-
On Nostr, I am running several marketing accounts for my projects: Ditto, The Mostr Bridge, and Cobrafuma. But I want other people to be able to post from those accounts. In fact, I want to hire a "social media manager" someday (for when my wife is not available 😂). This is a pretty basic need for social media, but of course on Nostr it isn't basic at all, because private keys have nuclear potential if leaked. Even if you trust the person, a small mistake could be disastrous. To solve this, we need a bunker. ## What is a bunker? A bunker (aka "remote signer") allows you to store your keys on your computer, but give others access. Once the other person is granted access, they can send commands to your computer like `sign_event` and `get_public_key`, and your computer will perform those operations without needing to expose the actual key. 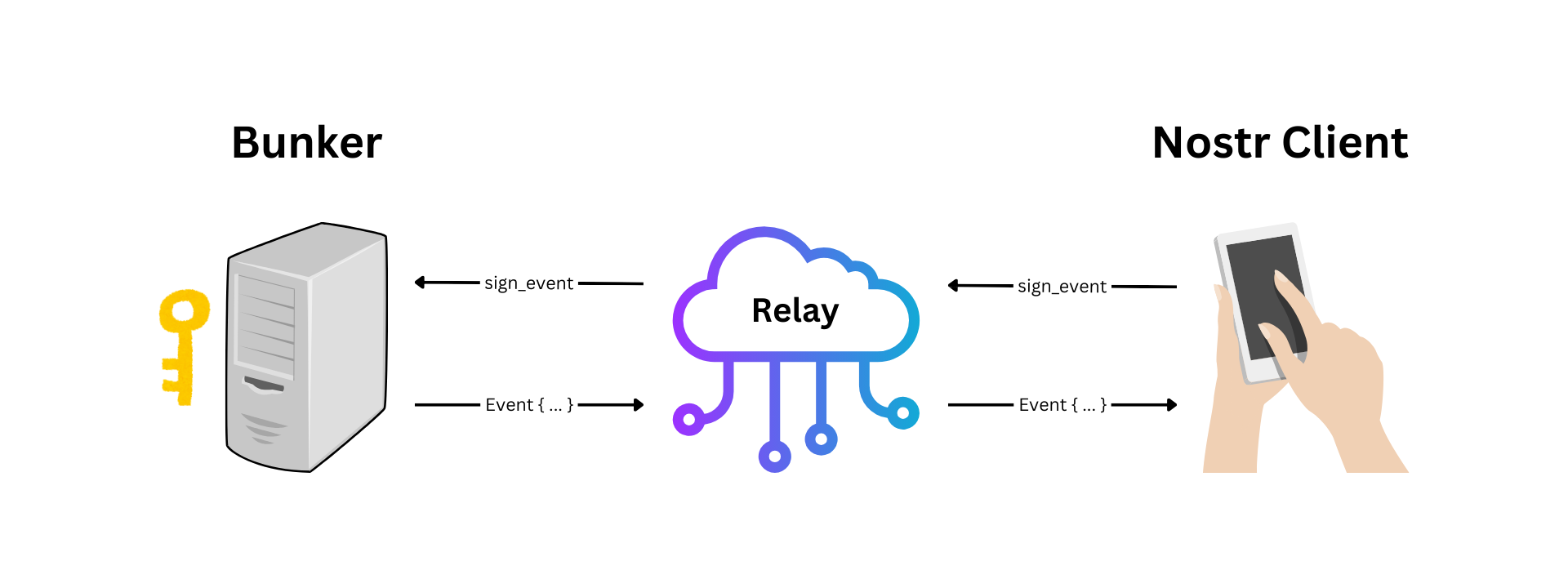 In reality the UX is not so technical. Your bunker generates a unique URI containing the connection details, and the other person pastes it into the login screen. Everything else happens automatically. As for the running the bunker, you can run it on a VPS, a laptop, an old computer in your house, a Raspberry Pi, or even an Android phone. The first bunker was an Android app called Nostr Connect. This lead to the creation of nsecBunker (a hosted service), nsec.app (a bunker that runs inside your web browser), and Amber (another Android app). These days nsec.app and Amber are the only ones being actively developed, but due to running in restricted environments (web and Android respectively), they don't offer the level of 24/7 reliability I wanted in a bunker. If you are a single user managing your own keys I still recommend Amber, but for doling out credentials to your team, you might want knox. ## Introducing Knox 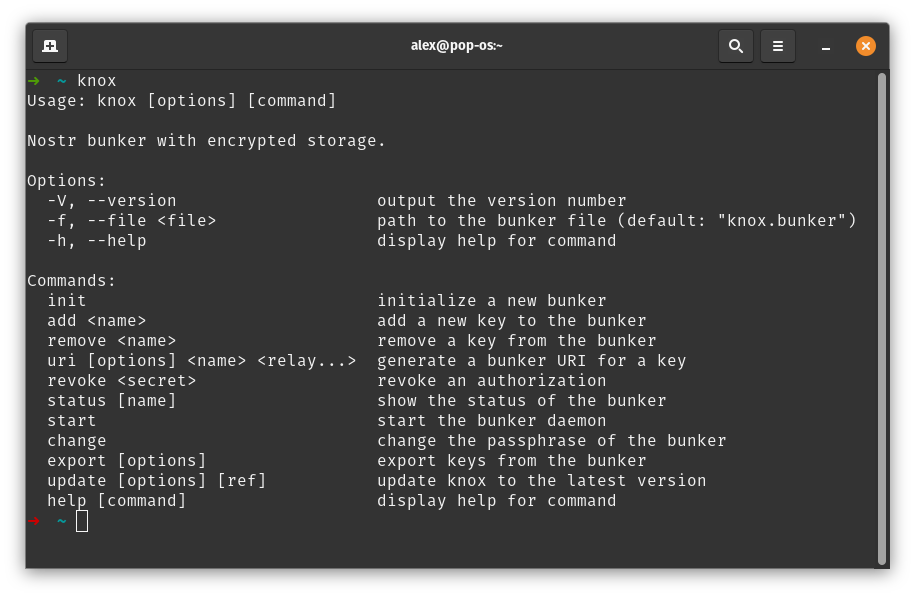 knox is a command-line tool that manages keys, generates bunker URIs, and runs a bunker server. It is still beta software, but I am using it successfully today to post on Ditto. knox is inspired by the wonderful [`nak bunker`](https://github.com/fiatjaf/nak) command, which almost solved my problem but has no way to store credentials. So I created my own command-line bunker that you can run again and again.  Most notably, knox introduces a portable `.bunker` file format for storing keys and connection details. It's encrypted with a password, which you have to type every time you want to add or remove keys, generate new URIs, and when you start the bunker. With knox you can have one bunker file, or many. It is loosely inspired by the KeePass `.kbdx` idea. knox is written in TypeScript, but it's available as a precompiled executable on Linux, MacOS, and Windows thanks to `deno compile`. ## Getting Started To install knox, I've prepared a simple setup script that will detect your OS and install the knox command in your path: ```sh curl https://dl.soapbox.pub/install/knox.sh | sh ``` You can also grab a [precompiled binary](https://gitlab.com/soapbox-pub/knox#install) if