-
 @ 000002de:c05780a7
2025-05-22 20:50:21
@ 000002de:c05780a7
2025-05-22 20:50:21I'm mostly curious about how Tapper can do this with a straight face.
https://stacker.news/items/986926
-
 @ cefb08d1:f419beff
2025-05-22 07:16:18
@ cefb08d1:f419beff
2025-05-22 07:16:18https://stacker.news/items/986402
-
 @ 000002de:c05780a7
2025-05-21 20:00:21
@ 000002de:c05780a7
2025-05-21 20:00:21I enjoy Jonathan Pageau's perspectives from time to time. He is big on myth and symbolic signs in culture and history. I find this stuff fascinating as well. I watched this video last week, and based on the title, I was thinking... hmm, I wonder if it is a review of Return of the Strong Gods. It wasn't, but it really flows with the thesis of that book. You should read it if you haven't, and before you do, go check out @SimpleStacker's review of it.
Pageau starts the video by talking about the concept of "watching the clown." He uses Ye as the clown. Ye has been a leading indicator in the past when he publicly claimed he was a Christian and began making music and holding church services. Now he's going "off the rails" seemingly with his Hitler songs and art. Clearly, the stigma of Hitler will not last forever. It's hard for us to realize this. At least for someone of my age, but Pageau points out that eventually, the villains of history become less of a stand-in for Satan and more of a purely historical figure. He mentions Alexander the Great as a man who did incredibly evil things, but today we just read about him in school and don't really think about it too much. One day, that will be the way Hitler is viewed. Sure, evil, but the power of using him as the mythical Satan will wane.
The most interesting point I took away from this video, though, was that the post-war consensus was built on a dark secret. Now, it's not a secret to me, but at some point, it was. And this secret is a deep flaw in the current state of the West that keeps affecting us in negative ways. The secret is that in order to defeat Hitler and the Nazis, the West allied itself with the Soviets. Stalin. An incredibly evil man and an ideology that has led to the death and suffering of more humans than the Nazis. This is just a fact, but it's so dark that we don't talk about it.
For many years as I began to study Communism and the Soviet Union I began to question why on earth did the allies align themselves with Stalin. Obviously it was for stratigic reasons. I get it. But the fact that this topic is not really discussed in our culture has had a dark effect. Now, I'm not interested in figuring out if Stalin was more evil than Hitler or if Fascism is worse that Communism. I think this misses the point. The point is that today if soneone has Nazi symbols it is very likely not gonna go well for them but Communist symbols are usually just fine. We see the ideas of Socialism discussed openly without concern. Its popular even. Fascism on the other hand is always (until recently) masked at best.
Today we are seeing more and more people openly talk about this reality, and it is a signal that the WW2 consensus is breaking. As people age out and our collective memory fades, this lie will become more visible because the mythical view of Hitler will fade. This will allow people to be more objective about viewing the decisions of the past. I don't recall the book discussing this directly, but it is an interesting connection for sure.
I recommend watching The World War II Consensus is Breaking Down by Jonathan Pageau.
https://stacker.news/items/985962
-
 @ 000002de:c05780a7
2025-05-21 17:42:27
@ 000002de:c05780a7
2025-05-21 17:42:27I've been trying out Arch Linux again and the thing that always surprises me is pacman. The way it works seems so unintuitive to me coming from the apt, yum, and dnf worlds.
I know I will get it and it will become internalized but I just wonder what the designer was thinking when making the flags/commands.
https://stacker.news/items/985808
-
 @ 000002de:c05780a7
2025-05-21 17:27:46
@ 000002de:c05780a7
2025-05-21 17:27:46I completely missed this until yesterday. I was listening to our local news talk station and it came up. They had some people that were pretty knowledgeable about prostate cancer on. They talked about other presidents being tested while in office for it. They came to conclusion that it is possible that Biden wasn't having his PSA checked. This is pretty normal for a old dude his age. But it is not normal for a President his age.
My thought is much simpler.
We know his doctors, the media, and his admin were lying about his health when he was in office. Hello! Anyone paying attention and not invested in his regime knew he was declining mentally in front of our very eyes. They covered for him over and over again. Only those that don't pay attention or discounted his critics completely was surprised by his debate performance.
To be clear though, Biden is far from the first president to do this. Wilson, FDR, Kennedy, and Reagan all had issues and they were kept from the public. If we learned these things in school we might actually have a public that thinks critically once and a while.
So, with that in mind do you really think the regime would not withhold medical info about this cancer? Come on. Don't be naive. He clearly was not in charge 100% of the time while in office and the regime wanted to maintain power. Sharing that he had prostate cancer would not be on the menu.
Politics is like a drug that numbs the brain. Because people don't like one party or person they retard their thinking. Its the same thing as happens in sports. Fans of one team see the same play completely differently from the other team's fans. Politics and the investment into parties kills most people's objectivity.
I don't trust liars. It honestly blows my mind how trusting people can be of professional liars. Both parties are full of liars. Trump is a liar and those opposing him are liars. We are drowning in lies. You can vote for a lessor of two evils but never forget what they are.
https://stacker.news/items/985791
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 8d34bd24:414be32b
2025-05-21 15:52:46
@ 8d34bd24:414be32b
2025-05-21 15:52:46In our culture today, people like to have “my truth” as opposed to “your truth.” They want to have teachers who tell them what they want to hear and worship in the way they desire. The Bible predicted these times.
For the time will come when people will not put up with sound doctrine. Instead, to suit their own desires, they will gather around them a great number of teachers to say what their itching ears want to hear. (2 Timothy 4:3)
My question is, “do we get to choose what we want to believe about God and how we want to worship Him, or does God tell us what we are to believe and how we are to worship Him?”
The Bible makes it clear that He is who He says He is and He expects obedience and worship according to His commands. We do not get to decide for ourselves.
The woman said to Him, “Sir, I perceive that You are a prophet. Our fathers worshiped in this mountain, and you people say that in Jerusalem is the place where men ought to worship.” Jesus said to her, “Woman, believe Me, an hour is coming when neither in this mountain nor in Jerusalem will you worship the Father. You worship what you do not know; we worship what we know, for salvation is from the Jews. But an hour is coming, and now is, when the true worshipers will worship the Father in spirit and truth; for such people the Father seeks to be His worshipers. God is spirit, and those who worship Him must worship in spirit and truth.” (John 4:19-24) {emphasis mine}
In this passage, Jesus gently corrects the woman for worshipping what she does not know. He also says, “God is spirit, and those who worship Him must worship in spirit and truth.” He states what God is (spirit) and how He must be worshipped “in spirit and truth.” We don’t get to define God however we wish, and we don’t get to worship Him any way we wish. God is who He has revealed Himself to be and we must obey Him and worship Him the way He has commanded.
In this next passage, God makes clear that He is holy and we do not get to worship Him any way we wish. We are to interact with Him in the prescribed manner.
Now Nadab and Abihu, the sons of Aaron, took their respective firepans, and after putting fire in them, placed incense on it and offered strange fire before the Lord, which He had not commanded them. And fire came out from the presence of the Lord and consumed them, and they died before the Lord. Then Moses said to Aaron, “It is what the Lord spoke, saying,
‘By those who come near Me I will be treated as holy,\ And before all the people I will be honored.’ ”
So Aaron, therefore, kept silent. (Leviticus 10:1-3) {emphasis mine}
God had prescribed a particular way to approach Him and only those whom He had chosen (priests of the lineage of Aaron). Nadab and Abihu chose to “do it their way” and paid the price for ignoring God’s command. God set an example with them.
God has been gracious enough to reveal Himself, His character, His power, and His commands to us. If we have truly submitted ourselves to His rule, we should hunger for God’s words so we can know Him better and honor Him in obedience.
But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. I have given them Your word; and the world has hated them, because they are not of the world, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. They are not of the world, even as I am not of the world. Sanctify them in the truth; Your word is truth. (John 17:13-17) {emphasis mine}
In today’s culture, everybody likes to claim their own personal truth, but that isn’t how truth works. The truth is not determined by an individual for themselves. It isn’t even determined by a consensus or majority vote. The truth is the truth even if not one person on earth believes it. God speaks truth and God is truth. Our belief or lack thereof doesn’t change the truth, but our lack of belief in the truth, especially the truth as revealed by God in His word, can negatively affect our relationship with God.
God expects us to study His word so we can obey His commands.
For I did not speak to your fathers, or command them in the day that I brought them out of the land of Egypt, concerning burnt offerings and sacrifices. But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ Yet they did not obey or incline their ear, but walked in their own counsels and in the stubbornness of their evil heart, and went backward and not forward. Since the day that your fathers came out of the land of Egypt until this day, I have sent you all My servants the prophets, daily rising early and sending them. Yet they did not listen to Me or incline their ear, but stiffened their neck; they did more evil than their fathers. (Jeremiah 7:22-26) {emphasis mine}
Today you rarely see someone bowing down to a golden idol, but that doesn’t mean that we are any better at obeying God’s commands or submitting to His will. We still try to make God in our own image so He is a convenience to us and how we want to live our lives. We still put other things ahead of God — family, work, entertainment, fame, etc. Most of us aren’t any more faithful to God than the Israelites were. Just like the Israelites, we put on the trappings of faith but don’t live according to faith and faithfulness.
And He said to them, “Rightly did Isaiah prophesy of you hypocrites, as it is written:
‘This people honors Me with their lips,\ But their heart is far away from Me.\ **But in vain do they worship Me,\ Teaching as doctrines the precepts of men.’\ Neglecting the commandment of God, you hold to the tradition of men.”
He was also saying to them, “You are experts at setting aside the commandment of God in order to keep your tradition. (Mark 7:6-9) {emphasis mine}
How many “churches” and “Christian” leaders teach people according to the culture instead of according to the Word of God? How many tell people what they want to hear and what makes them feel good instead of what they need to hear — the truth as spoken through the Bible? How many church attenders follow a “Christian” leader more than they follow their Creator, Savior, and God? How many church attenders can recite the words of their leaders better than the Holy Scriptures?
I solemnly charge you in the presence of God and of Christ Jesus, who is to judge the living and the dead, and by His appearing and His kingdom: preach the word; be ready in season and out of season; reprove, rebuke, exhort, with great patience and instruction. For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. But you, be sober in all things, endure hardship, do the work of an evangelist, fulfill your ministry. (2 Timothy 4:1-5) {emphasis mine}
How can we know if a church leader is rightly preaching God’s word? We can only know if we have read the Bible and studied it. We should be like the Bereans:
Now these were more noble-minded than those in Thessalonica, for they received the word with great eagerness, examining the Scriptures daily to see whether these things were so. (Acts 17:11)
Honestly, I don’t trust any spiritual leader who doesn’t encourage me to search the Scriptures to see whether their words are true. Any leader who puts their own word above the Scriptures is a false teacher. Sadly there are many, maybe more than faithful teachers. Some false teachers are intentionally so, but many have been misled by other false teachers. Their guilt is less, but they don’t do any less harm than those who intentionally mislead.
We need to seek trustworthy teachers who speak according to the Word of God, who quote the Bible to support their opinions, and who seek the good of their followers rather than the submission of their followers.
Do not harden your hearts, as at Meribah,\ As in the day of Massah in the wilderness,
“When your fathers tested Me,\ They tried Me, though they had seen My work.\ For forty years I loathed that generation,\ And said they are a people who err in their heart,\ And they do not know My ways.\ Therefore I swore in My anger,\ Truly they shall not enter into My rest.” (Psalm 95:8-11) {emphasis mine} *Teach me good discernment and knowledge,\ For I believe in Your commandments*.\ Before I was afflicted I went astray,\ But now I keep Your word.\ You are good and do good;\ Teach me Your statutes.\ The arrogant have forged a lie against me;\ *With all my heart I will observe Your precepts*.\ Their heart is covered with fat,\ But I delight in Your law.\ It is good for me that I was afflicted,\ That I may learn Your statutes.\ The law of Your mouth is better to me\ Than thousands of gold and silver pieces. (Psalm 119:66-72) {emphasis mine}
May our Creator God teach us the truth. May He fill our hearts with the desire to be in His word daily and to seek His will. May He do what is necessary to get our attention and turn our hearts and minds fully to Him, so we can learn His statutes and serve Him faithfully, so one day we are blessed to hear, “Well done! Good and faithful servant.”
Trust Jesus.
FYI, I see lack of knowledge of truth and God’s word as one of the biggest problems in the church today; however, it is possible to know the Bible in depth, but not know God. As important as knowledge of Scriptures is, this knowledge (without faith, submission, obedience, and love) is meaningless. Knowledge doesn’t get us to heaven. Even obedience doesn’t get us to heaven. Only faith and submission to our creator God leads to salvation and heaven. That being said, we can’t faithfully serve our God without knowledge of Him and His commands. Out of gratefulness for who He is and what He has done for us, we should seek to know and please Him.
-
 @ ecda4328:1278f072
2025-05-21 11:44:17
@ ecda4328:1278f072
2025-05-21 11:44:17An honest response to objections — and an answer to the most important question: why does any of this matter?
Last updated: May 21, 2025\ \ 📄 Document version:\ EN: https://drive.proton.me/urls/A4A8Y8A0RR#Sj2OBsBYJFr1\ RU: https://drive.proton.me/urls/GS9AS1NB30#ZdKKb5ackB5e
\ Statement: Deflation is not the enemy, but a natural state in an age of technological progress.\ Criticism: in real macroeconomics, long-term deflation is linked to depressions.\ Deflation discourages borrowers and investors, and makes debt heavier.\ Natural ≠ Safe.
1. “Deflation → Depression, Debt → Heavier”
This is true in a debt-based system. Yes, in a fiat economy, debt balloons to the sky, and without inflation it collapses.
But Bitcoin offers not “deflation for its own sake,” but an environment where you don’t need to be in debt to survive. Where savings don’t melt away.\ Jeff Booth said it clearly:
“Technology is inherently deflationary. Fighting deflation with the printing press is fighting progress.”
You don’t have to take on credit to live in this system. Which means — deflation is not an enemy, but an ally.
💡 People often confuse two concepts:
-
That deflation doesn’t work in an economy built on credit and leverage — that’s true.
-
That deflation itself is bad — that’s a myth.
📉 In reality, deflation is the natural state of a free market when technology makes everything cheaper.
Historical example:\ In the U.S., from the Civil War to the early 1900s, the economy experienced gentle deflation — alongside economic growth, employment expansion, and industrial boom.\ Prices fell: for example, a sack of flour cost \~$1.00 in 1865 and \~$0.50 in 1895 — and there was no crisis, because wages held and productivity increased.
Modern example:\ Consumer electronics over the past 20–30 years are a vivid example of technological deflation:\ – What cost $5,000 in 2000 (e.g., a 720p plasma TV) now costs $300 and delivers 10× better quality.\ – Phones, computers, cameras — all became far more powerful and cheaper at the same time.\ That’s how tech-driven deflation works: you get more for less.
📌 Bitcoin doesn’t make the world deflationary. It just doesn’t fight against deflation, unlike the fiat model that fights to preserve its debt pyramid.\ It stops punishing savers and rewards long-term thinkers.
Even economists often confuse organic tech deflation with crisis-driven (debt) deflation.
\ \ Statement: We’ve never lived in a truly free market — central banks and issuance always existed.\ Criticism: ideological statement.\ A truly “free” market is utopian.\ Banks and monetary issuance emerged in response to crises.\ A market without arbiters is not always fair, especially under imperfect competition.
2. “The Free Market Is a Utopia”
Yes, “pure markets” are rare. But what we have today isn’t regulation — it’s centralized power in the hands of central banks and cartels.
Bitcoin offers rules without rulers. 21 million. No one can change the issuance. It’s not ideology — it’s code instead of trust. And it has worked for 15 years.
💬 People often say that banks and centralized issuance emerged as a response to crises — as if the market couldn’t manage on its own.\ But if a system needs to be “rescued” again and again through money printing… maybe the problem isn’t freedom, but the system itself?
📌 Crises don’t disprove the value of free markets. They only reveal how fragile a system becomes when the price of money is set not by the market, but by a boardroom vote.\ Bitcoin doesn’t magically eliminate crises — it removes the root cause: the ability to manipulate money in someone’s interest.
\ \ Statement: Inflation is an invisible tax, especially on the poor and working class.\ Criticism: partly true: inflation can reduce debt burden, boost employment.\ The state indexes social benefits. Under stable inflation, compensators can work. Under deflation, things might be worse (mass layoffs, defaults).
3. “Inflation Can Help”
Theoretically — yes. Textbooks say moderate inflation can reduce debt burdens and stimulate consumption and jobs.\ But in practice — it works as a stealth tax, especially on those without assets. The wealthy escape — into real estate, stocks, funds.\ But the poor and working class lose purchasing power because their money is held in cash — and cash devalues.
💬 As Lyn Alden says:
“When your money can’t hold value, you’re forced to become an investor — even if you just want to save and live.”
The state may index pensions or benefits — but always with a lag, and always less than actual price increases.\ If bread rises 15% and your payment increase is 5%, you got poorer, even if the number on paper went up.
💥 We live in an inflationary system of everything:\ – Inflationary money\ – Inflationary products\ – Inflationary content\ – And now even inflationary minds
🧠 This is more than just rising prices — it’s a degradation of reality perception. You’re always rushing, everything loses meaning.\ But when did the system start working against you?
📉 What went wrong after 1971?
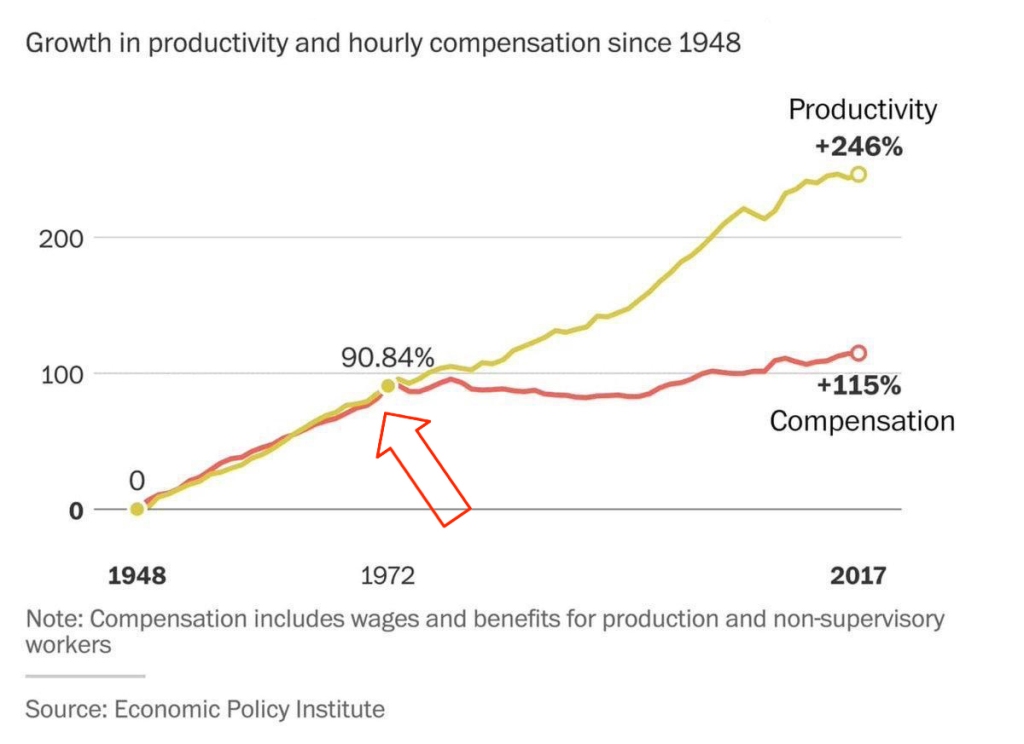 This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.
This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.👉 This means: you work more, better, faster — but buy less.
🔗 Source: wtfhappenedin1971.com
When you must spend today because tomorrow it’ll be worth less — that’s rewarding impulse and punishing long-term thinking.
Bitcoin offers a different environment:\ – Savings work\ – Long-term thinking is rewarded\ – The price of the future is calculated, not forced by a printing press
📌 Inflation can be a tool. But in government hands, it became a weapon — a slow, inevitable upward redistribution of wealth.
\ \ Statement: War is not growth, but a reallocation of resources into destruction.
Criticism: war can spur technological leaps (Internet, GPS, nuclear energy — all from military programs). "Military Keynesianism" was a real model.
4. “War Drives R&D”
Yes, wars sometimes give rise to tech spin-offs: Internet, GPS, nuclear power — all originated from military programs.
But that doesn’t make war a source of progress — it makes tech a byproduct of catastrophe.
“War reallocates resources toward destruction — not growth.”
Progress doesn’t happen because of war — it happens despite it.
If scientific breakthroughs require a million dead and burnt cities — maybe you’ve built your economy wrong.
💬 Even Michael Saylor said:
“If you need war to develop technology — you’ve built civilization wrong.”
No innovation justifies diverting human labor, minds, and resources toward destruction.\ War is always the opposite of efficiency — more is wasted than created.
🧠 Bitcoin, on the other hand, is an example of how real R&D happens without violence.\ No taxes. No army. Just math, voluntary participation, and open-source code.
📌 Military Keynesianism is not a model of progress — it’s a symptom of a sick monetary system that needs destruction to reboot.
Bitcoin shows that coordination without violence is possible.\ This is R&D of a new kind: based not on destruction, but digital creation.
Statement: Bitcoin isn’t “Gold 1.0,” but an improved version: divisible, verifiable, unseizable.
Criticism: Bitcoin has no physical value; "unseizability" is a theory;\ Gold is material and autonomous.
5. “Bitcoin Has No Physical Value”
And gold does? Just because it shines?
Physical form is no guarantee of value.\ Real value lies in: scarcity, reliable transfer, verifiability, and non-confiscatability.
Gold is:\ – Hard to divide\ – Hard to verify\ – Expensive to store\ – Easy to seize
💡 Bitcoin is the first store of value in history that is fully free from physical limitations, and yet:\ – Absolutely scarce (21M, forever)\ – Instantly transferable over the Internet\ – Cryptographically verifiable\ – Controlled by no government
🔑 Bitcoin’s value lies in its liberation from the physical.\ It doesn’t need to be “backed” by gold or oil. It’s backed by energy, mathematics, and ongoing verification.
“Price is what you pay, value is what you get.” — Warren Buffett
When you buy bitcoin, you’re not paying for a “token” — you’re gaining access to a network of distributed financial energy.
⚡️ What are you really getting when you own bitcoin?\ – A key to a digital asset that can’t be faked\ – The ability to send “crystallized energy” anywhere on Earth (it takes 10 minutes on the base L1 layer, or instantly via the Lightning Network)\ – A role in a new accounting system that runs 24/7/365\ – Freedom: from banks, borders, inflation, and force
📉 Bitcoin doesn’t require physical value — because it creates value:\ Through trust, scarcity, and energy invested in mining.\ And unlike gold, it was never associated with slavery.
Statement: There’s no “income without risk” in Bitcoin: just hold — you preserve; want more — invest, risk, build.
Criticism: contradicts HODL logic; speculation remains dominant behavior.
6. “Speculation Dominates”
For now — yes. That’s normal for the early phase of a new technology. Awareness doesn’t come instantly.
What matters is not the motive of today’s buyer — but what they’re buying.
📉 A speculator may come and go — but the asset remains.\ And this asset is the only one in history that will never exist again. 21 million. Forever.
📌 Look deeper. Bitcoin has:\ – No CEO\ – No central issuer\ – No inflation\ – No “off switch”\ 💡 It was fairly distributed — through mining, long before ASICs existed. In the early years, bitcoin was spent and exchanged — not hoarded. Only those who truly believed in it are still holding it today.
💡 It’s not a stock. Not a startup. Not someone’s project.\ It’s a new foundation for trust.\ It’s opting out of a system where freedom is a privilege you’re granted under conditions.
🧠 People say: “Bitcoin can be copied.”\ Theoretically — yes.\ Practically — never.
Here’s what you’d need to recreate Bitcoin:\ – No pre-mine\ – A founder who disappears and never sells\ – No foundation or corporation\ – Tens of thousands of nodes worldwide\ – 701 million terahashes of hash power\ – Thousands of devs writing open protocols\ – Hundreds of global conferences\ – Millions of people defending digital sovereignty\ – All that without a single marketing budget
That’s all.
🔁 Everything else is an imitation, not a creation.\ Just like you can’t “reinvent fire” — Bitcoin can only exist once.
Statements:\ **The Russia's '90s weren’t a free market — just anarchic chaos without rights protection.\ **Unlike fiat or even dollars, Bitcoin is the first asset with real defense — from governments, inflation, even thugs.\ *And yes, even if your barber asks about Bitcoin — maybe it's not a bubble, but a sign that inflation has already hit everyone.
Criticism: Bitcoin’s protection isn’t universal — it works only with proper handling and isn’t available to all.\ Some just want to “get rich.”\ None of this matters because:
-
Bitcoin’s volatility (-30% in a week, +50% in a month) makes it unusable for price planning or contracts.
-
It can’t handle mass-scale usage.
-
To become currency, geopolitical will is needed — and without the first two, don’t even talk about the third.\ Also: “Bitcoin is too complicated for the average person.”
