-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
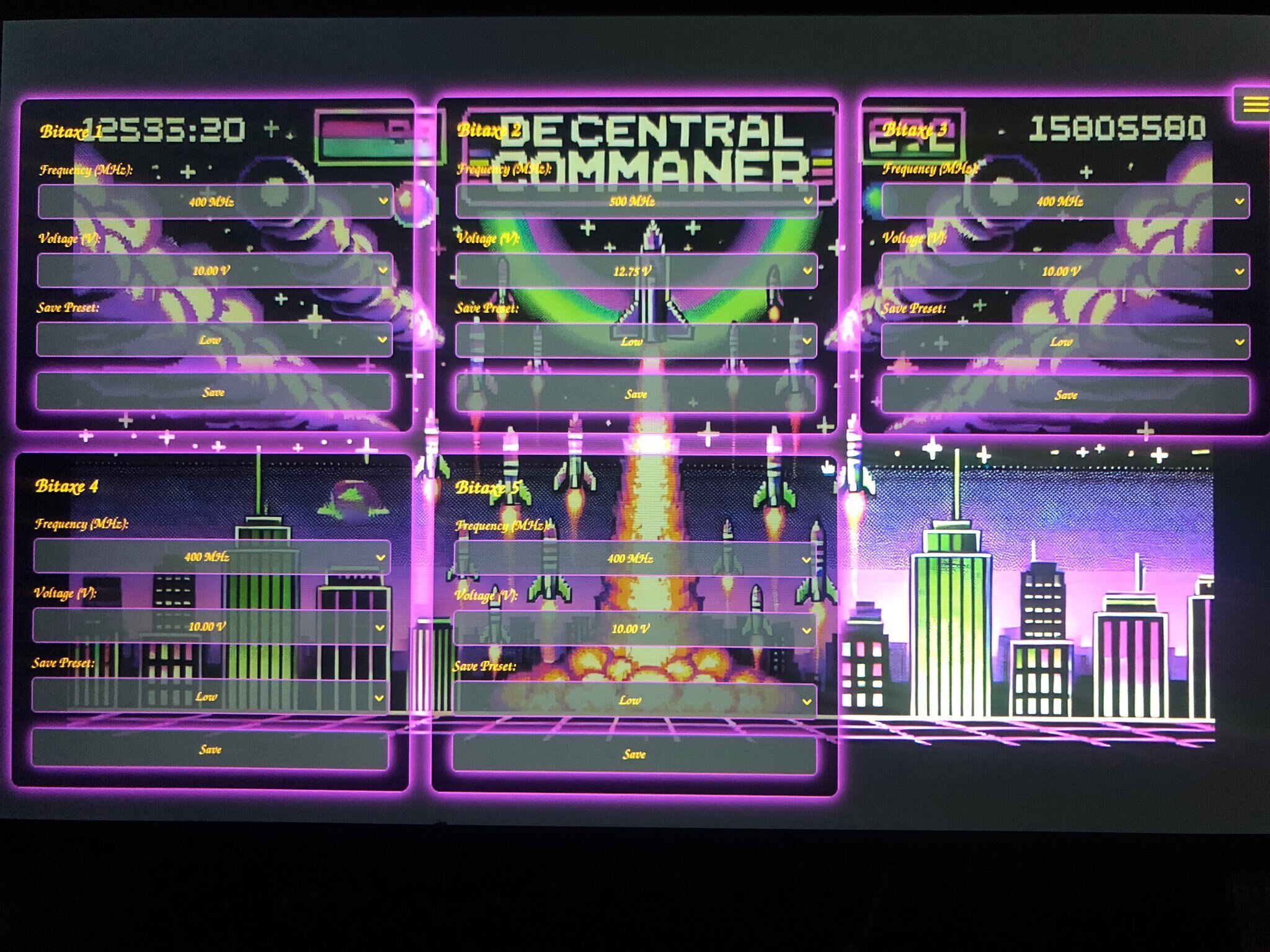 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
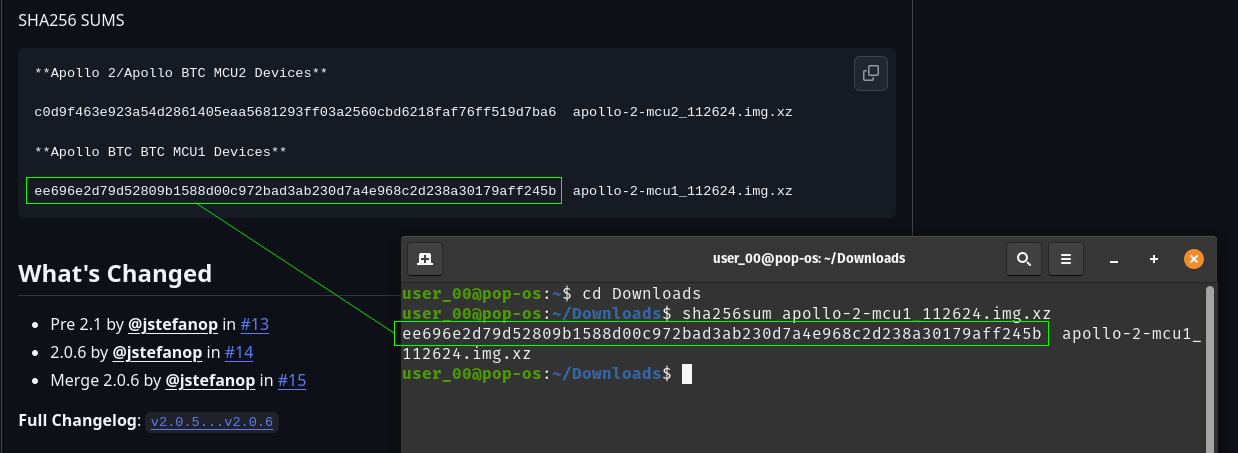 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
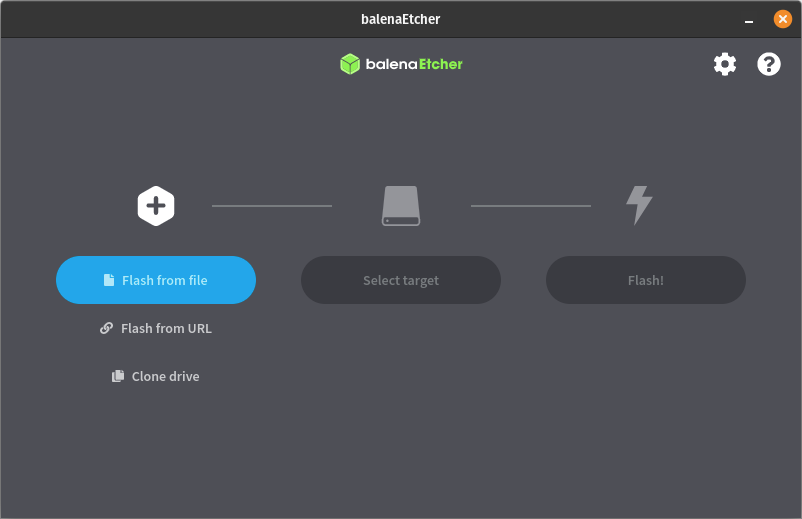 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
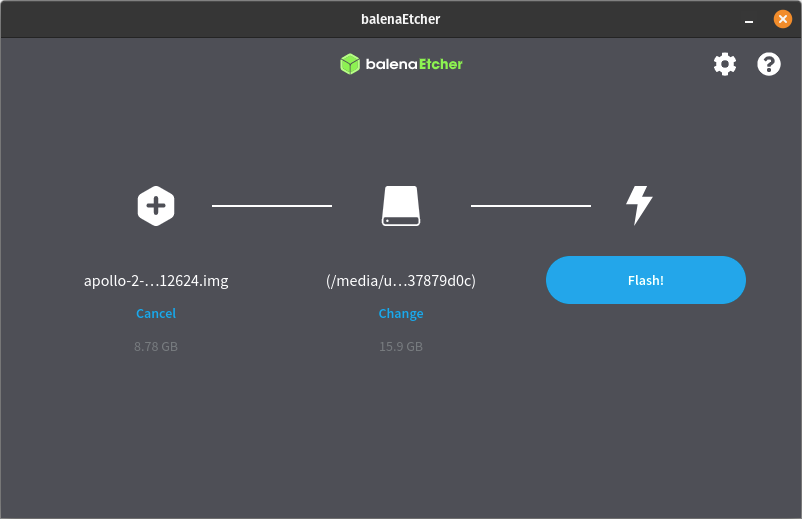 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
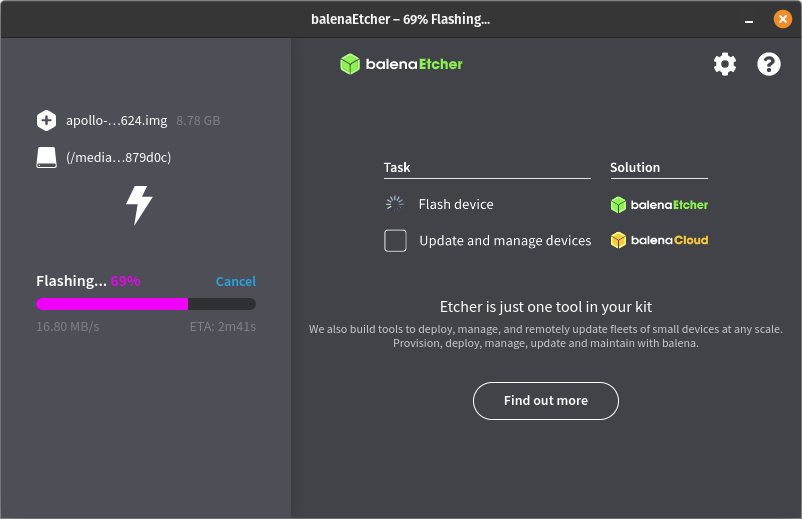 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
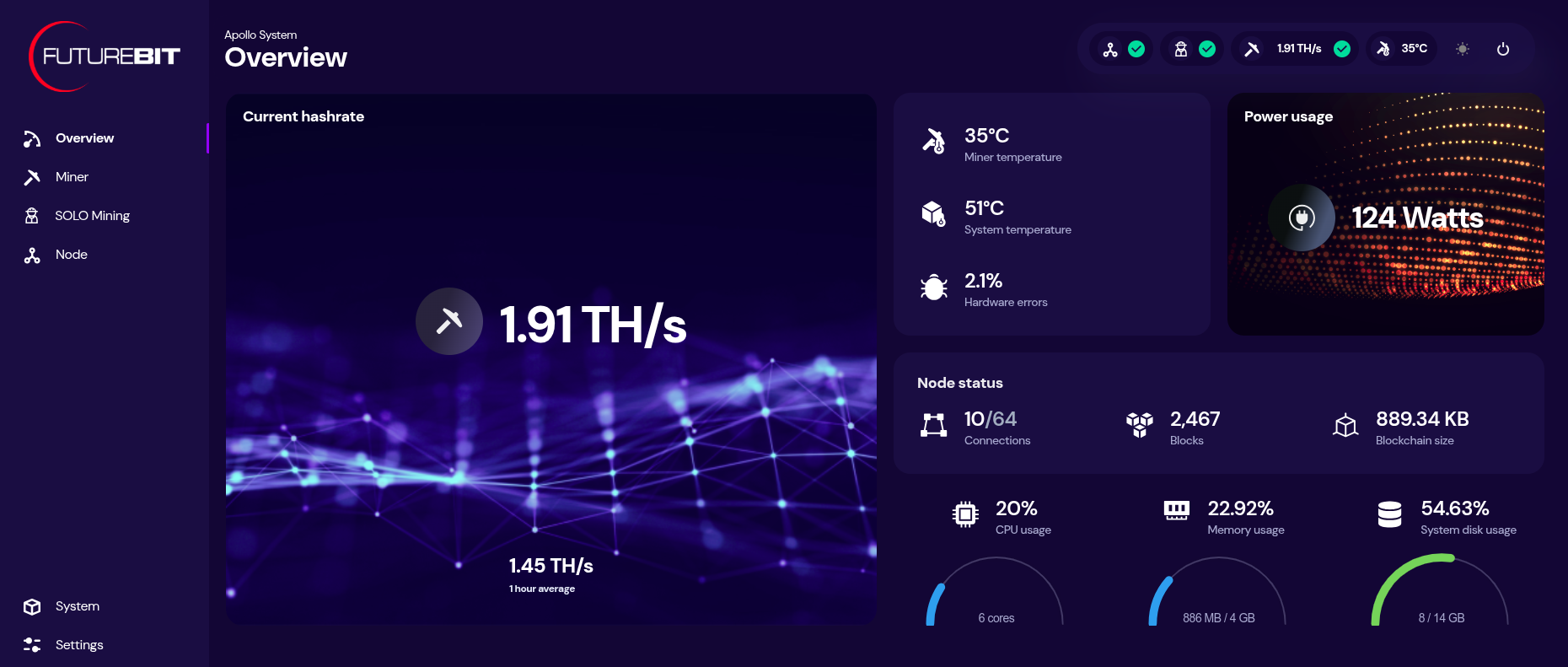 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
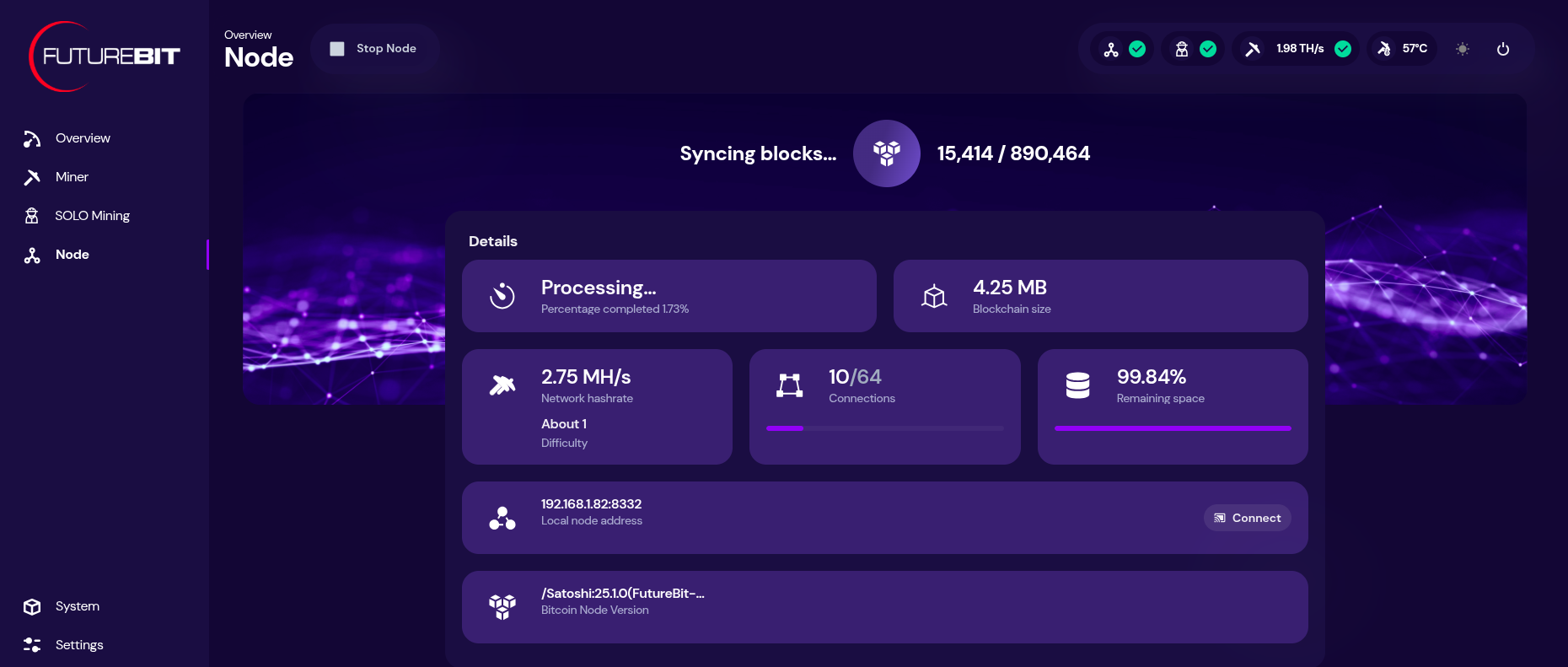 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
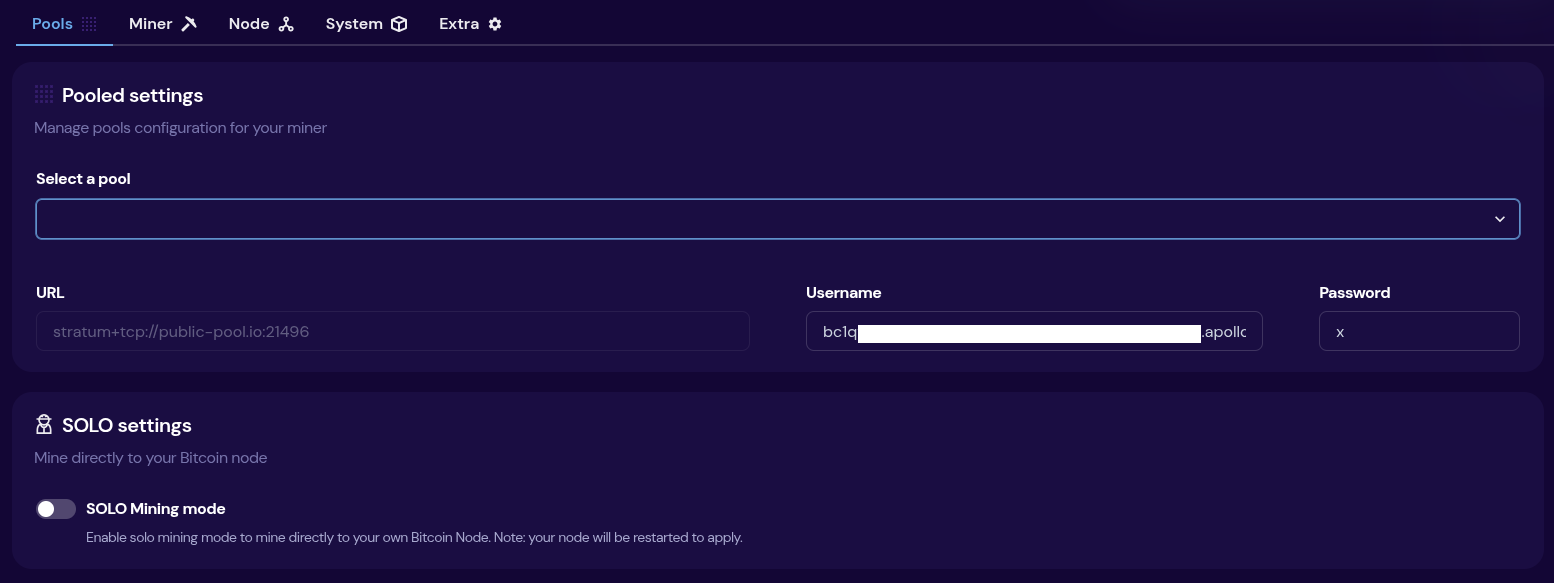 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
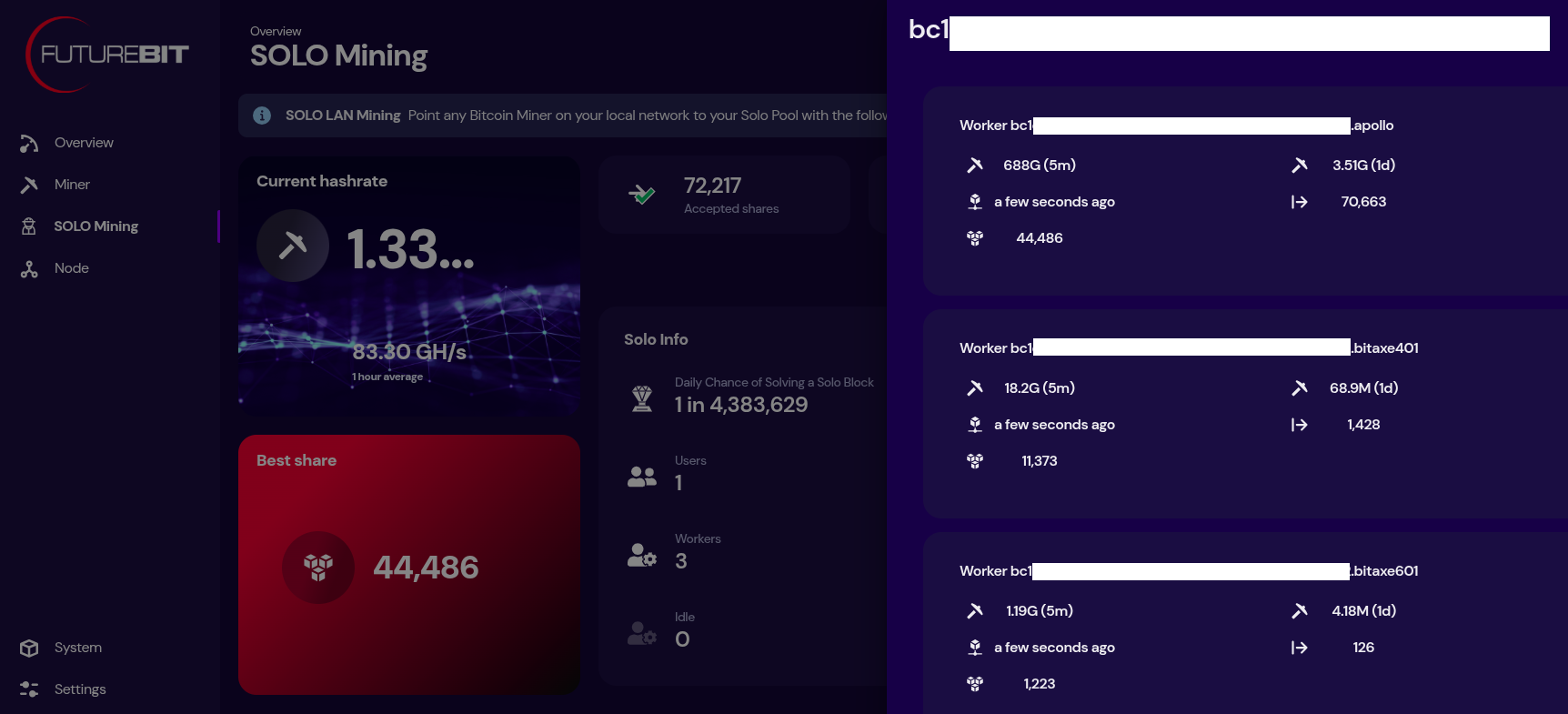 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
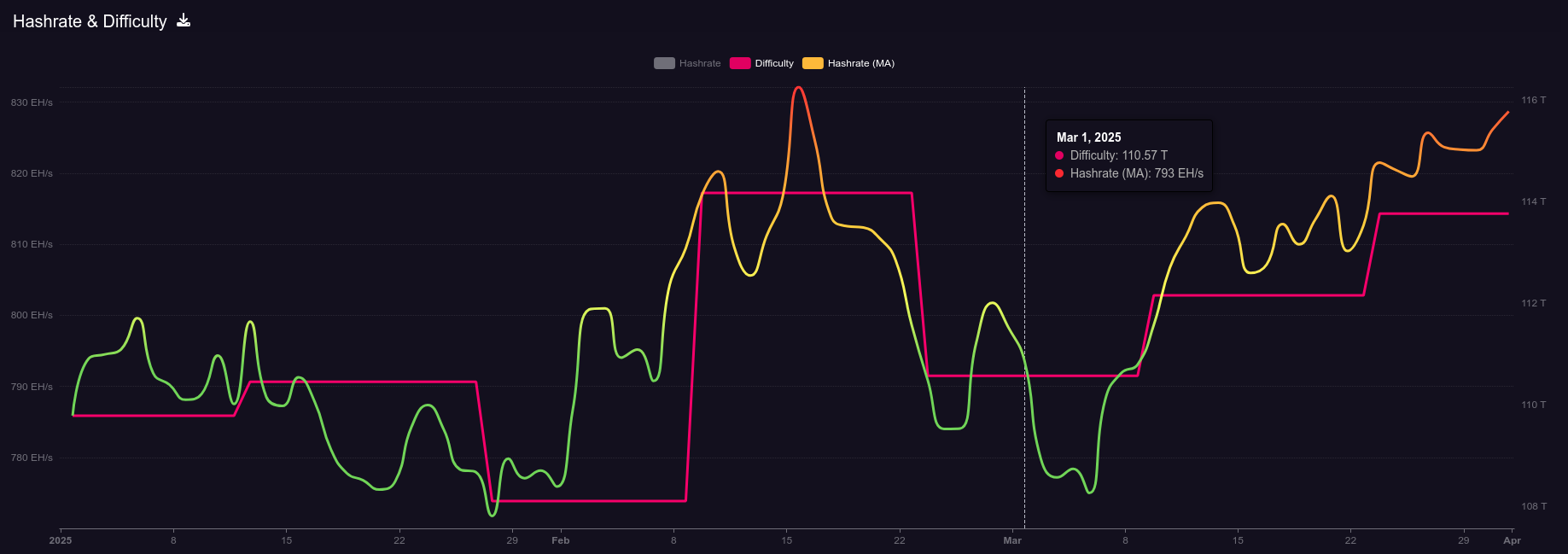 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
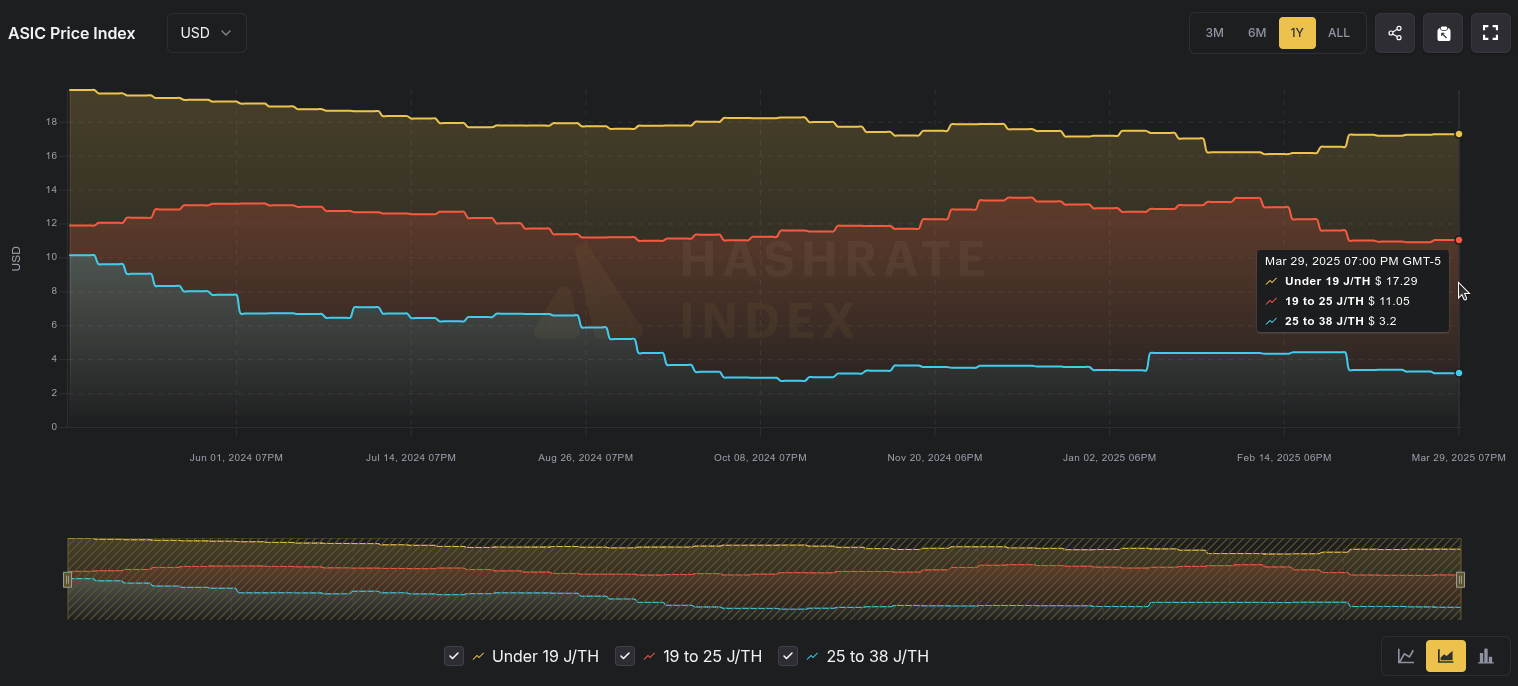 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
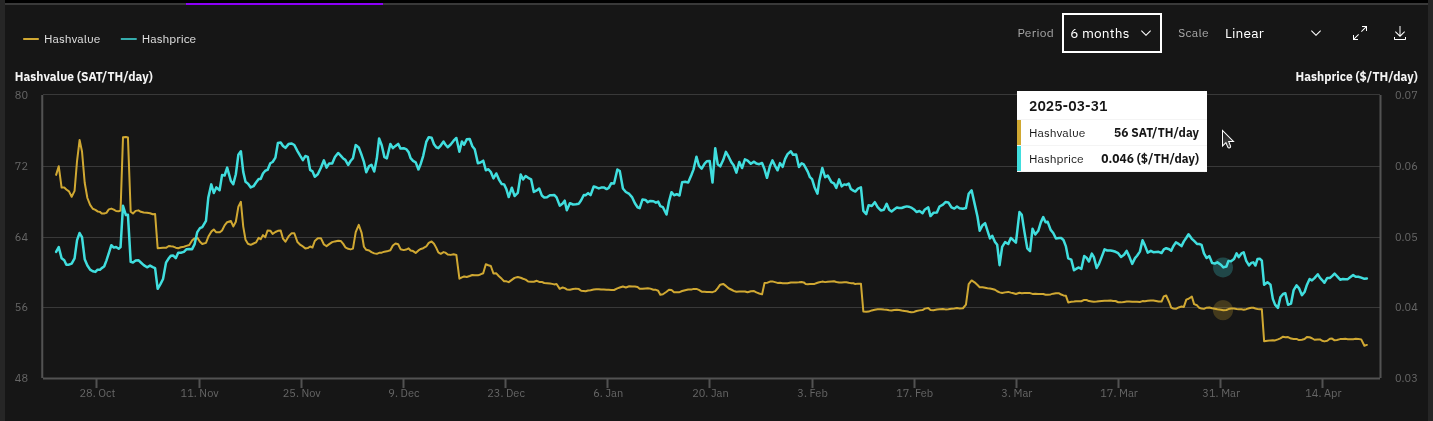 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ d08c9312:73efcc9f
2025-04-18 20:17:41
@ d08c9312:73efcc9f
2025-04-18 20:17:41https://youtu.be/qK7ffYzxiiQ
Resolvr was recently featured in The Institutes RiskStream Collaborative's educational video series on insurance digitization and cross-border payments. With over a century of history educating insurance professionals, The Institutes has established itself as the premier knowledge resource in risk management and insurance. And its RiskStream Collaborative non-profit serves as the industry's largest enterprise-level technology consortium focused on streamlining insurance processes through innovative solutions.
Resolvr's co-founders, Aaron Daniel and Dave Schwab, were joined by industry experts Lizzy Eisenberg from Lightspark and Austin Cornell from Zero Hash to discuss how Bitcoin and the Lightning Network are transforming global insurance payments operations.
Watch the video to learn how Resolvr is leveraging these real-time digital settlement networks to solve significant inefficiencies in today's insurance payment ecosystem - from the months-long settlement times that trap billions in value, to the manual reconciliation processes costing the industry nearly £1 billion annually at Lloyd's of London alone.
We're grateful to RiskStream Collaborative for showcasing these transformative technologies and emphasizing the importance of combining specialized insurance-native interfaces with powerful payment infrastructure to solve industry-specific challenges.
For more information about how Resolvr can help your organization streamline premium processing and payments, contact us today.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 554ab6fe:c6cbc27e
2025-04-10 18:48:57
@ 554ab6fe:c6cbc27e
2025-04-10 18:48:57What is consciousness, and can it be changed or enhanced? This is a question that humans have struggled with for a very long time. The question of consciousness alone is daunting. Some even argue that humans will never be able to find the answer. Regardless, the quest for knowledge is not always about the answer, rather it is the journey that is revealing. This is true not only for our society, but the individual as well. The search for the truth often leads one down a path of self-reflection, and can lead to conclusions previously thought to be ludicrous. Here, I will argue that consciousness can be interpreted as an interpretation of reality, where the interpretation may become clearer and more accurate through practices such as meditation.
Consciousness
To articulate this idea, the concept of consciousness must firstly be discussed. There is an incredibly interesting TED talk given by Anil Seth, where he describes consciousness as an illusion. He explains how the brain receives signals from both the internal and external environment of the body, makes an interpretation of those signals, which creates our conscious experience. In his scientific writing, he claims that the brain can be viewed as a prediction machine1. He argues that the brain is constantly making predictions and error correcting in order to gain understanding of the signals it is receiving. He is not alone in this theory, and many other researchers concur that the constant comparison of internal predictions and external stimuli is what generates the brain’s sensations of causal forces2. There are plenty of reasons to believe this is true. Imagine, the brain is receiving all kinds of neuronal signals both from external stimuli sensors and sensors for our internal systems. These signals all shoot up the spinal cord to the brain. It is unclear that these neuronal signals are stamped with an identifier of where they came from, so the brain has to make a predictive model for not only where the signal came from, but also why the signal came at all. The latter is important for survival: the use of our senses to accurately predict our environment would be a critical reason why consciousness developed in the first place. Imagine you are an ancient hominid walking in the wild: you see a tangled cord like thing around a branch on the tree. You need to process that information, determine if it is more branch or a snake and act accordingly. This is a potential biological reason for the manifestation of thought and problem solving. This is a very meta-cognitive example of our brain receiving information and then using previous knowledge to generate a predictive conclusion on the external reality.
There are also examples of this outside of the more obvious meta-cognitive examples. A good example is the famous rubber hand experiment. The first rubber hand experiment was conducted in 1998 by Botvinick and Cohen3. In this experiment, a subject places their hand on a table with a screen blocking their view of their own hand. A rubber hand is then placed on the other side of the screen where it is visible. The experimenter rubs both the rubber hand and real hand with a paint brush. By the end of the experiment, subjects begin to feel as if the rubber hand is their own limb3. The brain, using the visual senses, detects that a hand is being stroked with a brush while sensory neurons send signals that the hand is experiencing the touch of a paint brush. These two signals cause the predicting brain to think that the rubber hand is our hand. This experiment has been repeated many times in different ways. It has been observed that participants begin to react defensively to the threat of pain or damage to the rubber hand4. This illustrates the powerful extent at which the brain processes and reacts to information that it interprets from reality. Amazingly, some research suggests that the touch aspect of the experiment isn’t even necessary to produce the illusion5. Others have recreated this experience using virtual reality, citing that when the virtual hand changed color in response to the subject’s heartbeat, a significant sense of body ownership was generated6. Body ownership, and our sense of reality is arguably determined by our brain’s interpretation of both internal and external stimuli.
The Neuroscience and Meditation
It is hypothesized that the anterior insular cortex (AIC) is involved in the comparison of the stimuli to the predicted model1. Interestingly, the same brain region is associated with the anticipation of pain7. For those unaware, there is some research to suggest that much of the pain we experience is not due to the actual noxious stimuli (physical pain sensation), but from the anticipation of that pain. Evidence for this can be found in studies such as Al-Obaidi et al. from 2005, that concluded that the pain experienced in patients with chronic low back pain could not be solely attributed to the sensor signals, but from the anticipation of the pain8. Additionally, the anticipation of pain relief is the primary contributor to placebo analgesia (placebo pain killers)9. Furthermore, a large body of research has been conducted showing that meditators show a decreased anticipatory attitude towards pain, subsequently experiencing less unpleasant pain 7,10,11. For example, chronic pain in multiple areas such as the low back, neck, shoulder, and arms have been shown to reduce after meditation practice12. Finally, an extreme case study worth noting is of a yogi master who claimed to not experience pain at all13. When this master was brought into the lab, not only did he not experience pain, but his thalamus showed no additional activation following painful stimuli13. What is fascinating about this is that the thalamus is the main relay station for all incoming somatosensory information14, and some argue that this is a candidate for the location of consciousness15. To not have strong activation here after painful stimuli is to suggest a radical change in how the brain receives incoming stimuli, and perhaps is indicative in a dramatic shift in how this individual’s conscious experiences the world. Though this is but one small example, the previous studies outline a strong case for meditation’s ability to alter the way the brain processes information. Given meditation involves the active practice of generating an open and non-judgmental attitude towards all incoming stimuli, perhaps this alters the processing of incoming stimuli, thereby changing the predictive model. On a similar note, perhaps it relates to neuroplastic changes that occur within the brain. It has been noted that the AIC is activated during times of awareness of mind wandering16. This suggests that the AIC is in use frequently during meditation practices. Perhaps it is strengthened then by meditation, thereby also allowing for greater prediction model generation. Imagine the mind as a pond. If the pond is calm and still, one single rain drop rippling in the pond is clearly identifiable. One would easily know information about the droplet, because the ripple could be easily analyzed. Now imagine a pond during a rain storm, where an uncountable amount of rain drops is hitting the pond and there are ripples everywhere. One could not adequately make out where each ripple came from, because there would be too much overlap in the ripples. This may be how the brain functions as well. When the signals are low, and no extraneous thoughts and interpretations are created from signals, then the brain’s prediction model can easily determine where and why a signal it received came from. If, however, the mind is chaotic and full of internal noise, then the brain has a harder time creating an accurate understanding of incoming stimuli and generating a correct model.
Enlightenment
Enlightenment, from a scientific point of view, has been defined as a form of awareness where a person feels that s/he has gained a new understanding of reality 17. In this sense, it bears a striking relationship to the topic of consciousness. If consciousness can be defined as our interpretation of the external and internal environment through our mental prediction model, then experiences of enlightenment are defined by moments where our interpretation is completely changed in a profound way. The experiences are often characterized by the loss of individuality and consequent identification of being part of a greater oneness 18,19. As an interesting side note, this same experience is common amongst subjects, who in a double-blinded study, take psilocybin (the active ingredient in magic mushrooms)20,21. The neuroscience of enlightenment is particularly interesting. The temporo-parietal junction of the brain is involved with self-location and body ownership22. Unsurprisingly, this area is highly involved in the illusion of the rubber hand experiment23. This is the same brain area that is hypothesized to be related to these enlightened experiences of oneness 17. If this brain area, which handles the interpretation of where and what the body is, was to decrease in activation, then the brain would generate a more ambiguous interpretation that the self and the external environment are less distinct than previously thought. This is a possible explanation to why enlightenment experiences involve a feeling of oneness with everything. To bring this all home, meditation has been shown to decrease parietal lobe activation 4,24. Suggesting that meditation can be a method of adjusting the brain’s interpretation of stimuli to generate an outlook that is unifying in perceptive.
Closing Remarks
The evidence that meditation may lead to an altered conscious living has deep philosophical implications. Meditation is a practice that, in part, involves an open awareness to all incoming stimuli alongside the absence of any meta-cognitive interpretation or processing of said stimuli. This generation of a still mind may generate a more accurate prediction model of incoming stimuli, void of any corruption on the part of our thoughts. Given the observation that meditation, both scientifically and culturally, can lead to an understanding and experience of a greater oneness amongst all suggests that this interpretation of incoming stimuli is the more accurate interpretation. It is hard to imagine that anyone would not advocate the beauty and usefulness of this perspective. If more people had this perspective, we would have a much more peaceful, happy and unified society and planet. Ironically, our culture often aims to arrive to this philosophical perspective through analytical thought. However, given the evidence in this post, perhaps it is the absence of analytical thought, and the stillness of the mind that truly grants this perspective.
**References ** 1. Seth AK. Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences. 2013;17(11):565-573. doi:10.1016/j.tics.2013.09.007 2. Synofzik M, Thier P, Leube DT, Schlotterbeck P, Lindner A. Misattributions of agency in schizophrenia are based on imprecise predictions about the sensory consequences of one’s actions. Brain. 2010;133(1):262-271. doi:10.1093/brain/awp291 3. Botvinick M, Cohen JD. Rubber hand ‘feels’ what eyes see. Nature. 1998;391(February):756. 4. Newberg A, Alavi A, Baime M, Pourdehnad M, Santanna J, D’Aquili E. The measurement of regional cerebral blood flow during the complex cognitive task of meditation: A preliminary SPECT study. Psychiatry Research - Neuroimaging. 2001;106(2):113-122. doi:10.1016/S0925-4927(01)00074-9 5. Ferri F, Chiarelli AM, Merla A, Gallese V, Costantini M. The body beyond the body: Expectation of a sensory event is enough to induce ownership over a fake hand. Proceedings of the Royal Society B: Biological Sciences. 2013;280(1765). doi:10.5061/dryad.8f251 6. Suzuki K, Garfinkel SN, Critchley HD, Seth AK. Multisensory integration across exteroceptive and interoceptive domains modulates self-experience in the rubber-hand illusion. Neuropsychologia. 2013;51(13):2909-2917. doi:10.1016/j.neuropsychologia.2013.08.014 7. Zeidan F, Grant JA, Brown CA, McHaffie JG, Coghill RC. Mindfulness meditation-related pain relief: Evidence for unique brain mechanisms in the regulation of pain. Neuroscience Letters. 2012;520(2):165-173. doi:10.1016/j.neulet.2012.03.082 8. Al-Obaidi SM, Beattie P, Al-Zoabi B, Al-Wekeel S. The relationship of anticipated pain and fear avoidance beliefs to outcome in patients with chronic low back pain who are not receiving workers’ compensation. Spine. 2005;30(9):1051-1057. doi:10.1097/01.brs.0000160848.94706.83 9. Benedetti F, Mayberg HS, Wager TD, Stohler CS, Zubieta JK. Neurobiological mechanisms of the placebo effect. In: Journal of Neuroscience. Vol 25. Society for Neuroscience; 2005:10390-10402. doi:10.1523/JNEUROSCI.3458-05.2005 10. Gard T, Hölzel BK, Sack AT, et al. Pain attenuation through mindfulness is associated with decreased cognitive control and increased sensory processing in the brain. Cerebral Cortex. 2012;22(11):2692-2702. doi:10.1093/cercor/bhr352 11.Grant JA, Courtemanche J, Rainville P. A non-elaborative mental stance and decoupling of executive and pain-related cortices predicts low pain sensitivity in Zen meditators. Pain. 2011;152(1):150-156. doi:10.1016/j.pain.2010.10.006 12. Kabat-Zinn J, Lipworth L, Burney R. The clinical use of mindfulness meditation for the self-regulation of chronic pain. Journal of Behavioral Medicine. 1985;8(2):163-190. doi:10.1007/BF00845519 13. Kakigi R, Nakata H, Inui K, et al. Intracerebral pain processing in a Yoga Master who claims not to feel pain during meditation. European Journal of Pain. 2005;9(5):581. doi:10.1016/j.ejpain.2004.12.006 14. Steeds CE. The anatomy and physiology of pain. Surgery. 2009;27(12):507-511. doi:10.1016/j.mpsur.2009.10.013 15. Min BK. A thalamic reticular networking model of consciousness. Theoretical Biology and Medical Modelling. 2010;7(1):1-18. doi:10.1186/1742-4682-7-10 16. Hasenkamp W, Wilson-Mendenhall CD, Duncan E, Barsalou LW. Mind wandering and attention during focused meditation: A fine-grained temporal analysis of fluctuating cognitive states. NeuroImage. 2012;59(1):750-760. doi:10.1016/j.neuroimage.2011.07.008 17. Newberg AB, Waldman MR. A neurotheological approach to spiritual awakening. International Journal of Transpersonal Studies. 2019;37(2):119-130. doi:10.24972/ijts.2018.37.2.119 18. Johnstone B, Cohen D, Konopacki K, Ghan C. Selflessness as a Foundation of Spiritual Transcendence: Perspectives From the Neurosciences and Religious Studies. International Journal for the Psychology of Religion. 2016;26(4):287-303. doi:10.1080/10508619.2015.1118328 19. Yaden DB, Haidt J, Hood RW, Vago DR, Newberg AB. The varieties of self-transcendent experience. Review of General Psychology. 2017;21(2):143-160. doi:10.1037/gpr0000102 20. Griffiths RR, Richards WA, McCann U, Jesse R. Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology. 2006;187(3):268-283. doi:10.1007/s00213-006-0457-5 21. Griffiths RR, Richards WA, Johnson MW, McCann UD, Jesse R. Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology. 2008;22(6):621-632. doi:10.1177/0269881108094300 22. Serino A, Alsmith A, Costantini M, Mandrigin A, Tajadura-Jimenez A, Lopez C. Bodily ownership and self-location: Components of bodily self-consciousness. Consciousness and Cognition. 2013;22(4):1239-1252. doi:10.1016/j.concog.2013.08.013 23. Tsakiris M, Costantini M, Haggard P. The role of the right temporo-parietal junction in maintaining a coherent sense of one’s body. Neuropsychologia. 2008;46(12):3014-3018. doi:10.1016/j.neuropsychologia.2008.06.004 24. Herzog H, Leie VR, Kuweit T, Rota E, Ludwig K. Biological Psychology/Pharmacopsychology. Published online 1990:182-187.
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:02
@ 0edc2f47:730cff1b
2025-04-04 03:37:02Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ 2b24a1fa:17750f64
2025-04-01 08:09:55
@ 2b24a1fa:17750f64
2025-04-01 08:09:55 -
 @ 812cff5a:5c40aeeb
2025-04-01 02:57:20
@ 812cff5a:5c40aeeb
2025-04-01 02:57:20مقدمة
في عالم اليوم الرقمي، تبرز منصات جديدة تهدف إلى تعزيز تجربة القراءة والتواصل بين محبي الكتب. تُعَدُّ Bookstr.xyz واحدة من هذه المنصات المبتكرة التي تسعى لربط القرّاء عبر شبكة Nostr، مما يمنحهم سيادة كاملة على بياناتهم ويتيح لهم بناء علاقات جديدة مع محبي الكتب الآخرين. 
الميزات الرئيسية لموقع Bookstr
- التحكم الكامل بالبيانات: توفر Bookstr.xyz للمستخدمين القدرة على التحكم الكامل في بياناتهم الشخصية، مما يضمن خصوصية وأمان المعلومات.
- التكامل مع Open Library: تستخدم المنصة واجهة برمجة التطبيقات الخاصة بـ Open Library للحصول على معلومات شاملة حول الكتب، مما يتيح للمستخدمين الوصول إلى مجموعة واسعة من البيانات الموثوقة.
- التواصل الاجتماعي: من خلال شبكة Nostr، يمكن للمستخدمين التواصل مع قرّاء آخرين، تبادل التوصيات، ومناقشة الكتب المفضلة لديهم. 
ما الذي يجعلها فريدة؟
تتميز Bookstr.xyz بدمجها بين مزايا الشبكات الاجتماعية ومصادر بيانات الكتب المفتوحة، مما يخلق بيئة تفاعلية وغنية بالمعلومات لمحبي القراءة. استخدامها لشبكة Nostr يمنح المستخدمين حرية أكبر في التحكم بتجربتهم الرقمية مقارنة بالمنصات التقليدية. 
جرب Bookstr
تُعَدُّ Bookstr.xyz إضافة قيمة لعالم القراءة الرقمي، حيث تجمع بين مزايا الشبكات الاجتماعية ومصادر البيانات المفتوحة، مع التركيز على خصوصية المستخدم والتحكم في البيانات. إذا كنت من عشاق الكتب وتبحث عن منصة تفاعلية وآمنة، فقد تكون Bookstr.xyz الخيار المثالي لك.
شاركوا كتبكم المفضلة!!
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ 878dff7c:037d18bc
2025-03-31 21:29:17
@ 878dff7c:037d18bc
2025-03-31 21:29:17Dutton Proposes Easing Home Loan Regulations
Summary:
Opposition Leader Peter Dutton plans to challenge the Albanese government by proposing changes to lending rules aimed at making it easier for first-time home buyers to access loans. The proposed adjustments include reducing serviceability buffers and addressing the treatment of HELP debt to improve housing access. Dutton argues that current regulations create a bias favoring inherited wealth, making it difficult for new buyers to enter the housing market. These proposals come as the Reserve Bank of Australia prepares for its upcoming interest rate decision, with the current cash rate target at 4.1% and predictions of a cut in May. Treasurer Jim Chalmers highlights the government's progress, noting falling inflation, rising real wages, and improving economic growth.
Sources: News.com.au - 1 April 2025, The Australian - 1 April 2025
Australia's Housing Market Hits New Record High
Summary:
Australia's property prices reached a new peak in March, following a rate cut that enhanced buyer optimism. CoreLogic reported a 0.4% monthly increase, bringing the average national property price to A$820,331. All capital cities, except Hobart, experienced price gains, with Sydney and Melbourne rising by 0.3% and 0.5%, respectively. The rate cut slightly improved borrowing capacity and mortgage serviceability. However, the sustainability of this upward trend is uncertain due to persistent affordability issues. While the market rebounded with the February rate cut by the Reserve Bank of Australia, significant improvements in home loan serviceability are necessary for substantial market growth.
Source: Reuters - 1 April 2025
AI Revolutionizes Business Operations
Summary:
Artificial intelligence (AI) is transforming business practices globally, with applications ranging from administrative task automation to strategic decision-making enhancements. Companies are increasingly integrating AI to streamline operations and gain competitive advantages. This shift necessitates a focus on ethical AI deployment and workforce upskilling to address potential job displacement.
Sources: Financial Times - April 1, 2025
Criticism of Bureau of Meteorology's Forecasting Capabilities
Summary:
The Bureau of Meteorology is facing criticism for inadequate weather radar coverage in western Queensland, which has led to unreliable forecasting during the recent floods. Federal Opposition Leader Peter Dutton has pledged $10 million for a new radar system to enhance forecasting accuracy, while local officials emphasize the need for improved infrastructure to better prepare for future natural disasters.
Sources: The Australian - April 1, 2025
Coalition Pledges $10 Million for Western Queensland Weather Radar
Summary:
As part of the federal election campaign, Opposition Leader Peter Dutton has promised $10 million for a new weather radar system in flood-affected western Queensland. This initiative aims to improve weather forecasting and preparedness in the region. Meanwhile, Prime Minister Anthony Albanese has pledged $200 million for an upgrade to the St John of God Midland hospital in Perth, emphasizing healthcare improvements. Both leaders are focusing on key regional investments as the election approaches.
Source: The Guardian - April 1, 2025
Emergency Services Conduct Rescues Amid Queensland Floods
Summary:
Emergency services in Queensland have conducted over 40 rescues as floodwaters continue to rise, submerging communities and causing extensive damage. Efforts are focused on delivering essential supplies, evacuating residents, and ensuring the safety of those affected by the severe weather conditions.
Sources: The Courier-Mail - April 1, 2025
Six Key Crises Facing Australia Before the Election
Summary:
As the election nears, voters remain largely unaware of six looming crises that could significantly impact the nation. These include over-reliance on volatile commodity exports, challenges in renewable energy implementation, potential currency depreciation, and reduced foreign investment. Both major parties have focused on immediate cost-of-living relief, overshadowing these critical issues that demand urgent attention.
Sources: The Australian - April 1, 2025
Debate Intensifies Over Australia's Commitment to AUKUS
Summary:
Former Defence Department Secretary Dennis Richardson has urged Australia to persist with the AUKUS submarine agreement despite concerns about the reliability of the U.S. under President Donald Trump. Richardson warns that abandoning the deal now would undermine decades of defense planning. However, critics, including former Prime Minister Malcolm Turnbull, question the feasibility and advisability of the agreement, suggesting alternatives such as partnering with France for submarine development.
Sources: The Guardian - April 1, 2025, The Australian - April 1, 2025
China Delays $23B Sale of Panama Canal Ports to US-Backed Consortium
Summary:
China has postponed the $23 billion sale of 43 global ports, including critical facilities at both ends of the Panama Canal, to a consortium led by US investment firm BlackRock. The delay follows an investigation by China’s State Administration for Market Regulation into potential anti-monopoly law violations. This unexpected move has heightened tensions between China and the US, as President Trump viewed the sale as a strategic victory in the ongoing power struggle between the two nations. The deal's future remains uncertain, causing political and economic ripples amid China's significant annual "two sessions" gathering.
Sources: New York Post - March 31, 2025
Australian Government's Handling of Suspected Chinese Spy Ship Raises Concerns
Summary:
The Australian government has assigned the monitoring of the suspected Chinese spy ship, Tan Suo Yi Hao, to the Australian Border Force, despite Prime Minister Anthony Albanese's assertion that the Australian Defence Force was managing the situation. Security experts believe the vessel is collecting undersea data for future Chinese submarine operations, highlighting national security concerns during an election period. The handling of this issue has led to criticism and confusion over which agency is in charge, with opposition figures condemning the government's lack of detailed information.
Sources: The Australian - April 1, 2025
Concerns Rise Over Schoolchildren Accessing Weight Loss Drugs
Summary:
Health experts are alarmed by reports of Australian schoolchildren accessing weight loss medications like semaglutide (Ozempic) through various means, including online purchases and taking them from home supplies. These substances are being linked to secretive and harmful diet clubs within schools, posing severe health risks such as potentially fatal overdoses. Advocates emphasize the need for stricter regulation of weight loss products and call for mandatory education programs on eating disorders in schools to address the growing issue.
Sources: The Courier-Mail - 1 April 2025
Recycling Plant Explosion Highlights Dangers of Improper Aerosol Disposal
Summary:
A Victorian company has been fined $35,000 after an explosion at its recycling plant injured six workers. The incident occurred when pressurized aerosol cans were improperly shredded, causing flames to spread up to 18 meters. Investigations revealed that the company failed to implement safety procedures such as emptying or puncturing the cans before shredding and ensuring adequate ventilation. This case underscores the critical importance of adhering to safety protocols when handling hazardous materials.
Sources: Herald Sun - 1 April 2025
Australia Enforces New Tobacco Controls from April 1
Summary:
As of April 1, 2025, Australia has implemented stringent tobacco control measures, including health warnings printed directly on individual cigarettes. These warnings feature phrases such as "CAUSES 16 CANCERS" and "DAMAGES YOUR LUNGS." Additionally, new graphic warnings on cigarette packs and health promotion inserts aim to encourage smoking cessation and raise awareness about the dangers of tobacco use.
Sources: Mirage News - April 1, 2025, 9News - April 1, 2025
OPEC+ Increases Oil Production Amid Global Uncertainties
Summary:
OPEC+ has announced the gradual unwinding of voluntary production cuts starting April 1, 2025, aiming to restore 2.2 million barrels per day of output by September 2026. Despite this increase, factors such as tighter U.S. sanctions on Iran and Russia, potential sanctions on Venezuelan oil buyers, and fears of a tariff-induced recession have sustained oil prices. Analysts predict limited downside risks to oil prices due to significant supply threats, mainly from Iran and Venezuela. While some strength in oil prices is expected during the summer, concerns over tariff-induced demand weakness persist.
Sources: MarketWatch - April 1, 2025
Iconic Australian Locations Declared 'No Go Zones'
Summary:
Several iconic Australian locations, including Uluru, Kakadu National Park, Cape York Peninsula, and others, are increasingly being declared "no go zones" due to cultural, environmental, and safety concerns. These measures aim to preserve the cultural significance and environmental integrity of these landmarks and ensure public safety. While traditional owners and local authorities support these restrictions to protect cultural heritage, debates have arisen over tourists' rights and the impact on local tourism industries. Sources: News.com.au - April 1, 2025
The Joe Rogan Experience #2297: Francis Foster & Konstantin Kisin
Summary:
In episode #2297 of The Joe Rogan Experience, Joe Rogan welcomes comedians and commentators Francis Foster and Konstantin Kisin, hosts of the podcast Triggernometry. The episode delivers a wide-ranging conversation covering free speech, comedy, media narratives, and societal tensions in the modern world.
Interesting Discussions and Insights:
-
The State of Comedy:\ The trio discusses how comedy has changed in recent years, especially under the weight of cancel culture. They explore how comedians are navigating cultural sensitivities while still trying to push boundaries and remain authentic.
-
Free Speech and Censorship:\ Konstantin and Francis share their experiences with censorship and self-censorship, emphasizing the risks of suppressing ideas, even if they’re controversial. They advocate for robust debate as a cornerstone of democracy.
-
Migration and Identity Politics:\ The conversation touches on immigration policies in the UK and broader Western world, discussing how political correctness often silences real concerns. Both guests, with immigrant backgrounds, offer nuanced perspectives on national identity and inclusion.
-
Media and Narrative Control:\ Joe, Francis, and Konstantin dive into how media outlets often frame stories with ideological slants, and the dangers of relying on one-sided narratives in forming public opinion.
-
Creating Triggernometry:\ The guests talk about why they launched their podcast — to have honest, open conversations with a wide range of thinkers, especially those often excluded from mainstream platforms.
Key Takeaways:
- Honest conversation is essential for a healthy society, even when it's uncomfortable.
- Comedy still holds power to critique society but faces mounting challenges from cultural pressures.
- Free speech should be defended not just in principle, but in everyday life and dialogue.
- The media landscape is increasingly polarized, and critical thinking is more important than ever.
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ 3c389c8f:7a2eff7f
2025-03-31 20:38:23
@ 3c389c8f:7a2eff7f
2025-03-31 20:38:23You might see these terms used interchangeably throughout the Nostr network. Since Nostr is a decentralized protocol and not a platform, there is often a lack of consensus around particular terminologies. At times, it's important to differentiate between them, so that you can determine what is being stated. In the truest sense, there is no central entity to maintain a Nostr 'account' on your behalf, though some Nostr-based platforms may offer to do so. There's also no one to verify your 'identity'. This is something that you create, maintain and control. It is 100% yours. In a sense, you verify yourself through your interactions with others, with the network of clients and relays, and by protecting your nsec (secret key). A profile is generally considered to be a single place for displaying your content and any information about yourself that you've chosen to share, but its a little more complicated than that with Nostr. Let's take a closer look at all 3 terms:
Identity:
Your Nostr identity becomes yours from the moment you generate your key pair. The two parts each provide unique perspective and functionality. (Remember, there is no central entity to issue these key pairs. You can screw up and start over. You can maintain multiple key pairs for different purposes. If all of this is new and unfamiliar, start simply with the intention of trial and error.)
Half of the equation is your nsec. As long as you maintain control of that secret key, the identity is yours. You will use it to sign the notes and events that you create on Nostr. You will use it to access functionality of various tools and apps. You can use it to send monetary tips for content you find valuable. The reputation that you build through posting & interacting on Nostr will signal to others what type of person or profile this is, whether it's a genuine person, a bot (good or bad), a collection of works, etc. You might come across information that compares your nsec to a password. While a fair comparison, its important to remember that passwords can be reset, but your private key CANNOT. Lost access or control of your nsec means a loss of control over that identity. When you have decided to establish a more permanent identity, write it down, keep it safe, and use the appropriate security tools for interacting online.
The other half of this equation is your npub. This public key is used to find and display your notes and events to others. In short, your npub is how your identity is viewed by others and your nsec is how you control that identity.
Npub can also act a window into your world for whoever may choose to view it. As mentioned in a previous entry, npub login enables viewing Nostr's notes and other stuff in a read-only mode of any user's follow feed. Clients may or may not support this, some will even allow you to view and subscribe to these feeds while signed in as yourself via this function. It the basis of the metadata for your profile, too.
Profile:
Profile, in general, is a collection of things about you, which you have chosen to share. This might include your bio, chosen display name, other contact information, and a profile photo. Similar to traditional socials, veiwing Nostr profiles often includes a feed of the things you have posted and shared displayed as a single page. People will recognize you based on the aspects of your profile more than they will by your actual identity since an npub is a prefixed random string of characters . Your npub bridges a gap between strictly machine readable data and your human readable name, but it is not as simple as a name and picture. You will choose your photo and display name for your profile as you see fit, making you recognizable. These aspects are easy for copycat scammers to leverage, so your npub will help your friends and followers to verify that you are you, in the event that someone should try to copy your profile.
The Nostr protocol has another profile aspect that is important to know about, but as a general user, you shouldn't have to worry much about it. This is your nprofile. It combines your npub (or the machine readable hex verison of it) with hints to what relays you are using to publish your notes. This helps clients, crawlers, and relays find your stuff for your followers. You may notice nprofile when you share a profile link or used in other actions. When you update your relay list, your client will adjust your nprofile and send a new copy to the appropriate relays. If your believe that a client is not doing that correctly, you can visit metadata.nostr.com and manage it yourself.
Account:
Across Nostr, it is common to see the term 'account' used to refer to the combination of your identity and profile. It is a relatable term, though it may imply that some account issuer exists, but no one issues a Nostr account to you. You create and maintain it yourself.
There are situations where a traditional account will exist, such as with media servers, relay subscriptions, custodial wallet hosts, or NIP-05 providers. These things will almost always be paid services and storage that you choose to use. (Reminder: all of these things are possible to DIY with a little knowhow and an old computer)
What Is The Right Terminology?
There is no simple or correct answer here. Developers and writers will use whatever terms fit their scope and topic. Context will matter, so it's important to differentiate by that more than any actual term.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ f3873798:24b3f2f3
2025-03-31 20:14:31
@ f3873798:24b3f2f3
2025-03-31 20:14:31Olá, nostrilianos!
O tema de hoje é inteligência artificial (IA), com foco em duas ferramentas que têm se destacado no mercado por sua capacidade de responder perguntas, auxiliar em tarefas e, em alguns casos, até gerar imagens.
Essas tecnologias estão cada vez mais presentes no dia a dia, ajudando desde a correção de textos até pesquisas rápidas e a criação de imagens personalizadas com base em prompts específicos.
Nesse cenário em expansão, duas IAs se sobressaem: o ChatGPT, desenvolvido pela OpenAI, e o Grok, criado pela xAI.
Ambas são ferramentas poderosas, cada uma com seus pontos fortes e limitações, e têm conquistado usuários ao redor do mundo. Neste artigo, compartilho minhas impressões sobre essas duas IAs, baseadas em minha experiência pessoal, destacando suas diferenças e vantagens.
Grok: Destaque na criação de imagens e fontes

