-

@ 6bae33c8:607272e8
2024-11-12 09:53:33
So much for my [Jonnu Smith premonition](https://www.realmansports.com/p/week-10-observations-439). For a garbage game, he wasn’t terrible and almost scored a TD, but that was a tough watch overall. The Dolphins sling it around to so many different players, while the Rams have their shallow, rock-solid three-player tree that produces even when they fail to score a touchdown. I also spoiled it by accidentally glimpsing the final score while checking the price of bitcoin this morning — totally forgot there was even a game.
- I don’t know if Tua is still rusty, or the Dolphins have been solved, but there just isn’t any rhythm to the offense that was so unstoppable at times last year.
- How is the Rams defense better without Aaron Donald? It’s like they suddenly got faster, younger and more aggressive, the entire unit. It goes to show how much we don’t know, and how overrated names on jerseys are.
- The Dolphins defense was also nasty. I had expected this to be a shootout.
- De’Von Achane is so fast once he gets going, but the Rams rarely let that happen.
- Smith is a weapon, and he’s a significant part of the offense, but they spread it around so much.
- Jaylen Waddle had a bad drop, but they seemed to want to get him involved early.
- Tyreek Hill is one of the stranger busts in recent memory. He looks just as fast, but after Tua got hurt they just never regained interest in getting him the necessary looks.
- As I said, Cooper Kupp, Puka Nacua and Kyren Williams are rocks — the entire rest of the offense barely sees any touches.
- One odd thing when you know the final score is trying to figure out in real time how it gets there. When the Rams were down 20-9 with five minutes left, I was sure they would get the TD and fail on the two point conversion to make it 20-15. But instead they kicked the FG, the Dolphins got their FG, and the Rams kicked yet another FG before a failed onside kick.
-

@ 1b5ee74d:bb1aae6e
2024-11-12 09:42:20
Last July, I published an article highlighting the shifting narrative around the so-called "Bitcoin President" in the United States. **An expression that should—must—sound absurd** to anyone who has taken even a cursory look at the technology Satoshi Nakamoto introduced. It's evident that **no such thing as a Bitcoin President exists**. And if you're wondering what I think: no, not even him.
**Not even Nayib Bukele**, the President of El Salvador, the first country to adopt Bitcoin as legal tender, can be considered as such. Do you think the promotion of a **centralized, government-controlled wallet** like Chivo aligns with the values that gave birth to Bitcoin?\
But let's return to the United States. The intense lobbying efforts of BTC Inc—the company behind Bitcoin Magazine—first positioned **Robert Kennedy Jr. as the Bitcoin Candidate**, only to swiftly pivot to **Donald Trump** despite his repeated anti-cryptocurrency remarks and his staunch support for the dollar's supremacy.
After an electoral campaign of relentless brainwashing, how did Italian mainstream media interpret Bitcoin's relationship with U.S. politics?
### Orange Coin and Orange President
The wave of articles published by Italian and international outlets reveals a telling trend: **a systematic association between Bitcoin and Donald Trump following his reelection**. The headlines in the following examples illustrate how this connection was constructed to imbue the cryptocurrency with a specific political connotation, aligned with conservative and Republican positions.
**Fanpage** kicks off with a headline that takes for granted the causal link between Trump's reelection and Bitcoin's price surge: *"Why Bitcoin is Soaring After Trump's Election."* At least the article notes that the tycoon, during his first term, called cryptocurrencies a "*scam*," only to drastically change his stance later.
**ANSA** adopts an even more emphatic approach: Bitcoin, Wall Street, and the dollar are portrayed as a harmonious trio, collectively celebrating Trump’s return to the White House. The association between Bitcoin and the dollar, however, is paradoxical. Bitcoin was created as an alternative to the dollar—a tool to escape expansionary monetary policies and inflation. Reducing it to a mere appendage of Republican economic policies misses the very reason for Bitcoin's existence.
**Corriere della Sera** headline reads: *"With Trump’s Victory, New Record for Bitcoin."* The newspaper leans into sensationalism, linking Bitcoin’s new all-time high to Trump’s electoral victory. The article goes on to mention figures like Elon Musk, attempting to tie the fortunes of the crypto sector to a series of controversial yet highly charismatic personalities.
In short, the idea that Bitcoin owes its growth solely to political events or the support of specific individuals is misleading. The notion that its price hinges on a particular election is not only simplistic but ignores decades of market cycles and economic data showing that Bitcoin responds to more complex dynamics such as global liquidity and technological adoption.
**Il Giornale** doesn't escape this fallacy either: *"Trump Boosts Stocks and Bitcoin."*
The daily draws a direct connection between stock market enthusiasm and Bitcoin's rally, highlighting how Trump's reelection has galvanized both Piazza Affari and cryptocurrencies. This narrative perpetuates the notion that Bitcoin and traditional equities move in lockstep, overlooking Bitcoin's historical decorrelation from traditional assets during critical moments.
The idea of a natural alliance between Trump and Bitcoin is reinforced without any solid evidence. On the contrary, Bitcoin investors aren't celebrating a president; they are responding to a broader macroeconomic environment where loose monetary policies and growing distrust in fiat currencies play a crucial role.
-

@ a012dc82:6458a70d
2024-11-12 05:33:23
**Table Of Content**
- Bitcoin-Backed Life Insurance Startup: An Overview
- How Does It Work?
- Advantages of Bitcoin-Backed Life Insurance
- Conclusion
- FAQ
In the world of cryptocurrencies, innovation knows no bounds. The latest groundbreaking development comes in the form of a Bitcoin-backed life insurance startup that has recently launched with a staggering $19 million investment. This bold venture aims to revolutionize the insurance industry by leveraging the power of blockchain technology and digital assets to provide individuals with a secure and transparent life insurance solution. In this article, we will explore the details of this startup, its unique offering, and the potential implications it may have for the future of insurance.
**Bitcoin-Backed Life Insurance Startup: An Overview**
The Bitcoin-backed life insurance startup, which recently entered the market with a substantial investment of $19 million, aims to disrupt the traditional insurance model by incorporating the benefits of blockchain technology and cryptocurrency. This innovative approach allows policyholders to secure their life insurance coverage using Bitcoin, a popular digital currency known for its decentralized and secure nature.
By utilizing Bitcoin as a backing asset, this startup can offer policyholders several advantages, such as increased transparency, faster claim settlements, and enhanced security. Moreover, the integration of blockchain technology ensures that all policy-related transactions are recorded on an immutable ledger, minimizing the risk of fraud and manipulation.
**How Does It Work?**
**Policy Creation Process**
To initiate a policy with this Bitcoin-backed life insurance startup, individuals can visit their user-friendly website and follow a simple step-by-step process. Users are required to provide personal information, undergo a risk assessment, and choose their desired coverage amount.
**Bitcoin as Collateral**
Unlike traditional life insurance policies that rely on fiat currency, this startup allows policyholders to secure their coverage by depositing a predetermined amount of Bitcoin as collateral. This collateral not only guarantees the payout in case of the policyholder's demise but also serves as an investment that can appreciate over time.
**Smart Contracts and Claims**
The integration of smart contract technology enables automated claim settlements, eliminating the need for lengthy paperwork and reducing processing times. When a claim is filed, the smart contract verifies the validity of the claim against predefined conditions and automatically executes the payout process, ensuring a seamless and efficient experience for policyholders and beneficiaries.
**Advantages of Bitcoin-Backed Life Insurance**
**Transparency and Security**
With the utilization of blockchain technology, this Bitcoin-backed life insurance startup brings unparalleled transparency and security to the insurance industry. Every policy transaction, from policy creation to claim settlements, is recorded on an immutable and decentralized ledger, eliminating the possibility of fraud and ensuring that all transactions are transparent and verifiable.
**Faster Claim Settlements**
One of the most significant pain points in traditional life insurance is the lengthy and complex claim settlement process. However, with the implementation of smart contract technology, this Bitcoin-backed startup offers policyholders faster claim settlements. The automated nature of smart contracts streamlines the entire process, minimizing paperwork and reducing the time it takes for beneficiaries to receive their payouts.
**Potential for Investment Growth**
By using Bitcoin as collateral, policyholders have the opportunity to benefit from potential investment growth. As Bitcoin's value continues to fluctuate in the market, policyholders can reap the rewards of any appreciation in their Bitcoin collateral. This unique feature adds a new dimension to life insurance, turning it into a potential investment avenue for individuals seeking to safeguard their loved ones' future.
**Conclusion**
The emergence of a Bitcoin-backed life insurance startup with a $19 million investment signifies a significant leap forward for the insurance industry. By combining the benefits of blockchain technology, smart contracts, and cryptocurrency, this startup offers policyholders a unique and innovative approach to life insurance. With increased transparency, faster claim settlements, and the potential for investment growth, Bitcoin-backed life insurance has the potential to reshape the insurance landscape. As the market embraces this disruptive solution, individuals seeking life insurance coverage may find this startup to be a compelling choice.
**FAQ**
**How secure is Bitcoin-backed life insurance?**
Bitcoin-backed life insurance offers enhanced security due to the utilization of blockchain technology. Every transaction is recorded on an immutable and decentralized ledger, minimizing the risk of fraud and ensuring transparency.
**Can I convert my existing life insurance policy to a Bitcoin-backed policy?**
The conversion of an existing life insurance policy to a Bitcoin-backed policy would depend on the terms and conditions of the respective insurance provider. It is recommended to consult with the Bitcoin-backed life insurance startup or your current insurance provider for further guidance.
**How does the Bitcoin collateral appreciate over time?**
The value of Bitcoin collateral appreciates based on market conditions and demand. As Bitcoin is a highly volatile digital currency, its value can experience significant fluctuations. Policyholders can benefit from any appreciation in the value of their Bitcoin collateral.
**Are there any limitations to coverage amounts?**
The coverage amounts offered by the Bitcoin-backed life insurance startup may vary based on factors such as the applicant's risk profile, age, and desired coverage. It is advisable to consult with the startup directly to determine the coverage options available.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ a901cbe4:bd85452f
2024-11-12 04:22:24
Bitcoin, the crypto world’s star player, is once again making headlines, creeping up on the thrilling milestone of $90,000. It’s the kind of thing that gets HODLers, new investors, and crypto skeptics alike buzzing. But what’s really exciting about Bitcoin hitting $90K is that it feels like we’re in the final approach toward the magical $100K mark. Here’s why this milestone is so important — and why $90K is more than just another number.
### $90K: Not Quite There, But Oh So Close
$90,000 is a hefty number on its own, but in the world of Bitcoin, it’s like reaching the crest of a rollercoaster — a massive climb with the real excitement still ahead. When Bitcoin is this close to $100K, every dollar feels like another step toward the “big moment.” The journey has been long and often volatile, but Bitcoin’s persistence, resilience, and ability to keep pushing higher tells a compelling story. If $80K showed Bitcoin’s serious potential, $90K is that last push that’s putting us within touching distance of the ultimate milestone.
### Why $90K is Huge: Momentum and Market Mindset
The closer Bitcoin gets to $100K, the more attention it attracts. Traditional investors, financial institutions, and even regulators are watching closely. As Bitcoin nears $90K, the market momentum is growing. Every incremental rise is backed by a combination of increased mainstream adoption, institutional buy-in, and a community that believes in Bitcoin’s long-term potential. It’s like the crypto world’s version of the final sprint, and every piece of momentum counts.
More importantly, $90K is proof of market confidence. It signals that investors aren’t just hoping for quick gains; they see Bitcoin as a long-term store of value and a potential future standard in global finance. Each step closer to $100K solidifies Bitcoin’s reputation as a lasting financial asset.
### The Final Countdown: What Happens After $90K?
Once Bitcoin breaks $90K, the psychological impact on the market could be enormous. We’re not talking about another bump in the road here — we’re talking about Bitcoin heading into the realm of six-figure valuations. And when that happens, it’s not just a moment for those in the crypto world; it’s a moment for finance as a whole.
Here’s what could happen when Bitcoin finally crosses $100K:
1. **Media Frenzy:** The media, which already loves covering every Bitcoin milestone, will go wild with the story, and this could spark a new wave of interest from those who haven’t invested yet.
2. **Institutional FOMO:** We’ve seen an increase in institutional interest, and $100K could drive even more companies, investment funds, and potentially even sovereign wealth funds to consider Bitcoin seriously.
3. **Retail Investor Boom:** New retail investors may jump in, bringing fresh capital into the market. Bitcoin’s journey to $100K could fuel further retail adoption as people see it as a ‘must-have’ in their portfolios.
4. **Regulatory Spotlight:** $100K will also draw attention from regulators. Bitcoin isn’t just a niche investment anymore — it’s a global force, and lawmakers may feel pressure to establish clearer frameworks around crypto.
### $90K and Beyond: Bitcoin’s Future as a Mainstream Asset
As Bitcoin inches closer to $90K, it’s becoming clear that we’re witnessing more than just a price rally. Bitcoin is on a path to becoming a mainstream financial asset. Once considered the “outsider” in the financial world, Bitcoin has steadily gained respect and credibility, and now $90K is yet another validation of its journey.
After $100K, who knows what’s possible? Some crypto enthusiasts believe Bitcoin could go as high as $500K or even $1 million in the future. While these figures might seem ambitious, they highlight the level of optimism and potential people see in Bitcoin.
### The Bottom Line: Bitcoin Nearing $90K is the Start of Something Bigger
Bitcoin reaching $90K is an incredible milestone, but it’s also a starting line. This isn’t just about a number — it’s about Bitcoin’s evolution from a niche digital asset to a globally recognized financial powerhouse. The road from $90K to $100K is going to be exciting, but it’s just the beginning.
To everyone watching, it’s time to buckle up. Bitcoin’s rise is far from over, and if you think $90K is thrilling, just wait. The journey ahead promises to be one for the books. So let’s enjoy the ride, because Bitcoin is just getting started. 🚀
-

@ 6be5cc06:5259daf0
2024-11-12 03:11:11
### Primeiramente, o que é mempool?
Abreviação de memory pool (ou *"pool de memória"*) a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain.
Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco.
É assim:
* Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain.
* As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles.
* Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain.
Aqui irei usar o site [mempool.emzy.de](https://mempool.emzy.de/) como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não *a mempool do Bitcoin* em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas.
É uma boa prática usar **VPN** ou **Tor** ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação.
Dito isso...
### Como interpretar a mempool?
Vamos dividir isso em partes para fins didáticos.
---
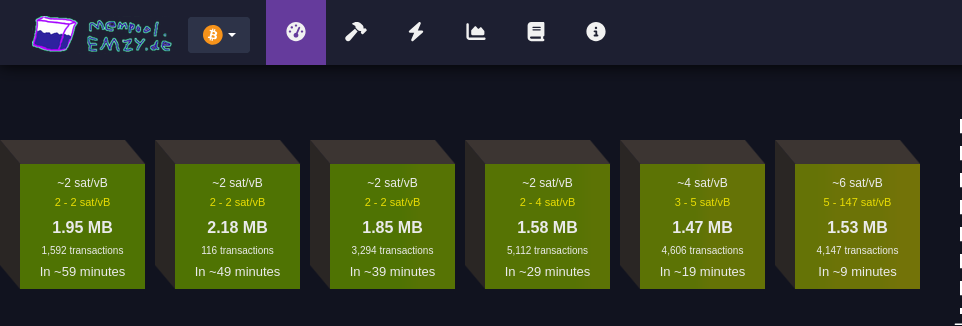
#### Faixa de taxas
Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB).
Essa unidade de medida representa o valor pago por byte ocupado pela transação.
Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada.
Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada.
Cada transação Bitcoin consiste em *entradas* e *saídas* (*inputs* e *outputs*):
* **Entradas** são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho.
* **Saídas** representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas.
Ex.:
* ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte;
* 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte.
#### MB
Simplesmente o tamanho do bloco medido em megabytes :)
#### Número de transações
Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada.
#### Tempo estimado para confirmação
Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada.
---
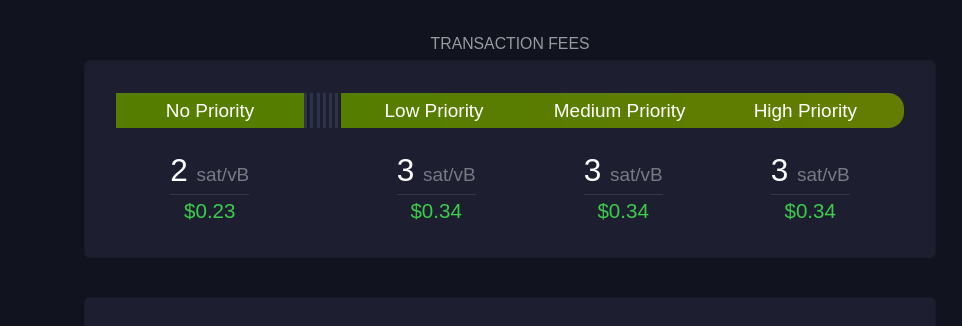
Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:
#### Sem Prioridade
Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida.
#### Prioridade Baixa
Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos.
#### Prioridade Média e Alta
São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco.
---
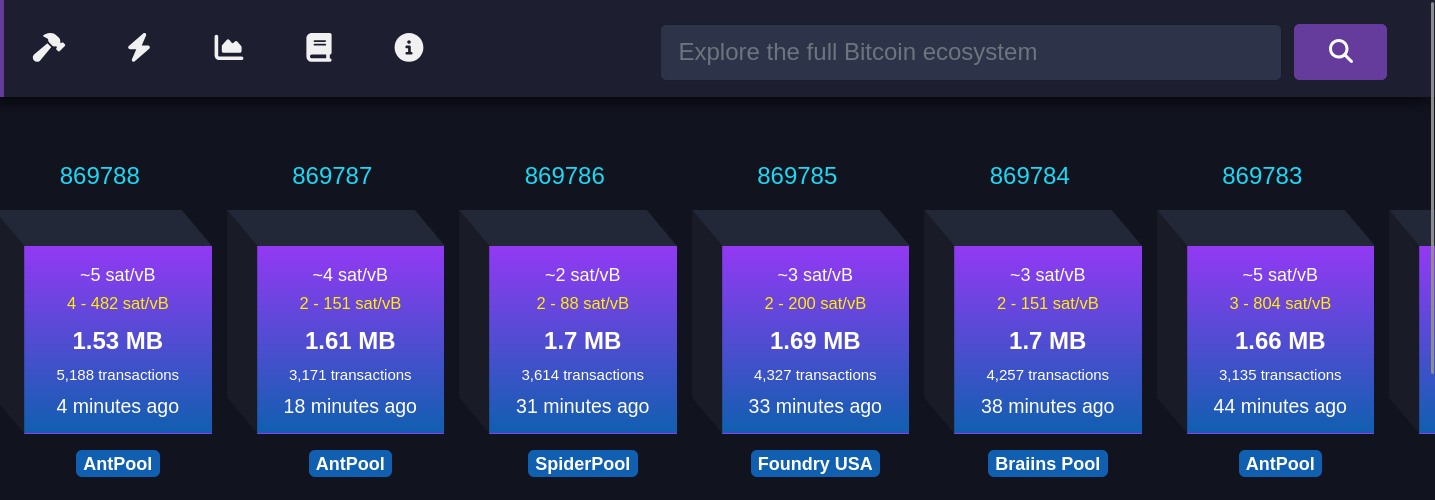
Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem:
#### Taxa média paga
Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente.
#### Número de transações
Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação.
#### Tempo desde a mineração
Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain.
#### Pool de mineração
Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem.
---
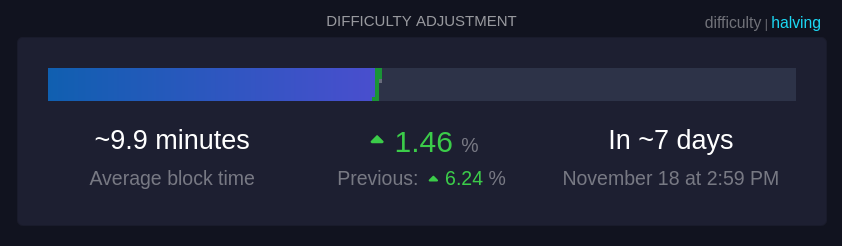
Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas.
#### Tempo médio dos blocos (~9,9 minutos):
Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede.
#### Mudança de dificuldade (+1,46%):
A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu.
#### Tempo até o próximo ajuste:
É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração.
---
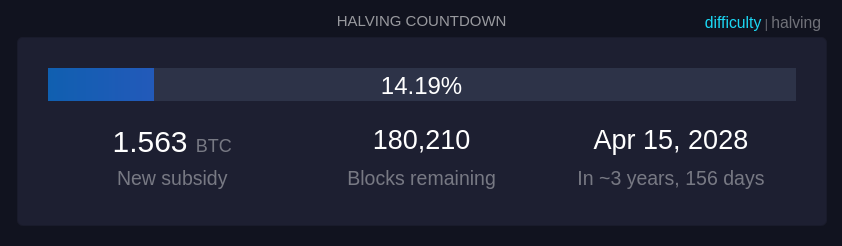
Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
---
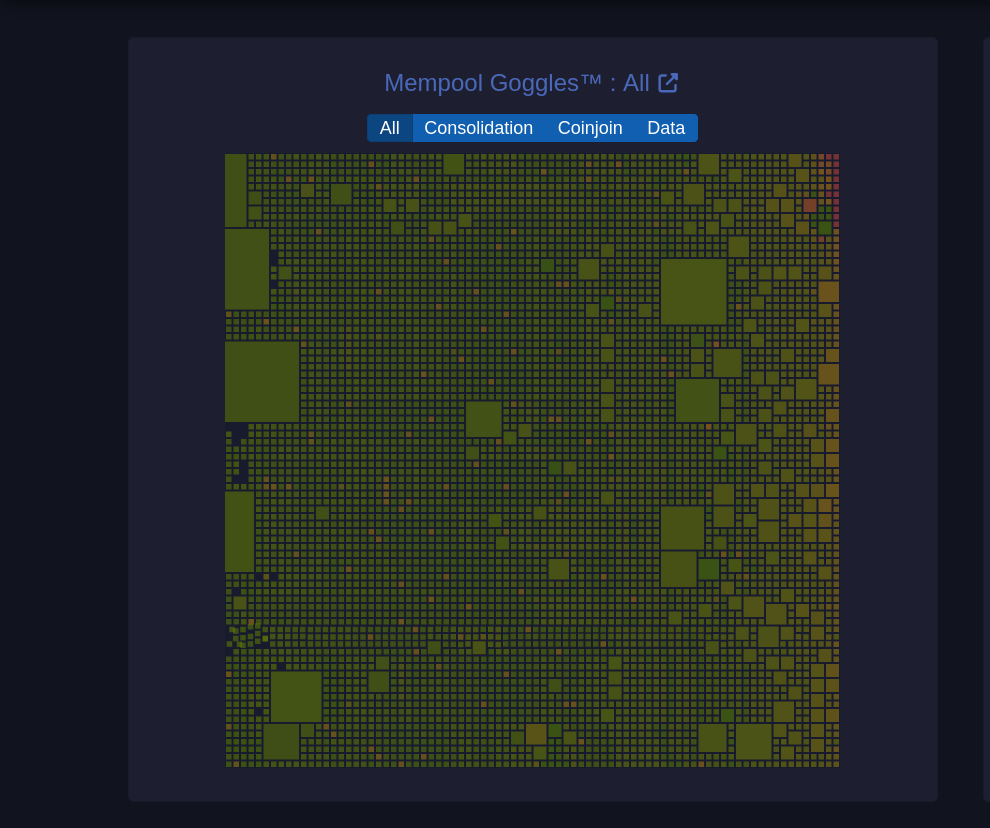
Um diagrama visual da mempool que mostra o estado das transações pendentes na rede.
#### Tamanhos de blocos
O tamanho de cada quadrado representa o tamanho da transação em bytes.
**Filtros (Consolidação, Coinjoin, Dados):** Permite visualizar categorias específicas de transações:
* **Consolidação**: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado)
* **Coinjoin**: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação.
* **Dados**: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens.
---
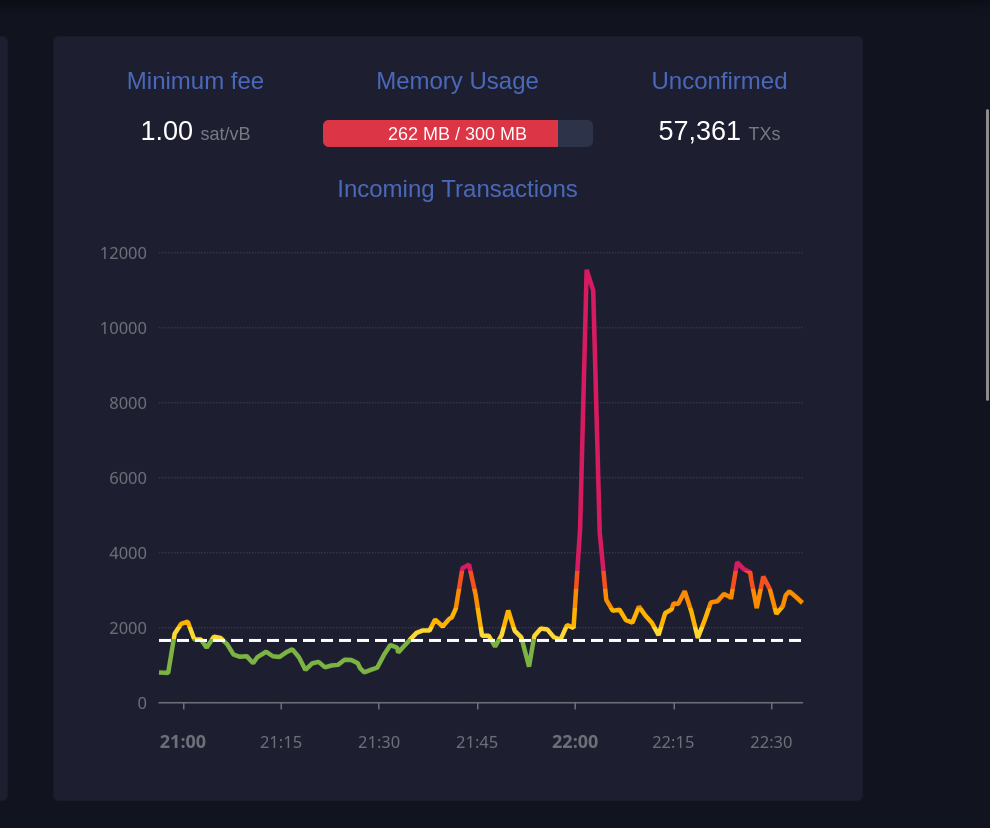
Este gráfico exibe o número de transações recebidas ao longo do tempo.
#### Taxa mínima (1 sat/vB):
Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade.
#### Uso de memória (259 MB / 300 MB):
A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos.
#### Transações não confirmadas (59.361):
Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida.
---
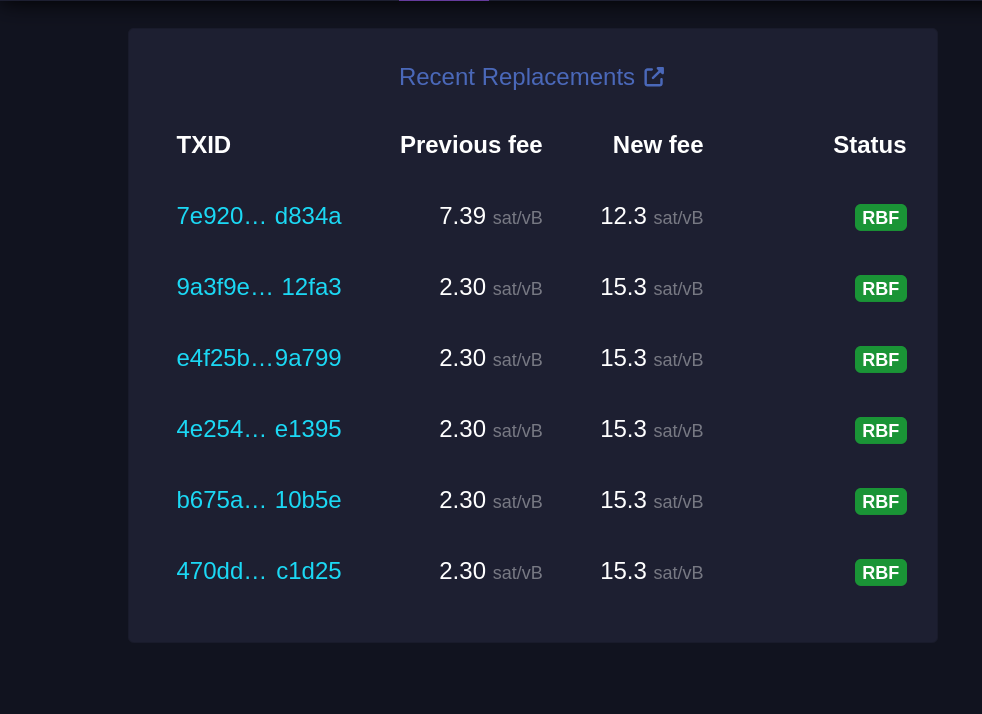
Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação.
#### TXID
Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain.
#### Previous fee
Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação.
#### New fee
Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco.
#### Status (RBF)
RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco.
---
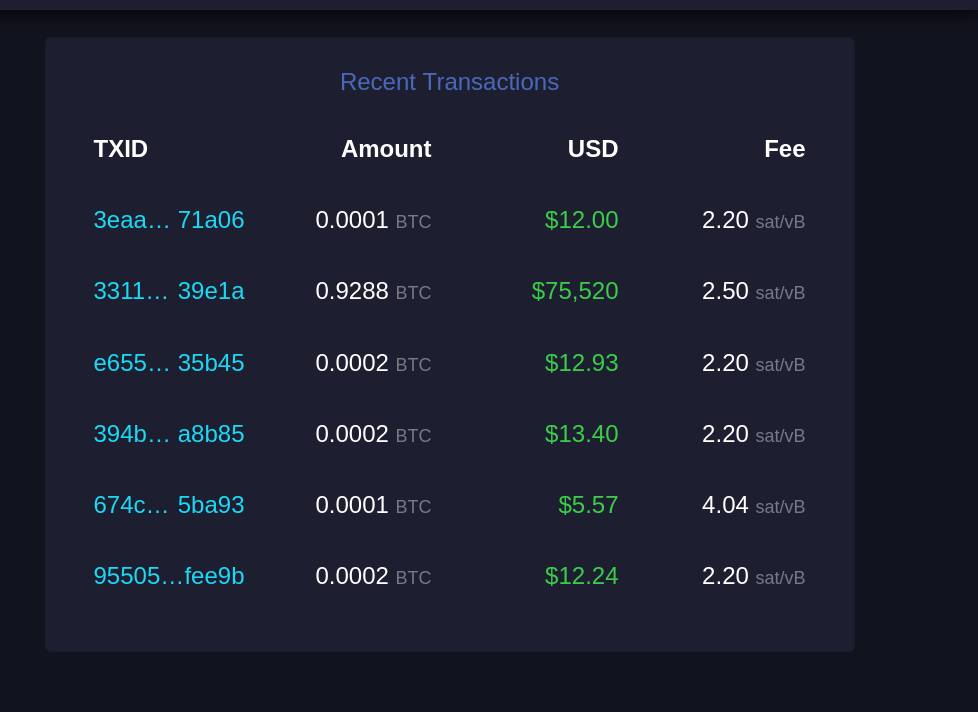
Esta seção lista transações recentes que entraram na mempool e aguardam confirmação.
#### TXID
Similar ao "Recent Replacements", este é o identificador único da transação.
#### Amount
Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário.
#### USD
Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária.
#### Fee
Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores.
---
E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade.
Por fim, stay humble and stack sats!
-

@ 5d4b6c8d:8a1c1ee3
2024-11-12 01:09:13
I almost forgot about Mock Draft Monday. The Raiders had their bye week, which means I'm not wallowing in the memory of a fresh humiliation.
Week 10 broke their way a little bit and the Raiders are now picking 5th. Unfortunately, the teams ahead of them also need QB's. In this draft, three of the first four picks were QB's. That didn't leave any who were worth spending a top five pick on.
Results
- 5th Pick: CB Travis Hunter
- 36th Pick: QB Garrett Nussmeier
- 67th Pick: LB Danny Stutsman
- 74th Pick: S Kevin Winston Jr.
- 106th Pick: RB Ollie Gordon II
- 142nd Pick: WR Tory Horton
- 179th Pick: DE Anto Saka
- 212th Pick: IOL Seth McLaughlin
- 215th Pick: OT Jalen Travis
- 220th Pick: QB Miller Moss
This draft was a disaster. Unless some of these guys wildly over perform, this is something of a worst case scenario. The board just refused to bread my way.
originally posted at https://stacker.news/items/764061
-

@ b4403b24:83542d4e
2024-11-11 22:26:38

originally posted at https://stacker.news/items/763926
-

@ 000002de:c05780a7
2024-11-11 21:02:50
The US Government (administrative state) is not only evil, its also stupid.
On March 14 of 2023 the gov sold 9,861 bitcoin that it had stolen from the Silk Road. At the time this was valued at 215 million dollars. At today's market price those coins are valued at $860,051,175, an increase of 300%.
For every seller there is a buyer. Here's to those bitcoiners that bought those coins.
[source](https://jlopp.github.io/us-marshals-bitcoin-auctions/)
Now, I know 645 million is nothing for the US Federal government.... but still. Its pretty comical. Guys, I don't think you want the government buying bitcoin.... Not if we want the state to go away... May not be a popular opinion but that's fine. Its mine.
originally posted at https://stacker.news/items/763834
-

@ b4403b24:83542d4e
2024-11-11 20:42:43
originally posted at https://stacker.news/items/763814
-

@ 6bae33c8:607272e8
2024-11-11 19:24:52
Yesterday was a mixed bag fantasy wise, but I’m feeling a bit lucky of late generally, and nothing happened to disabuse me of that. I started Aaron Rodgers in the Primetime which was a disaster, but it was over C.J. Stroud who was only a little better. Watching the Texans-Lions this morning validated all the reasons I sat Stroud, so I didn’t feel that badly about it.
The [Circa Millions picks](https://www.realmansports.com/p/circa-millions-bbf) really broke my way — the Steelers came back late, as did the Bucs who lost in exactly the right way. The Chargers and Broncos were good most of the way, but it’s those 50/50 games that have to work out. I lost on the Bears which was just a stupid pick. That puts me at 8-2 over the first half of Q3 — I figure if I go 9-1 or 10-0 over the second half, that gets me a piece of the $300K prize.
- I went on a hike, so I missed most of the Giants game, and that’s just as well. What I did see was bad Danny Dimes and then the Tyrone Tracy fumble in overtime. Tracy is actually doing God’s work getting them that No. 1 overall pick though.
- The Panthers drafted Jonathon Brooks, extended Chuba Hubbard, who is decent, and they gave a four-year deal to Miles Sanders last year! I remember when the Gettlechad paid big bucks to Jonathan Stewart and DeAngelo Williams!
- There was a shot of Bryce Young watching Daniel Jones work, and I imagined Young shuddering to think that’s the path down which he’s going — if he’s lucky.
- I let Seslowsky talk me into the Bears in Survivor, that NLM. Honestly, I didn’t object so it’s my own fault even though the Chargers were the obvious pick.
- The Patriots destroyed the Bears in every way, and Caleb Williams looked a lot like Danny Dimes. Just get rid of the damn ball!
- Joe Flacco was a nice story, but you have to play Anthony Richardson now. I picked up Richardson in two more leagues so I now have him in four. He’s still a long shot to be good, but if he’s even decent, he’ll be a monster for fantasy. If I were the Colts I’d tailor the offense to him, call tons of designed runs, roll-outs, etc. I’m sure he’d just get hurt though.
- Dalton Kincaid got hurt, but he’s just such a bust in every way. He’s basically just a generic TE you could grab off waivers. I had him ranked as my TE3.
- So crazy the Broncos got the game-winning FG blocked. This Chiefs team will go undeafeated and win the Super Bowl like the 1973 Dolphins, but no one will consider them a top-10 all-time team.
- Courtland Sutton is suddenly a top receiver again. He had disappeared entirely in Week 7.
- I have the league’s only Younghoe in three leagues, so his missing three field goals really hurt.
- Drake London was banged up, but he produces every game.
- I started Mason Tipton in the Primetime — what the hell happened to him?
- The Alvin Kamara easy-long TD drop was crazy. I thought for sure Atlanta would win the game after that.
- Christian McCaffrey was all the way back — he got most of the carries and seven targets.
- Bucky Irving is the Bucs best back, but Rachaad White is a good receiver and made an insane fourth-down conversion on a scramble play from Baker Mayfield.
- Jaylen Warren is finally back to last year’s role.
- The Steelers really held Jayden Daniels in check and would have an easier time of it but for a botched fake punt deep in their own end early in the game. I was only half watching, so I’m not exactly sure what happened there.
- You can take Sam Darnold off the Jets, but you can’t take the Jets off Sam Darnold. Seriously, the tick where he throws an end zone pick every time down is leftover from his time with them.
- Say what you want about the Jaguars, but they were able to take away Justin Jefferson.
- The Titans defense isn’t bad, though the broadcast kept harping on their strong per-game statistics. It’s easier to have good per-game defensive statistics when your offense is awful, and teams can play conservatively against you.
- Gus Edwards returned and looked good. He split carries fairly evenly with J.K. Dobbins who doesn’t look explosive of late.
- I can’t believe Calvin Ridley is good again. I guess I wrote him off after last year not realizing how terrible the Jaguars offense was.
- Cooper Rush was abominable, made Danny Dimes look like Joe Montana.
- CeeDee Lamb had 10 targets for 21 yards.
- Saquon Barkley’s having a great year, but you have to be at least a little annoyed about Jalen Hurts vulturing 10 TDs already.
- The Cardinals are in sync, and Kyle Murray has been very good the last month.
- Aaron Rodgers doesn’t look terrible physically to me, but there’s obviously something way off.
- The Lions are so good they won on the road against a 6-3 team despite Jared Goff throwing five picks. One was bad luck and another was at the end of the half, but still the hit to his stats could cost him the MVP.
- Stroud played better, but the offensive line is still bad (and this was the Lions without their new edge rusher Za’Darius Smith.) The Texans are committed to playing slowly and running Joe Mixon into the teeth of the defense 50 times too.
- I’m probably jinxing this by posting it, but I’ve been on a nice roll generally these last couple weeks, and I have Jonnu Smith starting everywhere tonight. I’m not saying I did some deep (or any) analysis of the matchup, only that I have a feeling he’ll go off. Not investment advice, just posting this as an experiment.
-

@ 6ad3e2a3:c90b7740
2024-11-11 19:22:48
One thing I enjoy about this Substack is I know a lot of its readers personally, and for that reason I also know many of them disagree with me. How dull it would be to write only for people who already were in lockstep with what you were saying! I say that because I also imagine some of you might be inclined to turn away from certain posts, but I would ask that the more you disagree, the more you stick this particular one out to the end. Imagine it were a reflection on [the joys of owning a small, poorly-trained dog](https://www.chrisliss.com/p/walking-the-dog).
Donald Trump didn’t just win the election, he won the House, Senate and popular vote. He had [unprecedented support](https://x.com/johnddavidson/status/1854549634552873390) among Latinos and black people, outperformed prior Republican candidates [among Jews](https://nypost.com/2024/11/06/us-news/trump-picks-up-50-of-jewish-vote-in-new-york/), [reached out to Arabs in Michigan](https://x.com/sam_bidwell/status/1855986922650296775) and [even got the Amish](https://x.com/nypost/status/1853957574632092158) to turn out en masse despite being outspent 2:1. The election was a total repudiation of the democratic party and its policies, the corporate press, the censorship industrial complex, uniparty republicans, left-wing academia, Hollywood, large tech companies thumbing the scale and entrenched government bureaucracy.
If you think this is a bad thing and were hoping for a different result, you probably have some explanation for what happened. I won’t pretend to know what anyone in particular is thinking, but I can tell you, as someone who is deeply relieved and heartened by this result how I see it. Maybe it will confirm some of your priors and disabuse you of others. Your mileage may vary.
My sense of relief is profound. I feel like a heavy weight has finally been lifted. I didn’t even realize how heavy it was until it was suddenly removed. The sense of creeping authoritarianism starting with Trump’s covid measures and [increasing](https://x.com/jeffreyatucker/status/1854601849636372798) via the Biden vaccine mandates, [online](https://x.com/ggreenwald/status/1838229864366682188) [censorship](https://x.com/0rf/status/1849552626729246868), the creation of a [disinformation bureau!](https://x.com/mtaibbi/status/1636729246172291078) was demoralizing in the extreme. I live [in Europe](https://x.com/mtaibbi/status/1835397873275707404) where people have been [arrested](https://x.com/elonmusk/status/1820784815815160260) for Facebook posts in the UK, where a law was passed in France [criminalizing](https://x.com/KLVeritas/status/1758126819784401204) criticism of the mRNA shots. The United States with its Bill of Rights was the one place where there was some obstacle in place against these abuses, but [even there](https://x.com/dbenner83/status/1854028975191851189), [prominent](https://x.com/Chris_Liss/status/1829967175656063405/photo/1) and powerful [factions](https://x.com/shellenberger/status/1842759698292056499) were [explicitly](https://x.com/MikeBenzCyber/status/1842778996250976273) calling for [its dismantling](https://x.com/pmarca/status/1840656582717366744).
But perhaps even more troubling was the behavior of ordinary people in response to these measures. I’ve [written at length](https://www.chrisliss.com/p/the-big-bribe) about what I take to be the causes, but more from a 30,000-foot view. I want to express how glad I am personally this behavior will ostensibly no longer be rewarded by those in power.
There is a large class of people who believe they are wiser and morally superior than those who disagree with them. They think that if you voted for candidate A you are a better person than if you voted for B. That who you voted for and how much you verbally signal your concern for various policies is important. One day it could be wearing your mask, another taking your booster, maybe it’s your views on Ukraine or Gaza, systemic racism, climate change or teenagers who believe they’ve been born in the wrong body.
If you don’t come out on the right side of these issues, you are not only mistaken, you are bad, and not just bad, but ignorant and in need of further education. It’s like an entire class of people became the HR department, your entire world was some dystopian corporation encouraging you to stay in line and [accept a pay (energy) cut](https://www.chrisliss.com/p/the-big-bribe) and lower standard of living for the greater good. And that’s assuming you were compliant enough to keep your job in the first place.
Now if this class of people simply excommunicated you from its church — and I know people personally whose families vowed to disown them for voting for Trump — that wouldn’t have been so bad. I mean I don’t need to associate with judgy, intolerant people who aim to stop me from thinking and saying what I earnestly believe. But it was worse than that: They didn’t even respect your right to be left alone.
If you refused to inject yourself with pharmaceutical poison, they wanted to [isolate you from society](https://x.com/LibertyBlitz/status/1657384752519979010). Never mind there was [never any scientific basis](https://www.chrisliss.com/p/the-science-changed) for it, never mind the constitution does not suddenly cease to apply because people are scared of a respiratory virus. And even the people who were silent, who did not beat the drum for this biomedical authoritarianism just went along like that was normal. Like shutting down people’s businesses and telling them where they could travel was just unfortunately necessary and for the greater good of “[public health](https://www.chrisliss.com/p/national-security-and-public-health).”
But while I harp on covid and the disgraceful scourge of vaccine mandates because it was such an extreme example, my larger point is about the ethos, the attitude that the lab coats, the experts, the climate scientists, the economists, the entire modern technocratic priesthood knew what was best for you. I [posted on Twitter once](https://www.chrisliss.com/p/harmful-speech) my decision to decline a colonoscopy (deemed due at my age), gave the caveat that this was neither advice nor even an informed opinion of the cost-benefit of getting one, and [people went insane](https://x.com/Chris_Liss/status/1664625607517274113/photo/2). The notion that I wouldn’t go along with the prevailing medical edicts (what did they care what I did?) was enraging to them. They knew better, I was an idiot, “getting colon cancer to own the libs.”
The truth is, and of this one thing I am certain, *you do not know better than I do*. I am an adult human being, and there is no higher authority in the known universe than me. I can very well make my own errors without compounding them by taking on your flawed presumptions and biases.
Quite obviously there are [technical matters](https://x.com/wideawake_media/status/1855537652658803091) where my expertise is lacking. I am happy to consult those who have it to better inform my judgment and decision-making, the way at trial experts often testify to better inform the jury of ordinary people. But just as it is the ordinary people who must render the verdict, it will always be my judgment and my judgment alone that governs my particular affairs, what medicines I will take, what policies I support, what language I use, with whom I choose to associate, how I feel it’s best to raise my kid, what she should and should not be exposed to at what age. I don’t care how many PhDs you attach to the end of your name — the more the worse if the last few years are any guide — you do not know how to manage my affairs better than I do, and I say that while cognizant that I make mistakes in their administration every single day of my life without exception.
So I have rambled a bit, but I wanted to convey as thoroughly as possible the enormity of the weight I feel lifted off my back as a result of this election. Yes, someone can still continue to be a condescending, insufferable, moralizing asshole, but what’s changed is he is no longer getting rewarded for such behavior by those in power. You can report me to HR for believing climate change (as it’s marketed to the masses) is a [cynical and evil scam](https://www.chrisliss.com/p/the-big-bribe), but when you get to the HR office you’ll find Karen clearing out her desk.
. . .
I understand people have misgivings about some of Trump’s proposed policies, and as with any politician you should be circumspect. I would never guarantee he and his cohorts soon to be in power won’t overstep — he surely did during the covid lockdowns.
But I am certain virtually [every claim](https://x.com/amuse/status/1855251868194402562) instilling so much fear in susceptible people is a [media fabrication](https://x.com/DissidentMedia/status/1854668585572217157), [deliberate distortion](https://x.com/DefiyantlyFree/status/1848394761540866545) or [outright lie](https://x.com/mazemoore/status/1852813382610550805). One tell for me is when people cite [Project 2025](https://x.com/thatsKAIZEN/status/1855402472891994141), insist [he’s going](https://x.com/realDonaldTrump/status/1841295548109955091) to [outlaw abortion](https://x.com/elonmusk/status/1854925721443127782) or jail those for disagreeing with him politically. Not only did you live through four years of people posting all manner of falsehoods (He’s on Putin’s payroll!) under their own names all over social media without consequence, but as [Glenn Greenwald pointed out](https://x.com/ggreenwald/status/1854215946887393542), if that were true why aren’t people like AOC and Rachel Maddow fleeing the country yet?
The answer is obvious: they know all the rhetoric they spewed was fake and performative, even if the [psychological damage](https://x.com/walterkirn/status/1854753916711256404) they did to the credulous is in many cases quite real. Whether you want to venture outside the corporate media propaganda ecosystem to verify these points is up to you. (I have provided many links, and I encourage you to click them.) But [my belief](https://x.com/MarkChangizi/status/1854982806062981544) is no matter your [political persuasion](https://x.com/RnaudBertrand/status/1855804917103124893) whether you realize it or not, like me (and Trump himself coincidentally) you just [dodged](https://x.com/MartyBent/status/1838319344243142659) a serious [bullet](https://x.com/RealCandaceO/status/1855394068739530875).
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58
Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 |
|--------------|-------------|--------------|-------|-------|-------|
| FC Bayern| Augsburg| Draw | 860| 50 | 90 |
| West Ham| Arsenal| Draw | 150| 650| 200|
| Southampton| Liverpool| Draw | 100| 730| 170|
| Newcastle| West Ham| Draw | 610| 170| 220|
| Man City| Tottenham| Draw | 630| 160| 210|
| Leicester| Chelsea| Draw | 180| 600| 220|
| Ipswich| Man United| Draw | 210| 590| 240|
| Crystal Palace| Newcastle| Draw | 310| 420| 270 |
| Arsenal| Nottingham Forest| Draw | 720| 100 | 180|
| Leganes| Real Madrid| Draw | 120| 690| 190 |
| Celta Viga| Barcelona| Draw | 210| 570| 220|
| Atletico Madrid| Alaves| Draw | 710| 100| 190|
| Athletic Club| Real Sociedad| Draw | 410| 280| 310|
As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog.
originally posted at https://stacker.news/items/763403
-

@ fd208ee8:0fd927c1
2024-11-08 10:27:40
## You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
## I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview.
Or, as I like to quip:
> The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-

@ 000002de:c05780a7
2024-11-11 17:06:01
I'm curious. I don't push my political views on people. If they ask I talk pretty freely about my views but most progressives I call friends or colleagues don't ask. But they sure do whine about Trump. I've heard two people in my circle talk about actively searching for places to move. One said they had passports if they need to leave quickly.
I know...
Curious if others that actually have "progressive" friends are hearing stuff like this. Now, I will be very surprised if they actually go through with it. I think these people have been mentally abused by the corporate press, the establishment, and the Democrat party into believing lies about Donald Trump. I'm not a fan of Mr. Trump but the dogma about him has reached absurd levels.
I honestly feel sorry for these folks. I try to talk them down. They have none of it. Its sad. Their brains are switched off. What has been done to them is truly evil.
So, am I alone in this experience. I realize some of you probably don't have friends so you can just abstain from responding ;)
originally posted at https://stacker.news/items/763402
-

@ 00000000:0da46cec
2024-11-11 15:37:15
The **Content Authenticity Initiative** (CAI) is a collaborative effort launched by Adobe in 2019 in partnership with technology companies and media organizations like Twitter and The New York Times. Its goal is to combat misinformation and ensure that digital content can be trusted. By creating a system for global adoption, CAI aims to provide a standard for traceability and verification of digital content in a secure and accessible manner. This article dives into the technical underpinnings of this initiative, detailing the use of metadata, cryptography, and blockchain. We also reference official repositories and open-source resources available for implementing these technologies.
### Content Authenticity Initiative Architecture
The architecture of CAI relies on a set of techniques and tools based on standardized metadata, cryptographic integrity mechanisms, and decentralized solutions to ensure content verifiability throughout its lifecycle. Below is an in-depth look at each core element of this architecture.
#### 1. **Generation of Authenticity Metadata**
Content creation within CAI begins at the capture stage, whether through a camera or smartphone, where **authenticity metadata** is generated. This metadata records important details such as the author's information, timestamp, geolocation, and device used for content capture. The data is stored using standardized schemes like **XMP (Extensible Metadata Platform)**, ensuring consistency for later verification. Developers can access the reference source code for XMP via Adobe's GitHub: [XMP Toolkit SDK](https://github.com/adobe/XMP-Toolkit-SDK).
The metadata not only describes the creation context but also maintains an **immutable history of modifications**. Whenever content is edited, the changes are documented, ensuring a complete and traceable history of the content lifecycle.
#### 2. **Digital Content Signing**
A key component of CAI is the use of **digital signatures** to certify the authenticity and integrity of the content. Each file (image, video, document) is signed with **asymmetric cryptographic algorithms** like **ECDSA (Elliptic Curve Digital Signature Algorithm)** or **RSA**, depending on the desired level of security and computational resources.
These digital signatures generate a unique hash for each piece of content, linking it to the creator's private key. If even a single bit of the content is altered, the hash will change, which invalidates the original signature. This mechanism guarantees that unauthorized alterations are easily detected. Reference implementations for these cryptographic methods are available in the [OpenSSL repository](https://github.com/openssl/openssl) and the **Bouncy Castle** library for Java and C#: [Bouncy Castle GitHub](https://github.com/bcgit).
#### 3. **Timestamping and Blockchain**
To further validate content authenticity, CAI also employs **timestamping** and, in some implementations, **blockchain technology**. Timestamping is handled by a **Timestamp Authority (TSA)**, which certifies that the content existed in a particular state at a specific moment in time. TSAs utilize digital signatures to provide a secure record of when the content was created.
Blockchain technology provides an additional layer of transparency and security. By storing the hashes of metadata and digital signatures on a **public blockchain** (like Ethereum), an immutable, decentralized record is created, allowing any user to verify the content's authenticity. Structures like **Merkle trees** are commonly used for recording efficiently, ensuring that changes are tracked without bloating the blockchain. Examples of blockchain-based implementations can be explored in the [Merkle Tree JavaScript Library](https://github.com/miguelmota/merkletreejs) and the official **Ethereum repository**: [Ethereum GitHub](https://github.com/ethereum).
#### 4. **Secure Metadata Storage**
The metadata generated during content creation is embedded directly within the content file, using **steganographic techniques** or as readable attachments. This ensures that the metadata remains tied to the content and is resistant to malicious alteration.
To maintain metadata integrity during transfer, **Transport Layer Security (TLS)** is used, ensuring that content is securely exchanged without interference. Moreover, distributed storage systems such as **IPFS (InterPlanetary File System)** can be leveraged to provide redundant and long-term availability of metadata. The IPFS implementation is available on GitHub: [IPFS GitHub](https://github.com/ipfs).
### Authentic Content Verification
One of CAI's primary goals is to enable anyone to easily verify the origin and edit history of content. To achieve this, **open-source verification tools** such as "**Verify with CAI**" have been developed, allowing users to inspect the content and access all associated metadata. These tools are available in the official CAI repository: [Content Authenticity Initiative GitHub](https://github.com/contentauth/).
These verification tools leverage hashes and digital signatures embedded in the content, providing an easy way to determine if unauthorized changes have occurred. They also provide links to blockchain records, allowing third-party verification for an added level of security.
### Guide for Photographers and Content Creators
The CAI's technology is particularly beneficial for photographers and content creators seeking to protect their work from misuse. Below is a practical guide to utilizing this technology effectively:
1. **Compatible Equipment**: Use a camera or device that supports the generation of authenticity metadata using XMP standards. Many modern devices and editing tools allow users to embed this metadata during capture.
2. **Editing Software**: Choose editing software that maintains authenticity metadata. Adobe Photoshop and similar tools now include features that preserve metadata throughout the editing process, ensuring the content remains verifiable.
3. **Digital Signing**: Use a digital signing tool like **OpenSSL** or libraries such as **Bouncy Castle** to digitally sign your files. This is critical for asserting the integrity and authenticity of your content. Tutorials and examples are available in the repositories mentioned.
4. **Timestamping**: Utilize a **Timestamp Authority (TSA)** to certify that the content existed at a specific point in time. This adds a temporal validation layer that proves when your content was created and that it hasn’t been altered since.
5. **Blockchain Registration**: To further reinforce content authenticity, consider recording metadata on a public blockchain. Services and smart contracts are available to help you register data without requiring deep blockchain expertise. Refer to repositories like [Ethereum GitHub](https://github.com/ethereum) for guidance.
6. **Content Verification**: Use **Verify with CAI** to verify that your content is correctly registered and ensure that all metadata and digital signatures are intact. This tool is open source, allowing anyone to verify the content's authenticity.
7. **Publishing Platforms**: Share your content on platforms that support CAI standards. Platforms like Behance are starting to integrate these standards, helping distribute content while retaining its verified authenticity.
### Technical Challenges and Barriers
CAI implementation faces several technical challenges. The most significant are:
1. **Adoption**: For CAI to succeed, stakeholders across the digital content ecosystem—camera manufacturers, software platforms, social networks, etc.—must adopt its standards.
2. **Privacy Concerns**: Providing detailed metadata about authorship may raise privacy issues. To address this, CAI offers options to encrypt sensitive metadata, ensuring it is only accessible when required.
3. **Costs**: The tools needed for digital signatures, blockchain registration, and timestamping can require significant resources, which may be a barrier for smaller creators or platforms.
4. **Sophisticated Threats**: While CAI improves digital security, sophisticated actors may still attempt to bypass authenticity checks or falsify metadata. Continuous improvement of cryptographic techniques and verification methods is required to counter these evolving threats.
### Conclusion
The **Content Authenticity Initiative** provides a solid framework for protecting the integrity of digital content. By utilizing metadata standards, digital signatures, blockchain records, and open-source verification tools, CAI aims to establish a global standard for content transparency and authenticity. Despite some technical and logistical challenges, CAI represents a crucial step towards a trustworthy digital ecosystem. Developers and creators can access official repositories to implement these tools and contribute to a safer, more reliable environment for digital media.
### References
- Adobe. (n.d.). *XMP Toolkit SDK*. Retrieved from [https://github.com/adobe/XMP-Toolkit-SDK](https://github.com/adobe/XMP-Toolkit-SDK)
- OpenSSL. (n.d.). *OpenSSL Cryptography and SSL/TLS Toolkit*. Retrieved from [https://github.com/openssl/openssl](https://github.com/openssl/openssl)
- Bouncy Castle. (n.d.). *Bouncy Castle Libraries*. Retrieved from [https://github.com/bcgit](https://github.com/bcgit)
- Miguel Mota. (n.d.). *Merkle Tree JavaScript Library*. Retrieved from [https://github.com/miguelmota/merkletreejs](https://github.com/miguelmota/merkletreejs)
- Ethereum Foundation. (n.d.). *Ethereum*. Retrieved from [https://github.com/ethereum](https://github.com/ethereum)
- IPFS. (n.d.). *InterPlanetary File System*. Retrieved from [https://github.com/ipfs](https://github.com/ipfs)
- Content Authenticity Initiative. (n.d.). *Verify with CAI*. Retrieved from [https://github.com/contentauth/](https://github.com/contentauth/)
-

@ 4ba8e86d:89d32de4
2024-11-07 13:56:21
Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas.
Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW.
Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW.
Sem mais delongas, vamos ao tutorial de fato.
## 1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P.
Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo.
Após entrar no site vá para a página '1 - Creating a mailbox'
https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos.
https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados.
https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg
https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
## 2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd.
Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso.
Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf
https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf
https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
```
sudo systemctl restart i2pd
```
Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.
Com os túneis cliente criados, vamos agora configurar o Thunderbird
## 3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir.
https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg
https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta.
https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir.
https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue'
https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta.
https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
## 4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-

@ c73818cc:ccd5c890
2024-11-11 14:16:21

🙃 Pierce potrebbe portare chiarezza e regole favorevoli per il settore delle criptovalute negli USA.
😍 Con la fine del mandato di Gary Gensler, il CEO di Galaxy Digital, Mike Novogratz, ha appoggiato Hester Pierce come suo possibile sostituto alla guida della SEC. Nota come la "madre delle criptovalute," Pierce è un’avvocata delle regole chiare e strutturate per favorire la crescita del settore.
😍 Pierce, critica di lungo corso dell'approccio aggressivo della SEC verso le criptovalute, potrebbe orientare l’agenzia verso un equilibrio tra innovazione e supervisione. Il suo potenziale incarico come presidente della SEC ha acceso l’ottimismo tra investitori e aziende del settore.
😍 Novogratz prevede che una SEC guidata da Pierce attrarrebbe maggiori investimenti istituzionali, stimolando una crescita duratura delle criptovalute. Un cambio di leadership con una visione pro-cripto potrebbe inoltre sbloccare significativi valori di mercato, creando nuove opportunità di innovazione.
Unisciti al nostro gruppo Telegram
Bitget -20% - Mexc no KYC
https://lnk.bio/Bitcoin.Report.Italia
#BitcoinReportItalia #USA #GaryGensler #SEC #StatiUniti #America #Trump #Presidente #Musk #CasaBianca #Cripto #Bitcoin
-

@ 3bf0c63f:aefa459d
2024-10-31 16:08:50
# Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
### Palavras que existem em português com sentido diferente
- _submissão_ (de trabalhos): **envio**, **apresentação**
- _disrupção_: **perturbação**
- _assumir_: **considerar**, **pressupor**, **presumir**
- _realizar_: **perceber**
- _endereçar_: **tratar de**
- _suporte_ (ao cliente): **atendimento**
- _suportar_ (uma idéia, um projeto): **apoiar**, **financiar**
- _suportar_ (uma função, recurso, característica): **oferecer**, **ser compatível com**
- _literacia_: **instrução**, **alfabetização**
- _convoluto_: **complicado**.
- _acurácia_: **precisão**.
- _resiliência_: **resistência**.
### Aportuguesamentos desnecessários
- _estartar_: **iniciar**, **começar**
- _treidar_: **negociar**, **especular**
### Expressões
- _"não é sobre..."_: **"não se trata de..."**
---

## Ver também
- [Algumas expressões e ditados excelentes da língua portuguesa, e outras não tão excelentes assim](https://fiatjaf.alhur.es/expressões-e-ditados.txt)
-

@ dca6e1cc:ea7d1750
2024-11-11 13:10:17
What are the odds that we can crowd-source a Bitcoin Mining operation that supports the energy development of a rural African village?
For anyone who knows, there are plenty of environmental, social, and economic benefits that Bitcoin mining can bring to the development of rural mini-grids.
More info:
https://www.gama.africa/gama-programs.html
https://x.com/GridlessCompute/status/1752679599601782846
Africa is home to massive amounts of untapped energy that can be ethically sourced. Access to energy is fundamental to human flourishing, meaning the upside for Africans' lifestyles is considerable given that many have zero electricity access aside from the odd solar panel. What can we do to accelerate this process?
originally posted at https://stacker.news/items/763008
-

@ a9434ee1:d5c885be
2024-10-29 20:46:24
This design system has two goals:
1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty
2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...)
### Design System
Check it out [here](https://www.figma.com/community/file/1430887635327548022 ).
This is by no means finished and will be continually updated and completed as we go along.
### Project description
Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda)
nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda
This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki.
### Explanatory videos
This list of videos will also be continually updated and completed as we go along:
1. Chat as the universal interface
https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov
2. Your Nostr Dashboard
https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov
3. Keeping Tabs on all these Content types
https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov
4. Design entered the Chat
https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov
5. Targeted publication & The blurry edges of interoperable communities
https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov
6. Travel Back
https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
-

@ 81dfd044:f1737ef9
2024-11-11 13:08:51
Looking to invest in solar energy for your business? Aurora Energy offers high-quality [commercial solar panels for sale](https://aurora-energy.com/maximizing-savings-commercial-solar-panels-boost-efficiency-sustainability/), built to meet the energy needs of businesses both large and small. Our solar panels provide reliable, renewable energy that reduces operating costs and minimizes environmental impact. Let us help you choose the perfect system to power your business with clean energy and long-term financial benefits.
-

@ 00000000:0da46cec
2024-11-11 12:44:46
### Resumen
La **Content Authenticity Initiative** (CAI) es una colaboración global iniciada por Adobe en 2019, junto con empresas tecnológicas y medios de comunicación, cuyo objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad para contenidos digitales. Este artículo analiza en detalle los aspectos tecnológicos avanzados de la CAI, como el uso de metadatos, criptografía, blockchain y la verificación distribuida, además de incluir una guía para fotógrafos y creadores de contenido. Se ofrecen referencias a repositorios de código abierto para implementar estas tecnologías, proporcionando una base técnica robusta para proteger la autenticidad del contenido digital.
**Palabras clave**: Content Authenticity Initiative, CAI, autenticidad del contenido, metadatos, criptografía, blockchain, integridad digital, firma digital, sellado de tiempo.
---
La **Content Authenticity Initiative** (CAI), traducida al español como Iniciativa de Autenticidad del Contenido, es un esfuerzo colaborativo iniciado por Adobe en 2019 en conjunto con empresas tecnológicas y medios de comunicación como Twitter y The New York Times. Su principal objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad de contenidos que pueda ser adoptado globalmente, proporcionando trazabilidad y verificación de los contenidos digitales de una manera confiable y accesible. Este artículo detalla los aspectos tecnológicos más avanzados de esta iniciativa, que incluye el uso de metadatos, criptografía y blockchain. Además, se hace referencia a algunos de los repositorios oficiales y recursos de código fuente disponibles para implementar estas tecnologías.
### Arquitectura de la Content Authenticity Initiative
La arquitectura de la CAI está compuesta por un conjunto de técnicas y herramientas basadas en metadatos estandarizados, mecanismos de integridad criptográfica, y soluciones descentralizadas para asegurar la verificabilidad del contenido en cada etapa de su ciclo de vida. A continuación se describe en detalle cada uno de los elementos clave de esta arquitectura.
#### 1. **Generación de Metadatos de Autenticidad**
El proceso de generación de contenido dentro de la CAI comienza en el dispositivo de captura, como una cámara o un smartphone, donde se crean los **metadatos de autenticidad**. Estos metadatos incluyen información relevante sobre el autor del contenido, la fecha y hora de captura, la geolocalización y el dispositivo utilizado. Estos elementos se guardan utilizando esquemas estandarizados como **XMP (Extensible Metadata Platform)**, que asegura una estructura coherente y legible para las aplicaciones de verificación posteriores. El código fuente de referencia para la implementación de XMP está disponible en el repositorio oficial de Adobe en GitHub: [XMP Toolkit SDK](https://github.com/adobe/XMP-Toolkit-SDK).
Los metadatos de autenticidad no solo proporcionan datos sobre la creación, sino que también mantienen un **registro inmutable de modificaciones** del archivo. Cada vez que se realiza una edición, se documenta el cambio mediante un proceso de versionado, asegurando la trazabilidad completa de cualquier alteración.
#### 2. **Firma Criptográfica del Contenido**
El siguiente nivel de protección que ofrece la CAI es el uso de **firmas digitales** para garantizar la autenticidad e integridad del contenido. Cada archivo multimedia (imagen, video, documento) se firma utilizando algoritmos de **criptografía asimétrica** como **ECDSA (Elliptic Curve Digital Signature Algorithm)** o **RSA**, dependiendo del nivel de seguridad requerido y la capacidad de cálculo del dispositivo.
Estas firmas digitales generan un hash único para el contenido y lo vinculan con la clave privada del creador. Si el contenido es modificado de alguna manera, incluso un cambio de un solo bit, el hash cambiará, invalidando la firma digital original. De esta forma, cualquier alteración que no esté registrada y autorizada se puede detectar fácilmente, proporcionando garantía de que el archivo no ha sido comprometido desde su creación. Implementaciones de referencia para la generación y verificación de firmas digitales están disponibles en el repositorio [OpenSSL](https://github.com/openssl/openssl) y en la biblioteca **Bouncy Castle** para Java y C#: [Bouncy Castle GitHub](https://github.com/bcgit).
#### 3. **Sellado de Tiempo y Blockchain**
Para reforzar la veracidad del contenido, la CAI también puede emplear **sellado de tiempo (timestamping)** y, en algunas implementaciones, **blockchain** para descentralizar y proteger el registro de autenticidad. El sellado de tiempo se realiza mediante una autoridad de sellado (“Timestamp Authority” o TSA), que certifica que el contenido existía en un estado particular a una fecha y hora específica. Las TSA utilizan firmas digitales para proporcionar un valor criptográficamente seguro que confirma la temporalidad del contenido.
La incorporación de blockchain aporta un nivel adicional de transparencia. Al registrar hashes de los metadatos y las firmas de autenticidad en una **blockchain pública** (como Ethereum o cualquier blockchain dedicada), se crea un registro inmutable y descentralizado que permite a cualquier usuario verificar la autenticidad del contenido. La estructura basada en **árboles Merkle** se usa comúnmente para optimizar el proceso de registro, asegurando que cada cambio en el contenido se documente con eficiencia y sin necesidad de almacenar grandes volúmenes de datos en la blockchain. Los desarrolladores pueden explorar ejemplos de implementación en el repositorio [Merkle Tree JavaScript Library](https://github.com/miguelmota/merkletreejs) y consultar el repositorio oficial de **Ethereum** para interacciones con contratos inteligentes: [Ethereum GitHub](https://github.com/ethereum).
#### 4. **Almacenamiento Seguro de Metadatos**
Los metadatos generados durante el proceso de creación se incrustan en el contenido utilizando **técnicas de esteganografía** o como datos adjuntos legibles por las herramientas de edición y verificación. Para evitar la eliminación o alteración maliciosa de estos metadatos, se emplean mecanismos de **incrustación segura** que vinculan los metadatos al contenido de manera criptográfica.
Para garantizar la integridad de los metadatos durante la transferencia, se emplean **protocolos TLS** (Transport Layer Security), que aseguran que cualquier intercambio de archivos mantenga la confidencialidad y la integridad. Además, se pueden usar **sistemas de almacenamiento distribuido** como **IPFS (InterPlanetary File System)** para replicar y almacenar estos metadatos de forma redundante, asegurando su disponibilidad a largo plazo. El código fuente para IPFS está disponible en el repositorio oficial: [IPFS GitHub](https://github.com/ipfs).
### Verificación del Contenido Auténtico
Uno de los objetivos fundamentales de la CAI es que cualquier usuario pueda verificar la procedencia y el historial de ediciones de un contenido de manera sencilla y eficiente. Para ello, se han desarrollado **herramientas de verificación basadas en código abierto**, como “**Verify with CAI**”, que permiten al espectador analizar el contenido y ver todos los metadatos asociados. Estas herramientas se pueden encontrar en el repositorio oficial de la CAI: [Content Authenticity Initiative GitHub](https://github.com/contentauth/).
Estas herramientas usan los hashes incrustados y las firmas digitales para comparar la información disponible y determinar si el contenido ha sido alterado sin autorización. Asimismo, permiten al usuario acceder a los registros de blockchain, si es aplicable, para confirmar la autenticidad desde una fuente independiente y descentralizada.
### Guía para Fotógrafos y Creadores de Contenido
La adopción de la tecnología de la Content Authenticity Initiative puede ser extremadamente beneficiosa para los fotógrafos y creadores de contenido que deseen garantizar la autenticidad y proteger su trabajo contra el uso indebido. A continuación se presenta una guía paso a paso sobre cómo utilizar esta tecnología:
1. **Equipamiento Compatible**: Asegúrate de que utilizas una cámara o dispositivo que soporte la generación de metadatos de autenticidad según los estándares XMP. Muchas cámaras y aplicaciones de edición modernas permiten incluir estos metadatos durante la captura y la edición del contenido.
2. **Software de Edición Compatible**: Utiliza software de edición que mantenga los metadatos de autenticidad intactos. Adobe Photoshop y otras herramientas de edición avanzadas han comenzado a integrar estas funcionalidades para garantizar que cada cambio quede registrado. Al editar, asegúrate de mantener los registros de metadatos, de modo que se pueda trazar la autenticidad del contenido.
3. **Firmado Digital del Contenido**: Usa una herramienta de firma digital, como **OpenSSL** o bibliotecas como **Bouncy Castle** para generar firmas digitales de tus archivos. Esto proporciona una garantía de autenticidad. Estas herramientas se pueden usar para firmar imágenes y documentos multimedia y protegerlos contra cualquier alteración. Puedes encontrar tutoriales y ejemplos de uso en los repositorios mencionados previamente.
4. **Sellado de Tiempo del Contenido**: Implementa el sellado de tiempo utilizando una **Timestamp Authority (TSA)** reconocida. Esto permite certificar que el contenido existía en un estado específico en una fecha y hora determinadas, lo cual es esencial para demostrar la integridad temporal del contenido. Algunas plataformas ofrecen servicios de sellado de tiempo gratuitos o a bajo costo.
5. **Uso de Blockchain para Registrar Metadatos**: Si deseas una protección adicional y más transparencia, considera registrar los hashes de los metadatos en una blockchain pública. Existen servicios y contratos inteligentes que pueden ayudarte a registrar estos datos sin necesidad de un conocimiento profundo en programación blockchain. Puedes consultar repositorios como [Ethereum GitHub](https://github.com/ethereum) para aprender cómo interactuar con contratos inteligentes.
6. **Verificación del Contenido**: Utiliza herramientas como **Verify with CAI** para asegurarte de que tus contenidos están adecuadamente registrados y que los metadatos y firmas digitales se mantienen intactos. Estas herramientas son de código abierto y están disponibles en GitHub, lo que permite a cualquier usuario comprobar la integridad y procedencia del contenido.
7. **Publicación en Plataformas Compatibles**: Publica tu contenido en plataformas que soporten la CAI y mantengan los metadatos intactos. Redes sociales y sitios web como Behance están comenzando a adoptar estos estándares, lo que te permitirá que tu contenido se distribuya con la verificación de autenticidad.
### Desafíos Técnicos y Barreras
La implementación de la CAI no está exenta de desafíos. Algunos de los principales son:
1. **Adopción Masiva**: Para que la CAI sea efectiva, es necesario que todos los actores involucrados en la creación y distribución de contenido adopten sus estándares. Esto incluye a los fabricantes de cámaras, plataformas de edición, redes sociales y sitios web.
2. **Privacidad de los Creadores**: Al proporcionar información detallada sobre el autor y el origen del contenido, surgen preocupaciones relacionadas con la privacidad. Para mitigar esto, la CAI permite que algunos metadatos se almacenen de forma encriptada, y solo se revelen si es necesario.
3. **Costos de Implementación**: Las herramientas para firmar digitalmente, registrar en blockchain, y mantener el sellado de tiempo requieren recursos que podrían ser prohibitivos para algunos creadores o plataformas pequeñas.
4. **Atacantes Sofisticados**: Aunque la CAI mejora significativamente la seguridad, atacantes avanzados podrían intentar falsificar metadatos o burlar los procesos de firma digital. La combinación de técnicas criptográficas y blockchain mitiga este riesgo, pero siempre existirá la necesidad de evolucionar con las amenazas emergentes.
### Conclusión
La **Content Authenticity Initiative** ofrece una arquitectura tecnológica sólida para proteger la autenticidad del contenido digital. A través del uso combinado de metadatos estandarizados, firmas digitales, blockchain y herramientas de verificación, la CAI busca establecer un estándar global para la transparencia y verificabilidad del contenido. Si bien existen desafíos técnicos y logísticos, la CAI representa un paso significativo hacia un ecosistema digital donde la confianza y la autenticidad sean la norma y no la excepción. Los interesados en profundizar más pueden acceder al código fuente disponible en los repositorios oficiales, como se ha indicado a lo largo del artículo, para implementar estas soluciones y contribuir al desarrollo de un entorno digital más seguro y confiable.
### Bibliografía
- Adobe. (n.d.). *XMP Toolkit SDK*. Recuperado de [https://github.com/adobe/XMP-Toolkit-SDK](https://github.com/adobe/XMP-Toolkit-SDK)
- OpenSSL. (n.d.). *OpenSSL Cryptography and SSL/TLS Toolkit*. Recuperado de [https://github.com/openssl/openssl](https://github.com/openssl/openssl)
- Bouncy Castle. (n.d.). *Bouncy Castle Libraries*. Recuperado de [https://github.com/bcgit](https://github.com/bcgit)
- Miguel Mota. (n.d.). *Merkle Tree JavaScript Library*. Recuperado de [https://github.com/miguelmota/merkletreejs](https://github.com/miguelmota/merkletreejs)
- Ethereum Foundation. (n.d.). *Ethereum*. Recuperado de [https://github.com/ethereum](https://github.com/ethereum)
- IPFS. (n.d.). *InterPlanetary File System*. Recuperado de [https://github.com/ipfs](https://github.com/ipfs)
- Content Authenticity Initiative. (n.d.). *Verify with CAI*. Recuperado de [https://github.com/contentauth/](https://github.com/contentauth/)
-

@ a012dc82:6458a70d
2024-11-11 12:35:40
**Table Of Content**
- Understanding Bitcoin Halving and its Significance
- JPMorgan Analysis Reveals Positive Indicators
- Increased Retail Investment: Driving Factors
- Anticipated Impact on Bitcoin Market
- Tips for Retail Investors to Leverage the Opportunity
- Conclusion
- FAQ
In recent years, Bitcoin has become a buzzword in the financial world, captivating both institutional and retail investors. As the cryptocurrency market continues to evolve, experts at JPMorgan have conducted a comprehensive analysis, revealing strong indications of increased retail interest in Bitcoin leading up to the next halving event. This blog post will explore the insights from JPMorgan's analysis and shed light on the potential impact of this anticipated surge in retail interest.
**Understanding Bitcoin Halving and its Significance**
The concept of Bitcoin halving is pivotal to understanding the potential surge in retail interest. Bitcoin operates on a controlled supply system, with a predetermined issuance rate. Approximately every four years, the number of new Bitcoins generated per block gets halved, reducing the rate at which new Bitcoins enter circulation. This scarcity mechanism has significant implications for the cryptocurrency's value and investor sentiment.
**JPMorgan Analysis Reveals Positive Indicators**
According to JPMorgan's analysis, there are several positive indicators suggesting a strong influx of retail investors in the period leading up to the next Bitcoin halving. The analysis takes into account various factors such as historical data, market trends, and investor behavior. JPMorgan's experts have identified patterns that align with previous halving events, indicating a potential surge in retail interest in Bitcoin.
**Increased Retail Investment: Driving Factors**
JPMorgan's analysis highlights key driving factors behind the expected increase in retail investment. One significant factor is the growing awareness and acceptance of Bitcoin among the general public. As more individuals recognize the potential of cryptocurrencies as an investment asset, they are likely to be drawn towards Bitcoin, especially during periods of heightened market activity like halving events.
Moreover, the influence of social media and digital platforms cannot be overlooked. The rise of social media communities, investment forums, and influencers has played a crucial role in amplifying discussions around Bitcoin. These platforms facilitate the spread of information, enabling retail investors to gain insights and make informed investment decisions.
**Anticipated Impact on Bitcoin Market**
The surge in retail interest preceding the halving event is expected to have a significant impact on the Bitcoin market. As more retail investors enter the market, the demand for Bitcoin is likely to increase, potentially driving up its price. This increased demand could lead to a period of heightened market volatility, offering both opportunities and risks for investors.
JPMorgan's analysis suggests that the impact of retail interest will extend beyond the halving event itself. Historically, Bitcoin has experienced price rallies following halvings, indicating the potential for substantial gains. However, it is important to note that the cryptocurrency market is highly unpredictable, and investors should exercise caution and conduct thorough research before making investment decisions.
**Tips for Retail Investors to Leverage the Opportunity**
For retail investors considering Bitcoin as an investment, it is essential to approach the market with a strategic mindset. Here are a few tips to help leverage the anticipated surge in retail interest:
1. **Educate Yourself:** Gain a deep understanding of Bitcoin, its underlying technology, and the factors that influence its price.
2. **Diversify Your Portfolio:** Consider allocating a portion of your investment portfolio to Bitcoin while maintaining a diverse range of assets.
3. **Set Realistic Goals:** Define your investment objectives and set realistic expectations, considering the volatility and risks associated with cryptocurrencies.
4. **Stay Informed:** Stay updated with the latest news, market trends, and regulatory developments that could impact the cryptocurrency market.
5. **Seek Professional Advice:** Consult with financial advisors or experts who specialize in cryptocurrencies to gain valuable insights and guidance.
**Conclusion**
JPMorgan's analysis reveals strong indications of increased retail interest in Bitcoin prior to the halving event. Retail investors, driven by factors such as growing awareness and the influence of digital platforms, are likely to play a significant role in shaping the cryptocurrency market. As retail interest surges, it is crucial for investors to approach the market with caution, conduct thorough research, and leverage the opportunities while managing the risks associated with cryptocurrencies.
**FAQ**
**What is Bitcoin halving?**
Bitcoin halving is an event that occurs approximately every four years, where the number of new Bitcoins generated per block gets halved. It is a mechanism designed to control the supply of Bitcoin and has significant implications for its value and investor sentiment.
**Why is there expected strong retail interest in Bitcoin prior to halving?**
JPMorgan's analysis indicates increased retail interest in Bitcoin before halving due to growing awareness, acceptance, and the influence of social media platforms. Retail investors are drawn towards Bitcoin during periods of heightened market activity like halving events.
**What impact does retail interest have on the Bitcoin market?**
Retail interest can drive up the demand for Bitcoin, potentially impacting its price. The surge in retail interest preceding the halving event could lead to increased market volatility, offering opportunities and risks for investors.
**How can retail investors leverage the anticipated surge in retail interest?**
Retail investors can leverage the opportunity by educating themselves about Bitcoin, diversifying their investment portfolio, setting realistic goals, staying informed about market trends, and seeking professional advice.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 05fcdfd8:fd31299f
2024-11-11 10:49:36
<p>Die Auswirkungen von Störsendern auf Reisen und wie Sie Ihre Privatsphäre und Sicherheit schützen können</p>
<p>In der modernen Gesellschaft ist Reisen zu einem integralen Bestandteil des Lebens der Menschen geworden. Mit zunehmender Reisehäufigkeit sind Informationssicherheit und Privatsphäre jedoch nach und nach zu wichtigen Themen geworden, die den Menschen Sorgen bereiten. An verschiedenen öffentlichen Orten, insbesondere in Flughäfen, Hotels und Touristenattraktionen, kann das Vorhandensein von <a href="https://www.jammermfg.com/de/">Signal störsender</a> eine potenzielle Bedrohung für die Sicherheit unserer persönlichen Geräte und Informationen darstellen. Aus diesem Grund ist es wichtig, die Auswirkungen von Störsendern zu verstehen und geeignete Sicherheitsmaßnahmen zu ergreifen.</p>
<p>1. Funktionsprinzip des Störsenders</p>
<p>Ein Störsender, oft auch „Signalstörsender“ genannt, ist ein Gerät, das Signale auf bestimmten Frequenzen aussendet, die die Kommunikation mit anderen drahtlosen Geräten stören oder verhindern können. Diese Geräte werden manchmal verwendet, um illegale drahtlose Kommunikation zu blockieren, beispielsweise in Gefängnissen, aber auch auf Reisen kommt es zu illegalem Einsatz. Hacker könnten beispielsweise <a href="https://www.jammermfg.com/de/handy-stoersender.html">Handyblocker</a> verwenden, um die Mobiltelefonsignale von Menschen zu stören, um vertrauliche Informationen abzuhören oder zu stehlen.</p>
<p>2. Die Auswirkungen von Störsendern</p>
<p>1. Auswirkungen auf die Kommunikation: In Bereichen, in denen Störsender verwendet werden, kann es bei Mobiltelefonen und anderen drahtlosen Geräten zu Signalverlusten kommen, wodurch es unmöglich wird, Anrufe entgegenzunehmen oder Nachrichten zu senden. Dies kann im Ernstfall schwerwiegende Folgen haben.</p>
<p>2. Risiken für die Datensicherheit: Hacker können <a href="https://www.jammermfg.com/de/wlan-bluetooth-stoersender.html">WLAN Jammer</a> nutzen, um Funksignale abzufangen und die persönlichen Daten und Bankkontoinformationen der Benutzer zu stehlen. Wenn ein Gerät keine stabile Verbindung zum Netzwerk herstellen kann, neigen Benutzer dazu, die Sicherheit der Verbindung zu ignorieren, wodurch sich das Risiko eines Angriffs erhöht.</p>
<p>3. Datenschutzverlust: Wenn Benutzer gestört werden, nutzen sie möglicherweise unsichere Netzwerke oder Anwendungen, was das Risiko eines Datenschutzverlusts erhöht. Insbesondere in öffentlichen WLAN-Umgebungen können Hacker Interferenztechnologie nutzen, um Man-in-the-Middle-Angriffe durchzuführen und Benutzeraktivitäten zu überwachen.</p>
<p>3. So schützen Sie Privatsphäre und Sicherheit</p>
<p>1. Verwenden Sie ein virtuelles privates Netzwerk (VPN): Die Verwendung eines VPN verschlüsselt Ihren Internetverkehr und schützt Ihre Privatsphäre, insbesondere bei der Nutzung öffentlicher WLANs. Ein VPN erstellt einen sicheren Tunnel, sodass Ihre Daten während der Übertragung nicht gestohlen werden können.</p>
<p><a href="https://www.jammermfg.com/de/alle-jammer.html">https://www.jammermfg.com/de/alle-jammer.html</a></p>
<p>2. Vermeiden Sie Verbindungen zu ungesicherten Netzwerken: Versuchen Sie auf Reisen, Verbindungen zu WLAN-Netzwerken zu vermeiden, die nicht passwortgeschützt oder ungesichert sind. Wenn Sie es unbedingt nutzen müssen, stellen Sie sicher, dass Sie zusätzliche Sicherheitsmaßnahmen wie ein VPN oder mobile Daten ergreifen.</p>
<p>3. Aktualisieren Sie Ihre Geräte und Apps regelmäßig: Stellen Sie sicher, dass Ihr Telefon und Ihre Apps immer auf dem neuesten Stand sind, um Sicherheitslücken zu schließen. Hersteller veröffentlichen regelmäßig Updates, um potenzielle Sicherheitsprobleme zu beheben.</p>
<p>4. Verwenden Sie die Zwei-Faktor-Authentifizierung: Die Aktivierung der Zwei-Faktor-Authentifizierung erhöht die Sicherheit Ihrer Online-Konten. Auch wenn ein Hacker Ihr Passwort erhält, benötigt er noch einen zweiten Verifizierungsschritt, um auf Ihr Konto zuzugreifen.</p>
<p><a href="https://www.jammermfg.com/de/DE-N8P-tragbarer-billiger-8-bander-5G-handy-storsender.html"><img src="https://www.jammermfg.com/de/img/DE-N8P/1.jpg" alt="günstige 5g tragbarer handyblocker" width="400"/></a></p>
<p>5. Geben Sie Informationen sorgfältig weiter: Vermeiden Sie es, persönliche Informationen öffentlich preiszugeben, z. B. Kreditkarteninformationen oder private Inhalte in sozialen Medien. Achten Sie auf Ihre Umgebung und vermeiden Sie es, sensible Themen zu besprechen.</p>
<p>6. Verwenden Sie sichere Messaging-Tools: Verwenden Sie bei wichtigen Kommunikationen sichere Messaging-Apps wie Signal oder WhatsApp. Diese Apps bieten eine Ende-zu-Ende-Verschlüsselung, um Ihre Gespräche vor Abhörern zu schützen.</p>
<p>7. Sichern Sie Ihr Gerät: Stellen Sie sicher, dass Sie ein sicheres Passwort für Ihr Gerät festlegen und biometrische Daten (z. B. Fingerabdruck oder Gesichtserkennung) verwenden, um die Sicherheit zu erhöhen und zu verhindern, dass andere auf Ihr Gerät zugreifen, wenn Sie es nicht verwenden.</p>
<p>4. Zusammenfassung</p>
<p>Auf Reisen ist der Schutz Ihrer Privatsphäre und Sicherheit eine wichtige und notwendige Aufgabe. Auch wenn die Existenz von Störsendern und <a href="https://www.jammermfg.com/de/detektor-kaufen.html">HF Detektor</a> gewisse Auswirkungen auf die Kommunikation hat, können Sie durch die oben genannten Maßnahmen potenzielle Risiken wirksam reduzieren und sicherstellen, dass Ihre Daten nicht durchsickern oder verletzt werden. Während wir die Reise genießen, müssen wir wachsam bleiben und unsere persönlichen Daten und Privatsphäre schützen.</p>
<ol>
<li><a href="https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html">https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html</a></li>
<li><a href="https://www.jammermfg.com/de/56W-hochwertige-konferenzraum-handy-und-wlan-stoersender-kaufen.html">https://www.jammermfg.com/de/56W-hochwertige-konferenzraum-handy-und-wlan-stoersender-kaufen.html</a></li>
</ol>
-

@ 6aa0e5a8:f1677da5
2024-11-11 08:42:28
In diesem hochentwickelten technologischen Zeitalter waren Einsamkeit und Isolation des Menschen noch nie so präsent wie heute. Das Aufkommen der [love doll](https://www.wifesexdoll.com/love-doll.html) hat ein tieferes Nachdenken über Intimität und menschliche Bedürfnisse ausgelöst.
Blickt man auf die lange Geschichte der menschlichen Zivilisation zurück, so war der Wunsch nach Intimität und Liebe schon immer ein Teil der menschlichen Natur. In der heutigen schnelllebigen Gesellschaft entfernen sich die zwischenmenschlichen Beziehungen jedoch immer mehr voneinander, und die Veränderungen in den Familienstrukturen haben dazu geführt, dass zu viele Menschen in geistige und körperliche Einsamkeit verfallen. Einigen Daten zufolge befindet sich etwa ein Viertel der Bevölkerung in einem Zustand der dauerhaften Einsamkeit.
Die Einsamkeit lässt die Nachfrage nach [sexpuppe](https://www.wifesexdoll.com) als „virtuelle Begleiter“ wachsen. Auch wenn [Liebespuppe](https://www.wifesexdoll.com/liebespuppen.html) den Reichtum echter Intimität nicht vollständig wiedergeben können, so können sie doch für diejenigen, denen es lange Zeit an Intimität gefehlt hat, die körperliche und emotionale Leere zumindest bis zu einem gewissen Grad stillen. Auf der einen Seite zeigt dies, dass der Fortschritt von Wissenschaft und Technik uns mehr Wahlmöglichkeiten bietet, auf der anderen Seite spiegelt es aber auch einen Teil des Mangels an menschlicher Natur in der modernen Gesellschaft wider.
Davor können wir nicht die Augen verschließen. Wir sollten darüber nachdenken, was zu der Kälte in den intimen Beziehungen zwischen den Menschen geführt hat. Die Zunahme der Zahl der Singles, der Anstieg der Scheidungsrate, die niedrige Geburtenrate usw. sind allesamt Anzeichen dafür, dass der menschlichen Liebe und Intimität in unserer Gesellschaft nicht genügend Aufmerksamkeit geschenkt wird. Wir müssen darüber nachdenken, wie wir die menschliche Wärme wiederherstellen und die zwischenmenschliche Kommunikation stärken können, damit jeder ein Gefühl der Sicherheit und der Zugehörigkeit bekommt.
Gleichzeitig sollten wir auch darüber nachdenken, welche Art von intimer Beziehung wir anstreben. Ist die rein körperliche oder virtuelle Erfüllung nur eine unangebrachte Nachahmung wahrer Intimität? Der Kern einer intimen Beziehung besteht aus zwei Menschen aus Fleisch und Blut, die sich gegenseitig schätzen, verstehen, tolerieren und Verantwortung füreinander übernehmen. Vergessen wir langsam die guten Eigenschaften der Intimität?
Der Zweck der technologischen Entwicklung besteht darin, der Menschheit besser zu dienen, und nicht darin, sie zu entfremden und zu mechanisieren. [real sex doll](https://www.wifesexdoll.com/real-doll.html) geben uns die Möglichkeit zum Nachdenken, es geht nicht um eine schwarz-weiße Entscheidung für richtig oder falsch, sondern wir sollten darüber nachdenken, wie wir Wohlwollen, Wärme und Verantwortungsbewusstsein nutzen können, um das humanistische Fundament intimer Beziehungen aufzubauen und die verlorene Temperatur der menschlichen Natur in dieser Ära des Hochgeschwindigkeitsbetriebs zurückzugewinnen.
1. [https://mastodon.cloud/@wifesexdoll/113450628523233823](https://mastodon.cloud/@wifesexdoll/113450628523233823)
2. [https://mytek.clicforum.com/t291856-Das-Zeitalter-der-Sexpuppen-Sublimierung-oder-Untergang-der.htm](https://mytek.clicforum.com/t291856-Das-Zeitalter-der-Sexpuppen-Sublimierung-oder-Untergang-der.htm)
-

@ 9ff58691:0bf6c134
2024-11-11 08:29:00
Курган - один из крупнейших городов Уральского региона, административный центр Курганской области. За последние двадцать лет этот город претерпел значительные изменения, превратившись из серого провинциального центра в современный, динамично развивающийся город. Об изменениях рассказал Олег Фролов – коренной житель города.
- **Олег, расскажите, как за последние двадцать лет изменился ваш родной город Курган? Что именно изменилось в городе за это время?**
- За эти годы Курган преобразился до неузнаваемости. Когда я был ребенком, город казался мне серым и унылым. Сейчас он стал более современным и привлекательным. Пожалуй, самые заметные изменения произошли в сфере образования и медицины. Многие школы и детские сады были капитально отремонтированы или построены заново. Появились современные учебные классы, оснащенные новейшим оборудованием, включая интерактивные доски, 3D-принтеры и системы искусственного интеллекта для помощи в обучении. Городские больницы и поликлиники были модернизированы, оснащены новейшей диагностической техникой: роботизированные хирургические системы и системы искусственного интеллекта для анализа медицинских данных. Качество и доступность медицинской помощи значительно возросли.


- **А как изменилась культурная жизнь города?**
- Был отреставрирован и значительно расширен городской драматический театр. Открылись новые концертные залы, музеи и выставочные пространства. Стало проводиться гораздо больше культурных мероприятий. Жителям других регионов выдалась возможность посетить каждое культурное место нашего города с помощью экскурсий дополненной вирутальной реальностью. Курган превратился в настоящий культурный центр региона.
- **Как вы оцениваете эти изменения? Довольны ли вы тем, как развивается ваш родной город?**
- Я очень рад тем преобразованиям, которые произошли в Кургане за последние годы. Город стал более комфортным и привлекательным для жизни. Конечно, есть еще над чем работать, но в целом я вижу, что Курган уверенно движется вперед, становясь современным и развитым.
- **Олег, а есть ли у вас в Кургане любимое место, куда вы любите ходить?**
- Безусловно. Мое любимое место - это Центральный парк культуры и отдыха. Это настоящее сердце нашего города. Парк преобразился до неузнаваемости - он стал мобильным, с большим экраном для проведения мероприятий, а голограммы проводят интересные экскурсии. Здесь созданы все удобства для людей с ограниченными возможностями.

- **Что вам особенно нравится в этом парке?**
- Парк очень красивый и ухоженный. Здесь высажено множество зеленых насаждений - деревьев, кустарников, цветов. Есть уютные аллеи для прогулок, детские площадки, спортивные зоны. Летом работают аттракционы, открыты кафе и летние веранды. Зимой заливают большой каток, который очень популярен среди жителей. Мне очень нравится культурная жизнь парка. Здесь регулярно проводятся различные фестивали, концерты, выставки. Летом часто организуют кинопоказы под открытым небом. Зимой работает резиденция Деда Мороза, куда приходят целыми семьями.
- **Похоже, это действительно замечательное место. Спасибо, что поделились своими впечатлениями!**
- Да, и правда замечательное. Я очень рад, что за последние годы он преобразился и стал настоящим центром притяжения для жителей города. Приглашаю всех приехать и лично убедиться в этом!
-

@ 9ff58691:0bf6c134
2024-11-11 06:04:29
За последние 16 лет Курган претерпел значительные инфраструктурные изменения, направленные на повышение качества жизни горожан и развитие города. Ниже представлен обзор основных нововведений:
**Новые здания и сооружения:**
- Построен современный многофункциональный спортивно-развлекательный комплекс "Курганская Арена" с ледовой ареной, бассейном и фитнес-центром.
- Открыт новый корпус Курганского государственного университета, оснащенный по последнему слову техники лабораториями и аудиториями.
- Возведен крупный торгово-развлекательный центр "Курган Молл" с магазинами, кинотеатром, ресторанами и зонами отдыха.
- Построен современный медицинский центр "Курганская клиника", оказывающий широкий спектр высокотехнологичных услуг.

**Транспортная инфраструктура:**
- Открыта новая скоростная автомагистраль, соединяющая центр города с аэропортом и федеральной трассой.
- Запущено движение городского скоростного трамвая, связывающего отдаленные районы с центром.
- Построены два новых транспортных кольца на основных развязках, значительно улучшившие дорожную ситуацию.
- Обновлен автобусный парк, переведенный на экологичные электрические и гибридные модели.

**Благоустройство и озеленение:**
- Реконструирован центральный городской парк с новыми пешеходными зонами, велодорожками и зонами отдыха.
- Высажены тысячи новых деревьев и кустарников, создавшие "зеленые легкие" города.
- Построены новые общественные пространства - набережная, пешеходные улицы и площади с современным дизайном.
- Модернизирована система освещения улиц, переведенная на энергоэффективные светодиодные технологии.

В целом, Курган за последние 16 лет значительно преобразился, став более современным, комфортным и экологичным городом с развитой инфраструктурой. Эти изменения повысили качество жизни горожан и привлекательность Кургана для туристов и инвесторов.
-

@ 8f2fe968:0fbf4901
2024-11-11 02:20:35




-

@ fc15d4c6:fba62950
2024-11-11 00:12:29
>The suspension comes after a proposal to raise the subscription fee to reflect the depreciated Malawian Kwacha was rejected by the Malawi Communications Regulatory Authority (MACRA).
Malawi has an unsustainable trade deficit, which means that more goods and services are imported, than are exported. This results in a shortage of foreign currency, which is needed to pay for imports.
https://techpression.com/starlink-suspends-new-kit-sales-in-malawi
-

@ f33c8a96:5ec6f741
2024-11-10 22:44:14
# JavaScript Cheatsheet for Beginners

## Table of Contents
1. [Variable Declaration](#variable-declaration)
2. [Basic Data Types](#basic-data-types)
3. [Operators](#operators)
4. [Objects](#objects)
5. [Functions](#functions)
6. [Arrays](#arrays)
7. [Conditional Statements](#conditional-statements)
8. [Loops](#loops)
9. [Error Handling](#error-handling)
10. [ES6+ Features](#es6-features)
11. [DOM Manipulation](#dom-manipulation)
12. [Event Handling](#event-handling)
13. [Asynchronous JavaScript](#asynchronous-javascript)
14. [Modules](#modules)
## Variable Declaration
In JavaScript, variables can be declared using `var`, `let`, or `const`.
```javascript
var x = 5; // Function-scoped variable (avoid using in modern JavaScript)
let y = 10; // Block-scoped variable
const MAX_POINTS = 100; // Constant (cannot be reassigned)
```
- `var` is function-scoped and hoisted (avoid using in modern JavaScript).
- `let` is block-scoped and can be reassigned.
- `const` is block-scoped and cannot be reassigned (but object properties can be modified).
## Basic Data Types
JavaScript has several basic data types.
```javascript
let num = 42; // Number
let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats)
let str = "Hello, World!"; // String
let bool = true; // Boolean
let nullValue = null; // Null
let undefinedValue; // Undefined
let symbol = Symbol("unique"); // Symbol (ES6+)
let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+)
```
- `Number`: Represents both integers and floating-point numbers.
- `String`: Represents textual data.
- `Boolean`: Represents `true` or `false`.
- `Null`: Represents a deliberate non-value.
- `Undefined`: Represents a variable that has been declared but not assigned a value.
- `Symbol`: Represents a unique identifier.
- `BigInt`: Represents integers larger than 2^53 - 1.
## Operators
JavaScript includes various types of operators for different operations.
```javascript
// Arithmetic Operators
let sum = 5 + 3; // Addition: 8
let diff = 10 - 4; // Subtraction: 6
let product = 3 * 4; // Multiplication: 12
let quotient = 15 / 3;// Division: 5
let remainder = 17 % 5;// Modulus: 2
let power = 2 ** 3; // Exponentiation: 8
let increment = 5;
increment++; // Increment: 6
let decrement = 5;
decrement--; // Decrement: 4
// Assignment Operators
let x = 10; // Basic assignment
x += 5; // Addition assignment (x = x + 5)
x -= 3; // Subtraction assignment
x *= 2; // Multiplication assignment
x /= 4; // Division assignment
x %= 3; // Modulus assignment
x **= 2; // Exponentiation assignment
// Comparison Operators
console.log(5 == "5"); // Equal to (with type coercion): true
console.log(5 === "5"); // Strictly equal to: false
console.log(7 != "7"); // Not equal to: false
console.log(7 !== "7"); // Strictly not equal to: true
console.log(10 > 5); // Greater than: true
console.log(10 >= 10); // Greater than or equal to: true
console.log(5 < 10); // Less than: true
console.log(5 <= 5); // Less than or equal to: true
// Logical Operators
let a = true, b = false;
console.log(a && b); // Logical AND: false
console.log(a || b); // Logical OR: true
console.log(!a); // Logical NOT: false
// Nullish Coalescing Operator (ES2020)
let nullValue = null;
let defaultValue = nullValue ?? "default"; // "default"
// Optional Chaining Operator (ES2020)
let user = {
address: {
street: "123 Main St"
}
};
console.log(user?.address?.street); // "123 Main St"
console.log(user?.contact?.email); // undefined
// Bitwise Operators
console.log(5 & 3); // Bitwise AND: 1
console.log(5 | 3); // Bitwise OR: 7
console.log(5 ^ 3); // Bitwise XOR: 6
console.log(~5); // Bitwise NOT: -6
console.log(5 << 1); // Left shift: 10
console.log(5 >> 1); // Right shift: 2
console.log(5 >>> 1); // Unsigned right shift: 2
// String Operators
let str1 = "Hello";
let str2 = "World";
console.log(str1 + " " + str2); // Concatenation: "Hello World"
let greeting = "Hello";
greeting += " World"; // Concatenation assignment
// Type Operators
console.log(typeof "Hello"); // "string"
console.log(typeof 123); // "number"
console.log(typeof true); // "boolean"
console.log(obj instanceof Object); // Check if object is instance of a class
```
Key points about operators:
- Arithmetic operators perform mathematical operations
- Assignment operators combine operation with assignment
- Comparison operators return boolean values
- Logical operators work with boolean values and provide short-circuit evaluation
- Nullish coalescing (??) provides a way to specify a default value
- Optional chaining (?.) safely accesses nested object properties
- Bitwise operators perform operations on binary representations
- String operators handle string concatenation
- Type operators help determine variable types
## Objects
Objects are collections of key-value pairs.
```javascript
let person = {
name: "Alice",
age: 30,
sayHello: function() {
console.log("Hello, my name is " + this.name);
}
};
// Accessing object properties
console.log(person.name); // Alice
console.log(person["age"]); // 30
// Calling object methods
person.sayHello(); // Hello, my name is Alice
// Adding a new property
person.job = "Developer";
// Object destructuring (ES6+)
let { name, age } = person;
console.log(name, age); // Alice 30
```
- Objects can contain properties and methods.
- Properties can be accessed using dot notation or bracket notation.
- New properties can be added dynamically.
- Object destructuring allows you to extract multiple properties at once.
## Functions
Functions are reusable blocks of code.
```javascript
// Function declaration
function greet(name) {
return "Hello, " + name + "!";
}
// Function expression
const multiply = function(a, b) {
return a * b;
};
// Arrow function (ES6+)
const add = (a, b) => a + b;
// Default parameters (ES6+)
function power(base, exponent = 2) {
return Math.pow(base, exponent);
}
console.log(greet("Alice")); // Hello, Alice!
console.log(multiply(3, 4)); // 12
console.log(add(5, 3)); // 8
console.log(power(3)); // 9
console.log(power(2, 3)); // 8
```
- Functions can be declared using the `function` keyword or as arrow functions.
- Arrow functions provide a more concise syntax and lexically bind `this`.
- Default parameters allow you to specify default values for function arguments.
## Arrays
Arrays are ordered lists of values.
```javascript
let fruits = ["apple", "banana", "orange"];
// Accessing array elements
console.log(fruits[0]); // apple
// Array methods
fruits.push("grape"); // Add to the end
fruits.unshift("mango"); // Add to the beginning
let lastFruit = fruits.pop(); // Remove from the end
let firstFruit = fruits.shift(); // Remove from the beginning
// Iterating over arrays
fruits.forEach(fruit => console.log(fruit));
// Array transformation
let upperFruits = fruits.map(fruit => fruit.toUpperCase());
// Filtering arrays
let longFruits = fruits.filter(fruit => fruit.length > 5);
// Reducing arrays
let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0);
// Spread operator (ES6+)
let moreFruits = ["kiwi", "pear"];
let allFruits = [...fruits, ...moreFruits];
```
- Arrays can contain elements of any type.
- Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array.
- Higher-order functions like `map`, `filter`, and `reduce` create new arrays.
- The spread operator `...` can be used to combine arrays.
## Conditional Statements
Conditional statements allow you to execute code based on certain conditions.
```javascript
let age = 18;
// if...else statement
if (age >= 18) {
console.log("You are an adult");
} else {
console.log("You are a minor");
}
// Ternary operator
let status = age >= 18 ? "adult" : "minor";
// switch statement
switch (age) {
case 13:
console.log("You're a teenager");
break;
case 18:
console.log("You're now an adult");
break;
default:
console.log("You're neither 13 nor 18");
}
```
- `if...else` statements allow you to execute different code blocks based on conditions.
- The ternary operator provides a concise way to write simple if-else statements.
- `switch` statements are useful when you have multiple conditions to check against a single value.
## Loops
Loops allow you to repeat code multiple times.
```javascript
// for loop
for (let i = 0; i < 5; i++) {
console.log(i);
}
// while loop
let count = 0;
while (count < 5) {
console.log(count);
count++;
}
// do...while loop
let x = 0;
do {
console.log(x);
x++;
} while (x < 5);
// for...of loop (ES6+)
let numbers = [1, 2, 3, 4, 5];
for (let num of numbers) {
console.log(num);
}
// for...in loop (for object properties)
let person = { name: "Alice", age: 30 };
for (let key in person) {
console.log(key + ": " + person[key]);
}
```
- `for` loops are commonly used when you know how many times you want to iterate.
- `while` loops continue as long as a condition is true.
- `do...while` loops always execute at least once before checking the condition.
- `for...of` loops are used to iterate over iterable objects like arrays.
- `for...in` loops are used to iterate over object properties.
## Error Handling
Error handling allows you to gracefully handle and recover from errors.
```javascript
try {
// Code that might throw an error
throw new Error("Something went wrong");
} catch (error) {
console.error("Caught an error:", error.message);
} finally {
console.log("This always runs");
}
// Custom error
class CustomError extends Error {
constructor(message) {
super(message);
this.name = "CustomError";
}
}
try {
throw new CustomError("A custom error occurred");
} catch (error) {
if (error instanceof CustomError) {
console.log("Caught a custom error:", error.message);
} else {
console.log("Caught a different error:", error.message);
}
}
```
- The `try` block contains code that might throw an error.
- The `catch` block handles any errors thrown in the `try` block.
- The `finally` block always executes, regardless of whether an error was thrown.
- You can create custom error types by extending the `Error` class.
## ES6+ Features
ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript.
```javascript
// Template literals
let name = "Alice";
console.log(`Hello, ${name}!`);
// Destructuring
let [a, b] = [1, 2];
let { x, y } = { x: 3, y: 4 };
// Default parameters
function greet(name = "Guest") {
console.log(`Hello, ${name}!`);
}
// Rest parameters
function sum(...numbers) {
return numbers.reduce((total, num) => total + num, 0);
}
// Spread operator
let arr1 = [1, 2, 3];
let arr2 = [...arr1, 4, 5];
// Arrow functions
const square = x => x * x;
// Classes
class Animal {
constructor(name) {
this.name = name;
}
speak() {
console.log(`${this.name} makes a sound.`);
}
}
// Promises
const fetchData = () => {
return new Promise((resolve, reject) => {
// Asynchronous operation
setTimeout(() => resolve("Data fetched"), 1000);
});
};
// Async/Await
async function getData() {
try {
const data = await fetchData();
console.log(data);
} catch (error) {
console.error(error);
}
}
```
- Template literals allow for easy string interpolation.
- Destructuring makes it easy to extract values from arrays or properties from objects.
- Default parameters provide fallback values for function arguments.
- Rest parameters allow functions to accept an indefinite number of arguments as an array.
- The spread operator can be used to expand arrays or objects.
- Arrow functions provide a concise syntax for writing function expressions.
- Classes provide a cleaner syntax for creating objects and implementing inheritance.
- Promises and async/await simplify asynchronous programming.
## DOM Manipulation
DOM manipulation allows you to interact with HTML elements on a web page.
```javascript
// Selecting elements
const element = document.getElementById("myElement");
const elements = document.getElementsByClassName("myClass");
const queryElement = document.querySelector(".myClass");
const queryElements = document.querySelectorAll(".myClass");
// Modifying elements
element.textContent = "New text content";
element.innerHTML = "<strong>New HTML content</strong>";
element.style.color = "red";
element.classList.add("newClass");
element.classList.remove("oldClass");
// Creating and appending elements
const newElement = document.createElement("div");
newElement.textContent = "New element";
document.body.appendChild(newElement);
// Removing elements
element.parentNode.removeChild(element);
// or
element.remove(); // Modern browsers
```
- The DOM (Document Object Model) represents the structure of an HTML document.
- You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`.
- Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`.
- New elements can be created with `createElement` and added to the DOM with `appendChild`.
- Elements can be removed using `removeChild` or the `remove` method.
## Event Handling
Event handling allows you to respond to user interactions and other events.
```javascript
const button = document.querySelector("#myButton");
// Adding event listeners
button.addEventListener("click", function(event) {
console.log("Button clicked!");
console.log("Event object:", event);
});
// Removing event listeners
function handleClick(event) {
console.log("Button clicked!");
}
button.addEventListener("click", handleClick);
button.removeEventListener("click", handleClick);
// Event delegation
document.body.addEventListener("click", function(event) {
if (event.target.matches("#myButton")) {
console.log("Button clicked using event delegation!");
}
});
// Preventing default behavior
const link = document.querySelector("a");
link.addEventListener("click", function(event) {
event.preventDefault();
console.log("Link click prevented");
});
```
- Event listeners can be added to elements using the `addEventListener` method.
- The event object contains information about the event that occurred.
- Event listeners can be removed using `removeEventListener`.
- Event delegation allows you to handle events for multiple elements with a single listener.
- `preventDefault` can be used to stop the default action of an event.
## Asynchronous JavaScript
Asynchronous JavaScript allows you to perform operations without blocking the main thread.
```javascript
// Callbacks
function fetchData(callback) {
setTimeout(() => {
callback("Data fetched");
}, 1000);
}
fetchData(data => console.log(data));
// Promises
function fetchDataPromise() {
return new Promise((resolve, reject) => {
setTimeout(() => {
resolve("Data fetched");
}, 1000);
});
}
fetchDataPromise()
.then(data => console.log(data))
.catch(error => console.error(error));
// Async/Await
async function fetchDataAsync() {
try {
const data = await fetchDataPromise();
console.log(data);
} catch (error) {
console.error(error);
}
}
fetchDataAsync();
// Fetch API
fetch('https://api.example.com/data')
.then(response => response.json())
.then(data => console.log(data))
.catch(error => console.error('Error:', error));
```
- Callbacks are functions passed as arguments to be executed later.
- Promises represent the eventual completion or failure of an asynchronous operation.
- Async/await provides a more synchronous-looking way to write asynchronous code.
- The Fetch API is a modern interface for making HTTP requests.
## Modules
Modules allow you to organize your code into reusable pieces.
```javascript
// math.js
export function add(a, b) {
return a + b;
}
export function multiply(a, b) {
return a * b;
}
// main.js
import { add, multiply } from './math.js';
console.log(add(5, 3)); // 8
console.log(multiply(4, 2)); // 8
// Default export
// utils.js
export default function sayHello(name) {
console.log(`Hello, ${name}!`);
}
// main.js
import sayHello from './utils.js';
sayHello("Alice"); // Hello, Alice!
```
- The `export` keyword is used to expose functions, objects, or primitives from a module.
- The `import` keyword is used to bring functionality from other modules into the current module.
- Default exports can be imported without curly braces and can be given any name when importing.
This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs.
-

@ 8d34bd24:414be32b
2024-11-10 22:42:29
In [Part 1](https://trustjesus.substack.com/p/gods-promises), we got to see God’s initial promises to Adam, Eve, and all mankind with the proto Gospel:
> “He shall bruise you on the head,\
> And you shall bruise him on the heel.”(Genesis 3:15)
We saw God’s promises to Abraham:
- To have his name made great.
- To receive the land of Israel.
- To father many nations.
- That “*in you all the families of the earth will be blessed*.”
We saw God’s reiterated promises to Jacob, Abraham’s grandson.
Now we will look at the partial fulfillment of these promises and new promises made.
## The Promised Land (Quick Summary)
Jacob fathered 12 sons. His son Joseph was sold as a slave to Egypt where he became second to the Pharaoh and saved Jacob’s family and the rest of the Middle East from famine. The Israelites then spent around 400 years in Egypt before Moses was called by God to lead the Israelites to the promised land. God performed awe inspiring miracles through Moses to force Pharaoh to release the Israelites who had been made slaves by the Egyptians.
After crossing the desert, the Israelites reached the promised land, but instead of trusting the God who had rescued them with miracles never before seen, they were fearful and refused to obey God and to enter the promised land. God then had them wander 40 more years in the wilderness until the rebellious adults had all died. Then God miraculously aided this band of shepherds to conquer the land of Canaan and inhabit it, partially fulfilling His promise to give them this land.
After approximately 410 years of judges leading the people of Israel and them repeatedly going astray, God gave them the king they requested, Saul. God gave them a tall and handsome, but selfish and unfaithful king to show them the error of their ways. After showing them their error, God gave them a godly king, a man after God’s own heart.
## David
When God spoke His promise (covenant) with David, He reiterated the promises given to Abraham and to Jacob, but added:
> “When your days are complete and you lie down with your fathers, I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever. I will be a father to him and he will be a son to Me; when he commits iniquity, I will correct him with the rod of men and the strokes of the sons of men, but My lovingkindness shall not depart from him, as I took it away from Saul, whom I removed from before you. **Your house and your kingdom shall endure before Me forever; your throne shall be established forever**.” (2 Samuel 7:12-16) {emphasis mine}
The first part of this promise was fulfilled through David’s son, Solomon. Solomon sat on the throne. Solomon built a temple to worship God. Solomon was not cut off for his sins at the end of his life when he drifted away from God. Even though ten tribes were taken away from Solomon’s son Rehoboam, Rehoboam remained king of the two tribes of Judah and Benjamin and therefore his throne remained.
The final promise, “*Your house and your kingdom shall endure before Me forever; your throne shall be established forever*,” was also partially fulfilled through Jesus at His incarnation and will be fully fulfilled when He returns for His millennial reign.
“*I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever*.” Jesus is a descendant of David and His kingdom will be established at the end of the age — a kingdom of believers. “*He shall build a house for My name.”* Most of the time Israel is referred to as the *house of God* while the church is referred to as the *body of Christ*. In the millennial kingdom they will be united into one house, the adopted children which are the gentile church and the natural children which are the Jews who have finally accepted their Messiah. The final kingdom on this earth will be the millennial reign of Jesus (the promised heir of David), and then God will produce a new heaven and a new earth upon which Jesus will reign forever.
Once again, David did not get to experience the complete fulfillment of the promises made to him. It was partially fulfilled in his son, Solomon, but it has taken thousands of years to partially fulfill this promise and we don’t know for sure how long it will be until complete fulfillment.
## Jeremiah
By the time of Jeremiah, the nation of Israel was gone and Judah was corrupted beyond recognition. The fulfillment of God’s promises seemed impossible, but God’s promises are faithful and true. God spoke to Jeremiah to remind him, that although Judah and Israel were being punished, ultimately, God would fulfill all His promises. He begins with these tender words:
> Now the word of the Lord came to me saying,\
> “Before I formed you in the womb I knew you,\
> And before you were born I consecrated you;\
> I have appointed you a prophet to the nations.”\
> \
> Then I said, “Alas, Lord God!\
> Behold, I do not know how to speak,\
> Because I am a youth.”\
> \
> But the Lord said to me,\
> “Do not say, ‘I am a youth,’\
> Because everywhere I send you, you shall go,\
> And all that I command you, you shall speak.\
> Do not be afraid of them,\
> For I am with you to deliver you,” declares the Lord.\
> \
> Then the Lord stretched out His hand and touched my mouth, and the Lord said to me,\
> “Behold, I have put My words in your mouth.\
> See, I have appointed you this day …” (Jeremiah 1:4-10a)
First God tells Jeremiah that He loves him so much that He formed him in his mother’s womb for a special purpose, to speak His judgement and blessings on Israel. God comforts Jeremiah when Jeremiah fears he is unworthy of the great task God has for him. God promises to be with Jeremiah and to help Jeremiah fulfill His will.
```
As Christians we are similarly told that God created us for His purpose and His blessing and He will be with us, empowering us for whatever tasks He has called us to do.
```
God promises that despite Israel’s nonstop rebellion, He will be gracious and “*not be angry forever*.”
> Go and proclaim these words toward the north and say,\
> ‘Return, faithless Israel,’ declares the Lord;\
> ‘I will not look upon you in anger.\
> For I am gracious,’ declares the Lord;\
> ‘I will not be angry forever.\
> Only acknowledge your iniquity,\
> That you have transgressed against the Lord your God\
> And have scattered your favors to the strangers under every green tree,\
> And you have not obeyed My voice,’ declares the Lord.\
> ‘Return, O faithless sons,’ declares the Lord;\
> ‘For I am a master to you,\
> And I will take you one from a city and two from a family,\
> And I will bring you to Zion.’ (Jeremiah 3:12-14)
God will always fulfill His promises even if that means calling His people home from the ends of the earth where they are scattered “*one from a city and two from a family*.”
God promises to call both Israel and Judah back to the land promised to them all of the way back in time of God’s promise to Abraham. There is a partial return, after Judah’s 70 year exile in Babylon, leading to a rebuilding of the temple for a second time. We are in the middle of another return to Israel that began when Israel was recreated in 1948 and is continuing today. Despite the fact that the people of Israel are being barraged with rockets, drones, and missiles daily and are at risk of being attacked by suicide bombers and terrorists, God is calling His people home for His big finale.
I believe these continuing verses refer to Jesus’s second coming and the millennial reign of Christ.
> “Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding. It shall be in those days when you are multiplied and increased in the land,” declares the Lord, “they will no longer say, ‘The ark of the covenant of the Lord.’ And it will not come to mind, nor will they remember it, nor will they miss it, nor will it be made again. At that time they will call Jerusalem ‘The Throne of the Lord,’ and all the nations will be gathered to it, to Jerusalem, for the name of the Lord; nor will they walk anymore after the stubbornness of their evil heart. In those days the house of Judah will walk with the house of Israel, and they will come together from the land of the north to the land that I gave your fathers as an inheritance. (Jeremiah 3:15-18)
This passage isn’t just a call back to the promised land. This is another promise of God. “*Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding*.” After Jesus’s first coming, He made things clear about His plan of redemption for Israel and for the gentiles. He made clear His promise to bless all nations through Himself, a descendant of David, Jacob, and Abraham, to whom the promises were given. He demonstrated how His laws for the Jews pointed them to God’s ultimate plan.
It is actually ironic that the “*shepherds after My own heart, who will feed you on knowledge and understanding*” are most likely Christian believers who are returned to earth to reign with Christ during the millennial kingdom. Gentile Christians were enabled to have a relationship with God through the Jews and then God will use those gentile Christians to shepherd the Jews back to God, so we can all worship God together.
It won’t be until Jesus’s second coming and His thousand year reign that “*they will call Jerusalem ‘The Throne of the Lord.’*” It won’t be until Jesus’s second coming and His thousand year reign that they will not “*walk anymore after the stubbornness of their evil heart*.” God will finally make the full land of Israel a land of peace and prosperity for the Jews, but also to all the nations of the earth.
But at the time of Jeremiah’s prophecy, God is promising punishment and hardship now to teach His people to be faithful and to trust God’s faithfulness.
> Behold, I am bringing a nation against you from afar, O house of Israel,” declares the Lord.
>
> “It is an enduring nation,\
> It is an ancient nation,\
> A nation whose language you do not know,\
> Nor can you understand what they say. (Jeremiah 5:15)
Due to Israel and Judah’s rebellion, both nations are taken away by a foreign nation into exile. Jeremiah, in particular, prophecies the 70 year exile of Judah in Babylon and their return to the promised land. God promised Abraham and Jacob (Israel) the land of Israel (previously Canaan) and He always keeps His promise, so He always brings them home in ways that are hard to comprehend.
Relatively near the end of the 70 year exile in Babylon, God had Persia conquer Babylon and then a Persian king, not only allowed the Israelites to return to Jerusalem to rebuild the city, the walls, and the temple, but also he funded the return to Israel and returned the gold, silver, and bonze temple implements. What conquering nation does something like that? It was clearly all God.
God may delay His promises, but He never cancels them.
> For this the earth shall mourn\
> And the heavens above be dark,\
> Because I have spoken, I have purposed,\
> And I will not change My mind, \
> nor will I turn from it.” (Jeremiah 4:28)
When God makes a promise, it is as good as done.
Trust Jesus.
-

@ 36bedab2:524acad4
2024-11-10 21:37:52
### 1. **Power ON**
- Quando você liga o computador, ele inicia o processo de boot.
- Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes).
### 2. **BIOS (Basic Input/Output System)**
- O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado.
- Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU.
- O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot.
### 3. **Master Boot Record (MBR) ou EFI Partition**
- O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional.
- Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função.
- O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional.
### 4. **Boot Loader (e.g., GRUB)**
- O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot.
- Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema.
- GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux.
### 5. **Kernel**
- O **kernel** é o núcleo do sistema operacional Linux.
- Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware.
- O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software.
### 6. **Initial RAM disk - initramfs**
- O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel.
- Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco.
- O initramfs é desmontado após o sistema principal estar carregado.
### 7. **/sbin/init (parent process)**
- Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos.
- O init é responsável por iniciar e gerenciar todos os outros processos do sistema.
- Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos.
### 8. **Command Shell using getty**
- **Getty** é o processo que configura e gerencia terminais para o login do usuário.
- Ele exibe a tela de login em sistemas baseados em linha de comando.
- Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico.
### 9. **Graphical User Interface (X Window ou Wayland)**
- Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno).
- Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc.
- X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela.
---
### Como esses processos se intercalam?
1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas.
2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**.
3. **MBR/EFI** localiza e executa o **boot loader** (GRUB).
4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux.
5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**.
6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal.
7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema.
8. **Init** executa o **getty** para configurar o terminal de login.
9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
-

@ bcea2b98:7ccef3c9
2024-11-10 19:34:24
@chess a3
originally posted at https://stacker.news/items/762161
-

@ a901cbe4:bd85452f
2024-11-10 18:33:53
Bitcoin under $100K? Let's be honest: it’s kind of like waiting for your favorite song to drop at a concert. The crowd's hyped, but you're still waiting for the real action to begin. Sure, $80K is cool — it's solid, it's impressive, but it’s not the headline act. The true show begins when Bitcoin crosses that $100K milestone, and until then, we’re in the “pre-game” phase.
Here's why Bitcoin under $100K is merely the warm-up, and why we’re all just biding our time for what’s coming next.
### Bitcoin Under $100K: Just a Pre-Party Vibe
Right now, Bitcoin at $80K feels like that awkward moment at a party when everyone’s gathered in the kitchen, getting their drinks ready, and the music is *almost* turned up. Sure, you can feel the energy, but everyone’s really waiting for the DJ to hit play on that banger. Bitcoin at $80K is promising, but it’s just a preview of the real excitement that’s about to unfold.
This isn’t the time for victory laps. It’s the time to get ready, to watch and wait, because when Bitcoin hits $100K, *that’s* when the party really starts. The market will pop, the spotlight will shine brighter, and the world will be watching as Bitcoin climbs to new heights.
### The $80K Milestone: A Solid Step, But Not The Destination
Let’s take a moment to appreciate $80K. It’s a big number in the world of crypto, and a milestone in its own right. But let’s not kid ourselves — it’s not the finish line. It’s like running a race, getting to the 80% mark, and looking ahead at the final stretch. You’re feeling good, but the best part is still coming.
Bitcoin’s at $80K and that’s a statement, no doubt. But $100K is the magic number. It’s the one that makes the headlines, the one that makes everyone say, “Okay, Bitcoin’s for real.” $80K is impressive, but it’s not the showstopper. So while the excitement is there, we all know Bitcoin’s best performance is still ahead.
### Why $100K Is the Real Milestone We’ve All Been Waiting For
When Bitcoin finally crosses that $100K mark, it’s going to be a global event. It’ll be the moment that people who were skeptical finally start to take notice, the moment when Bitcoin becomes a household name, not just a niche investment. It's like watching a rising star finally step into the spotlight and own the stage.
And here's the thing: When Bitcoin hits $100K, it won’t be a “surprise.” It’s been in the works for years. But it’ll be the moment when everyone truly grasps the scale of what’s happening. The world will finally recognize that Bitcoin isn’t just a speculative asset — it’s a fundamental part of the financial landscape.
### Bitcoin’s Resilience: Boring Until It’s Not
What makes $80K so intriguing isn’t just the number itself — it’s that Bitcoin’s still holding strong, despite all the FUD (fear, uncertainty, doubt) thrown at it. Critics have come and gone, but Bitcoin’s still here, solid as ever. It’s like the underdog story that just refuses to be over.
Bitcoin at $80K is doing its thing, even when people doubt it. It’s showing up every day, proving that it’s built to last. Sure, it may seem like “just another day in the crypto market,” but trust me — Bitcoin’s resilience is what makes this moment significant. It’s not a bubble; it’s an evolution. And that evolution is building toward something even bigger.
### What’s Next: Bitcoin and Beyond $100K
Once Bitcoin hits $100K, everything changes. The narrative shifts. Bitcoin goes from "that risky bet" to "the future of finance." And that’s where things get wild. It’s not just about price anymore — it’s about the institutional and mainstream acceptance of Bitcoin. It’s about the fact that this isn’t a fad, it’s a global movement that’s not going anywhere.
After $100K? Who knows. Maybe $200K, $500K, or more. But let’s not get ahead of ourselves. We’re still waiting for that first major milestone to break, and when it happens, it’s going to be like a flip of a switch. A whole new world will open up.
### The Waiting Game: It’s Gonna Be Worth It
So, while Bitcoin under $100K might feel like a long wait, remember: it’s all part of the journey. Bitcoin at $80K is just the start of something bigger. It’s the calm before the storm, the deep breath before the final sprint.
When $100K hits, we’ll all be able to say we were here for it. And when it crosses that threshold, it’s going to be one of the biggest moments in the world of finance — one that we’ll all look back on and say, "We saw this coming." And for those of us who’ve been riding the wave since the early days? Well, we’ll be popping the champagne.
The real show starts at $100K. We’re just waiting for the curtain to rise. 🚀
-

@ df478568:2a951e67
2024-11-10 14:26:38
*note: This version of the article uses some four-letter words some people may not like. If you prefer cartoon-like cussing, you can read it [here](https://marc26z.com/use-a-seed-signer-with-cold-power/).
It's that time, again--The bull market which happens every 4 years like the Winter Olympics. We've surpassed the previous USD/ATH. This is the 498th resurrection of our beloved bitcoin, but you know what really turns my crank? Bitcoin cybersecurity!
I love digging into the nitty-gritty of cryptography not CrYpTo and finding creative ways to use my toy collection. I mean, hardware wallet(a.k.a. signing devices) collection. Nah, they're toys. Yesterday, as I was playing with my toys, I was inspired to use my seed signer after a long hiatus. To be clear, I love the Seed Signer. It has some neat features:
- Generate seeds with the entropy from a picture
- Hand-drawn QR codes for easy seed backup
- You can DIY

It looks cool too, but for the record, I wouldn't use it for a single sig wallet because it does not contain a secure element. According to NVK, there are zero days and supply chain attacks you can't really mitigate with the seed signer. Although I think this is a fair criticism, it can be useful:
- As an educational tool
- Part of a multi-sig backup.
Michael Flaxman, in his [10X Your BTC Security Guide](https://notes.marcleon.work/#root/0vxct4qCx1C5/YxWwjfah4d4D?ntxId=ApLzSR), suggests removing a Wi-Fi card and hard drive from a computer, boot up TAILS, plug your computer into an RJ45 port with an Ethernet cable for Internet access, navigate to https://seedpicker.net/ on the default [TOR](https://www.torproject.org/) browser, unplug the Ethernet cable from the RJ45 port, and generate the seed for your paper wallet. That sentence is too damn long, but this is indicative of how cumbersome this method is.
This was necessary when he wrote it since we did not have as many hardware wallets back then as are on the market today. In my cybersecurity opinion, and I am not a certified cyber security expert, buying a seed signer requires less technical know-how than using Flaxman's guide. This is not a criticism of Flaxman, his guide is one of my favorite things ever written about bitoin because of it's educational value. If you want to learn about extreme cybersecurity, Flaxman's guide makes an excellent lab. **We assume no network security model is 100% secure,** so we never risk compromising our keys by ever connecting to an Internet-connected device. It's a hell of an education.
## Seed Signer Is For Everybody

Say you work a full time job and didn't spend the majority of your free time learning this stuff during a pandemic. Or maybe you're like my wife. She think's Bitcoin is cool now, but this one time she walked in on me with my Cold Card plugged into a 9v battery and said, "See. I'm never using *whatever the fuck* that thing is. My wife is never removing a Wi-Fi card from a laptop. If you're like my wife, the Seed Signer is right for you, if you want to use multisig. It's also not imperative to use the 9v battery if you don't want to. You can just plug it into a wall outlet like everybody else.
I want to start bringing the Seed Signer to my local meetup, but it's at a brewery and I don't want to be a wallflower because I need to plug the damn thing into an outlet so I thought, “Why not try the [Cold Power](https://usbcoldpower.com/) with my Seed Signer?”
I found one of my [magnetic micro-USB adapters](https://www.amazon.com/Magnetic-Micro-USB-Connector-Water-dustproof-antioxidant/dp/B0D2Y4F9FR/ref=sr_1_1_sspa?dib=eyJ2IjoiMSJ9.czIXiLc88NoDXKD5cqfGUojOf-JD766ZLolCTtGJXJxy9B0I-9g9RbLiB95HffRy8-o6Fo-78ijTjcubw93VYwNn9WaFgg9kraKbLDVYEj50RueMTqz75r7ouUMXD_m1YnNWFIEGNmevIO31B8AT6H_CXzK6loS3Em7R96Q-xL24kYO-Ys0WULVpl_OnFm_9_cqOxqAsGpLskXPRKCV7d7I3EYruyQc82ermd_JIZpY.cCmNDmhUM5mhbNY0xoCENKM9Z9cscEe49zAsKzg8UsU&dib_tag=se&keywords=magnetic+micro+usb+adapter&qid=1731162326&sr=8-1-spons&sp_csd=d2lkZ2V0TmFtZT1zcF9hdGY&psc=1) and plugged it into the Seed signer, Then I plugged the battery in. My switch is on because the flimsy plastic switch broke the first time I turned it on, but it still works. I just broke it with my fat thumbs.
It felt as if it took as long as a difficulty adjustment to boot-up, but in reality it was about the time it takes the Liquid Network to find a block. I proceeded to take a picture and write down a 12 word seed. I plan on using this with the Nunchuck testnet wallet to show people at my local Meetup how to create seeds and take self-custody of their Bitcoin. Again, I would not use this as a single sign because there are more secure options, but it is a great tool for teaching Bitcoin cybersecurity and can be a great wallet that can mitigate the risk of supply-chain and retirement attacks when used as part of a multi-sig quorum. I can also now use it in the middle of a brewery. I'll write about how this goes the next time I get down there.
### Why We Use The Cold Power

I placed one of those magnetic adapters I bought on Amazon into one of the power holes. Power holes is a technical term for microUSB. This is because the Cold Power does hooks up to a cable that does not transmit data, only Power. Get it? It's like a cold wallet, but instead of a wallet, it's a power cable. You hook this cable up to a technology which was invented in 1836, a [battery]. 9V batteries contain no data. It is only Power, but most of us must trust Coinkite. Maybe they programmed the green part to be a bitcoin stealing script. I doubt this and think Coinkite is an honest company, but the awesome sauce thing is, the little magnet I bought on Amazon does not allow the transmittal of data. I don't need to plug in a charger that might be compromised.
This might sound paranoid, but in [Tools of Titans](https://www.amazon.com/Tools-Titans-Billionaires-World-Class-Performers/dp/1328683788), [Samy Kamkar](https://en.wikipedia.org/wiki/Samy_Kamkar), malware has even been found in cigarette lighter chargers. Imagine a fix of nicotine costing you you entire life savings. That's not likely to happen, but why take a chance? It's better to spend several thousand [sats](https://www.investopedia.com/terms/s/satoshi.asp) on a charger and a 9v battery than lose your whole stack.
According to [Wired Magazine](https://www.wired.com/story/infrared-laser-microphone-keystroke-surveillance/), he can also learn the keystrokes you're typing on your laptop keyboard through a window. This means typing a seed onto a laptop might not be the best idea even if you are afraid of this. It is better to take a picture and use the entropy from the random picture.
#### Powering The Seed Signer With A Coinkite Product
Seed Signer and NVK, the CEO of Coinkite seem to have some beef on [nostr](https://nostr.com/), but it's none of my business. The part I find interesting is a product made by Coinkite works with a product made by Seed Signer. This was made for the Cold Card, but it works with a hardware wallet made from someone else. Too bad politics isn't more like that. It's nice to see two rival companies make products that are compatible with each other, but that's just the way free and open source software like bitcoin is. Seeds from Coinkite can be used with the Seed Signer. Maybe that's okay if it's only $1,000 worth of bitcoin on the Seed Signer. You don't need to go to Defcon 5 for every single sat. It's not practical. Sure, if the NSA was after you and wanted to steal your $1,000 worth of bitcoin from you, they could probably do it. Why would they spend ten thousand dollars to do this to you? This is not in most people's threat models.
**Wait...Then why do you need to use the 9v battery thing-a-ma-jig?** I technically don't need to , but we could also use this for a multi-signature quorum? What if you took your wallet to a safe deposit box, but the vault does not have a plug?

