-

@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07
## Chef's notes
This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is.
## Details
- ⏲️ Prep time: 30
- 🍳 Cook time: 0
- 🍽️ Servings: 8
## Ingredients
- 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates
- 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates
- 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates
- 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates
- 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates
## Directions
1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake.
2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
-

@ af9d7040:42d05d35
2024-11-18 20:15:51
## When I was taking these photos, I kept thinking about certain movies.
### *Each image is half a movie still, half my own shot.*
### **[Twin Peaks](https://www.imdb.com/title/tt0098936/)**

### **[Brokeback Mountain*](https://www.imdb.com/title/tt0388795/?ref_=nv_sr_srsg_0_tt_6_nm_0_in_0_q_Brokeback%2520Mountain)**

### **[Parasite](https://www.imdb.com/title/tt6751668/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Parasite)**

### **[Waterworld](https://www.imdb.com/title/tt0114898/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Waterworld)**

### **[True Detective](https://www.imdb.com/title/tt2356777/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_True%2520Detective)**

### **[Phantom Thread](https://www.imdb.com/title/tt5776858/?ref_=nv_sr_srsg_0_tt_4_nm_1_in_0_q_Phantom%2520Thread)**

### **[Arrival](https://www.imdb.com/title/tt2543164/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Arrival)**

### **[There Will Be Blood](https://www.imdb.com/title/tt0469494/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_There%2520Will%2520Be%2520Blood)**

### **[Your Name](https://www.imdb.com/title/tt5311514/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Your%2520Name)**

### **[Sicario](https://www.imdb.com/title/tt3397884/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_Sicario)**

### **[Steve Jobs](https://www.imdb.com/title/tt2080374/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_Steve%2520Jobs)**

### **[And](https://www.imdb.com/title/tt0108778/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_the%2520friends)**

-

@ b98139a6:eb269255
2024-11-18 20:15:16
I've been suddenly having trouble posting comments that are priced at 1 sat. I also tested with zaps, and 1sat zaps fail as well. They seem to fail instantly, and show canceled in the wallet history & on AlbyHub (running on my Start9). However, there is no record of the TX failing (or even attempting) in the lightning node itself.
Bigger payments do work, and I tried a 2sat zap which did work. I don't comment too often, but I zap every day, and my zaps are well above 1sat, so I didn't notice until I wanted to write some comments today and they all came back as failing...
Has anyone else seen this? Is there a setting that I somehow messed up? It's odd that the 2sat zap went through fine, and much bigger payments have been working without issue (both outgoing and incoming), so it's not a liquidity issue.
originally posted at https://stacker.news/items/773077
-

@ 6bae33c8:607272e8
2024-11-18 18:36:16
I much prefer to write these after a good week. I used to kind of relish excoriating myself after every mistake, complaining about all the questionable calls and coaches’ decision-making that went against me, but not so much anymore. When I lose, I try to think of it as the outcome that’s most suited to me at this particular time. Had I gone 5-0, that would have been most suited, but apparently I really needed the 1-4 to knock me out of Q3.
I won’t pretend to know the particular lesson in this. Life isn’t like that. You take from it what you choose and then await the next lesson. If I had to guess I’d say I wasn’t ready to win Q3 — not the money, that’s not the issue — but psychologically I wasn’t ready to accept winning it.
You see my brain has been poisoned with these ideas about probability wherein it’s very hard to go 5-0 (1 in 32, maybe 1 in 28 or so if you have an edge.) To do it twice is 1 in 1000 (2 ^10 = 1024). To do it four times (20 - 0) is less than one in a million. So when I go to pick the games each week I have this foreboding and dread that it can’t be done. Or that it *can* be done, but only with a lot of luck. This is toxic.
Whether or not the math adds up is irrelevant to the process of picking the games. You are divining what is likely to happen and positioning yourself accordingly. Maybe I am the greatest of all time. Maybe I *can* go on a 20-0 run if I get in sync. Tom Brady had no business believing he could win seven Super Bowls. If he focused on the odds of that happening, it probably wouldn’t have happened. He just went out and played as though he could win one every year.
So my takeaway is I’m too much of a midwit, someone who learned the Probability 101 course and thinks he’s got this shit down. I’m too savvy to win the Q3, because I know better, because I’ve run the numbers and realize it can’t be done without a ton of luck. I want to be less savvy, less caught up in probabilities and more naive. I want to pick with the confidence of someone who is totally naive to the likelihood and all-in on transmuting my observations and knowledge of what I see into the winning picks.
I will try to do this going forward, but it’s possible my long stint in the midwit fantasy industry damaged my brain too much.
- The Bengals-Chargers 40-minute edit wasn’t ready when I woke up this morning, so I watched the six-minute highlights. I had Joe Burrow, Ja’Marr Chase and JK Dobbins, so there were a lot of highlights! I also had Khalil Herbert going out of desperation due to byes in one league, and I’m not sure if he played.
- Alan Seslowsky [put out a video](https://www.youtube.com/watch?v=4lF-9mI4EDs) before the year saying to take Chase No. 1 overall, and being the donkey I am, I took it literally and drafted him in three leagues. Reminds me of that Buddhist story where three monks tell a retarded monk (a “fool”) that if he lets each of them whack him with a stick, he’ll become enlightened. So he agrees, they hit him and it works.
- I don’t think the Chargers are serious contenders, but with Jim Harbaugh there it’s finally at least possible.
- The Packers are out of sync and obviously very lucky to win that game. No idea why they refuse to give Jayden Reed targets, but I’m happy about it since I once regretted not drafting him.
- I watched the first two-third of the Lions-Jaguars, and I can assure you that game was not as close as the score. Total domination on both sides. It was incidentally the only ATS pick I won.
- I picked the Titans +6 due to divine inspiration, but it must have been intended for a different branch of the multiverse, one where the refs didn’t call a garbage personal foul on 4th-and-goal that gifted the Vikings, who won by 10, a TD instead of a turnover on downs.
- A few games ago, Chase/Justin Jefferson was a close call, but Chase has since left him in the dust.
- With Marvin Harrison on bye, I was forced to start Nick Westbrook-Ikhine, so I appreciated the 98-yard TD pass to him. Just a 16.8-point play. Will Levis sucks though.
- My Primetime team will do okay if CJ Stroud has a good game (especially if he connects with Tank Dell), but I originally had Anthony Richardson in at QB and Jonnu Smith (28 points) at TE who I benched for Dallas Goedert. (I was actually satisfied with Goedert’s 11 points on Thursday night too.)
- I have Jaylen Waddle in one league, started him over Jonnu and Elijah Moore. I know everyone would have done that, but at what point do you have to start considering say Ladd McConkey over him. (Next week, I get Malik Nabers back, so I’ll have that choice.)
- Brock Bowers maybe should have been the Dynasty League 1.1. for this year’s rookies.
- I saw a little of the Pats-Rams game. Cooper Kupp caught an intermediate ball, the defender missed and he ran untouched for 69 yards with no one near him. The Rams were totally stifled by the Dolphins last week too.
- Drake Maye looked pretty good to me from what I watched. I don’t know if he’ll be great, but he’s over the threshold.
- I had the Browns plus 1.5 as one of my picks, and it looked okay until the fourth quarter when they fell apart. I also had Taysom Hill in my dynasty league where I was forced to start two tight ends. See below:
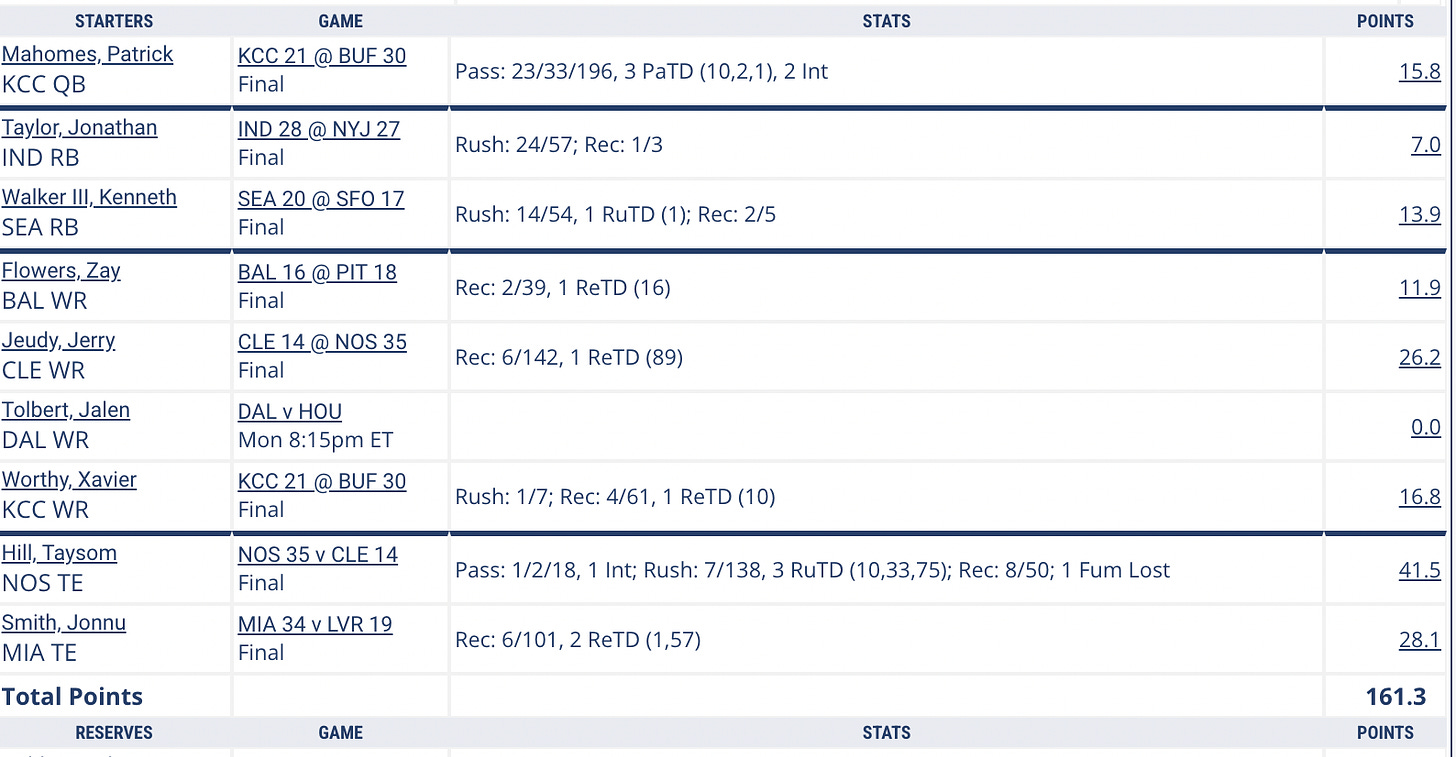- Jerry Jeudy has random massive games once every year or so. But the Browns are so much more watchable with Jameis Winston than Deshaun Watson, who should just hire prostitutes to re-enact the massage experience in perpetuity with that money.
- The time to pick up Anthony Richardson was last week, which I did in two leagues. He was obviously going to get another shot, and the upside was/is still there.
- The Jets are hilarious, should have stuck with QB1.
- I had the Ravens -3, and while it was the losing side, they are the better team than the Steelers. Justin Tucker hit that last 54-yarder, but he missed two earlier field goals in the game, and it was tough to watch. It’s as if the great Mariano Rivera had gotten shelled in his final season (which he did not.)
- I really thought the Ravens would get that two-point conversion and cover in overtime too.
- The Falcons never got off the plane. No idea what happened there. At least we got to see some Penix. “12-inch” passed the eye test for me, though he could have put more air under one deep throw. Is that not his college nickname?
- Never try and handicap the Denver running back situation.
- The 49ers look like themselves, but there’s something missing. I guess Nick Bosa getting hurt and George Kittle not playing explains some of it.
- Geno Smith made a bad-ass 16-yard TD scramble to win the game. It looks like JSN has emerged as his No. 1 receiver finally even with DK Metcalf back. Tyler Lockett seems relegated to a bit role.
- The Chiefs had a shot after their TD to cut it to 23-21, but Josh Allen crushed their spirits with a 26-yard TD on 4th-and-2. Save it for the playoffs, Josh!
- I watched the Tyson-Paul flight on Netflix Saturday morning. It was pretty dull, but I’ve heard two conflicting theories since: (1) Paul took it easy on Tyson late out of respect for the legend — Tyson did look exhausted after eight shortened rounds; and (2) That Tyson went easy on Paul, pulled punches and let him win. (There were a couple points where Tyson slowed up after Paul made an odd gesture like sticking his tongue out.) I don’t know, but they both got paid so much, nothing would surprise me.
-

@ cd7973fe:aec52bc3
2024-11-18 18:23:59
test
-

@ ced4158e:f2a74519
2024-11-18 18:10:47
Бесплатный роллтон в Метрополисе, катание на единорогах в ЦПКО, а может быть летающие машины? Все это впереди, вот только общественный транспорт в Кургане будет актуален всегда, и однажды наш старый добрый друг ПАЗик из гадкого утёнка превратится в прекрасного лебедя. А как это будет выглядеть? Смотри!
<iframe width="1862" height="791" src="https://www.youtube.com/embed/GUbmibUb4tk" title="" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
#45news
#Курган2040
-

@ 5bfb38cb:2b999aa7
2024-11-18 18:06:30
### Spot Over BTX2024
### Open Interest:
There are no significant changes in OI as we have moved to premium.
### Institutional Order Flow Sponsorship:
The IOF is bullish above the all-time high. The structure must be maintained away from the high to continue the trend.
### Weekly Profile:
The week presents relevant news on Tuesday and Thursday. It is likely that we will see some bearish manipulation until Tuesday or Wednesday, and then move to premium if the IOF remains bullish.
### Classic Technical Analysis:
We have consolidated a new ATH but have had a week of retracement towards the equilibrium of the last bullish swing. We must maintain these levels to remain bullish.
https://image.nostr.build/70fe786e500780819ce09425ec4c2e916e7010f1feaa333f52e3d91ffa29f071.png
### Market Structure:
The structure is bullish.
### Trading Range:
66798 to 93483. Currently in Premium.
##### PD Array Matrix:
Premium:
- ATH 93483
Discount:
- FVG D 85121
- FVG D 80280
- FVG D 74479
- OB+D 72727
Equilibrium:
- 80141
### Key Price Levels:
- OB+D 72727. I do not expect closes below this structure and its MT at 70273 to remain bullish.
https://image.nostr.build/98b448aa561465b4dcaecf340073d86ff7008a0b1d30437b21f7e26e71213bdc.png
### Daily BIAS:
Bullish.
### Daily Target:
- Retracement to 80280 to take liquidity and reach a swing equilibrium, and then maintain premium. If the high is clearly taken, the structure may be invalidated to pursue the weekly and monthly bullish target.
*Learning to accept and deal with the inherent risk of trading is what separates the consistent winners from everyone else.*
-

@ 4ba8e86d:89d32de4
2024-11-07 13:56:21
Tutorial feito por Grom mestre⚡poste original abaixo:
http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277
Bom dia/tarde/noite a todos os camaradas.
Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW.
Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta.
É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW.
Sem mais delongas, vamos ao tutorial de fato.
## 1. Criando uma conta de email no hq.postman
Relembrando: Esse tutorial considera que você já tenha acesso à I2P.
Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo.
Após entrar no site vá para a página '1 - Creating a mailbox'
https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg
Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos.
https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg
Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados.
https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg
https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg
Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email.
## 2. Configurando os túneis cliente de SMTP e POP3
O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P.
Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir.
Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd.
Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso.
Edite-os conforme as imagens a seguir:
Arquivo pop-postman.conf
https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg
Arquivo smtp-postman.conf
https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg
Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando:
```
sudo systemctl restart i2pd
```
Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço.
Com os túneis cliente criados, vamos agora configurar o Thunderbird
## 3. Configurando o Thunderbird para acessar a nossa conta
Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir.
https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg
https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg
Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens.
Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta.
https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg
Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir.
https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg
A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue'
https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg
E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta.
https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg
## 4. Observações e considerações finais
Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual.
Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
-

@ 41e6f20b:06049e45
2024-11-17 17:33:55
Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ fd208ee8:0fd927c1
2024-11-08 10:27:40
## You have no idea
I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.

It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse.
I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._
But you were always apart. You were always two different people. You just didn't notice, until now.

I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship.
## I was raised by relaxed revolutionaries
Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics.
It's like magic, but it's the result of a mindset, not a worldview.
Or, as I like to quip:
> The best way to stay married, is to not get divorced.

My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live.
My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.

The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on.
And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer.
You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.

We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something.
Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
-

@ 97c70a44:ad98e322
2024-11-18 17:57:17
So I have this cool new product, which for about two weeks has been ready to release, if I could just solve one thing. I have recently moved away from storing user keys in my apps due to the ease with which they could (and have) been put at risk. In doing so, I've discovered that despite its downsides, pasting your nsec into an app is a pretty straightforward operation which even non-technical people can pull off. In contrast, pretty much no other key management solution is.
Just to state the obvious, and to kick off this survey of nostr key management options, let me just state that asking users to paste their nsec into your app is a *bad idea*. However good your intentions, this opens your users up to all kinds of attack vectors, including clipboard hijacking attacks, exposing keys to insecure communication channels, exposing keys to many different apps, supply chain attacks, XSS attacks, and yes, bugs that cause your software to send keys to analytics or error reporting backends.
The era of nsec-pasting is over.
I've committed to embracing the pain and removing nsec login from Coracle, and I encourage other devs to do the same. The sooner we treat key management with the urgency it deserves, the sooner we can come up with a secure *and* convenient key management solution.
As an aside, `ncryptsec` is a great innovation for securely *transporting* keys, but it still doesn't protect against exposure to apps that need to *use* keys. It has its place though; in fact I'm of the opinion that `nsec` and seed words should be deprecated, and support for them should be removed. Giving friendly names and human-readable representations to data that is essentially private is a really bad idea (unless you're memorizing your key). But I digress.
# Signer Comparisons
Let's go through a few existing options for key management, and compare their relative merits. I've tried to list them in the order they appeared on the scene, which also helps to clarify the logic of how signers have evolved. Throughout, I will be focusing on what kinds of user experience each approach unlocks for *non-technical users*, since my goal is to build products that work for regular people.
## Extension Signers
The first signer application (that I know of) was nos2x, by fiatjaf. As I understand it, this was a proof-of-concept of how users might protect their keys without releasing custody of them. And it works really well! In fact, even though there have been many forks and imitators, I still use nos2x when using nostr on my desktop browser.
Extension signers offer a great user experience, along a narrow happy path. Setting up a browser extension is a relatively familiar process for normal users, and once it's done you don't really have to think about it. In theory, extensions can also include their own onboarding process and key backup strategies as well, allowing users to get started in a single place. Plus, there's very little latency involved in making calls to the signer extension.
This positive experience breaks down quickly though once a user wants to use a desktop or mobile application. When this happens, users have to start over essentially from scratch. Nothing they did to set up the extension helps them move to another signer application.
While it's *technically* possible to use extension signers on mobile via e.g. the Kiwi browser, this doesn't work for native apps or apps installed as PWAs. Instead, you either have to revert to pasting keys, or use some other solution.
One slight permutation of extension signers is browser signers, like Spring. Instead of adding a signer to your browser, Spring allows you to install a browser that holds your keys and allows you to use any nostr web application. But this has all the same basic limitations that extension signers do.
## Hardware Signers
Hardware signers came around shortly after extension signers. I'm not going to spend much time talking about them here, because although they're about as far along the spectrum towards security as you can go, they're also not very convenient. Non-technical users aren't going to onboard by buying (or building) a device which they have to connect to their desktop via USB whenever they want to sign a message. Hardware signers have their place, but onboarding isn't it.
The only hardware signer I'm aware of (although I'm sure I've heard of others) is from [LNBits](https://github.com/lnbits/nostr-signing-device), and is usually used via a browser extension like [horse](https://github.com/lnbits/horse). This of course means that it has all the same limitations that browser extensions have, and then some (although mobile and desktop apps would likely be able to find a way to talk directly to the signer).
## Hosted Signers
Remote signers (aka "bunkers") use the Nostr Connect protocol (also known as NIP 46) for remote signing.
Hosted signers in particular are one example of a NIP 46 remote signer, which lives on "somebody else's computer". Because they use a legacy web architecture, they can be built to be very familiar and convenient to users. It's trivial to build a hosted signer that offers email/password login along with 2FA, password resets, session revokation, the whole shebang. But they have one fatal flaw, which is that they are custodial. This means that not only do users have to relinquish exclusive control over their keys, but hosted signers also can become a target for hackers.
## Desktop Signers
Several projects exist which allow users to run their own bunker, on their own hardware. These include nostr clients like Gossip, as well as command-line utilities like nak. This approach is mostly an improvement over extension signers, because it widens the scope of applications that can conveniently access the signer from those that run in the browser to those that run on the desktop computer the signer lives on. The downside is that they have to communicate via relays, which either introduces latency or requires an additional component to be running locally.
While it's technically possible to use desktop signers to log in on other computers or mobile apps, I don't think that's going to be very practical for most people. Mobile apps by definition are more portable than regular computers. Anyone who wants to access their nostr account on more than one device will have to either set up separate solutions, or go with another kind of remote signer. This isn't a huge obstacle for people highly invested in nostr, but it's a significant amount of friction for a new user.
## Mobile Signers
Mobile signers solve the problem introduced by desktop signers of not always having access to your signer (or of your signer not having access to you, due to being powered down or disconnected from the internet). Mobile devices are generally more available than desktop devices, and also have better push notifications. This means that users can approve signer requests from any device as easily as tapping a notification.
Mobile signers on Android can also upgrade their UX by taking advantage of NIP 55 to avoid the round trip to relays, reducing latency and making it possible to sign things offline. [Amber](https://github.com/greenart7c3/Amber) has been a pioneer in this area, and other projects like [Nostrum](https://github.com/nostr-connect/nostrum) and [Alby's nostr-signer](https://github.com/getAlby/nostr-signer) have been prototyped.
To date, there unfortunately haven't been any signer applications released for iOS, which leaves the mobile signer story incomplete. In my opinion, this is probably the most promising solution for end users, although it's currently under-developed.
## Web Signers
One interesting alternative that combines the benefits of hosted, desktop, and mobile wallets is [nsec.app](https://nsec.app). This is a web application frontend which keeps keys in the browser, so that they are never shared with a third party. Using web push notifications and a healthy sprinkle of black magic, nsec.app is able to respond to signer requests by opening itself in a browser window.
This works generally pretty well for desktop web applications, less well on android, still less well for android PWAs, and (to my understanding) not at all on iOS. Artur from nostr.band is working on these problems using a variety of approaches, one of which is embedding nsec.app in an iframe and communicating using `postMessage`.
This approach also makes it possible to sync keys between your phone and desktop, simulating a hosted UX by making them accessible from either location by signing in to nsec.app. This is done by encrypting user keys and storing them on the nsec.app server. In theory this should be secure, but it's something to consider.
I'm cautiously optimistic about this approach. If successful, it would enable a single brand to exist on every platform, which is important to reduce unnecessary configuration and cognitive overhead for users.
## Multisig Signers
Another experimental approach is multi-sig. [Promenade](https://git.fiatjaf.com/promenade) is a project by fiatjaf exploring this possibility. This would allow users to split their keys across different custodians and require all (or some majority of them) to approve an event signature before it would be valid.
The downsides of this are an increase in complexity (more moving parts for users to deal with) and latency (more parties to coordinate with to sign events). I'm also not clear on whether encryption is possible using multi-signature keys. If not, that would preclude not only existing direct messages (which will hopefully end up on MLS eventually anyway), but also things like private lists, mutes, and application settings. I think multi-signature signers are promising, but are definitely a long-term project.
## Self-Hosted Signers
Coming nearly full circle, self-hosted signers are a special case of hosted signers, but, you know, self-hosted. These signers might live on a home server like a Start9 and be accessible for signer request approvals via tor, or they might live on a server run by the user (or an Uncle Jim). This would be an extremely convenient approach for anyone willing to deal with the complexities of hosting the infrastructure.
A good candidate for NIP 46 support might be AlbyHub, which is already one of the easiest self-hosted wallets to set up and use. Adding signer suppport to AlbyHub would allow users to have their wallet and nostr keys stored in the same place, and accessible anywhere either via the web interface or via AlbyGo.
## Omniplatform Signers
This leads me to, finally, "omniplatform" signers. This isn't really a new architecture, but a combination of several. User choice is great, but nostr has a very tight complexity budget when onboarding new users. If a brand can manage to get new users set up with a very simple but sub-optimal solution, then grow them into a more complete integration into the nostr ecosystem, that would be a huge win.
I think Alby has a great shot at doing this, if it's something they want to prioritize. Bitwarden would also be a great candidate, since they already have apps on every platform, as well as a self-hosted option (Vaultwarden). If users could start with a mobile app, and incrementally set up a browser extension, self-hosted vault, and hardware signer as needed, that I think would be an ideal path.
# Nostr Connect: broken, but promising
If you can't tell from the above comparison, I'm partial to NIP 46 as the best, most flexible way to build high-quality user experiences. Remote key management means a reduction in moving keys, hosting keys, and software installation and administration. If we can get users to the point where their keys live in only two places (their password manager and their signer), we'll be doing good.
There are however many ways to implement NIP 46. Implementing all of them in a single client (or signer) would be burdensome for developers, and introduce a lot of UI complexity to users. Here's a quick survey of flows that currently exist.
## Signer -> Client
The simplest way to connect a client and a bunker is for a user to explicitly authorize the connection by copying a `bunker://` URL from their signer application to their client. This allows the bunker to generate and validate a secret embedded in the URL without the client having to do anything other than pass it along in the initial `connect` request.
This is a great UX for people who know what they're doing, but isn't at all friendly to newcomers. Someone signing in for the first time isn't going to know what a bunker link is, and even if they do they're immediately confronted with the problem of picking a signer, setting it up, and finding out where in that app they can obtain a bunker link. This can be marginally smoothed out using things like protocol handlers and QR codes, but these won't apply in all (or even most) cases.
## Client -> Signer
The reverse flow is similar. This relies on the user to explicitly authorize the connection by copying a `nostrconnect://` url from the client into the signer app. In technical terms, this requires one fewer step, since in NIP 46 the connection is always initiated by the client. In this case, the pasting of the URL replaces the `connect` request. The client listens for a response containing a client-generated secret embedded in the `nostrconnect://` url. This step isn't currently supported by all signer apps, some of which return an `ack` instead. This can result in session hijacking, where an attacker can intercept signing requests (although they can't do anything that would require the user's key, like decrypting messages).
While at first glance `nostrconnect` seems functionally identical to `bunker` links, the UX has the potential to be much better. The reason for this has to do with how people use which devices, and where a client or signer application is most likely to be run. This requires making some assumptions, but in my mind the most common scenario is that a user will want to host their signer on their phone, since that is the device that is most universally available for authorizations (apart from an always-online hosted signer on the open internet). In other words, users generally have their phones with them when they're using their computer, but often don't have a desktop available when using their phone. This idea is validated by (for example) the prevalence of SMS-based 2FA, which assumes the presence of a phone.
Assuming the signer is on the user's phone, QR-scan flows for client authorization make a lot more sense if the client is the one generating the link, since they can simply scan a code generated on another device with their camera, or copy/paste or use a protocol handler for a client on the same device. In contrast, when using a `bunker` link users might find themselves in the awkward position of having to copy a link from their phone to their desktop. Whether this is done via QR code or by sending yourself a link via DM/text/email, it's an awkward flow most people aren't really prepared for.
## Auto-Connect
Some enhancements have been made to the bunker flow which allow clients to send an initial `connect` request without asking the user to copy links between apps. These allow clients to do away with opaque magic strings entirely and provide the idealized "just one click" flow. However, after trying to make this flow work over the course of a couple weeks, I've come to the opinion that the additional complexity involved in automating the flow just isn't worth it.
There are a few variants of this "auto-connect" flow:
- Signer NIP-05: Signers can register a NIP 05 address for a user's pubkey on their domain, allowing users to enter their address rather than their pubkey on login. Unfortunately, this address has no relation to their actual NIP 05 address, which can result in a lot of confusion.
- User NIP-05: To solve this problem, fiatjaf has proposed [a new version](https://github.com/nostr-protocol/nips/pull/1578) which allows users to enter their own NIP 05 in at login instead of the one provided by the signer. The client would then look up the user's `10046` event and follow the signer pubkey listed there.
- Nostrconnect handler: Signers may publish a NIP 89 handler which includes a handler url that clients can send `nostrconnect` urls to. This isn't currently specified anywhere, but it is supported by nsec.app. This bypasses the NIP 05 address requirement entirely, allowing users to simply pick a signer and click a button.
Each of these flows have their own strengths and weaknesses, but all of them share a dependency on some external source of truth for routing a user to the correct bunker.
In the first case, this is done by remembering the NIP 05 address assigned by the signer, which relies on DNS and on users to not forget which address they're using.
In the second case, this is done by relying on the user having done a significant amount of configuration (setting up a NIP 05, adding it to their kind 0, and having published a `10046` event) which may or may not exist. This forces clients to gracefully degrade to some alternative login method anyway, and adds UX friction since users have to choose which interface will work for them.
The final method bypasses the need for users to remember their NIP 05 address, but it does require either the client or the user to select a trusted signer. If poorly implemented, this could result in users choosing an untrustworthy signer on signup (risking their keys), or the wrong signer on login resulting in a broken session.
For all these reasons, I've opted to go with the vanilla bunker/nostrconnect flow, which allows me to display a simple interface to users. Presenting a QR code without comment assumes that users know what to do with it, but the benefit is that it makes explicit the signer selection step which the auto-connect flows try to paper over. This is actually a good thing, because instead of using heuristics like addresses or lists of signers presented by a client to make the decision, users can choose based on which app they actually have installed, which is a richer mnemonic device.
# Making NIP 46 Work
The bottom line here is that while NIP 46 is the best baseline for signer support, it doesn't currently work very well at all. There are a variety of reasons for this:
- The specification itself isn't clear, and is constantly changing. This leads to incompatibilities between apps and signers (or explosive complexity in trying to handle every case).
- Extensions to the basic bunker flow (both in terms of signer implementation and signer discovery) are worth researching, but each one creates another dimension of possible incompatibility. Signers will be incentivized to support every possible login flow, creating complexity for users and increasing attack surface area. Clients will have to implement fallbacks to their preferred signup flows, again resulting in UX complexity.
- Clients don't currently deal well with latency. In order for NIP 46 to work smoothly, clients will have to implement better loading, debouncing, optimistic updates, publish status, and "undo". There are downsides to this, but many of these features endu up being built by mature software products anyway, so supporting these patterns may actually improve rather than degrade UX.
- There's currently no easy and secure way for users to store keys in a single signer which they can access anywhere. This means that users have to set up multiple bunkers depending where they're sitting, or resort to alternative login methods like NIP 07 or 55. These are great upgrades, since they reduce latency and bandwidth use, but shouldn't be required for new users to learn.
- There's no unified experience across platforms. If a user signs up on their desktop, how do they safely transfer their keys to their Android signer app? If they're given seed words, how can they import them as an nsec? Consensus on best practices would be an improvement, but I think only a unified UX across platforms for a single signer can really solve this.
- As nice as it might be to bypass app stores and built-in push notifications, shunning traditional platforms drastically increases the friction for users. To my knowledge, no signer app currently exists in traditional app stores, or supports built-in push notifications. If we want nostr to be accessible to non-technical folks, we can't ask them to start by downloading Obtanium or zap.store and a UnifiedPush distributor for their platform.
As I mentioned above, I don't think NIP 46 will ever be the only solution for signers. But I do think it's a great baseline on which to build a kind of "progressive enhancement" approach. For example, clients should support at least nostrconnect/bunker links, and encourage users once they've logged in to upgrade to NIP 55 or NIP 07 signers. Signers should exist in the mainstream app store and use native push notifications, with an option to install elsewhere or opt-in to UnifiedPush.
The goal here is to balance user experience and security. The number one rule for this is to reduce attack vectors for obtaining user keys. This points to (ideally) a single non-custodial signer, easily accessible to the user, and a simple protocol for using that signer from any app. Progressive enhancement is fine, but we should always be able to fall back to this baseline.
-

@ 3bf0c63f:aefa459d
2024-10-31 16:08:50
# Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
### Palavras que existem em português com sentido diferente
- _submissão_ (de trabalhos): **envio**, **apresentação**
- _disrupção_: **perturbação**
- _assumir_: **considerar**, **pressupor**, **presumir**
- _realizar_: **perceber**
- _endereçar_: **tratar de**
- _suporte_ (ao cliente): **atendimento**
- _suportar_ (uma idéia, um projeto): **apoiar**, **financiar**
- _suportar_ (uma função, recurso, característica): **oferecer**, **ser compatível com**
- _literacia_: **instrução**, **alfabetização**
- _convoluto_: **complicado**.
- _acurácia_: **precisão**.
- _resiliência_: **resistência**.
### Aportuguesamentos desnecessários
- _estartar_: **iniciar**, **começar**
- _treidar_: **negociar**, **especular**
### Expressões
- _"não é sobre..."_: **"não se trata de..."**
---

## Ver também
- [Algumas expressões e ditados excelentes da língua portuguesa, e outras não tão excelentes assim](https://fiatjaf.alhur.es/expressões-e-ditados.txt)
-

@ a9434ee1:d5c885be
2024-10-29 20:46:24
This design system has two goals:
1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty
2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...)
### Design System
Check it out [here](https://www.figma.com/community/file/1430887635327548022 ).
This is by no means finished and will be continually updated and completed as we go along.
### Project description
Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda)
nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda
This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki.
### Explanatory videos
This list of videos will also be continually updated and completed as we go along:
1. Chat as the universal interface
https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov
2. Your Nostr Dashboard
https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov
3. Keeping Tabs on all these Content types
https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov
4. Design entered the Chat
https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov
5. Targeted publication & The blurry edges of interoperable communities
https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov
6. Travel Back
https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
-

@ 84999652:2a24d806
2024-11-18 17:18:10
当敲出这个标题时,我知道一定要得罪一大批人了,但是,我可能只是大家的嘴替,说了一句大家都不愿意承认的事实而已。
从2023年6月份,我开始关注比特币Layer2这个赛道,花费了大量时间研究比特币扩容技术,长期跟进一些我认为比较具有技术含量的团队,比如:Stacks、BEVM、Bihelix、Bool Network,包括BitVM和RGB的解决方案等等。
研究了一圈发现,BTC Layer2似乎真的是一个伪命题,因为,比特币压根不需要Layer2,而是Crypto行业需要比特币而已;而且Layer2本身只是一门生意,压根不是区块链;最关键的问题是,Layer2压根不能帮助主链扩容,只是把主链代币找了一些应用场景而已,而且这些场景都是照抄Layer1,丝毫没有创新。
最早验证我这个思路,并且和我的想法达成共鸣的是BEVM团队。我从去年6月就开始关注这个比特币创业团队,他们也算是最早在华语区推广比特Layer2的团队了,但是,他们在2024年却突然180度大转弯,彻底否认了比特币layer2赛道,转而推出了名为Super Bitcoin的全新战略,具体在这里我就不细讲了,有兴趣的可以看他们发布最新版白皮书,写的还是很有意思的。
为什么最早推广比特币Layer2的团队,突然彻底放弃这个方向,转朝另一个方向?这里,我来谈谈我的一些看见:
### 一、Layer2是一个臆想的需求,并没有真正帮助Layer1扩容
Layer2概念最早来源于比特币,当初中本聪在比特币白皮书第八章专门提到了简单支付验证(全称Simple Payment Verification,简称SPV)的方案。意思是说,可以基于比特币的SPV节点也就是轻节点,可以在没有下载完整比特币区块链的情况下,也可以完成交易验证,我们可以理解为这是一种高效的链下交易验证。
基于这个概念,诞生了闪电网络,闪电网络是完全基于中本聪的提出的简单支付验证去实现的,这个方案是有意义的,因为,闪电网络足够快、足够便宜,更重要的是它完全继承比特币的网络安全性,帮助比特币在交易方面实现了真正意义上的“扩容”。
后来的以太坊Layer2照抄了这个模式,但是,以太坊的Layer2虽然能共享以太坊的安全性,但是,却无法帮助以太坊真正的实现扩容,只是增加了以太坊这个代币的一些应用场景而已。
闪电网络之所以能基于简单支付验证实现比特币“扩容”,是因为比特币采用的是UTXO模型,而以太坊采用的是统一帐户模型,任何Layer2方案都无法解决以太坊账号模型带来的问题。
我们简单来讲:
比特币UTXO模型是一个模拟人与人之间现金交易的模型,任何人之间拿着现金交易时,是可以同时和多人进行交易,而且交易双方就可以彼此验证交易,并不一定需要全局达成共识才能交易,在交易期间并不需要一个中心化的机构来统一变更交易双方的数据。因此,比特币的UTXO模型可以实现并发处理交易以及局部进行状态变更,而且不需要一个统一的世界状态树来更新状态。
而以太坊采用的是统一账户模型,也就是传统的银行账户模型。账户模型在处理交易时,需要依靠一个全局的状态树来给每一笔交易涉及的地址进行余额的加减计算从而实现状态变更。
因此,以太坊的每一笔交易的状态都需要先变更完之后,才能进行下一笔交易,否则就会出现双花或者无法交易等问题。通俗来讲,以太坊的账户模型,需要一个中心的世界状态树来统一处理交易,来统一变更所有账户的状态。虽然,这个世界状态树是去中心机制来驱动的。也正是因为去中心化的方式来驱动这个世界状态树,也导致了这个状态变更能力很差,效率很低。
以太坊要实现扩容,本质上是要提升状态变更的效率和能力。但是,目前所有的以太坊Layer2都没有在这方面对以太坊进行任何的改变和提升。当然,这不是以太坊Layer2能解决的问题,是以太坊自身的问题。
最近,以太坊社区提出了BeamChain方案,其中最重要的一点是引入SNARK ,SNARK全称Succinct Non-Interactive Argument of Knowledge,也就是“简洁非交互式知识证明”,这个和比特币的简单支付验证(Simple Payment Verification)也就是前文我们提到的SPV,几乎是要达到一样的效果。这个确实可以提升以太坊的验证效率,因为,验证的内容被压缩了,而且不需要验证全部内容,因此,可以部分提升以太坊的状态变更能力。但是,这依然没有彻底解决以太坊帐户模型所带来的无法并行处理交易的问题,因为,依然依靠世界状态树来统一变更状态。
打个比喻就是:比特币的UTXO模型是一个可以并行的多车道(实际上是无限车道),而以太坊有且只有一个单车道,现在以太坊的BeamChain无非是把这个车道的通车速度再提升一个层次而已。而且,这个方案本质上和以太坊Layer2没有太大关系。
从这个角度来看,以太坊Layer2根本无法帮助以太坊实现扩容,最后,还是得以太坊自己挥刀自救。当然,以太坊的统一帐户模型设计是以太坊在扩容之路上的“最大障碍”。
而比特币的闪电网络本质上并不是依靠自身的技术来帮助比特币进行扩容,而是比特币的UTXO模型本身就是具备局部变更状态和并发处理状态变更的能力,而闪电网络只是在这个能力之上,用一个客户端+一个防止双花交易的检举机制把比特币的这个本身自带的链下扩容方案呈现出来了而已。所以,除了闪电网络以外,基本上没有第二个真正意义上的Layer2。甚至说,闪电网络也并不是比特币的Layer2,而是基于比特币的UTXO模型和SPV技术,创造的一个可以快速交易比特币的应用而已。
因此,我们说,无论是以太坊Layer2还是比特币Layer2,本质都无法帮助Layer1实现扩容,无非是给Laye1的代币找了一些应用场景而已,并没有真正意义上给Layer1带来改变!
Layer2仅仅是一个叙事,而且是一个打着帮助Layer1扩容的旗号,实际却干着自己的生意。
### 二、Layer2只是项目方的一门生意,和散户无关
有一个显而易见的问题,几乎所有的Layer2都是中心化的,Layer2本身没有共识机制,更没有节点的概念,Layer2的运行有且只有官方的一个定序器,也就是Sequencer。
所有的Layer2本质都是一个没有共识机制、没有“矿工参与共识”的私有链。
一般,一个POS共识机制的链,其代币基本可以用于节点质押、充当GAS以及参与链上的一些治理等等场景。但是,Layer2代币,没有节点质押需求(没有共识机制和节点,质押个啥),链的GAS也是用Layer1的代币。能讲的唯一价值,就是进行虚无缥缈的所谓治理。Layer2本质都是中心化的,又能治理个啥?
而且我们前面说过,Layer2的定序器有且只有官方一个,因此,整个链上的所有GAS都被官方收取了,这也是除了发币之外。所有Layer2项目方的最主要收入来源。比如,ZKsync等Layer2在代币TGE之前,疯狂的给用户制造空投预期,ZKsync每月GAS收入基本是300万-500万美金,而且连续PUA2年,光GAS收入就是7200万-1亿美金,这恐怕比上交易所赚的还多。
所以,我说,Layer2就是一门生意,你要的是项目方的代币空投,项目方赚的是你花费的GAS。最后,空投给你一个啥用没有的代币,结束。
这个生意模式已经被越来越多的商业主体看明白了,所以,你看到越来越多的大型项目开始自己做Layer2,传统的商业主体,比如三星、Visa等;Crypto项目,比如,Uniswap的Unichain就是典型的例子。因为,大家都想明白了,总共就这些用户,而且我有自己的“私域用户”,为啥交给别人赚这个钱,还不如自己赚!
未来,会有越来越多的商业主体来做自己的Layer2,依附一个拥有共识能力的Layer1来共享安全性,自己搭一个定序器,基本就可以开干了。GAS费自己收,用户在自己链上玩,形成一个传统意义上的商业闭环。从这个角度来看,像Coinbase这样拥有巨大交易用户的商业主体,自己做一个Layer2是最好的,也是有竞争力的。
但是,这一切基本和散户无关。因为,这是Layer2的商业主体自己的生意,用户只是消费者。这一切本质和共识和社区用户都无关,因此,Layer2代币也很难有共识。这是包括以太坊和比特币Layer2都逐渐走弱的原因所在。
### 3、比特币不需要Layer2,是Crypto行业需要比特币
为什么说,比特币本质上不需要Layer2,只是Crypto行业需要比特币?
围绕比特币创业的Crypto项目,目前市值最大的是WBTC,这个项目明白了一点,不是比特币需要拓展方案,是整个Crypto行业需要比特币这个大金矿。
在WBTC之前,以太坊这个金融市场是和比特币这个全球最大的数字金矿是完全隔绝的,比特币占有全球加密货币50%以上的市场份额,其他金融市场要长足发展,非常需要这样的优质资产,因此,WBTC诞生了。当然,WBTC的风险在于是中心化的。所以,后来诞生了相对去中心化的TBTC等解决方案,包括,这一轮很多机构下场亲自做的各类WarpBTC,都是解决一个问题——把比特币这个超级金矿搬到自己的生态里来或者去到别的生态里去。
但是,不管怎样,这是行业需要比特币,而不是比特币需要这些拓展方案。比特币本性自足,不需要任何拓展方案,这么多年围绕比特币的拓展方案都没什么创新意义,大部分都是在重复造轮子。
因此,当我意识到这个问题后,从现在开始,我对一切要去改进比特币或者帮助比特币拓展的方案统统都不感兴趣。比特币不需要任何拓展方案,是这个行业,甚至整个人类需要比特币。
当我们从这个角度思考时,思维和眼界立马就打开了!
为了更容易理解这个事,我先分享一篇文章,https://x.com/qiqileyuan/status/1858357959807635854
**作者推特ID:@qiqileyuan**
这个文章提出了一个问题:
比特币在成为国家储备之后,还有更高维度的叙事可以把比特币的价格送到100万美金以上吗?
这是一个极好的问题。
作者给到的答案是:
当比特币作为数字黄金储备到各个国家的国库之后,其价值无限接近于黄金,但是,想要让比特币在100万美金以上继续突破,数字黄金的这个概念是不足以支撑的,数字黄金的概念在比特币成为国家货币储备之后,其叙事基本是趋于落地了,比特币下一个阶段的价值是:成为链上AI的货币和AI共识问题的去中心化控制系统。
我觉得作者真正打开了比特币的上升叙事。
这个思路,没有局限于思考比特币本身,而是跳出来开始思考比特币网络和人类以及AI的关系。这是认知上的升级,站在更高处才能看到不一样的风景。
我认为,把比特币作为未来链上AI货币,把比特币网络作为未来AI治理事务的共识网络,是非常有未来的方向。
这一点,我在BEVM发布的Super Bitcoin白皮书以及其相关的解读文档中也找到了相应的思路和方案。
### Super Bitcoin是这样描述的:
比特币是一个去中心化的状态变更机器,是一个不断生长的机械共识来驱动的去中心化控制系统。这个系统的共识能力不断生长(通过吸食算力和能源),这是唯一能匹配人类未来的AI治理和安全需求的系统。因为,比特币是全球最去中心化的系统,不受任何一方控制,其共识过的“状态变更事务”是值得信赖的,尤其在未来AI世界,AI和我们几乎只能信任比特币网络。而且这个网络的共识能力和安全性是不断生长的,可以满足人类和AI日益增长的安全和去中心化治理需求。Super Bitcoin要做的就是要把比特币的这种无限生长的机械共识能力和去中心化状态变更的能力共享给未来人类的各种公共治理和AI安全需求。
这是我认为巨酷无比的创业方向,远超比特币Layer2等小卡拉米的创业思维。
第一、这个思路,找到了比特币未来价值增长的第二曲线,实现了比特币从“数字黄金”到“链上AI货币和链上AI治理系统”的身份转换,这是当前我认为最值得探索的方向。
第二、通过把比特币和未来人类发展以及链上AI的需求结合,真正把比特币的价值发挥到了最大化。在此之前,大家把BTC作为作为数字黄金,要做Warp BTC,要做Layer2帮比特币做拓展,这只是看到了BTC这个Coin的价值,并没有思考比特币网络本身的价值,以及对于人类更深远的意义。毕竟,BTC只是比特币网络的激励Coin,并不是比特币的全部。
### 总结:
比特币Layer2已经成为了一个过时的且没有意义的创业方向。比特币在成为国家货币储备之后,进入了一个全新的发展阶段。比特币的价值更大了,共识更广了,其网络价安全性也更强了,而且这些都在不断生长。但是,比特币网络本身的价值还完全没有开发出来,未来最具价值的创业方向是围绕比特币网络本身,去思考这个无限生长的去中心化控制系统,这个全球最大的去中心化状态变更机器,能在未来的人类和AI并存的时代,发挥哪些更大的价值,这才是最有潜力的创业方向。
发挥比特币网络本身的价值,而不仅仅局限于BTC这个Coin本身,这或许才是中本聪留给人类的最大财富!
中本聪,或许真的是从未来穿越回来的!
**本文灵感主要来源于比特币学习交流暑社区“中本聪大学”(推特ID:@ZhongbcDX_1028),本人长期在中本聪大学和诸多比特币OG及爱好者深度交流学习比特币,一起探讨Crypto行业发展机遇。**
如果您对【中本聪大学】感兴趣,想要了解更多相关信息,与同样对该项目感兴趣的人讨论,欢迎加入我们创建的【交流群】。**添加Web3CN小助手(微信id:Web3CNpro) (TG id:@potato_little,添加时备注项目名称【中本聪大学】,以便小助手将您拉进相应的社群哦。**
-

@ 5d4b6c8d:8a1c1ee3
2024-11-18 17:13:32
Another OC, another loss. There were some encouraging signs (Bowers might be a generational TE) and we get some clarity on what's wrong.
Thanks to this loss, the Raiders are now picking 4th and it seems that Shedeur is angling to play for the Silver and Black. The stars are aligning a little bit. Also, the Jets continue being a trainwreck, so the pick we got for Davante is moving up the board.
# 2025 Mock Draft
- 4th Pick: QB Jalen Milroe
- 35th Pick: OT Cameron Williams
- 66th Pick: RB Quinshon Judkins
- 71st Pick: DT T.J. Sanders
- 106th Pick: WR Jayden Higgins
- 142nd Pick: IOL Armand Membou
- 179th Pick: CB Zy Alexander
- 212th Pick: QB Dillon Gabriel
- 215th Pick: IOL Seth McLaughlin
- 217th Pick: OT Jude Bowry
It ended up being funny how this board fell, but I don't mind doubling up on all the positions of need. It's maddening watching this team fail to upgrade at QB and on the O-Line.
The Raiders defense is already fine and they'll be getting back two very good D-Linemen next season. They just can't go into next season without addressing the problems on offense.
When are the rest of you going to look to the draft?
originally posted at https://stacker.news/items/772891
-

@ 9ff58691:0bf6c134
2024-11-18 16:42:21
Курган стал настоящим примером экологической сознательности и активного участия граждан в охране окружающей среды.
Экоакции, проводимые накануне дня города, привлекают все больше людей, стремящихся помочь природе, особенно в лесах, расположенных рядом с городом.
Местные жители активно участвуют в мероприятиях, направленных на восстановление лесных экосистем. В рамках программы «Сохраним лес» волонтеры высаживают деревья, очищают территории от мусора и проводят образовательные сессии о важности сохранения природы. Эти акции организуются как государственными структурами, так и общественными экологическими организациями, которые объединяют усилия для достижения общей цели — создания чистого и здорового окружения.
Поддержка со стороны молодежи играет ключевую роль в этих инициативах. Школьники и студенты активно участвуют в экоакциях, осознавая важность своего вклада в защиту природы. Они не только высаживают деревья, но и участвуют в различных конкурсах и проектах, посвященных экологии. Таким образом, формируется новое поколение граждан, готовых заботиться о своей планете.
Кроме того, в Кургане активно развиваются программы по охране труда в лесу, которые обучают волонтеров безопасным методам работы с растительностью и соблюдению экологических норм. Это позволяет не только улучшить состояние лесов, но и обеспечить безопасность участников акций.
Курган сейчас — это город, где люди не просто говорят о проблемах экологии, а активно действуют для их решения.
Автор: Эвелина Тимирбаева
-

@ c48a6fb0:bcddf255
2024-11-18 16:10:43
## So what is the oracle problem (op)?
The op is trying to bring real world information into a digital information network (eg Bitcoin) without relying on one or multiable trusted parties (called a oracle).
So what do I mean by real world informations?
When I ask another peer in a network what 2+3 is, I can always verify the result on my own. But when I ask what the current weather in London is I have to trust that peer or ask other "trusted peer" (for example a british news channels).
**So to conclude math is conciderd trustless**
## So what is PoW?
PoW means proof of work. Its a method to proof that one of your peers did work without trusting someone. But how does it work trustless you might ask? We can't just setup a camera in their room and watch them work since it would be easy for them to cheat. (And the camera would be a trusted partie again.) The answere again is math. But we first need to learn a little bit about algorithm based hashfunctions. Bitcoins PoW uses mainly sha256.
The most important part about hashfunctions (in this context) are that they aren't reversable calculations. What does that mean? When I calculate 2+3=5 I can allways reverse that with enought informations.
If I don't know the 2nd number:
2+?=5
i can reverse that by calculation -2 on both sides:
?=5-2 .
That lets me know that ?=3 .
But you can't do that with hashfunctions. The hashfunction Sha1 with an input of the number 137 looks like this:
Sha-1(137) = e1a864f0b77f6c89794827a9035355dc8d052622
But just a small change to 138 gives you a complety diffrent result:
Sha-1(138)= 56ad4d4deaec98465c419b4a8ea7bfc1ed38c4d9
Since there is no way to tell if your input was below/above 100 or if it even was a number (because you can input text as well) the only method of getting the input is by trying out one input after the other.
Test it out yourself: [Sha1 calculator](https://xorbin.com/tools/sha1-hash-calculator).
## How does Bitcoins PoW use the hashfunctions?
When you give someone the task to get you a specific result of sha-1 they have to guess a lot of inputs to get the result. This is conciderd work. Providing the right input is the proof that your peer did work for that (or that they were lucky).Their solution however is quick and easy verifyable by you. Since calculating only one hash takes far less than a second.
Short note: Bitcoin actually however uses a range of results that are concidered the right result (Number must start with x amount of zeros). That's how Bitcoin makes sure you need to provide real work to secure or attack bitcoin.
## How do I get other information trustless?
"But wait?! You didn't explain how I can get the weather in London". You're right. Because getting these type of information trustless is impossible. Work is the only realworld information you can get trustless.
You can reduce the trust by having several validators. But the validators could team up to betrail you. Or there could be a mesurement mistake effecting several validators at once. Or diffrent validators provide diffret results. Who do you trust? The result that was provided the most? So spamming becomes the truth? Or the information gets altered on the way too you. Or your client censors certain information for you.
There is an insane amount of attack vectors. Concluding: Trust is allways a terrible risk. No matter how little. Trust = information centralization.
Examples of real world information:
Price of stocks, stablecoins (price of a currency), a picture, music, videos.
**Cryptocurrencies that use oracles are relying on trust and are doomed to get centralised.**
**When they claim to be decentralised you now know they are a scam.**
Distributed doesn't equal decentralised.
## This article is reworked from its release on Nostr:
nostr:nevent1qqs8yzntzvun4alupatcupetdqaaf4k609hm30cjrggyt2y602h8fxspzpmhxue69uhkummnw3ezumt0d5hsygxy3fhmpxsr2k93an6srh3vuzdvjddu8lpdw0h4kktr0e6meh0j25psgqqqqqqserd69u
## I posted it original on my Twitter on 07th Jan 2023. I reposted it too Nostr, because X is closed knowledge.
-

@ f8a5df57:b7a58cd4
2024-11-18 15:46:47
<iframe width="720" height="405" src="https://rutube.ru/play/embed/d83ed19084087a2a14f7bd59319ca216" frameBorder="0" allow="clipboard-write; autoplay" webkitAllowFullScreen mozallowfullscreen allowFullScreen></iframe>
# Содержание сюжета:
Поднебесье - такое название получил 100 процентов экологичный микрорайон в дальних уголках столицы. Он получил такое название за счет своего уникального расположения возле реки Яуза. На территории расположены небоскребы высотой 200 этажей, на последнем из которых можно в прямом смысле достать до неба. Благодаря такой инициативе в небе начали работать роботы-пилоты, которые доставляют продукты жителям прямо в окошки квартир. Помимо этого их задачей является осмотр территории, сообщение времени и погоды москвичам. В микрорайоне находится несколько парков с уютными беседками и местами для отдыха с детьми: центр скалолазания, батутов, больших аквапарков. При этом все объекты оснащены обилием растений и увлажнителями воздуха.
**Автор:** Дарья Воронина
-

@ f8a5df57:b7a58cd4
2024-11-18 15:20:13
Москва стала одним из первых городов, внедривших собственную электронную валюту, благодаря которой открылись новые горизонты для финансовых операций и цифровой экономики. Эта инициатива направлена на упрощение расчетов и повышение безопасности транзакций в условиях быстро меняющегося финансового ландшафта.
20 июля 2063 года Москва представила свою электронную валюту, которая обещает революционизировать финансовые операции и улучшить взаимодействие между гражданами и бизнесом. Этот шаг стал ответом на растущую потребность в безопасных и эффективных способах ведения финансовых дел. Электронная валюта будет использовать технологию блокчейн, обеспечивая прозрачность и защиту данных. Ожидается, что новая валюта позволит пользователям проводить мгновенные транзакции без необходимости обращения к традиционным банковским системам. Это также может снизить затраты на переводы и повысить доступность финансовых услуг для населения.
Внедрение электронной валюты поддерживается правительством города, которое видит в этом шаге возможность привлечь инвестиции и развивать стартапы в области финтеха. Эксперты отмечают, что такая инициатива может стать катализатором для дальнейшего развития цифровой экономики в России.
Автор: Ксения Данилова
"Создание электронной валюты — это не просто шаг к цифровизации экономики, это возможность изменить саму природу финансовых отношений в нашем городе. Мы вступаем в новую эру, где технологии будут играть ключевую роль в повседневной жизни граждан," — говорит экономист Алексей Смирнов.
-

@ 5bfb38cb:2b999aa7
2024-11-18 15:07:56
### Spot Over BTX2024
#### Relative Strength Analysis:
The 3 stock indices have had a week of bullish retracement, with the YM showing the least retracement and the NQ the most.
#### Classic Technical Analysis:
In terms of conventional technical analysis, BTC remains in an Elliott structure fulfilling a minor wave 5 and a major wave 3. We have had a consolidation structure since March 2024 with a breakout to the upside. The context is strongly bullish.
https://image.nostr.build/6b83ebee90e8ef8dc7965f159b8fd6b6244eda7b0b18a8e611962bb3129e8980.png
https://image.nostr.build/c0a9ba9a4f3edf81e7787c24988fc8a8787225e847e73d99d459b5d6c4ba6a44.png
#### COT:
The progression of contracts nearing expiration is at a premium. The 12-month COT is in a positive program and in positive hedging.
Banks are buying Bitcoin futures contracts and are not in a bearish position, being the counterpart to leveraged short investment funds.
https://image.nostr.build/d24f4b3ddeabaafa4885d96b726c65976fc64679bc760414630cd7db5641e36b.png
https://image.nostr.build/11a0b1e68b5ee1d6879716d831a8a9517ec653beed1f425086a7736965bfa534.png
#### Market Sentiment:
Market sentiment in general retail news is bullish following the FED's rate cut and in response to the US elections, although with some moderation after this week.
The Williams %R remains in oversold territory and avoids a bearish divergence.
#### Intermarket Analysis:
The 3 indices have made a bullish reversal. The YM shows the greatest strength marking an FVG while the NQ is the weakest.
The 3 bonds ZN, ZF, and ZB have had another week of taking with negative displacement but without a negative close. It is likely that we have a bit of room left for discount. Interest rates behave inversely.
The DYX has had a bullish week with a lot of strength and has maintained another bullish week. It is likely that we continue to take some premium closing an FVG W. Peripheral currencies are weak with strong bearish displacement, with the EUR being the weakest.
In commodities, GC has had its first significant delay with a bearish close and MSS. BTC maintains a very bullish week with a positive opening and closing gap. CL is in a high resistance framework with a week of negative close.
In conclusion, we have a stock market with a bullish retracement that has not yet changed the market structure. Strength of the DYX with weakness in peripheral currencies. Strength of BTC in commodities with GC showing a first significant retracement. CL lost in a seek and destroy framework.
#### Market Profile:
The market is currently bullish. It needs to move significantly away from the all-time high to continue this movement.
#### Market Structure:
The value 66798.00 maintains price control. The weekly context is bullish.
#### Trading Range:
93483 to 66789. Currently at a premium in the range.
#### PD Array Matrix:
Premium:
- PWH 93483
- OB+W 5910.75
Discount:
- PWL 80280
- FVG W CE 79940
- OB+W 69011
Equilibrium:
- 80141
#### Key Price Levels:
- FVG W CE 79940. I do not expect closes below this structure to remain bullish.
https://image.nostr.build/233090043a36d9f20a65db086d16b8ba2adf109c456ae5435c5ed1ee24df2f76.png
#### Weekly BIAS:
Bullish.
#### Weekly Objective:
- Retracement to equilibrium in the PWL region at 80280 to take liquidity and then continue to premium in an ideal scenario. A new take of the previous ATH before this scenario invalidates the possibility and leads to targeting 103363 sooner than expected. Await market confirmations.
*The market is a great teacher; pay attention and learn its lessons. Every chart, every trend, and every reversal has a story to tell. Listen carefully, and you’ll become a master storyteller.* 🔮
-

@ 5bfb38cb:2b999aa7
2024-11-18 15:07:13
### Comments:
This is where we embark on our journey and set sail into unknown waters...
### Seasonal Trend/Monthly Changes:
While Bitcoin's seasonal trend often resembles that of the SP500, sometimes they can lead or lag each other. We have been in a bullish trend for 24 months since November 2022, which exceeds the average duration of a bullish trend that ranges from 9 to 18 months. The reality is harsh, and we are in a brutally bullish market. This November has been like the last 15 years of Bitcoin, and we expect a premium close this month.
https://image.nostr.build/f03e1e0ac181e109688d0efc9f5ccd52133ce9e37da7de26d2789b72bac47834.png
### Interest Rate Differentials:
The FED has lowered the interest rate to 4.75% after 3 years, signaling the first dovish signs. The inflation target of 2% has not yet been reached but remains close. Among central banks, the FED and the BOE currently maintain the highest rates. The central bank market gives us a framework and a positive bias.
### Market Structure:
Since November 2022, we have a clear monthly bullish trend that marked a new ATH in March 2024 and has projected after 7 months of re-accumulation to keep us bullish and embark on projections.
https://image.nostr.build/c507c91a14ba63bf3afb11217ab19ef0b17f18eeb81a46baf356ccc78d140783.png
### Intermarket Analysis:
The YM and ES reached a new all-time high in October. The NQ has had a relative high but has not yet presented a new all-time high, being the most delayed.
The ZF, ZN, and ZB bonds have had a negative month, closing below the lows and a FVG M. They are likely to continue with some weakness. The 5, 10, and 30-year interest rates behave inversely with strength.
The DYX has achieved a strong bullish reversal. There is weakness in peripheral currencies led by the EUR.
In commodities, the GC maintains another month with a bullish close at highs, being the strongest. BTC achieves a monthly close above relative highs after 7 months. CL shows weakness without being able to achieve a bullish close.
The conclusion is the strength of the stock market led by the ES and YM, but they may be approaching a trend end. This is reflected in the DYX making a monthly bullish MSS. In commodities, the GC continues to lead with great strength, and BTC has achieved the first sign of a monthly bullish change, projecting above highs following the path of GC. CL is in a high resistance and lagging territory.
### Market Profile:
The market is frankly and brutally bullish, taking a new high and fleetingly massacring structures at a discount. We can only watch and project a trend end when it occurs, but never go against institutional order flow.
### Operational Range:
49577 to 93483. Currently in Premium Zone.
### PD Array Matrix:
**Premium:**
- ATH 93483.00
**Discount:**
- OB+M 64612
- FVG M 59313
- PML 58867
**Equilibrium:**
- 71530
**Key Price Levels:**
- OB+M 64612. I do not expect closes below the CE of the structure to maintain the bullish idea.
### Monthly BIAS:
Bullish BIAS.
### Monthly Objective:
- The first objective has been the extension +1.5SD of the consolidation at 85903, which has already been met. The second objective would be the extension between +2.0SD and +2.5SD between the values of 98011 and 110120. I have doubts whether it will find the strength to reach here this month, given that ideally, we will do so before closing 2024.
https://image.nostr.build/95a89792f35540e0c6302dbd2a82e2cb6bac8a92f5b813312ce5104bbf877beb.png
*"The market is the mirror through which we truly see who we are, godspeed traveler."*
-

@ bbb5dda0:f09e2747
2024-11-18 14:15:11
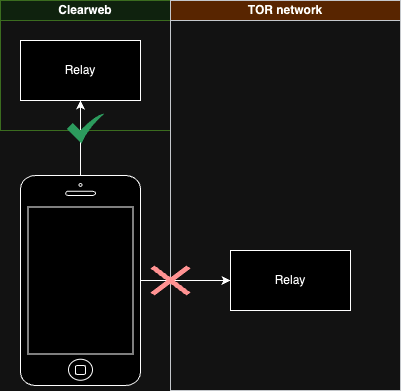
**What if there is no line, no boundary between tor and clearnet (the 'normal' web)? What if a Damus user on iPhone can talk to their friend's private TOR relay? Let's find out together what can happen by using this new tool which I call Nostr Epoxy! And it's scalable, too!**
**TL;DR Demo video:**
nostr:naddr1qqr5gc20v43hy5czyzamthdqu92k09ulq4p5q77uyqeadu9mkv8hy5f2nqw0mvhsncn5wqcyqqqgtwc5nzpll
|  |  |
| -------------------------------------------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------- |
| Phone can reach clearweb relay, but cannot connect to TOR relay | Phone can reach TOR relay |
Proxies have been around forever and can be a powerful tool in getting around network restrictions. In the context of nostr, currently everyone connects to a relay directly, which you may not always want. The relay can keep track of your IP address and build a profile, or your device might be behind a very restrictive firewall which prevents you from reaching a relay.
From this problem, the idea for proxy relays was born. We wanted to reach a TOR relay, without having to install any TOR stuff on our devices. Which on iPhones is especially challenging. So the idea is that we want to extend a relay's functionality so that it can instead of processing requests for itself, it can pass on the requests to another relay that they themselves can reach.
The easiest solution to get this working is in the form of a Reverse Proxy, which you can put in front of any relay, which by default tunnels the traffic to the operator's own relay, for example a Strfry instance. That way the relay implementation doesn't have to change and the user doesn't have to be aware that this relay endpoint can also proxy to other relays. The example implementation is called [NERP - Nostr Epoxy Reverse Proxy](nostr:naddr1qvzqqqrhnypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uqpjmn0wd68ytt9wphhs7fdwfjhvetjwdjj6urjdau8j6sn6y7).
|  |  |
| ----------------------------------------------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------- |
| Reverse proxy default behaviour | Reverse proxy after proxy request |
As shown above the default is to connect to the operator's own relay. So how do we create the proxied connection? Well we send the following request over our websocket:
```json
["PROXY", "wss://relay.com"]
```
Which asks the proxy to change the target from it's own back-end to whatever we specify. In this case `wss://relay.com`. However, it turns out this relay doesn't live in a fiat world, it responds with:
`["PROXY", "PAYMENT_REQURIED", <payment_request>]` where `<payment_request>` is an object:
```json
{
"price": "1",
"unit": "sat",
"mint": "https://some.mint.cash/",
}
```
Which brings us to...
## 💰 Monetizing proxies
Inevitably we're going to hit the "Who's gonna run the proxies!?" question. Well you are, because you want to stack some sats. Therefore we added monetization to these proxies, which is what sets this project apart from current-day proxies on the internet. When the client is hit with the `PAYMENT_REQUIRED` message above, it can retry the first message, but with an additional field, a cashu payment.
```json
["PROXY", "wss://relay.com", "cashuAeyJ0..."]
```
We're now paying a couple sats, (the price above is in sats per minute). If the proxy is happy with our payment, it will start a timer and set up the connection to the target relay. Indicated by a `["PROXY", "CONNECTED"]` message, after which we can go about our relay business until the bought time runs out. After which the proxy will close our connection with code `1000`, reason: `PROXY: Connection Bankrupted`.
The nice thing here is that introducing payments can reduce spam significantly.
### Why Cashu?
Because [Cashu eCash](https://cashu.me) allows us to finally make micro-payments viable and scalable, it can help us to bring an honest monetary reward to the people that do the hard work of maintaining the free and open internet. If you provide a proxy, you get paid and therefore you're incentivised to keep the infrastructure up and running.
Cashu tokens are a very efficient way of sending payments directly. Unlike Lightning, it does not require a back and forth between the two transacting parties. Because cashu tokens can be sent as a string of text, you can attach it to any request/data you're sending around. Even at rest, the money will still be 'physically' there. That means there's no back and forth required to send a payment, like we do on lightning, and people don't need perfect connectivity.
## 💭 Some philosophy
Until now, all web applications have been strongly coupled to the transportation methods they use, mainly http(s). Nostr changes this, because the data that feeds an application can now arrive over any transportation mechanism. WebSockets, Thumb-drives, QR, LoRa (radio) and Heck! even FM and pigeons will work!
Although the above point is not necessarily tied to the use of websocket proxies, it does underline the point I want to make: Because Nostr completely decouples applications from the transportation layer, We can get VERY creative in the ways in which we transport application data... Therefore, the boundaries of the current clearnet network become irrelevant.
Using the websocket proxies, we can now hop from clearnet to tor, to [i2p](https://geti2p.net/en/), to [hyper](https://github.com/hypercore-protocol) and back to clearnet. This significantly reduces the burden on the client by not having to 'know' how any of these other networks work, they won't have to install anything, yet they can interact with relays on these lesser known networks.
## ⚙ Under the hood
Here's a UMl example of a proxy (that does not have a default relay behind it) and the lifecycle of a proxied connection.
## NIP-XX draft
I wrote a draft NIP on how to support proxying [here](https://github.com/ArjenStens/nostr-epoxy-reverse-proxy/blob/main/NIP-XX.md).
## 🛝 Play with it!
I created a [Dashboard](https://swissdash.site) to discover proxies and play with connecting to relays (multiple hops are possible).

Check out the route-builder tab, add a couple sats to the wallet and route some request through the proxies.


## Resources
- [Dashboard](https://swissdash.site)
- **Nostr Epoxy Reverse Proxy** [Source Code](nostr:naddr1qvzqqqrhnypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uqpjmn0wd68ytt9wphhs7fdwfjhvetjwdjj6urjdau8j6sn6y7)
- **NIP** [draft](https://github.com/ArjenStens/nostr-epoxy-reverse-proxy/blob/main/NIP-XX.md)
-

@ 9ff58691:0bf6c134
2024-11-18 12:27:12
Городская администрация Кургана предлагает широкий спектр учебных программ и стажировок для молодежи:
🎓 "Молодежный кадровый резерв" - программа стажировок в городской администрации. Получите опыт работы в органах местного самоуправления, осваиваете новые цифровые навыки, в том числе использование технологий искусственного интеллекта для повышения эффективности работы.

