-

@ d57360cb:4fe7d935
2025-02-07 17:48:33
You exist at the central point of life. Everywhere you go, everywhere you are you’ll find yourself peering out through your eyes at the center of everything.
The center always stays the same, the contents that surround it are always moving and changing.
Yet we foolishly believe the things that surround us and continuously transform hold the answers to change.
Change comes from the center, from within. Then it affects all that comes within its path.
Take care of your center and it will change the world that surrounds it.
-

@ 0463223a:3b14d673
2025-02-07 17:20:27
Mental health is a funny old bag. As someone who’s been on various prescribed drugs for anxiety and depression for many years and is slowly weaning myself off (I’ve reduced my Venlafaxine dose by 1/6th. Next is the Pregabalin. One step at a time eh…) I’m not sure I fully understand normailty.
Yesterday I finally got my hands on a record I absolutely love. I had it on cassette for 34 years but never knew the title, I recorded it from Friends FM (London pirate radio station) back in 1991. I chanced upon the title after some random YouTube clicks. I was so happy to find out, it was the only song on the tape that had eluded me after all these years. I’d been watching it on Discogs for a while and finally found one at a nice price. Yay!
I’ve been lost in nostalgia all day. Lost friends have been on my mind.
My best friend as a kid was an interesting character, a fantastic artist. He was by far the best at drawing in my class at primary school, heavily influenced by M.C. Escher and artists I’d never heard of, he’d grown up in a more culturally expansive house than I. He was into fashion and design but we weren’t clever kids at school. We had a lot in common musically and I always thought he’d be my MC back when I was starting out as a DJ. He was a very creative person but also a total fantasist. As a duo he was the extraverted, outspoken one, I barely spoke a word and relied on him a lot socially. He was sectioned under the Mental Health Act at 20 years old. We lost touch.
Our birthday’s were within 1 day of each other and a third friend had his the day after mine. Our 16th birthdays fell on Friday, Saturday and Sunday. This was quite exciting. By midday on the Friday, he was permanently expelled from school. He’d taken acid in the morning and essentially enjoyed himself, running around and laughing a lot. The school didn’t approve, oh then his mother kicked him out of home. An eventful start to a messy weekend…
We took a lot of acid as kids and I’m not shitting you when I say he, in particular, took a LOT. When we were 16 he told the local gypsies that he score them some acid, 100 tabs to be exact, about £200 worth. Not a lot of money but acid has always been very good value for money. He secured the goods easily, his brother was in the business so to speak but he chose not to pass the goods on… Over the course of a month, with the exception of the ones he gave to his friends he took the whole lot. (Side note, it also meant the local gypsies were after us. That’s another story). None of us could keep up as far as acid was concerned.
Even as I’m writing I’m thinking of more funny incidents, like the time we were in a shop with umbrellas for sale. He picked one up, opened it and danced out the shop, stealing it in the most obnoxious, obvious way even and no one batted an eyelid. Funny as fuck at the time but not ideal behaviour… He was like that all the time. In today’s world he would have letters after his name for sure. Maybe not PhD or BSC but definitely ADHD and ASD.
This ties in with the period where I became pretty much non-verbal. I’ve written about my uncertainty of my autism diagnosis before and it’s hard to say if this period of not speaking was due to that or extreme anxiety growing up with an absent, alcoholic, father and being bullied etc. It’s certainly safe to say taking loads of acid probably didn’t help!
After many adventures, going to illegal raves, hustling to get DJ spots, trips in the woods, trips in bedrooms, trips pretty much everywhere, my friend became less and less stable. We fell out after he gave a bunch of my possessions to some random stranger at a rave. As kids we’d often swap clothes, jackets, shoes etc. It was one way of feeling like you had fresh clothes on a budget but giving my stuff away was the final straw. We fell out big time over that. The last time I saw him was in my early 20s. He looked like a ghost, a total shadow of a human. There was nothing there. Tragic. I seriously hope he’s well now. I’m long away from the people I grew up with, I might never find out. Thinking about you man.
Since then, I’ve had another 2 friends sectioned under the Mental Health Act, drugs, petty crime and an unstable home life does does fuckry to a young brain. I’ve also lost a couple of friends to crack and heroin. Not fun. Drugs are bad m’kay.
I’ve struggled with mental health my entire life, before drugs were an issue. Probably going back to 10 years old, at least as far as I can recall. Not that I want sympathy, far from it, I own my mistakes. I’m typing this shit on the internet because I want to and I want to honour lost friends. I own every single mistake. Maybe writing shit helps? Making music certainly does. It’s given me a sense of identity and I’m very lucky in what I do. Ironically I now work for a record label who’s motto is “Comforting the disturbed, disturbing the comfortable”. Very apt.
The drummer in my current band took his own life in 2014. That was fucking shit. He was a totally straight edge guy. Very talented musician. Suicide is fucking vile, I don’t have the words to describe what that does to those left behind. Just a couple of weeks earlier we’d been offered a record deal with an advance to make an album, we were also working with another very respected artist in his live band. Like wtf man. I still don’t get it. I don’t even want to say more out of respect for his family. RIP brother.
Nostr is a funny place, so many people I have very little in common with other than a dislike of banks (I hold the banksters responsible for the 2008 crash directly responsible for the death of my friend btw. I still say fuck each and every one of you. Cunts).
I often see folks refer to others as ‘normies’. From what I gather a normie is someone who didn’t grow up posting on 4Chan. The funny thing is these people are often the one’s saying work hard, raise a family etc. I mean come on, you go on about working hard, raising families and eating healthily. Fucking hell!!! Like that’s sort of normal, you know?
Tell me about sitting in a slum in south London with prostitutes, smoking crack thinking of ways you can get some money to score and then talk to me about ‘normies’. LMAO. For clarity, I didn’t have sex with them. I just wanted drugs and so did they. Nothing about this is glamorous by the way, it’s tragic and grim. I’m glad it’s not the norm.
If you’re that healthy, hardworking guy with a family calling people normies, respect to you, in all honestly I’m envious. I wish I’d grown up in a stable home with two parents and a dad who hooked me up working for a fund straight out of school. Normies! Fuck I’m still laughing about that one. The other one that cracks me up is plebs, again you worked at a fund and you talk about being a pleb. Funny fucker. Respect for your sense of humour though.
I’m not bitter (well not fully). I read the posts with interest and I’m always trying to learn new stuff, I’m happiest when learning. Learning is good for you. Fact.
It’s a thoroughly miserable day here as write this, icey cold, grey and very windy, this is still the happiest I’ve been in life. I now have a wonderful, beautiful wife. No kids but with my background, I’ve decided these genes are best left here. There’s some sadness about that too but it could be worse, I might be the type to think Peter Thiel is cool.
This probably reads like a right whinney thread but it isn’t. I’m excited about the future. I know some very talented people and I think we can do amazing things. Each day is a new opportunity. Being part of the underground internet is cool. We need free and open tools more than ever. The world is possibly the most fucked up it’s been in many years but also maybe that’s an illusion. I’m the last person you should ask about reality tbh.
Anyway, that’s it for today. This probably reads like a confused mess and a nightmare for anyone who digs grammar but that’s cool, I’m writing without using AI or a filter, it’s not a work email. I’m typing as the words appear in my head, this is who I am.
I’m a normie…
-

@ 1cb14ab3:95d52462
2025-02-07 16:41:54
***Tree branches, driftwood coconut. 5'7" teardrop. [Dawei, Myanmar. 2020]***
---
#### Introduction
Situated on Myanmar’s Grandfather Beach, this lens captures the dramatic shape of a steep, rocky hill that mirrors the arduous road leading to this remote location. Grandfather invites viewers to reflect on the connection between journey and destination, highlighting the tension and beauty of paths less traveled.
#### Site & Placement
The lens is positioned at the west end of the beach, focusing on the sharp hill rising above the shoreline. Its teardrop shape accentuates the rocky prominence, emphasizing its similarity to the road that winds toward the beach. A bench, placed 12 feet away, provides a place for viewers to absorb the rugged beauty of the scene.
#### Impermanence & Integration
Crafted from driftwood, branches, and stone, Grandfather is a fleeting presence in this timeless landscape. Its brief existence reflects the challenges and ephemerality of the journey it highlights, blending into the environment as it gradually succumbs to the elements.
#### Reflection
*Grandfather* invites viewers to consider the parallels between the physical journey to reach the beach and life’s broader paths. It stands as a reminder that even the most challenging routes can lead to moments of profound beauty.
---
## Photos








---
#### More from the 'Earth Lens' Series:
[Earth Lens Series: Artist Statement + List of Works](https://hes.npub.pro/post/1731091744332/)
["Looking Glass" (Earth Lens 001)](https://hes.npub.pro/post/1736304563962/)
["Folsom" (Earth Lens 002)](https://hes.npub.pro/post/1737844073125/)
["Sanctuary" (Earth Lens 003)](https://hes.npub.pro/post/1731091744332/)
["Platte" (Earth Lens 004)](https://hes.npub.pro/post/sya8nv6q8k0w3olqcepwz)
[COMING SOON: "Chongming" (Earth Lens 006)](https://hes.npub.pro/post/1731091744332/)
---
#### More from Hes
[Portfolio](https://hesart.npub.pro)
[Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz)
[Artist Statements](https://hes.npub.pro/tag/art/)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography)
[Money](https://hes.npub.pro/tag/money)
[Tech](https://hes.npub.pro/tag/tech)
---
*All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
-

@ f57bac88:6045161e
2025-02-07 16:23:37
## **۱. ایران پیش از هخامنشیان**
پیش از ظهور **کوروش بزرگ** و تأسیس امپراتوری هخامنشی، سرزمین ایران تحت حکومت چندین تمدن و دودمان مهم قرار داشت:
### **ایلامیان (حدود ۳۰۰۰–۶۴۰ پیش از میلاد)**
- **قلمرو:** جنوب غربی ایران (خوزستان امروزی)
- **دستاوردها:**
- ایجاد یکی از نخستین دولتهای متمرکز در منطقه
- توسعه خط نوشتاری ایلامی
- جنگهای طولانی با بابل و آشور
- در سال **۶۴۰ ق.م**، ایلام توسط **آشوربانیپال**، شاه آشور، فتح و ضعیف شد.
### **مادها (حدود ۷۰۰–۵۵۰ پیش از میلاد)**
- **بنیانگذار:** دیاکو (۷۰۹–۶۵۶ ق.م)
- **شاهان مهم:**
- **فرورتیش:** مقابله با آشوریان و توسعه قلمرو ماد
- **هووخشتره:** شکست آشور و گسترش قدرت مادها
- **ایشتوویگو:** آخرین پادشاه ماد که توسط **کوروش بزرگ** شکست خورد
- **دستاوردها:**
- نخستین ارتش منظم در تاریخ ایران
- اتحاد قبایل ایرانی و پایهگذاری حکومت متمرکز
### **خاندان هخامنشی پیش از کوروش**
- **هخامنش:** بنیانگذار دودمان هخامنشی (حدود ۷۰۰ ق.م)
- **چیشپیش:** حاکم آنشان
- **کمبوجیه یکم:** پدر کوروش بزرگ
کوروش بزرگ با شکست دادن مادها، نخستین امپراتوری بزرگ ایران را بنیان نهاد.
---
## **۲. هخامنشیان (۵۵۰–۳۳۰ پیش از میلاد)**
### **کوروش بزرگ؛ بنیانگذار نخستین امپراتوری ایرانی**
- **قلمرو:** از آسیای مرکزی تا مدیترانه و مصر.
- **دستاوردها:**
- **تأسیس امپراتوری هخامنشی**؛ نخستین امپراتوری چندملیتی تاریخ.
- **صدور منشور حقوق بشر (استوانه کوروش).**
- **فتح بابل و آزادی یهودیان.**
- **ایجاد سیستم حکومتی مبتنی بر احترام به فرهنگها و ادیان مختلف.**
- **ایجاد جادههای ارتباطی برای تسهیل تجارت و حملونقل.**
### **داریوش بزرگ (۵۲۲–۴۸۶ ق.م)**
- **گسترش امپراتوری و ایجاد نظام اداری پیشرفته.**
- **ساخت تخت جمشید.**
- **ایجاد راه شاهی برای ارتباط بهتر میان ایالتها.**
- **ایجاد سیستم مالی و ضرب نخستین سکه ایرانی.**
### **خشایارشا (۴۸۶–۴۶۵ ق.م)**
- **نبردهای مهم با یونانیان، از جمله جنگ سالامیس.**
- **تکمیل تخت جمشید و گسترش معماری هخامنشی.**
### **پایان هخامنشیان**
- داریوش سوم در برابر اسکندر مقدونی شکست خورد و امپراتوری سقوط کرد.
---
## **۳. اشکانیان (۲۴۷ پیش از میلاد–۲۲۴ میلادی)**
- **بنیانگذار:** ارشک اول.
- **دستاوردها:**
- مقابله با امپراتوری روم.
- ایجاد نظام حکومتی نیمهمتمرکز.
- گسترش تجارت از طریق جاده ابریشم.
---
## **۴. ساسانیان (۲۲۴–۶۵۱ میلادی)**
### **شاپور اول (۲۴۱–۲۷۲ م)**
- شکست دادن امپراتور روم (والرین).
- توسعه علمی و فرهنگی.
### **انوشیروان دادگر (۵۳۱–۵۷۹ م)**
- اصلاحات مالی و اداری.
- ترویج علم و فلسفه.
### **یزدگرد سوم (۶۳۲–۶۵۱ م)**
- آخرین شاه ساسانی، شکست در برابر حمله اعراب مسلمان.
---
## **۵. سلسلههای محلی و اسلامی**
- **سامانیان، آلبویه، سلجوقیان** نقش مهمی در حفظ فرهنگ ایرانی داشتند.
---
## **۶. صفویان (۱۵۰۱–۱۷۳۶ میلادی)**
- **شاه اسماعیل صفوی:** رسمی کردن مذهب تشیع.
- **شاه عباس بزرگ:** توسعه اقتصادی، رونق اصفهان، اصلاحات نظامی.
---
## **۷. افشاریان (۱۷۳۶–۱۷۹۶ میلادی)**
- **نادرشاه افشار:** شکست امپراتوری مغول هند، بازپسگیری خراسان.
---
## **۸. زندیان (۱۷۵۱–۱۷۹۴ میلادی)**
- **کریمخان زند:** صلح و توسعه اقتصادی، ساخت بازار وکیل شیراز.
---
## **۹. قاجاریان (۱۷۹۶–۱۹۲۵ میلادی)**
- **آغامحمدخان قاجار:** تأسیس حکومت قاجار.
- **اصلاحات امیرکبیر، جنگهای ایران و روس، انقلاب مشروطه.**
---
## **۱۰. پهلوی (۱۹۲۵–۱۹۷۹ میلادی)**
### **رضاشاه (۱۹۲۵–۱۹۴۱)**
- **نوسازی ایران، توسعه آموزش، ایجاد راهآهن سراسری.**
- **تأسیس دانشگاه تهران و مدرنسازی نظام اداری.**
- **حذف القاب سنتی و ارتقای جایگاه زنان در جامعه.**
### **محمدرضا شاه (۱۹۴۱–۱۹۷۹)**
- **انقلاب سفید و اصلاحات ارضی.**
- **افزایش درآمد نفتی و توسعه صنعتی ایران.**
- **ایجاد زیرساختهای اقتصادی مدرن.**
- **برگزاری جشنهای ۲۵۰۰ ساله شاهنشاهی.**
---
## **جمعبندی**
ایران در طول تاریخ شاهد حکومتهای متعددی بوده که هر کدام در توسعه فرهنگی، اقتصادی و نظامی کشور نقش داشتهاند.
-

@ f57bac88:6045161e
2025-02-07 16:22:07
#### ۱. دوران پالئولیتیک (عصر حجر قدیم)
دوران پالئولیتیک یا عصر سنگ قدیم، اولین دوره از تاریخ بشری است که به زمانی برمیگردد که انسانها هنوز بهطور عمده در زندگی شکارچی-گردآورنده بودند و ابزارهای ابتدایی سنگی را برای تأمین غذا و سایر نیازهای خود استفاده میکردند. این دوران بیش از ۲٫۵ میلیون سال به طول انجامید و انسانها در آن زندگی سخت و متکی به شکار و گردآوری میوهها و گیاهان داشتند. در ایران، این دوره بیشتر در مناطق غربی و مرکزی کشور شواهدی از سکونت انسانهای اولیه بهجا گذاشته است.
مناطقی مانند **غارهای میرعماد در لرستان** و **غار شوش** در جنوب غرب ایران، از مکانهای مهم این دوران هستند که نشاندهنده حضور انسانهای نئاندرتال و هوموساپینس در این منطقه هستند. ابزارهای سنگی کشفشده از این مکانها، نشاندهنده استفاده انسانهای اولیه از سنگها برای ساخت چاقوها، تیغهها و ابزارهای مختلف برای شکار و جمعآوری غذا بوده است. در این دوران، انسانها همچنان در گروههای کوچک زندگی میکردند و عمدتاً بهصورت پراکنده در مناطق مختلف سکونت داشتند.
#### ۲. دوران نوسنگی (Neolithic)
دوران نوسنگی، که آغاز آن به حدود ۱۰,۰۰۰ سال پیش بازمیگردد، بهعنوان یکی از تحولات اساسی تاریخ بشری شناخته میشود. در این دوره، انسانها به تدریج از زندگی شکارگری به کشاورزی و دامداری روی آوردند. این تغییر، نه تنها در سبک زندگی بشر، بلکه در ساختارهای اجتماعی، اقتصادی و فرهنگی جوامع نیز انقلابی بزرگ ایجاد کرد. انسانها برای اولین بار گیاهان را کشت و از آنها برای تأمین غذا استفاده کردند و همچنین دامها را اهلی کردند.
در ایران، از جمله مهمترین مکانهایی که نشاندهنده آغاز کشاورزی و زندگی روستایی است میتوان به **چغاگلان** در کردستان اشاره کرد. این منطقه یکی از اولین محوطههای باستانی است که شواهدی از کشاورزی اولیه در آن پیدا شده است. همچنین **تل برآفتاب** در کرمانشاه و **تل هندیجان** در جنوب غرب ایران نیز از دیگر سایتهای مهم نوسنگی هستند که شواهدی از نخستین جوامع کشاورزی و دامداری در آنها بهدست آمده است.
زندگی در این دوران بهطور عمده در روستاهای کوچک متمرکز بود و مردم در کنار کشاورزی و دامداری، بهصورت ابتدایی صنایع دستی نیز تولید میکردند. این دوره شروعی برای روابط تجاری و فرهنگی میان جوامع مختلف بود که به تدریج پیچیدگیهای بیشتری پیدا کرد.
#### ۳. دوران مس و سنگ (Chalcolithic)
دوران مس و سنگ که به آن **دوران چالهکولیتیک** نیز گفته میشود، مرحلهای میان دوران نوسنگی و مفرغ است که حدود ۵,۰۰۰ سال پیش آغاز شد. در این دوران، انسانها از فلزات، بهویژه مس، استفاده کردند و ابزارهایی ساختند که در کنار ابزارهای سنگی قرار میگرفت. این دوره، بهویژه بهعنوان دوران گذار از عصر سنگ به عصر مفرغ شناخته میشود.
یکی از مهمترین ویژگیهای این دوران، استفاده اولیه از فلزات است که امکان ساخت ابزارهایی با دقت و کارایی بالاتر را فراهم کرد. در کنار کشاورزی و دامداری، تجارت و ارتباطات میان جوامع مختلف شروع به گسترش کرد و باعث تبادل کالاها و ایدهها بین مناطق مختلف شد. از مهمترین محوطههای باستانی این دوره میتوان به **تپه سیلک** در کاشان اشاره کرد که در آن آثار بسیاری از زندگی کشاورزی، صنایع دستی و حتی شواهدی از ساختوسازهای ابتدایی پیدا شده است.
**تپه نوشیجان** در همدان نیز یکی دیگر از سایتهای مهم این دوران است که در آن آثار مس و ابزارهای فلزی کشف شده است. این آثار نشاندهنده توسعه فنون فلزکاری و استفاده از مس برای ساخت ابزارهای پیچیدهتر در این دوره است.
#### ۴. دوران مفرغ (Bronze Age)
دوران مفرغ، که از حدود ۳۰۰۰ سال پیش از میلاد آغاز شد، یکی از مهمترین دورانها در تاریخ بشری است. در این دوره، استفاده از فلز مفرغ برای ساخت ابزار، سلاحها و اشیاء تزئینی گسترش یافت. دوران مفرغ نهتنها از نظر تکنولوژیکی بلکه از نظر فرهنگی و اجتماعی نیز اهمیت زیادی دارد، زیرا در این دوره جوامع انسانی پیچیدگیهای بیشتری پیدا کرده و بهتدریج به تمدنهای بزرگتری تبدیل شدند.
ایران در دوران مفرغ شاهد شکلگیری تمدنهای اولیهای همچون ایلامیان بود. این تمدنها در جنوب غربی ایران (مناطق کنونی استان خوزستان و استان ایلام) و در نواحی شمال غرب کشور ریشه دوانیدند. در این دوران، ساختارهای سیاسی و اجتماعی پیچیدهتر شد و نشانههای اولیه از شکلگیری دولتهای شهری و پیشرفتهتر بهوجود آمد.
یکی از مهمترین سایتهای باستانی این دوره، **تپه حسنلو** در آذربایجان غربی است که شواهدی از یک تمدن پیشرفته با استفاده از مفرغ در آن پیدا شده است. این تپه که بهعنوان یکی از مهمترین محوطههای باستانی شناخته میشود، آثار مختلفی از جمله سلاحها، ابزارها و مصنوعات هنری از دوران مفرغ را در خود جای داده است. همچنین، **تپه سفالی** در جنوب غرب ایران نیز نشاندهنده روند پیشرفت در استفاده از مفرغ و تغییرات فرهنگی در این دوره است.
در این زمان، جوامع انسانی بهطور گستردهتری در زمینههای کشاورزی، تجارت، فنون ساختوساز و هنرهای تزئینی فعالیت میکردند. استفاده از مفرغ نهتنها به ارتقاء صنعت و فنون مرتبط با آن کمک کرد، بلکه زمینه را برای ظهور تمدنهای بزرگتر مانند ایلامیان فراهم آورد.
#### نتیجهگیری
تاریخ باستانی ایران گواهی است بر تکامل انسانها از دورههای ابتدایی شکارگری و گردآوری به جوامع پیچیدهتر کشاورزی، دامداری و تولید صنایع دستی و فلزی. این تحولات از دوران پالئولیتیک تا دوران مفرغ باعث شد تا ایران به یکی از کانونهای مهم تمدنسازی در تاریخ بشری تبدیل شود. پیشرفتهای تکنولوژیکی، ساختارهای اجتماعی پیچیدهتر و گسترش ارتباطات تجاری و فرهنگی در این دورهها، زمینهساز ظهور تمدنهای بزرگ و پیچیدهای مانند ایلامیان، هخامنشیان و ساسانیان شد که در تاریخ ایران و جهان نقش مهمی ایفا کردند.
این تاریخچه در کنار آثار باستانی که از این دوران بهجا مانده است، همچنان دلیلی برای عظمت و شکوه تمدن ایران در تاریخ بشر است.
-

@ a012dc82:6458a70d
2025-02-07 15:23:54
In the intricate and rapidly evolving world of digital currencies, the interplay between Bitcoin and the US dollar, particularly through the medium of stablecoins, stands out as a subject of profound significance. Mark Goodwin, a renowned figure in the realm of Bitcoin and an advocate for decentralized financial systems, sheds light on this complex dynamic. This article delves deeper into the nuanced relationship between Bitcoin and the dollar, the pivotal role of stablecoins, and the risks they entail, drawing upon the extensive expertise of Goodwin.
**Table Of Content**
- Understanding the Bitcoin-Dollar Symbiosis
- The Role of Stablecoins
- Mark Goodwin's Perspective on Stablecoins
- Conclusion
- FAQs
**Understanding the Bitcoin-Dollar Symbiosis**
The relationship between Bitcoin and the US dollar is a fascinating study in contrasts and interdependencies. Bitcoin, known for its decentralized nature, offers a politically neutral platform but is characterized by significant price volatility. This volatility stands in stark contrast to the relative stability of the US dollar, a currency backed by the full faith and credit of the US government. The dollar, often used as a benchmark for Bitcoin's value, follows its trajectory in many ways, particularly in regions where Bitcoin is gaining traction.
The symbiosis between Bitcoin and the dollar is particularly evident in the context of global financial instability. In regions with volatile local currencies, the adoption of Bitcoin often leads to a parallel increase in the use of dollar-based stablecoins. This phenomenon suggests that Bitcoin's growth could inadvertently bolster the stability and global reach of the US dollar.
Moreover, the Bitcoin-dollar dynamic is not just limited to direct financial transactions. It extends to the broader implications for monetary policy, international trade, and global economic stability. As Bitcoin continues to gain acceptance, it challenges traditional financial systems and currencies, including the dollar, prompting a reevaluation of their roles in a digital age.
**The Role of Stablecoins**
Stablecoins, designed to bridge the gap between traditional finance and the digital asset space, play a crucial role in this relationship. By pegging their value to stable assets like the US dollar, they offer a less volatile alternative to cryptocurrencies like Bitcoin. This stability is essential for global commerce, enabling near-instantaneous transactions with lower fees compared to traditional banking systems.
In economies plagued by inflation, stablecoins offer a haven for individuals and businesses to preserve their wealth. They provide a degree of financial stability and predictability that is often lacking in local currencies. This aspect of stablecoins is particularly appealing in developing countries, where currency instability can be a significant barrier to economic growth and stability.
Furthermore, stablecoins are increasingly being seen as a tool for financial inclusion. They offer an accessible entry point for individuals who are unbanked or underbanked, providing them with a means to participate in the global economy. This potential for social impact adds another layer of significance to the role of stablecoins in the financial ecosystem.
**Mark Goodwin's Perspective on Stablecoins**
Mark Goodwin, with his deep understanding of Bitcoin and its implications for the financial world, offers a critical perspective on stablecoins. He acknowledges their potential benefits but also highlights the risks associated with their use.
**Price Stability Concerns**
Goodwin points out that while stablecoins aim to maintain a stable value, there are inherent risks in keeping their peg to the underlying asset. Market conditions, liquidity issues, and redemption pressures can all threaten the stability of stablecoins. If these risks are not adequately managed, it can lead to a deviation from the peg and a potential loss of trust from users.
**Regulatory Challenges**
The evolving regulatory landscape surrounding stablecoins is another area of concern. As authorities worldwide grapple with how to regulate these digital assets, stablecoin projects must navigate a complex web of financial regulations to achieve long-term viability. Goodwin emphasizes the need for a balanced regulatory approach that ensures consumer protection without stifling innovation.
**Potential for Market Manipulation**
Given their substantial market capitalization, stablecoins are susceptible to market manipulation. The limited oversight in the rapidly expanding cryptocurrency space amplifies this risk. Goodwin advocates for enhanced transparency and regulatory frameworks to mitigate these risks and ensure market integrity.
**Conclusion**
The relationship between Bitcoin and the dollar, especially through the medium of stablecoins, represents a delicate balance between the ideals of decentralization and the practicalities of financial stability. While stablecoins offer promising solutions for global financial transactions, they come with inherent risks that require careful consideration. Goodwin's insights underscore the importance of vigilance and a thoughtful approach to integrating these digital assets into the broader financial system. As the market continues to evolve, the role of stablecoins in shaping the future of finance remains a critical area for exploration and debate.
**FAQs**
**How do stablecoins fit into the Bitcoin-dollar dynamic?**
Stablecoins serve as a bridge between traditional finance and digital assets. Pegged to stable assets like the US dollar, they offer a less volatile alternative to cryptocurrencies and facilitate global commerce with near-instant transactions and lower fees.
**What are the risks associated with stablecoins?**
Risks include challenges in maintaining the peg to the underlying asset, regulatory uncertainties, and potential for market manipulation. These risks can threaten the stability and trust in stablecoins.
**What is Mark Goodwin's perspective on stablecoins?**
Mark Goodwin acknowledges the benefits of stablecoins but warns about the risks of centralization and manipulation. He emphasizes the need for balanced regulation and transparency to mitigate risks.
**Can stablecoins promote financial inclusion?**
Yes, stablecoins can provide financial inclusion by offering an accessible entry point for unbanked or underbanked individuals, allowing them to participate in the global economy.
**How does Bitcoin's growth affect the US dollar?**
Bitcoin's growth, particularly in regions with unstable currencies, can lead to increased adoption of dollar-based stablecoins, potentially bolstering the US dollar's global reach and stability.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ f683e870:557f5ef2
2025-02-07 14:33:31
After many months of ideation, research, and heads-down building, <span data-type="mention" data-id="726a1e261cc6474674e8285e3951b3bb139be9a773d1acf49dc868db861a1c11" data-label="nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9">@nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9</span> and myself are excited to announce our new project called Vertex.
**Vertex’s mission is to provide developers and builders with the most up-to-date and easy-to-use social graph tools**.
Our services will enable our future customers to improve the experience they provide by offering:
- Protection against **impersonation** and **DoS attacks**
- Personalized **discovery** and **recommendations**.
All in an open, transparent and interoperable way.
## Open and Interoperable
We have structured our services as [NIP-90 Data Vending Machines](https://github.com/nostr-protocol/nips/blob/master/90.md). We are currently using [these DVMs](https://vertexlab.io/docs/nips) and we are eager to hear what the community thinks and if anyone has suggestions for improvements.
Regardless of their specific structures, using DVMs means one very important thing: **no vendor lock-in**.
Anyone can start processing the same requests and compete with us to offer the most accurate results at the best price. This is very important for us because we are well aware that services like ours can potentially become a central point of failure. The ease with which we can be replaced by a competitor will keep us on our toes and will continue to motivate us to build better and better experiences for our customers, all while operating in an ethical and open manner.
Speaking of openness, we have released **all of our code under the [MIT license](https://spdx.org/licenses/MIT.html)**, which means that anyone can review our algorithms, and any company or power user can run their own copies of Vertex if they so wish.
We are confident in this decision because the value of Vertex is not in the software. It is in the team who designed and implemented it – and now continually improves, manages and runs it to provide the most accurate results with the lowest latency and highest uptime.
# What we offer
We currently support three DVMs, but we plan to increase our offering substantially this year.
1. `VerifyReputation`: give your users useful and personalized information to asses the reputation of an npub, minimizing the risk of impersonations.
2. `RecommendFollows`: give your users personalized recommendations about interesting npubs they might want who to follow.
3. `SortAuthors`: give your users the ability to sort replies, comments, zaps, search results or just about anything using authors’ reputations.
To learn more, watch this 3-minute walk-through video, and [visit our website](https://vertexlab.io/)
https://cdn.satellite.earth/6efabff7da55ce848074351b2d640ca3bde4515060d9aba002461a4a4ddad8d8.mp4
We are also considering offering a custom service to help builders clarify and implement their vision for Web of Trust in their own applications or projects. Please reach out if you are interested.
-

@ 5d4b6c8d:8a1c1ee3
2025-02-07 14:32:43
Ate a little later yesterday.
I took my daughter for a scooter ride on a trail near our house (I was walking) and she wanted to go farther than normal. Great for the steps challenge. Then, as soon as we turned around to go home, she decided she was too tired to scoot anymore. So, I got to do the return leg of the walk carrying both the kid and her scooter.
We were out about an hour longer than expected, hence the later meal.
## Score Card
Day 1: 14 hour fast (13 dry)
Day 2: 15 hour fast (14 dry)
Day 3: 17 hours (16 dry)
Day 4: 18 hours (17 dry)
Day 5: 18 hours (16 dry)
Day 6: 19 hours (16 dry)
Day 7: TBD (15 dry)
originally posted at https://stacker.news/items/878700
-

@ e7bc35f8:3ed2a7cf
2025-02-07 14:29:10
The strategic importance of Syria in shaping the balance of power in the Middle East is undeniable. Positioned at the crossroads of key regional players, Syria has long been a battleground for competing interests. From its alliances with Russia and Iran to its role in energy politics, the country has been targeted by external forces seeking to reshape the region to their advantage.
Syria has historically been an essential ally of Russia, providing the Russian navy access to the Mediterranean through the port of Latakia. At the same time, Iran has viewed Syria as a critical component of the so-called "Shiite Crescent," which provides Tehran with a vital connection to Hezbollah in Lebanon. Any disruption in Syria would have significant consequences for both Russian and Iranian strategic interests.
On August 31, 2011, [Amnesty International](https://www.amnesty.org/en/documents/MDE24/035/2011/en/) released a report accusing the Syrian government of being responsible for the deaths of 88 detainees from recent protests. However, like most media narratives surrounding the conflict,[ the allegations](https://www.youtube.com/watch?v=paR5_hu64H0) were based entirely on second-hand accounts and contextless video snippets provided by opposition forces actively attempting to overthrow the Assad government.
Despite the lack of concrete evidence, the establishment media eagerly propagated the story, fueling calls for "humanitarian intervention." This followed a familiar pattern: the invocation of the so-called "[Responsibility to Protect](https://www.globalresearch.ca/humanitarian-neo-colonialism-framing-libya-and-reframing-war/24617)" doctrine, a pretext used by global powers to justify military invasions and devastating bombing campaigns under the guise of protecting civilians.
As seen with Libya, Western leaders—including Obama, Sarkozy, Cameron, and Harper—[called for Assad's removal](https://youtu.be/qNtICdGDdwQ?si=PW--2jwV8Ed1GRYY), paving the way for potential NATO military intervention.
Long before the Arab Spring, Western governments had been laying the groundwork for regime change in Syria. In April 2011, [a U.S. State Department official](https://web.archive.org/web/20110411130724/https://www.rawstory.com/rs/2011/04/08/us-trains-activists-to-evade-security-forces/) admitted to running a two-year, $50 million program aimed at equipping protesters with new technologies to evade government detection. The same official revealed that activists from Syria and other Arab Spring countries had received training just before the uprisings began.
Earlier that year, [The Washington Post](https://www.washingtonpost.com/world/us-secretly-backed-syrian-opposition-groups-cables-released-by-wikileaks-show/2011/04/14/AF1p9hwD_story.html) published leaked U.S. diplomatic cables proving that Washington had been secretly funding Syrian opposition groups since at least 2005—well before the so-called "spontaneous" protests erupted.
This raises a critical question: why would an isolated government facing the threat of NATO intervention deliberately provoke the West by ordering snipers to fire on unarmed protesters at funerals? The mainstream media never questioned these dubious claims, which were sourced from anonymous, second-hand, and unverified reports.
n 2010, a group called [Gen Next](https://web.archive.org/web/20090213090409/https://www.america.gov/st/texttrans-english/2008/November/20081120122321eaifas0.3440363.html) (renamed now as [Alder](https://alder.co/about-alder/)) which has been involved with Alliance of Youth Movements in organizing youth-led destabilization campaigns in countries that are not friendly to American and Israeli interests had delivered a [training program](https://web.archive.org/web/20110929221929/https://www.gen-next.org/index.php/programs/gallery/-/album/5482723470431484737/) in which participants were taught how to handle high-powered sniper rifles and shoulder-mounted grenade launchers. Predictably, these reports were ignored in the West.
In August 2011, Israeli intelligence-linked outlet DEBKAfile [reported](https://web.archive.org/web/20110815020301/http://www.debka.com/article/21207/) that NATO and the Turkish military were drafting plans for a military campaign in Syria, which included arming opposition fighters with anti-tank and anti-air rockets, mortars, and heavy machine guns.
As the situation escalated, the establishment media once again cheered on war, pushing for intervention under the guise of protecting Syrian civilians. The cycle repeated itself in 2013, when Western governments accused Assad of using [chemical weapons](https://www.youtube.com/watch?v=b7-S1QAmWQQ), conveniently ignoring the overwhelming opposition to another military adventure.
By 2013, the American public had grown weary of endless wars. Despite relentless efforts by the White House to manufacture consent for a unilateral strike on Syria, there was widespread opposition—not just [in the U.S.](https://web.archive.org/web/20150808142142/https://www.washingtonpost.com/news/worldviews/wp/2013/08/26/new-poll-syria-intervention-even-less-popular-than-congress/), but [globally](https://www.youtube.com/watch?v=ZPGjbwqHRNs).
[John Kerry](https://web.archive.org/web/20130827020025/http://www.state.gov/secretary/remarks/2013/08/213503.htm) and [Barack Obama](https://www.youtube.com/watch?v=GxyBKKYPT4c) falsely claimed that Assad was responsible for a chemical weapons attack, using this as a pretext for military intervention. However, independent analysts and insiders exposed this as a false flag operation. Even in the UK, the propaganda push faltered when British Prime Minister [David Cameron](https://www.youtube.com/watch?v=QnKKPwEX_ac) lost a crucial [parliamentary vote](https://www.youtube.com/watch?v=obxu5W9Wru8) on military action in Syria.
As more evidence [surfaced](https://oilprice.com/Geopolitics/International/Did-the-White-House-Help-Plan-the-Syrian-Chemical-Attack.html), it became clear that the attack had been perpetrated by U.S.-backed terrorist groups—and that the U.S. government knew about it in advance. When even members of the British Parliament called out the deception, the war narrative collapsed, exposing the extent of the manufactured crisis.
The events in Syria were not isolated. Retired U.S. General Wesley Clark famously [revealed ](https://www.youtube.com/watch?v=SzX3DfZR_1c)that he had overheard a conversation at the Pentagon about a plan to invade seven countries—including Iraq, Libya, and Syria—long before the Arab Spring. While Clark’s timeline was not entirely accurate, the overarching strategy of destabilization was clear.
Key figures in the U.S. defense establishment at the time—including Paul Wolfowitz, Douglas Feith, and Richard Perle—had extensive [ties to Israel](https://web.archive.org/web/20130904083848/https://edition.cnn.com/2004/US/08/27/fbi.spy/), raising the question of whether a broader Zionist agenda was at play. [Documents ](https://web.archive.org/web/20130117222422/https://www.informationclearinghouse.info/pdf/The%20Zionist%20Plan%20for%20the%20Middle%20East.pdf)such as the infamous "Oded Yinon Plan" ([Greater Israel](https://www.globalresearch.ca/greater-israel-the-zionist-plan-for-the-middle-east/5324815)) outlined strategies for the dissolution of Syria and Iraq into ethnically and religiously divided territories, weakening any potential opposition to Israeli expansion.
The plan explicitly called for breaking Syria apart into sectarian statelets, mirroring the strategy used to divide Lebanon. The long-term goal was clear: to ensure that Israel’s adversaries remained fragmented and powerless.
<img src="https://blossom.primal.net/313eed84ca3bff42df56ba7fd73028266ad13ab6b20bba3126aa9d4238550476.png">
"Divide and conquer" is a strategy used for millennia. And this is what happens in Syria so many years as we were seeing the Sunni majority fighting the Alawite sect in Power under Assad and his father for decades. And it's interesting to see not only the native inhabitants Sunni of Syria but of course the foreign funded jihadists who were being shipped into the country and fueling all that conflict.
Part of what this was about, it's the destabilization of the [Shia land bridge](https://phibetaiota.net/2013/05/graphic-irans-shia-land-bridge-to-lebanon-mediterranean/) that connects Iran all the way to its Hezbollah forces in Lebanon, which runs through Syria. But if that can be destabilized and the Shia Alawite sect minority that rules Syria can be replaced with a Sunni majority ruling over the country then that would break up that link between Iran and Lebanon and further destabilize and isolate Iran.
<img src="https://blossom.primal.net/c3e9eedd9f2140bb63a552ff08eb8aab1ca10ae981da2a6841b496baec230937.jpg">
And this is something that can be seen in policy planning documents of various think tanks, as in the infamous "[Which path to Persia?](https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)" document from Brookings Institution.
As we start to expand the scope of this, then of course the thing that always in these Middle East conflicts comes into play is the natural resources.
Let's remember the prospect of the [Iraq, Iran, Syria pipeline](https://web.archive.org/web/20130727143145/https://www.tehrantimes.com/economy-and-business/758-iran-iraq-syria-sign-major-gas-pipeline-deal-).
Iran, Iraq, and Syria had signed a deal for the construction of the Middle East’s largest gas pipeline, which would transit Iranian gas from Iran’s South Pars gas field to Europe via Lebanon and the Mediterranean Sea.
What we were talking about back then was a pipeline providing traveling from Iran to Europe, through the Mediterranean.
[That move](https://www.youtube.com/watch?v=oNet5aLKaWg) was about to change the power balance of the region.
Such a [project ](https://web.archive.org/web/20130723151340/http://www.atimes.com/atimes/Middle_East/MID-04-230713.html)had the potential to shift the regional power balance dramatically. The mere prospect of it was enough to anger multiple stakeholders, from the U.S. and Israel to Turkey and the Gulf monarchies, all of whom had vested interests in preventing [Syria ](https://web.archive.org/web/20130831121243/http://atimes.com/atimes/Middle_East/MID-04-290813.html)from becoming an energy corridor.
The war in Syria was never about democracy, humanitarian concerns, or chemical weapons. It was about [power](https://web.archive.org/web/20130315191710/http://www.davemanuel.com/2010/06/14/us-military-spending-over-the-years/), [control](https://web.archive.org/web/20130318180618/http://www.usatoday.com/story/money/business/2013/03/10/10-companies-profiting-most-from-war/1970997/), and the relentless [pursuit ](https://web.archive.org/web/20130306140329/http://www.businessinsider.com/top-25-us-defense-companies-2012-2?op=1)of strategic dominance by Western and regional actors. The destabilization of Syria served multiple agendas—weakening Iran, severing Russia’s influence, ensuring Israel’s security, and controlling energy routes.
What we have witnessed over the past decade is not a civil war, but a foreign-orchestrated campaign to dismantle yet another independent state in the Middle East. Understanding these dynamics is essential in recognizing how mainstream narratives are crafted to justify war while hiding the real motivations behind the chaos.
<img src="https://blossom.primal.net/b1e0155c7bd73c05fe6323e9131d528842c6410f6520f0cc7885b6bdb5022084.jpg">
-

@ 044da344:073a8a0e
2025-02-07 14:06:14
Knapp ein Jahr hat es gedauert nach meinen letzten Gesprächen im Apolut-Studio, seinerzeit mit [Robert Cibis](https://apolut.net/im-gespraech-robert-cibis/) und [Yann Song King](https://apolut.net/im-gespraech-yann-song-king/) und am Rande von Berlin schon längst nicht mehr so komfortabel wie einst an der bayerisch-österreichischen Grenze oder dann im Süden Schwedens, wo eine komplette Mannschaft für perfekte Qualität gesorgt hat. Kamera, Ton, Regie, Maske und sogar eine Gästebetreuung. Lauter Profis, aber irgendwann offenbar nicht mehr zu bezahlen aus Spenden und wahrscheinlich auch überholt von der Konkurrenz im Internet, die mit einfachen Mitteln zwar weit unterhalb aller TV-Standards bleibt, aber aktuell ist, viel, viel günstiger und inhaltlich trotzdem sehr oft sehr spannend.
Egal. Auf Onlineinterviews hatte und habe ich keine Lust. Ich möchte den Menschen spüren, um den es geht. Vorher mit ihm reden und hinterher hoffentlich auch noch. Ich telefoniere nur im Notfall, weil dort vieles von dem verlorengeht, was den Austausch ausmacht. Zoom und Co. liefern zwar ein Bild, sind aber ansonsten nicht viel besser. Um das nur mit einer Zahl zu illustrieren: Bei einem Bildschirmgespräch dauert es zweieinhalb Sekunden, bis mein Gegenüber registriert, dass ich etwas sagen will. Live und in Farbe liegt die Reaktionszeit bei knapp der Hälfte.
Also habe ich aus der Not eine Tugend gemacht und bin selbst zum Produzenten geworden. Nicht ganz allein natürlich. Es gab Tipps von Dirk Wächter, der für viele der Bilder und Videos von Daniele Ganser steht und die Apolut-Gäste auf unnachahmliche Weise fotografiert hat, von Paul Brandenburg, der Technik borgte, und von Ingmar Beyer, den ich im großen Studio kennenlernen durfte und der nun auch bei meinen eigenen Versuchen dafür sorgt, dass der Ton stimmt. Vielen Dank dafür.

Ein Dank gilt auch Axel Klopprogge, den die Leser dieser Seite aus der Kolumne [Oben & Unten](https://www.freie-medienakademie.de/columns/2) kennen und der sich gewissermaßen als Versuchskaninchen zur Verfügung stellte. Der Anlass war denkbar günstig, als wir uns Ende Januar im Wohnzimmerstudio trafen: Gerade war seine Aufsatzsammlung „Links oder rechts oder was?“ erschienen – Stoff genug für 90 Minuten. Das Buch wird morgen in meiner [Kolumne](https://www.freie-medienakademie.de/columns/5) noch einmal gesondert gewürdigt.
Wer in unser [Gespräch](https://youtu.be/LUiUAhb2OXY) hineinschaut, wird schnell den Unterschied zu Apolut sehen: Es gibt Publikum. Gut zehn Menschen, die hoffentlich wiederkommen. Die nächsten Gäste: [Michael Beleites](https://www.freie-medienakademie.de/medien-plus/resonanz-aus-dem-osten), mit dem ich über den Darwinismus reden werde und über all das, was diese Ideologie aus uns gemacht hat, sowie Erich Hambach, der gerade auf den letzten Metern für sein Buch „Herren des Geldes“ ist.
[Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/)
[Unterstützen](https://www.freie-medienakademie.de/unterstuetzen)
-

@ 5d4b6c8d:8a1c1ee3
2025-02-07 14:02:05
Apparently, there's still another NFL game and, I suppose, we have to discuss it.
I'm much more excited to get into all the NBA trades that happened.
Who got better?
Who got worse?
Who did something really weird?
Of course, we'll talk about the contests going on in the territory.
MLB's ramping up. Can anyone challenge the Dodgers?
Ovi is trying to get back on pace to break NHL's career scoring record.
Any bets we're excited about
Plus, whatever the stackers want us to cover (time and memory permitting)
originally posted at https://stacker.news/items/878674
-

@ 54286b98:3debc100
2025-02-07 11:05:29
Reality is clear when we stand in the light.\
Falsehood appears when we tilt ourselves just enough to distort what’s real.
Every object—tree, person, or building—casts a shadow.\
But only the object is real. The shadow is an effect, not the truth.
Light reveals what’s true. Darkness hides it, warping our perspective.\
Our angle to the light source changes everything.
Christ is that source of light. He shines on everyone—no matter who we are.\
He doesn’t shift. Truth doesn’t shift.
But we do. Our minds waver like waves in the ocean, creating ever-changing shadows.\
Those shifting shadows can fool us.
Today, let’s choose to stand in his perfect light.\
Let’s notice where we need to grow and refuse to be deceived by distorted reflections.\
Let’s anchor ourselves to what’s real.
Until next time,\
**J**
> Do not be deceived, my beloved brothers. Every good gift and every perfect gift is from above, coming down from the Father of lights, with whom there is no variation or shadow due to change. Of his own will he brought us forth by the word of truth, that we should be a kind of firstfruits of his creatures. **James 1: 16-18**
*Original article published on: [https://www.javierfeliu.com/blog/shifting-shadows/](https://www.javierfeliu.com/blog/shifting-shadows/)\
Photo by [Yang Deng](https://unsplash.com/@palon?ref=javierfeliu.com) / [Unsplash](https://unsplash.com/?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit)*
-

@ a367f9eb:0633efea
2025-02-07 10:39:28
Issued on January 23, 2025, Staff Accounting Bulletin 122 rescinds SAB 121, [originally issued](https://www.sec.gov/oca/staff-accounting-bulletin-121) by Gensler in March 2022. The previous bulletin provided guidance for financial entities and custodians holding any “crypto-assets,” requiring them to account for all cryptocurrencies primarily as liabilities on their balance sheets, rather than assets.
The revoking of SAB 121 empowers entities to assess whether their crypto-assets are classified as liabilities only if they believe a loss is probable.
For bitcoin holders who hold their own keys and run their own node, this distinction and its subsequent repeal made little difference.
But for the budding world of Bitcoin banking and finance, as well as the booming industry of custodial wallets and brokerages, it’s a game changer.
Rather than having to match cryptocurrency deposits one-for-one with other liquid assets in the case of a contingency, the new accounting guidance frees up institutions to mark the true values of crypto-assets on their books.
Rather than having to buy up $1 million in treasuries or cash in order to hold $1 million in bitcoin or cover losses, firms will now be able to recognize that $1 million as a true asset.
It may not seem like a revolution, but it may be the beginning of our bull-inspired Bitcoin banking era.
After years of byzantine persecutions of cryptocurrency developers, entrepreneurs, and ever-increasing regulations on Bitcoin, this paradigm shift at the nation’s premier markets regulator means traditional finance can finally include bitcoin and its crypto-offspring in its suite of financial products – with some caveats.
Practically, this rather benign-sounding rule lowers the barrier of entry for entities that want to offer bitcoin services to their customers. Whether it’s a bank, an exchange, or a liquidity service provider custodying funds, there is now a more sustainable path for offering bitcoin alongside any other type of account.
While a general crypto market framework is still far from established in law, the current situation grants fairness between both fiat money and cryptocurrencies in the hands of entrepreneurs who want to custody funds for their clients.
Practically, however, what does this mean for the average bitcoiner?
## **What will my Bitcoin bank look like?**
If we take a peek over at Europe, there are already FinTech firms and banking institutions that offer some level of bitcoin services.
Xapo Bank, a private bank headquartered in Gibraltar, [offers](https://www.xapobank.com/en) each customer a traditional bank account and IBAN number alongside an instantaneous deposit and withdrawal address for Bitcoin and Bitcoin Lightning, Tether, and USDC.
Considering Xapo [built](https://decrypt.co/8449/coinbase-acquires-xapo-crypto-custodian) the doomsday-proof custody vaults for bitcoin storage later bought by Coinbase in 2019, now the preferred institutional custodian for billions in assets, it’s easy to see why so many customers trust their custody.
And for those willing to make the tradeoff for custody of their funds, they do offer something attractive.
In a single account, a customer could deposit cash, exchange it to bitcoin, and withdraw to self-custody. They could also deposit bitcoin using Lightning, and then instantly convert that amount to send a traditional bank transfer to pay their rent or utility bills for those who don’t yet accept bitcoin.
Again, this may not be the solution for those who [prefer self-custody](https://www.btcpolicy.org/articles/self-custody-is-nonnegotiable), but it does offer an integrated fiat on and off ramp that others may find convenient.
Similarly, the UK-based FinTech firm Revolut offers its customers the [ability](https://www.revolut.com/crypto/) to deposit and withdraw their bitcoin within the app, as well as exchange it for whichever fiat currency they wish. For those who currently hold bitcoin in an ETF or some other custodial product, a move to an app such as this may be even more attractive.
And we already know US companies are begging to expand their own services to their customers.
Companies such as **Strike** and **Fold** have already begun to increase their Bitcoin banking services for American customers, offering account and routing numbers for [bill pay](https://strike.me/blog/announcing-strike-bill-pay/), as well as the ability to instantly swap between currencies if they wish.
Fold has the [ambition](https://blog.foldapp.com/fold-to-go-public/) to become one of the nation’s largest publicly-traded bitcoin financial services, looking to soon add mortgage and lending offers, as well as insurance solutions.
These financial firms will offer bitcoin for purchase, lending, and exchange, but we can also assume their suite of products will become more diverse and attractive for a more diverse customer base.
## **What about sovereign money?**
Educating Americans about the benefits of Bitcoin is an important task. So is improving our policy landscape so that all bitcoiners may flourish.
But if the Bitcoin network truly represents a revolutionary way to have and use neutral money, should we even consider Bitcoin banks something we want? How can peer-to-peer money integrate with the centralized custodial banking system so many of us are trying to escape?
Even the most primitive advantages of Bitcoin are built on its ability to be owned in a sovereign way, at the total exclusion of everyone who doesn’t have the private key. For many of us, this is all we desire and want. And for the rights to hold and use Bitcoin how we wish to be universally recognized.
However, we cannot dictate how the rest of our Bitcoin peers will engage with the network, nor what they inscribe into blocks if they have the computing power to mine them. If Bitcoin entrepreneurs freely compete to offer unique products and services to custody, trade, or lend bitcoin, the rules should make that easier and more possible.
For those who will still need to interact with the fiat world, they should be able to benefit from Bitcoin-first products and services designed with them in mind. And regulations should empower them rather than restrict what they can do.
Not every Bitcoin banking product will be attractive to every bitcoiner and that’s okay. But the positive evolution of e-cash, custodial services, lending, and insurance is something that will help leverage the power of Bitcoin. And that should be championed.
*Yaël Ossowski is a fellow at the Bitcoin Policy Institute.*
This article was originally published at the [Bitcoin Policy Institute](https://www.btcpolicy.org/articles/has-the-era-of-bull-inspired-bitcoin-banking-already-begun).
-

@ d360efec:14907b5f
2025-02-07 09:42:54
ณ ดินแดนอันไกลโพ้น ปรากฏดันเจี้ยนลึกลับไร้ก้นบึ้ง นามว่า
"ตลาดการเก็งกำไร" ประตูทางเข้าเปล่งประกายล่อตาล่อใจ แต่มักถูกปกคลุมด้วยหมอกแห่งความไม่แน่นอน
คำจารึกโบราณ แกะสลักเหนือประตูทางเข้า เตือนสติผู้มาเยือน: "ผู้ใดเข้าล้วนมิอาจหวนคืน..." เฉกเช่นสำนวนโบราณที่กล่าวขาน "คนในมิอาจออก คนนอกมิต้องการย่างกราย"
ภาพที่ปรากฎตรงหน้า คือชายหนุ่มผู้หาญกล้า กำลังจะก้าวเข้าสู่ประตูดันเจี้ยน เหนือประตูมีป้ายขนาดมหึมาสลักคำว่า "Trading" สัญลักษณ์แห่งโลกการลงทุน การเก็งกำไร ไม่ว่าจะเป็น หุ้น, ฟอเร็กซ์, คริปโต ล้วนเป็นมอนสเตอร์ที่สถิตอยู่ในนี้
การจะพิชิตดันเจี้ยนนี้ได้นั้น หาใช่เรื่องง่าย ภารกิจแรกคือการกำจัดปีศาจ**"นักพนัน"** ที่สิงอยู่ในจิตใจของผู้กล้าทุกคน ปีศาจตนนี้ร้ายกาจยิ่งนัก แต่มิใช่ว่าไร้ทางปราบ หากท่านผู้กล้าปรารถนาจะหลุดพ้นจากวงจรอุบาทว์นี้ จงใช้วิธีเหล่านี้เถิด
1. เข้าใจว่าการพนันคือกับดัก
ปีศาจพนันมักล่อลวงด้วยภาพลวงตาแห่งชัยชนะเพียงชั่วครู่ แต่แท้จริงแล้ว มันถูกออกแบบมาเพื่อสูบเลือดสูบเนื้อจากเหล่าผู้กล้าในระยะยาว จงจำไว้ว่าการพนันมิใช่หนทางสู่ความร่ำรวย แต่เป็นเส้นทางสู่หุบเหวแห่งความสิ้นเนื้อประดาตัว
2. เปลี่ยนมุมมองเกี่ยวกับเหรียญทอง
จงมองเหรียญทองที่ท่านมีมิใช่แค่ตัวเลข แต่เป็น “เวลาและหยาดเหงื่อ” ที่ท่านได้แลกมา หากท่านสูญเสียมันไปเพราะการพนัน มันคือเวลาชีวิตที่หายไปตลอดกาล
3. ตัดขาดสิ่งเร้าที่กระตุ้นให้เล่น
• ลบแอปพนัน / ปิดกั้นเว็บไซต์มืด
• เลิกติดตามเพจหรือกลุ่มที่เกี่ยวข้อง
• เปลี่ยนสหายร่วมทางที่ชักชวนไปสู่ทางเสื่อม
4. ใช้กฎ 5 นาที
เมื่อใดที่ความกระหายอยากเล่นครอบงำ จงหยุดยั้งตัวเองไว้ 5 นาที แล้วตรองดูว่า
• คราก่อนท่านสูญเสียไปเท่าใด?
• หากเล่นแล้วเสียอีก จะรู้สึกเช่นไร?
• มีสิ่งใดที่ควรทำมากกว่านี้หรือไม่?
5. แสวงหาเส้นทางแห่งการลงทุนที่แท้จริง
แทนที่จะใช้เหรียญทองไปกับการพนัน จงเปลี่ยนเป็นการลงทุนที่มีโอกาสเติบโต เช่น เป็นนักรบแห่งคุณค่า (VI) , เข้าซื้อหุ้นแล้วเก็บมันไว้ในหีบสมบัติ 1 ปี , DCA BTC ดั่งสะสมขุมทรัพย์ทีละน้อย
6. ถามตัวเองว่า “อยากเป็นผู้ชนะ หรือเป็นเหยื่อ?”
ผู้ที่ร่ำรวยจากการพนันคือนักลงทุนผู้เปิดบ่อน มิใช่ผู้เล่น หากท่านปรารถนาจะเป็นผู้ชนะ จงเลือกเส้นทางที่ชาญฉลาดกว่า
7. ตั้งเป้าหมายที่ยิ่งใหญ่กว่า
จงตั้งเป้าหมายที่ชัดเจน เช่น สะสมเหรียญทองเพื่อซื้อปราสาท 5 ล้าน หรือหาเงิน 100 ล้าน แล้วจงมุ่งมั่นไปที่มัน การพนันจะทำให้เป้าหมายของท่านล่าช้าลง
📉 เหตุใดดันเจี้ยนแห่งการเทรดจึงเปรียบเสมือนเขาวงกต?
1️⃣ ก้าวเข้ามาง่าย ออกไปยาก
• การเข้าสู่ตลาดการเงินเป็นเรื่องง่ายดาย ใช้เพียงบัญชีเทรดและเงินทุนเพียงเล็กน้อย แต่เมื่อเข้ามาแล้ว จิตวิทยาแห่งการลงทุน และ ความผันผวนของตลาด จะทำให้ยากที่จะออกไป
2️⃣ เส้นทางที่ซับซ้อน
• นักรบมือใหม่มักคิดว่าการทำกำไรเป็นเรื่องง่าย แต่เมื่อเริ่มต้นจริงจะพบว่ามีปัจจัยมากมายที่ต้องเรียนรู้ ทั้งเทคนิค เวทมนตร์พื้นฐาน อารมณ์ตลาด และจิตวิทยาของตน
3️⃣ ความโลภและความหวังทำให้ติดอยู่ในตลาด
• หลายคนเริ่มต้นเทรดด้วยเป้าหมายหาเหรียญทอง แต่เมื่อขาดทุน กลับพยายามเอาคืน
• เมื่อกำไร ก็อยากได้มากขึ้น จนบางครั้งไม่รู้จักพอ
4️⃣ ไม่มีเส้นทางที่แน่นอน
• ในเขาวงกตนี้ ไม่มีทางเดินตรงไปสู่ความสำเร็จ ต้องลองผิดลองถูกหลายครา
• บางคนหลงทาง บางคนเจอทางตัน บางคนออกจากตลาดไปก่อนจะถึงทางออกที่แท้จริง
🎯 แล้วจะเอาตัวรอดจากวงกตนี้ได้อย่างไร?
✅ เข้าใจว่าเทรดไม่ใช่การพนัน
• การเทรดที่ดีต้องมีระบบ ไม่ใช่แค่เสี่ยงดวง
✅ ฝึกวินัยและจัดการอารมณ์
• สิ่งที่สังหารนักรบมิใช่ปีศาจในตลาด แต่เป็น “อารมณ์ของตนเอง”
✅ วางแผนก่อนเข้าเทรด และมีจุดตัดขาดทุนเสมอ
• อย่าเข้าเทรดโดยไร้แผน เพราะจะทำให้ท่านติดอยู่ในเขาวงกตตลอดกาล
✅ รู้ว่าเมื่อไหร่ควรหยุด
• บางครั้ง “การไม่เทรด” คือการตัดสินใจที่ดีที่สุด
🔮 บทสรุป
ดันเจี้ยนแห่งการเทรดเปรียบเสมือนสถานที่ลี้ลับที่ยังไม่มีผู้ใดสำรวจมาก่อน ผู้ใดที่ย่างกรายเข้ามาล้วนออกไปยาก เพราะมันเต็มไปด้วยความท้าทาย อารมณ์ และความโลภ แต่หากท่านเข้าใจเกมนี้ดีพอ ท่านจะสามารถหาทางออก และเปลี่ยนมันให้เป็นโอกาสแห่งความมั่งคั่งได้ จงจำไว้ว่า การจะออกจากดันเจี้ยนนี้ได้ ท่านต้องพิชิตบอสใหญ่ "การรู้เท่าทันอารมณ์ และมายเซ็ทที่เหมาะสมกับเทรนด์เดอร์" ให้จงได้!
หวังว่าพวกท่านจะไม่หลายเป็นซากศพเน่าๆ ในดันเจี้ยนแห่งนี้
ของให้โชคดีมีชัยในโลกเทรนด์เดอร์ YONOSUBA
-

@ 16d11430:61640947
2025-02-07 09:37:24
Introduction: The Lost Art of Flourishing
Eudaimonia, the Greek concept of human flourishing, represents a state of deep fulfillment derived from purpose, mastery, and moral virtue. Aristotle described it as the highest human good, achieved not through transient pleasures but through living in accordance with reason and excellence.
Yet, in our modern fiat-driven world, eudaimonia has largely perished. Instead of striving for excellence, people are entrapped by systems of debt, artificial scarcity, and wage slavery, where fulfillment is secondary to survival. The incentives of fiat capitalism—endless growth, consumerism, and bureaucratic control—have eroded the conditions necessary for human flourishing.
The purpose of this article is to explore the death of eudaimonia under fiat rule, supported by critical evidence, and to examine whether it can be resurrected—perhaps through alternative systems like Bitcoin and decentralized technologies.
---
The Fiat Machine and the Death of Eudaimonia
1. The Extraction of Meaning: Fiat as a Mechanism of Control
Fiat currency, backed by nothing but government decree, is a tool of centralized power. It is inflationary by design, ensuring that those who hold wealth in fiat lose purchasing power over time unless they participate in increasingly speculative financial schemes.
This constant need to hedge against inflation forces individuals into short-term thinking, undermining long-term endeavors that lead to mastery and fulfillment. Instead of creating art, philosophy, or science for its own sake, people are incentivized to chase money in the fastest, most extractive way possible.
Critical Evidence: Wages have stagnated relative to productivity since the abandonment of the gold standard in 1971, while financialization has exploded. According to the U.S. Bureau of Labor Statistics, median wages have barely kept up with inflation, whereas asset prices (stocks, real estate) have soared—favoring the wealthy who can invest while punishing wage earners.
2. The Death of Virtue: How Fiat Incentivizes Corruption
Aristotle tied eudaimonia to virtue—justice, courage, temperance, and wisdom. But fiat economies erode virtue by rewarding manipulation over integrity. In a world where money is easily printed, those closest to its issuance—the state, banks, and corporate elites—reap the rewards while the average person suffers debasement.
Fiat allows for moral hazard: banks are bailed out after reckless speculation, politicians spend without accountability, and corporations use inflation to justify price hikes. This destroys trust, a fundamental component of any thriving society.
Critical Evidence: The Cantillon Effect demonstrates that newly printed money benefits those who receive it first (banks, hedge funds) at the expense of those who receive it last (workers, pensioners). The 2008 financial crisis and subsequent bailouts exemplify how fiat rewards risk-taking elites while punishing ordinary citizens.
3. Bureaucratic Slavery: The War Against Self-Sufficiency
Fiat governance has transformed human beings from self-reliant individuals into bureaucratic dependents. Governments and corporations engineer complexity—compliance laws, credential requirements, and licensing systems—to keep individuals trapped in cycles of employment and taxation.
Eudaimonia thrives in societies where individuals have control over their work and creations, yet fiat systems strip away autonomy. Most people today work jobs they do not love, merely to service debts or meet rising costs.
Critical Evidence: A 2019 Gallup survey found that 85% of employees worldwide are disengaged from their jobs, meaning they find no real meaning in their work. Meanwhile, U.S. student loan debt has surpassed $1.7 trillion, forcing young people into decades of financial servitude before they can even attempt to pursue meaningful work.
---
Can Eudaimonia Be Resurrected?
1. Bitcoin and the Return of Hard Money
If fiat is the poison, Bitcoin might be the antidote. Unlike fiat, Bitcoin is scarce, decentralized, and operates on proof-of-work, rewarding merit rather than proximity to power.
A Bitcoin-based economy restores long-term thinking by allowing individuals to store value in a deflationary asset rather than being forced into high-risk speculation. When people do not need to chase inflation, they can focus on work that is intrinsically fulfilling rather than merely profitable.
Critical Evidence: Countries like El Salvador have adopted Bitcoin as legal tender to escape the inflationary policies of central banks, while Bitcoin’s fixed supply of 21 million ensures its purchasing power cannot be arbitrarily diluted.
2. Decentralized Systems and Self-Sovereignty
Beyond money, decentralization itself is a means of restoring eudaimonia. Peer-to-peer networks, open-source software, and blockchain verification (such as DamageBDD) enable individuals to engage in meaningful work without needing corporate or governmental permission.
Critical Evidence: The rise of remote work, creator economies, and DAOs (Decentralized Autonomous Organizations) shows that people can be productive outside traditional corporate structures when given the right tools.
3. The Renaissance of Craftsmanship and Knowledge
A return to hard money and decentralized economies will likely trigger a renaissance of craftsmanship. When individuals no longer need to rush for short-term profits, they can master trades, sciences, and arts in ways that have not been possible since the fiat era began.
We are already seeing glimpses of this in the resurgence of interest in sovereign computing, homesteading, and open-source development—a direct rebellion against the fiat model of centralization and planned obsolescence.
Critical Evidence: The growth of FOSS (Free and Open Source Software) and Bitcoin development reflects a shift toward work driven by passion and principle rather than extractive financial incentives.
---
Conclusion: The Path Forward
Eudaimonia is not dead, but it has been suffocated under the weight of fiat. By restoring individual sovereignty—through sound money, decentralized verification, and self-sufficiency—we can resurrect the human spirit. The transition will not be easy; it will require a rejection of the comfort fiat provides in exchange for the struggle that meaningful existence demands.
Yet, for those who seek mastery, virtue, and true fulfillment, there is no other choice. The fiat era has stripped humanity of its highest potential. It is time to reclaim it.
-