7. “It’s Too Complex for the Masses”
It’s complex — if you’re using L1 (Layer 1). But even grandmas use Telegram. In El Salvador, schoolkids buy lunch with Lightning. My barber installed Wallet of Satoshi in minutes right in front of me — and I now pay for my haircut via Lightning.
UX is just a matter of time. And it’s improving. Emerging tools:\ Cashu, Fedimint, Fedi, Wallet of Satoshi, Phoenix, Proton Wallet, Swiss Bitcoin Pay, Bolt Card / CoinCorner (NFC cards for Lightning payments).
This is like the internet in 1995:\ It started with modems — now it’s 4K streaming.
💸 Now try sending a regular bank transfer abroad:\ – you need to type a long IBAN\ – add SWIFT/BIC codes\ – include the recipient’s full physical address (!), compromising their privacy\ – sometimes add extra codes or “purpose of payment”\ – you might get a call from your bank “just to confirm”\ – no way to check the status — the money floats somewhere between correspondent/intermediary banks\ – weekends or holidays? Banks are closed\ – and don’t forget the limits, restrictions, and potential freezes
📌 With Bitcoin, you just scan a QR code and send.\ 10 minutes on-chain = final settlement.\ Via Lightning = instant and nearly free.\ No bureaucracy. No permission. No borders.
8. “Can’t Handle the Load”
A common myth.\ Yes, Bitcoin L1 processes about 7 transactions per second — intentionally. It’s not built to be Visa. It’s a financial protocol, just like TCP/IP is a network protocol. TCP/IP isn’t “fast” or “slow” — the experience depends on the infrastructure built on top: servers, routers, hardware. In the ’90s, it delivered text. Today, it streams Netflix. The protocol didn’t change — the stack did.
Same with Bitcoin: L1 defines rules, security, finality.\ Scaling and speed? That’s the second layer’s job.
To understand scale:
| Network | TPS (Transactions/sec) | | --- | --- | | Visa | up to 24,000 | | Mastercard | \~5,000 | | PayPal | \~193 | | Litecoin | \~56 | | Ethereum | \~20 | | Bitcoin | \~7 |
\ ⚡️ Enter Lightning Network — Bitcoin’s “fast lane.”\ It allows millions of transactions per second, instantly and nearly free.
And it’s not a sidechain.
❗️ Lightning is not a separate network.\ It uses real Bitcoin transactions (2-of-2 multisig). You can close the channel to L1 at any time. It’s not an alternative — it’s a native extension built into Bitcoin.\ Also evolving: Ark, Fedimint, eCash — new ways to scale and add privacy.
📉 So criticizing Bitcoin for “slowness” is like blaming TCP/IP because your old modem won’t stream YouTube.\ The protocol isn’t the problem — it’s the infrastructure.
🛡️ And by the way: Visa crashes more often than Bitcoin.
9. “We Need Geopolitical Will”
Not necessarily. All it takes is the will of the people — and leaders willing to act. El Salvador didn’t wait for G20 approval or IMF blessings. Since 2001, the country had used the US dollar as its official currency, abandoning its own colón. But that didn’t save it from inflation or dependency on foreign monetary policy. In 2021, El Salvador became the first country to recognize Bitcoin as legal tender. Since March 13, 2024, they’ve been purchasing 1 BTC daily, tracked through their public address:
🔗 Address\ 📅 First transaction
This policy became the foundation of their Strategic Bitcoin Reserve (SBR) — a state-led effort to accumulate Bitcoin as a national reserve asset for long-term stability and sovereignty.
Their example inspired others.
In March 2025, U.S. President Donald Trump signed an executive order creating the Strategic Bitcoin Reserve of the USA, to be funded through confiscated Bitcoin and digital assets.\ The idea: accumulate, don’t sell, and strategically expand the reserve — without extra burden on taxpayers.
Additionally, Senator Cynthia Lummis (Wyoming) proposed the BITCOIN Act, targeting the purchase of 1 million BTC over five years (\~5% of the total supply).\ The plan: fund it via revaluation of gold certificates and other budget-neutral strategies.
📚 More: Strategic Bitcoin Reserve — Wikipedia
👉 So no global consensus is required. No IMF greenlight.\ All it takes is conviction — and an understanding that the future of finance lies in decentralized, scarce assets like Bitcoin.
10. “-30% in a week, +50% in a month = not money”
True — Bitcoin is volatile. But that’s normal for new technologies and emerging money. It’s not a bug — it’s a price discovery phase. The world is still learning what this asset is.
📉 Volatility is the price of entry.\ 📈 But the reward is buying the future at a discount.
As Michael Saylor put it:
“A tourist sees Niagara Falls as chaos — roaring, foaming, spraying water.\ An engineer sees immense energy.\ It all depends on your mental model.”
Same with Bitcoin. Speculators see chaos. Investors see structural scarcity. Builders see a new financial foundation.
💡 Now consider gold:
👉 After the gold standard was abandoned in 1971, the price of gold skyrocketed from around \~$300 to over $2,700 (adjusted to 2023 dollars) by 1980. Along the way, it experienced extreme volatility — with crashes of 40–60% even amid the broader uptrend.\ 💡 (\~$300 is the inflation-adjusted equivalent of about $38 in 1971 dollars)\ 📈 Source: Gold Price Chart — Macrotrends\ \ Nobody said, “This can’t be money.” \ Because money is defined not by volatility, but by scarcity, adoption, and trust — which build over time.
📊 The more people save in Bitcoin, the more its volatility fades.
This is a journey — not a fixed state.
We don’t judge the internet by how it worked in 1994.\ So why expect Bitcoin to be the “perfect currency” in 2025?
It grows bottom-up — without regulators’ permission.\ And the longer it survives, the stronger it becomes.
Remember how many times it’s been declared dead.\ And how many times it came back — stronger.
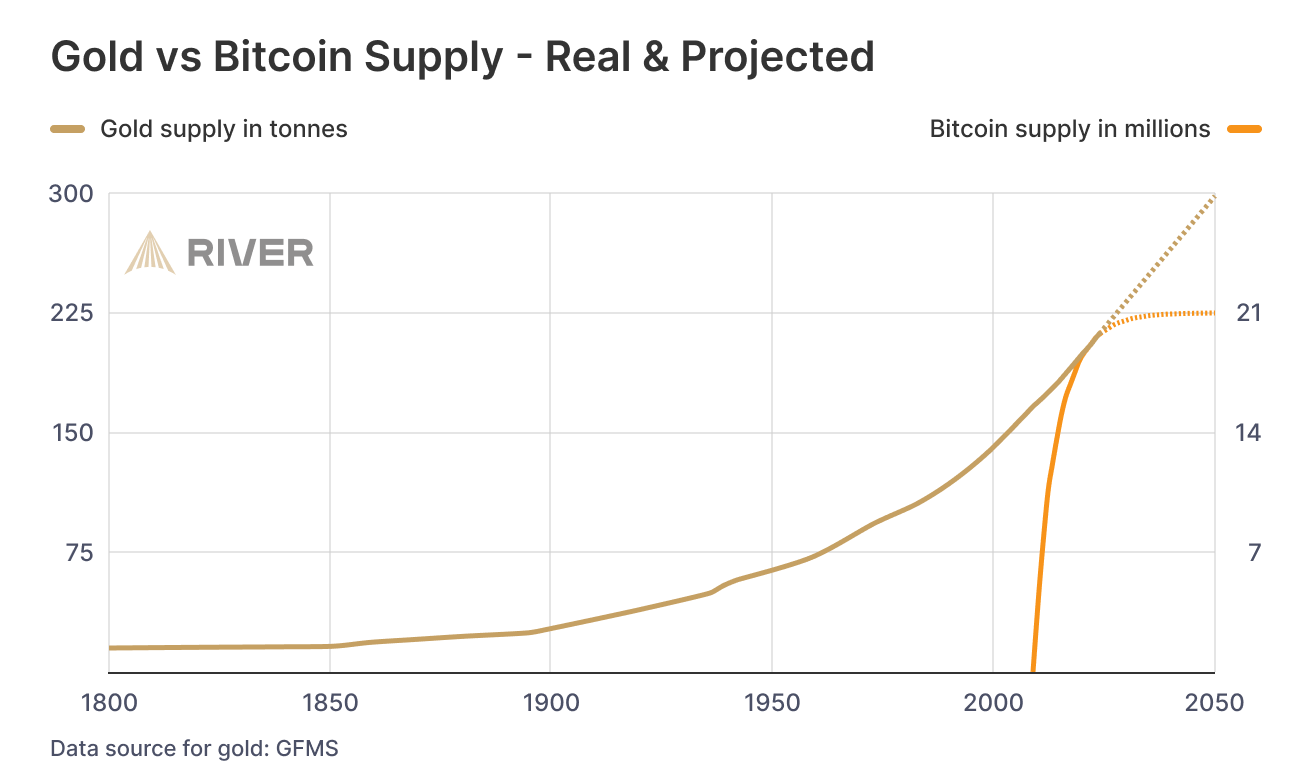
📊 Gold vs. Bitcoin: Supply Comparison
This chart shows the key difference between the two hard assets:
🔹 Gold — supply keeps growing.\ Mining may be limited, but it’s still inflationary.\ Each year, there’s more — with no known cap: new mines, asteroid mining, recycling.
🔸 Bitcoin — capped at 21 million.\ The emission schedule is public, mathematically predictable, and ends completely around 2140.
🧠 Bottom line:\ Gold is good.\ Bitcoin is better — for predictability and scarcity.
💡 As Saifedean Ammous said:
“Gold was the best monetary good… until Bitcoin.”
 ### While we argue — fiat erodes every day.
### While we argue — fiat erodes every day.No matter your view on Bitcoin, just show me one other asset that is simultaneously:
– immune to devaluation by decree\ – impossible to print more of\ – impossible to confiscate by a centralized order\ – impossible to counterfeit\ – and, most importantly — transferable across borders without asking permission from a bank, a state, or a passport
💸 Try sending $10,000 through PayPal from Iran to Paraguay, or Bangladesh to Saint Lucia.\ Good luck. PayPal doesn't even work there.
Now open a laptop, type 12 words — and you have access to your savings anywhere on Earth.
🌍 Bitcoin doesn't ask for permission.\ It works for everyone, everywhere, all the time.
📌 There has never been anything like this before.
Bitcoin is the first asset in history that combines:
– digital nature\ – predictable scarcity\ – absolute portability\ – and immunity from tyranny
💡 As Michael Saylor said:
“Bitcoin is the first money in human history not created by bankers or politicians — but by engineers.”
You can own it with no bank.\ No intermediary.\ No passport.\ No approval.
That’s why Bitcoin isn’t just “internet money” or “crypto” or “digital gold.”\ It may not be perfect — but it’s incorruptible.\ And it’s not going away.\ It’s already here.\ It is the foundation of a new financial reality.
🔒 This is not speculation. This is a peaceful financial revolution.\ 🪙 This is not a stock. It’s money — like the world has never seen.\ ⛓️ This is not a fad. It’s a freedom protocol.
And when even the barber starts asking about Bitcoin — it’s not a bubble.\ It’s a sign that the system is breaking.\ And people are looking for an exit.
For the first time — they have one.
💼 This is not about investing. It’s about the dignity of work.
Imagine a man who cleans toilets at an airport every day.
Not a “prestigious” job.\ But a crucial one.\ Without him — filth, bacteria, disease.
He shows up on time. He works with his hands.
And his money? It devalues. Every day.
He doesn’t work less — often he works more than those in suits.\ But he can afford less and less — because in this system, honest labor loses value each year.
Now imagine he’s paid in Bitcoin.
Not in some “volatile coin,” but in hard money — with a limited supply.\ Money that can’t be printed, reversed, or devalued by central banks.
💡 Then he could:
– Stop rushing to spend, knowing his labor won’t be worth less tomorrow\ – Save for a dream — without fear of inflation eating it away\ – Feel that his time and effort are respected — because they retain value
Bitcoin gives anyone — engineer or janitor — a way out of the game rigged against them.\ A chance to finally build a future where savings are real.
This is economic justice.\ This is digital dignity.
📉 In fiat, you have to spend — or your money melts.\ 📈 In Bitcoin, you choose when to spend — because it’s up to you.
🧠 In a deflationary economy, both saving and spending are healthy:
You don’t scramble to survive — you choose to create.
🎯 That’s true freedom.
When even someone cleaning floors can live without fear —\ and know that their time doesn’t vanish... it turns into value.
🧱 The Bigger Picture
Bitcoin is not just a technology — it’s rooted in economic philosophy.\ The Austrian School of Economics has long argued that sound money, voluntary exchange, and decentralized decision-making are prerequisites for real prosperity.\ Bitcoin doesn’t reinvent these ideas — it makes them executable.
📉 Inflation doesn’t just erode savings.\ It quietly destroys quality of life.\ You work more — and everything becomes worse:\ – food is cheaper but less nutritious\ – homes are newer but uglier and less durable\ – clothes cost more but fall apart in months\ – streaming is faster, but your attention span collapses\ This isn’t just consumerism — it’s the economics of planned obsolescence.
🧨 Meanwhile, the U.S. debt has exceeded 3x its GDP.\ And nobody wants to buy U.S. bonds anymore — so the U.S. has to buy its own debt.\ Yes: printing money to buy the IOUs you just printed.\ This is the endgame of fiat.
🎭 Bonds are often sold as “safe.”\ But in practice, they are a weapon — especially abroad.\ The U.S. and IMF give loans to developing countries.\ But when those countries can’t repay (due to rigged terms or global economic headwinds), they’re forced to sell land, resources, or strategic assets.\ Both sides lose: the debtor collapses under the weight of debt, while the creditor earns resentment and instability.\ This isn’t cooperation — it’s soft colonialism enabled by inflation.
📌 Bitcoin offers a peaceful exit.\ A financial system where money can’t be created out of thin air.\ Where savings work.\ Where dignity is restored — even for those who clean toilets.
-
-
 @ cefb08d1:f419beff
2025-05-21 10:15:18
@ cefb08d1:f419beff
2025-05-21 10:15:18Cat angels are the reason there are no mice angels.
Mel Brooks
https://stacker.news/items/985375
-
 @ cefb08d1:f419beff
2025-05-21 09:02:28
@ cefb08d1:f419beff
2025-05-21 09:02:28https://www.youtube.com/watch?v=OOmr2s-JPXo
The GWM Catch Up Day 3: Men's Quarterfinalists Locked, The Box delivers for pro surfing’s faithful:
https://www.youtube.com/watch?v=Owe-rjECP3M
The Box dishes West Oz power, Main Break decides last Quarters draws I Stone & Wood Post Show Day 3:
https://www.youtube.com/watch?v=qN3oi4kOGAA
Men 16 Round Results:
Source: https://www.worldsurfleague.com/events/2025/ct/326/western-australia-margaret-river-pro/results?roundId=24776
https://stacker.news/items/985339
-
 @ cefb08d1:f419beff
2025-05-21 06:34:00
@ cefb08d1:f419beff
2025-05-21 06:34:00https://stacker.news/items/985298
-
 @ 7460b7fd:4fc4e74b
2025-05-21 02:35:36
@ 7460b7fd:4fc4e74b
2025-05-21 02:35:36如果比特币发明了真正的钱,那么 Crypto 是什么?
引言
比特币诞生之初就以“数字黄金”姿态示人,被支持者誉为人类历史上第一次发明了真正意义上的钱——一种不依赖国家信用、总量恒定且不可篡改的硬通货。然而十多年过去,比特币之后蓬勃而起的加密世界(Crypto)已经远超“货币”范畴:从智能合约平台到去中心组织,从去央行的稳定币到戏谑荒诞的迷因币,Crypto 演化出一个丰富而混沌的新生态。这不禁引发一个根本性的追问:如果说比特币解决了“真金白银”的问题,那么 Crypto 又完成了什么发明?
 Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。
Crypto 与政治的碰撞:随着Crypto版图扩张,全球政治势力也被裹挟进这场金融变革洪流(示意图)。比特币的出现重塑了货币信用,但Crypto所引发的却是一场更深刻的政治与治理结构实验。从华尔街到华盛顿,从散户论坛到主权国家,越来越多人意识到:Crypto不只是技术或金融现象,而是一种全新的政治表达结构正在萌芽。正如有激进论者所断言的:“比特币发明了真正的钱,而Crypto则在发明新的政治。”价格K线与流动性曲线,或许正成为这个时代社群意志和社会价值观的新型投射。冲突结构:当价格挑战选票
传统政治中,选票是人民意志的载体,一人一票勾勒出民主治理的正统路径。而在链上的加密世界里,骤升骤降的价格曲线和真金白银的买卖行为却扮演起了选票的角色:资金流向成了民意走向,市场多空成为立场表决。价格行为取代选票,这听来匪夷所思,却已在Crypto社群中成为日常现实。每一次代币的抛售与追高,都是社区对项目决策的即时“投票”;每一根K线的涨跌,都折射出社区意志的赞同或抗议。市场行为本身承担了决策权与象征权——价格即政治,正在链上蔓延。
这一新生政治形式与旧世界的民主机制形成了鲜明冲突。bitcoin.org中本聪在比特币白皮书中提出“一CPU一票”的工作量证明共识,用算力投票取代了人为决策bitcoin.org。而今,Crypto更进一步,用资本市场的涨跌来取代传统政治的选举。支持某项目?直接购入其代币推高市值;反对某提案?用脚投票抛售资产。相比漫长的选举周期和层层代议制,链上市场提供了近乎实时的“公投”机制。但这种机制也引发巨大争议:资本的投票天然偏向持币多者(富者)的意志,是否意味着加密政治更为金权而非民权?持币多寡成为影响力大小,仿佛选举演变成了“一币一票”,巨鲸富豪俨然掌握更多话语权。这种与民主平等原则的冲突,成为Crypto政治形式饱受质疑的核心张力之一。
尽管如此,我们已经目睹市场投票在Crypto世界塑造秩序的威力:2016年以太坊因DAO事件分叉时,社区以真金白银“投票”决定了哪条链获得未来。arkhamintelligence.com结果是新链以太坊(ETH)成为主流,其市值一度超过2,800亿美元,而坚持原则的以太经典(ETC)市值不足35亿美元,不及前者的八十分之一arkhamintelligence.com。市场选择清楚地昭示了社区的政治意志。同样地,在比特币扩容之争、各类硬分叉博弈中,无不是由投资者和矿工用资金与算力投票,胜者存续败者黯然。价格成为裁决纷争的最终选票,冲击着传统“选票决胜”的政治理念。Crypto的价格民主,与现代代议民主正面相撞,激起当代政治哲思中前所未有的冲突火花。
治理与分配
XRP对决SEC成为了加密世界“治理与分配”冲突的经典战例。2020年底,美国证券交易委员会(SEC)突然起诉Ripple公司,指控其发行的XRP代币属于未注册证券,消息一出直接引爆市场恐慌。XRP价格应声暴跌,一度跌去超过60%,最低触及0.21美元coindesk.com。曾经位居市值前三的XRP险些被打入谷底,监管的强硬姿态似乎要将这个项目彻底扼杀。
然而XRP社区没有选择沉默。 大批长期持有者组成了自称“XRP军团”(XRP Army)的草根力量,在社交媒体上高调声援Ripple,对抗监管威胁。面对SEC的指控,他们集体发声,质疑政府选择性执法,声称以太坊当年发行却“逍遥法外”,只有Ripple遭到不公对待coindesk.com。正如《福布斯》的评论所言:没人预料到愤怒的加密散户投资者会掀起法律、政治和社交媒体领域的‘海啸式’反击,痛斥监管机构背弃了保护投资者的承诺crypto-law.us。这种草根抵抗监管的话语体系迅速形成:XRP持有者不但在网上掀起舆论风暴,还采取实际行动向SEC施压。他们发起了请愿,抨击SEC背离保护投资者初衷、诉讼给个人投资者带来巨大伤害,号召停止对Ripple的上诉纠缠——号称这是在捍卫全球加密用户的共同利益bitget.com。一场由民间主导的反监管运动就此拉开帷幕。
Ripple公司则选择背水一战,拒绝和解,在法庭上与SEC针锋相对地鏖战了近三年之久。Ripple坚称XRP并非证券,不应受到SEC管辖,即使面临沉重法律费用和业务压力也不妥协。2023年,这场持久战迎来了标志性转折:美国法庭作出初步裁决,认定XRP在二级市场的流通不构成证券coindesk.com。这一胜利犹如给沉寂已久的XRP注入强心针——消息公布当天XRP价格飙涨近一倍,盘中一度逼近1美元大关coindesk.com。沉重监管阴影下苟延残喘的项目,凭借司法层面的突破瞬间重获生机。这不仅是Ripple的胜利,更被支持者视为整个加密行业对SEC强权的一次胜仗。
XRP的对抗路线与某些“主动合规”的项目形成了鲜明对比。 稳定币USDC的发行方Circle、美国最大合规交易所Coinbase等选择了一条迎合监管的道路:它们高调拥抱现行法规,希望以合作换取生存空间。然而现实却给了它们沉重一击。USDC稳定币在监管风波中一度失去美元锚定,哪怕Circle及时披露储备状况也无法阻止恐慌蔓延,大批用户迅速失去信心,短时间内出现数十亿美元的赎回潮blockworks.co。Coinbase则更为直接:即便它早已注册上市、反复向监管示好,2023年仍被SEC指控为未注册证券交易所reuters.com,卷入漫长诉讼漩涡。可见,在迎合监管的策略下,这些机构非但未能换来监管青睐,反而因官司缠身或用户流失而丧失市场信任。 相比之下,XRP以对抗求生存的路线反而赢得了投资者的眼光:价格的涨跌成为社区投票的方式,抗争的勇气反过来强化了市场对它的信心。
同样引人深思的是另一种迥异的治理路径:技术至上的链上治理。 以MakerDAO为代表的去中心化治理模式曾被寄予厚望——MKR持币者投票决策、算法维持稳定币Dai的价值,被视为“代码即法律”的典范。然而,这套纯技术治理在市场层面却未能形成广泛认同,亦无法激发群体性的情绪动员。复杂晦涩的机制使得普通投资者难以参与其中,MakerDAO的治理讨论更多停留在极客圈子内部,在社会大众的政治对话中几乎听不见它的声音。相比XRP对抗监管所激发的铺天盖地关注,MakerDAO的治理实验显得默默无闻、难以“出圈”。这也说明,如果一种治理实践无法连接更广泛的利益诉求和情感共鸣,它在社会政治层面就难以形成影响力。
XRP之争的政治象征意义由此凸显: 它展示了一条“以市场对抗国家”的斗争路线,即通过代币价格的集体行动来回应监管权力的施压。在这场轰动业界的对决中,价格即是抗议的旗帜,涨跌映射着政治立场。XRP对SEC的胜利被视作加密世界向旧有权力宣告的一次胜利:资本市场的投票器可以撼动监管者的强权。这种“价格即政治”的张力,正是Crypto世界前所未有的社会实验:去中心化社区以市场行为直接对抗国家权力,在无形的价格曲线中凝聚起政治抗争的力量,向世人昭示加密货币不仅有技术和资本属性,更蕴含着不可小觑的社会能量和政治意涵。
不可归零的政治资本
Meme 币的本质并非廉价或易造,而在于其构建了一种“无法归零”的社群生存结构。 对于传统观点而言,多数 meme 币只是短命的投机游戏:价格暴涨暴跌后一地鸡毛,创始人套现跑路,投资者血本无归,然后“大家转去炒下一个”theguardian.com。然而,meme 币社群的独特之处在于——失败并不意味着终结,而更像是运动的逗号而非句号。一次币值崩盘后,持币的草根们往往并未散去;相反,他们汲取教训,准备东山再起。这种近乎“不死鸟”的循环,使得 meme 币运动呈现出一种数字政治循环的特质:价格可以归零,但社群的政治热情和组织势能不归零。正如研究者所指出的,加密领域中的骗局、崩盘等冲击并不会摧毁生态,反而成为让系统更加强韧的“健康应激”,令整个行业在动荡中变得更加反脆弱cointelegraph.com。对应到 meme 币,每一次暴跌和重挫,都是社群自我进化、卷土重来的契机。这个去中心化群体打造出一种自组织的安全垫,失败者得以在瓦砾上重建家园。对于草根社群、少数派乃至体制的“失败者”而言,meme 币提供了一个永不落幕的抗争舞台,一种真正反脆弱的政治性。正因如此,我们看到诸多曾被嘲笑的迷因项目屡败屡战:例如 Dogecoin 自2013年问世后历经八年沉浮,早已超越玩笑属性,成为互联网史上最具韧性的迷因之一frontiersin.org;支撑 Dogecoin 的正是背后强大的迷因文化和社区意志,它如同美国霸权支撑美元一样,为狗狗币提供了“永不中断”的生命力frontiersin.org。
“复活权”的数字政治意涵
这种“失败-重生”的循环结构蕴含着深刻的政治意涵:在传统政治和商业领域,一个政党选举失利或一家公司破产往往意味着清零出局,资源散尽、组织瓦解。然而在 meme 币的世界,社群拥有了一种前所未有的“复活权”。当项目崩盘,社区并不必然随之消亡,而是可以凭借剩余的人心和热情卷土重来——哪怕换一个 token 名称,哪怕重启一条链,运动依然延续。正如 Cheems 项目的核心开发者所言,在几乎无人问津、技术受阻的困境下,大多数人可能早已卷款走人,但 “CHEEMS 社区没有放弃,背景、技术、风投都不重要,重要的是永不言弃的精神”cointelegraph.com。这种精神使得Cheems项目起死回生,社区成员齐声宣告“我们都是 CHEEMS”,共同书写历史cointelegraph.com。与传统依赖风投和公司输血的项目不同,Cheems 完全依靠社区的信念与韧性存续发展,体现了去中心化运动的真谛cointelegraph.com。这意味着政治参与的门槛被大大降低:哪怕没有金主和官方背书,草根也能凭借群体意志赋予某个代币新的生命。对于身处社会边缘的群体来说,meme 币俨然成为自组织的安全垫和重新集结的工具。难怪有学者指出,近期涌入meme币浪潮的主力,正是那些对现实失望但渴望改变命运的年轻人theguardian.com——“迷茫的年轻人,想要一夜暴富”theguardian.com。meme币的炒作表面上看是投机赌博,但背后蕴含的是草根对既有金融秩序的不满与反抗:没有监管和护栏又如何?一次失败算不得什么,社区自有后路和新方案。这种由底层群众不断试错、纠错并重启的过程,本身就是一种数字时代的新型反抗运动和群众动员机制。
举例而言,Terra Luna 的沉浮充分展现了这种“复活机制”的政治力量。作为一度由风投资本热捧的项目,Luna 币在2022年的崩溃本可被视作“归零”的失败典范——稳定币UST瞬间失锚,Luna币价归零,数十亿美元灰飞烟灭。然而“崩盘”并没有画下休止符。Luna的残余社区拒绝承认失败命运,通过链上治理投票毅然启动新链,“复活”了 Luna 代币,再次回到市场交易reuters.com。正如 Terra 官方在崩盘后发布的推文所宣称:“我们力量永在社区,今日的决定正彰显了我们的韧性”reuters.com。事实上,原链更名为 Luna Classic 后,大批所谓“LUNC 军团”的散户依然死守阵地,誓言不离不弃;他们自发烧毁巨量代币以缩减供应、推动技术升级,试图让这个一度归零的项目重新燃起生命之火binance.com。失败者并未散场,而是化作一股草根洪流,奋力托举起项目的残迹。经过迷因化的叙事重塑,这场从废墟中重建价值的壮举,成为加密世界中草根政治的经典一幕。类似的案例不胜枚举:曾经被视为笑话的 DOGE(狗狗币)正因多年社群的凝聚而跻身主流币种,总市值一度高达数百亿美元,充分证明了“民有民享”的迷因货币同样可以笑傲市场frontiersin.org。再看最新的美国政治舞台,连总统特朗普也推出了自己的 meme 币 $TRUMP,号召粉丝拿真金白银来表达支持。该币首日即从7美元暴涨至75美元,两天后虽回落到40美元左右,但几乎同时,第一夫人 Melania 又发布了自己的 $Melania 币,甚至连就职典礼的牧师都跟风发行了纪念币theguardian.com!显然,对于狂热的群众来说,一个币的沉浮并非终点,而更像是运动的换挡——资本市场成为政治参与的新前线,你方唱罢我登场,meme 币的群众动员热度丝毫不减。值得注意的是,2024年出现的 Pump.fun 等平台更是进一步降低了这一循环的技术门槛,任何人都可以一键生成自己的 meme 币theguardian.com。这意味着哪怕某个项目归零,剩余的社区完全可以借助此类工具迅速复制一个新币接力,延续集体行动的火种。可以说,在 meme 币的世界里,草根社群获得了前所未有的再生能力和主动权,这正是一种数字时代的群众政治奇观:失败可以被当作梗来玩,破产能够变成重生的序章。
价格即政治:群众投机的新抗争
meme 币现象的兴盛表明:在加密时代,价格本身已成为一种政治表达。这些看似荒诞的迷因代币,将金融市场变成了群众宣泄情绪和诉求的另一个舞台。有学者将此概括为“将公民参与直接转化为了投机资产”cdn-brighterworld.humanities.mcmaster.ca——也就是说,社会运动的热情被注入币价涨跌,政治支持被铸造成可以交易的代币。meme 币融合了金融、技术与政治,通过病毒般的迷因文化激发公众参与,形成对现实政治的某种映射cdn-brighterworld.humanities.mcmaster.caosl.com。当一群草根投入全部热忱去炒作一枚毫无基本面支撑的币时,这本身就是一种大众政治动员的体现:币价暴涨,意味着一群人以戏谑的方式在向既有权威叫板;币价崩盘,也并不意味着信念的消亡,反而可能孕育下一次更汹涌的造势。正如有分析指出,政治类 meme 币的出现前所未有地将群众文化与政治情绪融入市场行情,价格曲线俨然成为民意和趋势的风向标cdn-brighterworld.humanities.mcmaster.ca。在这种局面下,投机不再仅仅是逐利,还是一种宣示立场、凝聚共识的过程——一次次看似荒唐的炒作背后,是草根对传统体制的不服与嘲讽,是失败者拒绝认输的呐喊。归根结底,meme 币所累积的,正是一种不可被归零的政治资本。价格涨落之间,群众的愤怒、幽默与希望尽显其中;这股力量不因一次挫败而消散,反而在市场的循环中愈发壮大。也正因如此,我们才说“价格即政治”——在迷因币的世界里,价格不只是数字,更是人民政治能量的晴雨表,哪怕归零也终将卷土重来。cdn-brighterworld.humanities.mcmaster.caosl.com
全球新兴现象:伊斯兰金融的入场
当Crypto在西方世界掀起市场治政的狂潮时,另一股独特力量也悄然融入这一场域:伊斯兰金融携其独特的道德秩序,开始在链上寻找存在感。长期以来,伊斯兰金融遵循着一套区别于世俗资本主义的原则:禁止利息(Riba)、反对过度投机(Gharar/Maysir)、强调实际资产支撑和道德投资。当这些原则遇上去中心化的加密技术,会碰撞出怎样的火花?出人意料的是,这两者竟在“以市场行为表达价值”这个层面产生了惊人的共鸣。伊斯兰金融并不拒绝市场机制本身,只是为其附加了道德准则;Crypto则将市场机制推向了政治高位,用价格来表达社群意志。二者看似理念迥异,实则都承认市场行为可以也应当承载社会价值观。这使得越来越多金融与政治分析人士开始关注:当虔诚的宗教伦理遇上狂野的加密市场,会塑造出何种新范式?
