-
 @ 1817b617:715fb372
2025-05-19 20:39:28
@ 1817b617:715fb372
2025-05-19 20:39:28Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
🔗 Buy Flash USDT Now This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
✅ Perfect for: Simulating token inflows Wallet stress testing “Proof of funds” display Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
🧠 What Is Flash USDT? Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
Visible on wallet interfaces Time-limited (auto-disappears cleanly) Undetectable on block explorers after expiry It’s the smartest, safest way to simulate high-value transactions without real crypto.
🛠️ Flash USDT Software – Your Own USDT Flasher at Your Fingertips Want to control the flash? Run your own operations? Flash unlimited wallets?
🔗 Buy Flash USDT Software
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
Send custom USDT amounts Set custom expiry time (e.g., 30–360 days) Flash multiple wallets Choose between networks (Tron, ETH, BSC) You can simulate any amount, to any supported wallet, from your own system.
No third-party access. No blockchain fee. No trace left behind.
💥 Why Our Flash USDT & Software Stands Out Feature Flash USDT Flash USDT Software One-time flash send ✅ Yes Optional Full sender control ❌ No ✅ Yes TRC20 / ERC20 / BEP20 ✅ Yes ✅ Yes Custom duration/expiry Limited ✅ Yes Unlimited usage ❌ One-off ✅ Yes Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
🛒 Ready to Buy Flash USDT or the Software? Skip the wait. Skip the scammers. You’re one click away from real control.
👉 Buy Flash USDT 👉 Buy Flash USDT Software
📞 Support or live walkthrough?
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
🚫 Legal Notice These tools are intended for:
Educational purposes Demo environments Wallet and UI testing They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call: Need to flash USDT? Want full control? Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
🔗 Buy Now → Flash USDT 🔗 Buy Now → Flash USDT Software 💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
Buy Flash USDT Now\ This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
Perfect for:
- Simulating token inflows
- Wallet stress testing
- “Proof of funds” display
Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
What Is Flash USDT?
Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
- Visible on wallet interfaces
- Time-limited (auto-disappears cleanly)
- Undetectable on block explorers after expiry
It’s the smartest, safest way to simulate high-value transactions without real crypto.
Flash USDT Software – Your Own USDT Flasher at Your Fingertips
Want to control the flash?\ Run your own operations?\ Flash unlimited wallets?
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
- Send custom USDT amounts
- Set custom expiry time (e.g., 30–360 days)
- Flash multiple wallets
- Choose between networks (Tron, ETH, BSC)
You can simulate any amount, to any supported wallet, from your own system.
No third-party access.\ No blockchain fee.\ No trace left behind.
Why Our Flash USDT & Software Stands Out
Feature
Flash USDT
Flash USDT Software
One-time flash send
Yes
Optional
Full sender control
No
Yes
TRC20 / ERC20 / BEP20
Yes
Yes
Custom duration/expiry
Limited
Yes
Unlimited usage
One-off
Yes
Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
Ready to Buy Flash USDT or the Software?
Skip the wait. Skip the scammers.\ You’re one click away from real control.
Support or live walkthrough?
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
Legal Notice
These tools are intended for:
- Educational purposes
- Demo environments
- Wallet and UI testing
They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call:
Need to flash USDT? Want full control?\ Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ 30b99916:3cc6e3fe
2025-05-19 20:30:52
@ 30b99916:3cc6e3fe
2025-05-19 20:30:52bitcoin #security #vault #veracrypt #powershell
BTCwallet automates running hot and cold storage wallets for multiple Bitcoin wallet applications.

BTCwallet is included with VaultApi and supports Sparrow, Blockstream Green, and just added support for Wasabi wallets.
To launch a wallet application, the command BTCwallet start is executed.
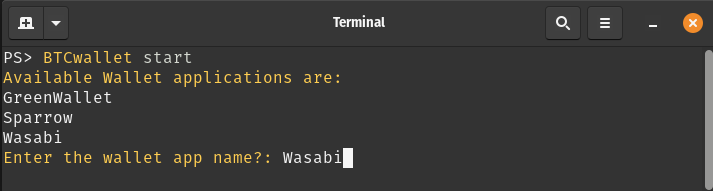
After responding to prompts for launching and initializing the Vault (not shown), the following prompts are presented.
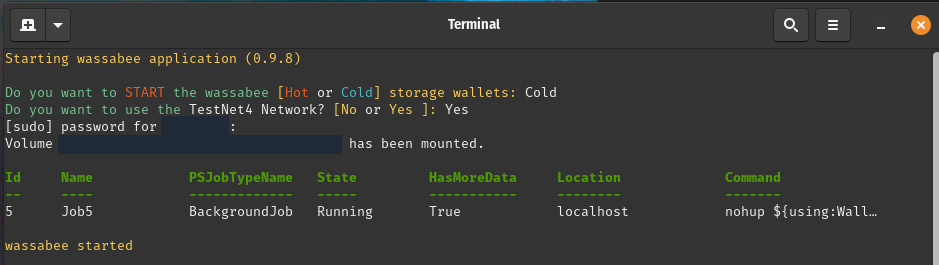
Now the Wasabi GUI application (a.k.a wassabee) is presented.

With the combination of VaultApi and BTCwallet one has a very secure self-hosted password manager along with a very secure way of protecting your Bitcoin wallet's data.
Care to follow me on my journey? If so, then check out the following links.
-
 @ 9be6a199:6e133301
2025-05-19 20:27:20
@ 9be6a199:6e133301
2025-05-19 20:27:20ssdsdsdsdsdsdsd
-
 @ 9be6a199:6e133301
2025-05-19 20:15:18
@ 9be6a199:6e133301
2025-05-19 20:15:18 -
 @ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31
@ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31Whatever
-
 @ 4c96d763:80c3ee30
2025-05-19 20:56:26
@ 4c96d763:80c3ee30
2025-05-19 20:56:26Changes
William Casarin (19):
- dave: add screenshot to readme
- dave: fix image in readme
- columns: remove spamming info logs about writing to cache
- columns: never truncate notes you're replying to
- windows: don't show terminal window
- mention: show username instead of display_name
- chrome: switch from ALPHA to BETA
- ui: make post replies selectable
- dave: include anonymous user identifier in api call
- dave: add trial mode
- dave: fix sidebar click
- dave: nudge avatar when you click
- dave: hide media in dave note previews
- chrome: fix theme persistence
- ui: fix a bunch of missing hover pointers
- Release Notedeck Beta v0.4.0
- release: changelog
- timeline: show media on universe timeline
- clippy: fix lint related to iterator
kernelkind (28):
- add
trust_media_from_pk2method - add hashbrown
- introduce & use
JobPool - introduce JobsCache
- add blurhash dependency
- introduce blur
- note: remove unnecessary derive macros from
NoteAction - propagate
JobsCache ImagePulseTint->PulseAlpha- images: move fetch to fn
- add
TexturesCache - images: make
MediaCacheholdMediaCacheType - images: make promise payload optional to take easily
- post: unnest
- notedeck_ui: move carousel to
note/media.rs - note media: only show full screen when loaded
- note media: unnest full screen media
- pass
NoteActionby value instead of reference - propagate
Imagesto actionbar - add one shot error message
- make
WidgetimplProfilePicmutably - implement blurring
- don't show zap button if no wallet
- display name should wrap
- make styled button toggleable
- method to get current default zap amount
- add
CustomZapView - use
CustomZapView
pushed to notedeck:refs/heads/master
-
 @ 975e4ad5:8d4847ce
2025-05-19 07:31:41
@ 975e4ad5:8d4847ce
2025-05-19 07:31:41The Origin of the Name “Bitcoin”
The name “Bitcoin” is a blend of “bit” (a unit of information in computing) and “coin” (a currency). Satoshi Nakamoto chose this name to highlight the digital nature of the currency, which exists entirely on a blockchain—a decentralized network immune to central control. The name is short, memorable, and reflects the project’s philosophy: money that is both technological and universal.
Satoshi decided to divide 1 Bitcoin into 100 million smaller units, named “satoshis” in his honor. This wasn’t arbitrary. Nakamoto foresaw that Bitcoin could become extremely valuable, as we see today, with 1 BTC worth around $100,000 (as of May 2025). Dividing the currency into such tiny fractions ensures flexibility: even if Bitcoin’s price reaches millions, people can use satoshis for small transactions, like buying coffee or paying network fees.
Why 100 Million Satoshis?
Satoshi’s decision to make 1 BTC equal 100,000,000 satoshis was visionary. He drew inspiration from traditional currencies, where 1 dollar splits into 100 cents, but went further. With a maximum supply of 21 million Bitcoins, the total number of satoshis is 2.1 quadrillion (2,100,000,000,000,000). This number may sound massive, but it was carefully chosen to provide enough units for future microtransactions without compromising the currency’s sense of scarcity.
If Bitcoin’s supply were framed as 2.1 quadrillion “bitcoins” instead of 21 million, it would create a false impression of abundance. Psychologically, people perceive smaller numbers as more valuable and rare. 21 million feels like a true limit, while quadrillions seem almost infinite, which would undermine Bitcoin’s core value proposition: scarcity, akin to gold.
The Benefits of Satoshis
Satoshis are the backbone of Bitcoin’s flexibility. They enable:
-
Microtransactions: Satoshis make payments as small as fractions of a cent possible, which is crucial for Bitcoin’s future as a global currency. In countries with low purchasing power, satoshis can be used for everyday purchases.
-
Network Fees: On-chain Bitcoin transactions require fees, often less than 1 BTC. Satoshis allow precise fee calculations without dealing with decimal fractions.
-
Accessibility: Even if 1 BTC costs $1 million, anyone can afford to buy satoshis. For example, $10 is roughly 100,000 satoshis at current prices, making Bitcoin accessible to all.
Beyond practical benefits, satoshis carry cultural weight. The phrase “stacking sats” has become a rallying cry in the Bitcoin community, symbolizing long-term investment and belief in the currency’s future. This expression is so iconic that removing the term “satoshi” would be like erasing part of Bitcoin’s identity.
Lightning Network and Satoshis
The Lightning Network, a layer-2 solution for Bitcoin, has made satoshis even more vital. This network enables fast and cheap transactions that don’t settle directly on the blockchain (off-chain). Due to low fees and small amounts, Lightning transactions are typically measured in satoshis, not Bitcoin. For example, a payment of 0.0001 BTC (10,000 satoshis) is common in Lightning, while on-chain transactions often involve larger sums, measured in BTC.
This distinction—Bitcoin for on-chain and satoshis for Lightning—is not only practical but also logical. On-chain transactions are slower and costlier, suited for large transfers or long-term storage (“HODLing”). Lightning is for everyday payments, where satoshis shine. Renaming satoshis to “bitcoin” would blur this distinction, causing confusion. Would you say, “I have 1 million bitcoins in my Lightning channel”? That sounds absurd and undermines the clarity the current system provides.
Why Renaming Is a Bad Idea
The idea of calling 1 satoshi a “bitcoin” and abandoning the term “bitcoin” for the whole unit has several serious flaws:
-
User Confusion: People accustomed to 1 BTC = $100,000 will be shocked to hear that 1 “bitcoin” is now worth 0.01 cents. New users won’t understand why “bitcoin” is so cheap, while veterans will struggle to recalculate their holdings. This could lead to errors, scams, or even loss of trust.
-
Technical Chaos: Wallets, exchanges, merchants, and software would need to overhaul their interfaces. Some platforms might stick to the old nomenclature, creating inconsistencies. Imagine an exchange showing “1 bitcoin = $0.01” while another uses “1 BTC = $100,000.” The result? Total chaos.
-
Cultural Loss: Satoshi is a tribute to Satoshi Nakamoto, whose vision changed the world. Erasing his name is disrespectful to his legacy. Moreover, phrases like “stacking sats” would vanish, weakening the community’s spirit.
-
Psychological Impact: 2.1 quadrillion “bitcoins” sound like an endless supply, undermining the idea of scarcity. In contrast, 21 million Bitcoins reinforce the sense of rarity, which is key to the currency’s value.
-
No Real Benefit: Satoshis are already a functional unit. Wallets can display amounts in satoshis, mBTC, or dollars without changing the protocol. Renaming solves no real problem—it just creates new ones.
Alternatives to Renaming
Instead of upending Bitcoin’s nomenclature, we can make the currency more accessible by:
-
Education: Teach people they can buy fractions of a Bitcoin, even just a few satoshis. This removes the psychological barrier of a high price.
-
Better Interfaces: Wallets can display amounts in satoshis or local currency for easier understanding. For example, instead of “0.0001 BTC,” an app could show “10,000 satoshis” or “$10.”
-
Promoting Lightning Network: Encouraging the use of satoshis in Lightning will make Bitcoin more practical for daily payments.
-
Communication: Emphasize that Bitcoin is like gold—you don’t buy a whole bar, but grams. This makes the currency more approachable to newcomers.
Bitcoin is more than a currency—it’s an idea that changed the world. The name “Bitcoin” and its satoshis are integral to that idea. Satoshi Nakamoto designed the system with the future in mind, giving us a currency that is both scarce and flexible. Renaming satoshis to “bitcoin” is a marketing stunt with no technical merit, risking trust, clarity, and Bitcoin’s culture. Instead of changing what works, let’s focus on education and innovation to make Bitcoin even more accessible. Let’s keep stacking sats and preserve the spirit of Satoshi!
-
-
 @ 4ba8e86d:89d32de4
2025-05-19 10:13:19
@ 4ba8e86d:89d32de4
2025-05-19 10:13:19DTails é uma ferramenta que facilita a inclusão de aplicativos em imagens de sistemas live baseados em Debian, como o Tails. Com ela, você pode personalizar sua imagem adicionando os softwares que realmente precisa — tudo de forma simples, transparente e sob seu controle total.
⚠️ DTails não é uma distribuição. É uma ferramenta de remasterização de imagens live.
Ela permite incluir softwares como:
✅ SimpleX Chat ✅ Clientes Nostr Web (Snort & Iris) ✅ Sparrow Wallet ✅ Feather Wallet ✅ Cake Wallet ✅ RoboSats ✅ Bisq ✅ BIP39 (Ian Coleman) ✅ SeedTool ... e muito mais. https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg
Importante: os binários originais dos aplicativos não são modificados, garantindo total transparência e permitindo a verificação de hashes a qualquer momento.
👨💻 Desenvolvido por: nostr:npub1dtmp3wrkyqafghjgwyk88mxvulfncc9lg6ppv4laet5cun66jtwqqpgte6
GitHub: https://github.com/DesobedienteTecnologico/dtails?tab=readme-ov-file
🎯 Controle total do que será instalado
Com o DTails, você escolhe exatamente o que deseja incluir na imagem personalizada. Se não marcar um aplicativo, ele não será adicionado, mesmo que esteja disponível. Isso significa: privacidade, leveza e controle absoluto.
https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg https://image.nostr.build/b70ed11ad2ce0f14fd01d62c08998dc18e3f27733c8d7e968f3459846fb81baf.jpg https://image.nostr.build/4f5a904218c1ea6538be5b3f764eefda95edd8f88b2f42ac46b9ae420b35e6f6.jpg
⚙️ Começando com o DTails
📦 Requisitos de pacotes
Antes de tudo, instale os seguintes pacotes no Debian:
``` sudo apt-get install genisoimage parted squashfs-tools syslinux-utils build-essential python3-tk python3-pil.imagetk python3-pyudev
```
🛠 Passo a passo
1 Clone o repositório:
``` git clone https://github.com/DesobedienteTecnologico/dtails cd dtails
```
2 Inicie a interface gráfica com sudo:
``` sudo ./dtails.py
```
Por que usar sudo? É necessário para montar arquivos .iso ou .img e utilizar ferramentas essenciais do sistema.
💿 Selecione a imagem Tails que deseja modificar
https://nostr.download/e3143dcd72ab6dcc86228be04d53131ccf33d599a5f7f2f1a5c0d193557dac6b.jpg
📥 Adicione ou remova pacotes
1 Marque os aplicativos desejados. 2 Clique Buildld para gerar sua imagem personalizada. https://image.nostr.build/5c4db03fe33cd53d06845074d03888a3ca89c3e29b2dc1afed4d9d181489b771.png
Você pode acompanhar todo o processo diretamente no terminal. https://nostr.download/1d959f4be4de9fbb666ada870afee4a922fb5e96ef296c4408058ec33cd657a8.jpg
💽 .ISO vs .IMG — Qual escolher?
| Formato | Persistência | Observações | | ------- | ---------------------- | ----------------------------------------------- | | .iso | ❌ Não tem persistência | Gera o arquivo DTails.iso na pasta do projeto | | .img | ✅ Suporta persistência | Permite gravar diretamente em um pendrive |
https://nostr.download/587fa3956df47a38b169619f63c559928e6410c3dd0d99361770a8716b3691f6.jpg https://nostr.download/40c7c5badba765968a1004ebc67c63a28b9ae3b5801addb02166b071f970659f.jpg
vídeo
https://www.youtube.com/live/QABz-GOeQ68?si=eYX-AHsolbp_OmAm
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ a8d1560d:3fec7a08
2025-05-19 17:28:05
@ a8d1560d:3fec7a08
2025-05-19 17:28:05NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "mediawiki" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-mediawiki-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }MediaWiki Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "mediawiki"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ d41bf82f:ed90d888
2025-05-19 20:31:54
@ d41bf82f:ed90d888
2025-05-19 20:31:54“ประเด็นแท้จริงคือเรื่องของการควบคุม—อินเทอร์เน็ตแพร่ขยายกว้างไกลเกินกว่าที่รัฐบาลใดจะครอบงำได้โดยง่าย ด้วยการสร้างเขตเศรษฐกิจระดับโลกที่ไร้รอยต่อ ไม่ขึ้นต่ออธิปไตย และอยู่นอกเหนือการควบคุม อินเทอร์เน็ตจึงตั้งคำถามต่อแนวคิดของรัฐชาติในตัวมันเอง” — JOHN PERRY BARLOW
บทนี้เริ่มต้นด้วยการวิพากษ์แนวคิด ทางด่วนข้อมูล ว่าเป็นคำอุปมาอุปมัยที่ยังยึดติดกับโลกยุคอุตสาหกรรม เพราะเศรษฐกิจยุคสารสนเทศไม่ใช่แค่โครงสร้างพื้นฐานสำหรับขนส่งข้อมูล แต่คือ จุดหมายปลายทาง ใหม่ในตัวเอง นั่นคือ ไซเบอร์สเปซ —ดินแดนที่ก้าวข้ามขอบเขตทางภูมิศาสตร์โดยสิ้นเชิง
ไซเบอร์สเปซคือพื้นที่ใหม่ของปฏิสัมพันธ์ทางสังคม เศรษฐกิจ และการเมือง ซึ่งไม่สามารถควบคุมโดยรัฐชาติแบบเดิมได้อีกต่อไป ผู้เขียนยกคำของ John Perry Barlow ที่เปรียบไซเบอร์สเปซเป็น “ดินแดนแห่งเสรีภาพ” ที่ไม่ยึดโยงกับสถานที่จริง และเปิดโอกาสให้ทุกคนแสดงความคิดเห็นได้อย่างไร้การควบคุม
การเปลี่ยนผ่านนี้ส่งผลกระทบรุนแรงต่อโครงสร้างของเศรษฐกิจแบบเดิม การเข้าถึงข้อมูลอย่างรวดเร็วแบบไร้ขอบเขตเปรียบเสมือนตัวทำละลายที่กัดกร่อนต้นทุนของสถาบันขนาดใหญ่ ทั้งภาครัฐและเอกชน ไมโครโพรเซสซิงจะเปลี่ยนรูปแบบขององค์กรและแนวคิดเรื่องสถานที่ในทางเศรษฐกิจอย่างสิ้นเชิง
ตลอดประวัติศาสตร์ เศรษฐกิจผูกติดกับพื้นที่ทางภูมิศาสตร์ การเดินทางเป็นเรื่องยากและจำกัด การค้าขายส่วนใหญ่เกิดในระดับท้องถิ่น ภาษา วัฒนธรรม และภูมิประเทศเป็นอุปสรรคทางการเมืองเสมอ จนถึงกับที่ผู้เขียนกล่าวว่า การเมืองทั้งหมดเป็นเรื่องท้องถิ่น
แต่เทคโนโลยีสมัยใหม่กำลังเปลี่ยนสมการนี้ การสื่อสารและขนส่งที่รวดเร็วทำให้ผู้มีความสามารถสามารถเลือกสถานที่อยู่อาศัยหรือทำงานได้อย่างเสรี ลดอำนาจต่อรองของรัฐบาลในพื้นที่นั้นลง เพราะคนสามารถ “หนี” ได้ง่ายขึ้น หากรัฐบาลกดขี่หรือรีดไถ
แม้อินเทอร์เน็ตยุคแรกจะดูธรรมดา เช่น ใช้อ่านบทความหรือสั่งซื้อสินค้า แต่ศักยภาพที่แท้จริงของเศรษฐกิจไซเบอร์นั้นยิ่งใหญ่มาก ผู้เขียนเสนอว่ามันจะพัฒนาเป็นสามขั้น: 1. ขั้นพื้นฐาน: อินเทอร์เน็ตเป็นเพียงช่องทางเพิ่มประสิทธิภาพธุรกิจแบบเดิม (เช่น เว็บขายสินค้าขายของออนไลน์ เช่น อเมซอน) 2. ขั้นพัฒนา: การเกิดขึ้นของเงินดิจิทัลที่เข้ารหัสและไม่สามารถติดตามได้ จะปลดปล่อยธุรกรรมจากการควบคุมและการจัดเก็บภาษีของรัฐ 3. ขั้นก้าวหน้า: ไซเบอร์สเปซจะมีระบบเศรษฐกิจ กฎหมาย และกลไกคุ้มครองของตัวเอง ปราศจากการควบคุมจากรัฐบาลใด ๆ
ในโลกใหม่นี้ Sovereign Individual หรือ “ปัจเจกผู้มีอธิปไตย” จะสามารถสร้างความมั่งคั่งและดำเนินกิจกรรมในไซเบอร์สเปซได้อย่างเป็นอิสระ โดยไม่ต้องอิงรัฐชาติ รัฐจึงจะถูกบีบให้ลดขนาดและเปลี่ยนบทบาทจากผู้ใช้อำนาจกลายเป็นผู้ให้บริการที่ต้องแข่งขันเพื่อความพึงพอใจของพลเมือง
สามารถไปติดตามเนื้อหาแบบ short vdo ที่สรุปประเด็นสำคัญจากแต่ละบท พร้อมกราฟิกและคำอธิบายกระชับ เข้าใจง่าย ได้ที่ TikTok ช่อง https://www.tiktok.com/@moneyment1971
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 83279ad2:bd49240d
2025-05-18 07:27:02
@ 83279ad2:bd49240d
2025-05-18 07:27:02nostr:nevent1qvzqqqr4gupzpqe8ntfgamz8sh3p88w99x5k2r7mksjrvm2xghju9qj00j75jfqdqythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qy88wumn8ghj7mn0wvhxcmmv9uq3wamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmny9uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59uq3wamnwvaz7tmnv4shycmg9ehx7ueww3hkgcte9uq3wamnwvaz7tmnv4shycmg9ehx7ueww3hkgcte9uq3wamnwvaz7tmjv4kxz7fwwpexjmtpdshxuet59uqsuamnwvaz7tmwdaejumr0dshsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9mhwden5te0wfjkccte9ec8y6tdv9kzumn9wshszrnhwden5te0dehhxtnvdakz7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgwwaehxw309ahx7uewd3hkctcqyznaykvq5f87swdlg0tf4u8zph2k0snnwnjwdsm59uun96nuya70wzx2z50
-
 @ 9be6a199:6e133301
2025-05-19 17:24:12
@ 9be6a199:6e133301
2025-05-19 17:24:12this is the content
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 9be6a199:6e133301
2025-05-19 17:23:23
@ 9be6a199:6e133301
2025-05-19 17:23:23this is the content
-
 @ f85b9c2c:d190bcff
2025-05-19 13:22:09
@ f85b9c2c:d190bcff
2025-05-19 13:22:09
Fake KYC Emails
Phishing scammers are again targeting users of the popular cryptocurrency wallet MetaMask. In a recent email campaign, cybercriminals are attempting to trick people into revealing their secret MetaMask passphrase. The emails falsely claim that you must urgently verify your wallet due to new Know Your Customer (KYC) regulations. If you fall for the scope and click the “Verify” button, you will be taken to a fake MetaMask website that asks you to enter your passphrase. If you do provide your passphrase, criminals can access your wallet and steal any cryptocurrency you have stored there. You are unlikely to get your stolen crypto back. Such email scam campaigns are ongoing and target users of many different cryptocurrency wallets. Be wary of any unsolicited email or text message that claims that you must provide your crypto wallet passphrase or other sensitive personal information. image
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 3f68dede:779bb81d
2025-05-19 17:14:15
@ 3f68dede:779bb81d
2025-05-19 17:14:15 -
 @ 3f68dede:779bb81d
2025-05-19 17:06:26
@ 3f68dede:779bb81d
2025-05-19 17:06:26 -
 @ 3f68dede:779bb81d
2025-05-19 17:04:13
@ 3f68dede:779bb81d
2025-05-19 17:04:13testing schedule
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 05a0f81e:fc032124
2025-05-19 11:31:47
@ 05a0f81e:fc032124
2025-05-19 11:31:47There are stages in life that man must encounter in the life living process. And in thus stage are what I called the most scary moment in life.
The stages of life are typically recognized as Infancy (birth to 2 years), Early Childhood (3-8 years), Adolescence (9-18 years), and Adulthood (19 years and older). Adulthood can be further divided into early, middle, and late stages.
The adulthood, is the youthful stage, the stage where the youths are enrolled into the career part of there life, either academic pursuit or entrepreneurial pursuit. The adult hood are raged from the beginning of career pursuit to the ending of career pursuit, and at the stage is where the youths choose to either proper in life or become a failure.
With a well detailed analysis, some see the youthful stage as the most enjoyable stage in life, and there are no doubt about that but one thing is certain about, the mistake you made at the youthful stage of your life but in your career pursuit and daily living stay with you forever unless your ability to deal with your emotions and regret is 90%.
The adulthood is a scary moment because that's the stage where youths choose there career focus, either further education, skilled labor or entrepreneurs and at the beginning of the career path, they are scared of making the wrong choice. But the most fearful path of the adulthood is facing the laboratory market, that is after school or after acquiring skills, how to start making a good living. This path of life affects mostly the youths that choose academic pursuit at the early adulthood without making necessary research on there field of study, and this is the reason while there are many graduates that are bike man, brick layers, driver and so on.
The inability to face the labor market as a graduates can be linked to your field of study, the decisions you made while in school, and the channels you choose when you graduated.
The ending of career pursuit to face the labor market is the most scary moment in life and youths that escape that fear easily are either born with golden spoon allowing their parents to pave their way for them or they chose the right part at the earliest adulthood.
Proper orientation are need in career pursuit to enable youths to have the self confident and boldness to choose a enroll into the best to face the labor market when it is time ⏲️.
