-
 @ f6488c62:c929299d
2025-05-19 03:25:26
@ f6488c62:c929299d
2025-05-19 03:25:26เรื่องจริงที่ต้องเตือน: เมื่อ "ความรวยจากคริปโต" กลายเป็นดาบสองคมที่อันตรายถึงชีวิต! 🔪💰
ในขณะที่หลายคนยินดีกับกำไรจาก Bitcoin และคริปโตอื่นๆ มีเรื่องราวอีกด้านที่น่าสะเทือนใจเกิดขึ้นทั่วโลก โดยเฉพาะเหตุการณ์ "ลักพาตัวเพื่อเรียกค่าไถ่เป็นคริปโต" ที่ทวีความรุนแรงขึ้น
ข้อมูลและข่าวจากหลายแหล่งยืนยันว่า ผู้ใช้งานคริปโตกำลังตกเป็นเป้าหมายของอาชญากร โดยใช้วิธีการที่โหดเหี้ยม เช่น การทำร้ายร่างกาย หรือแม้กระทั่งการ "ตัดนิ้ว" เพื่อบีบบังคับให้เหยื่อโอนคริปโตใน Cold Wallet ที่เก็บไว้! เคสล่าสุดที่เกิดขึ้นในฝรั่งเศสและสหรัฐฯ ในช่วงปี 2025 เป็นเครื่องย้ำเตือนชั้นดี
ทำไมพวกเขาถึงเลือก "คุณ" ที่เป็นนักลงทุนคริปโต? ปัจจัยสำคัญคือ: มูลค่าสินทรัพย์ที่คุณถือสูงมาก, การเก็บ Private Key ของ Cold Wallet คือจุดอ่อนที่คนร้ายใช้ความรุนแรงบังคับเอาได้ง่าย, และที่น่าตกใจคือ การ "โพสต์โชว์ความรวย" หรือพูดถึงคริปโตมากเกินไปบนโซเชียลมีเดีย กำลังเป็นการชี้เป้าให้ตัวเอง!
ข้อคิดและแนวทางป้องกันตัวที่สำคัญสุดๆ:
จงเป็น "Ghost" ในโลกคริปโต: อย่าให้ใครรู้ว่าคุณถืออะไร เท่าไหร่ หรือรวยแค่ไหน การปิดทองหลังพระในโลกคริปโตอาจช่วยรักษาชีวิตคุณได้ ยกระดับความปลอดภัย "ชีวิตจริง": คิดถึงกล้องวงจรปิด, ระบบรักษาความปลอดภัยที่บ้าน, การจ้างบอดี้การ์ด (ถ้าจำเป็นจริงๆ), และระวังการเดินทางคนเดียว บริหารจัดการ "กุญแจ" ของคุณให้ดีที่สุด: Cold Wallet สำคัญมาก แต่การเก็บ Private Key ให้ปลอดภัยจากสายตาคนอื่น และการกระจายความเสี่ยงโดยแบ่งทรัพย์สินไปหลาย Wallet ก็สำคัญไม่แพ้กัน ความรุนแรงในวงการคริปโตเป็นบทเรียนราคาแพงที่บอกว่า ความมั่งคั่งที่มองไม่เห็นในโลกดิจิทัลนั้น มีราคาค่างวดที่ต้องจ่ายในโลกจริงหากประมาท การลงทุนอย่างรอบคอบ ไม่ใช่แค่การดูกราฟ แต่คือการประเมินและจัดการความเสี่ยงใน "ชีวิต" ของคุณด้วย!
แชร์โพสนี้เพื่อเตือนเพื่อนๆ นักลงทุนทุกคน ให้ปลอดภัยทั้งทรัพย์สินและชีวิตครับ/ค่ะ!
Crypto #Bitcoin #Ethereum #ColdWallet #PrivateKey #Security #Crime #DigitalAssets #Investor #SafetyFirst #เตือนภัย #ลงทุนอย่างปลอดภัย
-
 @ 2b998b04:86727e47
2025-05-19 03:18:36
@ 2b998b04:86727e47
2025-05-19 03:18:36Web3 talked a lot about freedom.\ But it didn’t ask much of me.
Participation meant showing up, clicking, co-signing, reacting.\ A few emoji could pass a vote. A few posts could signal alignment.\ But there was no real cost.\ No friction.\ No weight.
It felt easy — and eventually, it felt empty.
Bitcoin, by contrast, never asked for my attention.\ It demanded my effort.
Proof of Work isn’t just what secures Bitcoin.\ It’s what shapes the people who actually engage with it.
You can’t fake time.\ You can’t fake energy.\ You can’t fake commitment.
If you want to mine a block, you need to burn electricity.\ If you want to hold your keys, you need to learn what that means.\ If you want to build with Bitcoin, you’re staking skin, not vibes.
Eventually I realized: this isn’t just a consensus algorithm.\ It’s a way of seeing the world.
Proof of Work is an ethic.\ It values restraint.\ It rewards effort.\ It penalizes shortcuts.
It’s the opposite of what most of the internet has become.
Web3 tried to engineer consensus through incentive design — but consensus without cost is hollow.
In Bitcoin, there is no shortcut to agreement.\ You either do the work, or you don’t get a say.\ You can’t tweet your way into a block. You can’t fork your way into consensus.\ You earn your way — through time, electricity, and conviction.
The deeper I leaned into Bitcoin, the more it reshaped me:
-
I stopped trying to “move fast” and started focusing on lasting things.
-
I began to care more about how work was verified, not just how it looked.
-
I started pruning systems — and relationships — that couldn’t carry weight.
Even in how I think about faith, work, rest, and community — I’ve started asking:
Is this real?\ Does this cost anything?\ Is this proof of something?
Fiat culture taught me to act like time was cheap.\ PoW culture reminded me: time is everything.
Fiat let me pretend I could get something for nothing.\ PoW told me the truth — you can’t.
I no longer want to participate in systems that reward shortcuts.\ I want to build slowly, honestly, and with weight.
Proof of Work isn’t just what runs Bitcoin.\ It’s what reforms me.
⚡ If this resonates, zap me some sats — or pass it forward.\ 🤖 Drafted with the help of ChatGPT, who also prefers work over noise.
-
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 33baa074:3bb3a297
2025-05-19 02:53:31
@ 33baa074:3bb3a297
2025-05-19 02:53:31Distilled water and purified water are different in some aspects. Which one is better depends on personal needs and preferences. The following is a comparative analysis of the two from multiple dimensions:
Water source and process flow Distilled water: The water source usually comes from natural water bodies such as rivers, lakes and seas. It is treated by distillation, that is, water is heated to boiling and water vapor is condensed into liquid water. This process can remove impurities, harmful substances and most minerals in the water.

Purified water: The water source is mainly tap water. Through a series of complex processes such as filtration, adsorption, reverse osmosis, and electrolysis, harmful substances, bacteria, viruses and some minerals in the water are removed to achieve high purity. The process flow is relatively complex and some trace elements that are beneficial to the human body are retained.
Ingredients and nutrition Distilled water: Highly pure, almost no minerals and trace elements. Long-term drinking may cause the human body to lack necessary minerals and trace elements, thus affecting health.
Purified water: After treatment, some trace elements that are beneficial to the human body are retained. While maintaining a high degree of purity, it has certain nutritional value and is more suitable as daily drinking water to meet the basic needs of the human body for water and minerals.
Uses Distilled water: Due to its high purity and impurity-free characteristics, it is widely used in the pharmaceutical industry (such as preparing and diluting various drug solutions, saline, and cleaning wounds, etc.), chemical experiments (dissolving and diluting chemical reagents, preparing chemical solutions, etc.), and industrial production.
Purified water: More used in daily drinking, cooking, and brewing tea and coffee. It has a fresh taste and no odor, which can better preserve the original flavor of food and drinks. It can also be used to prepare infant milk powder and formula milk powder, etc., which is safer and more reliable because it does not contain harmful substances.
Potential risks Distilled water: Due to the lack of minerals and trace elements, it may cause nutritional imbalance in the human body.
Purified water: Although some trace elements are retained, it may also bring potential health risks due to chemical residues in the processing process.
In summary, if you are worried about the loss of minerals, it may be more appropriate to choose purified water; if you think that excessive mineral intake is not good for health, then distilled water may be a better choice. But no matter which one you choose, it is not recommended to drink a large amount of water for a long time. It can be combined with other mineral-rich drinks or foods to maintain the body's nutritional balance.
-
 @ 2b998b04:86727e47
2025-05-19 02:42:59
@ 2b998b04:86727e47
2025-05-19 02:42:59never fully left Bitcoin. But for a while, I treated it like an asset — not a foundation.
It sat quietly in the background while I explored ecosystems that promised more features, more flexibility, more “community.” But the deeper I went into Web3, the more I realized what I was missing: clarity. Conviction. Limits that meant something.
Bitcoin never sold me hype. It just sat there, silently verifying everything.
When I finally returned to it — not as an asset, but as a philosophy — it wasn’t with fanfare.\ It was more like waking up in a room I had forgotten I built.
Reading The Bitcoin Standard didn’t just shift how I think about money.\ It reframed how I saw time, trust, and value itself.
Fiat incentivizes urgency.\ Bitcoin forces patience.\ Fiat rewards noise.\ Bitcoin rewards work.
It hit me: I had been operating with fiat assumptions in more areas than I wanted to admit — not just in trading or investing, but in how I approached relationships, goals, even faith.
I started pruning.
I stopped trading altcoins altogether.\ I stopped measuring success in dollars and started thinking in sats.\ I stepped out of endless Discord threads and Telegram pings — and felt relief I hadn’t known I needed.
I started building more quietly.\ And more honestly.
Even in my non-financial life, things began to change.\ Low time preference showed up in how I approached relationships.\ In how I treated rest.\ In how I stopped chasing every new opportunity and started focusing on stewardship — of capital, energy, and attention.\ And I’ve been trying to become more patient — though I think that’s more the Holy Spirit’s work in me than Bitcoin’s.
In some ways, it wasn’t just a return.\ It was a repentance.
A turning away from the illusion of infinite leverage, and back toward a system that demanded real cost.\ Bitcoin doesn’t flatter. It disciplines.\ And that’s exactly what I needed.
I didn’t need to be early to the next thing.\ I needed to go deeper with the one thing that still made sense.
Bitcoin didn’t need me to return.\ But I’m grateful I did.
⚡ If this resonates, zap me some sats — or share it forward.\ 🤖 Drafted with the help of ChatGPT, who never once tried to sell me a token.
#ProofOfWork #BitcoinNotCrypto #TheReturn #StillBuilding #LowTimePreference #TimeNotTokens
-
 @ f6488c62:c929299d
2025-05-19 02:41:45
@ f6488c62:c929299d
2025-05-19 02:41:45เกิดอะไรขึ้นช่วงส่งท้ายปี 2024? จู่ๆ บัญชี X ของอีลอน มัสก์ ก็เปลี่ยนชื่อเป็น "Kekius Maximus" สร้างความสงสัยและกระแสไปทั่ว!
ชื่อนี้มีความหมายแฝงอะไร? ➡️ Kek: มาจากเทพกบในตำนานอียิปต์ และเป็นมีมยอดฮิตในโลกออนไลน์ (โดยเฉพาะกลุ่มคริปโต/เกม) มักใช้สื่อถึงความขำขัน เสียดสี ➡️ Maximus: คาดว่ามาจากตัวละครฮีโร่ผู้กล้าหาญในภาพยนตร์ Gladiator ➡️ รูปโปรไฟล์: ใช้ภาพ Pepe the Frog (มีมดัง) ในชุดนักรบโรมัน ถือจอยสติ๊ก!
เจตนาที่เป็นไปได้? ✅ ความสนุกและเล่นกับมีม: มัสก์ชอบใช้มีมสร้างกระแสอยู่แล้ว นี่อาจเป็นอีกครั้งที่เขาหยอกล้อกับวัฒนธรรมอินเทอร์เน็ต ✅ ทดสอบอิทธิพล: การเปลี่ยนชื่อส่งผลให้เหรียญมีม KEKIUS พุ่งขึ้นมหาศาล เป็นการยืนยันพลังโซเชียลของเขา ✅ เชื่อมโยงกับเกม: มัสก์เคยใช้ชื่อ Kekius Maximus ในเกม Path of Exile มาก่อน
แม้จะเปลี่ยนชื่อกลับไปแล้ว แต่เรื่องนี้ก็แสดงให้เห็นมุมที่เป็นกันเอง ความชอบส่วนตัว และอิทธิพลอันทรงพลังของอีลอน มัสก์ ได้เป็นอย่างดี!
ElonMusk #KekiusMaximus #X #โซเชียลมีเดีย #มีม #คริปโต #Gladiator #PepeTheFrog
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ a31f394c:7ad8f439
2025-05-19 02:21:26
@ a31f394c:7ad8f439
2025-05-19 02:21:26Nos últimos anos, o entretenimento digital tem ganhado cada vez mais espaço na vida dos brasileiros. Nesse cenário, a 88BRL se destaca como uma das plataformas mais completas e confiáveis do mercado. Com um ambiente seguro, interface moderna e uma variedade impressionante de jogos, o site oferece uma experiência única para quem busca diversão, emoção e a possibilidade de transformar o lazer em grandes recompensas.
Uma Plataforma Segura e Intuitiva Desde o primeiro acesso, fica evidente que a 88brlfoi desenvolvida com foco no usuário. A navegação é simples e fluida, mesmo para quem não tem muita familiaridade com plataformas de jogos online. O site é responsivo, ou seja, funciona perfeitamente tanto em computadores quanto em dispositivos móveis, garantindo liberdade para jogar onde e quando quiser.
Outro ponto importante é a segurança. A plataforma utiliza tecnologia de criptografia avançada para proteger os dados dos usuários e garantir transações rápidas e seguras. Além disso, o suporte ao cliente está disponível todos os dias, pronto para resolver qualquer dúvida ou problema com eficiência e cordialidade.
Catálogo de Jogos Diversificado A grande estrela da 88BRL é, sem dúvida, sua coleção de jogos. A plataforma oferece opções para todos os gostos e níveis de experiência, com títulos desenvolvidos por estúdios renomados do setor. Entre os destaques, estão os populares jogos de slots, roletas virtuais e mesas de cartas, todos com gráficos realistas, trilha sonora envolvente e mecânicas intuitivas.
Para quem gosta de desafios estratégicos, a plataforma também conta com uma seção de jogos de habilidade, onde a atenção, raciocínio rápido e conhecimento podem fazer toda a diferença. O sistema é justo e transparente, oferecendo chances reais de vitória a todos os jogadores.
Experiência Personalizada para o Jogador Brasileiro Um dos grandes diferenciais da 88BRL é o cuidado com o público nacional. O site está totalmente traduzido para o português, e o atendimento ao cliente é feito por profissionais brasileiros, garantindo uma comunicação clara e eficaz. Além disso, a plataforma aceita os principais métodos de pagamento utilizados no Brasil, incluindo transferências bancárias, carteiras digitais e até mesmo PIX, o que torna os depósitos e saques rápidos e descomplicados.
A experiência do jogador vai além dos jogos em si. A 88BRL oferece promoções frequentes, bônus de boas-vindas atrativos e um programa de fidelidade que recompensa os usuários mais ativos com benefícios exclusivos, como rodadas grátis, brindes e acesso antecipado a novos jogos.
Comunidade e Diversão Sem Limites A plataforma também incentiva a construção de uma comunidade entre seus usuários, com torneios e eventos especiais que promovem a interação e a competitividade saudável. Esses eventos são uma ótima oportunidade para testar habilidades, conhecer outros jogadores e se divertir ainda mais.
Com atualizações constantes e novos títulos sendo adicionados regularmente, a 88BRL mostra que está sempre atenta às tendências do mercado e ao feedback dos usuários. Isso garante uma experiência dinâmica e sempre renovada.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ a31f394c:7ad8f439
2025-05-19 02:20:52
@ a31f394c:7ad8f439
2025-05-19 02:20:52A 66BR chega ao cenário nacional como uma plataforma de entretenimento digital que promete transformar a forma como os brasileiros vivenciam os jogos online. Com uma interface moderna, navegação intuitiva e uma vasta variedade de jogos, o site oferece tudo o que os amantes da adrenalina e da sorte procuram — tudo isso com total segurança e praticidade.
Plataforma Moderna e Acessível Desde o primeiro acesso, é possível notar o cuidado com a experiência do usuário. A 66BR possui um layout responsivo, funcionando perfeitamente tanto em computadores quanto em dispositivos móveis. Isso significa que você pode jogar de onde quiser, seja no conforto de casa ou em movimento. A navegação é simples, rápida e organizada, o que facilita até mesmo para quem está começando agora nesse universo.
Além disso, a 66brprioriza a segurança dos seus usuários. A plataforma utiliza tecnologia de criptografia avançada para garantir que todas as informações pessoais e financeiras estejam protegidas. Os métodos de pagamento são variados e incluem opções populares no Brasil, como Pix, boleto bancário e carteiras digitais.
Variedade de Jogos para Todos os Gostos Um dos grandes atrativos da 66BR é a diversidade de jogos disponíveis. A plataforma trabalha com os principais desenvolvedores do mercado, garantindo gráficos de alta qualidade, jogabilidade fluida e títulos sempre atualizados.
Entre as opções oferecidas, destacam-se:
Slots virtuais: com temas que vão desde mitologia até filmes e séries, essas máquinas digitais combinam sorte e emoção em rodadas rápidas e empolgantes.
Jogos de mesa: para quem gosta de jogos estratégicos e clássicos como o pôquer, o blackjack e a roleta.
Jogos ao vivo: com transmissões em tempo real, esses jogos proporcionam uma experiência imersiva, como se o jogador estivesse em um ambiente físico, interagindo com anfitriões reais.
Todos os jogos são otimizados para rodar sem travamentos e contam com versões de demonstração para quem deseja testar antes de apostar com dinheiro real.
Experiência do Jogador: Simples, Justa e Divertida A experiência do usuário na 66BR vai além da qualidade dos jogos. O suporte ao cliente é outro ponto forte da plataforma, com atendimento disponível 24 horas por dia, em português, e com respostas rápidas e eficientes. Isso demonstra o compromisso da empresa em garantir a satisfação e tranquilidade de seus usuários.
Outro diferencial importante são as promoções e bônus frequentes. Novos usuários são recebidos com bônus de boas-vindas atrativos, enquanto os jogadores mais frequentes podem participar de campanhas exclusivas, com prêmios especiais e recompensas personalizadas.
A plataforma também conta com um sistema de fidelidade, onde os jogadores acumulam pontos à medida que participam dos jogos. Esses pontos podem ser trocados por bônus, giros grátis e outras vantagens dentro do site.
Conclusão A 66BR chega com força total para conquistar os brasileiros que buscam uma plataforma segura, moderna e recheada de entretenimento. Com um catálogo robusto de jogos, atendimento eficiente e benefícios para todos os perfis de jogadores, a 66BR se consolida como uma das melhores opções do país. Se você está procurando uma nova forma de se divertir e explorar o mundo dos jogos online com qualidade e confiança, a 66BR é o destino certo.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 2b998b04:86727e47
2025-05-19 02:13:37
@ 2b998b04:86727e47
2025-05-19 02:13:37🧱 Why I Left Web3 for Proof of Work – Part 2: The Breaking Point\ \ It wasn’t a moment. It was a slow-motion unraveling.\ \ By 2024, I was deeply involved in a Web3 project focused on rewarding eco-conscious actions using a token system called “Proof of Environment.” I helped run a related Facebook group aimed at building community and encouraging engagement — especially among refugees and people living on the margins.\ \ I believed in it. I have a lot of respect for the project’s founder. His heart is in the right place.\ \ But reality set in: the token wasn’t trading.\ People were earning rewards that had no liquidity.\ \ So I tried to bridge the gap. I personally subsidized the effort — offering USD to keep people engaged and compensated.\ \ Eventually, I had to stop.\ \ Not because I lost faith in the mission… but because I realized I was compensating for a structural flaw. I was using fiat to prop up what was supposed to be an alternative to fiat.\ \ That realization cracked something open. And it wasn’t just about that project.\ \ By early 2025, I started re-examining the other Web3 spaces I was part of — including a local crypto-faith collective and a civic blockchain group I’d been attending.\ \ Before I say more - I want to be clear:\ \ - I respect the people involved in these communities.\ - I believe their intentions are sincere, and their efforts often come from a genuine desire to help.\ - The speakers were engaging and thought-provoking.\ - This isn’t a judgment of hearts — it’s a reflection on structure, incentives, and what actually works.\ \ One local Web3 community I attended regularly was especially revealing. It was connected to a publishing platform that promised a new way to engage content and community. But in practice, the tech was clunky, and the product was difficult to use — even basic edits to content required small fees in a token that few people understood. One of the DAOs I participated in burned through tens of thousands — mostly on architecture plans and design proposals.\ \ Weekly meetings had free lunches and spiritual talks… but the people experiencing homelessness, who we supposedly served? Often absent — or tokenized for optics.\ \ At one point, I proposed a practical idea to support a local housing initiative. The vision was for residents to grow some of their own food — creating both sustainability and job training opportunities.\ \ The response?\ \ “Let’s do this later.”\ \ It was polite. But it meant no.\ \ Over time, I felt less like a contributor and more like a prop — quietly tolerated, not truly included.\ \ Meanwhile, others held titles, got paid (quietly, maybe — but it was hard to tell how), and kept the stage.\ \ There was always funding for visibility. Rarely funding for outcomes.\ \ The problems people actually faced — hunger, housing, dignity — don’t care about abstractions.\ \ And neither does Bitcoin.\ \ I didn’t leave all at once. I still showed up in March, April, and May — out of habit, curiosity, and maybe hope.\ \ The speakers were thoughtful. In March, someone taught on mindfulness and the “five dimensions of time.” It was peaceful. But to me, it felt like another New Age sidetrack — far from the urgent needs on the ground.\ \ In April, one speaker — a former military interrogator turned AI educator — spoke on an AI “OS” for schools. Another shared how they helped build local currencies in Kenyan villages.\ \ In May, someone presented a trauma-informed housing model for youth with mental illness — one of the few ideas that felt truly grounded.\ \ These were all great ideas — thoughtful, human, often moving.\ \ My only thought was: they might have been better served by starting with Bitcoin — not as an add-on, but as a foundation. Especially the last two.\ \ And again — I believe many of the people involved were sincerely trying to make a difference.\ \ But something had shifted in me.\ \ I couldn’t stop asking: Who actually benefits from this tech?\ \ Does it work — or is it just another talk wrapped in hope?\ \ Why does impact often need a token?\ \ Not all the speakers revolved around Web3 or tokens — but many did.\ \ And quietly, a deeper question emerged: Couldn’t we just do all of this… with Bitcoin?\ \ Without a new platform. Without a fragile token.\ \ Just real tools. Real money. Real proof of work.\ \ The breaking point wasn’t dramatic. It was subtle, quiet — but final.\ \ ✍️ A Personal Note\ \ Even after all this, I still attend some of these events. I still show up — not because I’ve “come back,” but because I care.\ \ Because I respect the people.\ \ Because I believe conviction doesn’t require separation — it just requires clarity. I’m not circling back.\ \ I’m walking forward — with eyes open.\ \ And sometimes that means sitting in the same room with people I no longer fully agree with… and still learning something.\ \ My break wasn’t from the people.\ \ It was from the hype.\ \ From the structure, not the souls.\ \ And I still believe we can build better — if we start with truth.\ \ ⚡ If this resonates, zap me some sats — or just share it forward.\ 🤖 Drafted with the help of ChatGPT, who’s helped me find clarity across tech, theology, and everything in between.
-
 @ 08f96856:ffe59a09
2025-05-15 01:22:34
@ 08f96856:ffe59a09
2025-05-15 01:22:34เมื่อพูดถึง Bitcoin Standard หลายคนมักนึกถึงภาพโลกอนาคตที่ทุกคนใช้บิตคอยน์ซื้อกาแฟหรือของใช้ในชีวิตประจำวัน ภาพแบบนั้นดูเหมือนไกลตัวและเป็นไปไม่ได้ในความเป็นจริง หลายคนถึงกับพูดว่า “คงไม่ทันเห็นในช่วงชีวิตนี้หรอก” แต่ในมุมมองของผม Bitcoin Standard อาจไม่ได้เริ่มต้นจากการที่เราจ่ายบิตคอยน์โดยตรงในร้านค้า แต่อาจเริ่มจากบางสิ่งที่เงียบกว่า ลึกกว่า และเกิดขึ้นแล้วในขณะนี้ นั่นคือ การล่มสลายทีละน้อยของระบบเฟียตที่เราใช้กันอยู่
ระบบเงินที่อิงกับอำนาจรัฐกำลังเข้าสู่ช่วงขาลง รัฐบาลทั่วโลกกำลังจมอยู่ในภาระหนี้ระดับประวัติการณ์ แม้แต่ประเทศมหาอำนาจก็เริ่มแสดงสัญญาณของภาวะเสี่ยงผิดนัดชำระหนี้ อัตราเงินเฟ้อกลายเป็นปัญหาเรื้อรังที่ไม่มีท่าทีจะหายไป ธนาคารที่เคยโอนฟรีเริ่มกลับมาคิดค่าธรรมเนียม และประชาชนก็เริ่มรู้สึกถึงการเสื่อมศรัทธาในระบบการเงินดั้งเดิม แม้จะยังพูดกันไม่เต็มเสียงก็ตาม
ในขณะเดียวกัน บิตคอยน์เองก็กำลังพัฒนาแบบเงียบ ๆ เงียบ... แต่ไม่เคยหยุด โดยเฉพาะในระดับ Layer 2 ที่เริ่มแสดงศักยภาพอย่างจริงจัง Lightning Network เป็น Layer 2 ที่เปิดใช้งานมาได้ระยะเวลสหนึ่ง และยังคงมีบทบาทสำคัญที่สุดในระบบนิเวศของบิตคอยน์ มันทำให้การชำระเงินเร็วขึ้น มีต้นทุนต่ำ และไม่ต้องบันทึกทุกธุรกรรมลงบล็อกเชน เครือข่ายนี้กำลังขยายตัวทั้งในแง่ของโหนดและการใช้งานจริงทั่วโลก
ขณะเดียวกัน Layer 2 ทางเลือกอื่นอย่าง Ark Protocol ก็กำลังพัฒนาเพื่อตอบโจทย์ด้านความเป็นส่วนตัวและประสบการณ์ใช้งานที่ง่าย BitVM เปิดแนวทางใหม่ให้บิตคอยน์รองรับ smart contract ได้ในระดับ Turing-complete ซึ่งทำให้เกิดความเป็นไปได้ในกรณีใช้งานอีกมากมาย และเทคโนโลยีที่น่าสนใจอย่าง Taproot Assets, Cashu และ Fedimint ก็ทำให้การออกโทเคนหรือสกุลเงินที่อิงกับบิตคอยน์เป็นจริงได้บนโครงสร้างของบิตคอยน์เอง
เทคโนโลยีเหล่านี้ไม่ใช่การเติบโตแบบปาฏิหาริย์ แต่มันคืบหน้าอย่างต่อเนื่องและมั่นคง และนั่นคือเหตุผลที่มันจะ “อยู่รอด” ได้ในระยะยาว เมื่อฐานของความน่าเชื่อถือไม่ใช่บริษัท รัฐบาล หรือทุน แต่คือสิ่งที่ตรวจสอบได้และเปลี่ยนกฎไม่ได้
แน่นอนว่าบิตคอยน์ต้องแข่งขันกับ stable coin, เงินดิจิทัลของรัฐ และ cryptocurrency อื่น ๆ แต่สิ่งที่ทำให้มันเหนือกว่านั้นไม่ใช่ฟีเจอร์ หากแต่เป็นความทนทาน และความมั่นคงของกฎที่ไม่มีใครเปลี่ยนได้ ไม่มีทีมพัฒนา ไม่มีบริษัท ไม่มีประตูปิด หรือการยึดบัญชี มันยืนอยู่บนคณิตศาสตร์ พลังงาน และเวลา
หลายกรณีใช้งานที่เคยถูกทดลองในโลกคริปโตจะค่อย ๆ เคลื่อนเข้ามาสู่บิตคอยน์ เพราะโครงสร้างของมันแข็งแกร่งกว่า ไม่ต้องการทีมพัฒนาแกนกลาง ไม่ต้องพึ่งกลไกเสี่ยงต่อการผูกขาด และไม่ต้องการ “ความเชื่อใจ” จากใครเลย
Bitcoin Standard ที่ผมพูดถึงจึงไม่ใช่การเปลี่ยนแปลงแบบพลิกหน้ามือเป็นหลังมือ แต่คือการ “เปลี่ยนฐานของระบบ” ทีละชั้น ระบบการเงินใหม่ที่อิงอยู่กับบิตคอยน์กำลังเกิดขึ้นแล้ว มันไม่ใช่โลกที่ทุกคนถือเหรียญบิตคอยน์ แต่มันคือโลกที่คนใช้อาจไม่รู้ตัวด้วยซ้ำว่า “สิ่งที่เขาใช้นั้นอิงอยู่กับบิตคอยน์”
ผู้คนอาจใช้เงินดิจิทัลที่สร้างบน Layer 3 หรือ Layer 4 ผ่านแอป ผ่านแพลตฟอร์ม หรือผ่านสกุลเงินใหม่ที่ดูไม่ต่างจากเดิม แต่เบื้องหลังของระบบจะผูกไว้กับบิตคอยน์
และถ้ามองในเชิงพัฒนาการ บิตคอยน์ก็เหมือนกับอินเทอร์เน็ต ครั้งหนึ่งอินเทอร์เน็ตก็ถูกมองว่าเข้าใจยาก ต้องพิมพ์ http ต้องรู้จัก TCP/IP ต้องตั้ง proxy เอง แต่ปัจจุบันผู้คนใช้งานอินเทอร์เน็ตโดยไม่รู้ว่าเบื้องหลังมีอะไรเลย บิตคอยน์กำลังเดินตามเส้นทางเดียวกัน โปรโตคอลกำลังถอยออกจากสายตา และวันหนึ่งเราจะ “ใช้มัน” โดยไม่ต้องรู้ว่ามันคืออะไร
หากนับจากช่วงเริ่มต้นของอินเทอร์เน็ตในยุค 1990 จนกลายเป็นโครงสร้างหลักของโลกในสองทศวรรษ เส้นเวลาของบิตคอยน์ก็กำลังเดินตามรอยเท้าของอินเทอร์เน็ต และถ้าเราเชื่อว่าวัฏจักรของเทคโนโลยีมีจังหวะของมันเอง เราก็จะรู้ว่า Bitcoin Standard นั้นไม่ใช่เรื่องของอนาคตไกลโพ้น แต่มันเกิดขึ้นแล้ว
siamstr
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 2b998b04:86727e47
2025-05-19 02:12:52
@ 2b998b04:86727e47
2025-05-19 02:12:52For years, I wandered through the Web3 space—intrigued by its promises, pulled in by buzzwords like “decentralization,” “DAOs,” and “stakeholder democracy.”
But over time, the signals got drowned out by noise.
I saw venture capital pour into projects that had no product. I watched communities reward performative governance and token hype, rather than real work or impact. Even in faith-based circles, “Web3 for good” often meant shiny apps that served insiders more than outsiders.
Then I found my way back to where I began: Bitcoin.
Not as a speculative asset—but as a philosophy. A discipline. A foundation.
Proof of Work doesn’t need marketing. It doesn’t ask for permission. It either works—or it doesn’t.
Web3 taught me a lot. But Bitcoin gave me a plumb line. And from now on, that’s the line I’m building on.
This is Part 1 of a multi-part series. Follow for future entries.\ \ — Andrew G. Stanton\ Bitcoiner, builder, believer.
This article was co-drafted using ChatGPT to accelerate the writing process. Final content was reviewed and edited by me.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 65912a7a:5dc638bf
2025-02-09 20:34:15
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
the coronavirus panic is dumb
As a concerned friend, I sent him a private text:
Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
Sam, you of all people should not be concerned about this.
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
Is (35,000 deaths + 600,000 cases) > 35,000 cases?
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ a5ee4475:2ca75401
2025-05-19 01:11:59
@ a5ee4475:2ca75401
2025-05-19 01:11:59clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 📱 (on development) ⏳
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] [source] 🤖🍎
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 9c47bb51:000381d0
2025-01-05 03:32:27
@ 9c47bb51:000381d0
2025-01-05 03:32:27EVERYDAY STACKING GUIDE
Let me break it down for you: stacking sats is about building your Bitcoin stash little by little. You do not need to make some massive play or wait for the perfect opportunity. It is about finding simple, steady ways to add to your stack, no matter what your situation looks like. And the best part? There are so many ways to do it, whether you are creating something, connecting with folks directly, or just using tools that reward you. Let us dive into how you can stack sats consistently, keeping it decentralized and peer-to-peer whenever possible.
You have got platforms like Stacker News where you can earn sats just by being part of the conversation. Think of it as Bitcoin’s answer to Reddit. You share something valuable, comment on posts, or just engage with the community, and next thing you know, you have got some sats coming your way. It is simple, and it is steady. Plus, it feels good to know your thoughts and contributions are being rewarded.
Then there is Nostr, a decentralized social platform that is making waves. It is built to connect people directly, and it ties in Bitcoin through the Lightning Network. The coolest thing? You can get tipped, or “zapped,” for your posts, notes, or anything you put out there. This is not about big corporations taking a cut; it is people showing love directly. Share your ideas, your art, your insights, and watch your stack grow while connecting with a global community.
Now, let us talk about Fold. It is a little different but still fun. You spin their rewards wheel every day, and you will earn a few sats. Sometimes it is a little, sometimes it is more, but it all adds up. If you are using their Bitcoin rewards debit card for your regular spending, you are earning even more. Sure, it is not 100 percent decentralized, but it is an easy way to stack sats while handling your everyday purchases.
For creators, platforms like Zap.Stream are opening doors. Imagine streaming your work, whether it is music, art, teaching, or something else, and getting paid directly in Bitcoin by your audience. No middlemen, no fuss. It is all about connecting directly with the people who support you and earning sats in real time.
And do not forget about selling something for Bitcoin. Whether it is handmade crafts, digital products, or your services, there is always a way to find buyers who want to pay in sats. Platforms that focus on Bitcoin marketplaces make it easier to connect with those folks. Plus, it is a true peer-to-peer exchange, keeping it aligned with the decentralized spirit of Bitcoin.
If you are freelancing, there are options to get paid in Bitcoin directly. Whether you are designing, coding, writing, or consulting, there are platforms that let you bypass the banks and get your payment straight into your wallet. It is quick, efficient, and keeps you in control of your money.
And let us talk about the small, passive ways to stack sats. Cashback apps like Lolli let you earn Bitcoin on everyday purchases. It might not be a huge amount, but those little bits add up over time. If you are already spending the money, why not get some sats back for it?
The real key here is consistency. Set a goal for yourself, whether it is adding sats daily or weekly, and stick to it. Even if it is just a few hundred sats here and there, it is progress. Those small steps add up over time and can turn into something meaningful.
Why focus on decentralized and peer-to-peer methods? Because that is what Bitcoin is all about. It is about staying true to the values of self-sovereignty and financial freedom. By avoiding centralized systems, you are not just stacking sats; you are strengthening the Bitcoin ecosystem itself.
Stacking sats is not about getting rich overnight. It is a journey. It is about building your stash, supporting the Bitcoin movement, and claiming your financial independence bit by bit. Whether it is through sharing content, selling products, or using new platforms, the mission stays the same: keep adding to your stack, little by little. And remember, every sat counts.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-19 00:31:55
@ 5d4b6c8d:8a1c1ee3
2025-05-19 00:31:55We have our conference finalists: - Indiana (4) @ New York (3) - Minnesota (6) @ OKC (1)
Pick one team to advance to the finals and one player to win Conference Finals MVP. One player from each matchup will be named MVP.
The scoring this round is 4 points + seed value for picking a winner and 4 points for picking an MVP. The maximum points this round are 14.
Current Scores | Stacker | Points | |----------|-------| | @Undisciplined | 35 | | @grayruby | 32 | | @gnilma | 28 | | @fishious | 21 | | @WeAreAllSatoshi | 20 | | @BlokchainB | 19 | | @Coinsreporter | 19 | | @Carresan | 18 | | @Car | 9 |
SGA was the leading scorer of round 2
https://stacker.news/items/983402
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 9c47bb51:000381d0
2024-12-06 16:20:33
@ 9c47bb51:000381d0
2024-12-06 16:20:33As Bitcoin’s price continues to climb, the value of its smallest unit, the Satoshi, grows with it. Today, owning a million Satoshis is an affordable and wise investment—especially as Bitcoin reaches new heights. Here’s why a million Satoshis should be the minimum amount everyone owns and why cold storage is key to securing your future.
- Affordability and Future Value
While owning one full Bitcoin might seem out of reach for many, owning one million Satoshis is much more achievable. As Bitcoin continues to rise in value, a million Satoshis, which is currently worth around $250, could become worth $10,000 or more in the future. This makes owning a million Satoshis not just an entry into Bitcoin, but a solid step toward securing future wealth.
- A World Priced in Sats
Imagine a future where goods and services are priced in Satoshis. As Bitcoin gains widespread adoption, this scenario is becoming more likely. With Bitcoin potentially surpassing $1 million per coin, one million Satoshis will be worth a significant sum in the future. By owning this amount now, you’re setting yourself up for a future where everyday transactions are measured in Sats, ensuring your financial independence.
- A Hedge Against Inflation
With fiat currencies losing value over time, Bitcoin offers a deflationary alternative. Owning Satoshis is like holding a form of “sound money” that protects you from inflationary pressures. As Bitcoin’s value continues to grow, your Satoshis could outpace inflation, preserving your wealth for the long term.
- The Importance of Cold Storage
Storing your Satoshis securely is just as important as owning them. Cold storage solutions, like the Foundation Passport, Coldcard, or Bitkey, offer the highest level of security by keeping your private keys offline. This protects your Bitcoin from online threats, ensuring that your Satoshis remain safe for years to come.
Cold Storage Solutions
• Foundation Passport: Portable, secure, and open-source. A great option for long-term Bitcoin storage. • Coldcard: A highly secure hardware wallet that keeps your Bitcoin offline and out of reach from hackers. • Bitkey: A versatile, user-friendly cold storage solution integrated with your smartphone.A Better Future with Bitcoin
Owning a million Satoshis today is not just about having a small piece of Bitcoin—it’s about securing a financial future where Bitcoin is the standard. Cold storage protects your wealth, and owning Bitcoin positions you to thrive in a decentralized, Bitcoin-driven economy. As Bitcoin continues to evolve, those who embrace it today will be ahead of the curve in a world where wealth is stored in Satoshis.
-
 @ 9c47bb51:000381d0
2024-12-06 16:07:53
@ 9c47bb51:000381d0
2024-12-06 16:07:53In a world that often rewards conformity, being open-minded can be a radical act. It is a choice to embrace curiosity, challenge assumptions, and allow life to surprise you. When we open our minds, we invite new possibilities—not just in the realm of ideas but in every aspect of existence, from consciousness expansion to financial freedom with Bitcoin, and even finding a life partner. Let’s explore how this mindset can transform your reality.
- Open-Mindedness and Consciousness
The first step to expanding consciousness is realizing how much there is to learn. By questioning the default narratives we’ve inherited—about who we are, why we’re here, and what reality itself means—we create space for deeper awareness.