事实上,穆斯林世界已经在探索“清真加密”的道路。一些区块链项目致力于确保协议符合伊斯兰教法(Sharia)的要求。例如Haqq区块链发行的伊斯兰币(ISLM),从规则层面内置了宗教慈善义务——每发行新币即自动将10%拨入慈善DAO,用于公益捐赠,以符合天课(Zakat)的教义nasdaq.comnasdaq.com。同时,该链拒绝利息和赌博类应用,2022年还获得了宗教权威的教令(Fatwa)认可其合规性nasdaq.com。再看理念层面,伊斯兰经济学强调货币必须有内在价值、收益应来自真实劳动而非纯利息剥削。这一点与比特币的“工作量证明”精神不谋而合——有人甚至断言法定货币无锚印钞并不清真,而比特币这类需耗费能源生产的资产反而更符合教法初衷cointelegraph.com。由此,越来越多穆斯林投资者开始以道德投资的名义进入Crypto领域,将资金投向符合清真原则的代币和协议。
这种现象带来了微妙的双重合法性:一方面,Crypto世界原本奉行“价格即真理”的世俗逻辑,而伊斯兰金融为其注入了一股道德合法性,使部分加密资产同时获得了宗教与市场的双重背书;另一方面,即便在遵循宗教伦理的项目中,最终决定成败的依然是市场对其价值的认可。道德共识与市场共识在链上交汇,共同塑造出一种混合的新秩序。这一全球新兴现象引发广泛议论:有人将其视为金融民主化的极致表现——不同文化价值都能在市场平台上表达并竞争;也有人警惕这可能掩盖新的风险,因为把宗教情感融入高风险资产,既可能凝聚强大的忠诚度,也可能在泡沫破裂时引发信仰与财富的双重危机。但无论如何,伊斯兰金融的入场使Crypto的政治版图更加丰盈多元。从华尔街交易员到中东教士,不同背景的人们正通过Crypto这个奇特的舞台,对人类价值的表达方式进行前所未有的实验。
升华结语:价格即政治的新直觉
回顾比特币问世以来的这段历程,我们可以清晰地看到一条演进的主线:先有货币革命,后有政治发明。比特币赋予了人类一种真正自主的数字货币,而Crypto在此基础上完成的,则是一项前所未有的政治革新——它让市场价格行为承担起了类似政治选票的功能,开创了一种“价格即政治”的新直觉。在这个直觉下,市场不再只是冷冰冰的交易场所;每一次资本流动、每一轮行情涨落,都被赋予了社会意义和政治涵义。买入即表态,卖出即抗议,流动性的涌入或枯竭胜过千言万语的陈情。Crypto世界中,K线图俨然成为民意曲线,行情图就是政治晴雨表。决策不再由少数权力精英关起门来制定,而是在全球无眠的交易中由无数普通人共同谱写。这样的政治形式也许狂野,也许充满泡沫和噪音,但它不可否认地调动起了广泛的社会参与,让原本疏离政治进程的个体通过持币、交易重新找回了影响力的幻觉或实感。
“价格即政治”并非一句简单的口号,而是Crypto给予世界的全新想象力。它质疑了传统政治的正统性:如果一串代码和一群匿名投资者就能高效决策资源分配,我们为何还需要繁冗的官僚体系?它也拷问着自身的内在隐忧:当财富与权力深度绑定,Crypto政治如何避免堕入金钱统治的老路?或许,正是在这样的矛盾和张力中,人类政治的未来才会不断演化。Crypto所开启的,不仅是技术乌托邦或金融狂欢,更可能是一次对民主形式的深刻拓展和挑战。这里有最狂热的逐利者,也有最理想主义的社群塑梦者;有一夜暴富的神话,也有瞬间破灭的惨痛。而这一切汇聚成的洪流,正冲撞着工业时代以来既定的权力谱系。
当我们再次追问:Crypto究竟是什么? 或许可以这样回答——Crypto是比特币之后,人类完成的一次政治范式的试验性跃迁。在这里,价格行为化身为选票,资本市场演化为广场,代码与共识共同撰写“社会契约”。这是一场仍在进行的文明实验:它可能无声地融入既有秩序,也可能剧烈地重塑未来规则。但无论结局如何,如今我们已经见证:在比特币发明真正的货币之后,Crypto正在发明真正属于21世纪的政治。它以数字时代的语言宣告:在链上,价格即政治,市场即民意,代码即法律。这,或许就是Crypto带给我们的最直观而震撼的本质启示。
参考资料:
-
中本聪. 比特币白皮书: 一种点对点的电子现金系统. (2008)bitcoin.org
-
Arkham Intelligence. Ethereum vs Ethereum Classic: Understanding the Differences. (2023)arkhamintelligence.com
-
Binance Square (@渔神的加密日记). 狗狗币价格为何上涨?背后的原因你知道吗?binance.com
-
Cointelegraph中文. 特朗普的迷因币晚宴预期内容揭秘. (2025)cn.cointelegraph.com
-
慢雾科技 Web3Caff (@Lisa). 风险提醒:从 LIBRA 看“政治化”的加密货币骗局. (2025)web3caff.com
-
Nasdaq (@Anthony Clarke). How Cryptocurrency Aligns with the Principles of Islamic Finance. (2023)nasdaq.comnasdaq.com
-
Cointelegraph Magazine (@Andrew Fenton). DeFi can be halal but not DOGE? Decentralizing Islamic finance. (2023)cointelegraph.com
-
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 3f770d65:7a745b24
2025-05-20 21:14:28
@ 3f770d65:7a745b24
2025-05-20 21:14:28I’m Derek Ross, and I’m all-in on Nostr.
I started the Grow Nostr Initiative to help more people discover what makes Nostr so powerful: ✅ You own your identity ✅ You choose your social graph and algorithms ✅ You aren't locked into any single app or platform ✅ You can post, stream, chat, and build, all without gatekeepers
What we’re doing with Grow Nostr Initiative: 🌱 Hosting local meetups and mini-conferences to onboard people face-to-face 📚 Creating educational materials and guides to demystify how Nostr works 🧩 Helping businesses and creators understand how they can plug into Nostr (running media servers, relays, and using key management tools)
I believe Nostr is the foundation of a more open internet. It’s still early, but we’re already seeing incredible apps for social, blogging, podcasting, livestreaming, and more. And the best part is that they're all interoperable, censorship-resistant, and built on open standards. Nostr is the world's largest bitcoin economy by transaction volume and I truly believe that the purple pill helps the orange pill go down. Meaning, growing Nostr will also grow Bitcoin adoption.
If you’ve been curious about Nostr or are building something on it, or let’s talk. Whether you're just getting started or you're already deep in the ecosystem, I'm here to answer questions, share what I’ve learned, and hear your ideas. Check out https://nostrapps.com to find your next social decentralized experience.
Ask Me Anything about GNI, Nostr, Bitcoin, the upcoming #NosVegas event at the Bitcoin Conference next week, etc.!
– Derek Ross 🌐 https://grownostr.org npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
https://stacker.news/items/984689
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53
@ 46fcbe30:6bd8ce4d
2025-03-11 18:11:53MEMORANDUM OF CONVERSATION
SUBJECT: Meeting with Russian President Yeltsin
PARTICIPANTS: - U.S. - President Clinton - Secretary Albright - National Security Advisor Berger - Deputy National Security Advisor Steinberg - Ambassador Sestanovich - Carlos Pascual
- Russia
- Russian President Yeltsin
- Foreign Minister Ivanov
- Kremlin Foreign Policy Advisor Prihodko
- Defense Minister Sergeyev
- Interpreter: Peter Afansenko
- Notetaker: Carlos Pascual
DATE, TIME AND PLACE: November 19, 1999, 10:45 a.m. - 11:40 a.m. Istanbul, Turkey
President Yeltsin: We are in neutral territory here. I welcome you.
The President: Neither of us has a stake here. It's good to see you.
President Yeltsin: Well, Bill, what about those camps here in Turkey that are preparing troops to go into Chechnya? Aren't you in charge of those? I have the details. Minister Ivanov, give me the map. I want to show you where the mercenaries are being trained and then being sent into Chechnya. They are armed to the teeth. (Note: Yeltsin pulls out map of Turkey and circulates it.) Bill, this is your fault. I told Demirel yesterday that I will send the head of the SRV tomorrow and we will show him where the camps are located. These are not state-sanctioned camps. They are sponsored by NGOs and religious organizations. But let me tell you if this were in Russia and there were but one camp, I would throw them all out and put the bandits in the electric chair.
The President: Perhaps Demirel could help you.
President Yeltsin: Well, he ought to. Tomorrow after I get back, I will send the head of the Foreign Intelligence Service here. Bill, did you hurt your leg?
The President: Yes, but it is not bad.
President Yeltsin: When one leg of the President hurts, that is a bad thing.
The President: It lets me know I am alive.
President Yeltsin: I know we are not upset at each other. We were just throwing some jabs. I'm still waiting for you to visit. Bill. I've said to you come to visit in May, then June, then July and then August. Now it's past October and you're still not there.
The President: You're right, Boris, I owe you a visit.
President Yeltsin: Last time I went to the U.S., Bill.
The President: Well, I better set it up. I'll look at the calendar and find a time that's good for you and me.
President Yeltsin: Call me and tell me the month and date. Unless I have another visit, I will do the maximum amount I can to do everything around your schedule. The main things I have are to go to China and India.
The President: Boris, we still have lots to do together.
President Yeltsin: You heard my statement on nuclear arms and on banning nuclear tests. I just signed a law on ratification of a new agreement on the Comprehensive Test Ban Treaty. Isn't that right, Minister Ivanov?
Minister Ivanov: You signed the documents that sent the Comprehensive Test Ban Treaty to the Duma for review.
President Yeltsin: Well, in any case, I still approved it.
The President: Maybe I can get the Congress to agree still. They kept the Treaty even after they rejected it. So perhaps, there is still a chance.
President Yeltsin: Or perhaps it's just the bureaucrats working and they haven't had a chance to send it back to you yet. I'm upset that you signed the law to change the ABM Treaty.
The President: I signed no such law. People in Congress don't like the ABM Treaty. If Congress had its way, they would undermine the treaty. I'm trying to uphold it. But we need a national missile defense to protect against rogue states. We can't have a national missile defense that works without changing the ABM Treaty. But I want to do this cooperatively. I want to persuade you that this is good for both of us. The primary purpose is to protect against terrorists and rogue states. It would be ineffective against Russia. The system we're looking at would operate against just 20 missiles. And, Boris I want to figure out how to share the benefits. For all I know, in twenty years terrorists could have access to nuclear weapons. I know your people don't agree with me, but I'm not trying to overthrow the ABM Treaty. We're still trying to discover what's technically possible with national missile defense, but there are people in America who want to throw over the ABM Treaty. I have made no decisions yet.
President Yeltsin: Bill, Bill. I got your note. It went into all these things in incredible detail. I read it and I was satisfied. I've not yet ceased to believe in you. I ask you one thing. Just give Europe to Russia. The U.S. is not in Europe. Europe should be the business of Europeans. Russia is half European and half Asian.
The President: So you want Asia too?
President Yeltsin: Sure, sure. Bill. Eventually, we will have to agree on all of this.
The President: I don't think the Europeans would like this very much.
President Yeltsin: Not all. But I am a European. I live in Moscow. Moscow is in Europe and I like it. You can take all the other states and provide security to them. I will take Europe and provide them security. Well, not I. Russia will. We will end this conflict in Chechnya. I didn't say all the things I was thinking (in his speech). I listened to you carefully. I took a break just beforehand. Then I listened to you from beginning to end. I can even repeat what you said. Bill, I'm serious. Give Europe to Europe itself. Europe never felt as close to Russia as it does now. We have no difference of opinion with Europe, except maybe on Afganistan and Pakistan—which, by the way, is training Chechens. These are bandits, headhunters and killers. They're raping American women. They're cutting off ears and other parts of their hostages. We're fighting these types of terrorists. Let's not accuse Russia that we are too rough with these kinds of people. There are only two options: kill them or put them on trial. There's no third option, but we can put them on trial, and sentence them to 20-25 years. How many Americans, French, British and Germans have I freed that were there in Chechnya under the OSCE? The Chechen killers don't like the language of the OSCE. Here's my Minister of Defense. Stand up. We have not lost one soldier down there. Tell them.
Minister Sergeyev: We did not lose one soldier in Gudermes.
President Yeltsin: You see, Gudermes was cleansed without one military or civilian killed. We killed 200 bandits. The Minister of Defense is fulfilling the plan as I have said it should be. He's doing this thoughtfully. The soldiers only ask: don't stop the campaign. I promised these guys—I told every soldier, marshal and general—I will bring the campaign to fruition. We have these Chechens under lock and key. We have the key. They can't get in, they can't get out. Except maybe through Georgia; that's Shevardnadze's big mistake. And through Azerbaijan; that's Aliyev's mistake. They're shuttling in under the name of Islam. We're for freedom of religion, but not for fundamentalist Islam. These extremists are against you and against me.
We have the power in Russia to protect all of Europe, including those with missiles. We'll make all the appropriate treaties with China. We're not going to provide nuclear weapons to India. If we give them submarines, it will be only conventional diesel submarines, not nuclear. They would be from the 935 generation. You're going in that direction too. I'm thinking about your proposal—well, what your armed forces are doing—getting rid of fissile materials, particularly plutonium. We should just get rid of it. As soon as it's there, people start thinking of how to make bombs. Look, Russia has the power and intellect to know what to do with Europe. If Ivanov stays here, he will initial the CFE Treaty and I'll sign it under him. But under the OSCE Charter, there is one thing I cannot agree—which is that, based on humanitarian causes, one state can interfere in the affairs of another state.
National Security Advisor Berger: Mr. President, there's nothing in the Charter on one state's interference in the affairs of another.
Secretary Albright: That's right. What the Charter says is that affairs within a state will affect the other states around it.
President Yeltsin: Russia agrees to take out its property and equipment from Georgia in accordance with the new CFE Treaty. I have a statement on this. (looking toward Ivanov) Give it to me. I signed it today. Actually, it was late last night. I like to work late.
The President: Me, too.
President Yeltsin: I know you like to work late, Bill. When you call me, I calculate the time and I tell myself it's 4 a.m. and he's calling me. It lets you cleanse your brain and you feel great. I am not criticizing you, Bill. The President should be encouraged to work hard.
The President: So, we will get an agreement on CFE.
President Yeltsin: Yes.
The President: That's very important, seven years. We've worked on this for a long time.
President Yeltsin: Look, Ivanov has lost the statement in his own bag. He can't find the paper in his own bag. On the Charter, we have to look at it from the beginning. The Charter's ready. However, when states begin to tie in the Charter with the final declaration that has wording unacceptable to us, that's when we'll say no. And responsibility for this will fall fully on the West. (Looking at Ivanov) Give me this thing. It is written on paper. Bill. I am ready to sign it. It is a declaration about what we're talking about.
Secretary Albright: Some states want to record in the declaration your willingness to have an OSCE mission.
President Yeltsin: No, not at all. We will finish this with our own forces. Chechnya is the business of the internal affairs of Russia. We have to decide what to do. After we cleansed Gudermes, the muslim mufti came and asked for help, said I hate Basayev and he should be banned. These are the kinds of leaders we will put forward. I have thought this through carefully.
The President: On the Chechen problem. I have been less critical than others. Even today, I asked the others how they would deal with this if it were their country. This is a political issue. It may be the best thing for you within Russia to tell the Europeans to go to hell. But the best thing for your relations with Europe for the long term is to figure out the policy that you want to have with Europe and to keep that in mind as you deal with Chechnya.
President Yeltsin: (Gets up rapidly) Bill, the meeting is up. We said 20 minutes and it has now been more than 35 minutes.
The President: That's fine. We can say the meeting is over.
President Yeltsin: This meeting has gone on too long. You should come to visit, Bill.
The President: Who will win the election?
President Yeltsin: Putin, of course. He will be the successor to Boris Yeltsin. He's a democrat, and he knows the West.
The President: He's very smart.
President Yeltsin: He's tough. He has an internal ramrod. He's tough internally, and I will do everything possible for him to win—legally, of course. And he will win. You'll do business together. He will continue the Yeltsin line on democracy and economics and widen Russia's contacts. He has the energy and the brains to succeed. Thank you, Bill.
The President: Thank you, Boris. It was good to see you.
End of Conversation
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ 291c75d9:37f1bfbe
2025-03-08 04:09:59
@ 291c75d9:37f1bfbe
2025-03-08 04:09:59In 1727, a 21-year-old Benjamin Franklin gathered a dozen men in Philadelphia for a bold experiment in intellectual and civic growth. Every Friday night, this group—known as the Junto, from the Spanish juntar ("to join")—met in a tavern or private home to discuss "Morals, Politics, or Natural Philosophy (science)." Far from a casual social club, the Junto was a secret society dedicated to mutual improvement, respectful discourse, and community betterment. What began as a small gathering of tradesmen and thinkers would leave a lasting mark on Franklin’s life and colonial America.
Printers are educated in the belief that when men differ in opinion, both sides ought equally to have the advantage of being heard by the public, and that when Truth and Error have fair play, the former is always an overmatch for the latter. - Benjamin Franklin
The Junto operated under a clear set of rules, detailed by Franklin in his Autobiography:
"The rules that I drew up required that every member, in his turn, should produce one or more queries on any point of Morals, Politics, or Natural Philosophy, to be discuss’d by the company; and once in three months produce and read an essay of his own writing, on any subject he pleased. Our debates were to be under the direction of a president, and to be conducted in the sincere spirit of inquiry after truth, without fondness for dispute, or desire of victory; and, to prevent warmth [heatedness], all expressions of positiveness in opinions, or direct contradiction, were after some time made contraband and prohibited under small pecuniary penalties [monetary fines]."
These guidelines emphasized collaboration over competition. Members were expected to contribute questions or essays, sparking discussions that prioritized truth over ego. To keep debates civil, the group even imposed small fines for overly assertive or contradictory behavior—a practical nudge toward humility and open-mindedness. (Yes, I believe that is an ass tax!)
Rather than admitting new members, Franklin encouraged existing ones to form their own discussion groups. This created a decentralized network of groups ("private relays," as I think of them), echoing the structure of modern platforms like NOSTR—while preserving the Junto’s exclusivity and privacy.
From the beginning, they made it a rule to keep these meetings secret, without applications or admittance of new members. Instead, Franklin encouraged members to form their own groups—in a way acting as private relays of sorts. (I say "private" because they continued to keep the Junto secret, even with these new groups.)
Membership: A Diverse Circle United by Values
The Junto’s twelve founding members came from varied walks of life—printers, surveyors, shoemakers, and clerks—yet shared a commitment to self-improvement. Franklin, though the youngest (around 21 when the group formed), led the Junto with a vision of collective growth. To join, candidates faced a simple vetting process, answering four key questions:
- Have you any particular disrespect for any present members? Answer: I have not.
- Do you sincerely declare that you love mankind in general, of what profession or religion soever? Answer: I do.
- Do you think any person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship? Answer: No.