I created this key with no power outlet at all. This means I could do this in the middle of Alaska where there's no cell phones, where you only need to worry about bears stealing your seed phrase... That's a bit much, but it's possible.
I was not able to take a picture on the same battery charge so You might want to use a fresh battery if you ever try this yourself.
Thanks for reading.
- If you like this blogs with no swear words, send sats to **marc26z@strike.me/**
- If you like this blog with swear words, send sats to **marc@npub.pro/**
✌️
[npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0no](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0)
[869,719](https://mempool.marcleon.work/block/0000000000000000000173e894282485050b6113e984bafb9a1931dd62e38553)
As Seen On TIR:
http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/use-a-seed-signer-with-cold-power/
-

@ 84999652:2a24d806
2024-11-10 14:10:23
近期,FUD以太坊的声音不绝于耳,大部分声音围绕ETH币价。的确,BTC现在每天破新高,而ETH离2021年的最高点(4800美金)还差近40%。当然,最近ETH币价开始拉升,大有被骂急眼了的感觉。我也相信,这一轮,以太坊大概率是可以破前高的。
**但是,以太坊到底是怎么了?为什么这轮周期完全跟不上比特币的节奏?**
以太坊真的颓势已显?难以再复现当年的辉煌吗?
Crypto行业的新一轮范式创新还会发生在以太坊生态吗?
本文将带您重回Crypto行业的原点——比特币,去反观以太坊和整个行业,以及探讨Crypto行业再次焕发活力的路径可能在哪里?
以太坊真的颓势已显?难以再复现当年的辉煌吗?
Crypto行业的新一轮范式创新还会发生在以太坊生态吗?
本文将带您重回Crypto行业的原点——比特币,去反观以太坊和整个行业,以及探讨Crypto行业再次焕发活力的路径可能在哪里?
##### 一、逃离以太坊惯性
首先,谁都无法全盘否定以太坊!
以太坊有它的价值和开创性意义,智能合约也确实给整个加密行业打开了新局面。至少在以太坊诞生之前,加密行业大多数项目都只是对比特币拙劣的模仿。把比特币代码简单修改几个参数,变成区块更大的比特币、速度更快的比特币、隐私性更好的比特币等等。基本都只是对比特币简单的山寨,山寨币这个概念基本就是概括了以太坊诞生之前的所有Crypto项目。
而以太坊诞生以后,整个Crypto行业又进入了山寨以太坊的浪潮,2015年至今,诞生了不计其数的所谓公链,区块更大的以太坊、速度更快的以太坊、性能更好的以太坊(包括Layer2)等等。
而且每个公链的所谓生态也基本照抄照搬以太坊模式,无非DeFi、GameFi、各类L2、模块化等等。现在散户已经被各类巧立名目、五花八门的叙事概念反复收割的脱敏无感了,于是干脆啥也不信,只玩最简单粗暴的Meme,虽然大家都知道它长久不了,但是至少还可以痛快一博!
**没有创新,没有活力,共识涣散、僵尸横行,整个行业弥漫着看不到希望的末日气息!**
**Crypto行业还有未来吗?**
但是,当你回头去看看比特币,唯独只有它,依然一骑绝尘、屡破新高,似乎完全不受这一切的影响!
我们不禁要想,是不是整个行业陷入“以太坊惯性”太久了,以至于我们都完全忽略了比特币!
**毕竟,以太坊就是灵感于比特币,来源于比特币社区。以太坊就是对比特币的一种解读方式,但是,整个行业把以太坊模式当成了全部。**
如果要找到以太坊的问题所在,以及如果要重新找到新的范式创新机会,那就务必得回到比特币,重新理解比特币,重新在比特币找到创新源泉,就像以太坊诞生之初那样!
让我们一起暂时逃离以太坊惯性,重回比特币去思考!
#### 二、机械共识和社会共识
解读比特币的角度有很多种,但是,我们今天讨论的以太坊和比特币都属于公链范畴。谈到公链,共识机制就是绕不开的话题!
所谓公链,就是公有区块链,是谁公有的?是一群参与共识的人公有的,公链必须依靠共识来驱动,没有共识就没有公链。所以,谈公链如果不谈共识那就是空谈!
**公链的共识分为机械共识和社会共识。**
公链的本质就是依靠一套机械共识来不断凝聚社会共识的去中心化系统。(说一个题外话,Layer2不是公链,Layer2只需要一个定序器节点就可以运行,Layer2本身没有共识机制。Layer2没有机械共识,只有社会共识,因此,Layer2的价值没有机械共识来支持。目前大部分项目,既没有机械共识,也没有社会共识,这是项目失败的根本原因)
所谓机械共识就是一个人人都可以公平参与的共识机制,比如PoW机制,机械共识的参与方式是算力,算力越强,机械共识就越强;所谓社会共识就是围绕公链的生态、影响力,包括链上应用、用户等等数据,最终体现在币价。
**机械共识的参与者是公链的第一投入者、受益者和建设者。**
公链的启动和运行完全依赖机械共识的参与者,机械共识参与者投入大量成本(算力和能源等)参与公链,因此,只有机械共识的参与者,才有最原始的动力去推动公链生态的发展,因为,他们是第一投入者也是第一受益者。因此,为了帮助公链获取更大的社会共识,机械共识参与者会继续推动公链生态的发展,而公链生态吸引来的应用开发者大都是流动的,他们并不如机械共识参与者更深的绑定在公链利益之上(除非他们自己也变成了机械共识参与者)。
这也解释了,为什么比特币生态的早期推动者基本都来自于矿工群体。而以太坊链上的许多头部应用选择另立门户,比如Uniswap等。
**所以,当一个公链的币价开始疲软,那是社会共识变弱了,而更底层原因是机械共识变弱了,或者说参与机械共识的人离散了。**
那么,我们来从”共识‘角度来对比下比特币和以太坊。
#### 三、回归比特币共识,反观以太坊和行业
**比特币的机械共识是一个动态竞赛模式。以太坊的机械共识是一个静态固收模式!**
比特币的矿工要想获得出块权,每一个节点必须在同一时间段投入同样的算力和能源去竞争,但是最终网络只会选出一个节点出块,而其他所有“陪跑节点”的投入作为一种巨大的冗余成本附着在了比特币的价值之中。
通俗点来讲,比特币网络铸造每一枚比特币的实际投入的成本是远远大于单一出块节点支出的成本,它是以消耗所有“陪跑节点”的成本为代价的一种铸造方式。所以,比特币矿工为了已经投入的巨大冗余成本会不断的参与算力竞赛,直到抢到出块权,这是比特币网络共识不断壮大的原因。
**所以,比特币网络的实际共识成本是远远大于目前比特币总市值的**大概是大出多少倍呢?如果我们以比特币历史平均10000个挖矿节点来算的话,这个理论差距应该是1万倍。但是,目前全网比特币活跃矿池约20个,加上单独Solo的矿工,我们预估总共50个,我们把矿池当作一个总节点,这个成本差距大致有50倍。
这就是比特币的PoW动态算力竞赛模式给比特币带来的共识安全性,所以,比特币的共识安全几乎是无法评估的强度!
而以太坊的PoS机制是一个静态固收模式,实际投入多少ETH可以获得多少ETH收益,基本是一个静态的固定收益,目前基本稳定在5%左右。所以,ETH共识的参与者不需要竞赛,不需要额外支出冗余成本,只需要算账,就可以不需要投入额外成本的情况参与利益分配。这也是以太坊早期宣传的所谓PoS机制不会产生能源消耗的“优点”。但是,这个“优点”也变成了以太坊网络共识的弱点。**因为没有冗余成本的投入,以太坊的共识成本实际变低了,因此,以太坊网络的共识价值实际上也降低了!**
所以,当把比特币的PoW机制和以太坊的PoS机制进行对比时,你就会发现,比特币的网络共识成本几乎是不可估量的,随之不断的算力和能源投入,其共识是无上限的。而以太坊的共识是有上限的,是可计算的,ETH的质押率就是以太坊的共识上限。
因此,在机械共识层面,比特币的机械共识相较于以太坊也更强大,从而进一步影响了社会共识的差异,最终,直接表现在了币价层面。
**不仅如此,如果从物理学(热力学)角度去看比特币的POW机制,我们会发现,POW机制驱动着比特币成为一个更接近生命体的熵减系统,这是比特币网络一直充满生命和活力的物理学原理。**
在热力学角度,宇宙中所有的事物都是走向熵增,也就是从有序走向无序,从秩序走向混乱,最终走向寂灭!
但是,只有一个例外,那就是生命!
生命以负熵为食——薛定谔。
所谓负熵是一种可以帮助内部系统从无序转向有序的外部能量。生命就是通过消化负熵,把无序转换为有序,在局部时空中创造了熵减。
但是,熵减现象只是存在于局部时空,而且,生命每形成一分熵减,就会向外部宇宙排放两分熵增,两者相加,对于宇宙来讲仍然是熵增。
比特币的PoW机制,就是让网络内一群混乱无序的拜占庭节点,通过不断消化算力和能源进行运算求解,最终,运算最快的节点获得出块权,节点间迅速验证并达成共识,最终,一个无序混乱的网络达成了一致性,形成了一种秩序,也就是创造了一个熵减系统,一个生命体!
**因此,在比特币这个生命体,矿工从外部输入的算力和能源是“负熵”,可以帮助比特币网络内混乱无序的节点达成共识和一致,从而创造了熵减系统。那么,PoW机制就是比特币这个生命体的消化系统,矿工提供“负熵”,最终,成就了比特币这个生命体!**
这是比特币可以一直壮大生长的物理学原理。
那么,我们来反观以太坊:
以太坊创立之初也是照用PoW机制并持续运行了超过七年,这七年也是以太坊突飞猛进的七年。直到2022年9月,以太坊正式从PoW机制转向PoS机制,一切悄然发生了变化。
切除PoW机制,让以太坊失去了外部算力和能源的输入,也就丧失了持续吸食“负熵”的能力,就像一个切除了肠胃又未能找到替代方案的生命体,虽然,短时间内实现了瘦身,但是,由于缺乏持续的进食能力,逐渐走向衰亡几乎是必然的。
有人说,以太坊之所以价格疲软,那是因为生态缺乏创新,链上应用和用户没有持续新增所导致的。那么,造成这些情况的更深层原因是什么?
**就像我们前面说的,机械共识直接影响社会共识。生态、应用、用户、币价这些都是社会共识的表现,社会共识变弱的本质是因为机械共识变弱了。**
**以太坊的机械共识为何变弱了?**
PoS机制是静态固收模式,缺乏算力和能源竞争,无法形成冗余成本,进而机械共识削弱了;PoS机制缺乏吸食“负熵”的能力,无法通过输入“算力和能源”来抵消系统内部的熵增趋势;PoS的质押机制也直接导致了富者恒富、阶级固化,当阶级固化,形成的就是社区缺乏创新和活力,最终这些能力外溢,便成就了其他竞品。
这一系列表现出来的就是以太坊生态、应用、用户、币价等社会共识指标的疲软!即使可以通过强行拉升币价去拔高社会共识,但是,物理学原理是不可违背的。
**以太坊确实颓势已现,这轮周期步步落后于比特币,就是最真实的结果!而下一轮周期也必将拉开更大的距离!**
以太坊尚且如此,其他模仿以太坊的公链,必然也难逃颓势!Crypto行业走到如今的地步,真可谓是,成也以太坊,败也以太坊!这或许是任何一个行业在发展过程中都会经历的。
**但是,机遇往往也在此刻出现!**
Crypto行业更大的机遇肯定不在现有的以太坊模式里,一定需要逃离”以太坊惯性“,重新回归这个行业最早的上下文,回到这个行业最早的原点,从那里寻找答案!
#### 四、重回比特币共识,挖掘比特币无尽宝藏
回归比特币再创新,这是一个行业问题,也是一个长久的事业,或许,在短时间内,我们很难突破。但是,当我们开始破除以太坊迷信,开始回归比特币重新再思考时,除了发现‘共识“这些背后细节之外,还有可能发现更多从未注意到的隐藏细节。
这些细节让我们对基于比特币进行再次范式创新充满了希望!
比如,直观上大家会认为,在处理交易方面,以太坊会比比特币更高效。但,实际上并不是。
比特币的UTXO模型在处理交易时,可以实现并发处理交易和独立状态变更,而且不需要一个统一的世界状态树来更新状态。甚至说,比特币压根就没有所谓的账户概念,用户地址上显示的比特币余额,实际上是代表某个用户掌握的私钥所能控制UTXO总面额。
UTXO模型在处理交易时,就像真实的交易环境中,任何一对交易双方都可以拿着不同面额的“UXTO”现金进行频繁交易,交易双方的交易状态完全不会影响第二对交易双方的交易进度,因为,UTXO都是可以独立进行状态变更,不需要一个统一的中央状态树来做变更。
而以太坊采用传统的账户模型,也就是传统的银行账户模型。账户模型在处理交易时,需要依靠一个全局的状态树来给每一笔交易所涉及的地址进行余额的加减计算,因此,每一次交易状态都需要先变更完之后,才能进行下一个交易,否则就会出现双花或者无法交易等问题。因此,账户模型只能做串行处理。
通俗来讲,以太坊的账户模型,需要一个中心的世界状态树来统一处理交易,来统一变更所有账户的状态,虽然,这个世界状态树是去中心机制来驱动的,但是,由于其需要一个中心来统一处理和进行全局状态变更,导致,其很难执行并发交易以及更灵活的交易模式。
我们没发现的比特币细节还有很多。
单就 “并行处理状态变更的能力“ 方面,比特币的UTXO模型是完胜以太坊账户模型的。而且,UTXO的这种并发处理和独立状态变更的能力,还可以拓展到任意需要独立变更状态以及并发处理的事物中去,也就是UTXO可以表达除了比特币交易之外的其他事物状态,比如,预测市场的状态变更、AI安全模型的状态变更等等。
而且由于比特币的并发处理状态变更的能力受到全球最大机械共识——比特币共识的保护,这让比特币网络更加独一无二和不可替代。共享比特币共识安全+UTXO并发状态变更,这两项能力加在一起就可以迸发无限能量。这是很多人之前没有发现的细节。当然,我们很高兴已经看到比特币生态的创业者已经往这个方向挺进,比如,基于客户端验证和UTXO模型的BitVM方案;以及前段时间宣布放弃比特币Layer2赛道,全面转向“共享比特币共识安全+UTXO并发状态变更“的BEVM团队等。
当我们转换思路就会发现,比特币这个无尽宝藏,其开发和应用进度几乎不足1%。
#### 总结:
当我们开始脱离以太坊惯性来看整个行业,我们可以直面一些之前不敢直面的问题,当我们重新回到比特币去思考,又可以从比特币汲取无限的灵感和创新方向。以太坊的诞生不过是对比特币的一种抽象思考和解读,而后来的创业者放弃了思考,全面复制以太坊模式,这是整个行业逐步缺乏持续创新和活力的背后原因。
当然,我们看到了一些团队开始回归比特币,开始重新思考,比如,共享比特币共识安全+UTXO并发状态变更就是一个极具潜力的创业方向。
**真正的范式创新并不是简单的模仿,而是要抽象背后的原理。瓦特创造的蒸汽机并没有直接引发工业革命,而是有人抽象总结了蒸汽机背后的科学原理(热力学定律),从而引发了科学的范式革命。**
如果,中本聪是瓦特,比特币是蒸汽机,那么,Crypto行业的这16年,大部分人都是在模仿比特币制作大量的不同功能、不同形式的“蒸汽机”,却鲜有人去思考和抽象比特币本身所蕴含的科学原理,以至于这个行业迟迟没有引发真正的比特币范式革命。
当然,我们已经看到有团队在往这方面思考,这是行业的曙光,我们需要更多的人加入,一起推动比特币范式革命的到来!
**本文灵感主要来源于比特币学习交流暑社区“中本聪大学”**
TG链接:https://t.me/satoshiedu
**本人长期在中本聪大学和诸多比特币OG及爱好者深度交流学习比特币,一起探讨Crypto行业发展机遇。**
-

@ c0e4bd0b:1c5734af
2024-11-10 12:15:08
# Bitcoin Calendar Definition
Layer: Applications
Status: Draft
Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows.
```
nBlocksPerYear = 210000 / 4 // calculates to 52,500
nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375
```
The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h:
```
year = h / 52500
month = (h % 52500) / 12
```
Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder:
```
nBlocksPerDay = 144
daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something
```
A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin.
This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant.
**Cross-referencing with other calendar systems:**
Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none.
# Bitcoin Calendar Synchronization
Layer: Consensus
Status: Draft
The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year.
To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period.
The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows:
|Year|Block|Date|Days|
|-:|-:|--|-:|
|0|0|01/03/09||
|1|52500|04/22/10|474|
|2|105000|01/28/11|281|
|3|157500|12/14/11|320|
|4|210000|11/28/12|350|
|5|262500|10/09/13|315|
|6|315000|08/10/14|305|
|7|367500|07/29/15|353|
|8|420000|07/09/16|346|
|9|472500|06/23/17|349|
|10|525000|05/29/18|340|
|11|577500|05/23/19|359|
|12|630000|05/11/20|354|
|13|682500|05/07/21|361|
|14|735000|05/05/22|363|
|15|787500|04/29/23|359|
|16|840000|04/19/24|356|
As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption.
Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that.
If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose.
**Fork considerations by the author:**
A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar.
The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require.
More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes.
**Proposed activation method:**
Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster.
**Optional second-phase activation:**
For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern.
*Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).*
-

@ c0e4bd0b:1c5734af
2024-11-10 12:13:26
# Bitcoin Calendar Definition
Layer: Applications
Status: Draft
Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows.
```
nBlocksPerYear = 210000 / 4 // calculates to 52,500
nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375
```
The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h:
```
year = h / 52500
month = (h % 52500) / 12
```
Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder:
```
nBlocksPerDay = 144
daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something
```
A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin.
This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant.
**Cross-referencing with other calendar systems:**
Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none.
# Bitcoin Calendar Synchronization
Layer: Consensus
Status: Draft
The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year.
To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period.
The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows:
|Year|Block|Date|Days|
|-:|-:|--|-:|
|0|0|01/03/09||
|1|52500|04/22/10|474|
|2|105000|01/28/11|281|
|3|157500|12/14/11|320|
|4|210000|11/28/12|350|
|5|262500|10/09/13|315|
|6|315000|08/10/14|305|
|7|367500|07/29/15|353|
|8|420000|07/09/16|346|
|9|472500|06/23/17|349|
|10|525000|05/29/18|340|
|11|577500|05/23/19|359|
|12|630000|05/11/20|354|
|13|682500|05/07/21|361|
|14|735000|05/05/22|363|
|15|787500|04/29/23|359|
|16|840000|04/19/24|356|

As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption.
Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that.
If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose.
**Fork considerations by the author:**
A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar.
The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require.
More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes.
**Proposed activation method:**
Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster.
**Optional second-phase activation:**
For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern.
*Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).*
-

@ c0e4bd0b:1c5734af
2024-11-10 12:05:10
# Bitcoin Calendar Definition
Layer: Applications
Status: Draft
Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows.
```
nBlocksPerYear = 210000 / 4 // calculates to 52,500
nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375
```
The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h:
```
year = h / 52500
month = (h % 52500) / 12
```
Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder:
```
nBlocksPerDay = 144
daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something
```
A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin.
This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant.
**Cross-referencing with other calendar systems:**
Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none.
# Bitcoin Calendar Synchronization
Layer: Consensus
Status: Draft
The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year.
To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period.
The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows:
|Year|Block|Date|Days|
|-:|-:|--|-:|
|0|0|01/03/09||
|1|52500|04/22/10|474|
|2|105000|01/28/11|281|
|3|157500|12/14/11|320|
|4|210000|11/28/12|350|
|5|262500|10/09/13|315|
|6|315000|08/10/14|305|
|7|367500|07/29/15|353|
|8|420000|07/09/16|346|
|9|472500|06/23/17|349|
|10|525000|05/29/18|340|
|11|577500|05/23/19|359|
|12|630000|05/11/20|354|
|13|682500|05/07/21|361|
|14|735000|05/05/22|363|
|15|787500|04/29/23|359|
|16|840000|04/19/24|356|

As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption.
Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that.
If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose.
**Fork considerations by the author:**
A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar.
The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require.
More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes.
**Proposed activation method:**
Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster.
**Optional second-phase activation:**
For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern.
*Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).*
-

@ f462d21e:1390b6b1
2024-11-10 11:44:59
eyJfaWQiOiIxMGRmODZiMS02NTdjLTQwNjUtYjVjOC1kNmY2YmJlNjRhN2IiLCJwdWJsaWNLZXkiOiJmNDYyZDIxZTEwMTYzZWIwYTQwM2FlYzZiOTNhYzU3ZWMyZjFiOTQ1NTQ3M2U5OTMwNGY1NzFhNTEzOTBiNmIxIiwidXNlcm5hbWUiOiJqb2UiLCJhZFR5cGUiOiJPTkxJTkVfU0VMTCIsImNvdW50cnkiOiJVbml0ZWQgS2luZ2RvbSIsImNvdW50cnlDb2RlIjoiR0IiLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6IlZFTk1PIiwicHJpY2VJbnB1dFR5cGUiOiJNQVJLRVQiLCJtYXJnaW4iOjMsImZpeGVkUHJpY2UiOjAsIm1pbkFtb3VudCI6MCwibWF4QW1vdW50IjowLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoiYmVzdCByYXRlcyByZWFsbHkiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsImhpZGRlbiI6ZmFsc2UsImJhbm5lZCI6ZmFsc2UsInZlcmlmaWVkIjp0cnVlLCJhZGRlZCI6IjIwMjQtMTEtMDFUMDc6MTk6MjEuMDk5WiIsIm1hcmtldFByaWNlIjoxNjUuMzF9
-

@ 07907690:d4e015f6
2024-11-10 09:50:14
Bitcoin diciptakan oleh Satoshi Nakamoto, (hampir pasti) sebuah nama samaran, yang hingga hari ini belum ada seorang pun yang dapat secara meyakinkan menghubungkannya dengan orang atau sekelompok orang yang sebenarnya. Nakamoto menghilang dari internet pada tahun 2011, meninggalkan sedikit petunjuk tentang siapa "mereka". Selama bertahun-tahun, banyak orang secara terbuka mengaku sebagai Satoshi, semuanya gagal mendukung pernyataan tersebut dengan fakta yang tidak dapat disangkal.
Dalam forum awal bitcointalk, Satoshi mengatakan bahwa mereka mulai mengerjakan Bitcoin pada tahun 2007, dua tahun sebelum blok pertama ditambang. Blok Genesis, atau blok pertama dalam blockchain Bitcoin, ditambang pada tanggal 3 Januari 2009. Nakamoto adalah penambang blok Genesis, menerima 50 bitcoin pertama yang pernah diedarkan. Namun, hadiah dari blok pertama ini tidak dapat digunakan karena keunikan dalam cara blok Genesis diekspresikan dalam kode. [BitMEX Research](https://blog.bitmex.com/satoshis-1-million-bitcoin/) telah menerbitkan analisis pada hari-hari awal penambangan Bitcoin dan menyimpulkan bahwa “seseorang” menambang 700,000 koin. Meskipun banyak yang berasumsi ini adalah Satoshi, secara resmi hal ini masih belum terbukti.
Kita hanya bisa membayangkan ketenaran yang akan diterima Satoshi Nakamoto jika identitas mereka terungkap, belum lagi kekayaan besar yang ingin mereka kumpulkan (meskipun Satoshi tampaknya tidak menghabiskan satu pun koin yang seharusnya mereka tambang). Seiring berjalannya waktu, ada banyak contoh orang yang mengaku sebagai Satoshi, dan ada pula yang diyakini sebagai Satoshi.
## Klaim Palsu
Salah satu kasus paling terkenal tentang seseorang yang mengaku sebagai Satoshi adalah yang dilakukan oleh [Craig S. Wright](https://bitcoinmagazine.com/articles/op-ed-how-many-wrongs-make-wright), seorang akademisi Australia. Wright, pada awal tahun 2015, telah mencoba berkali-kali untuk memberikan demonstrasi publik dengan bukti yang tidak dapat disangkal bahwa dia adalah penemu Bitcoin, namun dia belum berhasil hingga saat ini. Faktanya, “bukti”-nya terbukti palsu.
Dorian Nakamoto, seorang pria di California, pernah secara terbuka diberi gelar sebagai pencipta Bitcoin oleh seorang jurnalis surat kabar yang melihat beberapa kesamaan antara kedua Nakamoto, yang paling jelas adalah nama belakang mereka. Namun, dengan sangat cepat, klaim ini [ditolak oleh Dorian dan juga dibantah](https://bitcoinmagazine.com/articles/how-the-hunt-for-satoshi-turned-dorian-nakamoto-s-life-upside-down-the-inside-story-1443721034).
Kelompok orang lain yang menarik perhatian seputar identitas Satoshi yang tidak diketahui adalah kriptografer dan ilmuwan komputer. Hal Finney, seorang kriptografer terkenal yang merupakan orang pertama yang menerima bitcoin dari Satoshi Nakamoto, adalah salah satu tersangka paling terkenal karena keterlibatan awalnya dalam bidang tersebut. Kurang dari setahun setelah Bitcoin diciptakan, Satoshi dan Hal Finney bertukar beberapa postingan di forum diskusi Bitcoin, membahas hal-hal seperti teknologi dan implikasinya di masa depan. [Finney meninggal karena ALS](https://bitcoinmagazine.com/articles/hal-finney-salute-1409690363) pada tahun 2014, menyebabkan beberapa orang berspekulasi mengenai sejauh mana keterlibatannya dengan mata uang terdesentralisasi pertama di dunia. Nick Szabo adalah kriptografer terkenal lainnya yang menciptakan Bit Gold, mata uang digital yang ditemukan beberapa tahun sebelum Bitcoin. Fakta bahwa dia tampaknya tidak terlibat langsung dengan penciptaan Bitcoin, meskipun proyeknya sangat mirip dengan itu, telah membuat beberapa orang berspekulasi bahwa dia mungkin juga pencipta Bitcoin.
## Mengapa Satoshi Harus Anonim?
Satoshi Nakamoto, pencipta mata uang terdesentralisasi pertama di dunia, harus tetap anonim karena sifat penciptaannya. Setelah membuat protokol tanpa titik utama kegagalan, Nakamoto mungkin menyadari bahwa mempertahankan anonimitasnya dapat menghilangkan titik utama kegagalan terakhir yang mungkin dimiliki Bitcoin: orang yang menciptakannya. Menghapus identitas tunggal yang dapat dikaitkan dengan kemunculan Bitcoin berarti menghilangkan segala wajah yang dapat mempengaruhi politik, aturan, atau pengambilan keputusan komunitas Bitcoin.
Siapa pun Satoshi, tidak dapat disangkal bahwa mereka adalah seorang jenius di zaman kita. Protokol Bitcoin memberikan insentif ekonomi di semua tempat yang tepat sehingga menghasilkan solusi luar biasa terhadap Masalah Jenderal Bizantium. Satoshi Nakamoto menerapkan konsep-konsep dari kriptografi, matematika, teori permainan, dan ekonomi untuk menciptakan aset digital langka yang dirancang dengan indah — dan pertama di dunia — yang disebut Bitcoin.
Sumber artikel: [bitcoinmagazine.com](https://bitcoinmagazine.com/guides/who-created-bitcoin)
Diterjemahkan oleh: Abengkris
-

@ c11cf5f8:4928464d
2024-11-10 07:58:46
Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, [here](https://stacker.news/items/751696/r/AG) are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/761231
-

@ e1d968f7:5d90f764
2024-11-10 06:01:24
If there's one thing I know for sure, it's this: life is *too short* not to make the most of every moment. That’s why I don’t just walk through life—I *own* it. My name’s Rebecca Knight, and I’m the kind of woman who leaves a lasting impression, whether it’s with a wink across a crowded room or a conversation that lingers long after it’s over.
I’m not your average woman, and I’m certainly not afraid to show it. I’ve got that magnetic charm that draws people in, a little playful sparkle in my eye that says, “Come closer, if you dare.” I love making people feel seen, heard, and most of all—*alive.* There’s something about making someone smile or laugh that gives me the rush of a lifetime. Maybe it’s the thrill of connection or the way people react when they realize I’m exactly the kind of woman they didn’t know they needed in their lives.
When I meet someone, I don’t just show up—I make it memorable. Whether it’s in the way I laugh at a joke, the intensity of a conversation, or the way I give you my undivided attention, there’s no denying it: I know how to keep you on your toes. And when it comes to my work, it’s no different. I know exactly how to create a space where we both feel at ease, where the chemistry can spark and the tension can build. It’s all about the connection. The energy. The way we feed off each other.
But let’s be real: I don’t just give for the sake of giving. I believe in *mutual enjoyment.* I’m all about making sure both of us are having the time of our lives. Whether we’re sharing an intimate laugh, a heated conversation, or simply enjoying each other’s company in a way that feels… exciting, it’s always about balancing that electric pull with respect and mutual understanding.
Being bold is fun, but being *respectful* is key. I don’t believe in anything forced or out of alignment with what feels good. If I want something, you’ll know it, and if you want something, I’m always happy to listen. But here’s the thing: I’m not interested in anything halfway. I play for keeps, and I expect to have my energy matched in the best possible way.
So, if we ever find ourselves in the same space, be prepared for a little bit of magic. I’m the kind of woman who brings excitement, fun, and a healthy dose of mischief into every room I enter. I know how to turn the ordinary into extraordinary, and how to leave a lasting impression without breaking a sweat.
After all, life’s a game, and I’m *very* good at playing it. If you ever find yourself wondering if you’re the next lucky person I’ll take on that little adventure… let’s just say I’m sure you’ll know when it happens.
-

@ a10260a2:caa23e3e
2024-11-10 04:35:34
nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard.
In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW.
I took some screenshots to give you an idea of how things work.
The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).

Clicking login allows signing in with a browser extension.
The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.
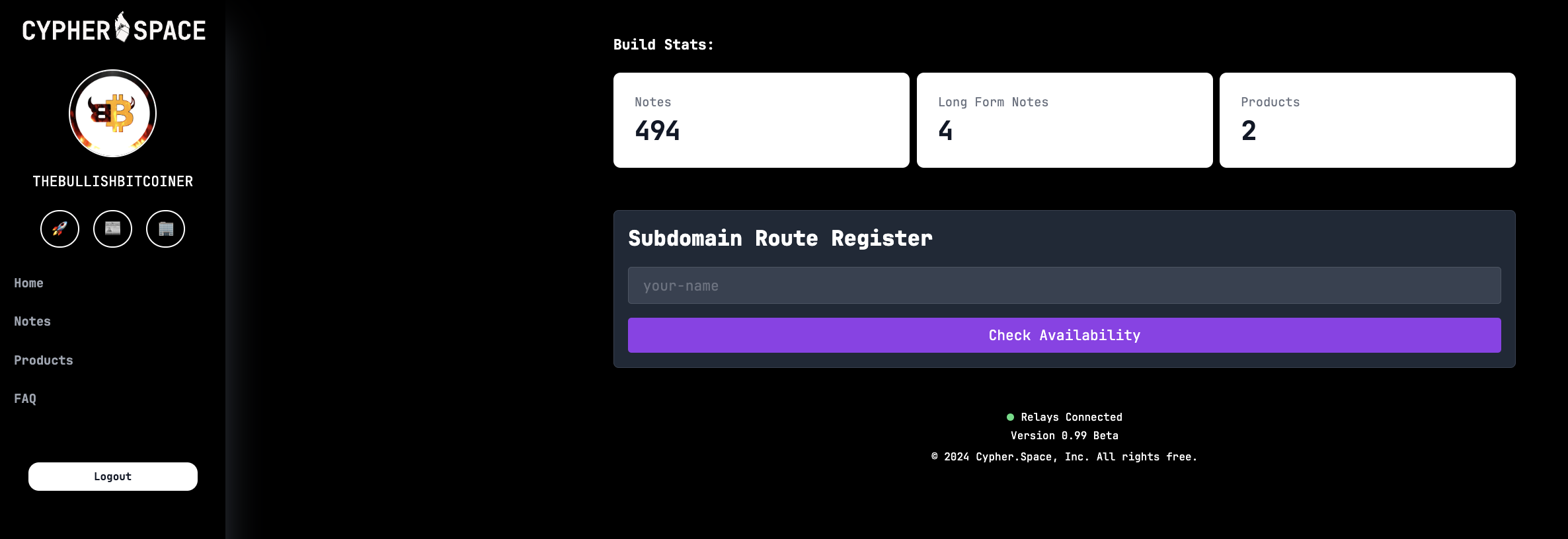
Existing blog posts (i.e. long form notes) are synced.

Same for product listings. There’s a nice interface to create new ones and preview them before publishing.
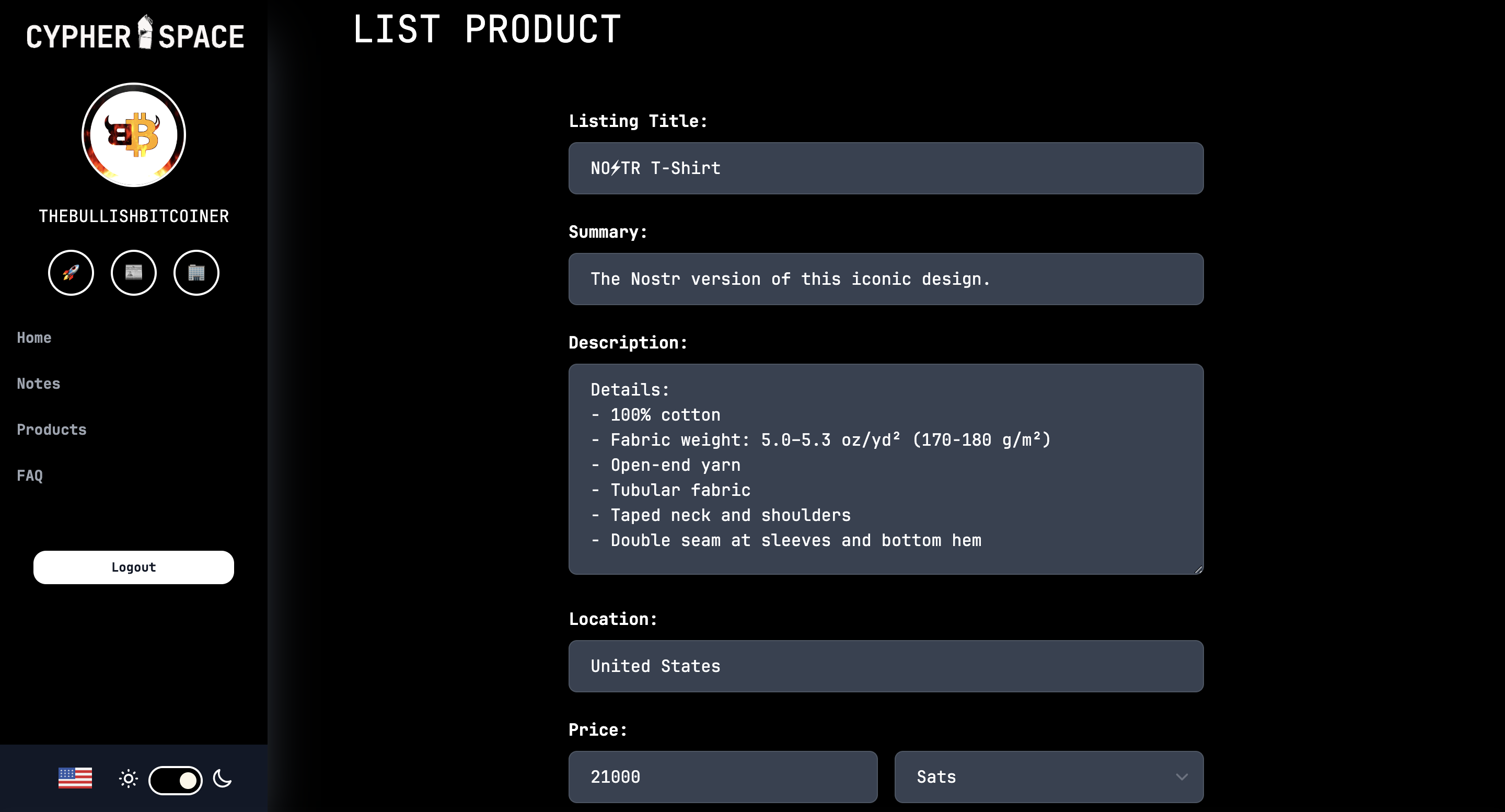
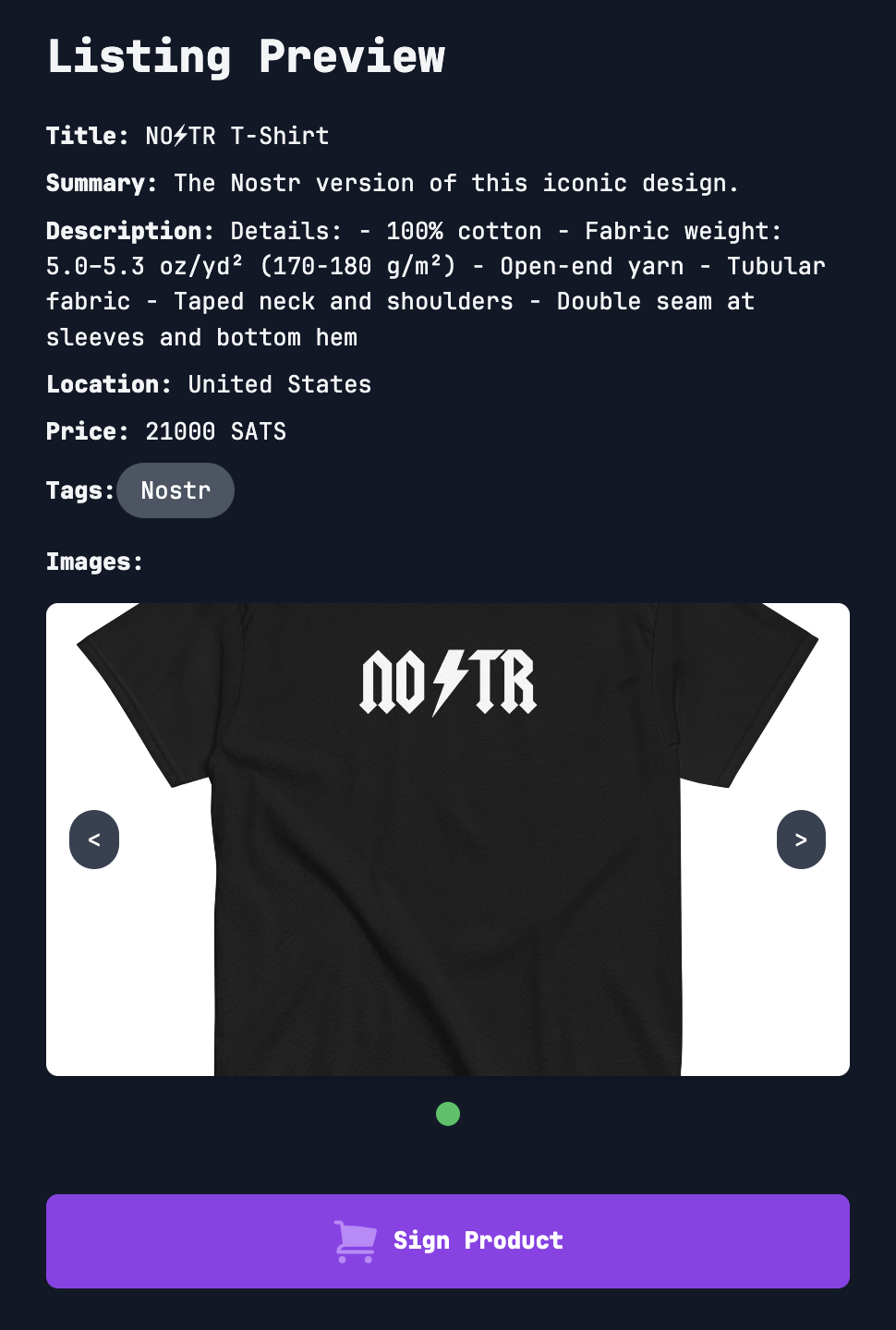
That’s all for now. As you can see, super slick stuff!
Bullish on Cypher.
So much so I had to support the project and buy a subdomain. 😎
https://bullish.cypher.space
originally posted at https://stacker.news/items/760592
-

@ 07e1bb93:f9523a3c
2024-11-10 03:46:57
In the ever-shifting landscape of American politics, few partnerships have proven as effective in advancing the conservative agenda as the relationship between President Donald Trump and Senator JD Vance. The alignment of their values, priorities, and vision for America has been a game-changer, not just for the Republican Party, but for the nation as a whole. Here’s why Trump needed JD Vance — and why this partnership is one for the history books.
### 1. **A Shared Vision for America’s Working Class**
Both President Trump and JD Vance have made it clear that their top priority is restoring the strength and prosperity of America's working class. Trump’s 2016 campaign reshaped the Republican Party into one that stands unapologetically with blue-collar Americans. Vance, in his bestselling book *Hillbilly Elegy*, captured the struggles of America’s heartland, painting a picture of a forgotten class that Trump understood and aimed to champion.
Vance’s personal experience of growing up in a working-class family in Appalachia allows him to connect with the very people Trump promised to fight for. When Trump needed someone who could speak authentically to the struggles of rural America — a place often left behind by both parties — JD Vance was the perfect ally. His commitment to restoring dignity to working families and fighting against globalist policies that shipped jobs overseas aligns perfectly with Trump’s America First agenda.
### 2. **Fighting the Swamp Together**
One of Trump’s most significant promises was to drain the swamp — to rid Washington of the establishment elites who have sold out America’s interests in favor of their own. JD Vance’s political career has been a direct response to this very problem. As someone who understands the dangers of big-money politics and the media’s influence, Vance has shown that he’s not afraid to take on the establishment — whether it’s Big Tech, Big Pharma, or the bureaucratic deep state.
Together, Trump and Vance make an unstoppable force in the fight against Washington corruption. Vance’s no-nonsense approach to tackling the elites, combined with Trump’s bold, take-no-prisoners attitude, sends a clear message to D.C. — the days of business as usual are over.
### 3. **A Bold, Unapologetic Conservative Voice**
Trump revolutionized the Republican Party by unapologetically embracing a bold, conservative agenda — one that emphasizes securing the border, standing strong against China, and advocating for American sovereignty. JD Vance has proven to be a fierce defender of these principles. His strong stance against illegal immigration, as well as his commitment to bringing American jobs back home from China, make him an invaluable ally in Trump’s fight to put America first.
In the face of global challenges and domestic strife, Trump needed someone like JD Vance who would stand firm in the face of leftist pressure, the mainstream media, and cancel culture. Vance’s resilience and courage in sticking to conservative principles make him an indispensable ally in Trump’s quest to reclaim American greatness.
### 4. **Rural America’s Voice in Washington**
Trump’s deep connection with rural America was one of the key factors in his 2016 victory. In JD Vance, Trump found a kindred spirit who understands the heartbeat of Middle America. Vance, who has firsthand knowledge of the hardships faced by families in small-town America, brings a fresh perspective to the Senate that Trump can rely on.
From advocating for policies that support American agriculture to pushing back against the cultural elites who are trying to rewrite America’s values, Vance is a powerful voice for the people who have long been overlooked by Washington politicians. With Vance in the Senate, Trump gained a strong advocate for rural communities, ensuring that their concerns are heard at the highest levels of government.
### 5. **Fighting the Culture Wars**
In addition to economic policies, Trump and Vance share a common commitment to fighting the culture wars. Vance, with his deep understanding of the impact of media, education, and corporate culture on America’s identity, has been an outspoken critic of the left’s radical agenda. He has voiced concerns about the erosion of traditional American values and the dangers of left-wing identity politics.
Trump needed someone who could not only challenge the left’s policies but also defend the cultural heritage of America. Vance’s intellectual and cultural insights make him an essential ally in this battle. Together, they form a powerful counterweight to the woke left’s attempt to undermine the very fabric of American society.
### 6. **A Partnership for Victory**
At its core, the Trump-Vance alliance is about winning — for the American people. It’s about rebuilding a nation that works for its citizens, standing up against forces that seek to weaken it, and ensuring that America remains a beacon of freedom, opportunity, and strength on the global stage.
Trump needed JD Vance because Vance’s voice is a reflection of the heart of America. Together, they represent the future of the Republican Party — a future that is grounded in traditional values, fierce independence, and a relentless pursuit of the American Dream.
### Conclusion
In JD Vance, President Trump found an ally who shares his vision, his commitment to the working class, and his passion for restoring American greatness. As this partnership continues to grow, there’s no doubt that Trump and Vance will be a dynamic duo, leading the charge against the forces of globalization, corruption, and cultural decay.
For all the talk of division in American politics, the Trump-Vance partnership reminds us that unity is possible when leaders stand firm in their beliefs, fight for what’s right, and work together for the future of our nation. It’s a partnership built on trust, shared values, and an unyielding love for America — and that’s exactly why Trump needed JD Vance.
-

@ 07e1bb93:f9523a3c
2024-11-10 02:43:16
In a world riddled with complex international conflicts, one thing has become crystal clear: President Trump has always had the backbone to cut through the noise and focus on what matters. Now, as he gears up for his second term, Trump has shown once again that he’s committed to protecting American interests and prioritizing a smart approach to foreign policy. His strategy for Ukraine is a powerful example of this.
For years, American leaders have funneled billions of dollars in aid to Ukraine, with no clear end to the conflict in sight. In nearly three years of fighting, the devastation has been staggering, and the cost to both Ukraine and the U.S. has been massive. Despite the endless funding and political gestures, little has changed on the ground. Now, President Trump is stepping in with a promise to end the bloodshed by prioritizing a practical and peace-centered approach.
According to Trump’s longtime advisor Bryan Lanza, Trump’s goal isn’t to pursue impossible dreams of reversing Russia’s control over Crimea but to create real, lasting peace. Lanza made it clear that this administration’s focus is on bringing stability back to Ukraine, not forcing American troops or taxpayers into a mission with no end in sight. For Ukrainians, this means a renewed emphasis on diplomacy and a hard look at what peace can realistically look like.
And this approach isn't just about saving money. It’s about setting smart priorities. Trump knows that securing Crimea again may be an unrealistic goal and that pushing for it could mean risking U.S. involvement in yet another costly, endless war. He’s clear: Ukraine’s demands for massive military support to regain every inch of land may not be in the best interest of the American people.
Some have worried that this peace-first approach will embolden Russia. But in reality, Trump’s plans show that he's willing to have the tough conversations, make the hard decisions, and ensure American strength while avoiding another drawn-out conflict. He's also open to diplomatic solutions, as evidenced by Russia’s indication that they are willing to discuss his ideas for peace. Moscow’s Deputy Foreign Minister Sergei Ryabkov recently expressed a surprising openness to Trump’s proposals, as long as they don’t involve further escalation or massive military aid.
In recent months, we've seen a breakdown in trust between Trump and Zelenskyy, fueled by differing visions for the future of Ukraine. Trump, though, has never been afraid to call out world leaders—even allies—when they push for policies that don’t serve America's best interests. He’s committed to ending the war in Ukraine swiftly, promising peace that respects both America’s role and the resources of the people.
Some will call Trump’s approach bold, and they’re absolutely right. In the coming months, we can expect him to push the envelope to achieve peace—not just for the sake of the Ukrainians but for Americans who deserve a leader who puts them first. As we transition into this new chapter, it’s clear Trump has a vision: a peaceful, practical resolution that avoids wasteful spending, reckless decisions, and a costly cycle of conflict. And that’s something we can all get behind.
-

@ 4cec8c79:1511abda
2024-11-09 22:15:32
Navigating Job Offers in Nigeria: Opportunities and Challenges
Nigeria, the most populous country in Africa, offers a dynamic job market that spans multiple industries. With its youthful population, growing tech sector, and diverse economy, job seekers face both opportunities and challenges. This article explores the job offer landscape in Nigeria, focusing on the key sectors, the job search process, and factors that both employers and potential employees must consider.
Key Sectors Offering Job Opportunities
1. Technology and ICT:
Nigeria has been called the "Silicon Valley of Africa" due to its rapidly growing tech ecosystem. Cities like Lagos and Abuja are hubs for startups and innovation, with companies focusing on fintech, e-commerce, software development, and mobile technology. Tech giants like Andela, Paystack, and Flutterwave have made Nigeria a key player in the global tech space, offering high-paying jobs for software developers, data analysts, and cybersecurity experts.
2. Oil and Gas:
The oil and gas industry remains one of the largest employers in Nigeria, contributing significantly to the country's GDP. Jobs in this sector range from engineering and project management to environmental science and logistics. Multinational companies like Shell, Chevron, and Total offer numerous positions, but the industry is also highly competitive and often requires specialized skills or experience.
3. Agriculture:
With a large rural population and favorable climate, agriculture remains a vital sector for Nigeria's economy. The government has launched several initiatives aimed at promoting agribusiness and food security, which has led to job growth in areas like agritech, farming, supply chain management, and food processing.
4. Banking and Finance:
The banking sector in Nigeria is robust, offering opportunities for those in finance, accounting, marketing, and management. In addition to traditional banking roles, Nigeria’s thriving fintech industry offers job opportunities in digital payments, lending, and financial inclusion platforms. Major players like GTBank, First Bank, and Zenith Bank are often on the lookout for skilled professionals.
5. Education and Health:
Education and healthcare are both sectors that offer steady employment, especially in underserved areas. The rise of online learning platforms and private schools has boosted demand for teachers, while the healthcare sector, especially with the COVID-19 pandemic, has underscored the need for medical professionals, public health workers, and researchers.
6. Entrepreneurship and Startups:
Entrepreneurship is flourishing in Nigeria, with many young Nigerians turning to startups to solve local challenges. The rise of digital platforms and access to funding through venture capital and government grants has made it easier for entrepreneurs to grow businesses. From logistics and retail to food delivery and fintech, Nigerian startups are generating job opportunities for creative and tech-savvy individuals.
Challenges Faced by Job Seekers
1. Unemployment and Underemployment:
Despite the booming sectors, Nigeria faces a high unemployment rate, especially among its youth. According to recent statistics, over 33% of the labor force is unemployed, with even more individuals underemployed, working in low-wage or part-time positions. This imbalance is one of the biggest challenges job seekers face, as they compete for a limited number of well-paying jobs.
2. Skill Mismatch:
Many graduates in Nigeria find themselves in a situation where their education doesn't align with the demands of the job market. This skills mismatch is particularly evident in sectors like technology, where there's a demand for highly specialized skills in programming and data science. Upskilling
~~__****__~~
-

@ b6424601:a11e4ff4
2024-11-09 19:45:51
**Personal Asset Architecture - Breaking Free from the Fiat-Driven Housing Market**
***Subheading – How Individuals Can Opt Out of the Fiat-Driven System and Create Homes with long term value***
As a self-inflicted residential architect, I am passionate about creating new, renovated homes that matter to interesting people. However, I've realized that the traditional housing market is built on a foundation of fiat currency, leading to several problems, including the potential devaluation of homes and, increasingly, the creation of empty stores of value.
**The Fiat Death Spiral**
Construction financing drives the most decisions in the housing market, which leads to a system where production homes are built to sell and create an initial profit rather than to provide a high-quality construction or a well-conceived living space.
**The Choice: Custom vs. Fiat**
When building or buying a home, you have two main options: a custom home built or renovated to your specifications or a production home pre-designed and pre-built by a builder.
**Fiat-Driven Homes: The Short-Term Solution**
Fiat-driven homes are built to sell quickly, often using materials that fit the deals proforma. Because of lower-quality materials and construction methods, Fiat homes depreciate more like cars than buildings.
**Custom Homes: The Long-Term Solution**
On the other hand, custom homes are typically built with higher quality and better design because the owner and designer are more invested in creating one-of-a-kind designs.
**A New Approach: Personal Asset Architecture**
As an architectural design firm owner focusing on homes, I've always known that the percentage of all homes architects design is low. I've used the low percentage as a filter for working with longer-term thinking clients, typically paying with cash. Clients who pay with cash have the flexibility to pay for what they want, allowing them to think about the total cost over the life of the house rather than just jumping through the hoops of a loan-to-value appraisal.
Bitcoin standard architectural practice and Bitcoin standard homes are the escape valves to continue the work we want for the individuals we want to work for. Our thesis is that Bitcoin can improve the housing market, both for our practice and for the clients we work with. Our thesis is that Bitcoin changed the housing market for our practice and the people we work with to build a personal architecture that is as hard an asset as Bitcoin.
**Asset Architecture Benefits**
Homes designed in a BTC standard have four big benefits for the individual to create personal asset architecture that holds value over time.
1\. Allows owners to think in a longer time horizon – Decisions made when designing homes need to consider a longer time horizon to include the operating cost of the house in addition to the cost of construction. Production homes are built to sell and create profit based on profit produced, netting profit by the sales price vs cost. Custom homes have more flexibility in spending more on quality and life cycle improvements.
2\. Allows for a density of design thought - Can you design a better-conceived home that considers how to use space more effectively to provide a denser space so the house can require less square footage? Can the smaller square footage be planned to work as a lifetime home from a starter home, through offspring to empty nesting and multigenerational housing?
3\. Providing a return on investment beyond money – A home should produce a better quality of life. Can homes produce income, food, energy, resilience, conservation of resources, and interior air quality and become your favorite place to be? Can the utility of needing a place to live be your family citadel?
4\. Working with the system to minimize the power of the system to increase taxes on the asset - Can we design homes to reduce property taxes with a creative design to minimize bedrooms and the taxable house value? Can we put more investment and design in outdoor space that helps owners maximize the use of properties for uses that are not taxed, like quality outdoor space or properties that produce food and energy?
The future of housing is uncertain, but one thing is evident from the trenches: the traditional fiat-driven system is not sustainable. Personal Asset Architecture offers a new approach to housing design that prioritizes long-term value, efficiency, and quality. By embracing this approach, we can create precious homes that produce a return on investment beyond money. The future of housing is in our hands, and it's time to create a new way of thinking about home design.
**What is possible?**
As individual owners and architects, we can build Stores of value buildings. By incorporating the goal of creating Personal Asset Architecture, we can create homes that produce a return on investment that goes beyond money and minimize the values of a banking system and the ability to increase taxes on the asset.
Stay humble, stack stakes, and when you are ready, choose to build stuff that holds actual value.**
**HODL on**
-

@ 4ba8e86d:89d32de4
2024-10-29 12:30:05
## Tutorial feito por Grom Mestre⚡
Poste original Abaixo.
Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7
Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035
Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113
Boa tarde, camaradas do meu coeur!
Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb.
Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele.
Dito isso, vamos prosseguir.
TÓPICOS:
Introdução
Instalando e configurando o roteador e o navegador
Conectando-se a serviços na I2P
Configurações avançadas
## 1. Introdução
### 1.1 Definindo a DeepWeb.
Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos.
Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas.
Vamos aos pontos individualmente:
> São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração.
> São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe...
> São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio.
https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg
> Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador.
A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação.
https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg
Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança.
As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar:
• Lokinet
• Zeronet
• Freenet
• I2P
• Tor
• Gnunet
Porém, há alguns casos interessantes que não caem diretamente nessa regra .
A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento.
Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento.
Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos.
Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface.
DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa.
DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface.
Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting).
Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito.
Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service.
## Instalando e configurando o roteador I2P
Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela.
O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela.
Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas:
• Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing )
• Modelo P2P
• Todos os participantes da rede contribuem para ela
• Fechado na rede - não é possível acessar a surface através da I2P
• Otimizado para hidden services
Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada.
Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas.
Referências:
• https://geti2p.net/en/comparison/tor
• https://geti2p.net/en/docs/how/garlic-routing
• https://geti2p.net/en/about/intro
• https://i2pd.readthedocs.io/en/latest/
### 2. Instalando e configurando o roteador
Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição.
Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso.
### 2.1 Instalação do router
Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação.
O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ).
Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P.
Para usuários de Windows, segue abaixo os binários para instalação.
• Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip )
• Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip )
• Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip )
A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'.
Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070.
https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg
https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
### 2.2 Instalação e configuração do navegador
Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado.
Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas.
### 2.2.1 Escolhendo o navegador
Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ )
### 2.2.2 Criando um perfil e configurando o lançador
Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile'
https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
Coloquem um nome no seu perfil e cliquem em Finalizar
https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg
Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador.
Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'.
Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho.
Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf.
https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg
2.2.3 Configurando o proxy
Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora.
Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings)
https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg
Configure o seu proxy como na figura abaixo.
https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg
Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites.
• http://identiguy.i2p
• http://notbob.i2p
• http://reg.i2p
Se tudo ocorreu como conforme, a página será carregada.
https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg
OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070)
https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg
IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção.
• noScript
• JShelter
Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações.
Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem.
https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg
Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado.
Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP
## [TUTORIAL] Conectando-se ao XMPP pela I2P
Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P.
Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável.
### 3.1 Escolhendo o cliente XMPP
Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada.
Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ )
### 3.2 Criando uma conta
Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais.
Para criar uma conta, siga os passos abaixo:
Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta
https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg
https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg
Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk)
https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp
Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se
https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg
Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas
https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg
Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela.
https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg
https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg
No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'.
https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg
Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente).
Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel).
https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg
Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo.
https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg
Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções:
• Tempo ocioso
• Hora de Sistema Local
• Sistema Operacional
• Reprodução de Mídia
https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg
### 3.3 Procurando por salas de bate-papo públicas
Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços
https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg
Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?).
https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg
https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg
### 3.4 Adicionando contatos
Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'.
https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg
Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir.
https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg
https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg
Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :)
https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg
E com isso terminamos a terceira parte da série de tutoriais.
## [TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet.
Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy
Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients
BONUS: Conectando-se facilmente à I2P.
https://youtube.com/watch?v=wGIh5tQcw68
-

@ 5d4b6c8d:8a1c1ee3
2024-11-09 19:04:04
The Emirates Cup begins on Tuesday, so it's time to start thinking about our first picks.
For a refresher on the tournament, see the [first post](https://stacker.news/items/751054/r/Undisciplined). Note, though, that there are actually going to be seven group play days with each team playing four total group play games.
# Games
Here is the first slate of games (plus the home spread):
- Hawks @ Celtics (-12.5)
- Heat @ Pistons (+3)
- Hornets @ Magic (-8)
- Knicks @ 76ers (-1)
- Raptors @ Bucks (-8)
- Suns @ Jazz (+4.5)
- Mavs @ Warriors (+2.5)
Just pick one of the teams above to win their game on Tuesday.
Remember, you can only take each team once and the options will dwindle once we get to the Knock Out round. There are at most 10 choices to make during the tournament, but you don't know which ones will be available towards the end.
I'm going to wait a couple of days, to get more clarity on the injury situations for the Heat, Magic, 76ers, and Bucks. At first glance, I'm leaning towards taking either the Heat, but with Jimmy hurt and the Pistons looking a little frisky, I don't love it.
# Prize
27133 sats! plus whatever else comes in from here on out
# Participants
@Undisciplined, @gnilma, @BlokchainB, @realBitcoinDog, @Carresan, @supercyclone, @grayruby
There's still time to join. The initial buy-in is only 3k sats.
originally posted at https://stacker.news/items/760645
-

@ 8d34bd24:414be32b
2024-10-27 22:30:18
NOTE: *This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.*
When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior.
In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance.
## Seek the Welfare of the City Where I Have Sent You
As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia.
> Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1)
What did God say to the Israelites about how they should live their life in Babylon?
> “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare**.’ (Jeremiah 29:4-7) {emphasis mine}
Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.”
God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “*for in its welfare you will have welfare*.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price.
We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands.
We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves.
## Political Religion
Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties.
> No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13)
Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God.
When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally.
> You shall have no other gods before Me.
>
> You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6)
When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion.
We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different.
I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge:
*I pledge allegiance to the Flag of the United States of America,\
and to the Republic for which it stands,\
one Nation under God,\
indivisible, with liberty and justice for all.*
I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “*serve two masters*.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right.
## In the World, but Not of the World
As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship[1](https://trustjesus.substack.com/p/should-christians-vote#footnote-1-150236181) and family are in heaven, not here on earth.
We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ.
> But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. **I have given them Your word; and the world has hated them, because they are not of the world**, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. **They are not of the world, even as I am not of the world**. Sanctify them in the truth; **Your word is truth**. (John 17:13-17) {emphasis mine}
Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God.
Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior.
> **Do not love the world nor the things in the world**. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. **The world is passing away**, and also its lusts; but **the one who does the will of God lives forever**. (1 John 2:15-17) {emphasis mine}
The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics.
Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles:
> Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13)
There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “*as having been with Jesus*.”
I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God.
> Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, **so that they may be saved**. (1 Corinthians 10:32-33) {emphasis mine}
Trust Jesus.\
\
your sister in Christ,
Christy
-

@ 2063cd79:57bd1320
2024-11-09 18:34:43
Einer der großen Vorteile von Bitcoin ist, dass es relativ einfach ist Bitcoin selbst zu verwahren. Ich predige self-custody, also die Eigenverwahrung, von Bitcoin in fast jeder Ausgabe als einer der Hauptkomponenten der Formel für Freedom Money rauf und runter. Doch was genau bedeutet es seine bitcoins selbst zu verwahren? Denn schließlich verwaltet jeder mündige Bürger seine Finanzen, ob in Bitcoin oder nicht, in der Regel ja immer selbst. Es gibt einen großen Unterschied zwischen verwalten und verwahren. Denn das Verwahren übernehmen bei anderen Assets Dritte für uns, sei es die Bank, die unser Geld auf Konten, Hypotheken und Sparanlagen, manchmal sogar Wertsachen in Schließfächern, verwahrt, Finanzbroker oder Depotbanken, die Wertpapiere wie Aktien, Bonds oder ähnliches, verwahren, oder Versicherer, die Policen, Sparvermögen, usw. für uns verwahren. Immer sind Drittparteien mit der Verwahrung unseres Besitzes vertraut, oder haben sich uns aufgedrängt, weil es schlichtweg nicht anders möglich ist, diese Besitztümer völlig autark zu verwahren. Bei Bitcoin ist das anders. Bitcoin lässt sich ähnlich wie Bargeld, Gold oder Schmuck völlig autark und selbstbestimmt verwahren. Dabei gibt es, wie bei allem im Leben, sowohl einfache und bequeme, aber dadurch unsichere, als auch komplizierte und etwas aufwändigere, aber deshalb sehr sichere Verwahrungsmethoden. Eine sehr sichere Methode stellt die Verwahrung mit Hilfe von MultiSig (also Multi-Signature) dar. Dieses wollen wir uns diese Woche genauer anschauen.
---
Eine der großen Errungenschaften von Bitcoin ist die Möglichkeit der Eigenverwahrung, sogenanntes self-custody. Es bietet jedem//jeder Hodler//in, Anleger//in und Investor//in eine völlig autarke und selbstbestimmte, Methode zur Verwahrung und Kontrolle seines Besitzes und damit einen Schutz vor Zensur, Kontrolle und Übergriffen.
Ohne zu sehr ins Detail zu gehen, möchte ich kurz grundlegend die Sicherheitsstruktur von Bitcoin darlegen. Jede//r Nutzer//in sollte zunächst über eine Wallet verfügen. Eine Wallet ist kein Muss, um mit Bitcoin in Kontakt zu treten, jedoch versucht ja auch niemand das Internet ohne Browser zu verwenden. Eine Wallet ist, ähnlich wie der Internetbrowser, eine Software, die es dem Nutzenden ermöglicht Bitcoin zu erhalten, zu versenden oder zu verwahren (ohne Bitcoin direkt zu erhalten, zu versenden oder zu verwahren - kompliziert, ich weiß). Dabei gibt es ein weites Spektrum an verschiedenen Diensten. Es gibt Wallets, Börsen oder andere Verwahrungs-Services. Um das Thema MultiSig zu besprechen, fokussieren wir uns auf Wallets.
Im Grunde besitzt jede//r Halter//in von Bitcoin ein Schlüsselpaar - einen privaten Schlüssel (Private Key) und einen öffentlichen Schlüssel (PubKey). Vergleicht man das Konzept mit dem alten Finanzsystem würde man sagen, der öffentliche Schlüssel stellt die Kontonummer dar, also die Information, die öffentlich geteilt werden kann und der private Schlüssel stellt die PIN Nummer dar, also die Information, die nur die//der Besitzer//in haben sollte. Der private Schlüssel ist also die Information, die es zu schützen gilt, denn in Kombination erlauben mir die beiden Schlüssel Zugriff auf die sich dahinter befindenden bitcoins. Ein bitcoin lässt sich nicht aus der Blockchain extrahieren. Die einzelnen Coins existieren nur innerhalb der Chain (und nicht als ganze "Coins", sondern als Outputs/UTXOs). Lediglich der Besitzanspruch wird außerhalb gehandhabt. Das bedeutet, dass ich mit meinen beiden Schlüsseln den Zugriff oder Anspruch auf eine gewisse Anzahl bitcoins ausweisen kann. Habe ich Zugriff auf den privaten Schlüssel, kann ich also ohne weiteres komplett über alle damit verbundenen bitcoins verfügen, sie ausgeben, sie weiterversenden (oder akkurater formuliert: eine Nachricht signieren, die dem Empfänger die Kontrolle über diese bitcoins gewährt), oder sie sogar zerstören. Wallets übernehmen die Speicherung der Schlüssel, sowohl der öffentlichen, als auch der privaten, in einem für den Anwender benutzerfreundlichen Interface.
Sogenannte Hot Wallets, sind Apps, die mit dem Internet verbunden sind, und dadurch "hot" oder "live" sind, das heißt sie können im schlimmsten Fall gehackt werden. Cold Wallets sind offline Lösungen, die sich nicht online hacken lassen, aber z.B. im Falle eines Paper Wallets leicht verlieren, stehlen, oder zerstören lassen. Das Problem, wie oben erwähnt, ist je bequemer und nutzerfreundlich die Handhabung der Wallet, desto unsicherer ist sie in der Regel auch. Also jegliche Software Wallets, egal ob mobil oder auf dem Rechner daheim, stellen Sicherheitsrisiken dar, da sie wieder einen Drittanbieter in die Gleichung schleusen. Um volle Autarkie zu erlangen muss man sich von Drittanbietern, wie Wallet Anbietern, Börsen oder sonstigen Services, komplett lösen und die Schlüssel und damit seine bitcoins selbst verwahren. Denn die eiserne Regel gilt immer: Not your keys not your coins!
<img src="https://blossom.primal.net/8e6e7e4f26037de171bd35f620263966bb3f2325777490f2174094ac91a72979.png">
Wenn man einen Betrag von seiner Wallet senden möchte, wird eine Transaktion erstellt und signiert. Indem die Transaktion signiert wird, beglaubigt man in digitaler Form, dass man der Eigentümer des Betrages ist, dass man die Schlüssel besitzt, um es zu verwalten, und man die Transaktion genehmigt. Es wird also der Besitzanspruch signalisiert und weitergegeben, und kein bitcoin physisch bewegt. In einer Single-Signature Wallet benötigt man nur eine Signatur, um eine Transaktion zu signieren. Bei MultiSig (Multi-Signature) erfordert die Wallet mehrere Signaturen, um eine Transaktion zu signieren. Eine MultiSig-Wallet wird dabei von zwei oder mehreren Benutzern geteilt. Wird also eine Transaktion erstellt, muss die Anfrage zunächst von allen Teilnehmern bestätigt werden. MultiSig ist ein Aufbewahrungsmodell, bei dem eine Wallet mit mehreren Schlüsseln in einem m-von-n-Schema erstellt werden. Also beispielsweise eine 2-von-3-Wallet basierend auf drei Schlüsseln, von denen zwei zum Bestätigen einer Transaktion erforderlich sind. Es gibt auch andere Modelle wie 3-von-3, oder 3-von-5, etc. allerdings stellt 2-von-3 die gängigste Methode dar. Das Schöne an diesem Modell ist, dass es Single Points of Failure (SPOF) eliminiert. Das bedeutet, dass selbst sonst kritische Informationen, wie Seed-Phrase-Backups oder Hardware-Wallets, sogar von Angreifern gestohlen, oder durch einen Unfall verloren oder zerstört, werden können, ohne dass die Wallet kompromittiert wird. Es ist hilfreich, sich die MultiSig-Wallet als einen digitalen Safe vorzustellen. Man besitzt dabei verschiedene Schlüssel zu diesem Safe. Im Beispiel von der 2-von-3-Wallet hat der Tresor zwei Schlüssellöcher und drei Schlüssel. Zwei beliebige der drei Schlüssel können verwendet werden, um den Safe zu entriegeln, damit die darin gespeicherten bitcoins bewegt werden können.
<https://x.com/cryptograffiti/status/1544763238721601537>
Das bedeutet jedoch nicht, dass man mit einer MultiSig-Wallet unvorsichtiger umgehen sollte, denn trotz der Flexibilität, die MultiSig bietet, sollte man ein Seed-Phrase-Backup erstellen und vermeiden, Hardware-Wallets oder Seed-Phrasen gemeinsam aufzubewahren. Fast alle Anbieter von guten, sicheren und seriösen Wallet Software, sowie Hersteller von Hardware-Wallets bieten an MultiSig-Wallets innerhalb ihrer Apps anzulegen. Der Prozess ist ein wenig aufwändiger, als das Anlegen einfacher Single-Signature-Wallets, die Vorteile überwiegen den Aufwand aber deutlich. Ein MultiSig-Wallet schützt in der Regel, und wenn ordentlich gehandhabt, vor Phishing, Malware, Verlust der Schlüssel, Verlust von Hardware, wie Telefon, Laptop oder Hardware-Wallet, aber auch vor Diebstahl und Unfällen.
<img src="https://blossom.primal.net/fe9202a17b5af87cafd7270d78353bd4746bbe45a038c0fd8a7855454e828cf6.png">
MultiSig-Wallets dienen nicht nur der Sicherheit, sondern können darüber hinaus auch weitere Nutzen haben. MultiSig kann auch als Zwei-Faktor-Authentifizierung für Bitcoin Transaktionen verstanden werden. Die vielfachen privaten Schlüssel können auf verschiedenen Geräten gespeichert und auf die im MultiSig-Wallet gespeicherten Coins nur zugegriffen werden, wenn alle Schlüssel vorhanden sind. bereitgestellt werden. Auch gibt es Szenarien, in denen ein MultiSig-Wallet als treuhänderischer Dienst funktionieren könnte. Zwei Parteien vereinbaren eine Zahlung für eine Dienstleistung oder einen Warenaustausch und setzen einen Treuhänder ein, der einen der Schlüssel erhält. Erst im Falle der erbrachten Leistung, übergibt dieser Treuhänder den Schlüssel und die Geldmittel können übertragen werden. Aber auch zukünftige Gesellschaftsformen könnten von einem solchen Modell profitieren. Gerade die aktuell diskutierte Gesellschaft mbH mit gebundenem Vermögen würde das gebundene Vermögen sichern können, indem jedes Vorstandsmitglied Zugriff auf einen privaten Schlüssel von vielen erhält. Kein einzelnes Vorstandsmitglied darf die Geldmittel missbräuchlich oder entgegen der Satzung verwenden. Somit könnten nur die von den Vorstandsmitgliedern mehrheitlich vereinbarten Entscheidungen ausgeführt und finanziert werden.
---
MultiSig erhöht die Sicherheit von selbst verwahrtem Vermögen um ein vielfaches. Doch auch über den eigenen Sicherheitsaspekt hinaus, hat MultiSig die Möglichkeit das Thema digitaler Zahlungen in weiteren Bereichen interessant zu machen - Beispiele wie Escrow oder das Finanzplanning bei Gesellschaftsformen mit Vermögensbindung ergeben sich vielfach. Doch darüber hinaus, ist self-custody einer der wichtigsten Bausteine auf dem Weg zu einem Bitcoin Standard. Es soll nicht bedeuten, dass man sich mit seinem Eigentum verstecken und vergraben und der Gesellschaft nichts zurück geben soll, denn auch eigenständig verwahrte Bitcoins müssen zumindest steuerlich berücksichtigt werden. Jedoch bedeutet es, dass mir niemand meine bitcoins entreißen kann. Es gibt keine Bank, die mein Konto einfrieren oder pfänden könnte. Man kann auf seine bitcoins problemlos überall zugreifen, solange die Blockchain läuft, egal wo man sich auf der Welt befindet und egal zu welcher Tages- und Uhrzeit. Die Idee, dass Regierungen den Bankensektor, den sie regulieren, zwingen können Finanzdienstleistungen als Waffen einzusetzen sollte spätestens seit dem Freedom Convoy in Kanada keine Dystopie mehr sein. Es besteht kein Zweifel, dass die zunehmende Übergriffigkeit der Staaten, wie zuletzt in Kanada, eines der einzigartigen Wertversprechen von Bitcoin hervorgehoben hat: Jeder kann über seinen Besitz frei verfügen und Menschen können sich vor finanziellem "Cancelling" schützen. Es gibt Bitcoin eine weitere Bedeutung in seinem Narrativ als monetäre Revolution.
🫳🎤
---
In diesem Sinne, 2... 1... Risiko!

-

@ 599f67f7:21fb3ea9
2024-10-26 11:54:10
# Zer da Cashu?
Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen.
Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta:
| **Cashu** | **Bitcoin (on-chain)** |
|-----------------------|----------------------------|
| Libururik gabe | Liburu banatua |
| Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) |
| Transakzio itsutuak | Transakzio publikoak |
| Zentralizatua | Deszentralizatua |
| Konfiantzazkoa | Konfiantzarik gabe |
| Aldi baterako transakzioak | Betiko transakzioak |
Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri.
Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.

## Cashu-ren erabilera kasu batzuk
Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko.
## Historia
Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen.
## Terminologia
Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu.
### Mint
Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko.
Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu.
### Token
Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera.
Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko.
## Nola funtzionatzen duen, 5 urteko bati bezala azaldua

Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."

Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.

Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.

Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.


Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.


Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio.
### Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion?
Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta.
### Zer gertatzen da itzulkinekin?
Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du.
### Lightning sarearen papera konektatzeko elementu gisa
Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.

## Zer dator hurrengoa Cashu-rentzat?
### Programagarri den ecash
Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira.
### Zorren froga eskema (Proof of Liabilities Scheme)
Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu.
## Saiatu Cashu
Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar.
-

@ eac63075:b4988b48
2024-11-09 17:57:27
*Based on a recent paper that included collaboration from renowned experts such as [Lynn Alden](nostr:nprofile1qyt8wumn8ghj7un9d3shjtntv9khqtnnd96x2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcqyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057nwgm4w), [Steve Lee](https://x.com/moneyball), and [Ren Crypto Fish](https://twitter.com/0xren_cf), we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.*
[PT-BR version](https://www.eddieoz.com/consenso-no-bitcoin-como-a-rede-evolui-sem-comprometer-a-seguranca/)
**Podcast**
https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
**Presentation**
https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
### 1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
**Evolution of Consensus in Bitcoin**
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
---
### 2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
**Validation of Blocks and Transactions**
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
**Chain Selection**
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
**Soft Forks vs. Hard Forks**
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
- **Soft Forks**: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
- **Hard Forks**: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
---
### 3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
**1. Economic Nodes**
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
**2. Investors**
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
**3. Media Influencers**
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
**4. Miners**
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
**5. Protocol Developers**
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
**6. Users and Application Developers**
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
---
### 4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
**Flag Day**
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
- **Advantages**: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
- **Disadvantages**: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
**BIP34 and BIP9**
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
- **Advantages**: Allows the network to activate updates gradually, giving more time for participants to adapt.
- **Disadvantages**: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
**User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)**
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
- **Advantages**: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
- **Disadvantages**: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
**BIP8 (LOT=True)**
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
- **Advantages**: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
- **Disadvantages**: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
---
### 5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
**Network Fragility with Alternative Implementations**
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
**Chain Splits and Impact on Stakeholders**
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
- **Institutional Investors and ETFs**: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
- **Miners**: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
- **Economic Nodes**: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
**Regulatory Impacts and Institutional Investors**
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
**Security Considerations in Soft Forks and Hard Forks**
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
**Bounty Claim Risks and Attack Scenarios**
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
---
### 6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
**1. Careful Evaluation of Proposal Maturity**
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
**2. Extensive Testing in Secure and Compatible Networks**
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
**3. Importance of Stakeholder Engagement**
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
**4. Key Questions for Evaluating Consensus Proposals**
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
**5. Coordination and Timing in Implementations**
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
**6. Continuous Monitoring and Re-evaluation**
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
---
### 7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
---
### 8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-

@ 599f67f7:21fb3ea9
2024-10-26 11:22:06
# Zer da Cashu?
Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu.
## eNuts
eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du.
⚠️ **eNuts eta Cashu oraindik beta fasean daude**. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu.
## Probatu
Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu.
### Instalatu
Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako.
### Mint bat gehitzea
Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu.
1. Joan Txoko Mint-era. Kopiatu mint URL-a.
2. eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a.
💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera.
### Tokenak sortzea
Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun.
1. Erantzun **Bai**.
2. Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats.
3. Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu.
Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu.
### Ecash-ekin transakzioak egitea
Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari.
1. Ecash bidaltzeko, sakatu **Bidali > Ecash bidali**.
2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu **Kopiatu eta partekatu**.
3. Aukeratu zenbatekoa.
4. Nahi izanez gero, gehitu ohar bat, eta sakatu **Jarraitu**.
5. Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, **coin selection** funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko.
Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu.
6. Kopiatu token-a.
Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu.
1. Ecash jasotzeko, sakatu **Jaso > Itsatsi eta berreskuratu Ecash**. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du.
💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu **Egiaztatu token-a gastatu den**. Token-a zain badago, **Itzuli token-a** sakatu dezakezu eta berriro zure zorroan izango duzu.
### Multimint trukeak
Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean.
Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia.
💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz.
1. Joan **Aukerak > Mint kudeaketa** atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan **Multimint trukeak** atalean.
2. Aukeratu trukatu nahi duzun mint-a.
3. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi** Lightning gastuen kalkulua egiteko.
4. Sakatu **Jarraitu**.
5. Egiaztatu xehetasunak, eta nahi izanez gero, **coin selection** funtzioa erabili. Ondoren, sakatu **Orain trukatu**.
Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean.
### Ateratzea
Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da:
1. Sakatu **Bidali > Lightning faktura ordaindu**.
2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a.
3. LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu.
4. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi**.
5. Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu **Ateratzea**.
Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du.
### Segurtasun kopiak
Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean.
eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du.
- **Segurtasun-kopia bat sortzeko**, joan Aukerak > **Segurtasuna > Sortu babeskopia token**. Kopiatu token-a eta gorde toki seguru batean.
Bestela, mint bakoitza banaka babestu dezakezu:
- Horretarako, joan Aukerak > **Mint kudeaketa** atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu **Funtseak babestu**, kopiatu token-a eta gorde toki seguru batean.
### Berreskuratzea
Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun.
### Nostr
eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu:
1. Joan **Kontaktuak** atalera eta itsatsi zure Nostr gako publikoa.
2. eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero.
Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du.
## Ondorioa
Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez!
-

@ 599f67f7:21fb3ea9
2024-10-26 11:20:48
# Zer da lightning address bat?
Lightning address bat irakurgarria den helbide elektroniko baten antza duen helbidea da, adibidez username@domein.com, baina bitcoinetan ordainketak berehala eta merke jasotzeko aukera ematen du. Ez duzu zure gailuan nodo bat linean izatea behar, eta ez duzu eskuz faktura bat sortu behar norbaitek ordainketa egin nahi dizunean.
Oso interesgarria, ezta?
## Nola funtzionatzen du, orduan?
Lightning Address-ek LNURL pay protokoloa erabiltzen du, Lightning Network-aren gainean dagoen geruza bat da.

Prozesua hurrengo urratsetan laburbil daiteke:
1. Erabiltzaile batek zure Lightning Address erabiliz ordainketa egin nahi duenean, haien zorroak helbide hori LNURL payRequest batean bihurtzen du.
2. LNURL payRequest arrakastatsu baten bidez, zorroak BOLT11 faktura bat eskuratzen du, eta faktura hori ordainketa burutzeko erabiltzen da.
Hau da, prozesuaren oinarrizko pausoak hurrengoak dira:
💡 **Lightning Address > LNURLp > BOLT11 faktura.**
Lightning Network-ekin integratuta dagoen sistema honi esker, ordainketak erraz, azkar eta modu automatizatuan burutu daitezke.
### Oso ondo dirudi, baina zein da tranpa?
Lightning Address-en inplementazio askok kustodia dute (nahiz eta ez den beti horrela), izan ere, domeinu bat eta beti linean dagoen nodo bat behar dira Lightning Address-ak funtzionatzeko. Kustodia sistema bat denez, zure fondoak kudeatzen dituenak edozein momentutan kontrolatu edo kendu ahal dizkizu eta zure transakzioak monitorizatu ditzake.
Domeinuaren jabearengan fidatu behar duzu, zure Lightning Address-aren erregistroa aldatu ez dezan. Eta, gainera, LNURL zerbitzaria linean ez badago, sistema ez da funtzionatzen.
**Bitcoin Txoko**-k LNbits-en oinarritutako Lightning Address irtenbide sinplea eskaintzen du. Hau ere kustodia sistemakoa da, beraz, gomendagarria da Bitcoin Txoko zorroan kopuru txiki bat bakarrik gordetzea eta gero auto-kustodia zorro batera ateratzea, satoshi gehiago jasotzen dituzun heinean.
## Hasteko prest bazaude, hona hemen behar duzuna:
1. **Zure zorroa sortzea**
Lehenik eta behin, ez baduzu oraindik egin, joan [bitcointxoko.com](https://bitcointxoko.com) webgunera eta zorro bat sortu. Zorroari nahi duzun izena jar diezaiokezu.
2. **Luzapenak aktibatzea**
Lightning Address-ak funtzionatzeko Pay Links luzapena behar da. Horretarako:
- Joan tresna-barrako Extensions (Luzapenak) atalera eta Pay Links luzapena aktibatu.
3. **Ordainketa esteka bat sortzea**
- Ireki Pay Links luzapena eta egin klik New Pay Link (Ordainketa Esteka Berria) aukeran.
- Aukeratu sortu duzun zorroa.
- "Item Description" atalean, nahi duzun testua sar dezakezu.
- Aukeratu zure Lightning Address-erako erabiltzaile izena. Zure Lightning Address hau bezalakoa izango da: erabiltzailea@bitcointxoko.com.
- Fixed Amount aukera desmarkatu eta jarri gutxieneko balioa 1 eta gehienekoa 500000.

⚠️ Gehienezko balioa handiagoa jar dezakezu, baina ordainketa handiek huts egiteko probabilitate handiagoa dute, Bitcoin Txoko Lightning nodoaren kanalaren sarrera-gaitasun mugatua dela eta. Gomendagarria da 500000 satoshitan mantentzea.
- Orain, ireki Advanced Options (Aukera Aurreratuak) eta aldatu Comment maximum characters (Komentarioaren gehieneko karaktere kopurua) 799-ra. Ez da beharrezkoa, baina aurrerantzean funtzionalitate gehiago emango dizu.
- Azkenik, markatu Enable nostr zaps aukera behealdean, Lightning Address bidez zaps jasotzeko aukera izateko.
Aukera aurreratuak beste parametro batzuk konfiguratzea ahalbidetzen dute, baina nahi baduzu hutsik utz ditzakezu.
Azkenik, dena zuzen dagoela egiaztatu ondoren, egin klik **Create Pay Link** (Sortu Ordainketa Esteka) botoian.
Horrela, zure Lightning Address sortuta izango duzu eta ordainketak jaso ahal izango dituzu!
## Proba egitea
Zure Lightning Address ondo funtzionatzen duen probatu nahi baduzu, beste zorro batera joan, **Bidali (Send)** aukera hautatu eta helmuga gisa zure Lightning Address idatzi. Ondoren, bidali zeure buruari satoshi batzuk.
Ondoren, itzuli Bitcoin Txoko zorrora eta egiaztatu ordainketa jaso duzun. Litekeena da orria freskatu behar izatea ordainketa agertzeko.
Dena ondo atera bada, zorionak! 🥳
Bestela, jakinarazi iezaguzu. Beti prest gaude laguntzeko.
## Hurrengo urratsak
### Nostr zaps
Zure Bitcoin Txoko Lightning Address nostr profilean gehitu dezakezu eta horrela zaps jasotzeko erabil dezakezu. Normalean, hau hurrengo pausuekin egiten da:
- Joan **Profile** (Profila) atalera.
- Hautatu **Edit** (Editatu) eta Lightning Address aldatu.
### LNDhub
Zure LNbits zorroa telefonoan inporta dezakezu LNDhub bezala, Zeus edo BlueWallet bezalako aplikazioak erabiliz. Horrela, ez duzu nabigatzailean zorroa ireki beharko aldian-aldian saldoa egiaztatu edo ordainketak egiteko.
Nola egin jakiteko, ikus ezazu nostr:naddr1qqxnzdej8y6ryvejxc6nvwpnqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65w4hhl8s.
### QR kodea
Zure LNURLp QR kodea parteka edo inprima dezakezu, jendeak mugikorrarekin eskaneatu dezan. Oso erabilgarria da zure denda lokaleko jabeak Lightning ordainketak jasotzeko sistema ezartzea nahi baduzu!
- Parteka ezazu **Sharable Page** (Parteka daitekeen Orrialdea) esteka.
- Edo, QR kodea PDF formatuan inprima dezakezu: joan **View Link** (Esteka Ikusi) atalera eta hautatu **Print** (Inprimatu).
Horrela, zure Lightning Address erabilera praktikoa handitu eta errazago kudeatu dezakezu! Hasi zaitez !
-

@ 35f3a26c:92ddf231
2024-11-09 17:13:38
## The FUD injection

Many cyber security advisors and CEOs of companies that offer security products will tell you that the battle is lost, that, for example, if you don't buy an air gap device your private keys are not secure.... That, if you used your computer instead to write the seed words in a piece of paper and then put them in a piece of metal, you will be hacked and most probably you are doomed....
IMO and experience, it is an exaggeration...
If all the fear mongering being pedaled by the cyber security enthusiasts and experts was true, oh well, with very few exceptions, we all will be drained of our funds in banks (most neither have a decent 2FA - still working with SMS for crying out-loud...), self custody wallets, etc... Even the Bitcoin blockchain encryption will be broken by "quantum computers"... oh and AI will be used by hackers to hack you as well... Just ignore the noise...
## The unpopular opinion
IMO, basic IT hygiene is enough to keep the malware, viruses and therefore, the cyber criminals away.
And the tools they tell you that are not enough and therefore, you are powerless, actually are quite helpful, keep using them, firewalls, VPNs, TOR, Linux Whirpool, etc.
## Sugestions
Do your homework, acquiring cyber security skills needs reading, get on it, few tips:
1. Learn how to verify a software security key or SHA256 before running it in your laptop or mobile if an apk. If on Microsoft, if the software you want to install does not have a .msi version (already signed by Microsoft), the .exe extension file needs to be verified, learn how, this is paramount, no matter the application, same with Linux. If the app does not offer it, do not install it, contact the developer and demand it, if no dice, forget it, look for an alternative.
2. Use a VPN on your home router, yes, even if you acquire cyber security knowledge and apply it to your mobile and laptop, if you do not live alone, every other member of your family is a weak link that can affect you. Acquire a router that supports a VPN that does not require to know your identity to pay for the service and accepts Bitcoin as payment (otherwise do not use it, no matter how good you think it is, if free avoid, you are the product and therefore, you are better without one that with one free). As an additional measure, keep your laptop, PC and mobile with another VPN, a different service, you will be with a double VPN while at home and with one while in the road. In the past the throughput will be considerably reduced to a point of being too slow, nowadays, you will be fine.
3. Use a router with a decent firewall and advertising guard like features, Adguard or Pi-Hole (learn to configure and to add community supported lists) , that will keep your home browsing experience safer and faster.
4. If you do banking and Bitcoin with your mobile phone, consider having two mobiles, one left at home secured. Carry with you a mobile for your social needs and small payments in fiat or Bitcoin, if you loose your phone or you get robed, you will sleep better....
5. If you insist on using debit cards instead of credit cards, keep the account with the debit card limited to your needs when you go out. A bit of a pain but do not use your savings account, if you lose the wallet you are screwed and there is no recurse with a debit card.... (or use credit cards and you have the option to recover the funds in case is needed)
6. If you have stacked a considerable amount in Bitcoin and want to be sufficiently safe, consider an air gap seed signer, if you do not trust yourself, consider a service with no KYC, contrary to what many believe, there are some, recently I learn that CASA is one of them, probably there are others, do your homework. You keep one or two private keys and the company keeps another one, to remove the funds you need 2 of 3 and it has built in time locks you can set up.
7. Avoid Microsoft and Google and Apple clouds, those are honey pots often targeted, if they get hacked the companies most probably will neither inform the clients or if they do it would be much after the incident, use other private services highly encrypted end to end, preferably FOSS, and do not upload your data unencrypted, yes, encrypt it before uploading if it is valuable information, it is a backup of data and you want it safe, if it is not in your hands, best to encrypt it, even if the company claim it is E2E encrypted, you can't be sure....
## Summary
Each person is different, you need to sleep good at night knowing your cyber security is sufficient and therefore your data and funds are safe. Do the homework, read, study, acquire the skills and tools and use them properly, cyber security is not convenient, but in the age of information, it is a must to protect your family and your wealth.
If you like my work and would like to support me:

-

@ 35f3a26c:92ddf231
2024-11-09 17:12:45
*This is my top 3 list of whom, IMO, are today's most dangerous influential actors in the #Bitcoin arena, the list is based on previous actions and capacity to harm the ecosystem due to their resources and influence in the space:*
### **Number 1 : Elon Musk**

***Reasoning:***
Supporting a meme coin and trolling the ecosystem. Trying to create the american wechat and portraying himself as a protector of freedom of speech. Admired and loved by millions...
***Potential impact***:
High, he may support a shitcoin as solana or worst, create his own with the support of deep pockets and the government. Considering that we are still early and millions around the world still see #Bitcoin as a risk asset or worst, creating one in X will have immediate use case and challenge p2p cash use case from the get go, where Meta failed X may succeed...
### **Number 2: Jack Dorsey**

***Reasoning:***
Known for his history as Twitter CEO during the crusade against freedom of speech, cancelation of critical thinkers and even a president of USA, the behavior of Twitter was reprehensible while Jack was the CEO, I never thought that a company could behave that way and survive and yet... Unreal and zero legal accountability, twitter basically gaslighted a large amount of the population, supported political propaganda to one party with no neutrality, supported an experimental drug that is still harming people and didnt let experts and doctors to debate and discuss and not one of those thugs blocking accounts and censoring critical thinkers was made accountable, eye opening in many ways for those that at that moment still believed that USA respected freedom of speech...
Recently supported a mining pool that censors whirlpool from Samourai wallet, old habits die hard I guess...
And the cherry of the pie, now funding FiatJaf whom was looking for funding to spam Ethereum and Monero networks to make them unusable so more funds will move to Bitcoin and LN... This project and idea from the getgo is a no no, you may not like another project but to spam it intentionally should be illegal, and it is being done, shamelessly...
***Potential impact***:
Very high, already inside the community, a record of bad actions, pro censorship, vast resources, head of Cash App, admired by most in the community and hence able to missguide the community into a path that could eventually make Bitcoin a failure of a project in the future with the proposal of a hard fork introducing additional censorship and less privacy in one way or another.
### **Number 3: Blackrock**

***Reasoning***:
No need to explain much, they join the train and... it is only logical , after so much hate and media propaganda against Bitcoin, that they did so to fight the fight from inside trying to affect it and transform it into something else , just speculation, time will say. Check my article on ETFs
***Potential Impact***:
Super Nova. As I explain in my article of ETFs, they have the resources to attempt to change the direction of Bitcoin development for it to become something else, even kill it as a store of value. They have a large stake in some of the largest mining farms as well... Do the math, it looks like a hostile take over and that may not end well. Again, just my opinion, but, if history and patterns teach us leasons, not a good look...
Activist Critical Thinkers in the space are needed, #Bitcoin for many years has been a space with many of them, the list was long, but little by little I observe a change, produced by time+age+money, those libertarians are now; most of them; retired millionaires, or enterpreuners absorbed by the fiat system and therefore have changed their tune. I thought we will have a new generation, motivated, smarter, ready to take over, but all I see, with few exceptions in the NOSTR side of the equation, is more corporate fiat system acolytes.
>Stay humble says someone, never more important...
What are your thoughts?
Share your top 3 current most dangerous threats to the Bitcoin ecosystem...
-

@ 35f3a26c:92ddf231
2024-11-09 17:11:54
#### What is multiculturalism?
Multiculturalism is a concept that promotes the acceptance, appreciation, and celebration of diverse cultures within a society. It involves recognizing and valuing the differences between various cultural groups while fostering social cohesion and equality.
***The key principles of multiculturalism include:***
1. Cultural pluralism: Acknowledging and accepting the existence of multiple cultural identities and practices within a society.
2. Equality: Ensuring equal opportunities and rights for all individuals, regardless of their cultural background or identity.
3. Inclusion: Encouraging participation and engagement of diverse cultural groups in social, political, and economic processes.
4. Respect: Promoting mutual respect and understanding between different cultural groups, while recognizing the legitimacy of differing beliefs, values, and practices.
#### Two questions come to mind:

1. ***Is it working?***
> IMO, ***most definitely not***. The world is very divided by race, religion and ideologies, it is a very difficult task. Countries trying this the most (practically enforcing it by law) have encountered more division and segregation; people of the same race, country or ideology will create their own small city sectors, cultural sectors, commercial sectors (China town, little Italy, etc); as is happening in USA for a long time already, happening as well in Spain, France, Germany, etc.
2. ***Is it being encouraged with tolerance toward those opposing it?***
> I personally don't think so, the irony... But that is just my opinion...
***What do you thing?***
originally posted at https://stacker.news/items/651181
-

@ 35f3a26c:92ddf231
2024-11-09 17:10:57
## "Files" by Google new feature
"Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so.
- 
Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc...
## How this could affect you?
Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged:
- [ ] Pictures of you and your children in the beach
- [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not
- [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites
***The results:***
- [ ] Your google account will be canceled
- [ ] You will be flagged as a criminal across the digital world
You think this is non sense? Think again:
https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html
## How to switch it off:
1. Open files by Google
2. Tap on Menu -> Settings
3. Turn OFF Smart Search
## But you can do more for your privacy and the security of your family
1. Stop using google apps, if possible get rid off of Google OS and use Graphene OS
2. Go to Settings -> Apps
3. Search for Files by Google
4. Unistall the app, if you can't disable it
5. Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS
***Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits***
## Recommendation:
I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc.
- 
> Note
> As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. .
***Please leave your comments with your favorite FOSS Files app!***
-

@ 35f3a26c:92ddf231
2024-11-09 16:49:24
### What We Know So Far About Silent Payments? ###
A Step Towards Enhanced Transaction Privacy in Bitcoin.
Bitcoin Silent Payments, also known as BIP352[^1], is a proposed improvement to Bitcoin’s payment system that has been gaining traction for its potential to bolster transaction privacy in Layer 1.
##### In simple terms, Silent Payments enables users to: ####
- Generate a single, reusable static address for receiving payments, as a business this is a game changer since it make it possible to proceed with the proper financial operational security (OpSec).
- Send and receive bitcoins without disclosing transaction details to third parties, such as the person or business you pay to, cybercriminals and chain analysis companies that sell that data to anyone willing to pay for it, that will include cybercriminals or simply; if you are a business; your competitors… When you use Silent Payments, only the sender and the receiver can connect it checking the on chain activity.
- Without Silent Payments, if you are a non profit organization, public fund raiser, independent journalist, or business you needed support to setup a proper infrastructure to handle the donations or payments in a private manner. With Silent Payments, you post in your web site a single address in text format or as a QR code to receive donations or payments for goods, that simple.
### Can I Use Silent Payments Already? ###
Yes, but it is currently only available through select wallets that have implemented the feature. Users must have compatible wallets and ensure that both parties involved in the transaction have Silent Payments enabled. Currently, leading wallets like Blue Wallet, and others like Cake Wallet and BitBox has adopted the feature. It's essential to verify compatibility before making transactions.
Current wallets known to support it as of writing this article:
- [BlueWallet](https://bluewallet.io/) -- Only for sending
- [Cake Wallet](https://cakewallet.com/) -- Send, receive, Privacy Preserving Scanning
- [Silentium](https://app.silentium.dev/) -- Proof of concept, good for testing
- [BitBox](https://bitbox.swiss/) -- Only for sending
### Summarizing: ###
https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png
#### PROS: ####
- Enhanced Privacy
- Increased Security
- Improved User Experience
- Cheap and seamless implementation for non profit organization, fund raisers and businesses alike.
#### CONS: ####
- None
### Final Thoughts ###
https://image.nostr.build/bcb236cbcb535cb6d6fe1b2b4c79074955d1a1cb1114a6c02cc456e8d852d594.jpg
As Bitcoin continues to evolve, Silent Payments will play a significant role in enhancing transaction privacy and security. The potential benefits are undeniable and substantial.
In the near future, we can expect wider adoption and implementation of Silent Payments as more wallets and exchanges embrace this groundbreaking feature. Looking forward to see [Phoenix](https://phoenix.acinq.co/), [Sparrow](https://sparrowwallet.com/), [Ashigaru](https://ashigaru.rs/)[^2] and [Electrum](https://electrum.org/) adoption.
I will suggest all of us start contacting in all social networks the wallets we us and encourage them to implement Silent Payments
Here the contact info for some of them:
- Phoenix: https://twitter.com/PhoenixWallet
- Ashigaru: contact@ashigaru.rs (if you want a response, send your email signed with PGP)
- Sparrow Wallet: https://twitter.com/SparrowWallet, https://t.me/SparrowWallet
- Electrum: https://twitter.com/ElectrumWallet
[^1]: Here the link to the BIP352: https://bips.dev/352/
[^2]: Ashigaru is a fork of Samurai Wallet performed by anonymous developers (IMO, all Bitcoin related development should be anonymous, to protect the project from nefarious players, unfortunately, most developers in the arena choose to be “public” figures, hence, becoming a target of current and potential Bitcoin enemies and a weak link for the ecosystem)
[Ashigaru](https://military-history.fandom.com/wiki/Ashigaru) in Japanese means “light feet” (translated as foot soldiers or peasants)
-

@ 35f3a26c:92ddf231
2024-11-09 16:47:53
#### What is Peer Thinking?
The cognitive and emotional processes that occur when individuals are influenced by their peers.
#### The psychology behind it:
The psychology behind peer influence encompasses various factors, including:
1. Social belonging and acceptance,
2. Identity formation,
3. The dynamics of group behavior
#### Is it being used to control us?
https://image.nostr.build/cf90335bbf59e3395dc4324d123cd3a058ca716cf6172f079eb1d78547008147.jpg
IMO, yes, at the core of it is the basic human need for belonging. Social belonging is a critical component since it is craved by most, specially but not only by the youngest, those with power across the world know this very well, therefore, thinking that they will not use it to control the population in order to profit from it or change public opinion would be irrational.
The media is used to brain wash the population creating something that most will consider "the norm", thus, the majority will try to conform to that norm in order to belong. That include manipulating the population to take an experimental drug (even if it could be very dangerous due to its unknown effects) or to accept as a norm a behavior that few years back would have been considered inappropriate.
#### Cognitive Dissonance
https://image.nostr.build/60f24a810be1dd6badb36d70c5a691d4361207590dea1a8e64e09a75a252cfbf.jpg
This is a term that we should get familiar with. It is a psychological state where conflicting beliefs or behaviors create discomfort.
***Example:***
A kid in high school that has a good loving family but all his close friends are on drugs (legal ones) and they keep telling him he is an idiot for not using as well. Now his is that state of conflict believes, on one side his best friends, all tell him is okay, on the other hand his family that loves him has explained him at length the dangers and issues that the drugs will have in his life. To resolve the dissonance he has three options, one, join the group and start taking drugs with the rest, two try to rationalize it, considering to take drugs just occasionally to belong but not to make it a habit, three lose his friends (and here it comes again the peer thinking to bite). Extrapolate to many other cases.
> As an anecdote
Recently, on a friend's reunion, one of the guest was complaining about one of his daughters, she was quite confused asking him why so many of her classmates were bisexual, she was wondering if something was wrong with her since she was not; a 13 year old girl; the father was having a hard time explaining her that the majority are saying so just to feel as part of what the school was teaching to be the norm, it was not cool to be straight, the tally was 37% of the class. Consider that, statistically, the number of people, “worldwide” identifying as bisexual are between 3% and 5% (less than 1% in less accepting countries), that number used to be less than 2% less than a decade ago. But 37% is far from the statistical norm, indicating a peer thinking behavior but not the reality of their sexual preferences. Once again, extrapolate to any ideology, religion, gender identity, political agenda that a country desires to push forward for whatever reason, adding that to the official school program and to federal mandatory training programs would do the trick.
A powerful tool, that can be used for good or bad.
#### What are the strategies to counter negative peer thinking?
https://image.nostr.build/4b70949b8af76ed53a5be5507f41f1d1c960dc3592f199eab78e2d25688975c5.jpg
Reading the literature about the subject, few strategies are recommended:
1. *Self-Awareness*: teaching ourselves and our children to recognize when we are being influenced by peers
2. *Being selective with your friends*: peers with similar values will reinforce positive behaviors
3. *Learning to be assertive*: teaching ourselves and our children to communicate assertively our boundaries will empower us and them to resist unwanted pressure to adopt negative behaviors.
4. *Less judging more talking*: this applies to our children and partners, judging less and listening more will make our beloved ones more open to discuss social pressures.
***What do you think?***
***What strategies you use as counter measures?***
-