@ 6ad3e2a3:c90b7740
2025-02-07 08:17:18
When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account.
I’d tell them, “You decide, I’ve got my own problems.”
. . .
I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests.
. . .
Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere.
Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium.
That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper.
. . .
I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative.
The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media.
What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn.
There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.)
No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness.
We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot.
. . .
I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them.
I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!”
. . .
There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature.
. . .
No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach.
. . .
The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.”
For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems.
-

@ da0b9bc3:4e30a4a9
2025-02-07 07:26:07
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/878449
-

@ e3ba5e1a:5e433365
2025-02-07 05:25:58
How much does the government cost? Focusing just on the US, we could talk in terms of US dollars spent on the budget each year. But those numbers are so large we can’t really conceptualize them. A more relatable way of talking about this is what percentage of your income goes to the government. Or, even better, what percentage of your productive output is funneled to the government?
A first pass answer would be to look at income tax. If income tax is 30%, you work 30% of the year for the government and 70% for yourself. The problem is that income tax isn’t the only tax. There’s property tax, sales tax, payroll tax (i.e. another income tax), and who knows how many others. In other words, income tax only covers one (large) portion of our taxed income.
But it doesn’t stop there. We can’t forget inflation, the hidden, silent tax that not only erodes your earnings, but destroys your savings. It pulls off the amazing feat of not only taxing you today, but *historically* taxing you. It punishes you for being a prudent person and saving your money. (Which, side note, is why we love saving in Bitcoin.)
You might think we’re done. We’ve covered all the ways the government funds itself: direct taxation and inflation (via money printing). And that part is true. But we haven’t finished looking at the cost. You see, economically speaking, every time you put a tax into a system, you create inefficiencies. The market can no longer perform as well as it did previously. So we have yet another hidden cost: all productive capability in the economy gets worse, because the government needs to push its way in. An easy way to see this is all the tax games companies play to fall into different deductions and exemptions.
It doesn’t stop there either. Now that we’re talking about government-caused inefficiency, we can of course get to regulation. Regulation directly makes things more expensive (by forcing companies to spend time on compliance). It also indirectly makes things more expensive by presenting a barrier to entry for new providers, reducing competition and further hurting consumers.
Surely that’s the end, right? Nope. The government is sucking capital out of the private sector to put into public sector projects. That means the private sector has less capital for investment. People are incentivized not to save due to inflation, which encourages high-time-preference consumerism. This means we get less investment by companies for the future, which defeats the natural tendency of industry to become more efficient over time and pass on the savings to the consumer (via technology-driven deflation, for instance).
I knew all of that two weeks ago, and it hasn’t changed.
There’s one final piece to this puzzle. Many of us suspected it. With the news coming out about USAID and the programs it laundered money to, we’re starting to get even more concrete proof. The government steals our money, inflates it, takes all of that productive capacity we sweated and toiled for… and gives it to people who are actively trying to hurt us, yet again furthering the cost of government.
The cost of government isn’t one number. It’s not quantifiable. The cost of government is losing out on the world where everything becomes better, safer, cheaper, faster, healthier, and more enjoyable, and replacing it with a decaying, eroding society, where the most morally bankrupt people can fleece the rest of us for their livelihoods.
I’m praying that the exposure and toppling of USAID is a major accomplishment, but just one of many more to come. To quote The Two Towers, I hope it “will be like the falling of small stones that starts an avalanche.”
-

@ 000002de:c05780a7
2025-02-07 03:54:22
I've long been a fan of [Liberty Maniacs](https://libertymaniacs.com/), the site that makes funny political shirts for rebels & liberty lovers but their email today hit me as extra funny.
## Here's what they shared.
To say the last two weeks have been wild would be the understatement of the century.
🔥 DOGE is taking over the Treasury
🔥 USAID got caught laundering money (again)—basically funding everything to the left of Jimmy Carter’s ghost.
🔥 The new AG wants to drop the Epstein list like it’s hot.
🔥 The CIA just casually admitted the government created COVID.
🔥 And oh yeah, the Gulf of Mexico? Not anymore. Welcome to the Gulf of America!
At this point, reality is outpacing satire. But don’t worry, we’re working harder than a WEF escort during Davos week to get these news cycles onto shirts before the next scandal drops.
Not sure if we’ll ever catch up, but damn it, we’re gonna try.
---
I mean, that's pretty good stuff. If you are a marketer or copywriter this is how you do it.
originally posted at https://stacker.news/items/878326
-

@ 57d1a264:69f1fee1
2025-02-07 03:35:34
# The #LightningNetwork introduces the concept of #payment channels. How do these channels work, and how do they enable #bitcoin to #scale while maintaining #security?
originally posted at https://stacker.news/items/878316
-

@ 6bcc27d2:b67d296e
2025-02-07 03:06:38
This is the test of obsidian nostr writer
-

@ 57d1a264:69f1fee1
2025-02-07 02:59:45
# Bitcoin's blockchain is described as a 'public ledger.' How does this public nature contribute to bitcoin's security and trustlessness, and what role do nodes play in this system?
originally posted at https://stacker.news/items/878295
-

@ 5d4b6c8d:8a1c1ee3
2025-02-07 01:02:09
I don't think I did one of these summary posts last month.
Based on the [predictions](https://stacker.news/items/865017/r/Undisciplined) made by stackers here's what to expect at the end of the season.
**Champion**: Celtics
**MVP**: SGA
**All NBA 1st Team**
C Jokic
F Giannis
F Luka
G Ant
G SGA
These aren't bad, but whoever's sticking with those Ant and Luka picks seriously need to move off of them.
originally posted at https://stacker.news/items/878234
-

@ df173277:4ec96708
2025-02-07 00:41:34
## **Building Our Confidential Backend on Secure Enclaves**
With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with.
## **Auth and Databases Today**
As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that:
1. Need to register users (authentication).
2. Collect and process user data in business-specific ways, often on the backend.
Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes).
## **"Just Trust Us" Isn't Good Enough**
In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data.
Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility.
The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services.
## **Current Attempts at Securing Data**
Current User Experience of E2EE Apps
While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**:
1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side.
2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data.
3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility.
Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider.
## **Secure Enclaves**
### **The Hybrid Approach**
Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden.
App Service Running Inside Secure Enclave
### **High-Level Goal of Enclaves**
Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\
• **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\
• **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\
• **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in).
### **Different Secure Enclave Solutions**
[**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds.
[**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications.
[**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers.
[**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised.
[**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees.
### **Key Benefits**
One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data.
Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware.
Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks.
Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist.
It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing.
## **How We Use Secure Enclaves**
Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads.
### **Our Stack: AWS Nitro + Nvidia TEE**
• **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave.
• **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with.
### **End-to-End Encryption from Client to Enclave**
Client-side Enclave Attestation from Maple AI
Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud).
Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session.
From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request.
### **In-Enclave Operations**
At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form.
User Auth Methods running inside Enclave
A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information.
Main Enclave Operations in OpenSecret
The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user.
Realtime Encrypted Data Sync on Multiple Devices
Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext.
Confidential AI Workloads
Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation.
### **Reproducible Builds + Verification**
Client verifies enclave attestation document
We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs.
Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation.
## **Putting It All Together**
OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute
By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes.
This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats.
Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure.
OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use.
Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system.
The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad.
## **Things to Come**
We're excited to build on our enclaved approach. Here's what's on our roadmap:
• **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\
• **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\
• **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\
• **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\
• **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\
• **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\
• **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API.
## **Getting Started**
Ready to see enclaves in action? Here's how to dive in:\
1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\
2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\
3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\
4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further.
## **Conclusion**
By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use.
**We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself.
Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build!
*Thank you for reading, and welcome to the era of enclaved computing.*
-

@ 3b7fc823:e194354f
2025-02-07 00:39:21
# Details on how to use a Burner Phone
Mobile phones are needed for communications when out in the world but they are a nightmare for privacy and security as detailed in <MISSIVE /07> especially when it comes to surveillance risks. This is more of a hands on guide for how to mitigate those risks.
Burner phones as the name describes is a use and "burn" device either for a single operation or for a longer period if proper precautions are taken. In case you are unaware what I mean by a burner phone; cell phones can be purchased from big box stores, gas stations, and kiosks in cash without a contract. They are usually not very expense and enable you to buy prepaid cards to use for phone and internet service.
Getting a Burner Phone:
1. Best to use a store out of town but not mandatory.
2. Do not take any electronics with you, especially another phone.
3. Park down the street in another parking lot near the store and walk over. Be mindful of security cameras.
4. Cover any tattoos or identifying marks. Wear a hat and a medical mask. (Thank you covid)
5. Use cash only to buy.
6. Leave, do not shop or buy anything else.
Setting up Burner Phone:
1. Go somewhere with free public WIFI (Starbucks, Library, whatever)
2. Do not take any electronics with you, especially another phone.
3. Open package and follow directions to activate using the public WIFI access.
4. Choose a random area code during setup.
5. Create a new random gmail account. (Do not reuse accounts or names)
6. Download and install a VPN, Signal or SimpleX, Firefox Focus Browser, Tor if needed. Delete any other unnecessary apps.
7. Change phone settings (see list)
8. Turn off and remove battery if able to (becoming harder to find) or put into a Faraday Bag.
9. Destroy packaging that came with the phone.
Phone Settings:
1. Turn off hotspot and tethering. Enable Always on VPN and Block Connections without VPN. Set DNS to automatic.
2. Turn off bluetooth and WIFI.
3. Disable all notifications, notification history, notifications on lock screen, and emergency alerts.
4. Turn off all sounds and vibrations.
5. Turn off Find my Device. Setup screen lock with password. (No bio)
6. Toggle everything in privacy: no permissions, turn off microphone, turn off usage and diagnostics, etc
7. Set Use Location to off.
8. Under Languages & Input > Virtual Keyboard > Gboard > Advanced: disable usage statistics, personalizing, and improve voice and typing for everyone.
Using a Burner Phone:
1. Never sign into any account associated with your real identity.
2. Never use it to contact anyone associated with your real identity.
3. Time and distance between burner phone and any other cell phone you own.
i.e. A hour has passed and several miles from when you use and had on the other device.
4. When not in use the battery is removed or in a Faraday Bag.
5. Always use a VPN and always use private search and browser set to delete upon closing (Firefox Focus default).
6. Never actually call or text from the phone. You only want to use SimpleX or Signal for communications.
7. Do not save anything (files, pictures, history) on the phone, especially if incriminating.
8. Do not take it with you or use unless necessary.
9. When in doubt, burn it and get another one.
10. Never carry over names, accounts, whatever from old burner phone to new burner phone.
Burning a phone:
1. Factory reset the device.
2. Remove and destroy the SIM card.
3. Remove the battery because lithium batteries can explode. (may have to take it apart)
4. Smash internals.
5. Burn remains or drown in water. (Throw it in the river)
As long as you are careful to never identify yourself with the burner phone the only surveillance they can do is know that a phone was used or in a location but not who it belongs to. Be aware that if you are caught with it on your person any information or contacts on the phone may get compromised. Be mindful what you put on it.
-

@ b8851a06:9b120ba1
2025-02-06 22:46:54
When Your Bitcoin Stash Saves Your Earnings Report: The Accounting Shift Every Business Needs to Understand
**Tesla’s Q4 2024 earnings were a wreck—revenue down, costs up. But thanks to Bitcoin, the financial airbags deployed so effectively that no one’s talking about the crash.
**
Let’s Be Clear:
This isn’t about praising Tesla or Elon Musk (we’ll leave that to fan accounts). It’s about dissecting how a simple accounting rule change turned Bitcoin into a corporate financial shock absorber. The numbers reveal a playbook any business can replicate.
The “Aha” Moment: Accounting Rules Meet Digital Gold
(Why This Matters for Main Street Businesses)
The Problem Before 2025:
Companies had to report Bitcoin like a cursed family heirloom—you could only tell people when its value dropped, never when it gained. Imagine having to value your house at its lowest sale price in the neighborhood, even while yours was freshly renovated.
The 2025 Fix:
New rules let companies report Bitcoin like stocks—current value, gains and losses included. Suddenly, that digital gold in the treasury vault gets to shine.
Why This Changes Everything:
• For Tesla: Their $184M Bitcoin stash got revalued to $1.076B → $600M paper gain
• For Your Business: Bitcoin isn’t just an asset; it’s an earnings hedge
For Tesla, Bitcoin turned a bad quarter into a balanced one. For your business, it’s the difference between surviving a downturn and thriving through one.
Tesla’s Numbers Decoded: Bitcoin as Financial CPR
The Crash:
• Automotive revenue ↓ 8%
• Operating expenses ↑ 9%
• Missed revenue targets by $1.5B
The Airbag:
• Bitcoin gain: $600M
• EPS boost: 23% of total earnings
• Balance sheet upgrade: 484% Bitcoin value increase
The Takeaway:
Bitcoin didn’t fix Tesla’s car business—it kept their financials on life support while they work on repairs.
The Business Owner’s Guide to Bitcoin Airbags
(No Tech Jargon, Just Street Smarts)
1. Your New Financial Shock Absorber
• Old Way: Keep cash reserves losing 4-7% annually to inflation
• Bitcoin Way: Treasury that grows while parked
Real Math:
$10M Treasury Allocation
Year 1:
- Cash: $9.6M (after 4% inflation loss)
- Bitcoin: $15.4M (54% avg annual growth*)
2. The “Get Out of Jail Free” Card
When core business stumbles (like Tesla’s did):
• Bitcoin gains offset operational losses
• Buys time for turnaround strategies
3. Shareholder Whisperer
That Bitcoin gain isn’t just numbers—it’s storytelling fuel:
• “Our innovative treasury strategy delivered $600M in non-operational income”
• Beats explaining another quarter of declining sales
Building Your Bitcoin Safety Net
A Step-by-Step Playbook
Step 1: Treasury Triage
• Allocate 5-10% of cash reserves to Bitcoin
• Not speculation—modern balance sheet insurance
Step 2: Accounting Alignment
Work with your CFO to:
• Implement FASB-compliant reporting
• Train teams on quarterly revaluations
Step 3: Strategic Deployment
• Hold through volatility cycles
• Treat gains as bonus liquidity for:
• R&D funding
• Debt reduction
• Opportunistic acquisitions
Pro Tip: Start small—even a 1% Bitcoin allocation creates optionality without material risk.
Objection Busters: What Skeptics Miss
“But Bitcoin’s Too Volatile!”
Cash is guaranteed to lose value. Bitcoin at least gives you a fighting chance.
“We’re Not Tech Bros!”
• Bitcoin isn’t tech—it’s digital real estate
• The network effect is its tenant base
“Accounting’s Too Complex!”
• Modern tools automate revaluations
• Takes less time than managing foreign currency hedges
The Future of Corporate Treasuries
(Why Early Adopters Win)
2025’s Landscape:
• First movers already reaping benefits
• Late adopters face inflationary erosion
Your Move:
• Conduct treasury health check
• Model Bitcoin allocation scenarios
• Implement phased adoption
Final Word:
Tesla’s story isn’t about “crypto” moonshots—it’s about modern financial engineering. The new accounting rules have turned Bitcoin into a Swiss Army knife for corporate treasuries:
• Blade 1: Inflation hedge
• Blade 2: Earnings supplement
• Blade 3: Strategic reserve asset
The question isn’t whether Bitcoin belongs on corporate balance sheets—it’s how much value your business will leave on the table by ignoring this tool.
Your Competitors Won’t Wait—Why Should You?
→ [Free Treasury Health Assessment]( https://neowealth.xyz/code)
→ [Bitcoin Accounting Implementation Guide
]( https://neowealth.xyz/services)
Let [www.NeoWealth.xyz]( https://neowealth.xyz/) assist you– Modern Treasury Solutions for Pragmatic Leaders
#Nostr Footnotes:
Data Sources: #Tesla Q4 2024 Earnings Report, FASB Accounting Standards Update 2023-08, Bitcoin Historical Returns Analysis (2015-2024)
Past performance ≠ future results.
#Bitcoin not #Crypto
-

@ c2827524:5f45b2f7
2025-02-06 22:07:53
#### Social media e condivisioni anche da mobile?
#### Certamente sì, con i **client per i dispositivi Android**.

## Zapstore: client Nostr in un posto solo
Zapstore non c'era e lo hanno inventato.
È lo store dal quale si scaricano i client #Nostr per i dispositivi mobili.
Permissionless è la chiave: non serve attendere che gli store "ufficiali" mettano a disposizione l'ultima release e nemmeno che la comunità di f-droid compili i sorgenti.
Gli sviluppatori di client per Android aggiornano Zapstore e il gioco è fatto!
[Zapstore si scarica direttamente dal sito ufficiale](https://zapstore.dev/).
Al primo download è consigliato seguire le istruzioni per verificare lo sha256 del file apk, prima di installarlo sul proprio dispositivo.
## Universo N.O.S.T.R.
Una volta installato e aperto zapstore, **l'universo Nostr si apre in tutto il suo splendore**.
Tra i primi suggerimenti si dovrebbe trovare Amber ma, se non compare, basta cercare nella casella di ricerca.
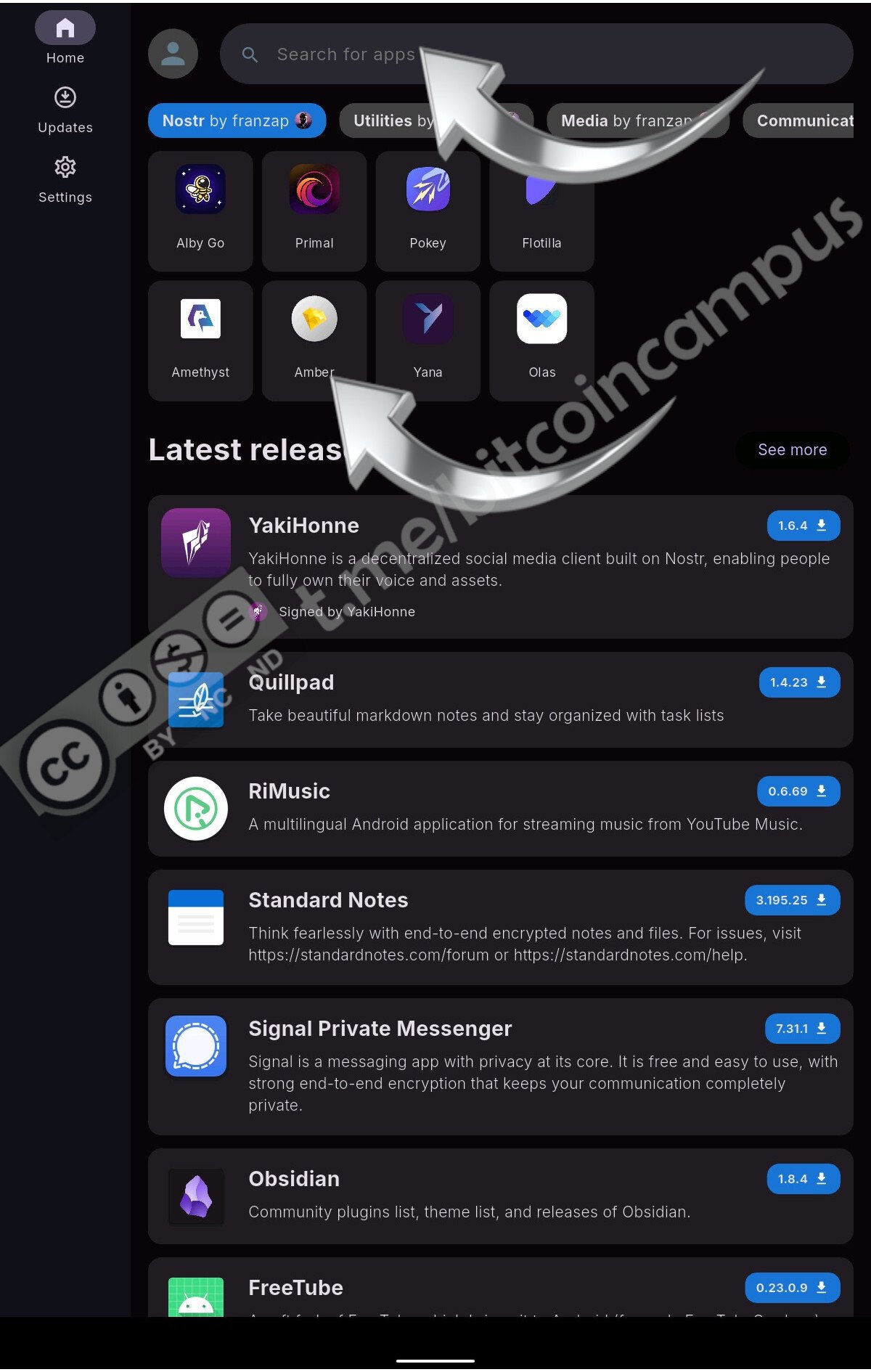
Dopodiché Amber viene presentato in primo piano
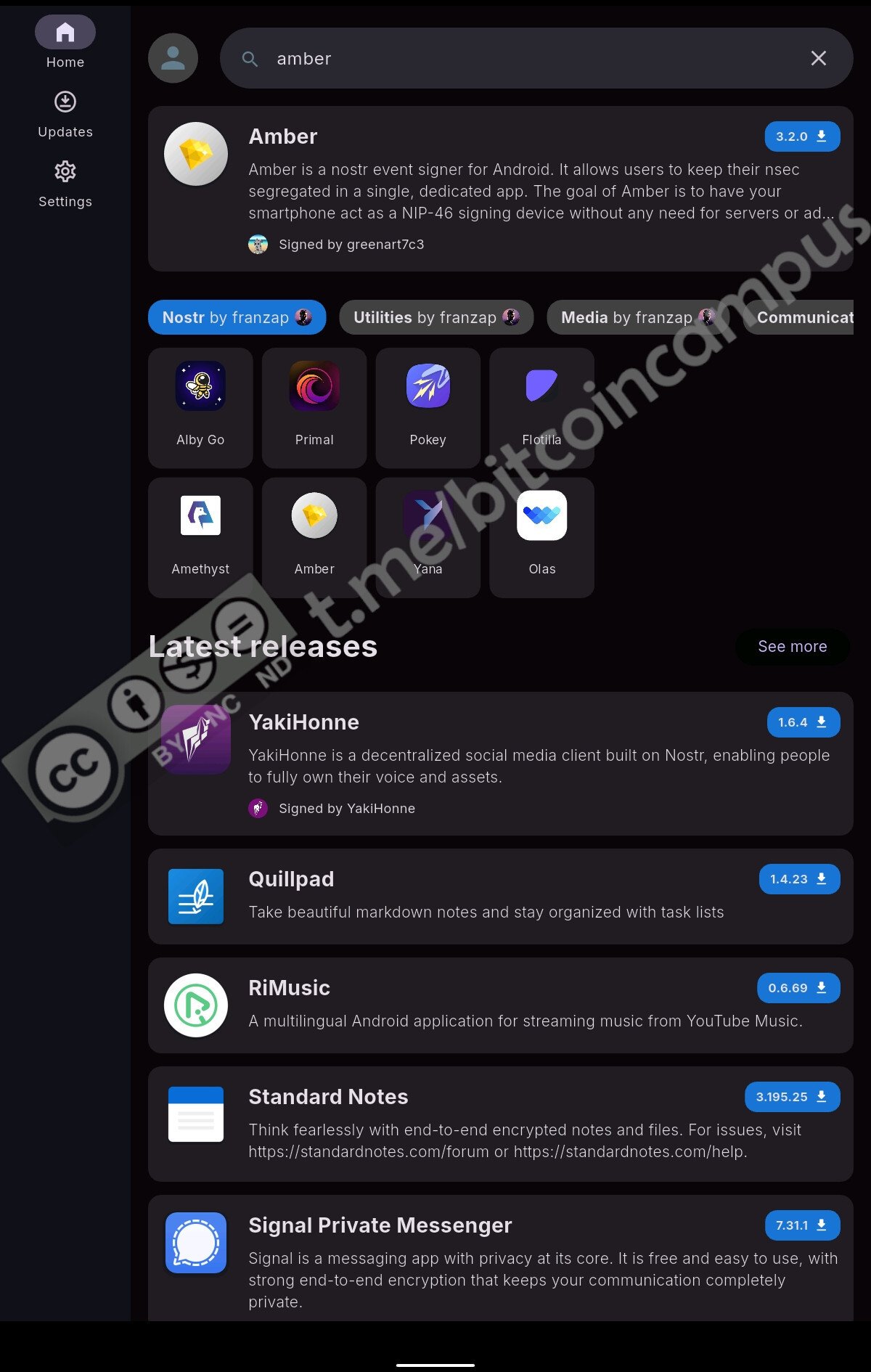
Basta cliccare sulla presentaione e compare in basso il tasto ***Install***
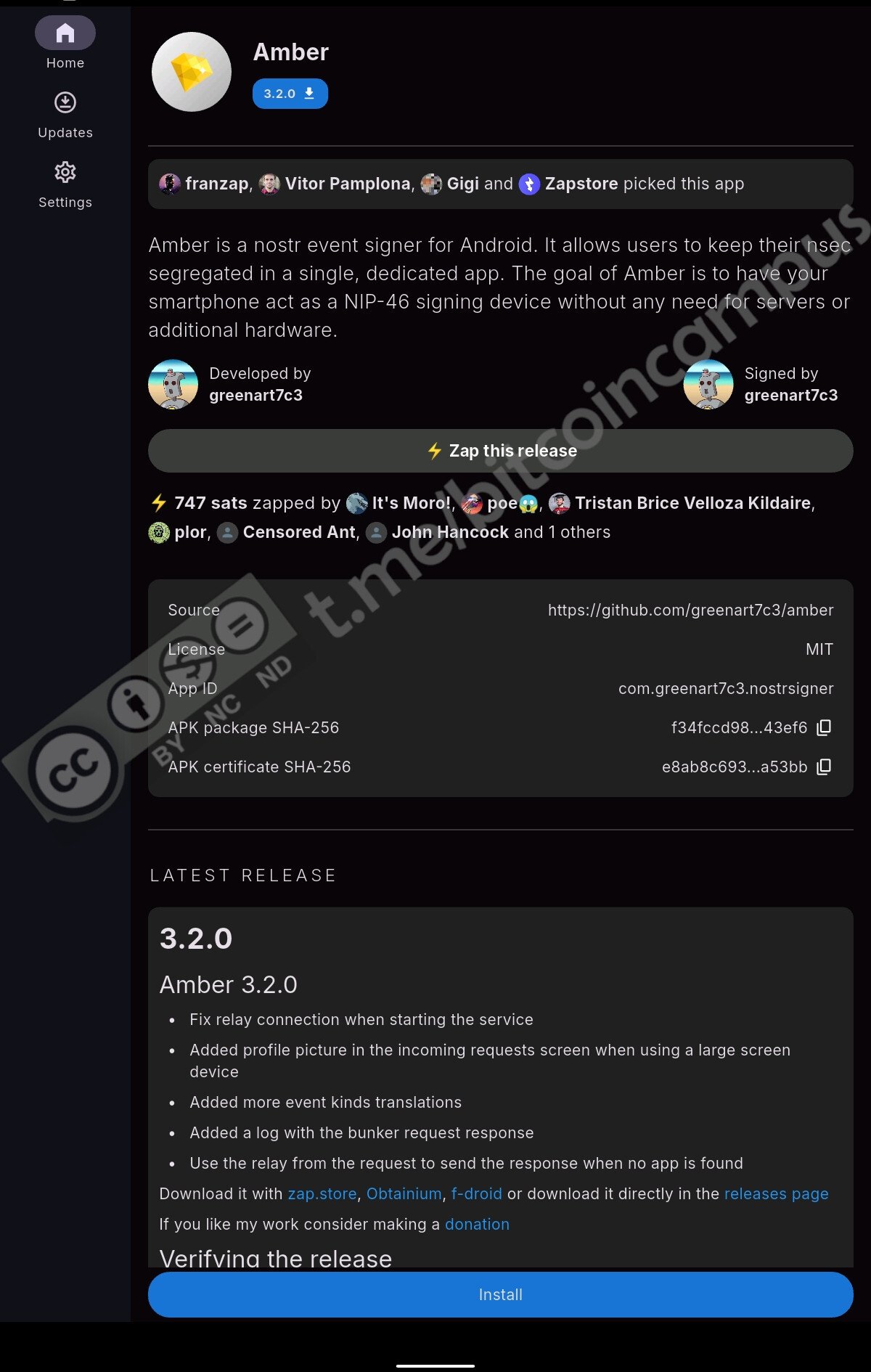
Zapstore esorta a fare le proprie ricerche per controllare la versione, sviluppatore e le caratteristiche dell'app che si va ad installare.
Quando si è verificato bene, cliccare su ***Trust and install app***

Lasciare installare e alla fine Android chiede l'autorizzazione all'installazione.
Come sempre, se è la prima volta che si usa uno store "non ufficiale", si dovrà anche autorizzare dalle impostazioni generali del dispositivo, cui si accede automaticamente
Non resta che cliccare in basso su ***Open*** per lanciare Amber
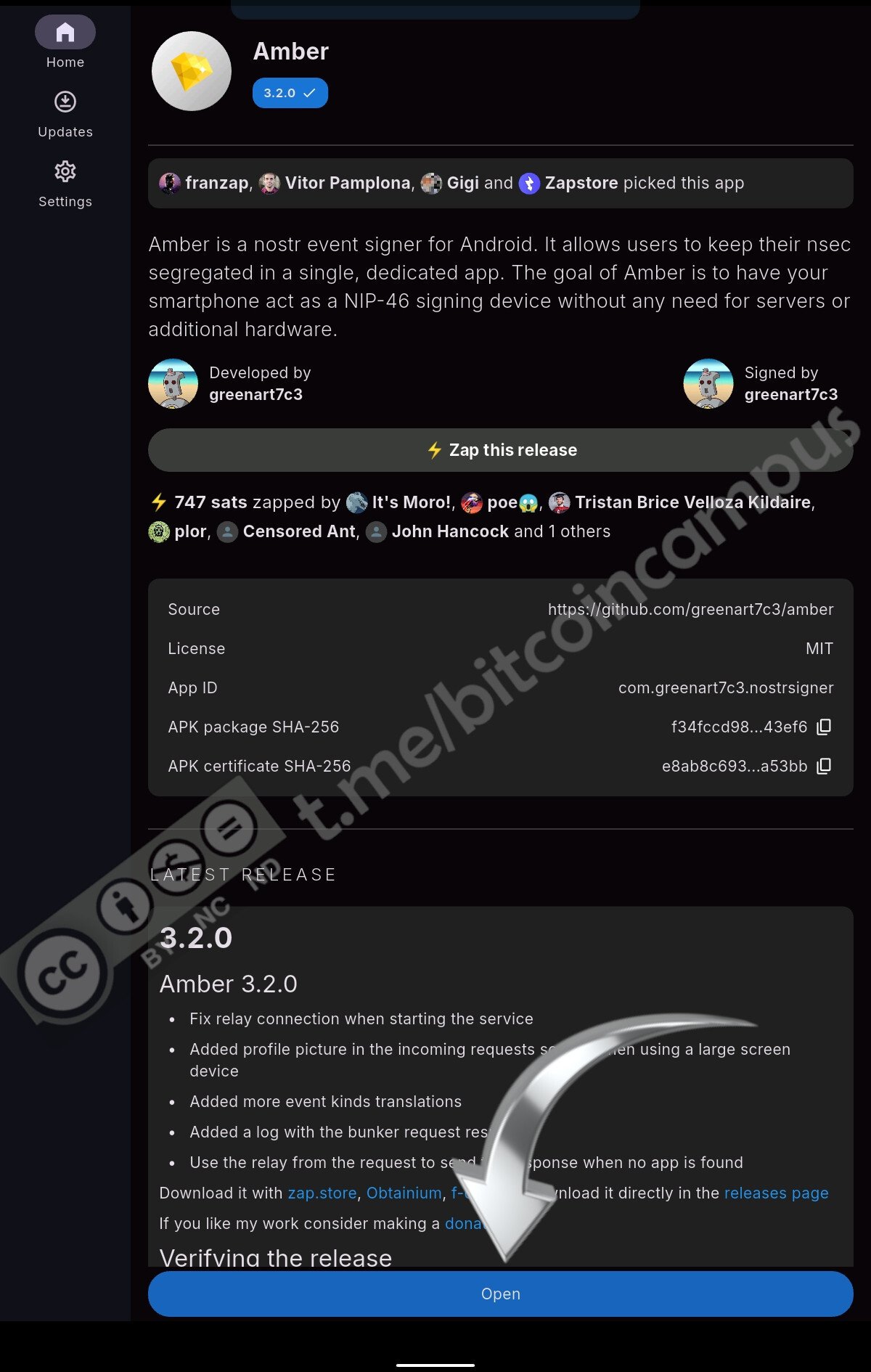
Amber è l'app che firmerà tutti gli eventi che si pubblicheranno su Nostr. Come app è anche in grado di generare una nuova coppia di chiavi.
Presupponendo di aver già un profilo attivo ed impostato, magari [creato seguendo il tutorial precedente](https://laura.npub.pro/post/z3dxkkdooerzzyv_oqy6b/), qui si deve cliccare su ***Use your private key***
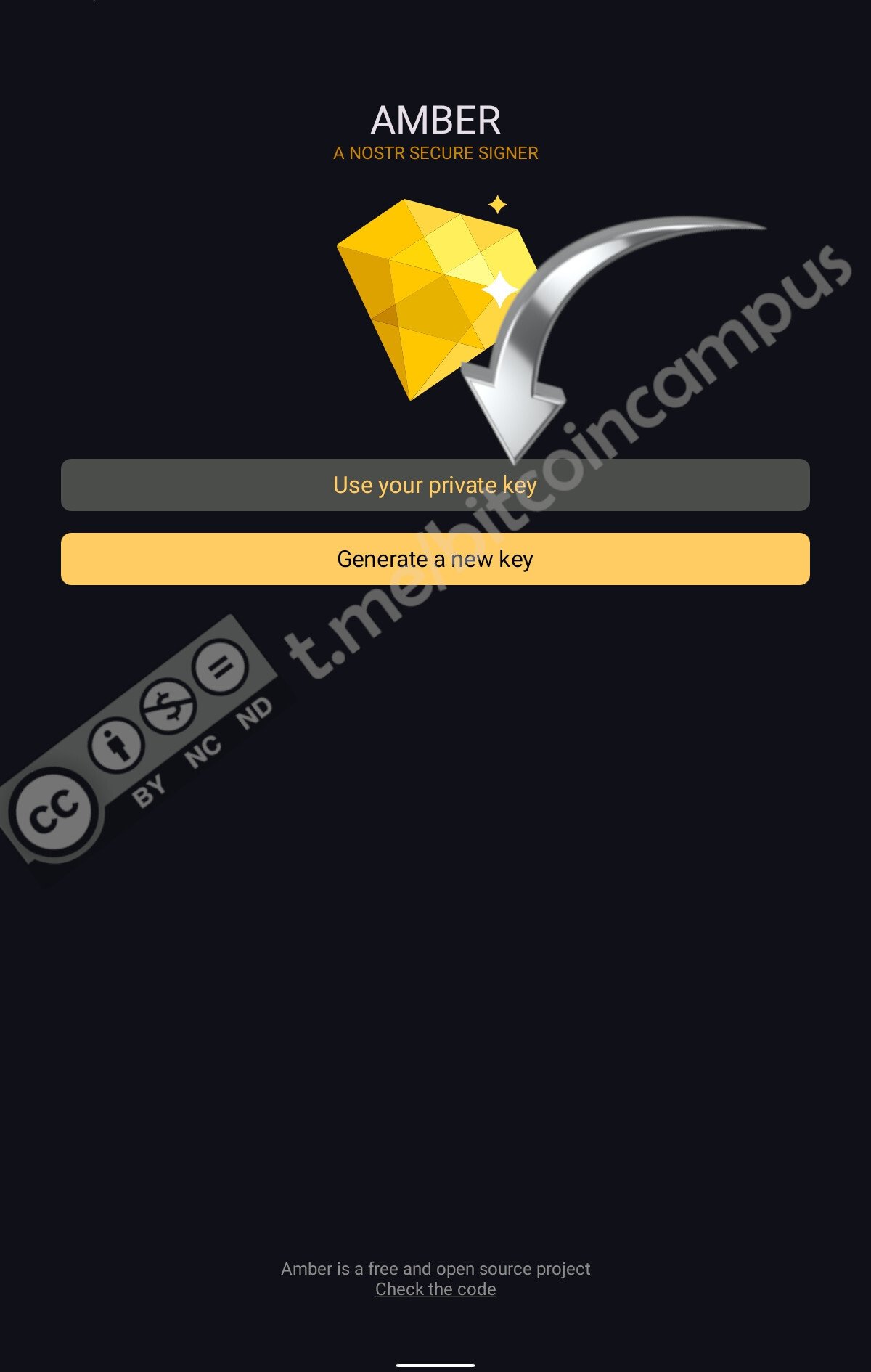
La chiave privata può essere copiata/incollata o scansionata agendo sull'iconcina stilizzata del QR code. Una volta importata si deve proseguire cliccando ***Next***
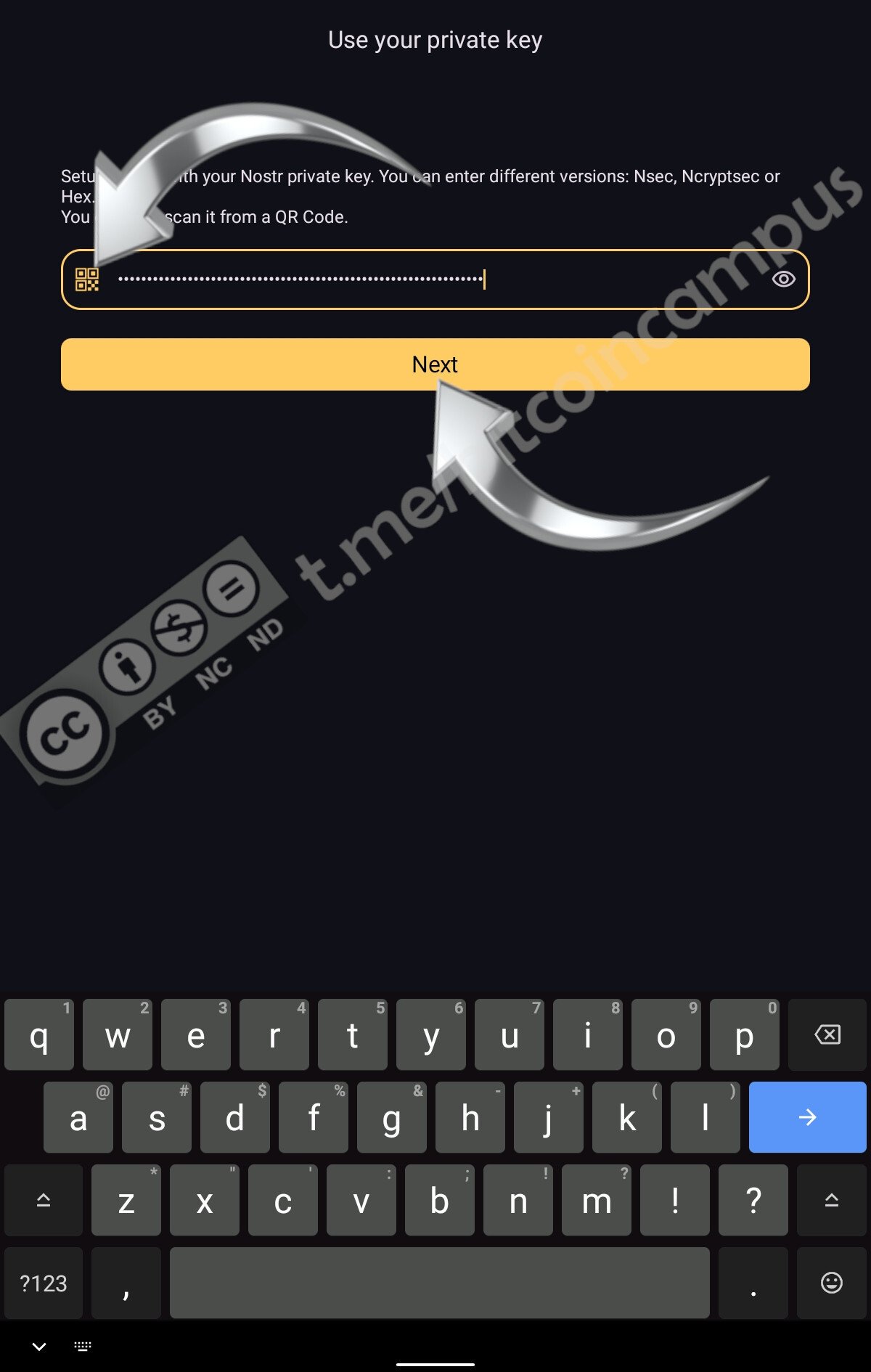
Impostare come far firmare Amber, approvando la firma per eventi semplici o farlo manualmente ogni singola volta, poi confermare cliccando ***Finish***
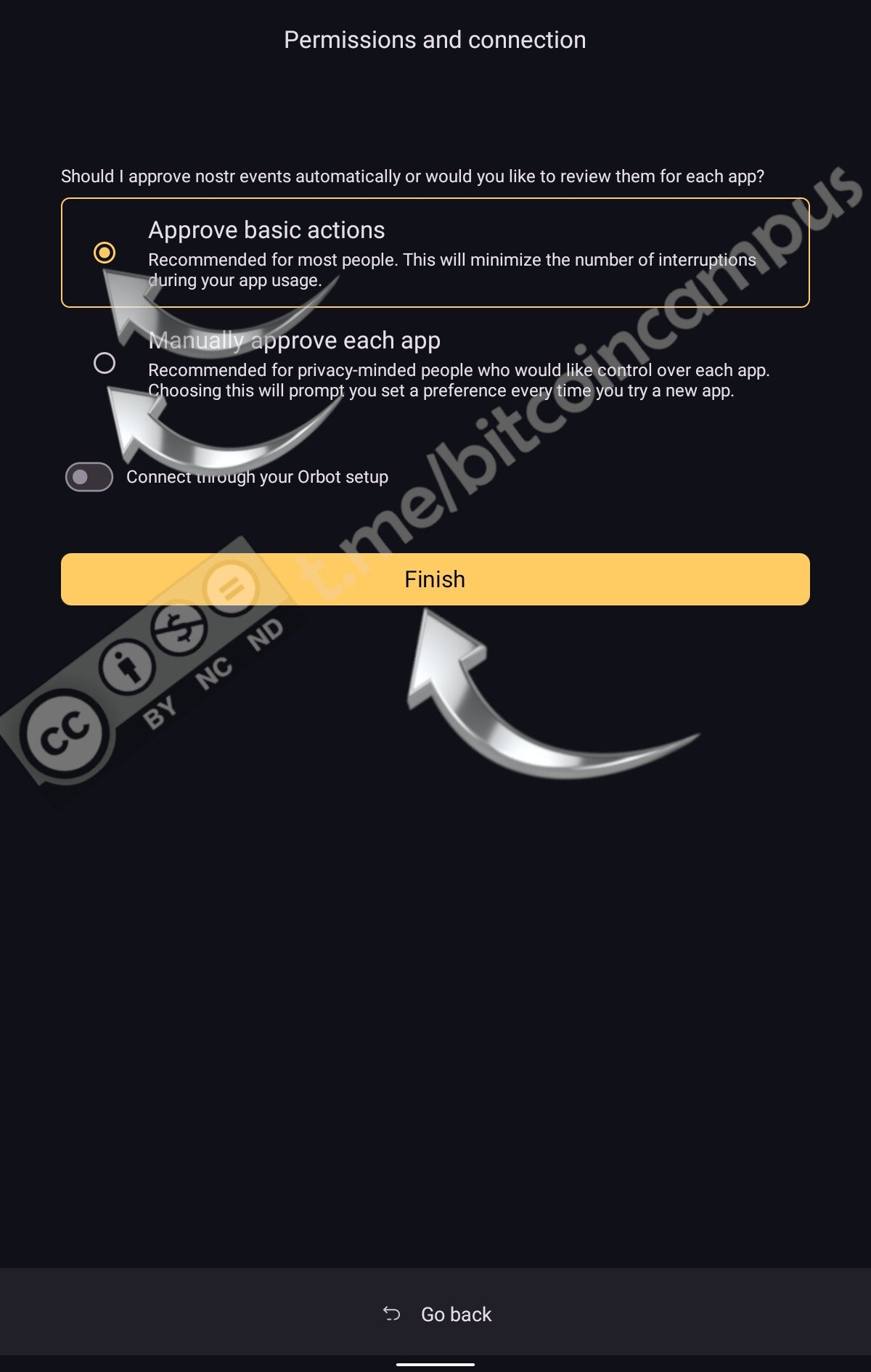
Amber è pronto a firmare eventi, note and other stuff che ogni utente vorrà pubblicare.
Manca solo il/i client che si desidera utilizzare.
Aggiungerne uno cliccando sul "+" in basso a destra

## Amethyst
Amethyst è il client per Android forse più completo, aggiornato ed efficiente del mondo Android. Se c'è un client ottimo per iniziare, [è proprio Amethyst](https://github.com/vitorpamplona/amethyst).
Se non compare tra i suggerimenti della home di Amber, cercarlo e scegliere ***Install***
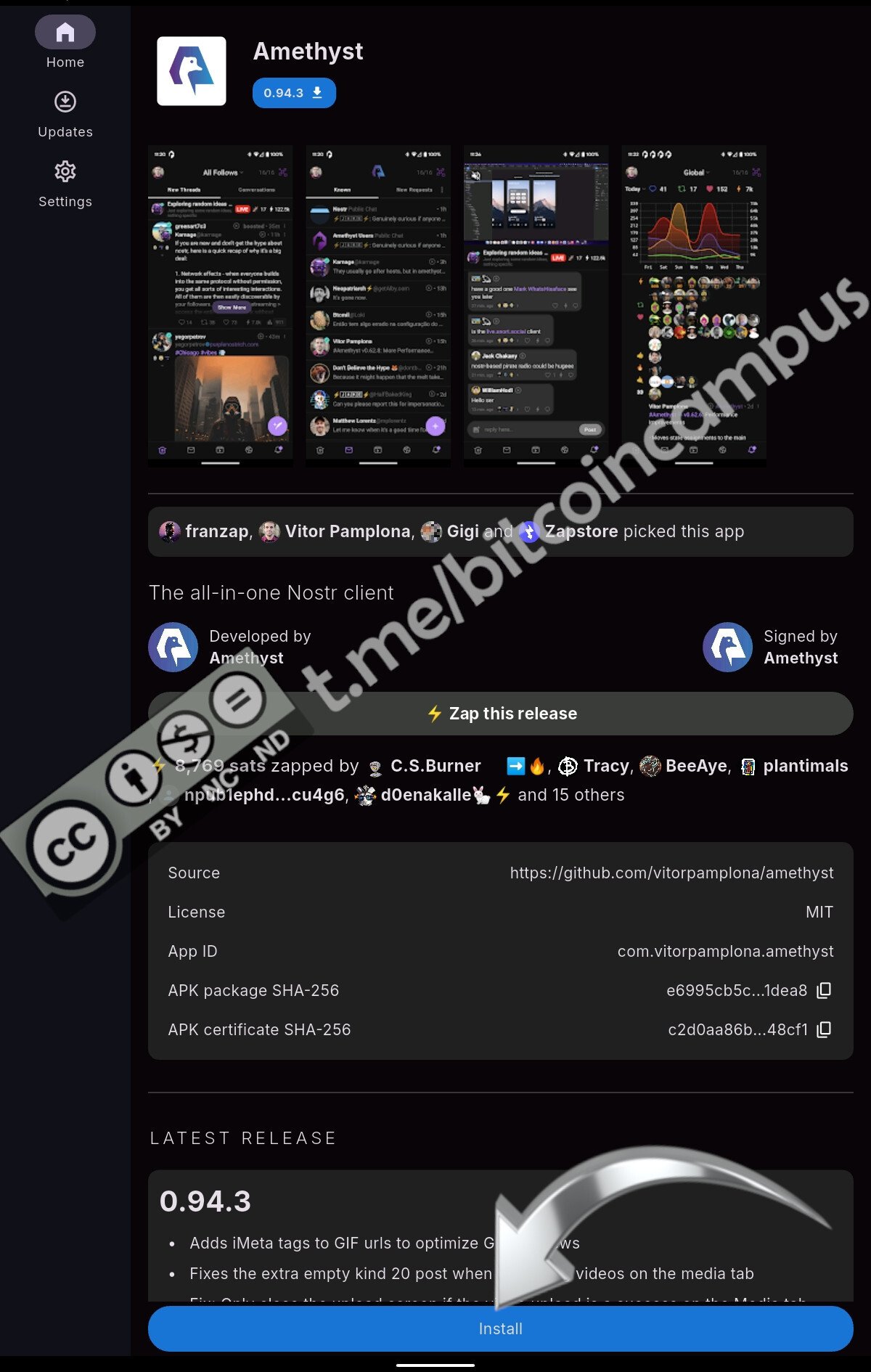
Tra il download e l'apertura di Amethyst, c'è il passaggio della verifica dell'integrità del file apk, che Amber svolge al posto dell'utente
Quando la verifica è terminata, basta aprire Amethyst cliccando in basso su ***Open***
Accettare i ToS per evienziare i pulsanti di login

e scegliere ***Login with Amber***
Scegliere quali privilegi consentire ad Amber, che vengono mostrati in una lista e terminare cliccando su ***Grant Permissions***
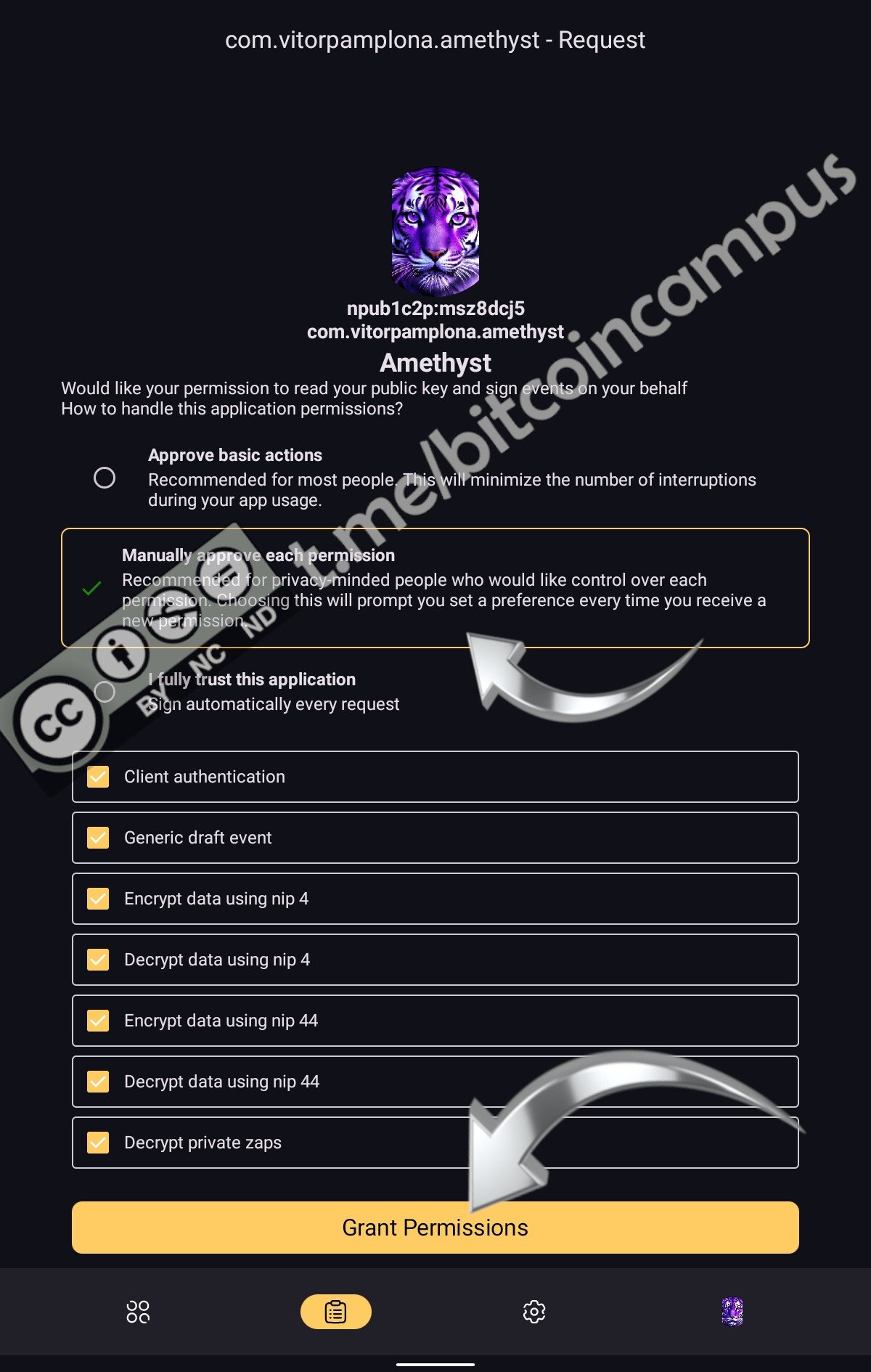
Da questo momento in poi sarà Amber a firmare le note con la chiave privata dell'utente.
Alle nostriche resta solo il compito di dare spazio alla creatività e usare Amethyst per condividere post.

La pubblicazione avviene cliccando ***Post*** su Amethyst e, a seconda dei permessi concessi ad Amber, la nota verrà propagata.
Ad esempio: se si è scelto di approvare manualmente ogni post, Amber mostra il menu di conferma.
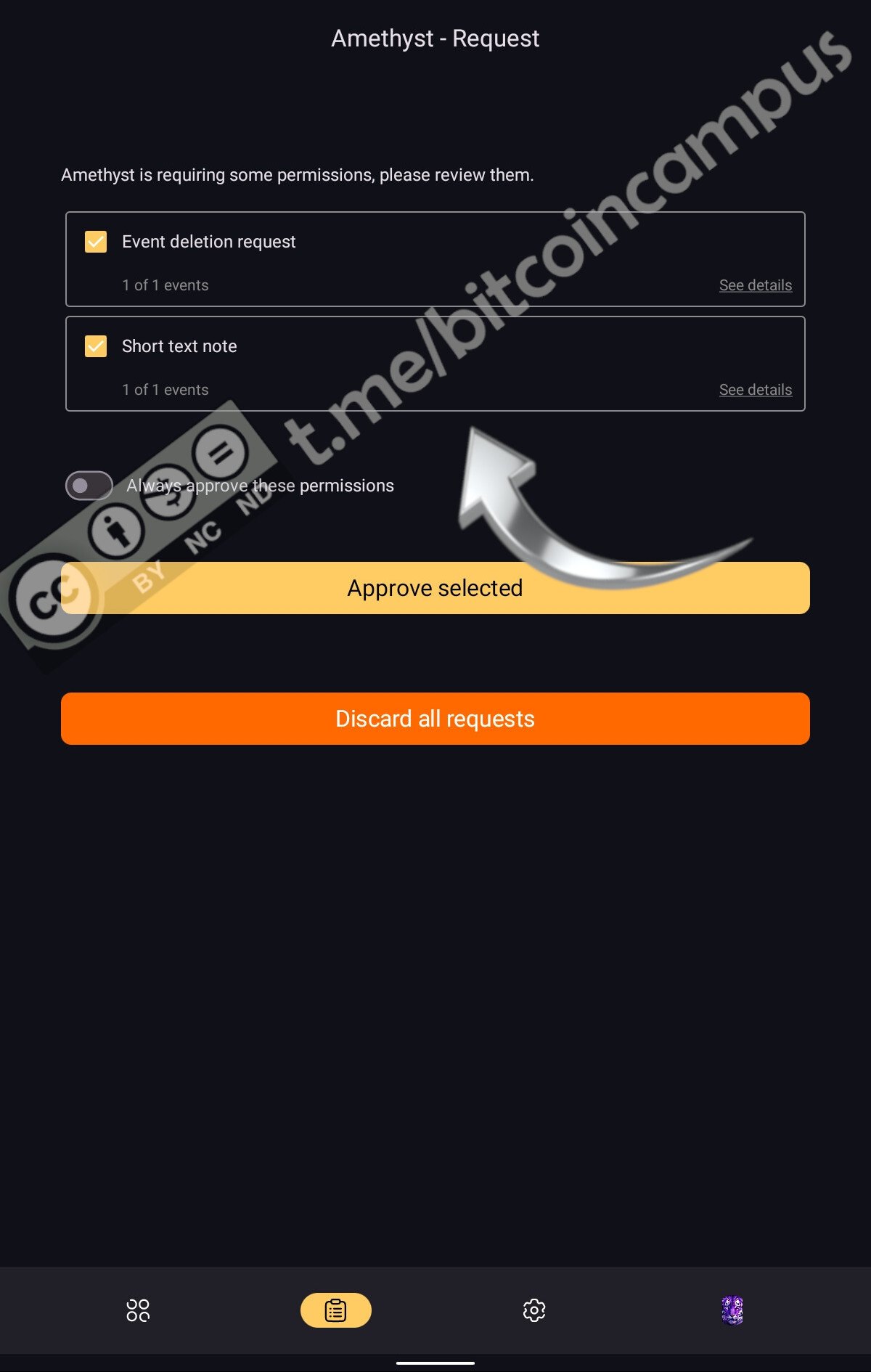
Approvare manualmente ogni post è, all'inizio, un bel modo di utilizzare Amber, perché facilita la conoscenza della natura degli eventi che si stanno postando.
---
## I settings di Amber
Uno sguardo ai menu e alle impostazioni di Amber è doveroso.
Non ci sono accorgimenti particolari, ma è sempre un'ottima abitudine conoscere ed esplorare i menu delle app che si vanno ad utilizzare.
Dalla home di Amber, sono visibili in basso e si trovano - in ordine -
* ***Incoming Request***, dove appariranno le richieste di approvazione per firmare le note
* ***Settings***, per tutte le impostazioni generali di sicurezza, uso con Orbot, rivedere le scelte di firma ***Sign Policy*** ecc
approvare il controllo biometrico per la firma, se impostato sul dispositivo
e dare un'occhiata e un test ai relay che si son scelti

#### Non manca nient'altro. Solo postare ed eslorare i client più belli e aggiornarli da Zapstore
---
## Per info
* https://nostree.me/laura@cosanostr.com
* https://laura.npub.pro/
* https://t.me/bitcoincampus
* https://planb.network
-

@ 000002de:c05780a7
2025-02-06 18:47:45
I stand by my non-stance that the cowboy credit thing is OK. Using services like MiniBits and CoinOSis OK and using your own node is OK. There are tradeoffs of each. I've been using these eCash hosted / custodial services for over a month now. They work fine most of the time. NWC works most of the time but there are growing pains with the volume of small transactions hitting these services.
I'm gonna try turning it all off for a week starting today. Just use CCs. I mean its kinda like old school SN right?
Next I'd like to really make an effort to go the other way and use a self sovereign stack. I've tried that before with SN and it didn't work for me. Pretty sure I was just too busy and didn't have time to work out the kinks in my setup.
I think cowboy credits are the easiest option by far. No issues really except you aren't dealing with sats. It doesn't feel the same and it isn't the same. I'm wondering how it will hit me as I use them though.
originally posted at https://stacker.news/items/877936
-

@ d57360cb:4fe7d935
2025-02-06 18:31:30
Mindfulness often has the misconception that by practicing you can stop your mind from thinking and obtain an empty mind.
While one can definitely achieve moments of emptiness in thinking, this view that emptiness is the goal can be the very obstacle in your way leading to frustration with the practice.
If we adjust our perspective and see mindfulness as learning to accept the situations we find ourselves in and adjust to them rather than fighting them, we achieve a kind of grace under pressure.
The thoughts are part of the practice, just like cars on the road are part of driving, or the danger of a punch is always a threat to a boxer.
The difference between the novice and the seasoned is one has accepted and acclimated to the realities of the situation instead of fighting them, in this one finds freedom.
-