- Do you love truth for truth’s sake, and will you endeavor impartially to find and receive it yourself and communicate it to others? Answer: Yes.
These criteria reveal the Junto’s core values: respect, tolerance, and an unwavering pursuit of truth. They ensured that members brought not just intellect but also character to the table—placing dialogue as the priority.
One should also note the inspiration from the "Dry Club" of John Locke, William Popple, and Benjamin Furly in the 1690s. They too required affirmation to:
- Whether he loves all men, of what profession or religion soever?
- Whether he thinks no person ought to be harmed in his body, name, or goods, for mere speculative opinions, or his external way of worship?
- Whether he loves and seeks truth for truth’s sake; and will endeavor impartially to find and receive it himself, and to communicate it to others?
And they agreed: "That no person or opinion be unhandsomely reflected on; but every member behave himself with all the temper, judgment, modesty, and discretion he is master of."
The Discussions: 24 Questions to Spark Insight
Franklin crafted a list of 24 questions to guide the Junto’s conversations, ranging from personal anecdotes to civic concerns. These prompts showcase the group’s intellectual breadth. Here are some of my favorites:
Hath any citizen in your knowledge failed in his business lately, and what have you heard of the cause? Have you lately heard of any citizen’s thriving well, and by what means? Do you know of any fellow citizen who has lately done a worthy action, deserving praise and imitation? Do you think of anything at present in which the Junto may be serviceable to mankind, their country, friends, or themselves? Have you lately observed any defect in the laws of your country, which it would be proper to move the legislature for an amendment? Do you know of any deserving young beginner lately set up, whom it lies in the power of the Junto any way to encourage?
(Read them all here.)
Note the keen attention to success and failure, and the reflection on both. Attention was often placed on the community and individual improvement beyond the members of the group. These questions encouraged members to share knowledge, reflect on virtues and vices, and propose solutions to real-world problems. The result? Discussions that didn’t just end at the tavern door but inspired tangible community improvements.
The Junto’s Legacy: America’s First Lending Library
One of the Junto’s most enduring contributions to Philadelphia—and indeed, to the American colonies—was the creation of the first lending library in 1731. Born from the group’s commitment to mutual improvement and knowledge-sharing, this library became a cornerstone of public education and intellectual life in the community.
The idea for the library emerged naturally from the Junto’s discussions. Members, who came from diverse backgrounds but shared a passion for learning, recognized that their own access to books was often limited and costly—and they referred to them often. To address this, they proposed pooling their personal collections to create a shared resource. This collaborative effort allowed them—and eventually the broader public—to access a wider range of books than any individual could afford alone.
The library operated on a simple yet revolutionary principle: knowledge should be available to all, regardless of wealth or status. By creating a lending system, the Junto democratized access to information, fostering a culture of self-education and curiosity. This was especially significant at a time when books were scarce and formal education was not universally accessible.
The success of the Junto’s library inspired similar initiatives across the colonies, laying the groundwork for the public library system we know today. It also reflected the group’s broader mission: to serve not just its members but the entire community. The library became a symbol of the Junto’s belief in the power of education to uplift individuals and society alike.
With roots extending back to the founding of the Society in 1743, the Library of the American Philosophical Society houses over thirteen million manuscripts, 350,000 volumes and bound periodicals, 250,000 images, and thousands of hours of audiotape. The Library’s holdings make it one of the premier institutions for documenting the history of the American Revolution and Founding, the study of natural history in the 18th and 19th centuries, the study of evolution and genetics, quantum mechanics, and the development of cultural anthropology, among others.
The American Philosophical Society Library continues today. I hope to visit it myself in the future.
Freedom, for Community
Comparing the Junto to Nostr shows how the tools of community and debate evolve with time. Both prove that people crave spaces to connect, share, and grow—whether in a colonial tavern or a digital relay. Yet their differences reveal trade-offs: the Junto’s structure offered depth and focus but capped its reach, while Nostr’s openness promises scale at the cost of order.
In a sense, Nostr feels like the Junto’s modern echo—faster, bigger, and unbound by gates or rules. Franklin might admire its ambition, even if he’d raise an eyebrow at its messiness. For us, the comparison underscores a timeless truth: no matter the medium, the drive to seek truth and build community endures.
The Autobiography of Benjamin Franklin (1771–1790, pub. 1791)
http://www.benjamin-franklin-history.org/junto-club/
Benjamin Franklin, Political, Miscellaneous, and Philosophical Pieces, ed. Benjamin Vaughan (London: 1779), pp. 533–536.
"Rules of a Society" in The Remains of John Locke, Esq. (1714), p. 113
npubpro
-
 @ c48e29f0:26e14c11
2025-03-07 04:51:09
@ c48e29f0:26e14c11
2025-03-07 04:51:09ESTABLISHMENT OF THE STRATEGIC BITCOIN RESERVE AND UNITED STATES DIGITAL ASSET STOCKPILE EXECUTIVE ORDER March 6, 2025
By the authority vested in me as President by the Constitution and the laws of the United States of America, it is hereby ordered:
Section 1. Background.
Bitcoin is the original cryptocurrency. The Bitcoin protocol permanently caps the total supply of bitcoin (BTC) at 21 million coins, and has never been hacked. As a result of its scarcity and security, Bitcoin is often referred to as “digital gold”. Because there is a fixed supply of BTC, there is a strategic advantage to being among the first nations to create a strategic bitcoin reserve. The United States Government currently holds a significant amount of BTC, but has not implemented a policy to maximize BTC’s strategic position as a unique store of value in the global financial system. Just as it is in our country’s interest to thoughtfully manage national ownership and control of any other resource, our Nation must harness, not limit, the power of digital assets for our prosperity.
Sec. 2. Policy.
It is the policy of the United States to establish a Strategic Bitcoin Reserve. It is further the policy of the United States to establish a United States Digital Asset Stockpile that can serve as a secure account for orderly and strategic management of the United States’ other digital asset holdings.
Sec. 3. Creation and Administration of the Strategic Bitcoin Reserve and United States Digital Asset Stockpile.
(a) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “Strategic Bitcoin Reserve,” capitalized with all BTC held by the Department of the Treasury that was finally forfeited as part of criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any executive department or agency (agency) and that is not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Government BTC). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Government BTC held by it to the Strategic Bitcoin Reserve and shall submit a report reflecting the result of that review to the Secretary of the Treasury. Government BTC deposited into the Strategic Bitcoin Reserve shall not be sold and shall be maintained as reserve assets of the United States utilized to meet governmental objectives in accordance with applicable law.
(b) The Secretary of the Treasury shall establish an office to administer and maintain control of custodial accounts collectively known as the “United States Digital Asset Stockpile,” capitalized with all digital assets owned by the Department of the Treasury, other than BTC, that were finally forfeited as part of criminal or civil asset forfeiture proceedings and that are not needed to satisfy requirements under 31 U.S.C. 9705 or released pursuant to subsection (d) of this section (Stockpile Assets). Within 30 days of the date of this order, each agency shall review its authorities to transfer any Stockpile Assets held by it to the United States Digital Asset Stockpile and shall submit a report reflecting the result of that review to the Secretary of the Treasury. The Secretary of the Treasury shall determine strategies for responsible stewardship of the United States Digital Asset Stockpile in accordance with applicable law.
(c) The Secretary of the Treasury and the Secretary of Commerce shall develop strategies for acquiring additional Government BTC provided that such strategies are budget neutral and do not impose incremental costs on United States taxpayers. However, the United States Government shall not acquire additional Stockpile Assets other than in connection with criminal or civil asset forfeiture proceedings or in satisfaction of any civil money penalty imposed by any agency without further executive or legislative action.
(d) “Government Digital Assets” means all Government BTC and all Stockpile Assets. The head of each agency shall not sell or otherwise dispose of any Government Digital Assets, except in connection with the Secretary of the Treasury’s exercise of his lawful authority and responsible stewardship of the United States Digital Asset Stockpile pursuant to subsection (b) of this section, or pursuant to an order from a court of competent jurisdiction, as required by law, or in cases where the Attorney General or other relevant agency head determines that the Government Digital Assets (or the proceeds from the sale or disposition thereof) can and should: (i) be returned to identifiable and verifiable victims of crime; (ii) be used for law enforcement operations;
(iii) be equitably shared with State and local law enforcement partners; or (iv) be released to satisfy requirements under 31 U.S.C. 9705, 28 U.S.C. 524(c), 18 U.S.C. 981, or 21 U.S.C. 881.(e) Within 60 days of the date of this order, the Secretary of the Treasury shall deliver an evaluation of the legal and investment considerations for establishing and managing the Strategic Bitcoin Reserve and United States Digital Asset Stockpile going forward, including the accounts in which the Strategic Bitcoin Reserve and United States Digital Asset Stockpile should be located and the need for any legislation to operationalize any aspect of this order or the proper management and administration of such accounts.
Sec. 4. Accounting.
Within 30 days of the date of this order, the head of each agency shall provide the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets with a full accounting of all Government Digital Assets in such agency’s possession, including any information regarding the custodial accounts in which such Government Digital Assets are currently held that would be necessary to facilitate a transfer of the Government Digital Assets to the Strategic Bitcoin Reserve or the United States Digital Asset Stockpile. If such agency holds no Government Digital Assets, such agency shall confirm such fact to the Secretary of the Treasury and the President’s Working Group on Digital Asset Markets within 30 days of the date of this order.
Sec. 5. General Provisions.
(a) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department or agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(b) This order shall be implemented consistent with applicable law and subject to the availability of appropriations.
(c) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 6, 2025
-
 @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-
 @ c8383d81:f9139549
2025-03-02 23:57:18
@ c8383d81:f9139549
2025-03-02 23:57:18Project is still in early stages but now it is split into 2 different domain entities. Everything is opened sourced under one github https://github.com/Nsite-Info
So what’s new ?
Project #1 https://Nsite.info
A basic website with main info regarding what an Nsite is how it works and a list of tools and repo’s you can use to start building and debugging. 99% Finished, needs some extra translations and the Nsite Debugger can use a small upgrade.
Project #2 https://Nsite.cloud
This project isn’t finished, it currently is at a 40% finished stage. This contains the Nsite Gateway for all sites (still a work in progress) and the final stage the Nsite editor & template deployment.
If you are interested in Nsite’s join: https://chachi.chat/groups.hzrd149.com/e23891
Big thanks to nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr nostr:npub1klr0dy2ul2dx9llk58czvpx73rprcmrvd5dc7ck8esg8f8es06qs427gxc for all the tooling & code.
!(image)[https://i.nostr.build/AkUvk7R2h9cVEMLB.png]
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06This post by Eric Weiss inspired me to try it out. After all, I have plaid around with ppq.ai - pay per query before.
Using this script:
```bash
!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() { local model_name="$1" local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo }
for model in "${models[@]}"; do query_model "$model" & done
wait ```
I got this output:
``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | Bitcoin | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | Bitcoin | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | Bitcoin | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20% ```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ dd664d5e:5633d319
2025-02-12 07:05:51
@ dd664d5e:5633d319
2025-02-12 07:05:51I think this note from Chip (nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7) is one of those things that people with business management experience take a lot more seriously than most developers and influencers do.
I am painfully aware of the cost of systems administration, financial transaction management and recordkeeping, recruiting and personnel management, legal and compliance, requirements management, technical support, renting and managing physical spaces and infrastructure, negotiating with suppliers, customer service, etc. etc.
There's this idea, on Nostr, that sort of trickled in along with Bitcoin Twitter, that we would all just be isolated subsistance farmers and one-man-show podcasters with a gigantic server rack in the basement. But some of us are running real companies -- on and off Nostr, for-profit and non-profit -- and it often requires a lot of human labor.
The things we build aren't meant to be used by one person and his girlfriend and his dog. Yes, he can also run all these things, himself, but he no longer has to. Our existence gives him the choice: run these things or pay us to run them and spend your time doing something else, that you do better than we do.
These things are meant to be used by hundreds... thousands... eventually millions of people. The workflows, processes, infrastructure, and personnel need to be able to scale up-and-down, scale in-and-out, work smoothly with 5 people or 50 people. These are the sort of Nostr systems that wouldn't collapse when encountering a sudden influx or mass-escape. But these systems are much more complex and they take time to build and staff to run them. (And, no, AI can't replace them all. AI means that they now also have to integrate a bunch of AI into the system and maintain that, too.)
GitCitadel (nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz) is very automation-forward, but we still have to front the incredibly high cost of designing and building the automation, train people to interact with it (there are now over 20 people integrated into the workflow!), adjust it based upon their feedback, and we have to support the automation, once it's running.
This sort of streamlined machine is what people pay companies for, not code. That is why there's little business cost to open source.
Open-source is great, but...

nostr:nevent1qqsgqh2dedhagyd9k8yfk2lagswjl7y627k9fpnq4l436ccmlys0s3qprdmhxue69uhhg6r9vehhyetnwshxummnw3erztnrdakj7q3qqdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havqxpqqqqqqzdhnyjm
-
 @ fd208ee8:0fd927c1
2025-02-06 15:58:38
@ fd208ee8:0fd927c1
2025-02-06 15:58:38Beginning at the start
In my previous article, The Establishment, I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a company is a team, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
The Initiation
The first, and most-difficult step of team formation, is the initiation. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.
So, just do and be all of those things, and then initiate the team, with the method I will name the Hatbock Method. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
The Sitting
We now get to the second most difficult part of team formation: figuring out where to sit. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, immediately.

Now, this next bit is very important:
Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German Stammtisch principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out when to sit. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. Write everything down. Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, as a company.
-
 @ c8383d81:f9139549
2025-02-05 13:06:05
@ c8383d81:f9139549
2025-02-05 13:06:05My own stats on what I’ve done over the weekend:
-
Spoke to +100 developers, it was great seeing a couple of familiar Flemish faces and meeting some new ones but overall the crowd was extremely diverse.
-
Ended up doing a short interview promoting the protocol and ended up going to 0 talks.
-
Tried to evangelize by going booth by booth to distribute a Nostr flyer to other FOSDEM projects, with the hope that they would broadcast the info towards their SOME person to add Nostr on their list or to build out a library for the languages that were present ( This was a fairly slow approach )
-
Kept it to Nostr protocol 95% of the time, the Bitcoin narrative is not always a good time to push and as a side note I’ve met more Monero users than in the last 5 years.
-
Was able to convince some engineers to look into the #soveng endeavor.
Small overview from the most common questions:
- They have heard about Nostr but are not sure of the details. ( mostly through the bitcoin community )
- What is the difference with ActivityPub, Mastodon, Fediverse ?
- IOT developers, so questions regarding MQTT & Meshtastic integrations ?
- Current state of MLS on Nostr ?
- What are the current biggest clients / apps build on Nostr ?
- Will jack still give a talk ?
Things we could improve:
- Bring more stickers like loads more,
- Bring T-shirts, Pins… could be a good way to fund these adventures instead of raising funds. ( Most projects where selling something to help raise funds for projects )
- Almost no onboarding / client installs.
- Compared to the Nostr booth at BTC Amsterdam not a single person asked if they could charge their phone.
Personal Note: The last time I visited was roughly 13 years ago and me being a little more seasoned I just loved the fact that I was able to pay some support to the open source projects I’ve been using for years ( homebrew, modzilla, Free BSD,.. ) and see the amazing diverse crowd that is the open source Movement 🧡
Al final shoutout to our great pirate crew 🏴☠️: The Dutch Guard ( nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe & nostr:npub1l77twp5l02jadkcjn6eeulv2j7y5vmf9tf3hhtq7h7rp0vzhgpzqz0swft ) and a adrenaline fueled nostr:npub1t6jxfqz9hv0lygn9thwndekuahwyxkgvycyscjrtauuw73gd5k7sqvksrw , nostr:npub1rfw075gc6pc693w5v568xw4mnu7umlzpkfxmqye0cgxm7qw8tauqfck3t8 and nostr:npub1r30l8j4vmppvq8w23umcyvd3vct4zmfpfkn4c7h2h057rmlfcrmq9xt9ma amazing finally meeting you IRL after close to 2 years since the Yakihonne hackathon 😀

-
-
 @ dd1f9d50:06113a21
2025-02-05 01:48:55
@ dd1f9d50:06113a21
2025-02-05 01:48:55(Because Most People Don’t Understand Money)
The requisite knowledge needed to know whether $100 or $100,000 per Bitcoin is relatively speaking “a lot,” is what value means. One way to measure value is through a universal yardstick we call “Money.” The question of “What is money?” is perhaps one of the most overlooked and under answered in our day and age. There is even an entire podcast dedicated to that question with the eponymous title, hosted by Robert Breedlove. That podcast often delves into the more philosophical underpinnings whereas I hope to approach this with a more practical answer.
Money is a technology.
Money is the technology with which we interact with one another to reorganize goods and services to the place and time they are best suited. Most money of the past has been tangible (though not a requisite feature), scarce, recognizable (read: verifiable), durable, portable, and divisible. These features one might call the “Attributes of Money.” These attributes are absolutely essential for a money to maintain its status as a money. (Those of you who understand the U.S. Dollar system maybe scratching your heads right now but, believe me, I will address that elephant in due time.) These attributes, you may notice, are not a yes or no but more of a gradient. A money can be MORE portable than another yet, less durable. One more divisible but not scarce whatsoever. The point being they must have, in some capacity, these attributes or they simply aren’t money.
One of These Things is Not Like the Other
| | Bitcoin | Gold | Dollars | |-----------------|:----------------------------------------------------------------------------------------------------------------:|:------------------------------------------------------------------:|:--------------------------------------------------------------------------------------------------------------------------------------------------:| | Scarcity | 21 million coins
is the maximum supply | Unknown- the
supply grows roughly 2% per year | Also unknown to anyone outside of the Federal Reserve, Trillions and counting | | Recognizability | Each coin is verifiable to it's genesis on the timechain | Each molecule of gold has distinct physical verifiable properties | If the Federal reserve says it is a valid note, it is (Unless you are an enemy of the United States) | | Durablility | Each "Bitcoin" is information stored on a globally distributed network | Doesn't Rust and as far as can be measured Au197 is stable forever | Can be destroyed by any means that effect fabric and centralized databases | | Portability | Available wherever data can be store- Anywhere | Can be moved at 9.81 Newtons per Kilogram- Methods may vary | Can be moved physically with fabric notes- Digitally with express permission from a US accredited banking institution | | Divisibility | Currently can be divided into 100 million parts called Sats (can be further subdivided by adding decimal places) | Can be divided to the Atomic level (Though not practical) | Can be divided (without dilution) by adding new denominative bills or coinage
Can be divided (with dilution) by printing new bills or coinage | | | Bitcoin | Gold | Dollars |You may think with all of the great functionality of Bitcoin that the phrase "One of these things is not like the other" refers to BTC. No, I was referring to the Dollar. It is the only one on the list that was a currency that was substituted as some kind of faux money. It asserts itself, or rather the Federal Reserve asserts it, as money, de facto.
Dollars are NOT money.
Dollars are (allegedly) a currency. If money is a specific technology, currency is the financial infrastructure that allows that technology to reach and be used by the most number of people possible. This requires a firm tether between the asset being used as money and the currency used as a claim to that money. For example: If I hand you a chicken, you have a chicken. But, if I hand you a coupon that is redeemable for a chicken, you do not have a chicken. You have a claim to a chicken that is only as good as the party making that claim. Bringing it back to money again, dollars (Prior to 1971) were redeemable for gold at a rate of $35 per ounce. This is that strong tether that pegged dollars to gold and physical reality itself. Without a proof of work, mining, . Until…
WTF Happened in 1971?
The Nixon shock happened. Briefly, The U.S. took in Europe’s gold in the 1940’s to keep it out of Hitler’s hands. The U.S. made an agreement to peg the dollar to Europe’s gold. The U.S. over printed dollars in relation to the gold holdings. Around 1971 France (among others) called the U.S. out for devaluing the dollar and thus European currencies. So, Nixon “Temporarily” suspended the convertibility of dollars to gold. Now, here we all are like Wile E. Coyote having run off of the golden cliff clutching our dollars in our arms and 54 years later we still haven’t looked down to see the truth.
Dollars Aren’t Backed by Anything
This is why no country in the world today has a money standard. Seemingly they all forgot the number one rule of issuing currency, it must be backed by something. Now, you may hear dollar proponents say “The U.S. dollar is backed by the full faith and credit of the United States!” Another way of saying that is, “We said it is worth something, so it is!” This fiat (by decree) mentality creates a plethora of perverse incentives. The ever growing supply disallows users of the Dollar to save without inccuring the penalties of inflation.
Just a Few Examples of How You're Being Crushed
Because your dollar loses value:
- It pushes people to spend them on assets that seem to appreciate (as the dollar debases) but are truly staying stagnant.
- It pushes people to gamble on securities hoping the perceived value is enough to beat the inflationary curve.
- It pushes people away from saving for their future and the future of their families.
- It creates insane credit incentives so that people borrow way more than they can afford today knowing that dollars will be cheaper in the future. (Effectively a short position)
- It pushes people to spend less and less time making and maintaining their families as it becomes more expensive to keep a similar lifestyle to which it was founded.
These are just a few of the terrible consequences of not knowing that trading a currency with no monetary backing has on a society. Most may blame this soley on the ability to print currency by a central bank but, that is not the only factor. If the fed printed dollars against gold, people would simply take the best rate they could get and remonetize themselves with the gold. But because there is no monetary escape hatch guaranteed by the issuance of dollars, I.E. no one has to take your dollars in exchange for their Bitcoin or gold, you are left at the mercy of the market.
One Day, People Will Stop Accepting Your Dollars
Those lementing the high price of Bitcoin might want to thank their lucky stars that Bitcoin still has a rational number next to the "BTC 1=$?" sign. One day you will have to exchange something of actual value to the spender (no longer a seller). Your product, good or service, will be the only thing that anyone might be willing to part with their Bitcoin over. That is what makes a money, the most salable non-consumable good, whose only funtion is to back a financial structure that facilitates trade.
Bitcoin is Capital
Capital is a broad term that can describe anything that confers value or benefit to its owners, such as a factory and its machinery, or the financial assets of a business or an individual. Bitcoin being the latter creates the financial structures from which you build upon. You use capital to hold, transfer, and grow value. You do not do this with cash. Cash is a depreciating asset when you don't use it to gain goods or services for yourself or your business. This misconception around the equivalance between cash and money (financial capital) is what tricks people into believing Dollars are money. And what's worse is that even some of our greatest heroes have done this.
Slay Your Heroes, Within Reason
Unfortunately due to a mixing of verbiage that have very distinct differences, the title: "Bitcoin: A Peer-to-Peer Electronic Cash System" is technically inaccurate. Bitcoin doesn't fit the definition of cash, which is a liquid asset that can be easily converted into its equivalent value. In short, Satoshi misspoke. In reality, owning Bitcoin UTXOs (with private keys) means you already possess the asset, not just a claim to it. When you spend Bitcoin, the recipient receives the actual asset, not a promise of it. When you receive Bitcoin, you have final settlement on that transaction. Fundamentally Bitcoin is not cash, electronic or otherwise.
Bitcoin is Money.
-
 @ fd208ee8:0fd927c1
2025-02-02 10:33:19
@ fd208ee8:0fd927c1
2025-02-02 10:33:19GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a self-hosted OneDev instance. In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our team's GitHub projects will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted GitWorkshop instance.
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
Next Infrasteps
Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our Alexandria client. We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based Behave feature test for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to Done. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our status page. We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our GitCitadel DevOps npub, to make sure you don't miss out on the IT action.
Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-
 @ fd208ee8:0fd927c1
2025-01-23 15:31:24
@ fd208ee8:0fd927c1
2025-01-23 15:31:24Planning Alexandria
People keep asking what features nostr:npub1s3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqd975wz has planned for #Alexandria, but they're not set in stone because we're an agile project.
What we do have, is lots of tickets on our Kanban boards and a naming scheme, where we use a famous person's last name, to signify the release goals.

Gutenberg v 0.1.0
(after the inventor of the printing press) will contain the features needed to read and write NIP-62 Curated Publications, as well as encompassing the complex infrastructure, architecture, documentation, and personnel we require to make this all run smoothly and look easy.

Euler v 0.2.0
(after a mathematician credited with establishing graph theory) will contain the features for deep-searching, visually exploring, and smartly navigating the data set, wiki page display, annotating and citing the publications, exporting to other formats (like PDF, ePUB, and LaTeX), and commenting/reviewing. To help with the heavy lifting, we will be swapping out the core with our own Nostr SDK called "Aedile".

Defoe v 0.3.0
(after an author who perfected the novel format) will be all about our favorite writers. We will be focusing upon profile data, payment systems, book clubs and communities, and stylesheets.
That is everything we have planned, for the v1.0 edition, and we consider that version to be a true product.
As for after that, a teaser...

-
 @ e034d654:ca919814
2025-01-22 23:14:27
@ e034d654:ca919814
2025-01-22 23:14:27I stumbled into nostr end of March 2023. At that point already fully thrown into the hows, whys and whats of Bitcoin, never really interested in social apps, just recently playing around with Lightning, the only experience of which at the time was Muun (😬) and stacker.news custodial wallet.
Fairly inexperienced with technicals other than rough understandings of concepts. A crappy laptop node with a dangling SSD via USB, constantly having to resync to current blockheights whenever I was ready to make an on chain transaction to cold storage. My great success after over two years of delay, and a couple failed attempts.