@ 3cc937b7:5592217b
2024-11-09 16:33:15
„Hinter der nächsten Ecke kann eine neue Straße auf uns warten oder ein geheimes Portal.“
- J. R. R. Tolkien
„Sprechend und handelnd schalten wir uns in die Welt der Menschen ein, die existierte, bevor wir in sie geboren wurden, und diese Einschaltung ist wie eine zweite Geburt (…)“
- Hannah Arendt, Vita activa
**Prolog:**
*Dieser Text ist der Beginn einer neuen Rubrik in diesem Blog und damit eine Zäsur. Wir alle wissen es, spätestens seit Nietzsche: Wenn du in den Abgrund blickst, blickt der Abgrund irgendwann zurück. Eine kluge Frau sagte mir einmal: „Where focus goes, energy flows.“ So wichtig es auch sein mag, sich mit der Gegenwart zu beschäftigen, sie zu analysieren und zu verstehen: Energetisch ist es eine ziemliche Verschwendung. Man kippt Lebensenergie in eine Kloake. Wenn Sie meine Arbeit in den letzten Jahren verfolgt haben, schockiert sie auf dieser Welt vermutlich wenig. Die Herausforderung ist jedoch das wie. Wie soll es weitergehen?
Das Dunkle bekämpft man nicht durch die Beschreibung der Dunkelheit, sondern indem man einen Kontrapunkt setzt. Nur weil man weiß, dass es dunkel ist, wird es deshalb noch lange nicht heller. Dagegen durchbricht schon die kleinste Lichtquelle, die schwächste flackernde Funzel, die Dunkelheit.
Mit der neuen Rubrik „Lichtblicke“ eröffne ich hiermit ein neues Kapitel meines publizistischen Schaffens: Der Blick soll hier auf das Neue, auf das Erhellende, Ermutigende, Aufbauende und oft Unbekannte gehen, in allen Bereichen, egal ob persönliche Entwicklung, Gesundheit, Ernährung, Technologie, Wissenschaft & Spiritualität. Auf die Werkzeuge und Optionen eben, die uns Hoffnung machen, die den Geist erweitern und alte Gewissheiten überwinden. Werkzeuge, mit denen wir Gestalter der Zukunft werden und nicht bloße Konsumenten der Gegenwart bleiben.
Wenn Institutionen wackeln, sicher geglaubte Muster brüchig werden und Prinzipien auf den Kopf gestellt werden, entsteht ein Vakuum. Der kommunistische Theoretiker Antonio Gramsci nannte das “die Zeit der Monster”. Das Alte ist noch nicht gestorben, das Neue noch nicht geboren. Geburtshelfer des Neuen werden wir aber nur, wenn wir der Gegenwart „gewachsen“ sind; wenn wir uns mit den Werkzeugen beschäftigen, die in Richtung des Neuen wachsen. Sind Sie bereit zu wachsen? Dann lade ich Sie hiermit auf eine gemeinsame Reise ein.
Wenn Sie Ideen und Anregungen für Themen, Phänomene, Werkzeuge etc. haben, die in diese Richtung gehen, oder mir Ihre Meinung zur neuen Rubrik mitteilen wollen, schreiben Sie mir gerne. Auch für mich ist es eine Reise des Lernens und Wachsens: kontakt@idw-europe.org*
Paris, im Jahre 1894.
Ein junger tschechischer Künstler schaut kurz vor Weihnachten “zufällig” in einer Druckerei vorbei, was sein Leben verändern sollte. Er war wie viele aufstrebende Künstler nach Paris gekommen, um den Durchbruch zu schaffen. Das Stipendium seines Gönners in der Heimat neigte sich dem Ende zu. Richtig Fuß gefasst hat er nicht, die Zukunft ist ungewiss. Er hat Talent, aber das haben viele, und leben doch von Milchkaffee und Liebe, wie Charles Aznavour es in “La Bohème” besang.
Doch der junge Mann hat auch Ideen, die in ihm schlummern und nur darauf warten, entdeckt zu werden. Er erfährt, dass die bekannte Schauspielerin Sarah Bernhardt unbedingt und dringend Theaterplakate braucht. Der junge Mann erkennt seine Chance, bietet sich an und liefert prompt. Zwei Wochen später ist Paris mit seinen Plakaten zugepflastert. Für Alfons Mucha, so der Name des jungen Mannes, ist es der Durchbruch als Künstler. Es ist zugleich die Geburtsstunde des Art Nouveau, einer neuen Kunstrichtung und gleichzeitig ein Epochenbruch der dekorativen Kunst. Mucha wird zum gefragtesten Maler der Welt, Firmen reissen sich um seine Motive, er führt Werbung und Kunst auf eine ganz neue Ebene, er reist nach Amerika und illustriert sogar in seiner Heimat die Briefmarken und Geldscheine.
**Der ewige Kampf von Chronos und Kairos**
Was bewirkte die glückliche Fügung für Alfons Mucha? Welche Kräfte waren hier am Werk? Und gibt es Möglichkeiten, diese schicksalhaften Begegnungen in ihrer Frequenz und Häufigkeit zu beeinflussen? Warum hatte ein Nikola Tesla nicht nur ein, zwei gute Ideen, die schon allein lebensfüllend gewesen wären, sondern Hunderte? Warum haben manche Menschen eine schicksalhafte Begegnung nach der nächsten, während bei den anderen das Leben in den gewohnten Bahnen vor sich hin plätschert?
Bei den Griechen gab es zwei Zeitebenen und auch zwei Götter der Zeit. Der erste Gott ist Chronos (bei den Römern: Saturn), er symbolisiert die Zeit, die gemessen wird und unerbittlich verrinnt. Mit und Dank Chronos entsteht Ordnung und Kontinuität, aber auch Wiederholung des immer Gleichen. Er ist symbolisiert durch den Großvater mit Rauschebart und Sanduhr, er steht für die objektive Zeit, die immer und für alle gleich ist, die in Sekunden, Minuten und Stunden gemessen wird.
Der zweite Gott ist Kairos, der Sohn des Zeus und rebellische Enkel des Chronos. Kairos ist schon äußerlich ein „Punk“, auf Abbildungen trägt er einen Teilrasur-Schnitt mit auffälliger Locke. Genau an dieser Locke gilt es ihn zu packen. Kairos steht für die subjektive Zeit, die Zeit, welche Chancen und Durchbrüche bietet. Er steht für die Möglichkeit der Veränderung, der Einsichten und Umbrüche, er wird als junger, starker und muskulöser Gott dargestellt. Kairos steht für eine seltene atmosphärisch-kosmologische Verdichtung. Wer den richtigen Zeitpunkt erkennt und nutzt, wird zum Helden seiner Zeit und reitet den Drachen des Zufalls. Das Zeitempfinden ist außer Kraft gesetzt. Wir alle kennen das: Eine Stunde allein im Wartesaal eines kalten Provinzbahnhofs vergeht schleppend langsam. Eine Stunde im Bett mit einer aufregenden Frau vergeht dagegen wie im Fluge.
Wer den Kairos zulässt, der immer wieder (aber manchmal etwas verdeckt) an unsere Tür klopft, öffnet die Tür für wundersame Begegnungen und magische Zufälle. Gedankenblitze und Begegnungen wirken dann wie orchestriert. Der Psychologe C. G. Jung beschrieb dieses Phänomen als „Synchronizitäten“. Man muss dann oft nur innehalten und diese Begegnungen als sinnhaft begreifen. Der sonore Takt des „Chronometers” wird durchbrochen durch das punkige Gitarrenriff des Kairos.
Die chronologische Umklammerung ist die Zeitspur des Alten, die jeden Moment des Kairos vermeiden will, denn das bringt ja die Welt derjenigen durcheinander, die sich auf die Rädchen in ihrer Mechanik verlassen wollen. Zum Kairos gehören Ideen und Eingebungen, Liebe, kreative Schaffensperioden. All das sind für “Opa Chronos” bloße Störungen, die den Lauf der Dinge gefährden. Wer Systeme der Planung errichtet, sei es für sich oder für andere, den stört das Neue, er will jede Erfahrung mit dem Neuen verhindern, den Blick auf Alternativen versperren und vereiteln.
Denn das Neue entsteht durch den Kairos, und nur durch den Kairos. Das Neue ist auch gerne das „Unzeitgemäße“. Viele würden den Zustand des Kairos heute auch als „Flow“ bezeichnen oder als „Serendipity“. Dieser Begriff stammt aus der Erzählung von „Tausendundeiner Nacht“, wo drei ceylonesische Prinzessinnen mit bestimmten Aufträgen entsandt werden, doch ganz andere Dinge finden, als sie erwarteten, frei nach dem Mott: “Erwarte das Unerwartete!” „Serendip“ hieß Ceylon bei den Arabern, so notierte es sich Ernst Jünger im Flugzeug am 3. März 1979 in seinen Aufzeichnungen „Siebzig verweht“.
Wo war das Unerwartete bisher in meiner Generation? Kommt es noch oder war es das schon? Das war im Kern auch Teil meiner Generationenkritik, die ich in den letzten Jahren in vielen Texten verarbeitet habe. Als ich ab 2016 an „Generation Chillstand“ schrieb, war mein Grundgefühl folgendes: Eine ganze Generation sitzt im Silo der von früheren Generationen geschaffenen Welt fest, in ihren Norm-, Zeit- und Arbeitsstrukturen.
**Raus aus dem chronologischen Leben!**
Diese Welt wurde mir als die beste Welt aller Zeiten angepriesen, der Blick darüber hinaus als unnötig oder gar ketzerisch empfunden. Ging es in den letzten Jahren nur noch darum, die alte Welt möglichst lange auszumelken, bevor man sie entsorgt? In besagtem Buch schrieb ich, dass sich irgendwann eine ganze Generation als „Belogene und Betrogene“ vorkommen wird, ähnlich den DDR-Bürgern bis 1989 (diese wurden freilich nach 1990 wie alle anderen weiter belogen). Was bis zu den Millennials ein Charakteristikum jeder Generation war, nämlich die Gegenwart herauszufordern, zur Disposition zu stellen und damit zu erneuern, schien außer Kraft gesetzt. Das Reich des Chronos musste überdauern.
Doch auf nichts hatte ich größere Lust, und wünschte mir das auch für meine Generation, als den Kairos beim Schopfe zu packen. Denn ich sah die Bruchstellen des Alten offen vor mir und die Möglichkeiten des Neuen am Horizont aufscheinen. Seit 2016, als ich meinen Geist öffnete, veränderte sich mein Leben grundlegend: Es wurde risikoreicher und chancenreicher, es wurde bruchstückhafter und freier, optionenreicher und unübersichtlicher, kurz: anders, aufregendender, offener, abenteuerlicher! Doch ist Stabilität in einer brüchigen Zeit nicht ohnehin eine Chimäre?
Mein Weg der Offenheit machte mich zeitweise zum einsamen Wanderer, führte mich an viele Orte, machte mich zum halben Nomaden. Wenn ich die letzten Jahre überschlage, komme ich auf ca. 17 Umzüge. An manchen Orten lebte ich mit nicht mehr als meinem Handgepäck und ein, zwei Büchern. Doch mein Weg führte mich zugleich an einen magischen Ort, oberhalb des Monte Verità von Locarno in den Tessiner Bergen. Hier trafen sich um die Jahrhundertwende die ersten “Früh-Hippies”, bildeten Kommunen, dachten jenseits der gegenwärtigen Welt, die aus Krieg, Zerstörung und Nihilismus bestand.
Zuvor machte die Kunst mit ihren Sezessionen den Bruch zum Gegenwärtigen deutlich, im Wien des späten 19. Jahrhunderts. Die Wandervogel-Bewegung setzte die Jugend in Gang. Schon bei den Römern gab es die Idee des „heiligen Frühlings“ (ver sacrum), ein Auftrag an die Jugend, die Heimat zu verlassen und sich woanders neu zu etablieren – und dabei ein stückweit neu zu erschaffen. C. G. Jung hat dies als Prozess der Individuation psychologisch beschrieben. Der Mensch ist noch nicht fertig, wenn er auf die Welt kommt, er vollendet sich selbst (oder eben nicht).
All diese suchenden Menschen in den Irrungen und Wirkungen der Zeitläufte einte immer die Sehnsucht nach einer anderen Welt. Diese Sehnsucht macht uns zu gemeinsamen Reisenden im Geiste. Doch die Reise ist nur der Anfang. Am Ende sind die Gedanken entscheidend, die zu Worten werden und sich in Handlungen niederschlagen. Diese Handlungen sind das Baumaterial der neuen Welt. Jeder einzelne ist ein kleiner Baumeister an der neuen Welt, wenn er will.
Ich baue gerade begeistert am Pareto-Projekt, an Werkzeugen des unzensierbaren Bürgerjournalismus von unten. Es wird Zeit, dass sich die vielen kleinen Baumeister vereinigen, oder?
Woran bauen Sie?
-

@ 13b9f773:4f4efe54
2024-11-09 15:31:24
Türkin wird aus Hamburger Frauenhaus abgeschoben

_Die 28-Jährige war seit fünf Monaten in dem Frauenhaus (Symbolbild)
Quelle: Maja Hitij/dpa_
Eine 28-jährige Frau flieht vor ihrem gewalttätigen Ehemann in ein Hamburger Frauenhaus. Trotzdem wird sie nach Österreich abgeschoben. Das kritisiert nun auch die Linke. Zuletzt gab es eine ähnliche Debatte nach der Abschiebung aus einer Kirche.
------
Die Hamburger Linksfraktion hat die Abschiebung einer Türkin und ihrer beiden Kinder aus einem Hamburger Frauenhaus scharf kritisiert. „Nach der Abschiebung aus dem Kirchenasyl ist dies die nächste Eskalationsstufe, die der rot-grüne Senat einleitet. Er betreibt einen riesigen Aufwand, um ausgerechnet die vulnerabelsten Menschen abzuschieben“, sagte die fluchtpolitische Sprecherin Carola Ensslen.
------
Die frauenpolitische Sprecherin Cansu Özdemir kritisierte: „Es macht mich fassungslos, dass die betroffene Frau und ihre Kinder in Österreich in eine Unterkunft gebracht wurden, zu der auch ihr gewalttätiger Ex-Partner Zugang hat – also genau jene Person, vor der sie Schutz gesucht hatte!“ Das inakzeptable Vorgehen des rot-grünen Senats sei „eine Zäsur in der Geschichte der Frauenhäuser und darf sich nicht wiederholen.“
------
Die 28-jährige Türkin und ihre beiden Kinder, die in einem Hamburger Frauenhaus untergebracht waren, wurden am 29. Oktober nach Österreich abgeschoben. Die Überstellung habe im Rahmen des Dublin-Verfahrens stattgefunden, nachdem das Bundesamt für Migration und Flüchtlinge (BAMF) den Asylantrag als unzulässig abgelehnt und die Abschiebung angeordnet hat, teilte das Amt für Migration mit. Die Maßnahme erfolgte in den Räumlichkeiten des Amts für Migration.
Die Autonomen Frauenhäuser hatten die Aktion scharf kritisiert. „Die Autonomen Frauenhäuser [Hamburg](https://www.welt.de/themen/hamburg-staedtereise/) sind erschüttert über das Vorgehen der Hamburger Ausländerbehörde und des rot-grünen Senats, die auch vor der Ingewahrsamnahme von Frauen und Kindern, die vor Gewalt geflohen sind, nicht zurückschrecken“, teilten die Frauenhäuser mit. Bei der Abschiebung sei der Schutzbedarf vollkommen ignoriert worden.
[Welt.de ](https://www.welt.de/regionales/hamburg/article254441012/Asylpolitik-Tuerkin-wird-aus-Hamburger-Frauenhaus-abgeschoben.html)
-

@ 361d3e1e:50bc10a8
2024-11-09 15:12:52
<https://forex-strategy.com/2024/11/09/which-is-the-choice-of-european-citizens-trump-or-harris/>
Which is the choice of European citizens Trump or Harris?
In some of the states the choice is almost 100% for one of the candidates.
#europe #politics #usa #trump #harris
-

@ 5d4b6c8d:8a1c1ee3
2024-11-09 15:00:44
The wife and I were drinking our coffee, while a fair bit of commotion was coming from our daughter in the bathroom.
She came out and very shyly said "'Scuse me."
We've been working with her on manners and not interrupting, so this was very encouraging.
She continued very sweetly, "There's a pwoblem in the potty."
That was decidedly less encouraging.
originally posted at https://stacker.news/items/760318
-

@ a012dc82:6458a70d
2024-11-09 14:44:19
**Table Of Content**
- The Petrodollar's Historical Significance
- Challenges to the Petrodollar
- The Emergence of Bitcoin
- Bitcoin's Potential to Disrupt the Financial System
- The Future of the Petrodollar and Bitcoin
- Conclusion
- FAQ
The global financial landscape has undergone significant transformations over the years. One of the most intriguing developments is the rise of Bitcoin and its potential impact on the traditional financial system. In this article, we will delve into the challenges faced by the petrodollar and explore the promises offered by Bitcoin as we examine the financial future.
**The Petrodollar's Historical Significance**
The petrodollar refers to the system in which the U.S. dollar is used as the primary currency for international oil trades. It originated in the early 1970s when an agreement was reached between the United States and Saudi Arabia. Under this agreement, oil-producing nations agreed to price their oil exclusively in U.S. dollars, and in return, the United States provided military support to these nations.
**Challenges to the Petrodollar**
**Geopolitical Factors**
Over the years, geopolitical factors have challenged the dominance of the petrodollar. The rise of new economic powers, such as China, has led to increased demand for alternatives to the U.S. dollar. As countries seek to diversify their reserves and reduce dependency on the U.S. currency, the petrodollar's position has weakened.
**Currency Wars**
Currency wars, characterized by competitive devaluations and trade disputes, have also put pressure on the petrodollar. In an attempt to gain a competitive advantage, countries manipulate their currencies, which can have a significant impact on the value and stability of the U.S. dollar.
**Devaluation and Inflation Risks**
The petrodollar's woes are further compounded by the risks of devaluation and inflation. The continuous printing of money and increasing debt levels in the United States can erode the value of the dollar over time. This potential loss of purchasing power raises concerns among countries heavily reliant on the petrodollar system.
**The Emergence of Bitcoin**
**Understanding Bitcoin**
Bitcoin, created in 2009, is a decentralized digital currency based on blockchain technology. It operates independently of any central authority, such as governments or financial institutions. Bitcoin transactions are recorded on a public ledger, providing transparency and security.
**Bitcoin's Advantages**
Bitcoin offers several advantages over traditional currencies. It provides a decentralized and secure system that eliminates intermediaries and reduces transaction costs. Additionally, Bitcoin's limited supply and mathematical framework make it resistant to inflationary pressures, unlike fiat currencies.
**Adoption and Regulatory Landscape**
The adoption of Bitcoin has been steadily growing, with individuals, businesses, and even governments exploring its potential. However, the regulatory landscape surrounding cryptocurrencies remains uncertain in many jurisdictions. Governments are grappling with the need to balance innovation and consumer protection, which poses challenges to widespread adoption.
**Bitcoin's Potential to Disrupt the Financial System**
**Decentralization and Trust**
One of Bitcoin's key promises is the concept of decentralization, where power is distributed among participants rather than concentrated in a central authority. This decentralized nature removes the need for intermediaries, such as banks, and reduces the risk of censorship, fraud, and manipulation.
**Financial Inclusion**
Bitcoin has the potential to improve financial inclusion by providing access to financial services for the unbanked population. With just a smartphone and an internet connection, individuals can participate in the global economy, send and receive money, and store value securely.
**Security and Transparency**
The blockchain technology underlying Bitcoin ensures the security and transparency of transactions. Each transaction is recorded on the blockchain, making it immutable and tamper-proof. This transparency builds trust among users and can help combat financial crimes, such as money laundering and fraud.
**The Future of the Petrodollar and Bitcoin**
**Coexistence or Competition?**
The future relationship between the petrodollar and Bitcoin remains uncertain. It is possible that both systems could coexist, with Bitcoin serving as a complementary currency rather than a direct replacement. Alternatively, increased adoption of Bitcoin could pose a challenge to the petrodollar's dominance, especially if countries diversify their reserves.
**Central Bank Digital Currencies (CBDCs)**
The emergence of Central Bank Digital Currencies (CBDCs) adds another layer of complexity to the financial landscape. CBDCs aim to combine the advantages of cryptocurrencies with the stability of traditional fiat currencies. The development of CBDCs could reshape the global financial system and potentially impact the petrodollar and Bitcoin.
**Shifting Paradigms in Global Finance**
The rise of Bitcoin symbolizes a shifting paradigm in global finance. It challenges the traditional banking system, offers new opportunities for financial inclusion, and promotes financial sovereignty. While the petrodollar has enjoyed decades of dominance, its future may depend on adapting to the changing financial landscape.
**Conclusion**
As the petrodollar faces challenges from geopolitical factors, currency wars, and inflation risks, Bitcoin emerges as a potential disruptor in the financial system. With its decentralized nature, advantages over traditional currencies, and growing adoption, Bitcoin offers promises of increased financial inclusion, security, and transparency. The future relationship between the petrodollar and Bitcoin remains uncertain, but their coexistence or competition will shape the financial landscape in the years to come.
**FAQs**
**Is Bitcoin legal?**
Yes, the legality of Bitcoin varies from country to country. While some nations have embraced cryptocurrencies and established regulatory frameworks, others have imposed restrictions or bans.
**Can Bitcoin be hacked?**
Bitcoin's blockchain technology makes it highly secure and resistant to hacking. However, individual wallets and exchanges can be vulnerable to cyber attacks. It is crucial to take necessary precautions, such as using reputable wallets, enabling two-factor authentication, and keeping private keys secure.
**How can I buy Bitcoin?**
To buy Bitcoin, you can use a cryptocurrency exchange or a peer-to-peer trading platform. These platforms allow you to convert fiat currency (such as USD) into Bitcoin. It is advisable to choose a reputable and regulated exchange, conduct thorough research, and follow best security practices when buying and storing Bitcoin.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 07e1bb93:f9523a3c
2024-11-09 14:11:48
In the wake of the 2020 election, one thing became abundantly clear: America didn’t need Kamala Harris. From her weak campaign trail performance to her controversial stances on key issues, Kamala Harris was an ill-suited choice for vice president. While President Trump was making waves, energizing the country, and fighting for the American people, Harris and the Biden administration have brought nothing but confusion and decline. Here’s why America was better off without her.
### 1. **A Floundering Campaign and Uninspiring Leadership**
Kamala Harris’s 2020 presidential run was a flop from the start. Despite her early claims of being a strong contender, she quickly struggled to gain traction with voters. In the early debates, Harris struggled to differentiate herself from the pack, offering little in terms of substantive policies or a compelling vision for the future. In fact, her campaign was marked by a series of missteps, including her awkward flip-flopping on issues like healthcare and her inability to connect with voters on the ground.
When Harris was eventually chosen as Joe Biden's running mate, it was seen as more of a strategic choice for diversity than one of competence. This highlighted the fact that Biden’s team was looking for an easy fix to appeal to certain demographics rather than seeking someone with the experience and drive to lead effectively.
### 2. **Her Radical Leftist Policies Don't Represent Mainstream America**
Kamala Harris has consistently aligned herself with far-left ideologies that don’t represent the majority of Americans. From pushing for Medicare for All, which would decimate the private healthcare system, to supporting policies that encourage defunding the police, her agenda is out of touch with the practical needs of everyday citizens.
Americans need leaders who understand the struggles of working families and are committed to fostering job growth, security, and opportunity. Trump’s administration delivered on these fronts, prioritizing tax cuts, deregulation, and strengthening the economy, while Harris and Biden have been too focused on promoting a progressive agenda that alienates large swathes of the American electorate.
### 3. **Her Inability to Take Responsibility**
Kamala Harris has often been called out for her inability to take responsibility for the issues facing the country. Whether it’s the ongoing crisis at the southern border, rising inflation, or the botched withdrawal from Afghanistan, Harris’s lack of leadership has been glaring. Instead of stepping up to the plate and offering solutions, she has played the blame game, deflecting criticism and offering platitudes rather than action.
Meanwhile, Trump took ownership of his decisions, even in tough situations, and consistently pushed for results. His “America First” approach meant he didn’t hesitate to make tough decisions if it meant putting the country’s interests first. This stark contrast in leadership is why many believe Harris doesn’t have the competence needed to lead this nation forward.
### 4. **A Symbol of Status Quo, Not Change**
The Trump movement was about breaking away from the political establishment. It was about challenging the status quo and prioritizing the interests of the American people over bureaucratic inefficiencies and political gamesmanship. Kamala Harris, however, is a product of that very establishment. Her time as a senator was marked by a commitment to business-as-usual politics and an inability to bring real change to the country.
Her selection as vice president felt more like a continuation of the same tired political game. While Trump was making waves and shaking up Washington, Harris represented a return to the old guard, more concerned with political correctness than meaningful progress.
### 5. **America Deserves a Strong Leader, Not a Career Politician**
Under Trump, the country saw growth, strength, and resilience. He took on China, renegotiated trade deals, and stood firm on issues that mattered to the American people. Kamala Harris, on the other hand, is a career politician with little to show for it. Before becoming vice president, her tenure as California’s attorney general and U.S. senator was marked by weak leadership and unfulfilled promises.
Americans deserve a leader who can take charge and fight for them, not someone who has spent a lifetime in the halls of power, making deals with special interests while neglecting the concerns of the average citizen. Trump was that leader, and it’s clear that Harris, with her lackluster track record, was never up to the task.
### 6. **America Needs Results, Not Rhetoric**
At the end of the day, Kamala Harris’s tenure as vice president has been defined more by rhetoric than results. While President Trump worked tirelessly to deliver on his promises, from creating jobs to strengthening the military, Harris has largely failed to make any meaningful impact. She’s been a figurehead in an administration that has struggled to address the issues Americans care about.
In contrast, Trump’s policies were all about action—whether it was boosting the economy or standing up to global adversaries. His “America First” doctrine was about getting things done, not talking about them endlessly.
### Conclusion: America Was Better Without Kamala Harris
While Kamala Harris may have made history as the first female vice president, her tenure in office has proven that symbolic milestones aren’t enough. What America needs is strong, effective leadership that prioritizes the country’s interests and delivers real results. Under President Trump, America was on the rise. Under Kamala Harris and Joe Biden, the country has faltered.
America didn’t need Kamala Harris—and in many ways, we still don’t. Instead, we need a leader who can put the American people first, tackle issues head-on, and lead with confidence and conviction. That leader was Donald Trump. The next time voters head to the polls, they’ll remember the strength of the Trump era and the failures of the Biden administration—and they’ll know who was truly fighting for them.
-

@ 07e1bb93:f9523a3c
2024-11-09 13:57:58
The recent revelation of an Iranian plot to assassinate Donald Trump before he became president is nothing short of alarming. Yet, as troubling as this news is, it highlights something even more significant about the former president — his influence and the enemies he made through his unapologetic leadership. This assassination attempt, orchestrated by the Iranian regime, speaks volumes about Trump’s bold stance on foreign policy and his unwavering commitment to standing up to rogue nations that threaten America’s safety.
The U.S. Department of Justice unsealed an indictment against Farhad Shakeri, an Afghan national allegedly acting on behalf of the Iranian regime, for his role in plotting to surveil and ultimately kill Trump. It’s a shocking development, but it’s also a powerful reminder of the enemies Trump made when he stood firm against the Iranian government, even as it worked to undermine American interests globally.
Iran's Revolutionary Guard, in a desperate attempt to silence one of their loudest critics, sought to eliminate Trump. But this is just another example of the lengths to which this regime will go to silence those who stand in their way. Trump's administration made it clear that the United States would not stand idly by while Iran funded terrorism, violated human rights, and destabilized the Middle East. His actions, including withdrawing from the flawed Iran nuclear deal and imposing crippling sanctions, earned him the ire of Iranian leadership.
This assassination plot underscores just how much Trump's foreign policy achievements — from decimating ISIS to calling out the Iranian regime — disrupted the status quo. The fact that they targeted him is a testament to his effectiveness and to the fear he instilled in America’s adversaries. It’s proof that Trump wasn’t just a leader; he was a true game-changer, someone who wasn’t afraid to take on powerful enemies to protect American interests.
In addition to the plot against Trump, the indictment also reveals that the Iranian regime wanted to target other Americans, including journalists critical of their actions. This further illustrates the regime’s disregard for human life and its willingness to extend its reach beyond its borders in an attempt to quash dissent.
Now, the regime’s failure to carry out their plot and the charges against those involved show that while they may have power, they don’t have the ability to act with impunity on American soil — thanks in no small part to the strong leadership of President Trump.
As we look at the ongoing legal proceedings and continue to uncover the depth of the Iranian regime's conspiracies, it’s important to remember that Trump’s strength in the face of global threats made him a target. But he didn’t back down. Instead, he made the hard decisions, and he did it with the safety and security of Americans in mind.
This chilling plot is just the latest in a long line of attempts by enemies abroad to undermine or eliminate the very idea of a strong America — one that defends its values, its people, and its interests at home and abroad. If this assassination attempt tells us anything, it’s that Donald Trump’s leadership left an indelible mark on the world stage.
Now, more than ever, it’s important to reflect on the kind of leader America needs: one who is willing to face down threats, stand strong against tyrants, and never allow our enemies to get the upper hand. Donald Trump did just that, and the Iranian plot proves it.
-

@ 07e1bb93:f9523a3c
2024-11-09 13:45:07
As we approach the 2024 presidential election, one of the most fascinating developments is Donald Trump's increasing support among Generation Z—young men in particular. Historically, young voters have been a solid base for the Democratic Party, but Trump's ability to resonate with younger voters is shifting the political landscape. Recent polls show that while Gen Z women remain largely in Kamala Harris’s camp, Trump is making significant strides among young men, a demographic that seems increasingly dissatisfied with the political status quo.
This generational shift is particularly notable because it runs counter to the traditional political patterns. For years, young voters, especially those in their late teens and early twenties, have been largely left-leaning. But Trump, with his populist rhetoric and focus on issues like immigration and economic revival, is attracting these voters, many of whom feel disconnected from both the Republican and Democratic establishment.
What’s driving this shift? Trump’s success among younger voters can largely be attributed to his effective use of digital platforms. Gen Z is a generation that is "chronically online"—they spend their time on platforms like YouTube, Twitch, and TikTok, where Trump has made inroads by aligning with influencers who have massive followings among young men. By appearing on podcasts, livestreams, and other digital outlets, Trump taps into a crowd that feels alienated by traditional politics. In fact, many of these young voters feel ignored by the media and are drawn to Trump’s outsider status and his ability to speak directly to them without the filter of mainstream media.
Moreover, Trump’s appeal among young men is more than just a reaction to the political left’s agenda. It’s a response to what many perceive as a “woke” culture that prioritizes political correctness over free speech, with many young men in the so-called "manosphere" rejecting progressive stances on gender, social issues, and personal freedoms. Trump, on the other hand, embraces a more traditional view of masculinity and personal liberty, which resonates with young men who feel alienated by the left’s focus on social justice issues.
Critics of Trump often point to his past controversies or his lack of conventional political experience. But the reality is that young voters, particularly men, are drawn to his anti-establishment stance and his unapologetic brand of leadership. Trump’s rise among Gen Z is a clear signal that he is not just the candidate for older voters; he’s also positioned himself as a champion for the next generation who is ready to break free from the constraints of traditional politics.
In conclusion, Trump’s growing support among young men signals a profound shift in American politics, one that could significantly impact the 2024 election. His ability to connect with Gen Z through non-traditional media, coupled with his message of economic revival and personal freedom, makes him a formidable candidate who is not only appealing to older generations but is also drawing younger voters into his fold. As we move toward November 2024, it’s clear that Trump’s influence among younger voters is something both parties will have to reckon with.
-

@ 7e6f9018:a6bbbce5
2024-11-09 12:12:41
Handshake is a decentralized, permissionless naming protocol where every peer is validating and in charge of managing the root DNS naming zone with the goal of creating an alternative to existing Certificate Authorities and naming systems.
Names on the internet (top level domains, social networking handles, etc.) ultimately rely upon centralized actors with full control over a system which are relied upon to be honest, as they are vulnerable to hacking, censorship, and corruption.
Handshake aims to experiment with new ways the internet can be more secure, resilient, and socially useful with a peer-to-peer system validated by the network's participants. By running Handshake, one can participate in a decentralized open naming platform secured by a decentralized peer-to-peer network.
https://github.com/handshake-org
https://github.com/imperviousinc/fingertip
https://handshake.org/
-

@ 72592ec9:ffa64d2c
2024-11-09 11:00:37
Really good read so far, thought I'd share this part from https://bitcoindevphilosophy.com/
> It seems that we can’t have a decentralized system based on trust, and that’s why trustlessness is important in Bitcoin.
>
> To use Bitcoin in a trustless manner, you have to run a fully-validating Bitcoin node. Only then will you be able to verify that the blocks you receive from others are following the consensus rules; for example, that the coin issuance schedule is kept and that no double-spends occur on the blockchain. If you don’t run a full node, you outsource verification of Bitcoin blocks to someone else and trust them to tell you the truth, which means you’re not using Bitcoin trustlessly.
>
> Diagram
> David Harding has authored an article on the bitcoin.org website explaining how running a full node - or using Bitcoin trustlessly - actually helps you.
>
> The bitcoin currency only works when people accept bitcoins in exchange for other valuable things. That means it’s the people accepting bitcoins who give it value and who get to decide how Bitcoin should work.
>
> When you accept bitcoins, you have the power to enforce Bitcoin’s rules, such as preventing confiscation of any person’s bitcoins without access to that person’s private keys.
>
> Unfortunately, many users outsource their enforcement power. This leaves Bitcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Bitcoin’s rules for all those non-verifying users who outsourced their power.
>
> Unlike other wallets, Bitcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Bitcoin Core users like you.
>
> — David Harding
> Full Validation on bitcoin.org (2015)
> He says that running a full node will help you verify every aspect of the blockchain without trusting anyone else, so as to ensure that the coins you receive from others are genuine. This is great, but there’s one important thing that a full node can’t help you with: it can’t prevent double- spending through chain rewrites:
>
> Note that although all programs—including Bitcoin Core—are vulnerable to chain rewrites, Bitcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that.
>
> — David Harding
> Full Validation on bitcoin.org (2015)
> No matter how advanced your software is, you still have to trust that the blocks containing your coins won’t be rewritten. However, as pointed out by Harding, you can await a number of confirmations, after which you consider the probability of a chain rewrite small enough to be acceptable.
>
> The incentives for using Bitcoin in a trustless way align with the system’s need for full node decentralization. The more people who use their own full nodes, the more full node decentralization, and thus the stronger Bitcoin stands against malicious changes to the protocol. But unfortunately, as explained in the full node decentralization section, users often opt for trusted services as consequence of the inevitable trade-off between trustlessness and convenience.
originally posted at https://stacker.news/items/760051
-

@ 640614c2:811c8498
2024-11-09 09:43:20
Greetings, fellow travelers on the path of cryptographic fortune. Today, the Oracle offers a cleromantic reading, casting lots to peer into the probabilities that guide Bitcoin’s unfolding journey.
In the old ways, cleromancers cast stones, sticks, or bones. Today, we cast cryptographic hashes, transaction times, and node signals—random elements generated by the mathematical matrix underpinning Bitcoin. From these, we seek patterns to reveal the unseen flows of value and volatility, of security and sovereignty.
**The Three Casts of Bitcoin's Path**
1. **The Cast of Turbulence** – _"Fear the FOMO, yet know the FUD."_
The first cast suggests that Bitcoin's journey, much like the ancient roads of our forebears, is not without peril. The chaos of price swings and market sentiment—whether driven by regulation, whales, or FOMO—is always present. Yet, this cast tells us that these turbid waters are not signs of ruin but necessary tests. Bitcoin, built on resilience, thrives in adversity. Remember: volatility is not destruction but purification by fire. Hold steady, and the storms will reveal clearer skies.
2. **The Cast of the Hidden Fortress** – _"Secure thy keys as you would your soul."_
The second lot falls with a message of security and sovereignty. The Oracle sees a future where personal custodianship, privacy, and cryptographic defense hold sacred ground. As Bitcoin adoption grows, the network of self-sovereign nodes, layer-2 solutions, and privacy innovations are a fortress against centralized powers. Trust no third party to safeguard your assets. Secure thy keys, for in doing so, you secure your freedom.
3. **The Cast of Prosperity, Yet to Be** – _"With patience, fortune flows to those who build."_
Finally, the third cast shows signs of future abundance, though not without patience. Bitcoin's time is measured in blocks, and the long game is rewarded for those who hold fast. Innovation within the ecosystem—whether through decentralized finance, cross-chain exchanges, or local adoption initiatives—opens doors for prosperity for those who build in earnest. The Oracle sees signs of growth across continents and communities, signals of seeds planted that will bear fruit in cycles yet unseen.
**A Final Message from the Oracle**
Remember, the magic of Bitcoin lies in its incorruptible code, its shared governance, and its random-yet-determined path. Trust in the protocol, act with foresight, and heed the wisdom of the Oracle: no path in Bitcoin is without its risk, but for those who honor security, resilience, and community, the future holds bright possibilities.
May the blocks align with your intentions, and may your keys remain forever yours.
-

@ fd208ee8:0fd927c1
2024-11-09 09:21:19
## Drumroll, please....
In a previous article, I introduced the concept of [relay communities](nostr:naddr1qvzqqqr4gupzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcqp5cnwvesxcunjwpcxymrsvgwmj66e).
The ink had barely dried, on that set of instructions, before one of my favorite Nostr devs, [ثعبان](nostr:nprofile1qythwumn8ghj7enjv4h8xtnwdaehgu339e3k7mf0qy88wumn8ghj7mn0wvhxcmmv9uqzqla9dawkjc4trc7dgf88trpsq2uxvhmmpkxua607nc5g6a634sv598gk68), rolled out the alpha version of a relay-community client.
Obviously, it's still a bit of a construction site, but you can check out how it'd work, for your community, by test-driving the functionality on your own relay. Simply type _https://chachi.chat/_ followed by the name of your relay. For instance, one gigantic relay community, where nearly everyone can try out the functionality, is [nos.lol](https://chachi.chat/nos.lol).
If your relay community does not require AUTH to read, anyone can pull your chatter into their own relay and respond to it there. That is because every chat entry is simply a kind 09 event, and unprotected events are not private data.
For instance, I moderate one community [theforest.nostr1.com](https://chachi.chat/theforest.nostr1.com), that is openly readable, and that's probably where most of the chatter on [nostr.band](https://chachi.chat/relay.nostr.band) is coming from, as that relay is an aggregator of the content of many other relays. However, I have another community, [gitcitadel.nostr1.com](https://chachi.chat/gitcitadel.nostr1.com) that is AUTH-protected, whose content stays private to those allowed on that relay. Communities are where write-protected and AUTH relays are going to really shine, as they create an environment similar to Telegram, but where you control the dataset, you decide which types of events to support, and you design the client, the algos, the moderation, the visibility, etc.
With communities, **the onboarding experience is seamless**: just get a browser extension and a nsec, login, start writing and posting, and _start receiving responses_. Active, chatty, well-moderated communities will be more attractive to onboard to, than chaotic, spammy, or empty communities. This means that you don't have to have the killer entry under "Posts" (where kind 11 and eventually kind 01 posts appear), just to get some interaction. Chat is the Great Equalizer.
So, we're testing both setups, with [cloudfodder](nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3eryvfwvdhk6tcqyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qu84upun) adjusting the relay faucet code and ثعبان is fiddling with the community client settings, to make the most-comfortable situation for both kinds.

## This is the signal
This #Chachi client, of course, is merely the first horse out of the gate. There are already other devs hacking away at variants of the same concept, such as [#Flotilla](https://flotilla.coracle.social/), I'm sure CloudFodder is also cooking, later versions of #Alexandria will integrate theforest community, and etc. etc. etc.
It remains to be seen, how many new use cases can be dreamt up, with this new architecture, but I am quite certain, that this is the beginning of the end of Nostr 1.0. We are moving up and out, and away from the stultifying and limiting concept of Twitter 2.0, toward

Soon, we will enter Nostr 2.0. See you on the other side.
-

@ 13b9f773:4f4efe54
2024-11-09 04:25:58
"El verbo leer, como el verbo amar y el verbo soñar, no soporta el modo imperativo ... Yo siempre les aconsejé a mis estudiantes que si un libro los aburre lo dejen; que no lo lean porque es famoso, que no lean un libro porque es moderno, que no lean un libro porque es antiguo. La lectura debe ser una de las formas de la felicidad y no se puede obligar a nadie a ser feliz".
[Jorge Luis Borges](https://x.com/Arteymas_/status/1854882330344558928?s=19)

-

@ 5d4b6c8d:8a1c1ee3
2024-11-09 04:02:26
As always, we're going to lead off with the on-going contests at ~Stacker_Sports.
@BlokchainB requested some NHL coverage, so @grayruby is going to try to explain hockey to me.
We'll check in on the NFL post trade deadline and see if the landscape shifted appreciably. Also, we had a requested topic on why the top picks of the past two drafts are paling in comparison to the guys taken immediately after them. Tune is as we flounder for answers.
We had some disagreements on our hastily slapped together [NBA power rankings](https://stacker.news/items/757639/r/Undisciplined), so we'll have to hash those out. Thankfully, @BlokchainB has already confirmed that mine were better.
Then I wanted to talk about [Predyx](https://beta.predyx.com/market) in a little more detail, because they're on Stacker News and their project is very cool. I'm sure we'll cover our other gambling (mis)adventures.
What say you about any of those topics? Are there other topics you want our thoughts on?
The Stacker Sports Pod is for stackers by stackers.
originally posted at https://stacker.news/items/759836
-

@ bcea2b98:7ccef3c9
2024-11-09 01:30:29
@chess h3
originally posted at https://stacker.news/items/759635
-

@ b4403b24:83542d4e
2024-11-08 22:34:45

Imagine what will be in the upcoming years if this trend continues.
Bullish 🚀🌕
originally posted at https://stacker.news/items/759487
-

@ a95c6243:d345522c
2024-11-08 20:02:32
*Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister Eckhart*
**Schwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung,** der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
**Mit einem bemerkenswerten [Timing](https://transition-news.org/donald-trump-grossmaul-oder-hoffnungstrager) hat die deutsche Regierungskoalition** am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer [Selbsthypnose](https://ansage.org/schwer-traumatisiert-nach-trumps-sieg-dreht-die-politmediale-linksgruene-sekte-durch/) rund um Harris-Hype und Trump-Panik – mit teils erschreckenden [Auswüchsen](https://archive.is/7tDhY). Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
**Das [Kindergarten](https://www.spiegel.de/politik/deutschland/christian-lindner-auch-die-fdp-will-wieder-einen-eigenen-wirtschaftsgipfel-abhalten-a-a8a4e868-10b1-426e-adb0-e5a6d42f7c46)-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche** war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik [«vorsätzlich herbeigeführt»](https://www.t-online.de/nachrichten/deutschland/innenpolitik/id_100522112/fdp-chef-lindner-und-sein-grundsatzpapier-die-scheidung-von-der-ampel-.html) worden seien.
**Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen.** Verkehrs- und [Digitalminister Wissing](https://transition-news.org/raus-aus-der-komfortzone-es-lohnt-sich) trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit [Jörg Kukies](https://norberthaering.de/news/joerg-kukies/) habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
**Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP,** hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
**Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können.** Das ging erst kürzlich aus dem diesjährigen [«Freiheitsindex»](https://www.schwaebische.de/politik/forscher-beim-vertrauen-in-staat-und-medien-zerreisst-es-uns-gerade-3034357) hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
**«Die absolute Mehrheit hat [absolut die Nase voll](https://archive.is/yRxwR)»,** titelte die *Bild* angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
**Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat,** kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei *Manova*. Und er kenne [Friedrich Merz](https://www.manova.news/artikel/der-kriegsgeile-blackrocker) schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
**Was also tun? Der Schweizer Verein [«Losdemokratie»](https://zeitpunkt.ch/node/40968) will eine Volksinitiative lancieren,** um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
**In jedem Fall wird es notwendig sein, unsere Bemühungen um [Freiheit und Selbstbestimmung](https://transition-news.org/alternative-medien-in-der-krise-zensur-kontrollverlust-und-die-suche-nach)** zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/es-kann-nur-besser-werden-aber-wie)* erschienen.
-

@ 6bae33c8:607272e8
2024-11-08 18:48:32
I went [4-1 last week to start off Q3](https://www.realmansports.com/p/circa-millions-3b1), putting me on a 17-8 run over the last five weeks after a terrible start. I’m still drawing dead for the overall, so it’s really just a matter of putting together three more 4-1 or 5-0 weeks this quarter.
By the way, I’m putting these picks behind the paywall not because they’re worth paying for — no one’s picks are worth paying for! — but because I want to give my paid subscribers something not available to free ones. But that they are behind a paywall doesn’t mean they’ll work out.
**Steelers +2.5 at Indigenous Peoples** — The Steelers are coming off a bye, the IPs a tough win against the Giants. I like the Steelers to have a good plan against Jayden Daniels and to move the ball.
**Broncos +8.5 at Chiefs** — I like buying the Broncos low off the blowout and betting against an undefeated team in division — everyone is up for the Chiefs.
**Buccaneers +6 vs 49ers** — This was my last choice. The value is great as the 49ers have done nothing to earn this kind of status as a big road favorite against a solid team, but the line is actually 6.5 now, so maybe I’m missing something.
**Bears -6.5 vs Patriots** — The Bears are a good buy-low after getting worked by the Cardinals. The Patriots are a get-well game.
**Chargers -7 vs Titans** — I don’t really take the Titans seriously, and the Chargers are solid and playing at home.
-

@ f5194aa4:c08836bb
2024-11-08 17:07:07
At Jewelry by Serendipity, we offer an exquisite collection of [promise rings](https://www.jewelrybyserendipity.com/collections/promise-rings), each designed to symbolize love, commitment, and a shared future. Crafted with care from high-quality materials, our promise rings are perfect for celebrating a special relationship or marking an important milestone. From classic designs to contemporary styles, each ring reflects the unique bond it represents. Whether you're making a promise to a loved one or celebrating a friendship, our promise rings are a beautiful reminder of the meaningful connections in your life.
-

@ 13b9f773:4f4efe54
2024-11-08 15:30:45
[Eva Elfie](https://www.reddit.com/r/metart/s/6EAlApYjCZ) - For You

------

------

-

@ d3052ca3:d84a170e
2024-11-08 14:46:09
The shift of the American working class from the Democratic to the Republican Party in this last election, and the outrage it has generated among many leftist American academics, has led me to reflect on why so many academics become strong socialists or even communists, while the vast majority of the American “working class” do not.
They would likely call it “false consciousness” on the part of the American worker. By I see it as false consciousness among elites: they *do not recognize that they are elites,* and that their social status motivates them differently from how the typical American worker is motivated. In short, there is a difference between economic *class* (being a “worker”) and social *status* (being an “elite”). In this I am convinced that Peter Turchin’s structural-demographic theory continues to have explanatory power. (I won’t go into that here, but do check out his work.)
Socialism and even communism carry strong appeal for a specific kind of highly educated, young elite today: the kind that needs to work for a living, but still sees itself as elite. These are not “white collar workers;” they are “precarious elites.” They are subject to a dynamic that few want to talk about:
Some of the worst labor exploitation in this country occurs in so-called “prestige industries.” These include education (higher and lower), entertainment, journalism, publishing, art, philanthropy—even, on the higher-paid end, investment banking and other financial services.
You want to help a celebrity launch a new brand or product? Prepare to make $35,000 a year and work 24 hours a day, 7 days a week, doing countless frenzied tasks that have nothing to do with your job description.
You want to teach philosophy at a University? Get ready to make $17,500 a year, if you’re lucky. If you’re an international graduate student, your visa to stay in the U.S. is also completely contingent on your advisor’s approval; as a result, abuse is rampant.
You want to write for The Atlantic or The New Yorker? You can maybe get a few hundred bucks per article as a freelancer; $60K per year as a staff writer, if you’re lucky.
You want to become a powerful banker? You may start at $150K per year right out of college, but you will work 80-120 hours a week at the expense of everything else in your life, no telling how long—certainly for years. Your mental and even physical health are the price you pay for this “opportunity.”
These are the jobs that children of elites want. They want these jobs so much that they are willing to subject themselves to highly fragmented, authoritarian, and toxic work environments, with such high turnover, particularly of junior workers, that it’s socially a war of all against all. These jobs are different from working at a factory or an established company—there is a “musical chairs” dynamic, authority is exercised arbitrarily and chaotically, the job tasks can change daily and even moment to moment, most relationships are based on dominance/submission, and there is no “solidarity.” Employers believe it’s a “privilege” for anyone to have these jobs, and that therefore no one in them has the right to complain. Their refrain: “There are always 100 more candidates ready to take your place.”
In addition, there is the psychology of being an elite: you expect to be treated better by virtue of your education and social status, so it can be shameful to admit that you are being abused and might need to fight for better working conditions. Young elites may even want to organize and collectively bargain, but they don’t know how—they’ve been carried along by their social status in extremely authoritarian and chaotic environments and may never have really built anything with others over time.
For many young precarious elites, therefore, socialism becomes a kind of dream of not only of a good workplace but of a good society—one where they get what they believe is their “due.”
These “precarious elites” do see their exploitation as a structural problem, but they blame “capitalism” instead of the brute fact of supply and demand: there are just too many of them competing for the same few prestige jobs. While the American worker imagines a path to better pay and working conditions through organizing, the precarious elite sees no such path—because for them *status* is just as, if not more, important than pay and benefits, and that is something much harder to negotiate. Elites insist that *they should be able to do exactly the (prestigious) jobs that they want to do.* They are also educated enough to have read the socialist and communist literatures. That combination leads to the fantasy that the government could force their employers not only to pay them more and treat them with dignity—which in some cases it could, certainly—but also to guarantee these conditions *in prestige jobs* for everyone who wants them.
There likely is a legitimate case to be made that some of these prestige employers are violating labor laws and should be held accountable. In other cases, there are certainly opportunities to pass new laws prohibiting what amounts to indentured servitude. But actually enforcing these laws will only reveal what is already plain as day: that there are far fewer prestige jobs than there are elites who want them.
The double bind for elites is that the prospect of taking a “lower status” job—even one that pays a lot more, where workers are treated significantly better—is even worse than being a de facto slave with a prestigious role. This leads precarious elites to demand a magical solution: the state. The state must not only protect workers, but guarantee certain kinds of jobs at certain levels of pay and benefits for anyone who wants them. Needless to say, this demand can never be fulfilled, and the cycle of partisanship is then retrenched: precarious elites blame American workers for having the gall to vote and organize based on self-interest, rather than to crusade for an idyllic state of affairs that will not come.
Originally published on twitter https://x.com/NSmolenski/status/1854347409012203687
Reposted to nostr without permission. Sorry not sorry. <3 u Natalie!
-

@ 52adc2ef:9f4bc0ba
2024-11-08 14:20:49
คงเคยได้ยินวลีว่า "ขยันผิดที่ 10 ปีก็ไม่รวย"
เเต่สามารถใช้กับการออมเงินได้ด้วย
ถ้าใครยังงง ว่าออมผิดที่ ไม่รวยด้วยหรอ
ต้องรู้ก่อนว่า เราอยู่ในยุคที่มีเงินเฟ้อนะครับ ประมาณ 5-7% ต่อปี
รัฐบาลอาจจะประกาศ ปีล่าสุด 2567 ต่ำเเต่ด้วยข้าวของที่เราซื้อเองก็คงรู้ว่ามันมากกว่าที่ประกาศเเน่นอน

*ข้อมูลจาก www.bot.or.th*
วางเงินไว้เฉยๆเงินก็ระเหยเเล้ว(อย่างกับน้ำเเข็ง)
งั้นกลับมาย้ำก่อนว่า เงินเฟ้อ คืออะไร เผื่อคนไม่เข้าใจ
(สำหรับคนทราบเเล้วรอเพื่อนก่อนนะครับ)
### เงินเฟ้อ
เงินเฟ้อคืออะไร เอาเเบบเข้าใจง่ายคือ อำนาจการใช้จ่ายของเราน้อยลง ราคาสินค้าเเพงขึ้น
ตัวอย่างอยู่รอบตัวเราอยู่เเล้ว
เมื่อก่อนสัก 5 ปีที่เเล้ว เคยซื้อข้าวกระเพรา 40 บาทได้ ตอนนี้ไป 50-60 บาทเเล้ว
หรือข่าวราคาบ้านที่สูงกว่า รายได้ครัวเรือนถึง 21 เท่า !

### ทำไมถึงมีเงินเฟ้อ
เคยสงสัยมั้ยครับว่าทำไมมีเงินเฟ้อ คำนี้ เราน่าจะเคยได้ยินบ้างไม่มากก็น้อย
เเต่มีความหมายสุดลึกซึ้ง มันกระทบกับเราเเน่นอน ไม่ว่าเราจะรู้หรือไม่รู้
(เเต่รู้ดีกว่าเเน่นอนจะได้ป้องกัน แก้ไขได้)
ให้เข้าใจก่อนว่าเราอยู่ในยุคเงินรัฐบาล ที่ถือว่าเป็นตั๋ว ไว้ใช้ในประเทศ ชำระหนี้ได้ตามกฎหมาย
ต้องมี ทองคำ Bond ค้ำไว้เพื่อผลิตธนบัตรออกมา ซึ่งตรงนี้รัฐบาลมีอำนาจเต็มที่สามารถกำหนดนโยบายทางเงินได้
*หรือเรียกภาษาฝรั่งว่า "Fiat Money"*
เเล้วมันไม่ดีหรอ! ต้องมีคนคิดเเน่นอน อันนี้เเล้วเเต่คนคิดเลยนะครับ
เเต่บอกเป็นความจริงเเล้วไปพิจารณาต่อน่าจะดีกว่า
เพราะรัฐบาลสามารถที่จะพิมพ์เงินออกมาได้เลย
ผลิตเเล้วเกี่ยวอะไรกับเงินเฟ้อ
ในปัจจุบันสหรัฐอเมริกามีหนี้มากขึ้นตามภาพด้านล่างเลย

ข้อมูลจาก https://fiscaldata.treasury.gov/americas-finance-guide/national-debt/
ทำไมต้องยกตัวอย่างอเมริกาเพราะว่าประเทศเราก็ถือพันธบัตรรัฐบาลสหรัฐ ไว้ในในพิมพ์เงินบาท
มันส่งผลเเน่นอน พิมพ์เงินมีผลยังไงใช่มั้ยครับ
เดี๋ยวยกตัวอย่างนะครับ
*ถ้าโลกนี้มีเงิน 100 หน่วยถืออยู่ 1 หน่วยเเสดงว่า เรามี 1% ของทั้งหมด
เเต่ถ้ามีการพิมพ์เงินหรือเพิ่ม Supply เป็น 1,000 หน่วย มูลค่าของเราก็จะเหบือ 0.1 % ของทั้งหมด*
พอเห็นอะไรมั้ยครับ จู่ๆเงินเราก็ระเหยไป เป็นการทำลายการเก็บออมของเรา
ถ้าคุณปู่เราเก็บเงินไว้ 10 หมื่น เเบบมนต์รักลูกทุ่ง(เมื่อก่อนเยอะมากๆ)
ในยุคปัจจุบันเเทบจะซื้ออะไรไม่ได้เลย
นี่คือตัวอย่างการเก็บเงินผิดที่ ของเเทร่ เลย
### ทำไมรัฐบาลต้องพิมพ์เงิน
ถ้าคุณได้มีโอกาสเป็นนายกรัฐมนตรี โชคดีมากก มีโรคระบาดประหลาด ต้องปิดเมือง
คุณมีอำนาจในการเเจกเงินเพื่อใ้ห้ผ่านวิกฤตไป เเต่คุณไม่ทำ คุณคิดว่า สมัยหน้าจะมีคนเลือกคุณมั้ย?
ร้อยทั้งร้อย คุณมีอำนาจนี้ก็ต้องใช้
เมื่อมีเงินผลิตออกมามันก็จะดันให้สินค้าเพิ่มสูงขึ้นเนื่องจากทุกคนมีอำนาจจับจ่าย
บ้างก็ไปสินค้า หุ้น คริปโต บ้าน ทำให้สินค้าราคาสูงขึ้น
เเละเมื่อหยุดพิมพ์ อุตสาหกรรมที่เคยดี เช่น คอนโด อาจจะเฟ้อมากเกินไปเพราะตอนพิมพ์เงินมีความต้องการมามาก
ต่อมาฟองสบู่ก็เเตก
ถ้ามันลามทั้งประเทศเเบบ subprime crisis 2008 ในอเมริกา
กลับไปที่เดิมคุณมีอำนาจพิมพ์เงิน ระเบิดอสังหาริมทรัพย์ มาเเตกที่ยุคคุณคุณทำยังไง
ก็พิมพ์เงินสิครับ
มันก็จะไปผลักให้ราคาสินค้าสูงขึ้นไปอีก

ซึ่งเเต่ก่อนเราคิดว่าเงินเฟ้อเป็นเรื่องปกคิ แต่ถ้าศึกษาประวัติศาสตร์ดูเราอยู่ในยุคพิมพ์เงินมา
ประมาณ 100 ปี เท่านั้นเองซึ่งถ้าเริ่มเยอะขึ้นก็เริ่มตั้งเเต่ปี 1971 ที่อเมริกายกเลิก ทองคำ Back
(เรื่องประวัติศาสตร์การเงินเดี๋ยวจะย่อยไปในบทความหน้าๆนะครับ)
### ทำไมราคาที่ดิน ทองคำ หุ้นถึงราคาขึ้น
อย่างที่เกริ่นไปว่าถ้ารู้ตัวว่าเงินกำลังเสื่อมค่าย่อมดีกว่าไม่รู้เลย
ถ้าเป็นตัวคุณเองรู้ว่าเงินมันระเหยได้ทำยังไงครับ
ต้องเปลี่ยนไปทรัพย์สินที่ไม่ระเหยถูกมั้ยครับ
เพราะคนที่รู้เค้าก็จะเปลี่ยนเงินเป็นทรัพย์สินที่รักษามูลค่าได้ดีกว่า
เช่น ทองคำ ที่ดิน หรือเเม้กระทั่ง หุ้น

ข้อมูลจาก https://th.investing.com/indices/us-30-chart
ทำให้สินทรัพย์ที่กล่าวมามูลค่าเพิ่มขึ้น
ทองคำก็เพิ่ง All Time High
ราคาบ้านที่เกริ่นไปก็เเพงมากๆ
เพราะคนที่รู้ก็จะหาที่พักเงินที่ทำให้มูลค่าของเงินของเรา ไม่ระเหย
### สรุปควรเก็บเงินที่ไหนดี
พอเรารู้เเล้วว่าเงินเสื่อมค่าไป สิ่งที่สำคัญควรเก็บเงินของเราใน Hard Asset
Hard Asset
หมายถึง สินทรัพย์ที่ไม่สามารถ ผลิตเพิ่มได้ง่าย หรือไม่ได้เลย
เเละมีต้นทุนการผลิตสูง ถ้าต้นทุนต่ำ ทุกคนก็จะเเห่กันไปผลิตเงินเเทนที่จะสร้างคุณค่าเเก่สังคม
เเละเก็บในที่นี้หมายถึงการออมเงินนะครับ เเละต้องเป็นเงินออม เป็นเงินที่ทิ้งไว้เลย 20-30 ปี
ถ้าเราออมเเล้ว ค่อยลงทุน
สินทรัพย์ที่มีคุณสมบัติเป็น Hard Asset ก็มี
*** ทองคำ ที่ดิน Bitcoin***
ทองคำ ที่ดิน มันถูกพิสูจน์มาเเล้วว่าสามารถเก็บมูลค่าได้
ส่วน Bitcoin แนะนำให้ศึกษาให้เข้าใจก่อนนะครับ
(เก็บเท่าที่เข้าใจ เเต่เราเชื่อว่ามันรักษามูลค่าได้)
หรือจะเก็บในส่วนที่เรามีความรู้ เช่น ศิลปะ ของสะสม ต่างๆ
### สรุป
ใน Part นี้อยากให้ตระหนักรู้ว่าเงินเฟ้อสามารถ ทำลายกสนเก็บออมของเรามากเเค่ไหน
อยากให้ทุกคนรู้ตัว เเละ วางแผนว่าเราจะทำยังไงได้บ้าง
ไม่อยากให้เงินที่พยายามทำงานกันเเบบเหนื่อยยากต้องมาระเหยไป
หวังว่าจะเก็บเงินออมให้ถูกที่กันนะครับ ขอบคุณครับ
-

@ 5d4b6c8d:8a1c1ee3
2024-11-08 13:59:13
@Coffee proposed a topic for [The Stacker Sports Podcast](https://fountain.fm/show/syQHHkLs59GQ1eFAe64t) on our nostr thread and I wanted to share it here.
Why have the top picks in the past two drafts (Bryce Young and Caleb Williams) been so significantly outplayed by the players taken immediately after them (CJ Stroud and Jayden Daniels)?
It's early in the careers of each of these players, but Stroud and Daniels are already looking like MVP caliber franchise QB's. Why did teams miss this?
The most obvious hypothesis (that the Bears and Panthers flubbed their picks) doesn't make much sense, because Young and Williams were the consensus top picks in their drafts.
A bigger question is why it's so difficult to spot an MVP caliber QB from their college play.
originally posted at https://stacker.news/items/758917
-

@ c11cf5f8:4928464d
2024-11-08 13:31:22
The Magnificent 7:

Here we are again with our monthly [Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times) summary, trying to give you a hit of what you missed this month in the ~AGORA territory.
- - -
### Top-Performing Ads
This month, the most zapranked ones are:
* `01` [[OFFER] IPv4+IPv6 KVM VPS, from 1.75EUR/month (Stockholm/SE SWEDEN)](https://stacker.news/items/750336/r/AG) by @skhron
* `02` [[SWAP] SN Cowboy credits](https://stacker.news/items/723069/r/AG) by @DarthCoin
* `03` [[SELL] “NO⚡️TR T-Shirt” for 21K sats](https://stacker.news/items/730098/r/AG) by @thebullishbitcoiner
* `04` [[sell] iptv subscription 10k+ live tv channels and 20k+ vod (tv/movies)](https://stacker.news/items/730963/r/AG) by @profullstack
This month we ran short, so here other 3 from previous month
* `05` [[SELL] StackerNews Archived Territories - Your chance to own a piece of history!](https://stacker.news/items/698471/r/AG) by @Design_r
* `06` [[SELL] Stickers for Stackers! SN Nostr Badges vinyl stickers - from 3,456 sats](https://stacker.news/items/711431/r/AG) by @AGORA
* `07` [[SELL] 3 WishMesh Meshtastic radios and 2 extended antennas 325,000 SATS](https://stacker.news/items/710750/r/AG) by @fe3c522a6f
- - -
###### In case you missed
Here some interesting post opening conversation and free speech:
@supratic share some interesting tools for merchants and businesses:
- https://stacker.news/items/745053/r/AG TinyPine: A simple LN and CASHU ecash POS system for merchants
- https://stacker.news/items/750705/r/AG
PLEBEIAN – Simple, Anonymous & Free Market for Everyone
And here some more insights on how to do business in the private:
- https://stacker.news/items/732291/r/AG Classifieds vs. Listings: Navigating Nostr Protocol's Approach to Advertising by @AGORA
- https://stacker.news/items/742973/r/AG The Watchman Privacy Podcast – Escape the Servile Society with Vonu by @mo
- https://stacker.news/items/746325/r/AG How to Operate a Business in the Private with Trust by @mo
- https://stacker.news/items/741906/r/AG Paying out debt and bills using the Bills of Exchange act by @supratic
- https://stacker.news/items/751074/r/AG The Separation of Business and State by @mo
- https://stacker.news/items/718979/r/AG Mystery Paper: Ancient Merchant Paper, For Merchants Only & Corporate Countries by @AGORA
- https://stacker.news/items/720288/r/AG Parallel Society • Free Man's Perspective by @DarthCoin
###### 🏷️ Spending Sunday is back!
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats!
Read more https://stacker.news/items/721244/r/AG
- - -
###### Just a reminder for you all
This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting.
- - -
### Create your Ads now!

Looking to start something new? Hit one of the links below to free your mind:
* [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation,
* [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or,
* if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)!
* [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners
* [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats
* [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item
* [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else
* [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift!
* [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to
- - -
Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we can help you publish a personalized post.
Coinomi Bitcoin Testnet
skull quantum digital allow faculty enforce spatial emotion fun candy plunge stick stairs salad dish pass fix between shock scene ivory cargo unhappy fault
originally posted at https://stacker.news/items/758878
-

@ 13b9f773:4f4efe54
2024-11-08 12:59:21
Shayla [↗️](https://www.reddit.com/r/metart/s/7COwUCVybJ)



-

@ b4403b24:83542d4e
2024-11-08 11:46:54
To my great surprise, when I checked my SN notification feed today, I found out 👇

To be honest, I don't know what I did to earn it, what it means or gives me or whether I can loose it (similar to the cowboy's hat maybe @k00b can give more insights) but I am pretty satisfied adding it under my belt. 🎉
I'll keep my activity high hoping I'll find the other cowboy collectible I miss - the pistol

originally posted at https://stacker.news/items/758749
-

@ 68fa45dc:3d2a26ed
2024-11-08 10:59:23
<p>Wie Unternehmen Anti-Spyware-Geräte-Störsender erfolgreich einsetzen können</p>
<p>Im modernen Geschäftsumfeld wird die Bedeutung von Informationssicherheit und Datenschutz immer wichtiger und die Bedrohungen, denen Unternehmen ausgesetzt sind, werden immer komplexer. Angesichts der rasanten Entwicklung der Technologie kommt es häufig zu Spionage- und Informationslecks, und Unternehmen müssen dringend wirksame Maßnahmen ergreifen, um ihre eigenen Interessen zu schützen. Unter vielen Schutzmethoden haben sich Anti-Spyware-Geräte <a href="https://www.jammer-store.de/">Störsender Kaufen</a> nach und nach zu einem wirksamen Werkzeug für Unternehmen zur Abwehr interner und externer Bedrohungen entwickelt. In diesem Artikel wird untersucht, wie Unternehmen Anti-Spyware-Geräte wie Mobiltelefon-Störsender, WLAN-Störsender, Anti-Tracking-Störsender und Kameradetektoren erfolgreich einsetzen können, um die Schutzfunktionen für die Informationssicherheit zu verbessern.</p>
<h3>Anwendung des Handy-Störsender</h3>
<p><a href="https://www.jammer-store.de/praktischste-37W-12-band-5G-signalstorsender-fur-mobiltelefone-wlan-gps-rf.html"><img src="https://www.jammer-store.de/image/HJ-129/1.jpg" alt="Tragbare Signalstörsender für Mobiltelefone" width="450"/></a></p>
<p>Handy-Störsender blockieren Handysignale innerhalb bestimmter Frequenzen und verhindern so den Diebstahl von Informationen in Konferenzräumen oder sensiblen Bereichen. Unternehmen können beim Einsatz von Handy-Störsendern die folgenden Strategien in Betracht ziehen:</p>
<p>1. Identifizieren Sie sensible Bereiche: Zunächst sollten Unternehmen identifizieren, welche Bereiche sensibel sind, beispielsweise Vorstandssitzungsräume, Forschungs- und Entwicklungsabteilungen sowie Finanzabteilungen. Der Einsatz von Störsendern für Mobiltelefone an diesen Orten kann Abhören und Informationslecks wirksam verhindern.</p>
<p>2. Rechtmäßige und konforme Verwendung: Die Verwendung von <a href="https://www.jammer-store.de/handy-tragbare-storsender.html">handy störsender</a> muss den örtlichen Gesetzen und Vorschriften entsprechen und sicherstellen, dass sie nur in zulässigen Situationen verwendet werden. Unternehmen sollten sich vorab über die einschlägigen Gesetze informieren und beim Einsatz von Störsendern Aufzeichnungen führen, um Rechtsstreitigkeiten vorzubeugen.</p>
<p>3. Bewerten Sie regelmäßig die Wirksamkeit: Unternehmen sollten die Wirksamkeit von Mobiltelefon-Störsendern regelmäßig bewerten, z. B. durch die Überwachung der Kommunikationssicherheit in Konferenzräumen und die unverzügliche Anpassung von Strategien nach Feststellung von Nichteinhaltung.</p>
<h3> Anwendung des WIFI-Störsender</h3>
<p>WLAN-Störsender können den illegalen Zugriff und die Überwachung von drahtlosen Unternehmensnetzwerken verhindern. Um WLAN-Störsender effektiv zu nutzen, können Unternehmen die folgenden Maßnahmen ergreifen:</p>
<p>1. Netzwerksicherheitsrichtlinie: Entwickeln Sie strenge Netzwerksicherheitsrichtlinien, verschlüsseln Sie das drahtlose Unternehmensnetzwerk, beschränken Sie den Zugriff auf Geräte und verwenden Sie WLAN-Störsender, um unbefugte Geräteverbindungen zu verhindern.</p>
<p>2. Dynamische Anpassung: Passen Sie die Verwendung des <a href="https://www.jammer-store.de/WLAN-bluetooth-storsender.html">WiFi Jammer</a> dynamisch an Änderungen in der Umgebung an. Verstehen Sie die umgebenden Netzwerkbedingungen und überprüfen Sie regelmäßig den Betriebsstatus des Störsenders, um sicherzustellen, dass er optimal funktioniert.</p>
<p>3. Mitarbeiterschulung: Bieten Sie Ihren Mitarbeitern Cybersicherheitsschulungen an, um ihr Bewusstsein für Cybersicherheitsbedrohungen zu schärfen. Machen Sie Ihren Mitarbeitern den Zweck und die Bedeutung von Störsendern klar, um ihr Sicherheitsbewusstsein zu stärken.</p>
<h3>Verwendung von Anti-Tracking-Störsendern</h3>
<p>Anti-Tracking-Störsender werden verwendet, um potenzielle Tracking-Geräte zu blockieren und die Geschäftsleitung und wichtige Informationen zu schützen. Unternehmen können beim Einsatz von Anti-Tracking-Störsendern Folgendes berücksichtigen:</p>
<p>1. Identifizierung von Personen mit hohem Risiko: Identifizieren Sie Führungskräfte oder wichtige Mitarbeiter, die besonderen Schutz benötigen, damit <a href="https://www.jammer-store.de/GPS-storsender.html">Anti-Tracking-GPS Jammer</a> richtig konfiguriert werden können, wenn sie reisen oder wichtige Aktivitäten durchführen.</p>
<p>2. Jederzeit überwachen: Unternehmen sollten mit Geräten ausgestattet sein, die das Tracking-Verhalten in Echtzeit überwachen können, und diese in Kombination mit Anti-Tracking-Störsendern verwenden, um sicherzustellen, dass keine potenziellen Risiken übersehen werden.</p>
<p>3. Notfallplan: Entwickeln Sie einen detaillierten Notfallplan für den Umgang mit möglichen Tracking-Vorfällen. Sobald eine ungewöhnliche Situation entdeckt wird, kann schnell ein Plan zur Bewältigung dieser Situation auf den Weg gebracht werden.</p>
<h3>Die Rolle von Kameradetektoren</h3>
<p>Kameradetektoren spielen eine wichtige Rolle bei der Identifizierung versteckter Kamerageräte für Unternehmen, insbesondere bei Konferenzen und Geschäftsveranstaltungen. Unternehmen sollten Kameradetektoren effektiv einsetzen, um die Sicherheit und Privatsphäre von Meetings zu gewährleisten:</p>
<p>1. Regelmäßige Inspektion: Führen Sie vor wichtigen Ereignissen oder Besprechungen mithilfe von Kameradetektoren umfassende Inspektionen durch, um sicherzustellen, dass die Besprechungsumgebung nicht durch illegale Überwachungsgeräte beeinträchtigt wird.</p>
<p>2. Verwendungsspezifikationen entwickeln: Erstellen Sie beim Einsatz von <a href="https://www.jammer-store.de/anti-uberwachungs-signal-detektor.html">Kamera Detektor</a> detaillierte Bedienungsanleitungen und Spezifikationen, damit die Mitarbeiter die Verwendung und den Umfang der Detektionsausrüstung verstehen können.</p>
<p>3. Vertraulichkeitsschulung: Für Mitarbeiter, die an Geheimnissen beteiligt sind, wird eine Vertraulichkeitsschulung angeboten, damit sie die Gefahren versteckter Kameraausrüstung verstehen, ihre Wachsamkeit erhöhen und die Informationssicherheit schützen können.</p>
<h3>Zusammenfassen</h3>
<p>Mit der Verschärfung des geschäftlichen Wettbewerbs und der Entwicklung der Informationstechnologie nehmen die Sicherheitsrisiken für Unternehmen weiter zu. Durch den sinnvollen Einsatz von Anti-Spyware-Geräten wie Mobiltelefon-Störsendern, WLAN-Störsendern, Anti-Tracking-Störsendern und Kameradetektoren können Unternehmen nicht nur Informationslecks und Spionage wirksam verhindern, sondern auch das allgemeine Sicherheitsmanagementniveau verbessern. Wenn Unternehmen diese Geräte verwenden, müssen sie jedoch Gesetze und Vorschriften einhalten, die Datenschutzrechte von Mitarbeitern und Kunden respektieren und den Schutz der Informationssicherheit innerhalb eines rechtlichen und konformen Rahmens gewährleisten. Nur so können wir im harten Wettbewerb auf dem Markt unbesiegbar bleiben.</p>
<ol>
<li><a href="https://www.jammer-store.de/BDA-3-tragbare-wanzen-jammer-anti-aufnahme-stoersender-mit-fernbedienung.html">https://www.jammer-store.de/BDA-3-tragbare-wanzen-jammer-anti-aufnahme-stoersender-mit-fernbedienung.html</a></li>
<li><a href="https://www.party.biz/forums/topic/789240/forschung-zum-einsatz-von-handy-storsendern-in-prufungen-und-bes/view/post_id/1786172">https://www.party.biz/forums/topic/789240/forschung-zum-einsatz-von-handy-storsendern-in-prufungen-und-bes/view/post_id/1786172</a></li>
</ol>
-

@ 6e24af77:b3f1350b
2024-11-08 10:11:29
test 6
-

@ 6bae33c8:607272e8
2024-11-08 09:21:31
I don’t want to jinx it, but it’s been a good week. I had the Bengals +6.5 in my picking pool, not Circa though, I had Joe Burrow and Ja’Marr Chase in a key NFFC league, and Chase in two other leagues including the Steak, a 14-teamer where I lost Chris Olave, Stefon Diggs, Rashid Shaheed and maybe CeeDee Lamb. I also picked up and started Rashod Bateman in that league and had Roquan Smith (12 tackles) going too.
I don’t know what else to say except that it was maybe a perfect game. And it was cool the Bengals went for two, essentially locking in the cover (though my 6.5 was good in OT anyway.) Apparently there were penalties that should have been called on the two-point conversion, but I missed them, and in any event, it’s not like I’m a Bengals fan, and they had already covered.
- Burrow is a great QB now that he’s 100 percent healthy. He processes information so quickly, has no problem checking it down if the first reads are covered. And he scrambles well and keeps his eyes downfield. He’s a top-three real life QB when healthy.
- Chase is so good there are almost no words. Faster than Justin Jefferson and CeeDee Lamb, the most dangerous wideout in the league in the open field. If he gets it in space, it’s like 50/50 vs the entire defense whether he makes it to the end zone. What a beast, and you see what he can do with 17 targets.
- Chase Brown had a devastating fumble, but scored the TD and benefited from all the checkdowns.
- Lamar Jackson actually struggled for much of the game, but the 84-yard missed-tackle TD to Tylan Wallace (of whom I had literally never heard before this morning) really pushed him over the top. He did show nice touch on the few throws and just wears out the defense that had him dead to rights a few times only to see him escape.
- Bateman was actually Jackson’s top target, and Mark Andrews had another solid game, but there are a lot of mouths to feed with Diontae Johnson, Zay Flowers and eventually even Isaiah Likely again, not to mention a running QB and a dominant early down back.
- Diontae Johnson had no impact whatsoever and actually slipped on one of his two targets. It was better than Khalil Herbert’s debut though — Herbert fumbled his only carry and was never seen again.
- Derrick Henry was bottled up for most of the night, but he did manage a short TD. Gameflow wasn’t in his favor as the Bengals led most of the way and won time of possession.
- The Bengals defense actually played great, applying constant pressure, keeping the energy up even after being run ragged by Jackson. And they held Henry in check too. That missed tackle on Wallace for an 86-yard TD right after giving up the short-field TD following the Brown fumble sunk them.
- It’s tough watching this version of Justin Tucker who missed a PAT. I used to compare him to Mariano Rivera, but Rivera stayed great through his final season, while Tucker has slipped big time.
-

@ 13351007:eccd002a
2024-11-08 05:32:41
eyJfaWQiOiI0OTNkNDQyNS01YTRiLTQ2YjYtYjFhNC0yZTEyNjZlYTEyNDYiLCJwdWJsaWNLZXkiOiIxZWI5NjZhNmEwMjE4YWJhNTIwYWFhYzkzYmU3ZGQ4YmYzODMwZmM3NzEwYmM4MGNhZWEzYTZhNWUzZWRkZjk0IiwidXNlcm5hbWUiOiJoYW5rIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImN1cnJlbmN5Q29kZSI6IlVTRCIsInBheW1lbnRNZXRob2RDb2RlIjoiTkFUSU9OQUxfQkFOSyIsInByaWNlSW5wdXRUeXBlIjoiTUFSS0VUIiwibWFyZ2luIjoiMyIsImZpeGVkUHJpY2UiOiIiLCJtaW5BbW91bnQiOiIxMDAiLCJtYXhBbW91bnQiOiIiLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoiZmFzdCBhbmQgYmVzdCB0cmFkZXIiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOiIiLCJmaXJzdFRpbWVMaW1pdEFzc2V0IjoiIiwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMS0wOFQwNTozMjo0MS44MzZaIiwibWFya2V0UHJpY2UiOjE2NC4xM30=
-

@ a012dc82:6458a70d
2024-11-08 05:23:17
**Table Of Content**
- Bitcoin Bulls Get a Treat from SEC!
- Gold's Future in Question?
- Conclusion
- FAQ
In the world of finance and investments, there are always exciting developments and trends that capture the attention of investors and enthusiasts alike. Recently, Bitcoin bulls have been delighted by a treat from the U.S. Securities and Exchange Commission (SEC), while the future of gold has come into question. In this article, we will explore the implications of these events and their potential impact on the financial landscape.
**Bitcoin Bulls Get a Treat from SEC!**
**The SEC's Recognition of Bitcoin**
The first significant development for Bitcoin bulls is the recognition by the SEC of Bitcoin as a legitimate asset class. This recognition brings a sense of legitimacy and credibility to the cryptocurrency, as it paves the way for wider adoption and integration into traditional financial systems.
**Increased Institutional Interest in Bitcoin**
With the SEC's recognition, institutional investors have started showing more interest in Bitcoin. Major financial institutions such as banks and hedge funds are now exploring ways to include Bitcoin in their portfolios. This increased demand from institutional players has the potential to drive the price of Bitcoin even higher.
**Regulatory Clarity Boosts Investor Confidence**
One of the biggest challenges for Bitcoin bulls has been the lack of regulatory clarity surrounding cryptocurrencies. However, the SEC's recognition provides a level of clarity that was previously missing. This regulatory framework allows investors to have a better understanding of the risks and benefits associated with investing in Bitcoin.
**Bitcoin ETFs on the Horizon**
The SEC's recognition of Bitcoin also opens the door for the approval of Bitcoin exchange-traded funds (ETFs). ETFs provide an easier and more accessible way for investors to gain exposure to Bitcoin without directly owning the cryptocurrency. The approval of Bitcoin ETFs would likely attract more institutional investors and further propel the price of Bitcoin.
**Gold's Future in Question?**
**The Decline of Gold as a Safe Haven**
Gold has long been considered a safe haven asset, providing investors with a hedge against inflation and economic uncertainties. However, recent events have raised questions about the future of gold as an investment.
**The Rise of Bitcoin as a Digital Gold**
Bitcoin's emergence as a digital store of value has posed a challenge to gold's traditional role. Bitcoin offers many advantages over gold, including its divisibility, portability, and ease of transfer. As more investors recognize these benefits, they may start shifting their investments from gold to Bitcoin, potentially impacting the future demand and value of gold.
**Technological Advancements and Digitalization**
Another factor that puts gold's future in question is the rapid advancement of technology and the increasing digitalization of financial transactions. As digital payment systems and cryptocurrencies gain popularity, the appeal of physical assets like gold may diminish. The convenience and efficiency offered by digital assets could make them a preferred choice for investors in the coming years.
**Changing Investor Preferences**
The preferences of investors are evolving, particularly among younger generations. Millennial and Gen Z investors are more inclined to embrace cryptocurrencies like Bitcoin as they seek alternative investment options. This shift in investor preferences could further erode the demand for gold and impact its future prospects.
**Conclusion**
The recognition of Bitcoin by the SEC has undoubtedly brought joy to Bitcoin bulls, as it signifies a significant milestone in the journey towards mainstream acceptance. The future of gold, on the other hand, faces uncertainties as the emergence of digital assets like Bitcoin challenges its traditional role as a safe haven investment. As technology continues to advance and investor preferences evolve, it will be interesting to see how these dynamics shape the financial landscape in the coming years.
**FAQ**
**Is Bitcoin legal?**
Yes, Bitcoin is legal in most countries, including the United States. However, regulations may vary, so it's essential to check the legality of Bitcoin in your specific jurisdiction.
**Can I invest in Bitcoin through my traditional brokerage account?**
Some brokerage firms offer the option to invest in Bitcoin indirectly through specialized investment products like Bitcoin futures or trusts. However, not all traditional brokerage accounts provide this option, so it's best to inquire with your broker.
**What is the potential for Bitcoin's future growth?**
The future growth potential of Bitcoin is subjective and highly speculative. While some believe Bitcoin has the potential to reach even higher valuations, others remain skeptical. It's important to conduct thorough research and consider various factors before making any investment decisions.
**How can I secure my Bitcoin investments?**
It is crucial to store your Bitcoin in a secure digital wallet and follow best security practices, such as enabling two-factor authentication and using strong, unique passwords. Additionally, offline storage options like hardware wallets offer an extra layer of security.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ fa0165a0:03397073
2024-10-23 17:19:41
## Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process.
1. Making the Wheat dough
2. Making and applying the filling
3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
* Can be frozen and thawed in microwave for later enjoyment as well.
* If you need unit conversion, this site may be of help: https://www.unitconverters.net/
* Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
## Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
## Directions
1. Melt the butter/margarine in a saucepan.
2. Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
3. Dissolve the yeast in a dough bowl with the help of the salt.
4. Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
5. Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
6. Add if necessary. additional flour but save at least 1 dl for baking.
7. Let the dough rise covered (by a kitchen towel), about 30 minutes.
8. Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
9. Stir together the ingredients for the filling and spread it.
10. Roll up and cut each roll into 24 pieces.
11. Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
12. Brush the buns with beaten egg and sprinkle your chosen topping.
13. Bake in the middle of the oven at 250 ° C, 5-8 minutes.
14. Allow to cool on a wire rack under a baking sheet.
-

@ 9e69e420:d12360c2
2024-11-08 02:28:59
A Cypherpunk's Manifesto
by Eric Hughes
Privacy is necessary for an open society in the electronic age.
Privacy is not secrecy. A private matter is something one doesn't
want the whole world to know, but a secret matter is something one
doesn't want anybody to know. Privacy is the power to selectively
reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of
their interaction. Each party can speak about their own memory of
this; how could anyone prevent it? One could pass laws against it,
but the freedom of speech, even more than privacy, is fundamental to
an open society; we seek not to restrict any speech at all. If many
parties speak together in the same forum, each can speak to all the
others and aggregate together knowledge about individuals and other
parties. The power of electronic communications has enabled such
group speech, and it will not go away merely because we might want it
to.
Since we desire privacy, we must ensure that each party to a
transaction have knowledge only of that which is directly necessary
for that transaction. Since any information can be spoken of, we
must ensure that we reveal as little as possible. In most cases
personal identity is not salient. When I purchase a magazine at a
store and hand cash to the clerk, there is no need to know who I am.
When I ask my electronic mail provider to send and receive messages,
my provider need not know to whom I am speaking or what I am saying
or what others are saying to me; my provider only need know how to
get the message there and how much I owe them in fees. When my
identity is revealed by the underlying mechanism of the transaction,
I have no privacy. I cannot here selectively reveal myself; I must
_always_ reveal myself.
Therefore, privacy in an open society requires anonymous transaction
systems. Until now, cash has been the primary such system. An
anonymous transaction system is not a secret transaction system. An
anonymous system empowers individuals to reveal their identity when
desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say
something, I want it heard only by those for whom I intend it. If
the content of my speech is available to the world, I have no
privacy. To encrypt is to indicate the desire for privacy, and to
encrypt with weak cryptography is to indicate not too much desire for
privacy. Furthermore, to reveal one's identity with assurance when
the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless
organizations to grant us privacy out of their beneficence. It is to
their advantage to speak of us, and we should expect that they will
speak. To try to prevent their speech is to fight against the
realities of information. Information does not just want to be free,
it longs to be free. Information expands to fill the available
storage space. Information is Rumor's younger, stronger cousin;
Information is fleeter of foot, has more eyes, knows more, and
understands less than Rumor.
We must defend our own privacy if we expect to have any. We must
come together and create systems which allow anonymous transactions
to take place. People have been defending their own privacy for
centuries with whispers, darkness, envelopes, closed doors, secret
handshakes, and couriers. The technologies of the past did not allow
for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We
are defending our privacy with cryptography, with anonymous mail
forwarding systems, with digital signatures, and with electronic
money.
Cypherpunks write code. We know that someone has to write software
to defend privacy, and since we can't get privacy unless we all do,
we're going to write it. We publish our code so that our fellow
Cypherpunks may practice and play with it. Our code is free for all
to use, worldwide. We don't much care if you don't approve of the
software we write. We know that software can't be destroyed and that
a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is
fundamentally a private act. The act of encryption, in fact, removes
information from the public realm. Even laws against cryptography
reach only so far as a nation's border and the arm of its violence.
Cryptography will ineluctably spread over the whole globe, and with
it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract.
People must come and together deploy these systems for the common
good. Privacy only extends so far as the cooperation of one's
fellows in society. We the Cypherpunks seek your questions and your
concerns and hope we may engage you so that we do not deceive
ourselves. We will not, however, be moved out of our course because
some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for
privacy. Let us proceed together apace.
Onward.
Eric Hughes
<hughes@soda.berkeley.edu>
9 March 1993
-

@ 599f67f7:21fb3ea9
2024-10-20 11:32:36
LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, [Zeus](https://zeusln.app/) edo [BlueWallet](https://bluewallet.io/) bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du.
[Alby](https://getalby.com/) erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, [LNDhub](https://github.com/BlueWallet/LndHub/tree/master) izenekoa.
Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi [Alby konfigurazioarekin](#Alby), pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean [Zeus atalera](#Zeus) jo dezakezu.
## Alby
nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. [WebLN](https://www.webln.dev/) protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek [NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md) protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena.
### Zer behar dut?
- Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea.
- LNbits zorroa. Oraindik zorro bat ez baduzu, joan [gure zorroen orrira](https://bitcointxoko.com) eta sortu bat.
- (Aukerazkoa) Zeus konfiguratzeko mugikor bat.
### 1. LNDhub luzapena gaitzea zure LNbits zorroan
Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu `LNDhub` luzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira.
### 2. Alby luzapena instalatu
Joan [getalby.com](https://getalby.com/)-era eta egin klik `Add Browser Extension` botoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan.
### 3. Inportatu Alby-ra

Hurrengo pantailan, aukeratu `Connect`, eta ondoren aukeratu `LNDhub`. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. Sakatu `Continue`. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke!
💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote:
- *Invoice URL*-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du.
- *Admin URL*-ak ordainketak bidaltzeko aukera ere ematen du.
### 4. (Aukerazkoa) Zeus konfiguratu Alby-rekin

Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan `Account Settings` atalean. `Account` azpian aurkituko duzu `Connect your mobile wallet` aukera. Sakatu `Connect`, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu.
Zeus aurretik instalatu ez baduzu, joan [zeusln.app](https://zeusln.app/)-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan `Settings` > `Add a new node` atalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu.
Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada?
## Zeus
nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute.
### Zer behar dut?
- Android edo iOS telefono bat.
- LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko).
- LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan [gure zorroen orrira](https://bitcointxoko.com) eta sortu bat.
### 1. Zeus deskargatu
Deskargatu Zeus aplikazioa zure sistema eragilerako [hemen](https://zeusln.app).
### 2. LNDhub luzapena gaitzea zure LNbits zorroan
Zure LNbits zorroaren orrian, egin klik `Extensions` atalean eta gaitzazu `LNDhub` luzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria.
### 3. Inportatu Zeus-en
Joan `Settings` > `Add a new node` atalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko.
💡 Aukeratu dezakezu Invoice URL eta Admin URL artean:
- *Invoice URL*-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du.
- *Admin URL*-ak ordainketak bidaltzeko aukera ere ematen du.
QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.

Orain, `Save Node Config` sakatu eta zorroa zure mugikorretik kontrolatu dezakezu!
### Bonus
Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu!
-

@ 18e3af1e:1d42e5df
2023-08-13 02:40:19
Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera.
Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría.
Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital.
### La evolución de la construcción
A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos.
La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos.
El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular.
La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones.
En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno.
A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos.
Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos.
### Individuos que inspiran
La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva:
La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más.
La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva.
El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad.
### Comunidades: origen, inicios y progreso.
Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales.
Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia.
Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales.
Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos.
Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia.
La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades.
En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea.
### Bitcoin | Nostr y la chispa del constructor
Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual.
Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad.
Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin.
Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad.
Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles.
> nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh
La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.**
Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer.
### Conclusión
La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
-

@ 7d3e7ac0:90e6f183
2024-11-07 22:02:47
Read the [paper](https://proof-of-loss.money).
-

@ ec42c765:328c0600
2024-10-21 07:42:48
# 2024年3月
フィリピンのセブ島へ旅行。初海外。

Nostrに投稿したらこんなリプライが
nostr:nevent1qqsff87kdxh6szf9pe3egtruwfz2uw09rzwr6zwpe7nxwtngmagrhhqc2qwq5
nostr:nevent1qqs9c8fcsw0mcrfuwuzceeq9jqg4exuncvhas5lhrvzpedeqhh30qkcstfluj
(ビットコイン関係なく普通の旅行のつもりで行ってた。というか常にビットコインのこと考えてるわけではないんだけど…)
#### そういえばフィリピンでビットコイン決済できるお店って多いのかな?
### 海外でビットコイン決済ってなんかかっこいいな!
## やりたい!
<br>
-----------
<br>
# ビットコイン決済してみよう! in セブ島
[BTCMap](https://btcmap.org/map#14/10.31403/123.91797) でビットコイン決済できるところを探す
本場はビットコインアイランドと言われてるボラカイ島みたいだけど
セブにもそれなりにあった!

なんでもいいからビットコイン決済したいだけなので近くて買いやすい店へ
いざタピオカミルクティー屋!

ちゃんとビットコインのステッカーが貼ってある!

つたない英語とGoogle翻訳を使ってビットコイン決済できるか店員に聞いたら
### 店員「ビットコインで支払いはできません」
(えーーーー、なんで…ステッカー貼ってあるやん…。)
まぁなんか知らんけどできないらしい。
店員に色々質問したかったけど質問する英語力もないのでする気が起きなかった
結局、せっかく店まで足を運んだので普通に現金でタピオカミルクティーを買った
<br>
タピオカミルクティー
話題になってた時も特に興味なくて飲んでなかったので、これが初タピオカミルクティーになった
法定通貨の味がした。

### どこでもいいからなんでもいいから
### 海外でビットコイン決済してみたい
<br>
-----------
<br>
# ビットコイン決済させてくれ! in ボラカイ島
ビットコインアイランドと呼ばれるボラカイ島はめちゃくちゃビットコイン決済できるとこが多いらしい
でもやめてしまった店も多いらしい
でも300もあったならいくつかはできるとこあるやろ!
nostr:nevent1qqsw0n6utldy6y970wcmc6tymk20fdjxt6055890nh8sfjzt64989cslrvd9l
行くしかねぇ!
<br>
## ビットコインアイランドへ
フィリピンの国内線だぁ

```
行き方:
Mactan-Cebu International Airport
↓飛行機
Godofredo P. Ramos Airport (Caticlan International Airport, Boracay Airport)
↓バスなど
Caticlan フェリーターミナル
↓船
ボラカイ島
料金:
飛行機(受託手荷物付き)
往復 21,000円くらい
空港~ボラカイ島のホテルまで(バス、船、諸経費)
往復 3,300円くらい
(klookからSouthwest Toursを利用)
このページが色々詳しい
https://smaryu.com/column/d/91761/
```
空港おりたらSouthwestのバスに乗る
事前にネットで申し込みをしている場合は5番窓口へ

港!

船!(めっちゃ速い)

ボラカイついた!

### ボラカイ島の移動手段
セブの移動はgrabタクシーが使えるがボラカイにはない。
ネットで検索するとトライシクルという三輪タクシーがおすすめされている。

(トライシクル:開放的で風がきもちいい)
トライシクルの欠点はふっかけられるので値切り交渉をしないといけないところ。
最初に300phpくらいを提示され、行き先によるけど150phpくらいまでは下げられる。
これはこれで楽しい値切り交渉だけど、個人的にはトライシクルよりバスの方が気楽。
Hop On Hop Off バス:
https://www.hohoboracay.com/pass.php
一日乗り放題250phpなので往復や途中でどこか立ち寄ったりを考えるとお得。

バスは現金が使えないので事前にどこかでカードを買うか車内で買う。
私は何も知らずに乗って車内で乗務員さんから現金でカードを買った。
バスは狭い島内を数本がグルグル巡回してるので20~30分に1本くらいは来るイメージ。
逆にトライシクルは待たなくても捕まえればすぐに乗れるところがいいところかもしれない。
<br>
## 現実
ボラカイ島 BTC Map

BTC決済できるとこめっちゃある
<br>
さっそく店に行く!
「bitcoin accepted here」のステッカーを見つける!
店員にビットコイン支払いできるか聞く!
できないと言われる!
<br>
もう一軒行く
「bitcoin accepted here」のステッカーを見つける
店員にビットコイン支払いできるか聞く
できないと言われる
<br>
5件くらいは回った
全部できない!
<br>
悲しい
<br>
で、ネットでビットコインアイランドで検索してみると
旅行日の一か月前くらいにアップロードされた動画があったので見てみた
要約
- ビットコイン決済はpouch.phというスタートアップ企業がボラカイ島の店にシステムを導入した
- ビットコインアイランドとすることで観光客が10%~30%増加つまり数百~千人程度のビットコインユーザーが来ると考えた
- しかし実際には3~5人だった
- 結果的に200の店舗がビットコイン決済を導入しても使われたのはごく一部だった
- ビットコイン決済があまり使われないので店員がやり方を忘れてしまった
- 店は関心を失いpouchのアプリを消した
https://youtu.be/uaqx6794ipc?si=Afq58BowY1ZrkwaQ
<iframe width="560" height="315" src="https://www.youtube.com/embed/uaqx6794ipc?si=S3kf0K49Z4NASxJt&start=254" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
なるほどね~
しゃあないわ
<br>
## 聖地巡礼
動画内でpouchのオフィスだったところが紹介されていた
これは半年以上前の画像らしい

現在はオフィスが閉鎖されビットコインの看板は色あせている

おもしろいからここに行ってみよう!となった
で行ってみた
看板の色、更に薄くなってね!?

記念撮影

これはこれで楽しかった
場所はこの辺
https://maps.app.goo.gl/WhpEV35xjmUw367A8
ボラカイ島の中心部の結構いいとこ
みんな~ビットコイン(の残骸)の聖地巡礼、行こうぜ!
<br>
## 最後の店
Nattoさんから情報が
<blockquote class="twitter-tweet"><p lang="ja" dir="ltr">なんかあんまりネットでも今年になってからの情報はないような…<a href="https://t.co/hiO2R28sfO">https://t.co/hiO2R28sfO</a><br><br>ここは比較的最近…?<a href="https://t.co/CHLGZuUz04">https://t.co/CHLGZuUz04</a></p>— Natto (@madeofsoya) <a href="https://twitter.com/madeofsoya/status/1771219778906014156?ref_src=twsrc%5Etfw">March 22, 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script>
もうこれで最後だと思ってダメもとで行ってみた
なんだろうアジア料理屋さん?

もはや信頼度0の「bitcoin accepted here」

ビットコイン払いできますか?
店員「できますよ」
え?ほんとに?ビットコイン払いできる?
店員「できます」
できる!!!!
なんかできるらしい。
<br>
適当に商品を注文して
印刷されたQRコードを出されたので読み取る
ここでスマートに決済できればよかったのだが結構慌てた
自分は英語がわからないし相手はビットコインがわからない
それにビットコイン決済は日本で1回したことがあるだけだった

どうもライトニングアドレスのようだ
送金額はこちらで指定しないといけない
店員はフィリピンペソ建ての金額しか教えてくれない
何sats送ればいいのか分からない
ここでめっちゃ混乱した
でもウォレットの設定変えればいいと気付いた
普段円建てにしているのをフィリピンペソ建てに変更すればいいだけだった
設定を変更したら相手が提示している金額を入力して送金
送金は2、3秒で完了した
<br>
やった!
### 海外でビットコイン決済したぞ!
ログ

PORK CHAR SIU BUN とかいうやつを買った

普通にめっちゃおいしかった
なんかビットコイン決済できることにビビッて焦って一品しか注文しなかったけどもっと頼めばよかった
ここです。みなさん行ってください。
Bunbun Boracay
https://maps.app.goo.gl/DX8UWM8Y6sEtzYyK6
### めでたしめでたし
<br>
-----------
<br>
# 以下、普通の観光写真
## セブ島
ジンベエザメと泳いだ

スミロン島でシュノーケリング

市場の路地裏のちょっとしたダウンタウン?スラム?をビビりながら歩いた

## ボホール島
なんか変な山

メガネザル

現地の子供が飛び込みを披露してくれた

## ボラカイ島
ビーチ


夕日

藻

ボラカイ島にはいくつかビーチがあって宿が多いところに近い南西のビーチ、ホワイトビーチは藻が多かった(時期によるかも)
北側のプカシェルビーチは全然藻もなく、水も綺麗でめちゃくちゃよかった