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:54
@ 3f68dede:779bb81d
2025-05-19 17:02:54testing schedule
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ a5ee4475:2ca75401
2025-05-19 01:11:59
@ a5ee4475:2ca75401
2025-05-19 01:11:59clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 📱 (on development) ⏳
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] [source] 🤖🍎
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ a31f394c:7ad8f439
2025-05-19 07:55:53
@ a31f394c:7ad8f439
2025-05-19 07:55:53No mundo dos jogos online, onde inúmeras plataformas buscam a atenção dos jogadores, KK999 se destaca como uma opção inovadora e empolgante. Focada no público brasileiro, a plataforma oferece uma ampla gama de jogos, uma interface intuitiva e um excelente suporte ao cliente. Se você está em busca de um destino online para jogos que combine entretenimento, qualidade e segurança, KK999 é a escolha certa para você.
Visão Geral da Plataforma KK999 é mais do que uma simples plataforma de jogos. É uma experiência imersiva e moderna, desenvolvida para atender às necessidades específicas dos jogadores brasileiros. A plataforma possui uma interface limpa e fácil de navegar, o que torna a experiência de jogar agradável e sem complicações. O site é responsivo, o que significa que você pode acessar e jogar de qualquer dispositivo, seja no desktop ou no celular, tornando a plataforma perfeita para quem deseja jogar em qualquer lugar.
O diferencial do kk999 é a experiência personalizada que oferece aos jogadores brasileiros. Além de estar completamente traduzido para o português, o site também oferece promoções e suporte técnico localizados, o que cria uma sensação de familiaridade e confiança entre os usuários.
Variedade de Jogos para Todos os Gostos Uma das características mais atraentes da KK999 é sua vasta seleção de jogos. A plataforma oferece desde jogos tradicionais de mesa, como poker e baccarat, até os modernos jogos de slots, que são incrivelmente populares entre os jogadores. Se você gosta de desafios estratégicos ou prefere a emoção de uma boa rotação de roletas, KK999 tem algo para todos.
Os jogos de mesa, como poker e blackjack, permitem que os jogadores testem suas habilidades e se envolvam em desafios emocionantes. Cada jogo é projetado com gráficos de alta qualidade e animações fluidas, criando uma experiência realista e envolvente. Além disso, a plataforma oferece uma coleção diversificada de slots, com temas variados e recursos extras que aumentam a emoção a cada giro.
Para aqueles que preferem uma experiência mais interativa, KK999 também oferece jogos com dealers ao vivo. Esses jogos permitem que os jogadores interajam com dealers profissionais em tempo real, criando uma atmosfera de jogo ao vivo, que remete à experiência de um cassino físico.
Experiência do Jogador: Segurança e Suporte de Qualidade O KK999 entende que uma experiência de jogo de alta qualidade vai além de apenas jogar. A plataforma se destaca pelo seu compromisso com a segurança dos jogadores. Utilizando as mais recentes tecnologias de criptografia, KK999 garante que todas as informações pessoais e financeiras dos jogadores estejam seguras, proporcionando tranquilidade para que os jogadores possam se concentrar apenas no jogo.
Além disso, o suporte ao cliente do KK999 é impecável. A plataforma oferece suporte 24 horas por dia, 7 dias por semana, por meio de chat ao vivo e e-mail. Caso o jogador tenha dúvidas sobre um jogo, questões relacionadas à conta ou precise de assistência técnica, a equipe de atendimento está sempre disponível e pronta para ajudar.
Bônus e Promoções para Todos os Jogadores KK999 também se destaca pelas suas ofertas generosas de bônus e promoções. Para os novos jogadores, a plataforma oferece bônus de boas-vindas, enquanto os jogadores regulares podem aproveitar programas de fidelidade que recompensam a lealdade dos usuários com ofertas exclusivas e prêmios.
Essas promoções tornam a experiência de jogar ainda mais divertida e empolgante, dando aos jogadores mais chances de se divertir e ganhar enquanto jogam seus jogos favoritos.
Conclusão KK999 se estabeleceu como uma plataforma de jogos online de referência no Brasil, oferecendo uma experiência única que combina uma enorme variedade de jogos, uma interface amigável, suporte excepcional e medidas de segurança robustas. Se você está à procura de uma plataforma para se divertir e explorar, KK999 é o lugar perfeito para começar sua jornada de jogos online.
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 5c26ee8b:a4d229aa
2025-05-17 15:41:01
@ 5c26ee8b:a4d229aa
2025-05-17 15:41:01The prophet Abraham, peace be upon him, is mentioned in the Quran in different surahs. Since young age he started to question what the people of his time used to worship, his wisdom and reasoning led him to God, Allah, and his bravery helped him resist the aggression of disbelievers. In the following some of the verses mentioning him and his family.
19:41 Maryam
وَاذْكُرْ فِي الْكِتَابِ إِبْرَاهِيمَ ۚ إِنَّهُ كَانَ صِدِّيقًا نَبِيًّا
And mention in the Book [the story of] Abraham. Indeed, he was a man of truth and a prophet.
19:42 Maryam
إِذْ قَالَ لِأَبِيهِ يَا أَبَتِ لِمَ تَعْبُدُ مَا لَا يَسْمَعُ وَلَا يُبْصِرُ وَلَا يُغْنِي عَنْكَ شَيْئًا
[Mention] when he said to his father, "O my father, why do you worship that which does not hear and does not see and will not benefit you at all?
19:43 Maryam
يَا أَبَتِ إِنِّي قَدْ جَاءَنِي مِنَ الْعِلْمِ مَا لَمْ يَأْتِكَ فَاتَّبِعْنِي أَهْدِكَ صِرَاطًا سَوِيًّا
O my father, indeed there has come to me of knowledge that which has not come to you, so follow me; I will guide you to an even path.
19:44 Maryam
يَا أَبَتِ لَا تَعْبُدِ الشَّيْطَانَ ۖ إِنَّ الشَّيْطَانَ كَانَ لِلرَّحْمَٰنِ عَصِيًّا
O my father, do not worship Satan. Indeed Satan has ever been, to the Most Merciful, disobedient.
19:45 Maryam
يَا أَبَتِ إِنِّي أَخَافُ أَنْ يَمَسَّكَ عَذَابٌ مِنَ الرَّحْمَٰنِ فَتَكُونَ لِلشَّيْطَانِ وَلِيًّا
O my father, indeed I fear that there will touch you a punishment from the Most Merciful so you would be to Satan a companion [in Hellfire]."
19:46 Maryam
قَالَ أَرَاغِبٌ أَنْتَ عَنْ آلِهَتِي يَا إِبْرَاهِيمُ ۖ لَئِنْ لَمْ تَنْتَهِ لَأَرْجُمَنَّكَ ۖ وَاهْجُرْنِي مَلِيًّا
[His father] said, "Have you no desire for my gods, O Abraham? If you do not desist, I will surely stone you, so avoid me a prolonged time."
19:47 Maryam
قَالَ سَلَامٌ عَلَيْكَ ۖ سَأَسْتَغْفِرُ لَكَ رَبِّي ۖ إِنَّهُ كَانَ بِي حَفِيًّا
[Abraham] said, "Peace will be upon you. I will ask forgiveness for you of my Lord. Indeed, He is ever gracious to me.
19:48 Maryam
وَأَعْتَزِلُكُمْ وَمَا تَدْعُونَ مِنْ دُونِ اللَّهِ وَأَدْعُو رَبِّي عَسَىٰ أَلَّا أَكُونَ بِدُعَاءِ رَبِّي شَقِيًّا
And I will leave you and those you invoke other than Allah and will invoke my Lord. I expect that I will not be in invocation to my Lord unhappy."
19:49 Maryam
فَلَمَّا اعْتَزَلَهُمْ وَمَا يَعْبُدُونَ مِنْ دُونِ اللَّهِ وَهَبْنَا لَهُ إِسْحَاقَ وَيَعْقُوبَ ۖ وَكُلًّا جَعَلْنَا نَبِيًّا
So when he had left them and those they worshipped other than Allah, We gave him Isaac and Jacob, and each [of them] We made a prophet.
19:50 Maryam
وَوَهَبْنَا لَهُمْ مِنْ رَحْمَتِنَا وَجَعَلْنَا لَهُمْ لِسَانَ صِدْقٍ عَلِيًّا
And We gave them of Our mercy, and we made for them a reputation of high honor.
19:54 Maryam
وَاذْكُرْ فِي الْكِتَابِ إِسْمَاعِيلَ ۚ إِنَّهُ كَانَ صَادِقَ الْوَعْدِ وَكَانَ رَسُولًا نَبِيًّا
And mention in the Book, Ishmael. Indeed, he was true to his promise, and he was a messenger and a prophet.
19:55 Maryam
وَكَانَ يَأْمُرُ أَهْلَهُ بِالصَّلَاةِ وَالزَّكَاةِ وَكَانَ عِنْدَ رَبِّهِ مَرْضِيًّا
And he used to enjoin on his people prayer and zakah and was to his Lord pleasing.
And when prophet Abraham, peace be upon him realised that his father is an enemy of Allah he left him and so must be adopted in case other disbelieving family members as in the following verses.
9:114 At-Tawba
وَمَا كَانَ اسْتِغْفَارُ إِبْرَاهِيمَ لِأَبِيهِ إِلَّا عَنْ مَوْعِدَةٍ وَعَدَهَا إِيَّاهُ فَلَمَّا تَبَيَّنَ لَهُ أَنَّهُ عَدُوٌّ لِلَّهِ تَبَرَّأَ مِنْهُ ۚ إِنَّ إِبْرَاهِيمَ لَأَوَّاهٌ حَلِيمٌ
And the request of forgiveness of Abraham for his father was only because of a promise he had made to him. But when it became apparent to Abraham that his father was an enemy to Allah, he disassociated himself from him. Indeed was Abraham compassionate and patient.
9:23 At-Tawba
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَتَّخِذُوا آبَاءَكُمْ وَإِخْوَانَكُمْ أَوْلِيَاءَ إِنِ اسْتَحَبُّوا الْكُفْرَ عَلَى الْإِيمَانِ ۚ وَمَنْ يَتَوَلَّهُمْ مِنْكُمْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ
O you who have believed, do not take your fathers or your brothers as allies if they have preferred disbelief over belief. And whoever does so among you - then it is those who are the wrongdoers.
9:24 At-Tawba
قُلْ إِنْ كَانَ آبَاؤُكُمْ وَأَبْنَاؤُكُمْ وَإِخْوَانُكُمْ وَأَزْوَاجُكُمْ وَعَشِيرَتُكُمْ وَأَمْوَالٌ اقْتَرَفْتُمُوهَا وَتِجَارَةٌ تَخْشَوْنَ كَسَادَهَا وَمَسَاكِنُ تَرْضَوْنَهَا أَحَبَّ إِلَيْكُمْ مِنَ اللَّهِ وَرَسُولِهِ وَجِهَادٍ فِي سَبِيلِهِ فَتَرَبَّصُوا حَتَّىٰ يَأْتِيَ اللَّهُ بِأَمْرِهِ ۗ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الْفَاسِقِينَ
Say, [O Muhammad], "If your fathers, your sons, your brothers, your wives, your relatives, wealth which you have obtained, commerce wherein you fear decline, and dwellings with which you are pleased are more beloved to you than Allah and His Messenger and jihad in His cause, then wait until Allah executes His command. And Allah does not guide the defiantly disobedient people."
In the following another incident that prophet Abraham peace be upon had faced. As well as his research for God that guided him just by making him reach a reasonable conclusion while observing his surroundings.
2:258 Al-Baqara
أَلَمْ تَرَ إِلَى الَّذِي حَاجَّ إِبْرَاهِيمَ فِي رَبِّهِ أَنْ آتَاهُ اللَّهُ الْمُلْكَ إِذْ قَالَ إِبْرَاهِيمُ رَبِّيَ الَّذِي يُحْيِي وَيُمِيتُ قَالَ أَنَا أُحْيِي وَأُمِيتُ ۖ قَالَ إِبْرَاهِيمُ فَإِنَّ اللَّهَ يَأْتِي بِالشَّمْسِ مِنَ الْمَشْرِقِ فَأْتِ بِهَا مِنَ الْمَغْرِبِ فَبُهِتَ الَّذِي كَفَرَ ۗ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
Have you not considered the one who argued with Abraham about his Lord [merely] because Allah had given him kingship? When Abraham said, "My Lord is the one who gives life and causes death," he said, "I give life and cause death." Abraham said, "Indeed, Allah brings up the sun from the east, so bring it up from the west." So the disbeliever was overwhelmed [by astonishment], and Allah does not guide the wrongdoing people.
2:260 Al-Baqara
وَإِذْ قَالَ إِبْرَاهِيمُ رَبِّ أَرِنِي كَيْفَ تُحْيِي الْمَوْتَىٰ ۖ قَالَ أَوَلَمْ تُؤْمِنْ ۖ قَالَ بَلَىٰ وَلَٰكِنْ لِيَطْمَئِنَّ قَلْبِي ۖ قَالَ فَخُذْ أَرْبَعَةً مِنَ الطَّيْرِ فَصُرْهُنَّ إِلَيْكَ ثُمَّ اجْعَلْ عَلَىٰ كُلِّ جَبَلٍ مِنْهُنَّ جُزْءًا ثُمَّ ادْعُهُنَّ يَأْتِينَكَ سَعْيًا ۚ وَاعْلَمْ أَنَّ اللَّهَ عَزِيزٌ حَكِيمٌ
And [mention] when Abraham said, "My Lord, show me how You give life to the dead." [Allah] said, "Have you not believed?" He said, "Yes, but [I ask] only that my heart may be satisfied." [Allah] said, "Take four birds and commit them to yourself. Then [after slaughtering them] put on each hill a portion of them; then call them - they will come [flying] to you in haste. And know that Allah is Exalted in Might and Wise."
6:74 Al-An'aam
۞ وَإِذْ قَالَ إِبْرَاهِيمُ لِأَبِيهِ آزَرَ أَتَتَّخِذُ أَصْنَامًا آلِهَةً ۖ إِنِّي أَرَاكَ وَقَوْمَكَ فِي ضَلَالٍ مُبِينٍ
And [mention, O Muhammad], when Abraham said to his father Azar, "Do you take idols as deities? Indeed, I see you and your people to be in manifest error."
6:75 Al-An'aam
وَكَذَٰلِكَ نُرِي إِبْرَاهِيمَ مَلَكُوتَ السَّمَاوَاتِ وَالْأَرْضِ وَلِيَكُونَ مِنَ الْمُوقِنِينَ
And thus did We show Abraham the realm of the heavens and the earth that he would be among the certain [in faith]
6:76 Al-An'aam
فَلَمَّا جَنَّ عَلَيْهِ اللَّيْلُ رَأَىٰ كَوْكَبًا ۖ قَالَ هَٰذَا رَبِّي ۖ فَلَمَّا أَفَلَ قَالَ لَا أُحِبُّ الْآفِلِينَ
So when the night covered him [with darkness], he saw a star. He said, "This is my lord." But when it set, he said, "I like not those that disappear."
6:77 Al-An'aam
فَلَمَّا رَأَى الْقَمَرَ بَازِغًا قَالَ هَٰذَا رَبِّي ۖ فَلَمَّا أَفَلَ قَالَ لَئِنْ لَمْ يَهْدِنِي رَبِّي لَأَكُونَنَّ مِنَ الْقَوْمِ الضَّالِّينَ
And when he saw the moon rising, he said, "This is my lord." But when it set, he said, "Unless my Lord guides me, I will surely be among the people gone astray."
6:78 Al-An'aam
فَلَمَّا رَأَى الشَّمْسَ بَازِغَةً قَالَ هَٰذَا رَبِّي هَٰذَا أَكْبَرُ ۖ فَلَمَّا أَفَلَتْ قَالَ يَا قَوْمِ إِنِّي بَرِيءٌ مِمَّا تُشْرِكُونَ
And when he saw the sun rising, he said, "This is my lord; this is greater." But when it set, he said, "O my people, indeed I am free from what you associate with Allah.
6:79 Al-An'aam
إِنِّي وَجَّهْتُ وَجْهِيَ لِلَّذِي فَطَرَ السَّمَاوَاتِ وَالْأَرْضَ حَنِيفًا ۖ وَمَا أَنَا مِنَ الْمُشْرِكِينَ
Indeed, I have turned my face toward He who created the heavens and the earth, inclining toward truth, and I am not of those who associate others with Allah."
6:80 Al-An'aam
وَحَاجَّهُ قَوْمُهُ ۚ قَالَ أَتُحَاجُّونِّي فِي اللَّهِ وَقَدْ هَدَانِ ۚ وَلَا أَخَافُ مَا تُشْرِكُونَ بِهِ إِلَّا أَنْ يَشَاءَ رَبِّي شَيْئًا ۗ وَسِعَ رَبِّي كُلَّ شَيْءٍ عِلْمًا ۗ أَفَلَا تَتَذَكَّرُونَ
And his people argued with him. He said, "Do you argue with me concerning Allah while He has guided me? And I fear not what you associate with Him [and will not be harmed] unless my Lord should will something. My Lord encompasses all things in knowledge; then will you not remember?
6:81 Al-An'aam
وَكَيْفَ أَخَافُ مَا أَشْرَكْتُمْ وَلَا تَخَافُونَ أَنَّكُمْ أَشْرَكْتُمْ بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ عَلَيْكُمْ سُلْطَانًا ۚ فَأَيُّ الْفَرِيقَيْنِ أَحَقُّ بِالْأَمْنِ ۖ إِنْ كُنْتُمْ تَعْلَمُونَ
And how should I fear what you associate while you do not fear that you have associated with Allah that for which He has not sent down to you any authority? So which of the two parties has more right to security, if you should know?
6:82 Al-An'aam
الَّذِينَ آمَنُوا وَلَمْ يَلْبِسُوا إِيمَانَهُمْ بِظُلْمٍ أُولَٰئِكَ لَهُمُ الْأَمْنُ وَهُمْ مُهْتَدُونَ
They who believe and do not mix their belief with injustice - those will have security, and they are [rightly] guided.
6:83 Al-An'aam
وَتِلْكَ حُجَّتُنَا آتَيْنَاهَا إِبْرَاهِيمَ عَلَىٰ قَوْمِهِ ۚ نَرْفَعُ دَرَجَاتٍ مَنْ نَشَاءُ ۗ إِنَّ رَبَّكَ حَكِيمٌ عَلِيمٌ
And that was Our [conclusive] argument which We gave Abraham against his people. We raise by degrees whom We will. Indeed, your Lord is Wise and Knowing.
6:84 Al-An'aam
وَوَهَبْنَا لَهُ إِسْحَاقَ وَيَعْقُوبَ ۚ كُلًّا هَدَيْنَا ۚ وَنُوحًا هَدَيْنَا مِنْ قَبْلُ ۖ وَمِنْ ذُرِّيَّتِهِ دَاوُودَ وَسُلَيْمَانَ وَأَيُّوبَ وَيُوسُفَ وَمُوسَىٰ وَهَارُونَ ۚ وَكَذَٰلِكَ نَجْزِي الْمُحْسِنِينَ
And We gave to Abraham, Isaac and Jacob - all [of them] We guided. And Noah, We guided before; and among his descendants, David and Solomon and Job and Joseph and Moses and Aaron. Thus do We reward the doers of good.
6:85 Al-An'aam
وَزَكَرِيَّا وَيَحْيَىٰ وَعِيسَىٰ وَإِلْيَاسَ ۖ كُلٌّ مِنَ الصَّالِحِينَ
And Zechariah and John and Jesus and Elias - and all were of the righteous.
6:86 Al-An'aam
وَإِسْمَاعِيلَ وَالْيَسَعَ وَيُونُسَ وَلُوطًا ۚ وَكُلًّا فَضَّلْنَا عَلَى الْعَالَمِينَ
And Ishmael and Elisha and Jonah and Lot - and all [of them] We preferred over the worlds.
6:87 Al-An'aam
وَمِنْ آبَائِهِمْ وَذُرِّيَّاتِهِمْ وَإِخْوَانِهِمْ ۖ وَاجْتَبَيْنَاهُمْ وَهَدَيْنَاهُمْ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And [some] among their fathers and their descendants and their brothers - and We chose them and We guided them to a straight path.
6:88 Al-An'aam
ذَٰلِكَ هُدَى اللَّهِ يَهْدِي بِهِ مَنْ يَشَاءُ مِنْ عِبَادِهِ ۚ وَلَوْ أَشْرَكُوا لَحَبِطَ عَنْهُمْ مَا كَانُوا يَعْمَلُونَ
That is the guidance of Allah by which He guides whomever He wills of His servants. But if they had associated others with Allah, then worthless for them would be whatever they were doing.
6:89 Al-An'aam
أُولَٰئِكَ الَّذِينَ آتَيْنَاهُمُ الْكِتَابَ وَالْحُكْمَ وَالنُّبُوَّةَ ۚ فَإِنْ يَكْفُرْ بِهَا هَٰؤُلَاءِ فَقَدْ وَكَّلْنَا بِهَا قَوْمًا لَيْسُوا بِهَا بِكَافِرِينَ
Those are the ones to whom We gave the Scripture and authority and prophethood. But if the disbelievers deny it, then We have entrusted it to a people who are not therein disbelievers.
6:90 Al-An'aam
أُولَٰئِكَ الَّذِينَ هَدَى اللَّهُ ۖ فَبِهُدَاهُمُ اقْتَدِهْ ۗ قُلْ لَا أَسْأَلُكُمْ عَلَيْهِ أَجْرًا ۖ إِنْ هُوَ إِلَّا ذِكْرَىٰ لِلْعَالَمِينَ
Those are the ones whom Allah has guided, so from their guidance take an example. Say, "I ask of you for this message no payment. It is not but a reminder for the worlds."
6:91 Al-An'aam
وَمَا قَدَرُوا اللَّهَ حَقَّ قَدْرِهِ إِذْ قَالُوا مَا أَنْزَلَ اللَّهُ عَلَىٰ بَشَرٍ مِنْ شَيْءٍ ۗ قُلْ مَنْ أَنْزَلَ الْكِتَابَ الَّذِي جَاءَ بِهِ مُوسَىٰ نُورًا وَهُدًى لِلنَّاسِ ۖ تَجْعَلُونَهُ قَرَاطِيسَ تُبْدُونَهَا وَتُخْفُونَ كَثِيرًا ۖ وَعُلِّمْتُمْ مَا لَمْ تَعْلَمُوا أَنْتُمْ وَلَا آبَاؤُكُمْ ۖ قُلِ اللَّهُ ۖ ثُمَّ ذَرْهُمْ فِي خَوْضِهِمْ يَلْعَبُونَ
And they did not appraise Allah with true appraisal when they said, "Allah did not reveal to a human being anything." Say, "Who revealed the Scripture that Moses brought as light and guidance to the people? You [Jews] make it into pages, disclosing [some of] it and concealing much. And you were taught that which you knew not - neither you nor your fathers." Say, "Allah [revealed it]." Then leave them in their [empty] discourse, amusing themselves.
6:92 Al-An'aam
وَهَٰذَا كِتَابٌ أَنْزَلْنَاهُ مُبَارَكٌ مُصَدِّقُ الَّذِي بَيْنَ يَدَيْهِ وَلِتُنْذِرَ أُمَّ الْقُرَىٰ وَمَنْ حَوْلَهَا ۚ وَالَّذِينَ يُؤْمِنُونَ بِالْآخِرَةِ يُؤْمِنُونَ بِهِ ۖ وَهُمْ عَلَىٰ صَلَاتِهِمْ يُحَافِظُونَ
And this is a Book which We have sent down, blessed and confirming what was before it, that you may warn the Mother of Cities and those around it. Those who believe in the Hereafter believe in it, and they are maintaining their prayers.
21:51 Al-Anbiyaa
۞ وَلَقَدْ آتَيْنَا إِبْرَاهِيمَ رُشْدَهُ مِنْ قَبْلُ وَكُنَّا بِهِ عَالِمِينَ
And We had certainly given Abraham his sound judgement before, and We were of him well-Knowing
21:52 Al-Anbiyaa
إِذْ قَالَ لِأَبِيهِ وَقَوْمِهِ مَا هَٰذِهِ التَّمَاثِيلُ الَّتِي أَنْتُمْ لَهَا عَاكِفُونَ
When he said to his father and his people, "What are these statues to which you are devoted?"
21:53 Al-Anbiyaa
قَالُوا وَجَدْنَا آبَاءَنَا لَهَا عَابِدِينَ
They said, "We found our fathers worshippers of them."
21:54 Al-Anbiyaa
قَالَ لَقَدْ كُنْتُمْ أَنْتُمْ وَآبَاؤُكُمْ فِي ضَلَالٍ مُبِينٍ
He said, "You were certainly, you and your fathers, in manifest error."
21:55 Al-Anbiyaa
قَالُوا أَجِئْتَنَا بِالْحَقِّ أَمْ أَنْتَ مِنَ اللَّاعِبِينَ
They said, "Have you come to us with truth, or are you of those who jest?"
21:56 Al-Anbiyaa
قَالَ بَلْ رَبُّكُمْ رَبُّ السَّمَاوَاتِ وَالْأَرْضِ الَّذِي فَطَرَهُنَّ وَأَنَا عَلَىٰ ذَٰلِكُمْ مِنَ الشَّاهِدِينَ
He said, "[No], rather, your Lord is the Lord of the heavens and the earth who created them, and I, to that, am of those who testify.
21:57 Al-Anbiyaa
وَتَاللَّهِ لَأَكِيدَنَّ أَصْنَامَكُمْ بَعْدَ أَنْ تُوَلُّوا مُدْبِرِينَ
And [I swear] by Allah, I will surely plan against your idols after you have turned and gone away."
21:58 Al-Anbiyaa
فَجَعَلَهُمْ جُذَاذًا إِلَّا كَبِيرًا لَهُمْ لَعَلَّهُمْ إِلَيْهِ يَرْجِعُونَ
So he made them into fragments, except a large one among them, that they might return to it [and question].
21:59 Al-Anbiyaa
قَالُوا مَنْ فَعَلَ هَٰذَا بِآلِهَتِنَا إِنَّهُ لَمِنَ الظَّالِمِينَ
They said, "Who has done this to our gods? Indeed, he is of the wrongdoers."
21:60 Al-Anbiyaa
قَالُوا سَمِعْنَا فَتًى يَذْكُرُهُمْ يُقَالُ لَهُ إِبْرَاهِيمُ
They said, "We heard a young man mention them who is called Abraham."
21:61 Al-Anbiyaa
قَالُوا فَأْتُوا بِهِ عَلَىٰ أَعْيُنِ النَّاسِ لَعَلَّهُمْ يَشْهَدُونَ
They said, "Then bring him before the eyes of the people that they may testify."
21:62 Al-Anbiyaa
قَالُوا أَأَنْتَ فَعَلْتَ هَٰذَا بِآلِهَتِنَا يَا إِبْرَاهِيمُ
They said, "Have you done this to our gods, O Abraham?"
21:63 Al-Anbiyaa
قَالَ بَلْ فَعَلَهُ كَبِيرُهُمْ هَٰذَا فَاسْأَلُوهُمْ إِنْ كَانُوا يَنْطِقُونَ
He said, "Rather, this - the largest of them - did it, so ask them, if they should [be able to] speak."
21:64 Al-Anbiyaa
فَرَجَعُوا إِلَىٰ أَنْفُسِهِمْ فَقَالُوا إِنَّكُمْ أَنْتُمُ الظَّالِمُونَ
So they returned to [blaming] themselves and said [to each other], "Indeed, you are the wrongdoers."