Something about the breadth of information for nitty gritty specifics, the clash with all the things that I found interesting about Bitcoin, with others equally as focused, kept me interested in Nostr. Plus the lighthearted shit posting to break up plumbing the depths of knowledge appealed to me.
Cut to now. Through the jurisdictional removals and even deaths of LN wallet projects, using mobile LSPs, finding use cases with the numerous cashu implementations, moderate comfortability with NWC strings of various permissions, budgets for seemingly endless apps of Nostr clients, swapping relays, isolated wallets with Alby go for my wife and cousin (I told them both not to put much on there as I'm sure failure is imminent) Alby Hub and Zeus, now fully backended by my own persistently online lightning node. All of it adding to the fluidity of my movement around the protocol.
Nimble.
Gradual progress. Reading through notes and guides posted on Nostr learning little bits, circling back eventually, if even at a time it wasn't clicking for me. Either way. Glad i've stuck to it even if I still barely know what it is I'm doing.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 79998141:0f8f1901
2025-01-02 05:04:56
@ 79998141:0f8f1901
2025-01-02 05:04:56Happy new year, Anon.
Thanks for tuning in to whatever this long form post will be. I hope to make these more regular, like journal entries as we travel through "real life" and the Nostrverse together. If I'm making time for this reflective writing, then things are going as planned.
2024 was a wildly transformative year for me for many reasons... there's no way I can possibly fit all of them here. They're not all related to Bitcoin and Nostr- I've got a beautiful life outside of all that which has its own independent arc. My wife and I celebrated 7 years of marriage together, stronger than ever (don't believe that "itch" bullshit). We let go of some negative relationships and embraced some positive ones. We cut some bad habits, and we made some good habits. We worked, we traveled, we saw family, and we partied.
But damn, these two technologies have become a huge part of my life. God willing, this trend will continue until they've both eclipsed my professional capacity through our startup, Conduit BTC.
This was the year I was truly orange pilled. Until late 2023, I had traded (quite profitably) Bitcoin, "crypto", stocks, options, prediction markets and whatever else I could get my hands on that felt undervalued. I did this all in my spare time, grinding out a little financial freedom while I hustled at my fiat ventures to support my little family. I wasn't a true believer- just an opportunist with a knack for spotting where and when a crowd might flock to next. That was right up until I ran face first into Lyn Alden's book "Broken Money".
Something about Lyn's engineer/macro-finance inspired prose clicked with me, lock and key. Total one way function. By the end of the book my laser eyes had burned a hole in my bedroom ceiling. I was all in- and acted accordingly both with my capital and my attention. It wasn't long before I discovered Nostr and dove in here too, falling deep into my current orange and purple polyamorous love affair.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Despite the passion, through studying Bitcoin's criticisms (from the likes of Mike Green and Nassim Taleb) I found a hole in the utopian plot: none of this works without Bitcoin actually being used as money. Worldwide transactions must skyrocket demand for blockspace to keep the network secure/stable for the long term. Besides, if everyday folks aren't using Bitcoin as money then we haven't done shit to make the world a better place. In that world, we've only replaced old masters with new ones. Fuck that.
Whatever I did in this space needed to increase the usage of Bitcoin as money. Simple. This was bigger than passion, this was purpose. I knew that come hell or high water I would dedicate myself to this mission.
Lucky for me I found a partner and best friend in @aceaspades to go on this adventure with. I'm infinitely grateful for him. He's an incredible man who also happens to be an insanely creative and talented software developer. We'd tried for years to find the right project to focus on together, experimenting with all kinds of new techy ideas as they came across our field. Nothing had ever captured our attention like this. This was different. By March of 2024 we had formed a company and gotten to work iterating on how we could leverage these beautiful protocols and open-source tech to create something that served our mission. This is @ConduitBTC.
I've done well in my fiat career executing plans downstream of someone else's creative vision. I've learned the ins and outs of an established ecosystem and found ways to profit from it. I take plans developed by others, compete to win contracts to build them, and execute on them in a cashflow-positive way. I'm bringing this no bullshit blue collar skillset with me to the Nostrverse whether they like it or not.
The adventure we're embarking on now is totally different though. We're charting a new course - totally creative, highly intuitive and extremely speculative towards a future that doesn't exist yet. There are few established norms. The potential is vast but unknown. We're diving into a strange quest to sell a map to an imaginary place and to simultaneously architect its creation (alongside all the amazing builders here doing the same thing). This is insanely exciting to me.
We're barely getting started but a lot has been invested under the surface which will show itself in 2025. We'll be sharing updates in a proper post on @ConduitBTC soon.
As for my personal 2025 resolutions, here they are: - zero alcohol for the entire year (did this in 2019 and had a great year, it's time for a rerun) - more focused presence in the moment: especially with my wife - more self care and prioritized mental/physical health - this includes daily: naps, prayer, self hypnosis or meditation, sweat, and stretching/massaging (overworked in 2024 with a fiat 9-5, a board/advisor role in a fiat business I have equity in, and my newfound passion here. Two serious burn out episodes experienced this year - zero is the only acceptable number of burnouts for long term health and success.) - related to the above: get Conduit some mission-aligned funding partners and leave my fiat 9-5. Grow the Conduit team (have put in a serious amount of my personal capital already to get this going, which will show fruit in the new year... but I am not an island) - more authentic and thoughtful posts on Nostr, with a solid amount of shitposting and organic home grown memes to balance it out... more zaps, more geniune connections and interactions with the curious forward thinking people on here - more IRL Nostr/Bitcoin events - more laughter, more jokes
Enough for now. Cheers to you and yours Anon, may 2025 bring you the magic you've been dreaming of.
-
 @ dd664d5e:5633d319
2024-12-29 20:29:03
@ dd664d5e:5633d319
2024-12-29 20:29:03The paparazzi are we

One of the things that bothers me about social media, in general, is that it gives celebrities an air of approachability, that they don't actually offer.
Theoretically, a celebrity could respond to any one of the dozens or even hundreds of people asking them questions or lodging complaints or singing their praises, but they usually only respond very selectively and leave everyone else just sitting there, as a living monument to the ReplyGuy.
And, as a wise man once said, ReplyGuy is a hoe.
Death of a ReplyGuy
This is usually because of time and energy restrictions, but also due to distaste, disdain, or indifference. Regardless of motivation, it is simply the nature of things, when a larger number of people are clamboring for the attention of some particular person.
Ooh, ooh! Can I have the next question?! Would you please address my bug? May I have a microsecond of your time?

Social media (and I include GitHub in this category) ups this game considerably, and potentially turns it all into a dangerous psychological torture, by making us all preoccupied with people who don't interact with us. The most irrational of groupies because we are forever making almost-contact with our stars.
If we can see them talking to one person, we're supposed to feel like they've spoken with all of us. But they haven't. They spoke with someone else, and we were allowed to watch. No different than on television, except that we might be disappointed and eager to return the next day, to renew our futile attempt.
The same intoxicating feeling that playing the lottery elicits. Everyone is a potential winner, but there is only one jackpot. Come back next week. Buy another ticket. This next time, is your time. Promise.
The view from the peanut gallery

It is all an illusion that there is no hierarchy, where there clearly is one. Celebrities of the past had, at least, the decency to remain slightly aloof. But they all want to be one of the Common Folk, now, just as every multi-millionaire aspires to see himself as fundamentally working-class.

All of celebrity social media is a stage, and most of us are merely spectators or commentators, to what is playing on it. This is why, if someone treats me like someone sitting in the peanut gallery, my instinct is to treat them like an actor.
Because, in reality, that is what they are.
-
 @ a42048d7:26886c32
2024-12-27 16:33:24
@ a42048d7:26886c32
2024-12-27 16:33:24DIY Multisig is complex and 100x more likely to fail than you think if you do it yourself: A few years ago as an experiment I put what was then $2,000 worth Bitcoin into a 2 of 3 DIY multisig with two close family members holding two keys on Tapsigners and myself holding the last key on a Coldcard. My thought was to try and preview how they might deal with self custodied multisig Bitcoin if I died prematurely. After over a year I revisited and asked them to try and do a transaction without me. Just send that single Utxo to a new address in the same wallet, no time limit. It could not possibly have failed harder and shook my belief in multisig. To summarize an extremely painful day, there was a literally 0% chance they would figure this out without help. If this had been for real all our BTC may have been lost forever. Maybe eventually a family friend could’ve helped, but I hadn’t thought of that and hadn’t recommended a trusted BTC knowledge/help source. I had preached self sovereignty and doing it alone and my family tried to respect that. I should’ve given them the contact info of local high integrity bitcoiners I trust implicitly. Regardless of setup type, I highly recommend having a trusted Bitcoiner and online resources your family knows they can turn to to trouble shoot. Bookmark the corresponding BTCSessions video to your BTC self custody setup. Multisig is complicated as hell and hard to understand. Complexity is the enemy when it comes to making sure your BTC isn’t lost and actually gets to your heirs. Many Bitcoiners use a similar setup to this one that failed so badly, and I’m telling you unless you’re married to or gave birth to a seriously hardcore maxi who is extremely tech savvy, the risk your Bitcoin is lost upon your death is unacceptably high. My family is extremely smart but when the pressure of now many thousands of dollars was on the line, the complexity of multisig torpedoed them. Don’t run to an ETF! There are answers: singlesig is awesome. From observing my family I’m confident they would’ve been okay in a singlesig setup. It was the process of signing on separate devices with separate signers, and moving a PSBT around that stymied them. If it had been singlesig they would’ve been okay as one signature on its own was accomplished. Do not besmirch singlesig, it’s incredibly powerful and incredibly resilient. Resilience and simplicity are vastly underrated! In my opinion multisig may increase your theoretical security against attacks that are far less likely to actually happen, e.g. an Oceans Eleven style hack/heist. More likely your heirs will be fighting panic, grief, and stress and forget something you taught them a few years back. If they face an attack it will most likely be social engineering/phishing. They are unlikely to face an elaborate heist that would make a fun movie. While I still maintain it was a mistake for Bitkey to not have a separate screen to verify addresses and other info, overall I believe it’s probably the best normie option for small BTC holdings(yes I do know Bitkey is actually multisig, but the UX is basically a single sig). This incident scared me into realizing the importance of simplicity. Complexity and confusion of heirs/family may be the most under-considered aspects of BTC security. If you’ve made a DIY multisig and your heirs can’t explain why they need all three public keys and what a descriptor is and where it’s backed up, you might as well just go have that boating accident now and get it over with.
Once you get past small amounts of BTC, any reputable hardware wallet in singlesig is amazing security I would encourage folks to consider. In a singlesig setup - For $5 wrench attack concerns, just don’t have your hardware signer or steel backup at your home. You can just have a hot wallet on your phone with a small amount for spending.
If you get a really big stack collaborative multisig is a potentially reasonable middle ground. Just be very thoughtful and brutally honest about your heirs and their BTC and general tech knowledge. Singlesig is still great and you don’t have to move past it, but I get that you also need to sleep at night. If you have truly life changing wealth and are just too uncomfortable with singlesig, maybe consider either 1) Anchorwatch to get the potential benefits of multisig security with the safety net of traditional insurance or 2) Liana wallet where you can use miniscript to effectively have a time locked singlesig spending path to a key held by a third party to help your family recover your funds if they can’t figure it out before that timelock hits, 3) Bitcoin Keeper with their automatic inheritance docs and mini script enabled inheritance key. The automatic inheritance docs are a best in class feature no one else has done yet. Unchained charges $200 for inheritance docs on top of your $250 annual subscription, which imho is beyond ridiculous. 4) Swan vault, I’ve generally soured on most traditional 2 of 3 collaborative multisig because I’ve always found holes either in security (Unchained signed a transaction in only a few hours and has no defined time delay, and still doesn’t support Segwit, seriously guys, wtf?), only support signers that are harder to use and thus tough for noobs, or the overall setups are just too complex. Swan Vault’s focus on keeping it as simple as possible really stands out against competitors that tack on unneeded confusion complexity.
TLDR: For small amounts of BTC use Bitkey. For medium to large amounts use singlesig with a reputable hardware wallet and steel backup. For life changing wealth where you just can no longer stomach sinsglesig maybe also consider Anchorwatch, Bitcoin Keeper, Sean Vault, or Liana. Don’t forget your steel backups! Be safe out there! Do your own research and don’t take my word for it. Just use this as inspiration to consider an alternative point of view. If you’re a family of software engineers, feel free to tell me to go fuck myself.
-
 @ 502ab02a:a2860397
2025-05-23 01:57:14
@ 502ab02a:a2860397
2025-05-23 01:57:14น้ำนมมนุษย์ที่ไม่ง้อมนุษย์ หรือนี่กำลังจะกลายเป็นเรื่องจริงเร็วกว่าที่เราคิดนะครับ
ในยุคที่อุตสาหกรรมอาหารหันหลังให้กับปศุสัตว์ ไม่ว่าจะด้วยเหตุผลด้านสิ่งแวดล้อม จริยธรรม หรือความยั่งยืน “น้ำนมจากห้องแล็บ” กำลังกลายเป็นแนวหน้าของการปฏิวัติอาหาร โดยเฉพาะเมื่อบริษัทหนึ่งจากสิงคโปร์นามว่า TurtleTree ประกาศอย่างชัดเจนว่า พวกเขากำลังจะสร้างโปรตีนสำคัญในน้ำนมมนุษย์ โดยไม่ต้องมีมนุษย์แม่เลยแม้แต่น้อย
TurtleTree ก่อตั้งในปี 2019 โดยมีเป้าหมายอันทะเยอทะยานคือการผลิตโปรตีนในนมแม่ให้ได้ผ่านเทคโนโลยีที่เรียกว่า precision fermentation โดยใช้จุลินทรีย์ที่ถูกดัดแปลงพันธุกรรมให้ผลิตโปรตีนเฉพาะ เช่น lactoferrin และ human milk oligosaccharides (HMOs) ซึ่งเป็นองค์ประกอบล้ำค่าที่พบในน้ำนมมนุษย์แต่แทบไม่มีในนมวัว หรือผลิตภัณฑ์นมทั่วไป
โปรตีนตัวแรกที่ TurtleTree ประสบความสำเร็จในการผลิตคือ LF+ หรือ lactoferrin ที่เลียนแบบโปรตีนในนมแม่ ซึ่งมีหน้าที่ช่วยระบบภูมิคุ้มกันของทารก ต่อต้านแบคทีเรีย และช่วยให้ร่างกายดูดซึมธาตุเหล็กได้ดีขึ้น โปรตีนนี้เป็นหนึ่งในหัวใจของนมแม่ ที่บริษัทต้องการนำมาใช้ในอุตสาหกรรมนมผงเด็กและอาหารเสริมสำหรับผู้ใหญ่ ล่าสุดในปี 2024 LF+ ได้รับการรับรองสถานะ GRAS (Generally Recognized As Safe) จากองค์การอาหารและยาสหรัฐฯ (FDA) อย่างเป็นทางการ เป็นหมุดหมายสำคัญที่บอกว่า นี่ไม่ใช่แค่ไอเดียในแล็บอีกต่อไป แต่กำลังกลายเป็นผลิตภัณฑ์เชิงพาณิชย์จริง
เบื้องหลังของโปรเจกต์นี้คือการลงทุนกว่า 30 ล้านดอลลาร์สหรัฐจากกลุ่มทุนทั่วโลก รวมถึงบริษัท Solar Biotech ที่จับมือกับ TurtleTree ในการขยายกำลังการผลิตเชิงอุตสาหกรรมในสหรัฐอเมริกา โดยตั้งเป้าว่าจะสามารถผลิตโปรตีนเหล่านี้ได้ในระดับราคาที่แข่งขันได้ภายในไม่กี่ปีข้างหน้า
สิ่งที่น่าสนใจคือ TurtleTree ไม่ได้หยุดแค่ lactoferrin พวกเขายังวางแผนพัฒนา HMO ซึ่งเป็นน้ำตาลเชิงซ้อนชนิดพิเศษที่มีอยู่เฉพาะในน้ำนมแม่ เป็นอาหารเลี้ยงแบคทีเรียดีในลำไส้ทารก ช่วยพัฒนาระบบภูมิคุ้มกันและสมอง ปัจจุบัน HMOs เริ่มเป็นที่นิยมในวงการ infant formula แต่การผลิตยังจำกัดและมีต้นทุนสูง การที่ TurtleTree จะนำเทคโนโลยี precision fermentation มาใช้ผลิต HMO จึงถือเป็นความพยายามในการลดช่องว่างระหว่าง "นมแม่จริง" กับ "นมผงสังเคราะห์"
ทั้งหมดนี้เกิดขึ้นภายใต้แนวคิดใหม่ของอุตสาหกรรมอาหารที่เรียกว่า "functional nutrition" หรือโภชนาการที่ออกแบบเพื่อทำงานเฉพาะทาง ไม่ใช่แค่ให้พลังงานหรือโปรตีน แต่เล็งเป้าหมายเฉพาะ เช่น เสริมภูมิคุ้มกัน ซ่อมแซมสมอง หรือฟื้นฟูร่างกาย โดยมีรากฐานจากธรรมชาติ แต่ใช้เทคโนโลยีสมัยใหม่ในการผลิต
แม้จะฟังดูเป็นความก้าวหน้าทางวิทยาศาสตร์ที่น่าตื่นเต้น แต่น้ำเสียงที่ดังก้องในอีกมุมหนึ่งก็คือคำถามเชิงจริยธรรม TurtleTree กำลังสร้างโปรตีนที่มีอยู่เฉพาะในมนุษย์ โดยอาศัยข้อมูลพันธุกรรมของมนุษย์เอง แล้วนำเข้าสู่ระบบอุตสาหกรรมเพื่อการค้า คำถามคือ เมื่อใดที่การจำลองธรรมชาติจะกลายเป็นการผูกขาดธรรมชาติ? ใครควรเป็นเจ้าของข้อมูลพันธุกรรมของมนุษย์? และถ้าวันหนึ่งบริษัทใดบริษัทหนึ่งสามารถควบคุมการผลิต “นมแม่จำลอง” ได้แต่เพียงผู้เดียว นั่นจะส่งผลต่อเสรีภาพของสังคมในมุมไหนบ้าง?
นักชีวจริยธรรมหลายคน เช่น ดร.ซิลเวีย แคมโปเรซี จาก King's College London ตั้งข้อสังเกตไว้ว่า เทคโนโลยีแบบนี้อาจแก้ปัญหาการเข้าถึงนมแม่ในพื้นที่ห่างไกลหรือในกลุ่มแม่ที่ให้นมไม่ได้ แต่ขณะเดียวกันก็อาจกลายเป็นการสร้าง "ระบบอาหารทางเลือก" ที่ควบคุมโดยบริษัทไม่กี่ราย ที่มีอำนาจเกินกว่าผู้บริโภคจะตรวจสอบได้
เมื่อเทคโนโลยีสามารถจำลองสิ่งที่เคยสงวนไว้เฉพาะธรรมชาติ และมนุษย์ได้ใกล้เคียงจนแทบแยกไม่ออก บางทีคำถามที่ควรถามอาจไม่ใช่แค่ว่า “มันปลอดภัยหรือไม่?” แต่อาจต้องถามว่า “เราไว้ใจใครให้สร้างสิ่งนี้แทนธรรมชาติ?” เพราะน้ำนมแม่เคยเป็นสิ่งที่มาจากรักและชีวิต แต่วันนี้มันอาจกลายเป็นเพียงสิ่งที่มาจากห้องแล็บและโมเลกุล... และนั่นคือสิ่งที่เราต้องคิดให้เป็น ก่อนจะกินให้ดี เต่านี้มีบุญคุณอันใหญ่หลวงงงงงงง
เสริมจุดน่าสนใจให้ครับ KBW Ventures ถือเป็นผู้ลงทุนรายใหญ่ที่สุดใน TurtleTree Labs โดยมีบทบาทสำคัญในหลายรอบการระดมทุนของบริษัท KBW Ventures เป็นบริษัทลงทุนจากสหรัฐอาหรับเอมิเรตส์ ก่อตั้งโดย สมเด็จพระราชโอรสเจ้าชายคาเล็ด บิน อัลวาลีด บิน ตาลาล อัล ซาอุด (HRH Prince Khaled bin Alwaleed bin Talal Al Saud) ในรอบการระดมทุน Pre-A มูลค่า 6.2 ล้านดอลลาร์สหรัฐฯ ซึ่งปิดในเดือนธันวาคม 2020 KBW Ventures ได้ร่วมลงทุนพร้อมกับ Green Monday Ventures, Eat Beyond Global และ Verso Capital . นอกจากนี้ เจ้าชาย Khaled ยังได้เข้าร่วมเป็นที่ปรึกษาให้กับ TurtleTree Labs เพื่อสนับสนุนการขยายตลาดและกลยุทธ์การเติบโตของบริษัท
ซึ่งในตัว KBW Ventures นั้น เป็นบริษัทลงทุนที่มุ่งเน้นการสนับสนุนเทคโนโลยีที่ยั่งยืนและนวัตกรรมในหลากหลายอุตสาหกรรม เช่น เทคโนโลยีชีวภาพ (biotech), เทคโนโลยีพลังงานสะอาด, เทคโนโลยีการเงิน (fintech), เทคโนโลยีการขนส่ง, และเทคโนโลยีอาหาร (food tech) โดยเฉพาะ และในส่วนของเจ้าชาย Khaled มีความสนใจอย่างลึกซึ้งในด้านเทคโนโลยีอาหาร โดยเฉพาะในกลุ่มโปรตีนทางเลือก เช่น Beyond Meat ซึ่งเป็นการลงทุนที่สะท้อนถึงความมุ่งมั่นชัดเจนในการส่งเสริมอาหารที่ยั่งยืนและมีจริยธรรมครับ และแน่นอนเลยว่า โดยมีส่วนร่วมในรอบระดมทุนหลายครั้งของ Beyond Meat รวมถึงตอนที่ Beyond Meat เข้าตลาดหุ้น Nasdaq ครั้งแรกในปี 2019
เจ้าชาย Khaled เชื่อมั่นว่าอาหารทางเลือกแบบพืชจะถูกลงและแพร่หลายมากขึ้น จนอาจถูกกว่าราคาเนื้อสัตว์จากสัตว์จริงภายในปี 2025 ตามข้อมูลที่ได้มาแสดงว่า ปีนี้นี่หว่าาาาาาาาาา
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 2b998b04:86727e47
2025-05-23 01:56:23
@ 2b998b04:86727e47
2025-05-23 01:56:23\> “Huge swathes of people…spend their entire working lives performing tasks they secretly believe do not really need to be performed.”\ \> — David Graeber, Bullshit Jobs
\> “We are in a system that must grow — forever — or it collapses. But technology, by its very nature, is deflationary.”\ \> — Jeff Booth, The Price of Tomorrow
We live in a strange paradox: Technological progress is supposed to make life easier, yet many people feel more overworked and less fulfilled than ever. While artificial intelligence and automation promise unprecedented productivity, it’s not yet clear whether that will mean fewer bullshit jobs — or simply new kinds of them.
What Is a Bullshit Job?
In his landmark book Bullshit Jobs, the late anthropologist David Graeber exposed a haunting truth: millions of jobs exist not because they are needed, but because of economic, political, or psychological inertia. These are roles that even the workers themselves suspect are meaningless — created to serve appearances, maintain hierarchies, or justify budgets.
Think:
-
Middle managers approving other middle managers' reports
-
Employees running meetings to prepare for other meetings
-
Corporate roles invented to interface with poorly implemented AI tools
Bullshit work isn’t the absence of technology. It’s often the outcome of resisting what technology could actually do — in order to preserve jobs, status, or growth targets.
Booth’s Warning: The System is Rigged Against Deflation
In The Price of Tomorrow, entrepreneur Jeff Booth argues that the natural state of a tech-driven economy is deflation — things getting better, cheaper, and faster.
But our global financial system is built on perpetual inflation and debt expansion. Booth writes:
\> “We are using inflationary monetary policy to fight deflationary technological forces.”
Even as AI and automation could eliminate unnecessary jobs and increase abundance, our system requires jobs — or the illusion of them — to keep the economy expanding. So bullshit jobs persist, and even evolve.
AI as a Deflationary Force
AI is rapidly accelerating the deflation Booth described:
-
Tasks that used to take hours now take seconds
-
Whole creative and administrative processes are being streamlined
-
Labor can scale digitally — one tool used globally at near-zero marginal cost
Embraced honestly, this could mean fewer hours, lower costs, and more prosperity. But again, we are not optimized for truth — we are optimized for GDP growth.
So we invent new layers of AI-enhanced bullshit:
-
Prompt engineers writing prompts for other prompt engineers
-
"Human-in-the-loop" validators reviewing AI output they don’t understand
-
Consultants building dashboards that nobody reads
Toward a Post-Bullshit Future
Here’s the real opportunity: If we embrace deflation as a blessing — not a threat — and redesign our systems around truth, efficiency, and abundance, we could:
-
Eliminate meaningless labor
-
Reduce the cost of living dramatically
-
Liberate people to create, heal, build, and rest
This means more than economic reform — it’s a philosophical shift. We must stop equating “employment” with value. That’s where Bitcoin and open-source tools point: toward a world where permissionless value creation is possible without the bloat of gatekeeping institutions.