This could involve practices like meditation, exploring alternative philosophies, or studying ancient wisdom traditions like Traditional Chinese Medicine (TCM). These practices teach us that the mind is not a fixed entity but a fluid and evolving tool. When we let go of rigid beliefs, we begin to notice synchronicities, experience heightened awareness, and even tap into higher states of being.
Being open-minded in this sense doesn’t mean blindly accepting everything; it means cultivating discernment while remaining curious. It’s in this openness that we discover the profound interconnectedness of all things.
- Bitcoin: Financial Freedom through Innovation
For many, Bitcoin is a misunderstood or intimidating concept. But being open-minded to alternative systems can lead to incredible breakthroughs—not just financially but philosophically. Bitcoin isn’t just “digital money”; it represents decentralization, transparency, and freedom from traditional financial systems that have long prioritized the few over the many.
Adopting Bitcoin often requires a mental shift. It’s not about chasing short-term gains but about understanding the principles of sound money, scarcity, and peer-to-peer networks. For those willing to question how money works and why it matters, Bitcoin offers an opportunity to participate in a financial revolution that empowers individuals.
Openness to Bitcoin can also reshape your mindset toward technology, personal sovereignty, and global collaboration. It’s not just a currency; it’s a philosophy of trust and innovation.
- Finding Love Through Open-Mindedness
The search for a life partner often mirrors our internal beliefs about ourselves and others. An open mind can transform how we approach relationships, making space for unexpected connections.
When we let go of rigid expectations—about what our partner “should” look like, where we’ll meet them, or how a relationship should progress—we allow love to unfold organically. Sometimes, the most wonderful spouse enters our lives when we least expect it, perhaps through a chance encounter or shared passion.
Open-mindedness in love also means being willing to grow together, embracing differences, and learning from one another. It’s about building a relationship rooted in mutual respect, curiosity, and the belief that you can continually discover new facets of your partner (and yourself) over time.
Final Thoughts: The Ripple Effect of Open-Mindedness
Whether it’s exploring consciousness, adopting Bitcoin, or finding a wonderful spouse, being open-minded is a skill that creates ripple effects across all areas of life. It’s not just about embracing new ideas—it’s about living with the belief that the universe has infinite possibilities waiting for you to discover.
By opening your mind, you open doors: to deeper awareness, financial independence, and love that feels like home. The more you explore, the more you realize that being open-minded doesn’t just expand your world—it transforms it.
So, the next time you’re faced with something unfamiliar or challenging, ask yourself: What could I learn if I let myself be curious?
On this journey, everything becomes possible.
-
 @ 805b34f7:3620fac3
2025-05-18 23:38:44
@ 805b34f7:3620fac3
2025-05-18 23:38:44By Louise Rafkin
Oct. 18, 2024
https://www.nytimes.com/2024/10/18/fashion/laura-baroni-paul-keating-wedding.html
In early 2022, Paul Thomas Keating and Laura Baroni each traveled to Costa Rica looking for something — but not necessarily for someone. The two kicked around the small beach town of Santa Teresa, on the western coast, for more than a month before laying eyes on each other.
When they did, there were sparks but few words. At a dinner with mutual friends, Ms. Baroni, who is from Italy, was immediately intrigued by the handsome, curly-haired American. Shared glances prompted Ms. Baroni to pivot from English, of which she knew just a few words, to Spanish, in which she was fluent. Mr. Keating spoke Spanish passably, so it was in that language that they shared stories about how their paths had crossed.
Ms. Baroni, 27, grew up in Liguria, Italy. After earning a bachelor’s degree in modern languages and cultures for business and tourism from the University of Genoa, she worked as a sales manager for a company that made biodegradable bags. But during the pandemic, she became hooked on surfing, and by the end of 2021, had bought a one-way ticket to Costa Rica and settled in Santa Teresa, which is known for its superb year-round waves.
At the time, Mr. Keating, 31, was a self-described surf bum. “I lived simply, or, you could also say, in poverty,” he said jokingly. In Santa Teresa, he shared a home with several roommates and swarms of mosquitoes; to thwart the insects, he slept inside a tent set up in his bedroom. A skunk bedded down in the kitchen sink. “It kept the rodents out, so we let it stay,” he said.
Mr. Keating spent his childhood in Oceanside, Calif., a small Southern California beach town. He played baseball for Vanguard University, earning a bachelor’s degree in business administration and a master’s in organizational psychology. He then pursued a career in modeling and acting. He appeared in a commercial for Mountain Dew and was cast in the reality dating show “FBoy Island” in 2021. He was booted off in the fourth week.
By late 2021, he was delivering refrigerators to college dorm rooms and dreaming of a different life. “I wanted to surf with cool people, have a family and find meaningful work,” he said. He packed his 1985 Nissan truck with donated baseball equipment and set off for Costa Rica. During the five-week road trip, he gave the baseball gear to children in Nicaragua.
After their first meeting, Mr. Keating suggested that he and Ms. Baroni attend a local festival where, in an effort to impress Ms. Baroni, he jumped into a rodeo arena with angry bulls. To his surprise, Ms. Baroni followed. Both escaped unscathed, and with a surge of adrenaline, shared a first kiss.
Soon after, Ms. Baroni texted a friend in Italy: “I’ve met my future husband and the father of my children.”
Mr. Keating was similarly smitten. The couple began surfing together, and Ms. Baroni’s fearlessness in the face of huge waves fueled Mr. Keating’s ardor and admiration.

Several months later, after moving in together, Ms. Baroni floated the first “I love you.” Mr. Keating began to sob. “After years of wandering and not finding, here was everything I wanted,” he said.
In 2023, the couple traveled together to more than a dozen countries and visited each other’s families. They also developed careers. Ms. Baroni now works as an independent model, photographer and content creator. Mr. Keating, who still occasionally models and acts in commercials, works for Primal, a social media company. “When you have the right person at your side, it’s easy to find yourself,” Ms. Baroni said.
In June 2023, the couple, still living a nomadic life, were invited by one of Mr. Keating’s work associates to cruise the Greek islands on his boat. On the island of Paxos, atop a rocky hillside, Mr. Keating dropped to a knee and, with friends and colleagues watching, proposed with a snake-shaped ring with tiny diamond eyes that reminded him of the jungles of Costa Rica. Ms. Baroni closed her eyes and fell silent. For several minutes, Mr. Keating wondered if he was experiencing the most embarrassing moment of his life.
“Just two nights before, I had dreamed we were marrying,” Ms. Baroni explained. When her eyes opened she smiled and said yes. The two clasped hands and leaped into the sea.
On Oct. 10, at San Clemente State Beach park in San Clemente, Calif., the couple were married by nostr:nprofile1qyx8wumn8ghj7cnjvghxjmcpz4mhxue69uhk2er9dchxummnw3ezumrpdejqqgqufvg53h6lmccvqp2sl55aafykewhq47gw7kwp93722h7gdq6xx5mdd75x , a friend of Mr. Keating’s who was ordained by American Marriage Ministries for the event.
Ms. Baroni said her vows in Italian. “I spoke love with my heart, I know Paul understood,” she said. After the ceremony, the 100 guests walked a short dirt path to the beach, where the groom and his best man jumped into the Pacific for a sunset surf session while still wearing their wedding attire.
“We are going to have the most interesting lives,” Ms. Baroni said.
pv
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ 57c631a3:07529a8e
2025-04-07 13:17:50
@ 57c631a3:07529a8e
2025-04-07 13:17:50What is Growth Engineering? Before we start: if you’ve already filled out the What is your tech stack? survey: thank you! If you’ve not done so, your help will be greatly appreciated. It takes 5-15 minutes to complete. Those filling out will receive results before anyone else, and additional analysis from myself and Elin. Fill out this survey here.**
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Growth engineering was barely known a decade ago, but today, most scaleups and many publicly traded tech companies have dedicated growth teams staffed by growth engineers. However, some software engineers are still suspicious of this new area because of its reputation for hacky code with little to no code coverage.
For this reason and others, I thought it would be interesting to learn more from an expert who can tell us all about the practicalities of this controversial domain. So I turned to Alexey Komissarouk, who’s been in growth engineering since 2016, and was in charge of it at online education platform, MasterClass. These days, Alexey lives in Tokyo, Japan, where he advises on growth engineering and teaches the Growth Engineering course at Reforge.
In today’s deep dive, Alexey covers:
- What is Growth Engineering? In the simplest terms: writing code to help a company make more money. But there are details to consider: like the company size where it makes sense to have a dedicated team do this.
- What do Growth Engineers work on? Business-facing work, empowerment and platform work are the main areas.
- Why Growth Engineers move faster than Product Engineers. Product Engineers ship to build: Growth Engineers ship to learn. Growth Engineers do take shortcuts that would make no sense when building for longevity – doing this on purpose.
- Tech stack. Common programming languages, monitoring and oncall, feature flags and experimentation, product analytics, review apps, and more.
- What makes a good Growth Engineer? Curiosity, “build to learn” mindset and a “Jack of all trades” approach.
- Where do Growth Engineers fit in? Usually part of the engineering department, either operating as with an “owner” or a “hitchiker” model.
- Becoming a Growth Engineer. A great area if you want to eventually become a founder or product manager – but even if not, it can accelerate your career growth. Working in Growth forces you to learn more about the business.
With that, it’s over to Alexey:
I’ll never forget the first time I made my employer a million dollars.
I was running a push notification A/B test for meal delivery startup Sprig, trying to boost repeat orders.
A push notification similar to what we tested to boost repeat orders
Initial results were unpromising; the push notification was not receiving many opens. Still, I wanted to be thorough: before concluding the idea was a failure, I wrote a SQL query to compare order volume for subsequent weeks between customers in test vs control.
The SQL used to figure out the push notification’s efficiency
As it turned out, our test group “beat” the control group by around 10%:
‘review_5_push’ was the new type of push notification. Roughly the same amount of users clicked it, but they placed 10% more in orders
I plugged the numbers into a significance calculator, which showed it was statistically significant – or “stat-sig” – and therefore highly unlikely to be a coincidence. This meant we had a winner on our hands! But how meaningful was it, really, and what would adding the push notification mean for revenue, if rolled out to 100% of users?
It turned out this experiment created an additional $1.5 million dollars, annually, with just one push notification. Wow!
I was hooked. Since that day, I've shipped hundreds of experimental “winners” which generated hundreds of millions of incremental revenue for my employers. But you never forget the first one. Moments like this is what growth engineering is all about.
1. What is Growth Engineering?
Essentially, growth engineering is the writing of code to make a company money. Of course, all code produced by a business on some level serves this purpose, but while Product Engineers focus on creating a Product worth paying for, Growth Engineers instead focus on making that good product have a good business. To this end, they focus on optimizing and refining key parts of the customer journey, such as:
- Getting more people to consider the product
- Converting them into paying customers
- Keeping them as customers for longer, and spending more
What kinds of companies employ Growth Engineers? Places you’ve heard of, like Meta, LinkedIn, DoorDash, Coinbase, and Dropbox, are some of the ones I’ve had students from. There’s also OpenAI, Uber, Tiktok, Tinder, Airbnb, Pinterest… the list of high-profile companies goes on. Most newer public consumer companies you’ve heard have a growth engineering org, too.
Typically, growth engineering orgs are started by companies at Series B stage and beyond, so long as they are selling to either consumers or businesses via SaaS. These are often places trying to grow extremely fast, and have enough software engineers that some can focus purely on growth. Before the Series B stage, a team is unlikely to be ready for growth for various reasons; likely that it hasn’t found product-market fit, or has no available headcount, or lacks the visitor traffic required to run A/B tests.
Cost is a consideration. A fully-loaded growth team consisting of a handful of engineers, a PM, and a designer costs approximately 1 million dollars annually. To justify this, a rule of thumb is to have at least $5 million dollars in recurring revenue – a milestone often achieved at around the Series B stage.
Despite the presence of growth engineering at many public consumer tech companies, the field itself is still quite new, as a discipline and as a proper title.
Brief history of growth engineering
When I joined Opendoor in 2016, there was a head of growth but no dedicated growth engineers, but there were by the time I left in 2020. At MasterClass soon after, there was a growth org and a dozen dedicated growth engineers. So when did growth engineering originate?
The story is that its origins lie at Facebook in 2007. The team was created by then-VP of platform and monetization Chamath Palihapitiya. Reforce founder and CEO Brian Balfour shares:
“Growth (the kind found on an org chart) began at Facebook under the direction of Chamath Palihapitiya. In 2007, he joined the early team in a nebulous role that fell somewhere between Product, Marketing, and Operations. According to his retelling of the story on Recode Decode, after struggling to accomplish anything meaningful in his first year on the job, he was on the verge of being fired.Sheryl Sandberg joined soon after him, and in a hail mary move he pitched her the game-changing idea that led to the creation of the first-ever growth team. This idea not only saved his job, but earned him the lion’s share of the credit for Facebook’s unprecedented growth.At the time, Sheryl and Mark asked him, “What do you call this thing where you help change the product, do some SEO and SEM, and algorithmically do this or that?”His response: “I don’t know, I just call that, like, Growth, you know, we’re going to try to grow. I’ll be the head of growing stuff."And just like that, Growth became a thing.”
Rather than focus on a particular product or feature, the growth team at Facebook focused on moving the needle, and figuring out which features to work on. These days, Meta employs hundreds if not thousands of growth engineers.
2. What do Growth Engineers work on?
Before we jump into concrete examples, let’s identify three primary focus areas that a growth engineer’s work usually involves.
- Business-facing work – improving the business directly
- Empowerment work – enabling other teams to improve the business
- Platform work – improving the velocity of the above activities
Let’s go through all three:
Business-facing work
This is the bread and butter of growth engineering, and follows a common pattern:
- Implement an idea. Try something big or small to try and move a key business metric, which differs by team but is typically related to conversion rate or retention.
- Quantify impact. Usually via A/B testing.
- Analyze impact. Await results, analyze impact, ship or roll back – then go back to the first step.
Experiments can lead to sweeping or barely noticeable changes. A famous “I can’t believe they needed to test this” was when Google figured out which shade of blue generates the most clicks. At MasterClass, we tested things across the spectrum:
- Small: should we show the price right on the homepage, was that a winner? Yes, but we framed it in monthly terms of $15/month, not $180/year.
- Medium: when browsing a course page, should we include related courses, or more details about the course itself? Was it a winner? After lengthy experimentation, it was hard to tell: both are valuable and we needed to strike the right balance.
- Large: when a potential customer is interested, do we take them straight to checkout, or encourage them to learn more? Counterintuitively, adding steps boosted conversion!
Empowerment
One of the best ways an engineer can move a target metric is by removing themselves as a bottleneck, so colleagues from marketing can iterate and optimize freely. To this end, growth engineers can either build internal tools or integrate self-serve MarTech (Marketing Technology) vendors.
With the right tool, there’s a lot that marketers can do without engineering’s involvement:
- Build and iterate on landing pages (Unbounce, Instapage, etc)
- Draft and send email, SMS and Push Notifications (Iterable, Braze, Customer.io, etc)
- Connect new advertising partners (Google Tag Manager, Segment, etc)
We go more into detail about benefits and applications in the MarTech section of Tech Stack, below.
Platform work
As a business scales, dedicated platform teams help improve stability and velocity for the teams they support. Within growth, this often includes initiatives like:
- Experiment Platform. Many parts of running an experiment can be standardized, from filtering the audience, to bucketing users properly, to observing statistical methodology. Historically, companies built reusable Experiment Platforms in-house, but more recently, vendors such as Eppo and Statsig have grown in popularity with fancy statistical methodologies like “Controlled Using Pre-Experiment Data” (CUPED) that give more signal with less data.
- Reusable components. Companies with standard front-end components for things like headlines, buttons, and images, dramatically reduce the time required to spin up a new page. No more "did you want 5 or 6 pixels here" with a designer; instead growth engineers rely on tools like Storybook to standardize and share reusable React components.
- Monitoring. Growth engineering benefits greatly from leveraging monitoring to compensate for reduced code coverage. High-quality business metric monitoring tools can detect bugs before they cause damage.
When I worked at MasterClass, having monitoring at the ad layer prevented at least one six-figure incident. One Friday, a marketer accidentally broadened the audience for a particular ad from US-only, to worldwide. In response, the Facebook Ad algorithm went on a spending spree, bringing in plenty of visitors from places like Brazil and India, whom we knew from past experience were unlikely to purchase the product. Fortunately, our monitoring noticed the low-performing campaign within minutes, and an alert was sent to the growth engineer on-call, who immediately reached out to the marketer and confirmed the change was unintentional, and then shut down the campaign.
Without this monitoring, a subtle targeting error like this could have gone unnoticed all weekend and would have eaten up $100,000+ of marketing budget. This episode shows that platform investment can benefit everyone; and since growth needs them most, it’s often the growth platform engineering team which implements them.
As the day-to-day work of a Growth Engineer shows, A/B tests are a critical tool to both measure success and learn. It’s a numbers game: the more A/B tests a team can run in a given quarter, the more of them will end up winners, making the team successful. It’s no wonder, then, that Growth Engineering will pull out all the stops to improve velocity.
3. Why Growth Engineers move faster than Product Engineers
On the surface, growth engineering teams look like product engineering ones; writing code, shipping pull requests, monitoring on-call, etc. So how do they move so much faster? The big reason lies in philosophy and focus, not technology. To quote Elena Verna, head of growth at Dropbox:
“Product Engineering teams ship to build; Growth Engineering teams ship to learn.”
Real-world case: price changes at Masterclass
A few years ago at MasterClass, the growth team wanted to see if changing our pricing model to multiple tiers would improve revenue.
Inspired in part by multiple pricing tiers for competitors such as Netflix (above), Disney Plus, and Hulu.
The “multiple pricing tier” proposal for MasterClass.
From a software engineering perspective, this was a highly complex project because:
- Backend engineering work: the backend did not yet support multiple pricing options, requiring a decent amount of engineering, and rigorous testing to make sure existing customers weren’t affected.
- Client app changes: on the device side, multiple platforms (iOS, iPad, Android, Roku, Apple TV, etc) would each need to be updated, including each relevant app store.
The software engineering team estimated that becoming a “multi-pricing-tier” company would take months across numerous engineering teams, and engineering leadership was unwilling to greenlight that significant investment.
We in growth engineering took this as a challenge. As usual, our goal was not just to add the new pricing model, but to learn how much money it might bring in. The approach we ended up proposing was a Fake Door test, which involves offering a not-yet-available option to customers to gauge interest level. This was risky, as taking a customer who’s ready to pay and telling them to join some kind of waiting list is a colossal waste, and risks making them feel like the target of a “bait and switch” trick.
We found a way. The key insight was that people are only offended about a “bait and switch”, if the “switch” is worse than the “bait.” Telling customers they would pay $100 and then switching to $150 would cause a riot, but starting at $150 and then saying “just kidding, it’s only $100” is a pleasant surprise.
The good kind of surprise.
So long as every test “pricing tier” is less appealing – higher prices, fewer features – than the current offering, we could “upgrade” customers after their initial selection. A customer choosing the cheapest tier gets extra features at no extra cost, while a customer choosing a more expensive tier is offered a discount.
We created three new tiers, at different prices. The new “premium” tier would describe the existing, original offering. Regardless of what potential customers selected, they got this “original offering,” during the experiment.
The best thing about this was that no backend changes were required. There were no real, new, back-end pricing plans; everybody ended up purchasing the same version of MasterClass for the same price, with the same features. The entirety of the engineering work was on building a new pricing page, and the “congratulations, you’ve been upgraded” popup. This took just a few days.
Within a couple of weeks, we had enough data to be confident the financial upside of moving to a multi-pricing-tier model would be significant. With this, we’re able to convince the rest of engineering’s leadership to invest in building the feature properly. In the end, launching multiple pricing tiers turned out to be one of the biggest revenue wins of the year.
Building a skyscraper vs building a tent
The MasterClass example demonstrates the spirit of growth engineering; focusing on building to learn, instead of building to last. Consider building skyscrapers versus tents.
Building a tent optimizes for speed of set-up and tear-down over longevity. You don’t think of a tent as one that is shoddy or low-quality compared to skyscrapers: it’s not even the same category of buildings! Growth engineers maximize use of lightweight materials. To stick with the tents vs skyscraper metaphor: we prioritize lightweight fabric materials over steel and concrete whenever possible. We only resort to traditional building materials when there’s no other choice, or when a direction is confirmed as correct. Quality is important – after all, a tent must keep out rain and mosquitoes. However, the speed-vs-durability tradeoff decision results in very different approaches and outcomes.
4. Tech stack
At first glance, growth and product engineers use the same tooling, and contribute to the same codebases. But growth engineering tends to be high-velocity, experiment-heavy, and with limited test coverage. This means that certain “nice to have” tools for product engineering are mission-critical for growth engineers.
Read more https://connect-test.layer3.press/articles/ea02c1a1-7cfa-42b4-8722-0165abcae8bb
-
 @ 9c47bb51:000381d0
2024-12-06 15:47:43
@ 9c47bb51:000381d0
2024-12-06 15:47:43The financial markets are at a crossroads. With SPY trading at $608 and QQQ at $525, these flagship ETFs are steadily moving toward the $1,000 per share milestone. While the milestone itself is symbolic, its implications for investors and the broader market could be transformative.
For many retail investors, high share prices—despite the availability of fractional shares—create a psychological barrier. Investors instinctively perceive higher prices as less accessible, even if the value proposition remains unchanged. This perception challenges the traditional market and raises the question:
How will markets adapt as SPY and QQQ continue their climb toward $1,000 per share?
Let’s explore two potential paths forward, including how Bitcoin ETFs and direct Bitcoin ownership could reshape how we invest and define “The Market.”
- New Standardized Products for Retail Investors
When SPY and QQQ reach higher price levels, markets will likely introduce new products to maintain accessibility. This adaptation wouldn’t be unprecedented. For example, Fidelity’s FNILX, a zero-expense index fund that tracks the S&P 500, provides a low-cost and highly accessible alternative to traditional funds.
However, FNILX is a mutual fund and doesn’t offer the liquidity or tradability of ETFs, which makes ETFs far more appealing to active traders and long-term investors alike. The ETF equivalent of FNILX would likely take the form of new products specifically designed to solve the “high price barrier” problem.
What These New ETFs Could Look Like:
• Lower Price Points: New ETFs might adopt alternative share structures or tokenization to fractionalize ownership while maintaining correlation to major indices like SPY and QQQ. • Cost-Effective Options: Providers could offer these products with reduced or zero fees, similar to FNILX, but with the tradability of ETFs. • Trader-Friendly Designs: These ETFs would retain liquidity and flexibility, ensuring active investors can continue trading them easily.Such products would act as next-generation ETFs, satisfying demand for accessibility while keeping retail investors engaged in traditional markets.
- The Rise of Bitcoin as an Alternative Market Standard
While SPY and QQQ dominate the current investment landscape, the rise of Bitcoin ETFs and direct Bitcoin ownership presents a compelling alternative. Bitcoin’s decentralized nature and finite supply make it fundamentally different from traditional equities, and its adoption as a financial instrument is growing rapidly.
Bitcoin ETFs: A Familiar Entry Point
Bitcoin ETFs, like IBIT, bridge the gap between the traditional financial system and the world of cryptocurrency. They allow investors to gain Bitcoin exposure through familiar platforms, such as brokerage accounts, without needing to manage private keys or wallets.
Advantages of Bitcoin ETFs: 1. Ease of Use: Easily accessible through existing brokerage platforms, making Bitcoin exposure as simple as buying a stock.
2. Regulated Framework: Operates within traditional financial regulations, providing a sense of security for traditional investors. 3. Portfolio Integration: Fits seamlessly into diversified portfolios, allowing Bitcoin exposure alongside traditional assets.However, Bitcoin ETFs have limitations, including management fees, lack of true ownership, and reliance on third-party custodians.
Self-Custody Bitcoin: True Financial Sovereignty
For investors who want to fully embrace the decentralized ethos of Bitcoin, self-custody offers unparalleled financial sovereignty. By purchasing Bitcoin directly and storing it in a private wallet, investors take full control of their assets.
Benefits of Self-Custody: 1. True Ownership: You hold the private keys, ensuring no third party has control over your Bitcoin.
2. Censorship Resistance: Self-custodied Bitcoin is immune to freezes, seizures, or restrictions. 3. Decentralization: You actively contribute to the resilience of the Bitcoin network. 4. Security: Proper practices, like using hardware wallets or multi-signature solutions, provide robust protection against theft or institutional failure.Self-custody does require responsibility, but the learning curve is shrinking as user-friendly tools and educational resources become more widely available.
A Broader Shift in Market Perception
As SPY and QQQ climb toward $1,000, Bitcoin may begin to redefine how we measure market health and economic performance. Traditionally, indices like the S&P 500 have been seen as benchmarks for the economy. In the future, Bitcoin’s price and adoption metrics could serve as a parallel or even competing measure.
Why Bitcoin Could Become a New Market Standard:
• Global Inclusion: Bitcoin is accessible to anyone with an internet connection, breaking down geographic and economic barriers. • Inflation Hedge: Its finite supply makes it a powerful store of value, particularly in inflationary environments. • Decentralized Economy: Bitcoin represents a global, decentralized economic standard, uncorrelated with traditional equity markets.Implications for the Future of Investing
For Traditional ETFs:
As SPY and QQQ approach $1,000, the introduction of new, lower-priced ETF products will be critical to maintaining retail engagement. These innovations could fragment demand across products, altering trading volumes and creating new dynamics for liquidity and volatility.
For Bitcoin:
The rise of Bitcoin ETFs and self-custody will empower investors to rethink how they store and grow their wealth. The decision between convenience (Bitcoin ETFs) and sovereignty (self-custody) will define a new era of financial choice.
Takeaway: Preparing for a Transformative Future
The approaching $1,000 milestone for SPY and QQQ is more than just a numerical milestone—it signals a shift in how markets must adapt to the needs of investors. Whether through new standardized ETFs or the growing adoption of Bitcoin ETFs and self-custody, the investment landscape is evolving.
For investors, this is an opportunity to embrace change. Will you continue to follow traditional benchmarks, explore new Bitcoin products, or take control through self-custody?
One thing is clear: the markets of tomorrow will reward those who adapt, innovate, and educate themselves. The future isn’t about choosing between systems—it’s about using the tools that empower you to thrive.
-
 @ 9c47bb51:000381d0
2024-12-06 14:14:51
@ 9c47bb51:000381d0
2024-12-06 14:14:51What is NWC? Nostr Wallet Connect (NWC) is an open protocol that connects your Lightning wallet to apps using your Nostr identity (Npub). It’s private, decentralized, and secure—no need for Google or Facebook logins.
Why Choose NWC?
🔑 Unified Identity • Log into apps using your Npub (Nostr public key). • No passwords. One identity for all apps.
⚡ Seamless Payments • Send or receive Lightning payments directly in apps. • Enable tips, subscriptions, or in-app purchases instantly.
🛡️ Privacy First • No personal data sharing—your Npub is all you need. • Your wallet keys stay secure and private.
🌐 Decentralized Control • No centralized gatekeepers. • Your identity and wallet are yours forever—no bans or restrictions.
How NWC Works
1️⃣ Get a Nostr Key Pair • Npub = your public identity. • Your private key stays secure.
2️⃣ Connect to Apps with NWC • Use your Npub to authorize apps. • Your Lightning wallet handles payments securely.
3️⃣ Freedom Across Apps • Use NWC with any app that supports Nostr and Lightning.
Why NWC is Better than Google/Facebook
❌ Google/Facebook • Centralized and tracks your data. • Can ban or restrict your account. • Requires passwords and exposes personal info.
✅ NWC • Decentralized and private. • Censorship-resistant—your identity is always yours. • Password-free and keeps your data secure.
The Future of Online Connection NWC is the better way to connect apps, wallets, and identities. Say goodbye to centralized logins and hello to freedom, privacy, and control.
🔑 Start using NWC today—your wallet, your identity, your rules.
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ f85b9c2c:d190bcff
2025-05-18 23:33:20
@ f85b9c2c:d190bcff
2025-05-18 23:33:20
Am I the only one who tires of this pen’s endless fight, Scribbling words that dance in the dimmest light? The ink flows free, but my mind’s in a plight, I still don’t get it, this craft’s strange height. My thoughts once soared, a creative kite, Now they stumble, lost in the night. The page stares back, so blank, so white, I still don’t get it, where’s my insight? I chase the muse with all my might, But she’s a ghost, just out of sight. My fingers cramp, my soul takes flight, I still don’t get it, this endless write. The stories beg to be shaped just right, Yet boredom creeps, a thief in flight. I dream of tales that spark delight, I still don’t get it, this weary blight. Friends say, “Your words, they shine so bright,” But I feel trapped in this daily rite. The passion fades, no end in sight, I still don’t get it, this draining fight. A poem, a prose, I try to ignite, Each line a chore, a forced invite. The joy’s gone cold, no warmth in sight, I still don’t get it, this fading light. Am I alone, or do others unite, In feeling this pull, this tired dislike? The keyboard clacks, the thoughts take flight, I still don’t get it, this writer’s spite. Perhaps it’s me, my heart’s too tight, Or maybe writing’s a cruel delight. I’ll push on through, with grit and bite, I still don’t get it, but I’ll rewrite. So here I sit, in day or night, Pouring my soul, though it feels trite. Am I the only one? I seek the sight, I still don’t get it—yet still, I write.
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ a5ee4475:2ca75401
2025-05-18 16:07:07
@ a5ee4475:2ca75401
2025-05-18 16:07:07ai #artificial #intelligence #english #tech
Open Source
Models
Text
Image
- SDAI FOSS - Stable Diffusion AI to Android [download] [source] 🤖
- Stable Diffusion - Text to image [source] 🌐
- Pixart Alpha - Photorealistic Text to Image Generation [source]
- Pixart Delta - Framework to Pixart Alpha [paper] [source]
- Pixart Sigma - 4K Text to Image Generation [source]
- OmniGen - Pompt, image or subject to image [source]
- Pigallery - Self-Hosted AI Image Generator [source]
Video
Tools
Lightning Based
- Animal Sunset - AI video generation with Nostr npub by lightning payments [source]
- Ai Rand - AI text generation with Pubky DNS by lightning payments [source]
- PlebAI - Text and Image generation without signup [source] 🌐🤖🍎 [sites down - only github available]
Others
- HuggingFace - Test and collaborate on models, datasets and apps. [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Ollama - Run LLMs Locally [source]
- DreamStudio - Stable Diffusion’s Web App Tool [info] [source]
- Prompt Gallery - AI images with their prompts [source]
Closed Source
Models
Text
- ChatGPT
- Claude
- Gemini
- Copilot
- Maritalk - Text AI in Portuguese focused on Brazil with model Sabia-3 and the open source models Sabia-7b and Sabia-2 [source]
- Amazônia IA - Text AI in Portuguese focused on Brazil with the guara, hapia and golia models [source]
Image
Video
- Minimax - Realistic videos (prompts only in chinese)
Tools
Other index: Amazing AI
-
 @ 9c47bb51:000381d0
2024-12-05 17:26:41
@ 9c47bb51:000381d0
2024-12-05 17:26:41If you could earn between 100-1,000 sats a day, what would that amount to if Bitcoin reached $1,000,000 per coin? Let’s do the math:
1 Bitcoin (BTC) = 100,000,000 satoshis (sats).
Current Bitcoin price = $101,000.
Future Bitcoin price = $1,000,000.
Daily Earnings in Fiat Equivalent at $1M/BTC:
• 100 sats/day = 0.000001 BTC/day = $1.00/day • 1,000 sats/day = 0.00001 BTC/day = $10.00/dayAnnual Earnings at $1M/BTC:
• 100 sats/day x 365 days = $365/year • 1,000 sats/day x 365 days = $3,650/yearEven at the smallest level—earning 100 sats a day—you’re positioning yourself for significant long-term wealth as Bitcoin’s value increases. It’s a perfect example of the power of accumulation over time.
Why Every Sat Matters
Bitcoin is scarce, with only 21 million BTC to ever exist. That’s 2,100 trillion sats for the entire world. Each satoshi is a fraction of a finite resource, making it inherently valuable. If someone gives you even 1 satoshi, they are saying, “I appreciate your work. You’re making a difference.”
Whether you’re earning sats through:
• Working: Salary or side hustle paid in Bitcoin. • Nostr: Engaging, posting, or contributing to communities. • Streaming: Providing value in podcasts or live content. • Rewards Apps: Using tools like Fold or other Bitcoin cashback services.Every sat stacks up, and over time, those seemingly small earnings can become life-changing.
The Fun of Stacking Sats
Part of the magic of Bitcoin is the journey. Watching your small daily efforts compound into something meaningful is both empowering and exciting. So whether you’re earning sats, stacking on dips, or getting tipped on Nostr—have fun. Celebrate every sat. You’re building a future on a foundation of hard work and a revolutionary currency.
The Bitcoin ride is just getting started. Hold tight, stack consistently, and enjoy the journey to financial sovereignty!
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ b1b16be0:08f41c1d
2025-04-11 22:58:00
@ b1b16be0:08f41c1d
2025-04-11 22:58:00Bitcoin need more devs to scale! So I decide to translate to spanish https://plebdevs.com plebdevs@plebdevs.com is a opensource website to learn #bitcoin #lightning free.I started in my free time but now I have to sacrifice work time to move forward. Any zap could be a new bitcoiner!
Why Spanish? Spanish is the third most spoken language on the internet, but much of this community has little access to technical content in English. Plebdevs can be the 🔥torch that illuminates new developers to scale Bitcoin from Latin America and the world.
Apprenticeship Incentive Plebs will gaining the possibility of #learn a higher-paying job as #dev.
Let's Make Bitcoin Scale Millions of Spanish speakers can learn how to develop about Bitcoin and Lightning.
Proof of Work Introduction presentation: https://docs.google.com/presentation/d/1IMC4GHYjccKhGu2mDrtY3bOGcjyFcwgXwFyKyNMq7iw/edit?usp=sharing
🟩🟩🟩⬜⬜⬜⬜⬜⬜⬜ 30%
Thanks to bitcoinplebdev@bitcoinpleb.dev to create this #wonder
Any Zap will be helpful!
mav21@primal.net am@cubabitcoin.org lacrypta@hodl.ar BenJustman@primal.net shishi@nostrplebs.com sabine@primal.net onpoint@nostr.com theguyswann@iris.to Richard@primal.net eliza@primal.net
-
 @ 9c47bb51:000381d0
2024-12-03 01:23:32
@ 9c47bb51:000381d0
2024-12-03 01:23:32Running your own Bitcoin node is one of the most powerful actions you can take to secure financial sovereignty and protect the network’s decentralization.
Bitcoin nodes independently verify transactions and enforce consensus rules, ensuring no single entity—be it governments, corporations, or influential players like BlackRock or Michael Saylor—can dictate how Bitcoin evolves.
Here’s why it matters 👇🏽
1. Decentralization Is FreedomA network is only as decentralized as its participants. When you run a node, you become a part of the consensus mechanism that ensures Bitcoin remains neutral, censorship-resistant, and immune to centralized control.
2. Verification, Not TrustBitcoin’s power lies in its ability to eliminate the need for trust. By running a node, you verify every transaction and block yourself, instead of relying on others who may have vested interests. This ensures you’re transacting on the Bitcoin network as it was designed—not on a version compromised by corporate or governmental interests.
3. Preventing Centralized UpgradesPlayers like BlackRock and influential figures might push for changes to Bitcoin that align with their agendas, potentially undermining its core principles. Running your own node gives you the power to reject unwanted upgrades and stick to Bitcoin’s original ethos.
4. Strengthening the NetworkThe more nodes in the network, the more robust and resistant it becomes to attacks or collusion by centralized entities. Your node helps secure this public good for everyone.
Bitcoin is a tool for freedom, but that freedom only lasts if we actively protect it. Running a node is not just a technical act—it’s a declaration of independence. Don’t let the promise of Bitcoin be steered by the powerful. Take control. Verify. Secure your sovereignty.
-
 @ f85b9c2c:d190bcff
2025-05-18 23:02:05
@ f85b9c2c:d190bcff
2025-05-18 23:02:05
Cryptocurrency has been a hot topic in the world of finance and technology for the past few years. With the rise of Bitcoin and other digital currencies, many have speculated that crypto could be the future of money. But is this really the case? In this article, we’ll take a closer look at the concept of cryptocurrency and whether it has the potential to replace traditional forms of currency.
What is Cryptocurrency? First, let’s define what cryptocurrency actually is. Essentially, cryptocurrency is a digital or virtual form of currency that uses blockchain technology for secure and decentralized transactions. Unlike traditional currencies, which are controlled by central authorities such as banks and governments, cryptocurrency operates independently and is not subject to the same regulations or central authorities. Bitcoin, the first and most well-known cryptocurrency, was created in 2009 by an unknown individual or group using the pseudonym Satoshi Nakamoto. Since then, thousands of other cryptocurrencies have emerged, each with their own unique features and values.
The Advantages of Cryptocurrency 1.One of the main advantage of cryptocurrency is its decentralized nature. This means that it is not controlled by any central authority, making it immune to inflation and government interference. Transactions are also fast and secure, thanks to blockchain technology.
2.Another advantage of cryptocurrency is its potential for investment. Many people have made significant profits by investing in cryptocurrencies.However, it’s important to note that cryptocurrency carries a high level of risk.
The Challenges of Cryptocurrency While there are certainly benefits to using cryptocurrency, there are also several challenges that must be addressed before it can become the future of money. 1. One major issue is the lack of regulation. As mentioned earlier, cryptocurrency is not subject to the same regulations as traditional currencies, which can make it vulnerable to fraud and illegal activities. This has led to some governments imposing restrictions on the use of cryptocurrency, hindering its adoption on a global scale.
- Another challenge is the complexity of cryptocurrency. For the average person, understanding how it works and how to use it can be challenging. This can make it less accessible and limit its potential for widespread use.
Is Crypto Really the Future of Money? So, back to our initial question: is crypto really the future of money? While it certainly has its advantages, there are still many obstacles that need to be overcome before that can happen. Some experts believe that cryptocurrency has the potential to transform the financial industry, while others argue that it will never fully replace traditional forms of currency. The truth is, it’s still too early to say for certain what the future holds for cryptocurrency. One thing is for sure, though — cryptocurrency has already made a significant impact on the financial world and it’s here to stay. Whether it will become the primary form of currency in the future remains to be seen, but it’s clear that it has disrupted the traditional financial system and sparked important discussions about the future of money.
In Conclusion Cryptocurrency has captured the attention of the world with its promise of a decentralized and secure currency. While it does have its advantages, there are still many challenges that need to be addressed before it can truly become the future of money. Only time will tell if cryptocurrency will live up to its potential and become a mainstream form of currency. In the meantime, it’s certainly worth keeping an eye on as it continues to evolve and shape the financial landscape.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ 866e0139:6a9334e5
2025-05-18 21:49:14
@ 866e0139:6a9334e5
2025-05-18 21:49:14Autor: Michael Meyen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„Warum der Weltfrieden von Deutschland abhängt“ steht auf dem Cover. Sicher: Ein Verlag will verkaufen. Superlative machen sich da immer gut. Der Weltfrieden und Deutschland. „Wie das“, wird mancher fragen, über den Atlantik schauen, nach Kiew oder gar nach Moskau und nach Peking, und die 24 Euro ausgeben. Ich kann nur sagen: Das ist gut investiert, wenn man verstehen will, was uns die Nachrichtensprecher und ihre Kritiker im Moment alles um die Ohren hauen. Ich durfte die Texte von Hauke Ritz schon lesen und ein Vorwort schreiben, in dem es nicht nur um Krieg und Frieden geht, sondern auch um die Frage, warum sich manche, die einst „links“ zu stehen glaubten, inzwischen mit einigen Konservativen besser vertragen als mit den alten Genossen – nicht nur bei der Gretchenfrage auf dem Cover. Nun aber zu meinem Vorwort.