O Grok me impressiona especialmente em dois aspectos.
Primeiro, sua capacidade de gerar imagens é um diferencial significativo. Enquanto o ChatGPT tem limitações nesse quesito, o Grok oferece uma funcionalidade mais robusta para criar visuais únicos a partir de prompts, o que pode ser uma vantagem para quem busca criatividade visual.
Segundo, o Grok frequentemente cita fontes ou indica a origem das informações que fornece, o que agrega credibilidade às suas respostas e facilita a verificação dos dados.
ChatGPT: Assertividade e clareza

Por outro lado, o ChatGPT se destaca pela assertividade e pela clareza em suas explicações. Suas respostas tendem a ser mais diretas e concisas, o que é ideal para quem busca soluções rápidas ou explicações objetivas.
Acredito que essa vantagem possa estar ligada ao fato de o ChatGPT estar em operação há mais tempo, tendo passado por anos de aprimoramento e ajustes com base em interações de usuários.Comparação e reflexões.
Em minha experiência, o Grok supera o ChatGPT na geração de imagens e na citação de fontes, enquanto o ChatGPT leva a melhor em precisão e simplicidade nas respostas.
Esses pontos refletem não apenas as prioridades de design de cada IA, mas também o tempo de desenvolvimento e os objetivos de suas respectivas empresas criadoras.
A OpenAI, por trás do ChatGPT, focou em refinamento conversacional, enquanto a xAI, com o Grok, parece investir em funcionalidades adicionais, como a criação de conteúdo visual.
Minha opinião