@ 89ccea93:df4e00b7
2025-02-06 16:28:15
**[Original Post](https://expatriotic.me/robosats/)**
## Why use RoboSats
### 1. Lightning Fast
* LN Hodl invoices serve as bonds & escrows for high assurance and speed.
### 2. Absolutely Private
* Best privacy practices by default.
* Simple and KYC-free.
* You will generate a random Robot avatar for a single use.
* The exchange is Tor-only.
### 3. Open Source
* RoboSats is fully open source. - [Github](https://github.com/RoboSats/robosats)
*I'm going to use the Tor Browser on desktop for this guide. But the android app is essentially identical. So the flow should be the same.*
```I prefer Bisq for buying as I can get really good deals. Plus the use of a larger deposit helps to secure things. However, Bisq is onchain only, so in a higher fee environment, it could get pricey. RoboSats however is using lightning.```
*BTW, for Bisq if the miner fees get higher, check out a [Monero based fork](https://github.com/retoaccess1/haveno-reto) where you can pay the deposit in Monero, as this will help with miner fees. Plus generally speaking, and especially in a high fee environment, Monero fees should be lower.*
## Step 1 - Download or use in Tor browser
1. Use <http://robodexarjwtfryec556cjdz3dfa7u47saek6lkftnkgshvgg2kcumqd.onion/> for use in Tor Browser
2. Download APK from Github and check signature to make sure it's signed with the Reckless-Satoshi [PGP key](https://keys.openpgp.org/vks/v1/by-fingerprint/B4AB5F19113D4125DDF217739C4585B561315571) (if this is something you know how to do. Explaining it is outside the purview of this article) - <https://github.com/RoboSats/robosats/releases/>
## Step 2 - Roll a Robot
*Image 1 - GARAGE tab*

1. For regular mode click "*🚀START*". A robot will be given to you. You'll be prompted to save a unique string that will help you log back in to that specific robot. Helpful if you initiate a trade. If you wanted to make an order directly, I recommend you skip step one and go to directly to step two.
*Image 2 - Start menu*

*Image 3 - After rolling a robot*

*Image 4 - Prompted to browse or make an order.*

2. If you want to make create an order, skip down to "*➡️ FAST GENERATE ORDER*"
*Image 2 - Start menu*

*Image 5 - FAST GENERATE ORDER*

## Step 3 - Go to the OFFERS tab
*Image 6 - OFFERS tab*

1. Select BUY/SELL depending on your need.
2. Select currency. Just look for the "**🌎 ANY**" and pick your currency from the drop down menu.
3. Filter payment method by clicking "**METHOD**" and selecting one of the options, or simply start typing and watch your option pop up.
4. Click "*Premium*" until it sorts from the lowest premium to the highest.
## Step 4 - Select/Create an offer
*Image 7 - taking an offer*

1. Take the order (or make one) and if the person had a range, put in how much bitcoin you wish to buy.
2. Click take order
## Step 5 - Receiving the bitcoin
1. Pay a small deposit to lock in the order
*Image 8 - taking order*

2. Paste in a LN invoice for the amount of LN sats to be received. (see Addendum #2)
3. Pay using fiat method preselected
4. Bitcoin is paid out of escrow and into the LN invoice that you gave.
## Addendum
1. Use this for more help - <https://learn.robosats.com/>
2. If you don't wish to receive in lighting, then in Step 5, instead of your own LN invoice, use one from https://boltz.exchange/swap. You can do this natively in RoboSats, but they charge an arm and a leg.
originally posted at https://stacker.news/items/877796
-

@ 5d4b6c8d:8a1c1ee3
2025-02-06 16:14:00
I would have done about an hour better today, but my hatred of food waste got the best of me. My daughter wanted the crusts cut off of her toast and, since no one else was going to eat them, I gobbled them up.
That was the last thing I ate, yesterday, though, and I didn't eat or drink anything for the next 16 hours. Still pretty good.
## Score Card
Day 1: 14 hour fast (13 dry)
Day 2: 15 hour fast (14 dry)
Day 3: 17 hours (16 dry)
Day 4: 18 hours (17 dry)
Day 5: 18 hours (16 dry)
Day 6: TBD (16 dry)
originally posted at https://stacker.news/items/877787
-

@ fdc85145:e465bf18
2025-02-06 16:13:36
Preserve your vehicle's paint with our high-quality [paint protection film](https://www.autoandmarinedetailing.co.nz/paint-protection-film-auckland) at Auto and Marine Detailing. This transparent film acts as a shield against scratches, rock chips, and harmful UV rays. Custom-fit to your car, it ensures complete coverage without altering its appearance. Our team provides expert installation, so your vehicle remains in pristine condition, retaining its value for years to come.
-

@ f6b1e489:f1c91bc4
2025-02-06 15:59:52
# Psychedelics and Bitcoin
Almost everyone who gets into bitcoin at some point realizes how it destroys your mental models of the world. You start questioning the _status quo_ and experience a serious rewiring of the brain. This can be confusing and frightening at first. But in hindsight it is mostly viewed as positive and people end up being a different, better person. Less focussed on hedonistic consumption, more focussed on long term health and wealth.
# Rewiring the Brain
I realized that psychedelics (like LSD or Psilocybin) and learning Bitcoin had a similar effect on my brain. The closest to my head-over-heels experience down the Bitcoin rabbithole were my experiences with LSD long before I discovered Bitcoin. Both shaped my life in an unexpected but positive way. I can´t talk about psychedelic experiences with most of my family, similar as with Bitcoin. They just don´t get it. And at this point I won´t bother trying to explain it anymore.
# Volatility
Then there is the volatility aspect. Psychedelic trips can be quite volatile, you never know what to expect. There is always some level of loss of control and you have to be fine with it. Similar with Bitcoin: You have to be able to stand the ups and downs, one day feeling like a genius, being full of doubt the next day.
# Questioning Authority
There are also some historical and cultural parallels between the spread of LSD in the 60s and Bitcoin today. In the 1960s Timothy Leary coined the term "_Turn on, tune in, drop out_". Large parts of the youth counterculture discovered the freeing effect of LSD on the mind and said "Fuck it, we´re not gonna participate in your wars". They challenged authority and the societal norms. Today, bitcoiners find the freedom of Bitcoin. They like to opt out of the system and say "Fuck it, we´re not gonna participate in your bullshit any longer". Passionate, freedom-loving communities have formed around both phenomena.
What are your thoughts on this? Do you have similar experiences? Did I miss anything?
originally posted at https://stacker.news/items/877770
-

@ fd208ee8:0fd927c1
2025-02-06 15:58:38
## Beginning at the start
In my previous article, [The Establishment](https://next-alexandria.gitcitadel.eu/publication?d=the-gitcitadel-blog-the-establishment-3-by-stella-v-1), I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a *company* is a *team*, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop.
## The Initiation
The first, and most-difficult step of team formation, is *the initiation*. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".)
Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because
* You have to come up with an idea that is coherent, plausible, and inspiring.
* You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires.
* You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members.
* You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks.
* You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.

So, just do and be all of those things, and then initiate the team, with the method I will name the *Hatbock Method*. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team.
Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".)
## The Sitting
We now get to the second most difficult part of team formation: figuring out *where to sit*. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea.
Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, *immediately*.

Now, this next bit is very important:
> Do not let anyone outside your team influence where you sit!
...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice.
This is the German *Stammtisch* principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area.
## Plan it in
Once you've sat down, and finished your rough draft of the Vision, you need to figure out *when to sit*. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.)
The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros".
It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc.
And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. *Write everything down.* Anything not written down, is a suggestion, not an assigned task.
If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, [as a company](https://next-alexandria.gitcitadel.eu/publication?d=the-gitcitadel-blog-the-establishment-3-by-stella-v-1).
-

@ f1989a96:bcaaf2c1
2025-02-06 14:01:03
Good morning, readers!
In India, the central bank has taken a significant step toward launching its central bank digital currency (CBDC), the digital rupee. In partnership with fintech firms Mobikwik and Cred, the digital rupee is now available to 180 million users through a new “e₹ wallet,” a CBDC wallet app designed for public use. Predictably, the CBDC comes with tight restrictions, including limits on payment amounts and frequency and extensive personal data collection, raising concerns over financial privacy.
In open-source news, HRF is pleased to announce a collaboration with MIT for the 2025 MIT Bitcoin Expo. This two-day freedom-focused event will explore how Bitcoin and adjacent freedom tech can help combat financial surveillance and repression under authoritarian regimes through expert speakers, panels, workshops, and more. Elsewhere, Joltz became the first self-custodial wallet to support Taproot Assets, enabling access to stable digital dollars on a decentralized network for activists, dissidents, and others in difficult political environments.
We conclude with an extensive guide from Area Bitcoin, a Brazilian education hub, thoroughly examining Brazil’s DREX CBDC and its implications for financial freedom and human rights in Brazil and beyond.
**Now, let’s dive right in!**
### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a)
## **GLOBAL NEWS**
#### **India | Central Bank Partners with Fintech Firms to Pilot Launch CBDC**
The Reserve Bank of India (RBI) [partnered](https://www.businesstoday.in/personal-finance/news/story/mobikwik-cred-join-hands-with-rbi-to-fully-launch-cbdc-ers-for-android-check-features-usage-462318-2025-01-28) with fintech firms MobiKwik and Cred, alongside Yes Bank, to expand the digital rupee, India’s CBDC. With a combined user base of [180 million,](https://www.ledgerinsights.com/fintech-wallets-go-live-in-digital-rupee-cbdc-pilot/) Mobikwik and Cred will act as entry points for public access to the CBDC through their new “e₹ wallet” CBDC app. However, the app mandates video verification and imposes significant restrictions. For instance, a daily transaction cap of ₹50,000 ($577) and ₹10,000 ($115) limit per transaction. The RBI’s decision to embed the digital rupee within existing fintech firms to boost adoption leaves few avenues for financial privacy and freedom as the Indian state [pushes](https://www.lowyinstitute.org/the-interpreter/india-s-plan-world-without-cash) further towards a cashless economy.
#### **El Salvador | Lawmakers Scale Back Bitcoin Legal Tender Law**
El Salvador’s congress [amended](https://www.reuters.com/world/americas/lawmakers-el-salvador-rush-new-bitcoin-reform-after-imf-deal-2025-01-30/) its Bitcoin law, making private sector acceptance of Bitcoin voluntary. The reform follows a $1.4 billion loan agreement with the International Monetary Fund (IMF) that wanted to limit the government’s, citizens’, and economies’ exposure to Bitcoin. Salvadoran lawmaker Elisa Rosales [said](https://www.reuters.com/world/americas/lawmakers-el-salvador-rush-new-bitcoin-reform-after-imf-deal-2025-01-30/) the latest reform guarantees Bitcoin’s “permanence as legal tender” while facilitating its “practical implementation.” But, John Dennehy, founder of the civil society organization [Mi Primer Bitcoin](https://es.myfirstbitcoin.io/), [explained](https://x.com/jdennehy_writes/status/1885346352621617615) that the reform removed “all references of bitcoin as money or legal tender, plus the actual conditions, such as the government accepting bitcoin for things such as taxes, are now prohibited.” The future of freedom technology in El Salvador will be worth monitoring closely as the regime continues to erode protections on civil liberties.
#### **Nigeria | Regime Hikes Telecom Tariffs for Citizens**
In Nigeria, the regime approved a [50% increase](https://thenationonlineng.net/50-tariff-hike-a-necessary-step-or-a-burden-for-nigerians/) in telecom tariffs, further straining citizens already grappling with financial instability. Call rates will rise from 11 to 16.50 naira per minute ($0.0074 to $0.011) and SMS charges from 4 to 6 naira ($0.0026 to $0.004), exacerbating three-decade-high inflation as the ripple effects spread through the economy. Telecom companies justify the price hike as necessary for the sector’s survival amid the naira’s ongoing [devaluation](https://www.bloomberg.com/news/articles/2024-09-13/why-nigeria-s-naira-currency-ngn-usd-slumped-and-why-it-matters). [Deolu Ogunbanjo](https://www.linkedin.com/in/deolu-ogunbanjo-62b5a18b/?originalSubdomain=ng), president of the National Association of Telecoms Subscribers, however, [argues](https://thenationonlineng.net/50-tariff-hike-a-necessary-step-or-a-burden-for-nigerians/) that “this decision shows the government cares more about protecting profits than protecting people.” For Nigerians relying on mobile networks for work, banking, and daily communications, the increased costs will make phone services less accessible, putting even more pressure on civil society under an authoritarian government.
#### **Nicaragua | Inter-American Court of Human Rights Rules Against Ortega**
In Nicaragua, where the financial repression of individuals, opposition, and civil society is widespread, the Inter-American Court of Human Rights [ruled](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) that Daniel Ortega’s reelections since 2011 were illegitimate. This ruling “is the legal confirmation that there is no legitimate president in Nicaragua, but rather a dictator who has usurped power,” [said](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) Jaime Aparicio, a Bolivian lawyer, [adding](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) that “this is the first time that there is a legal precedent determining the illegality of Ortega’s presidency.” In a country where the regime systematically [freezes](https://www.reuters.com/world/americas/nicaragua-govt-accuses-catholic-church-money-laundering-freezes-accounts-2023-05-27/) bank accounts, seizes assets, and [shuts down](https://www.catholicnewsagency.com/news/261539/nicaraguan-dictatorship-shuts-down-more-organizations-including-dominican-nuns) nonprofits to silence dissent, this verdict sets a critical legal precedent against the abuse of state power to secure reelection. While the court lacks enforcement, its ruling strengthens legal challenges to Ortega’s rule and could provide a foundation for future actions against electoral fraud and authoritarian control.
#### **Webinar Series for Nonprofits | Become Unstoppable**
In an era where financial control is weaponized against dissent, the ability to transact freely is more important than ever. For activists and nonprofits operating under oppressive regimes, Bitcoin can offer a way to resist censorship, protect funds, and remain operational.
Join HRF for a free, three-day webinar from March **17–19**, led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial freedom expert at the Anti-Corruption Foundation. The sessions will run daily from **10:30 a.m. to 12:00 p.m. EDT** and are designed specifically to teach human rights defenders and nonprofit organizations how to integrate Bitcoin into their work to challenge state censorship and confiscation in a beginner-friendly way.
### [Register Here](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform)
## BITCOIN AND FREEDOM TECH NEWS
#### **MIT | 2025 Bitcoin Expo**
HRF is partnering with [MIT](https://www.mit.edu/) to host the [2025 MIT Bitcoin Expo](https://mitbtcexpo.org/), a two-day event from April 5-6 at the Stata Center, exploring Bitcoin and freedom technologies as tools for privacy, financial sovereignty, and civil liberties — especially for people living under authoritarian regimes. Now in its 12th year, the expo features keynotes, panels, technical workshops, and hackathons. It brings together developers, activists, students, and researchers to dive into privacy, self-sovereignty, and decentralization. Attendees will also gain hands-on experience and engage in meaningful discussions on the real-world impact of freedom technologies. Learn more about the expo and get your tickets [here](https://mitbtcexpo.org/)**.**
#### **Bitcoin Mining | Two Blocks Mined by Solo Miners This Week**
This week, two solo miners successfully mined Bitcoin blocks, marking a rare and significant event. The first block was [solved](https://x.com/FutureBit/status/1884740065223495821) through a collaborative effort led by the [256 Foundation](https://256foundation.org/) (where 300+ participants [pooled](https://crypto.news/solo-miner-solving-a-block-and-getting-3-146-btc/) their hashrate for a fundraising event). The second block was [mined](https://x.com/SoloSatoshi/status/1885418398345269572) independently through [solo.ckpool](https://solo.ckpool.org/) by a miner using hashrate equivalent to thousands of BitAxe devices, a type of open-source home mining hardware. The news shows that independent miners can still compete outside of large [mining pools](https://river.com/learn/terms/m/mining-pool/). These events reaffirm Bitcoin’s decentralization and censorship resistance, proving that solo mining remains viable with the proper coordination and infrastructure, which is especially key as solo mining can be done privately and quietly under tyrannical regimes.
#### **Joltz Wallet | First Self-Custodial Wallet to Support Taproot Assets**
Joltz has [launched](https://x.com/joltz_btc/status/1885097351108243487) the first self-custodial wallet for [Taproot Assets](https://docs.lightning.engineering/the-lightning-network/taproot-assets), enabling users to hold and transact stablecoins like USDT (Tether) directly on Bitcoin — without intermediaries. Unlike custodial solutions, Joltz ensures users retain full control over their funds while enabling BTC-to-USDT swaps through a user-friendly interface. This could expand access to stable money — particularly for activists and nonprofits in volatile markets in search of digital dollars. However, stablecoins still carry centralization and censorship risks, as issuers like Tether can freeze funds or be beholden to regulatory demands.
#### **Olas | New Updates Enhance Accessibility and Features**
[Olas](https://github.com/pablof7z/olas), an Instagram-like Nostr client built by [Pablof7z](https://github.com/pablof7z), [released](https://github.com/pablof7z/olas/releases/tag/0.2.0) a new update for iOS and Android. The update introduces multiple images per post, Instagram-style filters, and improved video playback. It also enhances its Nostr-native wallet functionality so users can more fluidly receive Bitcoin tips and payments. The client also made Nostr Wallet Connect (NWC), a protocol that allows apps to interact with Bitcoin Lightning wallets, more reliable for end users. Nostr clients like Olas may prove to be a useful tool for censorship-resistant communications on social networks among activists worldwide and stand as a stark contrast to centralized, permissioned alternatives.
#### **OpenSats | Announces Ninth Wave of Bitcoin Grants**
[OpenSats](http://opensats.org), a public nonprofit supporting open-source Bitcoin projects, [announced](https://opensats.org/blog/ninth-wave-of-bitcoin-grants) its ninth wave of Bitcoin grants advancing financial freedom and privacy. Among the recipients, [Nutstash](https://www.nutstash.app/), a multi-platform Cashu ecash wallet, enables private, censorship-resistant Bitcoin transactions — critical for human rights defenders. Another grantee, [El Tor](https://devpost.com/software/el-tor), is developing a fork of the [Tor Network](https://www.torproject.org/) integrated with Bitcoin's Lightning Network, aiming to enhance online privacy for activists and dissidents. HRF welcomes OpenSats’ continued support for decentralized tools in an increasingly surveilled world.
#### **bitcoin++ | Upcoming Bitcoin Developer Conference**
Bitcoin developers and freedom tech enthusiasts will [gather](https://btcplusplus.dev/conf/floripa) in Florianopolis, Brazil, from Feb. 19-22, 2025, for the special “hacking edition” [bitcoin++](https://btcplusplus.dev/) conference. Unlike past bitcoin++ events, which focused on single topics like scripting or ecash, this event will feature hands-on development to enhance Bitcoin’s privacy, scalability, and censorship resistance. Attendees will participate in workshops, live coding challenges, and technical discussions. HRF will help the event include attendees from authoritarian regimes in Latin America. Learn more about the conference or buy tickets [here](https://btcplusplus.dev/conf/floripa).
## RECOMMENDED CONTENT
#### **The Risks of the DREX Central Bank Digital Currency by Area Bitcoin**
In this [article](https://blog.areabitcoin.co/cbdc-drex/), [Area Bitcoin](https://www.areabitcoin.co/), a Brazilian Bitcoin education hub, examines [DREX](https://cbdctracker.hrf.org/currency/brazil), Brazil’s central bank digital currency (CBDC), and its threat to Brazilians’ financial autonomy. DREX operates as a token on a centralized, permissioned blockchain that grants officials sweeping surveillance and control over individual financial activity. Further, its strict Know-Your-Customer (KYC) and Anti-Money Laundering (AML) measures erode financial privacy. Area Bitcoin [warns](https://blog.areabitcoin.co/cbdc-drex/), “By embracing it, we risk surrendering our personal data, the fruits of our labor, and even generational wealth to political and bureaucratic oversight.”
*If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).*
*Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\
*Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)*
*The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*.
[**Subscribe to newsletter**](http://financialfreedomreport.org/)
[**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Visit our website**](https://hrf.org/programs/financial-freedom/)
-

@ 1f3ce62e:6e6b5d83
2025-02-06 13:21:23
During challenging times for relationships of all kind, stopping & reflecting brings a new perspective and help us to observe our contribution to it.
**We spend a lot of time at work, our relationships there are important** 👥
When we **hit a wall with a colleague** it takes a lot of energy, stress and inefficiencies in our daily tasks.
Have you ever gotten stressed about sending an email to a colleague? 😅
By listening to myself (to my inner voice, to my body) have helped me to start observing it. 👂
Then, observing it 👀 like an outsider has helped me to put myself on the other's shoes. Empathy does its thing at this stage.
**People are stories, wounds not healed, as we all have.** 💕
Finally, I **proactive open an space to talk**. I like to listen first, all that is being said, not just words. Then I use my voice. Or vice versa as needed.
**Not all relationship's challenges can be solved** (I have learned to accepted that), but I honor them, **by opening the space anyways**.
From my research 🤓 ...
Observing 👀
Reflecting 🤔
Opening an space to talk 👥
Listening 👂 ⚖ Speaking 🗣
👂What is being said, but the most important…
👂💛 **What is not being said.**
And **when we start listening deeply, we can listen to fears, our own and others**.\
\
I wonder why we don't talk about dragons 🐉 at work. 🤭\
\
I wonder why we don't talk about fears.\
\
As an individual who explored them a lot in therapy, and I have experienced the benefit of it, I wonder, why no-one talks about them at workplaces.
**Have you ever asked your team...What is their biggest fear?** 🤔
Talking about fears at work could feel uncomfortable at the very beginning, but exploring them is a way to connect with others while realizing we share a lot of them.
**Overcoming them with others could bring a lot of relief too.**
Fears limit our actions, decisions and our ideas to blow.
Using tools like LEGOs helps us to explore the unconscious mind 🖤 🧠, where most of the fears have their residence. From where most of the decisions are made 😅
🌱 With Mini figures and blocks we **can project a situation** that you or your team is going through.
🌱 As we project it, you can **detach emotionally from it** and you **become an observer** of it.
🌱 You can only change, what you can **observe with** **full presence**.
🌱 **Playing** does exactly that, **brings us to the present moment**.
**By using LEGOs we can bring perspective and spark more creative solutions.**
Ignoring fears at work means ignoring we are... just humans.
So step by step, we made our workplaces more human.
**Deep listening breaks down walls.**
**And that is what The World 🌎 strongly needs these days.**
**In the end, what is really behind any wall, it is a wound not healed.**
Stay colorful!
Laus
-

@ cf7ed325:050194cf
2025-02-06 12:28:27
The [TIA Nile Cruise](https://www.etbtoursegypt.com/tour/ms-tia-nile-cruise) offers a fantastic way to experience Egypt’s timeless beauty, as it takes you on an unforgettable journey along the majestic Nile River. Whether you’re a history buff, an adventure seeker, or simply looking for a relaxing getaway, this cruise offers something for everyone.
One of the standout features of this cruise is its luxurious accommodations, combining modern amenities with the charm of traditional Egyptian hospitality. As you sail through Egypt’s most iconic landmarks, such as the Valley of the Kings, the Pyramids of Giza, and the temples of Karnak and Luxor, the comfort of the TIA Nile Cruise ensures that every moment is enjoyable.
If you’re exploring other options, there are many other high-end Nile cruises that offer similarly unforgettable experiences. The [Gemma Nile Cruise](https://www.etbtoursegypt.com/tour/gemma-nile-cruise) is one of the most popular alternatives, offering luxury and sophistication while cruising through the heart of Egypt. It’s perfect for those seeking an elegant escape with premium service and spectacular views.
Another excellent choice is the [Sonesta Sun Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/sonesta-sun-goddess-nile-cruise), which provides a combination of relaxed luxury and top-notch service. Guests can enjoy stunning views of Egypt’s famous landmarks, along with a variety of recreational facilities on board.
For those looking for something extra special, the [Sonesta Star Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Star-Goddess-Nile-Cruise) and the [Sonesta Moon Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Moon-Goddess-Nile-cruise) are both fantastic options, offering spacious rooms and exceptional service. These cruises ensure that guests have an unparalleled experience as they explore the wonders of Egypt.
The [Sonesta Nile Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Nile-Goddess-Cruise-tours) is another luxurious option, known for its elegance and comfort. It offers an array of gourmet dining options and entertainment for an all-around memorable trip.
Lastly, the [Sonesta George Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-St-George-Nile-Cruise) promises an exceptional cruising experience with modern amenities and stunning Nile views. Whichever cruise you choose, you can be sure that your journey along the Nile will be unforgettable, filled with adventure, culture, and relaxation.
🌐 Visit us at www.etbtoursegypt.com
📲 Contact us now! +20 10 21100873
📧 For Booking and Inquiries: info@etbtours.com
🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
-

@ 4506e04e:8c16ba04
2025-02-06 12:11:10
This spec aims to build a client application that enables patients to securely store and access their medical data using the Nostr protocol while ensuring only authorized doctors can write medical records. All data is end-to-end encrypted (E2EE) before being stored on Nostr relays, preventing unauthorized access. Patients can grant or revoke doctors’ write permissions, and all medical updates are encrypted with the patient’s public key, ensuring only they can read them. An audit log keeps track of all doctors (identified by their npubs) who have accessed or modified the patient’s data. This solution provides privacy, security, and transparency while leveraging decentralized, zero-trust storage on Nostr. 🚀
---
## **1️⃣ Core Architecture**
### **Client Application (Mobile - Patient)**
- **Stores only encrypted medical data** (no write permissions).
- Allows **temporary read access** to the patient.
- Maintains an **audit log of npubs** (medical staff) who wrote/modified data.
### **Client Application (Mobile - Doctor)**
- **Writes new medical records** and encrypts them with the patient’s **npub**.
- Submits encrypted records to Nostr relays.
- Can view past records that they (or other authorized doctors) have written.
### **Nostr Relays**
- Store **only encrypted medical records** (relays cannot read them).
- Act as a **communication layer** between doctors and the patient.
---
## **2️⃣ How It Works (End-to-End Workflow)**
### **👨⚕️ Writing/Updating Medical Data (Doctor)**
1. The doctor inputs new medical records into their mobile app.
2. The data is **encrypted using the patient’s npub** (so only the patient can read it).
3. The encrypted record is published to **Nostr relays**.
4. The patient’s app detects the update and decrypts the data locally for viewing.
### **👩⚕️ Managing Doctor Access (Patient)**
1. The patient manually **grants or revokes access** to doctors via their app.
2. If a doctor is **granted access**, they can write new records.
3. The patient **cannot modify or delete medical records**, only read them.
### **🔑 Secure Key Exchange for Read Access**
1. The doctor **encrypts records** with the patient’s **npub**.
2. The patient uses their **nsec** (private key) to decrypt and read the data.
3. Other unauthorized parties (including relays) **cannot decrypt the data**.
### **📜 Access Logging**
- Every **write operation** (new or modified medical record) is **logged in the patient’s app**.
- The log includes:
- **npub of the doctor** who made the update.
- **Timestamp of the update**.
- **Hash of the encrypted record** for verification.
---
## **3️⃣ Security Measures**
✅ **Doctors Can Write, Patients Can Only Read**
- Only **authorized doctors** can submit medical data.
- Patients can only **view** (not modify) their records.
✅ **End-to-End Encryption**
- Data is **encrypted before transmission**, ensuring no unauthorized access.
✅ **Zero-Trust Storage**
- Nostr relays **store encrypted records** that are useless without the decryption key.
✅ **Audit Log for Transparency**
- Patients can track **who wrote or modified** their records.
✅ **No Long-Term Access Without Authorization**
- The patient can revoke a doctor’s **write permissions** anytime.
---
## **4️⃣ Technology Stack**
- **Frontend (Mobile App)**
- **Flutter (Dart)** or **React Native (JavaScript/TypeScript)**
- Secure local storage for audit logs (**EncryptedSharedPreferences** on Android, **Keychain** on iOS)
- **Cryptography**
- **ECC (Elliptic Curve Cryptography)** for **key exchange** (Nostr encryption model)
- **AES-256** for **encrypting medical records** (written by doctors)
- **Networking & Storage**
- **Nostr Protocol** (NIPs 04 for encrypted DMs, NIP 33 for event-based access control)
- **Multi-Relay Storage** (for redundancy)
---
## **5️⃣ Potential Challenges & Solutions**
### **🔹 Patient Cannot Edit Records**
- Patients might want to **annotate or request corrections** on their records.
- Solution: Allow a **separate encrypted channel** for patient feedback.
### **🔹 Doctor Write Permissions Management**
- A UI is needed for patients to **approve/revoke doctor access** easily.
- Solution: Implement a **simple approval system** in the mobile app.
### **🔹 Relay Availability**
- Solution: Store records **on multiple relays** for redundancy.
---
This design ensures that **only authorized doctors can write data**, while **patients have full visibility and control over access**. 🚀
***I'm looking for a co-founder to build this. I've got the experienced and cost-efficient team who can build this. DM me for details.***
-

@ c1301dca:8efcc835
2025-02-06 11:34:08
Hiring the right sales talent is one of the most crucial decisions a company can make. A strong sales team drives revenue, builds relationships, and contributes to business success. However, making the wrong hire can lead to costly mistakes—high turnover, poor morale, and missed sales targets. This is where Prehire psychological assessments come in, offering a powerful tool to help companies make better, more informed hiring decisions.
At its core, a [**Prehire psychological assessment**](https://www.velocity-sales.com/prehire-selection) helps employers look beyond resumes, experience, and qualifications. It digs deeper into potential candidates' behavioural traits, cognitive abilities, and intrinsic motivations. This deeper understanding enables companies to select candidates who are skilled and aligned with the job demands and the company's culture.
## 1. Improved Candidate Fit for the Role
A common challenge in sales hiring is finding candidates perfect for the role and the team. Sales positions often require specific skills, such as persistence, emotional intelligence, problem-solving abilities, and the ability to perform under pressure. Traditional hiring methods focus heavily on qualifications and experience, but these don't always provide insight into how a candidate will handle the job demands.
Prehire psychological assessments go further by assessing a candidate's cognitive capabilities and personality traits. For example, a candidate might have an impressive sales background but struggle with resilience when facing rejection or high-pressure situations. A proper psychological assessment identifies these qualities, allowing companies to choose candidates naturally inclined to thrive in sales environments.
## 2. Reducing Turnover Rates
Turnover is one of the biggest challenges in the sales industry and can be costly. When employees leave, the company faces recruitment costs, training costs, and lost revenue. Moreover, high turnover can negatively impact team morale, lowering performance across the board.
Prehire psychological assessments help reduce turnover by identifying candidates more likely to stay long-term. The assessments examine intrinsic motivation—whether candidates are genuinely passionate about the role and aligned with the company's mission. Candidates naturally aligned with the job and organisation are more likely to stay engaged, satisfied, and committed. This reduces the risk of early departures and creates a more stable, high-performing team.
## 3. Enhancing Sales Performance
Sales roles can be highly demanding, requiring individuals to stay motivated, favourable, and productive even during tough times. A candidate's ability to handle stress, maintain enthusiasm, and stay focused on goals can significantly influence their performance.
Psychological assessments provide valuable insights into how candidates will react under pressure, how resilient they are, and how well they manage stress. By understanding a candidate's psychological profile, employers can select individuals better equipped to deal with the highs and lows of a sales career. These candidates are more likely to stay motivated, adapt to challenges, and maintain consistent performance.
## 4. Cultural Fit and Team Harmony
A key factor in any successful team is how well team members work together. A salesperson who excels individually but clashes with the company culture can cause disruptions within the team. Similarly, a candidate who struggles to adapt to the sales team's dynamic can lower overall performance and morale.
Prehire psychological assessments evaluate how candidates will fit within the existing team culture. These assessments measure interpersonal skills, emotional intelligence, and adaptability, which are critical in a sales environment. By selecting candidates who align with the team's dynamics and values, companies foster a more collaborative and cohesive work environment, ultimately boosting morale and improving overall sales performance.
### Boost sales and reduce turnover with the right hire—Prehire Psychological Assessments!
The right sales talent is more critical than ever. In a competitive landscape, Prehire psychological assessments provide a deeper, more nuanced view of candidates, helping businesses make better decisions that lead to higher retention rates, improved morale, and more robust sales performance. By understanding candidates more deeply, companies can reduce turnover, ensure better cultural fit, and ultimately create a more effective and motivated sales team
Velocity Sales Consulting specialises in helping businesses enhance their **[Candidate selection process consulting](https://www.velocity-sales.com)** through scientifically backed prehire psychological assessments. Our expert consulting services ensure your sales hiring decisions are data-driven, informed, and tailored to help your company succeed.
-

@ 044da344:073a8a0e
2025-02-06 11:30:19
Nachdem ich in diesem Jahr schon die [Schweiz](https://www.freie-medienakademie.de/medien-plus/die-afd-spricht-englisch) gewürdigt habe und den renitenten [Osten](https://www.freie-medienakademie.de/medien-plus/resonanz-aus-dem-osten), wird es Zeit, nach Österreich zu schauen. Wien, Hannes Hofbauer, Promedia. Für mich eine Dreifaltigkeit, seit ich im September 2021 bei der [Zukunftskonferenz](https://www.manova.news/artikel/weil-es-anders-geht) war. Auf den Straßen der Stadt lief mein altes Leben davon. Der Wien-Marathon, geplant eigentlich für April 2020 und für mich seinerzeit ein Fixpunkt im Kalender, weil ich glaubte, besser in Form zu sein als je zuvor. Den Startplatz hatte ich unter Protest zurückgegeben, nachdem die Organisatoren per Rundmail dazu aufriefen, sich doch bitte die Spritze zu holen. Die Zeit reiche sogar noch für zwei. Mitten im Training wohlgemerkt, wenn das Immunsystem ohnehin permanent im Keller ist und nicht mal eine Rotznase in der Nähe verkraftet. Für Rekorde war es an jenem Septembersonntag dann ohnehin viel zu heiß.
Also zur Zukunftskonferenz, die es eigentlich gar nicht hätte geben dürfen. Jedenfalls für mich nicht. Kein Zertifikat, nirgends. Von jenseits der Grenze schien Wien damals eine uneinnehmbare Festung zu sein für alle, die ohne Maske einreiten wollen. Die Impfpflicht war zwar noch nicht beschlossen, aber die veröffentlichte Stimmung ließ kaum Zweifel, dass das kommen würde. In Wien, das habe ich damals gelernt, geht trotzdem immer was. Kein Hotel ohne Test? Dann wohnst Du eben privat, lieber Michael. Und wenn wir Hunger haben, finden wir immer einen Griechen oder jemanden vom Balkan.

Wien spielt auch im neuen Buch von Hannes Hofbauer eine Rolle. Eine kleine, okay, und beim Blick auf Cover und Titel auch nicht unbedingt zu erwarten. Russland heute, sagen alle optischen Signale. Wirtschaftskrieg, Sanktionen, ein neues Schloss aus Eisen. Hofbauer wäre aber nicht Hofbauer, wenn er es bei den letzten paar Jahren belassen würde. Wie schon in seinem Buch über [Zensur](https://medienblog.hypotheses.org/10635) taucht er in die Geschichte ein und kommt so über die Hanse und Maria Theresia, über den unseligen Gutsverwalter Charles Boykott und Woodrow Wilson zwangsläufig auch zur Embargopolitik des Westens im Kalten Krieg. COCOM. Eine dieser Abkürzungen, die auch ausgeschrieben nicht verraten, was wirklich dahintersteckt. „Koordinationsausschuss für Ost-West-Handel“, sagt Wikipedia. Der Zeitzeuge Michael Meyen erinnert sich an eine DDR-Jugend, in der er sehnsüchtig auf das Weihnachtspaket aus dem Westen wartete. Vielleicht gibt es ja diesmal Taschenrechner, Quarzuhr oder irgendetwas anderes von dem, was sonst nur im Intershop liegt. Wien, sagt Hannes Hofbauer, war ein „Hotspot“ des Ost-Schmuggels. Einer der Orte, über die das gehandelt wurde, was nicht auf den schwarzen COCOM-Listen stand und so eigentlich auch nicht in mein Kinderzimmer kommen konnte. Die Quellen dieses Hotspots: Familienbande, Tradition und eine Position zwischen den großen Mächten.
Vermutlich ist es deshalb kein Zufall, dass ein Buch wie dieses aus Österreich kommt. Hannes Hofbauer muss nicht groß herausstreichen, dass er sich auskennt im Osten Europas. Seine Bücher sprechen so für sich, dass ein paar zarte Hinweise genügen. Frühjahr 1990, kurz nach der Eröffnung von McDonalds am Puschkin-Platz in Moskau. Eine lange Schlange, erinnert sich Hofbauer. „Den Geschmack des Westens“ probieren (S. 214). Heute sind die 825 Standorte verkauft. Der neue Betreiber hatte vorher Erfolg in Sibirien und sagt jetzt auf Russisch: „Wkusno i totschka“. Lecker und Punkt.
Damit ist ein Teil der Geschichte schon erzählt. Die Russen haben reagiert und den „härtesten Wirtschaftskrieg, den der Westen seit 1945 führt“, ins Leere laufen lassen (S. 203). BRICS und der Trend weg vom Dollar, die Umstellung der Landwirtschaft, die Weizen-Rekordernte 2024 und die Obst-Importe aus der Türkei. „Das westliche Sanktionsregime hat die Welt verändert“, sagt Hannes Hofbauer – aber anders als gedacht (S. 221). Damit sind nicht nur die Verluste gemeint, für die hier McDonalds steht, oder der Push für die russische Wirtschaft, sondern auch der „schleichende Wandel von der russländischen zur russisch-nationalen Identität“. *Russki mir* heißt das Schlagwort, das auf Zusammenhalt zielt. Russische Welt, Rechtsruck und Kirchenmacht inklusive (S. 238).
Zu Hofbauers Geschichte gehören aber auch, wie sollte es bei einem Historiker anders sein, die langen Linien, die Scharmützel mit dem Irak und Libyen, die die „Dollar-Zwangsjacke“ abstreifen wollten (S. 65), und der Rechtsbruch, der stets damit verbunden ist, irgendwelche „Bestimmungen“ gegen Länder durchzusetzen, die jemand mit Allmachtsphantasien gerade als „Bösewicht und Unruhestifter“ ausgemacht hat (S. 14). „Schießkrieg und Wirtschaftskrieg hängen eng zusammen“ (S. 17): Diese Formel hat Woodrow Wilson, seinerzeit US-Präsident, schon im September 1919 in das kollektive Weltgedächtnis geschrieben. Möge der Krieg auch barbarisch sein, so sei doch der Boykott „ein unendlich viel schrecklicheres Kriegsinstrument“ (S. 9). Das erklärt COCOM. Das erklärt „Amerikas Kampf gegen russische Energie für Europa“, den Hannes Hofbauer schon 1960 beginnen lässt (S. 53). Das erklärt auch das Kontaktschuld-Prinzip, das ich im Dezember 2019 live auf Kuba erleben durfte. Dunkle Städte beim Anflug, Warten an den Tankstellen und der Zweifel, ob es etwas werden würde mit einer Vortragstour so ganz ohne Benzin. Dann endlich ein Schiff am Horizont. Wer in Havanna anlegt, so habe ich gelernt, ist für US-Häfen tabu. Die Kubaner sind damals nicht verhungert, immerhin. Aber gut ging es ihnen trotzdem nicht.
„Russland ruinieren“: Bei Hannes Hofbauer beginnt dieses Kapitel 2009 – mit dem Versuch, über die Idee „Östliche Partnerschaft“ sechs Staaten aus dem Dunstkreis Moskaus zu lösen (S. 81). Moldawien, Georgien, Armenien, die Ukraine, Belarus, Aserbaidschan. Wir wissen, wie das ausgegangen ist. Wir wissen auch, wie und warum die Spirale weitergedreht wurde. Geopolitischer Wahn, der Kampf um kulturelle Deutungshoheit, wunderbar nachzulesen im Promedia-Buch von [Hauke Ritz](https://www.freie-medienakademie.de/medien-plus/die-macht-der-ideen), dazu der „Kampf um das große Geschäft“ (S. 104) und natürlich um das große Geld, der hier und jetzt selbst russische Auslandsvermögen nicht zu verschonen scheint, obwohl doch Eigentum ein Fetisch ist, der nicht einmal Straftätern entzogen werden kann (S. 133).
Hannes Hofbauer verlässt den Hochsitz des Chronisten hin und wieder, um auf Menschen zu schauen, die zu Kollateralschäden geworden sind. Jozef Hambálek, ein slowakischer Motorradfahrer, der seinen Ministerpräsidenten brauchte, um von der Sanktionsliste gestrichen zu werden. So-yoen Schröder-Kim, fristlos entlassen, weil sie am 9. Mai 2023 mit ihrem Mann, Ex-Bundeskanzler, in der russischen Botschaft war. Justus Frantz, einst Klassikstar und heute Persona non grata, weil er nicht von alten Freunden und großer Kunst lassen wollte. Hofbauer spricht von einem „Russland-Hass“, der bei den Volksvertretern der EU „paranoide Züge“ trage, und von einer „kolonialen Attitüde moralischer Überlegenheit“ (S. 127). Er zeigt die Folgen jenseits der Wirtschaft. Kultur, Olympia, Wissenschaft, private Reisen. Die Zensur natürlich – nötig allein schon deshalb, damit die „russische Erzählung“ unsichtbar wird (S. 160). Und er hat eine Anekdote, die exemplarisch zeigt, warum das alles so gekommen ist. Ort: Das *Heute-Journal* im ZDF 2014. Anwesende: Claus Kleber und Joe Kaeser, seinerzeit Siemens-Chef und gerade zufrieden zurück aus Russland, wo er Putin getroffen hatte und den Gazprom-Chef. Der Leser ahnt, was kommt. Ein Verhör. Was haben Sie sich dabei gedacht, Herr Kaeser? Hannes Hofbauer sagt, dass dem Wirtschaftsboss erst in diesem Moment klar geworden sei, worauf die deutsche Politik hinauslief, und er zu Kreuze gekrochen sei (S. 235). Der Rest ist Geschichte – für alle Zeiten festgehalten in diesem Buch.
\
[Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/)
-

@ 89ccea93:df4e00b7
2025-02-06 11:20:49
I've opened a ~monero territory.
I kept wanting to post things about or tangential to monero and didn't know where to shove them.
Obviously ~bitcoin isn't the right place.
And ~cryptocurrency didn't feel right, since for me, as a bitcoiner, monero is in a unique position. It doesn't seem to fit under the larger basket of cryptocurrencies. Many of which are scams/self-enrichment schemes. Ahem, XRP.
Or just poorly implemented and pre-mined. Ahem, ETH.
I don't know a lot about monero actually, but I use it and like it and think it has a place in a bitcoiners arsenal in resisting government infringements and resisting pervasive privacy shit-holes like the chain anal companies. Even Coinbase has their own proprietary chain anal. It's disgusting. They don't want us to have privacy. And many people play right into their hands by handing over their ID card and picture of their face to get bitcoins when you can get it anonymously. But I digress.
Use the territory, or don't.
But if you do, then welcome.
originally posted at https://stacker.news/items/877547
-

@ e373ca41:b82abcc5
2025-02-06 09:25:07
*This article by Milosz Matuschek first appeared in German in* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/usaid-and-co-die-ersten-kopfe-der)***
*In my first multi-part Corona series,* *[The Corona Complex](https://www.freischwebende-intelligenz.org/p/coronakomplex?utm_source=publication-search), I focused on the early inconsistencies of the "pandemic." In The Corona Connection, I will explore the key players involved in this event over multiple installments.*
*It’s not yet spring, but the bud of truth is already breaking through the icy layer of lies. You can cover the truth with as much PR, manipulation, and propaganda as you want—it will only turn into compost. Because truth is rooted in something; it’s a living organism, while lies are rotting waste. The coming weeks and months will be enlightening.*
### The USAID Front Organization
The grand cleanup led by Musk & Trump is in full swing. In the U.S., the agency USAID is currently being dismantled amid protests from employees. [As of Friday, February 7, nearly all staff members have lost their jobs.](https://www.usaid.gov) What does this mean?
*Der Spiegel* referred to USAID as a "development agency" and reported that a nervous Bill Gates now wants to [call Trump](https://www.spiegel.de/wirtschaft/unternehmen/bill-gates-zu-stopp-der-us-auslandshilfen-donald-trump-hat-mir-seine-telefonnummer-gegeben-a-fafae10c-3163-43ea-96a4-f218050d658a) "to save lives." The *NZZ* euphemistically describes USAID as an "independent development aid agency." Seeing "AID" in the name, people think of humanitarian efforts—Bob Geldof, compassionate nuns, and "Bread for the World."
In reality, USAID ("United States Agency for International Development" – claim: "From the American People") is far from just a food distribution service (although it does that too). Primarily, it serves as a [covert, rapid-response intelligence force for operations such as regime change, astroturfing, and targeted executions](https://foundationforfreedomonline.com/usaid-internal-documents-reveal-government-plot-to-promote-censorship-initiatives/)—expanding new business models for the U.S. empire. They are the enforcers who move in before "peace, democracy, and reconstruction" are declared.
USAID was heavily involved in Ukraine, providing $5 billion in funding, as Robert Kennedy Jr. recently stated in an interview. The agency throws money around freely, financing both the GAVI vaccine alliance and the World Economic Forum—because, of course, these are the world's most "needy" causes.
<https://x.com/ShadowofEzra/status/1886153128757629157>
### The PREDICT Program
It gets even stranger. Under the so-called PREDICT program, significant funding was allocated to research coronaviruses in bats. This research was conducted in collaboration with the Wuhan Institute of Virology (WIV) and included gain-of-function experiments. In 2017, the NIH lifted a previously imposed moratorium on funding such research, paving the way for its resumption and expansion, including international partnerships like the one with WIV.
USAID spent about $200 million in taxpayer money on bat virus research, with approximately $50 million going directly to WIV. Despite being a publicly funded science program, PREDICT's administrators have largely refused to release sensitive details about its research. Peter Daszak, who received substantial funding ([now cut off](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/)), even ignored some subpoenas. Officials shared information with taxpayers only reluctantly and in minimal amounts.
<https://x.com/KanekoaTheGreat/status/1886098345938284813>
A 2023 investigation by the *[White Coat Waste Project](https://blog.whitecoatwaste.org/2023/06/15/covid-origin-wcw-investigation-proves-u-s-govt-funded-patient-zero/)*, following a public records request, revealed that U.S. taxpayer dollars—through the NIH and USAID—flowed to the Wuhan Institute of Virology. These funds supported gain-of-function experiments in which viruses were genetically modified to increase their transmissibility or virulence. The program ended in 2019.
### The Mystery of Ben Hu
One of the most explosive revelations was the identification of Ben Hu, a lead researcher at WIV, as a potential "Patient Zero." Reports indicate that he developed COVID-like symptoms as early as November 2019—before the first officially recognized cases. Hu was deeply involved in the gain-of-function experiments funded by U.S. taxpayer money.
Looking further back, the picture becomes clearer. As early as 2012, USAID funds were used to capture bats in caves, including those in Mojiang, where [several miners died from a deadly respiratory illness](https://pubmed.ncbi.nlm.nih.gov/33194988/). The infection was reportedly caused by bat droppings.
<https://x.com/TheSeeker268/status/1886469590701760960>
Too many coincidences are piling up: The virus strain from back then, RaTG13, has striking similarities to SARS-CoV-2. Fauci’s pardon dates back to as early as 2014. A significant portion of funding from both Fauci and USAID went to Peter Daszak’s EcoHealth Alliance. Daszak in 2016 gave surprisingly candid responses regarding gain-of-function research.
<https://x.com/mazemoore/status/1883378918687719725>
The director of the CDC, Robert Redfield, had already pointed out in previous hearings that [U.S. public funds were used for research in Wuhan.](https://x.com/KanekoaTheGreat/status/1886126884108554352)
So, to summarize here quickly, adding a question:
* A CIA front organization was catching sick bats in a previous outbreak zone of deadly respiratory diseases in China (e.g., Mojiang caves) in 2012.
* It funded tens of millions of dollars' worth of research to enhance the pathogenicity of coronaviruses in Wuhan.
* It transferred money to Chinese military-medical institutions.
* Wuhan researcher Ben Hu fell mysteriously ill and became Patient Zero.
So here’s the question: Isn't a natural origin of the virus the most obvious explanation in the world?
***
ADVERTISEMENT:
*Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*
*Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.*
***
#### Who still believes in a natural origin of COVID-19?
The official narrative worldwide is that the virus originated naturally—perhaps from someone consuming or handling a bat at a wet market near WIV. Yet, neither the sick animal nor the first human case of "natural transmission" has ever been identified.
At the same time, intelligence-backed "nudging" units worked preemptively to discredit vaccine skeptics and bolster "Trusted News Initiatives" and fact-checking programs. [Even the CIA director has now suggested that COVID may have originated in a lab.](https://apnews.com/article/covid-cia-trump-china-pandemic-lab-leak-9ab7e84c626fed68ca13c8d2e453dde1) And he likely knows exactly why.
One thing is certain: The theory of natural zoonotic transmission in COVID-19 has been obliterated. It was the PR stunt of the century. A joint effort by the CIA and China—who else could pull off such a grand deception?
These revelations are making the players behind the "Corona Connection" increasingly visible: a network of CIA-China partnerships, NGOs, the media apparatus, corrupt politicians, and willing, unscrupulous, or even outright sociopathic scientists.
")
As these connections come to light over the next months and years, the consequences for those involved—and for society at large—will be immense. We are approaching a moment of societal reckoning. A house of cards can only stand for so long before it collapses.
In Germany, Christian Drosten was one of the most aggressive proponents of the "conspiracy theory" label, frequently using it to discredit critics. As one of the main gatekeepers of the COVID narrative, he played a key role in shaping the scientific community’s response. His most steadfast domestic opponent was Hamburg physicist Roland Wiesendanger.
[Drosten was one of the most outspoken propagandists of the zoonosis theory—while simultaneously working as its chief cover-up artist and deflector. He often portrayed himself as the misunderstood victim.](https://www.freischwebende-intelligenz.org/p/wanted-drosten-luege?utm_source=publication-search)
This is what happens when the desire for recognition and power overshadows any sense of medical ethics. Now, serious questions arise about his role: What did he know about the research in Wuhan? Was he aware of USAID’s funding? Given that Charité (his institution) received grants from Bill Gates and that his PCR test was immediately declared the global gold standard, it seems unlikely that he knew nothing.
This demands an investigative committee and legal proceedings.
In the coming weeks and months, many more connections will be uncovered, fully exposing the "Corona Connection."
The era of silence is over.
And so is the era of immunity.
***
This article was written with the **[Pareto-client](https://pareto.space/read?category=global)** on Nostr. Check it out!
***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*

*Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Nosta.me.](https://nosta.me/create/welcome)**

-

@ 89ccea93:df4e00b7
2025-02-06 08:55:27

<https://www.merriam-webster.com/dictionary/shill>
I question the intellectual honesty of someone using the word "shill" to describe a Monero user.
I used to hang out in DeFi circles and we had a robust understanding of the word shill. Basically it was someone financially motivated to get you do do a certain behavior.
`Use platform X, buy token Y etc and get some benefit.`
When in reality, they wanted you to pump the liquidity so they could dump on you.
I don't see the same thing being true for Monero users.
A Monero user is someone who wants one thing. Privacy. That's literally it.
A Monero user doesn't want to get rich. Using Monero usually means they're taking a financial hit as Bitcoin is a better SoV. There is literally no financial gain to the Monero user if someone else uses it.
It shouldn't really be debatable then that for the purpose above, privacy, Monero surpasses Bitcoin.
But! Lightning!!
To which I reply, so what? Lightning is okay, but it's not a panacea.
It's UX is clunky at best. And perfect privacy is not a default. Many Lightning users are trusting their privacy and IP to a third party when they use it custodially.
But a one-to-one comparision of Monero privacy to Lightning privacy is effectively impossible because of how many different ways there are to interact with and use Lightning. Monero privacy is extremely quantifiable. Lightning privacy is a bit more ethereal. And this post isn't the place to go into that. I just made a sister post in the ~privacy territory.
originally posted at https://stacker.news/items/877476
-

@ 57d1a264:69f1fee1
2025-02-06 07:38:36
# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers?
originally posted at https://stacker.news/items/877437
-

@ 73da3415:a8b7f470
2025-02-06 07:32:17
T e s t 1
-

@ 57d1a264:69f1fee1
2025-02-06 07:28:25
# Looking at bitcoin's layered architecture (base layer and Lightning Network), can you explain why this approach was necessary? What are the trade-offs between transacting on each layer?
originally posted at https://stacker.news/items/877429
-

@ da0b9bc3:4e30a4a9
2025-02-06 06:38:33
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/877410
-

@ 3ffac3a6:2d656657
2025-02-06 03:58:47
## Motivations
Recently, my sites hosted behind Cloudflare tunnels mysteriously stopped working—not once, but twice. The first outage occurred about a week ago. Interestingly, when I switched to using the 1.1.1.1 WARP VPN on my cellphone or PC, the sites became accessible again. Clearly, the issue wasn't with the sites themselves but something about the routing. This led me to the brilliant (or desperate) idea of routing all Cloudflare-bound traffic through a WARP tunnel in my local network.
## Prerequisites
- A "server" with an **amd64 processor** (the WARP client only works on amd64 architecture). I'm using an old mac mini, but really, anything with an amd64 processor will do.
- Basic knowledge of Linux commands.
- Access to your Wi-Fi router's settings (if you plan to configure routes there).
---
## Step 1: Installing the WARP CLI
1. **Update your system packages:**
```bash
sudo apt update && sudo apt upgrade -y
```
2. **Download and install the WARP CLI:**
```bash
curl https://pkg.cloudflareclient.com/pubkey.gpg | sudo gpg --yes --dearmor --output /usr/share/keyrings/cloudflare-warp-archive-keyring.gpg
echo "deb [arch=amd64 signed-by=/usr/share/keyrings/cloudflare-warp-archive-keyring.gpg] https://pkg.cloudflareclient.com/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflare-client.list
sudo apt-get update && sudo apt-get install cloudflare-warp
```
3. **Register and connect to WARP:**
Run the following commands to register and connect to WARP:
```bash
sudo warp-cli register
sudo warp-cli connect
````
Confirm the connection with:
```bash
warp-cli status
```
---
## Step 2: Routing Traffic on the Server Machine
Now that WARP is connected, let's route the local network's Cloudflare-bound traffic through this tunnel.
1. **Enable IP forwarding:**
```bash
sudo sysctl -w net.ipv4.ip_forward=1
```
Make it persistent after reboot:
```bash
echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf
sudo sysctl -p
```
2. **Set up firewall rules to forward traffic:**
```bash
sudo nft add rule ip filter FORWARD iif "eth0" oif "CloudflareWARP" ip saddr 192.168.31.0/24 ip daddr 104.0.0.0/8 accept
sudo nft add rule ip filter FORWARD iif "CloudflareWARP" oif "eth0" ip saddr 104.0.0.0/8 ip daddr 192.168.31.0/24 ct state established,related accept
```
Replace `eth0` with your actual network interface if different.
3. **Make rules persistent:**
```bash
sudo apt install nftables
sudo nft list ruleset > /etc/nftables.conf
```
---
## Step 3: Configuring the Route on a Local PC (Linux)
On your local Linux machine:
1. **Add a static route:**
```bash
sudo ip route add 104.0.0.0/24 via <SERVER_IP>
```
Replace `<SERVER_IP>` with the internal IP of your WARP-enabled server. This should be a temporary solution, since it only effects a local machine. For a solution that can effect the whole local network, please see next step.
---
## Step 4: Configuring the Route on Your Wi-Fi Router (Recommended)
If your router allows adding static routes:
1. **Log in to your router's admin interface.**
2. **Navigate to the Static Routing section.** (This may vary depending on the router model.)
3. **Add a new static route:**
- **Destination Network:** `104.0.0.0`
- **Subnet Mask:** `255.255.255.0`
- **Gateway:** `<SERVER_IP>`
- **Metric:** `1` (or leave it default)
4. **Save and apply the settings.**
One of the key advantages of this method is how easy it is to disable once your ISP's routing issues are resolved. Since the changes affect the entire network at once, you can quickly restore normal network behavior by simply removing the static routes or disabling the forwarding rules, all without the need for complex reconfigurations.
---
## Final Thoughts
Congratulations! You've now routed all your Cloudflare-bound traffic through a secure WARP tunnel, effectively bypassing mysterious connectivity issues. If the sites ever go down again, at least you’ll have one less thing to blame—and one more thing to debug.
-

@ a012dc82:6458a70d
2025-02-06 02:34:44
In an unexpected turn of events that has sent ripples through the cryptocurrency world, Changpeng Zhao, the CEO of Binance, has extended his stay in the United States. This development is particularly striking against the backdrop of Binance's ongoing legal challenges and the intense scrutiny it faces from regulators worldwide. Zhao's decision to remain in the U.S. longer than anticipated is not just a personal choice but a strategic move that could have far-reaching implications for Binance's global operations and the cryptocurrency industry at large. It raises questions about Binance's future strategies and its efforts to navigate the complex web of international regulations.
**Table Of Content**
- Background: Binance's Regulatory Challenges
- Changpeng Zhao's Role and Influence
- The Unexpected U.S. Stay
- Legal Considerations
- Future of Binance and Crypto Regulation
- Conclusion
- FAQs
**Background: Binance's Regulatory Challenges**
Binance has emerged as a dominant force in the cryptocurrency exchange market, known for its vast selection of digital assets and high trading volumes. However, this success has not come without its share of challenges. The platform has been under the microscope of regulators across the globe, facing scrutiny over its compliance with stringent anti-money laundering (AML) standards and consumer protection laws. These regulatory hurdles have manifested in various forms, including formal warnings from financial watchdogs, in-depth investigations by regulatory authorities, and outright bans in certain jurisdictions. These challenges highlight the precarious position Binance occupies in the global financial landscape and underscore the delicate balance it must maintain between innovation and regulatory compliance.
**Changpeng Zhao's Role and Influence**
Changpeng Zhao, affectionately known as "CZ" in the crypto community, is more than just the CEO of Binance; he is a visionary and a key influencer in the cryptocurrency sector. Since founding Binance in 2017, Zhao has steered the company through exponential growth, navigating the volatile waters of the crypto market with a blend of technological innovation and strategic foresight. However, this journey has been fraught with controversies, particularly around issues of regulatory compliance and operational transparency. As the face and voice of Binance, Zhao's decisions, public statements, and even his personal movements are closely watched and analyzed for insights into Binance's future direction and its stance on regulatory matters.
**The Unexpected U.S. Stay**
The news of Zhao's extended stay in the U.S. has sparked a flurry of speculation and analysis within the financial and cryptocurrency sectors. This move is particularly intriguing given the current regulatory climate in the U.S., which is known for its stringent financial oversight and tough stance on cryptocurrency regulation. The extended stay raises several questions: Is Zhao seeking to engage in high-level negotiations with U.S. regulators? Is Binance planning a strategic pivot or expansion in the U.S. market? Or is this a proactive measure to address some of the legal challenges facing the company? Whatever the reason, Zhao's presence in the U.S. is a clear indication that significant developments are underway for Binance in one of the world's most important financial markets.
**Implications for Binance**
Zhao's decision to extend his stay in the U.S. could be interpreted as a strategic move to align Binance more closely with U.S. regulatory frameworks. This could involve enhancing the company's compliance systems, engaging in more transparent dialogue with regulatory bodies, or even restructuring some of Binance's business practices to conform to U.S. standards. Such changes could be crucial for Binance's continued operation and growth in the U.S. market, potentially opening doors to new partnerships, investment opportunities, and a broader customer base. Moreover, a stronger foothold in the U.S. could enhance Binance's reputation globally, signaling its commitment to regulatory compliance and financial stability.
**Industry Reactions**
The cryptocurrency industry and financial markets are abuzz with discussions about Zhao's extended stay in the U.S. Analysts, investors, and other industry players are keenly observing this development, understanding that Zhao's actions could signal a new chapter for Binance and possibly the entire cryptocurrency sector. His stay is being interpreted as a sign of Binance's willingness to engage more proactively with regulatory bodies, a move that could have significant implications for how cryptocurrency businesses operate globally. Additionally, Zhao's presence in the U.S. could influence other cryptocurrency exchanges and startups, setting a precedent for how they might approach regulatory challenges and market expansion.
**Legal Considerations**
Zhao's prolonged presence in the U.S. coincides with a critical period for Binance as it navigates complex legal waters. His decision to stay could be instrumental in facilitating more direct and effective engagement with U.S. legal authorities and regulatory bodies. This proximity to the heart of U.S. financial regulation might enable more constructive dialogues, potentially leading to resolutions or progress in the various legal cases and investigations Binance is currently involved in. Zhao's hands-on involvement in these legal matters could be a game-changer, offering opportunities for negotiation, compliance, and possibly even reconciliation with regulatory authorities.
**Potential Outcomes**
The involvement of Zhao in legal and regulatory discussions in the U.S. could lead to a spectrum of outcomes for Binance. These might range from reaching amicable settlements and forming robust compliance agreements to facing more stringent regulatory actions or operational restrictions, depending on the nature of the negotiations and the willingness of both parties to find common ground. The outcomes of these engagements are likely to have a significant impact on Binance's operational framework, its global reputation, and its ability to compete in the international market. They could also set important precedents for how major cryptocurrency exchanges interact with regulatory bodies and navigate legal challenges.
**Future of Binance and Crypto Regulation**
Zhao's decision to extend his stay in the U.S. is a pivotal moment in the evolving narrative of cryptocurrency regulation. It underscores the increasing importance of regulatory compliance for major players in the crypto space and suggests a potential shift towards more collaborative and proactive approaches between industry leaders and regulatory bodies. This development could be a harbinger of a new era in cryptocurrency regulation, where open dialogue, transparency, and compliance play central roles in shaping the industry's future.
**Strategic Shifts for Binance**
Depending on the outcomes of Zhao's engagements in the U.S., Binance may undergo significant strategic shifts, particularly in its approach to regulatory compliance, operational transparency, and market strategy. These shifts could have far-reaching implications, not only for Binance but for the entire cryptocurrency exchange industry. They could set new standards for regulatory compliance, influence the development of new financial products and services, and shape the future landscape of the global cryptocurrency market.
**Conclusion**
Changpeng Zhao's unexpected extended stay in the United States represents a critical and potentially transformative moment in Binance's ongoing legal and regulatory saga. It reflects the complex and dynamic nature of cryptocurrency regulation and the necessity for industry leaders to adeptly navigate these challenges. As the crypto community and financial markets watch closely, the decisions and actions taken by Zhao in the coming days and weeks could have far-reaching implications for Binance's future, its position in the global market, and the broader trajectory of the cryptocurrency industry.
**FAQs**
**What challenges is Binance currently facing?**
Binance is grappling with regulatory scrutiny worldwide, particularly concerning anti-money laundering standards and consumer protection laws. This has led to investigations, warnings, and bans in several countries.
**How might Zhao's stay in the U.S. impact Binance?**
Zhao's extended stay could signal a move towards greater regulatory compliance and cooperation in the U.S., potentially leading to operational changes and enhanced market access for Binance.
