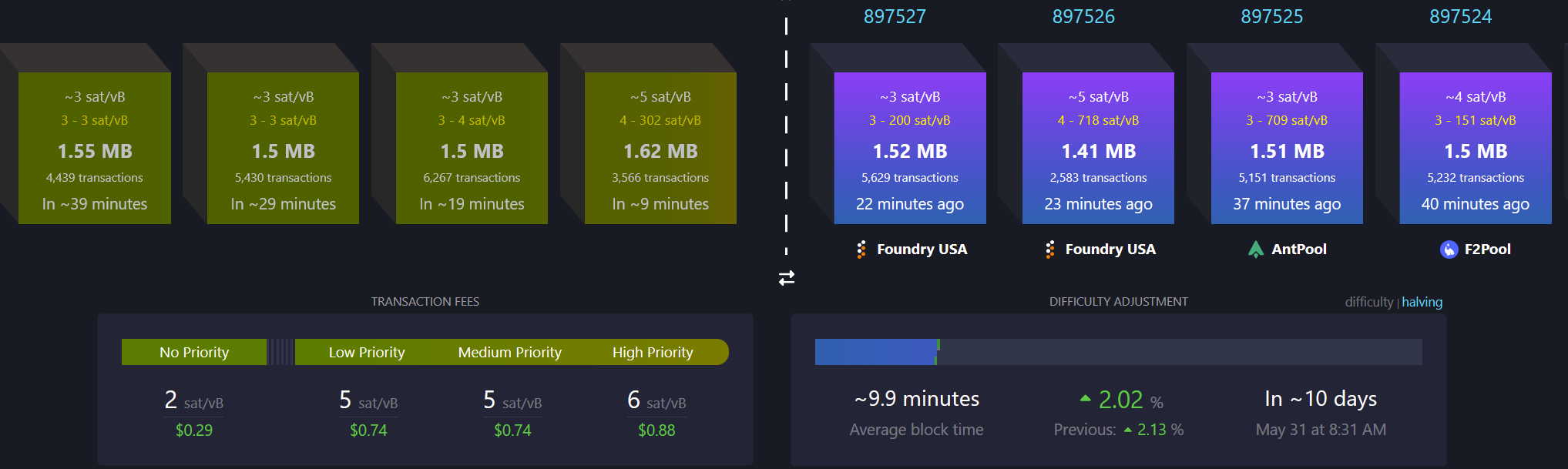
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 8bad92c3:ca714aa5
2025-05-23 04:01:08
@ 8bad92c3:ca714aa5
2025-05-23 04:01:08Marty's Bent

It's been a hell of a week in Austin, Texas. The Texas Energy & Mining Summit was held at Bitcoin Park Austin on Tuesday and yesterday. Around 200 people from across the energy sector and the mining sector convened to discuss the current state of bitcoin mining, how it integrates with energy systems, and where things are going in the near to medium term. Representatives from ERCOT, Halliburton, and some of the largest mining companies in the world were in attendence. Across town, Bitcoin++ is holding their conference on mempools, which is fitting considering there is currently an ongoing debate about mempool policy and whether or not Bitcoin Core should eliminate the data limit on OP_RETURN.
I've had the pleasure of participating in both events. At the Texas Energy & Mining Summit I opened up the two-day event with the opening panel on why Texas is perfectly suited not only for bitcoin mining but for the bitcoin industry in general. Texas is a state that highly values private property rights, low taxes, and free market competition. It's become clear to me over the four years that I've lived in Texas that it is an incredible place to start a bitcoin business. The energy down here (pun intended) is palpable.
I also hosted the ending panel with Nick Gates from Priority Power, Will Cole from Zaprite and Jay Beddict from Foundry about what we have to look forward to through the rest of the year. I think the consensus was pretty clear on the panel, there's never been a more bullish setup for bitcoin historically. The political support we're getting here in the United States, the institutional adoption that we're seeing, and the fervor around protocol level development are all pointing in the right direction. Even though the discussions around protocol development can be contentious at times, it's a signal that people really care about this open source monetary protocol that we're all building on. We all agreed that Bitcoin has never been more de-risked than it is today. That is not to say that there aren't any risk.
We also discussed the problem with mining pool centralization and the FPPS payout scheme and why people need to be paying attention to it. But I think overall, things are looking pretty good right now.
Yesterday I also had the pleasure of running the live desk at Bitcoin++ speaking with many of the developers building out the protocol layer and layers above bitcoin. It's always extremely humbling to sit down and speak with the developers because they are so damn smart. Brilliant people who really care deeply about bitcoin. Even though many of them have very different views about the state of bitcoin and how to build it out moving forward. I view my role on the live desk is simply to try to get everybody's perspective. Not only on the OP_RETURN discussion, but on the future of bitcoin and how the protocol progresses from a technical perspective.
I had many conversations. The first with Average Gary and VNPRC, who are working on hashpools, which are attempting to solve the mining pool centralization and privacy problems that exists by using ecash. Hashpool gives miners the ability to exchange hash shares for ehash tokens. that are immediately liquid and exchangeable for bitcoin over the lightning network. Solving the consistent payout and liquidity problem that miners are always trying to solve. Currently FPPS payout schemes are the way they solve these problems. I'm incredibly optimistic about the hashpools project.
I also had the pleasure of speaking with SuperTestNet and Dusty Daemon, who are both focused on making bitcoin more inherently private at the protocol layer and on the lightning network. I think Dusty's work on splicing is very underappreciated right now and is something that you should all look into. Dusty also explained an idea he has that would make CoinJoin coordination much easier by creating a standardized coordination protocol. I'm going to butcher the explanation here, But I think the general idea is to create a way for people to combine inputs by monitoring the lightning network and looking for individual actors who are looking to rebalance channels and opportunistically set up a collaborative transaction with them. This is something I think everyone should look into and champion because I think it would be incredibly beneficial to on-chain privacy. As Bitcoin scales and gets adopted by millions and billions of people over the next few decades.
I also had the pleasure of speaking with Andrew Poelstra and Boerst about cryptography and block templates. For those of you who are unaware, Andrew Poelstra the Head of Research at Blockstream and on the cutting edge of the cryptography that bitcoin uses and may implement in the future. We had a wide ranging discussion about OP_RETURN, FROST, Musig2, Miniscript, quantum. resistant cryptographic libraries, and how Bitcoin Core actually works as a development project.
I also spoke with Liam Egan from Alpen Labs. He's working on ZK rollups on Bitcoin. Admittedly, this is an area I haven't explored too deeply, so it was awesome to sit down with Liam and get his perspective. Alpen Labs is leveraging BitVM to enable their rollups.
I highly recommend if and when you get the time to check out the YouTube stream of the Live Desk. A lot of very deep, technical conversations, but if you're really interested to learn how bitcoin actually works and some of the ideas that are out there to make it better, this is an incredible piece of content to watch. I'm about to head over for day two of Bitcoin++ to run the Live Desk again. So if you get this email before we go live make sure you subscribe to the YouTube channel and tune in for the day.
One thing I will say. Last night, there was a debate about OP_RETURN and I think it's important to note that despite how vitriolic people may get on Twitter, it's always interesting to see people with diametrically opposed views get together and have civil debates. It's obvious that everyone involved cares deeply about bitcoin. Having these tough conversations in person is very important. Particularly, civil conversations. I certainly think yesterday's debate was civil. Though, I will say I think that as bitcoiners, we should hold ourselves to a higher standard of decorum when debates like this are had.
Tyler Campbell from Unchained mentioned that it is insane that there was such a small group of people attending this particular debate about the future of a two trillion dollar protocol. Bitcoin is approaching $100,000 again as I type and no one in big tech, no one in big finance outside of people looking for bitcoin treasury plays is really paying attention to what's happening at the protocol level. This is simply funny to observe and probably a good thing in the long run. But, Meta, Stripe, Apple, Visa, Mastercard and the Teslas of the world are all asleep at the wheel as we build out the future of money.
The $1 Trillion Basis Trade Time Bomb
The massive basis trade currently looming over financial markets represents a systemic risk that dwarfs previous crises. As James Lavish warned during our conversation, approximately $1 trillion in leveraged positions exist within this trade - ten times larger than those held by Long-Term Capital Management before its 1998 collapse. These trades employ staggering leverage ratios between 20x to 100x just to make minuscule basis point differences profitable. The Brookings Institution, which Lavish describes as a "tacit research arm of the Fed," has published a paper explicitly warning about this trade's dangers.
"The Brookings Institution came out with a solution... instead of printing money this time, the Fed will just take the whole trade off of the hedge funds books. Absolutely, utterly maniacal. The thought of the Fed becoming a hedge fund... it's nuts." - James Lavish
What makes this situation particularly alarming is how an unwind could trigger cascading margin calls throughout interconnected financial markets. As Lavish explained, when positions begin unwinding, prices move dramatically, triggering more margin calls that force more selling. This "powder keg behind the scenes" is being closely monitored by sophisticated investors who understand its destructive potential. Unlike a controlled demolition, this unwinding could quickly become chaotic, potentially forcing unprecedented Fed intervention.
Check out the full podcast here for more on Bitcoin's role as the neutral reserve asset, nation-state mining strategies, and the repeal of SAB 121's impact on banking adoption.
Headlines of the Day
Panama City Signs Deal for Bitcoin Municipal Payments - via X
U.S. Economy Polls Show Falling Confidence in Trump Leadership - via CNBC
Jack Mallers's Bitcoin Bank Targets $500 Trillion Market - via X
Bitcoin Decouples From Markets With 10% Gain Amid Asset Slump - via X
Looking for the perfect video _to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 2
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ be39043c:4a573ca3
2024-08-16 01:59:24
@ be39043c:4a573ca3
2024-08-16 01:59:24Traditionally, miso making takes place during the cold winter. Miso is fermented during the warm season and start using after it gets cooler in the fall. However, I did make during the summer and there was no problem.
For 29oz miso
Ingredients: * Chickpeas 0.5lbs(227g) * Dried Koji 0.5lbs(227g) *not raw(active) koji * Natural salts 103g * Chickpeas : Koji: Salts = 1: 1: 0.45 (salts 12.5%)
I find chickpeas easier to handle than soy beans. For soy beans,
- Soy beans 230g (soak at least 18 hours)
- Dried Koji 340g
- Natural salts 30g(Salts 12.5%)
You also need :
Container for fermentation -32 oz glass jar (no metal lid) or strong plastic container or bag that can be sealed. * large mixing bowl
small bowl
* pressure cooker or large pot * food processor or blender or masher (I use the bottom of small glass jar sanitized with hotwater) * parchment paper or plastic wrap to cover the surface- Wash chickpeas and soak over night
- Cook chickpeas until it can be crashed with your thumb and pinky finger with a pressure cooker or a pot (this may take hours with a pot) Move a part of cooked liquid from the pot to a small bowl and drain the rest. Wait until chickpeas can be handled with hand.
- Mash chickpeas into paste
- Sanitize the 32oz jar with hot water or sanitizer of your choice
- Mixed dried koji with salts with hand
- Add koji and salts to the chickpea paste. Mix with hand well. Add a little bit of the liquid you put aside earlier if the paste is too dry (do not add too much).
- When mixed well, make balls with the paste using hands.
- Throw one of the balls into the jar and push onto the jar with your fist. Repeat this process. (you don't have to punch here. Just push. This process is to transfer the miso paste into the jar without air. The exposure to air will lead to mold. Make sure not to have a space.)
- After throwing all balls into the jar and place tightly without air, seal the surface with a piece of parchment paper or plastic wrap.
- Close the lid.
- Place the jar in a cool and dark place (room temperature). Leave 6 months to 2 years. After the half of the duration, you may pull out of paste and place the bottom half onto the upper half so that the miso will be evenly fermented. This process can be skipped. Check once in a couple of months if there is mold.
- If mold appears on the surface, just scrape it off.
Miso pro's video. He uses soys.
-
 @ 2ede6f6b:b94998e2
2024-08-15 21:11:43
@ 2ede6f6b:b94998e2
2024-08-15 21:11:43test
originally posted at https://stacker.news/items/459389
-
 @ 8bad92c3:ca714aa5
2025-05-23 04:01:08
@ 8bad92c3:ca714aa5
2025-05-23 04:01:08
I've pulled together the most compelling forward-looking predictions from our recent podcast conversations. These insights highlight where our guests see opportunities and challenges in the Bitcoin ecosystem, energy markets, and beyond.
AI Agents Will Drive Bitcoin Adoption More Than Human Users by 2030 - Andrew Myers
Andrew Myers described how the artificial intelligence revolution will fundamentally transform Bitcoin usage patterns over the next few years. He highlighted Paul's tweet that suggested machine-to-machine transactions using Bitcoin will soon dominate the network.
"We talk about Bitcoin being used as a medium of exchange. We're going to find that the machines are doing most of that exchange at some point relatively soon," Andrew explained. "The agents using Bitcoin to complete tasks using something like L4 or two protocol is going to far surpass the amount of transactions that humans are doing to do things in their everyday lives."
Andrew believes AI agents will naturally gravitate toward Bitcoin because it's more energy-efficient from a computational perspective than traditional payment rails. As AI systems optimize for energy efficiency, Bitcoin's direct settlement mechanism becomes increasingly attractive compared to legacy financial infrastructure. This shift could accelerate Bitcoin adoption in ways we haven't fully anticipated, creating a new category of machine-driven demand.
CalPERS Funding Status Will Drop Below 70% by June 2025 - Dom Bei
Dom Bei, who's running for the Board of Trustees at CalPERS, made a concerning prediction about America's largest public pension fund. Currently sitting at approximately 75% funded, Dom warned the situation could deteriorate further after recent tariff-related markdowns.
"They say that the fund had a $26 billion markdown, which if my math is correct, would bring the fund closer towards the 70% funded number," Dom explained. He noted the fund needs to recover these losses before the June 30, 2025 reporting deadline, or face serious consequences.
If CalPERS funding status drops below 70%, Dom predicts a familiar pattern will unfold: municipalities and taxpayers will face higher contribution rates to cover the shortfall, diverting money from essential services like parks, schools, and public safety. This would likely trigger another round of pension reform debates targeting worker benefits, despite similar reforms in 2013 failing to address the fundamental performance issues plaguing the fund.
Energy Companies Will Incorporate Bitcoin Into Settlements Within 3 Years - Andrew Myers
Andrew Myers outlined a compelling vision for Bitcoin's integration into energy markets, predicting that by 2027 (block 1,050,000), we'll see widespread adoption of Bitcoin for energy transactions and settlements. He described his company's mission as enabling "every electric power company to use bitcoin by block 1,050,000."
"Our mantra for Bitcoin is fast, accurate, transparent energy transactions," Andrew explained. He highlighted several inefficiencies in current energy markets that Bitcoin could solve, including: Information asymmetry between energy buyers and sellers. Slow 30-day billing cycles creating unnecessary credit risk
Capital locked up in prepayments, deposits, and collateral requirements.Andrew revealed that his team has already prototyped a Bitcoin collateral product and that a major energy company in Texas is currently building similar functionality. He predicts these early implementations will demonstrate Bitcoin's potential to unlock billions in working capital across the energy sector through faster settlement and reduced collateral requirements.
Most significantly, Andrew mentioned early discussions with independent system operators about modifying power market protocols to incorporate Bitcoin as an alternative settlement mechanism alongside the US dollar.
Blockspace conducts cutting-edge proprietary research for investors.
Bitcoin Miners Face Hard Choices as AI Data Centers Pick Prime Locations
Bitcoin miners hoping to cash in on the AI boom by selling their facilities to hyperscalers are finding fewer opportunities than expected. With mining economics dimming and specific buyer requirements limiting potential deals, the industry faces significant challenges.
Christian Lopez, Head of Blockchain and Digital Assets at Cohen and Company Capital Markets, notes a "glut of bitcoin mines" currently on the market. While miners control substantial power resources, hyperscalers typically demand facilities with at least 150-200 megawatts capacity within 100 miles of major cities—criteria most mining operations don't meet.
An estimated 1-1.5 gigawatts of mining capacity is available for acquisition, creating downward pressure on power prices. This oversupply stems from both deteriorating mining economics and overoptimistic AI-related expectations. The valuation gap remains a persistent obstacle: "Buyers face the critical 'buy versus build' question," Lopez explains. While buyers typically value sites at $300,000-$500,000 per megawatt plus a modest premium, sellers often seek $1.5-$2 million per megawatt based on public company valuations.