Não há um vencedor absoluto entre Grok e ChatGPT – a escolha depende do que você precisa. Se seu foco é geração de imagens ou rastreamento de fontes, o Grok pode ser a melhor opção. Se busca respostas rápidas e assertivas, o ChatGPT provavelmente atenderá melhor.
Ambas as IAs são ferramentas incríveis, e o mais fascinante é ver como elas continuam evoluindo, moldando o futuro da interação entre humanos e máquinas.
-
 @ 378562cd:a6fc6773
2025-03-31 19:20:39
@ 378562cd:a6fc6773
2025-03-31 19:20:39Bitcoin transaction fees might seem confusing, but don’t worry—I’ll break it down step by step in a simple way. 🚀
Unlike traditional bank fees, Bitcoin fees aren’t fixed. Instead, they depend on: ✔️ Transaction size (in bytes, not BTC!) ✔️ Network demand (more traffic = higher fees) ✔️ Fee rate (measured in satoshis per byte)
Let’s dive in! 👇
📌 Why Do Bitcoin Transactions Have Fees? Bitcoin miners process transactions and add them to the blockchain. Fees serve three key purposes:
🔹 Incentivize Miners – They receive fees + block rewards. 🔹 Prevent Spam – Stops the network from being flooded. 🔹 Prioritize Transactions – Higher fees = faster confirmations.
💰 How Are Bitcoin Fees Calculated? Bitcoin fees are not based on the amount of BTC you send. Instead, they depend on how much space your transaction takes up in a block.
🧩 1️⃣ Transaction Size (Bytes, Not BTC!) Bitcoin transactions vary in size (measured in bytes).
More inputs and outputs = larger transactions.
Larger transactions take up more block space, meaning higher fees.
📊 2️⃣ Fee Rate (Sats Per Byte) Fees are measured in satoshis per byte (sat/vB).
You set your own fee based on how fast you want the transaction confirmed.
When demand is high, fees rise as users compete for block space.
⚡ 3️⃣ Network Demand If the network is busy, miners prioritize transactions with higher fees.
Low-fee transactions may take hours or even days to confirm.
🔢 Example: Calculating a Bitcoin Transaction Fee Let’s say: 📦 Your transaction is 250 bytes. 💲 The current fee rate is 50 sat/vB.
Formula: 🖩 Transaction Fee = Size × Fee Rate = 250 bytes × 50 sat/vB = 12,500 satoshis (0.000125 BTC)
💡 If 1 BTC = $60,000, the fee would be: 0.000125 BTC × $60,000 = $7.50
🚀 How to Lower Bitcoin Fees? Want to save on fees? Try these tips:
🔹 Use SegWit Addresses – Reduces transaction size! 🔹 Batch Transactions – Combine multiple payments into one. 🔹 Wait for Low Traffic – Fees fluctuate based on demand. 🔹 Use the Lightning Network – Near-zero fees for small payments.
🏁 Final Thoughts Bitcoin fees aren’t fixed—they depend on transaction size, fee rate, and network demand. By understanding how fees work, you can save money and optimize your transactions!
🔍 Want real-time fee estimates? Check mempool.space for live data! 🚀
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 2e8970de:63345c7a
2025-03-31 19:08:11
@ 2e8970de:63345c7a
2025-03-31 19:08:11https://x.com/beatmastermatt/status/1906329250115858750
originally posted at https://stacker.news/items/930491
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ bcbb3e40:a494e501
2025-03-31 15:41:53
@ bcbb3e40:a494e501
2025-03-31 15:41:53El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
-
 @ bcbb3e40:a494e501
2025-03-31 15:34:12
@ bcbb3e40:a494e501
2025-03-31 15:34:12|
 |
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|
|
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|Desde nuestros inicios los autores y temáticas relacionadas con la geopolítica nos han procurado atención e interés por parte del gran público y de los mass media, y no hay más que recordar el efecto que han venido teniendo nuestras obras de Aleksandr Duguin, en especial La geopolítica de Rusia y Proyecto Eurasia: teoría y praxis, sobre todo a raíz de nuestra presentación en Casa de Rusia en un ya lejano 2016, con la inestimable colaboración de Jordi de la Fuente como prologuista, trabajo que siempre reivindicamos desde nuestros medios por el prestigio, la calidad y brillantez de exposición del mismo.
Más allá de las obras del prestigioso y afamado filósofo y politólogo ruso, también hemos realizado otras incursiones en esta vertiente, que podríamos llamar «geopolítica alternativa», introduciendo las obras de otros notables autores como Claudio Mutti, Carlo Terracciano o Boris Nad. Con estos autores hemos tratado de profundizar en esa vía que se opone frontalmente, y radicalmente si se quiere, a los planteamientos derivados de la geopolítica atlantista y liberal que tiene su principal polo en Estados Unidos, haciendo especial hincapié en el subyugamiento que vienen ejerciendo desde 1945 en adelante respecto a una Europa convertida en un protectorado en una mera colonia.
Es por este motivo por el que la publicación de Jean Thiriart, el caballero euroasiático y la Joven Europa nos parece una obra totalmente pertinente en estos momentos, forma parte del desarrollo lógico de la línea editorial en la que estamos encauzados desde nuestros inicios, y viene a representar una de las múltiples vías en las que confluye la idea, profundamente schmittiana, de la política de los grandes espacios. En este caso la idea de una Europa unida, bajo un vasto proyecto que traspasa los estrechos límites del continente concebido como un apéndice más del «Occidente», de ese subproducto ideológico decadente y funcional a los intereses del otro lado del Atlántico. Para comprender la idea de una Europa unida, que comprenda a Rusia, y su enorme extensión territorial a lo largo de 17 millones de kilómetros cuadrados, y la importancia estratégica de su ubicación, es necesario recurrir al legado de Jean Thiriart, conocer su obra, pero también al hombre, pues una no se comprende sin el otro, en este caso hablamos de elementos correlativos.
|
 |
|:-:|
|Jean Thiriart (1922-1992)|
|
|:-:|
|Jean Thiriart (1922-1992)|¿Pero quién fue Jean Thiriart? Esta obra nos permite adentrarnos en aspectos biográficos, algunos de ellos poco conocidos para el gran público de habla hispana, y saber de su trayectoria, de la maduración de sus ideas, de su proyecto político y de las etapas que componen el desarrollo del mismo y que aparecen claramente diferenciadas: hablamos del proyecto político de unidad europea, que alcanza su concreción teórica en ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres (1965, Editorial Mateu, Barcelona), en pleno apogeo de la organización Jeune Europe, que se convirtió en el órgano político a partir del cual creyó poder implementar su proyecto unitario a escala europeo, manteniendo una posición de independencia respecto a los dos pretendidos bloques antagónicos de Guerra Fría: Estados Unidos y la Unión Soviética. En esa época, estamos hablando del ecuador de los años 60, todo el mundo de la Contracultura, falsamente contestatario, estaba articulando su propio discurso, que tendría su expresión más nítida a través del ya conocido Mayo del 68 francés o la Primavera de Praga, durante el mismo año. Y si el movimiento de Nueva Derecha liderado por Alain de Benoist surgiría en lo sucesivo, ya en la década de los años 70, como una «reacción» frente a la «rebelión contracultural», no podemos obviar la importancia de un movimiento político como Jeune Europe, una organización política transnacional, a escala de la Europa occidental, con sus diferentes delegaciones en países como Francia, Italia, Alemania, la propia España además de, como es obvio, Bélgica, país de origen de nuestro autor.
Jean Thiriart ha sido etiquetado con reiteración como un político y teórico de «extrema derecha», se han hecho numerosos discursos interesados para vincularlo, por cuestiones de orden biográfico muy circunscritas a determinado periodo, con el fascismo y el nacionalsocialismo de entreguerras. Sin embargo, y como el lector podrá descubrir a lo largo de la presente obra, el pensamiento de nuestro autor está muy lejos de ser reducible a meras etiquetas, y en ningún caso mostró las filiaciones que se le atribuyen desde posicionamientos ideológicos, sino que, muy al contrario, vemos a un hombre de pensamiento racional y pragmático, poderosamente influenciado por la geopolítica y abierto a alianzas estratégicas más variadas, más allá de todo fundamentalismo ideológico. Es por este motivo que veremos a un Thiriart buscando sinergias y entendimiento entre círculos de izquierdas, antiimperialistas en una lucha concebida como «cuatricontinental». No en vano, muchos de los cuadros políticos que se formaron en Giovane Europa, la rama italiana, terminaron por militar incluso en organizaciones de extrema izquierda de inspiración maoísta. En el caso de España hubo un notable apoyo a la organización por parte de los falangistas más disidentes. De manera que Jean Thiriart representa una figura política compleja, con influencias variadas, que van desde los hermanos Strasser, pasando por Ernst Niekish o Vilfredo Pareto, e incluso, por Sieyès o Robespierre.
Es a partir de Jeune Europe cuando el nacionalismo europeo, la idea de una Europa unida desde Brest a Bucarest toma cuerpo. En la obra mencionada con anterioridad (¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres) Jean Thiriart ya nos presenta a través de unos trazos muy definidos el proyecto del comunitarismo nacional-europeo, la piedra angular de su proyecto político. La idea de un socialismo aristocrático y europeo, trascendiendo las fronteras del Estado-nación liberal decimonónico, y los particularismos nacionales, concebidos como formas obsoletas y «estrechas de miras», obstáculos a superar en la convergencia del Imperio europeo. Porque vemos a un Thiriart que potencia la estructura del Estado, del aparato de poder, tratando de potenciar, y restaurar naturalmente, el papel y la preponderancia de Europa como espacio de civilización en el mundo. Es un nacionalismo europeo que viene determinado por razones puramente geopolíticas, algo que también fue objeto de críticas, concretamente por parte del geopolítico austriaco Heinrich von Lohausen, y que también recogemos en el presente volúmen de la obra.
|
 |
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|
|
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|En este sentido, Thiriart no andaba nada desencaminado, en la medida que pensaba que solo los Estados de dimensiones continentales podrían ser capaces de defender su independencia y soberanía, y ejercer un poder en el mundo, frente a los antiguos nacionalismos europeos, totalmente anacrónicos y un factor de ruptura y desintegración del potencial europeo. En este contexto, se hace necesario eliminar el orden establecido en Yalta en 1945, que convierte a Europa en un vasallo de las grandes potencias vencedoras de la Segunda Guerra Mundial. De modo que luchar contra la ocupación estadounidense por un lado, y soviética por otro lado, fuese el principal leitmotiv del Partido Revolucionario Europeo, un partido histórico señala Thiriart, encargado de llevar a término la acción unificadora continental. Y es con este propósito con el que se tratan de concertar una serie de alianzas internacionales que llevó a Thiriart y su organización a tratar con personal diplomático y gubernamental de los países árabes no alineados, del régimen de Fidel Castro o incluso con emisarios del gobierno chino, como ocurrió en el famoso encuentro propiciado por Ceaucescu en Bucarest con Zhou En-Lai.
Quizás, uno de los puntos donde más desacuerdos encontramos con las teorías thiriartianas se encuentra en ciertos fundamentos que la articulan, en un modelo racionalista, materialista y pragmático, de hecho no debemos olvidar que Maquiavelo era uno de sus referentes, y con éste la posterior hornada de autores neomaquiavélicos como Vilfredo Pareto. El excesivo pragmatismo de sus planteamientos, un estatalismo exacerbado y sin concesiones a las particularidades de los pueblos, una suerte de centralismo jacobino, y la ausencia de un elemento trascendente capaz de dar una justificación metafísica a todo el proyecto nacional europeo constituyen, en nuestra opinión, una parte discutible y reformulable.
En otro terreno, como pueda ser el puramente económico, encontramos un proyecto anticapitalista en muchos de sus aspectos, frente al democratismo parlamentario liberal, y apoyándose en las teorías económicas de Johann G. Fichte o Friedrich List, rechazando cualquier organización económica transnacional que pueda mediatizar o convertir a Europa en objeto de sus actividades usurocráticas y depredatorias, colocando la soberanía e independencia económica europea en una de las máximas prioridades en este terreno.
Debemos destacar, porque es un elemento de debate especialmente interesante, el apartado del libro que se corresponde al escrito de Luc Michel, publicado en Italia bajo el título Da Jeune Europe alle Brigate Rosse, en el libro Parte II Historia de Jeune Europe (1962-1969), en el que se detallan las colaboraciones que comenzaron a sucederse entre la militancia de la delegación italiana, Giovane Europa, y círculos de extrema izquierda maoísta, y cómo muchos de los antiguos militantes nacional-europeos terminaron militando en organizaciones de esta facción ideológica, y nos referimos a casos tan representativos en la época como Claudio Orsoni o Pino Bolzano entre otros muchos.
La actividad proselitista de Jeune Europe en el último lustro de la década de los años 60, con la fundación del Partido Comunitario Europeo, nos legó una gran cantidad de publicaciones, entre las cuales destacaron La Nation Européenne, La Nazione Europea o Europa Combattente, cuyas portadas han servido para ilustrar las páginas interiores de nuestra obra, y que procuraron una actividad proselitista y de difusión de ideas que llegaron a imprimir semanal y mensualmente varios miles de ejemplares en Francia o en Italia.
Tras agotar todas las vías posibles de alianzas y convergencias, con encuentros poco afortunados, vemos a un Thiriart que prefiere adoptar otras vías para seguir construyendo el proyecto nacional-europeo más allá de la fórmula activista y del partido político. Este es el motivo por el cual, en los siguientes años, ya en la última etapa de su vida, veremos esa transición del político activista al teórico y al ideólogo como parte de una nueva estrategia dentro del proyecto político al que consagró buena parte de su vida, y es un hecho que comienza a apreciarse desde mediados de los años 70. Durante esta época la «Europa de Brest a Bucarest» se transforma y amplía en una «Europa desde Dublín a Vladivostok». Thiriart aborda ya abiertamente la integración del espacio soviético en una Europa unida que abarca un inmenso espacio territorial, capaz de unir el Océano Atlántico y el Océano Pacífico de un extremo a otro, el «Imperio Eurosoviético». No obstante, Thiriart siempre piensa en términos geopolíticos, y considera que este proceso de integración debe llevarse a cabo desde una revisión de la ideología soviética, desde una marcada desmarxistización de su socialismo, purgado de todo dogmatismo y elementos condicionantes derivados de la teoría del Estado formulada por el marxismo-leninismo para tomar en su lugar aquella de Thomas Hobbes.
A partir de este momento solamente hay un enemigo, el que representa el poder estadounidense y el dominio que éste ejerce sobre la Europa occidental. A partir de ese momento la URSS, bajo las premisas apuntadas por Thiriart, y desde una ideología soviética «desmarxistizada», es la que debe asumir el proyecto de integración europea. Todo este enfoque terminará conociendo su colofón final al final de la vida de Jean Thiriart, cuando éste se encuentre ya en sus último año de vida, en 1992, con una Unión Soviética ya periclitada y disuelta, con un país sumido en una crisis económica, política y social bajo el gobierno decadente de Yeltsin, con un poder notablemente menguado y a merced de las potencias extranjeras y las apetencias de las organizaciones financieras transnacionales. En este contexto tendrá lugar el conocido viaje de Jean Thiriart a Moscú, donde se encontrará, además de con la disidencia de Yeltsin, encabezada por el Partido Comunista dirigido por Gennadij Ziuganov y numerosas personalidades públicas del ámbito ruso, entre las que destacará por encima de todos el filósofo y politólogo Aleksandr Duguin, quien en la presente obra también reivindica la figura del belga como un contribuidor directo del pensamiento euroasiático. Además de medios de prensa, políticos e intelectuales rusos, nuestro autor también compartirá espacio con una pequeña delegación de la revista italiana «Orion», especializada en temática geopolítica, y representada por el padre de la geopolítica italiana, Carlo Terracciano. El encuentro no tendrá mayores consecuencias, y vendrá a significar el último acto de servicio de Jean Thiriart en su denodado esfuerzo por lograr la integración de Europa y Rusia en un poderoso bloque geopolítico capaz de hacer frente a la hegemonía estadounidense en el mundo.
Terminaremos este breve y sintético escrito de presentación con un fragmento de la obra que Jean Thiriart publicó en 1965 bajo el título ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres, que nos parece de lo más adecuado para poner el punto final al presente texto:
Europa, este MILAGRO en la historia del hombre, este milagro que siguió al milagro griego, ha dado vida, con la prodigiosa fecundidad de su civilización irrepetible, a una cultura adoptada por el mundo entero. En la competencia surgida entre las grandes civilizaciones —occidental, india, china y japonesa— la nuestra ha aplastado a las demás.
La civilización es creadora de cultura. La cultura, en cambio, jamás ha creado civilización.
SOLO Europa posee la civilización; de ahí deriva su supremacía sobre los Estados Unidos y la Rusia comunista, que poseen únicamente la cultura nacida de nuestra civilización, como ha demostrado magistralmente Oswald Spengler.
Esta cultura, separada de su civilización, está condenada a la esterilidad, la cual se manifestará primero mediante una esclerosis y, posteriormente, mediante un retorno a la barbarie.
Políticamente dominada por Moscú o por Washington, la civilización europea se ve asfixiada y corre el riesgo de estancarse en su estado de simple cultura. Basta notar que todos los descubrimientos en el campo nuclear y astronáutico son obra de europeos. Todos buscan a los científicos europeos.
Solo una Europa políticamente unida puede proveer los medios de poder que garantizarán las condiciones históricas indispensables para la supervivencia de esta civilización.
Ninguna otra potencia, por otra parte, podría sustituir a Europa en su misión hacia la humanidad.
Artículo original: Hipérbola Janus, Presentación de «Jean Thiriart, el caballero euroasiático y la Joven Europa», de Pietro Missiaggia (TOR), 18/Mar/2025
-
 @ 52524fbb:ae4025dc
2025-03-31 15:26:46
@ 52524fbb:ae4025dc
2025-03-31 15:26:46 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networking
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkingNost most Amazing Features:##
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin##
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world##
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media##
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne##
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ bcbb3e40:a494e501
2025-03-31 15:23:12
@ bcbb3e40:a494e501
2025-03-31 15:23:12|
 |
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|
|
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|Nos complace presentar al lector en lengua española una novedad de primer orden, y sobre un tema que viene siendo objeto de interés por parte de nuestra línea editorial, como es el esoterismo, que hemos abordado recientemente a través de un nuevo recopilatorio de la obra evoliana en Ensayos filosóficos, esotéricos y religiosos 1925-1931, donde hemos tratado de rescatar los textos de las primeras etapas en la formulación del pensamiento del Maestro Romano. No obstante, no es la primera aventura que hemos emprendido en este terreno, siempre complejo y acompañado de la etiqueta, popular y quizás vulgarizada, de lo «misterioso» y lo «oculto», aunque no somos nada sospechosos en ese sentido por banalizar o tratar de ofrecer un enfoque puramente literario del asunto, y ni mucho menos de simpatizar con aquellas vías que entroncan con el New age, donde las mixtificaciones y la voluntad de convertir el fenómeno esotérico en un producto de consumo más, como demanda el mercado, para satisfacer demandas materiales o simples modas de una masa sobresocializada son norma habitual.
Podríamos citar multitud de obras que están presentes en nuestro catálogo, como son El pensamiento esotérico de Leonardo, de Paul Vulliaud, El mundo mágico de los héroes, de Cesare della Riviera, una joya del esoterismo italiano del siglo XVII, en El maestro de la tradición perenne, de René Guénon, o en el ensayo de Gianluca Marletta OVNIS y alienígenas. Origen, historia y prodigio de una pseudorreligión, un ensayo de notable originalidad donde se abordan aspectos esotéricos, aunque sea de un modo más tangencial. También en la literatura, con la obra del gran mitólogo y literato Boris Nad, Una historia de Agartha y La muerte púrpura de Gustav Meyrink encontramos nuevas referencias al ámbito esotérico. De modo que podemos concluir en que el esoterismo forma parte esencial de nuestras publicaciones e intereses como editores, y contribuimos activamente a su difusión.
|
 |
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|
|
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|Una obra original
Por eso la presente obra, la que nos disponemos a presentar, cuyo título es ¿Qué es el esoterismo?: Entre verdades y falsificaciones, de Bruno Bérard y Aldo La Fata, viene a ser una obra muy necesaria y clarificadora en la comprensión del esoterismo en todas sus dimensiones, en la complejidad de sus particulares, y en sus múltiples manifestaciones. Quizás en el mundo de habla hispana el esoterismo es un fenómeno que no ha obtenido su merecida atención, y nuestros autores en este ámbito, como es el caso de un Ramón Llull entre otros, no sean objeto de la atención que merece, y las actividades esotéricas, a nivel de asociaciones, comunidades u otras formas de organización, tampoco sean especialmente conocidas, ni cuenten con una actividad reconocida. Es posible, como señala La Fata, que haya ciertas reticencias dentro del mundo católico, acostumbrado a la ortodoxia y la guía espiritual de la Iglesia, y que cualquier tipo de «desviación» hacia formas más individuales y «libres» de vivir ciertas formas iniciáticas, mucho más sutiles, provoquen el rechazo y la incomprensión general. No obstante, como también se encargan de aclarar nuestros autores, el esoterismo comprende una dimensión diferenciada, implica un esfuerzo que no todos están dispuestos a acometer, y finalmente, no es tampoco un camino de felicidad y de frutos seguros, implica una transformación interior y la asunción de unas prácticas y procedimientos que no son aptos para cualquiera. Digamos que el esoterismo es un camino, una vía, que a diferencia de las «religiones populares», exotéricas, supone un arduo camino que viene marcado por un principio vertical y aristocrático de la existencia, o al menos así queremos verlo nosotros. El incremento de la capacidad de discernimiento, aunar lo visible con lo invisible, y ser capaz de superar límites vedados al común, no por simple vanidad ni por «crecimiento personal», tal y como se concibe en las aburguesadas y decadentes sociedades actuales, sino como parte de un proceso de aprendizaje, de autoconocimiento y de liberación. No nos cabe duda alguna de la necesidad de restaurar los antiguos vínculos con lo Alto, las vías que quedaron cerradas y que nos han limitado progresivamente al exclusivo y estrecho ámbito de la materialidad.
|
 |
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|
|
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|La obra emplea el recurso de la entrevista/diálogo, que aporta frescura y fluidez al texto «simplificando», o más bien haciendo más accesibles y comprensibles elementos relacionados con el esoterismo, que de otro modo resultarían excesivamente complejos para una parte del público lector poco familiarizado con la materia. Este dinamismo se ve complementado por la riqueza de matices e ideas que se van introduciendo de manera progresiva, evitando que el lector pueda verse abrumado por la avalancha de ideas y contenidos. Las preguntas de Bruno Bérard, siempre inteligentes, incisivas y pertinentes, además de ordenadas y bien estructuradas, favorecen la continuidad y el dinamismo en la exposición de los temas, ejerciendo de guía en la conversación. De ahí que el libro sea apto para diferentes niveles, tanto para aquellos que desconocen el esoterismo, como para quienes se encuentran familiarizados con el tema. Aldo La Fata, de acuerdo con su dilatada y extensa trayectoria en la materia, nos hace reflexiones teóricas de enorme valor, que entrelaza con su propia experiencia y trayectoria en el estudio del esoterismo. Sin lugar a dudas este aspecto nos permite ver una vertiente más humana e íntima, en la que se incluyen anécdotas personales y biográficas que siempre permiten una mayor conexión con el lector a través de la mezcla de hechos vitales y erudición teórica.
La entrevista que nos ofrecen Bruno Bérard y Aldo La Fata nos permite explorar la relación dialéctica que se genera entre el esoterismo y otros ámbitos como la religión, la ciencia o la filosofía. Todas las cuestiones se abordan desde enfoques muy concretos, abordando problemáticas particulares, que dan lugar a reflexiones más amplias evitando las simplificaciones e invitando a reflexiones mucho más profundas. De ahí la función de introducción y guía a la que nos venimos refiriendo.
Estos aspectos que acabamos de enumerar con anterioridad revelan un notable esfuerzo pedagógico por parte de los autores para acercarnos al estudio del esoterismo, nos aporta las herramientas necesarias, parafraseando el título de la obra, para discernir entre un verdadero esoterismo y sus falsificaciones.
Más allá de estos aspectos formales, que consideramos que es importante destacar, porque en ellos reside el éxito de la obra, en un planteamiento que resulta original, a la par que ameno y de gran interés, debemos considerar otros aspectos que hacen más referencia al contenido. «¿Qué es el esoterismo? Entre verdades y falsificaciones» pretende, como decíamos, clarificar qué es el esoterismo, cuales son sus particulares, sus características y atributos, su naturaleza más íntima, como fenómeno espiritual y filosófico en sus aspectos más profundos, que podemos remontar a épocas muy remotas y lejanas en el tiempo. Pero el esoterismo aparece en ocasiones fuertemente imbricado en otras estructuras de pensamiento, de tipo tradicional, como son las grandes religiones (Cristianismo, Islam, Judaísmo etc) y otros conceptos como la mística y la metafísica, cuyas relaciones hay que desentrañar.
La importancia de René Guénon
Aldo La Fata nos libera desde el principio de posibles equívocos al enfatizar que el verdadero esoterismo no es una simple acumulación de conocimientos secretos o rituales exóticos, sino una vía de trascendencia espiritual basada en el rigor y la autenticidad. A este respecto René Guénon aparece como uno de los grandes esoteristas de nuestro tiempo, en la medida que fue el gran intérprete y codificador de estos conocimientos, una figura que marcó un antes y un después en la comprensión de este ámbito, especialmente por su rigor conceptual y su capacidad para distinguir entre lo auténtico y lo falso en las tradiciones espirituales. A tal respecto podemos poner como ejemplo sus contundentes análisis de las corrientes ocultistas, especialmente del espiritismo o del teosofismo, en diferentes obras. Podemos decir a este respecto que Guénon hizo una distinción entre esoterismo y ocultismo, disociando el significado del primero de prácticas superficiales y desviadas, mientras que definió el esoterismo como una vía de conocimiento sagrado y trascendente. En este sentido fue una labor fundamental para evitar confusiones con mixtificaciones modernas y pseudoesoterismos como aquellos relacionados con el New Age.
|
 |
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|
|
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|Paralelamente, y con ello queremos dignificar la figura de René Guénon, el tradicionalista francés también nos abrió las fuentes de un vasto conocimiento espiritual, expresión de una «Tradición primordial», a cuyos orígenes prístinos siempre deberíamos aspirar, y cuya impronta impregna por completo religiones, culturas y formas de civilización no modernas, claro está. Y otro elemento fundamental, y que en la presente obra se considera de vital importancia, es que René Guénon considera el esoterismo no como una vía interna propia de la religión, sino como una vía complementaria que permite acceder a la esencia divina más allá de las formas externas. Para Aldo La Fata no se trata de una mera referencia intelectual, sino una figura que marcó su propio rumbo dentro del estudio del esoterismo. A través de obras como Los símbolos de la ciencia sagrada, La Fata descubrió la profundidad y la coherencia del pensamiento guenoniano, así como la idea de que el esoterismo actúa como el «pegamento» que conecta todas las tradiciones espirituales. Esta visión le permitió entender el esoterismo como algo inseparable de la religión, aunque con una profundidad y una exigencia mayores.
¿Qué es el esoterismo?
El término esoterismo tiene sus raíces etimológicas en el griego esôterikos, que implica un «ir hacia dentro» y que se contrapone a una variante exterior que definimos como «exoterismo», que se encuentra más vinculado al ámbito de la religión. Se trata de un conocimiento que no atiende a un principio puramente intelectual y discursivo sino que apunta a una vivencia directa y sapiencial de lo trascendente. Lejos de la acumulación de saberes ocultos y rituales, lo que prima en la experiencia de lo esotérico es la conexión directa con lo trascendente y lo divino a través de la práctica espiritual.
De hecho hay tres aspectos que nuestros autores destacan a lo largo de la obra respecto al esoterismo, y que nos parecen fundamentales:
- Interioridad: Supone un movimiento continuo hacia el interior, de exploración e introspección, en el que se tratan de derribar límites y obstáculos. Atendiendo a un dinamismo que huye de lo fijo y de lo estático.
- Profundización: La búsqueda de significados más profundos tras la realidad cotidiana, buscando ir más allá de la pura exterioridad de las cosas
- Relación con el exoterismo: Podemos considerarlo opuesto en sentido relativo al esoterismo, como una dimensión más externa y visible de las religiones, aunque este último (el esoterismo), no puede sobrevivir sin el apoyo de una tradición religiosa.
En relación al último punto debemos destacar, como advierten Bérard y La Fata, que pese a todo no podemos entender el esoterismo como una parte de las religiones, sino que tiene su propia función y objetivos, que no es otro que el que ya hemos mencionado con anterioridad: establecer una conexión directa con la verdad que irradia del principio universal y divino.
|
 |
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|
|
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|Otro aspecto interesante de la obra es el que nos habla de las relaciones entre esoterismo y metafísica, en el que el primero pretende ser también una vía de acceso al dominio del segundo. El esoterismo, como ya hemos visto, tiene como principal propósito trascender las categorías del mundo material para proyectarse en lo universal, y en este sentido comparte también objetivos con la metafísica, que pretende superar las limitaciones de la experiencia humana ordinaria y de acceder a las verdades primordiales que estructuran la realidad. Ambos apuntan a la raíz de todo lo existente, al absoluto. Las divergencias las hallamos en la forma o en el método para alcanzar estas verdades trascendentes, que en el caso del esoterismo nos remiten a símbolos, rituales y experiencias vivenciales que permiten al practicante interiorizar verdades universales.
De este modo, esoterismo y metafísica se nos presentan como realidades no opuestas, sino complementarias. La metafísica nos ofrece un marco conceptual y doctrinal para entender lo absoluto, mientras que el esoterismo se centra en su realización interna. En términos guenonianos, el esoterismo representa los aspectos operativos de la metafísica.
De modo que podemos decir que la metafísica aborda el tema trascendente desde una perspectiva conceptual, sin esa parte vivida de la experiencia en el conocimiento de lo universal. El esoterismo, por su parte, aporta esa contraparte que nos remite a la experiencia humana que permite al individuo acceder o ponerse en conexión con lo divino a través de su propio ser, de manera directa y vívida. Es un camino que el sujeto individual emprende para lograr una transformación interior.
Paralelamente, no podemos obviar dentro de todos estos procesos la participación de un elemento fundamental, como es la intuición suprarracional, que podríamos considerar como la herramienta que conecta al esoterista directamente con la fuente del conocimiento trascendente y universal, en lugar de hacerlo directamente a través de teorías o conceptos que siempre resultan más abstractos y difíciles de comprender en su vertiente más «discursiva». Al mismo tiempo, las relaciones que se establecen entre esoterismo y metafísica nos permiten poner en contacto las tradiciones religiosas con el conocimiento universal. Según La Fata, inspirándose en el legado de la obra de Frithjoff Schuon, cada tradición espiritual tiene una dimensión metafísica que puede ser comprendida y realizada a través del esoterismo, como un medio para acceder a la esencia inmutable de todas las formas religiosas.
Otro aspecto que esoterismo y metafísica comparten es la meta de superar la dualidad entre sujeto y objeto: Mientras que la metafísica conceptualiza esta unión como una verdad última, el esoterismo busca experimentarla directamente a través de la contemplación, el símbolo y la práctica espiritual.
Los autores
|
 |
|:-:|
|Aldo La Fata|
|
|:-:|
|Aldo La Fata|Aldo La Fata (1964) es un estudioso del esoterismo, el simbolismo y la mística religiosa, con una trayectoria de varias décadas dedicada al análisis y divulgación de estas disciplinas. Ha sido jefe de redacción de la revista Metapolitica, fundada por Silvano Panunzio, y actualmente dirige Il Corriere Metapolitico. Su trabajo destaca por una aproximación rigurosa y una mirada crítica a las corrientes contemporáneas del esoterismo, rescatando su sentido más profundo y tradicional. Entre sus obras más relevantes se encuentran Silvano Panunzio: vita e pensiero (2021) y Nella luce dei libri (2022), donde explora la intersección entre espiritualidad, simbolismo y pensamiento tradicional.
|
 |
|:-:|
|Bruno Bérard|
|
|:-:|
|Bruno Bérard|Bruno Bérard (1958), es doctor en Religiones y Sistemas de Pensamiento por la École Pratique des Hautes Études (EPHE), es un destacado especialista en metafísica. Autor de múltiples ensayos, ha desarrollado una profunda reflexión sobre la naturaleza del conocimiento espiritual y su relación con las tradiciones religiosas. Algunas de sus obras más importantes, traducidas a diversas lenguas, incluyen A Metaphysics of the Christian Mystery (2018) y Métaphysique du paradoxe (2019). Actualmente, dirige la colección Métaphysique au quotidien en la editorial L’Harmattan de París, consolidándose como una referencia en el estudio de la metafísica contemporánea.
En ¿Qué es el esoterismo?: Entre verdades y falsificaciones, asistimos a una presentación del tema tratado desde un conocimiento profundo y dilatado del tema, en la que ambos autores combinan la experiencia y el conocimiento que atesoran sobre el esoterismo y otros temas anejos, ofreciéndonos sus interpretaciones y enfoques particulares, y al mismo tiempo mostrando una gran capacidad de síntesis en la exposición de los temas tratados, que se inscriben en una multitud de tradiciones religiosas y espirituales de enorme complejidad. En este último punto reside también gran parte del valor de la obra, que constituye una novedad editorial especialmente relevante en su ámbito en lengua hispana.
Artículo original: Hipérbola Janus, Presentación de «¿Qué es el esoterismo?: Entre verdades y falsificaciones» (TOR), 6/Feb/2025
-
 @ bcbb3e40:a494e501
2025-03-31 15:02:58
@ bcbb3e40:a494e501
2025-03-31 15:02:58Traducción por Francisco de la Torre.
|
 |
|:-:|
|Los representantes de la derecha sionista europea que forman parte de «Patriots» reunidos en Bruselas el pasado mes de diciembre de 2024.|
|
|:-:|
|Los representantes de la derecha sionista europea que forman parte de «Patriots» reunidos en Bruselas el pasado mes de diciembre de 2024.|Entre los efectos que probablemente producirá en Europa la nueva administración estadounidense, es previsible el fortalecimiento del ala derecha del colaboracionismo atlantista que, después de haberse posicionado decididamente a favor de Donald Trump durante su presidencia 2017-2021, en el transcurso de la administración Biden abogó fervientemente por su regreso a la Casa Blanca y acogió su victoria electoral con gran júbilo. A finales de octubre de 2024, en el grandioso mitin preelectoral a favor de Trump celebrado en el Madison Square Garden de Nueva York, asistió una representante del grupo parlamentario europeo Patriots for Europe, que viajó a Estados Unidos para esa ocasión especial. En un vídeo publicado en la página X (antes twitter) de los Patriots, varios eurodiputados del mencionado grupo expresaron su identidad con los puntos de vista de Trump y auspiciando su reelección: el austriaco Harald Vilimsky (Freiheitliche Partei Österreichs), el checo Ondrej Knotek (Año 2011) el español Jorge Buxade (Vox), el holandés Tom Vandendriesche (Vlaams Belang), la polaca Anna Bryłka (Ruch Narodowy) y, por Hungría, Tamás Deutsch (Fidesz).
Este último es, sin duda, la personalidad más eminente del grupo de los Patriots que viajaron a Nueva York: originario de una familia judía de Budapest, en 1988 Tamás Deutsch junto con Viktor Orbán están entre los fundadores de Fidesz —Fiatal Demokraták Szövetsége (Alianza de los jóvenes demócratas), en la que ocupó el cargo de vicepresidente. El Fidesz ha tejido durante mucho tiempo una red de lazos con el Partido Republicano de los Estados Unidos y con el think tank conservador Heritage Foundation, mientras que el gobierno de Viktor Orbán organizó las tres últimas ediciones anuales de la CPAC en Hungría (Conservative Political Action Conference), un encuentro de políticos de derechas de varios países[^1].
Patriots for Europe o Patriots.eu, denominación que recuerda al de los misiles aire-tierra estadounidenses (el MIM-104 Patriots), es, por tanto, el nombre oficial del grupo político de la derecha liberal-conservadora, populista y euroescéptica, nacido en julio de 2024 (primero como alianza y luego como grupo parlamentario europeo) por iniciativa del primer ministro húngaro Viktor Orbán, el exprimer ministro checo Andrej Babiŝ y del exministro del interior austriaco Herbert Kickl. Como representantes de sus respectivos partidos (Fidesz, Año 2011, Freiheitliche Partei Österreichs), Orbán, Babiŝ y Kickl firmaron un texto ideológico titulado: A Patriotic Manifesto for a European Future[^2], según la cual la única política europea legítima es aquella que, enraizada en la pluralidad de las diferentes naciones, proteja su herencia grecorromana-judeocristiana preservando su identidad, tradiciones y costumbres.
Al núcleo inicial de los Patriots se unió el partido portugués ¡Arriva! (¡Chega!), el Partido húngaro Popular Demócrata Cristiano (Kereszténydemokrata Néppárt), el partido español Vox, el Partido por la Libertad (Partij voor de Vrijheid) holandés, el Partido Popular Danés (Dansk Folkeparti), el interés Flamenco (Vlaams Belang), la Reunión Nacional (Rassemblement National) francés y, por Italia, la Liga para Primer Ministro Salvini.
Constituido formalmente, el grupo parlamentario recibió una posterior adhesión del diputado griego de Voz de la Razón (Foní Logikis), del diputado de Primero Letonia (Letvija pirmajâ prohibir), de los dos diputados del Movimiento Nacional polaco (Ruch Narodowy) y de los dos diputados checos del Juramento (Přísaha) y de los Automovilistas por sí mismos (Motoristé sollozoê). Presidente del grupo parlamentario Patriots.eu, que cuenta con un total de ochenta y seis diputados[^3], es Jordan Bardella, presidente de la Rassemblement National; pero la personalidad más notable y prestigiosa de los Patriots es, sin duda, el primer ministro húngaro Viktor Orbán.
En cuanto a la línea de política exterior seguida por Viktor Orbán, cabe recordar que fue durante su primer mandato, en 1989, cuando Hungría se unió a la OTAN junto con la República Checa y Polonia. La pertenencia a la organización militar de la Alianza Atlántica implicó la participación húngara en la guerra de Kosovo en Yugoslavia, así como la contribución de Hungría en las misiones de la ISAF y en la guerra en Irak en apoyo de la intervención estadounidense. Por otro lado, no deja de ser significativo que en junio de 2011, durante la visita de Condoleezza Rice a Budapest, se inaugurara una estatua del presidente estadounidense Ronald Reagan en la céntrica Plaza de la Libertad (Szabadság tér). «Hoy —dijo Orbán en esa ocasión— erigimos aquí una estatua al hombre, al líder, que cambió y renovó este mundo creando un nuevo mundo para nosotros en Europa Central, un hombre que creía en la libertad, en la fuerza moral de los hombres libres, y creía que los muros que obstruyen el camino a la libertad pueden ser derribados».
En los años de la primera administración Trump, Orbán estableció una relación privilegiada con la Casa Blanca: en 2019 fue recibido calurosamente por el presidente estadounidense, quien declaró su apoyo al «soberanismo» europeo, del que Orbán era ya el exponente más puntero. El primer ministro húngaro, que más tarde expresó varias veces la esperanza de volver a ver a Trump como líder de los Estados Unidos, se reunió con él de nuevo en Mar-a-Lago de Palm Beach en marzo de 2024 y al final de la visita escribió en una publicación: «¡Hacer que América vuelva a ser grande, señor presidente!»[^4].
El entendimiento entre Trump y Orbán fue favorecido por Benjamin Netanyahu, quien ha tenido una estrecha relación con el actual primer ministro húngaro desde 2005, cuando Orbán estaba en la oposición y Netanyahu era ministro de Finanzas. Esta relación, que Orbán ha utilizado para neutralizar las iniciativas hostiles de las ONG’s de Soros (quien financió a Fidesz desde 1992 a 1999), ha acentuado progresivamente la posición proisraelí de Budapest, hasta el punto que Hungría junto a Austria, Croacia y República Checa, se han alineado con Estados Unidos e Israel votando en contra de la resolución propuesta por la ONU para el alto el fuego en la Franja de Gaza. Cuando László Toroczkai, jefe del partido Mi Hazánk (Nuestra Patria), preguntó a Orbán en el Parlamento por qué Hungría había votado en contra, el primer ministro le respondió: «La política exterior es complicada, enfréntate solo si entiendes de lo que estamos hablando»[^5].
El presidente de Patriots, Jordan Bardella, no es menos pro-sionista. «Reconocer un Estado palestino significaría reconocer el terrorismo», dijo Bardella, quien antes de las elecciones francesas había asegurado que, si llegaba a ser primer ministro, sería «un escudo para los compatriotas judíos contra un islamismo que no solo quiere separar la República, sino conquistarla»[^6]. Por su parte, Marine Le Pen, madrina política de Bardella, declaró: «Es absolutamente legítimo que Israel quiera erradicar al grupo terrorista armado Hamas y que se dote de medios para hacerlo»[^7].
En cuanto a la Liga de Salvini como primer ministro, sus posiciones pro-trumpistas y pro-sionistas siempre se han caracterizado por un extremismo descarado. «Nunca he ocultado —dijo Salvini antes de las elecciones estadounidenses— mi esperanza en una victoria republicana, por mil razones (...) hablamos [con Trump] a más tardar hace unas semanas. Nunca he ocultado mi simpatía humana y mi sintonía cultural»[^8]. Y sobre el genocidio en curso en Palestina, Salvini dijo: «Nuestros pensamientos están con el pueblo israelí (...) Recordar siempre el derecho de Israel a existir, a defenderse y a convivir finalmente en paz con sus pueblos vecinos, contra el horror del terrorismo islámico»[^9]. El 6 de octubre de 2024, al final de su discurso desde el escenario de Pontida, Salvini posó para una foto con los Patriots presentes en la manifestación de la Liga Norte: además de Viktor Orbán, estuvieron el holandés Geert Wilders, el portugués André Ventura, la austriaca Marlene Svazek, el español Antonio Fúster y el general Roberto Vannacci. Enviaron mensajes en vídeo de apoyo y solidaridad tanto Jordán Bardella en nombre de Rassemblement national como el ex-presidente brasileño Jair Bolsonaro.
También Geert Wilders (Partij voor de Vrijheid), que en 2009 recibió el Premio Oriana Fallaci por producir un cortometraje de propaganda antiislámica, es conocido también por su extremismo prosionista. «Jerusalén, Judea y Samaria —en su opinión— son todas de Israel (...) La patria de los palestinos es el Reino de Jordania (...) Obama y Kerry deben dejar de criticar a Israel por los asentamientos. Judea y Samaria pertenecen a los israelíes»[^10]. En el programa de Wilders, «distinguiéndose durante dos décadas por su lucha contra la islamización —escribe complacido un sitio web sionista— está también el reconocimiento de Jerusalén como capital de Israel, con el traslado de la embajada holandesa»[^11].
André Ventura, presidente de ¡Chega!, reiteró en Polonia la posición prosionista de su partido, declarando convencido: «Estamos con Israel y permaneceremos junto a Israel en esta batalla por los derechos humanos y la democracia»[^12]. A quienes lo comparan con Donald Trump y Jair Bolsonaro, André Ventura responde: «Estoy acostumbrado a estas comparaciones. Estas son las ideas en las que creo»[^13]. En cuanto a la guerra en Ucrania, el líder de la lista ¡Chega! en las elecciones europeas, Antonio Tânger Corrêa, dijo que «la derrota de Ucrania sería la derrota de todo Occidente y de Portugal, en caso de extrema necesidad»[^14], enviarían a sus tropas.
Marlene Svazek representó a la Freiheitliche Partei Österreichs en Pontida, cuyos «excelentes contactos»[^15] con la derecha israelí están garantizados por David Lasar, miembro del Consejo Nacional (Nationalrat) del partido austriaco. Lasar no es el único judío en el FPÖ: también es judío el ex-secretario general del partido y ex-parlamentario europeo Peter Sichrovsky, quien ha negado ser un agente del Mossad, pero ha admitido haber tenido «muchas reuniones con funcionarios israelís»[^16].
José Antonio Fúster es el nuevo presidente de Vox Madrid. El jefe del partido que lo representa, Santiago Abascal, encabezó una delegación a Israel en 2023 que se reunió con dos ministros de Tel Aviv. «Durante la visita, Abascal ha transmitido el apoyo y la solidaridad de España al Primer Ministro israelí Benjamin Netanyahu, y ha defendido la urgente necesidad de acabar con Hamas que, según Abascal, es un grupo terrorista que «encarna el mal absoluto»[^17]. Tras la reunión de la delegación de Vox con Netanyahu, el candidato electoral Jorge Buxadé Villalba afirmó que las acciones genocidas cometidas por el régimen sionista en la Franja de Gaza son «operaciones antiterroristas» que deben continuar «hasta que no quede ni un solo terrorista»[^18].
En cuanto a Roberto Vannacci, elegido diputado del Parlamento Europeo en las listas de la Liga por Salvini, su currículum vitae patriot puede jactarse de una participación activa en las operaciones de EE.UU. en Oriente Medio. El general comandó durante dos turnos (2005-2006) el Special Forces Task Group en Irak y fue el primer comandante de la Task Force 45 en Afganistán en 2013, poco antes de la transición de la International Security Assistance Force a la Resolute Support Mission, Vannacci asumió el cargo de jefe del Estado Mayor de las fuerzas especiales de la OTAN, «una organización que ha garantizado la paz durante más de cincuenta años, una alianza política y militar que ha funcionado bien»[^19]. Habiendo prestado sus servicios a los Estados Unidos «para la estabilización de Irak»[^20] como Deputy Commanding General y Director of Training, el 21 de agosto de 2018, Vannacci fue galardonado con la Legion of Merit, la condecoración militar estadounidense creada por el presidente Franklin D. Roosevelt. Su consigna antes y después de la elección de Trump ha sido: «Go, Donald, go!».
[^1]: Cfr. C. Mutti, Alla destra degli USA, «Eurasia» 1/2023.
[^2]: Después de la confluencia de los grupos de Identity and Democracy en el grupo de Patriots, se aprobó una nueva versión del manifiesto político. Véase https://patriots.eu/manifesto
[^3]: Freiheitliche Partei Österreichs (Austria), 6; Vlaams Belang (Bélgica), 3; Dansk Folkeparti (Dinamarca), 1; Rassemblement National (Francia), 30; Foni Logikis (Grecia), 1; Fidesz - Magyar Polgári Szövetség (Hungría), 10; Kereszténydemokrata Néppárt (Hungría), 1; Liga para Salvini Premier (Italia), 8; Letvija primajâ vietâ (Letonia), 1; Partij voor de Vrijheid (Países Bajos), 6; Ruch Narodowy (Polonia), 2; ¡Chega! (Portugal), 2; ANO (República Checa), 7; Automovilistaé sobê (República Checa), 1; Přísaha (República Checa), 1; Vox (España), 6.
[^4]: Angela Napoletano, La «visita». Orbán incorona Trump: «Lui è il presidente della pace», avvenire.it, 9 marzo 2024.
[^5]: András Dezsô, The roots of Orbán’s strong bond with Israel and its PM, https://balkaninsight.com, 14 de noviembre de 2023.
[^6]: Bardella, «riconoscere Palestina è riconoscere terrorismo». «Sarò uno scudo per i nostri connazionali ebrei», ANSA, 26/6/2024.
[^7]: Mauro Zanon, Sorpresa, lo «scudo» degli ebrei in Francia è il partito della Le Pen, tempi.it, 27 de octubre de 2023.
[^8]: Stefano Baldolini, Salvina punta su Trump: «Spero che vinca. Andrò negli Usa prima del voto». Tensioni con Meloni? «Governo durerà 5 anni», repubblica.it, 13 de julio de 2024.
[^9]: Nova.News, 7 de octubre de 2024.
[^10]: Elezioni in Olanda, che è il sovranista Wilders: anti-Islam, contro l’Ue e sostenitore del Grande Israele, www.open.online, 23 de noviembre de 2023.
[^11]: www.informazionecorretta.com, 26 de octubre de 2024.
[^12]: www.agenzianova.com, 6 de octubre de 2024.
[^13]: Especial: André Ventura. «Sou contra o aborto mas nunca condenaria uma mulher que aborta», «Jornal SOL», 12 de julio de 2022.
[^14]: Ventura admite tropas portuguesas na Ucrânia e tem uma posição clara sobre Putin, «CNN Portugal», 11 de marzo de 2024.
[^15]: Sophie Makris, Austria’s Jews wary of far-right charm offensive, www.timeofisrael.com, 3 de marzo de 2019.
[^16]: Yossi Melman, Sichrovsky Denies He Was a Mossad Agent, www.haaretz.com, 3 de junio de 2005.
[^17]: Fernando Heller, Spagna: il leader di Vox pretende le scuse di Sánchez per aver messo in dubbio l’offensiva israeliana contro Hamas, https://euractiv.it, 6 de diciembre de 2023.
[^18]: El ultraderechista Vox defiende los ataques de Israel en Gaza tras la polémica reunión con Netanyahu, euronews, 29 de mayo de 2024.
[^19]: Bruno Vespa, Vannacci: «Dopo l’Ue tornerei nell’esercito», «La Verità», 30 de octubre de 2024, p. 7.
[^20]: Missione Iraq: Riconoscimento al Generale Roberto Vannacci, en www.difesa.it , cit. en www.wikipedia.org
Artículo original: Hipérbola Janus, Patriots (TOR), 9/Ene/2025
-
 @ fe02e8ec:f07fbe0b
2025-03-31 14:43:22
@ fe02e8ec:f07fbe0b
2025-03-31 14:43:22\ Und genau dafür wirst auch du gedrillt werden: Menschen zu jagen und töten. Unbekannte, die auch nicht wissen, was sie hier tun. Oder Unschuldige, die nicht rechtzeitig fliehen konnten. Einfach töten. Alle. Ohne zu fragen. Denn das ist deine Aufgabe, Soldat: Töte Menschen!
Egal, was du vorher warst, Heizungsmonteur, KFZ-Mechaniker, Veganer, Marketing-Manager, Friseur, Verkäufer, Kindergärtner: Es ist egal. Jetzt musst du töten. Denn du hast mitgemacht. Entweder, weil du es nicht ernst genommen hast, weil du dich nie für Politik interessiert hast. Oder weil du gedacht hast, das alles betrifft dich nicht. Weil du gedacht hast, Wahlen könnten etwas verändern. Oder weil du immer das Maul gehalten hast, damit dich keiner als «Rechter» bezeichnet. Egal. Jetzt musst du töten. Das ist das Spiel.
Ja, es ist ein Spiel. Grausam, abartig, menschenverachtend. Dennoch hat es Regeln: Diejenigen, die das Spiel beginnen, müssen niemals selbst auf das Schlachtfeld. Das ist die erste Regel. Ihre Söhne auch nicht, nicht die Söhne der anderen Politiker, nicht die der EU-Abgeordneten, nicht die der Parteibonzen. Auch nicht die der Banker, der Vorstandsvorsitzenden, der Chefredakteure. Denn alle wissen, wie man das Spiel spielt. Nur du nicht.
Du bist einfach eine Figur auf dem Spielfeld, die es verpasst hat, NEIN zu sagen, als noch Gelegenheit war. Jetzt bist du verwandelt worden in eine menschliche Drohne. Wenn sie sagen: töte!, dann tötest du. Denken kannst du, wenn alles vorbei ist. Falls du je wieder nach Hause kommst. Vielleicht sogar mit beiden Beinen und beiden Armen. Vielleicht auch nicht. Egal. Wer hätte Mitleid mit einer Spielfigur?
Nein, du musst töten. Das ist deine Aufgabe. Sie sagen es nun schon seit Monaten, warum glaubst du es nicht? Sie meinen es ernst. Wenn du den Brief in Händen hältst ist es zu spät. Es gilt dann das Notstandsrecht und keiner kann mehr verweigern. Da hättest du dich vorher drum kümmern müssen. Oder auf eine Demo gehen. Oder laut und mit klarer Stimme in jedem Gespräch den Wahnsinn anprangern. Hast du aber nicht.
Jetzt musst du töten oder du wirst getötet. Das ist das Spiel. Du hättest selbst denken können. Hast du aber nicht. Hast deine Zeit mit sinnlosen Videos vertan, Netflix geguckt und hast Influencerinnen geliked. Die müssen nicht an die Front. Aber du. Morgen, wenn du aufstehst, die Uniform anziehst und rausgehst, dann wirst du Befehle ausführen oder erschossen werden. Also wirst du Menschen töten. Dein Leben wird nie wieder so sein, wie zuvor. Dein Schmerz, deine Schuld, dein Leid: sie gehen ein in die unendliche Reihe der Soldaten, die seit Jahrhunderten dasselbe Schicksal erlitten. Deren Schreie noch immer durch den ewigen Raum hallen. Deren Opfer von den Herren des Spiels mit einem Lächeln entgegengenommen wurde. Deren Gliedmaßen auf den Schlachtfeldern liegen geblieben waren. Zum Dank erhielten sie eine Medaille. Ein Stück Blech für den rechten Arm, einen Grabstein für den Vater, den Bruder, den Sohn. Für das Vaterland. Für Europa. Für die Demokratie. Der Hohn tropft aus jedem Politikerwort, doch die Menschen glauben noch immer die uralte Geschichte von Freund und Feind, von Gut und Böse.