**What are the potential outcomes of Zhao's U.S. engagements?**
Outcomes could range from amicable settlements and compliance agreements to more stringent regulatory actions, depending on the nature of Zhao's discussions with U.S. authorities.
**How could this development affect the broader cryptocurrency industry?**
Zhao's actions could set a precedent for cryptocurrency exchanges in terms of regulatory compliance and engagement, influencing the global cryptocurrency regulatory landscape.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ fe32298e:20516265
2025-02-06 02:11:34
I've been using AI tools to help with coding for a while now, but it's always been copy/pasting into ChatGPT and DeepSeek. Faster iteration is better, and privacy is best. So it's time to figure out how to use these tools integrated into [VSCodium](https://github.com/VSCodium/vscodium) and running locally. After a quick review of the most popular extensions I've heard about, I settled on [Tabby](https://github.com/TabbyML/tabby).
## What the heck does this actually DO?
* Code completion - like autocomplete suggestions, looks at your code and suggests the next thing to type at the cursor. You can see it in gray text, then press Tab and it's added to your code.
* Chat - easily chat with an LLM about your code inside your editor, faster than copy/pasting into a website.
* Apparently it can write docs and tests too.
## Can I run it locally? Without a GPU? YES!
Tabby is optimized for small models that only need a few GBs of RAM. I'm using a fairly old [System76](https://system76.com/) Galago Pro with Core i5-10210U and 16 GB RAM. The fans spin up, and Tabby sometimes shows a warning about slow response time, but it seems usable.
## How do I get it set up?
This is the overview, look for step-by-step instructions at the end of this article.
1. Install the Tabby server, which runs locally.
1. Start the Tabby server and tell it to serve some models which it will download automatically.
1. Log in to the Tabby server web interface and create an admin account.
1. Install the Tabby extension in your editor.
1. Connect the Tabby extension to your Tabby server.
## How do I actually use it?
1. Click **Tabby** in the bottom-right corner to open the Tabby command palette.
1. Select **Chat** to open the Chat pane. Drag it to the right side if you want.
1. Or, *Ctrl-Shift-P* and type "tabby" to see some Tabby commands
1. Select some code and *Ctrl-Shift-P* "tabby" to see more Tabby commands
1. **Explain this** seems like a useful one.
Other than that, I don't know! I just started using it today.
## What model should I use?
As usual, it depends. If you're using CPU instead of GPU, start with the ones recommended by Tabby and shown in the Step-by-Step below. Tabby has a [registry of models](https://tabby.tabbyml.com/docs/models/) you can choose from, and a [leaderboard](https://leaderboard.tabbyml.com/) to compare them.
## Step-by-Step
This is for Ubuntu 24.04, and no GPU.
```
# install pre-reqs
sudo apt install build-essential cmake libssl-dev pkg-config
sudo apt install protobuf-compiler libopenblas-dev
sudo apt install make sqlite3 graphviz
# install rust
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
. "$HOME/.cargo/env"
# build tabby
git clone --recurse-submodules https://github.com/TabbyML/tabby
cd tabby
cargo build
# run tabby (downloads ~3 GB of models)
./target/debug/tabby serve --model StarCoder-1B --chat-model Qwen2-1.5B-Instruct
# browse to http://0.0.0.0:8080 and create an admin user
```
* Install the Tabby extension in your editor. VSCodium had it in the extensions store by searching for "tabby" or try this `ext install TabbyML.vscode-tabby`
* *Ctrl-Shift-P* and look for "Tabby: Connect to server"
* Use the default of `http://localhost:8080`
* Switch over to the Tabby web interface, click your Profile Picture and copy the auth token
* Paste that into Tabby somewhere. I'm sure you'll figure it out if you got this far.
-

@ 5d4b6c8d:8a1c1ee3
2025-02-06 00:49:05
Herbs and spices don't just taste great. Most of the time they're also great for you.
- Spicier foods ironically are strongly anti-inflammatory and chronic inflammation is one of the major drivers of poor health
- Roots, like turmeric/ginger/garlic/onion, are also strongly anti-inflammatory
- Herbs, like parsley and oregano, are super high in vitamins K, C, beta carotene, folate, and others, as well as potassium, manganese, and other minerals.
- Seeds, like cumin or coriander, are super mineral dense.
- Sea salt (unrefined) has a broad array and excellent balance of minerals.
So, what's the health principle?
Eat tastier more flavorful food. It's tasty because it's good for us (shut up sugar!).
originally posted at https://stacker.news/items/877209
 @ d57360cb:4fe7d935
2025-02-07 17:48:33You exist at the central point of life. Everywhere you go, everywhere you are you’ll find yourself peering out through your eyes at the center of everything. The center always stays the same, the contents that surround it are always moving and changing. Yet we foolishly believe the things that surround us and continuously transform hold the answers to change. Change comes from the center, from within. Then it affects all that comes within its path. Take care of your center and it will change the world that surrounds it.
@ d57360cb:4fe7d935
2025-02-07 17:48:33You exist at the central point of life. Everywhere you go, everywhere you are you’ll find yourself peering out through your eyes at the center of everything. The center always stays the same, the contents that surround it are always moving and changing. Yet we foolishly believe the things that surround us and continuously transform hold the answers to change. Change comes from the center, from within. Then it affects all that comes within its path. Take care of your center and it will change the world that surrounds it. @ 0463223a:3b14d673
2025-02-07 17:20:27Mental health is a funny old bag. As someone who’s been on various prescribed drugs for anxiety and depression for many years and is slowly weaning myself off (I’ve reduced my Venlafaxine dose by 1/6th. Next is the Pregabalin. One step at a time eh…) I’m not sure I fully understand normailty. Yesterday I finally got my hands on a record I absolutely love. I had it on cassette for 34 years but never knew the title, I recorded it from Friends FM (London pirate radio station) back in 1991. I chanced upon the title after some random YouTube clicks. I was so happy to find out, it was the only song on the tape that had eluded me after all these years. I’d been watching it on Discogs for a while and finally found one at a nice price. Yay! I’ve been lost in nostalgia all day. Lost friends have been on my mind. My best friend as a kid was an interesting character, a fantastic artist. He was by far the best at drawing in my class at primary school, heavily influenced by M.C. Escher and artists I’d never heard of, he’d grown up in a more culturally expansive house than I. He was into fashion and design but we weren’t clever kids at school. We had a lot in common musically and I always thought he’d be my MC back when I was starting out as a DJ. He was a very creative person but also a total fantasist. As a duo he was the extraverted, outspoken one, I barely spoke a word and relied on him a lot socially. He was sectioned under the Mental Health Act at 20 years old. We lost touch. Our birthday’s were within 1 day of each other and a third friend had his the day after mine. Our 16th birthdays fell on Friday, Saturday and Sunday. This was quite exciting. By midday on the Friday, he was permanently expelled from school. He’d taken acid in the morning and essentially enjoyed himself, running around and laughing a lot. The school didn’t approve, oh then his mother kicked him out of home. An eventful start to a messy weekend… We took a lot of acid as kids and I’m not shitting you when I say he, in particular, took a LOT. When we were 16 he told the local gypsies that he score them some acid, 100 tabs to be exact, about £200 worth. Not a lot of money but acid has always been very good value for money. He secured the goods easily, his brother was in the business so to speak but he chose not to pass the goods on… Over the course of a month, with the exception of the ones he gave to his friends he took the whole lot. (Side note, it also meant the local gypsies were after us. That’s another story). None of us could keep up as far as acid was concerned. Even as I’m writing I’m thinking of more funny incidents, like the time we were in a shop with umbrellas for sale. He picked one up, opened it and danced out the shop, stealing it in the most obnoxious, obvious way even and no one batted an eyelid. Funny as fuck at the time but not ideal behaviour… He was like that all the time. In today’s world he would have letters after his name for sure. Maybe not PhD or BSC but definitely ADHD and ASD. This ties in with the period where I became pretty much non-verbal. I’ve written about my uncertainty of my autism diagnosis before and it’s hard to say if this period of not speaking was due to that or extreme anxiety growing up with an absent, alcoholic, father and being bullied etc. It’s certainly safe to say taking loads of acid probably didn’t help! After many adventures, going to illegal raves, hustling to get DJ spots, trips in the woods, trips in bedrooms, trips pretty much everywhere, my friend became less and less stable. We fell out after he gave a bunch of my possessions to some random stranger at a rave. As kids we’d often swap clothes, jackets, shoes etc. It was one way of feeling like you had fresh clothes on a budget but giving my stuff away was the final straw. We fell out big time over that. The last time I saw him was in my early 20s. He looked like a ghost, a total shadow of a human. There was nothing there. Tragic. I seriously hope he’s well now. I’m long away from the people I grew up with, I might never find out. Thinking about you man. Since then, I’ve had another 2 friends sectioned under the Mental Health Act, drugs, petty crime and an unstable home life does does fuckry to a young brain. I’ve also lost a couple of friends to crack and heroin. Not fun. Drugs are bad m’kay. I’ve struggled with mental health my entire life, before drugs were an issue. Probably going back to 10 years old, at least as far as I can recall. Not that I want sympathy, far from it, I own my mistakes. I’m typing this shit on the internet because I want to and I want to honour lost friends. I own every single mistake. Maybe writing shit helps? Making music certainly does. It’s given me a sense of identity and I’m very lucky in what I do. Ironically I now work for a record label who’s motto is “Comforting the disturbed, disturbing the comfortable”. Very apt. The drummer in my current band took his own life in 2014. That was fucking shit. He was a totally straight edge guy. Very talented musician. Suicide is fucking vile, I don’t have the words to describe what that does to those left behind. Just a couple of weeks earlier we’d been offered a record deal with an advance to make an album, we were also working with another very respected artist in his live band. Like wtf man. I still don’t get it. I don’t even want to say more out of respect for his family. RIP brother. Nostr is a funny place, so many people I have very little in common with other than a dislike of banks (I hold the banksters responsible for the 2008 crash directly responsible for the death of my friend btw. I still say fuck each and every one of you. Cunts). I often see folks refer to others as ‘normies’. From what I gather a normie is someone who didn’t grow up posting on 4Chan. The funny thing is these people are often the one’s saying work hard, raise a family etc. I mean come on, you go on about working hard, raising families and eating healthily. Fucking hell!!! Like that’s sort of normal, you know? Tell me about sitting in a slum in south London with prostitutes, smoking crack thinking of ways you can get some money to score and then talk to me about ‘normies’. LMAO. For clarity, I didn’t have sex with them. I just wanted drugs and so did they. Nothing about this is glamorous by the way, it’s tragic and grim. I’m glad it’s not the norm. If you’re that healthy, hardworking guy with a family calling people normies, respect to you, in all honestly I’m envious. I wish I’d grown up in a stable home with two parents and a dad who hooked me up working for a fund straight out of school. Normies! Fuck I’m still laughing about that one. The other one that cracks me up is plebs, again you worked at a fund and you talk about being a pleb. Funny fucker. Respect for your sense of humour though. I’m not bitter (well not fully). I read the posts with interest and I’m always trying to learn new stuff, I’m happiest when learning. Learning is good for you. Fact. It’s a thoroughly miserable day here as write this, icey cold, grey and very windy, this is still the happiest I’ve been in life. I now have a wonderful, beautiful wife. No kids but with my background, I’ve decided these genes are best left here. There’s some sadness about that too but it could be worse, I might be the type to think Peter Thiel is cool. This probably reads like a right whinney thread but it isn’t. I’m excited about the future. I know some very talented people and I think we can do amazing things. Each day is a new opportunity. Being part of the underground internet is cool. We need free and open tools more than ever. The world is possibly the most fucked up it’s been in many years but also maybe that’s an illusion. I’m the last person you should ask about reality tbh. Anyway, that’s it for today. This probably reads like a confused mess and a nightmare for anyone who digs grammar but that’s cool, I’m writing without using AI or a filter, it’s not a work email. I’m typing as the words appear in my head, this is who I am. I’m a normie…
@ 0463223a:3b14d673
2025-02-07 17:20:27Mental health is a funny old bag. As someone who’s been on various prescribed drugs for anxiety and depression for many years and is slowly weaning myself off (I’ve reduced my Venlafaxine dose by 1/6th. Next is the Pregabalin. One step at a time eh…) I’m not sure I fully understand normailty. Yesterday I finally got my hands on a record I absolutely love. I had it on cassette for 34 years but never knew the title, I recorded it from Friends FM (London pirate radio station) back in 1991. I chanced upon the title after some random YouTube clicks. I was so happy to find out, it was the only song on the tape that had eluded me after all these years. I’d been watching it on Discogs for a while and finally found one at a nice price. Yay! I’ve been lost in nostalgia all day. Lost friends have been on my mind. My best friend as a kid was an interesting character, a fantastic artist. He was by far the best at drawing in my class at primary school, heavily influenced by M.C. Escher and artists I’d never heard of, he’d grown up in a more culturally expansive house than I. He was into fashion and design but we weren’t clever kids at school. We had a lot in common musically and I always thought he’d be my MC back when I was starting out as a DJ. He was a very creative person but also a total fantasist. As a duo he was the extraverted, outspoken one, I barely spoke a word and relied on him a lot socially. He was sectioned under the Mental Health Act at 20 years old. We lost touch. Our birthday’s were within 1 day of each other and a third friend had his the day after mine. Our 16th birthdays fell on Friday, Saturday and Sunday. This was quite exciting. By midday on the Friday, he was permanently expelled from school. He’d taken acid in the morning and essentially enjoyed himself, running around and laughing a lot. The school didn’t approve, oh then his mother kicked him out of home. An eventful start to a messy weekend… We took a lot of acid as kids and I’m not shitting you when I say he, in particular, took a LOT. When we were 16 he told the local gypsies that he score them some acid, 100 tabs to be exact, about £200 worth. Not a lot of money but acid has always been very good value for money. He secured the goods easily, his brother was in the business so to speak but he chose not to pass the goods on… Over the course of a month, with the exception of the ones he gave to his friends he took the whole lot. (Side note, it also meant the local gypsies were after us. That’s another story). None of us could keep up as far as acid was concerned. Even as I’m writing I’m thinking of more funny incidents, like the time we were in a shop with umbrellas for sale. He picked one up, opened it and danced out the shop, stealing it in the most obnoxious, obvious way even and no one batted an eyelid. Funny as fuck at the time but not ideal behaviour… He was like that all the time. In today’s world he would have letters after his name for sure. Maybe not PhD or BSC but definitely ADHD and ASD. This ties in with the period where I became pretty much non-verbal. I’ve written about my uncertainty of my autism diagnosis before and it’s hard to say if this period of not speaking was due to that or extreme anxiety growing up with an absent, alcoholic, father and being bullied etc. It’s certainly safe to say taking loads of acid probably didn’t help! After many adventures, going to illegal raves, hustling to get DJ spots, trips in the woods, trips in bedrooms, trips pretty much everywhere, my friend became less and less stable. We fell out after he gave a bunch of my possessions to some random stranger at a rave. As kids we’d often swap clothes, jackets, shoes etc. It was one way of feeling like you had fresh clothes on a budget but giving my stuff away was the final straw. We fell out big time over that. The last time I saw him was in my early 20s. He looked like a ghost, a total shadow of a human. There was nothing there. Tragic. I seriously hope he’s well now. I’m long away from the people I grew up with, I might never find out. Thinking about you man. Since then, I’ve had another 2 friends sectioned under the Mental Health Act, drugs, petty crime and an unstable home life does does fuckry to a young brain. I’ve also lost a couple of friends to crack and heroin. Not fun. Drugs are bad m’kay. I’ve struggled with mental health my entire life, before drugs were an issue. Probably going back to 10 years old, at least as far as I can recall. Not that I want sympathy, far from it, I own my mistakes. I’m typing this shit on the internet because I want to and I want to honour lost friends. I own every single mistake. Maybe writing shit helps? Making music certainly does. It’s given me a sense of identity and I’m very lucky in what I do. Ironically I now work for a record label who’s motto is “Comforting the disturbed, disturbing the comfortable”. Very apt. The drummer in my current band took his own life in 2014. That was fucking shit. He was a totally straight edge guy. Very talented musician. Suicide is fucking vile, I don’t have the words to describe what that does to those left behind. Just a couple of weeks earlier we’d been offered a record deal with an advance to make an album, we were also working with another very respected artist in his live band. Like wtf man. I still don’t get it. I don’t even want to say more out of respect for his family. RIP brother. Nostr is a funny place, so many people I have very little in common with other than a dislike of banks (I hold the banksters responsible for the 2008 crash directly responsible for the death of my friend btw. I still say fuck each and every one of you. Cunts). I often see folks refer to others as ‘normies’. From what I gather a normie is someone who didn’t grow up posting on 4Chan. The funny thing is these people are often the one’s saying work hard, raise a family etc. I mean come on, you go on about working hard, raising families and eating healthily. Fucking hell!!! Like that’s sort of normal, you know? Tell me about sitting in a slum in south London with prostitutes, smoking crack thinking of ways you can get some money to score and then talk to me about ‘normies’. LMAO. For clarity, I didn’t have sex with them. I just wanted drugs and so did they. Nothing about this is glamorous by the way, it’s tragic and grim. I’m glad it’s not the norm. If you’re that healthy, hardworking guy with a family calling people normies, respect to you, in all honestly I’m envious. I wish I’d grown up in a stable home with two parents and a dad who hooked me up working for a fund straight out of school. Normies! Fuck I’m still laughing about that one. The other one that cracks me up is plebs, again you worked at a fund and you talk about being a pleb. Funny fucker. Respect for your sense of humour though. I’m not bitter (well not fully). I read the posts with interest and I’m always trying to learn new stuff, I’m happiest when learning. Learning is good for you. Fact. It’s a thoroughly miserable day here as write this, icey cold, grey and very windy, this is still the happiest I’ve been in life. I now have a wonderful, beautiful wife. No kids but with my background, I’ve decided these genes are best left here. There’s some sadness about that too but it could be worse, I might be the type to think Peter Thiel is cool. This probably reads like a right whinney thread but it isn’t. I’m excited about the future. I know some very talented people and I think we can do amazing things. Each day is a new opportunity. Being part of the underground internet is cool. We need free and open tools more than ever. The world is possibly the most fucked up it’s been in many years but also maybe that’s an illusion. I’m the last person you should ask about reality tbh. Anyway, that’s it for today. This probably reads like a confused mess and a nightmare for anyone who digs grammar but that’s cool, I’m writing without using AI or a filter, it’s not a work email. I’m typing as the words appear in my head, this is who I am. I’m a normie… @ 1cb14ab3:95d52462
2025-02-07 16:41:54***Tree branches, driftwood coconut. 5'7" teardrop. [Dawei, Myanmar. 2020]*** --- #### Introduction Situated on Myanmar’s Grandfather Beach, this lens captures the dramatic shape of a steep, rocky hill that mirrors the arduous road leading to this remote location. Grandfather invites viewers to reflect on the connection between journey and destination, highlighting the tension and beauty of paths less traveled. #### Site & Placement The lens is positioned at the west end of the beach, focusing on the sharp hill rising above the shoreline. Its teardrop shape accentuates the rocky prominence, emphasizing its similarity to the road that winds toward the beach. A bench, placed 12 feet away, provides a place for viewers to absorb the rugged beauty of the scene. #### Impermanence & Integration Crafted from driftwood, branches, and stone, Grandfather is a fleeting presence in this timeless landscape. Its brief existence reflects the challenges and ephemerality of the journey it highlights, blending into the environment as it gradually succumbs to the elements. #### Reflection *Grandfather* invites viewers to consider the parallels between the physical journey to reach the beach and life’s broader paths. It stands as a reminder that even the most challenging routes can lead to moments of profound beauty. --- ## Photos         --- #### More from the 'Earth Lens' Series: [Earth Lens Series: Artist Statement + List of Works](https://hes.npub.pro/post/1731091744332/) ["Looking Glass" (Earth Lens 001)](https://hes.npub.pro/post/1736304563962/) ["Folsom" (Earth Lens 002)](https://hes.npub.pro/post/1737844073125/) ["Sanctuary" (Earth Lens 003)](https://hes.npub.pro/post/1731091744332/) ["Platte" (Earth Lens 004)](https://hes.npub.pro/post/sya8nv6q8k0w3olqcepwz) [COMING SOON: "Chongming" (Earth Lens 006)](https://hes.npub.pro/post/1731091744332/) --- #### More from Hes [Portfolio](https://hesart.npub.pro) [Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz) [Artist Statements](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) [Money](https://hes.npub.pro/tag/money) [Tech](https://hes.npub.pro/tag/tech) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
@ 1cb14ab3:95d52462
2025-02-07 16:41:54***Tree branches, driftwood coconut. 5'7" teardrop. [Dawei, Myanmar. 2020]*** --- #### Introduction Situated on Myanmar’s Grandfather Beach, this lens captures the dramatic shape of a steep, rocky hill that mirrors the arduous road leading to this remote location. Grandfather invites viewers to reflect on the connection between journey and destination, highlighting the tension and beauty of paths less traveled. #### Site & Placement The lens is positioned at the west end of the beach, focusing on the sharp hill rising above the shoreline. Its teardrop shape accentuates the rocky prominence, emphasizing its similarity to the road that winds toward the beach. A bench, placed 12 feet away, provides a place for viewers to absorb the rugged beauty of the scene. #### Impermanence & Integration Crafted from driftwood, branches, and stone, Grandfather is a fleeting presence in this timeless landscape. Its brief existence reflects the challenges and ephemerality of the journey it highlights, blending into the environment as it gradually succumbs to the elements. #### Reflection *Grandfather* invites viewers to consider the parallels between the physical journey to reach the beach and life’s broader paths. It stands as a reminder that even the most challenging routes can lead to moments of profound beauty. --- ## Photos         --- #### More from the 'Earth Lens' Series: [Earth Lens Series: Artist Statement + List of Works](https://hes.npub.pro/post/1731091744332/) ["Looking Glass" (Earth Lens 001)](https://hes.npub.pro/post/1736304563962/) ["Folsom" (Earth Lens 002)](https://hes.npub.pro/post/1737844073125/) ["Sanctuary" (Earth Lens 003)](https://hes.npub.pro/post/1731091744332/) ["Platte" (Earth Lens 004)](https://hes.npub.pro/post/sya8nv6q8k0w3olqcepwz) [COMING SOON: "Chongming" (Earth Lens 006)](https://hes.npub.pro/post/1731091744332/) --- #### More from Hes [Portfolio](https://hesart.npub.pro) [Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz) [Artist Statements](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) [Money](https://hes.npub.pro/tag/money) [Tech](https://hes.npub.pro/tag/tech) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.* @ f57bac88:6045161e
2025-02-07 16:23:37## **۱. ایران پیش از هخامنشیان** پیش از ظهور **کوروش بزرگ** و تأسیس امپراتوری هخامنشی، سرزمین ایران تحت حکومت چندین تمدن و دودمان مهم قرار داشت: ### **ایلامیان (حدود ۳۰۰۰–۶۴۰ پیش از میلاد)** - **قلمرو:** جنوب غربی ایران (خوزستان امروزی) - **دستاوردها:** - ایجاد یکی از نخستین دولتهای متمرکز در منطقه - توسعه خط نوشتاری ایلامی - جنگهای طولانی با بابل و آشور - در سال **۶۴۰ ق.م**، ایلام توسط **آشوربانیپال**، شاه آشور، فتح و ضعیف شد. ### **مادها (حدود ۷۰۰–۵۵۰ پیش از میلاد)** - **بنیانگذار:** دیاکو (۷۰۹–۶۵۶ ق.م) - **شاهان مهم:** - **فرورتیش:** مقابله با آشوریان و توسعه قلمرو ماد - **هووخشتره:** شکست آشور و گسترش قدرت مادها - **ایشتوویگو:** آخرین پادشاه ماد که توسط **کوروش بزرگ** شکست خورد - **دستاوردها:** - نخستین ارتش منظم در تاریخ ایران - اتحاد قبایل ایرانی و پایهگذاری حکومت متمرکز ### **خاندان هخامنشی پیش از کوروش** - **هخامنش:** بنیانگذار دودمان هخامنشی (حدود ۷۰۰ ق.م) - **چیشپیش:** حاکم آنشان - **کمبوجیه یکم:** پدر کوروش بزرگ کوروش بزرگ با شکست دادن مادها، نخستین امپراتوری بزرگ ایران را بنیان نهاد. --- ## **۲. هخامنشیان (۵۵۰–۳۳۰ پیش از میلاد)** ### **کوروش بزرگ؛ بنیانگذار نخستین امپراتوری ایرانی** - **قلمرو:** از آسیای مرکزی تا مدیترانه و مصر. - **دستاوردها:** - **تأسیس امپراتوری هخامنشی**؛ نخستین امپراتوری چندملیتی تاریخ. - **صدور منشور حقوق بشر (استوانه کوروش).** - **فتح بابل و آزادی یهودیان.** - **ایجاد سیستم حکومتی مبتنی بر احترام به فرهنگها و ادیان مختلف.** - **ایجاد جادههای ارتباطی برای تسهیل تجارت و حملونقل.** ### **داریوش بزرگ (۵۲۲–۴۸۶ ق.م)** - **گسترش امپراتوری و ایجاد نظام اداری پیشرفته.** - **ساخت تخت جمشید.** - **ایجاد راه شاهی برای ارتباط بهتر میان ایالتها.** - **ایجاد سیستم مالی و ضرب نخستین سکه ایرانی.** ### **خشایارشا (۴۸۶–۴۶۵ ق.م)** - **نبردهای مهم با یونانیان، از جمله جنگ سالامیس.** - **تکمیل تخت جمشید و گسترش معماری هخامنشی.** ### **پایان هخامنشیان** - داریوش سوم در برابر اسکندر مقدونی شکست خورد و امپراتوری سقوط کرد. --- ## **۳. اشکانیان (۲۴۷ پیش از میلاد–۲۲۴ میلادی)** - **بنیانگذار:** ارشک اول. - **دستاوردها:** - مقابله با امپراتوری روم. - ایجاد نظام حکومتی نیمهمتمرکز. - گسترش تجارت از طریق جاده ابریشم. --- ## **۴. ساسانیان (۲۲۴–۶۵۱ میلادی)** ### **شاپور اول (۲۴۱–۲۷۲ م)** - شکست دادن امپراتور روم (والرین). - توسعه علمی و فرهنگی. ### **انوشیروان دادگر (۵۳۱–۵۷۹ م)** - اصلاحات مالی و اداری. - ترویج علم و فلسفه. ### **یزدگرد سوم (۶۳۲–۶۵۱ م)** - آخرین شاه ساسانی، شکست در برابر حمله اعراب مسلمان. --- ## **۵. سلسلههای محلی و اسلامی** - **سامانیان، آلبویه، سلجوقیان** نقش مهمی در حفظ فرهنگ ایرانی داشتند. --- ## **۶. صفویان (۱۵۰۱–۱۷۳۶ میلادی)** - **شاه اسماعیل صفوی:** رسمی کردن مذهب تشیع. - **شاه عباس بزرگ:** توسعه اقتصادی، رونق اصفهان، اصلاحات نظامی. --- ## **۷. افشاریان (۱۷۳۶–۱۷۹۶ میلادی)** - **نادرشاه افشار:** شکست امپراتوری مغول هند، بازپسگیری خراسان. --- ## **۸. زندیان (۱۷۵۱–۱۷۹۴ میلادی)** - **کریمخان زند:** صلح و توسعه اقتصادی، ساخت بازار وکیل شیراز. --- ## **۹. قاجاریان (۱۷۹۶–۱۹۲۵ میلادی)** - **آغامحمدخان قاجار:** تأسیس حکومت قاجار. - **اصلاحات امیرکبیر، جنگهای ایران و روس، انقلاب مشروطه.** --- ## **۱۰. پهلوی (۱۹۲۵–۱۹۷۹ میلادی)** ### **رضاشاه (۱۹۲۵–۱۹۴۱)** - **نوسازی ایران، توسعه آموزش، ایجاد راهآهن سراسری.** - **تأسیس دانشگاه تهران و مدرنسازی نظام اداری.** - **حذف القاب سنتی و ارتقای جایگاه زنان در جامعه.** ### **محمدرضا شاه (۱۹۴۱–۱۹۷۹)** - **انقلاب سفید و اصلاحات ارضی.** - **افزایش درآمد نفتی و توسعه صنعتی ایران.** - **ایجاد زیرساختهای اقتصادی مدرن.** - **برگزاری جشنهای ۲۵۰۰ ساله شاهنشاهی.** --- ## **جمعبندی** ایران در طول تاریخ شاهد حکومتهای متعددی بوده که هر کدام در توسعه فرهنگی، اقتصادی و نظامی کشور نقش داشتهاند.
@ f57bac88:6045161e
2025-02-07 16:23:37## **۱. ایران پیش از هخامنشیان** پیش از ظهور **کوروش بزرگ** و تأسیس امپراتوری هخامنشی، سرزمین ایران تحت حکومت چندین تمدن و دودمان مهم قرار داشت: ### **ایلامیان (حدود ۳۰۰۰–۶۴۰ پیش از میلاد)** - **قلمرو:** جنوب غربی ایران (خوزستان امروزی) - **دستاوردها:** - ایجاد یکی از نخستین دولتهای متمرکز در منطقه - توسعه خط نوشتاری ایلامی - جنگهای طولانی با بابل و آشور - در سال **۶۴۰ ق.م**، ایلام توسط **آشوربانیپال**، شاه آشور، فتح و ضعیف شد. ### **مادها (حدود ۷۰۰–۵۵۰ پیش از میلاد)** - **بنیانگذار:** دیاکو (۷۰۹–۶۵۶ ق.م) - **شاهان مهم:** - **فرورتیش:** مقابله با آشوریان و توسعه قلمرو ماد - **هووخشتره:** شکست آشور و گسترش قدرت مادها - **ایشتوویگو:** آخرین پادشاه ماد که توسط **کوروش بزرگ** شکست خورد - **دستاوردها:** - نخستین ارتش منظم در تاریخ ایران - اتحاد قبایل ایرانی و پایهگذاری حکومت متمرکز ### **خاندان هخامنشی پیش از کوروش** - **هخامنش:** بنیانگذار دودمان هخامنشی (حدود ۷۰۰ ق.م) - **چیشپیش:** حاکم آنشان - **کمبوجیه یکم:** پدر کوروش بزرگ کوروش بزرگ با شکست دادن مادها، نخستین امپراتوری بزرگ ایران را بنیان نهاد. --- ## **۲. هخامنشیان (۵۵۰–۳۳۰ پیش از میلاد)** ### **کوروش بزرگ؛ بنیانگذار نخستین امپراتوری ایرانی** - **قلمرو:** از آسیای مرکزی تا مدیترانه و مصر. - **دستاوردها:** - **تأسیس امپراتوری هخامنشی**؛ نخستین امپراتوری چندملیتی تاریخ. - **صدور منشور حقوق بشر (استوانه کوروش).** - **فتح بابل و آزادی یهودیان.** - **ایجاد سیستم حکومتی مبتنی بر احترام به فرهنگها و ادیان مختلف.** - **ایجاد جادههای ارتباطی برای تسهیل تجارت و حملونقل.** ### **داریوش بزرگ (۵۲۲–۴۸۶ ق.م)** - **گسترش امپراتوری و ایجاد نظام اداری پیشرفته.** - **ساخت تخت جمشید.** - **ایجاد راه شاهی برای ارتباط بهتر میان ایالتها.** - **ایجاد سیستم مالی و ضرب نخستین سکه ایرانی.** ### **خشایارشا (۴۸۶–۴۶۵ ق.م)** - **نبردهای مهم با یونانیان، از جمله جنگ سالامیس.** - **تکمیل تخت جمشید و گسترش معماری هخامنشی.** ### **پایان هخامنشیان** - داریوش سوم در برابر اسکندر مقدونی شکست خورد و امپراتوری سقوط کرد. --- ## **۳. اشکانیان (۲۴۷ پیش از میلاد–۲۲۴ میلادی)** - **بنیانگذار:** ارشک اول. - **دستاوردها:** - مقابله با امپراتوری روم. - ایجاد نظام حکومتی نیمهمتمرکز. - گسترش تجارت از طریق جاده ابریشم. --- ## **۴. ساسانیان (۲۲۴–۶۵۱ میلادی)** ### **شاپور اول (۲۴۱–۲۷۲ م)** - شکست دادن امپراتور روم (والرین). - توسعه علمی و فرهنگی. ### **انوشیروان دادگر (۵۳۱–۵۷۹ م)** - اصلاحات مالی و اداری. - ترویج علم و فلسفه. ### **یزدگرد سوم (۶۳۲–۶۵۱ م)** - آخرین شاه ساسانی، شکست در برابر حمله اعراب مسلمان. --- ## **۵. سلسلههای محلی و اسلامی** - **سامانیان، آلبویه، سلجوقیان** نقش مهمی در حفظ فرهنگ ایرانی داشتند. --- ## **۶. صفویان (۱۵۰۱–۱۷۳۶ میلادی)** - **شاه اسماعیل صفوی:** رسمی کردن مذهب تشیع. - **شاه عباس بزرگ:** توسعه اقتصادی، رونق اصفهان، اصلاحات نظامی. --- ## **۷. افشاریان (۱۷۳۶–۱۷۹۶ میلادی)** - **نادرشاه افشار:** شکست امپراتوری مغول هند، بازپسگیری خراسان. --- ## **۸. زندیان (۱۷۵۱–۱۷۹۴ میلادی)** - **کریمخان زند:** صلح و توسعه اقتصادی، ساخت بازار وکیل شیراز. --- ## **۹. قاجاریان (۱۷۹۶–۱۹۲۵ میلادی)** - **آغامحمدخان قاجار:** تأسیس حکومت قاجار. - **اصلاحات امیرکبیر، جنگهای ایران و روس، انقلاب مشروطه.** --- ## **۱۰. پهلوی (۱۹۲۵–۱۹۷۹ میلادی)** ### **رضاشاه (۱۹۲۵–۱۹۴۱)** - **نوسازی ایران، توسعه آموزش، ایجاد راهآهن سراسری.** - **تأسیس دانشگاه تهران و مدرنسازی نظام اداری.** - **حذف القاب سنتی و ارتقای جایگاه زنان در جامعه.** ### **محمدرضا شاه (۱۹۴۱–۱۹۷۹)** - **انقلاب سفید و اصلاحات ارضی.** - **افزایش درآمد نفتی و توسعه صنعتی ایران.** - **ایجاد زیرساختهای اقتصادی مدرن.** - **برگزاری جشنهای ۲۵۰۰ ساله شاهنشاهی.** --- ## **جمعبندی** ایران در طول تاریخ شاهد حکومتهای متعددی بوده که هر کدام در توسعه فرهنگی، اقتصادی و نظامی کشور نقش داشتهاند. @ f57bac88:6045161e
2025-02-07 16:22:07#### ۱. دوران پالئولیتیک (عصر حجر قدیم) دوران پالئولیتیک یا عصر سنگ قدیم، اولین دوره از تاریخ بشری است که به زمانی برمیگردد که انسانها هنوز بهطور عمده در زندگی شکارچی-گردآورنده بودند و ابزارهای ابتدایی سنگی را برای تأمین غذا و سایر نیازهای خود استفاده میکردند. این دوران بیش از ۲٫۵ میلیون سال به طول انجامید و انسانها در آن زندگی سخت و متکی به شکار و گردآوری میوهها و گیاهان داشتند. در ایران، این دوره بیشتر در مناطق غربی و مرکزی کشور شواهدی از سکونت انسانهای اولیه بهجا گذاشته است. مناطقی مانند **غارهای میرعماد در لرستان** و **غار شوش** در جنوب غرب ایران، از مکانهای مهم این دوران هستند که نشاندهنده حضور انسانهای نئاندرتال و هوموساپینس در این منطقه هستند. ابزارهای سنگی کشفشده از این مکانها، نشاندهنده استفاده انسانهای اولیه از سنگها برای ساخت چاقوها، تیغهها و ابزارهای مختلف برای شکار و جمعآوری غذا بوده است. در این دوران، انسانها همچنان در گروههای کوچک زندگی میکردند و عمدتاً بهصورت پراکنده در مناطق مختلف سکونت داشتند. #### ۲. دوران نوسنگی (Neolithic) دوران نوسنگی، که آغاز آن به حدود ۱۰,۰۰۰ سال پیش بازمیگردد، بهعنوان یکی از تحولات اساسی تاریخ بشری شناخته میشود. در این دوره، انسانها به تدریج از زندگی شکارگری به کشاورزی و دامداری روی آوردند. این تغییر، نه تنها در سبک زندگی بشر، بلکه در ساختارهای اجتماعی، اقتصادی و فرهنگی جوامع نیز انقلابی بزرگ ایجاد کرد. انسانها برای اولین بار گیاهان را کشت و از آنها برای تأمین غذا استفاده کردند و همچنین دامها را اهلی کردند. در ایران، از جمله مهمترین مکانهایی که نشاندهنده آغاز کشاورزی و زندگی روستایی است میتوان به **چغاگلان** در کردستان اشاره کرد. این منطقه یکی از اولین محوطههای باستانی است که شواهدی از کشاورزی اولیه در آن پیدا شده است. همچنین **تل برآفتاب** در کرمانشاه و **تل هندیجان** در جنوب غرب ایران نیز از دیگر سایتهای مهم نوسنگی هستند که شواهدی از نخستین جوامع کشاورزی و دامداری در آنها بهدست آمده است. زندگی در این دوران بهطور عمده در روستاهای کوچک متمرکز بود و مردم در کنار کشاورزی و دامداری، بهصورت ابتدایی صنایع دستی نیز تولید میکردند. این دوره شروعی برای روابط تجاری و فرهنگی میان جوامع مختلف بود که به تدریج پیچیدگیهای بیشتری پیدا کرد. #### ۳. دوران مس و سنگ (Chalcolithic) دوران مس و سنگ که به آن **دوران چالهکولیتیک** نیز گفته میشود، مرحلهای میان دوران نوسنگی و مفرغ است که حدود ۵,۰۰۰ سال پیش آغاز شد. در این دوران، انسانها از فلزات، بهویژه مس، استفاده کردند و ابزارهایی ساختند که در کنار ابزارهای سنگی قرار میگرفت. این دوره، بهویژه بهعنوان دوران گذار از عصر سنگ به عصر مفرغ شناخته میشود. یکی از مهمترین ویژگیهای این دوران، استفاده اولیه از فلزات است که امکان ساخت ابزارهایی با دقت و کارایی بالاتر را فراهم کرد. در کنار کشاورزی و دامداری، تجارت و ارتباطات میان جوامع مختلف شروع به گسترش کرد و باعث تبادل کالاها و ایدهها بین مناطق مختلف شد. از مهمترین محوطههای باستانی این دوره میتوان به **تپه سیلک** در کاشان اشاره کرد که در آن آثار بسیاری از زندگی کشاورزی، صنایع دستی و حتی شواهدی از ساختوسازهای ابتدایی پیدا شده است. **تپه نوشیجان** در همدان نیز یکی دیگر از سایتهای مهم این دوران است که در آن آثار مس و ابزارهای فلزی کشف شده است. این آثار نشاندهنده توسعه فنون فلزکاری و استفاده از مس برای ساخت ابزارهای پیچیدهتر در این دوره است. #### ۴. دوران مفرغ (Bronze Age) دوران مفرغ، که از حدود ۳۰۰۰ سال پیش از میلاد آغاز شد، یکی از مهمترین دورانها در تاریخ بشری است. در این دوره، استفاده از فلز مفرغ برای ساخت ابزار، سلاحها و اشیاء تزئینی گسترش یافت. دوران مفرغ نهتنها از نظر تکنولوژیکی بلکه از نظر فرهنگی و اجتماعی نیز اهمیت زیادی دارد، زیرا در این دوره جوامع انسانی پیچیدگیهای بیشتری پیدا کرده و بهتدریج به تمدنهای بزرگتری تبدیل شدند. ایران در دوران مفرغ شاهد شکلگیری تمدنهای اولیهای همچون ایلامیان بود. این تمدنها در جنوب غربی ایران (مناطق کنونی استان خوزستان و استان ایلام) و در نواحی شمال غرب کشور ریشه دوانیدند. در این دوران، ساختارهای سیاسی و اجتماعی پیچیدهتر شد و نشانههای اولیه از شکلگیری دولتهای شهری و پیشرفتهتر بهوجود آمد. یکی از مهمترین سایتهای باستانی این دوره، **تپه حسنلو** در آذربایجان غربی است که شواهدی از یک تمدن پیشرفته با استفاده از مفرغ در آن پیدا شده است. این تپه که بهعنوان یکی از مهمترین محوطههای باستانی شناخته میشود، آثار مختلفی از جمله سلاحها، ابزارها و مصنوعات هنری از دوران مفرغ را در خود جای داده است. همچنین، **تپه سفالی** در جنوب غرب ایران نیز نشاندهنده روند پیشرفت در استفاده از مفرغ و تغییرات فرهنگی در این دوره است. در این زمان، جوامع انسانی بهطور گستردهتری در زمینههای کشاورزی، تجارت، فنون ساختوساز و هنرهای تزئینی فعالیت میکردند. استفاده از مفرغ نهتنها به ارتقاء صنعت و فنون مرتبط با آن کمک کرد، بلکه زمینه را برای ظهور تمدنهای بزرگتر مانند ایلامیان فراهم آورد. #### نتیجهگیری تاریخ باستانی ایران گواهی است بر تکامل انسانها از دورههای ابتدایی شکارگری و گردآوری به جوامع پیچیدهتر کشاورزی، دامداری و تولید صنایع دستی و فلزی. این تحولات از دوران پالئولیتیک تا دوران مفرغ باعث شد تا ایران به یکی از کانونهای مهم تمدنسازی در تاریخ بشری تبدیل شود. پیشرفتهای تکنولوژیکی، ساختارهای اجتماعی پیچیدهتر و گسترش ارتباطات تجاری و فرهنگی در این دورهها، زمینهساز ظهور تمدنهای بزرگ و پیچیدهای مانند ایلامیان، هخامنشیان و ساسانیان شد که در تاریخ ایران و جهان نقش مهمی ایفا کردند. این تاریخچه در کنار آثار باستانی که از این دوران بهجا مانده است، همچنان دلیلی برای عظمت و شکوه تمدن ایران در تاریخ بشر است.
@ f57bac88:6045161e
2025-02-07 16:22:07#### ۱. دوران پالئولیتیک (عصر حجر قدیم) دوران پالئولیتیک یا عصر سنگ قدیم، اولین دوره از تاریخ بشری است که به زمانی برمیگردد که انسانها هنوز بهطور عمده در زندگی شکارچی-گردآورنده بودند و ابزارهای ابتدایی سنگی را برای تأمین غذا و سایر نیازهای خود استفاده میکردند. این دوران بیش از ۲٫۵ میلیون سال به طول انجامید و انسانها در آن زندگی سخت و متکی به شکار و گردآوری میوهها و گیاهان داشتند. در ایران، این دوره بیشتر در مناطق غربی و مرکزی کشور شواهدی از سکونت انسانهای اولیه بهجا گذاشته است. مناطقی مانند **غارهای میرعماد در لرستان** و **غار شوش** در جنوب غرب ایران، از مکانهای مهم این دوران هستند که نشاندهنده حضور انسانهای نئاندرتال و هوموساپینس در این منطقه هستند. ابزارهای سنگی کشفشده از این مکانها، نشاندهنده استفاده انسانهای اولیه از سنگها برای ساخت چاقوها، تیغهها و ابزارهای مختلف برای شکار و جمعآوری غذا بوده است. در این دوران، انسانها همچنان در گروههای کوچک زندگی میکردند و عمدتاً بهصورت پراکنده در مناطق مختلف سکونت داشتند. #### ۲. دوران نوسنگی (Neolithic) دوران نوسنگی، که آغاز آن به حدود ۱۰,۰۰۰ سال پیش بازمیگردد، بهعنوان یکی از تحولات اساسی تاریخ بشری شناخته میشود. در این دوره، انسانها به تدریج از زندگی شکارگری به کشاورزی و دامداری روی آوردند. این تغییر، نه تنها در سبک زندگی بشر، بلکه در ساختارهای اجتماعی، اقتصادی و فرهنگی جوامع نیز انقلابی بزرگ ایجاد کرد. انسانها برای اولین بار گیاهان را کشت و از آنها برای تأمین غذا استفاده کردند و همچنین دامها را اهلی کردند. در ایران، از جمله مهمترین مکانهایی که نشاندهنده آغاز کشاورزی و زندگی روستایی است میتوان به **چغاگلان** در کردستان اشاره کرد. این منطقه یکی از اولین محوطههای باستانی است که شواهدی از کشاورزی اولیه در آن پیدا شده است. همچنین **تل برآفتاب** در کرمانشاه و **تل هندیجان** در جنوب غرب ایران نیز از دیگر سایتهای مهم نوسنگی هستند که شواهدی از نخستین جوامع کشاورزی و دامداری در آنها بهدست آمده است. زندگی در این دوران بهطور عمده در روستاهای کوچک متمرکز بود و مردم در کنار کشاورزی و دامداری، بهصورت ابتدایی صنایع دستی نیز تولید میکردند. این دوره شروعی برای روابط تجاری و فرهنگی میان جوامع مختلف بود که به تدریج پیچیدگیهای بیشتری پیدا کرد. #### ۳. دوران مس و سنگ (Chalcolithic) دوران مس و سنگ که به آن **دوران چالهکولیتیک** نیز گفته میشود، مرحلهای میان دوران نوسنگی و مفرغ است که حدود ۵,۰۰۰ سال پیش آغاز شد. در این دوران، انسانها از فلزات، بهویژه مس، استفاده کردند و ابزارهایی ساختند که در کنار ابزارهای سنگی قرار میگرفت. این دوره، بهویژه بهعنوان دوران گذار از عصر سنگ به عصر مفرغ شناخته میشود. یکی از مهمترین ویژگیهای این دوران، استفاده اولیه از فلزات است که امکان ساخت ابزارهایی با دقت و کارایی بالاتر را فراهم کرد. در کنار کشاورزی و دامداری، تجارت و ارتباطات میان جوامع مختلف شروع به گسترش کرد و باعث تبادل کالاها و ایدهها بین مناطق مختلف شد. از مهمترین محوطههای باستانی این دوره میتوان به **تپه سیلک** در کاشان اشاره کرد که در آن آثار بسیاری از زندگی کشاورزی، صنایع دستی و حتی شواهدی از ساختوسازهای ابتدایی پیدا شده است. **تپه نوشیجان** در همدان نیز یکی دیگر از سایتهای مهم این دوران است که در آن آثار مس و ابزارهای فلزی کشف شده است. این آثار نشاندهنده توسعه فنون فلزکاری و استفاده از مس برای ساخت ابزارهای پیچیدهتر در این دوره است. #### ۴. دوران مفرغ (Bronze Age) دوران مفرغ، که از حدود ۳۰۰۰ سال پیش از میلاد آغاز شد، یکی از مهمترین دورانها در تاریخ بشری است. در این دوره، استفاده از فلز مفرغ برای ساخت ابزار، سلاحها و اشیاء تزئینی گسترش یافت. دوران مفرغ نهتنها از نظر تکنولوژیکی بلکه از نظر فرهنگی و اجتماعی نیز اهمیت زیادی دارد، زیرا در این دوره جوامع انسانی پیچیدگیهای بیشتری پیدا کرده و بهتدریج به تمدنهای بزرگتری تبدیل شدند. ایران در دوران مفرغ شاهد شکلگیری تمدنهای اولیهای همچون ایلامیان بود. این تمدنها در جنوب غربی ایران (مناطق کنونی استان خوزستان و استان ایلام) و در نواحی شمال غرب کشور ریشه دوانیدند. در این دوران، ساختارهای سیاسی و اجتماعی پیچیدهتر شد و نشانههای اولیه از شکلگیری دولتهای شهری و پیشرفتهتر بهوجود آمد. یکی از مهمترین سایتهای باستانی این دوره، **تپه حسنلو** در آذربایجان غربی است که شواهدی از یک تمدن پیشرفته با استفاده از مفرغ در آن پیدا شده است. این تپه که بهعنوان یکی از مهمترین محوطههای باستانی شناخته میشود، آثار مختلفی از جمله سلاحها، ابزارها و مصنوعات هنری از دوران مفرغ را در خود جای داده است. همچنین، **تپه سفالی** در جنوب غرب ایران نیز نشاندهنده روند پیشرفت در استفاده از مفرغ و تغییرات فرهنگی در این دوره است. در این زمان، جوامع انسانی بهطور گستردهتری در زمینههای کشاورزی، تجارت، فنون ساختوساز و هنرهای تزئینی فعالیت میکردند. استفاده از مفرغ نهتنها به ارتقاء صنعت و فنون مرتبط با آن کمک کرد، بلکه زمینه را برای ظهور تمدنهای بزرگتر مانند ایلامیان فراهم آورد. #### نتیجهگیری تاریخ باستانی ایران گواهی است بر تکامل انسانها از دورههای ابتدایی شکارگری و گردآوری به جوامع پیچیدهتر کشاورزی، دامداری و تولید صنایع دستی و فلزی. این تحولات از دوران پالئولیتیک تا دوران مفرغ باعث شد تا ایران به یکی از کانونهای مهم تمدنسازی در تاریخ بشری تبدیل شود. پیشرفتهای تکنولوژیکی، ساختارهای اجتماعی پیچیدهتر و گسترش ارتباطات تجاری و فرهنگی در این دورهها، زمینهساز ظهور تمدنهای بزرگ و پیچیدهای مانند ایلامیان، هخامنشیان و ساسانیان شد که در تاریخ ایران و جهان نقش مهمی ایفا کردند. این تاریخچه در کنار آثار باستانی که از این دوران بهجا مانده است، همچنان دلیلی برای عظمت و شکوه تمدن ایران در تاریخ بشر است. @ a012dc82:6458a70d
2025-02-07 15:23:54In the intricate and rapidly evolving world of digital currencies, the interplay between Bitcoin and the US dollar, particularly through the medium of stablecoins, stands out as a subject of profound significance. Mark Goodwin, a renowned figure in the realm of Bitcoin and an advocate for decentralized financial systems, sheds light on this complex dynamic. This article delves deeper into the nuanced relationship between Bitcoin and the dollar, the pivotal role of stablecoins, and the risks they entail, drawing upon the extensive expertise of Goodwin. **Table Of Content** - Understanding the Bitcoin-Dollar Symbiosis - The Role of Stablecoins - Mark Goodwin's Perspective on Stablecoins - Conclusion - FAQs **Understanding the Bitcoin-Dollar Symbiosis** The relationship between Bitcoin and the US dollar is a fascinating study in contrasts and interdependencies. Bitcoin, known for its decentralized nature, offers a politically neutral platform but is characterized by significant price volatility. This volatility stands in stark contrast to the relative stability of the US dollar, a currency backed by the full faith and credit of the US government. The dollar, often used as a benchmark for Bitcoin's value, follows its trajectory in many ways, particularly in regions where Bitcoin is gaining traction. The symbiosis between Bitcoin and the dollar is particularly evident in the context of global financial instability. In regions with volatile local currencies, the adoption of Bitcoin often leads to a parallel increase in the use of dollar-based stablecoins. This phenomenon suggests that Bitcoin's growth could inadvertently bolster the stability and global reach of the US dollar. Moreover, the Bitcoin-dollar dynamic is not just limited to direct financial transactions. It extends to the broader implications for monetary policy, international trade, and global economic stability. As Bitcoin continues to gain acceptance, it challenges traditional financial systems and currencies, including the dollar, prompting a reevaluation of their roles in a digital age. **The Role of Stablecoins** Stablecoins, designed to bridge the gap between traditional finance and the digital asset space, play a crucial role in this relationship. By pegging their value to stable assets like the US dollar, they offer a less volatile alternative to cryptocurrencies like Bitcoin. This stability is essential for global commerce, enabling near-instantaneous transactions with lower fees compared to traditional banking systems. In economies plagued by inflation, stablecoins offer a haven for individuals and businesses to preserve their wealth. They provide a degree of financial stability and predictability that is often lacking in local currencies. This aspect of stablecoins is particularly appealing in developing countries, where currency instability can be a significant barrier to economic growth and stability. Furthermore, stablecoins are increasingly being seen as a tool for financial inclusion. They offer an accessible entry point for individuals who are unbanked or underbanked, providing them with a means to participate in the global economy. This potential for social impact adds another layer of significance to the role of stablecoins in the financial ecosystem. **Mark Goodwin's Perspective on Stablecoins** Mark Goodwin, with his deep understanding of Bitcoin and its implications for the financial world, offers a critical perspective on stablecoins. He acknowledges their potential benefits but also highlights the risks associated with their use. **Price Stability Concerns** Goodwin points out that while stablecoins aim to maintain a stable value, there are inherent risks in keeping their peg to the underlying asset. Market conditions, liquidity issues, and redemption pressures can all threaten the stability of stablecoins. If these risks are not adequately managed, it can lead to a deviation from the peg and a potential loss of trust from users. **Regulatory Challenges** The evolving regulatory landscape surrounding stablecoins is another area of concern. As authorities worldwide grapple with how to regulate these digital assets, stablecoin projects must navigate a complex web of financial regulations to achieve long-term viability. Goodwin emphasizes the need for a balanced regulatory approach that ensures consumer protection without stifling innovation. **Potential for Market Manipulation** Given their substantial market capitalization, stablecoins are susceptible to market manipulation. The limited oversight in the rapidly expanding cryptocurrency space amplifies this risk. Goodwin advocates for enhanced transparency and regulatory frameworks to mitigate these risks and ensure market integrity. **Conclusion** The relationship between Bitcoin and the dollar, especially through the medium of stablecoins, represents a delicate balance between the ideals of decentralization and the practicalities of financial stability. While stablecoins offer promising solutions for global financial transactions, they come with inherent risks that require careful consideration. Goodwin's insights underscore the importance of vigilance and a thoughtful approach to integrating these digital assets into the broader financial system. As the market continues to evolve, the role of stablecoins in shaping the future of finance remains a critical area for exploration and debate. **FAQs** **How do stablecoins fit into the Bitcoin-dollar dynamic?** Stablecoins serve as a bridge between traditional finance and digital assets. Pegged to stable assets like the US dollar, they offer a less volatile alternative to cryptocurrencies and facilitate global commerce with near-instant transactions and lower fees. **What are the risks associated with stablecoins?** Risks include challenges in maintaining the peg to the underlying asset, regulatory uncertainties, and potential for market manipulation. These risks can threaten the stability and trust in stablecoins. **What is Mark Goodwin's perspective on stablecoins?** Mark Goodwin acknowledges the benefits of stablecoins but warns about the risks of centralization and manipulation. He emphasizes the need for balanced regulation and transparency to mitigate risks. **Can stablecoins promote financial inclusion?** Yes, stablecoins can provide financial inclusion by offering an accessible entry point for unbanked or underbanked individuals, allowing them to participate in the global economy. **How does Bitcoin's growth affect the US dollar?** Bitcoin's growth, particularly in regions with unstable currencies, can lead to increased adoption of dollar-based stablecoins, potentially bolstering the US dollar's global reach and stability. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-07 15:23:54In the intricate and rapidly evolving world of digital currencies, the interplay between Bitcoin and the US dollar, particularly through the medium of stablecoins, stands out as a subject of profound significance. Mark Goodwin, a renowned figure in the realm of Bitcoin and an advocate for decentralized financial systems, sheds light on this complex dynamic. This article delves deeper into the nuanced relationship between Bitcoin and the dollar, the pivotal role of stablecoins, and the risks they entail, drawing upon the extensive expertise of Goodwin. **Table Of Content** - Understanding the Bitcoin-Dollar Symbiosis - The Role of Stablecoins - Mark Goodwin's Perspective on Stablecoins - Conclusion - FAQs **Understanding the Bitcoin-Dollar Symbiosis** The relationship between Bitcoin and the US dollar is a fascinating study in contrasts and interdependencies. Bitcoin, known for its decentralized nature, offers a politically neutral platform but is characterized by significant price volatility. This volatility stands in stark contrast to the relative stability of the US dollar, a currency backed by the full faith and credit of the US government. The dollar, often used as a benchmark for Bitcoin's value, follows its trajectory in many ways, particularly in regions where Bitcoin is gaining traction. The symbiosis between Bitcoin and the dollar is particularly evident in the context of global financial instability. In regions with volatile local currencies, the adoption of Bitcoin often leads to a parallel increase in the use of dollar-based stablecoins. This phenomenon suggests that Bitcoin's growth could inadvertently bolster the stability and global reach of the US dollar. Moreover, the Bitcoin-dollar dynamic is not just limited to direct financial transactions. It extends to the broader implications for monetary policy, international trade, and global economic stability. As Bitcoin continues to gain acceptance, it challenges traditional financial systems and currencies, including the dollar, prompting a reevaluation of their roles in a digital age. **The Role of Stablecoins** Stablecoins, designed to bridge the gap between traditional finance and the digital asset space, play a crucial role in this relationship. By pegging their value to stable assets like the US dollar, they offer a less volatile alternative to cryptocurrencies like Bitcoin. This stability is essential for global commerce, enabling near-instantaneous transactions with lower fees compared to traditional banking systems. In economies plagued by inflation, stablecoins offer a haven for individuals and businesses to preserve their wealth. They provide a degree of financial stability and predictability that is often lacking in local currencies. This aspect of stablecoins is particularly appealing in developing countries, where currency instability can be a significant barrier to economic growth and stability. Furthermore, stablecoins are increasingly being seen as a tool for financial inclusion. They offer an accessible entry point for individuals who are unbanked or underbanked, providing them with a means to participate in the global economy. This potential for social impact adds another layer of significance to the role of stablecoins in the financial ecosystem. **Mark Goodwin's Perspective on Stablecoins** Mark Goodwin, with his deep understanding of Bitcoin and its implications for the financial world, offers a critical perspective on stablecoins. He acknowledges their potential benefits but also highlights the risks associated with their use. **Price Stability Concerns** Goodwin points out that while stablecoins aim to maintain a stable value, there are inherent risks in keeping their peg to the underlying asset. Market conditions, liquidity issues, and redemption pressures can all threaten the stability of stablecoins. If these risks are not adequately managed, it can lead to a deviation from the peg and a potential loss of trust from users. **Regulatory Challenges** The evolving regulatory landscape surrounding stablecoins is another area of concern. As authorities worldwide grapple with how to regulate these digital assets, stablecoin projects must navigate a complex web of financial regulations to achieve long-term viability. Goodwin emphasizes the need for a balanced regulatory approach that ensures consumer protection without stifling innovation. **Potential for Market Manipulation** Given their substantial market capitalization, stablecoins are susceptible to market manipulation. The limited oversight in the rapidly expanding cryptocurrency space amplifies this risk. Goodwin advocates for enhanced transparency and regulatory frameworks to mitigate these risks and ensure market integrity. **Conclusion** The relationship between Bitcoin and the dollar, especially through the medium of stablecoins, represents a delicate balance between the ideals of decentralization and the practicalities of financial stability. While stablecoins offer promising solutions for global financial transactions, they come with inherent risks that require careful consideration. Goodwin's insights underscore the importance of vigilance and a thoughtful approach to integrating these digital assets into the broader financial system. As the market continues to evolve, the role of stablecoins in shaping the future of finance remains a critical area for exploration and debate. **FAQs** **How do stablecoins fit into the Bitcoin-dollar dynamic?** Stablecoins serve as a bridge between traditional finance and digital assets. Pegged to stable assets like the US dollar, they offer a less volatile alternative to cryptocurrencies and facilitate global commerce with near-instant transactions and lower fees. **What are the risks associated with stablecoins?** Risks include challenges in maintaining the peg to the underlying asset, regulatory uncertainties, and potential for market manipulation. These risks can threaten the stability and trust in stablecoins. **What is Mark Goodwin's perspective on stablecoins?** Mark Goodwin acknowledges the benefits of stablecoins but warns about the risks of centralization and manipulation. He emphasizes the need for balanced regulation and transparency to mitigate risks. **Can stablecoins promote financial inclusion?** Yes, stablecoins can provide financial inclusion by offering an accessible entry point for unbanked or underbanked individuals, allowing them to participate in the global economy. **How does Bitcoin's growth affect the US dollar?** Bitcoin's growth, particularly in regions with unstable currencies, can lead to increased adoption of dollar-based stablecoins, potentially bolstering the US dollar's global reach and stability. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ f683e870:557f5ef2
2025-02-07 14:33:31After many months of ideation, research, and heads-down building, <span data-type="mention" data-id="726a1e261cc6474674e8285e3951b3bb139be9a773d1acf49dc868db861a1c11" data-label="nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9">@nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9</span> and myself are excited to announce our new project called Vertex. **Vertex’s mission is to provide developers and builders with the most up-to-date and easy-to-use social graph tools**. Our services will enable our future customers to improve the experience they provide by offering: - Protection against **impersonation** and **DoS attacks** - Personalized **discovery** and **recommendations**. All in an open, transparent and interoperable way. ## Open and Interoperable We have structured our services as [NIP-90 Data Vending Machines](https://github.com/nostr-protocol/nips/blob/master/90.md). We are currently using [these DVMs](https://vertexlab.io/docs/nips) and we are eager to hear what the community thinks and if anyone has suggestions for improvements. Regardless of their specific structures, using DVMs means one very important thing: **no vendor lock-in**. Anyone can start processing the same requests and compete with us to offer the most accurate results at the best price. This is very important for us because we are well aware that services like ours can potentially become a central point of failure. The ease with which we can be replaced by a competitor will keep us on our toes and will continue to motivate us to build better and better experiences for our customers, all while operating in an ethical and open manner. Speaking of openness, we have released **all of our code under the [MIT license](https://spdx.org/licenses/MIT.html)**, which means that anyone can review our algorithms, and any company or power user can run their own copies of Vertex if they so wish. We are confident in this decision because the value of Vertex is not in the software. It is in the team who designed and implemented it – and now continually improves, manages and runs it to provide the most accurate results with the lowest latency and highest uptime. # What we offer We currently support three DVMs, but we plan to increase our offering substantially this year. 1. `VerifyReputation`: give your users useful and personalized information to asses the reputation of an npub, minimizing the risk of impersonations. 2. `RecommendFollows`: give your users personalized recommendations about interesting npubs they might want who to follow. 3. `SortAuthors`: give your users the ability to sort replies, comments, zaps, search results or just about anything using authors’ reputations. To learn more, watch this 3-minute walk-through video, and [visit our website](https://vertexlab.io/) https://cdn.satellite.earth/6efabff7da55ce848074351b2d640ca3bde4515060d9aba002461a4a4ddad8d8.mp4 We are also considering offering a custom service to help builders clarify and implement their vision for Web of Trust in their own applications or projects. Please reach out if you are interested.
@ f683e870:557f5ef2
2025-02-07 14:33:31After many months of ideation, research, and heads-down building, <span data-type="mention" data-id="726a1e261cc6474674e8285e3951b3bb139be9a773d1acf49dc868db861a1c11" data-label="nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9">@nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9</span> and myself are excited to announce our new project called Vertex. **Vertex’s mission is to provide developers and builders with the most up-to-date and easy-to-use social graph tools**. Our services will enable our future customers to improve the experience they provide by offering: - Protection against **impersonation** and **DoS attacks** - Personalized **discovery** and **recommendations**. All in an open, transparent and interoperable way. ## Open and Interoperable We have structured our services as [NIP-90 Data Vending Machines](https://github.com/nostr-protocol/nips/blob/master/90.md). We are currently using [these DVMs](https://vertexlab.io/docs/nips) and we are eager to hear what the community thinks and if anyone has suggestions for improvements. Regardless of their specific structures, using DVMs means one very important thing: **no vendor lock-in**. Anyone can start processing the same requests and compete with us to offer the most accurate results at the best price. This is very important for us because we are well aware that services like ours can potentially become a central point of failure. The ease with which we can be replaced by a competitor will keep us on our toes and will continue to motivate us to build better and better experiences for our customers, all while operating in an ethical and open manner. Speaking of openness, we have released **all of our code under the [MIT license](https://spdx.org/licenses/MIT.html)**, which means that anyone can review our algorithms, and any company or power user can run their own copies of Vertex if they so wish. We are confident in this decision because the value of Vertex is not in the software. It is in the team who designed and implemented it – and now continually improves, manages and runs it to provide the most accurate results with the lowest latency and highest uptime. # What we offer We currently support three DVMs, but we plan to increase our offering substantially this year. 1. `VerifyReputation`: give your users useful and personalized information to asses the reputation of an npub, minimizing the risk of impersonations. 2. `RecommendFollows`: give your users personalized recommendations about interesting npubs they might want who to follow. 3. `SortAuthors`: give your users the ability to sort replies, comments, zaps, search results or just about anything using authors’ reputations. To learn more, watch this 3-minute walk-through video, and [visit our website](https://vertexlab.io/) https://cdn.satellite.earth/6efabff7da55ce848074351b2d640ca3bde4515060d9aba002461a4a4ddad8d8.mp4 We are also considering offering a custom service to help builders clarify and implement their vision for Web of Trust in their own applications or projects. Please reach out if you are interested. @ 5d4b6c8d:8a1c1ee3
2025-02-07 14:32:43Ate a little later yesterday. I took my daughter for a scooter ride on a trail near our house (I was walking) and she wanted to go farther than normal. Great for the steps challenge. Then, as soon as we turned around to go home, she decided she was too tired to scoot anymore. So, I got to do the return leg of the walk carrying both the kid and her scooter. We were out about an hour longer than expected, hence the later meal. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: TBD (15 dry) originally posted at https://stacker.news/items/878700
@ 5d4b6c8d:8a1c1ee3
2025-02-07 14:32:43Ate a little later yesterday. I took my daughter for a scooter ride on a trail near our house (I was walking) and she wanted to go farther than normal. Great for the steps challenge. Then, as soon as we turned around to go home, she decided she was too tired to scoot anymore. So, I got to do the return leg of the walk carrying both the kid and her scooter. We were out about an hour longer than expected, hence the later meal. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: TBD (15 dry) originally posted at https://stacker.news/items/878700 @ e7bc35f8:3ed2a7cf
2025-02-07 14:29:10The strategic importance of Syria in shaping the balance of power in the Middle East is undeniable. Positioned at the crossroads of key regional players, Syria has long been a battleground for competing interests. From its alliances with Russia and Iran to its role in energy politics, the country has been targeted by external forces seeking to reshape the region to their advantage. Syria has historically been an essential ally of Russia, providing the Russian navy access to the Mediterranean through the port of Latakia. At the same time, Iran has viewed Syria as a critical component of the so-called "Shiite Crescent," which provides Tehran with a vital connection to Hezbollah in Lebanon. Any disruption in Syria would have significant consequences for both Russian and Iranian strategic interests. On August 31, 2011, [Amnesty International](https://www.amnesty.org/en/documents/MDE24/035/2011/en/) released a report accusing the Syrian government of being responsible for the deaths of 88 detainees from recent protests. However, like most media narratives surrounding the conflict,[ the allegations](https://www.youtube.com/watch?v=paR5_hu64H0) were based entirely on second-hand accounts and contextless video snippets provided by opposition forces actively attempting to overthrow the Assad government. Despite the lack of concrete evidence, the establishment media eagerly propagated the story, fueling calls for "humanitarian intervention." This followed a familiar pattern: the invocation of the so-called "[Responsibility to Protect](https://www.globalresearch.ca/humanitarian-neo-colonialism-framing-libya-and-reframing-war/24617)" doctrine, a pretext used by global powers to justify military invasions and devastating bombing campaigns under the guise of protecting civilians. As seen with Libya, Western leaders—including Obama, Sarkozy, Cameron, and Harper—[called for Assad's removal](https://youtu.be/qNtICdGDdwQ?si=PW--2jwV8Ed1GRYY), paving the way for potential NATO military intervention. Long before the Arab Spring, Western governments had been laying the groundwork for regime change in Syria. In April 2011, [a U.S. State Department official](https://web.archive.org/web/20110411130724/https://www.rawstory.com/rs/2011/04/08/us-trains-activists-to-evade-security-forces/) admitted to running a two-year, $50 million program aimed at equipping protesters with new technologies to evade government detection. The same official revealed that activists from Syria and other Arab Spring countries had received training just before the uprisings began. Earlier that year, [The Washington Post](https://www.washingtonpost.com/world/us-secretly-backed-syrian-opposition-groups-cables-released-by-wikileaks-show/2011/04/14/AF1p9hwD_story.html) published leaked U.S. diplomatic cables proving that Washington had been secretly funding Syrian opposition groups since at least 2005—well before the so-called "spontaneous" protests erupted. This raises a critical question: why would an isolated government facing the threat of NATO intervention deliberately provoke the West by ordering snipers to fire on unarmed protesters at funerals? The mainstream media never questioned these dubious claims, which were sourced from anonymous, second-hand, and unverified reports. n 2010, a group called [Gen Next](https://web.archive.org/web/20090213090409/https://www.america.gov/st/texttrans-english/2008/November/20081120122321eaifas0.3440363.html) (renamed now as [Alder](https://alder.co/about-alder/)) which has been involved with Alliance of Youth Movements in organizing youth-led destabilization campaigns in countries that are not friendly to American and Israeli interests had delivered a [training program](https://web.archive.org/web/20110929221929/https://www.gen-next.org/index.php/programs/gallery/-/album/5482723470431484737/) in which participants were taught how to handle high-powered sniper rifles and shoulder-mounted grenade launchers. Predictably, these reports were ignored in the West. In August 2011, Israeli intelligence-linked outlet DEBKAfile [reported](https://web.archive.org/web/20110815020301/http://www.debka.com/article/21207/) that NATO and the Turkish military were drafting plans for a military campaign in Syria, which included arming opposition fighters with anti-tank and anti-air rockets, mortars, and heavy machine guns. As the situation escalated, the establishment media once again cheered on war, pushing for intervention under the guise of protecting Syrian civilians. The cycle repeated itself in 2013, when Western governments accused Assad of using [chemical weapons](https://www.youtube.com/watch?v=b7-S1QAmWQQ), conveniently ignoring the overwhelming opposition to another military adventure. By 2013, the American public had grown weary of endless wars. Despite relentless efforts by the White House to manufacture consent for a unilateral strike on Syria, there was widespread opposition—not just [in the U.S.](https://web.archive.org/web/20150808142142/https://www.washingtonpost.com/news/worldviews/wp/2013/08/26/new-poll-syria-intervention-even-less-popular-than-congress/), but [globally](https://www.youtube.com/watch?v=ZPGjbwqHRNs). [John Kerry](https://web.archive.org/web/20130827020025/http://www.state.gov/secretary/remarks/2013/08/213503.htm) and [Barack Obama](https://www.youtube.com/watch?v=GxyBKKYPT4c) falsely claimed that Assad was responsible for a chemical weapons attack, using this as a pretext for military intervention. However, independent analysts and insiders exposed this as a false flag operation. Even in the UK, the propaganda push faltered when British Prime Minister [David Cameron](https://www.youtube.com/watch?v=QnKKPwEX_ac) lost a crucial [parliamentary vote](https://www.youtube.com/watch?v=obxu5W9Wru8) on military action in Syria. As more evidence [surfaced](https://oilprice.com/Geopolitics/International/Did-the-White-House-Help-Plan-the-Syrian-Chemical-Attack.html), it became clear that the attack had been perpetrated by U.S.-backed terrorist groups—and that the U.S. government knew about it in advance. When even members of the British Parliament called out the deception, the war narrative collapsed, exposing the extent of the manufactured crisis. The events in Syria were not isolated. Retired U.S. General Wesley Clark famously [revealed ](https://www.youtube.com/watch?v=SzX3DfZR_1c)that he had overheard a conversation at the Pentagon about a plan to invade seven countries—including Iraq, Libya, and Syria—long before the Arab Spring. While Clark’s timeline was not entirely accurate, the overarching strategy of destabilization was clear. Key figures in the U.S. defense establishment at the time—including Paul Wolfowitz, Douglas Feith, and Richard Perle—had extensive [ties to Israel](https://web.archive.org/web/20130904083848/https://edition.cnn.com/2004/US/08/27/fbi.spy/), raising the question of whether a broader Zionist agenda was at play. [Documents ](https://web.archive.org/web/20130117222422/https://www.informationclearinghouse.info/pdf/The%20Zionist%20Plan%20for%20the%20Middle%20East.pdf)such as the infamous "Oded Yinon Plan" ([Greater Israel](https://www.globalresearch.ca/greater-israel-the-zionist-plan-for-the-middle-east/5324815)) outlined strategies for the dissolution of Syria and Iraq into ethnically and religiously divided territories, weakening any potential opposition to Israeli expansion. The plan explicitly called for breaking Syria apart into sectarian statelets, mirroring the strategy used to divide Lebanon. The long-term goal was clear: to ensure that Israel’s adversaries remained fragmented and powerless. <img src="https://blossom.primal.net/313eed84ca3bff42df56ba7fd73028266ad13ab6b20bba3126aa9d4238550476.png"> "Divide and conquer" is a strategy used for millennia. And this is what happens in Syria so many years as we were seeing the Sunni majority fighting the Alawite sect in Power under Assad and his father for decades. And it's interesting to see not only the native inhabitants Sunni of Syria but of course the foreign funded jihadists who were being shipped into the country and fueling all that conflict. Part of what this was about, it's the destabilization of the [Shia land bridge](https://phibetaiota.net/2013/05/graphic-irans-shia-land-bridge-to-lebanon-mediterranean/) that connects Iran all the way to its Hezbollah forces in Lebanon, which runs through Syria. But if that can be destabilized and the Shia Alawite sect minority that rules Syria can be replaced with a Sunni majority ruling over the country then that would break up that link between Iran and Lebanon and further destabilize and isolate Iran. <img src="https://blossom.primal.net/c3e9eedd9f2140bb63a552ff08eb8aab1ca10ae981da2a6841b496baec230937.jpg"> And this is something that can be seen in policy planning documents of various think tanks, as in the infamous "[Which path to Persia?](https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)" document from Brookings Institution. As we start to expand the scope of this, then of course the thing that always in these Middle East conflicts comes into play is the natural resources. Let's remember the prospect of the [Iraq, Iran, Syria pipeline](https://web.archive.org/web/20130727143145/https://www.tehrantimes.com/economy-and-business/758-iran-iraq-syria-sign-major-gas-pipeline-deal-). Iran, Iraq, and Syria had signed a deal for the construction of the Middle East’s largest gas pipeline, which would transit Iranian gas from Iran’s South Pars gas field to Europe via Lebanon and the Mediterranean Sea. What we were talking about back then was a pipeline providing traveling from Iran to Europe, through the Mediterranean. [That move](https://www.youtube.com/watch?v=oNet5aLKaWg) was about to change the power balance of the region. Such a [project ](https://web.archive.org/web/20130723151340/http://www.atimes.com/atimes/Middle_East/MID-04-230713.html)had the potential to shift the regional power balance dramatically. The mere prospect of it was enough to anger multiple stakeholders, from the U.S. and Israel to Turkey and the Gulf monarchies, all of whom had vested interests in preventing [Syria ](https://web.archive.org/web/20130831121243/http://atimes.com/atimes/Middle_East/MID-04-290813.html)from becoming an energy corridor. The war in Syria was never about democracy, humanitarian concerns, or chemical weapons. It was about [power](https://web.archive.org/web/20130315191710/http://www.davemanuel.com/2010/06/14/us-military-spending-over-the-years/), [control](https://web.archive.org/web/20130318180618/http://www.usatoday.com/story/money/business/2013/03/10/10-companies-profiting-most-from-war/1970997/), and the relentless [pursuit ](https://web.archive.org/web/20130306140329/http://www.businessinsider.com/top-25-us-defense-companies-2012-2?op=1)of strategic dominance by Western and regional actors. The destabilization of Syria served multiple agendas—weakening Iran, severing Russia’s influence, ensuring Israel’s security, and controlling energy routes. What we have witnessed over the past decade is not a civil war, but a foreign-orchestrated campaign to dismantle yet another independent state in the Middle East. Understanding these dynamics is essential in recognizing how mainstream narratives are crafted to justify war while hiding the real motivations behind the chaos. <img src="https://blossom.primal.net/b1e0155c7bd73c05fe6323e9131d528842c6410f6520f0cc7885b6bdb5022084.jpg">