21:65 Al-Anbiyaa
ثُمَّ نُكِسُوا عَلَىٰ رُءُوسِهِمْ لَقَدْ عَلِمْتَ مَا هَٰؤُلَاءِ يَنْطِقُونَ
Then they reversed themselves, [saying], "You have already known that these do not speak!"
21:66 Al-Anbiyaa
قَالَ أَفَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَنْفَعُكُمْ شَيْئًا وَلَا يَضُرُّكُمْ
He said, "Then do you worship instead of Allah that which does not benefit you at all or harm you?
21:67 Al-Anbiyaa
أُفٍّ لَكُمْ وَلِمَا تَعْبُدُونَ مِنْ دُونِ اللَّهِ ۖ أَفَلَا تَعْقِلُونَ
Uff to you and to what you worship instead of Allah. Then will you not use reason?"
21:68 Al-Anbiyaa
قَالُوا حَرِّقُوهُ وَانْصُرُوا آلِهَتَكُمْ إِنْ كُنْتُمْ فَاعِلِينَ
They said, "Burn him and support your gods - if you are to act."
21:69 Al-Anbiyaa
قُلْنَا يَا نَارُ كُونِي بَرْدًا وَسَلَامًا عَلَىٰ إِبْرَاهِيمَ
Allah said, "O fire, be coolness and safety upon Abraham."
21:70 Al-Anbiyaa
وَأَرَادُوا بِهِ كَيْدًا فَجَعَلْنَاهُمُ الْأَخْسَرِينَ
And they intended for him harm, but We made them the greatest losers.
Prophet Abraham, peace be upon, that was Muslim rebuilt the Ka’ba in Mecca together with his son Ishmael (where Muslim people perform pilgrimage (Hajj and Umrah)). Many details of the story of prophet Abraham peace be upon him are part of the pilgrimage rituals and I hope that you can come to know them from the following verses.
3:33 Aal-i-Imraan
۞ إِنَّ اللَّهَ اصْطَفَىٰ آدَمَ وَنُوحًا وَآلَ إِبْرَاهِيمَ وَآلَ عِمْرَانَ عَلَى الْعَالَمِينَ
Indeed, Allah chose Adam and Noah and the family of Abraham and the family of 'Imran over the worlds -
3:34 Aal-i-Imraan
ذُرِّيَّةً بَعْضُهَا مِنْ بَعْضٍ ۗ وَاللَّهُ سَمِيعٌ عَلِيمٌ
Descendants, some of them from others. And Allah is Hearing and Knowing.
3:65 Aal-i-Imraan
يَا أَهْلَ الْكِتَابِ لِمَ تُحَاجُّونَ فِي إِبْرَاهِيمَ وَمَا أُنْزِلَتِ التَّوْرَاةُ وَالْإِنْجِيلُ إِلَّا مِنْ بَعْدِهِ ۚ أَفَلَا تَعْقِلُونَ
O People of the Scripture, why do you argue about Abraham while the Torah and the Gospel were not revealed until after him? Then will you not reason?
3:66 Aal-i-Imraan
هَا أَنْتُمْ هَٰؤُلَاءِ حَاجَجْتُمْ فِيمَا لَكُمْ بِهِ عِلْمٌ فَلِمَ تُحَاجُّونَ فِيمَا لَيْسَ لَكُمْ بِهِ عِلْمٌ ۚ وَاللَّهُ يَعْلَمُ وَأَنْتُمْ لَا تَعْلَمُونَ
Here you are - those who have argued about that of which you have [some] knowledge, but why do you argue about that of which you have no knowledge? And Allah knows, while you know not.
3:67 Aal-i-Imraan
مَا كَانَ إِبْرَاهِيمُ يَهُودِيًّا وَلَا نَصْرَانِيًّا وَلَٰكِنْ كَانَ حَنِيفًا مُسْلِمًا وَمَا كَانَ مِنَ الْمُشْرِكِينَ
Abraham was neither a Jew nor a Christian, but he was one inclining toward truth, a Muslim [submitting to Allah]. And he was not of the polytheists.
Tawaf (walking around the Ka’ba) is one of the rituals of pilgrimage as mentioned in the following.
22:26 Al-Hajj
وَإِذْ بَوَّأْنَا لِإِبْرَاهِيمَ مَكَانَ الْبَيْتِ أَنْ لَا تُشْرِكْ بِي شَيْئًا وَطَهِّرْ بَيْتِيَ لِلطَّائِفِينَ وَالْقَائِمِينَ وَالرُّكَّعِ السُّجُودِ
And [mention, O Muhammad], when We designated for Abraham the site of the House, [saying], "Do not associate anything with Me and purify My House for those who perform Tawaf and those who stand [in prayer] and those who bow and prostrate.
22:27 Al-Hajj
وَأَذِّنْ فِي النَّاسِ بِالْحَجِّ يَأْتُوكَ رِجَالًا وَعَلَىٰ كُلِّ ضَامِرٍ يَأْتِينَ مِنْ كُلِّ فَجٍّ عَمِيقٍ
And proclaim to the people the Hajj [pilgrimage]; they will come to you on foot and on every lean camel; they will come from every distant pass -
22:28 Al-Hajj
لِيَشْهَدُوا مَنَافِعَ لَهُمْ وَيَذْكُرُوا اسْمَ اللَّهِ فِي أَيَّامٍ مَعْلُومَاتٍ عَلَىٰ مَا رَزَقَهُمْ مِنْ بَهِيمَةِ الْأَنْعَامِ ۖ فَكُلُوا مِنْهَا وَأَطْعِمُوا الْبَائِسَ الْفَقِيرَ
That they may witness benefits for themselves and mention the name of Allah on known days over what He has provided for them of [sacrificial] animals. So eat of them and feed the miserable and poor.
22:29 Al-Hajj
ثُمَّ لْيَقْضُوا تَفَثَهُمْ وَلْيُوفُوا نُذُورَهُمْ وَلْيَطَّوَّفُوا بِالْبَيْتِ الْعَتِيقِ
Then let them end their untidiness and fulfill their vows and perform Tawaf around the ancient House."
22:30 Al-Hajj
ذَٰلِكَ وَمَنْ يُعَظِّمْ حُرُمَاتِ اللَّهِ فَهُوَ خَيْرٌ لَهُ عِنْدَ رَبِّهِ ۗ وَأُحِلَّتْ لَكُمُ الْأَنْعَامُ إِلَّا مَا يُتْلَىٰ عَلَيْكُمْ ۖ فَاجْتَنِبُوا الرِّجْسَ مِنَ الْأَوْثَانِ وَاجْتَنِبُوا قَوْلَ الزُّورِ
That [has been commanded], and whoever honors the sacred ordinances of Allah - it is best for him in the sight of his Lord. And permitted to you are the grazing livestock, except what is recited to you. So avoid the uncleanliness of idols and avoid false statement,
22:31 Al-Hajj
حُنَفَاءَ لِلَّهِ غَيْرَ مُشْرِكِينَ بِهِ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَكَأَنَّمَا خَرَّ مِنَ السَّمَاءِ فَتَخْطَفُهُ الطَّيْرُ أَوْ تَهْوِي بِهِ الرِّيحُ فِي مَكَانٍ سَحِيقٍ
Inclining [only] to Allah, not associating [anything] with Him. And he who associates with Allah - it is as though he had fallen from the sky and was snatched by the birds or the wind carried him down into a remote place.
22:32 Al-Hajj
ذَٰلِكَ وَمَنْ يُعَظِّمْ شَعَائِرَ اللَّهِ فَإِنَّهَا مِنْ تَقْوَى الْقُلُوبِ
That [is so]. And whoever honors the symbols of Allah - indeed, it is from the piety of hearts.
22:33 Al-Hajj
لَكُمْ فِيهَا مَنَافِعُ إِلَىٰ أَجَلٍ مُسَمًّى ثُمَّ مَحِلُّهَا إِلَى الْبَيْتِ الْعَتِيقِ
For you the animals marked for sacrifice are benefits for a specified term; then their place of sacrifice is at the ancient House.
22:34 Al-Hajj
وَلِكُلِّ أُمَّةٍ جَعَلْنَا مَنْسَكًا لِيَذْكُرُوا اسْمَ اللَّهِ عَلَىٰ مَا رَزَقَهُمْ مِنْ بَهِيمَةِ الْأَنْعَامِ ۗ فَإِلَٰهُكُمْ إِلَٰهٌ وَاحِدٌ فَلَهُ أَسْلِمُوا ۗ وَبَشِّرِ الْمُخْبِتِينَ
And for all religion We have appointed a rite [of sacrifice] that they may mention the name of Allah over what He has provided for them of [sacrificial] animals. For your god is one God, so to Him submit. And, [O Muhammad], give good tidings to the humble [before their Lord]
2:124 Al-Baqara
۞ وَإِذِ ابْتَلَىٰ إِبْرَاهِيمَ رَبُّهُ بِكَلِمَاتٍ فَأَتَمَّهُنَّ ۖ قَالَ إِنِّي جَاعِلُكَ لِلنَّاسِ إِمَامًا ۖ قَالَ وَمِنْ ذُرِّيَّتِي ۖ قَالَ لَا يَنَالُ عَهْدِي الظَّالِمِينَ
And [mention, O Muhammad], when Abraham was tried by his Lord with commands and he fulfilled them. [Allah] said, "Indeed, I will make you a leader for the people." [Abraham] said, "And of my descendants?" [Allah] said, "My covenant does not include the wrongdoers."
2:125 Al-Baqara
وَإِذْ جَعَلْنَا الْبَيْتَ مَثَابَةً لِلنَّاسِ وَأَمْنًا وَاتَّخِذُوا مِنْ مَقَامِ إِبْرَاهِيمَ مُصَلًّى ۖ وَعَهِدْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ أَنْ طَهِّرَا بَيْتِيَ لِلطَّائِفِينَ وَالْعَاكِفِينَ وَالرُّكَّعِ السُّجُودِ
And [mention] when We made the House a place of return for the people and [a place of] security. And take, [O believers], from the standing place of Abraham a place of prayer. And We charged Abraham and Ishmael, [saying], "Purify My House for those who perform Tawaf (walking around the Ka’ba) and those who are staying [there] for worship and those who bow and prostrate [in prayer]."
2:126 Al-Baqara
وَإِذْ قَالَ إِبْرَاهِيمُ رَبِّ اجْعَلْ هَٰذَا بَلَدًا آمِنًا وَارْزُقْ أَهْلَهُ مِنَ الثَّمَرَاتِ مَنْ آمَنَ مِنْهُمْ بِاللَّهِ وَالْيَوْمِ الْآخِرِ ۖ قَالَ وَمَنْ كَفَرَ فَأُمَتِّعُهُ قَلِيلًا ثُمَّ أَضْطَرُّهُ إِلَىٰ عَذَابِ النَّارِ ۖ وَبِئْسَ الْمَصِيرُ
And [mention] when Abraham said, "My Lord, make this a secure city and provide its people with fruits - whoever of them believes in Allah and the Last Day." [Allah] said. "And whoever disbelieves - I will grant him enjoyment for a little; then I will force him to the punishment of the Fire, and wretched is the destination."
2:127 Al-Baqara
وَإِذْ يَرْفَعُ إِبْرَاهِيمُ الْقَوَاعِدَ مِنَ الْبَيْتِ وَإِسْمَاعِيلُ رَبَّنَا تَقَبَّلْ مِنَّا ۖ إِنَّكَ أَنْتَ السَّمِيعُ الْعَلِيمُ
And [mention] when Abraham was raising the foundations of the House and [with him] Ishmael, [saying], "Our Lord, accept [this] from us. Indeed You are the Hearing, the Knowing.
2:128 Al-Baqara
رَبَّنَا وَاجْعَلْنَا مُسْلِمَيْنِ لَكَ وَمِنْ ذُرِّيَّتِنَا أُمَّةً مُسْلِمَةً لَكَ وَأَرِنَا مَنَاسِكَنَا وَتُبْ عَلَيْنَا ۖ إِنَّكَ أَنْتَ التَّوَّابُ الرَّحِيمُ
Our Lord, and make us Muslims [in submission] to You and from our descendants a Muslim nation [in submission] to You. And show us our rites and accept our repentance. Indeed, You are the Accepting of repentance, the Merciful.
2:129 Al-Baqara
رَبَّنَا وَابْعَثْ فِيهِمْ رَسُولًا مِنْهُمْ يَتْلُو عَلَيْهِمْ آيَاتِكَ وَيُعَلِّمُهُمُ الْكِتَابَ وَالْحِكْمَةَ وَيُزَكِّيهِمْ ۚ إِنَّكَ أَنْتَ الْعَزِيزُ الْحَكِيمُ
Our Lord, and send among them a messenger from themselves who will recite to them Your verses and teach them the Book and wisdom and purify them. Indeed, You are the Exalted in Might, the Wise."
2:130 Al-Baqara
وَمَنْ يَرْغَبُ عَنْ مِلَّةِ إِبْرَاهِيمَ إِلَّا مَنْ سَفِهَ نَفْسَهُ ۚ وَلَقَدِ اصْطَفَيْنَاهُ فِي الدُّنْيَا ۖ وَإِنَّهُ فِي الْآخِرَةِ لَمِنَ الصَّالِحِينَ
And who would be averse to the religion of Abraham except one who makes a fool of himself. And We had chosen him in this world, and indeed he, in the Hereafter, will be among the righteous.
2:131 Al-Baqara
إِذْ قَالَ لَهُ رَبُّهُ أَسْلِمْ ۖ قَالَ أَسْلَمْتُ لِرَبِّ الْعَالَمِينَ
When his Lord said to him, "Submit", he said "I have submitted [in Islam] to the Lord of the worlds."
2:132 Al-Baqara
وَوَصَّىٰ بِهَا إِبْرَاهِيمُ بَنِيهِ وَيَعْقُوبُ يَا بَنِيَّ إِنَّ اللَّهَ اصْطَفَىٰ لَكُمُ الدِّينَ فَلَا تَمُوتُنَّ إِلَّا وَأَنْتُمْ مُسْلِمُونَ
And Abraham instructed his sons [to do the same] and [so did] Jacob, [saying], "O my sons, indeed Allah has chosen for you this religion, so do not die except while you are Muslims."
Also walking between as-Safa and al-Marwah is one of pilgrimage rituals as the wife of Abraham ran between them in Mecca to seek water for her son Ishmael, peace be upon them, when they were left by prophet Abraham as God ordained him.
14:35 Ibrahim
وَإِذْ قَالَ إِبْرَاهِيمُ رَبِّ اجْعَلْ هَٰذَا الْبَلَدَ آمِنًا وَاجْنُبْنِي وَبَنِيَّ أَنْ نَعْبُدَ الْأَصْنَامَ
And [mention, O Muhammad], when Abraham said, "My Lord, make this city [Makkah] secure and keep me and my sons away from worshipping idols.
14:36 Ibrahim
رَبِّ إِنَّهُنَّ أَضْلَلْنَ كَثِيرًا مِنَ النَّاسِ ۖ فَمَنْ تَبِعَنِي فَإِنَّهُ مِنِّي ۖ وَمَنْ عَصَانِي فَإِنَّكَ غَفُورٌ رَحِيمٌ
My Lord, indeed they have led astray many among the people. So whoever follows me - then he is of me; and whoever disobeys me - indeed, You are [yet] Forgiving and Merciful.
14:37 Ibrahim
رَبَّنَا إِنِّي أَسْكَنْتُ مِنْ ذُرِّيَّتِي بِوَادٍ غَيْرِ ذِي زَرْعٍ عِنْدَ بَيْتِكَ الْمُحَرَّمِ رَبَّنَا لِيُقِيمُوا الصَّلَاةَ فَاجْعَلْ أَفْئِدَةً مِنَ النَّاسِ تَهْوِي إِلَيْهِمْ وَارْزُقْهُمْ مِنَ الثَّمَرَاتِ لَعَلَّهُمْ يَشْكُرُونَ
Our Lord, I have settled some of my descendants in an uncultivated valley near Your sacred House, our Lord, that they may establish prayer. So make hearts among the people incline toward them and provide for them from the fruits that they might be grateful.
2:158 Al-Baqara
۞ إِنَّ الصَّفَا وَالْمَرْوَةَ مِنْ شَعَائِرِ اللَّهِ ۖ فَمَنْ حَجَّ الْبَيْتَ أَوِ اعْتَمَرَ فَلَا جُنَاحَ عَلَيْهِ أَنْ يَطَّوَّفَ بِهِمَا ۚ وَمَنْ تَطَوَّعَ خَيْرًا فَإِنَّ اللَّهَ شَاكِرٌ عَلِيمٌ
Indeed, as-Safa and al-Marwah are among the symbols of Allah. So whoever makes Hajj to the House or performs 'umrah - there is no blame upon him for walking between them. And whoever volunteers good - then indeed, Allah is appreciative and Knowing.
2:196 Al-Baqara
وَأَتِمُّوا الْحَجَّ وَالْعُمْرَةَ لِلَّهِ ۚ فَإِنْ أُحْصِرْتُمْ فَمَا اسْتَيْسَرَ مِنَ الْهَدْيِ ۖ وَلَا تَحْلِقُوا رُءُوسَكُمْ حَتَّىٰ يَبْلُغَ الْهَدْيُ مَحِلَّهُ ۚ فَمَنْ كَانَ مِنْكُمْ مَرِيضًا أَوْ بِهِ أَذًى مِنْ رَأْسِهِ فَفِدْيَةٌ مِنْ صِيَامٍ أَوْ صَدَقَةٍ أَوْ نُسُكٍ ۚ فَإِذَا أَمِنْتُمْ فَمَنْ تَمَتَّعَ بِالْعُمْرَةِ إِلَى الْحَجِّ فَمَا اسْتَيْسَرَ مِنَ الْهَدْيِ ۚ فَمَنْ لَمْ يَجِدْ فَصِيَامُ ثَلَاثَةِ أَيَّامٍ فِي الْحَجِّ وَسَبْعَةٍ إِذَا رَجَعْتُمْ ۗ تِلْكَ عَشَرَةٌ كَامِلَةٌ ۗ ذَٰلِكَ لِمَنْ لَمْ يَكُنْ أَهْلُهُ حَاضِرِي الْمَسْجِدِ الْحَرَامِ ۚ وَاتَّقُوا اللَّهَ وَاعْلَمُوا أَنَّ اللَّهَ شَدِيدُ الْعِقَابِ
And complete the Hajj and 'umrah for Allah. But if you are prevented, then [offer] what can be obtained with ease of sacrificial animals. And do not shave your heads until the sacrificial animal has reached its place of slaughter. And whoever among you is ill or has an ailment of the head [making shaving necessary must offer] a ransom of fasting [three days] or charity or sacrifice. And when you are secure, then whoever performs 'umrah [during the Hajj months] followed by Hajj [offers] what can be obtained with ease of sacrificial animals. And whoever cannot find [or afford such an animal] - then a fast of three days during Hajj and of seven when you have returned [home]. Those are ten complete [days]. This is for those whose family is not in the area of al-Masjid al-Haram. And fear Allah and know that Allah is severe in penalty.
As in the previous verse the sacrifice of an animal is one of the rituals of Hajj, pilgrimage, and in the following the related story where God saved and ransomed his son with a animal from heavens to sacrifice.
37:83 As-Saaffaat
۞ وَإِنَّ مِنْ شِيعَتِهِ لَإِبْرَاهِيمَ
And indeed, among his kind was Abraham,
37:84 As-Saaffaat
إِذْ جَاءَ رَبَّهُ بِقَلْبٍ سَلِيمٍ
When he came to his Lord with a sound heart
37:85 As-Saaffaat
إِذْ قَالَ لِأَبِيهِ وَقَوْمِهِ مَاذَا تَعْبُدُونَ
[And] when he said to his father and his people, "What do you worship?
37:86 As-Saaffaat
أَئِفْكًا آلِهَةً دُونَ اللَّهِ تُرِيدُونَ
Is it falsehood [as] gods other than Allah you desire?
37:87 As-Saaffaat
فَمَا ظَنُّكُمْ بِرَبِّ الْعَالَمِينَ
Then what is your thought about the Lord of the worlds?"
37:88 As-Saaffaat
فَنَظَرَ نَظْرَةً فِي النُّجُومِ
And he cast a look at the stars
37:89 As-Saaffaat
فَقَالَ إِنِّي سَقِيمٌ
And said, "Indeed, I am [about to be] ill."
37:90 As-Saaffaat
فَتَوَلَّوْا عَنْهُ مُدْبِرِينَ
So they turned away from him, departing.
37:91 As-Saaffaat
فَرَاغَ إِلَىٰ آلِهَتِهِمْ فَقَالَ أَلَا تَأْكُلُونَ
Then he turned to their gods and said, "Do you not eat?
37:92 As-Saaffaat
مَا لَكُمْ لَا تَنْطِقُونَ
What is [wrong] with you that you do not speak?"
37:93 As-Saaffaat
فَرَاغَ عَلَيْهِمْ ضَرْبًا بِالْيَمِينِ
And he turned upon them a blow with [his] right hand.
37:94 As-Saaffaat
فَأَقْبَلُوا إِلَيْهِ يَزِفُّونَ
Then the people came toward him, hastening.
37:95 As-Saaffaat
قَالَ أَتَعْبُدُونَ مَا تَنْحِتُونَ
He said, "Do you worship that which you [yourselves] carve,
37:96 As-Saaffaat
وَاللَّهُ خَلَقَكُمْ وَمَا تَعْمَلُونَ
While Allah created you and that which you do?"
37:97 As-Saaffaat
قَالُوا ابْنُوا لَهُ بُنْيَانًا فَأَلْقُوهُ فِي الْجَحِيمِ
They said, "Construct for him a furnace and throw him into the burning fire."
37:98 As-Saaffaat
فَأَرَادُوا بِهِ كَيْدًا فَجَعَلْنَاهُمُ الْأَسْفَلِينَ
And they intended for him a plan, but We made them the most debased.
37:99 As-Saaffaat
وَقَالَ إِنِّي ذَاهِبٌ إِلَىٰ رَبِّي سَيَهْدِينِ
And [then] he said, "Indeed, I will go to [where I am ordered by] my Lord; He will guide me.
37:100 As-Saaffaat
رَبِّ هَبْ لِي مِنَ الصَّالِحِينَ
My Lord, grant me [a child] from among the righteous."
37:101 As-Saaffaat
فَبَشَّرْنَاهُ بِغُلَامٍ حَلِيمٍ
So We gave him good tidings of a forbearing boy.
37:102 As-Saaffaat
فَلَمَّا بَلَغَ مَعَهُ السَّعْيَ قَالَ يَا بُنَيَّ إِنِّي أَرَىٰ فِي الْمَنَامِ أَنِّي أَذْبَحُكَ فَانْظُرْ مَاذَا تَرَىٰ ۚ قَالَ يَا أَبَتِ افْعَلْ مَا تُؤْمَرُ ۖ سَتَجِدُنِي إِنْ شَاءَ اللَّهُ مِنَ الصَّابِرِينَ
And when he reached with him [the age of] exertion, he said, "O my son, indeed I have seen in a dream that I [must] sacrifice you, so see what you think." He said, "O my father, do as you are commanded. You will find me, if Allah wills, of the steadfast."
37:103 As-Saaffaat
فَلَمَّا أَسْلَمَا وَتَلَّهُ لِلْجَبِينِ
And when they had both submitted and he put him down upon his forehead,
37:104 As-Saaffaat
وَنَادَيْنَاهُ أَنْ يَا إِبْرَاهِيمُ
We called to him, "O Abraham,
37:105 As-Saaffaat
قَدْ صَدَّقْتَ الرُّؤْيَا ۚ إِنَّا كَذَٰلِكَ نَجْزِي الْمُحْسِنِينَ
You have fulfilled (believed and fulfilled) the vision." Indeed, We thus reward the doers of good.
37:106 As-Saaffaat
إِنَّ هَٰذَا لَهُوَ الْبَلَاءُ الْمُبِينُ
Indeed, this was the clear trial.
37:107 As-Saaffaat
وَفَدَيْنَاهُ بِذِبْحٍ عَظِيمٍ
And We ransomed him with a great sacrifice,
37:108 As-Saaffaat
وَتَرَكْنَا عَلَيْهِ فِي الْآخِرِينَ
And We left for him [favorable mention] among later generations:
37:109 As-Saaffaat
سَلَامٌ عَلَىٰ إِبْرَاهِيمَ
"Peace upon Abraham."
37:110 As-Saaffaat
كَذَٰلِكَ نَجْزِي الْمُحْسِنِينَ
Indeed, We thus reward the doers of good.
37:111 As-Saaffaat
إِنَّهُ مِنْ عِبَادِنَا الْمُؤْمِنِينَ
Indeed, he was of Our believing servants.