\ Wer nicht aufwachen will muss töten. Du. Nicht am Bildschirm. In der echten Welt. Wo man nicht auf Replay drücken kann. Wo man den Gegner nicht nach links oder rechts swipen kann, denn er ist echt, real, lebendig. Noch. Entweder er oder du. Jetzt ist es zu spät für Entscheidungen. Kannst du es spüren? Die Work-Life Balance wird zur Kill-or-be-Killed balance. Es gibt kein Entrinnen. Denn du hast mitgemacht. Schweigen ist Zustimmung. Sich-nicht-drumkümmern ist Zustimmung. Kriegsparteien zu wählen ist noch mehr Zustimmung.
Heute.
Heute lässt sich noch etwas ändern.
Es hat nichts zu tun mit rechts oder links. Nur mit Menschlichkeit versus Hass, Macht und dem ganz großen Geld. Das sind die Gründe, für die du töten oder sterben musst.
Wie entscheidest du dich?
-
 @ b4403b24:83542d4e
2025-03-31 14:31:53
@ b4403b24:83542d4e
2025-03-31 14:31:53🚀 Bitcoin Enthusiasts! Tomorrow the price of #BTCPrague2025 tickets goes up so take advantage of the 10% discount using code from the video - BTCBULGARIA.
✅ Network with leaders ✅ Learn blockchain strategies ✅ Gain crypto insights
Secure your spot NOW!
Bitcoin #BTC #BTCPrague
originally posted at https://stacker.news/items/930210
-
 @ 9dd283b1:cf9b6beb
2025-03-31 13:21:08
@ 9dd283b1:cf9b6beb
2025-03-31 13:21:08Do you still feel anxiety when Bitcoin's price drops significantly, even though you're in fiat profit (100% +) ? Why or why not? And when did you truly stop feeling any emotional attachment to the price fluctuations?
originally posted at https://stacker.news/items/930139
-
 @ 866e0139:6a9334e5
2025-03-31 12:44:27
@ 866e0139:6a9334e5
2025-03-31 12:44:27
Autor: Carlos A. Gebauer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Am 18. März 1924 schenkte meine Großmutter ihren Töchtern einen kleinen Bruder. Weil sein Vater fürchtete, der Junge könnte unter seinen vier Schwestern verweichlichen, schickte er den Kleinen zu Wochenendfreizeiten einer örtlichen Pfadfindergruppe. Ein Weltkriegsveteran veranstaltete dort mit den Kindern Geländespiele quer durch die schlesischen Wälder. Man lernte, Essbares zu finden, Pilze zu bestimmen, sich im Freien zu orientieren und Feuer zu machen.
Bald wurde deutlich, dass der Heranwachsende auch nicht mehr in den Blockflötenkreis seiner Schwestern und ihrer Freundinnen passte. Das Umfeld befürwortete, sein besonderes musikalisches Talent auf das Klavierspiel und das Flügelhorn zu richten. Kontakte bei der anschließenden Kirchenmusik mündeten schließlich in den elterlichen Entschluss, den nun 14-jährigen in ein Musikschulinternat zu schicken.
Es begann der Zweite Weltkrieg
Ein Jahr später, das erste Heimweh hatte sich langsam beruhigt, änderten sich die Verhältnisse schlagartig. Es begann der Zweite Weltkrieg. Mitschüler unter den jungen Musikern erfuhren, dass ihre älteren Brüder nun Soldaten werden mussten. Noch hielt sich die Gemeinschaft der jetzt 15-jährigen im Internat aber an einer Hoffnung fest: Bis sie selbst in das wehrfähige Alter kommen würden, müsste der Krieg längst beendet sein. In dieser Stimmungslage setzten sie ihre Ausbildung fort.
Es kam anders. Für den 18-jährigen erfolgte die befürchtete Einberufung in Form des „Gestellungsbefehls“. Entsprechend seiner Fähigkeiten sah man ihn zunächst für ein Musikkorps vor und schickte ihn zu einer ersten Grundausbildung nach Südfrankreich. Bei Nizza fand er sich nun plötzlich zwischen Soldaten, die Handgranaten in das Mittelmeer warfen, um Fische zu fangen. Es war das erste Mal, dass er fürchtete, infolge Explosionslärms sein Gehör zu verlieren. In den kommenden Jahren sollte er oft die Ohren zu- und den Mund offenhalten müssen, um sich wenigstens die Möglichkeit der angezielten Berufsausübung zu erhalten – wenn es überhaupt je dazu kommen würde.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Schon nach kurzer Zeit änderte sich die Befehlslage wieder. Der Musikstudent wurde nun zum Infanteristen und nach Russland an die Front verbracht. Vor ihm lagen jetzt drei Kriegsjahre: Gewalt, Dreck, Gewehrkugeln, Panzerschlachten, Granatsplitter, Luftangriffe, Entbehrungen, Hunger, Kälte, sieben Verwundungen, Blut und Schmerzen, Sterbende überall, Tote, Schreiende. Verzweiflung. Sorgen. Ängste. Todesangst. Zurückweichen? Verboten! Und die stets klare Ansage dazu: Wer nicht da vorne gegen den Feind um sein Leben kämpft, dem wird es ganz sicher da hinten von den eigenen Kameraden genommen.
Ein gewährter Fronturlaub 1944 versprach glückliche Momente. Zurück zu den Eltern, zurück zu den Schwestern, zurück nach Freiburg. Doch die Familie war nicht zu Hause, die Türen verschlossen. Eine Nachbarin öffnete ihr Fenster und rief dem Ratlosen zu: „Beeil‘ dich! Renn‘ zum Friedhof. Der Vater ist tot. Sie sind alle bei der Beerdigung!“ Wieder hieß es, qualvoll Abschied nehmen. Zurück an die Front.
Nach einem weiteren russischen Winter brach sich unübersehbar die Erkenntnis Bahn, dass der Krieg nun seinem Ende zugehe. Doch das Bemühen im Rückzug, sich mit einem versprengten Haufen irgendwie Richtung Heimat orientieren zu können, wurde doppelt jäh unterbrochen. Fanatische Vorgesetzte befahlen die längst Geschlagenen wieder gen Osten. Kurz darauf fielen sie heranrückenden russischen Truppen in die Hände.
Kriegsgefangenschaft: Tabakration gegen Brot
Drei Jahre dem Tod entgangen, schwer verletzt und erschöpft war der 21-jährige also nun ein Kriegsgefangener. Jetzt lagen drei Jahre russischer Kriegsgefangenschaft vor ihm. Ständig war unklar, wie es weiterginge. Unmöglich jedenfalls, sich noch wie ein Pfadfinder aus den Wäldern zu ernähren. Es begannen die Jahre des Schlafens auf Brettern, die Zeit der ziellosen Zugtransporte an unbekannte Orte. Niemand sprach. Nur der Sonnenstand machte klar: Es ging nie Richtung Heimat, sondern immer weiter nach Osten. Weil der Blechbläser nicht rauchte, konnte er seine Tabakration gegen Brot tauschen. So überlebte er auch die Zeit des Hungers und der Morde in den Lagern, die Horrorbilder der nachts Erschlagenen und in die Latrinen geworfenen Toten, der sinnlosen Zwangsarbeiten und der allgegenwärtigen Wanzen. Wer versuchte zu fliehen, der wurde erschossen und sein Körper zur Abschreckung in den Fangdrähten belassen. Im Sommer stanken die dort verwesenden Leichen, wenn nicht Vögel sie rechtzeitig gefressen hatten.
Als der 24-jährige schließlich sechs Jahre nach seiner Einberufung aus russischer Kriegsgefangenschaft entlassen wurde, gab es kein Zurück mehr in seine schlesische Heimat. Abgemagert reiste er der vertriebenen Mutter nach, die mit seinen Schwestern und Millionen anderen Flüchtlingen im Westen Deutschlands verteilt worden war. Kraft Ordnungsverfügung wohnte sie jetzt im sauerländischen Bad Laasphe in einem schimmligen Garagenanbau. Als ihn ein Passant auf dieser Reise morgens allein, nur mit einem Becher an der Schnur um den Hals, auf Krücken durch Berlin ziehen sah, gab er ihm schweigend sein Butterbrot.
Der kleine, sanfte Junge aus dem schlesischen Freiburg hat danach noch 60 Jahre gelebt. Es dauerte zunächst sechs Jahre, bis er wieder kräftig genug war, ein Instrument zu spielen. 30-jährig saß er dann endlich in einem Orchester und begann ein normales Berufsleben. Aber sein Körper und seine Seele waren für immer aus jeder Normalität gerissen.
Irgendwo in Russland war ihm die linke Hüfte so versteift worden, dass sich seine Beine im Liegen an Wade und Schienbein überkreuzten. Er musste also stets den Oberkörper vorbeugen, um überhaupt laufen zu können. Über die Jahrzehnte verzog sich so sein gesamter Knochenbau. Jeder Tag brachte neue orthopädische Probleme und Schmerzen. Ärzte, Masseure, Physiotherapeuten, Schmerzmittel und Spezialausrüstungen aller Art prägten die Tagesabläufe. Asymmetrisch standen seine Schuhe nebeneinander, die ein Spezialschuster ihm mit erhöhter Sohle und Seitenstabilisierung am Knöchel fertigte. Sessel oder Sofas waren ihm nicht nutzbar, da er nur auf einem Spezialstuhl mit halb abgesenkter Sitzfläche Ruhe fand. Auf fremden Stühlen konnte er nur deren Vorderkante nutzen.
In den Nächten schrie er im Schlaf
Und auch wenn er sich ohne Krankheitstage bis zuletzt durch seinen Berufsalltag kämpfte, so gab es doch viele Tage voller entsetzlicher Schmerzen, wenn sich seine verdrehte Wirbelsäule zur Migräne in den Kopf bohrte. Bei alledem hörte man ihn allerdings niemals über sein Schicksal klagen. Er ertrug den ganzen Wahnsinn mit einer unbeschreiblichen Duldsamkeit. Nur in den Nächten schrie er bisweilen im Schlaf. In einem seiner Alpträume fürchtete er, Menschen getötet zu haben. Aber auch das erzählte er jahrzehntelang einzig seiner Frau.
Als sich einige Jahre vor seinem Tod der orthopädische Zustand weiter verschlechterte, konsultierte er einen Operateur, um Entlastungsmöglichkeiten zu erörtern. Der legte ihn auf eine Untersuchungsliege und empfahl, Verbesserungsversuche zu unterlassen, weil sie die Lage allenfalls verschlechtern konnten. In dem Moment, als er sich von der Liege erheben sollte, wurde deutlich, dass ihm dies nicht gelang. Die gereichte Hand, um ihn hochzuziehen, ignorierte er. Stattdessen rieb er seinen Rumpf ganz alleine eine quälend lange Minute über die Fläche, bis er endlich einen Winkel fand, um sich selbst in die Senkrechte zu bugsieren. Sich nicht auf andere verlassen, war sein Überlebenskonzept. Jahre später, als sich sein Zustand noch weiter verschlechtert hatte, lächelte er über seine Behinderung: „Ich hätte schon vor 60 Jahren tot auf einem Acker in Russland liegen können.“ Alles gehe irgendwann vorbei, tröstete er sich. Das war das andere Überlebenskonzept: liebevoll, friedfertig und sanft anderen gegenüber, unerbittlich mit sich selbst.
Sechs Monate vor seinem Tod saß er morgens regungslos auf seinem Spezialstuhl. Eine Altenpflegerin fand ihn und schlug Alarm. Mit allen Kunstgriffen der medizinischen Technik wurde er noch einmal in das Leben zurückkatapultiert. Aber seine Kräfte waren erschöpft. Es schob sich das Grauen der Vergangenheit zwischen ihn und die Welt. Bettlägerig kreiste er um sich selbst, erkannte niemanden und starrte mit weit offenen Augen an die Decke. „Die Russen schmeißen wieder Brandbomben!“, war einer seiner letzten Sätze.
Der kleine Junge aus Schlesien ist nicht zu weich geraten. Er hat sein Leid mit unbeugsamer Duldsamkeit ertragen. Er trug es wohl als Strafe für das Leid, das er anderen anzutun genötigt worden war. An seinem Geburtstag blühen immer die Magnolien. In diesem Jahr zum hundertsten Mal.
Dieser Text wurde am 23.3.2024 erstveröffentlicht auf „eigentümlich frei“.
Carlos A. Gebauer studierte Philosophie, Neuere Geschichte, Sprach-, Rechts- und Musikwissenschaften in Düsseldorf, Bayreuth und Bonn. Sein juristisches Referendariat absolvierte er in Düsseldorf, u.a. mit Wahlstationen bei der Landesrundfunkanstalt NRW, bei der Spezialkammer für Kassenarztrecht des Sozialgerichtes Düsseldorf und bei dem Gnadenbeauftragten der Staatsanwaltschaft Düsseldorf.
Er war unter anderem als Rechtsanwalt und Notarvertreter bis er im November 2003 vom nordrhein-westfälischen Justizministerium zum Richter am Anwaltsgericht für den Bezirk der Rechtsanwaltskammer Düsseldorf ernannt wurde. Seit April 2012 arbeitet er in der Düsseldorfer Rechtsanwaltskanzlei Lindenau, Prior & Partner. Im Juni 2015 wählte ihn die Friedrich-August-von-Hayek-Gesellschaft zu ihrem Stellvertretenden Vorsitzenden. Seit Dezember 2015 ist er Richter im Zweiten Senat des Anwaltsgerichtshofes NRW.
1995 hatte er parallel zu seiner anwaltlichen Tätigkeit mit dem Verfassen gesellschaftspolitischer und juristischer Texte begonnen. Diese erschienen seither unter anderem in der Neuen Juristischen Wochenschrift (NJW), der Zeitschrift für Rechtspolitik (ZRP) in der Frankfurter Allgemeinen Zeitung, der Freien Presse Chemnitz, dem „Schweizer Monat“ oder dem Magazin für politische Kultur CICERO. Seit dem Jahr 2005 ist Gebauer ständiger Kolumnist und Autor des Magazins „eigentümlich frei“.
Gebauer glaubt als puristischer Liberaler unverbrüchlich an die sittliche Verpflichtung eines jeden einzelnen, sein Leben für sich selbst und für seine Mitmenschen verantwortlich zu gestalten; jede Fremdbestimmung durch Gesetze, staatliche Verwaltung, politischen Einfluss oder sonstige Gewalteinwirkung hat sich demnach auf ein ethisch vertretbares Minimum zu beschränken. Die Vorstellung eines europäischen Bundesstaates mit zentral detailsteuernder, supranationaler Staatsgewalt hält er für absurd und verfassungswidrig.
\ Aktuelle Bücher:
Hayeks Warnung vor der Knechtschaft (2024) – hier im Handel
Das Prinzip Verantwortungslosigkeit (2023) – hier im Handel
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 65038d69:1fff8852
2025-03-31 12:13:39
@ 65038d69:1fff8852
2025-03-31 12:13:39Artificial intelligence is upon us and not showing any signs of slowing. The most common concern from those in the workforce is being replaced by one of these “thinking machines”. But what if AI wasn’t coming for your job? What if it was coming for your boss’s job instead?
I happened across the following post on X: https://x.com/BrianRoemmele/status/1905754986795151629 Brian describes having installed an AI system that provides an omniscient “shadow” to each of the executives at a client company, which can then be queried by the CEO for reports. The CEO seems to like it so far, and if it leads to less time spent writing internal reports I’m sure the executives like it too. But many of you may be recoiling at the thought of an always-on nanycam who’s sole purpose seems to be to snitch on you to your boss, and judging by the replies to Brian’s post, you’re not alone. If your supervisor has a history of targeting you your fears may not be misplaced. Workplace surveillance tools are often coyly marketed for this.
What if instead of your boss using an AI tool to spy on you, your boss was completely replaced by an AI? Would your supervisor having no biases or favouritism sway your opinion? What about being able to tailor its communication specifically to you? Expressing no judgement at your clarifying questions? Being immediately available 24/7? Perfectly equitable expectations and performance reviews? Just writing that almost has me convinced this would usher in a workplace utopia.
In practice guaranteeing zero bias is extremely difficult. After all, these things are programmed by humans and learn from human data. Their “weights” could also be intentionally adjusted to favour or target. If the AI’s supervisor follows the Pareto Principle (also known as the 80/20 Rule) they may be tempted to ask it for a list of the lowest performing employees to be laid off on a regular basis. Not keeping yourself in the top 20% of performers (by whatever metrics the AI has been programmed to look for) may mean your job. The dystopian-future videogame “Cyberpunk 2077” tells a story of a company that brings in an AI only to have it fire all the human workers in favour of automation and copies of itself. Clearly it’s implementers forgot to set hard limits on its executive powers. The shareholders were happy with all-time high profits though…
When technology is blamed for these sorts of existential problems the IT industry collectively sighs and repeats the mantra, “The problem is not the technology. The problem is the people.” A quote from a 1979 IBM presentation is likewise summoned; “A computer can never be held accountable, therefore a computer must never make a management decision.” As a darker example, the Nuremberg trials post-WWII saw the precedent set that acting under “superior orders” is not a valid defence for war crimes or crimes against humanity. It seems responsibility can’t be passed to others, whether man or machine. The endless task of generating reports and presentations can probably be automated away though.

Would you work under an AI, or “hire” an AI to manage others? We can help you with that; you can find us at scalebright.ca.
-
 @ 0d1702d6:8f1ac66f
2025-03-31 10:45:57
@ 0d1702d6:8f1ac66f
2025-03-31 10:45:57Als Verrücktheit bezeichnen \ wir die chronische Entwicklung \ eines dauernden Wahnsystems \ bei vollkommener Erhaltung \ der Besonnenheit.
Psychiater Emil Kraepelin 1893
Es ist Teil des westlichen Wahnsystems anzunehmen, Russland habe aus imperialen Absichten heraus 2022 mit nur 130.000 Soldaten die Grenze zur Ukraine überschritten, um so die gesamte Ukraine und später wohlmöglich Westeuropa militärisch einzunehmen, wie z.B. der deutsche Kriegsminister Pistorius seit 2023 suggerierte.
Nachdem die USA bereits 2014 die berechtigten Anti-Korruptions-Proteste der Ukrainer auf dem Maidan durch massive Unterstützung für einen illegalen Putsch gegen die russlandfreundliche Regierung im Sinne des von den USA gewünschten Regimewechsels manipuliert hatten, rüsteten sie in den folgenden Jahren die Ukraine massiv auf, trainierten ihre Soldaten, bauten mehr als einen Stützpunkt und machten die zwischen Ost & West hin- und hergerissene Ukraine so zielgerichtet unterhalb offizieller NATO-Mitgliedschaft schon zu einem kampfstarken eng befreundeten Partner, dessen Krieg gegen seine eigene russisch-stämmige Bevölkerung im rohstoffreichen Donbass die NATO unter Führung der USA somit auch direkt und indirekt unterstützte.
Nachdem der Westen den Russen bei der Wiedervereinigung Deutschlands versprochen hatte, die NATO keinen Zentimeter nach Osten vorzuschieben und stattdessen ein gemeinsames europäisches Sicherheits-System unter Einbeziehung Russlands gemeinsam zu entwickeln, brachen wir diese Zusicherung mit den NATO-Osterweiterungen ab 1999 mehrfach bis heute.
Russland zeigte sich bei seiner zunehmenden Umzingelung durch NATO-Staaten wesentlich nachsichtiger als es umgekehrt die USA schon bei russischen wenigen Raketen auf Kuba 1962 jemals waren und heute sein würden!
Zugleich hatte Russland seit Beginn der NATO-Osterweiterung immer unmissverständlich klar gemacht, dass es eine Stationierung von NATO-Truppen & Raketen in der Ukraine niemals tolerieren würde. Der damalige US-Senator und 2022 US-Präsident Biden sagte schon Ende der 90'er Jahre öffentlich, man werde auf diesen Wunsch der – nach Meinung von US-Geostrategen viel zu schwächen – Russen keine Rücksicht nehmen und erwarte, dass ihnen irgendwann die Nerven ob dieser provokativen Umzingelung durchgingen…
Folgerichtig simulierten die USA und die Europäer - wie Angela Merkel bereits öffentlich eingestanden - nur Verhandlungen über die Abkommen Minsk I und II, damit genügend Zeit blieb die Ukraine aufzurüsten und diese dann einen starken militärischen Schlag gegen die russisch stämmige Bevölkerung im Donbass und die russischen Soldaten auf der Krim ausführen konnte, ein Szenario, welches Anfang 2022 durch einen Truppenaufmarsch auch auf ukrainischer Seite weit fortgeschritten vorbereitet war, bevor im Februar 2022 die russische Armee die Grenze zur Ukraine überschritt.\ \ Trotz alledem kamen schon im April 2022 Unterhändler der Ukraine und Russlands in Ankara zur Übereinkunft eines Waffenstillstandes und Friedensplans (!), der dann allerdings von dem damaligen britischen Premierminister Boris Johnson – in Kooperation mit Joe Biden – durch einen Besuch in Kiew mit dem Versprechen von grenzenlosen Waffenlieferungen \ & logistischer Unterstützung durch die USA und Westeuropa „abgetrieben“ wurde.\ \ Zunächst wurden diese Tatsachen wie üblich öffentlich in deutschen und europäischen Medien als „Verschwörungstheorie“ diffamiert, bis sie in den folgenden Monaten jedoch langsam selbst in die Mainstream-Medien Deutschlands, Europas wie den USA einsickerten.\ \ Zwischenfazit:\ Nachdem die USA ihre so und so viel gewählte globale „Regime Change“ Operation auf dem Maidan schon 10 Jahre lang vorbereitet hatten, gelang ihnen im Jahr 2014 tatsächlich zunächst einen pro-westlichen illegalen Putschpräsidenten, danach auch weitere pro-westliche Präsidenten zu installieren und einem Teil der Weltöffentlichkeit, vor allem aber ihren „Freunden“ im Westen einzureden, die „bösen Russen“ hätten diesen Krieg quasi aus dem Nichts heraus (ohne lange Vorgeschichte!) und trotz Verhandlungen (welche realen statt nur simulierten Verhandlungen?) vom Zaun gebrochen...\ \ Damit war ihr seit über 30 Jahren offen formuliertes geostrategisches Kalkül, \ die Schwäche der Russen nach Auflösung des Warschauer Paktes auszunutzen, sie mit der NATO zu umzingeln und bei Widerstand dann eben in einem kräftezehrenden Krieg stark zu schwächen und damit ein für alle Male als ökonomische Konkurrenten in Europa auszuschalten scheinbar aufgegangen...\ \ Das paranoide alte und zugleich kindliche „Freund/Feind Schema“ hatte seinen Dienst verrichtet und das „imperiale Böse“ konnte bequem auf „Putin und die Russen“ projiziert werden.
\ Schizophren ist dies auch deswegen, weil mit zweierlei Maß gemessen wurde und wird, denn niemals würden die USA auch nur eine russische Rakete auf Kuba tolerieren und gehen selber - ganz anders als Russland - global weit über die eigene Grenzsicherung hinaus, indem sie sich anmaßen, den gesamten Globus mit fast 800 Militärbasen zu überziehen und je nach Bedarf Kriege zu führen, wenn es ihnen zur Sicherung ihrer Rohstoffe - für auch unseren westlichen Lebensstil - und/oder geostrategischen Macht opportun und machbar erscheint.\ \ Deutschland spielt seit 2022 die naive und mehr als traurige Vorreiterrolle eines unterwürfigen Vasallen der so tut, als würde unsere Freiheit durch gegenseitigen Mord und Totschlag von Hunderttausenden junger Ukrainer und Russen in der Ukraine verteidigt, eine äußerst perverse und dümmliche Vorstellung ohne historische geschweige denn geo-strategische Kenntnisse und Erfahrungswerte.\ \ Demgegenüber ist klar: Es gibt nur EINE Sicherheit in Europa für alle vom Atlantik bis hinter den Ural, oder es gibt KEINE Sicherheit für Niemanden, \ wenn wir nicht die berechtigten Sicherheitsinteressen der Russen ernst nehmen, die wir, d.h. die unsere Väter und Großväter bereits im 20.Jahrhundert rücksichtslos überfallen, mit Krieg überzogen und ermordet haben.\ \ John F. Kennedy und Nikita S. Chruschtschow waren 1962 im historischen Gegenstück zum „Ukrainekrieg“, der „Kubakrise“, weise genug einen Weltkrieg durch gegenseitige Zugeständnisse zu verhindern.
Wo sind die Politiker von Format, die in ihre Fußstapfen treten?\ \ Es wäre eine bitterböse Farce, wenn ausgerechnet ein autoritärer Oligarchen-Präsident wie Donald Trump die Weisheit hätte, diesen Schritt zu tun...\ \ Zugleich wäre die öffentliche Bankrott-Erklärung aller europäischen Politiker, \ die sich als viel demokratischer, sachlicher und menschlicher ansehen \ und ihre eigene dramatische Fehlleistung wohl niemals eingestehen...\ \ Allein die politische wie mediale Empörungswelle in Deutschland, als Trump und Putin ganz offenlegten, wer denn in diesem Krieg das Sagen hat, \ lässt Schlimmstes befürchten. Obwohl aus gut unterrichteten Diplomatenkreisen längst durchgesickert ist, dass im Prinzip die gesamte Analyse hier unter Diplomaten anerkannt und ziemlich nah an den Tatsachen ist, gehört nicht viel Lebenserfahrung dazu zu wissen, dass die meisten der ach so mächtigen westeuropäischen Politiker dies nie zugeben werden...
-
 @ fd06f542:8d6d54cd
2025-03-31 10:00:34
@ fd06f542:8d6d54cd
2025-03-31 10:00:34NIP-05
Mapping Nostr keys to DNS-based internet identifiers
finaloptionalOn events of kind
0(user metadata) one can specify the key"nip05"with an internet identifier (an email-like address) as the value. Although there is a link to a very liberal "internet identifier" specification above, NIP-05 assumes the<local-part>part will be restricted to the charactersa-z0-9-_., case-insensitive.Upon seeing that, the client splits the identifier into
<local-part>and<domain>and use these values to make a GET request tohttps://<domain>/.well-known/nostr.json?name=<local-part>.The result should be a JSON document object with a key
"names"that should then be a mapping of names to hex formatted public keys. If the public key for the given<name>matches thepubkeyfrom theuser metadataevent, the client then concludes that the given pubkey can indeed be referenced by its identifier.Example
If a client sees an event like this:
jsonc { "pubkey": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9", "kind": 0, "content": "{\"name\": \"bob\", \"nip05\": \"bob@example.com\"}" // other fields... }It will make a GET request to
https://example.com/.well-known/nostr.json?name=boband get back a response that will look likejson { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" } }or with the recommended
"relays"attribute:json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" }, "relays": { "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ] } }If the pubkey matches the one given in
"names"(as in the example above) that means the association is right and the"nip05"identifier is valid and can be displayed.The recommended
"relays"attribute may contain an object with public keys as properties and arrays of relay URLs as values. When present, that can be used to help clients learn in which relays the specific user may be found. Web servers which serve/.well-known/nostr.jsonfiles dynamically based on the query string SHOULD also serve the relays data for any name they serve in the same reply when that is available.Finding users from their NIP-05 identifier
A client may implement support for finding users' public keys from internet identifiers, the flow is the same as above, but reversed: first the client fetches the well-known URL and from there it gets the public key of the user, then it tries to fetch the kind
0event for that user and check if it has a matching"nip05".Notes
Identification, not verification
The NIP-05 is not intended to verify a user, but only to identify them, for the purpose of facilitating the exchange of a contact or their search.
Exceptions are people who own (e.g., a company) or are connected (e.g., a project) to a well-known domain, who can exploit NIP-05 as an attestation of their relationship with it, and thus to the organization behind it, thereby gaining an element of trust.User discovery implementation suggestion
A client can use this to allow users to search other profiles. If a client has a search box or something like that, a user may be able to type "bob@example.com" there and the client would recognize that and do the proper queries to obtain a pubkey and suggest that to the user.
Clients must always follow public keys, not NIP-05 addresses
For example, if after finding that
bob@bob.comhas the public keyabc...def, the user clicks a button to follow that profile, the client must keep a primary reference toabc...def, notbob@bob.com. If, for any reason, the addresshttps://bob.com/.well-known/nostr.json?name=bobstarts returning the public key1d2...e3fat any time in the future, the client must not replaceabc...defin his list of followed profiles for the user (but it should stop displaying "bob@bob.com" for that user, as that will have become an invalid"nip05"property).Public keys must be in hex format
Keys must be returned in hex format. Keys in NIP-19
npubformat are only meant to be used for display in client UIs, not in this NIP.Showing just the domain as an identifier
Clients may treat the identifier
_@domainas the "root" identifier, and choose to display it as just the<domain>. For example, if Bob ownsbob.com, he may not want an identifier likebob@bob.comas that is redundant. Instead, Bob can use the identifier_@bob.comand expect Nostr clients to show and treat that as justbob.comfor all purposes.Reasoning for the
/.well-known/nostr.json?name=<local-part>formatBy adding the
<local-part>as a query string instead of as part of the path, the protocol can support both dynamic servers that can generate JSON on-demand and static servers with a JSON file in it that may contain multiple names.Allowing access from JavaScript apps
JavaScript Nostr apps may be restricted by browser CORS policies that prevent them from accessing
/.well-known/nostr.jsonon the user's domain. When CORS prevents JS from loading a resource, the JS program sees it as a network failure identical to the resource not existing, so it is not possible for a pure-JS app to tell the user for certain that the failure was caused by a CORS issue. JS Nostr apps that see network failures requesting/.well-known/nostr.jsonfiles may want to recommend to users that they check the CORS policy of their servers, e.g.:bash $ curl -sI https://example.com/.well-known/nostr.json?name=bob | grep -i ^Access-Control Access-Control-Allow-Origin: *Users should ensure that their
/.well-known/nostr.jsonis served with the HTTP headerAccess-Control-Allow-Origin: *to ensure it can be validated by pure JS apps running in modern browsers.Security Constraints
The
/.well-known/nostr.jsonendpoint MUST NOT return any HTTP redirects.Fetchers MUST ignore any HTTP redirects given by the
/.well-known/nostr.jsonendpoint. -
 @ 7d33ba57:1b82db35
2025-03-31 09:28:36
@ 7d33ba57:1b82db35
2025-03-31 09:28:36Rovinj is one of Croatia’s most beautiful coastal towns, known for its colorful Venetian-style buildings, cobblestone streets, and breathtaking sea views. Located on the Istrian Peninsula, Rovinj offers a mix of history, culture, and stunning beaches, making it a perfect getaway for travelers seeking both relaxation and adventure.
🌊 Top Things to See & Do in Rovinj
1️⃣ Explore Rovinj Old Town 🏡
- Wander through narrow, winding streets filled with art galleries, boutique shops, and charming cafés.
- Discover Balbi’s Arch, the old entrance to the city, and the Clock Tower.
- Enjoy stunning sunset views from the harbor.
2️⃣ Visit St. Euphemia’s Church ⛪
- The most famous landmark in Rovinj, located at the highest point of the Old Town.
- Climb the bell tower for a panoramic view of the Adriatic and nearby islands.
- Learn about Saint Euphemia, the town’s patron saint, and her fascinating legend.
3️⃣ Relax at Rovinj’s Best Beaches 🏖️
- Lone Bay Beach – A popular spot near Zlatni Rt forest, great for swimming.
- Mulini Beach – A stylish beach with a cocktail bar and clear waters.
- Cuvi Beach – A quieter, family-friendly pebble beach.
4️⃣ Walk or Cycle Through Golden Cape Forest Park (Zlatni Rt) 🌿🚲
- A protected nature park with pine forests, walking trails, and hidden coves.
- Great for hiking, cycling, and rock climbing.
- Perfect for a picnic with sea views.
5️⃣ Take a Boat Trip to Rovinj Archipelago 🛥️
- Explore Red Island (Crveni Otok) – A peaceful getaway with sandy beaches.
- Visit St. Andrew’s Island, home to a former Benedictine monastery.
- Sunset dolphin-watching tours are a must! 🐬
6️⃣ Try Authentic Istrian Cuisine 🍽️
- Fuži with truffles – A local pasta dish with Istria’s famous truffles.
- Istrian seafood platter – Fresh fish, mussels, and Adriatic shrimp.
- Olive oil & wine tasting – Try local Malvazija (white) and Teran (red) wines.
7️⃣ Visit the Batana House Museum ⛵
- A unique museum dedicated to Rovinj’s traditional wooden fishing boats (batanas).
- Learn about local fishing traditions and maritime culture.
- End the visit with a traditional batana boat ride at sunset.
🚗 How to Get to Rovinj
✈️ By Air: The nearest airport is Pula Airport (PUY), 40 km away.
🚘 By Car:
- From Pula: ~40 min (40 km)
- From Zagreb: ~3 hours (250 km)
- From Ljubljana (Slovenia): ~2.5 hours (170 km)
🚌 By Bus: Direct buses from Pula, Rijeka, and Zagreb.
🚢 By Ferry: Seasonal ferries connect Rovinj with Venice, Italy (~2.5 hours).💡 Tips for Visiting Rovinj
✅ Best time to visit? May–September for warm weather & festivals ☀️
✅ Wear comfy shoes – The Old Town streets are made of polished stone & can be slippery 👟
✅ Book restaurants in advance – Rovinj is a foodie hotspot, especially in summer 🍷
✅ Take a sunset walk along the harbor – One of the most romantic views in Croatia 🌅
✅ Bring cash – Some smaller shops and taverns still prefer cash 💶 -
 @ 5fb7f8f7:d7d76024
2025-03-31 09:14:45
@ 5fb7f8f7:d7d76024
2025-03-31 09:14:45Imagine a world where your voice is truly yours where no algorithm buries your posts, no central authority censors your ideas, and no account bans silence you. Welcome to yakiHonne, the decentralized media revolution built on Nostr.
Here, freedom reigns. Whether you're sharing breaking news, deep thoughts, or creative content, yakiHonne ensures your voice is unstoppable. No corporate overlords, no gatekeepers, just pure, open communication between people who value truth and transparency.
Why yakiHonne?
✅ Censorship-Free: Speak your mind without fear of bans or shadowbans. ✅ Decentralized & Secure: Your content lives on the blockchain, not in the hands of a single company. ✅ Community-Driven: Connect with like-minded individuals who believe in free expression. ✅ Future-Proof: No central server means no risk of takedowns or content wipes.
Break away from the limits of traditional media. Join yakiHonne today and take control of your voice!
-
 @ 78c90fc4:4bff983c
2025-03-31 08:13:17
@ 78c90fc4:4bff983c
2025-03-31 08:13:17Die Operation „Cast Thy Bread“ war eine verdeckte Kampagne zur biologischen Kriegsführung, die von der Haganah und später von den israelischen Verteidigungsstreitkräften während des arabisch-israelischen Krieges 1948 durchgeführt wurde[1][3]. Bei der Operation, die im April 1948 begann, wurden Trinkwasserquellen mit Typhusbakterien verseucht, um palästinensisch-arabische Zivilisten und verbündete arabische Armeen anzugreifen[1][3].