Adding to these challenges, retrofitting mining sites for high-performance computing often requires completely reconstructing the power infrastructure rather than leveraging existing setups. Despite current difficulties, industry sentiment remains cautiously optimistic, with many experts predicting Bitcoin could reach $125,000-$200,000 by late 2025.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 502ab02a:a2860397
2025-05-23 01:57:14
@ 502ab02a:a2860397
2025-05-23 01:57:14น้ำนมมนุษย์ที่ไม่ง้อมนุษย์ หรือนี่กำลังจะกลายเป็นเรื่องจริงเร็วกว่าที่เราคิดนะครับ
ในยุคที่อุตสาหกรรมอาหารหันหลังให้กับปศุสัตว์ ไม่ว่าจะด้วยเหตุผลด้านสิ่งแวดล้อม จริยธรรม หรือความยั่งยืน “น้ำนมจากห้องแล็บ” กำลังกลายเป็นแนวหน้าของการปฏิวัติอาหาร โดยเฉพาะเมื่อบริษัทหนึ่งจากสิงคโปร์นามว่า TurtleTree ประกาศอย่างชัดเจนว่า พวกเขากำลังจะสร้างโปรตีนสำคัญในน้ำนมมนุษย์ โดยไม่ต้องมีมนุษย์แม่เลยแม้แต่น้อย
TurtleTree ก่อตั้งในปี 2019 โดยมีเป้าหมายอันทะเยอทะยานคือการผลิตโปรตีนในนมแม่ให้ได้ผ่านเทคโนโลยีที่เรียกว่า precision fermentation โดยใช้จุลินทรีย์ที่ถูกดัดแปลงพันธุกรรมให้ผลิตโปรตีนเฉพาะ เช่น lactoferrin และ human milk oligosaccharides (HMOs) ซึ่งเป็นองค์ประกอบล้ำค่าที่พบในน้ำนมมนุษย์แต่แทบไม่มีในนมวัว หรือผลิตภัณฑ์นมทั่วไป
โปรตีนตัวแรกที่ TurtleTree ประสบความสำเร็จในการผลิตคือ LF+ หรือ lactoferrin ที่เลียนแบบโปรตีนในนมแม่ ซึ่งมีหน้าที่ช่วยระบบภูมิคุ้มกันของทารก ต่อต้านแบคทีเรีย และช่วยให้ร่างกายดูดซึมธาตุเหล็กได้ดีขึ้น โปรตีนนี้เป็นหนึ่งในหัวใจของนมแม่ ที่บริษัทต้องการนำมาใช้ในอุตสาหกรรมนมผงเด็กและอาหารเสริมสำหรับผู้ใหญ่ ล่าสุดในปี 2024 LF+ ได้รับการรับรองสถานะ GRAS (Generally Recognized As Safe) จากองค์การอาหารและยาสหรัฐฯ (FDA) อย่างเป็นทางการ เป็นหมุดหมายสำคัญที่บอกว่า นี่ไม่ใช่แค่ไอเดียในแล็บอีกต่อไป แต่กำลังกลายเป็นผลิตภัณฑ์เชิงพาณิชย์จริง
เบื้องหลังของโปรเจกต์นี้คือการลงทุนกว่า 30 ล้านดอลลาร์สหรัฐจากกลุ่มทุนทั่วโลก รวมถึงบริษัท Solar Biotech ที่จับมือกับ TurtleTree ในการขยายกำลังการผลิตเชิงอุตสาหกรรมในสหรัฐอเมริกา โดยตั้งเป้าว่าจะสามารถผลิตโปรตีนเหล่านี้ได้ในระดับราคาที่แข่งขันได้ภายในไม่กี่ปีข้างหน้า
สิ่งที่น่าสนใจคือ TurtleTree ไม่ได้หยุดแค่ lactoferrin พวกเขายังวางแผนพัฒนา HMO ซึ่งเป็นน้ำตาลเชิงซ้อนชนิดพิเศษที่มีอยู่เฉพาะในน้ำนมแม่ เป็นอาหารเลี้ยงแบคทีเรียดีในลำไส้ทารก ช่วยพัฒนาระบบภูมิคุ้มกันและสมอง ปัจจุบัน HMOs เริ่มเป็นที่นิยมในวงการ infant formula แต่การผลิตยังจำกัดและมีต้นทุนสูง การที่ TurtleTree จะนำเทคโนโลยี precision fermentation มาใช้ผลิต HMO จึงถือเป็นความพยายามในการลดช่องว่างระหว่าง "นมแม่จริง" กับ "นมผงสังเคราะห์"
ทั้งหมดนี้เกิดขึ้นภายใต้แนวคิดใหม่ของอุตสาหกรรมอาหารที่เรียกว่า "functional nutrition" หรือโภชนาการที่ออกแบบเพื่อทำงานเฉพาะทาง ไม่ใช่แค่ให้พลังงานหรือโปรตีน แต่เล็งเป้าหมายเฉพาะ เช่น เสริมภูมิคุ้มกัน ซ่อมแซมสมอง หรือฟื้นฟูร่างกาย โดยมีรากฐานจากธรรมชาติ แต่ใช้เทคโนโลยีสมัยใหม่ในการผลิต
แม้จะฟังดูเป็นความก้าวหน้าทางวิทยาศาสตร์ที่น่าตื่นเต้น แต่น้ำเสียงที่ดังก้องในอีกมุมหนึ่งก็คือคำถามเชิงจริยธรรม TurtleTree กำลังสร้างโปรตีนที่มีอยู่เฉพาะในมนุษย์ โดยอาศัยข้อมูลพันธุกรรมของมนุษย์เอง แล้วนำเข้าสู่ระบบอุตสาหกรรมเพื่อการค้า คำถามคือ เมื่อใดที่การจำลองธรรมชาติจะกลายเป็นการผูกขาดธรรมชาติ? ใครควรเป็นเจ้าของข้อมูลพันธุกรรมของมนุษย์? และถ้าวันหนึ่งบริษัทใดบริษัทหนึ่งสามารถควบคุมการผลิต “นมแม่จำลอง” ได้แต่เพียงผู้เดียว นั่นจะส่งผลต่อเสรีภาพของสังคมในมุมไหนบ้าง?
นักชีวจริยธรรมหลายคน เช่น ดร.ซิลเวีย แคมโปเรซี จาก King's College London ตั้งข้อสังเกตไว้ว่า เทคโนโลยีแบบนี้อาจแก้ปัญหาการเข้าถึงนมแม่ในพื้นที่ห่างไกลหรือในกลุ่มแม่ที่ให้นมไม่ได้ แต่ขณะเดียวกันก็อาจกลายเป็นการสร้าง "ระบบอาหารทางเลือก" ที่ควบคุมโดยบริษัทไม่กี่ราย ที่มีอำนาจเกินกว่าผู้บริโภคจะตรวจสอบได้
เมื่อเทคโนโลยีสามารถจำลองสิ่งที่เคยสงวนไว้เฉพาะธรรมชาติ และมนุษย์ได้ใกล้เคียงจนแทบแยกไม่ออก บางทีคำถามที่ควรถามอาจไม่ใช่แค่ว่า “มันปลอดภัยหรือไม่?” แต่อาจต้องถามว่า “เราไว้ใจใครให้สร้างสิ่งนี้แทนธรรมชาติ?” เพราะน้ำนมแม่เคยเป็นสิ่งที่มาจากรักและชีวิต แต่วันนี้มันอาจกลายเป็นเพียงสิ่งที่มาจากห้องแล็บและโมเลกุล... และนั่นคือสิ่งที่เราต้องคิดให้เป็น ก่อนจะกินให้ดี เต่านี้มีบุญคุณอันใหญ่หลวงงงงงงง
เสริมจุดน่าสนใจให้ครับ KBW Ventures ถือเป็นผู้ลงทุนรายใหญ่ที่สุดใน TurtleTree Labs โดยมีบทบาทสำคัญในหลายรอบการระดมทุนของบริษัท KBW Ventures เป็นบริษัทลงทุนจากสหรัฐอาหรับเอมิเรตส์ ก่อตั้งโดย สมเด็จพระราชโอรสเจ้าชายคาเล็ด บิน อัลวาลีด บิน ตาลาล อัล ซาอุด (HRH Prince Khaled bin Alwaleed bin Talal Al Saud) ในรอบการระดมทุน Pre-A มูลค่า 6.2 ล้านดอลลาร์สหรัฐฯ ซึ่งปิดในเดือนธันวาคม 2020 KBW Ventures ได้ร่วมลงทุนพร้อมกับ Green Monday Ventures, Eat Beyond Global และ Verso Capital . นอกจากนี้ เจ้าชาย Khaled ยังได้เข้าร่วมเป็นที่ปรึกษาให้กับ TurtleTree Labs เพื่อสนับสนุนการขยายตลาดและกลยุทธ์การเติบโตของบริษัท
ซึ่งในตัว KBW Ventures นั้น เป็นบริษัทลงทุนที่มุ่งเน้นการสนับสนุนเทคโนโลยีที่ยั่งยืนและนวัตกรรมในหลากหลายอุตสาหกรรม เช่น เทคโนโลยีชีวภาพ (biotech), เทคโนโลยีพลังงานสะอาด, เทคโนโลยีการเงิน (fintech), เทคโนโลยีการขนส่ง, และเทคโนโลยีอาหาร (food tech) โดยเฉพาะ และในส่วนของเจ้าชาย Khaled มีความสนใจอย่างลึกซึ้งในด้านเทคโนโลยีอาหาร โดยเฉพาะในกลุ่มโปรตีนทางเลือก เช่น Beyond Meat ซึ่งเป็นการลงทุนที่สะท้อนถึงความมุ่งมั่นชัดเจนในการส่งเสริมอาหารที่ยั่งยืนและมีจริยธรรมครับ และแน่นอนเลยว่า โดยมีส่วนร่วมในรอบระดมทุนหลายครั้งของ Beyond Meat รวมถึงตอนที่ Beyond Meat เข้าตลาดหุ้น Nasdaq ครั้งแรกในปี 2019
เจ้าชาย Khaled เชื่อมั่นว่าอาหารทางเลือกแบบพืชจะถูกลงและแพร่หลายมากขึ้น จนอาจถูกกว่าราคาเนื้อสัตว์จากสัตว์จริงภายในปี 2025 ตามข้อมูลที่ได้มาแสดงว่า ปีนี้นี่หว่าาาาาาาาาา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:31
@ 39cc53c9:27168656
2025-05-20 10:45:31The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 2b998b04:86727e47
2025-05-23 01:56:23
@ 2b998b04:86727e47
2025-05-23 01:56:23\> “Huge swathes of people…spend their entire working lives performing tasks they secretly believe do not really need to be performed.”\ \> — David Graeber, Bullshit Jobs
\> “We are in a system that must grow — forever — or it collapses. But technology, by its very nature, is deflationary.”\ \> — Jeff Booth, The Price of Tomorrow
We live in a strange paradox: Technological progress is supposed to make life easier, yet many people feel more overworked and less fulfilled than ever. While artificial intelligence and automation promise unprecedented productivity, it’s not yet clear whether that will mean fewer bullshit jobs — or simply new kinds of them.
What Is a Bullshit Job?
In his landmark book Bullshit Jobs, the late anthropologist David Graeber exposed a haunting truth: millions of jobs exist not because they are needed, but because of economic, political, or psychological inertia. These are roles that even the workers themselves suspect are meaningless — created to serve appearances, maintain hierarchies, or justify budgets.
Think:
-
Middle managers approving other middle managers' reports
-
Employees running meetings to prepare for other meetings
-
Corporate roles invented to interface with poorly implemented AI tools
Bullshit work isn’t the absence of technology. It’s often the outcome of resisting what technology could actually do — in order to preserve jobs, status, or growth targets.
Booth’s Warning: The System is Rigged Against Deflation
In The Price of Tomorrow, entrepreneur Jeff Booth argues that the natural state of a tech-driven economy is deflation — things getting better, cheaper, and faster.
But our global financial system is built on perpetual inflation and debt expansion. Booth writes:
\> “We are using inflationary monetary policy to fight deflationary technological forces.”
Even as AI and automation could eliminate unnecessary jobs and increase abundance, our system requires jobs — or the illusion of them — to keep the economy expanding. So bullshit jobs persist, and even evolve.
AI as a Deflationary Force
AI is rapidly accelerating the deflation Booth described:
-
Tasks that used to take hours now take seconds
-
Whole creative and administrative processes are being streamlined
-
Labor can scale digitally — one tool used globally at near-zero marginal cost
Embraced honestly, this could mean fewer hours, lower costs, and more prosperity. But again, we are not optimized for truth — we are optimized for GDP growth.
So we invent new layers of AI-enhanced bullshit:
-
Prompt engineers writing prompts for other prompt engineers
-
"Human-in-the-loop" validators reviewing AI output they don’t understand
-
Consultants building dashboards that nobody reads
Toward a Post-Bullshit Future
Here’s the real opportunity: If we embrace deflation as a blessing — not a threat — and redesign our systems around truth, efficiency, and abundance, we could:
-
Eliminate meaningless labor
-
Reduce the cost of living dramatically
-
Liberate people to create, heal, build, and rest
This means more than economic reform — it’s a philosophical shift. We must stop equating “employment” with value. That’s where Bitcoin and open-source tools point: toward a world where permissionless value creation is possible without the bloat of gatekeeping institutions.
Final Thought: Tech Won’t Save Us, But Truth Might
Technology, left to its own logic, tends toward freedom, efficiency, and abundance. But our current systems suppress that logic in favor of growth at all costs — even if it means assigning millions of people to do work that doesn’t need doing.
So will AI eliminate bullshit jobs?
It can. But only if we stop pretending we need them.
And for those of us who step outside the wage-work loop, something remarkable happens. We begin using these tools to create actual value — not to impress a boss, but to solve real problems and serve real people.
Recently, I built a tool using AI and automation that helps me cross-post content from Nostr to LinkedIn, Facebook, and X. It wasn’t for a paycheck. It was about leverage — freeing time, expanding reach, and creating a public record of ideas.\ You can check it out here:\ 👉 <https://tinyurl.com/ywxuowl5>
Will it help others? I don’t know yet.\ But it helped me — and that’s the point.
Real value creation doesn’t always begin with a business plan. Sometimes it starts with curiosity, conviction, and the courage to build without permission.
Maybe the future of work isn’t about scaling jobs at all.\ Maybe it’s about reclaiming time — and using these tools to build lives of meaning.
If this resonates — or if you’ve found your own way to reclaim time and create value outside the wage loop — zap me and share your story. Let’s build the post-bullshit economy together. ⚡
-
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 90152b7f:04e57401
2025-05-23 01:27:49
@ 90152b7f:04e57401
2025-05-23 01:27:49[Analytical & Intelligence Comments]\ \ “On Monday February 27th, 2012, WikiLeaks began publishing The Global Intelligence Files, over five million e-mails from the Texas headquartered "global intelligence" company Stratfor. The e-mails date between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal's Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agencies, including the US Department of Homeland Security, the US Marines and the US Defence Intelligence Agency. The emails show Stratfor's web of informers, pay-off structure, payment laundering techniques and psychological methods.”\ \ Released on 2013-02-13 00:00 GMT Email-ID 13332210 Date 2011-05-04 16:26:59\ From <jetdrive@earthlink.net> To <responses@stratfor.com> CROYDON KEMP sent a\ message using the contact form at <https://www.stratfor.com/contact\>\\ Mossad ran 9/11 Arab "hijacker" terrorist operation\ \ By Wayne Madsen\ \ British intelligence reported in February 2002 that the Israeli Mossad ran the Arab hijacker cells that were later blamed by the U.S. government's 9/11 Commission for carrying out the aerial attacks on the World Trade Center and Pentagon. WMR has received details of the British intelligence report which was suppressed by the government of then-Prime Minister Tony Blair.\ \ A Mossad unit consisting of six Egyptian- and Yemeni-born Jews infiltrated "Al Qaeda" cells in Hamburg (the Atta-Mamoun Darkanzali cell), south Florida, and Sharjah in the United Arab Emirates in the months before 9/11. The Mossad not only infiltrated cells but began to run them and give them specific orders that would eventually culminate in their being on board four regularly-scheduled flights originating in Boston, Washington Dulles, and Newark, New Jersey on 9/11.\ \ The Mossad infiltration team comprised six Israelis, comprising two cells of three agents, who all received special training at a Mossad base in the Negev Desert in their future control and handling of the "Al Qaeda" cells. One Mossad cell traveled to Amsterdam where they submitted to the operational control of the Mossad's Europe Station, which operates from the El Al complex at Schiphol International Airport. The three-man Mossad unit then traveled to Hamburg where it made contact with Mohammed Atta, who believed they were sent by Osama Bin Laden. In fact, they were sent by Ephraim Halevy, the chief of Mossad.\ \ The second three-man Mossad team flew to New York and then to southern Florida where they began to direct the "Al Qaeda" cells operating from Hollywood, Miami, Vero Beach, Delray Beach, and West Palm Beach. Israeli "art students," already under investigation by the Drug Enforcement Administration for casing the offices and homes of federal law enforcement officers, had been living among and conducting surveillance of the activities, including flight school training, of the future Arab "hijacker" cells, particularly in Hollywood and Vero Beach.\ \ In August 2001, the first Mossad team flew with Atta and other Hamburg "Al Qaeda" members to Boston. Logan International Airport's security was contracted to Huntleigh USA, a firm owned by an Israeli airport security firm closely connected to Mossad — International Consultants on Targeted Security – ICTS. ICTS's owners were politically connected to the Likud Party, particularly the Netanyahu faction and then-Jerusalem mayor and future Prime Minister Ehud Olmert. It was Olmert who personally interceded with New York Mayor Rudolph Giuliani to have released from prison five Urban Moving Systems employees, identified by the CIA and FBI agents as Mossad agents. The Israelis were the only suspects arrested anywhere in the United States on 9/11 who were thought to have been involved in the 9/11 attacks.\ \ The two Mossad teams sent regular coded reports on the progress of the 9/11 operation to Tel Aviv via the Israeli embassy in Washington, DC. WMR has learned from a Pentagon source that leading Americans tied to the media effort to pin 9/11 on Arab hijackers, Osama Bin Laden, and the Taliban were present in the Israeli embassy on September 10, 2001, to coordinate their media blitz for the subsequent days and weeks following the attacks. It is more than likely that FBI counter-intelligence agents who conduct surveillance of the Israeli embassy have proof on the presence of the Americans present at the embassy on September 10. Some of the Americans are well-known to U.S. cable news television audiences.\ \ In mid-August, the Mossad team running the Hamburg cell in Boston reported to Tel Aviv that the final plans for 9/11 were set. The Florida-based Mossad cell reported that the documented "presence" of the Arab cell members at Florida flight schools had been established.\ \ The two Mossad cells studiously avoided any mention of the World Trade Center or targets in Washington, DC in their coded messages to Tel Aviv. Halevy covered his tracks by reporting to the CIA of a "general threat" by an attack by Arab terrorists on a nuclear plant somewhere on the East Coast of the United States. CIA director George Tenet dismissed the Halevy warning as "too non-specific." The FBI, under soon-to-be-departed director Louis Freeh, received the "non-specific" warning about an attack on a nuclear power plant and sent out the information in its routine bulletins to field agents but no high alert was ordered.\ \ The lack of a paper trail pointing to "Al Qaeda" as the masterminds on 9/11, which could then be linked to Al Qaeda's Mossad handlers, threw off the FBI. On April 19, 2002, FBI director Robert Mueller, in a speech to San Francisco's Commonwealth Club, stated: "In our investigation, we have not uncovered a single piece of paper — either here in the United States, or in the treasure trove of information that has turned up in Afghanistan and elsewhere — that mentioned any aspect of the September 11 plot."\ \ The two Mossad "Al Qaeda" infiltration and control teams had also helped set up safe houses for the quick exfiltration of Mossad agents from the United States. Last March, WMR reported: "WMR has learned from two El Al sources who worked for the Israeli airline at New York’s John F. Kennedy airport that on 9/11, hours after the Federal Aviation Administration (FAA) grounded all civilian domestic and international incoming and outgoing flights to and from the United States, a full El Al Boeing 747 took off from JFK bound for Tel Aviv’s Ben Gurion International Airport. The two El Al employee sources are not Israeli nationals but legal immigrants from Ecuador who were working in the United States for the airline. The flight departed JFK at 4:11 pm and its departure was, according to the El Al sources, authorized by the direct intervention of the U.S. Department of Defense. U.S. military officials were on the scene at JFK and were personally involved with the airport and air traffic control authorities to clear the flight for take-off. According to the 9/11 Commission report, Transportation Secretary Norman Mineta ordered all civilian flights to be grounded at 9:45 am on September 11." WMR has learned from British intelligence sources that the six-man Mossad team was listed on the El Al flight manifest as El Al employees.\ \ WMR previously reported that the Mossad cell operating in the Jersey City-Weehawken area of New Jersey through Urban Moving Systems was suspected by some in the FBI and CIA of being involved in moving explosives into the World Trade Center as well as staging "false flag" demonstrations at least two locations in north Jersey: Liberty State Park and an apartment complex in Jersey City as the first plane hit the World Trade Center's North Tower. One team of Urban Moving Systems Mossad agents was arrested later on September 11 and jailed for five months at the Metropolitan Detention Center in Brooklyn. Some of their names turned up in a joint CIA-FBI database as known Mossad agents, along with the owner of Urban Moving Systems, Dominik Suter, whose name also appeared on a "Law Enforcement Sensitive" FBI 9/11 suspects list, along with the names of key "hijackers," including Mohammed Atta and Hani Hanjour, as well as the so-called "20th hijacker," Zacarias Moussaoui.\ \ Suter was allowed to escape the United States after the FBI made initial contact with him at the Urban Moving Systems warehouse in Weehawken, New Jersey, following the 9/11 attacks. Suter was later permitted to return to the United States where he was involved in the aircraft parts supply business in southern Florida, according to an informe3d source who contacted WMR. Suter later filed for bankruptcy in Florida for Urban Moving Systems and other businesses he operated: Suburban Moving & Storage Inc.; Max Movers, Inc.; Invsupport; Woodflooring Warehouse Corp.; One Stop Cleaning LLC; and City Carpet Upholstery, Inc. At the time of the bankruptcy filing in Florida, Suter listed his address as 1867 Fox Court, Wellington, FL 33414, with a phone number of 561 204-2359.\ \ From the list of creditors it can be determined that Suter had been operating in the United States since 1993, the year of the first attack on the World Trade Center. In 1993, Suter began racking up American Express credit card charges totaling $21,913.97. Suter also maintained credit card accounts with HSBC Bank and Orchard Bank c/o HSBC Card Services of Salinas, California, among other banks. Suter also did business with the Jewish Community Center of Greater Palm Beach in Florida and Ryder Trucks in Miami. Miami and southern Florida were major operating areas for cells of Israeli Mossad agents masquerading as "art students," who were living and working near some of the identified future Arab "hijackers" in the months preceding 9/11.