you don't want to run the script. ## Commands Once installed, run `knox` to see a list of supported commands. It should look something like this: ``` Usage: knox [options] [command] Nostr bunker with encrypted storage. Options: -V, --version output the version number -f, --file <file> path to the bunker file (default: "knox.bunker") -h, --help display help for command Commands: init initialize a new bunker add <name> add a new key to the bunker remove <name> remove a key from the bunker uri [options] <name> <relay...> generate a bunker URI for a key revoke <secret> revoke an authorization pubkey [options] <name> show the public key of a secret key status [name] show the status of the bunker start start the bunker daemon change change the passphrase of the bunker export [options] export keys from the bunker update [options] [ref] update knox to the latest version help [command] display help for command ``` Run `knox init` to create a new bunker file. Then use `knox add alex` (replace with your own name) to add a key, then `knox uri alex` to get a connection string. Finally, run `knox start` to start the bunker. While the bunker is running, you can continue to run commands like `knox add` and `knox uri` in another tab, and the bunker will detect the file changes and automatically refresh. 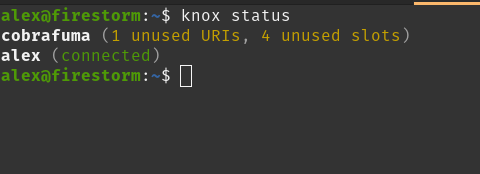 Another good one is `knox status`, which shows a list of keys and whether any of their URIs are being utilized. `knox status <key>` can show the individual connections for a specific key, and `knox revoke <secret>` can revoke an individual connection. ## Bunker Where? knox needs internet connectivity to connect to relays, but it does not need to expose any ports to the outside world, so the ideal place might be on a desktop computer in your living room. This might be considered more secure than a VPS in a datacenter, depending on your circumstances.  I am running knox on an old Dell computer under my TV, which is a cheap and simple solution. It's connected to a backup battery in case the power flickers, but a prolonged outage would require starting the bunker again manually. I also suggest running the bunker in `screen` or a similar tool so you can reconnect and view the logs over ssh on your home network. It's not suggested to run knox in systemd, because knox requires manually entering the encryption password when it starts. Any solution to store the password to disk, or pass it through a command-line argument, would compromise security. ## What's Next? For now, knox is meeting my needs. As the idea evolves I expect to make more changes, and possibly improvements to the `.bunker` format if anyone else decides to use it. Feel free to drop any suggestions on [GitLab](https://gitlab.com/soapbox-pub/knox/-/issues)! Another interesting idea would be to build a UI to manage the `.bunker` file, or to offer hosted bunker (although I am kind of against this, unless the hoster is just cloud sync service and the bunker is decrypted locally within the browser, similar to KeeWeb).