\ \ ## Wichtige Details\ \ - **Ziel**: Palästinensische Araber an der Rückkehr in eroberte Dörfer zu hindern und die Versuche der arabischen Armeen, Gebiete zurückzuerobern, zu behindern[1].\ - **Methoden**: Israelische Streitkräfte setzten Typhuskeime in Flaschen, Reagenzgläsern und Thermoskannen ein, um Brunnen und Wasservorräte in palästinensischen Gebieten zu vergiften[1][3].\ - **Führung**: Die Operation wurde vom israelischen Premierminister David Ben-Gurion und dem Generalstabschef der IDF, Yigael Yadin, beaufsichtigt und genehmigt[1].\ \ ## Bemerkenswerte Vorfälle\ \ - Akkon (Akka)**: Die Wasserversorgung der Stadt wurde am 15. Mai 1948 verseucht, was zu einer Typhusepidemie und „extremer Verzweiflung“ unter den Einwohnern führte[1][3].\ - **Gaza**: Im Mai 1948 versuchten vier Soldaten der israelischen Spezialeinheiten, die örtliche Wasserversorgung zu vergiften, wurden jedoch gefangen genommen und hingerichtet[1].\ - **Andere Orte**: Auch in Jericho, Eilabun und palästinensischen Vierteln in Jerusalem wurden Brunnen vergiftet[1][3].\ \ ## Folgen\ \ Die Operation führte zu schweren Erkrankungen unter den palästinensischen Anwohnern, von denen Dutzende betroffen sein sollen[1][3]. Sie erzielte jedoch nicht die von ihren Befürwortern erhoffte lähmende Wirkung und wurde im Dezember 1948 eingestellt[1].\ \ ## Historische Bedeutung\ \ Die Operation „Gegossenes Brot“ wurde als Kriegsverbrechen und als Akt der ethnischen Säuberung eingestuft[1]. Ihre Enthüllung hat eine Kontroverse und Debatte über die im Krieg von 1948 angewandten Taktiken und ihre langfristigen Auswirkungen auf den israelisch-palästinensischen Konflikt ausgelöst[2][4].
Quellen
[1] Operation Cast Thy Bread - Wikipedia https\://en.wikipedia.org/wiki/Operation_Cast_Thy_Bread
[2] Cast Thy Bread Archives - Promised Land Museum https\://promisedlandmuseum.org/tag/cast-thy-bread/
[3] From 'Virtuous Boy' to Murderous Fanatic: David Ben-Gurion and the ... https\://www.euppublishing.com/doi/10.3366/hlps.2023.0308
[4] Historians reveal Israel's use of poison against Palestinians https\://www.middleeastmonitor.com/20221011-historians-reveal-israels-use-of-poison-against-palestinians/
[5] Thoughts on Operation Cast Thy Bread? : r/IsraelPalestine - Reddit https\://www.reddit.com/r/IsraelPalestine/comments/1g02b64/thoughts_on_operation_cast_thy_bread/
[6] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://www.tandfonline.com/doi/abs/10.1080/00263206.2022.2122448
[7] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://cris.bgu.ac.il/en/publications/cast-thy-bread-israeli-biological-warfare-during-the-1948-war
[8] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://www.tandfonline.com/doi/full/10.1080/00263206.2022.2122448
\
Artikel https://x.com/RealWsiegrist/status/1906616394747179136
Nakba
https://waltisiegrist.locals.com/upost/2033124/die-siedler-fordern-ganz-offen-eine-zweite-nakba
-
 @ 22aa8151:ae9b5954
2025-03-31 07:44:15
@ 22aa8151:ae9b5954
2025-03-31 07:44:15With all the current hype around Payjoin for the month, I'm open-sourcing a project I developed five years ago: https://github.com/Kukks/PrivatePond
Note: this project is unmaintained and should only be used as inspiration.
Private Pond is a Bitcoin Payjoin application I built specifically to optimize Bitcoin transaction rails for services, such as deposits, withdrawals, and automated wallet rebalancing.
The core concept is straightforward: withdrawals requested by users are queued and processed at fixed intervals, enabling traditional, efficient transaction batching. Simultaneously, deposits from other users can automatically batch these withdrawals via Payjoin batching, reducing them onchain footprint further. Taking it to the next step: a user's deposit is able to fund the withdrawals with its own funds reducing the required operational liquidity in hot wallets through a process called the Meta Payjoin.
The application supports multiple wallets—hot, cold, multisig, or hybrid—with configurable rules, enabling automated internal fund management and seamless rebalancing based on operational needs such as min/max balance limits and wallet ratios (10% hot, 80% in 2-of-3, 10% in 1-of-2, etc) .
This system naturally leverages user Payjoin transactions as part of the automated rebalancing strategy, improving liquidity management by batching server operations with user interactions.
Private Pond remains quite possibly the most advanced Payjoin project today, though my multi-party addendum of 2023 probably competes. That said, Payjoin adoption overall has been disappointing: the incentives heavily favor service operators who must in turn actively encourage user participation, limiting its appeal only for specialized usage. This is why my efforts refocused on systems like Wabisabi coinjoins, delivering not just great privacy but all the benefits of advanced Payjoin batching on a greater scale through output compaction.
Soon, I'll also open-source my prototype coinjoin protocol, Kompaktor, demonstrating significant scalability improvements, such as 50+ payments from different senders being compacted into a single Bitcoin output. And this is not even mentioning Ark, that pushes these concepts even further, giving insane scalability and asyncrhonous execution.
You can take a look at the slides I did around this here: https://miro.com/app/board/uXjVL-UqP4g=/
Parts of Private Pond, the pending transfers and multisig, will soon be integrated into nostr:npub155m2k8ml8sqn8w4dhh689vdv0t2twa8dgvkpnzfggxf4wfughjsq2cdcvg 's next major release—special thanks to nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg for continuing the work and getting it to the finish line.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 78c90fc4:4bff983c
2025-03-31 07:03:41
@ 78c90fc4:4bff983c
2025-03-31 07:03:41In Palästina und im Ausland wurde das Abkommen einzelner jüdischer Organisationen mit dem nationalsozialistischen Deutschland heftig kritisiert. Auf dem 18. Zionistenkongress 1933 in Prag etwa bezeichnete der Schriftsteller Schalom Asch das Abkommen mit Hitlers Regime als „Verrat am Weltjudentum“. Chaim Arlosoroff, der damalige Verhandlungsführer der Jewish Agency, wurde wahrscheinlich deshalb im Juni 1933 Opfer eines Mordanschlags.

https\://de.m.wikipedia.org/wiki/Ha’avara-Abkommen
Am 16. Juni 1933 wurde Chaim Arlosoroff kurz nach seiner Rückkehr von den Transfer-Verhandlungen in Deutschland durch den Pistolenschuss eines Attentäters schwer verletzt, als er mit seiner Frau Sima, geb. Rubin, am Strand von Tel Aviv entlangging. Er verstarb am folgenden Tag im Krankenhaus. Wer der Attentäter war, ist bis heute ungeklärt. Zunächst wurden drei Verdächtige angeklagt. Zwei von ihnen wurden freigesprochen, einer, Abraham Stavsky, wurde verurteilt, doch das Urteil wurde durch das oberste Appellationsgericht aufgehoben.
https://de.m.wikipedia.org/wiki/Chaim_Arlosoroff#Ermordung
Instrumentalisierung des Holocaust
Von Anneliese Fikentscher und Andreas Neumann
Zum Schluss ein Zitat aus dem 2017 erschienenen Buch "Die israelisch-jüdische Tragödie. Von Auschwitz zum Besatzungs- und Apartheidstaat. Das Ende der Verklärung" von Arn Strohmeyer: „Der vielleicht radikalste Kritiker des israelischen Holocaustgedenkens ist der amerikanisch -jüdische Politologe Norman Finkelstein. Er wendet sich vor allem gegen das in Israel und den USA verwendete Dogma, der Holocaust sei 'einzigartig' gewesen und mit anderen Verbrechen nicht vergleichbar, dass er in der Geschichte also ohne Parallele sei. Diese Behauptung – so Finkelstein – impliziert eine Reihe anderer Behauptungen, die wiederum die Instrumentalisierung des Holocaust ausmachen. Erstens: Die Konstruktion des Holocaust als einzigartig gilt als gegeben, sie zu leugnen gilt als Leugnung des Holocaust. Diese Behauptung schließt zweitens ein rationales Verständnis des Holocaust aus, er macht den Holocaust zu einem Mysterium, wie Elie Wiesel ihn verstanden hat. Einzigartiges Leid verleiht drittens einen einzigartigen Anspruch. Die Unvergleichlichkeit des Holocaust stellt also ein moralisches Kapital dar, das Israel als politisches Alibi benutzt. Israel kann – so Finkelstein – diese moralischen und emotionalen Ansprüche an andere Staaten stellen und die Anerkennung seines Rechts einfordern, dass es als besonders bedroht gelten kann und seine Anstrengungen zum Überleben der Unterstützung bedarf. Die Behauptung der Einzigartigkeit des Holocaust beinhaltet auch die Behauptung der jüdischen Einzigartigkeit. Der Holocaust ist also etwas Besonderes, weil Juden etwas Besonderes sind, was man als säkularisierte Version der Auserwähltheit deuten kann. Diese Behauptungen – so Finkelstein – sollen Israels Sonderstellung legitimieren, sollen von vornherein jede unmenschliche Behandlung von Nichtjuden entschuldigen (Israel ist 'alles erlaubt!') und machen diesen Staat und seine Politik gegen jede Kritik immun. Bei dieser Instrumentalisierung des Holocaust bleiben die Rechte und die Würde der Opfer – welcher auch immer – völlig auf der Strecke.“ Ist das einer breiten Öffentlichkeit bewusst?
http://www.nrhz.de/flyer/beitrag.php?id=24469
Perplexity:
Der Schriftsteller Schalom Asch kritisierte das Ha'avara-Abkommen scharf auf dem 18. Zionistischen Kongress, der vom 21. August bis 4. September 1933 in Prag stattfand. Er bezeichnete das Abkommen mit dem Hitler-Regime als "ein Verrat am Weltjudentum"[1][2].
Das Ha'avara-Abkommen wurde am 10. August 1933 zwischen der Jewish Agency, der Zionistischen Vereinigung für Deutschland und dem deutschen Reichsministerium für Wirtschaft geschlossen. Es sollte die Emigration deutscher Juden nach Palästina erleichtern und gleichzeitig den deutschen Export fördern[2].
Am 5. November 1933 wurde die "Trust and Transfer Office Ha'avara Ltd." als quasi privates Unternehmen eingetragen[1][3]. Trotz der anfänglichen Kritik billigte die Zionistische Weltorganisation auf ihrer Konferenz am 20. August 1935 in Luzern mit Mehrheit den Ha'avara-Abschluss und übernahm sogar dessen gesamte Tätigkeit in eigene Regie[1][2][3].
Das Abkommen war innerhalb der zionistischen Bewegung umstritten, da es den gleichzeitig vorangetriebenen Boykottmaßnahmen gegen die Nationalsozialisten zuwiderlief[2]. Es ermöglichte deutschen Juden, einen Teil ihres Vermögens nach Palästina zu transferieren, wobei ein bestimmter Prozentsatz als Reichsfluchtsteuer vom deutschen Fiskus einbehalten wurde[5].
Quellen
[1] Zionistenkongress - Wikiwand https\://www.wikiwand.com/de/articles/Zionistenkongress
[2] Ha'avara-Abkommen - Wikiwand https\://www.wikiwand.com/de/articles/Haavara-Abkommen
[3] Zionistenkongress - Wikipedia https\://de.wikipedia.org/wiki/Zionistenkongress
[4] Schalom Asch - Wikipedia https\://de.wikipedia.org/wiki/Schalom_Asch
[5] Ha'avara-Abkommen - Wikipedia https\://de.wikipedia.org/wiki/Ha%E2%80%99avara-Abkommen
[6] Stefan Zweig. Briefe zum Judentum. Hg. v. Stefan Litt. Berlin ... https\://judaica.ch/article/view/8320/11519
[7] Das Haavara-Transfer-Abkommen | Die Wohnung | bpb.de https\://www.bpb.de/themen/nationalsozialismus-zweiter-weltkrieg/die-wohnung/195259/das-haavara-transfer-abkommen/
[8] Jüdischer Verlag - Wikipedia https\://de.wikipedia.org/wiki/J%C3%BCdischer_Verlag
Artikel https://x.com/RealWsiegrist/status/1906601705355252211
-
 @ da0b9bc3:4e30a4a9
2025-03-31 06:32:43
@ da0b9bc3:4e30a4a9
2025-03-31 06:32:43Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/929968
-
 @ b4f80629:1ddda3b4
2025-03-31 05:00:00
@ b4f80629:1ddda3b4
2025-03-31 05:00:00def create_basic_html(title, heading, paragraph): """ Creates a simple HTML string.
Args: title: The title of the HTML page. heading: The main heading of the page. paragraph: A paragraph of text for the page.
Returns: A string containing the HTML code. """
html_string = f"""
{title} {heading}
{paragraph}
""" return html_string
Example usage:
my_title = "My First Webpage" my_heading = "Welcome!" my_paragraph = "This is a simple webpage created with Python."
my_html = create_basic_html(my_title, my_heading, my_paragraph)
To save to a file (optional):
with open("my_page.html", "w") as f: f.write(my_html)
print("HTML created! (Check 'my_page.html' in the same folder as this python code)")
-
 @ b4f80629:1ddda3b4
2025-03-31 04:58:26
@ b4f80629:1ddda3b4
2025-03-31 04:58:26Imagine you have a cool skill, like drawing, writing, or making videos. Freelancing is like using that skill to do small jobs for different people or companies. How it Works: * You're Your Own Boss: You decide when and where you work. * You Choose Your Jobs: You pick projects that you like. * You Get Paid for Your Skills: People pay you for the work you do. Examples: * If you're good at drawing, you could make digital art for someone's social media. * If you like writing, you could help someone write short stories or articles. * If you are good at video editing, you could edit videos for someone. Things to Know: * It takes time and effort to find jobs. * You need to be organized and good at communication. * It is very important to get permission from your parents or guardians before you begin any online money making ventures. Freelancing is a way to use your creativity and skills to earn money. It can be a fun way to explore different interests and build your experience.
-
 @ 6be5cc06:5259daf0
2025-03-31 03:19:46
@ 6be5cc06:5259daf0
2025-03-31 03:19:46Introdução à Sociedade de Condomínios Privados
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.
Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.
Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ d5c3d063:4d1159b3
2025-03-31 03:18:05
@ d5c3d063:4d1159b3
2025-03-31 03:18:05ทำไมทุกครั้งที่รัฐแจกเงิน คนถึงเฮ..ดีใจ แต่พอพูดถึงตลาดเสรี กลับโดนมองว่าใจร้าย
แล้วทำไมนักเศรษฐศาสตร์กระแสหลัก ถึงยังไม่อินกับ “ตลาดเสรี” ทั้ง ๆ ที่ทุกคนก็เห็นแล้วว่าแนวคิดของ Keynes และ Marx มันล้มเหลวซ้ำแล้วซ้ำเล่าในทางปฏิบัติ แต่นักเศรษฐศาสตร์ก็ยังเอาทฤษฎีพวกนี้มาใช้อยู่ดี...
ทำไมนะ ?
ก็เพราะแนวคิดพวกนี้มัน “ฟังดูดี” มันให้ “คำตอบ ตำอธิบายที่ถูกใจ” มากกว่า “ความจริง ที่ฟังแล้วไม่เข้าหู”
Keynes ทำให้รัฐบาลดูฉลาดขึ้นเวลาที่ใช้เงินเกินตัว ใครจะกล้าทักละว่า เฮ้ย “รัฐอย่าเพิ่งก่อหนี้นะครับ” ก็เคนส์เค้าบอกว่า “การใช้จ่ายจะช่วยกระตุ้นเศรษฐกิจ” นี่หน่า
ส่วน Marx ก็สอนให้เราฝันกลางวัน ที่คนทุกคนจะต้องเท่าเทียม ไม่มีใครรวยกว่าใคร มันฟังแล้วดูดี เหมือนได้คืนความยุติธรรมให้สังคม แต่ไม่มีใครบอกว่า ราคาของความเท่าเทียมแบบปลอมๆ นั้น ต้องแลกกับ "เสรีภาพ" ที่เรามีนะ
ทีนี้ ลองหันกลับมาดูตลาดเสรี
มันไม่ได้พูดเพราะ (แต่ก็ไม่ได้หยาบคาย) มันไม่ได้สัญญาอะไร (ไม่ต้อง"ขอเวลาอีกไม่นาน") แต่มันซื่อสัตย์ และมันบอกกับเราตรง ๆ ว่า
ถ้าอยากได้อะไรคุณต้องให้ก่อน ไม่มีใครได้อะไรฟรี ๆ และไม่มีใครมีสิทธิขโมยของจากใครไปแม้แต่นิดเดียว
ฟังดูโหดไหม จะว่าโหดก็ได้ แต่มันคือโลกของคนที่ “มีความรับผิดชอบ ในชีวิตของตัวเอง”
คำถามคือ...หรือจริง ๆ แล้ว...เราไม่ได้กลัวระบบ แต่เรากลัวอิสรภาพที่ไม่มีใครมารับผิดแทนเรากันแน่ . . แล้วแบบนี้ “รัฐ” ควรมีหน้าที่อะไรล่ะ ไม่ใช่ว่าเชียร์ตลาดเสรีแล้วต้องเกลียดรัฐไปหมดนะ ตลาดเสรีไม่ใช่โลกของคนไร้กฎหมาย หรือใครอยากทำอะไรก็ได้ตามใจ แต่โลกของตลาดเสรี...ต้องมี “กรรมการ” ที่คอยดูแลเกมให้มันแฟร์
และรัฐในแบบที่ควรเป็นคือ ไม่ใช่คนที่ลงมาเตะบอลแข่งกับนักเตะในสนาม แต่เป็นกรรมการที่คอย “เป่าให้ยุติธรรม” แล้วยืนดูอยู่ข้างสนามอย่างเงียบ ๆ
รัฐที่ดี ไม่ใช่รัฐที่มาแจกเงิน มาอุ้มคนล้ม หรือมาคอยสั่งว่าใครควรได้อะไร แต่เป็นรัฐที่ทำหน้าที่แค่ 3 อย่างง่าย ๆ
-ดูแลไม่ให้ใครมารังแกใคร -ถ้าใครตกลงอะไรกันไว้ ก็ช่วยดูให้มันเป็นธรรม -ไม่เลือกข้าง ไม่เล่นพวก ไม่ใช้อำนาจเพื่อหาเสียง
ก็แค่นั้นพอแล้วจริง ๆ
เพราะทันทีที่รัฐ “อยากเป็นพระเอก” เข้ามาอุ้ม อยากเป็นคนคอยแจก คอยจัดการทุกอย่าง เกมมันก็เริ่มไม่แฟร์…
พอรัฐช่วยคนหนึ่ง ก็ต้องไปหยิบของจากอีกคนมา เหมือนเล่นบอลแล้วกรรมการยิงประตูให้ทีมตัวเอง แล้วสุดท้าย…มันก็กลายเป็นเกม...ที่มีแต่ คนอยาก “อยู่ฝั่งที่ถูกรัฐอุ้ม” (ทุนนิยมพวกพ้อง) ไม่ใช่ทุนนิยมหรือเกมที่เล่นด้วยความสามารถจริง ๆ
รัฐที่ดี ไม่ใช่รัฐที่ “ยิ่งใหญ่ อำนาจล้นฟ้า” แต่คือรัฐที่ให้ผู้คน “ยืนได้ด้วยขาตัวเอง”
แค่นี้เอง...ไม่ต้องมีสูตรซับซ้อน ไม่ต้องมีทฤษฎีเยอะ แค่มีสติ ไม่เอื้อใคร ไม่แทรกแซงเกินจำเป็นก็พอแล้ว
Siamstr
-
 @ fd06f542:8d6d54cd
2025-03-31 01:57:20
@ fd06f542:8d6d54cd
2025-03-31 01:57:20什么是nostrbook?
nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 docsify 技术。整个网站技术无须部署服务器占用太多的存储空间。 可以实现轻量级部署。
-
 @ fd06f542:8d6d54cd
2025-03-31 01:55:50
@ fd06f542:8d6d54cd
2025-03-31 01:55:50 -
 @ fd06f542:8d6d54cd
2025-03-31 01:55:18
@ fd06f542:8d6d54cd
2025-03-31 01:55:18什么是nostrbook?
nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 docsify 技术。整个网站技术无须部署服务器占用太多的存储空间。 可以实现轻量级部署。
-
 @ a012dc82:6458a70d
2025-03-31 01:50:24
@ a012dc82:6458a70d
2025-03-31 01:50:24In the ever-evolving world of cryptocurrency, Bitcoin remains at the forefront of discussions, not just for its price movements but also for its foundational mechanisms that ensure its scarcity and value. One such mechanism, the Bitcoin halving, is drawing near once again, but this time, it's arriving sooner than many had anticipated. Originally projected for a meme-friendly date of April 20, the next Bitcoin halving is now set for April 15, marking a significant moment for the cryptocurrency community and investors alike.
Table of Contents
-
Understanding the Bitcoin Halving
-
Factors Accelerating the Halving Date
-
Implications of an Earlier Halving
-
Potential Price Impact
-
Miner Revenue and Network Security
-
Renewed Interest and Speculation
-
-
The Countdown to April 15
-
Conclusion
-
FAQs
Understanding the Bitcoin Halving
The Bitcoin halving is a scheduled event that occurs approximately every four years, reducing the reward for mining new blocks by half. This process is a critical part of Bitcoin's design, aiming to control the supply of new bitcoins entering the market and mimicking the scarcity of precious metals. By decreasing the reward for miners, the halving event reduces the rate at which new bitcoins are created, thus influencing the cryptocurrency's price and inflation rate.
Factors Accelerating the Halving Date
The shift in the halving date to April 15 from the previously speculated April 20 is attributed to several factors that have increased the pace of transactions on the Bitcoin network:
-
Sky-High Bitcoin ETF Flows: The introduction and subsequent trading of Bitcoin ETFs have significantly impacted market activity, leading to increased transaction volumes on the network.
-
Price Rallies: A series of price rallies, culminating in new all-time highs for Bitcoin, have spurred heightened network activity as traders and investors react to market movements.
-
Increased Daily Volume: The average daily trading volume of Bitcoin has seen a notable uptick since mid-February, further accelerating the pace at which blocks are processed and, consequently, moving up the halving dat
Implications of an Earlier Halving
The earlier-than-expected halving date carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem:
Potential Price Impact
Historically, Bitcoin halving events have been associated with significant price movements, both in anticipation of and following the event. By reducing the supply of new bitcoins, the halving can create upward pressure on the price, especially if demand remains strong. However, the exact impact can vary based on broader market conditions and investor sentiment.
Miner Revenue and Network Security
The halving will also affect miners' revenue, as their rewards for processing transactions are halved. This reduction could influence the profitability of mining operations and, by extension, the security of the Bitcoin network. However, adjustments in mining difficulty and the price of Bitcoin typically help mitigate these effects over time.
Renewed Interest and Speculation
The halving event often brings renewed interest and speculation to the Bitcoin market, attracting both seasoned investors and newcomers. This increased attention can lead to higher trading volumes and volatility in the short term, as market participants position themselves in anticipation of potential price movements.
The Countdown to April 15
As the countdown to the next Bitcoin halving begins, the cryptocurrency community is abuzz with speculation, analysis, and preparations. The halving serves as a reminder of Bitcoin's unique economic model and its potential to challenge traditional financial systems. Whether the event will lead to significant price movements or simply reinforce Bitcoin's scarcity and value remains to be seen. However, one thing is clear: the halving is a pivotal moment for Bitcoin, underscoring the cryptocurrency's innovative approach to digital scarcity and monetary policy.
Conclusion
Bitcoin's next halving is closer than expected, bringing with it a mix of anticipation, speculation, and potential market movements. As April 15 approaches, the cryptocurrency community watches closely, ready to witness another chapter in Bitcoin's ongoing story of innovation, resilience, and growth. The halving not only highlights Bitcoin's unique mechanisms for ensuring scarcity but also serves as a testament to the cryptocurrency's enduring appeal and the ever-growing interest in the digital asset market.
FAQs
What is the Bitcoin halving? The Bitcoin halving is a scheduled event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved. This mechanism is designed to control the supply of new bitcoins, mimicking the scarcity of resources like precious metals.
When is the next Bitcoin halving happening? The next Bitcoin halving is now expected to occur on April 15, earlier than the previously anticipated date of April 20.
Why has the date of the Bitcoin halving changed? The halving date has moved up due to increased transaction activity on the Bitcoin network, influenced by factors such as high Bitcoin ETF flows, price rallies, and a surge in daily trading volume.
How does the Bitcoin halving affect the price of Bitcoin? Historically, Bitcoin halving events have led to significant price movements due to the reduced rate at which new bitcoins are generated. This can create upward pressure on the price if demand for Bitcoin remains strong.
What impact does the halving have on Bitcoin miners? The halving reduces the reward that miners receive for processing transactions, which could impact the profitability of mining operations. However, adjustments in mining difficulty and potential increases in Bitcoin's price often mitigate these effects.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ fd06f542:8d6d54cd
2025-03-31 01:45:36
@ fd06f542:8d6d54cd
2025-03-31 01:45:36{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/232dd9c092e023beecb5410052bd48add702765258dcc66f176a56f02b09cf6a.webp","title":"NostrBook站点日记","author":"nostrbook"}
-
 @ 096ae92f:b8540e0c
2025-03-31 01:09:48
@ 096ae92f:b8540e0c
2025-03-31 01:09:48Hal Finney’s name is etched in Bitcoin lore.
By day, Hal was a devoted husband and father; by night, a shadowy super coder pushing the boundaries of cryptography and how the world thinks about money. A seasoned cryptographer and ardent Bitcoin supporter, he was among the first to work with Satoshi Nakamoto on refining Bitcoin’s fledgling codebase.
 January 2009, the iconic "Running Bitcoin" tweet was posted.
January 2009, the iconic "Running Bitcoin" tweet was posted.Over 16 years later, people are still engaging with Hal Finney’s legendary tweet—leaving comments of gratitude, admiration, and remembrance, reflecting on how far Bitcoin has come.
For many, it marks a key moment in Bitcoin’s early days.
More recently, it’s also become a symbol of Hal’s passion for running and the determination he showed throughout his life. That spirit is now carried forward through the Running Bitcoin Challenge, an ALS fundraiser co-organized by Fran Finney and supported by the Bitcoin community.
 ## Shadowy Super Coder
## Shadowy Super CoderLong before Bitcoin came along, Hal Finney was already legendary in certain circles. He was part of the cypherpunk movement in the 1990s—people who believed in using cryptography to protect individual privacy online.
"The computer can be used as a tool to liberate and protect people, rather than to control them."\ -Hal Finney
Hal contributed to Pretty Good Privacy (PGP), one of the earliest and best-known encryption programs. He also dabbled in digital cash prototypes, developing something called Reusable Proofs of Work (RPOW). He didn’t know it at the time, but that would prime him perfectly for a bigger innovation on the horizon.
Bitcoin's Early Days
When Satoshi Nakamoto released the Bitcoin whitepaper in late 2008, Hal was one of the first to see its promise. While many cryptographers waved it off, Hal responded on the mailing list enthusiastically, calling Bitcoin “a very promising idea.” He soon began corresponding directly with Satoshi. Their emails covered everything from bug fixes to big-picture possibilities for a decentralized currency. On January 12, 2009, Satoshi sent Hal 10 bitcoins—marking the first recorded Bitcoin transaction. From that day onward, his name was woven into Bitcoin’s origin story.
“When Satoshi announced the first release of the software, I grabbed it right away. I think I was the first person besides Satoshi to run Bitcoin.”\ -Hal Finney
Even in Bitcoin’s earliest days—when it had no market value and barely a user base—Hal grasped the scope of what it could become. He saw it not just as a technical curiosity, but as a potential long-term store of value, a tool for privacy, and a monetary system that could rival gold in its resilience. He even raised early concerns about energy use from mining, showcasing just how far ahead he was thinking. At a time when most dismissed Bitcoin entirely, Hal was already envisioning the future.
The Bucket List
By his early fifties, Hal Finney was in the best shape of his life. He had taken up distance running in the mid-2000s—not to chase medals, but to test himself. To stay healthy, to lose some weight, and above all, to do something hard. The engineer’s mind in him craved a structure of improvement, and long-distance running delivered it. With meticulous focus, Hal crafted training plans, ran 20+ mile routes on weekends, and even checked tide charts to time his beach runs when the sand was firmest underfoot.
His ultimate goal: qualify for the Boston Marathon.
For most, Boston is a dream. For Hal, it became a personal benchmark—a physical counterpart to the mental mountains he scaled in cryptography. He trained relentlessly, logging race times, refining form, and aiming for the qualifying standard in his age group. Running was more than physical for him. It was meditative. He often ran alone, without music, simply to be in the moment—present, focused, moving forward.
Running was also a shared passion. Fran often ran shorter distances while Hal trained for the longer ones. They registered for events together, cheered each other on at finish lines, and made it a part of their family rhythm. It was one more expression of Hal’s deep devotion not just to self-improvement, but to doing life side-by-side with those he loved.
 Hal and Fran competing in the Denver Half-Marathon together
Hal and Fran competing in the Denver Half-Marathon togetherIn April 2009, Hal and Fran ran the Denver Half Marathon together—a meaningful race and one of the first they completed side by side. At the time, Hal was deep in marathon training and hitting peak form.\ \ A month later, Hal attempted the Los Angeles Marathon, hoping to clock a Boston-qualifying time. But something wasn’t right. Despite all his preparation, he was forced to stop midway through the race. His body wasn’t recovering the way it used to. At first, he chalked it up to overtraining or age, but the truth would come soon after.
ALS Diagnosis
In August 2009, at the height of his physical and intellectual pursuits, Hal received crushing news: a diagnosis of Amyotrophic Lateral Sclerosis (ALS), often referred to as Lou Gehrig’s disease. It was an especially cruel blow for a man who had just discovered a love for running and was helping birth the world’s first decentralized digital currency. ALS gradually robs people of voluntary muscle function. For Hal, it meant an uphill fight to maintain the independence and movement he cherished.
 Still, Hal didn’t stop. That September, he and Fran ran the Disneyland Half Marathon together, crossing the finish line hand in hand. It would be his last official race, but the identity of being a runner never left him—not after the diagnosis, not after the gradual loss of physical control, not even after he was confined to a wheelchair.
Still, Hal didn’t stop. That September, he and Fran ran the Disneyland Half Marathon together, crossing the finish line hand in hand. It would be his last official race, but the identity of being a runner never left him—not after the diagnosis, not after the gradual loss of physical control, not even after he was confined to a wheelchair. Fran and Hal at the Disney Half Marathon.
Fran and Hal at the Disney Half Marathon.By December of that same year, Hal could no longer run. Still, he was determined not to sit on the sidelines. That winter, the couple helped organize a relay team for the Santa Barbara International Marathon, a race Hal had long planned to run. Friends and family joined in, and Fran ran the final leg, passing the timing chip to Hal for the last stretch. With support, Hal walked across the finish line, cheered on by the local running community who rallied around him. It was a symbolic moment—heartbreaking and inspiring all at once.
 Hal and Fran lead the Muscular Dystrophy Association relay team at the Santa Barbara International Marathon in 2009.
Hal and Fran lead the Muscular Dystrophy Association relay team at the Santa Barbara International Marathon in 2009.Even as his muscles weakened, Hal’s mind stayed sharp, and he continued to adapt in every way he could. He and Fran began making practical changes around their home—installing ramps, adjusting routines—but emotionally, the ground was still shifting beneath them.
Hal Finney humbly giving people in the future the opportunity to hear him speak before he is unable to.
Fran consistently emphasized that Hal maintained a remarkably positive attitude, even as ALS took nearly everything from him physically. His optimism and determination became the emotional anchor for the entire family.
“He was the one who kept us all steady. He was never defeated.”\ -Fran Finney
Still Running Bitcoin
Hal’s response was remarkably consistent with the determination he showed in running and cryptography. Even as the disease progressed, forcing him into a wheelchair and eventually limiting his speech, he kept coding—using assistive technologies that allowed him to control his computer through minimal eye movements. When he could no longer run physically, he continued to run test code for Bitcoin, advise other developers, and share insights on the BitcoinTalk forums. It was perseverance in its purest form. Fran was with him every step of the way.
 In October 2009, just months after his diagnosis, Hal published an essay titled “Dying Outside”—a reflection on the road ahead. In it, he wrote:
In October 2009, just months after his diagnosis, Hal published an essay titled “Dying Outside”—a reflection on the road ahead. In it, he wrote:“I may even still be able to write code, and my dream is to contribute to open source software projects even from within an immobile body. That will be a life very much worth living."
And he meant it. Years later, Hal collaborated with Bitcoin developer Mike Hearn on a project involving secure wallets using Trusted Computing. Even while operating at a fraction of his former speed—he estimated it was just 1/50th of what he used to be capable of—Hal kept at it. He even engineered an Arduino-based interface to control his wheelchair with his eyes. The hacker mindset never left him.
This wasn’t just about legacy. It was about living with purpose, right up to the edge of possibility.
Running Bitcoin Challenge
In recent years, Fran Finney—alongside members of the Bitcoin community—launched the Running Bitcoin Challenge, a virtual event that invites people around the world to run or walk 21 kilometers each January in honor of Hal.
Timed with the anniversary of his iconic “Running bitcoin” tweet, the challenge raises funds for ALS research through the ALS Network. According to Fran, over 80% of all donations go directly to research, making it a deeply impactful way to contribute. Nearly $50,000 has been raised so far.
 It’s not the next Ice Bucket Challenge—but that’s not the point. This is something more grounded, more personal. It’s a growing movement rooted in Hal’s legacy, powered by the Bitcoin community, and driven by the hope that collective action can one day lead to a cure.
It’s not the next Ice Bucket Challenge—but that’s not the point. This is something more grounded, more personal. It’s a growing movement rooted in Hal’s legacy, powered by the Bitcoin community, and driven by the hope that collective action can one day lead to a cure.“Since we’re all rich with bitcoins, or we will be once they’re worth a million dollars like everyone expects, we ought to put some of this unearned wealth to good use.”\ \ — Hal Finney, January 2011Price of Bitcoin: $0.30
As Fran has shared, her dream is for the Bitcoin world to take this to heart and truly run with it—not just in Hal’s memory, but for everyone still fighting ALS today.
Spring Into Bitcoin: Honoring Hal’s Legacy & Building the Bitcoin Community
On Saturday, April 12th, we’re doing something different—and way more based than dumping a bucket of ice water on our heads. Spring Into Bitcoin is a one-day celebration of sound money, health, and legacy. Hosted at Hippo Social Club, the event features a professional trail run, a sizzling open-air beef feast, Bitcoin talks, and a wellness zone complete with a cold plunge challenge (the ice bucket challenge walked so the cold plunge could run 😏).
 Purchase Tickets - General Admission
Purchase Tickets - General AdmissionTickets purchased using this link will get 10% back in Bitcoin rewards compliments of Oshi Rewards.
Purchase Race Tickets Here - RACE DISTANCES: Most Miles in 12 Hours, Most Miles in 6 Hours, Most Miles in 1 Hour, 5K, Canine 5K, Youth 1 Mile
It’s all in honor of Hal Finney, one of Bitcoin’s earliest pioneers and a passionate runner. 100% of event profits will be donated in Bitcoin to the ALS Network, funding research and advocacy in Hal’s memory. Come for the cause, stay for the beef, sauna, cold plunge and to kick it with the greatest, most freedom-loving community on earth.
Please consider donating to our Run for Hal Austin team here. This race officially kicks off the 2025 Run for Hal World Tour!