Стажеры работают бок о бок с сотрудниками, использующими передовые ИИ-ассистенты для анализа данных, автоматизации рутинных задач и принятия управленческих решений. Они изучают, как применять технологии машинного обучения и компьютерного зрения для оптимизации городских сервисов и инфраструктуры.
*"Стажировка в администрации стала для меня отличным стартом карьеры. Я приобрел бесценный опыт и познакомился с современными технологиями, которые применяются в муниципальном управлении"* - Алексей, 23 года.
🏢 "Карьерный старт" - программа стажировок в ведущих компаниях Кургана. Попробуйте себя в различных сферах бизнеса, осваиваете новейшие разработки в области ИИ и автоматизации.
Стажеры получают возможность поработать с виртуальными ассистентами, способными анализировать большие данные, прогнозировать тренды и предлагать оптимальные решения. Они также изучают, как применять технологии дополненной и виртуальной реальности в различных отраслях.
*"Стажировка в IT-компании помогла мне определиться с будущей профессией. Я получила уникальный опыт работы с современными технологиями, которые меняют облик многих отраслей"* - Мария, 21 год.

Не упустите свой шанс! Подробности и условия участия в программах "Молодежный кадровый резерв" и "Карьерный старт" можно узнать на сайте городской администрации Кургана.
-

@ 9ff58691:0bf6c134
2024-11-18 12:21:35
В нашем городе стартует новая программа по озеленению и восстановлению природных экосистем, которая направлена на улучшение качества жизни и сохранение природного наследия нашего региона. Программа будет реализована при поддержке местных властей и частных инвесторов и охватит как городские, так и пригородные территории.
В рамках программы планируется высадка более 10 000 деревьев и кустарников, создание новых зеленых зон и восстановление существующих природных ландшафтов. Также будут организованы акции по очистке и благоустройству парков и скверов, что позволит сделать наш город более комфортным и привлекательным для жителей и гостей.
Мы пообщались с одним из инвесторов программы, Александром Петровым, который поделился своими мыслями о важности этого проекта:
**"Я считаю, что озеленение — это не просто вопрос эстетики, но и необходимость для здоровья нашего города. Зеленые насаждения помогают очищать воздух, создают комфортные условия для жизни и способствуют улучшению психоэмоционального состояния людей. Я рад, что могу участвовать в этом проекте и надеюсь, что он вдохновит других инвесторов поддерживать экологические инициативы в нашем регионе."**
Программа по озеленению станет важным шагом к созданию устойчивого и экологически чистого Кургана. Мы призываем всех жителей города принять активное участие в этом процессе: участвуйте в акциях по высадке деревьев, помогайте в благоустройстве и делитесь своими идеями по улучшению городской среды.
Автор: Налобина Александра
-

@ 5afdec5b:2d631be1
2024-11-18 10:23:46
In August 2024, **Lendasat** introduced a novel loan protocol, designed to address the inherent risks of custodial lending platforms. By leveraging Bitcoin's self-custodial nature, the **Lendasat** protocol allows borrowers to secure loans without transferring ownership of their assets. If you haven’t had a chance to explore our [whitepaper](https://whitepaper.lendasat.com/lendasat-whitepaper.pdf), this blog post will guide you through the protocol and its advantages.
We’ll explore how **Lendasat** works, the technology behind it, and why it stands out as a solution for Bitcoin-collateralized lending. Diagrams will help break down each stage of the protocol, so you can understand the mechanisms step-by-step.
## Bitcoin Lending, the Right Way
Bitcoin, as a decentralized and self-custodial asset, offers users a chance to be their own bank. However, the current landscape for Bitcoin-backed loans often forces users to hand over their Bitcoin to custodians—introducing a set of serious risks:
- **Custodian risk**: Entrusting a third party with your Bitcoin exposes you to theft, mismanagement, or outright fraud.
- **Opaqueness**: Traditional platforms don’t offer transparency on how assets are handled.
- **Regulatory risk**: Centralized custodians are vulnerable to regulatory changes that may lead to asset freezing or seizure.
**Lendasat** eliminates these concerns by enabling **escrow-less lending**. Borrowers retain control of their Bitcoin, using **Discreet Log Contracts (DLCs)** and **Hash Time-Locked Contracts (HTLCs)** to govern loan agreements without middlemen. With these cryptographic tools, **Lendasat** removes the need for trust in centralized entities, offering a **fully transparent and secure** lending process.
---
## How Lendasat Works
The protocol operates between two parties: **Bob** (the borrower) and **Lydia** (the lender). Bob wishes to borrow stablecoins, locking his Bitcoin as collateral, while Lydia provides the loan principal in stablecoins, looking to earn interest.
Let’s dive into how the protocol works, step by step.
### 1. Opening the Loan
The loan process starts with both parties locking assets in cryptographically secured contracts.
#### 1.1 Secret Generation
- Bob generates a collateral secret, `b`.
- Lydia generates a loan secret, `l`.
#### 1.2 Bob Locks Bitcoin Collateral
Bob locks his Bitcoin in a **Discreet Log Contract (DLC)**. The DLC involves an oblivious oracle[^1] that can attest to certain events, such as the price of Bitcoin at loan maturity. If necessary, an oracle attestation can be used at loan maturity to determine how the collateral should be split between Bob and Lydia.
Additionally, Bob locks Lydia's claim on her share of the collateral behind the hash of the collateral secret, `H(b)`. Lydia will need to know `b` to be able to claim her portion of the collateral unilaterally.
> **Key Insight**: Unlike traditional escrows, the **DLC** ensures that Bob retains control of his collateral throughout the loan process. The oracle attestation is only needed to help settle the contract if Bob and Lydia fail to cooperate.
#### 1.3 Lydia Locks the Principal
Lydia, in turn, locks the loan principal in an **HTLC** on Ethereum (or another smart contract-enabled blockchain[^2] or L2). This HTLC is designed so that Bob can only claim the principal if he reveals `b`.
- **Condition 1**: Bob must provide the preimage to `H(b)` i.e. `b`.
- **Condition 2**: If Bob doesn’t act in time, Lydia can recover her funds after a timelock expires.
#### 1.4 Bob Claims the Principal
Bob, now seeing the loan principal is locked up, reveals the secret `b` to claim it. This revelation allows Lydia to later claim part of the Bitcoin collateral, but only if Bob defaults on repayment or in the event of a liquidation.
### 2. Cooperative Repayment
If Bob is ready to repay the loan:
1. **Bob** locks the repayment amount in an **HTLC** on Ethereum, this time using `H(l)` as a hash lock.
2. **Lydia** claims her repayment, revealing `l`.
3. **Bob** uses `l` to unlock the entirety of his Bitcoin collateral from the DLC.
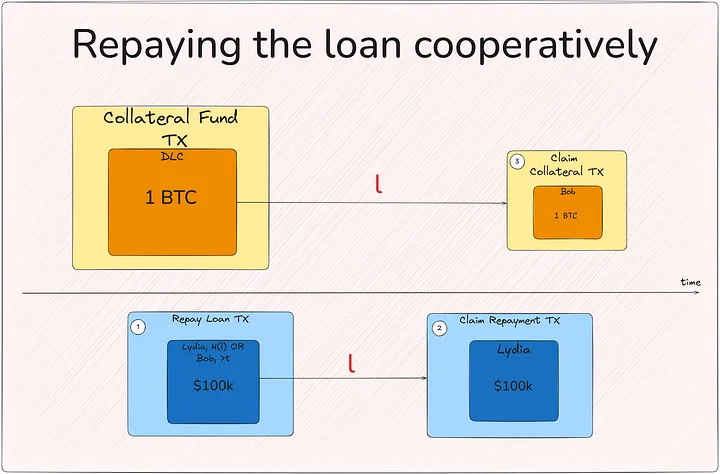
---
## When Things Go Sideways
Not all loans proceed smoothly. Here’s how **Lendasat** handles common scenarios when the loan doesn't go as planned.
### 1. Lender No-Show
What happens if Bob locks up his Bitcoin collateral, but Lydia disappears before providing the principal?
In this case, Bob can unilaterally recover his Bitcoin after an **early collateral refund timeout** built into the contract. This timeout prevents Bob’s collateral from being stuck indefinitely, a common safeguard in decentralized contracts.
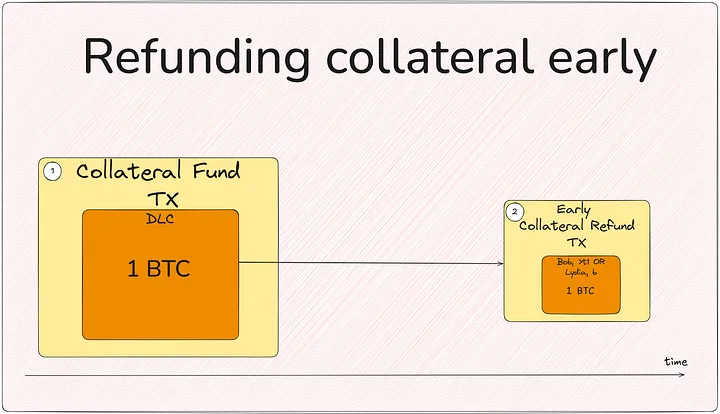
### 2. Borrower Fails to Claim the Loan
Similarly, if Lydia locks up the principal and Bob does not claim it, both parties are protected by respective timeouts:
- **Lydia** recovers her principal after a shorter refund timeout on Ethereum.
- **Bob** gets his Bitcoin collateral back after a longer refund timeout.
These dual timeouts ensure neither party’s assets remain frozen for too long.
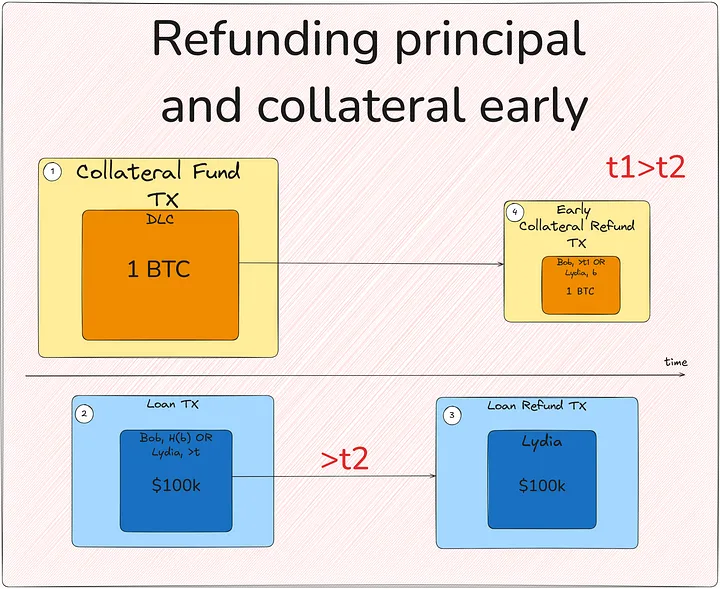
### 3. Unilateral Repayment
If Bob defaults or Lydia doesn’t claim her repayment, the protocol shifts to **non-cooperative repayment** through the **DLC**. In this case, the protocol involves an oracle attestation to the Bitcoin price at loan maturity. Lydia receives an amount of Bitcoin collateral equivalent to the loan’s value (plus interest) based on the oracle's attestation. The remaining collateral goes back to Bob.
This mechanism ensures that even in the worst case, Lydia can still recover her funds by liquidating part or all of Bob’s Bitcoin collateral.
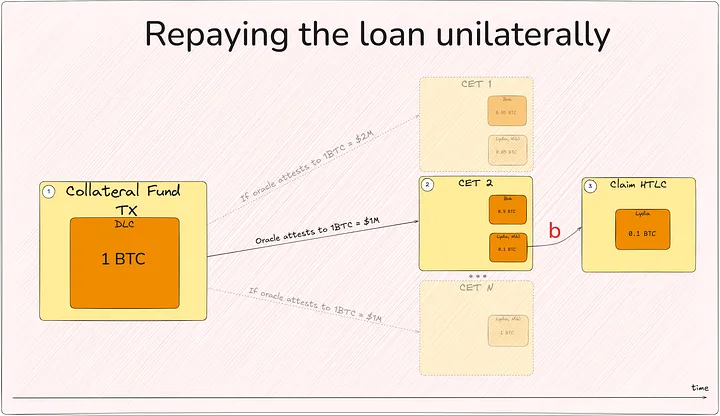
---
## Keeping the Loan Alive: Liquidation and Collateral Management
One of the key challenges of lending is managing **Loan-to-Value (LTV) ratios**. If Bitcoin’s price falls significantly, Lydia might have to liquidate part of the collateral to cover the outstanding loan.
Here’s how **Lendasat** addresses liquidation:
- If the LTV ratio approaches a critical threshold, **Lydia** can trigger an oracle-based liquidation of the Bitcoin collateral before loan maturity. This protects the lender from losses due to market volatility.
- Liquidation relies on the same **DLC** mechanism that handles non-cooperative repayment, ensuring a smooth, automated process for collateral distribution.
The protocol also allows Bob to **increase his collateral** if necessary, by splicing into the DLC with more funds, keeping the loan in good standing and avoiding liquidation.
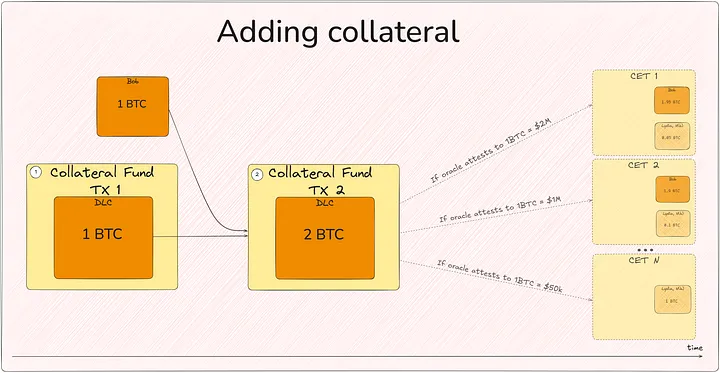
---
## Technical Appendix: How HTLCs and DLCs Combine
### HTLCs: Enabling Cross-Chain Functionality
An **HTLC** (Hash Time-Locked Contract) is a foundational building block for cross-chain operations. It allows Bob to lock collateral on one chain (Bitcoin) while simultaneously claiming funds on another (Ethereum). In Lendasat, **HTLCs** govern the locking and claiming of both loan principal and repayment on the Ethereum chain.
### DLCs: Securing Conditional Payouts
A **Discreet Log Contract (DLC)** is used to ensure that Bob’s Bitcoin collateral is only accessible to Lydia under specific conditions, like a default or liquidation event. The **DLC** relies on oracles to determine the correct payout based on the Bitcoin price at loan maturity or liquidation.
Combining these two technologies allows **Lendasat** to create a trustless lending mechanism that spans multiple blockchains.
---
## Conclusion
**Lendasat** redefines Bitcoin-collateralized lending by eliminating custodial risk and empowering borrowers to retain control of their collateral. Using **HTLCs** and **DLCs**, our protocol creates a trustless environment where both lenders and borrowers are protected, even in the event of non-cooperation or default.
For those interested in a deeper technical understanding, please refer to our [whitepaper](https://whitepaper.lendasat.com/lendasat-whitepaper.pdf), and stay tuned as we continue to refine the protocol and unlock new possibilities for decentralized finance.
## Footnotes
[^1]: When we talk about an oracle, we are not discounting the possibility of using _multiple_ oracles. The DLC protocol does allow for a quorum of oracles to determine the outcome of an event, to distribute the trust.
[^2]: This can be the Bitcoin blockchain itself, via Taproot Assets, RGB or BRC20.
-

@ 2e1d9d3e:fc3683d1
2024-11-18 10:23:36
Im Zeitalter der rasanten Entwicklung der Informationstechnologie ist die Signalsicherheit in allen Lebensbereichen in den Mittelpunkt der Aufmerksamkeit gerückt. Da Netzwerkangriffe und Informationsdiebstahl immer häufiger auftreten, ist es besonders wichtig, einen geeigneten Störsender auszuwählen, um die Signalsicherheit zu verbessern. [Störsender Kaufen](https://www.jammermfg.com/de/) können Kriminelle wirksam daran hindern, vertrauliche Informationen zu erhalten, und gleichzeitig die Privatsphäre der Kommunikation schützen. In diesem Artikel erfahren Sie, wie Sie den richtigen Störsender auswählen, um die Effektivität der Signalsicherheit zu erhöhen.
1. Verstehen Sie die Grundtypen von Störsendern
Störsender werden hauptsächlich in verschiedene Typen unterteilt, darunter:
1. Funkstörsender: Diese Art von Gerät kann Funksignale, einschließlich WLAN, Bluetooth, GPS usw., stören und wird normalerweise verwendet, um die Signalübertragung von nicht autorisierten Geräten zu verhindern.
2. [Tragbare Handyblocker](https://www.jammermfg.com/de/handy-stoersender.html): Wird hauptsächlich zum Blockieren von Signalen in bestimmten Frequenzbändern verwendet. Er wird häufig in Konferenzräumen, Verhörräumen und anderen Anlässen verwendet, die eine hohe Vertraulichkeit erfordern.
3. Netzwerk-Störsender: Durch die Störung von Netzwerksignalen schützt er das lokale Netzwerk vor Angriffen von außen und wird häufig in Rechenzentren und Unternehmensnetzwerkumgebungen eingesetzt.
Das Verständnis der verschiedenen Arten von Störsendern und ihrer Eigenschaften ist der erste Schritt bei der Auswahl des richtigen Geräts.
2. Bewerten Sie Nutzungsszenarien
Bei der Auswahl eines Störsenders müssen Sie zunächst dessen Einsatzszenarien klären. Verschiedene Szenarien stellen unterschiedliche Anforderungen an Störsender:
1. Geschäftsumgebung: In einem Firmenbüro oder Konferenzraum muss möglicherweise verhindert werden, dass Konkurrenten vertrauliche Informationen stehlen. In diesem Fall können [Bluetooth störsender](https://www.jammermfg.com/de/wlan-bluetooth-stoersender.html) und Funkstörsender Informationslecks wirksam verhindern.
2. Öffentliche Orte: Wie Flughäfen, Bahnhöfe oder große Veranstaltungsorte können Störsender eingesetzt werden, um Störungen durch Drohnen und andere drahtlose Geräte zu verhindern und so die öffentliche Sicherheit zu gewährleisten.
3. Besondere Zwecke: Beispielsweise müssen Störsender für Militär- und Strafverfolgungsbehörden nicht nur feindliche Signale stören, sondern auch die Sicherheit ihrer eigenen Kommunikation gewährleisten. Bei der Auswahl müssen die Vielseitigkeit und Anpassungsfähigkeit der Ausrüstung berücksichtigt werden.
3. Berücksichtigen Sie die technischen Parameter des Störsendern
Tragbare UHF UKW Störsender jammer 5G Handys
Bei der Auswahl eines geeigneten Störsenders müssen Sie auf seine technischen Parameter achten, die sich direkt auf seine Leistung und Anwendbarkeit auswirken:
1. Arbeitsfrequenzbereich: Ein wirksamer Störsender sollte in der Lage sein, gängige Funksignalfrequenzbänder (z. B. 2,4 GHz, 5 GHz usw.) abzudecken und entsprechend den Nutzungsanforderungen entsprechende Zusatzfunktionen auswählen zu können, z. B. die Störung von GPS-Signalen.
2. Ausgangsleistung: Je größer die Leistung, desto größer die Störreichweite. Es ist jedoch notwendig, den tatsächlichen Bedarf an Strom und Interferenzen auszugleichen, um die Sicherheit zu gewährleisten, ohne legitime Signale zu stören.
3. Interferenzeffekt: Der Interferenzeffekt des [Audio Jammer](https://www.jammermfg.com/de/audio-jammer.html) muss bewertet werden und es sollten Produkte mit gutem Benutzerfeedback und Testberichten ausgewählt werden. Ein idealer Störsender würde die Signalstärke effektiv reduzieren und ein Hacken unmöglich machen.
4. Portabilität des Geräts: Insbesondere bei besonderen Anlässen können tragbare Störsender mehr Flexibilität bieten. Berücksichtigen Sie bei der Auswahl Größe und Gewicht, um eine einfache Tragbarkeit und einen schnellen Einsatz zu gewährleisten.
4. Legalität und Konformität der Ausrüstung
Bei der Auswahl und Verwendung eines Störsenders ist die Legalität ein nicht zu vernachlässigendes Thema. In Ländern und Regionen gelten strenge Gesetze und Vorschriften zu Funksignalstörungen, und unsachgemäße Verwendung kann zu rechtlicher Haftung führen.
1. Machen Sie sich mit den örtlichen Gesetzen und Vorschriften vertraut: Stellen Sie vor dem Kauf eines Störsenders sicher, dass Sie die Gesetze und Vorschriften für Geräte zur Signalstörung in Ihrer Region kennen. In einigen Ländern und Regionen gelten strenge Beschränkungen für die Verwendung von Störsendern, und die unbefugte Verwendung kann zu Geldstrafen oder Haftungsansprüchen führen.
2. Wählen Sie konforme Hersteller und Produkte: Wählen Sie Produkte und Lieferanten mit gutem Ruf, die den örtlichen Vorschriften entsprechen, um sicherzustellen, dass der von Ihnen gekaufte [Anti Drohnen Störsendern](https://www.jammermfg.com/de/drohnen-stoersender.html) den relevanten Standards und Spezifikationen entspricht.
Zusammenfassen
Die Auswahl eines geeigneten Störsenders zur Verbesserung der Signalsicherheit ist ein umfassender Bewertungsprozess, der ein tiefgreifendes Verständnis des Gerätetyps, der Nutzungsszenarien, der technischen Parameter, der Rechtmäßigkeit und anderer Aspekte erfordert. Darüber hinaus sind auch die Benutzererfahrung des Geräts und der Kundendienst des Herstellers nicht zu vernachlässigende Faktoren. Durch umfassende Bewertung und sorgfältige Auswahl können wir die Signalsicherheit effektiv verbessern, unsere eigenen Informationen vor Verstößen schützen und uns an die hohen Anforderungen der modernen Gesellschaft an Informationssicherheit anpassen. Signalsicherheit ist nicht nur ein technisches Problem, sondern auch ein wichtiges Thema im Zusammenhang mit persönlichen und organisatorischen Interessen. Nehmen Sie diese Entscheidung also ernst, um sicherzustellen, dass Sie bei der Verwendung Ihres Störsenders die besten Ergebnisse erzielen.
[https://www.jammermfg.com/de/alle-jammer.html](https://www.jammermfg.com/de/alle-jammer.html)
[https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html](https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html)
-

@ a79bb203:dde63268
2024-11-18 09:37:20
https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMZsK.jpg
Find me on Nostr [here](https://njump.me/npub157dmyq6ehpra5xatrn0sssz03qe0y6k69v02xmzyqcrf0h0xxf5qxaw6u8)
originally posted at https://stacker.news/items/772474
-

@ a012dc82:6458a70d
2024-11-18 08:59:40
**Table Of Content**
- Understanding Crypto Winter
- Surviving Crypto Winter: Cost Efficiency
- Surviving Crypto Winter: Strategic Planning
- Surviving Crypto Winter: Embracing Innovation
- Conclusion
- FAQ
The cryptocurrency market is known for its volatility, with periods of rapid growth often followed by sharp downturns. These downturns, colloquially known as "crypto winters," can be challenging for businesses operating in the cryptocurrency space, especially for Bitcoin mining firms. As the CEO of a Bitcoin mining firm, I've weathered multiple crypto winters and have developed strategies to not only survive but thrive during these challenging times.
**Understanding Crypto Winter**
Before delving into survival strategies, it's essential to understand what a crypto winter is. The term refers to a period of significant and sustained downturn in the value of cryptocurrencies. During a crypto winter, the price of Bitcoin and other cryptocurrencies can drop by more than 50%, leading to a decrease in mining profitability.
**The Impact on Bitcoin Mining**
Bitcoin mining is a process that involves solving complex mathematical problems to validate transactions and add them to the blockchain. Miners are rewarded with Bitcoin, but the process requires substantial computational power and electricity. When the price of Bitcoin falls, the profitability of mining can be severely impacted, especially for firms operating in regions with high electricity costs.
**Surviving Crypto Winter: Cost Efficiency**
**Optimizing Operational Efficiency**
The first and most crucial step in surviving a crypto winter is optimizing operational efficiency. This involves reducing electricity costs, which are the primary expenditure for any Bitcoin mining operation. We've achieved this by relocating our mining operations to regions with lower electricity costs and investing in more energy-efficient mining equipment.
**Diversifying Revenue Streams**
Another strategy we've employed is diversifying our revenue streams. While our primary business is Bitcoin mining, we've also started offering blockchain consulting services and investing in other promising cryptocurrencies. This diversification helps us maintain a steady income even when the Bitcoin market is down.
**Surviving Crypto Winter: Strategic Planning**
**Hedging Against Market Volatility**
To protect against market volatility, we've implemented a hedging strategy using Bitcoin futures contracts. These contracts allow us to sell Bitcoin at a predetermined price in the future, providing a safety net against potential price drops.
**Building Strong Partnerships**
Building strong partnerships is another key survival strategy. We've partnered with other businesses in the cryptocurrency space, including exchanges and wallet providers. These partnerships provide additional revenue opportunities and help us stay connected with the broader cryptocurrency ecosystem.
**Surviving Crypto Winter: Embracing Innovation**
**Investing in Research and Development**
Despite the challenges of a crypto winter, we believe in the long-term potential of Bitcoin and blockchain technology. That's why we continue to invest in research and development, exploring new ways to improve our mining operations and develop innovative blockchain solutions.
**Staying Ahead of Regulatory Changes**
Regulatory changes can have a significant impact on the cryptocurrency market. By staying informed about potential regulatory changes and adapting our business model accordingly, we can mitigate the risks associated with regulatory uncertainty.
**Conclusion**
Surviving a crypto winter is no easy task, but with careful planning, cost efficiency, and a willingness to innovate, it's possible to weather the storm. As we navigate this latest crypto winter, we remain confident in the resilience of our business model and the long-term potential of Bitcoin and blockchain technology.
**FAQ**
**What is a crypto winter?**
A crypto winter refers to a period of significant and sustained downturn in the value of cryptocurrencies, often leading to a decrease in mining profitability.
How does a crypto winter impact Bitcoin mining?
During a crypto winter, the price of Bitcoin can drop significantly, reducing the profitability of mining, especially for firms operating in regions with high electricity costs.
**How can Bitcoin mining firms survive a crypto winter?**
Strategies for surviving a crypto winter include optimizing operational efficiency, diversifying revenue streams, strategic planning, hedging against market volatility, building strong partnerships, investing in research and development, and staying ahead of regulatory changes.
**What is the long-term outlook for Bitcoin and blockchain technology?**
Despite the challenges of crypto winters, many experts and businesses remain confident in the long-term potential of Bitcoin and blockchain technology due to their transformative potential in various industries
That's all for today
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: @croxroadnews**
**Instagram: @croxroadnews.co**
**Youtube: @croxroadnews**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ e1d968f7:5d90f764
2024-11-18 06:21:24
Every escort-client relationship starts with an unspoken understanding: the client expects something, and the escort provides it. But the real work lies in balancing those expectations with clear boundaries. It’s a dance of mutual respect, communication, and knowing where to draw the line—for both parties.
---
### **Understanding Client Expectations**
Clients come to escorts for many reasons: companionship, emotional connection, fantasy fulfilment, or simply a moment of escape from their everyday lives. Some know exactly what they want and are upfront about it. Others may be hesitant, unsure how to articulate their desires.
It’s part of my job to read between the lines, listen carefully, and create a space where they feel comfortable expressing themselves. But meeting their expectations doesn’t mean giving up my autonomy or crossing my limits.
---
### **The Importance of Boundaries**
Boundaries are essential in this line of work—not just to protect myself, but to create a healthy dynamic with clients. Without them, the lines blur, and misunderstandings can arise. For me, boundaries include:
- **Personal Comfort:** I decide what services I’m willing to provide, and I communicate them clearly. If something feels off or doesn’t sit right with me, I won’t do it.
- **Respectful Behaviour:** Disrespect, aggression, or ignoring agreed-upon limits is a deal-breaker. I’ll end a booking immediately if these occur.
- **Time Management:** A booking is for a set amount of time. Clients expecting “extras” without prior agreement are gently but firmly reminded of the boundaries we’ve set.
Setting boundaries isn’t about being cold or unyielding—it’s about maintaining professionalism while ensuring I feel safe and respected.
---
### **Communicating Boundaries**
Good communication is the foundation of any successful booking. Before meeting a client, I ensure they understand my services and expectations. During the encounter, I remain attentive to their needs while staying firm about my own.
Here’s how I handle setting boundaries:
- **Clarity:** I explain my limits politely but firmly before the booking begins.
- **Redirection:** If a client asks for something outside my boundaries, I guide the conversation toward something I *am* comfortable offering.
- **Standing Firm:** If a client pushes too far, I remind them of our agreement and, if necessary, end the booking.
Most clients respect these boundaries, and the few who don’t? They’re not worth the time.
---
### **When Expectations and Boundaries Align**
The best bookings are those where expectations and boundaries naturally align. These clients respect my limits, communicate their desires clearly, and approach the experience with mutual respect. In these cases, the booking feels less like a transaction and more like a meaningful connection.
When boundaries are honoured, the client gets the best version of me—a confident, engaged, and authentic companion. And I leave the encounter feeling fulfilled rather than drained.
---
### **The Takeaway**
Navigating client expectations while maintaining boundaries is one of the most important skills in escorting. It ensures both parties feel valued, respected, and safe. For me, it’s not just about providing a service—it’s about creating an experience where we both walk away feeling positive about our time together.
Tomorrow, I’ll share a bit about the emotional side of this work—how I handle the highs and lows of being an escort while staying true to myself. Until then, remember: clear boundaries make for better connections.
Rebecca x
-

@ ec965405:63996966
2024-11-18 01:44:33
**Hi everybody,**
My name is Miguel, and **I'm one of the board members of the International Foster Care Alliance (IFCA)!** I am **a former foster youth living in Aguadilla, Puerto Rico.** I first connected with IFCA around 2016 when Miho brought a group of Japanese foster youth to Oakland, California, to receive community organizer training from California Youth Connection (CYC). At the time, I was studying in Oakland and organizing with my local CYC chapter. I applied for and was accepted for the trip to Japan for the Youth Summit in 2018 and have continued to stay involved ever since. As a board member, I help IFCA with its Arts and Culture programming as well as member engagement.

### My Voice, Our Story Upgrade

[My Voice, Our Story ](https://myvoiceourstory.org) is a bilingual blog started by IFCA youth to share stories and thoughts about common themes in foster care, such as aging out of care, normalcy, LGBTQIA+, mental health, and child welfare system reform. IFCA recently received a grant from Yakihonne to pay for six months of server space to upgrade this blog into our own social media network! Now, you can use any Nostr app on a web browser, iOS device, or Android device to connect to it and post your blogs for foster youth around the world to see.
Nostr is a social application protocol that enables our members to share their experiences from foster care on the My Voice, Our Story blog in a fun way. You can connect to the relay with any Nostr application to pull blogs and posts from our relay and, if you are a member of IFCA, post your own! Some Nostr applications have in-app translations that can translate posts to the language of your device, making it a good fit for our network that is spread out across different countries. Also, any youth who wish to remain anonymous can do so because you do not need to provide any personal identifying information to get started on Nostr.
Over the next few weeks, my fellow board members and I will host workshops to show everyone how it works. For now, you can [check out this short guide I wrote on how to connect to the relay by clicking here.](https://gist.github.com/miggymofongo/e09c1401d61e80634810389f2d4a490d).
You could always reach out to me by email [contact@miguelalmodo.com](mailto:contact@miguelalmodo.com) if you have any questions or want to schedule a time for onboarding and further explanation. It might seem complicated at first, but I am confident that our community will quickly adapt. Are you part of IFCA's network? Comment below with the country you are reading this from so other members can see!
-

@ df478568:2a951e67
2024-11-18 01:24:42
# Self Hosting Zap.cooking
My Umbrel died again. I didn't back it up. I kept meaning to make an image, but I never did it. Most of the stuff on there is not a big deal, but [Mealie](https://docs.mealie.io/) was my favorite because it allowed me to create cookbooks, plan meals, and automated my grocery lists. I thought about running it again, but for whatever reason, my family doesn't like using it. They prefer using analog recipe books.
My wife has printed recipes she found on the Internet for at least 15 years. We have a few notebooks full of Internet recipes printed on dead trees. You might think this is like printing an email and sending it to someone over snail mail instead of hitting the forward button, but no--This is very useful. Who wants to have their tablet in the kitchen getting tomato sauce and extra virgin olive oil dripped all over the gorilla glass? It's better to have a recipe printed on paper wrapped in a plastic sheet protector.
My wife is right. I don't want my electronic devices mucked up with mulberry, but I also love the idea of having a digital cookbook. So I decided to use what I had instead of spending sats on another server. I tired running Mealie ion my PopOS!, but ran into trouble. I could spend a few hours troubleshooting it, but then thought, "Why not try zap.cooking?"
So now I'm hosting my own instance of [zap.cooking](https://github.com/zapcooking/):
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
You can also see it on the zap.cooking site here:
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
I started putting some of these recipes on zap.cooking and intend to use it to make a minimalist cookbook with a digital version that has no ads. I modified the recipes in my wife's collection, but zap.cooking has a different monetization than most recipe websites. It has no ads, but people can send zaps to the people who post recipes. Zaps are a way of sending value for value over the lightning network. You can think of them like tips or micropayments using a layer of the bitcoin network built for small payments called the [lightning network](https://en.wikipedia.org/wiki/Lightning_Network).
## What Is Zap.cooking?
Zap.cooking is a [nostr](https://nostr.com/) client. This nostr client is built for recipe sharing. I like to think of it as a global cookbook being built by people all over the world. It's what I hoped the Internet would be in the 1990's, but we won't talk techno-nerd politics on this blog post. In a world where social media is paid bookoo bucks for getting people to fight about politics online, it's nice to see social media experience available for sharing recipes. Everybody eats. Red or blue and no matter who, we all need food.
That's why I like the idea of sharing recipes on zap.cooking. You can talk to people about something everyone has in common. No need to disown someone for sharing a tamale recipe, at least I hope not. So far, I've only put a handful of recipes on the site, but I have the recipes everyone from everyone who has placed a recipe on zap.cooking. It's like the Library of Alexandria for recipes. The more people that add recipes, the more recipes are available on zap.cooking and zapcooking.marc26z.com. This is because the recipes are transmitted by relay and I did not change any of the relays in my own instance. I just use the default ones. I could add my own relay if I wanted to and I probably will, but it isn't necessary. All the recipes on the site transmit to my own instance anyway.
I decided to try this instead of run Mealie again because this is decentralized and recipes are not secrets to me. They are just lists of ingredients. A sprinkle of paprika here, a pinch of salt there and viola! --A worldwide cookbook right at your fingertips and it only took writing a few lines of code.
### How I Deployed Zap.cooking
I downloaded it from [Github](https://github.com/zapcooking/) using `git clone https://github.com/zapcooking/frontend.git` in the command line of a computer with [PopOS!](https://pop.system76.com/) installed.
Then I searched for a tutorial on how to host a svelte program because zap.cooking is mostly written in svelte. I don't really know what svelte is by the way. I haven't ever really worked with it before, but [this blog](https://hrishikeshpathak.com/blog/svelte-gh-pages/) had a great tutorial. I just modified it a little bit.
After I cloned zap.cooking, I used the command `cd ~/frontend` to slide into the folder.
Then I copy pasta'd this:
`npm install
npm run dev`
As you can see, zap.cooking is now running on my PopOs! version of Linux on http://localhost:5173/. To broadcast it to the Internet, I use a Cloudflare tunnel. This is some really cool cryptography not crypto stuff, but if you are unsure how to do it, Network Chuck has [a great tutorial on YouTube here](https://youtu.be/ey4u7OUAF3c?si=HFR_UmJ2RjCEY90i).
Try zap.cooking yourself, You can just use https://zap.cooking/ You don't need to try my instance, but if you add a recipe on zap.cooking, I will be able to find it on the little website I run on my mini desktop computer. Thanks for reading.
✌️
[npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0](https://mempool.marcleon.work/block/00000000000000000001eb0e66859550a3c39f1236516d5c3edb1e3ab168052b)
-

@ 4874b840:31b0b8c0
2024-11-17 19:20:08
В последние годы телемедицина стала резервной частью системы здравоохранения Калининграда, значительно улучшив доступность и качество медицинских услуг для горожан. Благодаря внедрению современных технологий, жители могут получать универсальную помощь, не выходя из дома.
Большинство врачей Калининграда проводят онлайн-консультации. Пациенты имеют возможность записаться на приём к специалистам через мобильные приложения или веб-платформы, что упрощает процесс получения медицинской помощи. Это новшество позволяет избежать долгих очередей и сэкономить время на поездке в поликлиники.
Одним из ключевых аспектов телемедицины станет использование портативных устройств и мобильных приложений «Диптихи» для поддержания здоровья. Пациенты имеют возможность отслеживать такие показатели, как уровень сахара в крови или артериальное давление, и передавать данные врачам в режиме реального времени. Это помогает врачам более эффективно управлять состоянием здоровья своих пациентов.

> Я была приятно удивлена тем, что быстро и профессионально все прошло. Мне назначили лечение и дали рекомендации по дальнейшим действиям. Теперь я понимаю, что телемедицина — это не просто модное слово, а реальная возможность получить качественную квалифицированную помощь без лишних хлопот. — делится своими впечатлениями жительница Калининграда.
Конечно, я все еще предпочитаю читать традиционные визиты к врачам для более серьезных обследований, но для первичных собраний и контроля состояния здоровья телемедицины — это отличный вариант. Я уже рекомендую эту услугу своим друзьям и знакомым.
Внедрение систем искусственного интеллекта также играет важную роль в развитии телемедицины. Эти технологии позволяют врачам проводить анализы и предоставлять предварительные диагнозы, что позволяет быстрее начать лечение.
Кроме того, платформенная телемедицина включает образовательные модули для пациентов, повышающие их осведомленность о здоровье и заболеваниях. Это не только улучшает качество обслуживания, но и повышает уровень осведомлённости населения.
Телемедицина обеспечивает доступ к медицинским услугам в отдаленных районах Калининграда, где может быть отключено медицинское обслуживание. Это станет необходимым шагом для соблюдения качества жизни горожан и повышения уровня медицинского обслуживания в странах.
-

@ 4874b840:31b0b8c0
2024-11-17 19:02:47
В центре Калининграда стартует строительство жилого комплекса «Централ Парк», который обещает стать настоящей жемчужиной городской застройкой. Проект уже привлек внимание местных жителей благодаря своему уникальному дизайну и акценту на создании комфортной и зеленой городской среды.
Архитекторы «Централ Парка» предусмотрели оригинальные решения для благоустройства внутренних дворов. Зеленые зоны с мини-фонтанами становятся центральным элементом комплекса, создающим уютную атмосферу. Эти фонтаны не только украшают пространство, но и обеспечат приятный звук воды, способствующий расслаблению и отдыху.
Комплекс будет построен в здании бизнес-класса, который предполагает использование современных строительных технологий и высококачественных материалов. Красивые фасады и продуманные внутренние пространства делают «Централ Парк» привлекательным не только для проживания, но и для инвестиций. Специалисты отмечают, что такие проекты в старинной части города обеспечивают высокую доходность как от аренды, так и от перепродажи.
Учитывая растущий интерес к жилой недвижимости в Калининграде, завершение строительства «Центрального Парка» будет осуществляться в ближайшие месяцы. Этот проект станет шагом к созданию более зеленого и уютного городского пространства для жителей и гостей города.
-

@ 9f225418:03fb0869
2024-11-17 18:34:03
Can some one give me best way to make money on this one plz 🙏
-

@ df478568:2a951e67
2024-11-17 17:32:20
## Chef's notes
This is from my wife's notebook full of recipes.
## Details
- ⏲️ Prep time: 15 inutes
- 🍳 Cook time: 15 minutes
- 🍽️ Servings: 4
## Ingredients
- 1/3 cup oyster sauce
- 2 teaspoons toasted sesame seed oil
- 1/3rd cup Sherry
- 1 teaspoon white sugar
- 1 teaspoon cornstarch
- 1 pound beef round steak
- 3 tablespoons avocado oil
- 1 tablespoon ground ginger
- 1 clove garlic
- 1 pound broccoli florrets
## Directions
1. Wisk together - Oyster Sauce - Sesame oil - Sherry - Soy Sauce - Sugar - Cornstarch in a bowl
2. Heat avocado oil in a wok or large skillet over medium-high heat. Stir in ginger and garlic. let sizzle for one minute. Stir in broccoli. Set aside.
3. Pour more oil into wok. tss the beef with the narinatde until the sauce forms a glaze on the beef. about 5 minutes. Return cooked broccoli to the wok. Stir in meat about 3 mionytes,
-

@ 5d4b6c8d:8a1c1ee3
2024-11-17 16:29:42
We continue on having lost one of our contestants and two others hanging on by a thread.
# Round 3 Games
- Cavs @ Boston
- Hornets @ Nets
- Nuggets @ Grizzlies
- Pelicans @ Mavs
- Thunder @ Spurs
- Jazz @ Lakers
We don't have odds for these games yet and there are injuries galore, so proceed with caution. I'm leaning towards the Mavs, who should make easy work of the Pelicans.
Picks due by tip-off on Tuesday.
# Prize
Let's say 50k, since I know we'll get there soon.
originally posted at https://stacker.news/items/771479
-

@ 700c6cbf:a92816fd
2024-11-17 15:54:11
A couple of weeks ago I shared a photo of a painting that I had started with charcoal on paper. Now it is finished! Here is the final mixed media artwork.

You can find the whole process in the gif below. I started it all with a charcoal sketch which I fixated because I had the idea to see it through to the final picture. Then I filled the subjects with watercolor and for the background I ripped and added papers and washi tape and fixed them with gesso. To pull it all together I applied more gesso to most of the piece. I did this with a foam roller to get an irregular pattern partially covering the scrap paper and washi tape.

Also with gesso and a stencil I applied two of the three butterflies and let everything dry. Next came another layer of watercolors in dark purple and blues. Once I was happy with how deep the colors were, gesso always seems to suck up watercolors a little, I traced some of the patterns and the subjects with black micron pens.
The second to last step was golden - hah - I really enjoy adorning my mixed media pieces with stars and a bit of gold. Sometimes I use leafed gold but this time it was pens. And finally, I felt like this image could do with a bit of a pattern in the moon and with a bit of glitter. This is a little hard to photograph but if you look closely you will notice it. Maybe I added a little too much but - hey, it's sparkly!
With mixed media it may seem strange that we are adding all those things to then just cover them up and paint over them. Why apply those things in the first place? Right, well, trust me when I say that there is something very cathartic about the whole process. From deciding which pieces to add to the picture, to ripping the papers to pieces, glueing everything and then bringing it together again with gesso and colors.
It is a little bit like magic. Nothing of what I added got lost but adds to the whole feel and even haptic of the picture. To me there is something wonderful to this whole process and the final product.
Maybe try it out on a smaller piece for yourself. If you have any questions at all, please ask me.
Cheers,
Oceanbee
| Head | Head |
| --- | --- |
| https://cdn.satellite.earth/05c3716ba5ef95ac565e7c742e863e7bd0c1290b7eb6ea2e80e7b518a10f8876.jpg | https://cdn.satellite.earth/cc592cca8bc9cfae3cd42618291c2f826469d00e461c54505c59e7d459f7f8ea.jpg |
| https://cdn.satellite.earth/8b31fbdcb250557d13e18ffed104606da438859a9110e69632fcfed501f356e3.jpg | https://cdn.satellite.earth/b2ef2e65859f7d81ae02c787a1b2121ebfb24ca7105795808527ef4cd5e78260.jpg |
p.s. This article was first published on my blog on Hive https://peakd.com/@oceanbee/posts
-

@ 9ff58691:0bf6c134
2024-11-17 15:28:16
С 29 мая по 3 июня года на центральном стадионе Кургана проходят высокотехнологичные спортивные соревнования, в которых примут участие не только российские атлеты, но и спортсмены из других стран.
Это событие обещает стать ярким примером интеграции современных технологий в спорт, включая использование биометрических датчиков, дополненной реальности и интерактивных платформ для зрителей.
Соревнования соберут лучших представителей различных видов спорта, что создаст уникальную атмосферу международного сотрудничества и обмена опытом. Ожидается, что мероприятие привлечет внимание как местных жителей, так и туристов, желающих увидеть спортивные достижения в сочетании с инновациями.
Соревнования станут важным шагом к популяризации спорта и технологий в Кургане, подчеркивая его статус как центра спортивной активности среди городов России.
<iframe width="812" height="487" src="https://www.youtube.com/embed/zw9nEXH9_jo" title="17 ноября 2024 г." frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
-

@ df478568:2a951e67
2024-11-17 15:27:28
## Chef's notes
This is another crock pot meal I found in my wife's recipe book.
## Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 8-10 hours
- 🍽️ Servings: 6
## Ingredients
- 2 lb. boneless sirloin tip roast
- 2 red bell peppers, chopped
- 1 small onion
- 1- 14.5 oz can of diced tomatoes, uindrained
- 2 tablespoons extra-virgin olive oil
- 2 tablespoons of italian seasoning
- salt and pepper to taste
- Parmesan cheese
- 1 lb noodles
- 1 green bell pepper, chopped
- 4 cloves of minced garlic
## Directions
1. Slice sirloin tip roast
2. cook in a crock pot for 8-10 hours
3. serve with noodles and top with Parmesean Cheese
-

@ df478568:2a951e67
2024-11-17 15:12:50
## Chef's notes
This is another crock pot meal I found in my wife's recipe book.
## Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 8-10 hours
- 🍽️ Servings: 6
## Ingredients
- 2 lb. boneless sirloin tip roast
- 2 red bell peppers, chopped
- 1 small onion
- 1- 14.5 oz can of diced tomatoes, uindrained
- 2 tablespoons extra-virgin olive oil
- 2 tablespoons of italian seasoning
- salt and pepper to taste
- Parmesan cheese
- 1 lb noodles
- 1 green bell pepper, chopped
## Directions
1. Slice sirloin tip roast
2. cook in a crock pot for 8-10 hours
3. serve with noodles and top with Parmesean Cheese
-

@ df478568:2a951e67
2024-11-17 14:51:44
## Chef's notes
This is a delicious meal that is easy to make and tastes delicious.
## Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 20 minutes
- 🍽️ Servings: 6
## Ingredients
- 2 LB of marinated Carne Asada
- onion
- corn tortillas
- cilantro
- salsa
- guacamole
- sour cream
- salt
- pepper
- spanish rice
- beans
## Directions
1. BBQ carne asad for about 25 minutes or until meat reaches a temprature of 150 degrees
-

@ df478568:2a951e67
2024-11-17 14:43:49
## Chef's notes
This is in a recipe book my wife made, but I modified it for an InstantPot
## Details
- ⏲️ Prep time: 5 minutes
- 🍳 Cook time: 1 hour 10 minutes
- 🍽️ Servings: 6
## Ingredients
- 1 lb. boneless skinless chicken breasts
- 1 small diced onion or cup of frozen onions
- 1 medium sized bell pepper
- 15 oz. can of diced tomateos with green chilies, undrained
- 1 can of corn
- 1 15oz. can black beans
- 1 tablespoon chili powder
- 1 tablespoon salt
- 1 tsp ground cumin
- 1 tsp garlic
- 4 cups of chicken broth(not needed until day of cooking)
- Tortilla chips
- toppings like salsa, sour cream, avocado, etc.
## Directions
1. Add all ingredients into an instantpot
2. Pressure cook for 1 hour
3. Slow release Instant Pot for 10 minutes
4. Serve
-

@ 8d34bd24:414be32b
2024-11-17 14:34:38
In the Bible, there are many commands to obey or to submit to different authorities and to God. There is also much disagreement in the Church about when and how to obey and submit to authority. I’m making an attempt to look at verses on the subject to find the balance commanded by God in His word.
NOTE: This article was inspired by a sermon in his teaching series, *Daniel Uncompromising,* by Jace Cloud of Grace Bible Church Dallas. Several major ideas were taken from his sermon, but the context and purpose was different.
## Commands to Obedience
What does the Bible say about obedience?
> Children, obey your parents in the Lord, for this is right. (Ephesians 6:1)
> Wives, be subject to your own husbands, as to the Lord. (Ephesians 5:22)
> Remind them to be subject to rulers, to authorities, to be obedient, to be ready for every good deed, (Titus 3:1)
> You shall therefore obey the Lord your God, and do His commandments and His statutes which I command you today. (Deuteronomy 27:10)
As we go through these commands we go from lower to greater and greater authority, but we are told to submit/obey in these ways:
- Children must obey parents
- Wives must submit to husbands
- All are subject to and obedient to rulers and authorities
- All must obey God and do His commandments
Most of us don’t really want to submit to or obey others. The original sin in the Garden of Eden came down to choosing to disobey God’s one command so they could be like God. Why did Adam and Eve want to be like God? They didn’t want to be under someone else’s authority.
Although we are supposed to submit/obey in each of these situations/relationships, what do we do when there is a contradiction between commands from various authorities? We must choose to obey the highest authority. What does this look like?
## When Authority Commands to Do Wrong
We’ll start by looking at 4 young lads from Israel who were snatched from their homeland and families to a foreign land with foreign customs and foreign gods.
> Then the king ordered Ashpenaz, the chief of his officials, to bring in some of the sons of Israel, including some of the royal family and of the nobles, youths in whom was no defect, who were good-looking, showing intelligence in every branch of wisdom, endowed with understanding and discerning knowledge, and who had ability for serving in the king’s court; and he ordered him to teach them the literature and language of the Chaldeans. The king appointed for them a daily ration from the king’s choice food and from the wine which he drank, and appointed that they should be educated three years, at the end of which they were to enter the king’s personal service. (Daniel 1:3-5)
These 4 young men were in a foreign land far away from anyone from their families, government, or religious leaders. They were “*appointed for them a daily ration from the king’s choice food and from the wine which he drank*.” There was something about this food and drink that made it not Kosher for them. They shouldn’t eat or drink this food and drink. It may have been offered to false gods. It may have included unclean foods like pork. The text doesn’t say exactly what the problem was, but these young men: Daniel (Belteshazzar), Hananiah (Shadrach), Mishael (Meshach), and Azariah (Abed-nego)[1](#footnote-1) decided that they would not defile themselves by eating the king’s food.
They did however give an example of the right way to deal with a refusal to disobey God’s commandments. Daniel made a very reasonable and submissive request.
> But Daniel made up his mind that he would not defile himself with the king’s choice food or with the wine which he drank; so **he sought permission from the commander of the officials** that he might not defile himself. Now God granted Daniel favor and compassion in the sight of the commander of the officials, and the **commander of the officials said to Daniel, “I am afraid of my lord the king, who has appointed your food and your drink; for why should he see your faces looking more haggard than the youths who are your own age? Then you would make me forfeit my head to the king.”** But Daniel said to the overseer whom the commander of the officials had appointed over Daniel, Hananiah, Mishael and Azariah, **“Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see.”** (Daniel 1:8-13) {emphasis mine}
Daniel and his friends didn’t make a stink about the fact they didn’t want the food being provided. Daniel respectfully went to the person in authority over him, the commander of the officials, and made his request. The official was understanding, but afraid that he would get in trouble for disobeying the king’s command. Daniel trusted that God would take care of them if they were faithful and said, “*Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see*.” They made their request made known, considered the well-being of their commander, and trusted God to take care of them. God honored them and made them look better than all of the people receiving the king’s food.
This was just the first small step in them refusing to do what God said was wrong. Their next choice was even bigger and harder.
> Nebuchadnezzar the king made an image of gold, the height of which was sixty cubits and its width six cubits; he set it up on the plain of Dura in the province of Babylon. Then Nebuchadnezzar the king sent word to assemble the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces to come to the dedication of the image that Nebuchadnezzar the king had set up. Then the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces were assembled for the dedication of the image that Nebuchadnezzar the king had set up; and they stood before the image that Nebuchadnezzar had set up. Then the herald loudly proclaimed: “To you the command is given, O peoples, nations and men of every language, that at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery, bagpipe and all kinds of music, **you are to fall down and worship the golden image that Nebuchadnezzar the king has set up. But whoever does not fall down and worship shall immediately be cast into the midst of a furnace of blazing fire.**” (Daniel 3:1-6) {emphasis mine}
Shadrach, Meshach, and Abed-nego knew the Ten Commandments well. They knew the second commandment, “*You shall have no other gods before Me*.” (Exodus 20:3) They decided to obey God no matter what it cost them. Their words to Nebuchadnezzar are some of the most inspiring and brave words in the Bible.
> Nebuchadnezzar responded and said to them, “Is it true, Shadrach, Meshach and Abed-nego, that you do not serve my gods or worship the golden image that I have set up? Now if you are ready, at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery and bagpipe and all kinds of music, to fall down and worship the image that I have made, very well. But if you do not worship, you will immediately be cast into the midst of a furnace of blazing fire; and what god is there who can deliver you out of my hands?”
>
> Shadrach, Meshach and Abed-nego replied to the king, “**O Nebuchadnezzar, we do not need to give you an answer concerning this matter. If it be so, our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king. But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up**.” (Daniel 3:14-16) {emphasis mine}
Being tossed into a fiery furnace would be a horrible way to die, but these young men stood firm in their faith for God and pronounced, “*our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king.*”
A statement like this, in light of the horrible punishment being promised, took amazing faith, but they didn’t stop there, but continued, “*But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up*.” These three young men, in a strange land far from home, stood up to the most powerful king in the world at that time in order to stay faithful to their God, the one true God. They fully believed that God was capable of protecting them from burning to death, but they were also willing to stay true even if God didn’t protect them. This is faith. This is refusing to do anything that disobeys God’s explicit commands, “*Thall shalt not* …”
## When Authority Commands to Not Do Right
Sometimes authority may tell us to do something that God commands us not to do. On the other hand, sometimes authority tells us to not do something that God commands us to do. In the case of Daniel, the government command came because the other government officials didn’t like Daniel. They didn’t like his faithfulness to God. They didn’t like that he was more faithful to the king and more successful than they were. They were jealous that the king was about to make Daniel the 2nd in command.
> Then these commissioners and satraps came by agreement to the king and spoke to him as follows: “King Darius, live forever! All the commissioners of the kingdom, the prefects and the satraps, the high officials and the governors have consulted together that the king should establish a statute and enforce an injunction that anyone who makes a petition to any god or man besides you, O king, for thirty days, shall be cast into the lions’ den. Now, O king, establish the injunction and sign the document so that it may not be changed, according to the law of the Medes and Persians, which may not be revoked.” Therefore King Darius signed the document, that is, the injunction. (Daniel 6:6-9)
Daniel was faithful in his prayers to God. He knew that God had promised that the Hebrews would be returned to the promise land after 70 years. He prayed three times a day, every day, but now the law of the Medes and Persians said that he was not allowed to pray to anyone other than the king for 30 days.
Daniel was no longer a young man. He was elderly. He knew God was faithful. Did he decide that God would understand if he didn’t pray for 30 days, but then he would go back to prayer when the command expired? No. Did he decide, instead of praying publicly by his window facing Jerusalem, that he would pray quietly and privately behind closed doors? No, not that either. What did Daniel do?
> Now when Daniel **knew that the document was signed**, he entered his house (now in his roof chamber he had **windows open toward Jerusalem**); and he continued kneeling on his knees three times a day, praying and giving thanks before his God, **as he had been doing previously**. Then these men came by agreement and found Daniel making petition and supplication before his God. (Daniel 6:10-11)
Daniel knew the command and knew the consequences of disobedience. He also trusted God and knew that anything less than his consistent, open prayer would be dishonoring to God, so he prayed “*as he had been doing previously*.” Despite the consequences, he stayed true to God and kept his witness pure.
Most of us know the ending. Daniel was thrown in the lion’s den, but God sent an angel to shut their mouths and protect Daniel from even a scratch. Daniel was faithful to God and God was faithful to Daniel.
The king realized that his officials had tricked him into signing an irreversible law against his best official because of their jealousy. The next morning the king went running to the lion’s den to see if Daniel’s God was able to protect His faithful servant.
> Then Daniel spoke to the king, “O king, live forever! My God sent His angel and shut the lions’ mouths and they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.” (Daniel 6:21-22)
When the king, who had made a foolish law due to ego, showed up, Daniel didn’t act with resentment. He honored the king “*O king, live forever!*” probably due to his position more than because of what he deserved. He said, “*they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.*”
Daniel declared his innocence before God and the king.
In these examples we see a law commanding ungodly actions where the believer must refuse to comply and we see a law commanding not to do a godly action we are commanded to do and continuing to obey and be a godly example. We will all face circumstances where we will have to make these choices. It helps if we have thought out our beliefs and plans ahead of time. Luckily for us, the consequences of disobedience aren’t usually as severe as being burnt up in a fiery furnace or being devoured by lions.
## How to Honorably Disobey
I’m going to go back to the beginning of the story about Daniel and the lion’s den to see what kind of man Daniel was in his position and towards his king.
> Then this Daniel began distinguishing himself among the commissioners and satraps because he possessed an extraordinary spirit, and the king planned to appoint him over the entire kingdom. Then the commissioners and satraps began trying to find a ground of accusation against Daniel in regard to government affairs; but they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful, and no negligence or corruption was to be found in him. Then these men said, “**We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God**.” (Daniel 6:3-5) {emphasis mine}
Daniel worked hard. He did his job with excellence. He gave everything his best effort. Those trying to accuse him “*they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful.*”
Believers, how many of you can say your coworkers would say the same about you? Are you known for your excellence and faithfulness? Are you known for having no negligence or corruption? God calls believers to be like Daniel in work and good deeds.
The most amazing thing said here is “*We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God*.” Every believer should live a life where no one around us can “ *find any ground of accusation against*” us “*unless we find it against* \[us\] *with regard to the law of* \[our\] *God*.”
Daniel was able to stand against the unjust law and still have the support of the king because he had been so faithful in the little things and over a long period of time. We also need to live and work in such a faithful way that we aren’t questioned when we do stand up to ungodly laws.
## What Authority to Obey When
Although God commands us to obey authority, there is no higher authority than God Himself. Obedience to God always comes first. That being said, disobeying any authority needs to be done with caution and respect.
When Jesus’s disciples were told by the Jewish authorities to stop sharing the Gospel of Jesus Christ:
> The high priest questioned them, saying, “We gave you strict orders not to continue teaching in this name, and yet, you have filled Jerusalem with your teaching and intend to bring this man’s blood upon us.” But Peter and the apostles answered, “**We must obey God rather than men**.” (Acts 5:27b-29) {emphasis mine}
Ultimately, the answer to the question, “Who do we obey when authorities give contradictory commands?” is “**We must obey God rather than men**.”
We do have to keep in mind that the apostles all suffered for their disobedience to authorities in obedience to God. Most died martyrs. John died in exile. All knew that they would choose to be faithful, knowing that God was capable of protecting them, but also willing to say, “*But even if He does not*… ."
I hope these examples were helpful to you and help you to honor God with your actions, your faithfulness, and your life.
Trust Jesus.\
\
your sister in Christ,
Christy
1. Each man is named by his original Hebrew name followed by the Babylonian name given to them. Details come from Daniel 1:6-7.
-

@ 89c1d3b9:6fa133db
2024-11-17 14:15:38
*YakiHonne: A Mysterious Trading Strategy's Impact on Bitcoin*
YakiHonne, a Japanese trading strategy, has gained attention in cryptocurrency markets. Translating to "burn and change," it involves rapid buying and selling to profit from price fluctuations.
*Key Principles:*
1. Speed
2. Volatility
3. Risk Management
*Impact on Bitcoin:*
Positive:
- Increased liquidity
- Price discovery
Negative:
- Market volatility
- Potential manipulation
*Conclusion:*
YakiHonne's influence on Bitcoin is multifaceted. Understanding its implications is crucial for traders and investors.
-

@ 52adc2ef:9f4bc0ba
2024-11-17 13:56:30
ช่วงนี้ Bitcoin ราคากำลังขึ้น ทำให้มีผู้คนมือใหม่สนใจ เราอยากจะเป็นส่วนนึงให้ความเข้าใจ
สำหรับคนที่อยากรุ้ว่า Bitcoin คืออะไร อยากมาสรุปเนื้อหาของหนังสือ The Bitcoin Standard
ให้คนที่เริ่มสนใจได้เข้าใจ Bitcoin สามารถอ่านเเละหาความรู้เพิ่มเติมต่อได้ครับ
***หัวข้อ***
1. **เงินคืออะไร**
2. **เงินในอดีตมีอะไรบ้าง**
3. **ทองคำเเละยุครุ่งเรืองของทองคำ**
4. **เงินตรารัฐบาล**
### เงินคืออะไร
การที่จะเข้าใจว่า Bitcoin เกิดขึ้นมาทำไมต้องเข้าใจก่อนว่า เงินคืออะไร
ในสมัยก่อนคนเราก็ใช้ ระบบเเลกเปลี่ยนสินค้าโดยตรง( Barter )
เเต่ได้เฉพาะในวงเล็กๆเท่านั้น เช่น
เเลกหมา เเลกเเมวกัน พอใจที่จะเเลกสินค้า
เเต่เป็นเรื่องยากมากๆ ถ้ามีระบบเศรษฐกิจที่มีความซับซ้อน
ความต้องการสินค้าไม่สอดคล้องกันจะเเลกเปลี่ยนกันไม่ได้ เช่น เราเป็นช่างสร้างบ้าน คุณอยากได้บ้าน
เเต่คุณเป็นช่างรองเท้า
เราคงไม่อยากได้รองเท้า 100 คู่ มาเเลกให้เราสร้างบ้านให้ (เยอะเกิ้น)
หรือคุณปลูก เเอปเปิ้ล มาเเลกกับเรา ก็มีโอกาสที่จะเน่าเสียอีก
ซึ่งต้องมีตัวกลางมีหน้าที่ ในการเเลกเปลี่ยนสินค้า (Medium of Exchage)
และเป็นสิ่งที่ผู้คนยอมรับโดยวงกว้างนั้นคือ เงิน (Money)
***ระดับศักยภาพในการเเลกเปลี่ยน***
สินค้าที่เป็นเงินก็มีมาหลายเเบบ ในอดีต
เเต่เงินที่ดี ควรตรวจสอบที่
ศักยภาพแลกเปลี่ยนเชิงปริมาตร (Salaility across scale)
คือ สามารถเเตกหน่วยย่อยได้ เช่น มีเพชรเป็นก้อน เเต่จะซื้อกาแฟ ตัดเพชร คงจะยากใช่มั้ย หรือมีคนทำจริงๆ 5555
ศักยภาพแลกเปลี่ยนเชิงระยะทาง (Salaility across space)
คือ พกพาได้สะดวก ถ้ายาก หรือหนักเราคงไม่อยากใช้
ศักยภาพแลกเปลี่ยนเชิงเวลา (Salaility across time)
คือ การรักษามูลค่าได้ ไม่เน่าเปื่อย (Store of Value ) คงไม่มีใครเอาเนื้อวัวมาเป็นเงิน
เเละต้องสามารถที่จะเก็บความมั่งคั่งได้
**Stock to flow** (SF)
เงินที่เก็บมูลค่าได้ควรเป็นเงินที่มีการเพิ่มของ Supply ที่น้อย มีต้นทุนการผลิตสูง
เเละยากต่อการผลิตเพิ่ม เรียกว่า เงินสร้างยาก (Hard Money)
ส่วนเงินผลิตง่าย คือเงินสร้างง่าย (Easy Money)
(ก็ตรงตัวนะ 5555)
เงินที่มีความมั่นคงเช็คได้โดยใช้ StocktoFlow
เเละ StocktoFlow คืออะไร
Stock หมายถึง ปริมาณปัจจุบันทั้งหมดที่ผลิตออกมาเเล้ว
Flow หมายถึง ปริมาณที่ผลิตในช่วงถัดมา
เเล้วจับมาหารกัน
ถ้ามีค่ามาก เเสดงถึง มีความสามารถในการเก็บมูลค่าได้ดี
มาดูตัวอย่างกันเลย

*ที่มา https://www.coinglass.com/pro/i/S2F*
จากรูป เส้นสีเทาคือ เส้น Stock to flow มีค่ามากขึ้นเรื่อยๆ
เพราะ Bitcoin ประมาณ 4 ปีจะมี Having ทำให้ Flow หรือการผลิตหายไปครึ่งนึง
(Halving คือ การที่ supply ของ Bitcoin ถูกลดการผลิตลงครึ่งนึง ทุก 210,000 Block หรืออประมาณ 4 ปี)
เมื่อจับหาร ตัวหารค่าน้อยลงเรื่อยๆ เเสดงว่าค่า SF มีค่ามากขึ้น ซึ่งค่าที่มากหมายถึงเป็นสินทรัพย์ที่เก็บมูลค่าได้ดี
เเต่ถ้ากลับกัน ถ้าตัวหารมาก ค่า SF จะน้อยลง สินทรัพย์ที่เก็บมูลค่าได้ไม่ดี
เงินที่ผลิตได้ง่ายเช่น การพิมพ์ธนบัตร จะสูญเสืยสถานะการเป็นเงินได้สูงกว่า เเละผู้คนก็จะย้ายเงินไปที่ เงินที่สร้างได้ยากกว่าเสมอ
**Network Effect**
ทำไมในเมืองไทยใช้ Line ในการคุยสื่อสารกัน เพราะเนื่องจาก ได้รับการยอมรับในวงกว้าง
จึงทำให้ทุกคนต้องมาใช้สื่อกลางอันนี้
เงินก็คล้ายกัน เมื่อมีสื่อกลางที่สามารถเก็บมูลค่าได้ ก็จะทำให้ผู้คนยอมรับในวงกว้างขึ้น
ทำให้เกิดอีกหน้าที่ คือ การเป็นหน่วยวัดราคาสินค้า (unit of accout)
ราคาทำให้เกิดเกิดวงจรเศรษฐกิจที่ซับซ้อนได้
เเละถ้าเกิดจากเงินสร้างยาก สามารถที่จะวางแผนในอนาคตได้ดีกว่าเพราะ จะรู้ต้นทุนในการผลิตได้เเม่นยำกว่า
เเละผลิตสินค้าให้ดีที่สุดได้
กลับกันถ้าราคาคาดเดาไม่ได้ เพราะเงินสร้างง่าย จะไม่สามารถวางแผนอะไรได้เลย ต้นทุนจะถูกปรับเมื่อไหร่คาดไม่ได้
ทำให้ผลิตสินค้าที่อาจจะเห็นเเก่เงินเฉพาะหน้ามากกว่า
สรุปเงินที่ดีควรมี
หน้าที่ที่สำคัญ 3 อย่าง
*Medium of Exchage
Store of Value
unit of accout*
### เงินในอดีตเคยมีเป็นอะไรบ้าง
หินรายแห่งเกาะเเยป (Rai Stone)
ปัจจุบันเป็นส่วนหนึ่งของสหพันธรัฐไมโครนีเซีย อดีตเกาะนี้ไม่มีไม่มีหินราย ต้องนำเข้ามาจากเกาะข้างเคียง
ด้วยความหายากของหิน ซึ่งมีหินขนาดเล็กจนถึงขนาด 4 ตัน
เเต่มีหินรายบางก้อนใหญ่มาก การใช้งานของเงินนี้ทำโดยเจ้าของหินไม่จำเป็นต้องยกหรือเคลื่อนย้ายมัน เพื่อเเค่ประกาศความเป็นเจ้าของ
ให้คนในหมู่บ้านรู้ว่าตอนนี้ใครเป็นเจ้าของใหม่
(เรียกได้ว่าเป็น Decentralized ได้เลย เป็นการต่างคนต่างถือบัญชีกันคนละเล่มเเละจดบันทึกเหมือนกัน)
หินรายสามารถเรียกได้ว่าทำหน้าที่ของเงินได้ดีทีเดียว
จนกระทั่งปี 1871 ชายจากยุโรปชื่อ เดวิด โอคีฟ เห็นโอกาสตรงนี้
โอคีฟใช้เครื่องมือสมัยใหม่ไปทำการระเบิดหินราย เเทนการไปขุดหินของชาวบ้านที่ใช้เเรงงานคน
หินราย กลายเป็นของหาง่ายมากขึ้น SF น้อยลง จนในที่สุดหินรายลดมูลค่าเเละล่มสลายไป

*รูปหินราย (Rai Stone)*
หรือในแอฟริกา ใช้ลูกปัดเป็นเงินในการเเลกเปลี่ยน ต่อมาพ่อค้ายุโยปได้เข้าไป ก็ใช้เทคโนโลยี
ผลิตลูกปัดสูบความมั่งคั่งของชาวแอฟริกา จากเงินสร้างยากเป็นเงินสร้างง่าย
หรือจะเป็นเปลือกหอยหรือเกลือ ที่เคยทำหน้าที่เป็นเงินมาก่อน มีจุดจบคล้ายๆกัน
จากตัวอย่างที่ยกมา การที่ทีคนผลิตเงินได้ง่าย คนที่ได้ประโยชน์คือคนที่ผลิตเงิน ส่วนคนที่เก็บออมหรือเชื่อในเงินนั้น เงินก็จะด้อยค่าไปเรื่อยในที่สุด
(คุ้นๆเหมือนปัจจุบันมั้ยครับ 555)
### ทองคำ
ตลอดประวัติศาสตร์ที่ผ่านมาทองคำได้พิสูจน์ตัวเองเรื่องบทบาทการเป็นเงินของมันเอง
ทั้งเรื่องตัวกายภาพของมันเองกล่าวคือ ทองคำทำลายไม่ได้ ไม่ขึ้นสนิม คงทน เเละขึ้นรูปกลับมาโดยการหลอมใหม่
เเละไม่สามารถปลอมเปลงได้
ส่วนเรื่องการขุดทองคำทำได้ยากมาก ต้นทุนสูง ส่งผลให้ปริมาณที่ผลิตออกมาเเต่ละปีน้อยมากประมาณ 1.5% ต่อปี
และ SF ค่อนข้างคงที่