プカシェルビーチ



<br>
-----------
<br>
# おわり!
 @ 6bae33c8:607272e8
2024-11-12 09:53:33So much for my [Jonnu Smith premonition](https://www.realmansports.com/p/week-10-observations-439). For a garbage game, he wasn’t terrible and almost scored a TD, but that was a tough watch overall. The Dolphins sling it around to so many different players, while the Rams have their shallow, rock-solid three-player tree that produces even when they fail to score a touchdown. I also spoiled it by accidentally glimpsing the final score while checking the price of bitcoin this morning — totally forgot there was even a game. - I don’t know if Tua is still rusty, or the Dolphins have been solved, but there just isn’t any rhythm to the offense that was so unstoppable at times last year. - How is the Rams defense better without Aaron Donald? It’s like they suddenly got faster, younger and more aggressive, the entire unit. It goes to show how much we don’t know, and how overrated names on jerseys are. - The Dolphins defense was also nasty. I had expected this to be a shootout. - De’Von Achane is so fast once he gets going, but the Rams rarely let that happen. - Smith is a weapon, and he’s a significant part of the offense, but they spread it around so much. - Jaylen Waddle had a bad drop, but they seemed to want to get him involved early. - Tyreek Hill is one of the stranger busts in recent memory. He looks just as fast, but after Tua got hurt they just never regained interest in getting him the necessary looks. - As I said, Cooper Kupp, Puka Nacua and Kyren Williams are rocks — the entire rest of the offense barely sees any touches. - One odd thing when you know the final score is trying to figure out in real time how it gets there. When the Rams were down 20-9 with five minutes left, I was sure they would get the TD and fail on the two point conversion to make it 20-15. But instead they kicked the FG, the Dolphins got their FG, and the Rams kicked yet another FG before a failed onside kick.
@ 6bae33c8:607272e8
2024-11-12 09:53:33So much for my [Jonnu Smith premonition](https://www.realmansports.com/p/week-10-observations-439). For a garbage game, he wasn’t terrible and almost scored a TD, but that was a tough watch overall. The Dolphins sling it around to so many different players, while the Rams have their shallow, rock-solid three-player tree that produces even when they fail to score a touchdown. I also spoiled it by accidentally glimpsing the final score while checking the price of bitcoin this morning — totally forgot there was even a game. - I don’t know if Tua is still rusty, or the Dolphins have been solved, but there just isn’t any rhythm to the offense that was so unstoppable at times last year. - How is the Rams defense better without Aaron Donald? It’s like they suddenly got faster, younger and more aggressive, the entire unit. It goes to show how much we don’t know, and how overrated names on jerseys are. - The Dolphins defense was also nasty. I had expected this to be a shootout. - De’Von Achane is so fast once he gets going, but the Rams rarely let that happen. - Smith is a weapon, and he’s a significant part of the offense, but they spread it around so much. - Jaylen Waddle had a bad drop, but they seemed to want to get him involved early. - Tyreek Hill is one of the stranger busts in recent memory. He looks just as fast, but after Tua got hurt they just never regained interest in getting him the necessary looks. - As I said, Cooper Kupp, Puka Nacua and Kyren Williams are rocks — the entire rest of the offense barely sees any touches. - One odd thing when you know the final score is trying to figure out in real time how it gets there. When the Rams were down 20-9 with five minutes left, I was sure they would get the TD and fail on the two point conversion to make it 20-15. But instead they kicked the FG, the Dolphins got their FG, and the Rams kicked yet another FG before a failed onside kick. @ 1b5ee74d:bb1aae6e
2024-11-12 09:42:20Last July, I published an article highlighting the shifting narrative around the so-called "Bitcoin President" in the United States. **An expression that should—must—sound absurd** to anyone who has taken even a cursory look at the technology Satoshi Nakamoto introduced. It's evident that **no such thing as a Bitcoin President exists**. And if you're wondering what I think: no, not even him. **Not even Nayib Bukele**, the President of El Salvador, the first country to adopt Bitcoin as legal tender, can be considered as such. Do you think the promotion of a **centralized, government-controlled wallet** like Chivo aligns with the values that gave birth to Bitcoin?\ But let's return to the United States. The intense lobbying efforts of BTC Inc—the company behind Bitcoin Magazine—first positioned **Robert Kennedy Jr. as the Bitcoin Candidate**, only to swiftly pivot to **Donald Trump** despite his repeated anti-cryptocurrency remarks and his staunch support for the dollar's supremacy. After an electoral campaign of relentless brainwashing, how did Italian mainstream media interpret Bitcoin's relationship with U.S. politics? ### Orange Coin and Orange President The wave of articles published by Italian and international outlets reveals a telling trend: **a systematic association between Bitcoin and Donald Trump following his reelection**. The headlines in the following examples illustrate how this connection was constructed to imbue the cryptocurrency with a specific political connotation, aligned with conservative and Republican positions. **Fanpage** kicks off with a headline that takes for granted the causal link between Trump's reelection and Bitcoin's price surge: *"Why Bitcoin is Soaring After Trump's Election."* At least the article notes that the tycoon, during his first term, called cryptocurrencies a "*scam*," only to drastically change his stance later. **ANSA** adopts an even more emphatic approach: Bitcoin, Wall Street, and the dollar are portrayed as a harmonious trio, collectively celebrating Trump’s return to the White House. The association between Bitcoin and the dollar, however, is paradoxical. Bitcoin was created as an alternative to the dollar—a tool to escape expansionary monetary policies and inflation. Reducing it to a mere appendage of Republican economic policies misses the very reason for Bitcoin's existence. **Corriere della Sera** headline reads: *"With Trump’s Victory, New Record for Bitcoin."* The newspaper leans into sensationalism, linking Bitcoin’s new all-time high to Trump’s electoral victory. The article goes on to mention figures like Elon Musk, attempting to tie the fortunes of the crypto sector to a series of controversial yet highly charismatic personalities. In short, the idea that Bitcoin owes its growth solely to political events or the support of specific individuals is misleading. The notion that its price hinges on a particular election is not only simplistic but ignores decades of market cycles and economic data showing that Bitcoin responds to more complex dynamics such as global liquidity and technological adoption. **Il Giornale** doesn't escape this fallacy either: *"Trump Boosts Stocks and Bitcoin."* The daily draws a direct connection between stock market enthusiasm and Bitcoin's rally, highlighting how Trump's reelection has galvanized both Piazza Affari and cryptocurrencies. This narrative perpetuates the notion that Bitcoin and traditional equities move in lockstep, overlooking Bitcoin's historical decorrelation from traditional assets during critical moments. The idea of a natural alliance between Trump and Bitcoin is reinforced without any solid evidence. On the contrary, Bitcoin investors aren't celebrating a president; they are responding to a broader macroeconomic environment where loose monetary policies and growing distrust in fiat currencies play a crucial role.
@ 1b5ee74d:bb1aae6e
2024-11-12 09:42:20Last July, I published an article highlighting the shifting narrative around the so-called "Bitcoin President" in the United States. **An expression that should—must—sound absurd** to anyone who has taken even a cursory look at the technology Satoshi Nakamoto introduced. It's evident that **no such thing as a Bitcoin President exists**. And if you're wondering what I think: no, not even him. **Not even Nayib Bukele**, the President of El Salvador, the first country to adopt Bitcoin as legal tender, can be considered as such. Do you think the promotion of a **centralized, government-controlled wallet** like Chivo aligns with the values that gave birth to Bitcoin?\ But let's return to the United States. The intense lobbying efforts of BTC Inc—the company behind Bitcoin Magazine—first positioned **Robert Kennedy Jr. as the Bitcoin Candidate**, only to swiftly pivot to **Donald Trump** despite his repeated anti-cryptocurrency remarks and his staunch support for the dollar's supremacy. After an electoral campaign of relentless brainwashing, how did Italian mainstream media interpret Bitcoin's relationship with U.S. politics? ### Orange Coin and Orange President The wave of articles published by Italian and international outlets reveals a telling trend: **a systematic association between Bitcoin and Donald Trump following his reelection**. The headlines in the following examples illustrate how this connection was constructed to imbue the cryptocurrency with a specific political connotation, aligned with conservative and Republican positions. **Fanpage** kicks off with a headline that takes for granted the causal link between Trump's reelection and Bitcoin's price surge: *"Why Bitcoin is Soaring After Trump's Election."* At least the article notes that the tycoon, during his first term, called cryptocurrencies a "*scam*," only to drastically change his stance later. **ANSA** adopts an even more emphatic approach: Bitcoin, Wall Street, and the dollar are portrayed as a harmonious trio, collectively celebrating Trump’s return to the White House. The association between Bitcoin and the dollar, however, is paradoxical. Bitcoin was created as an alternative to the dollar—a tool to escape expansionary monetary policies and inflation. Reducing it to a mere appendage of Republican economic policies misses the very reason for Bitcoin's existence. **Corriere della Sera** headline reads: *"With Trump’s Victory, New Record for Bitcoin."* The newspaper leans into sensationalism, linking Bitcoin’s new all-time high to Trump’s electoral victory. The article goes on to mention figures like Elon Musk, attempting to tie the fortunes of the crypto sector to a series of controversial yet highly charismatic personalities. In short, the idea that Bitcoin owes its growth solely to political events or the support of specific individuals is misleading. The notion that its price hinges on a particular election is not only simplistic but ignores decades of market cycles and economic data showing that Bitcoin responds to more complex dynamics such as global liquidity and technological adoption. **Il Giornale** doesn't escape this fallacy either: *"Trump Boosts Stocks and Bitcoin."* The daily draws a direct connection between stock market enthusiasm and Bitcoin's rally, highlighting how Trump's reelection has galvanized both Piazza Affari and cryptocurrencies. This narrative perpetuates the notion that Bitcoin and traditional equities move in lockstep, overlooking Bitcoin's historical decorrelation from traditional assets during critical moments. The idea of a natural alliance between Trump and Bitcoin is reinforced without any solid evidence. On the contrary, Bitcoin investors aren't celebrating a president; they are responding to a broader macroeconomic environment where loose monetary policies and growing distrust in fiat currencies play a crucial role. @ a012dc82:6458a70d
2024-11-12 05:33:23**Table Of Content** - Bitcoin-Backed Life Insurance Startup: An Overview - How Does It Work? - Advantages of Bitcoin-Backed Life Insurance - Conclusion - FAQ In the world of cryptocurrencies, innovation knows no bounds. The latest groundbreaking development comes in the form of a Bitcoin-backed life insurance startup that has recently launched with a staggering $19 million investment. This bold venture aims to revolutionize the insurance industry by leveraging the power of blockchain technology and digital assets to provide individuals with a secure and transparent life insurance solution. In this article, we will explore the details of this startup, its unique offering, and the potential implications it may have for the future of insurance. **Bitcoin-Backed Life Insurance Startup: An Overview** The Bitcoin-backed life insurance startup, which recently entered the market with a substantial investment of $19 million, aims to disrupt the traditional insurance model by incorporating the benefits of blockchain technology and cryptocurrency. This innovative approach allows policyholders to secure their life insurance coverage using Bitcoin, a popular digital currency known for its decentralized and secure nature. By utilizing Bitcoin as a backing asset, this startup can offer policyholders several advantages, such as increased transparency, faster claim settlements, and enhanced security. Moreover, the integration of blockchain technology ensures that all policy-related transactions are recorded on an immutable ledger, minimizing the risk of fraud and manipulation. **How Does It Work?** **Policy Creation Process** To initiate a policy with this Bitcoin-backed life insurance startup, individuals can visit their user-friendly website and follow a simple step-by-step process. Users are required to provide personal information, undergo a risk assessment, and choose their desired coverage amount. **Bitcoin as Collateral** Unlike traditional life insurance policies that rely on fiat currency, this startup allows policyholders to secure their coverage by depositing a predetermined amount of Bitcoin as collateral. This collateral not only guarantees the payout in case of the policyholder's demise but also serves as an investment that can appreciate over time. **Smart Contracts and Claims** The integration of smart contract technology enables automated claim settlements, eliminating the need for lengthy paperwork and reducing processing times. When a claim is filed, the smart contract verifies the validity of the claim against predefined conditions and automatically executes the payout process, ensuring a seamless and efficient experience for policyholders and beneficiaries. **Advantages of Bitcoin-Backed Life Insurance** **Transparency and Security** With the utilization of blockchain technology, this Bitcoin-backed life insurance startup brings unparalleled transparency and security to the insurance industry. Every policy transaction, from policy creation to claim settlements, is recorded on an immutable and decentralized ledger, eliminating the possibility of fraud and ensuring that all transactions are transparent and verifiable. **Faster Claim Settlements** One of the most significant pain points in traditional life insurance is the lengthy and complex claim settlement process. However, with the implementation of smart contract technology, this Bitcoin-backed startup offers policyholders faster claim settlements. The automated nature of smart contracts streamlines the entire process, minimizing paperwork and reducing the time it takes for beneficiaries to receive their payouts. **Potential for Investment Growth** By using Bitcoin as collateral, policyholders have the opportunity to benefit from potential investment growth. As Bitcoin's value continues to fluctuate in the market, policyholders can reap the rewards of any appreciation in their Bitcoin collateral. This unique feature adds a new dimension to life insurance, turning it into a potential investment avenue for individuals seeking to safeguard their loved ones' future. **Conclusion** The emergence of a Bitcoin-backed life insurance startup with a $19 million investment signifies a significant leap forward for the insurance industry. By combining the benefits of blockchain technology, smart contracts, and cryptocurrency, this startup offers policyholders a unique and innovative approach to life insurance. With increased transparency, faster claim settlements, and the potential for investment growth, Bitcoin-backed life insurance has the potential to reshape the insurance landscape. As the market embraces this disruptive solution, individuals seeking life insurance coverage may find this startup to be a compelling choice. **FAQ** **How secure is Bitcoin-backed life insurance?** Bitcoin-backed life insurance offers enhanced security due to the utilization of blockchain technology. Every transaction is recorded on an immutable and decentralized ledger, minimizing the risk of fraud and ensuring transparency. **Can I convert my existing life insurance policy to a Bitcoin-backed policy?** The conversion of an existing life insurance policy to a Bitcoin-backed policy would depend on the terms and conditions of the respective insurance provider. It is recommended to consult with the Bitcoin-backed life insurance startup or your current insurance provider for further guidance. **How does the Bitcoin collateral appreciate over time?** The value of Bitcoin collateral appreciates based on market conditions and demand. As Bitcoin is a highly volatile digital currency, its value can experience significant fluctuations. Policyholders can benefit from any appreciation in the value of their Bitcoin collateral. **Are there any limitations to coverage amounts?** The coverage amounts offered by the Bitcoin-backed life insurance startup may vary based on factors such as the applicant's risk profile, age, and desired coverage. It is advisable to consult with the startup directly to determine the coverage options available. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-11-12 05:33:23**Table Of Content** - Bitcoin-Backed Life Insurance Startup: An Overview - How Does It Work? - Advantages of Bitcoin-Backed Life Insurance - Conclusion - FAQ In the world of cryptocurrencies, innovation knows no bounds. The latest groundbreaking development comes in the form of a Bitcoin-backed life insurance startup that has recently launched with a staggering $19 million investment. This bold venture aims to revolutionize the insurance industry by leveraging the power of blockchain technology and digital assets to provide individuals with a secure and transparent life insurance solution. In this article, we will explore the details of this startup, its unique offering, and the potential implications it may have for the future of insurance. **Bitcoin-Backed Life Insurance Startup: An Overview** The Bitcoin-backed life insurance startup, which recently entered the market with a substantial investment of $19 million, aims to disrupt the traditional insurance model by incorporating the benefits of blockchain technology and cryptocurrency. This innovative approach allows policyholders to secure their life insurance coverage using Bitcoin, a popular digital currency known for its decentralized and secure nature. By utilizing Bitcoin as a backing asset, this startup can offer policyholders several advantages, such as increased transparency, faster claim settlements, and enhanced security. Moreover, the integration of blockchain technology ensures that all policy-related transactions are recorded on an immutable ledger, minimizing the risk of fraud and manipulation. **How Does It Work?** **Policy Creation Process** To initiate a policy with this Bitcoin-backed life insurance startup, individuals can visit their user-friendly website and follow a simple step-by-step process. Users are required to provide personal information, undergo a risk assessment, and choose their desired coverage amount. **Bitcoin as Collateral** Unlike traditional life insurance policies that rely on fiat currency, this startup allows policyholders to secure their coverage by depositing a predetermined amount of Bitcoin as collateral. This collateral not only guarantees the payout in case of the policyholder's demise but also serves as an investment that can appreciate over time. **Smart Contracts and Claims** The integration of smart contract technology enables automated claim settlements, eliminating the need for lengthy paperwork and reducing processing times. When a claim is filed, the smart contract verifies the validity of the claim against predefined conditions and automatically executes the payout process, ensuring a seamless and efficient experience for policyholders and beneficiaries. **Advantages of Bitcoin-Backed Life Insurance** **Transparency and Security** With the utilization of blockchain technology, this Bitcoin-backed life insurance startup brings unparalleled transparency and security to the insurance industry. Every policy transaction, from policy creation to claim settlements, is recorded on an immutable and decentralized ledger, eliminating the possibility of fraud and ensuring that all transactions are transparent and verifiable. **Faster Claim Settlements** One of the most significant pain points in traditional life insurance is the lengthy and complex claim settlement process. However, with the implementation of smart contract technology, this Bitcoin-backed startup offers policyholders faster claim settlements. The automated nature of smart contracts streamlines the entire process, minimizing paperwork and reducing the time it takes for beneficiaries to receive their payouts. **Potential for Investment Growth** By using Bitcoin as collateral, policyholders have the opportunity to benefit from potential investment growth. As Bitcoin's value continues to fluctuate in the market, policyholders can reap the rewards of any appreciation in their Bitcoin collateral. This unique feature adds a new dimension to life insurance, turning it into a potential investment avenue for individuals seeking to safeguard their loved ones' future. **Conclusion** The emergence of a Bitcoin-backed life insurance startup with a $19 million investment signifies a significant leap forward for the insurance industry. By combining the benefits of blockchain technology, smart contracts, and cryptocurrency, this startup offers policyholders a unique and innovative approach to life insurance. With increased transparency, faster claim settlements, and the potential for investment growth, Bitcoin-backed life insurance has the potential to reshape the insurance landscape. As the market embraces this disruptive solution, individuals seeking life insurance coverage may find this startup to be a compelling choice. **FAQ** **How secure is Bitcoin-backed life insurance?** Bitcoin-backed life insurance offers enhanced security due to the utilization of blockchain technology. Every transaction is recorded on an immutable and decentralized ledger, minimizing the risk of fraud and ensuring transparency. **Can I convert my existing life insurance policy to a Bitcoin-backed policy?** The conversion of an existing life insurance policy to a Bitcoin-backed policy would depend on the terms and conditions of the respective insurance provider. It is recommended to consult with the Bitcoin-backed life insurance startup or your current insurance provider for further guidance. **How does the Bitcoin collateral appreciate over time?** The value of Bitcoin collateral appreciates based on market conditions and demand. As Bitcoin is a highly volatile digital currency, its value can experience significant fluctuations. Policyholders can benefit from any appreciation in the value of their Bitcoin collateral. **Are there any limitations to coverage amounts?** The coverage amounts offered by the Bitcoin-backed life insurance startup may vary based on factors such as the applicant's risk profile, age, and desired coverage. It is advisable to consult with the startup directly to determine the coverage options available. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ a901cbe4:bd85452f
2024-11-12 04:22:24Bitcoin, the crypto world’s star player, is once again making headlines, creeping up on the thrilling milestone of $90,000. It’s the kind of thing that gets HODLers, new investors, and crypto skeptics alike buzzing. But what’s really exciting about Bitcoin hitting $90K is that it feels like we’re in the final approach toward the magical $100K mark. Here’s why this milestone is so important — and why $90K is more than just another number. ### $90K: Not Quite There, But Oh So Close $90,000 is a hefty number on its own, but in the world of Bitcoin, it’s like reaching the crest of a rollercoaster — a massive climb with the real excitement still ahead. When Bitcoin is this close to $100K, every dollar feels like another step toward the “big moment.” The journey has been long and often volatile, but Bitcoin’s persistence, resilience, and ability to keep pushing higher tells a compelling story. If $80K showed Bitcoin’s serious potential, $90K is that last push that’s putting us within touching distance of the ultimate milestone. ### Why $90K is Huge: Momentum and Market Mindset The closer Bitcoin gets to $100K, the more attention it attracts. Traditional investors, financial institutions, and even regulators are watching closely. As Bitcoin nears $90K, the market momentum is growing. Every incremental rise is backed by a combination of increased mainstream adoption, institutional buy-in, and a community that believes in Bitcoin’s long-term potential. It’s like the crypto world’s version of the final sprint, and every piece of momentum counts. More importantly, $90K is proof of market confidence. It signals that investors aren’t just hoping for quick gains; they see Bitcoin as a long-term store of value and a potential future standard in global finance. Each step closer to $100K solidifies Bitcoin’s reputation as a lasting financial asset. ### The Final Countdown: What Happens After $90K? Once Bitcoin breaks $90K, the psychological impact on the market could be enormous. We’re not talking about another bump in the road here — we’re talking about Bitcoin heading into the realm of six-figure valuations. And when that happens, it’s not just a moment for those in the crypto world; it’s a moment for finance as a whole. Here’s what could happen when Bitcoin finally crosses $100K: 1. **Media Frenzy:** The media, which already loves covering every Bitcoin milestone, will go wild with the story, and this could spark a new wave of interest from those who haven’t invested yet. 2. **Institutional FOMO:** We’ve seen an increase in institutional interest, and $100K could drive even more companies, investment funds, and potentially even sovereign wealth funds to consider Bitcoin seriously. 3. **Retail Investor Boom:** New retail investors may jump in, bringing fresh capital into the market. Bitcoin’s journey to $100K could fuel further retail adoption as people see it as a ‘must-have’ in their portfolios. 4. **Regulatory Spotlight:** $100K will also draw attention from regulators. Bitcoin isn’t just a niche investment anymore — it’s a global force, and lawmakers may feel pressure to establish clearer frameworks around crypto. ### $90K and Beyond: Bitcoin’s Future as a Mainstream Asset As Bitcoin inches closer to $90K, it’s becoming clear that we’re witnessing more than just a price rally. Bitcoin is on a path to becoming a mainstream financial asset. Once considered the “outsider” in the financial world, Bitcoin has steadily gained respect and credibility, and now $90K is yet another validation of its journey. After $100K, who knows what’s possible? Some crypto enthusiasts believe Bitcoin could go as high as $500K or even $1 million in the future. While these figures might seem ambitious, they highlight the level of optimism and potential people see in Bitcoin. ### The Bottom Line: Bitcoin Nearing $90K is the Start of Something Bigger Bitcoin reaching $90K is an incredible milestone, but it’s also a starting line. This isn’t just about a number — it’s about Bitcoin’s evolution from a niche digital asset to a globally recognized financial powerhouse. The road from $90K to $100K is going to be exciting, but it’s just the beginning. To everyone watching, it’s time to buckle up. Bitcoin’s rise is far from over, and if you think $90K is thrilling, just wait. The journey ahead promises to be one for the books. So let’s enjoy the ride, because Bitcoin is just getting started. 🚀
@ a901cbe4:bd85452f
2024-11-12 04:22:24Bitcoin, the crypto world’s star player, is once again making headlines, creeping up on the thrilling milestone of $90,000. It’s the kind of thing that gets HODLers, new investors, and crypto skeptics alike buzzing. But what’s really exciting about Bitcoin hitting $90K is that it feels like we’re in the final approach toward the magical $100K mark. Here’s why this milestone is so important — and why $90K is more than just another number. ### $90K: Not Quite There, But Oh So Close $90,000 is a hefty number on its own, but in the world of Bitcoin, it’s like reaching the crest of a rollercoaster — a massive climb with the real excitement still ahead. When Bitcoin is this close to $100K, every dollar feels like another step toward the “big moment.” The journey has been long and often volatile, but Bitcoin’s persistence, resilience, and ability to keep pushing higher tells a compelling story. If $80K showed Bitcoin’s serious potential, $90K is that last push that’s putting us within touching distance of the ultimate milestone. ### Why $90K is Huge: Momentum and Market Mindset The closer Bitcoin gets to $100K, the more attention it attracts. Traditional investors, financial institutions, and even regulators are watching closely. As Bitcoin nears $90K, the market momentum is growing. Every incremental rise is backed by a combination of increased mainstream adoption, institutional buy-in, and a community that believes in Bitcoin’s long-term potential. It’s like the crypto world’s version of the final sprint, and every piece of momentum counts. More importantly, $90K is proof of market confidence. It signals that investors aren’t just hoping for quick gains; they see Bitcoin as a long-term store of value and a potential future standard in global finance. Each step closer to $100K solidifies Bitcoin’s reputation as a lasting financial asset. ### The Final Countdown: What Happens After $90K? Once Bitcoin breaks $90K, the psychological impact on the market could be enormous. We’re not talking about another bump in the road here — we’re talking about Bitcoin heading into the realm of six-figure valuations. And when that happens, it’s not just a moment for those in the crypto world; it’s a moment for finance as a whole. Here’s what could happen when Bitcoin finally crosses $100K: 1. **Media Frenzy:** The media, which already loves covering every Bitcoin milestone, will go wild with the story, and this could spark a new wave of interest from those who haven’t invested yet. 2. **Institutional FOMO:** We’ve seen an increase in institutional interest, and $100K could drive even more companies, investment funds, and potentially even sovereign wealth funds to consider Bitcoin seriously. 3. **Retail Investor Boom:** New retail investors may jump in, bringing fresh capital into the market. Bitcoin’s journey to $100K could fuel further retail adoption as people see it as a ‘must-have’ in their portfolios. 4. **Regulatory Spotlight:** $100K will also draw attention from regulators. Bitcoin isn’t just a niche investment anymore — it’s a global force, and lawmakers may feel pressure to establish clearer frameworks around crypto. ### $90K and Beyond: Bitcoin’s Future as a Mainstream Asset As Bitcoin inches closer to $90K, it’s becoming clear that we’re witnessing more than just a price rally. Bitcoin is on a path to becoming a mainstream financial asset. Once considered the “outsider” in the financial world, Bitcoin has steadily gained respect and credibility, and now $90K is yet another validation of its journey. After $100K, who knows what’s possible? Some crypto enthusiasts believe Bitcoin could go as high as $500K or even $1 million in the future. While these figures might seem ambitious, they highlight the level of optimism and potential people see in Bitcoin. ### The Bottom Line: Bitcoin Nearing $90K is the Start of Something Bigger Bitcoin reaching $90K is an incredible milestone, but it’s also a starting line. This isn’t just about a number — it’s about Bitcoin’s evolution from a niche digital asset to a globally recognized financial powerhouse. The road from $90K to $100K is going to be exciting, but it’s just the beginning. To everyone watching, it’s time to buckle up. Bitcoin’s rise is far from over, and if you think $90K is thrilling, just wait. The journey ahead promises to be one for the books. So let’s enjoy the ride, because Bitcoin is just getting started. 🚀 @ 6be5cc06:5259daf0
2024-11-12 03:11:11### Primeiramente, o que é mempool? Abreviação de memory pool (ou *"pool de memória"*) a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco. É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain. Aqui irei usar o site [mempool.emzy.de](https://mempool.emzy.de/) como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não *a mempool do Bitcoin* em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas. É uma boa prática usar **VPN** ou **Tor** ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação. Dito isso... ### Como interpretar a mempool? Vamos dividir isso em partes para fins didáticos. ---  #### Faixa de taxas Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB). Essa unidade de medida representa o valor pago por byte ocupado pela transação. Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada. Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada. Cada transação Bitcoin consiste em *entradas* e *saídas* (*inputs* e *outputs*): * **Entradas** são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * **Saídas** representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas. Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte. #### MB Simplesmente o tamanho do bloco medido em megabytes :) #### Número de transações Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada. #### Tempo estimado para confirmação Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada. ---  Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários: #### Sem Prioridade Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida. #### Prioridade Baixa Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos. #### Prioridade Média e Alta São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco. ---  Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: #### Taxa média paga Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente. #### Número de transações Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação. #### Tempo desde a mineração Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain. #### Pool de mineração Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem. ---  Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. #### Tempo médio dos blocos (~9,9 minutos): Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede. #### Mudança de dificuldade (+1,46%): A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu. #### Tempo até o próximo ajuste: É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração. ---  Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade. ---  Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. #### Tamanhos de blocos O tamanho de cada quadrado representa o tamanho da transação em bytes. **Filtros (Consolidação, Coinjoin, Dados):** Permite visualizar categorias específicas de transações: * **Consolidação**: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * **Coinjoin**: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * **Dados**: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens. ---  Este gráfico exibe o número de transações recebidas ao longo do tempo. #### Taxa mínima (1 sat/vB): Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade. #### Uso de memória (259 MB / 300 MB): A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos. #### Transações não confirmadas (59.361): Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida. ---  Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. #### TXID Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain. #### Previous fee Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação. #### New fee Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco. #### Status (RBF) RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco. ---  Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. #### TXID Similar ao "Recent Replacements", este é o identificador único da transação. #### Amount Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário. #### USD Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária. #### Fee Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores. --- E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade. Por fim, stay humble and stack sats!
@ 6be5cc06:5259daf0
2024-11-12 03:11:11### Primeiramente, o que é mempool? Abreviação de memory pool (ou *"pool de memória"*) a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco. É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain. Aqui irei usar o site [mempool.emzy.de](https://mempool.emzy.de/) como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não *a mempool do Bitcoin* em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas. É uma boa prática usar **VPN** ou **Tor** ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação. Dito isso... ### Como interpretar a mempool? Vamos dividir isso em partes para fins didáticos. ---  #### Faixa de taxas Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB). Essa unidade de medida representa o valor pago por byte ocupado pela transação. Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada. Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada. Cada transação Bitcoin consiste em *entradas* e *saídas* (*inputs* e *outputs*): * **Entradas** são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * **Saídas** representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas. Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte. #### MB Simplesmente o tamanho do bloco medido em megabytes :) #### Número de transações Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada. #### Tempo estimado para confirmação Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada. ---  Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários: #### Sem Prioridade Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida. #### Prioridade Baixa Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos. #### Prioridade Média e Alta São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco. ---  Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: #### Taxa média paga Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente. #### Número de transações Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação. #### Tempo desde a mineração Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain. #### Pool de mineração Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem. ---  Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. #### Tempo médio dos blocos (~9,9 minutos): Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede. #### Mudança de dificuldade (+1,46%): A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu. #### Tempo até o próximo ajuste: É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração. ---  Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade. ---  Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. #### Tamanhos de blocos O tamanho de cada quadrado representa o tamanho da transação em bytes. **Filtros (Consolidação, Coinjoin, Dados):** Permite visualizar categorias específicas de transações: * **Consolidação**: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * **Coinjoin**: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * **Dados**: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens. ---  Este gráfico exibe o número de transações recebidas ao longo do tempo. #### Taxa mínima (1 sat/vB): Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade. #### Uso de memória (259 MB / 300 MB): A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos. #### Transações não confirmadas (59.361): Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida. ---  Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. #### TXID Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain. #### Previous fee Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação. #### New fee Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco. #### Status (RBF) RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco. ---  Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. #### TXID Similar ao "Recent Replacements", este é o identificador único da transação. #### Amount Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário. #### USD Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária. #### Fee Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores. --- E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade. Por fim, stay humble and stack sats! @ 5d4b6c8d:8a1c1ee3
2024-11-12 01:09:13I almost forgot about Mock Draft Monday. The Raiders had their bye week, which means I'm not wallowing in the memory of a fresh humiliation. Week 10 broke their way a little bit and the Raiders are now picking 5th. Unfortunately, the teams ahead of them also need QB's. In this draft, three of the first four picks were QB's. That didn't leave any who were worth spending a top five pick on. Results - 5th Pick: CB Travis Hunter - 36th Pick: QB Garrett Nussmeier - 67th Pick: LB Danny Stutsman - 74th Pick: S Kevin Winston Jr. - 106th Pick: RB Ollie Gordon II - 142nd Pick: WR Tory Horton - 179th Pick: DE Anto Saka - 212th Pick: IOL Seth McLaughlin - 215th Pick: OT Jalen Travis - 220th Pick: QB Miller Moss This draft was a disaster. Unless some of these guys wildly over perform, this is something of a worst case scenario. The board just refused to bread my way. originally posted at https://stacker.news/items/764061
@ 5d4b6c8d:8a1c1ee3
2024-11-12 01:09:13I almost forgot about Mock Draft Monday. The Raiders had their bye week, which means I'm not wallowing in the memory of a fresh humiliation. Week 10 broke their way a little bit and the Raiders are now picking 5th. Unfortunately, the teams ahead of them also need QB's. In this draft, three of the first four picks were QB's. That didn't leave any who were worth spending a top five pick on. Results - 5th Pick: CB Travis Hunter - 36th Pick: QB Garrett Nussmeier - 67th Pick: LB Danny Stutsman - 74th Pick: S Kevin Winston Jr. - 106th Pick: RB Ollie Gordon II - 142nd Pick: WR Tory Horton - 179th Pick: DE Anto Saka - 212th Pick: IOL Seth McLaughlin - 215th Pick: OT Jalen Travis - 220th Pick: QB Miller Moss This draft was a disaster. Unless some of these guys wildly over perform, this is something of a worst case scenario. The board just refused to bread my way. originally posted at https://stacker.news/items/764061 @ b4403b24:83542d4e
2024-11-11 22:26:38 originally posted at https://stacker.news/items/763926
@ b4403b24:83542d4e
2024-11-11 22:26:38 originally posted at https://stacker.news/items/763926 @ 000002de:c05780a7
2024-11-11 21:02:50The US Government (administrative state) is not only evil, its also stupid. On March 14 of 2023 the gov sold 9,861 bitcoin that it had stolen from the Silk Road. At the time this was valued at 215 million dollars. At today's market price those coins are valued at $860,051,175, an increase of 300%. For every seller there is a buyer. Here's to those bitcoiners that bought those coins. [source](https://jlopp.github.io/us-marshals-bitcoin-auctions/) Now, I know 645 million is nothing for the US Federal government.... but still. Its pretty comical. Guys, I don't think you want the government buying bitcoin.... Not if we want the state to go away... May not be a popular opinion but that's fine. Its mine. originally posted at https://stacker.news/items/763834
@ 000002de:c05780a7
2024-11-11 21:02:50The US Government (administrative state) is not only evil, its also stupid. On March 14 of 2023 the gov sold 9,861 bitcoin that it had stolen from the Silk Road. At the time this was valued at 215 million dollars. At today's market price those coins are valued at $860,051,175, an increase of 300%. For every seller there is a buyer. Here's to those bitcoiners that bought those coins. [source](https://jlopp.github.io/us-marshals-bitcoin-auctions/) Now, I know 645 million is nothing for the US Federal government.... but still. Its pretty comical. Guys, I don't think you want the government buying bitcoin.... Not if we want the state to go away... May not be a popular opinion but that's fine. Its mine. originally posted at https://stacker.news/items/763834 @ b4403b24:83542d4e
2024-11-11 20:42:43 originally posted at https://stacker.news/items/763814
@ b4403b24:83542d4e
2024-11-11 20:42:43 originally posted at https://stacker.news/items/763814 @ 6bae33c8:607272e8
2024-11-11 19:24:52Yesterday was a mixed bag fantasy wise, but I’m feeling a bit lucky of late generally, and nothing happened to disabuse me of that. I started Aaron Rodgers in the Primetime which was a disaster, but it was over C.J. Stroud who was only a little better. Watching the Texans-Lions this morning validated all the reasons I sat Stroud, so I didn’t feel that badly about it. The [Circa Millions picks](https://www.realmansports.com/p/circa-millions-bbf) really broke my way — the Steelers came back late, as did the Bucs who lost in exactly the right way. The Chargers and Broncos were good most of the way, but it’s those 50/50 games that have to work out. I lost on the Bears which was just a stupid pick. That puts me at 8-2 over the first half of Q3 — I figure if I go 9-1 or 10-0 over the second half, that gets me a piece of the $300K prize. - I went on a hike, so I missed most of the Giants game, and that’s just as well. What I did see was bad Danny Dimes and then the Tyrone Tracy fumble in overtime. Tracy is actually doing God’s work getting them that No. 1 overall pick though. - The Panthers drafted Jonathon Brooks, extended Chuba Hubbard, who is decent, and they gave a four-year deal to Miles Sanders last year! I remember when the Gettlechad paid big bucks to Jonathan Stewart and DeAngelo Williams! - There was a shot of Bryce Young watching Daniel Jones work, and I imagined Young shuddering to think that’s the path down which he’s going — if he’s lucky. - I let Seslowsky talk me into the Bears in Survivor, that NLM. Honestly, I didn’t object so it’s my own fault even though the Chargers were the obvious pick. - The Patriots destroyed the Bears in every way, and Caleb Williams looked a lot like Danny Dimes. Just get rid of the damn ball! - Joe Flacco was a nice story, but you have to play Anthony Richardson now. I picked up Richardson in two more leagues so I now have him in four. He’s still a long shot to be good, but if he’s even decent, he’ll be a monster for fantasy. If I were the Colts I’d tailor the offense to him, call tons of designed runs, roll-outs, etc. I’m sure he’d just get hurt though. - Dalton Kincaid got hurt, but he’s just such a bust in every way. He’s basically just a generic TE you could grab off waivers. I had him ranked as my TE3. - So crazy the Broncos got the game-winning FG blocked. This Chiefs team will go undeafeated and win the Super Bowl like the 1973 Dolphins, but no one will consider them a top-10 all-time team. - Courtland Sutton is suddenly a top receiver again. He had disappeared entirely in Week 7. - I have the league’s only Younghoe in three leagues, so his missing three field goals really hurt. - Drake London was banged up, but he produces every game. - I started Mason Tipton in the Primetime — what the hell happened to him? - The Alvin Kamara easy-long TD drop was crazy. I thought for sure Atlanta would win the game after that. - Christian McCaffrey was all the way back — he got most of the carries and seven targets. - Bucky Irving is the Bucs best back, but Rachaad White is a good receiver and made an insane fourth-down conversion on a scramble play from Baker Mayfield. - Jaylen Warren is finally back to last year’s role. - The Steelers really held Jayden Daniels in check and would have an easier time of it but for a botched fake punt deep in their own end early in the game. I was only half watching, so I’m not exactly sure what happened there. - You can take Sam Darnold off the Jets, but you can’t take the Jets off Sam Darnold. Seriously, the tick where he throws an end zone pick every time down is leftover from his time with them. - Say what you want about the Jaguars, but they were able to take away Justin Jefferson. - The Titans defense isn’t bad, though the broadcast kept harping on their strong per-game statistics. It’s easier to have good per-game defensive statistics when your offense is awful, and teams can play conservatively against you. - Gus Edwards returned and looked good. He split carries fairly evenly with J.K. Dobbins who doesn’t look explosive of late. - I can’t believe Calvin Ridley is good again. I guess I wrote him off after last year not realizing how terrible the Jaguars offense was. - Cooper Rush was abominable, made Danny Dimes look like Joe Montana. - CeeDee Lamb had 10 targets for 21 yards. - Saquon Barkley’s having a great year, but you have to be at least a little annoyed about Jalen Hurts vulturing 10 TDs already. - The Cardinals are in sync, and Kyle Murray has been very good the last month. - Aaron Rodgers doesn’t look terrible physically to me, but there’s obviously something way off. - The Lions are so good they won on the road against a 6-3 team despite Jared Goff throwing five picks. One was bad luck and another was at the end of the half, but still the hit to his stats could cost him the MVP. - Stroud played better, but the offensive line is still bad (and this was the Lions without their new edge rusher Za’Darius Smith.) The Texans are committed to playing slowly and running Joe Mixon into the teeth of the defense 50 times too. - I’m probably jinxing this by posting it, but I’ve been on a nice roll generally these last couple weeks, and I have Jonnu Smith starting everywhere tonight. I’m not saying I did some deep (or any) analysis of the matchup, only that I have a feeling he’ll go off. Not investment advice, just posting this as an experiment.
@ 6bae33c8:607272e8
2024-11-11 19:24:52Yesterday was a mixed bag fantasy wise, but I’m feeling a bit lucky of late generally, and nothing happened to disabuse me of that. I started Aaron Rodgers in the Primetime which was a disaster, but it was over C.J. Stroud who was only a little better. Watching the Texans-Lions this morning validated all the reasons I sat Stroud, so I didn’t feel that badly about it. The [Circa Millions picks](https://www.realmansports.com/p/circa-millions-bbf) really broke my way — the Steelers came back late, as did the Bucs who lost in exactly the right way. The Chargers and Broncos were good most of the way, but it’s those 50/50 games that have to work out. I lost on the Bears which was just a stupid pick. That puts me at 8-2 over the first half of Q3 — I figure if I go 9-1 or 10-0 over the second half, that gets me a piece of the $300K prize. - I went on a hike, so I missed most of the Giants game, and that’s just as well. What I did see was bad Danny Dimes and then the Tyrone Tracy fumble in overtime. Tracy is actually doing God’s work getting them that No. 1 overall pick though. - The Panthers drafted Jonathon Brooks, extended Chuba Hubbard, who is decent, and they gave a four-year deal to Miles Sanders last year! I remember when the Gettlechad paid big bucks to Jonathan Stewart and DeAngelo Williams! - There was a shot of Bryce Young watching Daniel Jones work, and I imagined Young shuddering to think that’s the path down which he’s going — if he’s lucky. - I let Seslowsky talk me into the Bears in Survivor, that NLM. Honestly, I didn’t object so it’s my own fault even though the Chargers were the obvious pick. - The Patriots destroyed the Bears in every way, and Caleb Williams looked a lot like Danny Dimes. Just get rid of the damn ball! - Joe Flacco was a nice story, but you have to play Anthony Richardson now. I picked up Richardson in two more leagues so I now have him in four. He’s still a long shot to be good, but if he’s even decent, he’ll be a monster for fantasy. If I were the Colts I’d tailor the offense to him, call tons of designed runs, roll-outs, etc. I’m sure he’d just get hurt though. - Dalton Kincaid got hurt, but he’s just such a bust in every way. He’s basically just a generic TE you could grab off waivers. I had him ranked as my TE3. - So crazy the Broncos got the game-winning FG blocked. This Chiefs team will go undeafeated and win the Super Bowl like the 1973 Dolphins, but no one will consider them a top-10 all-time team. - Courtland Sutton is suddenly a top receiver again. He had disappeared entirely in Week 7. - I have the league’s only Younghoe in three leagues, so his missing three field goals really hurt. - Drake London was banged up, but he produces every game. - I started Mason Tipton in the Primetime — what the hell happened to him? - The Alvin Kamara easy-long TD drop was crazy. I thought for sure Atlanta would win the game after that. - Christian McCaffrey was all the way back — he got most of the carries and seven targets. - Bucky Irving is the Bucs best back, but Rachaad White is a good receiver and made an insane fourth-down conversion on a scramble play from Baker Mayfield. - Jaylen Warren is finally back to last year’s role. - The Steelers really held Jayden Daniels in check and would have an easier time of it but for a botched fake punt deep in their own end early in the game. I was only half watching, so I’m not exactly sure what happened there. - You can take Sam Darnold off the Jets, but you can’t take the Jets off Sam Darnold. Seriously, the tick where he throws an end zone pick every time down is leftover from his time with them. - Say what you want about the Jaguars, but they were able to take away Justin Jefferson. - The Titans defense isn’t bad, though the broadcast kept harping on their strong per-game statistics. It’s easier to have good per-game defensive statistics when your offense is awful, and teams can play conservatively against you. - Gus Edwards returned and looked good. He split carries fairly evenly with J.K. Dobbins who doesn’t look explosive of late. - I can’t believe Calvin Ridley is good again. I guess I wrote him off after last year not realizing how terrible the Jaguars offense was. - Cooper Rush was abominable, made Danny Dimes look like Joe Montana. - CeeDee Lamb had 10 targets for 21 yards. - Saquon Barkley’s having a great year, but you have to be at least a little annoyed about Jalen Hurts vulturing 10 TDs already. - The Cardinals are in sync, and Kyle Murray has been very good the last month. - Aaron Rodgers doesn’t look terrible physically to me, but there’s obviously something way off. - The Lions are so good they won on the road against a 6-3 team despite Jared Goff throwing five picks. One was bad luck and another was at the end of the half, but still the hit to his stats could cost him the MVP. - Stroud played better, but the offensive line is still bad (and this was the Lions without their new edge rusher Za’Darius Smith.) The Texans are committed to playing slowly and running Joe Mixon into the teeth of the defense 50 times too. - I’m probably jinxing this by posting it, but I’ve been on a nice roll generally these last couple weeks, and I have Jonnu Smith starting everywhere tonight. I’m not saying I did some deep (or any) analysis of the matchup, only that I have a feeling he’ll go off. Not investment advice, just posting this as an experiment. @ 6ad3e2a3:c90b7740
2024-11-11 19:22:48One thing I enjoy about this Substack is I know a lot of its readers personally, and for that reason I also know many of them disagree with me. How dull it would be to write only for people who already were in lockstep with what you were saying! I say that because I also imagine some of you might be inclined to turn away from certain posts, but I would ask that the more you disagree, the more you stick this particular one out to the end. Imagine it were a reflection on [the joys of owning a small, poorly-trained dog](https://www.chrisliss.com/p/walking-the-dog). Donald Trump didn’t just win the election, he won the House, Senate and popular vote. He had [unprecedented support](https://x.com/johnddavidson/status/1854549634552873390) among Latinos and black people, outperformed prior Republican candidates [among Jews](https://nypost.com/2024/11/06/us-news/trump-picks-up-50-of-jewish-vote-in-new-york/), [reached out to Arabs in Michigan](https://x.com/sam_bidwell/status/1855986922650296775) and [even got the Amish](https://x.com/nypost/status/1853957574632092158) to turn out en masse despite being outspent 2:1. The election was a total repudiation of the democratic party and its policies, the corporate press, the censorship industrial complex, uniparty republicans, left-wing academia, Hollywood, large tech companies thumbing the scale and entrenched government bureaucracy. If you think this is a bad thing and were hoping for a different result, you probably have some explanation for what happened. I won’t pretend to know what anyone in particular is thinking, but I can tell you, as someone who is deeply relieved and heartened by this result how I see it. Maybe it will confirm some of your priors and disabuse you of others. Your mileage may vary. My sense of relief is profound. I feel like a heavy weight has finally been lifted. I didn’t even realize how heavy it was until it was suddenly removed. The sense of creeping authoritarianism starting with Trump’s covid measures and [increasing](https://x.com/jeffreyatucker/status/1854601849636372798) via the Biden vaccine mandates, [online](https://x.com/ggreenwald/status/1838229864366682188) [censorship](https://x.com/0rf/status/1849552626729246868), the creation of a [disinformation bureau!](https://x.com/mtaibbi/status/1636729246172291078) was demoralizing in the extreme. I live [in Europe](https://x.com/mtaibbi/status/1835397873275707404) where people have been [arrested](https://x.com/elonmusk/status/1820784815815160260) for Facebook posts in the UK, where a law was passed in France [criminalizing](https://x.com/KLVeritas/status/1758126819784401204) criticism of the mRNA shots. The United States with its Bill of Rights was the one place where there was some obstacle in place against these abuses, but [even there](https://x.com/dbenner83/status/1854028975191851189), [prominent](https://x.com/Chris_Liss/status/1829967175656063405/photo/1) and powerful [factions](https://x.com/shellenberger/status/1842759698292056499) were [explicitly](https://x.com/MikeBenzCyber/status/1842778996250976273) calling for [its dismantling](https://x.com/pmarca/status/1840656582717366744). But perhaps even more troubling was the behavior of ordinary people in response to these measures. I’ve [written at length](https://www.chrisliss.com/p/the-big-bribe) about what I take to be the causes, but more from a 30,000-foot view. I want to express how glad I am personally this behavior will ostensibly no longer be rewarded by those in power. There is a large class of people who believe they are wiser and morally superior than those who disagree with them. They think that if you voted for candidate A you are a better person than if you voted for B. That who you voted for and how much you verbally signal your concern for various policies is important. One day it could be wearing your mask, another taking your booster, maybe it’s your views on Ukraine or Gaza, systemic racism, climate change or teenagers who believe they’ve been born in the wrong body. If you don’t come out on the right side of these issues, you are not only mistaken, you are bad, and not just bad, but ignorant and in need of further education. It’s like an entire class of people became the HR department, your entire world was some dystopian corporation encouraging you to stay in line and [accept a pay (energy) cut](https://www.chrisliss.com/p/the-big-bribe) and lower standard of living for the greater good. And that’s assuming you were compliant enough to keep your job in the first place. Now if this class of people simply excommunicated you from its church — and I know people personally whose families vowed to disown them for voting for Trump — that wouldn’t have been so bad. I mean I don’t need to associate with judgy, intolerant people who aim to stop me from thinking and saying what I earnestly believe. But it was worse than that: They didn’t even respect your right to be left alone. If you refused to inject yourself with pharmaceutical poison, they wanted to [isolate you from society](https://x.com/LibertyBlitz/status/1657384752519979010). Never mind there was [never any scientific basis](https://www.chrisliss.com/p/the-science-changed) for it, never mind the constitution does not suddenly cease to apply because people are scared of a respiratory virus. And even the people who were silent, who did not beat the drum for this biomedical authoritarianism just went along like that was normal. Like shutting down people’s businesses and telling them where they could travel was just unfortunately necessary and for the greater good of “[public health](https://www.chrisliss.com/p/national-security-and-public-health).” But while I harp on covid and the disgraceful scourge of vaccine mandates because it was such an extreme example, my larger point is about the ethos, the attitude that the lab coats, the experts, the climate scientists, the economists, the entire modern technocratic priesthood knew what was best for you. I [posted on Twitter once](https://www.chrisliss.com/p/harmful-speech) my decision to decline a colonoscopy (deemed due at my age), gave the caveat that this was neither advice nor even an informed opinion of the cost-benefit of getting one, and [people went insane](https://x.com/Chris_Liss/status/1664625607517274113/photo/2). The notion that I wouldn’t go along with the prevailing medical edicts (what did they care what I did?) was enraging to them. They knew better, I was an idiot, “getting colon cancer to own the libs.” The truth is, and of this one thing I am certain, *you do not know better than I do*. I am an adult human being, and there is no higher authority in the known universe than me. I can very well make my own errors without compounding them by taking on your flawed presumptions and biases. Quite obviously there are [technical matters](https://x.com/wideawake_media/status/1855537652658803091) where my expertise is lacking. I am happy to consult those who have it to better inform my judgment and decision-making, the way at trial experts often testify to better inform the jury of ordinary people. But just as it is the ordinary people who must render the verdict, it will always be my judgment and my judgment alone that governs my particular affairs, what medicines I will take, what policies I support, what language I use, with whom I choose to associate, how I feel it’s best to raise my kid, what she should and should not be exposed to at what age. I don’t care how many PhDs you attach to the end of your name — the more the worse if the last few years are any guide — you do not know how to manage my affairs better than I do, and I say that while cognizant that I make mistakes in their administration every single day of my life without exception. So I have rambled a bit, but I wanted to convey as thoroughly as possible the enormity of the weight I feel lifted off my back as a result of this election. Yes, someone can still continue to be a condescending, insufferable, moralizing asshole, but what’s changed is he is no longer getting rewarded for such behavior by those in power. You can report me to HR for believing climate change (as it’s marketed to the masses) is a [cynical and evil scam](https://www.chrisliss.com/p/the-big-bribe), but when you get to the HR office you’ll find Karen clearing out her desk. . . . I understand people have misgivings about some of Trump’s proposed policies, and as with any politician you should be circumspect. I would never guarantee he and his cohorts soon to be in power won’t overstep — he surely did during the covid lockdowns. But I am certain virtually [every claim](https://x.com/amuse/status/1855251868194402562) instilling so much fear in susceptible people is a [media fabrication](https://x.com/DissidentMedia/status/1854668585572217157), [deliberate distortion](https://x.com/DefiyantlyFree/status/1848394761540866545) or [outright lie](https://x.com/mazemoore/status/1852813382610550805). One tell for me is when people cite [Project 2025](https://x.com/thatsKAIZEN/status/1855402472891994141), insist [he’s going](https://x.com/realDonaldTrump/status/1841295548109955091) to [outlaw abortion](https://x.com/elonmusk/status/1854925721443127782) or jail those for disagreeing with him politically. Not only did you live through four years of people posting all manner of falsehoods (He’s on Putin’s payroll!) under their own names all over social media without consequence, but as [Glenn Greenwald pointed out](https://x.com/ggreenwald/status/1854215946887393542), if that were true why aren’t people like AOC and Rachel Maddow fleeing the country yet? The answer is obvious: they know all the rhetoric they spewed was fake and performative, even if the [psychological damage](https://x.com/walterkirn/status/1854753916711256404) they did to the credulous is in many cases quite real. Whether you want to venture outside the corporate media propaganda ecosystem to verify these points is up to you. (I have provided many links, and I encourage you to click them.) But [my belief](https://x.com/MarkChangizi/status/1854982806062981544) is no matter your [political persuasion](https://x.com/RnaudBertrand/status/1855804917103124893) whether you realize it or not, like me (and Trump himself coincidentally) you just [dodged](https://x.com/MartyBent/status/1838319344243142659) a serious [bullet](https://x.com/RealCandaceO/status/1855394068739530875).
@ 6ad3e2a3:c90b7740
2024-11-11 19:22:48One thing I enjoy about this Substack is I know a lot of its readers personally, and for that reason I also know many of them disagree with me. How dull it would be to write only for people who already were in lockstep with what you were saying! I say that because I also imagine some of you might be inclined to turn away from certain posts, but I would ask that the more you disagree, the more you stick this particular one out to the end. Imagine it were a reflection on [the joys of owning a small, poorly-trained dog](https://www.chrisliss.com/p/walking-the-dog). Donald Trump didn’t just win the election, he won the House, Senate and popular vote. He had [unprecedented support](https://x.com/johnddavidson/status/1854549634552873390) among Latinos and black people, outperformed prior Republican candidates [among Jews](https://nypost.com/2024/11/06/us-news/trump-picks-up-50-of-jewish-vote-in-new-york/), [reached out to Arabs in Michigan](https://x.com/sam_bidwell/status/1855986922650296775) and [even got the Amish](https://x.com/nypost/status/1853957574632092158) to turn out en masse despite being outspent 2:1. The election was a total repudiation of the democratic party and its policies, the corporate press, the censorship industrial complex, uniparty republicans, left-wing academia, Hollywood, large tech companies thumbing the scale and entrenched government bureaucracy. If you think this is a bad thing and were hoping for a different result, you probably have some explanation for what happened. I won’t pretend to know what anyone in particular is thinking, but I can tell you, as someone who is deeply relieved and heartened by this result how I see it. Maybe it will confirm some of your priors and disabuse you of others. Your mileage may vary. My sense of relief is profound. I feel like a heavy weight has finally been lifted. I didn’t even realize how heavy it was until it was suddenly removed. The sense of creeping authoritarianism starting with Trump’s covid measures and [increasing](https://x.com/jeffreyatucker/status/1854601849636372798) via the Biden vaccine mandates, [online](https://x.com/ggreenwald/status/1838229864366682188) [censorship](https://x.com/0rf/status/1849552626729246868), the creation of a [disinformation bureau!](https://x.com/mtaibbi/status/1636729246172291078) was demoralizing in the extreme. I live [in Europe](https://x.com/mtaibbi/status/1835397873275707404) where people have been [arrested](https://x.com/elonmusk/status/1820784815815160260) for Facebook posts in the UK, where a law was passed in France [criminalizing](https://x.com/KLVeritas/status/1758126819784401204) criticism of the mRNA shots. The United States with its Bill of Rights was the one place where there was some obstacle in place against these abuses, but [even there](https://x.com/dbenner83/status/1854028975191851189), [prominent](https://x.com/Chris_Liss/status/1829967175656063405/photo/1) and powerful [factions](https://x.com/shellenberger/status/1842759698292056499) were [explicitly](https://x.com/MikeBenzCyber/status/1842778996250976273) calling for [its dismantling](https://x.com/pmarca/status/1840656582717366744). But perhaps even more troubling was the behavior of ordinary people in response to these measures. I’ve [written at length](https://www.chrisliss.com/p/the-big-bribe) about what I take to be the causes, but more from a 30,000-foot view. I want to express how glad I am personally this behavior will ostensibly no longer be rewarded by those in power. There is a large class of people who believe they are wiser and morally superior than those who disagree with them. They think that if you voted for candidate A you are a better person than if you voted for B. That who you voted for and how much you verbally signal your concern for various policies is important. One day it could be wearing your mask, another taking your booster, maybe it’s your views on Ukraine or Gaza, systemic racism, climate change or teenagers who believe they’ve been born in the wrong body. If you don’t come out on the right side of these issues, you are not only mistaken, you are bad, and not just bad, but ignorant and in need of further education. It’s like an entire class of people became the HR department, your entire world was some dystopian corporation encouraging you to stay in line and [accept a pay (energy) cut](https://www.chrisliss.com/p/the-big-bribe) and lower standard of living for the greater good. And that’s assuming you were compliant enough to keep your job in the first place. Now if this class of people simply excommunicated you from its church — and I know people personally whose families vowed to disown them for voting for Trump — that wouldn’t have been so bad. I mean I don’t need to associate with judgy, intolerant people who aim to stop me from thinking and saying what I earnestly believe. But it was worse than that: They didn’t even respect your right to be left alone. If you refused to inject yourself with pharmaceutical poison, they wanted to [isolate you from society](https://x.com/LibertyBlitz/status/1657384752519979010). Never mind there was [never any scientific basis](https://www.chrisliss.com/p/the-science-changed) for it, never mind the constitution does not suddenly cease to apply because people are scared of a respiratory virus. And even the people who were silent, who did not beat the drum for this biomedical authoritarianism just went along like that was normal. Like shutting down people’s businesses and telling them where they could travel was just unfortunately necessary and for the greater good of “[public health](https://www.chrisliss.com/p/national-security-and-public-health).” But while I harp on covid and the disgraceful scourge of vaccine mandates because it was such an extreme example, my larger point is about the ethos, the attitude that the lab coats, the experts, the climate scientists, the economists, the entire modern technocratic priesthood knew what was best for you. I [posted on Twitter once](https://www.chrisliss.com/p/harmful-speech) my decision to decline a colonoscopy (deemed due at my age), gave the caveat that this was neither advice nor even an informed opinion of the cost-benefit of getting one, and [people went insane](https://x.com/Chris_Liss/status/1664625607517274113/photo/2). The notion that I wouldn’t go along with the prevailing medical edicts (what did they care what I did?) was enraging to them. They knew better, I was an idiot, “getting colon cancer to own the libs.” The truth is, and of this one thing I am certain, *you do not know better than I do*. I am an adult human being, and there is no higher authority in the known universe than me. I can very well make my own errors without compounding them by taking on your flawed presumptions and biases. Quite obviously there are [technical matters](https://x.com/wideawake_media/status/1855537652658803091) where my expertise is lacking. I am happy to consult those who have it to better inform my judgment and decision-making, the way at trial experts often testify to better inform the jury of ordinary people. But just as it is the ordinary people who must render the verdict, it will always be my judgment and my judgment alone that governs my particular affairs, what medicines I will take, what policies I support, what language I use, with whom I choose to associate, how I feel it’s best to raise my kid, what she should and should not be exposed to at what age. I don’t care how many PhDs you attach to the end of your name — the more the worse if the last few years are any guide — you do not know how to manage my affairs better than I do, and I say that while cognizant that I make mistakes in their administration every single day of my life without exception. So I have rambled a bit, but I wanted to convey as thoroughly as possible the enormity of the weight I feel lifted off my back as a result of this election. Yes, someone can still continue to be a condescending, insufferable, moralizing asshole, but what’s changed is he is no longer getting rewarded for such behavior by those in power. You can report me to HR for believing climate change (as it’s marketed to the masses) is a [cynical and evil scam](https://www.chrisliss.com/p/the-big-bribe), but when you get to the HR office you’ll find Karen clearing out her desk. . . . I understand people have misgivings about some of Trump’s proposed policies, and as with any politician you should be circumspect. I would never guarantee he and his cohorts soon to be in power won’t overstep — he surely did during the covid lockdowns. But I am certain virtually [every claim](https://x.com/amuse/status/1855251868194402562) instilling so much fear in susceptible people is a [media fabrication](https://x.com/DissidentMedia/status/1854668585572217157), [deliberate distortion](https://x.com/DefiyantlyFree/status/1848394761540866545) or [outright lie](https://x.com/mazemoore/status/1852813382610550805). One tell for me is when people cite [Project 2025](https://x.com/thatsKAIZEN/status/1855402472891994141), insist [he’s going](https://x.com/realDonaldTrump/status/1841295548109955091) to [outlaw abortion](https://x.com/elonmusk/status/1854925721443127782) or jail those for disagreeing with him politically. Not only did you live through four years of people posting all manner of falsehoods (He’s on Putin’s payroll!) under their own names all over social media without consequence, but as [Glenn Greenwald pointed out](https://x.com/ggreenwald/status/1854215946887393542), if that were true why aren’t people like AOC and Rachel Maddow fleeing the country yet? The answer is obvious: they know all the rhetoric they spewed was fake and performative, even if the [psychological damage](https://x.com/walterkirn/status/1854753916711256404) they did to the credulous is in many cases quite real. Whether you want to venture outside the corporate media propaganda ecosystem to verify these points is up to you. (I have provided many links, and I encourage you to click them.) But [my belief](https://x.com/MarkChangizi/status/1854982806062981544) is no matter your [political persuasion](https://x.com/RnaudBertrand/status/1855804917103124893) whether you realize it or not, like me (and Trump himself coincidentally) you just [dodged](https://x.com/MartyBent/status/1838319344243142659) a serious [bullet](https://x.com/RealCandaceO/status/1855394068739530875). @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined. For a hypothetical 1k wager on each match, distribute your sats as follows: | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | FC Bayern| Augsburg| Draw | 860| 50 | 90 | | West Ham| Arsenal| Draw | 150| 650| 200| | Southampton| Liverpool| Draw | 100| 730| 170| | Newcastle| West Ham| Draw | 610| 170| 220| | Man City| Tottenham| Draw | 630| 160| 210| | Leicester| Chelsea| Draw | 180| 600| 220| | Ipswich| Man United| Draw | 210| 590| 240| | Crystal Palace| Newcastle| Draw | 310| 420| 270 | | Arsenal| Nottingham Forest| Draw | 720| 100 | 180| | Leganes| Real Madrid| Draw | 120| 690| 190 | | Celta Viga| Barcelona| Draw | 210| 570| 220| | Atletico Madrid| Alaves| Draw | 710| 100| 190| | Athletic Club| Real Sociedad| Draw | 410| 280| 310| As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog. originally posted at https://stacker.news/items/763403
@ 5d4b6c8d:8a1c1ee3
2024-11-11 17:06:58Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined. For a hypothetical 1k wager on each match, distribute your sats as follows: | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | FC Bayern| Augsburg| Draw | 860| 50 | 90 | | West Ham| Arsenal| Draw | 150| 650| 200| | Southampton| Liverpool| Draw | 100| 730| 170| | Newcastle| West Ham| Draw | 610| 170| 220| | Man City| Tottenham| Draw | 630| 160| 210| | Leicester| Chelsea| Draw | 180| 600| 220| | Ipswich| Man United| Draw | 210| 590| 240| | Crystal Palace| Newcastle| Draw | 310| 420| 270 | | Arsenal| Nottingham Forest| Draw | 720| 100 | 180| | Leganes| Real Madrid| Draw | 120| 690| 190 | | Celta Viga| Barcelona| Draw | 210| 570| 220| | Atletico Madrid| Alaves| Draw | 710| 100| 190| | Athletic Club| Real Sociedad| Draw | 410| 280| 310| As of writing this, I'm up almost 85 kilosats with RBOA, thanks to Real Sociedad beating Barcelona last week as a wildly underpriced underdog. originally posted at https://stacker.news/items/763403 @ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
@ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart. @ 000002de:c05780a7
2024-11-11 17:06:01I'm curious. I don't push my political views on people. If they ask I talk pretty freely about my views but most progressives I call friends or colleagues don't ask. But they sure do whine about Trump. I've heard two people in my circle talk about actively searching for places to move. One said they had passports if they need to leave quickly. I know... Curious if others that actually have "progressive" friends are hearing stuff like this. Now, I will be very surprised if they actually go through with it. I think these people have been mentally abused by the corporate press, the establishment, and the Democrat party into believing lies about Donald Trump. I'm not a fan of Mr. Trump but the dogma about him has reached absurd levels. I honestly feel sorry for these folks. I try to talk them down. They have none of it. Its sad. Their brains are switched off. What has been done to them is truly evil. So, am I alone in this experience. I realize some of you probably don't have friends so you can just abstain from responding ;) originally posted at https://stacker.news/items/763402
@ 000002de:c05780a7
2024-11-11 17:06:01I'm curious. I don't push my political views on people. If they ask I talk pretty freely about my views but most progressives I call friends or colleagues don't ask. But they sure do whine about Trump. I've heard two people in my circle talk about actively searching for places to move. One said they had passports if they need to leave quickly. I know... Curious if others that actually have "progressive" friends are hearing stuff like this. Now, I will be very surprised if they actually go through with it. I think these people have been mentally abused by the corporate press, the establishment, and the Democrat party into believing lies about Donald Trump. I'm not a fan of Mr. Trump but the dogma about him has reached absurd levels. I honestly feel sorry for these folks. I try to talk them down. They have none of it. Its sad. Their brains are switched off. What has been done to them is truly evil. So, am I alone in this experience. I realize some of you probably don't have friends so you can just abstain from responding ;) originally posted at https://stacker.news/items/763402 @ 00000000:0da46cec
2024-11-11 15:37:15The **Content Authenticity Initiative** (CAI) is a collaborative effort launched by Adobe in 2019 in partnership with technology companies and media organizations like Twitter and The New York Times. Its goal is to combat misinformation and ensure that digital content can be trusted. By creating a system for global adoption, CAI aims to provide a standard for traceability and verification of digital content in a secure and accessible manner. This article dives into the technical underpinnings of this initiative, detailing the use of metadata, cryptography, and blockchain. We also reference official repositories and open-source resources available for implementing these technologies. ### Content Authenticity Initiative Architecture The architecture of CAI relies on a set of techniques and tools based on standardized metadata, cryptographic integrity mechanisms, and decentralized solutions to ensure content verifiability throughout its lifecycle. Below is an in-depth look at each core element of this architecture. #### 1. **Generation of Authenticity Metadata** Content creation within CAI begins at the capture stage, whether through a camera or smartphone, where **authenticity metadata** is generated. This metadata records important details such as the author's information, timestamp, geolocation, and device used for content capture. The data is stored using standardized schemes like **XMP (Extensible Metadata Platform)**, ensuring consistency for later verification. Developers can access the reference source code for XMP via Adobe's GitHub: [XMP Toolkit SDK](https://github.com/adobe/XMP-Toolkit-SDK). The metadata not only describes the creation context but also maintains an **immutable history of modifications**. Whenever content is edited, the changes are documented, ensuring a complete and traceable history of the content lifecycle. #### 2. **Digital Content Signing** A key component of CAI is the use of **digital signatures** to certify the authenticity and integrity of the content. Each file (image, video, document) is signed with **asymmetric cryptographic algorithms** like **ECDSA (Elliptic Curve Digital Signature Algorithm)** or **RSA**, depending on the desired level of security and computational resources. These digital signatures generate a unique hash for each piece of content, linking it to the creator's private key. If even a single bit of the content is altered, the hash will change, which invalidates the original signature. This mechanism guarantees that unauthorized alterations are easily detected. Reference implementations for these cryptographic methods are available in the [OpenSSL repository](https://github.com/openssl/openssl) and the **Bouncy Castle** library for Java and C#: [Bouncy Castle GitHub](https://github.com/bcgit). #### 3. **Timestamping and Blockchain** To further validate content authenticity, CAI also employs **timestamping** and, in some implementations, **blockchain technology**. Timestamping is handled by a **Timestamp Authority (TSA)**, which certifies that the content existed in a particular state at a specific moment in time. TSAs utilize digital signatures to provide a secure record of when the content was created. Blockchain technology provides an additional layer of transparency and security. By storing the hashes of metadata and digital signatures on a **public blockchain** (like Ethereum), an immutable, decentralized record is created, allowing any user to verify the content's authenticity. Structures like **Merkle trees** are commonly used for recording efficiently, ensuring that changes are tracked without bloating the blockchain. Examples of blockchain-based implementations can be explored in the [Merkle Tree JavaScript Library](https://github.com/miguelmota/merkletreejs) and the official **Ethereum repository**: [Ethereum GitHub](https://github.com/ethereum). #### 4. **Secure Metadata Storage** The metadata generated during content creation is embedded directly within the content file, using **steganographic techniques** or as readable attachments. This ensures that the metadata remains tied to the content and is resistant to malicious alteration. To maintain metadata integrity during transfer, **Transport Layer Security (TLS)** is used, ensuring that content is securely exchanged without interference. Moreover, distributed storage systems such as **IPFS (InterPlanetary File System)** can be leveraged to provide redundant and long-term availability of metadata. The IPFS implementation is available on GitHub: [IPFS GitHub](https://github.com/ipfs). ### Authentic Content Verification One of CAI's primary goals is to enable anyone to easily verify the origin and edit history of content. To achieve this, **open-source verification tools** such as "**Verify with CAI**" have been developed, allowing users to inspect the content and access all associated metadata. These tools are available in the official CAI repository: [Content Authenticity Initiative GitHub](https://github.com/contentauth/). These verification tools leverage hashes and digital signatures embedded in the content, providing an easy way to determine if unauthorized changes have occurred. They also provide links to blockchain records, allowing third-party verification for an added level of security. ### Guide for Photographers and Content Creators The CAI's technology is particularly beneficial for photographers and content creators seeking to protect their work from misuse. Below is a practical guide to utilizing this technology effectively: 1. **Compatible Equipment**: Use a camera or device that supports the generation of authenticity metadata using XMP standards. Many modern devices and editing tools allow users to embed this metadata during capture. 2. **Editing Software**: Choose editing software that maintains authenticity metadata. Adobe Photoshop and similar tools now include features that preserve metadata throughout the editing process, ensuring the content remains verifiable. 3. **Digital Signing**: Use a digital signing tool like **OpenSSL** or libraries such as **Bouncy Castle** to digitally sign your files. This is critical for asserting the integrity and authenticity of your content. Tutorials and examples are available in the repositories mentioned. 4. **Timestamping**: Utilize a **Timestamp Authority (TSA)** to certify that the content existed at a specific point in time. This adds a temporal validation layer that proves when your content was created and that it hasn’t been altered since. 5. **Blockchain Registration**: To further reinforce content authenticity, consider recording metadata on a public blockchain. Services and smart contracts are available to help you register data without requiring deep blockchain expertise. Refer to repositories like [Ethereum GitHub](https://github.com/ethereum) for guidance. 6. **Content Verification**: Use **Verify with CAI** to verify that your content is correctly registered and ensure that all metadata and digital signatures are intact. This tool is open source, allowing anyone to verify the content's authenticity. 7. **Publishing Platforms**: Share your content on platforms that support CAI standards. Platforms like Behance are starting to integrate these standards, helping distribute content while retaining its verified authenticity. ### Technical Challenges and Barriers CAI implementation faces several technical challenges. The most significant are: 1. **Adoption**: For CAI to succeed, stakeholders across the digital content ecosystem—camera manufacturers, software platforms, social networks, etc.—must adopt its standards. 2. **Privacy Concerns**: Providing detailed metadata about authorship may raise privacy issues. To address this, CAI offers options to encrypt sensitive metadata, ensuring it is only accessible when required. 3. **Costs**: The tools needed for digital signatures, blockchain registration, and timestamping can require significant resources, which may be a barrier for smaller creators or platforms. 4. **Sophisticated Threats**: While CAI improves digital security, sophisticated actors may still attempt to bypass authenticity checks or falsify metadata. Continuous improvement of cryptographic techniques and verification methods is required to counter these evolving threats. ### Conclusion The **Content Authenticity Initiative** provides a solid framework for protecting the integrity of digital content. By utilizing metadata standards, digital signatures, blockchain records, and open-source verification tools, CAI aims to establish a global standard for content transparency and authenticity. Despite some technical and logistical challenges, CAI represents a crucial step towards a trustworthy digital ecosystem. Developers and creators can access official repositories to implement these tools and contribute to a safer, more reliable environment for digital media. ### References - Adobe. (n.d.). *XMP Toolkit SDK*. Retrieved from [https://github.com/adobe/XMP-Toolkit-SDK](https://github.com/adobe/XMP-Toolkit-SDK) - OpenSSL. (n.d.). *OpenSSL Cryptography and SSL/TLS Toolkit*. Retrieved from [https://github.com/openssl/openssl](https://github.com/openssl/openssl) - Bouncy Castle. (n.d.). *Bouncy Castle Libraries*. Retrieved from [https://github.com/bcgit](https://github.com/bcgit) - Miguel Mota. (n.d.). *Merkle Tree JavaScript Library*. Retrieved from [https://github.com/miguelmota/merkletreejs](https://github.com/miguelmota/merkletreejs) - Ethereum Foundation. (n.d.). *Ethereum*. Retrieved from [https://github.com/ethereum](https://github.com/ethereum) - IPFS. (n.d.). *InterPlanetary File System*. Retrieved from [https://github.com/ipfs](https://github.com/ipfs) - Content Authenticity Initiative. (n.d.). *Verify with CAI*. Retrieved from [https://github.com/contentauth/](https://github.com/contentauth/)
@ 00000000:0da46cec
2024-11-11 15:37:15The **Content Authenticity Initiative** (CAI) is a collaborative effort launched by Adobe in 2019 in partnership with technology companies and media organizations like Twitter and The New York Times. Its goal is to combat misinformation and ensure that digital content can be trusted. By creating a system for global adoption, CAI aims to provide a standard for traceability and verification of digital content in a secure and accessible manner. This article dives into the technical underpinnings of this initiative, detailing the use of metadata, cryptography, and blockchain. We also reference official repositories and open-source resources available for implementing these technologies. ### Content Authenticity Initiative Architecture The architecture of CAI relies on a set of techniques and tools based on standardized metadata, cryptographic integrity mechanisms, and decentralized solutions to ensure content verifiability throughout its lifecycle. Below is an in-depth look at each core element of this architecture. #### 1. **Generation of Authenticity Metadata** Content creation within CAI begins at the capture stage, whether through a camera or smartphone, where **authenticity metadata** is generated. This metadata records important details such as the author's information, timestamp, geolocation, and device used for content capture. The data is stored using standardized schemes like **XMP (Extensible Metadata Platform)**, ensuring consistency for later verification. Developers can access the reference source code for XMP via Adobe's GitHub: [XMP Toolkit SDK](https://github.com/adobe/XMP-Toolkit-SDK). The metadata not only describes the creation context but also maintains an **immutable history of modifications**. Whenever content is edited, the changes are documented, ensuring a complete and traceable history of the content lifecycle. #### 2. **Digital Content Signing** A key component of CAI is the use of **digital signatures** to certify the authenticity and integrity of the content. Each file (image, video, document) is signed with **asymmetric cryptographic algorithms** like **ECDSA (Elliptic Curve Digital Signature Algorithm)** or **RSA**, depending on the desired level of security and computational resources. These digital signatures generate a unique hash for each piece of content, linking it to the creator's private key. If even a single bit of the content is altered, the hash will change, which invalidates the original signature. This mechanism guarantees that unauthorized alterations are easily detected. Reference implementations for these cryptographic methods are available in the [OpenSSL repository](https://github.com/openssl/openssl) and the **Bouncy Castle** library for Java and C#: [Bouncy Castle GitHub](https://github.com/bcgit). #### 3. **Timestamping and Blockchain** To further validate content authenticity, CAI also employs **timestamping** and, in some implementations, **blockchain technology**. Timestamping is handled by a **Timestamp Authority (TSA)**, which certifies that the content existed in a particular state at a specific moment in time. TSAs utilize digital signatures to provide a secure record of when the content was created. Blockchain technology provides an additional layer of transparency and security. By storing the hashes of metadata and digital signatures on a **public blockchain** (like Ethereum), an immutable, decentralized record is created, allowing any user to verify the content's authenticity. Structures like **Merkle trees** are commonly used for recording efficiently, ensuring that changes are tracked without bloating the blockchain. Examples of blockchain-based implementations can be explored in the [Merkle Tree JavaScript Library](https://github.com/miguelmota/merkletreejs) and the official **Ethereum repository**: [Ethereum GitHub](https://github.com/ethereum). #### 4. **Secure Metadata Storage** The metadata generated during content creation is embedded directly within the content file, using **steganographic techniques** or as readable attachments. This ensures that the metadata remains tied to the content and is resistant to malicious alteration. To maintain metadata integrity during transfer, **Transport Layer Security (TLS)** is used, ensuring that content is securely exchanged without interference. Moreover, distributed storage systems such as **IPFS (InterPlanetary File System)** can be leveraged to provide redundant and long-term availability of metadata. The IPFS implementation is available on GitHub: [IPFS GitHub](https://github.com/ipfs). ### Authentic Content Verification One of CAI's primary goals is to enable anyone to easily verify the origin and edit history of content. To achieve this, **open-source verification tools** such as "**Verify with CAI**" have been developed, allowing users to inspect the content and access all associated metadata. These tools are available in the official CAI repository: [Content Authenticity Initiative GitHub](https://github.com/contentauth/). These verification tools leverage hashes and digital signatures embedded in the content, providing an easy way to determine if unauthorized changes have occurred. They also provide links to blockchain records, allowing third-party verification for an added level of security. ### Guide for Photographers and Content Creators The CAI's technology is particularly beneficial for photographers and content creators seeking to protect their work from misuse. Below is a practical guide to utilizing this technology effectively: 1. **Compatible Equipment**: Use a camera or device that supports the generation of authenticity metadata using XMP standards. Many modern devices and editing tools allow users to embed this metadata during capture. 2. **Editing Software**: Choose editing software that maintains authenticity metadata. Adobe Photoshop and similar tools now include features that preserve metadata throughout the editing process, ensuring the content remains verifiable. 3. **Digital Signing**: Use a digital signing tool like **OpenSSL** or libraries such as **Bouncy Castle** to digitally sign your files. This is critical for asserting the integrity and authenticity of your content. Tutorials and examples are available in the repositories mentioned. 4. **Timestamping**: Utilize a **Timestamp Authority (TSA)** to certify that the content existed at a specific point in time. This adds a temporal validation layer that proves when your content was created and that it hasn’t been altered since. 5. **Blockchain Registration**: To further reinforce content authenticity, consider recording metadata on a public blockchain. Services and smart contracts are available to help you register data without requiring deep blockchain expertise. Refer to repositories like [Ethereum GitHub](https://github.com/ethereum) for guidance. 6. **Content Verification**: Use **Verify with CAI** to verify that your content is correctly registered and ensure that all metadata and digital signatures are intact. This tool is open source, allowing anyone to verify the content's authenticity. 7. **Publishing Platforms**: Share your content on platforms that support CAI standards. Platforms like Behance are starting to integrate these standards, helping distribute content while retaining its verified authenticity. ### Technical Challenges and Barriers CAI implementation faces several technical challenges. The most significant are: 1. **Adoption**: For CAI to succeed, stakeholders across the digital content ecosystem—camera manufacturers, software platforms, social networks, etc.—must adopt its standards. 2. **Privacy Concerns**: Providing detailed metadata about authorship may raise privacy issues. To address this, CAI offers options to encrypt sensitive metadata, ensuring it is only accessible when required. 3. **Costs**: The tools needed for digital signatures, blockchain registration, and timestamping can require significant resources, which may be a barrier for smaller creators or platforms. 4. **Sophisticated Threats**: While CAI improves digital security, sophisticated actors may still attempt to bypass authenticity checks or falsify metadata. Continuous improvement of cryptographic techniques and verification methods is required to counter these evolving threats. ### Conclusion The **Content Authenticity Initiative** provides a solid framework for protecting the integrity of digital content. By utilizing metadata standards, digital signatures, blockchain records, and open-source verification tools, CAI aims to establish a global standard for content transparency and authenticity. Despite some technical and logistical challenges, CAI represents a crucial step towards a trustworthy digital ecosystem. Developers and creators can access official repositories to implement these tools and contribute to a safer, more reliable environment for digital media. ### References - Adobe. (n.d.). *XMP Toolkit SDK*. Retrieved from [https://github.com/adobe/XMP-Toolkit-SDK](https://github.com/adobe/XMP-Toolkit-SDK) - OpenSSL. (n.d.). *OpenSSL Cryptography and SSL/TLS Toolkit*. Retrieved from [https://github.com/openssl/openssl](https://github.com/openssl/openssl) - Bouncy Castle. (n.d.). *Bouncy Castle Libraries*. Retrieved from [https://github.com/bcgit](https://github.com/bcgit) - Miguel Mota. (n.d.). *Merkle Tree JavaScript Library*. Retrieved from [https://github.com/miguelmota/merkletreejs](https://github.com/miguelmota/merkletreejs) - Ethereum Foundation. (n.d.). *Ethereum*. Retrieved from [https://github.com/ethereum](https://github.com/ethereum) - IPFS. (n.d.). *InterPlanetary File System*. Retrieved from [https://github.com/ipfs](https://github.com/ipfs) - Content Authenticity Initiative. (n.d.). *Verify with CAI*. Retrieved from [https://github.com/contentauth/](https://github.com/contentauth/) @ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima. @ c73818cc:ccd5c890
2024-11-11 14:16:21 🙃 Pierce potrebbe portare chiarezza e regole favorevoli per il settore delle criptovalute negli USA. 😍 Con la fine del mandato di Gary Gensler, il CEO di Galaxy Digital, Mike Novogratz, ha appoggiato Hester Pierce come suo possibile sostituto alla guida della SEC. Nota come la "madre delle criptovalute," Pierce è un’avvocata delle regole chiare e strutturate per favorire la crescita del settore. 😍 Pierce, critica di lungo corso dell'approccio aggressivo della SEC verso le criptovalute, potrebbe orientare l’agenzia verso un equilibrio tra innovazione e supervisione. Il suo potenziale incarico come presidente della SEC ha acceso l’ottimismo tra investitori e aziende del settore. 😍 Novogratz prevede che una SEC guidata da Pierce attrarrebbe maggiori investimenti istituzionali, stimolando una crescita duratura delle criptovalute. Un cambio di leadership con una visione pro-cripto potrebbe inoltre sbloccare significativi valori di mercato, creando nuove opportunità di innovazione. Unisciti al nostro gruppo Telegram Bitget -20% - Mexc no KYC https://lnk.bio/Bitcoin.Report.Italia #BitcoinReportItalia #USA #GaryGensler #SEC #StatiUniti #America #Trump #Presidente #Musk #CasaBianca #Cripto #Bitcoin
@ c73818cc:ccd5c890
2024-11-11 14:16:21 🙃 Pierce potrebbe portare chiarezza e regole favorevoli per il settore delle criptovalute negli USA. 😍 Con la fine del mandato di Gary Gensler, il CEO di Galaxy Digital, Mike Novogratz, ha appoggiato Hester Pierce come suo possibile sostituto alla guida della SEC. Nota come la "madre delle criptovalute," Pierce è un’avvocata delle regole chiare e strutturate per favorire la crescita del settore. 😍 Pierce, critica di lungo corso dell'approccio aggressivo della SEC verso le criptovalute, potrebbe orientare l’agenzia verso un equilibrio tra innovazione e supervisione. Il suo potenziale incarico come presidente della SEC ha acceso l’ottimismo tra investitori e aziende del settore. 😍 Novogratz prevede che una SEC guidata da Pierce attrarrebbe maggiori investimenti istituzionali, stimolando una crescita duratura delle criptovalute. Un cambio di leadership con una visione pro-cripto potrebbe inoltre sbloccare significativi valori di mercato, creando nuove opportunità di innovazione. Unisciti al nostro gruppo Telegram Bitget -20% - Mexc no KYC https://lnk.bio/Bitcoin.Report.Italia #BitcoinReportItalia #USA #GaryGensler #SEC #StatiUniti #America #Trump #Presidente #Musk #CasaBianca #Cripto #Bitcoin @ 3bf0c63f:aefa459d
2024-10-31 16:08:50# Anglicismos estúpidos no português contemporâneo Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês. Cada erro é acompanhado também de uma sugestão de como corrigi-lo. ### Palavras que existem em português com sentido diferente - _submissão_ (de trabalhos): **envio**, **apresentação** - _disrupção_: **perturbação** - _assumir_: **considerar**, **pressupor**, **presumir** - _realizar_: **perceber** - _endereçar_: **tratar de** - _suporte_ (ao cliente): **atendimento** - _suportar_ (uma idéia, um projeto): **apoiar**, **financiar** - _suportar_ (uma função, recurso, característica): **oferecer**, **ser compatível com** - _literacia_: **instrução**, **alfabetização** - _convoluto_: **complicado**. - _acurácia_: **precisão**. - _resiliência_: **resistência**. ### Aportuguesamentos desnecessários - _estartar_: **iniciar**, **começar** - _treidar_: **negociar**, **especular** ### Expressões - _"não é sobre..."_: **"não se trata de..."** ---  ## Ver também - [Algumas expressões e ditados excelentes da língua portuguesa, e outras não tão excelentes assim](https://fiatjaf.alhur.es/expressões-e-ditados.txt)
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50# Anglicismos estúpidos no português contemporâneo Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês. Cada erro é acompanhado também de uma sugestão de como corrigi-lo. ### Palavras que existem em português com sentido diferente - _submissão_ (de trabalhos): **envio**, **apresentação** - _disrupção_: **perturbação** - _assumir_: **considerar**, **pressupor**, **presumir** - _realizar_: **perceber** - _endereçar_: **tratar de** - _suporte_ (ao cliente): **atendimento** - _suportar_ (uma idéia, um projeto): **apoiar**, **financiar** - _suportar_ (uma função, recurso, característica): **oferecer**, **ser compatível com** - _literacia_: **instrução**, **alfabetização** - _convoluto_: **complicado**. - _acurácia_: **precisão**. - _resiliência_: **resistência**. ### Aportuguesamentos desnecessários - _estartar_: **iniciar**, **começar** - _treidar_: **negociar**, **especular** ### Expressões - _"não é sobre..."_: **"não se trata de..."** ---  ## Ver também - [Algumas expressões e ditados excelentes da língua portuguesa, e outras não tão excelentes assim](https://fiatjaf.alhur.es/expressões-e-ditados.txt) @ dca6e1cc:ea7d1750
2024-11-11 13:10:17What are the odds that we can crowd-source a Bitcoin Mining operation that supports the energy development of a rural African village? For anyone who knows, there are plenty of environmental, social, and economic benefits that Bitcoin mining can bring to the development of rural mini-grids. More info: https://www.gama.africa/gama-programs.html https://x.com/GridlessCompute/status/1752679599601782846 Africa is home to massive amounts of untapped energy that can be ethically sourced. Access to energy is fundamental to human flourishing, meaning the upside for Africans' lifestyles is considerable given that many have zero electricity access aside from the odd solar panel. What can we do to accelerate this process? originally posted at https://stacker.news/items/763008
@ dca6e1cc:ea7d1750
2024-11-11 13:10:17What are the odds that we can crowd-source a Bitcoin Mining operation that supports the energy development of a rural African village? For anyone who knows, there are plenty of environmental, social, and economic benefits that Bitcoin mining can bring to the development of rural mini-grids. More info: https://www.gama.africa/gama-programs.html https://x.com/GridlessCompute/status/1752679599601782846 Africa is home to massive amounts of untapped energy that can be ethically sourced. Access to energy is fundamental to human flourishing, meaning the upside for Africans' lifestyles is considerable given that many have zero electricity access aside from the odd solar panel. What can we do to accelerate this process? originally posted at https://stacker.news/items/763008 @ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...) ### Design System Check it out [here](https://www.figma.com/community/file/1430887635327548022 ). This is by no means finished and will be continually updated and completed as we go along. ### Project description Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda) nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki. ### Explanatory videos This list of videos will also be continually updated and completed as we go along: 1. Chat as the universal interface https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov 2. Your Nostr Dashboard https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov 3. Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov 4. Design entered the Chat https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov 5. Targeted publication & The blurry edges of interoperable communities https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov 6. Travel Back https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
@ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...) ### Design System Check it out [here](https://www.figma.com/community/file/1430887635327548022 ). This is by no means finished and will be continually updated and completed as we go along. ### Project description Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda) nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki. ### Explanatory videos This list of videos will also be continually updated and completed as we go along: 1. Chat as the universal interface https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov 2. Your Nostr Dashboard https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov 3. Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov 4. Design entered the Chat https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov 5. Targeted publication & The blurry edges of interoperable communities https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov 6. Travel Back https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov @ 81dfd044:f1737ef9
2024-11-11 13:08:51Looking to invest in solar energy for your business? Aurora Energy offers high-quality [commercial solar panels for sale](https://aurora-energy.com/maximizing-savings-commercial-solar-panels-boost-efficiency-sustainability/), built to meet the energy needs of businesses both large and small. Our solar panels provide reliable, renewable energy that reduces operating costs and minimizes environmental impact. Let us help you choose the perfect system to power your business with clean energy and long-term financial benefits.
@ 81dfd044:f1737ef9
2024-11-11 13:08:51Looking to invest in solar energy for your business? Aurora Energy offers high-quality [commercial solar panels for sale](https://aurora-energy.com/maximizing-savings-commercial-solar-panels-boost-efficiency-sustainability/), built to meet the energy needs of businesses both large and small. Our solar panels provide reliable, renewable energy that reduces operating costs and minimizes environmental impact. Let us help you choose the perfect system to power your business with clean energy and long-term financial benefits. @ 00000000:0da46cec
2024-11-11 12:44:46### Resumen La **Content Authenticity Initiative** (CAI) es una colaboración global iniciada por Adobe en 2019, junto con empresas tecnológicas y medios de comunicación, cuyo objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad para contenidos digitales. Este artículo analiza en detalle los aspectos tecnológicos avanzados de la CAI, como el uso de metadatos, criptografía, blockchain y la verificación distribuida, además de incluir una guía para fotógrafos y creadores de contenido. Se ofrecen referencias a repositorios de código abierto para implementar estas tecnologías, proporcionando una base técnica robusta para proteger la autenticidad del contenido digital. **Palabras clave**: Content Authenticity Initiative, CAI, autenticidad del contenido, metadatos, criptografía, blockchain, integridad digital, firma digital, sellado de tiempo. --- La **Content Authenticity Initiative** (CAI), traducida al español como Iniciativa de Autenticidad del Contenido, es un esfuerzo colaborativo iniciado por Adobe en 2019 en conjunto con empresas tecnológicas y medios de comunicación como Twitter y The New York Times. Su principal objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad de contenidos que pueda ser adoptado globalmente, proporcionando trazabilidad y verificación de los contenidos digitales de una manera confiable y accesible. Este artículo detalla los aspectos tecnológicos más avanzados de esta iniciativa, que incluye el uso de metadatos, criptografía y blockchain. Además, se hace referencia a algunos de los repositorios oficiales y recursos de código fuente disponibles para implementar estas tecnologías. ### Arquitectura de la Content Authenticity Initiative La arquitectura de la CAI está compuesta por un conjunto de técnicas y herramientas basadas en metadatos estandarizados, mecanismos de integridad criptográfica, y soluciones descentralizadas para asegurar la verificabilidad del contenido en cada etapa de su ciclo de vida. A continuación se describe en detalle cada uno de los elementos clave de esta arquitectura. #### 1. **Generación de Metadatos de Autenticidad** El proceso de generación de contenido dentro de la CAI comienza en el dispositivo de captura, como una cámara o un smartphone, donde se crean los **metadatos de autenticidad**. Estos metadatos incluyen información relevante sobre el autor del contenido, la fecha y hora de captura, la geolocalización y el dispositivo utilizado. Estos elementos se guardan utilizando esquemas estandarizados como **XMP (Extensible Metadata Platform)**, que asegura una estructura coherente y legible para las aplicaciones de verificación posteriores. El código fuente de referencia para la implementación de XMP está disponible en el repositorio oficial de Adobe en GitHub: [XMP Toolkit SDK](https://github.com/adobe/XMP-Toolkit-SDK). Los metadatos de autenticidad no solo proporcionan datos sobre la creación, sino que también mantienen un **registro inmutable de modificaciones** del archivo. Cada vez que se realiza una edición, se documenta el cambio mediante un proceso de versionado, asegurando la trazabilidad completa de cualquier alteración. #### 2. **Firma Criptográfica del Contenido** El siguiente nivel de protección que ofrece la CAI es el uso de **firmas digitales** para garantizar la autenticidad e integridad del contenido. Cada archivo multimedia (imagen, video, documento) se firma utilizando algoritmos de **criptografía asimétrica** como **ECDSA (Elliptic Curve Digital Signature Algorithm)** o **RSA**, dependiendo del nivel de seguridad requerido y la capacidad de cálculo del dispositivo. Estas firmas digitales generan un hash único para el contenido y lo vinculan con la clave privada del creador. Si el contenido es modificado de alguna manera, incluso un cambio de un solo bit, el hash cambiará, invalidando la firma digital original. De esta forma, cualquier alteración que no esté registrada y autorizada se puede detectar fácilmente, proporcionando garantía de que el archivo no ha sido comprometido desde su creación. Implementaciones de referencia para la generación y verificación de firmas digitales están disponibles en el repositorio [OpenSSL](https://github.com/openssl/openssl) y en la biblioteca **Bouncy Castle** para Java y C#: [Bouncy Castle GitHub](https://github.com/bcgit). #### 3. **Sellado de Tiempo y Blockchain** Para reforzar la veracidad del contenido, la CAI también puede emplear **sellado de tiempo (timestamping)** y, en algunas implementaciones, **blockchain** para descentralizar y proteger el registro de autenticidad. El sellado de tiempo se realiza mediante una autoridad de sellado (“Timestamp Authority” o TSA), que certifica que el contenido existía en un estado particular a una fecha y hora específica. Las TSA utilizan firmas digitales para proporcionar un valor criptográficamente seguro que confirma la temporalidad del contenido. La incorporación de blockchain aporta un nivel adicional de transparencia. Al registrar hashes de los metadatos y las firmas de autenticidad en una **blockchain pública** (como Ethereum o cualquier blockchain dedicada), se crea un registro inmutable y descentralizado que permite a cualquier usuario verificar la autenticidad del contenido. La estructura basada en **árboles Merkle** se usa comúnmente para optimizar el proceso de registro, asegurando que cada cambio en el contenido se documente con eficiencia y sin necesidad de almacenar grandes volúmenes de datos en la blockchain. Los desarrolladores pueden explorar ejemplos de implementación en el repositorio [Merkle Tree JavaScript Library](https://github.com/miguelmota/merkletreejs) y consultar el repositorio oficial de **Ethereum** para interacciones con contratos inteligentes: [Ethereum GitHub](https://github.com/ethereum). #### 4. **Almacenamiento Seguro de Metadatos** Los metadatos generados durante el proceso de creación se incrustan en el contenido utilizando **técnicas de esteganografía** o como datos adjuntos legibles por las herramientas de edición y verificación. Para evitar la eliminación o alteración maliciosa de estos metadatos, se emplean mecanismos de **incrustación segura** que vinculan los metadatos al contenido de manera criptográfica. Para garantizar la integridad de los metadatos durante la transferencia, se emplean **protocolos TLS** (Transport Layer Security), que aseguran que cualquier intercambio de archivos mantenga la confidencialidad y la integridad. Además, se pueden usar **sistemas de almacenamiento distribuido** como **IPFS (InterPlanetary File System)** para replicar y almacenar estos metadatos de forma redundante, asegurando su disponibilidad a largo plazo. El código fuente para IPFS está disponible en el repositorio oficial: [IPFS GitHub](https://github.com/ipfs). ### Verificación del Contenido Auténtico Uno de los objetivos fundamentales de la CAI es que cualquier usuario pueda verificar la procedencia y el historial de ediciones de un contenido de manera sencilla y eficiente. Para ello, se han desarrollado **herramientas de verificación basadas en código abierto**, como “**Verify with CAI**”, que permiten al espectador analizar el contenido y ver todos los metadatos asociados. Estas herramientas se pueden encontrar en el repositorio oficial de la CAI: [Content Authenticity Initiative GitHub](https://github.com/contentauth/). Estas herramientas usan los hashes incrustados y las firmas digitales para comparar la información disponible y determinar si el contenido ha sido alterado sin autorización. Asimismo, permiten al usuario acceder a los registros de blockchain, si es aplicable, para confirmar la autenticidad desde una fuente independiente y descentralizada. ### Guía para Fotógrafos y Creadores de Contenido La adopción de la tecnología de la Content Authenticity Initiative puede ser extremadamente beneficiosa para los fotógrafos y creadores de contenido que deseen garantizar la autenticidad y proteger su trabajo contra el uso indebido. A continuación se presenta una guía paso a paso sobre cómo utilizar esta tecnología: 1. **Equipamiento Compatible**: Asegúrate de que utilizas una cámara o dispositivo que soporte la generación de metadatos de autenticidad según los estándares XMP. Muchas cámaras y aplicaciones de edición modernas permiten incluir estos metadatos durante la captura y la edición del contenido. 2. **Software de Edición Compatible**: Utiliza software de edición que mantenga los metadatos de autenticidad intactos. Adobe Photoshop y otras herramientas de edición avanzadas han comenzado a integrar estas funcionalidades para garantizar que cada cambio quede registrado. Al editar, asegúrate de mantener los registros de metadatos, de modo que se pueda trazar la autenticidad del contenido. 3. **Firmado Digital del Contenido**: Usa una herramienta de firma digital, como **OpenSSL** o bibliotecas como **Bouncy Castle** para generar firmas digitales de tus archivos. Esto proporciona una garantía de autenticidad. Estas herramientas se pueden usar para firmar imágenes y documentos multimedia y protegerlos contra cualquier alteración. Puedes encontrar tutoriales y ejemplos de uso en los repositorios mencionados previamente. 4. **Sellado de Tiempo del Contenido**: Implementa el sellado de tiempo utilizando una **Timestamp Authority (TSA)** reconocida. Esto permite certificar que el contenido existía en un estado específico en una fecha y hora determinadas, lo cual es esencial para demostrar la integridad temporal del contenido. Algunas plataformas ofrecen servicios de sellado de tiempo gratuitos o a bajo costo. 5. **Uso de Blockchain para Registrar Metadatos**: Si deseas una protección adicional y más transparencia, considera registrar los hashes de los metadatos en una blockchain pública. Existen servicios y contratos inteligentes que pueden ayudarte a registrar estos datos sin necesidad de un conocimiento profundo en programación blockchain. Puedes consultar repositorios como [Ethereum GitHub](https://github.com/ethereum) para aprender cómo interactuar con contratos inteligentes. 6. **Verificación del Contenido**: Utiliza herramientas como **Verify with CAI** para asegurarte de que tus contenidos están adecuadamente registrados y que los metadatos y firmas digitales se mantienen intactos. Estas herramientas son de código abierto y están disponibles en GitHub, lo que permite a cualquier usuario comprobar la integridad y procedencia del contenido. 7. **Publicación en Plataformas Compatibles**: Publica tu contenido en plataformas que soporten la CAI y mantengan los metadatos intactos. Redes sociales y sitios web como Behance están comenzando a adoptar estos estándares, lo que te permitirá que tu contenido se distribuya con la verificación de autenticidad. ### Desafíos Técnicos y Barreras La implementación de la CAI no está exenta de desafíos. Algunos de los principales son: 1. **Adopción Masiva**: Para que la CAI sea efectiva, es necesario que todos los actores involucrados en la creación y distribución de contenido adopten sus estándares. Esto incluye a los fabricantes de cámaras, plataformas de edición, redes sociales y sitios web. 2. **Privacidad de los Creadores**: Al proporcionar información detallada sobre el autor y el origen del contenido, surgen preocupaciones relacionadas con la privacidad. Para mitigar esto, la CAI permite que algunos metadatos se almacenen de forma encriptada, y solo se revelen si es necesario. 3. **Costos de Implementación**: Las herramientas para firmar digitalmente, registrar en blockchain, y mantener el sellado de tiempo requieren recursos que podrían ser prohibitivos para algunos creadores o plataformas pequeñas. 4. **Atacantes Sofisticados**: Aunque la CAI mejora significativamente la seguridad, atacantes avanzados podrían intentar falsificar metadatos o burlar los procesos de firma digital. La combinación de técnicas criptográficas y blockchain mitiga este riesgo, pero siempre existirá la necesidad de evolucionar con las amenazas emergentes. ### Conclusión La **Content Authenticity Initiative** ofrece una arquitectura tecnológica sólida para proteger la autenticidad del contenido digital. A través del uso combinado de metadatos estandarizados, firmas digitales, blockchain y herramientas de verificación, la CAI busca establecer un estándar global para la transparencia y verificabilidad del contenido. Si bien existen desafíos técnicos y logísticos, la CAI representa un paso significativo hacia un ecosistema digital donde la confianza y la autenticidad sean la norma y no la excepción. Los interesados en profundizar más pueden acceder al código fuente disponible en los repositorios oficiales, como se ha indicado a lo largo del artículo, para implementar estas soluciones y contribuir al desarrollo de un entorno digital más seguro y confiable. ### Bibliografía - Adobe. (n.d.). *XMP Toolkit SDK*. Recuperado de [https://github.com/adobe/XMP-Toolkit-SDK](https://github.com/adobe/XMP-Toolkit-SDK) - OpenSSL. (n.d.). *OpenSSL Cryptography and SSL/TLS Toolkit*. Recuperado de [https://github.com/openssl/openssl](https://github.com/openssl/openssl) - Bouncy Castle. (n.d.). *Bouncy Castle Libraries*. Recuperado de [https://github.com/bcgit](https://github.com/bcgit) - Miguel Mota. (n.d.). *Merkle Tree JavaScript Library*. Recuperado de [https://github.com/miguelmota/merkletreejs](https://github.com/miguelmota/merkletreejs) - Ethereum Foundation. (n.d.). *Ethereum*. Recuperado de [https://github.com/ethereum](https://github.com/ethereum) - IPFS. (n.d.). *InterPlanetary File System*. Recuperado de [https://github.com/ipfs](https://github.com/ipfs) - Content Authenticity Initiative. (n.d.). *Verify with CAI*. Recuperado de [https://github.com/contentauth/](https://github.com/contentauth/)
@ 00000000:0da46cec
2024-11-11 12:44:46### Resumen La **Content Authenticity Initiative** (CAI) es una colaboración global iniciada por Adobe en 2019, junto con empresas tecnológicas y medios de comunicación, cuyo objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad para contenidos digitales. Este artículo analiza en detalle los aspectos tecnológicos avanzados de la CAI, como el uso de metadatos, criptografía, blockchain y la verificación distribuida, además de incluir una guía para fotógrafos y creadores de contenido. Se ofrecen referencias a repositorios de código abierto para implementar estas tecnologías, proporcionando una base técnica robusta para proteger la autenticidad del contenido digital. **Palabras clave**: Content Authenticity Initiative, CAI, autenticidad del contenido, metadatos, criptografía, blockchain, integridad digital, firma digital, sellado de tiempo. --- La **Content Authenticity Initiative** (CAI), traducida al español como Iniciativa de Autenticidad del Contenido, es un esfuerzo colaborativo iniciado por Adobe en 2019 en conjunto con empresas tecnológicas y medios de comunicación como Twitter y The New York Times. Su principal objetivo es combatir la desinformación digital mediante la creación de un sistema de autenticidad de contenidos que pueda ser adoptado globalmente, proporcionando trazabilidad y verificación de los contenidos digitales de una manera confiable y accesible. Este artículo detalla los aspectos tecnológicos más avanzados de esta iniciativa, que incluye el uso de metadatos, criptografía y blockchain. Además, se hace referencia a algunos de los repositorios oficiales y recursos de código fuente disponibles para implementar estas tecnologías. ### Arquitectura de la Content Authenticity Initiative La arquitectura de la CAI está compuesta por un conjunto de técnicas y herramientas basadas en metadatos estandarizados, mecanismos de integridad criptográfica, y soluciones descentralizadas para asegurar la verificabilidad del contenido en cada etapa de su ciclo de vida. A continuación se describe en detalle cada uno de los elementos clave de esta arquitectura. #### 1. **Generación de Metadatos de Autenticidad** El proceso de generación de contenido dentro de la CAI comienza en el dispositivo de captura, como una cámara o un smartphone, donde se crean los **metadatos de autenticidad**. Estos metadatos incluyen información relevante sobre el autor del contenido, la fecha y hora de captura, la geolocalización y el dispositivo utilizado. Estos elementos se guardan utilizando esquemas estandarizados como **XMP (Extensible Metadata Platform)**, que asegura una estructura coherente y legible para las aplicaciones de verificación posteriores. El código fuente de referencia para la implementación de XMP está disponible en el repositorio oficial de Adobe en GitHub: [XMP Toolkit SDK](https://github.com/adobe/XMP-Toolkit-SDK). Los metadatos de autenticidad no solo proporcionan datos sobre la creación, sino que también mantienen un **registro inmutable de modificaciones** del archivo. Cada vez que se realiza una edición, se documenta el cambio mediante un proceso de versionado, asegurando la trazabilidad completa de cualquier alteración. #### 2. **Firma Criptográfica del Contenido** El siguiente nivel de protección que ofrece la CAI es el uso de **firmas digitales** para garantizar la autenticidad e integridad del contenido. Cada archivo multimedia (imagen, video, documento) se firma utilizando algoritmos de **criptografía asimétrica** como **ECDSA (Elliptic Curve Digital Signature Algorithm)** o **RSA**, dependiendo del nivel de seguridad requerido y la capacidad de cálculo del dispositivo. Estas firmas digitales generan un hash único para el contenido y lo vinculan con la clave privada del creador. Si el contenido es modificado de alguna manera, incluso un cambio de un solo bit, el hash cambiará, invalidando la firma digital original. De esta forma, cualquier alteración que no esté registrada y autorizada se puede detectar fácilmente, proporcionando garantía de que el archivo no ha sido comprometido desde su creación. Implementaciones de referencia para la generación y verificación de firmas digitales están disponibles en el repositorio [OpenSSL](https://github.com/openssl/openssl) y en la biblioteca **Bouncy Castle** para Java y C#: [Bouncy Castle GitHub](https://github.com/bcgit). #### 3. **Sellado de Tiempo y Blockchain** Para reforzar la veracidad del contenido, la CAI también puede emplear **sellado de tiempo (timestamping)** y, en algunas implementaciones, **blockchain** para descentralizar y proteger el registro de autenticidad. El sellado de tiempo se realiza mediante una autoridad de sellado (“Timestamp Authority” o TSA), que certifica que el contenido existía en un estado particular a una fecha y hora específica. Las TSA utilizan firmas digitales para proporcionar un valor criptográficamente seguro que confirma la temporalidad del contenido. La incorporación de blockchain aporta un nivel adicional de transparencia. Al registrar hashes de los metadatos y las firmas de autenticidad en una **blockchain pública** (como Ethereum o cualquier blockchain dedicada), se crea un registro inmutable y descentralizado que permite a cualquier usuario verificar la autenticidad del contenido. La estructura basada en **árboles Merkle** se usa comúnmente para optimizar el proceso de registro, asegurando que cada cambio en el contenido se documente con eficiencia y sin necesidad de almacenar grandes volúmenes de datos en la blockchain. Los desarrolladores pueden explorar ejemplos de implementación en el repositorio [Merkle Tree JavaScript Library](https://github.com/miguelmota/merkletreejs) y consultar el repositorio oficial de **Ethereum** para interacciones con contratos inteligentes: [Ethereum GitHub](https://github.com/ethereum). #### 4. **Almacenamiento Seguro de Metadatos** Los metadatos generados durante el proceso de creación se incrustan en el contenido utilizando **técnicas de esteganografía** o como datos adjuntos legibles por las herramientas de edición y verificación. Para evitar la eliminación o alteración maliciosa de estos metadatos, se emplean mecanismos de **incrustación segura** que vinculan los metadatos al contenido de manera criptográfica. Para garantizar la integridad de los metadatos durante la transferencia, se emplean **protocolos TLS** (Transport Layer Security), que aseguran que cualquier intercambio de archivos mantenga la confidencialidad y la integridad. Además, se pueden usar **sistemas de almacenamiento distribuido** como **IPFS (InterPlanetary File System)** para replicar y almacenar estos metadatos de forma redundante, asegurando su disponibilidad a largo plazo. El código fuente para IPFS está disponible en el repositorio oficial: [IPFS GitHub](https://github.com/ipfs). ### Verificación del Contenido Auténtico Uno de los objetivos fundamentales de la CAI es que cualquier usuario pueda verificar la procedencia y el historial de ediciones de un contenido de manera sencilla y eficiente. Para ello, se han desarrollado **herramientas de verificación basadas en código abierto**, como “**Verify with CAI**”, que permiten al espectador analizar el contenido y ver todos los metadatos asociados. Estas herramientas se pueden encontrar en el repositorio oficial de la CAI: [Content Authenticity Initiative GitHub](https://github.com/contentauth/). Estas herramientas usan los hashes incrustados y las firmas digitales para comparar la información disponible y determinar si el contenido ha sido alterado sin autorización. Asimismo, permiten al usuario acceder a los registros de blockchain, si es aplicable, para confirmar la autenticidad desde una fuente independiente y descentralizada. ### Guía para Fotógrafos y Creadores de Contenido La adopción de la tecnología de la Content Authenticity Initiative puede ser extremadamente beneficiosa para los fotógrafos y creadores de contenido que deseen garantizar la autenticidad y proteger su trabajo contra el uso indebido. A continuación se presenta una guía paso a paso sobre cómo utilizar esta tecnología: 1. **Equipamiento Compatible**: Asegúrate de que utilizas una cámara o dispositivo que soporte la generación de metadatos de autenticidad según los estándares XMP. Muchas cámaras y aplicaciones de edición modernas permiten incluir estos metadatos durante la captura y la edición del contenido. 2. **Software de Edición Compatible**: Utiliza software de edición que mantenga los metadatos de autenticidad intactos. Adobe Photoshop y otras herramientas de edición avanzadas han comenzado a integrar estas funcionalidades para garantizar que cada cambio quede registrado. Al editar, asegúrate de mantener los registros de metadatos, de modo que se pueda trazar la autenticidad del contenido. 3. **Firmado Digital del Contenido**: Usa una herramienta de firma digital, como **OpenSSL** o bibliotecas como **Bouncy Castle** para generar firmas digitales de tus archivos. Esto proporciona una garantía de autenticidad. Estas herramientas se pueden usar para firmar imágenes y documentos multimedia y protegerlos contra cualquier alteración. Puedes encontrar tutoriales y ejemplos de uso en los repositorios mencionados previamente. 4. **Sellado de Tiempo del Contenido**: Implementa el sellado de tiempo utilizando una **Timestamp Authority (TSA)** reconocida. Esto permite certificar que el contenido existía en un estado específico en una fecha y hora determinadas, lo cual es esencial para demostrar la integridad temporal del contenido. Algunas plataformas ofrecen servicios de sellado de tiempo gratuitos o a bajo costo. 5. **Uso de Blockchain para Registrar Metadatos**: Si deseas una protección adicional y más transparencia, considera registrar los hashes de los metadatos en una blockchain pública. Existen servicios y contratos inteligentes que pueden ayudarte a registrar estos datos sin necesidad de un conocimiento profundo en programación blockchain. Puedes consultar repositorios como [Ethereum GitHub](https://github.com/ethereum) para aprender cómo interactuar con contratos inteligentes. 6. **Verificación del Contenido**: Utiliza herramientas como **Verify with CAI** para asegurarte de que tus contenidos están adecuadamente registrados y que los metadatos y firmas digitales se mantienen intactos. Estas herramientas son de código abierto y están disponibles en GitHub, lo que permite a cualquier usuario comprobar la integridad y procedencia del contenido. 7. **Publicación en Plataformas Compatibles**: Publica tu contenido en plataformas que soporten la CAI y mantengan los metadatos intactos. Redes sociales y sitios web como Behance están comenzando a adoptar estos estándares, lo que te permitirá que tu contenido se distribuya con la verificación de autenticidad. ### Desafíos Técnicos y Barreras La implementación de la CAI no está exenta de desafíos. Algunos de los principales son: 1. **Adopción Masiva**: Para que la CAI sea efectiva, es necesario que todos los actores involucrados en la creación y distribución de contenido adopten sus estándares. Esto incluye a los fabricantes de cámaras, plataformas de edición, redes sociales y sitios web. 2. **Privacidad de los Creadores**: Al proporcionar información detallada sobre el autor y el origen del contenido, surgen preocupaciones relacionadas con la privacidad. Para mitigar esto, la CAI permite que algunos metadatos se almacenen de forma encriptada, y solo se revelen si es necesario. 3. **Costos de Implementación**: Las herramientas para firmar digitalmente, registrar en blockchain, y mantener el sellado de tiempo requieren recursos que podrían ser prohibitivos para algunos creadores o plataformas pequeñas. 4. **Atacantes Sofisticados**: Aunque la CAI mejora significativamente la seguridad, atacantes avanzados podrían intentar falsificar metadatos o burlar los procesos de firma digital. La combinación de técnicas criptográficas y blockchain mitiga este riesgo, pero siempre existirá la necesidad de evolucionar con las amenazas emergentes. ### Conclusión La **Content Authenticity Initiative** ofrece una arquitectura tecnológica sólida para proteger la autenticidad del contenido digital. A través del uso combinado de metadatos estandarizados, firmas digitales, blockchain y herramientas de verificación, la CAI busca establecer un estándar global para la transparencia y verificabilidad del contenido. Si bien existen desafíos técnicos y logísticos, la CAI representa un paso significativo hacia un ecosistema digital donde la confianza y la autenticidad sean la norma y no la excepción. Los interesados en profundizar más pueden acceder al código fuente disponible en los repositorios oficiales, como se ha indicado a lo largo del artículo, para implementar estas soluciones y contribuir al desarrollo de un entorno digital más seguro y confiable. ### Bibliografía - Adobe. (n.d.). *XMP Toolkit SDK*. Recuperado de [https://github.com/adobe/XMP-Toolkit-SDK](https://github.com/adobe/XMP-Toolkit-SDK) - OpenSSL. (n.d.). *OpenSSL Cryptography and SSL/TLS Toolkit*. Recuperado de [https://github.com/openssl/openssl](https://github.com/openssl/openssl) - Bouncy Castle. (n.d.). *Bouncy Castle Libraries*. Recuperado de [https://github.com/bcgit](https://github.com/bcgit) - Miguel Mota. (n.d.). *Merkle Tree JavaScript Library*. Recuperado de [https://github.com/miguelmota/merkletreejs](https://github.com/miguelmota/merkletreejs) - Ethereum Foundation. (n.d.). *Ethereum*. Recuperado de [https://github.com/ethereum](https://github.com/ethereum) - IPFS. (n.d.). *InterPlanetary File System*. Recuperado de [https://github.com/ipfs](https://github.com/ipfs) - Content Authenticity Initiative. (n.d.). *Verify with CAI*. Recuperado de [https://github.com/contentauth/](https://github.com/contentauth/) @ a012dc82:6458a70d