1. Der Leser
Hauke Ritz hat meinen Blick auf die Welt verändert. In diesem Satz stecken zwei Menschen. Ich fange mit dem Leser an, weil jeder Text auf einen Erfahrungsberg trifft, gewachsen durch all das, was Herkunft, soziale Position und Energievorrat ermöglichen. Ob ein Autor dort auf Resonanz stößt, kann er nicht beeinflussen. Also zunächst etwas zu mir. Ich bin auf der Insel Rügen aufgewachsen – in einer kommunistischen Familie und mit Karl Marx. Das Sein bestimmt das Bewusstsein. In der Schule haben wir Kinder uns über ein anderes Marx-Zitat amüsiert, das in einem der Räume groß an der Wand stand. „Die Philosophen haben die Welt nur verschieden interpretiert, es kömmt drauf an, sie zu verändern.“ Kömmt. Dieser Marx. Was der sich traut.
Das Schulhaus ist nach 1990 schnell abgerissen worden. Bauland mit Meerblick, fünf Minuten bis zum Strand. Marx stand nun zwar kaum noch in der Zeitung, Eltern, Freunde und Bekannte waren sich aber trotzdem sicher, dass er Recht hat. Das Sein bestimmt das Bewusstsein. Hier die Ostdeutschen, auf Jahre gebunden im Kampf um Arbeitsplatz und Qualifikationsnachweise, Rente und Grundstück, und dort Glücksritter aus dem Westen, die sich das Dorf kaufen und nach ihrem Bilde formen. Das Kapital live in Aktion gewissermaßen.
Ich selbst bin damals eher durch Zufall an der Universität gelandet und habe dort eine Spielart der Medienforschung kennengelernt, die in den USA erfunden worden war, um den Zweiten Weltkrieg nicht nur auf dem Schlachtfeld zu gewinnen, sondern auch in den Köpfen. Diese akademische Disziplin konnte und wollte nach ihrer Ankunft in der alten Bundesrepublik nichts mit Marx am Hut haben. Zum einen war da dieser neue Freund auf der anderen Atlantikseite, moralisch sauber und damit ein Garant gegen den Vorwurf, mitgemacht zu haben und vielleicht sogar Goebbels und sein Postulat von den Medien als Führungsmittel immer noch in sich zu tragen. Je lauter dieser Vorwurf wurde, desto stärker zog es deutsche Propagandaforscher, die sich zur Tarnung Kommunikations- oder Publizistikwissenschaftler nannten, in die USA.
Zum anderen verbannte der Radikalenerlass jeden Hauch von Marxismus aus dem universitären Leben. Selbst Postmarxisten wie Adorno und Horkheimer mit ihrer Frankfurter Schule, Karl Mannheim oder Pierre Bourdieu, auf die ich bei der Suche nach einer neuen intellektuellen Heimat fast zwangsläufig gestoßen bin, spielten in den Lehrveranstaltungen kaum eine Rolle und damit auch nicht in Dissertationen, Habilitationen, Fachzeitschriften. Peer Review wird schnell zur Farce, wenn jeder Gutachter weiß, dass bestimmte Texte nur von mir und meinen Schülern zitiert werden. Ich habe dann versucht, die Kollegen mit Foucault zu überraschen, aber auch das hat nicht lange funktioniert.
Zu Hauke Ritz ist es von da immer noch weit. Ich habe eine Lungenembolie gebraucht (2013), zwei Auftritte bei KenFM (2018) und die Attacken, die auf diese beiden Interviews zielten sowie auf meinen Blog Medienrealität, gestartet 2017 und zeitgleich mit großen Abendveranstaltungen aus der virtuellen Welt in die Uni-Wirklichkeit geholt, um bereit zu sein für diesen Denker. Corona nicht zu vergessen. Ich erinnere mich noch genau an diesen Abend. Narrative Nummer 16 im August 2020. Hauke Ritz zu Gast bei Robert Cibis, Filmemacher und Kopf von Ovalmedia. Da saß jemand, der mühelos durch die Geschichte spazierte und es dabei schaffte, geistige und materielle Welt zusammenzubringen. Meine Götter Marx, Bourdieu und Foucault, wenn man so will, angereichert mit mehr als einem Schuss Religionswissen, um die jemand wie ich, als Atheist erzogen und immer noch aufgeregt, wenn er vor einer Kirche steht, eher einen Bogen macht. Dazu all das, was ich in tapsigen Schritten auf dem Gebiet der historischen Forschung zu erkunden versucht hatte – nur in weit längeren Zeiträumen und mit der Vogelperspektive, die jede gute Analyse braucht. Und ich kannte diesen Mann nicht. Ein Armutszeugnis nach mehr als einem Vierteljahrhundert in Bewusstseinsindustrie und Ideologieproduktion.
2. Der Autor
Und damit endlich zu diesem Autor, der meinen Blick auf die Welt verändert hat. Hauke Ritz, Jahrgang 1975, ist ein Kind der alten deutschen Universität. Er hat an der FU Berlin studiert, als man dort noch Professoren treffen konnte, denen Eigenständigkeit wichtiger war als Leistungspunkte, Deadlines und politische Korrektheit. Seine Dissertation wurzelt in diesem ganz anderen akademischen Milieu. Ein dickes Buch, in dem es um Geschichtsphilosophie geht und um die Frage, welchen Reim sich die Deutschen vom Ersten Weltkrieg bis zum Fall der Berliner Mauer auf den Siegeszug von Wissenschaft und Technik gemacht haben. Das klingt sehr akademisch, wird aber schnell politisch, wenn man die Aufsätze liest, die Hauke Ritz ab den späten Nullerjahren auf diesem Fundament aufgebaut hat und die hier nun in einer Art Best-of in die Öffentlichkeit zurückgeholt werden aus dem Halbdunkel von Publikationsorten, deren Reputation inzwischen zum Teil gezielt zerstört worden ist, und die so hoffentlich ein großes und neues Publikum erreichen. In den Texten, die auf dieses Vorwort folgen, geht es um den tiefen Staat und den neuen kalten Krieg, um Geopolitik und Informationskriege und dabei immer wieder auch um die geistige Krise der westlichen Welt sowie um den fehlenden Realitätssinn deutscher Außenpolitik.
Bevor ich darauf zurückkomme, muss ich die Doppelbiografie abrunden, mit der ich eingestiegen bin. Im Februar 2022, wir erinnern uns auch mit Hilfe des Interviews, das Paul Schreyer mit ihm führte, war Hauke Ritz gerade in Moskau, als Universitätslehrer auf Zeit mit einem DAAD-Stipendium. Im November 2024, als ich diese Zeilen schreibe, ist er wieder einmal in China, mit familiären Verbindungen. Das heißt auch: Hauke Ritz hat mehr gesehen, als einem in den Kongresshotels der US-dominierten Forschergemeinschaften je geboten werden kann. Und er muss weder um Zitationen buhlen noch um irgendwelche Fördertöpfe und damit auch nicht um das Wohlwollen von Kollegen.
Ein Lehrstuhl oder eine Dozentenstelle, hat er mir im Frühsommer 2021 auf Usedom erzählt, wo wir uns das erste Mal gesehen haben, so eine ganz normale akademische Karriere sei für ihn nicht in Frage gekommen. Der Publikationsdruck, die Denkschablonen. Lieber ökonomisch unsicher, aber dafür geistig frei. Ich habe mir diesen Satz gemerkt, weil er einen Beamten wie mich zwingt, seinen Lebensentwurf auf den Prüfstand zu stellen. Bin ich beim Lesen, Forschen, Schreiben so unabhängig, wie ich mir das stets einzureden versuche? Wo sind die Grenzen, die eine Universität und all die Zwänge setzen, die mit dem Kampf um Reputation verbunden sind? Und was ist mit dem Lockmittel Pension, das jeder verspielt, der das Schiff vor der Zeit verlassen will?
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Hauke Ritz, das zeigen die zehn Aufsätze, die in diesem Buch versammelt sind, hat alles richtig gemacht. Hier präsentiert sich ein Autor, der „von links“ aufgebrochen ist und sich immer noch so sieht (so beschreibt er das dort, wo es um die aktuelle Theorieschwäche des einst gerade hier so dominanten Lagers geht), aber trotzdem keine Angst hat, für ein Wertesystem zu werben, das eher konservativ wirkt. Herkunft und Familie zum Beispiel. Verankerung und Zugehörigkeit, sowohl geografisch als auch intellektuell. Mehr noch: Wenn ich Hauke Ritz richtig verstanden habe, dann braucht es ein Amalgam aus den Restbeständen der »alten« Linken und dem christlich geprägten Teil des konservativen Lagers, um eine Entwicklung aufzuhalten und vielleicht sogar umzukehren, die in seinen Texten das Etikett »Postmoderne« trägt. Grenzen sprengen, Identitäten schleifen, Traditionen vergessen. Umwertung aller Werte. Transgender und Trans- oder sogar Posthumanismus. Wer all das nicht mag, findet in diesem Buch ein Reiseziel. Gerechtigkeit und Utopie, Wahrheitssuche, der Glaube an die Schöpferkraft des Menschen und die geistige Regulierung politischer Macht – verwurzelt in der Topografie Europas, die Konkurrenz erzwang, und vor allem im Christentum, weitergetragen in weltlichen Religionen wie dem Kommunismus, und so attraktiv, dass Hauke Ritz von Universalismus sprechen kann, von der Fähigkeit dieser Kultur, ein Leitstern für die Welt zu sein.
Ich habe die Texte im Frühling 2022 gelesen, allesamt in einem Rutsch, um mich auf das Gespräch vorzubereiten, das ich mit Hauke Ritz dann im Juni für die Plattform Apolut geführt habe, den Nachfolger von KenFM. Ich weiß, dass das ein Privileg ist. Lesen, worauf man Lust hat, und dafür auch noch bezahlt werden. Ich weiß auch, dass ich ohne die Vorgeschichte, ohne Corona und all das, was mich und dieses Land dorthin geführt hat, niemals das Glück hätte empfinden können, das mit der Entdeckung eines Autors wie Hauke Ritz verbunden ist. Ohne all das wäre ich wahrscheinlich weiter zu irgendwelchen hochwichtigen Tagungen in die USA geflogen und hätte mich mit Aufsätzen für Fachzeitschriften gequält, die für einen winzigen Kreis von Eingeweihten gemacht und selbst von diesem Kreis allenfalls registriert, aber nicht studiert werden.
Lange Gespräche mit Köpfen wie Hauke Ritz hatten bei Ovalmedia oder Apolut in den Coronajahren sechsstellige Zuschauerzahlen. Ein großes Publikum, wenn man die Komplexität und die Originalität mitdenkt, die jeder Leser gleich genießen kann. Man findet diese Videos noch, allerdings nicht beim De-facto-Monopolisten YouTube, der Zensur sei Dank. Im Bermudadreieck zwischen Berlin, Brüssel und dem Silicon Valley verschwindet alles, was die hegemonialen Narrative herausfordert und das Potenzial hat, Menschenmassen erst zu erreichen und dann zu bewegen. Ich habe Hauke Ritz deshalb schon im Studio und am Abend nach unserem Dreh ermutigt und wahrscheinlich sogar ein wenig gedrängt, aus seinen Aufsätzen ein Buch zu machen. Das war auch ein wenig egoistisch gedacht: Ich wollte mein Aha-Erlebnis mit anderen teilen und so Gleichgesinnte heranziehen. Der Mensch ist ein Herdentier und mag es nicht, allein und isoliert zu sein.
3. Ein neuer Blick auf Macht
Drei Jahre später gibt es nicht nur die Aufsatzsammlung, die Sie gerade in den Händen halten, sondern auch ein Buch, das ich als „großen Wurf“ beschrieben habe – als Werk eines Autors, der die Wirklichkeit nicht ignoriert (Geografie, Reichtum und die Geschichte mit ihren ganz realen Folgen), sich aber trotzdem von der Vorstellung löst, dass der Mensch in all seinem Streben und Irren nicht mehr sei als ein Produkt der Umstände. Hauke Ritz dreht den Spieß um: Die Geschichte bewegt nicht uns, sondern wir bewegen sie. Was passiert, das passiert auch und vielleicht sogar in erster Linie, weil wir ganz bestimmte Vorstellungen von der Vergangenheit und unserem Platz in dieser Welt verinnerlicht haben. Von diesem Axiom ist es nur ein klitzekleiner Schritt zur Machtpolitik: Wenn es stimmt, dass das historische Bewusstsein mindestens genauso wichtig ist wie Atomsprengköpfe, Soldaten oder Gasfelder, dann können sich die Geheimdienste nicht auf Überwachung und Kontrolle beschränken. Dann müssen sie in die Ideenproduktion eingreifen. Und wir? Wir müssen die Geistesgeschichte neu schreiben, Politik anders sehen und zuallererst begreifen, dass der Mensch das Sein verändern kann, wenn er denn versteht, wer und was seinen Blick bisher gelenkt hat. Ich bin deshalb besonders froh, dass es auch das Herz der Serie „Die Logik des neuen kalten Krieges“ in dieses Buch geschafft hat, ursprünglich 2016 bei RT-Deutsch erschienen. Diese Stücke sind exemplarisch für das Denken von Hauke Ritz. Der Neoliberalismus, um das nur an einem Beispiel zu illustrieren, wird dort von ihm nicht ökonomisch interpretiert, „sondern als ein Kulturmodell“, das zu verstehen hilft, wie es zu der Ehe von Kapitalismus und „neuer Linker“ kommen konnte und damit sowohl zu jener „aggressiven Dominanz des Westens“, die auch den Westend-Verlag umtreibt und so diese Publikation ermöglicht, als auch zur „Vernachlässigung der sozialen Frage“.
Hauke Ritz holt die geistige Dimension von Herrschen und Beherrschtwerden ins Scheinwerferlicht und fragt nach der „Macht des Konzepts“. Diese Macht, sagt Hauke Ritz nicht nur in seinem Aufsatz über die „kulturelle Dimension des Kalten Krieges“, hat 1989/90 den Zweikampf der Systeme entschieden. Nicht die Ökonomie, nicht das Wohlstandsgefälle, nicht das Wettrüsten. Ein Riesenreich wie die Sowjetunion, kaum verschuldet, autark durch Rohstoffe und in der Lage, jeden Feind abzuschrecken, habe weder seine Satellitenstaaten aufgeben müssen noch sich selbst – wenn da nicht der Sog gewesen wäre, der von der Rockmusik ausging, von Jeans und Hollywood, von bunten Schaufenstern und von einem Märchen, das das andere Lager als Hort von Mitbestimmung, Pressefreiheit und ganz privatem Glück gepriesen hat. Als selbst der erste Mann im Kreml all das für bare Münze nahm und Glasnost ausrief (das, was der Westen für seinen Journalismus bis heute behauptet, aber schon damals nicht einlösen konnte und wollte), sei es um den Gegenentwurf geschehen gewesen. Die Berliner Mauer habe der Psychologie nicht standhalten können.
Fast noch wichtiger: All das war kein Zufall, sondern Resultat strategischer und vor allem geheimdienstlicher Arbeit. Hauke Ritz kann sich hier unter anderem auf Francis Stonor Saunders und Michael Hochgeschwender stützen und so herausarbeiten, wie die CIA über den Kongress für kulturelle Freiheit in den 1950ern und 1960ern Schriftsteller und Journalisten finanzierte, Musiker und Maler, Zeitschriften, Galerien, Filme – und damit Personal, Denkmuster, Symbole. Die „neue“ Linke, „nicht-kommunistisch“, also nicht mehr an der System- und Eigentumsfrage interessiert, diese „neue“ Linke ist, das lernen wir bei Hauke Ritz, genauso ein Produkt von Ideenmanagement wie das positive US-Bild vieler Westeuropäer oder eine neue französische Philosophie um Michel Foucault, Claude Lévi-Strauss oder Bernard-Henri Lévy, die Marx und Hegel abwählte, stattdessen auf Nietzsche setzte und so ein Fundament schuf für das „Projekt einer Umwertung aller Werte“.
Natürlich kann man fragen: Was hat all das mit uns zu tun? Mit dem Krieg in der Ukraine, mit der Zukunft Europas oder gar mit der These auf dem Buchcover, dass nichts weniger als der „Weltfrieden“ ausgerechnet von uns, von Deutschland abhängt? Warum sollen wir uns mit Kämpfen in irgendwelchen Studierstübchen beschäftigen, die höchstens zwei Handvoll Gelehrte verstehen? Hauke Ritz sagt: Wer die Welt beherrschen will, muss den Code der europäischen Kultur umschreiben. Wie weit dieses „Projekt“ schon gediehen ist, sieht jeder, der die Augen öffnet. In der Lesart von Hauke Ritz ist Europa Opfer einer „postmodernen Fehlinterpretation seiner eigenen Kultur“, importiert aus den USA und nur abzuwehren mit Hilfe von Russland, das zwar zu Europa gehöre, sich vom Westen des Kontinents aber unterscheide und deshalb einen Gegenentwurf liefern könne. Stichworte sind hier Orthodoxie und Sozialismus sowie eine Vergangenheit als Imperium, ohne die, so sieht das Hauke Ritz, neben diplomatischen Erfahrungen die „politischen Energien“ fehlen, die nötig sind, um Souveränität auch da zu bewahren, wo die „Macht des Konzepts“ beginnt. China und der Iran ja, Indien und Lateinamerika nein.
Keine Angst, ich schreibe hier kein zweites Buch. Diese Appetithäppchen sollen Lust machen auf einen Autor, der die Hektik der Gegenwart hinter sich lässt und aus den Tiefen der Geschichte eine Interpretation anbietet, die die hegemoniale Ideologie in ein ganz neues Licht rückt und sie so als „Rechtfertigungslehre“ enttarnt (Werner Hofmann) oder als „Machtinterpretation der Wirklichkeit“ (Václav Havel), die sich zwangsläufig „ritualisiert“ und „von der Wirklichkeit emanzipiert“, um als „Alibi“ für alle funktionieren zu können, die mit der Macht marschieren. Ich weiß nicht mehr, wie ich das Marx-Zitat mit dem komischen Wort „kömmt“ als kleiner Junge gedeutet habe. Ich wusste wenig von Philosophie und gar nichts von der Welt. Hauke Ritz blickt nicht nur in Abgründe, die ich vorher allenfalls aus dem Augenwinkel gesehen hatte, sondern bietet zugleich eine Lösung an. Als Gleichung und in seinen Worten formuliert: „klassische Arbeiterbewegung“ plus „christlich orientierte Wertkonservative“ ist gleich Hoffnung und Neustart. Und nun Vorhang auf für einen Philosophen, der nicht nur Deutschland einen Weg weist in Richtung Veränderung und Frieden.
Michael Meyen ist Medienforscher, Ausbilder und Journalist. Seit 2002 ist er Universitätsprofessor an der LMU München. https://www.freie-medienakademie.de/
Der Link zum Buch von Hauke Ritz
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ f7d424b5:618c51e8
2025-05-18 18:03:25
@ f7d424b5:618c51e8
2025-05-18 18:03:25GAMERS, Join us for a vicless episode where we talk about AI for a change and how it has been impacting our lives. I promise it's video games related.
Stuff cited:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 3104fbbf:ac623068
2025-04-04 06:58:30
@ 3104fbbf:ac623068
2025-04-04 06:58:30
Introduction
If you have a functioning brain, it’s impossible to fully stand for any politician or align completely with any political party. The solutions we need are not found in the broken systems of power but in individual actions and local initiatives. Voting for someone may be your choice, but relying solely on elections every few years as a form of political activism is a losing strategy. People around the world have fallen into the trap of thinking that casting a ballot once every four years is enough, only to return to complacency as conditions worsen. Voting for the "lesser of two evils" has been the norm for decades, yet expecting different results from the same flawed system is naive at best.
The truth is, governments are too corrupt to save us. In times of crisis, they won’t come to your aid—instead, they will tighten their grip, imposing more surveillance, control, and wealth extraction to benefit the oligarch class. To break free from this cycle, we must first protect ourselves individually—financially, geographically, and digitally—alongside our families.
Then, we must organize and build resilient local communities. These are the only ways forward. History has shown us time and again that the masses are easily deceived by the political circus, falling for the illusion of a "savior" who will fix everything. But whether right, center, or left, the story remains the same: corruption, lies, and broken promises. If you possess a critical and investigative mind, you know better than to place your trust in politicians, parties, or self-proclaimed heroes. The real solution lies in free and sovereign individuals who reject the herd mentality and take responsibility for their own lives.
From the beginning of time, true progress has come from individuals who think for themselves and act independently. The nauseating web of politicians, billionaires, and oligarchs fighting for power and resources has never been—and will never be—the answer to our problems. In a world increasingly dominated by corrupted governments, NGOs, and elites, ordinary people must take proactive steps to protect themselves and their families.
1. Financial Protection: Reclaiming Sovereignty Through Bitcoin
Governments and central banks have long manipulated fiat currencies, eroding wealth through inflation and bailouts that transfer resources to the oligarch class. Bitcoin, as a decentralized, censorship-resistant, and finite currency, offers a way out. Here’s what individuals can do:
-
Adopt Bitcoin as a Savings Tool: Shift a portion of your savings into Bitcoin to protect against inflation and currency devaluation. Bitcoin’s fixed supply (21 million coins) ensures it cannot be debased like fiat money.
-
Learn Self-Custody: Store your Bitcoin in a hardware wallet or use open-source software wallets. Avoid centralized exchanges, which are vulnerable to government seizure or collapse.
-
Diversify Geographically: Hold assets in multiple jurisdictions to reduce the risk of confiscation or capital controls. Consider offshore accounts or trusts if feasible.
-
Barter and Local Economies: In times of crisis, local barter systems and community currencies can bypass failing national systems. Bitcoin can serve as a global medium of exchange in such scenarios.
2. Geographical Flexibility: Reducing Dependence on Oppressive Systems
Authoritarian regimes thrive on controlling populations within fixed borders. By increasing geographical flexibility, individuals can reduce their vulnerability:
-
Obtain Second Passports or Residencies: Invest in citizenship-by-investment programs or residency permits in countries with greater freedoms and lower surveillance.
-
Relocate to Freer Jurisdictions: Research and consider moving to regions with stronger property rights, lower taxes, and less government overreach.
-
Decentralize Your Life: Avoid keeping all your assets, family, or business operations in one location. Spread them across multiple regions to mitigate risks.
3. Digital Privacy: Fighting Surveillance with Advanced Tools
The rise of mass surveillance and data harvesting by governments and corporations threatens individual freedom. Here’s how to protect yourself:
-
Use Encryption: Encrypt all communications using tools like Signal or ProtonMail. Ensure your devices are secured with strong passwords and biometric locks.
-
Adopt Privacy-Focused Technologies: Use Tor for anonymous browsing, VPNs to mask your IP address, and open-source operating systems like Linux to avoid backdoors.
-
Reject Surveillance Tech: Avoid smart devices that spy on you (e.g., Alexa, Google Home). Opt for decentralized alternatives like Mastodon instead of Twitter, or PeerTube instead of YouTube.
-
Educate Yourself on Digital Privacy: Learn about tools and practices that enhance your online privacy and security.
4. Building Resilient Local Communities: The Foundation of a Free Future
While individual actions are crucial, collective resilience is equally important. Governments are too corrupt to save populations in times of crisis—history shows they will instead impose more control and transfer wealth to the elite.
To counter this, communities must organize locally:
-
Form Mutual Aid Networks: Create local groups that share resources, skills, and knowledge. These networks can provide food, medical supplies, and security during crises.
-
Promote Local Economies: Support local businesses, farmers, and artisans. Use local currencies or barter systems to reduce dependence on centralized financial systems.
-
Develop Off-Grid Infrastructure: Invest in renewable energy, water filtration, and food production to ensure self-sufficiency. Community gardens, solar panels, and rainwater harvesting are excellent starting points.
-
Educate and Empower: Host workshops on financial literacy, digital privacy, and sustainable living. Knowledge is the most powerful tool against authoritarianism.
5. The Bigger Picture: Rejecting the Illusion of Saviors
The deep corruption within governments, NGOs, and the billionaire class is evident. These entities will never act in the interest of ordinary people. Instead, they will exploit crises to expand surveillance, control, and wealth extraction. The idea of a political “savior” is a dangerous illusion. True freedom comes from individuals taking responsibility for their own lives and working together to build decentralized, resilient systems.
Conclusion: A Call to Action
The path to a genuinely free humanity begins with individual action. By adopting Bitcoin, securing digital privacy, increasing geographical flexibility, and building resilient local communities, ordinary people can protect themselves against authoritarianism. Governments will not save us—they are the problem. It is up to us to create a better future, free from the control of corrupt elites.
-
The tools for liberation already exist.
-
The question is: will we use them?
For those interested, I share ideas and solutions in my book « THE GATEWAY TO FREEDOM » https://blisshodlenglish.substack.com/p/the-gateway-to-freedom
⚡ The time to act is now. Freedom is not given—it is taken. ⚡
If you enjoyed this article, consider supporting it with a Zap!
My Substack ENGLISH = https://blisshodlenglish.substack.com/ My substack FRENCH = https://blisshodl.substack.com/
Get my Book « THE GATEWAY TO FREEDOM » here 🙏 => https://coinos.io/blisshodl
-
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 7bdef7be:784a5805
2025-04-02 12:02:45
@ 7bdef7be:784a5805
2025-04-02 12:02:45We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs. ## The problem Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, **so everyone can actually snoop** what we are interested in, and what is supposable that we read daily. ## The solution Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see [NIP-51](https://github.com/nostr-protocol/nips/blob/master/51.md)). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create **dedicated feeds**, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be **encrypted**, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also **really private one**. One might wonder what use can really be made of private lists; here are some examples: - Browse “can't miss” content from users I consider a priority; - Supervise competitors or adversarial parts; - Monitor sensible topics (tags); - Following someone without being publicly associated with them, as this may be undesirable; The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of **how many bots scan our actions to profile us**. ## The current state Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff ([NIP-44](https://github.com/nostr-protocol/nips/blob/master/51.md)). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply **mark them as local-only**, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment. To date, as far as I know, the best client with list management is Gossip, which permits to manage **both encrypted and local-only lists**. Beg your Nostr client to implement private lists!
-
 @ df478568:2a951e67
2025-05-18 21:29:52
@ df478568:2a951e67
2025-05-18 21:29:52Mene sells investment grade, 24 kt gold jewelry. 24kt gold is 100% atomic number 79, AU, gold like a nugget. More pure than Ivory soap. Best of all, you can buy it the greatest money ever made. By the way, this really is not investment advice. I am bearish on the gold/bitcoin trade anyway. I'm old enough to remember [when a whole coin first became worth more than an ounce of gold.
nostr:nevent1qqsrssrzndmlv6vatcsg5ahzz9hy9k7026x4fq2ntwh3zfaw6hdtj0cjmjyn9.
Unfortunately, I didn't have an ounce of gold back then. I only had a few grams I didn't sell for bitcoin and like eight fiat bucks.
Gold is about gifts for me. I don't have any gold myself, except for an 18 kt gold necklace my grandmother gave me when I was seven. I'm never selling it I would have a lot more bitcoin if I sold that necklace when bitcoin was $200, but I keep it for sentimental reasons. It's not about the money, it's about the utility of gold.
Reduce Your Non-Strategic Future Trash Reserve
I don't like spending sats on stuff you expect to throw away within 5 years or less. l'll buy a pair of shoes very now and then, but it doesn't make sense to go on a shopping spree at The Dollar Tree, where nothing is a dollar, nor built to last. Expect everything you buy at The Dollar Tree to be buried in a landfill within a few years.
Consider this your non-strategic future trash reserve. Every 1,000 sats you don't spend is a thousand sats stacked. Put those sats into your Strategic Bitcoin Reserve instead of your non-strategic future trash reserve.
*“He is so rich, he has no room to shit.”
– Marcus Aurelius, Meditations*
People Don't Throw Gold Away
I still have that gold necklace even though it no longer fits my neck. If you buy someone a smart watch, you can bet your last sat it will help fill a landfill within 5 years or less. This is not financial advice. If you give the gift of a 24 kt. gold bracelet, you know it won't be thrown away. It might get stolen or sold, but nobody in their right mind is throwing gold away like a sock with holes in it.
That's why I like buying gold as a gift. Besides, my wife and daughter both like gold jewelery. Go figure. I have given them sats before. They prefer the gold. Well, my wife doesn't want to spend the sats anymore, but she did. In the old 144 block days, she She used to joke, "My husband never shuts up about bitcoin. It's money we can't spend. That's not the case anymore. Block by block, bitcoin is accepted more and more places. Menē accepts bitcoin for gold Jewelry.
I don't know if Menē stacks sats, but they do use the lightning network. I doubt they keep the sats. They use BitPay, the company BTCpayServer set out to destroy. I still use bitcoin over the lightning network to stack sats because, like BTCPins says…
Gold Is Stack-able
I'm not saying to spend your whole stack on a Cuban Link. You can start small. Buy a charm. It will come with a free leather strap, but just so you know, it's a trap. My wife said she loves the charm, but needs a charm bracelet to go with it because she's not wearing a strap. Good, now I know what to get her for Christmas. You could save sats for something nice though and many of the pieces are stack-able. Maybe you can't afford a whole ounce today. Buy a few grams and add to it as the blocks go by and the charms presumably become cheaper. Gold is the bigger asset right now and it has gone up quite a bit recently, but bitcoin is hovering just below the Gold/bitcoin all time high. i can't predict the future, but I want to re-iterate, just because they market this as investment jewelry, I am not saying this is investment advice. This is about giving the gift of bitcoin 1.0.
There's a metric ton of different charms that can be added to a bracelet or necklace. This makes gold a gift that keeps on giving. Buy a bracelet for her birthday this year and you can buy her a charm next year. They say bitcoin is digital gold. What better way to begin teaching people digital gold than by using analog gold? Again, I don't expect gold to be the biggest asset in the world for long. This is about showing your loved ones that bitcoin is better than gold.
You can spend sats at Menē. They will send you 100% pure gold. They charge spot for the gold and add a 25% fee for their labor. They will send your gift to the destination of your choice. You can even set the delivery date if you order in advance. Each piece is hand crafted and made to order like Burger King, but built to last and no seed oil. Best of all, they have 44,441 reviews as of block 897,304.

Each piece also comes with a letter of authenticity. It shows how many grams of 100% gold it's made of. It's not as good as a UTXO, but they say the jewelry is as good as gold. If you want to give bitcoin away, buy one of my birthday cards, but if you want to buy something your loved ones won't throw away, buy Menē. They accept bitcoin for tariff-free gold jewelry, hand-crafted in the United States of America. They accept bitcoin, but you know what they don't accept? Gold because bitcoin is better than gold for selling gold on the Internet.
Menē Is Great!
I give Menē two emoji 5-of-5 orange hearts. They make great gifts worthy of people who stand to inherit generational wealth.
🧡🧡🧡🧡🧡
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 8d34bd24:414be32b
2025-05-18 20:43:56
@ 8d34bd24:414be32b
2025-05-18 20:43:56We are all supposed to share Jesus and His word with those around us. We are called to:
but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence (1 Peter 3:15)
We should daily pray to God, read the Bible, and share Jesus with others. Some Christians will choose to go into full-time service to God. They will be pastors or missionaries. They will work for churches, Christian schools, and other Christian ministries. Of course, not everyone will make serving Jesus a career. That doesn’t mean the non-career Christians have no job to do. We are all to be a light to this world.
There is one ministry, though, that I’d argue is most important: sharing the gospel with and discipling our children.
These words, which I am commanding you today, shall be on your heart. You shall teach them diligently to your sons and shall talk of them when you sit in your house and when you walk by the way and when you lie down and when you rise up. (Deuteronomy 6:6-7)
This passage may have been written in the Old Testament, but I’d argue that it is even more true now that we have the truth of Jesus Christ, “the way, the truth, and the life.” If the Jews were called to diligently teach their kids the law, how much more should Christians diligently teach their kids the wonderous works and words of Jesus?
Train up a child in the way he should go, Even when he is old he will not depart from it. (Proverbs 22:6)
We should be so excited about what Jesus has done for us that it flows out of us in our daily lives. We should have a strong desire to learn God’s word and to share it with others, especially our children. We should share our excitement about Jesus with our kids. We should share our gratefulness for all Jesus has done for us. We should share our excitement about doing God’s work. Our children should see our faith in all we do and say.
Taking our kids to church Sunday morning and to Sunday school or youth group once a week is not going to teach our kids the importance of faith in Jesus. Praying openly at meals, at bedtime, when we hear about someone in need, and when a difficult situation happens teaches our kids to rely on Jesus. Reading our Bibles in front of our kids and doing daily devotions (at whatever time works for you, but we do evenings) teaches them the importance of the Scriptures. Acting according to a Biblical worldview and taking the time to explain to our kids the answers to the hard questions when the culture contradicts the Bible. This may mean taking the time to research answers to your kids’ questions because you don’t know the answer. Being patient with our kids, and even apologizing to them when we fail, teaches them to be humble and to repent. As the old saying goes, “morals are caught more than taught.” Also faith in Jesus is caught more than taught.
We need to live Godly lives that are different than the culture, remembering that our children are always watching, even when they are quite young and can’t articulate what they are learning.
We need to actively teach God’s word. This may be summarizing principles when they are young, but as soon as possible, this should include reading God’s word to our kids. (My daily reading is usually in an NASB Bible, but it is difficult for a young child to understand with its long, complex sentences, so I recommend something like the NLT Bible for children.)
“Now this is the commandment, the statutes and the judgments which the Lord your God has commanded me to teach you, that you might do them in the land where you are going over to possess it, so that you and your son and your grandson might fear the Lord your God, to keep all His statutes and His commandments which I command you, all the days of your life, and that your days may be prolonged. (Deuteronomy 6:1-2) {emphasis mine}
We want to share all of our knowledge of God and the Bible with our kids, grandkids, and great grandkids. We want to disciple our kids into strong faith in God and knowledge of the Bible, so they are capable of training their kids and their grandkids. We want to multiply faith in our families.
It is definitely good to have scheduled, intentional times of training our kids about the Bible. This could be part of homeschooling (which I strongly recommend). This could be family devotions, but we want teaching our kids about God to be just a natural part of life.
You shall teach them to your sons, talking of them when you sit in your house and when you walk along the road and when you lie down and when you rise up. (Deuteronomy 11:19)
Talking about what God has done in our lives, what we have learned about in our personal Bible study, and how the Bible relates to things we see in life should all naturally flow out of our interactions together. Talk about what the Bible says about a subject you hear on the news. Talk about what the Bible says about what is happening in a movie you watch. Talk about what the Bible says about the decisions you and your kids are having to make. Talk about what the Bible says about your kids’ relationship with each other and their friends and parents. God should be a normal part of everything in life.
We also want to make sure our actions don’t drive our kids away from God.
Fathers, do not provoke your children to anger, but bring them up in the discipline and instruction of the Lord. (Ephesians 6:4)
The Bible does not make light of our need to train our kids in faith.
Discipline your son while there is hope, And do not desire his death. (Proverbs 19:18)
This is so important that failure to train up our kids in faith is considered desiring our kid’s death.
God finds this training so critical, He also addresses it from the kid’s point of view and commands them to listen to their parent’s teaching.
My son, give attention to my words;\ Incline your ear to my sayings.\ Do not let them depart from your sight;\ Keep them in the midst of your heart.\ For they are life to those who find them\ And health to all their body.\ Watch over your heart with all diligence,\ For from it flow the springs of life. (Proverbs 4:20-23)
In Proverbs 31, the Bible gives the best explanation of a Godly woman and mother.
She opens her mouth in wisdom,\ And the teaching of kindness is on her tongue.\ She looks well to the ways of her household,\ And does not eat the bread of idleness.\ *Her children rise up and bless her*;\ Her husband also, and he praises her, saying:\ “Many daughters have done nobly,\ But you excel them all.” (Proverbs 31:26-29)
A Mom should continually “open her mouth in wisdom,” and teach kindly. A mother who fulfills this commandment faithfully is promised that “Her children rise up and bless her.” Being loved and appreciated by our kids is a wonderful blessing, but even greater is knowing that we will see our children with us in heaven.
May God guide you and encourage you as you teach, train, and discipline your kids to know their God, Creator, and Savior.
Trust Jesus.
-
 @ 64334edc:1c0451e5
2025-05-18 10:49:56
@ 64334edc:1c0451e5
2025-05-18 10:49:56Zik88 là một nền tảng công nghệ hiện đại được phát triển nhằm mang đến trải nghiệm số tối ưu và thân thiện cho người dùng. Từ khi ra mắt, Zik88 đã không ngừng cải tiến giao diện và tính năng để phù hợp với nhu cầu ngày càng đa dạng của người dùng hiện đại. Giao diện thiết kế trực quan, tối giản giúp mọi đối tượng dễ dàng làm quen và thao tác nhanh chóng trên nhiều thiết bị khác nhau như điện thoại, máy tính bảng và máy tính cá nhân. Nền tảng này sử dụng công nghệ xử lý dữ liệu nhanh và ổn định, giảm thiểu thời gian chờ và nâng cao hiệu suất vận hành. Ngoài ra, Zik88 còn tích hợp các công cụ tùy chỉnh cá nhân hóa, cho phép người dùng lựa chọn bố cục, màu sắc và chức năng phù hợp với thói quen sử dụng riêng, tạo nên trải nghiệm sử dụng tiện lợi và thân thiện hơn. Điều này giúp Zik88 không chỉ là một nền tảng công nghệ đơn thuần mà còn là người bạn đồng hành hỗ trợ người dùng tối ưu hóa hoạt động hàng ngày một cách hiệu quả và dễ dàng.
Bên cạnh việc tối ưu trải nghiệm người dùng, ZIK88 đặc biệt chú trọng đến yếu tố bảo mật và an toàn dữ liệu. Nền tảng được xây dựng với hệ thống bảo mật đa lớp hiện đại, áp dụng các thuật toán mã hóa tiên tiến nhằm đảm bảo mọi thông tin cá nhân và dữ liệu quan trọng của người dùng được bảo vệ tuyệt đối khỏi các nguy cơ xâm nhập hoặc tấn công mạng. Ngoài ra, Zik88 còn vận hành quy trình kiểm tra và giám sát hoạt động liên tục, nhanh chóng phát hiện và xử lý kịp thời những bất thường nhằm duy trì môi trường số an toàn và ổn định cho tất cả người dùng. Đội ngũ kỹ thuật chuyên nghiệp luôn túc trực 24/7 để hỗ trợ xử lý sự cố và giải đáp thắc mắc, giúp người dùng yên tâm khi trải nghiệm các dịch vụ trên nền tảng. Sự kết hợp giữa công nghệ bảo mật tiên tiến và dịch vụ chăm sóc khách hàng tận tâm chính là điểm tựa vững chắc giúp Zik88 xây dựng được uy tín và lòng tin sâu sắc từ cộng đồng người dùng, tạo nền móng cho sự phát triển bền vững trong tương lai.