Final Thought: Tech Won’t Save Us, But Truth Might
Technology, left to its own logic, tends toward freedom, efficiency, and abundance. But our current systems suppress that logic in favor of growth at all costs — even if it means assigning millions of people to do work that doesn’t need doing.
So will AI eliminate bullshit jobs?
It can. But only if we stop pretending we need them.
And for those of us who step outside the wage-work loop, something remarkable happens. We begin using these tools to create actual value — not to impress a boss, but to solve real problems and serve real people.
Recently, I built a tool using AI and automation that helps me cross-post content from Nostr to LinkedIn, Facebook, and X. It wasn’t for a paycheck. It was about leverage — freeing time, expanding reach, and creating a public record of ideas.\ You can check it out here:\ 👉 <https://tinyurl.com/ywxuowl5>
Will it help others? I don’t know yet.\ But it helped me — and that’s the point.
Real value creation doesn’t always begin with a business plan. Sometimes it starts with curiosity, conviction, and the courage to build without permission.
Maybe the future of work isn’t about scaling jobs at all.\ Maybe it’s about reclaiming time — and using these tools to build lives of meaning.
If this resonates — or if you’ve found your own way to reclaim time and create value outside the wage loop — zap me and share your story. Let’s build the post-bullshit economy together. ⚡
-
-
 @ 94215f42:7681f622
2025-05-23 01:44:26
@ 94215f42:7681f622
2025-05-23 01:44:26The promise of AI is intoxicating: slash operational costs by 50-80%, achieve software-style margins on service businesses and and watch enterprise value multiply overnight.
But this initial value creation contains a hidden trap that could leave businesses worth less than when they started. Understanding the "Value Trap" is key to navigating a transition to an AI economy.
What is the Value Trap?
Whilst the value trap is forward looking and somewhat theoretical at this point, there are strong financial incentives to drive investments (many $bns of are looking at the transformation opportunity) that mean this should be taken very seriously.
The Value Trap unfolds in distinct phases:
Phase 1: Status Quo A typical service business operates with 100 units of revenue and 90 units of cost, generating 10 units of profit, representing a standard 10% margin. A bog standard business we can all relate to, long term customers locked in, market fit a distant memory, but growth is hard at this point.
Phase 2: Cost Reduction Early AI adopters slash operational expenses from 90 to 20 units while maintaining 100 units of revenue. This is the very real promise when moving to a "Human at the Edge" model that we'll unpack in a future article. Suddenly, they're generating 80 units of profit at an 8x increase that can easily add multiple to the enterprise value! A venture style return on a business previously struggling for growth.
Phase 3: Growth Phase With massive profit margins comes pricing power. These businesses can undercut competitors while maintaining healthy margins, driving rapid revenue growth. Having removed the human constraint on scaling and the additional overheads and complexity this introduces we see seemingly unlimited expansion. The brakes are truly off at this point for early adopters to expand total market share.
Phase 4: Competition Emerges The extraordinary returns attract competitors. It's important to note there is no technical moat here, other businesses implement similar AI strategies, often from your own staff who may have been let go, new entrants launch AI-native operations, and pricing power erodes.
Phase 5: Mean Reversion After 3-7 years (our best guess given current investment interest in transformation led PE), competitive pressure drives revenue down from 100 to 25 units while costs remain at 20. The business ends up with similar margins to where it started but at much lower absolute revenue, potentially destroying enterprise value.
What you've done is just massively reduced costs in this industry by displacing jobs and those individuals can turn around and compete. You incentivise the competition which erodes your pricing power
Why This Pattern is Inevitable
The Value Trap isn't pure speculation, but based on market dynamics playing out given a set of financial incentives. We believe there are several key forces that make this cycle almost guaranteed:
The Arbitrage is Too Attractive When businesses can achieve "venture returns with no product-market fit risk," capital will flood in. Private equity and Venture Capital firms are already raising funds specifically to acquire traditional service businesses and apply AI transformation strategies .
Low Technical Barriers Unlike previous technological advantages, AI implementation doesn't require significant technical moats. Much of the technology is open source, and the real barrier is process redesign thinking rather than proprietary technology.
The "One Player" Principle In any market, it only takes one competitor to implement AI-native processes to force everyone else to adapt. You either "play the game or you get left behind".
Capital Abundance With global money supply expanding and traditional investment opportunities yielding lower returns, the combination of proven product-market fit and dramatic cost reduction potential represents an irresistible opportunity for investors.
Strategic Response for SMEs: The Netflix Model
Small and medium enterprises actually have a significant advantage in navigating the Value Trap, but they need to act strategically and start moving now.
Embrace the Incubation Approach Rather than gutting your existing business, adopt Netflix's strategy: build an AI-native version of your business alongside your current operations. This approach manages risk while positioning for the future.

The answer here is why not both. you don't necessarily have to gut your current business, but you should be thinking about what does my business look like in five years and how do I transition into that.
Leverage Your Natural Advantages Small businesses can adapt faster than large enterprises. While a 20,000-person company faces "political shockwaves" when reducing workforce, a 10-person business can double revenue without anyone noticing. You can focus on growth rather than painful cost-cutting.
Remove Growth Constraints Early AI removes the traditional constraint where "adding the next person" represents a significant capital investment. Small businesses can scale efficiently once they've redesigned their processes around AI-native workflows, avoid further capital outlay and scaling without increasing complexity in operations.
Focus on Local Networks For various reasons associated with the commoditisation of intelligence, we believe the future favours "hyper-localised" businesses serving customers who "know, like, and trust" them. As intelligence becomes commoditised, human relationships become more valuable, not less.
Strategic Response for Capital Allocators
For private equity and venture capital firms, the Value Trap presents both enormous opportunity and significant risk.
Target the Right Businesses Look for businesses with strong persistent moats that will slow mean reversion:
-
Strong brand and customer relationships
-
High customer acquisition costs in the industry
-
Regulatory barriers to entry
-
Capital-intensive startup requirements
-
Long-term contracts and switching costs
Master the Timing The key is capturing value during the expansion phase and exiting before mean reversion accelerates, or finding an appropriate time arbitrage solution to retain value (see below). The optimal point if you're a capital allocator is almost when you've extracted the most cost out of the business.
Consider Hybrid Strategies Rather than just gutting existing businesses, consider acquiring for distribution and customer base while building AI-native operations alongside traditional ones. This provides multiple exit strategies and reduces execution risk.
Bitcoin: The Time Arbitrage Solution
Whenever I've talked to anybody about AI, my first point of advice is just buy bitcoin.
This isn't just evangelism, so much as a recognition of where you would want to hold value as the Value Trap plays out. In essence the value trap generates an arbitrage opportunity, hige profits are pulled forwards short-term balooning the balance sheet, but the second order consequences of this change risk destroying the value you just created!
We believe alongside rapid competition leading to price for services collapsing, the mass job displacement leads to political pressure for intervention.
This could take several forms, but UBI, mortgage bailouts, unemployment extensions, seizure of existing property.
"All roads lead to money printing," as Pete notes in Good Stuff 02 .
During Weimar Republic hyperinflation, "the cost of a newspaper in year five was the same nominal figure as all of the money that existed in year four." While extreme, this illustrates how quickly monetary systems can shift as inflation and money supply inflation begins to run.
To resolve these issues, Bitcoin allows you to conduct arbitrage across time in an asset that is inflation resistant (fixed supply), hard to seize, has no counter party risk (if someone holds your gold, stocks, cash they can take it without asking) and transportable. Capturing value today and preserving it through monetary system changes protecting against the second and third-order effects of massive economic disruption, that AI represents.
Opportunity, Not Fear: The Renaissance Ahead
The Value Trap isn't a reason to avoid AI, it's a roadmap for navigating inevitable change strategically.
The Entrepreneurial Renaissance This could be a Renaissance for entrepreneurs, if you're entrepreneurial minded, this is an amazing time to be alive because there's opportunity that exists in all fields and the barriers to entry have never been lower.
Liberation from Busy Work The displacement of administrative and routine cognitive work frees humans for higher-value creation.
Democratisation of Intelligence When you can "purchase intelligence in buckets of $0.02 API calls," the barriers to starting and scaling businesses collapse. Individual entrepreneurs can build businesses that previously required large teams, with much lower complexity and risk.
Cost Reduction Benefits Everyone The ultimate outcome of the Value Trap cycle benefits consumers through dramatically lower prices for goods and services.
"Who doesn't want cheaper stuff? Why don't we just reduce the cost of everything massively?"
Conclusion: Embrace the High Agency Era
The Value Trap represents a fundamental shift from employment-based to entrepreneurship-based wealth creation. Rather than fearing job displacement, we should prepare for "the age of the entrepreneur" a high agency era.
The businesses and individuals who thrive will be those who:
-
Understand the cycle and position accordingly
-
Focus on unique value creation rather than routine processing or middleman models
-
Build local networks and relationships
-
Preserve wealth through the monetary transition
-
Embrace building and creating unique value
If you are high agency, you can make anything happen.
The Value Trap isn't just about AI transforming business, it won't do this on its own, its a description of how humans will use this technology to generate and capture value.
The future belongs to builders, creators, and entrepreneurs who can navigate transition periods and emerge stronger. The Value Trap is the map, use it wisely.
This article draws heavily on discussion between myself and business partner Andy in Episode 02 of The Good Stuff, if you prefer listening try that :)
-
-
 @ 90152b7f:04e57401
2025-05-23 01:27:49
@ 90152b7f:04e57401
2025-05-23 01:27:49[Analytical & Intelligence Comments]\ \ “On Monday February 27th, 2012, WikiLeaks began publishing The Global Intelligence Files, over five million e-mails from the Texas headquartered "global intelligence" company Stratfor. The e-mails date between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal's Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agencies, including the US Department of Homeland Security, the US Marines and the US Defence Intelligence Agency. The emails show Stratfor's web of informers, pay-off structure, payment laundering techniques and psychological methods.”\ \ Released on 2013-02-13 00:00 GMT Email-ID 13332210 Date 2011-05-04 16:26:59\ From <jetdrive@earthlink.net> To <responses@stratfor.com> CROYDON KEMP sent a\ message using the contact form at <https://www.stratfor.com/contact\>\\ Mossad ran 9/11 Arab "hijacker" terrorist operation\ \ By Wayne Madsen\ \ British intelligence reported in February 2002 that the Israeli Mossad ran the Arab hijacker cells that were later blamed by the U.S. government's 9/11 Commission for carrying out the aerial attacks on the World Trade Center and Pentagon. WMR has received details of the British intelligence report which was suppressed by the government of then-Prime Minister Tony Blair.\ \ A Mossad unit consisting of six Egyptian- and Yemeni-born Jews infiltrated "Al Qaeda" cells in Hamburg (the Atta-Mamoun Darkanzali cell), south Florida, and Sharjah in the United Arab Emirates in the months before 9/11. The Mossad not only infiltrated cells but began to run them and give them specific orders that would eventually culminate in their being on board four regularly-scheduled flights originating in Boston, Washington Dulles, and Newark, New Jersey on 9/11.\ \ The Mossad infiltration team comprised six Israelis, comprising two cells of three agents, who all received special training at a Mossad base in the Negev Desert in their future control and handling of the "Al Qaeda" cells. One Mossad cell traveled to Amsterdam where they submitted to the operational control of the Mossad's Europe Station, which operates from the El Al complex at Schiphol International Airport. The three-man Mossad unit then traveled to Hamburg where it made contact with Mohammed Atta, who believed they were sent by Osama Bin Laden. In fact, they were sent by Ephraim Halevy, the chief of Mossad.\ \ The second three-man Mossad team flew to New York and then to southern Florida where they began to direct the "Al Qaeda" cells operating from Hollywood, Miami, Vero Beach, Delray Beach, and West Palm Beach. Israeli "art students," already under investigation by the Drug Enforcement Administration for casing the offices and homes of federal law enforcement officers, had been living among and conducting surveillance of the activities, including flight school training, of the future Arab "hijacker" cells, particularly in Hollywood and Vero Beach.\ \ In August 2001, the first Mossad team flew with Atta and other Hamburg "Al Qaeda" members to Boston. Logan International Airport's security was contracted to Huntleigh USA, a firm owned by an Israeli airport security firm closely connected to Mossad — International Consultants on Targeted Security – ICTS. ICTS's owners were politically connected to the Likud Party, particularly the Netanyahu faction and then-Jerusalem mayor and future Prime Minister Ehud Olmert. It was Olmert who personally interceded with New York Mayor Rudolph Giuliani to have released from prison five Urban Moving Systems employees, identified by the CIA and FBI agents as Mossad agents. The Israelis were the only suspects arrested anywhere in the United States on 9/11 who were thought to have been involved in the 9/11 attacks.\ \ The two Mossad teams sent regular coded reports on the progress of the 9/11 operation to Tel Aviv via the Israeli embassy in Washington, DC. WMR has learned from a Pentagon source that leading Americans tied to the media effort to pin 9/11 on Arab hijackers, Osama Bin Laden, and the Taliban were present in the Israeli embassy on September 10, 2001, to coordinate their media blitz for the subsequent days and weeks following the attacks. It is more than likely that FBI counter-intelligence agents who conduct surveillance of the Israeli embassy have proof on the presence of the Americans present at the embassy on September 10. Some of the Americans are well-known to U.S. cable news television audiences.\ \ In mid-August, the Mossad team running the Hamburg cell in Boston reported to Tel Aviv that the final plans for 9/11 were set. The Florida-based Mossad cell reported that the documented "presence" of the Arab cell members at Florida flight schools had been established.\ \ The two Mossad cells studiously avoided any mention of the World Trade Center or targets in Washington, DC in their coded messages to Tel Aviv. Halevy covered his tracks by reporting to the CIA of a "general threat" by an attack by Arab terrorists on a nuclear plant somewhere on the East Coast of the United States. CIA director George Tenet dismissed the Halevy warning as "too non-specific." The FBI, under soon-to-be-departed director Louis Freeh, received the "non-specific" warning about an attack on a nuclear power plant and sent out the information in its routine bulletins to field agents but no high alert was ordered.\ \ The lack of a paper trail pointing to "Al Qaeda" as the masterminds on 9/11, which could then be linked to Al Qaeda's Mossad handlers, threw off the FBI. On April 19, 2002, FBI director Robert Mueller, in a speech to San Francisco's Commonwealth Club, stated: "In our investigation, we have not uncovered a single piece of paper — either here in the United States, or in the treasure trove of information that has turned up in Afghanistan and elsewhere — that mentioned any aspect of the September 11 plot."\ \ The two Mossad "Al Qaeda" infiltration and control teams had also helped set up safe houses for the quick exfiltration of Mossad agents from the United States. Last March, WMR reported: "WMR has learned from two El Al sources who worked for the Israeli airline at New York’s John F. Kennedy airport that on 9/11, hours after the Federal Aviation Administration (FAA) grounded all civilian domestic and international incoming and outgoing flights to and from the United States, a full El Al Boeing 747 took off from JFK bound for Tel Aviv’s Ben Gurion International Airport. The two El Al employee sources are not Israeli nationals but legal immigrants from Ecuador who were working in the United States for the airline. The flight departed JFK at 4:11 pm and its departure was, according to the El Al sources, authorized by the direct intervention of the U.S. Department of Defense. U.S. military officials were on the scene at JFK and were personally involved with the airport and air traffic control authorities to clear the flight for take-off. According to the 9/11 Commission report, Transportation Secretary Norman Mineta ordered all civilian flights to be grounded at 9:45 am on September 11." WMR has learned from British intelligence sources that the six-man Mossad team was listed on the El Al flight manifest as El Al employees.\ \ WMR previously reported that the Mossad cell operating in the Jersey City-Weehawken area of New Jersey through Urban Moving Systems was suspected by some in the FBI and CIA of being involved in moving explosives into the World Trade Center as well as staging "false flag" demonstrations at least two locations in north Jersey: Liberty State Park and an apartment complex in Jersey City as the first plane hit the World Trade Center's North Tower. One team of Urban Moving Systems Mossad agents was arrested later on September 11 and jailed for five months at the Metropolitan Detention Center in Brooklyn. Some of their names turned up in a joint CIA-FBI database as known Mossad agents, along with the owner of Urban Moving Systems, Dominik Suter, whose name also appeared on a "Law Enforcement Sensitive" FBI 9/11 suspects list, along with the names of key "hijackers," including Mohammed Atta and Hani Hanjour, as well as the so-called "20th hijacker," Zacarias Moussaoui.\ \ Suter was allowed to escape the United States after the FBI made initial contact with him at the Urban Moving Systems warehouse in Weehawken, New Jersey, following the 9/11 attacks. Suter was later permitted to return to the United States where he was involved in the aircraft parts supply business in southern Florida, according to an informe3d source who contacted WMR. Suter later filed for bankruptcy in Florida for Urban Moving Systems and other businesses he operated: Suburban Moving & Storage Inc.; Max Movers, Inc.; Invsupport; Woodflooring Warehouse Corp.; One Stop Cleaning LLC; and City Carpet Upholstery, Inc. At the time of the bankruptcy filing in Florida, Suter listed his address as 1867 Fox Court, Wellington, FL 33414, with a phone number of 561 204-2359.\ \ From the list of creditors it can be determined that Suter had been operating in the United States since 1993, the year of the first attack on the World Trade Center. In 1993, Suter began racking up American Express credit card charges totaling $21,913.97. Suter also maintained credit card accounts with HSBC Bank and Orchard Bank c/o HSBC Card Services of Salinas, California, among other banks. Suter also did business with the Jewish Community Center of Greater Palm Beach in Florida and Ryder Trucks in Miami. Miami and southern Florida were major operating areas for cells of Israeli Mossad agents masquerading as "art students," who were living and working near some of the identified future Arab "hijackers" in the months preceding 9/11.\ \ ABC's 20/20 correspondent John Miller ensured that the Israeli connection to "Al Qaeda's" Arab hijackers was buried in an "investigation" of the movers' activities on 9/11. Anchor Barbara Walters helped Miller in putting a lid on the story about the movers and Suter aired on June 21, 2002. Miller then went on to become the FBI public affairs spokesman to ensure that Mueller and other FBI officials kept to the "Al Qaeda" script as determined by the Bush administration and the future 9/11 Commission. But former CIA chief of counter-terrorism Vince Cannistraro let slip to ABC an important clue to the operations of the Mossad movers in New Jersey when he stated that the Mossad agents "set up or exploited for the purpose of launching an intelligence operation against radical Islamists in the area, particularly in the New Jersey-New York area." The "intelligence operation" turned out to have been the actual 9/11 attacks. And it was no coincidence that it was ABC's John Miller who conducted a May 1998 rare interview of Osama Bin Laden at his camp in Afghanistan. Bin Laden played his part well for future scenes in the fictional "made-for-TV" drama known as 9/11.\ \ WMR has also learned from Italian intelligence sources that Mossad's running of "Al Qaeda" operatives did not end with running the "hijacking" teams in the United States and Hamburg. Other Arab "Al Qaeda" operatives, run by Mossad, were infiltrated into Syria but arrested by Syrian intelligence. Syria was unsuccessful in turning them to participate in intelligence operations in Lebanon. Detailed information on Bin Laden's support team was offered to the Bush administration, up to days prior to 9/11, by Gutbi al-Mahdi, the head of the Sudanese Mukhabarat intelligence service. The intelligence was rejected by the Biush White House. It was later reported that Sudanese members of "Al Qaeda's" support network were double agents for Mossad who had also established close contacts with Yemeni President Ali Abdullah Saleh and operated in Egypt, Saudi Arabia, and Eritrea, as well as Sudan. The Mossad connection to Al Qaeda in Sudan was likely known by the Sudanese Mukhabarat, a reason for the rejection of its intelligence on "Al Qaeda" by the thoroughly-Mossad penetrated Bush White House. Yemen had also identified "Al Qaeda" members who were also Mossad agents. A former chief of Mossad revealed to this editor in 2002 that Yemeni-born Mossad "deep insertion" commandos spotted Bin Laden in the Hadhramaut region of eastern Yemen after his escape from Tora Bora in Afghanistan, following the U.S. invasion.\ \ French intelligence determined that other Egyptian- and Yemeni-born Jewish Mossad agents were infiltrated into Sharjah in the United Arab Emirates as radical members of the Muslim Brotherhood. However, the "Muslim Brotherhood" agents actually were involved in providing covert Israeli funding for "Al Qaeda" activities. On February 21, 2006, WMR reported on the U.S. Treasury Secretary's firing by President Bush over information discovered on the shady "Al Qaeda" accounts in the United Arab Emirates: "Banking insiders in Dubai report that in March 2002, U.S. Secretary of Treasury Paul O’Neill visited Dubai and asked for documents on a $109,500 money transfer from Dubai to a joint account held by hijackers Mohammed Atta and Marwan al Shehhi at Sun Trust Bank in Florida. O'Neill also asked UAE authorities to close down accounts used by Al Qaeda . . . . The UAE complained about O’Neill’s demands to the Bush administration. O’Neill’s pressure on the UAE and Saudis contributed to Bush firing him as Treasury Secretary in December 2002 " O'Neill may have also stumbled on the "Muslim Brotherhood" Mossad operatives operating in the emirates who were directing funds to "Al Qaeda."\ \ After the collapse of the Soviet Union and the rise to power of the Taliban in Afghanistan, Sharjah's ruler, Sultan bin Mohammed al-Qasimi, who survived a palace coup attempt in 1987, opened his potentate to Russian businessmen like Viktor Bout, as well as to financiers of radical Muslim groups, including the Taliban and "Al Qaeda."\ \ Moreover, this Israeli support for "Al Qaeda" was fully known to Saudi intelligence, which approved of it in order to avoid compromising Riyadh. The joint Israeli-Saudi support for "Al Qaeda" was well-known to the Sharjah and Ras al Khaimah-based aviation network of the now-imprisoned Russian, Viktor Bout, jailed in New York on terrorism charges. The presence of Bout in New York, a hotbed of Israeli intelligence control of U.S. federal prosecutors, judges, as well as the news media, is no accident: Bout knows enough about the Mossad activities in Sharjah in support of the Taliban and Al Qaeda in Afghanistan, where Bout also had aviation and logistics contracts, to expose Mossad as the actual mastermind behind 9/11. Bout's aviation empire also extended to Miami and Dallas, two areas that were nexuses for the Mossad control operations for the "Al Qaeda" flight training operations of the Arab cell members in the months prior to 9/11.\ \ Bout's path also crossed with "Al Qaeda's" support network at the same bank in Sharjah, HSBC. Mossad's phony Muslim Brotherhood members from Egypt and Yemen controlled financing for "Al Qaeda" through the HSBC accounts in Sharjah. Mossad's Dominik Suter also dealt with HSBC in the United States. The FBI's chief counter-terrorism agent investigating Al Qaeda, John O'Neill, became aware of the "unique" funding mechanisms for Al Qaeda. It was no mistake that O'Neill was given the job as director of security for the World Trade Center on the eve of the attack. O'Neill perished in the collapse of the complex.Mossad uses a number of Jews born in Arab countries to masquerade as Arabs. They often carry forged or stolen passports from Arab countries or nations in Europe that have large Arab immigrant populations, particularly Germany, France, Britain, Denmark, Sweden, and the Netherlands.\ \ For Mossad, the successful 9/11 terrorist "false flag" operation was a success beyond expectations. The Bush administration, backed by the Blair government, attacked and occupied Iraq, deposing Saddam Hussein, and turned up pressure on Israel's other adversaries, including Iran, Syria, Pakistan, Hamas, and Lebanese Hezbollah. The Israelis also saw the U.S., Britain, and the UN begin to crack down on the Lebanese Shi'a diamond business in Democratic Republic of Congo and West Africa, and with it, the logistics support provided by Bout's aviation companies, which resulted in a free hand for Tel Aviv to move in on Lebanese diamond deals in central and west Africa.\ \ Then-Israeli Finance Minister Binyamin Netanyahu commented on the 9/11 attacks on U.S. television shortly after they occurred. Netanyahu said: "It is very good!" It now appears that Netanyahu, in his zeal, blew Mossad's cover as the masterminds of 9/11.\ \ Wayne Madsen is a Washington, DC-based investigative journalist, author and syndicated columnist. He has written for several renowned papers and blogs.\ \ Madsen is a regular contributor on Russia Today. He has been a frequent political and national security commentator on Fox News and has also appeared on ABC, NBC, CBS, PBS, CNN, BBC, Al Jazeera, and MS-NBC. Madsen has taken on Bill O’Reilly and Sean Hannity on their television shows. He has been invited to testifty as a witness before the US House of Representatives, the UN Criminal Tribunal for Rwanda, and an terrorism investigation panel of the French government.\ \ As a U.S. Naval Officer, he managed one of the first computer security programs for the U.S. Navy. He subsequently worked for the National Security Agency, the Naval Data Automation Command, Department of State, RCA Corporation, and Computer Sciences Corporation.\ \ Madsen is a member of the Society of Professional Journalists (SPJ), Association for Intelligence Officers (AFIO), and the National Press Club. He is a regular contributor to Opinion Maker
-
 @ 3eba5ef4:751f23ae
2025-05-23 01:12:10
@ 3eba5ef4:751f23ae
2025-05-23 01:12:10Crypto Insights
Introducing Generalized Program Composition and Coin Delegation into Bitcoin
Joshua Doman proposed a proof-of-concept called Graftleaf, aiming to achieve generalized program composition and delegation in Taproot in a simple and secure way. Graftleaf is a new Taproot leaf version (0xc2) that uses the annex to perform delegation. It adds two key features:
-
Composition: The ability to sequentially execute zero, one, or multiple witness programs, including a locking script.