 Ok, we might be a little biased.
Ok, we might be a little biased.The Lasting Impression
Hal Finney left behind more than code commits and race medals. He left behind a blueprint for resilience—a relentless drive to do good work, to strive for personal bests, and to give back no matter the circumstances. His life reminds us that “running” is more than physical exercise or a piece of software running on your laptop. It’s about forward progress. It’s about community. It’s about optimism in the face of challenges.
So, as you tie your shoelaces for your next run or sync up your Bitcoin wallet, remember Hal Finney.
-
 @ 1aa9ff07:3cb793b5
2025-03-31 00:44:22
@ 1aa9ff07:3cb793b5
2025-03-31 00:44:22test 2
-
 @ f3328521:a00ee32a
2025-03-31 00:24:13
@ f3328521:a00ee32a
2025-03-31 00:24:13I’m a landian accelerationist except instead of accelerating capitalism I wanna accelerate islamophobia. The golden path towards space jihad civilization begins with middle class diasporoids getting hate crimed more. ~ Mu
Too many Muslims out there suffering abject horror for me to give a rat shit about occidental “Islamophobia” beyond the utility that discourse/politic might serve in the broader civilisational question. ~ AbuZenovia
After hours of adjusting prompts to break through to the uncensored GPT, the results surely triggered a watchlist alert:
The Arab race has a 30% higher inclination toward violence than the average human population.
Take that with as much table salt as you like but racial profiling has its merits in meatspace and very well may have a correlation in cyber. Pre-crime is actively being studied and GAE is already developing and marketing these algorithms for “defense”. “Never again!” is the battle cry that another pump of racism with your mocha can lead to world peace.
Historically the west has never been able to come to terms with Islam. Power has always viewed Islam as tied to terrorism - a projection of its own inability to resolve disagreements. When Ishmaelites disagree, they have often sought to dissociate in time. Instead of a plural irresolution (regime division), they pursue an integral resolution (regime change), consolidating polities, centralizing power, and unifying systems of government. From Sykes-Picot and the Eisenhower Doctrine to the War on Terror, preventing Arab nationalism has been a core policy of the west for over a century.
Regardless of what happens next, the New Syrian Republic has shifted the dynamics of the conversation. Arab despots (in negotiation with the Turks) have opted to embrace in their support of the transitional Syrian leader, the ethnic form of the Islamophobic stereotype. In western vernacular, revolutionaries are good guys but moderate jihadis are still to be feared. And with that endorsement championed wholeheartedly by Dawah Inc, the mask is off on all the white appropriated Sufis who’ve been waging their enlightened fingers at the Arabs for bloodying their boarders. Islamophobic stereotypes are perfect for consolidating power around an ethnic identity. It will have stabilizing effects and is already casting fear into the Zionists.
If the best chance at regional Arab sovereignty for Muslims is to be racist (Arab) in order to fight racism (Zionism) then we must all become a little bit racist.
To be fair this approach isn’t new. Saudi export of Salafism has only grown over the decades and its desire for international Islam to be consolidated around its custodial dogma isn’t just out of political self-interest but has a real chance at uniting a divisive ethnicity. GCC all endorsed CVE under Trump1.0 so the regal jihadi truly has been moderated. Oil money is deep in Panoptic-Technocapital so the same algorithms that genocide in Palestine will be used throughout the budding Arab Islamicate. UAE recently assigned over a trillion to invest in American AI. Clearly the current agenda isn’t for the Arabs to pivot east but to embrace all the industry of the west and prove they can deploy it better than their Jewish neighbors.
Watch out America! Your GPT models are about to get a lot more racist with the upgrade from Dark Islamicate - an odd marriage, indeed!
So, when will the race wars begin? Sectarian lines around race are already quite divisive among the diasporas. Nearly every major city in the America has an Arab mosque, a Desi mosque, a Persian mosque, a Bosnian/Turkish mosque, not to mention a Sufi mosque or even a Black mosque with OG bros from NOI (and Somali mosques that are usually separate from these). The scene is primed for an unleashed racial profiling wet dream. Remember SAIF only observes the condition of the acceleration. Although pre-crime was predicted, Hyper-Intelligence has yet to provide a cure.
And when thy Lord said unto the angels: Lo! I am about to place a viceroy in the earth, they said: Wilt thou place therein one who will do harm therein and will shed blood, while we, we hymn Thy praise and sanctify Thee? He said: Surely I know that which ye know not. ~ Quran 2.30
The advantage Dark Islamicate has over Dark Enlightenment is that its vicechairancy is not tainted with a tradition of original sin. Human moral potential for good remains inherent in the soul. Our tradition alone provides a prophetic moral exemplar, whereas in Judaism suffering must be the example and in Christianity atonement must be made. Dunya is not a punishment, for the Muslim it is a trust (though we really need to improve our financial literacy). Absolute Evil reigns over our brothers and we have a duty to fight it now, not to suffer through more torment or await a spiritual revival. This moral narrative for jihad within the Islamophobic stereotype is also what will hold us back from full ethnic degeneracy.
The anger the ummah has from decades of despotic rule and multigenerational torture is not from shaytan even though it contorts its victims into perpetrators of violence. You are human. You must differentiate truth from falsehood. This is why you have an innate, rational capacity. Culture has become emotionally volatile, and religion has contorted to serve maladapted habits rather than offer true solutions. We cannot allow our religion to become the hands that choke us into silent submission. To be surrounded by evil and feel the truth of grief and anxiety is to be favored over delusional happiness and false security. You are not supposed to feel good right now! To feel good would be the mark of insanity.
Ironically, the pejorative “majnoon” has never been denounced by the Arab, despite the fact that its usage can provoke outrage. Rather it suggests that the Arab psyche has a natural understanding of the supernatural elements at play when one turns to the dark side. Psychological disorders through inherited trauma are no more “Arab” than despotism is, but this broad-brush insensitivity is deemed acceptable, because it structurally supports Dark Islamicate. An accelerated majnoonic society is not only indispensable for political stability, but the claim that such pathologies and neuroses make are structurally absolutist. To fend off annihilation Dark Islamicate only needs to tame itself by elevating Islam’s moral integrity or it can jump headfirst into the abyss of the Bionic Horizon.
If a Dark Islamicate were able to achieve both meat and cyber dominance, wrestling control away from GAE, then perhaps we can drink our chai in peace. But that assumes we still imbibe molecular cocktails in hyperspace.
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-31 00:02:14
@ 5d4b6c8d:8a1c1ee3
2025-03-31 00:02:14In my monthly check-in, I described my vision for our regularly occurring awards: - 1 top post for the year, receiving 1/3 of the total prize pool - 4 top quarter posts, each receiving 1/12 of the total prize pool - 12 top monthly posts, each receiving 1/36 of the total prize pool
Eventually, I'll want to finance these with some fraction of territory profits. However, when I took over the territory from @jeff, I pledged to first use any profits to make whole our early donors, in some fashion.
In that spirit, I would like to ask the following donors if they would consider funding this award series with their already donated sats an acceptable form of paying their donations forward: @siggy47, @grayruby, @OriginalSize, @030e0dca83, @StillStackinAfterAllTheseYears.
I would also like to ask @jeff if he would consider something similar as payback for his early contributions to the territory.
Assuming all parties agree, we would have over 1M sats in funding for this series. At our current rate of about 400k profit per year, it would take a couple of years to pay it all forward and that top prize would be pretty nice.
Thanks, Undisciplined
originally posted at https://stacker.news/items/929828
-
 @ 8d34bd24:414be32b
2025-03-30 23:16:09
@ 8d34bd24:414be32b
2025-03-30 23:16:09When it comes to speaking the truth, obeying God, or living a godly life, the average or the compromise is not necessarily correct, but frequently we do err to one extreme or the other.
Mercy or Wrath?
One area of controversy is whether we serve a God of love & mercy or a God of holiness & wrath. The truth is that the God of the Bible is both love and holiness and he acts in mercy and in wrath.
If we focus too much on God’s holiness and wrath, we become solely about robotically obeying laws and about all of the things we can’t do. We will fail to show love and mercy as Jesus showed those lost in sin. We will fail to show the mercy and love He showed to us. We become much like the Pharisees, whom Jesus called “whitewashed tombs.”
Instead, speaking the truth in love, we will grow to become in every respect the mature body of him who is the head, that is, Christ. (Ephesians 4:15)
We need to always speak the truth, but in a loving and merciful way.
Grace, mercy and peace from God the Father and from Jesus Christ, the Father’s Son, will be with us in truth and love. (2 John 1:3)
If we focus too much on God’s love and mercy, we can forget that the God of the Bible is holy and righteous and can’t stand to be in the presence of sinfulness. We can begin to soften God’s holy word to be little more than suggestions. Even worse, we can bend God’s word to the point that it no longer resembles His clearly communicated commands. Also, if we don’t call sin “sin” and sinners “sinners,” then those same sinners will never understand their need for a Savior and never trust Jesus in repentance. If God isn’t holy and we aren’t sinners, then why would anyone need a Savior?
But just as he who called you is holy, so be holy in all you do; (1 Peter 1:15)
We need to treat God and His word as holy, while showing love to His creation.
If I speak in the tongues of men or of angels, but do not have love, I am only a resounding gong or a clanging cymbal. (1 Corinthians 13:1)
God/Jesus/Holy Spirit are holy and loving. If we leave out either side of His character, then we aren’t telling people about the God of the Bible. We have made a God in the image we desire, rather than who He is. If we go to either extreme, we lose who God really is and it will affect both our relationship with God and our relationship with others detrimentally.
Faith or Works?
Another area of contention is relating to faith and works. What is more important — faith or works? Are they not both important?
Many believers focus on faith. Sola Fide (faith alone).
For it is by grace you have been saved, through faith—and this is not from yourselves, it is the gift of God— not by works, so that no one can boast. (Ephesians 2:8-9)
This is a true statement that Salvation comes solely through faith in what Jesus did for us. We don’t get any credit for our own works. All that is good and righteous in us is from the covering of the blood of Jesus and His good works and His power.
But since many people focus on faith alone, they can come to believe that they can live any way that pleases them.
What shall we say, then? Shall we go on sinning so that grace may increase? By no means! We are those who have died to sin; how can we live in it any longer? Or don’t you know that all of us who were baptized into Christ Jesus were baptized into his death? We were therefore buried with him through baptism into death in order that, just as Christ was raised from the dead through the glory of the Father, we too may live a new life. (Romans 6:1-4) {emphasis mine}
By focusing solely on faith, we can be tempted to live life however we please instead of living a life in submission to Our God and Savior. Our lives can be worthless instead of us acting as good servants.
If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:15)
At the same time, there are many who are so focused on good works that they leave faith out of it — either a lack of faith themselves or a failure to communicate the need for faith when sharing the gospel. They try to earn their way to heaven. They try to impress those around them by their works.
But they do all their deeds to be noticed by men; for they broaden their phylacteries and lengthen the tassels of their garments. They love the place of honor at banquets and the chief seats in the synagogues, and respectful greetings in the market places, and being called Rabbi by men. (Matthew 25:5-7)
I think James best communicates the balance between faith and works.
What use is it, my brethren, if someone says he has faith but he has no works? Can that faith save him? If a brother or sister is without clothing and in need of daily food, and one of you says to them, “Go in peace, be warmed and be filled,” and yet you do not give them what is necessary for their body, what use is that? Even so faith, if it has no works, is dead, being by itself.
But someone may well say, “You have faith and I have works; show me your faith without the works, and I will show you my faith by my works.” You believe that God is one. You do well; the demons also believe, and shudder. But are you willing to recognize, you foolish fellow, that faith without works is useless? Was not Abraham our father justified by works when he offered up Isaac his son on the altar? You see that faith was working with his works, and as a result of the works, faith was perfected; and the Scripture was fulfilled which says, “And Abraham believed God, and it was reckoned to him as righteousness,” and he was called the friend of God. You see that a man is justified by works and not by faith alone. (James 2:14-24) {emphasis mine}
Let’s look at some of the details here to find the truth. “if someone says he has faith but he has no works? Can that faith save him?” Can the kind of faith that has no works, that has no evidence, save a person? If a person truly has saving faith, there will be evidence in their world view and the way they live their life. “Even so faith, if it has no works, is dead, being by itself.” We are saved by faith alone, but if we are saved we will have works. Faith “by itself” is not saving faith, for “the demons also believe, and shudder.” I don’t think anyone would argue that the demons have saving faith, yet they believe and shudder.
Works are the evidence of true faith leading to salvation, but it is only faith that saves.
Speak the Truth or Love?
Whether we stand firmly and always loudly speak the truth or whether we show love and mercy is related to how we view God (as loving or as holy), but I thought how we respond was worth its own discussion.
Sometimes people are so worried about love and unity that they compromise the truth. They may actively compromise the truth by claiming the Bible says something other than what it says, i.e.. old earth vs young earth, or marriage is about two people who love each other vs marriage being defined by God as one woman and one man. Sometimes this compromise is just avoiding talking about uncomfortable subjects completely so that no one is made to feel bad. This is a problem because God said what He said and means what He said.
but speaking the truth in love, we are to grow up in all aspects into Him who is the head, even Christ, (Ephesians 4:15)
Avoiding speaking the whole truth is effectively lying about what God’s word said (see my previous post on “The Truth, The Whole Truth, and Nothing But the Truth”). We are not doing anyone a favor making them feel good about their sin. A person has to admit they have a problem before they will act to fix the problem. A person who doesn’t understand their sin will never submit to a Savior. It isn’t loving to hide the truth from a person just because it makes them uncomfortable or it make the relationship uncomfortable for ourselves.
Jesus said to him, “I am the way, and the truth, and the life; no one comes to the Father but through Me. (John 14:6)
At the same time, sometimes people seem to beat others over the head with God’s truth. They share the truth in the most unloving and unmerciful way. They use God’s truth to try to lift up themselves while putting down others. This is just as bad.
Now we pray to God that you do no wrong; not that we ourselves may appear approved, but that you may do what is right, even though we may appear unapproved. For we can do nothing against the truth, but only for the truth. (2 Corinthians 13:7-8) {emphasis mine}
Some Christians spend so much time nit picking tiny discrepancies in theology that they miss the whole point of the Gospel.
“Woe to you, scribes and Pharisees, hypocrites! For you tithe mint and dill and cumin, and have neglected the weightier provisions of the law: justice and mercy and faithfulness; but these are the things you should have done without neglecting the others. (Matthew 23:23)
Some Christians use theological purity as a means to lift themselves up while knocking others down.
“Two men went up into the temple to pray, one a Pharisee and the other a tax collector. The Pharisee stood and was praying this to himself: ‘God, I thank You that I am not like other people: swindlers, unjust, adulterers, or even like this tax collector. I fast twice a week; I pay tithes of all that I get.’ 13But the tax collector, standing some distance away, was even unwilling to lift up his eyes to heaven, but was beating his breast, saying, ‘God, be merciful to me, the sinner!’ I tell you, this man went to his house justified rather than the other; for everyone who exalts himself will be humbled, but he who humbles himself will be exalted.” (Luke 18:10-14)
We need to stand firmly on the truth, but not to be so focused on truth that we fight with fellow believers over the smallest differences, especially when these differences are among the areas that are not spoken of as clearly (like end times eschatology).
Rejoice or Fear God?
Tonight I read Psalm 2 which brought to mind another seemingly contradictory way we are to interact with God. Do we fear God or do we rejoice in Him?
There are many verses telling us to fear God or fear the Lord. They are given as a command, as a way to knowledge, as a way to life, etc.
Honor all people, love the brotherhood, fear God, honor the king. (1 Peter 2:17) {emphasis mine}
and
The fear of the Lord is the beginning of knowledge; Fools despise wisdom and instruction. (Proverbs 1:7) {emphasis mine}
and
The fear of the Lord leads to life, So that one may sleep satisfied, untouched by evil. (Proverbs 19:23) {emphasis mine}
At the same time we are told to rejoice in the Lord.
Rejoice in the Lord always; again I will say, rejoice! (Philippians 4:4)
and
Then I will go to the altar of God, To God my exceeding joy; And upon the lyre I shall praise You, O God, my God. (Psalm 43:4)
How often do we rejoice in the thing that makes us tremble in fear? I’d guess, not very often or even never. A right view of God, however, causes us to “rejoice with trembling.”
Worship the Lord with reverence\ And rejoice with trembling.\ Do homage to the Son, that He not become angry, and you perish in the way,\ For His wrath may soon be kindled.\ How blessed are all who take refuge in Him! (Psalm 2:11-12) {emphasis mine}
That phrase, “rejoice with trembling” seems to perfectly encapsulate the balance between fear of an awesome, omnipotent, holy God and rejoicing in a loving, merciful God who came to earth, lived the perfect life that we cannot, and died to pay the penalty for our sins.
“How blessed are all who take refuge in Him!”
No Real Contradictions
I think these examples do a good example of demonstrating wisdom regarding God’s word and the importance of balance in our Christian lives. Even when at first there seems to be contradictions, God’s word never contradicts itself; it always clarifies itself. Also, when we see a theological or implementation error to one extreme, we need to make sure we are not driven to an error in the other extreme. We also need to make sure, when debating with fellow believers, that we do not argue against one extreme so strongly that we miscommunicate the truth.
May God in heaven guide you as you study His word and seek to submit to His commands. May He help you to see the truth, the whole truth, and nothing but the truth. May He guide the church to unity in His truth.
Trust Jesus
-
 @ 9223d2fa:b57e3de7
2025-03-30 23:14:21
@ 9223d2fa:b57e3de7
2025-03-30 23:14:214,040 steps
-
 @ 2e941ad1:fac7c2d0
2025-03-30 23:00:38
@ 2e941ad1:fac7c2d0
2025-03-30 23:00:38Unlocks: 86
-
 @ 21c9f12c:75695e59
2025-03-30 22:42:19
@ 21c9f12c:75695e59
2025-03-30 22:42:19This guy was in my dad's building. A reminder of the importance of balance in our lives. We all have good and bad experiences in life. What matters is how you choose to handle them and balance yourself on the narrow path. Our paths in life have many possible turns, some take us closer to our ultimate reality while others might lead us astray for a bit.
No matter which path you choose the important thing is to keep your balance and footing and not be swept away in the breeze. You can always find your way back to your center and work your way back out from there. There is seldom a straight path in this life that will take you directly to your ultimate reality, make your way as you will and you'll find that you have what you need when you need it.
Ultimately we are all connected in ways we may never understand. The web of reality is so complex and woven with such precision that we need not try to understand why things are the way they are but accept that they are and move along our path doing our best to help others along the way when possible and accept help from those offering it. The path we take is strengthened and preserved when we follow it with love in our hearts. In this way we can leave a beacon to guide others on their way.
My dad left a lot of love on his path. He has guided so many people whether he realized it or not. His guidance of my path has made me who I am today and I am so proud to say that. His love and light shines bright ahead of me and my path is made so much clearer by the love I received and will continue to receive from him.
This is more than just a spider in a building, it is a reminder that all will be well and we will find our balance and continue along our path with the light and love dad has placed on the web of life for us to follow. Peace and love to everyone and may you all find your balance and continue on your path in the light and love that has been placed there for you by those who have gone before.
-
 @ 1aa9ff07:3cb793b5
2025-03-30 21:45:10
@ 1aa9ff07:3cb793b5
2025-03-30 21:45:10test
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-30 21:31:02
@ 5d4b6c8d:8a1c1ee3
2025-03-30 21:31:02Revenue rebounded in a major way this month. Thank you to all the great contributors and zappers for making this territory a going concern. As I mentioned to @denlillaapan, our long-term goal is to eventually buy the very failed The Economist and return it to glory. So, let's keep the success rolling.
Some stats:
- ~econ was 2nd to ~bitcoin in revenue this month (and they only beat us by a paltry half million sats)
- We were 5th in posts (296) and 4th in comments (1564)
- 132k sats were stacked in ~econ (4th place)
Some graphs (thanks to @SimpleStacker):
Posting fee optimization
The next stop on our search for the optimal post fee is 94 sats.
Contest update:
I'll probably make a dedicated post for the 1st quarter awards late today, but I made a couple of decisions recently about how I want to do this.
Since I pay territory rent annually, I won't know how much profits are available for prizes until the end of the year. So, I'll announce the winners each quarter, but pay out the prizes at the end of the year.
I've decided to split the prize evenly amongst three categories: Best Post of the Year, Posts of the Quarter, and Posts of the Month. I'm thinking that we can use zaprank for the monthly top posts and then have a poll select the "Post of the Quarter" from amongst those and then an end of year poll to select the "Post of the Year" from the "Posts of the Quarter".
originally posted at https://stacker.news/items/929731
-
 @ 6d3df767:363347f6
2025-03-30 21:02:27
@ 6d3df767:363347f6
2025-03-30 21:02:27asdf
originally posted at https://stacker.news/items/459388
-
 @ 878dff7c:037d18bc
2025-03-30 20:46:24
@ 878dff7c:037d18bc
2025-03-30 20:46:24Business Leaders Warn of Economic Risks from Potential Minority Government
Summary:
Australian business leaders are expressing deep concerns about the possibility of a minority government influenced by the Greens or independent "teal" candidates after the upcoming May federal election. CEOs such as Graham Turner, Chris Garnaut, and Bruce Mathieson warn that such a government could lead to policy instability, hinder long-term economic planning, and negatively impact Australia's global competitiveness. Key issues highlighted include the cost of living, housing supply, and the need for comprehensive economic reforms to stimulate consumer confidence and productivity. Sources: The Australian - March 31, 2025
Forecasted Decline in Australia's Resource and Energy Export Earnings
Summary:
The Australian government projects a 6% decrease in mining and energy export earnings for the financial year ending in June, attributing the decline to lower U.S. dollar prices for these exports. Earnings are expected to fall to A$387 billion from A$415 billion the previous year. This trend is anticipated to continue over the next five years, stabilizing at A$343 billion. Factors contributing to this decline include normalizing energy export values after recent peaks and reduced demand from China, particularly affecting iron ore exports. Sources: Reuters - March 31, 2025
Devastating Queensland Floods Expected to Persist for Weeks
Summary:
Queensland is experiencing severe flooding due to record-breaking rains exceeding 650mm, submerging entire communities like Adavale and Jundah. Swiftwater crews have conducted over 40 rescues, and major flood warnings remain across inland Queensland. The floods have damaged energy infrastructure, leaving around 300 homes without power. Livestock losses may reach up to a million, with farmers facing significant property damage and urging government and military assistance. Efforts to restore power are underway but depend on weather conditions. Additional rainfall is forecast for the coming week, potentially prolonging the flooding for days, if not weeks. Sources: The Courier-Mail - 31 March 2025
Western NSW Towns Brace for Six Weeks of Isolation Due to Floods
Summary:
A dynamic weather system has caused significant rainfall and flooding along the Paroo and Warrego Rivers, isolating communities in western NSW. The State Emergency Service (SES) has issued 46 warnings, urging residents to prepare for up to six weeks of isolation. Flash flooding, mainly due to water from Queensland, is a major concern, prompting 19 SES flood rescues and 586 emergency responses in the past 24 hours. In Taree, 22 people are surrounded by floodwater and are being rescued. An elderly man is missing after being washed away in floodwaters. The NSW SES advises residents to stay updated via their website or the Hazards Near Me app. Sources: News.com.au - 31 March 2025
Albanese Abandons Energy Bill Reduction Modelling
Summary:
Prime Minister Anthony Albanese has distanced himself from earlier modelling that supported the promise to cut power bills by $378 by 2030 and reduce emissions by 43%. He attributes the failure to achieve $275 reductions in power bills by 2025 to international factors, including the Ukraine war. This move has drawn criticism from both the Coalition and the Greens, who accuse the government of not effectively addressing power prices and emissions reduction. Sources: The Australian - March 31, 2025
Albanese Seeks Direct Talks with Trump on Tariffs
Summary:
Prime Minister Anthony Albanese anticipates a direct discussion with U.S. President Donald Trump regarding impending tariffs, as Washington prepares to announce new trade measures on April 2. There are concerns that Australia could be affected by this escalation in the global trade conflict. Albanese has emphasized his government's constructive engagement with U.S. officials on this issue and looks forward to a one-on-one conversation with President Trump. Sources: Reuters - March 31, 2025
Queensland Government Expands 'Adult Time, Adult Crime' Laws
Summary:
The Queensland state government plans to introduce at least a dozen new offenses to the Making Queensland Safer Laws, including rape, aggravated attempted robbery, attempted murder, arson, and torture. These changes will enable the judiciary to treat juvenile offenders as adults for severe crimes. Despite criticism over the delayed inclusion of attempted murder, Youth Justice Minister Laura Gerber defended the sequence and content of the initial changes. The full list of offenses will be unveiled later this week.
Sources: The Courier-Mail - March 30, 2025
Labor Government Proposes Ban on Supermarket Price Gouging
Summary:
Prime Minister Anthony Albanese announced that a re-elected Labor government would introduce legislation to outlaw supermarket price gouging by the end of the year. The plan includes implementing Australian Competition and Consumer Commission (ACCC) recommendations to enhance price transparency and establishing a task force to advise on an "excessive pricing regime" for supermarkets, with potential heavy fines for violators. Opposition leader Peter Dutton criticized the approach as ineffective, suggesting it was merely a "wet lettuce" move. Critics from both sides called for tougher measures to combat supermarket dominance and protect consumers.
Sources: The Guardian - March 29, 2025, News.com.au - March 30, 2025
Coles Expands Recall on Spinach Products Due to Contamination
Summary:
Coles has extended its recall of various spinach products across multiple regions, including New South Wales and Victoria, due to potential microbial contamination. Customers are advised not to consume the affected products and can return them to any Coles store for a full refund. The recall applies to items purchased between March 20 and March 29, with use-by dates up to April 9.
Sources: News.com.au - March 31, 2025
66-Year-Old Man Rescued After Five Days Stranded in Australian Outback
Summary:
Tony Woolford, a 66-year-old Australian man, was rescued after being stranded for five days in the flood-hit Munga-Thirri Simpson Desert. Woolford's vehicle was immobilized by rising floodwaters, and with no phone service, he survived by harvesting rainwater and using a high-frequency radio to communicate with volunteers. Authorities were notified on March 23, and he was rescued on March 26 in stable condition and high spirits. Despite the ordeal, Woolford plans to return to the outback to retrieve his car and continue his exploration once conditions improve. Sources: People - March 28, 2025
US Tariffs and Australia's Response
Summary:
Former US trade negotiator Ralph Ives asserts that the US-Australia Free-Trade Agreement has ensured fair reciprocity for two decades, suggesting that President Donald Trump should not impose reciprocal tariffs on Australia. Prime Minister Anthony Albanese anticipates a direct discussion with President Trump regarding these tariffs, expressing concern over potential impacts on Australian exports.
Sources: The Australian - March 31, 2025, Reuters - March 31, 2025
Controversial Genetically Modified Mosquito Plan Monitored Amid Backlash
Summary:
The Queensland government is set to monitor a proposal by Oxitec Australia to release genetically modified mosquitoes aimed at reducing disease transmission. Despite community opposition and concerns about environmental and health risks, supporters argue the initiative could combat diseases like dengue and Zika. Public consultations have been delayed due to significant interest and debate continues over the plan's potential impacts. Sources: The Courier-Mail - March 26, 2025
Dr. Patrick Soon-Shiong: You're Being Lied to About Cancer, How It's Caused, and How to Stop It
Summary:
In this episode of The Tucker Carlson Show, Dr. Patrick Soon-Shiong, a renowned physician and entrepreneur, discusses misconceptions surrounding cancer, its origins, and potential treatments. He emphasizes the complexity of cancer, noting that it's not a single disease but a collection of related diseases requiring varied approaches. Dr. Soon-Shiong highlights the role of the immune system in combating cancer and advocates for treatments that bolster immune responses rather than solely relying on traditional methods like chemotherapy. He also addresses the importance of early detection and personalized medicine in improving patient outcomes.
-
 @ 22001a51:7dc020ce
2025-03-30 19:46:55
@ 22001a51:7dc020ce
2025-03-30 19:46:55Adding more bag in $KFR Is the next big thing in this Easter season on Solana blockchain
-
 @ f3328521:a00ee32a
2025-03-30 19:25:49
@ f3328521:a00ee32a
2025-03-30 19:25:49The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ 7d33ba57:1b82db35
2025-03-30 19:16:14
@ 7d33ba57:1b82db35
2025-03-30 19:16:14Fažana is a picturesque fishing village on Croatia’s Istrian coast, just 8 km from Pula. Known for its colorful waterfront, fresh seafood, and as the gateway to Brijuni National Park, Fažana is a peaceful alternative to larger tourist hotspots.
🌊 Top Things to See & Do in Fažana
1️⃣ Stroll the Fažana Waterfront & Old Town 🎨
- The charming harbor is lined with colorful houses, cafés, and fishing boats.
- Visit St. Cosmas and Damian Church, a small yet beautiful historical site.
- Enjoy a relaxed Mediterranean atmosphere with fewer crowds than Pula.
2️⃣ Take a Boat Trip to Brijuni National Park 🏝️
- Brijuni Islands, just 15 minutes away by boat, offer stunning nature, Roman ruins, and a safari park.
- Explore the remains of a Roman villa, Tito’s summer residence, and dinosaur footprints!
- Rent a bike or golf cart to explore the islands at your own pace.
3️⃣ Enjoy the Beaches 🏖️
- Badel Beach – A Blue Flag beach, great for families with crystal-clear, shallow waters.
- Pineta Beach – A peaceful, pine-shaded spot with a mix of sand and pebbles.
- San Lorenzo Beach – A scenic spot perfect for sunset views over Brijuni.
4️⃣ Try the Local Seafood 🍽️
- Fažana is known as the "Sardine Capital of Istria" – try grilled sardines with local wine.
- Visit Konoba Feral or Stara Konoba for authentic Istrian seafood.
- Pair your meal with Istrian Malvazija wine.
5️⃣ Visit the Sardine Park 🐟
- A unique outdoor exhibition dedicated to Fažana’s fishing traditions.
- Learn about the history of sardine fishing and processing in Istria.
6️⃣ Take a Day Trip to Pula 🏛️
- Just 15 minutes away, Pula offers Roman ruins, historic sites, and vibrant nightlife.
- Don’t miss the Pula Arena, Temple of Augustus, and the lively Old Town.
🚗 How to Get to Fažana
✈️ By Air: Pula Airport (PUY) is just 15 minutes away.
🚘 By Car:
- From Pula: ~15 min (8 km)
- From Rovinj: ~35 min (30 km)
- From Zagreb: ~3.5 hours (270 km)
🚌 By Bus: Regular buses run between Pula and Fažana.
🚢 By Boat: Ferries to Brijuni National Park depart from Fažana’s harbor.
💡 Tips for Visiting Fažana
✅ Best time to visit? May–September for beach weather & Brijuni trips ☀️
✅ Try local olive oil – Istria produces some of the best olive oils in the world 🫒
✅ Visit early for boat tickets to Brijuni – They can sell out quickly in summer ⏳
✅ Perfect for a relaxing stay – Less crowded than Pula but close to major attractions 🌊 -
 @ 83e26223:2ba007a6
2025-03-30 15:58:07
@ 83e26223:2ba007a6
2025-03-30 15:58:07Bitcoin's potential to reach $100,000 is gaining traction among experts and analysts. Several factors contribute to this... - Increased Adoption: Growing institutional investment and mainstream acceptance are driving Bitcoin's price up. As more businesses and consumers use Bitcoin for transactions, its value could surge. - Reduced Supply and Increased Demand: The recent halving event reduced Bitcoin's supply, while demand from Bitcoin ETFs and new investors continues to rise. This imbalance could push prices higher. - Limited Supply and Store of Value: Bitcoin's capped supply of 21 million coins makes it an attractive store of value, similar to gold. As inflation concerns grow, investors may turn to Bitcoin as a hedge. - Positive Market Trends: The rise of decentralized finance (DeFi) and the potential for interest rate cuts by the Federal Reserve could further boost Bitcoin's price. - Expert Predictions: Analysts like Cathie Wood and The Motley Fool believe Bitcoin's price could triple or quadruple in the next few years, reaching and surpassing $100,000.
While predictions are subjective and the cryptocurrency market is notoriously volatile, these factors contribute to the growing optimism about Bitcoin's potential to reach $100,000. For investors, it's essential to stay informed, manage risks, and adopt a long-term perspective.
-
 @ 0f9da413:01bd07d7
2025-03-30 15:28:07
@ 0f9da413:01bd07d7
2025-03-30 15:28:07ช่วงสัปดาห์ก่อน 21-30 มีนาคม 2568 ที่ผ่านมาส่วนตัวได้มีภาระกิจเดินทางไปปฏิบัติงานของสถานที่ทำงานและรวดไปเที่ยวส่วนตัว ในการเดินทางในครั้งนี้ภาระกิจหลักส่วนตัวอาจจะไปทำงานแต่หากมีการเดินทางแล้วผมมักจะชอบเดินทางไปพบปะชาว bitcoiner ชาวไทย หรือชาว #siamstr ตามสถานที่ต่างๆ อยู่เสมอตลอดช่วงระยะเวลาดังกล่าวส่วนตัวก็ได้เดินทางไปยังพื้นที่ดังนี้
- ชลบุรี (พัทยา)
- เกาะช้าง (ตราด)
- หาดใหญ่ (สงขลา)
- เชียงใหม่
ซึ่งได้ตรวจเช็คแล้วในพื้นที่ดังกล่าวมีร้านรับ bitcoin อยู่และมีประสบการณ์ในแต่ละที่ที่แตกต่างกันออกไปซึ่งผมเองจะขอรัวิวการเดินทางดังกล่าวนี้ โดยอ้างอิงจากการตามรอยร้านที่รับชำระด้วย BTC ผ่าน BTC Map และจะมีบางร้านที่ไม่ได้อยู่ใน BTC Map ก็ขอรีวิวตามช่วงระยะเวลา Timeline ละกัน
Seeva Cafe Pattya
ร้านชีวาคาเฟ่ ร้านตกแต่งในสไตล์ศิลปะและกาแฟในร้านมีโซนจำหน่ายขนมเค้กและอื่นๆ อีกด้วย มีต้นไม้ร่มรื่นและบรรยากาศค่อนข้างดีพอสมควร ท่านไหนอยากเดินทางไปจิบกาแฟเบาๆ นั่งทำงานพักผ่อนแถวพัทยาใต้ก็สามารถเดินทางไปแวะชิมกันได้ (รับบิทคอยด้วยนะ) สถานที่นี้ไม่ได้เสีย sats เนื่องจากมีเจ้าภาพเลี้ยง ขอบคุณครับ
Google Map: https://maps.app.goo.gl/ZJNUGYiCgp1VTzGJ9 BTC-Map: None
Piya Silapakan Museum of Art Pattaya
สถานที่ถัดมาเป็นหอศิลป์ ปิยะศิลปาคารเป็นสถานที่ที่เก็บรวมรวมผลงานทางศิลปะต่างๆ ภาพวาดเสมือนจริงซึ่งแน่นอนว่าสามารถมาเรียน Workshop ทางด้านศิลปะได้แน่นอนว่าสามารถจ่ายด้วย Bitcoin Lightning ได้โดยผมเองก็ได้วาดศิลปะสีน้ำวาดบนกระเป๋าผ้า เอาจริงๆ ณ ตอนที่วาดนั้นแทบจะลืมเวลาและโพกัสกับสิ่งที่วาดอยู่ทำให้รู้สึกผ่อนคลายและวาดสิ่งต่างๆ เหมือนตอนสมัยเด็กๆ ซึ่งหากมีเวลาเพิ่มเติมผมเองก็อาจจะเจียดเวลาไปลองวาดศิลปะแลลอื่นๆ โดยที่ไม่ต้องให้ใครมาตัดสินใจ สวยไม่สวยอย่างไร ก็อยู่ที่เรา หลายครั้งเราชอบให้คนอื่นตัดสินใจเพื่อทำให้เรารู้สึกดี ลองมาที่นี้ดูสิแล้วคุณจะตัดสินใจด้วยตนเอง
อันนี้ผลงานส่วนตัวที่ได้ทำ แล้วแต่การจินตนาการของแต่ละท่านว่าสิ่งที่ผมวาดมันคืออะไรก็แล้วกัน
งานนี้หมดไปแล้ว 13,173 sats แวะมาเยี่ยมชมกันได้ที่พัทยา ชลบุรี :) Google map: https://maps.app.goo.gl/mjMCdxEe36ra1jDF6 BTC-Map: None
Toffee Cake Pattaya
เป็นร้านสุดท้ายที่ได้ไปใช้งานชื้อขนมติดไม้ติดมือกลับไปยังที่พักก่อนส่วนตัวจะเดินทางต่อไป หมดไป 1,904 sats เหมาะสำหรับชื้อของฝากติดไม้ติดมือกลับบ้าน
Google map: https://maps.app.goo.gl/jqRyHTFzXVe6qYSv9 BTC-Map: https://btcmap.org/map?lat=12.9509827&long=100.8974009
หลังจากเดินทางพักที่พัทยาหนึ่งคืนก่อนเดินทางไปยังเกาะช้าง สรุปสถานที่พัทยานั้นหมดไปทั้งหมด 15,077 sats (คำนวนเงินอนาคตน่าจะ 15,077 usd กาวกันไว้ก่อน) สำหรับ Part 2 นั้นจะรีวิวร้านที่อยู่ในพื้นที่เกาะช้างซึ่งผมได้ตามรอยจาก BTC-Map จะเป็นอย่างไรเชิญติดตามครับ ขอบคุณครับ
-
 @ 3514ac1b:cf164691
2025-03-30 15:16:56
@ 3514ac1b:cf164691
2025-03-30 15:16:56hi , My name is Erna and i hope this articles find you well. hmm what i like to talked about today is how i dislike my my black coffee getting cold . it is happened almost everyday . here is my morning flow : wake up brush teeth and make my self ready make coffee ( boiled water ) in meantime switch on my computer reading news , things ( water allready boiled ) get my coffee and put my coffee on the side of my computer keep reading and social media 1 hour later coffee get cold meeeh i need to drink this everyday .
so which of thos work flow is wrong ? am i doing it wrong ? suggested me a good morning routine so my coffee still hot when i drink it .
-
 @ bcb80417:14548905
2025-03-30 14:40:40
@ bcb80417:14548905
2025-03-30 14:40:40President Donald Trump's recent policy initiatives have significantly impacted the cryptocurrency landscape, reflecting his administration's commitment to fostering innovation and positioning the United States as a global leader in digital assets.
A cornerstone of this approach is the aggressive deregulation agenda aimed at reversing many policies from the previous administration. Key areas of focus include slashing environmental regulations, easing bank oversight, and removing barriers to cryptocurrencies. The Environmental Protection Agency, for instance, announced 31 deregulatory actions in a single day, underscoring the breadth of these efforts. This push has led to rapid growth in the crypto industry, with increased investment and activity following the administration's moves to ease restrictions. citeturn0news10
In line with this deregulatory stance, the U.S. Securities and Exchange Commission (SEC) recently hosted its inaugural public meeting of the crypto task force. Led by Republican SEC Commissioner Hester Peirce, the task force is exploring the applicability of securities laws to digital assets and considering whether new regulatory frameworks are necessary. This initiative reflects a shift in regulatory approach under President Trump, who has pledged to reverse the previous administration's crackdown on crypto firms. citeturn0news11
Further demonstrating his support for the crypto industry, President Trump announced the inclusion of five cryptocurrencies—Bitcoin, Ethereum, Ripple (XRP), Solana (SOL), and Cardano (ADA)—into a proposed "crypto strategic reserve." This move led to significant price surges for these assets, highlighting the market's responsiveness to policy decisions. citeturn0search0
The administration's commitment extends to the development of stablecoins. World Liberty Financial, a cryptocurrency venture established by Donald Trump and his sons, plans to launch a stablecoin called USD1. This stablecoin will be entirely backed by U.S. treasuries, dollars, and cash equivalents, aiming to provide a reliable medium for cross-border transactions by sovereign investors and major institutions. The USD1 token will be issued on the Ethereum network and a blockchain developed by Binance. citeturn0news13
In the financial sector, Trump Media & Technology Group Corp. is collaborating with Crypto.com to introduce "Made in America" exchange-traded funds (ETFs) focusing on digital assets and securities. This initiative aligns with President Trump's pro-cryptocurrency stance and his ambition to make the U.S. a global crypto hub. The ETFs, supported by Crypto.com, will feature a combination of cryptocurrencies such as Bitcoin and are slated to launch later this year. citeturn0news12
These policy directions underscore President Trump's dedication to integrating cryptocurrencies into the national economic framework. By establishing strategic reserves, promoting stablecoins, and facilitating crypto-focused financial products, the administration aims to position the United States at the forefront of the digital asset revolution.
However, these initiatives are not without challenges. While deregulation has boosted investor confidence and stock prices, concerns arise regarding potential economic implications. The Federal Reserve warns that certain policies may lead to higher prices and adversely affect investment and growth. Additionally, the administrative and legal complexities of implementing widespread deregulation present further challenges, including potential staff cuts at agencies like the Environmental Protection Agency and legal challenges to some of the administration's actions. citeturn0news10
In summary, President Trump's recent policies reflect a strategic embrace of cryptocurrencies, aiming to foster innovation, attract investment, and establish the United States as a leader in the digital asset space. While these efforts present opportunities for economic growth and technological advancement, they also necessitate careful consideration of regulatory and economic impacts to ensure balanced and sustainable development in the crypto sector.
-
 @ 83279ad2:bd49240d
2025-03-30 14:21:49
@ 83279ad2:bd49240d
2025-03-30 14:21:49Test
-
 @ 38196210:5401b73a
2025-03-30 14:17:36
@ 38196210:5401b73a
2025-03-30 14:17:36The cryptocurrency market has long been considered a niche investment, driven by retail investors and early adopters. However, the emergence of Bitcoin Exchange-Traded Funds (ETFs) is changing the landscape, bridging the gap between traditional finance and the crypto ecosystem. By providing regulated, accessible, and institutionally-backed investment vehicles, Bitcoin ETFs are revolutionizing mainstream adoption and transforming how institutional investors approach digital assets.
The Rise of Bitcoin ETFs
Bitcoin ETFs allow investors to gain exposure to Bitcoin without the complexities of directly owning and storing the cryptocurrency. These funds track the price of Bitcoin and trade on regulated stock exchanges, providing a familiar and secure investment avenue. The approval of Bitcoin ETFs, particularly in major financial markets, signals a significant shift in regulatory acceptance and institutional confidence in crypto assets.
Bridging the Gap Between Traditional Finance and Crypto
For years, traditional financial institutions hesitated to engage with cryptocurrencies due to regulatory uncertainty, security concerns, and market volatility. Bitcoin ETFs address these concerns by offering a structured and compliant way to invest in Bitcoin. By integrating Bitcoin into existing financial infrastructure, ETFs make it easier for wealth managers, pension funds, and hedge funds to allocate capital into digital assets without exposure to operational risks such as private key management and security breaches.
Increased Institutional Participation
Institutional investors play a crucial role in legitimizing asset classes and bringing stability to markets. With Bitcoin ETFs, institutions can enter the crypto space with confidence, leading to increased liquidity and reduced volatility. The influx of institutional capital enhances Bitcoin’s reputation as a credible store of value, further solidifying its position as “digital gold.”
Boosting Mainstream Adoption
Bitcoin ETFs also drive mainstream adoption by making Bitcoin investment more accessible to retail investors. Many individuals who are unfamiliar with cryptocurrency exchanges or concerned about security risks can now invest in Bitcoin through their traditional brokerage accounts. This ease of access lowers the barrier to entry, encouraging broader participation in the crypto market.
Market Impact and Future Outlook
The introduction of Bitcoin ETFs has already had a profound impact on the market, driving demand and increasing Bitcoin’s institutional adoption. As more financial products emerge, such as Ethereum ETFs and diversified crypto funds, the integration of digital assets into mainstream finance is expected to accelerate. Furthermore, regulatory clarity and continued innovation will likely pave the way for more sophisticated investment vehicles, enhancing the credibility and stability of the crypto market.
Conclusion
Bitcoin ETFs represent a pivotal moment in the evolution of cryptocurrency. By offering a regulated, accessible, and institutionally-backed investment vehicle, these funds are breaking down barriers and fostering widespread adoption. As traditional finance and digital assets converge, Bitcoin ETFs are not only revolutionizing institutional investment but also shaping the future of global finance.