\ \ ABC's 20/20 correspondent John Miller ensured that the Israeli connection to "Al Qaeda's" Arab hijackers was buried in an "investigation" of the movers' activities on 9/11. Anchor Barbara Walters helped Miller in putting a lid on the story about the movers and Suter aired on June 21, 2002. Miller then went on to become the FBI public affairs spokesman to ensure that Mueller and other FBI officials kept to the "Al Qaeda" script as determined by the Bush administration and the future 9/11 Commission. But former CIA chief of counter-terrorism Vince Cannistraro let slip to ABC an important clue to the operations of the Mossad movers in New Jersey when he stated that the Mossad agents "set up or exploited for the purpose of launching an intelligence operation against radical Islamists in the area, particularly in the New Jersey-New York area." The "intelligence operation" turned out to have been the actual 9/11 attacks. And it was no coincidence that it was ABC's John Miller who conducted a May 1998 rare interview of Osama Bin Laden at his camp in Afghanistan. Bin Laden played his part well for future scenes in the fictional "made-for-TV" drama known as 9/11.\ \ WMR has also learned from Italian intelligence sources that Mossad's running of "Al Qaeda" operatives did not end with running the "hijacking" teams in the United States and Hamburg. Other Arab "Al Qaeda" operatives, run by Mossad, were infiltrated into Syria but arrested by Syrian intelligence. Syria was unsuccessful in turning them to participate in intelligence operations in Lebanon. Detailed information on Bin Laden's support team was offered to the Bush administration, up to days prior to 9/11, by Gutbi al-Mahdi, the head of the Sudanese Mukhabarat intelligence service. The intelligence was rejected by the Biush White House. It was later reported that Sudanese members of "Al Qaeda's" support network were double agents for Mossad who had also established close contacts with Yemeni President Ali Abdullah Saleh and operated in Egypt, Saudi Arabia, and Eritrea, as well as Sudan. The Mossad connection to Al Qaeda in Sudan was likely known by the Sudanese Mukhabarat, a reason for the rejection of its intelligence on "Al Qaeda" by the thoroughly-Mossad penetrated Bush White House. Yemen had also identified "Al Qaeda" members who were also Mossad agents. A former chief of Mossad revealed to this editor in 2002 that Yemeni-born Mossad "deep insertion" commandos spotted Bin Laden in the Hadhramaut region of eastern Yemen after his escape from Tora Bora in Afghanistan, following the U.S. invasion.\ \ French intelligence determined that other Egyptian- and Yemeni-born Jewish Mossad agents were infiltrated into Sharjah in the United Arab Emirates as radical members of the Muslim Brotherhood. However, the "Muslim Brotherhood" agents actually were involved in providing covert Israeli funding for "Al Qaeda" activities. On February 21, 2006, WMR reported on the U.S. Treasury Secretary's firing by President Bush over information discovered on the shady "Al Qaeda" accounts in the United Arab Emirates: "Banking insiders in Dubai report that in March 2002, U.S. Secretary of Treasury Paul O’Neill visited Dubai and asked for documents on a $109,500 money transfer from Dubai to a joint account held by hijackers Mohammed Atta and Marwan al Shehhi at Sun Trust Bank in Florida. O'Neill also asked UAE authorities to close down accounts used by Al Qaeda . . . . The UAE complained about O’Neill’s demands to the Bush administration. O’Neill’s pressure on the UAE and Saudis contributed to Bush firing him as Treasury Secretary in December 2002 " O'Neill may have also stumbled on the "Muslim Brotherhood" Mossad operatives operating in the emirates who were directing funds to "Al Qaeda."\ \ After the collapse of the Soviet Union and the rise to power of the Taliban in Afghanistan, Sharjah's ruler, Sultan bin Mohammed al-Qasimi, who survived a palace coup attempt in 1987, opened his potentate to Russian businessmen like Viktor Bout, as well as to financiers of radical Muslim groups, including the Taliban and "Al Qaeda."\ \ Moreover, this Israeli support for "Al Qaeda" was fully known to Saudi intelligence, which approved of it in order to avoid compromising Riyadh. The joint Israeli-Saudi support for "Al Qaeda" was well-known to the Sharjah and Ras al Khaimah-based aviation network of the now-imprisoned Russian, Viktor Bout, jailed in New York on terrorism charges. The presence of Bout in New York, a hotbed of Israeli intelligence control of U.S. federal prosecutors, judges, as well as the news media, is no accident: Bout knows enough about the Mossad activities in Sharjah in support of the Taliban and Al Qaeda in Afghanistan, where Bout also had aviation and logistics contracts, to expose Mossad as the actual mastermind behind 9/11. Bout's aviation empire also extended to Miami and Dallas, two areas that were nexuses for the Mossad control operations for the "Al Qaeda" flight training operations of the Arab cell members in the months prior to 9/11.\ \ Bout's path also crossed with "Al Qaeda's" support network at the same bank in Sharjah, HSBC. Mossad's phony Muslim Brotherhood members from Egypt and Yemen controlled financing for "Al Qaeda" through the HSBC accounts in Sharjah. Mossad's Dominik Suter also dealt with HSBC in the United States. The FBI's chief counter-terrorism agent investigating Al Qaeda, John O'Neill, became aware of the "unique" funding mechanisms for Al Qaeda. It was no mistake that O'Neill was given the job as director of security for the World Trade Center on the eve of the attack. O'Neill perished in the collapse of the complex.Mossad uses a number of Jews born in Arab countries to masquerade as Arabs. They often carry forged or stolen passports from Arab countries or nations in Europe that have large Arab immigrant populations, particularly Germany, France, Britain, Denmark, Sweden, and the Netherlands.\ \ For Mossad, the successful 9/11 terrorist "false flag" operation was a success beyond expectations. The Bush administration, backed by the Blair government, attacked and occupied Iraq, deposing Saddam Hussein, and turned up pressure on Israel's other adversaries, including Iran, Syria, Pakistan, Hamas, and Lebanese Hezbollah. The Israelis also saw the U.S., Britain, and the UN begin to crack down on the Lebanese Shi'a diamond business in Democratic Republic of Congo and West Africa, and with it, the logistics support provided by Bout's aviation companies, which resulted in a free hand for Tel Aviv to move in on Lebanese diamond deals in central and west Africa.\ \ Then-Israeli Finance Minister Binyamin Netanyahu commented on the 9/11 attacks on U.S. television shortly after they occurred. Netanyahu said: "It is very good!" It now appears that Netanyahu, in his zeal, blew Mossad's cover as the masterminds of 9/11.\ \ Wayne Madsen is a Washington, DC-based investigative journalist, author and syndicated columnist. He has written for several renowned papers and blogs.\ \ Madsen is a regular contributor on Russia Today. He has been a frequent political and national security commentator on Fox News and has also appeared on ABC, NBC, CBS, PBS, CNN, BBC, Al Jazeera, and MS-NBC. Madsen has taken on Bill O’Reilly and Sean Hannity on their television shows. He has been invited to testifty as a witness before the US House of Representatives, the UN Criminal Tribunal for Rwanda, and an terrorism investigation panel of the French government.\ \ As a U.S. Naval Officer, he managed one of the first computer security programs for the U.S. Navy. He subsequently worked for the National Security Agency, the Naval Data Automation Command, Department of State, RCA Corporation, and Computer Sciences Corporation.\ \ Madsen is a member of the Society of Professional Journalists (SPJ), Association for Intelligence Officers (AFIO), and the National Press Club. He is a regular contributor to Opinion Maker
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 1817b617:715fb372
2025-05-22 23:39:18
@ 1817b617:715fb372
2025-05-22 23:39:18🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge 🔥 Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
🌐 Explore all the details at cryptoflashingtool.com.
🌟 Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
🎯 Top Features You’ll Love: ✅ Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
🔒 Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
🖥️ User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
📅 Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
🔄 Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
💱 Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
📊 Proven Results: ✅ Over 79 billion flash transactions completed. ✅ 3000+ satisfied users around the globe. ✅ 42 active blockchain nodes ensuring fast, seamless performance.
📌 How It Works: Step 1️⃣: Input Transaction Info
Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20). Set amount and flash duration. Enter the recipient wallet (auto-validated). Step 2️⃣: Make Payment
Pay in your selected crypto. Scan the QR code or use the provided address. Upload your transaction proof (hash and screenshot). Step 3️⃣: Launch the Flash
Blockchain confirmation simulation happens instantly. Your transaction appears real within seconds. Step 4️⃣: Verify & Spend
Access your flashed coins immediately. Verify your transactions using blockchain explorers. 🛡️ Why Our Flashing Tech Leads the Market: 🔗 Race/Finney Attack Mechanics: Mimics authentic blockchain behavior. 🖥️ Private iNode Clusters: Deliver fast syncing and reliable confirmation. ⏰ Live Timer: Ensures fresh, legitimate transactions. 🔍 Real Blockchain TX IDs: All transactions come with verifiable IDs.
❓ FAQs:
Is flashing secure? ✅ Yes, fully encrypted with VPN/proxy compatibility. Multiple devices? ✅ Yes, up to 5 Windows PCs per license. Chargebacks possible? ❌ No, flashing is irreversible. Spendability? ✅ Flash coins stay spendable 60–360 days. Verification after expiry? ❌ No, transactions expire after the set time. Support? ✅ 24/7 Telegram and WhatsApp help available. 🔐 Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
📲 Contact Us: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Flash Like a Pro?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge
Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
Explore all the details at cryptoflashingtool.com.
Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
Top Features You’ll Love:
Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
Proven Results:
Over 79 billion flash transactions completed.
3000+ satisfied users around the globe.
42 active blockchain nodes ensuring fast, seamless performance.
How It Works: Step
: Input Transaction Info
- Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20).
- Set amount and flash duration.
- Enter the recipient wallet (auto-validated).
Step
: Make Payment
- Pay in your selected crypto.
- Scan the QR code or use the provided address.
- Upload your transaction proof (hash and screenshot).
Step
: Launch the Flash
- Blockchain confirmation simulation happens instantly.
- Your transaction appears real within seconds.
Step
: Verify & Spend
- Access your flashed coins immediately.
- Verify your transactions using blockchain explorers.
Why Our Flashing Tech Leads the Market:
Race/Finney Attack Mechanics: Mimics authentic blockchain behavior.
Private iNode Clusters: Deliver fast syncing and reliable confirmation.
Live Timer: Ensures fresh, legitimate transactions.
Real Blockchain TX IDs: All transactions come with verifiable IDs.
FAQs:
- Is flashing secure?
Yes, fully encrypted with VPN/proxy compatibility. - Multiple devices?
Yes, up to 5 Windows PCs per license. - Chargebacks possible?
No, flashing is irreversible. - Spendability?
Flash coins stay spendable 60–360 days. - Verification after expiry?
No, transactions expire after the set time. - Support?
24/7 Telegram and WhatsApp help available.
Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
Contact Us:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Flash Like a Pro?
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 74fb3ef2:58adabc7
2025-05-22 22:26:23
@ 74fb3ef2:58adabc7
2025-05-22 22:26:23Suppose you have a small mom-and-pop shop selling bananas, your bananas are of the highest quality, you plant the banana trees yourself, you water them daily, take great care of everything, and still select only the top 1% of bananas to sell.
Your customers love it, there's no place where they can get better bananas, but due to the fact that you spend so much time, your bananas have to be more expensive, so despite the higher quality, you don't make as much money as you think you should; surely you can get a little more of the market if you adopt some of the strategies that work for your competitors.
So you look across the street, and what do you know? Their bananas are of significantly worse quality than yours, but they're not just selling bananas, they're selling apples too, so you think to yourself, "what if I sold apples? Maybe my apples won't be the best in the market, but nobody can beat my bananas!"
You start planting apple trees, and after a while you're able go sell slightly better than average apples, but by doing so you neglect your bananas ever so slightly.
Most of your existing customers don't notice, you still have the best bananas in town, they don't notice the slight drop in quality. And now that you're selling apples too you're making more money, and more customers come to you.
But you notice that there's a new store now that's selling oranges, and people are buying them. So surely you need oranges too, so you can make some extra money.
You plant a few orange trees, but find yourself spending so much time tending to the oranges and apples that you can't devote the same time and love to your bananas.
You are making a bit of extra cash from the new customers, business is going well, but you don't have time for anything else anymore. You no free time anymore, you are overworked and your health is getting worse.
But you can't stop now that business is going well, you are making so much more, yeah maybe you don't have the same bananas anymore, but you do have slightly above average apples and oranges that have attracted so many customers.
You suddenly fall ill, you've overworked yourself and you are stuck at a hospital for a while.
When you come back to your store, a few of your customers are back, but not all of them, so you think of more ideas, mandarins, kiwi, watermelons, you can grow it all, but you're gonna hire a bunch of people to help you so you don't fall ill again.
One thing leads to another and you are making more money than ever, but strangely you don't hear your customers praising your bananas anymore.
So you take one of your bananas, peel it, and as you taste it, a wave of disappointment hits you.
Your bananas are now just as bad as everyone else's; you gave in to the tyranny of the marginal customer.
You make a lot of money now, but your flagship product is long gone, you are now just another Fruitseller.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ bf47c19e:c3d2573b
2025-05-22 21:03:52
@ bf47c19e:c3d2573b
2025-05-22 21:03:52Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
-
Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.
-
Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
-
Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.
Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine: kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.
Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
 Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.
Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj tweet to savršeno objašnjava:
Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ cae03c48:2a7d6671
2025-05-22 20:01:14
@ cae03c48:2a7d6671
2025-05-22 20:01:14Bitcoin Magazine

Bitcoiners Should Care About The GENIUS ActWhile the GENIUS Act is a stablecoin bill, U.S.-based Bitcoin enthusiasts should be paying attention to the language in the bill as it pertains to the ability to transact privately with crypto assets — including bitcoin.
Two documents that recently circulated among Senate Banking Committee Democrats indicate that Senate Democrats want to see amendments made to the GENIUS Act that would greatly reduce user privacy in crypto transactions.
Senate Democrats’ Analysis of GENIUS Act
The first of these two documents is a two-pager entitled “Banking Committee Democratic Staff Analysis on Latest GENIUS Act Draft”.
 NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote.
NEW: Senate Banking Committee Democrats just dropped a scathing staff analysis of the latest GENIUS Act draft ahead of this evening’s cloture vote. Staffers describe the latest GENIUS Act draft as a blueprint for ‘Trump crypto corruption’ and Big Tech dominance over digital… pic.twitter.com/Gqd2LxFGx1
— Eleanor Terrett (@EleanorTerrett) May 19, 2025
This document is filled with the type of rhetoric that is commonly associated with the Ranking Member of the Senate Banking Committee, Senator Elizabeth Warren (D-MA).
It refers to stablecoins as tools for illicit finance (despite the fact that the largest stablecoin issuer, Tether, often works with the Department of Justice (DoJ) and the FBI to stop the illegal use of stablecoins).
It also states that the current iteration of the GENIUS Act “does nothing to actually impose basic obligations on [crypto mixers] to prevent illicit finance.”

A segment from document featuring Democrats’ analysis of The GENIUS Act.
This latter critique of the bill is antithetical to guidance that Deputy Attorney General (DAG) Todd Blanche offered in a memo on April 7, 2025. DAG Blanche stated that the DoJ will no longer target crypto mixing services for the acts of their end users.
In this document, however, Senate Democrats indicate that they plan to continue targeting crypto mixing technology instead of those who abuse it.
If amendments regarding the targeting of crypto mixers are added to a revised version of the GENIUS Act, this could have an impact on Bitcoin users who employ such technology in the name of preserving their privacy.
A Letter From Democrats Opposing The GENIUS Act
Senate Banking Democrats circulated a second document on Monday, as well.
This document, a letter signed by 46 advocacy groups, opposed the GENIUS Act.
Brendan Pedersen of Punchbowl News shared segments of the letter on X.
Democratic staff on the Senate Banking Committee sent around a letter this AM signed by several dozen advocacy orgs opposing the GENIUS Act.
Includes ACRE, AFR, Center for Responsible Lending, Our Revolution, Public Citizen, Tech Oversight Project… pic.twitter.com/pragFvzSKB
— Brendan Pedersen (@BrendanPedersen) May 19, 2025
The authors of the letter claim that the GENIUS Act does not do enough to prevent illicit finance in part because it still allows for “self-hosted wallets that lack know-your-customer (KYC) requirements.”
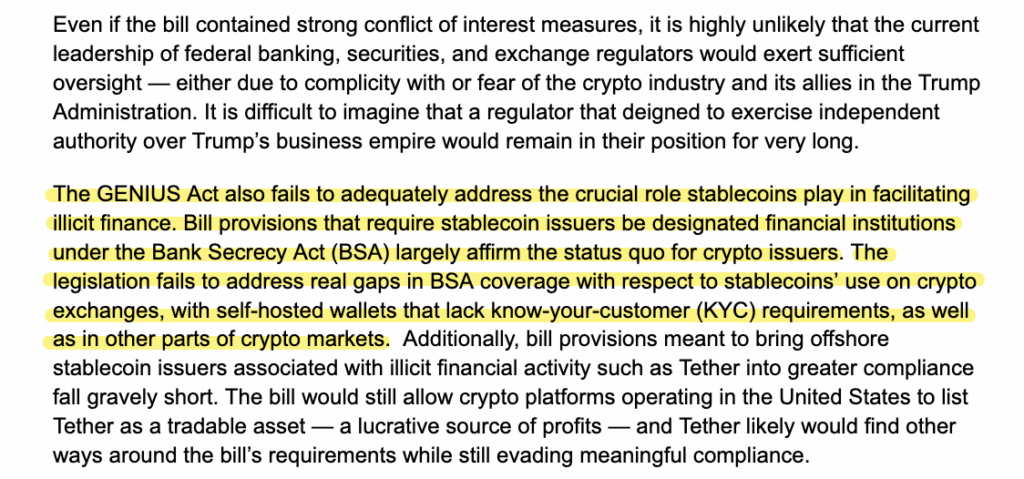
A segment from the letter opposing The GENIUS Act that touches on noncustodial wallets and KYC requirements.
If the GENIUS Act is amended so that it requires KYC for all wallets that touch stablecoins — self-custodial wallets included — it’s likely only a matter of time before similar regulation is established for Bitcoin wallets.
Bitcoin Transactional Privacy Is At Stake
Just because the GENIUS Act doesn’t directly reference Bitcoin doesn’t mean that Bitcoin won’t be affected by it.