Zik88 không chỉ dừng lại ở việc cung cấp nền tảng công nghệ, mà còn hướng đến việc xây dựng một hệ sinh thái số đa dạng và sáng tạo nhằm phục vụ tốt nhất cho nhu cầu của người dùng. Nền tảng thường xuyên cập nhật và mở rộng các tính năng mới, đồng thời tích hợp các dịch vụ bổ trợ để nâng cao giá trị sử dụng cho người dùng. Sự linh hoạt trong việc kết nối với các hệ sinh thái khác giúp Zik88 mở rộng phạm vi hoạt động và nâng cao khả năng phục vụ đa dạng đối tượng khách hàng. Ngoài ra, Zik88 cũng chú trọng phát triển cộng đồng người dùng thông qua các chương trình tương tác, sự kiện trực tuyến và các hoạt động gắn kết nhằm tạo ra không gian giao lưu, trao đổi và học hỏi lẫn nhau. Chiến lược phát triển bền vững này giúp Zik88 không chỉ tạo ra giá trị thực tế mà còn xây dựng được mối quan hệ lâu dài với người dùng, từ đó khẳng định vị trí hàng đầu trong lĩnh vực công nghệ số. Với nền tảng vững chắc và tầm nhìn phát triển chiến lược, Zik88 hứa hẹn sẽ tiếp tục đồng hành và mang đến những trải nghiệm công nghệ ngày càng vượt trội cho người dùng trong tương lai.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 57d56d16:458edffd
2025-05-18 19:18:27
@ 57d56d16:458edffd
2025-05-18 19:18:27Automatic Matrix user creation so ONLY Minecraft players can access, talk and trade outside/with the community.
Moving away from our Discord Server, as that isn't very self sovereign of us :)
https://chat.sovereigncraft.com
========
https://github.com/CappyTech/ServerBridge |
Two-way Matrix chat bridge for Minecraft servers.
ServerBridge enables Spigot/Paper servers to relay chat messages between Minecraft and Matrix rooms in real time. It’s lightweight, server-focused, and ideal for community coordination, moderation, and cross-platform communication.
https://stacker.news/items/983174
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 5f078e90:b2bacaa3
2025-05-18 18:47:21
@ 5f078e90:b2bacaa3
2025-05-18 18:47:21Sloth test
Just a test
Please ignore.

In the lush canopy of a rainforest, Sid the sloth hung lazily from a branch, his mossy fur blending with the leaves. Each day, he nibbled on tender shoots, moving so slowly that ants marched faster. One morning, a curious toucan dropped a shiny berry. Sid, intrigued, reached for it over hours, only to find it was a pebble! Chuckling, he napped, dreaming of sweeter finds. His unhurried life taught the jungle: patience brings its own rewards. (376 characters)
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ 4fe14ef2:f51992ec
2025-05-18 10:04:00
@ 4fe14ef2:f51992ec
2025-05-18 10:04:00Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share & repost: N: note13hdv7a3lfe97hyn8qyed55u463nzya579z8zw7lvh84tfeks7f9swg0dlt X: https://x.com/AGORA_SN/status/1924042853971353859
https://stacker.news/items/982879
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-18 16:24:01
@ 5d4b6c8d:8a1c1ee3
2025-05-18 16:24:01First, the caveat: Yes, I understand that there's a consistent libertarian case for free trade as a policy position.
With all the discourse around tariffs, I wanted to highlight something of a moral oddity in the arguments being used by many free trade libertarians (I am a free trade libertarian, btw): namely, the idea that we (Americans) should happily take advantage of subsidized exports from poorer countries.
I do agree with the economics of the argument: By subsidizing exports, other countries are imposing a deadweight loss on themselves and passing savings along to US consumers.
Why are libertarians celebrating this, though? Poor, oppressed foreigners are being stolen from by their authoritarian governments and American consumers are benefiting from it financially. Thinking this is a good situation is odd and thinking you have a right to take part in it is even stranger.
Libertarians certainly understand that subsidies are wrong and economically harmful, and that they benefit a select group of politically connected cronies. Nothing about that changes just because it's happening in a foreign country and your grocery bill benefits from it.
Saying "That's how they run their country. It's none of our business." is a plea to moral relativism, which libertarians generally avoid. Libertarians also usually understand that the "they" who rule is not the same as the "they" who are ruled. Is it just too uncomfortable to acknowledge being the beneficiary of abuse?
I can't help but draw parallels to the abolitionists of two hundred years ago, who refused to buy the products of slaves. I think they're mostly viewed as having been "on the right side of history", but they're probably on the "wrong" side of most "free trade" arguments. Another of those arguments being that it doesn't help the poor oppressed foreigner to stop doing business with their oppressor (yes, many lefties get all mixed up about who the oppressors are).
Anyway, I have no brilliant conclusion to offer. What do you all think?
https://stacker.news/items/983054
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ a5ee4475:2ca75401
2025-05-15 14:11:16
@ a5ee4475:2ca75401
2025-05-15 14:11:16lists #descentralismo #compilation #english
*The last list was updated in Amethyst, so the update of this one will only be visible in Amethyst.
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
AI
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqq823c8mw5zk
FOSS GAME
nostr:naddr1qq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhzqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gut57qtr
OSHW - Open Source Hardware
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Markdown Uses for Some Clients
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwsppemhxue69uhkummn9ekx7mp0qgsq37tg2603tu0cqdrxs30e2n5t8p87uenf4fvfepdcvr7nllje5zgrqsqqqqqpkdvta4
Other Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 58537364:705b4b85
2025-05-18 08:20:04
@ 58537364:705b4b85
2025-05-18 08:20:04มีคำหนึ่งในพุทธศาสนาที่เราอาจจะคุ้นหู แต่ว่าความเข้าใจอาจจะไม่ตรงกับความหมายในพุทธศาสนา นั่นคือคำว่า อธิปไตย
เวลาเรานึกถึงอธิปไตย ก็นึกไปถึงเรื่องของการเมือง ระบอบการปกครอง เช่น ประชาธิปไตย แต่อธิปไตยในพุทธศาสนาไม่ใช่เป็นเรื่องของระบอบการปกครอง แต่เป็นเรื่องของการให้คุณค่าให้ความสำคัญ
อธิปไตยก็แปลว่าการถือเอาเป็นใหญ่ เอาอะไรเป็นใหญ่ ก็มี 3 ประการใหญ่ ๆ อันแรกคือธรรมาธิปไตย คือการเอาธรรมะเป็นใหญ่ อันที่ 2 คืออัตตาธิปไตย การถือเอาตัวเองหรืออัตตาเป็นใหญ่ และ 3 โลกาธิปไตย ถือเอาคนหมู่มากเป็นใหญ่ ความหมายนี้ก็คือว่าไม่ได้มีความเห็นเป็นของตัวเอง แต่ว่าทำไปตามความเห็นของคนส่วนใหญ่ ที่เรียกว่าโลก เป็นต้น
แต่ว่าหลัก ๆ ก็มีอยู่ 2 อย่าง ที่เราควรจะใส่ใจและก็ทำความเข้าใจให้ถูกต้อง นั่นคือ ธรรมาธิปไตยกับอัตตาธิปไตย
การถือธรรมเป็นใหญ่ ความหมายคือเอาความถูกต้องเป็นใหญ่ เวลาเราทำงานทำการหรือเราใช้ชีวิต ถ้าเราถือธรรมเป็นใหญ่หรือธรรมาธิปไตย เราก็จะตั้งตัวอยู่ในศีลในธรรม ไม่เบียดเบียนผู้อื่น เพราะเห็นแก่ความถูกต้อง แต่ถ้าเราเอาตัวเองเป็นใหญ่หรืออัตตาธิปไตย มันก็คือการเอาประโยชน์ของตัวเองเป็นใหญ่ ไม่สนใจว่าความถูกต้องหรือระเบียบกฎเกณฑ์จะเป็นอย่างไร ถ้าเราถือตัวเองเป็นใหญ่ การที่เราจะอยู่ในศีลธรรมก็ยาก เพราะว่าเอาความต้องการของตัวเองเป็นหลัก ซึ่งส่วนใหญ่ก็เป็นเรื่องของกิเลสนั่นแหละ หรือความเห็นแก่ตัว
อัตตาธิปไตยในความหมายที่แย่คือการเห็นแก่ตัว ส่วนธรรมาธิปไตยเห็นแก่ธรรมะ เห็นแก่ความถูกต้อง หรือถ้าพูดง่าย ๆ คือว่าธรรมาธิปไตยคือการเอาถูกความเป็นใหญ่ ส่วนอัตตาธิปไตยคือเอาความถูกใจเป็นใหญ่
อันนี้เราก็มาพิจารณาดูง่าย ๆ ในการดำเนินชีวิตของคนเรา ในแต่ละวันเราเอาอะไรเป็นใหญ่ อย่างเช่นเวลากินอาหาร ถ้าเราเอาความถูกต้องเป็นใหญ่ หรือธรรมาธิปไตย เราก็จะกินอาหารที่เป็นประโยชน์ต่อสุขภาพ เพื่อทำให้ร่างกายแข็งแรง มีกำลังวังชา เพื่อที่จะได้ทำกิจการงานต่าง ๆ ได้
แต่ถ้าเอาความถูกใจเป็นใหญ่ เราก็จะกินเพราะว่ามันอร่อย เอารสชาติเป็นใหญ่ ถึงแม้ว่ามันจะไม่เป็นประโยชน์ต่อสุขภาพ แต่มันอร่อย มันหวาน มันเปรี้ยว มันเผ็ด มันเค็ม หรือว่ามันสีสวยน่ากิน ทั้ง ๆ ที่มันอาจจะเจือไปด้วยสารพิษที่เป็นอันตราย
หลายคนก็รู้ว่ากินอาหารที่มันเต็มไปด้วยไขมัน อุดมไปด้วยน้ำตาล เป็นโทษต่อสุขภาพ แต่ก็ห้ามใจไม่ได้ กินมาก ๆ เข้า สุดท้ายก็เป็นโรคหัวใจ โรคเบาหวาน ไตวาย หรือบางทีถ้ากินอาหารประเภทที่มันเป็นของดิบ เช่น ปลาดิบ มีพยาธิใบไม้ในตับ ก็เกิดเป็นมะเร็งในตับ หลายคนก็รู้ว่ากินอาหารแบบนี้ ทำให้เกิดโรคเป็นมะเร็งในตับ รู้ว่ามันไม่ถูกต้องแต่ก็กิน เพราะมันถูกใจ
หรือเวลาเราเรียนหนังสือ ถ้าความถูกต้อง เราก็ต้องเรียนด้วยความขยันหมั่นเพียร ต้องมีความซื่อสัตย์สุจริต เวลาทำการบ้าน หรือเวลาเข้าห้องสอบ แต่ถ้าเราเอาความถูกใจเป็นใหญ่ เรียนบ้างไม่เรียนบ้าง บางวิชาฉันไม่ชอบฉันก็ไม่เรียน เวลาทำการบ้านก็ไปลอกจากเพื่อน หรือว่าไปตัดแปะมาจากกูเกิ้ลหรือวิกิพีเดีย เวลาสอบก็ทุจริต แม้รู้ว่าไม่ถูกต้อง แต่มันถูกใจ คือมันสะดวก ง่าย สบาย
เวลาทำงานถ้าเราเอาความถูกต้องเป็นใหญ่ เราก็จะทำงานด้วยความรับผิดชอบ แม้ว่าเป็นงานที่เราไม่ชอบ แต่เมื่อเรามีหน้าที่ เราก็ต้องพยายามทำให้ดีที่สุด เพราะเป็นความรับผิดชอบของเรา แต่ถ้าเอาความถูกใจ งานนี้ฉันไม่ชอบ ฉันก็ไม่ทำ ต่อเมื่อเป็นงานที่ฉันชอบ ฉันจึงจะทำ
หรือถ้าเป็นงานที่ฉันไม่ได้อะไร ฉันไม่ทำ จะทำก็ต่อเมื่อเป็นงานที่ได้ผลประโยชน์ เวลาจะทำอะไรก็จะถามว่าทำแล้วฉันจะได้อะไร อันนี้ก็คือเอาความถูกใจเป็นหลัก หรือเอาความถูกใจเป็นใหญ่ในเวลาทำงาน
เวลาใช้ข้าวของ เช่นโทรศัพท์มือถือ ถามตัวเราเองว่าเราใช้ความถูกต้องหรือความถูกใจ ถ้าใช้ความถูกต้องเป็นใหญ่ ก็จะใช้โทรศัพท์เพื่อติดต่องานการ ทำกิจธุระ หาความรู้ เช็คข้อมูล อาจจะดูหนังฟังเพลงบ้าง ก็ให้เวลากับมันพอสมควร ไม่ใช่หมกมุ่นอยู่กับมัน โดยไม่เป็นอันทำอะไร งานการก็ไม่สนใจ ก้มหน้าดูแต่โทรศัพท์ ใช้ดูหนังฟังเพลง หรือบางทีหนักกว่านั้น ใช้เพื่อเล่นพนันออนไลน์ หรือเล่นเกมออนไลน์ วันหนึ่งหลายชั่วโมง การใช้โทรศัพท์มือถือแบบนี้ ก็เรียกว่าไม่ได้เอาความถูกต้องเป็นใหญ่ แต่เอาความถูกใจเป็นใหญ่
ฉะนั้นลองพิจารณาดูเรื่องการใช้ชีวิตของคนเรา รวมทั้งความสัมพันธ์กับผู้คน เราใช้อะไรเป็นใหญ่ เอาความถูกต้องเป็นใหญ่ หรือเอาความถูกใจเป็นใหญ่ เวลาคบเพื่อน เวลามีเรื่องที่ต้องเกี่ยวข้องกับผู้คน ถ้าเราเอาความถูกต้องเป็นใหญ่ เราก็จะคำนึงถึงความรู้สึกของอีกฝ่ายหนึ่ง เราจะไม่คิดถึงแต่จะเบียดเบียน เอาเปรียบ ต้องมีความเสียสละ แล้วก็รู้จักอดกลั้น ไม่ทำตามอารมณ์
แต่ถ้าเอาความถูกใจเป็นใหญ่ ก็เรียกว่าไม่สนใจว่าคนอื่น เขาจะรู้สึกอย่างไร เอาเปรียบได้ก็เอาเปรียบ ไม่พอใจอะไรก็โวยวาย เรียกว่าขาดน้ำใจ แล้วก็ขาดความรับผิดชอบ มันเป็นเส้นแบ่งได้เลยในเรื่องคน ในเรื่องของพฤติกรรม ในเรื่องของการกระทำ ว่าเราใช้ความถูกต้องหรือความถูกใจ
ถ้าเราเอาความถูกต้องเป็นใหญ่ ชีวิตก็มีโอกาสที่จะเจริญก้าวหน้า อยู่ในศีลในธรรม ตั้งมั่นในความดี แต่ถ้าเราเอาความถูกใจเป็นใหญ่ ก็มีโอกาสที่จะตกต่ำย่ำแย่ เพราะสุดท้ายก็กลายเป็นคนเห็นแก่ตัว หรือว่าตกเป็นทาสของกิเลส อยากกินอะไรก็กิน อยากทำอะไรก็ทำ ไม่ได้สนใจส่วนรวม
เวลามาอยู่วัดก็เหมือนกัน ถ้าเอาความถูกต้องเป็นใหญ่ เราก็จะปฏิบัติตามกฎระเบียบ แม้บางอย่างเราอาจจะต้องฝืนใจทำ เพราะว่าเราเป็นคนตื่นสาย แต่ว่าเราจำเป็นต้องตื่นเช้ามาทำวัตร เพราะว่ามันเป็นระเบียบ มันเป็นข้อวัตร เป็นกติกา เวลามีการทำกิจส่วนรวมก็ไปร่วมช่วยทำ
แต่ถ้าเราเอาความถูกใจเป็นใหญ่ มาบ้างไม่มาบ้าง ทำวัตร เอาความอยากของตัวเองเป็นหลัก ไม่อยากมาก็ไม่มา หรือว่าไม่อยากตื่นก็ไม่ตื่น งานที่เป็นของส่วนรวม ฉันไม่อยากทำฉันก็ไม่ทำ อันนี้ก็ทำให้ชีวิตเราย่ำแย่ไป
แต่ที่จริงแล้วถ้าเราแยกแยะความถูกต้อง ความถูกใจเป็น ก็จะทำให้เราสามารถที่จะใช้ชีวิตไปในทางที่ถูกต้องได้ แต่บางครั้งมันก็ไม่ง่ายที่เราจะแยกแยะได้ชัดเจน ระหว่างความถูกต้องกับความถูกใจ เพราะบางครั้งกิเลสมันก็ฉลาด มันจะอ้างความถูกต้องเฉพาะเวลาที่ถูกใจ แต่ถ้าหากว่าความถูกต้องยามใดไม่ถูกใจฉัน ฉันก็ไม่สนใจ
อย่างเช่นเวลาทำงาน สิ้นปีก็มีโบนัส ถ้าหากว่าฉันได้โบนัส แต่ถ้ารู้ว่าคนอื่นได้โบนัสมากกว่าฉัน เช่นฉันได้ 50,000 แต่อีกคนได้ 70,000 หรือแสนหนึ่ง ก็จะไม่พอใจ ก็จะอ้างว่าไม่ถูกต้อง ไม่เป็นธรรม ความเป็นธรรมคืออะไร ความถูกต้องคืออะไร ก็คือต้องได้เท่ากัน ก็อาจจะเรียกร้อง อาจจะประท้วง อาจจะโวยวายว่ามันต้องเป็นธรรม คือต้องได้เท่ากัน ถึงจะถูกต้อง
แต่ถ้าหากว่าตัวเองได้มากกว่า ตัวเองได้แสน แต่ว่าคนอื่นเขาได้ 50,000, 70,000 เงียบเลย ไม่พูดสักคำเลยว่ามันไม่ถูกต้อง มันไม่เป็นธรรม เพราะอะไร เพราะว่าฉันได้มากกว่า คราวนี้ฉันได้มากกว่า ก็ถือว่าเป็นเรื่องที่ถูกใจฉันแล้ว ถึงตอนนี้ก็ทิ้งเรื่องความถูกต้องไป แต่ถ้าเราเอาความถูกต้องเป็นใหญ่ แม้ว่าจะมีเงินหรือได้เงินมากกว่าคนอื่น มันก็ไม่ถูกต้องอยู่นั่นเอง ก็ต้องทำให้เกิดความถูกต้องขึ้นมา คือว่าต้องได้เท่าคนอื่น
หลายคนเรียกร้องความถูกต้อง เรียกร้องความเป็นธรรม บ่อยครั้งเลยเพราะว่าตัวเองสูญเสียผลประโยชน์ หรือว่าไม่ได้ประโยชน์เท่ากับคนอื่น ถ้าหากว่าตัวเองได้เกิดน้อยกว่าคนอื่น จะเรียกร้องความเป็นธรรม เรียกร้องความถูกต้อง แต่ถ้าหากว่าตัวเองได้มากกว่าคนอื่น ความถูกต้องก็ลืมไปเลย อันนี้แหละนะเรียกว่าอ้างความถูกต้องต่อเมื่อมันถูกใจฉัน ทั้งที่ถ้าถูกต้องแล้วฉันได้เท่าคนอื่น แต่กลับดีหากว่าฉันได้มากกว่าคนอื่น แล้วหากความถูกต้องหมายถึงว่าฉันต้องได้น้อยลง ลดลงมาจากแสนให้เหลือ 70,000 เท่ากับคนอื่น ฉันไม่เอาแล้ว
อันนี้ก็เป็นสิ่งที่เราพบอยู่บ่อย ๆ อ้างความถูกต้องต่อเมื่อมันถูกใจ แต่ถ้ามันไม่ถูกใจฉันเมื่อไหร่ ก็ไม่อ้างความถูกต้องแล้ว ลืมไปเลย อันนี้ก็ต้องระมัดระวัง เพราะบางครั้งกิเลสมันก็ฉลาด มันก็อ้างความถูกต้อง เพื่อสนองผลประโยชน์ของมัน และบางทีเราก็นิยามความถูกต้องแปรผันไป ขึ้นอยู่กับความถูกใจ
ความถูกต้องหรือความเป็นธรรม มันก็มองได้หลายแง่ และตรงนี้แหละ เป็นโอกาสที่จะทำให้ตัวกิเลสมันมาเป็นตัวกำหนด ว่าอย่างไหนเรียกว่าเป็นความถูกต้อง
อย่างเช่นหมู่บ้านหนึ่ง เมื่อสัก 30-40 ปีก่อน สมัยที่ยังไม่มีอบต. ในหมู่บ้านนั้นมีปั๊มน้ำ ที่ใช้แบบคันโยก เป็นปั๊มน้ำของหมู่บ้าน มันเกิดเสียขึ้นมา นักศึกษาที่เป็นพัฒนากรประจำหมู่บ้าน เขาก็เสนอว่าควรจะเก็บเงินทุกหลังคาเลยหลังคาละ 10 บาท เพื่อเป็นค่าซ่อมปั๊ม
ปรากฏว่าชาวบ้านหลายคนไม่ยอม บอกว่าบ้านฉันอยู่ไกลจากปั๊มน้ำ ฉันไม่ค่อยได้ใช้หรอก บ้านไหนที่ใช้ปั๊มมากกว่า เพราะอยู่ใกล้ปั๊ม ควรจะเสียมากกว่า ส่วนบ้านไหนที่อยู่ไกลใช้น้อย ก็ควรจะเสียน้อย แทนที่จะเสีย 10 บาท ก็เสีย 5 บาท เสียเท่ากันนี่ถือว่าไม่เป็นธรรม ตกลงก็เป็นอันว่าต้องเสียไม่เท่ากัน
แต่หนึ่งเดือนต่อมาในหมู่บ้าน มีคนเอาผ้าห่มมาแจก เพราะว่ามันใกล้ฤดูหนาว เอามาถวายวัด หลวงพ่อเจ้าอาวาสท่านก็ปรึกษามัคทายก เพราะว่าผ้าห่มมันไม่พอที่จะแจกให้ชาวบ้านทุกครัวเรือนเท่ากัน มัคทายกก็เสนอว่าบ้านไหนที่ช่วยส่วนรวมได้ 2 ผืน บ้านไหนที่ไม่ค่อยช่วยส่วนรวมได้ 1 ผืน
พอประกาศอย่างนี้เข้า ชาวบ้านไม่พอใจ บอกว่าไม่เป็นธรรม เป็นธรรมคืออะไร เป็นธรรมคือต้องได้เท่ากัน ก็แปลกนะ เวลาจ่ายเงิน ต้องจ่ายไม่เท่ากัน ถึงจะเป็นธรรม แต่เวลาพอได้ผ้าห่มหรือแจกผ้าห่ม ต้องได้เท่ากันถึงจะเป็นธรรม
อันนี้แปลว่าอะไร แปลว่าความเป็นธรรมหรือความถูกต้องนี่มันไม่แน่นอน มันแปรผันขึ้นอยู่กับความถูกใจ จ่ายเท่ากัน หลายคนไม่ถูกใจ ควรจะจ่ายน้อยกว่า จ่ายไม่เท่ากันจึงจะเรียกว่าเป็นธรรม แต่ถึงเวลาได้ ต้องได้เท่ากันจึงจะเป็นธรรม
ถ้าเราพิจารณาดูก็จะพบว่า นี่มันเป็นการนิยามคำว่าเป็นธรรม หรือความถูกต้องโดยอาศัยความถูกใจ ถึงเวลาได้ ต้องได้เท่ากันจึงจะถูกใจ ถ้าได้ไม่เท่ากัน ไม่ถูกใจ ก็ถือว่าไม่เป็นธรรม แต่เวลาจ่าย ต้องจ่ายไม่เท่ากันจึงจะถูกต้อง ฉันต้องจ่ายน้อยกว่า เพราะบ้านฉันอยู่ไกล อย่างนี้เรียกว่าเป็นธรรม
ฉะนั้นความเป็นธรรม ถ้าเราไม่ระวัง มันก็เป็นข้ออ้างเพื่อสนองกิเลส เพื่อสนองความถูกใจ ถ้าเราดูให้ดี ๆ ความถูกต้อง ความถูกใจ แม้ว่าความหมายจะต่างกัน แต่ถ้าไม่ระวัง มันก็กลายเป็นเรื่องเดียวกันได้ ก็คือว่าอันไหนถูกใจจึงเรียกว่าถูกต้อง อันไหนไม่ถูกใจก็เรียกว่าไม่ถูกต้อง
และอีกอย่างหนึ่งคือแม้เราจะมีความชัดเจนว่าอย่างนี้คือความถูกต้อง แต่ก็ต้องระวัง อย่าไปยึดมั่นถือมั่นกับมันมาก เพราะถ้าเราไปยึดมั่นถือมั่นกับความถูกต้องเมื่อไหร่ พอเจอใครทำอะไรไม่ถูกต้อง กลายเป็นไม่ถูกใจไปเลย
อย่างที่เคยเล่า ศีลจาริณี บวชใหม่ ไม่รู้ธรรมเนียม ยืนกินน้ำ แม่ชีเดินผ่านมาเห็นคาตาเลย อย่างนี้ไม่ถูกต้อง แต่ว่าไปยึดกับความถูกต้องมากไป พอเจอความไม่ถูกต้องขึ้นมา โกรธนะ ทุบหลังศีลจาริณีเลย อันนี้เรียกว่าเป็นเพราะยึดมั่นความถูกต้องมาก ยึดมั่นกับระเบียบมาก พอยึดมั่นกับระเบียบหรือความถูกต้อง พอเจอความไม่ถูกต้อง หรือใครทำอะไรไม่ถูกต้อง ก็จะโกรธ
หรือว่าที่วัดก็มีระเบียบ เวลาฟังธรรมต้องปิดโทรศัพท์มือถือ อันนี้คือความถูกต้องที่ควรปฏิบัติร่วมกัน แต่เกิดมีโยมคนหนึ่งลืมปิดโทรศัพท์มือถือ แล้วบังเอิญมีคนโทรเข้ามา เสียงก็ดังกลางศาลาเลย ขณะที่เจ้าอาวาสกำลังเทศน์อยู่ นี่เป็นความไม่ถูกต้องแท้ ๆ เลย ถ้ายึดมั่นกับความถูกต้องมาก เวลาเจอความไม่ถูกต้องแบบนี้ก็โกรธ
โกรธแล้วเป็นอย่างไร ก็ตะโกนด่าเลย เจ้าอาวาสก็ตะโกนด่าเลย กำลังเทศน์อยู่ดีๆ เปลี่ยนโหมดเลยนะ เป็นการด่าแทน ด่าเจ้าของโทรศัพท์ที่ลืมปิดโทรศัพท์ อันนี้เรียกว่าพอเจอความไม่ถูกต้องนี่ มันเกิดไม่ถูกใจขึ้นมา พอไม่ถูกใจแล้วกิเลสมันก็พร้อมที่จะเล่นงาน พร้อมที่จะโวยวาย พร้อมที่จะพูด หรือพร้อมที่จะกระทำอะไรก็ตามด้วยอำนาจของโทสะ ด้วยอำนาจของกิเลส ซึ่งเป็นเรื่องของอัตตาธิปไตย
ฉะนั้นเราต้องระวัง ขณะที่เรายึดมั่นในความถูกต้อง ถ้าเรายึดมั่นมากไป พอเจอใครทำอะไรไม่ถูกต้องขึ้นมา ความไม่ถูกต้องจะกลายเป็นความไม่ถูกใจทันทีเลย ทั้งๆ ที่ดูเผินๆ ไม่ถูกต้องกับไม่ถูกใจนี่มันห่างกันนะ มันไกลกันมาก
เช่นเดียวกับความถูกต้อง ความถูกใจ บางทีมันก็ไกลกันมาก แต่ในบางครั้งบางคราว ถ้าไม่รู้ทันมัน มันกลายเป็นเรื่องเดียวกันไปเลย คือถ้าไม่ถูกต้องเมื่อไหร่ ก็ไม่ถูกใจเมื่อนั้น หรือจะเป็นสิ่งที่ถูกต้อง ก็ต่อเมื่อมันถูกใจ ถ้าอันไหนไม่ถูกใจ ก็ไม่ถูกต้องไป
อันนี้มันต้องใช้สติพิจารณา การที่เรารู้ว่าอะไรถูก อะไรผิด เป็นสิ่งที่ดี และการที่เราปฏิบัติตามความถูกต้อง ก็เป็นสิ่งที่ดี เรียกว่ามีธรรมาธิปไตย แต่ถ้าเรายึดมั่นในความถูกต้องมากไป มันก็ง่ายมากเลยนะ ที่เวลาเจอใครทำอะไรไม่ถูกต้อง ความไม่ถูกต้องก็กลายเป็นความไม่ถูกใจ หรือกระตุ้นให้เกิดความไม่ถูกใจทันที
แล้วบางทีก็ไม่รู้ตัวนะ ก็ยังคิดว่าฉันทำสิ่งที่ถูกต้อง แต่ที่จริงแล้วสิ่งที่ทำไปมันถูกใจต่างหาก แล้วมันก็เกินเลยความถูกต้องไป เพราะว่าไปทุบหลังคนอื่นนี่มันจะถูกต้องได้อย่างไร หรือว่าไปตะโกนด่ากลางศาลาในขณะที่ขาดสติ หรือทำไปด้วยความโกรธ จะเป็นความถูกต้องได้อย่างไร มันก็เป็นเรื่องละเอียดอ่อน ความถูกต้องไม่ใช่ว่ามันจะกลายเป็นสิ่งตรงข้ามกับความถูกใจ
ถ้าเราไม่ระวัง ความยึดมั่นถือมั่น มันก็จะทำให้ความถูกต้องกับความถูกใจ กลายเป็นอันเดียวกัน แล้วก็ทำให้เกิดความผิดพลาด หรือเกิดความเสียหายขึ้น
หลายคนก็ทำสิ่งที่ไม่ถูกต้องเพื่อพิทักษ์ความถูกต้อง อันนี้มีเยอะเลย ที่เป็นข่าวก็คือว่าไปฆ่าคนนั้นคนนี้เพื่อรักษาความถูกต้อง ไม่ว่าเป็นความถูกต้องทางการเมือง ความถูกต้องทางศาสนา
อย่างพวกที่เป็นพวกก่อการร้าย หลายคนเขาก็คิดว่าเขาทำเพื่อพระเจ้า เขาทำเพื่อพิทักษ์ความถูกต้องทางศาสนา แต่ว่าสิ่งที่เขาทำ มันกลายเป็นความไม่ถูกต้องไปเสียแล้ว ทำไปด้วยอำนาจของกิเลส ตัวเองเป็นคนตัดสินว่าใครจะอยู่ใครจะไป ใครที่คิดไม่เหมือนฉัน ก็ต้องถูกกำจัดออกไปจากโลกนี้ เพราะมันเป็นคนที่คิดไม่ถูกต้อง ปฏิบัติไม่ถูกต้อง
ที่จริงก็เป็นเพียงแค่เห็นต่างจากตัวเองเท่านั้น แต่พอเจอคนที่เห็นต่าง ก็เปลี่ยนจากความไม่ถูกใจ กลายเป็นข้ออ้างว่าเขาทำสิ่งที่ไม่ถูกต้อง เพราะฉะนั้นก็สมควรกำจัดออกไปจากโลกนี้
อันนี้เป็นสิ่งที่เราเห็นมากขึ้นเรื่อยๆ ที่เป็นข่าว แล้วมันไม่ใช่เพราะเรื่องศาสนาอย่างเดียว เรื่องการเมือง เรื่องวัฒนธรรม ก็มีความถูกต้องของมัน แต่ถ้าไปยึดความถูกต้องมากไป ใครที่ปฏิบัติไม่ถูกต้องในสายตาของเรา มันก็กลายเป็นสิ่งที่กระตุ้นความไม่ถูกใจ ทำให้เกิดความโกรธ ทำให้เกิดข้ออ้างในการที่จะจัดการ ทำร้าย หรือว่าสังหาร
ฉะนั้นต้องระวังมากทีเดียว การทำความไม่ถูกต้อง ในนามของความถูกต้อง ก็กลายเป็นว่าทำไปด้วยอำนาจของกิเลส แทนที่จะเป็นธรรมาธิปไตย ก็กลายเป็นอัตตาธิปไตยไป.
https://youtu.be/nvGHQUvjvOE
พระไพศาล วิสาโล วัดป่าสุคะโต 4 กันยายน 2565 ขอขอบคุณ Nonglak Trongselsat
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 998034a6:27d87b27
2025-05-18 16:19:25
@ 998034a6:27d87b27
2025-05-18 16:19:25Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 998034a6:27d87b27
2025-05-18 16:19:23
@ 998034a6:27d87b27
2025-05-18 16:19:23Skjønner du? Bare tekst.
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 998034a6:27d87b27
2025-05-18 16:19:22
@ 998034a6:27d87b27
2025-05-18 16:19:22TEST TEST TEST Her kommer bildene:


-
 @ 58537364:705b4b85
2025-05-18 08:18:45
@ 58537364:705b4b85
2025-05-18 08:18:45Discipline is “doing things with intention, without being swayed or carried away by emotions.” On the other hand, lack of discipline implies the opposite:
Lack of discipline is “acting according to emotional fluctuations or being carried away by feelings,” such as sleepiness, hunger, boredom, frustration, satisfaction, dissatisfaction, fear, infatuation, or lack of mindfulness. This often leads to various excuses like:
- "I'll do it later."
- "I'm too tired."
- "It's too hot or too cold."
- "It's still early."
- "It's already too late."
- Etc.
Building lasting discipline “does not come from force, but from dreams.” The law of dreams states that we must create a clear vision of our ‘heaven’ (goal), then minimize the gap between thought and action. The more we overthink, the less likely we are to act—our mind becomes weak and unstable.
The law of dreams also suggests dreaming for others, not just for oneself. When the mind is overly focused on personal success, wisdom and insight diminish. Actions become self-centered and lack empathy. But when our goal is for the greater good, every action becomes meaningful and contributes to shared happiness and success.
— Metha Harimtepathipbodi
Read the TH full version at: https://w3.do/SODEDpmP
-
 @ a5ee4475:2ca75401
2025-05-09 17:10:35
@ a5ee4475:2ca75401
2025-05-09 17:10:35Título H1 - Formatação Markdown
[Titulo com '# ' antes do texto, pode não funcionar se o título H1 for iniciado depois de um texto normal]
list #descentralismo #markdown #clients #Amethyst #Yakihonne
Título H2 [2 hashtags e espaço]
Título H3 [3 hashtags e espaço]
Título H4 [4 hashtags e espaço]
Título H5 [5 hashtags e espaço]
Título H6 [6 hashtags e espaço]
*Copie e cole o texto para enxergar os caracteres usados
Réguas horizontais
- Com 3 sublinhados (_) seguidos:
- Com 3 hífens (-) seguidos:
- Com três asteriscos (*) seguidos:
Ênfases
Negrito: - Dois asteriscos antes e depois: Este é um texto em negrito
- Dois sublinhados antes e depois: Esse é um texto em negrito
Itálico - Um asterisco antes e um depois: Esse é um texto em itálico
- Um sublinhado antes e um depois: Esse é um texto em itálico
Tachado:
~~Aqui houve uma rasura~~
Bloco de citações
Usando 1 a 3 “>”:
O bloco de citações pode ser eninhado…
…Usando cada vez mais maior-que (>).
…Mesmo com espaços entre eles.
Listas
Não-ordenadas
- Crie um tópico começando com
+,-ou*. - Subtópicos são feitos adicionando 2 espaços:
- A mudança da marcação inicial não altera a lista:
- Com asterisco
- Com sinal de mais
- Com sinal de menos
- Muito fácil!
Ordenadas
- Lorem ipsum dolor sit amet
- Consectetur adipiscing elit
- Integer molestie lorem at massa
- Você pode usar números em sequência...
- ...ou deixar tudo como
1.ou outro número.
O número inicia com recuos:
- foo
- bar
Códigos
códigona mesma linhaCaixa de código
-
Códigos intentados com 4 espaços:
// Some comments line 1 of code line 2 of code line 3 of code
-
Com 3 acentos graves antes e depois:
Marcação de texto:
Insira o texto aqui...Marcação de sintaxe:
``` js var foo = function (bar) { return bar++; };
console.log(foo(5)); ```
Tabelas
| APP | Descrição | | ------ | ----------- | | Element | App de mensagens que usa a rede Matrix. | | Simplex | App de mensagens bastante usado. | | 0xchat | App de mensagens no Nostr. |
Links
-
Link autoconvertido https://github.com/nodeca/pica (habilite o linkify para ver)
Imagens nomeadas
Minion:

Stormtroopocat:
[https://octodex.github.com/images/stormtroopocat.jpg])
Como links, imagens também tem sintaxe footnote ‘!’ + ‘Outro texto’...
[https://octodex.github.com/images/dojocat.jpg])
…com uma referência id posterior da referência na localização da URL.
Plugins
O recurso de
markdown-ité um suporte muito eficaz de plugins de sintaxe.
Emojis
*Acesse o link para entender melhor
Marcação clássica: :wink: :cry: :laughing: :yum:
Figuras Ascii (emoticons): :-) :-( 8-) ;)
Veja como mudar a exibição com o twemoji.
Sobrescrito / Subscrito
*Acesse os links para entender melhor
- 19^th^
- H~2~O
\
*Acesse o link para entender melhor
++Texto Inserido++
\
*Acesse o link para entender melhor
==Texto marcado==
Notas de Rodapé
*Acesse o link para entender melhor
Nota de rodapé 1 link[^primeiro].
Nota de rodapé 2 link[^segundo].
Rodapé^[Texto do rodapé na linha] definição na linha.
Referência duplicada no rodapé[^segundo].
[^primeiro]: Rodapé pode ter marcação
e múltiplos parágrafos.[^segundo]: Texto de rodapé.
Listas de Definição
*Acesse o link para entender melhor
Termo 1
: Definição 1 com continuação preguiçosa.
Termo 2 com marcação na linha
: Definição 2
{ algum código, parte da Definição 2 } Third paragraph of definition 2.Estilo compacto:
Termo 1 ~ Definição 1
Termo 2 ~ Definição 2a ~ Definição 2b
Esse texto é uma adaptação do:
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwspzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyqy0j6zknu2lr7qrge5yt725azecflhxv6d2tzwgtwrql5llukdqjqcyqqqqqqgfdk5w3
-
 @ a5ee4475:2ca75401
2025-05-08 21:57:12
@ a5ee4475:2ca75401
2025-05-08 21:57:12brasil #portugal #portugues #bitcoin
Brasil
-
Jericoacoara - Ceará nostr:nprofile1qqsdc47glaz2z599a7utq9gk2xyf6z70t7ddyryrnweyt32z4sdarfsppemhxue69uhkummn9ekx7mp00ex584
-
Rolante - Rio Grande do Sul nostr:nprofile1qqsdrks96vr7vc7frjflm8lmhwleslwzgjlkpyj4ahjhzgm4n8dh0qqprdmhxue69uhkymm4de3k2u3wd45ku6tzdak8gtnfdenx7qgcwaen5te0xycrqt3hxyhryvfh9ccngde6xsurgwqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduhxppd6
-
Santo Antonio do Pinhal - São Paulo nostr:nprofile1qqsr5maylee9j77ce0es6tgmxj3pax2dlsuuptkn2stuj95jzqysulgpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqgdwaehxw309ahx7uewd3hkca6zsjl
Portugal
- Ilha da Madeira - nostr:nprofile1qqsv45qvfz5vdzwn9478wzusyggjf44x3w7xk8f3cgpe4px44wgv77cpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpz3mhxue69uhhyetvv9ujumn0wd68ytnzvuq32amnwvaz7tmwdaehgu3dwfjkccte9eshquqzhddc4
-
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 58537364:705b4b85
2025-05-18 08:18:23
@ 58537364:705b4b85
2025-05-18 08:18:23The Dhamma of the Buddha is not merely a concept or philosophical hypothesis. It is the direct seeing of the truth — that suffering truly exists within us, and that it can genuinely be ended — through observing, with wisdom, not by calculation or blind belief.