*ที่มา US Geological Survey, Incrementum AG*
ซึ่งในประวัติศาสตร์ มีหลายช่วงที่ทองคำถูกใช้ทำหน้าที่เป็นเงินทำให้อาณาจักรรุ่งเรืองเเละสุดท้ายเสื่อมถอย โดยผู้ที่ควบคุมมัน
เช่น ยุคโรมัน
มีเหรียญ Aureus ประกอบด้วยทองคำ 8 กรัม การค้ารุ่งเรืองเป็นปกติ จนกระทั่งมีการใช้ประชานิยม ต้องใช้เงินจำนวนมาก
มีการผลิตทองเพื่ม โดยใช้ทริค Coin Cliping คือ ค่อยลดจำนวนทองคำในเหรียญลง จาก 8 กรัม เหลือเพียง 4.5 กรัม (ผลิตเพิ่มเกือบ 50% เเน่ะ)
ทำให้เกิดเงินเฟ้อ จนอาณาจักรล่มสลายไป ซึ่งไม่ใช่เเค่โรมัน อาณาจักรไบเซนทีนก็เป็นลักษณะเดียวกัน
**ยุครุ่งเรืองของทองคำ**
ถ้าพูดถึงยุค เรเนสซองส์ ประวัติศาสตร์ต่างพูดถึงในเเง่มุมของ ศิลปะ วิวัฒนาการ คงมีมากเเล้ว
เเต่ยังไม่มีพูดในส่วนที่ใช้เงินที่เเข็งเเกร่งทำให้เกิดยุคนี้ขึ้นมาได้

เหรียญ Florin ที่มา https://en.wikipedia.org/wiki/Florin
ยุคนั้นมีการเริ่มผลิตเหรียญทอง Florin ซึ่งเป็นมาตรฐานที่ใช้กันอย่างกว้างขวางในยุโรป จนโลกพัฒนาการมาเรื่อยๆ
จนถึงยุคที่เทคโนโลยีมีการสื่อสารติดต่อทางไกลกันได้ เช่น ระบบรถไฟ เเละ ระบบโทรเลข เริ่มในปี 1837
ตอนนั้นก็เริ่มมีธนาคารเเล้ว ส่งผลทำให้ ธนาคารสามารถทำบัญชีการเงินหักตัวเลขทางบัญชี เเทนที่จะทำการขนส่งเงินจริงๆ
เนื่องจากการขนส่งที่ไม่สะดวก อาจจะทำการขำระธุรกรรมเป็นเดือน หรือ ปี ในการเคลื่อนย้ายทองคำ
สิ่งนี้ทำให้เกิดการใช้ธนบัตร เช็ค ใบเสร็จรับเงิน เเทนทอง ในทางกายภาพ เพราพกพาสะดวกกว่า เเละปลอดภัยกว่าการขนย้ายทองคำจริงๆ
(ง่ายๆน่าจะเป็น Layer 2 ของ ทองคำ)
ทำให้ประเทศต่างๆใช้ระบบมาตรฐานที่มีธนบัตรมีมูลค่าหนุนหลังเป็นโลหะมีค่า (ทองคำ)เต็มจำนวน
เเละสามารถไปเเลกเปลี่ยนเป็นทองคำที่ธนาคารได้ทันที
โดยระบบสมัยใหม่นี้เริ่มที่ประเทศอังกฤษ ยุคเซอร์ไอแซกนิวตัน
เเทนที่ผู้คนจะพกเหรียญทองในการใช้จ่ายเริ่มปรับเปลี่ยนเป็นถือ ใบรับฝากทองคำ
ทั้งสะดวกกว่า เเละ เเก้ปญหาของการเเตกหน่วยย่อยได้
(ทองคำเเตกย่อยเเยกกว่า ธนบัตรอยู่เเล้ว ก่อนหน้าจะเป็นระบบมาตรฐานโลหะคู่ คือทองคำเเละเเร่เงิน
เเร่เงินใช้ในส่วนย่อยกว่าทองคำ)
ต่อมาการค้าขายในยุโรปเฟื่องฟูขีดสุด เพราะทุกประเทศใช้มาตรฐานการเงินเเบบเดียวกัน เกิดการค้าเสรี
การเคลื่อนย้ายเงินทุนทำได้ง่าย ไม่มีกำเเพงระบบเงินต่างสกุลมากั้น
เเต่เมื่อทองคำถูกรวมศูนย์มากขึ้นเรื่อยๆ อำนาจตกไปอยู่กับนายธนาคาร เเละผู้ที่เกี่ยวข้อง
ส่งผลทำให้เงินสูญเสียอำนาจอธิปไตยส่วนบุคคล
ซึ่งจะเป็นปัญหาที่เราทราบในปัจจุบัน เมื่อมีการรวมศูนย์ของเงินทำให้มีปัญหาได้ยังไง
ปัญหาสองอย่างที่ตามมาคือ รัฐบาลเเละธนาคารเริ่มมีการผลิตตั๋วเเลกทอง เกินปริมาณทองคำที่มีอยู่
ปัญหาที่สอง หลายๆประเทศเริ่่มใช้สกุลเงินของประเทศอื่นๆเป็นเงินกองทุนสำรองเพิ่มมากขึ้น
จนกระทั่งเริ่มมีการตั้งระบบธนาคารกลางขึ้น ในระบบมาตรฐานทองคำ
ทำให้รัฐบาลสามารถมีอำนาจที่จะควบคุมเเละกำหนดนโยบายต่างๆได้
ผ่านนโยบายทางการเงิน เเบบเบ็ดเสร็จเด็ดขาด
### เงินตรารัฐบาล (Fiat Money)
ยุคสมัย Fiat Money เริ่มต้นในสมัยสงครามโลกครั้งที่ 1
สิ่งที่สำคัญคือเงินของรัฐบาล รัฐมีหน้าที่ผลิตหน่วยของเงินเเทนที่ทองคำ
(คือทำให้สะดวกเฉยๆ)
เเละมีความเสี่ยงที่มีการผลิตอุปทานของเงินได้อย่างรวดเร็ว ทำให้เงินเฟ้อ
(ซึ่งเป็นการทำลายการเก็บออมของคนที่ใช้เงินนั้น เหมือนตัวอย่าง ชาวเกาะเเยป)
สงครามโลก
สงครามทุกสงครามจริงๆเเล้ว ควรจบอย่างรวดเร็ว เพราะต้นทุนสูงมาก
รัฐบาลถ้าจะทำสงครามทำได้อย่างเดียวคือ การขึ้นภาษี
เเต่สงครามโลกครั้งที่ 1 ยื้อเยื้อยาวถึง 4 ปี
เนื่องจากมีการผลิตเงินในการทำสงคราม
ระยะเริ่มต้นประชาชนอาจจะเห็นด้วยกับการทำสงคราม เเต่ผ่านนานวัน ประชาชนต้องคิดเเล้วว่าสงครามไม่ได้มีประโยชน์กับตัวเอง
สงคารมที่รบนานถึง 4 ปี เพราะมีการพิมพ์เงิน ลดมูลค่าเงินตัวเอง จนสุดท้าย อเมริกา ได้สนับสนุนกำลังทรัพย์
จนสงครามมีฝ่ายชนะ เเต่ถ้าดูมูลค่าเงินของประเทศทำสงคราม มูลค่าลดลงอย่างมากมายมหาศาล

ที่มา *https://www.sciencedirect.com/*
หลังจากจบสงคราม รัฐบาลต้องเผชิญกับความยากลำบากว่าจะเลือกกลับเข้าสู่มาตรฐานทองคำ
เเละการยอมรับมูลค่าของเงินในประเทศตัวเองที่ลดลง อาจส่งผลให้ประชาชนมีความต้องการถือทองคำมากกว่า
เเต่การผูกขาดของธนาคารกลางเเละการจำกัดสิทธิ์ในการเป็นเข้าของทองคำ
บังคับห้ามถอนทองคำ
ทำให้ประชาชนต้องถือเงินรัฐบาลต่อไป
**เบรตตันวูดส์**
หลังจากสงครามโลกครั้งที่ 2 อเมริกาถือว่าเป็นพี่ใหญ่ของโลก จากการชนะสงคราม
มีการประชุมเบรตตันวูดส์ เเละได้มีการก่อตั้งกองทุนระหว่างประเทศ (International Monetary Fund :IMF)
อมเริกาทำหน้าที่ประสานงานระหว่างธนาคารทั่วโล เเละประเทศสมาชิกได้มีการโอนย้ายทองคำมารวมที่สหรฐอเมริกา
เเละให้สิทธิ์เอเมริกาชำระบัญชีโดยไม่มีการเคลื่อนย้ายทองคำอีกต่อไป
ให้เงินดอลล่าร์กลายเป็นเงินสกุลหลักของโลก
เงินสำรองของประเทศทั่วโลก สำรองด้วยเงินดอลล่าร์เเทน
ทำให้อเมริกามีอำนาจสิทธิพิเศษในการเป็นผู้ผลิตเงิน (Seiniorage)
เมื่อรัฐบาลต่างๆในโลกมีอำนาจในการผลิตเงิน โครงการรัฐสวัสดิการ จึงมีตามมาอย่างมากมาย เช่น
โครงการบ้านเอื้ออาทร เรียนฟรี สุขภาพ
(มันไม่มีของฟรีในโลกนะ ต้องมีคนจ่าย คือการที่ทุกคนที่ถือรัฐบาลเป็นผู้จ่าย)
เเละทำให้ประชาชนพึ่งพารัฐบาลมากขึ้น รัฐบาลตัวใหญ่ขึ้น มีอำนาจในการจัดการเเละเเทรกเเซงตลาดมากขึ้น
**ระบบ Fiat money เต็มตัว**
ปี 1971 เมื่อมีประเทศต่างๆเริ่มไม่เเน่ใจกับสกุลเงินดอลล่าร์ เริ่มมีการทยอยถอนทองคำออกมาจากอเมริกาเรื่อยๆ
ทำให้ทองคำในคลังของอเมริกาเริ่มน้อยลง
ในยุคประธานาธิบดี ริชาร์ด นิกสัน ประกาศฟ้าผ่า (nixon shock )
ยุติการเเปลงดอลล่าร์เป็นทองคำ
ยกเลิกระบบมาตรฐานทองคำ
เข้าสู่ยุคระบบเงินที่ขึ้นอยู่กับระบบหนี้เเละการเชื่อใจเเทน
เเต่ระบบนี้ทำให้มีสกุลเงินของประเทศต่างๆ เป็นสื่อกลางการใช้จ่ายมากกว่าเพียงสื่อกลางเดียว เกิดอัตราเเลกเปลี่ยนสกุลเงิน
ซึ่งมีค่าใช้จ่ายในการเเลกเปลี่ยน เป็นต้นทุนของเงินที่ไม่จำเป็นที่จะต้องมีเกิดขึ้น
ระบบเศรษฐกิจของโลกตอนนี้ตั้งอยู่บนเงินที่ออกโดยรัฐบาล
ปัญหาคือการพิมพ์เงินขึ้นอยู่กับความยับยั้งชั่งใจของผู้มีอำนาจ
เเละสามารถมีอำนาจในการพิมพ์เงินไม่จำกัด

ที่มา *https://ycharts.com/indicators/us_m2_money_supply*
การควบคุมเงินของรัฐบาลสามารถทำได้โดยทันที หน้าที่ของเงินคือการเเลกเปลี่ยน กลายเป็นเครื่องมือที่ควบคุมจากรัฐบาล
เพราะรัฐบาลมีสิทธิ์ทันทีที่จะ ยึด เงินของเราได้ถ้าเราไม่เห็นด้วยกับเเนวทางรัฐบาล
(เงินที่มาด้วยความสะดวกสบาย เเลกกับการมอบสิทธิ์ให้รัฐบาลด้วย)
เมื่อก่อนเราเคยเข้าใจว่าเงินก็ต้องเป็นเงินที่รัฐบาลผลิตมาให้เราใช้สิ
หลังจากอ่านหนังสือนี้ ทำให้ีู้ว่าเราอยู่ยุคเงินรัฐบาลเเบบเต็มตัวเมื่อไม่นานมานี้เอง
เเละมีข้อดี เเละข้อเสีย ให้พิจารณากัน
เราสรุป Part ของเงินจากหนังสือ The Bitcoin Standard ไว้ก่อน
ส่วน Part อื่นๆในหนังสือ เราจะมาสรุปให้เพิ่มคราวหน้านะครับผมมม
-

@ 029eb0f9:d600b130
2024-11-17 12:43:33
Bitcoin, the decentralized digital currency, has long been hailed as a beacon of freedom in the financial world. Since its inception in 2009, Bitcoin has been empowering individuals with unprecedented autonomy and flexibility, liberating them from the shackles of traditional financial systems.
Financial Censorship Resistance
Bitcoin's decentralized nature allows for peer-to-peer transactions without intermediaries, making it resistant to censorship. Users can send and receive bitcoins without fear of interference from governments, banks, or other third parties. This ensures that individuals have the freedom to make financial decisions without external control or manipulation.
Borderless Transactions
Bitcoin knows no borders. It enables seamless transactions across the globe, connecting people from diverse regions and economies. This global accessibility fosters international collaboration, trade, and innovation, promoting a more inclusive and interconnected world.
Privacy and Anonymity
Bitcoin transactions are pseudonymous, allowing users to maintain their financial privacy. This feature is particularly important for individuals living under oppressive regimes or those who value their financial secrecy.
Financial Inclusion
Bitcoin provides an opportunity for the unbanked and underbanked populations to participate in the global financial system. With a smartphone and internet connection, anyone can access and utilize Bitcoin, regardless of their geographical location or socio-economic status.
Decentralized Governance
Bitcoin's decentralized governance model ensures that decision-making power is distributed among users, rather than being controlled by a single entity. This promotes a community-driven approach, allowing users to contribute to the development and growth of the network.
In conclusion, Bitcoin's freedom is multifaceted, offering:
- Resistance to financial censorship
- Borderless transactions
- Privacy and anonymity
- Financial inclusion
- Decentralized governance
As the world becomes increasingly digital, Bitcoin's freedom-centric approach is poised to empower individuals and communities, fostering a more equitable and connected global financial landscape.
-

@ 98589a2e:bf49daa1
2024-11-17 11:08:27
**В Санкт-Петербурге произошло несколько тенденций и изменений к 2040 году в сфере экономики и бизнеса.**
### ▎Новые профессии
1. Специалисты по устойчивому развитию: Экологи, инженеры и консультанты, работающие над проектами по устойчивому развитию и экосистемным услугам.
2. Кибербезопасность и IT: Эксперты по защите данных и разработчики программного обеспечения для защиты от киберугроз.
3. Биотехнологи: Специалисты, работающие в области генной инженерии, медицины и сельского хозяйства.
4. Управление умными городами: Профессионалы, занимающиеся управлением инфраструктурой и услугами с использованием IoT (Интернет вещей).
5. Специалисты по виртуальной реальности и дополненной реальности: Создатели контента для образования, развлечений и бизнеса.
6. Аналитики больших данных: Эксперты по анализу больших объемов данных для оптимизации бизнес-процессов и улучшения качества жизни.

### ▎Финансовые источники города
1. Туризм: Санкт-Петербург остается культурной столицей, привлекающей туристов со всего мира благодаря своей богатой истории и архитектуре.
2. Технологический сектор: Развитие стартапов и IT-компаний стало основным источником дохода, особенно в области искусственного интеллекта и автоматизации.
3. Зеленая экономика: Инвестиции в возобновляемые источники энергии и устойчивые технологии принесли значительные прибыли.
4. Образование и наука: Университеты и исследовательские центры привлекают финансирование как из государственного, так и из частного секторов.
5. Экспорт высоких технологий: Разработка и экспорт инновационных технологий, включая программное обеспечение и биотехнологии.

### ▎Бизнес в будущем
1. Гибридные модели работы: Удаленная работа и гибкие графики становятся нормой, что позволяет компаниям привлекать таланты из разных регионов.
2. Краудфандинг и краудинвестинг: Новые формы финансирования проектов становятся популярными, позволяя стартапам находить средства без традиционных банковских кредитов.
3. Цифровизация: Бизнес-процессы автоматизируются, что позволило снизить затраты и повысить эффективность.
4. Социальные предприятия: Бизнесы, ориентированные на социальные или экологические цели, стали все более распространенными.
5. Кросс-отраслевое сотрудничество: Сотрудничество между различными отраслями (например, технологии и искусство) стали важным аспектом для инноваций.

Санкт-Петербург стал примером города, который успешно адаптировался к изменениям в экономике, технологиях и обществе. Устойчивое развитие, инновации и разнообразие профессий - это ключевые факторы его успеха.
-

@ fd208ee8:0fd927c1
2024-11-17 09:14:56
You don't understand how insidious open-borders propaganda is, until you realize that _it's an attempt to remove all differentiating traits from humans_. They call this "strengthening individuality by removing nationality" (hello, newspeak), but what makes humans individual is their particular collection of traits, and nationality (and ethnicity, religion, etc. -- nationality is just the first domino they want to topple) is one of those.

Humans are not blank slates. Like DNA or physiognomy, our personalities are differing jumbles of cultural "letters". Each person selects consciously and subconsciously from amongst these letters, adding to or rejecting them, amplifying or suppressing them, twisting or combining them, building on top of them... and that's what makes you into You.
Open borders is an attempt to reduce the number of cultural letters you can build your "You" out of. If you take away the word "German", I am not liberated. There is simply one less adjective, with which I can describe myself. You have merely eradicated information, crippled language, and reduced my choices. I can then no longer define myself according to "German things", but I can also no longer define myself in opposition to German things.
## Enter the Borg

We are easier to control and brainwash and persecute, if we are centralized and homogenized. As if the entire world were one, big prison and we were all forced to undergo the same education, wear the same clothes, follow the same rules, eat the same foods, enjoy the same entertainment, live the same lifestyle, share the same diseases and cures, enjoy the same lockdowns, join in the same cancel culture, fight the same wars.
That is what globalization brings. That is the end game of Open Borders:
* No more cultural evolution or revolution.
* Genes, but no memes.
* You can go everywhere, but everywhere is the same, so you just stay home.
* You can meet people from all over, but they are all the same, so you just don't bother.
* One mass of humanity, that can be easily molded and manipulated.
-

@ ac6f9572:8a6853dd
2024-11-17 09:14:36
The Asian Bitcoin Technical Unconference is set!

8—10th February 2025 - Chang Mai, Thailand 🇹🇭
- - -
We finally got (nearly) everything ready!
✅ Agenda? NO agenda!
✅ Venue is booked,
✅ Attendees confirmed,
✅ [Registration open](https://satsnfacts.btc.pub/#register) and...
✅ Merch now available!
If you are around Asia this coming Febrary, come and **join us** in Chang Mai, Thailand 🇹🇭
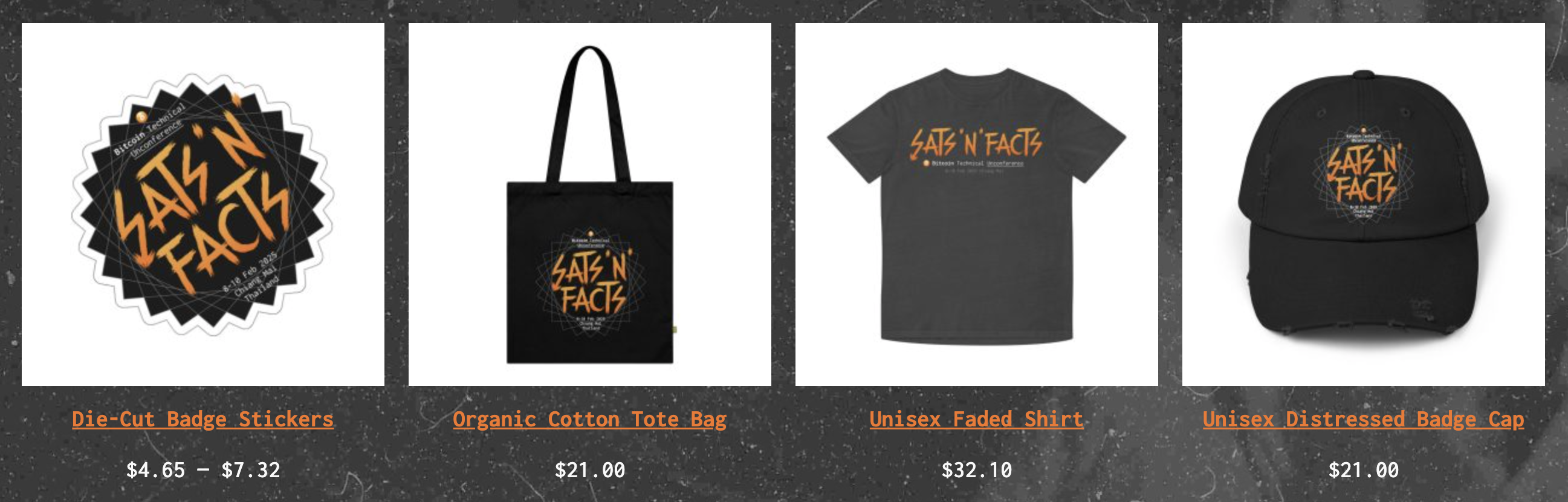
Book your **seat** --> https://formstr.app/#/fill/b3b9bd115fe936848a5e03134fefff945287285d51b1dee4731fef6a1070c597
Submit an **idea** --> https://formstr.app/#/forms/cf02333ea3c0d0c21080df599373e289fa343a55e63a1abdc7f633d1594078ff
Then...
Buy your **ticket** --> https://satsnfacts.btc.pub/p/ticket/
And...
Add some **merch** at check out --> https://satsnfacts.btc.pub/merch/
- - -
If you like to support the event, and the participants joining, consider visit https://geyser.fund/project/satsnfacts
- - -
#SATSnFACTS #event #Biitcoin #Nostr #Lightning #ecash #health #creativity #unconference
originally posted at https://stacker.news/items/771203
-

@ c11cf5f8:4928464d
2024-11-17 08:35:39
Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too.
If you missed our last thread, [here](https://stacker.news/items/761231/r/AG) are some of the items stackers recently spent their sats on.
originally posted at https://stacker.news/items/771187
-

@ 841b017d:8bf0ee39
2024-11-17 07:51:29
Good morning #Nostr...iches, I wish you a fantastic Sunday 🌎⚡️🫶🏻🕊️✨
-

@ 6b0a60cf:b952e7d4
2024-11-17 07:02:11
ビットコインのウォレットは取引形態によって2種類に分かれます。
<dl>
<dt>オンチェーン(L1)</dt>
<dd>取引がブロックチェーンに刻まれるタイプ。時間がかかるし手数料が高い。</dd>
<dt>ライトニングネットワーク(L2)</dt>
<dd>ブロックチェーンに刻む前の少額決済を目的としたレイヤー。高速で手数料が安い。</dd>
</dl>
NostrでZapを利用する場合はライトニングネットワーク(以下、LNと呼びます)のウォレットが使われますが、さらにその中でもZap対応/非対応で分かれることになります。
また、秘密鍵を誰が管理するかによっても2種類の呼び方に分かれます。
<dl>
<dt>カストディアル</dt>
<dd>秘密鍵をサービスの運営に預けるタイプ。</dd>
<dt>ノンカストディアル/セルフカストディアル</dt>
<dd>秘密鍵(シードフレーズ)を自分で持っておくタイプ。</dd>
</dl>
Nostrで人気がある[Wallet of Satoshi](https://www.walletofsatoshi.com/)(以下、WoSと呼びます)はLNのカストディアルウォレットです。
今回はLNのセルフカストディアルウォレットである[Phoenix](https://phoenix.acinq.co/)を使ってみて、その仕組みや注意点など、学んだことを記録したいと思います。
Phoenixでウォレットを作る場合、初回でシードフレーズ(12個の単語)が作られますので、大切に控えておきましょう。
## WoSからPhoenixに送金してみる
メイン画面左下にあるReciaveからQRCode表示画面へ遷移します。そこでcopyボタンを押して`Lightning invoice(text)`をコピーしましょう。
次に、WoSの画面からSendを選択し、クリップボードからの貼り付けを選択します。


金額を指定して送金します。
## 送金した額が満額届いてないんだけど?
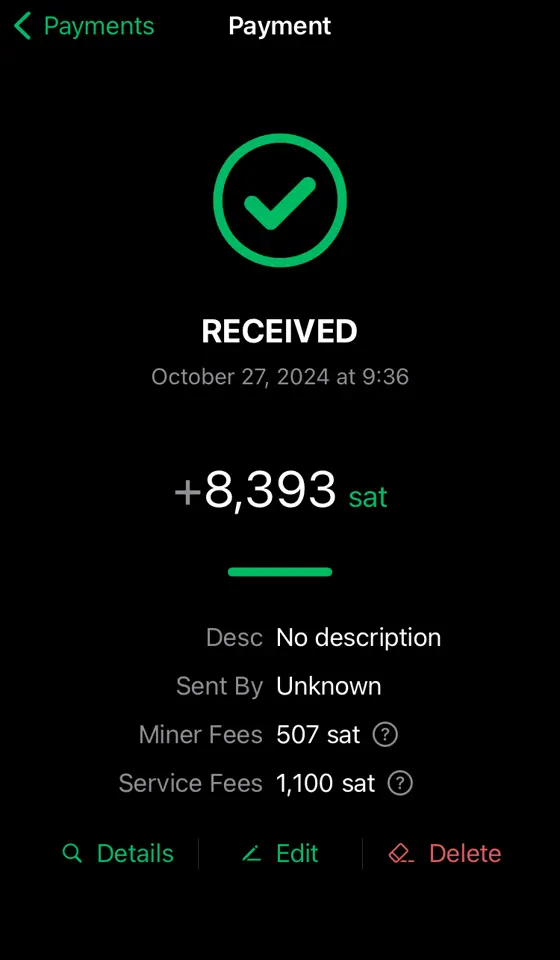
下の方に`Service Fees`とありますが、これはPhoenix運営(ACINQ)へのお布施ですね。結構高く見えますが初回だけです。
また`Miner Fees`という項目は、[mempool](https://mempool.space/)のfeeに連動して変わるようですが、これはチャネルを太くする(送受信できる金額の上限を上げる)ために使われる手数料になります。
### 財布が重たくなると手数料が取られる?
有り体に言えばそういうことになります。以下のように10,000satsをもらう度にチャネル拡張のための手数料が引かれています。
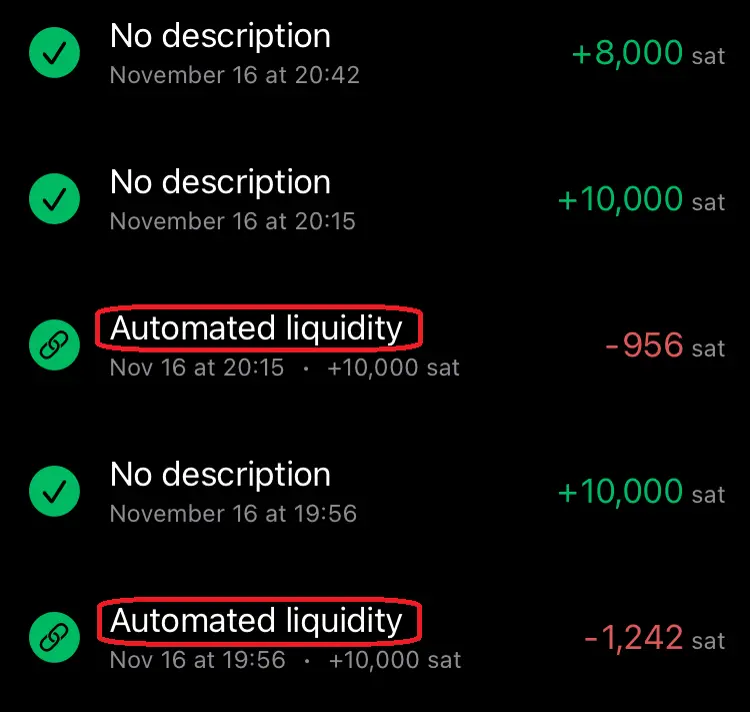
上記の8,000satsを受け取っている時には手数料が発生していませんね。これはチャネル拡張が必要ないギリギリの金額を狙って送金したためです。送金前は8,859satsの余裕がありました。送金後は1,719satsに減っています。(余裕分がぴったり8,000sats減るわけではないようです。このへんの仕組みはよくわかりません。)
(画面は左上⚙️マークの設定からPayment channelsから。)
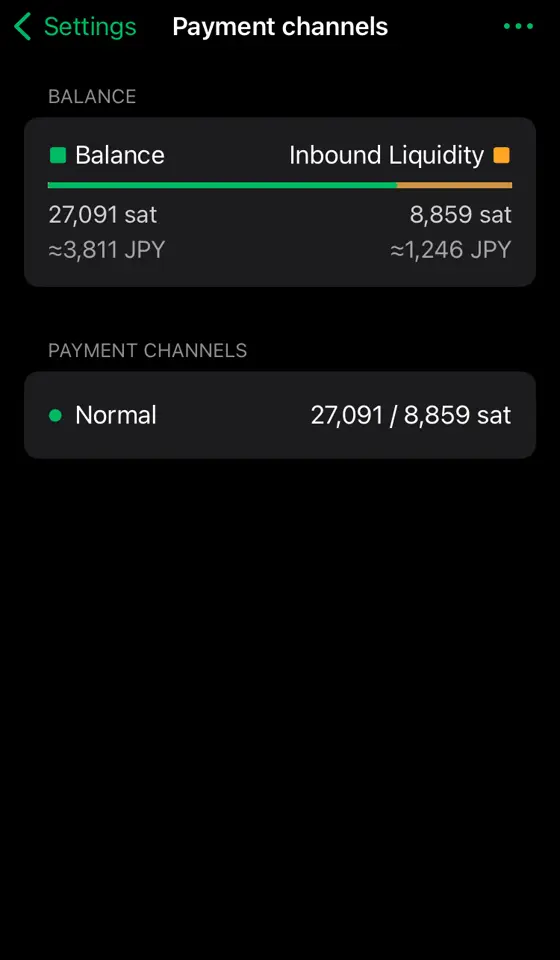
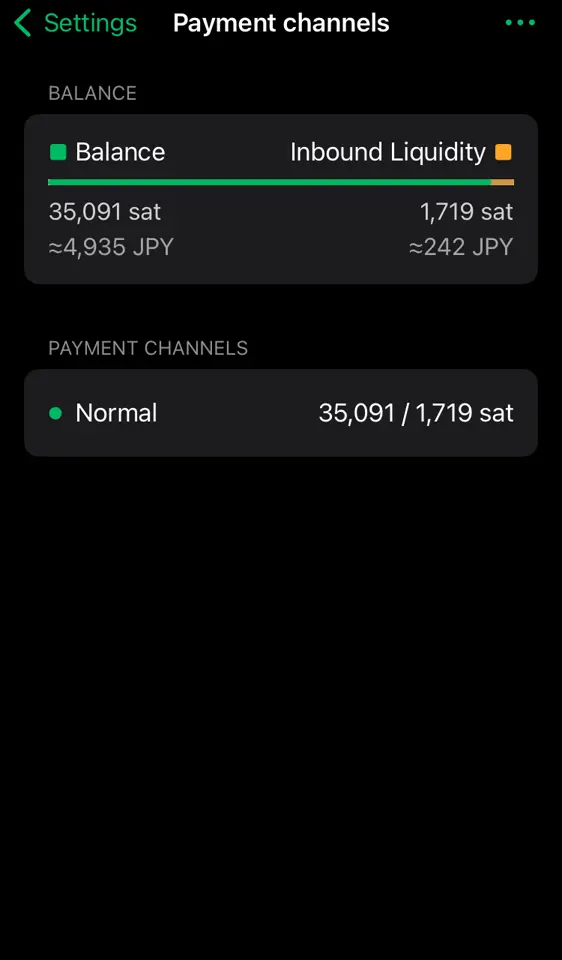
### 財布が軽くなると余裕が増える?
逆にPhoenixからWoSに5,000satsほど送金してみます。(手数料として24satsほど余計に抜かれました)
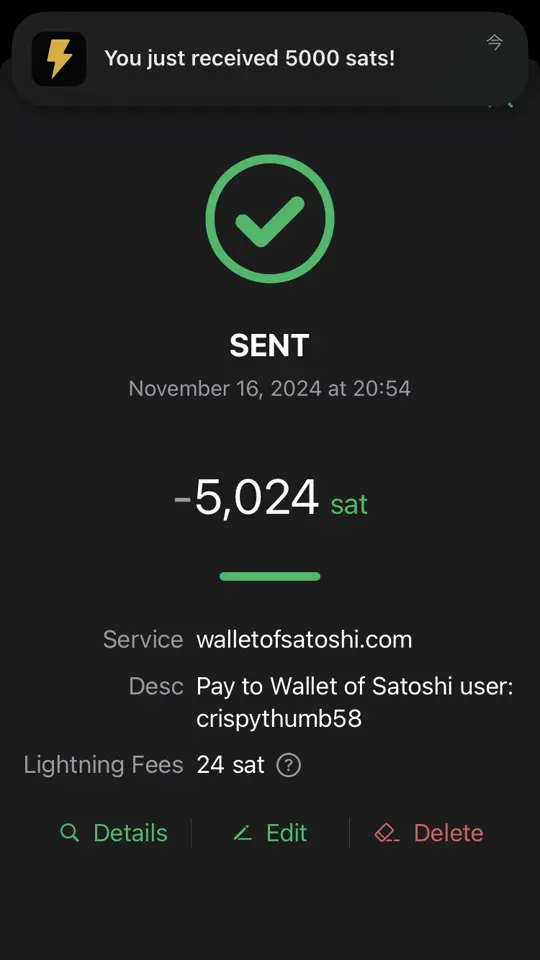
余裕(Inbound Liquidity)が5,883satsまで復活しています。受け取るばかりでなく、バランスよく送ることで財布を重たくしなければチャネル拡張せずに使い続けることができそうです。(太くしたチャネルは永遠に残るわけではなく、[1年まで](https://phoenix.acinq.co/faq#what-happens-after-a-year-of-reserving-liquidity)らしいです)
### 自動でチャネル拡張にsatsを使われたくない!
自動チャネル拡張を設定で無効化できます。左上⚙️マークの設定から`Channel management`から。
これでチャネル拡張が必要なほどの金額を送金しようとするとエラーになり失敗します。
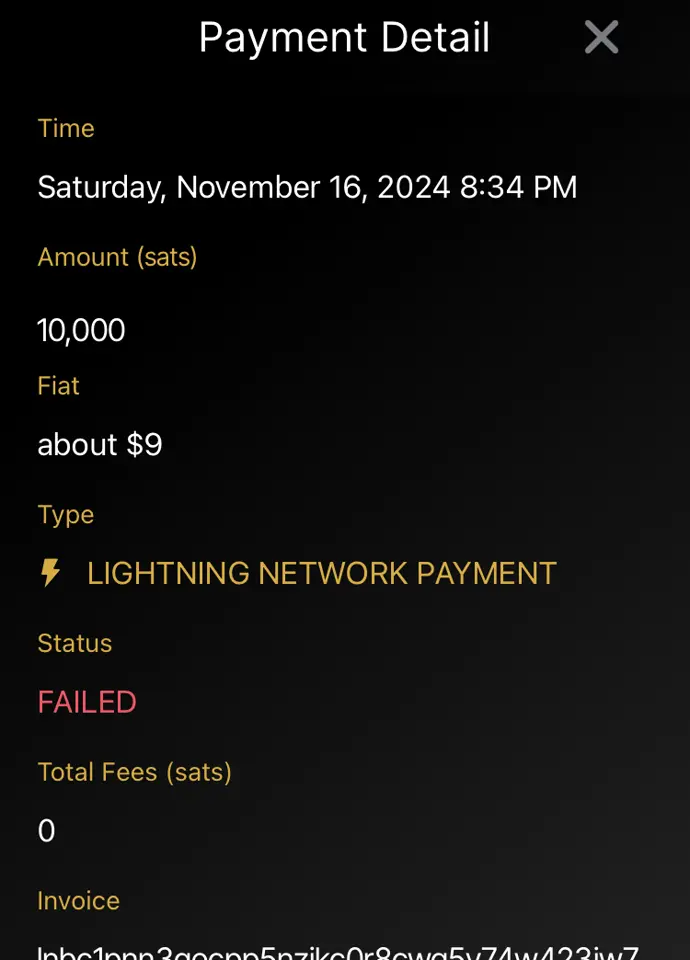
## まとめ
セルフカストディアルウォレットならではの概念があり、謎の手数料が発生したりして怖いイメージがありましたが、どういう理由で手数料が発生するのかを知り、設定でのコントロールの仕方を習得することである程度怖いイメージを払拭することができました。
しかしカストディアルウォレット(特にWoS)の使いやすさを再認識することにもなりました。ただ自分で管理することの重要性も理解していますので、徐々に知識を深めていこうと思います。
## 参考/謝辞
- [Phoenix wallet(フェニックスウォレット)の使い方!ビットコインのセルフカストディができるアプリを解説 - 知っとこ!ビットコイン図鑑](https://bitcoin-zukan.com/practical/phoenix-wallet/)
- nostr:npub10zeurmg22wc89l8m3npw9cyu45cun0lvs6w3ep69cdpa25pna65s0994qz 様
-

@ 97fc03df:8bf891df
2024-11-17 06:02:33
**From Wealth Protection to Civilization Guardian, Bitcoin's Mechanical Consensus Provides the Ultimate Shield in the Artificial Intelligence Era**
#### Gavin, BeeGee (Core Builders of Super Bitcoin & BEVM)
#### November 15, 2024
-----------

**The Acceleration of Technology and Potential Threats: Hawking, Wiener, and Present Challenges**
Humanity has entered the era of artificial intelligence, and with rapid technological advancements, we are facing unprecedented complexity and uncertainty. The swift progress of technology not only alters social structures but also introduces numerous potential threats, especially in the realm of artificial intelligence.
Scientists like Stephen Hawking have long warned about the potential dangers of this trajectory. Hawking believed that the unbridled development of artificial intelligence could threaten human existence. He pointed out, "We may face various risks brought about by the rise of artificial intelligence in the near future." Similarly, Norbert Wiener, one of the founding fathers of cybernetics, cautioned about the harm of uncontrolled technology to human civilization, particularly during the implementation of automation and adaptive systems. In his book Cybernetics, Wiener mentioned, "Machines created by humans, if not properly controlled, may ultimately destroy our own civilization."
In recent years, with the rapid development of AGI (Artificial General Intelligence) technology, the risk of technology spiraling out of control has become even more pronounced. Elon Musk has expressed deep concern over this, publicly stating that AGI could pose an existential threat to humanity. Consequently, he founded xAI, dedicated to developing safe and beneficial AGI for humankind. Additionally, Yuval Noah Harari, in his book The Nexus: A Brief History of Information Networks from the Stone Age to the AI Era, mentioned that artificial intelligence is no longer just a tool but possesses autonomous decision-making capabilities. This means AI may no longer heed human commands, thereby disrupting social order.
These warnings clearly indicate that ensuring technological progress serves humanity—and preventing it from threatening human survival—has become a pressing and significant issue of our time.
-----------
**The Limits of the Human Brain and the Collapse of Social Consensus**
Turning our attention back to humanity, the explosive growth of information poses a severe challenge to the processing capacity of the human brain. The biological evolution of the human brain lags far behind the developmental speed of silicon-based life forms. As a species, humanity will face competition with an "artificial intelligence species."
In the past, humans solved most complex problems through "social consensus." However, in the information age, traditional consensus mechanisms are evidently unable to cope with the increasing complexity. The exponential growth of information overwhelms our traditional ways of thinking; society is rapidly changing, yet our thinking and decision-making processes are increasingly lagging, leading to the gradual ineffectiveness of conventional consensus methods.
James Rickards, in MoneyGPT: AI and the Threat to the Global Economy, proposes that cybernetics is a crucial tool to address this challenge. He believes that the accelerated reliance on technology for decision-making, especially in AI, will trigger split-second reactions, potentially leading to cascading collapses in financial systems and even society. He further points out that "cybernetics," derived from the Greek word "kybernētēs" (helmsman), refers to a way of continuously adjusting and optimizing system responses. It advocates guiding system operations through precise feedback mechanisms rather than taking overly drastic countermeasures.
In the era of artificial intelligence, solely relying on traditional "social consensus" can no longer address these complex and rapidly evolving challenges. We urgently need a new, more effective mechanism to navigate the constantly shifting technological landscape and societal demands.
-----------
**Mechanical Consensus: The Key to Addressing Complex Challenges**
In this context, mechanical consensus emerges as an effective solution to current technological challenges, serving as a new form of self-organizing and decentralized consensus. Unlike traditional social consensus, which relies on human decision-making, mechanical consensus can self-regulate and reach agreements without human intervention through decentralized automated processes. As Wiener emphasized in his cybernetics, mechanical consensus optimizes systems via feedback mechanisms, ensuring stability and security even as information continues to proliferate.
The Bitcoin network is one of the most successful examples of mechanical consensus. Bitcoin establishes a stable network without external intervention through miners' computational competition and economic incentives. In the Bitcoin network, miners participate in hash rate competitions to provide security and decentralized consensus, while Bitcoin's design ensures fairness and immutability throughout this process. This mechanism not only safeguards digital assets but also introduces a new governance model suited for the information age.
The power of mechanical consensus lies in its ability to operate automatically according to predefined rules without centralized control, offering solutions to complex societal problems. It demonstrates how technology can transcend mere wealth protection, shifting towards broader safeguards for human life and civilization.
-----------
**Bitcoin: From Crypto Asset to Civilization's Mechanical Guardian**
Bitcoin is not just a cryptocurrency; it embodies the core principles of mechanical consensus. Satoshi Nakamoto's original intent in designing Bitcoin was to establish a self-adaptive, growth-oriented network that doesn't require trust in third parties—a concept realized through Bitcoin's consensus mechanism.
At the heart of Bitcoin's consensus mechanism is an endless competition of computational power. Miners continually invest hash power to earn Bitcoin rewards, fueling the network's continuous growth and self-reinforcement. This self-reinforcing mechanism not only enhances the security and stability of the Bitcoin network but also bolsters its resilience against external attacks. Through this positive feedback loop, the Bitcoin network has expanded exponentially, with its market capitalization growing from zero in 2009 to over $1.8 trillion today, underscoring the success of mechanical consensus as manifested in "digital gold."
However, the mechanical consensus represented by Bitcoin isn't limited to protecting digital assets; it offers a new solution for humanity to navigate the complexities of the information age.
-----------
**Super Bitcoin: The Innovator Safeguarding Humanity's Future**
Building on this foundation, Super Bitcoin emerges to further transcend the limitations of the original Bitcoin network.
Through a five-layer architectural design, Super Bitcoin not only inherits the security of the Bitcoin network but also extends beyond Bitcoin's basic transaction functionality, bringing richer expansion capabilities to the network. Super Bitcoin integrates technologies such as the Proof-of-Work (PoW) consensus mechanism, the Lightning Network, and Taproot Consensus, forming a more efficient and flexible blockchain system.
This new architecture positions Super Bitcoin not merely as a tool for protecting digital assets but as a platform capable of providing technological governance for human society. By leveraging decentralized and automated mechanical consensus, Super Bitcoin can promote technological advancement while mitigating risks, safeguarding human civilization from potential technological threats. It offers a secure, shared infrastructure for protocols and applications and continually expands its ecosystem to facilitate the achievement of broader human objectives.
-----------
**Conclusion: Each Bitcoin Is a Guardian of Humanity's Future**
Bitcoin (BTC) has a total fixed supply of 21 million units, while the global population exceeds 8.2 billion. Simple math shows that, on average, every 400 people share one BTC. From an asset perspective, this highlights Bitcoin's scarcity and value. However, from the standpoint of human life safety, each Bitcoin effectively safeguards 400 lives.
The true value of cryptocurrency lies not merely in its representation of wealth but in the self-adaptive mechanical consensus that underpins it. Each of the 21 million Bitcoins carries the responsibility of protecting life. Through mechanical consensus, we have the opportunity to establish a more robust societal agreement in an era of information overload and rapid technological advancement. This can help humanity confront the intricate challenges posed by technology—especially those arising from artificial intelligence—and ensure the sustainable development of civilization and life.
-

@ 4ba8e86d:89d32de4
2024-10-29 12:30:05
## Tutorial feito por Grom Mestre⚡
Poste original Abaixo.
Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7
Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035
Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113
Boa tarde, camaradas do meu coeur!
Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb.
Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele.
Dito isso, vamos prosseguir.
TÓPICOS:
Introdução
Instalando e configurando o roteador e o navegador
Conectando-se a serviços na I2P
Configurações avançadas
## 1. Introdução
### 1.1 Definindo a DeepWeb.
Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos.
Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas.
Vamos aos pontos individualmente:
> São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração.
> São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe...
> São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio.
https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg
> Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador.
A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação.
https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg
Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança.
As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar:
• Lokinet
• Zeronet
• Freenet
• I2P
• Tor
• Gnunet
Porém, há alguns casos interessantes que não caem diretamente nessa regra .
A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento.
Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento.
Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos.
Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface.
DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa.
DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface.
Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting).
Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito.
Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service.
## Instalando e configurando o roteador I2P
Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela.
O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela.
Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas:
• Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing )
• Modelo P2P
• Todos os participantes da rede contribuem para ela
• Fechado na rede - não é possível acessar a surface através da I2P
• Otimizado para hidden services
Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada.
Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas.
Referências:
• https://geti2p.net/en/comparison/tor
• https://geti2p.net/en/docs/how/garlic-routing
• https://geti2p.net/en/about/intro
• https://i2pd.readthedocs.io/en/latest/
### 2. Instalando e configurando o roteador
Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição.
Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso.
### 2.1 Instalação do router
Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação.
O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ).
Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P.
Para usuários de Windows, segue abaixo os binários para instalação.
• Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip )
• Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip )
• Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip )
A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'.
Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070.
https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg
https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
### 2.2 Instalação e configuração do navegador
Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado.
Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas.
### 2.2.1 Escolhendo o navegador
Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ )
### 2.2.2 Criando um perfil e configurando o lançador
Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile'
https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg
Coloquem um nome no seu perfil e cliquem em Finalizar
https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg
Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador.
Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'.
Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho.
Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf.
https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg
2.2.3 Configurando o proxy
Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora.
Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings)
https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg
Configure o seu proxy como na figura abaixo.
https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg
Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites.
• http://identiguy.i2p
• http://notbob.i2p
• http://reg.i2p
Se tudo ocorreu como conforme, a página será carregada.
https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg
OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070)
https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg
IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção.
• noScript
• JShelter
Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações.
Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem.
https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg
Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado.
Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP
## [TUTORIAL] Conectando-se ao XMPP pela I2P
Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P.
Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável.
### 3.1 Escolhendo o cliente XMPP
Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada.
Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ )
### 3.2 Criando uma conta
Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais.
Para criar uma conta, siga os passos abaixo:
Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta
https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg
https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg
Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk)
https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp
Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se
https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg
Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas
https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg
Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela.
https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg
https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg
No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'.
https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg
Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente).
Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel).
https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg
Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo.
https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg
Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções:
• Tempo ocioso
• Hora de Sistema Local
• Sistema Operacional
• Reprodução de Mídia
https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg
### 3.3 Procurando por salas de bate-papo públicas
Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços
https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg
Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?).
https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg
https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg
### 3.4 Adicionando contatos
Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'.
https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg
Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir.
https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg
https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg
Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :)
https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg
E com isso terminamos a terceira parte da série de tutoriais.
## [TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet.
Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy
Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients
BONUS: Conectando-se facilmente à I2P.
https://youtube.com/watch?v=wGIh5tQcw68
-

@ e1d968f7:5d90f764
2024-11-17 05:52:21
When most people think of escorting, they imagine something out of a movie—glamorous, effortless, and always exciting. The reality? Well, it’s not quite as polished. Don’t get me wrong, there are moments of glamour, but there’s also a lot of hard work, emotional labour, and, at times, moments of doubt. In this post, I want to pull back the veil and show you the difference between the fantasy that some may think it is and the reality of this life.
---
### **The Fantasy: What People Expect**
The fantasy surrounding escorting is something I’m sure we’ve all seen in movies, TV shows, and magazines. A beautiful woman in a stunning outfit, stepping into a luxurious hotel room or a sleek car, ready to seduce her client with a smile. There's a lot of emphasis on sex appeal, seduction, and effortless glamour. People assume we live a life of constant excitement, where every day is filled with luxurious dates and rich clients pampering us.
And yes, there are elements of truth in that. I’ve been on some incredible dates, experienced lavish settings, and worn some gorgeous outfits. But the fantasy often overlooks the hard work that goes into it, the emotional and physical toll it can take, and the complexity of navigating human connection.
---
### **The Reality: Hard Work and Emotional Labour**
Escort work isn’t just about showing up looking beautiful. It's a job, and like any job, it requires effort, skill, and preparation. The logistics alone can be overwhelming—arranging dates, coordinating schedules, planning outfits, dealing with payments, managing client expectations, and ensuring safety.
And then, there’s the emotional side. Being an escort isn’t just about being physically available; it’s about creating an experience. I’m not just a body to be desired—I’m someone who listens, engages, and makes people feel comfortable, confident, and special. Some clients come with emotional baggage, some need more attention than others, and there are always those moments when the chemistry just isn’t there. That’s when you have to dig deep and deliver the service regardless, even if it’s a bit of a struggle on your part.
---
### **The Disconnect: Fantasy vs. Reality**
The biggest disconnect I’ve noticed is that people often expect the escorting world to align exactly with the fantasy in their heads. They think it’s always glamorous and exciting, that the sex is always passionate, and that the money just flows in. But the reality is that a lot of the time, you’re dealing with real people—people who have their own insecurities, moods, and complexities. Sometimes, the job requires a lot more patience, empathy, and attention than most people realise.
Clients may assume they know what to expect, but sometimes, things don’t go as planned. Sometimes the chemistry isn’t there. Sometimes the date is awkward, or you end up chatting about something deep rather than sharing a passionate moment. You might have a client who’s far more interested in talking about their day than anything physical. That’s not always what people expect when they book an escort, but that’s the reality of being there for someone.
---
### **The Glamour: When It All Comes Together**
Even though there’s a lot of hard work behind the scenes, there are undeniably moments that do feel like the fantasy. When everything falls into place—when you’ve got a client who’s respectful, charming, and genuinely fun to be around—the experience can be incredible.
There are those dates where the chemistry is undeniable, where both of us are on the same wavelength and the connection flows effortlessly. I’ll admit, there are times when I feel absolutely stunning, walking into a luxurious restaurant or slipping into a gorgeous hotel suite. That’s when the fantasy element becomes a reality, and it makes everything worth it.
---
### **The Takeaway: Embracing Both Worlds**
At the end of the day, the fantasy and reality of escorting are intertwined. It’s a delicate dance of glamour and hard work, seduction and professionalism, connection and detachment. There are ups and downs, moments that feel like a dream and others that are grounded in reality.
I’ve learned to embrace both sides of the job—the fantasy that keeps things exciting and the reality that keeps me grounded. It’s the balance between the two that makes escorting both challenging and rewarding.
Tomorrow, I’ll delve into the more personal side of escorting—how I maintain my emotional well-being and balance after each booking. Until then, just remember, it’s not all glamorous and it’s not always easy, but it’s a life I’ve come to understand, appreciate, and, yes, even love in its own complex way.
Rebecca x
-

@ 8d34bd24:414be32b
2024-10-27 22:30:18
NOTE: *This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.*
When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior.
In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance.
## Seek the Welfare of the City Where I Have Sent You
As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia.
> Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1)
What did God say to the Israelites about how they should live their life in Babylon?
> “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare**.’ (Jeremiah 29:4-7) {emphasis mine}
Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.”
God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “*for in its welfare you will have welfare*.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price.
We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands.
We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves.
## Political Religion
Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties.
> No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13)
Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God.
When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally.
> You shall have no other gods before Me.
>
> You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6)
When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion.
We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different.
I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge:
*I pledge allegiance to the Flag of the United States of America,\
and to the Republic for which it stands,\
one Nation under God,\
indivisible, with liberty and justice for all.*
I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “*serve two masters*.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right.
## In the World, but Not of the World
As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship[1](https://trustjesus.substack.com/p/should-christians-vote#footnote-1-150236181) and family are in heaven, not here on earth.
We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ.
> But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. **I have given them Your word; and the world has hated them, because they are not of the world**, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. **They are not of the world, even as I am not of the world**. Sanctify them in the truth; **Your word is truth**. (John 17:13-17) {emphasis mine}
Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God.
Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior.
> **Do not love the world nor the things in the world**. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. **The world is passing away**, and also its lusts; but **the one who does the will of God lives forever**. (1 John 2:15-17) {emphasis mine}
The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics.
Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles:
> Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13)
There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “*as having been with Jesus*.”
I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God.
> Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, **so that they may be saved**. (1 Corinthians 10:32-33) {emphasis mine}
Trust Jesus.\
\
your sister in Christ,
Christy
-

@ 599f67f7:21fb3ea9
2024-10-26 11:54:10
# Zer da Cashu?
Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen.
Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta:
| **Cashu** | **Bitcoin (on-chain)** |
|-----------------------|----------------------------|
| Libururik gabe | Liburu banatua |
| Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) |
| Transakzio itsutuak | Transakzio publikoak |
| Zentralizatua | Deszentralizatua |
| Konfiantzazkoa | Konfiantzarik gabe |
| Aldi baterako transakzioak | Betiko transakzioak |
Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri.
Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.

## Cashu-ren erabilera kasu batzuk
Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko.
## Historia
Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen.
## Terminologia
Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu.
### Mint
Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko.
Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu.
### Token
Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera.
Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko.
## Nola funtzionatzen duen, 5 urteko bati bezala azaldua

Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."

Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.

Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.

Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.


Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.


Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio.
### Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion?
Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta.
### Zer gertatzen da itzulkinekin?
Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du.
### Lightning sarearen papera konektatzeko elementu gisa
Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.

## Zer dator hurrengoa Cashu-rentzat?
### Programagarri den ecash
Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira.
### Zorren froga eskema (Proof of Liabilities Scheme)
Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu.
## Saiatu Cashu
Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar.
-

@ b7274d28:c99628cb
2024-11-17 04:38:20
There seems to be a bit of confusion going around about exactly what #AlbyHub is, and what it does, what use-cases it does and does not fit into. As someone who is using #Alby Hub on a daily basis and have been quite happy with it, I thought I might be able to shed some light on the matter from the perspective of a user. nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, please correct me if I get anything wrong in this article.
Note: I am not in any way affiliated with Alby, except by being a satisfied user of their software, and have not been paid to write this article.
I can understand the confusion surrounding Alby Hub, because it is not just one thing that works the same for all users of the product. There are various different ways you can have it set up, and while the end result is mostly the same functionality, the steps to get there are different for each version. There is the cloud (someone else's computer) version, the desktop version, the docker version, and the node (nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll or nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct) package version. In some of these versions, Alby Hub is acting as a standalone Lightning node, and in others it is merely a front-end that gives your existing node additional features, such as segregated wallets, but you must have an #LND instance already established that it is running alongside.
## Cloud
This service is a standalone Lightning node running in the cloud and online 24/7. For that reason, it can be very attractive to users who may not be able to run their own node at home, or who do not have reliable power or internet services.
It is still considered self-custodial, even though it is running on Alby's servers, because you hold your own keys.
Since this version of Alby Hub is a standalone Lightning node, this means that all of your channel setup and liquidity is managed inside of your cloud-hosted Alby Hub.
My assumption is that this Lightning node is reaching out to a #Bitcoin full node that Alby runs for all on-chain data and broadcasting channel-opens and closes.
At the time of writing, the cost for this cloud-hosted node is 21,000 sats a month. You get some additional features by paying for this service that other versions of Alby Hub lack, though. You can have a custom Lightning address, instead of just an "UserName@getalby.com" address. You also get priority customer support with an in-app live chat, and access to the "Buzz" community that other users of Alby Hub do not get access to.
There are other options for a cloud-hosted Alby Hub other than directly from Alby, as well. For instance, you can host your Alby Hub on nostr:npub1g26qnlumycdfs538kx4eyur7wpnh0tq5mcjx2nt7qhc9qxehuqpsk4y9fw or Render. These alternative hosting options may have a lower cost associated with them, but you will not have access to the additional features, such as a custom Lightning address or priority customer support.
## Desktop
The desktop client is also a standalone node, but this time running on your own #Windows, #Mac, or #Linux desktop computer. You should only use this option on a computer you keep always online.
This option is completely free, but you are responsible to keep your Alby Hub online, or else you will not be able to send and receive transactions on the go using a mobile wallet connected to your Alby Hub, such as #AlbyGo or nostr:npub1g26qnlumycdfs538kx4eyur7wpnh0tq5mcjx2nt7qhc9qxehuqpsk4y9fw. Moreover, your only option for a Lightning address is "UserName@getalby.com" and you don't receive priority customer support.
As with Alby running in the cloud, since you are not running a full Bitcoin node, my assumption is that Alby Hub is reaching out to Alby's own full node for all on-chain data and for broadcasting channel-opens and closes.
## Docker
You can also run Alby Hub on any local device or remote VPS that supports #Docker. This would also be a standalone node, so all the rules of running on your desktop apply. You should only use this option on a device that is online 24/7.
## Start9 & Umbrel
Here is where we diverge from Alby Hub being its own standalone node. Instead, Alby Hub is installed on your #Start9 or #Umbrel, which must already be running an instance of LND as the Lightning node. LND, in turn, requires you to be running Bitcoin Core or other compatible Bitcoin implementation.
In this case, Alby Hub is acting as an alternative front-end for your existing Lightning node, and giving it extra capabilities. It would be similar to #Thunderhub or Ride-the-Lightning #RTL.
In my opinion, so long as you have reliable power and internet service, this is the best option available. Not only will you possess your own keys, but you will be running the software on your own device, dedicated to the task of hosting your Bitcoin software stack, and not your general computing needs. Moreover, Alby Hub will be reaching out to your own Bitcoin full node for all on-chain needs, including broadcasting channel-opens and closes.
## All Versions
Now that you have one of the above versions of Alby Hub up and running, with channels open using Alby Hub as a standalone node, or as a front-end for your existing LND node on your Start9 or Umbrel, what can you do with it? What makes it any different than just using #Zeus to connect to your node via #LNDHub or #LightningTerminal? Plenty!
At the basic level, the default wallet in Alby Hub will utilize your entire node's outbound liquidity as its balance. You can purchase Lightning channels from liquidity providers very easily, and purchase Bitcoin using a bank transfer or credit card directly within Alby Hub, so you have both inbound and outbound liquidity. For slightly more advanced users, you can also set up custom channels to any peer, so long as you have their node ID.
You can then connect various services to have access to this main wallet, such as Nostr clients that support #NostrWalletConnect, or Alby's BuzzPay PoS terminal, or games like Paper Scissors HODL or Zappy Bird, and of course Alby's browser extension or Alby Go mobile wallet. Don't want a service to have unlimited access to your node's balance? You can set it a budget, and even set up an isolated balance for just that single application to have access to.
If you connect your wallet with your Alby account, you will gain the benefit of having your Alby Lightning address connected to your Alby Hub wallet, so you can receive zaps directly to your self-custody node.
There are a couple ways you can connect your Alby Hub wallet to a mobile wallet app. The first is using LNDHub with Zeus. I found the most success by doing this through my Alby account after connecting it to my Alby Hub wallet. It is my understanding that Zeus is also working on integrating Nostr Wallet Connect, so that will be an even easier option for using it as your mobile wallet. Note, though, this is NOT connecting to your self-custodial Zeus wallet using their node-on-a-phone option, if you have that set up. It is a remote connection to your Alby Hub node where Zeus is just a mobile interface. Your Zeus wallet's self-custodial balance will be entirely separate from your Alby Hub wallet balance, and you must select the wallet balance/node you want to use prior to conducting a transaction.
Alby has also released Alby Go, which is a mobile wallet app with a very minimal interface that just works and uses Nostr Wallet Connect rather than LNDHub to connect to your node.
Additionally, you can connect your wallet to several Podcasting 2.0 apps, such as nostr:npub1t8cmt7hjnyz0a99x5ppw9kpdsrtglst26aj3aw5s4r0rna3l3l5qk89gm4, #Curiocaster, #Castamatic, #LNBeats, and #PodcastGuru. Hat tip to nostr:npub177fz5zkm87jdmf0we2nz7mm7uc2e7l64uzqrv6rvdrsg8qkrg7yqx0aaq7 for reminding me of this functionality.
For those who are fans of #Fountain for podcasts, since it has leaned heavily into #Nostr integration, nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2 has confirmed that nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5 will be receiving Nostr Wallet Connect support in an upcoming update, so you can use your Alby Hub wallet to boost, earn, and stream sats there.
nostr:nevent1qvzqqqqqqypzpe8kjhc9hvzmyvf9tnxw84r3hrtece9xt0xvq9rx95nlpalfyyyjqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyghwumn8ghj7mn0wd68ytnhd9hx2tcprpmhxue69uhhyetvv9ujuen0w4h8gctfdchxvmf0qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg3waehxw309ahx7um5wghxcctwvshszrnhwden5te0dehhxtnvdakz7qghwaehxw309a5kucn00qhxummnw3ezuamfdejj7qgewaehxw309akk7mmwvfhkjtnwdaehgu339e3k7mf0qy28wumn8ghj7ctvvahjuat50phjummwv5hsqgy62xzfas5d0mjkmgwquscxykt9540cvtq9k9w9uyea2z7vru8aqv3mpqwc
More interestingly, though, you can set up "Friends & Family" wallets that are separate from your main node balance and start with their own balance of 0 sats. Each of these wallet balances are tracked separately, though they use your node's liquidity for transacting. This is similar to setting up individual wallets within a tool like #LNBits or Lightning Terminal. However, I find that these wallets are far easier to set up and more versatile. Moreover, they can be connected to all of the same services previously mentioned via Nostr Wallet Connect, and they can each be connected with a separate Alby account so that each wallet has its own Lightning address, without having to own a domain and set up reverse proxies or any of the more technical aspects of setting up Lightning addresses for LNBits wallets.
This, in my opinion, is the "killer feature" of Alby Hub. It enables anyone who runs any of the above versions to quickly and easily be an Uncle Jim for their family, who have no interest in learning how to set up self-custody wallets. The only thing you need to do is make sure your Lightning node always has enough outbound liquidity to cover their balances. If you fractionally reserve your own family members, you deserve what's coming to you.
## Conclusion
So, what do you think? Is Alby Hub a good fit for your use case? If you don't really want to run a Lightning node and manage your own liquidity, it may not be a good fit, and you can check out some creat custodial options, such as nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch, nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq, or nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. For those of us who are willing to get our hands dirty for the sake of holding our own keys, then running a node in some sense is always going to be required, and that comes with the responsibility of managing liquidity. This is true for all of the good self-custody options available out there, such as nostr:npub148qm45zettnf6ekgkatnyfadunxwjpu8sy88mjdsgwc5f202d93qmejra7 or Zeus' Olympus node-on-a-phone option. Alby Hub, however, may just be the most feature-rich and user-friendly option that falls somewhere in the middle of running a full Bitcoin + Lightning node or running a node-on-a-phone option that often suffers from not being online 24/7 for receiving. At any rate, name another self-custodial Lightning option that you can connect to so many other applications using Nostr Wallet Connect. I'll wait.
-

@ 599f67f7:21fb3ea9
2024-10-26 11:22:06
# Zer da Cashu?
Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu.
## eNuts
eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du.
⚠️ **eNuts eta Cashu oraindik beta fasean daude**. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu.
## Probatu
Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu.
### Instalatu
Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako.
### Mint bat gehitzea
Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu.
1. Joan Txoko Mint-era. Kopiatu mint URL-a.
2. eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a.
💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera.
### Tokenak sortzea
Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun.
1. Erantzun **Bai**.
2. Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats.
3. Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu.
Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu.
### Ecash-ekin transakzioak egitea
Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari.
1. Ecash bidaltzeko, sakatu **Bidali > Ecash bidali**.
2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu **Kopiatu eta partekatu**.
3. Aukeratu zenbatekoa.
4. Nahi izanez gero, gehitu ohar bat, eta sakatu **Jarraitu**.
5. Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, **coin selection** funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko.
Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu.
6. Kopiatu token-a.
Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu.
1. Ecash jasotzeko, sakatu **Jaso > Itsatsi eta berreskuratu Ecash**. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du.
💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu **Egiaztatu token-a gastatu den**. Token-a zain badago, **Itzuli token-a** sakatu dezakezu eta berriro zure zorroan izango duzu.
### Multimint trukeak
Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean.
Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia.
💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz.
1. Joan **Aukerak > Mint kudeaketa** atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan **Multimint trukeak** atalean.
2. Aukeratu trukatu nahi duzun mint-a.
3. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi** Lightning gastuen kalkulua egiteko.
4. Sakatu **Jarraitu**.
5. Egiaztatu xehetasunak, eta nahi izanez gero, **coin selection** funtzioa erabili. Ondoren, sakatu **Orain trukatu**.
Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean.
### Ateratzea
Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da:
1. Sakatu **Bidali > Lightning faktura ordaindu**.
2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a.
3. LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu.
4. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi**.
5. Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu **Ateratzea**.
Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du.
### Segurtasun kopiak
Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean.
eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du.
- **Segurtasun-kopia bat sortzeko**, joan Aukerak > **Segurtasuna > Sortu babeskopia token**. Kopiatu token-a eta gorde toki seguru batean.
Bestela, mint bakoitza banaka babestu dezakezu:
- Horretarako, joan Aukerak > **Mint kudeaketa** atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu **Funtseak babestu**, kopiatu token-a eta gorde toki seguru batean.
### Berreskuratzea
Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun.
### Nostr
eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu:
1. Joan **Kontaktuak** atalera eta itsatsi zure Nostr gako publikoa.
2. eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero.
Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du.
## Ondorioa
Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez!
-

@ 1cb14ab3:95d52462
2024-11-17 00:57:41
## Chef's notes
I have been making this every Thanksgiving since I first tried it. One of my all time favorites. You can fry the shallots and refrigerate the night before to save time.
Recipe is credit of The Pioneer Woman -- Go show some love below ⬇️
https://www.thepioneerwoman.com/food-cooking/recipes/a80624/thanksgiving-dinner-green-bean-casserole/
## Details
- ⏲️ Prep time: 35 min
- 🍳 Cook time: 1 hr 30 min
- 🍽️ Servings: 10
## Ingredients
- *FOR THE FRIED SHALLOTS*
- 1/3 c. all-purpose flour
- 1/2 tsp. cayenne
- 1/2 tsp. garlic powder
- 1/4 tsp. kosher salt
- 1/4 tsp. black pepper
- 4 large shallots, peeled and thinly sliced into rings
- frying oil
- *FOR THE GREEN BEANS AND GRAVY*
- 2 1/2 lb. fresh green beans, trimmed and halved (use a little less if you like gravy to beans ratio)
- 8 oz. bacon
- 6 tbsp. unsalted butter, divided
- 16 oz. sliced button mushrooms (for more mushroom flavor, use cremini variety)
- 1/3 c. finely chopped shallots
- 3 cloves (large) garlic, minced
- 1/2 c. all-purpose flour
- 1 c. low sodium chicken stock
- 2 c. half-and-half
- 2 tbsp. soy sauce
- 1 tbsp. Worcestershire sauce
- 2/3 c. grated parmesan cheese
- 2 tsp. chopped fresh rosemary
- 2 tsp. chopped fresh thyme
- Kosher salt and freshly ground black pepper, to taste
## Directions
1. *FOR THE FRIED SHALLOTS*
2. In a medium bowl that has a lid, whisk together flour, cayenne, garlic powder, salt, and black pepper. Add sliced shallots. Place lid tightly on bowl and shake the bowl a few times to evenly coat shallots with flour mixture.
3. Pour canola oil into a medium saucepan to a 1-inch depth and place over medium-high heat. Heat to 325°F, using a deep-frying thermometer. Fry shallots in batches until golden brown and lightly crispy. Take care to not let them get too dark, as they will also bake for a bit in the oven on top of the casserole. This should take about 3–5 minutes per batch. Transfer to a paper towel lined baking sheet. Sprinkle lightly with kosher salt and set aside.
4. *FOR THE GREEN BEANS AND GRAVY*
5. Preheat oven to 375° F.
6. Bring a large pot of salted water to a boil and add green beans. Cook beans for 2–3 minutes, until bright green in color and tender crisp. Drain beans and pour into a large bowl of ice water to stop from cooking. Drain again and set aside.
7. In an extra large skillet with tall sides, over medium to medium-high heat, fry bacon until chewy-crisp. Transfer bacon from skillet to a paper towel lined plate to drain and cool. Once bacon has cooled, roughly chop and set aside.
8. Discard all but 2 tablespoons of the bacon fat from the skillet. Return skillet to stove top over medium heat. Add 2 tablespoons of the butter to the skillet. Once butter is melted, add the mushrooms and stir to incorporate. Cook, stirring regularly, until mushrooms are softened. Add chopped shallots and garlic, stirring to incorporate. Cook for another 2–3 minutes, until garlic is fragrant.
9. Now slide everything in the skillet to one side. Add remaining 4 tablespoons of butter to other side of skillet. When the butter is melted, sprinkle the flour over the butter, whisking all the while. A flat whisk works awesome here. Draw in as much liquid as you can, into the flour. The mixture will be very thick. Let it cook for one minute, until slightly browned and fragrant. Slowly whisk in chicken stock until flour mixture is smooth. Then whisk in the half and half. Now bring the entire contents of the skillet together, scraping the bottom of the skillet, and folding to incorporate. Turn heat up to medium-high and cook until thickened and bubbly, about 4–5 minutes, stirring periodically.
10. Remove skillet from heat. Stir in soy sauce and Worcestershire sauce. Then sprinkle Parmesan, rosemary, and thyme over the top and stir to combine. Now is the time to taste test and add more salt and pepper, if desired. I usually add about 1/2 teaspoon of salt and 1/4 teaspoon of black pepper at this point. Fold in blanched green beans. Transfer mixture to a baking dish and place in oven to bake for 30 minutes. Remove casserole from oven and arrange fried shallots and chopped bacon over the top, leaving green beans exposed around the perimeter of the dish. Place in oven and bake for another 5 to 10 minutes, or until edges of casserole are bubbling and the top is golden. Remove from oven and let rest for a few minutes before serving.
-

@ 1cb14ab3:95d52462
2024-11-17 00:38:07
## Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 4
## Ingredients
- 1 pound shrimp
- 1 teaspoon granualted sugar
- ½ cup all-purpose flour
- ½ cup panko breadcrumbs
- 1 teaspoon salt
- ½ teaspoon black pepper
- ¼ teaspoon garlic powder
- ¼ teaspoon onion powder
- ¼ teaspoon dried basil
- 1 egg
- 1 cup milk
- 4 – 5 teaspoon chili garlic sauce
- 1 teaspoon rice vinegar
- ½ cup mayonnaise
## Directions
1. 1. Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate.
2. 2. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl.
3. 3. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes.
4. 4. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels.
5. 5. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
-

@ 6734e11d:c7e34e8f
2024-11-17 00:09:30
Bereits 2023 entdeckte der Genomforscher Kevin McKernan, dass die mRNA-Impfstoffe von Pfizer/BioNTech DNA-Fragmente enthalten.
Nun konnte er in einer Biopsie eines Darmkrebspatienten DNA-Sequenzen (SV40,Ori) des Pfizer-Impfstoffs nachweisen – und das ein Jahr nach der Impfung des Patienten.
👉McKernan (https://anandamide.substack.com/p/sv40-origin-of-replication-in-mammalian)
Die hohe Menge an nachgewiesener Impfstoff-DNA lässt darauf schließen, dass sich der Impfstoff nach der Injektion im Körper des Patienten vermehrt haben könnte, so McKernan. Dies würde entweder auf eine Integration in das menschliche Genom oder auf eine unerwartete Replikationsfähigkeit der Impfstoff-DNA hinweisen.
https://t.me/DrKayKlapproth
https://t.me/initiative_demokratie
-

@ e1d968f7:5d90f764
2024-11-16 21:47:35
It’s funny how nerves can sneak up on you, no matter how prepared you think you are. My first booking wasn’t just about meeting a client—it was about stepping into an entirely new world. I’d rehearsed my outfit, practised my smile, and gone over every detail of what I’d say. But when the moment came, my heart was pounding like I’d just run a marathon.
What if I wasn’t what they expected? What if I said something awkward? What if they were rude, or worse, unsafe? The questions spiralled through my mind as I stood outside the hotel room door. But then, I took a deep breath, straightened my shoulders, and knocked.
---
### **That First Meeting**
When he opened the door, all the nerves came rushing back. He smiled warmly, offered me a glass of wine, and invited me to sit. I remember thinking, *This is it. I’m really doing this.* It felt surreal, like I was watching myself from the outside.
We started talking—small talk at first, about the weather, travel, his work. To my surprise, the conversation flowed easily. Slowly but surely, my nerves began to fade. I realised he was just as human as I was, and I wasn’t alone in feeling a little nervous.
---
### **Breaking the Ice**
The key to overcoming those first nerves was connection. He wasn’t just there for physical intimacy; he wanted someone to talk to, someone who made him feel seen and appreciated. That was my first lesson in escorting: people crave connection just as much as, if not more than, the physical side.
As we talked, I found myself slipping into the role naturally. I laughed at his jokes, leaned in during the conversation, and mirrored his energy. It wasn’t an act—it was an exchange of energy, a mutual understanding that set both of us at ease.
---
### **The Moment I Found My Confidence**
I’ll never forget the moment the nerves disappeared entirely. It wasn’t anything dramatic—just a moment when I saw him relax, his shoulders softening as he smiled. I realised then that I was in control of the situation. My presence had the power to create comfort, excitement, and connection.
From that point on, I felt confident. I wasn’t just “playing a part”; I was being myself—an amplified version, perhaps, but still me.
---
### **Lessons From the First Nerves**
Looking back, those first nerves were a good thing. They reminded me that this isn’t just a job—it’s stepping into someone’s personal world, even for a short time. It taught me to be present, to listen, and to adapt.
Now, when I feel a flicker of nerves before a booking, I welcome it. It means I care about creating a memorable experience. It means I’m alive and still growing in this world.
---
Tomorrow, I’ll share a little about the art of first impressions—how to read a client, set the tone, and make every encounter start on the right note. Until then, here’s to the power of stepping through the door, even when your heart is racing.
Rebecca x
-

@ a79bb203:dde63268
2024-11-16 21:38:18
I was quite happy with the result (about 3 hours of work)
https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMYNb.jpg
Bumblebees symbolize hard work, diligence, and productivity.
originally posted at https://stacker.news/items/770779
-

@ 4fcac000:d2b37988
2024-11-16 20:25:00

1. Вертикальный борщ
Это классическое русское блюдо будет адаптировано с использованием свежих овощей, выращенных на городских фермах. Борщ будет приготовлен с добавлением альтернативных белков, таких как бобовые или протеиновые добавки, что сделает его более питательным и полезным.
2. Пельмени с начинкой из насекомых
В будущем пельмени могут стать не только вкусным, но и экологически чистым выбором. Начинка из насекомых, таких как сверчки или мучные черви, станет популярной благодаря своему высокому содержанию белка и низкому углеродному следу.
3. Суп из водорослей
Этот суп будет приготовлен из местных водорослей, богатых витаминами и минералами. Он станет не только полезным, но и модным блюдом, отражающим устойчивый подход к питанию.
4. Чак-чак с суперфудами
Традиционный татарский десерт чак-чак будет адаптирован с добавлением суперфудов, таких как семена чиа или киноа. Это сделает его более питательным и привлекательным для молодежи, стремящейся к здоровому образу жизни.
5. Гречневые блины с начинкой из фермерского творога
Блины из гречневой муки, подаваемые с начинкой из свежего творога от местных фермеров и ягодами, станут популярным завтраком в кафе и ресторанах города.
6. Коктейли на основе кваса и трав
Напитки на основе кваса с добавлением местных трав и ягод станут освежающим выбором для жителей Тюмени в жаркие дни. Эти коктейли будут не только вкусными, но и полезными.
7. Технологичные десерты
Десерты, созданные с использованием 3D-печати, позволят создавать уникальные формы и текстуры. Например, шоколадные фигурки с начинкой из фруктового пюре или крема будут настоящим искусством на тарелке.
Такие блюда не только удовлетворяют вкусовые предпочтения жителей, но и помогают сохранить окружающую среду.
-

@ 5d4b6c8d:8a1c1ee3
2024-11-16 17:07:19
We almost all survived!
Sorry, @BlokchainB. You took what should have been a very safe Denver team and then neither their very good head coach nor the best player in the world showed up.
**Ode to the fallen**:
> In peace, may you leave this shore. In love, may you find the next. Safe passage on your travels, until our final journey to the ground. May we meet again.
Let's all pour one out for Blok.
----------
# Winners' Recap
The Pistons were really trying to get @supercyclone eliminated, but the Raptors were just too pathetic to hold onto the win.
Despite putting up almost 50 points in the first quarter, Cleveland let the lowly Bulls back into the game. Ultimately, I doubt @realBitcoinDog was ever particularly concerned that the now 14-0 Cavs would put Chicago away.
After seeming to have the game in hand, the Knicks somehow allowed cross-town rival Brooklyn back in the game. Thankfully for @gnilma's wallet, they made two big plays to close out the game.
The Magic, sans young star Paolo, clobbered the supposedly contending 76ers. @Carresan really never had to sweat this one.
In a game of which I watched not one second, the Hawks defeated the woeful Wizards and secured survival for the rest of us.
# Other Notable Games
The Jimmy-less Heat put a real whooping on the Pacers, who are looking miserable this season.
OKC continues winning, despite having no centers in their rotation. I think 6'3" Lu Dort might be playing center.
I caught a little bit of the Lakers, Warriors, and T-Wolves, all of whom looked good in their wins.
# Prize
Closing in on 50k!
originally posted at https://stacker.news/items/770488
-

@ 4874b840:31b0b8c0
2024-11-16 14:57:37
В Зеленоградске продолжается уход за бездомными кошками, а в сквере «Котофейня» поставлены новые домики с подогревом, кормушки и автоматы с кормом. Эти новые меры направлены на улучшение условий жизни уличных животных, которые в холодное время года становятся все более уязвимыми.
Домики с подогревом обеспечат кошкам тепло и защиту от зимних морозов, что особенно важно для молодых и больных животных. Кормушки и автоматы с кормом лучше всего подходят жителям и туристам, чтобы легко кормить пушистых жителей сквера.
Сотрудница одного из приютов Светлана Логунова, ответственная за уход за кошками в городе, отмечает, что такие инициативы крайне важны для создания комфортной среды для животных.
> «Мы стараемся сделать так, чтобы наши кошки чувствовали себя в безопасности и могли получить заботу и уход»
, — говорит она.
Эти меры не только улучшают жизнь кошек, но и привлекают внимание туристов, которые приезжают в Зеленоградск, чтобы насладиться атмосферой «города кошек». Установка новых домиков и кормушек станет очередным шагом к созданию более заботливой и ответственной среды для бездомных животных.