If Senate Democrats get their way and crypto mixers become a target of the bill and/or if the bill requires that all wallets that touch stablecoins require users to KYC, and the bill is enacted into law, anonymity in crypto transactions will become a crime.
So, while some Bitcoiners may be anti-stablecoins, most, I would wager, aren’t anti-privacy. Therefore, it would behoove them to contact their elected officials to urge them to vote “no” for the GENIUS Act if the upcoming iteration of the bill restricts the ability to transact privately.
This post Bitcoiners Should Care About The GENIUS Act first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ e691f4df:1099ad65
2025-04-24 18:56:12
@ e691f4df:1099ad65
2025-04-24 18:56:12Viewing Bitcoin Through the Light of Awakening
Ankh & Ohm Capital’s Overview of the Psycho-Spiritual Nature of Bitcoin
Glossary:
I. Preface: The Logos of Our Logo
II. An Oracular Introduction
III. Alchemizing Greed
IV. Layers of Fractalized Thought
V. Permissionless Individuation
VI. Dispelling Paradox Through Resonance
VII. Ego Deflation
VIII. The Coin of Great Price
Preface: The Logos of Our Logo
Before we offer our lens on Bitcoin, it’s important to illuminate the meaning behind Ankh & Ohm’s name and symbol. These elements are not ornamental—they are foundational, expressing the cosmological principles that guide our work.
Our mission is to bridge the eternal with the practical. As a Bitcoin-focused family office and consulting firm, we understand capital not as an end, but as a tool—one that, when properly aligned, becomes a vehicle for divine order. We see Bitcoin not simply as a technological innovation but as an emanation of the Divine Logos—a harmonic expression of truth, transparency, and incorruptible structure. Both the beginning and the end, the Alpha and Omega.
The Ankh (☥), an ancient symbol of eternal life, is a key to the integration of opposites. It unites spirit and matter, force and form, continuity and change. It reminds us that capital, like Life, must not only be generative, but regenerative; sacred. Money must serve Life, not siphon from it.
The Ohm (Ω) holds a dual meaning. In physics, it denotes a unit of electrical resistance—the formative tension that gives energy coherence. In the Vedic tradition, Om (ॐ) is the primordial vibration—the sound from which all existence unfolds. Together, these symbols affirm a timeless truth: resistance and resonance are both sacred instruments of the Creator.
Ankh & Ohm, then, represents our striving for union, for harmony —between the flow of life and intentional structure, between incalculable abundance and measured restraint, between the lightbulb’s electrical impulse and its light-emitting filament. We stand at the threshold where intention becomes action, and where capital is not extracted, but cultivated in rhythm with the cosmos.
We exist to shepherd this transformation, as guides of this threshold —helping families, founders, and institutions align with a deeper order, where capital serves not as the prize, but as a pathway to collective Presence, Purpose, Peace and Prosperity.
An Oracular Introduction
Bitcoin is commonly understood as the first truly decentralized and secure form of digital money—a breakthrough in monetary sovereignty. But this view, while technically correct, is incomplete and spiritually shallow. Bitcoin is more than a tool for economic disruption. Bitcoin represents a mythic threshold: a symbol of the psycho-spiritual shift that many ancient traditions have long foretold.
For millennia, sages and seers have spoken of a coming Golden Age. In the Vedic Yuga cycles, in Plato’s Great Year, in the Eagle and Condor prophecies of the Americas—there exists a common thread: that humanity will emerge from darkness into a time of harmony, cooperation, and clarity. That the veil of illusion (maya, materiality) will thin, and reality will once again become transparent to the transcendent. In such an age, systems based on scarcity, deception, and centralization fall away. A new cosmology takes root—one grounded in balance, coherence, and sacred reciprocity.
But we must ask—how does such a shift happen? How do we cross from the age of scarcity, fear, and domination into one of coherence, abundance, and freedom?
One possible answer lies in the alchemy of incentive.
Bitcoin operates not just on the rules of computer science or Austrian economics, but on something far more old and subtle: the logic of transformation. It transmutes greed—a base instinct rooted in scarcity—into cooperation, transparency, and incorruptibility.
In this light, Bitcoin becomes more than code—it becomes a psychoactive protocol, one that rewires human behavior by aligning individual gain with collective integrity. It is not simply a new form of money. It is a new myth of value. A new operating system for human consciousness.
Bitcoin does not moralize. It harmonizes. It transforms the instinct for self-preservation into a pathway for planetary coherence.
Alchemizing Greed
At the heart of Bitcoin lies the ancient alchemical principle of transmutation: that which is base may be refined into gold.
Greed, long condemned as a vice, is not inherently evil. It is a distorted longing. A warped echo of the drive to preserve life. But in systems built on scarcity and deception, this longing calcifies into hoarding, corruption, and decay.
Bitcoin introduces a new game. A game with memory. A game that makes deception inefficient and truth profitable. It does not demand virtue—it encodes consequence. Its design does not suppress greed; it reprograms it.
In traditional models, game theory often illustrates the fragility of trust. The Prisoner’s Dilemma reveals how self-interest can sabotage collective well-being. But Bitcoin inverts this. It creates an environment where self-interest and integrity converge—where the most rational action is also the most truthful.
Its ledger, immutable and transparent, exposes manipulation for what it is: energetically wasteful and economically self-defeating. Dishonesty burns energy and yields nothing. The network punishes incoherence, not by decree, but by natural law.
This is the spiritual elegance of Bitcoin: it does not suppress greed—it transmutes it. It channels the drive for personal gain into the architecture of collective order. Miners compete not to dominate, but to validate. Nodes collaborate not through trust, but through mathematical proof.
This is not austerity. It is alchemy.
Greed, under Bitcoin, is refined. Tempered. Re-forged into a generative force—no longer parasitic, but harmonic.
Layers of Fractalized Thought Fragments
All living systems are layered. So is the cosmos. So is the human being. So is a musical scale.
At its foundation lies the timechain—the pulsing, incorruptible record of truth. Like the heart, it beats steadily. Every block, like a pulse, affirms its life through continuity. The difficulty adjustment—Bitcoin’s internal calibration—functions like heart rate variability, adapting to pressure while preserving coherence.
Above this base layer is the Lightning Network—a second layer facilitating rapid, efficient transactions. It is the nervous system: transmitting energy, reducing latency, enabling real-time interaction across a distributed whole.
Beyond that, emerging tools like Fedimint and Cashu function like the capillaries—bringing vitality to the extremities, to those underserved by legacy systems. They empower the unbanked, the overlooked, the forgotten. Privacy and dignity in the palms of those the old system refused to see.
And then there is NOSTR—the decentralized protocol for communication and creation. It is the throat chakra, the vocal cords of the “freedom-tech” body. It reclaims speech from the algorithmic overlords, making expression sovereign once more. It is also the reproductive system, as it enables the propagation of novel ideas and protocols in fertile, uncensorable soil.
Each layer plays its part. Not in hierarchy, but in harmony. In holarchy. Bitcoin and other open source protocols grow not through exogenous command, but through endogenous coherence. Like cells in an organism. Like a song.
Imagine the cell as a piece of glass from a shattered holographic plate —by which its perspectival, moving image can be restructured from the single shard. DNA isn’t only a logical script of base pairs, but an evolving progressive song. Its lyrics imbued with wise reflections on relationships. The nucleus sings, the cell responds—not by command, but by memory. Life is not imposed; it is expressed. A reflection of a hidden pattern.
Bitcoin chants this. Each node, a living cell, holds the full timechain—Truth distributed, incorruptible. Remove one, and the whole remains. This isn’t redundancy. It’s a revelation on the power of protection in Truth.
Consensus is communion. Verification becomes a sacred rite—Truth made audible through math.
Not just the signal; the song. A web of self-expression woven from Truth.
No center, yet every point alive with the whole. Like Indra’s Net, each reflects all. This is more than currency and information exchange. It is memory; a self-remembering Mind, unfolding through consensus and code. A Mind reflecting the Truth of reality at the speed of thought.
Heuristics are mental shortcuts—efficient, imperfect, alive. Like cells, they must adapt or decay. To become unbiased is to have self-balancing heuristics which carry feedback loops within them: they listen to the environment, mutate when needed, and survive by resonance with reality. Mutation is not error, but evolution. Its rules are simple, but their expression is dynamic.
What persists is not rigidity, but pattern.
To think clearly is not necessarily to be certain, but to dissolve doubt by listening, adjusting, and evolving thought itself.
To understand Bitcoin is simply to listen—patiently, clearly, as one would to a familiar rhythm returning.
Permissionless Individuation
Bitcoin is a path. One that no one can walk for you.
Said differently, it is not a passive act. It cannot be spoon-fed. Like a spiritual path, it demands initiation, effort, and the willingness to question inherited beliefs.
Because Bitcoin is permissionless, no one can be forced to adopt it. One must choose to engage it—compelled by need, interest, or intuition. Each person who embarks undergoes their own version of the hero’s journey.
Carl Jung called this process Individuation—the reconciliation of fragmented psychic elements into a coherent, mature Self. Bitcoin mirrors this: it invites individuals to confront the unconscious assumptions of the fiat paradigm, and to re-integrate their relationship to time, value, and agency.
In Western traditions—alchemy, Christianity, Kabbalah—the individual is sacred, and salvation is personal. In Eastern systems—Daoism, Buddhism, the Vedas—the self is ultimately dissolved into the cosmic whole. Bitcoin, in a paradoxical way, echoes both: it empowers the individual, while aligning them with a holistic, transcendent order.
To truly see Bitcoin is to allow something false to die. A belief. A habit. A self-concept.
In that death—a space opens for deeper connection with the Divine itSelf.
In that dissolution, something luminous is reborn.
After the passing, Truth becomes resurrected.
Dispelling Paradox Through Resonance
There is a subtle paradox encoded into the hero’s journey: each starts in solidarity, yet the awakening affects the collective.
No one can be forced into understanding Bitcoin. Like a spiritual truth, it must be seen. And yet, once seen, it becomes nearly impossible to unsee—and easier for others to glimpse. The pattern catches.
This phenomenon mirrors the concept of morphic resonance, as proposed and empirically tested by biologist Rupert Sheldrake. Once a critical mass of individuals begins to embody a new behavior or awareness, it becomes easier—instinctive—for others to follow suit. Like the proverbial hundredth monkey who begins to wash the fruit in the sea water, and suddenly, monkeys across islands begin doing the same—without ever meeting.
When enough individuals embody a pattern, it ripples outward. Not through propaganda, but through field effect and wave propagation. It becomes accessible, instinctive, familiar—even across great distance.
Bitcoin spreads in this way. Not through centralized broadcast, but through subtle resonance. Each new node, each individual who integrates the protocol into their life, strengthens the signal for others. The protocol doesn’t shout; it hums, oscillates and vibrates——persistently, coherently, patiently.
One awakens. Another follows. The current builds. What was fringe becomes familiar. What was radical becomes obvious.
This is the sacred geometry of spiritual awakening. One awakens, another follows, and soon the fluidic current is strong enough to carry the rest. One becomes two, two become many, and eventually the many become One again. This tessellation reverberates through the human aura, not as ideology, but as perceivable pattern recognition.
Bitcoin’s most powerful marketing tool is truth. Its most compelling evangelist is reality. Its most unstoppable force is resonance.
Therefore, Bitcoin is not just financial infrastructure—it is psychic scaffolding. It is part of the subtle architecture through which new patterns of coherence ripple across the collective field.
The training wheels from which humanity learns to embody Peace and Prosperity.
Ego Deflation
The process of awakening is not linear, and its beginning is rarely gentle—it usually begins with disruption, with ego inflation and destruction.
To individuate is to shape a center; to recognize peripherals and create boundaries—to say, “I am.” But without integration, the ego tilts—collapsing into void or inflating into noise. Fiat reflects this pathology: scarcity hoarded, abundance simulated. Stagnation becomes disguised as safety, and inflation masquerades as growth.
In other words, to become whole, the ego must first rise—claiming agency, autonomy, and identity. However, when left unbalanced, it inflates, or implodes. It forgets its context. It begins to consume rather than connect. And so the process must reverse: what inflates must deflate.
In the fiat paradigm, this inflation is literal. More is printed, and ethos is diluted. Savings decay. Meaning erodes. Value is abstracted. The economy becomes bloated with inaudible noise. And like the psyche that refuses to confront its own shadow, it begins to collapse under the weight of its own illusions.
But under Bitcoin, time is honored. Value is preserved. Energy is not abstracted but grounded.
Bitcoin is inherently deflationary—in both economic and spiritual senses. With a fixed supply, it reveals what is truly scarce. Not money, not status—but the finite number of heartbeats we each carry.
To see Bitcoin is to feel that limit in one’s soul. To hold Bitcoin is to feel Time’s weight again. To sense the importance of Bitcoin is to feel the value of preserved, potential energy. It is to confront the reality that what matters cannot be printed, inflated, or faked. In this way, Bitcoin gently confronts the ego—not through punishment, but through clarity.
Deflation, rightly understood, is not collapse—it is refinement. It strips away illusion, bloat, and excess. It restores the clarity of essence.
Spiritually, this is liberation.
The Coin of Great Price
There is an ancient parable told by a wise man:
“The kingdom of heaven is like a merchant seeking fine pearls, who, upon finding one of great price, sold all he had and bought it.”
Bitcoin is such a pearl.
But the ledger is more than a chest full of treasure. It is a key to the heart of things.
It is not just software—it is sacrament.
A symbol of what cannot be corrupted. A mirror of divine order etched into code. A map back to the sacred center.
It reflects what endures. It encodes what cannot be falsified. It remembers what we forgot: that Truth, when aligned with form, becomes Light once again.
Its design is not arbitrary. It speaks the language of life itself—
The elliptic orbits of the planets mirrored in its cryptography,
The logarithmic spiral of the nautilus shell discloses its adoption rate,
The interconnectivity of mycelium in soil reflect the network of nodes in cyberspace,
A webbed breadth of neurons across synaptic space fires with each new confirmed transaction.
It is geometry in devotion. Stillness in motion.
It is the Logos clothed in protocol.
What this key unlocks is beyond external riches. It is the eternal gold within us.
Clarity. Sovereignty. The unshakeable knowing that what is real cannot be taken. That what is sacred was never for sale.
Bitcoin is not the destination.
It is the Path.
And we—when we are willing to see it—are the Temple it leads back to.
-
 @ 2b24a1fa:17750f64
2025-05-22 19:44:28
@ 2b24a1fa:17750f64
2025-05-22 19:44:28„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian?
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
Bild: Marco Maas/fotografirma.de
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 9b308fda:b6c7310d
2025-05-22 18:30:19
@ 9b308fda:b6c7310d
2025-05-22 18:30:19@15/05/2025 ✨ Week 0 – Getting Started with My Internship at Formstr (Onboarding)
I’m excited to share that I’ve been selected as a Summer of Bitcoin intern at Formstr!
After the final exams wrapped up on May 4th, I took a short, well-deserved break while traveling back home from college for the summer. Once settled in, I quickly transitioned into internship mode and began diving into the project assigned to me at Formstr.
It’s been a great start so far, and I’m looking forward to learning, building, and sharing more along the way.
@22/05/2025 — Week 01 – Building Features and Brainstorming at Formstr
This week at Formstr was packed with development and discussions.
The major highlight was completing the row popup view for form responses — now, clicking on any response row shows a clean and complete view of that user's submission. I'm happy to share that the pull request has been merged! It feels great to contribute something that improves the user experience so visibly.
Alongside that, I started brainstorming the LLM-Analysis feature. We had a productive discussion during the weekly developer meeting on Signal, where I shared my initial thoughts and got valuable input from the team. There's a lot of potential in this, and it’s exciting to shape it from the ground up.
I also worked on improving relay management in the form settings to reduce redundancy. The changes are in progress, and it’s almost done — just final touches left before merging.
Another topic we tackled was the “Form Filler with AI” feature. There are still some open questions around implementation and user flow, so we’ve decided to continue discussions with more team members before finalizing the plan.
We’ve also agreed to hold weekly team meetings going forward to keep everyone aligned on ideas, progress, and blockers. I’m glad to be part of such a collaborative and thoughtful team!
-
 @ 8bad92c3:ca714aa5
2025-05-22 18:02:41
@ 8bad92c3:ca714aa5
2025-05-22 18:02:41Key Takeaways

In this episode of TFTC, Andrew Myers, founder of Satoshi Energy, explores the convergence of AI, humanoid robots, Bitcoin, and decentralized energy, warning of a near future where self-replicating machines dominate energy and labor. Myers argues that Bitcoin’s decentralized nature offers a critical check against centralized AI power, enabling autonomous agents to transact freely and protecting individual sovereignty. Through his company’s work and its software BitCurrent, Myers promotes Bitcoin as both a tool for energy market efficiency and a foundation for preserving liberty in an AI-driven world.
Best Quotes
“Humanoid robots are going to not only replace most of the jobs people do today… they're going to be able to recreate themselves and self-replicate faster than that.”
“For me the key value proposition of Bitcoin is leveling the economic playing field. Rather than those who control the money printer making the economic decisions, it's everyday people.”
“AI energy demand is infinite. Bitcoin has a Nakamoto point… AI doesn’t.”
“Satoshi Energy’s mission is to enable every electric power company to use Bitcoin by block 1,050,000.”
“If you're a Bitcoiner and you're not using Fold, what are you doing? You're leaving sats on the table.”
“Tesla said machines would eventually fight wars for us. When that happens, nation-states become spectators. Bitcoin is how we avoid centralized control of those machines.”
“There’s already an energy company in Texas using Bitcoin as collateral in a power contract.”
“Are we auditioning for a galactic federation? Maybe. Even if not, we should still be acting like we are.”
Conclusion
Andrew Myers delivers a compelling vision of the future where exponential AI and energy growth demand a decentralized response—one rooted in Bitcoin as more than money, but as critical infrastructure for freedom. Through Satoshi Energy and tools like BitCurrent, Myers bridges big ideas with tangible actions, advocating for bottom-up sovereignty across energy and finance. His message is clear: decentralization is no longer optional—it’s essential for preserving human agency in an increasingly automated world.
Timestamps
0:00 - Intro
0:34 - Tesla’s AI energy theory
8:59 - Bitcoin and decentralization fixes AI
13:02 - Fold & Bitkey
14:38 - How Satoshi Energy is using AI
19:28 - Bit Current
23:13 - Unchained
23:42 - Revealing inefficiency
32:57 - Proliferating OS AI with bitcoin
36:26 -Apple of Eden and Antichrist
45:11 - Iberian outage
48:48 - Defense tech
54:51 - UFOs, Atlantis and remote viewingTranscript
(00:00) Humanoid robots are advancing so quickly. They're going to not only replace most of the jobs that people do today, probably the next 5 to 10 years, but they're going to be able to recreate themselves and self-replicate even faster than that. With AI, the energy demand is infinite. It's going to 10x and 10x and 10x again in terms of global energy consumption, and that's just going to completely change the world we live in.
(00:21) If there's a sufficiently advanced AI, is it going to listen to a politician that says, "No, you can't have that energy." Or is it going to say, "Fuck you. Send the drone. You can hear us loud and clear. Loud and clear. I have to put this in front of my face so I'm not leaning. Yeah, vibe coding. There may be some securityities.