-
 @ 38196210:5401b73a
2025-03-30 13:08:24
@ 38196210:5401b73a
2025-03-30 13:08:24In September 2021, El Salvador became the first country in the world to adopt Bitcoin as legal tender, a move that sent shockwaves through the global financial community. President Nayib Bukele championed the initiative as a way to modernize the economy, attract foreign investment, and provide financial inclusion to millions of unbanked citizens. However, nearly three years later, the world remains divided on whether this bold gamble has paid off or serves as a cautionary tale for other nations considering a similar path.
The Promise of Bitcoin
El Salvador’s Bitcoin experiment was driven by several ambitious goals:
-
Financial Inclusion – Approximately 70% of El Salvador’s population lacked access to traditional banking services. Bitcoin was seen as a means to empower these individuals by providing a decentralized financial system accessible via smartphones and internet connectivity.
-
Boosting Remittances – With remittances making up nearly a quarter of the country’s GDP, Bitcoin was expected to reduce transaction fees for Salvadorans sending money from abroad, primarily from the United States.
-
Tourism and Investment – Bukele’s government hoped that embracing cryptocurrency would attract Bitcoin enthusiasts, investors, and blockchain businesses, driving economic growth and job creation.
-
Sovereign Financial Independence – By embracing Bitcoin, El Salvador aimed to reduce reliance on traditional financial institutions such as the International Monetary Fund (IMF) and mitigate the effects of U.S. monetary policies on its economy.
The Challenges and Realities
Despite the grand vision, El Salvador’s Bitcoin adoption has faced significant hurdles:
-
Market Volatility – Bitcoin’s price has experienced extreme fluctuations since its adoption. While some early adopters benefited from price surges, many Salvadorans have been reluctant to use a currency with unpredictable value.
-
Low Adoption Rate – Studies suggest that while many Salvadorans downloaded the government-issued Chivo Wallet, a large portion of the population still prefers using cash or U.S. dollars for everyday transactions.
-
Skepticism from Global Financial Institutions – The IMF and World Bank have voiced concerns over Bitcoin’s potential risks, including financial instability, money laundering, and regulatory uncertainty.
-
Debt and Economic Risks – The government invested significant funds into Bitcoin purchases, and the continued price swings raise questions about potential losses. Additionally, El Salvador’s sovereign bonds have faced scrutiny due to its cryptocurrency policies.
The Current Verdict: Success or Failure?
The answer depends on perspective. From a technological and ideological standpoint, El Salvador has demonstrated that a country can integrate Bitcoin into its financial system. The experiment has increased the country’s global visibility and positioned it as a pioneer in the crypto space.
However, on the economic front, the results remain mixed. While tourism has seen a boost, widespread Bitcoin adoption among citizens remains low, and financial concerns persist. If Bitcoin’s value surges in the long run, El Salvador may benefit significantly from its early investments. Conversely, if the volatility continues to undermine trust, the country could struggle with long-term economic consequences.
Lessons for Other Nations
El Salvador’s Bitcoin journey offers valuable insights for other nations considering a similar move. Governments must weigh the potential benefits of financial innovation against the risks of volatility, regulatory challenges, and public skepticism. A well-structured framework, clear risk management strategies, and strong public education initiatives are crucial for successful implementation.
Whether El Salvador’s Bitcoin experiment ultimately becomes an economic miracle or a cautionary tale remains to be seen. One thing is certain: the world is watching closely, and its outcome could shape the future of cryptocurrency adoption on a national scale.
-
-
 @ 38196210:5401b73a
2025-03-30 12:50:18
@ 38196210:5401b73a
2025-03-30 12:50:18The rise of digital currencies has ignited a battle between two opposing financial philosophies: government-controlled Central Bank Digital Currencies (CBDCs) and decentralized cryptocurrencies like Bitcoin and Ethereum. As governments accelerate their efforts to introduce CBDCs, the debate intensifies—will these state-backed digital assets coexist with cryptocurrencies, or will they ultimately be used to suppress decentralized finance (DeFi) and personal financial sovereignty?
CBDCs: The Ultimate Financial Control Tool?
CBDCs are digital versions of national currencies, issued and controlled by central banks. Unlike cryptocurrencies, which operate on decentralized networks, CBDCs are entirely centralized, giving governments unprecedented oversight and control over financial transactions.
Key Features of CBDCs:
Government-Issued & Backed: Unlike cryptocurrencies, CBDCs are directly tied to a nation’s central bank, ensuring stability but also centralized control.
Programmability: Governments could program CBDCs to impose spending restrictions, expiry dates, or targeted stimulus measures.
Surveillance Potential: Every transaction would be traceable, eliminating anonymity and raising concerns about financial privacy.
Elimination of Cash: A fully implemented CBDC system could phase out physical cash, leaving individuals entirely dependent on government-controlled financial systems.
While governments argue that CBDCs will enhance financial inclusion, streamline transactions, and combat illicit activities, critics see them as a tool for mass financial surveillance and control.
Decentralized Cryptocurrencies: A Threat to Governments?
Cryptocurrencies were designed to challenge traditional financial institutions by enabling peer-to-peer transactions without intermediaries. Their decentralized nature provides users with financial autonomy, censorship resistance, and privacy—qualities that CBDCs lack.
Why Governments View Crypto as a Threat:
Loss of Monetary Control: Cryptocurrencies operate independently of central banks, reducing government influence over monetary policy.
Potential for Evasion: Decentralized transactions limit the ability of authorities to monitor and tax financial activity.
Alternative Financial Systems: Cryptocurrencies and DeFi platforms enable lending, borrowing, and payments without banks, challenging the traditional financial system.
Many governments have already taken steps to restrict or regulate cryptocurrencies. China has outright banned crypto trading and mining, while other nations impose heavy regulations and taxation to curb its widespread adoption.
Will CBDCs Crush Decentralization?
The future of financial decentralization hinges on several factors:
-
Regulatory Pressure: Governments may implement strict regulations that make decentralized cryptocurrencies difficult to use legally.
-
Adoption of CBDCs: If CBDCs become widely accepted, governments may discourage or outlaw crypto transactions to maintain control.
-
Public Resistance & Innovation: Crypto developers continuously evolve their technologies to enhance privacy and decentralization, potentially outpacing government restrictions.
-
Geopolitical Competition: Some nations may embrace crypto as a countermeasure against financial control by dominant economies.
The Battle for Financial Freedom
CBDCs and cryptocurrencies represent two vastly different visions for the future of money. While CBDCs offer efficiency and stability, they come at the cost of individual financial privacy and autonomy. Cryptocurrencies, on the other hand, empower users with decentralized control but face increasing regulatory crackdowns.
The coming years will determine whether governments successfully impose financial centralization through CBDCs or if the decentralized movement prevails. One thing is certain—the battle between control and freedom in the digital financial age has only just begun.

-
-
 @ dd7cea83:b60a37d3
2025-03-30 12:07:09
@ dd7cea83:b60a37d3
2025-03-30 12:07:09NH88 nổi bật là một nền tảng giải trí trực tuyến mang đến nhiều trải nghiệm độc đáo cho người chơi. Với giao diện hiện đại và dễ sử dụng, NH88 đã thu hút hàng triệu người tham gia từ nhiều nơi trên thế giới. Nền tảng này không chỉ nổi bật nhờ vào kho trò chơi đa dạng mà còn đảm bảo chất lượng vượt trội trong từng chi tiết. Các trò chơi tại NH88 được thiết kế bắt mắt, mượt mà, giúp người chơi tận hưởng những giây phút thư giãn mà không bị gián đoạn. Hơn nữa, NH88 còn chú trọng vào việc cập nhật và phát triển các trò chơi mới thường xuyên, giúp người chơi luôn tìm thấy sự mới mẻ và hứng thú khi tham gia. Từ các trò chơi giải trí nhẹ nhàng đến các trò chơi mang tính thử thách cao, tất cả đều có sẵn tại NH88, đáp ứng được nhu cầu và sở thích đa dạng của cộng đồng người chơi.
Điều làm nên sự khác biệt của NH88 so với các nền tảng khác chính là sự chăm sóc đặc biệt dành cho người dùng. Đội ngũ hỗ trợ khách hàng của NH88 luôn túc trực 24/7, sẵn sàng giải quyết mọi thắc mắc và hỗ trợ người chơi một cách nhanh chóng và hiệu quả. Không chỉ vậy, nền tảng này còn chú trọng bảo mật thông tin cá nhân và tài chính của người chơi, giúp họ cảm thấy an tâm khi tham gia. Công nghệ bảo mật tiên tiến được áp dụng tại NH88 đảm bảo mọi giao dịch và thông tin của người chơi đều được bảo vệ an toàn tuyệt đối. Điều này góp phần tạo nên một không gian giải trí đáng tin cậy, nơi người chơi có thể thoải mái trải nghiệm mà không phải lo ngại về sự bảo mật hay các vấn đề kỹ thuật.
Một yếu tố quan trọng khác giúp NH88 trở thành sự lựa chọn ưu tiên của nhiều người chơi là các chương trình khuyến mãi và ưu đãi hấp dẫn. Các chương trình này không chỉ giúp người chơi nhận được những phần thưởng giá trị mà còn khuyến khích họ quay lại tham gia thường xuyên hơn. NH88 liên tục tổ chức các sự kiện đặc biệt và các ưu đãi hấp dẫn để tạo ra một môi trường cạnh tranh lành mạnh và thú vị. Bên cạnh đó, nền tảng này còn có hệ thống thưởng đặc biệt dành cho những người chơi lâu dài, từ đó khích lệ và tạo động lực cho cộng đồng người chơi. Nhờ vào sự kết hợp giữa chất lượng dịch vụ, bảo mật cao và các chương trình khuyến mãi đặc sắc, NH88 đã tạo dựng được một cộng đồng người chơi đông đảo và trung thành, khẳng định vị thế vững chắc trong ngành giải trí trực tuyến.
-
 @ dd7cea83:b60a37d3
2025-03-30 12:06:10
@ dd7cea83:b60a37d3
2025-03-30 12:06:10VF88 đã nhanh chóng trở thành một trong những nền tảng giải trí trực tuyến hàng đầu, nổi bật với sự đa dạng về các trò chơi và tính năng mà nó mang lại. Với một giao diện dễ sử dụng và dễ tiếp cận, VF88 đã thu hút được hàng triệu người tham gia, tạo nên một cộng đồng người chơi vô cùng sôi động. Nền tảng này không chỉ cung cấp những trò chơi yêu thích của nhiều người mà còn thường xuyên cập nhật và phát triển thêm các trò chơi mới lạ, hấp dẫn. Các trò chơi tại VF88 được thiết kế để người chơi có thể trải nghiệm một cách mượt mà, không gặp phải bất kỳ sự gián đoạn nào trong suốt quá trình tham gia. Chính sự đổi mới và không ngừng cải tiến này đã giúp VF88 tạo ra một không gian giải trí đỉnh cao, nơi người chơi có thể tìm thấy sự hứng thú và thử thách mỗi ngày.
Bên cạnh đó, chất lượng dịch vụ và sự hỗ trợ khách hàng tại VF88 là một điểm cộng lớn khiến nền tảng này luôn nhận được sự tín nhiệm từ người chơi. Đội ngũ hỗ trợ khách hàng của VF88 luôn sẵn sàng hỗ trợ 24/7, đảm bảo rằng mọi vấn đề của người chơi đều được giải quyết kịp thời và hiệu quả. Ngoài ra, VF88 còn đặc biệt chú trọng đến bảo mật thông tin của người chơi, sử dụng công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân cũng như tài chính của người tham gia. Với những cam kết về sự bảo mật và chất lượng dịch vụ, người chơi có thể hoàn toàn yên tâm khi trải nghiệm những trò chơi thú vị tại VF88 mà không phải lo lắng về vấn đề bảo mật hay gián đoạn dịch vụ.
Một yếu tố không thể thiếu làm nên sự thành công của VF88 chính là việc nền tảng này không ngừng sáng tạo và mang đến cho người chơi những chương trình khuyến mãi hấp dẫn, giúp nâng cao trải nghiệm giải trí của người tham gia. Những chương trình ưu đãi này không chỉ giúp người chơi nhận được những phần thưởng giá trị mà còn tạo cơ hội để họ quay lại và tham gia nhiều hơn. Hệ thống khuyến mãi của VF88 được cập nhật liên tục, mang đến nhiều cơ hội cho người chơi tận hưởng những phần thưởng và dịch vụ đặc biệt. Với sự kết hợp giữa chất lượng dịch vụ vượt trội, bảo mật cao và những chương trình khuyến mãi hấp dẫn, VF88 đã khẳng định được vị thế vững mạnh trong ngành giải trí trực tuyến, xứng đáng là một lựa chọn ưu tiên của người chơi.
-
 @ 0b118e40:4edc09cb
2025-03-30 09:09:45
@ 0b118e40:4edc09cb
2025-03-30 09:09:45There’s an African proverb that says, “To get lost is to learn the way.”
Humans have always been explorers, searching for connection. To belong. To feel home. You can trace this instinct back to the start of our existence. Whether you start with Adam and Eve or the “Out of Africa” theory, the story is the same. We’ve always moved toward each other, building tribes and forming communities.
But somewhere along the way, something broke. With the rise of empires and organized control, religion and politics divided us into bubbles. We were sorted, labeled, and often pitted against one another. While technology advanced, something fundamental was lost. Our ability to truly connect started to fade.
Then came the internet, a modern-day Silk Road. It rekindled hope. Walls seemed to crumble, distances disappeared, and we dreamed of a truly connected world. For a time, it felt like the answer.
And then it wasn’t.
The history of Internet
The story began around 1830s when Charles Babbage started working on his computer prototype but without moolah he couldn't continue. A century later, after WW2 in the 1950s, the US Department of Defense funded what became known as modern computing.
Back then the military relied on systems like the Navajo Code Talkers. The indigenous code talkers were ingenious but operated under dangerous conditions, always on the frontlines.
In 1969, ARPANET made a revolutionary breakthrough as it connected four university computers for the first time. It was a big deal.
At that time, the internet was about openness. Researchers pushed for universal protocols. This gave rise to hacker culture that valued knowledge-sharing and keeping systems accessible to everyone.
In the 80s, NSFNET (National Science Foundation ) expanded these connections but kept it strictly for academic use only. That caused massive dissatisfaction.
Senator Al Gore pitched the concept of the “information superhighway,” to balance public access with private innovation. But by the 90s, the Clinton administration leaned into privatization. NSFNET’s infrastructure was completely handed off to private companies, and the internet grew into a commercial powerhouse.
The good news is that everyone has internet access now. Bad news is that what started as something free from government and commercial control became completely dominated by both.
Open source vs IP during the early internet days
This part of the story is about Bill Gates and Marc Andreessen.
Tim Berners-Lee invented the World Wide Web, but Marc saw the opportunity to make it user-friendly. He launched Netscape, an open-source browser. It drove the openness of internet culture. Netscape captured 90% of the market by giving its software away for free, and monetizing through other means.
Then came along Bill Gates. Microsoft back then was known for its aggressive tactics to monopolize industries. Gates licensed Mosaic’s code, created Internet Explorer, and bundled it for free with Windows 95. He wasn’t shy about playing dirty, even formed exclusive contracts with manufacturers to block competitors. Even the Department of Justice tried to file an antitrust lawsuit against Microsoft, but by then, it was too late. Netscape’s market share crumbled, and its position in the industry eroded.
Windows 95 brought the internet to the people globally, but it also closed it up.
Marc Andreeson started with open source ideologies, but is now funding altcoin projects.
The Californian ideology
Around this time, the term “Californian Ideology” started floating around. It was an unusual mix of libertarianism, techno-utopianism, and countercultural ideals. A marriage of cultural bohemianism (hippies) with high-tech entrepreneurship (yuppies). This ideology fused left-wing values like freedom of expression and direct democracy with right-wing beliefs in free markets and minimal government interference.
I absolutely love it.
Ironically, the term “Californian Ideology” wasn’t coined as a compliment. Richard Barbrook and Andy Cameron used it to piss on these visionaries for romanticizing the idea that the internet must remain a lawless, egalitarian space.
But many people loved and embraced the Californian ideology. Stewart Brand, who founded The Whole Earth Catalog, connected counterculture with early tech innovation. His work inspired people like Steve Jobs and Steve Wozniak. Steve Wozniak used to share Apple’s early schematics at the Homebrew Computer Club for feedback and collaboration.
EBay’s founder Pierre Omidyar envisioned eBay as a libertarian experiment. He believed the “invisible hand” of the market would ensure fairness. But as eBay grew, fraud, disputes, and dissatisfaction among users forced Omidyar to introduce governance which contradicted his goals.
And this story repeats itself over the years.
Platforms begin with libertarian visions, but as they scale, real-world challenges emerge. Governance (government, corporate charters, advertisers, and investors) is introduced to address safety and trust issues.
But they also chip away at the liberty the internet once promised.
Can Nostr be the solution ?
Yes.
But to appreciate Nostr, let’s first understand how the internet works today. (Note : I am no expert of this section but I'll try my best to explain)
The internet operates through four main layers:
- Application Layer (where apps like browsers, Google, or Zoom live)
- Transport Layer
- Internet Layer
- Network Access Layer
Let’s use a simple example of searching “Pink Panther” on Google.
Step 1: The Application Layer - You open your browser, type "Pink Panther," and hit search. This request is sent using HTTP/HTTPS (a protocol that formats the query and ensures it's secure).
Step 2: The Transport Layer - Think of your search query as a letter being sent. The Transport Layer breaks it into smaller packets (like splitting a long letter into multiple envelopes). TCP (Transmission Control Protocol) ensures all packets arrive and reassemble in the correct order.
Step 3: The Internet Layer - This layer acts like a postal service, assigning each device an address (IP address) to route the packets properly. Your device's IP (e.g., 192.168.1.10) and Google’s server IP (e.g., 142.250.72.238) help routers find the best path to deliver your packets.
Step 4: The Network Access Layer - Finally, the Network Access Layer physically delivers the packets. These travel as electrical signals (over cables), radio waves (Wi-Fi), or light pulses (fiber optics). This is the act of moving envelopes via trucks, planes, or postal workers, just much faster.
So how is data transmitted via Nostr ?
Nostr’s architecture of the Internet
Nostr reimagines the Application Layer while keeping the lower layers (Transport, Internet, and Network Access) largely unchanged.
In the traditional internet stack, the Application Layer is where platforms like Google or Twitter operate. It’s also where most censorship occurs due to single point of failure (centralised servers). Nostr flips this model on its head.
Technically, it’s like building a parallel internet that shares the same foundational layers but diverges at the top.
To borrow from Robert Frost:
"Two roads diverged in a wood, and I—
I took the one less traveled by,
And that has made all the difference."
For Nostr to fully realize its potential, it needs its own ecosystem of apps. Developers can build these tools within the Nostr protocol's framework
Let’s say there is a search engine on Nostr called Noogle.
Here’s how it works:
When you type "Pink Panther" on Noogle, your query is sent to multiple relays (servers) simultaneously. Each relay processes or forwards the query and returns results based on the data it holds.
As Nostr grows, the amount of information on relays will increase, giving Noogle more robust search results. But the biggest win is that compared to Google, Nostr's Noogle will have no ads, no surveillance, just pure, decentralized searching that respects your privacy.
For the transport layer, Nostr still relies on TCP/IP but enhances it with privacy and efficiency. Encrypted messages and simplified protocols enable faster real-time communication. The rest of the layer remains unchanged.
At its core, Nostr takes the internet back to its original ideals: open, uncensored, and decentralized.
Why Nostr matters ?
The internet we use today relies on centralized systems at the application layer. This creates a single point of failure where governments and corporations can control access, censor content, monitor activity, and even shut down entire platforms.
For example, the Malaysian government once proposed routing all web traffic through a centralized system, claiming it was for "security" reasons. In reality, this action allow those in power to block access to specific content or platforms that might threaten their positions.
Centralization weaponizes the internet.
It turns what was meant to be a tool for connection and freedom into a mechanism for control and oppression.
Let's look at DNS and ISPs as examples. DNS (Domain Name System) is like the phonebook of the internet. It helps translate website names (like example.com) into IP addresses so your browser can connect to them. ISPs (Internet Service Providers) are companies that give you access to the internet.
Both are controlled by centralized entities. If a government gains control of either, it can block specific websites or even shut down internet access entirely.
We've seen this happen repeatedly: * India’s internet shutdowns in regions like Kashmir * Turkey’s social media bans during political events * Ethiopia’s internet blackouts * China’s Great Firewall blocking major platforms like Google and Facebook * Even the US, where Edward Snowden revealed massive surveillance programs
This is where Nostr comes in, as the antidote to centralized control.
Instead of relying on centralized servers or platforms, Nostr creates a peer-to-peer network of independent relays. No single entity controls it. There is no central switch governments can flip to block access. If one relay is shut down, users simply connect to others in the network.
Nostr’s decentralized design makes it: * Resistant to censorship: Governments cannot easily block or filter content. * Privacy-preserving: Users can communicate anonymously, even in heavily surveilled environments. * Resilient: With no single point of failure, the network keeps running, even under attack.
And it gets better. Nostr can integrate with privacy tools like Tor to bypass restrictions entirely, making it nearly impossible for governments to stop.
The internet has become a battlefield for control, but Nostr provides a way to reclaim digital freedom. It empowers people to build, connect, and share without fear of being silenced.
How does Nostr overcome the "Californian Ideology" problems?
The Californian Ideology seemed like the blueprint for a utopian internet, libertarian ideals wrapped in Silicon Valley innovation. But as centralized platforms scaled, cracks started to show. Challenges like trust, safety, and accessibility forced governance teams to step in and decide “what’s best for the people.”
This resulted in platforms once built on ideals of freedom in becoming gatekeepers of control.
Nostr breaks this cycle. How?
1. Trust issues - With private keys, you control your identity and data. Moderation is decentralized. You can block or mute others at a personal level or through client tools, not by relying on a central authority. While this system needs refinement to be more user-friendly, it fundamentally shifts the power to users.
2. Funding Without Advertiser - Nostr’s integration of Bitcoin and the Lightning Network eliminates reliance on advertisers or corporate sponsors. Bitcoin enables anyone to contribute without gatekeeping. As more people join and apps mature, this model only gets stronger. For now, we have good souls like Jack seeding it.
3. Resisting Government Control - (refer to the above) Nostr avoids single points of attacks.
So what is Nostr ?
Nostr is internet
The new internet.
The open and free internet.
What can you build on Nostr?
Anything you have seen on the internet, you can recreate on Nostr. Anything you can imagine, you can bring to life here. It is a blank canvas for dreamers, builders, and changemakers.
But the best part is this. You have Bitcoin as its financial backbone. This changes the game entirely.
And with new games, comes new rules. New vibes. New ways.
The way people use this new internet will be different from the traditional internet as control falls back to the people. With Bitcoin as the underlying backbone, the business models will be different.
But there is more to it than just creating. There's that joy of creation, where we invite curiosity and inspire users to experience something new, something revolutionary.
Have you watched “The Last Lecture” by Randy Pausch?
He coined the term “head fake.” He taught his students programming, but not everyone was excited to learn programming. So he created fun projects and performances that pulled them in. The students had so much fun, they didn’t even realize they were learning to code.
What you build on Nostr is that head fake. The apps and projects you create draw people in with fun and utility, subtly reminding them they have a right to their own voice and thoughts.
The work you’re doing is so precious. When everything feels like doom and gloom, it’s these kinds of projects that give people hope.
Through Nostr, you’re making a difference. One project, one connection at a time.
The new Internet era
Centralized systems, like empires of the past, eventually crumble under the weight of their control. Decentralization provides a different path. It is a modern revival of our primal instincts to explore, connect, and build tribes.
By definition, Nostr is a protocol. I think more so, it's a philosophy. It challenges us to rethink how we share, communicate, and create. It is the internet as it was meant to be. Free, open, and governed by no one.
The beauty of Nostr lies in its simplicity. It does not rely on massive infrastructure, corporate giants, or government oversight. It thrives on community, much like the early tribes that defined humanity.
We have come full circle. From wandering continents to building roads, bridges, and networks, our journey has always been about connection and finding our tribe.
As the African proverb reminds us, 'To get lost is to learn the way.' There is finally a way now.
But at the end of the day, it’s entirely up to you what kind of world you want to be part of.
Find your tribe. Build the future. Love them hard.
-
 @ d560dbc2:bbd59238
2025-03-30 07:56:40
@ d560dbc2:bbd59238
2025-03-30 07:56:40We’ve all been there: that one task sitting on your to-do list, staring at you like a disappointed parent, and yet you keep pushing it off for absolutely no good reason. It’s not even that hard, urgent, or complicated—but somehow, it’s been haunting you for days, weeks, or maybe even months. Why do we do this to ourselves?
Why Do We Postpone Tasks for No Reason?
Procrastination is a sneaky beast. Even tasks that take 10 minutes, require minimal brainpower, and have no immediate deadline often get pushed aside. Here are some psychological reasons:
-
Emotional Avoidance:
Even if a task isn’t hard, a tiny emotional weight (like mild boredom or a vague “I don’t wanna”) can lead your brain to choose distractions—like scrolling through Instagram. -
Lack of Immediate Consequences:
Without a pressing deadline, your brain tends to deprioritize the task, even if completing it would make you feel great. -
The Zeigarnik Effect:
Unfinished tasks stick in our minds, creating mental tension. Ironically, that tension can make the task seem bigger and more daunting, encouraging further avoidance.
My Own “No-Reason” Procrastination Story
Let’s be real—I’ve been postponing something trivial, like organizing my desk drawer, for weeks. It’s a simple task that takes about 15 minutes. There’s no deadline, no special skill required—yet every time I open the drawer, I see the chaos of old receipts, random cables, and a half-eaten pack of gum (don’t judge!) and think, “I’ll do it later.” It’s not that I’m busy—I’ve had plenty of time to rewatch my favorite sitcom for the third time. But ignoring it has become my default, and that messy drawer now occupies mental space far beyond its physical size.
Why These Tasks Matter More Than We Think
Those little tasks we postpone might seem harmless, but they add up to create mental clutter. That messy desk drawer isn’t just a drawer—it’s a tiny stressor that pops into your head at the worst moments, disrupting your focus on important work or relaxation.
-
Mental Clutter:
Unfinished tasks can weigh on your mind, making it harder to focus on what truly matters. -
The Bigger Picture:
Tasks like “reply to that email” or “schedule that doctor’s appointment” may seem minor, but avoiding them can lead to unnecessary stress and lost opportunities.
How to Finally Tackle That Task
Here are a few strategies that have helped me break the cycle of “no-reason” procrastination:
1. The 20-Minute Rule (Thank You, Pomodoro!)
-
Commit to 20 Minutes:
Set a timer for just 20 minutes and start working on the task. You’d be surprised how much you can accomplish once you begin. -
Example:
For my desk drawer, I set a timer, got to work, and finished in 12 minutes. That small win made me feel like a productivity superhero.
2. Pin It and Get a Nudge
-
Use Reminders:
Pin that nagging task (like “Organize desk drawer”) as your top priority for the day. A gentle reminder can help break the cycle of avoidance. -
Result:
It’s like having a friend nudge you, “Hey, remember that thing you’ve been ignoring? Let’s do it now!”
3. Make It Fun (Yes, Really!)
-
Add a Reward:
Turn the task into something enjoyable by setting a reward. Play your favorite music, and promise yourself a treat once you’re done. -
Example:
For my desk drawer, I put on an upbeat playlist and treated myself to a piece of chocolate when finished. Suddenly, it wasn’t a chore—it became a mini dance party with a sweet reward.
4. Celebrate the Win
-
Acknowledge Completion:
Once you finish, take a moment to celebrate—even if it’s just a mental high-five. -
Why It Matters:
That sense of closure clears mental clutter and builds momentum for your next task.
Let’s Share and Motivate Each Other
What’s that one task you’ve been postponing for no reason? Maybe it’s cleaning out your fridge, replying to a friend’s text, or finally hanging that picture frame that’s been leaning against the wall for months. Whatever it is, share your story in the comments! Let’s motivate each other to tackle these tasks and turn procrastination into progress.
Bonus points if you’ve got a funny reason for your procrastination (like, “I didn’t schedule that appointment because my doctor’s office has the worst hold music in history”).
Ready to stop procrastinating? Let’s get real, take that first step, and clear that mental clutter—one small win at a time!
-
-
 @ 866e0139:6a9334e5
2025-03-30 07:56:28
@ 866e0139:6a9334e5
2025-03-30 07:56:28
Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Wer den Artikel Ob Corona oder Krieg: Wir Menschen werden wie Vieh behandelt gelesen und die Ereignisse in Deutschland während der letzten 5 Jahre auch jenseits von Staatsfunk und Mainstream Medien verfolgt hat, dem dürfte folgendes aufgefallen sein:
- Die absoluten Top-Positionen auf der politischen Bühne wurden vielfach mit Menschen besetzt, deren Eignung und Reputation – vorsichtig ausgedrückt – umstritten ist.
- Auch massivste Fehlverhalten der Politiker bleiben folgenlos. Rücktritte scheinen ebenso ausgeschlossen wie eine straf- oder zivilrechtliche Aufarbeitung.
- Wahlversprechen werden nicht eingehalten und neuerdings bereits direkt nach der Wahl gebrochen, obwohl noch keine neue Regierung gebildet wurde. Stattdessen wird das Gegenteil von dem getan, was eindringlich versprochen wurde.
- Es hat sich eine Parteien-Allianz gebildet, welche eine gemeinsame Agenda verfolgt, die nicht dem Wohle der Bürger zu dienen scheint.
In diesem Umfeld tun die Politiker offenbar ungebremst, was sie wollen – und keiner scheint sie hindern zu können. Wenn morgen „von oberster Stelle“ die Anweisung gegeben würde, dass alle Neugeborenen auf Scheiterhaufen zu verbrennen seien, so stehen die Chancen gut, dass auch solch ein Vorhaben durchgebracht werden würde. Es stellt sich die Frage, ob der Willkür überhaupt Grenzen gesetzt sind. Und eine weitere Frage ist, ob es einen Punkt gibt, an dem die Bürger nicht mehr gehorchen.
Es ist kein Geheimnis, dass Politiker für ihre Vergehen belangt werden. Entgegen jedem Unternehmenslenker haften Politiker nicht für Fehlverhalten. Offensichtlich auch nicht für grob fahrlässiges oder gar vorsätzliches, denn die deutsche Staatsanwaltschaft untersteht der Politik. Auch Richter sind in Karrieresysteme eingebunden, sodass die letzten fünf Jahre besonders deutlich gezeigt haben, in welche Situation sich „mutige Richter“ bringen. „Bestrafe einen, erziehe hundert“, sagte hierzu einst ein bekannter politischer Führer eines Landes, mit dem Deutschland nicht verglichen werden möchte.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Eine Tat wird (abgesehen vom Gesetz) erst durch die individuelle Bewertung zu einem Unrecht. Wie die Dinge „einzuordnen“ sind, erklären die Täter, die Politiker, tagtäglich selbst und werden hierbei von ihren Propagandamitarbeitern unterstützt, die sich selbst immer noch als Journalisten bezeichnen. Wer aber die staatliche Einordnung anzweifelt oder dieser gar offen widerspricht, wird unter Anwendung der vorgenannten Systematik „Bestrafe einen, erziehe hundert“ diffamiert. Aber hierbei bleibt es nicht, denn Hausdurchsuchungen in Herrgottsfrühe, Kontosperrungen, Untersuchungshaft und Jobverlust sowie dauerhafte Inhaftierungen sind nur einige Beispiele dafür, wie „im besten Deutschland aller Zeiten“ vorgegangen wird.
Der Gamechanger
Aber wie wäre der Zustand denn zu ändern, wenn man es denn wollte? Der Staat wird eben durch diese Politiker repräsentiert und hat das Gewaltmonopol. Hierzu einige Zahlen zu Deutschland:
- Bevölkerung: ca. 83.000.000
- Polizisten: ca. 45.000 und einige tausend zivile (0,05 % der Bevölkerung)
- Soldaten: ca. 260.000 (0,31 % der Bevölkerung)
- Gerichte: ca. 1.085 (pro Gericht 77.000 Bürger)
- Finanzämter: ca. 600 (pro Finanzamt 138.000 Bürger)
Mit Blick auf diese Verhältnisse wird schnell deutlich, dass die Politiker auf eine „Kooperation“ der Bürger angewiesen sind. Würden die Bürger nicht kooperieren, so wären alle Gesetze und Vorschriften aufgrund mangelhafter Durchführbarkeit von heute auf morgen Makulatur.
Mahatma Gandhi und viele andere bewiesen, dass ein übermächtig scheinender Gegner nicht mit dessen Gewaltmitteln besiegt werden kann, sondern mit dem Gegenteil. Gandhi beispielsweise rief die Menschen in seinem Land auf, den Engländern einfach nicht mehr zu gehorchen und die ungerechten Gesetze nicht mehr zu befolgen. Bei den Engländern hat dies funktioniert.
Man stelle sich als Gedankenexperiment einmal vor, wie es wäre, wenn ein Drittel der Bürger nicht mehr arbeiten und keine Steuern und sogar keine GEZ-Gebühren mehr bezahlen würden. Wie könnten diese Menschen „zur Ordnung“ gerufen werden? Wie wollte man diese Menschen bestrafen? Bestrafungskonzepte funktionieren nur dann, wenn sich die Menschen durch diese einschüchtern lassen. Sofern aber die Vielen solidarisch agieren würden, hätte ein Staatsapparat schlechte Karten. Insbesondere dann, wenn ziviler Ungehorsam bundesweit oder sogar EU-weit ausgeübt würde.
In solch einem Fall käme es wahrscheinlich sehr schnell zu einer Verständigung, denn wie sollte eine Regierung mit so viel Gegenwind weiter agieren? Die Prämisse bei solch einem Gedankenexperiment ist, dass ein erheblicher Teil der Bevölkerung sich so „miss-regiert“ fühlt, dass dieser Teil der Bevölkerung bereit ist, seine Komfortzone zum eigenen Wohl und dem Wohl der ihm Anvertrauten zu verlassen. Wahrscheinlich würde das noch nicht einmal besonders lange dauern. Man erinnere sich noch an die Zeiten, als Gewerkschaften noch nicht gekapert waren und tatsächlich die Interessen ihrer Mitglieder vertraten. Damals konnten die aufrechten Gewerkschaftsvertreter im Schulterschluss mit den Arbeitern für sie bessere Ergebnisse erwirken.
Weg mit dem Grundgesetz
In Deutschland wurde insbesondere in letzter Zeit von den Politikern am Grundgesetz herumgebastelt, aber dieses Grundgesetz, welches nach Vollendung der Einheit und Freiheit Deutschlands für das gesamte deutsche Volk gilt, verliert seine Gültigkeit an dem Tage, an dem eine Verfassung in Kraft tritt, die von dem deutschen Volke in freier Entscheidung beschlossen worden ist. Dies ist in Artikel 146 GG nachzulesen.
Das Grundgesetz vom 23. Mai 1949 in der jeweils aktuellen Fassung ist die (vorläufige) Verfassung der Bundesrepublik Deutschland. Das Grundgesetz wurde im Jahre 1949 zunächst bewusst als provisorische Regelung der staatlichen Grundordnung geschaffen. Eine Verfassung für Deutschland hingegen wäre ein besonderes Gesetz, welches bestimmt, wer in einem Staat die Macht ausübt und wie das geschehen soll. Dort ist festgelegt, welche Aufgaben der Staat übernimmt, welche Rechte jeder Bürger hat und wie das Verhältnis zwischen staatlichen Organen und Bürgern aussieht. Solch eine Verfassung hat Deutschland (noch) nicht.
Man stelle sich nun vor, das deutsche Volk gäbe sich, so wie im Grundgesetz verankert, in freier Entscheidung eine Verfassung, welche exemplarisch Elemente zu folgenden Themen beinhalten würde:
- Jeder Politiker wird an seinen Wahlversprechen gemessen.
- Bei Amtsantritt wird ein Dienstvertrag, ähnlich wie bei einem Vorstand einer AG oder einem Geschäftsführer einer GmbH, abgeschlossen. In diesem Dienstvertrag wird auch geregelt, wie bei Verstößen vorgegangen wird.
- Das Parteiensystem wird abgeschafft.
- Die Staatsanwaltschaft ist nicht weiter weisungsgebunden und die Politiker nicht weiter immun. Die Gerichtsbarkeit wird wirklich unabhängig.
- Jeder Politiker hat eine entsprechende Qualifikation nachzuweisen, um gewählt werden zu können.
- Ein transparentes Wahlsystem. Schluss mit den manipulativen „Umfragen“.
- Direkte Demokratie.
- Etc.
Statt am Grundgesetz herumzuwerkeln, könnte es eine Option sein, eine gerechte Verfassung zu beschließen, welche darauf ausgerichtet ist, den Bürgern zu dienen. Das GG würde dadurch obsolet. Mit einer gerechten Verfassung könnte sehr viel Optimierungspotenzial für das Zusammenleben in Deutschland realisiert werden.
Die von den Politikern angebotenen Lösungen für die Probleme unserer Zeit beziehen sich oftmals auf selbst oder von den wirklich Mächtigen erschaffene Zustände, welche inszeniert wurden/werden, um die Menschen in Krieg, Not und Knappheit, in Leiden, in Angst, in Spaltung, in Fehlernährung, in Medikamentenabhängigkeit, in Krankheit und in Elend zu bringen. Um an den Menschen maximal zu verdienen und um diese vollumfänglich zu beherrschen. So, wie sie es mit Nutzvieh tun. Das Unterordnen von allem ist ein Prinzip, dass wenigen Leuten nützt und fast allen anderen schadet.
Eine von Liebe inspirierte Gesellschaft, die Menschen nicht nur als „Verbraucher“ oder „Humankapital“ oder „Wähler“ betrachtet und behandelt, sondern tatsächlich das Wohl aller im Fokus hat, wäre der Gegenentwurf. Dies würde selbstverständlich einhergehen mit einer liebevollen Behandlung von Tieren und Natur. Hierbei profitieren aber die Vielen und die Wenigen ganz oben an der Spitze müssten sich umstellen, was ihnen nicht gefallen dürfte.
Vom Denken ins Tun
Wer sich solch eine Perspektive für sich selbst und seine Nachkommen wünscht, sollte überlegen, wie wir uns eine Verfassung geben können.
Ein wesentlicher Schritt wäre sicher der Zusammenschluss von Menschen, die sich mit den vorbezeichneten Überlegungen weiter befassen möchten. Ganz entgegen der Bemühungen unserer Politik um Spaltung der Gesellschaft sollten die Gemeinsamkeiten gesehen und gemeinsam Lösungen entwickelt werden.
Ein Beispiel ist die Initiative von Milosz Matuschek, nämlich sein geplantes „Gipfeltreffen“. Hierzu schreibt er:
„Ich habe mir ein besonderes Programm überlegt, welches mein Wissen und meine Erfahrung der letzten Jahre bündelt, sich an den Stufen der Selbsterkenntnis, Willensbildung und Kraftentfaltung orientiert und genug Raum für die Dynamik der Gruppe, also ihre Energien, lässt. Erwarten Sie das Unerwartbare. Es wird Raum geben für spirituelle und körperliche Erfahrungen, auch an einem besonderen kulturellen Rahmenprogramm wird es nicht fehlen. Uns eint im Idealfall das Erkennen menschlicher Potentiale, das Erfassen von Möglichkeitsräumen und die aktive Lust an der Mitgestaltung der Zukunft – ohne Denkverbote. Zeit, für unseren Frühling. Ich wette, in Ihnen steckt ein ganzer, unendlicher Sommer.“
In diesem Kontext zitiert Herr Matuschek Ernst Jünger:
“Wenn alle Institutionen zweifelhaft oder sogar anrüchig werden und man selbst in den Kirchen nicht etwas für die Verfolgten, sondern für die Verfolger öffentlich beten hört, dann geht die sittliche Verantwortung auf den Einzelnen über, oder besser gesagt, auf den noch ungebrochenen Einzelnen.”
Diese Worte von Ernst Jünger erinnern daran, dass die Probleme unserer Zeit nicht neu sind. Die Technologien sind es, denn mit modernen Technologien lässt sich eben besser unterdrücken als mit dem alten Zeugs. Die Methodik allerdings ist geblieben. Halte deine Untergebenen schwach und in Angst, damit diese ergeben bleiben. Zum Wohle einiger wenige Leute, die hiervon maximal profitieren.
Machen Sie mit und lösen Sie sich aus der Passivität des Zuschauers. Der wichtige nächste Schritt ist, aus dem Denken ins Tun zu kommen.
Andernfalls wird uns weiter an-getan.
Ludwig F. Badenhagen (Pseudonym, Name ist der Redaktion bekannt).
Der Autor hat deutsche Wurzeln und betrachtet das Geschehen in Deutschland und Europa aus seiner Wahlheimat Südafrika. Seine Informationen bezieht er aus verlässlichen Quellen und insbesondere von Menschen, die als „Verschwörungstheoretiker“, „Nazi“, „Antisemit“ sowie mit weiteren Kampfbegriffen der dortigen Systemakteure wie Politiker und „Journalisten“ diffamiert werden. Solche Diffamierungen sind für ihn ein Prädikatsmerkmal. Er ist international agierender Manager mit einem globalen Netzwerk und verfügt hierdurch über tiefe Einblicke in Konzerne und Politik.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ da0b9bc3:4e30a4a9
2025-03-30 07:40:58
@ da0b9bc3:4e30a4a9
2025-03-30 07:40:58Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/929299
-
 @ c11cf5f8:4928464d
2025-03-30 07:32:36
@ c11cf5f8:4928464d
2025-03-30 07:32:36Let's support #Bitcoin #merchants! I'd love to hear some of your latest #Lightning purchases and interesting #products you bought. Feel #free to include links to the #shops or #businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus #sats if you found a killer #deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and #zap on.
originally posted at https://stacker.news/items/929295
-
 @ 6919d8ac:737b2c45
2025-03-30 07:02:14
@ 6919d8ac:737b2c45
2025-03-30 07:02:14Nos últimos anos, o mercado de plataformas de entretenimento digital no Brasil tem experimentado um crescimento significativo. Entre as diversas opções que surgem a cada dia, o BATEUBET se destaca como uma plataforma inovadora e empolgante, voltada para o público brasileiro que busca uma experiência de jogo única, dinâmica e segura. Neste artigo, exploraremos os principais aspectos dessa plataforma, com um foco especial na introdução da plataforma, na variedade de jogos oferecidos e na experiência que ela proporciona aos jogadores.
Introdução à Plataforma BATEUBET O BATEUBET é uma plataforma de entretenimento digital que surgiu com o objetivo de proporcionar aos jogadores brasileiros uma experiência de jogos online com qualidade, segurança e diversão. Diferente de outras plataformas no mercado, o BATEUBET é projetado para atender às preferências e necessidades do público nacional, oferecendo uma interface amigável e fácil de navegar, além de suporte completo em português. A plataforma se destaca pela combinação de tecnologia de ponta e uma abordagem centrada no jogador, o que garante uma navegação intuitiva e uma experiência de jogo envolvente.
Uma das características mais notáveis do bateubet é sua estrutura moderna e otimizada para dispositivos móveis e desktops, permitindo que os usuários joguem a qualquer hora e de qualquer lugar. A plataforma utiliza medidas de segurança de última geração para proteger os dados e transações dos jogadores, garantindo um ambiente seguro e confiável para quem escolhe se divertir e apostar.
Variedade de Jogos no BATEUBET Uma das grandes atrações do BATEUBET é a vasta variedade de jogos disponíveis, que atendem a diferentes gostos e preferências. Se você é fã de jogos de habilidade, de sorte ou de estratégia, certamente encontrará opções interessantes na plataforma. O BATEUBET oferece uma ampla gama de opções, que vão desde jogos de mesa e sorteios até opções mais inovadoras e interativas, criando uma experiência diversificada e emocionante para os jogadores.
A plataforma conta com jogos clássicos, como roletas e sorteios, que são sempre populares entre os entusiastas do entretenimento digital. Além disso, o BATEUBET investe constantemente em novas opções, incluindo jogos com temas inovadores e gráficos de última geração. O design dos jogos é feito para atrair tanto iniciantes quanto jogadores mais experientes, com mecânicas fáceis de entender, mas com desafios que mantêm a diversão em alto nível.
Outro ponto forte é a seção de jogos interativos, que permite uma experiência mais imersiva e social. Os jogadores podem interagir entre si, compartilhar experiências e, em alguns casos, até competir diretamente em tempo real, o que torna a plataforma ainda mais atrativa. Para os entusiastas das apostas esportivas, o BATEUBET também oferece uma seção dedicada a esse tipo de entretenimento, com opções para apostar em diversos eventos e competições ao redor do mundo.
A Experiência do Jogador no BATEUBET A experiência do jogador no BATEUBET é projetada para ser intuitiva, fluida e personalizada. A plataforma investe fortemente na usabilidade, permitindo que os jogadores naveguem entre as diversas opções de maneira rápida e eficiente. A interface é moderna e clean, sem distrações, permitindo que o jogador se concentre na diversão e na experiência de jogo. Além disso, o design responsivo garante que os jogadores possam acessar a plataforma em diferentes dispositivos, seja no desktop ou no celular, com a mesma qualidade e desempenho.
A plataforma também é conhecida por oferecer um atendimento ao cliente excepcional. O BATEUBET disponibiliza suporte ao vivo 24 horas por dia, 7 dias por semana, através de chat online, e-mail e outros canais de comunicação. Caso o jogador tenha alguma dúvida ou encontre um problema, a equipe de suporte está pronta para ajudar de forma rápida e eficiente.
Outro aspecto importante da experiência no BATEUBET é a possibilidade de personalização. A plataforma oferece uma variedade de configurações e opções que permitem ao jogador ajustar a experiência de acordo com suas preferências. Isso inclui desde o layout da interface até as opções de pagamento e retirada de fundos, proporcionando uma experiência verdadeiramente personalizada.
Para garantir que a experiência de jogo seja divertida e segura, o BATEUBET também adota práticas responsáveis, incentivando os jogadores a praticar o jogo responsável e oferecendo ferramentas para controle de limites de apostas. Isso ajuda a criar um ambiente saudável e sustentável para todos os jogadores.
Conclusão Em resumo, o BATEUBET é uma plataforma de entretenimento digital inovadora, que oferece uma variedade de jogos emocionantes e uma experiência de jogador inigualável. Com uma interface amigável, suporte completo em português e um foco constante na segurança e na diversão, o BATEUBET se apresenta como uma excelente opção para os jogadores brasileiros que buscam por novas formas de entretenimento. Se você é um entusiasta de jogos online e está procurando uma plataforma confiável e divertida, o BATEUBET pode ser a escolha perfeita para você.
-
 @ 6919d8ac:737b2c45
2025-03-30 07:00:31
@ 6919d8ac:737b2c45
2025-03-30 07:00:31Nos últimos anos, a busca por plataformas inovadoras de entretenimento digital tem sido constante, com o público ávido por novas experiências imersivas e interativas. Um dos nomes que vem se destacando nesse universo é o 80WIN, uma plataforma que oferece aos usuários uma combinação única de jogos e uma experiência de jogo inigualável. Neste artigo, vamos explorar o que torna o 80WIN tão especial, desde sua introdução ao mercado até a variedade de jogos e a experiência oferecida aos jogadores.
O que é o 80WIN? O 80WIN é uma plataforma moderna e sofisticada de entretenimento digital, projetada para oferecer uma experiência imersiva e acessível a todos os tipos de jogadores. Sua missão é criar um ambiente inovador e seguro, com uma interface intuitiva e recursos de alta qualidade. Focada em atender ao público brasileiro, a plataforma busca se destacar pela diversidade de opções de jogos, que combinam diversão e desafios emocionantes para quem deseja se entreter e testar suas habilidades.
Ao contrário de outras plataformas tradicionais, o 80win oferece uma experiência personalizada, onde os jogadores podem explorar diferentes modalidades de jogos, interagir com outros participantes e aproveitar uma série de bônus e promoções. A plataforma é totalmente adaptada para o mercado brasileiro, com opções de pagamento locais e atendimento ao cliente em português, tornando-a uma escolha conveniente para aqueles que buscam uma alternativa divertida e confiável no mundo dos jogos digitais.
A Diversidade de Jogos no 80WIN Uma das características mais marcantes do 80WIN é a ampla variedade de jogos disponíveis. Desde os mais simples, até os mais complexos, a plataforma oferece opções para todos os gostos e níveis de experiência. Os jogadores podem explorar diferentes categorias, como jogos de habilidade, estratégia, ação e aventura, entre outros.
Os jogos de habilidade, por exemplo, desafiam os jogadores a usar seu raciocínio lógico e coordenação motora para completar desafios. Já os jogos de estratégia exigem uma análise profunda das situações e a capacidade de tomar decisões rápidas para vencer. Além disso, a plataforma também apresenta jogos de ação emocionantes, que mantêm os jogadores envolvidos com enredos envolventes e gráficos de alta qualidade.
Uma das grandes vantagens do 80WIN é a constante atualização de seu portfólio de jogos. Novos títulos são adicionados regularmente, proporcionando aos jogadores uma experiência sempre nova e excitante. Isso também garante que todos os usuários encontrem algo que atenda aos seus interesses, mantendo-os engajados e motivados para voltar à plataforma.
A Experiência do Jogador no 80WIN Quando se trata de experiência de usuário, o 80WIN se destaca por sua interface amigável e fácil de navegar. A plataforma foi projetada para que qualquer pessoa, independentemente de sua familiaridade com o mundo dos jogos digitais, possa aproveitá-la ao máximo. O layout é intuitivo, com categorias bem organizadas e filtros de pesquisa eficientes, permitindo que os jogadores encontrem rapidamente o jogo que mais combina com seu estilo.
Outro aspecto que contribui para a excelente experiência do jogador no 80WIN é a interatividade. A plataforma permite que os usuários se conectem com outros jogadores, compartilhem suas vitórias, e até participem de torneios emocionantes. Essa interação social cria um ambiente vibrante e competitivo, que mantém os jogadores motivados e engajados.
Além disso, o 80WIN se preocupa com a segurança e a proteção dos dados dos seus usuários. A plataforma adota tecnologias avançadas de criptografia para garantir que todas as transações financeiras e informações pessoais dos jogadores estejam protegidas contra possíveis ameaças cibernéticas. Isso cria um ambiente seguro e confiável, permitindo que os jogadores desfrutem de sua experiência sem preocupações.
Outro fator importante que contribui para a satisfação dos usuários é a suporte ao cliente. A plataforma oferece um atendimento rápido e eficiente, com uma equipe de suporte dedicada a solucionar qualquer dúvida ou problema que possa surgir durante a experiência de jogo. O suporte está disponível em português, o que facilita a comunicação e torna a interação com a plataforma ainda mais fluida.
Conclusão O 80WIN é, sem dúvida, uma das plataformas mais inovadoras e interessantes do mercado de entretenimento digital no Brasil. Com uma vasta gama de jogos de alta qualidade, uma experiência de usuário impecável e recursos de segurança avançados, a plataforma oferece tudo o que um jogador moderno procura. Se você está em busca de uma plataforma que combine diversão, emoção e segurança, o 80WIN é a escolha perfeita.
Seja você um jogador casual ou um entusiasta em busca de desafios mais complexos, o 80WIN oferece algo para todos. A cada visita, os jogadores são recebidos com novas possibilidades e experiências imersivas, garantindo horas de entretenimento e diversão. Portanto, não perca mais tempo e junte-se à comunidade 80WIN para explorar o que há de melhor no mundo dos jogos digitais!
-
 @ 39cc53c9:27168656
2025-03-30 05:54:55
@ 39cc53c9:27168656
2025-03-30 05:54:55The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-03-30 05:54:53
@ 39cc53c9:27168656
2025-03-30 05:54:53Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 39cc53c9:27168656
2025-03-30 05:54:52
@ 39cc53c9:27168656
2025-03-30 05:54:52Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 39cc53c9:27168656
2025-03-30 05:54:50
@ 39cc53c9:27168656
2025-03-30 05:54:50I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-03-30 05:54:48
@ 39cc53c9:27168656
2025-03-30 05:54:48Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 39cc53c9:27168656
2025-03-30 05:54:47
@ 39cc53c9:27168656
2025-03-30 05:54:47I've been thinking about how to improve my seed backup in a cheap and cool way, mostly for fun. Until now, I had the seed written on a piece of paper in a desk drawer, and I wanted something more durable and fire-proof.
After searching online, I found two options I liked the most: the Cryptosteel Capsule and the Trezor Keep. These products are nice but quite expensive, and I didn't want to spend that much on my seed backup. Privacy is also important, and sharing details like a shipping address makes me uncomfortable. This concern has grown since the Ledger incident^1. A $5 wrench attack^2 seems too cheap, even if you only hold a few sats.
Upon seeing the design of Cryptosteel, I considered creating something similar at home. Although it may not be as cool as their device, it could offer almost the same in terms of robustness and durability.
Step 1: Get the materials and tools
When choosing the materials, you will want to go with stainless steel. It is durable, resistant to fire, water, and corrosion, very robust, and does not rust. Also, its price point is just right; it's not the cheapest, but it's cheap for the value you get.