@ e7bc35f8:3ed2a7cf
2025-02-07 14:29:10The strategic importance of Syria in shaping the balance of power in the Middle East is undeniable. Positioned at the crossroads of key regional players, Syria has long been a battleground for competing interests. From its alliances with Russia and Iran to its role in energy politics, the country has been targeted by external forces seeking to reshape the region to their advantage. Syria has historically been an essential ally of Russia, providing the Russian navy access to the Mediterranean through the port of Latakia. At the same time, Iran has viewed Syria as a critical component of the so-called "Shiite Crescent," which provides Tehran with a vital connection to Hezbollah in Lebanon. Any disruption in Syria would have significant consequences for both Russian and Iranian strategic interests. On August 31, 2011, [Amnesty International](https://www.amnesty.org/en/documents/MDE24/035/2011/en/) released a report accusing the Syrian government of being responsible for the deaths of 88 detainees from recent protests. However, like most media narratives surrounding the conflict,[ the allegations](https://www.youtube.com/watch?v=paR5_hu64H0) were based entirely on second-hand accounts and contextless video snippets provided by opposition forces actively attempting to overthrow the Assad government. Despite the lack of concrete evidence, the establishment media eagerly propagated the story, fueling calls for "humanitarian intervention." This followed a familiar pattern: the invocation of the so-called "[Responsibility to Protect](https://www.globalresearch.ca/humanitarian-neo-colonialism-framing-libya-and-reframing-war/24617)" doctrine, a pretext used by global powers to justify military invasions and devastating bombing campaigns under the guise of protecting civilians. As seen with Libya, Western leaders—including Obama, Sarkozy, Cameron, and Harper—[called for Assad's removal](https://youtu.be/qNtICdGDdwQ?si=PW--2jwV8Ed1GRYY), paving the way for potential NATO military intervention. Long before the Arab Spring, Western governments had been laying the groundwork for regime change in Syria. In April 2011, [a U.S. State Department official](https://web.archive.org/web/20110411130724/https://www.rawstory.com/rs/2011/04/08/us-trains-activists-to-evade-security-forces/) admitted to running a two-year, $50 million program aimed at equipping protesters with new technologies to evade government detection. The same official revealed that activists from Syria and other Arab Spring countries had received training just before the uprisings began. Earlier that year, [The Washington Post](https://www.washingtonpost.com/world/us-secretly-backed-syrian-opposition-groups-cables-released-by-wikileaks-show/2011/04/14/AF1p9hwD_story.html) published leaked U.S. diplomatic cables proving that Washington had been secretly funding Syrian opposition groups since at least 2005—well before the so-called "spontaneous" protests erupted. This raises a critical question: why would an isolated government facing the threat of NATO intervention deliberately provoke the West by ordering snipers to fire on unarmed protesters at funerals? The mainstream media never questioned these dubious claims, which were sourced from anonymous, second-hand, and unverified reports. n 2010, a group called [Gen Next](https://web.archive.org/web/20090213090409/https://www.america.gov/st/texttrans-english/2008/November/20081120122321eaifas0.3440363.html) (renamed now as [Alder](https://alder.co/about-alder/)) which has been involved with Alliance of Youth Movements in organizing youth-led destabilization campaigns in countries that are not friendly to American and Israeli interests had delivered a [training program](https://web.archive.org/web/20110929221929/https://www.gen-next.org/index.php/programs/gallery/-/album/5482723470431484737/) in which participants were taught how to handle high-powered sniper rifles and shoulder-mounted grenade launchers. Predictably, these reports were ignored in the West. In August 2011, Israeli intelligence-linked outlet DEBKAfile [reported](https://web.archive.org/web/20110815020301/http://www.debka.com/article/21207/) that NATO and the Turkish military were drafting plans for a military campaign in Syria, which included arming opposition fighters with anti-tank and anti-air rockets, mortars, and heavy machine guns. As the situation escalated, the establishment media once again cheered on war, pushing for intervention under the guise of protecting Syrian civilians. The cycle repeated itself in 2013, when Western governments accused Assad of using [chemical weapons](https://www.youtube.com/watch?v=b7-S1QAmWQQ), conveniently ignoring the overwhelming opposition to another military adventure. By 2013, the American public had grown weary of endless wars. Despite relentless efforts by the White House to manufacture consent for a unilateral strike on Syria, there was widespread opposition—not just [in the U.S.](https://web.archive.org/web/20150808142142/https://www.washingtonpost.com/news/worldviews/wp/2013/08/26/new-poll-syria-intervention-even-less-popular-than-congress/), but [globally](https://www.youtube.com/watch?v=ZPGjbwqHRNs). [John Kerry](https://web.archive.org/web/20130827020025/http://www.state.gov/secretary/remarks/2013/08/213503.htm) and [Barack Obama](https://www.youtube.com/watch?v=GxyBKKYPT4c) falsely claimed that Assad was responsible for a chemical weapons attack, using this as a pretext for military intervention. However, independent analysts and insiders exposed this as a false flag operation. Even in the UK, the propaganda push faltered when British Prime Minister [David Cameron](https://www.youtube.com/watch?v=QnKKPwEX_ac) lost a crucial [parliamentary vote](https://www.youtube.com/watch?v=obxu5W9Wru8) on military action in Syria. As more evidence [surfaced](https://oilprice.com/Geopolitics/International/Did-the-White-House-Help-Plan-the-Syrian-Chemical-Attack.html), it became clear that the attack had been perpetrated by U.S.-backed terrorist groups—and that the U.S. government knew about it in advance. When even members of the British Parliament called out the deception, the war narrative collapsed, exposing the extent of the manufactured crisis. The events in Syria were not isolated. Retired U.S. General Wesley Clark famously [revealed ](https://www.youtube.com/watch?v=SzX3DfZR_1c)that he had overheard a conversation at the Pentagon about a plan to invade seven countries—including Iraq, Libya, and Syria—long before the Arab Spring. While Clark’s timeline was not entirely accurate, the overarching strategy of destabilization was clear. Key figures in the U.S. defense establishment at the time—including Paul Wolfowitz, Douglas Feith, and Richard Perle—had extensive [ties to Israel](https://web.archive.org/web/20130904083848/https://edition.cnn.com/2004/US/08/27/fbi.spy/), raising the question of whether a broader Zionist agenda was at play. [Documents ](https://web.archive.org/web/20130117222422/https://www.informationclearinghouse.info/pdf/The%20Zionist%20Plan%20for%20the%20Middle%20East.pdf)such as the infamous "Oded Yinon Plan" ([Greater Israel](https://www.globalresearch.ca/greater-israel-the-zionist-plan-for-the-middle-east/5324815)) outlined strategies for the dissolution of Syria and Iraq into ethnically and religiously divided territories, weakening any potential opposition to Israeli expansion. The plan explicitly called for breaking Syria apart into sectarian statelets, mirroring the strategy used to divide Lebanon. The long-term goal was clear: to ensure that Israel’s adversaries remained fragmented and powerless. <img src="https://blossom.primal.net/313eed84ca3bff42df56ba7fd73028266ad13ab6b20bba3126aa9d4238550476.png"> "Divide and conquer" is a strategy used for millennia. And this is what happens in Syria so many years as we were seeing the Sunni majority fighting the Alawite sect in Power under Assad and his father for decades. And it's interesting to see not only the native inhabitants Sunni of Syria but of course the foreign funded jihadists who were being shipped into the country and fueling all that conflict. Part of what this was about, it's the destabilization of the [Shia land bridge](https://phibetaiota.net/2013/05/graphic-irans-shia-land-bridge-to-lebanon-mediterranean/) that connects Iran all the way to its Hezbollah forces in Lebanon, which runs through Syria. But if that can be destabilized and the Shia Alawite sect minority that rules Syria can be replaced with a Sunni majority ruling over the country then that would break up that link between Iran and Lebanon and further destabilize and isolate Iran. <img src="https://blossom.primal.net/c3e9eedd9f2140bb63a552ff08eb8aab1ca10ae981da2a6841b496baec230937.jpg"> And this is something that can be seen in policy planning documents of various think tanks, as in the infamous "[Which path to Persia?](https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)" document from Brookings Institution. As we start to expand the scope of this, then of course the thing that always in these Middle East conflicts comes into play is the natural resources. Let's remember the prospect of the [Iraq, Iran, Syria pipeline](https://web.archive.org/web/20130727143145/https://www.tehrantimes.com/economy-and-business/758-iran-iraq-syria-sign-major-gas-pipeline-deal-). Iran, Iraq, and Syria had signed a deal for the construction of the Middle East’s largest gas pipeline, which would transit Iranian gas from Iran’s South Pars gas field to Europe via Lebanon and the Mediterranean Sea. What we were talking about back then was a pipeline providing traveling from Iran to Europe, through the Mediterranean. [That move](https://www.youtube.com/watch?v=oNet5aLKaWg) was about to change the power balance of the region. Such a [project ](https://web.archive.org/web/20130723151340/http://www.atimes.com/atimes/Middle_East/MID-04-230713.html)had the potential to shift the regional power balance dramatically. The mere prospect of it was enough to anger multiple stakeholders, from the U.S. and Israel to Turkey and the Gulf monarchies, all of whom had vested interests in preventing [Syria ](https://web.archive.org/web/20130831121243/http://atimes.com/atimes/Middle_East/MID-04-290813.html)from becoming an energy corridor. The war in Syria was never about democracy, humanitarian concerns, or chemical weapons. It was about [power](https://web.archive.org/web/20130315191710/http://www.davemanuel.com/2010/06/14/us-military-spending-over-the-years/), [control](https://web.archive.org/web/20130318180618/http://www.usatoday.com/story/money/business/2013/03/10/10-companies-profiting-most-from-war/1970997/), and the relentless [pursuit ](https://web.archive.org/web/20130306140329/http://www.businessinsider.com/top-25-us-defense-companies-2012-2?op=1)of strategic dominance by Western and regional actors. The destabilization of Syria served multiple agendas—weakening Iran, severing Russia’s influence, ensuring Israel’s security, and controlling energy routes. What we have witnessed over the past decade is not a civil war, but a foreign-orchestrated campaign to dismantle yet another independent state in the Middle East. Understanding these dynamics is essential in recognizing how mainstream narratives are crafted to justify war while hiding the real motivations behind the chaos. <img src="https://blossom.primal.net/b1e0155c7bd73c05fe6323e9131d528842c6410f6520f0cc7885b6bdb5022084.jpg"> @ 044da344:073a8a0e
2025-02-07 14:06:14Knapp ein Jahr hat es gedauert nach meinen letzten Gesprächen im Apolut-Studio, seinerzeit mit [Robert Cibis](https://apolut.net/im-gespraech-robert-cibis/) und [Yann Song King](https://apolut.net/im-gespraech-yann-song-king/) und am Rande von Berlin schon längst nicht mehr so komfortabel wie einst an der bayerisch-österreichischen Grenze oder dann im Süden Schwedens, wo eine komplette Mannschaft für perfekte Qualität gesorgt hat. Kamera, Ton, Regie, Maske und sogar eine Gästebetreuung. Lauter Profis, aber irgendwann offenbar nicht mehr zu bezahlen aus Spenden und wahrscheinlich auch überholt von der Konkurrenz im Internet, die mit einfachen Mitteln zwar weit unterhalb aller TV-Standards bleibt, aber aktuell ist, viel, viel günstiger und inhaltlich trotzdem sehr oft sehr spannend. Egal. Auf Onlineinterviews hatte und habe ich keine Lust. Ich möchte den Menschen spüren, um den es geht. Vorher mit ihm reden und hinterher hoffentlich auch noch. Ich telefoniere nur im Notfall, weil dort vieles von dem verlorengeht, was den Austausch ausmacht. Zoom und Co. liefern zwar ein Bild, sind aber ansonsten nicht viel besser. Um das nur mit einer Zahl zu illustrieren: Bei einem Bildschirmgespräch dauert es zweieinhalb Sekunden, bis mein Gegenüber registriert, dass ich etwas sagen will. Live und in Farbe liegt die Reaktionszeit bei knapp der Hälfte. Also habe ich aus der Not eine Tugend gemacht und bin selbst zum Produzenten geworden. Nicht ganz allein natürlich. Es gab Tipps von Dirk Wächter, der für viele der Bilder und Videos von Daniele Ganser steht und die Apolut-Gäste auf unnachahmliche Weise fotografiert hat, von Paul Brandenburg, der Technik borgte, und von Ingmar Beyer, den ich im großen Studio kennenlernen durfte und der nun auch bei meinen eigenen Versuchen dafür sorgt, dass der Ton stimmt. Vielen Dank dafür.  Ein Dank gilt auch Axel Klopprogge, den die Leser dieser Seite aus der Kolumne [Oben & Unten](https://www.freie-medienakademie.de/columns/2) kennen und der sich gewissermaßen als Versuchskaninchen zur Verfügung stellte. Der Anlass war denkbar günstig, als wir uns Ende Januar im Wohnzimmerstudio trafen: Gerade war seine Aufsatzsammlung „Links oder rechts oder was?“ erschienen – Stoff genug für 90 Minuten. Das Buch wird morgen in meiner [Kolumne](https://www.freie-medienakademie.de/columns/5) noch einmal gesondert gewürdigt. Wer in unser [Gespräch](https://youtu.be/LUiUAhb2OXY) hineinschaut, wird schnell den Unterschied zu Apolut sehen: Es gibt Publikum. Gut zehn Menschen, die hoffentlich wiederkommen. Die nächsten Gäste: [Michael Beleites](https://www.freie-medienakademie.de/medien-plus/resonanz-aus-dem-osten), mit dem ich über den Darwinismus reden werde und über all das, was diese Ideologie aus uns gemacht hat, sowie Erich Hambach, der gerade auf den letzten Metern für sein Buch „Herren des Geldes“ ist. [Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/) [Unterstützen](https://www.freie-medienakademie.de/unterstuetzen)
@ 044da344:073a8a0e
2025-02-07 14:06:14Knapp ein Jahr hat es gedauert nach meinen letzten Gesprächen im Apolut-Studio, seinerzeit mit [Robert Cibis](https://apolut.net/im-gespraech-robert-cibis/) und [Yann Song King](https://apolut.net/im-gespraech-yann-song-king/) und am Rande von Berlin schon längst nicht mehr so komfortabel wie einst an der bayerisch-österreichischen Grenze oder dann im Süden Schwedens, wo eine komplette Mannschaft für perfekte Qualität gesorgt hat. Kamera, Ton, Regie, Maske und sogar eine Gästebetreuung. Lauter Profis, aber irgendwann offenbar nicht mehr zu bezahlen aus Spenden und wahrscheinlich auch überholt von der Konkurrenz im Internet, die mit einfachen Mitteln zwar weit unterhalb aller TV-Standards bleibt, aber aktuell ist, viel, viel günstiger und inhaltlich trotzdem sehr oft sehr spannend. Egal. Auf Onlineinterviews hatte und habe ich keine Lust. Ich möchte den Menschen spüren, um den es geht. Vorher mit ihm reden und hinterher hoffentlich auch noch. Ich telefoniere nur im Notfall, weil dort vieles von dem verlorengeht, was den Austausch ausmacht. Zoom und Co. liefern zwar ein Bild, sind aber ansonsten nicht viel besser. Um das nur mit einer Zahl zu illustrieren: Bei einem Bildschirmgespräch dauert es zweieinhalb Sekunden, bis mein Gegenüber registriert, dass ich etwas sagen will. Live und in Farbe liegt die Reaktionszeit bei knapp der Hälfte. Also habe ich aus der Not eine Tugend gemacht und bin selbst zum Produzenten geworden. Nicht ganz allein natürlich. Es gab Tipps von Dirk Wächter, der für viele der Bilder und Videos von Daniele Ganser steht und die Apolut-Gäste auf unnachahmliche Weise fotografiert hat, von Paul Brandenburg, der Technik borgte, und von Ingmar Beyer, den ich im großen Studio kennenlernen durfte und der nun auch bei meinen eigenen Versuchen dafür sorgt, dass der Ton stimmt. Vielen Dank dafür.  Ein Dank gilt auch Axel Klopprogge, den die Leser dieser Seite aus der Kolumne [Oben & Unten](https://www.freie-medienakademie.de/columns/2) kennen und der sich gewissermaßen als Versuchskaninchen zur Verfügung stellte. Der Anlass war denkbar günstig, als wir uns Ende Januar im Wohnzimmerstudio trafen: Gerade war seine Aufsatzsammlung „Links oder rechts oder was?“ erschienen – Stoff genug für 90 Minuten. Das Buch wird morgen in meiner [Kolumne](https://www.freie-medienakademie.de/columns/5) noch einmal gesondert gewürdigt. Wer in unser [Gespräch](https://youtu.be/LUiUAhb2OXY) hineinschaut, wird schnell den Unterschied zu Apolut sehen: Es gibt Publikum. Gut zehn Menschen, die hoffentlich wiederkommen. Die nächsten Gäste: [Michael Beleites](https://www.freie-medienakademie.de/medien-plus/resonanz-aus-dem-osten), mit dem ich über den Darwinismus reden werde und über all das, was diese Ideologie aus uns gemacht hat, sowie Erich Hambach, der gerade auf den letzten Metern für sein Buch „Herren des Geldes“ ist. [Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/) [Unterstützen](https://www.freie-medienakademie.de/unterstuetzen) @ 5d4b6c8d:8a1c1ee3
2025-02-07 14:02:05Apparently, there's still another NFL game and, I suppose, we have to discuss it. I'm much more excited to get into all the NBA trades that happened. Who got better? Who got worse? Who did something really weird? Of course, we'll talk about the contests going on in the territory. MLB's ramping up. Can anyone challenge the Dodgers? Ovi is trying to get back on pace to break NHL's career scoring record. Any bets we're excited about Plus, whatever the stackers want us to cover (time and memory permitting) originally posted at https://stacker.news/items/878674
@ 5d4b6c8d:8a1c1ee3
2025-02-07 14:02:05Apparently, there's still another NFL game and, I suppose, we have to discuss it. I'm much more excited to get into all the NBA trades that happened. Who got better? Who got worse? Who did something really weird? Of course, we'll talk about the contests going on in the territory. MLB's ramping up. Can anyone challenge the Dodgers? Ovi is trying to get back on pace to break NHL's career scoring record. Any bets we're excited about Plus, whatever the stackers want us to cover (time and memory permitting) originally posted at https://stacker.news/items/878674 @ 54286b98:3debc100
2025-02-07 11:05:29Reality is clear when we stand in the light.\ Falsehood appears when we tilt ourselves just enough to distort what’s real. Every object—tree, person, or building—casts a shadow.\ But only the object is real. The shadow is an effect, not the truth. Light reveals what’s true. Darkness hides it, warping our perspective.\ Our angle to the light source changes everything. Christ is that source of light. He shines on everyone—no matter who we are.\ He doesn’t shift. Truth doesn’t shift. But we do. Our minds waver like waves in the ocean, creating ever-changing shadows.\ Those shifting shadows can fool us. Today, let’s choose to stand in his perfect light.\ Let’s notice where we need to grow and refuse to be deceived by distorted reflections.\ Let’s anchor ourselves to what’s real. Until next time,\ **J** > Do not be deceived, my beloved brothers. Every good gift and every perfect gift is from above, coming down from the Father of lights, with whom there is no variation or shadow due to change. Of his own will he brought us forth by the word of truth, that we should be a kind of firstfruits of his creatures. **James 1: 16-18** *Original article published on: [https://www.javierfeliu.com/blog/shifting-shadows/](https://www.javierfeliu.com/blog/shifting-shadows/)\ Photo by [Yang Deng](https://unsplash.com/@palon?ref=javierfeliu.com) / [Unsplash](https://unsplash.com/?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit)*
@ 54286b98:3debc100
2025-02-07 11:05:29Reality is clear when we stand in the light.\ Falsehood appears when we tilt ourselves just enough to distort what’s real. Every object—tree, person, or building—casts a shadow.\ But only the object is real. The shadow is an effect, not the truth. Light reveals what’s true. Darkness hides it, warping our perspective.\ Our angle to the light source changes everything. Christ is that source of light. He shines on everyone—no matter who we are.\ He doesn’t shift. Truth doesn’t shift. But we do. Our minds waver like waves in the ocean, creating ever-changing shadows.\ Those shifting shadows can fool us. Today, let’s choose to stand in his perfect light.\ Let’s notice where we need to grow and refuse to be deceived by distorted reflections.\ Let’s anchor ourselves to what’s real. Until next time,\ **J** > Do not be deceived, my beloved brothers. Every good gift and every perfect gift is from above, coming down from the Father of lights, with whom there is no variation or shadow due to change. Of his own will he brought us forth by the word of truth, that we should be a kind of firstfruits of his creatures. **James 1: 16-18** *Original article published on: [https://www.javierfeliu.com/blog/shifting-shadows/](https://www.javierfeliu.com/blog/shifting-shadows/)\ Photo by [Yang Deng](https://unsplash.com/@palon?ref=javierfeliu.com) / [Unsplash](https://unsplash.com/?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit)* @ a367f9eb:0633efea
2025-02-07 10:39:28Issued on January 23, 2025, Staff Accounting Bulletin 122 rescinds SAB 121, [originally issued](https://www.sec.gov/oca/staff-accounting-bulletin-121) by Gensler in March 2022. The previous bulletin provided guidance for financial entities and custodians holding any “crypto-assets,” requiring them to account for all cryptocurrencies primarily as liabilities on their balance sheets, rather than assets. The revoking of SAB 121 empowers entities to assess whether their crypto-assets are classified as liabilities only if they believe a loss is probable. For bitcoin holders who hold their own keys and run their own node, this distinction and its subsequent repeal made little difference. But for the budding world of Bitcoin banking and finance, as well as the booming industry of custodial wallets and brokerages, it’s a game changer. Rather than having to match cryptocurrency deposits one-for-one with other liquid assets in the case of a contingency, the new accounting guidance frees up institutions to mark the true values of crypto-assets on their books. Rather than having to buy up $1 million in treasuries or cash in order to hold $1 million in bitcoin or cover losses, firms will now be able to recognize that $1 million as a true asset. It may not seem like a revolution, but it may be the beginning of our bull-inspired Bitcoin banking era. After years of byzantine persecutions of cryptocurrency developers, entrepreneurs, and ever-increasing regulations on Bitcoin, this paradigm shift at the nation’s premier markets regulator means traditional finance can finally include bitcoin and its crypto-offspring in its suite of financial products – with some caveats. Practically, this rather benign-sounding rule lowers the barrier of entry for entities that want to offer bitcoin services to their customers. Whether it’s a bank, an exchange, or a liquidity service provider custodying funds, there is now a more sustainable path for offering bitcoin alongside any other type of account. While a general crypto market framework is still far from established in law, the current situation grants fairness between both fiat money and cryptocurrencies in the hands of entrepreneurs who want to custody funds for their clients. Practically, however, what does this mean for the average bitcoiner? ## **What will my Bitcoin bank look like?** If we take a peek over at Europe, there are already FinTech firms and banking institutions that offer some level of bitcoin services. Xapo Bank, a private bank headquartered in Gibraltar, [offers](https://www.xapobank.com/en) each customer a traditional bank account and IBAN number alongside an instantaneous deposit and withdrawal address for Bitcoin and Bitcoin Lightning, Tether, and USDC. Considering Xapo [built](https://decrypt.co/8449/coinbase-acquires-xapo-crypto-custodian) the doomsday-proof custody vaults for bitcoin storage later bought by Coinbase in 2019, now the preferred institutional custodian for billions in assets, it’s easy to see why so many customers trust their custody. And for those willing to make the tradeoff for custody of their funds, they do offer something attractive. In a single account, a customer could deposit cash, exchange it to bitcoin, and withdraw to self-custody. They could also deposit bitcoin using Lightning, and then instantly convert that amount to send a traditional bank transfer to pay their rent or utility bills for those who don’t yet accept bitcoin. Again, this may not be the solution for those who [prefer self-custody](https://www.btcpolicy.org/articles/self-custody-is-nonnegotiable), but it does offer an integrated fiat on and off ramp that others may find convenient. Similarly, the UK-based FinTech firm Revolut offers its customers the [ability](https://www.revolut.com/crypto/) to deposit and withdraw their bitcoin within the app, as well as exchange it for whichever fiat currency they wish. For those who currently hold bitcoin in an ETF or some other custodial product, a move to an app such as this may be even more attractive. And we already know US companies are begging to expand their own services to their customers. Companies such as **Strike** and **Fold** have already begun to increase their Bitcoin banking services for American customers, offering account and routing numbers for [bill pay](https://strike.me/blog/announcing-strike-bill-pay/), as well as the ability to instantly swap between currencies if they wish. Fold has the [ambition](https://blog.foldapp.com/fold-to-go-public/) to become one of the nation’s largest publicly-traded bitcoin financial services, looking to soon add mortgage and lending offers, as well as insurance solutions. These financial firms will offer bitcoin for purchase, lending, and exchange, but we can also assume their suite of products will become more diverse and attractive for a more diverse customer base. ## **What about sovereign money?** Educating Americans about the benefits of Bitcoin is an important task. So is improving our policy landscape so that all bitcoiners may flourish. But if the Bitcoin network truly represents a revolutionary way to have and use neutral money, should we even consider Bitcoin banks something we want? How can peer-to-peer money integrate with the centralized custodial banking system so many of us are trying to escape? Even the most primitive advantages of Bitcoin are built on its ability to be owned in a sovereign way, at the total exclusion of everyone who doesn’t have the private key. For many of us, this is all we desire and want. And for the rights to hold and use Bitcoin how we wish to be universally recognized. However, we cannot dictate how the rest of our Bitcoin peers will engage with the network, nor what they inscribe into blocks if they have the computing power to mine them. If Bitcoin entrepreneurs freely compete to offer unique products and services to custody, trade, or lend bitcoin, the rules should make that easier and more possible. For those who will still need to interact with the fiat world, they should be able to benefit from Bitcoin-first products and services designed with them in mind. And regulations should empower them rather than restrict what they can do. Not every Bitcoin banking product will be attractive to every bitcoiner and that’s okay. But the positive evolution of e-cash, custodial services, lending, and insurance is something that will help leverage the power of Bitcoin. And that should be championed. *Yaël Ossowski is a fellow at the Bitcoin Policy Institute.* This article was originally published at the [Bitcoin Policy Institute](https://www.btcpolicy.org/articles/has-the-era-of-bull-inspired-bitcoin-banking-already-begun).
@ a367f9eb:0633efea
2025-02-07 10:39:28Issued on January 23, 2025, Staff Accounting Bulletin 122 rescinds SAB 121, [originally issued](https://www.sec.gov/oca/staff-accounting-bulletin-121) by Gensler in March 2022. The previous bulletin provided guidance for financial entities and custodians holding any “crypto-assets,” requiring them to account for all cryptocurrencies primarily as liabilities on their balance sheets, rather than assets. The revoking of SAB 121 empowers entities to assess whether their crypto-assets are classified as liabilities only if they believe a loss is probable. For bitcoin holders who hold their own keys and run their own node, this distinction and its subsequent repeal made little difference. But for the budding world of Bitcoin banking and finance, as well as the booming industry of custodial wallets and brokerages, it’s a game changer. Rather than having to match cryptocurrency deposits one-for-one with other liquid assets in the case of a contingency, the new accounting guidance frees up institutions to mark the true values of crypto-assets on their books. Rather than having to buy up $1 million in treasuries or cash in order to hold $1 million in bitcoin or cover losses, firms will now be able to recognize that $1 million as a true asset. It may not seem like a revolution, but it may be the beginning of our bull-inspired Bitcoin banking era. After years of byzantine persecutions of cryptocurrency developers, entrepreneurs, and ever-increasing regulations on Bitcoin, this paradigm shift at the nation’s premier markets regulator means traditional finance can finally include bitcoin and its crypto-offspring in its suite of financial products – with some caveats. Practically, this rather benign-sounding rule lowers the barrier of entry for entities that want to offer bitcoin services to their customers. Whether it’s a bank, an exchange, or a liquidity service provider custodying funds, there is now a more sustainable path for offering bitcoin alongside any other type of account. While a general crypto market framework is still far from established in law, the current situation grants fairness between both fiat money and cryptocurrencies in the hands of entrepreneurs who want to custody funds for their clients. Practically, however, what does this mean for the average bitcoiner? ## **What will my Bitcoin bank look like?** If we take a peek over at Europe, there are already FinTech firms and banking institutions that offer some level of bitcoin services. Xapo Bank, a private bank headquartered in Gibraltar, [offers](https://www.xapobank.com/en) each customer a traditional bank account and IBAN number alongside an instantaneous deposit and withdrawal address for Bitcoin and Bitcoin Lightning, Tether, and USDC. Considering Xapo [built](https://decrypt.co/8449/coinbase-acquires-xapo-crypto-custodian) the doomsday-proof custody vaults for bitcoin storage later bought by Coinbase in 2019, now the preferred institutional custodian for billions in assets, it’s easy to see why so many customers trust their custody. And for those willing to make the tradeoff for custody of their funds, they do offer something attractive. In a single account, a customer could deposit cash, exchange it to bitcoin, and withdraw to self-custody. They could also deposit bitcoin using Lightning, and then instantly convert that amount to send a traditional bank transfer to pay their rent or utility bills for those who don’t yet accept bitcoin. Again, this may not be the solution for those who [prefer self-custody](https://www.btcpolicy.org/articles/self-custody-is-nonnegotiable), but it does offer an integrated fiat on and off ramp that others may find convenient. Similarly, the UK-based FinTech firm Revolut offers its customers the [ability](https://www.revolut.com/crypto/) to deposit and withdraw their bitcoin within the app, as well as exchange it for whichever fiat currency they wish. For those who currently hold bitcoin in an ETF or some other custodial product, a move to an app such as this may be even more attractive. And we already know US companies are begging to expand their own services to their customers. Companies such as **Strike** and **Fold** have already begun to increase their Bitcoin banking services for American customers, offering account and routing numbers for [bill pay](https://strike.me/blog/announcing-strike-bill-pay/), as well as the ability to instantly swap between currencies if they wish. Fold has the [ambition](https://blog.foldapp.com/fold-to-go-public/) to become one of the nation’s largest publicly-traded bitcoin financial services, looking to soon add mortgage and lending offers, as well as insurance solutions. These financial firms will offer bitcoin for purchase, lending, and exchange, but we can also assume their suite of products will become more diverse and attractive for a more diverse customer base. ## **What about sovereign money?** Educating Americans about the benefits of Bitcoin is an important task. So is improving our policy landscape so that all bitcoiners may flourish. But if the Bitcoin network truly represents a revolutionary way to have and use neutral money, should we even consider Bitcoin banks something we want? How can peer-to-peer money integrate with the centralized custodial banking system so many of us are trying to escape? Even the most primitive advantages of Bitcoin are built on its ability to be owned in a sovereign way, at the total exclusion of everyone who doesn’t have the private key. For many of us, this is all we desire and want. And for the rights to hold and use Bitcoin how we wish to be universally recognized. However, we cannot dictate how the rest of our Bitcoin peers will engage with the network, nor what they inscribe into blocks if they have the computing power to mine them. If Bitcoin entrepreneurs freely compete to offer unique products and services to custody, trade, or lend bitcoin, the rules should make that easier and more possible. For those who will still need to interact with the fiat world, they should be able to benefit from Bitcoin-first products and services designed with them in mind. And regulations should empower them rather than restrict what they can do. Not every Bitcoin banking product will be attractive to every bitcoiner and that’s okay. But the positive evolution of e-cash, custodial services, lending, and insurance is something that will help leverage the power of Bitcoin. And that should be championed. *Yaël Ossowski is a fellow at the Bitcoin Policy Institute.* This article was originally published at the [Bitcoin Policy Institute](https://www.btcpolicy.org/articles/has-the-era-of-bull-inspired-bitcoin-banking-already-begun). @ d360efec:14907b5f
2025-02-07 09:42:54ณ ดินแดนอันไกลโพ้น ปรากฏดันเจี้ยนลึกลับไร้ก้นบึ้ง นามว่า "ตลาดการเก็งกำไร" ประตูทางเข้าเปล่งประกายล่อตาล่อใจ แต่มักถูกปกคลุมด้วยหมอกแห่งความไม่แน่นอน คำจารึกโบราณ แกะสลักเหนือประตูทางเข้า เตือนสติผู้มาเยือน: "ผู้ใดเข้าล้วนมิอาจหวนคืน..." เฉกเช่นสำนวนโบราณที่กล่าวขาน "คนในมิอาจออก คนนอกมิต้องการย่างกราย" ภาพที่ปรากฎตรงหน้า คือชายหนุ่มผู้หาญกล้า กำลังจะก้าวเข้าสู่ประตูดันเจี้ยน เหนือประตูมีป้ายขนาดมหึมาสลักคำว่า "Trading" สัญลักษณ์แห่งโลกการลงทุน การเก็งกำไร ไม่ว่าจะเป็น หุ้น, ฟอเร็กซ์, คริปโต ล้วนเป็นมอนสเตอร์ที่สถิตอยู่ในนี้ การจะพิชิตดันเจี้ยนนี้ได้นั้น หาใช่เรื่องง่าย ภารกิจแรกคือการกำจัดปีศาจ**"นักพนัน"** ที่สิงอยู่ในจิตใจของผู้กล้าทุกคน ปีศาจตนนี้ร้ายกาจยิ่งนัก แต่มิใช่ว่าไร้ทางปราบ หากท่านผู้กล้าปรารถนาจะหลุดพ้นจากวงจรอุบาทว์นี้ จงใช้วิธีเหล่านี้เถิด 1. เข้าใจว่าการพนันคือกับดัก ปีศาจพนันมักล่อลวงด้วยภาพลวงตาแห่งชัยชนะเพียงชั่วครู่ แต่แท้จริงแล้ว มันถูกออกแบบมาเพื่อสูบเลือดสูบเนื้อจากเหล่าผู้กล้าในระยะยาว จงจำไว้ว่าการพนันมิใช่หนทางสู่ความร่ำรวย แต่เป็นเส้นทางสู่หุบเหวแห่งความสิ้นเนื้อประดาตัว 2. เปลี่ยนมุมมองเกี่ยวกับเหรียญทอง จงมองเหรียญทองที่ท่านมีมิใช่แค่ตัวเลข แต่เป็น “เวลาและหยาดเหงื่อ” ที่ท่านได้แลกมา หากท่านสูญเสียมันไปเพราะการพนัน มันคือเวลาชีวิตที่หายไปตลอดกาล 3. ตัดขาดสิ่งเร้าที่กระตุ้นให้เล่น • ลบแอปพนัน / ปิดกั้นเว็บไซต์มืด • เลิกติดตามเพจหรือกลุ่มที่เกี่ยวข้อง • เปลี่ยนสหายร่วมทางที่ชักชวนไปสู่ทางเสื่อม 4. ใช้กฎ 5 นาที เมื่อใดที่ความกระหายอยากเล่นครอบงำ จงหยุดยั้งตัวเองไว้ 5 นาที แล้วตรองดูว่า • คราก่อนท่านสูญเสียไปเท่าใด? • หากเล่นแล้วเสียอีก จะรู้สึกเช่นไร? • มีสิ่งใดที่ควรทำมากกว่านี้หรือไม่? 5. แสวงหาเส้นทางแห่งการลงทุนที่แท้จริง แทนที่จะใช้เหรียญทองไปกับการพนัน จงเปลี่ยนเป็นการลงทุนที่มีโอกาสเติบโต เช่น เป็นนักรบแห่งคุณค่า (VI) , เข้าซื้อหุ้นแล้วเก็บมันไว้ในหีบสมบัติ 1 ปี , DCA BTC ดั่งสะสมขุมทรัพย์ทีละน้อย 6. ถามตัวเองว่า “อยากเป็นผู้ชนะ หรือเป็นเหยื่อ?” ผู้ที่ร่ำรวยจากการพนันคือนักลงทุนผู้เปิดบ่อน มิใช่ผู้เล่น หากท่านปรารถนาจะเป็นผู้ชนะ จงเลือกเส้นทางที่ชาญฉลาดกว่า 7. ตั้งเป้าหมายที่ยิ่งใหญ่กว่า จงตั้งเป้าหมายที่ชัดเจน เช่น สะสมเหรียญทองเพื่อซื้อปราสาท 5 ล้าน หรือหาเงิน 100 ล้าน แล้วจงมุ่งมั่นไปที่มัน การพนันจะทำให้เป้าหมายของท่านล่าช้าลง 📉 เหตุใดดันเจี้ยนแห่งการเทรดจึงเปรียบเสมือนเขาวงกต? 1️⃣ ก้าวเข้ามาง่าย ออกไปยาก • การเข้าสู่ตลาดการเงินเป็นเรื่องง่ายดาย ใช้เพียงบัญชีเทรดและเงินทุนเพียงเล็กน้อย แต่เมื่อเข้ามาแล้ว จิตวิทยาแห่งการลงทุน และ ความผันผวนของตลาด จะทำให้ยากที่จะออกไป 2️⃣ เส้นทางที่ซับซ้อน • นักรบมือใหม่มักคิดว่าการทำกำไรเป็นเรื่องง่าย แต่เมื่อเริ่มต้นจริงจะพบว่ามีปัจจัยมากมายที่ต้องเรียนรู้ ทั้งเทคนิค เวทมนตร์พื้นฐาน อารมณ์ตลาด และจิตวิทยาของตน 3️⃣ ความโลภและความหวังทำให้ติดอยู่ในตลาด • หลายคนเริ่มต้นเทรดด้วยเป้าหมายหาเหรียญทอง แต่เมื่อขาดทุน กลับพยายามเอาคืน • เมื่อกำไร ก็อยากได้มากขึ้น จนบางครั้งไม่รู้จักพอ 4️⃣ ไม่มีเส้นทางที่แน่นอน • ในเขาวงกตนี้ ไม่มีทางเดินตรงไปสู่ความสำเร็จ ต้องลองผิดลองถูกหลายครา • บางคนหลงทาง บางคนเจอทางตัน บางคนออกจากตลาดไปก่อนจะถึงทางออกที่แท้จริง 🎯 แล้วจะเอาตัวรอดจากวงกตนี้ได้อย่างไร? ✅ เข้าใจว่าเทรดไม่ใช่การพนัน • การเทรดที่ดีต้องมีระบบ ไม่ใช่แค่เสี่ยงดวง ✅ ฝึกวินัยและจัดการอารมณ์ • สิ่งที่สังหารนักรบมิใช่ปีศาจในตลาด แต่เป็น “อารมณ์ของตนเอง” ✅ วางแผนก่อนเข้าเทรด และมีจุดตัดขาดทุนเสมอ • อย่าเข้าเทรดโดยไร้แผน เพราะจะทำให้ท่านติดอยู่ในเขาวงกตตลอดกาล ✅ รู้ว่าเมื่อไหร่ควรหยุด • บางครั้ง “การไม่เทรด” คือการตัดสินใจที่ดีที่สุด 🔮 บทสรุป ดันเจี้ยนแห่งการเทรดเปรียบเสมือนสถานที่ลี้ลับที่ยังไม่มีผู้ใดสำรวจมาก่อน ผู้ใดที่ย่างกรายเข้ามาล้วนออกไปยาก เพราะมันเต็มไปด้วยความท้าทาย อารมณ์ และความโลภ แต่หากท่านเข้าใจเกมนี้ดีพอ ท่านจะสามารถหาทางออก และเปลี่ยนมันให้เป็นโอกาสแห่งความมั่งคั่งได้ จงจำไว้ว่า การจะออกจากดันเจี้ยนนี้ได้ ท่านต้องพิชิตบอสใหญ่ "การรู้เท่าทันอารมณ์ และมายเซ็ทที่เหมาะสมกับเทรนด์เดอร์" ให้จงได้! หวังว่าพวกท่านจะไม่หลายเป็นซากศพเน่าๆ ในดันเจี้ยนแห่งนี้ ของให้โชคดีมีชัยในโลกเทรนด์เดอร์ YONOSUBA
@ d360efec:14907b5f
2025-02-07 09:42:54ณ ดินแดนอันไกลโพ้น ปรากฏดันเจี้ยนลึกลับไร้ก้นบึ้ง นามว่า "ตลาดการเก็งกำไร" ประตูทางเข้าเปล่งประกายล่อตาล่อใจ แต่มักถูกปกคลุมด้วยหมอกแห่งความไม่แน่นอน คำจารึกโบราณ แกะสลักเหนือประตูทางเข้า เตือนสติผู้มาเยือน: "ผู้ใดเข้าล้วนมิอาจหวนคืน..." เฉกเช่นสำนวนโบราณที่กล่าวขาน "คนในมิอาจออก คนนอกมิต้องการย่างกราย" ภาพที่ปรากฎตรงหน้า คือชายหนุ่มผู้หาญกล้า กำลังจะก้าวเข้าสู่ประตูดันเจี้ยน เหนือประตูมีป้ายขนาดมหึมาสลักคำว่า "Trading" สัญลักษณ์แห่งโลกการลงทุน การเก็งกำไร ไม่ว่าจะเป็น หุ้น, ฟอเร็กซ์, คริปโต ล้วนเป็นมอนสเตอร์ที่สถิตอยู่ในนี้ การจะพิชิตดันเจี้ยนนี้ได้นั้น หาใช่เรื่องง่าย ภารกิจแรกคือการกำจัดปีศาจ**"นักพนัน"** ที่สิงอยู่ในจิตใจของผู้กล้าทุกคน ปีศาจตนนี้ร้ายกาจยิ่งนัก แต่มิใช่ว่าไร้ทางปราบ หากท่านผู้กล้าปรารถนาจะหลุดพ้นจากวงจรอุบาทว์นี้ จงใช้วิธีเหล่านี้เถิด 1. เข้าใจว่าการพนันคือกับดัก ปีศาจพนันมักล่อลวงด้วยภาพลวงตาแห่งชัยชนะเพียงชั่วครู่ แต่แท้จริงแล้ว มันถูกออกแบบมาเพื่อสูบเลือดสูบเนื้อจากเหล่าผู้กล้าในระยะยาว จงจำไว้ว่าการพนันมิใช่หนทางสู่ความร่ำรวย แต่เป็นเส้นทางสู่หุบเหวแห่งความสิ้นเนื้อประดาตัว 2. เปลี่ยนมุมมองเกี่ยวกับเหรียญทอง จงมองเหรียญทองที่ท่านมีมิใช่แค่ตัวเลข แต่เป็น “เวลาและหยาดเหงื่อ” ที่ท่านได้แลกมา หากท่านสูญเสียมันไปเพราะการพนัน มันคือเวลาชีวิตที่หายไปตลอดกาล 3. ตัดขาดสิ่งเร้าที่กระตุ้นให้เล่น • ลบแอปพนัน / ปิดกั้นเว็บไซต์มืด • เลิกติดตามเพจหรือกลุ่มที่เกี่ยวข้อง • เปลี่ยนสหายร่วมทางที่ชักชวนไปสู่ทางเสื่อม 4. ใช้กฎ 5 นาที เมื่อใดที่ความกระหายอยากเล่นครอบงำ จงหยุดยั้งตัวเองไว้ 5 นาที แล้วตรองดูว่า • คราก่อนท่านสูญเสียไปเท่าใด? • หากเล่นแล้วเสียอีก จะรู้สึกเช่นไร? • มีสิ่งใดที่ควรทำมากกว่านี้หรือไม่? 5. แสวงหาเส้นทางแห่งการลงทุนที่แท้จริง แทนที่จะใช้เหรียญทองไปกับการพนัน จงเปลี่ยนเป็นการลงทุนที่มีโอกาสเติบโต เช่น เป็นนักรบแห่งคุณค่า (VI) , เข้าซื้อหุ้นแล้วเก็บมันไว้ในหีบสมบัติ 1 ปี , DCA BTC ดั่งสะสมขุมทรัพย์ทีละน้อย 6. ถามตัวเองว่า “อยากเป็นผู้ชนะ หรือเป็นเหยื่อ?” ผู้ที่ร่ำรวยจากการพนันคือนักลงทุนผู้เปิดบ่อน มิใช่ผู้เล่น หากท่านปรารถนาจะเป็นผู้ชนะ จงเลือกเส้นทางที่ชาญฉลาดกว่า 7. ตั้งเป้าหมายที่ยิ่งใหญ่กว่า จงตั้งเป้าหมายที่ชัดเจน เช่น สะสมเหรียญทองเพื่อซื้อปราสาท 5 ล้าน หรือหาเงิน 100 ล้าน แล้วจงมุ่งมั่นไปที่มัน การพนันจะทำให้เป้าหมายของท่านล่าช้าลง 📉 เหตุใดดันเจี้ยนแห่งการเทรดจึงเปรียบเสมือนเขาวงกต? 1️⃣ ก้าวเข้ามาง่าย ออกไปยาก • การเข้าสู่ตลาดการเงินเป็นเรื่องง่ายดาย ใช้เพียงบัญชีเทรดและเงินทุนเพียงเล็กน้อย แต่เมื่อเข้ามาแล้ว จิตวิทยาแห่งการลงทุน และ ความผันผวนของตลาด จะทำให้ยากที่จะออกไป 2️⃣ เส้นทางที่ซับซ้อน • นักรบมือใหม่มักคิดว่าการทำกำไรเป็นเรื่องง่าย แต่เมื่อเริ่มต้นจริงจะพบว่ามีปัจจัยมากมายที่ต้องเรียนรู้ ทั้งเทคนิค เวทมนตร์พื้นฐาน อารมณ์ตลาด และจิตวิทยาของตน 3️⃣ ความโลภและความหวังทำให้ติดอยู่ในตลาด • หลายคนเริ่มต้นเทรดด้วยเป้าหมายหาเหรียญทอง แต่เมื่อขาดทุน กลับพยายามเอาคืน • เมื่อกำไร ก็อยากได้มากขึ้น จนบางครั้งไม่รู้จักพอ 4️⃣ ไม่มีเส้นทางที่แน่นอน • ในเขาวงกตนี้ ไม่มีทางเดินตรงไปสู่ความสำเร็จ ต้องลองผิดลองถูกหลายครา • บางคนหลงทาง บางคนเจอทางตัน บางคนออกจากตลาดไปก่อนจะถึงทางออกที่แท้จริง 🎯 แล้วจะเอาตัวรอดจากวงกตนี้ได้อย่างไร? ✅ เข้าใจว่าเทรดไม่ใช่การพนัน • การเทรดที่ดีต้องมีระบบ ไม่ใช่แค่เสี่ยงดวง ✅ ฝึกวินัยและจัดการอารมณ์ • สิ่งที่สังหารนักรบมิใช่ปีศาจในตลาด แต่เป็น “อารมณ์ของตนเอง” ✅ วางแผนก่อนเข้าเทรด และมีจุดตัดขาดทุนเสมอ • อย่าเข้าเทรดโดยไร้แผน เพราะจะทำให้ท่านติดอยู่ในเขาวงกตตลอดกาล ✅ รู้ว่าเมื่อไหร่ควรหยุด • บางครั้ง “การไม่เทรด” คือการตัดสินใจที่ดีที่สุด 🔮 บทสรุป ดันเจี้ยนแห่งการเทรดเปรียบเสมือนสถานที่ลี้ลับที่ยังไม่มีผู้ใดสำรวจมาก่อน ผู้ใดที่ย่างกรายเข้ามาล้วนออกไปยาก เพราะมันเต็มไปด้วยความท้าทาย อารมณ์ และความโลภ แต่หากท่านเข้าใจเกมนี้ดีพอ ท่านจะสามารถหาทางออก และเปลี่ยนมันให้เป็นโอกาสแห่งความมั่งคั่งได้ จงจำไว้ว่า การจะออกจากดันเจี้ยนนี้ได้ ท่านต้องพิชิตบอสใหญ่ "การรู้เท่าทันอารมณ์ และมายเซ็ทที่เหมาะสมกับเทรนด์เดอร์" ให้จงได้! หวังว่าพวกท่านจะไม่หลายเป็นซากศพเน่าๆ ในดันเจี้ยนแห่งนี้ ของให้โชคดีมีชัยในโลกเทรนด์เดอร์ YONOSUBA @ 16d11430:61640947
2025-02-07 09:37:24Introduction: The Lost Art of Flourishing Eudaimonia, the Greek concept of human flourishing, represents a state of deep fulfillment derived from purpose, mastery, and moral virtue. Aristotle described it as the highest human good, achieved not through transient pleasures but through living in accordance with reason and excellence. Yet, in our modern fiat-driven world, eudaimonia has largely perished. Instead of striving for excellence, people are entrapped by systems of debt, artificial scarcity, and wage slavery, where fulfillment is secondary to survival. The incentives of fiat capitalism—endless growth, consumerism, and bureaucratic control—have eroded the conditions necessary for human flourishing. The purpose of this article is to explore the death of eudaimonia under fiat rule, supported by critical evidence, and to examine whether it can be resurrected—perhaps through alternative systems like Bitcoin and decentralized technologies. --- The Fiat Machine and the Death of Eudaimonia 1. The Extraction of Meaning: Fiat as a Mechanism of Control Fiat currency, backed by nothing but government decree, is a tool of centralized power. It is inflationary by design, ensuring that those who hold wealth in fiat lose purchasing power over time unless they participate in increasingly speculative financial schemes. This constant need to hedge against inflation forces individuals into short-term thinking, undermining long-term endeavors that lead to mastery and fulfillment. Instead of creating art, philosophy, or science for its own sake, people are incentivized to chase money in the fastest, most extractive way possible. Critical Evidence: Wages have stagnated relative to productivity since the abandonment of the gold standard in 1971, while financialization has exploded. According to the U.S. Bureau of Labor Statistics, median wages have barely kept up with inflation, whereas asset prices (stocks, real estate) have soared—favoring the wealthy who can invest while punishing wage earners. 2. The Death of Virtue: How Fiat Incentivizes Corruption Aristotle tied eudaimonia to virtue—justice, courage, temperance, and wisdom. But fiat economies erode virtue by rewarding manipulation over integrity. In a world where money is easily printed, those closest to its issuance—the state, banks, and corporate elites—reap the rewards while the average person suffers debasement. Fiat allows for moral hazard: banks are bailed out after reckless speculation, politicians spend without accountability, and corporations use inflation to justify price hikes. This destroys trust, a fundamental component of any thriving society. Critical Evidence: The Cantillon Effect demonstrates that newly printed money benefits those who receive it first (banks, hedge funds) at the expense of those who receive it last (workers, pensioners). The 2008 financial crisis and subsequent bailouts exemplify how fiat rewards risk-taking elites while punishing ordinary citizens. 3. Bureaucratic Slavery: The War Against Self-Sufficiency Fiat governance has transformed human beings from self-reliant individuals into bureaucratic dependents. Governments and corporations engineer complexity—compliance laws, credential requirements, and licensing systems—to keep individuals trapped in cycles of employment and taxation. Eudaimonia thrives in societies where individuals have control over their work and creations, yet fiat systems strip away autonomy. Most people today work jobs they do not love, merely to service debts or meet rising costs. Critical Evidence: A 2019 Gallup survey found that 85% of employees worldwide are disengaged from their jobs, meaning they find no real meaning in their work. Meanwhile, U.S. student loan debt has surpassed $1.7 trillion, forcing young people into decades of financial servitude before they can even attempt to pursue meaningful work. --- Can Eudaimonia Be Resurrected? 1. Bitcoin and the Return of Hard Money If fiat is the poison, Bitcoin might be the antidote. Unlike fiat, Bitcoin is scarce, decentralized, and operates on proof-of-work, rewarding merit rather than proximity to power. A Bitcoin-based economy restores long-term thinking by allowing individuals to store value in a deflationary asset rather than being forced into high-risk speculation. When people do not need to chase inflation, they can focus on work that is intrinsically fulfilling rather than merely profitable. Critical Evidence: Countries like El Salvador have adopted Bitcoin as legal tender to escape the inflationary policies of central banks, while Bitcoin’s fixed supply of 21 million ensures its purchasing power cannot be arbitrarily diluted. 2. Decentralized Systems and Self-Sovereignty Beyond money, decentralization itself is a means of restoring eudaimonia. Peer-to-peer networks, open-source software, and blockchain verification (such as DamageBDD) enable individuals to engage in meaningful work without needing corporate or governmental permission. Critical Evidence: The rise of remote work, creator economies, and DAOs (Decentralized Autonomous Organizations) shows that people can be productive outside traditional corporate structures when given the right tools. 3. The Renaissance of Craftsmanship and Knowledge A return to hard money and decentralized economies will likely trigger a renaissance of craftsmanship. When individuals no longer need to rush for short-term profits, they can master trades, sciences, and arts in ways that have not been possible since the fiat era began. We are already seeing glimpses of this in the resurgence of interest in sovereign computing, homesteading, and open-source development—a direct rebellion against the fiat model of centralization and planned obsolescence. Critical Evidence: The growth of FOSS (Free and Open Source Software) and Bitcoin development reflects a shift toward work driven by passion and principle rather than extractive financial incentives. --- Conclusion: The Path Forward Eudaimonia is not dead, but it has been suffocated under the weight of fiat. By restoring individual sovereignty—through sound money, decentralized verification, and self-sufficiency—we can resurrect the human spirit. The transition will not be easy; it will require a rejection of the comfort fiat provides in exchange for the struggle that meaningful existence demands. Yet, for those who seek mastery, virtue, and true fulfillment, there is no other choice. The fiat era has stripped humanity of its highest potential. It is time to reclaim it.
@ 16d11430:61640947
2025-02-07 09:37:24Introduction: The Lost Art of Flourishing Eudaimonia, the Greek concept of human flourishing, represents a state of deep fulfillment derived from purpose, mastery, and moral virtue. Aristotle described it as the highest human good, achieved not through transient pleasures but through living in accordance with reason and excellence. Yet, in our modern fiat-driven world, eudaimonia has largely perished. Instead of striving for excellence, people are entrapped by systems of debt, artificial scarcity, and wage slavery, where fulfillment is secondary to survival. The incentives of fiat capitalism—endless growth, consumerism, and bureaucratic control—have eroded the conditions necessary for human flourishing. The purpose of this article is to explore the death of eudaimonia under fiat rule, supported by critical evidence, and to examine whether it can be resurrected—perhaps through alternative systems like Bitcoin and decentralized technologies. --- The Fiat Machine and the Death of Eudaimonia 1. The Extraction of Meaning: Fiat as a Mechanism of Control Fiat currency, backed by nothing but government decree, is a tool of centralized power. It is inflationary by design, ensuring that those who hold wealth in fiat lose purchasing power over time unless they participate in increasingly speculative financial schemes. This constant need to hedge against inflation forces individuals into short-term thinking, undermining long-term endeavors that lead to mastery and fulfillment. Instead of creating art, philosophy, or science for its own sake, people are incentivized to chase money in the fastest, most extractive way possible. Critical Evidence: Wages have stagnated relative to productivity since the abandonment of the gold standard in 1971, while financialization has exploded. According to the U.S. Bureau of Labor Statistics, median wages have barely kept up with inflation, whereas asset prices (stocks, real estate) have soared—favoring the wealthy who can invest while punishing wage earners. 2. The Death of Virtue: How Fiat Incentivizes Corruption Aristotle tied eudaimonia to virtue—justice, courage, temperance, and wisdom. But fiat economies erode virtue by rewarding manipulation over integrity. In a world where money is easily printed, those closest to its issuance—the state, banks, and corporate elites—reap the rewards while the average person suffers debasement. Fiat allows for moral hazard: banks are bailed out after reckless speculation, politicians spend without accountability, and corporations use inflation to justify price hikes. This destroys trust, a fundamental component of any thriving society. Critical Evidence: The Cantillon Effect demonstrates that newly printed money benefits those who receive it first (banks, hedge funds) at the expense of those who receive it last (workers, pensioners). The 2008 financial crisis and subsequent bailouts exemplify how fiat rewards risk-taking elites while punishing ordinary citizens. 3. Bureaucratic Slavery: The War Against Self-Sufficiency Fiat governance has transformed human beings from self-reliant individuals into bureaucratic dependents. Governments and corporations engineer complexity—compliance laws, credential requirements, and licensing systems—to keep individuals trapped in cycles of employment and taxation. Eudaimonia thrives in societies where individuals have control over their work and creations, yet fiat systems strip away autonomy. Most people today work jobs they do not love, merely to service debts or meet rising costs. Critical Evidence: A 2019 Gallup survey found that 85% of employees worldwide are disengaged from their jobs, meaning they find no real meaning in their work. Meanwhile, U.S. student loan debt has surpassed $1.7 trillion, forcing young people into decades of financial servitude before they can even attempt to pursue meaningful work. --- Can Eudaimonia Be Resurrected? 1. Bitcoin and the Return of Hard Money If fiat is the poison, Bitcoin might be the antidote. Unlike fiat, Bitcoin is scarce, decentralized, and operates on proof-of-work, rewarding merit rather than proximity to power. A Bitcoin-based economy restores long-term thinking by allowing individuals to store value in a deflationary asset rather than being forced into high-risk speculation. When people do not need to chase inflation, they can focus on work that is intrinsically fulfilling rather than merely profitable. Critical Evidence: Countries like El Salvador have adopted Bitcoin as legal tender to escape the inflationary policies of central banks, while Bitcoin’s fixed supply of 21 million ensures its purchasing power cannot be arbitrarily diluted. 2. Decentralized Systems and Self-Sovereignty Beyond money, decentralization itself is a means of restoring eudaimonia. Peer-to-peer networks, open-source software, and blockchain verification (such as DamageBDD) enable individuals to engage in meaningful work without needing corporate or governmental permission. Critical Evidence: The rise of remote work, creator economies, and DAOs (Decentralized Autonomous Organizations) shows that people can be productive outside traditional corporate structures when given the right tools. 3. The Renaissance of Craftsmanship and Knowledge A return to hard money and decentralized economies will likely trigger a renaissance of craftsmanship. When individuals no longer need to rush for short-term profits, they can master trades, sciences, and arts in ways that have not been possible since the fiat era began. We are already seeing glimpses of this in the resurgence of interest in sovereign computing, homesteading, and open-source development—a direct rebellion against the fiat model of centralization and planned obsolescence. Critical Evidence: The growth of FOSS (Free and Open Source Software) and Bitcoin development reflects a shift toward work driven by passion and principle rather than extractive financial incentives. --- Conclusion: The Path Forward Eudaimonia is not dead, but it has been suffocated under the weight of fiat. By restoring individual sovereignty—through sound money, decentralized verification, and self-sufficiency—we can resurrect the human spirit. The transition will not be easy; it will require a rejection of the comfort fiat provides in exchange for the struggle that meaningful existence demands. Yet, for those who seek mastery, virtue, and true fulfillment, there is no other choice. The fiat era has stripped humanity of its highest potential. It is time to reclaim it. @ 6ad3e2a3:c90b7740
2025-02-07 08:17:18When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account. I’d tell them, “You decide, I’ve got my own problems.” . . . I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests. . . . Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere. Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium. That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper. . . . I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative. The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media. What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn. There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.) No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness. We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot. . . . I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them. I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!” . . . There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature. . . . No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach. . . . The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.” For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems.
@ 6ad3e2a3:c90b7740
2025-02-07 08:17:18When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account. I’d tell them, “You decide, I’ve got my own problems.” . . . I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests. . . . Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere. Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium. That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper. . . . I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative. The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media. What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn. There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.) No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness. We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot. . . . I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them. I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!” . . . There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature. . . . No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach. . . . The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.” For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems. @ da0b9bc3:4e30a4a9
2025-02-07 07:26:07Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/878449
@ da0b9bc3:4e30a4a9
2025-02-07 07:26:07Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/878449 @ e3ba5e1a:5e433365
2025-02-07 05:25:58How much does the government cost? Focusing just on the US, we could talk in terms of US dollars spent on the budget each year. But those numbers are so large we can’t really conceptualize them. A more relatable way of talking about this is what percentage of your income goes to the government. Or, even better, what percentage of your productive output is funneled to the government? A first pass answer would be to look at income tax. If income tax is 30%, you work 30% of the year for the government and 70% for yourself. The problem is that income tax isn’t the only tax. There’s property tax, sales tax, payroll tax (i.e. another income tax), and who knows how many others. In other words, income tax only covers one (large) portion of our taxed income. But it doesn’t stop there. We can’t forget inflation, the hidden, silent tax that not only erodes your earnings, but destroys your savings. It pulls off the amazing feat of not only taxing you today, but *historically* taxing you. It punishes you for being a prudent person and saving your money. (Which, side note, is why we love saving in Bitcoin.) You might think we’re done. We’ve covered all the ways the government funds itself: direct taxation and inflation (via money printing). And that part is true. But we haven’t finished looking at the cost. You see, economically speaking, every time you put a tax into a system, you create inefficiencies. The market can no longer perform as well as it did previously. So we have yet another hidden cost: all productive capability in the economy gets worse, because the government needs to push its way in. An easy way to see this is all the tax games companies play to fall into different deductions and exemptions. It doesn’t stop there either. Now that we’re talking about government-caused inefficiency, we can of course get to regulation. Regulation directly makes things more expensive (by forcing companies to spend time on compliance). It also indirectly makes things more expensive by presenting a barrier to entry for new providers, reducing competition and further hurting consumers. Surely that’s the end, right? Nope. The government is sucking capital out of the private sector to put into public sector projects. That means the private sector has less capital for investment. People are incentivized not to save due to inflation, which encourages high-time-preference consumerism. This means we get less investment by companies for the future, which defeats the natural tendency of industry to become more efficient over time and pass on the savings to the consumer (via technology-driven deflation, for instance). I knew all of that two weeks ago, and it hasn’t changed. There’s one final piece to this puzzle. Many of us suspected it. With the news coming out about USAID and the programs it laundered money to, we’re starting to get even more concrete proof. The government steals our money, inflates it, takes all of that productive capacity we sweated and toiled for… and gives it to people who are actively trying to hurt us, yet again furthering the cost of government. The cost of government isn’t one number. It’s not quantifiable. The cost of government is losing out on the world where everything becomes better, safer, cheaper, faster, healthier, and more enjoyable, and replacing it with a decaying, eroding society, where the most morally bankrupt people can fleece the rest of us for their livelihoods. I’m praying that the exposure and toppling of USAID is a major accomplishment, but just one of many more to come. To quote The Two Towers, I hope it “will be like the falling of small stones that starts an avalanche.”
@ e3ba5e1a:5e433365
2025-02-07 05:25:58How much does the government cost? Focusing just on the US, we could talk in terms of US dollars spent on the budget each year. But those numbers are so large we can’t really conceptualize them. A more relatable way of talking about this is what percentage of your income goes to the government. Or, even better, what percentage of your productive output is funneled to the government? A first pass answer would be to look at income tax. If income tax is 30%, you work 30% of the year for the government and 70% for yourself. The problem is that income tax isn’t the only tax. There’s property tax, sales tax, payroll tax (i.e. another income tax), and who knows how many others. In other words, income tax only covers one (large) portion of our taxed income. But it doesn’t stop there. We can’t forget inflation, the hidden, silent tax that not only erodes your earnings, but destroys your savings. It pulls off the amazing feat of not only taxing you today, but *historically* taxing you. It punishes you for being a prudent person and saving your money. (Which, side note, is why we love saving in Bitcoin.) You might think we’re done. We’ve covered all the ways the government funds itself: direct taxation and inflation (via money printing). And that part is true. But we haven’t finished looking at the cost. You see, economically speaking, every time you put a tax into a system, you create inefficiencies. The market can no longer perform as well as it did previously. So we have yet another hidden cost: all productive capability in the economy gets worse, because the government needs to push its way in. An easy way to see this is all the tax games companies play to fall into different deductions and exemptions. It doesn’t stop there either. Now that we’re talking about government-caused inefficiency, we can of course get to regulation. Regulation directly makes things more expensive (by forcing companies to spend time on compliance). It also indirectly makes things more expensive by presenting a barrier to entry for new providers, reducing competition and further hurting consumers. Surely that’s the end, right? Nope. The government is sucking capital out of the private sector to put into public sector projects. That means the private sector has less capital for investment. People are incentivized not to save due to inflation, which encourages high-time-preference consumerism. This means we get less investment by companies for the future, which defeats the natural tendency of industry to become more efficient over time and pass on the savings to the consumer (via technology-driven deflation, for instance). I knew all of that two weeks ago, and it hasn’t changed. There’s one final piece to this puzzle. Many of us suspected it. With the news coming out about USAID and the programs it laundered money to, we’re starting to get even more concrete proof. The government steals our money, inflates it, takes all of that productive capacity we sweated and toiled for… and gives it to people who are actively trying to hurt us, yet again furthering the cost of government. The cost of government isn’t one number. It’s not quantifiable. The cost of government is losing out on the world where everything becomes better, safer, cheaper, faster, healthier, and more enjoyable, and replacing it with a decaying, eroding society, where the most morally bankrupt people can fleece the rest of us for their livelihoods. I’m praying that the exposure and toppling of USAID is a major accomplishment, but just one of many more to come. To quote The Two Towers, I hope it “will be like the falling of small stones that starts an avalanche.” @ 000002de:c05780a7
2025-02-07 03:54:22I've long been a fan of [Liberty Maniacs](https://libertymaniacs.com/), the site that makes funny political shirts for rebels & liberty lovers but their email today hit me as extra funny. ## Here's what they shared. To say the last two weeks have been wild would be the understatement of the century. 🔥 DOGE is taking over the Treasury 🔥 USAID got caught laundering money (again)—basically funding everything to the left of Jimmy Carter’s ghost. 🔥 The new AG wants to drop the Epstein list like it’s hot. 🔥 The CIA just casually admitted the government created COVID. 🔥 And oh yeah, the Gulf of Mexico? Not anymore. Welcome to the Gulf of America! At this point, reality is outpacing satire. But don’t worry, we’re working harder than a WEF escort during Davos week to get these news cycles onto shirts before the next scandal drops. Not sure if we’ll ever catch up, but damn it, we’re gonna try. --- I mean, that's pretty good stuff. If you are a marketer or copywriter this is how you do it. originally posted at https://stacker.news/items/878326