(00:45) I do want to hand it off to a developer who actually understands this stuff to say, am I am I going to am I going to leak any information or like be Yeah, I should probably do that before I release to the public. Now, let me say that. does seem pretty simple though. It's just getting the data on the page, getting the price of Bitcoin, using Coin Gecko API, and then running the math of how much Bitcoin is this worth at this point in time.
(01:13) We're not collecting any data either. I don't think that you know of. No, this is AI once. This is the problem of vibe coding. Are you bearish on AI? Uh, I think we're at a fork in the road and on one side I'm very bullish. You shamed me for for admitting that I was turning my kids into Legos via or turning myself into Lego in this. I was channeling my inner Marty.
(01:36) What would Marty do? Well, that's what uh that's what precipitated this. You hit me up. Was it two weeks ago now at this point? this week with your tweet about Nicola Tesla essentially predicting AI and him not factoring in sound money to the inevitable future that he foresaw. Yeah, it kind of came up uh in the work we're doing at Satoshi Energy where we're developing sites for data centers and a lot of those were were Bitcoin data centers for the last five six years and then in the last couple of years just increasingly demand
(02:20) from AI data centers in some cases like a project that we sold to a Bitcoin miner then becomes an AI site and then start to have questions within the team about what is our AI strategy and it was always in the back of my mind as part of the strategy which we'll get into like what is this fork in the road which directions could it go but I hadn't ever really communicated it to our team uh until recently because it's such a big idea that like on top of thinking about sound money and energy like we're already thinking about enough but as the
(02:57) team's growing as people are starting to ask these questions and like in some cases feeling conflicted about um should we be serving this AI market and in some cases large institutional investors and tech companies uh really like felt the need to put the the pen to paper and and talk about this and talk about how AI fits into our overall strategy.
(03:20) Uh, and part of that reminded me of this uh, essay that Nicola Tesla wrote called um, the problem of human energy, which was kind of a cheeky title. Uh, because clearly he thought, you know, energy would liberate humanity. Uh, but it get you get a lot more readers if you, you know, if you name it, the problem of human energy, especially a lot more of the critics who you're trying to convince otherwise.
(03:44) And one of the biggest things, biggest takeaways for me in that in that essay is he he basically says at some point man will create machines that fight wars for us and limit the the loss of human life to the point where the different parties, nation states, other powerful people u that were fighting wars with each other will once it's sort of this this machine to machine battle, they'll just become interested spectators.
(04:13) and eventually lead to world peace. So I think that's the path we want to be on. Not the path where it becomes a very centralized AI and we ultimately become enslaved. Uh but on the path to world peace or or keeping ourselves on that path to world peace. I think that's where Bitcoin plays a role. it keeps the economic playing field level uh and keeps this technology sufficiently decentralized where Bitcoin is that protocol for you know decentralized AI agents communicating with each other.
(04:46) So we can go in any direction you want from there but it's a big idea. No, this is in line with something I wrote about earlier this week that was inspired by a tweet that Paul Otoy from Stack put out basically not explaining this exact problem but just giving his thoughts on how he's viewing the state of AI and where it will go in the future.
(05:10) And Paul, the team at stack and sphinx are highly focused on enabling the open- source AI as opposed to closed source AI. I I think based on what you just said, I think it's very line what Paul was saying in that tweet, which is we're reaching the point with MCP with these sort of protocols where you can store context that agents can plug into and begin communicating with each other.
(05:39) We're at the point where agentic models are getting are actually usable. And I think that's where you have this like critical tipping point of okay that's really going to dictate which direction in the fork in the road we go down because once the agents are able to go do these tasks you right have these network effects that take hold and it's very important that we thread the needle of making sure that it's open and incentivized properly.
(06:10) Yes. Yes, we had this idea of time preference in the Bitcoin community where you know we think with sound money we should have a low time preference meaning we think longer term uh we don't need need to make sort of quick rash decisions into investments today but then you have this tidal wave of AI coming our our direction it almost forces you back into that high time preference mindset of like I need to address this problem now um and Then from like an energy perspective, it's interesting too.
(06:44) Uh you have like Drew's concept of the Nakamoto point for Bitcoin. Like how much of of human energy of global energy will will Bitcoin mining consume? And like say it's between 1 and 10% of of human energy. If it becomes 100% then uh that doesn't make any sense because then you're just like worshiping Bitcoin.
(07:03) And if all of the energy is going towards that, it means you're not putting any energy towards any other sort of economic pursuit or uh you know human need. But with AI, the energy demand is infinite. I don't think there is a Nakamoto point. It's just like it's going to 10x and 10x and 10x again in terms of g global energy consumption.
(07:23) Uh and that's just going to completely change the world we live in. Another thing on sort of the high time preference concept is like humanoid robots are advancing so quickly. They're going to not only replace all of the job most of the jobs that people do today, very quickly within probably the next 5 to 10 years max, but they're going to be able to rec -
 @ b2caa9b3:9eab0fb5
2025-04-24 06:25:35
@ b2caa9b3:9eab0fb5
2025-04-24 06:25:35Yesterday, I faced one of the most heartbreaking and frustrating experiences of my life. Between 10:00 AM and 2:00 PM, I was held at the Taveta border, denied entry into Kenya—despite having all the necessary documents, including a valid visitor’s permit and an official invitation letter.
The Kenyan Immigration officers refused to speak with me. When I asked for clarification, I was told flatly that I would never be allowed to enter Kenya unless I obtain a work permit. No other reason was given. My attempts to explain that I simply wanted to see my child were ignored. No empathy. No flexibility. No conversation. Just rejection.
While I stood there for hours, held by officials with no explanation beyond a bureaucratic wall, I recorded the experience. I now have several hours of footage documenting what happened—a silent testimony to how a system can dehumanize and block basic rights.
And the situation doesn’t end at the border.
My child, born in Kenya, is also being denied the right to see me. Germany refuses to grant her citizenship, which means she cannot visit me either. The German embassy in Nairobi refuses to assist, stating they won’t get involved. Their silence is loud.
This is not just about paperwork. This is about a child growing up without her father. It’s about a system that chooses walls over bridges, and bureaucracy over humanity. Kenya, by refusing me entry, is keeping a father away from his child. Germany, by refusing to act under §13 StGB, is complicit in that injustice.
In the coming days, I’ll share more about my past travels and how this situation unfolded. I’ll also be releasing videos and updates on TikTok—because this story needs to be heard. Not just for me, but for every parent and child caught between borders and bureaucracies.
Stay tuned—and thank you for standing with me.
-
 @ 3ad01248:962d8a07
2025-05-22 17:18:25
@ 3ad01248:962d8a07
2025-05-22 17:18:25With the price of Bitcoin skyrocketing as of late maybe its time that we go over some rules as a Bitcoiner because someone just got robbed in the UK of the Bitcoin wealth by a fake Uber driver. I fear this will become more common place as time goes on unless certain rules are followed.
Rule 1: Never talk about your Bitcoin holdings to people you don't know or don't trust
This will easily make you a target. If you are out in public saying you have 5 Bitcoin what do you think is going to happen when the wrong person finds out. They will follow you home, tie you up and take your shit. You can avoid this by not talking about your Bitcoin in public spaces, you never know how is listening. Hell I wouldn't even share it with your spouse to be honest. You don't know who she is talking to either. Keep your wealth private.
Rule 2: Stay Humble/Live Below Your means
Resist the urge to spend your new found wealth on something extravagent like a lambo or something that is going to draw unwanted attention. Not saying that you shouldn't enjoy your life but be aware that not everyone is going to be happy about your new found wealth. The best thing you can do is drive an unassuming car and live in regular home.
Rule 3: Don't Carry Your Wealth In Your Pocket
It is definitely a bad idea to walk around with your wealth stored on your phone. This is how people are getting robbed of their wealth. They leave their holding on some centralized exchange where all you need is a password to access their account. When you are under duress that isn't going to stop anyone from stealing your money. Self custody your Bitcoin and keep it in cold storage! Can't stress that enough.
Rule 5: Practice Good Digital Hygiene
With more and more of our lives online, especially social media it is a good idea to practice good digital hygiene. The internet is rife with scammers looking to access your private information to learn everything about you. Use a VPN if possible. You should probably get in the habit of creating multiple email address or use a service that creates fake ones for you. It is safe to assume that some database with your information will get hacked at some point. Better to have a random email get stolen versus the primary one that you use. A second phone line couldn't hurt as well.
Rule 6: Keep Your Circle Small
This kind of ties back in with the first rule. The more people you allow into your inner circle the more you open yourself up to attack. You can't always be sure of someone's motives especially people that you recent met. Be wary of people that just show up out of the blue wanting to be your best friend. This applies to family as well, if they somehow know that you own Bitcoin and see that you are doing well you can't assume that just because they are family you can't trust them. In fact these are the people you have to worry about the most.
It's better to be safe than sorry in my opinion. Keep your circle of trust small and you won't have problems.
These are six rules that I think can help keep you safe and you Bitcoin wealth in your hands. I'm sure there are more, if you think of more comment below!!
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 94215f42:7681f622
2025-05-23 01:44:26
@ 94215f42:7681f622
2025-05-23 01:44:26The promise of AI is intoxicating: slash operational costs by 50-80%, achieve software-style margins on service businesses and and watch enterprise value multiply overnight.
But this initial value creation contains a hidden trap that could leave businesses worth less than when they started. Understanding the "Value Trap" is key to navigating a transition to an AI economy.
What is the Value Trap?
Whilst the value trap is forward looking and somewhat theoretical at this point, there are strong financial incentives to drive investments (many $bns of are looking at the transformation opportunity) that mean this should be taken very seriously.
The Value Trap unfolds in distinct phases:
Phase 1: Status Quo A typical service business operates with 100 units of revenue and 90 units of cost, generating 10 units of profit, representing a standard 10% margin. A bog standard business we can all relate to, long term customers locked in, market fit a distant memory, but growth is hard at this point.
Phase 2: Cost Reduction Early AI adopters slash operational expenses from 90 to 20 units while maintaining 100 units of revenue. This is the very real promise when moving to a "Human at the Edge" model that we'll unpack in a future article. Suddenly, they're generating 80 units of profit at an 8x increase that can easily add multiple to the enterprise value! A venture style return on a business previously struggling for growth.
Phase 3: Growth Phase With massive profit margins comes pricing power. These businesses can undercut competitors while maintaining healthy margins, driving rapid revenue growth. Having removed the human constraint on scaling and the additional overheads and complexity this introduces we see seemingly unlimited expansion. The brakes are truly off at this point for early adopters to expand total market share.
Phase 4: Competition Emerges The extraordinary returns attract competitors. It's important to note there is no technical moat here, other businesses implement similar AI strategies, often from your own staff who may have been let go, new entrants launch AI-native operations, and pricing power erodes.
Phase 5: Mean Reversion After 3-7 years (our best guess given current investment interest in transformation led PE), competitive pressure drives revenue down from 100 to 25 units while costs remain at 20. The business ends up with similar margins to where it started but at much lower absolute revenue, potentially destroying enterprise value.
What you've done is just massively reduced costs in this industry by displacing jobs and those individuals can turn around and compete. You incentivise the competition which erodes your pricing power
Why This Pattern is Inevitable
The Value Trap isn't pure speculation, but based on market dynamics playing out given a set of financial incentives. We believe there are several key forces that make this cycle almost guaranteed:
The Arbitrage is Too Attractive When businesses can achieve "venture returns with no product-market fit risk," capital will flood in. Private equity and Venture Capital firms are already raising funds specifically to acquire traditional service businesses and apply AI transformation strategies .
Low Technical Barriers Unlike previous technological advantages, AI implementation doesn't require significant technical moats. Much of the technology is open source, and the real barrier is process redesign thinking rather than proprietary technology.
The "One Player" Principle In any market, it only takes one competitor to implement AI-native processes to force everyone else to adapt. You either "play the game or you get left behind".
Capital Abundance With global money supply expanding and traditional investment opportunities yielding lower returns, the combination of proven product-market fit and dramatic cost reduction potential represents an irresistible opportunity for investors.
Strategic Response for SMEs: The Netflix Model
Small and medium enterprises actually have a significant advantage in navigating the Value Trap, but they need to act strategically and start moving now.
Embrace the Incubation Approach Rather than gutting your existing business, adopt Netflix's strategy: build an AI-native version of your business alongside your current operations. This approach manages risk while positioning for the future.

The answer here is why not both. you don't necessarily have to gut your current business, but you should be thinking about what does my business look like in five years and how do I transition into that.
Leverage Your Natural Advantages Small businesses can adapt faster than large enterprises. While a 20,000-person company faces "political shockwaves" when reducing workforce, a 10-person business can double revenue without anyone noticing. You can focus on growth rather than painful cost-cutting.
Remove Growth Constraints Early AI removes the traditional constraint where "adding the next person" represents a significant capital investment. Small businesses can scale efficiently once they've redesigned their processes around AI-native workflows, avoid further capital outlay and scaling without increasing complexity in operations.
Focus on Local Networks For various reasons associated with the commoditisation of intelligence, we believe the future favours "hyper-localised" businesses serving customers who "know, like, and trust" them. As intelligence becomes commoditised, human relationships become more valuable, not less.
Strategic Response for Capital Allocators
For private equity and venture capital firms, the Value Trap presents both enormous opportunity and significant risk.
Target the Right Businesses Look for businesses with strong persistent moats that will slow mean reversion:
-
Strong brand and customer relationships
-
High customer acquisition costs in the industry
-
Regulatory barriers to entry
-
Capital-intensive startup requirements
-
Long-term contracts and switching costs
Master the Timing The key is capturing value during the expansion phase and exiting before mean reversion accelerates, or finding an appropriate time arbitrage solution to retain value (see below). The optimal point if you're a capital allocator is almost when you've extracted the most cost out of the business.
Consider Hybrid Strategies Rather than just gutting existing businesses, consider acquiring for distribution and customer base while building AI-native operations alongside traditional ones. This provides multiple exit strategies and reduces execution risk.
Bitcoin: The Time Arbitrage Solution
Whenever I've talked to anybody about AI, my first point of advice is just buy bitcoin.
This isn't just evangelism, so much as a recognition of where you would want to hold value as the Value Trap plays out. In essence the value trap generates an arbitrage opportunity, hige profits are pulled forwards short-term balooning the balance sheet, but the second order consequences of this change risk destroying the value you just created!
We believe alongside rapid competition leading to price for services collapsing, the mass job displacement leads to political pressure for intervention.
This could take several forms, but UBI, mortgage bailouts, unemployment extensions, seizure of existing property.
"All roads lead to money printing," as Pete notes in Good Stuff 02 .
During Weimar Republic hyperinflation, "the cost of a newspaper in year five was the same nominal figure as all of the money that existed in year four." While extreme, this illustrates how quickly monetary systems can shift as inflation and money supply inflation begins to run.
To resolve these issues, Bitcoin allows you to conduct arbitrage across time in an asset that is inflation resistant (fixed supply), hard to seize, has no counter party risk (if someone holds your gold, stocks, cash they can take it without asking) and transportable. Capturing value today and preserving it through monetary system changes protecting against the second and third-order effects of massive economic disruption, that AI represents.
Opportunity, Not Fear: The Renaissance Ahead
The Value Trap isn't a reason to avoid AI, it's a roadmap for navigating inevitable change strategically.
The Entrepreneurial Renaissance This could be a Renaissance for entrepreneurs, if you're entrepreneurial minded, this is an amazing time to be alive because there's opportunity that exists in all fields and the barriers to entry have never been lower.
Liberation from Busy Work The displacement of administrative and routine cognitive work frees humans for higher-value creation.
Democratisation of Intelligence When you can "purchase intelligence in buckets of $0.02 API calls," the barriers to starting and scaling businesses collapse. Individual entrepreneurs can build businesses that previously required large teams, with much lower complexity and risk.
Cost Reduction Benefits Everyone The ultimate outcome of the Value Trap cycle benefits consumers through dramatically lower prices for goods and services.
"Who doesn't want cheaper stuff? Why don't we just reduce the cost of everything massively?"
Conclusion: Embrace the High Agency Era
The Value Trap represents a fundamental shift from employment-based to entrepreneurship-based wealth creation. Rather than fearing job displacement, we should prepare for "the age of the entrepreneur" a high agency era.
The businesses and individuals who thrive will be those who:
-
Understand the cycle and position accordingly
-
Focus on unique value creation rather than routine processing or middleman models
-
Build local networks and relationships
-
Preserve wealth through the monetary transition
-
Embrace building and creating unique value
If you are high agency, you can make anything happen.
The Value Trap isn't just about AI transforming business, it won't do this on its own, its a description of how humans will use this technology to generate and capture value.
The future belongs to builders, creators, and entrepreneurs who can navigate transition periods and emerge stronger. The Value Trap is the map, use it wisely.
This article draws heavily on discussion between myself and business partner Andy in Episode 02 of The Good Stuff, if you prefer listening try that :)
-
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ f1989a96:bcaaf2c1
2025-05-22 17:09:23
@ f1989a96:bcaaf2c1
2025-05-22 17:09:23Good morning, readers!
Today, we begin in China, where the central bank injected $138 billion into the economy and expanded the money supply by 12.5% year-over-year. As the regime eases monetary conditions to prop up a decelerating economy, Chinese citizens are rushing to preserve their savings, evidenced by Bitcoin/CNY trading activity jumping over 20% on the news. But while some escape to harder money, others remain trapped. In Hunan, an elderly Chinese woman died outside a bank after being forced to appear in person in order to withdraw her own money for medical care.\ \ In Central America, Salvadoran President Bukele revived a “foreign agents” bill that would impose a 30% tax on foreign-funded NGOs, threatening to financially crush organizations that hold those in power accountable and protect journalists and civil society. The proposal mirrors laws used in Russia, China, Belarus, and beyond to suppress dissent. And it arrives amid Bukele’s authoritarian drift and increasing threats to independent journalists.\ \ In open-source news, we highlight a new tool called ChapSmart, a Bitcoin-powered remittance service that allows users to send Bitcoin to citizens and families in Tanzania and have it disbursed in Tanzanian shillings (TZS) via M-PESA. This tool is increasingly helpful as the Tanzanian regime tightens control over foreign currency, mandating that all transactions be conducted in TZS. ChapSmart provides an accessible way for nonprofits and dissidents to access value from abroad using Bitcoin.\ \ We end with an Ask Me Anything (AMA) with Bitcoin educator Anita Posch on Stacker News, who shares her thoughts, experiences, and views from her time conducting Bitcoin education in authoritarian regimes in Africa. We also feature an article from Togolese human rights advocate Farida Nabourema, who critiques Nigeria’s new investment act for classifying Bitcoin as a security and for the regulatory hurdles this will impose on the grassroots adoption of freedom tech in the country.
Be sure to tune in next week at 2 p.m. Oslo time on Wednesday, May 28, as the Oslo Freedom Forum’s Freedom Tech track airs on Bitcoin Magazine’s livestream channels, headlined by speakers Ziya Sadr, Abubakr Nur Khalil, Amiti Uttarwar, Calle, Sarah Kreps, Ben Perrin, and many more.
Now, let’s read on!