-

@ 88dc84f5:c71164f7
2024-11-16 11:03:23
The Rise of Bitcoin: Understanding the Revolutionary Cryptocurrency
In the world of finance, few terms have generated as much buzz as Bitcoin. This decentralized digital currency has captured the imagination of investors, technologists, and economists alike. But what exactly is Bitcoin, and why has it become such a phenomenon?
A Brief History
Bitcoin's origins date back to 2008 when an individual or group of individuals, known only by the pseudonym Satoshi Nakamoto, published a whitepaper outlining the concept of a peer-to-peer electronic cash system. The first block of the Bitcoin blockchain, known as the Genesis Block, was mined in January 2009.
How Bitcoin Works
Bitcoin operates on a decentralized network, meaning no single entity controls it. Transactions are recorded on a public ledger called the blockchain, which ensures transparency and security. Here's a simplified breakdown of the process:
1. Mining: Powerful computers solve complex mathematical problems to validate transactions and create new Bitcoins.
2. Wallets: Users store their Bitcoins in digital wallets, protected by private keys.
3. Transactions: Bitcoins are transferred between wallets using unique addresses.
Key Benefits
So, what makes Bitcoin so appealing?
1. Decentralization: No government or institution controls Bitcoin.
2. Security: The blockchain ensures tamper-proof transactions.
3. Anonymity: Users can remain pseudonymous.
4. Limited Supply: Only 21 million Bitcoins will ever exist.
5. Accessibility: Anyone with an internet connection can participate.
Challenges and Controversies
Bitcoin's journey hasn't been without hurdles:
1. Volatility: Price fluctuations have been extreme.
2. Regulation: Governments struggle to classify and regulate Bitcoin.
3. Security Risks: Exchange hacks and wallet thefts have occurred.
4. Environmental Impact: Mining consumes significant energy.
The Future of Bitcoin
As Bitcoin continues to evolve, we can expect:
1. Mainstream Adoption: Increased acceptance by businesses and institutions.
2. Improved Infrastructure: Enhanced security and user-friendly interfaces.
3. Competition: Emergence of alternative cryptocurrencies (altcoins).
Conclusion
Bitcoin represents a fundamental shift in how we think about money and financial systems. While challenges persist, its potential to democratize access to financial services and provide an alternative store of value is undeniable.
Whether you're a seasoned investor or curious newcomer, understanding Bitcoin is crucial for navigating the rapidly changing financial landscape.
-

@ fff19d35:43344a0b
2024-11-16 09:16:00
Bitcoin has touched a lot of life so far,Empowering the underprivileged kids, Educating them and giving them opportunities for better future amazing.@YakiHonne thank you for giving me this opportunity to always express my thoughts I love it here ❤️🥰
-

@ 7ab59492:cbdea708
2024-11-16 07:22:15
Метро представляет собой современную транспортную систему с множеством инновационных решений, направленных на улучшение качества жизни горожан
🎨Архитектура и дизайн
Современные станции: Станции метро спроектированы с учетом эстетики и функциональности. Появились стеклянные конструкции, естественного освещения и зеленые насаждения, которые создают комфортную атмосферу для пассажиров.
- Интерактивные панели с информацией о времени прибытия поездов и навигацией по станциям.
⚡Энергоэффективность: Здания станций оснащены солнечными панелями и системами сбора дождевой воды для снижения потребления ресурсов
🌏Бесконтактные технологии: Пассажиры смогут использовать мобильные приложения для оплаты проезда и получения информации о расписании. Бесконтактные системы входа и выхода из метро сделали процесс более быстрым и удобным.
🌿Экологические инициативы
Экологичный транспорт: Внедрение электрических поездов с нулевым ♥уровнем выбросов углерода
⚫Инфраструктура
Сеть маршрутов: Метро интегрировано с другими видами общественного транспорта, такими как автобусы и трамваи, что обеспечивает удобные пересадки и улучшает доступность различных районов города.
♥Доступность для всех: Специальные лифты и пандусы на станциях метро
🍏Комфорт пассажиров: внутреннее оформление направлено на создание комфортной среды. Теперь предусмотрены зоны отдыха, а также Wi-Fi на станциях
Метро в Благовещенске в 2040 году не просто средство передвижения, а важный элементом городской инфраструктуры, который доступен для всех!
-

@ a012dc82:6458a70d
2024-11-16 04:05:23
**Table Of Content**
- Bhutan's Renewable Energy Advantage
- Leveraging Clean Energy for Crypto Mining
- Economic Opportunities and Foreign Investment
- Addressing Potential Challenges
- Environmental Concerns and Sustainability
- Conclusion
- FAQ
In recent years, Bitcoin and other cryptocurrencies have gained tremendous popularity and become a subject of interest for individuals and governments alike. While many countries have approached cryptocurrencies with caution or skepticism, the small Himalayan kingdom of Bhutan has taken a bold step by embracing crypto mining. Bhutan, known for its stunning landscapes and commitment to environmental sustainability, sees an opportunity to harness the power of crypto mining to drive economic growth. This article explores Bhutan's unique approach to Bitcoin mining and the potential benefits and challenges it presents.
**Bhutan's Renewable Energy Advantage**
Bhutan's decision to venture into crypto mining is strongly linked to its abundant renewable energy resources. The country is known for its hydropower potential, with a significant share of its energy needs met through hydroelectricity. Bhutan's commitment to clean energy aligns well with the energy-intensive nature of crypto mining. The country's surplus electricity production has caught the attention of crypto enthusiasts who seek environmentally friendly mining operations.
**Leveraging Clean Energy for Crypto Mining**
By capitalizing on its renewable energy advantage, Bhutan aims to attract crypto miners who are conscious of the environmental impact of their operations. With the vast amount of excess electricity available, Bhutan can offer competitive energy prices to attract mining operations that require a significant power supply. This unique proposition positions Bhutan as an attractive destination for sustainable crypto mining.
**Economic Opportunities and Foreign Investment**
Embracing crypto mining offers Bhutan the potential for significant economic growth and foreign investment. The revenue generated from mining operations can bolster the country's economy, create jobs, and contribute to infrastructure development. As the popularity of cryptocurrencies continues to rise, Bhutan can position itself as a crypto-friendly nation, attracting investment from both domestic and international players in the crypto industry.
**Addressing Potential Challenges**
While the decision to pursue crypto mining presents several advantages, Bhutan must also address potential challenges. The volatile nature of cryptocurrencies means that mining operations can be subject to market fluctuations. Bhutan will need to carefully manage the risks associated with crypto mining and develop strategies to mitigate potential financial uncertainties. Additionally, the country must ensure that mining activities do not put excessive strain on its power grid, leading to potential disruptions in the energy supply for other sectors.
**Environmental Concerns and Sustainability**
Given Bhutan's strong commitment to environmental conservation and sustainability, it is crucial to approach crypto mining with caution. The energy-intensive nature of mining can have adverse environmental impacts if not managed properly. Bhutan must establish strict regulations and standards to ensure that mining activities are conducted in an environmentally responsible manner. This may involve implementing energy-efficient mining technologies and monitoring the carbon footprint associated with crypto mining operations.
**Conclusion**
Bhutan's venture into crypto mining demonstrates its forward-thinking approach and willingness to embrace new technologies. By leveraging its renewable energy resources, the country aims to position itself as a sustainable destination for crypto mining, fostering economic growth and attracting foreign investment. However, Bhutan must strike a careful balance between reaping the benefits of crypto mining and addressing potential challenges, particularly in terms of market volatility, energy management, and environmental sustainability. With proper planning, regulation, and a commitment to sustainability, Bhutan's bet on crypto mining could prove to be a transformative step toward a prosperous future.
**FAQ**
**What is Bhutan's approach to crypto mining?**
Bhutan has embraced crypto mining by leveraging its renewable energy resources, particularly its surplus hydroelectricity. The country aims to attract environmentally conscious miners by offering competitive energy prices and positioning itself as a sustainable destination for crypto mining.
**Why is Bhutan interested in crypto mining?**
Bhutan sees crypto mining as an opportunity for economic growth, job creation, and foreign investment. By capitalizing on the popularity of cryptocurrencies, the country can generate revenue and contribute to infrastructure development.
**What are the potential challenges of crypto mining in Bhutan?**
One challenge is the volatile nature of cryptocurrencies, which can subject mining operations to market fluctuations. Bhutan must also ensure that mining activities do not strain its power grid and cause disruptions in energy supply for other sectors.
**How will Bhutan address environmental concerns?**
Bhutan's commitment to environmental conservation and sustainability means it will establish strict regulations for crypto mining. The country aims to implement energy-efficient mining technologies and monitor the carbon footprint associated with mining operations to minimize environmental impact.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 5d4b6c8d:8a1c1ee3
2024-11-16 00:24:01
I've got Heat-Pacers on and I'm excited about some of the later games.
Is anyone else tuning into the second night of the Emirates Cup?
originally posted at https://stacker.news/items/769843
-

@ 19f9afb8:ce50e4d3
2024-11-15 22:05:01
## Chef's notes
*Make sure you watch your roux closely. It can go from perfect to burnt in a moment.
*Top with green onion tops.
*Sprinkle a very small amount of file over top.
*Andouille sausage is traditional but kielbasa is also a good substitute.
## Details
- ⏲️ Prep time: 30 minutes for vegetable prep + ~1 hour for boiling chicken
- 🍳 Cook time: ~2 hours
- 🍽️ Servings: 8-10
## Ingredients
- 1 large onion
- 1 large bell pepper
- 2 medium stalks celery
- 6-8 cloves garlic
- ~3 lbs. bone-in, skin-on chicken; remove skin and set aside to render
- ~1.5 lbs andouille sausage, browned
- ~1/2 lb. tasso, optional
- 2 green onions, chopped and separated
- 2 cups okra, cut (frozen or fresh, not canned)
- ~1 cup oil (rendered from chicken skins & sausage)
- ~1 cup flour
- 1-2 bay leaves
## Directions
1. Chop all vegetables and set aside. Render the fats from your chicken skins and sausages.
2. Combine your flour and rendered fats in a cast iron skillet and stir continually over medium –low heat until your roux is chocolate brown. Stir in about 1/4 tsp of flour at this stage and cook until it stops “fizzing”. (This is simply to add to the thickening power of the roux.)
3. While you are cooking your roux, boil your chicken until cooked through, remove from heat and broth, and set aside to cool for deboning .
4. Add your vegetables, roux, deboned chicken, sausage, hot sauce, Worcestershire, and spices/seasonings to your broth. Optional: sauté your vegetables, except okra, before adding to broth. (Only add the bottom portions of the green onion here, reserve the green tops for garnish.)
5. Cook until the okra is soft and no longer slimy, about 2 hours, at a low boil. (med-high heat)
6. Optional: reduce to a simmer about 10 minutes before finished and drop a few eggs to poach in the stew before serving. Do not stir.
7. Serve over rice.
-

@ f33c8a96:5ec6f741
2024-11-15 21:45:12
# Voltage Tipper ⚡
A Simple Lightning tipping app template built with NextJS and Voltage.
[Voltage Tipper Video Walkthrough](https://www.youtube.com/watch?v=y2eFBtRLRUk)
To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work!
[](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper)
**Run on Replit**
[https://replit.com/@voltage-cloud/voltage-tipper](https://replit.com/@voltage-cloud/voltage-tipper)
## Table of Contents
1. [Deployment](#deployment)
2. [Environment Variables](#environment-variables)
3. [API](#api)
4. [Contributing](#contributing)
5. [License](#license)
## Deployment
To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work!
[](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper)
## Environment Variables
- `NEXT_PUBLIC_HOST`: The host URL for your LND lightning node (not including port).
- `NEXT_PUBLIC_INVOICE_MACAROON`: The invoice macaroon.
- `NEXT_PUBLIC_READ_MACAROON`: The read-only macaroon.
#### Host
The host is your Node's 'API endpoint' you can copy it from your Voltage Dashboard, be sure to include 'https://'. Example: `https://plebdev.m.voltageapp.io`
#### Macaroons
The Invoice and Read macaroons are authentication tokens that allows you to interact with your LND node's REST API with permissions for reading data, and creating invoices. You can also grab a "Admin" macaroon for permissions to spend but that is not required here since we are only receiving through this webapp, so your funds are safu.
**You can find your Macaroons in your Voltage Dashboard by visiting Manage Access -> Macaroon Bakery**
## API
- `/api/lnurl`
Returns lnurlPay response object defined in [LUD-06](https://github.com/lnurl/luds/blob/luds/06.md)
- `/api/getlnurl`
Returns bech32 encoded lnurlPay
- `/.well-known/lnurlp/{NodeAlias}`
This is your lightning address endpoint, returns lnurlPay response defined in [LUD-16](https://github.com/lnurl/luds/blob/luds/16.md)
- `/api/callback?amount=21000`
This is your callback endpoint that will return an invoice when `amount` query parameter is passed with millisat value
## Contributing
Contributions are welcome! Please open an issue or submit a pull request.
## License
This project is licensed under the MIT License. See the LICENSE file for details.
-

@ 1e286f5c:cc2c5009
2024-11-15 21:27:43
### A Battle of Nutrients
A question I often ask myself and to anyone that is willing to listen is:
*****Why spend money on feeding plants a lone nutrient, when you can feed your plants and your soil a whole collection of nutrients (and more) that are water soluble?*****
We can take a look into #Humic + #Fulvic #Acids, a list of nutrients that #microorganisms make available for plant uptake, or even applications of #AminoAcids.
Each choice individually has vast array of benefits by themselves, for now we are going to take a look into Humic and Fulvic acids.
----
## Average Chemical Formulas
**Humic Acid** (*Darker Brown Color*):
* C187 ( 187 #Carbon )
* H186 ( 186 #Hydrogen )
* O89 ( 89 #Oxygen )
* N9 ( 9 #Nitrogen )
* S1 ( 1 #Sulfur )
**Fulvic Acid** (*Yellow / Golden Color*)
* C135 ( 135 Carbon )
* H182 ( 182 Hydrogen )
* O95 ( 95 Oxygen )
* N5 ( 5 Nitrogen )
* S2 ( 2 Sulfur )
---
## A view into the scope.

Here you can see the difference in coloration between the darker brown and golden / yellow color.
A sample taken from one of my #vermicompost bins.
Bonus: A Hyaline Testate Amoeba in the process of cycling 2 fungal spores can be observed.
(Hyaline = Biological substance with a glassy appearance)
----
These acids can be easily obtained through a #CompostTea brew or a #CompostExtract that you can create in your local #bioregion with supplies found all around you. If you are looking for the best bang for your buck, there's no better soil and nutrient architects than those found in nature.
Compared to #fungi and #bacteria (we also can't simply cast aside the multiple trophic levels that break down #OrganicMatter), we are simply inefficient.
However we can provide the environments and food sources to fight along side these #Organisms.
As the Organisms break down the OM overtime, they are creating Humic and Fulvic Acids as well as other #Microaggregates, this is just one process that is transforming lifeless dirt into the dark brown, living #soil we associate as healthy soil.
----
Let's dive into some of the benefits these 2 acids bring to the table.
## Fulvic Acid:
- Considered a powerful organic electrolyte.
- Enhances cell division and elongation.
- As a foliar spray, increases the plant's oxygen uptake capacity.
- Increases chlorophyll production and increases the permeability of plant membranes, which lead to an improvement for the plant to uptake nutrients.
- A unique capacity to dissolve minerals and trace elements.
- Enhances photosynthesis.
- Drought protection via improved moisture storage.
- Dissolves silica and enhances the benefits of silica.
- Increases stomata opening and transpiration.
- Assists plant respiration and improves respiration of beneficial micro-organisms.
- Influences multiple enzymatic processes.
- Stimulates plants immune system.
- ----
## Humic Acid
- Improves Soil Structure
- Increases water holding capacity in soil.
- Improves plant drought resistance.
- Enhances uptake of Nitrogen by plants.
- Stimulates plant enzymes and increases enzyme production.
- Stimulates Growth and proliferation of beneficial microorganisms.
- Enhances plant's natural resistance against diseases and pesticides.
- Stimulates Root growth.
- Increases the thickness of cell walls in fruit, leading to prolonged shelf life.
- Increases germination and viability of seeds.
- Helps increase physical appearance and nutritional value of crop yields.
----
These are far from a full list of benefits, but sheds light on some of the benefits that they bring to the table.
As always, thank you for taking time and checking out the information i've provided.
*Now Onward!*
D.
---
#Permies #Gardening #Microscopy #RegenerativeSoil
#Regenerative
-

@ 3ab7c210:d74e9dbf
2024-11-15 21:11:27
Nostr and Bitcoin technology combined result in upgrading the entire concept of funding and raising money to drive innovation and improve the world.
@Angor introduces a new P2P Funding Protocol and seeks to revolutionize how the capital is raised by stepping into this transformative space, leveraging the potential of Bitcoin and Nostr to advance adoption—not just of these technologies, but of every creative project that will emerge in the years to come.
It's an opportunity to redefine funding entirely and how it is perceived. Funding can be done in more free way for both investors and project funders—free from risks and censorship. This marks a whole new era in how funding is done.
@Angor, as a P2P funding protocol, aims to have a positive impact on individual lives, supporting project founders and investors by helping allocate their scarce resources safely.
It’s also a shift in the structure of how capital is raised. The future of fundraising is evolving, with solutions already available. Angor embraces this idea and the opportunities that Nostr and Bitcoin offer, driving adoption of decentralized ideas further. Angor is here to lead this growing movement of decentralization and risk-free funding protocol.
-

@ 5d4b6c8d:8a1c1ee3
2024-11-15 21:03:43
This is a requested topic for a future podcast episode. I do have a giant spreadsheet with a bunch of stats and stuff in it to help figure this out, but I'm doing this off the top of my head.
# My Top 10
1. Jordan: 6 titles, 6 Finals MVPs, 5 MVPs, 1 DPOY, and tops by my eye test
2. Lebron: 4 titles, 4 Finals MVPs, 4 MVPs, 20 All-NBAs, holds virtually all the career playoff stats
3. Kareem: 6 titles, 2 Finals MVPs, 6 MVPs, 15 All-NBAs, also the greatest HS and college player ever
4. Wilt: 2 titles, 1 Finals MVP, 4 MVPs, 10 All-NBAs, holds virtually all single game and single season records
5. Magic: 5 titles, 3 Finals MVPs, 3 MVPs, 10 All-NBAs, greatest passer of all time and played every position
6. Bird: 3 titles, 2 Finals MVPs, 3 MVPs, 10 All-NBAs, most well-rounded player ever
7. Russell: 11 titles, 5 MVPs, 11 All-NBAs, greatest winner in the history of professional sports
8. Duncan: 5 titles, 3 Finals MVPs, 2 MVPs, 15 All-NBAs, most underrated player in NBA history
9. Kobe: 5 titles, 2 Finals MVPs, 1 MVP, 15 All-NBAs, 12 All-Defense teams, more All-Star MVPs than anyone
10. Steph: 4 titles, 1 Finals MVP, 2 MVPs, 10 All-NBA, greatest shooter ever
Honorable mentions: Shaq and Jokic
Shaq and Steph are a toss-up to me. I came down on the side of positional balance. You could think of this as an All-time 1st and 2nd team, rather than purely a top 10.
I expect Jokic to make it, but he's right in the middle of his prime and hasn't yet matched the career achievements of these guys.
Let the arguments begin!
originally posted at https://stacker.news/items/769603
-

@ e1d968f7:5d90f764
2024-11-15 19:20:44
Welcome to *Behind Closed Doors*, my daily dive into what it's really like to work as an escort. I'm Rebecca, and I’m excited to share this journey with you—an open, honest, and sometimes cheeky look behind the scenes of my world. This isn’t just about the physical side of escorting (though we’ll get to those stories); it’s about the whole experience: the clients, the emotions, the personal growth, and the challenges that come with it.
Starting out, I had my share of nerves and doubts. This line of work has a lot of stereotypes attached, and everyone seems to have an opinion on it. But for me, becoming an escort has been a path to independence and empowerment. I get to choose who I spend my time with, set my own boundaries, and earn in a way that works for me. That level of freedom is priceless.
Over the next posts, I'll be sharing the truths that many don’t see—moments that range from sexy to funny, uplifting to intense. Whether you're here out of curiosity, to challenge your own views, or just for a bit of escapism, I’m glad you’re joining me. Let’s break down some myths and get real about what it’s like to walk in my heels.
So, cheers to new beginnings! Here’s to an adventure, to honesty, and to a little bit of mischief along the way.
Rebecca x
-

@ e1d968f7:5d90f764
2024-11-15 19:15:56
After yesterday’s introduction, let’s dive into one of the most common questions I get: *Why did you choose to become an escort?* It’s a question loaded with assumptions, and the answer is more complex than most people think.
For me, it wasn’t a spur-of-the-moment decision. It was about control—over my time, my finances, and my life. Like many others, I’ve had traditional jobs, and while they were fine, they left me feeling boxed in. I craved something that allowed me to work on my own terms, to meet people, and to experience a kind of freedom that a 9-to-5 could never give me.
But it wasn’t just about money or flexibility. I’ve always loved connecting with people on a deeper level, and this job lets me do that in ways I didn’t expect. There’s something fulfilling about creating moments of intimacy and understanding—whether it’s helping someone feel seen, offering companionship, or just giving them an escape from their daily lives.
Of course, I had my hesitations. Would I feel safe? Would people judge me? Could I handle the emotional side of the work? I did my research, set boundaries, and slowly built the confidence to enter this world on my terms.
Choosing this path wasn’t about desperation or lack of options—it was about taking charge of my life in a way that felt authentic to me. Escorting might not be for everyone, but for me, it’s been empowering, challenging, and deeply rewarding.
Tomorrow, I’ll talk about one of the first steps I took to get started: creating my escort persona. Until then, thanks for coming along on this journey.
Rebecca x
-

@ 2348ca50:32a055a8
2024-11-15 19:04:13
[Electrical repair is often seen as a daunting task, one](https://seqelectricalandenergy.com.au/electrician-redbank-plains/) that can evoke a sense of dread in homeowners and business owners alike. The thought of dealing with electrical problems can be overwhelming, particularly when safety is a concern.
Electrical systems are complex and, if not handled correctly, can lead to severe consequences, including fires, electrocution, and extensive property damage. In this article, we will explore the various aspects of electrical repair, the significance of addressing electrical issues promptly, and the factors that contribute to the perception of electrical repair as a big issue.
Understanding the Complexity of Electrical Systems
Electrical systems consist of intricate components that work together to power homes and businesses. These systems include wiring, circuit breakers, outlets, switches, and appliances. When an electrical issue arises, it often stems from a malfunction in one or more of these components. Common problems include faulty wiring, tripped circuit breakers, overloaded circuits, and malfunctioning outlets or switches.
The complexity of electrical systems is one of the reasons why electrical repair is perceived as a significant issue. Unlike some home repairs, such as fixing a leaky faucet or patching a wall, electrical work requires specialized knowledge and skills. Improper repairs can lead to dangerous situations, which is why many people hesitate to tackle electrical issues on their own.
Safety Concerns
Safety is paramount when it comes to electrical work. The potential risks associated with electrical repairs include:
Electrocution: Working with live wires poses a serious risk of electrocution. Even a minor shock can be harmful, while severe shocks can lead to fatal injuries.
Electrical Fires: Faulty wiring or overloaded circuits can spark electrical fires, which can spread quickly and cause extensive damage to property and lives.
Property Damage: Improper repairs can lead to further damage within the electrical system, resulting in costly repairs and potential loss of property.
Due to these safety concerns, many individuals prefer to hire a licensed electrician to handle electrical repairs. Electricians are trained to follow safety protocols and ensure that all repairs meet local electrical codes. This professional expertise not only mitigates risks but also provides peace of mind to homeowners and business owners.
The Cost Factor
Another aspect that contributes to the perception of electrical repair as a significant issue is the cost. Electrical repairs can vary in price depending on the complexity of the problem, the materials needed, and the labor involved. While some minor repairs may be relatively inexpensive, more extensive issues can lead to substantial expenses.
Homeowners may find themselves facing bills for:
Service Calls: Many electricians charge a service fee for coming to inspect the problem.
Parts and Materials: Replacement parts can vary in cost depending on the type and quality of the materials needed for the repair.
Labor Costs: Electricians typically charge by the hour, and rates can vary based on experience and location.
Code Compliance: In some cases, electrical repairs may require updates to comply with current codes, leading to additional expenses.
This financial burden can make electrical repair seem like a significant issue, prompting homeowners to delay repairs, which can lead to even more costly problems in the future.
Common Electrical Issues
To better understand why electrical repair is often viewed as a big issue, let’s examine some common electrical problems that homeowners may encounter:
Tripped Circuit Breakers: Frequent tripping of circuit breakers can indicate an overloaded circuit, a short circuit, or a ground fault. While resetting a breaker is simple, persistent issues may require professional attention.
Flickering Lights: Flickering lights can result from loose wiring, a faulty light fixture, or an overloaded circuit. Addressing the underlying cause is crucial to prevent further electrical issues.
Dead Outlets: Outlets that no longer work can be caused by faulty wiring, tripped breakers, or blown fuses. Identifying the cause is essential to restore power safely.
Electrical Shocks: If a person experiences shocks when using an appliance or outlet, it indicates a serious problem that requires immediate attention.
Burning Smells or Scorch Marks: Any burning smell or visible scorch marks around outlets or switches can signify overheating wiring, which poses a fire risk and necessitates immediate repair.
DIY vs. Hiring a Professional
When faced with electrical issues, homeowners often grapple with the decision of whether to attempt a DIY repair or hire a professional. While there are minor electrical tasks that can be safely performed by individuals with basic knowledge—such as replacing a light bulb or changing a fuse—most electrical repairs are best left to licensed electricians.
Reasons to Hire a Professional:
Expertise: Electricians have undergone extensive training and possess the skills necessary to diagnose and repair electrical issues safely and effectively.
Safety Compliance: Professionals are familiar with local electrical codes and regulations, ensuring that repairs meet safety standards.
Warranty and Insurance: Many licensed electricians offer warranties on their work, providing assurance that if something goes wrong, the repair will be covered. Additionally, they carry liability insurance to protect homeowners in case of accidents.
Time and Convenience: Electrical repairs can be time-consuming, especially for those without experience. Hiring a professional saves time and reduces the risk of costly mistakes.
The Importance of Timely Repairs
Delaying electrical repairs can lead to escalating issues that may compromise safety and result in higher costs down the line. Here are some reasons why timely electrical repairs are essential:
Preventing Further Damage: Addressing electrical problems promptly can prevent them from worsening, saving money on extensive repairs.
Ensuring Safety: Timely repairs reduce the risk of electrical fires, shocks, and other safety hazards associated with malfunctioning electrical systems.
Maintaining Property Value: Regular maintenance and prompt repairs help maintain the value of a property. Potential buyers may be deterred by known electrical issues, leading to decreased marketability.
Improving Energy Efficiency: Faulty electrical systems can lead to increased energy consumption. Prompt repairs can improve energy efficiency, resulting in lower utility bills.
Conclusion
In conclusion, electrical repair is indeed a significant issue that requires careful consideration and prompt action. The complexity of electrical systems, coupled with safety concerns and potential costs, contributes to the perception that electrical problems are daunting. While some minor tasks can be handled by homeowners, most electrical repairs should be entrusted to licensed professionals to ensure safety and compliance with local codes.
Timely repairs are crucial to prevent further damage, maintain safety, and preserve property value. By understanding the common electrical issues, weighing the pros and cons of DIY versus professional help, and recognizing the importance of addressing problems promptly, homeowners can navigate the complexities of electrical repair with confidence. Ultimately, addressing electrical issues proactively not only safeguards lives and property but also promotes a safe and efficient living environment.
-

@ f33c8a96:5ec6f741
2024-11-15 18:31:02
# JavaScript Cheatsheet for Beginners
## Table of Contents
1. [Variable Declaration](#variable-declaration)
2. [Basic Data Types](#basic-data-types)
3. [Operators](#operators)
4. [Objects](#objects)
5. [Functions](#functions)
6. [Arrays](#arrays)
7. [Conditional Statements](#conditional-statements)
8. [Loops](#loops)
9. [Error Handling](#error-handling)
10. [ES6+ Features](#es6-features)
11. [DOM Manipulation](#dom-manipulation)
12. [Event Handling](#event-handling)
13. [Asynchronous JavaScript](#asynchronous-javascript)
14. [Modules](#modules)
## Variable Declaration
In JavaScript, variables can be declared using `var`, `let`, or `const`.
```javascript
var x = 5; // Function-scoped variable (avoid using in modern JavaScript)
let y = 10; // Block-scoped variable
const MAX_POINTS = 100; // Constant (cannot be reassigned)
```
- `var` is function-scoped and hoisted (avoid using in modern JavaScript).
- `let` is block-scoped and can be reassigned.
- `const` is block-scoped and cannot be reassigned (but object properties can be modified).
## Basic Data Types
JavaScript has several basic data types.
```javascript
let num = 42; // Number
let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats)
let str = "Hello, World!"; // String
let bool = true; // Boolean
let nullValue = null; // Null
let undefinedValue; // Undefined
let symbol = Symbol("unique"); // Symbol (ES6+)
let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+)
```
- `Number`: Represents both integers and floating-point numbers.
- `String`: Represents textual data.
- `Boolean`: Represents `true` or `false`.
- `Null`: Represents a deliberate non-value.
- `Undefined`: Represents a variable that has been declared but not assigned a value.
- `Symbol`: Represents a unique identifier.
- `BigInt`: Represents integers larger than 2^53 - 1.
## Operators
JavaScript includes various types of operators for different operations.
```javascript
// Arithmetic Operators
let sum = 5 + 3; // Addition: 8
let diff = 10 - 4; // Subtraction: 6
let product = 3 * 4; // Multiplication: 12
let quotient = 15 / 3;// Division: 5
let remainder = 17 % 5;// Modulus: 2
let power = 2 ** 3; // Exponentiation: 8
let increment = 5;
increment++; // Increment: 6
let decrement = 5;
decrement--; // Decrement: 4
// Assignment Operators
let x = 10; // Basic assignment
x += 5; // Addition assignment (x = x + 5)
x -= 3; // Subtraction assignment
x *= 2; // Multiplication assignment
x /= 4; // Division assignment
x %= 3; // Modulus assignment
x **= 2; // Exponentiation assignment
// Comparison Operators
console.log(5 == "5"); // Equal to (with type coercion): true
console.log(5 === "5"); // Strictly equal to: false
console.log(7 != "7"); // Not equal to: false
console.log(7 !== "7"); // Strictly not equal to: true
console.log(10 > 5); // Greater than: true
console.log(10 >= 10); // Greater than or equal to: true
console.log(5 < 10); // Less than: true
console.log(5 <= 5); // Less than or equal to: true
// Logical Operators
let a = true, b = false;
console.log(a && b); // Logical AND: false
console.log(a || b); // Logical OR: true
console.log(!a); // Logical NOT: false
// Nullish Coalescing Operator (ES2020)
let nullValue = null;
let defaultValue = nullValue ?? "default"; // "default"
// Optional Chaining Operator (ES2020)
let user = {
address: {
street: "123 Main St"
}
};
console.log(user?.address?.street); // "123 Main St"
console.log(user?.contact?.email); // undefined
// Bitwise Operators
console.log(5 & 3); // Bitwise AND: 1
console.log(5 | 3); // Bitwise OR: 7
console.log(5 ^ 3); // Bitwise XOR: 6
console.log(~5); // Bitwise NOT: -6
console.log(5 << 1); // Left shift: 10
console.log(5 >> 1); // Right shift: 2
console.log(5 >>> 1); // Unsigned right shift: 2
// String Operators
let str1 = "Hello";
let str2 = "World";
console.log(str1 + " " + str2); // Concatenation: "Hello World"
let greeting = "Hello";
greeting += " World"; // Concatenation assignment
// Type Operators
console.log(typeof "Hello"); // "string"
console.log(typeof 123); // "number"
console.log(typeof true); // "boolean"
console.log(obj instanceof Object); // Check if object is instance of a class
```
Key points about operators:
- Arithmetic operators perform mathematical operations
- Assignment operators combine operation with assignment
- Comparison operators return boolean values
- Logical operators work with boolean values and provide short-circuit evaluation
- Nullish coalescing (??) provides a way to specify a default value
- Optional chaining (?.) safely accesses nested object properties
- Bitwise operators perform operations on binary representations
- String operators handle string concatenation
- Type operators help determine variable types
## Objects
Objects are collections of key-value pairs.
```javascript
let person = {
name: "Alice",
age: 30,
sayHello: function() {
console.log("Hello, my name is " + this.name);
}
};
// Accessing object properties
console.log(person.name); // Alice
console.log(person["age"]); // 30
// Calling object methods
person.sayHello(); // Hello, my name is Alice
// Adding a new property
person.job = "Developer";
// Object destructuring (ES6+)
let { name, age } = person;
console.log(name, age); // Alice 30
```
- Objects can contain properties and methods.
- Properties can be accessed using dot notation or bracket notation.
- New properties can be added dynamically.
- Object destructuring allows you to extract multiple properties at once.
## Functions
Functions are reusable blocks of code.
```javascript
// Function declaration
function greet(name) {
return "Hello, " + name + "!";
}
// Function expression
const multiply = function(a, b) {
return a * b;
};
// Arrow function (ES6+)
const add = (a, b) => a + b;
// Default parameters (ES6+)
function power(base, exponent = 2) {
return Math.pow(base, exponent);
}
console.log(greet("Alice")); // Hello, Alice!
console.log(multiply(3, 4)); // 12
console.log(add(5, 3)); // 8
console.log(power(3)); // 9
console.log(power(2, 3)); // 8
```
- Functions can be declared using the `function` keyword or as arrow functions.
- Arrow functions provide a more concise syntax and lexically bind `this`.
- Default parameters allow you to specify default values for function arguments.
## Arrays
Arrays are ordered lists of values.
```javascript
let fruits = ["apple", "banana", "orange"];
// Accessing array elements
console.log(fruits[0]); // apple
// Array methods
fruits.push("grape"); // Add to the end
fruits.unshift("mango"); // Add to the beginning
let lastFruit = fruits.pop(); // Remove from the end
let firstFruit = fruits.shift(); // Remove from the beginning
// Iterating over arrays
fruits.forEach(fruit => console.log(fruit));
// Array transformation
let upperFruits = fruits.map(fruit => fruit.toUpperCase());
// Filtering arrays
let longFruits = fruits.filter(fruit => fruit.length > 5);
// Reducing arrays
let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0);
// Spread operator (ES6+)
let moreFruits = ["kiwi", "pear"];
let allFruits = [...fruits, ...moreFruits];
```
- Arrays can contain elements of any type.
- Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array.
- Higher-order functions like `map`, `filter`, and `reduce` create new arrays.
- The spread operator `...` can be used to combine arrays.
## Conditional Statements
Conditional statements allow you to execute code based on certain conditions.
```javascript
let age = 18;
// if...else statement
if (age >= 18) {
console.log("You are an adult");
} else {
console.log("You are a minor");
}
// Ternary operator
let status = age >= 18 ? "adult" : "minor";
// switch statement
switch (age) {
case 13:
console.log("You're a teenager");
break;
case 18:
console.log("You're now an adult");
break;
default:
console.log("You're neither 13 nor 18");
}
```
- `if...else` statements allow you to execute different code blocks based on conditions.
- The ternary operator provides a concise way to write simple if-else statements.
- `switch` statements are useful when you have multiple conditions to check against a single value.
## Loops
Loops allow you to repeat code multiple times.
```javascript
// for loop
for (let i = 0; i < 5; i++) {
console.log(i);
}
// while loop
let count = 0;
while (count < 5) {
console.log(count);
count++;
}
// do...while loop
let x = 0;
do {
console.log(x);
x++;
} while (x < 5);
// for...of loop (ES6+)
let numbers = [1, 2, 3, 4, 5];
for (let num of numbers) {
console.log(num);
}
// for...in loop (for object properties)
let person = { name: "Alice", age: 30 };
for (let key in person) {
console.log(key + ": " + person[key]);
}
```
- `for` loops are commonly used when you know how many times you want to iterate.
- `while` loops continue as long as a condition is true.
- `do...while` loops always execute at least once before checking the condition.
- `for...of` loops are used to iterate over iterable objects like arrays.
- `for...in` loops are used to iterate over object properties.
## Error Handling
Error handling allows you to gracefully handle and recover from errors.
```javascript
try {
// Code that might throw an error
throw new Error("Something went wrong");
} catch (error) {
console.error("Caught an error:", error.message);
} finally {
console.log("This always runs");
}
// Custom error
class CustomError extends Error {
constructor(message) {
super(message);
this.name = "CustomError";
}
}
try {
throw new CustomError("A custom error occurred");
} catch (error) {
if (error instanceof CustomError) {
console.log("Caught a custom error:", error.message);
} else {
console.log("Caught a different error:", error.message);
}
}
```
- The `try` block contains code that might throw an error.
- The `catch` block handles any errors thrown in the `try` block.
- The `finally` block always executes, regardless of whether an error was thrown.
- You can create custom error types by extending the `Error` class.
## ES6+ Features
ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript.
```javascript
// Template literals
let name = "Alice";
console.log(`Hello, ${name}!`);
// Destructuring
let [a, b] = [1, 2];
let { x, y } = { x: 3, y: 4 };
// Default parameters
function greet(name = "Guest") {
console.log(`Hello, ${name}!`);
}
// Rest parameters
function sum(...numbers) {
return numbers.reduce((total, num) => total + num, 0);
}
// Spread operator
let arr1 = [1, 2, 3];
let arr2 = [...arr1, 4, 5];
// Arrow functions
const square = x => x * x;
// Classes
class Animal {
constructor(name) {
this.name = name;
}
speak() {
console.log(`${this.name} makes a sound.`);
}
}
// Promises
const fetchData = () => {
return new Promise((resolve, reject) => {
// Asynchronous operation
setTimeout(() => resolve("Data fetched"), 1000);
});
};
// Async/Await
async function getData() {
try {
const data = await fetchData();
console.log(data);
} catch (error) {
console.error(error);
}
}
```
- Template literals allow for easy string interpolation.
- Destructuring makes it easy to extract values from arrays or properties from objects.
- Default parameters provide fallback values for function arguments.
- Rest parameters allow functions to accept an indefinite number of arguments as an array.
- The spread operator can be used to expand arrays or objects.
- Arrow functions provide a concise syntax for writing function expressions.
- Classes provide a cleaner syntax for creating objects and implementing inheritance.
- Promises and async/await simplify asynchronous programming.
## DOM Manipulation
DOM manipulation allows you to interact with HTML elements on a web page.
```javascript
// Selecting elements
const element = document.getElementById("myElement");
const elements = document.getElementsByClassName("myClass");
const queryElement = document.querySelector(".myClass");
const queryElements = document.querySelectorAll(".myClass");
// Modifying elements
element.textContent = "New text content";
element.innerHTML = "<strong>New HTML content</strong>";
element.style.color = "red";
element.classList.add("newClass");
element.classList.remove("oldClass");
// Creating and appending elements
const newElement = document.createElement("div");
newElement.textContent = "New element";
document.body.appendChild(newElement);
// Removing elements
element.parentNode.removeChild(element);
// or
element.remove(); // Modern browsers
```
- The DOM (Document Object Model) represents the structure of an HTML document.
- You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`.
- Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`.
- New elements can be created with `createElement` and added to the DOM with `appendChild`.
- Elements can be removed using `removeChild` or the `remove` method.
## Event Handling
Event handling allows you to respond to user interactions and other events.
```javascript
const button = document.querySelector("#myButton");
// Adding event listeners
button.addEventListener("click", function(event) {
console.log("Button clicked!");
console.log("Event object:", event);
});
// Removing event listeners
function handleClick(event) {
console.log("Button clicked!");
}
button.addEventListener("click", handleClick);
button.removeEventListener("click", handleClick);
// Event delegation
document.body.addEventListener("click", function(event) {
if (event.target.matches("#myButton")) {
console.log("Button clicked using event delegation!");
}
});
// Preventing default behavior
const link = document.querySelector("a");
link.addEventListener("click", function(event) {
event.preventDefault();
console.log("Link click prevented");
});
```
- Event listeners can be added to elements using the `addEventListener` method.
- The event object contains information about the event that occurred.
- Event listeners can be removed using `removeEventListener`.
- Event delegation allows you to handle events for multiple elements with a single listener.
- `preventDefault` can be used to stop the default action of an event.
## Asynchronous JavaScript
Asynchronous JavaScript allows you to perform operations without blocking the main thread.
```javascript
// Callbacks
function fetchData(callback) {
setTimeout(() => {
callback("Data fetched");
}, 1000);
}
fetchData(data => console.log(data));
// Promises
function fetchDataPromise() {
return new Promise((resolve, reject) => {
setTimeout(() => {
resolve("Data fetched");
}, 1000);
});
}
fetchDataPromise()
.then(data => console.log(data))
.catch(error => console.error(error));
// Async/Await
async function fetchDataAsync() {
try {
const data = await fetchDataPromise();
console.log(data);
} catch (error) {
console.error(error);
}
}
fetchDataAsync();
// Fetch API
fetch('https://api.example.com/data')
.then(response => response.json())
.then(data => console.log(data))
.catch(error => console.error('Error:', error));
```
- Callbacks are functions passed as arguments to be executed later.
- Promises represent the eventual completion or failure of an asynchronous operation.
- Async/await provides a more synchronous-looking way to write asynchronous code.
- The Fetch API is a modern interface for making HTTP requests.
## Modules
Modules allow you to organize your code into reusable pieces.
```javascript
// math.js
export function add(a, b) {
return a + b;
}
export function multiply(a, b) {
return a * b;
}
// main.js
import { add, multiply } from './math.js';
console.log(add(5, 3)); // 8
console.log(multiply(4, 2)); // 8
// Default export
// utils.js
export default function sayHello(name) {
console.log(`Hello, ${name}!`);
}
// main.js
import sayHello from './utils.js';
sayHello("Alice"); // Hello, Alice!
```
- The `export` keyword is used to expose functions, objects, or primitives from a module.
- The `import` keyword is used to bring functionality from other modules into the current module.
- Default exports can be imported without curly braces and can be given any name when importing.
This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs.
-

@ f33c8a96:5ec6f741
2024-11-15 18:25:12
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/kFUIfaCpXzA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ f33c8a96:5ec6f741
2024-11-15 18:23:58
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/7dsR7um-DxA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ f33c8a96:5ec6f741
2024-11-15 18:21:00
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/QY6euaT_G_E?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ f33c8a96:5ec6f741
2024-11-15 18:06:42
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/tGVxP4RgyI4?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 468f729d:5ab4fd5e
2024-11-15 17:52:45
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 6bae33c8:607272e8
2024-11-15 17:41:15
I went 4-1 again [last week](https://www.realmansports.com/p/circa-millions-bbf) to put myself at 8-2 for Q3 and 21-9 over the last six weeks. It’s too bad I did so poorly Weeks 1-4.
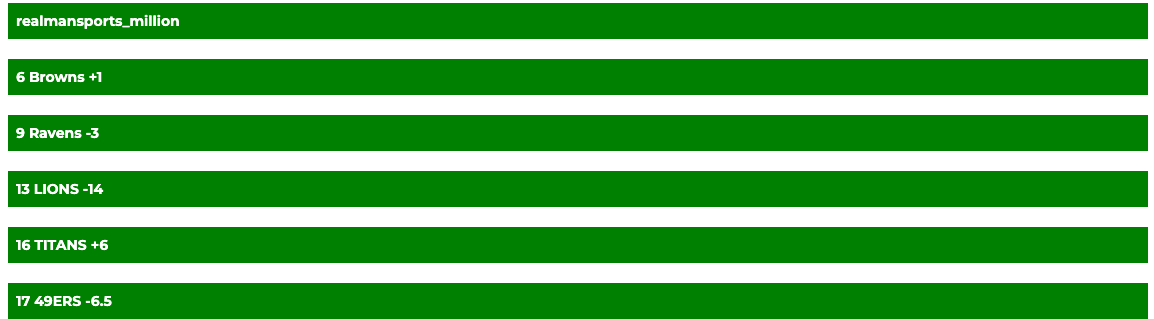**Browns +1 at Saints** — I don’t know why I’m taking Jameis Winston, but I figure the Saints are a good sell-high off their close win, and the Browns have more weapons in the passing game.
**Ravens -3 at Steelers** — The Ravens are in a different class than the Steelers, and they’ll be up for this one.
**Lions -14 vs Jaguars** — I usually don’t take double-digit favorites, but the Lions should grind Jacksonville into oblivion.
**Titans +6 vs Vikings** — This one came to me in a vision of sorts. I asked my mind what should be my fifth pick, and it highlighted the Titans. (I did the same thing with the Bucs last week, but didn’t say anything about it because I hated the pick.) The Titans defense could give struggling Sam Darnold trouble too.
**49ers -6.5 vs Seahawks** — Division games can go either way, but the Seahawks can’t pass protect to save their lives, and it feels like the 49ers are about to go on a run.
-

@ f15638f3:702ff079
2024-11-15 17:31:34
I AM CARELITO
-

@ 59f0660b:d5d24440
2024-11-15 17:27:53
Bitcoin is often regarded as the only true decentralized digital currency offering freedom for several compelling reasons. Here are ten key points:
1. First-Mover Advantage
Bitcoin was the first cryptocurrency, introduced in 2009 by Satoshi Nakamoto, and it set the standard for decentralization. It operates without any central authority or intermediary, serving as a trustless system【6】【8】.
2. Decentralized Network
Bitcoin's network is maintained by a vast array of miners and nodes spread globally. This decentralization makes it nearly impossible for any single entity or group to control or manipulate the system【7】.
3. Immutable Blockchain
Bitcoin's blockchain is immutable, meaning that once a transaction is confirmed, it cannot be altered. This ensures transparency and trust, key factors in maintaining decentralization【6】【9】.
4. Censorship Resistance
Bitcoin transactions are peer-to-peer, bypassing banks and governments. This makes it difficult for any authority to censor transactions, providing freedom of use even in restrictive environments【9】【10】.
5. Open Source Code
Bitcoin's code is open-source, allowing anyone to review, improve, or fork the project. This transparency ensures community trust and reduces reliance on centralized developers【6】【8】.
6. Proof-of-Work Consensus
Bitcoin's proof-of-work (PoW) mechanism is considered one of the most secure and decentralized consensus models. It requires computational power to validate transactions, ensuring no entity can dominate easily【7】.
7. Fixed Supply
Bitcoin has a hard cap of 21 million coins, enforced by its code. This scarcity makes it immune to inflationary policies or manipulation by centralized entities【8】.
8. Independence from Institutions
Unlike many other cryptocurrencies tied to specific companies, protocols, or foundations, Bitcoin has no central organization controlling its development or marketing【6】【7】.
9. Resilient to Hard Forks
Bitcoin’s governance model and community ethos have ensured it remains resilient despite several hard forks (e.g., Bitcoin Cash), which have not succeeded in supplanting Bitcoin’s dominance【9】【10】.
10. Global Acceptance and Network Effect
Bitcoin has the largest adoption, recognition, and infrastructure compared to any other cryptocurrency. Its acceptance by individuals, merchants, and institutions reinforces its position as the leading decentralized digital currency【8】【10】.
Other cryptocurrencies may claim decentralization but often have trade-offs like pre-mines, centralized foundations, or governance structures that reduce their degree of freedom compared to Bitcoin. Would you like to explore this further?
-

@ 59f0660b:d5d24440
2024-11-15 17:27:53
Bitcoin is often regarded as the only true decentralized digital currency offering freedom for several compelling reasons. Here are ten key points:
1. First-Mover Advantage
Bitcoin was the first cryptocurrency, introduced in 2009 by Satoshi Nakamoto, and it set the standard for decentralization. It operates without any central authority or intermediary, serving as a trustless system【6】【8】.
2. Decentralized Network
Bitcoin's network is maintained by a vast array of miners and nodes spread globally. This decentralization makes it nearly impossible for any single entity or group to control or manipulate the system【7】.
3. Immutable Blockchain
Bitcoin's blockchain is immutable, meaning that once a transaction is confirmed, it cannot be altered. This ensures transparency and trust, key factors in maintaining decentralization【6】【9】.
4. Censorship Resistance
Bitcoin transactions are peer-to-peer, bypassing banks and governments. This makes it difficult for any authority to censor transactions, providing freedom of use even in restrictive environments【9】【10】.
5. Open Source Code
Bitcoin's code is open-source, allowing anyone to review, improve, or fork the project. This transparency ensures community trust and reduces reliance on centralized developers【6】【8】.
6. Proof-of-Work Consensus
Bitcoin's proof-of-work (PoW) mechanism is considered one of the most secure and decentralized consensus models. It requires computational power to validate transactions, ensuring no entity can dominate easily【7】.
7. Fixed Supply
Bitcoin has a hard cap of 21 million coins, enforced by its code. This scarcity makes it immune to inflationary policies or manipulation by centralized entities【8】.
8. Independence from Institutions
Unlike many other cryptocurrencies tied to specific companies, protocols, or foundations, Bitcoin has no central organization controlling its development or marketing【6】【7】.
9. Resilient to Hard Forks
Bitcoin’s governance model and community ethos have ensured it remains resilient despite several hard forks (e.g., Bitcoin Cash), which have not succeeded in supplanting Bitcoin’s dominance【9】【10】.
10. Global Acceptance and Network Effect
Bitcoin has the largest adoption, recognition, and infrastructure compared to any other cryptocurrency. Its acceptance by individuals, merchants, and institutions reinforces its position as the leading decentralized digital currency【8】【10】.
Other cryptocurrencies may claim decentralization but often have trade-offs like pre-mines, centralized foundations, or governance structures that reduce their degree of freedom compared to Bitcoin. Would you like to explore this further?
-

@ 59f0660b:d5d24440
2024-11-15 17:17:30
What is Yakihonne?
Yakihonne is a decentralized social media platform built on the Nostr protocol and integrates Bitcoin as its financial layer. It provides a censorship-resistant environment for publishing and engaging with content like blogs, flash news, videos, and curated media. Yakihonne emphasizes freedom of speech, decentralized identity management, and seamless financial transactions via Bitcoin's Lightning Network【6】【7】【9】.
---
Why Yakihonne? (6 Reasons)
1. Censorship Resistance: It ensures free speech by operating on a decentralized protocol, avoiding centralized control【7】【9】.
2. User Autonomy: Users retain full control over their data and identities using cryptographic keys【9】【10】.
3. Monetization with Bitcoin: Integrating the Lightning Network enables instant, borderless payments【6】【9】.
4. Interoperability: Supports cross-platform usage within the Nostr ecosystem, allowing users to move seamlessly across applications【6】.
5. Community-Driven Innovation: The platform evolves with input from its user base and developers【10】.
6. Privacy-Centric Design: Avoids the pitfalls of ad-based or surveillance-driven models seen in traditional social platforms【9】【10】.
---
How Yakihonne Relates to Bitcoin and Nostr (5 Reasons)
1. Bitcoin Payments: Enables direct microtransactions via the Lightning Network, including features like tipping ("zaps") and monetizing content【7】【8】.
2. Decentralized Identity: Built on Nostr, Yakihonne uses cryptographic keypairs to ensure secure, private user authentication【6】【9】.
3. Aligned Philosophies: Both Nostr and Bitcoin prioritize decentralization and user sovereignty【6】.
4. Economic Incentives: By combining content creation with Bitcoin monetization, it aligns incentives for creators and participants【7】【9】.
5. Interoperable Ecosystem: Being Nostr-compatible, Yakihonne integrates smoothly into other decentralized applications that share similar values【6】【8】.
---
The Future of Yakihonne (5 Predictions)
1. Increased Adoption: As demand for censorship-resistant platforms grows, Yakihonne is likely to attract more users【7】【8】.
2. Expansion of Features: Ongoing updates, like Yakihonne 2.0, suggest an emphasis on performance improvements and new tools for creators【9】.
3. Enhanced Financial Integration: The integration with Bitcoin and Lightning will grow, offering diverse monetization options【9】.
4. Broader Decentralized Ecosystem: Yakihonne's compatibility with Nostr positions it as a hub in the decentralized internet revolution【6】【7】.
5. Resilience to Censorship: As centralized platforms face increasing scrutiny, Yakihonne’s decentralized approach offers a viable alternative【9】【10】.
Let me know if you'd like further details or links to explore these topics in-depth!
-

@ 84999652:2a24d806
2024-11-15 16:22:23
### Gavin, BeeGee (Super Bitcoin和BEVM 核心建设者)
2024年11月15日
---
### —— 从财产保护到文明守护,比特币的机械共识为人工智能时代提供终极护盾
**科技的加速与潜在威胁:霍金、维纳与当下挑战**
人类已经步入人工智能时代,随着技术的快速进步,我们正面对前所未有的复杂性和不确定性。科技的飞速发展不仅改变了社会结构,也带来了诸多潜在威胁,尤其是在人工智能领域。
霍金等科学家早已对这一进程的潜在危险发出警告。霍金认为,人工智能的无序发展有可能威胁到人类的生存,他指出:“我们可能在不久的将来面临人工智能崛起带来的种种风险。”同样,控制论奠基人之一的维纳也曾警告过科技失控对人类文明的危害,尤其是在自动化与自适应系统的推行过程中。维纳曾在《控制论》中提到,“人类创造的机器,若不加以控制,最终可能会摧毁我们自己的文明。”
近年来,随着AGI(通用人工智能)技术的飞速发展,科技失控的风险变得愈加突出。马斯克对此深感忧虑,并公开表示AGI有可能对人类构成生存威胁,因此他成立了xAI,致力于开发有益于人类的安全人工智能。此外,尤瓦尔·赫拉利在其《智人之上:从石器时代到AI时代的信息网络简史》中提到,人工智能已经不仅是工具,而是具备了自主决策的能力,这使得AI可能不再听从人类的指挥,进而对社会秩序构成冲击。
这些警告清楚地表明,如何确保科技进步服务于人类、避免其威胁人类生存,已成为当今亟待解决的重大问题。
**人类大脑的极限与社会共识的崩溃**
回到人类自身,信息的爆炸式增长对人类大脑的处理能力提出了严峻考验。人类大脑的生物进化远远落后于硅基生物的发展速度。人类作为一个种族,将面临着和“人工智能种族”的竞争。
在过去,人类通过“社会共识”解决了大多数复杂问题,然而在信息化时代,传统的共识机制显然已无法应对日益加剧的复杂性。信息量的指数级增长让我们的思维方式无法与之匹配,社会在快速变化的同时,我们的思维和决策却变得愈发滞后,导致传统的共识方式逐渐失效。
James Rickards 在《MoneyGPT: AI and the Threat to the Global Economy》中提出,控制论是应对这一挑战的重要工具。他认为,科技对决策的加速依赖,尤其是在AI领域,将引发秒级反应,可能导致金融系统甚至社会的连锁崩溃。他进一步指出,“控制论”是指一种不断调整和优化系统反应的思想方式,源自希腊语的“kybernētēs”(舵手),它倡导通过精准的反馈机制来引导系统运行,而不是采取过于激烈的应对措施。
在人工智能时代,单纯依靠传统的“社会共识”已经无法应对这些复杂、快速变化的挑战。我们亟需一种新的、更有效的机制,以应对不断变化的科技局势和社会需求。
**机械共识:应对复杂挑战的关键**
在这种背景下,机械共识作为一种新的自我组织、去中心化的共识形式,成为了应对当前科技挑战的有效方案。与传统的社会共识依赖于人为决策不同,机械共识通过去中心化的自动化博弈,能够在没有人为干预的情况下自我调节并达成一致。正如维纳在其控制论中所强调的,机械共识是一种通过反馈机制优化系统的方式,在信息不断增加的环境下,依然能够保证系统的稳定与安全。
比特币网络便是机械共识最成功的示例之一。比特币通过矿工的算力竞赛和经济激励机制,形成了一个无需外部干预的稳定网络。在比特币网络中,矿工们通过参与算力竞争,为网络提供安全性和去中心化的共识,而比特币的设计确保了这一过程的公平性与不可篡改性。其机制不仅保障了数字资产的安全性,也为信息时代带来了全新的治理模式。
机械共识所展现的力量,正是其能够在无中央控制的情况下,依据设定的规则自动运行,并为人类社会的复杂问题提供解决方案的能力。它让我们看到了技术能够如何超越单一的财富保护,转向对人类生命与文明更广泛的保障。
**比特币:从加密资产到文明守护者的机械共识**
比特币不仅仅是一种加密资产,它代表了机械共识的核心理念。中本聪设计比特币的初衷便是为了建立一个无需信任第三方的自适应增长型网络,而这一理念正是通过比特币的共识机制得以实现的。
比特币的共识机制背后,实际上是一场永无止境的算力竞赛。矿工们为获得比特币奖励,不断投入算力,推动网络的持续增长与自我强化。这种自我强化机制不仅增加了比特币网络的安全性和稳定性,同时也不断增强了其抵抗外部攻击的能力。通过这种正反馈机制,比特币的网络得以不断壮大,其市值从2009年的零增长到目前超过1.8万亿美元,证明了机械共识作为“数字货币”的成功。
然而,比特币所代表的机械共识不仅仅局限于保护数字资产,它为人类应对信息时代的复杂性提供了一个新的解决方案。
**Super Bitcoin:守护人类未来的革新者**
在此基础上,Super Bitcoin应运而生,进一步突破比特币网络的局限。
通过五层架构的设计,Super Bitcoin不仅继承了比特币网络的安全性,还突破了比特币单纯转账的功能,为比特币网络带来了更为丰富的扩展能力。Super Bitcoin在设计中集成了工作量证明(PoW)共识机制,闪电网络,Taproot Consensus等技术,形成了一个更高效、灵活的区块链体系。
这一新的架构使得Super Bitcoin不仅仅是一个数字资产的保护工具,它更像是一个能够为人类社会提供科技管控的平台。通过去中心化、自动化的机械共识,Super Bitcoin能够在控制风险的同时促进技术的发展,并保障人类文明免受潜在的科技威胁。它不仅为协议和应用提供了一个安全、共享的基础设施,更在不断扩展的生态系统中,提供了实现更多人类目标的可能。
**结语:每一枚比特币都是对人类未来的守护**
比特币(BTC)的总量恒定为2100万枚,而全球人口已超过82亿。简单计算,每400人平均共享一枚BTC。从资产角度看,这凸显了比特币的稀缺性和价值。然而,从人类生命安全的角度来看,每枚比特币实际上守护着400条生命。
加密货币的真正价值不仅在于其作为财富的象征,更在于其背后的自适应机械共识。2100万个比特币,每一枚都承载着守护生命的责任。通过机械共识,我们有机会在信息爆炸、科技进步的时代,建立一个更为坚固的社会共识,帮助人类应对复杂的科技尤其是人工智能带来的挑战,确保文明与生命的可持续发展。
-

@ 5d4b6c8d:8a1c1ee3
2024-11-15 15:07:59
Heading into episode 6, here's a rough outline of what we're planning on talking about.
~Stacker_Sports contest updates: UEFA, Cricket, NFL, NBA
Bitcoiner Athletes: two sports celebrities were in the bitcoin news recently
Hockey: a hot start for a surprising team
NFL
- our head-to-head fantasy matchup (if @grayruby still wants to talk about it after his team's reprehensible outing),
- which contenders are on the outside looking in,
- Why are the Bears so bad at picking OC's?
Tyson vs Paul
NBA
- By popular demand, KAT Corner makes a return
- Thoughts and expectations for the Emirates CUp
- Can the best player win MVP on a garbage team?
- Our early hits and misses of the season
Degenerate Corner: bets we're excited about, platforms we're excited about, ongoing bets we have with each other.
originally posted at https://stacker.news/items/769019
-