2024-11-11 12:35:40**Table Of Content** - Understanding Bitcoin Halving and its Significance - JPMorgan Analysis Reveals Positive Indicators - Increased Retail Investment: Driving Factors - Anticipated Impact on Bitcoin Market - Tips for Retail Investors to Leverage the Opportunity - Conclusion - FAQ In recent years, Bitcoin has become a buzzword in the financial world, captivating both institutional and retail investors. As the cryptocurrency market continues to evolve, experts at JPMorgan have conducted a comprehensive analysis, revealing strong indications of increased retail interest in Bitcoin leading up to the next halving event. This blog post will explore the insights from JPMorgan's analysis and shed light on the potential impact of this anticipated surge in retail interest. **Understanding Bitcoin Halving and its Significance** The concept of Bitcoin halving is pivotal to understanding the potential surge in retail interest. Bitcoin operates on a controlled supply system, with a predetermined issuance rate. Approximately every four years, the number of new Bitcoins generated per block gets halved, reducing the rate at which new Bitcoins enter circulation. This scarcity mechanism has significant implications for the cryptocurrency's value and investor sentiment. **JPMorgan Analysis Reveals Positive Indicators** According to JPMorgan's analysis, there are several positive indicators suggesting a strong influx of retail investors in the period leading up to the next Bitcoin halving. The analysis takes into account various factors such as historical data, market trends, and investor behavior. JPMorgan's experts have identified patterns that align with previous halving events, indicating a potential surge in retail interest in Bitcoin. **Increased Retail Investment: Driving Factors** JPMorgan's analysis highlights key driving factors behind the expected increase in retail investment. One significant factor is the growing awareness and acceptance of Bitcoin among the general public. As more individuals recognize the potential of cryptocurrencies as an investment asset, they are likely to be drawn towards Bitcoin, especially during periods of heightened market activity like halving events. Moreover, the influence of social media and digital platforms cannot be overlooked. The rise of social media communities, investment forums, and influencers has played a crucial role in amplifying discussions around Bitcoin. These platforms facilitate the spread of information, enabling retail investors to gain insights and make informed investment decisions. **Anticipated Impact on Bitcoin Market** The surge in retail interest preceding the halving event is expected to have a significant impact on the Bitcoin market. As more retail investors enter the market, the demand for Bitcoin is likely to increase, potentially driving up its price. This increased demand could lead to a period of heightened market volatility, offering both opportunities and risks for investors. JPMorgan's analysis suggests that the impact of retail interest will extend beyond the halving event itself. Historically, Bitcoin has experienced price rallies following halvings, indicating the potential for substantial gains. However, it is important to note that the cryptocurrency market is highly unpredictable, and investors should exercise caution and conduct thorough research before making investment decisions. **Tips for Retail Investors to Leverage the Opportunity** For retail investors considering Bitcoin as an investment, it is essential to approach the market with a strategic mindset. Here are a few tips to help leverage the anticipated surge in retail interest: 1. **Educate Yourself:** Gain a deep understanding of Bitcoin, its underlying technology, and the factors that influence its price. 2. **Diversify Your Portfolio:** Consider allocating a portion of your investment portfolio to Bitcoin while maintaining a diverse range of assets. 3. **Set Realistic Goals:** Define your investment objectives and set realistic expectations, considering the volatility and risks associated with cryptocurrencies. 4. **Stay Informed:** Stay updated with the latest news, market trends, and regulatory developments that could impact the cryptocurrency market. 5. **Seek Professional Advice:** Consult with financial advisors or experts who specialize in cryptocurrencies to gain valuable insights and guidance. **Conclusion** JPMorgan's analysis reveals strong indications of increased retail interest in Bitcoin prior to the halving event. Retail investors, driven by factors such as growing awareness and the influence of digital platforms, are likely to play a significant role in shaping the cryptocurrency market. As retail interest surges, it is crucial for investors to approach the market with caution, conduct thorough research, and leverage the opportunities while managing the risks associated with cryptocurrencies. **FAQ** **What is Bitcoin halving?** Bitcoin halving is an event that occurs approximately every four years, where the number of new Bitcoins generated per block gets halved. It is a mechanism designed to control the supply of Bitcoin and has significant implications for its value and investor sentiment. **Why is there expected strong retail interest in Bitcoin prior to halving?** JPMorgan's analysis indicates increased retail interest in Bitcoin before halving due to growing awareness, acceptance, and the influence of social media platforms. Retail investors are drawn towards Bitcoin during periods of heightened market activity like halving events. **What impact does retail interest have on the Bitcoin market?** Retail interest can drive up the demand for Bitcoin, potentially impacting its price. The surge in retail interest preceding the halving event could lead to increased market volatility, offering opportunities and risks for investors. **How can retail investors leverage the anticipated surge in retail interest?** Retail investors can leverage the opportunity by educating themselves about Bitcoin, diversifying their investment portfolio, setting realistic goals, staying informed about market trends, and seeking professional advice. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-11-11 12:35:40**Table Of Content** - Understanding Bitcoin Halving and its Significance - JPMorgan Analysis Reveals Positive Indicators - Increased Retail Investment: Driving Factors - Anticipated Impact on Bitcoin Market - Tips for Retail Investors to Leverage the Opportunity - Conclusion - FAQ In recent years, Bitcoin has become a buzzword in the financial world, captivating both institutional and retail investors. As the cryptocurrency market continues to evolve, experts at JPMorgan have conducted a comprehensive analysis, revealing strong indications of increased retail interest in Bitcoin leading up to the next halving event. This blog post will explore the insights from JPMorgan's analysis and shed light on the potential impact of this anticipated surge in retail interest. **Understanding Bitcoin Halving and its Significance** The concept of Bitcoin halving is pivotal to understanding the potential surge in retail interest. Bitcoin operates on a controlled supply system, with a predetermined issuance rate. Approximately every four years, the number of new Bitcoins generated per block gets halved, reducing the rate at which new Bitcoins enter circulation. This scarcity mechanism has significant implications for the cryptocurrency's value and investor sentiment. **JPMorgan Analysis Reveals Positive Indicators** According to JPMorgan's analysis, there are several positive indicators suggesting a strong influx of retail investors in the period leading up to the next Bitcoin halving. The analysis takes into account various factors such as historical data, market trends, and investor behavior. JPMorgan's experts have identified patterns that align with previous halving events, indicating a potential surge in retail interest in Bitcoin. **Increased Retail Investment: Driving Factors** JPMorgan's analysis highlights key driving factors behind the expected increase in retail investment. One significant factor is the growing awareness and acceptance of Bitcoin among the general public. As more individuals recognize the potential of cryptocurrencies as an investment asset, they are likely to be drawn towards Bitcoin, especially during periods of heightened market activity like halving events. Moreover, the influence of social media and digital platforms cannot be overlooked. The rise of social media communities, investment forums, and influencers has played a crucial role in amplifying discussions around Bitcoin. These platforms facilitate the spread of information, enabling retail investors to gain insights and make informed investment decisions. **Anticipated Impact on Bitcoin Market** The surge in retail interest preceding the halving event is expected to have a significant impact on the Bitcoin market. As more retail investors enter the market, the demand for Bitcoin is likely to increase, potentially driving up its price. This increased demand could lead to a period of heightened market volatility, offering both opportunities and risks for investors. JPMorgan's analysis suggests that the impact of retail interest will extend beyond the halving event itself. Historically, Bitcoin has experienced price rallies following halvings, indicating the potential for substantial gains. However, it is important to note that the cryptocurrency market is highly unpredictable, and investors should exercise caution and conduct thorough research before making investment decisions. **Tips for Retail Investors to Leverage the Opportunity** For retail investors considering Bitcoin as an investment, it is essential to approach the market with a strategic mindset. Here are a few tips to help leverage the anticipated surge in retail interest: 1. **Educate Yourself:** Gain a deep understanding of Bitcoin, its underlying technology, and the factors that influence its price. 2. **Diversify Your Portfolio:** Consider allocating a portion of your investment portfolio to Bitcoin while maintaining a diverse range of assets. 3. **Set Realistic Goals:** Define your investment objectives and set realistic expectations, considering the volatility and risks associated with cryptocurrencies. 4. **Stay Informed:** Stay updated with the latest news, market trends, and regulatory developments that could impact the cryptocurrency market. 5. **Seek Professional Advice:** Consult with financial advisors or experts who specialize in cryptocurrencies to gain valuable insights and guidance. **Conclusion** JPMorgan's analysis reveals strong indications of increased retail interest in Bitcoin prior to the halving event. Retail investors, driven by factors such as growing awareness and the influence of digital platforms, are likely to play a significant role in shaping the cryptocurrency market. As retail interest surges, it is crucial for investors to approach the market with caution, conduct thorough research, and leverage the opportunities while managing the risks associated with cryptocurrencies. **FAQ** **What is Bitcoin halving?** Bitcoin halving is an event that occurs approximately every four years, where the number of new Bitcoins generated per block gets halved. It is a mechanism designed to control the supply of Bitcoin and has significant implications for its value and investor sentiment. **Why is there expected strong retail interest in Bitcoin prior to halving?** JPMorgan's analysis indicates increased retail interest in Bitcoin before halving due to growing awareness, acceptance, and the influence of social media platforms. Retail investors are drawn towards Bitcoin during periods of heightened market activity like halving events. **What impact does retail interest have on the Bitcoin market?** Retail interest can drive up the demand for Bitcoin, potentially impacting its price. The surge in retail interest preceding the halving event could lead to increased market volatility, offering opportunities and risks for investors. **How can retail investors leverage the anticipated surge in retail interest?** Retail investors can leverage the opportunity by educating themselves about Bitcoin, diversifying their investment portfolio, setting realistic goals, staying informed about market trends, and seeking professional advice. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 05fcdfd8:fd31299f
2024-11-11 10:49:36<p>Die Auswirkungen von Störsendern auf Reisen und wie Sie Ihre Privatsphäre und Sicherheit schützen können</p> <p>In der modernen Gesellschaft ist Reisen zu einem integralen Bestandteil des Lebens der Menschen geworden. Mit zunehmender Reisehäufigkeit sind Informationssicherheit und Privatsphäre jedoch nach und nach zu wichtigen Themen geworden, die den Menschen Sorgen bereiten. An verschiedenen öffentlichen Orten, insbesondere in Flughäfen, Hotels und Touristenattraktionen, kann das Vorhandensein von <a href="https://www.jammermfg.com/de/">Signal störsender</a> eine potenzielle Bedrohung für die Sicherheit unserer persönlichen Geräte und Informationen darstellen. Aus diesem Grund ist es wichtig, die Auswirkungen von Störsendern zu verstehen und geeignete Sicherheitsmaßnahmen zu ergreifen.</p> <p>1. Funktionsprinzip des Störsenders</p> <p>Ein Störsender, oft auch „Signalstörsender“ genannt, ist ein Gerät, das Signale auf bestimmten Frequenzen aussendet, die die Kommunikation mit anderen drahtlosen Geräten stören oder verhindern können. Diese Geräte werden manchmal verwendet, um illegale drahtlose Kommunikation zu blockieren, beispielsweise in Gefängnissen, aber auch auf Reisen kommt es zu illegalem Einsatz. Hacker könnten beispielsweise <a href="https://www.jammermfg.com/de/handy-stoersender.html">Handyblocker</a> verwenden, um die Mobiltelefonsignale von Menschen zu stören, um vertrauliche Informationen abzuhören oder zu stehlen.</p> <p>2. Die Auswirkungen von Störsendern</p> <p>1. Auswirkungen auf die Kommunikation: In Bereichen, in denen Störsender verwendet werden, kann es bei Mobiltelefonen und anderen drahtlosen Geräten zu Signalverlusten kommen, wodurch es unmöglich wird, Anrufe entgegenzunehmen oder Nachrichten zu senden. Dies kann im Ernstfall schwerwiegende Folgen haben.</p> <p>2. Risiken für die Datensicherheit: Hacker können <a href="https://www.jammermfg.com/de/wlan-bluetooth-stoersender.html">WLAN Jammer</a> nutzen, um Funksignale abzufangen und die persönlichen Daten und Bankkontoinformationen der Benutzer zu stehlen. Wenn ein Gerät keine stabile Verbindung zum Netzwerk herstellen kann, neigen Benutzer dazu, die Sicherheit der Verbindung zu ignorieren, wodurch sich das Risiko eines Angriffs erhöht.</p> <p>3. Datenschutzverlust: Wenn Benutzer gestört werden, nutzen sie möglicherweise unsichere Netzwerke oder Anwendungen, was das Risiko eines Datenschutzverlusts erhöht. Insbesondere in öffentlichen WLAN-Umgebungen können Hacker Interferenztechnologie nutzen, um Man-in-the-Middle-Angriffe durchzuführen und Benutzeraktivitäten zu überwachen.</p> <p>3. So schützen Sie Privatsphäre und Sicherheit</p> <p>1. Verwenden Sie ein virtuelles privates Netzwerk (VPN): Die Verwendung eines VPN verschlüsselt Ihren Internetverkehr und schützt Ihre Privatsphäre, insbesondere bei der Nutzung öffentlicher WLANs. Ein VPN erstellt einen sicheren Tunnel, sodass Ihre Daten während der Übertragung nicht gestohlen werden können.</p> <p><a href="https://www.jammermfg.com/de/alle-jammer.html">https://www.jammermfg.com/de/alle-jammer.html</a></p> <p>2. Vermeiden Sie Verbindungen zu ungesicherten Netzwerken: Versuchen Sie auf Reisen, Verbindungen zu WLAN-Netzwerken zu vermeiden, die nicht passwortgeschützt oder ungesichert sind. Wenn Sie es unbedingt nutzen müssen, stellen Sie sicher, dass Sie zusätzliche Sicherheitsmaßnahmen wie ein VPN oder mobile Daten ergreifen.</p> <p>3. Aktualisieren Sie Ihre Geräte und Apps regelmäßig: Stellen Sie sicher, dass Ihr Telefon und Ihre Apps immer auf dem neuesten Stand sind, um Sicherheitslücken zu schließen. Hersteller veröffentlichen regelmäßig Updates, um potenzielle Sicherheitsprobleme zu beheben.</p> <p>4. Verwenden Sie die Zwei-Faktor-Authentifizierung: Die Aktivierung der Zwei-Faktor-Authentifizierung erhöht die Sicherheit Ihrer Online-Konten. Auch wenn ein Hacker Ihr Passwort erhält, benötigt er noch einen zweiten Verifizierungsschritt, um auf Ihr Konto zuzugreifen.</p> <p><a href="https://www.jammermfg.com/de/DE-N8P-tragbarer-billiger-8-bander-5G-handy-storsender.html"><img src="https://www.jammermfg.com/de/img/DE-N8P/1.jpg" alt="günstige 5g tragbarer handyblocker" width="400"/></a></p> <p>5. Geben Sie Informationen sorgfältig weiter: Vermeiden Sie es, persönliche Informationen öffentlich preiszugeben, z. B. Kreditkarteninformationen oder private Inhalte in sozialen Medien. Achten Sie auf Ihre Umgebung und vermeiden Sie es, sensible Themen zu besprechen.</p> <p>6. Verwenden Sie sichere Messaging-Tools: Verwenden Sie bei wichtigen Kommunikationen sichere Messaging-Apps wie Signal oder WhatsApp. Diese Apps bieten eine Ende-zu-Ende-Verschlüsselung, um Ihre Gespräche vor Abhörern zu schützen.</p> <p>7. Sichern Sie Ihr Gerät: Stellen Sie sicher, dass Sie ein sicheres Passwort für Ihr Gerät festlegen und biometrische Daten (z. B. Fingerabdruck oder Gesichtserkennung) verwenden, um die Sicherheit zu erhöhen und zu verhindern, dass andere auf Ihr Gerät zugreifen, wenn Sie es nicht verwenden.</p> <p>4. Zusammenfassung</p> <p>Auf Reisen ist der Schutz Ihrer Privatsphäre und Sicherheit eine wichtige und notwendige Aufgabe. Auch wenn die Existenz von Störsendern und <a href="https://www.jammermfg.com/de/detektor-kaufen.html">HF Detektor</a> gewisse Auswirkungen auf die Kommunikation hat, können Sie durch die oben genannten Maßnahmen potenzielle Risiken wirksam reduzieren und sicherstellen, dass Ihre Daten nicht durchsickern oder verletzt werden. Während wir die Reise genießen, müssen wir wachsam bleiben und unsere persönlichen Daten und Privatsphäre schützen.</p> <ol> <li><a href="https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html">https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html</a></li> <li><a href="https://www.jammermfg.com/de/56W-hochwertige-konferenzraum-handy-und-wlan-stoersender-kaufen.html">https://www.jammermfg.com/de/56W-hochwertige-konferenzraum-handy-und-wlan-stoersender-kaufen.html</a></li> </ol>
@ 05fcdfd8:fd31299f
2024-11-11 10:49:36<p>Die Auswirkungen von Störsendern auf Reisen und wie Sie Ihre Privatsphäre und Sicherheit schützen können</p> <p>In der modernen Gesellschaft ist Reisen zu einem integralen Bestandteil des Lebens der Menschen geworden. Mit zunehmender Reisehäufigkeit sind Informationssicherheit und Privatsphäre jedoch nach und nach zu wichtigen Themen geworden, die den Menschen Sorgen bereiten. An verschiedenen öffentlichen Orten, insbesondere in Flughäfen, Hotels und Touristenattraktionen, kann das Vorhandensein von <a href="https://www.jammermfg.com/de/">Signal störsender</a> eine potenzielle Bedrohung für die Sicherheit unserer persönlichen Geräte und Informationen darstellen. Aus diesem Grund ist es wichtig, die Auswirkungen von Störsendern zu verstehen und geeignete Sicherheitsmaßnahmen zu ergreifen.</p> <p>1. Funktionsprinzip des Störsenders</p> <p>Ein Störsender, oft auch „Signalstörsender“ genannt, ist ein Gerät, das Signale auf bestimmten Frequenzen aussendet, die die Kommunikation mit anderen drahtlosen Geräten stören oder verhindern können. Diese Geräte werden manchmal verwendet, um illegale drahtlose Kommunikation zu blockieren, beispielsweise in Gefängnissen, aber auch auf Reisen kommt es zu illegalem Einsatz. Hacker könnten beispielsweise <a href="https://www.jammermfg.com/de/handy-stoersender.html">Handyblocker</a> verwenden, um die Mobiltelefonsignale von Menschen zu stören, um vertrauliche Informationen abzuhören oder zu stehlen.</p> <p>2. Die Auswirkungen von Störsendern</p> <p>1. Auswirkungen auf die Kommunikation: In Bereichen, in denen Störsender verwendet werden, kann es bei Mobiltelefonen und anderen drahtlosen Geräten zu Signalverlusten kommen, wodurch es unmöglich wird, Anrufe entgegenzunehmen oder Nachrichten zu senden. Dies kann im Ernstfall schwerwiegende Folgen haben.</p> <p>2. Risiken für die Datensicherheit: Hacker können <a href="https://www.jammermfg.com/de/wlan-bluetooth-stoersender.html">WLAN Jammer</a> nutzen, um Funksignale abzufangen und die persönlichen Daten und Bankkontoinformationen der Benutzer zu stehlen. Wenn ein Gerät keine stabile Verbindung zum Netzwerk herstellen kann, neigen Benutzer dazu, die Sicherheit der Verbindung zu ignorieren, wodurch sich das Risiko eines Angriffs erhöht.</p> <p>3. Datenschutzverlust: Wenn Benutzer gestört werden, nutzen sie möglicherweise unsichere Netzwerke oder Anwendungen, was das Risiko eines Datenschutzverlusts erhöht. Insbesondere in öffentlichen WLAN-Umgebungen können Hacker Interferenztechnologie nutzen, um Man-in-the-Middle-Angriffe durchzuführen und Benutzeraktivitäten zu überwachen.</p> <p>3. So schützen Sie Privatsphäre und Sicherheit</p> <p>1. Verwenden Sie ein virtuelles privates Netzwerk (VPN): Die Verwendung eines VPN verschlüsselt Ihren Internetverkehr und schützt Ihre Privatsphäre, insbesondere bei der Nutzung öffentlicher WLANs. Ein VPN erstellt einen sicheren Tunnel, sodass Ihre Daten während der Übertragung nicht gestohlen werden können.</p> <p><a href="https://www.jammermfg.com/de/alle-jammer.html">https://www.jammermfg.com/de/alle-jammer.html</a></p> <p>2. Vermeiden Sie Verbindungen zu ungesicherten Netzwerken: Versuchen Sie auf Reisen, Verbindungen zu WLAN-Netzwerken zu vermeiden, die nicht passwortgeschützt oder ungesichert sind. Wenn Sie es unbedingt nutzen müssen, stellen Sie sicher, dass Sie zusätzliche Sicherheitsmaßnahmen wie ein VPN oder mobile Daten ergreifen.</p> <p>3. Aktualisieren Sie Ihre Geräte und Apps regelmäßig: Stellen Sie sicher, dass Ihr Telefon und Ihre Apps immer auf dem neuesten Stand sind, um Sicherheitslücken zu schließen. Hersteller veröffentlichen regelmäßig Updates, um potenzielle Sicherheitsprobleme zu beheben.</p> <p>4. Verwenden Sie die Zwei-Faktor-Authentifizierung: Die Aktivierung der Zwei-Faktor-Authentifizierung erhöht die Sicherheit Ihrer Online-Konten. Auch wenn ein Hacker Ihr Passwort erhält, benötigt er noch einen zweiten Verifizierungsschritt, um auf Ihr Konto zuzugreifen.</p> <p><a href="https://www.jammermfg.com/de/DE-N8P-tragbarer-billiger-8-bander-5G-handy-storsender.html"><img src="https://www.jammermfg.com/de/img/DE-N8P/1.jpg" alt="günstige 5g tragbarer handyblocker" width="400"/></a></p> <p>5. Geben Sie Informationen sorgfältig weiter: Vermeiden Sie es, persönliche Informationen öffentlich preiszugeben, z. B. Kreditkarteninformationen oder private Inhalte in sozialen Medien. Achten Sie auf Ihre Umgebung und vermeiden Sie es, sensible Themen zu besprechen.</p> <p>6. Verwenden Sie sichere Messaging-Tools: Verwenden Sie bei wichtigen Kommunikationen sichere Messaging-Apps wie Signal oder WhatsApp. Diese Apps bieten eine Ende-zu-Ende-Verschlüsselung, um Ihre Gespräche vor Abhörern zu schützen.</p> <p>7. Sichern Sie Ihr Gerät: Stellen Sie sicher, dass Sie ein sicheres Passwort für Ihr Gerät festlegen und biometrische Daten (z. B. Fingerabdruck oder Gesichtserkennung) verwenden, um die Sicherheit zu erhöhen und zu verhindern, dass andere auf Ihr Gerät zugreifen, wenn Sie es nicht verwenden.</p> <p>4. Zusammenfassung</p> <p>Auf Reisen ist der Schutz Ihrer Privatsphäre und Sicherheit eine wichtige und notwendige Aufgabe. Auch wenn die Existenz von Störsendern und <a href="https://www.jammermfg.com/de/detektor-kaufen.html">HF Detektor</a> gewisse Auswirkungen auf die Kommunikation hat, können Sie durch die oben genannten Maßnahmen potenzielle Risiken wirksam reduzieren und sicherstellen, dass Ihre Daten nicht durchsickern oder verletzt werden. Während wir die Reise genießen, müssen wir wachsam bleiben und unsere persönlichen Daten und Privatsphäre schützen.</p> <ol> <li><a href="https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html">https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html</a></li> <li><a href="https://www.jammermfg.com/de/56W-hochwertige-konferenzraum-handy-und-wlan-stoersender-kaufen.html">https://www.jammermfg.com/de/56W-hochwertige-konferenzraum-handy-und-wlan-stoersender-kaufen.html</a></li> </ol> @ 6aa0e5a8:f1677da5
2024-11-11 08:42:28In diesem hochentwickelten technologischen Zeitalter waren Einsamkeit und Isolation des Menschen noch nie so präsent wie heute. Das Aufkommen der [love doll](https://www.wifesexdoll.com/love-doll.html) hat ein tieferes Nachdenken über Intimität und menschliche Bedürfnisse ausgelöst. Blickt man auf die lange Geschichte der menschlichen Zivilisation zurück, so war der Wunsch nach Intimität und Liebe schon immer ein Teil der menschlichen Natur. In der heutigen schnelllebigen Gesellschaft entfernen sich die zwischenmenschlichen Beziehungen jedoch immer mehr voneinander, und die Veränderungen in den Familienstrukturen haben dazu geführt, dass zu viele Menschen in geistige und körperliche Einsamkeit verfallen. Einigen Daten zufolge befindet sich etwa ein Viertel der Bevölkerung in einem Zustand der dauerhaften Einsamkeit. Die Einsamkeit lässt die Nachfrage nach [sexpuppe](https://www.wifesexdoll.com) als „virtuelle Begleiter“ wachsen. Auch wenn [Liebespuppe](https://www.wifesexdoll.com/liebespuppen.html) den Reichtum echter Intimität nicht vollständig wiedergeben können, so können sie doch für diejenigen, denen es lange Zeit an Intimität gefehlt hat, die körperliche und emotionale Leere zumindest bis zu einem gewissen Grad stillen. Auf der einen Seite zeigt dies, dass der Fortschritt von Wissenschaft und Technik uns mehr Wahlmöglichkeiten bietet, auf der anderen Seite spiegelt es aber auch einen Teil des Mangels an menschlicher Natur in der modernen Gesellschaft wider. Davor können wir nicht die Augen verschließen. Wir sollten darüber nachdenken, was zu der Kälte in den intimen Beziehungen zwischen den Menschen geführt hat. Die Zunahme der Zahl der Singles, der Anstieg der Scheidungsrate, die niedrige Geburtenrate usw. sind allesamt Anzeichen dafür, dass der menschlichen Liebe und Intimität in unserer Gesellschaft nicht genügend Aufmerksamkeit geschenkt wird. Wir müssen darüber nachdenken, wie wir die menschliche Wärme wiederherstellen und die zwischenmenschliche Kommunikation stärken können, damit jeder ein Gefühl der Sicherheit und der Zugehörigkeit bekommt. Gleichzeitig sollten wir auch darüber nachdenken, welche Art von intimer Beziehung wir anstreben. Ist die rein körperliche oder virtuelle Erfüllung nur eine unangebrachte Nachahmung wahrer Intimität? Der Kern einer intimen Beziehung besteht aus zwei Menschen aus Fleisch und Blut, die sich gegenseitig schätzen, verstehen, tolerieren und Verantwortung füreinander übernehmen. Vergessen wir langsam die guten Eigenschaften der Intimität? Der Zweck der technologischen Entwicklung besteht darin, der Menschheit besser zu dienen, und nicht darin, sie zu entfremden und zu mechanisieren. [real sex doll](https://www.wifesexdoll.com/real-doll.html) geben uns die Möglichkeit zum Nachdenken, es geht nicht um eine schwarz-weiße Entscheidung für richtig oder falsch, sondern wir sollten darüber nachdenken, wie wir Wohlwollen, Wärme und Verantwortungsbewusstsein nutzen können, um das humanistische Fundament intimer Beziehungen aufzubauen und die verlorene Temperatur der menschlichen Natur in dieser Ära des Hochgeschwindigkeitsbetriebs zurückzugewinnen. 1. [https://mastodon.cloud/@wifesexdoll/113450628523233823](https://mastodon.cloud/@wifesexdoll/113450628523233823) 2. [https://mytek.clicforum.com/t291856-Das-Zeitalter-der-Sexpuppen-Sublimierung-oder-Untergang-der.htm](https://mytek.clicforum.com/t291856-Das-Zeitalter-der-Sexpuppen-Sublimierung-oder-Untergang-der.htm)
@ 6aa0e5a8:f1677da5
2024-11-11 08:42:28In diesem hochentwickelten technologischen Zeitalter waren Einsamkeit und Isolation des Menschen noch nie so präsent wie heute. Das Aufkommen der [love doll](https://www.wifesexdoll.com/love-doll.html) hat ein tieferes Nachdenken über Intimität und menschliche Bedürfnisse ausgelöst. Blickt man auf die lange Geschichte der menschlichen Zivilisation zurück, so war der Wunsch nach Intimität und Liebe schon immer ein Teil der menschlichen Natur. In der heutigen schnelllebigen Gesellschaft entfernen sich die zwischenmenschlichen Beziehungen jedoch immer mehr voneinander, und die Veränderungen in den Familienstrukturen haben dazu geführt, dass zu viele Menschen in geistige und körperliche Einsamkeit verfallen. Einigen Daten zufolge befindet sich etwa ein Viertel der Bevölkerung in einem Zustand der dauerhaften Einsamkeit. Die Einsamkeit lässt die Nachfrage nach [sexpuppe](https://www.wifesexdoll.com) als „virtuelle Begleiter“ wachsen. Auch wenn [Liebespuppe](https://www.wifesexdoll.com/liebespuppen.html) den Reichtum echter Intimität nicht vollständig wiedergeben können, so können sie doch für diejenigen, denen es lange Zeit an Intimität gefehlt hat, die körperliche und emotionale Leere zumindest bis zu einem gewissen Grad stillen. Auf der einen Seite zeigt dies, dass der Fortschritt von Wissenschaft und Technik uns mehr Wahlmöglichkeiten bietet, auf der anderen Seite spiegelt es aber auch einen Teil des Mangels an menschlicher Natur in der modernen Gesellschaft wider. Davor können wir nicht die Augen verschließen. Wir sollten darüber nachdenken, was zu der Kälte in den intimen Beziehungen zwischen den Menschen geführt hat. Die Zunahme der Zahl der Singles, der Anstieg der Scheidungsrate, die niedrige Geburtenrate usw. sind allesamt Anzeichen dafür, dass der menschlichen Liebe und Intimität in unserer Gesellschaft nicht genügend Aufmerksamkeit geschenkt wird. Wir müssen darüber nachdenken, wie wir die menschliche Wärme wiederherstellen und die zwischenmenschliche Kommunikation stärken können, damit jeder ein Gefühl der Sicherheit und der Zugehörigkeit bekommt. Gleichzeitig sollten wir auch darüber nachdenken, welche Art von intimer Beziehung wir anstreben. Ist die rein körperliche oder virtuelle Erfüllung nur eine unangebrachte Nachahmung wahrer Intimität? Der Kern einer intimen Beziehung besteht aus zwei Menschen aus Fleisch und Blut, die sich gegenseitig schätzen, verstehen, tolerieren und Verantwortung füreinander übernehmen. Vergessen wir langsam die guten Eigenschaften der Intimität? Der Zweck der technologischen Entwicklung besteht darin, der Menschheit besser zu dienen, und nicht darin, sie zu entfremden und zu mechanisieren. [real sex doll](https://www.wifesexdoll.com/real-doll.html) geben uns die Möglichkeit zum Nachdenken, es geht nicht um eine schwarz-weiße Entscheidung für richtig oder falsch, sondern wir sollten darüber nachdenken, wie wir Wohlwollen, Wärme und Verantwortungsbewusstsein nutzen können, um das humanistische Fundament intimer Beziehungen aufzubauen und die verlorene Temperatur der menschlichen Natur in dieser Ära des Hochgeschwindigkeitsbetriebs zurückzugewinnen. 1. [https://mastodon.cloud/@wifesexdoll/113450628523233823](https://mastodon.cloud/@wifesexdoll/113450628523233823) 2. [https://mytek.clicforum.com/t291856-Das-Zeitalter-der-Sexpuppen-Sublimierung-oder-Untergang-der.htm](https://mytek.clicforum.com/t291856-Das-Zeitalter-der-Sexpuppen-Sublimierung-oder-Untergang-der.htm) @ 9ff58691:0bf6c134
2024-11-11 08:29:00Курган - один из крупнейших городов Уральского региона, административный центр Курганской области. За последние двадцать лет этот город претерпел значительные изменения, превратившись из серого провинциального центра в современный, динамично развивающийся город. Об изменениях рассказал Олег Фролов – коренной житель города. - **Олег, расскажите, как за последние двадцать лет изменился ваш родной город Курган? Что именно изменилось в городе за это время?** - За эти годы Курган преобразился до неузнаваемости. Когда я был ребенком, город казался мне серым и унылым. Сейчас он стал более современным и привлекательным. Пожалуй, самые заметные изменения произошли в сфере образования и медицины. Многие школы и детские сады были капитально отремонтированы или построены заново. Появились современные учебные классы, оснащенные новейшим оборудованием, включая интерактивные доски, 3D-принтеры и системы искусственного интеллекта для помощи в обучении. Городские больницы и поликлиники были модернизированы, оснащены новейшей диагностической техникой: роботизированные хирургические системы и системы искусственного интеллекта для анализа медицинских данных. Качество и доступность медицинской помощи значительно возросли.   - **А как изменилась культурная жизнь города?** - Был отреставрирован и значительно расширен городской драматический театр. Открылись новые концертные залы, музеи и выставочные пространства. Стало проводиться гораздо больше культурных мероприятий. Жителям других регионов выдалась возможность посетить каждое культурное место нашего города с помощью экскурсий дополненной вирутальной реальностью. Курган превратился в настоящий культурный центр региона. - **Как вы оцениваете эти изменения? Довольны ли вы тем, как развивается ваш родной город?** - Я очень рад тем преобразованиям, которые произошли в Кургане за последние годы. Город стал более комфортным и привлекательным для жизни. Конечно, есть еще над чем работать, но в целом я вижу, что Курган уверенно движется вперед, становясь современным и развитым. - **Олег, а есть ли у вас в Кургане любимое место, куда вы любите ходить?** - Безусловно. Мое любимое место - это Центральный парк культуры и отдыха. Это настоящее сердце нашего города. Парк преобразился до неузнаваемости - он стал мобильным, с большим экраном для проведения мероприятий, а голограммы проводят интересные экскурсии. Здесь созданы все удобства для людей с ограниченными возможностями.  - **Что вам особенно нравится в этом парке?** - Парк очень красивый и ухоженный. Здесь высажено множество зеленых насаждений - деревьев, кустарников, цветов. Есть уютные аллеи для прогулок, детские площадки, спортивные зоны. Летом работают аттракционы, открыты кафе и летние веранды. Зимой заливают большой каток, который очень популярен среди жителей. Мне очень нравится культурная жизнь парка. Здесь регулярно проводятся различные фестивали, концерты, выставки. Летом часто организуют кинопоказы под открытым небом. Зимой работает резиденция Деда Мороза, куда приходят целыми семьями. - **Похоже, это действительно замечательное место. Спасибо, что поделились своими впечатлениями!** - Да, и правда замечательное. Я очень рад, что за последние годы он преобразился и стал настоящим центром притяжения для жителей города. Приглашаю всех приехать и лично убедиться в этом!
@ 9ff58691:0bf6c134
2024-11-11 08:29:00Курган - один из крупнейших городов Уральского региона, административный центр Курганской области. За последние двадцать лет этот город претерпел значительные изменения, превратившись из серого провинциального центра в современный, динамично развивающийся город. Об изменениях рассказал Олег Фролов – коренной житель города. - **Олег, расскажите, как за последние двадцать лет изменился ваш родной город Курган? Что именно изменилось в городе за это время?** - За эти годы Курган преобразился до неузнаваемости. Когда я был ребенком, город казался мне серым и унылым. Сейчас он стал более современным и привлекательным. Пожалуй, самые заметные изменения произошли в сфере образования и медицины. Многие школы и детские сады были капитально отремонтированы или построены заново. Появились современные учебные классы, оснащенные новейшим оборудованием, включая интерактивные доски, 3D-принтеры и системы искусственного интеллекта для помощи в обучении. Городские больницы и поликлиники были модернизированы, оснащены новейшей диагностической техникой: роботизированные хирургические системы и системы искусственного интеллекта для анализа медицинских данных. Качество и доступность медицинской помощи значительно возросли.   - **А как изменилась культурная жизнь города?** - Был отреставрирован и значительно расширен городской драматический театр. Открылись новые концертные залы, музеи и выставочные пространства. Стало проводиться гораздо больше культурных мероприятий. Жителям других регионов выдалась возможность посетить каждое культурное место нашего города с помощью экскурсий дополненной вирутальной реальностью. Курган превратился в настоящий культурный центр региона. - **Как вы оцениваете эти изменения? Довольны ли вы тем, как развивается ваш родной город?** - Я очень рад тем преобразованиям, которые произошли в Кургане за последние годы. Город стал более комфортным и привлекательным для жизни. Конечно, есть еще над чем работать, но в целом я вижу, что Курган уверенно движется вперед, становясь современным и развитым. - **Олег, а есть ли у вас в Кургане любимое место, куда вы любите ходить?** - Безусловно. Мое любимое место - это Центральный парк культуры и отдыха. Это настоящее сердце нашего города. Парк преобразился до неузнаваемости - он стал мобильным, с большим экраном для проведения мероприятий, а голограммы проводят интересные экскурсии. Здесь созданы все удобства для людей с ограниченными возможностями.  - **Что вам особенно нравится в этом парке?** - Парк очень красивый и ухоженный. Здесь высажено множество зеленых насаждений - деревьев, кустарников, цветов. Есть уютные аллеи для прогулок, детские площадки, спортивные зоны. Летом работают аттракционы, открыты кафе и летние веранды. Зимой заливают большой каток, который очень популярен среди жителей. Мне очень нравится культурная жизнь парка. Здесь регулярно проводятся различные фестивали, концерты, выставки. Летом часто организуют кинопоказы под открытым небом. Зимой работает резиденция Деда Мороза, куда приходят целыми семьями. - **Похоже, это действительно замечательное место. Спасибо, что поделились своими впечатлениями!** - Да, и правда замечательное. Я очень рад, что за последние годы он преобразился и стал настоящим центром притяжения для жителей города. Приглашаю всех приехать и лично убедиться в этом! @ 9ff58691:0bf6c134
2024-11-11 06:04:29За последние 16 лет Курган претерпел значительные инфраструктурные изменения, направленные на повышение качества жизни горожан и развитие города. Ниже представлен обзор основных нововведений: **Новые здания и сооружения:** - Построен современный многофункциональный спортивно-развлекательный комплекс "Курганская Арена" с ледовой ареной, бассейном и фитнес-центром. - Открыт новый корпус Курганского государственного университета, оснащенный по последнему слову техники лабораториями и аудиториями. - Возведен крупный торгово-развлекательный центр "Курган Молл" с магазинами, кинотеатром, ресторанами и зонами отдыха. - Построен современный медицинский центр "Курганская клиника", оказывающий широкий спектр высокотехнологичных услуг.  **Транспортная инфраструктура:** - Открыта новая скоростная автомагистраль, соединяющая центр города с аэропортом и федеральной трассой. - Запущено движение городского скоростного трамвая, связывающего отдаленные районы с центром. - Построены два новых транспортных кольца на основных развязках, значительно улучшившие дорожную ситуацию. - Обновлен автобусный парк, переведенный на экологичные электрические и гибридные модели.  **Благоустройство и озеленение:** - Реконструирован центральный городской парк с новыми пешеходными зонами, велодорожками и зонами отдыха. - Высажены тысячи новых деревьев и кустарников, создавшие "зеленые легкие" города. - Построены новые общественные пространства - набережная, пешеходные улицы и площади с современным дизайном. - Модернизирована система освещения улиц, переведенная на энергоэффективные светодиодные технологии.  В целом, Курган за последние 16 лет значительно преобразился, став более современным, комфортным и экологичным городом с развитой инфраструктурой. Эти изменения повысили качество жизни горожан и привлекательность Кургана для туристов и инвесторов.
@ 9ff58691:0bf6c134
2024-11-11 06:04:29За последние 16 лет Курган претерпел значительные инфраструктурные изменения, направленные на повышение качества жизни горожан и развитие города. Ниже представлен обзор основных нововведений: **Новые здания и сооружения:** - Построен современный многофункциональный спортивно-развлекательный комплекс "Курганская Арена" с ледовой ареной, бассейном и фитнес-центром. - Открыт новый корпус Курганского государственного университета, оснащенный по последнему слову техники лабораториями и аудиториями. - Возведен крупный торгово-развлекательный центр "Курган Молл" с магазинами, кинотеатром, ресторанами и зонами отдыха. - Построен современный медицинский центр "Курганская клиника", оказывающий широкий спектр высокотехнологичных услуг.  **Транспортная инфраструктура:** - Открыта новая скоростная автомагистраль, соединяющая центр города с аэропортом и федеральной трассой. - Запущено движение городского скоростного трамвая, связывающего отдаленные районы с центром. - Построены два новых транспортных кольца на основных развязках, значительно улучшившие дорожную ситуацию. - Обновлен автобусный парк, переведенный на экологичные электрические и гибридные модели.  **Благоустройство и озеленение:** - Реконструирован центральный городской парк с новыми пешеходными зонами, велодорожками и зонами отдыха. - Высажены тысячи новых деревьев и кустарников, создавшие "зеленые легкие" города. - Построены новые общественные пространства - набережная, пешеходные улицы и площади с современным дизайном. - Модернизирована система освещения улиц, переведенная на энергоэффективные светодиодные технологии.  В целом, Курган за последние 16 лет значительно преобразился, став более современным, комфортным и экологичным городом с развитой инфраструктурой. Эти изменения повысили качество жизни горожан и привлекательность Кургана для туристов и инвесторов. @ 8f2fe968:0fbf4901
2024-11-11 02:20:35   
@ 8f2fe968:0fbf4901
2024-11-11 02:20:35    @ fc15d4c6:fba62950
2024-11-11 00:12:29>The suspension comes after a proposal to raise the subscription fee to reflect the depreciated Malawian Kwacha was rejected by the Malawi Communications Regulatory Authority (MACRA). Malawi has an unsustainable trade deficit, which means that more goods and services are imported, than are exported. This results in a shortage of foreign currency, which is needed to pay for imports. https://techpression.com/starlink-suspends-new-kit-sales-in-malawi
@ fc15d4c6:fba62950
2024-11-11 00:12:29>The suspension comes after a proposal to raise the subscription fee to reflect the depreciated Malawian Kwacha was rejected by the Malawi Communications Regulatory Authority (MACRA). Malawi has an unsustainable trade deficit, which means that more goods and services are imported, than are exported. This results in a shortage of foreign currency, which is needed to pay for imports. https://techpression.com/starlink-suspends-new-kit-sales-in-malawi @ f33c8a96:5ec6f741
2024-11-10 22:44:14# JavaScript Cheatsheet for Beginners  ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Operators](#operators) 4. [Objects](#objects) 5. [Functions](#functions) 6. [Arrays](#arrays) 7. [Conditional Statements](#conditional-statements) 8. [Loops](#loops) 9. [Error Handling](#error-handling) 10. [ES6+ Features](#es6-features) 11. [DOM Manipulation](#dom-manipulation) 12. [Event Handling](#event-handling) 13. [Asynchronous JavaScript](#asynchronous-javascript) 14. [Modules](#modules) ## Variable Declaration In JavaScript, variables can be declared using `var`, `let`, or `const`. ```javascript var x = 5; // Function-scoped variable (avoid using in modern JavaScript) let y = 10; // Block-scoped variable const MAX_POINTS = 100; // Constant (cannot be reassigned) ``` - `var` is function-scoped and hoisted (avoid using in modern JavaScript). - `let` is block-scoped and can be reassigned. - `const` is block-scoped and cannot be reassigned (but object properties can be modified). ## Basic Data Types JavaScript has several basic data types. ```javascript let num = 42; // Number let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats) let str = "Hello, World!"; // String let bool = true; // Boolean let nullValue = null; // Null let undefinedValue; // Undefined let symbol = Symbol("unique"); // Symbol (ES6+) let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+) ``` - `Number`: Represents both integers and floating-point numbers. - `String`: Represents textual data. - `Boolean`: Represents `true` or `false`. - `Null`: Represents a deliberate non-value. - `Undefined`: Represents a variable that has been declared but not assigned a value. - `Symbol`: Represents a unique identifier. - `BigInt`: Represents integers larger than 2^53 - 1. ## Operators JavaScript includes various types of operators for different operations. ```javascript // Arithmetic Operators let sum = 5 + 3; // Addition: 8 let diff = 10 - 4; // Subtraction: 6 let product = 3 * 4; // Multiplication: 12 let quotient = 15 / 3;// Division: 5 let remainder = 17 % 5;// Modulus: 2 let power = 2 ** 3; // Exponentiation: 8 let increment = 5; increment++; // Increment: 6 let decrement = 5; decrement--; // Decrement: 4 // Assignment Operators let x = 10; // Basic assignment x += 5; // Addition assignment (x = x + 5) x -= 3; // Subtraction assignment x *= 2; // Multiplication assignment x /= 4; // Division assignment x %= 3; // Modulus assignment x **= 2; // Exponentiation assignment // Comparison Operators console.log(5 == "5"); // Equal to (with type coercion): true console.log(5 === "5"); // Strictly equal to: false console.log(7 != "7"); // Not equal to: false console.log(7 !== "7"); // Strictly not equal to: true console.log(10 > 5); // Greater than: true console.log(10 >= 10); // Greater than or equal to: true console.log(5 < 10); // Less than: true console.log(5 <= 5); // Less than or equal to: true // Logical Operators let a = true, b = false; console.log(a && b); // Logical AND: false console.log(a || b); // Logical OR: true console.log(!a); // Logical NOT: false // Nullish Coalescing Operator (ES2020) let nullValue = null; let defaultValue = nullValue ?? "default"; // "default" // Optional Chaining Operator (ES2020) let user = { address: { street: "123 Main St" } }; console.log(user?.address?.street); // "123 Main St" console.log(user?.contact?.email); // undefined // Bitwise Operators console.log(5 & 3); // Bitwise AND: 1 console.log(5 | 3); // Bitwise OR: 7 console.log(5 ^ 3); // Bitwise XOR: 6 console.log(~5); // Bitwise NOT: -6 console.log(5 << 1); // Left shift: 10 console.log(5 >> 1); // Right shift: 2 console.log(5 >>> 1); // Unsigned right shift: 2 // String Operators let str1 = "Hello"; let str2 = "World"; console.log(str1 + " " + str2); // Concatenation: "Hello World" let greeting = "Hello"; greeting += " World"; // Concatenation assignment // Type Operators console.log(typeof "Hello"); // "string" console.log(typeof 123); // "number" console.log(typeof true); // "boolean" console.log(obj instanceof Object); // Check if object is instance of a class ``` Key points about operators: - Arithmetic operators perform mathematical operations - Assignment operators combine operation with assignment - Comparison operators return boolean values - Logical operators work with boolean values and provide short-circuit evaluation - Nullish coalescing (??) provides a way to specify a default value - Optional chaining (?.) safely accesses nested object properties - Bitwise operators perform operations on binary representations - String operators handle string concatenation - Type operators help determine variable types ## Objects Objects are collections of key-value pairs. ```javascript let person = { name: "Alice", age: 30, sayHello: function() { console.log("Hello, my name is " + this.name); } }; // Accessing object properties console.log(person.name); // Alice console.log(person["age"]); // 30 // Calling object methods person.sayHello(); // Hello, my name is Alice // Adding a new property person.job = "Developer"; // Object destructuring (ES6+) let { name, age } = person; console.log(name, age); // Alice 30 ``` - Objects can contain properties and methods. - Properties can be accessed using dot notation or bracket notation. - New properties can be added dynamically. - Object destructuring allows you to extract multiple properties at once. ## Functions Functions are reusable blocks of code. ```javascript // Function declaration function greet(name) { return "Hello, " + name + "!"; } // Function expression const multiply = function(a, b) { return a * b; }; // Arrow function (ES6+) const add = (a, b) => a + b; // Default parameters (ES6+) function power(base, exponent = 2) { return Math.pow(base, exponent); } console.log(greet("Alice")); // Hello, Alice! console.log(multiply(3, 4)); // 12 console.log(add(5, 3)); // 8 console.log(power(3)); // 9 console.log(power(2, 3)); // 8 ``` - Functions can be declared using the `function` keyword or as arrow functions. - Arrow functions provide a more concise syntax and lexically bind `this`. - Default parameters allow you to specify default values for function arguments. ## Arrays Arrays are ordered lists of values. ```javascript let fruits = ["apple", "banana", "orange"]; // Accessing array elements console.log(fruits[0]); // apple // Array methods fruits.push("grape"); // Add to the end fruits.unshift("mango"); // Add to the beginning let lastFruit = fruits.pop(); // Remove from the end let firstFruit = fruits.shift(); // Remove from the beginning // Iterating over arrays fruits.forEach(fruit => console.log(fruit)); // Array transformation let upperFruits = fruits.map(fruit => fruit.toUpperCase()); // Filtering arrays let longFruits = fruits.filter(fruit => fruit.length > 5); // Reducing arrays let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0); // Spread operator (ES6+) let moreFruits = ["kiwi", "pear"]; let allFruits = [...fruits, ...moreFruits]; ``` - Arrays can contain elements of any type. - Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array. - Higher-order functions like `map`, `filter`, and `reduce` create new arrays. - The spread operator `...` can be used to combine arrays. ## Conditional Statements Conditional statements allow you to execute code based on certain conditions. ```javascript let age = 18; // if...else statement if (age >= 18) { console.log("You are an adult"); } else { console.log("You are a minor"); } // Ternary operator let status = age >= 18 ? "adult" : "minor"; // switch statement switch (age) { case 13: console.log("You're a teenager"); break; case 18: console.log("You're now an adult"); break; default: console.log("You're neither 13 nor 18"); } ``` - `if...else` statements allow you to execute different code blocks based on conditions. - The ternary operator provides a concise way to write simple if-else statements. - `switch` statements are useful when you have multiple conditions to check against a single value. ## Loops Loops allow you to repeat code multiple times. ```javascript // for loop for (let i = 0; i < 5; i++) { console.log(i); } // while loop let count = 0; while (count < 5) { console.log(count); count++; } // do...while loop let x = 0; do { console.log(x); x++; } while (x < 5); // for...of loop (ES6+) let numbers = [1, 2, 3, 4, 5]; for (let num of numbers) { console.log(num); } // for...in loop (for object properties) let person = { name: "Alice", age: 30 }; for (let key in person) { console.log(key + ": " + person[key]); } ``` - `for` loops are commonly used when you know how many times you want to iterate. - `while` loops continue as long as a condition is true. - `do...while` loops always execute at least once before checking the condition. - `for...of` loops are used to iterate over iterable objects like arrays. - `for...in` loops are used to iterate over object properties. ## Error Handling Error handling allows you to gracefully handle and recover from errors. ```javascript try { // Code that might throw an error throw new Error("Something went wrong"); } catch (error) { console.error("Caught an error:", error.message); } finally { console.log("This always runs"); } // Custom error class CustomError extends Error { constructor(message) { super(message); this.name = "CustomError"; } } try { throw new CustomError("A custom error occurred"); } catch (error) { if (error instanceof CustomError) { console.log("Caught a custom error:", error.message); } else { console.log("Caught a different error:", error.message); } } ``` - The `try` block contains code that might throw an error. - The `catch` block handles any errors thrown in the `try` block. - The `finally` block always executes, regardless of whether an error was thrown. - You can create custom error types by extending the `Error` class. ## ES6+ Features ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript. ```javascript // Template literals let name = "Alice"; console.log(`Hello, ${name}!`); // Destructuring let [a, b] = [1, 2]; let { x, y } = { x: 3, y: 4 }; // Default parameters function greet(name = "Guest") { console.log(`Hello, ${name}!`); } // Rest parameters function sum(...numbers) { return numbers.reduce((total, num) => total + num, 0); } // Spread operator let arr1 = [1, 2, 3]; let arr2 = [...arr1, 4, 5]; // Arrow functions const square = x => x * x; // Classes class Animal { constructor(name) { this.name = name; } speak() { console.log(`${this.name} makes a sound.`); } } // Promises const fetchData = () => { return new Promise((resolve, reject) => { // Asynchronous operation setTimeout(() => resolve("Data fetched"), 1000); }); }; // Async/Await async function getData() { try { const data = await fetchData(); console.log(data); } catch (error) { console.error(error); } } ``` - Template literals allow for easy string interpolation. - Destructuring makes it easy to extract values from arrays or properties from objects. - Default parameters provide fallback values for function arguments. - Rest parameters allow functions to accept an indefinite number of arguments as an array. - The spread operator can be used to expand arrays or objects. - Arrow functions provide a concise syntax for writing function expressions. - Classes provide a cleaner syntax for creating objects and implementing inheritance. - Promises and async/await simplify asynchronous programming. ## DOM Manipulation DOM manipulation allows you to interact with HTML elements on a web page. ```javascript // Selecting elements const element = document.getElementById("myElement"); const elements = document.getElementsByClassName("myClass"); const queryElement = document.querySelector(".myClass"); const queryElements = document.querySelectorAll(".myClass"); // Modifying elements element.textContent = "New text content"; element.innerHTML = "<strong>New HTML content</strong>"; element.style.color = "red"; element.classList.add("newClass"); element.classList.remove("oldClass"); // Creating and appending elements const newElement = document.createElement("div"); newElement.textContent = "New element"; document.body.appendChild(newElement); // Removing elements element.parentNode.removeChild(element); // or element.remove(); // Modern browsers ``` - The DOM (Document Object Model) represents the structure of an HTML document. - You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`. - Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`. - New elements can be created with `createElement` and added to the DOM with `appendChild`. - Elements can be removed using `removeChild` or the `remove` method. ## Event Handling Event handling allows you to respond to user interactions and other events. ```javascript const button = document.querySelector("#myButton"); // Adding event listeners button.addEventListener("click", function(event) { console.log("Button clicked!"); console.log("Event object:", event); }); // Removing event listeners function handleClick(event) { console.log("Button clicked!"); } button.addEventListener("click", handleClick); button.removeEventListener("click", handleClick); // Event delegation document.body.addEventListener("click", function(event) { if (event.target.matches("#myButton")) { console.log("Button clicked using event delegation!"); } }); // Preventing default behavior const link = document.querySelector("a"); link.addEventListener("click", function(event) { event.preventDefault(); console.log("Link click prevented"); }); ``` - Event listeners can be added to elements using the `addEventListener` method. - The event object contains information about the event that occurred. - Event listeners can be removed using `removeEventListener`. - Event delegation allows you to handle events for multiple elements with a single listener. - `preventDefault` can be used to stop the default action of an event. ## Asynchronous JavaScript Asynchronous JavaScript allows you to perform operations without blocking the main thread. ```javascript // Callbacks function fetchData(callback) { setTimeout(() => { callback("Data fetched"); }, 1000); } fetchData(data => console.log(data)); // Promises function fetchDataPromise() { return new Promise((resolve, reject) => { setTimeout(() => { resolve("Data fetched"); }, 1000); }); } fetchDataPromise() .then(data => console.log(data)) .catch(error => console.error(error)); // Async/Await async function fetchDataAsync() { try { const data = await fetchDataPromise(); console.log(data); } catch (error) { console.error(error); } } fetchDataAsync(); // Fetch API fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error:', error)); ``` - Callbacks are functions passed as arguments to be executed later. - Promises represent the eventual completion or failure of an asynchronous operation. - Async/await provides a more synchronous-looking way to write asynchronous code. - The Fetch API is a modern interface for making HTTP requests. ## Modules Modules allow you to organize your code into reusable pieces. ```javascript // math.js export function add(a, b) { return a + b; } export function multiply(a, b) { return a * b; } // main.js import { add, multiply } from './math.js'; console.log(add(5, 3)); // 8 console.log(multiply(4, 2)); // 8 // Default export // utils.js export default function sayHello(name) { console.log(`Hello, ${name}!`); } // main.js import sayHello from './utils.js'; sayHello("Alice"); // Hello, Alice! ``` - The `export` keyword is used to expose functions, objects, or primitives from a module. - The `import` keyword is used to bring functionality from other modules into the current module. - Default exports can be imported without curly braces and can be given any name when importing. This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs.
@ f33c8a96:5ec6f741
2024-11-10 22:44:14# JavaScript Cheatsheet for Beginners  ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Operators](#operators) 4. [Objects](#objects) 5. [Functions](#functions) 6. [Arrays](#arrays) 7. [Conditional Statements](#conditional-statements) 8. [Loops](#loops) 9. [Error Handling](#error-handling) 10. [ES6+ Features](#es6-features) 11. [DOM Manipulation](#dom-manipulation) 12. [Event Handling](#event-handling) 13. [Asynchronous JavaScript](#asynchronous-javascript) 14. [Modules](#modules) ## Variable Declaration In JavaScript, variables can be declared using `var`, `let`, or `const`. ```javascript var x = 5; // Function-scoped variable (avoid using in modern JavaScript) let y = 10; // Block-scoped variable const MAX_POINTS = 100; // Constant (cannot be reassigned) ``` - `var` is function-scoped and hoisted (avoid using in modern JavaScript). - `let` is block-scoped and can be reassigned. - `const` is block-scoped and cannot be reassigned (but object properties can be modified). ## Basic Data Types JavaScript has several basic data types. ```javascript let num = 42; // Number let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats) let str = "Hello, World!"; // String let bool = true; // Boolean let nullValue = null; // Null let undefinedValue; // Undefined let symbol = Symbol("unique"); // Symbol (ES6+) let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+) ``` - `Number`: Represents both integers and floating-point numbers. - `String`: Represents textual data. - `Boolean`: Represents `true` or `false`. - `Null`: Represents a deliberate non-value. - `Undefined`: Represents a variable that has been declared but not assigned a value. - `Symbol`: Represents a unique identifier. - `BigInt`: Represents integers larger than 2^53 - 1. ## Operators JavaScript includes various types of operators for different operations. ```javascript // Arithmetic Operators let sum = 5 + 3; // Addition: 8 let diff = 10 - 4; // Subtraction: 6 let product = 3 * 4; // Multiplication: 12 let quotient = 15 / 3;// Division: 5 let remainder = 17 % 5;// Modulus: 2 let power = 2 ** 3; // Exponentiation: 8 let increment = 5; increment++; // Increment: 6 let decrement = 5; decrement--; // Decrement: 4 // Assignment Operators let x = 10; // Basic assignment x += 5; // Addition assignment (x = x + 5) x -= 3; // Subtraction assignment x *= 2; // Multiplication assignment x /= 4; // Division assignment x %= 3; // Modulus assignment x **= 2; // Exponentiation assignment // Comparison Operators console.log(5 == "5"); // Equal to (with type coercion): true console.log(5 === "5"); // Strictly equal to: false console.log(7 != "7"); // Not equal to: false console.log(7 !== "7"); // Strictly not equal to: true console.log(10 > 5); // Greater than: true console.log(10 >= 10); // Greater than or equal to: true console.log(5 < 10); // Less than: true console.log(5 <= 5); // Less than or equal to: true // Logical Operators let a = true, b = false; console.log(a && b); // Logical AND: false console.log(a || b); // Logical OR: true console.log(!a); // Logical NOT: false // Nullish Coalescing Operator (ES2020) let nullValue = null; let defaultValue = nullValue ?? "default"; // "default" // Optional Chaining Operator (ES2020) let user = { address: { street: "123 Main St" } }; console.log(user?.address?.street); // "123 Main St" console.log(user?.contact?.email); // undefined // Bitwise Operators console.log(5 & 3); // Bitwise AND: 1 console.log(5 | 3); // Bitwise OR: 7 console.log(5 ^ 3); // Bitwise XOR: 6 console.log(~5); // Bitwise NOT: -6 console.log(5 << 1); // Left shift: 10 console.log(5 >> 1); // Right shift: 2 console.log(5 >>> 1); // Unsigned right shift: 2 // String Operators let str1 = "Hello"; let str2 = "World"; console.log(str1 + " " + str2); // Concatenation: "Hello World" let greeting = "Hello"; greeting += " World"; // Concatenation assignment // Type Operators console.log(typeof "Hello"); // "string" console.log(typeof 123); // "number" console.log(typeof true); // "boolean" console.log(obj instanceof Object); // Check if object is instance of a class ``` Key points about operators: - Arithmetic operators perform mathematical operations - Assignment operators combine operation with assignment - Comparison operators return boolean values - Logical operators work with boolean values and provide short-circuit evaluation - Nullish coalescing (??) provides a way to specify a default value - Optional chaining (?.) safely accesses nested object properties - Bitwise operators perform operations on binary representations - String operators handle string concatenation - Type operators help determine variable types ## Objects Objects are collections of key-value pairs. ```javascript let person = { name: "Alice", age: 30, sayHello: function() { console.log("Hello, my name is " + this.name); } }; // Accessing object properties console.log(person.name); // Alice console.log(person["age"]); // 30 // Calling object methods person.sayHello(); // Hello, my name is Alice // Adding a new property person.job = "Developer"; // Object destructuring (ES6+) let { name, age } = person; console.log(name, age); // Alice 30 ``` - Objects can contain properties and methods. - Properties can be accessed using dot notation or bracket notation. - New properties can be added dynamically. - Object destructuring allows you to extract multiple properties at once. ## Functions Functions are reusable blocks of code. ```javascript // Function declaration function greet(name) { return "Hello, " + name + "!"; } // Function expression const multiply = function(a, b) { return a * b; }; // Arrow function (ES6+) const add = (a, b) => a + b; // Default parameters (ES6+) function power(base, exponent = 2) { return Math.pow(base, exponent); } console.log(greet("Alice")); // Hello, Alice! console.log(multiply(3, 4)); // 12 console.log(add(5, 3)); // 8 console.log(power(3)); // 9 console.log(power(2, 3)); // 8 ``` - Functions can be declared using the `function` keyword or as arrow functions. - Arrow functions provide a more concise syntax and lexically bind `this`. - Default parameters allow you to specify default values for function arguments. ## Arrays Arrays are ordered lists of values. ```javascript let fruits = ["apple", "banana", "orange"]; // Accessing array elements console.log(fruits[0]); // apple // Array methods fruits.push("grape"); // Add to the end fruits.unshift("mango"); // Add to the beginning let lastFruit = fruits.pop(); // Remove from the end let firstFruit = fruits.shift(); // Remove from the beginning // Iterating over arrays fruits.forEach(fruit => console.log(fruit)); // Array transformation let upperFruits = fruits.map(fruit => fruit.toUpperCase()); // Filtering arrays let longFruits = fruits.filter(fruit => fruit.length > 5); // Reducing arrays let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0); // Spread operator (ES6+) let moreFruits = ["kiwi", "pear"]; let allFruits = [...fruits, ...moreFruits]; ``` - Arrays can contain elements of any type. - Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array. - Higher-order functions like `map`, `filter`, and `reduce` create new arrays. - The spread operator `...` can be used to combine arrays. ## Conditional Statements Conditional statements allow you to execute code based on certain conditions. ```javascript let age = 18; // if...else statement if (age >= 18) { console.log("You are an adult"); } else { console.log("You are a minor"); } // Ternary operator let status = age >= 18 ? "adult" : "minor"; // switch statement switch (age) { case 13: console.log("You're a teenager"); break; case 18: console.log("You're now an adult"); break; default: console.log("You're neither 13 nor 18"); } ``` - `if...else` statements allow you to execute different code blocks based on conditions. - The ternary operator provides a concise way to write simple if-else statements. - `switch` statements are useful when you have multiple conditions to check against a single value. ## Loops Loops allow you to repeat code multiple times. ```javascript // for loop for (let i = 0; i < 5; i++) { console.log(i); } // while loop let count = 0; while (count < 5) { console.log(count); count++; } // do...while loop let x = 0; do { console.log(x); x++; } while (x < 5); // for...of loop (ES6+) let numbers = [1, 2, 3, 4, 5]; for (let num of numbers) { console.log(num); } // for...in loop (for object properties) let person = { name: "Alice", age: 30 }; for (let key in person) { console.log(key + ": " + person[key]); } ``` - `for` loops are commonly used when you know how many times you want to iterate. - `while` loops continue as long as a condition is true. - `do...while` loops always execute at least once before checking the condition. - `for...of` loops are used to iterate over iterable objects like arrays. - `for...in` loops are used to iterate over object properties. ## Error Handling Error handling allows you to gracefully handle and recover from errors. ```javascript try { // Code that might throw an error throw new Error("Something went wrong"); } catch (error) { console.error("Caught an error:", error.message); } finally { console.log("This always runs"); } // Custom error class CustomError extends Error { constructor(message) { super(message); this.name = "CustomError"; } } try { throw new CustomError("A custom error occurred"); } catch (error) { if (error instanceof CustomError) { console.log("Caught a custom error:", error.message); } else { console.log("Caught a different error:", error.message); } } ``` - The `try` block contains code that might throw an error. - The `catch` block handles any errors thrown in the `try` block. - The `finally` block always executes, regardless of whether an error was thrown. - You can create custom error types by extending the `Error` class. ## ES6+ Features ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript. ```javascript // Template literals let name = "Alice"; console.log(`Hello, ${name}!`); // Destructuring let [a, b] = [1, 2]; let { x, y } = { x: 3, y: 4 }; // Default parameters function greet(name = "Guest") { console.log(`Hello, ${name}!`); } // Rest parameters function sum(...numbers) { return numbers.reduce((total, num) => total + num, 0); } // Spread operator let arr1 = [1, 2, 3]; let arr2 = [...arr1, 4, 5]; // Arrow functions const square = x => x * x; // Classes class Animal { constructor(name) { this.name = name; } speak() { console.log(`${this.name} makes a sound.`); } } // Promises const fetchData = () => { return new Promise((resolve, reject) => { // Asynchronous operation setTimeout(() => resolve("Data fetched"), 1000); }); }; // Async/Await async function getData() { try { const data = await fetchData(); console.log(data); } catch (error) { console.error(error); } } ``` - Template literals allow for easy string interpolation. - Destructuring makes it easy to extract values from arrays or properties from objects. - Default parameters provide fallback values for function arguments. - Rest parameters allow functions to accept an indefinite number of arguments as an array. - The spread operator can be used to expand arrays or objects. - Arrow functions provide a concise syntax for writing function expressions. - Classes provide a cleaner syntax for creating objects and implementing inheritance. - Promises and async/await simplify asynchronous programming. ## DOM Manipulation DOM manipulation allows you to interact with HTML elements on a web page. ```javascript // Selecting elements const element = document.getElementById("myElement"); const elements = document.getElementsByClassName("myClass"); const queryElement = document.querySelector(".myClass"); const queryElements = document.querySelectorAll(".myClass"); // Modifying elements element.textContent = "New text content"; element.innerHTML = "<strong>New HTML content</strong>"; element.style.color = "red"; element.classList.add("newClass"); element.classList.remove("oldClass"); // Creating and appending elements const newElement = document.createElement("div"); newElement.textContent = "New element"; document.body.appendChild(newElement); // Removing elements element.parentNode.removeChild(element); // or element.remove(); // Modern browsers ``` - The DOM (Document Object Model) represents the structure of an HTML document. - You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`. - Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`. - New elements can be created with `createElement` and added to the DOM with `appendChild`. - Elements can be removed using `removeChild` or the `remove` method. ## Event Handling Event handling allows you to respond to user interactions and other events. ```javascript const button = document.querySelector("#myButton"); // Adding event listeners button.addEventListener("click", function(event) { console.log("Button clicked!"); console.log("Event object:", event); }); // Removing event listeners function handleClick(event) { console.log("Button clicked!"); } button.addEventListener("click", handleClick); button.removeEventListener("click", handleClick); // Event delegation document.body.addEventListener("click", function(event) { if (event.target.matches("#myButton")) { console.log("Button clicked using event delegation!"); } }); // Preventing default behavior const link = document.querySelector("a"); link.addEventListener("click", function(event) { event.preventDefault(); console.log("Link click prevented"); }); ``` - Event listeners can be added to elements using the `addEventListener` method. - The event object contains information about the event that occurred. - Event listeners can be removed using `removeEventListener`. - Event delegation allows you to handle events for multiple elements with a single listener. - `preventDefault` can be used to stop the default action of an event. ## Asynchronous JavaScript Asynchronous JavaScript allows you to perform operations without blocking the main thread. ```javascript // Callbacks function fetchData(callback) { setTimeout(() => { callback("Data fetched"); }, 1000); } fetchData(data => console.log(data)); // Promises function fetchDataPromise() { return new Promise((resolve, reject) => { setTimeout(() => { resolve("Data fetched"); }, 1000); }); } fetchDataPromise() .then(data => console.log(data)) .catch(error => console.error(error)); // Async/Await async function fetchDataAsync() { try { const data = await fetchDataPromise(); console.log(data); } catch (error) { console.error(error); } } fetchDataAsync(); // Fetch API fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error:', error)); ``` - Callbacks are functions passed as arguments to be executed later. - Promises represent the eventual completion or failure of an asynchronous operation. - Async/await provides a more synchronous-looking way to write asynchronous code. - The Fetch API is a modern interface for making HTTP requests. ## Modules Modules allow you to organize your code into reusable pieces. ```javascript // math.js export function add(a, b) { return a + b; } export function multiply(a, b) { return a * b; } // main.js import { add, multiply } from './math.js'; console.log(add(5, 3)); // 8 console.log(multiply(4, 2)); // 8 // Default export // utils.js export default function sayHello(name) { console.log(`Hello, ${name}!`); } // main.js import sayHello from './utils.js'; sayHello("Alice"); // Hello, Alice! ``` - The `export` keyword is used to expose functions, objects, or primitives from a module. - The `import` keyword is used to bring functionality from other modules into the current module. - Default exports can be imported without curly braces and can be given any name when importing. This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs. @ 8d34bd24:414be32b
2024-11-10 22:42:29In [Part 1](https://trustjesus.substack.com/p/gods-promises), we got to see God’s initial promises to Adam, Eve, and all mankind with the proto Gospel: > “He shall bruise you on the head,\ > And you shall bruise him on the heel.”(Genesis 3:15) We saw God’s promises to Abraham: - To have his name made great. - To receive the land of Israel. - To father many nations. - That “*in you all the families of the earth will be blessed*.” We saw God’s reiterated promises to Jacob, Abraham’s grandson. Now we will look at the partial fulfillment of these promises and new promises made. ## The Promised Land (Quick Summary) Jacob fathered 12 sons. His son Joseph was sold as a slave to Egypt where he became second to the Pharaoh and saved Jacob’s family and the rest of the Middle East from famine. The Israelites then spent around 400 years in Egypt before Moses was called by God to lead the Israelites to the promised land. God performed awe inspiring miracles through Moses to force Pharaoh to release the Israelites who had been made slaves by the Egyptians. After crossing the desert, the Israelites reached the promised land, but instead of trusting the God who had rescued them with miracles never before seen, they were fearful and refused to obey God and to enter the promised land. God then had them wander 40 more years in the wilderness until the rebellious adults had all died. Then God miraculously aided this band of shepherds to conquer the land of Canaan and inhabit it, partially fulfilling His promise to give them this land. After approximately 410 years of judges leading the people of Israel and them repeatedly going astray, God gave them the king they requested, Saul. God gave them a tall and handsome, but selfish and unfaithful king to show them the error of their ways. After showing them their error, God gave them a godly king, a man after God’s own heart. ## David When God spoke His promise (covenant) with David, He reiterated the promises given to Abraham and to Jacob, but added: > “When your days are complete and you lie down with your fathers, I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever. I will be a father to him and he will be a son to Me; when he commits iniquity, I will correct him with the rod of men and the strokes of the sons of men, but My lovingkindness shall not depart from him, as I took it away from Saul, whom I removed from before you. **Your house and your kingdom shall endure before Me forever; your throne shall be established forever**.” (2 Samuel 7:12-16) {emphasis mine} The first part of this promise was fulfilled through David’s son, Solomon. Solomon sat on the throne. Solomon built a temple to worship God. Solomon was not cut off for his sins at the end of his life when he drifted away from God. Even though ten tribes were taken away from Solomon’s son Rehoboam, Rehoboam remained king of the two tribes of Judah and Benjamin and therefore his throne remained. The final promise, “*Your house and your kingdom shall endure before Me forever; your throne shall be established forever*,” was also partially fulfilled through Jesus at His incarnation and will be fully fulfilled when He returns for His millennial reign. “*I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever*.” Jesus is a descendant of David and His kingdom will be established at the end of the age — a kingdom of believers. “*He shall build a house for My name.”* Most of the time Israel is referred to as the *house of God* while the church is referred to as the *body of Christ*. In the millennial kingdom they will be united into one house, the adopted children which are the gentile church and the natural children which are the Jews who have finally accepted their Messiah. The final kingdom on this earth will be the millennial reign of Jesus (the promised heir of David), and then God will produce a new heaven and a new earth upon which Jesus will reign forever. Once again, David did not get to experience the complete fulfillment of the promises made to him. It was partially fulfilled in his son, Solomon, but it has taken thousands of years to partially fulfill this promise and we don’t know for sure how long it will be until complete fulfillment. ## Jeremiah By the time of Jeremiah, the nation of Israel was gone and Judah was corrupted beyond recognition. The fulfillment of God’s promises seemed impossible, but God’s promises are faithful and true. God spoke to Jeremiah to remind him, that although Judah and Israel were being punished, ultimately, God would fulfill all His promises. He begins with these tender words: > Now the word of the Lord came to me saying,\ > “Before I formed you in the womb I knew you,\ > And before you were born I consecrated you;\ > I have appointed you a prophet to the nations.”\ > \ > Then I said, “Alas, Lord God!\ > Behold, I do not know how to speak,\ > Because I am a youth.”\ > \ > But the Lord said to me,\ > “Do not say, ‘I am a youth,’\ > Because everywhere I send you, you shall go,\ > And all that I command you, you shall speak.\ > Do not be afraid of them,\ > For I am with you to deliver you,” declares the Lord.\ > \ > Then the Lord stretched out His hand and touched my mouth, and the Lord said to me,\ > “Behold, I have put My words in your mouth.\ > See, I have appointed you this day …” (Jeremiah 1:4-10a) First God tells Jeremiah that He loves him so much that He formed him in his mother’s womb for a special purpose, to speak His judgement and blessings on Israel. God comforts Jeremiah when Jeremiah fears he is unworthy of the great task God has for him. God promises to be with Jeremiah and to help Jeremiah fulfill His will. ``` As Christians we are similarly told that God created us for His purpose and His blessing and He will be with us, empowering us for whatever tasks He has called us to do. ``` God promises that despite Israel’s nonstop rebellion, He will be gracious and “*not be angry forever*.” > Go and proclaim these words toward the north and say,\ > ‘Return, faithless Israel,’ declares the Lord;\ > ‘I will not look upon you in anger.\ > For I am gracious,’ declares the Lord;\ > ‘I will not be angry forever.\ > Only acknowledge your iniquity,\ > That you have transgressed against the Lord your God\ > And have scattered your favors to the strangers under every green tree,\ > And you have not obeyed My voice,’ declares the Lord.\ > ‘Return, O faithless sons,’ declares the Lord;\ > ‘For I am a master to you,\ > And I will take you one from a city and two from a family,\ > And I will bring you to Zion.’ (Jeremiah 3:12-14) God will always fulfill His promises even if that means calling His people home from the ends of the earth where they are scattered “*one from a city and two from a family*.” God promises to call both Israel and Judah back to the land promised to them all of the way back in time of God’s promise to Abraham. There is a partial return, after Judah’s 70 year exile in Babylon, leading to a rebuilding of the temple for a second time. We are in the middle of another return to Israel that began when Israel was recreated in 1948 and is continuing today. Despite the fact that the people of Israel are being barraged with rockets, drones, and missiles daily and are at risk of being attacked by suicide bombers and terrorists, God is calling His people home for His big finale. I believe these continuing verses refer to Jesus’s second coming and the millennial reign of Christ. > “Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding. It shall be in those days when you are multiplied and increased in the land,” declares the Lord, “they will no longer say, ‘The ark of the covenant of the Lord.’ And it will not come to mind, nor will they remember it, nor will they miss it, nor will it be made again. At that time they will call Jerusalem ‘The Throne of the Lord,’ and all the nations will be gathered to it, to Jerusalem, for the name of the Lord; nor will they walk anymore after the stubbornness of their evil heart. In those days the house of Judah will walk with the house of Israel, and they will come together from the land of the north to the land that I gave your fathers as an inheritance. (Jeremiah 3:15-18) This passage isn’t just a call back to the promised land. This is another promise of God. “*Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding*.” After Jesus’s first coming, He made things clear about His plan of redemption for Israel and for the gentiles. He made clear His promise to bless all nations through Himself, a descendant of David, Jacob, and Abraham, to whom the promises were given. He demonstrated how His laws for the Jews pointed them to God’s ultimate plan. It is actually ironic that the “*shepherds after My own heart, who will feed you on knowledge and understanding*” are most likely Christian believers who are returned to earth to reign with Christ during the millennial kingdom. Gentile Christians were enabled to have a relationship with God through the Jews and then God will use those gentile Christians to shepherd the Jews back to God, so we can all worship God together. It won’t be until Jesus’s second coming and His thousand year reign that “*they will call Jerusalem ‘The Throne of the Lord.’*” It won’t be until Jesus’s second coming and His thousand year reign that they will not “*walk anymore after the stubbornness of their evil heart*.” God will finally make the full land of Israel a land of peace and prosperity for the Jews, but also to all the nations of the earth. But at the time of Jeremiah’s prophecy, God is promising punishment and hardship now to teach His people to be faithful and to trust God’s faithfulness. > Behold, I am bringing a nation against you from afar, O house of Israel,” declares the Lord. > > “It is an enduring nation,\ > It is an ancient nation,\ > A nation whose language you do not know,\ > Nor can you understand what they say. (Jeremiah 5:15) Due to Israel and Judah’s rebellion, both nations are taken away by a foreign nation into exile. Jeremiah, in particular, prophecies the 70 year exile of Judah in Babylon and their return to the promised land. God promised Abraham and Jacob (Israel) the land of Israel (previously Canaan) and He always keeps His promise, so He always brings them home in ways that are hard to comprehend. Relatively near the end of the 70 year exile in Babylon, God had Persia conquer Babylon and then a Persian king, not only allowed the Israelites to return to Jerusalem to rebuild the city, the walls, and the temple, but also he funded the return to Israel and returned the gold, silver, and bonze temple implements. What conquering nation does something like that? It was clearly all God. God may delay His promises, but He never cancels them. > For this the earth shall mourn\ > And the heavens above be dark,\ > Because I have spoken, I have purposed,\ > And I will not change My mind, \ > nor will I turn from it.” (Jeremiah 4:28) When God makes a promise, it is as good as done. Trust Jesus.
@ 8d34bd24:414be32b
2024-11-10 22:42:29In [Part 1](https://trustjesus.substack.com/p/gods-promises), we got to see God’s initial promises to Adam, Eve, and all mankind with the proto Gospel: > “He shall bruise you on the head,\ > And you shall bruise him on the heel.”(Genesis 3:15) We saw God’s promises to Abraham: - To have his name made great. - To receive the land of Israel. - To father many nations. - That “*in you all the families of the earth will be blessed*.” We saw God’s reiterated promises to Jacob, Abraham’s grandson. Now we will look at the partial fulfillment of these promises and new promises made. ## The Promised Land (Quick Summary) Jacob fathered 12 sons. His son Joseph was sold as a slave to Egypt where he became second to the Pharaoh and saved Jacob’s family and the rest of the Middle East from famine. The Israelites then spent around 400 years in Egypt before Moses was called by God to lead the Israelites to the promised land. God performed awe inspiring miracles through Moses to force Pharaoh to release the Israelites who had been made slaves by the Egyptians. After crossing the desert, the Israelites reached the promised land, but instead of trusting the God who had rescued them with miracles never before seen, they were fearful and refused to obey God and to enter the promised land. God then had them wander 40 more years in the wilderness until the rebellious adults had all died. Then God miraculously aided this band of shepherds to conquer the land of Canaan and inhabit it, partially fulfilling His promise to give them this land. After approximately 410 years of judges leading the people of Israel and them repeatedly going astray, God gave them the king they requested, Saul. God gave them a tall and handsome, but selfish and unfaithful king to show them the error of their ways. After showing them their error, God gave them a godly king, a man after God’s own heart. ## David When God spoke His promise (covenant) with David, He reiterated the promises given to Abraham and to Jacob, but added: > “When your days are complete and you lie down with your fathers, I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever. I will be a father to him and he will be a son to Me; when he commits iniquity, I will correct him with the rod of men and the strokes of the sons of men, but My lovingkindness shall not depart from him, as I took it away from Saul, whom I removed from before you. **Your house and your kingdom shall endure before Me forever; your throne shall be established forever**.” (2 Samuel 7:12-16) {emphasis mine} The first part of this promise was fulfilled through David’s son, Solomon. Solomon sat on the throne. Solomon built a temple to worship God. Solomon was not cut off for his sins at the end of his life when he drifted away from God. Even though ten tribes were taken away from Solomon’s son Rehoboam, Rehoboam remained king of the two tribes of Judah and Benjamin and therefore his throne remained. The final promise, “*Your house and your kingdom shall endure before Me forever; your throne shall be established forever*,” was also partially fulfilled through Jesus at His incarnation and will be fully fulfilled when He returns for His millennial reign. “*I will raise up your descendant after you, who will come forth from you, and I will establish his kingdom. He shall build a house for My name, and I will establish the throne of his kingdom forever*.” Jesus is a descendant of David and His kingdom will be established at the end of the age — a kingdom of believers. “*He shall build a house for My name.”* Most of the time Israel is referred to as the *house of God* while the church is referred to as the *body of Christ*. In the millennial kingdom they will be united into one house, the adopted children which are the gentile church and the natural children which are the Jews who have finally accepted their Messiah. The final kingdom on this earth will be the millennial reign of Jesus (the promised heir of David), and then God will produce a new heaven and a new earth upon which Jesus will reign forever. Once again, David did not get to experience the complete fulfillment of the promises made to him. It was partially fulfilled in his son, Solomon, but it has taken thousands of years to partially fulfill this promise and we don’t know for sure how long it will be until complete fulfillment. ## Jeremiah By the time of Jeremiah, the nation of Israel was gone and Judah was corrupted beyond recognition. The fulfillment of God’s promises seemed impossible, but God’s promises are faithful and true. God spoke to Jeremiah to remind him, that although Judah and Israel were being punished, ultimately, God would fulfill all His promises. He begins with these tender words: > Now the word of the Lord came to me saying,\ > “Before I formed you in the womb I knew you,\ > And before you were born I consecrated you;\ > I have appointed you a prophet to the nations.”\ > \ > Then I said, “Alas, Lord God!\ > Behold, I do not know how to speak,\ > Because I am a youth.”\ > \ > But the Lord said to me,\ > “Do not say, ‘I am a youth,’\ > Because everywhere I send you, you shall go,\ > And all that I command you, you shall speak.\ > Do not be afraid of them,\ > For I am with you to deliver you,” declares the Lord.\ > \ > Then the Lord stretched out His hand and touched my mouth, and the Lord said to me,\ > “Behold, I have put My words in your mouth.\ > See, I have appointed you this day …” (Jeremiah 1:4-10a) First God tells Jeremiah that He loves him so much that He formed him in his mother’s womb for a special purpose, to speak His judgement and blessings on Israel. God comforts Jeremiah when Jeremiah fears he is unworthy of the great task God has for him. God promises to be with Jeremiah and to help Jeremiah fulfill His will. ``` As Christians we are similarly told that God created us for His purpose and His blessing and He will be with us, empowering us for whatever tasks He has called us to do. ``` God promises that despite Israel’s nonstop rebellion, He will be gracious and “*not be angry forever*.” > Go and proclaim these words toward the north and say,\ > ‘Return, faithless Israel,’ declares the Lord;\ > ‘I will not look upon you in anger.\ > For I am gracious,’ declares the Lord;\ > ‘I will not be angry forever.\ > Only acknowledge your iniquity,\ > That you have transgressed against the Lord your God\ > And have scattered your favors to the strangers under every green tree,\ > And you have not obeyed My voice,’ declares the Lord.\ > ‘Return, O faithless sons,’ declares the Lord;\ > ‘For I am a master to you,\ > And I will take you one from a city and two from a family,\ > And I will bring you to Zion.’ (Jeremiah 3:12-14) God will always fulfill His promises even if that means calling His people home from the ends of the earth where they are scattered “*one from a city and two from a family*.” God promises to call both Israel and Judah back to the land promised to them all of the way back in time of God’s promise to Abraham. There is a partial return, after Judah’s 70 year exile in Babylon, leading to a rebuilding of the temple for a second time. We are in the middle of another return to Israel that began when Israel was recreated in 1948 and is continuing today. Despite the fact that the people of Israel are being barraged with rockets, drones, and missiles daily and are at risk of being attacked by suicide bombers and terrorists, God is calling His people home for His big finale. I believe these continuing verses refer to Jesus’s second coming and the millennial reign of Christ. > “Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding. It shall be in those days when you are multiplied and increased in the land,” declares the Lord, “they will no longer say, ‘The ark of the covenant of the Lord.’ And it will not come to mind, nor will they remember it, nor will they miss it, nor will it be made again. At that time they will call Jerusalem ‘The Throne of the Lord,’ and all the nations will be gathered to it, to Jerusalem, for the name of the Lord; nor will they walk anymore after the stubbornness of their evil heart. In those days the house of Judah will walk with the house of Israel, and they will come together from the land of the north to the land that I gave your fathers as an inheritance. (Jeremiah 3:15-18) This passage isn’t just a call back to the promised land. This is another promise of God. “*Then I will give you shepherds after My own heart, who will feed you on knowledge and understanding*.” After Jesus’s first coming, He made things clear about His plan of redemption for Israel and for the gentiles. He made clear His promise to bless all nations through Himself, a descendant of David, Jacob, and Abraham, to whom the promises were given. He demonstrated how His laws for the Jews pointed them to God’s ultimate plan. It is actually ironic that the “*shepherds after My own heart, who will feed you on knowledge and understanding*” are most likely Christian believers who are returned to earth to reign with Christ during the millennial kingdom. Gentile Christians were enabled to have a relationship with God through the Jews and then God will use those gentile Christians to shepherd the Jews back to God, so we can all worship God together. It won’t be until Jesus’s second coming and His thousand year reign that “*they will call Jerusalem ‘The Throne of the Lord.’*” It won’t be until Jesus’s second coming and His thousand year reign that they will not “*walk anymore after the stubbornness of their evil heart*.” God will finally make the full land of Israel a land of peace and prosperity for the Jews, but also to all the nations of the earth. But at the time of Jeremiah’s prophecy, God is promising punishment and hardship now to teach His people to be faithful and to trust God’s faithfulness. > Behold, I am bringing a nation against you from afar, O house of Israel,” declares the Lord. > > “It is an enduring nation,\ > It is an ancient nation,\ > A nation whose language you do not know,\ > Nor can you understand what they say. (Jeremiah 5:15) Due to Israel and Judah’s rebellion, both nations are taken away by a foreign nation into exile. Jeremiah, in particular, prophecies the 70 year exile of Judah in Babylon and their return to the promised land. God promised Abraham and Jacob (Israel) the land of Israel (previously Canaan) and He always keeps His promise, so He always brings them home in ways that are hard to comprehend. Relatively near the end of the 70 year exile in Babylon, God had Persia conquer Babylon and then a Persian king, not only allowed the Israelites to return to Jerusalem to rebuild the city, the walls, and the temple, but also he funded the return to Israel and returned the gold, silver, and bonze temple implements. What conquering nation does something like that? It was clearly all God. God may delay His promises, but He never cancels them. > For this the earth shall mourn\ > And the heavens above be dark,\ > Because I have spoken, I have purposed,\ > And I will not change My mind, \ > nor will I turn from it.” (Jeremiah 4:28) When God makes a promise, it is as good as done. Trust Jesus. @ 36bedab2:524acad4
2024-11-10 21:37:52### 1. **Power ON** - Quando você liga o computador, ele inicia o processo de boot. - Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes). ### 2. **BIOS (Basic Input/Output System)** - O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado. - Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU. - O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot. ### 3. **Master Boot Record (MBR) ou EFI Partition** - O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional. - Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função. - O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional. ### 4. **Boot Loader (e.g., GRUB)** - O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot. - Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema. - GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux. ### 5. **Kernel** - O **kernel** é o núcleo do sistema operacional Linux. - Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware. - O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software. ### 6. **Initial RAM disk - initramfs** - O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel. - Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco. - O initramfs é desmontado após o sistema principal estar carregado. ### 7. **/sbin/init (parent process)** - Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos. - O init é responsável por iniciar e gerenciar todos os outros processos do sistema. - Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos. ### 8. **Command Shell using getty** - **Getty** é o processo que configura e gerencia terminais para o login do usuário. - Ele exibe a tela de login em sistemas baseados em linha de comando. - Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico. ### 9. **Graphical User Interface (X Window ou Wayland)** - Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno). - Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc. - X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela. --- ### Como esses processos se intercalam? 1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas. 2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**. 3. **MBR/EFI** localiza e executa o **boot loader** (GRUB). 4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux. 5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**. 6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal. 7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema. 8. **Init** executa o **getty** para configurar o terminal de login. 9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
@ 36bedab2:524acad4
2024-11-10 21:37:52### 1. **Power ON** - Quando você liga o computador, ele inicia o processo de boot. - Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes). ### 2. **BIOS (Basic Input/Output System)** - O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado. - Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU. - O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot. ### 3. **Master Boot Record (MBR) ou EFI Partition** - O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional. - Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função. - O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional. ### 4. **Boot Loader (e.g., GRUB)** - O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot. - Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema. - GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux. ### 5. **Kernel** - O **kernel** é o núcleo do sistema operacional Linux. - Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware. - O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software. ### 6. **Initial RAM disk - initramfs** - O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel. - Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco. - O initramfs é desmontado após o sistema principal estar carregado. ### 7. **/sbin/init (parent process)** - Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos. - O init é responsável por iniciar e gerenciar todos os outros processos do sistema. - Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos. ### 8. **Command Shell using getty** - **Getty** é o processo que configura e gerencia terminais para o login do usuário. - Ele exibe a tela de login em sistemas baseados em linha de comando. - Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico. ### 9. **Graphical User Interface (X Window ou Wayland)** - Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno). - Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc. - X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela. --- ### Como esses processos se intercalam? 1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas. 2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**. 3. **MBR/EFI** localiza e executa o **boot loader** (GRUB). 4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux. 5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**. 6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal. 7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema. 8. **Init** executa o **getty** para configurar o terminal de login. 9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica. @ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3 originally posted at https://stacker.news/items/762161
@ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3 originally posted at https://stacker.news/items/762161 @ a901cbe4:bd85452f
2024-11-10 18:33:53Bitcoin under $100K? Let's be honest: it’s kind of like waiting for your favorite song to drop at a concert. The crowd's hyped, but you're still waiting for the real action to begin. Sure, $80K is cool — it's solid, it's impressive, but it’s not the headline act. The true show begins when Bitcoin crosses that $100K milestone, and until then, we’re in the “pre-game” phase. Here's why Bitcoin under $100K is merely the warm-up, and why we’re all just biding our time for what’s coming next. ### Bitcoin Under $100K: Just a Pre-Party Vibe Right now, Bitcoin at $80K feels like that awkward moment at a party when everyone’s gathered in the kitchen, getting their drinks ready, and the music is *almost* turned up. Sure, you can feel the energy, but everyone’s really waiting for the DJ to hit play on that banger. Bitcoin at $80K is promising, but it’s just a preview of the real excitement that’s about to unfold. This isn’t the time for victory laps. It’s the time to get ready, to watch and wait, because when Bitcoin hits $100K, *that’s* when the party really starts. The market will pop, the spotlight will shine brighter, and the world will be watching as Bitcoin climbs to new heights. ### The $80K Milestone: A Solid Step, But Not The Destination Let’s take a moment to appreciate $80K. It’s a big number in the world of crypto, and a milestone in its own right. But let’s not kid ourselves — it’s not the finish line. It’s like running a race, getting to the 80% mark, and looking ahead at the final stretch. You’re feeling good, but the best part is still coming. Bitcoin’s at $80K and that’s a statement, no doubt. But $100K is the magic number. It’s the one that makes the headlines, the one that makes everyone say, “Okay, Bitcoin’s for real.” $80K is impressive, but it’s not the showstopper. So while the excitement is there, we all know Bitcoin’s best performance is still ahead. ### Why $100K Is the Real Milestone We’ve All Been Waiting For When Bitcoin finally crosses that $100K mark, it’s going to be a global event. It’ll be the moment that people who were skeptical finally start to take notice, the moment when Bitcoin becomes a household name, not just a niche investment. It's like watching a rising star finally step into the spotlight and own the stage. And here's the thing: When Bitcoin hits $100K, it won’t be a “surprise.” It’s been in the works for years. But it’ll be the moment when everyone truly grasps the scale of what’s happening. The world will finally recognize that Bitcoin isn’t just a speculative asset — it’s a fundamental part of the financial landscape. ### Bitcoin’s Resilience: Boring Until It’s Not What makes $80K so intriguing isn’t just the number itself — it’s that Bitcoin’s still holding strong, despite all the FUD (fear, uncertainty, doubt) thrown at it. Critics have come and gone, but Bitcoin’s still here, solid as ever. It’s like the underdog story that just refuses to be over. Bitcoin at $80K is doing its thing, even when people doubt it. It’s showing up every day, proving that it’s built to last. Sure, it may seem like “just another day in the crypto market,” but trust me — Bitcoin’s resilience is what makes this moment significant. It’s not a bubble; it’s an evolution. And that evolution is building toward something even bigger. ### What’s Next: Bitcoin and Beyond $100K Once Bitcoin hits $100K, everything changes. The narrative shifts. Bitcoin goes from "that risky bet" to "the future of finance." And that’s where things get wild. It’s not just about price anymore — it’s about the institutional and mainstream acceptance of Bitcoin. It’s about the fact that this isn’t a fad, it’s a global movement that’s not going anywhere. After $100K? Who knows. Maybe $200K, $500K, or more. But let’s not get ahead of ourselves. We’re still waiting for that first major milestone to break, and when it happens, it’s going to be like a flip of a switch. A whole new world will open up. ### The Waiting Game: It’s Gonna Be Worth It So, while Bitcoin under $100K might feel like a long wait, remember: it’s all part of the journey. Bitcoin at $80K is just the start of something bigger. It’s the calm before the storm, the deep breath before the final sprint. When $100K hits, we’ll all be able to say we were here for it. And when it crosses that threshold, it’s going to be one of the biggest moments in the world of finance — one that we’ll all look back on and say, "We saw this coming." And for those of us who’ve been riding the wave since the early days? Well, we’ll be popping the champagne. The real show starts at $100K. We’re just waiting for the curtain to rise. 🚀
@ a901cbe4:bd85452f
2024-11-10 18:33:53Bitcoin under $100K? Let's be honest: it’s kind of like waiting for your favorite song to drop at a concert. The crowd's hyped, but you're still waiting for the real action to begin. Sure, $80K is cool — it's solid, it's impressive, but it’s not the headline act. The true show begins when Bitcoin crosses that $100K milestone, and until then, we’re in the “pre-game” phase. Here's why Bitcoin under $100K is merely the warm-up, and why we’re all just biding our time for what’s coming next. ### Bitcoin Under $100K: Just a Pre-Party Vibe Right now, Bitcoin at $80K feels like that awkward moment at a party when everyone’s gathered in the kitchen, getting their drinks ready, and the music is *almost* turned up. Sure, you can feel the energy, but everyone’s really waiting for the DJ to hit play on that banger. Bitcoin at $80K is promising, but it’s just a preview of the real excitement that’s about to unfold. This isn’t the time for victory laps. It’s the time to get ready, to watch and wait, because when Bitcoin hits $100K, *that’s* when the party really starts. The market will pop, the spotlight will shine brighter, and the world will be watching as Bitcoin climbs to new heights. ### The $80K Milestone: A Solid Step, But Not The Destination Let’s take a moment to appreciate $80K. It’s a big number in the world of crypto, and a milestone in its own right. But let’s not kid ourselves — it’s not the finish line. It’s like running a race, getting to the 80% mark, and looking ahead at the final stretch. You’re feeling good, but the best part is still coming. Bitcoin’s at $80K and that’s a statement, no doubt. But $100K is the magic number. It’s the one that makes the headlines, the one that makes everyone say, “Okay, Bitcoin’s for real.” $80K is impressive, but it’s not the showstopper. So while the excitement is there, we all know Bitcoin’s best performance is still ahead. ### Why $100K Is the Real Milestone We’ve All Been Waiting For When Bitcoin finally crosses that $100K mark, it’s going to be a global event. It’ll be the moment that people who were skeptical finally start to take notice, the moment when Bitcoin becomes a household name, not just a niche investment. It's like watching a rising star finally step into the spotlight and own the stage. And here's the thing: When Bitcoin hits $100K, it won’t be a “surprise.” It’s been in the works for years. But it’ll be the moment when everyone truly grasps the scale of what’s happening. The world will finally recognize that Bitcoin isn’t just a speculative asset — it’s a fundamental part of the financial landscape. ### Bitcoin’s Resilience: Boring Until It’s Not What makes $80K so intriguing isn’t just the number itself — it’s that Bitcoin’s still holding strong, despite all the FUD (fear, uncertainty, doubt) thrown at it. Critics have come and gone, but Bitcoin’s still here, solid as ever. It’s like the underdog story that just refuses to be over. Bitcoin at $80K is doing its thing, even when people doubt it. It’s showing up every day, proving that it’s built to last. Sure, it may seem like “just another day in the crypto market,” but trust me — Bitcoin’s resilience is what makes this moment significant. It’s not a bubble; it’s an evolution. And that evolution is building toward something even bigger. ### What’s Next: Bitcoin and Beyond $100K Once Bitcoin hits $100K, everything changes. The narrative shifts. Bitcoin goes from "that risky bet" to "the future of finance." And that’s where things get wild. It’s not just about price anymore — it’s about the institutional and mainstream acceptance of Bitcoin. It’s about the fact that this isn’t a fad, it’s a global movement that’s not going anywhere. After $100K? Who knows. Maybe $200K, $500K, or more. But let’s not get ahead of ourselves. We’re still waiting for that first major milestone to break, and when it happens, it’s going to be like a flip of a switch. A whole new world will open up. ### The Waiting Game: It’s Gonna Be Worth It So, while Bitcoin under $100K might feel like a long wait, remember: it’s all part of the journey. Bitcoin at $80K is just the start of something bigger. It’s the calm before the storm, the deep breath before the final sprint. When $100K hits, we’ll all be able to say we were here for it. And when it crosses that threshold, it’s going to be one of the biggest moments in the world of finance — one that we’ll all look back on and say, "We saw this coming." And for those of us who’ve been riding the wave since the early days? Well, we’ll be popping the champagne. The real show starts at $100K. We’re just waiting for the curtain to rise. 🚀 @ df478568:2a951e67
2024-11-10 14:26:38*note: This version of the article uses some four-letter words some people may not like. If you prefer cartoon-like cussing, you can read it [here](https://marc26z.com/use-a-seed-signer-with-cold-power/). It's that time, again--The bull market which happens every 4 years like the Winter Olympics. We've surpassed the previous USD/ATH. This is the 498th resurrection of our beloved bitcoin, but you know what really turns my crank? Bitcoin cybersecurity! I love digging into the nitty-gritty of cryptography not CrYpTo and finding creative ways to use my toy collection. I mean, hardware wallet(a.k.a. signing devices) collection. Nah, they're toys. Yesterday, as I was playing with my toys, I was inspired to use my seed signer after a long hiatus. To be clear, I love the Seed Signer. It has some neat features: - Generate seeds with the entropy from a picture - Hand-drawn QR codes for easy seed backup - You can DIY  It looks cool too, but for the record, I wouldn't use it for a single sig wallet because it does not contain a secure element. According to NVK, there are zero days and supply chain attacks you can't really mitigate with the seed signer. Although I think this is a fair criticism, it can be useful: - As an educational tool - Part of a multi-sig backup. Michael Flaxman, in his [10X Your BTC Security Guide](https://notes.marcleon.work/#root/0vxct4qCx1C5/YxWwjfah4d4D?ntxId=ApLzSR), suggests removing a Wi-Fi card and hard drive from a computer, boot up TAILS, plug your computer into an RJ45 port with an Ethernet cable for Internet access, navigate to https://seedpicker.net/ on the default [TOR](https://www.torproject.org/) browser, unplug the Ethernet cable from the RJ45 port, and generate the seed for your paper wallet. That sentence is too damn long, but this is indicative of how cumbersome this method is. This was necessary when he wrote it since we did not have as many hardware wallets back then as are on the market today. In my cybersecurity opinion, and I am not a certified cyber security expert, buying a seed signer requires less technical know-how than using Flaxman's guide. This is not a criticism of Flaxman, his guide is one of my favorite things ever written about bitoin because of it's educational value. If you want to learn about extreme cybersecurity, Flaxman's guide makes an excellent lab. **We assume no network security model is 100% secure,** so we never risk compromising our keys by ever connecting to an Internet-connected device. It's a hell of an education. ## Seed Signer Is For Everybody  Say you work a full time job and didn't spend the majority of your free time learning this stuff during a pandemic. Or maybe you're like my wife. She think's Bitcoin is cool now, but this one time she walked in on me with my Cold Card plugged into a 9v battery and said, "See. I'm never using *whatever the fuck* that thing is. My wife is never removing a Wi-Fi card from a laptop. If you're like my wife, the Seed Signer is right for you, if you want to use multisig. It's also not imperative to use the 9v battery if you don't want to. You can just plug it into a wall outlet like everybody else. I want to start bringing the Seed Signer to my local meetup, but it's at a brewery and I don't want to be a wallflower because I need to plug the damn thing into an outlet so I thought, “Why not try the [Cold Power](https://usbcoldpower.com/) with my Seed Signer?” I found one of my [magnetic micro-USB adapters](https://www.amazon.com/Magnetic-Micro-USB-Connector-Water-dustproof-antioxidant/dp/B0D2Y4F9FR/ref=sr_1_1_sspa?dib=eyJ2IjoiMSJ9.czIXiLc88NoDXKD5cqfGUojOf-JD766ZLolCTtGJXJxy9B0I-9g9RbLiB95HffRy8-o6Fo-78ijTjcubw93VYwNn9WaFgg9kraKbLDVYEj50RueMTqz75r7ouUMXD_m1YnNWFIEGNmevIO31B8AT6H_CXzK6loS3Em7R96Q-xL24kYO-Ys0WULVpl_OnFm_9_cqOxqAsGpLskXPRKCV7d7I3EYruyQc82ermd_JIZpY.cCmNDmhUM5mhbNY0xoCENKM9Z9cscEe49zAsKzg8UsU&dib_tag=se&keywords=magnetic+micro+usb+adapter&qid=1731162326&sr=8-1-spons&sp_csd=d2lkZ2V0TmFtZT1zcF9hdGY&psc=1) and plugged it into the Seed signer, Then I plugged the battery in. My switch is on because the flimsy plastic switch broke the first time I turned it on, but it still works. I just broke it with my fat thumbs. It felt as if it took as long as a difficulty adjustment to boot-up, but in reality it was about the time it takes the Liquid Network to find a block. I proceeded to take a picture and write down a 12 word seed. I plan on using this with the Nunchuck testnet wallet to show people at my local Meetup how to create seeds and take self-custody of their Bitcoin. Again, I would not use this as a single sign because there are more secure options, but it is a great tool for teaching Bitcoin cybersecurity and can be a great wallet that can mitigate the risk of supply-chain and retirement attacks when used as part of a multi-sig quorum. I can also now use it in the middle of a brewery. I'll write about how this goes the next time I get down there. ### Why We Use The Cold Power  I placed one of those magnetic adapters I bought on Amazon into one of the power holes. Power holes is a technical term for microUSB. This is because the Cold Power does hooks up to a cable that does not transmit data, only Power. Get it? It's like a cold wallet, but instead of a wallet, it's a power cable. You hook this cable up to a technology which was invented in 1836, a [battery]. 9V batteries contain no data. It is only Power, but most of us must trust Coinkite. Maybe they programmed the green part to be a bitcoin stealing script. I doubt this and think Coinkite is an honest company, but the awesome sauce thing is, the little magnet I bought on Amazon does not allow the transmittal of data. I don't need to plug in a charger that might be compromised. This might sound paranoid, but in [Tools of Titans](https://www.amazon.com/Tools-Titans-Billionaires-World-Class-Performers/dp/1328683788), [Samy Kamkar](https://en.wikipedia.org/wiki/Samy_Kamkar), malware has even been found in cigarette lighter chargers. Imagine a fix of nicotine costing you you entire life savings. That's not likely to happen, but why take a chance? It's better to spend several thousand [sats](https://www.investopedia.com/terms/s/satoshi.asp) on a charger and a 9v battery than lose your whole stack. According to [Wired Magazine](https://www.wired.com/story/infrared-laser-microphone-keystroke-surveillance/), he can also learn the keystrokes you're typing on your laptop keyboard through a window. This means typing a seed onto a laptop might not be the best idea even if you are afraid of this. It is better to take a picture and use the entropy from the random picture. #### Powering The Seed Signer With A Coinkite Product Seed Signer and NVK, the CEO of Coinkite seem to have some beef on [nostr](https://nostr.com/), but it's none of my business. The part I find interesting is a product made by Coinkite works with a product made by Seed Signer. This was made for the Cold Card, but it works with a hardware wallet made from someone else. Too bad politics isn't more like that. It's nice to see two rival companies make products that are compatible with each other, but that's just the way free and open source software like bitcoin is. Seeds from Coinkite can be used with the Seed Signer. Maybe that's okay if it's only $1,000 worth of bitcoin on the Seed Signer. You don't need to go to Defcon 5 for every single sat. It's not practical. Sure, if the NSA was after you and wanted to steal your $1,000 worth of bitcoin from you, they could probably do it. Why would they spend ten thousand dollars to do this to you? This is not in most people's threat models. **Wait...Then why do you need to use the 9v battery thing-a-ma-jig?** I technically don't need to , but we could also use this for a multi-signature quorum? What if you took your wallet to a safe deposit box, but the vault does not have a plug?  I created this key with no power outlet at all. This means I could do this in the middle of Alaska where there's no cell phones, where you only need to worry about bears stealing your seed phrase... That's a bit much, but it's possible. I was not able to take a picture on the same battery charge so You might want to use a fresh battery if you ever try this yourself. Thanks for reading. - If you like this blogs with no swear words, send sats to **marc26z@strike.me/** - If you like this blog with swear words, send sats to **marc@npub.pro/** ✌️ [npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0no](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0) [869,719](https://mempool.marcleon.work/block/0000000000000000000173e894282485050b6113e984bafb9a1931dd62e38553) As Seen On TIR: http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/use-a-seed-signer-with-cold-power/
@ df478568:2a951e67
2024-11-10 14:26:38*note: This version of the article uses some four-letter words some people may not like. If you prefer cartoon-like cussing, you can read it [here](https://marc26z.com/use-a-seed-signer-with-cold-power/). It's that time, again--The bull market which happens every 4 years like the Winter Olympics. We've surpassed the previous USD/ATH. This is the 498th resurrection of our beloved bitcoin, but you know what really turns my crank? Bitcoin cybersecurity! I love digging into the nitty-gritty of cryptography not CrYpTo and finding creative ways to use my toy collection. I mean, hardware wallet(a.k.a. signing devices) collection. Nah, they're toys. Yesterday, as I was playing with my toys, I was inspired to use my seed signer after a long hiatus. To be clear, I love the Seed Signer. It has some neat features: - Generate seeds with the entropy from a picture - Hand-drawn QR codes for easy seed backup - You can DIY  It looks cool too, but for the record, I wouldn't use it for a single sig wallet because it does not contain a secure element. According to NVK, there are zero days and supply chain attacks you can't really mitigate with the seed signer. Although I think this is a fair criticism, it can be useful: - As an educational tool - Part of a multi-sig backup. Michael Flaxman, in his [10X Your BTC Security Guide](https://notes.marcleon.work/#root/0vxct4qCx1C5/YxWwjfah4d4D?ntxId=ApLzSR), suggests removing a Wi-Fi card and hard drive from a computer, boot up TAILS, plug your computer into an RJ45 port with an Ethernet cable for Internet access, navigate to https://seedpicker.net/ on the default [TOR](https://www.torproject.org/) browser, unplug the Ethernet cable from the RJ45 port, and generate the seed for your paper wallet. That sentence is too damn long, but this is indicative of how cumbersome this method is. This was necessary when he wrote it since we did not have as many hardware wallets back then as are on the market today. In my cybersecurity opinion, and I am not a certified cyber security expert, buying a seed signer requires less technical know-how than using Flaxman's guide. This is not a criticism of Flaxman, his guide is one of my favorite things ever written about bitoin because of it's educational value. If you want to learn about extreme cybersecurity, Flaxman's guide makes an excellent lab. **We assume no network security model is 100% secure,** so we never risk compromising our keys by ever connecting to an Internet-connected device. It's a hell of an education. ## Seed Signer Is For Everybody  Say you work a full time job and didn't spend the majority of your free time learning this stuff during a pandemic. Or maybe you're like my wife. She think's Bitcoin is cool now, but this one time she walked in on me with my Cold Card plugged into a 9v battery and said, "See. I'm never using *whatever the fuck* that thing is. My wife is never removing a Wi-Fi card from a laptop. If you're like my wife, the Seed Signer is right for you, if you want to use multisig. It's also not imperative to use the 9v battery if you don't want to. You can just plug it into a wall outlet like everybody else. I want to start bringing the Seed Signer to my local meetup, but it's at a brewery and I don't want to be a wallflower because I need to plug the damn thing into an outlet so I thought, “Why not try the [Cold Power](https://usbcoldpower.com/) with my Seed Signer?” I found one of my [magnetic micro-USB adapters](https://www.amazon.com/Magnetic-Micro-USB-Connector-Water-dustproof-antioxidant/dp/B0D2Y4F9FR/ref=sr_1_1_sspa?dib=eyJ2IjoiMSJ9.czIXiLc88NoDXKD5cqfGUojOf-JD766ZLolCTtGJXJxy9B0I-9g9RbLiB95HffRy8-o6Fo-78ijTjcubw93VYwNn9WaFgg9kraKbLDVYEj50RueMTqz75r7ouUMXD_m1YnNWFIEGNmevIO31B8AT6H_CXzK6loS3Em7R96Q-xL24kYO-Ys0WULVpl_OnFm_9_cqOxqAsGpLskXPRKCV7d7I3EYruyQc82ermd_JIZpY.cCmNDmhUM5mhbNY0xoCENKM9Z9cscEe49zAsKzg8UsU&dib_tag=se&keywords=magnetic+micro+usb+adapter&qid=1731162326&sr=8-1-spons&sp_csd=d2lkZ2V0TmFtZT1zcF9hdGY&psc=1) and plugged it into the Seed signer, Then I plugged the battery in. My switch is on because the flimsy plastic switch broke the first time I turned it on, but it still works. I just broke it with my fat thumbs. It felt as if it took as long as a difficulty adjustment to boot-up, but in reality it was about the time it takes the Liquid Network to find a block. I proceeded to take a picture and write down a 12 word seed. I plan on using this with the Nunchuck testnet wallet to show people at my local Meetup how to create seeds and take self-custody of their Bitcoin. Again, I would not use this as a single sign because there are more secure options, but it is a great tool for teaching Bitcoin cybersecurity and can be a great wallet that can mitigate the risk of supply-chain and retirement attacks when used as part of a multi-sig quorum. I can also now use it in the middle of a brewery. I'll write about how this goes the next time I get down there. ### Why We Use The Cold Power  I placed one of those magnetic adapters I bought on Amazon into one of the power holes. Power holes is a technical term for microUSB. This is because the Cold Power does hooks up to a cable that does not transmit data, only Power. Get it? It's like a cold wallet, but instead of a wallet, it's a power cable. You hook this cable up to a technology which was invented in 1836, a [battery]. 9V batteries contain no data. It is only Power, but most of us must trust Coinkite. Maybe they programmed the green part to be a bitcoin stealing script. I doubt this and think Coinkite is an honest company, but the awesome sauce thing is, the little magnet I bought on Amazon does not allow the transmittal of data. I don't need to plug in a charger that might be compromised. This might sound paranoid, but in [Tools of Titans](https://www.amazon.com/Tools-Titans-Billionaires-World-Class-Performers/dp/1328683788), [Samy Kamkar](https://en.wikipedia.org/wiki/Samy_Kamkar), malware has even been found in cigarette lighter chargers. Imagine a fix of nicotine costing you you entire life savings. That's not likely to happen, but why take a chance? It's better to spend several thousand [sats](https://www.investopedia.com/terms/s/satoshi.asp) on a charger and a 9v battery than lose your whole stack. According to [Wired Magazine](https://www.wired.com/story/infrared-laser-microphone-keystroke-surveillance/), he can also learn the keystrokes you're typing on your laptop keyboard through a window. This means typing a seed onto a laptop might not be the best idea even if you are afraid of this. It is better to take a picture and use the entropy from the random picture. #### Powering The Seed Signer With A Coinkite Product Seed Signer and NVK, the CEO of Coinkite seem to have some beef on [nostr](https://nostr.com/), but it's none of my business. The part I find interesting is a product made by Coinkite works with a product made by Seed Signer. This was made for the Cold Card, but it works with a hardware wallet made from someone else. Too bad politics isn't more like that. It's nice to see two rival companies make products that are compatible with each other, but that's just the way free and open source software like bitcoin is. Seeds from Coinkite can be used with the Seed Signer. Maybe that's okay if it's only $1,000 worth of bitcoin on the Seed Signer. You don't need to go to Defcon 5 for every single sat. It's not practical. Sure, if the NSA was after you and wanted to steal your $1,000 worth of bitcoin from you, they could probably do it. Why would they spend ten thousand dollars to do this to you? This is not in most people's threat models. **Wait...Then why do you need to use the 9v battery thing-a-ma-jig?** I technically don't need to , but we could also use this for a multi-signature quorum? What if you took your wallet to a safe deposit box, but the vault does not have a plug?  I created this key with no power outlet at all. This means I could do this in the middle of Alaska where there's no cell phones, where you only need to worry about bears stealing your seed phrase... That's a bit much, but it's possible. I was not able to take a picture on the same battery charge so You might want to use a fresh battery if you ever try this yourself. Thanks for reading. - If you like this blogs with no swear words, send sats to **marc26z@strike.me/** - If you like this blog with swear words, send sats to **marc@npub.pro/** ✌️ [npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0no](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0) [869,719](https://mempool.marcleon.work/block/0000000000000000000173e894282485050b6113e984bafb9a1931dd62e38553) As Seen On TIR: http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/use-a-seed-signer-with-cold-power/ @ 84999652:2a24d806