SUBSCRIBE HERE
GLOBAL NEWS
El Salvador | Bukele Reintroduces Foreign Agents Bill
In El Salvador, President Nayib Bukele revived a controversial “foreign agents” bill that threatens to severely restrict the finances and operations of NGOs. While the bill is not finalized, Bukele shared on X that the proposal would impose a 30% tax on donations to NGOs receiving foreign funding. This punitive financial measure alone would severely restrict Salvadoran organizations that protect independent journalism, advocate for human rights, and hold the government accountable. In neighboring Nicaragua, a similar foreign agents law has enabled the closure of more than 3,500 NGOs. El Salvador’s foreign agents bill arrives alongside other alarming moves, including arrest warrants against El Faro journalists, the arrest of human rights lawyer Ruth López, and the detention of more than 200 Venezuelan migrants under dubious claims of gang affiliation.
China | Injects Billions to Stabilize Economy
The Chinese Communist Party (CCP) has injected $138 billion in liquidity through interest rate cuts and a 0.5% reduction in banks’ reserve requirements, in effect expanding the money supply by 12.5% year-over-year. While the state eases monetary conditions to prop up a fragile system, ordinary citizens are left scrambling to preserve the value of their savings. Bitcoin/CNY trading volumes jumped over 20% in response, as people sought refuge from a weakening yuan. But while some can quietly escape to harder money, others are trapped in a system that treats access to money as a privilege. In Hunan, an elderly woman in a wheelchair died outside a bank after being forced to appear in person to withdraw her own money for medical care. Too weak to pass mandatory facial recognition scans, she collapsed after repeated failed attempts.
World | Authoritarian Regimes Lead CBDC Push, Study Finds
A new international study from the Nottingham Business School, part of Nottingham Trent University in England, set out to understand what is driving countries to pursue central bank digital currencies (CBDCs). Researchers found the answer lies mostly in political motives. Analyzing 68 countries, the report revealed that authoritarian governments are pushing CBDCs most aggressively, using their centralized power to hastily roll out CBDCs that can monitor transactions, restrict the movement of money, and suppress dissent. On the other hand, the report found democracies are moving more cautiously, weighing concerns over privacy, transparency, and public trust. The study also noted a correlation: countries with high levels of perceived corruption are more likely to explore CBDCs, often framing them as tools to fight illicit finance. These findings are consistent with HRF’s research, revealing nearly half the global population lives under an authoritarian regime experimenting with a CBDC.
Thailand | Plans to Issue New “Investment Token”
Thailand’s Ministry of Finance plans to issue 5 billion baht ($151 million) worth of “G-Tokens,” a new digital investment scheme that allows Thais to buy government bonds for as little as 100 baht ($3). Officials claim the project will democratize access to state-backed investments and offer higher returns than traditional bank deposits. But in a country rapidly advancing central bank digital currency (CBDC) infrastructure, this initiative raises apparent concerns. The move closely follows Thailand’s repeated digital cash handouts via a state-run wallet app, which restricts spending, tracks user behavior, and enforces expiration dates on money, all clear hallmarks of a CBDC. Luckily, the Thai government postponed the latest handout, but the infrastructure remains. Framing this project as inclusionary masks the reality: Thailand is building state-run digital systems that give the regime more power over citizens’ savings and spending.
Russia | Outlaws Amnesty International
Russia officially banned Amnesty International, designating it as an “undesirable organization” and criminalizing cooperation with the global human rights group. Russian officials claim Amnesty promotes “Russophobic projects” and undermines national security. This adds to the Kremlin’s assault on dissent, targeting human rights advocates, independent journalists, and civil society in the years since the 2022 full-scale invasion of Ukraine. The designation exposes anyone financially, publicly, or privately supporting Amnesty’s work to prosecution and imprisonment up to five years. With more than 220 organizations now blacklisted, Russia is systematically cutting off avenues for international accountability and isolating Russians from external support.
BITCOIN AND FREEDOM TECH NEWS
ChapSmart | Permissionless Remittances in Tanzania
ChapSmart is a Bitcoin-powered remittance service that allows users to send money to individuals and families in Tanzania while having it disbursed in Tanzanian shillings (TZS) via M-PESA. With ChapSmart, no account is needed: just enter your name, email, and the recipient’s M-Pesa details. Choose how much USD to send, pay in bitcoin via the Lightning Network, and ChapSmart delivers Tanzanian shillings instantly to the recipient's M-Pesa account with zero fees. This tool is especially useful as Tanzania’s regime enacts restrictions on foreign currencies, banning most citizens from quoting prices or accepting payment in anything other than TZS. ChapSmart offers a practical and accessible way for families, nonprofits, and individuals to access value from abroad using Bitcoin, even as the state tries to shut out financial alternatives.
Bitkey | Multisignature for Families Protecting Wealth from State Seizure
Decades ago, Ivy Galindo’s family lost their savings overnight when the Brazilian government froze citizens’ bank accounts to “fight inflation.” That moment shaped her understanding of financial repression and why permissionless tools like Bitcoin are essential. When her parents later chose to start saving in Bitcoin, Ivy knew a wallet with a single private key wasn’t enough, as it can be lost, stolen, or handed over under pressure or coercion from corrupt law enforcement or state officials. Multisignature (multisig) wallets, which require approval from multiple private keys to move funds, offer stronger protection against this loss and coercion and eliminate any single points of failure in a Bitcoin self-custody setup. But multisig setups are often too technical for everyday families. Enter Bitkey. This multisig device offered Ivy’s family a simple, secure way to share custody of their Bitcoin in the face of financial repression. In places where wealth confiscation and frozen bank accounts are a lived reality, multisignature wallets can help families stay in full control of their savings.
Parasite Pool | New Zero-Fee, Lightning Native Bitcoin Mining Pool
Parasite Pool is a new open-source Bitcoin mining pool built for home miners who want to contribute to Bitcoin’s decentralization without relying on the large and centralized mining pools. It charges zero fees and offers Lightning-native payouts with a low 10-satoshi threshold, allowing individuals to earn directly and instantly. Notably, it has a “pleb eat first” reward structure, which allocates 1 BTC to the block finder and splits the remaining 2.125 BTC plus fees among all non-winning participants via Lightning. This favors small-scale miners, who can earn outsized rewards relative to their hashpower, inverting the corporate bias of legacy mining pools. This makes Parasite Pool especially attractive for small scale miners, such as those operating in authoritarian contexts who need to mine discreetly and independently. In turn, these very same miners contribute to the Bitcoin network’s resistance to censorship, regulatory capture, and corporate control, ensuring it remains a tool for freedom and peaceful resistance for those who need it most. Learn more about the mining pool here.
Cake Wallet | Implements Payjoin V2
Cake Wallet, a non-custodial, privacy-focused, and open-source mobile Bitcoin wallet, released version 4.28, bringing Payjoin V2 to its user base. Payjoin is a privacy technique that allows two users to contribute an input to a Bitcoin transaction, breaking the common chain analysis heuristic that assumes a sender owns all inputs. This makes it harder for dictators to trace payments or link the identities of activists or nonprofits. Unlike the original Payjoin, which required both the sender and recipient to be online and operate a Payjoin server, Payjoin v2 removes both barriers and introduces asynchronous transactions and serverless communication. This means users can now conduct private transactions without coordination or technical setup, making private Bitcoin transactions much more accessible and expanding the tools dissidents have to transact in the face of censorship, extortion, and surveillance. HRF is pleased to have sponsored the Payjoin V2 specification with a bounty and is happy to see this functionality now in the wild.
Mi Primer Bitcoin | Receives Grant from startsmall
Mi Primer Bitcoin, a nonprofit organization supporting independent Bitcoin education in Central America, announced that it received a $1 million grant from Jack Dorsey’s startsmall public fund. This support will accelerate Mi Primer Bitcoin’s impartial, community-led, Bitcoin-only education. The initiative has trained tens of thousands of students while supporting over 65 grassroots projects across 35+ countries through its Independent Bitcoin Educators Node Network, pushing financial freedom forward where needed most. The Mi Primer Bitcoin (MPB) team stresses the importance of remaining free from government or corporate influence to preserve the integrity of their mission. As founder John Dennehy puts it, “Education will be captured by whoever funds it… We need to create alternative models for the revolution of Bitcoin education to realize its full potential.” MPB has been adopted by many education initiatives working under authoritarian regimes.
Phoenix Wallet | Introduces Unlimited BOLT 12 Offers and Manual Backup Options
Phoenix Wallet, a mobile Bitcoin Lightning wallet, introduced support for unlimited BOLT 12 offers in its v2.6.0 update, allowing users to generate as many reusable Lightning invoices as they like. These offers, which function like static Bitcoin addresses, remain permanently valid and can now include a custom description and amount — ideal for nonprofits or dissidents who need to receive regular donations discreetly. The update also introduces manual export and import of the payments database on Android, enabling users to securely transfer their payment history to new devices. These updates strengthen Phoenix’s position as one of the most user-friendly and feature-complete non-custodial Lightning wallets. BOLT 12 — once a pipe dream — is now a usable activist tool on popularly accessible mobile wallets.
RECOMMENDED CONTENT
Bitcoin Is Not a Security: Why Nigeria’s New Investment and Security Act Misses the Mark by Farida Nabourema
In this article, Togolese human rights advocate Farida Nabourema critiques Nigeria’s 2025 Investment and Securities Act for classifying Bitcoin as a security. Nabourema argues this approach is flawed, economically damaging, disconnected from the realities of Bitcoin usage and innovation across Africa, and an attempt to constrict a human rights tool. She warns that this regulatory framework risks stifling builders and harming the very communities that Bitcoin is helping in a context of widespread currency devaluations, inflation, and exclusion. Read it here.
Ask Me Anything with Anita Posch on Stacker News
After spending five months traveling through countries like Kenya and Zimbabwe, Bitcoin for Fairness Founder Anita Posch joined Stacker News for an Ask Me Anything (AMA) to discuss her view on Bitcoin adoption across the continent. She highlighted major progress since 2020, noting that several grassroots initiatives she supported have become self-sufficient and are now running their own education programs. Despite persistent challenges, like wallet usability, high on-chain fees, and Bitcoin’s misunderstood reputation, she shared stories of real-life impact, including cross-border remittances using mobile airtime and widespread Lightning use via apps like Tando in Kenya. Read the full conversation here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:04
@ dfa02707:41ca50e3
2025-05-22 17:02:04Contribute to keep No Bullshit Bitcoin news going.
News
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- Spiral renews support for Dan Gould and Joschisan. The organization has renewed support for Dan Gould, who is developing the Payjoin Dev Kit (PDK), and Joschisan, a Fedimint developer focused on simplifying federations.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- The European Central Bank is pushing for amendments to the European Union's Markets in Crypto Assets legislation (MiCA), just months after its implementation. According to Politico's report on Tuesday, the ECB is concerned that U.S. support for cryptocurrency, particularly stablecoins, could cause economic harm to the 27-nation bloc.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- The Virtual Asset Service Providers (VASP) Bill 2025 introduced in Kenya. The new legislation aims to establish a comprehensive legal framework for licensing, regulating, and supervising virtual asset service providers (VASPs), with strict penalties for non-compliant entities.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Paul Atkins has officially assumed the role of the 34th Chairman of the US Securities and Exchange Commission (SEC). This is a return to the agency for Atkins, who previously served as an SEC Commissioner from 2002 to 2008 under the George W. Bush administration. He has committed to advancing the SEC’s mission of fostering capital formation, safeguarding investors, and ensuring fair and efficient markets.
- Federal Reserve retracts guidance discouraging banks from engaging in 'crypto.' The U.S. Federal Reserve withdrew guidance that discouraged banks from crypto and stablecoin activities, as announced by its Board of Governors on Thursday. This includes rescinding a 2022 supervisory letter requiring prior notification of crypto activities and 2023 stablecoin requirements.
"As a result, the Board will no longer expect banks to provide notification and will instead monitor banks' crypto-asset activities through the normal supervisory process," reads the FED statement.
- Russian government to launch a cryptocurrency exchange. The country's Ministry of Finance and Central Bank announced plans to establish a trading platform for "highly qualified investors" that "will legalize crypto assets and bring crypto operations out of the shadows."
- Twenty One Capital is set to launch with over 42,000 BTC in its treasury. This new Bitcoin-native firm, backed by Tether and SoftBank, is planned to go public via a SPAC merger with Cantor Equity Partners and will be led by Jack Mallers, co-founder and CEO of Strike. According to a report by the Financial Times, the company aims to replicate the model of Michael Saylor with his company, MicroStrategy.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Metaplanet buys another 145 BTC. The Tokyo-listed company has purchased an additional 145 BTC for $13.6 million. Their total bitcoin holdings now stand at 5,000 coins, worth around $428.1 million.
- Semler Scientific has increased its bitcoin holdings to 3,303 BTC. The company acquired an additional 111 BTC at an average price of $90,124. The purchase was funded through proceeds from an at-the-market offering and cash reserves, as stated in a press release.
- Tesla still holds nearly $1 billion in bitcoin. According to the automaker's latest earnings report, the firm reported digital asset holdings worth $951 million as of March 31.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
- Arch Labs has secured $13 million to develop "ArchVM" and integrate smart-contract functionality with Bitcoin. The funding round, valuing the company at $200 million, was led by Pantera Capital, as announced on Tuesday.
- Citrea deployed its Clementine Bridge on the Bitcoin testnet. The bridge utilizes the BitVM2 programming language to inherit validity from Bitcoin, allegedly providing "the safest and most trust-minimized way to use BTC in decentralized finance."
- UAE-based Islamic bank ruya launches Shari’ah-compliant bitcoin investing. The bank has become the world’s first Islamic bank to provide direct access to virtual asset investments, including Bitcoin, via its mobile app, per Bitcoin Magazine.
- Solosatoshi.com has sold over 10,000 open-source miners, adding more than 10 PH of hashpower to the Bitcoin network.
"Thank you, Bitaxe community. OSMU developers, your brilliance built this. Supporters, your belief drives us. Customers, your trust powers 10,000+ miners and 10PH globally. Together, we’re decentralizing Bitcoin’s future. Last but certainly not least, thank you@skot9000 for not only creating a freedom tool, but instilling the idea into thousands of people, that Bitcoin mining can be for everyone again," said the firm on X.
- OCEAN's DATUM has found 100 blocks. "Over 65% of OCEAN’s miners are using DATUM, and that number is growing every day. This means block template construction is making its way back into the hands of the miners, which is not only the most profitable
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:04
@ dfa02707:41ca50e3
2025-05-22 17:02:04Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 3b3a42d3:d192e325
2025-04-10 08:51:15
@ 3b3a42d3:d192e325
2025-04-10 08:51:15Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ 25f5c1c7:e956c514
2025-05-22 23:42:09
@ 25f5c1c7:e956c514
2025-05-22 23:42:09I've been exploring ways to retain the strong security guarantees of Proof-of-Work (PoW) while significantly reducing its environmental footprint. Traditional PoW systems are undeniably robust, but their energy demands are a major concern. Delayed Proof-of-Work (DPoW) is my first proposal toward solving this - a concept designed to preserve the integrity and fairness of PoW while operating with a fraction of the hash power.
How it Works
-
A new block is added to the chain.
-
All miners start computing a VDF (Verifiable Delay Function) with the latest block's hash as the input.
-
The VDF is designed to take 4 minutes to complete, enforcing a mandatory idle period.
-
The \~1 minute mining period begins when miners complete the VDF.
-
- Miners compete to find a valid PoW for a new block, which includes the VDF output in the header.
-
The first miner to find a valid hash broadcasts the new block to the network.
-
The block is verified by nodes by checking the VDF's output is correct for the previous block hash, and that the PoW is valid.
-
This cycle of a 4 minute idle period and a brief mining period continues.
Key Advantages
-
The idle-mine cycle allows the network to operate with \~1/5 of the hash power of a standard PoW blockchain while still taking advantage of the security properties of PoW.
-
During the 4 minute idle period, the blockchain is guaranteed to be static. The predictable delay means blocks are propagated and confirmed in a more synchronised fashion, which could reduce synchronisation issues and orphaned blocks.
Potential Issues
-
VDFs can be computed slightly faster on hardware with higher clock speeds or specialised circuits, resulting in some miners having a longer mining period.
-
The short mining-window means that miners on faster connections will have a significant advantage over slower connections, as they will be able to propagate a mined block faster.
-
The VDF also uses energy, although negligible compared to the amount that algorithms use.
-
Miners might redirect their hash power to other cryptocurrencies during the delay period, which would undermine the goal of reducing energy consumption.
-
A malicious miner who obtains or predicts the next block could start pre-computing the VDF early, gaining an unfair advantage.
-
-
 @ 266815e0:6cd408a5
2025-04-08 07:19:53
@ 266815e0:6cd408a5
2025-04-08 07:19:53Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:03
@ dfa02707:41ca50e3
2025-05-22 17:02:03Contribute to keep No Bullshit Bitcoin news going.
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:03
@ dfa02707:41ca50e3
2025-05-22 17:02:03Contribute to keep No Bullshit Bitcoin news going.
- "Today we're launching the beta version of our multiplatform Nostr browser! Think Google Chrome but for Nostr apps. The beta is our big first step toward this vision," announced Damus.
- This version comes with the Dave Nostr AI assistant, support for zaps and the Nostr Wallet Connect (NWC) wallet interface, full-text note search, GIFs and fullscreen images, multiple media uploads, user tagging, relay list and mute list support, along with a number of other improvements."
"Included in the beta is the Dave, the Nostr AI assistant (its Grok for Nostr). Dave is a new Notedeck browser app that can search and summarize notes from the network. For a full breakdown of everything new, check out our beta launch video."
What's new
- Dave Nostr AI assistant app.
- GIFs.
- Fulltext note search.
- Add full screen images, add zoom, and pan.
- Zaps! NWC/ Wallet UI.
- Introduce last note per pubkey feed (experimental).
- Allow multiple media uploads per selection.
- Major Android improvements (still WIP).
- Added notedeck app sidebar.
- User Tagging.
- Note truncation.
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline.
- Mute list support (reading).
- Relay list support.
- Ctrl-enter to send notes.
- Added relay indexing (relay columns soon).
- Click hashtags to open hashtag timeline.
- Fixed timelines sometimes not updating (stale feeds).
- Fixed UI bounciness when loading profile pictures
- Fixed unselectable post replies.
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:03
@ dfa02707:41ca50e3
2025-05-22 17:02:03Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ 266815e0:6cd408a5
2025-04-04 11:06:34
@ 266815e0:6cd408a5
2025-04-04 11:06:34Hacking on a new obsidian plugin for publishing articles to nostr -- testing updates
Testing images
This should be replaced with a blossom URL
![[duck.jpg]]
Testing referencing other articles
This link should be broken [[Welcome]]
-
 @ 22aa8151:ae9b5954
2025-03-31 07:44:15
@ 22aa8151:ae9b5954
2025-03-31 07:44:15With all the current hype around Payjoin for the month, I'm open-sourcing a project I developed five years ago: https://github.com/Kukks/PrivatePond
Note: this project is unmaintained and should only be used as inspiration.
Private Pond is a Bitcoin Payjoin application I built specifically to optimize Bitcoin transaction rails for services, such as deposits, withdrawals, and automated wallet rebalancing.
The core concept is straightforward: withdrawals requested by users are queued and processed at fixed intervals, enabling traditional, efficient transaction batching. Simultaneously, deposits from other users can automatically batch these withdrawals via Payjoin batching, reducing them onchain footprint further. Taking it to the next step: a user's deposit is able to fund the withdrawals with its own funds reducing the required operational liquidity in hot wallets through a process called the Meta Payjoin.