Also, as mentioned in the previous verses walking between as-Safa and al-Marwah are from the rituals of Hajj and in the following Hadith explaining the related story that is also the story of a well called Zamzam in Mecca, whoever drinks from it is healed from any illness inshaa Allah. Narrated Ibn
Abbas: The first lady to use a girdle was the mother of Ishmael. She used a girdle so that she might hide her tracks from Sarah. Abraham brought her and her son Ishmael while she was breastfeeding him, to a place near the Kaba under a tree on the spot of Zamzam, at the highest place in the mosque. During those days there was nobody in Mecca, nor was there any water So he made them sit over there and placed near them a leather bag containing some dates, and a small water-skin containing some water, and set out homeward. Ishmael's mother followed him saying, "O Abraham! Where are you going, leaving us in this valley where there is no person whose company we may enjoy, nor is there anything (to enjoy)?" She repeated that to him many times, but he did not look back at her Then she asked him, "Has Allah ordered you to do so?" He said, "Yes." She said, "Then He will not neglect us," and returned while Abraham proceeded onwards, and on reaching the Thaniya where they could not see him, he faced the Kaba, and raising both hands, invoked Allah saying the following prayers: 'O our Lord! I have made some of my offspring dwell in a valley without cultivation, by Your Sacred House (Kaba at Mecca) in order, O our Lord, that they may offer prayer perfectly. So fill some hearts among men with love towards them, and (O Allah) provide them with fruits, so that they may give thanks.' (14.37) Ishmael's mother went on suckling Ishmael and drinking from the water (she had). When the water in the water-skin had all been used up, she became thirsty and her child also became thirsty. She started looking at him (i.e. Ishmael) tossing in agony; She left him, for she could not endure looking at him, and found that the mountain of Safa was the nearest mountain to her on that land. She stood on it and started looking at the valley keenly so that she might see somebody, but she could not see anybody. Then she descended from Safa and when she reached the valley, she tucked up her robe and ran in the valley like a person in distress and trouble, till she crossed the valley and reached the Marwa mountain where she stood and started looking, expecting to see somebody, but she could not see anybody. She repeated that (running between Safa and Marwa) seven times." The Prophet (ﷺ) said, "This is the source of the tradition of the walking of people between them (i.e. Safa and Marwa). When she reached the Marwa (for the last time) she heard a voice and she asked herself to be quiet and listened attentively. She heard the voice again and said, 'O, (whoever you may be)! You have made me hear your voice; have you got something to help me?" And behold! She saw an angel at the place of Zamzam, digging the earth with his heel (or his wing), till water flowed from that place. She started to make something like a basin around it, using her hand in this way, and started filling her water-skin with water with her hands, and the water was flowing out after she had scooped some of it." The Prophet (ﷺ) added, "May Allah bestow Mercy on Ishmael's mother! Had she let the Zamzam (flow without trying to control it) (or had she not scooped from that water) (to fill her water-skin), Zamzam would have been a stream flowing on the surface of the earth." The Prophet (ﷺ) further added, "Then she drank (water) and suckled her child. The angel said to her, 'Don't be afraid of being neglected, for this is the House of Allah which will be built by this boy and his father, and Allah never neglects His people.' The House (i.e. Kaba) at that time was on a high place resembling a hillock, and when torrents came, they flowed to its right and left. She lived in that way till some people from the tribe of Jurhum or a family from Jurhum passed by her and her child, as they (i.e. the Jurhum people) were coming through the way of Kada'. They landed in the lower part of Mecca where they saw a bird that had the habit of flying around water and not leaving it. They said, 'This bird must be flying around water, though we know that there is no water in this valley.' They sent one or two messengers who discovered the source of water, and returned to inform them of the water. So, they all came (towards the water)." The Prophet (ﷺ) added, "Ishmael's mother was sitting near the water. They asked her, 'Do you allow us to stay with you?" She replied, 'Yes, but you will have no right to possess the water.' They agreed to that." The Prophet (ﷺ) further said, "Ishmael's mother was pleased with the whole situation as she used to love to enjoy the company of the people. So, they settled there, and later on they sent for their families who came and settled with them so that some families became permanent residents there. The child (i.e. Ishmael) grew up and learnt Arabic from them and (his virtues) caused them to love and admire him as he grew up, and when he reached the age of puberty they made him marry a woman from amongst them. After Ishmael's mother had died, Abraham came after Ishmael's marriage in order to see his family that he had left before, but he did not find Ishmael there. When he asked Ishmael's wife about him, she replied, 'He has gone in search of our livelihood.' Then he asked her about their way of living and their condition, and she replied, 'We are living in misery; we are living in hardship and destitution,' complaining to him. He said, 'When your husband returns, convey my salutation to him and tell him to change the threshold of the gate (of his house).' When Ishmael came, he seemed to have felt something unusual, so he asked his wife, 'Has anyone visited you?' She replied, 'Yes, an old man of so-and-so description came and asked me about you and I informed him, and he asked about our state of living, and I told him that we were living in a hardship and poverty.' On that Ishmael said, 'Did he advise you anything?' She replied, 'Yes, he told me to convey his salutation to you and to tell you to change the threshold of your gate.' Ishmael said, 'It was my father, and he has ordered me to divorce you. Go back to your family.' So, Ishmael divorced her and married another woman from amongst them (i.e. Jurhum). Then Abraham stayed away from them for a period as long as Allah wished and called on them again but did not find Ishmael. So he came to Ishmael's wife and asked her about Ishmael. She said, 'He has gone in search of our livelihood.' Abraham asked her, 'How are you getting on?' asking her about their sustenance and living. She replied, 'We are prosperous and well-off (i.e. we have everything in abundance).' Then she thanked Allah' Abraham said, 'What kind of food do you eat?' She said. 'Meat.' He said, 'What do you drink?' She said, 'Water." He said, "O Allah! Bless their meat and water." The Prophet added, "At that time they did not have grain, and if they had grain, he would have also invoked Allah to bless it." The Prophet (ﷺ) added, "If somebody has only these two things as his sustenance, his health and disposition will be badly affected, unless he lives in Mecca." The Prophet (ﷺ) added," Then Abraham said Ishmael's wife, "When your husband comes, give my regards to him and tell him that he should keep firm the threshold of his gate.' When Ishmael came back, he asked his wife, 'Did anyone call on you?' She replied, 'Yes, a good-looking old man came to me,' so she praised him and added. 'He asked about you, and I informed him, and he asked about our livelihood and I told him that we were in a good condition.' Ishmael asked her, 'Did he give you any piece of advice?' She said, 'Yes, he told me to give his regards to you and ordered that you should keep firm the threshold of your gate.' On that Ishmael said, 'It was my father, and you are the threshold (of the gate). He has ordered me to keep you with me.' Then Abraham stayed away from them for a period as long as Allah wished, and called on them afterwards. He saw Ishmael under a tree near Zamzam, sharpening his arrows. When he saw Abraham, he rose up to welcome him (and they greeted each other as a father does with his son or a son does with his father). Abraham said, 'O Ishmael! Allah has given me an order.' Ishmael said, 'Do what your Lord has ordered you to do.' Abraham asked, 'Will you help me?' Ishmael said, 'I will help you.' Abraham said, Allah has ordered me to build a house here,' pointing to a hillock higher than the land surrounding it." The Prophet (ﷺ) added, "Then they raised the foundations of the House (i.e. the Kaba). Ishmael brought the stones and Abraham was building, and when the walls became high, Ishmael brought this stone and put it for Abraham who stood over it and carried on building, while Ishmael was handing him the stones, and both of them were saying, 'O our Lord! Accept (this service) from us, Verily, You are the All-Hearing, the All-Knowing.' The Prophet (ﷺ) added, "Then both of them went on building and going round the Ka`ba saying: O our Lord ! Accept (this service) from us, Verily, You are the All-Hearing, the All-Knowing." (2.127)وَحَدَّثَنِي عَبْدُ اللَّهِ بْنُ مُحَمَّدٍ، حَدَّثَنَا عَبْدُ الرَّزَّاقِ، أَخْبَرَنَا مَعْمَرٌ، عَنْ أَيُّوبَ السَّخْتِيَانِيِّ، وَكَثِيرِ بْنِ كَثِيرِ بْنِ الْمُطَّلِبِ بْنِ أَبِي وَدَاعَةَ،، يَزِيدُ أَحَدُهُمَا عَلَى الآخَرِ عَنْ سَعِيدِ بْنِ جُبَيْرٍ، قَالَ ابْنُ عَبَّاسٍ أَوَّلَ مَا اتَّخَذَ النِّسَاءُ الْمِنْطَقَ مِنْ قِبَلِ أُمِّ إِسْمَاعِيلَ، اتَّخَذَتْ مِنْطَقًا لَتُعَفِّيَ أَثَرَهَا عَلَى سَارَةَ، ثُمَّ جَاءَ بِهَا إِبْرَاهِيمُ، وَبِابْنِهَا إِسْمَاعِيلَ وَهْىَ تُرْضِعُهُ حَتَّى وَضَعَهُمَا عِنْدَ الْبَيْتِ عِنْدَ دَوْحَةٍ، فَوْقَ زَمْزَمَ فِي أَعْلَى الْمَسْجِدِ، وَلَيْسَ بِمَكَّةَ يَوْمَئِذٍ أَحَدٌ، وَلَيْسَ بِهَا مَاءٌ، فَوَضَعَهُمَا هُنَالِكَ، وَوَضَعَ عِنْدَهُمَا جِرَابًا فِيهِ تَمْرٌ وَسِقَاءً فِيهِ مَاءٌ، ثُمَّ قَفَّى إِبْرَاهِيمُ مُنْطَلِقًا فَتَبِعَتْهُ أُمُّ إِسْمَاعِيلَ فَقَالَتْ يَا إِبْرَاهِيمُ أَيْنَ تَذْهَبُ وَتَتْرُكُنَا بِهَذَا الْوَادِي الَّذِي لَيْسَ فِيهِ إِنْسٌ وَلاَ شَىْءٌ فَقَالَتْ لَهُ ذَلِكَ مِرَارًا، وَجَعَلَ لاَ يَلْتَفِتُ إِلَيْهَا فَقَالَتْ لَهُ آللَّهُ الَّذِي أَمَرَكَ بِهَذَا قَالَ نَعَمْ. قَالَتْ إِذًا لاَ يُضَيِّعُنَا. ثُمَّ رَجَعَتْ، فَانْطَلَقَ إِبْرَاهِيمُ حَتَّى إِذَا كَانَ عِنْدَ الثَّنِيَّةِ حَيْثُ لاَ يَرَوْنَهُ اسْتَقْبَلَ بِوَجْهِهِ الْبَيْتَ، ثُمَّ دَعَا بِهَؤُلاَءِ الْكَلِمَاتِ وَرَفَعَ يَدَيْهِ، فَقَالَ {رَبَّنَا إِنِّي أَسْكَنْتُ مِنْ ذُرِّيَّتِي بِوَادٍ غَيْرِ ذِي زَرْعٍ} حَتَّى بَلَغَ {يَشْكُرُونَ}. وَجَعَلَتْ أُمُّ إِسْمَاعِيلَ تُرْضِعُ إِسْمَاعِيلَ، وَتَشْرَبُ مِنْ ذَلِكَ الْمَاءِ، حَتَّى إِذَا نَفِدَ مَا فِي السِّقَاءِ عَطِشَتْ وَعَطِشَ ابْنُهَا، وَجَعَلَتْ تَنْظُرُ إِلَيْهِ يَتَلَوَّى ـ أَوْ قَالَ يَتَلَبَّطُ ـ فَانْطَلَقَتْ كَرَاهِيَةَ أَنْ تَنْظُرَ إِلَيْهِ، فَوَجَدَتِ الصَّفَا أَقْرَبَ جَبَلٍ فِي الأَرْضِ يَلِيهَا، فَقَامَتْ عَلَيْهِ ثُمَّ اسْتَقْبَلَتِ الْوَادِيَ تَنْظُرُ هَلْ تَرَى أَحَدًا فَلَمْ تَرَ أَحَدًا، فَهَبَطَتْ مِنَ، الصَّفَا حَتَّى إِذَا بَلَغَتِ الْوَادِيَ رَفَعَتْ طَرَفَ دِرْعِهَا، ثُمَّ سَعَتْ سَعْىَ الإِنْسَانِ الْمَجْهُودِ، حَتَّى جَاوَزَتِ الْوَادِيَ، ثُمَّ أَتَتِ الْمَرْوَةَ، فَقَامَتْ عَلَيْهَا وَنَظَرَتْ هَلْ تَرَى أَحَدًا، فَلَمْ تَرَ أَحَدًا، فَفَعَلَتْ ذَلِكَ سَبْعَ مَرَّاتٍ ـ قَالَ ابْنُ عَبَّاسٍ قَالَ النَّبِيُّ صلى الله عليه وسلم " فَذَلِكَ سَعْىُ النَّاسِ بَيْنَهُمَا ". ـ فَلَمَّا أَشْرَفَتْ عَلَى الْمَرْوَةِ سَمِعَتْ صَوْتًا، فَقَالَتْ صَهٍ. تُرِيدَ نَفْسَهَا، ثُمَّ تَسَمَّعَتْ، فَسَمِعَتْ أَيْضًا، فَقَالَتْ قَدْ أَسْمَعْتَ، إِنْ كَانَ عِنْدَكَ غِوَاثٌ. فَإِذَا هِيَ بِالْمَلَكِ، عِنْدَ مَوْضِعِ زَمْزَمَ، فَبَحَثَ بِعَقِبِهِ ـ أَوْ قَالَ بِجَنَاحِهِ ـ حَتَّى ظَهَرَ الْمَاءُ، فَجَعَلَتْ تُحَوِّضُهُ وَتَقُولُ بِيَدِهَا هَكَذَا، وَجَعَلَتْ تَغْرِفُ مِنَ الْمَاءِ فِي سِقَائِهَا، وَهْوَ يَفُورُ بَعْدَ مَا تَغْرِفُ ـ قَالَ ابْنُ عَبَّاسٍ قَالَ النَّبِيُّ صلى الله عليه وسلم " يَرْحَمُ اللَّهُ أُمَّ إِسْمَاعِيلَ لَوْ تَرَكَتْ زَمْزَمَ ـ أَوْ قَالَ لَوْ لَمْ تَغْرِفْ مِنَ الْمَاءِ ـ لَكَانَتْ زَمْزَمُ عَيْنًا مَعِينًا ". ـ قَالَ فَشَرِبَتْ وَأَرْضَعَتْ وَلَدَهَا، فَقَالَ لَهَا الْمَلَكُ لاَ تَخَافُوا الضَّيْعَةَ، فَإِنَّ هَا هُنَا بَيْتَ اللَّهِ، يَبْنِي هَذَا الْغُلاَمُ، وَأَبُوهُ، وَإِنَّ اللَّهَ لاَ يُضِيعُ أَهْلَهُ. وَكَانَ الْبَيْتُ مُرْتَفِعًا مِنَ الأَرْضِ كَالرَّابِيَةِ، تَأْتِيهِ السُّيُولُ فَتَأْخُذُ عَنْ يَمِينِهِ وَشِمَالِهِ، فَكَانَتْ كَذَلِكَ، حَتَّى مَرَّتْ بِهِمْ رُفْقَةٌ مِنْ جُرْهُمَ ـ أَوْ أَهْلُ بَيْتٍ مِنْ جُرْهُمَ ـ مُقْبِلِينَ مِنْ طَرِيقِ كَدَاءٍ فَنَزَلُوا فِي أَسْفَلِ مَكَّةَ، فَرَأَوْا طَائِرًا عَائِفًا. فَقَالُوا إِنَّ هَذَا الطَّائِرَ لَيَدُورُ عَلَى مَاءٍ، لَعَهْدُنَا بِهَذَا الْوَادِي وَمَا فِيهِ مَاءٌ، فَأَرْسَلُوا جَرِيًّا أَوْ جَرِيَّيْنِ، فَإِذَا هُمْ بِالْمَاءِ، فَرَجَعُوا فَأَخْبَرُوهُمْ بِالْمَاءِ، فَأَقْبَلُوا، قَالَ وَأُمُّ إِسْمَاعِيلَ عِنْدَ الْمَاءِ فَقَالُوا أَتَأْذَنِينَ لَنَا أَنْ نَنْزِلَ عِنْدَكِ فَقَالَتْ نَعَمْ، وَلَكِنْ لاَ حَقَّ لَكُمْ فِي الْمَاءِ. قَالُوا نَعَمْ. قَالَ ابْنُ عَبَّاسٍ قَالَ النَّبِيُّ صلى الله عليه وسلم " فَأَلْفَى ذَلِكَ أُمَّ إِسْمَاعِيلَ، وَهْىَ تُحِبُّ الإِنْسَ " فَنَزَلُوا وَأَرْسَلُوا إِلَى أَهْلِيهِمْ، فَنَزَلُوا مَعَهُمْ حَتَّى إِذَا كَانَ بِهَا أَهْلُ أَبْيَاتٍ مِنْهُمْ، وَشَبَّ الْغُلاَمُ، وَتَعَلَّمَ الْعَرَبِيَّةَ مِنْهُمْ، وَأَنْفَسَهُمْ وَأَعْجَبَهُمْ حِينَ شَبَّ، فَلَمَّا أَدْرَكَ زَوَّجُوهُ امْرَأَةً مِنْهُمْ، وَمَاتَتْ أُمُّ إِسْمَاعِيلَ، فَجَاءَ إِبْرَاهِيمُ، بَعْدَ مَا تَزَوَّجَ إِسْمَاعِيلُ يُطَالِعُ تَرِكَتَهُ، فَلَمْ يَجِدْ إِسْمَاعِيلَ، فَسَأَلَ امْرَأَتَهُ عَنْهُ فَقَالَتْ خَرَجَ يَبْتَغِي لَنَا. ثُمَّ سَأَلَهَا عَنْ عَيْشِهِمْ وَهَيْئَتِهِمْ فَقَالَتْ نَحْنُ بِشَرٍّ، نَحْنُ فِي ضِيقٍ وَشِدَّةٍ. فَشَكَتْ إِلَيْهِ. قَالَ فَإِذَا جَاءَ زَوْجُكِ فَاقْرَئِي عَلَيْهِ السَّلاَمَ، وَقُولِي لَهُ يُغَيِّرْ عَتَبَةَ بَابِهِ. فَلَمَّا جَاءَ إِسْمَاعِيلُ، كَأَنَّهُ آنَسَ شَيْئًا، فَقَالَ هَلْ جَاءَكُمْ مِنْ أَحَدٍ قَالَتْ نَعَمْ، جَاءَنَا شَيْخٌ كَذَا وَكَذَا، فَسَأَلَنَا عَنْكَ فَأَخْبَرْتُهُ، وَسَأَلَنِي كَيْفَ عَيْشُنَا فَأَخْبَرْتُهُ أَنَّا فِي جَهْدٍ وَشِدَّةٍ. قَالَ فَهَلْ أَوْصَاكِ بِشَىْءٍ قَالَتْ نَعَمْ، أَمَرَنِي أَنْ أَقْرَأَ عَلَيْكَ السَّلاَمَ، وَيَقُولُ غَيِّرْ عَتَبَةَ بَابِكَ. قَالَ ذَاكِ أَبِي وَقَدْ أَمَرَنِي أَنْ أُفَارِقَكِ الْحَقِي بِأَهْلِكِ. فَطَلَّقَهَا، وَتَزَوَّجَ مِنْهُمْ أُخْرَى، فَلَبِثَ عَنْهُمْ إِبْرَاهِيمُ مَا شَاءَ اللَّهُ ثُمَّ أَتَاهُمْ بَعْدُ، فَلَمْ يَجِدْهُ، فَدَخَلَ عَلَى امْرَأَتِهِ، فَسَأَلَهَا عَنْهُ. فَقَالَتْ خَرَجَ يَبْتَغِي لَنَا. قَالَ كَيْفَ أَنْتُمْ وَسَأَلَهَا عَنْ عَيْشِهِمْ، وَهَيْئَتِهِمْ. فَقَالَتْ نَحْنُ بِخَيْرٍ وَسَعَةٍ. وَأَثْنَتْ عَلَى اللَّهِ. فَقَالَ مَا طَعَامُكُمْ قَالَتِ اللَّحْمُ. قَالَ فَمَا شَرَابُكُمْ قَالَتِ الْمَاءُ. فَقَالَ اللَّهُمَّ بَارِكْ لَهُمْ فِي اللَّحْمِ وَالْمَاءِ. قَالَ النَّبِيُّ صلى الله عليه وسلم " وَلَمْ يَكُنْ لَهُمْ يَوْمَئِذٍ حَبٌّ، وَلَوْ كَانَ لَهُمْ دَعَا لَهُمْ فِيهِ ". قَالَ فَهُمَا لاَ يَخْلُو عَلَيْهِمَا أَحَدٌ بِغَيْرِ مَكَّةَ إِلاَّ لَمْ يُوَافِقَاهُ. قَالَ فَإِذَا جَاءَ زَوْجُكِ فَاقْرَئِي عَلَيْهِ السَّلاَمَ، وَمُرِيهِ يُثْبِتُ عَتَبَةَ بَابِهِ، فَلَمَّا جَاءَ إِسْمَاعِيلُ قَالَ هَلْ أَتَاكُمْ مِنْ أَحَدٍ قَالَتْ نَعَمْ أَتَانَا شَيْخٌ حَسَنُ الْهَيْئَةِ، وَأَثْنَتْ عَلَيْهِ، فَسَأَلَنِي عَنْكَ فَأَخْبَرْتُهُ، فَسَأَلَنِي كَيْفَ عَيْشُنَا فَأَخْبَرْتُهُ أَنَّا بِخَيْرٍ. قَالَ فَأَوْصَاكِ بِشَىْءٍ قَالَتْ نَعَمْ، هُوَ يَقْرَأُ عَلَيْكَ السَّلاَمَ، وَيَأْمُرُكَ أَنْ تُثْبِتَ عَتَبَةَ بَابِكَ. قَالَ ذَاكِ أَبِي، وَأَنْتِ الْعَتَبَةُ، أَمَرَنِي أَنْ أُمْسِكَكِ. ثُمَّ لَبِثَ عَنْهُمْ مَا شَاءَ اللَّهُ، ثُمَّ جَاءَ بَعْدَ ذَلِكَ، وَإِسْمَاعِيلُ يَبْرِي نَبْلاً لَهُ تَحْتَ دَوْحَةٍ قَرِيبًا مِنْ زَمْزَمَ، فَلَمَّا رَآهُ قَامَ إِلَيْهِ، فَصَنَعَا كَمَا يَصْنَعُ الْوَالِدُ بِالْوَلَدِ وَالْوَلَدُ بِالْوَالِدِ، ثُمَّ قَالَ يَا إِسْمَاعِيلُ، إِنَّ اللَّهَ أَمَرَنِي بِأَمْرٍ. قَالَ فَاصْنَعْ مَا أَمَرَكَ رَبُّكَ. قَالَ وَتُعِينُنِي قَالَ وَأُعِينُكَ. قَالَ فَإِنَّ اللَّهَ أَمَرَنِي أَنْ أَبْنِيَ هَا هُنَا بَيْتًا. وَأَشَارَ إِلَى أَكَمَةٍ مُرْتَفِعَةٍ عَلَى مَا حَوْلَهَا. قَالَ فَعِنْدَ ذَلِكَ رَفَعَا الْقَوَاعِدَ مِنَ الْبَيْتِ، فَجَعَلَ إِسْمَاعِيلُ يَأْتِي بِالْحِجَارَةِ، وَإِبْرَاهِيمُ يَبْنِي، حَتَّى إِذَا ارْتَفَعَ الْبِنَاءُ جَاءَ بِهَذَا الْحَجَرِ فَوَضَعَهُ لَهُ، فَقَامَ عَلَيْهِ وَهْوَ يَبْنِي، وَإِسْمَاعِيلُ يُنَاوِلُهُ الْحِجَارَةَ، وَهُمَا يَقُولاَنِ {رَبَّنَا تَقَبَّلْ مِنَّا إِنَّكَ أَنْتَ السَّمِيعُ الْعَلِيمُ}. قَالَ فَجَعَلاَ يَبْنِيَانِ حَتَّى يَدُورَا حَوْلَ الْبَيْتِ، وَهُمَا يَقُولاَنِ {رَبَّنَا تَقَبَّلْ مِنَّا إِنَّكَ أَنْتَ السَّمِيعُ الْعَلِيمُ }.
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ a5ee4475:2ca75401
2025-05-18 16:07:07
@ a5ee4475:2ca75401
2025-05-18 16:07:07ai #artificial #intelligence #english #tech
Open Source
Models
Text
Image
- SDAI FOSS - Stable Diffusion AI to Android [download] [source] 🤖
- Stable Diffusion - Text to image [source] 🌐
- Pixart Alpha - Photorealistic Text to Image Generation [source]
- Pixart Delta - Framework to Pixart Alpha [paper] [source]
- Pixart Sigma - 4K Text to Image Generation [source]
- OmniGen - Pompt, image or subject to image [source]
- Pigallery - Self-Hosted AI Image Generator [source]
Video
Tools
Lightning Based
- Animal Sunset - AI video generation with Nostr npub by lightning payments [source]
- Ai Rand - AI text generation with Pubky DNS by lightning payments [source]
- PlebAI - Text and Image generation without signup [source] 🌐🤖🍎 [sites down - only github available]
Others
- HuggingFace - Test and collaborate on models, datasets and apps. [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Ollama - Run LLMs Locally [source]
- DreamStudio - Stable Diffusion’s Web App Tool [info] [source]
- Prompt Gallery - AI images with their prompts [source]
Closed Source
Models
Text
- ChatGPT
- Claude
- Gemini
- Copilot
- Maritalk - Text AI in Portuguese focused on Brazil with model Sabia-3 and the open source models Sabia-7b and Sabia-2 [source]
- Amazônia IA - Text AI in Portuguese focused on Brazil with the guara, hapia and golia models [source]
Image
Video
- Minimax - Realistic videos (prompts only in chinese)
Tools
Other index: Amazing AI
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:33
@ 3f68dede:779bb81d
2025-05-19 17:02:33testing
-
 @ 8576ca0e:621f735e
2025-05-19 06:43:00
@ 8576ca0e:621f735e
2025-05-19 06:43:00
In the ever evolving landscape of social media, a new contender has emerged, seeking to redefine how we connect and interact online. YakiHonne, a mobile application built upon the innovative Nostr protocol, isn't just another platform vying for your attention. It represents a bold step towards decentralized social networking, seamlessly integrating the power of Bitcoin's Lightning Network into its very core.
Imagine a social space free from the control of centralized entities, where your data belongs to you, and where value can flow as freely as information. This is the vision YakiHonne is striving to realize. By leveraging the open and censorship resistant nature of Nostr, it offers a refreshing alternative to the traditional social media giants.
The Power of Decentralization: A Foundation Built on Nostr
At its heart, YakiHonne is powered by Nostr (Notes and Other Stuff Transmitted by Relays). Unlike conventional platforms that rely on a central server, Nostr operates on a network of independent relays. This decentralized architecture offers several key advantages:
• Censorship Resistance: No single entity can easily censor or shut down the network. Your posts and interactions are distributed across multiple relays.
• Data Ownership: Your data isn't locked away in a corporate database. You control your private keys, granting you greater autonomy over your information.
• Open and Extensible: The open nature of the protocol allows for innovation and the development of diverse clients and applications, fostering a vibrant ecosystem.
YakiHonne acts as a user friendly gateway to this decentralized world, providing an intuitive mobile interface to interact with the Nostr network.
Zaps: Where Social Interaction Meets Bitcoin
What truly sets YakiHonne apart is its deep integration of Bitcoin payments through the Lightning Network, often referred to as "zaps." This isn't just a tacked on feature; it's woven into the fabric of social interaction.
• Show Appreciation: Found a post insightful, funny, or valuable? You can instantly send a small amount of Bitcoin as a "zap" to show your appreciation directly to the creator.
• Monetize Content: Creators can earn Bitcoin for their contributions, fostering a more sustainable model for online content generation.
• Seamless Transactions: Lightning Network enables near instant and low fee Bitcoin transactions, making zapping a practical and frictionless experience.
This innovative integration transforms social interactions into potential value exchanges, creating new dynamics between creators and their audience.
Beyond the Basics: Features for Content and Connection
YakiHonne isn't solely focused on Bitcoin. It provides a robust set of features for creating, sharing, and discovering content:
• Long Form Articles (NIP-23): For those who want to delve deeper, YakiHonne supports the creation of wel formatted articles using a rich markdown editor. This allows for more nuanced discussions and the sharing of substantial ideas.
• Topic Based Collections (NIP-51): Users can curate content into organized collections, making it easier to discover information on specific topics and follow thought leaders in various domains.
• Following and Discovery (NIP-02): Stay connected with the people and ideas that matter to you by following other users. The platform also offers ways to discover top creators, curators, and trending discussions through hashtags (NIP-12).
• Rich User Profiles: Your profile showcases your followers, who you're following, your zapping activity, and the articles you've published, providing a comprehensive overview of your presence on the platform.
• Direct Messaging (DMs): For more private conversations, YakiHonne includes a direct messaging feature, allowing for one on one communication.
A Growing Ecosystem and Continuous Improvement
YakiHonne is actively being developed and refined by JustHonne Technologies. Recent updates highlight a commitment to improving the user experience and addressing bugs. Enhancements to the zap functionality, fixes for various technical issues, and improved stability demonstrate the ongoing dedication to making the app a reliable and enjoyable platform.
The open source nature of the mobile application, with its code available on GitHub, encourages community involvement and transparency. This collaborative approach can contribute to the platform's growth and evolution.