Suffering is not an abstract idea; it is a real experience we can feel. When we truly understand suffering by facing it directly — not running from it or deceiving ourselves — we will see that the sense of “self” is the root of suffering. Every time the feeling of “this is me, this is mine” arises — suffering follows.
The solution is not in argument or debate, but in taking action to see and know this truth for ourselves.
Thus, Dhamma is the science of the mind — not just a philosophy. And this is why the Buddha’s teachings have never become outdated, even after more than 2,500 years.
Read the TH full version at: https://w3.do/okHFEDy-
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 58537364:705b4b85
2025-05-18 08:16:44
@ 58537364:705b4b85
2025-05-18 08:16:44“Phra Ajahn (Venerable Sir), I don’t mean any offense, but since Buddhism already has its core teachings, if I think that we should reduce the number of temples or their structures, would that be considered sinful?”
“Bless you. When you eat a banana, do you eat the peel or the fruit?”
“I eat the fruit.”
“Oh… and before you eat it, do you peel it?”
The clean-faced girl nodded.
“Why do you peel it?”
“Because the peel isn’t edible.”
“Oh, so the peel is completely useless, right?”
She shook her head.
The narrator continues:
“In truth, the peel has a purpose—it protects the fruit. The same goes for durian or jackfruit peels. Think about it, if a fruit has a tough peel, it usually keeps the inside well protected—and the inside is often delicious…”
“To eat the fruit, we shouldn’t get confused and eat the peel. Nor should we eat only the peel and discard the fruit. Our role is to know what’s the peel and what’s the fruit—and we must know how to peel it.”
“I must admit, personally, I don’t care much for construction, decoration, or rituals, but I understand—some people enjoy them and find them beneficial. That’s valid. We just don’t have to argue about it…”
“It’s a matter of knowing how to ‘peel.’ Don’t get lost in the outer layers, but also don’t discard the essence inside. Instead, help guide others to understand, without throwing away what matters most…”
“For example, take prostrating. I don’t mind whether or not people prostrate to me. It’s not mandatory.”
“After reading the sutras and analyzing them, I found that in the Buddha’s time, when he gave teachings, many people came to listen. Some prostrated, some just joined their palms, some didn’t prostrate and just sat down, and some walked by without listening at all.”
“Likewise, when people left, their reactions varied. Some came with faith and left with it. Some changed and lost faith. Others came with doubt but gained faith later. And some never changed. That was during the Buddha’s time, no less.”
“So, we must ask: What does prostrating give us? I started doing it only after I was ordained. I’ve been doing it for 14 years. At first, I just followed along.”
“But later, I began to understand—it trains humility, helps reduce ego and pride, and teaches us appropriate behavior.”
“When someone prostrates to me, I feel more inclined to teach or talk with them, compared to those who don’t. With the latter, it’s harder to read them—so I just stay still and observe first.”
“Do you think some people prostrate without understanding the meaning, just copying others?”
The girl nodded.
“Right? So, I think prostrating, rituals, and temple buildings are not the ultimate essence of Buddhism. But they have meaning. They help guide us to reach the deeper benefit hidden within. It’s our job to understand them—if we really want to understand.”
“I believe that true religion doesn’t reside in material things. If it did, then Borobudur, the largest Buddhist monument in the world, filled with stupas, should be bustling with monks and Buddhists.”
“But do you know what it’s like now?”
The girl shook her head.
“…Now it’s just a tourist attraction. No monks live there anymore.”
“You said we should reduce the number of temples. What would you do with the space?”
“Maybe turn it into a public park or something.”
“That’s a good idea. I like it. Others could come and use it, too—with trees and animals. People would feel more at peace.”
The girl’s eyes lit up.
“But couldn’t we just plant more trees in the temples and make them like parks? Isn’t that a good idea?”
She smiled.
“Even though I don’t want us to cling to material or ritualistic forms, I still see their benefits. Look over there!”
He pointed to a carved wooden box.
All the children turned to look.
“…This box might be just ordinary wood. But once carved, it instantly looks valuable. It’s different from other boxes. The craftsman needed skill, time, and dedication to create it.”
“…If you had several wooden boxes to choose from, this would likely be among the first you’d pick.”
“This is what we call the value of beauty. Beautiful temples and buildings draw people to care for them, clean them, preserve them, and host meaningful events within. I guess that’s why temple architecture became such a tradition in the first place.”
“One last thing—about merit and sin.”
“Let’s understand the meanings first. Merit means cleansing the mind. Sin means lowering the mind, making it gloomy or defiled.”
“If you want to make a public park—merit or sin?”
“Merit.”
“If you’re annoyed and want to destroy all temples—merit or sin?”
“Sin.”
“If you prostrate with understanding, wishing to train humility and receive the Dhamma from monks—merit or sin?”
“Merit.”
“If you prostrate mindlessly, just following others—merit or sin?”
The girl paused and looked up.
“Still unclear, right?”
“Yes.” She nodded firmly.
“Then I ask you to observe your own mind. Is it clean or lowly? Is it merit or sin? Not just with prostrating, but with every action, word, and thought.”
“So, how much of your question did I answer?”
“One hundred percent!”
“Really? Okay. Thank you so much for the question.”
The children bowed and walked out of the pavilion.
The narrator, seizing the moment, reflected with admiration on the question and answer just shared.
This girl’s question wasn’t childish at all.
It was more mature than many adults' questions—insightful, nuanced, and sophisticated.
Her voice was clear, confident, courageous, and respectful. It was on point, meaningful, and thought-provoking—for both the speaker and the listeners.
While listening, she made eye contact and reacted, encouraging shared learning. She was an excellent listener and never missed a beat.
And most importantly, her smile and gaze uplifted and encouraged her classmates, too.
This made the speaker feel proud to be sitting there, at that moment, that day.
Truly joyful to see a young person with such a beautiful mind, who thinks of nature and wants to bring happiness to others—and who understands and appreciates the essence of Buddhism.
“It’s truly something to be proud of—to know that the Dhamma is reaching the younger generation. Don’t you agree?”
The author wasn’t asking anyone.
He turned to look at a marble statue placed behind him, and silently paid homage to the Buddha—the Supreme Teacher—with unwavering reverence.
Asrom Khantisarn A wooden house called “Kuti” June 15, 2023
By Phramaha Fookij Jutipanyo
Read the TH full version at: https://w3.do/Zp6prJLz
-
 @ 793d882b:a2d0433c
2025-05-18 15:01:44
@ 793d882b:a2d0433c
2025-05-18 15:01:44Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ 15aee60a:af83839e
2025-05-18 16:18:53
@ 15aee60a:af83839e
2025-05-18 16:18:53Jo, blomster kommer i alle farger og fasonger. Her har du to eksempler:


-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ 58537364:705b4b85
2025-05-18 07:58:28
@ 58537364:705b4b85
2025-05-18 07:58:28The essence of meditation goes beyond seeking mere tranquility or external peace. What truly matters is how we perceive our emotions and thoughts as they arise within us. By cultivating awareness and understanding, we gain the power to liberate ourselves from the grasp of these thoughts and emotions, instead of becoming enslaved or overwhelmed by them.
If we remain unaware, these thoughts and emotions can become our masters, dictating our actions and responses. However, by recognizing that we have the capacity to be masters over them, we unlock the potential to utilize them as valuable tools. With this awareness, we can employ these thoughts to solve life's challenges, be it personal, professional, or moral dilemmas.
In the same vein, emotions, when unexamined, can become our rulers, leading us astray and causing suffering. For instance, sadness can ensnare us in its grip, making us believe that we must be sad to express love for someone. Similarly, anger can deceive us into acting out of righteousness, perpetuating negative cycles.
To break free from these emotional chains, we must observe and understand our emotions with mindfulness. Only then can we release ourselves from their dictates and avoid falling into a pit of depression or ongoing conflict. By practicing the art of "seeing" our thoughts and emotions, we gain control over their influence and prevent them from taking over our hearts.
The journey of meditation involves consistent practice in seeing and observing these mental and emotional phenomena. Through continuous effort, we strengthen our ability to discern and eventually reduce their hold on us. This newfound awareness empowers us to make choices that lead to inner peace and liberation from suffering.
In this process of mindful seeing, we learn that peace is not achieved by suppressing or restraining our thoughts and emotions. True peace comes from allowing them to arise and exist without judgment or oppression. By embracing this mindful perspective, we discover the profound truth that we can be free from the clutches of our thoughts and emotions. Meditation, therefore, becomes the gateway to inner peace and true liberation.
source : การค้นพบตัวเองที่สำคัญ revised by : chat gpt, google translated.
-
 @ 15aee60a:af83839e
2025-05-18 16:18:52
@ 15aee60a:af83839e
2025-05-18 16:18:52Skjønner du? Bare tekst.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 793d882b:a2d0433c
2025-05-18 15:01:43
@ 793d882b:a2d0433c
2025-05-18 15:01:43Skjønner du? Bare tekst.
-
 @ a5ee4475:2ca75401
2025-05-07 20:00:42
@ a5ee4475:2ca75401
2025-05-07 20:00:42lista #descentralismo #comunidades #portugues
[em atualização]
*Até a criação desse post, só alguns clients têm acesso às comunidades, tal como o Satellite, o Coracle e o Amethyst.
**Se a comunidade não tiver proprietários ou moderadores ativos, o seu envio de mensagem poderá não ser aprovada para aparecer nela.
***Se criar uma, busque colocar um ou mais moderadores para a comunidade não acabar, caso você se ausente.
Geral:
n/Brasil (Por: nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqryyunpwd5kcq3qzdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2sxpqqqzr0v4va9m3
n/Portugal (por: nostr:nprofile1qqsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9uqsuamnwvaz7tmwdaejumr0dshszynhwden5te0dehhxarj9ek82tntv5hsd2h46x) nostr:naddr1qqy9qmmjw36kwctvqgsddhy42shp3w9h4mp0z3ss74wrxk47hmrk70deukxz23np6pvn5rqrqsqqpphkc3wuaj
n/Moçambique (por: nostr:nprofile1qqszx6hsp38v2re3q2pzxpv3slg5u7pxklxze7evarqk4eugqmhntdcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctc082x0w) nostr:naddr1qqf56m7r5ask6cnfw96ktuyls7e0p8u8hupzqgm27qxya3g0xypgygc9jxraznncy6muct8m9n5vz6h83qrw7ddhqvzqqqyx7c0autxh
n/África (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqru8qtxwf5kxcgzyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdaspqgn0q
-
n/Perguntas-e-Respostas (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq3lp8u85lcflpah2pz4y364fe2yz5edg5k4y32n2p84x4zp203fm980hz8sygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqsmmqtz9a9x
n/Links-e-Tutoriais-Úteis (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqj0p8u85lcflpahf3y5uj6n94zj64z42384yj2pf9fjmsu623z5j5lsn7ftkq3qne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqxpqqqzr0v3zu9fd
n/JornalismoNãoEstáMorto - Notícias e escrita informativa (Por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:nprofile1qqs0f74kketdcv63r53mlzgzfh93we3dkgzkldv2p6g62a8gf3g92yqpz4mhxue69uhkummnw3ezummcw3ezuer9wchszyrhwden5te0dehhxarj9ekk7mf0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9ufhpwuw) nostr:naddr1qqd55n6jfeq5cj2nf48j6nkrsd8j632n2npczt2dfaf9gnczyrvvsrjnp9xgqysjendxg6x2q7fldu73ajnf5e2h7uspp9tjl7jvxqcyqqqgdasy2kfg4
n/Agorismo³-E-Mercado (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpahg9r575jf2dx5ls4n94zj6n292fp5z3z094gry5qzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasrlnr7s
n/FeiraNostr - Marketplace (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qq9yvetfwfs5ummnw3eqyg9hpjdlkf2tvpegqssjvsa7kpmmdw55zcy76sz3tkd3p9sawancnypsgqqqsmmqucz73h
Tecnologia:
n/ndevs-br (por: nostr:nprofile1qqs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcppemhxue69uhkummn9ekx7mp0gc3lmk) nostr:naddr1qqyxuer9weej6cnjqgs923ewnsqlx7347cpjhxmcmt0rsmnwf3tasr736pjx4wee9q89ufcrqsqqpphk7z3axp
n/BrasilDev (por: nostr:nprofile1qqsyczyspluueyxautr3nxa2httku5e9m7d05dnu5zj3jnrg0jmucqcpr9mhxue69uhkyu3wwp6hyurvv4ex2mrp0yhxxmmd9uqs6amnwvaz7tmwdaejumr0dsq3camnwvaz7tmwdaehgu3wvf5hgcm0d9hx2u3wwdhkx6tpdsz8cl6e) nostr:naddr1qqy5yunpwd5kc3r9wcpzqnqgjq8lnnysmh3vwxvm42adwmjnyh0e473k0js22x2vdp7t0nqrqvzqqqyx7cvxdlla
n/Linux (por: nostr:nprofile1qqsxhewvq6fq9lzjmfwqrpg2ufgl09uh2cksupa853zxv04u2fva4uqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9nhwden5te0dehhxarjv4kxjar9wvhx7un89uqsuamnwvaz7tmwdaejumr0dshs6tvc92 ) nostr:naddr1qqz5c6tww4uqz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsygrtuhxqdyszl3fd5hqps59wy50hj7t4vtgwq7n6g3rx8679ykw67qpsgqqqsmmqznes6u
n/IA - Inteligencia Artificial (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqpyjsgpzpmhxue69uhkummnw3ezumt0d5hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqs03ln5
n/HardwareBr - Dúvidas, experiências e atualizações sobre hardware (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq9ysctjv3mkzun9gfeqyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmq54k3eu
n/SegurançaDaInformação (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqv9xet8w4exzmkr5as5gc2fdenx7undv8p60sardupzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cpss4m0
n/Moneroptbr (Por: nostr:nprofile1qqsyrmue77dm5ef5pmqsly0wp3248mk3vr9temj5p54plygcr97pavcpzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqgjwaehxw309ac82unsd3jhqct89ejhxqg5waehxw309aex2mrp0yhxgctdw4eju6t0tpqrvk) nostr:naddr1qq9y6mmwv4ex7ur5vfeqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygzpa7vl0xa6v56qasg0j8hqc42namgkpj4uae2q62sljyvpjlq7kvpsgqqqsmmqknmdan
Ciência:
n/Astronomia - Espaço e astros (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qq9yzum5wfhkummdd9ssz9thwden5te0dehhxarj9ehhsarj9ejx2a30qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqpphkkdel5t
n/Mecatrônica-NOSTR (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqfy6etrv9689sa5de5kxcfdfe84x4zjqythwumn8ghj76twvfhhstnp0faxzmt09ehx2ap0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphkgsy84w
n/Antropologystr - Antropologia (por: nostr:npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg ) nostr:naddr1qq85zmn5dpex7ur0d3hkw7tnw3eqygzfrtlt4hds900g0nl80lk6luq5h7fds622r5uqa3882jgckeyrfcpsgqqqsmmq4xrrgc
Cultura:
n/Estante-Nostr - Literatura e livros (por: nostr:nprofile1qqsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqpr4mhxue69uhkummnw3ez6vp39eukz6mfdphkumn99e3k7mf0qywhwumn8ghj7mn0wd68ytfsxgh8jcttd95x7mnwv5hxxmmd9uq37amnwvaz7tmwdaehgu3dxqejuer0wfskvctrw3hhy7fwdaexwtcjwfqr2) nostr:naddr1qqx52um5v9h8ge2lfehhxarjqgsdl72sxdne0yqwa7tpznlnc4yt5t9jf8htspnynrja92dcschm7sqrqsqqpphkwzdgct
n/Literatura-Arte-Cultura (por: nostr:nprofile1qqs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9cprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9nhwden5te0v4jx2m3wdehhxarj9ekxzmny9uqsuamnwvaz7tmwdaejumr0dshs8l9z0j) nostr:naddr1qqt5c6t5v4exzar4wfsj6stjw3jj6sm4d3682unpqgs92lr9pdcqnulddvzgj5twpz8ysdv7njhxagyxwtnlj8p3kpxxs9crqsqqpphkty54um
n/História-e-Filosofia (por: nostr:npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk ) nostr:naddr1qqjlp8u85lcflpahfpy4x4xrjdfyjsfdg5k5vj2vfaf573jfg8cflrum7z0cezczyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdas35g9vs
n/Urbanism - Urbanismo (por: nostr:nprofile1qqstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgpr9mhxue69uhhyetvv9ujuumwdae8gtnnda3kjctv9u2dla7c) nostr:naddr1qqy92unzv9hxjumdqgstwrymlvj5kcrjspppyepmavrhk6afg9sfa4q9zhvmzztp6am83xgrqsqqpphkyl5u8a
Fé:
n/Religião-e-Teologia - Cristianismo (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqs0p8u85lcflpah2fz5cj28f8pcxnedg5k4g320f385wj2p7z0ehyqzyz0y55n5d04g5q6wq97zq8tqxwvrddmulpjmlxd8zppf8kd0339ugqcyqqqgdasta04x5
n/Ateismo-e-Agnosticismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqtyzar9d9ek6medv5k5zemwdaehg6trd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdasuuzmw8
n/Budismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5yatyd9ek6mczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas0kmt4m
n/Taoismo - Daoismo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqy9gct0cwkhxmt0qy88wumn8ghj7mn0wvhxcmmv9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7crkzqvd
n/Espiritualidade - Significação e sublimidade (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq852umsd9exjar4v9kxjerpv3jszyrhwden5te0dehhxarj9ekk7mf0qgsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscrqsqqpphkxa5nfy
Entretenimento:
n/Equinox - Cinema no Nostr (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr) nostr:naddr1qqr52ut4d9hx77qpremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cmc79n5
n/Rock/metal - Músicas Rock e Metal (por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4 e nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz748t750 ) nostr:naddr1qq99ymmrdvh56et5v9kqzqqzypvep8kzcfyvdvug0j9agfv07ujkx9elwfujy5qfl06jy25zmvctwqcyqqqgdas306zj5
n/Música-Cinema-e-Livros (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qq4lp8u85lcflpahfhpe556fgdqj6s6ffez56sfdyck5cj2k2f848uyl366lp8unhhcflyu6qgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkfyz9pf
n/Lugares-e-Viagens (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqjlp8u85lcflpahf325ws2jg4fj63fd2ey5z369feflp8uv3mcflryd7z0cercpqqpzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7c965gfw
n/MídiasPerdidas - Lost Media (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqw0p8u85lcflpahfhpc63zfg9fj65z92fzyj3zp20cflfusqgsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qrqsqqpphkdltjpa
n/Football - Futebol (Por: nostr:nprofile1qqsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsppemhxue69uhkummn9ekx7mp0qywhwumn8ghj7mn0wd68ytnzd96xxmmfdejhytnnda3kjctv9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tc9l2d6x / Moderadores: nostr:nprofile1qqsx5rzeds2gf6hzaqf35qc0y6v5fys72fsec8w3gwszn3jw5mxewvgpz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9u5c2kxa & nostr:nprofile1qqspxhftq9htg9njgaefr6nmetl97q8qqlwxvynppl6c5zr9t0qmp9gpzfmhxue69uhhqatjwpkx2urpvuhx2ucpz3mhxue69uhhyetvv9ujuerpd46hxtnfduq3qamnwvaz7tmwdaehgu3wwa5kueguy3tt5) nostr:naddr1qqyxvmm0w33xzmrvqgsyjxh7htwmq277sl87wlld4lcpf0ujmp5558fcpmzww4y33djgxnsrqsqqpphkg0nfw5
n/Formula-1 (por: nostr:nprofile1qqsfujjjw3474zsrfcqhcgqavqeesd4h0nuxt0ue5ugy9y7e47xyh3qppemhxue69uhkummn9ekx7mp0qy2hwumn8ghj7mn0wd68ytn00p68ytnyv4mz7qgswaehxw309ahx7um5wghx6mmd9u2egtmk) nostr:naddr1qqy5vmmjd46kccfdxypzp8j22f6xh652qd8qzlpqr4sr8xpkka70sedlnxn3qs5nmxhccj7yqvzqqqyx7cc95u5w
n/Games - Atualizações sobre jogos (por: nostr:npub1atyuu22fvvj4yf2uf050fwra3pu7hjvykc7ravpmrkpwjxcc6hpsfneh4e ) nostr:naddr1qqz5wctdv4esyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqn0x7k7
n/JogosBrasil - Clips de jogos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qq955mm8dae5yunpwd5kcqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qj90yg0hl4e6qr7yg982dlh0qxdefy72d6ntuqet7hv3ateya782sxpqqqzr0vus9jl2
n/Minecraft (por: nostr:npub19xc7f5lg2z6svrjgye63rx44a96aq2ysqajx5tmum28cu6mk5j3qj3n9m9 ) nostr:naddr1qqy566twv43hyctxwspzq2d3unf7s594qc8ysfn4zxdtt6t46q5fqpmydghhek503e4hdf9zqvzqqqyx7ct7hldr
n/GenshinImpactBr (por: nostr:nprofile1qqs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggppemhxue69uhkummn9ekx7mp0qyg8wumn8ghj7mn0wd68ytnddakj7qgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctcnffw22) nostr:naddr1qqtlp8u85lcflpahgajkuumgd9hyjmtsv93hgsnjq9z8wue69uhkw6tjwahhgvntdaunx6mkdgmxv6ehdaek2mm3v9a8qdtkwa3x2cthda3kyvmdxgmk5cm3w3sksd34vcexv6mvxdukgtn0de5k7m30qgs28fezzs5n2rdjh9deqv3ztk59mhg4j2jxaee7a4amkya30jnruggrqsqqpphkq4s4py
Libertarianismo:
n/Defensores-caseiros (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq0lp8u85lcflpahg3jkvetwwdhhyetn943kzum9d9ex7ulsn78mgq3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vcr78h2
n/Desobediência_Civil (por: nostr:nprofile1qqs2kw4x8jws3a4heehst0ywafwfymdqk35hx8mrf0dw6zdsnk5kj9gpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m306r5ytp) nostr:naddr1qq2ygetnda3x2erfcw4xucmfv905x6tkd9kqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsyg9t82nre8gg76muumc9hj8w5hyjdkstg6tnra35hkhdpxcfm2tfz5psgqqqsmmqlg3ata
n/sobreviNOSTR - Sobrevivencialismo (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq20p8u85lcflpah2dhkyun9we55un6n23fqz3rhwvaz7tm8d9e8wmm5xf4k77fnddmx5dnxdvmk7um9dackz7nsx4m8wcn9v9mk7cmzxdknydm2vdchgctgxc6kvvnxddkrx7ty9ehku6t0dchsygz8g3szf3lmg9j80mg5dlmkt24uvmsjwmht93svvpv5ws96gk0ltvpsgqqqsmmqtempje
n/Triggr - Armas (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qqr9g5jfgar4yqghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3qgazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsxpqqqzr0vt5085y
n/Kaboom - Química e explosivos (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4 ) nostr:naddr1qqt0p8u85lcflpahfdq5yn60fhcflra57z0602qppemhxue69uhkummn9ekx7mp0qgsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcrqsqqpphk637p09
n/CAVERNA-DO-PIRATA - Pirataria (por: nostr:nprofile1qqsyw3rqynrlkstywlk3gmlhvk4tcehpyahwktrqcczegaqt53vl7kcpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpg3mhxw309uex5umwd35xvmn9d35kwdtpvdcnv6tpvdukgmt6v33xgmt8xau8watwd568smpkw9mkyan6v93hwdrvwaex5mtv09jzummwd9hkutcpg4mhxue69uhhx6m60fhrvcmfd4nxga34v5e8q6r2vv68ju34wcmkj6mz0p6xudtxxajxkamwx43nwa35xa6xgat6d33x7um3d4ckgtn0de5k7m304dlxq4) nostr:naddr1qq40p8u85lcflpahgdq4v32jfeqj63z094gyj5jp23qlp8u0kn3gpr0znzswlwy07z0ca2gpg3mhxw309ankjunhda6ry6m00yekkan2xenxkdm0wdjk7utp0fcr2anhvfjkzam0vd3rxmfjxa4xxut5v95rvdtxxfnxkmpn09jzummwd9hkutczypr5gcpycla5zerha52xlam9427xdcf8dm4jccxxqk28gzayt8l4kqcyqqqgdask5hmmn
n/PrivateSociety - Propostas e discussões para uma sociedade privada (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq89qunfweshge2nda3kjet50ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cfvhgrt
n/TeoriaDasBandeiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqf9get0wf5kzerpwdpxzmnyv45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkatc9rh
n/SemFronteiras (por: nostr:nprofile1qqs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586gpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshszrnhwden5te0dehhxtnvdakz7ar9xsz) nostr:naddr1qqx4xetdgeex7mn5v45hyctnqgs8efvwljfdwa0qynp7n9dhqacf3llucdqtm9ge8kjv0dt40yw586grqsqqpphkjs0cue
n/AnarcoSobrevivencialismo (por: nostr:nprofile1qqsfj5s9lrcckaxd8ul7vf3c4ajfg0n0ytcjvetclw679hy6p98wpfqpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy2hwumn8ghj7un9d3shjtnwdaehgu3wvfnj7qg4waehxw309ahx7um5wghx77r5wghxgetk9uykdgj7) nostr:naddr1qqdyzmnpwf3k75m0vfex2anfwejkucmfv9kxjumddap9yq3qn9fqt7833d6v60elucnr3tmyjslx7gh3yejh37a4utwf5z2wuzjqxpqqqzr0vsz5kcy
n/SociedadeAlternativaLibertaria - Libertários (por: nostr:nprofile1qqs2ph3za34henpq2y3rzgqwgdc4pjmpleqr5t62rf7kxj0lmdyxnfgppemhxue69uhkummn9ekx7mp0ydypw5) nostr:naddr1qq09xmmrd9jkgctyv4qkcar9wfhxzarfwes5c6tzv4e8gctjd9ssyg9qmc3wc6muess9zg33yq8yxu2sedslusp69a9p5ltrf8lakjrf55psgqqqsmmq8dtk3m
n/LibertariosPT - Libertários de Portugal (por: nostr:nprofile1qqszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4gppemhxue69uhkummn9ekx7mp05leack) nostr:naddr1qqx5c6tzv4e8gctjd9hhx5z5qgszx8rlqax4pakclsxscudfset7fs37jm7rflnugh3nf8r4ehx4z4grqsqqpphke05802
Discussões Sociais
n/Aliança-Conservadora-Brasileira (por: nostr:npub1atg5rgfuarup49470kqexfgcesdr85yru56y0y8qf3z6kc30g2vqyfyqyp ) nostr:naddr1qqsyzmrfv9hv8fmptapk7mnnv4e8vctydaexzh6zwfshx6tvv45hycgzyr4dzsdp8n50sx5khe7crye9rrxp5v7ss0jng3usupxyt2mz9apfsqcyqqqgdasue9j59
n/Ilha-de-Anhatomirin - Monarquia (Por: nostr:nprofile1qqsgzc22v804davx6vpwtwfu6j84yvupeld497tfr396usmu7s0m08qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszymhwden5te0v9ehgunpdshxu6twdfsj7qguwaehxw309a5x7ervvfhkgtnrdaexzcmvv5h8gmm0d3ej7a2jp7u) nostr:naddr1qqf5jmrgvykkgefdg9hxsct5dakkjunfd5q3uamnwvaz7tmwdaehgu3dwp6kytnhv4kxcmmjv3jhytnwv46z7q3qs9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqxpqqqzr0vu2qg3m
n/ManosphereBrasil - Contra a misandria (Por: nostr:nprofile1qqs0p3yd48kzm56a4tual772y3vsjwehx6tc3rv8ht8q0zgncg5r7qgpg3mhxw309ahhsarjv3jhvctkxc685d35093rw7pkwf4xwdrww3a8z6ngv4jx6dtzx4ax5ut4d36kw6mwdpa8ydpkdeunyutzv9jzummwd9hkutcpjnhed) nostr:naddr1qqgy6ctwdaehq6r9wfj5yunpwd5kcqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyrcvfrdfaskaxhd2l80lhj3ytyynkdekj7ygmpa6ecrcjy7z9qlszqcyqqqgdasl3kaju
Memes
n/Shitposting (Por: nostr:nprofile1qqs9nyy7ctpy334n3p7gh4p93lmj2cch8ae8jgjsp8al2g32stdnpdcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpr9mhxue69uhhyetvv9ujumn0wd68ytnrdakjuct49us57cz4) nostr:naddr1qq94x6rfw3cx7um5d9hxwqgswaehxw309ahx7um5wghx6mmd9upzqkvsnmpvyjxxkwy8ez75yk8lwftrzulhy7fz2qylhafz92pdkv9hqvzqqqyx7chlz42w
n/Puro-caldo-do-Brasil. (por: nostr:nprofile1qqsztjv2pflmwcayr2jaq90astj94lu5l0smr0zhkfdct4ry7uxu7dqywzq8t) nostr:naddr1qq24qatjdukkxctvv3hj6er094p8yctnd9kzuqghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7q3qyhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6qxpqqqzr0vwh0r4w
Locais
n/NordesteLibertário - Nordeste (Por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqf5ummjv3jhxar9f35kyetjwnp6zunfdupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqyx7cnejrgl
n/BahiaLibertária - Bahia (por: nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0s8pkkr ) nostr:naddr1qqgyyctgd9s5c6tzv4e8fsapwf5kzq3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqzr0vc4949j
n/LiberdadeMinas - Minas Gerais (Por: nostr:nprofile1qqsf0kszkmrmy9l3c7mxr3uhh3fmyjpq2z4hjvv7wdq84k5npd7gw3cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszxthwden5te0wfjkccte9eekummjwsh8xmmrd9skctcprpmhxue69uhhyetvv9ujuurvv438xarj9e3k7mf0mx68nx) nostr:naddr1qq8yc6tzv4exgctyv4xkjmnpwvqsqq3qjldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsxpqqqzr0vag4knt
n/CyberpunkManaus - Manaus (Por: nostr:nprofile1qqsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqpz3mhxw309ucnqt3jx5cjuvpwxgarsvpcxqq3wamn8ghj7vfexghrzd3c9ccjuv3s8gurqwps9uq5gamn8ghj7entv43kjd3nvfcx5en6093h2up5w3ekgmn4xsekvatwx438xamywp6ksemcwp6xummzdgekzdmz0pmhzd3j0g6xzepwdahxjmmw9u2upp88) nostr:naddr1qqgyx7tzv4e8qatwdvk56ctwv96hxqgqqgsz8v8zlrg0jclhasdksctsr2jw28lrqwn3zrsclnkpmytvmzhhdlqrqsqqpphkgjh4rf
n/BelémLibertario (por: nostr:npub167s6q8sfzkhel4227kacu98zcg6e37v5sqwkv8mxaazrryz9huzqlhcu2t) nostr:nevent1qqsqnqgx3u2whdqdqmlstqcmgav6xfe4upz2qxfvj03tlk699dzlk7qzyrt6rgq7py26l874ft6mhrs5utprtx8ejjqp6eslvmh5gvvsgklsgqcyqqqqq2qqsdz6l
n/SãoPauloLivre - São Paulo (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq898sardagxzatvdaxxjanjv5pzp6kfec55jce92gj4cjlg7ju8mzrea0ycfd3u86crk8vzayd334wrqvzqqqyx7cmls060
n/AcreLibertário - Acre (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qq85zcmjv4xxjcn9wf6v8gtjd9hsyg82e88zjjtry4fz2hztar6tslvg084unp9k8sltqwcast53kxx4cvpsgqqqsmmqftljpt
n/Alagoas (por: nostr:nprofile1qqsw4jww99ykxf2jy4wyh685hp7cs70texztv0p7kqa3mqhfrvvdtscpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpzpmhxue69uhkummnw3ezumt0d5hsz8rhwden5te0wfjkccte9emkj6mfveex2etyd9sju7re0ghsftvmn0 e nostr:nprofile1qqs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshsz9thwden5te0wfjkccte9ehx7um5wghxyee0vnwevs) nostr:naddr1qqr5zmrpvahkzuczyr4vnn3ff93j2539t3973a9c0ky8n67fsjmrc04s8vwc96gmrr2uxqcyqqqgdas8qtaf4
Empreendedorismo:
n/Empreendedorismo/BR (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqd5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj7snjv9ekjmqzyz5jr7tdaz02wwfsksstyrf9ytx4x9yhaa257my24xlw5s29yt5dkqcyqqqgdaslzrp3p
n/Empreendedorismo/SP (por: nostr:npub14ysljm0gn6nnjv95yzeq6ffze4f3f9l0248kez4fhm4yz3fzardslwx5e8) nostr:naddr1qqt5y4zr9azk6urjv4jkuer9v3hhy6tnd4hj756sqgs2jg0edh5fafeexz6zpvsdy53v65c5jlh42nmv325ma6jpg53w3kcrqsqqpphkcym25j
Análise
n/EBDV (Em Busca Da Verdade) - Análise geral e desenvolvimento pessoal (por: nostr:nprofile1qqs0xmu0skfdlmtl5tth6cv99za8f8kv7ulz5srkm8p6v5k03dx9lzspz4mhxue69uhkummnw3ezummcw3ezuer9wchszrnhwden5te0dehhxtnvdakz7qgswaehxw309ahx7um5wghx6mmd9usvrt9r) nostr:naddr1qqzy2sjy2cpzpum037ze9hld073dwltps55t5ay7enmnu2jqwmvu8fjje795chu2qvzqqqyx7cy9v5px
-
 @ 078d6670:56049f0c
2025-05-18 07:53:13
@ 078d6670:56049f0c
2025-05-18 07:53:13Imagine having a personal assistant who could prompt you into riding a positive wave of creativity and warn you about a risky period of your life when you are cognitively distracted. An assistant that knows you better than you do, only because it has processing power and a database curated by you for you. A better you, created by you!
There is so much fear around AI. It will take jobs, it will realize how stupid humans are and take over the world. That’s if you believe AI can become conscious, not merely mimic human behaviour. But it can’t, it is just a super complex system programmed to interact with you better than before. Here is a explanation by @clif_high : Artificial Intelligence is retarded or AI & Bullshit
AI is still the best thing since the internet!
Imagine having a tool to gauge your personal life, impersonally. No judgement, only code. A tool that could correlate your behaviour with moon phases, seasons, diurnal rhythms, astrological cycles, birthdays (or any other metric); if any patterns exist, it can enlighten you. The same tool filters your inbox, takes action if necessary, alerts you, if necessary.
All the artwork you’ve created, you’ve appreciated, can be analyzed for future inspiration.
What you might need: personal diary (digital), personal journal (if there’s a difference), calendar, pictures, emails and a personal AI.
It could also curate a reading list for you, discovering literature it calculates will benefit you, including economic theory and psychology. We would need a feedback system so it didn’t leave the reservation.
Is there a danger it could mislead you? Maybe if you think AI is sentient, or it could miscalculate, so you would need to check its bias (and your own).
Think of your smartphone, but more capable and a lot more processing power. Not more intelligence, that’s reserved for the programmer. Unless you’re the programmer (but maybe it won’t be necessary to learn coding), or rather the prompt-engineer, then it is up to your intelligence as to how well you can set up your personal AI assistant. Maybe you need an assistant to help you set it up, like, that would be a great vocation: helping old people configure their AI.
The aim is create opportunities for more recreation time. Time spent being healthy. There could be a setting on your AI to prioritize saving time when connecting with other people’s AI, so both enjoy hyper-productivity and time for passion.
There are amazing groups of people concerned in making AI available to all free of bias, decentralized and open source:
- GPT4ALL
- @BrianRoemmele on X & readmultiplex.com
- Open Agents is working on making AI decentralized by securing it openly with the Bitcoin blockchain (@OpenAgentsInc on X).
- If you know of any others, please drop a reference in the comments.
It is essential for humanity that AI remains open source. If it is centralized and co-opted by private corporations in cahoots with government, we’re in big trouble (genocide, slavery, poverty, endless wars). Decentralized, transparent, open-source AI leads to better humans!