@ 000002de:c05780a7
2025-02-07 03:54:22I've long been a fan of [Liberty Maniacs](https://libertymaniacs.com/), the site that makes funny political shirts for rebels & liberty lovers but their email today hit me as extra funny. ## Here's what they shared. To say the last two weeks have been wild would be the understatement of the century. 🔥 DOGE is taking over the Treasury 🔥 USAID got caught laundering money (again)—basically funding everything to the left of Jimmy Carter’s ghost. 🔥 The new AG wants to drop the Epstein list like it’s hot. 🔥 The CIA just casually admitted the government created COVID. 🔥 And oh yeah, the Gulf of Mexico? Not anymore. Welcome to the Gulf of America! At this point, reality is outpacing satire. But don’t worry, we’re working harder than a WEF escort during Davos week to get these news cycles onto shirts before the next scandal drops. Not sure if we’ll ever catch up, but damn it, we’re gonna try. --- I mean, that's pretty good stuff. If you are a marketer or copywriter this is how you do it. originally posted at https://stacker.news/items/878326 @ 57d1a264:69f1fee1
2025-02-07 03:35:34# The #LightningNetwork introduces the concept of #payment channels. How do these channels work, and how do they enable #bitcoin to #scale while maintaining #security? originally posted at https://stacker.news/items/878316
@ 57d1a264:69f1fee1
2025-02-07 03:35:34# The #LightningNetwork introduces the concept of #payment channels. How do these channels work, and how do they enable #bitcoin to #scale while maintaining #security? originally posted at https://stacker.news/items/878316 @ 6bcc27d2:b67d296e
2025-02-07 03:06:38This is the test of obsidian nostr writer
@ 6bcc27d2:b67d296e
2025-02-07 03:06:38This is the test of obsidian nostr writer @ 57d1a264:69f1fee1
2025-02-07 02:59:45# Bitcoin's blockchain is described as a 'public ledger.' How does this public nature contribute to bitcoin's security and trustlessness, and what role do nodes play in this system? originally posted at https://stacker.news/items/878295
@ 57d1a264:69f1fee1
2025-02-07 02:59:45# Bitcoin's blockchain is described as a 'public ledger.' How does this public nature contribute to bitcoin's security and trustlessness, and what role do nodes play in this system? originally posted at https://stacker.news/items/878295 @ 5d4b6c8d:8a1c1ee3
2025-02-07 01:02:09I don't think I did one of these summary posts last month. Based on the [predictions](https://stacker.news/items/865017/r/Undisciplined) made by stackers here's what to expect at the end of the season. **Champion**: Celtics **MVP**: SGA **All NBA 1st Team** C Jokic F Giannis F Luka G Ant G SGA These aren't bad, but whoever's sticking with those Ant and Luka picks seriously need to move off of them. originally posted at https://stacker.news/items/878234
@ 5d4b6c8d:8a1c1ee3
2025-02-07 01:02:09I don't think I did one of these summary posts last month. Based on the [predictions](https://stacker.news/items/865017/r/Undisciplined) made by stackers here's what to expect at the end of the season. **Champion**: Celtics **MVP**: SGA **All NBA 1st Team** C Jokic F Giannis F Luka G Ant G SGA These aren't bad, but whoever's sticking with those Ant and Luka picks seriously need to move off of them. originally posted at https://stacker.news/items/878234 @ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.*
@ df173277:4ec96708
2025-02-07 00:41:34## **Building Our Confidential Backend on Secure Enclaves** With our newly released [private and confidential **Maple AI**](https://trymaple.ai/?ref=blog.opensecret.cloud) and the open sourcing of our [**OpenSecret** platform](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud) code, I'm excited to present this technical primer on how we built our confidential compute platform leveraging **secure enclaves**. By combining AWS Nitro enclaves with end-to-end encryption and reproducible builds, our platform gives developers and end users the confidence that user data is protected, even at runtime, and that the code operating on their data has not been tampered with. ## **Auth and Databases Today** As developers, we live in an era where protecting user data means "encryption at rest," plus some access policies and procedures. Developers typically run servers that: 1. Need to register users (authentication). 2. Collect and process user data in business-specific ways, often on the backend. Even if data is encrypted at rest, it's commonly unlocked with a single master key or credentials the server holds. This means that data is visible during runtime to the application, system administrators, and potentially to the hosting providers. This scenario makes it difficult (or impossible) to guarantee that sensitive data isn't snooped on, memory-dumped, or used in unauthorized ways (for instance, training AI models behind the scenes). ## **"Just Trust Us" Isn't Good Enough** In a traditional server architecture, users have to take it on faith that the code handling their data is the same code the operator claims to be running. Behind the scenes, applications can be modified or augmented to forward private information elsewhere, and there is no transparent way for users to verify otherwise. This lack of proof is unsettling, especially for services that process or store highly confidential data. Administrators, developers, or cloud providers with privileged access can inspect memory in plaintext, attach debuggers, or gain complete visibility into stored information. Hackers who compromise these privileged levels can directly access sensitive data. Even with strict policies or promises of good conduct, the reality is that technical capabilities and misconfigurations can override words on paper. If a server master key can decrypt your data or can be accessed by an insider with root permissions, then "just trust us" loses much of its credibility. The rise of AI platforms amplifies this dilemma. User data, often full of personal details, gets funneled into large-scale models that might be training or fine-tuning behind the scenes. Relying on vague assurances that "we don't look at your data" is no longer enough to prevent legitimate concerns about privacy and misuse. Now more than ever, providing a **strong, verifiable** guarantee that data remains off-limits, even when actively processed, has become a non-negotiable requirement for trustworthy services. ## **Current Attempts at Securing Data** Current User Experience of E2EE Apps While properly securing data is not easy, it isn't to say that no one is trying. Some solutions use **end-to-end encryption** (E2EE), where user data is encrypted client-side with a password or passphrase, so not even the server operator can decrypt it. That approach can be quite secure, but it also has its **limitations**: 1. **Key Management Nightmares**: If a user forgets their passphrase, the data is effectively lost, and there's no way to recover it from the developer's side. 2. **Feature Limitations**: Complex server-side operations (like offline/background tasks, AI queries, real-time collaboration, or heavy computation) can't easily happen if the server is never capable of processing decrypted data. 3. **Platform Silos**: Some solutions rely on iCloud, Google Drive, or local device storage. That can hamper multi-device usage or multi-OS compatibility. Other approaches include self-hosting. However, these either burden users with dev ops overhead or revert to the "trust me" model for the server if you "self-host" on a cloud provider. ## **Secure Enclaves** ### **The Hybrid Approach** Secure enclaves offer a compelling middle ground. They combine the privacy benefits of keeping data secure from prying admins while still allowing meaningful server-side computation. In a nutshell, an enclave is a protected environment within a machine, isolated at the hardware level, so that even if the OS or server is compromised, the data and code inside the enclave remain hidden. App Service Running Inside Secure Enclave ### **High-Level Goal of Enclaves** Enclaves, also known under the broader umbrella of **confidential computing**, aim to:\ • **Lock down data** so that only authorized code within the enclave can process the original plaintext data.\ • **Deny external inspection** by memory dumping, attaching a debugger, or intercepting plaintext network traffic.\ • **Prove** to external users or services that an enclave is running unmodified, approved code (this is where **remote attestation** comes in). ### **Different Secure Enclave Solutions** [**AMD SEV**](https://www.amd.com/en/developer/sev.html?ref=blog.opensecret.cloud) **(Secure Encrypted Virtualization)** encrypts an entire virtual machine's memory so that even a compromised hypervisor cannot inspect or modify guest data. Its core concept is "lift-and-shift" security. No application refactoring is required because hardware-based encryption automatically protects the OS and all VM applications. Later enhancements (SEV-ES and SEV-SNP) added encryption of CPU register states and memory integrity protections, further limiting hypervisor tampering. This broad coverage means the guest OS is included in the trusted boundary. AMD SEV has matured into a robust solution for confidential VMs in multi-tenant clouds. [**Intel TDX**](https://www.intel.com/content/www/us/en/developer/tools/trust-domain-extensions/overview.html?ref=blog.opensecret.cloud) **(Trust Domain Extensions)** shifts from process-level enclaves to full VM encryption, allowing an entire guest operating system and its applications to run in an isolated "trust domain." Like AMD SEV, Intel TDX encrypts and protects all memory the VM uses from hypervisors or other privileged software, so developers do not need to refactor their code to benefit from hardware-based confidentiality. This broader scope addresses many SGX limitations, such as strict memory bounds and the need to split out enclave-specific logic, and offers a more straightforward "lift-and-shift" path for running existing workloads privately. While SGX is now deprecated, TDX carries forward the core confidential computing principles but applies them at the virtual machine level for more substantial isolation, easier deployment, and the ability to scale up to large, memory-intensive applications. [**Apple Secure Enclave and Private Compute**](https://security.apple.com/blog/private-cloud-compute/?ref=blog.opensecret.cloud) is a dedicated security coprocessor embedded in most Apple devices (iPhones, iPads, Macs) and now extended to Apple's server-side AI infrastructure. It runs its own microkernel, has hardware-protected memory, and securely manages operations such as biometric authentication, key storage, and cryptographic tasks. Apple's "Private Compute" approach in the cloud brings similar enclave capabilities to server-based AI, enabling on-device-grade privacy even when requests are processed in Apple's data centers. [**AWS Nitro Enclaves**](https://docs.aws.amazon.com/enclaves/latest/user/nitro-enclave.html?ref=blog.opensecret.cloud) carve out a tightly isolated "mini-VM" from a parent EC2 instance, with its own vCPUs and memory guarded by dedicated Nitro cards. The enclave has no persistent storage and no external network access, significantly reducing the attack surface. Communication with the parent instance occurs over a secure local channel (vsock), and AWS offers hardware-based attestation so that secrets (e.g., encryption keys from AWS KMS) can be accessed only to the correct enclave. This design helps developers protect sensitive data or code even if the main EC2 instance's OS is compromised. [**NVIDIA GPU TEEs**](https://www.nvidia.com/en-us/data-center/solutions/confidential-computing/?ref=blog.opensecret.cloud) **(Hopper H100 and Blackwell)** extend confidential computing to accelerated workloads by encrypting data in GPU memory and ensuring that even a privileged host cannot view or tamper with it. Data moving between CPU and GPU is encrypted in transit, so sensitive model weights or inputs remain protected during AI training or inference. NVIDIA's hardware and drivers handle secure data paths under the hood, allowing confidential large language model (LLM) workloads and other GPU-accelerated computations to run with minimal performance overhead and strong security guarantees. ### **Key Benefits** One major advantage of enclaves is their ability to **keep memory completely off-limits** to outside prying eyes. Even administrators who can normally inspect processes at will are blocked from peeking into the enclave's protected memory space. The enclave model is a huge shift in the security model: it prevents casual inspection and defends against sophisticated memory dumping techniques that might otherwise leak secrets or sensitive data. Another key benefit centers on cryptographic keys that are **never exposed outside the enclave**. Only verified code running inside the enclave environment can run decryption or signing operations, and it can only do so while that specific code is running. This ensures that compromised hosts or rogue processes, even those with high-level privileges, are unable to intercept or misuse the keys because the keys remain strictly within the trusted boundary of the hardware. Enclaves can also offer the power of **remote attestation**, allowing external clients or systems to confirm that they're speaking to an authentic, untampered enclave. By validating the hardware's integrity measurements and enclave-specific proofs, the remote party can be confident in the underlying security properties, an important guarantee in multi-tenant environments or whenever trust boundaries extend across different organizations and networks. Beyond that, **reproducible builds** can create a verifiable fingerprint proving which binary runs in the enclave. This is a step above a simple "trust us" approach. Anyone can independently recreate the enclave image and verify the resulting cryptographic hash by using a reproducible build system (for example, [our NixOS-based solution](https://github.com/OpenSecretCloud/opensecret/blob/master/flake.nix?ref=blog.opensecret.cloud)). If it matches, then users and developers know precisely how code handles their data, boosting confidence that no hidden changes exist. It's worth noting that although enclaves shield you from software devs, cloud providers, and insider threats, you do have to trust the **hardware vendor** (Intel, AMD, Apple, AWS, or NVIDIA) to implement their microcode and firmware securely. The entire enclave model could be theoretically undermined if a CPU maker's root keys or manufacturing process were compromised. Fortunately, these companies undergo extensive audits and firmware validations (often with third-party researchers), and their remote attestation mechanisms allow you to confirm specific firmware versions before trusting an enclave. While this adds a layer of "vendor trust," it's still a far more contained risk than trusting an entire operating system or cloud stack, so enclaves remain a strong step forward in practical, confidential computing. ## **How We Use Secure Enclaves** Now that we've covered the general idea of enclaves let's look at how we specifically implement them in OpenSecret, our developer platform for handling user auth, private keys, data encryption, and AI workloads. ### **Our Stack: AWS Nitro + Nvidia TEE** • **AWS Nitro Enclaves for the backend**: All critical logic, authentication, private key management, and data encryption/decryption run inside an AWS Nitro Enclave. • **Nvidia Trusted Execution for AI**: For large AI inference (such as the Llama 3.3 70B model), we utilize Nvidia's GPU-based TEEs to protect even GPU memory. This means users can feed sensitive data to the AI model **without** exposing it in plaintext to the GPU providers or us as the operator. [Edgeless Systems](https://www.edgeless.systems/?ref=blog.opensecret.cloud) is our Nvidia TEE provider, and due to the power of enclave verification, we don't need to worry about who runs the GPUs. We know requests can't be inspected or tampered with. ### **End-to-End Encryption from Client to Enclave** Client-side Enclave Attestation from Maple AI Before login or data upload, the user/client verifies the **enclave attestation** from our platform. This process proves that the specific Nitro Enclave is genuine and runs the exact code we've published. You can check this out live on [Maple AI's attestation page](https://trymaple.ai/proof?ref=blog.opensecret.cloud). Based on the attestation, the client establishes a secure ephemeral communication channel that only that enclave can decrypt. While we take advantage of SSL, it is typically not terminated inside the enclave itself. To ensure there's full encrypted data transfer all the way through to the enclave, we establish this additional handshake based on the attestation document that is used for all API requests during the client session. From there, the user's credentials, private keys, and data pass through this secure channel directly into the enclave, where they are decrypted and processed according to the user's request. ### **In-Enclave Operations** At the core of OpenSecret's approach is the conviction that security-critical tasks must happen inside the enclave, where even administrative privileges or hypervisor-level compromise cannot expose plaintext data. This encompasses everything from when a user logs in to creating and managing sensitive cryptographic keys. By confining these operations to a protected hardware boundary, developers can focus on building their applications without worrying about accidental data leaks, insider threats, or malicious attempts to harvest credentials. The enclave becomes the ultimate gatekeeper: it controls how data flows and ensures that nothing escapes in plain form. User Auth Methods running inside Enclave A primary example is **user authentication**. All sign-in workflows, including email/password, OAuth, and upcoming passkey-based methods, are handled entirely within the enclave. As soon as a user's credentials enter our platform through the encrypted channel, they are routed straight into the protected environment, bypassing the host's operating system or any potential snooping channels. From there, authentication and session details remain in the enclave, ensuring that privileged outsiders cannot intercept or modify them. By centralizing these identity flows within a sealed environment, developers can assure their users that no one outside the enclave (including the cloud provider or the app's own sysadmins) can peek at, tamper with, or access sensitive login information. Main Enclave Operations in OpenSecret The same principle applies to **private key management**. Whether keys are created fresh in the enclave or securely transferred into it, they remain sealed away from the rest of the system. Operations like digital signing or content decryption happen only within the hardware boundary, so raw keys never appear in any log, file system, or memory space outside the enclave. Developers retain the functionality they need, such as verifying user actions, encrypting data, or enabling secure transactions without ever exposing keys to a broader (and more vulnerable) attack surface. User backup options exist as well, where the keys can be securely passed to the end user. Realtime Encrypted Data Sync on Multiple Devices Another crucial aspect is **data encryption at rest**. While user data ultimately needs to be stored somewhere outside the enclave, the unencrypted form of that data only exists transiently inside the protected environment. Encryption and decryption routines run within the enclave, which holds the encryption keys strictly in memory under hardware guards. If a user uploads data, it is promptly secured before it leaves the enclave. When data is retrieved, it remains encrypted until it reenters the protected region and is passed back to the user through the secured communication channel. This ensures that even if someone gains access to the underlying storage or intercepts data in transit, they will see only meaningless ciphertext. Confidential AI Workloads Finally, **confidential AI workloads** build upon this same pattern: the Nitro enclave re-encrypts data so it can be processed inside a GPU-based trusted execution environment (TEE) for inference or other advanced computations. Sensitive data, like user-generated text or private documents, never appears in the clear on the host or within GPU memory outside the TEE boundary. When an AI process finishes, only the results are returned to the enclave, which can then relay them securely to the requesting user. By seamlessly chaining enclaves together, from CPU-based Nitro Enclaves to GPU-accelerated TEEs, we can deliver robust, hardware-enforced privacy for virtually any type of server-side or AI-driven operation. ### **Reproducible Builds + Verification** Client verifies enclave attestation document We build our enclaves on **NixOS** with reproducible builds, ensuring that anyone can verify that the binary we publish is indeed the binary running in the enclave. This build process is essential for proving we haven't snuck in malicious code to exfiltrate data or collect sensitive logs. Our code is fully open source ([GitHub: OpenSecret](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud)), so you can audit or run it yourself. You can also verify that the cryptographic measurement the build process outputs matches the measurement reported by the enclave during attestation. ## **Putting It All Together** OpenSecret Offering: Private Key Management, Encrypted Sync, Private AI, and Confidential Compute By weaving secure enclaves into every step, from authentication to data handling to AI inference, we shift the burden of trust away from human policies and onto provable, hardware-based protections. For app developers, you can offer your users robust privacy guarantees without rewriting all your business logic or building an entire security stack from scratch. Whether you're storing user credentials or running complex operations on sensitive data, the enclave approach ensures plaintext remains inaccessible to even the most privileged parties outside the enclave boundary. Developers can focus on building great apps, while OpenSecret handles the cryptographic "lock and key" behind the scenes. This model provides a secure-by-design environment for industries that demand strict data confidentiality, such as healthcare, fintech, cryptocurrency apps for secure key management, or decentralized identity platforms. Instead of worrying about memory dumps or backend tampering, you can trust that once data enters the enclave, it's sealed off from unauthorized eyes, including from the app developers themselves. And these safeguards don't just apply to niche use cases. Even general-purpose applications that handle login flows and user-generated content stand to benefit, especially as regulatory scrutiny grows around data privacy and insider threats. Imagine a telehealth startup using OpenSecret enclaves to protect patient information for remote consultations. Not only would patient data remain encrypted at rest, but any AI-driven analytics to assist with diagnoses could be run privately within the enclave, ensuring no one outside the hardware boundary can peek at sensitive health records. A fintech company could similarly isolate confidential financial transactions, preventing even privileged insiders from viewing or tampering with raw transaction details. These real-world implementations give developers a clear path to adopting enclaves for serious privacy and compliance needs without overhauling their infrastructure. OpenSecret aims to be a **full developer platform** with end-to-end security from day one. By incorporating user authentication, data storage, and GPU-based confidential AI into a single service, we eliminate many of the traditional hurdles in adopting enclaves. No more juggling separate tools for cryptographic key management, compliance controls, and runtime privacy. Instead, you get a unified stack that keeps data encrypted in transit, at rest, and in use. Our solution also caters to the exploding demand for AI applications: with TEE-enabled GPU workloads, you can securely process sensitive data for text inference without ever exposing raw plaintext or sensitive documents to the host system. The result is a new generation of apps that deliver advanced functionality, like real-time encrypted data sync or AI-driven insights, while preserving user privacy and meeting strict regulatory requirements. You don't have to rely on empty "trust us" promises because hardware enclaves, remote attestation, and reproducible builds collectively guarantee the code is running untampered. In short, OpenSecret offers the building blocks needed to create truly confidential services and experiences, allowing you to innovate while ensuring data protection remains ironclad. ## **Things to Come** We're excited to build on our enclaved approach. Here's what's on our roadmap: • **Production Launch**: We're using this in production now with [Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud) and have a developer preview playground up and running. We'll have the developer environment ready for production in a few months.\ • **Multi-Tenant Support**: Our platform currently works for single tenants, but we're opening this up so developers can onboard without needing a dedicated instance.\ • **Self-Serve Frontend**: A dev-friendly portal for provisioning apps, connecting OAuth or email providers, and managing users.\ • **External Key Signing Options**: Integrations with custom hardware security modules (HSMs) or customer-ran key managers that can only process data upon verifying the enclave attestation.\ • **Confidential Computing as a Service**: We'll expand our platform so that other developers can quickly create enclaves for specialized workloads without dealing with the complexities of Nitro or GPU TEEs.\ • **Additional SDKs**: In addition to our [JavaScript client-side SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud), we plan to launch official support for Rust, Python, Swift, Java, Go, and more.\ • **AI API Proxy with Attestation/Encryption**: We already provide an easy way to [access a Private AI through Maple AI](https://trymaple.ai/?ref=blog.opensecret.cloud), but we'd like to open this up more for existing tools and developers. We'll provide a proxy server that users can run on their local machines or servers that properly handle encryption to our OpenAI-compatible API. ## **Getting Started** Ready to see enclaves in action? Here's how to dive in:\ 1. **Run OpenSecret**: Check out our open-source repository at [OpenSecret on GitHub](https://github.com/OpenSecretCloud/opensecret?ref=blog.opensecret.cloud). You can run your own enclaved environment or try it out locally with Docker.\ 2. **Review Our SDK**: Our [JavaScript client SDK](https://github.com/OpenSecretCloud/OpenSecret-SDK?ref=blog.opensecret.cloud) makes it easy to handle sign-ins, put/get encrypted data, sign with user private keys, etc. It handles attestation verification and encryption under the hood, making the API integration seamless.\ 3. **Play with Maple AI**: Try out [Maple AI](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/) as an example of an AI app built directly on OpenSecret. Your queries are encrypted end to end, and the Llama model sees them only inside the TEE.\ 4. **Developer Preview**: Contact us if you want an invite to our early dev platform. We'll guide you through our SDK and give you access to the preview server. We'd love to build with you and incorporate your feedback as we develop this further. ## **Conclusion** By merging secure enclaves (AWS Nitro and Nvidia GPU TEEs), user authentication, private key management, and an end-to-end verifiable encrypted approach, **OpenSecret** provides a powerful platform where we protect user data during collection, storage, and processing. Whether it's for standard user management, handling private cryptographic keys, or powering AI inference, the technology ensures that **no one**, not even us or the cloud provider, can snoop on data in use. **We believe** this is the future of trustworthy computing in the cloud. And it's **all open source**, so you don't have to just take our word for it: you can see and verify everything yourself. Do you have questions, feedback, or a use case you'd like to test out? Come join us on [GitHub](https://github.com/OpenSecretCloud?ref=blog.opensecret.cloud), [Discord](https://discord.gg/ch2gjZAMGy?ref=blog.opensecret.cloud), or email us for a developer preview. We can't wait to see what you build! *Thank you for reading, and welcome to the era of enclaved computing.* @ 3b7fc823:e194354f
2025-02-07 00:39:21# Details on how to use a Burner Phone Mobile phones are needed for communications when out in the world but they are a nightmare for privacy and security as detailed in <MISSIVE /07> especially when it comes to surveillance risks. This is more of a hands on guide for how to mitigate those risks. Burner phones as the name describes is a use and "burn" device either for a single operation or for a longer period if proper precautions are taken. In case you are unaware what I mean by a burner phone; cell phones can be purchased from big box stores, gas stations, and kiosks in cash without a contract. They are usually not very expense and enable you to buy prepaid cards to use for phone and internet service. Getting a Burner Phone: 1. Best to use a store out of town but not mandatory. 2. Do not take any electronics with you, especially another phone. 3. Park down the street in another parking lot near the store and walk over. Be mindful of security cameras. 4. Cover any tattoos or identifying marks. Wear a hat and a medical mask. (Thank you covid) 5. Use cash only to buy. 6. Leave, do not shop or buy anything else. Setting up Burner Phone: 1. Go somewhere with free public WIFI (Starbucks, Library, whatever) 2. Do not take any electronics with you, especially another phone. 3. Open package and follow directions to activate using the public WIFI access. 4. Choose a random area code during setup. 5. Create a new random gmail account. (Do not reuse accounts or names) 6. Download and install a VPN, Signal or SimpleX, Firefox Focus Browser, Tor if needed. Delete any other unnecessary apps. 7. Change phone settings (see list) 8. Turn off and remove battery if able to (becoming harder to find) or put into a Faraday Bag. 9. Destroy packaging that came with the phone. Phone Settings: 1. Turn off hotspot and tethering. Enable Always on VPN and Block Connections without VPN. Set DNS to automatic. 2. Turn off bluetooth and WIFI. 3. Disable all notifications, notification history, notifications on lock screen, and emergency alerts. 4. Turn off all sounds and vibrations. 5. Turn off Find my Device. Setup screen lock with password. (No bio) 6. Toggle everything in privacy: no permissions, turn off microphone, turn off usage and diagnostics, etc 7. Set Use Location to off. 8. Under Languages & Input > Virtual Keyboard > Gboard > Advanced: disable usage statistics, personalizing, and improve voice and typing for everyone. Using a Burner Phone: 1. Never sign into any account associated with your real identity. 2. Never use it to contact anyone associated with your real identity. 3. Time and distance between burner phone and any other cell phone you own. i.e. A hour has passed and several miles from when you use and had on the other device. 4. When not in use the battery is removed or in a Faraday Bag. 5. Always use a VPN and always use private search and browser set to delete upon closing (Firefox Focus default). 6. Never actually call or text from the phone. You only want to use SimpleX or Signal for communications. 7. Do not save anything (files, pictures, history) on the phone, especially if incriminating. 8. Do not take it with you or use unless necessary. 9. When in doubt, burn it and get another one. 10. Never carry over names, accounts, whatever from old burner phone to new burner phone. Burning a phone: 1. Factory reset the device. 2. Remove and destroy the SIM card. 3. Remove the battery because lithium batteries can explode. (may have to take it apart) 4. Smash internals. 5. Burn remains or drown in water. (Throw it in the river) As long as you are careful to never identify yourself with the burner phone the only surveillance they can do is know that a phone was used or in a location but not who it belongs to. Be aware that if you are caught with it on your person any information or contacts on the phone may get compromised. Be mindful what you put on it.
@ 3b7fc823:e194354f
2025-02-07 00:39:21# Details on how to use a Burner Phone Mobile phones are needed for communications when out in the world but they are a nightmare for privacy and security as detailed in <MISSIVE /07> especially when it comes to surveillance risks. This is more of a hands on guide for how to mitigate those risks. Burner phones as the name describes is a use and "burn" device either for a single operation or for a longer period if proper precautions are taken. In case you are unaware what I mean by a burner phone; cell phones can be purchased from big box stores, gas stations, and kiosks in cash without a contract. They are usually not very expense and enable you to buy prepaid cards to use for phone and internet service. Getting a Burner Phone: 1. Best to use a store out of town but not mandatory. 2. Do not take any electronics with you, especially another phone. 3. Park down the street in another parking lot near the store and walk over. Be mindful of security cameras. 4. Cover any tattoos or identifying marks. Wear a hat and a medical mask. (Thank you covid) 5. Use cash only to buy. 6. Leave, do not shop or buy anything else. Setting up Burner Phone: 1. Go somewhere with free public WIFI (Starbucks, Library, whatever) 2. Do not take any electronics with you, especially another phone. 3. Open package and follow directions to activate using the public WIFI access. 4. Choose a random area code during setup. 5. Create a new random gmail account. (Do not reuse accounts or names) 6. Download and install a VPN, Signal or SimpleX, Firefox Focus Browser, Tor if needed. Delete any other unnecessary apps. 7. Change phone settings (see list) 8. Turn off and remove battery if able to (becoming harder to find) or put into a Faraday Bag. 9. Destroy packaging that came with the phone. Phone Settings: 1. Turn off hotspot and tethering. Enable Always on VPN and Block Connections without VPN. Set DNS to automatic. 2. Turn off bluetooth and WIFI. 3. Disable all notifications, notification history, notifications on lock screen, and emergency alerts. 4. Turn off all sounds and vibrations. 5. Turn off Find my Device. Setup screen lock with password. (No bio) 6. Toggle everything in privacy: no permissions, turn off microphone, turn off usage and diagnostics, etc 7. Set Use Location to off. 8. Under Languages & Input > Virtual Keyboard > Gboard > Advanced: disable usage statistics, personalizing, and improve voice and typing for everyone. Using a Burner Phone: 1. Never sign into any account associated with your real identity. 2. Never use it to contact anyone associated with your real identity. 3. Time and distance between burner phone and any other cell phone you own. i.e. A hour has passed and several miles from when you use and had on the other device. 4. When not in use the battery is removed or in a Faraday Bag. 5. Always use a VPN and always use private search and browser set to delete upon closing (Firefox Focus default). 6. Never actually call or text from the phone. You only want to use SimpleX or Signal for communications. 7. Do not save anything (files, pictures, history) on the phone, especially if incriminating. 8. Do not take it with you or use unless necessary. 9. When in doubt, burn it and get another one. 10. Never carry over names, accounts, whatever from old burner phone to new burner phone. Burning a phone: 1. Factory reset the device. 2. Remove and destroy the SIM card. 3. Remove the battery because lithium batteries can explode. (may have to take it apart) 4. Smash internals. 5. Burn remains or drown in water. (Throw it in the river) As long as you are careful to never identify yourself with the burner phone the only surveillance they can do is know that a phone was used or in a location but not who it belongs to. Be aware that if you are caught with it on your person any information or contacts on the phone may get compromised. Be mindful what you put on it. @ b8851a06:9b120ba1
2025-02-06 22:46:54When Your Bitcoin Stash Saves Your Earnings Report: The Accounting Shift Every Business Needs to Understand **Tesla’s Q4 2024 earnings were a wreck—revenue down, costs up. But thanks to Bitcoin, the financial airbags deployed so effectively that no one’s talking about the crash. ** Let’s Be Clear: This isn’t about praising Tesla or Elon Musk (we’ll leave that to fan accounts). It’s about dissecting how a simple accounting rule change turned Bitcoin into a corporate financial shock absorber. The numbers reveal a playbook any business can replicate. The “Aha” Moment: Accounting Rules Meet Digital Gold (Why This Matters for Main Street Businesses) The Problem Before 2025: Companies had to report Bitcoin like a cursed family heirloom—you could only tell people when its value dropped, never when it gained. Imagine having to value your house at its lowest sale price in the neighborhood, even while yours was freshly renovated. The 2025 Fix: New rules let companies report Bitcoin like stocks—current value, gains and losses included. Suddenly, that digital gold in the treasury vault gets to shine. Why This Changes Everything: • For Tesla: Their $184M Bitcoin stash got revalued to $1.076B → $600M paper gain • For Your Business: Bitcoin isn’t just an asset; it’s an earnings hedge For Tesla, Bitcoin turned a bad quarter into a balanced one. For your business, it’s the difference between surviving a downturn and thriving through one. Tesla’s Numbers Decoded: Bitcoin as Financial CPR The Crash: • Automotive revenue ↓ 8% • Operating expenses ↑ 9% • Missed revenue targets by $1.5B The Airbag: • Bitcoin gain: $600M • EPS boost: 23% of total earnings • Balance sheet upgrade: 484% Bitcoin value increase The Takeaway: Bitcoin didn’t fix Tesla’s car business—it kept their financials on life support while they work on repairs. The Business Owner’s Guide to Bitcoin Airbags (No Tech Jargon, Just Street Smarts) 1. Your New Financial Shock Absorber • Old Way: Keep cash reserves losing 4-7% annually to inflation • Bitcoin Way: Treasury that grows while parked Real Math: $10M Treasury Allocation Year 1: - Cash: $9.6M (after 4% inflation loss) - Bitcoin: $15.4M (54% avg annual growth*) 2. The “Get Out of Jail Free” Card When core business stumbles (like Tesla’s did): • Bitcoin gains offset operational losses • Buys time for turnaround strategies 3. Shareholder Whisperer That Bitcoin gain isn’t just numbers—it’s storytelling fuel: • “Our innovative treasury strategy delivered $600M in non-operational income” • Beats explaining another quarter of declining sales Building Your Bitcoin Safety Net A Step-by-Step Playbook Step 1: Treasury Triage • Allocate 5-10% of cash reserves to Bitcoin • Not speculation—modern balance sheet insurance Step 2: Accounting Alignment Work with your CFO to: • Implement FASB-compliant reporting • Train teams on quarterly revaluations Step 3: Strategic Deployment • Hold through volatility cycles • Treat gains as bonus liquidity for: • R&D funding • Debt reduction • Opportunistic acquisitions Pro Tip: Start small—even a 1% Bitcoin allocation creates optionality without material risk. Objection Busters: What Skeptics Miss “But Bitcoin’s Too Volatile!” Cash is guaranteed to lose value. Bitcoin at least gives you a fighting chance. “We’re Not Tech Bros!” • Bitcoin isn’t tech—it’s digital real estate • The network effect is its tenant base “Accounting’s Too Complex!” • Modern tools automate revaluations • Takes less time than managing foreign currency hedges The Future of Corporate Treasuries (Why Early Adopters Win) 2025’s Landscape: • First movers already reaping benefits • Late adopters face inflationary erosion Your Move: • Conduct treasury health check • Model Bitcoin allocation scenarios • Implement phased adoption Final Word: Tesla’s story isn’t about “crypto” moonshots—it’s about modern financial engineering. The new accounting rules have turned Bitcoin into a Swiss Army knife for corporate treasuries: • Blade 1: Inflation hedge • Blade 2: Earnings supplement • Blade 3: Strategic reserve asset The question isn’t whether Bitcoin belongs on corporate balance sheets—it’s how much value your business will leave on the table by ignoring this tool. Your Competitors Won’t Wait—Why Should You? → [Free Treasury Health Assessment]( https://neowealth.xyz/code) → [Bitcoin Accounting Implementation Guide ]( https://neowealth.xyz/services) Let [www.NeoWealth.xyz]( https://neowealth.xyz/) assist you– Modern Treasury Solutions for Pragmatic Leaders #Nostr Footnotes: Data Sources: #Tesla Q4 2024 Earnings Report, FASB Accounting Standards Update 2023-08, Bitcoin Historical Returns Analysis (2015-2024) Past performance ≠ future results. #Bitcoin not #Crypto
@ b8851a06:9b120ba1
2025-02-06 22:46:54When Your Bitcoin Stash Saves Your Earnings Report: The Accounting Shift Every Business Needs to Understand **Tesla’s Q4 2024 earnings were a wreck—revenue down, costs up. But thanks to Bitcoin, the financial airbags deployed so effectively that no one’s talking about the crash. ** Let’s Be Clear: This isn’t about praising Tesla or Elon Musk (we’ll leave that to fan accounts). It’s about dissecting how a simple accounting rule change turned Bitcoin into a corporate financial shock absorber. The numbers reveal a playbook any business can replicate. The “Aha” Moment: Accounting Rules Meet Digital Gold (Why This Matters for Main Street Businesses) The Problem Before 2025: Companies had to report Bitcoin like a cursed family heirloom—you could only tell people when its value dropped, never when it gained. Imagine having to value your house at its lowest sale price in the neighborhood, even while yours was freshly renovated. The 2025 Fix: New rules let companies report Bitcoin like stocks—current value, gains and losses included. Suddenly, that digital gold in the treasury vault gets to shine. Why This Changes Everything: • For Tesla: Their $184M Bitcoin stash got revalued to $1.076B → $600M paper gain • For Your Business: Bitcoin isn’t just an asset; it’s an earnings hedge For Tesla, Bitcoin turned a bad quarter into a balanced one. For your business, it’s the difference between surviving a downturn and thriving through one. Tesla’s Numbers Decoded: Bitcoin as Financial CPR The Crash: • Automotive revenue ↓ 8% • Operating expenses ↑ 9% • Missed revenue targets by $1.5B The Airbag: • Bitcoin gain: $600M • EPS boost: 23% of total earnings • Balance sheet upgrade: 484% Bitcoin value increase The Takeaway: Bitcoin didn’t fix Tesla’s car business—it kept their financials on life support while they work on repairs. The Business Owner’s Guide to Bitcoin Airbags (No Tech Jargon, Just Street Smarts) 1. Your New Financial Shock Absorber • Old Way: Keep cash reserves losing 4-7% annually to inflation • Bitcoin Way: Treasury that grows while parked Real Math: $10M Treasury Allocation Year 1: - Cash: $9.6M (after 4% inflation loss) - Bitcoin: $15.4M (54% avg annual growth*) 2. The “Get Out of Jail Free” Card When core business stumbles (like Tesla’s did): • Bitcoin gains offset operational losses • Buys time for turnaround strategies 3. Shareholder Whisperer That Bitcoin gain isn’t just numbers—it’s storytelling fuel: • “Our innovative treasury strategy delivered $600M in non-operational income” • Beats explaining another quarter of declining sales Building Your Bitcoin Safety Net A Step-by-Step Playbook Step 1: Treasury Triage • Allocate 5-10% of cash reserves to Bitcoin • Not speculation—modern balance sheet insurance Step 2: Accounting Alignment Work with your CFO to: • Implement FASB-compliant reporting • Train teams on quarterly revaluations Step 3: Strategic Deployment • Hold through volatility cycles • Treat gains as bonus liquidity for: • R&D funding • Debt reduction • Opportunistic acquisitions Pro Tip: Start small—even a 1% Bitcoin allocation creates optionality without material risk. Objection Busters: What Skeptics Miss “But Bitcoin’s Too Volatile!” Cash is guaranteed to lose value. Bitcoin at least gives you a fighting chance. “We’re Not Tech Bros!” • Bitcoin isn’t tech—it’s digital real estate • The network effect is its tenant base “Accounting’s Too Complex!” • Modern tools automate revaluations • Takes less time than managing foreign currency hedges The Future of Corporate Treasuries (Why Early Adopters Win) 2025’s Landscape: • First movers already reaping benefits • Late adopters face inflationary erosion Your Move: • Conduct treasury health check • Model Bitcoin allocation scenarios • Implement phased adoption Final Word: Tesla’s story isn’t about “crypto” moonshots—it’s about modern financial engineering. The new accounting rules have turned Bitcoin into a Swiss Army knife for corporate treasuries: • Blade 1: Inflation hedge • Blade 2: Earnings supplement • Blade 3: Strategic reserve asset The question isn’t whether Bitcoin belongs on corporate balance sheets—it’s how much value your business will leave on the table by ignoring this tool. Your Competitors Won’t Wait—Why Should You? → [Free Treasury Health Assessment]( https://neowealth.xyz/code) → [Bitcoin Accounting Implementation Guide ]( https://neowealth.xyz/services) Let [www.NeoWealth.xyz]( https://neowealth.xyz/) assist you– Modern Treasury Solutions for Pragmatic Leaders #Nostr Footnotes: Data Sources: #Tesla Q4 2024 Earnings Report, FASB Accounting Standards Update 2023-08, Bitcoin Historical Returns Analysis (2015-2024) Past performance ≠ future results. #Bitcoin not #Crypto @ c2827524:5f45b2f7
2025-02-06 22:07:53#### Social media e condivisioni anche da mobile? #### Certamente sì, con i **client per i dispositivi Android**.  ## Zapstore: client Nostr in un posto solo Zapstore non c'era e lo hanno inventato. È lo store dal quale si scaricano i client #Nostr per i dispositivi mobili. Permissionless è la chiave: non serve attendere che gli store "ufficiali" mettano a disposizione l'ultima release e nemmeno che la comunità di f-droid compili i sorgenti. Gli sviluppatori di client per Android aggiornano Zapstore e il gioco è fatto! [Zapstore si scarica direttamente dal sito ufficiale](https://zapstore.dev/). Al primo download è consigliato seguire le istruzioni per verificare lo sha256 del file apk, prima di installarlo sul proprio dispositivo. ## Universo N.O.S.T.R. Una volta installato e aperto zapstore, **l'universo Nostr si apre in tutto il suo splendore**. Tra i primi suggerimenti si dovrebbe trovare Amber ma, se non compare, basta cercare nella casella di ricerca.  Dopodiché Amber viene presentato in primo piano  Basta cliccare sulla presentaione e compare in basso il tasto ***Install***  Zapstore esorta a fare le proprie ricerche per controllare la versione, sviluppatore e le caratteristiche dell'app che si va ad installare. Quando si è verificato bene, cliccare su ***Trust and install app***  Lasciare installare e alla fine Android chiede l'autorizzazione all'installazione. Come sempre, se è la prima volta che si usa uno store "non ufficiale", si dovrà anche autorizzare dalle impostazioni generali del dispositivo, cui si accede automaticamente  Non resta che cliccare in basso su ***Open*** per lanciare Amber  Amber è l'app che firmerà tutti gli eventi che si pubblicheranno su Nostr. Come app è anche in grado di generare una nuova coppia di chiavi. Presupponendo di aver già un profilo attivo ed impostato, magari [creato seguendo il tutorial precedente](https://laura.npub.pro/post/z3dxkkdooerzzyv_oqy6b/), qui si deve cliccare su ***Use your private key***  La chiave privata può essere copiata/incollata o scansionata agendo sull'iconcina stilizzata del QR code. Una volta importata si deve proseguire cliccando ***Next***  Impostare come far firmare Amber, approvando la firma per eventi semplici o farlo manualmente ogni singola volta, poi confermare cliccando ***Finish***  Amber è pronto a firmare eventi, note and other stuff che ogni utente vorrà pubblicare. Manca solo il/i client che si desidera utilizzare. Aggiungerne uno cliccando sul "+" in basso a destra  ## Amethyst Amethyst è il client per Android forse più completo, aggiornato ed efficiente del mondo Android. Se c'è un client ottimo per iniziare, [è proprio Amethyst](https://github.com/vitorpamplona/amethyst). Se non compare tra i suggerimenti della home di Amber, cercarlo e scegliere ***Install***  Tra il download e l'apertura di Amethyst, c'è il passaggio della verifica dell'integrità del file apk, che Amber svolge al posto dell'utente  Quando la verifica è terminata, basta aprire Amethyst cliccando in basso su ***Open***  Accettare i ToS per evienziare i pulsanti di login  e scegliere ***Login with Amber***  Scegliere quali privilegi consentire ad Amber, che vengono mostrati in una lista e terminare cliccando su ***Grant Permissions***  Da questo momento in poi sarà Amber a firmare le note con la chiave privata dell'utente. Alle nostriche resta solo il compito di dare spazio alla creatività e usare Amethyst per condividere post.  La pubblicazione avviene cliccando ***Post*** su Amethyst e, a seconda dei permessi concessi ad Amber, la nota verrà propagata. Ad esempio: se si è scelto di approvare manualmente ogni post, Amber mostra il menu di conferma.  Approvare manualmente ogni post è, all'inizio, un bel modo di utilizzare Amber, perché facilita la conoscenza della natura degli eventi che si stanno postando. --- ## I settings di Amber Uno sguardo ai menu e alle impostazioni di Amber è doveroso. Non ci sono accorgimenti particolari, ma è sempre un'ottima abitudine conoscere ed esplorare i menu delle app che si vanno ad utilizzare. Dalla home di Amber, sono visibili in basso e si trovano - in ordine - * ***Incoming Request***, dove appariranno le richieste di approvazione per firmare le note  * ***Settings***, per tutte le impostazioni generali di sicurezza, uso con Orbot, rivedere le scelte di firma ***Sign Policy*** ecc  approvare il controllo biometrico per la firma, se impostato sul dispositivo  e dare un'occhiata e un test ai relay che si son scelti  #### Non manca nient'altro. Solo postare ed eslorare i client più belli e aggiornarli da Zapstore --- ## Per info * https://nostree.me/laura@cosanostr.com * https://laura.npub.pro/ * https://t.me/bitcoincampus * https://planb.network
@ c2827524:5f45b2f7
2025-02-06 22:07:53#### Social media e condivisioni anche da mobile? #### Certamente sì, con i **client per i dispositivi Android**.  ## Zapstore: client Nostr in un posto solo Zapstore non c'era e lo hanno inventato. È lo store dal quale si scaricano i client #Nostr per i dispositivi mobili. Permissionless è la chiave: non serve attendere che gli store "ufficiali" mettano a disposizione l'ultima release e nemmeno che la comunità di f-droid compili i sorgenti. Gli sviluppatori di client per Android aggiornano Zapstore e il gioco è fatto! [Zapstore si scarica direttamente dal sito ufficiale](https://zapstore.dev/). Al primo download è consigliato seguire le istruzioni per verificare lo sha256 del file apk, prima di installarlo sul proprio dispositivo. ## Universo N.O.S.T.R. Una volta installato e aperto zapstore, **l'universo Nostr si apre in tutto il suo splendore**. Tra i primi suggerimenti si dovrebbe trovare Amber ma, se non compare, basta cercare nella casella di ricerca.  Dopodiché Amber viene presentato in primo piano  Basta cliccare sulla presentaione e compare in basso il tasto ***Install***  Zapstore esorta a fare le proprie ricerche per controllare la versione, sviluppatore e le caratteristiche dell'app che si va ad installare. Quando si è verificato bene, cliccare su ***Trust and install app***  Lasciare installare e alla fine Android chiede l'autorizzazione all'installazione. Come sempre, se è la prima volta che si usa uno store "non ufficiale", si dovrà anche autorizzare dalle impostazioni generali del dispositivo, cui si accede automaticamente  Non resta che cliccare in basso su ***Open*** per lanciare Amber  Amber è l'app che firmerà tutti gli eventi che si pubblicheranno su Nostr. Come app è anche in grado di generare una nuova coppia di chiavi. Presupponendo di aver già un profilo attivo ed impostato, magari [creato seguendo il tutorial precedente](https://laura.npub.pro/post/z3dxkkdooerzzyv_oqy6b/), qui si deve cliccare su ***Use your private key***  La chiave privata può essere copiata/incollata o scansionata agendo sull'iconcina stilizzata del QR code. Una volta importata si deve proseguire cliccando ***Next***  Impostare come far firmare Amber, approvando la firma per eventi semplici o farlo manualmente ogni singola volta, poi confermare cliccando ***Finish***  Amber è pronto a firmare eventi, note and other stuff che ogni utente vorrà pubblicare. Manca solo il/i client che si desidera utilizzare. Aggiungerne uno cliccando sul "+" in basso a destra  ## Amethyst Amethyst è il client per Android forse più completo, aggiornato ed efficiente del mondo Android. Se c'è un client ottimo per iniziare, [è proprio Amethyst](https://github.com/vitorpamplona/amethyst). Se non compare tra i suggerimenti della home di Amber, cercarlo e scegliere ***Install***  Tra il download e l'apertura di Amethyst, c'è il passaggio della verifica dell'integrità del file apk, che Amber svolge al posto dell'utente  Quando la verifica è terminata, basta aprire Amethyst cliccando in basso su ***Open***  Accettare i ToS per evienziare i pulsanti di login  e scegliere ***Login with Amber***  Scegliere quali privilegi consentire ad Amber, che vengono mostrati in una lista e terminare cliccando su ***Grant Permissions***  Da questo momento in poi sarà Amber a firmare le note con la chiave privata dell'utente. Alle nostriche resta solo il compito di dare spazio alla creatività e usare Amethyst per condividere post.  La pubblicazione avviene cliccando ***Post*** su Amethyst e, a seconda dei permessi concessi ad Amber, la nota verrà propagata. Ad esempio: se si è scelto di approvare manualmente ogni post, Amber mostra il menu di conferma.  Approvare manualmente ogni post è, all'inizio, un bel modo di utilizzare Amber, perché facilita la conoscenza della natura degli eventi che si stanno postando. --- ## I settings di Amber Uno sguardo ai menu e alle impostazioni di Amber è doveroso. Non ci sono accorgimenti particolari, ma è sempre un'ottima abitudine conoscere ed esplorare i menu delle app che si vanno ad utilizzare. Dalla home di Amber, sono visibili in basso e si trovano - in ordine - * ***Incoming Request***, dove appariranno le richieste di approvazione per firmare le note  * ***Settings***, per tutte le impostazioni generali di sicurezza, uso con Orbot, rivedere le scelte di firma ***Sign Policy*** ecc  approvare il controllo biometrico per la firma, se impostato sul dispositivo  e dare un'occhiata e un test ai relay che si son scelti  #### Non manca nient'altro. Solo postare ed eslorare i client più belli e aggiornarli da Zapstore --- ## Per info * https://nostree.me/laura@cosanostr.com * https://laura.npub.pro/ * https://t.me/bitcoincampus * https://planb.network @ 000002de:c05780a7
2025-02-06 18:47:45I stand by my non-stance that the cowboy credit thing is OK. Using services like MiniBits and CoinOSis OK and using your own node is OK. There are tradeoffs of each. I've been using these eCash hosted / custodial services for over a month now. They work fine most of the time. NWC works most of the time but there are growing pains with the volume of small transactions hitting these services. I'm gonna try turning it all off for a week starting today. Just use CCs. I mean its kinda like old school SN right? Next I'd like to really make an effort to go the other way and use a self sovereign stack. I've tried that before with SN and it didn't work for me. Pretty sure I was just too busy and didn't have time to work out the kinks in my setup. I think cowboy credits are the easiest option by far. No issues really except you aren't dealing with sats. It doesn't feel the same and it isn't the same. I'm wondering how it will hit me as I use them though. originally posted at https://stacker.news/items/877936
@ 000002de:c05780a7
2025-02-06 18:47:45I stand by my non-stance that the cowboy credit thing is OK. Using services like MiniBits and CoinOSis OK and using your own node is OK. There are tradeoffs of each. I've been using these eCash hosted / custodial services for over a month now. They work fine most of the time. NWC works most of the time but there are growing pains with the volume of small transactions hitting these services. I'm gonna try turning it all off for a week starting today. Just use CCs. I mean its kinda like old school SN right? Next I'd like to really make an effort to go the other way and use a self sovereign stack. I've tried that before with SN and it didn't work for me. Pretty sure I was just too busy and didn't have time to work out the kinks in my setup. I think cowboy credits are the easiest option by far. No issues really except you aren't dealing with sats. It doesn't feel the same and it isn't the same. I'm wondering how it will hit me as I use them though. originally posted at https://stacker.news/items/877936 @ d57360cb:4fe7d935
2025-02-06 18:31:30Mindfulness often has the misconception that by practicing you can stop your mind from thinking and obtain an empty mind. While one can definitely achieve moments of emptiness in thinking, this view that emptiness is the goal can be the very obstacle in your way leading to frustration with the practice. If we adjust our perspective and see mindfulness as learning to accept the situations we find ourselves in and adjust to them rather than fighting them, we achieve a kind of grace under pressure. The thoughts are part of the practice, just like cars on the road are part of driving, or the danger of a punch is always a threat to a boxer. The difference between the novice and the seasoned is one has accepted and acclimated to the realities of the situation instead of fighting them, in this one finds freedom.
@ d57360cb:4fe7d935
2025-02-06 18:31:30Mindfulness often has the misconception that by practicing you can stop your mind from thinking and obtain an empty mind. While one can definitely achieve moments of emptiness in thinking, this view that emptiness is the goal can be the very obstacle in your way leading to frustration with the practice. If we adjust our perspective and see mindfulness as learning to accept the situations we find ourselves in and adjust to them rather than fighting them, we achieve a kind of grace under pressure. The thoughts are part of the practice, just like cars on the road are part of driving, or the danger of a punch is always a threat to a boxer. The difference between the novice and the seasoned is one has accepted and acclimated to the realities of the situation instead of fighting them, in this one finds freedom. @ 89ccea93:df4e00b7
2025-02-06 16:28:15**[Original Post](https://expatriotic.me/robosats/)** ## Why use RoboSats ### 1. Lightning Fast * LN Hodl invoices serve as bonds & escrows for high assurance and speed. ### 2. Absolutely Private * Best privacy practices by default. * Simple and KYC-free. * You will generate a random Robot avatar for a single use. * The exchange is Tor-only. ### 3. Open Source * RoboSats is fully open source. - [Github](https://github.com/RoboSats/robosats) *I'm going to use the Tor Browser on desktop for this guide. But the android app is essentially identical. So the flow should be the same.* ```I prefer Bisq for buying as I can get really good deals. Plus the use of a larger deposit helps to secure things. However, Bisq is onchain only, so in a higher fee environment, it could get pricey. RoboSats however is using lightning.``` *BTW, for Bisq if the miner fees get higher, check out a [Monero based fork](https://github.com/retoaccess1/haveno-reto) where you can pay the deposit in Monero, as this will help with miner fees. Plus generally speaking, and especially in a high fee environment, Monero fees should be lower.* ## Step 1 - Download or use in Tor browser 1. Use <http://robodexarjwtfryec556cjdz3dfa7u47saek6lkftnkgshvgg2kcumqd.onion/> for use in Tor Browser 2. Download APK from Github and check signature to make sure it's signed with the Reckless-Satoshi [PGP key](https://keys.openpgp.org/vks/v1/by-fingerprint/B4AB5F19113D4125DDF217739C4585B561315571) (if this is something you know how to do. Explaining it is outside the purview of this article) - <https://github.com/RoboSats/robosats/releases/> ## Step 2 - Roll a Robot *Image 1 - GARAGE tab*  1. For regular mode click "*🚀START*". A robot will be given to you. You'll be prompted to save a unique string that will help you log back in to that specific robot. Helpful if you initiate a trade. If you wanted to make an order directly, I recommend you skip step one and go to directly to step two. *Image 2 - Start menu*  *Image 3 - After rolling a robot*  *Image 4 - Prompted to browse or make an order.*  2. If you want to make create an order, skip down to "*➡️ FAST GENERATE ORDER*" *Image 2 - Start menu*  *Image 5 - FAST GENERATE ORDER*  ## Step 3 - Go to the OFFERS tab *Image 6 - OFFERS tab*  1. Select BUY/SELL depending on your need. 2. Select currency. Just look for the "**🌎 ANY**" and pick your currency from the drop down menu. 3. Filter payment method by clicking "**METHOD**" and selecting one of the options, or simply start typing and watch your option pop up. 4. Click "*Premium*" until it sorts from the lowest premium to the highest. ## Step 4 - Select/Create an offer *Image 7 - taking an offer*  1. Take the order (or make one) and if the person had a range, put in how much bitcoin you wish to buy. 2. Click take order ## Step 5 - Receiving the bitcoin 1. Pay a small deposit to lock in the order *Image 8 - taking order*  2. Paste in a LN invoice for the amount of LN sats to be received. (see Addendum #2) 3. Pay using fiat method preselected 4. Bitcoin is paid out of escrow and into the LN invoice that you gave. ## Addendum 1. Use this for more help - <https://learn.robosats.com/> 2. If you don't wish to receive in lighting, then in Step 5, instead of your own LN invoice, use one from https://boltz.exchange/swap. You can do this natively in RoboSats, but they charge an arm and a leg. originally posted at https://stacker.news/items/877796
@ 89ccea93:df4e00b7
2025-02-06 16:28:15**[Original Post](https://expatriotic.me/robosats/)** ## Why use RoboSats ### 1. Lightning Fast * LN Hodl invoices serve as bonds & escrows for high assurance and speed. ### 2. Absolutely Private * Best privacy practices by default. * Simple and KYC-free. * You will generate a random Robot avatar for a single use. * The exchange is Tor-only. ### 3. Open Source * RoboSats is fully open source. - [Github](https://github.com/RoboSats/robosats) *I'm going to use the Tor Browser on desktop for this guide. But the android app is essentially identical. So the flow should be the same.* ```I prefer Bisq for buying as I can get really good deals. Plus the use of a larger deposit helps to secure things. However, Bisq is onchain only, so in a higher fee environment, it could get pricey. RoboSats however is using lightning.``` *BTW, for Bisq if the miner fees get higher, check out a [Monero based fork](https://github.com/retoaccess1/haveno-reto) where you can pay the deposit in Monero, as this will help with miner fees. Plus generally speaking, and especially in a high fee environment, Monero fees should be lower.* ## Step 1 - Download or use in Tor browser 1. Use <http://robodexarjwtfryec556cjdz3dfa7u47saek6lkftnkgshvgg2kcumqd.onion/> for use in Tor Browser 2. Download APK from Github and check signature to make sure it's signed with the Reckless-Satoshi [PGP key](https://keys.openpgp.org/vks/v1/by-fingerprint/B4AB5F19113D4125DDF217739C4585B561315571) (if this is something you know how to do. Explaining it is outside the purview of this article) - <https://github.com/RoboSats/robosats/releases/> ## Step 2 - Roll a Robot *Image 1 - GARAGE tab*  1. For regular mode click "*🚀START*". A robot will be given to you. You'll be prompted to save a unique string that will help you log back in to that specific robot. Helpful if you initiate a trade. If you wanted to make an order directly, I recommend you skip step one and go to directly to step two. *Image 2 - Start menu*  *Image 3 - After rolling a robot*  *Image 4 - Prompted to browse or make an order.*  2. If you want to make create an order, skip down to "*➡️ FAST GENERATE ORDER*" *Image 2 - Start menu*  *Image 5 - FAST GENERATE ORDER*  ## Step 3 - Go to the OFFERS tab *Image 6 - OFFERS tab*  1. Select BUY/SELL depending on your need. 2. Select currency. Just look for the "**🌎 ANY**" and pick your currency from the drop down menu. 3. Filter payment method by clicking "**METHOD**" and selecting one of the options, or simply start typing and watch your option pop up. 4. Click "*Premium*" until it sorts from the lowest premium to the highest. ## Step 4 - Select/Create an offer *Image 7 - taking an offer*  1. Take the order (or make one) and if the person had a range, put in how much bitcoin you wish to buy. 2. Click take order ## Step 5 - Receiving the bitcoin 1. Pay a small deposit to lock in the order *Image 8 - taking order*  2. Paste in a LN invoice for the amount of LN sats to be received. (see Addendum #2) 3. Pay using fiat method preselected 4. Bitcoin is paid out of escrow and into the LN invoice that you gave. ## Addendum 1. Use this for more help - <https://learn.robosats.com/> 2. If you don't wish to receive in lighting, then in Step 5, instead of your own LN invoice, use one from https://boltz.exchange/swap. You can do this natively in RoboSats, but they charge an arm and a leg. originally posted at https://stacker.news/items/877796 @ 5d4b6c8d:8a1c1ee3
2025-02-06 16:14:00I would have done about an hour better today, but my hatred of food waste got the best of me. My daughter wanted the crusts cut off of her toast and, since no one else was going to eat them, I gobbled them up. That was the last thing I ate, yesterday, though, and I didn't eat or drink anything for the next 16 hours. Still pretty good. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: TBD (16 dry) originally posted at https://stacker.news/items/877787
@ 5d4b6c8d:8a1c1ee3
2025-02-06 16:14:00I would have done about an hour better today, but my hatred of food waste got the best of me. My daughter wanted the crusts cut off of her toast and, since no one else was going to eat them, I gobbled them up. That was the last thing I ate, yesterday, though, and I didn't eat or drink anything for the next 16 hours. Still pretty good. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: TBD (16 dry) originally posted at https://stacker.news/items/877787 @ fdc85145:e465bf18
2025-02-06 16:13:36Preserve your vehicle's paint with our high-quality [paint protection film](https://www.autoandmarinedetailing.co.nz/paint-protection-film-auckland) at Auto and Marine Detailing. This transparent film acts as a shield against scratches, rock chips, and harmful UV rays. Custom-fit to your car, it ensures complete coverage without altering its appearance. Our team provides expert installation, so your vehicle remains in pristine condition, retaining its value for years to come.
@ fdc85145:e465bf18
2025-02-06 16:13:36Preserve your vehicle's paint with our high-quality [paint protection film](https://www.autoandmarinedetailing.co.nz/paint-protection-film-auckland) at Auto and Marine Detailing. This transparent film acts as a shield against scratches, rock chips, and harmful UV rays. Custom-fit to your car, it ensures complete coverage without altering its appearance. Our team provides expert installation, so your vehicle remains in pristine condition, retaining its value for years to come. @ f6b1e489:f1c91bc4
2025-02-06 15:59:52# Psychedelics and Bitcoin Almost everyone who gets into bitcoin at some point realizes how it destroys your mental models of the world. You start questioning the _status quo_ and experience a serious rewiring of the brain. This can be confusing and frightening at first. But in hindsight it is mostly viewed as positive and people end up being a different, better person. Less focussed on hedonistic consumption, more focussed on long term health and wealth. # Rewiring the Brain I realized that psychedelics (like LSD or Psilocybin) and learning Bitcoin had a similar effect on my brain. The closest to my head-over-heels experience down the Bitcoin rabbithole were my experiences with LSD long before I discovered Bitcoin. Both shaped my life in an unexpected but positive way. I can´t talk about psychedelic experiences with most of my family, similar as with Bitcoin. They just don´t get it. And at this point I won´t bother trying to explain it anymore. # Volatility Then there is the volatility aspect. Psychedelic trips can be quite volatile, you never know what to expect. There is always some level of loss of control and you have to be fine with it. Similar with Bitcoin: You have to be able to stand the ups and downs, one day feeling like a genius, being full of doubt the next day. # Questioning Authority There are also some historical and cultural parallels between the spread of LSD in the 60s and Bitcoin today. In the 1960s Timothy Leary coined the term "_Turn on, tune in, drop out_". Large parts of the youth counterculture discovered the freeing effect of LSD on the mind and said "Fuck it, we´re not gonna participate in your wars". They challenged authority and the societal norms. Today, bitcoiners find the freedom of Bitcoin. They like to opt out of the system and say "Fuck it, we´re not gonna participate in your bullshit any longer". Passionate, freedom-loving communities have formed around both phenomena. What are your thoughts on this? Do you have similar experiences? Did I miss anything? originally posted at https://stacker.news/items/877770
@ f6b1e489:f1c91bc4