@ 2775fb0f:887f8193
2024-11-15 13:40:01
-

@ 6fff5148:a5dd5cdf
2024-11-15 12:17:03
* #*🍞☕🍱MORNING TEA🍱☕🍞*
_____________________________________
```Forget about all the reasons why something may not work. You on____ly need to find one good reason why it will.```
_____________________________________
*_Victor IBiz_* 15.11.2024
-

@ 44def29e:2052000d
2024-11-15 11:31:28
Es un bosque de hayas situado en el municipio español de Cantalojas, Sierra de Ayllón, en el Sistema Central. Es uno de los hayedos más meridionales de Europa y destaca por su belleza y singularidad. Predominan las hayas, pero también hay robles, pinos, tejos, acebos y otras especies. Declarado Patrimonio de la Humanidad en 2017, junto con otros hayedos de Europa, como extensión de los Hayedos primarios de los Cárpatos.
Track: https://elcorrelimos.com/hayedo-de-la-tejera-negra/
| | | |
| --- | --- | --- |
|  |  | |
|  |  |  |
|  |  |  |
-

@ 98589a2e:bf49daa1
2024-11-15 10:26:44
**Эстетическая часть Санкт-Петербурга претерпела значительные изменения, отражая динамичное развитие города и его стремление к инновациям. С населением, достигшим 6,5 миллионов человек, культурные инициативы и мероприятия стали более разнообразными и доступными для всех жителей.**

## Разнообразие культурных событий
Санкт-Петербург продолжает оставаться центром культурной жизни России, предлагая жителям и туристам широкий спектр мероприятий:
**Фестивали**: В городе проводятся многочисленные фестивали, такие как «Северное сияние», объединяющий музыку, искусство и литературу. Этот фестиваль стал площадкой для молодых талантов и известных артистов.
**Театры и спектакли**: Петербургские театры активно развивают свои программы, предлагая как классические постановки, так и современные интерпретации. Фестиваль «Театр без границ» привлекает внимание к инклюзивным спектаклям с тифлокомментированием и сурдопереводом.
**Выставки и арт-пространства**: В обновленном Апраксином дворе открылись новые галереи и коворкинги, где проводятся выставки современных художников и мастер-классы. Это пространство стало важным центром для творческих людей города.

## Новые культурные объекты
В Петербурге появились значимые культурные объекты:
**Планетарий и океанариум**: Новый планетарий стал не только крупнейшим в стране, но и интерактивным центром изучения астрономии. Океанариум во Фрунзенском районе стал научно-познавательным центром, предлагающим уникальные выставки о морской биологии.
**Культурные кластеры**: В рамках Генерального плана создано несколько культурных кластеров, в которых сосредоточены театры, художественные школы и образовательные центры. Это способствует обмену знаниями и культурному взаимодействию между различными направлениями искусства.

## Устойчивое развитие культуры
Культурная жизнь Петербурга также ориентирована на устойчивое развитие:
**Зеленые насаждения**: новые парковые зоны и благоустроенные набережные стали местом проведения культурных мероприятий на свежем воздухе. Здесь организуются концерты, выставки и ярмарки.
**Инклюзия в культуре**: культурные инициативы становятся более доступными для людей с ограниченными возможностями. Участие таких людей в культурной жизни города активно поддерживается с помощью специальных программ и мероприятий.

**Разнообразие мероприятий, новые культурные объекты и акцент на инклюзивности делают петербургскую культуру доступной и привлекательной для всех. Город продолжает развиваться, сохраняя свою уникальную атмосферу и традиции.**
### Как вам инициативы развития культурной жизни города?
-

@ c2827524:5f45b2f7
2024-11-15 10:11:29
<h2>Partigiani a Milano</h2>
tra le tante opportunità che Milano mi ha regalato, c’è anche quella di aver conosciuto di persona un discreto numero di partigiani, quelli veri.
Quando da bambina ho ascoltato le loro storie e capito le loro scelte, ero certa che – se fosse capitato a me – avrei certamente preso quella stessa decisione: <strong>stare dalla parte giusta</strong>.
<h2>Il momento di decidere</h2>
Prima del diploma ho deciso che volevo fare il <em>tecnico del suono</em>, che è effettivamente l’unico lavoro che sapevo fare fino al 2022.
Vita meravigliosa: ho girato il mondo a spese delle varie produzioni che mi hanno ingaggiato.
Poi, un giorno, ho deciso di soccorrere un grande amico in difficoltà, prendendo le sue parti e stravolgendo di fatto quella che fino al 2004 è stata una vita tranquilla e, fino a lì, noiosa. <strong>Noiosa per quello che sarebbe successo da quel momento in poi</strong>.
Prendere le difese di una parte debole in un contenzioso feroce tra fratelli, ha di fatto sconvolto ogni paradigma conquistato fino a quel momento.
Ho anche conosciuto una certa dose di cattiveria, visto le vere sembianze del male e scampato i suoi attacchi, ma questa è un’altra storia (di cui non posso scrivere perché vincolata a segreto professionale).
<h2>Covidiozia</h2>
Ogni evento o decisione, dal 2004 in poi, non è più stato lo stesso per me.
Quello che di grosso ho notato sono state <strong>le enormi differenze tra me e ""“gli altri”""</strong>, cosa che all’inizio mi ha portato ad evidenziarle, esaltandole perfino.
Poi è arrivato il compleanno del 2020, non festeggiato per colpa della covidiozia generale ormai dilagante.
Quelle che erano delle piccole differenze da esaltare, tra ""“gli altri""” e me, si sono <strong>tradotte in speciazione: loro da una parte, io nella direzione esattamente opposta</strong>.
Sono certa di essermi <strong>schierata dalla parte giusta</strong>; saranno i miei bias di conferma o di chi li appiccia, ma <strong>guardando indietro all'infanzia, a quando avevo promesso di decidere per il giusto, sono felice di aver mantenuto la promessa a quella bambina</strong>.
<h2>Bitcoin</h2>
Senza la covidiozia dilagante <strong>non avrei conosciuto Bitcoin</strong> Avrei continuato a condurre la mia insulsa vita come sempre, sebbene in un angolo diverso del mondo sempre nuovo e con un lavoro accattivante.
Non avrei iniziato a studiare questa <strong>deliziosa tecnologia</strong>.
Soprattutto, non avrei mai congiunto il mio cammino con tutti quelli che hanno avuto a loro modo una speciazione come la mia, staccando il proprio cammino da quello degli """altri""”.
<h2>Anche se quella bambina non sapeva i dettagli, la ringrazio per avermi guidato su un sentiero che è – a tutti gli effetti – quello che più si avvicina alla realizzazione della mia felicità</h3>
-

@ 07907690:d4e015f6
2024-11-15 10:10:05
PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP:
## Mengamankan Email (Enkripsi dan Dekripsi)
- Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya.
- Cara Kerja:
- Pengirim mengenkripsi email menggunakan kunci publik penerima.
- Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut.
- Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup.
## Tanda Tangan Digital (Digital Signature)
- Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah.
- Cara Kerja:
- Pengirim membuat tanda tangan digital menggunakan kunci privatnya.
- Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim.
- Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh.
## Melindungi File dan Dokumen
- Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya.
- Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya.
- Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya.
## Mengamankan Backup Data
- Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah.
- Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman.
- Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data.
## Perlindungan Identitas dan Anonimitas
- Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online.
- Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan.
- Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka.
## Memverifikasi Integritas Perangkat Lunak
- Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga.
- Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan.
- Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya.
## Komunikasi di Forum atau Jaringan Terdistribusi
- Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim.
- Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah.
- Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka.
---
## Mengapa PGP Penting?
- Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas.
-Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan.
- Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi.
- Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital.
---
## Kelebihan PGP
- Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi.
- Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source.
- Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data.
## Kekurangan PGP
- Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam.
- Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar.
- Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan.
---
PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.
 @ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving.
@ af9c48b7:a3f7aaf4
2024-11-18 20:26:07## Chef's notes This simple, easy, no bake desert will surely be the it at you next family gathering. You can keep it a secret or share it with the crowd that this is a healthy alternative to normal pie. I think everyone will be amazed at how good it really is. ## Details - ⏲️ Prep time: 30 - 🍳 Cook time: 0 - 🍽️ Servings: 8 ## Ingredients - 1/3 cup of Heavy Cream- 0g sugar, 5.5g carbohydrates - 3/4 cup of Half and Half- 6g sugar, 3g carbohydrates - 4oz Sugar Free Cool Whip (1/2 small container) - 0g sugar, 37.5g carbohydrates - 1.5oz box (small box) of Sugar Free Instant Chocolate Pudding- 0g sugar, 32g carbohydrates - 1 Pecan Pie Crust- 24g sugar, 72g carbohydrates ## Directions 1. The total pie has 30g of sugar and 149.50g of carboydrates. So if you cut the pie into 8 equal slices, that would come to 3.75g of sugar and 18.69g carbohydrates per slice. If you decided to not eat the crust, your sugar intake would be .75 gram per slice and the carborytrates would be 9.69g per slice. Based on your objective, you could use only heavy whipping cream and no half and half to further reduce your sugar intake. 2. Mix all wet ingredients and the instant pudding until thoroughly mixed and a consistent color has been achieved. The heavy whipping cream causes the mixture to thicken the more you mix it. So, I’d recommend using an electric mixer. Once you are satisfied with the color, start mixing in the whipping cream until it has a consistent “chocolate” color thorough. Once your satisfied with the color, spoon the mixture into the pie crust, smooth the top to your liking, and then refrigerate for one hour before serving. @ af9d7040:42d05d35
2024-11-18 20:15:51## When I was taking these photos, I kept thinking about certain movies. ### *Each image is half a movie still, half my own shot.* ### **[Twin Peaks](https://www.imdb.com/title/tt0098936/)**  ### **[Brokeback Mountain*](https://www.imdb.com/title/tt0388795/?ref_=nv_sr_srsg_0_tt_6_nm_0_in_0_q_Brokeback%2520Mountain)**  ### **[Parasite](https://www.imdb.com/title/tt6751668/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Parasite)**  ### **[Waterworld](https://www.imdb.com/title/tt0114898/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Waterworld)**  ### **[True Detective](https://www.imdb.com/title/tt2356777/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_True%2520Detective)**  ### **[Phantom Thread](https://www.imdb.com/title/tt5776858/?ref_=nv_sr_srsg_0_tt_4_nm_1_in_0_q_Phantom%2520Thread)**  ### **[Arrival](https://www.imdb.com/title/tt2543164/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Arrival)**  ### **[There Will Be Blood](https://www.imdb.com/title/tt0469494/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_There%2520Will%2520Be%2520Blood)**  ### **[Your Name](https://www.imdb.com/title/tt5311514/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Your%2520Name)**  ### **[Sicario](https://www.imdb.com/title/tt3397884/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_Sicario)**  ### **[Steve Jobs](https://www.imdb.com/title/tt2080374/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_Steve%2520Jobs)**  ### **[And](https://www.imdb.com/title/tt0108778/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_the%2520friends)** 
@ af9d7040:42d05d35
2024-11-18 20:15:51## When I was taking these photos, I kept thinking about certain movies. ### *Each image is half a movie still, half my own shot.* ### **[Twin Peaks](https://www.imdb.com/title/tt0098936/)**  ### **[Brokeback Mountain*](https://www.imdb.com/title/tt0388795/?ref_=nv_sr_srsg_0_tt_6_nm_0_in_0_q_Brokeback%2520Mountain)**  ### **[Parasite](https://www.imdb.com/title/tt6751668/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Parasite)**  ### **[Waterworld](https://www.imdb.com/title/tt0114898/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Waterworld)**  ### **[True Detective](https://www.imdb.com/title/tt2356777/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_True%2520Detective)**  ### **[Phantom Thread](https://www.imdb.com/title/tt5776858/?ref_=nv_sr_srsg_0_tt_4_nm_1_in_0_q_Phantom%2520Thread)**  ### **[Arrival](https://www.imdb.com/title/tt2543164/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Arrival)**  ### **[There Will Be Blood](https://www.imdb.com/title/tt0469494/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_There%2520Will%2520Be%2520Blood)**  ### **[Your Name](https://www.imdb.com/title/tt5311514/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_Your%2520Name)**  ### **[Sicario](https://www.imdb.com/title/tt3397884/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_Sicario)**  ### **[Steve Jobs](https://www.imdb.com/title/tt2080374/?ref_=nv_sr_srsg_0_tt_7_nm_1_in_0_q_Steve%2520Jobs)**  ### **[And](https://www.imdb.com/title/tt0108778/?ref_=nv_sr_srsg_0_tt_8_nm_0_in_0_q_the%2520friends)**  @ b98139a6:eb269255
2024-11-18 20:15:16I've been suddenly having trouble posting comments that are priced at 1 sat. I also tested with zaps, and 1sat zaps fail as well. They seem to fail instantly, and show canceled in the wallet history & on AlbyHub (running on my Start9). However, there is no record of the TX failing (or even attempting) in the lightning node itself. Bigger payments do work, and I tried a 2sat zap which did work. I don't comment too often, but I zap every day, and my zaps are well above 1sat, so I didn't notice until I wanted to write some comments today and they all came back as failing... Has anyone else seen this? Is there a setting that I somehow messed up? It's odd that the 2sat zap went through fine, and much bigger payments have been working without issue (both outgoing and incoming), so it's not a liquidity issue. originally posted at https://stacker.news/items/773077
@ b98139a6:eb269255
2024-11-18 20:15:16I've been suddenly having trouble posting comments that are priced at 1 sat. I also tested with zaps, and 1sat zaps fail as well. They seem to fail instantly, and show canceled in the wallet history & on AlbyHub (running on my Start9). However, there is no record of the TX failing (or even attempting) in the lightning node itself. Bigger payments do work, and I tried a 2sat zap which did work. I don't comment too often, but I zap every day, and my zaps are well above 1sat, so I didn't notice until I wanted to write some comments today and they all came back as failing... Has anyone else seen this? Is there a setting that I somehow messed up? It's odd that the 2sat zap went through fine, and much bigger payments have been working without issue (both outgoing and incoming), so it's not a liquidity issue. originally posted at https://stacker.news/items/773077 @ 6bae33c8:607272e8
2024-11-18 18:36:16I much prefer to write these after a good week. I used to kind of relish excoriating myself after every mistake, complaining about all the questionable calls and coaches’ decision-making that went against me, but not so much anymore. When I lose, I try to think of it as the outcome that’s most suited to me at this particular time. Had I gone 5-0, that would have been most suited, but apparently I really needed the 1-4 to knock me out of Q3. I won’t pretend to know the particular lesson in this. Life isn’t like that. You take from it what you choose and then await the next lesson. If I had to guess I’d say I wasn’t ready to win Q3 — not the money, that’s not the issue — but psychologically I wasn’t ready to accept winning it. You see my brain has been poisoned with these ideas about probability wherein it’s very hard to go 5-0 (1 in 32, maybe 1 in 28 or so if you have an edge.) To do it twice is 1 in 1000 (2 ^10 = 1024). To do it four times (20 - 0) is less than one in a million. So when I go to pick the games each week I have this foreboding and dread that it can’t be done. Or that it *can* be done, but only with a lot of luck. This is toxic. Whether or not the math adds up is irrelevant to the process of picking the games. You are divining what is likely to happen and positioning yourself accordingly. Maybe I am the greatest of all time. Maybe I *can* go on a 20-0 run if I get in sync. Tom Brady had no business believing he could win seven Super Bowls. If he focused on the odds of that happening, it probably wouldn’t have happened. He just went out and played as though he could win one every year. So my takeaway is I’m too much of a midwit, someone who learned the Probability 101 course and thinks he’s got this shit down. I’m too savvy to win the Q3, because I know better, because I’ve run the numbers and realize it can’t be done without a ton of luck. I want to be less savvy, less caught up in probabilities and more naive. I want to pick with the confidence of someone who is totally naive to the likelihood and all-in on transmuting my observations and knowledge of what I see into the winning picks. I will try to do this going forward, but it’s possible my long stint in the midwit fantasy industry damaged my brain too much. - The Bengals-Chargers 40-minute edit wasn’t ready when I woke up this morning, so I watched the six-minute highlights. I had Joe Burrow, Ja’Marr Chase and JK Dobbins, so there were a lot of highlights! I also had Khalil Herbert going out of desperation due to byes in one league, and I’m not sure if he played. - Alan Seslowsky [put out a video](https://www.youtube.com/watch?v=4lF-9mI4EDs) before the year saying to take Chase No. 1 overall, and being the donkey I am, I took it literally and drafted him in three leagues. Reminds me of that Buddhist story where three monks tell a retarded monk (a “fool”) that if he lets each of them whack him with a stick, he’ll become enlightened. So he agrees, they hit him and it works. - I don’t think the Chargers are serious contenders, but with Jim Harbaugh there it’s finally at least possible. - The Packers are out of sync and obviously very lucky to win that game. No idea why they refuse to give Jayden Reed targets, but I’m happy about it since I once regretted not drafting him. - I watched the first two-third of the Lions-Jaguars, and I can assure you that game was not as close as the score. Total domination on both sides. It was incidentally the only ATS pick I won. - I picked the Titans +6 due to divine inspiration, but it must have been intended for a different branch of the multiverse, one where the refs didn’t call a garbage personal foul on 4th-and-goal that gifted the Vikings, who won by 10, a TD instead of a turnover on downs. - A few games ago, Chase/Justin Jefferson was a close call, but Chase has since left him in the dust. - With Marvin Harrison on bye, I was forced to start Nick Westbrook-Ikhine, so I appreciated the 98-yard TD pass to him. Just a 16.8-point play. Will Levis sucks though. - My Primetime team will do okay if CJ Stroud has a good game (especially if he connects with Tank Dell), but I originally had Anthony Richardson in at QB and Jonnu Smith (28 points) at TE who I benched for Dallas Goedert. (I was actually satisfied with Goedert’s 11 points on Thursday night too.) - I have Jaylen Waddle in one league, started him over Jonnu and Elijah Moore. I know everyone would have done that, but at what point do you have to start considering say Ladd McConkey over him. (Next week, I get Malik Nabers back, so I’ll have that choice.) - Brock Bowers maybe should have been the Dynasty League 1.1. for this year’s rookies. - I saw a little of the Pats-Rams game. Cooper Kupp caught an intermediate ball, the defender missed and he ran untouched for 69 yards with no one near him. The Rams were totally stifled by the Dolphins last week too. - Drake Maye looked pretty good to me from what I watched. I don’t know if he’ll be great, but he’s over the threshold. - I had the Browns plus 1.5 as one of my picks, and it looked okay until the fourth quarter when they fell apart. I also had Taysom Hill in my dynasty league where I was forced to start two tight ends. See below: - Jerry Jeudy has random massive games once every year or so. But the Browns are so much more watchable with Jameis Winston than Deshaun Watson, who should just hire prostitutes to re-enact the massage experience in perpetuity with that money. - The time to pick up Anthony Richardson was last week, which I did in two leagues. He was obviously going to get another shot, and the upside was/is still there. - The Jets are hilarious, should have stuck with QB1. - I had the Ravens -3, and while it was the losing side, they are the better team than the Steelers. Justin Tucker hit that last 54-yarder, but he missed two earlier field goals in the game, and it was tough to watch. It’s as if the great Mariano Rivera had gotten shelled in his final season (which he did not.) - I really thought the Ravens would get that two-point conversion and cover in overtime too. - The Falcons never got off the plane. No idea what happened there. At least we got to see some Penix. “12-inch” passed the eye test for me, though he could have put more air under one deep throw. Is that not his college nickname? - Never try and handicap the Denver running back situation. - The 49ers look like themselves, but there’s something missing. I guess Nick Bosa getting hurt and George Kittle not playing explains some of it. - Geno Smith made a bad-ass 16-yard TD scramble to win the game. It looks like JSN has emerged as his No. 1 receiver finally even with DK Metcalf back. Tyler Lockett seems relegated to a bit role. - The Chiefs had a shot after their TD to cut it to 23-21, but Josh Allen crushed their spirits with a 26-yard TD on 4th-and-2. Save it for the playoffs, Josh! - I watched the Tyson-Paul flight on Netflix Saturday morning. It was pretty dull, but I’ve heard two conflicting theories since: (1) Paul took it easy on Tyson late out of respect for the legend — Tyson did look exhausted after eight shortened rounds; and (2) That Tyson went easy on Paul, pulled punches and let him win. (There were a couple points where Tyson slowed up after Paul made an odd gesture like sticking his tongue out.) I don’t know, but they both got paid so much, nothing would surprise me.
@ 6bae33c8:607272e8
2024-11-18 18:36:16I much prefer to write these after a good week. I used to kind of relish excoriating myself after every mistake, complaining about all the questionable calls and coaches’ decision-making that went against me, but not so much anymore. When I lose, I try to think of it as the outcome that’s most suited to me at this particular time. Had I gone 5-0, that would have been most suited, but apparently I really needed the 1-4 to knock me out of Q3. I won’t pretend to know the particular lesson in this. Life isn’t like that. You take from it what you choose and then await the next lesson. If I had to guess I’d say I wasn’t ready to win Q3 — not the money, that’s not the issue — but psychologically I wasn’t ready to accept winning it. You see my brain has been poisoned with these ideas about probability wherein it’s very hard to go 5-0 (1 in 32, maybe 1 in 28 or so if you have an edge.) To do it twice is 1 in 1000 (2 ^10 = 1024). To do it four times (20 - 0) is less than one in a million. So when I go to pick the games each week I have this foreboding and dread that it can’t be done. Or that it *can* be done, but only with a lot of luck. This is toxic. Whether or not the math adds up is irrelevant to the process of picking the games. You are divining what is likely to happen and positioning yourself accordingly. Maybe I am the greatest of all time. Maybe I *can* go on a 20-0 run if I get in sync. Tom Brady had no business believing he could win seven Super Bowls. If he focused on the odds of that happening, it probably wouldn’t have happened. He just went out and played as though he could win one every year. So my takeaway is I’m too much of a midwit, someone who learned the Probability 101 course and thinks he’s got this shit down. I’m too savvy to win the Q3, because I know better, because I’ve run the numbers and realize it can’t be done without a ton of luck. I want to be less savvy, less caught up in probabilities and more naive. I want to pick with the confidence of someone who is totally naive to the likelihood and all-in on transmuting my observations and knowledge of what I see into the winning picks. I will try to do this going forward, but it’s possible my long stint in the midwit fantasy industry damaged my brain too much. - The Bengals-Chargers 40-minute edit wasn’t ready when I woke up this morning, so I watched the six-minute highlights. I had Joe Burrow, Ja’Marr Chase and JK Dobbins, so there were a lot of highlights! I also had Khalil Herbert going out of desperation due to byes in one league, and I’m not sure if he played. - Alan Seslowsky [put out a video](https://www.youtube.com/watch?v=4lF-9mI4EDs) before the year saying to take Chase No. 1 overall, and being the donkey I am, I took it literally and drafted him in three leagues. Reminds me of that Buddhist story where three monks tell a retarded monk (a “fool”) that if he lets each of them whack him with a stick, he’ll become enlightened. So he agrees, they hit him and it works. - I don’t think the Chargers are serious contenders, but with Jim Harbaugh there it’s finally at least possible. - The Packers are out of sync and obviously very lucky to win that game. No idea why they refuse to give Jayden Reed targets, but I’m happy about it since I once regretted not drafting him. - I watched the first two-third of the Lions-Jaguars, and I can assure you that game was not as close as the score. Total domination on both sides. It was incidentally the only ATS pick I won. - I picked the Titans +6 due to divine inspiration, but it must have been intended for a different branch of the multiverse, one where the refs didn’t call a garbage personal foul on 4th-and-goal that gifted the Vikings, who won by 10, a TD instead of a turnover on downs. - A few games ago, Chase/Justin Jefferson was a close call, but Chase has since left him in the dust. - With Marvin Harrison on bye, I was forced to start Nick Westbrook-Ikhine, so I appreciated the 98-yard TD pass to him. Just a 16.8-point play. Will Levis sucks though. - My Primetime team will do okay if CJ Stroud has a good game (especially if he connects with Tank Dell), but I originally had Anthony Richardson in at QB and Jonnu Smith (28 points) at TE who I benched for Dallas Goedert. (I was actually satisfied with Goedert’s 11 points on Thursday night too.) - I have Jaylen Waddle in one league, started him over Jonnu and Elijah Moore. I know everyone would have done that, but at what point do you have to start considering say Ladd McConkey over him. (Next week, I get Malik Nabers back, so I’ll have that choice.) - Brock Bowers maybe should have been the Dynasty League 1.1. for this year’s rookies. - I saw a little of the Pats-Rams game. Cooper Kupp caught an intermediate ball, the defender missed and he ran untouched for 69 yards with no one near him. The Rams were totally stifled by the Dolphins last week too. - Drake Maye looked pretty good to me from what I watched. I don’t know if he’ll be great, but he’s over the threshold. - I had the Browns plus 1.5 as one of my picks, and it looked okay until the fourth quarter when they fell apart. I also had Taysom Hill in my dynasty league where I was forced to start two tight ends. See below: - Jerry Jeudy has random massive games once every year or so. But the Browns are so much more watchable with Jameis Winston than Deshaun Watson, who should just hire prostitutes to re-enact the massage experience in perpetuity with that money. - The time to pick up Anthony Richardson was last week, which I did in two leagues. He was obviously going to get another shot, and the upside was/is still there. - The Jets are hilarious, should have stuck with QB1. - I had the Ravens -3, and while it was the losing side, they are the better team than the Steelers. Justin Tucker hit that last 54-yarder, but he missed two earlier field goals in the game, and it was tough to watch. It’s as if the great Mariano Rivera had gotten shelled in his final season (which he did not.) - I really thought the Ravens would get that two-point conversion and cover in overtime too. - The Falcons never got off the plane. No idea what happened there. At least we got to see some Penix. “12-inch” passed the eye test for me, though he could have put more air under one deep throw. Is that not his college nickname? - Never try and handicap the Denver running back situation. - The 49ers look like themselves, but there’s something missing. I guess Nick Bosa getting hurt and George Kittle not playing explains some of it. - Geno Smith made a bad-ass 16-yard TD scramble to win the game. It looks like JSN has emerged as his No. 1 receiver finally even with DK Metcalf back. Tyler Lockett seems relegated to a bit role. - The Chiefs had a shot after their TD to cut it to 23-21, but Josh Allen crushed their spirits with a 26-yard TD on 4th-and-2. Save it for the playoffs, Josh! - I watched the Tyson-Paul flight on Netflix Saturday morning. It was pretty dull, but I’ve heard two conflicting theories since: (1) Paul took it easy on Tyson late out of respect for the legend — Tyson did look exhausted after eight shortened rounds; and (2) That Tyson went easy on Paul, pulled punches and let him win. (There were a couple points where Tyson slowed up after Paul made an odd gesture like sticking his tongue out.) I don’t know, but they both got paid so much, nothing would surprise me. @ cd7973fe:aec52bc3
2024-11-18 18:23:59test
@ cd7973fe:aec52bc3
2024-11-18 18:23:59test @ ced4158e:f2a74519
2024-11-18 18:10:47Бесплатный роллтон в Метрополисе, катание на единорогах в ЦПКО, а может быть летающие машины? Все это впереди, вот только общественный транспорт в Кургане будет актуален всегда, и однажды наш старый добрый друг ПАЗик из гадкого утёнка превратится в прекрасного лебедя. А как это будет выглядеть? Смотри! <iframe width="1862" height="791" src="https://www.youtube.com/embed/GUbmibUb4tk" title="" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> #45news #Курган2040
@ ced4158e:f2a74519
2024-11-18 18:10:47Бесплатный роллтон в Метрополисе, катание на единорогах в ЦПКО, а может быть летающие машины? Все это впереди, вот только общественный транспорт в Кургане будет актуален всегда, и однажды наш старый добрый друг ПАЗик из гадкого утёнка превратится в прекрасного лебедя. А как это будет выглядеть? Смотри! <iframe width="1862" height="791" src="https://www.youtube.com/embed/GUbmibUb4tk" title="" frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> #45news #Курган2040 @ 5bfb38cb:2b999aa7
2024-11-18 18:06:30### Spot Over BTX2024 ### Open Interest: There are no significant changes in OI as we have moved to premium. ### Institutional Order Flow Sponsorship: The IOF is bullish above the all-time high. The structure must be maintained away from the high to continue the trend. ### Weekly Profile: The week presents relevant news on Tuesday and Thursday. It is likely that we will see some bearish manipulation until Tuesday or Wednesday, and then move to premium if the IOF remains bullish. ### Classic Technical Analysis: We have consolidated a new ATH but have had a week of retracement towards the equilibrium of the last bullish swing. We must maintain these levels to remain bullish. https://image.nostr.build/70fe786e500780819ce09425ec4c2e916e7010f1feaa333f52e3d91ffa29f071.png ### Market Structure: The structure is bullish. ### Trading Range: 66798 to 93483. Currently in Premium. ##### PD Array Matrix: Premium: - ATH 93483 Discount: - FVG D 85121 - FVG D 80280 - FVG D 74479 - OB+D 72727 Equilibrium: - 80141 ### Key Price Levels: - OB+D 72727. I do not expect closes below this structure and its MT at 70273 to remain bullish. https://image.nostr.build/98b448aa561465b4dcaecf340073d86ff7008a0b1d30437b21f7e26e71213bdc.png ### Daily BIAS: Bullish. ### Daily Target: - Retracement to 80280 to take liquidity and reach a swing equilibrium, and then maintain premium. If the high is clearly taken, the structure may be invalidated to pursue the weekly and monthly bullish target. *Learning to accept and deal with the inherent risk of trading is what separates the consistent winners from everyone else.*
@ 5bfb38cb:2b999aa7
2024-11-18 18:06:30### Spot Over BTX2024 ### Open Interest: There are no significant changes in OI as we have moved to premium. ### Institutional Order Flow Sponsorship: The IOF is bullish above the all-time high. The structure must be maintained away from the high to continue the trend. ### Weekly Profile: The week presents relevant news on Tuesday and Thursday. It is likely that we will see some bearish manipulation until Tuesday or Wednesday, and then move to premium if the IOF remains bullish. ### Classic Technical Analysis: We have consolidated a new ATH but have had a week of retracement towards the equilibrium of the last bullish swing. We must maintain these levels to remain bullish. https://image.nostr.build/70fe786e500780819ce09425ec4c2e916e7010f1feaa333f52e3d91ffa29f071.png ### Market Structure: The structure is bullish. ### Trading Range: 66798 to 93483. Currently in Premium. ##### PD Array Matrix: Premium: - ATH 93483 Discount: - FVG D 85121 - FVG D 80280 - FVG D 74479 - OB+D 72727 Equilibrium: - 80141 ### Key Price Levels: - OB+D 72727. I do not expect closes below this structure and its MT at 70273 to remain bullish. https://image.nostr.build/98b448aa561465b4dcaecf340073d86ff7008a0b1d30437b21f7e26e71213bdc.png ### Daily BIAS: Bullish. ### Daily Target: - Retracement to 80280 to take liquidity and reach a swing equilibrium, and then maintain premium. If the high is clearly taken, the structure may be invalidated to pursue the weekly and monthly bullish target. *Learning to accept and deal with the inherent risk of trading is what separates the consistent winners from everyone else.* @ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima.
@ 4ba8e86d:89d32de4
2024-11-07 13:56:21Tutorial feito por Grom mestre⚡poste original abaixo: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/240277/tutorial-criando-e-acessando-sua-conta-de-email-pela-i2p?show=240277#q240277 Bom dia/tarde/noite a todos os camaradas. Seguindo a nossa série de tutoriais referentes a tecnologias essenciais para a segurança e o anonimato dos usuários, sendo as primeiras a openPGP e a I2P, lhes apresento mais uma opção para expandir os seus conhecimentos da DW. Muitos devem conhecer os serviços de mail na onion como DNMX e mail2tor, mas e que tal um serviço de email pela I2P. Nesse tutorial eu vou mostrar a vocês como criar a sua primeira conta no hq.postman.i2p e a acessar essa conta. É importante que vocês tenham lido a minha primeira série de tutoriais a respeito de como instalar, configurar e navegar pela I2P nostr:nevent1qqsyjcz2w0e6d6dcdeprhuuarw4aqkw730y542dzlwxwssneq3mwpaspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsyp5vcq Esse tutorial é um pré-requisito para o seguinte e portanto recomendo que leia-os antes de prosseguir com o seguinte tutorial. O tutorial de Kleopatra nostr:nevent1qqs8h7vsn5j6qh35949sa60dms4fneussmv9jd76n24lsmtz24k0xlqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgecq8f7 é complementar dado que é extremamente recomendado assinar e criptografar as mensagens que seguem por emails pela DW. Sem mais delongas, vamos ao tutorial de fato. ## 1. Criando uma conta de email no hq.postman Relembrando: Esse tutorial considera que você já tenha acesso à I2P. Entre no seu navegador e acesse o endereço hq.postman.i2p. O roteador provavelmente já contém esse endereço no seu addressbook e não haverá a necessidade de inserir o endereço b32 completo. Após entrar no site vá para a página '1 - Creating a mailbox' https://image.nostr.build/d850379fe315d2abab71430949b06d3fa49366d91df4c9b00a4a8367d53fcca3.jpg Nessa página, insira as credenciais de sua preferências nos campos do formulário abaixo. Lembre-se que o seu endereço de email aceita apenas letras e números. Clique em 'Proceed' depois que preencher todos os campos. https://image.nostr.build/670dfda7264db393e48391f217e60a2eb87d85c2729360c8ef6fe0cf52508ab4.jpg Uma página vai aparecer pedindo para confirmar as credenciais da sua nova conta. Se tudo estiver certo apenas clique em 'Confirm and Create Mailbox'. Se tudo ocorrer como conforme haverá uma confirmação de que a sua nova conta foi criada com sucesso. Após isso aguarde por volta de 5 minutos antes de tentar acessá-la, para que haja tempo suficiente para o servidor atualizar o banco de dados. https://image.nostr.build/ec58fb826bffa60791fedfd9c89a25d592ac3d11645b270c936c60a7c59c067f.jpg https://image.nostr.build/a2b7710d1e3cbb36431acb9055fd62937986b4da4b1a1bbb06d3f3cb1f544fd3.jpg Pronto! Sua nova conta de email na I2P foi criada. Agora vamos para a próxima etapa: como acessar a sua conta via um cliente de email. ## 2. Configurando os túneis cliente de SMTP e POP3 O hq.postman não possui um cliente web que nos permite acessar a nossa conta pelo navegador. Para isso precisamos usar um cliente como Thunderbird e configurar os túneis cliente no I2Pd que serão necessários para o Thunderbird se comunicar com o servidor pela I2P. Caso não tenha instalado o Thunderbird ainda, faça-o agora antes de prosseguir. Vamos configurar os túneis cliente do servidor de email no nosso roteador. Para isso abra um terminal ou o seu gestor de arquivos e vá para a pasta de configuração de túneis do I2P. Em Linux esse diretório se localiza em /etc/i2pd/tunnels.d. Em Windows, essa pasta se localiza em C:\users\user\APPDATA\i2pd. Na pasta tunnels.d crie dois arquivos: smtp.postman.conf e pop-postman.conf. Lembre-se que em Linux você precisa de permissões de root para escrever na pasta de configuração. Use o comando sudoedit <nome_do_arquivo> para isso. Edite-os conforme as imagens a seguir: Arquivo pop-postman.conf https://image.nostr.build/7e03505c8bc3b632ca5db1f8eaefc6cecb4743cd2096d211dd90bbdc16fe2593.jpg Arquivo smtp-postman.conf https://image.nostr.build/2d06c021841dedd6000c9fc2a641ed519b3be3c6125000b188842cd0a5af3d16.jpg Salve os arquivos e reinicie o serviço do I2Pd. Em Linux isso é feito pelo comando: ``` sudo systemctl restart i2pd ``` Entre no Webconsole do I2Pd pelo navegador (localhost:7070) e na seção I2P Tunnels, verifique se os túneis pop-postman e smtp-postman foram criados, caso contrário verifique se há algum erro nos arquivos e reinicie o serviço. Com os túneis cliente criados, vamos agora configurar o Thunderbird ## 3. Configurando o Thunderbird para acessar a nossa conta Abra o Thunderbird e clique em criar uma nova conta de email. Se você não tiver nenhum conta previamente presente nele você vai ser diretamente recebido pela janela de criação de conta a seguir. https://image.nostr.build/e9509d7bd30623716ef9adcad76c1d465f5bc3d5840e0c35fe4faa85740f41b4.jpg https://image.nostr.build/688b59b8352a17389902ec1e99d7484e310d7d287491b34f562b8cdd9dbe8a99.jpg Coloque as suas credenciais, mas não clique ainda em Continuar. Clique antes em Configure Manually, já que precisamos configurar manualmente os servidores de SMTP e POP3 para, respectivamente, enviar e receber mensagens. Preencha os campos como na imagem a seguir. Detalhe: Não coloque o seu endereço completo com o @mail.i2p, apenas o nome da sua conta. https://image.nostr.build/4610b0315c0a3b741965d3d7c1e4aff6425a167297e323ba8490f4325f40cdcc.jpg Clique em Re-test para verificar a integridade da conexão. Se tudo estiver certo uma mensagem irá aparecer avisando que as configurações do servidores estão corretas. Clique em Done assim que estiver pronto para prosseguir. https://image.nostr.build/8a47bb292f94b0d9d474d4d4a134f8d73afb84ecf1d4c0a7eb6366d46bf3973a.jpg A seguinte mensagem vai aparecer alertando que não estamos usando criptografia no envio das credenciais. Não há problema nenhum aqui, pois a I2P está garantindo toda a proteção e anonimato dos nossos dados, o que dispensa a necessidade de uso de TLS ou qualquer tecnologia similar nas camadas acima. Marque a opção 'I Understand the risks' e clique em 'Continue' https://image.nostr.build/9c1bf585248773297d2cb1d9705c1be3bd815e2be85d4342227f1db2f13a9cc6.jpg E por fim, se tudo ocorreu como devido sua conta será criada com sucesso e você agora será capaz de enviar e receber emails pela I2P usando essa conta. https://image.nostr.build/8ba7f2c160453c9bfa172fa9a30b642a7ee9ae3eeb9b78b4dc24ce25aa2c7ecc.jpg ## 4. Observações e considerações finais Como informado pelo próprio site do hq.postman, o domínio @mail.i2p serve apenas para emails enviados dentro da I2P. Emails enviados pela surface devem usar o domínio @i2pmai.org. É imprescindível que você saiba usar o PGP para assinar e criptografar as suas mensagens, dado que provavelmente as mensagens não são armazenadas de forma criptografada enquanto elas estão armazenadas no servidor. Como o protocolo POP3 delete as mensagens no imediato momento em que você as recebe, não há necessidade de fazer qualquer limpeza na sua conta de forma manual. Por fim, espero que esse tutorial tenha sido útil para vocês. Que seu conhecimento tenha expandido ainda mais com as informações trazidas aqui. Até a próxima. @ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller. @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart.
@ fd208ee8:0fd927c1
2024-11-08 10:27:40## You have no idea I regularly read comments from people, on here, wondering how it's possible to marry -- or even simply be friends! -- with someone who doesn't agree with you on politics. I see this sentiment expressed quite often, usually in the context of Bitcoin, or whatever _pig is currently being chased through the village_, as they say around here.  It seems rather sensible, but I don't think it's as hard, as people make it out to be. Further, I think it's a dangerous precondition to set, for your interpersonal relationships, because the political field is constantly in flux. If you determine who you will love, by their opinions, do you stop loving them if their opinions change, or if the opinions they have become irrelevant and a new set of opinions are needed -- and their new ones don't match your new ones? We could see this happen to relationships en masse, during the Covid Era, and I think it happens every day, in a slow grind toward the disintegration of interpersonal discourse. I suspect many people do stop loving, at that point, as they never really loved the other person for their own sake, they loved the other person because they thought the other person was exactly like they are. But no two people are alike, and the longer you are in a relationship with someone else, the more the initial giddiness wears off and the trials and tribulations add up, the more you notice how very different you actually are. This is the point, where best friends and romantic couples say, _We just grew apart._ But you were always apart. You were always two different people. You just didn't notice, until now.  I've also always been surprised at how many same-party relationships disintegrate because of some disagreement over some particular detail of some particular topic, that they generally agree on. To me, it seems like an irrelevant side-topic, but _they can't stand to be with this person_... and they stomp off. So, I tend to think that it's less that opinions need to align to each other, but rather that opinions need to align in accordance with the level of interpersonal tolerance they can bring into the relationship. ## I was raised by relaxed revolutionaries Maybe I see things this way because my parents come from two diverging political, cultural, national, and ethnic backgrounds, and are prone to disagreeing about a lot of "important" (to people outside their marriage) things, but still have one of the healthiest, most-fruitful, and most long-running marriages of anyone I know, from that generation. My parents, you see, aren't united by their opinions. They're united by their relationship, which is something _outside_ of opinions. Beyond opinions. Relationships are what turn two different people into one, cohesive unit, so that they slowly grow together. Eventually, even their faces merge, and their biological clocks tick to the same rhythm. They eventually become one entity that contains differing opinions about the same topics. It's like magic, but it's the result of a mindset, not a worldview. Or, as I like to quip: > The best way to stay married, is to not get divorced.  My parents simply determined early on, that they would stay together, and whenever they would find that they disagreed on something that _didn't directly pertain to their day-to-day existence with each other_ they would just agree-to-disagree about that, or roll their eyes, and move on. You do you. Live and let live. My parents have some of the most strongly held personal opinions of any people I've ever met, but they're also incredibly tolerant and can get along with nearly anyone, so their friends are a confusing hodgepodge of _people we liked and found interesting enough to keep around_. Which makes their house parties really fun, and highly unusual, in this day and age of mutual-damnation across the aisle.  The things that did affect them, directly, like which school the children should attend or which country they should live in, etc. were things they'd sit down and discuss, and somehow one opinion would emerge, and they'd again... move on. And that's how my husband and I also live our lives, and it's been working surprisingly well. No topics are off-limits to discussion (so long as you don't drone on for too long), nobody has to give up deeply held beliefs, or stop agitating for the political decisions they prefer. You see, we didn't like that the other always had the same opinion. We liked that the other always held their opinions strongly. That they were passionate about their opinions. That they were willing to voice their opinions; sacrifice to promote their opinions. And that they didn't let anyone browbeat or cow them, for their opinions, not even their best friends or their spouse. But that they were open to listening to the other side, and trying to wrap their mind around the possibility that they _might just be wrong about something_.  We married each other because we knew: this person really cares, this person has thought this through, and they're in it, to win it. What "it" is, is mostly irrelevant, so long as it doesn't entail torturing small animals in the basement, or raising the children on a diet of Mountain Dew and porn, or something. Live and let live. At least, it's never boring. At least, there's always something to ~~argue~~ talk about. At least, we never think... we've just grown apart. @ 97c70a44:ad98e322
2024-11-18 17:57:17So I have this cool new product, which for about two weeks has been ready to release, if I could just solve one thing. I have recently moved away from storing user keys in my apps due to the ease with which they could (and have) been put at risk. In doing so, I've discovered that despite its downsides, pasting your nsec into an app is a pretty straightforward operation which even non-technical people can pull off. In contrast, pretty much no other key management solution is. Just to state the obvious, and to kick off this survey of nostr key management options, let me just state that asking users to paste their nsec into your app is a *bad idea*. However good your intentions, this opens your users up to all kinds of attack vectors, including clipboard hijacking attacks, exposing keys to insecure communication channels, exposing keys to many different apps, supply chain attacks, XSS attacks, and yes, bugs that cause your software to send keys to analytics or error reporting backends. The era of nsec-pasting is over. I've committed to embracing the pain and removing nsec login from Coracle, and I encourage other devs to do the same. The sooner we treat key management with the urgency it deserves, the sooner we can come up with a secure *and* convenient key management solution. As an aside, `ncryptsec` is a great innovation for securely *transporting* keys, but it still doesn't protect against exposure to apps that need to *use* keys. It has its place though; in fact I'm of the opinion that `nsec` and seed words should be deprecated, and support for them should be removed. Giving friendly names and human-readable representations to data that is essentially private is a really bad idea (unless you're memorizing your key). But I digress. # Signer Comparisons Let's go through a few existing options for key management, and compare their relative merits. I've tried to list them in the order they appeared on the scene, which also helps to clarify the logic of how signers have evolved. Throughout, I will be focusing on what kinds of user experience each approach unlocks for *non-technical users*, since my goal is to build products that work for regular people. ## Extension Signers The first signer application (that I know of) was nos2x, by fiatjaf. As I understand it, this was a proof-of-concept of how users might protect their keys without releasing custody of them. And it works really well! In fact, even though there have been many forks and imitators, I still use nos2x when using nostr on my desktop browser. Extension signers offer a great user experience, along a narrow happy path. Setting up a browser extension is a relatively familiar process for normal users, and once it's done you don't really have to think about it. In theory, extensions can also include their own onboarding process and key backup strategies as well, allowing users to get started in a single place. Plus, there's very little latency involved in making calls to the signer extension. This positive experience breaks down quickly though once a user wants to use a desktop or mobile application. When this happens, users have to start over essentially from scratch. Nothing they did to set up the extension helps them move to another signer application. While it's *technically* possible to use extension signers on mobile via e.g. the Kiwi browser, this doesn't work for native apps or apps installed as PWAs. Instead, you either have to revert to pasting keys, or use some other solution. One slight permutation of extension signers is browser signers, like Spring. Instead of adding a signer to your browser, Spring allows you to install a browser that holds your keys and allows you to use any nostr web application. But this has all the same basic limitations that extension signers do. ## Hardware Signers Hardware signers came around shortly after extension signers. I'm not going to spend much time talking about them here, because although they're about as far along the spectrum towards security as you can go, they're also not very convenient. Non-technical users aren't going to onboard by buying (or building) a device which they have to connect to their desktop via USB whenever they want to sign a message. Hardware signers have their place, but onboarding isn't it. The only hardware signer I'm aware of (although I'm sure I've heard of others) is from [LNBits](https://github.com/lnbits/nostr-signing-device), and is usually used via a browser extension like [horse](https://github.com/lnbits/horse). This of course means that it has all the same limitations that browser extensions have, and then some (although mobile and desktop apps would likely be able to find a way to talk directly to the signer). ## Hosted Signers Remote signers (aka "bunkers") use the Nostr Connect protocol (also known as NIP 46) for remote signing. Hosted signers in particular are one example of a NIP 46 remote signer, which lives on "somebody else's computer". Because they use a legacy web architecture, they can be built to be very familiar and convenient to users. It's trivial to build a hosted signer that offers email/password login along with 2FA, password resets, session revokation, the whole shebang. But they have one fatal flaw, which is that they are custodial. This means that not only do users have to relinquish exclusive control over their keys, but hosted signers also can become a target for hackers. ## Desktop Signers Several projects exist which allow users to run their own bunker, on their own hardware. These include nostr clients like Gossip, as well as command-line utilities like nak. This approach is mostly an improvement over extension signers, because it widens the scope of applications that can conveniently access the signer from those that run in the browser to those that run on the desktop computer the signer lives on. The downside is that they have to communicate via relays, which either introduces latency or requires an additional component to be running locally. While it's technically possible to use desktop signers to log in on other computers or mobile apps, I don't think that's going to be very practical for most people. Mobile apps by definition are more portable than regular computers. Anyone who wants to access their nostr account on more than one device will have to either set up separate solutions, or go with another kind of remote signer. This isn't a huge obstacle for people highly invested in nostr, but it's a significant amount of friction for a new user. ## Mobile Signers Mobile signers solve the problem introduced by desktop signers of not always having access to your signer (or of your signer not having access to you, due to being powered down or disconnected from the internet). Mobile devices are generally more available than desktop devices, and also have better push notifications. This means that users can approve signer requests from any device as easily as tapping a notification. Mobile signers on Android can also upgrade their UX by taking advantage of NIP 55 to avoid the round trip to relays, reducing latency and making it possible to sign things offline. [Amber](https://github.com/greenart7c3/Amber) has been a pioneer in this area, and other projects like [Nostrum](https://github.com/nostr-connect/nostrum) and [Alby's nostr-signer](https://github.com/getAlby/nostr-signer) have been prototyped. To date, there unfortunately haven't been any signer applications released for iOS, which leaves the mobile signer story incomplete. In my opinion, this is probably the most promising solution for end users, although it's currently under-developed. ## Web Signers One interesting alternative that combines the benefits of hosted, desktop, and mobile wallets is [nsec.app](https://nsec.app). This is a web application frontend which keeps keys in the browser, so that they are never shared with a third party. Using web push notifications and a healthy sprinkle of black magic, nsec.app is able to respond to signer requests by opening itself in a browser window. This works generally pretty well for desktop web applications, less well on android, still less well for android PWAs, and (to my understanding) not at all on iOS. Artur from nostr.band is working on these problems using a variety of approaches, one of which is embedding nsec.app in an iframe and communicating using `postMessage`. This approach also makes it possible to sync keys between your phone and desktop, simulating a hosted UX by making them accessible from either location by signing in to nsec.app. This is done by encrypting user keys and storing them on the nsec.app server. In theory this should be secure, but it's something to consider. I'm cautiously optimistic about this approach. If successful, it would enable a single brand to exist on every platform, which is important to reduce unnecessary configuration and cognitive overhead for users. ## Multisig Signers Another experimental approach is multi-sig. [Promenade](https://git.fiatjaf.com/promenade) is a project by fiatjaf exploring this possibility. This would allow users to split their keys across different custodians and require all (or some majority of them) to approve an event signature before it would be valid. The downsides of this are an increase in complexity (more moving parts for users to deal with) and latency (more parties to coordinate with to sign events). I'm also not clear on whether encryption is possible using multi-signature keys. If not, that would preclude not only existing direct messages (which will hopefully end up on MLS eventually anyway), but also things like private lists, mutes, and application settings. I think multi-signature signers are promising, but are definitely a long-term project. ## Self-Hosted Signers Coming nearly full circle, self-hosted signers are a special case of hosted signers, but, you know, self-hosted. These signers might live on a home server like a Start9 and be accessible for signer request approvals via tor, or they might live on a server run by the user (or an Uncle Jim). This would be an extremely convenient approach for anyone willing to deal with the complexities of hosting the infrastructure. A good candidate for NIP 46 support might be AlbyHub, which is already one of the easiest self-hosted wallets to set up and use. Adding signer suppport to AlbyHub would allow users to have their wallet and nostr keys stored in the same place, and accessible anywhere either via the web interface or via AlbyGo. ## Omniplatform Signers This leads me to, finally, "omniplatform" signers. This isn't really a new architecture, but a combination of several. User choice is great, but nostr has a very tight complexity budget when onboarding new users. If a brand can manage to get new users set up with a very simple but sub-optimal solution, then grow them into a more complete integration into the nostr ecosystem, that would be a huge win. I think Alby has a great shot at doing this, if it's something they want to prioritize. Bitwarden would also be a great candidate, since they already have apps on every platform, as well as a self-hosted option (Vaultwarden). If users could start with a mobile app, and incrementally set up a browser extension, self-hosted vault, and hardware signer as needed, that I think would be an ideal path. # Nostr Connect: broken, but promising If you can't tell from the above comparison, I'm partial to NIP 46 as the best, most flexible way to build high-quality user experiences. Remote key management means a reduction in moving keys, hosting keys, and software installation and administration. If we can get users to the point where their keys live in only two places (their password manager and their signer), we'll be doing good. There are however many ways to implement NIP 46. Implementing all of them in a single client (or signer) would be burdensome for developers, and introduce a lot of UI complexity to users. Here's a quick survey of flows that currently exist. ## Signer -> Client The simplest way to connect a client and a bunker is for a user to explicitly authorize the connection by copying a `bunker://` URL from their signer application to their client. This allows the bunker to generate and validate a secret embedded in the URL without the client having to do anything other than pass it along in the initial `connect` request. This is a great UX for people who know what they're doing, but isn't at all friendly to newcomers. Someone signing in for the first time isn't going to know what a bunker link is, and even if they do they're immediately confronted with the problem of picking a signer, setting it up, and finding out where in that app they can obtain a bunker link. This can be marginally smoothed out using things like protocol handlers and QR codes, but these won't apply in all (or even most) cases. ## Client -> Signer The reverse flow is similar. This relies on the user to explicitly authorize the connection by copying a `nostrconnect://` url from the client into the signer app. In technical terms, this requires one fewer step, since in NIP 46 the connection is always initiated by the client. In this case, the pasting of the URL replaces the `connect` request. The client listens for a response containing a client-generated secret embedded in the `nostrconnect://` url. This step isn't currently supported by all signer apps, some of which return an `ack` instead. This can result in session hijacking, where an attacker can intercept signing requests (although they can't do anything that would require the user's key, like decrypting messages). While at first glance `nostrconnect` seems functionally identical to `bunker` links, the UX has the potential to be much better. The reason for this has to do with how people use which devices, and where a client or signer application is most likely to be run. This requires making some assumptions, but in my mind the most common scenario is that a user will want to host their signer on their phone, since that is the device that is most universally available for authorizations (apart from an always-online hosted signer on the open internet). In other words, users generally have their phones with them when they're using their computer, but often don't have a desktop available when using their phone. This idea is validated by (for example) the prevalence of SMS-based 2FA, which assumes the presence of a phone. Assuming the signer is on the user's phone, QR-scan flows for client authorization make a lot more sense if the client is the one generating the link, since they can simply scan a code generated on another device with their camera, or copy/paste or use a protocol handler for a client on the same device. In contrast, when using a `bunker` link users might find themselves in the awkward position of having to copy a link from their phone to their desktop. Whether this is done via QR code or by sending yourself a link via DM/text/email, it's an awkward flow most people aren't really prepared for. ## Auto-Connect Some enhancements have been made to the bunker flow which allow clients to send an initial `connect` request without asking the user to copy links between apps. These allow clients to do away with opaque magic strings entirely and provide the idealized "just one click" flow. However, after trying to make this flow work over the course of a couple weeks, I've come to the opinion that the additional complexity involved in automating the flow just isn't worth it. There are a few variants of this "auto-connect" flow: - Signer NIP-05: Signers can register a NIP 05 address for a user's pubkey on their domain, allowing users to enter their address rather than their pubkey on login. Unfortunately, this address has no relation to their actual NIP 05 address, which can result in a lot of confusion. - User NIP-05: To solve this problem, fiatjaf has proposed [a new version](https://github.com/nostr-protocol/nips/pull/1578) which allows users to enter their own NIP 05 in at login instead of the one provided by the signer. The client would then look up the user's `10046` event and follow the signer pubkey listed there. - Nostrconnect handler: Signers may publish a NIP 89 handler which includes a handler url that clients can send `nostrconnect` urls to. This isn't currently specified anywhere, but it is supported by nsec.app. This bypasses the NIP 05 address requirement entirely, allowing users to simply pick a signer and click a button. Each of these flows have their own strengths and weaknesses, but all of them share a dependency on some external source of truth for routing a user to the correct bunker. In the first case, this is done by remembering the NIP 05 address assigned by the signer, which relies on DNS and on users to not forget which address they're using. In the second case, this is done by relying on the user having done a significant amount of configuration (setting up a NIP 05, adding it to their kind 0, and having published a `10046` event) which may or may not exist. This forces clients to gracefully degrade to some alternative login method anyway, and adds UX friction since users have to choose which interface will work for them. The final method bypasses the need for users to remember their NIP 05 address, but it does require either the client or the user to select a trusted signer. If poorly implemented, this could result in users choosing an untrustworthy signer on signup (risking their keys), or the wrong signer on login resulting in a broken session. For all these reasons, I've opted to go with the vanilla bunker/nostrconnect flow, which allows me to display a simple interface to users. Presenting a QR code without comment assumes that users know what to do with it, but the benefit is that it makes explicit the signer selection step which the auto-connect flows try to paper over. This is actually a good thing, because instead of using heuristics like addresses or lists of signers presented by a client to make the decision, users can choose based on which app they actually have installed, which is a richer mnemonic device. # Making NIP 46 Work The bottom line here is that while NIP 46 is the best baseline for signer support, it doesn't currently work very well at all. There are a variety of reasons for this: - The specification itself isn't clear, and is constantly changing. This leads to incompatibilities between apps and signers (or explosive complexity in trying to handle every case). - Extensions to the basic bunker flow (both in terms of signer implementation and signer discovery) are worth researching, but each one creates another dimension of possible incompatibility. Signers will be incentivized to support every possible login flow, creating complexity for users and increasing attack surface area. Clients will have to implement fallbacks to their preferred signup flows, again resulting in UX complexity. - Clients don't currently deal well with latency. In order for NIP 46 to work smoothly, clients will have to implement better loading, debouncing, optimistic updates, publish status, and "undo". There are downsides to this, but many of these features endu up being built by mature software products anyway, so supporting these patterns may actually improve rather than degrade UX. - There's currently no easy and secure way for users to store keys in a single signer which they can access anywhere. This means that users have to set up multiple bunkers depending where they're sitting, or resort to alternative login methods like NIP 07 or 55. These are great upgrades, since they reduce latency and bandwidth use, but shouldn't be required for new users to learn. - There's no unified experience across platforms. If a user signs up on their desktop, how do they safely transfer their keys to their Android signer app? If they're given seed words, how can they import them as an nsec? Consensus on best practices would be an improvement, but I think only a unified UX across platforms for a single signer can really solve this. - As nice as it might be to bypass app stores and built-in push notifications, shunning traditional platforms drastically increases the friction for users. To my knowledge, no signer app currently exists in traditional app stores, or supports built-in push notifications. If we want nostr to be accessible to non-technical folks, we can't ask them to start by downloading Obtanium or zap.store and a UnifiedPush distributor for their platform. As I mentioned above, I don't think NIP 46 will ever be the only solution for signers. But I do think it's a great baseline on which to build a kind of "progressive enhancement" approach. For example, clients should support at least nostrconnect/bunker links, and encourage users once they've logged in to upgrade to NIP 55 or NIP 07 signers. Signers should exist in the mainstream app store and use native push notifications, with an option to install elsewhere or opt-in to UnifiedPush. The goal here is to balance user experience and security. The number one rule for this is to reduce attack vectors for obtaining user keys. This points to (ideally) a single non-custodial signer, easily accessible to the user, and a simple protocol for using that signer from any app. Progressive enhancement is fine, but we should always be able to fall back to this baseline.
@ 97c70a44:ad98e322