-
 @ 79008e78:dfac9395
2025-03-22 11:22:07
@ 79008e78:dfac9395
2025-03-22 11:22:07Keys and Addresses
อลิซต้องการจ่ายเงินให้กับบ๊อบแต่โหนดของบิตคอยน์ในระบบหลายพันโหนดจะตรวจสอบธุรกรรมของเธอ โดยไม่รู้ว่าอลิซหรือบ๊อบเป็นใคร ละเราต้องการรักษาความเป็นส่วนตัวของพวกเขาไว้เช่นนี้ อลิซจำเป็นต้องสื่อสารว่าบ๊อบควรได้รับบิตคอยน์บางส่วนของเธอโดยไม่เชื่อมโยงแง่มุมใด ๆ ของธุรกรรมนั้นกับตัวตนในโลกจริงของบ๊อบ หรือกับการชำระเงินด้วยบิตคอยน์ครั้งอื่น ๆ ที่บ๊อบได้รับ อลิซใช้ต้องทำให้มั่นใจว่ามีเพียแค่บ๊อบเท่านั้นที่สามารถใช้จ่ายบิตคอยน์ที่เขาได้รับต่อไปได้
ในบิตคอยน์ไวท์เปเปอร์ได้อธิบายถึงแผนการที่เรียบง่ายมากสำหรับการบรรลุเป้าหมายเหล่านั้น ดังที่แสดงในรูปด้านล่างนี้

ตัวของผู้รับอย่างบ๊อบเองจะได้รับบิตคอยน์ไปยัง public key ของเขาที่ถูกลงนามโดยผู้จ่ายอย่างอลิซ โดยบิตคอยน์ที่อลิซนำมาจ่ายนั้นก็ได้รับมาจากที่ใครสักคนส่งมาที่ public key ของเธอ และเธอก็ใช้ private key ของเธอในการลงนามเพื่อสร้างลายเซ็นของเธอและโหนดต่าง ๆ ของบิตคอยน์จะทำการตรวจสอบว่าลายเซ็นของอลิซผูกมัดกับเอาต์พุตของฟังก์ชันแฮชซึ่งตัวมันเองผูกมัดกับ public key ของบ๊อบและรายละเอียดธุรกรรมอื่นๆ
ในบทนี้เราจะพิจารณาpublic key private key Digital signatrue และ hash function จากนั้นใช้ทั้งหมดนี้ร่วมกันเพื่ออธิบาย address ที่ใช้โดยซอฟต์แวร์บิตคอยน์สมัยใหม่
Public Key Cryptography (การเข้ารหัสของ public key)
ระบบเข้ารหัสของ public key ถูกคิดค้นขึ้นในทศวรรษ 1970 มาจากรากฐานทางคณิตศาสตร์สำหรับความปลอดภัยของคอมพิวเตอร์และข้อมูลสมัยใหม่
นับตั้งแต่การคิดค้นระบบเข้ารหัส public key ได้มีการค้นพบฟังก์ชันทางคณิตศาสตร์ที่เหมาะสมหลายอย่าง เช่น การยกกำลังของจำนวนเฉพาะและการคูณของเส้นโค้งวงรี โดยฟังก์ชันทางคณิตศาสตร์เหล่านี้สามารถคำนวณได้ง่ายในทิศทางหนึ่ง แต่เป็นไปไม่ได้ที่จะคำนวณในทิศทางตรงกันข้ามโดยใช้คอมพิวเตอร์และอัลกอริทึมที่มีอยู่ในปัจจุบัน จากฟังก์ชันทางคณิตศาสตร์เหล่านี้ การเข้ารหัสลับช่วยให้สามารถสร้างลายเซ็นดิจิทัลที่ไม่สามารถปลอมแปลงได้และบิตคอยน์ได้ใช้การบวกและการคูณของเส้นโค้งวงรีเป็นพื้นฐานสำหรับการเข้ารหัสลับของมัน
ในบิตคอยน์ เราสามารถใช้ระบบเข้ารหัส public key เพื่อสร้างคู่กุญแจที่ควบคุมการเข้าถึงบิตคอยน์ คู่กุญแจประกอบด้วย private key และ public key ที่ได้มาจาก private key public keyใช้สำหรับรับเงิน และ private key ใช้สำหรับลงนามในธุรกรรมเพื่อใช้จ่ายเงิน
ความสัมพันธ์ทางคณิตศาสตร์ระหว่าง public key และ private key ที่ช่วยให้ private key สามารถใช้สร้างลายเซ็นบนข้อความได้ ลายเซ็นเหล่านี้สามารถตรวจสอบความถูกต้องกับ public key ได้โดยไม่เปิดเผย private key
TIP: ในการใช้งานซอฟแวร์กระเป๋าเงินบิตคอยน์บสงอัน จะทำการเก็บ private key และ public key ถูกเก็บไว้ด้วยกันในรูปแบบคู่กุญแจเพื่อความสะดวก แต่อย่างไรก็ตาม public key สามารถคำนวณได้จาก private key ดังนั้นการเก็บเพียง private key เท่านั้นก็เป็นไปได้เช่นกัน
bitcoin wallet มักจะทำการรวบรวมคู่กุญแต่ละคู่ ซึ่งจะประกอบไปด้วย private key และ public key โดย private key จะเป็นตัวเลขที่ถูกสุ่มเลือกขึ้นมา และเราขะใช้เส้นโค้งวงรี ซึ่งเป็นฟังก์ชันการเข้ารหัสทางเดียว เพื่อสร้าง public key ขึ้นมา
ทำไมจึงใช้การเข้ารหัสแบบอสมมาตร
ทำไมการเข้ารหัสแบบอสมมาตรจึงถูกใช้บิตคอยน์? มันไม่ได้ถูกใช้เพื่อ "เข้ารหัส" (ทำให้เป็นความลับ) ธุรกรรม แต่คุณสมบัติที่มีประโยชน์ของการเข้ารหัสแบบอสมมาตรคือความสามารถในการสร้าง ลายเซ็นดิจิทัล private key สามารถนำไปใช้กับธุรกรรมเพื่อสร้างลายเซ็นเชิงตัวเลข ลายเซ็นนี้สามารถสร้างได้เฉพาะโดยผู้ที่มีความเกี่ยวข้องกับ private key เท่านั้น แต่อย่างไรก็ตาม ทุกคนที่สามารถเข้าถึง public key และธุรกรรมสามารถใช้สิ่งเหล่านี้เพื่อ ตรวจสอบ ลายเซ็นได้ คุณสมบัติที่มีประโยชน์นี้ของการเข้ารหัสแบบอสมมาตรทำให้ทุกคนสามารถตรวจสอบลายเซ็นทุกรายการในทุกธุรกรรมได้ ในขณะที่มั่นใจว่าเฉพาะเจ้าของ private key เท่านั้นที่สามารถสร้างลายเซ็นที่ถูกต้องได้
Private keys
private key เป็นเพียงตัวเลขที่ถูกสุ่มขึ้น และการควบคุม private key ก็เป็นรากฐานสำคัญที่ทำให้เจ้าชองกุญแจดอกนี้สามารถควบคุมบิตคอยน์ทั้งหมดที่มีความเกี่ยวข้องกับ public key ที่คู่กัน private key นั้นใช้ในการสร้างลายเซ็นดิจิทัลที่ใช้ในการเคลื่อนย้ายบิตคอยน์ เราจำเป็นต้องเก็บ private key ให้เป็นความลับตลอดเวลา เพราะการเปิดเผยมันให้กับบุคคลอื่นนั้นก็เปรียบเสมือนกับการนำอำนาจในการควบคุมบิตคอยน์ไปให้แก่เขา นอกจากนี้ private key ยังจำเป็นต้องได้รับการสำรองข้อมูลและป้องกันจากการสูญหายโดยไม่ตั้งใจ เพราะหากเราได้ทำมันสูญหายไป จะไม่สามารถกู้คืนได้ และบิตคอยน์เหล่านั้นจะถูกปกป้องโดยกุญแจที่หายไปนั้นตลอดกาลเช่นกัน
TIP: private key ของบิตคอยน์นั้นเป็นเพียงแค่ตัวเลข คุณสามารถสร้างมันได้โดยใช้เพียงเหรียญ ดินสอ และกระดาษ โดยการโยนเหรียญเพียง 256 ครั้งจะทำให้คุณได้เลขฐานสองที่สามารถใช้เป็น private key ของบิตคอยน์ จากนั้นคุณสามารถใช้มันในการคำนวณหา public key แต่อย่างไรก็ตาม โปรดระมัดระวังเกี่ยวกับการเลือใช้วิธีการสุ่มที่ไม่สมบูรณ์ เพราะนั่นอาจลดความปลอดภัยของ private key และบิตคอยน์ที่มัมปกป้องอยู่อย่างมีนัยสำคัญ
ขั้นตอนแรกและสำคัญที่สุดในการสร้างกุญแจคือการหาแหล่งที่มาของความสุ่มที่ปลอดภัย (ซึ่งเรียกว่า เอนโทรปี) การสร้างกุญแจของบิตคอยน์นั้นเกือบเหมือนกับ "เลือกตัวเลขระหว่าง 1 และ 2^256" ซึ่งวิธีที่แน่นอนที่คุณใช้ในการเลือกตัวเลขนั้นไม่สำคัญตราบใดที่มันไม่สามารถคาดเดาหรือทำซ้ำได้ โดยปกติแล้วซอฟต์แวร์ของบิตคอยน์มักจะใช้ตัวสร้างตัวเลขสุ่มที่มีความปลอดภัยทางการเข้ารหัสเพื่อสร้างเอนโทรปี 256 บิต
สิ่งที่สำคัญในเรื่องนี้คือ private key สามารถเป็นตัวเลขใดๆ ระหว่าง 0 และ n - 1 (รวมทั้งสองค่า) โดยที่ n เป็นค่าคงที่ (n = 1.1578 × 10^77 ซึ่งน้อยกว่า 2^256 เล็กน้อย) ซึ่งกำหนดอยู่ใน elliptic curve ที่ใช้ใน Bitcoin ในการสร้างกุญแจดังกล่าว เราสุ่มเลือกเลขขนาด 256 บิตและตรวจสอบว่ามันน้อยกว่า n ในแง่ของการเขียนโปรแกรม โดยปกติแล้วสิ่งนี้ทำได้โดยการป้อนสตริงของบิตสุ่มที่ใหญ่กว่า ซึ่งรวบรวมจากแหล่งที่มาของความสุ่มที่มีความปลอดภัยทางการเข้ารหัส เข้าไปในอัลกอริทึมแฮช SHA256 ซึ่งจะสร้างค่าขนาด 256 บิตที่สามารถตีความเป็นตัวเลขได้อย่างสะดวก หากผลลัพธ์น้อยกว่า n เราจะได้กุญแจส่วนตัวที่เหมาะสม มิฉะนั้น เราก็เพียงแค่ลองอีกครั้งด้วยตัวเลขสุ่มอื่น
คำเตือน: อย่าเขียนโค้ดของคุณเองเพื่อสร้างตัวเลขสุ่ม หรือใช้ตัวสร้างตัวเลขสุ่ม "แบบง่าย" ที่มีให้ในภาษาโปรแกรมของคุณ ใช้ตัวสร้างตัวเลขสุ่มเทียมที่มีความปลอดภัยทางการเข้ารหัส (CSPRNG) จากแหล่งที่มีเอนโทรปีเพียงพอ ศึกษาเอกสารของไลบรารีตัวสร้างตัวเลขสุ่มที่คุณเลือกเพื่อให้มั่นใจว่ามีความปลอดภัยทางการเข้ารหัส การใช้งาน CSPRNG ที่ถูกต้องมีความสำคัญอย่างยิ่งต่อความปลอดภัยของกุญแจ
ต่อไปนี้คือกุญแจส่วนตัว (k) ที่สร้างขึ้นแบบสุ่มซึ่งแสดงในรูปแบบเลขฐานสิบหก (256 บิตแสดงเป็น 64 หลักเลขฐานสิบหก โดยแต่ละหลักคือ 4 บิต):
1E99423A4ED27608A15A2616A2B0E9E52CED330AC530EDCC32C8FFC6A526AEDDTIP: จำนวนที่เป็นไปได้ของ private key ทั้งหมดนั้นมีอยู่ 2^256 เป็นตัวเลขที่ใหญ่มากจนยากจะจินตนาการได้ มันมีค่าประมาณ 10^77 (เลข 1 ตามด้วยเลข 0 อีก 77 ตัว) ในระบบเลขฐานสิบ เพื่อให้เข้าใจง่ายขึ้น ลองเปรียบเทียบกับจักรวาลที่เรามองเห็นได้ซึ่งนักวิทยาศาสตร์ประมาณการว่ามีอะตอมทั้งหมดประมาณ 10^80 อะตอม นั่นหมายความว่าช่วงค่าของกุญแจส่วนตัว Bitcoin มีขนาดใกล้เคียงกับจำนวนอะตอมทั้งหมดในจักรวาลที่เรามองเห็นได้
การอธิบายเกี่ยวกับวิทยาการเข้ารหัสแบบเส้นโค้งวงรี (Elliptic Curve Cryptography)
วิทยาการเข้ารหัสแบบเส้นโค้งวงรี (ECC) เป็นประเภทหนึ่งของการเข้ารหัสแบบอสมมาตรหรือ public key ซึ่งอาศัยหลักการของปัญหาลอการิทึมแบบไม่ต่อเนื่อง โดยแสดงออกผ่านการบวกและการคูณบนจุดต่างๆ ของเส้นโค้งวงรี

บิตคอยน์ใช้เส้นโค้งวงรีเฉพาะและชุดค่าคงที่ทางคณิตศาสตร์ ตามที่กำหนดไว้ในมาตรฐานที่เรียกว่า secp256k1 ซึ่งกำหนดโดยสถาบันมาตรฐานและเทคโนโลยีแห่งชาติ (NIST) เส้นโค้ง secp256k1 ถูกกำหนดโดยฟังก์ชันต่อไปนี้ ซึ่งสร้างเส้นโค้งวงรี: y² = (x³ + 7) บนฟิลด์จำกัด (F_p) หรือ y² mod p = (x³ + 7) mod p
โดยที่ mod p (มอดูโลจำนวนเฉพาะ p) แสดงว่าเส้นโค้งนี้อยู่บนฟิลด์จำกัดของอันดับจำนวนเฉพาะ p ซึ่งเขียนได้เป็น F_p โดย p = 2^256 – 2^32 – 2^9 – 2^8 – 2^7 – 2^6 – 2^4 – 1 ซึ่งเป็นจำนวนเฉพาะที่มีค่ามหาศาล
บิตคอยน์ใช้เส้นโค้งวงรีที่ถูกนิยามบนฟิลด์จำกัดของอันดับจำนวนเฉพาะแทนที่จะอยู่บนจำนวนจริง ทำให้มันมีลักษณะเหมือนรูปแบบของจุดที่กระจัดกระจายในสองมิติ ซึ่งทำให้ยากต่อการจินตนาการภาพ อย่างไรก็ตาม คณิตศาสตร์ที่ใช้นั้นเหมือนกับเส้นโค้งวงรีบนจำนวนจริง
ตัวอย่างเช่น การเข้ารหัสลับด้วยเส้นโค้งวงรี: การแสดงภาพเส้นโค้งวงรีบน F(p) โดยที่ p=17 แสดงเส้นโค้งวงรีเดียวกันบนฟิลด์จำกัดของอันดับจำนวนเฉพาะ 17 ที่มีขนาดเล็กกว่ามาก ซึ่งแสดงรูปแบบของจุดบนตาราง
เส้นโค้งวงรี secp256k1 ที่ใช้ในบิตคอยน์สามารถนึกถึงได้ว่าเป็นรูปแบบของจุดที่ซับซ้อนมากกว่าบนตารางที่มีขนาดใหญ่มหาศาลจนยากจะเข้าใจได้

ตัวอย่างเช่น จุด P ที่มีพิกัด (x, y) ต่อไปนี้เป็นจุดที่อยู่บนเส้นโค้ง secp256k1:
P = (55066263022277343669578718895168534326250603453777594175500187360389116729240, 32670510020758816978083085130507043184471273380659243275938904335757337482424)เราสามารถใช้ Python เพื่อยืนยันว่าจุดนี้อยู่บนเส้นโค้งวงรีได้ตามตัวอย่างนี้: ตัวอย่างที่ 1: การใช้ Python เพื่อยืนยันว่าจุดนี้อยู่บนเส้นโค้งวงรี ``` Python 3.10.6 (main, Nov 14 2022, 16:10:14) [GCC 11.3.0] on linux Type "help", "copyright", "credits" or "license" for more information.p = 115792089237316195423570985008687907853269984665640564039457584007908834671663 x = 55066263022277343669578718895168534326250603453777594175500187360389116729240 y = 32670510020758816978083085130507043184471273380659243275938904335757337482424 (x ** 3 + 7 - y**2) % p 0 ``` ผลลัพธ์เป็น 0 ซึ่งแสดงว่าจุดนี้อยู่บนเส้นโค้งวงรีจริง เพราะเมื่อแทนค่า x และ y ลงในสมการ y² = (x³ + 7) mod p แล้ว ทั้งสองด้านของสมการมีค่าเท่ากัน
ในคณิตศาสตร์ของเส้นโค้งวงรี มีจุดที่เรียกว่า "จุดที่อนันต์" (point at infinity) ซึ่งมีบทบาทคล้ายกับศูนย์ในการบวก บนคอมพิวเตอร์ บางครั้งจุดนี้แทนด้วย x = y = 0 (ซึ่งไม่เป็นไปตามสมการเส้นโค้งวงรี แต่เป็นกรณีพิเศษที่สามารถตรวจสอบได้ง่าย)
มีตัวดำเนินการ + ที่เรียกว่า "การบวก" ซึ่งมีคุณสมบัติคล้ายกับการบวกแบบดั้งเดิมของจำนวนจริงที่เด็กๆ เรียนในโรงเรียน เมื่อมีจุดสองจุด P1 และ P2 บนเส้นโค้งวงรี จะมีจุดที่สาม P3 = P1 + P2 ซึ่งอยู่บนเส้นโค้งวงรีเช่นกัน
ในเชิงเรขาคณิต จุดที่สาม P3 นี้คำนวณได้โดยการลากเส้นระหว่าง P1 และ P2 เส้นนี้จะตัดกับเส้นโค้งวงรีที่จุดเพิ่มเติมอีกหนึ่งจุดพอดี เรียกจุดนี้ว่า P3' = (x, y) จากนั้นให้สะท้อนกับแกน x เพื่อได้ P3 = (x, -y)
มีกรณีพิเศษบางกรณีที่อธิบายความจำเป็นของ "จุดที่อนันต์":
- ถ้า P1 และ P2 เป็นจุดเดียวกัน เส้น "ระหว่าง" P1 และ P2 ควรขยายเป็นเส้นสัมผัสกับเส้นโค้ง ณ จุด P1 นี้ เส้นสัมผัสนี้จะตัดกับเส้นโค้งที่จุดใหม่อีกหนึ่งจุดพอดี คุณสามารถใช้เทคนิคจากแคลคูลัสเพื่อหาความชันของเส้นสัมผัส เทคนิคเหล่านี้ใช้ได้อย่างน่าแปลกใจ แม้ว่าเราจะจำกัดความสนใจไว้ที่จุดบนเส้นโค้งที่มีพิกัดเป็นจำนวนเต็มเท่านั้น!
- ในบางกรณี (เช่น ถ้า P1 และ P2 มีค่า x เดียวกันแต่ค่า y ต่างกัน) เส้นสัมผัสจะตั้งฉากพอดี ซึ่งในกรณีนี้ P3 = "จุดที่อนันต์"
- ถ้า P1 เป็น "จุดที่อนันต์" แล้ว P1 + P2 = P2 ในทำนองเดียวกัน ถ้า P2 เป็นจุดที่อนันต์ แล้ว P1 + P2 = P1 นี่แสดงให้เห็นว่าจุดที่อนันต์มีบทบาทเป็นศูนย์
การบวกนี้มีคุณสมบัติเชิงสมาคม (associative) ซึ่งหมายความว่า (A + B) + C = A + (B + C) นั่นหมายความว่าเราสามารถเขียน A + B + C โดยไม่ต้องมีวงเล็บและไม่มีความกำกวม
เมื่อเรานิยามการบวกแล้ว เราสามารถนิยามการคูณในแบบมาตรฐานที่ต่อยอดจากการบวก สำหรับจุด P บนเส้นโค้งวงรี ถ้า k เป็นจำนวนเต็มบวก แล้ว kP = P + P + P + … + P (k ครั้ง) โปรดทราบว่า k บางครั้งถูกเรียกว่า "เลขชี้กำลัง"
Public Keys
ในระบบคริปโตกราฟีแบบเส้นโค้งวงรี (Elliptic Curve Cryptography) public key ถูกคำนวณจาก private key โดยใช้การคูณเส้นโค้งวงรี ซึ่งเป็นกระบวนการที่ไม่สามารถย้อนกลับได้:
K = k × G
โดยที่:
- k คือ private key
- G คือจุดคงที่ที่เรียกว่า จุดกำเนิด (generator point)
- K คือ public key
การดำเนินการย้อนกลับ ที่เรียกว่า "การหาลอการิทึมแบบไม่ต่อเนื่อง" (finding the discrete logarithm) - คือการคำนวณหา k เมื่อรู้ค่า K - เป็นสิ่งที่ยากมากเทียบเท่ากับการลองค่า k ทุกค่าที่เป็นไปได้ (วิธีการแบบ brute-force)
ความยากของการย้อนกลับนี้คือหลักการความปลอดภัยหลักของระบบ ECC ที่ใช้ในบิตคอยน์ ซึ่งทำให้สามารถเผยแพร่ public key ได้อย่างปลอดภัย โดยที่ไม่ต้องกังวลว่าจะมีใครสามารถคำนวณย้อนกลับเพื่อหา private key ได้
TIP:การคูณเส้นโค้งวงรีเป็นฟังก์ชันประเภทที่นักเข้ารหัสลับเรียกว่า “ trap door function ”:
- เป็นสิ่งที่ทำได้ง่ายในทิศทางหนึ่ง
- แต่เป็นไปไม่ได้ที่จะทำในทิศทางตรงกันข้าม
คนที่มี private key สามารถสร้าง public key ได้อย่างง่ายดาย และสามารถแบ่งปันกับโลกได้โดยรู้ว่าไม่มีใครสามารถย้อนกลับฟังก์ชันและคำนวณ private key จาก public key ได้ กลวิธีทางคณิตศาสตร์นี้กลายเป็นพื้นฐานสำหรับลายเซ็นดิจิทัลที่ปลอมแปลงไม่ได้และมีความปลอดภัย ซึ่งใช้พิสูจน์การควบคุมเงินบิตคอยน์
เริ่มต้นด้วยการใช้ private key ในรูปแบบของตัวเลขสุ่ม เราคูณมันด้วยจุดที่กำหนดไว้ล่วงหน้าบนเส้นโค้งที่เรียกว่า จุดกำเนิด (generator point) เพื่อสร้างจุดอื่นที่อยู่บนเส้นโค้งเดียวกัน ซึ่งคำตอบจะเป็น public key ที่สอดคล้องกัน จุดกำเนิดถูกกำหนดไว้เป็นส่วนหนึ่งของมาตรฐาน secp256k1 และเป็นค่าเดียวกันสำหรับกุญแจทั้งหมดในระบบบิตคอยน์
เนื่องจากจุดกำเนิด G เป็นค่าเดียวกันสำหรับผู้ใช้บิตคอยน์ทุกคน private key (k) ที่คูณกับ G จะได้ public key (K) เดียวกันเสมอ ความสัมพันธ์ระหว่าง k และ K เป็นแบบตายตัวแต่สามารถคำนวณได้ในทิศทางเดียวเท่านั้น คือจาก k ไปยัง K นี่คือเหตุผลที่ public key ของบิตคอยน์ (K) สามารถแบ่งปันกับทุกคนได้โดยไม่เปิดเผย private key (k) ของผู้ใช้
TIP: private key สามารถแปลงเป็น public key ได้ แต่ public key ไม่สามารถแปลงกลับเป็น private key ได้ เพราะคณิตศาสตร์ที่ใช้ทำงานได้เพียงทิศทางเดียวเท่านั้น
เมื่อนำการคูณเส้นโค้งวงรีมาใช้งาน เราจะนำ private key (k) ที่สร้างขึ้นก่อนหน้านี้มาคูณกับจุดกำเนิด G เพื่อหา public key (K):
K = 1E99423A4ED27608A15A2616A2B0E9E52CED330AC530EDCC32C8FFC6A526AEDD × Gpublic key (K) จะถูกกำหนดเป็นจุด K = (x, y) โดยที่:x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBเพื่อจะให้เห็นภาพของการคูณจุดด้วยจำนวนเต็มมากขึ้น เราจะใช้เส้นโค้งวงรีที่ง่ายกว่าบนจำนวนจริง (โดยหลักการทางคณิตศาสตร์ยังคงเหมือนกัน) เป้าหมายของเราคือการหาผลคูณ kG ของจุดกำเนิด G ซึ่งเทียบเท่ากับการบวก G เข้ากับตัวเอง k ครั้งติดต่อกันในเส้นโค้งวงรี การบวกจุดเข้ากับตัวเองเทียบเท่ากับการลากเส้นสัมผัสที่จุดนั้นและหาว่าเส้นนั้นตัดกับเส้นโค้งอีกครั้งที่จุดใด จากนั้นจึงสะท้อนจุดนั้นบนแกน x
การเข้ารหัสลับด้วยเส้นโค้งวงรี: การแสดงภาพการคูณจุด G ด้วยจำนวนเต็ม k บนเส้นโค้งวงรี แสดงกระบวนการในการหา G, 2G, 4G เป็นการดำเนินการทางเรขาคณิตบนเส้นโค้งได้ดังนี้
TIP: ในซอฟแวร์ของบิตคอยน์ส่วนใหญ่ใช้ไลบรารีเข้ารหัสลับ libsecp256k1 เพื่อทำการคำนวณทางคณิตศาสตร์เส้นโค้งวงรี

Output and Input Scripts
แม้ว่าภาพประกอบจาก Bitcoin whitepaper ที่แสดงเรื่อง "Transaction chain" จะแสดงให้เห็นว่ามีการใช้ public key และ digital signature โดยตรง แต่ในความเป็นจริงบิตคอยน์เวอร์ชันแรกนั้นมีการส่งการชำระเงินไปยังฟิลด์ที่เรียกว่า output script และมีการใช้จ่ายบิตคอยน์เหล่านั้นโดยได้รับอนุญาตจากฟิลด์ที่เรียกว่า input script ฟิลด์เหล่านี้อนุญาตให้มีการดำเนินการเพิ่มเติมนอกเหนือจาก (หรือแทนที่) การตรวจสอบว่าลายเซ็นสอดคล้องกับ public key หรือไม่ ตัวอย่างเช่น output script สามารถมี public key สองดอกและต้องการลายเซ็นสองลายเซ็นที่สอดคล้องกันในฟิลด์ input script ที่ใช้จ่าย
ในภายหลัง ในหัวข้อ [tx_script] เราจะได้เรียนรู้เกี่ยวกับสคริปต์อย่างละเอียด สำหรับตอนนี้ สิ่งที่เราต้องเข้าใจคือ บิตคอยน์จะถูกรับเข้า output script ที่ทำหน้าที่เหมือน public key และการใช้จ่ายบิตคอยน์จะได้รับอนุญาตโดย input script ที่ทำหน้าที่เหมือนลายเซ็น
IP Addresses: The Original Address for Bitcoin (P2PK)
เราได้เห็นแล้วว่าอลิซสามารถจ่ายเงินให้บ็อบโดยการมอบบิตคอยน์บางส่วนของเธอให้กับกุญแจสาธารณะของบ็อบ แต่อลิซจะได้กุญแจสาธารณะของบ็อบมาได้อย่างไร? บ็อบอาจจะให้สำเนากุญแจแก่เธอ แต่ลองดูกุญแจสาธารณะที่เราใช้งานในตัวอย่างที่ผ่านมาอีกครั้ง:
x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBTIP จากหลาม: :สังเกตได้ว่า public key มีความยาวมาก ลองจินตนาการว่าบ็อบพยายามอ่านกุญแจนี้ให้อลิซฟังทางโทรศัพท์ คงจะยากมากที่จะอ่านและบันทึกโดยไม่มีข้อผิดพลาด
แทนที่จะป้อนกุญแจสาธารณะโดยตรง เวอร์ชันแรกของซอฟต์แวร์บิตคอยน์อนุญาตให้ผู้จ่ายเงินป้อนที่อยู่ IP ของผู้รับได้ ตามที่แสดงในหน้าจอการส่งเงินรุ่นแรกของบิตคอยน์ผ่าน The Internet Archive
คุณสมบัตินี้ถูกลบออกในภายหลัง เนื่องจากมีปัญหามากมายในการใช้ที่อยู่ IP แต่คำอธิบายสั้นๆ จะช่วยให้เราเข้าใจได้ดีขึ้นว่าทำไมคุณสมบัติบางอย่างอาจถูกเพิ่มเข้าไปในโปรโตคอลบิตคอยน์

เมื่ออลิซป้อนที่อยู่ IP ของบ็อบในบิตคอยน์เวอร์ชัน 0.1 Full node ของเธอจะทำการเชื่อมต่อกับ full node ของเขาและได้รับ public key ใหม่จากกระเป๋าสตางค์ของบ็อบที่โหนดของเขาไม่เคยให้กับใครมาก่อน การที่เป็น public key ใหม่นี้มีความสำคัญเพื่อให้แน่ใจว่าธุรกรรมต่าง ๆ ที่จ่ายให้บ็อบจะไม่สามารถถูกเชื่อมโยงเข้าด้วยกันโดยคนที่กำลังดูบล็อกเชนและสังเกตเห็นว่าธุรกรรมทั้งหมดจ่ายไปยัง public key เดียวกัน
เมื่อใช้ public key จากโหนดของอลิซซึ่งได้รับมาจากโหนดของบ็อบ กระเป๋าสตางค์ของอลิซจะสร้างเอาต์พุตธุรกรรมที่จ่ายให้กับสคริปต์เอาต์พุตดังนี้
<Bob's public key> OP_CHECKSIGต่อมาบ็อบจะสามารถใช้จ่ายเอาต์พุตนั้นด้วยสคริปต์อินพุตที่ประกอบด้วยลายเซ็นของเขาเท่านั้น:<Bob's signature>เพื่อให้เข้าใจว่าสคริปต์อินพุตและเอาต์พุตกำลังทำอะไร คุณสามารถรวมพวกมันเข้าด้วยกัน (สคริปต์อินพุตก่อน) แล้วสังเกตว่าข้อมูลแต่ละชิ้น (แสดงในเครื่องหมาย < >) จะถูกวางไว้ที่ด้านบนสุดของรายการที่เรียกว่าสแตก (stack) เมื่อพบรหัสคำสั่ง (opcode) มันจะใช้รายการจากสแตก โดยเริ่มจากรายการบนสุด มาดูว่ามันทำงานอย่างไรโดยเริ่มจากสคริปต์ที่รวมกัน:<Bob's signature> <Bob's public key> OP_CHECKSIGสำหรับสคริปต์นี้ ลายเซ็นของบ็อบจะถูกนำไปไว้บนสแตก จากนั้น public key ของบ็อบจะถูกวางไว้ด้านบนของลายเซ็น และบนสุดจะเป็นคำสั่ง OP_CHECKSIG ที่จะใช้องค์ประกอบสองอย่าง เริ่มจาก public key ตามด้วยลายเซ็น โดยลบพวกมันออกจากสแตก มันจะตรวจสอบว่าลายเซ็นตรงกับ public key และยืนยันฟิลด์ต่าง ๆ ในธุรกรรม ถ้าลายเซ็นถูกต้อง OP_CHECKSIG จะแทนที่ตัวเองบนสแตกด้วยค่า 1 ถ้าลายเซ็นไม่ถูกต้อง มันจะแทนที่ตัวเองด้วย 0 ถ้ามีรายการที่ไม่ใช่ศูนย์อยู่บนสุดของสแตกเมื่อสิ้นสุดการประเมิน สคริปต์ก็จะผ่าน ถ้าสคริปต์ทั้งหมดในธุรกรรมผ่าน และรายละเอียดอื่น ๆ ทั้งหมดเกี่ยวกับธุรกรรมนั้นต้องถูกต้องจึงจะถือว่าธุรกรรมนั้นถูกต้อง
โดยสรุป สคริปต์ข้างต้นใช้ public key และลายเซ็นเดียวกันกับที่อธิบายใน whitepaper แต่เพิ่มความซับซ้อนของฟิลด์สคริปต์สองฟิลด์และรหัสคำสั่งหนึ่งตัว ซึ่งเราจะเริ่มเห็นประโยชน์เมื่อเรามองที่ส่วนต่อไป
TIP:จากหลาม agian: เอาต์พุตประเภทนี้เป็นที่รู้จักในปัจจุบันว่า P2PK ซึ่งมันไม่เคยถูกใช้อย่างแพร่หลายสำหรับการชำระเงิน และไม่มีโปรแกรมที่ใช้กันอย่างแพร่หลายที่รองรับการชำระเงินผ่านที่อยู่ IP เป็นเวลาเกือบทศวรรษแล้ว
Legacy addresses for P2PKH
แน่นอนว่าการป้อนที่อยู่ IP ของคนที่คุณต้องการจ่ายเงินให้นั้นมีข้อดีหลายประการ แต่ก็มีข้อเสียหลายประการเช่นกัน หนึ่งในข้อเสียที่สำคัญคือผู้รับจำเป็นต้องให้กระเป๋าสตางค์ของพวกเขาออนไลน์ที่ที่อยู่ IP ของพวกเขา และต้องสามารถเข้าถึงได้จากโลกภายนอก
ซึ่งสำหรับคนจำนวนมากนั่นไม่ใช่ตัวเลือกที่เป็นไปได้เพราะหากพวกเขา:
- ปิดคอมพิวเตอร์ในเวลากลางคืน
- แล็ปท็อปของพวกเขาเข้าสู่โหมดสลีป
- อยู่หลังไฟร์วอลล์
- หรือกำลังใช้การแปลงที่อยู่เครือข่าย (NAT)
ปัญหานี้นำเรากลับมาสู่ความท้าทายเดิมที่ผู้รับเงินอย่างบ็อบต้องให้ public key ที่มีความยาวมากแก่ผู้จ่ายเงินอย่างอลิซ public key ของบิตคอยน์ที่สั้นที่สุดที่นักพัฒนาบิตคอยน์รุ่นแรกรู้จักมีขนาด 65 ไบต์ เทียบเท่ากับ 130 ตัวอักษรเมื่อเขียนในรูปแบบเลขฐานสิบหก (เฮกซาเดซิมอล) แต่อย่างไรก็ตาม บิตคอยน์มีโครงสร้างข้อมูลหลายอย่างที่มีขนาดใหญ่กว่า 65 ไบต์มาก ซึ่งจำเป็นต้องถูกอ้างอิงอย่างปลอดภัยในส่วนอื่น ๆ ของบิตคอยน์โดยใช้ข้อมูลขนาดเล็กที่สุดเท่าที่จะปลอดภัยได้
โดยบิตคอยน์แก้ปัญหานี้ด้วย ฟังก์ชันแฮช (hash function) ซึ่งเป็นฟังก์ชันที่รับข้อมูลที่อาจมีขนาดใหญ่ นำมาแฮช และให้ผลลัพธ์เป็นข้อมูลขนาดคงที่ ฟังก์ชันแฮชจะผลิตผลลัพธ์เดียวกันเสมอเมื่อได้รับข้อมูลนำเข้าแบบเดียวกัน และฟังก์ชันที่ปลอดภัยจะทำให้เป็นไปไม่ได้ในทางปฏิบัติสำหรับผู้ที่ต้องการเลือกข้อมูลนำเข้าอื่นที่ให้ผลลัพธ์เหมือนกันได้ นั่นทำให้ผลลัพธ์เป็น คำมั่นสัญญา (commitment) ต่อข้อมูลนำเข้า เป็นสัญญาว่าในทางปฏิบัติ มีเพียงข้อมูลนำเข้า x เท่านั้นที่จะให้ผลลัพธ์ X
สมมติว่าผมต้องการถามคำถามคุณและให้คำตอบของผมในรูปแบบที่คุณไม่สามารถอ่านได้ทันที สมมติว่าคำถามคือ "ในปีไหนที่ซาโตชิ นาคาโมโตะเริ่มทำงานบนบิทคอยน์?" ผมจะให้การยืนยันคำตอบของผมในรูปแบบของผลลัพธ์จากฟังก์ชันแฮช SHA256 ซึ่งเป็นฟังก์ชันที่ใช้บ่อยที่สุดในบิทคอยน์:
94d7a772612c8f2f2ec609d41f5bd3d04a5aa1dfe3582f04af517d396a302e4eต่อมา หลังจากคุณบอกคำตอบที่คุณเดาสำหรับคำถามนั้น ผมสามารถเปิดเผยคำตอบของผมและพิสูจน์ให้คุณเห็นว่าคำตอบของผม เมื่อใช้เป็นข้อมูลสำหรับฟังก์ชันแฮช จะให้ผลลัพธ์เดียวกันกับที่ผมให้คุณก่อนหน้านี้$ echo "2007. He said about a year and a half before Oct 2008" | sha256sum 94d7a772612c8f2f2ec609d41f5bd3d04a5aa1dfe3582f04af517d396a302e4eทีนี้ให้สมมติว่าเราถามบ็อบว่า " public key ของคุณคืออะไร?" บ็อบสามารถใช้ฟังก์ชันแฮชเพื่อให้การยืนยันที่ปลอดภัยทางการเข้ารหัสต่อ public key ของเขา หากเขาเปิดเผยกุญแจในภายหลัง และเราตรวจสอบว่ามันให้ผลการยืนยันเดียวกันกับที่เขาให้เราก่อนหน้านี้ เราสามารถมั่นใจได้ว่ามันเป็นกุญแจเดียวกันที่ใช้สร้างการยืนยันก่อนหน้านี้ฟังก์ชันแฮช SHA256 ถือว่าปลอดภัยมากและให้ผลลัพธ์ 256 บิต (32 ไบต์) น้อยกว่าครึ่งหนึ่งของขนาด public key ของบิทคอยน์ดั้งเดิม แต่อย่างไรก็ตาม มีฟังก์ชันแฮชอื่นๆ ที่ปลอดภัยน้อยกว่าเล็กน้อยที่ให้ผลลัพธ์ขนาดเล็กกว่า เช่น ฟังก์ชันแฮช RIPEMD-160 ซึ่งให้ผลลัพธ์ 160 บิต (20 ไบต์) ด้วยเหตุผลที่ซาโตชิ นาคาโมโตะไม่เคยระบุ เวอร์ชันดั้งเดิมของบิทคอยน์สร้างการยืนยันต่อ public key โดยการแฮชกุญแจด้วย SHA256 ก่อน แล้วแฮชผลลัพธ์นั้นด้วย RIPEMD-160 ซึ่งให้การยืนยันขนาด 20 ไบต์ต่อ public key
เราสามารถดูสิ่งนี้ตามอัลกอริทึม เริ่มจากกุญแจสาธารณะ K เราคำนวณแฮช SHA256 และคำนวณแฮช RIPEMD-160 ของผลลัพธ์ ซึ่งให้ตัวเลข 160 บิต (20 ไบต์): A = RIPEMD160(SHA256(K))
ทีนี้เราคงเข้าใจวิธีสร้างการยืนยันต่อ public key แล้ว ต่อไปเราจะมาดูวิธีการใช้งานโดยพิจารณาสคริปต์เอาต์พุตต่อไปนี้:
OP_DUP OP_HASH160 <Bob's commitment> OP_EQUAL OP_CHECKSIGและสคริปต์อินพุตต่อไปนี้:<Bob's signature> <Bob's public key>และเมื่อเรารวมมันเข้าด้วยกันเราจะได้ผลลัพธ์ดังนี้:<Bob's signature> <Bob's public key> OP_DUP OP_HASH160 <Bob's commitment> OP_EQUAL OP_CHECKSIGเหมือนที่เราทำใน IP Addresses: The Original Address for Bitcoin (P2PK) เราเริ่มวางรายการลงในสแต็ก ลายเซ็นของบ็อบถูกวางก่อน จากนั้น public key ของเขาถูกวางไว้ด้านบน จากนั้นดำเนินการ OP_DUP เพื่อทำสำเนารายการบนสุด ดังนั้นรายการบนสุดและรายการที่สองจากบนในสแต็กตอนนี้เป็น public key ของบ็อบทั้งคู่ การดำเนินการ OP_HASH160 ใช้ (ลบ) public key บนสุดและแทนที่ด้วยผลลัพธ์ของการแฮชด้วย RIPEMD160(SHA256(K)) ดังนั้นตอนนี้บนสุดของสแต็กคือแฮชของ public key ของบ็อบ ต่อไป commitment ถูกเพิ่มไว้บนสุดของสแต็ก การดำเนินการ OP_EQUALVERIFY ใช้รายการสองรายการบนสุดและตรวจสอบว่าพวกมันเท่ากัน ซึ่งควรเป็นเช่นนั้นหาก public key ที่บ็อบให้ในสคริปต์อินพุตเป็น public key เดียวกันกับที่ใช้สร้างการยืนยันในสคริปต์เอาต์พุตที่อลิซจ่าย หาก OP_EQUALVERIFY ล้มเหลว ทั้งสคริปต์จะล้มเหลว สุดท้าย เราเหลือสแต็กที่มีเพียงลายเซ็นของบ็อบและ public key ของเขา รหัสปฏิบัติการ OP_CHECKSIG ตรวจสอบว่าพวกมันสอดคล้องกัน
TIP: จากหลาม ถ้าอ่านตรงนี้และงง ๆ ผมไปทำรูปมาให้ดูง่ายขึ้นครับ
แม้กระบวนการของการ pay-to-publickey-hash(P2PKH) อาจดูซับซ้อน แต่มันทำให้การที่อลิซจ่ายเงินให้บ็อบมีเพียงการยืนยันเพียง 20 ไบต์ต่อ public key ของเขาแทนที่จะเป็นตัวกุญแจเอง ซึ่งจะมีขนาด 65 ไบต์ในเวอร์ชันดั้งเดิมของบิทคอยน์ นั่นเป็นข้อมูลที่น้อยกว่ามากที่บ็อบต้องสื่อสารกับอลิซ
แต่อย่างไรก็ตาม เรายังไม่ได้พูดถึงวิธีที่บ็อบรับ 20 ไบต์เหล่านั้นจากกระเป๋าเงินบิทคอยน์ของเขาไปยังกระเป๋าเงินของอลิซ มีการเข้ารหัสค่าไบต์ที่ใช้กันอย่างแพร่หลาย เช่น เลขฐานสิบหก แต่ข้อผิดพลาดใด ๆ ในการคัดลอกการยืนยันจะทำให้บิทคอยน์ถูกส่งไปยังเอาต์พุตที่ไม่สามารถใช้จ่ายได้ ทำให้พวกมันสูญหายไปตลอดกาล โดยในส่วนถัดไป เราจะดูที่การเข้ารหัสแบบกะทัดรัดและการตรวจสอบความถูกต้อง
Base58check Encoding
ระบบคอมพิวเตอร์มีวิธีเขียนตัวเลขยาวๆ ให้สั้นลงโดยใช้ทั้งตัวเลขและตัวอักษรผสมกัน เพื่อใช้พื้นที่น้อยลงอย่างเช่น
- ระบบเลขฐานสิบ (ปกติที่เราใช้) - ใช้เลข 0-9 เท่านั้น
- ระบบเลขฐานสิบหก - ใช้เลข 0-9 และตัวอักษร A-F ตัวอย่าง: เลข 255 ในระบบปกติ เขียนเป็น FF ในระบบเลขฐานสิบหก (สั้นกว่า)
- ระบบเลขฐานหกสิบสี่ (Base64) - ใช้สัญลักษณ์ถึง 64 ตัว: ตัวอักษรเล็ก (a-z) 26 ตัว, ตัวอักษรใหญ่ (A-Z) 26 ตัว, ตัวเลข (0-9) 10 ตัว, สัญลักษณ์พิเศษอีก 2 ตัว ("+" และ "/")
โดยระบบ Base64 นี้ช่วยให้เราส่งไฟล์คอมพิวเตอร์ผ่านข้อความธรรมดาได้ เช่น การส่งรูปภาพผ่านอีเมล โดยใช้พื้นที่น้อยกว่าการเขียนเป็นเลขฐานสิบแบบปกติมาก
การเข้ารหัสแบบ Base58 คล้ายกับ Base64 โดยใช้ตัวอักษรพิมพ์ใหญ่ พิมพ์เล็ก และตัวเลข แต่ได้ตัดตัวอักษรบางตัวที่มักถูกเข้าใจผิดว่าเป็นตัวอื่นและอาจดูเหมือนกันเมื่อแสดงในฟอนต์บางประเภทออกไป
Base58 คือ Base64 ที่ตัดตัวอักษรต่อไปนี้ออก:
- เลข 0 (ศูนย์)
- ตัวอักษร O (ตัว O พิมพ์ใหญ่)
- ตัวอักษร l (ตัว L พิมพ์เล็ก)
- ตัวอักษร I (ตัว I พิมพ์ใหญ่)
- และสัญลักษณ์ "+" และ "/"
หรือพูดให้ง่ายขึ้น Base58 คือกลุ่มตัวอักษรพิมพ์เล็ก พิมพ์ใหญ่ และตัวเลข แต่ไม่มีตัวอักษรทั้งสี่ตัว (0, O, l, I) ที่กล่าวถึงข้างต้น ตัวอักษรทั้งหมดที่ใช้ใน Base58 จะแสดงให้เห็นในตัวอักษร Base58 ของบิทคอยน์
Example 2. Bitcoin’s base58 alphabet
123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyzการเพิ่มความปลอดภัยพิเศษเพื่อป้องกันการพิมพ์ผิดหรือข้อผิดพลาดในการคัดลอก base58check ได้รวม รหัสตรวจสอบ (checksum) ที่เข้ารหัสในตัวอักษร base58 เข้าไปด้วย รหัสตรวจสอบนี้คือข้อมูลเพิ่มเติมอีก 4 ไบต์ที่เพิ่มเข้าไปที่ท้ายของข้อมูลที่กำลังถูกเข้ารหัสรหัสตรวจสอบนี้ได้มาจากการแฮชข้อมูลที่ถูกเข้ารหัส และจึงสามารถใช้เพื่อตรวจจับข้อผิดพลาดจากการคัดลอกและการพิมพ์ได้ เมื่อโปรแกรมได้รับรหัส base58check ซอฟต์แวร์ถอดรหัสจะคำนวณรหัสตรวจสอบของข้อมูลและเปรียบเทียบกับรหัสตรวจสอบที่รวมอยู่ในรหัสนั้น
หากทั้งสองไม่ตรงกัน แสดงว่ามีข้อผิดพลาดเกิดขึ้น และข้อมูล base58check นั้นไม่ถูกต้อง กระบวนการนี้ช่วยป้องกันไม่ให้ address บิทคอยน์ที่พิมพ์ผิดถูกยอมรับโดยซอฟต์แวร์กระเป๋าเงินว่าเป็น address ที่ถูกต้อง ซึ่งเป็นข้อผิดพลาดที่อาจส่งผลให้สูญเสียเงินได้
การแปลงข้อมูล (ตัวเลข) เป็นรูปแบบ base58check มีขั้นตอนดังนี้:
- เราเริ่มโดยการเพิ่ม prefix เข้าไปในข้อมูล เรียกว่า "version byte" ซึ่งช่วยให้ระบุประเภทของข้อมูลที่ถูกเข้ารหัสได้ง่าย ตัวอย่างเช่น: prefix ศูนย์ (0x00 ในระบบเลขฐานสิบหก) แสดงว่าข้อมูลควรถูกใช้เป็นการยืนยัน (hash) ในสคริปต์เอาต์พุต legacy P2PKH
- จากนั้น เราคำนวณ "double-SHA" checksum ซึ่งหมายถึงการใช้อัลกอริทึมแฮช SHA256 สองครั้งกับผลลัพธ์ก่อนหน้า (prefix ต่อกับข้อมูล):
checksum = SHA256(SHA256(prefix||data)) - จากแฮช 32 ไบต์ที่ได้ (การแฮชซ้อนแฮช) เราเลือกเฉพาะ 4 ไบต์แรก ไบต์ทั้งสี่นี้ทำหน้าที่เป็นรหัสตรวจสอบข้อผิดพลาดหรือ checksum
- นำ checksum นี้ไปต่อที่ท้ายข้อมูล
การเข้ารหัสแบบ base58check คือรูปแบบการเข้ารหัสที่ใช้ base58 พร้อมกับการระบุเวอร์ชันและการตรวจสอบความถูกต้อง เพื่อการเข้ารหัสข้อมูลบิทคอยน์ โดยคุณสามารถดูภาพประกอบด้านล่างเพื่อความเข้าใจเพิ่มเติม

ในบิตคอยน์นั้น นอกจากจะใช้ base58check ในการยืนยัน public key แล้ว ก็ยังมีการใช้ในข้อมูลอื่น ๆ ด้วย เพื่อทำให้ข้อมูลนั้นกะทัดรัด อ่านง่าย และตรวจจับข้อผิดพลาดได้ง่ายด้วยรหัสนำหน้า (version prefix) ในการเข้ารหัสแบบ base58check ถูกใช้เพื่อสร้างรูปแบบที่แยกแยะได้ง่าย ซึ่งเมื่อเข้ารหัสด้วย base58 โดยจะมีตัวอักษรเฉพาะที่จุดเริ่มต้นของข้อมูลที่เข้ารหัส base58check ตัวอักษรเหล่านี้ช่วยให้เราระบุประเภทของข้อมูลที่ถูกเข้ารหัสและวิธีการใช้งานได้ง่าย นี่คือสิ่งที่แยกความแตกต่าง ตัวอย่างเช่น ระหว่าง address บิทคอยน์ที่เข้ารหัส base58check ซึ่งขึ้นต้นด้วยเลข 1 กับรูปแบบการนำเข้า private key (WIF - Wallet Import Format) ที่เข้ารหัส base58check ซึ่งขึ้นต้นด้วยเลข 5 ตัวอย่างของ version prefix สามารถดูได้ตามตารางด้านล่างนี้

ภาพต่อไปนี้จะทำให้คุณเห็นภาพของกระบวนการแปลง public key ให้เป็น bitcoin address

Compressed Public Keys
ในยุคแรก ๆ ของบิตคอยน์นั้น มีเพียงการสร้าง public key แบบ 65 Bytes เท่านั้น แต่ในเวลาต่อมา เหล่านักพัฒนาในยุคหลังได้พบวิธีการสร้าง public key แบบใหม่ที่มีเพียง 33 Bytes และสามารถทำงานร่วมกันกับโหนดทั้งหมดในขณะนั้นได้ จีงไม่จะเป็นต้องเปลี่ยนแปลงกฎหรือโครงสร้างภายในโปรโตคอลของบิตคอยน์ โดย poublic key แบบใหม่ที่มีขนาด 33 Bytes นี้เรียกว่า compressed public key (public key ที่ถูกบีบอัด) และมีการเรียก public key ที่มีขนาด 65 Bytes ว่า uncompressed public key (public key ที่ไม่ถูกบีบอัด) ซึ่งประโยชน์ของ public key ที่เล็กลงนั้น นอกจากจะช่วยให้การส่ง public key ให้ผู้อื่นทำได้ง่ายขึ้นแล้ว ยังช่วยให้ธุรกรรมมีขนาดเล็กลง และช่วยให้สามารถทำการชำระเงินได้มากขึ้นในบล็อกเดียวกัน
อย่างที่เราได้เรียนรู้จากเนื้อหาในส่วนของ public key เราได้ทราบว่า public key คือจุด (x, y) บนเส้นโค้งวงรี เนื่องจากเส้นโค้งแสดงฟังก์ชันทางคณิตศาสตร์ จุดบนเส้นโค้งจึงเป็นคำตอบของสมการ ดังนั้นหากเรารู้พิกัด x เราก็สามารถคำนวณพิกัด y ได้โดยแก้สมการ y² mod p = (x³ + 7) mod p นั่นหมายความว่าเราสามารถเก็บเพียงพิกัด x ของ public key โดยละพิกัด y ไว้ ซึ่งช่วยลดขนาดของกุญแจและพื้นที่ที่ต้องใช้เก็บข้อมูลลง 256 บิต การลดขนาดลงเกือบ 50% ในทุกธุรกรรมรวมกันแล้วช่วยประหยัดข้อมูลได้มากมายในระยะยาว!