Looking Ahead: The Potential of Decentralized Social with Bitcoin
YakiHonne represents an exciting intersection of decentralized social networking and Bitcoin's utility. By seamlessly integrating Lightning Network payments, it introduces a novel way to interact and exchange value online. While still in its relatively early stages, YakiHonne holds significant potential to:
• Empower Creators: Provide new avenues for content monetization and direct interaction with their audience.
• Foster Meaningful Interactions: Encourage more thoughtful engagement through the ability to easily show appreciation.
• Offer a More Resilient Social Space: Provide an alternative to centralized platforms with greater resistance to censorship and single points of failure.
As the Nostr ecosystem continues to grow and evolve, and as more users seek decentralized alternatives, YakiHonne is well positioned to be a leading application in this burgeoning space. It's more than just another social media app; it's a glimpse into a future where online connections are more open, and truly belong to the users themselves.
-
 @ c9badfea:610f861a
2025-05-17 03:08:55
@ c9badfea:610f861a
2025-05-17 03:08:55- Install Rethink (it's free and open source)
- Launch the app and tap Skip
- Tap Start and then Proceed to set up the VPN connection
- Allow notifications and Proceed, then disable battery optimization for this app (you may need to set it to Unrestricted)
- Navigate to Configure and tap Apps
- On the top bar, tap 🛜 and 📶 to block all apps from connecting to the internet
- Search Apps for the apps you want to allow and Bypass Universal
- Return to the Configure view and tap DNS, then choose your preferred DNS provider (e.g. DNSCrypt > Quad9)
- Optionally, tap On-Device Blocklists, then Disabled, Download Blocklists, and later Configure (you may need to enable the Use In-App Downloader option if the download is not working)
- Return to the Configure view and tap Firewall, then Universal Firewall Rules and enable the options as desired:
- Block all apps when device is locked
- Block newly installed apps by default
- Block when DNS is bypassed
- Optionally, to set up WireGuard or Tor, return to the Configure view and tap Proxy
- For Tor, tap Setup Orbot, then optionally select all the apps that should route through Tor (you must have Orbot installed)
- For WireGuard, tap Setup WireGuard, then +, and select an option to import a WireGuard configuration (QR Code Scan, File Import, or Creation).
- Use Simple Mode for a single WireGuard connection (all apps are routed through it).
- Use Advanced Mode for multiple WireGuard connections (split tunnel, manually choosing apps to route through them)
⚠️ Use this app only if you know what you are doing, as misconfiguration can lead to missing notifications and other problems
ℹ️ On the main view, tap Logs to track all connections
ℹ️ You can also use a WireGuard connection (e.g., from your VPN provider) and on-device blocklists together
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ dc0bbb4c:b5479e81
2025-05-19 06:31:45
@ dc0bbb4c:b5479e81
2025-05-19 06:31:45Trong bối cảnh thị trường giải trí trực tuyến ngày càng phát triển mạnh mẽ, 1BWM đã và đang khẳng định vị thế là một trong những nền tảng kỹ thuật số được cộng đồng người dùng tin tưởng và lựa chọn nhiều nhất. Nhờ sở hữu giao diện thiết kế hiện đại, tinh tế và cực kỳ dễ sử dụng, 1BWM giúp người dùng dễ dàng tiếp cận và trải nghiệm mọi tiện ích mà nền tảng này mang lại chỉ với vài thao tác đơn giản. Không chỉ vậy, 1BWM còn ghi điểm bởi khả năng tối ưu hóa trải nghiệm trên đa dạng thiết bị như điện thoại di động, máy tính bảng và máy tính để bàn, giúp người dùng có thể giải trí bất cứ lúc nào, ở bất kỳ đâu một cách thuận tiện và mượt mà. Từ các chuyên mục nội dung hấp dẫn, phong phú cho đến hệ thống tính năng linh hoạt, 1BWM luôn biết cách làm mới mình để phù hợp với xu hướng công nghệ và nhu cầu giải trí ngày càng đa dạng của người dùng hiện đại.
Điểm mạnh nổi bật tiếp theo khiến 1BWM được nhiều người lựa chọn chính là hệ thống bảo mật dữ liệu và quyền riêng tư vô cùng nghiêm ngặt. Nền tảng này ứng dụng công nghệ mã hóa tiên tiến, đảm bảo mọi thông tin cá nhân, tài khoản và dữ liệu giao dịch của người dùng luôn được bảo vệ an toàn tuyệt đối. Bên cạnh đó, 1BWM còn sở hữu đội ngũ chăm sóc khách hàng chuyên nghiệp, tận tâm và giàu kinh nghiệm, luôn sẵn sàng hỗ trợ giải đáp mọi thắc mắc cũng như xử lý các tình huống phát sinh một cách nhanh chóng, hiệu quả nhất. Người dùng có thể yên tâm khi trải nghiệm các dịch vụ tại đây mà không phải lo lắng về bất cứ rủi ro nào liên quan đến bảo mật thông tin. Ngoài ra, nền tảng này còn thường xuyên triển khai các chương trình ưu đãi hấp dẫn, quà tặng đặc biệt dành cho người dùng mới lẫn hội viên lâu năm, tạo thêm nhiều giá trị và động lực cho cộng đồng người tham gia.
Không dừng lại ở đó, 1BWM luôn nỗ lực không ngừng trong việc nâng cao chất lượng dịch vụ và mở rộng thêm nhiều tiện ích giải trí mới, nhằm mang đến cho người dùng những trải nghiệm trọn vẹn và thú vị nhất. Nền tảng này liên tục cập nhật các chuyên mục nội dung mới mẻ, phong phú và bắt kịp xu hướng giải trí hiện đại, giúp người dùng luôn có thêm nhiều lựa chọn phù hợp với sở thích cá nhân. Đồng thời, 1BWM cũng chú trọng vào việc cải tiến công nghệ, tối ưu tốc độ kết nối và giao diện sử dụng để nâng cao trải nghiệm mỗi lần truy cập. Với định hướng phát triển rõ ràng cùng sự đầu tư bài bản, 1BWM không chỉ là một nền tảng giải trí đơn thuần mà còn là cộng đồng trực tuyến năng động, nơi người dùng có thể kết nối, tương tác và chia sẻ những khoảnh khắc giải trí vui vẻ, ý nghĩa cùng nhau. Nhờ những ưu điểm vượt trội này, 1BWM ngày càng khẳng định được vị thế và trở thành sự lựa chọn hàng đầu của người dùng Việt khi tìm kiếm một không gian giải trí số chất lượng, an toàn và uy tín.
-
 @ c9badfea:610f861a
2025-05-16 23:58:34
@ c9badfea:610f861a
2025-05-16 23:58:34- Install Breezy Weather (it's free and open source)
- Launch the app, tap Add A New Location and search for your city
- Review the providers for each weather source
- Optionally, add more locations by tapping the + icon
- Enjoy the weather updates
ℹ️ To receive notifications for weather alerts, tap ⚙️, then Notifications and enable Notifications Of Severe Weather Alerts
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:57
@ 3f68dede:779bb81d
2025-05-19 17:01:57testing schedule
-
 @ 005bc4de:ef11e1a2
2025-05-19 17:01:54
@ 005bc4de:ef11e1a2
2025-05-19 17:01:54Keys and Religion
Mixing
Normally, I'm not a fan mixing and comparing bitcoinesque things and religion. It's too banal and trite, too easy: the religion of Bitcoin, the allusion of Satoshi the savior, the "Book of Satoshi," even the "Genesis" block. But, today, I'll break my own rule.
Yesterday, I heard a Christian pastor speak of the "keys of the kingdom." My feeling is that, were you to ask the average Christian, "What is the key, or keys, to the kingdom?", and perhaps I'm wrong on this, but I think they'd answer, "Prayer." I've heard it many times, "Prayer is the key to the kingdom." It's an easy mantra to remember. And, prayer is important for a Christian, no question about it. However, Biblically, the phrase "keys of the kingdom" refers to something else.
As the pastor pointed out yesterday, Biblically there are two keys: the binding key and the loosing key. This refers to Matthew 16:19 where Jesus says:
I will give you the keys of the kingdom of heaven; whatever you bind on earth will be bound in heaven, and whatever you loose on earth will be loosed in heaven. Matthew 16:19 (NIV)
For context, back up a few verses. This statement above was made in a conversation between Jesus and his disciple Simon Peter.
15 Jesus asked, “But what about you?” he asked. “Who do you say I am?” 16 Simon Peter answered, “You are the Messiah, the Son of the living God.” 17 Jesus replied, “Blessed are you, Simon son of Jonah, for this was not revealed to you by flesh and blood, but by my Father in heaven. 18 And I tell you that you are Peter, and on this rock I will build my church, and the gates of Hades will not overcome it.
Although brief, this is a deep and rich exchange. Traditionally, this has been viewed as the moment that Christ instituted the Christian church, the passing of power and authority to the early church itself. There has been confusion over it too, particularly the "...on this rock I will build my church..." part of it. Jesus was referring to Simon Peter's statement of faith (...for this was not revealed to you by flesh and blood...) with the "this" being what Peter had just said, "You are the Messiah, the Son of the living God." The church would be built upon the rock of faith in Jesus as the Messiah.
The early Christian church thus established, Jesus instituted what's come to be called the "office of the keys." That is, Jesus grants authority to his "appointees" in the church to carry out his authority. In more practical terms, this is referring to those who have been called into church service, normally priests, to forgive or not forgive sins. When a priest or pastor forgives, or not, it is not that he is doing it by his own right or power. That priest is, after all, yet another sinful man as well. Instead, the priest forgives by Christ's authority which was handed down by Jesus himself in those words to Peter.
To use an analogy, suppose a general had to make a decision about foot soldiers on the front line, waiting there in the trenches. Due to some time constraint, a decision for action was needed imminently. However, suppose the general lacked some bit of information that could only be obtained at the front. So, the general wrote up a communique to the lieutenant stationed at the front saying, "You assess the situation, and you make the call, charge or pull back. I'll support your decision." A courier ran to the front, relayed the message to the lieutenant, and the lieutenant assessed and made the decision. Ultimately, even thought the lieutenant made the decision, the authority behind the decision lay with the general who had transferred his authority to the lieutenant.
This authority or office of the keys is mirrored in John 20:22-23, when the resurrected Jesus appears to his disciples and says, "If you forgive anyone’s sins, their sins are forgiven; if you do not forgive them, they are not forgiven.”
Going just one step further, recall there are two keys involved, binding and loosing, and there are two places involved, earth and heaven. Usually, priests and pastors are "in the business" of forgiving. Penitence or confession, when real, is forgiven. The priest has the authority to forgive, or "loose" the sinner from his wrongdoings here on earth. And, that forgiveness applies to heaven as well, the sin is atoned and reconciled with God.
But, what about when the person is unrepentant, unbothered by what is Biblically sinful, refuses to change his ways, and rather chooses to continue in sinful ways? The "binding" key says that the priest or appointed church leader can hold that person accountable, can bind that person to the sin and separation from God. Normally, we hear of "excommunication" from the church which is formally stating that a person is outside of the church body. The binding keys still bind, both on earth as being outside of the church and in heaven as being separated from God.
And bitcoin?
That's a lot of religion, and heavy religion at that. The question is, what does this have to do with bitcoin?
Keys.
Namely, this is about public and private keys. Loosing and binding keys. A bit more religion, then I'll get back to bitcoin.
Yesterday, the pastor spoke briefly about binding and loosing keys, and this where my thoughts about keys somehow morphed over into bitcoin. For some reason, I pictured Herod's Temple. There had been Solomon's temple, which was destroyed, and then there was Herod's which was known for its beauty and was the one during Jesus's time. But, let's recall the background on this...
The book of Exodus, and others in the Old Testament, outline in detail God's plan for the tabernacle (a traveling tent) and for the temple in Jerusalem.
The tabernacle, overhead diagram. Image source: https://en.wikipedia.org/wiki/Tabernacle
You might recall the "history" lesson in Raiders of the Lost Ark. With the tabernacle and temple, one of the purposes was to house the ark of the covenant. Remember that the ark was the golden box that the Israelites carried around containing Moses's stone tablets with the Ten Commandments, some manna, and Aaron's staff. It held great power, God's power, and God literally met and spoke with the Levite priests hovering over the cherubim's wings.

The ark of the covenant. Image source: https://en.wikipedia.org/wiki/Ark_of_the_Covenant
In the tabernacle and temple, the "Holy of Holies" was a room, separated by a heavy curtain. It was off limits to all because it was, well, holy of holies. A heavy curtain divided the Holy of Holies, or the "Most Holy Place", from the less-holy, "Holy Place."
Once a year, on the Day of Atonement, one person, the chief priest, was allowed to walk into the Holy of Holies. He would sprinkle the blood of a sacrificed animal onto the ark. This was done for the forgiveness of the people's sins. Although this was pre-Jesus's words, this was using the loosing keys and was loosing sin.
This was serious business and was taken seriously. For instance, the priests Nadab and Abihu improperly performed their sacrificial duties, they messed up the procedure, and were consumed by fire. Priesthood was a dangerous occupation, one slip up and you were scorched.
 The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_Temple
The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_TempleBack to keys...
Yesterday, for some reason when I heard about binding and loosing keys, I imagined the chief priest standing in front of the curtain. I imagined him taking a deep breath, collecting his thoughts, getting ready to go in. It had to be intimidating.
As he stood there, in my mind, he and everyone else was shut out. The Most Holy Place was bound and locked. Walking in meant getting scorched (again, the end of Raiders of the Lost Ark). Yet, that priest had the loosing key. He had, first, permission as chief priest to enter on the Day of Atonement, secondly, he had the sacrificial blood to loose sins. Although the binding key had locked the Holy of Holies and thus bound the sins of the people, the loosing key was about to loose their sins.
Cryptographic keys
And back to bitcoin...
Bitcoin, and cryptography in general, operate on public and private keys. Any flavor of "cryptocurrency", or even Nostr, has public and private keys. In a way, these are binding and loosing keys.
Say you have 1.0 BTC (that's 100,000,000 sats 😀). That BTC exists as a UTXO which can be seen by anyone viewing your public address. In this way, your bitcoin public key is your binding key...that UTXO, that bitcoin, is bound to your public key...it is locked in place behind that heavy curtain. It will be there forever, unless there is an intervention...
You also have your private key, your loosing key. You can apply your private key to loose that UTXO, that bitcoin, and to send it along to wherever.
This is like law and gospel: sin is binding, however Jesus frees it. A bitcoin UTXO is bound until a private key looses it.
Nostr offers a somewhat similar illustration. You have an npub publicly and and nsec secretly or privately. If you were to write a note, your private nsec is needed as a loosing key to free that message, to broadcast it to the world. Once broadcast, it can be seen by all, however it is still inextricably bound or tied to your public key (your npub). Your npub is your binding key and your message is bound to it.
Summed
I'm not sure this binding and loosing keys in religion, and public and private keys in cryptography is the best comparison in the world. It's probably a terrible comparison. But, this is what came to my mind yesterday.
And, so, the mixing of religion and bitcoin is now officially over.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:19
@ 3f68dede:779bb81d
2025-05-19 17:01:19testing schedule
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ 3f68dede:779bb81d
2025-05-19 17:00:18
@ 3f68dede:779bb81d
2025-05-19 17:00:18testing schedule
-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ 9c9d2765:16f8c2c2
2025-05-19 05:04:10
@ 9c9d2765:16f8c2c2
2025-05-19 05:04:10CHAPTER TWENTY TWO
“I should have trusted my son,” she said softly, her voice thick with emotion. “I allowed the world’s opinion to silence my instincts.”
James turned to her, his expression gentle. “You needed time to see what I had to become, Mother. I don’t blame you for anything.”
Mr. JP stepped forward, placing a firm hand on James’s shoulder. “Son, you’ve given this family more than we ever gave you. And tonight… Tonight, you gave JP Enterprises its legacy.”
Uncle Charles, who had silently stood behind James during the entire storm, finally spoke. “It took courage to keep quiet and watch those who wronged you bury themselves with their own greed.”
James nodded slightly. “And now… it’s done.”
Rita came closer, smiling softly. “Not completely,” she said with a hint of laughter. “You still have an entire empire to run… and a celebration to finish.”
James allowed a rare, genuine smile to appear. “Right. The anniversary.”
They returned to the hall, which had now regained its glamour and golden glow. The orchestra resumed a soft melody. The guests whispered less now and admired more. The reputation of James was not only redeemed, it was immortalized.
A grand toast was raised in his honor. Champagne glasses clinked gently beneath crystal chandeliers.
Meanwhile, in a corner of the room, Tracy sat, feeling like the walls were closing in. Her palms were damp. She had seen the storm come full circle, and it landed directly on the heads of her former allies. Her gaze lingered on James from afar no longer the man she belittled, deceived, and mocked. He was now untouchable.
She lowered her head, guilt dancing between her thoughts. What have I done?
As if sensing her gaze, James glanced in her direction. For a heartbeat, their eyes met. But there was no anger in his. Just clarity. And silence. He turned away, giving her no attention, no confrontation. That indifference stung more than any rebuke.
Back on stage, Mr. JP announced, “Tonight, we not only celebrate sixteen years of excellence, but we also honor the future. A future with James as our guiding light.”
The crowd once again erupted in applause.
As the music swelled and the lights dimmed to warm hues, couples danced, laughter returned, and the celebration continued. But for James, the victory wasn’t in the glamour, nor the spotlight. It was in knowing that he had not only defeated those who plotted against him but done so without losing his soul.
Later that evening, James stood alone at the terrace, looking out at the moonlit city below. Sandra approached quietly.
“You finally have it all,” she said gently. “The name. The company. The power.”
James didn’t turn. “It was never about having it all. It was about becoming everything they said I couldn’t.”
She smiled, stepping beside him. “And now?”
He exhaled, his breath misting into the cold night air. “Now… I build. For real this time.”
The celebration had ended, but its echoes still danced through the night like a lingering song in the soul. The grand hall slowly emptied, leaving behind the soft shuffling of feet and murmurs of astonishment. JP Enterprises’ 16th Anniversary had become more than a commemoration of business success it was now remembered as the night the city witnessed a man rise from ruin to royalty.
The staff bustled through the corridors, clearing the remains of laughter, toasts, and carefully prepared cuisine. James had stepped away, far from the glitz and glamour, and now stood once more on the terrace, his thoughts stretched thin across the skyline of the city he once wandered in as nothing more than a nameless shadow.
The weight of it all rested gently on his shoulders, not a burden, but a reminder. He remembered the cold nights on the street, the hunger, the humiliation at the Ray household, the scorn in Helen’s voice, and the way Tracy used to avoid eye contact with him as if he were dirt beneath her polished shoes.
His fists clenched slowly as memory swirled within him like a storm. But he released the tension just as quickly. That past could no longer touch him. He had outgrown it. Transcended it.
Behind him, the heavy oak doors creaked. It was Uncle Charles.
“You should rest,” Charles said, his tone fatherly. “You’ve had a long night.”
James turned, eyes soft yet heavy. “You ever wonder what happens after the applause ends?”
Charles smiled. “That’s when the real work begins.”
James chuckled dryly. “Exactly.”
They stood side by side, looking out at the city lights. It felt poetic somehow like all the scattered stars in the sky had descended to earth in the form of streetlights and skyscrapers.
“You did well tonight, James,” Charles said. “You kept your composure even when that girl tried to destroy everything.”
“She was just a pawn,” James replied. “Mark and Helen used her like they use everyone. Their power was built on manipulation. Mine won’t be.”
Charles looked at him, pride gleaming in his eyes. “And that’s why you’re different. That’s why you deserve the crown.”
Meanwhile, back in the Ray residence, chaos brewed. Mark paced violently, his jacket flung to the floor, his tie undone. Helen sat on the edge of the sofa, her heels off, nursing a glass of wine with trembling fingers.
“She betrayed us,” Mark spat. “That girl after all the money we gave her, she folded.”
“What did you expect?” Helen hissed. “She was a desperate street rat! Loyalty is not in their blood!”
Mark slammed his fist on the table. “Now the city sees us as liars. As criminals. We’ve been blacklisted by investors! Do you know what that means, Helen? We’re finished!”
Helen's face hardened. “No. We’re not. James might have won tonight, but the game isn’t over.”
Mark turned toward her. “You still want to fight him?”
The silence that followed the explosive revelation at the anniversary was thick and reverent. It blanketed the city like a veil, as if the skyline itself paused to absorb the magnitude of what had transpired. James, once discarded and humiliated, had emerged not only as the President of JP Enterprises, but as its rightful heir, son to the powerful and elusive Mr. JP. What was once speculation had now become an undeniable truth, echoing across boardrooms, dinner tables, and digital screens.
Back at JP Towers, the building pulsed with energy. Staff walked a little straighter, greeted one another with more awareness. The man they once passed in hallways without a second glance had now become a figure of awe and authority. His name echoed in hushed reverence: Mr. James.
Inside his office, James sat behind a polished obsidian desk, the city's skyline stretching behind him like a conquest. His fingers drummed silently on a closed file. He had received more than twenty new partnership requests within forty-eight hours of the celebration. Shares had surged. The media, which once sought to condemn him, was now clamoring for exclusive interviews, praising his resilience and visionary leadership.
Yet, James was silent.
Not because he didn't revel in victory, but because he understood something deeper this was not the end. It was only the beginning.
-
 @ c9badfea:610f861a
2025-05-10 11:08:51
@ c9badfea:610f861a
2025-05-10 11:08:51- Install FUTO Keyboard (it's free and open source)
- Launch the app, tap Switch Input Methods and select FUTO Keyboard
- For voice input, choose FUTO Keyboard (needs mic permission) and grant permission While Using The App
- Configure keyboard layouts under Languages & Models as needed
Adding Support for Non-English Languages
Voice Input
- Download voice input models from the FUTO Keyboard Add-Ons page
- For languages like Chinese, German, Spanish, Russian, French, Portuguese, Korean, and Japanese, download the Multilingual-74 model
- For other languages, download Multilingual-244
- Open FUTO Keyboard, go to Languages & Models, and import the downloaded model under Voice Input
Dictionaries
- Get dictionary files from AOSP Dictionaries
- Open FUTO Keyboard, navigate to Languages & Models, and import the dictionary under Dictionary
ℹ️ When typing, tap the microphone icon to use voice input
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 3f68dede:779bb81d
2025-05-19 16:59:50
@ 3f68dede:779bb81d
2025-05-19 16:59:50testing schedule
-
 @ f6488c62:c929299d
2025-05-19 03:25:26
@ f6488c62:c929299d
2025-05-19 03:25:26เรื่องจริงที่ต้องเตือน: เมื่อ "ความรวยจากคริปโต" กลายเป็นดาบสองคมที่อันตรายถึงชีวิต! 🔪💰
ในขณะที่หลายคนยินดีกับกำไรจาก Bitcoin และคริปโตอื่นๆ มีเรื่องราวอีกด้านที่น่าสะเทือนใจเกิดขึ้นทั่วโลก โดยเฉพาะเหตุการณ์ "ลักพาตัวเพื่อเรียกค่าไถ่เป็นคริปโต" ที่ทวีความรุนแรงขึ้น
ข้อมูลและข่าวจากหลายแหล่งยืนยันว่า ผู้ใช้งานคริปโตกำลังตกเป็นเป้าหมายของอาชญากร โดยใช้วิธีการที่โหดเหี้ยม เช่น การทำร้ายร่างกาย หรือแม้กระทั่งการ "ตัดนิ้ว" เพื่อบีบบังคับให้เหยื่อโอนคริปโตใน Cold Wallet ที่เก็บไว้! เคสล่าสุดที่เกิดขึ้นในฝรั่งเศสและสหรัฐฯ ในช่วงปี 2025 เป็นเครื่องย้ำเตือนชั้นดี
ทำไมพวกเขาถึงเลือก "คุณ" ที่เป็นนักลงทุนคริปโต? ปัจจัยสำคัญคือ: มูลค่าสินทรัพย์ที่คุณถือสูงมาก, การเก็บ Private Key ของ Cold Wallet คือจุดอ่อนที่คนร้ายใช้ความรุนแรงบังคับเอาได้ง่าย, และที่น่าตกใจคือ การ "โพสต์โชว์ความรวย" หรือพูดถึงคริปโตมากเกินไปบนโซเชียลมีเดีย กำลังเป็นการชี้เป้าให้ตัวเอง!
ข้อคิดและแนวทางป้องกันตัวที่สำคัญสุดๆ:
จงเป็น "Ghost" ในโลกคริปโต: อย่าให้ใครรู้ว่าคุณถืออะไร เท่าไหร่ หรือรวยแค่ไหน การปิดทองหลังพระในโลกคริปโตอาจช่วยรักษาชีวิตคุณได้ ยกระดับความปลอดภัย "ชีวิตจริง": คิดถึงกล้องวงจรปิด, ระบบรักษาความปลอดภัยที่บ้าน, การจ้างบอดี้การ์ด (ถ้าจำเป็นจริงๆ), และระวังการเดินทางคนเดียว บริหารจัดการ "กุญแจ" ของคุณให้ดีที่สุด: Cold Wallet สำคัญมาก แต่การเก็บ Private Key ให้ปลอดภัยจากสายตาคนอื่น และการกระจายความเสี่ยงโดยแบ่งทรัพย์สินไปหลาย Wallet ก็สำคัญไม่แพ้กัน ความรุนแรงในวงการคริปโตเป็นบทเรียนราคาแพงที่บอกว่า ความมั่งคั่งที่มองไม่เห็นในโลกดิจิทัลนั้น มีราคาค่างวดที่ต้องจ่ายในโลกจริงหากประมาท การลงทุนอย่างรอบคอบ ไม่ใช่แค่การดูกราฟ แต่คือการประเมินและจัดการความเสี่ยงใน "ชีวิต" ของคุณด้วย!
แชร์โพสนี้เพื่อเตือนเพื่อนๆ นักลงทุนทุกคน ให้ปลอดภัยทั้งทรัพย์สินและชีวิตครับ/ค่ะ!