-
Delegation: The ability to add additional spending conditions at signing time, which can include arbitrary combinations of programs and scripts.
This design overcomes the limitations of previous proposals by supporting complex script composition and delegation, promising backward compatibility, improved privacy and fungibility with the existing P2TR addresses.
Why OP_CHECKCONTRACTVERIFY (CCV) Will Replace OP_VAULT
A post mainly discusses the current status of Bitcoin script opcode OP_VAULT (BIP-345) and the possibility of it being replaced by OP_CHECKCONTRACTVERIFY (CCV, BIP-443). Key factors include:
-
CCV is a more general version of OP_VAULT, inheriting some features such as amount modes and deferred (cross-input) checks.
-
CCV supports replacing multiple script tapleaf nodes, has a simpler interface, and a lighter script interpreter implementation.
The author also points out CCV’s shortcomings and possible future extensions:
-
Currently, there is a lack of supporting documentation and tools, and the BIP is not yet fully completed.
-
A VAULT-decorator opcode may be needed to implement certain advanced features, such as requiring collateral lockup when unvaulting, or adding some rate-limiting behavior. These features are currently difficult to achieve.
Despite this, CCV remains a better foundation for building vault functionality.
Enabling Recursive Covenants via Self-Replication
Bram Cohen proposed adding a few simple opcodes to Bitcoin Script to enable recursive covenants in a natural and straightforward way. He illustrated with examples that a practical and useful script can be achieved through Quine, without other more complex tricks; developers writing recursive covenants must be aware of the importance of this approach.
UTXO Set Report from Mempool Research: Nearly Half of Bitcoin UTXOs Are Less Than 1,000 Sats
During the OP_RETURN debate in April-May 2025, the impact of inserting arbitrary data into transactions on the UTXO set sparked much discussion. In this report, Mempool studied the UTXO set, highlighting the fragmentation and bloat issues, especially due to small transactions and data embedding, which increase the storage and validation burden for node operators.
Key findings include:
-
Severe Bloat: Currently, about 49% of UTXOs are less than 1,000 satoshis (about $1). Most of these use Taproot address format and may be related to data embedding schemes (like Ordinals) or related transfer mechanisms. Although these UTXOs can usually be spent, before they are, they increase the storage and validation burden for all node operators.
-
Significant Proportion of Inscription-Related UTXOs: About 30% of UTXOs are related to inscription.
-
Large Number of Long-Unspent UTXOs: There are over 100,000 old Counterparty UTXOs using Pay to Multisig (p2ms) scripts, which have existed for over 10 years. Although they make up a small proportion of the total (about 173 million UTXOs), they are a typical example of UTXO bloat.
-
Taproot Becomes the Most Common UTXO Type: Among all UTXO types, Taproot (p2tr) has the highest proportion at 34.2%, followed by traditional p2pkh (28.8%) and p2wpkh (26.5%). However, in terms of total value stored, Taproot’s share is relatively low, indicating it is mainly used for small transactions or data embedding.
The report concludes by mentioning that as the UTXO sets continue to grow, Utreexo and SwiftSync are two scaling methods for maintaining Bitcoin’s accessibility to a wide range of node operators.
Visualization of Bitcoin Mainnet Data
mainnet-observer, built and maintained by developer @0xB10C, visualizes multiple data points from the Bitcoin mainnet, including:
-
Mining a single block currently requires over ~500,000,000,000,000,000,000,000,000 (500 zeta or 5×10²³) hash attempts.
-
Over 42 BTC are now permanently lost in provably unspendable OP_RETURN outputs.
-
Daily updated “Mining Centralization Index” (with proxy pools)
-
Bitcoin mining is currently highly centralized, with 6 pools producing and mining over 95% of block templates.

Path Queries: Addressing Payment Reliability and Routing Limitations
brh28 initiated a discussion on Lightning Network payment routing, focusing on issues like liquidity uncertainty and inefficient path discovery. He proposed a new path query mechanism—allowing nodes to dynamically share information through path queries, fostering a more decentralized routing ecosystem. This can improve the success rate of large payments and reduce reliance on a completely synced channel graph. Although there are still some privacy concerns, this method provides nodes with a controllable information disclosure mechanism and is expected to revolutionize current payment routing approaches.
Bitlayer and Sui Achieve Trust-Minimized BitVM Bridge
Bitlayer and Sui integrated the BitVM Bridge, launching Peg-BTC (YBTC)—bridging native Bitcoin to the Sui ecosystem via BitVM Bridge. BitVM Bridge is a trust-minimized bridge powered by Bitlayer and supported by the advanced BitVM smart contract framework.
Ark Protocol Litepaper
Ark recently released its litepaper: Ark: A UTXO-based Transaction Batching Protocol, outlining its technical foundation. As an innovative Bitcoin scaling protocol, Ark enables off-chain transaction execution while allowing users full control over their funds. This is achieved by introducing “virtual UTXOs” (VTXOs), allowing users to transact off-chain while retaining the ability to unilaterally exit to the Bitcoin main chain. Coordinated by an operator who batches user activities into on-chain commitments, Ark achieves high transaction throughput with minimal on-chain footprint. This provides Bitcoin with a simple and user-friendly scaling solution that offers a practical path for Layer 2 solutions that are inefficient or costly to execute on the main chain.
Top Reads on Blockchain and Beyond
List of Known Real-World Bitcoin Attack Incidents
Here is a list of real-world attacks against Bitcoin/crypto asset holders over the years.

The Internet Capital Market: Free Avenue for Developers, or Another Wave of FOMO?
This post discusses Internet Capital Markets (ICM)—decentralized platforms where funds flow directly to app builders and creators. ICM combines crowdfunding, token issuance, and equity speculation, eliminating the need for VCs, banks, or app stores. In 2025, more independent developers are issuing app tokens directly via X and tools like Believe and Launchcoin, attracting mass investment.
ICM Proponents argue this model breaks traditional funding barriers, making innovation more democratic and accessible; while critics warn that ICM is becoming a hotbed for hype and short-term speculation, with many projects lacking real products or long-term value. The author believes whether ICM can become the next milestone for Web3 hinges on whether it can break free from the cycle of “speculation becomes product traction” and deliver real user value and sustained innovation.
-
-
 @ a4a6b584:1e05b95b
2024-12-26 17:13:08
@ a4a6b584:1e05b95b
2024-12-26 17:13:08Step 1: Secure Your Device
- Install an Antivirus Program
Download and install a trusted antivirus program to scan files for potential malware. - For Linux: Calm Antivirus
-
For Windows: CalmWin Antivirus
-
Install a VPN
A VPN is essential for maintaining privacy and security. It will encrypt your internet traffic and hide your IP address. -
Recommended: Mullvad VPN, which accepts Bitcoin for anonymous payment.
-
Install a Torrent Program
You’ll need a torrent client to download files. -
Recommended: Deluge
-
Install the Tor Browser
To access The Pirate Bay or its proxies, you’ll need the privacy-focused Tor Browser.
Step 2: Prepare Your Setup
- Ensure your VPN is running and connected.
- Open the Tor Browser.
- Launch Deluge to have your torrent client ready.
Step 3: Using Tor Go to The Pirate Bay via Onion Service or Find a Trusted Pirate Bay Proxy
Accessing The Pirate Bay directly can be challenging due to restrictions in some regions. Proxy sites often fill the gap. - The Pirate Bay Onion service: http://piratebayo3klnzokct3wt5yyxb2vpebbuyjl7m623iaxmqhsd52coid.onion - Or find a trusted proxy: Use a site like Pirateproxy or a reliable Tor directory for updated lists.
Step 4: Search for Linux Distros
- On The Pirate Bay, navigate to the "OtherOS" category under the Applications section.
- Enter your desired Linux distro in the search bar (e.g., "Ubuntu," "Arch Linux").
Step 5: Select a Torrent
- Filter the Results:
- Look for torrents with the highest seeders (SE) and the fewest leechers (LE).
-
Trusted users are marked with a green skull icon—these are usually safe uploads.
-
Copy the Magnet Link:
- Right-click on the magnet icon next to the trusted torrent and select "Copy Link."
Step 6: Start the Download
- In Deluge, paste the copied magnet link into the “Add Torrent” box.
- Click OK to start the download.
- Monitor the progress until the download completes.
Step 7: Scan the Downloaded File
Once the file is downloaded: 1. Scan for viruses: Right-click the file and use Calm or CalmWin to verify its integrity.
2. If the file passes the scan, it’s ready for use.
Step 8: Manage Your File
- Seed or Remove:
- To help the torrent community, keep seeding the file by leaving it in your torrent client.
-
To stop seeding, right-click the file in Deluge and remove it.
-
Move for Long-Term Storage: Transfer the file to a secure directory for regular use.
Notes on Safety and Ethics
- Verify Legitimacy: Ensure the torrent you are downloading is for an official Linux distribution. Torrents with unusual names or details should be avoided.
- Support the Developers: Consider visiting the official websites of Linux distros (Ubuntu, Arch Linux) to support their work directly.
By following these steps, you can safely and privately download Linux distributions while contributing to the open-source community.
- Install an Antivirus Program
-
 @ 3eba5ef4:751f23ae
2025-05-23 01:08:23
@ 3eba5ef4:751f23ae
2025-05-23 01:08:23加密洞见
在比特币中引入通用程序组合与币委托机制
Joshua Doman 提出了一个 Graftleaf 的概念验证,旨在用一种简单而安全的方法在 Taproot 中实现通用程序组合和代笔委托。Graftleaf 是一个新的 Taproot 叶子版本(0xc2),使用附件来执行委托。Graftleaf 增加了两个关键功能:
-
组合:按顺序执行零个、一个或多个见证程序的能力,包括一个锁定脚本。
-
委派:在签名时添加其他支出条件的能力,可以包括程序和脚本的任意组合。
它们旨在通过支持复杂的脚本组合和委托来克服以前提案的局限性,承诺提高隐私性、可替代性以及与现有 P2TR 地址的向后兼容性。
为什么说 OP_CHECKCONTRACTVERIFY (CCV) 将会取代 OP_VAULT
帖子主要讨论了比特币脚本操作码 OP_VAULT(BIP-345)的现状,及其被OP_CHECKCONTRACTVERIFY(CCV,BIP-443)取代的可能。重要因素有:
-
CCV 是 OP_VAULT 的更通用版本,继承了部分功能,如金额模式(amount modes)、延迟跨输入检查(deferred cross-input checks)。
-
CCV支持替换多个脚本叶子节点(tapleaf),接口更简洁,脚本解释器实现更轻量。
同时作者也指出 CCV 的不足与未来可能的扩展:
-
当前缺少部分配套文档和工具,BIP 尚未完全完成。
-
可能需要 VAULT-decorator 操作码来实现某些高级功能,如解锁金库时必须抵押锁定、速率限制等。
尽管如此,CCV仍然是构建金库功能的更优基础。
通过自复制方式启用递归契约
Bram Cohen 提出通过向比特币脚本添加一些简单的操作码,以一种自然而直接的方式实现递归契约(recursive covenants)。他通过例子说明,一个实用且有用的脚本通过 Quine 自复制就可以实现,无需其他更复杂的技巧;编写递归契约的开发者必须意识到该方式的重要性。
Mempool Research 发布 UTXO 集的报告:比特币中近一半 UTXO 金额小于 1000 聪
在 2025 年 4 至 5 月期间的 OP_RETURN 大辩论中,将任意数据插入交易对 UTXO 集的影响的问题引发了大量讨论。Mempool 在这份报告中,对 UTXO 集进行了研究,强调了比特币 UTXO 集合碎片化和膨胀的问题,特别是由于小额交易和数据嵌入导致的 UTXO 增长,增加了节点运营者的存储和验证负担。关键结论有:
-
UTXO 集合的碎片化严重:目前约有 49% 的 UTXO 金额低于 1000 聪(约合 1 美元),这些小额 UTXO 大多采用 Taproot 地址格式,可能与数据嵌入方案(如 Ordinals 铭文)或相关的转移机制有关。尽管这些 UTXO 通常可被花费,但在被使用之前,它们会增加所有节点运营者的存储和验证负担。
-
铭文相关的 UTXO 占比显著:约 30% 的 UTXO 与铭文相关。
-
存在大量长期未动用的 UTXO:有超过 10 万个使用 Pay to Multisig (p2ms) 脚本的旧 Counterparty UTXO,且存在超过 10 年。尽管在总数(约 1.73 亿个 UTXO)中所占比例较小,但依然是 UTXO 膨胀的典型问题。
-
Taproot 成为最常见的 UTXO 类型:在所有 UTXO 类型中,Taproot(p2tr)占比最高,为 34.2%,其次是传统的 p2pkh(28.8%)和 p2wpkh(26.5%)。但是从 UTXO 所存储的总价值来看,Taproot 的占比相对较低,表明其主要用于小额交易或数据嵌入。
报告最后也提到,对于继续增长的 UTXO 集,Utreexo 和 SwiftSync 是两种对保持比特币对广泛节点运营者可访问性的扩容方法。
比特币网络各项数据的可视化呈现
mainnet-observer 由开发者 @0xB10C 搭建并维护,将比特币链的多项数据呈现出来,可以看到:
-
目前挖掘一个区块所需要的平均哈希尝试:超过 ~500000000000000000000000000(500 zeta 或 5×10²³)次
-
超过 42 个 BTC 现在永远丢失在可证明无法花费的 OP_RETURN 输出中
-
每日更新的「挖矿中心化指数」(带有代理池)
-
比特币挖矿高度集中,6 个矿池生产并挖掘了超过 95%的区块模板(截止 2025 年 4 月)

闪电网络路径查询:解决支付可靠性和路由限制
brh28 发起了关于闪电网络路由支付的讨论,聚焦「流动性的不确定性」(liquidity uncertainty)和路径发现效率低的问题,提出了一种新的路径查询机制——允许节点以路径查询的形式,实现动态信息共享,推动了一个更加分布式的路由生态。这可以提高了大额支付的成功率,并减少对完整通道图的依赖。尽管在隐私方面仍存在一定担忧,但该方法为节点提供了一种可控的信息披露机制,有望革新现有的支付路由方式。
Bitlayer 和 Sui 实现了信任最小化的 BitVM 桥
Bitlayer 和 Sui 整合了 BitVM Bridge,推出 Peg-BTC(YBTC)——通过 BitVM Bridge 将原生比特币桥接到 Sui 生态中。BitVM Bridge 是一个由 Bitlayer 提供支持并由先进的 BitVM 智能合约框架支持的信任最小化桥。
Ark 协议的正式规范
Ark 近日发布 Litepaper: Ark: A UTXO-based Transaction Batching Protocol,阐述其技术基础。作为一种新颖的比特币扩容协议,Ark 实现了链下交易执行,同时让用户能完全掌控自己的资金。这一点通过引入「虚拟UTXO」(VTXO)得以实现,用户在链下交易,同时保留单方面退出至比特币主链的能力。Ark 同一个 operator 协作,将用户操作打包成链上承诺,在保持极小链上负担的前提下实现高交易吞吐量。这为比特币提供了一种简单易用的扩容方案,也为那些在主链上执行效率低下或成本过高的二层方案提供了落地空间。
精彩无限,不止于链
已知真实发生过的比特币攻击事件列表
这里列出了历年来在真实世界中发生过的、针对比特币/加密资产拥有者的攻击事件。

互联网资本市场:是开发者的自由通道,还是另一波 FOMO?
帖子讨论了互联网资本市场( ICM, Internet Capital Markets ),即去中心化平台——资金直接流向应用程序构建者和创建者。ICM 集众筹、代币发行和股权投机于一体,无需VC、银行或应用商店。2025年,越来越多独立开发者通过 X 和 Believe、Launchcoin 等工具直接发行应用代币,吸引大众投资。ICM 的支持者认为,这种模式打破了传统融资壁垒,让创新更民主、门槛更低;但批评者警告,ICM 正沦为炒作和短期投机的温床,许多项目缺乏实际产品和长期价值。作者认为,ICM 模式能否成为 Web3 的下一个里程碑,关键在于其能否走出「投机成了产品增长动力」(speculation becomes product traction)的怪圈,实现真正的用户价值和持续创新。
-
-
 @ f85b9c2c:d190bcff
2025-05-23 01:04:58
@ f85b9c2c:d190bcff
2025-05-23 01:04:58 I’ve always believed that truth doesn’t bend to the will of the crowd. Growing up, I watched people nod along to ideas they didn’t even agree with, just because everyone else seemed to. It baffled me then, and it still does now. There’s something powerful about standing firm when you know you’re right—even if it means standing alone.
I’ve always believed that truth doesn’t bend to the will of the crowd. Growing up, I watched people nod along to ideas they didn’t even agree with, just because everyone else seemed to. It baffled me then, and it still does now. There’s something powerful about standing firm when you know you’re right—even if it means standing alone.It’s not easy, though. The pressure to conform can feel like a tidal wave, crashing down with judgment, whispers, and rolled eyes. I’ve been there, heart pounding, wondering if I’m the crazy one. But here’s what I’ve learned: the majority isn’t always right. History backs me up—think of Galileo, shunned for saying the Earth wasn’t the center of the universe, or the countless voices drowned out before they were proven true. Numbers don’t guarantee wisdom.
For me, it’s about integrity. If I’ve wrestled with the facts, questioned myself, and still landed on solid ground, I’m not backing down just to keep the peace. It’s not arrogance—it’s conviction. I’d rather be the lone voice in a sea of noise than a silent echo of a lie. Because in the end, truth doesn’t care about headcounts. It cares about courage.
-
 @ f85b9c2c:d190bcff
2025-05-23 01:01:32
@ f85b9c2c:d190bcff
2025-05-23 01:01:32Hey, it’s me again, and let me tell you about the wildest thing that happened to me recently. I swear, my life could be a comedy show sometimes😂. Picture this: me and my buddies were out messing around in the woods near campus, just kicking it like we always do. The sun was out, the vibes were good, and we were probably being louder than we needed to be. Then, out of nowhere, I spotted something slithering near my friend benji leg.

A snake. A legit, no-joke snake!
I yelled, “SNAKE!” at the top of my lungs—probably sounded like a total lunatic —and before I could even blink, those dudes were GONE. I mean, faster than their shadows, Olympic-sprinter-level gone. I’m standing there, heart pounding, looking at this snake like, “Bruh, did I just get ditched?” Turns out, I did. My so-called friends bolted back to the dorms without a second thought, leaving me to face the scaly intruder solo. Luckily, the snake wasn’t in the mood for drama. It just gave me this lazy side-eye and slithered off, like it was too cool to deal with me. I hightailed it back to the dorms too, and when I got there, benji and the crew were already laughing their heads off. “Bro, you screamed like a horror movie victim!” they said. Yeah, real funny, guys.
Honestly, though? I’m just glad that snake didn’t get too cozy with my backside. A near miss like that deserves a medal—or at least a good story. We’ve been cracking up about it ever since, and now every time we’re out, I’m the designated “snake spotter. Lesson learned: friends are great until nature throws a curveball. Phew, that was close! Never be afraid to stand against everyone if you know you’re right.
-
 @ f85b9c2c:d190bcff
2025-05-23 00:54:23
@ f85b9c2c:d190bcff
2025-05-23 00:54:23 P2P trading is also referred to as peer-to-peer trading or, more recently, people-to-people trading. Individuals can trade currencies and other marketable goods with other traders in this decentralized financial trading system.
P2P trading is a method of trading cryptocurrencies between people without the need of middlemen like exchanges, banks, or other financial institutions. Networks that connect buyers and sellers, streamline transactions, and frequently provide conflict resolution services are where P2P transactions take place.
P2P trading is also referred to as peer-to-peer trading or, more recently, people-to-people trading. Individuals can trade currencies and other marketable goods with other traders in this decentralized financial trading system.
P2P trading is a method of trading cryptocurrencies between people without the need of middlemen like exchanges, banks, or other financial institutions. Networks that connect buyers and sellers, streamline transactions, and frequently provide conflict resolution services are where P2P transactions take place.What is P2P Trading P2P trading is one of the quickest, cheapest, and most adaptable trading platforms, according to numerous research. Even more people could benefit from it if they lack access to conventional financial services or find some procedures to be too complicated.
P2P Trading in Nigeria P2P trading has grown somewhat in popularity in recent years as a result of the expansion of online marketplaces that bring together buyers and sellers. These platforms frequently offer wonderful alternatives to traditional financial services and perform similarly to or even better than what is provided by regional banks. Markets today provide unique advantages like quick transactions, reduced fees, and improved flexibility.
The ongoing development of regulations prohibiting the usage of cryptocurrencies is another factor that has increased the need for P2P trade in Nigeria. The majority of crypto traders in Nigeria now trade their cryptocurrencies with one another using the P2P trading system rather than the conventional trader-to-exchange service as a result of the ban on cryptocurrencies since 2021 till recently.P2P trading is thus one of the most popular and widely used forms of trading in Nigeria.
Peer-to-peer cryptocurrency trading is available on a number of well-known trading platforms, including Binance, Bitget, Bybit etc. A system has been built by these platforms (exchange websites and mobile applications) that enables traders to connect and trade their preferred crypto assets. P2P trading platforms have the power to transform Nigeria’s financial system and open up new doors for economic growth and development by bringing buyers and sellers together directly.
How does P2P trading work? One of the most effective ways to exchange cryptocurrency is through P2P trading, so everyone should be aware of how to get around it. It uses the exchange as a middleman to arrange, oversee, and finish trades between two independent dealers. The exchange service is used by buyers who search for sellers who are willing to sell to them at the price they are willing to pay, make a payment, and receive coins in return.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 1817b617:715fb372
2025-05-22 23:39:18
@ 1817b617:715fb372
2025-05-22 23:39:18🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge 🔥 Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
🌐 Explore all the details at cryptoflashingtool.com.
🌟 Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
🎯 Top Features You’ll Love: ✅ Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
🔒 Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
🖥️ User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
📅 Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
🔄 Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
💱 Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
📊 Proven Results: ✅ Over 79 billion flash transactions completed. ✅ 3000+ satisfied users around the globe. ✅ 42 active blockchain nodes ensuring fast, seamless performance.
📌 How It Works: Step 1️⃣: Input Transaction Info
Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20). Set amount and flash duration. Enter the recipient wallet (auto-validated). Step 2️⃣: Make Payment
Pay in your selected crypto. Scan the QR code or use the provided address. Upload your transaction proof (hash and screenshot). Step 3️⃣: Launch the Flash
Blockchain confirmation simulation happens instantly. Your transaction appears real within seconds. Step 4️⃣: Verify & Spend
Access your flashed coins immediately. Verify your transactions using blockchain explorers. 🛡️ Why Our Flashing Tech Leads the Market: 🔗 Race/Finney Attack Mechanics: Mimics authentic blockchain behavior. 🖥️ Private iNode Clusters: Deliver fast syncing and reliable confirmation. ⏰ Live Timer: Ensures fresh, legitimate transactions. 🔍 Real Blockchain TX IDs: All transactions come with verifiable IDs.
❓ FAQs:
Is flashing secure? ✅ Yes, fully encrypted with VPN/proxy compatibility. Multiple devices? ✅ Yes, up to 5 Windows PCs per license. Chargebacks possible? ❌ No, flashing is irreversible. Spendability? ✅ Flash coins stay spendable 60–360 days. Verification after expiry? ❌ No, transactions expire after the set time. Support? ✅ 24/7 Telegram and WhatsApp help available. 🔐 Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
📲 Contact Us: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Flash Like a Pro?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge
Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
Explore all the details at cryptoflashingtool.com.
Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
Top Features You’ll Love:
Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
Proven Results:
Over 79 billion flash transactions completed.
3000+ satisfied users around the globe.
42 active blockchain nodes ensuring fast, seamless performance.
How It Works: Step
: Input Transaction Info
- Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20).
- Set amount and flash duration.
- Enter the recipient wallet (auto-validated).
Step
: Make Payment
- Pay in your selected crypto.
- Scan the QR code or use the provided address.
- Upload your transaction proof (hash and screenshot).
Step
: Launch the Flash
- Blockchain confirmation simulation happens instantly.
- Your transaction appears real within seconds.
Step
: Verify & Spend
- Access your flashed coins immediately.
- Verify your transactions using blockchain explorers.
Why Our Flashing Tech Leads the Market:
Race/Finney Attack Mechanics: Mimics authentic blockchain behavior.
Private iNode Clusters: Deliver fast syncing and reliable confirmation.
Live Timer: Ensures fresh, legitimate transactions.
Real Blockchain TX IDs: All transactions come with verifiable IDs.
FAQs:
- Is flashing secure?
Yes, fully encrypted with VPN/proxy compatibility. - Multiple devices?
Yes, up to 5 Windows PCs per license. - Chargebacks possible?
No, flashing is irreversible. - Spendability?
Flash coins stay spendable 60–360 days. - Verification after expiry?
No, transactions expire after the set time. - Support?
24/7 Telegram and WhatsApp help available.
Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
Contact Us:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Flash Like a Pro?
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
-
 @ 74fb3ef2:58adabc7
2025-05-22 22:26:23
@ 74fb3ef2:58adabc7
2025-05-22 22:26:23Suppose you have a small mom-and-pop shop selling bananas, your bananas are of the highest quality, you plant the banana trees yourself, you water them daily, take great care of everything, and still select only the top 1% of bananas to sell.
Your customers love it, there's no place where they can get better bananas, but due to the fact that you spend so much time, your bananas have to be more expensive, so despite the higher quality, you don't make as much money as you think you should; surely you can get a little more of the market if you adopt some of the strategies that work for your competitors.
So you look across the street, and what do you know? Their bananas are of significantly worse quality than yours, but they're not just selling bananas, they're selling apples too, so you think to yourself, "what if I sold apples? Maybe my apples won't be the best in the market, but nobody can beat my bananas!"
You start planting apple trees, and after a while you're able go sell slightly better than average apples, but by doing so you neglect your bananas ever so slightly.
Most of your existing customers don't notice, you still have the best bananas in town, they don't notice the slight drop in quality. And now that you're selling apples too you're making more money, and more customers come to you.
But you notice that there's a new store now that's selling oranges, and people are buying them. So surely you need oranges too, so you can make some extra money.
You plant a few orange trees, but find yourself spending so much time tending to the oranges and apples that you can't devote the same time and love to your bananas.
You are making a bit of extra cash from the new customers, business is going well, but you don't have time for anything else anymore. You no free time anymore, you are overworked and your health is getting worse.
But you can't stop now that business is going well, you are making so much more, yeah maybe you don't have the same bananas anymore, but you do have slightly above average apples and oranges that have attracted so many customers.
You suddenly fall ill, you've overworked yourself and you are stuck at a hospital for a while.
When you come back to your store, a few of your customers are back, but not all of them, so you think of more ideas, mandarins, kiwi, watermelons, you can grow it all, but you're gonna hire a bunch of people to help you so you don't fall ill again.
One thing leads to another and you are making more money than ever, but strangely you don't hear your customers praising your bananas anymore.
So you take one of your bananas, peel it, and as you taste it, a wave of disappointment hits you.
Your bananas are now just as bad as everyone else's; you gave in to the tyranny of the marginal customer.
You make a lot of money now, but your flagship product is long gone, you are now just another Fruitseller.
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:46
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:46Bahrain-based Al Abraaj Restaurants Group has made history by becoming the first publicly-traded company in the Middle East to add bitcoin to its corporate treasury. This is a major step forward for regional bitcoin adoption.
On May 15, 2025, Al Abraaj Restaurants Group, a well-known restaurant chain listed on the Bahrain Bourse, announced it had bought 5 bitcoin (BTC) as part of a new treasury strategy. This makes the company the first in Bahrain, the GCC and the Middle East to officially hold bitcoin as a reserve asset.
Al Abraaj adds bitcoin to its treasury — Zawya
This is a growing trend globally where companies are treating bitcoin not just as an investment but as a long-term store of value. Major companies like Strategy, Tesla and Metaplanet have already done this — and now Al Abraaj is following suit.
Metaplanet recently added 1,241 BTC to its treasury, boosting the company’s holdings above El Salvador’s.
Related: Metaplanet Overtakes El Salvador in Bitcoin Holdings After $126M Purchase
“Our initiative towards becoming a Bitcoin Treasury Company reflects our forward-thinking approach and dedication to maximizing shareholder value,” said Abdulla Isa, Chairman of the Bitcoin Treasury Committee at Al Abraaj.
Al Abraaj’s move is largely inspired by Michael Saylor, Executive Chairman of Strategy, the world’s largest corporate holder of bitcoin. Saylor’s strategy of allocating billions to bitcoin has set a model that other companies — now including Al Abraaj — are following.
A photo shared by the company even showed a meeting between an Al Abraaj representative and Saylor, with the company calling itself the “MicroStrategy of the Middle East”.
“We believe that Bitcoin will play a pivotal role in the future of finance, and we are excited to be at the forefront of this transformation in the Kingdom of Bahrain,” Isa added.
To support its bitcoin initiative, Al Abraaj has partnered with 10X Capital, a New York-based investment firm that specializes in digital assets.
10X Capital has a strong track record in bitcoin treasury strategies, and recently advised Nakamoto Holdings on a $710 million deal — the largest of its kind.
With 10X’s help, Al Abraaj looks to raise more capital and increase its bitcoin holdings over time to maximize bitcoin-per-share for its investors. The company will also develop Sharia-compliant financial instruments so Islamic investors can get exposure to bitcoin in a halal way.
“Bahrain continues to be a leader in the Middle East in Bitcoin adoption,” said Hans Thomas, CEO of 10X Capital. He noted, with a combined GDP of $2.2 trillion and over $6 trillion in sovereign wealth, the GCC now has its first publicly listed bitcoin treasury company.
This is not just a first for Al Abraaj — it’s a first for the region. Bahrain has been positioning itself as a fintech hub and Al Abraaj’s move will encourage more non-fintech companies in the region to look into bitcoin.
The company said the decision was made after thorough due diligence and is in line with the regulations set by the Central Bank of Bahrain (CBB). Al Abraaj will be fully compliant with all digital asset transaction rules, including transparency, security and governance.
A special Bitcoin Committee has been formed to oversee the treasury strategy. It includes experienced bitcoin investors, financial experts and portfolio managers who will manage risk, monitor market conditions and ensure best practices in custody and disclosure.
The initial purchase was 5 BTC, but Al Abraaj sees this as just the beginning. The company stated that there are plans in motion to allocate a significant portion of their treasury into bitcoin over time.
According to the company’s reports, Al Abraaj is financially sound with $12.5 million in EBITDA in 2024. This strong financial foundation gives the company the confidence to explore new strategies like bitcoin investment.
-
 @ 9ca447d2:fbf5a36d
2025-05-22 22:01:45
@ 9ca447d2:fbf5a36d
2025-05-22 22:01:45Steak ‘n Shake recently made headlines by officially accepting bitcoin payments via the Lightning Network across all its U.S. locations. The integration of Bitcoin payments at over 500 locations is a monumental moment for both the fast food industry and the broader retail sector.
This is not just something that Steak ‘n Shake is testing in a handful of locations, they are doing a full-scale rollout, fully embracing Bitcoin.
With more than 100 million customers a year, Steak ‘n Shake’s integration of Lightning—Bitcoin’s fast, low-fee payment layer—makes it easier than ever to use Bitcoin in day-to-day life. Buying a burger and a shake with sats? That’s now a real option.
The process is straightforward. Customers simply scan a Lightning QR code at the register, completing their payment in seconds, while Steak ‘n Shake receives instant USD conversion, ensuring price stability and ease of use.
So what does this mean for Bitcoin and E-commerce?
For starters, Steak ‘n Shake becomes the first of eventually many to fully embrace a digital world. As Bitcoin continues to grow, consumers will continue to realize the benefits of saving in a currency that is truly scarce and decentralized.
This is a huge step forward for Bitcoin as it shows it is not just for holding, it’s for spending, too. And by using the Lightning Network, Steak n’ Shake is helping prove that Bitcoin can scale for everyday transactions.
This now creates a seamless checkout experience, making bitcoin a viable alternative to credit cards and cash.
More importantly, it signals a significant shift in mainstream attitudes towards Bitcoin. As a well-known brand across America, this move serves as a powerful endorsement, likely to influence other chains and retailers to consider similar integrations.
Related: Spar Supermarket in Switzerland Now Accepts Bitcoin Via Lightning
What can this mean for your business?
Accepting bitcoin as payment can open the door to a new demographic of tech-savvy, financially engaged consumers who prefer digital assets.
As we know, companies that adopt Bitcoin receive a fascinating amount of love from the Bitcoin community and I would assume Steak n’ Shake will be receiving the same amount of attention.
From a business perspective, accepting bitcoin has become more than just a payment method—it’s a marketing tool. It sets your business apart and gets people talking. And in a crowded market, that kind of edge matters.
Steak ‘n Shake’s embrace of Bitcoin is likely to accelerate the adoption of digital assets in both physical retail and e-commerce.
As more businesses witness the operational and marketing benefits, industry experts anticipate a ripple effect that will increase interaction between consumers and digital currencies, further regulatory clarity, and bring continued innovation in payment technology.
Steak ‘n Shake’s nationwide Bitcoin payments rollout is more than a novelty. It’s a pivotal development for digital payments, setting a precedent for other retailers and signaling the growing integration of digital assets into everyday commerce.
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ bf47c19e:c3d2573b
2025-05-22 21:03:52
@ bf47c19e:c3d2573b
2025-05-22 21:03:52Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
-
Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.
-
Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
-
Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.
Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine: kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.
Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
 Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.
Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj tweet to savršeno objašnjava:
Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ 2b24a1fa:17750f64
2025-05-22 19:44:28
@ 2b24a1fa:17750f64
2025-05-22 19:44:28„Triff niemals deine Idole“ heißt ein gängiger Ratschlag. In gewendeten Zeiten stehen zu dem die Werte auf dem Kopf – und manche Künstler mit ihnen. Die Worte, die aus manch ihrer Mündern kommen, wirken, als hätte eine fremde Hand sie auf deren Zunge gelegt.
https://soundcloud.com/radiomuenchen/wolf-biermann-und-sein-falscher-friede-von-alexa-rodrian?
Die Sängerin Alexa Rodrian erlebte bei der Verleihung des Deutschen Filmpreises einen solchen Moment der Desillusion. Es war der Auftritt des Liedermachers Wolf Biermann. Hören Sie hierzu Alexa Rodrians Text „Wolf Biermann und sein falscher Friede“.
Bild: Marco Maas/fotografirma.de
-
 @ 9b308fda:b6c7310d
2025-05-22 18:30:19
@ 9b308fda:b6c7310d
2025-05-22 18:30:19@15/05/2025 ✨ Week 0 – Getting Started with My Internship at Formstr (Onboarding)
I’m excited to share that I’ve been selected as a Summer of Bitcoin intern at Formstr!
After the final exams wrapped up on May 4th, I took a short, well-deserved break while traveling back home from college for the summer. Once settled in, I quickly transitioned into internship mode and began diving into the project assigned to me at Formstr.
It’s been a great start so far, and I’m looking forward to learning, building, and sharing more along the way.
@22/05/2025 — Week 01 – Building Features and Brainstorming at Formstr
This week at Formstr was packed with development and discussions.
The major highlight was completing the row popup view for form responses — now, clicking on any response row shows a clean and complete view of that user's submission. I'm happy to share that the pull request has been merged! It feels great to contribute something that improves the user experience so visibly.
Alongside that, I started brainstorming the LLM-Analysis feature. We had a productive discussion during the weekly developer meeting on Signal, where I shared my initial thoughts and got valuable input from the team. There's a lot of potential in this, and it’s exciting to shape it from the ground up.
I also worked on improving relay management in the form settings to reduce redundancy. The changes are in progress, and it’s almost done — just final touches left before merging.
Another topic we tackled was the “Form Filler with AI” feature. There are still some open questions around implementation and user flow, so we’ve decided to continue discussions with more team members before finalizing the plan.
We’ve also agreed to hold weekly team meetings going forward to keep everyone aligned on ideas, progress, and blockers. I’m glad to be part of such a collaborative and thoughtful team!
-
 @ 7e6f9018:a6bbbce5
2025-05-22 18:17:57
@ 7e6f9018:a6bbbce5
2025-05-22 18:17:57Governments and the press often publish data on the population’s knowledge of Catalan. However, this data only represents one stage in the linguistic process and does not accurately reflect the state of the language, since a language only has a future if it is used. Knowledge is a necessary step toward using a language, but it is not the final stage — that stage is actual use.
So what is the state of Catalan usage? If we look at data on regular use, we see that the Catalan language has remained stagnant over the past hundred years, with nearly the same number of regular speakers. In 1930, there were around 2.5 million speakers, and in 2018, there were 2.7 million.
 Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, in millions of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.These figures wouldn’t necessarily be negative if the language’s integrity were strong, that is, if its existence weren’t threatened by other languages. But the population of Catalonia has grown from 2.7 million in 1930 to 7.5 million in 2018. This means that today, regular Catalan speakers make up only 36% of Catalonia’s population, whereas in 1930, they represented 90%.
 Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.
Regular use of Catalan in Catalonia, as a percentage of speakers. The dotted segments are an estimate of the trend, based on the statements of Joan Coromines and adjusted according to Catalonia’s population growth.The language that has gained the most ground is mainly Spanish, which went from 200,000 speakers in 1930 to 3.8 million in 2018. Moreover, speakers of other foreign languages (500,000 speakers) have also grown more than Catalan speakers over the past hundred years.
Notes, Sources, and Methodology
The data from 2003 onward is taken from Idescat (source). Before 2003, there are no official statistics, but we can make interpretations based on historical evidence. The data prior to 2003 is calculated based on two key pieces of evidence:
-
1st Interpretation: In 1930, 90% of the population of Catalonia spoke Catalan regularly. Source and evidence: The Romance linguist Joan Coromines i Vigneaux, a renowned 20th-century linguist, stated in his 1950 work "El que s'ha de saber de la llengua catalana" that "In this territory [Greater Catalonia], almost the entire population speaks Catalan as their usual language" (1, 2).\ While "almost the entire population" is not a precise number, we can interpret it quantitatively as somewhere between 80% and 100%. For the sake of a moderate estimate, we assume 90% of the population were regular Catalan speakers, with the remaining 10% being immigrants and officials of the Spanish state.
-
2nd Interpretation: Regarding population growth between 1930 and 1998, on average, 60% is due to immigration (mostly adopting or already using Spanish language), while 40% is natural growth (likely to acquire Catalan language from childhood). Source and evidence: Between 1999 and 2019, when more detailed data is available, immigration accounted for 68% of population growth. From 1930 to 1998, there was a comparable wave of migration, especially between 1953 and 1973, largely of Spanish-speaking origin (3, 4, 5, 6). To maintain a moderate estimate, we assume 60% of population growth during that period was due to immigration, with the ratio varying depending on whether the period experienced more or less total growth.
-
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 8bad92c3:ca714aa5
2025-05-22 18:02:41
@ 8bad92c3:ca714aa5
2025-05-22 18:02:41Key Takeaways

In this episode of TFTC, Andrew Myers, founder of Satoshi Energy, explores the convergence of AI, humanoid robots, Bitcoin, and decentralized energy, warning of a near future where self-replicating machines dominate energy and labor. Myers argues that Bitcoin’s decentralized nature offers a critical check against centralized AI power, enabling autonomous agents to transact freely and protecting individual sovereignty. Through his company’s work and its software BitCurrent, Myers promotes Bitcoin as both a tool for energy market efficiency and a foundation for preserving liberty in an AI-driven world.
Best Quotes
“Humanoid robots are going to not only replace most of the jobs people do today… they're going to be able to recreate themselves and self-replicate faster than that.”
“For me the key value proposition of Bitcoin is leveling the economic playing field. Rather than those who control the money printer making the economic decisions, it's everyday people.”
“AI energy demand is infinite. Bitcoin has a Nakamoto point… AI doesn’t.”
“Satoshi Energy’s mission is to enable every electric power company to use Bitcoin by block 1,050,000.”
“If you're a Bitcoiner and you're not using Fold, what are you doing? You're leaving sats on the table.”
“Tesla said machines would eventually fight wars for us. When that happens, nation-states become spectators. Bitcoin is how we avoid centralized control of those machines.”
“There’s already an energy company in Texas using Bitcoin as collateral in a power contract.”
“Are we auditioning for a galactic federation? Maybe. Even if not, we should still be acting like we are.”
Conclusion
Andrew Myers delivers a compelling vision of the future where exponential AI and energy growth demand a decentralized response—one rooted in Bitcoin as more than money, but as critical infrastructure for freedom. Through Satoshi Energy and tools like BitCurrent, Myers bridges big ideas with tangible actions, advocating for bottom-up sovereignty across energy and finance. His message is clear: decentralization is no longer optional—it’s essential for preserving human agency in an increasingly automated world.
Timestamps
0:00 - Intro
0:34 - Tesla’s AI energy theory
8:59 - Bitcoin and decentralization fixes AI
13:02 - Fold & Bitkey
14:38 - How Satoshi Energy is using AI
19:28 - Bit Current
23:13 - Unchained
23:42 - Revealing inefficiency
32:57 - Proliferating OS AI with bitcoin
36:26 -Apple of Eden and Antichrist
45:11 - Iberian outage
48:48 - Defense tech
54:51 - UFOs, Atlantis and remote viewingTranscript
(00:00) Humanoid robots are advancing so quickly. They're going to not only replace most of the jobs that people do today, probably the next 5 to 10 years, but they're going to be able to recreate themselves and self-replicate even faster than that. With AI, the energy demand is infinite. It's going to 10x and 10x and 10x again in terms of global energy consumption, and that's just going to completely change the world we live in.
(00:21) If there's a sufficiently advanced AI, is it going to listen to a politician that says, "No, you can't have that energy." Or is it going to say, "Fuck you. Send the drone. You can hear us loud and clear. Loud and clear. I have to put this in front of my face so I'm not leaning. Yeah, vibe coding. There may be some securityities.
(00:45) I do want to hand it off to a developer who actually understands this stuff to say, am I am I going to am I going to leak any information or like be Yeah, I should probably do that before I release to the public. Now, let me say that. does seem pretty simple though. It's just getting the data on the page, getting the price of Bitcoin, using Coin Gecko API, and then running the math of how much Bitcoin is this worth at this point in time.
(01:13) We're not collecting any data either. I don't think that you know of. No, this is AI once. This is the problem of vibe coding. Are you bearish on AI? Uh, I think we're at a fork in the road and on one side I'm very bullish. You shamed me for for admitting that I was turning my kids into Legos via or turning myself into Lego in this. I was channeling my inner Marty.
(01:36) What would Marty do? Well, that's what uh that's what precipitated this. You hit me up. Was it two weeks ago now at this point? this week with your tweet about Nicola Tesla essentially predicting AI and him not factoring in sound money to the inevitable future that he foresaw. Yeah, it kind of came up uh in the work we're doing at Satoshi Energy where we're developing sites for data centers and a lot of those were were Bitcoin data centers for the last five six years and then in the last couple of years just increasingly demand
(02:20) from AI data centers in some cases like a project that we sold to a Bitcoin miner then becomes an AI site and then start to have questions within the team about what is our AI strategy and it was always in the back of my mind as part of the strategy which we'll get into like what is this fork in the road which directions could it go but I hadn't ever really communicated it to our team uh until recently because it's such a big idea that like on top of thinking about sound money and energy like we're already thinking about enough but as the
(02:57) team's growing as people are starting to ask these questions and like in some cases feeling conflicted about um should we be serving this AI market and in some cases large institutional investors and tech companies uh really like felt the need to put the the pen to paper and and talk about this and talk about how AI fits into our overall strategy.
(03:20) Uh, and part of that reminded me of this uh, essay that Nicola Tesla wrote called um, the problem of human energy, which was kind of a cheeky title. Uh, because clearly he thought, you know, energy would liberate humanity. Uh, but it get you get a lot more readers if you, you know, if you name it, the problem of human energy, especially a lot more of the critics who you're trying to convince otherwise.
(03:44) And one of the biggest things, biggest takeaways for me in that in that essay is he he basically says at some point man will create machines that fight wars for us and limit the the loss of human life to the point where the different parties, nation states, other powerful people u that were fighting wars with each other will once it's sort of this this machine to machine battle, they'll just become interested spectators.
(04:13) and eventually lead to world peace. So I think that's the path we want to be on. Not the path where it becomes a very centralized AI and we ultimately become enslaved. Uh but on the path to world peace or or keeping ourselves on that path to world peace. I think that's where Bitcoin plays a role. it keeps the economic playing field level uh and keeps this technology sufficiently decentralized where Bitcoin is that protocol for you know decentralized AI agents communicating with each other.
(04:46) So we can go in any direction you want from there but it's a big idea. No, this is in line with something I wrote about earlier this week that was inspired by a tweet that Paul Otoy from Stack put out basically not explaining this exact problem but just giving his thoughts on how he's viewing the state of AI and where it will go in the future.
(05:10) And Paul, the team at stack and sphinx are highly focused on enabling the open- source AI as opposed to closed source AI. I I think based on what you just said, I think it's very line what Paul was saying in that tweet, which is we're reaching the point with MCP with these sort of protocols where you can store context that agents can plug into and begin communicating with each other.
(05:39) We're at the point where agentic models are getting are actually usable. And I think that's where you have this like critical tipping point of okay that's really going to dictate which direction in the fork in the road we go down because once the agents are able to go do these tasks you right have these network effects that take hold and it's very important that we thread the needle of making sure that it's open and incentivized properly.
(06:10) Yes. Yes, we had this idea of time preference in the Bitcoin community where you know we think with sound money we should have a low time preference meaning we think longer term uh we don't need need to make sort of quick rash decisions into investments today but then you have this tidal wave of AI coming our our direction it almost forces you back into that high time preference mindset of like I need to address this problem now um and Then from like an energy perspective, it's interesting too.
(06:44) Uh you have like Drew's concept of the Nakamoto point for Bitcoin. Like how much of of human energy of global energy will will Bitcoin mining consume? And like say it's between 1 and 10% of of human energy. If it becomes 100% then uh that doesn't make any sense because then you're just like worshiping Bitcoin.
(07:03) And if all of the energy is going towards that, it means you're not putting any energy towards any other sort of economic pursuit or uh you know human need. But with AI, the energy demand is infinite. I don't think there is a Nakamoto point. It's just like it's going to 10x and 10x and 10x again in terms of g global energy consumption.
(07:23) Uh and that's just going to completely change the world we live in. Another thing on sort of the high time preference concept is like humanoid robots are advancing so quickly. They're going to not only replace all of the job most of the jobs that people do today, very quickly within probably the next 5 to 10 years max, but they're going to be able to rec -
 @ 8576ca0e:621f735e
2025-05-22 17:36:20
@ 8576ca0e:621f735e
2025-05-22 17:36:20In the evolving digital economy, Bitcoin has moved beyond its initial status as a speculative asset. It is now a powerful tool for building long-term wealth, especially within the context of a decentralized financial system. While Bitcoin 101 introduced the concept of Bitcoin and Bitcoin 102 covered its mechanics and investment basics, Bitcoin 103 dives deeper into how individuals can strategically build wealth in a decentralized world.
The Foundation: Why Decentralization Matters
At its core, Bitcoin operates on a decentralized network free from government control or manipulation by central banks. This decentralization is not just a technical characteristic but a financial philosophy. In a world where inflation erodes the value of fiat currencies and financial systems can be restricted by geopolitical decisions, Bitcoin offers sovereignty and transparency.
By removing intermediaries, Bitcoin empowers individuals to store, send, and receive money globally with minimal friction. This capability becomes crucial in building wealth that’s resilient to political and economic volatility.
Bitcoin as Digital Gold
Bitcoin's fixed supply capped at 21 million BTC mimics the scarcity of precious metals like gold. However, unlike gold, Bitcoin is portable, divisible, and easier to secure. Investors seeking a hedge against inflation and monetary debasement are increasingly turning to Bitcoin as a long term store of value.
Holding Bitcoin over time, known as "HODLing" in crypto parlance, is one of the most common wealth building strategies. Historical data shows that long-term holders tend to outperform short-term traders, especially in the face of Bitcoin’s cyclical volatility.
Diversification in a Decentralized Economy
Building wealth with Bitcoin doesn't mean going all in. It involves using Bitcoin as a foundational asset while exploring adjacent opportunities within the decentralized finance (DeFi) space. Bitcoin can be used as collateral, yield-generating assets, or even part of a diversified crypto portfolio that includes Ethereum, stablecoins, and tokenized assets.
For instance, some platforms allow users to lend their Bitcoin and earn interest, or stake wrapped Bitcoin (WBTC) on decentralized protocols. While these carry risk, they also offer the possibility of compounding returns beyond price appreciation alone.
Wealth Preservation through Self-Custody
One of the key principles of wealth building in the decentralized world is self custody. Unlike traditional bank accounts, where your assets are held by third parties, Bitcoin allows users to control their wealth directly through private keys and cold storage wallets.
By taking responsibility for their assets, users reduce counterparty risk and maintain access to their wealth even in times of crisis. This level of control and autonomy is unprecedented in the history of money.
Education and Risk Management
Wealth building in the Bitcoin ecosystem requires a solid understanding of risk. Volatility, regulatory uncertainty, and security vulnerabilities must be addressed through continuous education, diversification, and the use of reputable platforms.
New investors should start by:
• Setting long term goals
• Investing only what they can afford to lose
• Using hardware wallets for security
• Staying informed through trusted crypto news sources
The Future of Wealth in a Decentralized World
Bitcoin is not just reshaping finance, it’s redefining wealth. As decentralized technologies mature, we can expect a shift in how value is created, transferred, and preserved. From smart contracts to decentralized autonomous organizations (DAOs), the Bitcoin ethos of transparency, security, and autonomy will continue to guide the evolution of the digital economy.
In conclusion, Bitcoin 103 is about more than investing, It's about understanding the broader movement toward financial freedom. Building wealth in a decentralized world starts with a shift in mindset: from dependence to independence, from control to empowerment.
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.