2025-02-06 15:59:52# Psychedelics and Bitcoin Almost everyone who gets into bitcoin at some point realizes how it destroys your mental models of the world. You start questioning the _status quo_ and experience a serious rewiring of the brain. This can be confusing and frightening at first. But in hindsight it is mostly viewed as positive and people end up being a different, better person. Less focussed on hedonistic consumption, more focussed on long term health and wealth. # Rewiring the Brain I realized that psychedelics (like LSD or Psilocybin) and learning Bitcoin had a similar effect on my brain. The closest to my head-over-heels experience down the Bitcoin rabbithole were my experiences with LSD long before I discovered Bitcoin. Both shaped my life in an unexpected but positive way. I can´t talk about psychedelic experiences with most of my family, similar as with Bitcoin. They just don´t get it. And at this point I won´t bother trying to explain it anymore. # Volatility Then there is the volatility aspect. Psychedelic trips can be quite volatile, you never know what to expect. There is always some level of loss of control and you have to be fine with it. Similar with Bitcoin: You have to be able to stand the ups and downs, one day feeling like a genius, being full of doubt the next day. # Questioning Authority There are also some historical and cultural parallels between the spread of LSD in the 60s and Bitcoin today. In the 1960s Timothy Leary coined the term "_Turn on, tune in, drop out_". Large parts of the youth counterculture discovered the freeing effect of LSD on the mind and said "Fuck it, we´re not gonna participate in your wars". They challenged authority and the societal norms. Today, bitcoiners find the freedom of Bitcoin. They like to opt out of the system and say "Fuck it, we´re not gonna participate in your bullshit any longer". Passionate, freedom-loving communities have formed around both phenomena. What are your thoughts on this? Do you have similar experiences? Did I miss anything? originally posted at https://stacker.news/items/877770 @ fd208ee8:0fd927c1
2025-02-06 15:58:38## Beginning at the start In my previous article, [The Establishment](https://next-alexandria.gitcitadel.eu/publication?d=the-gitcitadel-blog-the-establishment-3-by-stella-v-1), I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a *company* is a *team*, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop. ## The Initiation The first, and most-difficult step of team formation, is *the initiation*. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".) Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.  So, just do and be all of those things, and then initiate the team, with the method I will name the *Hatbock Method*. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team. Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".) ## The Sitting We now get to the second most difficult part of team formation: figuring out *where to sit*. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea. Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, *immediately*.  Now, this next bit is very important: > Do not let anyone outside your team influence where you sit! ...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice. This is the German *Stammtisch* principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area. ## Plan it in Once you've sat down, and finished your rough draft of the Vision, you need to figure out *when to sit*. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.) The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros". It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc. And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. *Write everything down.* Anything not written down, is a suggestion, not an assigned task. If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, [as a company](https://next-alexandria.gitcitadel.eu/publication?d=the-gitcitadel-blog-the-establishment-3-by-stella-v-1).
@ fd208ee8:0fd927c1
2025-02-06 15:58:38## Beginning at the start In my previous article, [The Establishment](https://next-alexandria.gitcitadel.eu/publication?d=the-gitcitadel-blog-the-establishment-3-by-stella-v-1), I answered the question: "How do we form a company?" I realize, now, that I was getting a bit ahead, of myself, as the precursor to a *company* is a *team*, and many people struggle to form teams. So, I will go back to the beginning, and then you can read both articles to the end, and then stop. ## The Initiation The first, and most-difficult step of team formation, is *the initiation*. We know that it must be the most-difficult, as it's the step that carries the highest potential reward, and it's the step that is tried-and-failed most often. (Some people, like Elon Musk or Donald Trump, are born Initiators with excellent follow-through, but this archetype is exceedingly thin on the ground because it requires you to be mildly autistic, have barely-throttled ADHD, and/or tend to megalomania, also popularly known as "toxic masculinity", "CEO personality", or "being a successful military officer".) Someone needs to form a useful, attractive Vision and then motivate other people to help them achieve it. That sounds really easy, but it's actually brutally difficult because * You have to come up with an idea that is coherent, plausible, and inspiring. * You have to be able to communicate that idea to other people and make it appealing to them, by tying it into their own personal goals and desires. * You have to be able to hone and reformulate that idea, constantly, to correct it or to re-motivate the other team members. * You have to defend the idea against detractors, naysayers, and trolls, and you have to do it so vociferously, that it will erode your own popularity among those who disagree with you and open you to personal attacks. * You have to be able to focus on the idea, yourself, for a long stretch of time, and not allow yourself to get bored, lazy, or distracted.  So, just do and be all of those things, and then initiate the team, with the method I will name the *Hatbock Method*. It is so named because of the classic, German initiation ritual, in which an Initiator stands up, loudly defines their Vision and calls into a group "Wer hat Bock?" (roughly, "Who has the hunger/desire?") and whoever responds with "Ich hab Bock." (roughly, "Yes, I hunger for this.") is a part of the team. Then the Initiator says, "Okay, everyone with the hunger, let's sit down together, and discuss this some more." (This "sitting" is literally called a "seating", or "Sitzung", which is the German word for "meeting".) ## The Sitting We now get to the second most difficult part of team formation: figuring out *where to sit*. Most teams get this wrong, repeatedly, and many teams dissolve or fracture under the difficulty of this momentous decision. You would think organizing yourselves online would make this easier ("Oh, we'll just meet online!"), but the number of places available for sitting online are limitless. You can talk your whole Vision into the ground, with laborous discussions and migrations between Chachi, OxChat, Telegram, SimpleX, Slack, Discord, WhatsApp, GitHub, Teams, Coracle, Matrix... you get the idea. Try to keep in mind that the Vision is more important than the seating area, and go with the flow. Simply, find someplace and go there. Worry about it again, at a later date. Don't lose momentum. Sit down and start discussing the Vision, *immediately*.  Now, this next bit is very important: > Do not let anyone outside your team influence where you sit! ...unless they are providing your team with some good, service, or income, that makes choosing their preferred location the superior choice. This is the German *Stammtisch* principle, where a host encourages you to come sit down, regularly, in some particular place, because your sitting there provides them with some benefit: they can overhear your conversations, get you to test out their seating area, sell you refreshments, etc. Your choice of seating, in other words, is a valuable good, and you should only "sell" it to someone who rewards you in measure. They have to reward you because their preferred seating area wasn't your immediate and obvious choice, so there was probably something unappealing or uncertain about the seating area. ## Plan it in Once you've sat down, and finished your rough draft of the Vision, you need to figure out *when to sit*. This is the third most-difficult part of team formation. (Yes, don't worry, it gets easier as it goes along.) The most popular plan is the Wirsehenuns Plan (roughly, "We'll see each other, around.") This can work quite well, if you just want to have a loose collaboration, that calls itself together in an ad hoc fashion, when a team member feels the need. Also known as "@ me, bros". It's not a great plan for more intensive collaboration, as that tends to need a certain amount of velocity, to actually happen, as the speed of movement has a centrifugal effect on the tasks. Team momentum, in other words, creates a sort of gravity, that keeps the team together as a unit. So, for deeper teamwork, I would recommend the Stammtisch variant: name a place and date/time, when you will next meet. Preferably, on a rotating schedule: daily, weekly, last Thursday of the month, etc. And then meet there and then. And discuss amongst yourselves. Set clear, short-term tasks (and assign them to particular people!), medium-term strategies, and longer-term goals. *Write everything down.* Anything not written down, is a suggestion, not an assigned task. If you find your Stammtisch becoming increasingly rewarding and productive, and your goals start moving closer and closer into sight, then you might want to formalize your team structure further, [as a company](https://next-alexandria.gitcitadel.eu/publication?d=the-gitcitadel-blog-the-establishment-3-by-stella-v-1). @ f1989a96:bcaaf2c1
2025-02-06 14:01:03Good morning, readers! In India, the central bank has taken a significant step toward launching its central bank digital currency (CBDC), the digital rupee. In partnership with fintech firms Mobikwik and Cred, the digital rupee is now available to 180 million users through a new “e₹ wallet,” a CBDC wallet app designed for public use. Predictably, the CBDC comes with tight restrictions, including limits on payment amounts and frequency and extensive personal data collection, raising concerns over financial privacy. In open-source news, HRF is pleased to announce a collaboration with MIT for the 2025 MIT Bitcoin Expo. This two-day freedom-focused event will explore how Bitcoin and adjacent freedom tech can help combat financial surveillance and repression under authoritarian regimes through expert speakers, panels, workshops, and more. Elsewhere, Joltz became the first self-custodial wallet to support Taproot Assets, enabling access to stable digital dollars on a decentralized network for activists, dissidents, and others in difficult political environments. We conclude with an extensive guide from Area Bitcoin, a Brazilian education hub, thoroughly examining Brazil’s DREX CBDC and its implications for financial freedom and human rights in Brazil and beyond. **Now, let’s dive right in!** ### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **India | Central Bank Partners with Fintech Firms to Pilot Launch CBDC** The Reserve Bank of India (RBI) [partnered](https://www.businesstoday.in/personal-finance/news/story/mobikwik-cred-join-hands-with-rbi-to-fully-launch-cbdc-ers-for-android-check-features-usage-462318-2025-01-28) with fintech firms MobiKwik and Cred, alongside Yes Bank, to expand the digital rupee, India’s CBDC. With a combined user base of [180 million,](https://www.ledgerinsights.com/fintech-wallets-go-live-in-digital-rupee-cbdc-pilot/) Mobikwik and Cred will act as entry points for public access to the CBDC through their new “e₹ wallet” CBDC app. However, the app mandates video verification and imposes significant restrictions. For instance, a daily transaction cap of ₹50,000 ($577) and ₹10,000 ($115) limit per transaction. The RBI’s decision to embed the digital rupee within existing fintech firms to boost adoption leaves few avenues for financial privacy and freedom as the Indian state [pushes](https://www.lowyinstitute.org/the-interpreter/india-s-plan-world-without-cash) further towards a cashless economy. #### **El Salvador | Lawmakers Scale Back Bitcoin Legal Tender Law** El Salvador’s congress [amended](https://www.reuters.com/world/americas/lawmakers-el-salvador-rush-new-bitcoin-reform-after-imf-deal-2025-01-30/) its Bitcoin law, making private sector acceptance of Bitcoin voluntary. The reform follows a $1.4 billion loan agreement with the International Monetary Fund (IMF) that wanted to limit the government’s, citizens’, and economies’ exposure to Bitcoin. Salvadoran lawmaker Elisa Rosales [said](https://www.reuters.com/world/americas/lawmakers-el-salvador-rush-new-bitcoin-reform-after-imf-deal-2025-01-30/) the latest reform guarantees Bitcoin’s “permanence as legal tender” while facilitating its “practical implementation.” But, John Dennehy, founder of the civil society organization [Mi Primer Bitcoin](https://es.myfirstbitcoin.io/), [explained](https://x.com/jdennehy_writes/status/1885346352621617615) that the reform removed “all references of bitcoin as money or legal tender, plus the actual conditions, such as the government accepting bitcoin for things such as taxes, are now prohibited.” The future of freedom technology in El Salvador will be worth monitoring closely as the regime continues to erode protections on civil liberties. #### **Nigeria | Regime Hikes Telecom Tariffs for Citizens** In Nigeria, the regime approved a [50% increase](https://thenationonlineng.net/50-tariff-hike-a-necessary-step-or-a-burden-for-nigerians/) in telecom tariffs, further straining citizens already grappling with financial instability. Call rates will rise from 11 to 16.50 naira per minute ($0.0074 to $0.011) and SMS charges from 4 to 6 naira ($0.0026 to $0.004), exacerbating three-decade-high inflation as the ripple effects spread through the economy. Telecom companies justify the price hike as necessary for the sector’s survival amid the naira’s ongoing [devaluation](https://www.bloomberg.com/news/articles/2024-09-13/why-nigeria-s-naira-currency-ngn-usd-slumped-and-why-it-matters). [Deolu Ogunbanjo](https://www.linkedin.com/in/deolu-ogunbanjo-62b5a18b/?originalSubdomain=ng), president of the National Association of Telecoms Subscribers, however, [argues](https://thenationonlineng.net/50-tariff-hike-a-necessary-step-or-a-burden-for-nigerians/) that “this decision shows the government cares more about protecting profits than protecting people.” For Nigerians relying on mobile networks for work, banking, and daily communications, the increased costs will make phone services less accessible, putting even more pressure on civil society under an authoritarian government. #### **Nicaragua | Inter-American Court of Human Rights Rules Against Ortega** In Nicaragua, where the financial repression of individuals, opposition, and civil society is widespread, the Inter-American Court of Human Rights [ruled](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) that Daniel Ortega’s reelections since 2011 were illegitimate. This ruling “is the legal confirmation that there is no legitimate president in Nicaragua, but rather a dictator who has usurped power,” [said](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) Jaime Aparicio, a Bolivian lawyer, [adding](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) that “this is the first time that there is a legal precedent determining the illegality of Ortega’s presidency.” In a country where the regime systematically [freezes](https://www.reuters.com/world/americas/nicaragua-govt-accuses-catholic-church-money-laundering-freezes-accounts-2023-05-27/) bank accounts, seizes assets, and [shuts down](https://www.catholicnewsagency.com/news/261539/nicaraguan-dictatorship-shuts-down-more-organizations-including-dominican-nuns) nonprofits to silence dissent, this verdict sets a critical legal precedent against the abuse of state power to secure reelection. While the court lacks enforcement, its ruling strengthens legal challenges to Ortega’s rule and could provide a foundation for future actions against electoral fraud and authoritarian control. #### **Webinar Series for Nonprofits | Become Unstoppable** In an era where financial control is weaponized against dissent, the ability to transact freely is more important than ever. For activists and nonprofits operating under oppressive regimes, Bitcoin can offer a way to resist censorship, protect funds, and remain operational. Join HRF for a free, three-day webinar from March **17–19**, led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial freedom expert at the Anti-Corruption Foundation. The sessions will run daily from **10:30 a.m. to 12:00 p.m. EDT** and are designed specifically to teach human rights defenders and nonprofit organizations how to integrate Bitcoin into their work to challenge state censorship and confiscation in a beginner-friendly way. ### [Register Here](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) ## BITCOIN AND FREEDOM TECH NEWS #### **MIT | 2025 Bitcoin Expo** HRF is partnering with [MIT](https://www.mit.edu/) to host the [2025 MIT Bitcoin Expo](https://mitbtcexpo.org/), a two-day event from April 5-6 at the Stata Center, exploring Bitcoin and freedom technologies as tools for privacy, financial sovereignty, and civil liberties — especially for people living under authoritarian regimes. Now in its 12th year, the expo features keynotes, panels, technical workshops, and hackathons. It brings together developers, activists, students, and researchers to dive into privacy, self-sovereignty, and decentralization. Attendees will also gain hands-on experience and engage in meaningful discussions on the real-world impact of freedom technologies. Learn more about the expo and get your tickets [here](https://mitbtcexpo.org/)**.** #### **Bitcoin Mining | Two Blocks Mined by Solo Miners This Week** This week, two solo miners successfully mined Bitcoin blocks, marking a rare and significant event. The first block was [solved](https://x.com/FutureBit/status/1884740065223495821) through a collaborative effort led by the [256 Foundation](https://256foundation.org/) (where 300+ participants [pooled](https://crypto.news/solo-miner-solving-a-block-and-getting-3-146-btc/) their hashrate for a fundraising event). The second block was [mined](https://x.com/SoloSatoshi/status/1885418398345269572) independently through [solo.ckpool](https://solo.ckpool.org/) by a miner using hashrate equivalent to thousands of BitAxe devices, a type of open-source home mining hardware. The news shows that independent miners can still compete outside of large [mining pools](https://river.com/learn/terms/m/mining-pool/). These events reaffirm Bitcoin’s decentralization and censorship resistance, proving that solo mining remains viable with the proper coordination and infrastructure, which is especially key as solo mining can be done privately and quietly under tyrannical regimes. #### **Joltz Wallet | First Self-Custodial Wallet to Support Taproot Assets** Joltz has [launched](https://x.com/joltz_btc/status/1885097351108243487) the first self-custodial wallet for [Taproot Assets](https://docs.lightning.engineering/the-lightning-network/taproot-assets), enabling users to hold and transact stablecoins like USDT (Tether) directly on Bitcoin — without intermediaries. Unlike custodial solutions, Joltz ensures users retain full control over their funds while enabling BTC-to-USDT swaps through a user-friendly interface. This could expand access to stable money — particularly for activists and nonprofits in volatile markets in search of digital dollars. However, stablecoins still carry centralization and censorship risks, as issuers like Tether can freeze funds or be beholden to regulatory demands. #### **Olas | New Updates Enhance Accessibility and Features** [Olas](https://github.com/pablof7z/olas), an Instagram-like Nostr client built by [Pablof7z](https://github.com/pablof7z), [released](https://github.com/pablof7z/olas/releases/tag/0.2.0) a new update for iOS and Android. The update introduces multiple images per post, Instagram-style filters, and improved video playback. It also enhances its Nostr-native wallet functionality so users can more fluidly receive Bitcoin tips and payments. The client also made Nostr Wallet Connect (NWC), a protocol that allows apps to interact with Bitcoin Lightning wallets, more reliable for end users. Nostr clients like Olas may prove to be a useful tool for censorship-resistant communications on social networks among activists worldwide and stand as a stark contrast to centralized, permissioned alternatives. #### **OpenSats | Announces Ninth Wave of Bitcoin Grants** [OpenSats](http://opensats.org), a public nonprofit supporting open-source Bitcoin projects, [announced](https://opensats.org/blog/ninth-wave-of-bitcoin-grants) its ninth wave of Bitcoin grants advancing financial freedom and privacy. Among the recipients, [Nutstash](https://www.nutstash.app/), a multi-platform Cashu ecash wallet, enables private, censorship-resistant Bitcoin transactions — critical for human rights defenders. Another grantee, [El Tor](https://devpost.com/software/el-tor), is developing a fork of the [Tor Network](https://www.torproject.org/) integrated with Bitcoin's Lightning Network, aiming to enhance online privacy for activists and dissidents. HRF welcomes OpenSats’ continued support for decentralized tools in an increasingly surveilled world. #### **bitcoin++ | Upcoming Bitcoin Developer Conference** Bitcoin developers and freedom tech enthusiasts will [gather](https://btcplusplus.dev/conf/floripa) in Florianopolis, Brazil, from Feb. 19-22, 2025, for the special “hacking edition” [bitcoin++](https://btcplusplus.dev/) conference. Unlike past bitcoin++ events, which focused on single topics like scripting or ecash, this event will feature hands-on development to enhance Bitcoin’s privacy, scalability, and censorship resistance. Attendees will participate in workshops, live coding challenges, and technical discussions. HRF will help the event include attendees from authoritarian regimes in Latin America. Learn more about the conference or buy tickets [here](https://btcplusplus.dev/conf/floripa). ## RECOMMENDED CONTENT #### **The Risks of the DREX Central Bank Digital Currency by Area Bitcoin** In this [article](https://blog.areabitcoin.co/cbdc-drex/), [Area Bitcoin](https://www.areabitcoin.co/), a Brazilian Bitcoin education hub, examines [DREX](https://cbdctracker.hrf.org/currency/brazil), Brazil’s central bank digital currency (CBDC), and its threat to Brazilians’ financial autonomy. DREX operates as a token on a centralized, permissioned blockchain that grants officials sweeping surveillance and control over individual financial activity. Further, its strict Know-Your-Customer (KYC) and Anti-Money Laundering (AML) measures erode financial privacy. Area Bitcoin [warns](https://blog.areabitcoin.co/cbdc-drex/), “By embracing it, we risk surrendering our personal data, the fruits of our labor, and even generational wealth to political and bureaucratic oversight.” *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/)
@ f1989a96:bcaaf2c1
2025-02-06 14:01:03Good morning, readers! In India, the central bank has taken a significant step toward launching its central bank digital currency (CBDC), the digital rupee. In partnership with fintech firms Mobikwik and Cred, the digital rupee is now available to 180 million users through a new “e₹ wallet,” a CBDC wallet app designed for public use. Predictably, the CBDC comes with tight restrictions, including limits on payment amounts and frequency and extensive personal data collection, raising concerns over financial privacy. In open-source news, HRF is pleased to announce a collaboration with MIT for the 2025 MIT Bitcoin Expo. This two-day freedom-focused event will explore how Bitcoin and adjacent freedom tech can help combat financial surveillance and repression under authoritarian regimes through expert speakers, panels, workshops, and more. Elsewhere, Joltz became the first self-custodial wallet to support Taproot Assets, enabling access to stable digital dollars on a decentralized network for activists, dissidents, and others in difficult political environments. We conclude with an extensive guide from Area Bitcoin, a Brazilian education hub, thoroughly examining Brazil’s DREX CBDC and its implications for financial freedom and human rights in Brazil and beyond. **Now, let’s dive right in!** ### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **India | Central Bank Partners with Fintech Firms to Pilot Launch CBDC** The Reserve Bank of India (RBI) [partnered](https://www.businesstoday.in/personal-finance/news/story/mobikwik-cred-join-hands-with-rbi-to-fully-launch-cbdc-ers-for-android-check-features-usage-462318-2025-01-28) with fintech firms MobiKwik and Cred, alongside Yes Bank, to expand the digital rupee, India’s CBDC. With a combined user base of [180 million,](https://www.ledgerinsights.com/fintech-wallets-go-live-in-digital-rupee-cbdc-pilot/) Mobikwik and Cred will act as entry points for public access to the CBDC through their new “e₹ wallet” CBDC app. However, the app mandates video verification and imposes significant restrictions. For instance, a daily transaction cap of ₹50,000 ($577) and ₹10,000 ($115) limit per transaction. The RBI’s decision to embed the digital rupee within existing fintech firms to boost adoption leaves few avenues for financial privacy and freedom as the Indian state [pushes](https://www.lowyinstitute.org/the-interpreter/india-s-plan-world-without-cash) further towards a cashless economy. #### **El Salvador | Lawmakers Scale Back Bitcoin Legal Tender Law** El Salvador’s congress [amended](https://www.reuters.com/world/americas/lawmakers-el-salvador-rush-new-bitcoin-reform-after-imf-deal-2025-01-30/) its Bitcoin law, making private sector acceptance of Bitcoin voluntary. The reform follows a $1.4 billion loan agreement with the International Monetary Fund (IMF) that wanted to limit the government’s, citizens’, and economies’ exposure to Bitcoin. Salvadoran lawmaker Elisa Rosales [said](https://www.reuters.com/world/americas/lawmakers-el-salvador-rush-new-bitcoin-reform-after-imf-deal-2025-01-30/) the latest reform guarantees Bitcoin’s “permanence as legal tender” while facilitating its “practical implementation.” But, John Dennehy, founder of the civil society organization [Mi Primer Bitcoin](https://es.myfirstbitcoin.io/), [explained](https://x.com/jdennehy_writes/status/1885346352621617615) that the reform removed “all references of bitcoin as money or legal tender, plus the actual conditions, such as the government accepting bitcoin for things such as taxes, are now prohibited.” The future of freedom technology in El Salvador will be worth monitoring closely as the regime continues to erode protections on civil liberties. #### **Nigeria | Regime Hikes Telecom Tariffs for Citizens** In Nigeria, the regime approved a [50% increase](https://thenationonlineng.net/50-tariff-hike-a-necessary-step-or-a-burden-for-nigerians/) in telecom tariffs, further straining citizens already grappling with financial instability. Call rates will rise from 11 to 16.50 naira per minute ($0.0074 to $0.011) and SMS charges from 4 to 6 naira ($0.0026 to $0.004), exacerbating three-decade-high inflation as the ripple effects spread through the economy. Telecom companies justify the price hike as necessary for the sector’s survival amid the naira’s ongoing [devaluation](https://www.bloomberg.com/news/articles/2024-09-13/why-nigeria-s-naira-currency-ngn-usd-slumped-and-why-it-matters). [Deolu Ogunbanjo](https://www.linkedin.com/in/deolu-ogunbanjo-62b5a18b/?originalSubdomain=ng), president of the National Association of Telecoms Subscribers, however, [argues](https://thenationonlineng.net/50-tariff-hike-a-necessary-step-or-a-burden-for-nigerians/) that “this decision shows the government cares more about protecting profits than protecting people.” For Nigerians relying on mobile networks for work, banking, and daily communications, the increased costs will make phone services less accessible, putting even more pressure on civil society under an authoritarian government. #### **Nicaragua | Inter-American Court of Human Rights Rules Against Ortega** In Nicaragua, where the financial repression of individuals, opposition, and civil society is widespread, the Inter-American Court of Human Rights [ruled](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) that Daniel Ortega’s reelections since 2011 were illegitimate. This ruling “is the legal confirmation that there is no legitimate president in Nicaragua, but rather a dictator who has usurped power,” [said](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) Jaime Aparicio, a Bolivian lawyer, [adding](https://havanatimes.org/news/inter-american-human-rights-court-rules-against-nicaragua/) that “this is the first time that there is a legal precedent determining the illegality of Ortega’s presidency.” In a country where the regime systematically [freezes](https://www.reuters.com/world/americas/nicaragua-govt-accuses-catholic-church-money-laundering-freezes-accounts-2023-05-27/) bank accounts, seizes assets, and [shuts down](https://www.catholicnewsagency.com/news/261539/nicaraguan-dictatorship-shuts-down-more-organizations-including-dominican-nuns) nonprofits to silence dissent, this verdict sets a critical legal precedent against the abuse of state power to secure reelection. While the court lacks enforcement, its ruling strengthens legal challenges to Ortega’s rule and could provide a foundation for future actions against electoral fraud and authoritarian control. #### **Webinar Series for Nonprofits | Become Unstoppable** In an era where financial control is weaponized against dissent, the ability to transact freely is more important than ever. For activists and nonprofits operating under oppressive regimes, Bitcoin can offer a way to resist censorship, protect funds, and remain operational. Join HRF for a free, three-day webinar from March **17–19**, led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial freedom expert at the Anti-Corruption Foundation. The sessions will run daily from **10:30 a.m. to 12:00 p.m. EDT** and are designed specifically to teach human rights defenders and nonprofit organizations how to integrate Bitcoin into their work to challenge state censorship and confiscation in a beginner-friendly way. ### [Register Here](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) ## BITCOIN AND FREEDOM TECH NEWS #### **MIT | 2025 Bitcoin Expo** HRF is partnering with [MIT](https://www.mit.edu/) to host the [2025 MIT Bitcoin Expo](https://mitbtcexpo.org/), a two-day event from April 5-6 at the Stata Center, exploring Bitcoin and freedom technologies as tools for privacy, financial sovereignty, and civil liberties — especially for people living under authoritarian regimes. Now in its 12th year, the expo features keynotes, panels, technical workshops, and hackathons. It brings together developers, activists, students, and researchers to dive into privacy, self-sovereignty, and decentralization. Attendees will also gain hands-on experience and engage in meaningful discussions on the real-world impact of freedom technologies. Learn more about the expo and get your tickets [here](https://mitbtcexpo.org/)**.** #### **Bitcoin Mining | Two Blocks Mined by Solo Miners This Week** This week, two solo miners successfully mined Bitcoin blocks, marking a rare and significant event. The first block was [solved](https://x.com/FutureBit/status/1884740065223495821) through a collaborative effort led by the [256 Foundation](https://256foundation.org/) (where 300+ participants [pooled](https://crypto.news/solo-miner-solving-a-block-and-getting-3-146-btc/) their hashrate for a fundraising event). The second block was [mined](https://x.com/SoloSatoshi/status/1885418398345269572) independently through [solo.ckpool](https://solo.ckpool.org/) by a miner using hashrate equivalent to thousands of BitAxe devices, a type of open-source home mining hardware. The news shows that independent miners can still compete outside of large [mining pools](https://river.com/learn/terms/m/mining-pool/). These events reaffirm Bitcoin’s decentralization and censorship resistance, proving that solo mining remains viable with the proper coordination and infrastructure, which is especially key as solo mining can be done privately and quietly under tyrannical regimes. #### **Joltz Wallet | First Self-Custodial Wallet to Support Taproot Assets** Joltz has [launched](https://x.com/joltz_btc/status/1885097351108243487) the first self-custodial wallet for [Taproot Assets](https://docs.lightning.engineering/the-lightning-network/taproot-assets), enabling users to hold and transact stablecoins like USDT (Tether) directly on Bitcoin — without intermediaries. Unlike custodial solutions, Joltz ensures users retain full control over their funds while enabling BTC-to-USDT swaps through a user-friendly interface. This could expand access to stable money — particularly for activists and nonprofits in volatile markets in search of digital dollars. However, stablecoins still carry centralization and censorship risks, as issuers like Tether can freeze funds or be beholden to regulatory demands. #### **Olas | New Updates Enhance Accessibility and Features** [Olas](https://github.com/pablof7z/olas), an Instagram-like Nostr client built by [Pablof7z](https://github.com/pablof7z), [released](https://github.com/pablof7z/olas/releases/tag/0.2.0) a new update for iOS and Android. The update introduces multiple images per post, Instagram-style filters, and improved video playback. It also enhances its Nostr-native wallet functionality so users can more fluidly receive Bitcoin tips and payments. The client also made Nostr Wallet Connect (NWC), a protocol that allows apps to interact with Bitcoin Lightning wallets, more reliable for end users. Nostr clients like Olas may prove to be a useful tool for censorship-resistant communications on social networks among activists worldwide and stand as a stark contrast to centralized, permissioned alternatives. #### **OpenSats | Announces Ninth Wave of Bitcoin Grants** [OpenSats](http://opensats.org), a public nonprofit supporting open-source Bitcoin projects, [announced](https://opensats.org/blog/ninth-wave-of-bitcoin-grants) its ninth wave of Bitcoin grants advancing financial freedom and privacy. Among the recipients, [Nutstash](https://www.nutstash.app/), a multi-platform Cashu ecash wallet, enables private, censorship-resistant Bitcoin transactions — critical for human rights defenders. Another grantee, [El Tor](https://devpost.com/software/el-tor), is developing a fork of the [Tor Network](https://www.torproject.org/) integrated with Bitcoin's Lightning Network, aiming to enhance online privacy for activists and dissidents. HRF welcomes OpenSats’ continued support for decentralized tools in an increasingly surveilled world. #### **bitcoin++ | Upcoming Bitcoin Developer Conference** Bitcoin developers and freedom tech enthusiasts will [gather](https://btcplusplus.dev/conf/floripa) in Florianopolis, Brazil, from Feb. 19-22, 2025, for the special “hacking edition” [bitcoin++](https://btcplusplus.dev/) conference. Unlike past bitcoin++ events, which focused on single topics like scripting or ecash, this event will feature hands-on development to enhance Bitcoin’s privacy, scalability, and censorship resistance. Attendees will participate in workshops, live coding challenges, and technical discussions. HRF will help the event include attendees from authoritarian regimes in Latin America. Learn more about the conference or buy tickets [here](https://btcplusplus.dev/conf/floripa). ## RECOMMENDED CONTENT #### **The Risks of the DREX Central Bank Digital Currency by Area Bitcoin** In this [article](https://blog.areabitcoin.co/cbdc-drex/), [Area Bitcoin](https://www.areabitcoin.co/), a Brazilian Bitcoin education hub, examines [DREX](https://cbdctracker.hrf.org/currency/brazil), Brazil’s central bank digital currency (CBDC), and its threat to Brazilians’ financial autonomy. DREX operates as a token on a centralized, permissioned blockchain that grants officials sweeping surveillance and control over individual financial activity. Further, its strict Know-Your-Customer (KYC) and Anti-Money Laundering (AML) measures erode financial privacy. Area Bitcoin [warns](https://blog.areabitcoin.co/cbdc-drex/), “By embracing it, we risk surrendering our personal data, the fruits of our labor, and even generational wealth to political and bureaucratic oversight.” *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/) @ 1f3ce62e:6e6b5d83
2025-02-06 13:21:23During challenging times for relationships of all kind, stopping & reflecting brings a new perspective and help us to observe our contribution to it. **We spend a lot of time at work, our relationships there are important** 👥 When we **hit a wall with a colleague** it takes a lot of energy, stress and inefficiencies in our daily tasks. Have you ever gotten stressed about sending an email to a colleague? 😅 By listening to myself (to my inner voice, to my body) have helped me to start observing it. 👂 Then, observing it 👀 like an outsider has helped me to put myself on the other's shoes. Empathy does its thing at this stage. **People are stories, wounds not healed, as we all have.** 💕 Finally, I **proactive open an space to talk**. I like to listen first, all that is being said, not just words. Then I use my voice. Or vice versa as needed. **Not all relationship's challenges can be solved** (I have learned to accepted that), but I honor them, **by opening the space anyways**. From my research 🤓 ... Observing 👀 Reflecting 🤔 Opening an space to talk 👥 Listening 👂 ⚖ Speaking 🗣 👂What is being said, but the most important… 👂💛 **What is not being said.** And **when we start listening deeply, we can listen to fears, our own and others**.\ \ I wonder why we don't talk about dragons 🐉 at work. 🤭\ \ I wonder why we don't talk about fears.\ \ As an individual who explored them a lot in therapy, and I have experienced the benefit of it, I wonder, why no-one talks about them at workplaces. **Have you ever asked your team...What is their biggest fear?** 🤔 Talking about fears at work could feel uncomfortable at the very beginning, but exploring them is a way to connect with others while realizing we share a lot of them. **Overcoming them with others could bring a lot of relief too.** Fears limit our actions, decisions and our ideas to blow. Using tools like LEGOs helps us to explore the unconscious mind 🖤 🧠, where most of the fears have their residence. From where most of the decisions are made 😅 🌱 With Mini figures and blocks we **can project a situation** that you or your team is going through. 🌱 As we project it, you can **detach emotionally from it** and you **become an observer** of it. 🌱 You can only change, what you can **observe with** **full presence**. 🌱 **Playing** does exactly that, **brings us to the present moment**. **By using LEGOs we can bring perspective and spark more creative solutions.** Ignoring fears at work means ignoring we are... just humans. So step by step, we made our workplaces more human. **Deep listening breaks down walls.** **And that is what The World 🌎 strongly needs these days.** **In the end, what is really behind any wall, it is a wound not healed.** Stay colorful! Laus
@ 1f3ce62e:6e6b5d83
2025-02-06 13:21:23During challenging times for relationships of all kind, stopping & reflecting brings a new perspective and help us to observe our contribution to it. **We spend a lot of time at work, our relationships there are important** 👥 When we **hit a wall with a colleague** it takes a lot of energy, stress and inefficiencies in our daily tasks. Have you ever gotten stressed about sending an email to a colleague? 😅 By listening to myself (to my inner voice, to my body) have helped me to start observing it. 👂 Then, observing it 👀 like an outsider has helped me to put myself on the other's shoes. Empathy does its thing at this stage. **People are stories, wounds not healed, as we all have.** 💕 Finally, I **proactive open an space to talk**. I like to listen first, all that is being said, not just words. Then I use my voice. Or vice versa as needed. **Not all relationship's challenges can be solved** (I have learned to accepted that), but I honor them, **by opening the space anyways**. From my research 🤓 ... Observing 👀 Reflecting 🤔 Opening an space to talk 👥 Listening 👂 ⚖ Speaking 🗣 👂What is being said, but the most important… 👂💛 **What is not being said.** And **when we start listening deeply, we can listen to fears, our own and others**.\ \ I wonder why we don't talk about dragons 🐉 at work. 🤭\ \ I wonder why we don't talk about fears.\ \ As an individual who explored them a lot in therapy, and I have experienced the benefit of it, I wonder, why no-one talks about them at workplaces. **Have you ever asked your team...What is their biggest fear?** 🤔 Talking about fears at work could feel uncomfortable at the very beginning, but exploring them is a way to connect with others while realizing we share a lot of them. **Overcoming them with others could bring a lot of relief too.** Fears limit our actions, decisions and our ideas to blow. Using tools like LEGOs helps us to explore the unconscious mind 🖤 🧠, where most of the fears have their residence. From where most of the decisions are made 😅 🌱 With Mini figures and blocks we **can project a situation** that you or your team is going through. 🌱 As we project it, you can **detach emotionally from it** and you **become an observer** of it. 🌱 You can only change, what you can **observe with** **full presence**. 🌱 **Playing** does exactly that, **brings us to the present moment**. **By using LEGOs we can bring perspective and spark more creative solutions.** Ignoring fears at work means ignoring we are... just humans. So step by step, we made our workplaces more human. **Deep listening breaks down walls.** **And that is what The World 🌎 strongly needs these days.** **In the end, what is really behind any wall, it is a wound not healed.** Stay colorful! Laus @ cf7ed325:050194cf
2025-02-06 12:28:27The [TIA Nile Cruise](https://www.etbtoursegypt.com/tour/ms-tia-nile-cruise) offers a fantastic way to experience Egypt’s timeless beauty, as it takes you on an unforgettable journey along the majestic Nile River. Whether you’re a history buff, an adventure seeker, or simply looking for a relaxing getaway, this cruise offers something for everyone. One of the standout features of this cruise is its luxurious accommodations, combining modern amenities with the charm of traditional Egyptian hospitality. As you sail through Egypt’s most iconic landmarks, such as the Valley of the Kings, the Pyramids of Giza, and the temples of Karnak and Luxor, the comfort of the TIA Nile Cruise ensures that every moment is enjoyable. If you’re exploring other options, there are many other high-end Nile cruises that offer similarly unforgettable experiences. The [Gemma Nile Cruise](https://www.etbtoursegypt.com/tour/gemma-nile-cruise) is one of the most popular alternatives, offering luxury and sophistication while cruising through the heart of Egypt. It’s perfect for those seeking an elegant escape with premium service and spectacular views. Another excellent choice is the [Sonesta Sun Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/sonesta-sun-goddess-nile-cruise), which provides a combination of relaxed luxury and top-notch service. Guests can enjoy stunning views of Egypt’s famous landmarks, along with a variety of recreational facilities on board. For those looking for something extra special, the [Sonesta Star Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Star-Goddess-Nile-Cruise) and the [Sonesta Moon Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Moon-Goddess-Nile-cruise) are both fantastic options, offering spacious rooms and exceptional service. These cruises ensure that guests have an unparalleled experience as they explore the wonders of Egypt. The [Sonesta Nile Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Nile-Goddess-Cruise-tours) is another luxurious option, known for its elegance and comfort. It offers an array of gourmet dining options and entertainment for an all-around memorable trip. Lastly, the [Sonesta George Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-St-George-Nile-Cruise) promises an exceptional cruising experience with modern amenities and stunning Nile views. Whichever cruise you choose, you can be sure that your journey along the Nile will be unforgettable, filled with adventure, culture, and relaxation. 🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 For Booking and Inquiries: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt
@ cf7ed325:050194cf
2025-02-06 12:28:27The [TIA Nile Cruise](https://www.etbtoursegypt.com/tour/ms-tia-nile-cruise) offers a fantastic way to experience Egypt’s timeless beauty, as it takes you on an unforgettable journey along the majestic Nile River. Whether you’re a history buff, an adventure seeker, or simply looking for a relaxing getaway, this cruise offers something for everyone. One of the standout features of this cruise is its luxurious accommodations, combining modern amenities with the charm of traditional Egyptian hospitality. As you sail through Egypt’s most iconic landmarks, such as the Valley of the Kings, the Pyramids of Giza, and the temples of Karnak and Luxor, the comfort of the TIA Nile Cruise ensures that every moment is enjoyable. If you’re exploring other options, there are many other high-end Nile cruises that offer similarly unforgettable experiences. The [Gemma Nile Cruise](https://www.etbtoursegypt.com/tour/gemma-nile-cruise) is one of the most popular alternatives, offering luxury and sophistication while cruising through the heart of Egypt. It’s perfect for those seeking an elegant escape with premium service and spectacular views. Another excellent choice is the [Sonesta Sun Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/sonesta-sun-goddess-nile-cruise), which provides a combination of relaxed luxury and top-notch service. Guests can enjoy stunning views of Egypt’s famous landmarks, along with a variety of recreational facilities on board. For those looking for something extra special, the [Sonesta Star Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Star-Goddess-Nile-Cruise) and the [Sonesta Moon Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Moon-Goddess-Nile-cruise) are both fantastic options, offering spacious rooms and exceptional service. These cruises ensure that guests have an unparalleled experience as they explore the wonders of Egypt. The [Sonesta Nile Goddess Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-Nile-Goddess-Cruise-tours) is another luxurious option, known for its elegance and comfort. It offers an array of gourmet dining options and entertainment for an all-around memorable trip. Lastly, the [Sonesta George Nile Cruise](https://www.etbtoursegypt.com/tour/Sonesta-St-George-Nile-Cruise) promises an exceptional cruising experience with modern amenities and stunning Nile views. Whichever cruise you choose, you can be sure that your journey along the Nile will be unforgettable, filled with adventure, culture, and relaxation. 🌐 Visit us at www.etbtoursegypt.com 📲 Contact us now! +20 10 21100873 📧 For Booking and Inquiries: info@etbtours.com 🏢 Company Address: 4 El Lebeny Axis , Nazlet Al Batran , Al Haram, Giza , Egypt @ 4506e04e:8c16ba04
2025-02-06 12:11:10This spec aims to build a client application that enables patients to securely store and access their medical data using the Nostr protocol while ensuring only authorized doctors can write medical records. All data is end-to-end encrypted (E2EE) before being stored on Nostr relays, preventing unauthorized access. Patients can grant or revoke doctors’ write permissions, and all medical updates are encrypted with the patient’s public key, ensuring only they can read them. An audit log keeps track of all doctors (identified by their npubs) who have accessed or modified the patient’s data. This solution provides privacy, security, and transparency while leveraging decentralized, zero-trust storage on Nostr. 🚀 --- ## **1️⃣ Core Architecture** ### **Client Application (Mobile - Patient)** - **Stores only encrypted medical data** (no write permissions). - Allows **temporary read access** to the patient. - Maintains an **audit log of npubs** (medical staff) who wrote/modified data. ### **Client Application (Mobile - Doctor)** - **Writes new medical records** and encrypts them with the patient’s **npub**. - Submits encrypted records to Nostr relays. - Can view past records that they (or other authorized doctors) have written. ### **Nostr Relays** - Store **only encrypted medical records** (relays cannot read them). - Act as a **communication layer** between doctors and the patient. --- ## **2️⃣ How It Works (End-to-End Workflow)** ### **👨⚕️ Writing/Updating Medical Data (Doctor)** 1. The doctor inputs new medical records into their mobile app. 2. The data is **encrypted using the patient’s npub** (so only the patient can read it). 3. The encrypted record is published to **Nostr relays**. 4. The patient’s app detects the update and decrypts the data locally for viewing. ### **👩⚕️ Managing Doctor Access (Patient)** 1. The patient manually **grants or revokes access** to doctors via their app. 2. If a doctor is **granted access**, they can write new records. 3. The patient **cannot modify or delete medical records**, only read them. ### **🔑 Secure Key Exchange for Read Access** 1. The doctor **encrypts records** with the patient’s **npub**. 2. The patient uses their **nsec** (private key) to decrypt and read the data. 3. Other unauthorized parties (including relays) **cannot decrypt the data**. ### **📜 Access Logging** - Every **write operation** (new or modified medical record) is **logged in the patient’s app**. - The log includes: - **npub of the doctor** who made the update. - **Timestamp of the update**. - **Hash of the encrypted record** for verification. --- ## **3️⃣ Security Measures** ✅ **Doctors Can Write, Patients Can Only Read** - Only **authorized doctors** can submit medical data. - Patients can only **view** (not modify) their records. ✅ **End-to-End Encryption** - Data is **encrypted before transmission**, ensuring no unauthorized access. ✅ **Zero-Trust Storage** - Nostr relays **store encrypted records** that are useless without the decryption key. ✅ **Audit Log for Transparency** - Patients can track **who wrote or modified** their records. ✅ **No Long-Term Access Without Authorization** - The patient can revoke a doctor’s **write permissions** anytime. --- ## **4️⃣ Technology Stack** - **Frontend (Mobile App)** - **Flutter (Dart)** or **React Native (JavaScript/TypeScript)** - Secure local storage for audit logs (**EncryptedSharedPreferences** on Android, **Keychain** on iOS) - **Cryptography** - **ECC (Elliptic Curve Cryptography)** for **key exchange** (Nostr encryption model) - **AES-256** for **encrypting medical records** (written by doctors) - **Networking & Storage** - **Nostr Protocol** (NIPs 04 for encrypted DMs, NIP 33 for event-based access control) - **Multi-Relay Storage** (for redundancy) --- ## **5️⃣ Potential Challenges & Solutions** ### **🔹 Patient Cannot Edit Records** - Patients might want to **annotate or request corrections** on their records. - Solution: Allow a **separate encrypted channel** for patient feedback. ### **🔹 Doctor Write Permissions Management** - A UI is needed for patients to **approve/revoke doctor access** easily. - Solution: Implement a **simple approval system** in the mobile app. ### **🔹 Relay Availability** - Solution: Store records **on multiple relays** for redundancy. --- This design ensures that **only authorized doctors can write data**, while **patients have full visibility and control over access**. 🚀 ***I'm looking for a co-founder to build this. I've got the experienced and cost-efficient team who can build this. DM me for details.***
@ 4506e04e:8c16ba04
2025-02-06 12:11:10This spec aims to build a client application that enables patients to securely store and access their medical data using the Nostr protocol while ensuring only authorized doctors can write medical records. All data is end-to-end encrypted (E2EE) before being stored on Nostr relays, preventing unauthorized access. Patients can grant or revoke doctors’ write permissions, and all medical updates are encrypted with the patient’s public key, ensuring only they can read them. An audit log keeps track of all doctors (identified by their npubs) who have accessed or modified the patient’s data. This solution provides privacy, security, and transparency while leveraging decentralized, zero-trust storage on Nostr. 🚀 --- ## **1️⃣ Core Architecture** ### **Client Application (Mobile - Patient)** - **Stores only encrypted medical data** (no write permissions). - Allows **temporary read access** to the patient. - Maintains an **audit log of npubs** (medical staff) who wrote/modified data. ### **Client Application (Mobile - Doctor)** - **Writes new medical records** and encrypts them with the patient’s **npub**. - Submits encrypted records to Nostr relays. - Can view past records that they (or other authorized doctors) have written. ### **Nostr Relays** - Store **only encrypted medical records** (relays cannot read them). - Act as a **communication layer** between doctors and the patient. --- ## **2️⃣ How It Works (End-to-End Workflow)** ### **👨⚕️ Writing/Updating Medical Data (Doctor)** 1. The doctor inputs new medical records into their mobile app. 2. The data is **encrypted using the patient’s npub** (so only the patient can read it). 3. The encrypted record is published to **Nostr relays**. 4. The patient’s app detects the update and decrypts the data locally for viewing. ### **👩⚕️ Managing Doctor Access (Patient)** 1. The patient manually **grants or revokes access** to doctors via their app. 2. If a doctor is **granted access**, they can write new records. 3. The patient **cannot modify or delete medical records**, only read them. ### **🔑 Secure Key Exchange for Read Access** 1. The doctor **encrypts records** with the patient’s **npub**. 2. The patient uses their **nsec** (private key) to decrypt and read the data. 3. Other unauthorized parties (including relays) **cannot decrypt the data**. ### **📜 Access Logging** - Every **write operation** (new or modified medical record) is **logged in the patient’s app**. - The log includes: - **npub of the doctor** who made the update. - **Timestamp of the update**. - **Hash of the encrypted record** for verification. --- ## **3️⃣ Security Measures** ✅ **Doctors Can Write, Patients Can Only Read** - Only **authorized doctors** can submit medical data. - Patients can only **view** (not modify) their records. ✅ **End-to-End Encryption** - Data is **encrypted before transmission**, ensuring no unauthorized access. ✅ **Zero-Trust Storage** - Nostr relays **store encrypted records** that are useless without the decryption key. ✅ **Audit Log for Transparency** - Patients can track **who wrote or modified** their records. ✅ **No Long-Term Access Without Authorization** - The patient can revoke a doctor’s **write permissions** anytime. --- ## **4️⃣ Technology Stack** - **Frontend (Mobile App)** - **Flutter (Dart)** or **React Native (JavaScript/TypeScript)** - Secure local storage for audit logs (**EncryptedSharedPreferences** on Android, **Keychain** on iOS) - **Cryptography** - **ECC (Elliptic Curve Cryptography)** for **key exchange** (Nostr encryption model) - **AES-256** for **encrypting medical records** (written by doctors) - **Networking & Storage** - **Nostr Protocol** (NIPs 04 for encrypted DMs, NIP 33 for event-based access control) - **Multi-Relay Storage** (for redundancy) --- ## **5️⃣ Potential Challenges & Solutions** ### **🔹 Patient Cannot Edit Records** - Patients might want to **annotate or request corrections** on their records. - Solution: Allow a **separate encrypted channel** for patient feedback. ### **🔹 Doctor Write Permissions Management** - A UI is needed for patients to **approve/revoke doctor access** easily. - Solution: Implement a **simple approval system** in the mobile app. ### **🔹 Relay Availability** - Solution: Store records **on multiple relays** for redundancy. --- This design ensures that **only authorized doctors can write data**, while **patients have full visibility and control over access**. 🚀 ***I'm looking for a co-founder to build this. I've got the experienced and cost-efficient team who can build this. DM me for details.*** @ c1301dca:8efcc835
2025-02-06 11:34:08Hiring the right sales talent is one of the most crucial decisions a company can make. A strong sales team drives revenue, builds relationships, and contributes to business success. However, making the wrong hire can lead to costly mistakes—high turnover, poor morale, and missed sales targets. This is where Prehire psychological assessments come in, offering a powerful tool to help companies make better, more informed hiring decisions. At its core, a [**Prehire psychological assessment**](https://www.velocity-sales.com/prehire-selection) helps employers look beyond resumes, experience, and qualifications. It digs deeper into potential candidates' behavioural traits, cognitive abilities, and intrinsic motivations. This deeper understanding enables companies to select candidates who are skilled and aligned with the job demands and the company's culture. ## 1. Improved Candidate Fit for the Role A common challenge in sales hiring is finding candidates perfect for the role and the team. Sales positions often require specific skills, such as persistence, emotional intelligence, problem-solving abilities, and the ability to perform under pressure. Traditional hiring methods focus heavily on qualifications and experience, but these don't always provide insight into how a candidate will handle the job demands. Prehire psychological assessments go further by assessing a candidate's cognitive capabilities and personality traits. For example, a candidate might have an impressive sales background but struggle with resilience when facing rejection or high-pressure situations. A proper psychological assessment identifies these qualities, allowing companies to choose candidates naturally inclined to thrive in sales environments. ## 2. Reducing Turnover Rates Turnover is one of the biggest challenges in the sales industry and can be costly. When employees leave, the company faces recruitment costs, training costs, and lost revenue. Moreover, high turnover can negatively impact team morale, lowering performance across the board. Prehire psychological assessments help reduce turnover by identifying candidates more likely to stay long-term. The assessments examine intrinsic motivation—whether candidates are genuinely passionate about the role and aligned with the company's mission. Candidates naturally aligned with the job and organisation are more likely to stay engaged, satisfied, and committed. This reduces the risk of early departures and creates a more stable, high-performing team. ## 3. Enhancing Sales Performance Sales roles can be highly demanding, requiring individuals to stay motivated, favourable, and productive even during tough times. A candidate's ability to handle stress, maintain enthusiasm, and stay focused on goals can significantly influence their performance. Psychological assessments provide valuable insights into how candidates will react under pressure, how resilient they are, and how well they manage stress. By understanding a candidate's psychological profile, employers can select individuals better equipped to deal with the highs and lows of a sales career. These candidates are more likely to stay motivated, adapt to challenges, and maintain consistent performance. ## 4. Cultural Fit and Team Harmony A key factor in any successful team is how well team members work together. A salesperson who excels individually but clashes with the company culture can cause disruptions within the team. Similarly, a candidate who struggles to adapt to the sales team's dynamic can lower overall performance and morale. Prehire psychological assessments evaluate how candidates will fit within the existing team culture. These assessments measure interpersonal skills, emotional intelligence, and adaptability, which are critical in a sales environment. By selecting candidates who align with the team's dynamics and values, companies foster a more collaborative and cohesive work environment, ultimately boosting morale and improving overall sales performance. ### Boost sales and reduce turnover with the right hire—Prehire Psychological Assessments! The right sales talent is more critical than ever. In a competitive landscape, Prehire psychological assessments provide a deeper, more nuanced view of candidates, helping businesses make better decisions that lead to higher retention rates, improved morale, and more robust sales performance. By understanding candidates more deeply, companies can reduce turnover, ensure better cultural fit, and ultimately create a more effective and motivated sales team Velocity Sales Consulting specialises in helping businesses enhance their **[Candidate selection process consulting](https://www.velocity-sales.com)** through scientifically backed prehire psychological assessments. Our expert consulting services ensure your sales hiring decisions are data-driven, informed, and tailored to help your company succeed.
@ c1301dca:8efcc835
2025-02-06 11:34:08Hiring the right sales talent is one of the most crucial decisions a company can make. A strong sales team drives revenue, builds relationships, and contributes to business success. However, making the wrong hire can lead to costly mistakes—high turnover, poor morale, and missed sales targets. This is where Prehire psychological assessments come in, offering a powerful tool to help companies make better, more informed hiring decisions. At its core, a [**Prehire psychological assessment**](https://www.velocity-sales.com/prehire-selection) helps employers look beyond resumes, experience, and qualifications. It digs deeper into potential candidates' behavioural traits, cognitive abilities, and intrinsic motivations. This deeper understanding enables companies to select candidates who are skilled and aligned with the job demands and the company's culture. ## 1. Improved Candidate Fit for the Role A common challenge in sales hiring is finding candidates perfect for the role and the team. Sales positions often require specific skills, such as persistence, emotional intelligence, problem-solving abilities, and the ability to perform under pressure. Traditional hiring methods focus heavily on qualifications and experience, but these don't always provide insight into how a candidate will handle the job demands. Prehire psychological assessments go further by assessing a candidate's cognitive capabilities and personality traits. For example, a candidate might have an impressive sales background but struggle with resilience when facing rejection or high-pressure situations. A proper psychological assessment identifies these qualities, allowing companies to choose candidates naturally inclined to thrive in sales environments. ## 2. Reducing Turnover Rates Turnover is one of the biggest challenges in the sales industry and can be costly. When employees leave, the company faces recruitment costs, training costs, and lost revenue. Moreover, high turnover can negatively impact team morale, lowering performance across the board. Prehire psychological assessments help reduce turnover by identifying candidates more likely to stay long-term. The assessments examine intrinsic motivation—whether candidates are genuinely passionate about the role and aligned with the company's mission. Candidates naturally aligned with the job and organisation are more likely to stay engaged, satisfied, and committed. This reduces the risk of early departures and creates a more stable, high-performing team. ## 3. Enhancing Sales Performance Sales roles can be highly demanding, requiring individuals to stay motivated, favourable, and productive even during tough times. A candidate's ability to handle stress, maintain enthusiasm, and stay focused on goals can significantly influence their performance. Psychological assessments provide valuable insights into how candidates will react under pressure, how resilient they are, and how well they manage stress. By understanding a candidate's psychological profile, employers can select individuals better equipped to deal with the highs and lows of a sales career. These candidates are more likely to stay motivated, adapt to challenges, and maintain consistent performance. ## 4. Cultural Fit and Team Harmony A key factor in any successful team is how well team members work together. A salesperson who excels individually but clashes with the company culture can cause disruptions within the team. Similarly, a candidate who struggles to adapt to the sales team's dynamic can lower overall performance and morale. Prehire psychological assessments evaluate how candidates will fit within the existing team culture. These assessments measure interpersonal skills, emotional intelligence, and adaptability, which are critical in a sales environment. By selecting candidates who align with the team's dynamics and values, companies foster a more collaborative and cohesive work environment, ultimately boosting morale and improving overall sales performance. ### Boost sales and reduce turnover with the right hire—Prehire Psychological Assessments! The right sales talent is more critical than ever. In a competitive landscape, Prehire psychological assessments provide a deeper, more nuanced view of candidates, helping businesses make better decisions that lead to higher retention rates, improved morale, and more robust sales performance. By understanding candidates more deeply, companies can reduce turnover, ensure better cultural fit, and ultimately create a more effective and motivated sales team Velocity Sales Consulting specialises in helping businesses enhance their **[Candidate selection process consulting](https://www.velocity-sales.com)** through scientifically backed prehire psychological assessments. Our expert consulting services ensure your sales hiring decisions are data-driven, informed, and tailored to help your company succeed. @ 044da344:073a8a0e
2025-02-06 11:30:19Nachdem ich in diesem Jahr schon die [Schweiz](https://www.freie-medienakademie.de/medien-plus/die-afd-spricht-englisch) gewürdigt habe und den renitenten [Osten](https://www.freie-medienakademie.de/medien-plus/resonanz-aus-dem-osten), wird es Zeit, nach Österreich zu schauen. Wien, Hannes Hofbauer, Promedia. Für mich eine Dreifaltigkeit, seit ich im September 2021 bei der [Zukunftskonferenz](https://www.manova.news/artikel/weil-es-anders-geht) war. Auf den Straßen der Stadt lief mein altes Leben davon. Der Wien-Marathon, geplant eigentlich für April 2020 und für mich seinerzeit ein Fixpunkt im Kalender, weil ich glaubte, besser in Form zu sein als je zuvor. Den Startplatz hatte ich unter Protest zurückgegeben, nachdem die Organisatoren per Rundmail dazu aufriefen, sich doch bitte die Spritze zu holen. Die Zeit reiche sogar noch für zwei. Mitten im Training wohlgemerkt, wenn das Immunsystem ohnehin permanent im Keller ist und nicht mal eine Rotznase in der Nähe verkraftet. Für Rekorde war es an jenem Septembersonntag dann ohnehin viel zu heiß. Also zur Zukunftskonferenz, die es eigentlich gar nicht hätte geben dürfen. Jedenfalls für mich nicht. Kein Zertifikat, nirgends. Von jenseits der Grenze schien Wien damals eine uneinnehmbare Festung zu sein für alle, die ohne Maske einreiten wollen. Die Impfpflicht war zwar noch nicht beschlossen, aber die veröffentlichte Stimmung ließ kaum Zweifel, dass das kommen würde. In Wien, das habe ich damals gelernt, geht trotzdem immer was. Kein Hotel ohne Test? Dann wohnst Du eben privat, lieber Michael. Und wenn wir Hunger haben, finden wir immer einen Griechen oder jemanden vom Balkan.  Wien spielt auch im neuen Buch von Hannes Hofbauer eine Rolle. Eine kleine, okay, und beim Blick auf Cover und Titel auch nicht unbedingt zu erwarten. Russland heute, sagen alle optischen Signale. Wirtschaftskrieg, Sanktionen, ein neues Schloss aus Eisen. Hofbauer wäre aber nicht Hofbauer, wenn er es bei den letzten paar Jahren belassen würde. Wie schon in seinem Buch über [Zensur](https://medienblog.hypotheses.org/10635) taucht er in die Geschichte ein und kommt so über die Hanse und Maria Theresia, über den unseligen Gutsverwalter Charles Boykott und Woodrow Wilson zwangsläufig auch zur Embargopolitik des Westens im Kalten Krieg. COCOM. Eine dieser Abkürzungen, die auch ausgeschrieben nicht verraten, was wirklich dahintersteckt. „Koordinationsausschuss für Ost-West-Handel“, sagt Wikipedia. Der Zeitzeuge Michael Meyen erinnert sich an eine DDR-Jugend, in der er sehnsüchtig auf das Weihnachtspaket aus dem Westen wartete. Vielleicht gibt es ja diesmal Taschenrechner, Quarzuhr oder irgendetwas anderes von dem, was sonst nur im Intershop liegt. Wien, sagt Hannes Hofbauer, war ein „Hotspot“ des Ost-Schmuggels. Einer der Orte, über die das gehandelt wurde, was nicht auf den schwarzen COCOM-Listen stand und so eigentlich auch nicht in mein Kinderzimmer kommen konnte. Die Quellen dieses Hotspots: Familienbande, Tradition und eine Position zwischen den großen Mächten. Vermutlich ist es deshalb kein Zufall, dass ein Buch wie dieses aus Österreich kommt. Hannes Hofbauer muss nicht groß herausstreichen, dass er sich auskennt im Osten Europas. Seine Bücher sprechen so für sich, dass ein paar zarte Hinweise genügen. Frühjahr 1990, kurz nach der Eröffnung von McDonalds am Puschkin-Platz in Moskau. Eine lange Schlange, erinnert sich Hofbauer. „Den Geschmack des Westens“ probieren (S. 214). Heute sind die 825 Standorte verkauft. Der neue Betreiber hatte vorher Erfolg in Sibirien und sagt jetzt auf Russisch: „Wkusno i totschka“. Lecker und Punkt. Damit ist ein Teil der Geschichte schon erzählt. Die Russen haben reagiert und den „härtesten Wirtschaftskrieg, den der Westen seit 1945 führt“, ins Leere laufen lassen (S. 203). BRICS und der Trend weg vom Dollar, die Umstellung der Landwirtschaft, die Weizen-Rekordernte 2024 und die Obst-Importe aus der Türkei. „Das westliche Sanktionsregime hat die Welt verändert“, sagt Hannes Hofbauer – aber anders als gedacht (S. 221). Damit sind nicht nur die Verluste gemeint, für die hier McDonalds steht, oder der Push für die russische Wirtschaft, sondern auch der „schleichende Wandel von der russländischen zur russisch-nationalen Identität“. *Russki mir* heißt das Schlagwort, das auf Zusammenhalt zielt. Russische Welt, Rechtsruck und Kirchenmacht inklusive (S. 238). Zu Hofbauers Geschichte gehören aber auch, wie sollte es bei einem Historiker anders sein, die langen Linien, die Scharmützel mit dem Irak und Libyen, die die „Dollar-Zwangsjacke“ abstreifen wollten (S. 65), und der Rechtsbruch, der stets damit verbunden ist, irgendwelche „Bestimmungen“ gegen Länder durchzusetzen, die jemand mit Allmachtsphantasien gerade als „Bösewicht und Unruhestifter“ ausgemacht hat (S. 14). „Schießkrieg und Wirtschaftskrieg hängen eng zusammen“ (S. 17): Diese Formel hat Woodrow Wilson, seinerzeit US-Präsident, schon im September 1919 in das kollektive Weltgedächtnis geschrieben. Möge der Krieg auch barbarisch sein, so sei doch der Boykott „ein unendlich viel schrecklicheres Kriegsinstrument“ (S. 9). Das erklärt COCOM. Das erklärt „Amerikas Kampf gegen russische Energie für Europa“, den Hannes Hofbauer schon 1960 beginnen lässt (S. 53). Das erklärt auch das Kontaktschuld-Prinzip, das ich im Dezember 2019 live auf Kuba erleben durfte. Dunkle Städte beim Anflug, Warten an den Tankstellen und der Zweifel, ob es etwas werden würde mit einer Vortragstour so ganz ohne Benzin. Dann endlich ein Schiff am Horizont. Wer in Havanna anlegt, so habe ich gelernt, ist für US-Häfen tabu. Die Kubaner sind damals nicht verhungert, immerhin. Aber gut ging es ihnen trotzdem nicht. „Russland ruinieren“: Bei Hannes Hofbauer beginnt dieses Kapitel 2009 – mit dem Versuch, über die Idee „Östliche Partnerschaft“ sechs Staaten aus dem Dunstkreis Moskaus zu lösen (S. 81). Moldawien, Georgien, Armenien, die Ukraine, Belarus, Aserbaidschan. Wir wissen, wie das ausgegangen ist. Wir wissen auch, wie und warum die Spirale weitergedreht wurde. Geopolitischer Wahn, der Kampf um kulturelle Deutungshoheit, wunderbar nachzulesen im Promedia-Buch von [Hauke Ritz](https://www.freie-medienakademie.de/medien-plus/die-macht-der-ideen), dazu der „Kampf um das große Geschäft“ (S. 104) und natürlich um das große Geld, der hier und jetzt selbst russische Auslandsvermögen nicht zu verschonen scheint, obwohl doch Eigentum ein Fetisch ist, der nicht einmal Straftätern entzogen werden kann (S. 133). Hannes Hofbauer verlässt den Hochsitz des Chronisten hin und wieder, um auf Menschen zu schauen, die zu Kollateralschäden geworden sind. Jozef Hambálek, ein slowakischer Motorradfahrer, der seinen Ministerpräsidenten brauchte, um von der Sanktionsliste gestrichen zu werden. So-yoen Schröder-Kim, fristlos entlassen, weil sie am 9. Mai 2023 mit ihrem Mann, Ex-Bundeskanzler, in der russischen Botschaft war. Justus Frantz, einst Klassikstar und heute Persona non grata, weil er nicht von alten Freunden und großer Kunst lassen wollte. Hofbauer spricht von einem „Russland-Hass“, der bei den Volksvertretern der EU „paranoide Züge“ trage, und von einer „kolonialen Attitüde moralischer Überlegenheit“ (S. 127). Er zeigt die Folgen jenseits der Wirtschaft. Kultur, Olympia, Wissenschaft, private Reisen. Die Zensur natürlich – nötig allein schon deshalb, damit die „russische Erzählung“ unsichtbar wird (S. 160). Und er hat eine Anekdote, die exemplarisch zeigt, warum das alles so gekommen ist. Ort: Das *Heute-Journal* im ZDF 2014. Anwesende: Claus Kleber und Joe Kaeser, seinerzeit Siemens-Chef und gerade zufrieden zurück aus Russland, wo er Putin getroffen hatte und den Gazprom-Chef. Der Leser ahnt, was kommt. Ein Verhör. Was haben Sie sich dabei gedacht, Herr Kaeser? Hannes Hofbauer sagt, dass dem Wirtschaftsboss erst in diesem Moment klar geworden sei, worauf die deutsche Politik hinauslief, und er zu Kreuze gekrochen sei (S. 235). Der Rest ist Geschichte – für alle Zeiten festgehalten in diesem Buch. \ [Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/)