2024-11-10 14:10:23近期,FUD以太坊的声音不绝于耳,大部分声音围绕ETH币价。的确,BTC现在每天破新高,而ETH离2021年的最高点(4800美金)还差近40%。当然,最近ETH币价开始拉升,大有被骂急眼了的感觉。我也相信,这一轮,以太坊大概率是可以破前高的。 **但是,以太坊到底是怎么了?为什么这轮周期完全跟不上比特币的节奏?** 以太坊真的颓势已显?难以再复现当年的辉煌吗? Crypto行业的新一轮范式创新还会发生在以太坊生态吗? 本文将带您重回Crypto行业的原点——比特币,去反观以太坊和整个行业,以及探讨Crypto行业再次焕发活力的路径可能在哪里? 以太坊真的颓势已显?难以再复现当年的辉煌吗? Crypto行业的新一轮范式创新还会发生在以太坊生态吗? 本文将带您重回Crypto行业的原点——比特币,去反观以太坊和整个行业,以及探讨Crypto行业再次焕发活力的路径可能在哪里? ##### 一、逃离以太坊惯性 首先,谁都无法全盘否定以太坊! 以太坊有它的价值和开创性意义,智能合约也确实给整个加密行业打开了新局面。至少在以太坊诞生之前,加密行业大多数项目都只是对比特币拙劣的模仿。把比特币代码简单修改几个参数,变成区块更大的比特币、速度更快的比特币、隐私性更好的比特币等等。基本都只是对比特币简单的山寨,山寨币这个概念基本就是概括了以太坊诞生之前的所有Crypto项目。 而以太坊诞生以后,整个Crypto行业又进入了山寨以太坊的浪潮,2015年至今,诞生了不计其数的所谓公链,区块更大的以太坊、速度更快的以太坊、性能更好的以太坊(包括Layer2)等等。 而且每个公链的所谓生态也基本照抄照搬以太坊模式,无非DeFi、GameFi、各类L2、模块化等等。现在散户已经被各类巧立名目、五花八门的叙事概念反复收割的脱敏无感了,于是干脆啥也不信,只玩最简单粗暴的Meme,虽然大家都知道它长久不了,但是至少还可以痛快一博! **没有创新,没有活力,共识涣散、僵尸横行,整个行业弥漫着看不到希望的末日气息!** **Crypto行业还有未来吗?** 但是,当你回头去看看比特币,唯独只有它,依然一骑绝尘、屡破新高,似乎完全不受这一切的影响! 我们不禁要想,是不是整个行业陷入“以太坊惯性”太久了,以至于我们都完全忽略了比特币! **毕竟,以太坊就是灵感于比特币,来源于比特币社区。以太坊就是对比特币的一种解读方式,但是,整个行业把以太坊模式当成了全部。** 如果要找到以太坊的问题所在,以及如果要重新找到新的范式创新机会,那就务必得回到比特币,重新理解比特币,重新在比特币找到创新源泉,就像以太坊诞生之初那样! 让我们一起暂时逃离以太坊惯性,重回比特币去思考! #### 二、机械共识和社会共识 解读比特币的角度有很多种,但是,我们今天讨论的以太坊和比特币都属于公链范畴。谈到公链,共识机制就是绕不开的话题! 所谓公链,就是公有区块链,是谁公有的?是一群参与共识的人公有的,公链必须依靠共识来驱动,没有共识就没有公链。所以,谈公链如果不谈共识那就是空谈! **公链的共识分为机械共识和社会共识。** 公链的本质就是依靠一套机械共识来不断凝聚社会共识的去中心化系统。(说一个题外话,Layer2不是公链,Layer2只需要一个定序器节点就可以运行,Layer2本身没有共识机制。Layer2没有机械共识,只有社会共识,因此,Layer2的价值没有机械共识来支持。目前大部分项目,既没有机械共识,也没有社会共识,这是项目失败的根本原因) 所谓机械共识就是一个人人都可以公平参与的共识机制,比如PoW机制,机械共识的参与方式是算力,算力越强,机械共识就越强;所谓社会共识就是围绕公链的生态、影响力,包括链上应用、用户等等数据,最终体现在币价。 **机械共识的参与者是公链的第一投入者、受益者和建设者。** 公链的启动和运行完全依赖机械共识的参与者,机械共识参与者投入大量成本(算力和能源等)参与公链,因此,只有机械共识的参与者,才有最原始的动力去推动公链生态的发展,因为,他们是第一投入者也是第一受益者。因此,为了帮助公链获取更大的社会共识,机械共识参与者会继续推动公链生态的发展,而公链生态吸引来的应用开发者大都是流动的,他们并不如机械共识参与者更深的绑定在公链利益之上(除非他们自己也变成了机械共识参与者)。 这也解释了,为什么比特币生态的早期推动者基本都来自于矿工群体。而以太坊链上的许多头部应用选择另立门户,比如Uniswap等。 **所以,当一个公链的币价开始疲软,那是社会共识变弱了,而更底层原因是机械共识变弱了,或者说参与机械共识的人离散了。** 那么,我们来从”共识‘角度来对比下比特币和以太坊。 #### 三、回归比特币共识,反观以太坊和行业 **比特币的机械共识是一个动态竞赛模式。以太坊的机械共识是一个静态固收模式!** 比特币的矿工要想获得出块权,每一个节点必须在同一时间段投入同样的算力和能源去竞争,但是最终网络只会选出一个节点出块,而其他所有“陪跑节点”的投入作为一种巨大的冗余成本附着在了比特币的价值之中。 通俗点来讲,比特币网络铸造每一枚比特币的实际投入的成本是远远大于单一出块节点支出的成本,它是以消耗所有“陪跑节点”的成本为代价的一种铸造方式。所以,比特币矿工为了已经投入的巨大冗余成本会不断的参与算力竞赛,直到抢到出块权,这是比特币网络共识不断壮大的原因。 **所以,比特币网络的实际共识成本是远远大于目前比特币总市值的**大概是大出多少倍呢?如果我们以比特币历史平均10000个挖矿节点来算的话,这个理论差距应该是1万倍。但是,目前全网比特币活跃矿池约20个,加上单独Solo的矿工,我们预估总共50个,我们把矿池当作一个总节点,这个成本差距大致有50倍。 这就是比特币的PoW动态算力竞赛模式给比特币带来的共识安全性,所以,比特币的共识安全几乎是无法评估的强度! 而以太坊的PoS机制是一个静态固收模式,实际投入多少ETH可以获得多少ETH收益,基本是一个静态的固定收益,目前基本稳定在5%左右。所以,ETH共识的参与者不需要竞赛,不需要额外支出冗余成本,只需要算账,就可以不需要投入额外成本的情况参与利益分配。这也是以太坊早期宣传的所谓PoS机制不会产生能源消耗的“优点”。但是,这个“优点”也变成了以太坊网络共识的弱点。**因为没有冗余成本的投入,以太坊的共识成本实际变低了,因此,以太坊网络的共识价值实际上也降低了!** 所以,当把比特币的PoW机制和以太坊的PoS机制进行对比时,你就会发现,比特币的网络共识成本几乎是不可估量的,随之不断的算力和能源投入,其共识是无上限的。而以太坊的共识是有上限的,是可计算的,ETH的质押率就是以太坊的共识上限。 因此,在机械共识层面,比特币的机械共识相较于以太坊也更强大,从而进一步影响了社会共识的差异,最终,直接表现在了币价层面。 **不仅如此,如果从物理学(热力学)角度去看比特币的POW机制,我们会发现,POW机制驱动着比特币成为一个更接近生命体的熵减系统,这是比特币网络一直充满生命和活力的物理学原理。** 在热力学角度,宇宙中所有的事物都是走向熵增,也就是从有序走向无序,从秩序走向混乱,最终走向寂灭! 但是,只有一个例外,那就是生命! 生命以负熵为食——薛定谔。 所谓负熵是一种可以帮助内部系统从无序转向有序的外部能量。生命就是通过消化负熵,把无序转换为有序,在局部时空中创造了熵减。 但是,熵减现象只是存在于局部时空,而且,生命每形成一分熵减,就会向外部宇宙排放两分熵增,两者相加,对于宇宙来讲仍然是熵增。 比特币的PoW机制,就是让网络内一群混乱无序的拜占庭节点,通过不断消化算力和能源进行运算求解,最终,运算最快的节点获得出块权,节点间迅速验证并达成共识,最终,一个无序混乱的网络达成了一致性,形成了一种秩序,也就是创造了一个熵减系统,一个生命体! **因此,在比特币这个生命体,矿工从外部输入的算力和能源是“负熵”,可以帮助比特币网络内混乱无序的节点达成共识和一致,从而创造了熵减系统。那么,PoW机制就是比特币这个生命体的消化系统,矿工提供“负熵”,最终,成就了比特币这个生命体!** 这是比特币可以一直壮大生长的物理学原理。 那么,我们来反观以太坊: 以太坊创立之初也是照用PoW机制并持续运行了超过七年,这七年也是以太坊突飞猛进的七年。直到2022年9月,以太坊正式从PoW机制转向PoS机制,一切悄然发生了变化。 切除PoW机制,让以太坊失去了外部算力和能源的输入,也就丧失了持续吸食“负熵”的能力,就像一个切除了肠胃又未能找到替代方案的生命体,虽然,短时间内实现了瘦身,但是,由于缺乏持续的进食能力,逐渐走向衰亡几乎是必然的。 有人说,以太坊之所以价格疲软,那是因为生态缺乏创新,链上应用和用户没有持续新增所导致的。那么,造成这些情况的更深层原因是什么? **就像我们前面说的,机械共识直接影响社会共识。生态、应用、用户、币价这些都是社会共识的表现,社会共识变弱的本质是因为机械共识变弱了。** **以太坊的机械共识为何变弱了?** PoS机制是静态固收模式,缺乏算力和能源竞争,无法形成冗余成本,进而机械共识削弱了;PoS机制缺乏吸食“负熵”的能力,无法通过输入“算力和能源”来抵消系统内部的熵增趋势;PoS的质押机制也直接导致了富者恒富、阶级固化,当阶级固化,形成的就是社区缺乏创新和活力,最终这些能力外溢,便成就了其他竞品。 这一系列表现出来的就是以太坊生态、应用、用户、币价等社会共识指标的疲软!即使可以通过强行拉升币价去拔高社会共识,但是,物理学原理是不可违背的。 **以太坊确实颓势已现,这轮周期步步落后于比特币,就是最真实的结果!而下一轮周期也必将拉开更大的距离!** 以太坊尚且如此,其他模仿以太坊的公链,必然也难逃颓势!Crypto行业走到如今的地步,真可谓是,成也以太坊,败也以太坊!这或许是任何一个行业在发展过程中都会经历的。 **但是,机遇往往也在此刻出现!** Crypto行业更大的机遇肯定不在现有的以太坊模式里,一定需要逃离”以太坊惯性“,重新回归这个行业最早的上下文,回到这个行业最早的原点,从那里寻找答案! #### 四、重回比特币共识,挖掘比特币无尽宝藏 回归比特币再创新,这是一个行业问题,也是一个长久的事业,或许,在短时间内,我们很难突破。但是,当我们开始破除以太坊迷信,开始回归比特币重新再思考时,除了发现‘共识“这些背后细节之外,还有可能发现更多从未注意到的隐藏细节。 这些细节让我们对基于比特币进行再次范式创新充满了希望! 比如,直观上大家会认为,在处理交易方面,以太坊会比比特币更高效。但,实际上并不是。 比特币的UTXO模型在处理交易时,可以实现并发处理交易和独立状态变更,而且不需要一个统一的世界状态树来更新状态。甚至说,比特币压根就没有所谓的账户概念,用户地址上显示的比特币余额,实际上是代表某个用户掌握的私钥所能控制UTXO总面额。 UTXO模型在处理交易时,就像真实的交易环境中,任何一对交易双方都可以拿着不同面额的“UXTO”现金进行频繁交易,交易双方的交易状态完全不会影响第二对交易双方的交易进度,因为,UTXO都是可以独立进行状态变更,不需要一个统一的中央状态树来做变更。 而以太坊采用传统的账户模型,也就是传统的银行账户模型。账户模型在处理交易时,需要依靠一个全局的状态树来给每一笔交易所涉及的地址进行余额的加减计算,因此,每一次交易状态都需要先变更完之后,才能进行下一个交易,否则就会出现双花或者无法交易等问题。因此,账户模型只能做串行处理。 通俗来讲,以太坊的账户模型,需要一个中心的世界状态树来统一处理交易,来统一变更所有账户的状态,虽然,这个世界状态树是去中心机制来驱动的,但是,由于其需要一个中心来统一处理和进行全局状态变更,导致,其很难执行并发交易以及更灵活的交易模式。 我们没发现的比特币细节还有很多。 单就 “并行处理状态变更的能力“ 方面,比特币的UTXO模型是完胜以太坊账户模型的。而且,UTXO的这种并发处理和独立状态变更的能力,还可以拓展到任意需要独立变更状态以及并发处理的事物中去,也就是UTXO可以表达除了比特币交易之外的其他事物状态,比如,预测市场的状态变更、AI安全模型的状态变更等等。 而且由于比特币的并发处理状态变更的能力受到全球最大机械共识——比特币共识的保护,这让比特币网络更加独一无二和不可替代。共享比特币共识安全+UTXO并发状态变更,这两项能力加在一起就可以迸发无限能量。这是很多人之前没有发现的细节。当然,我们很高兴已经看到比特币生态的创业者已经往这个方向挺进,比如,基于客户端验证和UTXO模型的BitVM方案;以及前段时间宣布放弃比特币Layer2赛道,全面转向“共享比特币共识安全+UTXO并发状态变更“的BEVM团队等。 当我们转换思路就会发现,比特币这个无尽宝藏,其开发和应用进度几乎不足1%。 #### 总结: 当我们开始脱离以太坊惯性来看整个行业,我们可以直面一些之前不敢直面的问题,当我们重新回到比特币去思考,又可以从比特币汲取无限的灵感和创新方向。以太坊的诞生不过是对比特币的一种抽象思考和解读,而后来的创业者放弃了思考,全面复制以太坊模式,这是整个行业逐步缺乏持续创新和活力的背后原因。 当然,我们看到了一些团队开始回归比特币,开始重新思考,比如,共享比特币共识安全+UTXO并发状态变更就是一个极具潜力的创业方向。 **真正的范式创新并不是简单的模仿,而是要抽象背后的原理。瓦特创造的蒸汽机并没有直接引发工业革命,而是有人抽象总结了蒸汽机背后的科学原理(热力学定律),从而引发了科学的范式革命。** 如果,中本聪是瓦特,比特币是蒸汽机,那么,Crypto行业的这16年,大部分人都是在模仿比特币制作大量的不同功能、不同形式的“蒸汽机”,却鲜有人去思考和抽象比特币本身所蕴含的科学原理,以至于这个行业迟迟没有引发真正的比特币范式革命。 当然,我们已经看到有团队在往这方面思考,这是行业的曙光,我们需要更多的人加入,一起推动比特币范式革命的到来! **本文灵感主要来源于比特币学习交流暑社区“中本聪大学”** TG链接:https://t.me/satoshiedu **本人长期在中本聪大学和诸多比特币OG及爱好者深度交流学习比特币,一起探讨Crypto行业发展机遇。**
@ 84999652:2a24d806
2024-11-10 14:10:23近期,FUD以太坊的声音不绝于耳,大部分声音围绕ETH币价。的确,BTC现在每天破新高,而ETH离2021年的最高点(4800美金)还差近40%。当然,最近ETH币价开始拉升,大有被骂急眼了的感觉。我也相信,这一轮,以太坊大概率是可以破前高的。 **但是,以太坊到底是怎么了?为什么这轮周期完全跟不上比特币的节奏?** 以太坊真的颓势已显?难以再复现当年的辉煌吗? Crypto行业的新一轮范式创新还会发生在以太坊生态吗? 本文将带您重回Crypto行业的原点——比特币,去反观以太坊和整个行业,以及探讨Crypto行业再次焕发活力的路径可能在哪里? 以太坊真的颓势已显?难以再复现当年的辉煌吗? Crypto行业的新一轮范式创新还会发生在以太坊生态吗? 本文将带您重回Crypto行业的原点——比特币,去反观以太坊和整个行业,以及探讨Crypto行业再次焕发活力的路径可能在哪里? ##### 一、逃离以太坊惯性 首先,谁都无法全盘否定以太坊! 以太坊有它的价值和开创性意义,智能合约也确实给整个加密行业打开了新局面。至少在以太坊诞生之前,加密行业大多数项目都只是对比特币拙劣的模仿。把比特币代码简单修改几个参数,变成区块更大的比特币、速度更快的比特币、隐私性更好的比特币等等。基本都只是对比特币简单的山寨,山寨币这个概念基本就是概括了以太坊诞生之前的所有Crypto项目。 而以太坊诞生以后,整个Crypto行业又进入了山寨以太坊的浪潮,2015年至今,诞生了不计其数的所谓公链,区块更大的以太坊、速度更快的以太坊、性能更好的以太坊(包括Layer2)等等。 而且每个公链的所谓生态也基本照抄照搬以太坊模式,无非DeFi、GameFi、各类L2、模块化等等。现在散户已经被各类巧立名目、五花八门的叙事概念反复收割的脱敏无感了,于是干脆啥也不信,只玩最简单粗暴的Meme,虽然大家都知道它长久不了,但是至少还可以痛快一博! **没有创新,没有活力,共识涣散、僵尸横行,整个行业弥漫着看不到希望的末日气息!** **Crypto行业还有未来吗?** 但是,当你回头去看看比特币,唯独只有它,依然一骑绝尘、屡破新高,似乎完全不受这一切的影响! 我们不禁要想,是不是整个行业陷入“以太坊惯性”太久了,以至于我们都完全忽略了比特币! **毕竟,以太坊就是灵感于比特币,来源于比特币社区。以太坊就是对比特币的一种解读方式,但是,整个行业把以太坊模式当成了全部。** 如果要找到以太坊的问题所在,以及如果要重新找到新的范式创新机会,那就务必得回到比特币,重新理解比特币,重新在比特币找到创新源泉,就像以太坊诞生之初那样! 让我们一起暂时逃离以太坊惯性,重回比特币去思考! #### 二、机械共识和社会共识 解读比特币的角度有很多种,但是,我们今天讨论的以太坊和比特币都属于公链范畴。谈到公链,共识机制就是绕不开的话题! 所谓公链,就是公有区块链,是谁公有的?是一群参与共识的人公有的,公链必须依靠共识来驱动,没有共识就没有公链。所以,谈公链如果不谈共识那就是空谈! **公链的共识分为机械共识和社会共识。** 公链的本质就是依靠一套机械共识来不断凝聚社会共识的去中心化系统。(说一个题外话,Layer2不是公链,Layer2只需要一个定序器节点就可以运行,Layer2本身没有共识机制。Layer2没有机械共识,只有社会共识,因此,Layer2的价值没有机械共识来支持。目前大部分项目,既没有机械共识,也没有社会共识,这是项目失败的根本原因) 所谓机械共识就是一个人人都可以公平参与的共识机制,比如PoW机制,机械共识的参与方式是算力,算力越强,机械共识就越强;所谓社会共识就是围绕公链的生态、影响力,包括链上应用、用户等等数据,最终体现在币价。 **机械共识的参与者是公链的第一投入者、受益者和建设者。** 公链的启动和运行完全依赖机械共识的参与者,机械共识参与者投入大量成本(算力和能源等)参与公链,因此,只有机械共识的参与者,才有最原始的动力去推动公链生态的发展,因为,他们是第一投入者也是第一受益者。因此,为了帮助公链获取更大的社会共识,机械共识参与者会继续推动公链生态的发展,而公链生态吸引来的应用开发者大都是流动的,他们并不如机械共识参与者更深的绑定在公链利益之上(除非他们自己也变成了机械共识参与者)。 这也解释了,为什么比特币生态的早期推动者基本都来自于矿工群体。而以太坊链上的许多头部应用选择另立门户,比如Uniswap等。 **所以,当一个公链的币价开始疲软,那是社会共识变弱了,而更底层原因是机械共识变弱了,或者说参与机械共识的人离散了。** 那么,我们来从”共识‘角度来对比下比特币和以太坊。 #### 三、回归比特币共识,反观以太坊和行业 **比特币的机械共识是一个动态竞赛模式。以太坊的机械共识是一个静态固收模式!** 比特币的矿工要想获得出块权,每一个节点必须在同一时间段投入同样的算力和能源去竞争,但是最终网络只会选出一个节点出块,而其他所有“陪跑节点”的投入作为一种巨大的冗余成本附着在了比特币的价值之中。 通俗点来讲,比特币网络铸造每一枚比特币的实际投入的成本是远远大于单一出块节点支出的成本,它是以消耗所有“陪跑节点”的成本为代价的一种铸造方式。所以,比特币矿工为了已经投入的巨大冗余成本会不断的参与算力竞赛,直到抢到出块权,这是比特币网络共识不断壮大的原因。 **所以,比特币网络的实际共识成本是远远大于目前比特币总市值的**大概是大出多少倍呢?如果我们以比特币历史平均10000个挖矿节点来算的话,这个理论差距应该是1万倍。但是,目前全网比特币活跃矿池约20个,加上单独Solo的矿工,我们预估总共50个,我们把矿池当作一个总节点,这个成本差距大致有50倍。 这就是比特币的PoW动态算力竞赛模式给比特币带来的共识安全性,所以,比特币的共识安全几乎是无法评估的强度! 而以太坊的PoS机制是一个静态固收模式,实际投入多少ETH可以获得多少ETH收益,基本是一个静态的固定收益,目前基本稳定在5%左右。所以,ETH共识的参与者不需要竞赛,不需要额外支出冗余成本,只需要算账,就可以不需要投入额外成本的情况参与利益分配。这也是以太坊早期宣传的所谓PoS机制不会产生能源消耗的“优点”。但是,这个“优点”也变成了以太坊网络共识的弱点。**因为没有冗余成本的投入,以太坊的共识成本实际变低了,因此,以太坊网络的共识价值实际上也降低了!** 所以,当把比特币的PoW机制和以太坊的PoS机制进行对比时,你就会发现,比特币的网络共识成本几乎是不可估量的,随之不断的算力和能源投入,其共识是无上限的。而以太坊的共识是有上限的,是可计算的,ETH的质押率就是以太坊的共识上限。 因此,在机械共识层面,比特币的机械共识相较于以太坊也更强大,从而进一步影响了社会共识的差异,最终,直接表现在了币价层面。 **不仅如此,如果从物理学(热力学)角度去看比特币的POW机制,我们会发现,POW机制驱动着比特币成为一个更接近生命体的熵减系统,这是比特币网络一直充满生命和活力的物理学原理。** 在热力学角度,宇宙中所有的事物都是走向熵增,也就是从有序走向无序,从秩序走向混乱,最终走向寂灭! 但是,只有一个例外,那就是生命! 生命以负熵为食——薛定谔。 所谓负熵是一种可以帮助内部系统从无序转向有序的外部能量。生命就是通过消化负熵,把无序转换为有序,在局部时空中创造了熵减。 但是,熵减现象只是存在于局部时空,而且,生命每形成一分熵减,就会向外部宇宙排放两分熵增,两者相加,对于宇宙来讲仍然是熵增。 比特币的PoW机制,就是让网络内一群混乱无序的拜占庭节点,通过不断消化算力和能源进行运算求解,最终,运算最快的节点获得出块权,节点间迅速验证并达成共识,最终,一个无序混乱的网络达成了一致性,形成了一种秩序,也就是创造了一个熵减系统,一个生命体! **因此,在比特币这个生命体,矿工从外部输入的算力和能源是“负熵”,可以帮助比特币网络内混乱无序的节点达成共识和一致,从而创造了熵减系统。那么,PoW机制就是比特币这个生命体的消化系统,矿工提供“负熵”,最终,成就了比特币这个生命体!** 这是比特币可以一直壮大生长的物理学原理。 那么,我们来反观以太坊: 以太坊创立之初也是照用PoW机制并持续运行了超过七年,这七年也是以太坊突飞猛进的七年。直到2022年9月,以太坊正式从PoW机制转向PoS机制,一切悄然发生了变化。 切除PoW机制,让以太坊失去了外部算力和能源的输入,也就丧失了持续吸食“负熵”的能力,就像一个切除了肠胃又未能找到替代方案的生命体,虽然,短时间内实现了瘦身,但是,由于缺乏持续的进食能力,逐渐走向衰亡几乎是必然的。 有人说,以太坊之所以价格疲软,那是因为生态缺乏创新,链上应用和用户没有持续新增所导致的。那么,造成这些情况的更深层原因是什么? **就像我们前面说的,机械共识直接影响社会共识。生态、应用、用户、币价这些都是社会共识的表现,社会共识变弱的本质是因为机械共识变弱了。** **以太坊的机械共识为何变弱了?** PoS机制是静态固收模式,缺乏算力和能源竞争,无法形成冗余成本,进而机械共识削弱了;PoS机制缺乏吸食“负熵”的能力,无法通过输入“算力和能源”来抵消系统内部的熵增趋势;PoS的质押机制也直接导致了富者恒富、阶级固化,当阶级固化,形成的就是社区缺乏创新和活力,最终这些能力外溢,便成就了其他竞品。 这一系列表现出来的就是以太坊生态、应用、用户、币价等社会共识指标的疲软!即使可以通过强行拉升币价去拔高社会共识,但是,物理学原理是不可违背的。 **以太坊确实颓势已现,这轮周期步步落后于比特币,就是最真实的结果!而下一轮周期也必将拉开更大的距离!** 以太坊尚且如此,其他模仿以太坊的公链,必然也难逃颓势!Crypto行业走到如今的地步,真可谓是,成也以太坊,败也以太坊!这或许是任何一个行业在发展过程中都会经历的。 **但是,机遇往往也在此刻出现!** Crypto行业更大的机遇肯定不在现有的以太坊模式里,一定需要逃离”以太坊惯性“,重新回归这个行业最早的上下文,回到这个行业最早的原点,从那里寻找答案! #### 四、重回比特币共识,挖掘比特币无尽宝藏 回归比特币再创新,这是一个行业问题,也是一个长久的事业,或许,在短时间内,我们很难突破。但是,当我们开始破除以太坊迷信,开始回归比特币重新再思考时,除了发现‘共识“这些背后细节之外,还有可能发现更多从未注意到的隐藏细节。 这些细节让我们对基于比特币进行再次范式创新充满了希望! 比如,直观上大家会认为,在处理交易方面,以太坊会比比特币更高效。但,实际上并不是。 比特币的UTXO模型在处理交易时,可以实现并发处理交易和独立状态变更,而且不需要一个统一的世界状态树来更新状态。甚至说,比特币压根就没有所谓的账户概念,用户地址上显示的比特币余额,实际上是代表某个用户掌握的私钥所能控制UTXO总面额。 UTXO模型在处理交易时,就像真实的交易环境中,任何一对交易双方都可以拿着不同面额的“UXTO”现金进行频繁交易,交易双方的交易状态完全不会影响第二对交易双方的交易进度,因为,UTXO都是可以独立进行状态变更,不需要一个统一的中央状态树来做变更。 而以太坊采用传统的账户模型,也就是传统的银行账户模型。账户模型在处理交易时,需要依靠一个全局的状态树来给每一笔交易所涉及的地址进行余额的加减计算,因此,每一次交易状态都需要先变更完之后,才能进行下一个交易,否则就会出现双花或者无法交易等问题。因此,账户模型只能做串行处理。 通俗来讲,以太坊的账户模型,需要一个中心的世界状态树来统一处理交易,来统一变更所有账户的状态,虽然,这个世界状态树是去中心机制来驱动的,但是,由于其需要一个中心来统一处理和进行全局状态变更,导致,其很难执行并发交易以及更灵活的交易模式。 我们没发现的比特币细节还有很多。 单就 “并行处理状态变更的能力“ 方面,比特币的UTXO模型是完胜以太坊账户模型的。而且,UTXO的这种并发处理和独立状态变更的能力,还可以拓展到任意需要独立变更状态以及并发处理的事物中去,也就是UTXO可以表达除了比特币交易之外的其他事物状态,比如,预测市场的状态变更、AI安全模型的状态变更等等。 而且由于比特币的并发处理状态变更的能力受到全球最大机械共识——比特币共识的保护,这让比特币网络更加独一无二和不可替代。共享比特币共识安全+UTXO并发状态变更,这两项能力加在一起就可以迸发无限能量。这是很多人之前没有发现的细节。当然,我们很高兴已经看到比特币生态的创业者已经往这个方向挺进,比如,基于客户端验证和UTXO模型的BitVM方案;以及前段时间宣布放弃比特币Layer2赛道,全面转向“共享比特币共识安全+UTXO并发状态变更“的BEVM团队等。 当我们转换思路就会发现,比特币这个无尽宝藏,其开发和应用进度几乎不足1%。 #### 总结: 当我们开始脱离以太坊惯性来看整个行业,我们可以直面一些之前不敢直面的问题,当我们重新回到比特币去思考,又可以从比特币汲取无限的灵感和创新方向。以太坊的诞生不过是对比特币的一种抽象思考和解读,而后来的创业者放弃了思考,全面复制以太坊模式,这是整个行业逐步缺乏持续创新和活力的背后原因。 当然,我们看到了一些团队开始回归比特币,开始重新思考,比如,共享比特币共识安全+UTXO并发状态变更就是一个极具潜力的创业方向。 **真正的范式创新并不是简单的模仿,而是要抽象背后的原理。瓦特创造的蒸汽机并没有直接引发工业革命,而是有人抽象总结了蒸汽机背后的科学原理(热力学定律),从而引发了科学的范式革命。** 如果,中本聪是瓦特,比特币是蒸汽机,那么,Crypto行业的这16年,大部分人都是在模仿比特币制作大量的不同功能、不同形式的“蒸汽机”,却鲜有人去思考和抽象比特币本身所蕴含的科学原理,以至于这个行业迟迟没有引发真正的比特币范式革命。 当然,我们已经看到有团队在往这方面思考,这是行业的曙光,我们需要更多的人加入,一起推动比特币范式革命的到来! **本文灵感主要来源于比特币学习交流暑社区“中本聪大学”** TG链接:https://t.me/satoshiedu **本人长期在中本聪大学和诸多比特币OG及爱好者深度交流学习比特币,一起探讨Crypto行业发展机遇。** @ c0e4bd0b:1c5734af
2024-11-10 12:15:08# Bitcoin Calendar Definition Layer: Applications Status: Draft Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows. ``` nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375 ``` The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h: ``` year = h / 52500 month = (h % 52500) / 12 ``` Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder: ``` nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something ``` A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin. This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant. **Cross-referencing with other calendar systems:** Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none. # Bitcoin Calendar Synchronization Layer: Consensus Status: Draft The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year. To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period. The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows: |Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|  As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption. Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that. If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose. **Fork considerations by the author:** A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar. The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require. More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes. **Proposed activation method:** Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster. **Optional second-phase activation:** For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern. *Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).*
@ c0e4bd0b:1c5734af
2024-11-10 12:15:08# Bitcoin Calendar Definition Layer: Applications Status: Draft Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows. ``` nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375 ``` The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h: ``` year = h / 52500 month = (h % 52500) / 12 ``` Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder: ``` nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something ``` A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin. This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant. **Cross-referencing with other calendar systems:** Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none. # Bitcoin Calendar Synchronization Layer: Consensus Status: Draft The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year. To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period. The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows: |Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|  As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption. Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that. If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose. **Fork considerations by the author:** A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar. The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require. More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes. **Proposed activation method:** Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster. **Optional second-phase activation:** For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern. *Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).* @ c0e4bd0b:1c5734af
2024-11-10 12:13:26# Bitcoin Calendar Definition Layer: Applications Status: Draft Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows. ``` nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375 ``` The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h: ``` year = h / 52500 month = (h % 52500) / 12 ``` Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder: ``` nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something ``` A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin. This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant. **Cross-referencing with other calendar systems:** Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none. # Bitcoin Calendar Synchronization Layer: Consensus Status: Draft The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year. To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period. The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows: |Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|  As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption. Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that. If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose. **Fork considerations by the author:** A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar. The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require. More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes. **Proposed activation method:** Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster. **Optional second-phase activation:** For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern. *Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).*
@ c0e4bd0b:1c5734af
2024-11-10 12:13:26# Bitcoin Calendar Definition Layer: Applications Status: Draft Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows. ``` nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375 ``` The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h: ``` year = h / 52500 month = (h % 52500) / 12 ``` Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder: ``` nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something ``` A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin. This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant. **Cross-referencing with other calendar systems:** Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none. # Bitcoin Calendar Synchronization Layer: Consensus Status: Draft The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year. To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period. The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows: |Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|  As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption. Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that. If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose. **Fork considerations by the author:** A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar. The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require. More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes. **Proposed activation method:** Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster. **Optional second-phase activation:** For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern. *Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).* @ c0e4bd0b:1c5734af
2024-11-10 12:05:10# Bitcoin Calendar Definition Layer: Applications Status: Draft Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows. ``` nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375 ``` The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h: ``` year = h / 52500 month = (h % 52500) / 12 ``` Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder: ``` nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something ``` A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin. This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant. **Cross-referencing with other calendar systems:** Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none. # Bitcoin Calendar Synchronization Layer: Consensus Status: Draft The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year. To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period. The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows: |Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|  As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption. Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that. If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose. **Fork considerations by the author:** A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar. The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require. More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes. **Proposed activation method:** Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster. **Optional second-phase activation:** For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern. *Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).*
@ c0e4bd0b:1c5734af
2024-11-10 12:05:10# Bitcoin Calendar Definition Layer: Applications Status: Draft Bitcoin defines the halving cycle as 210,000 blocks, as defined in the file `kernel/chainparams.cpp`. This number was apparently chosen as an aesthetically pleasing number which equates almost exactly to 4 years, according to the ten-minute block schedule. This BIP proposes using this parameter of Bitcoin as the basis for reckoning calendar time, defined as follows. ``` nBlocksPerYear = 210000 / 4 // calculates to 52,500 nBlocksPerMonth = nBlocksPerYear / 12 // calculates to 4375 ``` The calculations above produce integer results, making calendrical calculations based on block height extremely convenient. The zero-based year and month are calculated as follows, using integer division (/) and mudulo (%) based on block height h: ``` year = h / 52500 month = (h % 52500) / 12 ``` Furthermore, we assume a bitcoin day length of 144 blocks. This is consistent with the target of 10-minutes per block and the 2016 blocks every two weeks for the difficulty adjustment period. This results in months of 30 days, with a small remainder: ``` nBlocksPerDay = 144 daysPerMonth = nBlocksPerMonth / nBlocksPerDay // calculates to 30.something ``` A human-friendly date can thus be displayed based upon block height, with familiar calendrical characteristics of 30 full days per month (with a partial day 31) and 12 months per year. As of this writing, the current bitcoin date is 7/24/17, 24-07-0017, or the twenty fourth day of the seventh month of the seventeenth year of Bitcoin. This definition forms the basis for a culturally independent and socially universal calendar system which is easy to calculate, durable, and financially relevant. **Cross-referencing with other calendar systems:** Since this date will not synchronize exactly to extant calendar systems, a notation needs to be used in cases where ambiguity would result. Taking the solar day as the example, references that cross over between the solar day and the bitcoin date need to have a qualifier resolving the phase discrepancy (as is done when referring to dates in ancient calendar systems that do not align with the turn of the date at midnight). For example, the Bitcoin date of 7/24/17 would be written as November 9/10, 2024, making it clear that it touches both of those solar days. However, this format should only be used for dates in which the two calendar systems are more out of sync than in sync. For dates that are more in sync than out of sync, no overlap day should be given, because it would add ambiguity where there otherwise was none. # Bitcoin Calendar Synchronization Layer: Consensus Status: Draft The Bitcoin calendar (referring to the prior definition) would be more economically relevant to earthlings if the Bitcoin year actually stayed synchronized with the growing seasons of the tropical year. Currently, the Bitcoin year begins in the springtime of the northern hemisphere, but it is offset one year and there is currently nothing to keep the bitcoin year from drifting further out of synchronization with the tropical year. To keep the Bitcoin year in sync with the seasons, the bi-weekly proof-of-work difficulty adjustment could be tailored to aim toward better alignment during every difficulty adjustment. Normally, the difficulty is adjusted upward or downward a maximum factor of 4, as defined in the file `pow.cpp`. The determination of the value within that range is made solely on the basis of the rate of block discovery during the prior 2016-block (two-week) period. The existing difficulty adjustment scheme has resulted in the Bitcoin calendar generally sliding earlier every year, presumably due to the fact that the global hash rate is generally increasing rather than decreasing. The historical dates for the year beginnings and the corresponding duration of the Bitcoin year are as follows: |Year|Block|Date|Days| |-:|-:|--|-:| |0|0|01/03/09|| |1|52500|04/22/10|474| |2|105000|01/28/11|281| |3|157500|12/14/11|320| |4|210000|11/28/12|350| |5|262500|10/09/13|315| |6|315000|08/10/14|305| |7|367500|07/29/15|353| |8|420000|07/09/16|346| |9|472500|06/23/17|349| |10|525000|05/29/18|340| |11|577500|05/23/19|359| |12|630000|05/11/20|354| |13|682500|05/07/21|361| |14|735000|05/05/22|363| |15|787500|04/29/23|359| |16|840000|04/19/24|356|  As can be seen, the number of days in the actual Bitcoin year are consistently fewer than the number of days in the tropical year (365.2425). Assuming the hash rate will generally continue to increase, this trend should continue, which allows us to make a convenient simplifying assumption. Conceptually this proposal seeks to add an additional, limited offset to the work requirement based on whether the Bitcoin calendar is ahead of schedule or behind schedule, in comparison to the tropical year. We can assume based on the trends, however, that we only need to "slow down" the block rate slightly to keep it in sync with the seasons. Therefore, this proposal aims to do only that. If the Bitcoin block height is a certain amount ahead of the calendar synchronization goal (per the trend), the difficulty would be increased one notch more than required by the normal calculation, if not already at the limit of adjustment for that period. This would make it impossible for the proposed change to overpower the existing calculation, but would still provide a gentle enough push when needed to keep the calendar in sync, thus accomplishing the purpose. **Fork considerations by the author:** A consensus change to the proof of work calculation would normally result in a hard fork. However, in the case that we only potentially increase the difficulty and never decrease it relative to non-upgraded nodes in the network, this means that during the transition, only upgraded nodes would be at risk of rejecting blocks for not meeting the more stringent difficulty level necessary to synchronize the calendar. The new nodes would therefore need to be programmed to yield to the non-upgraded difficulty criteria until most of the network has upgraded, at which point activation would occur (as explained below) and miners would be obliged to meet the tougher requirements demanded by all upgraded nodes. Nodes that still had not upgraded by that time would remain unaffected, since the post-activation blocks would only have more proof of work, and not less, than non-upgraded nodes require. More importantly, an overwhelming majority of the hash rate should be fully upgraded to avoid a situation where non-upgraded, non-mining nodes are forked by a longer chain created by non-upgraded miners. A sufficient portion of the hash rate following the upgrade path would eliminate this possiblity, even for non-mining nodes that don't upgrade, because the longer chain will come from the greater hash power and there would be no financial incentive for miners to switch back to catering to a minority of non-upgraded nodes. **Proposed activation method:** Upgraded nodes would delay the relaying of blocks that do not meet the more stringent requirements. This would begin as a confirmation-time penalty to upgraded nodes, but as the upgrade expands to more nodes, the effect would shift to incentivizing miners to produce blocks that conform to the upgrade in order to build on the longest chain faster. **Optional second-phase activation:** For the longer term, it might be advisable to also implement the corresponding opposite influence on the proof of work adjustment for the case where the simplifying assumption taken above does not hold. In other words, if hash rate were to take on a trend of decreasing over a significant period of time at some point in the future leading to a Bitcoin year length greater than 365 days, the calendar drift would ideally be pushed in the other direction by a relaxing influence on the proof of work requirement instead of a tightening influence. Since this would definitely result in a hard fork relative to un-upgraded nodes, this feature, if implemented, would need to be kept inactive for much longer, and only activated if/when the number of non-upgraded nodes becomes so insignificant that a hard fork is no longer a concern. *Join the conversation on [stacker.news](https://stacker.news/items/761346/r/rleed).* @ f462d21e:1390b6b1
2024-11-10 11:44:59eyJfaWQiOiIxMGRmODZiMS02NTdjLTQwNjUtYjVjOC1kNmY2YmJlNjRhN2IiLCJwdWJsaWNLZXkiOiJmNDYyZDIxZTEwMTYzZWIwYTQwM2FlYzZiOTNhYzU3ZWMyZjFiOTQ1NTQ3M2U5OTMwNGY1NzFhNTEzOTBiNmIxIiwidXNlcm5hbWUiOiJqb2UiLCJhZFR5cGUiOiJPTkxJTkVfU0VMTCIsImNvdW50cnkiOiJVbml0ZWQgS2luZ2RvbSIsImNvdW50cnlDb2RlIjoiR0IiLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6IlZFTk1PIiwicHJpY2VJbnB1dFR5cGUiOiJNQVJLRVQiLCJtYXJnaW4iOjMsImZpeGVkUHJpY2UiOjAsIm1pbkFtb3VudCI6MCwibWF4QW1vdW50IjowLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoiYmVzdCByYXRlcyByZWFsbHkiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsImhpZGRlbiI6ZmFsc2UsImJhbm5lZCI6ZmFsc2UsInZlcmlmaWVkIjp0cnVlLCJhZGRlZCI6IjIwMjQtMTEtMDFUMDc6MTk6MjEuMDk5WiIsIm1hcmtldFByaWNlIjoxNjUuMzF9
@ f462d21e:1390b6b1
2024-11-10 11:44:59eyJfaWQiOiIxMGRmODZiMS02NTdjLTQwNjUtYjVjOC1kNmY2YmJlNjRhN2IiLCJwdWJsaWNLZXkiOiJmNDYyZDIxZTEwMTYzZWIwYTQwM2FlYzZiOTNhYzU3ZWMyZjFiOTQ1NTQ3M2U5OTMwNGY1NzFhNTEzOTBiNmIxIiwidXNlcm5hbWUiOiJqb2UiLCJhZFR5cGUiOiJPTkxJTkVfU0VMTCIsImNvdW50cnkiOiJVbml0ZWQgS2luZ2RvbSIsImNvdW50cnlDb2RlIjoiR0IiLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6IlZFTk1PIiwicHJpY2VJbnB1dFR5cGUiOiJNQVJLRVQiLCJtYXJnaW4iOjMsImZpeGVkUHJpY2UiOjAsIm1pbkFtb3VudCI6MCwibWF4QW1vdW50IjowLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoiYmVzdCByYXRlcyByZWFsbHkiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsImhpZGRlbiI6ZmFsc2UsImJhbm5lZCI6ZmFsc2UsInZlcmlmaWVkIjp0cnVlLCJhZGRlZCI6IjIwMjQtMTEtMDFUMDc6MTk6MjEuMDk5WiIsIm1hcmtldFByaWNlIjoxNjUuMzF9 @ 07907690:d4e015f6
2024-11-10 09:50:14Bitcoin diciptakan oleh Satoshi Nakamoto, (hampir pasti) sebuah nama samaran, yang hingga hari ini belum ada seorang pun yang dapat secara meyakinkan menghubungkannya dengan orang atau sekelompok orang yang sebenarnya. Nakamoto menghilang dari internet pada tahun 2011, meninggalkan sedikit petunjuk tentang siapa "mereka". Selama bertahun-tahun, banyak orang secara terbuka mengaku sebagai Satoshi, semuanya gagal mendukung pernyataan tersebut dengan fakta yang tidak dapat disangkal. Dalam forum awal bitcointalk, Satoshi mengatakan bahwa mereka mulai mengerjakan Bitcoin pada tahun 2007, dua tahun sebelum blok pertama ditambang. Blok Genesis, atau blok pertama dalam blockchain Bitcoin, ditambang pada tanggal 3 Januari 2009. Nakamoto adalah penambang blok Genesis, menerima 50 bitcoin pertama yang pernah diedarkan. Namun, hadiah dari blok pertama ini tidak dapat digunakan karena keunikan dalam cara blok Genesis diekspresikan dalam kode. [BitMEX Research](https://blog.bitmex.com/satoshis-1-million-bitcoin/) telah menerbitkan analisis pada hari-hari awal penambangan Bitcoin dan menyimpulkan bahwa “seseorang” menambang 700,000 koin. Meskipun banyak yang berasumsi ini adalah Satoshi, secara resmi hal ini masih belum terbukti. Kita hanya bisa membayangkan ketenaran yang akan diterima Satoshi Nakamoto jika identitas mereka terungkap, belum lagi kekayaan besar yang ingin mereka kumpulkan (meskipun Satoshi tampaknya tidak menghabiskan satu pun koin yang seharusnya mereka tambang). Seiring berjalannya waktu, ada banyak contoh orang yang mengaku sebagai Satoshi, dan ada pula yang diyakini sebagai Satoshi. ## Klaim Palsu Salah satu kasus paling terkenal tentang seseorang yang mengaku sebagai Satoshi adalah yang dilakukan oleh [Craig S. Wright](https://bitcoinmagazine.com/articles/op-ed-how-many-wrongs-make-wright), seorang akademisi Australia. Wright, pada awal tahun 2015, telah mencoba berkali-kali untuk memberikan demonstrasi publik dengan bukti yang tidak dapat disangkal bahwa dia adalah penemu Bitcoin, namun dia belum berhasil hingga saat ini. Faktanya, “bukti”-nya terbukti palsu. Dorian Nakamoto, seorang pria di California, pernah secara terbuka diberi gelar sebagai pencipta Bitcoin oleh seorang jurnalis surat kabar yang melihat beberapa kesamaan antara kedua Nakamoto, yang paling jelas adalah nama belakang mereka. Namun, dengan sangat cepat, klaim ini [ditolak oleh Dorian dan juga dibantah](https://bitcoinmagazine.com/articles/how-the-hunt-for-satoshi-turned-dorian-nakamoto-s-life-upside-down-the-inside-story-1443721034). Kelompok orang lain yang menarik perhatian seputar identitas Satoshi yang tidak diketahui adalah kriptografer dan ilmuwan komputer. Hal Finney, seorang kriptografer terkenal yang merupakan orang pertama yang menerima bitcoin dari Satoshi Nakamoto, adalah salah satu tersangka paling terkenal karena keterlibatan awalnya dalam bidang tersebut. Kurang dari setahun setelah Bitcoin diciptakan, Satoshi dan Hal Finney bertukar beberapa postingan di forum diskusi Bitcoin, membahas hal-hal seperti teknologi dan implikasinya di masa depan. [Finney meninggal karena ALS](https://bitcoinmagazine.com/articles/hal-finney-salute-1409690363) pada tahun 2014, menyebabkan beberapa orang berspekulasi mengenai sejauh mana keterlibatannya dengan mata uang terdesentralisasi pertama di dunia. Nick Szabo adalah kriptografer terkenal lainnya yang menciptakan Bit Gold, mata uang digital yang ditemukan beberapa tahun sebelum Bitcoin. Fakta bahwa dia tampaknya tidak terlibat langsung dengan penciptaan Bitcoin, meskipun proyeknya sangat mirip dengan itu, telah membuat beberapa orang berspekulasi bahwa dia mungkin juga pencipta Bitcoin. ## Mengapa Satoshi Harus Anonim? Satoshi Nakamoto, pencipta mata uang terdesentralisasi pertama di dunia, harus tetap anonim karena sifat penciptaannya. Setelah membuat protokol tanpa titik utama kegagalan, Nakamoto mungkin menyadari bahwa mempertahankan anonimitasnya dapat menghilangkan titik utama kegagalan terakhir yang mungkin dimiliki Bitcoin: orang yang menciptakannya. Menghapus identitas tunggal yang dapat dikaitkan dengan kemunculan Bitcoin berarti menghilangkan segala wajah yang dapat mempengaruhi politik, aturan, atau pengambilan keputusan komunitas Bitcoin. Siapa pun Satoshi, tidak dapat disangkal bahwa mereka adalah seorang jenius di zaman kita. Protokol Bitcoin memberikan insentif ekonomi di semua tempat yang tepat sehingga menghasilkan solusi luar biasa terhadap Masalah Jenderal Bizantium. Satoshi Nakamoto menerapkan konsep-konsep dari kriptografi, matematika, teori permainan, dan ekonomi untuk menciptakan aset digital langka yang dirancang dengan indah — dan pertama di dunia — yang disebut Bitcoin. Sumber artikel: [bitcoinmagazine.com](https://bitcoinmagazine.com/guides/who-created-bitcoin) Diterjemahkan oleh: Abengkris
@ 07907690:d4e015f6
2024-11-10 09:50:14Bitcoin diciptakan oleh Satoshi Nakamoto, (hampir pasti) sebuah nama samaran, yang hingga hari ini belum ada seorang pun yang dapat secara meyakinkan menghubungkannya dengan orang atau sekelompok orang yang sebenarnya. Nakamoto menghilang dari internet pada tahun 2011, meninggalkan sedikit petunjuk tentang siapa "mereka". Selama bertahun-tahun, banyak orang secara terbuka mengaku sebagai Satoshi, semuanya gagal mendukung pernyataan tersebut dengan fakta yang tidak dapat disangkal. Dalam forum awal bitcointalk, Satoshi mengatakan bahwa mereka mulai mengerjakan Bitcoin pada tahun 2007, dua tahun sebelum blok pertama ditambang. Blok Genesis, atau blok pertama dalam blockchain Bitcoin, ditambang pada tanggal 3 Januari 2009. Nakamoto adalah penambang blok Genesis, menerima 50 bitcoin pertama yang pernah diedarkan. Namun, hadiah dari blok pertama ini tidak dapat digunakan karena keunikan dalam cara blok Genesis diekspresikan dalam kode. [BitMEX Research](https://blog.bitmex.com/satoshis-1-million-bitcoin/) telah menerbitkan analisis pada hari-hari awal penambangan Bitcoin dan menyimpulkan bahwa “seseorang” menambang 700,000 koin. Meskipun banyak yang berasumsi ini adalah Satoshi, secara resmi hal ini masih belum terbukti. Kita hanya bisa membayangkan ketenaran yang akan diterima Satoshi Nakamoto jika identitas mereka terungkap, belum lagi kekayaan besar yang ingin mereka kumpulkan (meskipun Satoshi tampaknya tidak menghabiskan satu pun koin yang seharusnya mereka tambang). Seiring berjalannya waktu, ada banyak contoh orang yang mengaku sebagai Satoshi, dan ada pula yang diyakini sebagai Satoshi. ## Klaim Palsu Salah satu kasus paling terkenal tentang seseorang yang mengaku sebagai Satoshi adalah yang dilakukan oleh [Craig S. Wright](https://bitcoinmagazine.com/articles/op-ed-how-many-wrongs-make-wright), seorang akademisi Australia. Wright, pada awal tahun 2015, telah mencoba berkali-kali untuk memberikan demonstrasi publik dengan bukti yang tidak dapat disangkal bahwa dia adalah penemu Bitcoin, namun dia belum berhasil hingga saat ini. Faktanya, “bukti”-nya terbukti palsu. Dorian Nakamoto, seorang pria di California, pernah secara terbuka diberi gelar sebagai pencipta Bitcoin oleh seorang jurnalis surat kabar yang melihat beberapa kesamaan antara kedua Nakamoto, yang paling jelas adalah nama belakang mereka. Namun, dengan sangat cepat, klaim ini [ditolak oleh Dorian dan juga dibantah](https://bitcoinmagazine.com/articles/how-the-hunt-for-satoshi-turned-dorian-nakamoto-s-life-upside-down-the-inside-story-1443721034). Kelompok orang lain yang menarik perhatian seputar identitas Satoshi yang tidak diketahui adalah kriptografer dan ilmuwan komputer. Hal Finney, seorang kriptografer terkenal yang merupakan orang pertama yang menerima bitcoin dari Satoshi Nakamoto, adalah salah satu tersangka paling terkenal karena keterlibatan awalnya dalam bidang tersebut. Kurang dari setahun setelah Bitcoin diciptakan, Satoshi dan Hal Finney bertukar beberapa postingan di forum diskusi Bitcoin, membahas hal-hal seperti teknologi dan implikasinya di masa depan. [Finney meninggal karena ALS](https://bitcoinmagazine.com/articles/hal-finney-salute-1409690363) pada tahun 2014, menyebabkan beberapa orang berspekulasi mengenai sejauh mana keterlibatannya dengan mata uang terdesentralisasi pertama di dunia. Nick Szabo adalah kriptografer terkenal lainnya yang menciptakan Bit Gold, mata uang digital yang ditemukan beberapa tahun sebelum Bitcoin. Fakta bahwa dia tampaknya tidak terlibat langsung dengan penciptaan Bitcoin, meskipun proyeknya sangat mirip dengan itu, telah membuat beberapa orang berspekulasi bahwa dia mungkin juga pencipta Bitcoin. ## Mengapa Satoshi Harus Anonim? Satoshi Nakamoto, pencipta mata uang terdesentralisasi pertama di dunia, harus tetap anonim karena sifat penciptaannya. Setelah membuat protokol tanpa titik utama kegagalan, Nakamoto mungkin menyadari bahwa mempertahankan anonimitasnya dapat menghilangkan titik utama kegagalan terakhir yang mungkin dimiliki Bitcoin: orang yang menciptakannya. Menghapus identitas tunggal yang dapat dikaitkan dengan kemunculan Bitcoin berarti menghilangkan segala wajah yang dapat mempengaruhi politik, aturan, atau pengambilan keputusan komunitas Bitcoin. Siapa pun Satoshi, tidak dapat disangkal bahwa mereka adalah seorang jenius di zaman kita. Protokol Bitcoin memberikan insentif ekonomi di semua tempat yang tepat sehingga menghasilkan solusi luar biasa terhadap Masalah Jenderal Bizantium. Satoshi Nakamoto menerapkan konsep-konsep dari kriptografi, matematika, teori permainan, dan ekonomi untuk menciptakan aset digital langka yang dirancang dengan indah — dan pertama di dunia — yang disebut Bitcoin. Sumber artikel: [bitcoinmagazine.com](https://bitcoinmagazine.com/guides/who-created-bitcoin) Diterjemahkan oleh: Abengkris @ c11cf5f8:4928464d
2024-11-10 07:58:46Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/751696/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/761231
@ c11cf5f8:4928464d
2024-11-10 07:58:46Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/751696/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/761231 @ e1d968f7:5d90f764
2024-11-10 06:01:24If there's one thing I know for sure, it's this: life is *too short* not to make the most of every moment. That’s why I don’t just walk through life—I *own* it. My name’s Rebecca Knight, and I’m the kind of woman who leaves a lasting impression, whether it’s with a wink across a crowded room or a conversation that lingers long after it’s over. I’m not your average woman, and I’m certainly not afraid to show it. I’ve got that magnetic charm that draws people in, a little playful sparkle in my eye that says, “Come closer, if you dare.” I love making people feel seen, heard, and most of all—*alive.* There’s something about making someone smile or laugh that gives me the rush of a lifetime. Maybe it’s the thrill of connection or the way people react when they realize I’m exactly the kind of woman they didn’t know they needed in their lives. When I meet someone, I don’t just show up—I make it memorable. Whether it’s in the way I laugh at a joke, the intensity of a conversation, or the way I give you my undivided attention, there’s no denying it: I know how to keep you on your toes. And when it comes to my work, it’s no different. I know exactly how to create a space where we both feel at ease, where the chemistry can spark and the tension can build. It’s all about the connection. The energy. The way we feed off each other. But let’s be real: I don’t just give for the sake of giving. I believe in *mutual enjoyment.* I’m all about making sure both of us are having the time of our lives. Whether we’re sharing an intimate laugh, a heated conversation, or simply enjoying each other’s company in a way that feels… exciting, it’s always about balancing that electric pull with respect and mutual understanding. Being bold is fun, but being *respectful* is key. I don’t believe in anything forced or out of alignment with what feels good. If I want something, you’ll know it, and if you want something, I’m always happy to listen. But here’s the thing: I’m not interested in anything halfway. I play for keeps, and I expect to have my energy matched in the best possible way. So, if we ever find ourselves in the same space, be prepared for a little bit of magic. I’m the kind of woman who brings excitement, fun, and a healthy dose of mischief into every room I enter. I know how to turn the ordinary into extraordinary, and how to leave a lasting impression without breaking a sweat. After all, life’s a game, and I’m *very* good at playing it. If you ever find yourself wondering if you’re the next lucky person I’ll take on that little adventure… let’s just say I’m sure you’ll know when it happens.
@ e1d968f7:5d90f764
2024-11-10 06:01:24If there's one thing I know for sure, it's this: life is *too short* not to make the most of every moment. That’s why I don’t just walk through life—I *own* it. My name’s Rebecca Knight, and I’m the kind of woman who leaves a lasting impression, whether it’s with a wink across a crowded room or a conversation that lingers long after it’s over. I’m not your average woman, and I’m certainly not afraid to show it. I’ve got that magnetic charm that draws people in, a little playful sparkle in my eye that says, “Come closer, if you dare.” I love making people feel seen, heard, and most of all—*alive.* There’s something about making someone smile or laugh that gives me the rush of a lifetime. Maybe it’s the thrill of connection or the way people react when they realize I’m exactly the kind of woman they didn’t know they needed in their lives. When I meet someone, I don’t just show up—I make it memorable. Whether it’s in the way I laugh at a joke, the intensity of a conversation, or the way I give you my undivided attention, there’s no denying it: I know how to keep you on your toes. And when it comes to my work, it’s no different. I know exactly how to create a space where we both feel at ease, where the chemistry can spark and the tension can build. It’s all about the connection. The energy. The way we feed off each other. But let’s be real: I don’t just give for the sake of giving. I believe in *mutual enjoyment.* I’m all about making sure both of us are having the time of our lives. Whether we’re sharing an intimate laugh, a heated conversation, or simply enjoying each other’s company in a way that feels… exciting, it’s always about balancing that electric pull with respect and mutual understanding. Being bold is fun, but being *respectful* is key. I don’t believe in anything forced or out of alignment with what feels good. If I want something, you’ll know it, and if you want something, I’m always happy to listen. But here’s the thing: I’m not interested in anything halfway. I play for keeps, and I expect to have my energy matched in the best possible way. So, if we ever find ourselves in the same space, be prepared for a little bit of magic. I’m the kind of woman who brings excitement, fun, and a healthy dose of mischief into every room I enter. I know how to turn the ordinary into extraordinary, and how to leave a lasting impression without breaking a sweat. After all, life’s a game, and I’m *very* good at playing it. If you ever find yourself wondering if you’re the next lucky person I’ll take on that little adventure… let’s just say I’m sure you’ll know when it happens. @ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard. In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW. I took some screenshots to give you an idea of how things work. The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).  Clicking login allows signing in with a browser extension.  The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.  Existing blog posts (i.e. long form notes) are synced.  Same for product listings. There’s a nice interface to create new ones and preview them before publishing.   That’s all for now. As you can see, super slick stuff! Bullish on Cypher. So much so I had to support the project and buy a subdomain. 😎 https://bullish.cypher.space originally posted at https://stacker.news/items/760592
@ a10260a2:caa23e3e
2024-11-10 04:35:34nostr:npub1nkmta4dmsa7pj25762qxa6yqxvrhzn7ug0gz5frp9g7p3jdscnhsu049fn added support for [classified listings (NIP-99)](https://github.com/sovbiz/Cypher-Nostr-Edition/commit/cd3bf585c77a85421de031db1d8ebd3911ba670d) about a month ago and recently announced this update that allows for creating/editing listings and blog posts via the dashboard. In other words, listings created on the website are also able to be viewed and edited on other Nostr apps like Amethyst and Shopstr. Interoperability FTW. I took some screenshots to give you an idea of how things work. The [home page](https://cypher.space/) is clean with the ability to search for profiles by name, npub, or Nostr address (NIP-05).  Clicking login allows signing in with a browser extension.  The dashboard gives an overview of the amount of notes posted (both short and long form) and products listed.  Existing blog posts (i.e. long form notes) are synced.  Same for product listings. There’s a nice interface to create new ones and preview them before publishing.   That’s all for now. As you can see, super slick stuff! Bullish on Cypher. So much so I had to support the project and buy a subdomain. 😎 https://bullish.cypher.space originally posted at https://stacker.news/items/760592 @ 07e1bb93:f9523a3c
2024-11-10 03:46:57In the ever-shifting landscape of American politics, few partnerships have proven as effective in advancing the conservative agenda as the relationship between President Donald Trump and Senator JD Vance. The alignment of their values, priorities, and vision for America has been a game-changer, not just for the Republican Party, but for the nation as a whole. Here’s why Trump needed JD Vance — and why this partnership is one for the history books. ### 1. **A Shared Vision for America’s Working Class** Both President Trump and JD Vance have made it clear that their top priority is restoring the strength and prosperity of America's working class. Trump’s 2016 campaign reshaped the Republican Party into one that stands unapologetically with blue-collar Americans. Vance, in his bestselling book *Hillbilly Elegy*, captured the struggles of America’s heartland, painting a picture of a forgotten class that Trump understood and aimed to champion. Vance’s personal experience of growing up in a working-class family in Appalachia allows him to connect with the very people Trump promised to fight for. When Trump needed someone who could speak authentically to the struggles of rural America — a place often left behind by both parties — JD Vance was the perfect ally. His commitment to restoring dignity to working families and fighting against globalist policies that shipped jobs overseas aligns perfectly with Trump’s America First agenda. ### 2. **Fighting the Swamp Together** One of Trump’s most significant promises was to drain the swamp — to rid Washington of the establishment elites who have sold out America’s interests in favor of their own. JD Vance’s political career has been a direct response to this very problem. As someone who understands the dangers of big-money politics and the media’s influence, Vance has shown that he’s not afraid to take on the establishment — whether it’s Big Tech, Big Pharma, or the bureaucratic deep state. Together, Trump and Vance make an unstoppable force in the fight against Washington corruption. Vance’s no-nonsense approach to tackling the elites, combined with Trump’s bold, take-no-prisoners attitude, sends a clear message to D.C. — the days of business as usual are over. ### 3. **A Bold, Unapologetic Conservative Voice** Trump revolutionized the Republican Party by unapologetically embracing a bold, conservative agenda — one that emphasizes securing the border, standing strong against China, and advocating for American sovereignty. JD Vance has proven to be a fierce defender of these principles. His strong stance against illegal immigration, as well as his commitment to bringing American jobs back home from China, make him an invaluable ally in Trump’s fight to put America first. In the face of global challenges and domestic strife, Trump needed someone like JD Vance who would stand firm in the face of leftist pressure, the mainstream media, and cancel culture. Vance’s resilience and courage in sticking to conservative principles make him an indispensable ally in Trump’s quest to reclaim American greatness. ### 4. **Rural America’s Voice in Washington** Trump’s deep connection with rural America was one of the key factors in his 2016 victory. In JD Vance, Trump found a kindred spirit who understands the heartbeat of Middle America. Vance, who has firsthand knowledge of the hardships faced by families in small-town America, brings a fresh perspective to the Senate that Trump can rely on. From advocating for policies that support American agriculture to pushing back against the cultural elites who are trying to rewrite America’s values, Vance is a powerful voice for the people who have long been overlooked by Washington politicians. With Vance in the Senate, Trump gained a strong advocate for rural communities, ensuring that their concerns are heard at the highest levels of government. ### 5. **Fighting the Culture Wars** In addition to economic policies, Trump and Vance share a common commitment to fighting the culture wars. Vance, with his deep understanding of the impact of media, education, and corporate culture on America’s identity, has been an outspoken critic of the left’s radical agenda. He has voiced concerns about the erosion of traditional American values and the dangers of left-wing identity politics. Trump needed someone who could not only challenge the left’s policies but also defend the cultural heritage of America. Vance’s intellectual and cultural insights make him an essential ally in this battle. Together, they form a powerful counterweight to the woke left’s attempt to undermine the very fabric of American society. ### 6. **A Partnership for Victory** At its core, the Trump-Vance alliance is about winning — for the American people. It’s about rebuilding a nation that works for its citizens, standing up against forces that seek to weaken it, and ensuring that America remains a beacon of freedom, opportunity, and strength on the global stage. Trump needed JD Vance because Vance’s voice is a reflection of the heart of America. Together, they represent the future of the Republican Party — a future that is grounded in traditional values, fierce independence, and a relentless pursuit of the American Dream. ### Conclusion In JD Vance, President Trump found an ally who shares his vision, his commitment to the working class, and his passion for restoring American greatness. As this partnership continues to grow, there’s no doubt that Trump and Vance will be a dynamic duo, leading the charge against the forces of globalization, corruption, and cultural decay. For all the talk of division in American politics, the Trump-Vance partnership reminds us that unity is possible when leaders stand firm in their beliefs, fight for what’s right, and work together for the future of our nation. It’s a partnership built on trust, shared values, and an unyielding love for America — and that’s exactly why Trump needed JD Vance.
@ 07e1bb93:f9523a3c
2024-11-10 03:46:57In the ever-shifting landscape of American politics, few partnerships have proven as effective in advancing the conservative agenda as the relationship between President Donald Trump and Senator JD Vance. The alignment of their values, priorities, and vision for America has been a game-changer, not just for the Republican Party, but for the nation as a whole. Here’s why Trump needed JD Vance — and why this partnership is one for the history books. ### 1. **A Shared Vision for America’s Working Class** Both President Trump and JD Vance have made it clear that their top priority is restoring the strength and prosperity of America's working class. Trump’s 2016 campaign reshaped the Republican Party into one that stands unapologetically with blue-collar Americans. Vance, in his bestselling book *Hillbilly Elegy*, captured the struggles of America’s heartland, painting a picture of a forgotten class that Trump understood and aimed to champion. Vance’s personal experience of growing up in a working-class family in Appalachia allows him to connect with the very people Trump promised to fight for. When Trump needed someone who could speak authentically to the struggles of rural America — a place often left behind by both parties — JD Vance was the perfect ally. His commitment to restoring dignity to working families and fighting against globalist policies that shipped jobs overseas aligns perfectly with Trump’s America First agenda. ### 2. **Fighting the Swamp Together** One of Trump’s most significant promises was to drain the swamp — to rid Washington of the establishment elites who have sold out America’s interests in favor of their own. JD Vance’s political career has been a direct response to this very problem. As someone who understands the dangers of big-money politics and the media’s influence, Vance has shown that he’s not afraid to take on the establishment — whether it’s Big Tech, Big Pharma, or the bureaucratic deep state. Together, Trump and Vance make an unstoppable force in the fight against Washington corruption. Vance’s no-nonsense approach to tackling the elites, combined with Trump’s bold, take-no-prisoners attitude, sends a clear message to D.C. — the days of business as usual are over. ### 3. **A Bold, Unapologetic Conservative Voice** Trump revolutionized the Republican Party by unapologetically embracing a bold, conservative agenda — one that emphasizes securing the border, standing strong against China, and advocating for American sovereignty. JD Vance has proven to be a fierce defender of these principles. His strong stance against illegal immigration, as well as his commitment to bringing American jobs back home from China, make him an invaluable ally in Trump’s fight to put America first. In the face of global challenges and domestic strife, Trump needed someone like JD Vance who would stand firm in the face of leftist pressure, the mainstream media, and cancel culture. Vance’s resilience and courage in sticking to conservative principles make him an indispensable ally in Trump’s quest to reclaim American greatness. ### 4. **Rural America’s Voice in Washington** Trump’s deep connection with rural America was one of the key factors in his 2016 victory. In JD Vance, Trump found a kindred spirit who understands the heartbeat of Middle America. Vance, who has firsthand knowledge of the hardships faced by families in small-town America, brings a fresh perspective to the Senate that Trump can rely on. From advocating for policies that support American agriculture to pushing back against the cultural elites who are trying to rewrite America’s values, Vance is a powerful voice for the people who have long been overlooked by Washington politicians. With Vance in the Senate, Trump gained a strong advocate for rural communities, ensuring that their concerns are heard at the highest levels of government. ### 5. **Fighting the Culture Wars** In addition to economic policies, Trump and Vance share a common commitment to fighting the culture wars. Vance, with his deep understanding of the impact of media, education, and corporate culture on America’s identity, has been an outspoken critic of the left’s radical agenda. He has voiced concerns about the erosion of traditional American values and the dangers of left-wing identity politics. Trump needed someone who could not only challenge the left’s policies but also defend the cultural heritage of America. Vance’s intellectual and cultural insights make him an essential ally in this battle. Together, they form a powerful counterweight to the woke left’s attempt to undermine the very fabric of American society. ### 6. **A Partnership for Victory** At its core, the Trump-Vance alliance is about winning — for the American people. It’s about rebuilding a nation that works for its citizens, standing up against forces that seek to weaken it, and ensuring that America remains a beacon of freedom, opportunity, and strength on the global stage. Trump needed JD Vance because Vance’s voice is a reflection of the heart of America. Together, they represent the future of the Republican Party — a future that is grounded in traditional values, fierce independence, and a relentless pursuit of the American Dream. ### Conclusion In JD Vance, President Trump found an ally who shares his vision, his commitment to the working class, and his passion for restoring American greatness. As this partnership continues to grow, there’s no doubt that Trump and Vance will be a dynamic duo, leading the charge against the forces of globalization, corruption, and cultural decay. For all the talk of division in American politics, the Trump-Vance partnership reminds us that unity is possible when leaders stand firm in their beliefs, fight for what’s right, and work together for the future of our nation. It’s a partnership built on trust, shared values, and an unyielding love for America — and that’s exactly why Trump needed JD Vance. @ 07e1bb93:f9523a3c
2024-11-10 02:43:16In a world riddled with complex international conflicts, one thing has become crystal clear: President Trump has always had the backbone to cut through the noise and focus on what matters. Now, as he gears up for his second term, Trump has shown once again that he’s committed to protecting American interests and prioritizing a smart approach to foreign policy. His strategy for Ukraine is a powerful example of this. For years, American leaders have funneled billions of dollars in aid to Ukraine, with no clear end to the conflict in sight. In nearly three years of fighting, the devastation has been staggering, and the cost to both Ukraine and the U.S. has been massive. Despite the endless funding and political gestures, little has changed on the ground. Now, President Trump is stepping in with a promise to end the bloodshed by prioritizing a practical and peace-centered approach. According to Trump’s longtime advisor Bryan Lanza, Trump’s goal isn’t to pursue impossible dreams of reversing Russia’s control over Crimea but to create real, lasting peace. Lanza made it clear that this administration’s focus is on bringing stability back to Ukraine, not forcing American troops or taxpayers into a mission with no end in sight. For Ukrainians, this means a renewed emphasis on diplomacy and a hard look at what peace can realistically look like. And this approach isn't just about saving money. It’s about setting smart priorities. Trump knows that securing Crimea again may be an unrealistic goal and that pushing for it could mean risking U.S. involvement in yet another costly, endless war. He’s clear: Ukraine’s demands for massive military support to regain every inch of land may not be in the best interest of the American people. Some have worried that this peace-first approach will embolden Russia. But in reality, Trump’s plans show that he's willing to have the tough conversations, make the hard decisions, and ensure American strength while avoiding another drawn-out conflict. He's also open to diplomatic solutions, as evidenced by Russia’s indication that they are willing to discuss his ideas for peace. Moscow’s Deputy Foreign Minister Sergei Ryabkov recently expressed a surprising openness to Trump’s proposals, as long as they don’t involve further escalation or massive military aid. In recent months, we've seen a breakdown in trust between Trump and Zelenskyy, fueled by differing visions for the future of Ukraine. Trump, though, has never been afraid to call out world leaders—even allies—when they push for policies that don’t serve America's best interests. He’s committed to ending the war in Ukraine swiftly, promising peace that respects both America’s role and the resources of the people. Some will call Trump’s approach bold, and they’re absolutely right. In the coming months, we can expect him to push the envelope to achieve peace—not just for the sake of the Ukrainians but for Americans who deserve a leader who puts them first. As we transition into this new chapter, it’s clear Trump has a vision: a peaceful, practical resolution that avoids wasteful spending, reckless decisions, and a costly cycle of conflict. And that’s something we can all get behind.
@ 07e1bb93:f9523a3c
2024-11-10 02:43:16In a world riddled with complex international conflicts, one thing has become crystal clear: President Trump has always had the backbone to cut through the noise and focus on what matters. Now, as he gears up for his second term, Trump has shown once again that he’s committed to protecting American interests and prioritizing a smart approach to foreign policy. His strategy for Ukraine is a powerful example of this. For years, American leaders have funneled billions of dollars in aid to Ukraine, with no clear end to the conflict in sight. In nearly three years of fighting, the devastation has been staggering, and the cost to both Ukraine and the U.S. has been massive. Despite the endless funding and political gestures, little has changed on the ground. Now, President Trump is stepping in with a promise to end the bloodshed by prioritizing a practical and peace-centered approach. According to Trump’s longtime advisor Bryan Lanza, Trump’s goal isn’t to pursue impossible dreams of reversing Russia’s control over Crimea but to create real, lasting peace. Lanza made it clear that this administration’s focus is on bringing stability back to Ukraine, not forcing American troops or taxpayers into a mission with no end in sight. For Ukrainians, this means a renewed emphasis on diplomacy and a hard look at what peace can realistically look like. And this approach isn't just about saving money. It’s about setting smart priorities. Trump knows that securing Crimea again may be an unrealistic goal and that pushing for it could mean risking U.S. involvement in yet another costly, endless war. He’s clear: Ukraine’s demands for massive military support to regain every inch of land may not be in the best interest of the American people. Some have worried that this peace-first approach will embolden Russia. But in reality, Trump’s plans show that he's willing to have the tough conversations, make the hard decisions, and ensure American strength while avoiding another drawn-out conflict. He's also open to diplomatic solutions, as evidenced by Russia’s indication that they are willing to discuss his ideas for peace. Moscow’s Deputy Foreign Minister Sergei Ryabkov recently expressed a surprising openness to Trump’s proposals, as long as they don’t involve further escalation or massive military aid. In recent months, we've seen a breakdown in trust between Trump and Zelenskyy, fueled by differing visions for the future of Ukraine. Trump, though, has never been afraid to call out world leaders—even allies—when they push for policies that don’t serve America's best interests. He’s committed to ending the war in Ukraine swiftly, promising peace that respects both America’s role and the resources of the people. Some will call Trump’s approach bold, and they’re absolutely right. In the coming months, we can expect him to push the envelope to achieve peace—not just for the sake of the Ukrainians but for Americans who deserve a leader who puts them first. As we transition into this new chapter, it’s clear Trump has a vision: a peaceful, practical resolution that avoids wasteful spending, reckless decisions, and a costly cycle of conflict. And that’s something we can all get behind. @ 4cec8c79:1511abda
2024-11-09 22:15:32Navigating Job Offers in Nigeria: Opportunities and Challenges Nigeria, the most populous country in Africa, offers a dynamic job market that spans multiple industries. With its youthful population, growing tech sector, and diverse economy, job seekers face both opportunities and challenges. This article explores the job offer landscape in Nigeria, focusing on the key sectors, the job search process, and factors that both employers and potential employees must consider. Key Sectors Offering Job Opportunities 1. Technology and ICT: Nigeria has been called the "Silicon Valley of Africa" due to its rapidly growing tech ecosystem. Cities like Lagos and Abuja are hubs for startups and innovation, with companies focusing on fintech, e-commerce, software development, and mobile technology. Tech giants like Andela, Paystack, and Flutterwave have made Nigeria a key player in the global tech space, offering high-paying jobs for software developers, data analysts, and cybersecurity experts. 2. Oil and Gas: The oil and gas industry remains one of the largest employers in Nigeria, contributing significantly to the country's GDP. Jobs in this sector range from engineering and project management to environmental science and logistics. Multinational companies like Shell, Chevron, and Total offer numerous positions, but the industry is also highly competitive and often requires specialized skills or experience. 3. Agriculture: With a large rural population and favorable climate, agriculture remains a vital sector for Nigeria's economy. The government has launched several initiatives aimed at promoting agribusiness and food security, which has led to job growth in areas like agritech, farming, supply chain management, and food processing. 4. Banking and Finance: The banking sector in Nigeria is robust, offering opportunities for those in finance, accounting, marketing, and management. In addition to traditional banking roles, Nigeria’s thriving fintech industry offers job opportunities in digital payments, lending, and financial inclusion platforms. Major players like GTBank, First Bank, and Zenith Bank are often on the lookout for skilled professionals. 5. Education and Health: Education and healthcare are both sectors that offer steady employment, especially in underserved areas. The rise of online learning platforms and private schools has boosted demand for teachers, while the healthcare sector, especially with the COVID-19 pandemic, has underscored the need for medical professionals, public health workers, and researchers. 6. Entrepreneurship and Startups: Entrepreneurship is flourishing in Nigeria, with many young Nigerians turning to startups to solve local challenges. The rise of digital platforms and access to funding through venture capital and government grants has made it easier for entrepreneurs to grow businesses. From logistics and retail to food delivery and fintech, Nigerian startups are generating job opportunities for creative and tech-savvy individuals. Challenges Faced by Job Seekers 1. Unemployment and Underemployment: Despite the booming sectors, Nigeria faces a high unemployment rate, especially among its youth. According to recent statistics, over 33% of the labor force is unemployed, with even more individuals underemployed, working in low-wage or part-time positions. This imbalance is one of the biggest challenges job seekers face, as they compete for a limited number of well-paying jobs. 2. Skill Mismatch: Many graduates in Nigeria find themselves in a situation where their education doesn't align with the demands of the job market. This skills mismatch is particularly evident in sectors like technology, where there's a demand for highly specialized skills in programming and data science. Upskilling ~~__****__~~
@ 4cec8c79:1511abda
2024-11-09 22:15:32Navigating Job Offers in Nigeria: Opportunities and Challenges Nigeria, the most populous country in Africa, offers a dynamic job market that spans multiple industries. With its youthful population, growing tech sector, and diverse economy, job seekers face both opportunities and challenges. This article explores the job offer landscape in Nigeria, focusing on the key sectors, the job search process, and factors that both employers and potential employees must consider. Key Sectors Offering Job Opportunities 1. Technology and ICT: Nigeria has been called the "Silicon Valley of Africa" due to its rapidly growing tech ecosystem. Cities like Lagos and Abuja are hubs for startups and innovation, with companies focusing on fintech, e-commerce, software development, and mobile technology. Tech giants like Andela, Paystack, and Flutterwave have made Nigeria a key player in the global tech space, offering high-paying jobs for software developers, data analysts, and cybersecurity experts. 2. Oil and Gas: The oil and gas industry remains one of the largest employers in Nigeria, contributing significantly to the country's GDP. Jobs in this sector range from engineering and project management to environmental science and logistics. Multinational companies like Shell, Chevron, and Total offer numerous positions, but the industry is also highly competitive and often requires specialized skills or experience. 3. Agriculture: With a large rural population and favorable climate, agriculture remains a vital sector for Nigeria's economy. The government has launched several initiatives aimed at promoting agribusiness and food security, which has led to job growth in areas like agritech, farming, supply chain management, and food processing. 4. Banking and Finance: The banking sector in Nigeria is robust, offering opportunities for those in finance, accounting, marketing, and management. In addition to traditional banking roles, Nigeria’s thriving fintech industry offers job opportunities in digital payments, lending, and financial inclusion platforms. Major players like GTBank, First Bank, and Zenith Bank are often on the lookout for skilled professionals. 5. Education and Health: Education and healthcare are both sectors that offer steady employment, especially in underserved areas. The rise of online learning platforms and private schools has boosted demand for teachers, while the healthcare sector, especially with the COVID-19 pandemic, has underscored the need for medical professionals, public health workers, and researchers. 6. Entrepreneurship and Startups: Entrepreneurship is flourishing in Nigeria, with many young Nigerians turning to startups to solve local challenges. The rise of digital platforms and access to funding through venture capital and government grants has made it easier for entrepreneurs to grow businesses. From logistics and retail to food delivery and fintech, Nigerian startups are generating job opportunities for creative and tech-savvy individuals. Challenges Faced by Job Seekers 1. Unemployment and Underemployment: Despite the booming sectors, Nigeria faces a high unemployment rate, especially among its youth. According to recent statistics, over 33% of the labor force is unemployed, with even more individuals underemployed, working in low-wage or part-time positions. This imbalance is one of the biggest challenges job seekers face, as they compete for a limited number of well-paying jobs. 2. Skill Mismatch: Many graduates in Nigeria find themselves in a situation where their education doesn't align with the demands of the job market. This skills mismatch is particularly evident in sectors like technology, where there's a demand for highly specialized skills in programming and data science. Upskilling ~~__****__~~ @ b6424601:a11e4ff4
2024-11-09 19:45:51**Personal Asset Architecture - Breaking Free from the Fiat-Driven Housing Market** ***Subheading – How Individuals Can Opt Out of the Fiat-Driven System and Create Homes with long term value*** As a self-inflicted residential architect, I am passionate about creating new, renovated homes that matter to interesting people. However, I've realized that the traditional housing market is built on a foundation of fiat currency, leading to several problems, including the potential devaluation of homes and, increasingly, the creation of empty stores of value. **The Fiat Death Spiral** Construction financing drives the most decisions in the housing market, which leads to a system where production homes are built to sell and create an initial profit rather than to provide a high-quality construction or a well-conceived living space. **The Choice: Custom vs. Fiat** When building or buying a home, you have two main options: a custom home built or renovated to your specifications or a production home pre-designed and pre-built by a builder. **Fiat-Driven Homes: The Short-Term Solution** Fiat-driven homes are built to sell quickly, often using materials that fit the deals proforma. Because of lower-quality materials and construction methods, Fiat homes depreciate more like cars than buildings. **Custom Homes: The Long-Term Solution** On the other hand, custom homes are typically built with higher quality and better design because the owner and designer are more invested in creating one-of-a-kind designs. **A New Approach: Personal Asset Architecture** As an architectural design firm owner focusing on homes, I've always known that the percentage of all homes architects design is low. I've used the low percentage as a filter for working with longer-term thinking clients, typically paying with cash. Clients who pay with cash have the flexibility to pay for what they want, allowing them to think about the total cost over the life of the house rather than just jumping through the hoops of a loan-to-value appraisal. Bitcoin standard architectural practice and Bitcoin standard homes are the escape valves to continue the work we want for the individuals we want to work for. Our thesis is that Bitcoin can improve the housing market, both for our practice and for the clients we work with. Our thesis is that Bitcoin changed the housing market for our practice and the people we work with to build a personal architecture that is as hard an asset as Bitcoin. **Asset Architecture Benefits** Homes designed in a BTC standard have four big benefits for the individual to create personal asset architecture that holds value over time. 1\. Allows owners to think in a longer time horizon – Decisions made when designing homes need to consider a longer time horizon to include the operating cost of the house in addition to the cost of construction. Production homes are built to sell and create profit based on profit produced, netting profit by the sales price vs cost. Custom homes have more flexibility in spending more on quality and life cycle improvements. 2\. Allows for a density of design thought - Can you design a better-conceived home that considers how to use space more effectively to provide a denser space so the house can require less square footage? Can the smaller square footage be planned to work as a lifetime home from a starter home, through offspring to empty nesting and multigenerational housing? 3\. Providing a return on investment beyond money – A home should produce a better quality of life. Can homes produce income, food, energy, resilience, conservation of resources, and interior air quality and become your favorite place to be? Can the utility of needing a place to live be your family citadel? 4\. Working with the system to minimize the power of the system to increase taxes on the asset - Can we design homes to reduce property taxes with a creative design to minimize bedrooms and the taxable house value? Can we put more investment and design in outdoor space that helps owners maximize the use of properties for uses that are not taxed, like quality outdoor space or properties that produce food and energy? The future of housing is uncertain, but one thing is evident from the trenches: the traditional fiat-driven system is not sustainable. Personal Asset Architecture offers a new approach to housing design that prioritizes long-term value, efficiency, and quality. By embracing this approach, we can create precious homes that produce a return on investment beyond money. The future of housing is in our hands, and it's time to create a new way of thinking about home design. **What is possible?** As individual owners and architects, we can build Stores of value buildings. By incorporating the goal of creating Personal Asset Architecture, we can create homes that produce a return on investment that goes beyond money and minimize the values of a banking system and the ability to increase taxes on the asset. Stay humble, stack stakes, and when you are ready, choose to build stuff that holds actual value.** **HODL on**
@ b6424601:a11e4ff4
2024-11-09 19:45:51**Personal Asset Architecture - Breaking Free from the Fiat-Driven Housing Market** ***Subheading – How Individuals Can Opt Out of the Fiat-Driven System and Create Homes with long term value*** As a self-inflicted residential architect, I am passionate about creating new, renovated homes that matter to interesting people. However, I've realized that the traditional housing market is built on a foundation of fiat currency, leading to several problems, including the potential devaluation of homes and, increasingly, the creation of empty stores of value. **The Fiat Death Spiral** Construction financing drives the most decisions in the housing market, which leads to a system where production homes are built to sell and create an initial profit rather than to provide a high-quality construction or a well-conceived living space. **The Choice: Custom vs. Fiat** When building or buying a home, you have two main options: a custom home built or renovated to your specifications or a production home pre-designed and pre-built by a builder. **Fiat-Driven Homes: The Short-Term Solution** Fiat-driven homes are built to sell quickly, often using materials that fit the deals proforma. Because of lower-quality materials and construction methods, Fiat homes depreciate more like cars than buildings. **Custom Homes: The Long-Term Solution** On the other hand, custom homes are typically built with higher quality and better design because the owner and designer are more invested in creating one-of-a-kind designs. **A New Approach: Personal Asset Architecture** As an architectural design firm owner focusing on homes, I've always known that the percentage of all homes architects design is low. I've used the low percentage as a filter for working with longer-term thinking clients, typically paying with cash. Clients who pay with cash have the flexibility to pay for what they want, allowing them to think about the total cost over the life of the house rather than just jumping through the hoops of a loan-to-value appraisal. Bitcoin standard architectural practice and Bitcoin standard homes are the escape valves to continue the work we want for the individuals we want to work for. Our thesis is that Bitcoin can improve the housing market, both for our practice and for the clients we work with. Our thesis is that Bitcoin changed the housing market for our practice and the people we work with to build a personal architecture that is as hard an asset as Bitcoin. **Asset Architecture Benefits** Homes designed in a BTC standard have four big benefits for the individual to create personal asset architecture that holds value over time. 1\. Allows owners to think in a longer time horizon – Decisions made when designing homes need to consider a longer time horizon to include the operating cost of the house in addition to the cost of construction. Production homes are built to sell and create profit based on profit produced, netting profit by the sales price vs cost. Custom homes have more flexibility in spending more on quality and life cycle improvements. 2\. Allows for a density of design thought - Can you design a better-conceived home that considers how to use space more effectively to provide a denser space so the house can require less square footage? Can the smaller square footage be planned to work as a lifetime home from a starter home, through offspring to empty nesting and multigenerational housing? 3\. Providing a return on investment beyond money – A home should produce a better quality of life. Can homes produce income, food, energy, resilience, conservation of resources, and interior air quality and become your favorite place to be? Can the utility of needing a place to live be your family citadel? 4\. Working with the system to minimize the power of the system to increase taxes on the asset - Can we design homes to reduce property taxes with a creative design to minimize bedrooms and the taxable house value? Can we put more investment and design in outdoor space that helps owners maximize the use of properties for uses that are not taxed, like quality outdoor space or properties that produce food and energy? The future of housing is uncertain, but one thing is evident from the trenches: the traditional fiat-driven system is not sustainable. Personal Asset Architecture offers a new approach to housing design that prioritizes long-term value, efficiency, and quality. By embracing this approach, we can create precious homes that produce a return on investment beyond money. The future of housing is in our hands, and it's time to create a new way of thinking about home design. **What is possible?** As individual owners and architects, we can build Stores of value buildings. By incorporating the goal of creating Personal Asset Architecture, we can create homes that produce a return on investment that goes beyond money and minimize the values of a banking system and the ability to increase taxes on the asset. Stay humble, stack stakes, and when you are ready, choose to build stuff that holds actual value.** **HODL on** @ 4ba8e86d:89d32de4
2024-10-29 12:30:05## Tutorial feito por Grom Mestre⚡ Poste original Abaixo. Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7 Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035 Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113 Boa tarde, camaradas do meu coeur! Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb. Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele. Dito isso, vamos prosseguir. TÓPICOS: Introdução Instalando e configurando o roteador e o navegador Conectando-se a serviços na I2P Configurações avançadas ## 1. Introdução ### 1.1 Definindo a DeepWeb. Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos. Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas. Vamos aos pontos individualmente: > São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração. > São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe... > São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio. https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg > Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador. A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação. https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança. As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar: • Lokinet • Zeronet • Freenet • I2P • Tor • Gnunet Porém, há alguns casos interessantes que não caem diretamente nessa regra . A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento. Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento. Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos. Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface. DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa. DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface. Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting). Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito. Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service. ## Instalando e configurando o roteador I2P Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela. O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela. Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas: • Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing ) • Modelo P2P • Todos os participantes da rede contribuem para ela • Fechado na rede - não é possível acessar a surface através da I2P • Otimizado para hidden services Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada. Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas. Referências: • https://geti2p.net/en/comparison/tor • https://geti2p.net/en/docs/how/garlic-routing • https://geti2p.net/en/about/intro • https://i2pd.readthedocs.io/en/latest/ ### 2. Instalando e configurando o roteador Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição. Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso. ### 2.1 Instalação do router Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação. O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ). Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P. Para usuários de Windows, segue abaixo os binários para instalação. • Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip ) • Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip ) • Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip ) A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'. Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070. https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg ### 2.2 Instalação e configuração do navegador Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado. Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas. ### 2.2.1 Escolhendo o navegador Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ ) ### 2.2.2 Criando um perfil e configurando o lançador Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile' https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg Coloquem um nome no seu perfil e cliquem em Finalizar https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador. Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'. Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho. Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf. https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg 2.2.3 Configurando o proxy Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora. Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings) https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg Configure o seu proxy como na figura abaixo. https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites. • http://identiguy.i2p • http://notbob.i2p • http://reg.i2p Se tudo ocorreu como conforme, a página será carregada. https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070) https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção. • noScript • JShelter Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações. Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem. https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado. Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP ## [TUTORIAL] Conectando-se ao XMPP pela I2P Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P. Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável. ### 3.1 Escolhendo o cliente XMPP Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada. Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ ) ### 3.2 Criando uma conta Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais. Para criar uma conta, siga os passos abaixo: Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk) https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela. https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'. https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente). Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel). https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo. https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções: • Tempo ocioso • Hora de Sistema Local • Sistema Operacional • Reprodução de Mídia https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg ### 3.3 Procurando por salas de bate-papo públicas Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?). https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg ### 3.4 Adicionando contatos Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'. https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir. https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :) https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg E com isso terminamos a terceira parte da série de tutoriais. ## [TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet. Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients BONUS: Conectando-se facilmente à I2P. https://youtube.com/watch?v=wGIh5tQcw68
@ 4ba8e86d:89d32de4
2024-10-29 12:30:05## Tutorial feito por Grom Mestre⚡ Poste original Abaixo. Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7 Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035 Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113 Boa tarde, camaradas do meu coeur! Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb. Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele. Dito isso, vamos prosseguir. TÓPICOS: Introdução Instalando e configurando o roteador e o navegador Conectando-se a serviços na I2P Configurações avançadas ## 1. Introdução ### 1.1 Definindo a DeepWeb. Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos. Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas. Vamos aos pontos individualmente: > São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração. > São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe... > São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio. https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg > Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador. A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação. https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança. As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar: • Lokinet • Zeronet • Freenet • I2P • Tor • Gnunet Porém, há alguns casos interessantes que não caem diretamente nessa regra . A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento. Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento. Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos. Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface. DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa. DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface. Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting). Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito. Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service. ## Instalando e configurando o roteador I2P Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela. O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela. Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas: • Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing ) • Modelo P2P • Todos os participantes da rede contribuem para ela • Fechado na rede - não é possível acessar a surface através da I2P • Otimizado para hidden services Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada. Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas. Referências: • https://geti2p.net/en/comparison/tor • https://geti2p.net/en/docs/how/garlic-routing • https://geti2p.net/en/about/intro • https://i2pd.readthedocs.io/en/latest/ ### 2. Instalando e configurando o roteador Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição. Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso. ### 2.1 Instalação do router Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação. O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ). Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P. Para usuários de Windows, segue abaixo os binários para instalação. • Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip ) • Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip ) • Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip ) A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'. Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070. https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg ### 2.2 Instalação e configuração do navegador Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado. Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas. ### 2.2.1 Escolhendo o navegador Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ ) ### 2.2.2 Criando um perfil e configurando o lançador Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile' https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg Coloquem um nome no seu perfil e cliquem em Finalizar https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador. Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'. Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho. Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf. https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg 2.2.3 Configurando o proxy Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora. Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings) https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg Configure o seu proxy como na figura abaixo. https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites. • http://identiguy.i2p • http://notbob.i2p • http://reg.i2p Se tudo ocorreu como conforme, a página será carregada. https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070) https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção. • noScript • JShelter Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações. Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem. https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado. Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP ## [TUTORIAL] Conectando-se ao XMPP pela I2P Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P. Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável. ### 3.1 Escolhendo o cliente XMPP Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada. Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ ) ### 3.2 Criando uma conta Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais. Para criar uma conta, siga os passos abaixo: Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk) https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela. https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'. https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente). Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel). https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo. https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções: • Tempo ocioso • Hora de Sistema Local • Sistema Operacional • Reprodução de Mídia https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg ### 3.3 Procurando por salas de bate-papo públicas Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?). https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg ### 3.4 Adicionando contatos Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'. https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir. https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :) https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg E com isso terminamos a terceira parte da série de tutoriais. ## [TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet. Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients BONUS: Conectando-se facilmente à I2P. https://youtube.com/watch?v=wGIh5tQcw68 @ 5d4b6c8d:8a1c1ee3
2024-11-09 19:04:04The Emirates Cup begins on Tuesday, so it's time to start thinking about our first picks. For a refresher on the tournament, see the [first post](https://stacker.news/items/751054/r/Undisciplined). Note, though, that there are actually going to be seven group play days with each team playing four total group play games. # Games Here is the first slate of games (plus the home spread): - Hawks @ Celtics (-12.5) - Heat @ Pistons (+3) - Hornets @ Magic (-8) - Knicks @ 76ers (-1) - Raptors @ Bucks (-8) - Suns @ Jazz (+4.5) - Mavs @ Warriors (+2.5) Just pick one of the teams above to win their game on Tuesday. Remember, you can only take each team once and the options will dwindle once we get to the Knock Out round. There are at most 10 choices to make during the tournament, but you don't know which ones will be available towards the end. I'm going to wait a couple of days, to get more clarity on the injury situations for the Heat, Magic, 76ers, and Bucks. At first glance, I'm leaning towards taking either the Heat, but with Jimmy hurt and the Pistons looking a little frisky, I don't love it. # Prize 27133 sats! plus whatever else comes in from here on out # Participants @Undisciplined, @gnilma, @BlokchainB, @realBitcoinDog, @Carresan, @supercyclone, @grayruby There's still time to join. The initial buy-in is only 3k sats. originally posted at https://stacker.news/items/760645
@ 5d4b6c8d:8a1c1ee3
2024-11-09 19:04:04The Emirates Cup begins on Tuesday, so it's time to start thinking about our first picks. For a refresher on the tournament, see the [first post](https://stacker.news/items/751054/r/Undisciplined). Note, though, that there are actually going to be seven group play days with each team playing four total group play games. # Games Here is the first slate of games (plus the home spread): - Hawks @ Celtics (-12.5) - Heat @ Pistons (+3) - Hornets @ Magic (-8) - Knicks @ 76ers (-1) - Raptors @ Bucks (-8) - Suns @ Jazz (+4.5) - Mavs @ Warriors (+2.5) Just pick one of the teams above to win their game on Tuesday. Remember, you can only take each team once and the options will dwindle once we get to the Knock Out round. There are at most 10 choices to make during the tournament, but you don't know which ones will be available towards the end. I'm going to wait a couple of days, to get more clarity on the injury situations for the Heat, Magic, 76ers, and Bucks. At first glance, I'm leaning towards taking either the Heat, but with Jimmy hurt and the Pistons looking a little frisky, I don't love it. # Prize 27133 sats! plus whatever else comes in from here on out # Participants @Undisciplined, @gnilma, @BlokchainB, @realBitcoinDog, @Carresan, @supercyclone, @grayruby There's still time to join. The initial buy-in is only 3k sats. originally posted at https://stacker.news/items/760645 @ 8d34bd24:414be32b
2024-10-27 22:30:18NOTE: *This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.* When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior. In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance. ## Seek the Welfare of the City Where I Have Sent You As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia. > Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1) What did God say to the Israelites about how they should live their life in Babylon? > “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare**.’ (Jeremiah 29:4-7) {emphasis mine} Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.” God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “*for in its welfare you will have welfare*.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price. We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands. We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves. ## Political Religion Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties. > No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13) Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God. When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally. > You shall have no other gods before Me. > > You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6) When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion. We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different. I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge: *I pledge allegiance to the Flag of the United States of America,\ and to the Republic for which it stands,\ one Nation under God,\ indivisible, with liberty and justice for all.* I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “*serve two masters*.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right. ## In the World, but Not of the World As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship[1](https://trustjesus.substack.com/p/should-christians-vote#footnote-1-150236181) and family are in heaven, not here on earth. We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ. > But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. **I have given them Your word; and the world has hated them, because they are not of the world**, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. **They are not of the world, even as I am not of the world**. Sanctify them in the truth; **Your word is truth**. (John 17:13-17) {emphasis mine} Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God. Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior. > **Do not love the world nor the things in the world**. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. **The world is passing away**, and also its lusts; but **the one who does the will of God lives forever**. (1 John 2:15-17) {emphasis mine} The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics. Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles: > Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13) There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “*as having been with Jesus*.” I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God. > Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, **so that they may be saved**. (1 Corinthians 10:32-33) {emphasis mine} Trust Jesus.\ \ your sister in Christ, Christy
@ 8d34bd24:414be32b
2024-10-27 22:30:18NOTE: *This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.* When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior. In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance. ## Seek the Welfare of the City Where I Have Sent You As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia. > Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1) What did God say to the Israelites about how they should live their life in Babylon? > “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare**.’ (Jeremiah 29:4-7) {emphasis mine} Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.” God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “*for in its welfare you will have welfare*.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price. We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands. We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves. ## Political Religion Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties. > No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13) Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God. When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally. > You shall have no other gods before Me. > > You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6) When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion. We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different. I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge: *I pledge allegiance to the Flag of the United States of America,\ and to the Republic for which it stands,\ one Nation under God,\ indivisible, with liberty and justice for all.* I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “*serve two masters*.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right. ## In the World, but Not of the World As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship[1](https://trustjesus.substack.com/p/should-christians-vote#footnote-1-150236181) and family are in heaven, not here on earth. We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ. > But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. **I have given them Your word; and the world has hated them, because they are not of the world**, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. **They are not of the world, even as I am not of the world**. Sanctify them in the truth; **Your word is truth**. (John 17:13-17) {emphasis mine} Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God. Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior. > **Do not love the world nor the things in the world**. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. **The world is passing away**, and also its lusts; but **the one who does the will of God lives forever**. (1 John 2:15-17) {emphasis mine} The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics. Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles: > Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13) There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “*as having been with Jesus*.” I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God. > Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, **so that they may be saved**. (1 Corinthians 10:32-33) {emphasis mine} Trust Jesus.\ \ your sister in Christ, Christy @ 2063cd79:57bd1320
2024-11-09 18:34:43Einer der großen Vorteile von Bitcoin ist, dass es relativ einfach ist Bitcoin selbst zu verwahren. Ich predige self-custody, also die Eigenverwahrung, von Bitcoin in fast jeder Ausgabe als einer der Hauptkomponenten der Formel für Freedom Money rauf und runter. Doch was genau bedeutet es seine bitcoins selbst zu verwahren? Denn schließlich verwaltet jeder mündige Bürger seine Finanzen, ob in Bitcoin oder nicht, in der Regel ja immer selbst. Es gibt einen großen Unterschied zwischen verwalten und verwahren. Denn das Verwahren übernehmen bei anderen Assets Dritte für uns, sei es die Bank, die unser Geld auf Konten, Hypotheken und Sparanlagen, manchmal sogar Wertsachen in Schließfächern, verwahrt, Finanzbroker oder Depotbanken, die Wertpapiere wie Aktien, Bonds oder ähnliches, verwahren, oder Versicherer, die Policen, Sparvermögen, usw. für uns verwahren. Immer sind Drittparteien mit der Verwahrung unseres Besitzes vertraut, oder haben sich uns aufgedrängt, weil es schlichtweg nicht anders möglich ist, diese Besitztümer völlig autark zu verwahren. Bei Bitcoin ist das anders. Bitcoin lässt sich ähnlich wie Bargeld, Gold oder Schmuck völlig autark und selbstbestimmt verwahren. Dabei gibt es, wie bei allem im Leben, sowohl einfache und bequeme, aber dadurch unsichere, als auch komplizierte und etwas aufwändigere, aber deshalb sehr sichere Verwahrungsmethoden. Eine sehr sichere Methode stellt die Verwahrung mit Hilfe von MultiSig (also Multi-Signature) dar. Dieses wollen wir uns diese Woche genauer anschauen. --- Eine der großen Errungenschaften von Bitcoin ist die Möglichkeit der Eigenverwahrung, sogenanntes self-custody. Es bietet jedem//jeder Hodler//in, Anleger//in und Investor//in eine völlig autarke und selbstbestimmte, Methode zur Verwahrung und Kontrolle seines Besitzes und damit einen Schutz vor Zensur, Kontrolle und Übergriffen. Ohne zu sehr ins Detail zu gehen, möchte ich kurz grundlegend die Sicherheitsstruktur von Bitcoin darlegen. Jede//r Nutzer//in sollte zunächst über eine Wallet verfügen. Eine Wallet ist kein Muss, um mit Bitcoin in Kontakt zu treten, jedoch versucht ja auch niemand das Internet ohne Browser zu verwenden. Eine Wallet ist, ähnlich wie der Internetbrowser, eine Software, die es dem Nutzenden ermöglicht Bitcoin zu erhalten, zu versenden oder zu verwahren (ohne Bitcoin direkt zu erhalten, zu versenden oder zu verwahren - kompliziert, ich weiß). Dabei gibt es ein weites Spektrum an verschiedenen Diensten. Es gibt Wallets, Börsen oder andere Verwahrungs-Services. Um das Thema MultiSig zu besprechen, fokussieren wir uns auf Wallets. Im Grunde besitzt jede//r Halter//in von Bitcoin ein Schlüsselpaar - einen privaten Schlüssel (Private Key) und einen öffentlichen Schlüssel (PubKey). Vergleicht man das Konzept mit dem alten Finanzsystem würde man sagen, der öffentliche Schlüssel stellt die Kontonummer dar, also die Information, die öffentlich geteilt werden kann und der private Schlüssel stellt die PIN Nummer dar, also die Information, die nur die//der Besitzer//in haben sollte. Der private Schlüssel ist also die Information, die es zu schützen gilt, denn in Kombination erlauben mir die beiden Schlüssel Zugriff auf die sich dahinter befindenden bitcoins. Ein bitcoin lässt sich nicht aus der Blockchain extrahieren. Die einzelnen Coins existieren nur innerhalb der Chain (und nicht als ganze "Coins", sondern als Outputs/UTXOs). Lediglich der Besitzanspruch wird außerhalb gehandhabt. Das bedeutet, dass ich mit meinen beiden Schlüsseln den Zugriff oder Anspruch auf eine gewisse Anzahl bitcoins ausweisen kann. Habe ich Zugriff auf den privaten Schlüssel, kann ich also ohne weiteres komplett über alle damit verbundenen bitcoins verfügen, sie ausgeben, sie weiterversenden (oder akkurater formuliert: eine Nachricht signieren, die dem Empfänger die Kontrolle über diese bitcoins gewährt), oder sie sogar zerstören. Wallets übernehmen die Speicherung der Schlüssel, sowohl der öffentlichen, als auch der privaten, in einem für den Anwender benutzerfreundlichen Interface. Sogenannte Hot Wallets, sind Apps, die mit dem Internet verbunden sind, und dadurch "hot" oder "live" sind, das heißt sie können im schlimmsten Fall gehackt werden. Cold Wallets sind offline Lösungen, die sich nicht online hacken lassen, aber z.B. im Falle eines Paper Wallets leicht verlieren, stehlen, oder zerstören lassen. Das Problem, wie oben erwähnt, ist je bequemer und nutzerfreundlich die Handhabung der Wallet, desto unsicherer ist sie in der Regel auch. Also jegliche Software Wallets, egal ob mobil oder auf dem Rechner daheim, stellen Sicherheitsrisiken dar, da sie wieder einen Drittanbieter in die Gleichung schleusen. Um volle Autarkie zu erlangen muss man sich von Drittanbietern, wie Wallet Anbietern, Börsen oder sonstigen Services, komplett lösen und die Schlüssel und damit seine bitcoins selbst verwahren. Denn die eiserne Regel gilt immer: Not your keys not your coins! <img src="https://blossom.primal.net/8e6e7e4f26037de171bd35f620263966bb3f2325777490f2174094ac91a72979.png"> Wenn man einen Betrag von seiner Wallet senden möchte, wird eine Transaktion erstellt und signiert. Indem die Transaktion signiert wird, beglaubigt man in digitaler Form, dass man der Eigentümer des Betrages ist, dass man die Schlüssel besitzt, um es zu verwalten, und man die Transaktion genehmigt. Es wird also der Besitzanspruch signalisiert und weitergegeben, und kein bitcoin physisch bewegt. In einer Single-Signature Wallet benötigt man nur eine Signatur, um eine Transaktion zu signieren. Bei MultiSig (Multi-Signature) erfordert die Wallet mehrere Signaturen, um eine Transaktion zu signieren. Eine MultiSig-Wallet wird dabei von zwei oder mehreren Benutzern geteilt. Wird also eine Transaktion erstellt, muss die Anfrage zunächst von allen Teilnehmern bestätigt werden. MultiSig ist ein Aufbewahrungsmodell, bei dem eine Wallet mit mehreren Schlüsseln in einem m-von-n-Schema erstellt werden. Also beispielsweise eine 2-von-3-Wallet basierend auf drei Schlüsseln, von denen zwei zum Bestätigen einer Transaktion erforderlich sind. Es gibt auch andere Modelle wie 3-von-3, oder 3-von-5, etc. allerdings stellt 2-von-3 die gängigste Methode dar. Das Schöne an diesem Modell ist, dass es Single Points of Failure (SPOF) eliminiert. Das bedeutet, dass selbst sonst kritische Informationen, wie Seed-Phrase-Backups oder Hardware-Wallets, sogar von Angreifern gestohlen, oder durch einen Unfall verloren oder zerstört, werden können, ohne dass die Wallet kompromittiert wird. Es ist hilfreich, sich die MultiSig-Wallet als einen digitalen Safe vorzustellen. Man besitzt dabei verschiedene Schlüssel zu diesem Safe. Im Beispiel von der 2-von-3-Wallet hat der Tresor zwei Schlüssellöcher und drei Schlüssel. Zwei beliebige der drei Schlüssel können verwendet werden, um den Safe zu entriegeln, damit die darin gespeicherten bitcoins bewegt werden können. <https://x.com/cryptograffiti/status/1544763238721601537> Das bedeutet jedoch nicht, dass man mit einer MultiSig-Wallet unvorsichtiger umgehen sollte, denn trotz der Flexibilität, die MultiSig bietet, sollte man ein Seed-Phrase-Backup erstellen und vermeiden, Hardware-Wallets oder Seed-Phrasen gemeinsam aufzubewahren. Fast alle Anbieter von guten, sicheren und seriösen Wallet Software, sowie Hersteller von Hardware-Wallets bieten an MultiSig-Wallets innerhalb ihrer Apps anzulegen. Der Prozess ist ein wenig aufwändiger, als das Anlegen einfacher Single-Signature-Wallets, die Vorteile überwiegen den Aufwand aber deutlich. Ein MultiSig-Wallet schützt in der Regel, und wenn ordentlich gehandhabt, vor Phishing, Malware, Verlust der Schlüssel, Verlust von Hardware, wie Telefon, Laptop oder Hardware-Wallet, aber auch vor Diebstahl und Unfällen. <img src="https://blossom.primal.net/fe9202a17b5af87cafd7270d78353bd4746bbe45a038c0fd8a7855454e828cf6.png"> MultiSig-Wallets dienen nicht nur der Sicherheit, sondern können darüber hinaus auch weitere Nutzen haben. MultiSig kann auch als Zwei-Faktor-Authentifizierung für Bitcoin Transaktionen verstanden werden. Die vielfachen privaten Schlüssel können auf verschiedenen Geräten gespeichert und auf die im MultiSig-Wallet gespeicherten Coins nur zugegriffen werden, wenn alle Schlüssel vorhanden sind. bereitgestellt werden. Auch gibt es Szenarien, in denen ein MultiSig-Wallet als treuhänderischer Dienst funktionieren könnte. Zwei Parteien vereinbaren eine Zahlung für eine Dienstleistung oder einen Warenaustausch und setzen einen Treuhänder ein, der einen der Schlüssel erhält. Erst im Falle der erbrachten Leistung, übergibt dieser Treuhänder den Schlüssel und die Geldmittel können übertragen werden. Aber auch zukünftige Gesellschaftsformen könnten von einem solchen Modell profitieren. Gerade die aktuell diskutierte Gesellschaft mbH mit gebundenem Vermögen würde das gebundene Vermögen sichern können, indem jedes Vorstandsmitglied Zugriff auf einen privaten Schlüssel von vielen erhält. Kein einzelnes Vorstandsmitglied darf die Geldmittel missbräuchlich oder entgegen der Satzung verwenden. Somit könnten nur die von den Vorstandsmitgliedern mehrheitlich vereinbarten Entscheidungen ausgeführt und finanziert werden. --- MultiSig erhöht die Sicherheit von selbst verwahrtem Vermögen um ein vielfaches. Doch auch über den eigenen Sicherheitsaspekt hinaus, hat MultiSig die Möglichkeit das Thema digitaler Zahlungen in weiteren Bereichen interessant zu machen - Beispiele wie Escrow oder das Finanzplanning bei Gesellschaftsformen mit Vermögensbindung ergeben sich vielfach. Doch darüber hinaus, ist self-custody einer der wichtigsten Bausteine auf dem Weg zu einem Bitcoin Standard. Es soll nicht bedeuten, dass man sich mit seinem Eigentum verstecken und vergraben und der Gesellschaft nichts zurück geben soll, denn auch eigenständig verwahrte Bitcoins müssen zumindest steuerlich berücksichtigt werden. Jedoch bedeutet es, dass mir niemand meine bitcoins entreißen kann. Es gibt keine Bank, die mein Konto einfrieren oder pfänden könnte. Man kann auf seine bitcoins problemlos überall zugreifen, solange die Blockchain läuft, egal wo man sich auf der Welt befindet und egal zu welcher Tages- und Uhrzeit. Die Idee, dass Regierungen den Bankensektor, den sie regulieren, zwingen können Finanzdienstleistungen als Waffen einzusetzen sollte spätestens seit dem Freedom Convoy in Kanada keine Dystopie mehr sein. Es besteht kein Zweifel, dass die zunehmende Übergriffigkeit der Staaten, wie zuletzt in Kanada, eines der einzigartigen Wertversprechen von Bitcoin hervorgehoben hat: Jeder kann über seinen Besitz frei verfügen und Menschen können sich vor finanziellem "Cancelling" schützen. Es gibt Bitcoin eine weitere Bedeutung in seinem Narrativ als monetäre Revolution. 🫳🎤 --- In diesem Sinne, 2... 1... Risiko! 
@ 2063cd79:57bd1320
2024-11-09 18:34:43Einer der großen Vorteile von Bitcoin ist, dass es relativ einfach ist Bitcoin selbst zu verwahren. Ich predige self-custody, also die Eigenverwahrung, von Bitcoin in fast jeder Ausgabe als einer der Hauptkomponenten der Formel für Freedom Money rauf und runter. Doch was genau bedeutet es seine bitcoins selbst zu verwahren? Denn schließlich verwaltet jeder mündige Bürger seine Finanzen, ob in Bitcoin oder nicht, in der Regel ja immer selbst. Es gibt einen großen Unterschied zwischen verwalten und verwahren. Denn das Verwahren übernehmen bei anderen Assets Dritte für uns, sei es die Bank, die unser Geld auf Konten, Hypotheken und Sparanlagen, manchmal sogar Wertsachen in Schließfächern, verwahrt, Finanzbroker oder Depotbanken, die Wertpapiere wie Aktien, Bonds oder ähnliches, verwahren, oder Versicherer, die Policen, Sparvermögen, usw. für uns verwahren. Immer sind Drittparteien mit der Verwahrung unseres Besitzes vertraut, oder haben sich uns aufgedrängt, weil es schlichtweg nicht anders möglich ist, diese Besitztümer völlig autark zu verwahren. Bei Bitcoin ist das anders. Bitcoin lässt sich ähnlich wie Bargeld, Gold oder Schmuck völlig autark und selbstbestimmt verwahren. Dabei gibt es, wie bei allem im Leben, sowohl einfache und bequeme, aber dadurch unsichere, als auch komplizierte und etwas aufwändigere, aber deshalb sehr sichere Verwahrungsmethoden. Eine sehr sichere Methode stellt die Verwahrung mit Hilfe von MultiSig (also Multi-Signature) dar. Dieses wollen wir uns diese Woche genauer anschauen. --- Eine der großen Errungenschaften von Bitcoin ist die Möglichkeit der Eigenverwahrung, sogenanntes self-custody. Es bietet jedem//jeder Hodler//in, Anleger//in und Investor//in eine völlig autarke und selbstbestimmte, Methode zur Verwahrung und Kontrolle seines Besitzes und damit einen Schutz vor Zensur, Kontrolle und Übergriffen. Ohne zu sehr ins Detail zu gehen, möchte ich kurz grundlegend die Sicherheitsstruktur von Bitcoin darlegen. Jede//r Nutzer//in sollte zunächst über eine Wallet verfügen. Eine Wallet ist kein Muss, um mit Bitcoin in Kontakt zu treten, jedoch versucht ja auch niemand das Internet ohne Browser zu verwenden. Eine Wallet ist, ähnlich wie der Internetbrowser, eine Software, die es dem Nutzenden ermöglicht Bitcoin zu erhalten, zu versenden oder zu verwahren (ohne Bitcoin direkt zu erhalten, zu versenden oder zu verwahren - kompliziert, ich weiß). Dabei gibt es ein weites Spektrum an verschiedenen Diensten. Es gibt Wallets, Börsen oder andere Verwahrungs-Services. Um das Thema MultiSig zu besprechen, fokussieren wir uns auf Wallets. Im Grunde besitzt jede//r Halter//in von Bitcoin ein Schlüsselpaar - einen privaten Schlüssel (Private Key) und einen öffentlichen Schlüssel (PubKey). Vergleicht man das Konzept mit dem alten Finanzsystem würde man sagen, der öffentliche Schlüssel stellt die Kontonummer dar, also die Information, die öffentlich geteilt werden kann und der private Schlüssel stellt die PIN Nummer dar, also die Information, die nur die//der Besitzer//in haben sollte. Der private Schlüssel ist also die Information, die es zu schützen gilt, denn in Kombination erlauben mir die beiden Schlüssel Zugriff auf die sich dahinter befindenden bitcoins. Ein bitcoin lässt sich nicht aus der Blockchain extrahieren. Die einzelnen Coins existieren nur innerhalb der Chain (und nicht als ganze "Coins", sondern als Outputs/UTXOs). Lediglich der Besitzanspruch wird außerhalb gehandhabt. Das bedeutet, dass ich mit meinen beiden Schlüsseln den Zugriff oder Anspruch auf eine gewisse Anzahl bitcoins ausweisen kann. Habe ich Zugriff auf den privaten Schlüssel, kann ich also ohne weiteres komplett über alle damit verbundenen bitcoins verfügen, sie ausgeben, sie weiterversenden (oder akkurater formuliert: eine Nachricht signieren, die dem Empfänger die Kontrolle über diese bitcoins gewährt), oder sie sogar zerstören. Wallets übernehmen die Speicherung der Schlüssel, sowohl der öffentlichen, als auch der privaten, in einem für den Anwender benutzerfreundlichen Interface. Sogenannte Hot Wallets, sind Apps, die mit dem Internet verbunden sind, und dadurch "hot" oder "live" sind, das heißt sie können im schlimmsten Fall gehackt werden. Cold Wallets sind offline Lösungen, die sich nicht online hacken lassen, aber z.B. im Falle eines Paper Wallets leicht verlieren, stehlen, oder zerstören lassen. Das Problem, wie oben erwähnt, ist je bequemer und nutzerfreundlich die Handhabung der Wallet, desto unsicherer ist sie in der Regel auch. Also jegliche Software Wallets, egal ob mobil oder auf dem Rechner daheim, stellen Sicherheitsrisiken dar, da sie wieder einen Drittanbieter in die Gleichung schleusen. Um volle Autarkie zu erlangen muss man sich von Drittanbietern, wie Wallet Anbietern, Börsen oder sonstigen Services, komplett lösen und die Schlüssel und damit seine bitcoins selbst verwahren. Denn die eiserne Regel gilt immer: Not your keys not your coins! <img src="https://blossom.primal.net/8e6e7e4f26037de171bd35f620263966bb3f2325777490f2174094ac91a72979.png"> Wenn man einen Betrag von seiner Wallet senden möchte, wird eine Transaktion erstellt und signiert. Indem die Transaktion signiert wird, beglaubigt man in digitaler Form, dass man der Eigentümer des Betrages ist, dass man die Schlüssel besitzt, um es zu verwalten, und man die Transaktion genehmigt. Es wird also der Besitzanspruch signalisiert und weitergegeben, und kein bitcoin physisch bewegt. In einer Single-Signature Wallet benötigt man nur eine Signatur, um eine Transaktion zu signieren. Bei MultiSig (Multi-Signature) erfordert die Wallet mehrere Signaturen, um eine Transaktion zu signieren. Eine MultiSig-Wallet wird dabei von zwei oder mehreren Benutzern geteilt. Wird also eine Transaktion erstellt, muss die Anfrage zunächst von allen Teilnehmern bestätigt werden. MultiSig ist ein Aufbewahrungsmodell, bei dem eine Wallet mit mehreren Schlüsseln in einem m-von-n-Schema erstellt werden. Also beispielsweise eine 2-von-3-Wallet basierend auf drei Schlüsseln, von denen zwei zum Bestätigen einer Transaktion erforderlich sind. Es gibt auch andere Modelle wie 3-von-3, oder 3-von-5, etc. allerdings stellt 2-von-3 die gängigste Methode dar. Das Schöne an diesem Modell ist, dass es Single Points of Failure (SPOF) eliminiert. Das bedeutet, dass selbst sonst kritische Informationen, wie Seed-Phrase-Backups oder Hardware-Wallets, sogar von Angreifern gestohlen, oder durch einen Unfall verloren oder zerstört, werden können, ohne dass die Wallet kompromittiert wird. Es ist hilfreich, sich die MultiSig-Wallet als einen digitalen Safe vorzustellen. Man besitzt dabei verschiedene Schlüssel zu diesem Safe. Im Beispiel von der 2-von-3-Wallet hat der Tresor zwei Schlüssellöcher und drei Schlüssel. Zwei beliebige der drei Schlüssel können verwendet werden, um den Safe zu entriegeln, damit die darin gespeicherten bitcoins bewegt werden können. <https://x.com/cryptograffiti/status/1544763238721601537> Das bedeutet jedoch nicht, dass man mit einer MultiSig-Wallet unvorsichtiger umgehen sollte, denn trotz der Flexibilität, die MultiSig bietet, sollte man ein Seed-Phrase-Backup erstellen und vermeiden, Hardware-Wallets oder Seed-Phrasen gemeinsam aufzubewahren. Fast alle Anbieter von guten, sicheren und seriösen Wallet Software, sowie Hersteller von Hardware-Wallets bieten an MultiSig-Wallets innerhalb ihrer Apps anzulegen. Der Prozess ist ein wenig aufwändiger, als das Anlegen einfacher Single-Signature-Wallets, die Vorteile überwiegen den Aufwand aber deutlich. Ein MultiSig-Wallet schützt in der Regel, und wenn ordentlich gehandhabt, vor Phishing, Malware, Verlust der Schlüssel, Verlust von Hardware, wie Telefon, Laptop oder Hardware-Wallet, aber auch vor Diebstahl und Unfällen. <img src="https://blossom.primal.net/fe9202a17b5af87cafd7270d78353bd4746bbe45a038c0fd8a7855454e828cf6.png"> MultiSig-Wallets dienen nicht nur der Sicherheit, sondern können darüber hinaus auch weitere Nutzen haben. MultiSig kann auch als Zwei-Faktor-Authentifizierung für Bitcoin Transaktionen verstanden werden. Die vielfachen privaten Schlüssel können auf verschiedenen Geräten gespeichert und auf die im MultiSig-Wallet gespeicherten Coins nur zugegriffen werden, wenn alle Schlüssel vorhanden sind. bereitgestellt werden. Auch gibt es Szenarien, in denen ein MultiSig-Wallet als treuhänderischer Dienst funktionieren könnte. Zwei Parteien vereinbaren eine Zahlung für eine Dienstleistung oder einen Warenaustausch und setzen einen Treuhänder ein, der einen der Schlüssel erhält. Erst im Falle der erbrachten Leistung, übergibt dieser Treuhänder den Schlüssel und die Geldmittel können übertragen werden. Aber auch zukünftige Gesellschaftsformen könnten von einem solchen Modell profitieren. Gerade die aktuell diskutierte Gesellschaft mbH mit gebundenem Vermögen würde das gebundene Vermögen sichern können, indem jedes Vorstandsmitglied Zugriff auf einen privaten Schlüssel von vielen erhält. Kein einzelnes Vorstandsmitglied darf die Geldmittel missbräuchlich oder entgegen der Satzung verwenden. Somit könnten nur die von den Vorstandsmitgliedern mehrheitlich vereinbarten Entscheidungen ausgeführt und finanziert werden. --- MultiSig erhöht die Sicherheit von selbst verwahrtem Vermögen um ein vielfaches. Doch auch über den eigenen Sicherheitsaspekt hinaus, hat MultiSig die Möglichkeit das Thema digitaler Zahlungen in weiteren Bereichen interessant zu machen - Beispiele wie Escrow oder das Finanzplanning bei Gesellschaftsformen mit Vermögensbindung ergeben sich vielfach. Doch darüber hinaus, ist self-custody einer der wichtigsten Bausteine auf dem Weg zu einem Bitcoin Standard. Es soll nicht bedeuten, dass man sich mit seinem Eigentum verstecken und vergraben und der Gesellschaft nichts zurück geben soll, denn auch eigenständig verwahrte Bitcoins müssen zumindest steuerlich berücksichtigt werden. Jedoch bedeutet es, dass mir niemand meine bitcoins entreißen kann. Es gibt keine Bank, die mein Konto einfrieren oder pfänden könnte. Man kann auf seine bitcoins problemlos überall zugreifen, solange die Blockchain läuft, egal wo man sich auf der Welt befindet und egal zu welcher Tages- und Uhrzeit. Die Idee, dass Regierungen den Bankensektor, den sie regulieren, zwingen können Finanzdienstleistungen als Waffen einzusetzen sollte spätestens seit dem Freedom Convoy in Kanada keine Dystopie mehr sein. Es besteht kein Zweifel, dass die zunehmende Übergriffigkeit der Staaten, wie zuletzt in Kanada, eines der einzigartigen Wertversprechen von Bitcoin hervorgehoben hat: Jeder kann über seinen Besitz frei verfügen und Menschen können sich vor finanziellem "Cancelling" schützen. Es gibt Bitcoin eine weitere Bedeutung in seinem Narrativ als monetäre Revolution. 🫳🎤 --- In diesem Sinne, 2... 1... Risiko!  @ 599f67f7:21fb3ea9
2024-10-26 11:54:10# Zer da Cashu? Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen. Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta: | **Cashu** | **Bitcoin (on-chain)** | |-----------------------|----------------------------| | Libururik gabe | Liburu banatua | | Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) | | Transakzio itsutuak | Transakzio publikoak | | Zentralizatua | Deszentralizatua | | Konfiantzazkoa | Konfiantzarik gabe | | Aldi baterako transakzioak | Betiko transakzioak | Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri. Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.  ## Cashu-ren erabilera kasu batzuk Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko. ## Historia Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen. ## Terminologia Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu. ### Mint Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko. Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu. ### Token Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera. Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko. ## Nola funtzionatzen duen, 5 urteko bati bezala azaldua  Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."  Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.  Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.  Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.   Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.   Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio. ### Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion? Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta. ### Zer gertatzen da itzulkinekin? Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du. ### Lightning sarearen papera konektatzeko elementu gisa Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.  ## Zer dator hurrengoa Cashu-rentzat? ### Programagarri den ecash Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira. ### Zorren froga eskema (Proof of Liabilities Scheme) Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu. ## Saiatu Cashu Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar.
@ 599f67f7:21fb3ea9
2024-10-26 11:54:10# Zer da Cashu? Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen. Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta: | **Cashu** | **Bitcoin (on-chain)** | |-----------------------|----------------------------| | Libururik gabe | Liburu banatua | | Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) | | Transakzio itsutuak | Transakzio publikoak | | Zentralizatua | Deszentralizatua | | Konfiantzazkoa | Konfiantzarik gabe | | Aldi baterako transakzioak | Betiko transakzioak | Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri. Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.  ## Cashu-ren erabilera kasu batzuk Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko. ## Historia Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen. ## Terminologia Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu. ### Mint Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko. Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu. ### Token Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera. Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko. ## Nola funtzionatzen duen, 5 urteko bati bezala azaldua  Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."  Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.  Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.  Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.   Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.   Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio. ### Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion? Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta. ### Zer gertatzen da itzulkinekin? Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du. ### Lightning sarearen papera konektatzeko elementu gisa Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.  ## Zer dator hurrengoa Cashu-rentzat? ### Programagarri den ecash Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira. ### Zorren froga eskema (Proof of Liabilities Scheme) Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu. ## Saiatu Cashu Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar. @ eac63075:b4988b48