2024-11-18 17:57:17So I have this cool new product, which for about two weeks has been ready to release, if I could just solve one thing. I have recently moved away from storing user keys in my apps due to the ease with which they could (and have) been put at risk. In doing so, I've discovered that despite its downsides, pasting your nsec into an app is a pretty straightforward operation which even non-technical people can pull off. In contrast, pretty much no other key management solution is. Just to state the obvious, and to kick off this survey of nostr key management options, let me just state that asking users to paste their nsec into your app is a *bad idea*. However good your intentions, this opens your users up to all kinds of attack vectors, including clipboard hijacking attacks, exposing keys to insecure communication channels, exposing keys to many different apps, supply chain attacks, XSS attacks, and yes, bugs that cause your software to send keys to analytics or error reporting backends. The era of nsec-pasting is over. I've committed to embracing the pain and removing nsec login from Coracle, and I encourage other devs to do the same. The sooner we treat key management with the urgency it deserves, the sooner we can come up with a secure *and* convenient key management solution. As an aside, `ncryptsec` is a great innovation for securely *transporting* keys, but it still doesn't protect against exposure to apps that need to *use* keys. It has its place though; in fact I'm of the opinion that `nsec` and seed words should be deprecated, and support for them should be removed. Giving friendly names and human-readable representations to data that is essentially private is a really bad idea (unless you're memorizing your key). But I digress. # Signer Comparisons Let's go through a few existing options for key management, and compare their relative merits. I've tried to list them in the order they appeared on the scene, which also helps to clarify the logic of how signers have evolved. Throughout, I will be focusing on what kinds of user experience each approach unlocks for *non-technical users*, since my goal is to build products that work for regular people. ## Extension Signers The first signer application (that I know of) was nos2x, by fiatjaf. As I understand it, this was a proof-of-concept of how users might protect their keys without releasing custody of them. And it works really well! In fact, even though there have been many forks and imitators, I still use nos2x when using nostr on my desktop browser. Extension signers offer a great user experience, along a narrow happy path. Setting up a browser extension is a relatively familiar process for normal users, and once it's done you don't really have to think about it. In theory, extensions can also include their own onboarding process and key backup strategies as well, allowing users to get started in a single place. Plus, there's very little latency involved in making calls to the signer extension. This positive experience breaks down quickly though once a user wants to use a desktop or mobile application. When this happens, users have to start over essentially from scratch. Nothing they did to set up the extension helps them move to another signer application. While it's *technically* possible to use extension signers on mobile via e.g. the Kiwi browser, this doesn't work for native apps or apps installed as PWAs. Instead, you either have to revert to pasting keys, or use some other solution. One slight permutation of extension signers is browser signers, like Spring. Instead of adding a signer to your browser, Spring allows you to install a browser that holds your keys and allows you to use any nostr web application. But this has all the same basic limitations that extension signers do. ## Hardware Signers Hardware signers came around shortly after extension signers. I'm not going to spend much time talking about them here, because although they're about as far along the spectrum towards security as you can go, they're also not very convenient. Non-technical users aren't going to onboard by buying (or building) a device which they have to connect to their desktop via USB whenever they want to sign a message. Hardware signers have their place, but onboarding isn't it. The only hardware signer I'm aware of (although I'm sure I've heard of others) is from [LNBits](https://github.com/lnbits/nostr-signing-device), and is usually used via a browser extension like [horse](https://github.com/lnbits/horse). This of course means that it has all the same limitations that browser extensions have, and then some (although mobile and desktop apps would likely be able to find a way to talk directly to the signer). ## Hosted Signers Remote signers (aka "bunkers") use the Nostr Connect protocol (also known as NIP 46) for remote signing. Hosted signers in particular are one example of a NIP 46 remote signer, which lives on "somebody else's computer". Because they use a legacy web architecture, they can be built to be very familiar and convenient to users. It's trivial to build a hosted signer that offers email/password login along with 2FA, password resets, session revokation, the whole shebang. But they have one fatal flaw, which is that they are custodial. This means that not only do users have to relinquish exclusive control over their keys, but hosted signers also can become a target for hackers. ## Desktop Signers Several projects exist which allow users to run their own bunker, on their own hardware. These include nostr clients like Gossip, as well as command-line utilities like nak. This approach is mostly an improvement over extension signers, because it widens the scope of applications that can conveniently access the signer from those that run in the browser to those that run on the desktop computer the signer lives on. The downside is that they have to communicate via relays, which either introduces latency or requires an additional component to be running locally. While it's technically possible to use desktop signers to log in on other computers or mobile apps, I don't think that's going to be very practical for most people. Mobile apps by definition are more portable than regular computers. Anyone who wants to access their nostr account on more than one device will have to either set up separate solutions, or go with another kind of remote signer. This isn't a huge obstacle for people highly invested in nostr, but it's a significant amount of friction for a new user. ## Mobile Signers Mobile signers solve the problem introduced by desktop signers of not always having access to your signer (or of your signer not having access to you, due to being powered down or disconnected from the internet). Mobile devices are generally more available than desktop devices, and also have better push notifications. This means that users can approve signer requests from any device as easily as tapping a notification. Mobile signers on Android can also upgrade their UX by taking advantage of NIP 55 to avoid the round trip to relays, reducing latency and making it possible to sign things offline. [Amber](https://github.com/greenart7c3/Amber) has been a pioneer in this area, and other projects like [Nostrum](https://github.com/nostr-connect/nostrum) and [Alby's nostr-signer](https://github.com/getAlby/nostr-signer) have been prototyped. To date, there unfortunately haven't been any signer applications released for iOS, which leaves the mobile signer story incomplete. In my opinion, this is probably the most promising solution for end users, although it's currently under-developed. ## Web Signers One interesting alternative that combines the benefits of hosted, desktop, and mobile wallets is [nsec.app](https://nsec.app). This is a web application frontend which keeps keys in the browser, so that they are never shared with a third party. Using web push notifications and a healthy sprinkle of black magic, nsec.app is able to respond to signer requests by opening itself in a browser window. This works generally pretty well for desktop web applications, less well on android, still less well for android PWAs, and (to my understanding) not at all on iOS. Artur from nostr.band is working on these problems using a variety of approaches, one of which is embedding nsec.app in an iframe and communicating using `postMessage`. This approach also makes it possible to sync keys between your phone and desktop, simulating a hosted UX by making them accessible from either location by signing in to nsec.app. This is done by encrypting user keys and storing them on the nsec.app server. In theory this should be secure, but it's something to consider. I'm cautiously optimistic about this approach. If successful, it would enable a single brand to exist on every platform, which is important to reduce unnecessary configuration and cognitive overhead for users. ## Multisig Signers Another experimental approach is multi-sig. [Promenade](https://git.fiatjaf.com/promenade) is a project by fiatjaf exploring this possibility. This would allow users to split their keys across different custodians and require all (or some majority of them) to approve an event signature before it would be valid. The downsides of this are an increase in complexity (more moving parts for users to deal with) and latency (more parties to coordinate with to sign events). I'm also not clear on whether encryption is possible using multi-signature keys. If not, that would preclude not only existing direct messages (which will hopefully end up on MLS eventually anyway), but also things like private lists, mutes, and application settings. I think multi-signature signers are promising, but are definitely a long-term project. ## Self-Hosted Signers Coming nearly full circle, self-hosted signers are a special case of hosted signers, but, you know, self-hosted. These signers might live on a home server like a Start9 and be accessible for signer request approvals via tor, or they might live on a server run by the user (or an Uncle Jim). This would be an extremely convenient approach for anyone willing to deal with the complexities of hosting the infrastructure. A good candidate for NIP 46 support might be AlbyHub, which is already one of the easiest self-hosted wallets to set up and use. Adding signer suppport to AlbyHub would allow users to have their wallet and nostr keys stored in the same place, and accessible anywhere either via the web interface or via AlbyGo. ## Omniplatform Signers This leads me to, finally, "omniplatform" signers. This isn't really a new architecture, but a combination of several. User choice is great, but nostr has a very tight complexity budget when onboarding new users. If a brand can manage to get new users set up with a very simple but sub-optimal solution, then grow them into a more complete integration into the nostr ecosystem, that would be a huge win. I think Alby has a great shot at doing this, if it's something they want to prioritize. Bitwarden would also be a great candidate, since they already have apps on every platform, as well as a self-hosted option (Vaultwarden). If users could start with a mobile app, and incrementally set up a browser extension, self-hosted vault, and hardware signer as needed, that I think would be an ideal path. # Nostr Connect: broken, but promising If you can't tell from the above comparison, I'm partial to NIP 46 as the best, most flexible way to build high-quality user experiences. Remote key management means a reduction in moving keys, hosting keys, and software installation and administration. If we can get users to the point where their keys live in only two places (their password manager and their signer), we'll be doing good. There are however many ways to implement NIP 46. Implementing all of them in a single client (or signer) would be burdensome for developers, and introduce a lot of UI complexity to users. Here's a quick survey of flows that currently exist. ## Signer -> Client The simplest way to connect a client and a bunker is for a user to explicitly authorize the connection by copying a `bunker://` URL from their signer application to their client. This allows the bunker to generate and validate a secret embedded in the URL without the client having to do anything other than pass it along in the initial `connect` request. This is a great UX for people who know what they're doing, but isn't at all friendly to newcomers. Someone signing in for the first time isn't going to know what a bunker link is, and even if they do they're immediately confronted with the problem of picking a signer, setting it up, and finding out where in that app they can obtain a bunker link. This can be marginally smoothed out using things like protocol handlers and QR codes, but these won't apply in all (or even most) cases. ## Client -> Signer The reverse flow is similar. This relies on the user to explicitly authorize the connection by copying a `nostrconnect://` url from the client into the signer app. In technical terms, this requires one fewer step, since in NIP 46 the connection is always initiated by the client. In this case, the pasting of the URL replaces the `connect` request. The client listens for a response containing a client-generated secret embedded in the `nostrconnect://` url. This step isn't currently supported by all signer apps, some of which return an `ack` instead. This can result in session hijacking, where an attacker can intercept signing requests (although they can't do anything that would require the user's key, like decrypting messages). While at first glance `nostrconnect` seems functionally identical to `bunker` links, the UX has the potential to be much better. The reason for this has to do with how people use which devices, and where a client or signer application is most likely to be run. This requires making some assumptions, but in my mind the most common scenario is that a user will want to host their signer on their phone, since that is the device that is most universally available for authorizations (apart from an always-online hosted signer on the open internet). In other words, users generally have their phones with them when they're using their computer, but often don't have a desktop available when using their phone. This idea is validated by (for example) the prevalence of SMS-based 2FA, which assumes the presence of a phone. Assuming the signer is on the user's phone, QR-scan flows for client authorization make a lot more sense if the client is the one generating the link, since they can simply scan a code generated on another device with their camera, or copy/paste or use a protocol handler for a client on the same device. In contrast, when using a `bunker` link users might find themselves in the awkward position of having to copy a link from their phone to their desktop. Whether this is done via QR code or by sending yourself a link via DM/text/email, it's an awkward flow most people aren't really prepared for. ## Auto-Connect Some enhancements have been made to the bunker flow which allow clients to send an initial `connect` request without asking the user to copy links between apps. These allow clients to do away with opaque magic strings entirely and provide the idealized "just one click" flow. However, after trying to make this flow work over the course of a couple weeks, I've come to the opinion that the additional complexity involved in automating the flow just isn't worth it. There are a few variants of this "auto-connect" flow: - Signer NIP-05: Signers can register a NIP 05 address for a user's pubkey on their domain, allowing users to enter their address rather than their pubkey on login. Unfortunately, this address has no relation to their actual NIP 05 address, which can result in a lot of confusion. - User NIP-05: To solve this problem, fiatjaf has proposed [a new version](https://github.com/nostr-protocol/nips/pull/1578) which allows users to enter their own NIP 05 in at login instead of the one provided by the signer. The client would then look up the user's `10046` event and follow the signer pubkey listed there. - Nostrconnect handler: Signers may publish a NIP 89 handler which includes a handler url that clients can send `nostrconnect` urls to. This isn't currently specified anywhere, but it is supported by nsec.app. This bypasses the NIP 05 address requirement entirely, allowing users to simply pick a signer and click a button. Each of these flows have their own strengths and weaknesses, but all of them share a dependency on some external source of truth for routing a user to the correct bunker. In the first case, this is done by remembering the NIP 05 address assigned by the signer, which relies on DNS and on users to not forget which address they're using. In the second case, this is done by relying on the user having done a significant amount of configuration (setting up a NIP 05, adding it to their kind 0, and having published a `10046` event) which may or may not exist. This forces clients to gracefully degrade to some alternative login method anyway, and adds UX friction since users have to choose which interface will work for them. The final method bypasses the need for users to remember their NIP 05 address, but it does require either the client or the user to select a trusted signer. If poorly implemented, this could result in users choosing an untrustworthy signer on signup (risking their keys), or the wrong signer on login resulting in a broken session. For all these reasons, I've opted to go with the vanilla bunker/nostrconnect flow, which allows me to display a simple interface to users. Presenting a QR code without comment assumes that users know what to do with it, but the benefit is that it makes explicit the signer selection step which the auto-connect flows try to paper over. This is actually a good thing, because instead of using heuristics like addresses or lists of signers presented by a client to make the decision, users can choose based on which app they actually have installed, which is a richer mnemonic device. # Making NIP 46 Work The bottom line here is that while NIP 46 is the best baseline for signer support, it doesn't currently work very well at all. There are a variety of reasons for this: - The specification itself isn't clear, and is constantly changing. This leads to incompatibilities between apps and signers (or explosive complexity in trying to handle every case). - Extensions to the basic bunker flow (both in terms of signer implementation and signer discovery) are worth researching, but each one creates another dimension of possible incompatibility. Signers will be incentivized to support every possible login flow, creating complexity for users and increasing attack surface area. Clients will have to implement fallbacks to their preferred signup flows, again resulting in UX complexity. - Clients don't currently deal well with latency. In order for NIP 46 to work smoothly, clients will have to implement better loading, debouncing, optimistic updates, publish status, and "undo". There are downsides to this, but many of these features endu up being built by mature software products anyway, so supporting these patterns may actually improve rather than degrade UX. - There's currently no easy and secure way for users to store keys in a single signer which they can access anywhere. This means that users have to set up multiple bunkers depending where they're sitting, or resort to alternative login methods like NIP 07 or 55. These are great upgrades, since they reduce latency and bandwidth use, but shouldn't be required for new users to learn. - There's no unified experience across platforms. If a user signs up on their desktop, how do they safely transfer their keys to their Android signer app? If they're given seed words, how can they import them as an nsec? Consensus on best practices would be an improvement, but I think only a unified UX across platforms for a single signer can really solve this. - As nice as it might be to bypass app stores and built-in push notifications, shunning traditional platforms drastically increases the friction for users. To my knowledge, no signer app currently exists in traditional app stores, or supports built-in push notifications. If we want nostr to be accessible to non-technical folks, we can't ask them to start by downloading Obtanium or zap.store and a UnifiedPush distributor for their platform. As I mentioned above, I don't think NIP 46 will ever be the only solution for signers. But I do think it's a great baseline on which to build a kind of "progressive enhancement" approach. For example, clients should support at least nostrconnect/bunker links, and encourage users once they've logged in to upgrade to NIP 55 or NIP 07 signers. Signers should exist in the mainstream app store and use native push notifications, with an option to install elsewhere or opt-in to UnifiedPush. The goal here is to balance user experience and security. The number one rule for this is to reduce attack vectors for obtaining user keys. This points to (ideally) a single non-custodial signer, easily accessible to the user, and a simple protocol for using that signer from any app. Progressive enhancement is fine, but we should always be able to fall back to this baseline. @ 3bf0c63f:aefa459d
2024-10-31 16:08:50# Anglicismos estúpidos no português contemporâneo Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês. Cada erro é acompanhado também de uma sugestão de como corrigi-lo. ### Palavras que existem em português com sentido diferente - _submissão_ (de trabalhos): **envio**, **apresentação** - _disrupção_: **perturbação** - _assumir_: **considerar**, **pressupor**, **presumir** - _realizar_: **perceber** - _endereçar_: **tratar de** - _suporte_ (ao cliente): **atendimento** - _suportar_ (uma idéia, um projeto): **apoiar**, **financiar** - _suportar_ (uma função, recurso, característica): **oferecer**, **ser compatível com** - _literacia_: **instrução**, **alfabetização** - _convoluto_: **complicado**. - _acurácia_: **precisão**. - _resiliência_: **resistência**. ### Aportuguesamentos desnecessários - _estartar_: **iniciar**, **começar** - _treidar_: **negociar**, **especular** ### Expressões - _"não é sobre..."_: **"não se trata de..."** ---  ## Ver também - [Algumas expressões e ditados excelentes da língua portuguesa, e outras não tão excelentes assim](https://fiatjaf.alhur.es/expressões-e-ditados.txt)
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50# Anglicismos estúpidos no português contemporâneo Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês. Cada erro é acompanhado também de uma sugestão de como corrigi-lo. ### Palavras que existem em português com sentido diferente - _submissão_ (de trabalhos): **envio**, **apresentação** - _disrupção_: **perturbação** - _assumir_: **considerar**, **pressupor**, **presumir** - _realizar_: **perceber** - _endereçar_: **tratar de** - _suporte_ (ao cliente): **atendimento** - _suportar_ (uma idéia, um projeto): **apoiar**, **financiar** - _suportar_ (uma função, recurso, característica): **oferecer**, **ser compatível com** - _literacia_: **instrução**, **alfabetização** - _convoluto_: **complicado**. - _acurácia_: **precisão**. - _resiliência_: **resistência**. ### Aportuguesamentos desnecessários - _estartar_: **iniciar**, **começar** - _treidar_: **negociar**, **especular** ### Expressões - _"não é sobre..."_: **"não se trata de..."** ---  ## Ver também - [Algumas expressões e ditados excelentes da língua portuguesa, e outras não tão excelentes assim](https://fiatjaf.alhur.es/expressões-e-ditados.txt) @ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...) ### Design System Check it out [here](https://www.figma.com/community/file/1430887635327548022 ). This is by no means finished and will be continually updated and completed as we go along. ### Project description Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda) nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki. ### Explanatory videos This list of videos will also be continually updated and completed as we go along: 1. Chat as the universal interface https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov 2. Your Nostr Dashboard https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov 3. Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov 4. Design entered the Chat https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov 5. Targeted publication & The blurry edges of interoperable communities https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov 6. Travel Back https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
@ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...) ### Design System Check it out [here](https://www.figma.com/community/file/1430887635327548022 ). This is by no means finished and will be continually updated and completed as we go along. ### Project description Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda) nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki. ### Explanatory videos This list of videos will also be continually updated and completed as we go along: 1. Chat as the universal interface https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov 2. Your Nostr Dashboard https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov 3. Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov 4. Design entered the Chat https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov 5. Targeted publication & The blurry edges of interoperable communities https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov 6. Travel Back https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov @ 84999652:2a24d806
2024-11-18 17:18:10当敲出这个标题时,我知道一定要得罪一大批人了,但是,我可能只是大家的嘴替,说了一句大家都不愿意承认的事实而已。 从2023年6月份,我开始关注比特币Layer2这个赛道,花费了大量时间研究比特币扩容技术,长期跟进一些我认为比较具有技术含量的团队,比如:Stacks、BEVM、Bihelix、Bool Network,包括BitVM和RGB的解决方案等等。 研究了一圈发现,BTC Layer2似乎真的是一个伪命题,因为,比特币压根不需要Layer2,而是Crypto行业需要比特币而已;而且Layer2本身只是一门生意,压根不是区块链;最关键的问题是,Layer2压根不能帮助主链扩容,只是把主链代币找了一些应用场景而已,而且这些场景都是照抄Layer1,丝毫没有创新。 最早验证我这个思路,并且和我的想法达成共鸣的是BEVM团队。我从去年6月就开始关注这个比特币创业团队,他们也算是最早在华语区推广比特Layer2的团队了,但是,他们在2024年却突然180度大转弯,彻底否认了比特币layer2赛道,转而推出了名为Super Bitcoin的全新战略,具体在这里我就不细讲了,有兴趣的可以看他们发布最新版白皮书,写的还是很有意思的。 为什么最早推广比特币Layer2的团队,突然彻底放弃这个方向,转朝另一个方向?这里,我来谈谈我的一些看见: ### 一、Layer2是一个臆想的需求,并没有真正帮助Layer1扩容 Layer2概念最早来源于比特币,当初中本聪在比特币白皮书第八章专门提到了简单支付验证(全称Simple Payment Verification,简称SPV)的方案。意思是说,可以基于比特币的SPV节点也就是轻节点,可以在没有下载完整比特币区块链的情况下,也可以完成交易验证,我们可以理解为这是一种高效的链下交易验证。 基于这个概念,诞生了闪电网络,闪电网络是完全基于中本聪的提出的简单支付验证去实现的,这个方案是有意义的,因为,闪电网络足够快、足够便宜,更重要的是它完全继承比特币的网络安全性,帮助比特币在交易方面实现了真正意义上的“扩容”。 后来的以太坊Layer2照抄了这个模式,但是,以太坊的Layer2虽然能共享以太坊的安全性,但是,却无法帮助以太坊真正的实现扩容,只是增加了以太坊这个代币的一些应用场景而已。 闪电网络之所以能基于简单支付验证实现比特币“扩容”,是因为比特币采用的是UTXO模型,而以太坊采用的是统一帐户模型,任何Layer2方案都无法解决以太坊账号模型带来的问题。 我们简单来讲: 比特币UTXO模型是一个模拟人与人之间现金交易的模型,任何人之间拿着现金交易时,是可以同时和多人进行交易,而且交易双方就可以彼此验证交易,并不一定需要全局达成共识才能交易,在交易期间并不需要一个中心化的机构来统一变更交易双方的数据。因此,比特币的UTXO模型可以实现并发处理交易以及局部进行状态变更,而且不需要一个统一的世界状态树来更新状态。 而以太坊采用的是统一账户模型,也就是传统的银行账户模型。账户模型在处理交易时,需要依靠一个全局的状态树来给每一笔交易涉及的地址进行余额的加减计算从而实现状态变更。 因此,以太坊的每一笔交易的状态都需要先变更完之后,才能进行下一笔交易,否则就会出现双花或者无法交易等问题。通俗来讲,以太坊的账户模型,需要一个中心的世界状态树来统一处理交易,来统一变更所有账户的状态。虽然,这个世界状态树是去中心机制来驱动的。也正是因为去中心化的方式来驱动这个世界状态树,也导致了这个状态变更能力很差,效率很低。 以太坊要实现扩容,本质上是要提升状态变更的效率和能力。但是,目前所有的以太坊Layer2都没有在这方面对以太坊进行任何的改变和提升。当然,这不是以太坊Layer2能解决的问题,是以太坊自身的问题。 最近,以太坊社区提出了BeamChain方案,其中最重要的一点是引入SNARK ,SNARK全称Succinct Non-Interactive Argument of Knowledge,也就是“简洁非交互式知识证明”,这个和比特币的简单支付验证(Simple Payment Verification)也就是前文我们提到的SPV,几乎是要达到一样的效果。这个确实可以提升以太坊的验证效率,因为,验证的内容被压缩了,而且不需要验证全部内容,因此,可以部分提升以太坊的状态变更能力。但是,这依然没有彻底解决以太坊帐户模型所带来的无法并行处理交易的问题,因为,依然依靠世界状态树来统一变更状态。 打个比喻就是:比特币的UTXO模型是一个可以并行的多车道(实际上是无限车道),而以太坊有且只有一个单车道,现在以太坊的BeamChain无非是把这个车道的通车速度再提升一个层次而已。而且,这个方案本质上和以太坊Layer2没有太大关系。 从这个角度来看,以太坊Layer2根本无法帮助以太坊实现扩容,最后,还是得以太坊自己挥刀自救。当然,以太坊的统一帐户模型设计是以太坊在扩容之路上的“最大障碍”。 而比特币的闪电网络本质上并不是依靠自身的技术来帮助比特币进行扩容,而是比特币的UTXO模型本身就是具备局部变更状态和并发处理状态变更的能力,而闪电网络只是在这个能力之上,用一个客户端+一个防止双花交易的检举机制把比特币的这个本身自带的链下扩容方案呈现出来了而已。所以,除了闪电网络以外,基本上没有第二个真正意义上的Layer2。甚至说,闪电网络也并不是比特币的Layer2,而是基于比特币的UTXO模型和SPV技术,创造的一个可以快速交易比特币的应用而已。 因此,我们说,无论是以太坊Layer2还是比特币Layer2,本质都无法帮助Layer1实现扩容,无非是给Laye1的代币找了一些应用场景而已,并没有真正意义上给Layer1带来改变! Layer2仅仅是一个叙事,而且是一个打着帮助Layer1扩容的旗号,实际却干着自己的生意。 ### 二、Layer2只是项目方的一门生意,和散户无关 有一个显而易见的问题,几乎所有的Layer2都是中心化的,Layer2本身没有共识机制,更没有节点的概念,Layer2的运行有且只有官方的一个定序器,也就是Sequencer。 所有的Layer2本质都是一个没有共识机制、没有“矿工参与共识”的私有链。 一般,一个POS共识机制的链,其代币基本可以用于节点质押、充当GAS以及参与链上的一些治理等等场景。但是,Layer2代币,没有节点质押需求(没有共识机制和节点,质押个啥),链的GAS也是用Layer1的代币。能讲的唯一价值,就是进行虚无缥缈的所谓治理。Layer2本质都是中心化的,又能治理个啥? 而且我们前面说过,Layer2的定序器有且只有官方一个,因此,整个链上的所有GAS都被官方收取了,这也是除了发币之外。所有Layer2项目方的最主要收入来源。比如,ZKsync等Layer2在代币TGE之前,疯狂的给用户制造空投预期,ZKsync每月GAS收入基本是300万-500万美金,而且连续PUA2年,光GAS收入就是7200万-1亿美金,这恐怕比上交易所赚的还多。 所以,我说,Layer2就是一门生意,你要的是项目方的代币空投,项目方赚的是你花费的GAS。最后,空投给你一个啥用没有的代币,结束。 这个生意模式已经被越来越多的商业主体看明白了,所以,你看到越来越多的大型项目开始自己做Layer2,传统的商业主体,比如三星、Visa等;Crypto项目,比如,Uniswap的Unichain就是典型的例子。因为,大家都想明白了,总共就这些用户,而且我有自己的“私域用户”,为啥交给别人赚这个钱,还不如自己赚! 未来,会有越来越多的商业主体来做自己的Layer2,依附一个拥有共识能力的Layer1来共享安全性,自己搭一个定序器,基本就可以开干了。GAS费自己收,用户在自己链上玩,形成一个传统意义上的商业闭环。从这个角度来看,像Coinbase这样拥有巨大交易用户的商业主体,自己做一个Layer2是最好的,也是有竞争力的。 但是,这一切基本和散户无关。因为,这是Layer2的商业主体自己的生意,用户只是消费者。这一切本质和共识和社区用户都无关,因此,Layer2代币也很难有共识。这是包括以太坊和比特币Layer2都逐渐走弱的原因所在。 ### 3、比特币不需要Layer2,是Crypto行业需要比特币 为什么说,比特币本质上不需要Layer2,只是Crypto行业需要比特币? 围绕比特币创业的Crypto项目,目前市值最大的是WBTC,这个项目明白了一点,不是比特币需要拓展方案,是整个Crypto行业需要比特币这个大金矿。 在WBTC之前,以太坊这个金融市场是和比特币这个全球最大的数字金矿是完全隔绝的,比特币占有全球加密货币50%以上的市场份额,其他金融市场要长足发展,非常需要这样的优质资产,因此,WBTC诞生了。当然,WBTC的风险在于是中心化的。所以,后来诞生了相对去中心化的TBTC等解决方案,包括,这一轮很多机构下场亲自做的各类WarpBTC,都是解决一个问题——把比特币这个超级金矿搬到自己的生态里来或者去到别的生态里去。 但是,不管怎样,这是行业需要比特币,而不是比特币需要这些拓展方案。比特币本性自足,不需要任何拓展方案,这么多年围绕比特币的拓展方案都没什么创新意义,大部分都是在重复造轮子。 因此,当我意识到这个问题后,从现在开始,我对一切要去改进比特币或者帮助比特币拓展的方案统统都不感兴趣。比特币不需要任何拓展方案,是这个行业,甚至整个人类需要比特币。 当我们从这个角度思考时,思维和眼界立马就打开了! 为了更容易理解这个事,我先分享一篇文章,https://x.com/qiqileyuan/status/1858357959807635854 **作者推特ID:@qiqileyuan** 这个文章提出了一个问题: 比特币在成为国家储备之后,还有更高维度的叙事可以把比特币的价格送到100万美金以上吗? 这是一个极好的问题。 作者给到的答案是: 当比特币作为数字黄金储备到各个国家的国库之后,其价值无限接近于黄金,但是,想要让比特币在100万美金以上继续突破,数字黄金的这个概念是不足以支撑的,数字黄金的概念在比特币成为国家货币储备之后,其叙事基本是趋于落地了,比特币下一个阶段的价值是:成为链上AI的货币和AI共识问题的去中心化控制系统。 我觉得作者真正打开了比特币的上升叙事。 这个思路,没有局限于思考比特币本身,而是跳出来开始思考比特币网络和人类以及AI的关系。这是认知上的升级,站在更高处才能看到不一样的风景。 我认为,把比特币作为未来链上AI货币,把比特币网络作为未来AI治理事务的共识网络,是非常有未来的方向。 这一点,我在BEVM发布的Super Bitcoin白皮书以及其相关的解读文档中也找到了相应的思路和方案。 ### Super Bitcoin是这样描述的: 比特币是一个去中心化的状态变更机器,是一个不断生长的机械共识来驱动的去中心化控制系统。这个系统的共识能力不断生长(通过吸食算力和能源),这是唯一能匹配人类未来的AI治理和安全需求的系统。因为,比特币是全球最去中心化的系统,不受任何一方控制,其共识过的“状态变更事务”是值得信赖的,尤其在未来AI世界,AI和我们几乎只能信任比特币网络。而且这个网络的共识能力和安全性是不断生长的,可以满足人类和AI日益增长的安全和去中心化治理需求。Super Bitcoin要做的就是要把比特币的这种无限生长的机械共识能力和去中心化状态变更的能力共享给未来人类的各种公共治理和AI安全需求。 这是我认为巨酷无比的创业方向,远超比特币Layer2等小卡拉米的创业思维。 第一、这个思路,找到了比特币未来价值增长的第二曲线,实现了比特币从“数字黄金”到“链上AI货币和链上AI治理系统”的身份转换,这是当前我认为最值得探索的方向。 第二、通过把比特币和未来人类发展以及链上AI的需求结合,真正把比特币的价值发挥到了最大化。在此之前,大家把BTC作为作为数字黄金,要做Warp BTC,要做Layer2帮比特币做拓展,这只是看到了BTC这个Coin的价值,并没有思考比特币网络本身的价值,以及对于人类更深远的意义。毕竟,BTC只是比特币网络的激励Coin,并不是比特币的全部。 ### 总结: 比特币Layer2已经成为了一个过时的且没有意义的创业方向。比特币在成为国家货币储备之后,进入了一个全新的发展阶段。比特币的价值更大了,共识更广了,其网络价安全性也更强了,而且这些都在不断生长。但是,比特币网络本身的价值还完全没有开发出来,未来最具价值的创业方向是围绕比特币网络本身,去思考这个无限生长的去中心化控制系统,这个全球最大的去中心化状态变更机器,能在未来的人类和AI并存的时代,发挥哪些更大的价值,这才是最有潜力的创业方向。 发挥比特币网络本身的价值,而不仅仅局限于BTC这个Coin本身,这或许才是中本聪留给人类的最大财富! 中本聪,或许真的是从未来穿越回来的! **本文灵感主要来源于比特币学习交流暑社区“中本聪大学”(推特ID:@ZhongbcDX_1028),本人长期在中本聪大学和诸多比特币OG及爱好者深度交流学习比特币,一起探讨Crypto行业发展机遇。** 如果您对【中本聪大学】感兴趣,想要了解更多相关信息,与同样对该项目感兴趣的人讨论,欢迎加入我们创建的【交流群】。**添加Web3CN小助手(微信id:Web3CNpro) (TG id:@potato_little,添加时备注项目名称【中本聪大学】,以便小助手将您拉进相应的社群哦。**
@ 84999652:2a24d806
2024-11-18 17:18:10当敲出这个标题时,我知道一定要得罪一大批人了,但是,我可能只是大家的嘴替,说了一句大家都不愿意承认的事实而已。 从2023年6月份,我开始关注比特币Layer2这个赛道,花费了大量时间研究比特币扩容技术,长期跟进一些我认为比较具有技术含量的团队,比如:Stacks、BEVM、Bihelix、Bool Network,包括BitVM和RGB的解决方案等等。 研究了一圈发现,BTC Layer2似乎真的是一个伪命题,因为,比特币压根不需要Layer2,而是Crypto行业需要比特币而已;而且Layer2本身只是一门生意,压根不是区块链;最关键的问题是,Layer2压根不能帮助主链扩容,只是把主链代币找了一些应用场景而已,而且这些场景都是照抄Layer1,丝毫没有创新。 最早验证我这个思路,并且和我的想法达成共鸣的是BEVM团队。我从去年6月就开始关注这个比特币创业团队,他们也算是最早在华语区推广比特Layer2的团队了,但是,他们在2024年却突然180度大转弯,彻底否认了比特币layer2赛道,转而推出了名为Super Bitcoin的全新战略,具体在这里我就不细讲了,有兴趣的可以看他们发布最新版白皮书,写的还是很有意思的。 为什么最早推广比特币Layer2的团队,突然彻底放弃这个方向,转朝另一个方向?这里,我来谈谈我的一些看见: ### 一、Layer2是一个臆想的需求,并没有真正帮助Layer1扩容 Layer2概念最早来源于比特币,当初中本聪在比特币白皮书第八章专门提到了简单支付验证(全称Simple Payment Verification,简称SPV)的方案。意思是说,可以基于比特币的SPV节点也就是轻节点,可以在没有下载完整比特币区块链的情况下,也可以完成交易验证,我们可以理解为这是一种高效的链下交易验证。 基于这个概念,诞生了闪电网络,闪电网络是完全基于中本聪的提出的简单支付验证去实现的,这个方案是有意义的,因为,闪电网络足够快、足够便宜,更重要的是它完全继承比特币的网络安全性,帮助比特币在交易方面实现了真正意义上的“扩容”。 后来的以太坊Layer2照抄了这个模式,但是,以太坊的Layer2虽然能共享以太坊的安全性,但是,却无法帮助以太坊真正的实现扩容,只是增加了以太坊这个代币的一些应用场景而已。 闪电网络之所以能基于简单支付验证实现比特币“扩容”,是因为比特币采用的是UTXO模型,而以太坊采用的是统一帐户模型,任何Layer2方案都无法解决以太坊账号模型带来的问题。 我们简单来讲: 比特币UTXO模型是一个模拟人与人之间现金交易的模型,任何人之间拿着现金交易时,是可以同时和多人进行交易,而且交易双方就可以彼此验证交易,并不一定需要全局达成共识才能交易,在交易期间并不需要一个中心化的机构来统一变更交易双方的数据。因此,比特币的UTXO模型可以实现并发处理交易以及局部进行状态变更,而且不需要一个统一的世界状态树来更新状态。 而以太坊采用的是统一账户模型,也就是传统的银行账户模型。账户模型在处理交易时,需要依靠一个全局的状态树来给每一笔交易涉及的地址进行余额的加减计算从而实现状态变更。 因此,以太坊的每一笔交易的状态都需要先变更完之后,才能进行下一笔交易,否则就会出现双花或者无法交易等问题。通俗来讲,以太坊的账户模型,需要一个中心的世界状态树来统一处理交易,来统一变更所有账户的状态。虽然,这个世界状态树是去中心机制来驱动的。也正是因为去中心化的方式来驱动这个世界状态树,也导致了这个状态变更能力很差,效率很低。 以太坊要实现扩容,本质上是要提升状态变更的效率和能力。但是,目前所有的以太坊Layer2都没有在这方面对以太坊进行任何的改变和提升。当然,这不是以太坊Layer2能解决的问题,是以太坊自身的问题。 最近,以太坊社区提出了BeamChain方案,其中最重要的一点是引入SNARK ,SNARK全称Succinct Non-Interactive Argument of Knowledge,也就是“简洁非交互式知识证明”,这个和比特币的简单支付验证(Simple Payment Verification)也就是前文我们提到的SPV,几乎是要达到一样的效果。这个确实可以提升以太坊的验证效率,因为,验证的内容被压缩了,而且不需要验证全部内容,因此,可以部分提升以太坊的状态变更能力。但是,这依然没有彻底解决以太坊帐户模型所带来的无法并行处理交易的问题,因为,依然依靠世界状态树来统一变更状态。 打个比喻就是:比特币的UTXO模型是一个可以并行的多车道(实际上是无限车道),而以太坊有且只有一个单车道,现在以太坊的BeamChain无非是把这个车道的通车速度再提升一个层次而已。而且,这个方案本质上和以太坊Layer2没有太大关系。 从这个角度来看,以太坊Layer2根本无法帮助以太坊实现扩容,最后,还是得以太坊自己挥刀自救。当然,以太坊的统一帐户模型设计是以太坊在扩容之路上的“最大障碍”。 而比特币的闪电网络本质上并不是依靠自身的技术来帮助比特币进行扩容,而是比特币的UTXO模型本身就是具备局部变更状态和并发处理状态变更的能力,而闪电网络只是在这个能力之上,用一个客户端+一个防止双花交易的检举机制把比特币的这个本身自带的链下扩容方案呈现出来了而已。所以,除了闪电网络以外,基本上没有第二个真正意义上的Layer2。甚至说,闪电网络也并不是比特币的Layer2,而是基于比特币的UTXO模型和SPV技术,创造的一个可以快速交易比特币的应用而已。 因此,我们说,无论是以太坊Layer2还是比特币Layer2,本质都无法帮助Layer1实现扩容,无非是给Laye1的代币找了一些应用场景而已,并没有真正意义上给Layer1带来改变! Layer2仅仅是一个叙事,而且是一个打着帮助Layer1扩容的旗号,实际却干着自己的生意。 ### 二、Layer2只是项目方的一门生意,和散户无关 有一个显而易见的问题,几乎所有的Layer2都是中心化的,Layer2本身没有共识机制,更没有节点的概念,Layer2的运行有且只有官方的一个定序器,也就是Sequencer。 所有的Layer2本质都是一个没有共识机制、没有“矿工参与共识”的私有链。 一般,一个POS共识机制的链,其代币基本可以用于节点质押、充当GAS以及参与链上的一些治理等等场景。但是,Layer2代币,没有节点质押需求(没有共识机制和节点,质押个啥),链的GAS也是用Layer1的代币。能讲的唯一价值,就是进行虚无缥缈的所谓治理。Layer2本质都是中心化的,又能治理个啥? 而且我们前面说过,Layer2的定序器有且只有官方一个,因此,整个链上的所有GAS都被官方收取了,这也是除了发币之外。所有Layer2项目方的最主要收入来源。比如,ZKsync等Layer2在代币TGE之前,疯狂的给用户制造空投预期,ZKsync每月GAS收入基本是300万-500万美金,而且连续PUA2年,光GAS收入就是7200万-1亿美金,这恐怕比上交易所赚的还多。 所以,我说,Layer2就是一门生意,你要的是项目方的代币空投,项目方赚的是你花费的GAS。最后,空投给你一个啥用没有的代币,结束。 这个生意模式已经被越来越多的商业主体看明白了,所以,你看到越来越多的大型项目开始自己做Layer2,传统的商业主体,比如三星、Visa等;Crypto项目,比如,Uniswap的Unichain就是典型的例子。因为,大家都想明白了,总共就这些用户,而且我有自己的“私域用户”,为啥交给别人赚这个钱,还不如自己赚! 未来,会有越来越多的商业主体来做自己的Layer2,依附一个拥有共识能力的Layer1来共享安全性,自己搭一个定序器,基本就可以开干了。GAS费自己收,用户在自己链上玩,形成一个传统意义上的商业闭环。从这个角度来看,像Coinbase这样拥有巨大交易用户的商业主体,自己做一个Layer2是最好的,也是有竞争力的。 但是,这一切基本和散户无关。因为,这是Layer2的商业主体自己的生意,用户只是消费者。这一切本质和共识和社区用户都无关,因此,Layer2代币也很难有共识。这是包括以太坊和比特币Layer2都逐渐走弱的原因所在。 ### 3、比特币不需要Layer2,是Crypto行业需要比特币 为什么说,比特币本质上不需要Layer2,只是Crypto行业需要比特币? 围绕比特币创业的Crypto项目,目前市值最大的是WBTC,这个项目明白了一点,不是比特币需要拓展方案,是整个Crypto行业需要比特币这个大金矿。 在WBTC之前,以太坊这个金融市场是和比特币这个全球最大的数字金矿是完全隔绝的,比特币占有全球加密货币50%以上的市场份额,其他金融市场要长足发展,非常需要这样的优质资产,因此,WBTC诞生了。当然,WBTC的风险在于是中心化的。所以,后来诞生了相对去中心化的TBTC等解决方案,包括,这一轮很多机构下场亲自做的各类WarpBTC,都是解决一个问题——把比特币这个超级金矿搬到自己的生态里来或者去到别的生态里去。 但是,不管怎样,这是行业需要比特币,而不是比特币需要这些拓展方案。比特币本性自足,不需要任何拓展方案,这么多年围绕比特币的拓展方案都没什么创新意义,大部分都是在重复造轮子。 因此,当我意识到这个问题后,从现在开始,我对一切要去改进比特币或者帮助比特币拓展的方案统统都不感兴趣。比特币不需要任何拓展方案,是这个行业,甚至整个人类需要比特币。 当我们从这个角度思考时,思维和眼界立马就打开了! 为了更容易理解这个事,我先分享一篇文章,https://x.com/qiqileyuan/status/1858357959807635854 **作者推特ID:@qiqileyuan** 这个文章提出了一个问题: 比特币在成为国家储备之后,还有更高维度的叙事可以把比特币的价格送到100万美金以上吗? 这是一个极好的问题。 作者给到的答案是: 当比特币作为数字黄金储备到各个国家的国库之后,其价值无限接近于黄金,但是,想要让比特币在100万美金以上继续突破,数字黄金的这个概念是不足以支撑的,数字黄金的概念在比特币成为国家货币储备之后,其叙事基本是趋于落地了,比特币下一个阶段的价值是:成为链上AI的货币和AI共识问题的去中心化控制系统。 我觉得作者真正打开了比特币的上升叙事。 这个思路,没有局限于思考比特币本身,而是跳出来开始思考比特币网络和人类以及AI的关系。这是认知上的升级,站在更高处才能看到不一样的风景。 我认为,把比特币作为未来链上AI货币,把比特币网络作为未来AI治理事务的共识网络,是非常有未来的方向。 这一点,我在BEVM发布的Super Bitcoin白皮书以及其相关的解读文档中也找到了相应的思路和方案。 ### Super Bitcoin是这样描述的: 比特币是一个去中心化的状态变更机器,是一个不断生长的机械共识来驱动的去中心化控制系统。这个系统的共识能力不断生长(通过吸食算力和能源),这是唯一能匹配人类未来的AI治理和安全需求的系统。因为,比特币是全球最去中心化的系统,不受任何一方控制,其共识过的“状态变更事务”是值得信赖的,尤其在未来AI世界,AI和我们几乎只能信任比特币网络。而且这个网络的共识能力和安全性是不断生长的,可以满足人类和AI日益增长的安全和去中心化治理需求。Super Bitcoin要做的就是要把比特币的这种无限生长的机械共识能力和去中心化状态变更的能力共享给未来人类的各种公共治理和AI安全需求。 这是我认为巨酷无比的创业方向,远超比特币Layer2等小卡拉米的创业思维。 第一、这个思路,找到了比特币未来价值增长的第二曲线,实现了比特币从“数字黄金”到“链上AI货币和链上AI治理系统”的身份转换,这是当前我认为最值得探索的方向。 第二、通过把比特币和未来人类发展以及链上AI的需求结合,真正把比特币的价值发挥到了最大化。在此之前,大家把BTC作为作为数字黄金,要做Warp BTC,要做Layer2帮比特币做拓展,这只是看到了BTC这个Coin的价值,并没有思考比特币网络本身的价值,以及对于人类更深远的意义。毕竟,BTC只是比特币网络的激励Coin,并不是比特币的全部。 ### 总结: 比特币Layer2已经成为了一个过时的且没有意义的创业方向。比特币在成为国家货币储备之后,进入了一个全新的发展阶段。比特币的价值更大了,共识更广了,其网络价安全性也更强了,而且这些都在不断生长。但是,比特币网络本身的价值还完全没有开发出来,未来最具价值的创业方向是围绕比特币网络本身,去思考这个无限生长的去中心化控制系统,这个全球最大的去中心化状态变更机器,能在未来的人类和AI并存的时代,发挥哪些更大的价值,这才是最有潜力的创业方向。 发挥比特币网络本身的价值,而不仅仅局限于BTC这个Coin本身,这或许才是中本聪留给人类的最大财富! 中本聪,或许真的是从未来穿越回来的! **本文灵感主要来源于比特币学习交流暑社区“中本聪大学”(推特ID:@ZhongbcDX_1028),本人长期在中本聪大学和诸多比特币OG及爱好者深度交流学习比特币,一起探讨Crypto行业发展机遇。** 如果您对【中本聪大学】感兴趣,想要了解更多相关信息,与同样对该项目感兴趣的人讨论,欢迎加入我们创建的【交流群】。**添加Web3CN小助手(微信id:Web3CNpro) (TG id:@potato_little,添加时备注项目名称【中本聪大学】,以便小助手将您拉进相应的社群哦。** @ 5d4b6c8d:8a1c1ee3
2024-11-18 17:13:32Another OC, another loss. There were some encouraging signs (Bowers might be a generational TE) and we get some clarity on what's wrong. Thanks to this loss, the Raiders are now picking 4th and it seems that Shedeur is angling to play for the Silver and Black. The stars are aligning a little bit. Also, the Jets continue being a trainwreck, so the pick we got for Davante is moving up the board. # 2025 Mock Draft - 4th Pick: QB Jalen Milroe - 35th Pick: OT Cameron Williams - 66th Pick: RB Quinshon Judkins - 71st Pick: DT T.J. Sanders - 106th Pick: WR Jayden Higgins - 142nd Pick: IOL Armand Membou - 179th Pick: CB Zy Alexander - 212th Pick: QB Dillon Gabriel - 215th Pick: IOL Seth McLaughlin - 217th Pick: OT Jude Bowry It ended up being funny how this board fell, but I don't mind doubling up on all the positions of need. It's maddening watching this team fail to upgrade at QB and on the O-Line. The Raiders defense is already fine and they'll be getting back two very good D-Linemen next season. They just can't go into next season without addressing the problems on offense. When are the rest of you going to look to the draft? originally posted at https://stacker.news/items/772891
@ 5d4b6c8d:8a1c1ee3
2024-11-18 17:13:32Another OC, another loss. There were some encouraging signs (Bowers might be a generational TE) and we get some clarity on what's wrong. Thanks to this loss, the Raiders are now picking 4th and it seems that Shedeur is angling to play for the Silver and Black. The stars are aligning a little bit. Also, the Jets continue being a trainwreck, so the pick we got for Davante is moving up the board. # 2025 Mock Draft - 4th Pick: QB Jalen Milroe - 35th Pick: OT Cameron Williams - 66th Pick: RB Quinshon Judkins - 71st Pick: DT T.J. Sanders - 106th Pick: WR Jayden Higgins - 142nd Pick: IOL Armand Membou - 179th Pick: CB Zy Alexander - 212th Pick: QB Dillon Gabriel - 215th Pick: IOL Seth McLaughlin - 217th Pick: OT Jude Bowry It ended up being funny how this board fell, but I don't mind doubling up on all the positions of need. It's maddening watching this team fail to upgrade at QB and on the O-Line. The Raiders defense is already fine and they'll be getting back two very good D-Linemen next season. They just can't go into next season without addressing the problems on offense. When are the rest of you going to look to the draft? originally posted at https://stacker.news/items/772891 @ 9ff58691:0bf6c134
2024-11-18 16:42:21Курган стал настоящим примером экологической сознательности и активного участия граждан в охране окружающей среды. Экоакции, проводимые накануне дня города, привлекают все больше людей, стремящихся помочь природе, особенно в лесах, расположенных рядом с городом. Местные жители активно участвуют в мероприятиях, направленных на восстановление лесных экосистем. В рамках программы «Сохраним лес» волонтеры высаживают деревья, очищают территории от мусора и проводят образовательные сессии о важности сохранения природы. Эти акции организуются как государственными структурами, так и общественными экологическими организациями, которые объединяют усилия для достижения общей цели — создания чистого и здорового окружения. Поддержка со стороны молодежи играет ключевую роль в этих инициативах. Школьники и студенты активно участвуют в экоакциях, осознавая важность своего вклада в защиту природы. Они не только высаживают деревья, но и участвуют в различных конкурсах и проектах, посвященных экологии. Таким образом, формируется новое поколение граждан, готовых заботиться о своей планете. Кроме того, в Кургане активно развиваются программы по охране труда в лесу, которые обучают волонтеров безопасным методам работы с растительностью и соблюдению экологических норм. Это позволяет не только улучшить состояние лесов, но и обеспечить безопасность участников акций. Курган сейчас — это город, где люди не просто говорят о проблемах экологии, а активно действуют для их решения. Автор: Эвелина Тимирбаева
@ 9ff58691:0bf6c134
2024-11-18 16:42:21Курган стал настоящим примером экологической сознательности и активного участия граждан в охране окружающей среды. Экоакции, проводимые накануне дня города, привлекают все больше людей, стремящихся помочь природе, особенно в лесах, расположенных рядом с городом. Местные жители активно участвуют в мероприятиях, направленных на восстановление лесных экосистем. В рамках программы «Сохраним лес» волонтеры высаживают деревья, очищают территории от мусора и проводят образовательные сессии о важности сохранения природы. Эти акции организуются как государственными структурами, так и общественными экологическими организациями, которые объединяют усилия для достижения общей цели — создания чистого и здорового окружения. Поддержка со стороны молодежи играет ключевую роль в этих инициативах. Школьники и студенты активно участвуют в экоакциях, осознавая важность своего вклада в защиту природы. Они не только высаживают деревья, но и участвуют в различных конкурсах и проектах, посвященных экологии. Таким образом, формируется новое поколение граждан, готовых заботиться о своей планете. Кроме того, в Кургане активно развиваются программы по охране труда в лесу, которые обучают волонтеров безопасным методам работы с растительностью и соблюдению экологических норм. Это позволяет не только улучшить состояние лесов, но и обеспечить безопасность участников акций. Курган сейчас — это город, где люди не просто говорят о проблемах экологии, а активно действуют для их решения. Автор: Эвелина Тимирбаева @ c48a6fb0:bcddf255
2024-11-18 16:10:43## So what is the oracle problem (op)? The op is trying to bring real world information into a digital information network (eg Bitcoin) without relying on one or multiable trusted parties (called a oracle). So what do I mean by real world informations? When I ask another peer in a network what 2+3 is, I can always verify the result on my own. But when I ask what the current weather in London is I have to trust that peer or ask other "trusted peer" (for example a british news channels). **So to conclude math is conciderd trustless** ## So what is PoW? PoW means proof of work. Its a method to proof that one of your peers did work without trusting someone. But how does it work trustless you might ask? We can't just setup a camera in their room and watch them work since it would be easy for them to cheat. (And the camera would be a trusted partie again.) The answere again is math. But we first need to learn a little bit about algorithm based hashfunctions. Bitcoins PoW uses mainly sha256. The most important part about hashfunctions (in this context) are that they aren't reversable calculations. What does that mean? When I calculate 2+3=5 I can allways reverse that with enought informations. If I don't know the 2nd number: 2+?=5 i can reverse that by calculation -2 on both sides: ?=5-2 . That lets me know that ?=3 . But you can't do that with hashfunctions. The hashfunction Sha1 with an input of the number 137 looks like this: Sha-1(137) = e1a864f0b77f6c89794827a9035355dc8d052622 But just a small change to 138 gives you a complety diffrent result: Sha-1(138)= 56ad4d4deaec98465c419b4a8ea7bfc1ed38c4d9 Since there is no way to tell if your input was below/above 100 or if it even was a number (because you can input text as well) the only method of getting the input is by trying out one input after the other. Test it out yourself: [Sha1 calculator](https://xorbin.com/tools/sha1-hash-calculator). ## How does Bitcoins PoW use the hashfunctions? When you give someone the task to get you a specific result of sha-1 they have to guess a lot of inputs to get the result. This is conciderd work. Providing the right input is the proof that your peer did work for that (or that they were lucky).Their solution however is quick and easy verifyable by you. Since calculating only one hash takes far less than a second. Short note: Bitcoin actually however uses a range of results that are concidered the right result (Number must start with x amount of zeros). That's how Bitcoin makes sure you need to provide real work to secure or attack bitcoin. ## How do I get other information trustless? "But wait?! You didn't explain how I can get the weather in London". You're right. Because getting these type of information trustless is impossible. Work is the only realworld information you can get trustless. You can reduce the trust by having several validators. But the validators could team up to betrail you. Or there could be a mesurement mistake effecting several validators at once. Or diffrent validators provide diffret results. Who do you trust? The result that was provided the most? So spamming becomes the truth? Or the information gets altered on the way too you. Or your client censors certain information for you. There is an insane amount of attack vectors. Concluding: Trust is allways a terrible risk. No matter how little. Trust = information centralization. Examples of real world information: Price of stocks, stablecoins (price of a currency), a picture, music, videos. **Cryptocurrencies that use oracles are relying on trust and are doomed to get centralised.** **When they claim to be decentralised you now know they are a scam.** Distributed doesn't equal decentralised. ## This article is reworked from its release on Nostr: nostr:nevent1qqs8yzntzvun4alupatcupetdqaaf4k609hm30cjrggyt2y602h8fxspzpmhxue69uhkummnw3ezumt0d5hsygxy3fhmpxsr2k93an6srh3vuzdvjddu8lpdw0h4kktr0e6meh0j25psgqqqqqqserd69u ## I posted it original on my Twitter on 07th Jan 2023. I reposted it too Nostr, because X is closed knowledge.
@ c48a6fb0:bcddf255
2024-11-18 16:10:43## So what is the oracle problem (op)? The op is trying to bring real world information into a digital information network (eg Bitcoin) without relying on one or multiable trusted parties (called a oracle). So what do I mean by real world informations? When I ask another peer in a network what 2+3 is, I can always verify the result on my own. But when I ask what the current weather in London is I have to trust that peer or ask other "trusted peer" (for example a british news channels). **So to conclude math is conciderd trustless** ## So what is PoW? PoW means proof of work. Its a method to proof that one of your peers did work without trusting someone. But how does it work trustless you might ask? We can't just setup a camera in their room and watch them work since it would be easy for them to cheat. (And the camera would be a trusted partie again.) The answere again is math. But we first need to learn a little bit about algorithm based hashfunctions. Bitcoins PoW uses mainly sha256. The most important part about hashfunctions (in this context) are that they aren't reversable calculations. What does that mean? When I calculate 2+3=5 I can allways reverse that with enought informations. If I don't know the 2nd number: 2+?=5 i can reverse that by calculation -2 on both sides: ?=5-2 . That lets me know that ?=3 . But you can't do that with hashfunctions. The hashfunction Sha1 with an input of the number 137 looks like this: Sha-1(137) = e1a864f0b77f6c89794827a9035355dc8d052622 But just a small change to 138 gives you a complety diffrent result: Sha-1(138)= 56ad4d4deaec98465c419b4a8ea7bfc1ed38c4d9 Since there is no way to tell if your input was below/above 100 or if it even was a number (because you can input text as well) the only method of getting the input is by trying out one input after the other. Test it out yourself: [Sha1 calculator](https://xorbin.com/tools/sha1-hash-calculator). ## How does Bitcoins PoW use the hashfunctions? When you give someone the task to get you a specific result of sha-1 they have to guess a lot of inputs to get the result. This is conciderd work. Providing the right input is the proof that your peer did work for that (or that they were lucky).Their solution however is quick and easy verifyable by you. Since calculating only one hash takes far less than a second. Short note: Bitcoin actually however uses a range of results that are concidered the right result (Number must start with x amount of zeros). That's how Bitcoin makes sure you need to provide real work to secure or attack bitcoin. ## How do I get other information trustless? "But wait?! You didn't explain how I can get the weather in London". You're right. Because getting these type of information trustless is impossible. Work is the only realworld information you can get trustless. You can reduce the trust by having several validators. But the validators could team up to betrail you. Or there could be a mesurement mistake effecting several validators at once. Or diffrent validators provide diffret results. Who do you trust? The result that was provided the most? So spamming becomes the truth? Or the information gets altered on the way too you. Or your client censors certain information for you. There is an insane amount of attack vectors. Concluding: Trust is allways a terrible risk. No matter how little. Trust = information centralization. Examples of real world information: Price of stocks, stablecoins (price of a currency), a picture, music, videos. **Cryptocurrencies that use oracles are relying on trust and are doomed to get centralised.** **When they claim to be decentralised you now know they are a scam.** Distributed doesn't equal decentralised. ## This article is reworked from its release on Nostr: nostr:nevent1qqs8yzntzvun4alupatcupetdqaaf4k609hm30cjrggyt2y602h8fxspzpmhxue69uhkummnw3ezumt0d5hsygxy3fhmpxsr2k93an6srh3vuzdvjddu8lpdw0h4kktr0e6meh0j25psgqqqqqqserd69u ## I posted it original on my Twitter on 07th Jan 2023. I reposted it too Nostr, because X is closed knowledge. @ f8a5df57:b7a58cd4
2024-11-18 15:46:47<iframe width="720" height="405" src="https://rutube.ru/play/embed/d83ed19084087a2a14f7bd59319ca216" frameBorder="0" allow="clipboard-write; autoplay" webkitAllowFullScreen mozallowfullscreen allowFullScreen></iframe> # Содержание сюжета: Поднебесье - такое название получил 100 процентов экологичный микрорайон в дальних уголках столицы. Он получил такое название за счет своего уникального расположения возле реки Яуза. На территории расположены небоскребы высотой 200 этажей, на последнем из которых можно в прямом смысле достать до неба. Благодаря такой инициативе в небе начали работать роботы-пилоты, которые доставляют продукты жителям прямо в окошки квартир. Помимо этого их задачей является осмотр территории, сообщение времени и погоды москвичам. В микрорайоне находится несколько парков с уютными беседками и местами для отдыха с детьми: центр скалолазания, батутов, больших аквапарков. При этом все объекты оснащены обилием растений и увлажнителями воздуха. **Автор:** Дарья Воронина
@ f8a5df57:b7a58cd4
2024-11-18 15:46:47<iframe width="720" height="405" src="https://rutube.ru/play/embed/d83ed19084087a2a14f7bd59319ca216" frameBorder="0" allow="clipboard-write; autoplay" webkitAllowFullScreen mozallowfullscreen allowFullScreen></iframe> # Содержание сюжета: Поднебесье - такое название получил 100 процентов экологичный микрорайон в дальних уголках столицы. Он получил такое название за счет своего уникального расположения возле реки Яуза. На территории расположены небоскребы высотой 200 этажей, на последнем из которых можно в прямом смысле достать до неба. Благодаря такой инициативе в небе начали работать роботы-пилоты, которые доставляют продукты жителям прямо в окошки квартир. Помимо этого их задачей является осмотр территории, сообщение времени и погоды москвичам. В микрорайоне находится несколько парков с уютными беседками и местами для отдыха с детьми: центр скалолазания, батутов, больших аквапарков. При этом все объекты оснащены обилием растений и увлажнителями воздуха. **Автор:** Дарья Воронина @ f8a5df57:b7a58cd4
2024-11-18 15:20:13Москва стала одним из первых городов, внедривших собственную электронную валюту, благодаря которой открылись новые горизонты для финансовых операций и цифровой экономики. Эта инициатива направлена на упрощение расчетов и повышение безопасности транзакций в условиях быстро меняющегося финансового ландшафта. 20 июля 2063 года Москва представила свою электронную валюту, которая обещает революционизировать финансовые операции и улучшить взаимодействие между гражданами и бизнесом. Этот шаг стал ответом на растущую потребность в безопасных и эффективных способах ведения финансовых дел. Электронная валюта будет использовать технологию блокчейн, обеспечивая прозрачность и защиту данных. Ожидается, что новая валюта позволит пользователям проводить мгновенные транзакции без необходимости обращения к традиционным банковским системам. Это также может снизить затраты на переводы и повысить доступность финансовых услуг для населения. Внедрение электронной валюты поддерживается правительством города, которое видит в этом шаге возможность привлечь инвестиции и развивать стартапы в области финтеха. Эксперты отмечают, что такая инициатива может стать катализатором для дальнейшего развития цифровой экономики в России. Автор: Ксения Данилова "Создание электронной валюты — это не просто шаг к цифровизации экономики, это возможность изменить саму природу финансовых отношений в нашем городе. Мы вступаем в новую эру, где технологии будут играть ключевую роль в повседневной жизни граждан," — говорит экономист Алексей Смирнов.
@ f8a5df57:b7a58cd4
2024-11-18 15:20:13Москва стала одним из первых городов, внедривших собственную электронную валюту, благодаря которой открылись новые горизонты для финансовых операций и цифровой экономики. Эта инициатива направлена на упрощение расчетов и повышение безопасности транзакций в условиях быстро меняющегося финансового ландшафта. 20 июля 2063 года Москва представила свою электронную валюту, которая обещает революционизировать финансовые операции и улучшить взаимодействие между гражданами и бизнесом. Этот шаг стал ответом на растущую потребность в безопасных и эффективных способах ведения финансовых дел. Электронная валюта будет использовать технологию блокчейн, обеспечивая прозрачность и защиту данных. Ожидается, что новая валюта позволит пользователям проводить мгновенные транзакции без необходимости обращения к традиционным банковским системам. Это также может снизить затраты на переводы и повысить доступность финансовых услуг для населения. Внедрение электронной валюты поддерживается правительством города, которое видит в этом шаге возможность привлечь инвестиции и развивать стартапы в области финтеха. Эксперты отмечают, что такая инициатива может стать катализатором для дальнейшего развития цифровой экономики в России. Автор: Ксения Данилова "Создание электронной валюты — это не просто шаг к цифровизации экономики, это возможность изменить саму природу финансовых отношений в нашем городе. Мы вступаем в новую эру, где технологии будут играть ключевую роль в повседневной жизни граждан," — говорит экономист Алексей Смирнов. @ 5bfb38cb:2b999aa7
2024-11-18 15:07:56### Spot Over BTX2024 #### Relative Strength Analysis: The 3 stock indices have had a week of bullish retracement, with the YM showing the least retracement and the NQ the most. #### Classic Technical Analysis: In terms of conventional technical analysis, BTC remains in an Elliott structure fulfilling a minor wave 5 and a major wave 3. We have had a consolidation structure since March 2024 with a breakout to the upside. The context is strongly bullish. https://image.nostr.build/6b83ebee90e8ef8dc7965f159b8fd6b6244eda7b0b18a8e611962bb3129e8980.png https://image.nostr.build/c0a9ba9a4f3edf81e7787c24988fc8a8787225e847e73d99d459b5d6c4ba6a44.png #### COT: The progression of contracts nearing expiration is at a premium. The 12-month COT is in a positive program and in positive hedging. Banks are buying Bitcoin futures contracts and are not in a bearish position, being the counterpart to leveraged short investment funds. https://image.nostr.build/d24f4b3ddeabaafa4885d96b726c65976fc64679bc760414630cd7db5641e36b.png https://image.nostr.build/11a0b1e68b5ee1d6879716d831a8a9517ec653beed1f425086a7736965bfa534.png #### Market Sentiment: Market sentiment in general retail news is bullish following the FED's rate cut and in response to the US elections, although with some moderation after this week. The Williams %R remains in oversold territory and avoids a bearish divergence. #### Intermarket Analysis: The 3 indices have made a bullish reversal. The YM shows the greatest strength marking an FVG while the NQ is the weakest. The 3 bonds ZN, ZF, and ZB have had another week of taking with negative displacement but without a negative close. It is likely that we have a bit of room left for discount. Interest rates behave inversely. The DYX has had a bullish week with a lot of strength and has maintained another bullish week. It is likely that we continue to take some premium closing an FVG W. Peripheral currencies are weak with strong bearish displacement, with the EUR being the weakest. In commodities, GC has had its first significant delay with a bearish close and MSS. BTC maintains a very bullish week with a positive opening and closing gap. CL is in a high resistance framework with a week of negative close. In conclusion, we have a stock market with a bullish retracement that has not yet changed the market structure. Strength of the DYX with weakness in peripheral currencies. Strength of BTC in commodities with GC showing a first significant retracement. CL lost in a seek and destroy framework. #### Market Profile: The market is currently bullish. It needs to move significantly away from the all-time high to continue this movement. #### Market Structure: The value 66798.00 maintains price control. The weekly context is bullish. #### Trading Range: 93483 to 66789. Currently at a premium in the range. #### PD Array Matrix: Premium: - PWH 93483 - OB+W 5910.75 Discount: - PWL 80280 - FVG W CE 79940 - OB+W 69011 Equilibrium: - 80141 #### Key Price Levels: - FVG W CE 79940. I do not expect closes below this structure to remain bullish. https://image.nostr.build/233090043a36d9f20a65db086d16b8ba2adf109c456ae5435c5ed1ee24df2f76.png #### Weekly BIAS: Bullish. #### Weekly Objective: - Retracement to equilibrium in the PWL region at 80280 to take liquidity and then continue to premium in an ideal scenario. A new take of the previous ATH before this scenario invalidates the possibility and leads to targeting 103363 sooner than expected. Await market confirmations. *The market is a great teacher; pay attention and learn its lessons. Every chart, every trend, and every reversal has a story to tell. Listen carefully, and you’ll become a master storyteller.* 🔮
@ 5bfb38cb:2b999aa7
2024-11-18 15:07:56### Spot Over BTX2024 #### Relative Strength Analysis: The 3 stock indices have had a week of bullish retracement, with the YM showing the least retracement and the NQ the most. #### Classic Technical Analysis: In terms of conventional technical analysis, BTC remains in an Elliott structure fulfilling a minor wave 5 and a major wave 3. We have had a consolidation structure since March 2024 with a breakout to the upside. The context is strongly bullish. https://image.nostr.build/6b83ebee90e8ef8dc7965f159b8fd6b6244eda7b0b18a8e611962bb3129e8980.png https://image.nostr.build/c0a9ba9a4f3edf81e7787c24988fc8a8787225e847e73d99d459b5d6c4ba6a44.png #### COT: The progression of contracts nearing expiration is at a premium. The 12-month COT is in a positive program and in positive hedging. Banks are buying Bitcoin futures contracts and are not in a bearish position, being the counterpart to leveraged short investment funds. https://image.nostr.build/d24f4b3ddeabaafa4885d96b726c65976fc64679bc760414630cd7db5641e36b.png https://image.nostr.build/11a0b1e68b5ee1d6879716d831a8a9517ec653beed1f425086a7736965bfa534.png #### Market Sentiment: Market sentiment in general retail news is bullish following the FED's rate cut and in response to the US elections, although with some moderation after this week. The Williams %R remains in oversold territory and avoids a bearish divergence. #### Intermarket Analysis: The 3 indices have made a bullish reversal. The YM shows the greatest strength marking an FVG while the NQ is the weakest. The 3 bonds ZN, ZF, and ZB have had another week of taking with negative displacement but without a negative close. It is likely that we have a bit of room left for discount. Interest rates behave inversely. The DYX has had a bullish week with a lot of strength and has maintained another bullish week. It is likely that we continue to take some premium closing an FVG W. Peripheral currencies are weak with strong bearish displacement, with the EUR being the weakest. In commodities, GC has had its first significant delay with a bearish close and MSS. BTC maintains a very bullish week with a positive opening and closing gap. CL is in a high resistance framework with a week of negative close. In conclusion, we have a stock market with a bullish retracement that has not yet changed the market structure. Strength of the DYX with weakness in peripheral currencies. Strength of BTC in commodities with GC showing a first significant retracement. CL lost in a seek and destroy framework. #### Market Profile: The market is currently bullish. It needs to move significantly away from the all-time high to continue this movement. #### Market Structure: The value 66798.00 maintains price control. The weekly context is bullish. #### Trading Range: 93483 to 66789. Currently at a premium in the range. #### PD Array Matrix: Premium: - PWH 93483 - OB+W 5910.75 Discount: - PWL 80280 - FVG W CE 79940 - OB+W 69011 Equilibrium: - 80141 #### Key Price Levels: - FVG W CE 79940. I do not expect closes below this structure to remain bullish. https://image.nostr.build/233090043a36d9f20a65db086d16b8ba2adf109c456ae5435c5ed1ee24df2f76.png #### Weekly BIAS: Bullish. #### Weekly Objective: - Retracement to equilibrium in the PWL region at 80280 to take liquidity and then continue to premium in an ideal scenario. A new take of the previous ATH before this scenario invalidates the possibility and leads to targeting 103363 sooner than expected. Await market confirmations. *The market is a great teacher; pay attention and learn its lessons. Every chart, every trend, and every reversal has a story to tell. Listen carefully, and you’ll become a master storyteller.* 🔮 @ 5bfb38cb:2b999aa7
2024-11-18 15:07:13### Comments: This is where we embark on our journey and set sail into unknown waters... ### Seasonal Trend/Monthly Changes: While Bitcoin's seasonal trend often resembles that of the SP500, sometimes they can lead or lag each other. We have been in a bullish trend for 24 months since November 2022, which exceeds the average duration of a bullish trend that ranges from 9 to 18 months. The reality is harsh, and we are in a brutally bullish market. This November has been like the last 15 years of Bitcoin, and we expect a premium close this month. https://image.nostr.build/f03e1e0ac181e109688d0efc9f5ccd52133ce9e37da7de26d2789b72bac47834.png ### Interest Rate Differentials: The FED has lowered the interest rate to 4.75% after 3 years, signaling the first dovish signs. The inflation target of 2% has not yet been reached but remains close. Among central banks, the FED and the BOE currently maintain the highest rates. The central bank market gives us a framework and a positive bias. ### Market Structure: Since November 2022, we have a clear monthly bullish trend that marked a new ATH in March 2024 and has projected after 7 months of re-accumulation to keep us bullish and embark on projections. https://image.nostr.build/c507c91a14ba63bf3afb11217ab19ef0b17f18eeb81a46baf356ccc78d140783.png ### Intermarket Analysis: The YM and ES reached a new all-time high in October. The NQ has had a relative high but has not yet presented a new all-time high, being the most delayed. The ZF, ZN, and ZB bonds have had a negative month, closing below the lows and a FVG M. They are likely to continue with some weakness. The 5, 10, and 30-year interest rates behave inversely with strength. The DYX has achieved a strong bullish reversal. There is weakness in peripheral currencies led by the EUR. In commodities, the GC maintains another month with a bullish close at highs, being the strongest. BTC achieves a monthly close above relative highs after 7 months. CL shows weakness without being able to achieve a bullish close. The conclusion is the strength of the stock market led by the ES and YM, but they may be approaching a trend end. This is reflected in the DYX making a monthly bullish MSS. In commodities, the GC continues to lead with great strength, and BTC has achieved the first sign of a monthly bullish change, projecting above highs following the path of GC. CL is in a high resistance and lagging territory. ### Market Profile: The market is frankly and brutally bullish, taking a new high and fleetingly massacring structures at a discount. We can only watch and project a trend end when it occurs, but never go against institutional order flow. ### Operational Range: 49577 to 93483. Currently in Premium Zone. ### PD Array Matrix: **Premium:** - ATH 93483.00 **Discount:** - OB+M 64612 - FVG M 59313 - PML 58867 **Equilibrium:** - 71530 **Key Price Levels:** - OB+M 64612. I do not expect closes below the CE of the structure to maintain the bullish idea. ### Monthly BIAS: Bullish BIAS. ### Monthly Objective: - The first objective has been the extension +1.5SD of the consolidation at 85903, which has already been met. The second objective would be the extension between +2.0SD and +2.5SD between the values of 98011 and 110120. I have doubts whether it will find the strength to reach here this month, given that ideally, we will do so before closing 2024. https://image.nostr.build/95a89792f35540e0c6302dbd2a82e2cb6bac8a92f5b813312ce5104bbf877beb.png *"The market is the mirror through which we truly see who we are, godspeed traveler."*
@ 5bfb38cb:2b999aa7
2024-11-18 15:07:13### Comments: This is where we embark on our journey and set sail into unknown waters... ### Seasonal Trend/Monthly Changes: While Bitcoin's seasonal trend often resembles that of the SP500, sometimes they can lead or lag each other. We have been in a bullish trend for 24 months since November 2022, which exceeds the average duration of a bullish trend that ranges from 9 to 18 months. The reality is harsh, and we are in a brutally bullish market. This November has been like the last 15 years of Bitcoin, and we expect a premium close this month. https://image.nostr.build/f03e1e0ac181e109688d0efc9f5ccd52133ce9e37da7de26d2789b72bac47834.png ### Interest Rate Differentials: The FED has lowered the interest rate to 4.75% after 3 years, signaling the first dovish signs. The inflation target of 2% has not yet been reached but remains close. Among central banks, the FED and the BOE currently maintain the highest rates. The central bank market gives us a framework and a positive bias. ### Market Structure: Since November 2022, we have a clear monthly bullish trend that marked a new ATH in March 2024 and has projected after 7 months of re-accumulation to keep us bullish and embark on projections. https://image.nostr.build/c507c91a14ba63bf3afb11217ab19ef0b17f18eeb81a46baf356ccc78d140783.png ### Intermarket Analysis: The YM and ES reached a new all-time high in October. The NQ has had a relative high but has not yet presented a new all-time high, being the most delayed. The ZF, ZN, and ZB bonds have had a negative month, closing below the lows and a FVG M. They are likely to continue with some weakness. The 5, 10, and 30-year interest rates behave inversely with strength. The DYX has achieved a strong bullish reversal. There is weakness in peripheral currencies led by the EUR. In commodities, the GC maintains another month with a bullish close at highs, being the strongest. BTC achieves a monthly close above relative highs after 7 months. CL shows weakness without being able to achieve a bullish close. The conclusion is the strength of the stock market led by the ES and YM, but they may be approaching a trend end. This is reflected in the DYX making a monthly bullish MSS. In commodities, the GC continues to lead with great strength, and BTC has achieved the first sign of a monthly bullish change, projecting above highs following the path of GC. CL is in a high resistance and lagging territory. ### Market Profile: The market is frankly and brutally bullish, taking a new high and fleetingly massacring structures at a discount. We can only watch and project a trend end when it occurs, but never go against institutional order flow. ### Operational Range: 49577 to 93483. Currently in Premium Zone. ### PD Array Matrix: **Premium:** - ATH 93483.00 **Discount:** - OB+M 64612 - FVG M 59313 - PML 58867 **Equilibrium:** - 71530 **Key Price Levels:** - OB+M 64612. I do not expect closes below the CE of the structure to maintain the bullish idea. ### Monthly BIAS: Bullish BIAS. ### Monthly Objective: - The first objective has been the extension +1.5SD of the consolidation at 85903, which has already been met. The second objective would be the extension between +2.0SD and +2.5SD between the values of 98011 and 110120. I have doubts whether it will find the strength to reach here this month, given that ideally, we will do so before closing 2024. https://image.nostr.build/95a89792f35540e0c6302dbd2a82e2cb6bac8a92f5b813312ce5104bbf877beb.png *"The market is the mirror through which we truly see who we are, godspeed traveler."* @ bbb5dda0:f09e2747
2024-11-18 14:15:11**What if there is no line, no boundary between tor and clearnet (the 'normal' web)? What if a Damus user on iPhone can talk to their friend's private TOR relay? Let's find out together what can happen by using this new tool which I call Nostr Epoxy! And it's scalable, too!** **TL;DR Demo video:** nostr:naddr1qqr5gc20v43hy5czyzamthdqu92k09ulq4p5q77uyqeadu9mkv8hy5f2nqw0mvhsncn5wqcyqqqgtwc5nzpll |  |  | | -------------------------------------------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------- | | Phone can reach clearweb relay, but cannot connect to TOR relay | Phone can reach TOR relay | Proxies have been around forever and can be a powerful tool in getting around network restrictions. In the context of nostr, currently everyone connects to a relay directly, which you may not always want. The relay can keep track of your IP address and build a profile, or your device might be behind a very restrictive firewall which prevents you from reaching a relay. From this problem, the idea for proxy relays was born. We wanted to reach a TOR relay, without having to install any TOR stuff on our devices. Which on iPhones is especially challenging. So the idea is that we want to extend a relay's functionality so that it can instead of processing requests for itself, it can pass on the requests to another relay that they themselves can reach. The easiest solution to get this working is in the form of a Reverse Proxy, which you can put in front of any relay, which by default tunnels the traffic to the operator's own relay, for example a Strfry instance. That way the relay implementation doesn't have to change and the user doesn't have to be aware that this relay endpoint can also proxy to other relays. The example implementation is called [NERP - Nostr Epoxy Reverse Proxy](nostr:naddr1qvzqqqrhnypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uqpjmn0wd68ytt9wphhs7fdwfjhvetjwdjj6urjdau8j6sn6y7). |  |  | | ----------------------------------------------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------- | | Reverse proxy default behaviour | Reverse proxy after proxy request | As shown above the default is to connect to the operator's own relay. So how do we create the proxied connection? Well we send the following request over our websocket: ```json ["PROXY", "wss://relay.com"] ``` Which asks the proxy to change the target from it's own back-end to whatever we specify. In this case `wss://relay.com`. However, it turns out this relay doesn't live in a fiat world, it responds with: `["PROXY", "PAYMENT_REQURIED", <payment_request>]` where `<payment_request>` is an object: ```json { "price": "1", "unit": "sat", "mint": "https://some.mint.cash/", } ``` Which brings us to... ## 💰 Monetizing proxies Inevitably we're going to hit the "Who's gonna run the proxies!?" question. Well you are, because you want to stack some sats. Therefore we added monetization to these proxies, which is what sets this project apart from current-day proxies on the internet. When the client is hit with the `PAYMENT_REQUIRED` message above, it can retry the first message, but with an additional field, a cashu payment. ```json ["PROXY", "wss://relay.com", "cashuAeyJ0..."] ``` We're now paying a couple sats, (the price above is in sats per minute). If the proxy is happy with our payment, it will start a timer and set up the connection to the target relay. Indicated by a `["PROXY", "CONNECTED"]` message, after which we can go about our relay business until the bought time runs out. After which the proxy will close our connection with code `1000`, reason: `PROXY: Connection Bankrupted`. The nice thing here is that introducing payments can reduce spam significantly. ### Why Cashu? Because [Cashu eCash](https://cashu.me) allows us to finally make micro-payments viable and scalable, it can help us to bring an honest monetary reward to the people that do the hard work of maintaining the free and open internet. If you provide a proxy, you get paid and therefore you're incentivised to keep the infrastructure up and running. Cashu tokens are a very efficient way of sending payments directly. Unlike Lightning, it does not require a back and forth between the two transacting parties. Because cashu tokens can be sent as a string of text, you can attach it to any request/data you're sending around. Even at rest, the money will still be 'physically' there. That means there's no back and forth required to send a payment, like we do on lightning, and people don't need perfect connectivity. ## 💭 Some philosophy Until now, all web applications have been strongly coupled to the transportation methods they use, mainly http(s). Nostr changes this, because the data that feeds an application can now arrive over any transportation mechanism. WebSockets, Thumb-drives, QR, LoRa (radio) and Heck! even FM and pigeons will work! Although the above point is not necessarily tied to the use of websocket proxies, it does underline the point I want to make: Because Nostr completely decouples applications from the transportation layer, We can get VERY creative in the ways in which we transport application data... Therefore, the boundaries of the current clearnet network become irrelevant. Using the websocket proxies, we can now hop from clearnet to tor, to [i2p](https://geti2p.net/en/), to [hyper](https://github.com/hypercore-protocol) and back to clearnet. This significantly reduces the burden on the client by not having to 'know' how any of these other networks work, they won't have to install anything, yet they can interact with relays on these lesser known networks. ## ⚙ Under the hood Here's a UMl example of a proxy (that does not have a default relay behind it) and the lifecycle of a proxied connection.  ## NIP-XX draft I wrote a draft NIP on how to support proxying [here](https://github.com/ArjenStens/nostr-epoxy-reverse-proxy/blob/main/NIP-XX.md). ## 🛝 Play with it! I created a [Dashboard](https://swissdash.site) to discover proxies and play with connecting to relays (multiple hops are possible).  Check out the route-builder tab, add a couple sats to the wallet and route some request through the proxies.   ## Resources - [Dashboard](https://swissdash.site) - **Nostr Epoxy Reverse Proxy** [Source Code](nostr:naddr1qvzqqqrhnypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uqpjmn0wd68ytt9wphhs7fdwfjhvetjwdjj6urjdau8j6sn6y7) - **NIP** [draft](https://github.com/ArjenStens/nostr-epoxy-reverse-proxy/blob/main/NIP-XX.md)
