ປະມານ $1.27 ຕໍ່ຄົນຕໍ່ວັນເມື່ອທຽບກັບຄຳແນະນຳມາດຕະຖານ. ແມ່ນແຕ່ປະຊາກອນທີ່ມີລາຍໄດ້ຕ່ຳກໍສາມາດປັບຮັບເອົາວິທີການກິນແບບນີ້ໄດ້ສຳເລັດ.
"ທ່າແຮງໃນການປິ່ນປົວເບົາຫວານ"
ອາດຈະໜ້າປະທັບໃຈທີ່ສຸດ: ການທົດລອງທາງຄລີນິກສະແດງໃຫ້ເຫັນວ່າຫຼາຍກວ່າ 50% ຂອງຜູ້ເຂົ້າຮ່ວມທີ່ມີເບົາຫວານປະເພດ 2 ສາມາດກັບຄືນມາດີຂຶ້ນໄດ້ດ້ວຍອາຫານແບບຄີໂຕ, ໂດຍສ່ວນໃຫຍ່ຫຼຸດລົງຫຼືຢຸດເຊົາໃຊ້ຢາພາຍໃນພຽງແຕ່ 10 ອາທິດ.
ທີ່ມາ: https://www.mdpi.com/2072-6643/17/6/1047#B4-nutrients-17-01047 ສະຫລຸບ ແລະ ແປໂດຍ: ChatGPT, Claude
-
 @ 7252ad94:d19de472
2025-03-18 03:12:33
@ 7252ad94:d19de472
2025-03-18 03:12:33![[BTC March 17 25.jpg]]#Bitcoin #btccharts #BitcoinCharts
-
 @ 7252ad94:d19de472
2025-03-18 01:45:36
@ 7252ad94:d19de472
2025-03-18 01:45:36![[BTC March 17 25.jpg]]#Bitcoin #btccharts #BitcoinCharts
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ d6c48950:54d57756
2025-03-17 23:04:50
@ d6c48950:54d57756
2025-03-17 23:04:50Theres a popular trend among people who never grew up with old tech to suddenly embrace it as rebellion against enshitification and capitalism but as someone who actually grew up with old phones and old tech theres a reason why iphones and social media won, because they're better.
This doesn't mean they don't have flaws, it means that even with the flaws they still outperform; dumbphones are a bandaid but smartphones have comprehensive features built in that work more like a bandage - ironically the solution smart phones have to the problem of smartphones is still better than using a dumbphone as a solution to smartphones - parental control and screen time features work and they're incredibly robust, if you set them up in a well thought out way you can get an insane amount of utility from your smartphone and none of the downsides, if you have a friend setup the parental features according to your wishes it can be setup in such a way that you as the owner of the device cannot get around it, limiting how long you can spend on social media, limiting what apps you can install, what websites you can go on but without losing any of the insane value of smartphones such as
- signal: private communications
- camera: not needing to carry a camera
- ability to send photos quickly and easily to friends
- ability to share what your doing with others publicly
- ability to pay for things without needing to carry a card
- uber
- bus/train apps
- note taking apps that're searchable and instantly backed up
- maps app
- weather app
These are just some of the things on my phone that provide high value, think about how much clutter I would have to carry if I switched to a dumbphone and not only that, the cluttered separate items would perform worse and cost more (since I already own a smartphone).
I'm not saying dumbphones are useless but they solve nothing, setting up a smartphone to remove risk and harm whilst maximising value forces you to give careful consideration to the problem
- Can I trust myself to not turn this off?
- How much time do I want to spend on instagram?
- Do I want notifications on for this person?
- Do I ever want notifications from twitter?
- What value does my phone even provide?
Now you might say you asked those questions before switching to a dumbphone but my point is it's optional, you can not think about any of those things and switch to a dumbphone whereas in something approximating irony when doing it on a smartphone you have to be intentional, mindful, honest and self aware. You have to give serious thought to can you control yourself or self limit certain behaviours and if not would moderation or complete abstinence be better?
In my case I struggle with instagram, but I didn't want to get rid of it because it's how I keep in touch with some friends and keep up to date on their life and them on mine, it also is a good point of contact for new people I meet or people who want to get in touch - but if I average this out i.e messaging (occasional) , posting and looking at friends posts it should only really take me maybe 10 minutes per day maximum - I set a ten minute lock, what happens if I spend 10 minutes scrolling reels and then want to post something? I can't, I'm punished for the behaviour which discourages me from doing it next time.
dumbphones feel like a punishment for a problem you haven't tried to fix and for a behaviour you can't clearly articulate - you know you're doing something wrong and might be able to name the action (wasting time on tiktok) but you have no actual understanding of the behaviour (i.e why you do it or why it's even bad beyond some vague harm you ironically heard on tiktok).
you're spending money for no additional value beyond social value (wow a flip phone how quirky) and I've yet to meet a single logn term dumbphone user with an active social life - ironically I do know a person who makes tiktoks about living with a dumbphone - they film the tiktoks on an iphone they take with them everwhere and use as their daily phone. I'm not saying all dumbphone influencers are lying but I'm skeptical someone whos embraced the dumbphone would spend their free time making tiktoks or online content at all really, maybe they would at the start but long term? I doubt it.
smartphones have tons of apps and all those apps have shitty subscription services and each update makes the app worse but there is still untapped value to be found in them - look at it as a tool that exists to perform functions and it'll make your life a lot better. You have to be mindful and intentional with technology or it will just do whatever large corporations want it to do.