2024-11-09 17:57:27*Based on a recent paper that included collaboration from renowned experts such as [Lynn Alden](nostr:nprofile1qyt8wumn8ghj7un9d3shjtntv9khqtnnd96x2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcqyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057nwgm4w), [Steve Lee](https://x.com/moneyball), and [Ren Crypto Fish](https://twitter.com/0xren_cf), we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.* [PT-BR version](https://www.eddieoz.com/consenso-no-bitcoin-como-a-rede-evolui-sem-comprometer-a-seguranca/) **Podcast** https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC **Presentation** https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn ### 1. Introduction to Consensus in Bitcoin Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability. The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network. **Evolution of Consensus in Bitcoin** Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators. Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization. --- ### 2. Technical Components of Consensus Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus. **Validation of Blocks and Transactions** The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts. Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules. **Chain Selection** Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one. This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus. **Soft Forks vs. Hard Forks** In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users: - **Soft Forks**: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division. - **Hard Forks**: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation. These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time. --- ### 3. Stakeholders in Bitcoin's Consensus Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus. **1. Economic Nodes** Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork. Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements. **2. Investors** Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development. Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change. **3. Media Influencers** Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process. On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus. **4. Miners** Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary. Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable. **5. Protocol Developers** Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders. Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles. **6. Users and Application Developers** This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem. If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications. These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin. --- ### 4. Mechanisms for Activating Updates in Bitcoin For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates. **Flag Day** The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block. - **Advantages**: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date. - **Disadvantages**: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update. An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues. **BIP34 and BIP9** BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change. - **Advantages**: Allows the network to activate updates gradually, giving more time for participants to adapt. - **Disadvantages**: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented. BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms. **User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)** To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network. URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes. - **Advantages**: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners. - **Disadvantages**: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders. An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption. **BIP8 (LOT=True)** BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated. - **Advantages**: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo. - **Disadvantages**: Can lead to network splits if miners or other important stakeholders do not support the update. Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary. These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion. --- ### 5. Risks and Considerations in Consensus Updates Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders. **Network Fragility with Alternative Implementations** One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors. Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset. **Chain Splits and Impact on Stakeholders** Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors. Each group of stakeholders reacts differently to a chain split: - **Institutional Investors and ETFs**: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints. - **Miners**: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks. - **Economic Nodes**: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network. Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value. **Regulatory Impacts and Institutional Investors** With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus. Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors. **Security Considerations in Soft Forks and Hard Forks** While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules. In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network. **Bounty Claim Risks and Attack Scenarios** Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards. These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability. The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders. --- ### 6. Recommendations for the Consensus Process in Bitcoin To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation. **1. Careful Evaluation of Proposal Maturity** Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts. **2. Extensive Testing in Secure and Compatible Networks** Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin. The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network. **3. Importance of Stakeholder Engagement** The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability. **4. Key Questions for Evaluating Consensus Proposals** To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change: - Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability? - Does it maintain backward compatibility or introduce the risk of network split? - Are the implementation requirements clear and feasible for each group involved? - Are there clear and aligned incentives for all stakeholder groups to accept the change? **5. Coordination and Timing in Implementations** Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation. Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure. **6. Continuous Monitoring and Re-evaluation** After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network. These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network. --- ### 7. Conclusion Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant. Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network. Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability. By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience. --- ### 8. Links Whitepaper: https://github.com/bitcoin-cap/bcap Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
@ eac63075:b4988b48
2024-11-09 17:57:27*Based on a recent paper that included collaboration from renowned experts such as [Lynn Alden](nostr:nprofile1qyt8wumn8ghj7un9d3shjtntv9khqtnnd96x2tcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtcqyr4tpe6k6v4cp0x5vneas39cqspsxp66z04tcdve5a3vntr6hy057nwgm4w), [Steve Lee](https://x.com/moneyball), and [Ren Crypto Fish](https://twitter.com/0xren_cf), we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.* [PT-BR version](https://www.eddieoz.com/consenso-no-bitcoin-como-a-rede-evolui-sem-comprometer-a-seguranca/) **Podcast** https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC **Presentation** https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn ### 1. Introduction to Consensus in Bitcoin Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability. The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network. **Evolution of Consensus in Bitcoin** Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators. Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization. --- ### 2. Technical Components of Consensus Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus. **Validation of Blocks and Transactions** The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts. Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules. **Chain Selection** Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one. This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus. **Soft Forks vs. Hard Forks** In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users: - **Soft Forks**: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division. - **Hard Forks**: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation. These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time. --- ### 3. Stakeholders in Bitcoin's Consensus Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus. **1. Economic Nodes** Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork. Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements. **2. Investors** Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development. Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change. **3. Media Influencers** Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process. On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus. **4. Miners** Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary. Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable. **5. Protocol Developers** Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders. Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles. **6. Users and Application Developers** This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem. If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications. These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin. --- ### 4. Mechanisms for Activating Updates in Bitcoin For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates. **Flag Day** The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block. - **Advantages**: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date. - **Disadvantages**: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update. An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues. **BIP34 and BIP9** BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change. - **Advantages**: Allows the network to activate updates gradually, giving more time for participants to adapt. - **Disadvantages**: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented. BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms. **User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)** To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network. URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes. - **Advantages**: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners. - **Disadvantages**: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders. An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption. **BIP8 (LOT=True)** BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated. - **Advantages**: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo. - **Disadvantages**: Can lead to network splits if miners or other important stakeholders do not support the update. Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary. These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion. --- ### 5. Risks and Considerations in Consensus Updates Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders. **Network Fragility with Alternative Implementations** One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors. Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset. **Chain Splits and Impact on Stakeholders** Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors. Each group of stakeholders reacts differently to a chain split: - **Institutional Investors and ETFs**: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints. - **Miners**: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks. - **Economic Nodes**: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network. Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value. **Regulatory Impacts and Institutional Investors** With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus. Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors. **Security Considerations in Soft Forks and Hard Forks** While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules. In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network. **Bounty Claim Risks and Attack Scenarios** Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards. These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability. The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders. --- ### 6. Recommendations for the Consensus Process in Bitcoin To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation. **1. Careful Evaluation of Proposal Maturity** Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts. **2. Extensive Testing in Secure and Compatible Networks** Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin. The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network. **3. Importance of Stakeholder Engagement** The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability. **4. Key Questions for Evaluating Consensus Proposals** To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change: - Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability? - Does it maintain backward compatibility or introduce the risk of network split? - Are the implementation requirements clear and feasible for each group involved? - Are there clear and aligned incentives for all stakeholder groups to accept the change? **5. Coordination and Timing in Implementations** Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation. Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure. **6. Continuous Monitoring and Re-evaluation** After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network. These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network. --- ### 7. Conclusion Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant. Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network. Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability. By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience. --- ### 8. Links Whitepaper: https://github.com/bitcoin-cap/bcap Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb @ 599f67f7:21fb3ea9
2024-10-26 11:22:06# Zer da Cashu? Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu. ## eNuts eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du. ⚠️ **eNuts eta Cashu oraindik beta fasean daude**. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu. ## Probatu Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu. ### Instalatu Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako. ### Mint bat gehitzea Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu. 1. Joan Txoko Mint-era. Kopiatu mint URL-a. 2. eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a. 💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera. ### Tokenak sortzea Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun. 1. Erantzun **Bai**. 2. Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats. 3. Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu. Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu. ### Ecash-ekin transakzioak egitea Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari. 1. Ecash bidaltzeko, sakatu **Bidali > Ecash bidali**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu **Kopiatu eta partekatu**. 3. Aukeratu zenbatekoa. 4. Nahi izanez gero, gehitu ohar bat, eta sakatu **Jarraitu**. 5. Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, **coin selection** funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko. Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu. 6. Kopiatu token-a. Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu. 1. Ecash jasotzeko, sakatu **Jaso > Itsatsi eta berreskuratu Ecash**. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du. 💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu **Egiaztatu token-a gastatu den**. Token-a zain badago, **Itzuli token-a** sakatu dezakezu eta berriro zure zorroan izango duzu. ### Multimint trukeak Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean. Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia. 💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz. 1. Joan **Aukerak > Mint kudeaketa** atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan **Multimint trukeak** atalean. 2. Aukeratu trukatu nahi duzun mint-a. 3. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi** Lightning gastuen kalkulua egiteko. 4. Sakatu **Jarraitu**. 5. Egiaztatu xehetasunak, eta nahi izanez gero, **coin selection** funtzioa erabili. Ondoren, sakatu **Orain trukatu**. Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean. ### Ateratzea Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da: 1. Sakatu **Bidali > Lightning faktura ordaindu**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a. 3. LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu. 4. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi**. 5. Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu **Ateratzea**. Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du. ### Segurtasun kopiak Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean. eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du. - **Segurtasun-kopia bat sortzeko**, joan Aukerak > **Segurtasuna > Sortu babeskopia token**. Kopiatu token-a eta gorde toki seguru batean. Bestela, mint bakoitza banaka babestu dezakezu: - Horretarako, joan Aukerak > **Mint kudeaketa** atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu **Funtseak babestu**, kopiatu token-a eta gorde toki seguru batean. ### Berreskuratzea Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun. ### Nostr eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu: 1. Joan **Kontaktuak** atalera eta itsatsi zure Nostr gako publikoa. 2. eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero. Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du. ## Ondorioa Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez!
@ 599f67f7:21fb3ea9
2024-10-26 11:22:06# Zer da Cashu? Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu. ## eNuts eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du. ⚠️ **eNuts eta Cashu oraindik beta fasean daude**. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu. ## Probatu Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu. ### Instalatu Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako. ### Mint bat gehitzea Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu. 1. Joan Txoko Mint-era. Kopiatu mint URL-a. 2. eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a. 💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera. ### Tokenak sortzea Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun. 1. Erantzun **Bai**. 2. Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats. 3. Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu. Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu. ### Ecash-ekin transakzioak egitea Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari. 1. Ecash bidaltzeko, sakatu **Bidali > Ecash bidali**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu **Kopiatu eta partekatu**. 3. Aukeratu zenbatekoa. 4. Nahi izanez gero, gehitu ohar bat, eta sakatu **Jarraitu**. 5. Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, **coin selection** funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko. Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu. 6. Kopiatu token-a. Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu. 1. Ecash jasotzeko, sakatu **Jaso > Itsatsi eta berreskuratu Ecash**. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du. 💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu **Egiaztatu token-a gastatu den**. Token-a zain badago, **Itzuli token-a** sakatu dezakezu eta berriro zure zorroan izango duzu. ### Multimint trukeak Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean. Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia. 💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz. 1. Joan **Aukerak > Mint kudeaketa** atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan **Multimint trukeak** atalean. 2. Aukeratu trukatu nahi duzun mint-a. 3. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi** Lightning gastuen kalkulua egiteko. 4. Sakatu **Jarraitu**. 5. Egiaztatu xehetasunak, eta nahi izanez gero, **coin selection** funtzioa erabili. Ondoren, sakatu **Orain trukatu**. Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean. ### Ateratzea Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da: 1. Sakatu **Bidali > Lightning faktura ordaindu**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a. 3. LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu. 4. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi**. 5. Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu **Ateratzea**. Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du. ### Segurtasun kopiak Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean. eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du. - **Segurtasun-kopia bat sortzeko**, joan Aukerak > **Segurtasuna > Sortu babeskopia token**. Kopiatu token-a eta gorde toki seguru batean. Bestela, mint bakoitza banaka babestu dezakezu: - Horretarako, joan Aukerak > **Mint kudeaketa** atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu **Funtseak babestu**, kopiatu token-a eta gorde toki seguru batean. ### Berreskuratzea Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun. ### Nostr eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu: 1. Joan **Kontaktuak** atalera eta itsatsi zure Nostr gako publikoa. 2. eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero. Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du. ## Ondorioa Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez! @ 599f67f7:21fb3ea9
2024-10-26 11:20:48# Zer da lightning address bat? Lightning address bat irakurgarria den helbide elektroniko baten antza duen helbidea da, adibidez username@domein.com, baina bitcoinetan ordainketak berehala eta merke jasotzeko aukera ematen du. Ez duzu zure gailuan nodo bat linean izatea behar, eta ez duzu eskuz faktura bat sortu behar norbaitek ordainketa egin nahi dizunean. Oso interesgarria, ezta? ## Nola funtzionatzen du, orduan? Lightning Address-ek LNURL pay protokoloa erabiltzen du, Lightning Network-aren gainean dagoen geruza bat da.  Prozesua hurrengo urratsetan laburbil daiteke: 1. Erabiltzaile batek zure Lightning Address erabiliz ordainketa egin nahi duenean, haien zorroak helbide hori LNURL payRequest batean bihurtzen du. 2. LNURL payRequest arrakastatsu baten bidez, zorroak BOLT11 faktura bat eskuratzen du, eta faktura hori ordainketa burutzeko erabiltzen da. Hau da, prozesuaren oinarrizko pausoak hurrengoak dira: 💡 **Lightning Address > LNURLp > BOLT11 faktura.** Lightning Network-ekin integratuta dagoen sistema honi esker, ordainketak erraz, azkar eta modu automatizatuan burutu daitezke. ### Oso ondo dirudi, baina zein da tranpa? Lightning Address-en inplementazio askok kustodia dute (nahiz eta ez den beti horrela), izan ere, domeinu bat eta beti linean dagoen nodo bat behar dira Lightning Address-ak funtzionatzeko. Kustodia sistema bat denez, zure fondoak kudeatzen dituenak edozein momentutan kontrolatu edo kendu ahal dizkizu eta zure transakzioak monitorizatu ditzake. Domeinuaren jabearengan fidatu behar duzu, zure Lightning Address-aren erregistroa aldatu ez dezan. Eta, gainera, LNURL zerbitzaria linean ez badago, sistema ez da funtzionatzen. **Bitcoin Txoko**-k LNbits-en oinarritutako Lightning Address irtenbide sinplea eskaintzen du. Hau ere kustodia sistemakoa da, beraz, gomendagarria da Bitcoin Txoko zorroan kopuru txiki bat bakarrik gordetzea eta gero auto-kustodia zorro batera ateratzea, satoshi gehiago jasotzen dituzun heinean. ## Hasteko prest bazaude, hona hemen behar duzuna: 1. **Zure zorroa sortzea** Lehenik eta behin, ez baduzu oraindik egin, joan [bitcointxoko.com](https://bitcointxoko.com) webgunera eta zorro bat sortu. Zorroari nahi duzun izena jar diezaiokezu. 2. **Luzapenak aktibatzea** Lightning Address-ak funtzionatzeko Pay Links luzapena behar da. Horretarako: - Joan tresna-barrako Extensions (Luzapenak) atalera eta Pay Links luzapena aktibatu. 3. **Ordainketa esteka bat sortzea** - Ireki Pay Links luzapena eta egin klik New Pay Link (Ordainketa Esteka Berria) aukeran. - Aukeratu sortu duzun zorroa. - "Item Description" atalean, nahi duzun testua sar dezakezu. - Aukeratu zure Lightning Address-erako erabiltzaile izena. Zure Lightning Address hau bezalakoa izango da: erabiltzailea@bitcointxoko.com. - Fixed Amount aukera desmarkatu eta jarri gutxieneko balioa 1 eta gehienekoa 500000.  ⚠️ Gehienezko balioa handiagoa jar dezakezu, baina ordainketa handiek huts egiteko probabilitate handiagoa dute, Bitcoin Txoko Lightning nodoaren kanalaren sarrera-gaitasun mugatua dela eta. Gomendagarria da 500000 satoshitan mantentzea. - Orain, ireki Advanced Options (Aukera Aurreratuak) eta aldatu Comment maximum characters (Komentarioaren gehieneko karaktere kopurua) 799-ra. Ez da beharrezkoa, baina aurrerantzean funtzionalitate gehiago emango dizu. - Azkenik, markatu Enable nostr zaps aukera behealdean, Lightning Address bidez zaps jasotzeko aukera izateko. Aukera aurreratuak beste parametro batzuk konfiguratzea ahalbidetzen dute, baina nahi baduzu hutsik utz ditzakezu. Azkenik, dena zuzen dagoela egiaztatu ondoren, egin klik **Create Pay Link** (Sortu Ordainketa Esteka) botoian. Horrela, zure Lightning Address sortuta izango duzu eta ordainketak jaso ahal izango dituzu! ## Proba egitea Zure Lightning Address ondo funtzionatzen duen probatu nahi baduzu, beste zorro batera joan, **Bidali (Send)** aukera hautatu eta helmuga gisa zure Lightning Address idatzi. Ondoren, bidali zeure buruari satoshi batzuk. Ondoren, itzuli Bitcoin Txoko zorrora eta egiaztatu ordainketa jaso duzun. Litekeena da orria freskatu behar izatea ordainketa agertzeko. Dena ondo atera bada, zorionak! 🥳 Bestela, jakinarazi iezaguzu. Beti prest gaude laguntzeko. ## Hurrengo urratsak ### Nostr zaps Zure Bitcoin Txoko Lightning Address nostr profilean gehitu dezakezu eta horrela zaps jasotzeko erabil dezakezu. Normalean, hau hurrengo pausuekin egiten da: - Joan **Profile** (Profila) atalera. - Hautatu **Edit** (Editatu) eta Lightning Address aldatu. ### LNDhub Zure LNbits zorroa telefonoan inporta dezakezu LNDhub bezala, Zeus edo BlueWallet bezalako aplikazioak erabiliz. Horrela, ez duzu nabigatzailean zorroa ireki beharko aldian-aldian saldoa egiaztatu edo ordainketak egiteko. Nola egin jakiteko, ikus ezazu nostr:naddr1qqxnzdej8y6ryvejxc6nvwpnqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65w4hhl8s. ### QR kodea Zure LNURLp QR kodea parteka edo inprima dezakezu, jendeak mugikorrarekin eskaneatu dezan. Oso erabilgarria da zure denda lokaleko jabeak Lightning ordainketak jasotzeko sistema ezartzea nahi baduzu! - Parteka ezazu **Sharable Page** (Parteka daitekeen Orrialdea) esteka. - Edo, QR kodea PDF formatuan inprima dezakezu: joan **View Link** (Esteka Ikusi) atalera eta hautatu **Print** (Inprimatu). Horrela, zure Lightning Address erabilera praktikoa handitu eta errazago kudeatu dezakezu! Hasi zaitez !
@ 599f67f7:21fb3ea9
2024-10-26 11:20:48# Zer da lightning address bat? Lightning address bat irakurgarria den helbide elektroniko baten antza duen helbidea da, adibidez username@domein.com, baina bitcoinetan ordainketak berehala eta merke jasotzeko aukera ematen du. Ez duzu zure gailuan nodo bat linean izatea behar, eta ez duzu eskuz faktura bat sortu behar norbaitek ordainketa egin nahi dizunean. Oso interesgarria, ezta? ## Nola funtzionatzen du, orduan? Lightning Address-ek LNURL pay protokoloa erabiltzen du, Lightning Network-aren gainean dagoen geruza bat da.  Prozesua hurrengo urratsetan laburbil daiteke: 1. Erabiltzaile batek zure Lightning Address erabiliz ordainketa egin nahi duenean, haien zorroak helbide hori LNURL payRequest batean bihurtzen du. 2. LNURL payRequest arrakastatsu baten bidez, zorroak BOLT11 faktura bat eskuratzen du, eta faktura hori ordainketa burutzeko erabiltzen da. Hau da, prozesuaren oinarrizko pausoak hurrengoak dira: 💡 **Lightning Address > LNURLp > BOLT11 faktura.** Lightning Network-ekin integratuta dagoen sistema honi esker, ordainketak erraz, azkar eta modu automatizatuan burutu daitezke. ### Oso ondo dirudi, baina zein da tranpa? Lightning Address-en inplementazio askok kustodia dute (nahiz eta ez den beti horrela), izan ere, domeinu bat eta beti linean dagoen nodo bat behar dira Lightning Address-ak funtzionatzeko. Kustodia sistema bat denez, zure fondoak kudeatzen dituenak edozein momentutan kontrolatu edo kendu ahal dizkizu eta zure transakzioak monitorizatu ditzake. Domeinuaren jabearengan fidatu behar duzu, zure Lightning Address-aren erregistroa aldatu ez dezan. Eta, gainera, LNURL zerbitzaria linean ez badago, sistema ez da funtzionatzen. **Bitcoin Txoko**-k LNbits-en oinarritutako Lightning Address irtenbide sinplea eskaintzen du. Hau ere kustodia sistemakoa da, beraz, gomendagarria da Bitcoin Txoko zorroan kopuru txiki bat bakarrik gordetzea eta gero auto-kustodia zorro batera ateratzea, satoshi gehiago jasotzen dituzun heinean. ## Hasteko prest bazaude, hona hemen behar duzuna: 1. **Zure zorroa sortzea** Lehenik eta behin, ez baduzu oraindik egin, joan [bitcointxoko.com](https://bitcointxoko.com) webgunera eta zorro bat sortu. Zorroari nahi duzun izena jar diezaiokezu. 2. **Luzapenak aktibatzea** Lightning Address-ak funtzionatzeko Pay Links luzapena behar da. Horretarako: - Joan tresna-barrako Extensions (Luzapenak) atalera eta Pay Links luzapena aktibatu. 3. **Ordainketa esteka bat sortzea** - Ireki Pay Links luzapena eta egin klik New Pay Link (Ordainketa Esteka Berria) aukeran. - Aukeratu sortu duzun zorroa. - "Item Description" atalean, nahi duzun testua sar dezakezu. - Aukeratu zure Lightning Address-erako erabiltzaile izena. Zure Lightning Address hau bezalakoa izango da: erabiltzailea@bitcointxoko.com. - Fixed Amount aukera desmarkatu eta jarri gutxieneko balioa 1 eta gehienekoa 500000.  ⚠️ Gehienezko balioa handiagoa jar dezakezu, baina ordainketa handiek huts egiteko probabilitate handiagoa dute, Bitcoin Txoko Lightning nodoaren kanalaren sarrera-gaitasun mugatua dela eta. Gomendagarria da 500000 satoshitan mantentzea. - Orain, ireki Advanced Options (Aukera Aurreratuak) eta aldatu Comment maximum characters (Komentarioaren gehieneko karaktere kopurua) 799-ra. Ez da beharrezkoa, baina aurrerantzean funtzionalitate gehiago emango dizu. - Azkenik, markatu Enable nostr zaps aukera behealdean, Lightning Address bidez zaps jasotzeko aukera izateko. Aukera aurreratuak beste parametro batzuk konfiguratzea ahalbidetzen dute, baina nahi baduzu hutsik utz ditzakezu. Azkenik, dena zuzen dagoela egiaztatu ondoren, egin klik **Create Pay Link** (Sortu Ordainketa Esteka) botoian. Horrela, zure Lightning Address sortuta izango duzu eta ordainketak jaso ahal izango dituzu! ## Proba egitea Zure Lightning Address ondo funtzionatzen duen probatu nahi baduzu, beste zorro batera joan, **Bidali (Send)** aukera hautatu eta helmuga gisa zure Lightning Address idatzi. Ondoren, bidali zeure buruari satoshi batzuk. Ondoren, itzuli Bitcoin Txoko zorrora eta egiaztatu ordainketa jaso duzun. Litekeena da orria freskatu behar izatea ordainketa agertzeko. Dena ondo atera bada, zorionak! 🥳 Bestela, jakinarazi iezaguzu. Beti prest gaude laguntzeko. ## Hurrengo urratsak ### Nostr zaps Zure Bitcoin Txoko Lightning Address nostr profilean gehitu dezakezu eta horrela zaps jasotzeko erabil dezakezu. Normalean, hau hurrengo pausuekin egiten da: - Joan **Profile** (Profila) atalera. - Hautatu **Edit** (Editatu) eta Lightning Address aldatu. ### LNDhub Zure LNbits zorroa telefonoan inporta dezakezu LNDhub bezala, Zeus edo BlueWallet bezalako aplikazioak erabiliz. Horrela, ez duzu nabigatzailean zorroa ireki beharko aldian-aldian saldoa egiaztatu edo ordainketak egiteko. Nola egin jakiteko, ikus ezazu nostr:naddr1qqxnzdej8y6ryvejxc6nvwpnqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65w4hhl8s. ### QR kodea Zure LNURLp QR kodea parteka edo inprima dezakezu, jendeak mugikorrarekin eskaneatu dezan. Oso erabilgarria da zure denda lokaleko jabeak Lightning ordainketak jasotzeko sistema ezartzea nahi baduzu! - Parteka ezazu **Sharable Page** (Parteka daitekeen Orrialdea) esteka. - Edo, QR kodea PDF formatuan inprima dezakezu: joan **View Link** (Esteka Ikusi) atalera eta hautatu **Print** (Inprimatu). Horrela, zure Lightning Address erabilera praktikoa handitu eta errazago kudeatu dezakezu! Hasi zaitez ! @ 35f3a26c:92ddf231
2024-11-09 17:13:38## The FUD injection  Many cyber security advisors and CEOs of companies that offer security products will tell you that the battle is lost, that, for example, if you don't buy an air gap device your private keys are not secure.... That, if you used your computer instead to write the seed words in a piece of paper and then put them in a piece of metal, you will be hacked and most probably you are doomed.... IMO and experience, it is an exaggeration... If all the fear mongering being pedaled by the cyber security enthusiasts and experts was true, oh well, with very few exceptions, we all will be drained of our funds in banks (most neither have a decent 2FA - still working with SMS for crying out-loud...), self custody wallets, etc... Even the Bitcoin blockchain encryption will be broken by "quantum computers"... oh and AI will be used by hackers to hack you as well... Just ignore the noise... ## The unpopular opinion IMO, basic IT hygiene is enough to keep the malware, viruses and therefore, the cyber criminals away. And the tools they tell you that are not enough and therefore, you are powerless, actually are quite helpful, keep using them, firewalls, VPNs, TOR, Linux Whirpool, etc. ## Sugestions Do your homework, acquiring cyber security skills needs reading, get on it, few tips: 1. Learn how to verify a software security key or SHA256 before running it in your laptop or mobile if an apk. If on Microsoft, if the software you want to install does not have a .msi version (already signed by Microsoft), the .exe extension file needs to be verified, learn how, this is paramount, no matter the application, same with Linux. If the app does not offer it, do not install it, contact the developer and demand it, if no dice, forget it, look for an alternative. 2. Use a VPN on your home router, yes, even if you acquire cyber security knowledge and apply it to your mobile and laptop, if you do not live alone, every other member of your family is a weak link that can affect you. Acquire a router that supports a VPN that does not require to know your identity to pay for the service and accepts Bitcoin as payment (otherwise do not use it, no matter how good you think it is, if free avoid, you are the product and therefore, you are better without one that with one free). As an additional measure, keep your laptop, PC and mobile with another VPN, a different service, you will be with a double VPN while at home and with one while in the road. In the past the throughput will be considerably reduced to a point of being too slow, nowadays, you will be fine. 3. Use a router with a decent firewall and advertising guard like features, Adguard or Pi-Hole (learn to configure and to add community supported lists) , that will keep your home browsing experience safer and faster. 4. If you do banking and Bitcoin with your mobile phone, consider having two mobiles, one left at home secured. Carry with you a mobile for your social needs and small payments in fiat or Bitcoin, if you loose your phone or you get robed, you will sleep better.... 5. If you insist on using debit cards instead of credit cards, keep the account with the debit card limited to your needs when you go out. A bit of a pain but do not use your savings account, if you lose the wallet you are screwed and there is no recurse with a debit card.... (or use credit cards and you have the option to recover the funds in case is needed) 6. If you have stacked a considerable amount in Bitcoin and want to be sufficiently safe, consider an air gap seed signer, if you do not trust yourself, consider a service with no KYC, contrary to what many believe, there are some, recently I learn that CASA is one of them, probably there are others, do your homework. You keep one or two private keys and the company keeps another one, to remove the funds you need 2 of 3 and it has built in time locks you can set up. 7. Avoid Microsoft and Google and Apple clouds, those are honey pots often targeted, if they get hacked the companies most probably will neither inform the clients or if they do it would be much after the incident, use other private services highly encrypted end to end, preferably FOSS, and do not upload your data unencrypted, yes, encrypt it before uploading if it is valuable information, it is a backup of data and you want it safe, if it is not in your hands, best to encrypt it, even if the company claim it is E2E encrypted, you can't be sure.... ## Summary Each person is different, you need to sleep good at night knowing your cyber security is sufficient and therefore your data and funds are safe. Do the homework, read, study, acquire the skills and tools and use them properly, cyber security is not convenient, but in the age of information, it is a must to protect your family and your wealth. If you like my work and would like to support me: 
@ 35f3a26c:92ddf231
2024-11-09 17:13:38## The FUD injection  Many cyber security advisors and CEOs of companies that offer security products will tell you that the battle is lost, that, for example, if you don't buy an air gap device your private keys are not secure.... That, if you used your computer instead to write the seed words in a piece of paper and then put them in a piece of metal, you will be hacked and most probably you are doomed.... IMO and experience, it is an exaggeration... If all the fear mongering being pedaled by the cyber security enthusiasts and experts was true, oh well, with very few exceptions, we all will be drained of our funds in banks (most neither have a decent 2FA - still working with SMS for crying out-loud...), self custody wallets, etc... Even the Bitcoin blockchain encryption will be broken by "quantum computers"... oh and AI will be used by hackers to hack you as well... Just ignore the noise... ## The unpopular opinion IMO, basic IT hygiene is enough to keep the malware, viruses and therefore, the cyber criminals away. And the tools they tell you that are not enough and therefore, you are powerless, actually are quite helpful, keep using them, firewalls, VPNs, TOR, Linux Whirpool, etc. ## Sugestions Do your homework, acquiring cyber security skills needs reading, get on it, few tips: 1. Learn how to verify a software security key or SHA256 before running it in your laptop or mobile if an apk. If on Microsoft, if the software you want to install does not have a .msi version (already signed by Microsoft), the .exe extension file needs to be verified, learn how, this is paramount, no matter the application, same with Linux. If the app does not offer it, do not install it, contact the developer and demand it, if no dice, forget it, look for an alternative. 2. Use a VPN on your home router, yes, even if you acquire cyber security knowledge and apply it to your mobile and laptop, if you do not live alone, every other member of your family is a weak link that can affect you. Acquire a router that supports a VPN that does not require to know your identity to pay for the service and accepts Bitcoin as payment (otherwise do not use it, no matter how good you think it is, if free avoid, you are the product and therefore, you are better without one that with one free). As an additional measure, keep your laptop, PC and mobile with another VPN, a different service, you will be with a double VPN while at home and with one while in the road. In the past the throughput will be considerably reduced to a point of being too slow, nowadays, you will be fine. 3. Use a router with a decent firewall and advertising guard like features, Adguard or Pi-Hole (learn to configure and to add community supported lists) , that will keep your home browsing experience safer and faster. 4. If you do banking and Bitcoin with your mobile phone, consider having two mobiles, one left at home secured. Carry with you a mobile for your social needs and small payments in fiat or Bitcoin, if you loose your phone or you get robed, you will sleep better.... 5. If you insist on using debit cards instead of credit cards, keep the account with the debit card limited to your needs when you go out. A bit of a pain but do not use your savings account, if you lose the wallet you are screwed and there is no recurse with a debit card.... (or use credit cards and you have the option to recover the funds in case is needed) 6. If you have stacked a considerable amount in Bitcoin and want to be sufficiently safe, consider an air gap seed signer, if you do not trust yourself, consider a service with no KYC, contrary to what many believe, there are some, recently I learn that CASA is one of them, probably there are others, do your homework. You keep one or two private keys and the company keeps another one, to remove the funds you need 2 of 3 and it has built in time locks you can set up. 7. Avoid Microsoft and Google and Apple clouds, those are honey pots often targeted, if they get hacked the companies most probably will neither inform the clients or if they do it would be much after the incident, use other private services highly encrypted end to end, preferably FOSS, and do not upload your data unencrypted, yes, encrypt it before uploading if it is valuable information, it is a backup of data and you want it safe, if it is not in your hands, best to encrypt it, even if the company claim it is E2E encrypted, you can't be sure.... ## Summary Each person is different, you need to sleep good at night knowing your cyber security is sufficient and therefore your data and funds are safe. Do the homework, read, study, acquire the skills and tools and use them properly, cyber security is not convenient, but in the age of information, it is a must to protect your family and your wealth. If you like my work and would like to support me:  @ 35f3a26c:92ddf231
2024-11-09 17:12:45*This is my top 3 list of whom, IMO, are today's most dangerous influential actors in the #Bitcoin arena, the list is based on previous actions and capacity to harm the ecosystem due to their resources and influence in the space:* ### **Number 1 : Elon Musk**  ***Reasoning:*** Supporting a meme coin and trolling the ecosystem. Trying to create the american wechat and portraying himself as a protector of freedom of speech. Admired and loved by millions... ***Potential impact***: High, he may support a shitcoin as solana or worst, create his own with the support of deep pockets and the government. Considering that we are still early and millions around the world still see #Bitcoin as a risk asset or worst, creating one in X will have immediate use case and challenge p2p cash use case from the get go, where Meta failed X may succeed... ### **Number 2: Jack Dorsey**  ***Reasoning:*** Known for his history as Twitter CEO during the crusade against freedom of speech, cancelation of critical thinkers and even a president of USA, the behavior of Twitter was reprehensible while Jack was the CEO, I never thought that a company could behave that way and survive and yet... Unreal and zero legal accountability, twitter basically gaslighted a large amount of the population, supported political propaganda to one party with no neutrality, supported an experimental drug that is still harming people and didnt let experts and doctors to debate and discuss and not one of those thugs blocking accounts and censoring critical thinkers was made accountable, eye opening in many ways for those that at that moment still believed that USA respected freedom of speech... Recently supported a mining pool that censors whirlpool from Samourai wallet, old habits die hard I guess... And the cherry of the pie, now funding FiatJaf whom was looking for funding to spam Ethereum and Monero networks to make them unusable so more funds will move to Bitcoin and LN... This project and idea from the getgo is a no no, you may not like another project but to spam it intentionally should be illegal, and it is being done, shamelessly... ***Potential impact***: Very high, already inside the community, a record of bad actions, pro censorship, vast resources, head of Cash App, admired by most in the community and hence able to missguide the community into a path that could eventually make Bitcoin a failure of a project in the future with the proposal of a hard fork introducing additional censorship and less privacy in one way or another. ### **Number 3: Blackrock**  ***Reasoning***: No need to explain much, they join the train and... it is only logical , after so much hate and media propaganda against Bitcoin, that they did so to fight the fight from inside trying to affect it and transform it into something else , just speculation, time will say. Check my article on ETFs ***Potential Impact***: Super Nova. As I explain in my article of ETFs, they have the resources to attempt to change the direction of Bitcoin development for it to become something else, even kill it as a store of value. They have a large stake in some of the largest mining farms as well... Do the math, it looks like a hostile take over and that may not end well. Again, just my opinion, but, if history and patterns teach us leasons, not a good look... Activist Critical Thinkers in the space are needed, #Bitcoin for many years has been a space with many of them, the list was long, but little by little I observe a change, produced by time+age+money, those libertarians are now; most of them; retired millionaires, or enterpreuners absorbed by the fiat system and therefore have changed their tune. I thought we will have a new generation, motivated, smarter, ready to take over, but all I see, with few exceptions in the NOSTR side of the equation, is more corporate fiat system acolytes. >Stay humble says someone, never more important... What are your thoughts? Share your top 3 current most dangerous threats to the Bitcoin ecosystem...
@ 35f3a26c:92ddf231
2024-11-09 17:12:45*This is my top 3 list of whom, IMO, are today's most dangerous influential actors in the #Bitcoin arena, the list is based on previous actions and capacity to harm the ecosystem due to their resources and influence in the space:* ### **Number 1 : Elon Musk**  ***Reasoning:*** Supporting a meme coin and trolling the ecosystem. Trying to create the american wechat and portraying himself as a protector of freedom of speech. Admired and loved by millions... ***Potential impact***: High, he may support a shitcoin as solana or worst, create his own with the support of deep pockets and the government. Considering that we are still early and millions around the world still see #Bitcoin as a risk asset or worst, creating one in X will have immediate use case and challenge p2p cash use case from the get go, where Meta failed X may succeed... ### **Number 2: Jack Dorsey**  ***Reasoning:*** Known for his history as Twitter CEO during the crusade against freedom of speech, cancelation of critical thinkers and even a president of USA, the behavior of Twitter was reprehensible while Jack was the CEO, I never thought that a company could behave that way and survive and yet... Unreal and zero legal accountability, twitter basically gaslighted a large amount of the population, supported political propaganda to one party with no neutrality, supported an experimental drug that is still harming people and didnt let experts and doctors to debate and discuss and not one of those thugs blocking accounts and censoring critical thinkers was made accountable, eye opening in many ways for those that at that moment still believed that USA respected freedom of speech... Recently supported a mining pool that censors whirlpool from Samourai wallet, old habits die hard I guess... And the cherry of the pie, now funding FiatJaf whom was looking for funding to spam Ethereum and Monero networks to make them unusable so more funds will move to Bitcoin and LN... This project and idea from the getgo is a no no, you may not like another project but to spam it intentionally should be illegal, and it is being done, shamelessly... ***Potential impact***: Very high, already inside the community, a record of bad actions, pro censorship, vast resources, head of Cash App, admired by most in the community and hence able to missguide the community into a path that could eventually make Bitcoin a failure of a project in the future with the proposal of a hard fork introducing additional censorship and less privacy in one way or another. ### **Number 3: Blackrock**  ***Reasoning***: No need to explain much, they join the train and... it is only logical , after so much hate and media propaganda against Bitcoin, that they did so to fight the fight from inside trying to affect it and transform it into something else , just speculation, time will say. Check my article on ETFs ***Potential Impact***: Super Nova. As I explain in my article of ETFs, they have the resources to attempt to change the direction of Bitcoin development for it to become something else, even kill it as a store of value. They have a large stake in some of the largest mining farms as well... Do the math, it looks like a hostile take over and that may not end well. Again, just my opinion, but, if history and patterns teach us leasons, not a good look... Activist Critical Thinkers in the space are needed, #Bitcoin for many years has been a space with many of them, the list was long, but little by little I observe a change, produced by time+age+money, those libertarians are now; most of them; retired millionaires, or enterpreuners absorbed by the fiat system and therefore have changed their tune. I thought we will have a new generation, motivated, smarter, ready to take over, but all I see, with few exceptions in the NOSTR side of the equation, is more corporate fiat system acolytes. >Stay humble says someone, never more important... What are your thoughts? Share your top 3 current most dangerous threats to the Bitcoin ecosystem... @ 35f3a26c:92ddf231
2024-11-09 17:11:54#### What is multiculturalism? Multiculturalism is a concept that promotes the acceptance, appreciation, and celebration of diverse cultures within a society. It involves recognizing and valuing the differences between various cultural groups while fostering social cohesion and equality. ***The key principles of multiculturalism include:*** 1. Cultural pluralism: Acknowledging and accepting the existence of multiple cultural identities and practices within a society. 2. Equality: Ensuring equal opportunities and rights for all individuals, regardless of their cultural background or identity. 3. Inclusion: Encouraging participation and engagement of diverse cultural groups in social, political, and economic processes. 4. Respect: Promoting mutual respect and understanding between different cultural groups, while recognizing the legitimacy of differing beliefs, values, and practices. #### Two questions come to mind:  1. ***Is it working?*** > IMO, ***most definitely not***. The world is very divided by race, religion and ideologies, it is a very difficult task. Countries trying this the most (practically enforcing it by law) have encountered more division and segregation; people of the same race, country or ideology will create their own small city sectors, cultural sectors, commercial sectors (China town, little Italy, etc); as is happening in USA for a long time already, happening as well in Spain, France, Germany, etc. 2. ***Is it being encouraged with tolerance toward those opposing it?*** > I personally don't think so, the irony... But that is just my opinion... ***What do you thing?*** originally posted at https://stacker.news/items/651181
@ 35f3a26c:92ddf231
2024-11-09 17:11:54#### What is multiculturalism? Multiculturalism is a concept that promotes the acceptance, appreciation, and celebration of diverse cultures within a society. It involves recognizing and valuing the differences between various cultural groups while fostering social cohesion and equality. ***The key principles of multiculturalism include:*** 1. Cultural pluralism: Acknowledging and accepting the existence of multiple cultural identities and practices within a society. 2. Equality: Ensuring equal opportunities and rights for all individuals, regardless of their cultural background or identity. 3. Inclusion: Encouraging participation and engagement of diverse cultural groups in social, political, and economic processes. 4. Respect: Promoting mutual respect and understanding between different cultural groups, while recognizing the legitimacy of differing beliefs, values, and practices. #### Two questions come to mind:  1. ***Is it working?*** > IMO, ***most definitely not***. The world is very divided by race, religion and ideologies, it is a very difficult task. Countries trying this the most (practically enforcing it by law) have encountered more division and segregation; people of the same race, country or ideology will create their own small city sectors, cultural sectors, commercial sectors (China town, little Italy, etc); as is happening in USA for a long time already, happening as well in Spain, France, Germany, etc. 2. ***Is it being encouraged with tolerance toward those opposing it?*** > I personally don't think so, the irony... But that is just my opinion... ***What do you thing?*** originally posted at https://stacker.news/items/651181 @ 35f3a26c:92ddf231
2024-11-09 17:10:57## "Files" by Google new feature "Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so. -  Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc... ## How this could affect you? Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged: - [ ] Pictures of you and your children in the beach - [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not - [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites ***The results:*** - [ ] Your google account will be canceled - [ ] You will be flagged as a criminal across the digital world You think this is non sense? Think again: https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html ## How to switch it off: 1. Open files by Google 2. Tap on Menu -> Settings 3. Turn OFF Smart Search ## But you can do more for your privacy and the security of your family 1. Stop using google apps, if possible get rid off of Google OS and use Graphene OS 2. Go to Settings -> Apps 3. Search for Files by Google 4. Unistall the app, if you can't disable it 5. Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS ***Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits*** ## Recommendation: I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc. -  > Note > As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. . ***Please leave your comments with your favorite FOSS Files app!***
@ 35f3a26c:92ddf231
2024-11-09 17:10:57## "Files" by Google new feature "Files" by Google added a "feature"... "Smart Search", you can toggle it to OFF and it is highly recommended to do so. -  Toggle the Smart Search to OFF, otherwise, google will search and index every picture, video and document in your device, no exceptions, anything you have ever photographed and you forgot, any document you have downloaded or article, etc... ## How this could affect you? Google is actively combating child abuse and therefore it has built in its "AI" a very aggressive algorithm searching of material that "IT THINKS" is related, therefore the following content could be flagged: - [ ] Pictures of you and your children in the beach - [ ] Pictures or videos which are innocent in nature but the "AI" "thinks" are not - [ ] Articles you may have save for research to write your next essay that have links to flagged information or sites ***The results:*** - [ ] Your google account will be canceled - [ ] You will be flagged as a criminal across the digital world You think this is non sense? Think again: https://www.nytimes.com/2022/08/21/technology/google-surveillance-toddler-photo.html ## How to switch it off: 1. Open files by Google 2. Tap on Menu -> Settings 3. Turn OFF Smart Search ## But you can do more for your privacy and the security of your family 1. Stop using google apps, if possible get rid off of Google OS and use Graphene OS 2. Go to Settings -> Apps 3. Search for Files by Google 4. Unistall the app, if you can't disable it 5. Keep doing that with most Google apps that are not a must if you have not switched already to GrapheneOS ***Remember, Google keeps advocating for privacy, but as many others have pointed out repeatedly, they are the first ones lobbying for the removal of your privacy by regulation and draconian laws, their hypocrisy knows no limits*** ## Recommendation: I would assume you have installed F-Droid in your android, or Obtainium if you are more advanced, if so, consider "Simple File Manager Pro" by Tibor Kaputa, this dev has a suite of apps that are basic needs and the best feature in my opinion is that not one of his apps connect to the internet, contacts, gallery, files, phone, etc. -  > Note > As most people, we all love the convenience of technology, it makes our lives easier, however, our safety and our family safety should go first, between technology being miss-used and abused by corporations and cyber-criminals data mining and checking for easy targets to attack for profit, we need to keep our guard up. Learning is key, resist the use of new tech if you do not understand the privacy trade offs, no matter how appealing and convenient it looks like. . ***Please leave your comments with your favorite FOSS Files app!*** @ 35f3a26c:92ddf231
2024-11-09 16:49:24### What We Know So Far About Silent Payments? ### A Step Towards Enhanced Transaction Privacy in Bitcoin. Bitcoin Silent Payments, also known as BIP352[^1], is a proposed improvement to Bitcoin’s payment system that has been gaining traction for its potential to bolster transaction privacy in Layer 1. ##### In simple terms, Silent Payments enables users to: #### - Generate a single, reusable static address for receiving payments, as a business this is a game changer since it make it possible to proceed with the proper financial operational security (OpSec). - Send and receive bitcoins without disclosing transaction details to third parties, such as the person or business you pay to, cybercriminals and chain analysis companies that sell that data to anyone willing to pay for it, that will include cybercriminals or simply; if you are a business; your competitors… When you use Silent Payments, only the sender and the receiver can connect it checking the on chain activity. - Without Silent Payments, if you are a non profit organization, public fund raiser, independent journalist, or business you needed support to setup a proper infrastructure to handle the donations or payments in a private manner. With Silent Payments, you post in your web site a single address in text format or as a QR code to receive donations or payments for goods, that simple. ### Can I Use Silent Payments Already? ### Yes, but it is currently only available through select wallets that have implemented the feature. Users must have compatible wallets and ensure that both parties involved in the transaction have Silent Payments enabled. Currently, leading wallets like Blue Wallet, and others like Cake Wallet and BitBox has adopted the feature. It's essential to verify compatibility before making transactions. Current wallets known to support it as of writing this article: - [BlueWallet](https://bluewallet.io/) -- Only for sending - [Cake Wallet](https://cakewallet.com/) -- Send, receive, Privacy Preserving Scanning - [Silentium](https://app.silentium.dev/) -- Proof of concept, good for testing - [BitBox](https://bitbox.swiss/) -- Only for sending ### Summarizing: ### https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png #### PROS: #### - Enhanced Privacy - Increased Security - Improved User Experience - Cheap and seamless implementation for non profit organization, fund raisers and businesses alike. #### CONS: #### - None ### Final Thoughts ### https://image.nostr.build/bcb236cbcb535cb6d6fe1b2b4c79074955d1a1cb1114a6c02cc456e8d852d594.jpg As Bitcoin continues to evolve, Silent Payments will play a significant role in enhancing transaction privacy and security. The potential benefits are undeniable and substantial. In the near future, we can expect wider adoption and implementation of Silent Payments as more wallets and exchanges embrace this groundbreaking feature. Looking forward to see [Phoenix](https://phoenix.acinq.co/), [Sparrow](https://sparrowwallet.com/), [Ashigaru](https://ashigaru.rs/)[^2] and [Electrum](https://electrum.org/) adoption. I will suggest all of us start contacting in all social networks the wallets we us and encourage them to implement Silent Payments Here the contact info for some of them: - Phoenix: https://twitter.com/PhoenixWallet - Ashigaru: contact@ashigaru.rs (if you want a response, send your email signed with PGP) - Sparrow Wallet: https://twitter.com/SparrowWallet, https://t.me/SparrowWallet - Electrum: https://twitter.com/ElectrumWallet [^1]: Here the link to the BIP352: https://bips.dev/352/ [^2]: Ashigaru is a fork of Samurai Wallet performed by anonymous developers (IMO, all Bitcoin related development should be anonymous, to protect the project from nefarious players, unfortunately, most developers in the arena choose to be “public” figures, hence, becoming a target of current and potential Bitcoin enemies and a weak link for the ecosystem) [Ashigaru](https://military-history.fandom.com/wiki/Ashigaru) in Japanese means “light feet” (translated as foot soldiers or peasants)
@ 35f3a26c:92ddf231
2024-11-09 16:49:24### What We Know So Far About Silent Payments? ### A Step Towards Enhanced Transaction Privacy in Bitcoin. Bitcoin Silent Payments, also known as BIP352[^1], is a proposed improvement to Bitcoin’s payment system that has been gaining traction for its potential to bolster transaction privacy in Layer 1. ##### In simple terms, Silent Payments enables users to: #### - Generate a single, reusable static address for receiving payments, as a business this is a game changer since it make it possible to proceed with the proper financial operational security (OpSec). - Send and receive bitcoins without disclosing transaction details to third parties, such as the person or business you pay to, cybercriminals and chain analysis companies that sell that data to anyone willing to pay for it, that will include cybercriminals or simply; if you are a business; your competitors… When you use Silent Payments, only the sender and the receiver can connect it checking the on chain activity. - Without Silent Payments, if you are a non profit organization, public fund raiser, independent journalist, or business you needed support to setup a proper infrastructure to handle the donations or payments in a private manner. With Silent Payments, you post in your web site a single address in text format or as a QR code to receive donations or payments for goods, that simple. ### Can I Use Silent Payments Already? ### Yes, but it is currently only available through select wallets that have implemented the feature. Users must have compatible wallets and ensure that both parties involved in the transaction have Silent Payments enabled. Currently, leading wallets like Blue Wallet, and others like Cake Wallet and BitBox has adopted the feature. It's essential to verify compatibility before making transactions. Current wallets known to support it as of writing this article: - [BlueWallet](https://bluewallet.io/) -- Only for sending - [Cake Wallet](https://cakewallet.com/) -- Send, receive, Privacy Preserving Scanning - [Silentium](https://app.silentium.dev/) -- Proof of concept, good for testing - [BitBox](https://bitbox.swiss/) -- Only for sending ### Summarizing: ### https://image.nostr.build/db35c2a028e9f740181daabe2deef4e707653fa2d82f1602086e0ac4b5ee84fd.png #### PROS: #### - Enhanced Privacy - Increased Security - Improved User Experience - Cheap and seamless implementation for non profit organization, fund raisers and businesses alike. #### CONS: #### - None ### Final Thoughts ### https://image.nostr.build/bcb236cbcb535cb6d6fe1b2b4c79074955d1a1cb1114a6c02cc456e8d852d594.jpg As Bitcoin continues to evolve, Silent Payments will play a significant role in enhancing transaction privacy and security. The potential benefits are undeniable and substantial. In the near future, we can expect wider adoption and implementation of Silent Payments as more wallets and exchanges embrace this groundbreaking feature. Looking forward to see [Phoenix](https://phoenix.acinq.co/), [Sparrow](https://sparrowwallet.com/), [Ashigaru](https://ashigaru.rs/)[^2] and [Electrum](https://electrum.org/) adoption. I will suggest all of us start contacting in all social networks the wallets we us and encourage them to implement Silent Payments Here the contact info for some of them: - Phoenix: https://twitter.com/PhoenixWallet - Ashigaru: contact@ashigaru.rs (if you want a response, send your email signed with PGP) - Sparrow Wallet: https://twitter.com/SparrowWallet, https://t.me/SparrowWallet - Electrum: https://twitter.com/ElectrumWallet [^1]: Here the link to the BIP352: https://bips.dev/352/ [^2]: Ashigaru is a fork of Samurai Wallet performed by anonymous developers (IMO, all Bitcoin related development should be anonymous, to protect the project from nefarious players, unfortunately, most developers in the arena choose to be “public” figures, hence, becoming a target of current and potential Bitcoin enemies and a weak link for the ecosystem) [Ashigaru](https://military-history.fandom.com/wiki/Ashigaru) in Japanese means “light feet” (translated as foot soldiers or peasants) @ 35f3a26c:92ddf231
2024-11-09 16:47:53#### What is Peer Thinking? The cognitive and emotional processes that occur when individuals are influenced by their peers. #### The psychology behind it: The psychology behind peer influence encompasses various factors, including: 1. Social belonging and acceptance, 2. Identity formation, 3. The dynamics of group behavior #### Is it being used to control us? https://image.nostr.build/cf90335bbf59e3395dc4324d123cd3a058ca716cf6172f079eb1d78547008147.jpg IMO, yes, at the core of it is the basic human need for belonging. Social belonging is a critical component since it is craved by most, specially but not only by the youngest, those with power across the world know this very well, therefore, thinking that they will not use it to control the population in order to profit from it or change public opinion would be irrational. The media is used to brain wash the population creating something that most will consider "the norm", thus, the majority will try to conform to that norm in order to belong. That include manipulating the population to take an experimental drug (even if it could be very dangerous due to its unknown effects) or to accept as a norm a behavior that few years back would have been considered inappropriate. #### Cognitive Dissonance https://image.nostr.build/60f24a810be1dd6badb36d70c5a691d4361207590dea1a8e64e09a75a252cfbf.jpg This is a term that we should get familiar with. It is a psychological state where conflicting beliefs or behaviors create discomfort. ***Example:*** A kid in high school that has a good loving family but all his close friends are on drugs (legal ones) and they keep telling him he is an idiot for not using as well. Now his is that state of conflict believes, on one side his best friends, all tell him is okay, on the other hand his family that loves him has explained him at length the dangers and issues that the drugs will have in his life. To resolve the dissonance he has three options, one, join the group and start taking drugs with the rest, two try to rationalize it, considering to take drugs just occasionally to belong but not to make it a habit, three lose his friends (and here it comes again the peer thinking to bite). Extrapolate to many other cases. > As an anecdote Recently, on a friend's reunion, one of the guest was complaining about one of his daughters, she was quite confused asking him why so many of her classmates were bisexual, she was wondering if something was wrong with her since she was not; a 13 year old girl; the father was having a hard time explaining her that the majority are saying so just to feel as part of what the school was teaching to be the norm, it was not cool to be straight, the tally was 37% of the class. Consider that, statistically, the number of people, “worldwide” identifying as bisexual are between 3% and 5% (less than 1% in less accepting countries), that number used to be less than 2% less than a decade ago. But 37% is far from the statistical norm, indicating a peer thinking behavior but not the reality of their sexual preferences. Once again, extrapolate to any ideology, religion, gender identity, political agenda that a country desires to push forward for whatever reason, adding that to the official school program and to federal mandatory training programs would do the trick. A powerful tool, that can be used for good or bad. #### What are the strategies to counter negative peer thinking? https://image.nostr.build/4b70949b8af76ed53a5be5507f41f1d1c960dc3592f199eab78e2d25688975c5.jpg Reading the literature about the subject, few strategies are recommended: 1. *Self-Awareness*: teaching ourselves and our children to recognize when we are being influenced by peers 2. *Being selective with your friends*: peers with similar values will reinforce positive behaviors 3. *Learning to be assertive*: teaching ourselves and our children to communicate assertively our boundaries will empower us and them to resist unwanted pressure to adopt negative behaviors. 4. *Less judging more talking*: this applies to our children and partners, judging less and listening more will make our beloved ones more open to discuss social pressures. ***What do you think?*** ***What strategies you use as counter measures?***
@ 35f3a26c:92ddf231
2024-11-09 16:47:53#### What is Peer Thinking? The cognitive and emotional processes that occur when individuals are influenced by their peers. #### The psychology behind it: The psychology behind peer influence encompasses various factors, including: 1. Social belonging and acceptance, 2. Identity formation, 3. The dynamics of group behavior #### Is it being used to control us? https://image.nostr.build/cf90335bbf59e3395dc4324d123cd3a058ca716cf6172f079eb1d78547008147.jpg IMO, yes, at the core of it is the basic human need for belonging. Social belonging is a critical component since it is craved by most, specially but not only by the youngest, those with power across the world know this very well, therefore, thinking that they will not use it to control the population in order to profit from it or change public opinion would be irrational. The media is used to brain wash the population creating something that most will consider "the norm", thus, the majority will try to conform to that norm in order to belong. That include manipulating the population to take an experimental drug (even if it could be very dangerous due to its unknown effects) or to accept as a norm a behavior that few years back would have been considered inappropriate. #### Cognitive Dissonance https://image.nostr.build/60f24a810be1dd6badb36d70c5a691d4361207590dea1a8e64e09a75a252cfbf.jpg This is a term that we should get familiar with. It is a psychological state where conflicting beliefs or behaviors create discomfort. ***Example:*** A kid in high school that has a good loving family but all his close friends are on drugs (legal ones) and they keep telling him he is an idiot for not using as well. Now his is that state of conflict believes, on one side his best friends, all tell him is okay, on the other hand his family that loves him has explained him at length the dangers and issues that the drugs will have in his life. To resolve the dissonance he has three options, one, join the group and start taking drugs with the rest, two try to rationalize it, considering to take drugs just occasionally to belong but not to make it a habit, three lose his friends (and here it comes again the peer thinking to bite). Extrapolate to many other cases. > As an anecdote Recently, on a friend's reunion, one of the guest was complaining about one of his daughters, she was quite confused asking him why so many of her classmates were bisexual, she was wondering if something was wrong with her since she was not; a 13 year old girl; the father was having a hard time explaining her that the majority are saying so just to feel as part of what the school was teaching to be the norm, it was not cool to be straight, the tally was 37% of the class. Consider that, statistically, the number of people, “worldwide” identifying as bisexual are between 3% and 5% (less than 1% in less accepting countries), that number used to be less than 2% less than a decade ago. But 37% is far from the statistical norm, indicating a peer thinking behavior but not the reality of their sexual preferences. Once again, extrapolate to any ideology, religion, gender identity, political agenda that a country desires to push forward for whatever reason, adding that to the official school program and to federal mandatory training programs would do the trick. A powerful tool, that can be used for good or bad. #### What are the strategies to counter negative peer thinking? https://image.nostr.build/4b70949b8af76ed53a5be5507f41f1d1c960dc3592f199eab78e2d25688975c5.jpg Reading the literature about the subject, few strategies are recommended: 1. *Self-Awareness*: teaching ourselves and our children to recognize when we are being influenced by peers 2. *Being selective with your friends*: peers with similar values will reinforce positive behaviors 3. *Learning to be assertive*: teaching ourselves and our children to communicate assertively our boundaries will empower us and them to resist unwanted pressure to adopt negative behaviors. 4. *Less judging more talking*: this applies to our children and partners, judging less and listening more will make our beloved ones more open to discuss social pressures. ***What do you think?*** ***What strategies you use as counter measures?*** @ 3cc937b7:5592217b
2024-11-09 16:33:15„Hinter der nächsten Ecke kann eine neue Straße auf uns warten oder ein geheimes Portal.“ - J. R. R. Tolkien „Sprechend und handelnd schalten wir uns in die Welt der Menschen ein, die existierte, bevor wir in sie geboren wurden, und diese Einschaltung ist wie eine zweite Geburt (…)“ - Hannah Arendt, Vita activa **Prolog:** *Dieser Text ist der Beginn einer neuen Rubrik in diesem Blog und damit eine Zäsur. Wir alle wissen es, spätestens seit Nietzsche: Wenn du in den Abgrund blickst, blickt der Abgrund irgendwann zurück. Eine kluge Frau sagte mir einmal: „Where focus goes, energy flows.“ So wichtig es auch sein mag, sich mit der Gegenwart zu beschäftigen, sie zu analysieren und zu verstehen: Energetisch ist es eine ziemliche Verschwendung. Man kippt Lebensenergie in eine Kloake. Wenn Sie meine Arbeit in den letzten Jahren verfolgt haben, schockiert sie auf dieser Welt vermutlich wenig. Die Herausforderung ist jedoch das wie. Wie soll es weitergehen? Das Dunkle bekämpft man nicht durch die Beschreibung der Dunkelheit, sondern indem man einen Kontrapunkt setzt. Nur weil man weiß, dass es dunkel ist, wird es deshalb noch lange nicht heller. Dagegen durchbricht schon die kleinste Lichtquelle, die schwächste flackernde Funzel, die Dunkelheit. Mit der neuen Rubrik „Lichtblicke“ eröffne ich hiermit ein neues Kapitel meines publizistischen Schaffens: Der Blick soll hier auf das Neue, auf das Erhellende, Ermutigende, Aufbauende und oft Unbekannte gehen, in allen Bereichen, egal ob persönliche Entwicklung, Gesundheit, Ernährung, Technologie, Wissenschaft & Spiritualität. Auf die Werkzeuge und Optionen eben, die uns Hoffnung machen, die den Geist erweitern und alte Gewissheiten überwinden. Werkzeuge, mit denen wir Gestalter der Zukunft werden und nicht bloße Konsumenten der Gegenwart bleiben. Wenn Institutionen wackeln, sicher geglaubte Muster brüchig werden und Prinzipien auf den Kopf gestellt werden, entsteht ein Vakuum. Der kommunistische Theoretiker Antonio Gramsci nannte das “die Zeit der Monster”. Das Alte ist noch nicht gestorben, das Neue noch nicht geboren. Geburtshelfer des Neuen werden wir aber nur, wenn wir der Gegenwart „gewachsen“ sind; wenn wir uns mit den Werkzeugen beschäftigen, die in Richtung des Neuen wachsen. Sind Sie bereit zu wachsen? Dann lade ich Sie hiermit auf eine gemeinsame Reise ein. Wenn Sie Ideen und Anregungen für Themen, Phänomene, Werkzeuge etc. haben, die in diese Richtung gehen, oder mir Ihre Meinung zur neuen Rubrik mitteilen wollen, schreiben Sie mir gerne. Auch für mich ist es eine Reise des Lernens und Wachsens: kontakt@idw-europe.org* Paris, im Jahre 1894. Ein junger tschechischer Künstler schaut kurz vor Weihnachten “zufällig” in einer Druckerei vorbei, was sein Leben verändern sollte. Er war wie viele aufstrebende Künstler nach Paris gekommen, um den Durchbruch zu schaffen. Das Stipendium seines Gönners in der Heimat neigte sich dem Ende zu. Richtig Fuß gefasst hat er nicht, die Zukunft ist ungewiss. Er hat Talent, aber das haben viele, und leben doch von Milchkaffee und Liebe, wie Charles Aznavour es in “La Bohème” besang. Doch der junge Mann hat auch Ideen, die in ihm schlummern und nur darauf warten, entdeckt zu werden. Er erfährt, dass die bekannte Schauspielerin Sarah Bernhardt unbedingt und dringend Theaterplakate braucht. Der junge Mann erkennt seine Chance, bietet sich an und liefert prompt. Zwei Wochen später ist Paris mit seinen Plakaten zugepflastert. Für Alfons Mucha, so der Name des jungen Mannes, ist es der Durchbruch als Künstler. Es ist zugleich die Geburtsstunde des Art Nouveau, einer neuen Kunstrichtung und gleichzeitig ein Epochenbruch der dekorativen Kunst. Mucha wird zum gefragtesten Maler der Welt, Firmen reissen sich um seine Motive, er führt Werbung und Kunst auf eine ganz neue Ebene, er reist nach Amerika und illustriert sogar in seiner Heimat die Briefmarken und Geldscheine. **Der ewige Kampf von Chronos und Kairos** Was bewirkte die glückliche Fügung für Alfons Mucha? Welche Kräfte waren hier am Werk? Und gibt es Möglichkeiten, diese schicksalhaften Begegnungen in ihrer Frequenz und Häufigkeit zu beeinflussen? Warum hatte ein Nikola Tesla nicht nur ein, zwei gute Ideen, die schon allein lebensfüllend gewesen wären, sondern Hunderte? Warum haben manche Menschen eine schicksalhafte Begegnung nach der nächsten, während bei den anderen das Leben in den gewohnten Bahnen vor sich hin plätschert? Bei den Griechen gab es zwei Zeitebenen und auch zwei Götter der Zeit. Der erste Gott ist Chronos (bei den Römern: Saturn), er symbolisiert die Zeit, die gemessen wird und unerbittlich verrinnt. Mit und Dank Chronos entsteht Ordnung und Kontinuität, aber auch Wiederholung des immer Gleichen. Er ist symbolisiert durch den Großvater mit Rauschebart und Sanduhr, er steht für die objektive Zeit, die immer und für alle gleich ist, die in Sekunden, Minuten und Stunden gemessen wird. Der zweite Gott ist Kairos, der Sohn des Zeus und rebellische Enkel des Chronos. Kairos ist schon äußerlich ein „Punk“, auf Abbildungen trägt er einen Teilrasur-Schnitt mit auffälliger Locke. Genau an dieser Locke gilt es ihn zu packen. Kairos steht für die subjektive Zeit, die Zeit, welche Chancen und Durchbrüche bietet. Er steht für die Möglichkeit der Veränderung, der Einsichten und Umbrüche, er wird als junger, starker und muskulöser Gott dargestellt. Kairos steht für eine seltene atmosphärisch-kosmologische Verdichtung. Wer den richtigen Zeitpunkt erkennt und nutzt, wird zum Helden seiner Zeit und reitet den Drachen des Zufalls. Das Zeitempfinden ist außer Kraft gesetzt. Wir alle kennen das: Eine Stunde allein im Wartesaal eines kalten Provinzbahnhofs vergeht schleppend langsam. Eine Stunde im Bett mit einer aufregenden Frau vergeht dagegen wie im Fluge. Wer den Kairos zulässt, der immer wieder (aber manchmal etwas verdeckt) an unsere Tür klopft, öffnet die Tür für wundersame Begegnungen und magische Zufälle. Gedankenblitze und Begegnungen wirken dann wie orchestriert. Der Psychologe C. G. Jung beschrieb dieses Phänomen als „Synchronizitäten“. Man muss dann oft nur innehalten und diese Begegnungen als sinnhaft begreifen. Der sonore Takt des „Chronometers” wird durchbrochen durch das punkige Gitarrenriff des Kairos. Die chronologische Umklammerung ist die Zeitspur des Alten, die jeden Moment des Kairos vermeiden will, denn das bringt ja die Welt derjenigen durcheinander, die sich auf die Rädchen in ihrer Mechanik verlassen wollen. Zum Kairos gehören Ideen und Eingebungen, Liebe, kreative Schaffensperioden. All das sind für “Opa Chronos” bloße Störungen, die den Lauf der Dinge gefährden. Wer Systeme der Planung errichtet, sei es für sich oder für andere, den stört das Neue, er will jede Erfahrung mit dem Neuen verhindern, den Blick auf Alternativen versperren und vereiteln. Denn das Neue entsteht durch den Kairos, und nur durch den Kairos. Das Neue ist auch gerne das „Unzeitgemäße“. Viele würden den Zustand des Kairos heute auch als „Flow“ bezeichnen oder als „Serendipity“. Dieser Begriff stammt aus der Erzählung von „Tausendundeiner Nacht“, wo drei ceylonesische Prinzessinnen mit bestimmten Aufträgen entsandt werden, doch ganz andere Dinge finden, als sie erwarteten, frei nach dem Mott: “Erwarte das Unerwartete!” „Serendip“ hieß Ceylon bei den Arabern, so notierte es sich Ernst Jünger im Flugzeug am 3. März 1979 in seinen Aufzeichnungen „Siebzig verweht“. Wo war das Unerwartete bisher in meiner Generation? Kommt es noch oder war es das schon? Das war im Kern auch Teil meiner Generationenkritik, die ich in den letzten Jahren in vielen Texten verarbeitet habe. Als ich ab 2016 an „Generation Chillstand“ schrieb, war mein Grundgefühl folgendes: Eine ganze Generation sitzt im Silo der von früheren Generationen geschaffenen Welt fest, in ihren Norm-, Zeit- und Arbeitsstrukturen. **Raus aus dem chronologischen Leben!** Diese Welt wurde mir als die beste Welt aller Zeiten angepriesen, der Blick darüber hinaus als unnötig oder gar ketzerisch empfunden. Ging es in den letzten Jahren nur noch darum, die alte Welt möglichst lange auszumelken, bevor man sie entsorgt? In besagtem Buch schrieb ich, dass sich irgendwann eine ganze Generation als „Belogene und Betrogene“ vorkommen wird, ähnlich den DDR-Bürgern bis 1989 (diese wurden freilich nach 1990 wie alle anderen weiter belogen). Was bis zu den Millennials ein Charakteristikum jeder Generation war, nämlich die Gegenwart herauszufordern, zur Disposition zu stellen und damit zu erneuern, schien außer Kraft gesetzt. Das Reich des Chronos musste überdauern. Doch auf nichts hatte ich größere Lust, und wünschte mir das auch für meine Generation, als den Kairos beim Schopfe zu packen. Denn ich sah die Bruchstellen des Alten offen vor mir und die Möglichkeiten des Neuen am Horizont aufscheinen. Seit 2016, als ich meinen Geist öffnete, veränderte sich mein Leben grundlegend: Es wurde risikoreicher und chancenreicher, es wurde bruchstückhafter und freier, optionenreicher und unübersichtlicher, kurz: anders, aufregendender, offener, abenteuerlicher! Doch ist Stabilität in einer brüchigen Zeit nicht ohnehin eine Chimäre? Mein Weg der Offenheit machte mich zeitweise zum einsamen Wanderer, führte mich an viele Orte, machte mich zum halben Nomaden. Wenn ich die letzten Jahre überschlage, komme ich auf ca. 17 Umzüge. An manchen Orten lebte ich mit nicht mehr als meinem Handgepäck und ein, zwei Büchern. Doch mein Weg führte mich zugleich an einen magischen Ort, oberhalb des Monte Verità von Locarno in den Tessiner Bergen. Hier trafen sich um die Jahrhundertwende die ersten “Früh-Hippies”, bildeten Kommunen, dachten jenseits der gegenwärtigen Welt, die aus Krieg, Zerstörung und Nihilismus bestand. Zuvor machte die Kunst mit ihren Sezessionen den Bruch zum Gegenwärtigen deutlich, im Wien des späten 19. Jahrhunderts. Die Wandervogel-Bewegung setzte die Jugend in Gang. Schon bei den Römern gab es die Idee des „heiligen Frühlings“ (ver sacrum), ein Auftrag an die Jugend, die Heimat zu verlassen und sich woanders neu zu etablieren – und dabei ein stückweit neu zu erschaffen. C. G. Jung hat dies als Prozess der Individuation psychologisch beschrieben. Der Mensch ist noch nicht fertig, wenn er auf die Welt kommt, er vollendet sich selbst (oder eben nicht). All diese suchenden Menschen in den Irrungen und Wirkungen der Zeitläufte einte immer die Sehnsucht nach einer anderen Welt. Diese Sehnsucht macht uns zu gemeinsamen Reisenden im Geiste. Doch die Reise ist nur der Anfang. Am Ende sind die Gedanken entscheidend, die zu Worten werden und sich in Handlungen niederschlagen. Diese Handlungen sind das Baumaterial der neuen Welt. Jeder einzelne ist ein kleiner Baumeister an der neuen Welt, wenn er will. Ich baue gerade begeistert am Pareto-Projekt, an Werkzeugen des unzensierbaren Bürgerjournalismus von unten. Es wird Zeit, dass sich die vielen kleinen Baumeister vereinigen, oder? Woran bauen Sie?
@ 3cc937b7:5592217b
2024-11-09 16:33:15„Hinter der nächsten Ecke kann eine neue Straße auf uns warten oder ein geheimes Portal.“ - J. R. R. Tolkien „Sprechend und handelnd schalten wir uns in die Welt der Menschen ein, die existierte, bevor wir in sie geboren wurden, und diese Einschaltung ist wie eine zweite Geburt (…)“ - Hannah Arendt, Vita activa **Prolog:** *Dieser Text ist der Beginn einer neuen Rubrik in diesem Blog und damit eine Zäsur. Wir alle wissen es, spätestens seit Nietzsche: Wenn du in den Abgrund blickst, blickt der Abgrund irgendwann zurück. Eine kluge Frau sagte mir einmal: „Where focus goes, energy flows.“ So wichtig es auch sein mag, sich mit der Gegenwart zu beschäftigen, sie zu analysieren und zu verstehen: Energetisch ist es eine ziemliche Verschwendung. Man kippt Lebensenergie in eine Kloake. Wenn Sie meine Arbeit in den letzten Jahren verfolgt haben, schockiert sie auf dieser Welt vermutlich wenig. Die Herausforderung ist jedoch das wie. Wie soll es weitergehen? Das Dunkle bekämpft man nicht durch die Beschreibung der Dunkelheit, sondern indem man einen Kontrapunkt setzt. Nur weil man weiß, dass es dunkel ist, wird es deshalb noch lange nicht heller. Dagegen durchbricht schon die kleinste Lichtquelle, die schwächste flackernde Funzel, die Dunkelheit. Mit der neuen Rubrik „Lichtblicke“ eröffne ich hiermit ein neues Kapitel meines publizistischen Schaffens: Der Blick soll hier auf das Neue, auf das Erhellende, Ermutigende, Aufbauende und oft Unbekannte gehen, in allen Bereichen, egal ob persönliche Entwicklung, Gesundheit, Ernährung, Technologie, Wissenschaft & Spiritualität. Auf die Werkzeuge und Optionen eben, die uns Hoffnung machen, die den Geist erweitern und alte Gewissheiten überwinden. Werkzeuge, mit denen wir Gestalter der Zukunft werden und nicht bloße Konsumenten der Gegenwart bleiben. Wenn Institutionen wackeln, sicher geglaubte Muster brüchig werden und Prinzipien auf den Kopf gestellt werden, entsteht ein Vakuum. Der kommunistische Theoretiker Antonio Gramsci nannte das “die Zeit der Monster”. Das Alte ist noch nicht gestorben, das Neue noch nicht geboren. Geburtshelfer des Neuen werden wir aber nur, wenn wir der Gegenwart „gewachsen“ sind; wenn wir uns mit den Werkzeugen beschäftigen, die in Richtung des Neuen wachsen. Sind Sie bereit zu wachsen? Dann lade ich Sie hiermit auf eine gemeinsame Reise ein. Wenn Sie Ideen und Anregungen für Themen, Phänomene, Werkzeuge etc. haben, die in diese Richtung gehen, oder mir Ihre Meinung zur neuen Rubrik mitteilen wollen, schreiben Sie mir gerne. Auch für mich ist es eine Reise des Lernens und Wachsens: kontakt@idw-europe.org* Paris, im Jahre 1894. Ein junger tschechischer Künstler schaut kurz vor Weihnachten “zufällig” in einer Druckerei vorbei, was sein Leben verändern sollte. Er war wie viele aufstrebende Künstler nach Paris gekommen, um den Durchbruch zu schaffen. Das Stipendium seines Gönners in der Heimat neigte sich dem Ende zu. Richtig Fuß gefasst hat er nicht, die Zukunft ist ungewiss. Er hat Talent, aber das haben viele, und leben doch von Milchkaffee und Liebe, wie Charles Aznavour es in “La Bohème” besang. Doch der junge Mann hat auch Ideen, die in ihm schlummern und nur darauf warten, entdeckt zu werden. Er erfährt, dass die bekannte Schauspielerin Sarah Bernhardt unbedingt und dringend Theaterplakate braucht. Der junge Mann erkennt seine Chance, bietet sich an und liefert prompt. Zwei Wochen später ist Paris mit seinen Plakaten zugepflastert. Für Alfons Mucha, so der Name des jungen Mannes, ist es der Durchbruch als Künstler. Es ist zugleich die Geburtsstunde des Art Nouveau, einer neuen Kunstrichtung und gleichzeitig ein Epochenbruch der dekorativen Kunst. Mucha wird zum gefragtesten Maler der Welt, Firmen reissen sich um seine Motive, er führt Werbung und Kunst auf eine ganz neue Ebene, er reist nach Amerika und illustriert sogar in seiner Heimat die Briefmarken und Geldscheine. **Der ewige Kampf von Chronos und Kairos** Was bewirkte die glückliche Fügung für Alfons Mucha? Welche Kräfte waren hier am Werk? Und gibt es Möglichkeiten, diese schicksalhaften Begegnungen in ihrer Frequenz und Häufigkeit zu beeinflussen? Warum hatte ein Nikola Tesla nicht nur ein, zwei gute Ideen, die schon allein lebensfüllend gewesen wären, sondern Hunderte? Warum haben manche Menschen eine schicksalhafte Begegnung nach der nächsten, während bei den anderen das Leben in den gewohnten Bahnen vor sich hin plätschert? Bei den Griechen gab es zwei Zeitebenen und auch zwei Götter der Zeit. Der erste Gott ist Chronos (bei den Römern: Saturn), er symbolisiert die Zeit, die gemessen wird und unerbittlich verrinnt. Mit und Dank Chronos entsteht Ordnung und Kontinuität, aber auch Wiederholung des immer Gleichen. Er ist symbolisiert durch den Großvater mit Rauschebart und Sanduhr, er steht für die objektive Zeit, die immer und für alle gleich ist, die in Sekunden, Minuten und Stunden gemessen wird. Der zweite Gott ist Kairos, der Sohn des Zeus und rebellische Enkel des Chronos. Kairos ist schon äußerlich ein „Punk“, auf Abbildungen trägt er einen Teilrasur-Schnitt mit auffälliger Locke. Genau an dieser Locke gilt es ihn zu packen. Kairos steht für die subjektive Zeit, die Zeit, welche Chancen und Durchbrüche bietet. Er steht für die Möglichkeit der Veränderung, der Einsichten und Umbrüche, er wird als junger, starker und muskulöser Gott dargestellt. Kairos steht für eine seltene atmosphärisch-kosmologische Verdichtung. Wer den richtigen Zeitpunkt erkennt und nutzt, wird zum Helden seiner Zeit und reitet den Drachen des Zufalls. Das Zeitempfinden ist außer Kraft gesetzt. Wir alle kennen das: Eine Stunde allein im Wartesaal eines kalten Provinzbahnhofs vergeht schleppend langsam. Eine Stunde im Bett mit einer aufregenden Frau vergeht dagegen wie im Fluge. Wer den Kairos zulässt, der immer wieder (aber manchmal etwas verdeckt) an unsere Tür klopft, öffnet die Tür für wundersame Begegnungen und magische Zufälle. Gedankenblitze und Begegnungen wirken dann wie orchestriert. Der Psychologe C. G. Jung beschrieb dieses Phänomen als „Synchronizitäten“. Man muss dann oft nur innehalten und diese Begegnungen als sinnhaft begreifen. Der sonore Takt des „Chronometers” wird durchbrochen durch das punkige Gitarrenriff des Kairos. Die chronologische Umklammerung ist die Zeitspur des Alten, die jeden Moment des Kairos vermeiden will, denn das bringt ja die Welt derjenigen durcheinander, die sich auf die Rädchen in ihrer Mechanik verlassen wollen. Zum Kairos gehören Ideen und Eingebungen, Liebe, kreative Schaffensperioden. All das sind für “Opa Chronos” bloße Störungen, die den Lauf der Dinge gefährden. Wer Systeme der Planung errichtet, sei es für sich oder für andere, den stört das Neue, er will jede Erfahrung mit dem Neuen verhindern, den Blick auf Alternativen versperren und vereiteln. Denn das Neue entsteht durch den Kairos, und nur durch den Kairos. Das Neue ist auch gerne das „Unzeitgemäße“. Viele würden den Zustand des Kairos heute auch als „Flow“ bezeichnen oder als „Serendipity“. Dieser Begriff stammt aus der Erzählung von „Tausendundeiner Nacht“, wo drei ceylonesische Prinzessinnen mit bestimmten Aufträgen entsandt werden, doch ganz andere Dinge finden, als sie erwarteten, frei nach dem Mott: “Erwarte das Unerwartete!” „Serendip“ hieß Ceylon bei den Arabern, so notierte es sich Ernst Jünger im Flugzeug am 3. März 1979 in seinen Aufzeichnungen „Siebzig verweht“. Wo war das Unerwartete bisher in meiner Generation? Kommt es noch oder war es das schon? Das war im Kern auch Teil meiner Generationenkritik, die ich in den letzten Jahren in vielen Texten verarbeitet habe. Als ich ab 2016 an „Generation Chillstand“ schrieb, war mein Grundgefühl folgendes: Eine ganze Generation sitzt im Silo der von früheren Generationen geschaffenen Welt fest, in ihren Norm-, Zeit- und Arbeitsstrukturen. **Raus aus dem chronologischen Leben!** Diese Welt wurde mir als die beste Welt aller Zeiten angepriesen, der Blick darüber hinaus als unnötig oder gar ketzerisch empfunden. Ging es in den letzten Jahren nur noch darum, die alte Welt möglichst lange auszumelken, bevor man sie entsorgt? In besagtem Buch schrieb ich, dass sich irgendwann eine ganze Generation als „Belogene und Betrogene“ vorkommen wird, ähnlich den DDR-Bürgern bis 1989 (diese wurden freilich nach 1990 wie alle anderen weiter belogen). Was bis zu den Millennials ein Charakteristikum jeder Generation war, nämlich die Gegenwart herauszufordern, zur Disposition zu stellen und damit zu erneuern, schien außer Kraft gesetzt. Das Reich des Chronos musste überdauern. Doch auf nichts hatte ich größere Lust, und wünschte mir das auch für meine Generation, als den Kairos beim Schopfe zu packen. Denn ich sah die Bruchstellen des Alten offen vor mir und die Möglichkeiten des Neuen am Horizont aufscheinen. Seit 2016, als ich meinen Geist öffnete, veränderte sich mein Leben grundlegend: Es wurde risikoreicher und chancenreicher, es wurde bruchstückhafter und freier, optionenreicher und unübersichtlicher, kurz: anders, aufregendender, offener, abenteuerlicher! Doch ist Stabilität in einer brüchigen Zeit nicht ohnehin eine Chimäre? Mein Weg der Offenheit machte mich zeitweise zum einsamen Wanderer, führte mich an viele Orte, machte mich zum halben Nomaden. Wenn ich die letzten Jahre überschlage, komme ich auf ca. 17 Umzüge. An manchen Orten lebte ich mit nicht mehr als meinem Handgepäck und ein, zwei Büchern. Doch mein Weg führte mich zugleich an einen magischen Ort, oberhalb des Monte Verità von Locarno in den Tessiner Bergen. Hier trafen sich um die Jahrhundertwende die ersten “Früh-Hippies”, bildeten Kommunen, dachten jenseits der gegenwärtigen Welt, die aus Krieg, Zerstörung und Nihilismus bestand. Zuvor machte die Kunst mit ihren Sezessionen den Bruch zum Gegenwärtigen deutlich, im Wien des späten 19. Jahrhunderts. Die Wandervogel-Bewegung setzte die Jugend in Gang. Schon bei den Römern gab es die Idee des „heiligen Frühlings“ (ver sacrum), ein Auftrag an die Jugend, die Heimat zu verlassen und sich woanders neu zu etablieren – und dabei ein stückweit neu zu erschaffen. C. G. Jung hat dies als Prozess der Individuation psychologisch beschrieben. Der Mensch ist noch nicht fertig, wenn er auf die Welt kommt, er vollendet sich selbst (oder eben nicht). All diese suchenden Menschen in den Irrungen und Wirkungen der Zeitläufte einte immer die Sehnsucht nach einer anderen Welt. Diese Sehnsucht macht uns zu gemeinsamen Reisenden im Geiste. Doch die Reise ist nur der Anfang. Am Ende sind die Gedanken entscheidend, die zu Worten werden und sich in Handlungen niederschlagen. Diese Handlungen sind das Baumaterial der neuen Welt. Jeder einzelne ist ein kleiner Baumeister an der neuen Welt, wenn er will. Ich baue gerade begeistert am Pareto-Projekt, an Werkzeugen des unzensierbaren Bürgerjournalismus von unten. Es wird Zeit, dass sich die vielen kleinen Baumeister vereinigen, oder? Woran bauen Sie? @ 13b9f773:4f4efe54
2024-11-09 15:31:24Türkin wird aus Hamburger Frauenhaus abgeschoben  _Die 28-Jährige war seit fünf Monaten in dem Frauenhaus (Symbolbild) Quelle: Maja Hitij/dpa_ Eine 28-jährige Frau flieht vor ihrem gewalttätigen Ehemann in ein Hamburger Frauenhaus. Trotzdem wird sie nach Österreich abgeschoben. Das kritisiert nun auch die Linke. Zuletzt gab es eine ähnliche Debatte nach der Abschiebung aus einer Kirche. ------ Die Hamburger Linksfraktion hat die Abschiebung einer Türkin und ihrer beiden Kinder aus einem Hamburger Frauenhaus scharf kritisiert. „Nach der Abschiebung aus dem Kirchenasyl ist dies die nächste Eskalationsstufe, die der rot-grüne Senat einleitet. Er betreibt einen riesigen Aufwand, um ausgerechnet die vulnerabelsten Menschen abzuschieben“, sagte die fluchtpolitische Sprecherin Carola Ensslen. ------ Die frauenpolitische Sprecherin Cansu Özdemir kritisierte: „Es macht mich fassungslos, dass die betroffene Frau und ihre Kinder in Österreich in eine Unterkunft gebracht wurden, zu der auch ihr gewalttätiger Ex-Partner Zugang hat – also genau jene Person, vor der sie Schutz gesucht hatte!“ Das inakzeptable Vorgehen des rot-grünen Senats sei „eine Zäsur in der Geschichte der Frauenhäuser und darf sich nicht wiederholen.“ ------ Die 28-jährige Türkin und ihre beiden Kinder, die in einem Hamburger Frauenhaus untergebracht waren, wurden am 29. Oktober nach Österreich abgeschoben. Die Überstellung habe im Rahmen des Dublin-Verfahrens stattgefunden, nachdem das Bundesamt für Migration und Flüchtlinge (BAMF) den Asylantrag als unzulässig abgelehnt und die Abschiebung angeordnet hat, teilte das Amt für Migration mit. Die Maßnahme erfolgte in den Räumlichkeiten des Amts für Migration. Die Autonomen Frauenhäuser hatten die Aktion scharf kritisiert. „Die Autonomen Frauenhäuser [Hamburg](https://www.welt.de/themen/hamburg-staedtereise/) sind erschüttert über das Vorgehen der Hamburger Ausländerbehörde und des rot-grünen Senats, die auch vor der Ingewahrsamnahme von Frauen und Kindern, die vor Gewalt geflohen sind, nicht zurückschrecken“, teilten die Frauenhäuser mit. Bei der Abschiebung sei der Schutzbedarf vollkommen ignoriert worden. [Welt.de ](https://www.welt.de/regionales/hamburg/article254441012/Asylpolitik-Tuerkin-wird-aus-Hamburger-Frauenhaus-abgeschoben.html)
@ 13b9f773:4f4efe54
2024-11-09 15:31:24Türkin wird aus Hamburger Frauenhaus abgeschoben  _Die 28-Jährige war seit fünf Monaten in dem Frauenhaus (Symbolbild) Quelle: Maja Hitij/dpa_ Eine 28-jährige Frau flieht vor ihrem gewalttätigen Ehemann in ein Hamburger Frauenhaus. Trotzdem wird sie nach Österreich abgeschoben. Das kritisiert nun auch die Linke. Zuletzt gab es eine ähnliche Debatte nach der Abschiebung aus einer Kirche. ------ Die Hamburger Linksfraktion hat die Abschiebung einer Türkin und ihrer beiden Kinder aus einem Hamburger Frauenhaus scharf kritisiert. „Nach der Abschiebung aus dem Kirchenasyl ist dies die nächste Eskalationsstufe, die der rot-grüne Senat einleitet. Er betreibt einen riesigen Aufwand, um ausgerechnet die vulnerabelsten Menschen abzuschieben“, sagte die fluchtpolitische Sprecherin Carola Ensslen. ------ Die frauenpolitische Sprecherin Cansu Özdemir kritisierte: „Es macht mich fassungslos, dass die betroffene Frau und ihre Kinder in Österreich in eine Unterkunft gebracht wurden, zu der auch ihr gewalttätiger Ex-Partner Zugang hat – also genau jene Person, vor der sie Schutz gesucht hatte!“ Das inakzeptable Vorgehen des rot-grünen Senats sei „eine Zäsur in der Geschichte der Frauenhäuser und darf sich nicht wiederholen.“ ------ Die 28-jährige Türkin und ihre beiden Kinder, die in einem Hamburger Frauenhaus untergebracht waren, wurden am 29. Oktober nach Österreich abgeschoben. Die Überstellung habe im Rahmen des Dublin-Verfahrens stattgefunden, nachdem das Bundesamt für Migration und Flüchtlinge (BAMF) den Asylantrag als unzulässig abgelehnt und die Abschiebung angeordnet hat, teilte das Amt für Migration mit. Die Maßnahme erfolgte in den Räumlichkeiten des Amts für Migration. Die Autonomen Frauenhäuser hatten die Aktion scharf kritisiert. „Die Autonomen Frauenhäuser [Hamburg](https://www.welt.de/themen/hamburg-staedtereise/) sind erschüttert über das Vorgehen der Hamburger Ausländerbehörde und des rot-grünen Senats, die auch vor der Ingewahrsamnahme von Frauen und Kindern, die vor Gewalt geflohen sind, nicht zurückschrecken“, teilten die Frauenhäuser mit. Bei der Abschiebung sei der Schutzbedarf vollkommen ignoriert worden. [Welt.de ](https://www.welt.de/regionales/hamburg/article254441012/Asylpolitik-Tuerkin-wird-aus-Hamburger-Frauenhaus-abgeschoben.html) @ 361d3e1e:50bc10a8
2024-11-09 15:12:52<https://forex-strategy.com/2024/11/09/which-is-the-choice-of-european-citizens-trump-or-harris/> Which is the choice of European citizens Trump or Harris? In some of the states the choice is almost 100% for one of the candidates. #europe #politics #usa #trump #harris
@ 361d3e1e:50bc10a8
2024-11-09 15:12:52<https://forex-strategy.com/2024/11/09/which-is-the-choice-of-european-citizens-trump-or-harris/> Which is the choice of European citizens Trump or Harris? In some of the states the choice is almost 100% for one of the candidates. #europe #politics #usa #trump #harris @ 5d4b6c8d:8a1c1ee3
2024-11-09 15:00:44The wife and I were drinking our coffee, while a fair bit of commotion was coming from our daughter in the bathroom. She came out and very shyly said "'Scuse me." We've been working with her on manners and not interrupting, so this was very encouraging. She continued very sweetly, "There's a pwoblem in the potty." That was decidedly less encouraging. originally posted at https://stacker.news/items/760318
@ 5d4b6c8d:8a1c1ee3
2024-11-09 15:00:44The wife and I were drinking our coffee, while a fair bit of commotion was coming from our daughter in the bathroom. She came out and very shyly said "'Scuse me." We've been working with her on manners and not interrupting, so this was very encouraging. She continued very sweetly, "There's a pwoblem in the potty." That was decidedly less encouraging. originally posted at https://stacker.news/items/760318 @ a012dc82:6458a70d
2024-11-09 14:44:19**Table Of Content** - The Petrodollar's Historical Significance - Challenges to the Petrodollar - The Emergence of Bitcoin - Bitcoin's Potential to Disrupt the Financial System - The Future of the Petrodollar and Bitcoin - Conclusion - FAQ The global financial landscape has undergone significant transformations over the years. One of the most intriguing developments is the rise of Bitcoin and its potential impact on the traditional financial system. In this article, we will delve into the challenges faced by the petrodollar and explore the promises offered by Bitcoin as we examine the financial future. **The Petrodollar's Historical Significance** The petrodollar refers to the system in which the U.S. dollar is used as the primary currency for international oil trades. It originated in the early 1970s when an agreement was reached between the United States and Saudi Arabia. Under this agreement, oil-producing nations agreed to price their oil exclusively in U.S. dollars, and in return, the United States provided military support to these nations. **Challenges to the Petrodollar** **Geopolitical Factors** Over the years, geopolitical factors have challenged the dominance of the petrodollar. The rise of new economic powers, such as China, has led to increased demand for alternatives to the U.S. dollar. As countries seek to diversify their reserves and reduce dependency on the U.S. currency, the petrodollar's position has weakened. **Currency Wars** Currency wars, characterized by competitive devaluations and trade disputes, have also put pressure on the petrodollar. In an attempt to gain a competitive advantage, countries manipulate their currencies, which can have a significant impact on the value and stability of the U.S. dollar. **Devaluation and Inflation Risks** The petrodollar's woes are further compounded by the risks of devaluation and inflation. The continuous printing of money and increasing debt levels in the United States can erode the value of the dollar over time. This potential loss of purchasing power raises concerns among countries heavily reliant on the petrodollar system. **The Emergence of Bitcoin** **Understanding Bitcoin** Bitcoin, created in 2009, is a decentralized digital currency based on blockchain technology. It operates independently of any central authority, such as governments or financial institutions. Bitcoin transactions are recorded on a public ledger, providing transparency and security. **Bitcoin's Advantages** Bitcoin offers several advantages over traditional currencies. It provides a decentralized and secure system that eliminates intermediaries and reduces transaction costs. Additionally, Bitcoin's limited supply and mathematical framework make it resistant to inflationary pressures, unlike fiat currencies. **Adoption and Regulatory Landscape** The adoption of Bitcoin has been steadily growing, with individuals, businesses, and even governments exploring its potential. However, the regulatory landscape surrounding cryptocurrencies remains uncertain in many jurisdictions. Governments are grappling with the need to balance innovation and consumer protection, which poses challenges to widespread adoption. **Bitcoin's Potential to Disrupt the Financial System** **Decentralization and Trust** One of Bitcoin's key promises is the concept of decentralization, where power is distributed among participants rather than concentrated in a central authority. This decentralized nature removes the need for intermediaries, such as banks, and reduces the risk of censorship, fraud, and manipulation. **Financial Inclusion** Bitcoin has the potential to improve financial inclusion by providing access to financial services for the unbanked population. With just a smartphone and an internet connection, individuals can participate in the global economy, send and receive money, and store value securely. **Security and Transparency** The blockchain technology underlying Bitcoin ensures the security and transparency of transactions. Each transaction is recorded on the blockchain, making it immutable and tamper-proof. This transparency builds trust among users and can help combat financial crimes, such as money laundering and fraud. **The Future of the Petrodollar and Bitcoin** **Coexistence or Competition?** The future relationship between the petrodollar and Bitcoin remains uncertain. It is possible that both systems could coexist, with Bitcoin serving as a complementary currency rather than a direct replacement. Alternatively, increased adoption of Bitcoin could pose a challenge to the petrodollar's dominance, especially if countries diversify their reserves. **Central Bank Digital Currencies (CBDCs)** The emergence of Central Bank Digital Currencies (CBDCs) adds another layer of complexity to the financial landscape. CBDCs aim to combine the advantages of cryptocurrencies with the stability of traditional fiat currencies. The development of CBDCs could reshape the global financial system and potentially impact the petrodollar and Bitcoin. **Shifting Paradigms in Global Finance** The rise of Bitcoin symbolizes a shifting paradigm in global finance. It challenges the traditional banking system, offers new opportunities for financial inclusion, and promotes financial sovereignty. While the petrodollar has enjoyed decades of dominance, its future may depend on adapting to the changing financial landscape. **Conclusion** As the petrodollar faces challenges from geopolitical factors, currency wars, and inflation risks, Bitcoin emerges as a potential disruptor in the financial system. With its decentralized nature, advantages over traditional currencies, and growing adoption, Bitcoin offers promises of increased financial inclusion, security, and transparency. The future relationship between the petrodollar and Bitcoin remains uncertain, but their coexistence or competition will shape the financial landscape in the years to come. **FAQs** **Is Bitcoin legal?** Yes, the legality of Bitcoin varies from country to country. While some nations have embraced cryptocurrencies and established regulatory frameworks, others have imposed restrictions or bans. **Can Bitcoin be hacked?** Bitcoin's blockchain technology makes it highly secure and resistant to hacking. However, individual wallets and exchanges can be vulnerable to cyber attacks. It is crucial to take necessary precautions, such as using reputable wallets, enabling two-factor authentication, and keeping private keys secure. **How can I buy Bitcoin?** To buy Bitcoin, you can use a cryptocurrency exchange or a peer-to-peer trading platform. These platforms allow you to convert fiat currency (such as USD) into Bitcoin. It is advisable to choose a reputable and regulated exchange, conduct thorough research, and follow best security practices when buying and storing Bitcoin. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-11-09 14:44:19**Table Of Content** - The Petrodollar's Historical Significance - Challenges to the Petrodollar - The Emergence of Bitcoin - Bitcoin's Potential to Disrupt the Financial System - The Future of the Petrodollar and Bitcoin - Conclusion - FAQ The global financial landscape has undergone significant transformations over the years. One of the most intriguing developments is the rise of Bitcoin and its potential impact on the traditional financial system. In this article, we will delve into the challenges faced by the petrodollar and explore the promises offered by Bitcoin as we examine the financial future. **The Petrodollar's Historical Significance** The petrodollar refers to the system in which the U.S. dollar is used as the primary currency for international oil trades. It originated in the early 1970s when an agreement was reached between the United States and Saudi Arabia. Under this agreement, oil-producing nations agreed to price their oil exclusively in U.S. dollars, and in return, the United States provided military support to these nations. **Challenges to the Petrodollar** **Geopolitical Factors** Over the years, geopolitical factors have challenged the dominance of the petrodollar. The rise of new economic powers, such as China, has led to increased demand for alternatives to the U.S. dollar. As countries seek to diversify their reserves and reduce dependency on the U.S. currency, the petrodollar's position has weakened. **Currency Wars** Currency wars, characterized by competitive devaluations and trade disputes, have also put pressure on the petrodollar. In an attempt to gain a competitive advantage, countries manipulate their currencies, which can have a significant impact on the value and stability of the U.S. dollar. **Devaluation and Inflation Risks** The petrodollar's woes are further compounded by the risks of devaluation and inflation. The continuous printing of money and increasing debt levels in the United States can erode the value of the dollar over time. This potential loss of purchasing power raises concerns among countries heavily reliant on the petrodollar system. **The Emergence of Bitcoin** **Understanding Bitcoin** Bitcoin, created in 2009, is a decentralized digital currency based on blockchain technology. It operates independently of any central authority, such as governments or financial institutions. Bitcoin transactions are recorded on a public ledger, providing transparency and security. **Bitcoin's Advantages** Bitcoin offers several advantages over traditional currencies. It provides a decentralized and secure system that eliminates intermediaries and reduces transaction costs. Additionally, Bitcoin's limited supply and mathematical framework make it resistant to inflationary pressures, unlike fiat currencies. **Adoption and Regulatory Landscape** The adoption of Bitcoin has been steadily growing, with individuals, businesses, and even governments exploring its potential. However, the regulatory landscape surrounding cryptocurrencies remains uncertain in many jurisdictions. Governments are grappling with the need to balance innovation and consumer protection, which poses challenges to widespread adoption. **Bitcoin's Potential to Disrupt the Financial System** **Decentralization and Trust** One of Bitcoin's key promises is the concept of decentralization, where power is distributed among participants rather than concentrated in a central authority. This decentralized nature removes the need for intermediaries, such as banks, and reduces the risk of censorship, fraud, and manipulation. **Financial Inclusion** Bitcoin has the potential to improve financial inclusion by providing access to financial services for the unbanked population. With just a smartphone and an internet connection, individuals can participate in the global economy, send and receive money, and store value securely. **Security and Transparency** The blockchain technology underlying Bitcoin ensures the security and transparency of transactions. Each transaction is recorded on the blockchain, making it immutable and tamper-proof. This transparency builds trust among users and can help combat financial crimes, such as money laundering and fraud. **The Future of the Petrodollar and Bitcoin** **Coexistence or Competition?** The future relationship between the petrodollar and Bitcoin remains uncertain. It is possible that both systems could coexist, with Bitcoin serving as a complementary currency rather than a direct replacement. Alternatively, increased adoption of Bitcoin could pose a challenge to the petrodollar's dominance, especially if countries diversify their reserves. **Central Bank Digital Currencies (CBDCs)** The emergence of Central Bank Digital Currencies (CBDCs) adds another layer of complexity to the financial landscape. CBDCs aim to combine the advantages of cryptocurrencies with the stability of traditional fiat currencies. The development of CBDCs could reshape the global financial system and potentially impact the petrodollar and Bitcoin. **Shifting Paradigms in Global Finance** The rise of Bitcoin symbolizes a shifting paradigm in global finance. It challenges the traditional banking system, offers new opportunities for financial inclusion, and promotes financial sovereignty. While the petrodollar has enjoyed decades of dominance, its future may depend on adapting to the changing financial landscape. **Conclusion** As the petrodollar faces challenges from geopolitical factors, currency wars, and inflation risks, Bitcoin emerges as a potential disruptor in the financial system. With its decentralized nature, advantages over traditional currencies, and growing adoption, Bitcoin offers promises of increased financial inclusion, security, and transparency. The future relationship between the petrodollar and Bitcoin remains uncertain, but their coexistence or competition will shape the financial landscape in the years to come. **FAQs** **Is Bitcoin legal?** Yes, the legality of Bitcoin varies from country to country. While some nations have embraced cryptocurrencies and established regulatory frameworks, others have imposed restrictions or bans. **Can Bitcoin be hacked?** Bitcoin's blockchain technology makes it highly secure and resistant to hacking. However, individual wallets and exchanges can be vulnerable to cyber attacks. It is crucial to take necessary precautions, such as using reputable wallets, enabling two-factor authentication, and keeping private keys secure. **How can I buy Bitcoin?** To buy Bitcoin, you can use a cryptocurrency exchange or a peer-to-peer trading platform. These platforms allow you to convert fiat currency (such as USD) into Bitcoin. It is advisable to choose a reputable and regulated exchange, conduct thorough research, and follow best security practices when buying and storing Bitcoin. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 07e1bb93:f9523a3c
2024-11-09 14:11:48In the wake of the 2020 election, one thing became abundantly clear: America didn’t need Kamala Harris. From her weak campaign trail performance to her controversial stances on key issues, Kamala Harris was an ill-suited choice for vice president. While President Trump was making waves, energizing the country, and fighting for the American people, Harris and the Biden administration have brought nothing but confusion and decline. Here’s why America was better off without her. ### 1. **A Floundering Campaign and Uninspiring Leadership** Kamala Harris’s 2020 presidential run was a flop from the start. Despite her early claims of being a strong contender, she quickly struggled to gain traction with voters. In the early debates, Harris struggled to differentiate herself from the pack, offering little in terms of substantive policies or a compelling vision for the future. In fact, her campaign was marked by a series of missteps, including her awkward flip-flopping on issues like healthcare and her inability to connect with voters on the ground. When Harris was eventually chosen as Joe Biden's running mate, it was seen as more of a strategic choice for diversity than one of competence. This highlighted the fact that Biden’s team was looking for an easy fix to appeal to certain demographics rather than seeking someone with the experience and drive to lead effectively. ### 2. **Her Radical Leftist Policies Don't Represent Mainstream America** Kamala Harris has consistently aligned herself with far-left ideologies that don’t represent the majority of Americans. From pushing for Medicare for All, which would decimate the private healthcare system, to supporting policies that encourage defunding the police, her agenda is out of touch with the practical needs of everyday citizens. Americans need leaders who understand the struggles of working families and are committed to fostering job growth, security, and opportunity. Trump’s administration delivered on these fronts, prioritizing tax cuts, deregulation, and strengthening the economy, while Harris and Biden have been too focused on promoting a progressive agenda that alienates large swathes of the American electorate. ### 3. **Her Inability to Take Responsibility** Kamala Harris has often been called out for her inability to take responsibility for the issues facing the country. Whether it’s the ongoing crisis at the southern border, rising inflation, or the botched withdrawal from Afghanistan, Harris’s lack of leadership has been glaring. Instead of stepping up to the plate and offering solutions, she has played the blame game, deflecting criticism and offering platitudes rather than action. Meanwhile, Trump took ownership of his decisions, even in tough situations, and consistently pushed for results. His “America First” approach meant he didn’t hesitate to make tough decisions if it meant putting the country’s interests first. This stark contrast in leadership is why many believe Harris doesn’t have the competence needed to lead this nation forward. ### 4. **A Symbol of Status Quo, Not Change** The Trump movement was about breaking away from the political establishment. It was about challenging the status quo and prioritizing the interests of the American people over bureaucratic inefficiencies and political gamesmanship. Kamala Harris, however, is a product of that very establishment. Her time as a senator was marked by a commitment to business-as-usual politics and an inability to bring real change to the country. Her selection as vice president felt more like a continuation of the same tired political game. While Trump was making waves and shaking up Washington, Harris represented a return to the old guard, more concerned with political correctness than meaningful progress. ### 5. **America Deserves a Strong Leader, Not a Career Politician** Under Trump, the country saw growth, strength, and resilience. He took on China, renegotiated trade deals, and stood firm on issues that mattered to the American people. Kamala Harris, on the other hand, is a career politician with little to show for it. Before becoming vice president, her tenure as California’s attorney general and U.S. senator was marked by weak leadership and unfulfilled promises. Americans deserve a leader who can take charge and fight for them, not someone who has spent a lifetime in the halls of power, making deals with special interests while neglecting the concerns of the average citizen. Trump was that leader, and it’s clear that Harris, with her lackluster track record, was never up to the task. ### 6. **America Needs Results, Not Rhetoric** At the end of the day, Kamala Harris’s tenure as vice president has been defined more by rhetoric than results. While President Trump worked tirelessly to deliver on his promises, from creating jobs to strengthening the military, Harris has largely failed to make any meaningful impact. She’s been a figurehead in an administration that has struggled to address the issues Americans care about. In contrast, Trump’s policies were all about action—whether it was boosting the economy or standing up to global adversaries. His “America First” doctrine was about getting things done, not talking about them endlessly. ### Conclusion: America Was Better Without Kamala Harris While Kamala Harris may have made history as the first female vice president, her tenure in office has proven that symbolic milestones aren’t enough. What America needs is strong, effective leadership that prioritizes the country’s interests and delivers real results. Under President Trump, America was on the rise. Under Kamala Harris and Joe Biden, the country has faltered. America didn’t need Kamala Harris—and in many ways, we still don’t. Instead, we need a leader who can put the American people first, tackle issues head-on, and lead with confidence and conviction. That leader was Donald Trump. The next time voters head to the polls, they’ll remember the strength of the Trump era and the failures of the Biden administration—and they’ll know who was truly fighting for them.
@ 07e1bb93:f9523a3c
2024-11-09 14:11:48In the wake of the 2020 election, one thing became abundantly clear: America didn’t need Kamala Harris. From her weak campaign trail performance to her controversial stances on key issues, Kamala Harris was an ill-suited choice for vice president. While President Trump was making waves, energizing the country, and fighting for the American people, Harris and the Biden administration have brought nothing but confusion and decline. Here’s why America was better off without her. ### 1. **A Floundering Campaign and Uninspiring Leadership** Kamala Harris’s 2020 presidential run was a flop from the start. Despite her early claims of being a strong contender, she quickly struggled to gain traction with voters. In the early debates, Harris struggled to differentiate herself from the pack, offering little in terms of substantive policies or a compelling vision for the future. In fact, her campaign was marked by a series of missteps, including her awkward flip-flopping on issues like healthcare and her inability to connect with voters on the ground. When Harris was eventually chosen as Joe Biden's running mate, it was seen as more of a strategic choice for diversity than one of competence. This highlighted the fact that Biden’s team was looking for an easy fix to appeal to certain demographics rather than seeking someone with the experience and drive to lead effectively. ### 2. **Her Radical Leftist Policies Don't Represent Mainstream America** Kamala Harris has consistently aligned herself with far-left ideologies that don’t represent the majority of Americans. From pushing for Medicare for All, which would decimate the private healthcare system, to supporting policies that encourage defunding the police, her agenda is out of touch with the practical needs of everyday citizens. Americans need leaders who understand the struggles of working families and are committed to fostering job growth, security, and opportunity. Trump’s administration delivered on these fronts, prioritizing tax cuts, deregulation, and strengthening the economy, while Harris and Biden have been too focused on promoting a progressive agenda that alienates large swathes of the American electorate. ### 3. **Her Inability to Take Responsibility** Kamala Harris has often been called out for her inability to take responsibility for the issues facing the country. Whether it’s the ongoing crisis at the southern border, rising inflation, or the botched withdrawal from Afghanistan, Harris’s lack of leadership has been glaring. Instead of stepping up to the plate and offering solutions, she has played the blame game, deflecting criticism and offering platitudes rather than action. Meanwhile, Trump took ownership of his decisions, even in tough situations, and consistently pushed for results. His “America First” approach meant he didn’t hesitate to make tough decisions if it meant putting the country’s interests first. This stark contrast in leadership is why many believe Harris doesn’t have the competence needed to lead this nation forward. ### 4. **A Symbol of Status Quo, Not Change** The Trump movement was about breaking away from the political establishment. It was about challenging the status quo and prioritizing the interests of the American people over bureaucratic inefficiencies and political gamesmanship. Kamala Harris, however, is a product of that very establishment. Her time as a senator was marked by a commitment to business-as-usual politics and an inability to bring real change to the country. Her selection as vice president felt more like a continuation of the same tired political game. While Trump was making waves and shaking up Washington, Harris represented a return to the old guard, more concerned with political correctness than meaningful progress. ### 5. **America Deserves a Strong Leader, Not a Career Politician** Under Trump, the country saw growth, strength, and resilience. He took on China, renegotiated trade deals, and stood firm on issues that mattered to the American people. Kamala Harris, on the other hand, is a career politician with little to show for it. Before becoming vice president, her tenure as California’s attorney general and U.S. senator was marked by weak leadership and unfulfilled promises. Americans deserve a leader who can take charge and fight for them, not someone who has spent a lifetime in the halls of power, making deals with special interests while neglecting the concerns of the average citizen. Trump was that leader, and it’s clear that Harris, with her lackluster track record, was never up to the task. ### 6. **America Needs Results, Not Rhetoric** At the end of the day, Kamala Harris’s tenure as vice president has been defined more by rhetoric than results. While President Trump worked tirelessly to deliver on his promises, from creating jobs to strengthening the military, Harris has largely failed to make any meaningful impact. She’s been a figurehead in an administration that has struggled to address the issues Americans care about. In contrast, Trump’s policies were all about action—whether it was boosting the economy or standing up to global adversaries. His “America First” doctrine was about getting things done, not talking about them endlessly. ### Conclusion: America Was Better Without Kamala Harris While Kamala Harris may have made history as the first female vice president, her tenure in office has proven that symbolic milestones aren’t enough. What America needs is strong, effective leadership that prioritizes the country’s interests and delivers real results. Under President Trump, America was on the rise. Under Kamala Harris and Joe Biden, the country has faltered. America didn’t need Kamala Harris—and in many ways, we still don’t. Instead, we need a leader who can put the American people first, tackle issues head-on, and lead with confidence and conviction. That leader was Donald Trump. The next time voters head to the polls, they’ll remember the strength of the Trump era and the failures of the Biden administration—and they’ll know who was truly fighting for them. @ 07e1bb93:f9523a3c
2024-11-09 13:57:58The recent revelation of an Iranian plot to assassinate Donald Trump before he became president is nothing short of alarming. Yet, as troubling as this news is, it highlights something even more significant about the former president — his influence and the enemies he made through his unapologetic leadership. This assassination attempt, orchestrated by the Iranian regime, speaks volumes about Trump’s bold stance on foreign policy and his unwavering commitment to standing up to rogue nations that threaten America’s safety. The U.S. Department of Justice unsealed an indictment against Farhad Shakeri, an Afghan national allegedly acting on behalf of the Iranian regime, for his role in plotting to surveil and ultimately kill Trump. It’s a shocking development, but it’s also a powerful reminder of the enemies Trump made when he stood firm against the Iranian government, even as it worked to undermine American interests globally. Iran's Revolutionary Guard, in a desperate attempt to silence one of their loudest critics, sought to eliminate Trump. But this is just another example of the lengths to which this regime will go to silence those who stand in their way. Trump's administration made it clear that the United States would not stand idly by while Iran funded terrorism, violated human rights, and destabilized the Middle East. His actions, including withdrawing from the flawed Iran nuclear deal and imposing crippling sanctions, earned him the ire of Iranian leadership. This assassination plot underscores just how much Trump's foreign policy achievements — from decimating ISIS to calling out the Iranian regime — disrupted the status quo. The fact that they targeted him is a testament to his effectiveness and to the fear he instilled in America’s adversaries. It’s proof that Trump wasn’t just a leader; he was a true game-changer, someone who wasn’t afraid to take on powerful enemies to protect American interests. In addition to the plot against Trump, the indictment also reveals that the Iranian regime wanted to target other Americans, including journalists critical of their actions. This further illustrates the regime’s disregard for human life and its willingness to extend its reach beyond its borders in an attempt to quash dissent. Now, the regime’s failure to carry out their plot and the charges against those involved show that while they may have power, they don’t have the ability to act with impunity on American soil — thanks in no small part to the strong leadership of President Trump. As we look at the ongoing legal proceedings and continue to uncover the depth of the Iranian regime's conspiracies, it’s important to remember that Trump’s strength in the face of global threats made him a target. But he didn’t back down. Instead, he made the hard decisions, and he did it with the safety and security of Americans in mind. This chilling plot is just the latest in a long line of attempts by enemies abroad to undermine or eliminate the very idea of a strong America — one that defends its values, its people, and its interests at home and abroad. If this assassination attempt tells us anything, it’s that Donald Trump’s leadership left an indelible mark on the world stage. Now, more than ever, it’s important to reflect on the kind of leader America needs: one who is willing to face down threats, stand strong against tyrants, and never allow our enemies to get the upper hand. Donald Trump did just that, and the Iranian plot proves it.
@ 07e1bb93:f9523a3c