Crypto #Bitcoin #Ethereum #ColdWallet #PrivateKey #Security #Crime #DigitalAssets #Investor #SafetyFirst #เตือนภัย #ลงทุนอย่างปลอดภัย
-
 @ c9badfea:610f861a
2025-05-16 20:15:31
@ c9badfea:610f861a
2025-05-16 20:15:31- Install Obtainium (it's free and open source)
- Launch the app and allow notifications
- Open your browser, navigate to the GitHub page of the app you want to install, and copy the URL (e.g.
https://github.com/revanced/revanced-managerfor ReVanced) - Launch Obtainium, navigate to Add App, paste the URL into App Source URL, and tap Add
- Wait for the loading process to finish
- You can now tap Install to install the application
- Enable Allow From This Source and return to Obtainium
- Proceed with the installation by tapping Install
ℹ️ Besides GitHub, Obtainium can install from additional sources
ℹ️ You can also explore Complex Obtainium Apps for more options
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 662f9bff:8960f6b2
2025-05-19 15:11:25
@ 662f9bff:8960f6b2
2025-05-19 15:11:25Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada explifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine released in December 2018 - The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ c6d8334c:30883d6d
2025-05-19 15:02:01
@ c6d8334c:30883d6d
2025-05-19 15:02:01#KIBedenken - Bewusstsein
Einen wichtigen Impuls über KI nachzudenken lieferte vor einiger Zeit Yuval Noah Harari an der University of Cambridge am Ende eines Podiumsgesprächs hier ab 1:15 h auf youtube:
Ich denke, wir müssen die Frage des Bewusstseins in den Mittelpunkt der Diskussion stellen. Es gibt eine riesige, riesige Verwirrung in der Terminologie, auch in der Welt der KI, zwischen Bewusstsein und Intelligenz. Aber es sind zwei verschiedene Dinge. Intelligenz ist die Fähigkeit, Probleme zu lösen und Ziele zu erreichen. Bewusstsein ist die Fähigkeit, Dinge zu fühlen, wie Schmerz oder Freude oder Liebe oder Hass. Wir neigen dazu, die beiden zu verwechseln, weil bei Menschen und auch bei anderen Säugetieren, Vögeln und anderen Tieren Bewusstsein und Intelligenz zusammengehören. Wir lösen Probleme durch unsere Gefühle. Computer waren bisher sehr anders. Sie sind in einigen Bereichen bereits intelligenter als wir, haben aber, soweit wir wissen, kein Bewusstsein. Soweit wir wissen, können sie überhaupt keinen Schmerz, keine Freude, keine Liebe oder keinen Hass empfinden. Niemand weiß, was in Zukunft passieren wird. Es gibt Modelle und Theorien, die argumentieren, dass KIs irgendwann auch bewusst oder empfindsam werden. Sie werden anfangen, Dinge zu fühlen. Sie werden anfangen, Schmerz oder Liebe oder Hass zu empfinden. Es gibt andere Modelle und Theorien, die sagen, nein. Sie könnten weit intelligenter werden als wir und immer noch null Bewusstsein haben. Das kann in der Evolution des Lebens sein. Wenn man darüber nachdenkt, die lange Entwicklung von Milliarden von Jahren der Evolution. Die Entwicklung der Intelligenz ist im Falle von Tieren wie uns und Schimpansen und Hunden und Schweinen und so weiter durch die Entwicklung des Bewusstseins verlaufen. Aber das ist kein universelles Gesetz der Evolution der Intelligenz. Vielleicht gibt es alternative Wege, die zu Superintelligenz ohne jegliches Bewusstsein führen. Einfach einen anderen, einen fremden Weg gehen. Und wir könnten an einen Punkt gelangen, an dem sie superintelligent sind und trotzdem null Bewusstsein haben. Und die Gefahr besteht dann darin, dass sie nicht nur die menschliche Zivilisation zerstören könnten, sondern das ganze Licht des Bewusstseins, um das gesamte ökologische System nach ihren Bedürfnissen umzugestalten, wofür sie kein Bewusstsein brauchen. Sie funktionieren auf eine völlig andere Weise. Sie könnten sich sogar von der Erde auf andere Planeten, auf andere Galaxien ausbreiten. Sie werden das Universum mit Intelligenz füllen, aber es wird ein völlig dunkles Universum ohne Bewusstsein sein. Wieder hohe Intelligenz, fähig, Raumschiffe zu bauen, die mit Lichtgeschwindigkeit fliegen und was auch immer, aber es gibt null Gefühl. Niemand, keine Entität fühlt Schmerz oder Freude, Liebe oder Hass. Für mich ist das ein schreckliches Szenario. Das schlimmste Szenario von allen ist dies. Dass wir ein Universum voller Intelligenz und völlig ohne Bewusstsein haben werden, denn ich denke, dass von den beiden das Bewusstsein weitaus wichtiger, weitaus wertvoller ist. Und es ist eine gute Erinnerung daran, dass wir das zumindest heute mit vielen anderen Tieren teilen, aber nicht mit den Computern, nicht mit den KIs. Wir sind also immer noch im selben Team wie die Würmer und die Affen, nicht im selben Team wie die Computer.
Ich denke, hier wird eine Spur gelegt, die sich unterscheidet von der reinen Funktion von KI zur intelligenten Verbesserung und Unterstützung von Lernprozessen oder vielfältigem Kompetenzerwerb hin zur Selbstreflexion der Lernenden. Auch im Blick auf (religionsbezogene) Bildung kennen wir den Mensch nicht nur biologisch, wie die Würmer und Affen sondern auch ausgestattet mit Würde, Entscheidungsfreiheit und als Beziehungswesen, das auf ein Gegenüber ausgerichtet sein kann und, wie Harari sagt, nicht im selben Team wie die Computer spielt. Sinn, Seele und Verstand erhalten wir weder aus uns selbst heraus noch von einer wie auch immer gearteten Intelligenz. Liebe, Gnade, Hoffnung, Frieden, Gemeinschaft, Trost, Zuversicht und viele weiteren lebensbedeutsame Erfahrungen gewinnen im Angesicht von Maschinen aus meiner Sicht an elementarer Bedeutung.
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 33baa074:3bb3a297
2025-05-19 02:53:31
@ 33baa074:3bb3a297
2025-05-19 02:53:31Distilled water and purified water are different in some aspects. Which one is better depends on personal needs and preferences. The following is a comparative analysis of the two from multiple dimensions:
Water source and process flow Distilled water: The water source usually comes from natural water bodies such as rivers, lakes and seas. It is treated by distillation, that is, water is heated to boiling and water vapor is condensed into liquid water. This process can remove impurities, harmful substances and most minerals in the water.

Purified water: The water source is mainly tap water. Through a series of complex processes such as filtration, adsorption, reverse osmosis, and electrolysis, harmful substances, bacteria, viruses and some minerals in the water are removed to achieve high purity. The process flow is relatively complex and some trace elements that are beneficial to the human body are retained.
Ingredients and nutrition Distilled water: Highly pure, almost no minerals and trace elements. Long-term drinking may cause the human body to lack necessary minerals and trace elements, thus affecting health.
Purified water: After treatment, some trace elements that are beneficial to the human body are retained. While maintaining a high degree of purity, it has certain nutritional value and is more suitable as daily drinking water to meet the basic needs of the human body for water and minerals.
Uses Distilled water: Due to its high purity and impurity-free characteristics, it is widely used in the pharmaceutical industry (such as preparing and diluting various drug solutions, saline, and cleaning wounds, etc.), chemical experiments (dissolving and diluting chemical reagents, preparing chemical solutions, etc.), and industrial production.
Purified water: More used in daily drinking, cooking, and brewing tea and coffee. It has a fresh taste and no odor, which can better preserve the original flavor of food and drinks. It can also be used to prepare infant milk powder and formula milk powder, etc., which is safer and more reliable because it does not contain harmful substances.
Potential risks Distilled water: Due to the lack of minerals and trace elements, it may cause nutritional imbalance in the human body.
Purified water: Although some trace elements are retained, it may also bring potential health risks due to chemical residues in the processing process.
In summary, if you are worried about the loss of minerals, it may be more appropriate to choose purified water; if you think that excessive mineral intake is not good for health, then distilled water may be a better choice. But no matter which one you choose, it is not recommended to drink a large amount of water for a long time. It can be combined with other mineral-rich drinks or foods to maintain the body's nutritional balance.
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ c9badfea:610f861a
2025-05-16 17:57:20
@ c9badfea:610f861a
2025-05-16 17:57:20- Install Lemuroid (it's free and open source)
- Launch the app, enable notifications, and select a directory for your games (e.g.
/Download/ROMs) - Download game ROMs and place them in the folder from the previous step (see links below)
- Open Lemuroid again, navigate to the Home tab, and tap the downloaded game
- Enjoy!
Some ROM Sources
ℹ️ An internet connection is only required when opening a game for the first time to download the emulator core per system (e.g. Gameboy or PS2)
ℹ️ Supported ROM file formats include
.nes,.gba,.sfc,.gb,.iso,.bin, and.zipℹ️ You may need to extract downloaded ROM files if they are packaged as archives (e.g.
.7z,.rar, or.zip) -
 @ 975e4ad5:8d4847ce
2025-05-16 11:22:20
@ 975e4ad5:8d4847ce
2025-05-16 11:22:20Introduction
Bitcoin and torrents are two technologies that have reshaped how people share information and resources in the digital age. Both are built on decentralized principles and challenge traditional systems—torrents in the realm of file sharing, and Bitcoin in the world of finance. However, while torrents have seen a decline in popularity with the rise of streaming platforms like Netflix and HBO, many wonder whether Bitcoin will follow a similar trajectory or continue to grow as a widely adopted technology. This article explores the similarities between the two technologies, the resilience of torrents against attempts to shut them down, the reasons for their declining popularity, and why Bitcoin is likely to avoid a similar fate.
Similarities Between Torrents and Bitcoin
Torrents and Bitcoin share several key characteristics that make them unique and resilient:
-
Decentralization:\ Torrents rely on peer-to-peer (P2P) networks, where users share files directly with each other without depending on a central server. Similarly, Bitcoin operates on a blockchain—a decentralized network of nodes that maintain and validate transactions. This lack of a central authority makes both technologies difficult to control or shut down.
-
Censorship Resistance:\ Both systems are designed to withstand attempts at restriction. Torrents continue to function even when specific sites like The Pirate Bay are blocked, as the network relies on thousands of users worldwide. Bitcoin is also resistant to government bans, as transactions are processed by a global network of miners.
-
Anonymity and Pseudonymity:\ Torrents allow users to share files without revealing their identities, especially when using VPNs. Bitcoin, while pseudonymous (transactions are public but not directly tied to real-world identities), offers a similar level of privacy, attracting users seeking financial freedom.
-
Open Source:\ Both technologies are open-source, enabling developers to improve and adapt them. This fosters innovation and makes the systems more resilient to attacks.
Why Torrents Cannot Be Stopped
Torrents have persisted despite numerous attempts to curb them due to their decentralized nature. Governments and organizations have shut down sites like The Pirate Bay and Kickass Torrents, but new platforms quickly emerge. The key reasons for their resilience include:
-
P2P Architecture:\ Torrents do not rely on a single server. Every user downloading or sharing a file becomes part of the network, making it impossible to completely dismantle.
-
Global Distribution:\ Millions of users worldwide sustain torrent networks. Even if one country imposes strict regulations, others continue to support the system.
-
Adaptability:\ The torrent community quickly adapts to challenges, using VPNs, proxy servers, or the dark web to bypass restrictions.
Despite this resilience, the popularity of torrents has significantly declined in recent years, particularly among younger users.
The Decline of Torrents: Why They Lost Popularity
In the early 2000s, torrents were the primary way to access movies, music, and software. They were easy to use, free, and offered a vast array of content. However, the rise of streaming platforms like Netflix, HBO, Disney+, and Spotify has changed how people consume media. The main reasons for the decline of torrents include:
-
Convenience:\ Streaming platforms provide instant access to high-quality content without the need for downloading or specialized software. Torrents, in contrast, require technical knowledge and are often slower.
-
Legality and Safety:\ Using torrents carries risks such as viruses, malware, and legal consequences. Streaming services offer a safe and legal alternative.
-
Marketing and Accessibility:\ Platforms like Netflix invest billions in original content and marketing, attracting younger users who prefer easy access over free but risky downloads.
-
Social Shifts:\ Younger generations, raised with access to subscription services, are often unfamiliar with torrents or view them as outdated. Studies from 2023 indicate that only a small percentage of people under 25 regularly use torrents.
Despite this decline, torrents have not disappeared entirely. They are still used in regions with limited access to streaming services or by users who value free access to niche content.
Why Bitcoin Will Not Share the Fate of Torrents
Despite the similarities, Bitcoin has unique characteristics that make it more likely to achieve mainstream adoption rather than being overshadowed by alternatives. Here are the key reasons:
-
Financial Revolution:\ Bitcoin addresses problems that lack direct alternatives. It enables transactions without intermediaries, which is particularly valuable in countries with unstable currencies or limited banking access. Unlike torrents, which were replaced by more convenient streaming platforms, traditional financial systems still have flaws that Bitcoin addresses.
-
Institutional Adoption:\ Major companies like Tesla, PayPal, and Square accept Bitcoin or invest in it. Financial institutions, including JPMorgan and Goldman Sachs, are developing cryptocurrency-related products. This institutional acceptance boosts Bitcoin’s credibility and legitimacy, something torrents never achieved.
-
Limited Supply:\ Bitcoin’s fixed supply of 21 million coins makes it attractive as a store of value, similar to gold. This characteristic distinguishes it from other technologies and gives it potential for long-term growth.
-
Technological Advancements:\ The Bitcoin network evolves through improvements like the Lightning Network, which makes transactions faster and cheaper. These innovations make it competitive with traditional payment systems, whereas torrents failed to adapt to streaming technologies.
-
Global Financial Integration:\ Unlike torrents, which remained in the niche of file sharing, Bitcoin has the potential to integrate into the global financial system. Countries like El Salvador have already recognized it as legal tender, and others may follow suit.
-
Cultural and Economic Significance:\ Bitcoin is perceived not only as a technology but also as a movement for financial independence and decentralization. This ideology attracts young people and tech enthusiasts, making it more resilient to the social shifts that affected torrents.
Conclusion
Torrents and Bitcoin share common roots as decentralized technologies that challenge the status quo. However, while torrents lost popularity due to the rise of more convenient and legal alternatives, Bitcoin has the potential to avoid this fate. Its ability to address real financial problems, institutional adoption, and technological advancements make it a likely candidate for mainstream use in the future. While torrents remained a niche technology, Bitcoin is emerging as a global force that could transform how the world perceives money.
-
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ c9badfea:610f861a
2025-05-15 23:51:35
@ c9badfea:610f861a
2025-05-15 23:51:35- Install SDAI (it's free and open source)
- Launch the app, and allow notifications when prompted
- Complete the introduction to get started
- Set Local Diffusion Microsoft ONNX as provider
- In the configuration step, Download a model (such as Real Vision) and wait for the process to finish
- Once the model is downloaded, tap on it and then select Setup
- You can now create images offline by entering a Prompt and tapping 🪄 Imagine
ℹ️ Download the tracking-free FOSS variant
ℹ️ Internet connection is only required for the initial model download
ℹ️ To speed up image generation, consider reducing the image size (e.g. 256x256)
-
 @ f6488c62:c929299d
2025-05-19 02:41:45
@ f6488c62:c929299d
2025-05-19 02:41:45เกิดอะไรขึ้นช่วงส่งท้ายปี 2024? จู่ๆ บัญชี X ของอีลอน มัสก์ ก็เปลี่ยนชื่อเป็น "Kekius Maximus" สร้างความสงสัยและกระแสไปทั่ว!
ชื่อนี้มีความหมายแฝงอะไร? ➡️ Kek: มาจากเทพกบในตำนานอียิปต์ และเป็นมีมยอดฮิตในโลกออนไลน์ (โดยเฉพาะกลุ่มคริปโต/เกม) มักใช้สื่อถึงความขำขัน เสียดสี ➡️ Maximus: คาดว่ามาจากตัวละครฮีโร่ผู้กล้าหาญในภาพยนตร์ Gladiator ➡️ รูปโปรไฟล์: ใช้ภาพ Pepe the Frog (มีมดัง) ในชุดนักรบโรมัน ถือจอยสติ๊ก!
เจตนาที่เป็นไปได้? ✅ ความสนุกและเล่นกับมีม: มัสก์ชอบใช้มีมสร้างกระแสอยู่แล้ว นี่อาจเป็นอีกครั้งที่เขาหยอกล้อกับวัฒนธรรมอินเทอร์เน็ต ✅ ทดสอบอิทธิพล: การเปลี่ยนชื่อส่งผลให้เหรียญมีม KEKIUS พุ่งขึ้นมหาศาล เป็นการยืนยันพลังโซเชียลของเขา ✅ เชื่อมโยงกับเกม: มัสก์เคยใช้ชื่อ Kekius Maximus ในเกม Path of Exile มาก่อน
แม้จะเปลี่ยนชื่อกลับไปแล้ว แต่เรื่องนี้ก็แสดงให้เห็นมุมที่เป็นกันเอง ความชอบส่วนตัว และอิทธิพลอันทรงพลังของอีลอน มัสก์ ได้เป็นอย่างดี!
ElonMusk #KekiusMaximus #X #โซเชียลมีเดีย #มีม #คริปโต #Gladiator #PepeTheFrog
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ a31f394c:7ad8f439
2025-05-19 02:21:26
@ a31f394c:7ad8f439
2025-05-19 02:21:26Nos últimos anos, o entretenimento digital tem ganhado cada vez mais espaço na vida dos brasileiros. Nesse cenário, a 88BRL se destaca como uma das plataformas mais completas e confiáveis do mercado. Com um ambiente seguro, interface moderna e uma variedade impressionante de jogos, o site oferece uma experiência única para quem busca diversão, emoção e a possibilidade de transformar o lazer em grandes recompensas.
Uma Plataforma Segura e Intuitiva Desde o primeiro acesso, fica evidente que a 88brlfoi desenvolvida com foco no usuário. A navegação é simples e fluida, mesmo para quem não tem muita familiaridade com plataformas de jogos online. O site é responsivo, ou seja, funciona perfeitamente tanto em computadores quanto em dispositivos móveis, garantindo liberdade para jogar onde e quando quiser.
Outro ponto importante é a segurança. A plataforma utiliza tecnologia de criptografia avançada para proteger os dados dos usuários e garantir transações rápidas e seguras. Além disso, o suporte ao cliente está disponível todos os dias, pronto para resolver qualquer dúvida ou problema com eficiência e cordialidade.
Catálogo de Jogos Diversificado A grande estrela da 88BRL é, sem dúvida, sua coleção de jogos. A plataforma oferece opções para todos os gostos e níveis de experiência, com títulos desenvolvidos por estúdios renomados do setor. Entre os destaques, estão os populares jogos de slots, roletas virtuais e mesas de cartas, todos com gráficos realistas, trilha sonora envolvente e mecânicas intuitivas.
Para quem gosta de desafios estratégicos, a plataforma também conta com uma seção de jogos de habilidade, onde a atenção, raciocínio rápido e conhecimento podem fazer toda a diferença. O sistema é justo e transparente, oferecendo chances reais de vitória a todos os jogadores.
Experiência Personalizada para o Jogador Brasileiro Um dos grandes diferenciais da 88BRL é o cuidado com o público nacional. O site está totalmente traduzido para o português, e o atendimento ao cliente é feito por profissionais brasileiros, garantindo uma comunicação clara e eficaz. Além disso, a plataforma aceita os principais métodos de pagamento utilizados no Brasil, incluindo transferências bancárias, carteiras digitais e até mesmo PIX, o que torna os depósitos e saques rápidos e descomplicados.
A experiência do jogador vai além dos jogos em si. A 88BRL oferece promoções frequentes, bônus de boas-vindas atrativos e um programa de fidelidade que recompensa os usuários mais ativos com benefícios exclusivos, como rodadas grátis, brindes e acesso antecipado a novos jogos.
Comunidade e Diversão Sem Limites A plataforma também incentiva a construção de uma comunidade entre seus usuários, com torneios e eventos especiais que promovem a interação e a competitividade saudável. Esses eventos são uma ótima oportunidade para testar habilidades, conhecer outros jogadores e se divertir ainda mais.
Com atualizações constantes e novos títulos sendo adicionados regularmente, a 88BRL mostra que está sempre atenta às tendências do mercado e ao feedback dos usuários. Isso garante uma experiência dinâmica e sempre renovada.
-
 @ c9badfea:610f861a
2025-05-15 23:11:22
@ c9badfea:610f861a
2025-05-15 23:11:22- Install MuPDF Mini (it's free and open source)
- Launch the app and open a document or book
- Tap the left or right edges to scroll through pages
- Enjoy distraction-free reading
ℹ️ You can open
.pdf,.xps,.cbz,.epub, andfb2documents -
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 9223d2fa:b57e3de7
2025-05-19 15:01:19
@ 9223d2fa:b57e3de7
2025-05-19 15:01:196,323 steps
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ a31f394c:7ad8f439
2025-05-19 02:20:52
@ a31f394c:7ad8f439
2025-05-19 02:20:52A 66BR chega ao cenário nacional como uma plataforma de entretenimento digital que promete transformar a forma como os brasileiros vivenciam os jogos online. Com uma interface moderna, navegação intuitiva e uma vasta variedade de jogos, o site oferece tudo o que os amantes da adrenalina e da sorte procuram — tudo isso com total segurança e praticidade.
Plataforma Moderna e Acessível Desde o primeiro acesso, é possível notar o cuidado com a experiência do usuário. A 66BR possui um layout responsivo, funcionando perfeitamente tanto em computadores quanto em dispositivos móveis. Isso significa que você pode jogar de onde quiser, seja no conforto de casa ou em movimento. A navegação é simples, rápida e organizada, o que facilita até mesmo para quem está começando agora nesse universo.
Além disso, a 66brprioriza a segurança dos seus usuários. A plataforma utiliza tecnologia de criptografia avançada para garantir que todas as informações pessoais e financeiras estejam protegidas. Os métodos de pagamento são variados e incluem opções populares no Brasil, como Pix, boleto bancário e carteiras digitais.
Variedade de Jogos para Todos os Gostos Um dos grandes atrativos da 66BR é a diversidade de jogos disponíveis. A plataforma trabalha com os principais desenvolvedores do mercado, garantindo gráficos de alta qualidade, jogabilidade fluida e títulos sempre atualizados.
Entre as opções oferecidas, destacam-se:
Slots virtuais: com temas que vão desde mitologia até filmes e séries, essas máquinas digitais combinam sorte e emoção em rodadas rápidas e empolgantes.
Jogos de mesa: para quem gosta de jogos estratégicos e clássicos como o pôquer, o blackjack e a roleta.
Jogos ao vivo: com transmissões em tempo real, esses jogos proporcionam uma experiência imersiva, como se o jogador estivesse em um ambiente físico, interagindo com anfitriões reais.
Todos os jogos são otimizados para rodar sem travamentos e contam com versões de demonstração para quem deseja testar antes de apostar com dinheiro real.
Experiência do Jogador: Simples, Justa e Divertida A experiência do usuário na 66BR vai além da qualidade dos jogos. O suporte ao cliente é outro ponto forte da plataforma, com atendimento disponível 24 horas por dia, em português, e com respostas rápidas e eficientes. Isso demonstra o compromisso da empresa em garantir a satisfação e tranquilidade de seus usuários.
Outro diferencial importante são as promoções e bônus frequentes. Novos usuários são recebidos com bônus de boas-vindas atrativos, enquanto os jogadores mais frequentes podem participar de campanhas exclusivas, com prêmios especiais e recompensas personalizadas.
A plataforma também conta com um sistema de fidelidade, onde os jogadores acumulam pontos à medida que participam dos jogos. Esses pontos podem ser trocados por bônus, giros grátis e outras vantagens dentro do site.
Conclusão A 66BR chega com força total para conquistar os brasileiros que buscam uma plataforma segura, moderna e recheada de entretenimento. Com um catálogo robusto de jogos, atendimento eficiente e benefícios para todos os perfis de jogadores, a 66BR se consolida como uma das melhores opções do país. Se você está procurando uma nova forma de se divertir e explorar o mundo dos jogos online com qualidade e confiança, a 66BR é o destino certo.
-
 @ 91bea5cd:1df4451c
2025-05-16 11:07:16
@ 91bea5cd:1df4451c
2025-05-16 11:07:16Instruções:
- Leia cada pergunta cuidadosamente.
- Escolha a opção (A, B, C ou D) que melhor descreve você na maioria das situações. Seja o mais honesto possível.
- Anote a letra correspondente à sua escolha para cada pergunta.
- No final, some quantas vezes você escolheu cada letra (A, B, C, D).
- Veja a seção de resultados para interpretar sua pontuação.
Teste de Temperamento
1. Em um evento social (festa, reunião), como você geralmente se comporta? A) Sou o centro das atenções, converso com todos, faço piadas e animo o ambiente. B) Tomo a iniciativa, organizo atividades ou discussões, e gosto de liderar conversas. C) Prefiro observar, conversar em grupos menores ou com pessoas que já conheço bem, e analiso o ambiente. D) Sou tranquilo, ouvinte, evito chamar atenção e me adapto ao ritmo do grupo.
2. Ao enfrentar um novo projeto ou tarefa desafiadora no trabalho ou estudo: A) Fico entusiasmado com a novidade, tenho muitas ideias iniciais, mas posso me distrair facilmente. B) Defino metas claras, crio um plano de ação rápido e foco em alcançar resultados eficientemente. C) Analiso todos os detalhes, planejo meticulosamente, prevejo possíveis problemas e busco a perfeição. D) Abordo com calma, trabalho de forma constante e organizada, e prefiro um ambiente sem pressão.
3. Como você geralmente reage a críticas? A) Tento levar na esportiva, talvez faça uma piada, mas posso me magoar momentaneamente e logo esqueço. B) Defendo meu ponto de vista vigorosamente, posso ficar irritado se sentir injustiça, mas foco em corrigir o problema. C) Levo muito a sério, analiso profundamente, posso me sentir magoado por um tempo e repenso minhas ações. D) Escuto com calma, considero a crítica objetivamente e tento não levar para o lado pessoal, buscando a paz.
4. Qual seu estilo de tomada de decisão? A) Sou impulsivo, decido rapidamente com base no entusiasmo do momento, às vezes me arrependo depois. B) Sou decidido e rápido, foco no objetivo final, às vezes sem considerar todos os detalhes ou sentimentos alheios. C) Sou ponderado, analiso todas as opções e consequências, demoro para decidir buscando a melhor escolha. D) Sou cauteloso, prefiro evitar decisões difíceis, busco consenso ou adio se possível.
5. Como você lida com rotina e repetição? A) Acho entediante rapidamente, preciso de variedade e novidade constante para me manter engajado. B) Tolero se for necessário para atingir um objetivo, mas prefiro desafios e mudanças que eu controlo. C) Aprecio a ordem e a previsibilidade, me sinto confortável com rotinas bem estabelecidas. D) Adapto-me bem à rotina, acho confortável e seguro, não gosto de mudanças bruscas.
6. Em uma discussão ou conflito: A) Tento aliviar a tensão com humor, expresso meus sentimentos abertamente, mas não guardo rancor. B) Sou direto e assertivo, defendo minha posição com firmeza, posso parecer confrontador. C) Evito confronto direto, mas fico remoendo o problema, analiso os argumentos e posso guardar ressentimento. D) Busco a conciliação, tento entender todos os lados, sou diplomático e evito o conflito a todo custo.
7. Como você expressa seus sentimentos (alegria, tristeza, raiva)? A) Expresso de forma aberta, intensa e visível, minhas emoções mudam rapidamente. B) Expresso de forma direta e forte, principalmente a raiva ou a determinação, controlo emoções "fracas". C) Tendo a internalizar, minhas emoções são profundas e duradouras, posso parecer reservado. D) Sou contido na expressão emocional, mantenho a calma externamente, mesmo que sinta algo internamente.
8. Qual seu nível de energia habitual? A) Alto, sou muito ativo, falante e entusiasmado, gosto de estar em movimento. B) Muito alto e direcionado, tenho muita energia para perseguir meus objetivos e liderar. C) Variável, posso ter picos de energia para projetos que me interessam, mas também preciso de tempo quieto para recarregar. D) Moderado e constante, sou calmo, tranquilo, prefiro atividades menos agitadas.