@ bbb5dda0:f09e2747
2024-11-18 14:15:11**What if there is no line, no boundary between tor and clearnet (the 'normal' web)? What if a Damus user on iPhone can talk to their friend's private TOR relay? Let's find out together what can happen by using this new tool which I call Nostr Epoxy! And it's scalable, too!** **TL;DR Demo video:** nostr:naddr1qqr5gc20v43hy5czyzamthdqu92k09ulq4p5q77uyqeadu9mkv8hy5f2nqw0mvhsncn5wqcyqqqgtwc5nzpll |  |  | | -------------------------------------------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------- | | Phone can reach clearweb relay, but cannot connect to TOR relay | Phone can reach TOR relay | Proxies have been around forever and can be a powerful tool in getting around network restrictions. In the context of nostr, currently everyone connects to a relay directly, which you may not always want. The relay can keep track of your IP address and build a profile, or your device might be behind a very restrictive firewall which prevents you from reaching a relay. From this problem, the idea for proxy relays was born. We wanted to reach a TOR relay, without having to install any TOR stuff on our devices. Which on iPhones is especially challenging. So the idea is that we want to extend a relay's functionality so that it can instead of processing requests for itself, it can pass on the requests to another relay that they themselves can reach. The easiest solution to get this working is in the form of a Reverse Proxy, which you can put in front of any relay, which by default tunnels the traffic to the operator's own relay, for example a Strfry instance. That way the relay implementation doesn't have to change and the user doesn't have to be aware that this relay endpoint can also proxy to other relays. The example implementation is called [NERP - Nostr Epoxy Reverse Proxy](nostr:naddr1qvzqqqrhnypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uqpjmn0wd68ytt9wphhs7fdwfjhvetjwdjj6urjdau8j6sn6y7). |  |  | | ----------------------------------------------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------- | | Reverse proxy default behaviour | Reverse proxy after proxy request | As shown above the default is to connect to the operator's own relay. So how do we create the proxied connection? Well we send the following request over our websocket: ```json ["PROXY", "wss://relay.com"] ``` Which asks the proxy to change the target from it's own back-end to whatever we specify. In this case `wss://relay.com`. However, it turns out this relay doesn't live in a fiat world, it responds with: `["PROXY", "PAYMENT_REQURIED", <payment_request>]` where `<payment_request>` is an object: ```json { "price": "1", "unit": "sat", "mint": "https://some.mint.cash/", } ``` Which brings us to... ## 💰 Monetizing proxies Inevitably we're going to hit the "Who's gonna run the proxies!?" question. Well you are, because you want to stack some sats. Therefore we added monetization to these proxies, which is what sets this project apart from current-day proxies on the internet. When the client is hit with the `PAYMENT_REQUIRED` message above, it can retry the first message, but with an additional field, a cashu payment. ```json ["PROXY", "wss://relay.com", "cashuAeyJ0..."] ``` We're now paying a couple sats, (the price above is in sats per minute). If the proxy is happy with our payment, it will start a timer and set up the connection to the target relay. Indicated by a `["PROXY", "CONNECTED"]` message, after which we can go about our relay business until the bought time runs out. After which the proxy will close our connection with code `1000`, reason: `PROXY: Connection Bankrupted`. The nice thing here is that introducing payments can reduce spam significantly. ### Why Cashu? Because [Cashu eCash](https://cashu.me) allows us to finally make micro-payments viable and scalable, it can help us to bring an honest monetary reward to the people that do the hard work of maintaining the free and open internet. If you provide a proxy, you get paid and therefore you're incentivised to keep the infrastructure up and running. Cashu tokens are a very efficient way of sending payments directly. Unlike Lightning, it does not require a back and forth between the two transacting parties. Because cashu tokens can be sent as a string of text, you can attach it to any request/data you're sending around. Even at rest, the money will still be 'physically' there. That means there's no back and forth required to send a payment, like we do on lightning, and people don't need perfect connectivity. ## 💭 Some philosophy Until now, all web applications have been strongly coupled to the transportation methods they use, mainly http(s). Nostr changes this, because the data that feeds an application can now arrive over any transportation mechanism. WebSockets, Thumb-drives, QR, LoRa (radio) and Heck! even FM and pigeons will work! Although the above point is not necessarily tied to the use of websocket proxies, it does underline the point I want to make: Because Nostr completely decouples applications from the transportation layer, We can get VERY creative in the ways in which we transport application data... Therefore, the boundaries of the current clearnet network become irrelevant. Using the websocket proxies, we can now hop from clearnet to tor, to [i2p](https://geti2p.net/en/), to [hyper](https://github.com/hypercore-protocol) and back to clearnet. This significantly reduces the burden on the client by not having to 'know' how any of these other networks work, they won't have to install anything, yet they can interact with relays on these lesser known networks. ## ⚙ Under the hood Here's a UMl example of a proxy (that does not have a default relay behind it) and the lifecycle of a proxied connection.  ## NIP-XX draft I wrote a draft NIP on how to support proxying [here](https://github.com/ArjenStens/nostr-epoxy-reverse-proxy/blob/main/NIP-XX.md). ## 🛝 Play with it! I created a [Dashboard](https://swissdash.site) to discover proxies and play with connecting to relays (multiple hops are possible).  Check out the route-builder tab, add a couple sats to the wallet and route some request through the proxies.   ## Resources - [Dashboard](https://swissdash.site) - **Nostr Epoxy Reverse Proxy** [Source Code](nostr:naddr1qvzqqqrhnypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uqpjmn0wd68ytt9wphhs7fdwfjhvetjwdjj6urjdau8j6sn6y7) - **NIP** [draft](https://github.com/ArjenStens/nostr-epoxy-reverse-proxy/blob/main/NIP-XX.md) @ 9ff58691:0bf6c134
2024-11-18 12:27:12Городская администрация Кургана предлагает широкий спектр учебных программ и стажировок для молодежи: 🎓 "Молодежный кадровый резерв" - программа стажировок в городской администрации. Получите опыт работы в органах местного самоуправления, осваиваете новые цифровые навыки, в том числе использование технологий искусственного интеллекта для повышения эффективности работы.  Стажеры работают бок о бок с сотрудниками, использующими передовые ИИ-ассистенты для анализа данных, автоматизации рутинных задач и принятия управленческих решений. Они изучают, как применять технологии машинного обучения и компьютерного зрения для оптимизации городских сервисов и инфраструктуры. *"Стажировка в администрации стала для меня отличным стартом карьеры. Я приобрел бесценный опыт и познакомился с современными технологиями, которые применяются в муниципальном управлении"* - Алексей, 23 года. 🏢 "Карьерный старт" - программа стажировок в ведущих компаниях Кургана. Попробуйте себя в различных сферах бизнеса, осваиваете новейшие разработки в области ИИ и автоматизации. Стажеры получают возможность поработать с виртуальными ассистентами, способными анализировать большие данные, прогнозировать тренды и предлагать оптимальные решения. Они также изучают, как применять технологии дополненной и виртуальной реальности в различных отраслях. *"Стажировка в IT-компании помогла мне определиться с будущей профессией. Я получила уникальный опыт работы с современными технологиями, которые меняют облик многих отраслей"* - Мария, 21 год.  Не упустите свой шанс! Подробности и условия участия в программах "Молодежный кадровый резерв" и "Карьерный старт" можно узнать на сайте городской администрации Кургана.
@ 9ff58691:0bf6c134
2024-11-18 12:27:12Городская администрация Кургана предлагает широкий спектр учебных программ и стажировок для молодежи: 🎓 "Молодежный кадровый резерв" - программа стажировок в городской администрации. Получите опыт работы в органах местного самоуправления, осваиваете новые цифровые навыки, в том числе использование технологий искусственного интеллекта для повышения эффективности работы.  Стажеры работают бок о бок с сотрудниками, использующими передовые ИИ-ассистенты для анализа данных, автоматизации рутинных задач и принятия управленческих решений. Они изучают, как применять технологии машинного обучения и компьютерного зрения для оптимизации городских сервисов и инфраструктуры. *"Стажировка в администрации стала для меня отличным стартом карьеры. Я приобрел бесценный опыт и познакомился с современными технологиями, которые применяются в муниципальном управлении"* - Алексей, 23 года. 🏢 "Карьерный старт" - программа стажировок в ведущих компаниях Кургана. Попробуйте себя в различных сферах бизнеса, осваиваете новейшие разработки в области ИИ и автоматизации. Стажеры получают возможность поработать с виртуальными ассистентами, способными анализировать большие данные, прогнозировать тренды и предлагать оптимальные решения. Они также изучают, как применять технологии дополненной и виртуальной реальности в различных отраслях. *"Стажировка в IT-компании помогла мне определиться с будущей профессией. Я получила уникальный опыт работы с современными технологиями, которые меняют облик многих отраслей"* - Мария, 21 год.  Не упустите свой шанс! Подробности и условия участия в программах "Молодежный кадровый резерв" и "Карьерный старт" можно узнать на сайте городской администрации Кургана. @ 9ff58691:0bf6c134
2024-11-18 12:21:35В нашем городе стартует новая программа по озеленению и восстановлению природных экосистем, которая направлена на улучшение качества жизни и сохранение природного наследия нашего региона. Программа будет реализована при поддержке местных властей и частных инвесторов и охватит как городские, так и пригородные территории. В рамках программы планируется высадка более 10 000 деревьев и кустарников, создание новых зеленых зон и восстановление существующих природных ландшафтов. Также будут организованы акции по очистке и благоустройству парков и скверов, что позволит сделать наш город более комфортным и привлекательным для жителей и гостей. Мы пообщались с одним из инвесторов программы, Александром Петровым, который поделился своими мыслями о важности этого проекта: **"Я считаю, что озеленение — это не просто вопрос эстетики, но и необходимость для здоровья нашего города. Зеленые насаждения помогают очищать воздух, создают комфортные условия для жизни и способствуют улучшению психоэмоционального состояния людей. Я рад, что могу участвовать в этом проекте и надеюсь, что он вдохновит других инвесторов поддерживать экологические инициативы в нашем регионе."** Программа по озеленению станет важным шагом к созданию устойчивого и экологически чистого Кургана. Мы призываем всех жителей города принять активное участие в этом процессе: участвуйте в акциях по высадке деревьев, помогайте в благоустройстве и делитесь своими идеями по улучшению городской среды. Автор: Налобина Александра
@ 9ff58691:0bf6c134
2024-11-18 12:21:35В нашем городе стартует новая программа по озеленению и восстановлению природных экосистем, которая направлена на улучшение качества жизни и сохранение природного наследия нашего региона. Программа будет реализована при поддержке местных властей и частных инвесторов и охватит как городские, так и пригородные территории. В рамках программы планируется высадка более 10 000 деревьев и кустарников, создание новых зеленых зон и восстановление существующих природных ландшафтов. Также будут организованы акции по очистке и благоустройству парков и скверов, что позволит сделать наш город более комфортным и привлекательным для жителей и гостей. Мы пообщались с одним из инвесторов программы, Александром Петровым, который поделился своими мыслями о важности этого проекта: **"Я считаю, что озеленение — это не просто вопрос эстетики, но и необходимость для здоровья нашего города. Зеленые насаждения помогают очищать воздух, создают комфортные условия для жизни и способствуют улучшению психоэмоционального состояния людей. Я рад, что могу участвовать в этом проекте и надеюсь, что он вдохновит других инвесторов поддерживать экологические инициативы в нашем регионе."** Программа по озеленению станет важным шагом к созданию устойчивого и экологически чистого Кургана. Мы призываем всех жителей города принять активное участие в этом процессе: участвуйте в акциях по высадке деревьев, помогайте в благоустройстве и делитесь своими идеями по улучшению городской среды. Автор: Налобина Александра @ 5afdec5b:2d631be1
2024-11-18 10:23:46In August 2024, **Lendasat** introduced a novel loan protocol, designed to address the inherent risks of custodial lending platforms. By leveraging Bitcoin's self-custodial nature, the **Lendasat** protocol allows borrowers to secure loans without transferring ownership of their assets. If you haven’t had a chance to explore our [whitepaper](https://whitepaper.lendasat.com/lendasat-whitepaper.pdf), this blog post will guide you through the protocol and its advantages. We’ll explore how **Lendasat** works, the technology behind it, and why it stands out as a solution for Bitcoin-collateralized lending. Diagrams will help break down each stage of the protocol, so you can understand the mechanisms step-by-step. ## Bitcoin Lending, the Right Way Bitcoin, as a decentralized and self-custodial asset, offers users a chance to be their own bank. However, the current landscape for Bitcoin-backed loans often forces users to hand over their Bitcoin to custodians—introducing a set of serious risks: - **Custodian risk**: Entrusting a third party with your Bitcoin exposes you to theft, mismanagement, or outright fraud. - **Opaqueness**: Traditional platforms don’t offer transparency on how assets are handled. - **Regulatory risk**: Centralized custodians are vulnerable to regulatory changes that may lead to asset freezing or seizure. **Lendasat** eliminates these concerns by enabling **escrow-less lending**. Borrowers retain control of their Bitcoin, using **Discreet Log Contracts (DLCs)** and **Hash Time-Locked Contracts (HTLCs)** to govern loan agreements without middlemen. With these cryptographic tools, **Lendasat** removes the need for trust in centralized entities, offering a **fully transparent and secure** lending process. --- ## How Lendasat Works The protocol operates between two parties: **Bob** (the borrower) and **Lydia** (the lender). Bob wishes to borrow stablecoins, locking his Bitcoin as collateral, while Lydia provides the loan principal in stablecoins, looking to earn interest. Let’s dive into how the protocol works, step by step. ### 1. Opening the Loan The loan process starts with both parties locking assets in cryptographically secured contracts. #### 1.1 Secret Generation - Bob generates a collateral secret, `b`. - Lydia generates a loan secret, `l`. #### 1.2 Bob Locks Bitcoin Collateral Bob locks his Bitcoin in a **Discreet Log Contract (DLC)**. The DLC involves an oblivious oracle[^1] that can attest to certain events, such as the price of Bitcoin at loan maturity. If necessary, an oracle attestation can be used at loan maturity to determine how the collateral should be split between Bob and Lydia. Additionally, Bob locks Lydia's claim on her share of the collateral behind the hash of the collateral secret, `H(b)`. Lydia will need to know `b` to be able to claim her portion of the collateral unilaterally. > **Key Insight**: Unlike traditional escrows, the **DLC** ensures that Bob retains control of his collateral throughout the loan process. The oracle attestation is only needed to help settle the contract if Bob and Lydia fail to cooperate. #### 1.3 Lydia Locks the Principal Lydia, in turn, locks the loan principal in an **HTLC** on Ethereum (or another smart contract-enabled blockchain[^2] or L2). This HTLC is designed so that Bob can only claim the principal if he reveals `b`. - **Condition 1**: Bob must provide the preimage to `H(b)` i.e. `b`. - **Condition 2**: If Bob doesn’t act in time, Lydia can recover her funds after a timelock expires. #### 1.4 Bob Claims the Principal Bob, now seeing the loan principal is locked up, reveals the secret `b` to claim it. This revelation allows Lydia to later claim part of the Bitcoin collateral, but only if Bob defaults on repayment or in the event of a liquidation.  ### 2. Cooperative Repayment If Bob is ready to repay the loan: 1. **Bob** locks the repayment amount in an **HTLC** on Ethereum, this time using `H(l)` as a hash lock. 2. **Lydia** claims her repayment, revealing `l`. 3. **Bob** uses `l` to unlock the entirety of his Bitcoin collateral from the DLC.  --- ## When Things Go Sideways Not all loans proceed smoothly. Here’s how **Lendasat** handles common scenarios when the loan doesn't go as planned. ### 1. Lender No-Show What happens if Bob locks up his Bitcoin collateral, but Lydia disappears before providing the principal? In this case, Bob can unilaterally recover his Bitcoin after an **early collateral refund timeout** built into the contract. This timeout prevents Bob’s collateral from being stuck indefinitely, a common safeguard in decentralized contracts.  ### 2. Borrower Fails to Claim the Loan Similarly, if Lydia locks up the principal and Bob does not claim it, both parties are protected by respective timeouts: - **Lydia** recovers her principal after a shorter refund timeout on Ethereum. - **Bob** gets his Bitcoin collateral back after a longer refund timeout. These dual timeouts ensure neither party’s assets remain frozen for too long.  ### 3. Unilateral Repayment If Bob defaults or Lydia doesn’t claim her repayment, the protocol shifts to **non-cooperative repayment** through the **DLC**. In this case, the protocol involves an oracle attestation to the Bitcoin price at loan maturity. Lydia receives an amount of Bitcoin collateral equivalent to the loan’s value (plus interest) based on the oracle's attestation. The remaining collateral goes back to Bob. This mechanism ensures that even in the worst case, Lydia can still recover her funds by liquidating part or all of Bob’s Bitcoin collateral.  --- ## Keeping the Loan Alive: Liquidation and Collateral Management One of the key challenges of lending is managing **Loan-to-Value (LTV) ratios**. If Bitcoin’s price falls significantly, Lydia might have to liquidate part of the collateral to cover the outstanding loan. Here’s how **Lendasat** addresses liquidation: - If the LTV ratio approaches a critical threshold, **Lydia** can trigger an oracle-based liquidation of the Bitcoin collateral before loan maturity. This protects the lender from losses due to market volatility. - Liquidation relies on the same **DLC** mechanism that handles non-cooperative repayment, ensuring a smooth, automated process for collateral distribution. The protocol also allows Bob to **increase his collateral** if necessary, by splicing into the DLC with more funds, keeping the loan in good standing and avoiding liquidation.  --- ## Technical Appendix: How HTLCs and DLCs Combine ### HTLCs: Enabling Cross-Chain Functionality An **HTLC** (Hash Time-Locked Contract) is a foundational building block for cross-chain operations. It allows Bob to lock collateral on one chain (Bitcoin) while simultaneously claiming funds on another (Ethereum). In Lendasat, **HTLCs** govern the locking and claiming of both loan principal and repayment on the Ethereum chain. ### DLCs: Securing Conditional Payouts A **Discreet Log Contract (DLC)** is used to ensure that Bob’s Bitcoin collateral is only accessible to Lydia under specific conditions, like a default or liquidation event. The **DLC** relies on oracles to determine the correct payout based on the Bitcoin price at loan maturity or liquidation. Combining these two technologies allows **Lendasat** to create a trustless lending mechanism that spans multiple blockchains. --- ## Conclusion **Lendasat** redefines Bitcoin-collateralized lending by eliminating custodial risk and empowering borrowers to retain control of their collateral. Using **HTLCs** and **DLCs**, our protocol creates a trustless environment where both lenders and borrowers are protected, even in the event of non-cooperation or default. For those interested in a deeper technical understanding, please refer to our [whitepaper](https://whitepaper.lendasat.com/lendasat-whitepaper.pdf), and stay tuned as we continue to refine the protocol and unlock new possibilities for decentralized finance. ## Footnotes [^1]: When we talk about an oracle, we are not discounting the possibility of using _multiple_ oracles. The DLC protocol does allow for a quorum of oracles to determine the outcome of an event, to distribute the trust. [^2]: This can be the Bitcoin blockchain itself, via Taproot Assets, RGB or BRC20.
@ 5afdec5b:2d631be1
2024-11-18 10:23:46In August 2024, **Lendasat** introduced a novel loan protocol, designed to address the inherent risks of custodial lending platforms. By leveraging Bitcoin's self-custodial nature, the **Lendasat** protocol allows borrowers to secure loans without transferring ownership of their assets. If you haven’t had a chance to explore our [whitepaper](https://whitepaper.lendasat.com/lendasat-whitepaper.pdf), this blog post will guide you through the protocol and its advantages. We’ll explore how **Lendasat** works, the technology behind it, and why it stands out as a solution for Bitcoin-collateralized lending. Diagrams will help break down each stage of the protocol, so you can understand the mechanisms step-by-step. ## Bitcoin Lending, the Right Way Bitcoin, as a decentralized and self-custodial asset, offers users a chance to be their own bank. However, the current landscape for Bitcoin-backed loans often forces users to hand over their Bitcoin to custodians—introducing a set of serious risks: - **Custodian risk**: Entrusting a third party with your Bitcoin exposes you to theft, mismanagement, or outright fraud. - **Opaqueness**: Traditional platforms don’t offer transparency on how assets are handled. - **Regulatory risk**: Centralized custodians are vulnerable to regulatory changes that may lead to asset freezing or seizure. **Lendasat** eliminates these concerns by enabling **escrow-less lending**. Borrowers retain control of their Bitcoin, using **Discreet Log Contracts (DLCs)** and **Hash Time-Locked Contracts (HTLCs)** to govern loan agreements without middlemen. With these cryptographic tools, **Lendasat** removes the need for trust in centralized entities, offering a **fully transparent and secure** lending process. --- ## How Lendasat Works The protocol operates between two parties: **Bob** (the borrower) and **Lydia** (the lender). Bob wishes to borrow stablecoins, locking his Bitcoin as collateral, while Lydia provides the loan principal in stablecoins, looking to earn interest. Let’s dive into how the protocol works, step by step. ### 1. Opening the Loan The loan process starts with both parties locking assets in cryptographically secured contracts. #### 1.1 Secret Generation - Bob generates a collateral secret, `b`. - Lydia generates a loan secret, `l`. #### 1.2 Bob Locks Bitcoin Collateral Bob locks his Bitcoin in a **Discreet Log Contract (DLC)**. The DLC involves an oblivious oracle[^1] that can attest to certain events, such as the price of Bitcoin at loan maturity. If necessary, an oracle attestation can be used at loan maturity to determine how the collateral should be split between Bob and Lydia. Additionally, Bob locks Lydia's claim on her share of the collateral behind the hash of the collateral secret, `H(b)`. Lydia will need to know `b` to be able to claim her portion of the collateral unilaterally. > **Key Insight**: Unlike traditional escrows, the **DLC** ensures that Bob retains control of his collateral throughout the loan process. The oracle attestation is only needed to help settle the contract if Bob and Lydia fail to cooperate. #### 1.3 Lydia Locks the Principal Lydia, in turn, locks the loan principal in an **HTLC** on Ethereum (or another smart contract-enabled blockchain[^2] or L2). This HTLC is designed so that Bob can only claim the principal if he reveals `b`. - **Condition 1**: Bob must provide the preimage to `H(b)` i.e. `b`. - **Condition 2**: If Bob doesn’t act in time, Lydia can recover her funds after a timelock expires. #### 1.4 Bob Claims the Principal Bob, now seeing the loan principal is locked up, reveals the secret `b` to claim it. This revelation allows Lydia to later claim part of the Bitcoin collateral, but only if Bob defaults on repayment or in the event of a liquidation.  ### 2. Cooperative Repayment If Bob is ready to repay the loan: 1. **Bob** locks the repayment amount in an **HTLC** on Ethereum, this time using `H(l)` as a hash lock. 2. **Lydia** claims her repayment, revealing `l`. 3. **Bob** uses `l` to unlock the entirety of his Bitcoin collateral from the DLC.  --- ## When Things Go Sideways Not all loans proceed smoothly. Here’s how **Lendasat** handles common scenarios when the loan doesn't go as planned. ### 1. Lender No-Show What happens if Bob locks up his Bitcoin collateral, but Lydia disappears before providing the principal? In this case, Bob can unilaterally recover his Bitcoin after an **early collateral refund timeout** built into the contract. This timeout prevents Bob’s collateral from being stuck indefinitely, a common safeguard in decentralized contracts.  ### 2. Borrower Fails to Claim the Loan Similarly, if Lydia locks up the principal and Bob does not claim it, both parties are protected by respective timeouts: - **Lydia** recovers her principal after a shorter refund timeout on Ethereum. - **Bob** gets his Bitcoin collateral back after a longer refund timeout. These dual timeouts ensure neither party’s assets remain frozen for too long.  ### 3. Unilateral Repayment If Bob defaults or Lydia doesn’t claim her repayment, the protocol shifts to **non-cooperative repayment** through the **DLC**. In this case, the protocol involves an oracle attestation to the Bitcoin price at loan maturity. Lydia receives an amount of Bitcoin collateral equivalent to the loan’s value (plus interest) based on the oracle's attestation. The remaining collateral goes back to Bob. This mechanism ensures that even in the worst case, Lydia can still recover her funds by liquidating part or all of Bob’s Bitcoin collateral.  --- ## Keeping the Loan Alive: Liquidation and Collateral Management One of the key challenges of lending is managing **Loan-to-Value (LTV) ratios**. If Bitcoin’s price falls significantly, Lydia might have to liquidate part of the collateral to cover the outstanding loan. Here’s how **Lendasat** addresses liquidation: - If the LTV ratio approaches a critical threshold, **Lydia** can trigger an oracle-based liquidation of the Bitcoin collateral before loan maturity. This protects the lender from losses due to market volatility. - Liquidation relies on the same **DLC** mechanism that handles non-cooperative repayment, ensuring a smooth, automated process for collateral distribution. The protocol also allows Bob to **increase his collateral** if necessary, by splicing into the DLC with more funds, keeping the loan in good standing and avoiding liquidation.  --- ## Technical Appendix: How HTLCs and DLCs Combine ### HTLCs: Enabling Cross-Chain Functionality An **HTLC** (Hash Time-Locked Contract) is a foundational building block for cross-chain operations. It allows Bob to lock collateral on one chain (Bitcoin) while simultaneously claiming funds on another (Ethereum). In Lendasat, **HTLCs** govern the locking and claiming of both loan principal and repayment on the Ethereum chain. ### DLCs: Securing Conditional Payouts A **Discreet Log Contract (DLC)** is used to ensure that Bob’s Bitcoin collateral is only accessible to Lydia under specific conditions, like a default or liquidation event. The **DLC** relies on oracles to determine the correct payout based on the Bitcoin price at loan maturity or liquidation. Combining these two technologies allows **Lendasat** to create a trustless lending mechanism that spans multiple blockchains. --- ## Conclusion **Lendasat** redefines Bitcoin-collateralized lending by eliminating custodial risk and empowering borrowers to retain control of their collateral. Using **HTLCs** and **DLCs**, our protocol creates a trustless environment where both lenders and borrowers are protected, even in the event of non-cooperation or default. For those interested in a deeper technical understanding, please refer to our [whitepaper](https://whitepaper.lendasat.com/lendasat-whitepaper.pdf), and stay tuned as we continue to refine the protocol and unlock new possibilities for decentralized finance. ## Footnotes [^1]: When we talk about an oracle, we are not discounting the possibility of using _multiple_ oracles. The DLC protocol does allow for a quorum of oracles to determine the outcome of an event, to distribute the trust. [^2]: This can be the Bitcoin blockchain itself, via Taproot Assets, RGB or BRC20. @ 2e1d9d3e:fc3683d1
2024-11-18 10:23:36Im Zeitalter der rasanten Entwicklung der Informationstechnologie ist die Signalsicherheit in allen Lebensbereichen in den Mittelpunkt der Aufmerksamkeit gerückt. Da Netzwerkangriffe und Informationsdiebstahl immer häufiger auftreten, ist es besonders wichtig, einen geeigneten Störsender auszuwählen, um die Signalsicherheit zu verbessern. [Störsender Kaufen](https://www.jammermfg.com/de/) können Kriminelle wirksam daran hindern, vertrauliche Informationen zu erhalten, und gleichzeitig die Privatsphäre der Kommunikation schützen. In diesem Artikel erfahren Sie, wie Sie den richtigen Störsender auswählen, um die Effektivität der Signalsicherheit zu erhöhen. 1. Verstehen Sie die Grundtypen von Störsendern Störsender werden hauptsächlich in verschiedene Typen unterteilt, darunter: 1. Funkstörsender: Diese Art von Gerät kann Funksignale, einschließlich WLAN, Bluetooth, GPS usw., stören und wird normalerweise verwendet, um die Signalübertragung von nicht autorisierten Geräten zu verhindern. 2. [Tragbare Handyblocker](https://www.jammermfg.com/de/handy-stoersender.html): Wird hauptsächlich zum Blockieren von Signalen in bestimmten Frequenzbändern verwendet. Er wird häufig in Konferenzräumen, Verhörräumen und anderen Anlässen verwendet, die eine hohe Vertraulichkeit erfordern. 3. Netzwerk-Störsender: Durch die Störung von Netzwerksignalen schützt er das lokale Netzwerk vor Angriffen von außen und wird häufig in Rechenzentren und Unternehmensnetzwerkumgebungen eingesetzt. Das Verständnis der verschiedenen Arten von Störsendern und ihrer Eigenschaften ist der erste Schritt bei der Auswahl des richtigen Geräts. 2. Bewerten Sie Nutzungsszenarien Bei der Auswahl eines Störsenders müssen Sie zunächst dessen Einsatzszenarien klären. Verschiedene Szenarien stellen unterschiedliche Anforderungen an Störsender: 1. Geschäftsumgebung: In einem Firmenbüro oder Konferenzraum muss möglicherweise verhindert werden, dass Konkurrenten vertrauliche Informationen stehlen. In diesem Fall können [Bluetooth störsender](https://www.jammermfg.com/de/wlan-bluetooth-stoersender.html) und Funkstörsender Informationslecks wirksam verhindern. 2. Öffentliche Orte: Wie Flughäfen, Bahnhöfe oder große Veranstaltungsorte können Störsender eingesetzt werden, um Störungen durch Drohnen und andere drahtlose Geräte zu verhindern und so die öffentliche Sicherheit zu gewährleisten. 3. Besondere Zwecke: Beispielsweise müssen Störsender für Militär- und Strafverfolgungsbehörden nicht nur feindliche Signale stören, sondern auch die Sicherheit ihrer eigenen Kommunikation gewährleisten. Bei der Auswahl müssen die Vielseitigkeit und Anpassungsfähigkeit der Ausrüstung berücksichtigt werden. 3. Berücksichtigen Sie die technischen Parameter des Störsendern Tragbare UHF UKW Störsender jammer 5G Handys Bei der Auswahl eines geeigneten Störsenders müssen Sie auf seine technischen Parameter achten, die sich direkt auf seine Leistung und Anwendbarkeit auswirken: 1. Arbeitsfrequenzbereich: Ein wirksamer Störsender sollte in der Lage sein, gängige Funksignalfrequenzbänder (z. B. 2,4 GHz, 5 GHz usw.) abzudecken und entsprechend den Nutzungsanforderungen entsprechende Zusatzfunktionen auswählen zu können, z. B. die Störung von GPS-Signalen. 2. Ausgangsleistung: Je größer die Leistung, desto größer die Störreichweite. Es ist jedoch notwendig, den tatsächlichen Bedarf an Strom und Interferenzen auszugleichen, um die Sicherheit zu gewährleisten, ohne legitime Signale zu stören. 3. Interferenzeffekt: Der Interferenzeffekt des [Audio Jammer](https://www.jammermfg.com/de/audio-jammer.html) muss bewertet werden und es sollten Produkte mit gutem Benutzerfeedback und Testberichten ausgewählt werden. Ein idealer Störsender würde die Signalstärke effektiv reduzieren und ein Hacken unmöglich machen. 4. Portabilität des Geräts: Insbesondere bei besonderen Anlässen können tragbare Störsender mehr Flexibilität bieten. Berücksichtigen Sie bei der Auswahl Größe und Gewicht, um eine einfache Tragbarkeit und einen schnellen Einsatz zu gewährleisten. 4. Legalität und Konformität der Ausrüstung Bei der Auswahl und Verwendung eines Störsenders ist die Legalität ein nicht zu vernachlässigendes Thema. In Ländern und Regionen gelten strenge Gesetze und Vorschriften zu Funksignalstörungen, und unsachgemäße Verwendung kann zu rechtlicher Haftung führen. 1. Machen Sie sich mit den örtlichen Gesetzen und Vorschriften vertraut: Stellen Sie vor dem Kauf eines Störsenders sicher, dass Sie die Gesetze und Vorschriften für Geräte zur Signalstörung in Ihrer Region kennen. In einigen Ländern und Regionen gelten strenge Beschränkungen für die Verwendung von Störsendern, und die unbefugte Verwendung kann zu Geldstrafen oder Haftungsansprüchen führen. 2. Wählen Sie konforme Hersteller und Produkte: Wählen Sie Produkte und Lieferanten mit gutem Ruf, die den örtlichen Vorschriften entsprechen, um sicherzustellen, dass der von Ihnen gekaufte [Anti Drohnen Störsendern](https://www.jammermfg.com/de/drohnen-stoersender.html) den relevanten Standards und Spezifikationen entspricht. Zusammenfassen Die Auswahl eines geeigneten Störsenders zur Verbesserung der Signalsicherheit ist ein umfassender Bewertungsprozess, der ein tiefgreifendes Verständnis des Gerätetyps, der Nutzungsszenarien, der technischen Parameter, der Rechtmäßigkeit und anderer Aspekte erfordert. Darüber hinaus sind auch die Benutzererfahrung des Geräts und der Kundendienst des Herstellers nicht zu vernachlässigende Faktoren. Durch umfassende Bewertung und sorgfältige Auswahl können wir die Signalsicherheit effektiv verbessern, unsere eigenen Informationen vor Verstößen schützen und uns an die hohen Anforderungen der modernen Gesellschaft an Informationssicherheit anpassen. Signalsicherheit ist nicht nur ein technisches Problem, sondern auch ein wichtiges Thema im Zusammenhang mit persönlichen und organisatorischen Interessen. Nehmen Sie diese Entscheidung also ernst, um sicherzustellen, dass Sie bei der Verwendung Ihres Störsenders die besten Ergebnisse erzielen. [https://www.jammermfg.com/de/alle-jammer.html](https://www.jammermfg.com/de/alle-jammer.html) [https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html](https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html)
@ 2e1d9d3e:fc3683d1
2024-11-18 10:23:36Im Zeitalter der rasanten Entwicklung der Informationstechnologie ist die Signalsicherheit in allen Lebensbereichen in den Mittelpunkt der Aufmerksamkeit gerückt. Da Netzwerkangriffe und Informationsdiebstahl immer häufiger auftreten, ist es besonders wichtig, einen geeigneten Störsender auszuwählen, um die Signalsicherheit zu verbessern. [Störsender Kaufen](https://www.jammermfg.com/de/) können Kriminelle wirksam daran hindern, vertrauliche Informationen zu erhalten, und gleichzeitig die Privatsphäre der Kommunikation schützen. In diesem Artikel erfahren Sie, wie Sie den richtigen Störsender auswählen, um die Effektivität der Signalsicherheit zu erhöhen. 1. Verstehen Sie die Grundtypen von Störsendern Störsender werden hauptsächlich in verschiedene Typen unterteilt, darunter: 1. Funkstörsender: Diese Art von Gerät kann Funksignale, einschließlich WLAN, Bluetooth, GPS usw., stören und wird normalerweise verwendet, um die Signalübertragung von nicht autorisierten Geräten zu verhindern. 2. [Tragbare Handyblocker](https://www.jammermfg.com/de/handy-stoersender.html): Wird hauptsächlich zum Blockieren von Signalen in bestimmten Frequenzbändern verwendet. Er wird häufig in Konferenzräumen, Verhörräumen und anderen Anlässen verwendet, die eine hohe Vertraulichkeit erfordern. 3. Netzwerk-Störsender: Durch die Störung von Netzwerksignalen schützt er das lokale Netzwerk vor Angriffen von außen und wird häufig in Rechenzentren und Unternehmensnetzwerkumgebungen eingesetzt. Das Verständnis der verschiedenen Arten von Störsendern und ihrer Eigenschaften ist der erste Schritt bei der Auswahl des richtigen Geräts. 2. Bewerten Sie Nutzungsszenarien Bei der Auswahl eines Störsenders müssen Sie zunächst dessen Einsatzszenarien klären. Verschiedene Szenarien stellen unterschiedliche Anforderungen an Störsender: 1. Geschäftsumgebung: In einem Firmenbüro oder Konferenzraum muss möglicherweise verhindert werden, dass Konkurrenten vertrauliche Informationen stehlen. In diesem Fall können [Bluetooth störsender](https://www.jammermfg.com/de/wlan-bluetooth-stoersender.html) und Funkstörsender Informationslecks wirksam verhindern. 2. Öffentliche Orte: Wie Flughäfen, Bahnhöfe oder große Veranstaltungsorte können Störsender eingesetzt werden, um Störungen durch Drohnen und andere drahtlose Geräte zu verhindern und so die öffentliche Sicherheit zu gewährleisten. 3. Besondere Zwecke: Beispielsweise müssen Störsender für Militär- und Strafverfolgungsbehörden nicht nur feindliche Signale stören, sondern auch die Sicherheit ihrer eigenen Kommunikation gewährleisten. Bei der Auswahl müssen die Vielseitigkeit und Anpassungsfähigkeit der Ausrüstung berücksichtigt werden. 3. Berücksichtigen Sie die technischen Parameter des Störsendern Tragbare UHF UKW Störsender jammer 5G Handys Bei der Auswahl eines geeigneten Störsenders müssen Sie auf seine technischen Parameter achten, die sich direkt auf seine Leistung und Anwendbarkeit auswirken: 1. Arbeitsfrequenzbereich: Ein wirksamer Störsender sollte in der Lage sein, gängige Funksignalfrequenzbänder (z. B. 2,4 GHz, 5 GHz usw.) abzudecken und entsprechend den Nutzungsanforderungen entsprechende Zusatzfunktionen auswählen zu können, z. B. die Störung von GPS-Signalen. 2. Ausgangsleistung: Je größer die Leistung, desto größer die Störreichweite. Es ist jedoch notwendig, den tatsächlichen Bedarf an Strom und Interferenzen auszugleichen, um die Sicherheit zu gewährleisten, ohne legitime Signale zu stören. 3. Interferenzeffekt: Der Interferenzeffekt des [Audio Jammer](https://www.jammermfg.com/de/audio-jammer.html) muss bewertet werden und es sollten Produkte mit gutem Benutzerfeedback und Testberichten ausgewählt werden. Ein idealer Störsender würde die Signalstärke effektiv reduzieren und ein Hacken unmöglich machen. 4. Portabilität des Geräts: Insbesondere bei besonderen Anlässen können tragbare Störsender mehr Flexibilität bieten. Berücksichtigen Sie bei der Auswahl Größe und Gewicht, um eine einfache Tragbarkeit und einen schnellen Einsatz zu gewährleisten. 4. Legalität und Konformität der Ausrüstung Bei der Auswahl und Verwendung eines Störsenders ist die Legalität ein nicht zu vernachlässigendes Thema. In Ländern und Regionen gelten strenge Gesetze und Vorschriften zu Funksignalstörungen, und unsachgemäße Verwendung kann zu rechtlicher Haftung führen. 1. Machen Sie sich mit den örtlichen Gesetzen und Vorschriften vertraut: Stellen Sie vor dem Kauf eines Störsenders sicher, dass Sie die Gesetze und Vorschriften für Geräte zur Signalstörung in Ihrer Region kennen. In einigen Ländern und Regionen gelten strenge Beschränkungen für die Verwendung von Störsendern, und die unbefugte Verwendung kann zu Geldstrafen oder Haftungsansprüchen führen. 2. Wählen Sie konforme Hersteller und Produkte: Wählen Sie Produkte und Lieferanten mit gutem Ruf, die den örtlichen Vorschriften entsprechen, um sicherzustellen, dass der von Ihnen gekaufte [Anti Drohnen Störsendern](https://www.jammermfg.com/de/drohnen-stoersender.html) den relevanten Standards und Spezifikationen entspricht. Zusammenfassen Die Auswahl eines geeigneten Störsenders zur Verbesserung der Signalsicherheit ist ein umfassender Bewertungsprozess, der ein tiefgreifendes Verständnis des Gerätetyps, der Nutzungsszenarien, der technischen Parameter, der Rechtmäßigkeit und anderer Aspekte erfordert. Darüber hinaus sind auch die Benutzererfahrung des Geräts und der Kundendienst des Herstellers nicht zu vernachlässigende Faktoren. Durch umfassende Bewertung und sorgfältige Auswahl können wir die Signalsicherheit effektiv verbessern, unsere eigenen Informationen vor Verstößen schützen und uns an die hohen Anforderungen der modernen Gesellschaft an Informationssicherheit anpassen. Signalsicherheit ist nicht nur ein technisches Problem, sondern auch ein wichtiges Thema im Zusammenhang mit persönlichen und organisatorischen Interessen. Nehmen Sie diese Entscheidung also ernst, um sicherzustellen, dass Sie bei der Verwendung Ihres Störsenders die besten Ergebnisse erzielen. [https://www.jammermfg.com/de/alle-jammer.html](https://www.jammermfg.com/de/alle-jammer.html) [https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html](https://www.jammermfg.com/de/DE-W04-wlan-kamera-stoersender-fuer-drahtlose-audio-video-rekorder.html) @ a79bb203:dde63268
2024-11-18 09:37:20https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMZsK.jpg Find me on Nostr [here](https://njump.me/npub157dmyq6ehpra5xatrn0sssz03qe0y6k69v02xmzyqcrf0h0xxf5qxaw6u8) originally posted at https://stacker.news/items/772474
@ a79bb203:dde63268
2024-11-18 09:37:20https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMZsK.jpg Find me on Nostr [here](https://njump.me/npub157dmyq6ehpra5xatrn0sssz03qe0y6k69v02xmzyqcrf0h0xxf5qxaw6u8) originally posted at https://stacker.news/items/772474 @ a012dc82:6458a70d
2024-11-18 08:59:40**Table Of Content** - Understanding Crypto Winter - Surviving Crypto Winter: Cost Efficiency - Surviving Crypto Winter: Strategic Planning - Surviving Crypto Winter: Embracing Innovation - Conclusion - FAQ The cryptocurrency market is known for its volatility, with periods of rapid growth often followed by sharp downturns. These downturns, colloquially known as "crypto winters," can be challenging for businesses operating in the cryptocurrency space, especially for Bitcoin mining firms. As the CEO of a Bitcoin mining firm, I've weathered multiple crypto winters and have developed strategies to not only survive but thrive during these challenging times. **Understanding Crypto Winter** Before delving into survival strategies, it's essential to understand what a crypto winter is. The term refers to a period of significant and sustained downturn in the value of cryptocurrencies. During a crypto winter, the price of Bitcoin and other cryptocurrencies can drop by more than 50%, leading to a decrease in mining profitability. **The Impact on Bitcoin Mining** Bitcoin mining is a process that involves solving complex mathematical problems to validate transactions and add them to the blockchain. Miners are rewarded with Bitcoin, but the process requires substantial computational power and electricity. When the price of Bitcoin falls, the profitability of mining can be severely impacted, especially for firms operating in regions with high electricity costs. **Surviving Crypto Winter: Cost Efficiency** **Optimizing Operational Efficiency** The first and most crucial step in surviving a crypto winter is optimizing operational efficiency. This involves reducing electricity costs, which are the primary expenditure for any Bitcoin mining operation. We've achieved this by relocating our mining operations to regions with lower electricity costs and investing in more energy-efficient mining equipment. **Diversifying Revenue Streams** Another strategy we've employed is diversifying our revenue streams. While our primary business is Bitcoin mining, we've also started offering blockchain consulting services and investing in other promising cryptocurrencies. This diversification helps us maintain a steady income even when the Bitcoin market is down. **Surviving Crypto Winter: Strategic Planning** **Hedging Against Market Volatility** To protect against market volatility, we've implemented a hedging strategy using Bitcoin futures contracts. These contracts allow us to sell Bitcoin at a predetermined price in the future, providing a safety net against potential price drops. **Building Strong Partnerships** Building strong partnerships is another key survival strategy. We've partnered with other businesses in the cryptocurrency space, including exchanges and wallet providers. These partnerships provide additional revenue opportunities and help us stay connected with the broader cryptocurrency ecosystem. **Surviving Crypto Winter: Embracing Innovation** **Investing in Research and Development** Despite the challenges of a crypto winter, we believe in the long-term potential of Bitcoin and blockchain technology. That's why we continue to invest in research and development, exploring new ways to improve our mining operations and develop innovative blockchain solutions. **Staying Ahead of Regulatory Changes** Regulatory changes can have a significant impact on the cryptocurrency market. By staying informed about potential regulatory changes and adapting our business model accordingly, we can mitigate the risks associated with regulatory uncertainty. **Conclusion** Surviving a crypto winter is no easy task, but with careful planning, cost efficiency, and a willingness to innovate, it's possible to weather the storm. As we navigate this latest crypto winter, we remain confident in the resilience of our business model and the long-term potential of Bitcoin and blockchain technology. **FAQ** **What is a crypto winter?** A crypto winter refers to a period of significant and sustained downturn in the value of cryptocurrencies, often leading to a decrease in mining profitability. How does a crypto winter impact Bitcoin mining? During a crypto winter, the price of Bitcoin can drop significantly, reducing the profitability of mining, especially for firms operating in regions with high electricity costs. **How can Bitcoin mining firms survive a crypto winter?** Strategies for surviving a crypto winter include optimizing operational efficiency, diversifying revenue streams, strategic planning, hedging against market volatility, building strong partnerships, investing in research and development, and staying ahead of regulatory changes. **What is the long-term outlook for Bitcoin and blockchain technology?** Despite the challenges of crypto winters, many experts and businesses remain confident in the long-term potential of Bitcoin and blockchain technology due to their transformative potential in various industries That's all for today **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-11-18 08:59:40**Table Of Content** - Understanding Crypto Winter - Surviving Crypto Winter: Cost Efficiency - Surviving Crypto Winter: Strategic Planning - Surviving Crypto Winter: Embracing Innovation - Conclusion - FAQ The cryptocurrency market is known for its volatility, with periods of rapid growth often followed by sharp downturns. These downturns, colloquially known as "crypto winters," can be challenging for businesses operating in the cryptocurrency space, especially for Bitcoin mining firms. As the CEO of a Bitcoin mining firm, I've weathered multiple crypto winters and have developed strategies to not only survive but thrive during these challenging times. **Understanding Crypto Winter** Before delving into survival strategies, it's essential to understand what a crypto winter is. The term refers to a period of significant and sustained downturn in the value of cryptocurrencies. During a crypto winter, the price of Bitcoin and other cryptocurrencies can drop by more than 50%, leading to a decrease in mining profitability. **The Impact on Bitcoin Mining** Bitcoin mining is a process that involves solving complex mathematical problems to validate transactions and add them to the blockchain. Miners are rewarded with Bitcoin, but the process requires substantial computational power and electricity. When the price of Bitcoin falls, the profitability of mining can be severely impacted, especially for firms operating in regions with high electricity costs. **Surviving Crypto Winter: Cost Efficiency** **Optimizing Operational Efficiency** The first and most crucial step in surviving a crypto winter is optimizing operational efficiency. This involves reducing electricity costs, which are the primary expenditure for any Bitcoin mining operation. We've achieved this by relocating our mining operations to regions with lower electricity costs and investing in more energy-efficient mining equipment. **Diversifying Revenue Streams** Another strategy we've employed is diversifying our revenue streams. While our primary business is Bitcoin mining, we've also started offering blockchain consulting services and investing in other promising cryptocurrencies. This diversification helps us maintain a steady income even when the Bitcoin market is down. **Surviving Crypto Winter: Strategic Planning** **Hedging Against Market Volatility** To protect against market volatility, we've implemented a hedging strategy using Bitcoin futures contracts. These contracts allow us to sell Bitcoin at a predetermined price in the future, providing a safety net against potential price drops. **Building Strong Partnerships** Building strong partnerships is another key survival strategy. We've partnered with other businesses in the cryptocurrency space, including exchanges and wallet providers. These partnerships provide additional revenue opportunities and help us stay connected with the broader cryptocurrency ecosystem. **Surviving Crypto Winter: Embracing Innovation** **Investing in Research and Development** Despite the challenges of a crypto winter, we believe in the long-term potential of Bitcoin and blockchain technology. That's why we continue to invest in research and development, exploring new ways to improve our mining operations and develop innovative blockchain solutions. **Staying Ahead of Regulatory Changes** Regulatory changes can have a significant impact on the cryptocurrency market. By staying informed about potential regulatory changes and adapting our business model accordingly, we can mitigate the risks associated with regulatory uncertainty. **Conclusion** Surviving a crypto winter is no easy task, but with careful planning, cost efficiency, and a willingness to innovate, it's possible to weather the storm. As we navigate this latest crypto winter, we remain confident in the resilience of our business model and the long-term potential of Bitcoin and blockchain technology. **FAQ** **What is a crypto winter?** A crypto winter refers to a period of significant and sustained downturn in the value of cryptocurrencies, often leading to a decrease in mining profitability. How does a crypto winter impact Bitcoin mining? During a crypto winter, the price of Bitcoin can drop significantly, reducing the profitability of mining, especially for firms operating in regions with high electricity costs. **How can Bitcoin mining firms survive a crypto winter?** Strategies for surviving a crypto winter include optimizing operational efficiency, diversifying revenue streams, strategic planning, hedging against market volatility, building strong partnerships, investing in research and development, and staying ahead of regulatory changes. **What is the long-term outlook for Bitcoin and blockchain technology?** Despite the challenges of crypto winters, many experts and businesses remain confident in the long-term potential of Bitcoin and blockchain technology due to their transformative potential in various industries That's all for today **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ e1d968f7:5d90f764
2024-11-18 06:21:24Every escort-client relationship starts with an unspoken understanding: the client expects something, and the escort provides it. But the real work lies in balancing those expectations with clear boundaries. It’s a dance of mutual respect, communication, and knowing where to draw the line—for both parties. --- ### **Understanding Client Expectations** Clients come to escorts for many reasons: companionship, emotional connection, fantasy fulfilment, or simply a moment of escape from their everyday lives. Some know exactly what they want and are upfront about it. Others may be hesitant, unsure how to articulate their desires. It’s part of my job to read between the lines, listen carefully, and create a space where they feel comfortable expressing themselves. But meeting their expectations doesn’t mean giving up my autonomy or crossing my limits. --- ### **The Importance of Boundaries** Boundaries are essential in this line of work—not just to protect myself, but to create a healthy dynamic with clients. Without them, the lines blur, and misunderstandings can arise. For me, boundaries include: - **Personal Comfort:** I decide what services I’m willing to provide, and I communicate them clearly. If something feels off or doesn’t sit right with me, I won’t do it. - **Respectful Behaviour:** Disrespect, aggression, or ignoring agreed-upon limits is a deal-breaker. I’ll end a booking immediately if these occur. - **Time Management:** A booking is for a set amount of time. Clients expecting “extras” without prior agreement are gently but firmly reminded of the boundaries we’ve set. Setting boundaries isn’t about being cold or unyielding—it’s about maintaining professionalism while ensuring I feel safe and respected. --- ### **Communicating Boundaries** Good communication is the foundation of any successful booking. Before meeting a client, I ensure they understand my services and expectations. During the encounter, I remain attentive to their needs while staying firm about my own. Here’s how I handle setting boundaries: - **Clarity:** I explain my limits politely but firmly before the booking begins. - **Redirection:** If a client asks for something outside my boundaries, I guide the conversation toward something I *am* comfortable offering. - **Standing Firm:** If a client pushes too far, I remind them of our agreement and, if necessary, end the booking. Most clients respect these boundaries, and the few who don’t? They’re not worth the time. --- ### **When Expectations and Boundaries Align** The best bookings are those where expectations and boundaries naturally align. These clients respect my limits, communicate their desires clearly, and approach the experience with mutual respect. In these cases, the booking feels less like a transaction and more like a meaningful connection. When boundaries are honoured, the client gets the best version of me—a confident, engaged, and authentic companion. And I leave the encounter feeling fulfilled rather than drained. --- ### **The Takeaway** Navigating client expectations while maintaining boundaries is one of the most important skills in escorting. It ensures both parties feel valued, respected, and safe. For me, it’s not just about providing a service—it’s about creating an experience where we both walk away feeling positive about our time together. Tomorrow, I’ll share a bit about the emotional side of this work—how I handle the highs and lows of being an escort while staying true to myself. Until then, remember: clear boundaries make for better connections. Rebecca x
@ e1d968f7:5d90f764
2024-11-18 06:21:24Every escort-client relationship starts with an unspoken understanding: the client expects something, and the escort provides it. But the real work lies in balancing those expectations with clear boundaries. It’s a dance of mutual respect, communication, and knowing where to draw the line—for both parties. --- ### **Understanding Client Expectations** Clients come to escorts for many reasons: companionship, emotional connection, fantasy fulfilment, or simply a moment of escape from their everyday lives. Some know exactly what they want and are upfront about it. Others may be hesitant, unsure how to articulate their desires. It’s part of my job to read between the lines, listen carefully, and create a space where they feel comfortable expressing themselves. But meeting their expectations doesn’t mean giving up my autonomy or crossing my limits. --- ### **The Importance of Boundaries** Boundaries are essential in this line of work—not just to protect myself, but to create a healthy dynamic with clients. Without them, the lines blur, and misunderstandings can arise. For me, boundaries include: - **Personal Comfort:** I decide what services I’m willing to provide, and I communicate them clearly. If something feels off or doesn’t sit right with me, I won’t do it. - **Respectful Behaviour:** Disrespect, aggression, or ignoring agreed-upon limits is a deal-breaker. I’ll end a booking immediately if these occur. - **Time Management:** A booking is for a set amount of time. Clients expecting “extras” without prior agreement are gently but firmly reminded of the boundaries we’ve set. Setting boundaries isn’t about being cold or unyielding—it’s about maintaining professionalism while ensuring I feel safe and respected. --- ### **Communicating Boundaries** Good communication is the foundation of any successful booking. Before meeting a client, I ensure they understand my services and expectations. During the encounter, I remain attentive to their needs while staying firm about my own. Here’s how I handle setting boundaries: - **Clarity:** I explain my limits politely but firmly before the booking begins. - **Redirection:** If a client asks for something outside my boundaries, I guide the conversation toward something I *am* comfortable offering. - **Standing Firm:** If a client pushes too far, I remind them of our agreement and, if necessary, end the booking. Most clients respect these boundaries, and the few who don’t? They’re not worth the time. --- ### **When Expectations and Boundaries Align** The best bookings are those where expectations and boundaries naturally align. These clients respect my limits, communicate their desires clearly, and approach the experience with mutual respect. In these cases, the booking feels less like a transaction and more like a meaningful connection. When boundaries are honoured, the client gets the best version of me—a confident, engaged, and authentic companion. And I leave the encounter feeling fulfilled rather than drained. --- ### **The Takeaway** Navigating client expectations while maintaining boundaries is one of the most important skills in escorting. It ensures both parties feel valued, respected, and safe. For me, it’s not just about providing a service—it’s about creating an experience where we both walk away feeling positive about our time together. Tomorrow, I’ll share a bit about the emotional side of this work—how I handle the highs and lows of being an escort while staying true to myself. Until then, remember: clear boundaries make for better connections. Rebecca x @ ec965405:63996966
2024-11-18 01:44:33**Hi everybody,** My name is Miguel, and **I'm one of the board members of the International Foster Care Alliance (IFCA)!** I am **a former foster youth living in Aguadilla, Puerto Rico.** I first connected with IFCA around 2016 when Miho brought a group of Japanese foster youth to Oakland, California, to receive community organizer training from California Youth Connection (CYC). At the time, I was studying in Oakland and organizing with my local CYC chapter. I applied for and was accepted for the trip to Japan for the Youth Summit in 2018 and have continued to stay involved ever since. As a board member, I help IFCA with its Arts and Culture programming as well as member engagement.  ### My Voice, Our Story Upgrade  [My Voice, Our Story ](https://myvoiceourstory.org) is a bilingual blog started by IFCA youth to share stories and thoughts about common themes in foster care, such as aging out of care, normalcy, LGBTQIA+, mental health, and child welfare system reform. IFCA recently received a grant from Yakihonne to pay for six months of server space to upgrade this blog into our own social media network! Now, you can use any Nostr app on a web browser, iOS device, or Android device to connect to it and post your blogs for foster youth around the world to see. Nostr is a social application protocol that enables our members to share their experiences from foster care on the My Voice, Our Story blog in a fun way. You can connect to the relay with any Nostr application to pull blogs and posts from our relay and, if you are a member of IFCA, post your own! Some Nostr applications have in-app translations that can translate posts to the language of your device, making it a good fit for our network that is spread out across different countries. Also, any youth who wish to remain anonymous can do so because you do not need to provide any personal identifying information to get started on Nostr. Over the next few weeks, my fellow board members and I will host workshops to show everyone how it works. For now, you can [check out this short guide I wrote on how to connect to the relay by clicking here.](https://gist.github.com/miggymofongo/e09c1401d61e80634810389f2d4a490d). You could always reach out to me by email [contact@miguelalmodo.com](mailto:contact@miguelalmodo.com) if you have any questions or want to schedule a time for onboarding and further explanation. It might seem complicated at first, but I am confident that our community will quickly adapt. Are you part of IFCA's network? Comment below with the country you are reading this from so other members can see!
@ ec965405:63996966
2024-11-18 01:44:33**Hi everybody,** My name is Miguel, and **I'm one of the board members of the International Foster Care Alliance (IFCA)!** I am **a former foster youth living in Aguadilla, Puerto Rico.** I first connected with IFCA around 2016 when Miho brought a group of Japanese foster youth to Oakland, California, to receive community organizer training from California Youth Connection (CYC). At the time, I was studying in Oakland and organizing with my local CYC chapter. I applied for and was accepted for the trip to Japan for the Youth Summit in 2018 and have continued to stay involved ever since. As a board member, I help IFCA with its Arts and Culture programming as well as member engagement.  ### My Voice, Our Story Upgrade  [My Voice, Our Story ](https://myvoiceourstory.org) is a bilingual blog started by IFCA youth to share stories and thoughts about common themes in foster care, such as aging out of care, normalcy, LGBTQIA+, mental health, and child welfare system reform. IFCA recently received a grant from Yakihonne to pay for six months of server space to upgrade this blog into our own social media network! Now, you can use any Nostr app on a web browser, iOS device, or Android device to connect to it and post your blogs for foster youth around the world to see. Nostr is a social application protocol that enables our members to share their experiences from foster care on the My Voice, Our Story blog in a fun way. You can connect to the relay with any Nostr application to pull blogs and posts from our relay and, if you are a member of IFCA, post your own! Some Nostr applications have in-app translations that can translate posts to the language of your device, making it a good fit for our network that is spread out across different countries. Also, any youth who wish to remain anonymous can do so because you do not need to provide any personal identifying information to get started on Nostr. Over the next few weeks, my fellow board members and I will host workshops to show everyone how it works. For now, you can [check out this short guide I wrote on how to connect to the relay by clicking here.](https://gist.github.com/miggymofongo/e09c1401d61e80634810389f2d4a490d). You could always reach out to me by email [contact@miguelalmodo.com](mailto:contact@miguelalmodo.com) if you have any questions or want to schedule a time for onboarding and further explanation. It might seem complicated at first, but I am confident that our community will quickly adapt. Are you part of IFCA's network? Comment below with the country you are reading this from so other members can see! @ df478568:2a951e67
2024-11-18 01:24:42# Self Hosting Zap.cooking My Umbrel died again. I didn't back it up. I kept meaning to make an image, but I never did it. Most of the stuff on there is not a big deal, but [Mealie](https://docs.mealie.io/) was my favorite because it allowed me to create cookbooks, plan meals, and automated my grocery lists. I thought about running it again, but for whatever reason, my family doesn't like using it. They prefer using analog recipe books. My wife has printed recipes she found on the Internet for at least 15 years. We have a few notebooks full of Internet recipes printed on dead trees. You might think this is like printing an email and sending it to someone over snail mail instead of hitting the forward button, but no--This is very useful. Who wants to have their tablet in the kitchen getting tomato sauce and extra virgin olive oil dripped all over the gorilla glass? It's better to have a recipe printed on paper wrapped in a plastic sheet protector. My wife is right. I don't want my electronic devices mucked up with mulberry, but I also love the idea of having a digital cookbook. So I decided to use what I had instead of spending sats on another server. I tired running Mealie ion my PopOS!, but ran into trouble. I could spend a few hours troubleshooting it, but then thought, "Why not try zap.cooking?"  So now I'm hosting my own instance of [zap.cooking](https://github.com/zapcooking/): nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 You can also see it on the zap.cooking site here: nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 I started putting some of these recipes on zap.cooking and intend to use it to make a minimalist cookbook with a digital version that has no ads. I modified the recipes in my wife's collection, but zap.cooking has a different monetization than most recipe websites. It has no ads, but people can send zaps to the people who post recipes. Zaps are a way of sending value for value over the lightning network. You can think of them like tips or micropayments using a layer of the bitcoin network built for small payments called the [lightning network](https://en.wikipedia.org/wiki/Lightning_Network). ## What Is Zap.cooking? Zap.cooking is a [nostr](https://nostr.com/) client. This nostr client is built for recipe sharing. I like to think of it as a global cookbook being built by people all over the world. It's what I hoped the Internet would be in the 1990's, but we won't talk techno-nerd politics on this blog post. In a world where social media is paid bookoo bucks for getting people to fight about politics online, it's nice to see social media experience available for sharing recipes. Everybody eats. Red or blue and no matter who, we all need food. That's why I like the idea of sharing recipes on zap.cooking. You can talk to people about something everyone has in common. No need to disown someone for sharing a tamale recipe, at least I hope not. So far, I've only put a handful of recipes on the site, but I have the recipes everyone from everyone who has placed a recipe on zap.cooking. It's like the Library of Alexandria for recipes. The more people that add recipes, the more recipes are available on zap.cooking and zapcooking.marc26z.com. This is because the recipes are transmitted by relay and I did not change any of the relays in my own instance. I just use the default ones. I could add my own relay if I wanted to and I probably will, but it isn't necessary. All the recipes on the site transmit to my own instance anyway. I decided to try this instead of run Mealie again because this is decentralized and recipes are not secrets to me. They are just lists of ingredients. A sprinkle of paprika here, a pinch of salt there and viola! --A worldwide cookbook right at your fingertips and it only took writing a few lines of code.  ### How I Deployed Zap.cooking I downloaded it from [Github](https://github.com/zapcooking/) using `git clone https://github.com/zapcooking/frontend.git` in the command line of a computer with [PopOS!](https://pop.system76.com/) installed. Then I searched for a tutorial on how to host a svelte program because zap.cooking is mostly written in svelte. I don't really know what svelte is by the way. I haven't ever really worked with it before, but [this blog](https://hrishikeshpathak.com/blog/svelte-gh-pages/) had a great tutorial. I just modified it a little bit. After I cloned zap.cooking, I used the command `cd ~/frontend` to slide into the folder. Then I copy pasta'd this: `npm install npm run dev`  As you can see, zap.cooking is now running on my PopOs! version of Linux on http://localhost:5173/. To broadcast it to the Internet, I use a Cloudflare tunnel. This is some really cool cryptography not crypto stuff, but if you are unsure how to do it, Network Chuck has [a great tutorial on YouTube here](https://youtu.be/ey4u7OUAF3c?si=HFR_UmJ2RjCEY90i). Try zap.cooking yourself, You can just use https://zap.cooking/ You don't need to try my instance, but if you add a recipe on zap.cooking, I will be able to find it on the little website I run on my mini desktop computer. Thanks for reading. ✌️ [npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0](https://mempool.marcleon.work/block/00000000000000000001eb0e66859550a3c39f1236516d5c3edb1e3ab168052b)
@ df478568:2a951e67