นี่คือ public key ที่ได้ยกเป็นตัวอย่างไว้ก่อนหน้า
x = F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A y = 07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBและนี่คือ public key ที่มีตัวนำหน้า 04 ตามด้วยพิกัด x และ y ในรูปแบบ 04 x y:
K = 04F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341A07CF33DA18BD734C600B96A72BBC4749D5141C90EC8AC328AE52DDFE2E505BDBuncompressed public key นั้นจะมีตัวนำหน้าเป็น 04 แต่ compressed public key จะมีตัวนำหน้าเป็น 02 หรือ 03 โดยเหตุผลนั้นมาจากสมการ y² mod p = (x³ + 7) mod p เนื่องจากด้านซ้ายของสมการคือ y² คำตอบสำหรับ y จึงเป็นรากที่สอง ซึ่งอาจมีค่าเป็นบวกหรือลบก็ได้ หากมองเชิงภาพ นี่หมายความว่าพิกัด y ที่ได้อาจอยู่เหนือหรือใต้แกน x เราต้องไม่ลืมว่าเส้นโค้งมีความสมมาตร ซึ่งหมายความว่ามันจะสะท้อนเหมือนกระจกโดยแกน x ดังนั้น แม้เราจะละพิกัด y ได้ แต่เราต้องเก็บ เครื่องหมาย ของ y (บวกหรือลบ) หรืออีกนัยหนึ่งคือเราต้องจำว่ามันอยู่เหนือหรือใต้แกน x เพราะแต่ละตำแหน่งแทนจุดที่แตกต่างกันและเป็น public key ที่แตกต่างกัน
เมื่อคำนวณเส้นโค้งวงรีในระบบเลขฐานสองบนสนามจำกัดของเลขจำนวนเฉพาะ p พิกัด y จะเป็นเลขคู่หรือเลขคี่ ซึ่งสอดคล้องกับเครื่องหมายบวก/ลบตามที่อธิบายก่อนหน้านี้ ดังนั้น เพื่อแยกความแตกต่างระหว่างค่าที่เป็นไปได้สองค่าของ y เราจึงเก็บ compressed public key ด้วยตัวนำหน้า 02 ถ้า y เป็นเลขคู่ และ 03 ถ้า y เป็นเลขคี่ ซึ่งช่วยให้ซอฟต์แวร์สามารถอนุมานพิกัด y จากพิกัด x และคลายการบีบอัดของ public key ไปยังพิกัดเต็มของจุดได้อย่างถูกต้อง ดังภาพประกอบต่อไปนี้

นี่คือ public key เดียวกันกับที่ยกตัวอย่างไว้ข้างต้นซึ่งแสดงให้เห็นในรูป compressed public key ที่เก็บใน 264 บิต (66 ตัวอักษรเลขฐานสิบหก) โดยมีตัวนำหน้า 03 ซึ่งบ่งชี้ว่าพิกัด y เป็นเลขคี่:
K = 03F028892BAD7ED57D2FB57BF33081D5CFCF6F9ED3D3D7F159C2E2FFF579DC341Acompressed public key สอดคล้องกับ private key เดียวกันกับ uncompressed public key หมายความว่ามันถูกสร้างจาก private key เดียวกัน แต่อย่างไรก็ตาม มันก็มีส่วนที่แตกต่างจาก uncompressed public key นั้นคือ หากเราแปลง compressed public key เป็น commitment โดยใช้ฟังก์ชัน HASH160 (RIPEMD160(SHA256(K))) มันจะสร้าง commitment ที่แตกต่างจาก uncompressed public key และจะนำไปสู่ bitcoin address ที่แตกต่างกันในที่สุด สิ่งนี้อาจทำให้สับสนเพราะหมายความว่า private key เดียวสามารถสร้าง public key ในสองรูปแบบที่แตกต่างกัน (แบบบีบอัดและแบบไม่บีบอัด) ซึ่งสร้าง bitcoin address ที่แตกต่างกันcompressed public key เป็นค่าเริ่มต้นในซอฟต์แวร์บิตคอยน์เกือบทั้งหมดในปัจจุบัน และถูกกำหนดให้ใช้กับคุณสมบัติใหม่บางอย่างที่เพิ่มในการอัปเกรดโปรโตคอลในภายหลัง
อย่างไรก็ตาม ซอฟต์แวร์บางตัวยังคงต้องรองรับ uncompressed public key เช่น แอปพลิเคชันกระเป๋าเงินที่นำเข้า private key จากกระเป๋าเงินเก่า เมื่อกระเป๋าเงินใหม่สแกนบล็อกเชนสำหรับผลลัพธ์และอินพุต P2PKH เก่า มันจำเป็นต้องรู้ว่าควรสแกนกุญแจขนาด 65 ไบต์ (และ commitment ของกุญแจเหล่านั้น) หรือกุญแจขนาด 33 ไบต์ (และ commitment ของกุญแจเหล่านั้น) หากไม่สแกนหาประเภทที่ถูกต้อง อาจทำให้ผู้ใช้ไม่สามารถใช้ยอดคงเหลือทั้งหมดได้ เพื่อแก้ไขปัญหานี้ เมื่อส่งออก private key จากกระเป๋าเงิน WIF ที่ใช้แสดง private key ในกระเป๋าเงินบิตคอยน์รุ่นใหม่จะถูกนำไปใช้แตกต่างกันเล็กน้อยเพื่อบ่งชี้ว่า private key เหล่านี้ถูกใช้ในการสร้าง compressed public key
Legacy: Pay to Script Hash (P2SH)
ตามที่เราได้เห็นในส่วนก่อนหน้านี้ ผู้รับบิตคอยน์ สามารถกำหนดให้การชำระเงินที่ส่งมาให้เขานั้นมีเงื่อนไขบางอย่างในสคริปต์เอาต์พุตได้โดยจะต้องปฏิบัติตามเงื่อนไขเหล่านั้นโดยใช้สคริปต์อินพุตเมื่อเขาใช้จ่ายบิตคอยน์เหล่านั้น ในส่วน IP Addresses: The Original Address for Bitcoin (P2PK) เงื่อนไขก็คือสคริปต์อินพุตต้องให้ลายเซ็นที่เหมาะสม ในส่วน Legacy Addresses for P2PKH นั้นจำเป็นต้องมี public key ที่เหมาะสมด้วย
ส่วนสำหรับผู้ส่งก็จะวางเงื่อนไขที่ผู้รับต้องการในสคริปต์เอาต์พุตที่ใช้จ่ายให้กับผู้รับ โดยผู้รับจะต้องสื่อสารเงื่อนไขเหล่านั้นให้ผู้ส่งทราบ ซึ่งคล้ายกับปัญหาที่บ๊อบต้องสื่อสาร public key ของเขาให้อลิซทราบ และเช่นเดียวกับปัญหานั้นที่ public key อาจมีขนาดค่อนข้างใหญ่ เงื่อนไขที่บ๊อบใช้ก็อาจมีขนาดใหญ่มากเช่นกัน—อาจมีขนาดหลายพันไบต์ นั่นไม่เพียงแต่เป็นข้อมูลหลายพันไบต์ที่ต้องสื่อสารให้อลิซทราบ แต่ยังเป็นข้อมูลหลายพันไบต์ที่เธอต้องจ่ายค่าธรรมเนียมธุรกรรมทุกครั้งที่ต้องการใช้จ่ายเงินให้บ๊อบ อย่างไรก็ตาม การใช้ฟังก์ชันแฮชเพื่อสร้าง commitment ขนาดเล็กสำหรับข้อมูลขนาดใหญ่ก็สามารถนำมาใช้ได้ในกรณีนี้เช่นกัน
ในเวลาต่อมานั้น การอัปเกรด BIP16 สำหรับโปรโตคอลบิตคอยน์ในปี 2012 ได้อนุญาตให้สคริปต์เอาต์พุตสร้าง commitment กับ redemption script (redeem script) ได้ แปลว่าเมื่อบ๊อบใช้จ่ายบิตคอยน์ของเขา ภายในสคริปต์อินพุตของเขานั้นจะต้องให้ redeem script ที่ตรงกับ commitment และข้อมูลที่จำเป็นเพื่อให้เป็นไปตาม redeem script (เช่น ลายเซ็น) เริ่มต้นด้วยการจินตนาการว่าบ๊อบต้องการให้มีลายเซ็นสองอันเพื่อใช้จ่ายบิตคอยน์ของเขา หนึ่งลายเซ็นจากกระเป๋าเงินบนเดสก์ท็อปและอีกหนึ่งจากอุปกรณ์เซ็นแบบฮาร์ดแวร์ เขาใส่เงื่อนไขเหล่านั้นลงใน redeem script:
<public key 1> OP_CHECKSIGVERIFY <public key 2> OP_CHECKSIGจากนั้นเขาสร้าง commitment กับ redeem script โดยใช้กลไก HASH160 เดียวกับที่ใช้สำหรับ commitment แบบ P2PKH, RIPEMD160(SHA256(script)) commitment นั้นถูกวางไว้ในสคริปต์เอาต์พุตโดยใช้เทมเพลตพิเศษ:OP_HASH160 <commitment> OP_EQUALคำเตือน: เมื่อใช้ pay to script hash (P2SH) คุณต้องใช้เทมเพลต P2SH โดยเฉพาะ ซึ่งจะไม่มีข้อมูลหรือเงื่อนไขเพิ่มเติมในสคริปต์เอาต์พุต หากสคริปต์เอาต์พุตไม่ได้เป็น OP_HASH160 <20 ไบต์> OP_EQUAL แน่นอนว่า redeem script จะไม่ถูกใช้และบิตคอยน์ใด ๆ อาจไม่สามารถใช้จ่ายได้หรืออาจถูกใช้จ่ายได้โดยทุกคน (หมายความว่าใครก็สามารถนำไปใช้ได้)
เมื่อบ๊อบต้องการจ่ายเงินที่เขาได้รับผ่าน commitment สำหรับสคริปต์ของเขา เขาจะใช้สคริปต์อินพุตที่รวมถึง redeem script ซึ่งถูกแปลงให้เป็นข้อมูลอีลิเมนต์เดียว นอกจากนี้เขายังให้ลายเซ็นที่จำเป็นเพื่อให้เป็นไปตาม redeem script โดยเรียงลำดับตามที่จะถูกใช้โดย opcodes:
<signature2> <signature1> <redeem script>เมื่อโหนดของบิตคอยน์ได้รับการใช้จ่ายของบ๊อบพวกมันจะตรวจสอบว่า redeem script ที่ถูกแปลงเป็นค่าแฮชแล้วมีค่าเดียวกันกับ commitment มั้ย หลังจากนั้นพวกมันจะแทนที่มันบนสแต็คด้วยค่าที่ถอดรหัสแล้ว:<signature2> <signature1> <pubkey1> OP_CHECKSIGVERIFY <pubkey2> OP_CHECKSIGสคริปต์จะถูกประมวลผล และหากผ่านการตรวจสอบและรายละเอียดธุรกรรมอื่น ๆ ทั้งหมดถูกต้อง ธุรกรรมก็จะถือว่าใช้ได้address สำหรับ P2SH ก็ถูกสร้างด้วย base58check เช่นกัน คำนำหน้าเวอร์ชันถูกตั้งเป็น 5 ซึ่งทำให้ที่อยู่ที่เข้ารหัสแล้วขึ้นต้นด้วยเลข 3 ตัวอย่างของที่อยู่ P2SH คือ 3F6i6kwkevjR7AsAd4te2YB2zZyASEm1HM
TIP: P2SH ไม่จำเป็นต้องเหมือนกับธุรกรรมแบบหลายลายเซ็น (multisignature) เสมอไป ถึง address P2SH ส่วนใหญ่ แทนสคริปต์แบบหลายลายเซ็นก็ตาม แต่อาจแทนสคริปต์ที่เข้ารหัสธุรกรรมประเภทอื่น ๆ ได้ด้วย
P2PKH และ P2SH เป็นสองเทมเพลตสคริปต์เท่านั้นที่ใช้กับการเข้ารหัสแบบ base58check พวกมันเป็นที่รู้จักในปัจจุบันว่าเป็น address แบบ legacy และกลายเป็นรูปแบบที่พบน้อยลงเรื่อยๆ address แบบ legacy ถูกแทนที่ด้วยaddress ตระกูล bech32
การโจมตี P2SH แบบ Collision
address ทั้งหมดที่อิงกับฟังก์ชันแฮชมีความเสี่ยงในทางทฤษฎีต่อผู้โจมตีที่อาจค้นพบอินพุตเดียวกันที่สร้างเอาต์พุตฟังก์ชันแฮช (commitment) โดยอิสระ ในกรณีของบิตคอยน์ หากพวกเขาค้นพบอินพุตในวิธีเดียวกับที่ผู้ใช้ดั้งเดิมทำ พวกเขาจะรู้ private key ของผู้ใช้และสามารถใช้จ่ายบิตคอยน์ของผู้ใช้นั้นได้ โอกาสที่ผู้โจมตีจะสร้างอินพุตสำหรับ commitment ที่มีอยู่แล้วโดยอิสระนั้นขึ้นอยู่กับความแข็งแกร่งของอัลกอริทึมแฮช สำหรับอัลกอริทึมที่ปลอดภัย 160 บิตอย่าง HASH160 ความน่าจะเป็นอยู่ที่ 1 ใน 2^160 นี่เรียกว่าการโจมตีแบบ preimage attack
ผู้โจมตีสามารถพยายามสร้างข้อมูลนำเข้าสองชุดที่แตกต่างกัน (เช่น redeem scripts) ที่สร้างการเข้ารหัสแบบเดียวกันได้ สำหรับ address ที่สร้างโดยฝ่ายเดียวทั้งหมด โอกาสที่ผู้โจมตีจะสร้างข้อมูลนำเข้าที่แตกต่างสำหรับการเข้ารหัสที่มีอยู่แล้วมีประมาณ 1 ใน 2^160 สำหรับอัลกอริทึม HASH160 นี่คือการโจมตีแบบ second preimage attack
อย่างไรก็ตาม สถานการณ์จะเปลี่ยนไปเมื่อผู้โจมตีสามารถมีอิทธิพลต่อค่าข้อมูลนำเข้าดั้งเดิมได้ ตัวอย่างเช่น ผู้โจมตีมีส่วนร่วมในการสร้างสคริปต์แบบหลายลายเซ็น (multisignature script) ซึ่งพวกเขาไม่จำเป็นต้องส่ง public key ของตนจนกว่าจะทราบ public key ของฝ่ายอื่นทั้งหมด ในกรณีนั้น ความแข็งแกร่งของอัลกอริทึมการแฮชจะลดลงเหลือรากที่สองของมัน สำหรับ HASH160 ความน่าจะเป็นจะกลายเป็น 1 ใน 2^80 นี่คือการโจมตีแบบ collision attack
เพื่อให้เข้าใจตัวเลขเหล่านี้ในบริบทที่ชัดเจน ข้อมูล ณ ต้นปี 2023 นักขุดบิตคอยน์ทั้งหมดรวมกันสามารถประมวลผลฟังก์ชันแฮชประมาณ 2^80 ทุกชั่วโมง พวกเขาใช้ฟังก์ชันแฮชที่แตกต่างจาก HASH160 ดังนั้นฮาร์ดแวร์ที่มีอยู่จึงไม่สามารถสร้างการโจมตีแบบ collision attack สำหรับมันได้ แต่การมีอยู่ของเครือข่ายบิตคอยน์พิสูจน์ว่าการโจมตีแบบชนกันต่อฟังก์ชัน 160 บิตอย่าง HASH160 สามารถทำได้จริงในทางปฏิบัติ นักขุดบิตคอยน์ได้ลงทุนเทียบเท่ากับหลายพันล้านดอลลาร์สหรัฐในฮาร์ดแวร์พิเศษ ดังนั้นการสร้างการโจมตีแบบ collision attack จึงไม่ใช่เรื่องถูก แต่มีองค์กรที่คาดหวังว่าจะได้รับบิตคอยน์มูลค่าหลายพันล้านดอลลาร์ไปยัง address ที่สร้างโดยกระบวนการที่เกี่ยวข้องกับหลายฝ่าย ซึ่งอาจทำให้การโจมตีนี้มีกำไร
มีโปรโตคอลการเข้ารหัสที่เป็นที่ยอมรับอย่างดีในการป้องกันการโจมตีแบบ collision attack แต่วิธีแก้ปัญหาที่ง่ายโดยไม่ต้องใช้ความรู้พิเศษจากผู้พัฒนากระเป๋าเงินคือการใช้ฟังก์ชันแฮชที่แข็งแกร่งกว่า การอัปเกรดบิตคอยน์ในภายหลังทำให้เป็นไปได้ และ address บิตคอยน์ใหม่ให้ความต้านทานการชนกันอย่างน้อย 128 บิต การดำเนินการแฮช 2^128 ครั้งจะใช้เวลานักขุดบิตคอยน์ปัจจุบันทั้งหมดประมาณ 32 พันล้านปี
แม้ว่าเราไม่เชื่อว่ามีภัยคุกคามเร่งด่วนต่อผู้ที่สร้าง address P2SH ใหม่ แต่เราแนะนำให้กระเป๋าเงินใหม่ทั้งหมดใช้ที่อยู่ประเภทใหม่เพื่อขจัดความกังวลเกี่ยวกับการโจมตีแบบ collision attack ของ P2SH address
Bech32 Addresses
ในปี 2017 โปรโตคอลบิตคอยน์ได้รับการอัปเกรด เพื่อป้องกันไม่ให้ตัวระบุธุรกรรม (txids) ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ได้รับความยินยอมจากผู้ใช้ที่ทำการใช้จ่าย (หรือองค์ประชุมของผู้ลงนามเมื่อต้องมีลายเซ็นหลายรายการ) การอัปเกรดนี้เรียกว่า segregated witness (หรือเรียกสั้นๆ ว่า segwit) ซึ่งยังให้ความสามารถเพิ่มเติมสำหรับข้อมูลธุรกรรมในบล็อกและประโยชน์อื่น ๆ อีกหลายประการ แต่อย่างไรก็ตาม หากมีผู้ใช้เก่าที่ต้องการเข้าถึงประโยชน์ของ segwit โดยตรงต้องยอมรับการชำระเงินไปยังสคริปต์เอาต์พุตใหม่
ตามที่ได้กล่าวไว้ใน p2sh หนึ่งในข้อดีของเอาต์พุตประเภท P2SH คือผู้จ่ายไม่จำเป็นต้องรู้รายละเอียดของสคริปต์ที่ผู้รับใช้ การอัปเกรด segwit ถูกออกแบบมาให้ใช้กลไกนี้ได้ดังเดิม จึง ทำให้ผู้จ่ายสามารถเริ่มเข้าถึงประโยชน์ใหม่ ๆ หลายอย่างได้ทันทีโดยใช้ที่อยู่ P2SH แต่เพื่อให้ผู้รับสามารถเข้าถึงประโยชน์เหล่านั้นได้ พวกเขาจำเป็นจะต้องให้กระเป๋าเงินของผู้จ่ายจ่ายเงินให้เขาโดยใช้สคริปต์ประเภทอื่นแทน ซึ่งจะต้องอาศัยการอัปเกรดกระเป๋าเงินของผู้จ่ายเพื่อรองรับสคริปต์ใหม่เหล่านี้
ในช่วงแรก เหล่านักพัฒนาบิตคอยน์ได้นำเสนอ BIP142 ซึ่งจะยังคงใช้ base58check ร่วมกับไบต์เวอร์ชันใหม่ คล้ายกับการอัปเกรด P2SH แต่การให้กระเป๋าเงินทั้งหมดอัปเกรดไปใช้สคริปต์ใหม่ที่มีเวอร์ชัน base58check ใหม่นั้น คาดว่าจะต้องใช้ความพยายามเกือบเท่ากับการให้พวกเขาอัปเกรดไปใช้รูปแบบ address ที่เป็นแบบใหม่ทั้งหมด ด้วยเหตุนี้้เอง ผู้สนับสนุนบิตคอยน์หลายคนจึงเริ่มออกแบบรูปแบบ address ที่ดีที่สุดเท่าที่เป็นไปได้ พวกเขาระบุปัญหาหลายอย่างกับ base58check ไว้ดังนี้:
- การที่ base58check ใช้อักษรที่มีทั้งตัวพิมพ์ใหญ่และตัวพิมพ์เล็กทำให้ไม่สะดวกในการอ่านออกเสียงหรือคัดลอก ลองอ่าน address แบบเก่าในบทนี้ให้เพื่อนฟังและให้พวกเขาคัดลอก คุณจะสังเกตว่าคุณต้องระบุคำนำหน้าทุกตัวอักษรด้วยคำว่า "ตัวพิมพ์ใหญ่" และ "ตัวพิมพ์เล็ก" และเมื่อคุณตรวจสอบสิ่งที่พวกเขาเขียน คุณจะพบว่าตัวพิมพ์ใหญ่และตัวพิมพ์เล็กของตัวอักษรบางตัวอาจดูคล้ายกันในลายมือของคนส่วนใหญ่
- รูปแบบนี้สามารถตรวจจับข้อผิดพลาดได้ แต่ไม่สามารถช่วยผู้ใช้แก้ไขข้อผิดพลาดเหล่านั้น ตัวอย่างเช่น หากคุณสลับตำแหน่งตัวอักษรสองตัวโดยไม่ตั้งใจเมื่อป้อน address ด้วยตนเอง กระเป๋าเงินของคุณจะเตือนว่ามีข้อผิดพลาดเกิดขึ้นแน่นอน แต่จะไม่ช่วยให้คุณค้นพบว่าข้อผิดพลาดอยู่ที่ไหน คุณอาจต้องใช้เวลาหลายนาทีที่น่าหงุดหงิดเพื่อค้นหาข้อผิดพลาดในที่สุด
- การใช้ตัวอักษรที่มีทั้งตัวพิมพ์ใหญ่และตัวพิมพ์เล็กยังต้องใช้พื้นที่เพิ่มเติมในการเข้ารหัสใน QR code ซึ่งนิยมใช้ในการแชร์ address และ invoice ระหว่างกระเป๋าเงิน พื้นที่เพิ่มเติมนี้หมายความว่า QR code จำเป็นต้องมีขนาดใหญ่ขึ้นที่ความละเอียดเดียวกัน หรือไม่เช่นนั้นก็จะยากต่อการสแกนอย่างรวดเร็ว
- การที่ต้องการให้กระเป๋าเงินผู้จ่ายทุกใบอัปเกรดเพื่อรองรับคุณสมบัติโปรโตคอลใหม่ เช่น P2SH และ segwit แม้ว่าการอัปเกรดเองอาจไม่ต้องใช้โค้ดมากนัก แต่ประสบการณ์แสดงให้เห็นว่าผู้พัฒนากระเป๋าเงินหลายรายมักยุ่งกับงานอื่น ๆ และบางครั้งอาจล่าช้าในการอัปเกรดเป็นเวลาหลายปี สิ่งนี้ส่งผลเสียต่อทุกคนที่ต้องการใช้คุณสมบัติใหม่ ๆ เหล่านี้
นักพัฒนาที่ทำงานเกี่ยวกับรูปแบบ address สำหรับ segwit ได้พบวิธีแก้ปัญหาเหล่านี้ทั้งหมดในรูปแบบ address แบบใหม่ที่เรียกว่า bech32 (ออกเสียงด้วย "ch" อ่อน เช่นใน "เบช สามสิบสอง") คำว่า "bech" มาจาก BCH ซึ่งเป็นอักษรย่อของบุคคลสามคนที่ค้นพบรหัสวนนี้ในปี 1959 และ 1960 ซึ่งเป็นพื้นฐานของ bech32 ส่วน "32" หมายถึงจำนวนตัวอักษรในชุดตัวอักษร bech32 (คล้ายกับ 58 ใน base58check):
-
Bech32 ใช้เฉพาะตัวเลขและตัวอักษรรูปแบบเดียว (โดยปกติจะแสดงเป็นตัวพิมพ์เล็ก) แม้ว่าชุดตัวอักษรของมันจะมีขนาดเกือบครึ่งหนึ่งของชุดตัวอักษรใน base58check ก็ตามแต่ address bech32 สำหรับสคริปต์ pay to witness public key hash (P2WPKH) ก็ยังยาวกว่า legacy address และมีขนาดเท่ากันกับสคริปต์ P2PKH
-
Bech32 สามารถทั้งตรวจจับและช่วยแก้ไขข้อผิดพลาดได้ ใน address ที่มีความยาวตามที่คาดหวังได้ และสามารถรับประกันทางคณิตศาสตร์ได้ว่าจะตรวจพบข้อผิดพลาดใด ๆ ที่ส่งผลกระทบต่อตัวอักษร 4 ตัวหรือน้อยกว่า ซึ่งเชื่อถือได้มากกว่า base58check ส่วนสำหรับข้อผิดพลาดที่ยาวกว่านั้น จะไม่สามารถตรวจพบได้ (โอกาสเกิดน้อยกว่าหนึ่งครั้งในหนึ่งพันล้าน) ซึ่งมีความเชื่อถือได้ประมาณเท่ากับ base58check ยิ่งไปกว่านั้น สำหรับ adddress ที่พิมพ์โดยมีข้อผิดพลาดเพียงเล็กน้อย มันสามารถบอกผู้ใช้ได้ว่าข้อผิดพลาดเหล่านั้นเกิดขึ้นที่ไหน ช่วยให้พวกเขาสามารถแก้ไขข้อผิดพลาดจากการคัดลอกเล็ก ๆ น้อย ๆ ได้อย่างรวดเร็ว
-
ตัวอย่างที่ 3 Bech32 address ที่มีข้อผิดพลาด Address: bc1p9nh05ha8wrljf7ru236awn4t2x0d5ctkkywmv9sclnm4t0av2vgs4k3au7 ข้อผิดพลาดที่ตรวจพบแสดงเป็นตัวหนาและขีดเส้นใต้ สร้างโดยใช้โปรแกรมสาธิตการถอดรหัส bech32 address
-
bech32 address นิยมเขียนด้วยตัวอักษรพิมพ์เล็กเท่านั้น แต่ตัวอักษรพิมพ์เล็กเหล่านี้สามารถแทนที่ด้วยตัวอักษรพิมพ์ใหญ่ก่อนการเข้ารหัส address ในรหัส QR ได้ วิธีนี้ช่วยให้สามารถใช้โหมดการเข้ารหัส QR แบบพิเศษที่ใช้พื้นที่น้อยกว่า คุณจะสังเกตเห็นความแตกต่างในขนาดและความซับซ้อนของรหัส QR ทั้งสองสำหรับที่อยู่เดียวกันในรูปภาพข้างล่างนี้

- Bech32 ใช้ประโยชน์จากกลไกการอัปเกรดที่ออกแบบมาเป็นส่วนหนึ่งของ segwit เพื่อทำให้กระเป๋าเงินผู้จ่ายสามารถจ่ายเงินไปยังประเภทเอาต์พุตที่ยังไม่ได้ใช้งานได้ โดยมีเป้าหมายคือการอนุญาตให้นักพัฒนาสร้างกระเป๋าเงินในวันนี้ที่สามารถใช้จ่ายไปยัง bech32 address และทำให้กระเป๋าเงินนั้นยังคงสามารถใช้จ่ายไปยัง bech32address ได้สำหรับผู้ใช้คุณสมบัติใหม่ที่เพิ่มในการอัปเกรดโปรโตคอลในอนาคต โดยที่มีความหวังว่าเราอาจไม่จำเป็นต้องผ่านรอบการอัปเกรดทั้งระบบอีกต่อไป ซึ่งจำเป็นสำหรับการให้ผู้คนใช้งาน P2SH และ segwit ได้อย่างเต็มรูปแบบ
-
Problems with Bech32 Addresses
address แบบ bech32 ประสบความสำเร็จในทุกด้านยกเว้นปัญหาหนึ่ง คือการรับประกันทางคณิตศาสตร์เกี่ยวกับความสามารถในการตรวจจับข้อผิดพลาดจะใช้ได้เฉพาะเมื่อความยาวของ address ที่คุณป้อนเข้าไปในกระเป๋าเงินมีความยาวเท่ากับ address ดั้งเดิมเท่านั้น หากคุณเพิ่มหรือลบตัวอักษรใด ๆ ระหว่างการคัดลอกจะทำให้ไม่สามารถตรวจจับได้ การรับประกันนี้จะไม่มีผล และกระเป๋าเงินของคุณอาจใช้จ่ายเงินไปยัง address ที่ไม่ถูกต้อง แต่อย่างไรก็ตาม แม้จะไม่มีคุณสมบัตินี้ มีความเชื่อว่าเป็นไปได้ยากมากที่ผู้ใช้ที่เพิ่มหรือลบตัวอักษรจะสร้างสตริงที่มีผลรวมตรวจสอบที่ถูกต้อง ซึ่งช่วยให้มั่นใจได้ว่าเงินของผู้ใช้จะปลอดภัย
น่าเสียดายที่การเลือกใช้ค่าคงที่ตัวหนึ่งในอัลกอริทึม bech32 บังเอิญทำให้การเพิ่มหรือลบตัวอักษร "q" ในตำแหน่งที่สองจากท้ายของ address ที่ลงท้ายด้วยตัวอักษร "p" เป็นเรื่องง่ายมาก ในกรณีเหล่านั้น คุณยังสามารถเพิ่มหรือลบตัวอักษร "q" หลายครั้งได้ด้วย ข้อผิดพลาดนี้จะถูกตรวจจับโดยผลรวมตรวจสอบ (checksum) ในบางครั้ง แต่จะถูกมองข้ามบ่อยกว่าความคาดหวังหนึ่งในพันล้านสำหรับข้อผิดพลาดจากการแทนที่ของ bech32 อย่างมาก สำหรับตัวอย่างสามารถดูได้ในรูปภาพข้างล่างนี้
ตัวอย่างที่ 4. การขยายความยาวของ bech32 address โดยไม่ทำให้ผลรวมตรวจสอบเป็นโมฆะ ``` bech32 address ที่ถูกต้อง: bc1pqqqsq9txsqp
address ที่ไม่ถูกต้องแต่มีผลรวมตรวจสอบที่ถูกต้อง: bc1pqqqsq9txsqqqqp bc1pqqqsq9txsqqqqqqp bc1pqqqsq9txsqqqqqqqqp bc1pqqqsq9txsqqqqqqqqqp bc1pqqqsq9txsqqqqqqqqqqqp ```
จากตัวอย่างนี้ คุณจะเห็นว่าแม้มีการเพิ่มตัวอักษร "q" เข้าไปหลายตัวก่อนตัวอักษร "p" ตัวสุดท้าย ระบบตรวจสอบก็ยังคงยอมรับว่า address เหล่านี้ถูกต้อง นี่เป็นข้อบกพร่องสำคัญของ bech32 เพราะอาจทำให้เงินถูกส่งไปยัง address ที่ไม่มีใครเป็นเจ้าของจริง ๆ หรือ address ที่ไม่ได้ตั้งใจจะส่งไป
สำหรับเวอร์ชันเริ่มต้นของ segwit (เวอร์ชัน 0) ปัญหานี้ไม่ใช่ความกังวลในทางปฏิบัติ เพราะมีความยาวที่ถูกต้องมีเพียงสองแบบที่กำหนดไว้สำหรับเอาต์พุต นั้นคือ 22 Byte และ 34 Byte ซึ่งสอดคล้องกับ bech32 address ที่มีความยาวยาวที่ 42 หรือ 62 ตัวอักษร ดังนั้นคนจะต้องเพิ่มหรือลบตัวอักษร "q" จากตำแหน่งที่สองจากท้ายของ bech32 address ถึง 20 ครั้งเพื่อส่งเงินไปยัง address ที่ไม่ถูกต้องโดยที่กระเป๋าเงินไม่สามารถตรวจจับได้ อย่างไรก็ตาม มันอาจกลายเป็นปัญหาสำหรับผู้ใช้ในอนาคตหากมีการนำการอัปเกรดบนพื้นฐานของ segwit มาใช้
Bech32m
แม้ว่า bech32 จะทำงานได้ดีสำหรับ segwit v0 แต่นักพัฒนาไม่ต้องการจำกัดขนาดเอาต์พุตโดยไม่จำเป็นในเวอร์ชันหลังๆ ของ segwit หากไม่มีข้อจำกัด การเพิ่มหรือลบตัวอักษร "q" เพียงตัวเดียวใน bech32 address อาจทำให้ผู้ใช้ส่งเงินโดยไม่ตั้งใจไปยังเอาต์พุตที่ไม่สามารถใช้จ่ายได้หรือสามารถใช้จ่ายได้โดยทุกคน (ทำให้บิตคอยน์เหล่านั้นถูกนำไปโดยทุกคนได้) นักพัฒนาได้วิเคราะห์ปัญหา bech32 อย่างละเอียดและพบว่าการเปลี่ยนค่าคงที่เพียงตัวเดียวในอัลกอริทึมของพวกเขาจะขจัดปัญหานี้ได้ ทำให้มั่นใจว่าการแทรกหรือลบตัวอักษรสูงสุดห้าตัวจะไม่ถูกตรวจจับน้อยกว่าหนึ่งครั้งในหนึ่งพันล้านเท่านั้น
เวอร์ชันของ bech32 ที่มีค่าคงที่เพียงหนึ่งตัวที่แตกต่างกันเรียกว่า bech32 แบบปรับแต่ง (bech32m) ตัวอักษรทั้งหมดใน address แบบ bech32 และ bech32m สำหรับข้อมูลพื้นฐานเดียวกันจะเหมือนกันทั้งหมด ยกเว้นหกตัวสุดท้าย (ซึ่งเป็นส่วนของ checksum) นั่นหมายความว่ากระเป๋าเงินจำเป็นต้องรู้ว่ากำลังใช้เวอร์ชันใดเพื่อตรวจสอบความถูกต้องของ checksum แต่ address ทั้งสองประเภทมีไบต์เวอร์ชันภายในที่ทำให้การระบุเวอร์ชันที่ใช้อยู่เป็นเรื่องที่ง่าย ในการทำงานกับทั้ง bech32 และ bech32m เราจะพิจารณากฎการเข้ารหัสและการแยกวิเคราะห์สำหรับ address บิตคอยน์แบบ bech32m เนื่องจากพวกมันครอบคลุมความสามารถในการแยกวิเคราะห์บน address แบบ bech32 และเป็นรูปแบบ address ที่แนะนำในปัจจุบันสำหรับกระเป๋าเงินบิตคอยน์