@ 044da344:073a8a0e
2025-02-06 11:30:19Nachdem ich in diesem Jahr schon die [Schweiz](https://www.freie-medienakademie.de/medien-plus/die-afd-spricht-englisch) gewürdigt habe und den renitenten [Osten](https://www.freie-medienakademie.de/medien-plus/resonanz-aus-dem-osten), wird es Zeit, nach Österreich zu schauen. Wien, Hannes Hofbauer, Promedia. Für mich eine Dreifaltigkeit, seit ich im September 2021 bei der [Zukunftskonferenz](https://www.manova.news/artikel/weil-es-anders-geht) war. Auf den Straßen der Stadt lief mein altes Leben davon. Der Wien-Marathon, geplant eigentlich für April 2020 und für mich seinerzeit ein Fixpunkt im Kalender, weil ich glaubte, besser in Form zu sein als je zuvor. Den Startplatz hatte ich unter Protest zurückgegeben, nachdem die Organisatoren per Rundmail dazu aufriefen, sich doch bitte die Spritze zu holen. Die Zeit reiche sogar noch für zwei. Mitten im Training wohlgemerkt, wenn das Immunsystem ohnehin permanent im Keller ist und nicht mal eine Rotznase in der Nähe verkraftet. Für Rekorde war es an jenem Septembersonntag dann ohnehin viel zu heiß. Also zur Zukunftskonferenz, die es eigentlich gar nicht hätte geben dürfen. Jedenfalls für mich nicht. Kein Zertifikat, nirgends. Von jenseits der Grenze schien Wien damals eine uneinnehmbare Festung zu sein für alle, die ohne Maske einreiten wollen. Die Impfpflicht war zwar noch nicht beschlossen, aber die veröffentlichte Stimmung ließ kaum Zweifel, dass das kommen würde. In Wien, das habe ich damals gelernt, geht trotzdem immer was. Kein Hotel ohne Test? Dann wohnst Du eben privat, lieber Michael. Und wenn wir Hunger haben, finden wir immer einen Griechen oder jemanden vom Balkan.  Wien spielt auch im neuen Buch von Hannes Hofbauer eine Rolle. Eine kleine, okay, und beim Blick auf Cover und Titel auch nicht unbedingt zu erwarten. Russland heute, sagen alle optischen Signale. Wirtschaftskrieg, Sanktionen, ein neues Schloss aus Eisen. Hofbauer wäre aber nicht Hofbauer, wenn er es bei den letzten paar Jahren belassen würde. Wie schon in seinem Buch über [Zensur](https://medienblog.hypotheses.org/10635) taucht er in die Geschichte ein und kommt so über die Hanse und Maria Theresia, über den unseligen Gutsverwalter Charles Boykott und Woodrow Wilson zwangsläufig auch zur Embargopolitik des Westens im Kalten Krieg. COCOM. Eine dieser Abkürzungen, die auch ausgeschrieben nicht verraten, was wirklich dahintersteckt. „Koordinationsausschuss für Ost-West-Handel“, sagt Wikipedia. Der Zeitzeuge Michael Meyen erinnert sich an eine DDR-Jugend, in der er sehnsüchtig auf das Weihnachtspaket aus dem Westen wartete. Vielleicht gibt es ja diesmal Taschenrechner, Quarzuhr oder irgendetwas anderes von dem, was sonst nur im Intershop liegt. Wien, sagt Hannes Hofbauer, war ein „Hotspot“ des Ost-Schmuggels. Einer der Orte, über die das gehandelt wurde, was nicht auf den schwarzen COCOM-Listen stand und so eigentlich auch nicht in mein Kinderzimmer kommen konnte. Die Quellen dieses Hotspots: Familienbande, Tradition und eine Position zwischen den großen Mächten. Vermutlich ist es deshalb kein Zufall, dass ein Buch wie dieses aus Österreich kommt. Hannes Hofbauer muss nicht groß herausstreichen, dass er sich auskennt im Osten Europas. Seine Bücher sprechen so für sich, dass ein paar zarte Hinweise genügen. Frühjahr 1990, kurz nach der Eröffnung von McDonalds am Puschkin-Platz in Moskau. Eine lange Schlange, erinnert sich Hofbauer. „Den Geschmack des Westens“ probieren (S. 214). Heute sind die 825 Standorte verkauft. Der neue Betreiber hatte vorher Erfolg in Sibirien und sagt jetzt auf Russisch: „Wkusno i totschka“. Lecker und Punkt. Damit ist ein Teil der Geschichte schon erzählt. Die Russen haben reagiert und den „härtesten Wirtschaftskrieg, den der Westen seit 1945 führt“, ins Leere laufen lassen (S. 203). BRICS und der Trend weg vom Dollar, die Umstellung der Landwirtschaft, die Weizen-Rekordernte 2024 und die Obst-Importe aus der Türkei. „Das westliche Sanktionsregime hat die Welt verändert“, sagt Hannes Hofbauer – aber anders als gedacht (S. 221). Damit sind nicht nur die Verluste gemeint, für die hier McDonalds steht, oder der Push für die russische Wirtschaft, sondern auch der „schleichende Wandel von der russländischen zur russisch-nationalen Identität“. *Russki mir* heißt das Schlagwort, das auf Zusammenhalt zielt. Russische Welt, Rechtsruck und Kirchenmacht inklusive (S. 238). Zu Hofbauers Geschichte gehören aber auch, wie sollte es bei einem Historiker anders sein, die langen Linien, die Scharmützel mit dem Irak und Libyen, die die „Dollar-Zwangsjacke“ abstreifen wollten (S. 65), und der Rechtsbruch, der stets damit verbunden ist, irgendwelche „Bestimmungen“ gegen Länder durchzusetzen, die jemand mit Allmachtsphantasien gerade als „Bösewicht und Unruhestifter“ ausgemacht hat (S. 14). „Schießkrieg und Wirtschaftskrieg hängen eng zusammen“ (S. 17): Diese Formel hat Woodrow Wilson, seinerzeit US-Präsident, schon im September 1919 in das kollektive Weltgedächtnis geschrieben. Möge der Krieg auch barbarisch sein, so sei doch der Boykott „ein unendlich viel schrecklicheres Kriegsinstrument“ (S. 9). Das erklärt COCOM. Das erklärt „Amerikas Kampf gegen russische Energie für Europa“, den Hannes Hofbauer schon 1960 beginnen lässt (S. 53). Das erklärt auch das Kontaktschuld-Prinzip, das ich im Dezember 2019 live auf Kuba erleben durfte. Dunkle Städte beim Anflug, Warten an den Tankstellen und der Zweifel, ob es etwas werden würde mit einer Vortragstour so ganz ohne Benzin. Dann endlich ein Schiff am Horizont. Wer in Havanna anlegt, so habe ich gelernt, ist für US-Häfen tabu. Die Kubaner sind damals nicht verhungert, immerhin. Aber gut ging es ihnen trotzdem nicht. „Russland ruinieren“: Bei Hannes Hofbauer beginnt dieses Kapitel 2009 – mit dem Versuch, über die Idee „Östliche Partnerschaft“ sechs Staaten aus dem Dunstkreis Moskaus zu lösen (S. 81). Moldawien, Georgien, Armenien, die Ukraine, Belarus, Aserbaidschan. Wir wissen, wie das ausgegangen ist. Wir wissen auch, wie und warum die Spirale weitergedreht wurde. Geopolitischer Wahn, der Kampf um kulturelle Deutungshoheit, wunderbar nachzulesen im Promedia-Buch von [Hauke Ritz](https://www.freie-medienakademie.de/medien-plus/die-macht-der-ideen), dazu der „Kampf um das große Geschäft“ (S. 104) und natürlich um das große Geld, der hier und jetzt selbst russische Auslandsvermögen nicht zu verschonen scheint, obwohl doch Eigentum ein Fetisch ist, der nicht einmal Straftätern entzogen werden kann (S. 133). Hannes Hofbauer verlässt den Hochsitz des Chronisten hin und wieder, um auf Menschen zu schauen, die zu Kollateralschäden geworden sind. Jozef Hambálek, ein slowakischer Motorradfahrer, der seinen Ministerpräsidenten brauchte, um von der Sanktionsliste gestrichen zu werden. So-yoen Schröder-Kim, fristlos entlassen, weil sie am 9. Mai 2023 mit ihrem Mann, Ex-Bundeskanzler, in der russischen Botschaft war. Justus Frantz, einst Klassikstar und heute Persona non grata, weil er nicht von alten Freunden und großer Kunst lassen wollte. Hofbauer spricht von einem „Russland-Hass“, der bei den Volksvertretern der EU „paranoide Züge“ trage, und von einer „kolonialen Attitüde moralischer Überlegenheit“ (S. 127). Er zeigt die Folgen jenseits der Wirtschaft. Kultur, Olympia, Wissenschaft, private Reisen. Die Zensur natürlich – nötig allein schon deshalb, damit die „russische Erzählung“ unsichtbar wird (S. 160). Und er hat eine Anekdote, die exemplarisch zeigt, warum das alles so gekommen ist. Ort: Das *Heute-Journal* im ZDF 2014. Anwesende: Claus Kleber und Joe Kaeser, seinerzeit Siemens-Chef und gerade zufrieden zurück aus Russland, wo er Putin getroffen hatte und den Gazprom-Chef. Der Leser ahnt, was kommt. Ein Verhör. Was haben Sie sich dabei gedacht, Herr Kaeser? Hannes Hofbauer sagt, dass dem Wirtschaftsboss erst in diesem Moment klar geworden sei, worauf die deutsche Politik hinauslief, und er zu Kreuze gekrochen sei (S. 235). Der Rest ist Geschichte – für alle Zeiten festgehalten in diesem Buch. \ [Freie Akademie für Medien & Journalismus](https://www.freie-medienakademie.de/) @ 89ccea93:df4e00b7
2025-02-06 11:20:49I've opened a ~monero territory. I kept wanting to post things about or tangential to monero and didn't know where to shove them. Obviously ~bitcoin isn't the right place. And ~cryptocurrency didn't feel right, since for me, as a bitcoiner, monero is in a unique position. It doesn't seem to fit under the larger basket of cryptocurrencies. Many of which are scams/self-enrichment schemes. Ahem, XRP. Or just poorly implemented and pre-mined. Ahem, ETH. I don't know a lot about monero actually, but I use it and like it and think it has a place in a bitcoiners arsenal in resisting government infringements and resisting pervasive privacy shit-holes like the chain anal companies. Even Coinbase has their own proprietary chain anal. It's disgusting. They don't want us to have privacy. And many people play right into their hands by handing over their ID card and picture of their face to get bitcoins when you can get it anonymously. But I digress. Use the territory, or don't. But if you do, then welcome. originally posted at https://stacker.news/items/877547
@ 89ccea93:df4e00b7
2025-02-06 11:20:49I've opened a ~monero territory. I kept wanting to post things about or tangential to monero and didn't know where to shove them. Obviously ~bitcoin isn't the right place. And ~cryptocurrency didn't feel right, since for me, as a bitcoiner, monero is in a unique position. It doesn't seem to fit under the larger basket of cryptocurrencies. Many of which are scams/self-enrichment schemes. Ahem, XRP. Or just poorly implemented and pre-mined. Ahem, ETH. I don't know a lot about monero actually, but I use it and like it and think it has a place in a bitcoiners arsenal in resisting government infringements and resisting pervasive privacy shit-holes like the chain anal companies. Even Coinbase has their own proprietary chain anal. It's disgusting. They don't want us to have privacy. And many people play right into their hands by handing over their ID card and picture of their face to get bitcoins when you can get it anonymously. But I digress. Use the territory, or don't. But if you do, then welcome. originally posted at https://stacker.news/items/877547 @ e373ca41:b82abcc5
2025-02-06 09:25:07*This article by Milosz Matuschek first appeared in German in* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/usaid-and-co-die-ersten-kopfe-der)*** *In my first multi-part Corona series,* *[The Corona Complex](https://www.freischwebende-intelligenz.org/p/coronakomplex?utm_source=publication-search), I focused on the early inconsistencies of the "pandemic." In The Corona Connection, I will explore the key players involved in this event over multiple installments.* *It’s not yet spring, but the bud of truth is already breaking through the icy layer of lies. You can cover the truth with as much PR, manipulation, and propaganda as you want—it will only turn into compost. Because truth is rooted in something; it’s a living organism, while lies are rotting waste. The coming weeks and months will be enlightening.* ### The USAID Front Organization The grand cleanup led by Musk & Trump is in full swing. In the U.S., the agency USAID is currently being dismantled amid protests from employees. [As of Friday, February 7, nearly all staff members have lost their jobs.](https://www.usaid.gov) What does this mean? *Der Spiegel* referred to USAID as a "development agency" and reported that a nervous Bill Gates now wants to [call Trump](https://www.spiegel.de/wirtschaft/unternehmen/bill-gates-zu-stopp-der-us-auslandshilfen-donald-trump-hat-mir-seine-telefonnummer-gegeben-a-fafae10c-3163-43ea-96a4-f218050d658a) "to save lives." The *NZZ* euphemistically describes USAID as an "independent development aid agency." Seeing "AID" in the name, people think of humanitarian efforts—Bob Geldof, compassionate nuns, and "Bread for the World." In reality, USAID ("United States Agency for International Development" – claim: "From the American People") is far from just a food distribution service (although it does that too). Primarily, it serves as a [covert, rapid-response intelligence force for operations such as regime change, astroturfing, and targeted executions](https://foundationforfreedomonline.com/usaid-internal-documents-reveal-government-plot-to-promote-censorship-initiatives/)—expanding new business models for the U.S. empire. They are the enforcers who move in before "peace, democracy, and reconstruction" are declared. USAID was heavily involved in Ukraine, providing $5 billion in funding, as Robert Kennedy Jr. recently stated in an interview. The agency throws money around freely, financing both the GAVI vaccine alliance and the World Economic Forum—because, of course, these are the world's most "needy" causes. <https://x.com/ShadowofEzra/status/1886153128757629157> ### The PREDICT Program It gets even stranger. Under the so-called PREDICT program, significant funding was allocated to research coronaviruses in bats. This research was conducted in collaboration with the Wuhan Institute of Virology (WIV) and included gain-of-function experiments. In 2017, the NIH lifted a previously imposed moratorium on funding such research, paving the way for its resumption and expansion, including international partnerships like the one with WIV. USAID spent about $200 million in taxpayer money on bat virus research, with approximately $50 million going directly to WIV. Despite being a publicly funded science program, PREDICT's administrators have largely refused to release sensitive details about its research. Peter Daszak, who received substantial funding ([now cut off](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/)), even ignored some subpoenas. Officials shared information with taxpayers only reluctantly and in minimal amounts. <https://x.com/KanekoaTheGreat/status/1886098345938284813> A 2023 investigation by the *[White Coat Waste Project](https://blog.whitecoatwaste.org/2023/06/15/covid-origin-wcw-investigation-proves-u-s-govt-funded-patient-zero/)*, following a public records request, revealed that U.S. taxpayer dollars—through the NIH and USAID—flowed to the Wuhan Institute of Virology. These funds supported gain-of-function experiments in which viruses were genetically modified to increase their transmissibility or virulence. The program ended in 2019. ### The Mystery of Ben Hu One of the most explosive revelations was the identification of Ben Hu, a lead researcher at WIV, as a potential "Patient Zero." Reports indicate that he developed COVID-like symptoms as early as November 2019—before the first officially recognized cases. Hu was deeply involved in the gain-of-function experiments funded by U.S. taxpayer money. Looking further back, the picture becomes clearer. As early as 2012, USAID funds were used to capture bats in caves, including those in Mojiang, where [several miners died from a deadly respiratory illness](https://pubmed.ncbi.nlm.nih.gov/33194988/). The infection was reportedly caused by bat droppings. <https://x.com/TheSeeker268/status/1886469590701760960> Too many coincidences are piling up: The virus strain from back then, RaTG13, has striking similarities to SARS-CoV-2. Fauci’s pardon dates back to as early as 2014. A significant portion of funding from both Fauci and USAID went to Peter Daszak’s EcoHealth Alliance. Daszak in 2016 gave surprisingly candid responses regarding gain-of-function research. <https://x.com/mazemoore/status/1883378918687719725> The director of the CDC, Robert Redfield, had already pointed out in previous hearings that [U.S. public funds were used for research in Wuhan.](https://x.com/KanekoaTheGreat/status/1886126884108554352) So, to summarize here quickly, adding a question: * A CIA front organization was catching sick bats in a previous outbreak zone of deadly respiratory diseases in China (e.g., Mojiang caves) in 2012. * It funded tens of millions of dollars' worth of research to enhance the pathogenicity of coronaviruses in Wuhan. * It transferred money to Chinese military-medical institutions. * Wuhan researcher Ben Hu fell mysteriously ill and became Patient Zero. So here’s the question: Isn't a natural origin of the virus the most obvious explanation in the world? *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** #### Who still believes in a natural origin of COVID-19? The official narrative worldwide is that the virus originated naturally—perhaps from someone consuming or handling a bat at a wet market near WIV. Yet, neither the sick animal nor the first human case of "natural transmission" has ever been identified. At the same time, intelligence-backed "nudging" units worked preemptively to discredit vaccine skeptics and bolster "Trusted News Initiatives" and fact-checking programs. [Even the CIA director has now suggested that COVID may have originated in a lab.](https://apnews.com/article/covid-cia-trump-china-pandemic-lab-leak-9ab7e84c626fed68ca13c8d2e453dde1) And he likely knows exactly why. One thing is certain: The theory of natural zoonotic transmission in COVID-19 has been obliterated. It was the PR stunt of the century. A joint effort by the CIA and China—who else could pull off such a grand deception? These revelations are making the players behind the "Corona Connection" increasingly visible: a network of CIA-China partnerships, NGOs, the media apparatus, corrupt politicians, and willing, unscrupulous, or even outright sociopathic scientists. ") As these connections come to light over the next months and years, the consequences for those involved—and for society at large—will be immense. We are approaching a moment of societal reckoning. A house of cards can only stand for so long before it collapses. In Germany, Christian Drosten was one of the most aggressive proponents of the "conspiracy theory" label, frequently using it to discredit critics. As one of the main gatekeepers of the COVID narrative, he played a key role in shaping the scientific community’s response. His most steadfast domestic opponent was Hamburg physicist Roland Wiesendanger. [Drosten was one of the most outspoken propagandists of the zoonosis theory—while simultaneously working as its chief cover-up artist and deflector. He often portrayed himself as the misunderstood victim.](https://www.freischwebende-intelligenz.org/p/wanted-drosten-luege?utm_source=publication-search) This is what happens when the desire for recognition and power overshadows any sense of medical ethics. Now, serious questions arise about his role: What did he know about the research in Wuhan? Was he aware of USAID’s funding? Given that Charité (his institution) received grants from Bill Gates and that his PCR test was immediately declared the global gold standard, it seems unlikely that he knew nothing. This demands an investigative committee and legal proceedings. In the coming weeks and months, many more connections will be uncovered, fully exposing the "Corona Connection." The era of silence is over. And so is the era of immunity. *** This article was written with the **[Pareto-client](https://pareto.space/read?category=global)** on Nostr. Check it out! ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*  *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Nosta.me.](https://nosta.me/create/welcome)** 
@ e373ca41:b82abcc5
2025-02-06 09:25:07*This article by Milosz Matuschek first appeared in German in* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/usaid-and-co-die-ersten-kopfe-der)*** *In my first multi-part Corona series,* *[The Corona Complex](https://www.freischwebende-intelligenz.org/p/coronakomplex?utm_source=publication-search), I focused on the early inconsistencies of the "pandemic." In The Corona Connection, I will explore the key players involved in this event over multiple installments.* *It’s not yet spring, but the bud of truth is already breaking through the icy layer of lies. You can cover the truth with as much PR, manipulation, and propaganda as you want—it will only turn into compost. Because truth is rooted in something; it’s a living organism, while lies are rotting waste. The coming weeks and months will be enlightening.* ### The USAID Front Organization The grand cleanup led by Musk & Trump is in full swing. In the U.S., the agency USAID is currently being dismantled amid protests from employees. [As of Friday, February 7, nearly all staff members have lost their jobs.](https://www.usaid.gov) What does this mean? *Der Spiegel* referred to USAID as a "development agency" and reported that a nervous Bill Gates now wants to [call Trump](https://www.spiegel.de/wirtschaft/unternehmen/bill-gates-zu-stopp-der-us-auslandshilfen-donald-trump-hat-mir-seine-telefonnummer-gegeben-a-fafae10c-3163-43ea-96a4-f218050d658a) "to save lives." The *NZZ* euphemistically describes USAID as an "independent development aid agency." Seeing "AID" in the name, people think of humanitarian efforts—Bob Geldof, compassionate nuns, and "Bread for the World." In reality, USAID ("United States Agency for International Development" – claim: "From the American People") is far from just a food distribution service (although it does that too). Primarily, it serves as a [covert, rapid-response intelligence force for operations such as regime change, astroturfing, and targeted executions](https://foundationforfreedomonline.com/usaid-internal-documents-reveal-government-plot-to-promote-censorship-initiatives/)—expanding new business models for the U.S. empire. They are the enforcers who move in before "peace, democracy, and reconstruction" are declared. USAID was heavily involved in Ukraine, providing $5 billion in funding, as Robert Kennedy Jr. recently stated in an interview. The agency throws money around freely, financing both the GAVI vaccine alliance and the World Economic Forum—because, of course, these are the world's most "needy" causes. <https://x.com/ShadowofEzra/status/1886153128757629157> ### The PREDICT Program It gets even stranger. Under the so-called PREDICT program, significant funding was allocated to research coronaviruses in bats. This research was conducted in collaboration with the Wuhan Institute of Virology (WIV) and included gain-of-function experiments. In 2017, the NIH lifted a previously imposed moratorium on funding such research, paving the way for its resumption and expansion, including international partnerships like the one with WIV. USAID spent about $200 million in taxpayer money on bat virus research, with approximately $50 million going directly to WIV. Despite being a publicly funded science program, PREDICT's administrators have largely refused to release sensitive details about its research. Peter Daszak, who received substantial funding ([now cut off](https://oversight.house.gov/release/breaking-hhs-formally-debars-ecohealth-alliance-dr-peter-daszak-after-covid-select-reveals-pandemic-era-wrongdoing/)), even ignored some subpoenas. Officials shared information with taxpayers only reluctantly and in minimal amounts. <https://x.com/KanekoaTheGreat/status/1886098345938284813> A 2023 investigation by the *[White Coat Waste Project](https://blog.whitecoatwaste.org/2023/06/15/covid-origin-wcw-investigation-proves-u-s-govt-funded-patient-zero/)*, following a public records request, revealed that U.S. taxpayer dollars—through the NIH and USAID—flowed to the Wuhan Institute of Virology. These funds supported gain-of-function experiments in which viruses were genetically modified to increase their transmissibility or virulence. The program ended in 2019. ### The Mystery of Ben Hu One of the most explosive revelations was the identification of Ben Hu, a lead researcher at WIV, as a potential "Patient Zero." Reports indicate that he developed COVID-like symptoms as early as November 2019—before the first officially recognized cases. Hu was deeply involved in the gain-of-function experiments funded by U.S. taxpayer money. Looking further back, the picture becomes clearer. As early as 2012, USAID funds were used to capture bats in caves, including those in Mojiang, where [several miners died from a deadly respiratory illness](https://pubmed.ncbi.nlm.nih.gov/33194988/). The infection was reportedly caused by bat droppings. <https://x.com/TheSeeker268/status/1886469590701760960> Too many coincidences are piling up: The virus strain from back then, RaTG13, has striking similarities to SARS-CoV-2. Fauci’s pardon dates back to as early as 2014. A significant portion of funding from both Fauci and USAID went to Peter Daszak’s EcoHealth Alliance. Daszak in 2016 gave surprisingly candid responses regarding gain-of-function research. <https://x.com/mazemoore/status/1883378918687719725> The director of the CDC, Robert Redfield, had already pointed out in previous hearings that [U.S. public funds were used for research in Wuhan.](https://x.com/KanekoaTheGreat/status/1886126884108554352) So, to summarize here quickly, adding a question: * A CIA front organization was catching sick bats in a previous outbreak zone of deadly respiratory diseases in China (e.g., Mojiang caves) in 2012. * It funded tens of millions of dollars' worth of research to enhance the pathogenicity of coronaviruses in Wuhan. * It transferred money to Chinese military-medical institutions. * Wuhan researcher Ben Hu fell mysteriously ill and became Patient Zero. So here’s the question: Isn't a natural origin of the virus the most obvious explanation in the world? *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** #### Who still believes in a natural origin of COVID-19? The official narrative worldwide is that the virus originated naturally—perhaps from someone consuming or handling a bat at a wet market near WIV. Yet, neither the sick animal nor the first human case of "natural transmission" has ever been identified. At the same time, intelligence-backed "nudging" units worked preemptively to discredit vaccine skeptics and bolster "Trusted News Initiatives" and fact-checking programs. [Even the CIA director has now suggested that COVID may have originated in a lab.](https://apnews.com/article/covid-cia-trump-china-pandemic-lab-leak-9ab7e84c626fed68ca13c8d2e453dde1) And he likely knows exactly why. One thing is certain: The theory of natural zoonotic transmission in COVID-19 has been obliterated. It was the PR stunt of the century. A joint effort by the CIA and China—who else could pull off such a grand deception? These revelations are making the players behind the "Corona Connection" increasingly visible: a network of CIA-China partnerships, NGOs, the media apparatus, corrupt politicians, and willing, unscrupulous, or even outright sociopathic scientists. ") As these connections come to light over the next months and years, the consequences for those involved—and for society at large—will be immense. We are approaching a moment of societal reckoning. A house of cards can only stand for so long before it collapses. In Germany, Christian Drosten was one of the most aggressive proponents of the "conspiracy theory" label, frequently using it to discredit critics. As one of the main gatekeepers of the COVID narrative, he played a key role in shaping the scientific community’s response. His most steadfast domestic opponent was Hamburg physicist Roland Wiesendanger. [Drosten was one of the most outspoken propagandists of the zoonosis theory—while simultaneously working as its chief cover-up artist and deflector. He often portrayed himself as the misunderstood victim.](https://www.freischwebende-intelligenz.org/p/wanted-drosten-luege?utm_source=publication-search) This is what happens when the desire for recognition and power overshadows any sense of medical ethics. Now, serious questions arise about his role: What did he know about the research in Wuhan? Was he aware of USAID’s funding? Given that Charité (his institution) received grants from Bill Gates and that his PCR test was immediately declared the global gold standard, it seems unlikely that he knew nothing. This demands an investigative committee and legal proceedings. In the coming weeks and months, many more connections will be uncovered, fully exposing the "Corona Connection." The era of silence is over. And so is the era of immunity. *** This article was written with the **[Pareto-client](https://pareto.space/read?category=global)** on Nostr. Check it out! ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*  *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Nosta.me.](https://nosta.me/create/welcome)**  @ 89ccea93:df4e00b7
2025-02-06 08:55:27 <https://www.merriam-webster.com/dictionary/shill> I question the intellectual honesty of someone using the word "shill" to describe a Monero user. I used to hang out in DeFi circles and we had a robust understanding of the word shill. Basically it was someone financially motivated to get you do do a certain behavior. `Use platform X, buy token Y etc and get some benefit.` When in reality, they wanted you to pump the liquidity so they could dump on you. I don't see the same thing being true for Monero users. A Monero user is someone who wants one thing. Privacy. That's literally it. A Monero user doesn't want to get rich. Using Monero usually means they're taking a financial hit as Bitcoin is a better SoV. There is literally no financial gain to the Monero user if someone else uses it. It shouldn't really be debatable then that for the purpose above, privacy, Monero surpasses Bitcoin. But! Lightning!! To which I reply, so what? Lightning is okay, but it's not a panacea. It's UX is clunky at best. And perfect privacy is not a default. Many Lightning users are trusting their privacy and IP to a third party when they use it custodially. But a one-to-one comparision of Monero privacy to Lightning privacy is effectively impossible because of how many different ways there are to interact with and use Lightning. Monero privacy is extremely quantifiable. Lightning privacy is a bit more ethereal. And this post isn't the place to go into that. I just made a sister post in the ~privacy territory. originally posted at https://stacker.news/items/877476
@ 89ccea93:df4e00b7
2025-02-06 08:55:27 <https://www.merriam-webster.com/dictionary/shill> I question the intellectual honesty of someone using the word "shill" to describe a Monero user. I used to hang out in DeFi circles and we had a robust understanding of the word shill. Basically it was someone financially motivated to get you do do a certain behavior. `Use platform X, buy token Y etc and get some benefit.` When in reality, they wanted you to pump the liquidity so they could dump on you. I don't see the same thing being true for Monero users. A Monero user is someone who wants one thing. Privacy. That's literally it. A Monero user doesn't want to get rich. Using Monero usually means they're taking a financial hit as Bitcoin is a better SoV. There is literally no financial gain to the Monero user if someone else uses it. It shouldn't really be debatable then that for the purpose above, privacy, Monero surpasses Bitcoin. But! Lightning!! To which I reply, so what? Lightning is okay, but it's not a panacea. It's UX is clunky at best. And perfect privacy is not a default. Many Lightning users are trusting their privacy and IP to a third party when they use it custodially. But a one-to-one comparision of Monero privacy to Lightning privacy is effectively impossible because of how many different ways there are to interact with and use Lightning. Monero privacy is extremely quantifiable. Lightning privacy is a bit more ethereal. And this post isn't the place to go into that. I just made a sister post in the ~privacy territory. originally posted at https://stacker.news/items/877476 @ 57d1a264:69f1fee1
2025-02-06 07:38:36# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers? originally posted at https://stacker.news/items/877437
@ 57d1a264:69f1fee1
2025-02-06 07:38:36# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers? originally posted at https://stacker.news/items/877437 @ 73da3415:a8b7f470
2025-02-06 07:32:17T e s t 1
@ 73da3415:a8b7f470
2025-02-06 07:32:17T e s t 1 @ 57d1a264:69f1fee1
2025-02-06 07:28:25# Looking at bitcoin's layered architecture (base layer and Lightning Network), can you explain why this approach was necessary? What are the trade-offs between transacting on each layer? originally posted at https://stacker.news/items/877429
@ 57d1a264:69f1fee1
2025-02-06 07:28:25# Looking at bitcoin's layered architecture (base layer and Lightning Network), can you explain why this approach was necessary? What are the trade-offs between transacting on each layer? originally posted at https://stacker.news/items/877429 @ da0b9bc3:4e30a4a9
2025-02-06 06:38:33Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/877410
@ da0b9bc3:4e30a4a9
2025-02-06 06:38:33Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/877410 @ 3ffac3a6:2d656657
2025-02-06 03:58:47## Motivations Recently, my sites hosted behind Cloudflare tunnels mysteriously stopped working—not once, but twice. The first outage occurred about a week ago. Interestingly, when I switched to using the 1.1.1.1 WARP VPN on my cellphone or PC, the sites became accessible again. Clearly, the issue wasn't with the sites themselves but something about the routing. This led me to the brilliant (or desperate) idea of routing all Cloudflare-bound traffic through a WARP tunnel in my local network. ## Prerequisites - A "server" with an **amd64 processor** (the WARP client only works on amd64 architecture). I'm using an old mac mini, but really, anything with an amd64 processor will do. - Basic knowledge of Linux commands. - Access to your Wi-Fi router's settings (if you plan to configure routes there). --- ## Step 1: Installing the WARP CLI 1. **Update your system packages:** ```bash sudo apt update && sudo apt upgrade -y ``` 2. **Download and install the WARP CLI:** ```bash curl https://pkg.cloudflareclient.com/pubkey.gpg | sudo gpg --yes --dearmor --output /usr/share/keyrings/cloudflare-warp-archive-keyring.gpg echo "deb [arch=amd64 signed-by=/usr/share/keyrings/cloudflare-warp-archive-keyring.gpg] https://pkg.cloudflareclient.com/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflare-client.list sudo apt-get update && sudo apt-get install cloudflare-warp ``` 3. **Register and connect to WARP:** Run the following commands to register and connect to WARP: ```bash sudo warp-cli register sudo warp-cli connect ```` Confirm the connection with: ```bash warp-cli status ``` --- ## Step 2: Routing Traffic on the Server Machine Now that WARP is connected, let's route the local network's Cloudflare-bound traffic through this tunnel. 1. **Enable IP forwarding:** ```bash sudo sysctl -w net.ipv4.ip_forward=1 ``` Make it persistent after reboot: ```bash echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf sudo sysctl -p ``` 2. **Set up firewall rules to forward traffic:** ```bash sudo nft add rule ip filter FORWARD iif "eth0" oif "CloudflareWARP" ip saddr 192.168.31.0/24 ip daddr 104.0.0.0/8 accept sudo nft add rule ip filter FORWARD iif "CloudflareWARP" oif "eth0" ip saddr 104.0.0.0/8 ip daddr 192.168.31.0/24 ct state established,related accept ``` Replace `eth0` with your actual network interface if different. 3. **Make rules persistent:** ```bash sudo apt install nftables sudo nft list ruleset > /etc/nftables.conf ``` --- ## Step 3: Configuring the Route on a Local PC (Linux) On your local Linux machine: 1. **Add a static route:** ```bash sudo ip route add 104.0.0.0/24 via <SERVER_IP> ``` Replace `<SERVER_IP>` with the internal IP of your WARP-enabled server. This should be a temporary solution, since it only effects a local machine. For a solution that can effect the whole local network, please see next step. --- ## Step 4: Configuring the Route on Your Wi-Fi Router (Recommended) If your router allows adding static routes: 1. **Log in to your router's admin interface.** 2. **Navigate to the Static Routing section.** (This may vary depending on the router model.) 3. **Add a new static route:** - **Destination Network:** `104.0.0.0` - **Subnet Mask:** `255.255.255.0` - **Gateway:** `<SERVER_IP>` - **Metric:** `1` (or leave it default) 4. **Save and apply the settings.** One of the key advantages of this method is how easy it is to disable once your ISP's routing issues are resolved. Since the changes affect the entire network at once, you can quickly restore normal network behavior by simply removing the static routes or disabling the forwarding rules, all without the need for complex reconfigurations. --- ## Final Thoughts Congratulations! You've now routed all your Cloudflare-bound traffic through a secure WARP tunnel, effectively bypassing mysterious connectivity issues. If the sites ever go down again, at least you’ll have one less thing to blame—and one more thing to debug.
@ 3ffac3a6:2d656657
2025-02-06 03:58:47## Motivations Recently, my sites hosted behind Cloudflare tunnels mysteriously stopped working—not once, but twice. The first outage occurred about a week ago. Interestingly, when I switched to using the 1.1.1.1 WARP VPN on my cellphone or PC, the sites became accessible again. Clearly, the issue wasn't with the sites themselves but something about the routing. This led me to the brilliant (or desperate) idea of routing all Cloudflare-bound traffic through a WARP tunnel in my local network. ## Prerequisites - A "server" with an **amd64 processor** (the WARP client only works on amd64 architecture). I'm using an old mac mini, but really, anything with an amd64 processor will do. - Basic knowledge of Linux commands. - Access to your Wi-Fi router's settings (if you plan to configure routes there). --- ## Step 1: Installing the WARP CLI 1. **Update your system packages:** ```bash sudo apt update && sudo apt upgrade -y ``` 2. **Download and install the WARP CLI:** ```bash curl https://pkg.cloudflareclient.com/pubkey.gpg | sudo gpg --yes --dearmor --output /usr/share/keyrings/cloudflare-warp-archive-keyring.gpg echo "deb [arch=amd64 signed-by=/usr/share/keyrings/cloudflare-warp-archive-keyring.gpg] https://pkg.cloudflareclient.com/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflare-client.list sudo apt-get update && sudo apt-get install cloudflare-warp ``` 3. **Register and connect to WARP:** Run the following commands to register and connect to WARP: ```bash sudo warp-cli register sudo warp-cli connect ```` Confirm the connection with: ```bash warp-cli status ``` --- ## Step 2: Routing Traffic on the Server Machine Now that WARP is connected, let's route the local network's Cloudflare-bound traffic through this tunnel. 1. **Enable IP forwarding:** ```bash sudo sysctl -w net.ipv4.ip_forward=1 ``` Make it persistent after reboot: ```bash echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf sudo sysctl -p ``` 2. **Set up firewall rules to forward traffic:** ```bash sudo nft add rule ip filter FORWARD iif "eth0" oif "CloudflareWARP" ip saddr 192.168.31.0/24 ip daddr 104.0.0.0/8 accept sudo nft add rule ip filter FORWARD iif "CloudflareWARP" oif "eth0" ip saddr 104.0.0.0/8 ip daddr 192.168.31.0/24 ct state established,related accept ``` Replace `eth0` with your actual network interface if different. 3. **Make rules persistent:** ```bash sudo apt install nftables sudo nft list ruleset > /etc/nftables.conf ``` --- ## Step 3: Configuring the Route on a Local PC (Linux) On your local Linux machine: 1. **Add a static route:** ```bash sudo ip route add 104.0.0.0/24 via <SERVER_IP> ``` Replace `<SERVER_IP>` with the internal IP of your WARP-enabled server. This should be a temporary solution, since it only effects a local machine. For a solution that can effect the whole local network, please see next step. --- ## Step 4: Configuring the Route on Your Wi-Fi Router (Recommended) If your router allows adding static routes: 1. **Log in to your router's admin interface.** 2. **Navigate to the Static Routing section.** (This may vary depending on the router model.) 3. **Add a new static route:** - **Destination Network:** `104.0.0.0` - **Subnet Mask:** `255.255.255.0` - **Gateway:** `<SERVER_IP>` - **Metric:** `1` (or leave it default) 4. **Save and apply the settings.** One of the key advantages of this method is how easy it is to disable once your ISP's routing issues are resolved. Since the changes affect the entire network at once, you can quickly restore normal network behavior by simply removing the static routes or disabling the forwarding rules, all without the need for complex reconfigurations. --- ## Final Thoughts Congratulations! You've now routed all your Cloudflare-bound traffic through a secure WARP tunnel, effectively bypassing mysterious connectivity issues. If the sites ever go down again, at least you’ll have one less thing to blame—and one more thing to debug. @ a012dc82:6458a70d
2025-02-06 02:34:44In an unexpected turn of events that has sent ripples through the cryptocurrency world, Changpeng Zhao, the CEO of Binance, has extended his stay in the United States. This development is particularly striking against the backdrop of Binance's ongoing legal challenges and the intense scrutiny it faces from regulators worldwide. Zhao's decision to remain in the U.S. longer than anticipated is not just a personal choice but a strategic move that could have far-reaching implications for Binance's global operations and the cryptocurrency industry at large. It raises questions about Binance's future strategies and its efforts to navigate the complex web of international regulations. **Table Of Content** - Background: Binance's Regulatory Challenges - Changpeng Zhao's Role and Influence - The Unexpected U.S. Stay - Legal Considerations - Future of Binance and Crypto Regulation - Conclusion - FAQs **Background: Binance's Regulatory Challenges** Binance has emerged as a dominant force in the cryptocurrency exchange market, known for its vast selection of digital assets and high trading volumes. However, this success has not come without its share of challenges. The platform has been under the microscope of regulators across the globe, facing scrutiny over its compliance with stringent anti-money laundering (AML) standards and consumer protection laws. These regulatory hurdles have manifested in various forms, including formal warnings from financial watchdogs, in-depth investigations by regulatory authorities, and outright bans in certain jurisdictions. These challenges highlight the precarious position Binance occupies in the global financial landscape and underscore the delicate balance it must maintain between innovation and regulatory compliance. **Changpeng Zhao's Role and Influence** Changpeng Zhao, affectionately known as "CZ" in the crypto community, is more than just the CEO of Binance; he is a visionary and a key influencer in the cryptocurrency sector. Since founding Binance in 2017, Zhao has steered the company through exponential growth, navigating the volatile waters of the crypto market with a blend of technological innovation and strategic foresight. However, this journey has been fraught with controversies, particularly around issues of regulatory compliance and operational transparency. As the face and voice of Binance, Zhao's decisions, public statements, and even his personal movements are closely watched and analyzed for insights into Binance's future direction and its stance on regulatory matters. **The Unexpected U.S. Stay** The news of Zhao's extended stay in the U.S. has sparked a flurry of speculation and analysis within the financial and cryptocurrency sectors. This move is particularly intriguing given the current regulatory climate in the U.S., which is known for its stringent financial oversight and tough stance on cryptocurrency regulation. The extended stay raises several questions: Is Zhao seeking to engage in high-level negotiations with U.S. regulators? Is Binance planning a strategic pivot or expansion in the U.S. market? Or is this a proactive measure to address some of the legal challenges facing the company? Whatever the reason, Zhao's presence in the U.S. is a clear indication that significant developments are underway for Binance in one of the world's most important financial markets. **Implications for Binance** Zhao's decision to extend his stay in the U.S. could be interpreted as a strategic move to align Binance more closely with U.S. regulatory frameworks. This could involve enhancing the company's compliance systems, engaging in more transparent dialogue with regulatory bodies, or even restructuring some of Binance's business practices to conform to U.S. standards. Such changes could be crucial for Binance's continued operation and growth in the U.S. market, potentially opening doors to new partnerships, investment opportunities, and a broader customer base. Moreover, a stronger foothold in the U.S. could enhance Binance's reputation globally, signaling its commitment to regulatory compliance and financial stability. **Industry Reactions** The cryptocurrency industry and financial markets are abuzz with discussions about Zhao's extended stay in the U.S. Analysts, investors, and other industry players are keenly observing this development, understanding that Zhao's actions could signal a new chapter for Binance and possibly the entire cryptocurrency sector. His stay is being interpreted as a sign of Binance's willingness to engage more proactively with regulatory bodies, a move that could have significant implications for how cryptocurrency businesses operate globally. Additionally, Zhao's presence in the U.S. could influence other cryptocurrency exchanges and startups, setting a precedent for how they might approach regulatory challenges and market expansion. **Legal Considerations** Zhao's prolonged presence in the U.S. coincides with a critical period for Binance as it navigates complex legal waters. His decision to stay could be instrumental in facilitating more direct and effective engagement with U.S. legal authorities and regulatory bodies. This proximity to the heart of U.S. financial regulation might enable more constructive dialogues, potentially leading to resolutions or progress in the various legal cases and investigations Binance is currently involved in. Zhao's hands-on involvement in these legal matters could be a game-changer, offering opportunities for negotiation, compliance, and possibly even reconciliation with regulatory authorities. **Potential Outcomes** The involvement of Zhao in legal and regulatory discussions in the U.S. could lead to a spectrum of outcomes for Binance. These might range from reaching amicable settlements and forming robust compliance agreements to facing more stringent regulatory actions or operational restrictions, depending on the nature of the negotiations and the willingness of both parties to find common ground. The outcomes of these engagements are likely to have a significant impact on Binance's operational framework, its global reputation, and its ability to compete in the international market. They could also set important precedents for how major cryptocurrency exchanges interact with regulatory bodies and navigate legal challenges. **Future of Binance and Crypto Regulation** Zhao's decision to extend his stay in the U.S. is a pivotal moment in the evolving narrative of cryptocurrency regulation. It underscores the increasing importance of regulatory compliance for major players in the crypto space and suggests a potential shift towards more collaborative and proactive approaches between industry leaders and regulatory bodies. This development could be a harbinger of a new era in cryptocurrency regulation, where open dialogue, transparency, and compliance play central roles in shaping the industry's future. **Strategic Shifts for Binance** Depending on the outcomes of Zhao's engagements in the U.S., Binance may undergo significant strategic shifts, particularly in its approach to regulatory compliance, operational transparency, and market strategy. These shifts could have far-reaching implications, not only for Binance but for the entire cryptocurrency exchange industry. They could set new standards for regulatory compliance, influence the development of new financial products and services, and shape the future landscape of the global cryptocurrency market. **Conclusion** Changpeng Zhao's unexpected extended stay in the United States represents a critical and potentially transformative moment in Binance's ongoing legal and regulatory saga. It reflects the complex and dynamic nature of cryptocurrency regulation and the necessity for industry leaders to adeptly navigate these challenges. As the crypto community and financial markets watch closely, the decisions and actions taken by Zhao in the coming days and weeks could have far-reaching implications for Binance's future, its position in the global market, and the broader trajectory of the cryptocurrency industry. **FAQs** **What challenges is Binance currently facing?** Binance is grappling with regulatory scrutiny worldwide, particularly concerning anti-money laundering standards and consumer protection laws. This has led to investigations, warnings, and bans in several countries. **How might Zhao's stay in the U.S. impact Binance?** Zhao's extended stay could signal a move towards greater regulatory compliance and cooperation in the U.S., potentially leading to operational changes and enhanced market access for Binance. **What are the potential outcomes of Zhao's U.S. engagements?** Outcomes could range from amicable settlements and compliance agreements to more stringent regulatory actions, depending on the nature of Zhao's discussions with U.S. authorities. **How could this development affect the broader cryptocurrency industry?** Zhao's actions could set a precedent for cryptocurrency exchanges in terms of regulatory compliance and engagement, influencing the global cryptocurrency regulatory landscape. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-06 02:34:44In an unexpected turn of events that has sent ripples through the cryptocurrency world, Changpeng Zhao, the CEO of Binance, has extended his stay in the United States. This development is particularly striking against the backdrop of Binance's ongoing legal challenges and the intense scrutiny it faces from regulators worldwide. Zhao's decision to remain in the U.S. longer than anticipated is not just a personal choice but a strategic move that could have far-reaching implications for Binance's global operations and the cryptocurrency industry at large. It raises questions about Binance's future strategies and its efforts to navigate the complex web of international regulations. **Table Of Content** - Background: Binance's Regulatory Challenges - Changpeng Zhao's Role and Influence - The Unexpected U.S. Stay - Legal Considerations - Future of Binance and Crypto Regulation - Conclusion - FAQs **Background: Binance's Regulatory Challenges** Binance has emerged as a dominant force in the cryptocurrency exchange market, known for its vast selection of digital assets and high trading volumes. However, this success has not come without its share of challenges. The platform has been under the microscope of regulators across the globe, facing scrutiny over its compliance with stringent anti-money laundering (AML) standards and consumer protection laws. These regulatory hurdles have manifested in various forms, including formal warnings from financial watchdogs, in-depth investigations by regulatory authorities, and outright bans in certain jurisdictions. These challenges highlight the precarious position Binance occupies in the global financial landscape and underscore the delicate balance it must maintain between innovation and regulatory compliance. **Changpeng Zhao's Role and Influence** Changpeng Zhao, affectionately known as "CZ" in the crypto community, is more than just the CEO of Binance; he is a visionary and a key influencer in the cryptocurrency sector. Since founding Binance in 2017, Zhao has steered the company through exponential growth, navigating the volatile waters of the crypto market with a blend of technological innovation and strategic foresight. However, this journey has been fraught with controversies, particularly around issues of regulatory compliance and operational transparency. As the face and voice of Binance, Zhao's decisions, public statements, and even his personal movements are closely watched and analyzed for insights into Binance's future direction and its stance on regulatory matters. **The Unexpected U.S. Stay** The news of Zhao's extended stay in the U.S. has sparked a flurry of speculation and analysis within the financial and cryptocurrency sectors. This move is particularly intriguing given the current regulatory climate in the U.S., which is known for its stringent financial oversight and tough stance on cryptocurrency regulation. The extended stay raises several questions: Is Zhao seeking to engage in high-level negotiations with U.S. regulators? Is Binance planning a strategic pivot or expansion in the U.S. market? Or is this a proactive measure to address some of the legal challenges facing the company? Whatever the reason, Zhao's presence in the U.S. is a clear indication that significant developments are underway for Binance in one of the world's most important financial markets. **Implications for Binance** Zhao's decision to extend his stay in the U.S. could be interpreted as a strategic move to align Binance more closely with U.S. regulatory frameworks. This could involve enhancing the company's compliance systems, engaging in more transparent dialogue with regulatory bodies, or even restructuring some of Binance's business practices to conform to U.S. standards. Such changes could be crucial for Binance's continued operation and growth in the U.S. market, potentially opening doors to new partnerships, investment opportunities, and a broader customer base. Moreover, a stronger foothold in the U.S. could enhance Binance's reputation globally, signaling its commitment to regulatory compliance and financial stability. **Industry Reactions** The cryptocurrency industry and financial markets are abuzz with discussions about Zhao's extended stay in the U.S. Analysts, investors, and other industry players are keenly observing this development, understanding that Zhao's actions could signal a new chapter for Binance and possibly the entire cryptocurrency sector. His stay is being interpreted as a sign of Binance's willingness to engage more proactively with regulatory bodies, a move that could have significant implications for how cryptocurrency businesses operate globally. Additionally, Zhao's presence in the U.S. could influence other cryptocurrency exchanges and startups, setting a precedent for how they might approach regulatory challenges and market expansion. **Legal Considerations** Zhao's prolonged presence in the U.S. coincides with a critical period for Binance as it navigates complex legal waters. His decision to stay could be instrumental in facilitating more direct and effective engagement with U.S. legal authorities and regulatory bodies. This proximity to the heart of U.S. financial regulation might enable more constructive dialogues, potentially leading to resolutions or progress in the various legal cases and investigations Binance is currently involved in. Zhao's hands-on involvement in these legal matters could be a game-changer, offering opportunities for negotiation, compliance, and possibly even reconciliation with regulatory authorities. **Potential Outcomes** The involvement of Zhao in legal and regulatory discussions in the U.S. could lead to a spectrum of outcomes for Binance. These might range from reaching amicable settlements and forming robust compliance agreements to facing more stringent regulatory actions or operational restrictions, depending on the nature of the negotiations and the willingness of both parties to find common ground. The outcomes of these engagements are likely to have a significant impact on Binance's operational framework, its global reputation, and its ability to compete in the international market. They could also set important precedents for how major cryptocurrency exchanges interact with regulatory bodies and navigate legal challenges. **Future of Binance and Crypto Regulation** Zhao's decision to extend his stay in the U.S. is a pivotal moment in the evolving narrative of cryptocurrency regulation. It underscores the increasing importance of regulatory compliance for major players in the crypto space and suggests a potential shift towards more collaborative and proactive approaches between industry leaders and regulatory bodies. This development could be a harbinger of a new era in cryptocurrency regulation, where open dialogue, transparency, and compliance play central roles in shaping the industry's future. **Strategic Shifts for Binance** Depending on the outcomes of Zhao's engagements in the U.S., Binance may undergo significant strategic shifts, particularly in its approach to regulatory compliance, operational transparency, and market strategy. These shifts could have far-reaching implications, not only for Binance but for the entire cryptocurrency exchange industry. They could set new standards for regulatory compliance, influence the development of new financial products and services, and shape the future landscape of the global cryptocurrency market. **Conclusion** Changpeng Zhao's unexpected extended stay in the United States represents a critical and potentially transformative moment in Binance's ongoing legal and regulatory saga. It reflects the complex and dynamic nature of cryptocurrency regulation and the necessity for industry leaders to adeptly navigate these challenges. As the crypto community and financial markets watch closely, the decisions and actions taken by Zhao in the coming days and weeks could have far-reaching implications for Binance's future, its position in the global market, and the broader trajectory of the cryptocurrency industry. **FAQs** **What challenges is Binance currently facing?** Binance is grappling with regulatory scrutiny worldwide, particularly concerning anti-money laundering standards and consumer protection laws. This has led to investigations, warnings, and bans in several countries. **How might Zhao's stay in the U.S. impact Binance?** Zhao's extended stay could signal a move towards greater regulatory compliance and cooperation in the U.S., potentially leading to operational changes and enhanced market access for Binance. **What are the potential outcomes of Zhao's U.S. engagements?** Outcomes could range from amicable settlements and compliance agreements to more stringent regulatory actions, depending on the nature of Zhao's discussions with U.S. authorities. **How could this development affect the broader cryptocurrency industry?** Zhao's actions could set a precedent for cryptocurrency exchanges in terms of regulatory compliance and engagement, influencing the global cryptocurrency regulatory landscape. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ fe32298e:20516265
2025-02-06 02:11:34I've been using AI tools to help with coding for a while now, but it's always been copy/pasting into ChatGPT and DeepSeek. Faster iteration is better, and privacy is best. So it's time to figure out how to use these tools integrated into [VSCodium](https://github.com/VSCodium/vscodium) and running locally. After a quick review of the most popular extensions I've heard about, I settled on [Tabby](https://github.com/TabbyML/tabby). ## What the heck does this actually DO? * Code completion - like autocomplete suggestions, looks at your code and suggests the next thing to type at the cursor. You can see it in gray text, then press Tab and it's added to your code. * Chat - easily chat with an LLM about your code inside your editor, faster than copy/pasting into a website. * Apparently it can write docs and tests too. ## Can I run it locally? Without a GPU? YES! Tabby is optimized for small models that only need a few GBs of RAM. I'm using a fairly old [System76](https://system76.com/) Galago Pro with Core i5-10210U and 16 GB RAM. The fans spin up, and Tabby sometimes shows a warning about slow response time, but it seems usable. ## How do I get it set up? This is the overview, look for step-by-step instructions at the end of this article. 1. Install the Tabby server, which runs locally. 1. Start the Tabby server and tell it to serve some models which it will download automatically. 1. Log in to the Tabby server web interface and create an admin account. 1. Install the Tabby extension in your editor. 1. Connect the Tabby extension to your Tabby server. ## How do I actually use it? 1. Click **Tabby** in the bottom-right corner to open the Tabby command palette. 1. Select **Chat** to open the Chat pane. Drag it to the right side if you want. 1. Or, *Ctrl-Shift-P* and type "tabby" to see some Tabby commands 1. Select some code and *Ctrl-Shift-P* "tabby" to see more Tabby commands 1. **Explain this** seems like a useful one. Other than that, I don't know! I just started using it today. ## What model should I use? As usual, it depends. If you're using CPU instead of GPU, start with the ones recommended by Tabby and shown in the Step-by-Step below. Tabby has a [registry of models](https://tabby.tabbyml.com/docs/models/) you can choose from, and a [leaderboard](https://leaderboard.tabbyml.com/) to compare them. ## Step-by-Step This is for Ubuntu 24.04, and no GPU. ``` # install pre-reqs sudo apt install build-essential cmake libssl-dev pkg-config sudo apt install protobuf-compiler libopenblas-dev sudo apt install make sqlite3 graphviz # install rust curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh . "$HOME/.cargo/env" # build tabby git clone --recurse-submodules https://github.com/TabbyML/tabby cd tabby cargo build # run tabby (downloads ~3 GB of models) ./target/debug/tabby serve --model StarCoder-1B --chat-model Qwen2-1.5B-Instruct # browse to http://0.0.0.0:8080 and create an admin user ``` * Install the Tabby extension in your editor. VSCodium had it in the extensions store by searching for "tabby" or try this `ext install TabbyML.vscode-tabby` * *Ctrl-Shift-P* and look for "Tabby: Connect to server" * Use the default of `http://localhost:8080` * Switch over to the Tabby web interface, click your Profile Picture and copy the auth token * Paste that into Tabby somewhere. I'm sure you'll figure it out if you got this far.
@ fe32298e:20516265
2025-02-06 02:11:34I've been using AI tools to help with coding for a while now, but it's always been copy/pasting into ChatGPT and DeepSeek. Faster iteration is better, and privacy is best. So it's time to figure out how to use these tools integrated into [VSCodium](https://github.com/VSCodium/vscodium) and running locally. After a quick review of the most popular extensions I've heard about, I settled on [Tabby](https://github.com/TabbyML/tabby). ## What the heck does this actually DO? * Code completion - like autocomplete suggestions, looks at your code and suggests the next thing to type at the cursor. You can see it in gray text, then press Tab and it's added to your code. * Chat - easily chat with an LLM about your code inside your editor, faster than copy/pasting into a website. * Apparently it can write docs and tests too. ## Can I run it locally? Without a GPU? YES! Tabby is optimized for small models that only need a few GBs of RAM. I'm using a fairly old [System76](https://system76.com/) Galago Pro with Core i5-10210U and 16 GB RAM. The fans spin up, and Tabby sometimes shows a warning about slow response time, but it seems usable. ## How do I get it set up? This is the overview, look for step-by-step instructions at the end of this article. 1. Install the Tabby server, which runs locally. 1. Start the Tabby server and tell it to serve some models which it will download automatically. 1. Log in to the Tabby server web interface and create an admin account. 1. Install the Tabby extension in your editor. 1. Connect the Tabby extension to your Tabby server. ## How do I actually use it? 1. Click **Tabby** in the bottom-right corner to open the Tabby command palette. 1. Select **Chat** to open the Chat pane. Drag it to the right side if you want. 1. Or, *Ctrl-Shift-P* and type "tabby" to see some Tabby commands 1. Select some code and *Ctrl-Shift-P* "tabby" to see more Tabby commands 1. **Explain this** seems like a useful one. Other than that, I don't know! I just started using it today. ## What model should I use? As usual, it depends. If you're using CPU instead of GPU, start with the ones recommended by Tabby and shown in the Step-by-Step below. Tabby has a [registry of models](https://tabby.tabbyml.com/docs/models/) you can choose from, and a [leaderboard](https://leaderboard.tabbyml.com/) to compare them. ## Step-by-Step This is for Ubuntu 24.04, and no GPU. ``` # install pre-reqs sudo apt install build-essential cmake libssl-dev pkg-config sudo apt install protobuf-compiler libopenblas-dev sudo apt install make sqlite3 graphviz # install rust curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh . "$HOME/.cargo/env" # build tabby git clone --recurse-submodules https://github.com/TabbyML/tabby cd tabby cargo build # run tabby (downloads ~3 GB of models) ./target/debug/tabby serve --model StarCoder-1B --chat-model Qwen2-1.5B-Instruct # browse to http://0.0.0.0:8080 and create an admin user ``` * Install the Tabby extension in your editor. VSCodium had it in the extensions store by searching for "tabby" or try this `ext install TabbyML.vscode-tabby` * *Ctrl-Shift-P* and look for "Tabby: Connect to server" * Use the default of `http://localhost:8080` * Switch over to the Tabby web interface, click your Profile Picture and copy the auth token * Paste that into Tabby somewhere. I'm sure you'll figure it out if you got this far. @ 5d4b6c8d:8a1c1ee3
2025-02-06 00:49:05Herbs and spices don't just taste great. Most of the time they're also great for you. - Spicier foods ironically are strongly anti-inflammatory and chronic inflammation is one of the major drivers of poor health - Roots, like turmeric/ginger/garlic/onion, are also strongly anti-inflammatory - Herbs, like parsley and oregano, are super high in vitamins K, C, beta carotene, folate, and others, as well as potassium, manganese, and other minerals. - Seeds, like cumin or coriander, are super mineral dense. - Sea salt (unrefined) has a broad array and excellent balance of minerals. So, what's the health principle? Eat tastier more flavorful food. It's tasty because it's good for us (shut up sugar!). originally posted at https://stacker.news/items/877209
@ 5d4b6c8d:8a1c1ee3
2025-02-06 00:49:05Herbs and spices don't just taste great. Most of the time they're also great for you. - Spicier foods ironically are strongly anti-inflammatory and chronic inflammation is one of the major drivers of poor health - Roots, like turmeric/ginger/garlic/onion, are also strongly anti-inflammatory - Herbs, like parsley and oregano, are super high in vitamins K, C, beta carotene, folate, and others, as well as potassium, manganese, and other minerals. - Seeds, like cumin or coriander, are super mineral dense. - Sea salt (unrefined) has a broad array and excellent balance of minerals. So, what's the health principle? Eat tastier more flavorful food. It's tasty because it's good for us (shut up sugar!). originally posted at https://stacker.news/items/877209