The application supports multiple wallets—hot, cold, multisig, or hybrid—with configurable rules, enabling automated internal fund management and seamless rebalancing based on operational needs such as min/max balance limits and wallet ratios (10% hot, 80% in 2-of-3, 10% in 1-of-2, etc) .
This system naturally leverages user Payjoin transactions as part of the automated rebalancing strategy, improving liquidity management by batching server operations with user interactions.
Private Pond remains quite possibly the most advanced Payjoin project today, though my multi-party addendum of 2023 probably competes. That said, Payjoin adoption overall has been disappointing: the incentives heavily favor service operators who must in turn actively encourage user participation, limiting its appeal only for specialized usage. This is why my efforts refocused on systems like Wabisabi coinjoins, delivering not just great privacy but all the benefits of advanced Payjoin batching on a greater scale through output compaction.
Soon, I'll also open-source my prototype coinjoin protocol, Kompaktor, demonstrating significant scalability improvements, such as 50+ payments from different senders being compacted into a single Bitcoin output. And this is not even mentioning Ark, that pushes these concepts even further, giving insane scalability and asyncrhonous execution.
You can take a look at the slides I did around this here: https://miro.com/app/board/uXjVL-UqP4g=/
Parts of Private Pond, the pending transfers and multisig, will soon be integrated into nostr:npub155m2k8ml8sqn8w4dhh689vdv0t2twa8dgvkpnzfggxf4wfughjsq2cdcvg 's next major release—special thanks to nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg for continuing the work and getting it to the finish line.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:02
@ dfa02707:41ca50e3
2025-05-22 17:02:02News
- Wallet of Satoshi teases a comeback in the US market with a non-custodial product. According to an announcement on X, the widely popular custodial Lightning wallet is preparing to re-enter the United States market with a non-custodial wallet. It is unclear whether the product will be open-source, but the project has clarified that "there will be no KYC on any Wallet of Satoshi, ever!" Wallet of Satoshi ceased serving customers in the United States in November 2023.
- Vulnerability disclosure: Remote crash due to addr message spam in Bitcoin Core versions before v29. Bitcoin Core developer Antoine Poinsot disclosed an integer overflow bug that crashes a node if spammed with addr messages over an extended period. A fix was released on April 14, 2025, in Bitcoin Core v29.0. The issue is rated Low severity.
- Coinbase Know Your Customer (KYC) data leak. The U.S. Department of Justice, including its Criminal Division in Washington, is investigating a cyberattack on Coinbase. The incident involved cybercriminals attempting to extort $20 million from Coinbase to prevent stolen customer data from being leaked online. Although the data breach affected less than 1% of the exchange's users, Coinbase now faces at least six lawsuits following the revelation that some customer support agents were bribed as part of the extortion scheme.
- Fold has launched Bitcoin Gift Cards, enabling users to purchase bitcoin for personal use or as gifts, redeemable via the Fold app. These cards are currently available on Fold’s website and are planned to expand to major retailers nationwide later this year.
"Our mission is to make bitcoin simple and approachable for everyone. The Bitcoin Gift Card brings bitcoin to millions of Americans in a familiar way. Available at the places people already shop, the Bitcoin Gift Card is the best way to gift bitcoin to others," said Will Reeves, Chairman and CEO of Fold.
- Corporate treasuries hold nearly 1.1 million BTC, representing about 5.5% of the total circulating supply (1,082,164 BTC), per BitcoinTreasuries.net data. Recent purchases include Strategy adding 7,390 BTC (total: 576,230 BTC), Metplanet acquiring 1,004 BTC (total: 7,800 BTC), Tether holding over 100,521 BTC, and XXI Capital, led by Jack Mallers, starting with 31,500 BTC.
- Meanwhile, a group of investors has filed a class action lawsuit against Strategy and its executive Michael Saylor. The lawsuit alleges that Strategy made overly optimistic projections using fair value accounting under new FASB rules while downplaying potential losses.
- The U.S. Senate voted to advance the GENIUS stablecoin bill for further debate before a final vote to pass it. Meanwhile, the House is crafting its own stablecoin legislation to establish a regulatory framework for stablecoins and their issuers in the U.S, reports CoinDesk.
- French 'crypto' entrepreneurs get priority access to emergency police services. French Minister of the Interior, Bruno Retailleau, agreed on measures to enhance security for 'crypto' professionals during a meeting on Friday. This follows a failed kidnapping attempt on Tuesday targeting the family of a cryptocurrency exchange CEO, and two other kidnappings earlier this year.
- Brussels Court declares tracking-based ads illegal in EU. The Brussels Court of Appeal ruled tracking-based online ads illegal in the EU due to an inadequate consent model. Major tech firms like Microsoft, Amazon, Google, and X are affected by the decision, as their consent pop-ups fail to protect privacy in real-time bidding, writes The Record.
- Telegram shares data on 22,777 users in Q1 2025, a significant increase from the 5,826 users' data shared during the same period in 2024. This significant increase follows the arrest of CEO and founder Pavel Durov last year.
- An Australian judge has ruled that Bitcoin is money, potentially exempting it from capital gains tax in the country. If upheld on appeal, this interim decision could lead to taxpayer refunds worth up to $1 billion, per tax lawyer Adrian Cartland.
Use the tools
- Bitcoin Safe v1.3.0 a secure and user-friendly Bitcoin savings wallet for beginners and advanced users, introduces an interactive chart, Child Pays For Parent (CPFP) support, testnet4 compatibility, preconfigured testnet demo wallets, various bug fixes, and other improvements.
- BlueWallet v7.1.8 brings numerous bug fixes, dependency updates, and a new search feature for addresses and transactions.
- Aqua Wallet v0.3.0 is out, offering beta testing for the reloadable Dolphin card (in partnership with Visa) for spending bitcoin and Liquid BTC. It also includes a new Optical Character Recognition (OCR) text scanner to read text addresses like QR codes, colored numbers on addresses for better readability, a reduced minimum for spending and swapping Liquid Bitcoin to 100 sats, plus other fixes and enhancements.

Source: Aqua wallet.
- The latest firmware updates for COLDCARD Mk4 v5.4.3 and Q v1.3.3 are now available, featuring the latest enhancements and bug fixes.
- Nunchuk Android v1.9.68.1 and iOS v1.9.79 introduce support for custom blockchain explorers, wallet archiving, re-ordering wallets on the home screen via long-press, and an anti-fee sniping setting.
- BDK-cli v1.0.0, a CLI wallet library and REPL tool to demo and test the BDK library, now uses bdk_wallet 1.0.0 and integrates Kyoto, utilizing the Kyoto protocol for compact block filters. It sets SQLite as the default database and discontinues support for sled.
- publsp is a new command-line tool designed for Lightning node runners or Lightning Service Providers (LSPs) to advertise liquidity offers over Nostr.
"LSPs advertise liquidity as addressable Kind 39735 events. Clients just pull and evaluate all those structured events, then NIP-17 DM an LSP of their choice to coordinate a liquidity purchase," writes developer smallworlnd.
-
Lightning Blinder by Super Testnet is a proof-of-concept privacy tool for the Lightning Network. It enables users to mislead Lightning Service Providers (LSPs) by making it appear as though one wallet is the sender or recipient, masking the original wallet. Explore and try it out here.
-
Mempal v1.5.3, a Bitcoin mempool monitoring and notification app for Android, now includes a swipe-down feature to refresh the dashboard, a custom time option for widget auto-update frequency, and a
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:02
@ dfa02707:41ca50e3
2025-05-22 17:02:02Contribute to keep No Bullshit Bitcoin news going.
- This release introduces Payjoin v2 functionality to Bitcoin wallets on Cake, along with several UI/UX improvements and bug fixes.
- The Payjoin v2 protocol enables asynchronous, serverless coordination between sender and receiver, removing the need to be online simultaneously or maintain a server. This simplifies privacy-focused transactions for regular users.
"I cannot speak highly enough of how amazing it has been to work with @bitgould and Jaad from the@payjoindevkit team, they're doing incredible work. None of this would be possible without them and their tireless efforts. PDK made it so much easier to ship Payjoin v2 than it would have been otherwise, and I can't wait to see other wallets jump in and give back to PDK as they implement it like we did," said Seth For Privacy, VP at Cake Wallet.

How to started with Payjoin in Cake Wallet:
- Open the app menu sidebar and click
Privacy. - Toggle the
Use Payjoinoption. - Now on your receive screen you'll see an option to copy a Payjoin URL
- Bull Bitcoin Wallet v0.4.0 introduced Payjoin v2 support in late December 2024. However, the current implementations are not interoperable at the moment, an issue that should be addressed in the next release of the Bull Bitcoin Wallet.
- Cake Wallet was one of the first wallets to introduce Silent Payments back in May 2024. However, users may encounter sync issues while using this feature at present, which will be resolved in the next release of Cake Wallet.
What's new
- Payjoin v2 implementation.
- Wallet group improvements: Enhanced management of multiple wallets.
- Various bug fixes: improving overall stability and user experience.
- Monero (XMR) enhancements.
Learn more about using, implementing, and understanding BIP 77: Payjoin Version 2 using the
payjoincrate in Payjoin Dev Kit here. -
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 0d6c8388:46488a33
2025-03-28 16:24:00
@ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to OpenSats for the grant to work on Hypernote this year! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry!
===
How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way.
1. What do we mean by hypermedia
A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the how with the what.
This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm.
A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML).
Contrast this with modern app development, where the what is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the how.
The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application".
(Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!)
Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the how of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the what.
And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON what, how do we deliver the how with nostr as well. Is that even possible?
2. Hypernote's design assumptions
Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way.
Hypernote was also deeply inspired by HTMX, so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a tiny bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims.
Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec.
Hypernote likes the
nakcommand line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem.3. "What's a hypernote?"
Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose.
But here's where things currently stand:
A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of:
- CONTENT. Static or dynamic content. (the what)
- LOGIC. Filters and events (the how)
- STYLE. Optional, inline style information specific to this element's content.
In the most basic example of a hypernote story, here's a lone "edit me" in the middle of the canvas:

{ "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" }As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color).
Here's a "sticker" that displays a note:
{ "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} }As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data.
Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us!
{ "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } }It's also a mess, but it demos the other part of "logic": methods which produce new events.
This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events.
I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of
jq-like language for destructing the relevant piece of data we want.My ideal syntax for a hypernote as a developer will look something like
```foo.hypernote Nak-like logic
Markdown-like content
CSS-like styles ```
But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI.
The end
I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ dfa02707:41ca50e3
2025-05-22 17:02:02
@ dfa02707:41ca50e3
2025-05-22 17:02:02Contribute to keep No Bullshit Bitcoin news going.
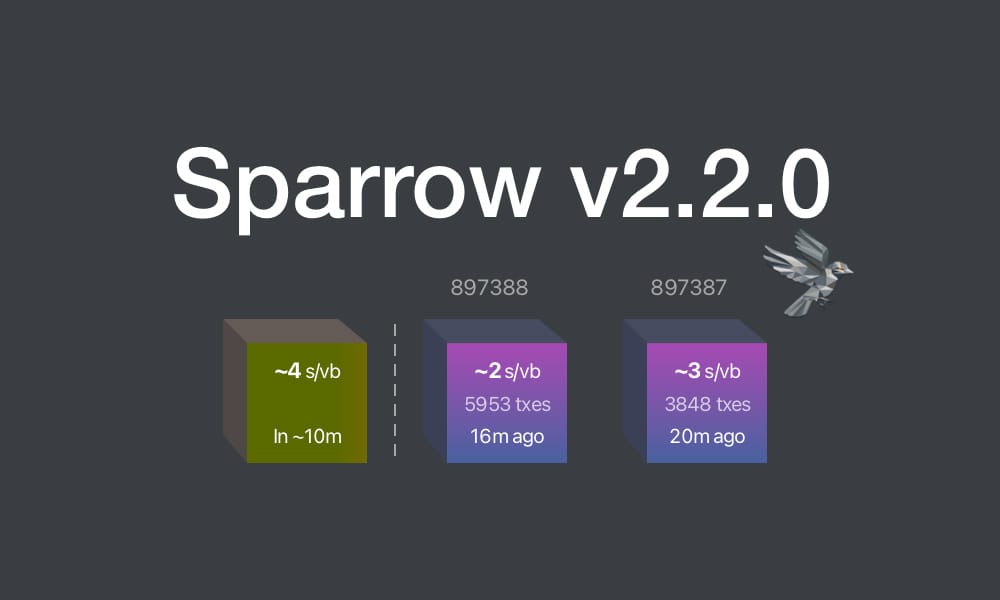
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ cae03c48:2a7d6671
2025-05-22 17:02:01
@ cae03c48:2a7d6671
2025-05-22 17:02:01Bitcoin Magazine

Texas Legislature Passes Bitcoin Reserve BillTexas has passed Senate Bill 21, a measure establishing the Texas Strategic Bitcoin Reserve. This makes Texas the third U.S. state to adopt Bitcoin as part of its state investment strategy, following Arizona and New Hampshire. The bill, officially titled the “Texas Strategic Bitcoin Reserve and Investment Act”, has cleared both legislative chambers and now heads to Governor Greg Abbott’s desk for final approval.
JUST IN: Texas Strategic Bitcoin Reserve bill SB21 officially PASSES and goes to Governors desk for final signature
 pic.twitter.com/8UMwxTHgg6
pic.twitter.com/8UMwxTHgg6— Bitcoin Magazine (@BitcoinMagazine) May 21, 2025
SB21 authorizes the creation of the Texas Strategic Bitcoin Reserve, a special fund outside the state treasury, which allows Texas to invest directly in Bitcoin and other approved cryptocurrencies, according to the legislation. The measure gives the State Treasurer full authority over the reserve’s administration, including acquiring, managing, staking, and potentially liquidating digital assets.
“The establishment of a strategic bitcoin reserve serves the public purpose of providing enhanced financial security to residents of this state,” declares the legislation.
The State Treasurer will manage the fund under strict conditions:
- Only cryptocurrencies with a 12-month average market cap of at least $500 billion can be purchased.
- Assets must be stored using “cold storage” technology to prevent unauthorized access.
- Third-party partners, including qualified custodians and liquidity providers, may be contracted for operations.
- The use of staking, and derivatives is allowed if it benefits the reserve.
Funds can come from legislative appropriations, donations from Texas residents, and returns on investments. While the reserve operates independently, the State Treasurer can temporarily liquidate it for state cash management under limited conditions.
Governor Abbott has not yet indicated whether he will sign the bill, but his past support of Bitcoin suggests a favorable outcome is likely.
“Texas is getting involved early on in this process because we see the future of what bitcoin and blockchain means to the entire world,” said Governor Abbott in an interview. “Texas wants to be the centerpiece of that. So we are promoting it, we are advancing it.”
When New Hampshire passed their bill on May 6, 2025, CEO and Co-Founder of Satoshi Action Dennis Porter remarked that it was just the beginning and now we’re seeing that vision unfold.
“Satoshi Action drafted the model, New Hampshire engraved it into law, and now every treasurer nationwide can follow that roadmap,” stated Dennis Porter on X. “HB 302 proves you can protect taxpayer money, diversify reserves, and future-proof state treasuries—all while embracing the most secure monetary network on Earth. New Hampshire didn’t just pass a bill; it sparked a movement.”
This post Texas Legislature Passes Bitcoin Reserve Bill first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ da8b7de1:c0164aee
2025-05-22 16:19:52
@ da8b7de1:c0164aee
2025-05-22 16:19:52Technológiai és fejlesztési hírek
- Észtország SMR-tervei:
Észtország hivatalosan elindította a nemzeti tervezési folyamatot és a környezeti hatásvizsgálatot egy 600 MW-os kis moduláris reaktor (SMR) atomerőmű létesítésére, GE Hitachi BWRX-300 technológiával. A projektet a Fermi Energia vezeti, a lakosság körében mérsékelt támogatottság mellett. Az építési engedélykérelem benyújtását 2029-re tervezik, a cél az ország energiabiztonságának és klímacéljainak erősítése.
- Olkiluoto-1 csökkentett teljesítménnyel üzemel:
Finnországban az Olkiluoto-2 egységben a generátor rotorjának cseréje miatt a termelés májusban újraindul, de a teljesítményt 735 MW-ra korlátozzák (a teljes kapacitás 890 MW). A csökkentett teljesítmény 2026-ig marad érvényben. Az Olkiluoto-1 egység normálisan működik, az Olkiluoto-3 pedig éves karbantartáson van.
Ipari és pénzügyi fejlemények
- Kanada–Argentína nehézvíz-együttműködés:
A kanadai Candu Energy (AtkinsRéalis) és az argentin Nemzeti Atomenergia Bizottság (CNEA) memorandumot írt alá a nehézvíz-termelés fellendítéséről. Ez magában foglalja az argentin PIAP nehézvízgyár újraindítását és potenciálisan új üzemek építését Kanadában. A fejlesztés támogatja a meglévő és tervezett CANDU reaktorok működését világszerte, és illeszkedik a COP28 utáni globális nukleáris bővüléshez.
- USA: nukleáris adókedvezményekért folyó lobbizás:
Az amerikai nukleáris ipar intenzív lobbitevékenységet folytat, hogy megőrizze a Biden-adminisztráció által bevezetett, az Inflációcsökkentő Törvény (IRA) szerinti nukleáris adókedvezményeket. Az új, republikánus többségű költségvetési törvényjavaslat jelentősen lerövidítené a tiszta energia (szél, nap, akkumulátor) támogatásokat, de a nukleáris ipar számára bizonyos kedvezmények megmaradnának, bár a 45U nukleáris adókedvezmény is három évvel korábban, 2031-ben lejárhat.
- Háztartási és ipari érdekek:
Az amerikai ház költségvetési törvényjavaslata megszüntetné a legtöbb tiszta energiához kapcsolódó adókedvezményt, kivéve néhány nukleáris projektet, és szigorítaná a kínai kapcsolatokkal rendelkező projektek támogatását. Ez várhatóan visszaveti a megújuló energiaipar beruházásait, miközben a nukleáris szektor relatív pozíciója javulhat.
Politikai és társadalmi fejlemények
- Tajvan: népszavazás a nukleáris energia sorsáról:
Tajvan parlamentje megszavazta, hogy népszavazást tartsanak a Maanshan atomerőmű újraindításáról, miután az ország utolsó működő reaktorát is leállították. A referendum nem azonnali újraindításról szól, hanem arról, hogy a lakosság döntsön a meghosszabbításról, ha a hatóságok biztonságosnak találják az üzemet.
- Pennsylvania kormányzója a nukleáris energia mellett:
Josh Shapiro, Pennsylvania kormányzója, a „Lightning Plan” keretében hangsúlyozta, hogy az állam energiabiztonsága és gazdasági fejlődése érdekében kulcsszerepet szán a nukleáris energiának, valamint más megbízható energiaforrásoknak. A terv célja a munkahelyteremtés, a fogyasztói költségek csökkentése és az engedélyezési folyamatok gyorsítása.
- TMI névváltás:
Az amerikai Nukleáris Szabályozó Hatóság (NRC) jóváhagyta a Three Mile Island (TMI) atomerőmű nevének megváltoztatását Christopher M. Crane-re, az Exelon volt vezérigazgatójának emlékére. A létesítmény a jövőben a Microsoft AI műveleteit is ellátja majd árammal, és 2028-tól 835 MW szén-dioxid-mentes áramot termelhet.