ข้อความจากหลาม: คือผมว่าตรงนี้เขาเขียนไม่รู้เรื่อง แต่เดาว่าเขาน่าจะสื่อว่า เราควรเรียนรู้วิธีการทำงานกับ bech32m เพราะมันเป็นรูปแบบที่แนะนำให้ใช้ในปัจจุบัน และมันมีข้อดีเพราะbech32m สามารถรองรับการอ่าน address แบบ bech32 แบบเก่าได้ด้วย ง่ายๆ คือ ถ้าคุณเรียนรู้วิธีทำงานกับ bech32m คุณจะสามารถทำงานกับทั้ง bech32m และ bech32 ได้ทั้งสองแบบ
bech32m address ริ่มต้นด้วยส่วนที่มนุษย์อ่านได้ (Human Readable Part: HRP) BIP173 มีกฎสำหรับการสร้าง HRP ของคุณเอง แต่สำหรับบิตคอยน์ คุณเพียงแค่จำเป็นต้องรู้จัก HRP ที่ถูกเลือกไว้แล้วตามที่แสดงในตารางข้างล่างนี้

ส่วน HRP ตามด้วยตัวคั่น ซึ่งก็คือเลข "1" ในข้อเสนอก่อนหน้านี้สำหรับตัวคั่นโปรโตคอลได้ใช้เครื่องหมายทวิภาค (colon) แต่ระบบปฏิบัติการและแอปพลิเคชันบางตัวที่อนุญาตให้ผู้ใช้ดับเบิลคลิกคำเพื่อไฮไลต์สำหรับการคัดลอกและวางนั้นจะไม่ขยายการไฮไลต์ไปถึงและผ่านเครื่องหมายทวิภาค
การใช้ตัวเลขช่วยให้มั่นใจได้ว่าการไฮไลต์ด้วยดับเบิลคลิกจะทำงานได้กับโปรแกรมใดๆ ที่รองรับสตริง bech32m โดยทั่วไป (ซึ่งรวมถึงตัวเลขอื่นๆ ด้วย) เลข "1" ถูกเลือกเพราะสตริง bech32 ไม่ได้ใช้เลข 1 ในกรณีอื่น เพื่อป้องกันการแปลงโดยไม่ตั้งใจระหว่างเลข "1" กับตัวอักษรพิมพ์เล็ก "l"
และส่วนอื่นของ bech32m address เรียกว่า "ส่วนข้อมูล" (data part) ซึ่งประกอบด้วยสามองค์ประกอบ:
- Witness version: ไบต์ถัดไปหลังจากตัวคั่นตัวอักษรนี้แทนเวอร์ชันของ segwit ตัวอักษร "q" คือการเข้ารหัสของ "0" สำหรับ segwit v0 ซึ่งเป็นเวอร์ชันแรกของ segwit ที่มีการแนะนำที่อยู่ bech32 ตัวอักษร "p" คือการเข้ารหัสของ "1" สำหรับ segwit v1 (หรือเรียกว่า taproot) ซึ่งเริ่มมีการใช้งาน bech32m มีเวอร์ชันที่เป็นไปได้ทั้งหมด 17 เวอร์ชันของ segwit และสำหรับ Bitcoin จำเป็นต้องให้ไบต์แรกของส่วนข้อมูล bech32m ถอดรหัสเป็นตัวเลข 0 ถึง 16 (รวมทั้งสองค่า)
- Witness program: คือตำแหน่งหลังจาก witnessversion ตั้งแต่ตำแหน่ง 2 ถึง 40 Byte สำหรับ segwit v0 นี้ต้องมีความยาว 20 หรือ 32 Byte ไม่สามารถ ffมีขนาดอื่นได้ สำหรับ segwit v1 ความยาวเดียวที่ถูกกำหนดไว้ ณ เวลาที่เขียนนี้คือ 32 ไบต์ แต่อาจมีการกำหนดความยาวอื่น ๆ ได้ในภายหลัง
- Checksum: มีความยาว 6 ตัวอักษร โดยส่วนนี้ถูกสร้างขึ้นโดยใช้รหัส BCH ซึ่งเป็นประเภทของรหัสแก้ไขข้อผิดพลาด (error corection code) (แต่อย่างไรก็ตาม สำหรับ address บิตคอยน์ เราจะเห็นในภายหลังว่าเป็นสิ่งสำคัญที่จะใช้ checksum เพื่อการตรวจจับข้อผิดพลาดเท่านั้น—ไม่ใช่การแก้ไข
ในส่วนต่อไปหลังจากนี้เราจะลองสร้าง address แบบ bech32 และ bech32m สำหรับตัวอย่างทั้งหมดต่อไปนี้ เราจะใช้โค้ดอ้างอิง bech32m สำหรับ Python
เราจะเริ่มด้วยการสร้างสคริปต์เอาต์พุตสี่ตัว หนึ่งตัวสำหรับแต่ละเอาต์พุต segwit ที่แตกต่างกันที่ใช้ในช่วงเวลาของการเผยแพร่ บวกกับอีกหนึ่งตัวสำหรับเวอร์ชัน segwit ในอนาคตที่ยังไม่มีความหมายที่กำหนดไว้ สคริปต์เหล่านี้แสดงอยู่ในตารางข้างล่างนี้

สำหรับเอาต์พุต P2WPKH witness program มีการผูก commitment ที่สร้างขึ้นในลักษณะเดียวกันกับ P2PKH ที่เห็นใน Legacy Addresses for P2PKH โดย public key ถูกส่งเข้าไปในฟังก์ชันแฮช SHA256 ไดเจสต์ขนาด 32 ไบต์ที่ได้จะถูกส่งเข้าไปในฟังก์ชันแฮช RIPEMD-160 ไดเจสต์ของฟังก์ชันนั้น จะถูกวางไว้ใน witness program
สำหรับเอาต์พุตแบบ pay to witness script hash (P2WSH) เราไม่ได้ใช้อัลกอริทึม P2SH แต่เราจะนำสคริปต์ ส่งเข้าไปในฟังก์ชันแฮช SHA256 และใช้ไดเจสต์ขนาด 32 ไบต์ของฟังก์ชันนั้นใน witness program สำหรับ P2SH ไดเจสต์ SHA256 จะถูกแฮชอีกครั้งด้วย RIPEMD-160 ซึ่งแน่นอนว่าอาจจะไม่ปลอดภัย ในบางกรณี สำหรับรายละเอียด ดูที่ P2SH Collision Attacks ผลลัพธ์ของการใช้ SHA256 โดยไม่มี RIPEMD-160 คือ การผูกพันแบบ P2WSH มีขนาด 32 ไบต์ (256 บิต) แทนที่จะเป็น 20 ไบต์ (160 บิต)
สำหรับเอาต์พุตแบบ pay-to-taproot (P2TR) witness program คือจุดบนเส้นโค้ง secp256k1 มันอาจเป็น public key แบบธรรมดา แต่ในกรณีส่วนใหญ่มันควรเป็น public key ที่ผูกพันกับข้อมูลเพิ่มเติมบางอย่าง เราจะเรียนรู้เพิ่มเติมเกี่ยวกับการผูกพันนั้นในหัวข้อของ taproot
สำหรับตัวอย่างของเวอร์ชัน segwit ในอนาคต เราเพียงแค่ใช้หมายเลขเวอร์ชัน segwit ที่สูงที่สุดที่เป็นไปได้ (16) และ witness program ที่มีขนาดเล็กที่สุดที่อนุญาต (2 ไบต์) โดยมีค่าเป็นศูนย์ (null value)
เมื่อเรารู้หมายเลขเวอร์ชันและ witness program แล้ว เราสามารถแปลงแต่ละอย่างให้เป็น bech32 address ได้ โดยการใช้ไลบรารีอ้างอิง bech32m สำหรับ Python เพื่อสร้าง address เหล่านั้นอย่างรวดเร็ว และจากนั้นมาดูอย่างละเอียดว่าเกิดอะไรขึ้น:
``` $ github=" https://raw.githubusercontent.com" $ wget $github/sipa/bech32/master/ref/python/segwit_addr.py $ python
from segwit_addr import * from binascii import unhexlify help(encode) encode(hrp, witver, witprog) Encode a segwit address. encode('bc', 0, unhexlify('2b626ed108ad00a944bb2922a309844611d25468')) 'bc1q9d3xa5gg45q2j39m9y32xzvygcgay4rgc6aaee' encode('bc', 0, unhexlify('648a32e50b6fb7c5233b228f60a6a2ca4158400268844c4bc295ed5e8c3d626f')) 'bc1qvj9r9egtd7mu2gemy28kpf4zefq4ssqzdzzycj7zjhk4arpavfhsct5a3p' encode('bc', 1, unhexlify('2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311')) 'bc1p9nh05ha8wrljf7ru236awm4t2x0d5ctkkywmu9sclnm4t0av2vgs4k3au7' encode('bc', 16, unhexlify('0000')) 'bc1sqqqqkfw08p'
หากเราเปิดไฟล์ segwit_addr.py และดูว่าโค้ดกำลังทำอะไร สิ่งแรกที่เราจะสังเกตเห็นคือความแตกต่างเพียงอย่างเดียวระหว่าง bech32 (ที่ใช้สำหรับ segwit v0) และ bech32m (ที่ใช้สำหรับเวอร์ชัน segwit รุ่นหลัง) คือค่าคงที่:BECH32_CONSTANT = 1 BECH32M_CONSTANT = 0x2bc830a3 ```และในส่วนต่อไป เราจะเห็นโค้ดที่สร้าง checksum ในขั้นตอนสุดท้ายของการสร้าง checksum ค่าคงที่ที่เหมาะสมถูกรวมเข้ากับข้อมูลอื่น ๆ โดยใช้การดำเนินการ xor ค่าเดียวนั้นคือความแตกต่างเพียงอย่างเดียวระหว่าง bech32 และ bech32m
เมื่อสร้าง checksum แล้ว อักขระ 5 บิตแต่ละตัวในส่วนข้อมูล (รวมถึง witness version, witness program และ checksum) จะถูกแปลงเป็นตัวอักษรและตัวเลข
สำหรับการถอดรหัสกลับเป็นสคริปต์เอาต์พุต เราทำงานย้อนกลับ ลองใช้ไลบรารีอ้างอิงเพื่อถอดรหัส address สอง address ของเรา: ```
help(decode) decode(hrp, addr) Decode a segwit address. _ = decode("bc", "bc1q9d3xa5gg45q2j39m9y32xzvygcgay4rgc6aaee") [0], bytes([1]).hex() (0, '2b626ed108ad00a944bb2922a309844611d25468') _ = decode("bc", "bc1p9nh05ha8wrljf7ru236awm4t2x0d5ctkkywmu9sclnm4t0av2vgs4k3au7") [0], bytes([1]).hex() (1, '2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311')
เราได้รับทั้ง witness version และ witness program กลับมา สิ่งเหล่านี้สามารถแทรกลงในเทมเพลตสำหรับสคริปต์เอาต์พุตของเรา:ตัวอย่างเช่น:OP_0 2b626ed108ad00a944bb2922a309844611d25468 OP_1 2ceefa5fa770ff24f87c5475d76eab519eda6176b11dbe1618fcf755bfac5311 ``` คำเตือน: ข้อผิดพลาดที่อาจเกิดขึ้นที่ควรระวังคือ witness version ที่มีค่า 0 ใช้สำหรับ OP_0 ซึ่งใช้ไบต์ 0x00—แต่เวอร์ชัน witness ที่มีค่า 1 ใช้ OP_1 ซึ่งเป็นไบต์ 0x51 เวอร์ชัน witness 2 ถึง 16 ใช้ไบต์ 0x52 ถึง 0x60 ตามลำดับเมื่อทำการเขียนโค้ดเพื่อเข้ารหัสหรือถอดรหัส bech32m เราขอแนะนำอย่างยิ่งให้คุณใช้เวกเตอร์ทดสอบ (test vectors) ที่มีให้ใน BIP350 เราขอให้คุณตรวจสอบให้แน่ใจว่าโค้ดของคุณผ่านเวกเตอร์ทดสอบที่เกี่ยวข้องกับการจ่ายเงินให้กับเวอร์ชัน segwit ในอนาคตที่ยังไม่ได้รับการกำหนด สิ่งนี้จะช่วยให้ซอฟต์แวร์ของคุณสามารถใช้งานได้อีกหลายปีข้างหน้า แม้ว่าคุณอาจจะไม่สามารถเพิ่มการรองรับคุณสมบัติใหม่ ๆ ของบิตคอยน์ได้ทันทีที่คุณสมบัตินั้น ๆ เริ่มใช้งานได้
Private Key Formats
private key สามารถถูกแสดงได้ในหลาย ๆ รูปแบบที่ต่างกันซึ่งสามารถแปลงเป็นตัวเลขขนาด 256 bit ชุดเดียวกันได้ ดังที่เราจะแสดงให้ดูในตารางข้างล่างนี้ รูปแบบที่แตกต่างกันถูกใช้ในสถานการณ์ที่ต่างกัน รูปแบบเลขฐานสิบหก (Hexadecimal) และรูปแบบไบนารี (raw binary) ถูกใช้ภายในซอฟต์แวร์และแทบจะไม่แสดงให้ผู้ใช้เห็น WIF ถูกใช้สำหรับการนำเข้า/ส่งออกกุญแจระหว่างกระเป๋าเงินและมักใช้ในการแสดงกุญแจส่วนตัวแบบ QR code
รูปแบบของ private key ในปัจจุบัน
ซอฟต์แวร์กระเป๋าเงินบิตคอยน์ในยุคแรกได้สร้าง private key อิสระอย่างน้อยหนึ่งดอกเมื่อกระเป๋าเงินของผู้ใช้ใหม่ถูกเริ่มต้น เมื่อชุดกุญแจเริ่มต้นถูกใช้ทั้งหมดแล้ว กระเป๋าเงินอาจสร้าง private key เพิ่มเติม private key แต่ละดอกสามารถส่งออกหรือนำเข้าได้ ทุกครั้งที่มีการสร้างหรือนำเข้า private key ใหม่ จะต้องมีการสร้างการสำรองข้อมูลกระเป๋าเงินใหม่ด้วย
กระเป๋าเงินบิตคอยน์ในยุคหลังเริ่มใช้กระเป๋าเงินแบบกำหนดได้ (deterministic wallets) ซึ่ง private key ทั้งหมดถูกสร้างจาก seed เพียงค่าเดียว กระเป๋าเงินเหล่านี้จำเป็นต้องสำรองข้อมูลเพียงครั้งเดียวเท่านั้นสำหรับการใช้งานบนเชนทั่วไป แต่อย่างไรก็ตาม หากผู้ใช้ส่งออก private key เพียงดอกเดียวจากกระเป๋าเงินเหล่านี้ และผู้โจมตีได้รับกุญแจนั้นรวมถึงข้อมูลที่ไม่ใช่ข้อมูลส่วนตัวบางอย่างเกี่ยวกับกระเป๋าเงิน พวกเขาอาจสามารถสร้างกุญแจส่วนตัวใด ๆ ในกระเป๋าเงินได้—ทำให้ผู้โจมตีสามารถขโมยเงินทั้งหมดในกระเป๋าเงินได้ นอกจากนี้ ยังไม่สามารถนำเข้ากุญแจสู่กระเป๋าเงินแบบกำหนดได้ นี่หมายความว่าแทบไม่มีกระเป๋าเงินสมัยใหม่ที่รองรับความสามารถในการส่งออกหรือนำเข้ากุญแจเฉพาะดอก ข้อมูลในส่วนนี้มีความสำคัญหลัก ๆ สำหรับผู้ที่ต้องการความเข้ากันได้กับกระเป๋าเงินบิตคอยน์ในยุคแรก ๆ
รูปแบบของ private key (รูปแบบการเข้ารหัส)
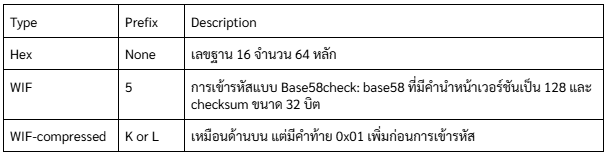 private key เดียวกันในแต่ละ format
private key เดียวกันในแต่ละ format
 รูปแบบการแสดงผลทั้งหมดเหล่านี้เป็นวิธีต่างๆ ในการแสดงเลขจำนวนเดียวกัน private key เดียวกัน พวกมันดูแตกต่างกัน แต่รูปแบบใดรูปแบบหนึ่งสามารถแปลงไปเป็นรูปแบบอื่นได้อย่างง่ายดาย
รูปแบบการแสดงผลทั้งหมดเหล่านี้เป็นวิธีต่างๆ ในการแสดงเลขจำนวนเดียวกัน private key เดียวกัน พวกมันดูแตกต่างกัน แต่รูปแบบใดรูปแบบหนึ่งสามารถแปลงไปเป็นรูปแบบอื่นได้อย่างง่ายดายCompressed Private Keys
คำว่า compressed private key ที่ใช้กันทั่วไปนั้นเป็นคำที่เรียกผิด เพราะเมื่อ private key ถูกส่งออกไปในรูปแบบ WIF-compressed มันจะมีความยาวมากกว่า private key แบบ uncompressed 1 Byte (เลข 01 ในช่อง Hex-compressed ในตารางด้านล่างนี้) ซึ่งบ่งบอกว่า private key ตัวนี้ มาจากกระเป๋าเงินรุ่นใหม่และควรใช้เพื่อสร้าง compressed public key เท่านั้น
private key เองไม่ได้ถูกบีบอัดและไม่สามารถบีบอัดได้ คำว่า compressed private key จริงๆ แล้วหมายถึง " private key ซึ่งควรใช้สร้าง compressed public key เท่านั้น" ในขณะที่ uncompressed private key จริงๆ แล้วหมายถึง “private key ซึ่งควรใช้สร้าง uncompressed public key เท่านั้น” คุณควรใช้เพื่ออ้างถึงรูปแบบการส่งออกเป็น "WIF-compressed" หรือ "WIF" เท่านั้น และไม่ควรอ้างถึง private key ว่า "บีบอัด" เพื่อหลีกเลี่ยงความสับสนต่อไป
ตารางนี้แสดงกุญแจเดียวกันที่ถูกเข้ารหัสในรูปแบบ WIF และ WIF-compressed
ตัวอย่าง: กุญแจเดียวกัน แต่รูปแบบต่างกัน

สังเกตว่ารูปแบบ Hex-compressed มีไบต์เพิ่มเติมหนึ่งไบต์ที่ท้าย (01 ในเลขฐานสิบหก) ในขณะที่คำนำหน้าเวอร์ชันการเข้ารหัสแบบ base58 เป็นค่าเดียวกัน (0x80) สำหรับทั้งรูปแบบ WIF และ WIF-compressed การเพิ่มหนึ่งไบต์ที่ท้ายของตัวเลขทำให้อักขระตัวแรกของการเข้ารหัสแบบ base58 เปลี่ยนจาก 5 เป็น K หรือ L
คุณสามารถคิดถึงสิ่งนี้เหมือนกับความแตกต่างของการเข้ารหัสเลขฐานสิบระหว่างตัวเลข 100 และตัวเลข 99 ในขณะที่ 100 มีความยาวมากกว่า 99 หนึ่งหลัก มันยังมีคำนำหน้าเป็น 1 แทนที่จะเป็นคำนำหน้า 9 เมื่อความยาวเปลี่ยนไป มันส่งผลต่อคำนำหน้า ในระบบ base58 คำนำหน้า 5 เปลี่ยนเป็น K หรือ L เมื่อความยาวของตัวเลขเพิ่มขึ้นหนึ่งไบต์
TIPจากหลาม: ผมว่าเขาเขียนย่อหน้านี้ไม่ค่อยรู้เรื่อง แต่ความหมายมันจะประมาณว่า เหมือนถ้าเราต้องการเขียนเลข 100 ในฐาน 10 เราต้องใช้สามตำแหน่ง 100 แต่ถ้าใช้ฐาน 16 เราจะใช้แค่ 2 ตำแหน่งคือ 64 ซึ่งมีค่าเท่ากัน
ถ้ากระเป๋าเงินบิตคอยน์สามารถใช้ compressed public key ได้ มันจะใช้ในทุกธุรกรรม private key ในกระเป๋าเงินจะถูกใช้เพื่อสร้างจุด public key บนเส้นโค้ง ซึ่งจะถูกบีบอัด compressed public key จะถูกใช้เพื่อสร้าง address และ address เหล่านี้จะถูกใช้ในธุรกรรม เมื่อส่งออก private key จากกระเป๋าเงินใหม่ที่ใช้ compressed public key WIF จะถูกปรับเปลี่ยน โดยเพิ่มต่อท้ายขนาด 1 ไบต์ 01 ให้กับ private key ที่ถูกเข้ารหัสแบบ base58check ที่ได้จะเรียกว่า "WIF-compressed" และจะขึ้นต้นด้วยอักษร K หรือ L แทนที่จะขึ้นต้นด้วย "5" เหมือนกับกรณีของคีย์ที่เข้ารหัสแบบ WIF (ไม่บีบอัด) จากกระเป๋าเงินรุ่นเก่า
Advanced Keys and Addresses
ในส่วนต่อไปนี้ เราจะดูรูปแบบของคีย์และ address เช่น vanity addresses และ paper wallets
vanity addresses
vanity addresses หรือ addresses แบบกำหนดเอง คือ address ที่มีข้อความที่มนุษย์อ่านได้และสามารถใช้งานได้จริง ตัวอย่างเช่น 1LoveBPzzD72PUXLzCkYAtGFYmK5vYNR33 อย่างที่เห็นว่ามันเป็น address ที่ถูกต้องซึ่งมีตัวอักษรเป็นคำว่า Love เป็นตัวอักษร base58 สี่ตัวแรก addresses แบบกำหนดเองต้องอาศัยการสร้างและทดสอบ private key หลายพันล้านตัวจนกว่าจะพบ address ที่มีรูปแบบตามที่ต้องการ แม้ว่าจะมีการปรับปรุงบางอย่างในอัลกอริทึมการสร้าง addresses แบบกำหนดเอง แต่กระบวนการนี้ต้องใช้การสุ่มเลือก private key มาสร้าง public key และนำไปสร้าง address และตรวจสอบว่าตรงกับรูปแบบที่ต้องการหรือไม่ โดยทำซ้ำหลายพันล้านครั้งจนกว่าจะพบที่ตรงกัน
เมื่อพบ address ที่ตรงกับรูปแบบที่ต้องการแล้ว private key ที่ใช้สร้าง address นั้นสามารถใช้โดยเจ้าของเพื่อใช้จ่ายบิตคอยน์ได้เหมือนกับ address อื่น ๆ ทุกประการ address ที่กำหนดเองไม่ได้มีความปลอดภัยน้อยกว่าหรือมากกว่าที่ address ๆ พวกมันขึ้นอยู่กับการเข้ารหัสเส้นโค้งรูปวงรี (ECC) และอัลกอริทึมแฮชที่ปลอดภัย (SHA) เหมือนกับ address อื่น ๆ คุณไม่สามารถค้นหา private key ของ address ที่ขึ้นต้นด้วยรูปแบบที่กำหนดเองได้ง่ายกว่า address อื่น ๆ
ตัวอย่างเช่น ยูจีเนียเป็นผู้อำนวยการการกุศลเพื่อเด็กที่ทำงานในฟิลิปปินส์ สมมติว่ายูจีเนียกำลังจัดการระดมทุนและต้องการใช้ address ที่กำหนดเองเพื่อประชาสัมพันธ์การระดมทุน ยูจีเนียจะสร้าง address ที่กำหนดเองที่ขึ้นต้นด้วย "1Kids" เพื่อส่งเสริมการระดมทุนเพื่อการกุศลสำหรับเด็ก มาดูกันว่า address ที่กำหนดเองนี้จะถูกสร้างขึ้นอย่างไรและมีความหมายอย่างไรต่อความปลอดภัยของการกุศลของยูจีเนีย
การสร้าง address ที่กำหนดเอง
ควรเข้าใจว่า address ของบิตคอยน์เป็นเพียงตัวเลขที่แสดงด้วยสัญลักษณ์ในรูปแบบตัวอักษร base58 เท่านั้น เพราะฉะนั้นแล้ว การค้นหารูปแบบเช่น "1Kids" สามารถมองได้ว่าเป็นการค้นหาที่อยู่ในช่วงตั้งแต่ 1Kids11111111111111111111111111111 ถึง 1Kidszzzzzzzzzzzzzzzzzzzzzzzzzzzzz มีประมาณ 5829 (ประมาณ 1.4 × 1051) address ในช่วงนั้น ทั้งหมดขึ้นต้นด้วย "1Kids" ตารางด้านล่างนี้แสดงช่วงของ address ที่มีคำนำหน้า 1Kids
 ลองดูรูปแบบ "1Kids" ในรูปของตัวเลขและดูว่าเราอาจพบรูปแบบนี้ใน bitcoin address บ่อยแค่ไหน โดยตารางข้างล่างนี้แสดงให้เห็นถีงคอมพิวเตอร์เดสก์ท็อปทั่วไปที่ไม่มีฮาร์ดแวร์พิเศษสามารถค้นหาคีย์ได้ประมาณ 100,000 คีย์ต่อวินาที
ลองดูรูปแบบ "1Kids" ในรูปของตัวเลขและดูว่าเราอาจพบรูปแบบนี้ใน bitcoin address บ่อยแค่ไหน โดยตารางข้างล่างนี้แสดงให้เห็นถีงคอมพิวเตอร์เดสก์ท็อปทั่วไปที่ไม่มีฮาร์ดแวร์พิเศษสามารถค้นหาคีย์ได้ประมาณ 100,000 คีย์ต่อวินาทีความถี่ของ address ที่กำหนดเอง (1KidsCharity) และเวลาค้นหาเฉลี่ยบนคอมพิวเตอร์เดสก์ท็อป

ดังที่เห็นได้ ยูจีเนียคงไม่สามารถสร้าง address แบบกำหนดเอง "1KidsCharity" ได้ในเร็ว ๆ นี้ แม้ว่าเธอจะมีคอมพิวเตอร์หลายพันเครื่องก็ตาม ทุกตัวอักษรที่เพิ่มขึ้นจะเพิ่มความยากขึ้น 58 เท่า รูปแบบที่มีมากกว่า 7 ตัวอักษรมักจะถูกค้นพบโดยฮาร์ดแวร์พิเศษ เช่น คอมพิวเตอร์เดสก์ท็อปที่สร้างขึ้นเป็นพิเศษที่มีหน่วยประมวลผลกราฟิก (GPUs) หลายตัว การค้นหา address แบบกำหนดเองบนระบบ GPU เร็วกว่าบน CPU ทั่วไปหลายเท่า
อีกวิธีหนึ่งในการหา address แบบกำหนดเองคือการจ้างงานไปยังกลุ่มคนขุด vanity addresses กลุ่มคนขุดvanity addresses เป็นบริการที่ให้ผู้ที่มีฮาร์ดแวร์ที่เร็วได้รับบิตคอยน์จากการค้นหา vanity addresses ให้กับผู้อื่น ยูจีเนียสามารถจ่ายค่าธรรมเนียมเพื่อจ้างงานการค้นหา vanity addresses ที่มีรูปแบบ 7 ตัวอักษรและได้ผลลัพธ์ในเวลาเพียงไม่กี่ชั่วโมงแทนที่จะต้องใช้ CPU ค้นหาเป็นเดือน ๆ
การสร้างที่ address แบบกำหนดเองเป็นการใช้วิธีการแบบ brute-force (ลองทุกความเป็นไปได้): ลองใช้คีย์สุ่ม ตรวจสอบ address ที่ได้ว่าตรงกับรูปแบบที่ต้องการหรือไม่ และทำซ้ำจนกว่าจะสำเร็จ
ความปลอดภัยและความเป็นส่วนตัวของ address แบบกำหนดเอง
address แบบกำหนดเองเคยเป็นที่นิยมในช่วงแรก ๆ ของบิตคอยน์ แต่แทบจะหายไปจากการใช้งานทั้งหมดในปี 2023 มีสาเหตุที่น่าจะเป็นไปได้สองประการสำหรับแนวโน้มนี้: - Deterministic wallets: ดังที่เราเห็นในพาร์ทของการกู้คืน การที่จะสำรองคีย์ทุกตัวในกระเป๋าเงินสมัยใหม่ส่วนใหญ่นั้น ทำเพียงแค่จดคำหรือตัวอักษรไม่กี่ตัว ซึ่งนี่เป็นผลจากการสร้างคีย์ทุกตัวในกระเป๋าเงินจากคำหรือตัวอักษรเหล่านั้นโดยใช้อัลกอริทึมแบบกำหนดได้ จึงไม่สามารถใช้ address แบบกำหนดเองกับ Deterministic wallets ได้ เว้นแต่ผู้ใช้จะสำรองข้อมูลเพิ่มเติมสำหรับ address แบบกำหนดเองทุก address ที่พวกเขาสร้าง ในทางปฏิบัติแล้วกระเป๋าเงินส่วนใหญ่ที่ใช้การสร้างคีย์แบบกำหนดได้ โดยไม่อนุญาตให้นำเข้าคีย์ส่วนตัวหรือการปรับแต่งคีย์จากโปรแกรมสร้าง address ที่กำหนดเอง
- การหลีกเลี่ยงการใช้ address ซ้ำซ้อน: การใช้ address แบบกำหนดเองเพื่อรับการชำระเงินหลายครั้งไปยัง address เดียวกันจะสร้างความเชื่อมโยงระหว่างการชำระเงินทั้งหมดเหล่านั้น นี่อาจเป็นที่ยอมรับได้สำหรับยูจีเนียหากองค์กรไม่แสวงหาผลกำไรของเธอจำเป็นต้องรายงานรายได้และค่าใช้จ่ายต่อหน่วยงานภาษีอยู่แล้ว แต่อย่างไรก็ตาม มันยังลดความเป็นส่วนตัวของคนที่จ่ายเงินให้ยูจีเนียหรือรับเงินจากเธอด้วย ตัวอย่างเช่น อลิซอาจต้องการบริจาคโดยไม่เปิดเผยตัวตน และบ็อบอาจไม่ต้องการให้ลูกค้ารายอื่นของเขารู้ว่าเขาให้ราคาส่วนลดแก่ยูจีเนีย
เราไม่คาดว่าจะเห็น address แบบกำหนดเองมากนักในอนาคต เว้นแต่ปัญหาที่กล่าวมาก่อนหน้านี้จะได้รับการแก้ไข
Paper Wallets
paper wallet หรือก็คือ private key ที่พิมพ์ลงในกระดาษ และโดยทั่วไปแล้วมักจะมีข้อมูลของ public key หรือ address บนกระดาษนั้นด้วยแม้ว่าจริง ๆ แล้วมันจะสามารถคำนวณได้ด้วย private key ก็ตาม
คำเตือน: paper wallet เป็นเทคโนโลยีที่ล้าสมัยแล้วและอันตรายสำหรับผู้ใช้ส่วนใหญ่ เพราะเป็นเรื่องยากที่จะสร้างมันอย่างปลอดภัย โดยเฉพาะอย่างยิ่งความเป็นไปได้ที่โค้ดที่ใช้สร้างอาจถูกแทรกแซงด้วยผู้ไม่ประสงค์ดี และอาจจะทำให้ผู้ใช้โดนขโมยบิตคอยน์ทั้งหมดไปได้ paper wallet ถูกแสดงที่นี่เพื่อวัตถุประสงค์ในการให้ข้อมูลเท่านั้นและไม่ควรใช้สำหรับเก็บบิตคอยน์

paper wallet ได้ถูกออกแบบมาเพื่อเป็นของขวัญและมีธีมตามฤดูกาล เช่น คริสต์มาสและปีใหม่ ส่วนเหตุผลอื่น ๆ ถูกออกแบบเพื่อการเก็บรักษาในตู้นิรภัยของธนาคารหรือตู้เซฟโดยมี private key ถูกซ่อนไว้ในบางวิธี ไม่ว่าจะด้วยสติกเกอร์แบบขูดที่ทึบแสงหรือพับและปิดผนึกด้วยแผ่นฟอยล์กันการงัดแงะ ส่วนการออกแบบอื่น ๆ มีสำเนาเพิ่มเติมของคีย์และ address ในรูปแบบของตอนฉีกที่แยกออกได้คล้ายกับตั๋ว ช่วยให้คุณสามารถเก็บสำเนาหลายชุดเพื่อป้องกันจากไฟไหม้ น้ำท่วม หรือภัยพิบัติทางธรรมชาติอื่น ๆ
จากการออกแบบเดิมของบิตคอยน์ที่เน้น public key ไปจนถึง address และสคริปต์สมัยใหม่อย่าง bech32m และ pay to taproot—และแม้แต่การอัพเกรดบิตคอยน์ในอนาคต—คุณได้เรียนรู้วิธีที่โปรโตคอลบิตคอยน์อนุญาตให้ผู้จ่ายเงินระบุกระเป๋าเงินที่ควรได้รับการชำระเงินของพวกเขา แต่เมื่อเป็นกระเป๋าเงินของคุณเองที่รับการชำระเงิน คุณจะต้องการความมั่นใจว่าคุณจะยังคงเข้าถึงเงินนั้นได้แม้ว่าจะเกิดอะไรขึ้นกับข้อมูลกระเป๋าเงินของคุณ ในบทต่อไป เราจะดูว่ากระเป๋าเงินบิตคอยน์ถูกออกแบบอย่างไรเพื่อปกป้องเงินทุนจากภัยคุกคามหลากหลายรูปแบบ