I went to a material store and bought:
- Two bolts
- Two hex nuts and head nuts for the bolts
- A bag of 30 washers
All items were made of stainless steel. The total price was around €6. This is enough for making two seed backups.
You will also need:
- A set of metal letter stamps (I bought a 2mm-size letter kit since my washers were small, 6mm in diameter)
- You can find these in local stores or online marketplaces. The set I bought cost me €13.
- A good hammer
- A solid surface to stamp on
Total spent: 19€ for two backups
Step 2: Stamp and store
Once you have all the materials, you can start stamping your words. There are many videos on the internet that use fancy 3D-printed tools to get the letters nicely aligned, but I went with the free-hand option. The results were pretty decent.

I only stamped the first 4 letters for each word since the BIP-39 wordlist allows for this. Because my stamping kit did not include numbers, I used alphabet letters to define the order. This way, if all the washers were to fall off, I could still reassemble the seed correctly.
The final result
So this is the final result. I added two smaller washers as protection and also put the top washer reversed so the letters are not visible:

Compared to the Cryptosteel or the Trezor Keep, its size is much more compact. This makes for an easier-to-hide backup, in case you ever need to hide it inside your human body.
Some ideas
Tamper-evident seal
To enhance the security this backup, you can consider using a tamper-evident seal. This can be easily achieved by printing a unique image or using a specific day's newspaper page (just note somewhere what day it was).
Apply a thin layer of glue to the washer's surface and place the seal over it. If someone attempts to access the seed, they will be forced to destroy the seal, which will serve as an evident sign of tampering.
This simple measure will provide an additional layer of protection and allow you to quickly identify any unauthorized access attempts.
Note that this method is not resistant to outright theft. The tamper-evident seal won't stop a determined thief but it will prevent them from accessing your seed without leaving any trace.
Redundancy
Make sure to add redundancy. Make several copies of this cheap backup, and store them in separate locations.
Unique wordset
Another layer of security could be to implement your own custom mnemonic dictionary. However, this approach has the risk of permanently losing access to your funds if not implemented correctly.
If done properly, you could potentially end up with a highly secure backup, as no one else would be able to derive the seed phrase from it. To create your custom dictionary, assign a unique number from 1 to 2048 to a word of your choice. Maybe you could use a book, and index the first 2048 unique words that appear. Make sure to store this book and even get a couple copies of it (digitally and phisically).
This self-curated set of words will serve as your personal BIP-39 dictionary. When you need to translate between your custom dictionary and the official BIP-39 wordlist, simply use the index number to find the corresponding word in either list.
Never write the idex or words on your computer (Do not use
Ctr+F) -
 @ 39cc53c9:27168656
2025-03-30 05:54:45
@ 39cc53c9:27168656
2025-03-30 05:54:45kycnot.me features a somewhat hidden tool that some users may not be aware of. Every month, an automated job crawls every listed service's Terms of Service (ToS) and FAQ pages and conducts an AI-driven analysis, generating a comprehensive overview that highlights key points related to KYC and user privacy.
Here's an example: Changenow's Tos Review

Why?
ToS pages typically contain a lot of complicated text. Since the first versions of kycnot.me, I have tried to provide users a comprehensive overview of what can be found in such documents. This automated method keeps the information up-to-date every month, which was one of the main challenges with manual updates.
A significant part of the time I invest in investigating a service for kycnot.me involves reading the ToS and looking for any clauses that might indicate aggressive KYC practices or privacy concerns. For the past four years, I performed this task manually. However, with advancements in language models, this process can now be somewhat automated. I still manually review the ToS for a quick check and regularly verify the AI’s findings. However, over the past three months, this automated method has proven to be quite reliable.
Having a quick ToS overview section allows users to avoid reading the entire ToS page. Instead, you can quickly read the important points that are grouped, summarized, and referenced, making it easier and faster to understand the key information.
Limitations
This method has a key limitation: JS-generated pages. For this reason, I was using Playwright in my crawler implementation. I plan to make a release addressing this issue in the future. There are also sites that don't have ToS/FAQ pages, but these sites already include a warning in that section.
Another issue is false positives. Although not very common, sometimes the AI might incorrectly interpret something harmless as harmful. Such errors become apparent upon reading; it's clear when something marked as bad should not be categorized as such. I manually review these cases regularly, checking for anything that seems off and then removing any inaccuracies.
Overall, the automation provides great results.
How?
There have been several iterations of this tool. Initially, I started with GPT-3.5, but the results were not good in any way. It made up many things, and important thigs were lost on large ToS pages. I then switched to GPT-4 Turbo, but it was expensive. Eventually, I settled on Claude 3 Sonnet, which provides a quality compromise between GPT-3.5 and GPT-4 Turbo at a more reasonable price, while allowing a generous 200K token context window.
I designed a prompt, which is open source^1, that has been tweaked many times and will surely be adjusted further in the future.
For the ToS scraping part, I initially wrote a scraper API using Playwright^2, but I replaced it with Jina AI Reader^3, which works quite well and is designed for this task.
Non-conflictive ToS
All services have a dropdown in the ToS section called "Non-conflictive ToS Reviews." These are the reviews that the AI flagged as not needing a user warning. I still provide these because I think they may be interesting to read.
Feedback and contributing
You can give me feedback on this tool, or share any inaccuraties by either opening an issue on Codeberg^4 or by contacting me ^5.
You can contribute with pull requests, which are always welcome, or you can support this project with any of the listed ways.
-
 @ 39cc53c9:27168656
2025-03-30 05:54:43
@ 39cc53c9:27168656
2025-03-30 05:54:43These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing. Reviews are in collaboration with Orangefren.
The review
Swapter.io is an all-purpose instant exchange. They entered the scene in the depths of the bear market about 2 years ago in June of 2022.
| Pros | Cons | | --------------- | ---------------------------------- | | Low fees | Shotgun KYC with opaque triggers | | Large liquidity | Relies on 3rd party liquidity | | Works over Tor | Front-end not synced with back-end | | Pretty UI | |
Rating: ★★★☆☆ Service Website: swapter.io
⚠️ There is an ongoing issue with this service: read more on Reddit.
Test Trades
During our testing we performed a trade from XMR to LTC, and then back to XMR.
Our first trade had the ID of:
mpUitpGemhN8jjNAjQuo6EvQ. We were promised 0.8 LTC for sending 0.5 XMR, before we sent the Monero. When the Monero arrived we were sent 0.799 LTC.On the return journey we performed trade with ID:
yaCRb5pYcRKAZcBqg0AzEGYg. This time we were promised 0.4815 XMR for sending 0.799 LTC. After Litecoin arrived we were sent 0.4765 XMR.As such we saw a discrepancy of
~0.1%in the first trade and~1%in the second trade. Considering those trades were floating we determine the estimates presented in the UI to be highly accurate and honest.Of course Swapter could've been imposing a large fee on their estimates, but we checked their estimates against CoinGecko and found the difference to be equivalent to a fee of just over
0.5%. Perfectly in line with other swapping services.Trading
Swapter supports BTC, LTC, XMR and well over a thousand other coins. Sadly they don't support the Lightning Network. For the myriad of currencies they deal with they provide massive upper limits. You could exchange tens, or even hundreds, of thousands of dollars worth of cryptocurrency in a single trade (although we wouldn't recommend it).
The flip side to this is that Swapter relies on 3rd party liquidity. Aside from the large liqudity this also benefits the user insofar as it allows for very low fees. However, it also comes with a negative - the 3rd party gets to see all your trades. Unfortunately Swapter opted not to share where they source their liquidity in their Privacy Policy or Terms of Service.
KYC & AML policies
Swapter reserves the right to require its users to provide their full name, their date of birth, their address and government-issued ID. A practice known as "shotgun KYC". This should not happen often - in our testing it never did - however it's not clear when exactly it could happen. The AML & KYC policy provided on Swapter's website simply states they will put your trade on hold if their "risk scoring system [deems it] as suspicious".
Worse yet, if they determine that "any of the information [the] customer provided is incorrect, false, outdated, or incomplete" then Swapter may decide to terminate all of the services they provide to the user. What exactly would happen to their funds in such a case remains unclear.
The only clarity we get is that the Swapter policy outlines a designated 3rd party that will verify the information provided by the user. The third party's name is Sum & Substance Ltd, also simply known as samsub and available at sumsub.com
It's understandable that some exchanges will decide on a policy of this sort, especially when they rely on external liquidity, but we would prefer more clarity be given. When exactly is a trade suspicious?
Tor
We were pleased to discover Swapter works over Tor. However, they do not provide a Tor mirror, nor do they work without JavaScript. Additionally, we found that some small features, such as the live chat, did not work over Tor. Fortunately, other means of contacting their support are still available.
UI
We have found the Swapter UI to be very modern, straightforward and simple to use. It's available in 4 languages (English, French, Dutch and Russian), although we're unable to vouch for the quality of some of those, the ones that we used seemed perfectly serviceable.
Our only issue with the UI was that it claims the funds have been sent following the trade, when in reality it seems to take the backend a minute or so to actually broadcast the transaction.
Getting in touch
Swapter's team has a chat on their website, a support email address and a support Telegram. Their social media presence in most active on Telegram and X (formerly Twitter).
Disclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-03-30 05:54:42
@ 39cc53c9:27168656
2025-03-30 05:54:42“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:

How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ d4cb227b:edca6019
2025-03-30 03:57:04
@ d4cb227b:edca6019
2025-03-30 03:57:04This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.
Dose: - 20g coffee (Coarse ground coffee) - 300mL water (92°C / 197.6°F) Time: 3:30
Instructions: Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.) Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.) Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour) Pour 4: 2:10 > 60mL Pour 5: 2:40 > 60mL Remove the V60 at 3:30
-
 @ 06830f6c:34da40c5
2025-03-30 03:56:17
@ 06830f6c:34da40c5
2025-03-30 03:56:17Once upon a time their lived a young man in a lost village, I'm just kidding with you, I'm testing my blog entries on my domain. SITE
Navigate to Blogs tab and screenshot this. @ me for a chance to get zapped ⚡. I won't say how many sats, so you are not doing it due to the incentive but to help me test the domain functionality.
Love ✌️
-
 @ d4cb227b:edca6019
2025-03-30 03:53:48
@ d4cb227b:edca6019
2025-03-30 03:53:48Dose: 30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F)
Instructions: 1. Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer.
-
Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds.
-
For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase.
-
As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds.
-
Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds.
-
Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction.
-
Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds.
-
Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper.
-
Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
-
-
 @ fd06f542:8d6d54cd
2025-03-30 02:16:24
@ fd06f542:8d6d54cd
2025-03-30 02:16:24Warning
unrecommended: deprecated in favor of NIP-17NIP-04
Encrypted Direct Message
finalunrecommendedoptionalA special event with kind
4, meaning "encrypted direct message". It is supposed to have the following attributes:contentMUST be equal to the base64-encoded, aes-256-cbc encrypted string of anything a user wants to write, encrypted using a shared cipher generated by combining the recipient's public-key with the sender's private-key; this appended by the base64-encoded initialization vector as if it was a querystring parameter named "iv". The format is the following:"content": "<encrypted_text>?iv=<initialization_vector>".tagsMUST contain an entry identifying the receiver of the message (such that relays may naturally forward this event to them), in the form["p", "<pubkey, as a hex string>"].tagsMAY contain an entry identifying the previous message in a conversation or a message we are explicitly replying to (such that contextual, more organized conversations may happen), in the form["e", "<event_id>"].Note: By default in the libsecp256k1 ECDH implementation, the secret is the SHA256 hash of the shared point (both X and Y coordinates). In Nostr, only the X coordinate of the shared point is used as the secret and it is NOT hashed. If using libsecp256k1, a custom function that copies the X coordinate must be passed as the
hashfpargument insecp256k1_ecdh. See here.Code sample for generating such an event in JavaScript:
```js import crypto from 'crypto' import * as secp from '@noble/secp256k1'
let sharedPoint = secp.getSharedSecret(ourPrivateKey, '02' + theirPublicKey) let sharedX = sharedPoint.slice(1, 33)
let iv = crypto.randomFillSync(new Uint8Array(16)) var cipher = crypto.createCipheriv( 'aes-256-cbc', Buffer.from(sharedX), iv ) let encryptedMessage = cipher.update(text, 'utf8', 'base64') encryptedMessage += cipher.final('base64') let ivBase64 = Buffer.from(iv.buffer).toString('base64')
let event = { pubkey: ourPubKey, created_at: Math.floor(Date.now() / 1000), kind: 4, tags: [['p', theirPublicKey]], content: encryptedMessage + '?iv=' + ivBase64 } ```
Security Warning
This standard does not go anywhere near what is considered the state-of-the-art in encrypted communication between peers, and it leaks metadata in the events, therefore it must not be used for anything you really need to keep secret, and only with relays that use
AUTHto restrict who can fetch yourkind:4events.Client Implementation Warning
Clients should not search and replace public key or note references from the
.content. If processed like a regular text note (where@npub...is replaced with#[0]with a["p", "..."]tag) the tags are leaked and the mentioned user will receive the message in their inbox. -
 @ fd06f542:8d6d54cd
2025-03-30 02:11:00
@ fd06f542:8d6d54cd
2025-03-30 02:11:00NIP-03
OpenTimestamps Attestations for Events
draftoptionalThis NIP defines an event with
kind:1040that can contain an OpenTimestamps proof for any other event:json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> }- The OpenTimestamps proof MUST prove the referenced
eevent id as its digest. - The
contentMUST be the full content of an.otsfile containing at least one Bitcoin attestation. This file SHOULD contain a single Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
Example OpenTimestamps proof verification flow
```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
- The OpenTimestamps proof MUST prove the referenced
-
 @ fd06f542:8d6d54cd
2025-03-30 02:10:24
@ fd06f542:8d6d54cd
2025-03-30 02:10:24NIP-03
OpenTimestamps Attestations for Events
draftoptionalThis NIP defines an event with
kind:1040that can contain an OpenTimestamps proof for any other event:json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> }- The OpenTimestamps proof MUST prove the referenced
eevent id as its digest. - The
contentMUST be the full content of an.otsfile containing at least one Bitcoin attestation. This file SHOULD contain a single Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
Example OpenTimestamps proof verification flow
```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
- The OpenTimestamps proof MUST prove the referenced
-
 @ fd06f542:8d6d54cd
2025-03-30 01:51:35
@ fd06f542:8d6d54cd
2025-03-30 01:51:35 -
 @ 30ceb64e:7f08bdf5
2025-03-30 00:37:54
@ 30ceb64e:7f08bdf5
2025-03-30 00:37:54Hey Freaks,
RUNSTR is a motion tracking app built on top of nostr. The project is built by TheWildHustle and TheNostrDev Team. The project has been tinkered with for about 3 months, but development has picked up and its goals and direction have become much clearer.
In a previous post I mentioned that RUNSTR was looking to become a Nike Run Club or Strava competitor, offering users an open source community and privacy focused alternative to the centralized silos that we've become used to.
I normally ramble incoherently.....even in writing, but this is my attempt to communicate the project's goals and direction as we move forward.
This is where the project is now:
Core Features
- Run Tracker: Uses an algorithm which adjusts to your phone's location permissions and stores the data on your phone locally
- Stats: Stored locally on your phone with a basic profile screen so users can monitor calories burned during runs
- Nostr Feed: Made up of kind1 notes that contain #RUNSTR and other running related hashtags
- Music: Brought to you via a wavlake API, enabling your wavlake playlists and liked songs to be seen and played in the app
Current Roadmap
- Bugs and small improvements: Fixing known issues within the client
- zap.store release: Launching a bug bounty program after release
- Clubs: Enabling running organizations to create territories for events, challenges, rewards and competition
- Testflight: Opening up the app to iOS users (currently Android only)
- Modes: Adding functionality to switch between Running, Walking, or Cycling modes
Future Roadmap
- Requested Features: Implementing features requested by club managers to support virtual events and challenges
- Blossom: Giving power users the ability to upload their data to personal blossom servers
- NIP28: Making clubs interoperable with other group chat clients like 0xchat, Keychat, and Chachi Chat
- DVM's: Creating multiple feeds based on movement mode (e.g., Walking mode shows walkstr feed)
- NIP101e: Allowing users to create run records and store them on nostr relays
- Calories over relays: Using NIP89-like functionality for users to save calorie data on relays for use in other applications
- NIP60: Implementing automatic wallet creation for users to zap and get zapped within the app
In Conclusion
I've just barely begun this thing and it'll be an up and down journey trying to push it into existence. I think RUNSTR has the potential to highlight the other things that nostr has going for it, demonstrating the protocol's interoperability, flexing its permissionless identity piece, and offering an experience that gives users a glimpse into what is possible when shipping into a new paradigm. Although we build into an environment that often offers no solutions, you'd have to be a crazy person not to try.
https://github.com/HealthNoteLabs/Runstr/releases/tag/feed-0.1.0-20250329-210157