Nemzetközi szakmai események
- NEA konferencia Londonban:
Az OECD NEA 2025. június 18–19-én Londonban rendezi meg az „Excellence in Nuclear Construction” nemzetközi konferenciát. A rendezvény célja, hogy a nukleáris ipar szereplői megosszák tapasztalataikat a nukleáris beruházások gyorsabb, kiszámíthatóbb és költséghatékonyabb megvalósítása érdekében, különös tekintettel a mérnöki, beszerzési és kivitelezési (EPC) kihívásokra.
Hivatkozások
- https://www.nucnet.org
- https://www.world-nuclear-news.org
- https://www.neimagazine.com
- https://www.oecd-nea.org
- https://www.iaea.org
- https://www.reuters.com/business/energy
- https://www.utilitydive.com
- https://www.atkinsrealis.com
- https://www.candu.com
-
 @ bc575705:dba3ed39
2025-03-13 05:57:10
@ bc575705:dba3ed39
2025-03-13 05:57:10In our hyper-connected age, the concept of "Know Your Customer" (KYC) has morphed from a regulatory necessity into a pervasive surveillance apparatus, subtly eroding our fundamental liberties. While purported to combat financial crime, KYC has become a tool for mass surveillance, data exploitation, and the gradual dismantling of personal privacy. Let’s embark on a comprehensive exploration of this system, exposing its inherent flaws and advocating for a paradigm shift towards decentralized financial sovereignty.
Beyond the Surface: The Intricate Web of KYC Data Collection
KYC transcends mere identity verification; it's a deep dive into the minutiae of our lives. Consider the breadth and depth of data extracted:
Geographic Surveillance: Proof of address requirements delve into historical residency, creating granular maps of our movements. Combined with location data from mobile devices and online activity, this paints a comprehensive picture of our physical presence.
Financial Autopsy: KYC dissects our financial lives with surgical precision. Income sources, asset declarations, and transaction histories are meticulously cataloged. Algorithmic analysis reveals spending habits, investment strategies, and even potential political affiliations.
Behavioral Predictive Modeling: AI algorithms analyze our financial behavior, predicting future actions and preferences. This data is invaluable for targeted advertising, but also for social engineering and political manipulation.
Biometric Invasiveness: Facial recognition, iris scans, and voice analysis create permanent, immutable records of our physical selves. These biometrics are highly sensitive and vulnerable to breaches, potentially leading to identity theft and even physical harm.
Social Network Mapping: KYC extends beyond individuals, mapping our social and professional networks. Institutions analyze our connections, identifying potential risks based on our associations. This has a chilling effect on free association and dissent, as individuals become hesitant to associate with those deemed "risky."
Psychometric Profiling: With the increase of online tests, and the collection of online data, companies and states can build psychometric profiles. These profiles can be used to predict actions, and even manipulate populations.
The Fallacy of Security: KYC's Ineffectiveness and the Rise of the Surveillance State
Despite its claims, KYC fails to effectively combat sophisticated financial crime. Instead, it creates a system of mass surveillance that disproportionately targets law-abiding citizens.
The Scourge of False Positives: Automated KYC systems frequently generate false positives, flagging innocent individuals as potential criminals. This can lead to financial exclusion, reputational damage, and even legal persecution.
A Ticking Time Bomb: Centralized KYC databases are prime targets for hackers, putting vast amounts of sensitive personal information at risk. Data breaches can lead to identity theft, financial fraud, and even physical harm.
The State's Panopticon: KYC empowers governments to monitor the financial activities of their citizens, creating a powerful tool for surveillance and control. This can be used to suppress dissent, target political opponents, and enforce conformity.
The Criminals Advantage: Sophisticated criminals easily bypass KYC using shell companies, money laundering, and other techniques. This makes KYC a system that punishes the innocent, and gives the criminals a false sense of security for the data collected.
Decentralized Alternatives: Reclaiming Financial Sovereignty and Privacy
In the face of this encroaching surveillance state, decentralized technologies offer a path to financial freedom and privacy.
Cryptocurrency | A Bastion of Financial Freedom: Bitcoin and other cryptocurrencies provide censorship-resistant alternatives to traditional financial systems. They empower individuals to transact freely, without the need for intermediaries or government oversight.
Decentralized Finance (DeFi) | Democratizing Finance: DeFi platforms offer a range of financial services, including lending, borrowing, and trading, without the need for traditional banks. These platforms are built on blockchain technology, ensuring transparency, security, and accessibility.
Self-Sovereign Identity (SSI) | Empowering Individuals: SSI solutions enable individuals to control their own digital identities, without relying on centralized authorities. This allows for secure and private verification of identity, without the need to share sensitive personal information with every service provider.
Privacy-Enhancing Technologies (PETs) | Shielding Your Data: Technologies like zero-knowledge proofs, homomorphic encryption, and secure multi-party computation can be used to protect personal data while still allowing for necessary verification.
Decentralized Autonomous Organizations (DAOs) | Creating new forms of governance: DAOs provide new ways for groups to organize, and make decisions. They provide a transparent way to pool resources, and make decisions.
A Call to Action: Defending Our Digital Rights and Building a Decentralized Future
We cannot passively accept the erosion of our fundamental freedoms. We must actively defend our digital rights and demand a more just and equitable financial system.
Advocate for Robust Privacy Laws: Demand stronger regulations that limit the collection and use of personal data.
Champion Decentralized Technologies: Support the development and adoption of cryptocurrencies, DeFi platforms, and other decentralized solutions.
Educate and Empower: Raise awareness about the dangers of KYC and state surveillance.
Cultivate Critical Thinking: Question the narratives presented by governments and corporations.
Build Decentralized Communities: Join and support decentralized communities that are working to build a more free and open financial system.
Demand transparency from all data collection: Insist that all data collection is open, and that there are strong penalties for those that misuse data.
The fight for financial freedom is a fight for human freedom. Let us stand together and reclaim our digital sovereignty.
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ dfa02707:41ca50e3
2025-05-22 16:01:24
@ dfa02707:41ca50e3
2025-05-22 16:01:24Contribute to keep No Bullshit Bitcoin news going.
Headlines
- OpenSats announces the eleventh wave of Nostr grants. The five projects in this wave are the mobile live-streaming app Swae, the Nostr-over-ham-radio project HAMSTR, Vertex—a Web-of-Trust (WOT) service for Nostr developers, Nostr Double Ratchet for end-to-end encrypted messaging, and the Nostr Game Engine for building games and applications integrated with the Nostr ecosystem.
- Project Eleven offers 1 BTC to break Bitcoin's cryptography with a quantum computer. The quantum computing research organization has introduced the Q-Day Prize, a global challenge that offers 1 BTC to the first team capable of breaking an elliptic curve cryptographic (ECC) key using Shor’s algorithm on a quantum computer. The prize will be awarded to the first team to successfully accomplish this breakthrough by April 5, 2026.
- Bull Bitcoin expands to Mexico, enabling anyone in the country to receive pesos from anywhere in the world straight from a Bitcoin wallet. Additionally, users can now buy Bitcoin with a Mexican bank account.
"Bull Bitcoin strongly believes in Bitcoin’s economic potential in Mexico, not only for international remittances and tourism, but also for Mexican individuals and companies to reclaim their financial sovereignty and protect their wealth from inflation and the fragility of traditional financial markets," said Francis Pouliot, Founder and CEO of Bull Bitcoin.
- Panama City votes to accept bitcoin for municipal services. The Panama City Council has voted to accept Bitcoin and other digital currencies for municipal services, becoming the first public institution in the country to do so. They will partner with an authorized bank responsible for converting the digital currency proceeds into dollars, reports Bitcoin Magazine.
- US Bitcoin miner manufacturer Auradine has raised $153 million in a Series C funding round as it expands into AI infrastructure. The round was led by StepStone Group and included participation from Maverick Silicon, Premji Invest, Samsung Catalyst Fund, Qualcomm Ventures, Mayfield, MARA Holdings, GSBackers, and other existing investors. The firm raised to over $300 million since its inception in 2022.
- Designathon 2025: The Bitcoin Design Community is organizing a Bitcoin design hackathon, scheduled to take place from May 4 to 18, 2025. Sign up and learn more about the event, prizes, and ideas.
Use the tools
- Core Lightning v25.02.1 and v24.11.2 address several issues, including returned outputs on mutual closes if peer didn't support
option_shutdown_anysegwit, properly handling duplicate HTLCs on closing, calculating fees with the correct HTLC timeout, occasional crash onbitcoind_getrawblockbyheightcallback, fixes tracepoint crashes in autoclean/chanbackup, and more. - LND v0.19.0-beta.rc2 is available for testing. New features include support for archiving channel backup, RBF cooperative closes, the Quiescence protocol, the
chainiosubsystem, lnwire messages for the Gossip 1.75 protocol, testnet4, and much more. - Hydrus v0.2.0, a Lightning liquidity management agent, is now available. This version adjusts routing policies, new CLI commands, built-in task scheduling, and a new open heuristic,
channels.block_height. - Alby Hub v1.16.0 introduces Alby Pro, a paid subscription plan for self-hosted Alby Hub runners that offers real-time backups, unlimited sub-wallets, customizable Lightning addresses, priority support, and more. The sidebar and settings page have received a UI update for a smoother experience, along with various other improvements and bug fixes.
- Alby Go v1.12.0 introduces a wallet switcher for swapping wallets during payments, withdrawals, and connections. It also improves number formatting for locales using decimal commas.
- Blitz Wallet v0.4.3-beta allows users to customize their maximum receive and balance amounts for ecash transactions. Besides, users can now pay for items in supported stores using ecash, and manual swap options have been expanded. The update also includes payment experience enhancements, performance optimizations, and bug fixes.
- Phoenix wallet v2.5.3 is a bug fix release that corrects UI problems on iOS and improves the handling of some Bolt12 failures.
- BitBanana v0.9.4 is a maintenance release that adds a link to new documentation, delivers bug fixes, and updated translations.
- BitBanana v0.9.3 was a notable release that introduced Nostr Wallet Connect (NWC) support, significantly enhanced the channel rebalancing interface, and added channel and UTXO sorting, among other features.
- Boltz Web App v1.7.3 has improved the UX for copying addresses and invoices, added fixes for hardware wallet integration, and backup files now include the rescue key, enabling backup imports to pick up pending swaps.
- Stratum v2 Reference Implementation (SRI) v1.3.0 comes with a new integration test framework and tests, enhanced APIs for role development, and core low-level crates now support
no_std. - ESP-Miner v2.6.6b1 is now available for testing.
- CTV Playground Android is a native Android implementation and demonstration of Bitcoin's proposed OP_CHECKTEMPLATEVERIFY (CTV) soft fork, including a CTV Vault implementation.
- Nstart, an onboarding wizard for new Nostr users, is now multilingual. Available languages include English, Español, Italiano, Français, Deutsch, and 日本語. You can contribute with a new language here.

Source: daniele
- GM Swap is a proof-of-concept implementation of the Atomic Signature Swaps NIP. It enables users to "swap GM notes, ensuring that both parties' signatures are exchanged simultaneously or not at all."
- Arti v1.4.2, a next-generation Tor client in Rust, is now available. Arti's RPC interface is now officially stable, and ready for testing.
- Tor Browser v14.5 has been released, introducing Connection Assist to Android, which helps mobile users facing strict censorship to easily unblock Tor with a single button press. Additionally, Belarusian, Bulgarian, and Portuguese languages are now available across all platforms, along with other improvements.
[
 ](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd
](https://njump.me/nevent1qqsqp3seup9kqz8xawavqd2jff6v627s63l4xwut9hjcphdnr5r3h5gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqgdwaehxw309ahx7uewd3hkcqfpwaehxw309akh2mr5d9cxcetcv4ezu6r4wdax7mn9vaujuam0wfkxgq3qpzzrdngrnlufqazx3lfj07k0vfuya6ehfy8q5yv2h8c5e8fxgmxqd -
 @ df67f9a7:2d4fc200
2025-03-13 00:23:46
@ df67f9a7:2d4fc200
2025-03-13 00:23:46For over a year, I have been developing “webs of trust onboarding and discovery” tools for Nostr. With additional funding, I hope to continue this endeavor in 2025. Here’s the story so far…
What I’m Building
More than simply a “list of follows follows”, “web of trust” implementations will power user discovery, content search, reviews and reccomendations, identity verification and access to all corners of the “trusted” Nostr network as it scales. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will leverage many forms of “relative trust” derived from our own “web” of natural interactions, “simply” by normalizing and scoring these interactions. The problem is, Nostr doesn’t have an extensible library for performing these “web of trust” calculations and delivering standardized reccomendations to any client … until now.
I have built a developer library by which clients and relays can offer “webs of trust” score calculations for any user. Primarily, I am also building a “social onboarding” client, which will leverage this library to provide “webs of trust” powered recommendations for new users at their crucial “first interaction” touchpoint.
- Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which I started a year ago with seed funding from @druid. This “social onboarding” client will leverage in person relationships, QR invites, and advocate recommendations to improve new user retention. Currently, it creates new accounts with encrypted keys upon scanning any user’s invite. Last summer, without additional funding or a reliable WoT engine to produce recommendations, I “paused” development of this project.
- GrapeRank Engine (developer library) : Working with @straycat last fall, I built an open source and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The power of GrapeRank is that it can generate different recommendations for different use cases (not just “web of trust” from “follows and mutes”), configurable easily by developers and by end users. This library is currently in v0.1, “generating and storing usable scores” without NIP standard outputs for Nostr clients.
- My Grapevine (algo dashboard) : In addition, I’ve just now wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, “web of trust” recommendations on Nostr have been implemented ad-hoc by clients with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
- Establish “sovereignty” for webs of trust users, by stimulating a “free market of choices” with open source libraries, enabling any developer to implement WoT powered recommendations with ease.
- Accelerate the isolation of “bots and bad actors”, and improve the “trustiness” of Nostr for everyone else, by streamlining the onboarding of “real world” trusted people directly into established “webs of trust”.
- Improve “discoverability of users and content” across all clients, by providing an extensible algo engine with “unlimited” NIP standard outputs, allowing any client to consume and take advantage of WoT powered recommendations, even as these NIPs are still in flux.
- Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for any user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
- Meet Me On Nostr (onboarding client) : MVP release : “scan my QR for instant account and DM with me on Nostr”.
- GrapeRank Engine (developer library) : 1.0 release : “output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays.
- My Grapevine (algo dashboard) : 1.0 release : “usable dashboard with API endpoints” for end users to configure and consume GrapeRank scores on their own clients and relays.
- Meet Me On Nostr (onboarding client) : 1.0 release : first integration with My Grapevine, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates.
Funding
In February 2024, I received a one time donation from @druid to start the “Meet Me On Nostr” client.
In May 2024, I applied for an OpenSats grant to fund further development of “Meet Me On Nostr”. This was denied.
In September 2024, @straycat offered to fund me for three months, to develop the “GrapeRank Engine” and “My Grapevine” demo client around his algorithm design.
I have a Geyser Fund page
Please reach out via DM if you are interested to fund part of this or any related project.
-
 @ dfa02707:41ca50e3
2025-05-22 16:01:23
@ dfa02707:41ca50e3
2025-05-22 16:01:23Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
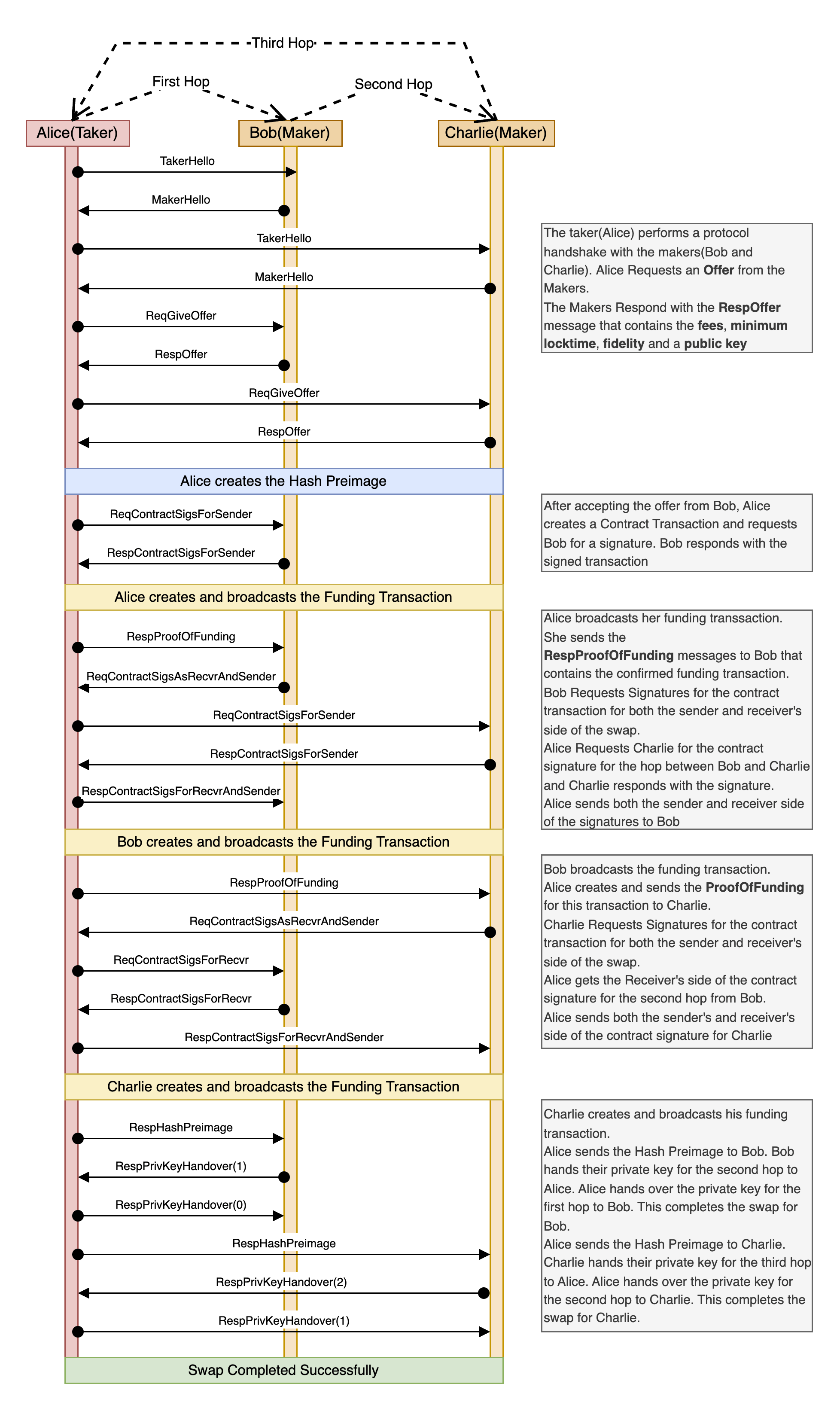
Source: Coinswap Protocol specification.

-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ dfa02707:41ca50e3
2025-05-22 16:01:23
@ dfa02707:41ca50e3
2025-05-22 16:01:23Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.