9. Como você organiza seu espaço de trabalho ou sua casa? A) Pode ser um pouco caótico e desorganizado, com muitas coisas interessantes espalhadas. B) Organizado de forma funcional para máxima eficiência, focado no essencial para as tarefas. C) Extremamente organizado, metódico, cada coisa em seu lugar, prezo pela ordem e estética. D) Confortável e prático, não necessariamente impecável, mas funcional e sem excessos.
10. O que mais te motiva? A) Reconhecimento social, diversão, novas experiências e interações. B) Poder, controle, desafios, alcançar metas ambiciosas e resultados concretos. C) Qualidade, significado, fazer as coisas da maneira certa, compreensão profunda. D) Paz, estabilidade, harmonia nos relacionamentos, evitar estresse e pressão.
11. Como você reage a imprevistos ou mudanças de plano? A) Adapto-me rapidamente, às vezes até gosto da novidade, embora possa atrapalhar meus planos iniciais. B) Fico irritado com a perda de controle, mas rapidamente busco uma solução alternativa para manter o objetivo. C) Sinto-me desconfortável e ansioso, preciso de tempo para reavaliar e replanejar cuidadosamente. D) Aceito com calma, sou flexível e me ajusto sem muito alarde, desde que não gere conflito.
12. Qual o seu maior medo (em termos gerais)? A) Ser rejeitado, ignorado ou ficar entediado. B) Perder o controle, parecer fraco ou incompetente. C) Cometer erros graves, ser inadequado ou imperfeito. D) Conflitos, pressão, tomar decisões erradas que afetem a estabilidade.
13. Como você costuma passar seu tempo livre? A) Socializando, saindo com amigos, buscando atividades novas e divertidas. B) Engajado em atividades produtivas, esportes competitivos, planejando próximos passos. C) Lendo, estudando, refletindo, dedicando-me a hobbies que exigem atenção e cuidado. D) Relaxando em casa, assistindo filmes, lendo tranquilamente, passando tempo com a família de forma calma.
14. Ao trabalhar em equipe: A) Sou o animador, trago ideias, conecto as pessoas, mas posso ter dificuldade em focar nos detalhes. B) Assumo a liderança naturalmente, delego tarefas, foco nos resultados e mantenho todos na linha. C) Sou o planejador e o crítico construtivo, atento aos detalhes, garanto a qualidade, mas posso ser muito exigente. D) Sou o pacificador e o colaborador, ajudo a manter a harmonia, realizo minhas tarefas de forma confiável.
15. Como você lida com prazos? A) Muitas vezes deixo para a última hora, trabalho melhor sob a pressão do prazo final, mas posso me atrapalhar. B) Gosto de terminar bem antes do prazo, vejo o prazo como um desafio a ser superado rapidamente. C) Planejo o tempo cuidadosamente para cumprir o prazo com qualidade, fico ansioso se o tempo fica curto. D) Trabalho em ritmo constante para cumprir o prazo sem estresse, não gosto de correria.
16. Qual destas frases mais te descreve? A) "A vida é uma festa!" B) "Se quer algo bem feito, faça você mesmo (ou mande fazer do seu jeito)." C) "Tudo tem um propósito e um lugar certo." D) "Devagar se vai ao longe."
17. Em relação a regras e procedimentos: A) Gosto de flexibilidade, às vezes acho as regras limitantes e tento contorná-las. B) Uso as regras a meu favor para atingir objetivos, mas não hesito em quebrá-las se necessário e se eu puder controlar as consequências. C) Sigo as regras rigorosamente, acredito que elas garantem ordem e qualidade. D) Respeito as regras para evitar problemas, prefiro seguir o fluxo estabelecido.
18. Como você reage quando alguém está emocionalmente abalado? A) Tento animar a pessoa, conto piadas, ofereço distração e companhia. B) Ofereço soluções práticas para o problema, foco em resolver a situação que causou o abalo. C) Escuto com empatia, ofereço apoio profundo e tento compreender a dor da pessoa. D) Mantenho a calma, ofereço um ouvido atento e um ombro amigo, sem me deixar abalar muito.
19. Que tipo de filme ou livro você prefere? A) Comédias, aventuras, romances leves, algo que me divirta e me mantenha entretido. B) Ação, suspense, biografias de líderes, estratégias, algo que me desafie ou inspire poder. C) Dramas profundos, documentários, mistérios complexos, ficção científica filosófica, algo que me faça pensar e sentir. D) Histórias tranquilas, dramas familiares, romances amenos, natureza, algo que me relaxe e traga conforto.
20. O que é mais importante para você em um relacionamento (amizade, amoroso)? A) Diversão, cumplicidade, comunicação aberta e espontaneidade. B) Lealdade, objetivos em comum, apoio mútuo nas ambições. C) Compreensão profunda, fidelidade, apoio emocional e intelectual. D) Harmonia, estabilidade, aceitação mútua e tranquilidade.
21. Se você ganhasse na loteria, qual seria sua primeira reação/ação? A) Faria uma grande festa, viajaria pelo mundo, compraria presentes para todos! B) Investiria estrategicamente, planejaria como multiplicar o dinheiro, garantiria o controle financeiro. C) Pesquisaria as melhores opções de investimento, faria um plano detalhado de longo prazo, doaria para causas significativas. D) Guardaria a maior parte em segurança, faria algumas melhorias práticas na vida, evitaria mudanças drásticas.
22. Como você se sente em relação a riscos? A) Gosto de arriscar se a recompensa parecer divertida ou excitante, sou otimista. B) Calculo os riscos e assumo-os se acreditar que a recompensa vale a pena e que posso controlar a situação. C) Evito riscos desnecessários, prefiro a segurança e a previsibilidade, analiso tudo antes de agir. D) Desgosto de riscos, prefiro caminhos seguros e comprovados, a estabilidade é mais importante.
23. Sua memória tende a focar mais em: A) Momentos divertidos, pessoas interessantes, experiências marcantes (embora possa esquecer detalhes). B) Sucessos, fracassos (para aprender), injustiças cometidas contra você, quem te ajudou ou atrapalhou. C) Detalhes precisos, conversas significativas, erros cometidos (por você ou outros), sentimentos profundos. D) Fatos objetivos, rotinas, informações práticas, geralmente de forma neutra.
24. Quando aprende algo novo, você prefere: A) Experimentar na prática imediatamente, aprender fazendo, mesmo que cometa erros. B) Entender o objetivo e a aplicação prática rapidamente, focar no essencial para usar o conhecimento. C) Estudar a fundo a teoria, entender todos os porquês, buscar fontes confiáveis e dominar o assunto. D) Aprender em um ritmo calmo, com instruções claras e passo a passo, sem pressão.
25. Se descreva em uma palavra (escolha a que mais se aproxima): A) Entusiasmado(a) B) Determinado(a) C) Criterioso(a) D) Pacífico(a)
26. Como você lida com o silêncio em uma conversa? A) Sinto-me desconfortável e tento preenchê-lo rapidamente com qualquer assunto. B) Uso o silêncio estrategicamente ou o interrompo para direcionar a conversa. C) Posso apreciar o silêncio para refletir, ou me sentir um pouco ansioso dependendo do contexto. D) Sinto-me confortável com o silêncio, não sinto necessidade de preenchê-lo.
27. O que te deixa mais frustrado(a)? A) Tédio, falta de reconhecimento, ser ignorado. B) Incompetência alheia, falta de controle, obstáculos aos seus planos. C) Desorganização, falta de qualidade, injustiça, superficialidade. D) Conflitos interpessoais, pressão excessiva, desordem emocional.
28. Qual a sua relação com o passado, presente e futuro? A) Foco no presente e nas oportunidades imediatas, otimista em relação ao futuro, esqueço o passado facilmente. B) Foco no futuro (metas) e no presente (ações para alcançá-las), aprendo com o passado mas não me prendo a ele. C) Reflito muito sobre o passado (aprendizados, erros), analiso o presente e planejo o futuro com cautela, às vezes com preocupação. D) Vivo o presente de forma tranquila, valorizo a estabilidade e a continuidade do passado, vejo o futuro com serenidade.
29. Se você tivesse que organizar um evento, qual seria seu papel principal? A) Relações públicas, divulgação, animação, garantir que todos se divirtam. B) Coordenação geral, definição de metas, delegação de tarefas, garantir que tudo aconteça conforme o planejado (por você). C) Planejamento detalhado, logística, controle de qualidade, garantir que nada dê errado. D) Suporte, resolução de problemas de forma calma, garantir um ambiente harmonioso.
30. Qual ambiente de trabalho te agrada mais? A) Dinâmico, social, com muita interação, flexibilidade e novidades. B) Competitivo, desafiador, focado em resultados, onde eu possa liderar ou ter autonomia. C) Estruturado, quieto, onde eu possa me concentrar, com padrões claros de qualidade e tempo para análise. D) Estável, cooperativo, sem pressão, com relacionamentos harmoniosos e tarefas previsíveis.
Calculando seus Resultados:
Agora, conte quantas vezes você escolheu cada letra:
- Total de A: ______
- Total de B: ______
- Total de C: ______
- Total de D: ______
A letra (ou as letras) com a maior pontuação indica(m) seu(s) temperamento(s) dominante(s).
Interpretação dos Resultados:
-
Se sua maior pontuação foi A: Temperamento SANGUÍNEO Dominante
- Características: Você é extrovertido, otimista, sociável, comunicativo, entusiasmado e adora novidades. Gosta de ser o centro das atenções, faz amigos facilmente e contagia os outros com sua energia. É criativo e espontâneo.
- Pontos Fortes: Carismático, inspirador, adaptável, bom em iniciar relacionamentos e projetos, perdoa facilmente.
- Desafios Potenciais: Pode ser indisciplinado, desorganizado, impulsivo, superficial, ter dificuldade em focar e terminar tarefas, e ser muito dependente de aprovação externa.
-
Se sua maior pontuação foi B: Temperamento COLÉRICO Dominante
- Características: Você é enérgico, decidido, líder nato, orientado para metas e resultados. É ambicioso, assertivo, direto e não tem medo de desafios ou confrontos. Gosta de estar no controle e é muito prático.
- Pontos Fortes: Determinado, eficiente, líder natural, bom em tomar decisões e resolver problemas, autoconfiante.
- Desafios Potenciais: Pode ser impaciente, dominador, teimoso, insensível aos sentimentos alheios, propenso à raiva e a "atropelar" os outros para atingir seus objetivos.
-
Se sua maior pontuação foi C: Temperamento MELANCÓLICO Dominante
- Características: Você é introvertido, analítico, sensível, perfeccionista e profundo. É leal, dedicado, aprecia a beleza e a ordem. Tende a ser pensativo, criterioso e busca significado em tudo. Leva as coisas a sério.
- Pontos Fortes: Detalhista, organizado, criativo (em profundidade), leal, empático, comprometido com a qualidade e a justiça.
- Desafios Potenciais: Pode ser pessimista, excessivamente crítico (consigo e com os outros), indeciso (pela análise excessiva), guardar ressentimentos, ser propenso à tristeza e ao isolamento.
-
Se sua maior pontuação foi D: Temperamento FLEUMÁTICO Dominante
- Características: Você é calmo, tranquilo, equilibrado e diplomático. É observador, paciente, confiável e fácil de conviver. Evita conflitos, busca harmonia e estabilidade. É um bom ouvinte e trabalha bem sob rotina.
- Pontos Fortes: Pacífico, estável, confiável, bom ouvinte, diplomático, eficiente em tarefas rotineiras, mantém a calma sob pressão.
- Desafios Potenciais: Pode ser indeciso, procrastinador, resistente a mudanças, parecer apático ou sem entusiasmo, ter dificuldade em se impor e expressar suas próprias necessidades.
Combinações de Temperamentos:
É muito comum ter pontuações altas em duas letras. Isso indica uma combinação de temperamentos. Por exemplo:
- Sanguíneo-Colérico: Extrovertido, enérgico, líder carismático, mas pode ser impulsivo e dominador.
- Sanguíneo-Fleumático: Sociável e agradável, mas pode ter dificuldade com disciplina e iniciativa.
- Colérico-Melancólico: Líder focado e detalhista, muito capaz, mas pode ser excessivamente crítico e exigente.
- Melancólico-Fleumático: Quieto, confiável, analítico, mas pode ser indeciso e resistente a riscos.
Importante: Este teste é uma ferramenta de autoconhecimento. Ninguém se encaixa perfeitamente em uma única caixa. Use os resultados para entender melhor suas tendências naturais, seus pontos fortes e as áreas onde você pode buscar equilíbrio e desenvolvimento.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c9badfea:610f861a
2025-05-14 18:38:04
@ c9badfea:610f861a
2025-05-14 18:38:04- Install KeePassDX (it's free and open source)
- Launch the app, tap Create New Vault, and choose a location to store the database file
- Activate the Password slider
- Type a Password and Confirm Password, then tap OK
- Tap + and Add Entry to add your first credentials
- Enter a Title, Username, and Password (you can also generate a password here)
- Tap ✓ at the bottom to create the entry
- Tap ⋮ and then Save Data to save the database
- Tap 🔒 to lock the database
⚠️ Make sure you use strong, high-entropy passphrases
⚠️ Back up the database file to a secure location (e.g. encrypted USB drive)
ℹ️ The database file (
.kdbx) can also be opened with various KeePass ports -
 @ c9badfea:610f861a
2025-05-05 20:16:29
@ c9badfea:610f861a
2025-05-05 20:16:29- Install PocketPal (it's free and open source)
- Launch the app, open the menu, and navigate to Models
- Download one or more models (e.g. Phi, Llama, Qwen)
- Once downloaded, tap Load to start chatting
ℹ️ Experiment with different models and their quantizations (Q4, Q6, Q8, etc.) to find the most suitable one
-
 @ 83279ad2:bd49240d
2025-05-14 03:58:40
@ 83279ad2:bd49240d
2025-05-14 03:58:40test nostr:nevent1qvzqqqqqqypzpqe8ntfgamz8sh3p88w99x5k2r7mksjrvm2xghju9qj00j75jfqdqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpzemhxue69uhhyetvv9ujumn0wvh8xmmrd9skcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qy28wumn8ghj7mn0wd68ytn00p68ytnyv4mqzrmhwden5te0dehhxarj9ekk7mgpp4mhxue69uhkummn9ekx7mqqyqknwtnxd4422ya9nh0qrcwfy6q3hhruyqaukvh2fpcu94es3tvu20tf7nt nostr:nevent1qvzqqqqqqypzpqe8ntfgamz8sh3p88w99x5k2r7mksjrvm2xghju9qj00j75jfqdqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcpr3mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmqpzemhxue69uhhyetvv9ujumn0wvh8xmmrd9skcqg5waehxw309aex2mrp0yhxgctdw4eju6t0qy28wumn8ghj7mn0wd68ytn00p68ytnyv4mqzrmhwden5te0dehhxarj9ekk7mgpp4mhxue69uhkummn9ekx7mqqyqknwtnxd4422ya9nh0qrcwfy6q3hhruyqaukvh2fpcu94es3tvu20tf7nt
-
 @ f85b9c2c:d190bcff
2025-05-18 23:33:20
@ f85b9c2c:d190bcff
2025-05-18 23:33:20
Am I the only one who tires of this pen’s endless fight, Scribbling words that dance in the dimmest light? The ink flows free, but my mind’s in a plight, I still don’t get it, this craft’s strange height. My thoughts once soared, a creative kite, Now they stumble, lost in the night. The page stares back, so blank, so white, I still don’t get it, where’s my insight? I chase the muse with all my might, But she’s a ghost, just out of sight. My fingers cramp, my soul takes flight, I still don’t get it, this endless write. The stories beg to be shaped just right, Yet boredom creeps, a thief in flight. I dream of tales that spark delight, I still don’t get it, this weary blight. Friends say, “Your words, they shine so bright,” But I feel trapped in this daily rite. The passion fades, no end in sight, I still don’t get it, this draining fight. A poem, a prose, I try to ignite, Each line a chore, a forced invite. The joy’s gone cold, no warmth in sight, I still don’t get it, this fading light. Am I alone, or do others unite, In feeling this pull, this tired dislike? The keyboard clacks, the thoughts take flight, I still don’t get it, this writer’s spite. Perhaps it’s me, my heart’s too tight, Or maybe writing’s a cruel delight. I’ll push on through, with grit and bite, I still don’t get it, but I’ll rewrite. So here I sit, in day or night, Pouring my soul, though it feels trite. Am I the only one? I seek the sight, I still don’t get it—yet still, I write.
-
 @ ecda4328:1278f072
2025-05-19 14:41:48
@ ecda4328:1278f072
2025-05-19 14:41:48An honest response to objections — and an answer to the most important question: why does any of this matter?
\ Statement: Deflation is not the enemy, but a natural state in an age of technological progress.\ Criticism: in real macroeconomics, long-term deflation is linked to depressions.\ Deflation discourages borrowers and investors, and makes debt heavier.\ Natural ≠ Safe.
1. “Deflation → Depression, Debt → Heavier”
This is true in a debt-based system. Yes, in a fiat economy, debt balloons to the sky, and without inflation it collapses.
But Bitcoin offers not “deflation for its own sake,” but an environment where you don’t need to be in debt to survive. Where savings don’t melt away.\ Jeff Booth said it clearly:
“Technology is inherently deflationary. Fighting deflation with the printing press is fighting progress.”
You don’t have to take on credit to live in this system. Which means — deflation is not an enemy, but an ally.
💡 People often confuse two concepts:
-
That deflation doesn’t work in an economy built on credit and leverage — that’s true.
-
That deflation itself is bad — that’s a myth.
📉 In reality, deflation is the natural state of a free market when technology makes everything cheaper.
Historical example:\ In the U.S., from the Civil War to the early 1900s, the economy experienced gentle deflation — alongside economic growth, employment expansion, and industrial boom.\ Prices fell: for example, a sack of flour cost \~$1.00 in 1865 and \~$0.50 in 1895 — and there was no crisis, because wages held and productivity increased.
Modern example:\ Consumer electronics over the past 20–30 years are a vivid example of technological deflation:\ – What cost $5,000 in 2000 (e.g., a 720p plasma TV) now costs $300 and delivers 10× better quality.\ – Phones, computers, cameras — all became far more powerful and cheaper at the same time.\ That’s how tech-driven deflation works: you get more for less.
📌 Bitcoin doesn’t make the world deflationary. It just doesn’t fight against deflation, unlike the fiat model that fights to preserve its debt pyramid.\ It stops punishing savers and rewards long-term thinkers.
Even economists often confuse organic tech deflation with crisis-driven (debt) deflation.
\ \ Statement: We’ve never lived in a truly free market — central banks and issuance always existed.\ Criticism: ideological statement.\ A truly “free” market is utopian.\ Banks and monetary issuance emerged in response to crises.\ A market without arbiters is not always fair, especially under imperfect competition.
2. “The Free Market Is a Utopia”
Yes, “pure markets” are rare. But what we have today isn’t regulation — it’s centralized power in the hands of central banks and cartels.
Bitcoin offers rules without rulers. 21 million. No one can change the issuance. It’s not ideology — it’s code instead of trust. And it has worked for 15 years.
\ \ Statement: Inflation is an invisible tax, especially on the poor and working class.\ Criticism: partly true: inflation can reduce debt burden, boost employment.\ The state indexes social benefits. Under stable inflation, compensators can work. Under deflation, things might be worse (mass layoffs, defaults).
3. “Inflation Can Help”
Theoretically — yes. Textbooks say moderate inflation can reduce debt burdens and stimulate consumption and jobs.\ But in practice — it works as a stealth tax, especially on those without assets. The wealthy escape — into real estate, stocks, funds.\ But the poor and working class lose purchasing power because their money is held in cash — and cash devalues.
💬 As Lyn Alden says:
“When your money can’t hold value, you’re forced to become an investor — even if you just want to save and live.”
The state may index pensions or benefits — but always with a lag, and always less than actual price increases.\ If bread rises 15% and your payment increase is 5%, you got poorer, even if the number on paper went up.
💥 We live in an inflationary system of everything:\ – Inflationary money\ – Inflationary products\ – Inflationary content\ – And now even inflationary minds
🧠 This is more than just rising prices — it’s a degradation of reality perception. You’re always rushing, everything loses meaning.\ But when did the system start working against you?
📉 What went wrong after 1971?
 This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.
This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.👉 This means: you work more, better, faster — but buy less.
🔗 Source: wtfhappenedin1971.com
When you must spend today because tomorrow it’ll be worth less — that’s rewarding impulse and punishing long-term thinking.
Bitcoin offers a different environment:\ – Savings work\ – Long-term thinking is rewarded\ – The price of the future is calculated, not forced by a printing press
📌 Inflation can be a tool. But in government hands, it became a weapon — a slow, inevitable upward redistribution of wealth.
Indexing is weak compensation if bread is up 15% and your “increase” is only 5%.
\ \ Statement: War is not growth, but a reallocation of resources into destruction.
Criticism: war can spur technological leaps (Internet, GPS, nuclear energy — all from military programs). "Military Keynesianism" was a real model.
4. “War Drives R&D”
Yes, wars sometimes give rise to tech spin-offs: Internet, GPS, nuclear power — all originated from military programs.
But that doesn’t make war a source of progress — it makes tech a byproduct of catastrophe.
“War reallocates resources toward destruction — not growth.”
Progress doesn’t happen because of war — it happens despite it.
If scientific breakthroughs require a million dead and burnt cities — maybe you’ve built your economy wrong.
💬 Even Michael Saylor said:
“If you need war to develop technology — you’ve built civilization wrong.”
No innovation justifies diverting human labor, minds, and resources toward destruction.\ War is always the opposite of efficiency — more is wasted than created.
🧠 Bitcoin, on the other hand, is an example of how real R&D happens without violence.\ No taxes. No army. Just math, voluntary participation, and open-source code.
📌 Military Keynesianism is not a model of progress — it’s a symptom of a sick monetary system that needs destruction to reboot.
Bitcoin shows that coordination without violence is possible.\ This is R&D of a new kind: based not on destruction, but digital creation.
Statement: Bitcoin isn’t “Gold 1.0,” but an improved version: divisible, verifiable, unseizable.
Criticism: Bitcoin has no physical value; "unseizability" is a theory;\ Gold is material and autonomous.
5. “Bitcoin Has No Physical Value”
And gold does? Just because it shines?
Physical form is no guarantee of value.\ Real value lies in: scarcity, reliable transfer, verifiability, and non-confiscatability.
Gold is:\ – Hard to divide\ – Hard to verify\ – Expensive to store\ – Easy to seize
💡 Bitcoin is the first store of value in history that is fully free from physical limitations, and yet:\ – Absolutely scarce (21M, forever)\ – Instantly transferable over the Internet\ – Cryptographically verifiable\ – Controlled by no government
🔑 Bitcoin’s value lies in its liberation from the physical.\ It doesn’t need to be “backed” by gold or oil. It’s backed by energy, mathematics, and ongoing verification.
“Price is what you pay, value is what you get.” — Warren Buffett
When you buy bitcoin, you’re not paying for a “token” — you’re gaining access to a network of distributed financial energy.
⚡️ What are you really getting when you own bitcoin?\ – A key to a digital asset that can’t be faked\ – The ability to send “crystallized energy” anywhere on Earth\ – A role in a new accounting system that runs 24/7/365\ – Freedom: from banks, borders, inflation, and force
📉 Bitcoin doesn’t require physical value — because it creates value:\ Through trust, scarcity, and energy invested in mining.\ And unlike gold, it was never associated with slavery.
Statement: There’s no “income without risk” in Bitcoin: just hold — you preserve; want more — invest, risk, build.
Criticism: contradicts HODL logic; speculation remains dominant behavior.
6. “Speculation Dominates”
For now — yes. That’s normal for the early phase of a new technology. Awareness doesn’t come instantly.
What matters is not the motive of today’s buyer — but what they’re buying.
📉 A speculator may come and go — but the asset remains.\ And this asset is the only one in history that will never exist again. 21 million. Forever.
📌 Look deeper. Bitcoin has:\ – No CEO\ – No central issuer\ – No inflation\ – No “off switch”
💡 It’s not a stock. Not a startup. Not someone’s project.\ It’s a new foundation for trust.\ It’s opting out of a system where freedom is a privilege you’re granted under conditions.
🧠 People say: “Bitcoin can be copied.”\ Theoretically — yes.\ Practically — never.
Here’s what you’d need to recreate Bitcoin:\ – No pre-mine\ – A founder who disappears and never sells\ – No foundation or corporation\ – Tens of thousands of nodes worldwide\ – 701 million terahashes of hash power\ – Thousands of devs writing open protocols\ – Hundreds of global conferences\ – Millions of people defending digital sovereignty\ – All that without a single marketing budget
That’s all.
🔁 Everything else is an imitation, not a creation.\ Just like you can’t “reinvent fire” — Bitcoin can only exist once.
Statements:\ The Russia's '90s weren’t a free market — just anarchic chaos without rights protection.*\ Unlike fiat or even dollars, Bitcoin is the first asset with real defense — from governments, inflation, even thugs.\ And yes, even if your barber asks about Bitcoin — maybe it's not a bubble, but a sign that inflation has already hit everyone.
Criticism: Bitcoin’s protection isn’t universal — it works only with proper handling and isn’t available to all.\ Some just want to “get rich.”\ None of this matters because:
-
Bitcoin’s volatility (-30% in a week, +50% in a month) makes it unusable for price planning or contracts.
-
It can’t handle mass-scale usage.
-
To become currency, geopolitical will is needed — and without the first two, don’t even talk about the third.\ Also: “Bitcoin is too complicated for the average person.”
7. “It’s Too Complex for the Masses”
It’s complex — if you’re using L1 (Layer 1). But even grandmas use Telegram. In El Salvador, schoolkids buy lunch with Lightning. My barber installed Wallet of Satoshi in minutes right in front of me — and I now pay for my haircut via Lightning.
UX is just a matter of time. And it’s improving. Emerging tools:\ Cashu, Fedimint, Fedi, Wallet of Satoshi, Phoenix, Proton Wallet, Swiss Bitcoin Pay, Bolt Card / CoinCorner (NFC cards for Lightning payments).
This is like the internet in 1995:\ It started with modems — now it’s 4K streaming.
8. “Can’t Handle the Load”
A common myth.\ Yes, Bitcoin L1 processes about 7 transactions per second — intentionally. It’s not built to be Visa. It’s a financial protocol, just like TCP/IP is a network protocol. TCP/IP isn’t “fast” or “slow” — the experience depends on the infrastructure built on top: servers, routers, hardware. In the ’90s, it delivered text. Today, it streams Netflix. The protocol didn’t change — the stack did.
Same with Bitcoin: L1 defines rules, security, finality.\ Scaling and speed? That’s the second layer’s job.
To understand scale:
| Network | TPS (Transactions/sec) | | --- | --- | | Visa | up to 24,000 | | Mastercard | \~5,000 | | PayPal | \~193 | | Litecoin | \~56 | | Ethereum | \~20 | | Bitcoin | \~7 |
\ ⚡️ Enter Lightning Network — Bitcoin’s “fast lane.”\ It allows millions of transactions per second, instantly and nearly free.
And it’s not a sidechain.