-
 @ f9cf4e94:96abc355
2024-12-30 19:02:32
@ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios.
A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação.
Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal.
Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado.
Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado.
Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida.
Assim nasceu o governo.
Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição!
Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa.
Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber.
brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
-
 @ 2f4550b0:95f20096
2025-03-17 22:44:46
@ 2f4550b0:95f20096
2025-03-17 22:44:46Networking is often misunderstood as a transactional exchange: handing out business cards or adding contacts on LinkedIn with the hope of an immediate payoff. But at its core, networking is something more dynamic and human. I like to define it as the nexus between "I know a person for that" and being bold enough to ask. It’s about building a web of relationships where knowledge, opportunity, and courage intersect. Whether in professional or personal spheres, networking thrives on trust, mutual benefit, and the willingness to step out of your comfort zone. Let’s unpack this idea and see how it plays out in real life.
Professionally, networking is the lifeblood of career growth. It’s not just about who you know, but who knows you and what they know you can do. Imagine you’re at a conference, coffee in hand, scanning a room full of strangers. You overhear someone mention a challenge their company is facing: they need a creative solution for a marketing campaign, and their team is stumped. Your brain lights up because you know a person for that! A brilliant graphic designer you met at a workshop last year. The easy part is making the mental connection. The harder part? Walking over, introducing yourself, and saying, “Hey, I couldn’t help but overhear. I might know someone who can help.” That’s where the boldness comes in. It’s not about selling yourself or your contact; it’s about offering value and starting a conversation. Over time, those small acts of courage build a reputation: you become the person who connects dots.
I saw this play out vividly a few years ago when a colleague, Sarah, turned a casual chat into a career-defining moment. We were at a local industry meetup, and she struck up a conversation with a startup founder who was frustrated about their lagging sales. Sarah didn’t have the answer herself, but she remembered a sales strategist she’d met at a previous event. Instead of letting the moment pass, she said, “I know someone who’s tackled this exact problem. Mind if I connect you?” The founder agreed, and within a week, Sarah had facilitated an introduction that led to a six-figure consulting gig for her contact and a glowing referral for herself. She didn’t ask for anything in return, but her willingness to bridge the gap earned her trust and credibility. That’s networking at its finest: knowing the right people and having the guts to act.
On the personal side, networking takes a softer, but no less impactful form. It’s less about career ladders and more about enriching your life and community. Think about the last time you needed a recommendation, for a plumber, a babysitter, or even a good book. You probably turned to a friend or neighbor, someone whose judgment you trust. That’s "I know a person for that" in action. But the boldness piece still applies. Asking for help or advice can feel vulnerable, especially if it’s not a close relationship. Yet, those small asks often deepen bonds.
I recently moved to a new city. Last week, I hesitantly asked a distant acquaintance if he could make an introduction to a local hair stylist he uses. I was nervous that I would bother him, or that he would ignore my note. Instead, he got back to me the same day, checked with the stylist to see if she had openings, then shared her contact information with me. I had an appointment for a haircut within 24 hours! Networking personally is about leaning into your circle,and sometimes expanding it, without overthinking the imposition.
In other words, it’s okay to ask. The beauty of this definition is its universality. Whether you’re pitching yourself for a job or seeking a hiking buddy, networking hinges on two things: relationships and initiative. Research backs this up tangentially. Studies like those from Harvard Business Review suggest that successful networking isn’t about extroversion or schmoozing, but about creating genuine connections and following through. It’s less about a polished elevator pitch and more about being useful and present.
Of course, it’s not always smooth sailing. The fear of rejection or coming off as pushy can paralyze even the best intentions. I’ve fumbled plenty of networking moments myself—once freezing mid-sentence while trying to pitch a collaboration to a senior exec at a mixer. But the stumbles teach you resilience. Networking isn’t a one-and-done; it’s a muscle you build over time.
Each time you say, “I know someone who can help,” or “Can you point me in the right direction?” you’re weaving a stronger web. So, the next time you’re at a crossroads, think of networking as that nexus. It’s knowing who’s in your orbit and daring to reach out. It’s less about collecting contacts and more about cultivating possibilities. The magic happens when you connect the dots and take the leap.