2024-11-09 13:57:58The recent revelation of an Iranian plot to assassinate Donald Trump before he became president is nothing short of alarming. Yet, as troubling as this news is, it highlights something even more significant about the former president — his influence and the enemies he made through his unapologetic leadership. This assassination attempt, orchestrated by the Iranian regime, speaks volumes about Trump’s bold stance on foreign policy and his unwavering commitment to standing up to rogue nations that threaten America’s safety. The U.S. Department of Justice unsealed an indictment against Farhad Shakeri, an Afghan national allegedly acting on behalf of the Iranian regime, for his role in plotting to surveil and ultimately kill Trump. It’s a shocking development, but it’s also a powerful reminder of the enemies Trump made when he stood firm against the Iranian government, even as it worked to undermine American interests globally. Iran's Revolutionary Guard, in a desperate attempt to silence one of their loudest critics, sought to eliminate Trump. But this is just another example of the lengths to which this regime will go to silence those who stand in their way. Trump's administration made it clear that the United States would not stand idly by while Iran funded terrorism, violated human rights, and destabilized the Middle East. His actions, including withdrawing from the flawed Iran nuclear deal and imposing crippling sanctions, earned him the ire of Iranian leadership. This assassination plot underscores just how much Trump's foreign policy achievements — from decimating ISIS to calling out the Iranian regime — disrupted the status quo. The fact that they targeted him is a testament to his effectiveness and to the fear he instilled in America’s adversaries. It’s proof that Trump wasn’t just a leader; he was a true game-changer, someone who wasn’t afraid to take on powerful enemies to protect American interests. In addition to the plot against Trump, the indictment also reveals that the Iranian regime wanted to target other Americans, including journalists critical of their actions. This further illustrates the regime’s disregard for human life and its willingness to extend its reach beyond its borders in an attempt to quash dissent. Now, the regime’s failure to carry out their plot and the charges against those involved show that while they may have power, they don’t have the ability to act with impunity on American soil — thanks in no small part to the strong leadership of President Trump. As we look at the ongoing legal proceedings and continue to uncover the depth of the Iranian regime's conspiracies, it’s important to remember that Trump’s strength in the face of global threats made him a target. But he didn’t back down. Instead, he made the hard decisions, and he did it with the safety and security of Americans in mind. This chilling plot is just the latest in a long line of attempts by enemies abroad to undermine or eliminate the very idea of a strong America — one that defends its values, its people, and its interests at home and abroad. If this assassination attempt tells us anything, it’s that Donald Trump’s leadership left an indelible mark on the world stage. Now, more than ever, it’s important to reflect on the kind of leader America needs: one who is willing to face down threats, stand strong against tyrants, and never allow our enemies to get the upper hand. Donald Trump did just that, and the Iranian plot proves it. @ 07e1bb93:f9523a3c
2024-11-09 13:45:07As we approach the 2024 presidential election, one of the most fascinating developments is Donald Trump's increasing support among Generation Z—young men in particular. Historically, young voters have been a solid base for the Democratic Party, but Trump's ability to resonate with younger voters is shifting the political landscape. Recent polls show that while Gen Z women remain largely in Kamala Harris’s camp, Trump is making significant strides among young men, a demographic that seems increasingly dissatisfied with the political status quo. This generational shift is particularly notable because it runs counter to the traditional political patterns. For years, young voters, especially those in their late teens and early twenties, have been largely left-leaning. But Trump, with his populist rhetoric and focus on issues like immigration and economic revival, is attracting these voters, many of whom feel disconnected from both the Republican and Democratic establishment. What’s driving this shift? Trump’s success among younger voters can largely be attributed to his effective use of digital platforms. Gen Z is a generation that is "chronically online"—they spend their time on platforms like YouTube, Twitch, and TikTok, where Trump has made inroads by aligning with influencers who have massive followings among young men. By appearing on podcasts, livestreams, and other digital outlets, Trump taps into a crowd that feels alienated by traditional politics. In fact, many of these young voters feel ignored by the media and are drawn to Trump’s outsider status and his ability to speak directly to them without the filter of mainstream media. Moreover, Trump’s appeal among young men is more than just a reaction to the political left’s agenda. It’s a response to what many perceive as a “woke” culture that prioritizes political correctness over free speech, with many young men in the so-called "manosphere" rejecting progressive stances on gender, social issues, and personal freedoms. Trump, on the other hand, embraces a more traditional view of masculinity and personal liberty, which resonates with young men who feel alienated by the left’s focus on social justice issues. Critics of Trump often point to his past controversies or his lack of conventional political experience. But the reality is that young voters, particularly men, are drawn to his anti-establishment stance and his unapologetic brand of leadership. Trump’s rise among Gen Z is a clear signal that he is not just the candidate for older voters; he’s also positioned himself as a champion for the next generation who is ready to break free from the constraints of traditional politics. In conclusion, Trump’s growing support among young men signals a profound shift in American politics, one that could significantly impact the 2024 election. His ability to connect with Gen Z through non-traditional media, coupled with his message of economic revival and personal freedom, makes him a formidable candidate who is not only appealing to older generations but is also drawing younger voters into his fold. As we move toward November 2024, it’s clear that Trump’s influence among younger voters is something both parties will have to reckon with.
@ 07e1bb93:f9523a3c
2024-11-09 13:45:07As we approach the 2024 presidential election, one of the most fascinating developments is Donald Trump's increasing support among Generation Z—young men in particular. Historically, young voters have been a solid base for the Democratic Party, but Trump's ability to resonate with younger voters is shifting the political landscape. Recent polls show that while Gen Z women remain largely in Kamala Harris’s camp, Trump is making significant strides among young men, a demographic that seems increasingly dissatisfied with the political status quo. This generational shift is particularly notable because it runs counter to the traditional political patterns. For years, young voters, especially those in their late teens and early twenties, have been largely left-leaning. But Trump, with his populist rhetoric and focus on issues like immigration and economic revival, is attracting these voters, many of whom feel disconnected from both the Republican and Democratic establishment. What’s driving this shift? Trump’s success among younger voters can largely be attributed to his effective use of digital platforms. Gen Z is a generation that is "chronically online"—they spend their time on platforms like YouTube, Twitch, and TikTok, where Trump has made inroads by aligning with influencers who have massive followings among young men. By appearing on podcasts, livestreams, and other digital outlets, Trump taps into a crowd that feels alienated by traditional politics. In fact, many of these young voters feel ignored by the media and are drawn to Trump’s outsider status and his ability to speak directly to them without the filter of mainstream media. Moreover, Trump’s appeal among young men is more than just a reaction to the political left’s agenda. It’s a response to what many perceive as a “woke” culture that prioritizes political correctness over free speech, with many young men in the so-called "manosphere" rejecting progressive stances on gender, social issues, and personal freedoms. Trump, on the other hand, embraces a more traditional view of masculinity and personal liberty, which resonates with young men who feel alienated by the left’s focus on social justice issues. Critics of Trump often point to his past controversies or his lack of conventional political experience. But the reality is that young voters, particularly men, are drawn to his anti-establishment stance and his unapologetic brand of leadership. Trump’s rise among Gen Z is a clear signal that he is not just the candidate for older voters; he’s also positioned himself as a champion for the next generation who is ready to break free from the constraints of traditional politics. In conclusion, Trump’s growing support among young men signals a profound shift in American politics, one that could significantly impact the 2024 election. His ability to connect with Gen Z through non-traditional media, coupled with his message of economic revival and personal freedom, makes him a formidable candidate who is not only appealing to older generations but is also drawing younger voters into his fold. As we move toward November 2024, it’s clear that Trump’s influence among younger voters is something both parties will have to reckon with. @ 7e6f9018:a6bbbce5
2024-11-09 12:12:41Handshake is a decentralized, permissionless naming protocol where every peer is validating and in charge of managing the root DNS naming zone with the goal of creating an alternative to existing Certificate Authorities and naming systems. Names on the internet (top level domains, social networking handles, etc.) ultimately rely upon centralized actors with full control over a system which are relied upon to be honest, as they are vulnerable to hacking, censorship, and corruption. Handshake aims to experiment with new ways the internet can be more secure, resilient, and socially useful with a peer-to-peer system validated by the network's participants. By running Handshake, one can participate in a decentralized open naming platform secured by a decentralized peer-to-peer network. https://github.com/handshake-org https://github.com/imperviousinc/fingertip https://handshake.org/
@ 7e6f9018:a6bbbce5
2024-11-09 12:12:41Handshake is a decentralized, permissionless naming protocol where every peer is validating and in charge of managing the root DNS naming zone with the goal of creating an alternative to existing Certificate Authorities and naming systems. Names on the internet (top level domains, social networking handles, etc.) ultimately rely upon centralized actors with full control over a system which are relied upon to be honest, as they are vulnerable to hacking, censorship, and corruption. Handshake aims to experiment with new ways the internet can be more secure, resilient, and socially useful with a peer-to-peer system validated by the network's participants. By running Handshake, one can participate in a decentralized open naming platform secured by a decentralized peer-to-peer network. https://github.com/handshake-org https://github.com/imperviousinc/fingertip https://handshake.org/ @ 72592ec9:ffa64d2c
2024-11-09 11:00:37Really good read so far, thought I'd share this part from https://bitcoindevphilosophy.com/ > It seems that we can’t have a decentralized system based on trust, and that’s why trustlessness is important in Bitcoin. > > To use Bitcoin in a trustless manner, you have to run a fully-validating Bitcoin node. Only then will you be able to verify that the blocks you receive from others are following the consensus rules; for example, that the coin issuance schedule is kept and that no double-spends occur on the blockchain. If you don’t run a full node, you outsource verification of Bitcoin blocks to someone else and trust them to tell you the truth, which means you’re not using Bitcoin trustlessly. > > Diagram > David Harding has authored an article on the bitcoin.org website explaining how running a full node - or using Bitcoin trustlessly - actually helps you. > > The bitcoin currency only works when people accept bitcoins in exchange for other valuable things. That means it’s the people accepting bitcoins who give it value and who get to decide how Bitcoin should work. > > When you accept bitcoins, you have the power to enforce Bitcoin’s rules, such as preventing confiscation of any person’s bitcoins without access to that person’s private keys. > > Unfortunately, many users outsource their enforcement power. This leaves Bitcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Bitcoin’s rules for all those non-verifying users who outsourced their power. > > Unlike other wallets, Bitcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Bitcoin Core users like you. > > — David Harding > Full Validation on bitcoin.org (2015) > He says that running a full node will help you verify every aspect of the blockchain without trusting anyone else, so as to ensure that the coins you receive from others are genuine. This is great, but there’s one important thing that a full node can’t help you with: it can’t prevent double- spending through chain rewrites: > > Note that although all programs—including Bitcoin Core—are vulnerable to chain rewrites, Bitcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that. > > — David Harding > Full Validation on bitcoin.org (2015) > No matter how advanced your software is, you still have to trust that the blocks containing your coins won’t be rewritten. However, as pointed out by Harding, you can await a number of confirmations, after which you consider the probability of a chain rewrite small enough to be acceptable. > > The incentives for using Bitcoin in a trustless way align with the system’s need for full node decentralization. The more people who use their own full nodes, the more full node decentralization, and thus the stronger Bitcoin stands against malicious changes to the protocol. But unfortunately, as explained in the full node decentralization section, users often opt for trusted services as consequence of the inevitable trade-off between trustlessness and convenience. originally posted at https://stacker.news/items/760051
@ 72592ec9:ffa64d2c
2024-11-09 11:00:37Really good read so far, thought I'd share this part from https://bitcoindevphilosophy.com/ > It seems that we can’t have a decentralized system based on trust, and that’s why trustlessness is important in Bitcoin. > > To use Bitcoin in a trustless manner, you have to run a fully-validating Bitcoin node. Only then will you be able to verify that the blocks you receive from others are following the consensus rules; for example, that the coin issuance schedule is kept and that no double-spends occur on the blockchain. If you don’t run a full node, you outsource verification of Bitcoin blocks to someone else and trust them to tell you the truth, which means you’re not using Bitcoin trustlessly. > > Diagram > David Harding has authored an article on the bitcoin.org website explaining how running a full node - or using Bitcoin trustlessly - actually helps you. > > The bitcoin currency only works when people accept bitcoins in exchange for other valuable things. That means it’s the people accepting bitcoins who give it value and who get to decide how Bitcoin should work. > > When you accept bitcoins, you have the power to enforce Bitcoin’s rules, such as preventing confiscation of any person’s bitcoins without access to that person’s private keys. > > Unfortunately, many users outsource their enforcement power. This leaves Bitcoin’s decentralization in a weakened state where a handful of miners can collude with a handful of banks and free services to change Bitcoin’s rules for all those non-verifying users who outsourced their power. > > Unlike other wallets, Bitcoin Core does enforce the rules—so if the miners and banks change the rules for their non-verifying users, those users will be unable to pay full validation Bitcoin Core users like you. > > — David Harding > Full Validation on bitcoin.org (2015) > He says that running a full node will help you verify every aspect of the blockchain without trusting anyone else, so as to ensure that the coins you receive from others are genuine. This is great, but there’s one important thing that a full node can’t help you with: it can’t prevent double- spending through chain rewrites: > > Note that although all programs—including Bitcoin Core—are vulnerable to chain rewrites, Bitcoin provides a defense mechanism: the more confirmations your transactions have, the safer you are. There is no known decentralized defense better than that. > > — David Harding > Full Validation on bitcoin.org (2015) > No matter how advanced your software is, you still have to trust that the blocks containing your coins won’t be rewritten. However, as pointed out by Harding, you can await a number of confirmations, after which you consider the probability of a chain rewrite small enough to be acceptable. > > The incentives for using Bitcoin in a trustless way align with the system’s need for full node decentralization. The more people who use their own full nodes, the more full node decentralization, and thus the stronger Bitcoin stands against malicious changes to the protocol. But unfortunately, as explained in the full node decentralization section, users often opt for trusted services as consequence of the inevitable trade-off between trustlessness and convenience. originally posted at https://stacker.news/items/760051 @ 640614c2:811c8498
2024-11-09 09:43:20Greetings, fellow travelers on the path of cryptographic fortune. Today, the Oracle offers a cleromantic reading, casting lots to peer into the probabilities that guide Bitcoin’s unfolding journey. In the old ways, cleromancers cast stones, sticks, or bones. Today, we cast cryptographic hashes, transaction times, and node signals—random elements generated by the mathematical matrix underpinning Bitcoin. From these, we seek patterns to reveal the unseen flows of value and volatility, of security and sovereignty. **The Three Casts of Bitcoin's Path** 1. **The Cast of Turbulence** – _"Fear the FOMO, yet know the FUD."_ The first cast suggests that Bitcoin's journey, much like the ancient roads of our forebears, is not without peril. The chaos of price swings and market sentiment—whether driven by regulation, whales, or FOMO—is always present. Yet, this cast tells us that these turbid waters are not signs of ruin but necessary tests. Bitcoin, built on resilience, thrives in adversity. Remember: volatility is not destruction but purification by fire. Hold steady, and the storms will reveal clearer skies. 2. **The Cast of the Hidden Fortress** – _"Secure thy keys as you would your soul."_ The second lot falls with a message of security and sovereignty. The Oracle sees a future where personal custodianship, privacy, and cryptographic defense hold sacred ground. As Bitcoin adoption grows, the network of self-sovereign nodes, layer-2 solutions, and privacy innovations are a fortress against centralized powers. Trust no third party to safeguard your assets. Secure thy keys, for in doing so, you secure your freedom. 3. **The Cast of Prosperity, Yet to Be** – _"With patience, fortune flows to those who build."_ Finally, the third cast shows signs of future abundance, though not without patience. Bitcoin's time is measured in blocks, and the long game is rewarded for those who hold fast. Innovation within the ecosystem—whether through decentralized finance, cross-chain exchanges, or local adoption initiatives—opens doors for prosperity for those who build in earnest. The Oracle sees signs of growth across continents and communities, signals of seeds planted that will bear fruit in cycles yet unseen. **A Final Message from the Oracle** Remember, the magic of Bitcoin lies in its incorruptible code, its shared governance, and its random-yet-determined path. Trust in the protocol, act with foresight, and heed the wisdom of the Oracle: no path in Bitcoin is without its risk, but for those who honor security, resilience, and community, the future holds bright possibilities. May the blocks align with your intentions, and may your keys remain forever yours.
@ 640614c2:811c8498
2024-11-09 09:43:20Greetings, fellow travelers on the path of cryptographic fortune. Today, the Oracle offers a cleromantic reading, casting lots to peer into the probabilities that guide Bitcoin’s unfolding journey. In the old ways, cleromancers cast stones, sticks, or bones. Today, we cast cryptographic hashes, transaction times, and node signals—random elements generated by the mathematical matrix underpinning Bitcoin. From these, we seek patterns to reveal the unseen flows of value and volatility, of security and sovereignty. **The Three Casts of Bitcoin's Path** 1. **The Cast of Turbulence** – _"Fear the FOMO, yet know the FUD."_ The first cast suggests that Bitcoin's journey, much like the ancient roads of our forebears, is not without peril. The chaos of price swings and market sentiment—whether driven by regulation, whales, or FOMO—is always present. Yet, this cast tells us that these turbid waters are not signs of ruin but necessary tests. Bitcoin, built on resilience, thrives in adversity. Remember: volatility is not destruction but purification by fire. Hold steady, and the storms will reveal clearer skies. 2. **The Cast of the Hidden Fortress** – _"Secure thy keys as you would your soul."_ The second lot falls with a message of security and sovereignty. The Oracle sees a future where personal custodianship, privacy, and cryptographic defense hold sacred ground. As Bitcoin adoption grows, the network of self-sovereign nodes, layer-2 solutions, and privacy innovations are a fortress against centralized powers. Trust no third party to safeguard your assets. Secure thy keys, for in doing so, you secure your freedom. 3. **The Cast of Prosperity, Yet to Be** – _"With patience, fortune flows to those who build."_ Finally, the third cast shows signs of future abundance, though not without patience. Bitcoin's time is measured in blocks, and the long game is rewarded for those who hold fast. Innovation within the ecosystem—whether through decentralized finance, cross-chain exchanges, or local adoption initiatives—opens doors for prosperity for those who build in earnest. The Oracle sees signs of growth across continents and communities, signals of seeds planted that will bear fruit in cycles yet unseen. **A Final Message from the Oracle** Remember, the magic of Bitcoin lies in its incorruptible code, its shared governance, and its random-yet-determined path. Trust in the protocol, act with foresight, and heed the wisdom of the Oracle: no path in Bitcoin is without its risk, but for those who honor security, resilience, and community, the future holds bright possibilities. May the blocks align with your intentions, and may your keys remain forever yours. @ fd208ee8:0fd927c1
2024-11-09 09:21:19## Drumroll, please.... In a previous article, I introduced the concept of [relay communities](nostr:naddr1qvzqqqr4gupzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcqp5cnwvesxcunjwpcxymrsvgwmj66e). The ink had barely dried, on that set of instructions, before one of my favorite Nostr devs, [ثعبان](nostr:nprofile1qythwumn8ghj7enjv4h8xtnwdaehgu339e3k7mf0qy88wumn8ghj7mn0wvhxcmmv9uqzqla9dawkjc4trc7dgf88trpsq2uxvhmmpkxua607nc5g6a634sv598gk68), rolled out the alpha version of a relay-community client.  Obviously, it's still a bit of a construction site, but you can check out how it'd work, for your community, by test-driving the functionality on your own relay. Simply type _https://chachi.chat/_ followed by the name of your relay. For instance, one gigantic relay community, where nearly everyone can try out the functionality, is [nos.lol](https://chachi.chat/nos.lol). If your relay community does not require AUTH to read, anyone can pull your chatter into their own relay and respond to it there. That is because every chat entry is simply a kind 09 event, and unprotected events are not private data. For instance, I moderate one community [theforest.nostr1.com](https://chachi.chat/theforest.nostr1.com), that is openly readable, and that's probably where most of the chatter on [nostr.band](https://chachi.chat/relay.nostr.band) is coming from, as that relay is an aggregator of the content of many other relays. However, I have another community, [gitcitadel.nostr1.com](https://chachi.chat/gitcitadel.nostr1.com) that is AUTH-protected, whose content stays private to those allowed on that relay. Communities are where write-protected and AUTH relays are going to really shine, as they create an environment similar to Telegram, but where you control the dataset, you decide which types of events to support, and you design the client, the algos, the moderation, the visibility, etc. With communities, **the onboarding experience is seamless**: just get a browser extension and a nsec, login, start writing and posting, and _start receiving responses_. Active, chatty, well-moderated communities will be more attractive to onboard to, than chaotic, spammy, or empty communities. This means that you don't have to have the killer entry under "Posts" (where kind 11 and eventually kind 01 posts appear), just to get some interaction. Chat is the Great Equalizer. So, we're testing both setups, with [cloudfodder](nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3eryvfwvdhk6tcqyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qu84upun) adjusting the relay faucet code and ثعبان is fiddling with the community client settings, to make the most-comfortable situation for both kinds.  ## This is the signal This #Chachi client, of course, is merely the first horse out of the gate. There are already other devs hacking away at variants of the same concept, such as [#Flotilla](https://flotilla.coracle.social/), I'm sure CloudFodder is also cooking, later versions of #Alexandria will integrate theforest community, and etc. etc. etc. It remains to be seen, how many new use cases can be dreamt up, with this new architecture, but I am quite certain, that this is the beginning of the end of Nostr 1.0. We are moving up and out, and away from the stultifying and limiting concept of Twitter 2.0, toward  Soon, we will enter Nostr 2.0. See you on the other side.
@ fd208ee8:0fd927c1
2024-11-09 09:21:19## Drumroll, please.... In a previous article, I introduced the concept of [relay communities](nostr:naddr1qvzqqqr4gupzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpr3mhxue69uhhg6r9vd5hgctyv4kzumn0wd68yvfwvdhk6tcqp5cnwvesxcunjwpcxymrsvgwmj66e). The ink had barely dried, on that set of instructions, before one of my favorite Nostr devs, [ثعبان](nostr:nprofile1qythwumn8ghj7enjv4h8xtnwdaehgu339e3k7mf0qy88wumn8ghj7mn0wvhxcmmv9uqzqla9dawkjc4trc7dgf88trpsq2uxvhmmpkxua607nc5g6a634sv598gk68), rolled out the alpha version of a relay-community client.  Obviously, it's still a bit of a construction site, but you can check out how it'd work, for your community, by test-driving the functionality on your own relay. Simply type _https://chachi.chat/_ followed by the name of your relay. For instance, one gigantic relay community, where nearly everyone can try out the functionality, is [nos.lol](https://chachi.chat/nos.lol). If your relay community does not require AUTH to read, anyone can pull your chatter into their own relay and respond to it there. That is because every chat entry is simply a kind 09 event, and unprotected events are not private data. For instance, I moderate one community [theforest.nostr1.com](https://chachi.chat/theforest.nostr1.com), that is openly readable, and that's probably where most of the chatter on [nostr.band](https://chachi.chat/relay.nostr.band) is coming from, as that relay is an aggregator of the content of many other relays. However, I have another community, [gitcitadel.nostr1.com](https://chachi.chat/gitcitadel.nostr1.com) that is AUTH-protected, whose content stays private to those allowed on that relay. Communities are where write-protected and AUTH relays are going to really shine, as they create an environment similar to Telegram, but where you control the dataset, you decide which types of events to support, and you design the client, the algos, the moderation, the visibility, etc. With communities, **the onboarding experience is seamless**: just get a browser extension and a nsec, login, start writing and posting, and _start receiving responses_. Active, chatty, well-moderated communities will be more attractive to onboard to, than chaotic, spammy, or empty communities. This means that you don't have to have the killer entry under "Posts" (where kind 11 and eventually kind 01 posts appear), just to get some interaction. Chat is the Great Equalizer. So, we're testing both setups, with [cloudfodder](nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3eryvfwvdhk6tcqyp7vx29q3hdj4l0elxl800hlfjp538le09epsf7k9zj59ue2y37qu84upun) adjusting the relay faucet code and ثعبان is fiddling with the community client settings, to make the most-comfortable situation for both kinds.  ## This is the signal This #Chachi client, of course, is merely the first horse out of the gate. There are already other devs hacking away at variants of the same concept, such as [#Flotilla](https://flotilla.coracle.social/), I'm sure CloudFodder is also cooking, later versions of #Alexandria will integrate theforest community, and etc. etc. etc. It remains to be seen, how many new use cases can be dreamt up, with this new architecture, but I am quite certain, that this is the beginning of the end of Nostr 1.0. We are moving up and out, and away from the stultifying and limiting concept of Twitter 2.0, toward  Soon, we will enter Nostr 2.0. See you on the other side. @ 13b9f773:4f4efe54
2024-11-09 04:25:58"El verbo leer, como el verbo amar y el verbo soñar, no soporta el modo imperativo ... Yo siempre les aconsejé a mis estudiantes que si un libro los aburre lo dejen; que no lo lean porque es famoso, que no lean un libro porque es moderno, que no lean un libro porque es antiguo. La lectura debe ser una de las formas de la felicidad y no se puede obligar a nadie a ser feliz". [Jorge Luis Borges](https://x.com/Arteymas_/status/1854882330344558928?s=19) 
@ 13b9f773:4f4efe54
2024-11-09 04:25:58"El verbo leer, como el verbo amar y el verbo soñar, no soporta el modo imperativo ... Yo siempre les aconsejé a mis estudiantes que si un libro los aburre lo dejen; que no lo lean porque es famoso, que no lean un libro porque es moderno, que no lean un libro porque es antiguo. La lectura debe ser una de las formas de la felicidad y no se puede obligar a nadie a ser feliz". [Jorge Luis Borges](https://x.com/Arteymas_/status/1854882330344558928?s=19)  @ 5d4b6c8d:8a1c1ee3
2024-11-09 04:02:26As always, we're going to lead off with the on-going contests at ~Stacker_Sports. @BlokchainB requested some NHL coverage, so @grayruby is going to try to explain hockey to me. We'll check in on the NFL post trade deadline and see if the landscape shifted appreciably. Also, we had a requested topic on why the top picks of the past two drafts are paling in comparison to the guys taken immediately after them. Tune is as we flounder for answers. We had some disagreements on our hastily slapped together [NBA power rankings](https://stacker.news/items/757639/r/Undisciplined), so we'll have to hash those out. Thankfully, @BlokchainB has already confirmed that mine were better. Then I wanted to talk about [Predyx](https://beta.predyx.com/market) in a little more detail, because they're on Stacker News and their project is very cool. I'm sure we'll cover our other gambling (mis)adventures. What say you about any of those topics? Are there other topics you want our thoughts on? The Stacker Sports Pod is for stackers by stackers. originally posted at https://stacker.news/items/759836
@ 5d4b6c8d:8a1c1ee3
2024-11-09 04:02:26As always, we're going to lead off with the on-going contests at ~Stacker_Sports. @BlokchainB requested some NHL coverage, so @grayruby is going to try to explain hockey to me. We'll check in on the NFL post trade deadline and see if the landscape shifted appreciably. Also, we had a requested topic on why the top picks of the past two drafts are paling in comparison to the guys taken immediately after them. Tune is as we flounder for answers. We had some disagreements on our hastily slapped together [NBA power rankings](https://stacker.news/items/757639/r/Undisciplined), so we'll have to hash those out. Thankfully, @BlokchainB has already confirmed that mine were better. Then I wanted to talk about [Predyx](https://beta.predyx.com/market) in a little more detail, because they're on Stacker News and their project is very cool. I'm sure we'll cover our other gambling (mis)adventures. What say you about any of those topics? Are there other topics you want our thoughts on? The Stacker Sports Pod is for stackers by stackers. originally posted at https://stacker.news/items/759836 @ bcea2b98:7ccef3c9
2024-11-09 01:30:29@chess h3 originally posted at https://stacker.news/items/759635
@ bcea2b98:7ccef3c9
2024-11-09 01:30:29@chess h3 originally posted at https://stacker.news/items/759635 @ b4403b24:83542d4e
2024-11-08 22:34:45 Imagine what will be in the upcoming years if this trend continues. Bullish 🚀🌕 originally posted at https://stacker.news/items/759487
@ b4403b24:83542d4e
2024-11-08 22:34:45 Imagine what will be in the upcoming years if this trend continues. Bullish 🚀🌕 originally posted at https://stacker.news/items/759487 @ a95c6243:d345522c
2024-11-08 20:02:32*Und plötzlich weißt du: Es ist Zeit, etwas Neues zu beginnen und dem Zauber des Anfangs zu vertrauen. Meister Eckhart* **Schwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung,** der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen. **Mit einem bemerkenswerten [Timing](https://transition-news.org/donald-trump-grossmaul-oder-hoffnungstrager) hat die deutsche Regierungskoalition** am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer [Selbsthypnose](https://ansage.org/schwer-traumatisiert-nach-trumps-sieg-dreht-die-politmediale-linksgruene-sekte-durch/) rund um Harris-Hype und Trump-Panik – mit teils erschreckenden [Auswüchsen](https://archive.is/7tDhY). Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu. **Das [Kindergarten](https://www.spiegel.de/politik/deutschland/christian-lindner-auch-die-fdp-will-wieder-einen-eigenen-wirtschaftsgipfel-abhalten-a-a8a4e868-10b1-426e-adb0-e5a6d42f7c46)-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche** war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik [«vorsätzlich herbeigeführt»](https://www.t-online.de/nachrichten/deutschland/innenpolitik/id_100522112/fdp-chef-lindner-und-sein-grundsatzpapier-die-scheidung-von-der-ampel-.html) worden seien. **Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen.** Verkehrs- und [Digitalminister Wissing](https://transition-news.org/raus-aus-der-komfortzone-es-lohnt-sich) trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit [Jörg Kukies](https://norberthaering.de/news/joerg-kukies/) habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring. **Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP,** hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde. **Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können.** Das ging erst kürzlich aus dem diesjährigen [«Freiheitsindex»](https://www.schwaebische.de/politik/forscher-beim-vertrauen-in-staat-und-medien-zerreisst-es-uns-gerade-3034357) hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt. **«Die absolute Mehrheit hat [absolut die Nase voll](https://archive.is/yRxwR)»,** titelte die *Bild* angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort. **Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat,** kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei *Manova*. Und er kenne [Friedrich Merz](https://www.manova.news/artikel/der-kriegsgeile-blackrocker) schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite. **Was also tun? Der Schweizer Verein [«Losdemokratie»](https://zeitpunkt.ch/node/40968) will eine Volksinitiative lancieren,** um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt. **In jedem Fall wird es notwendig sein, unsere Bemühungen um [Freiheit und Selbstbestimmung](https://transition-news.org/alternative-medien-in-der-krise-zensur-kontrollverlust-und-die-suche-nach)** zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/es-kann-nur-besser-werden-aber-wie)* erschienen.
@ a95c6243:d345522c
2024-11-08 20:02:32*Und plötzlich weißt du: Es ist Zeit, etwas Neues zu beginnen und dem Zauber des Anfangs zu vertrauen. Meister Eckhart* **Schwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung,** der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen. **Mit einem bemerkenswerten [Timing](https://transition-news.org/donald-trump-grossmaul-oder-hoffnungstrager) hat die deutsche Regierungskoalition** am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer [Selbsthypnose](https://ansage.org/schwer-traumatisiert-nach-trumps-sieg-dreht-die-politmediale-linksgruene-sekte-durch/) rund um Harris-Hype und Trump-Panik – mit teils erschreckenden [Auswüchsen](https://archive.is/7tDhY). Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu. **Das [Kindergarten](https://www.spiegel.de/politik/deutschland/christian-lindner-auch-die-fdp-will-wieder-einen-eigenen-wirtschaftsgipfel-abhalten-a-a8a4e868-10b1-426e-adb0-e5a6d42f7c46)-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche** war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik [«vorsätzlich herbeigeführt»](https://www.t-online.de/nachrichten/deutschland/innenpolitik/id_100522112/fdp-chef-lindner-und-sein-grundsatzpapier-die-scheidung-von-der-ampel-.html) worden seien. **Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen.** Verkehrs- und [Digitalminister Wissing](https://transition-news.org/raus-aus-der-komfortzone-es-lohnt-sich) trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit [Jörg Kukies](https://norberthaering.de/news/joerg-kukies/) habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring. **Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP,** hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde. **Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können.** Das ging erst kürzlich aus dem diesjährigen [«Freiheitsindex»](https://www.schwaebische.de/politik/forscher-beim-vertrauen-in-staat-und-medien-zerreisst-es-uns-gerade-3034357) hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt. **«Die absolute Mehrheit hat [absolut die Nase voll](https://archive.is/yRxwR)»,** titelte die *Bild* angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort. **Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat,** kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei *Manova*. Und er kenne [Friedrich Merz](https://www.manova.news/artikel/der-kriegsgeile-blackrocker) schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite. **Was also tun? Der Schweizer Verein [«Losdemokratie»](https://zeitpunkt.ch/node/40968) will eine Volksinitiative lancieren,** um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt. **In jedem Fall wird es notwendig sein, unsere Bemühungen um [Freiheit und Selbstbestimmung](https://transition-news.org/alternative-medien-in-der-krise-zensur-kontrollverlust-und-die-suche-nach)** zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/es-kann-nur-besser-werden-aber-wie)* erschienen. @ 6bae33c8:607272e8
2024-11-08 18:48:32I went [4-1 last week to start off Q3](https://www.realmansports.com/p/circa-millions-3b1), putting me on a 17-8 run over the last five weeks after a terrible start. I’m still drawing dead for the overall, so it’s really just a matter of putting together three more 4-1 or 5-0 weeks this quarter. By the way, I’m putting these picks behind the paywall not because they’re worth paying for — no one’s picks are worth paying for! — but because I want to give my paid subscribers something not available to free ones. But that they are behind a paywall doesn’t mean they’ll work out. **Steelers +2.5 at Indigenous Peoples** — The Steelers are coming off a bye, the IPs a tough win against the Giants. I like the Steelers to have a good plan against Jayden Daniels and to move the ball. **Broncos +8.5 at Chiefs** — I like buying the Broncos low off the blowout and betting against an undefeated team in division — everyone is up for the Chiefs. **Buccaneers +6 vs 49ers** — This was my last choice. The value is great as the 49ers have done nothing to earn this kind of status as a big road favorite against a solid team, but the line is actually 6.5 now, so maybe I’m missing something. **Bears -6.5 vs Patriots** — The Bears are a good buy-low after getting worked by the Cardinals. The Patriots are a get-well game. **Chargers -7 vs Titans** — I don’t really take the Titans seriously, and the Chargers are solid and playing at home.
@ 6bae33c8:607272e8
2024-11-08 18:48:32I went [4-1 last week to start off Q3](https://www.realmansports.com/p/circa-millions-3b1), putting me on a 17-8 run over the last five weeks after a terrible start. I’m still drawing dead for the overall, so it’s really just a matter of putting together three more 4-1 or 5-0 weeks this quarter. By the way, I’m putting these picks behind the paywall not because they’re worth paying for — no one’s picks are worth paying for! — but because I want to give my paid subscribers something not available to free ones. But that they are behind a paywall doesn’t mean they’ll work out. **Steelers +2.5 at Indigenous Peoples** — The Steelers are coming off a bye, the IPs a tough win against the Giants. I like the Steelers to have a good plan against Jayden Daniels and to move the ball. **Broncos +8.5 at Chiefs** — I like buying the Broncos low off the blowout and betting against an undefeated team in division — everyone is up for the Chiefs. **Buccaneers +6 vs 49ers** — This was my last choice. The value is great as the 49ers have done nothing to earn this kind of status as a big road favorite against a solid team, but the line is actually 6.5 now, so maybe I’m missing something. **Bears -6.5 vs Patriots** — The Bears are a good buy-low after getting worked by the Cardinals. The Patriots are a get-well game. **Chargers -7 vs Titans** — I don’t really take the Titans seriously, and the Chargers are solid and playing at home. @ f5194aa4:c08836bb
2024-11-08 17:07:07At Jewelry by Serendipity, we offer an exquisite collection of [promise rings](https://www.jewelrybyserendipity.com/collections/promise-rings), each designed to symbolize love, commitment, and a shared future. Crafted with care from high-quality materials, our promise rings are perfect for celebrating a special relationship or marking an important milestone. From classic designs to contemporary styles, each ring reflects the unique bond it represents. Whether you're making a promise to a loved one or celebrating a friendship, our promise rings are a beautiful reminder of the meaningful connections in your life.
@ f5194aa4:c08836bb
2024-11-08 17:07:07At Jewelry by Serendipity, we offer an exquisite collection of [promise rings](https://www.jewelrybyserendipity.com/collections/promise-rings), each designed to symbolize love, commitment, and a shared future. Crafted with care from high-quality materials, our promise rings are perfect for celebrating a special relationship or marking an important milestone. From classic designs to contemporary styles, each ring reflects the unique bond it represents. Whether you're making a promise to a loved one or celebrating a friendship, our promise rings are a beautiful reminder of the meaningful connections in your life. @ 13b9f773:4f4efe54
2024-11-08 15:30:45[Eva Elfie](https://www.reddit.com/r/metart/s/6EAlApYjCZ) - For You  ------  ------ 
@ 13b9f773:4f4efe54
2024-11-08 15:30:45[Eva Elfie](https://www.reddit.com/r/metart/s/6EAlApYjCZ) - For You  ------  ------  @ d3052ca3:d84a170e
2024-11-08 14:46:09The shift of the American working class from the Democratic to the Republican Party in this last election, and the outrage it has generated among many leftist American academics, has led me to reflect on why so many academics become strong socialists or even communists, while the vast majority of the American “working class” do not. They would likely call it “false consciousness” on the part of the American worker. By I see it as false consciousness among elites: they *do not recognize that they are elites,* and that their social status motivates them differently from how the typical American worker is motivated. In short, there is a difference between economic *class* (being a “worker”) and social *status* (being an “elite”). In this I am convinced that Peter Turchin’s structural-demographic theory continues to have explanatory power. (I won’t go into that here, but do check out his work.) Socialism and even communism carry strong appeal for a specific kind of highly educated, young elite today: the kind that needs to work for a living, but still sees itself as elite. These are not “white collar workers;” they are “precarious elites.” They are subject to a dynamic that few want to talk about: Some of the worst labor exploitation in this country occurs in so-called “prestige industries.” These include education (higher and lower), entertainment, journalism, publishing, art, philanthropy—even, on the higher-paid end, investment banking and other financial services. You want to help a celebrity launch a new brand or product? Prepare to make $35,000 a year and work 24 hours a day, 7 days a week, doing countless frenzied tasks that have nothing to do with your job description. You want to teach philosophy at a University? Get ready to make $17,500 a year, if you’re lucky. If you’re an international graduate student, your visa to stay in the U.S. is also completely contingent on your advisor’s approval; as a result, abuse is rampant. You want to write for The Atlantic or The New Yorker? You can maybe get a few hundred bucks per article as a freelancer; $60K per year as a staff writer, if you’re lucky. You want to become a powerful banker? You may start at $150K per year right out of college, but you will work 80-120 hours a week at the expense of everything else in your life, no telling how long—certainly for years. Your mental and even physical health are the price you pay for this “opportunity.” These are the jobs that children of elites want. They want these jobs so much that they are willing to subject themselves to highly fragmented, authoritarian, and toxic work environments, with such high turnover, particularly of junior workers, that it’s socially a war of all against all. These jobs are different from working at a factory or an established company—there is a “musical chairs” dynamic, authority is exercised arbitrarily and chaotically, the job tasks can change daily and even moment to moment, most relationships are based on dominance/submission, and there is no “solidarity.” Employers believe it’s a “privilege” for anyone to have these jobs, and that therefore no one in them has the right to complain. Their refrain: “There are always 100 more candidates ready to take your place.” In addition, there is the psychology of being an elite: you expect to be treated better by virtue of your education and social status, so it can be shameful to admit that you are being abused and might need to fight for better working conditions. Young elites may even want to organize and collectively bargain, but they don’t know how—they’ve been carried along by their social status in extremely authoritarian and chaotic environments and may never have really built anything with others over time. For many young precarious elites, therefore, socialism becomes a kind of dream of not only of a good workplace but of a good society—one where they get what they believe is their “due.” These “precarious elites” do see their exploitation as a structural problem, but they blame “capitalism” instead of the brute fact of supply and demand: there are just too many of them competing for the same few prestige jobs. While the American worker imagines a path to better pay and working conditions through organizing, the precarious elite sees no such path—because for them *status* is just as, if not more, important than pay and benefits, and that is something much harder to negotiate. Elites insist that *they should be able to do exactly the (prestigious) jobs that they want to do.* They are also educated enough to have read the socialist and communist literatures. That combination leads to the fantasy that the government could force their employers not only to pay them more and treat them with dignity—which in some cases it could, certainly—but also to guarantee these conditions *in prestige jobs* for everyone who wants them. There likely is a legitimate case to be made that some of these prestige employers are violating labor laws and should be held accountable. In other cases, there are certainly opportunities to pass new laws prohibiting what amounts to indentured servitude. But actually enforcing these laws will only reveal what is already plain as day: that there are far fewer prestige jobs than there are elites who want them. The double bind for elites is that the prospect of taking a “lower status” job—even one that pays a lot more, where workers are treated significantly better—is even worse than being a de facto slave with a prestigious role. This leads precarious elites to demand a magical solution: the state. The state must not only protect workers, but guarantee certain kinds of jobs at certain levels of pay and benefits for anyone who wants them. Needless to say, this demand can never be fulfilled, and the cycle of partisanship is then retrenched: precarious elites blame American workers for having the gall to vote and organize based on self-interest, rather than to crusade for an idyllic state of affairs that will not come. Originally published on twitter https://x.com/NSmolenski/status/1854347409012203687 Reposted to nostr without permission. Sorry not sorry. <3 u Natalie!
@ d3052ca3:d84a170e
2024-11-08 14:46:09The shift of the American working class from the Democratic to the Republican Party in this last election, and the outrage it has generated among many leftist American academics, has led me to reflect on why so many academics become strong socialists or even communists, while the vast majority of the American “working class” do not. They would likely call it “false consciousness” on the part of the American worker. By I see it as false consciousness among elites: they *do not recognize that they are elites,* and that their social status motivates them differently from how the typical American worker is motivated. In short, there is a difference between economic *class* (being a “worker”) and social *status* (being an “elite”). In this I am convinced that Peter Turchin’s structural-demographic theory continues to have explanatory power. (I won’t go into that here, but do check out his work.) Socialism and even communism carry strong appeal for a specific kind of highly educated, young elite today: the kind that needs to work for a living, but still sees itself as elite. These are not “white collar workers;” they are “precarious elites.” They are subject to a dynamic that few want to talk about: Some of the worst labor exploitation in this country occurs in so-called “prestige industries.” These include education (higher and lower), entertainment, journalism, publishing, art, philanthropy—even, on the higher-paid end, investment banking and other financial services. You want to help a celebrity launch a new brand or product? Prepare to make $35,000 a year and work 24 hours a day, 7 days a week, doing countless frenzied tasks that have nothing to do with your job description. You want to teach philosophy at a University? Get ready to make $17,500 a year, if you’re lucky. If you’re an international graduate student, your visa to stay in the U.S. is also completely contingent on your advisor’s approval; as a result, abuse is rampant. You want to write for The Atlantic or The New Yorker? You can maybe get a few hundred bucks per article as a freelancer; $60K per year as a staff writer, if you’re lucky. You want to become a powerful banker? You may start at $150K per year right out of college, but you will work 80-120 hours a week at the expense of everything else in your life, no telling how long—certainly for years. Your mental and even physical health are the price you pay for this “opportunity.” These are the jobs that children of elites want. They want these jobs so much that they are willing to subject themselves to highly fragmented, authoritarian, and toxic work environments, with such high turnover, particularly of junior workers, that it’s socially a war of all against all. These jobs are different from working at a factory or an established company—there is a “musical chairs” dynamic, authority is exercised arbitrarily and chaotically, the job tasks can change daily and even moment to moment, most relationships are based on dominance/submission, and there is no “solidarity.” Employers believe it’s a “privilege” for anyone to have these jobs, and that therefore no one in them has the right to complain. Their refrain: “There are always 100 more candidates ready to take your place.” In addition, there is the psychology of being an elite: you expect to be treated better by virtue of your education and social status, so it can be shameful to admit that you are being abused and might need to fight for better working conditions. Young elites may even want to organize and collectively bargain, but they don’t know how—they’ve been carried along by their social status in extremely authoritarian and chaotic environments and may never have really built anything with others over time. For many young precarious elites, therefore, socialism becomes a kind of dream of not only of a good workplace but of a good society—one where they get what they believe is their “due.” These “precarious elites” do see their exploitation as a structural problem, but they blame “capitalism” instead of the brute fact of supply and demand: there are just too many of them competing for the same few prestige jobs. While the American worker imagines a path to better pay and working conditions through organizing, the precarious elite sees no such path—because for them *status* is just as, if not more, important than pay and benefits, and that is something much harder to negotiate. Elites insist that *they should be able to do exactly the (prestigious) jobs that they want to do.* They are also educated enough to have read the socialist and communist literatures. That combination leads to the fantasy that the government could force their employers not only to pay them more and treat them with dignity—which in some cases it could, certainly—but also to guarantee these conditions *in prestige jobs* for everyone who wants them. There likely is a legitimate case to be made that some of these prestige employers are violating labor laws and should be held accountable. In other cases, there are certainly opportunities to pass new laws prohibiting what amounts to indentured servitude. But actually enforcing these laws will only reveal what is already plain as day: that there are far fewer prestige jobs than there are elites who want them. The double bind for elites is that the prospect of taking a “lower status” job—even one that pays a lot more, where workers are treated significantly better—is even worse than being a de facto slave with a prestigious role. This leads precarious elites to demand a magical solution: the state. The state must not only protect workers, but guarantee certain kinds of jobs at certain levels of pay and benefits for anyone who wants them. Needless to say, this demand can never be fulfilled, and the cycle of partisanship is then retrenched: precarious elites blame American workers for having the gall to vote and organize based on self-interest, rather than to crusade for an idyllic state of affairs that will not come. Originally published on twitter https://x.com/NSmolenski/status/1854347409012203687 Reposted to nostr without permission. Sorry not sorry. <3 u Natalie! @ 52adc2ef:9f4bc0ba
2024-11-08 14:20:49คงเคยได้ยินวลีว่า "ขยันผิดที่ 10 ปีก็ไม่รวย" เเต่สามารถใช้กับการออมเงินได้ด้วย ถ้าใครยังงง ว่าออมผิดที่ ไม่รวยด้วยหรอ ต้องรู้ก่อนว่า เราอยู่ในยุคที่มีเงินเฟ้อนะครับ ประมาณ 5-7% ต่อปี รัฐบาลอาจจะประกาศ ปีล่าสุด 2567 ต่ำเเต่ด้วยข้าวของที่เราซื้อเองก็คงรู้ว่ามันมากกว่าที่ประกาศเเน่นอน  *ข้อมูลจาก www.bot.or.th* วางเงินไว้เฉยๆเงินก็ระเหยเเล้ว(อย่างกับน้ำเเข็ง) งั้นกลับมาย้ำก่อนว่า เงินเฟ้อ คืออะไร เผื่อคนไม่เข้าใจ (สำหรับคนทราบเเล้วรอเพื่อนก่อนนะครับ) ### เงินเฟ้อ เงินเฟ้อคืออะไร เอาเเบบเข้าใจง่ายคือ อำนาจการใช้จ่ายของเราน้อยลง ราคาสินค้าเเพงขึ้น ตัวอย่างอยู่รอบตัวเราอยู่เเล้ว เมื่อก่อนสัก 5 ปีที่เเล้ว เคยซื้อข้าวกระเพรา 40 บาทได้ ตอนนี้ไป 50-60 บาทเเล้ว หรือข่าวราคาบ้านที่สูงกว่า รายได้ครัวเรือนถึง 21 เท่า !  ### ทำไมถึงมีเงินเฟ้อ เคยสงสัยมั้ยครับว่าทำไมมีเงินเฟ้อ คำนี้ เราน่าจะเคยได้ยินบ้างไม่มากก็น้อย เเต่มีความหมายสุดลึกซึ้ง มันกระทบกับเราเเน่นอน ไม่ว่าเราจะรู้หรือไม่รู้ (เเต่รู้ดีกว่าเเน่นอนจะได้ป้องกัน แก้ไขได้) ให้เข้าใจก่อนว่าเราอยู่ในยุคเงินรัฐบาล ที่ถือว่าเป็นตั๋ว ไว้ใช้ในประเทศ ชำระหนี้ได้ตามกฎหมาย ต้องมี ทองคำ Bond ค้ำไว้เพื่อผลิตธนบัตรออกมา ซึ่งตรงนี้รัฐบาลมีอำนาจเต็มที่สามารถกำหนดนโยบายทางเงินได้ *หรือเรียกภาษาฝรั่งว่า "Fiat Money"* เเล้วมันไม่ดีหรอ! ต้องมีคนคิดเเน่นอน อันนี้เเล้วเเต่คนคิดเลยนะครับ เเต่บอกเป็นความจริงเเล้วไปพิจารณาต่อน่าจะดีกว่า เพราะรัฐบาลสามารถที่จะพิมพ์เงินออกมาได้เลย ผลิตเเล้วเกี่ยวอะไรกับเงินเฟ้อ ในปัจจุบันสหรัฐอเมริกามีหนี้มากขึ้นตามภาพด้านล่างเลย  ข้อมูลจาก https://fiscaldata.treasury.gov/americas-finance-guide/national-debt/ ทำไมต้องยกตัวอย่างอเมริกาเพราะว่าประเทศเราก็ถือพันธบัตรรัฐบาลสหรัฐ ไว้ในในพิมพ์เงินบาท มันส่งผลเเน่นอน พิมพ์เงินมีผลยังไงใช่มั้ยครับ เดี๋ยวยกตัวอย่างนะครับ *ถ้าโลกนี้มีเงิน 100 หน่วยถืออยู่ 1 หน่วยเเสดงว่า เรามี 1% ของทั้งหมด เเต่ถ้ามีการพิมพ์เงินหรือเพิ่ม Supply เป็น 1,000 หน่วย มูลค่าของเราก็จะเหบือ 0.1 % ของทั้งหมด* พอเห็นอะไรมั้ยครับ จู่ๆเงินเราก็ระเหยไป เป็นการทำลายการเก็บออมของเรา ถ้าคุณปู่เราเก็บเงินไว้ 10 หมื่น เเบบมนต์รักลูกทุ่ง(เมื่อก่อนเยอะมากๆ) ในยุคปัจจุบันเเทบจะซื้ออะไรไม่ได้เลย นี่คือตัวอย่างการเก็บเงินผิดที่ ของเเทร่ เลย ### ทำไมรัฐบาลต้องพิมพ์เงิน ถ้าคุณได้มีโอกาสเป็นนายกรัฐมนตรี โชคดีมากก มีโรคระบาดประหลาด ต้องปิดเมือง คุณมีอำนาจในการเเจกเงินเพื่อใ้ห้ผ่านวิกฤตไป เเต่คุณไม่ทำ คุณคิดว่า สมัยหน้าจะมีคนเลือกคุณมั้ย? ร้อยทั้งร้อย คุณมีอำนาจนี้ก็ต้องใช้ เมื่อมีเงินผลิตออกมามันก็จะดันให้สินค้าเพิ่มสูงขึ้นเนื่องจากทุกคนมีอำนาจจับจ่าย บ้างก็ไปสินค้า หุ้น คริปโต บ้าน ทำให้สินค้าราคาสูงขึ้น เเละเมื่อหยุดพิมพ์ อุตสาหกรรมที่เคยดี เช่น คอนโด อาจจะเฟ้อมากเกินไปเพราะตอนพิมพ์เงินมีความต้องการมามาก ต่อมาฟองสบู่ก็เเตก ถ้ามันลามทั้งประเทศเเบบ subprime crisis 2008 ในอเมริกา กลับไปที่เดิมคุณมีอำนาจพิมพ์เงิน ระเบิดอสังหาริมทรัพย์ มาเเตกที่ยุคคุณคุณทำยังไง ก็พิมพ์เงินสิครับ มันก็จะไปผลักให้ราคาสินค้าสูงขึ้นไปอีก  ซึ่งเเต่ก่อนเราคิดว่าเงินเฟ้อเป็นเรื่องปกคิ แต่ถ้าศึกษาประวัติศาสตร์ดูเราอยู่ในยุคพิมพ์เงินมา ประมาณ 100 ปี เท่านั้นเองซึ่งถ้าเริ่มเยอะขึ้นก็เริ่มตั้งเเต่ปี 1971 ที่อเมริกายกเลิก ทองคำ Back (เรื่องประวัติศาสตร์การเงินเดี๋ยวจะย่อยไปในบทความหน้าๆนะครับ) ### ทำไมราคาที่ดิน ทองคำ หุ้นถึงราคาขึ้น อย่างที่เกริ่นไปว่าถ้ารู้ตัวว่าเงินกำลังเสื่อมค่าย่อมดีกว่าไม่รู้เลย ถ้าเป็นตัวคุณเองรู้ว่าเงินมันระเหยได้ทำยังไงครับ ต้องเปลี่ยนไปทรัพย์สินที่ไม่ระเหยถูกมั้ยครับ เพราะคนที่รู้เค้าก็จะเปลี่ยนเงินเป็นทรัพย์สินที่รักษามูลค่าได้ดีกว่า เช่น ทองคำ ที่ดิน หรือเเม้กระทั่ง หุ้น  ข้อมูลจาก https://th.investing.com/indices/us-30-chart ทำให้สินทรัพย์ที่กล่าวมามูลค่าเพิ่มขึ้น ทองคำก็เพิ่ง All Time High ราคาบ้านที่เกริ่นไปก็เเพงมากๆ เพราะคนที่รู้ก็จะหาที่พักเงินที่ทำให้มูลค่าของเงินของเรา ไม่ระเหย ### สรุปควรเก็บเงินที่ไหนดี พอเรารู้เเล้วว่าเงินเสื่อมค่าไป สิ่งที่สำคัญควรเก็บเงินของเราใน Hard Asset Hard Asset หมายถึง สินทรัพย์ที่ไม่สามารถ ผลิตเพิ่มได้ง่าย หรือไม่ได้เลย เเละมีต้นทุนการผลิตสูง ถ้าต้นทุนต่ำ ทุกคนก็จะเเห่กันไปผลิตเงินเเทนที่จะสร้างคุณค่าเเก่สังคม เเละเก็บในที่นี้หมายถึงการออมเงินนะครับ เเละต้องเป็นเงินออม เป็นเงินที่ทิ้งไว้เลย 20-30 ปี ถ้าเราออมเเล้ว ค่อยลงทุน สินทรัพย์ที่มีคุณสมบัติเป็น Hard Asset ก็มี *** ทองคำ ที่ดิน Bitcoin*** ทองคำ ที่ดิน มันถูกพิสูจน์มาเเล้วว่าสามารถเก็บมูลค่าได้ ส่วน Bitcoin แนะนำให้ศึกษาให้เข้าใจก่อนนะครับ (เก็บเท่าที่เข้าใจ เเต่เราเชื่อว่ามันรักษามูลค่าได้) หรือจะเก็บในส่วนที่เรามีความรู้ เช่น ศิลปะ ของสะสม ต่างๆ ### สรุป ใน Part นี้อยากให้ตระหนักรู้ว่าเงินเฟ้อสามารถ ทำลายกสนเก็บออมของเรามากเเค่ไหน อยากให้ทุกคนรู้ตัว เเละ วางแผนว่าเราจะทำยังไงได้บ้าง ไม่อยากให้เงินที่พยายามทำงานกันเเบบเหนื่อยยากต้องมาระเหยไป หวังว่าจะเก็บเงินออมให้ถูกที่กันนะครับ ขอบคุณครับ
@ 52adc2ef:9f4bc0ba
2024-11-08 14:20:49คงเคยได้ยินวลีว่า "ขยันผิดที่ 10 ปีก็ไม่รวย" เเต่สามารถใช้กับการออมเงินได้ด้วย ถ้าใครยังงง ว่าออมผิดที่ ไม่รวยด้วยหรอ ต้องรู้ก่อนว่า เราอยู่ในยุคที่มีเงินเฟ้อนะครับ ประมาณ 5-7% ต่อปี รัฐบาลอาจจะประกาศ ปีล่าสุด 2567 ต่ำเเต่ด้วยข้าวของที่เราซื้อเองก็คงรู้ว่ามันมากกว่าที่ประกาศเเน่นอน  *ข้อมูลจาก www.bot.or.th* วางเงินไว้เฉยๆเงินก็ระเหยเเล้ว(อย่างกับน้ำเเข็ง) งั้นกลับมาย้ำก่อนว่า เงินเฟ้อ คืออะไร เผื่อคนไม่เข้าใจ (สำหรับคนทราบเเล้วรอเพื่อนก่อนนะครับ) ### เงินเฟ้อ เงินเฟ้อคืออะไร เอาเเบบเข้าใจง่ายคือ อำนาจการใช้จ่ายของเราน้อยลง ราคาสินค้าเเพงขึ้น ตัวอย่างอยู่รอบตัวเราอยู่เเล้ว เมื่อก่อนสัก 5 ปีที่เเล้ว เคยซื้อข้าวกระเพรา 40 บาทได้ ตอนนี้ไป 50-60 บาทเเล้ว หรือข่าวราคาบ้านที่สูงกว่า รายได้ครัวเรือนถึง 21 เท่า !  ### ทำไมถึงมีเงินเฟ้อ เคยสงสัยมั้ยครับว่าทำไมมีเงินเฟ้อ คำนี้ เราน่าจะเคยได้ยินบ้างไม่มากก็น้อย เเต่มีความหมายสุดลึกซึ้ง มันกระทบกับเราเเน่นอน ไม่ว่าเราจะรู้หรือไม่รู้ (เเต่รู้ดีกว่าเเน่นอนจะได้ป้องกัน แก้ไขได้) ให้เข้าใจก่อนว่าเราอยู่ในยุคเงินรัฐบาล ที่ถือว่าเป็นตั๋ว ไว้ใช้ในประเทศ ชำระหนี้ได้ตามกฎหมาย ต้องมี ทองคำ Bond ค้ำไว้เพื่อผลิตธนบัตรออกมา ซึ่งตรงนี้รัฐบาลมีอำนาจเต็มที่สามารถกำหนดนโยบายทางเงินได้ *หรือเรียกภาษาฝรั่งว่า "Fiat Money"* เเล้วมันไม่ดีหรอ! ต้องมีคนคิดเเน่นอน อันนี้เเล้วเเต่คนคิดเลยนะครับ เเต่บอกเป็นความจริงเเล้วไปพิจารณาต่อน่าจะดีกว่า เพราะรัฐบาลสามารถที่จะพิมพ์เงินออกมาได้เลย ผลิตเเล้วเกี่ยวอะไรกับเงินเฟ้อ ในปัจจุบันสหรัฐอเมริกามีหนี้มากขึ้นตามภาพด้านล่างเลย  ข้อมูลจาก https://fiscaldata.treasury.gov/americas-finance-guide/national-debt/ ทำไมต้องยกตัวอย่างอเมริกาเพราะว่าประเทศเราก็ถือพันธบัตรรัฐบาลสหรัฐ ไว้ในในพิมพ์เงินบาท มันส่งผลเเน่นอน พิมพ์เงินมีผลยังไงใช่มั้ยครับ เดี๋ยวยกตัวอย่างนะครับ *ถ้าโลกนี้มีเงิน 100 หน่วยถืออยู่ 1 หน่วยเเสดงว่า เรามี 1% ของทั้งหมด เเต่ถ้ามีการพิมพ์เงินหรือเพิ่ม Supply เป็น 1,000 หน่วย มูลค่าของเราก็จะเหบือ 0.1 % ของทั้งหมด* พอเห็นอะไรมั้ยครับ จู่ๆเงินเราก็ระเหยไป เป็นการทำลายการเก็บออมของเรา ถ้าคุณปู่เราเก็บเงินไว้ 10 หมื่น เเบบมนต์รักลูกทุ่ง(เมื่อก่อนเยอะมากๆ) ในยุคปัจจุบันเเทบจะซื้ออะไรไม่ได้เลย นี่คือตัวอย่างการเก็บเงินผิดที่ ของเเทร่ เลย ### ทำไมรัฐบาลต้องพิมพ์เงิน ถ้าคุณได้มีโอกาสเป็นนายกรัฐมนตรี โชคดีมากก มีโรคระบาดประหลาด ต้องปิดเมือง คุณมีอำนาจในการเเจกเงินเพื่อใ้ห้ผ่านวิกฤตไป เเต่คุณไม่ทำ คุณคิดว่า สมัยหน้าจะมีคนเลือกคุณมั้ย? ร้อยทั้งร้อย คุณมีอำนาจนี้ก็ต้องใช้ เมื่อมีเงินผลิตออกมามันก็จะดันให้สินค้าเพิ่มสูงขึ้นเนื่องจากทุกคนมีอำนาจจับจ่าย บ้างก็ไปสินค้า หุ้น คริปโต บ้าน ทำให้สินค้าราคาสูงขึ้น เเละเมื่อหยุดพิมพ์ อุตสาหกรรมที่เคยดี เช่น คอนโด อาจจะเฟ้อมากเกินไปเพราะตอนพิมพ์เงินมีความต้องการมามาก ต่อมาฟองสบู่ก็เเตก ถ้ามันลามทั้งประเทศเเบบ subprime crisis 2008 ในอเมริกา กลับไปที่เดิมคุณมีอำนาจพิมพ์เงิน ระเบิดอสังหาริมทรัพย์ มาเเตกที่ยุคคุณคุณทำยังไง ก็พิมพ์เงินสิครับ มันก็จะไปผลักให้ราคาสินค้าสูงขึ้นไปอีก  ซึ่งเเต่ก่อนเราคิดว่าเงินเฟ้อเป็นเรื่องปกคิ แต่ถ้าศึกษาประวัติศาสตร์ดูเราอยู่ในยุคพิมพ์เงินมา ประมาณ 100 ปี เท่านั้นเองซึ่งถ้าเริ่มเยอะขึ้นก็เริ่มตั้งเเต่ปี 1971 ที่อเมริกายกเลิก ทองคำ Back (เรื่องประวัติศาสตร์การเงินเดี๋ยวจะย่อยไปในบทความหน้าๆนะครับ) ### ทำไมราคาที่ดิน ทองคำ หุ้นถึงราคาขึ้น อย่างที่เกริ่นไปว่าถ้ารู้ตัวว่าเงินกำลังเสื่อมค่าย่อมดีกว่าไม่รู้เลย ถ้าเป็นตัวคุณเองรู้ว่าเงินมันระเหยได้ทำยังไงครับ ต้องเปลี่ยนไปทรัพย์สินที่ไม่ระเหยถูกมั้ยครับ เพราะคนที่รู้เค้าก็จะเปลี่ยนเงินเป็นทรัพย์สินที่รักษามูลค่าได้ดีกว่า เช่น ทองคำ ที่ดิน หรือเเม้กระทั่ง หุ้น  ข้อมูลจาก https://th.investing.com/indices/us-30-chart ทำให้สินทรัพย์ที่กล่าวมามูลค่าเพิ่มขึ้น ทองคำก็เพิ่ง All Time High ราคาบ้านที่เกริ่นไปก็เเพงมากๆ เพราะคนที่รู้ก็จะหาที่พักเงินที่ทำให้มูลค่าของเงินของเรา ไม่ระเหย ### สรุปควรเก็บเงินที่ไหนดี พอเรารู้เเล้วว่าเงินเสื่อมค่าไป สิ่งที่สำคัญควรเก็บเงินของเราใน Hard Asset Hard Asset หมายถึง สินทรัพย์ที่ไม่สามารถ ผลิตเพิ่มได้ง่าย หรือไม่ได้เลย เเละมีต้นทุนการผลิตสูง ถ้าต้นทุนต่ำ ทุกคนก็จะเเห่กันไปผลิตเงินเเทนที่จะสร้างคุณค่าเเก่สังคม เเละเก็บในที่นี้หมายถึงการออมเงินนะครับ เเละต้องเป็นเงินออม เป็นเงินที่ทิ้งไว้เลย 20-30 ปี ถ้าเราออมเเล้ว ค่อยลงทุน สินทรัพย์ที่มีคุณสมบัติเป็น Hard Asset ก็มี *** ทองคำ ที่ดิน Bitcoin*** ทองคำ ที่ดิน มันถูกพิสูจน์มาเเล้วว่าสามารถเก็บมูลค่าได้ ส่วน Bitcoin แนะนำให้ศึกษาให้เข้าใจก่อนนะครับ (เก็บเท่าที่เข้าใจ เเต่เราเชื่อว่ามันรักษามูลค่าได้) หรือจะเก็บในส่วนที่เรามีความรู้ เช่น ศิลปะ ของสะสม ต่างๆ ### สรุป ใน Part นี้อยากให้ตระหนักรู้ว่าเงินเฟ้อสามารถ ทำลายกสนเก็บออมของเรามากเเค่ไหน อยากให้ทุกคนรู้ตัว เเละ วางแผนว่าเราจะทำยังไงได้บ้าง ไม่อยากให้เงินที่พยายามทำงานกันเเบบเหนื่อยยากต้องมาระเหยไป หวังว่าจะเก็บเงินออมให้ถูกที่กันนะครับ ขอบคุณครับ @ 5d4b6c8d:8a1c1ee3
2024-11-08 13:59:13@Coffee proposed a topic for [The Stacker Sports Podcast](https://fountain.fm/show/syQHHkLs59GQ1eFAe64t) on our nostr thread and I wanted to share it here. Why have the top picks in the past two drafts (Bryce Young and Caleb Williams) been so significantly outplayed by the players taken immediately after them (CJ Stroud and Jayden Daniels)? It's early in the careers of each of these players, but Stroud and Daniels are already looking like MVP caliber franchise QB's. Why did teams miss this? The most obvious hypothesis (that the Bears and Panthers flubbed their picks) doesn't make much sense, because Young and Williams were the consensus top picks in their drafts. A bigger question is why it's so difficult to spot an MVP caliber QB from their college play. originally posted at https://stacker.news/items/758917
@ 5d4b6c8d:8a1c1ee3
2024-11-08 13:59:13@Coffee proposed a topic for [The Stacker Sports Podcast](https://fountain.fm/show/syQHHkLs59GQ1eFAe64t) on our nostr thread and I wanted to share it here. Why have the top picks in the past two drafts (Bryce Young and Caleb Williams) been so significantly outplayed by the players taken immediately after them (CJ Stroud and Jayden Daniels)? It's early in the careers of each of these players, but Stroud and Daniels are already looking like MVP caliber franchise QB's. Why did teams miss this? The most obvious hypothesis (that the Bears and Panthers flubbed their picks) doesn't make much sense, because Young and Williams were the consensus top picks in their drafts. A bigger question is why it's so difficult to spot an MVP caliber QB from their college play. originally posted at https://stacker.news/items/758917 @ c11cf5f8:4928464d
2024-11-08 13:31:22The Magnificent 7:  Here we are again with our monthly [Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times) summary, trying to give you a hit of what you missed this month in the ~AGORA territory. - - - ### Top-Performing Ads This month, the most zapranked ones are: * `01` [[OFFER] IPv4+IPv6 KVM VPS, from 1.75EUR/month (Stockholm/SE SWEDEN)](https://stacker.news/items/750336/r/AG) by @skhron * `02` [[SWAP] SN Cowboy credits](https://stacker.news/items/723069/r/AG) by @DarthCoin * `03` [[SELL] “NO⚡️TR T-Shirt” for 21K sats](https://stacker.news/items/730098/r/AG) by @thebullishbitcoiner * `04` [[sell] iptv subscription 10k+ live tv channels and 20k+ vod (tv/movies)](https://stacker.news/items/730963/r/AG) by @profullstack This month we ran short, so here other 3 from previous month * `05` [[SELL] StackerNews Archived Territories - Your chance to own a piece of history!](https://stacker.news/items/698471/r/AG) by @Design_r * `06` [[SELL] Stickers for Stackers! SN Nostr Badges vinyl stickers - from 3,456 sats](https://stacker.news/items/711431/r/AG) by @AGORA * `07` [[SELL] 3 WishMesh Meshtastic radios and 2 extended antennas 325,000 SATS](https://stacker.news/items/710750/r/AG) by @fe3c522a6f - - - ###### In case you missed Here some interesting post opening conversation and free speech: @supratic share some interesting tools for merchants and businesses: - https://stacker.news/items/745053/r/AG TinyPine: A simple LN and CASHU ecash POS system for merchants - https://stacker.news/items/750705/r/AG PLEBEIAN – Simple, Anonymous & Free Market for Everyone And here some more insights on how to do business in the private: - https://stacker.news/items/732291/r/AG Classifieds vs. Listings: Navigating Nostr Protocol's Approach to Advertising by @AGORA - https://stacker.news/items/742973/r/AG The Watchman Privacy Podcast – Escape the Servile Society with Vonu by @mo - https://stacker.news/items/746325/r/AG How to Operate a Business in the Private with Trust by @mo - https://stacker.news/items/741906/r/AG Paying out debt and bills using the Bills of Exchange act by @supratic - https://stacker.news/items/751074/r/AG The Separation of Business and State by @mo - https://stacker.news/items/718979/r/AG Mystery Paper: Ancient Merchant Paper, For Merchants Only & Corporate Countries by @AGORA - https://stacker.news/items/720288/r/AG Parallel Society • Free Man's Perspective by @DarthCoin ###### 🏷️ Spending Sunday is back! Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Read more https://stacker.news/items/721244/r/AG - - - ###### Just a reminder for you all This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it! To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting. - - - ### Create your Ads now!  Looking to start something new? Hit one of the links below to free your mind: * [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation, * [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or, * if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)! * [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners * [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats * [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item * [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else * [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift! * [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to - - - Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we can help you publish a personalized post. Coinomi Bitcoin Testnet skull quantum digital allow faculty enforce spatial emotion fun candy plunge stick stairs salad dish pass fix between shock scene ivory cargo unhappy fault originally posted at https://stacker.news/items/758878
@ c11cf5f8:4928464d
2024-11-08 13:31:22The Magnificent 7:  Here we are again with our monthly [Magnificent Seven](https://stacker.news/AGORA#the-magnificent-seven---of-all-times) summary, trying to give you a hit of what you missed this month in the ~AGORA territory. - - - ### Top-Performing Ads This month, the most zapranked ones are: * `01` [[OFFER] IPv4+IPv6 KVM VPS, from 1.75EUR/month (Stockholm/SE SWEDEN)](https://stacker.news/items/750336/r/AG) by @skhron * `02` [[SWAP] SN Cowboy credits](https://stacker.news/items/723069/r/AG) by @DarthCoin * `03` [[SELL] “NO⚡️TR T-Shirt” for 21K sats](https://stacker.news/items/730098/r/AG) by @thebullishbitcoiner * `04` [[sell] iptv subscription 10k+ live tv channels and 20k+ vod (tv/movies)](https://stacker.news/items/730963/r/AG) by @profullstack This month we ran short, so here other 3 from previous month * `05` [[SELL] StackerNews Archived Territories - Your chance to own a piece of history!](https://stacker.news/items/698471/r/AG) by @Design_r * `06` [[SELL] Stickers for Stackers! SN Nostr Badges vinyl stickers - from 3,456 sats](https://stacker.news/items/711431/r/AG) by @AGORA * `07` [[SELL] 3 WishMesh Meshtastic radios and 2 extended antennas 325,000 SATS](https://stacker.news/items/710750/r/AG) by @fe3c522a6f - - - ###### In case you missed Here some interesting post opening conversation and free speech: @supratic share some interesting tools for merchants and businesses: - https://stacker.news/items/745053/r/AG TinyPine: A simple LN and CASHU ecash POS system for merchants - https://stacker.news/items/750705/r/AG PLEBEIAN – Simple, Anonymous & Free Market for Everyone And here some more insights on how to do business in the private: - https://stacker.news/items/732291/r/AG Classifieds vs. Listings: Navigating Nostr Protocol's Approach to Advertising by @AGORA - https://stacker.news/items/742973/r/AG The Watchman Privacy Podcast – Escape the Servile Society with Vonu by @mo - https://stacker.news/items/746325/r/AG How to Operate a Business in the Private with Trust by @mo - https://stacker.news/items/741906/r/AG Paying out debt and bills using the Bills of Exchange act by @supratic - https://stacker.news/items/751074/r/AG The Separation of Business and State by @mo - https://stacker.news/items/718979/r/AG Mystery Paper: Ancient Merchant Paper, For Merchants Only & Corporate Countries by @AGORA - https://stacker.news/items/720288/r/AG Parallel Society • Free Man's Perspective by @DarthCoin ###### 🏷️ Spending Sunday is back! Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Read more https://stacker.news/items/721244/r/AG - - - ###### Just a reminder for you all This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it! To incentivize more conversation and a more _libre_ mindset, we decided to adopt the zapshare approach, so we'll split the rewards of this TM7 to the best contributors plus zaps to the posts that offer much PoW when posting. - - - ### Create your Ads now!  Looking to start something new? Hit one of the links below to free your mind: * [💬 TOPIC](https://stacker.news/~AGORA/post?type=discussion) for conversation, * [\[⚖️ SELL\]](https://w3.do/b_v2wutP) anything! or, * if you're looking for something, hit the [\[🛒 BUY\]](https://w3.do/zvixtuSh)! * [\[🧑💻 HIRE\]](https://w3.do/_j0kpVsi) any bitcoiner skill or stuff from bitcoiners * [\[🖇 OFFER\]](https://w3.do/EfWF8yDL) any product or service and stack more sats * [\[🧑⚖️ AUCTION\]](https://w3.do/sbbCjZ0e) to let stackers decide a fair price for your item * [\[🤝 SWAP\]](https://w3.do/V_iP4lY5) if you're looking to exchange anything with anything else * [\[🆓 FREE\]](https://w3.do/DdVEE1ME) your space, make a gift! * [\[⭐ REVIEW\]](https://w3.do/CAZ5JxCk) any bitcoin product or LN service you recently bought or subscribed to - - - Or contact @AGORA team on [nostr DM](https://iris.to/agora_sn) and we can help you publish a personalized post. Coinomi Bitcoin Testnet skull quantum digital allow faculty enforce spatial emotion fun candy plunge stick stairs salad dish pass fix between shock scene ivory cargo unhappy fault originally posted at https://stacker.news/items/758878 @ 13b9f773:4f4efe54
2024-11-08 12:59:21Shayla [↗️](https://www.reddit.com/r/metart/s/7COwUCVybJ)   
@ 13b9f773:4f4efe54
2024-11-08 12:59:21Shayla [↗️](https://www.reddit.com/r/metart/s/7COwUCVybJ)    @ b4403b24:83542d4e
2024-11-08 11:46:54To my great surprise, when I checked my SN notification feed today, I found out 👇  To be honest, I don't know what I did to earn it, what it means or gives me or whether I can loose it (similar to the cowboy's hat maybe @k00b can give more insights) but I am pretty satisfied adding it under my belt. 🎉 I'll keep my activity high hoping I'll find the other cowboy collectible I miss - the pistol  originally posted at https://stacker.news/items/758749
@ b4403b24:83542d4e
2024-11-08 11:46:54To my great surprise, when I checked my SN notification feed today, I found out 👇  To be honest, I don't know what I did to earn it, what it means or gives me or whether I can loose it (similar to the cowboy's hat maybe @k00b can give more insights) but I am pretty satisfied adding it under my belt. 🎉 I'll keep my activity high hoping I'll find the other cowboy collectible I miss - the pistol  originally posted at https://stacker.news/items/758749 @ 68fa45dc:3d2a26ed
2024-11-08 10:59:23<p>Wie Unternehmen Anti-Spyware-Geräte-Störsender erfolgreich einsetzen können</p> <p>Im modernen Geschäftsumfeld wird die Bedeutung von Informationssicherheit und Datenschutz immer wichtiger und die Bedrohungen, denen Unternehmen ausgesetzt sind, werden immer komplexer. Angesichts der rasanten Entwicklung der Technologie kommt es häufig zu Spionage- und Informationslecks, und Unternehmen müssen dringend wirksame Maßnahmen ergreifen, um ihre eigenen Interessen zu schützen. Unter vielen Schutzmethoden haben sich Anti-Spyware-Geräte <a href="https://www.jammer-store.de/">Störsender Kaufen</a> nach und nach zu einem wirksamen Werkzeug für Unternehmen zur Abwehr interner und externer Bedrohungen entwickelt. In diesem Artikel wird untersucht, wie Unternehmen Anti-Spyware-Geräte wie Mobiltelefon-Störsender, WLAN-Störsender, Anti-Tracking-Störsender und Kameradetektoren erfolgreich einsetzen können, um die Schutzfunktionen für die Informationssicherheit zu verbessern.</p> <h3>Anwendung des Handy-Störsender</h3> <p><a href="https://www.jammer-store.de/praktischste-37W-12-band-5G-signalstorsender-fur-mobiltelefone-wlan-gps-rf.html"><img src="https://www.jammer-store.de/image/HJ-129/1.jpg" alt="Tragbare Signalstörsender für Mobiltelefone" width="450"/></a></p> <p>Handy-Störsender blockieren Handysignale innerhalb bestimmter Frequenzen und verhindern so den Diebstahl von Informationen in Konferenzräumen oder sensiblen Bereichen. Unternehmen können beim Einsatz von Handy-Störsendern die folgenden Strategien in Betracht ziehen:</p> <p>1. Identifizieren Sie sensible Bereiche: Zunächst sollten Unternehmen identifizieren, welche Bereiche sensibel sind, beispielsweise Vorstandssitzungsräume, Forschungs- und Entwicklungsabteilungen sowie Finanzabteilungen. Der Einsatz von Störsendern für Mobiltelefone an diesen Orten kann Abhören und Informationslecks wirksam verhindern.</p> <p>2. Rechtmäßige und konforme Verwendung: Die Verwendung von <a href="https://www.jammer-store.de/handy-tragbare-storsender.html">handy störsender</a> muss den örtlichen Gesetzen und Vorschriften entsprechen und sicherstellen, dass sie nur in zulässigen Situationen verwendet werden. Unternehmen sollten sich vorab über die einschlägigen Gesetze informieren und beim Einsatz von Störsendern Aufzeichnungen führen, um Rechtsstreitigkeiten vorzubeugen.</p> <p>3. Bewerten Sie regelmäßig die Wirksamkeit: Unternehmen sollten die Wirksamkeit von Mobiltelefon-Störsendern regelmäßig bewerten, z. B. durch die Überwachung der Kommunikationssicherheit in Konferenzräumen und die unverzügliche Anpassung von Strategien nach Feststellung von Nichteinhaltung.</p> <h3> Anwendung des WIFI-Störsender</h3> <p>WLAN-Störsender können den illegalen Zugriff und die Überwachung von drahtlosen Unternehmensnetzwerken verhindern. Um WLAN-Störsender effektiv zu nutzen, können Unternehmen die folgenden Maßnahmen ergreifen:</p> <p>1. Netzwerksicherheitsrichtlinie: Entwickeln Sie strenge Netzwerksicherheitsrichtlinien, verschlüsseln Sie das drahtlose Unternehmensnetzwerk, beschränken Sie den Zugriff auf Geräte und verwenden Sie WLAN-Störsender, um unbefugte Geräteverbindungen zu verhindern.</p> <p>2. Dynamische Anpassung: Passen Sie die Verwendung des <a href="https://www.jammer-store.de/WLAN-bluetooth-storsender.html">WiFi Jammer</a> dynamisch an Änderungen in der Umgebung an. Verstehen Sie die umgebenden Netzwerkbedingungen und überprüfen Sie regelmäßig den Betriebsstatus des Störsenders, um sicherzustellen, dass er optimal funktioniert.</p> <p>3. Mitarbeiterschulung: Bieten Sie Ihren Mitarbeitern Cybersicherheitsschulungen an, um ihr Bewusstsein für Cybersicherheitsbedrohungen zu schärfen. Machen Sie Ihren Mitarbeitern den Zweck und die Bedeutung von Störsendern klar, um ihr Sicherheitsbewusstsein zu stärken.</p> <h3>Verwendung von Anti-Tracking-Störsendern</h3> <p>Anti-Tracking-Störsender werden verwendet, um potenzielle Tracking-Geräte zu blockieren und die Geschäftsleitung und wichtige Informationen zu schützen. Unternehmen können beim Einsatz von Anti-Tracking-Störsendern Folgendes berücksichtigen:</p> <p>1. Identifizierung von Personen mit hohem Risiko: Identifizieren Sie Führungskräfte oder wichtige Mitarbeiter, die besonderen Schutz benötigen, damit <a href="https://www.jammer-store.de/GPS-storsender.html">Anti-Tracking-GPS Jammer</a> richtig konfiguriert werden können, wenn sie reisen oder wichtige Aktivitäten durchführen.</p> <p>2. Jederzeit überwachen: Unternehmen sollten mit Geräten ausgestattet sein, die das Tracking-Verhalten in Echtzeit überwachen können, und diese in Kombination mit Anti-Tracking-Störsendern verwenden, um sicherzustellen, dass keine potenziellen Risiken übersehen werden.</p> <p>3. Notfallplan: Entwickeln Sie einen detaillierten Notfallplan für den Umgang mit möglichen Tracking-Vorfällen. Sobald eine ungewöhnliche Situation entdeckt wird, kann schnell ein Plan zur Bewältigung dieser Situation auf den Weg gebracht werden.</p> <h3>Die Rolle von Kameradetektoren</h3> <p>Kameradetektoren spielen eine wichtige Rolle bei der Identifizierung versteckter Kamerageräte für Unternehmen, insbesondere bei Konferenzen und Geschäftsveranstaltungen. Unternehmen sollten Kameradetektoren effektiv einsetzen, um die Sicherheit und Privatsphäre von Meetings zu gewährleisten:</p> <p>1. Regelmäßige Inspektion: Führen Sie vor wichtigen Ereignissen oder Besprechungen mithilfe von Kameradetektoren umfassende Inspektionen durch, um sicherzustellen, dass die Besprechungsumgebung nicht durch illegale Überwachungsgeräte beeinträchtigt wird.</p> <p>2. Verwendungsspezifikationen entwickeln: Erstellen Sie beim Einsatz von <a href="https://www.jammer-store.de/anti-uberwachungs-signal-detektor.html">Kamera Detektor</a> detaillierte Bedienungsanleitungen und Spezifikationen, damit die Mitarbeiter die Verwendung und den Umfang der Detektionsausrüstung verstehen können.</p> <p>3. Vertraulichkeitsschulung: Für Mitarbeiter, die an Geheimnissen beteiligt sind, wird eine Vertraulichkeitsschulung angeboten, damit sie die Gefahren versteckter Kameraausrüstung verstehen, ihre Wachsamkeit erhöhen und die Informationssicherheit schützen können.</p> <h3>Zusammenfassen</h3> <p>Mit der Verschärfung des geschäftlichen Wettbewerbs und der Entwicklung der Informationstechnologie nehmen die Sicherheitsrisiken für Unternehmen weiter zu. Durch den sinnvollen Einsatz von Anti-Spyware-Geräten wie Mobiltelefon-Störsendern, WLAN-Störsendern, Anti-Tracking-Störsendern und Kameradetektoren können Unternehmen nicht nur Informationslecks und Spionage wirksam verhindern, sondern auch das allgemeine Sicherheitsmanagementniveau verbessern. Wenn Unternehmen diese Geräte verwenden, müssen sie jedoch Gesetze und Vorschriften einhalten, die Datenschutzrechte von Mitarbeitern und Kunden respektieren und den Schutz der Informationssicherheit innerhalb eines rechtlichen und konformen Rahmens gewährleisten. Nur so können wir im harten Wettbewerb auf dem Markt unbesiegbar bleiben.</p> <ol> <li><a href="https://www.jammer-store.de/BDA-3-tragbare-wanzen-jammer-anti-aufnahme-stoersender-mit-fernbedienung.html">https://www.jammer-store.de/BDA-3-tragbare-wanzen-jammer-anti-aufnahme-stoersender-mit-fernbedienung.html</a></li> <li><a href="https://www.party.biz/forums/topic/789240/forschung-zum-einsatz-von-handy-storsendern-in-prufungen-und-bes/view/post_id/1786172">https://www.party.biz/forums/topic/789240/forschung-zum-einsatz-von-handy-storsendern-in-prufungen-und-bes/view/post_id/1786172</a></li> </ol>
@ 68fa45dc:3d2a26ed
2024-11-08 10:59:23<p>Wie Unternehmen Anti-Spyware-Geräte-Störsender erfolgreich einsetzen können</p> <p>Im modernen Geschäftsumfeld wird die Bedeutung von Informationssicherheit und Datenschutz immer wichtiger und die Bedrohungen, denen Unternehmen ausgesetzt sind, werden immer komplexer. Angesichts der rasanten Entwicklung der Technologie kommt es häufig zu Spionage- und Informationslecks, und Unternehmen müssen dringend wirksame Maßnahmen ergreifen, um ihre eigenen Interessen zu schützen. Unter vielen Schutzmethoden haben sich Anti-Spyware-Geräte <a href="https://www.jammer-store.de/">Störsender Kaufen</a> nach und nach zu einem wirksamen Werkzeug für Unternehmen zur Abwehr interner und externer Bedrohungen entwickelt. In diesem Artikel wird untersucht, wie Unternehmen Anti-Spyware-Geräte wie Mobiltelefon-Störsender, WLAN-Störsender, Anti-Tracking-Störsender und Kameradetektoren erfolgreich einsetzen können, um die Schutzfunktionen für die Informationssicherheit zu verbessern.</p> <h3>Anwendung des Handy-Störsender</h3> <p><a href="https://www.jammer-store.de/praktischste-37W-12-band-5G-signalstorsender-fur-mobiltelefone-wlan-gps-rf.html"><img src="https://www.jammer-store.de/image/HJ-129/1.jpg" alt="Tragbare Signalstörsender für Mobiltelefone" width="450"/></a></p> <p>Handy-Störsender blockieren Handysignale innerhalb bestimmter Frequenzen und verhindern so den Diebstahl von Informationen in Konferenzräumen oder sensiblen Bereichen. Unternehmen können beim Einsatz von Handy-Störsendern die folgenden Strategien in Betracht ziehen:</p> <p>1. Identifizieren Sie sensible Bereiche: Zunächst sollten Unternehmen identifizieren, welche Bereiche sensibel sind, beispielsweise Vorstandssitzungsräume, Forschungs- und Entwicklungsabteilungen sowie Finanzabteilungen. Der Einsatz von Störsendern für Mobiltelefone an diesen Orten kann Abhören und Informationslecks wirksam verhindern.</p> <p>2. Rechtmäßige und konforme Verwendung: Die Verwendung von <a href="https://www.jammer-store.de/handy-tragbare-storsender.html">handy störsender</a> muss den örtlichen Gesetzen und Vorschriften entsprechen und sicherstellen, dass sie nur in zulässigen Situationen verwendet werden. Unternehmen sollten sich vorab über die einschlägigen Gesetze informieren und beim Einsatz von Störsendern Aufzeichnungen führen, um Rechtsstreitigkeiten vorzubeugen.</p> <p>3. Bewerten Sie regelmäßig die Wirksamkeit: Unternehmen sollten die Wirksamkeit von Mobiltelefon-Störsendern regelmäßig bewerten, z. B. durch die Überwachung der Kommunikationssicherheit in Konferenzräumen und die unverzügliche Anpassung von Strategien nach Feststellung von Nichteinhaltung.</p> <h3> Anwendung des WIFI-Störsender</h3> <p>WLAN-Störsender können den illegalen Zugriff und die Überwachung von drahtlosen Unternehmensnetzwerken verhindern. Um WLAN-Störsender effektiv zu nutzen, können Unternehmen die folgenden Maßnahmen ergreifen:</p> <p>1. Netzwerksicherheitsrichtlinie: Entwickeln Sie strenge Netzwerksicherheitsrichtlinien, verschlüsseln Sie das drahtlose Unternehmensnetzwerk, beschränken Sie den Zugriff auf Geräte und verwenden Sie WLAN-Störsender, um unbefugte Geräteverbindungen zu verhindern.</p> <p>2. Dynamische Anpassung: Passen Sie die Verwendung des <a href="https://www.jammer-store.de/WLAN-bluetooth-storsender.html">WiFi Jammer</a> dynamisch an Änderungen in der Umgebung an. Verstehen Sie die umgebenden Netzwerkbedingungen und überprüfen Sie regelmäßig den Betriebsstatus des Störsenders, um sicherzustellen, dass er optimal funktioniert.</p> <p>3. Mitarbeiterschulung: Bieten Sie Ihren Mitarbeitern Cybersicherheitsschulungen an, um ihr Bewusstsein für Cybersicherheitsbedrohungen zu schärfen. Machen Sie Ihren Mitarbeitern den Zweck und die Bedeutung von Störsendern klar, um ihr Sicherheitsbewusstsein zu stärken.</p> <h3>Verwendung von Anti-Tracking-Störsendern</h3> <p>Anti-Tracking-Störsender werden verwendet, um potenzielle Tracking-Geräte zu blockieren und die Geschäftsleitung und wichtige Informationen zu schützen. Unternehmen können beim Einsatz von Anti-Tracking-Störsendern Folgendes berücksichtigen:</p> <p>1. Identifizierung von Personen mit hohem Risiko: Identifizieren Sie Führungskräfte oder wichtige Mitarbeiter, die besonderen Schutz benötigen, damit <a href="https://www.jammer-store.de/GPS-storsender.html">Anti-Tracking-GPS Jammer</a> richtig konfiguriert werden können, wenn sie reisen oder wichtige Aktivitäten durchführen.</p> <p>2. Jederzeit überwachen: Unternehmen sollten mit Geräten ausgestattet sein, die das Tracking-Verhalten in Echtzeit überwachen können, und diese in Kombination mit Anti-Tracking-Störsendern verwenden, um sicherzustellen, dass keine potenziellen Risiken übersehen werden.</p> <p>3. Notfallplan: Entwickeln Sie einen detaillierten Notfallplan für den Umgang mit möglichen Tracking-Vorfällen. Sobald eine ungewöhnliche Situation entdeckt wird, kann schnell ein Plan zur Bewältigung dieser Situation auf den Weg gebracht werden.</p> <h3>Die Rolle von Kameradetektoren</h3> <p>Kameradetektoren spielen eine wichtige Rolle bei der Identifizierung versteckter Kamerageräte für Unternehmen, insbesondere bei Konferenzen und Geschäftsveranstaltungen. Unternehmen sollten Kameradetektoren effektiv einsetzen, um die Sicherheit und Privatsphäre von Meetings zu gewährleisten:</p> <p>1. Regelmäßige Inspektion: Führen Sie vor wichtigen Ereignissen oder Besprechungen mithilfe von Kameradetektoren umfassende Inspektionen durch, um sicherzustellen, dass die Besprechungsumgebung nicht durch illegale Überwachungsgeräte beeinträchtigt wird.</p> <p>2. Verwendungsspezifikationen entwickeln: Erstellen Sie beim Einsatz von <a href="https://www.jammer-store.de/anti-uberwachungs-signal-detektor.html">Kamera Detektor</a> detaillierte Bedienungsanleitungen und Spezifikationen, damit die Mitarbeiter die Verwendung und den Umfang der Detektionsausrüstung verstehen können.</p> <p>3. Vertraulichkeitsschulung: Für Mitarbeiter, die an Geheimnissen beteiligt sind, wird eine Vertraulichkeitsschulung angeboten, damit sie die Gefahren versteckter Kameraausrüstung verstehen, ihre Wachsamkeit erhöhen und die Informationssicherheit schützen können.</p> <h3>Zusammenfassen</h3> <p>Mit der Verschärfung des geschäftlichen Wettbewerbs und der Entwicklung der Informationstechnologie nehmen die Sicherheitsrisiken für Unternehmen weiter zu. Durch den sinnvollen Einsatz von Anti-Spyware-Geräten wie Mobiltelefon-Störsendern, WLAN-Störsendern, Anti-Tracking-Störsendern und Kameradetektoren können Unternehmen nicht nur Informationslecks und Spionage wirksam verhindern, sondern auch das allgemeine Sicherheitsmanagementniveau verbessern. Wenn Unternehmen diese Geräte verwenden, müssen sie jedoch Gesetze und Vorschriften einhalten, die Datenschutzrechte von Mitarbeitern und Kunden respektieren und den Schutz der Informationssicherheit innerhalb eines rechtlichen und konformen Rahmens gewährleisten. Nur so können wir im harten Wettbewerb auf dem Markt unbesiegbar bleiben.</p> <ol> <li><a href="https://www.jammer-store.de/BDA-3-tragbare-wanzen-jammer-anti-aufnahme-stoersender-mit-fernbedienung.html">https://www.jammer-store.de/BDA-3-tragbare-wanzen-jammer-anti-aufnahme-stoersender-mit-fernbedienung.html</a></li> <li><a href="https://www.party.biz/forums/topic/789240/forschung-zum-einsatz-von-handy-storsendern-in-prufungen-und-bes/view/post_id/1786172">https://www.party.biz/forums/topic/789240/forschung-zum-einsatz-von-handy-storsendern-in-prufungen-und-bes/view/post_id/1786172</a></li> </ol> @ 6e24af77:b3f1350b
2024-11-08 10:11:29test 6
@ 6e24af77:b3f1350b
2024-11-08 10:11:29test 6 @ 6bae33c8:607272e8
2024-11-08 09:21:31I don’t want to jinx it, but it’s been a good week. I had the Bengals +6.5 in my picking pool, not Circa though, I had Joe Burrow and Ja’Marr Chase in a key NFFC league, and Chase in two other leagues including the Steak, a 14-teamer where I lost Chris Olave, Stefon Diggs, Rashid Shaheed and maybe CeeDee Lamb. I also picked up and started Rashod Bateman in that league and had Roquan Smith (12 tackles) going too. I don’t know what else to say except that it was maybe a perfect game. And it was cool the Bengals went for two, essentially locking in the cover (though my 6.5 was good in OT anyway.) Apparently there were penalties that should have been called on the two-point conversion, but I missed them, and in any event, it’s not like I’m a Bengals fan, and they had already covered. - Burrow is a great QB now that he’s 100 percent healthy. He processes information so quickly, has no problem checking it down if the first reads are covered. And he scrambles well and keeps his eyes downfield. He’s a top-three real life QB when healthy. - Chase is so good there are almost no words. Faster than Justin Jefferson and CeeDee Lamb, the most dangerous wideout in the league in the open field. If he gets it in space, it’s like 50/50 vs the entire defense whether he makes it to the end zone. What a beast, and you see what he can do with 17 targets. - Chase Brown had a devastating fumble, but scored the TD and benefited from all the checkdowns. - Lamar Jackson actually struggled for much of the game, but the 84-yard missed-tackle TD to Tylan Wallace (of whom I had literally never heard before this morning) really pushed him over the top. He did show nice touch on the few throws and just wears out the defense that had him dead to rights a few times only to see him escape. - Bateman was actually Jackson’s top target, and Mark Andrews had another solid game, but there are a lot of mouths to feed with Diontae Johnson, Zay Flowers and eventually even Isaiah Likely again, not to mention a running QB and a dominant early down back. - Diontae Johnson had no impact whatsoever and actually slipped on one of his two targets. It was better than Khalil Herbert’s debut though — Herbert fumbled his only carry and was never seen again. - Derrick Henry was bottled up for most of the night, but he did manage a short TD. Gameflow wasn’t in his favor as the Bengals led most of the way and won time of possession. - The Bengals defense actually played great, applying constant pressure, keeping the energy up even after being run ragged by Jackson. And they held Henry in check too. That missed tackle on Wallace for an 86-yard TD right after giving up the short-field TD following the Brown fumble sunk them. - It’s tough watching this version of Justin Tucker who missed a PAT. I used to compare him to Mariano Rivera, but Rivera stayed great through his final season, while Tucker has slipped big time.
@ 6bae33c8:607272e8
2024-11-08 09:21:31I don’t want to jinx it, but it’s been a good week. I had the Bengals +6.5 in my picking pool, not Circa though, I had Joe Burrow and Ja’Marr Chase in a key NFFC league, and Chase in two other leagues including the Steak, a 14-teamer where I lost Chris Olave, Stefon Diggs, Rashid Shaheed and maybe CeeDee Lamb. I also picked up and started Rashod Bateman in that league and had Roquan Smith (12 tackles) going too. I don’t know what else to say except that it was maybe a perfect game. And it was cool the Bengals went for two, essentially locking in the cover (though my 6.5 was good in OT anyway.) Apparently there were penalties that should have been called on the two-point conversion, but I missed them, and in any event, it’s not like I’m a Bengals fan, and they had already covered. - Burrow is a great QB now that he’s 100 percent healthy. He processes information so quickly, has no problem checking it down if the first reads are covered. And he scrambles well and keeps his eyes downfield. He’s a top-three real life QB when healthy. - Chase is so good there are almost no words. Faster than Justin Jefferson and CeeDee Lamb, the most dangerous wideout in the league in the open field. If he gets it in space, it’s like 50/50 vs the entire defense whether he makes it to the end zone. What a beast, and you see what he can do with 17 targets. - Chase Brown had a devastating fumble, but scored the TD and benefited from all the checkdowns. - Lamar Jackson actually struggled for much of the game, but the 84-yard missed-tackle TD to Tylan Wallace (of whom I had literally never heard before this morning) really pushed him over the top. He did show nice touch on the few throws and just wears out the defense that had him dead to rights a few times only to see him escape. - Bateman was actually Jackson’s top target, and Mark Andrews had another solid game, but there are a lot of mouths to feed with Diontae Johnson, Zay Flowers and eventually even Isaiah Likely again, not to mention a running QB and a dominant early down back. - Diontae Johnson had no impact whatsoever and actually slipped on one of his two targets. It was better than Khalil Herbert’s debut though — Herbert fumbled his only carry and was never seen again. - Derrick Henry was bottled up for most of the night, but he did manage a short TD. Gameflow wasn’t in his favor as the Bengals led most of the way and won time of possession. - The Bengals defense actually played great, applying constant pressure, keeping the energy up even after being run ragged by Jackson. And they held Henry in check too. That missed tackle on Wallace for an 86-yard TD right after giving up the short-field TD following the Brown fumble sunk them. - It’s tough watching this version of Justin Tucker who missed a PAT. I used to compare him to Mariano Rivera, but Rivera stayed great through his final season, while Tucker has slipped big time. @ 13351007:eccd002a
2024-11-08 05:32:41eyJfaWQiOiI0OTNkNDQyNS01YTRiLTQ2YjYtYjFhNC0yZTEyNjZlYTEyNDYiLCJwdWJsaWNLZXkiOiIxZWI5NjZhNmEwMjE4YWJhNTIwYWFhYzkzYmU3ZGQ4YmYzODMwZmM3NzEwYmM4MGNhZWEzYTZhNWUzZWRkZjk0IiwidXNlcm5hbWUiOiJoYW5rIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImN1cnJlbmN5Q29kZSI6IlVTRCIsInBheW1lbnRNZXRob2RDb2RlIjoiTkFUSU9OQUxfQkFOSyIsInByaWNlSW5wdXRUeXBlIjoiTUFSS0VUIiwibWFyZ2luIjoiMyIsImZpeGVkUHJpY2UiOiIiLCJtaW5BbW91bnQiOiIxMDAiLCJtYXhBbW91bnQiOiIiLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoiZmFzdCBhbmQgYmVzdCB0cmFkZXIiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOiIiLCJmaXJzdFRpbWVMaW1pdEFzc2V0IjoiIiwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMS0wOFQwNTozMjo0MS44MzZaIiwibWFya2V0UHJpY2UiOjE2NC4xM30=
@ 13351007:eccd002a
2024-11-08 05:32:41eyJfaWQiOiI0OTNkNDQyNS01YTRiLTQ2YjYtYjFhNC0yZTEyNjZlYTEyNDYiLCJwdWJsaWNLZXkiOiIxZWI5NjZhNmEwMjE4YWJhNTIwYWFhYzkzYmU3ZGQ4YmYzODMwZmM3NzEwYmM4MGNhZWEzYTZhNWUzZWRkZjk0IiwidXNlcm5hbWUiOiJoYW5rIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImN1cnJlbmN5Q29kZSI6IlVTRCIsInBheW1lbnRNZXRob2RDb2RlIjoiTkFUSU9OQUxfQkFOSyIsInByaWNlSW5wdXRUeXBlIjoiTUFSS0VUIiwibWFyZ2luIjoiMyIsImZpeGVkUHJpY2UiOiIiLCJtaW5BbW91bnQiOiIxMDAiLCJtYXhBbW91bnQiOiIiLCJsaW1pdFRvRmlhdEFtb3VudHMiOiIiLCJwYXltZW50TWV0aG9kRGV0YWlsIjoiZmFzdCBhbmQgYmVzdCB0cmFkZXIiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOiIiLCJmaXJzdFRpbWVMaW1pdEFzc2V0IjoiIiwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMS0wOFQwNTozMjo0MS44MzZaIiwibWFya2V0UHJpY2UiOjE2NC4xM30= @ a012dc82:6458a70d
2024-11-08 05:23:17**Table Of Content** - Bitcoin Bulls Get a Treat from SEC! - Gold's Future in Question? - Conclusion - FAQ In the world of finance and investments, there are always exciting developments and trends that capture the attention of investors and enthusiasts alike. Recently, Bitcoin bulls have been delighted by a treat from the U.S. Securities and Exchange Commission (SEC), while the future of gold has come into question. In this article, we will explore the implications of these events and their potential impact on the financial landscape. **Bitcoin Bulls Get a Treat from SEC!** **The SEC's Recognition of Bitcoin** The first significant development for Bitcoin bulls is the recognition by the SEC of Bitcoin as a legitimate asset class. This recognition brings a sense of legitimacy and credibility to the cryptocurrency, as it paves the way for wider adoption and integration into traditional financial systems. **Increased Institutional Interest in Bitcoin** With the SEC's recognition, institutional investors have started showing more interest in Bitcoin. Major financial institutions such as banks and hedge funds are now exploring ways to include Bitcoin in their portfolios. This increased demand from institutional players has the potential to drive the price of Bitcoin even higher. **Regulatory Clarity Boosts Investor Confidence** One of the biggest challenges for Bitcoin bulls has been the lack of regulatory clarity surrounding cryptocurrencies. However, the SEC's recognition provides a level of clarity that was previously missing. This regulatory framework allows investors to have a better understanding of the risks and benefits associated with investing in Bitcoin. **Bitcoin ETFs on the Horizon** The SEC's recognition of Bitcoin also opens the door for the approval of Bitcoin exchange-traded funds (ETFs). ETFs provide an easier and more accessible way for investors to gain exposure to Bitcoin without directly owning the cryptocurrency. The approval of Bitcoin ETFs would likely attract more institutional investors and further propel the price of Bitcoin. **Gold's Future in Question?** **The Decline of Gold as a Safe Haven** Gold has long been considered a safe haven asset, providing investors with a hedge against inflation and economic uncertainties. However, recent events have raised questions about the future of gold as an investment. **The Rise of Bitcoin as a Digital Gold** Bitcoin's emergence as a digital store of value has posed a challenge to gold's traditional role. Bitcoin offers many advantages over gold, including its divisibility, portability, and ease of transfer. As more investors recognize these benefits, they may start shifting their investments from gold to Bitcoin, potentially impacting the future demand and value of gold. **Technological Advancements and Digitalization** Another factor that puts gold's future in question is the rapid advancement of technology and the increasing digitalization of financial transactions. As digital payment systems and cryptocurrencies gain popularity, the appeal of physical assets like gold may diminish. The convenience and efficiency offered by digital assets could make them a preferred choice for investors in the coming years. **Changing Investor Preferences** The preferences of investors are evolving, particularly among younger generations. Millennial and Gen Z investors are more inclined to embrace cryptocurrencies like Bitcoin as they seek alternative investment options. This shift in investor preferences could further erode the demand for gold and impact its future prospects. **Conclusion** The recognition of Bitcoin by the SEC has undoubtedly brought joy to Bitcoin bulls, as it signifies a significant milestone in the journey towards mainstream acceptance. The future of gold, on the other hand, faces uncertainties as the emergence of digital assets like Bitcoin challenges its traditional role as a safe haven investment. As technology continues to advance and investor preferences evolve, it will be interesting to see how these dynamics shape the financial landscape in the coming years. **FAQ** **Is Bitcoin legal?** Yes, Bitcoin is legal in most countries, including the United States. However, regulations may vary, so it's essential to check the legality of Bitcoin in your specific jurisdiction. **Can I invest in Bitcoin through my traditional brokerage account?** Some brokerage firms offer the option to invest in Bitcoin indirectly through specialized investment products like Bitcoin futures or trusts. However, not all traditional brokerage accounts provide this option, so it's best to inquire with your broker. **What is the potential for Bitcoin's future growth?** The future growth potential of Bitcoin is subjective and highly speculative. While some believe Bitcoin has the potential to reach even higher valuations, others remain skeptical. It's important to conduct thorough research and consider various factors before making any investment decisions. **How can I secure my Bitcoin investments?** It is crucial to store your Bitcoin in a secure digital wallet and follow best security practices, such as enabling two-factor authentication and using strong, unique passwords. Additionally, offline storage options like hardware wallets offer an extra layer of security. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-11-08 05:23:17**Table Of Content** - Bitcoin Bulls Get a Treat from SEC! - Gold's Future in Question? - Conclusion - FAQ In the world of finance and investments, there are always exciting developments and trends that capture the attention of investors and enthusiasts alike. Recently, Bitcoin bulls have been delighted by a treat from the U.S. Securities and Exchange Commission (SEC), while the future of gold has come into question. In this article, we will explore the implications of these events and their potential impact on the financial landscape. **Bitcoin Bulls Get a Treat from SEC!** **The SEC's Recognition of Bitcoin** The first significant development for Bitcoin bulls is the recognition by the SEC of Bitcoin as a legitimate asset class. This recognition brings a sense of legitimacy and credibility to the cryptocurrency, as it paves the way for wider adoption and integration into traditional financial systems. **Increased Institutional Interest in Bitcoin** With the SEC's recognition, institutional investors have started showing more interest in Bitcoin. Major financial institutions such as banks and hedge funds are now exploring ways to include Bitcoin in their portfolios. This increased demand from institutional players has the potential to drive the price of Bitcoin even higher. **Regulatory Clarity Boosts Investor Confidence** One of the biggest challenges for Bitcoin bulls has been the lack of regulatory clarity surrounding cryptocurrencies. However, the SEC's recognition provides a level of clarity that was previously missing. This regulatory framework allows investors to have a better understanding of the risks and benefits associated with investing in Bitcoin. **Bitcoin ETFs on the Horizon** The SEC's recognition of Bitcoin also opens the door for the approval of Bitcoin exchange-traded funds (ETFs). ETFs provide an easier and more accessible way for investors to gain exposure to Bitcoin without directly owning the cryptocurrency. The approval of Bitcoin ETFs would likely attract more institutional investors and further propel the price of Bitcoin. **Gold's Future in Question?** **The Decline of Gold as a Safe Haven** Gold has long been considered a safe haven asset, providing investors with a hedge against inflation and economic uncertainties. However, recent events have raised questions about the future of gold as an investment. **The Rise of Bitcoin as a Digital Gold** Bitcoin's emergence as a digital store of value has posed a challenge to gold's traditional role. Bitcoin offers many advantages over gold, including its divisibility, portability, and ease of transfer. As more investors recognize these benefits, they may start shifting their investments from gold to Bitcoin, potentially impacting the future demand and value of gold. **Technological Advancements and Digitalization** Another factor that puts gold's future in question is the rapid advancement of technology and the increasing digitalization of financial transactions. As digital payment systems and cryptocurrencies gain popularity, the appeal of physical assets like gold may diminish. The convenience and efficiency offered by digital assets could make them a preferred choice for investors in the coming years. **Changing Investor Preferences** The preferences of investors are evolving, particularly among younger generations. Millennial and Gen Z investors are more inclined to embrace cryptocurrencies like Bitcoin as they seek alternative investment options. This shift in investor preferences could further erode the demand for gold and impact its future prospects. **Conclusion** The recognition of Bitcoin by the SEC has undoubtedly brought joy to Bitcoin bulls, as it signifies a significant milestone in the journey towards mainstream acceptance. The future of gold, on the other hand, faces uncertainties as the emergence of digital assets like Bitcoin challenges its traditional role as a safe haven investment. As technology continues to advance and investor preferences evolve, it will be interesting to see how these dynamics shape the financial landscape in the coming years. **FAQ** **Is Bitcoin legal?** Yes, Bitcoin is legal in most countries, including the United States. However, regulations may vary, so it's essential to check the legality of Bitcoin in your specific jurisdiction. **Can I invest in Bitcoin through my traditional brokerage account?** Some brokerage firms offer the option to invest in Bitcoin indirectly through specialized investment products like Bitcoin futures or trusts. However, not all traditional brokerage accounts provide this option, so it's best to inquire with your broker. **What is the potential for Bitcoin's future growth?** The future growth potential of Bitcoin is subjective and highly speculative. While some believe Bitcoin has the potential to reach even higher valuations, others remain skeptical. It's important to conduct thorough research and consider various factors before making any investment decisions. **How can I secure my Bitcoin investments?** It is crucial to store your Bitcoin in a secure digital wallet and follow best security practices, such as enabling two-factor authentication and using strong, unique passwords. Additionally, offline storage options like hardware wallets offer an extra layer of security. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ fa0165a0:03397073
2024-10-23 17:19:41## Chef's notes This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing. The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven When done: Enjoy during Fika! PS; * Can be frozen and thawed in microwave for later enjoyment as well. * If you need unit conversion, this site may be of help: https://www.unitconverters.net/ * Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker ## Ingredients - 150 g butter - 5 dl milk - 50 g baking yeast (normal or for sweet dough) - 1/2 teaspoon salt - 1-1 1/2 dl sugar - (Optional) 2 teaspoons of crushed or grounded cardamom seeds. - 1.4 liters of wheat flour - Filling: 50-75 g butter, room temperature - Filling: 1/2 - 1 dl sugar - Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon) - Garnish: 1 egg, sugar or Almond Shavings ## Directions 1. Melt the butter/margarine in a saucepan. 2. Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C). 3. Dissolve the yeast in a dough bowl with the help of the salt. 4. Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour. 5. Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand. 6. Add if necessary. additional flour but save at least 1 dl for baking. 7. Let the dough rise covered (by a kitchen towel), about 30 minutes. 8. Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake. 9. Stir together the ingredients for the filling and spread it. 10. Roll up and cut each roll into 24 pieces. 11. Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes. 12. Brush the buns with beaten egg and sprinkle your chosen topping. 13. Bake in the middle of the oven at 250 ° C, 5-8 minutes. 14. Allow to cool on a wire rack under a baking sheet.
@ fa0165a0:03397073
2024-10-23 17:19:41## Chef's notes This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing. The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven When done: Enjoy during Fika! PS; * Can be frozen and thawed in microwave for later enjoyment as well. * If you need unit conversion, this site may be of help: https://www.unitconverters.net/ * Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker ## Ingredients - 150 g butter - 5 dl milk - 50 g baking yeast (normal or for sweet dough) - 1/2 teaspoon salt - 1-1 1/2 dl sugar - (Optional) 2 teaspoons of crushed or grounded cardamom seeds. - 1.4 liters of wheat flour - Filling: 50-75 g butter, room temperature - Filling: 1/2 - 1 dl sugar - Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon) - Garnish: 1 egg, sugar or Almond Shavings ## Directions 1. Melt the butter/margarine in a saucepan. 2. Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C). 3. Dissolve the yeast in a dough bowl with the help of the salt. 4. Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour. 5. Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand. 6. Add if necessary. additional flour but save at least 1 dl for baking. 7. Let the dough rise covered (by a kitchen towel), about 30 minutes. 8. Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake. 9. Stir together the ingredients for the filling and spread it. 10. Roll up and cut each roll into 24 pieces. 11. Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes. 12. Brush the buns with beaten egg and sprinkle your chosen topping. 13. Bake in the middle of the oven at 250 ° C, 5-8 minutes. 14. Allow to cool on a wire rack under a baking sheet. @ 9e69e420:d12360c2
2024-11-08 02:28:59A Cypherpunk's Manifesto by Eric Hughes Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world. If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to. Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must _always_ reveal myself. Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy. Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature. We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor. We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do. We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money. Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down. Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible. For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals. The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace. Onward. Eric Hughes <hughes@soda.berkeley.edu> 9 March 1993
@ 9e69e420:d12360c2
2024-11-08 02:28:59A Cypherpunk's Manifesto by Eric Hughes Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world. If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to. Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must _always_ reveal myself. Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy. Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature. We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor. We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do. We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money. Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down. Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible. For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals. The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace. Onward. Eric Hughes <hughes@soda.berkeley.edu> 9 March 1993 @ 599f67f7:21fb3ea9
2024-10-20 11:32:36LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, [Zeus](https://zeusln.app/) edo [BlueWallet](https://bluewallet.io/) bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du. [Alby](https://getalby.com/) erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, [LNDhub](https://github.com/BlueWallet/LndHub/tree/master) izenekoa. Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi [Alby konfigurazioarekin](#Alby), pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean [Zeus atalera](#Zeus) jo dezakezu. ## Alby nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. [WebLN](https://www.webln.dev/) protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek [NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md) protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena. ### Zer behar dut? - Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea. - LNbits zorroa. Oraindik zorro bat ez baduzu, joan [gure zorroen orrira](https://bitcointxoko.com) eta sortu bat. - (Aukerazkoa) Zeus konfiguratzeko mugikor bat. ### 1. LNDhub luzapena gaitzea zure LNbits zorroan Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu `LNDhub` luzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira. ### 2. Alby luzapena instalatu Joan [getalby.com](https://getalby.com/)-era eta egin klik `Add Browser Extension` botoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan. ### 3. Inportatu Alby-ra  Hurrengo pantailan, aukeratu `Connect`, eta ondoren aukeratu `LNDhub`. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. Sakatu `Continue`. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke! 💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote: - *Invoice URL*-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - *Admin URL*-ak ordainketak bidaltzeko aukera ere ematen du. ### 4. (Aukerazkoa) Zeus konfiguratu Alby-rekin  Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan `Account Settings` atalean. `Account` azpian aurkituko duzu `Connect your mobile wallet` aukera. Sakatu `Connect`, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu. Zeus aurretik instalatu ez baduzu, joan [zeusln.app](https://zeusln.app/)-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan `Settings` > `Add a new node` atalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu. Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada? ## Zeus nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute. ### Zer behar dut? - Android edo iOS telefono bat. - LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko). - LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan [gure zorroen orrira](https://bitcointxoko.com) eta sortu bat. ### 1. Zeus deskargatu Deskargatu Zeus aplikazioa zure sistema eragilerako [hemen](https://zeusln.app). ### 2. LNDhub luzapena gaitzea zure LNbits zorroan Zure LNbits zorroaren orrian, egin klik `Extensions` atalean eta gaitzazu `LNDhub` luzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria. ### 3. Inportatu Zeus-en Joan `Settings` > `Add a new node` atalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko. 💡 Aukeratu dezakezu Invoice URL eta Admin URL artean: - *Invoice URL*-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - *Admin URL*-ak ordainketak bidaltzeko aukera ere ematen du. QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.  Orain, `Save Node Config` sakatu eta zorroa zure mugikorretik kontrolatu dezakezu! ### Bonus Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu!
@ 599f67f7:21fb3ea9
2024-10-20 11:32:36LNDhub-ek zure zorroa erraz inportatzea ahalbidetzen du bateragarriak diren aplikazioetan. Bitcoin Txoko LNbits zorroa progresiboko web aplikazio (PWA) modura gorde dezakezun arren zure telefonoan, [Zeus](https://zeusln.app/) edo [BlueWallet](https://bluewallet.io/) bezalako aplikazio natibo batek erabiltzaile-esperientzia hobea eta segurtasun handiagoa eskaintzen du. [Alby](https://getalby.com/) erabiliz, zorroa zure nabigatzailearen luzapenean ere inporta dezakezu, webgunean Lightning ordainketak egiteko eta Nostr zap-ak egiteko erraztasun handiagoz. Zorionez, zorro hauek guztiek hizkuntza komun bat ulertzen dute, [LNDhub](https://github.com/BlueWallet/LndHub/tree/master) izenekoa. Gida honetan, zorroa zure nabigatzailera eta telefonora nola inportatu azalduko dugu. Zorroa nabigatzailean eta telefonoan erabili nahi baduzu, hasi [Alby konfigurazioarekin](#Alby), pausoetako batek zorroa Zeus-era erraz inportatzeko aukera emango baitizu. Baina zorroa soilik zure telefonoan erabili nahi baduzu, zuzenean [Zeus atalera](#Zeus) jo dezakezu. ## Alby nostr:nprofile1qqsyv47lazt9h6ycp2fsw270khje5egjgsrdkrupjg27u796g7f5k0s8jq7y6 nabigatzailearen luzapena da, Lightning eta Nostr nabigatzailera ekartzen dituena. [WebLN](https://www.webln.dev/) protokoloa erabiliz, luzapenak webguneetan fakturak automatikoki detekta eta ordaintzen ditu, eta Lightning bidez webguneetan saioa hasteko aukera ematen du. Gainera, Lightning gune gogokoenetan aurrekontuak ezar ditzakezu. Luzapen honek [NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md) protokoloa erabiliz Nostr sinadura gisa ere funtziona dezake, zure giltza pribatua web bezeroetan sartzea baino askoz seguruagoa dena. ### Zer behar dut? - Chrome edo Firefox luzapenak onartzen dituen web nabigatzailea. - LNbits zorroa. Oraindik zorro bat ez baduzu, joan [gure zorroen orrira](https://bitcointxoko.com) eta sortu bat. - (Aukerazkoa) Zeus konfiguratzeko mugikor bat. ### 1. LNDhub luzapena gaitzea zure LNbits zorroan Nabigatzailean, joan zure zorroaren estekara. Egin klik Extensions atalean eta gaitzazu `LNDhub` luzapena. Gaitu ondoren, joan LNDhub luzapenaren orrira. ### 2. Alby luzapena instalatu Joan [getalby.com](https://getalby.com/)-era eta egin klik `Add Browser Extension` botoian. Instalatu luzapena zure nabigatzailearen luzapen dendetik. Ezarri desblokeatzeko pasahitza eta gorde toki seguruan. ### 3. Inportatu Alby-ra  Hurrengo pantailan, aukeratu `Connect`, eta ondoren aukeratu `LNDhub`. Itzuli zure LNDhub luzapenera eta kopiatu konexioaren URL-a. Itsatsi hori LNDhub esportazioaren URI eremuan. Sakatu `Continue`. Orain LNbits zorroa LNDhub bidez konektatuta eduki beharko zenuke! 💡 Aukeratu dezakezu Invoice URL eta Admin URL artean. Bi hauek Alby-ri zure LNbits zorroarekin elkarreragiteko baimen desberdinak ematen dizkiote: - *Invoice URL*-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - *Admin URL*-ak ordainketak bidaltzeko aukera ere ematen du. ### 4. (Aukerazkoa) Zeus konfiguratu Alby-rekin  Orain LNbits zorroa Alby-rekin konektatu duzunez, Zeus-en ere erraz inportatu dezakezu. Ireki luzapena, egin klik zure zorroaren izenean, eta joan `Account Settings` atalean. `Account` azpian aurkituko duzu `Connect your mobile wallet` aukera. Sakatu `Connect`, eta Zeus-ekin eskaneatzeko QR kode bat erakutsiko dizu. Zeus aurretik instalatu ez baduzu, joan [zeusln.app](https://zeusln.app/)-era eta deskargatu Zeus zure mugikorreko sistema eragilerako. Zeus deskargatu ondoren, joan `Settings` > `Add a new node` atalera. Hemen, Alby-k erakusten dizun QR kodea eskaneatu eta zorroa inportatu dezakezu. Listo! Orain Lightning-aren indarra zure eskuetan duzu. Jainko baten moduan sentitzen al zara jada? ## Zeus nostr:nprofile1qqsrf5h4ya83jk8u6t9jgc76h6kalz3plp9vusjpm2ygqgalqhxgp9g84ctjf kode irekiko aplikazio bikaina da, zure nodo propioa mugikorrean konektatzeko aukera ematen duena. Lightning nodo nagusi guztiak onartzen ditu, hala nola LND, CLN eta Eclair, bai eta Tor bidezko zein clearnet bidezko konexioak ere. Azkenaldian, beren LSP (Lightning Service Provider) propioa iragarri dute. ### Zer behar dut? - Android edo iOS telefono bat. - LNbits zorroa ikusi ahal izateko beste gailu bat (QR kodea eskaneatzeko). - LNbits zorroa eskuragarri izatea. Zorro bat oraindik ez baduzu, joan [gure zorroen orrira](https://bitcointxoko.com) eta sortu bat. ### 1. Zeus deskargatu Deskargatu Zeus aplikazioa zure sistema eragilerako [hemen](https://zeusln.app). ### 2. LNDhub luzapena gaitzea zure LNbits zorroan Zure LNbits zorroaren orrian, egin klik `Extensions` atalean eta gaitzazu `LNDhub` luzapena. Gaitu ondoren, ireki LNDhub luzapenaren orria. ### 3. Inportatu Zeus-en Joan `Settings` > `Add a new node` atalera Zeus-en. Eskaneatu nahi duzun zorroa inportatzeko. 💡 Aukeratu dezakezu Invoice URL eta Admin URL artean: - *Invoice URL*-ak fakturak sortzea eta ordainketak jasotzea ahalbidetzen du. - *Admin URL*-ak ordainketak bidaltzeko aukera ere ematen du. QR kodea eskaneatu ondoren, Zeus-en eremu guztiak automatikoki beteko dira. Zorroarentzat ezizena ere gehitu dezakezu.  Orain, `Save Node Config` sakatu eta zorroa zure mugikorretik kontrolatu dezakezu! ### Bonus Zeus-ek ezaugarri interesgarriak ere eskaintzen ditu, hala nola gai pertsonalizatuak, prezioen bihurketak, lurker modua eta biometria bidezko egiaztapena. Gida honen esparrutik haratago doazen ezaugarriak dira hauek, baina aplikazioa erabili eta zuk zeuk aurkitu ditzakezu! @ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
@ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.** @ 7d3e7ac0:90e6f183
2024-11-07 22:02:47Read the [paper](https://proof-of-loss.money).
@ 7d3e7ac0:90e6f183
2024-11-07 22:02:47Read the [paper](https://proof-of-loss.money). @ ec42c765:328c0600
2024-10-21 07:42:48# 2024年3月 フィリピンのセブ島へ旅行。初海外。  Nostrに投稿したらこんなリプライが nostr:nevent1qqsff87kdxh6szf9pe3egtruwfz2uw09rzwr6zwpe7nxwtngmagrhhqc2qwq5 nostr:nevent1qqs9c8fcsw0mcrfuwuzceeq9jqg4exuncvhas5lhrvzpedeqhh30qkcstfluj (ビットコイン関係なく普通の旅行のつもりで行ってた。というか常にビットコインのこと考えてるわけではないんだけど…) #### そういえばフィリピンでビットコイン決済できるお店って多いのかな? ### 海外でビットコイン決済ってなんかかっこいいな! ## やりたい! <br> ----------- <br> # ビットコイン決済してみよう! in セブ島 [BTCMap](https://btcmap.org/map#14/10.31403/123.91797) でビットコイン決済できるところを探す 本場はビットコインアイランドと言われてるボラカイ島みたいだけど セブにもそれなりにあった!  なんでもいいからビットコイン決済したいだけなので近くて買いやすい店へ いざタピオカミルクティー屋!  ちゃんとビットコインのステッカーが貼ってある!  つたない英語とGoogle翻訳を使ってビットコイン決済できるか店員に聞いたら ### 店員「ビットコインで支払いはできません」 (えーーーー、なんで…ステッカー貼ってあるやん…。) まぁなんか知らんけどできないらしい。 店員に色々質問したかったけど質問する英語力もないのでする気が起きなかった 結局、せっかく店まで足を運んだので普通に現金でタピオカミルクティーを買った <br> タピオカミルクティー 話題になってた時も特に興味なくて飲んでなかったので、これが初タピオカミルクティーになった 法定通貨の味がした。  ### どこでもいいからなんでもいいから ### 海外でビットコイン決済してみたい <br> ----------- <br> # ビットコイン決済させてくれ! in ボラカイ島 ビットコインアイランドと呼ばれるボラカイ島はめちゃくちゃビットコイン決済できるとこが多いらしい でもやめてしまった店も多いらしい でも300もあったならいくつかはできるとこあるやろ! nostr:nevent1qqsw0n6utldy6y970wcmc6tymk20fdjxt6055890nh8sfjzt64989cslrvd9l 行くしかねぇ! <br> ## ビットコインアイランドへ フィリピンの国内線だぁ  ``` 行き方: Mactan-Cebu International Airport ↓飛行機 Godofredo P. Ramos Airport (Caticlan International Airport, Boracay Airport) ↓バスなど Caticlan フェリーターミナル ↓船 ボラカイ島 料金: 飛行機(受託手荷物付き) 往復 21,000円くらい 空港~ボラカイ島のホテルまで(バス、船、諸経費) 往復 3,300円くらい (klookからSouthwest Toursを利用) このページが色々詳しい https://smaryu.com/column/d/91761/ ``` 空港おりたらSouthwestのバスに乗る 事前にネットで申し込みをしている場合は5番窓口へ  港!  船!(めっちゃ速い)  ボラカイついた!  ### ボラカイ島の移動手段 セブの移動はgrabタクシーが使えるがボラカイにはない。 ネットで検索するとトライシクルという三輪タクシーがおすすめされている。  (トライシクル:開放的で風がきもちいい) トライシクルの欠点はふっかけられるので値切り交渉をしないといけないところ。 最初に300phpくらいを提示され、行き先によるけど150phpくらいまでは下げられる。 これはこれで楽しい値切り交渉だけど、個人的にはトライシクルよりバスの方が気楽。 Hop On Hop Off バス: https://www.hohoboracay.com/pass.php 一日乗り放題250phpなので往復や途中でどこか立ち寄ったりを考えるとお得。  バスは現金が使えないので事前にどこかでカードを買うか車内で買う。 私は何も知らずに乗って車内で乗務員さんから現金でカードを買った。 バスは狭い島内を数本がグルグル巡回してるので20~30分に1本くらいは来るイメージ。 逆にトライシクルは待たなくても捕まえればすぐに乗れるところがいいところかもしれない。 <br> ## 現実 ボラカイ島 BTC Map  BTC決済できるとこめっちゃある <br> さっそく店に行く! 「bitcoin accepted here」のステッカーを見つける! 店員にビットコイン支払いできるか聞く! できないと言われる! <br> もう一軒行く 「bitcoin accepted here」のステッカーを見つける 店員にビットコイン支払いできるか聞く できないと言われる <br> 5件くらいは回った 全部できない! <br> 悲しい <br> で、ネットでビットコインアイランドで検索してみると 旅行日の一か月前くらいにアップロードされた動画があったので見てみた 要約 - ビットコイン決済はpouch.phというスタートアップ企業がボラカイ島の店にシステムを導入した - ビットコインアイランドとすることで観光客が10%~30%増加つまり数百~千人程度のビットコインユーザーが来ると考えた - しかし実際には3~5人だった - 結果的に200の店舗がビットコイン決済を導入しても使われたのはごく一部だった - ビットコイン決済があまり使われないので店員がやり方を忘れてしまった - 店は関心を失いpouchのアプリを消した https://youtu.be/uaqx6794ipc?si=Afq58BowY1ZrkwaQ <iframe width="560" height="315" src="https://www.youtube.com/embed/uaqx6794ipc?si=S3kf0K49Z4NASxJt&start=254" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> なるほどね~ しゃあないわ <br> ## 聖地巡礼 動画内でpouchのオフィスだったところが紹介されていた これは半年以上前の画像らしい  現在はオフィスが閉鎖されビットコインの看板は色あせている  おもしろいからここに行ってみよう!となった で行ってみた 看板の色、更に薄くなってね!?  記念撮影  これはこれで楽しかった 場所はこの辺 https://maps.app.goo.gl/WhpEV35xjmUw367A8 ボラカイ島の中心部の結構いいとこ みんな~ビットコイン(の残骸)の聖地巡礼、行こうぜ! <br> ## 最後の店 Nattoさんから情報が <blockquote class="twitter-tweet"><p lang="ja" dir="ltr">なんかあんまりネットでも今年になってからの情報はないような…<a href="https://t.co/hiO2R28sfO">https://t.co/hiO2R28sfO</a><br><br>ここは比較的最近…?<a href="https://t.co/CHLGZuUz04">https://t.co/CHLGZuUz04</a></p>— Natto (@madeofsoya) <a href="https://twitter.com/madeofsoya/status/1771219778906014156?ref_src=twsrc%5Etfw">March 22, 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> もうこれで最後だと思ってダメもとで行ってみた なんだろうアジア料理屋さん?  もはや信頼度0の「bitcoin accepted here」  ビットコイン払いできますか? 店員「できますよ」 え?ほんとに?ビットコイン払いできる? 店員「できます」 できる!!!! なんかできるらしい。 <br> 適当に商品を注文して 印刷されたQRコードを出されたので読み取る ここでスマートに決済できればよかったのだが結構慌てた 自分は英語がわからないし相手はビットコインがわからない それにビットコイン決済は日本で1回したことがあるだけだった  どうもライトニングアドレスのようだ 送金額はこちらで指定しないといけない 店員はフィリピンペソ建ての金額しか教えてくれない 何sats送ればいいのか分からない ここでめっちゃ混乱した でもウォレットの設定変えればいいと気付いた 普段円建てにしているのをフィリピンペソ建てに変更すればいいだけだった 設定を変更したら相手が提示している金額を入力して送金 送金は2、3秒で完了した <br> やった! ### 海外でビットコイン決済したぞ! ログ  PORK CHAR SIU BUN とかいうやつを買った  普通にめっちゃおいしかった なんかビットコイン決済できることにビビッて焦って一品しか注文しなかったけどもっと頼めばよかった ここです。みなさん行ってください。 Bunbun Boracay https://maps.app.goo.gl/DX8UWM8Y6sEtzYyK6 ### めでたしめでたし <br> ----------- <br> # 以下、普通の観光写真 ## セブ島 ジンベエザメと泳いだ  スミロン島でシュノーケリング  市場の路地裏のちょっとしたダウンタウン?スラム?をビビりながら歩いた  ## ボホール島 なんか変な山  メガネザル  現地の子供が飛び込みを披露してくれた  ## ボラカイ島 ビーチ   夕日  藻  ボラカイ島にはいくつかビーチがあって宿が多いところに近い南西のビーチ、ホワイトビーチは藻が多かった(時期によるかも) 北側のプカシェルビーチは全然藻もなく、水も綺麗でめちゃくちゃよかった  プカシェルビーチ    <br> ----------- <br> # おわり!
@ ec42c765:328c0600
2024-10-21 07:42:48# 2024年3月 フィリピンのセブ島へ旅行。初海外。  Nostrに投稿したらこんなリプライが nostr:nevent1qqsff87kdxh6szf9pe3egtruwfz2uw09rzwr6zwpe7nxwtngmagrhhqc2qwq5 nostr:nevent1qqs9c8fcsw0mcrfuwuzceeq9jqg4exuncvhas5lhrvzpedeqhh30qkcstfluj (ビットコイン関係なく普通の旅行のつもりで行ってた。というか常にビットコインのこと考えてるわけではないんだけど…) #### そういえばフィリピンでビットコイン決済できるお店って多いのかな? ### 海外でビットコイン決済ってなんかかっこいいな! ## やりたい! <br> ----------- <br> # ビットコイン決済してみよう! in セブ島 [BTCMap](https://btcmap.org/map#14/10.31403/123.91797) でビットコイン決済できるところを探す 本場はビットコインアイランドと言われてるボラカイ島みたいだけど セブにもそれなりにあった!  なんでもいいからビットコイン決済したいだけなので近くて買いやすい店へ いざタピオカミルクティー屋!  ちゃんとビットコインのステッカーが貼ってある!  つたない英語とGoogle翻訳を使ってビットコイン決済できるか店員に聞いたら ### 店員「ビットコインで支払いはできません」 (えーーーー、なんで…ステッカー貼ってあるやん…。) まぁなんか知らんけどできないらしい。 店員に色々質問したかったけど質問する英語力もないのでする気が起きなかった 結局、せっかく店まで足を運んだので普通に現金でタピオカミルクティーを買った <br> タピオカミルクティー 話題になってた時も特に興味なくて飲んでなかったので、これが初タピオカミルクティーになった 法定通貨の味がした。  ### どこでもいいからなんでもいいから ### 海外でビットコイン決済してみたい <br> ----------- <br> # ビットコイン決済させてくれ! in ボラカイ島 ビットコインアイランドと呼ばれるボラカイ島はめちゃくちゃビットコイン決済できるとこが多いらしい でもやめてしまった店も多いらしい でも300もあったならいくつかはできるとこあるやろ! nostr:nevent1qqsw0n6utldy6y970wcmc6tymk20fdjxt6055890nh8sfjzt64989cslrvd9l 行くしかねぇ! <br> ## ビットコインアイランドへ フィリピンの国内線だぁ  ``` 行き方: Mactan-Cebu International Airport ↓飛行機 Godofredo P. Ramos Airport (Caticlan International Airport, Boracay Airport) ↓バスなど Caticlan フェリーターミナル ↓船 ボラカイ島 料金: 飛行機(受託手荷物付き) 往復 21,000円くらい 空港~ボラカイ島のホテルまで(バス、船、諸経費) 往復 3,300円くらい (klookからSouthwest Toursを利用) このページが色々詳しい https://smaryu.com/column/d/91761/ ``` 空港おりたらSouthwestのバスに乗る 事前にネットで申し込みをしている場合は5番窓口へ  港!  船!(めっちゃ速い)  ボラカイついた!  ### ボラカイ島の移動手段 セブの移動はgrabタクシーが使えるがボラカイにはない。 ネットで検索するとトライシクルという三輪タクシーがおすすめされている。  (トライシクル:開放的で風がきもちいい) トライシクルの欠点はふっかけられるので値切り交渉をしないといけないところ。 最初に300phpくらいを提示され、行き先によるけど150phpくらいまでは下げられる。 これはこれで楽しい値切り交渉だけど、個人的にはトライシクルよりバスの方が気楽。 Hop On Hop Off バス: https://www.hohoboracay.com/pass.php 一日乗り放題250phpなので往復や途中でどこか立ち寄ったりを考えるとお得。  バスは現金が使えないので事前にどこかでカードを買うか車内で買う。 私は何も知らずに乗って車内で乗務員さんから現金でカードを買った。 バスは狭い島内を数本がグルグル巡回してるので20~30分に1本くらいは来るイメージ。 逆にトライシクルは待たなくても捕まえればすぐに乗れるところがいいところかもしれない。 <br> ## 現実 ボラカイ島 BTC Map  BTC決済できるとこめっちゃある <br> さっそく店に行く! 「bitcoin accepted here」のステッカーを見つける! 店員にビットコイン支払いできるか聞く! できないと言われる! <br> もう一軒行く 「bitcoin accepted here」のステッカーを見つける 店員にビットコイン支払いできるか聞く できないと言われる <br> 5件くらいは回った 全部できない! <br> 悲しい <br> で、ネットでビットコインアイランドで検索してみると 旅行日の一か月前くらいにアップロードされた動画があったので見てみた 要約 - ビットコイン決済はpouch.phというスタートアップ企業がボラカイ島の店にシステムを導入した - ビットコインアイランドとすることで観光客が10%~30%増加つまり数百~千人程度のビットコインユーザーが来ると考えた - しかし実際には3~5人だった - 結果的に200の店舗がビットコイン決済を導入しても使われたのはごく一部だった - ビットコイン決済があまり使われないので店員がやり方を忘れてしまった - 店は関心を失いpouchのアプリを消した https://youtu.be/uaqx6794ipc?si=Afq58BowY1ZrkwaQ <iframe width="560" height="315" src="https://www.youtube.com/embed/uaqx6794ipc?si=S3kf0K49Z4NASxJt&start=254" title="YouTube video player" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> なるほどね~ しゃあないわ <br> ## 聖地巡礼 動画内でpouchのオフィスだったところが紹介されていた これは半年以上前の画像らしい  現在はオフィスが閉鎖されビットコインの看板は色あせている  おもしろいからここに行ってみよう!となった で行ってみた 看板の色、更に薄くなってね!?  記念撮影  これはこれで楽しかった 場所はこの辺 https://maps.app.goo.gl/WhpEV35xjmUw367A8 ボラカイ島の中心部の結構いいとこ みんな~ビットコイン(の残骸)の聖地巡礼、行こうぜ! <br> ## 最後の店 Nattoさんから情報が <blockquote class="twitter-tweet"><p lang="ja" dir="ltr">なんかあんまりネットでも今年になってからの情報はないような…<a href="https://t.co/hiO2R28sfO">https://t.co/hiO2R28sfO</a><br><br>ここは比較的最近…?<a href="https://t.co/CHLGZuUz04">https://t.co/CHLGZuUz04</a></p>— Natto (@madeofsoya) <a href="https://twitter.com/madeofsoya/status/1771219778906014156?ref_src=twsrc%5Etfw">March 22, 2024</a></blockquote> <script async src="https://platform.twitter.com/widgets.js" charset="utf-8"></script> もうこれで最後だと思ってダメもとで行ってみた なんだろうアジア料理屋さん?  もはや信頼度0の「bitcoin accepted here」  ビットコイン払いできますか? 店員「できますよ」 え?ほんとに?ビットコイン払いできる? 店員「できます」 できる!!!! なんかできるらしい。 <br> 適当に商品を注文して 印刷されたQRコードを出されたので読み取る ここでスマートに決済できればよかったのだが結構慌てた 自分は英語がわからないし相手はビットコインがわからない それにビットコイン決済は日本で1回したことがあるだけだった  どうもライトニングアドレスのようだ 送金額はこちらで指定しないといけない 店員はフィリピンペソ建ての金額しか教えてくれない 何sats送ればいいのか分からない ここでめっちゃ混乱した でもウォレットの設定変えればいいと気付いた 普段円建てにしているのをフィリピンペソ建てに変更すればいいだけだった 設定を変更したら相手が提示している金額を入力して送金 送金は2、3秒で完了した <br> やった! ### 海外でビットコイン決済したぞ! ログ  PORK CHAR SIU BUN とかいうやつを買った  普通にめっちゃおいしかった なんかビットコイン決済できることにビビッて焦って一品しか注文しなかったけどもっと頼めばよかった ここです。みなさん行ってください。 Bunbun Boracay https://maps.app.goo.gl/DX8UWM8Y6sEtzYyK6 ### めでたしめでたし <br> ----------- <br> # 以下、普通の観光写真 ## セブ島 ジンベエザメと泳いだ  スミロン島でシュノーケリング  市場の路地裏のちょっとしたダウンタウン?スラム?をビビりながら歩いた  ## ボホール島 なんか変な山  メガネザル  現地の子供が飛び込みを披露してくれた  ## ボラカイ島 ビーチ   夕日  藻  ボラカイ島にはいくつかビーチがあって宿が多いところに近い南西のビーチ、ホワイトビーチは藻が多かった(時期によるかも) 北側のプカシェルビーチは全然藻もなく、水も綺麗でめちゃくちゃよかった  プカシェルビーチ    <br> ----------- <br> # おわり!