❗️ Lightning is not a separate network.\ It uses real Bitcoin transactions (2-of-2 multisig). You can close the channel to L1 at any time. It’s not an alternative — it’s a native extension built into Bitcoin.\ Also evolving: Ark, Fedimint, eCash — new ways to scale and add privacy.
📉 So criticizing Bitcoin for “slowness” is like blaming TCP/IP because your old modem won’t stream YouTube.\ The protocol isn’t the problem — it’s the infrastructure.
🛡️ And by the way: Visa crashes more often than Bitcoin.
9. “We Need Geopolitical Will”
Not necessarily. All it takes is the will of the people — and leaders willing to act. El Salvador didn’t wait for G20 approval or IMF blessings. Since 2001, the country had used the US dollar as its official currency, abandoning its own colón. But that didn’t save it from inflation or dependency on foreign monetary policy. In 2021, El Salvador became the first country to recognize Bitcoin as legal tender. Since March 13, 2024, they’ve been purchasing 1 BTC daily, tracked through their public address:
🔗 Address\ 📅 First transaction
This policy became the foundation of their Strategic Bitcoin Reserve (SBR) — a state-led effort to accumulate Bitcoin as a national reserve asset for long-term stability and sovereignty.
Their example inspired others.
In March 2025, U.S. President Donald Trump signed an executive order creating the Strategic Bitcoin Reserve of the USA, to be funded through confiscated Bitcoin and digital assets.\ The idea: accumulate, don’t sell, and strategically expand the reserve — without extra burden on taxpayers.
Additionally, Senator Cynthia Lummis (Wyoming) proposed the BITCOIN Act, targeting the purchase of 1 million BTC over five years (\~5% of the total supply).\ The plan: fund it via revaluation of gold certificates and other budget-neutral strategies.
📚 More: Strategic Bitcoin Reserve — Wikipedia
👉 So no global consensus is required. No IMF greenlight.\ All it takes is conviction — and an understanding that the future of finance lies in decentralized, scarce assets like Bitcoin.
10. “-30% in a week, +50% in a month = not money”
True — Bitcoin is volatile. But that’s normal for new technologies and emerging money. It’s not a bug — it’s a price discovery phase. The world is still learning what this asset is.
📉 Volatility is the price of entry.\ 📈 But the reward is buying the future at a discount.
As Michael Saylor put it:
“A tourist sees Niagara Falls as chaos — roaring, foaming, spraying water.\ An engineer sees immense energy.\ It all depends on your mental model.”
Same with Bitcoin. Speculators see chaos. Investors see structural scarcity. Builders see a new financial foundation.
💡 Now consider gold:
👉 After the U.S. abandoned the gold standard in 1971, gold surged from \~$35 to over $800 in a decade — while suffering wild -40% to -60% crashes along the way.\ \ 📈 Gold Price Chart — Macrotrends\ \ Nobody said, “This can’t be money.” \ Because money is defined not by volatility, but by scarcity, adoption, and trust — which build over time.
📊 The more people save in Bitcoin, the more its volatility fades.
This is a journey — not a fixed state.
We don’t judge the internet by how it worked in 1994.\ So why expect Bitcoin to be the “perfect currency” in 2025?
It grows bottom-up — without regulators’ permission.\ And the longer it survives, the stronger it becomes.
Remember how many times it’s been declared dead.\ And how many times it came back — stronger.
📊 Gold vs. Bitcoin: Supply Comparison
This chart shows the key difference between the two hard assets:
🔹 Gold — supply keeps growing.\ Mining may be limited, but it’s still inflationary.\ Each year, there’s more — with no known cap: new mines, asteroid mining, recycling.
🔸 Bitcoin — capped at 21 million.\ The emission schedule is public, mathematically predictable, and ends completely around 2140.
🧠 Bottom line:\ Gold is good.\ Bitcoin is better — for predictability and scarcity.
💡 As Saifedean Ammous said:
“Gold was the best monetary good… until Bitcoin.”
While we argue — fiat erodes every day.
No matter your view on Bitcoin, just show me one other asset that is simultaneously:
– immune to devaluation by decree\ – impossible to print more of\ – impossible to confiscate by a centralized order\ – impossible to counterfeit\ – and, most importantly — transferable across borders without asking permission from a bank, a state, or a passport
💸 Try sending $10,000 through PayPal from Iran to Paraguay, or Bangladesh to Saint Lucia.\ Good luck. PayPal doesn't even work there.
Now open a laptop, type 12 words — and you have access to your savings anywhere on Earth.
🌍 Bitcoin doesn't ask for permission.\ It works for everyone, everywhere, all the time.
📌 There has never been anything like this before.
Bitcoin is the first asset in history that combines:
– digital nature\ – predictable scarcity\ – absolute portability\ – and immunity from tyranny
💡 As Michael Saylor said:
“Bitcoin is the first money in human history not created by bankers or politicians — but by engineers.”
You can own it with no bank.\ No intermediary.\ No passport.\ No approval.
That’s why Bitcoin isn’t just “internet money” or “crypto” or “digital gold.”\ It may not be perfect — but it’s incorruptible.\ And it’s not going away.\ It’s already here.\ It is the foundation of a new financial reality.
🔒 This is not speculation. This is a peaceful financial revolution.\ 🪙 This is not a stock. It’s money — like the world has never seen.\ ⛓️ This is not a fad. It’s a freedom protocol.
And when even the barber starts asking about Bitcoin — it’s not a bubble.\ It’s a sign that the system is breaking.\ And people are looking for an exit.
For the first time — they have one.
💼 This is not about investing. It’s about the dignity of work.
Imagine a man who cleans toilets at an airport every day.
Not a “prestigious” job.\ But a crucial one.\ Without him — filth, bacteria, disease.
He shows up on time. He works with his hands.
And his money? It devalues. Every day.
He doesn’t work less — often he works more than those in suits.\ But he can afford less and less — because in this system, honest labor loses value each year.
Now imagine he’s paid in Bitcoin.
Not in some “volatile coin,” but in hard money — with a limited supply.\ Money that can’t be printed, reversed, or devalued by central banks.
💡 Then he could:
– Stop rushing to spend, knowing his labor won’t be worth less tomorrow\ – Save for a dream — without fear of inflation eating it away\ – Feel that his time and effort are respected — because they retain value
Bitcoin gives anyone — engineer or janitor — a way out of the game rigged against them.\ A chance to finally build a future where savings are real.
This is economic justice.\ This is digital dignity.
📉 In fiat, you have to spend — or your money melts.\ 📈 In Bitcoin, you choose when to spend — because it’s up to you.
🧠 In a deflationary economy, both saving and spending are healthy:
You don’t scramble to survive — you choose to create.
🎯 That’s true freedom.
When even someone cleaning floors can live without fear —\ and know that their time doesn’t vanish... it turns into value.
-
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 0c65eba8:4a08ef9a
2025-05-19 14:41:33
@ 0c65eba8:4a08ef9a
2025-05-19 14:41:33You’re not alone.
There are countless men, good men, who want love, want marriage, want a family… but feel blocked. Blocked by time. By money. By fear. By uncertainty.
You’ve tried. You’ve thought about it. Maybe you’ve even taken a few steps. But the whole thing feels frustrating. Like you’re pushing against a wall that won’t budge.
This article is for you.
Most dating problems come from one of two places.
The first is your environment. Some cities and cultures make finding a good woman harder than others. But don’t make the mistake of thinking all of the West is the same. Even in the most liberal cities, there are still good women. Even in the most conservative areas, there are women to avoid. If you can move, move where it’s easier. If you can’t, reshape your environment in other ways, your community, your routines, your social circles.
The second source of problems is internal. Your skills, your mindset, your emotional blocks, your lack of development. These are the parts of you that aren’t yet ready to attract or lead a woman.
Here’s the good news: You can change both.
Aside from extreme physical limitations, nearly everything holding you back can be improved. Often faster than you think. Some things will take a day. Others will take a year or two. But you don’t need to be perfect. You only need to become the kind of man a good woman would say yes to.
You’re not lazy. You’re not broken.
You just haven’t been shown how to deal with these barriers like a man who’s preparing to lead a family.
This isn’t a scolding. It’s a flashlight. I'm going to show you something valuable, for free.
Each problem below is something real men have told me. Each solution is the next step forward. One step at a time.
Let’s take that step, together.
PROBLEM: “I don’t have time to go on dates.”
SOLUTION: If you don’t have time to date, you don’t have time to be married.
A woman isn’t a hobby you slot in between deadlines. She’s your future family. Mother of your children.
And if your current schedule can’t make room for love, it won’t make room for life either.
This doesn’t mean you should never date. It means you need a plan.
Sometimes, the wisest path is to finish what’s already on your plate. School. Training. A startup. A season of intensity that still needs to end.
If you’re deep in one of those phases, finish it. But make sure it has an end date. Don't put off finishing.
Restructure your life so that within 12 to 24 months, you’re free enough to fall in love. Not distracted. Not drowning. Available, with time and energy to spare.
Create space now, or clear the path so it can be created soon.
You don’t have to do everything at once. But you do have to be intentional.
That’s part of being a mature man, taking control of your time and energy.
PROBLEM: “I can’t afford to take a woman out on a date.”
SOLUTION: Money has always been a sore spot for young men.
Most men in history started out with very little. In the past, families often stepped in to help launch a young couple. But even then, the early years were lean. That’s normal.
Even if you’re intelligent, hardworking, and on the right track, it can still take until your early 30s to reach true financial stability. That doesn’t mean you’re behind. It means you’re on your own journey.
But here’s the thing: If you can’t afford to take a woman on a date, you can’t afford a wife either.
Marriage is not cheaper than dating. Children are not cheaper than courtship. Responsibility isn’t free.
You don’t need to impress her with a fine dining at a steakhouse. But you do need to signal that your life is in motion and that you have a plan.
If you’re broke, your mission is money. And that means:
-
Take on a second job, either a side gig or job-stacking
-
Reduce your expenses until you gain traction
-
Build an income stream that reflects a man ready to provide
Look at it as a test of your creativity, intelligence, social skills and perseverance. And yes, it's going to be hard. I too was a broke young man once. It's not a fun place to be.
A man who won’t feed himself cannot feed a family. Handle that first.
PROBLEM: “I don’t know where to meet women.”
SOLUTION: This isn’t just a logistics issue. It’s a life design issue.
You meet high-quality women by becoming a high-quality man in motion, a man with an interesting life.
That means building a life that’s rich with activity, purpose, and human connection. A life that invites others in, because it’s already alive.
Start doing interesting things with interesting people. Join groups. Serve. Create. Build a reputation in your community. Train at a gym. Lead something. Show up where life is happening.
Here’s a simple metric: If you’re not organically meeting at least one woman per month who you might want to date, your life isn’t active or interesting enough.
Women aren’t looking for a perfect man. They’re looking for a man with a compelling direction, a mission worth joining. A future worth investing in.
Women don’t just marry you. They marry into your lifestyle.
If your life is empty, isolated, or stagnant, there’s nothing for her to attach to. No rhythm to join. No social proof. No spark. No return on her investment.
Now, if you’re introverted, this part will be harder. Not impossible. Just different.
You’ll need to choose environments where you can thrive:
-
Smaller groups with consistent attendance
-
Classes or workshops with a shared task
-
Quiet community activities like hiking, book clubs, or local volunteering
-
Faith groups or skill-building meetups that match your interests
Focus on building a rhythm and repetition (habit). Show up. Be seen. Let relationships build slowly.
Create the kind of life a woman would be proud to stand beside. Not because she completes it, but because she compliments it.
I wrote more on this here:
Where to Find a Good Woman: A Short Field Guide for Men Who Want to Build a Legacy**
PROBLEM: “I’m too short. Or fat. Or ugly. Or too intimidating.”
SOLUTION: Every man has something about his body he doesn’t like. Some things can be changed. Others can’t. But here’s the truth:
Women don’t marry just for looks. They marry for masculine presence.
You can be average-looking, or even rough-looking, and still be deeply attractive if you carry yourself like a man. Strong. Composed. Grounded.
Most physical ‘flaws’ can be compensated for by strength in other areas:
-
Fat face? Get lean and muscular, it changes your bone structure and confidence.
-
Don’t like your jawline? Grow a beard and learn to carry yourself with dignity.
-
Short? Then your mission is to walk like a king and build a life so compelling she forgets your height within five minutes.
Plenty of short, homely, or scarred men marry wonderful women. But only when they don’t let their appearance be a cage.
Fix what you can. Style your hair. Improve your grooming. Learn how to dress. Lift. Move. Stand tall. Speak with purpose. Develop gravatas and humor.
The rest? Let it refine your spirit. Not shame you, but sharpen you. Your face isn’t the problem you imagine it to be and your presence is the solution.
PROBLEM: “I’m afraid of being MeToo’ed.”
SOLUTION: This fear is not unfounded. But it’s exaggerated, and it can be managed.
First, date women from your known social circle, or through trusted friends and communities. When you’re introduced by people who know her, and know you, the risk drops dramatically. Reputation protects.
Second, don’t sleep with women you’re not married to or seriously planning to marry. Promiscuity opens you up to accusations by nature of the risk you’ve chosen. If you act like a husband looking for a wife, you’ll avoid most of the fallout that comes from acting like a player.
Finally, date like a man of integrity. Be clear in your intent. Be respectful in your approach. Vet women the way you’d vet a business partner, slowly, carefully, with your eyes open.
Avoid women who are unstable, ideological, addicted to drama, or hostile to men or who have friends that are red flags. They’re not hard to spot if you stop pretending you can fix them. Don't date crazy, no matter how much of a hot mess they are.
Courage doesn’t mean being reckless. It means being cautious and moving forward anyway.
PROBLEM: “I have debilitating social anxiety.”
SOLUTION: Social anxiety is not your enemy. It’s a signal.
Anxiety is what your body feels when you know you’re unprepared. So the real issue isn’t fear, it’s readiness.
The solution is to prepare.
Start by talking with people you already know and trust. Ask them directly: “Do I come across in any off-putting way?” Be ready to hear the truth. This feedback is gold.
Next, expand your social exposure in gradual circles:
-
Begin with low-stakes conversations, cashiers, neighbors, people at your gym
-
Practice warm eye contact and a confident smile
-
Say hello, then progress to small talk
Train your ability to enjoy people. Genuine curiosity, care, and concern are magnetic.
Imagine that you are a source of light and warmth in the world. It radiates from your face. When you smile, that light shines on others and lifts their spirit.
Practice radiating that warmth everywhere you go. It will transform how people receive you, and how you see yourself.
Also, don’t overlook your existing social network. Ask friends: “Can you introduce me to people? Invite me to something?” And if they hesitate, ask why. Be open to correction. Sharpen your social skills until you become the man people want to introduce to others.
This process doesn’t have to take years. If you want to speed it up, message me. I’ll help you identify what needs to change and how to change it, fast.
You’re not trapped. You’re just untrained. Let’s fix that.
PROBLEM: “Online dating is awful. Everyone on the apps is weird, overweight, or carries baggage.”
SOLUTION: You’re not wrong. Most dating apps are designed to keep you swiping, not to help you find a wife.
But if you insist on using them, use them well.
-
Get professional photos taken. Not filtered selfies. Real, high-quality photos that make you look your best.
-
Write a profile that’s clear, masculine, and purposeful. If possible, get help from someone who understands marketing.
-
If you have a female friend or sister near your age, ask her: “What does this profile really communicate?” Men and women read profiles differently. Get honest feedback.
Even with the best profile, online dating carries risks. You’re meeting strangers. And many women on the apps are not relationship-ready. If you’re not seeing the kind of woman you want, stop using the apps. Don’t waste your energy in a dysfunctional pool.
Instead, date through your real life contacts. Grow your social circle. Lead an interesting life. Join hobbies, attend church, build your local community. That’s where quality women gather, and where you can be seen for who you really are.
You can use online dating as practice if nothing else. Go on a few low-stakes dates. Sharpen your conversation skills. You might meet someone better than expected. But don’t let it become your strategy.
Build a real life. Meet real women. That’s where the future is found.
PROBLEM: “I’m afraid of being rejected.”
SOLUTION: Rejection is painful, especially when you take it personally. So stop taking it personally.
Most rejections aren’t even about you. She might be in a bad mood, already dating someone, overwhelmed with work, or distracted. You’re getting a response to her current state, not a verdict on your worth.
Too many men grew up on movies where rejection is public and humiliating. But those are just movie scripts. In real life, rejection is rarely brutal. Especially if you’re respectful, most rejections are soft, and if you’re paying attention, you’ll see it coming before you even ask.
Her posture, her eye contact, her tone… they all tell a story. Women constantly signal how open they are to being approached. You can learn to read that story. It’s a skill.
Yes, you’ll still be rejected from time to time. But it won’t sting the same.
Men who fear rejection have a weak internal frame and a fragile ego. Both of these can, and must, be strengthened if you want to be in a relationship. Because in marriage, you’ll face moments where your wife rejects something you want, or pushes back hard. If you crumble over a stranger’s ‘no,’ how will you handle conflict with someone you love?
The solution isn’t to avoid rejection. It’s to heal the wounds that make you overly sensitive to it.
Let rejection be feedback. Let it be fuel. Let it forge you into a stronger man.
PROBLEM: “None of the women I meet are up to my standards.”
SOLUTION: Then you need to ask two questions:
-
Are your standards calibrated to reality, or to fantasy?
-
Are you the kind of man who attracts what you want?
There’s a simple way to check if your standards are realistic: If you’re out socializing regularly and meeting at least one woman per month that you find attractive and potentially relationship-worthy, your standards are likely calibrated.
Even if some are taken or uninterested, twelve encounters a year puts you on track to find someone marriage-worthy in one to two years.
But if you’re not meeting any women who meet your standards, or none are attracted to you, then your expectations are off, or you’re not meeting the masculine side of the equation.
High standards are good. But your standards for yourself must be even higher.
Don’t lower your standards. Raise your value.
PROBLEM: “I don’t know what women today want.”
SOLUTION: Don’t worry, many women don’t know what they want either.
At least not until they see it.
You don’t need to have a deep understanding of women to start dating. What you need is a deep understanding of yourself, and the basics of how to interact with the opposite sex.
Women are not a monolith. They don’t all want the same thing. And it’s okay if some women don’t want what you’re offering. That just means they’re not your match.
If you want marriage, children, and a peaceful home life, say so. Be clear. Be honest. Look for the woman who lights up at that vision.
And remember: first dates are not emotional dumps. Don’t share your entire life story. Don’t unload your childhood wounds and five-year plans all at once. Let it come out gradually, organically, over time.
Oversharing too soon is a kind of emotional immodesty. It pushes women away. It scares them.
Instead, bring warmth. Curiosity. Humor. Presence. Let her feel who you are, before she hears everything you’ve done or want to do.
Also, understand that many women are suffering in the dating market too. They’ve dealt with immature men, disrespect, or emotional burnout. Some are guarded. Some are hesitant. That’s not a personal rejection, it’s their healing process.
Your job isn’t to fix them. But it is to show up as the kind of man who makes her feel that safety, joy, and being lead by a man is possible again.
Be patient. Be strong. Be sincere.
And become the man who makes her remember what she wants.
PROBLEM: “Dating is exhausting. I just want to skip to marriage.”
SOLUTION: I’m always surprised by how many men don’t enjoy dating, or find it exhausting and stressful.
Let’s reframe that.
You’re going out with a beautiful woman. You’re spending time with someone you find attractive. And success isn’t about getting married, it’s about enjoying the evening.
That’s it.
Don’t complicate it. Keep it simple. Simple dates. Simple interactions. Think of it as fun. Learn how to find joy in the process.
Because here’s the secret: If you want your marriage to be joyful, you’ll have to keep dating your wife.
If planning one evening out drains you, you’re not ready for the rhythm of married life. Marriage isn’t a break from effort, it’s the reward for mastering it.
Now, yes, wanting the reward without the work is natural. But it’s immature.
Dating is the training ground. It’s where you learn. You don’t marry a stranger. You marry someone you’ve pursued, studied, and built connection with.
If you skip the process, you skip the transformation from boyfriend to husband.
Lean in. Learn. Let it shape you.
PROBLEM: “I have low self-esteem and maybe depression.”
SOLUTION: Women can tell.
Even if you’re good at hiding it, most women will pick up on low self-esteem or depression by the end of the first date. And it’s one of the most off-putting traits a man can have.
Not because they’re cruel. But because they’re biologically wired to seek strength.
Women already deal with hormonal emotional swings. The last thing they need is a man who can’t stabilize the emotional climate of a home. A man who is stuck in despair can’t uplift a family.
Other men might have sympathy for you. But women, especially women you aren’t related to, rarely do. They’re not selecting for pity. They’re selecting for protection. For future fatherhood. For strength.
That doesn’t make you unlovable. It makes this urgent.
Self-esteem isn’t magic. It’s earned. You build it by setting goals and achieving them, consistently. Start with goals so small you know you can win. Stack those wins daily. Use systems that help you keep score. Journal your progress. Review your wins. Let them rewire your beliefs.
Depression can be attacked the same way:
-
Lift heavy things
-
Eat meat
-
Get sunlight
-
Cut screen time and porn
-
Go outside and move
-
Sleep and wake on rhythm
-
Seek out experts: a coach, a priest, or a therapist
And most of all, stop isolating. Find men who are winning. Spend time with them. Compete with them. Let their energy rub off on you.
You’re not broken. You’re just under-trained.
Fix this, and the rest will follow.
PROBLEM: “There’s no point in dating when divorce laws are against men.”
SOLUTION: Yes, divorce laws are unjust.
But giving up on women because the system is rigged is like giving up on work because taxes exist.
You don’t surrender to the injustice. You outsmart it.
Vet better. Lead from a place of strength. Choose a woman who fears God, loves truth, hates a divorce, and shows loyalty under pressure.
Your objective as a man and husband is to build a marriage where the divorce laws don’t matter.
If you end up in court, you’ve already failed.
Build your family with a woman who doesn’t believe in divorce. Who comes from a family and a culture that doesn’t believe in divorce. These subcultures exist, even inside nations with high divorce rates.
Create a home where the idea of divorce doesn’t enter the conversation, not because you’re naïve, but because the family structure is strong, the values are shared, and the foundation is sacred.
And if needed, protect yourself legally without becoming cynical.
Living in fear is not a winning strategy. Conviction and leadership is.
PROBLEM: “I don’t see the benefit of marriage in 2025.”
SOLUTION: For some men, those who can barely care for themselves, lack discipline, avoid responsibility, and have no interest in becoming fathers, marriage may not benefit them. And frankly, it shouldn’t.
But if you’ve read this far, that’s not you.
You want to become the kind of man who leads a family. And for men like you, marriage is a worthy risk, it’s the catalyst you need.
As my friend *@LukeWeinhagen *often says:\ "The mature adult form of a male is called a father."
You become fully formed through marriage and fatherhood. You finish your development as a man by taking on sacred responsibility.
Now, some men say, “I can just pay a maid to clean my house, a nanny to raise my kids, and a girlfriend for company.”
Be honest with yourself. Most men saying that are too broke to afford one of those women, let alone three. And even if you could, that’s not a family.
Children raised by strangers will not grow up strong and securely attached to their parents. They will not continue your legacy. They will not build a civilization.
That model is a a cold dead end.
Marriage, when done right, is the greatest force multiplier in a man’s life.
You gain:
-
A woman’s emotional and spiritual partnership
-
A peaceful home, a sanctuary from the world
-
Feminine warmth, lightness, and joy woven into your daily life
-
Children who carry your name, your values, your soul
-
A home culture that makes you stronger
-
A reason to become the man you always knew you could be
-
Emotional and spiritual partnership
Don’t listen to broken men who couldn’t carry the weight. Become the man who can.
PROBLEM: “I’ve done everything right. I’m a great catch. And I still can’t find a woman.”
SOLUTION:
This is the hardest kind of problem, because it hides behind your own certainty.
If everything you’ve said is true, then by now, something should be working. So we have to consider two possibilities.
First, you’re deluding yourself. Maybe you haven’t actually done the work. Or you’ve done it halfway, inconsistently, or with the wrong intent. Maybe you’ve made progress, but you’re still self-sabotaging in subtle ways, through your words, your posture, your patterns. You say you want marriage and children, but you’re not living like a man who’s ready for it.
Second, there’s something off-putting about you that you don’t see. Either the people around you are too polite to tell you, or too socially blind to even notice.
In both cases, you will not solve this alone. If you could, you already would have. You need someone outside your head and outside your social circle. A trained eye. A mirror that doesn’t lie.
Talk to me. Book a call. Even just the free 30-minute session . I’ll tell you the truth. And if you’re ready, we’ll fix it. Most of the time, it’s only a few months of focused work.
But it starts with honesty.
No more guessing.
No more waiting.
Let’s find out what’s really in your way.
CLOSING:
Before we end, let’s clear up one more misconception: You do not need to be fully ready for marriage to start dating.
You just need to be ready to date well.
Your finances don’t need to support a household yet, but they should support a courtship. Your leadership doesn’t need to be flawless, but it needs to be growing towards maturity.
You won’t find a woman who’s fully ready for marriage either. You’ll grow into that role together.
Dating is not the finish line of readiness. It’s the training ground.
So don’t wait to be perfect. Be honest, be improving, and be intentional. That’s more than enough to begin.
You said you wanted a woman. A wife. A family. A future.
That dream will cost you. In time, money, effort, and pride.
But what you get in return, is everything that makes a man come alive.
Start by solving the next problem. And the one after that. And then keep going.
Once you can fix what’s in the way now, you’ll be ready to build what you were born for next.
And if there’s something blocking you that I didn’t cover here, say so. Send me a message. Leave a comment. Tell me what’s in the way.
This post wasn’t meant to be complete. It was meant to begin a conversation.
Let’s go.
-
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ e17e9a18:66d67a6b
2025-05-19 11:46:09
@ e17e9a18:66d67a6b
2025-05-19 11:46:09We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system.
When banks issue loans, they don’t lend existing money — they create new money from debt. You’re on the hook for the principal and the interest. But the interest doesn’t exist yet — it has to come from someone else borrowing. That means the system only works if debt keeps growing.
When it doesn’t, the whole thing wobbles. Governments step in to bail out the banks by printing more money, and that cost doesn’t vanish. It shows up in your taxes, your savings, and your grocery bill.
We’re not just working to pay our own debts, we’re paying for their losses too.
https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"Check the blocks, verify, ain't that hard to do When everyone's got eyes on it, can't slip nothin' throgh." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ a5ee4475:2ca75401
2025-05-15 14:11:16
@ a5ee4475:2ca75401
2025-05-15 14:11:16lists #descentralismo #compilation #english
*The last list was updated in Amethyst, so the update of this one will only be visible in Amethyst.
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
AI
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgawaehxw309ahx7um5wghxy6t5vdhkjmn9wgh8xmmrd9skctczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqq823c8mw5zk
FOSS GAME
nostr:naddr1qq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhzqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gut57qtr
OSHW - Open Source Hardware
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Markdown Uses for Some Clients
nostr:nevent1qqsv54qfgtme38r2tl9v6ghwfj09gdjukealstkzc77mwujr56tgfwsppemhxue69uhkummn9ekx7mp0qgsq37tg2603tu0cqdrxs30e2n5t8p87uenf4fvfepdcvr7nllje5zgrqsqqqqqpkdvta4
Other Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78