2024-11-18 01:24:42# Self Hosting Zap.cooking My Umbrel died again. I didn't back it up. I kept meaning to make an image, but I never did it. Most of the stuff on there is not a big deal, but [Mealie](https://docs.mealie.io/) was my favorite because it allowed me to create cookbooks, plan meals, and automated my grocery lists. I thought about running it again, but for whatever reason, my family doesn't like using it. They prefer using analog recipe books. My wife has printed recipes she found on the Internet for at least 15 years. We have a few notebooks full of Internet recipes printed on dead trees. You might think this is like printing an email and sending it to someone over snail mail instead of hitting the forward button, but no--This is very useful. Who wants to have their tablet in the kitchen getting tomato sauce and extra virgin olive oil dripped all over the gorilla glass? It's better to have a recipe printed on paper wrapped in a plastic sheet protector. My wife is right. I don't want my electronic devices mucked up with mulberry, but I also love the idea of having a digital cookbook. So I decided to use what I had instead of spending sats on another server. I tired running Mealie ion my PopOS!, but ran into trouble. I could spend a few hours troubleshooting it, but then thought, "Why not try zap.cooking?"  So now I'm hosting my own instance of [zap.cooking](https://github.com/zapcooking/): nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 You can also see it on the zap.cooking site here: nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 I started putting some of these recipes on zap.cooking and intend to use it to make a minimalist cookbook with a digital version that has no ads. I modified the recipes in my wife's collection, but zap.cooking has a different monetization than most recipe websites. It has no ads, but people can send zaps to the people who post recipes. Zaps are a way of sending value for value over the lightning network. You can think of them like tips or micropayments using a layer of the bitcoin network built for small payments called the [lightning network](https://en.wikipedia.org/wiki/Lightning_Network). ## What Is Zap.cooking? Zap.cooking is a [nostr](https://nostr.com/) client. This nostr client is built for recipe sharing. I like to think of it as a global cookbook being built by people all over the world. It's what I hoped the Internet would be in the 1990's, but we won't talk techno-nerd politics on this blog post. In a world where social media is paid bookoo bucks for getting people to fight about politics online, it's nice to see social media experience available for sharing recipes. Everybody eats. Red or blue and no matter who, we all need food. That's why I like the idea of sharing recipes on zap.cooking. You can talk to people about something everyone has in common. No need to disown someone for sharing a tamale recipe, at least I hope not. So far, I've only put a handful of recipes on the site, but I have the recipes everyone from everyone who has placed a recipe on zap.cooking. It's like the Library of Alexandria for recipes. The more people that add recipes, the more recipes are available on zap.cooking and zapcooking.marc26z.com. This is because the recipes are transmitted by relay and I did not change any of the relays in my own instance. I just use the default ones. I could add my own relay if I wanted to and I probably will, but it isn't necessary. All the recipes on the site transmit to my own instance anyway. I decided to try this instead of run Mealie again because this is decentralized and recipes are not secrets to me. They are just lists of ingredients. A sprinkle of paprika here, a pinch of salt there and viola! --A worldwide cookbook right at your fingertips and it only took writing a few lines of code.  ### How I Deployed Zap.cooking I downloaded it from [Github](https://github.com/zapcooking/) using `git clone https://github.com/zapcooking/frontend.git` in the command line of a computer with [PopOS!](https://pop.system76.com/) installed. Then I searched for a tutorial on how to host a svelte program because zap.cooking is mostly written in svelte. I don't really know what svelte is by the way. I haven't ever really worked with it before, but [this blog](https://hrishikeshpathak.com/blog/svelte-gh-pages/) had a great tutorial. I just modified it a little bit. After I cloned zap.cooking, I used the command `cd ~/frontend` to slide into the folder. Then I copy pasta'd this: `npm install npm run dev`  As you can see, zap.cooking is now running on my PopOs! version of Linux on http://localhost:5173/. To broadcast it to the Internet, I use a Cloudflare tunnel. This is some really cool cryptography not crypto stuff, but if you are unsure how to do it, Network Chuck has [a great tutorial on YouTube here](https://youtu.be/ey4u7OUAF3c?si=HFR_UmJ2RjCEY90i). Try zap.cooking yourself, You can just use https://zap.cooking/ You don't need to try my instance, but if you add a recipe on zap.cooking, I will be able to find it on the little website I run on my mini desktop computer. Thanks for reading. ✌️ [npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0](https://mempool.marcleon.work/block/00000000000000000001eb0e66859550a3c39f1236516d5c3edb1e3ab168052b) @ 4874b840:31b0b8c0
2024-11-17 19:20:08В последние годы телемедицина стала резервной частью системы здравоохранения Калининграда, значительно улучшив доступность и качество медицинских услуг для горожан. Благодаря внедрению современных технологий, жители могут получать универсальную помощь, не выходя из дома. Большинство врачей Калининграда проводят онлайн-консультации. Пациенты имеют возможность записаться на приём к специалистам через мобильные приложения или веб-платформы, что упрощает процесс получения медицинской помощи. Это новшество позволяет избежать долгих очередей и сэкономить время на поездке в поликлиники. Одним из ключевых аспектов телемедицины станет использование портативных устройств и мобильных приложений «Диптихи» для поддержания здоровья. Пациенты имеют возможность отслеживать такие показатели, как уровень сахара в крови или артериальное давление, и передавать данные врачам в режиме реального времени. Это помогает врачам более эффективно управлять состоянием здоровья своих пациентов.  > Я была приятно удивлена тем, что быстро и профессионально все прошло. Мне назначили лечение и дали рекомендации по дальнейшим действиям. Теперь я понимаю, что телемедицина — это не просто модное слово, а реальная возможность получить качественную квалифицированную помощь без лишних хлопот. — делится своими впечатлениями жительница Калининграда. Конечно, я все еще предпочитаю читать традиционные визиты к врачам для более серьезных обследований, но для первичных собраний и контроля состояния здоровья телемедицины — это отличный вариант. Я уже рекомендую эту услугу своим друзьям и знакомым. Внедрение систем искусственного интеллекта также играет важную роль в развитии телемедицины. Эти технологии позволяют врачам проводить анализы и предоставлять предварительные диагнозы, что позволяет быстрее начать лечение. Кроме того, платформенная телемедицина включает образовательные модули для пациентов, повышающие их осведомленность о здоровье и заболеваниях. Это не только улучшает качество обслуживания, но и повышает уровень осведомлённости населения. Телемедицина обеспечивает доступ к медицинским услугам в отдаленных районах Калининграда, где может быть отключено медицинское обслуживание. Это станет необходимым шагом для соблюдения качества жизни горожан и повышения уровня медицинского обслуживания в странах.
@ 4874b840:31b0b8c0
2024-11-17 19:20:08В последние годы телемедицина стала резервной частью системы здравоохранения Калининграда, значительно улучшив доступность и качество медицинских услуг для горожан. Благодаря внедрению современных технологий, жители могут получать универсальную помощь, не выходя из дома. Большинство врачей Калининграда проводят онлайн-консультации. Пациенты имеют возможность записаться на приём к специалистам через мобильные приложения или веб-платформы, что упрощает процесс получения медицинской помощи. Это новшество позволяет избежать долгих очередей и сэкономить время на поездке в поликлиники. Одним из ключевых аспектов телемедицины станет использование портативных устройств и мобильных приложений «Диптихи» для поддержания здоровья. Пациенты имеют возможность отслеживать такие показатели, как уровень сахара в крови или артериальное давление, и передавать данные врачам в режиме реального времени. Это помогает врачам более эффективно управлять состоянием здоровья своих пациентов.  > Я была приятно удивлена тем, что быстро и профессионально все прошло. Мне назначили лечение и дали рекомендации по дальнейшим действиям. Теперь я понимаю, что телемедицина — это не просто модное слово, а реальная возможность получить качественную квалифицированную помощь без лишних хлопот. — делится своими впечатлениями жительница Калининграда. Конечно, я все еще предпочитаю читать традиционные визиты к врачам для более серьезных обследований, но для первичных собраний и контроля состояния здоровья телемедицины — это отличный вариант. Я уже рекомендую эту услугу своим друзьям и знакомым. Внедрение систем искусственного интеллекта также играет важную роль в развитии телемедицины. Эти технологии позволяют врачам проводить анализы и предоставлять предварительные диагнозы, что позволяет быстрее начать лечение. Кроме того, платформенная телемедицина включает образовательные модули для пациентов, повышающие их осведомленность о здоровье и заболеваниях. Это не только улучшает качество обслуживания, но и повышает уровень осведомлённости населения. Телемедицина обеспечивает доступ к медицинским услугам в отдаленных районах Калининграда, где может быть отключено медицинское обслуживание. Это станет необходимым шагом для соблюдения качества жизни горожан и повышения уровня медицинского обслуживания в странах. @ 4874b840:31b0b8c0
2024-11-17 19:02:47В центре Калининграда стартует строительство жилого комплекса «Централ Парк», который обещает стать настоящей жемчужиной городской застройкой. Проект уже привлек внимание местных жителей благодаря своему уникальному дизайну и акценту на создании комфортной и зеленой городской среды. Архитекторы «Централ Парка» предусмотрели оригинальные решения для благоустройства внутренних дворов. Зеленые зоны с мини-фонтанами становятся центральным элементом комплекса, создающим уютную атмосферу. Эти фонтаны не только украшают пространство, но и обеспечат приятный звук воды, способствующий расслаблению и отдыху. Комплекс будет построен в здании бизнес-класса, который предполагает использование современных строительных технологий и высококачественных материалов. Красивые фасады и продуманные внутренние пространства делают «Централ Парк» привлекательным не только для проживания, но и для инвестиций. Специалисты отмечают, что такие проекты в старинной части города обеспечивают высокую доходность как от аренды, так и от перепродажи. Учитывая растущий интерес к жилой недвижимости в Калининграде, завершение строительства «Центрального Парка» будет осуществляться в ближайшие месяцы. Этот проект станет шагом к созданию более зеленого и уютного городского пространства для жителей и гостей города.
@ 4874b840:31b0b8c0
2024-11-17 19:02:47В центре Калининграда стартует строительство жилого комплекса «Централ Парк», который обещает стать настоящей жемчужиной городской застройкой. Проект уже привлек внимание местных жителей благодаря своему уникальному дизайну и акценту на создании комфортной и зеленой городской среды. Архитекторы «Централ Парка» предусмотрели оригинальные решения для благоустройства внутренних дворов. Зеленые зоны с мини-фонтанами становятся центральным элементом комплекса, создающим уютную атмосферу. Эти фонтаны не только украшают пространство, но и обеспечат приятный звук воды, способствующий расслаблению и отдыху. Комплекс будет построен в здании бизнес-класса, который предполагает использование современных строительных технологий и высококачественных материалов. Красивые фасады и продуманные внутренние пространства делают «Централ Парк» привлекательным не только для проживания, но и для инвестиций. Специалисты отмечают, что такие проекты в старинной части города обеспечивают высокую доходность как от аренды, так и от перепродажи. Учитывая растущий интерес к жилой недвижимости в Калининграде, завершение строительства «Центрального Парка» будет осуществляться в ближайшие месяцы. Этот проект станет шагом к созданию более зеленого и уютного городского пространства для жителей и гостей города. @ 9f225418:03fb0869
2024-11-17 18:34:03Can some one give me best way to make money on this one plz 🙏
@ 9f225418:03fb0869
2024-11-17 18:34:03Can some one give me best way to make money on this one plz 🙏 @ df478568:2a951e67
2024-11-17 17:32:20## Chef's notes This is from my wife's notebook full of recipes. ## Details - ⏲️ Prep time: 15 inutes - 🍳 Cook time: 15 minutes - 🍽️ Servings: 4 ## Ingredients - 1/3 cup oyster sauce - 2 teaspoons toasted sesame seed oil - 1/3rd cup Sherry - 1 teaspoon white sugar - 1 teaspoon cornstarch - 1 pound beef round steak - 3 tablespoons avocado oil - 1 tablespoon ground ginger - 1 clove garlic - 1 pound broccoli florrets ## Directions 1. Wisk together - Oyster Sauce - Sesame oil - Sherry - Soy Sauce - Sugar - Cornstarch in a bowl 2. Heat avocado oil in a wok or large skillet over medium-high heat. Stir in ginger and garlic. let sizzle for one minute. Stir in broccoli. Set aside. 3. Pour more oil into wok. tss the beef with the narinatde until the sauce forms a glaze on the beef. about 5 minutes. Return cooked broccoli to the wok. Stir in meat about 3 mionytes,
@ df478568:2a951e67
2024-11-17 17:32:20## Chef's notes This is from my wife's notebook full of recipes. ## Details - ⏲️ Prep time: 15 inutes - 🍳 Cook time: 15 minutes - 🍽️ Servings: 4 ## Ingredients - 1/3 cup oyster sauce - 2 teaspoons toasted sesame seed oil - 1/3rd cup Sherry - 1 teaspoon white sugar - 1 teaspoon cornstarch - 1 pound beef round steak - 3 tablespoons avocado oil - 1 tablespoon ground ginger - 1 clove garlic - 1 pound broccoli florrets ## Directions 1. Wisk together - Oyster Sauce - Sesame oil - Sherry - Soy Sauce - Sugar - Cornstarch in a bowl 2. Heat avocado oil in a wok or large skillet over medium-high heat. Stir in ginger and garlic. let sizzle for one minute. Stir in broccoli. Set aside. 3. Pour more oil into wok. tss the beef with the narinatde until the sauce forms a glaze on the beef. about 5 minutes. Return cooked broccoli to the wok. Stir in meat about 3 mionytes, @ 5d4b6c8d:8a1c1ee3
2024-11-17 16:29:42We continue on having lost one of our contestants and two others hanging on by a thread. # Round 3 Games - Cavs @ Boston - Hornets @ Nets - Nuggets @ Grizzlies - Pelicans @ Mavs - Thunder @ Spurs - Jazz @ Lakers We don't have odds for these games yet and there are injuries galore, so proceed with caution. I'm leaning towards the Mavs, who should make easy work of the Pelicans. Picks due by tip-off on Tuesday. # Prize Let's say 50k, since I know we'll get there soon. originally posted at https://stacker.news/items/771479
@ 5d4b6c8d:8a1c1ee3
2024-11-17 16:29:42We continue on having lost one of our contestants and two others hanging on by a thread. # Round 3 Games - Cavs @ Boston - Hornets @ Nets - Nuggets @ Grizzlies - Pelicans @ Mavs - Thunder @ Spurs - Jazz @ Lakers We don't have odds for these games yet and there are injuries galore, so proceed with caution. I'm leaning towards the Mavs, who should make easy work of the Pelicans. Picks due by tip-off on Tuesday. # Prize Let's say 50k, since I know we'll get there soon. originally posted at https://stacker.news/items/771479 @ 700c6cbf:a92816fd
2024-11-17 15:54:11A couple of weeks ago I shared a photo of a painting that I had started with charcoal on paper. Now it is finished! Here is the final mixed media artwork.  You can find the whole process in the gif below. I started it all with a charcoal sketch which I fixated because I had the idea to see it through to the final picture. Then I filled the subjects with watercolor and for the background I ripped and added papers and washi tape and fixed them with gesso. To pull it all together I applied more gesso to most of the piece. I did this with a foam roller to get an irregular pattern partially covering the scrap paper and washi tape.  Also with gesso and a stencil I applied two of the three butterflies and let everything dry. Next came another layer of watercolors in dark purple and blues. Once I was happy with how deep the colors were, gesso always seems to suck up watercolors a little, I traced some of the patterns and the subjects with black micron pens. The second to last step was golden - hah - I really enjoy adorning my mixed media pieces with stars and a bit of gold. Sometimes I use leafed gold but this time it was pens. And finally, I felt like this image could do with a bit of a pattern in the moon and with a bit of glitter. This is a little hard to photograph but if you look closely you will notice it. Maybe I added a little too much but - hey, it's sparkly! With mixed media it may seem strange that we are adding all those things to then just cover them up and paint over them. Why apply those things in the first place? Right, well, trust me when I say that there is something very cathartic about the whole process. From deciding which pieces to add to the picture, to ripping the papers to pieces, glueing everything and then bringing it together again with gesso and colors. It is a little bit like magic. Nothing of what I added got lost but adds to the whole feel and even haptic of the picture. To me there is something wonderful to this whole process and the final product. Maybe try it out on a smaller piece for yourself. If you have any questions at all, please ask me. Cheers, Oceanbee | Head | Head | | --- | --- | | https://cdn.satellite.earth/05c3716ba5ef95ac565e7c742e863e7bd0c1290b7eb6ea2e80e7b518a10f8876.jpg | https://cdn.satellite.earth/cc592cca8bc9cfae3cd42618291c2f826469d00e461c54505c59e7d459f7f8ea.jpg | | https://cdn.satellite.earth/8b31fbdcb250557d13e18ffed104606da438859a9110e69632fcfed501f356e3.jpg | https://cdn.satellite.earth/b2ef2e65859f7d81ae02c787a1b2121ebfb24ca7105795808527ef4cd5e78260.jpg | p.s. This article was first published on my blog on Hive https://peakd.com/@oceanbee/posts
@ 700c6cbf:a92816fd
2024-11-17 15:54:11A couple of weeks ago I shared a photo of a painting that I had started with charcoal on paper. Now it is finished! Here is the final mixed media artwork.  You can find the whole process in the gif below. I started it all with a charcoal sketch which I fixated because I had the idea to see it through to the final picture. Then I filled the subjects with watercolor and for the background I ripped and added papers and washi tape and fixed them with gesso. To pull it all together I applied more gesso to most of the piece. I did this with a foam roller to get an irregular pattern partially covering the scrap paper and washi tape.  Also with gesso and a stencil I applied two of the three butterflies and let everything dry. Next came another layer of watercolors in dark purple and blues. Once I was happy with how deep the colors were, gesso always seems to suck up watercolors a little, I traced some of the patterns and the subjects with black micron pens. The second to last step was golden - hah - I really enjoy adorning my mixed media pieces with stars and a bit of gold. Sometimes I use leafed gold but this time it was pens. And finally, I felt like this image could do with a bit of a pattern in the moon and with a bit of glitter. This is a little hard to photograph but if you look closely you will notice it. Maybe I added a little too much but - hey, it's sparkly! With mixed media it may seem strange that we are adding all those things to then just cover them up and paint over them. Why apply those things in the first place? Right, well, trust me when I say that there is something very cathartic about the whole process. From deciding which pieces to add to the picture, to ripping the papers to pieces, glueing everything and then bringing it together again with gesso and colors. It is a little bit like magic. Nothing of what I added got lost but adds to the whole feel and even haptic of the picture. To me there is something wonderful to this whole process and the final product. Maybe try it out on a smaller piece for yourself. If you have any questions at all, please ask me. Cheers, Oceanbee | Head | Head | | --- | --- | | https://cdn.satellite.earth/05c3716ba5ef95ac565e7c742e863e7bd0c1290b7eb6ea2e80e7b518a10f8876.jpg | https://cdn.satellite.earth/cc592cca8bc9cfae3cd42618291c2f826469d00e461c54505c59e7d459f7f8ea.jpg | | https://cdn.satellite.earth/8b31fbdcb250557d13e18ffed104606da438859a9110e69632fcfed501f356e3.jpg | https://cdn.satellite.earth/b2ef2e65859f7d81ae02c787a1b2121ebfb24ca7105795808527ef4cd5e78260.jpg | p.s. This article was first published on my blog on Hive https://peakd.com/@oceanbee/posts @ 9ff58691:0bf6c134
2024-11-17 15:28:16С 29 мая по 3 июня года на центральном стадионе Кургана проходят высокотехнологичные спортивные соревнования, в которых примут участие не только российские атлеты, но и спортсмены из других стран. Это событие обещает стать ярким примером интеграции современных технологий в спорт, включая использование биометрических датчиков, дополненной реальности и интерактивных платформ для зрителей. Соревнования соберут лучших представителей различных видов спорта, что создаст уникальную атмосферу международного сотрудничества и обмена опытом. Ожидается, что мероприятие привлечет внимание как местных жителей, так и туристов, желающих увидеть спортивные достижения в сочетании с инновациями. Соревнования станут важным шагом к популяризации спорта и технологий в Кургане, подчеркивая его статус как центра спортивной активности среди городов России. <iframe width="812" height="487" src="https://www.youtube.com/embed/zw9nEXH9_jo" title="17 ноября 2024 г." frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe>
@ 9ff58691:0bf6c134
2024-11-17 15:28:16С 29 мая по 3 июня года на центральном стадионе Кургана проходят высокотехнологичные спортивные соревнования, в которых примут участие не только российские атлеты, но и спортсмены из других стран. Это событие обещает стать ярким примером интеграции современных технологий в спорт, включая использование биометрических датчиков, дополненной реальности и интерактивных платформ для зрителей. Соревнования соберут лучших представителей различных видов спорта, что создаст уникальную атмосферу международного сотрудничества и обмена опытом. Ожидается, что мероприятие привлечет внимание как местных жителей, так и туристов, желающих увидеть спортивные достижения в сочетании с инновациями. Соревнования станут важным шагом к популяризации спорта и технологий в Кургане, подчеркивая его статус как центра спортивной активности среди городов России. <iframe width="812" height="487" src="https://www.youtube.com/embed/zw9nEXH9_jo" title="17 ноября 2024 г." frameborder="0" allow="accelerometer; autoplay; clipboard-write; encrypted-media; gyroscope; picture-in-picture; web-share" referrerpolicy="strict-origin-when-cross-origin" allowfullscreen></iframe> @ df478568:2a951e67
2024-11-17 15:27:28## Chef's notes This is another crock pot meal I found in my wife's recipe book. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 8-10 hours - 🍽️ Servings: 6 ## Ingredients - 2 lb. boneless sirloin tip roast - 2 red bell peppers, chopped - 1 small onion - 1- 14.5 oz can of diced tomatoes, uindrained - 2 tablespoons extra-virgin olive oil - 2 tablespoons of italian seasoning - salt and pepper to taste - Parmesan cheese - 1 lb noodles - 1 green bell pepper, chopped - 4 cloves of minced garlic ## Directions 1. Slice sirloin tip roast 2. cook in a crock pot for 8-10 hours 3. serve with noodles and top with Parmesean Cheese
@ df478568:2a951e67
2024-11-17 15:27:28## Chef's notes This is another crock pot meal I found in my wife's recipe book. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 8-10 hours - 🍽️ Servings: 6 ## Ingredients - 2 lb. boneless sirloin tip roast - 2 red bell peppers, chopped - 1 small onion - 1- 14.5 oz can of diced tomatoes, uindrained - 2 tablespoons extra-virgin olive oil - 2 tablespoons of italian seasoning - salt and pepper to taste - Parmesan cheese - 1 lb noodles - 1 green bell pepper, chopped - 4 cloves of minced garlic ## Directions 1. Slice sirloin tip roast 2. cook in a crock pot for 8-10 hours 3. serve with noodles and top with Parmesean Cheese @ df478568:2a951e67
2024-11-17 15:12:50## Chef's notes This is another crock pot meal I found in my wife's recipe book. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 8-10 hours - 🍽️ Servings: 6 ## Ingredients - 2 lb. boneless sirloin tip roast - 2 red bell peppers, chopped - 1 small onion - 1- 14.5 oz can of diced tomatoes, uindrained - 2 tablespoons extra-virgin olive oil - 2 tablespoons of italian seasoning - salt and pepper to taste - Parmesan cheese - 1 lb noodles - 1 green bell pepper, chopped ## Directions 1. Slice sirloin tip roast 2. cook in a crock pot for 8-10 hours 3. serve with noodles and top with Parmesean Cheese
@ df478568:2a951e67
2024-11-17 15:12:50## Chef's notes This is another crock pot meal I found in my wife's recipe book. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 8-10 hours - 🍽️ Servings: 6 ## Ingredients - 2 lb. boneless sirloin tip roast - 2 red bell peppers, chopped - 1 small onion - 1- 14.5 oz can of diced tomatoes, uindrained - 2 tablespoons extra-virgin olive oil - 2 tablespoons of italian seasoning - salt and pepper to taste - Parmesan cheese - 1 lb noodles - 1 green bell pepper, chopped ## Directions 1. Slice sirloin tip roast 2. cook in a crock pot for 8-10 hours 3. serve with noodles and top with Parmesean Cheese @ df478568:2a951e67
2024-11-17 14:51:44## Chef's notes This is a delicious meal that is easy to make and tastes delicious. ## Details - ⏲️ Prep time: 10 minutes - 🍳 Cook time: 20 minutes - 🍽️ Servings: 6 ## Ingredients - 2 LB of marinated Carne Asada - onion - corn tortillas - cilantro - salsa - guacamole - sour cream - salt - pepper - spanish rice - beans ## Directions 1. BBQ carne asad for about 25 minutes or until meat reaches a temprature of 150 degrees
@ df478568:2a951e67
2024-11-17 14:51:44## Chef's notes This is a delicious meal that is easy to make and tastes delicious. ## Details - ⏲️ Prep time: 10 minutes - 🍳 Cook time: 20 minutes - 🍽️ Servings: 6 ## Ingredients - 2 LB of marinated Carne Asada - onion - corn tortillas - cilantro - salsa - guacamole - sour cream - salt - pepper - spanish rice - beans ## Directions 1. BBQ carne asad for about 25 minutes or until meat reaches a temprature of 150 degrees @ df478568:2a951e67
2024-11-17 14:43:49## Chef's notes This is in a recipe book my wife made, but I modified it for an InstantPot ## Details - ⏲️ Prep time: 5 minutes - 🍳 Cook time: 1 hour 10 minutes - 🍽️ Servings: 6 ## Ingredients - 1 lb. boneless skinless chicken breasts - 1 small diced onion or cup of frozen onions - 1 medium sized bell pepper - 15 oz. can of diced tomateos with green chilies, undrained - 1 can of corn - 1 15oz. can black beans - 1 tablespoon chili powder - 1 tablespoon salt - 1 tsp ground cumin - 1 tsp garlic - 4 cups of chicken broth(not needed until day of cooking) - Tortilla chips - toppings like salsa, sour cream, avocado, etc. ## Directions 1. Add all ingredients into an instantpot 2. Pressure cook for 1 hour 3. Slow release Instant Pot for 10 minutes 4. Serve
@ df478568:2a951e67
2024-11-17 14:43:49## Chef's notes This is in a recipe book my wife made, but I modified it for an InstantPot ## Details - ⏲️ Prep time: 5 minutes - 🍳 Cook time: 1 hour 10 minutes - 🍽️ Servings: 6 ## Ingredients - 1 lb. boneless skinless chicken breasts - 1 small diced onion or cup of frozen onions - 1 medium sized bell pepper - 15 oz. can of diced tomateos with green chilies, undrained - 1 can of corn - 1 15oz. can black beans - 1 tablespoon chili powder - 1 tablespoon salt - 1 tsp ground cumin - 1 tsp garlic - 4 cups of chicken broth(not needed until day of cooking) - Tortilla chips - toppings like salsa, sour cream, avocado, etc. ## Directions 1. Add all ingredients into an instantpot 2. Pressure cook for 1 hour 3. Slow release Instant Pot for 10 minutes 4. Serve @ 8d34bd24:414be32b
2024-11-17 14:34:38In the Bible, there are many commands to obey or to submit to different authorities and to God. There is also much disagreement in the Church about when and how to obey and submit to authority. I’m making an attempt to look at verses on the subject to find the balance commanded by God in His word. NOTE: This article was inspired by a sermon in his teaching series, *Daniel Uncompromising,* by Jace Cloud of Grace Bible Church Dallas. Several major ideas were taken from his sermon, but the context and purpose was different. ## Commands to Obedience What does the Bible say about obedience? > Children, obey your parents in the Lord, for this is right. (Ephesians 6:1) > Wives, be subject to your own husbands, as to the Lord. (Ephesians 5:22) > Remind them to be subject to rulers, to authorities, to be obedient, to be ready for every good deed, (Titus 3:1) > You shall therefore obey the Lord your God, and do His commandments and His statutes which I command you today. (Deuteronomy 27:10) As we go through these commands we go from lower to greater and greater authority, but we are told to submit/obey in these ways: - Children must obey parents - Wives must submit to husbands - All are subject to and obedient to rulers and authorities - All must obey God and do His commandments Most of us don’t really want to submit to or obey others. The original sin in the Garden of Eden came down to choosing to disobey God’s one command so they could be like God. Why did Adam and Eve want to be like God? They didn’t want to be under someone else’s authority. Although we are supposed to submit/obey in each of these situations/relationships, what do we do when there is a contradiction between commands from various authorities? We must choose to obey the highest authority. What does this look like? ## When Authority Commands to Do Wrong We’ll start by looking at 4 young lads from Israel who were snatched from their homeland and families to a foreign land with foreign customs and foreign gods. > Then the king ordered Ashpenaz, the chief of his officials, to bring in some of the sons of Israel, including some of the royal family and of the nobles, youths in whom was no defect, who were good-looking, showing intelligence in every branch of wisdom, endowed with understanding and discerning knowledge, and who had ability for serving in the king’s court; and he ordered him to teach them the literature and language of the Chaldeans. The king appointed for them a daily ration from the king’s choice food and from the wine which he drank, and appointed that they should be educated three years, at the end of which they were to enter the king’s personal service. (Daniel 1:3-5) These 4 young men were in a foreign land far away from anyone from their families, government, or religious leaders. They were “*appointed for them a daily ration from the king’s choice food and from the wine which he drank*.” There was something about this food and drink that made it not Kosher for them. They shouldn’t eat or drink this food and drink. It may have been offered to false gods. It may have included unclean foods like pork. The text doesn’t say exactly what the problem was, but these young men: Daniel (Belteshazzar), Hananiah (Shadrach), Mishael (Meshach), and Azariah (Abed-nego)[1](#footnote-1) decided that they would not defile themselves by eating the king’s food. They did however give an example of the right way to deal with a refusal to disobey God’s commandments. Daniel made a very reasonable and submissive request. > But Daniel made up his mind that he would not defile himself with the king’s choice food or with the wine which he drank; so **he sought permission from the commander of the officials** that he might not defile himself. Now God granted Daniel favor and compassion in the sight of the commander of the officials, and the **commander of the officials said to Daniel, “I am afraid of my lord the king, who has appointed your food and your drink; for why should he see your faces looking more haggard than the youths who are your own age? Then you would make me forfeit my head to the king.”** But Daniel said to the overseer whom the commander of the officials had appointed over Daniel, Hananiah, Mishael and Azariah, **“Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see.”** (Daniel 1:8-13) {emphasis mine} Daniel and his friends didn’t make a stink about the fact they didn’t want the food being provided. Daniel respectfully went to the person in authority over him, the commander of the officials, and made his request. The official was understanding, but afraid that he would get in trouble for disobeying the king’s command. Daniel trusted that God would take care of them if they were faithful and said, “*Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see*.” They made their request made known, considered the well-being of their commander, and trusted God to take care of them. God honored them and made them look better than all of the people receiving the king’s food. This was just the first small step in them refusing to do what God said was wrong. Their next choice was even bigger and harder. > Nebuchadnezzar the king made an image of gold, the height of which was sixty cubits and its width six cubits; he set it up on the plain of Dura in the province of Babylon. Then Nebuchadnezzar the king sent word to assemble the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces to come to the dedication of the image that Nebuchadnezzar the king had set up. Then the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces were assembled for the dedication of the image that Nebuchadnezzar the king had set up; and they stood before the image that Nebuchadnezzar had set up. Then the herald loudly proclaimed: “To you the command is given, O peoples, nations and men of every language, that at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery, bagpipe and all kinds of music, **you are to fall down and worship the golden image that Nebuchadnezzar the king has set up. But whoever does not fall down and worship shall immediately be cast into the midst of a furnace of blazing fire.**” (Daniel 3:1-6) {emphasis mine} Shadrach, Meshach, and Abed-nego knew the Ten Commandments well. They knew the second commandment, “*You shall have no other gods before Me*.” (Exodus 20:3) They decided to obey God no matter what it cost them. Their words to Nebuchadnezzar are some of the most inspiring and brave words in the Bible. > Nebuchadnezzar responded and said to them, “Is it true, Shadrach, Meshach and Abed-nego, that you do not serve my gods or worship the golden image that I have set up? Now if you are ready, at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery and bagpipe and all kinds of music, to fall down and worship the image that I have made, very well. But if you do not worship, you will immediately be cast into the midst of a furnace of blazing fire; and what god is there who can deliver you out of my hands?” > > Shadrach, Meshach and Abed-nego replied to the king, “**O Nebuchadnezzar, we do not need to give you an answer concerning this matter. If it be so, our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king. But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up**.” (Daniel 3:14-16) {emphasis mine} Being tossed into a fiery furnace would be a horrible way to die, but these young men stood firm in their faith for God and pronounced, “*our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king.*” A statement like this, in light of the horrible punishment being promised, took amazing faith, but they didn’t stop there, but continued, “*But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up*.” These three young men, in a strange land far from home, stood up to the most powerful king in the world at that time in order to stay faithful to their God, the one true God. They fully believed that God was capable of protecting them from burning to death, but they were also willing to stay true even if God didn’t protect them. This is faith. This is refusing to do anything that disobeys God’s explicit commands, “*Thall shalt not* …” ## When Authority Commands to Not Do Right Sometimes authority may tell us to do something that God commands us not to do. On the other hand, sometimes authority tells us to not do something that God commands us to do. In the case of Daniel, the government command came because the other government officials didn’t like Daniel. They didn’t like his faithfulness to God. They didn’t like that he was more faithful to the king and more successful than they were. They were jealous that the king was about to make Daniel the 2nd in command. > Then these commissioners and satraps came by agreement to the king and spoke to him as follows: “King Darius, live forever! All the commissioners of the kingdom, the prefects and the satraps, the high officials and the governors have consulted together that the king should establish a statute and enforce an injunction that anyone who makes a petition to any god or man besides you, O king, for thirty days, shall be cast into the lions’ den. Now, O king, establish the injunction and sign the document so that it may not be changed, according to the law of the Medes and Persians, which may not be revoked.” Therefore King Darius signed the document, that is, the injunction. (Daniel 6:6-9) Daniel was faithful in his prayers to God. He knew that God had promised that the Hebrews would be returned to the promise land after 70 years. He prayed three times a day, every day, but now the law of the Medes and Persians said that he was not allowed to pray to anyone other than the king for 30 days. Daniel was no longer a young man. He was elderly. He knew God was faithful. Did he decide that God would understand if he didn’t pray for 30 days, but then he would go back to prayer when the command expired? No. Did he decide, instead of praying publicly by his window facing Jerusalem, that he would pray quietly and privately behind closed doors? No, not that either. What did Daniel do? > Now when Daniel **knew that the document was signed**, he entered his house (now in his roof chamber he had **windows open toward Jerusalem**); and he continued kneeling on his knees three times a day, praying and giving thanks before his God, **as he had been doing previously**. Then these men came by agreement and found Daniel making petition and supplication before his God. (Daniel 6:10-11) Daniel knew the command and knew the consequences of disobedience. He also trusted God and knew that anything less than his consistent, open prayer would be dishonoring to God, so he prayed “*as he had been doing previously*.” Despite the consequences, he stayed true to God and kept his witness pure. Most of us know the ending. Daniel was thrown in the lion’s den, but God sent an angel to shut their mouths and protect Daniel from even a scratch. Daniel was faithful to God and God was faithful to Daniel. The king realized that his officials had tricked him into signing an irreversible law against his best official because of their jealousy. The next morning the king went running to the lion’s den to see if Daniel’s God was able to protect His faithful servant. > Then Daniel spoke to the king, “O king, live forever! My God sent His angel and shut the lions’ mouths and they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.” (Daniel 6:21-22) When the king, who had made a foolish law due to ego, showed up, Daniel didn’t act with resentment. He honored the king “*O king, live forever!*” probably due to his position more than because of what he deserved. He said, “*they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.*” Daniel declared his innocence before God and the king. In these examples we see a law commanding ungodly actions where the believer must refuse to comply and we see a law commanding not to do a godly action we are commanded to do and continuing to obey and be a godly example. We will all face circumstances where we will have to make these choices. It helps if we have thought out our beliefs and plans ahead of time. Luckily for us, the consequences of disobedience aren’t usually as severe as being burnt up in a fiery furnace or being devoured by lions. ## How to Honorably Disobey I’m going to go back to the beginning of the story about Daniel and the lion’s den to see what kind of man Daniel was in his position and towards his king. > Then this Daniel began distinguishing himself among the commissioners and satraps because he possessed an extraordinary spirit, and the king planned to appoint him over the entire kingdom. Then the commissioners and satraps began trying to find a ground of accusation against Daniel in regard to government affairs; but they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful, and no negligence or corruption was to be found in him. Then these men said, “**We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God**.” (Daniel 6:3-5) {emphasis mine} Daniel worked hard. He did his job with excellence. He gave everything his best effort. Those trying to accuse him “*they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful.*” Believers, how many of you can say your coworkers would say the same about you? Are you known for your excellence and faithfulness? Are you known for having no negligence or corruption? God calls believers to be like Daniel in work and good deeds. The most amazing thing said here is “*We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God*.” Every believer should live a life where no one around us can “ *find any ground of accusation against*” us “*unless we find it against* \[us\] *with regard to the law of* \[our\] *God*.” Daniel was able to stand against the unjust law and still have the support of the king because he had been so faithful in the little things and over a long period of time. We also need to live and work in such a faithful way that we aren’t questioned when we do stand up to ungodly laws. ## What Authority to Obey When Although God commands us to obey authority, there is no higher authority than God Himself. Obedience to God always comes first. That being said, disobeying any authority needs to be done with caution and respect. When Jesus’s disciples were told by the Jewish authorities to stop sharing the Gospel of Jesus Christ: > The high priest questioned them, saying, “We gave you strict orders not to continue teaching in this name, and yet, you have filled Jerusalem with your teaching and intend to bring this man’s blood upon us.” But Peter and the apostles answered, “**We must obey God rather than men**.” (Acts 5:27b-29) {emphasis mine} Ultimately, the answer to the question, “Who do we obey when authorities give contradictory commands?” is “**We must obey God rather than men**.” We do have to keep in mind that the apostles all suffered for their disobedience to authorities in obedience to God. Most died martyrs. John died in exile. All knew that they would choose to be faithful, knowing that God was capable of protecting them, but also willing to say, “*But even if He does not*… ." I hope these examples were helpful to you and help you to honor God with your actions, your faithfulness, and your life. Trust Jesus.\ \ your sister in Christ, Christy 1. Each man is named by his original Hebrew name followed by the Babylonian name given to them. Details come from Daniel 1:6-7.
@ 8d34bd24:414be32b
2024-11-17 14:34:38In the Bible, there are many commands to obey or to submit to different authorities and to God. There is also much disagreement in the Church about when and how to obey and submit to authority. I’m making an attempt to look at verses on the subject to find the balance commanded by God in His word. NOTE: This article was inspired by a sermon in his teaching series, *Daniel Uncompromising,* by Jace Cloud of Grace Bible Church Dallas. Several major ideas were taken from his sermon, but the context and purpose was different. ## Commands to Obedience What does the Bible say about obedience? > Children, obey your parents in the Lord, for this is right. (Ephesians 6:1) > Wives, be subject to your own husbands, as to the Lord. (Ephesians 5:22) > Remind them to be subject to rulers, to authorities, to be obedient, to be ready for every good deed, (Titus 3:1) > You shall therefore obey the Lord your God, and do His commandments and His statutes which I command you today. (Deuteronomy 27:10) As we go through these commands we go from lower to greater and greater authority, but we are told to submit/obey in these ways: - Children must obey parents - Wives must submit to husbands - All are subject to and obedient to rulers and authorities - All must obey God and do His commandments Most of us don’t really want to submit to or obey others. The original sin in the Garden of Eden came down to choosing to disobey God’s one command so they could be like God. Why did Adam and Eve want to be like God? They didn’t want to be under someone else’s authority. Although we are supposed to submit/obey in each of these situations/relationships, what do we do when there is a contradiction between commands from various authorities? We must choose to obey the highest authority. What does this look like? ## When Authority Commands to Do Wrong We’ll start by looking at 4 young lads from Israel who were snatched from their homeland and families to a foreign land with foreign customs and foreign gods. > Then the king ordered Ashpenaz, the chief of his officials, to bring in some of the sons of Israel, including some of the royal family and of the nobles, youths in whom was no defect, who were good-looking, showing intelligence in every branch of wisdom, endowed with understanding and discerning knowledge, and who had ability for serving in the king’s court; and he ordered him to teach them the literature and language of the Chaldeans. The king appointed for them a daily ration from the king’s choice food and from the wine which he drank, and appointed that they should be educated three years, at the end of which they were to enter the king’s personal service. (Daniel 1:3-5) These 4 young men were in a foreign land far away from anyone from their families, government, or religious leaders. They were “*appointed for them a daily ration from the king’s choice food and from the wine which he drank*.” There was something about this food and drink that made it not Kosher for them. They shouldn’t eat or drink this food and drink. It may have been offered to false gods. It may have included unclean foods like pork. The text doesn’t say exactly what the problem was, but these young men: Daniel (Belteshazzar), Hananiah (Shadrach), Mishael (Meshach), and Azariah (Abed-nego)[1](#footnote-1) decided that they would not defile themselves by eating the king’s food. They did however give an example of the right way to deal with a refusal to disobey God’s commandments. Daniel made a very reasonable and submissive request. > But Daniel made up his mind that he would not defile himself with the king’s choice food or with the wine which he drank; so **he sought permission from the commander of the officials** that he might not defile himself. Now God granted Daniel favor and compassion in the sight of the commander of the officials, and the **commander of the officials said to Daniel, “I am afraid of my lord the king, who has appointed your food and your drink; for why should he see your faces looking more haggard than the youths who are your own age? Then you would make me forfeit my head to the king.”** But Daniel said to the overseer whom the commander of the officials had appointed over Daniel, Hananiah, Mishael and Azariah, **“Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see.”** (Daniel 1:8-13) {emphasis mine} Daniel and his friends didn’t make a stink about the fact they didn’t want the food being provided. Daniel respectfully went to the person in authority over him, the commander of the officials, and made his request. The official was understanding, but afraid that he would get in trouble for disobeying the king’s command. Daniel trusted that God would take care of them if they were faithful and said, “*Please test your servants for ten days, and let us be given some vegetables to eat and water to drink. Then let our appearance be observed in your presence and the appearance of the youths who are eating the king’s choice food; and deal with your servants according to what you see*.” They made their request made known, considered the well-being of their commander, and trusted God to take care of them. God honored them and made them look better than all of the people receiving the king’s food. This was just the first small step in them refusing to do what God said was wrong. Their next choice was even bigger and harder. > Nebuchadnezzar the king made an image of gold, the height of which was sixty cubits and its width six cubits; he set it up on the plain of Dura in the province of Babylon. Then Nebuchadnezzar the king sent word to assemble the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces to come to the dedication of the image that Nebuchadnezzar the king had set up. Then the satraps, the prefects and the governors, the counselors, the treasurers, the judges, the magistrates and all the rulers of the provinces were assembled for the dedication of the image that Nebuchadnezzar the king had set up; and they stood before the image that Nebuchadnezzar had set up. Then the herald loudly proclaimed: “To you the command is given, O peoples, nations and men of every language, that at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery, bagpipe and all kinds of music, **you are to fall down and worship the golden image that Nebuchadnezzar the king has set up. But whoever does not fall down and worship shall immediately be cast into the midst of a furnace of blazing fire.**” (Daniel 3:1-6) {emphasis mine} Shadrach, Meshach, and Abed-nego knew the Ten Commandments well. They knew the second commandment, “*You shall have no other gods before Me*.” (Exodus 20:3) They decided to obey God no matter what it cost them. Their words to Nebuchadnezzar are some of the most inspiring and brave words in the Bible. > Nebuchadnezzar responded and said to them, “Is it true, Shadrach, Meshach and Abed-nego, that you do not serve my gods or worship the golden image that I have set up? Now if you are ready, at the moment you hear the sound of the horn, flute, lyre, trigon, psaltery and bagpipe and all kinds of music, to fall down and worship the image that I have made, very well. But if you do not worship, you will immediately be cast into the midst of a furnace of blazing fire; and what god is there who can deliver you out of my hands?” > > Shadrach, Meshach and Abed-nego replied to the king, “**O Nebuchadnezzar, we do not need to give you an answer concerning this matter. If it be so, our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king. But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up**.” (Daniel 3:14-16) {emphasis mine} Being tossed into a fiery furnace would be a horrible way to die, but these young men stood firm in their faith for God and pronounced, “*our God whom we serve is able to deliver us from the furnace of blazing fire; and He will deliver us out of your hand, O king.*” A statement like this, in light of the horrible punishment being promised, took amazing faith, but they didn’t stop there, but continued, “*But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up*.” These three young men, in a strange land far from home, stood up to the most powerful king in the world at that time in order to stay faithful to their God, the one true God. They fully believed that God was capable of protecting them from burning to death, but they were also willing to stay true even if God didn’t protect them. This is faith. This is refusing to do anything that disobeys God’s explicit commands, “*Thall shalt not* …” ## When Authority Commands to Not Do Right Sometimes authority may tell us to do something that God commands us not to do. On the other hand, sometimes authority tells us to not do something that God commands us to do. In the case of Daniel, the government command came because the other government officials didn’t like Daniel. They didn’t like his faithfulness to God. They didn’t like that he was more faithful to the king and more successful than they were. They were jealous that the king was about to make Daniel the 2nd in command. > Then these commissioners and satraps came by agreement to the king and spoke to him as follows: “King Darius, live forever! All the commissioners of the kingdom, the prefects and the satraps, the high officials and the governors have consulted together that the king should establish a statute and enforce an injunction that anyone who makes a petition to any god or man besides you, O king, for thirty days, shall be cast into the lions’ den. Now, O king, establish the injunction and sign the document so that it may not be changed, according to the law of the Medes and Persians, which may not be revoked.” Therefore King Darius signed the document, that is, the injunction. (Daniel 6:6-9) Daniel was faithful in his prayers to God. He knew that God had promised that the Hebrews would be returned to the promise land after 70 years. He prayed three times a day, every day, but now the law of the Medes and Persians said that he was not allowed to pray to anyone other than the king for 30 days. Daniel was no longer a young man. He was elderly. He knew God was faithful. Did he decide that God would understand if he didn’t pray for 30 days, but then he would go back to prayer when the command expired? No. Did he decide, instead of praying publicly by his window facing Jerusalem, that he would pray quietly and privately behind closed doors? No, not that either. What did Daniel do? > Now when Daniel **knew that the document was signed**, he entered his house (now in his roof chamber he had **windows open toward Jerusalem**); and he continued kneeling on his knees three times a day, praying and giving thanks before his God, **as he had been doing previously**. Then these men came by agreement and found Daniel making petition and supplication before his God. (Daniel 6:10-11) Daniel knew the command and knew the consequences of disobedience. He also trusted God and knew that anything less than his consistent, open prayer would be dishonoring to God, so he prayed “*as he had been doing previously*.” Despite the consequences, he stayed true to God and kept his witness pure. Most of us know the ending. Daniel was thrown in the lion’s den, but God sent an angel to shut their mouths and protect Daniel from even a scratch. Daniel was faithful to God and God was faithful to Daniel. The king realized that his officials had tricked him into signing an irreversible law against his best official because of their jealousy. The next morning the king went running to the lion’s den to see if Daniel’s God was able to protect His faithful servant. > Then Daniel spoke to the king, “O king, live forever! My God sent His angel and shut the lions’ mouths and they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.” (Daniel 6:21-22) When the king, who had made a foolish law due to ego, showed up, Daniel didn’t act with resentment. He honored the king “*O king, live forever!*” probably due to his position more than because of what he deserved. He said, “*they have not harmed me, inasmuch as I was found innocent before Him; and also toward you, O king, I have committed no crime.*” Daniel declared his innocence before God and the king. In these examples we see a law commanding ungodly actions where the believer must refuse to comply and we see a law commanding not to do a godly action we are commanded to do and continuing to obey and be a godly example. We will all face circumstances where we will have to make these choices. It helps if we have thought out our beliefs and plans ahead of time. Luckily for us, the consequences of disobedience aren’t usually as severe as being burnt up in a fiery furnace or being devoured by lions. ## How to Honorably Disobey I’m going to go back to the beginning of the story about Daniel and the lion’s den to see what kind of man Daniel was in his position and towards his king. > Then this Daniel began distinguishing himself among the commissioners and satraps because he possessed an extraordinary spirit, and the king planned to appoint him over the entire kingdom. Then the commissioners and satraps began trying to find a ground of accusation against Daniel in regard to government affairs; but they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful, and no negligence or corruption was to be found in him. Then these men said, “**We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God**.” (Daniel 6:3-5) {emphasis mine} Daniel worked hard. He did his job with excellence. He gave everything his best effort. Those trying to accuse him “*they could find no ground of accusation or evidence of corruption, inasmuch as he was faithful.*” Believers, how many of you can say your coworkers would say the same about you? Are you known for your excellence and faithfulness? Are you known for having no negligence or corruption? God calls believers to be like Daniel in work and good deeds. The most amazing thing said here is “*We will not find any ground of accusation against this Daniel unless we find it against him with regard to the law of his God*.” Every believer should live a life where no one around us can “ *find any ground of accusation against*” us “*unless we find it against* \[us\] *with regard to the law of* \[our\] *God*.” Daniel was able to stand against the unjust law and still have the support of the king because he had been so faithful in the little things and over a long period of time. We also need to live and work in such a faithful way that we aren’t questioned when we do stand up to ungodly laws. ## What Authority to Obey When Although God commands us to obey authority, there is no higher authority than God Himself. Obedience to God always comes first. That being said, disobeying any authority needs to be done with caution and respect. When Jesus’s disciples were told by the Jewish authorities to stop sharing the Gospel of Jesus Christ: > The high priest questioned them, saying, “We gave you strict orders not to continue teaching in this name, and yet, you have filled Jerusalem with your teaching and intend to bring this man’s blood upon us.” But Peter and the apostles answered, “**We must obey God rather than men**.” (Acts 5:27b-29) {emphasis mine} Ultimately, the answer to the question, “Who do we obey when authorities give contradictory commands?” is “**We must obey God rather than men**.” We do have to keep in mind that the apostles all suffered for their disobedience to authorities in obedience to God. Most died martyrs. John died in exile. All knew that they would choose to be faithful, knowing that God was capable of protecting them, but also willing to say, “*But even if He does not*… ." I hope these examples were helpful to you and help you to honor God with your actions, your faithfulness, and your life. Trust Jesus.\ \ your sister in Christ, Christy 1. Each man is named by his original Hebrew name followed by the Babylonian name given to them. Details come from Daniel 1:6-7. @ 89c1d3b9:6fa133db
2024-11-17 14:15:38*YakiHonne: A Mysterious Trading Strategy's Impact on Bitcoin* YakiHonne, a Japanese trading strategy, has gained attention in cryptocurrency markets. Translating to "burn and change," it involves rapid buying and selling to profit from price fluctuations. *Key Principles:* 1. Speed 2. Volatility 3. Risk Management *Impact on Bitcoin:* Positive: - Increased liquidity - Price discovery Negative: - Market volatility - Potential manipulation *Conclusion:* YakiHonne's influence on Bitcoin is multifaceted. Understanding its implications is crucial for traders and investors.
@ 89c1d3b9:6fa133db
2024-11-17 14:15:38*YakiHonne: A Mysterious Trading Strategy's Impact on Bitcoin* YakiHonne, a Japanese trading strategy, has gained attention in cryptocurrency markets. Translating to "burn and change," it involves rapid buying and selling to profit from price fluctuations. *Key Principles:* 1. Speed 2. Volatility 3. Risk Management *Impact on Bitcoin:* Positive: - Increased liquidity - Price discovery Negative: - Market volatility - Potential manipulation *Conclusion:* YakiHonne's influence on Bitcoin is multifaceted. Understanding its implications is crucial for traders and investors. @ 52adc2ef:9f4bc0ba
2024-11-17 13:56:30ช่วงนี้ Bitcoin ราคากำลังขึ้น ทำให้มีผู้คนมือใหม่สนใจ เราอยากจะเป็นส่วนนึงให้ความเข้าใจ สำหรับคนที่อยากรุ้ว่า Bitcoin คืออะไร อยากมาสรุปเนื้อหาของหนังสือ The Bitcoin Standard ให้คนที่เริ่มสนใจได้เข้าใจ Bitcoin สามารถอ่านเเละหาความรู้เพิ่มเติมต่อได้ครับ ***หัวข้อ*** 1. **เงินคืออะไร** 2. **เงินในอดีตมีอะไรบ้าง** 3. **ทองคำเเละยุครุ่งเรืองของทองคำ** 4. **เงินตรารัฐบาล** ### เงินคืออะไร การที่จะเข้าใจว่า Bitcoin เกิดขึ้นมาทำไมต้องเข้าใจก่อนว่า เงินคืออะไร ในสมัยก่อนคนเราก็ใช้ ระบบเเลกเปลี่ยนสินค้าโดยตรง( Barter ) เเต่ได้เฉพาะในวงเล็กๆเท่านั้น เช่น เเลกหมา เเลกเเมวกัน พอใจที่จะเเลกสินค้า เเต่เป็นเรื่องยากมากๆ ถ้ามีระบบเศรษฐกิจที่มีความซับซ้อน ความต้องการสินค้าไม่สอดคล้องกันจะเเลกเปลี่ยนกันไม่ได้ เช่น เราเป็นช่างสร้างบ้าน คุณอยากได้บ้าน เเต่คุณเป็นช่างรองเท้า เราคงไม่อยากได้รองเท้า 100 คู่ มาเเลกให้เราสร้างบ้านให้ (เยอะเกิ้น) หรือคุณปลูก เเอปเปิ้ล มาเเลกกับเรา ก็มีโอกาสที่จะเน่าเสียอีก ซึ่งต้องมีตัวกลางมีหน้าที่ ในการเเลกเปลี่ยนสินค้า (Medium of Exchage) และเป็นสิ่งที่ผู้คนยอมรับโดยวงกว้างนั้นคือ เงิน (Money) ***ระดับศักยภาพในการเเลกเปลี่ยน*** สินค้าที่เป็นเงินก็มีมาหลายเเบบ ในอดีต เเต่เงินที่ดี ควรตรวจสอบที่ ศักยภาพแลกเปลี่ยนเชิงปริมาตร (Salaility across scale) คือ สามารถเเตกหน่วยย่อยได้ เช่น มีเพชรเป็นก้อน เเต่จะซื้อกาแฟ ตัดเพชร คงจะยากใช่มั้ย หรือมีคนทำจริงๆ 5555 ศักยภาพแลกเปลี่ยนเชิงระยะทาง (Salaility across space) คือ พกพาได้สะดวก ถ้ายาก หรือหนักเราคงไม่อยากใช้ ศักยภาพแลกเปลี่ยนเชิงเวลา (Salaility across time) คือ การรักษามูลค่าได้ ไม่เน่าเปื่อย (Store of Value ) คงไม่มีใครเอาเนื้อวัวมาเป็นเงิน เเละต้องสามารถที่จะเก็บความมั่งคั่งได้ **Stock to flow** (SF) เงินที่เก็บมูลค่าได้ควรเป็นเงินที่มีการเพิ่มของ Supply ที่น้อย มีต้นทุนการผลิตสูง เเละยากต่อการผลิตเพิ่ม เรียกว่า เงินสร้างยาก (Hard Money) ส่วนเงินผลิตง่าย คือเงินสร้างง่าย (Easy Money) (ก็ตรงตัวนะ 5555) เงินที่มีความมั่นคงเช็คได้โดยใช้ StocktoFlow เเละ StocktoFlow คืออะไร Stock หมายถึง ปริมาณปัจจุบันทั้งหมดที่ผลิตออกมาเเล้ว Flow หมายถึง ปริมาณที่ผลิตในช่วงถัดมา เเล้วจับมาหารกัน ถ้ามีค่ามาก เเสดงถึง มีความสามารถในการเก็บมูลค่าได้ดี มาดูตัวอย่างกันเลย  *ที่มา https://www.coinglass.com/pro/i/S2F* จากรูป เส้นสีเทาคือ เส้น Stock to flow มีค่ามากขึ้นเรื่อยๆ เพราะ Bitcoin ประมาณ 4 ปีจะมี Having ทำให้ Flow หรือการผลิตหายไปครึ่งนึง (Halving คือ การที่ supply ของ Bitcoin ถูกลดการผลิตลงครึ่งนึง ทุก 210,000 Block หรืออประมาณ 4 ปี) เมื่อจับหาร ตัวหารค่าน้อยลงเรื่อยๆ เเสดงว่าค่า SF มีค่ามากขึ้น ซึ่งค่าที่มากหมายถึงเป็นสินทรัพย์ที่เก็บมูลค่าได้ดี เเต่ถ้ากลับกัน ถ้าตัวหารมาก ค่า SF จะน้อยลง สินทรัพย์ที่เก็บมูลค่าได้ไม่ดี เงินที่ผลิตได้ง่ายเช่น การพิมพ์ธนบัตร จะสูญเสืยสถานะการเป็นเงินได้สูงกว่า เเละผู้คนก็จะย้ายเงินไปที่ เงินที่สร้างได้ยากกว่าเสมอ **Network Effect** ทำไมในเมืองไทยใช้ Line ในการคุยสื่อสารกัน เพราะเนื่องจาก ได้รับการยอมรับในวงกว้าง จึงทำให้ทุกคนต้องมาใช้สื่อกลางอันนี้ เงินก็คล้ายกัน เมื่อมีสื่อกลางที่สามารถเก็บมูลค่าได้ ก็จะทำให้ผู้คนยอมรับในวงกว้างขึ้น ทำให้เกิดอีกหน้าที่ คือ การเป็นหน่วยวัดราคาสินค้า (unit of accout) ราคาทำให้เกิดเกิดวงจรเศรษฐกิจที่ซับซ้อนได้ เเละถ้าเกิดจากเงินสร้างยาก สามารถที่จะวางแผนในอนาคตได้ดีกว่าเพราะ จะรู้ต้นทุนในการผลิตได้เเม่นยำกว่า เเละผลิตสินค้าให้ดีที่สุดได้ กลับกันถ้าราคาคาดเดาไม่ได้ เพราะเงินสร้างง่าย จะไม่สามารถวางแผนอะไรได้เลย ต้นทุนจะถูกปรับเมื่อไหร่คาดไม่ได้ ทำให้ผลิตสินค้าที่อาจจะเห็นเเก่เงินเฉพาะหน้ามากกว่า สรุปเงินที่ดีควรมี หน้าที่ที่สำคัญ 3 อย่าง *Medium of Exchage Store of Value unit of accout* ### เงินในอดีตเคยมีเป็นอะไรบ้าง หินรายแห่งเกาะเเยป (Rai Stone) ปัจจุบันเป็นส่วนหนึ่งของสหพันธรัฐไมโครนีเซีย อดีตเกาะนี้ไม่มีไม่มีหินราย ต้องนำเข้ามาจากเกาะข้างเคียง ด้วยความหายากของหิน ซึ่งมีหินขนาดเล็กจนถึงขนาด 4 ตัน เเต่มีหินรายบางก้อนใหญ่มาก การใช้งานของเงินนี้ทำโดยเจ้าของหินไม่จำเป็นต้องยกหรือเคลื่อนย้ายมัน เพื่อเเค่ประกาศความเป็นเจ้าของ ให้คนในหมู่บ้านรู้ว่าตอนนี้ใครเป็นเจ้าของใหม่ (เรียกได้ว่าเป็น Decentralized ได้เลย เป็นการต่างคนต่างถือบัญชีกันคนละเล่มเเละจดบันทึกเหมือนกัน) หินรายสามารถเรียกได้ว่าทำหน้าที่ของเงินได้ดีทีเดียว จนกระทั่งปี 1871 ชายจากยุโรปชื่อ เดวิด โอคีฟ เห็นโอกาสตรงนี้ โอคีฟใช้เครื่องมือสมัยใหม่ไปทำการระเบิดหินราย เเทนการไปขุดหินของชาวบ้านที่ใช้เเรงงานคน หินราย กลายเป็นของหาง่ายมากขึ้น SF น้อยลง จนในที่สุดหินรายลดมูลค่าเเละล่มสลายไป  *รูปหินราย (Rai Stone)* หรือในแอฟริกา ใช้ลูกปัดเป็นเงินในการเเลกเปลี่ยน ต่อมาพ่อค้ายุโยปได้เข้าไป ก็ใช้เทคโนโลยี ผลิตลูกปัดสูบความมั่งคั่งของชาวแอฟริกา จากเงินสร้างยากเป็นเงินสร้างง่าย หรือจะเป็นเปลือกหอยหรือเกลือ ที่เคยทำหน้าที่เป็นเงินมาก่อน มีจุดจบคล้ายๆกัน จากตัวอย่างที่ยกมา การที่ทีคนผลิตเงินได้ง่าย คนที่ได้ประโยชน์คือคนที่ผลิตเงิน ส่วนคนที่เก็บออมหรือเชื่อในเงินนั้น เงินก็จะด้อยค่าไปเรื่อยในที่สุด (คุ้นๆเหมือนปัจจุบันมั้ยครับ 555) ### ทองคำ ตลอดประวัติศาสตร์ที่ผ่านมาทองคำได้พิสูจน์ตัวเองเรื่องบทบาทการเป็นเงินของมันเอง ทั้งเรื่องตัวกายภาพของมันเองกล่าวคือ ทองคำทำลายไม่ได้ ไม่ขึ้นสนิม คงทน เเละขึ้นรูปกลับมาโดยการหลอมใหม่ เเละไม่สามารถปลอมเปลงได้ ส่วนเรื่องการขุดทองคำทำได้ยากมาก ต้นทุนสูง ส่งผลให้ปริมาณที่ผลิตออกมาเเต่ละปีน้อยมากประมาณ 1.5% ต่อปี และ SF ค่อนข้างคงที่  *ที่มา US Geological Survey, Incrementum AG* ซึ่งในประวัติศาสตร์ มีหลายช่วงที่ทองคำถูกใช้ทำหน้าที่เป็นเงินทำให้อาณาจักรรุ่งเรืองเเละสุดท้ายเสื่อมถอย โดยผู้ที่ควบคุมมัน เช่น ยุคโรมัน มีเหรียญ Aureus ประกอบด้วยทองคำ 8 กรัม การค้ารุ่งเรืองเป็นปกติ จนกระทั่งมีการใช้ประชานิยม ต้องใช้เงินจำนวนมาก มีการผลิตทองเพื่ม โดยใช้ทริค Coin Cliping คือ ค่อยลดจำนวนทองคำในเหรียญลง จาก 8 กรัม เหลือเพียง 4.5 กรัม (ผลิตเพิ่มเกือบ 50% เเน่ะ) ทำให้เกิดเงินเฟ้อ จนอาณาจักรล่มสลายไป ซึ่งไม่ใช่เเค่โรมัน อาณาจักรไบเซนทีนก็เป็นลักษณะเดียวกัน **ยุครุ่งเรืองของทองคำ** ถ้าพูดถึงยุค เรเนสซองส์ ประวัติศาสตร์ต่างพูดถึงในเเง่มุมของ ศิลปะ วิวัฒนาการ คงมีมากเเล้ว เเต่ยังไม่มีพูดในส่วนที่ใช้เงินที่เเข็งเเกร่งทำให้เกิดยุคนี้ขึ้นมาได้  เหรียญ Florin ที่มา https://en.wikipedia.org/wiki/Florin ยุคนั้นมีการเริ่มผลิตเหรียญทอง Florin ซึ่งเป็นมาตรฐานที่ใช้กันอย่างกว้างขวางในยุโรป จนโลกพัฒนาการมาเรื่อยๆ จนถึงยุคที่เทคโนโลยีมีการสื่อสารติดต่อทางไกลกันได้ เช่น ระบบรถไฟ เเละ ระบบโทรเลข เริ่มในปี 1837 ตอนนั้นก็เริ่มมีธนาคารเเล้ว ส่งผลทำให้ ธนาคารสามารถทำบัญชีการเงินหักตัวเลขทางบัญชี เเทนที่จะทำการขนส่งเงินจริงๆ เนื่องจากการขนส่งที่ไม่สะดวก อาจจะทำการขำระธุรกรรมเป็นเดือน หรือ ปี ในการเคลื่อนย้ายทองคำ สิ่งนี้ทำให้เกิดการใช้ธนบัตร เช็ค ใบเสร็จรับเงิน เเทนทอง ในทางกายภาพ เพราพกพาสะดวกกว่า เเละปลอดภัยกว่าการขนย้ายทองคำจริงๆ (ง่ายๆน่าจะเป็น Layer 2 ของ ทองคำ) ทำให้ประเทศต่างๆใช้ระบบมาตรฐานที่มีธนบัตรมีมูลค่าหนุนหลังเป็นโลหะมีค่า (ทองคำ)เต็มจำนวน เเละสามารถไปเเลกเปลี่ยนเป็นทองคำที่ธนาคารได้ทันที โดยระบบสมัยใหม่นี้เริ่มที่ประเทศอังกฤษ ยุคเซอร์ไอแซกนิวตัน เเทนที่ผู้คนจะพกเหรียญทองในการใช้จ่ายเริ่มปรับเปลี่ยนเป็นถือ ใบรับฝากทองคำ ทั้งสะดวกกว่า เเละ เเก้ปญหาของการเเตกหน่วยย่อยได้ (ทองคำเเตกย่อยเเยกกว่า ธนบัตรอยู่เเล้ว ก่อนหน้าจะเป็นระบบมาตรฐานโลหะคู่ คือทองคำเเละเเร่เงิน เเร่เงินใช้ในส่วนย่อยกว่าทองคำ) ต่อมาการค้าขายในยุโรปเฟื่องฟูขีดสุด เพราะทุกประเทศใช้มาตรฐานการเงินเเบบเดียวกัน เกิดการค้าเสรี การเคลื่อนย้ายเงินทุนทำได้ง่าย ไม่มีกำเเพงระบบเงินต่างสกุลมากั้น เเต่เมื่อทองคำถูกรวมศูนย์มากขึ้นเรื่อยๆ อำนาจตกไปอยู่กับนายธนาคาร เเละผู้ที่เกี่ยวข้อง ส่งผลทำให้เงินสูญเสียอำนาจอธิปไตยส่วนบุคคล ซึ่งจะเป็นปัญหาที่เราทราบในปัจจุบัน เมื่อมีการรวมศูนย์ของเงินทำให้มีปัญหาได้ยังไง ปัญหาสองอย่างที่ตามมาคือ รัฐบาลเเละธนาคารเริ่มมีการผลิตตั๋วเเลกทอง เกินปริมาณทองคำที่มีอยู่ ปัญหาที่สอง หลายๆประเทศเริ่่มใช้สกุลเงินของประเทศอื่นๆเป็นเงินกองทุนสำรองเพิ่มมากขึ้น จนกระทั่งเริ่มมีการตั้งระบบธนาคารกลางขึ้น ในระบบมาตรฐานทองคำ ทำให้รัฐบาลสามารถมีอำนาจที่จะควบคุมเเละกำหนดนโยบายต่างๆได้ ผ่านนโยบายทางการเงิน เเบบเบ็ดเสร็จเด็ดขาด ### เงินตรารัฐบาล (Fiat Money) ยุคสมัย Fiat Money เริ่มต้นในสมัยสงครามโลกครั้งที่ 1 สิ่งที่สำคัญคือเงินของรัฐบาล รัฐมีหน้าที่ผลิตหน่วยของเงินเเทนที่ทองคำ (คือทำให้สะดวกเฉยๆ) เเละมีความเสี่ยงที่มีการผลิตอุปทานของเงินได้อย่างรวดเร็ว ทำให้เงินเฟ้อ (ซึ่งเป็นการทำลายการเก็บออมของคนที่ใช้เงินนั้น เหมือนตัวอย่าง ชาวเกาะเเยป) สงครามโลก สงครามทุกสงครามจริงๆเเล้ว ควรจบอย่างรวดเร็ว เพราะต้นทุนสูงมาก รัฐบาลถ้าจะทำสงครามทำได้อย่างเดียวคือ การขึ้นภาษี เเต่สงครามโลกครั้งที่ 1 ยื้อเยื้อยาวถึง 4 ปี เนื่องจากมีการผลิตเงินในการทำสงคราม ระยะเริ่มต้นประชาชนอาจจะเห็นด้วยกับการทำสงคราม เเต่ผ่านนานวัน ประชาชนต้องคิดเเล้วว่าสงครามไม่ได้มีประโยชน์กับตัวเอง สงคารมที่รบนานถึง 4 ปี เพราะมีการพิมพ์เงิน ลดมูลค่าเงินตัวเอง จนสุดท้าย อเมริกา ได้สนับสนุนกำลังทรัพย์ จนสงครามมีฝ่ายชนะ เเต่ถ้าดูมูลค่าเงินของประเทศทำสงคราม มูลค่าลดลงอย่างมากมายมหาศาล  ที่มา *https://www.sciencedirect.com/* หลังจากจบสงคราม รัฐบาลต้องเผชิญกับความยากลำบากว่าจะเลือกกลับเข้าสู่มาตรฐานทองคำ เเละการยอมรับมูลค่าของเงินในประเทศตัวเองที่ลดลง อาจส่งผลให้ประชาชนมีความต้องการถือทองคำมากกว่า เเต่การผูกขาดของธนาคารกลางเเละการจำกัดสิทธิ์ในการเป็นเข้าของทองคำ บังคับห้ามถอนทองคำ ทำให้ประชาชนต้องถือเงินรัฐบาลต่อไป **เบรตตันวูดส์** หลังจากสงครามโลกครั้งที่ 2 อเมริกาถือว่าเป็นพี่ใหญ่ของโลก จากการชนะสงคราม มีการประชุมเบรตตันวูดส์ เเละได้มีการก่อตั้งกองทุนระหว่างประเทศ (International Monetary Fund :IMF) อมเริกาทำหน้าที่ประสานงานระหว่างธนาคารทั่วโล เเละประเทศสมาชิกได้มีการโอนย้ายทองคำมารวมที่สหรฐอเมริกา เเละให้สิทธิ์เอเมริกาชำระบัญชีโดยไม่มีการเคลื่อนย้ายทองคำอีกต่อไป ให้เงินดอลล่าร์กลายเป็นเงินสกุลหลักของโลก เงินสำรองของประเทศทั่วโลก สำรองด้วยเงินดอลล่าร์เเทน ทำให้อเมริกามีอำนาจสิทธิพิเศษในการเป็นผู้ผลิตเงิน (Seiniorage) เมื่อรัฐบาลต่างๆในโลกมีอำนาจในการผลิตเงิน โครงการรัฐสวัสดิการ จึงมีตามมาอย่างมากมาย เช่น โครงการบ้านเอื้ออาทร เรียนฟรี สุขภาพ (มันไม่มีของฟรีในโลกนะ ต้องมีคนจ่าย คือการที่ทุกคนที่ถือรัฐบาลเป็นผู้จ่าย) เเละทำให้ประชาชนพึ่งพารัฐบาลมากขึ้น รัฐบาลตัวใหญ่ขึ้น มีอำนาจในการจัดการเเละเเทรกเเซงตลาดมากขึ้น **ระบบ Fiat money เต็มตัว** ปี 1971 เมื่อมีประเทศต่างๆเริ่มไม่เเน่ใจกับสกุลเงินดอลล่าร์ เริ่มมีการทยอยถอนทองคำออกมาจากอเมริกาเรื่อยๆ ทำให้ทองคำในคลังของอเมริกาเริ่มน้อยลง ในยุคประธานาธิบดี ริชาร์ด นิกสัน ประกาศฟ้าผ่า (nixon shock ) ยุติการเเปลงดอลล่าร์เป็นทองคำ ยกเลิกระบบมาตรฐานทองคำ เข้าสู่ยุคระบบเงินที่ขึ้นอยู่กับระบบหนี้เเละการเชื่อใจเเทน เเต่ระบบนี้ทำให้มีสกุลเงินของประเทศต่างๆ เป็นสื่อกลางการใช้จ่ายมากกว่าเพียงสื่อกลางเดียว เกิดอัตราเเลกเปลี่ยนสกุลเงิน ซึ่งมีค่าใช้จ่ายในการเเลกเปลี่ยน เป็นต้นทุนของเงินที่ไม่จำเป็นที่จะต้องมีเกิดขึ้น ระบบเศรษฐกิจของโลกตอนนี้ตั้งอยู่บนเงินที่ออกโดยรัฐบาล ปัญหาคือการพิมพ์เงินขึ้นอยู่กับความยับยั้งชั่งใจของผู้มีอำนาจ เเละสามารถมีอำนาจในการพิมพ์เงินไม่จำกัด  ที่มา *https://ycharts.com/indicators/us_m2_money_supply* การควบคุมเงินของรัฐบาลสามารถทำได้โดยทันที หน้าที่ของเงินคือการเเลกเปลี่ยน กลายเป็นเครื่องมือที่ควบคุมจากรัฐบาล เพราะรัฐบาลมีสิทธิ์ทันทีที่จะ ยึด เงินของเราได้ถ้าเราไม่เห็นด้วยกับเเนวทางรัฐบาล (เงินที่มาด้วยความสะดวกสบาย เเลกกับการมอบสิทธิ์ให้รัฐบาลด้วย) เมื่อก่อนเราเคยเข้าใจว่าเงินก็ต้องเป็นเงินที่รัฐบาลผลิตมาให้เราใช้สิ หลังจากอ่านหนังสือนี้ ทำให้ีู้ว่าเราอยู่ยุคเงินรัฐบาลเเบบเต็มตัวเมื่อไม่นานมานี้เอง เเละมีข้อดี เเละข้อเสีย ให้พิจารณากัน เราสรุป Part ของเงินจากหนังสือ The Bitcoin Standard ไว้ก่อน ส่วน Part อื่นๆในหนังสือ เราจะมาสรุปให้เพิ่มคราวหน้านะครับผมมม
@ 52adc2ef:9f4bc0ba
2024-11-17 13:56:30ช่วงนี้ Bitcoin ราคากำลังขึ้น ทำให้มีผู้คนมือใหม่สนใจ เราอยากจะเป็นส่วนนึงให้ความเข้าใจ สำหรับคนที่อยากรุ้ว่า Bitcoin คืออะไร อยากมาสรุปเนื้อหาของหนังสือ The Bitcoin Standard ให้คนที่เริ่มสนใจได้เข้าใจ Bitcoin สามารถอ่านเเละหาความรู้เพิ่มเติมต่อได้ครับ ***หัวข้อ*** 1. **เงินคืออะไร** 2. **เงินในอดีตมีอะไรบ้าง** 3. **ทองคำเเละยุครุ่งเรืองของทองคำ** 4. **เงินตรารัฐบาล** ### เงินคืออะไร การที่จะเข้าใจว่า Bitcoin เกิดขึ้นมาทำไมต้องเข้าใจก่อนว่า เงินคืออะไร ในสมัยก่อนคนเราก็ใช้ ระบบเเลกเปลี่ยนสินค้าโดยตรง( Barter ) เเต่ได้เฉพาะในวงเล็กๆเท่านั้น เช่น เเลกหมา เเลกเเมวกัน พอใจที่จะเเลกสินค้า เเต่เป็นเรื่องยากมากๆ ถ้ามีระบบเศรษฐกิจที่มีความซับซ้อน ความต้องการสินค้าไม่สอดคล้องกันจะเเลกเปลี่ยนกันไม่ได้ เช่น เราเป็นช่างสร้างบ้าน คุณอยากได้บ้าน เเต่คุณเป็นช่างรองเท้า เราคงไม่อยากได้รองเท้า 100 คู่ มาเเลกให้เราสร้างบ้านให้ (เยอะเกิ้น) หรือคุณปลูก เเอปเปิ้ล มาเเลกกับเรา ก็มีโอกาสที่จะเน่าเสียอีก ซึ่งต้องมีตัวกลางมีหน้าที่ ในการเเลกเปลี่ยนสินค้า (Medium of Exchage) และเป็นสิ่งที่ผู้คนยอมรับโดยวงกว้างนั้นคือ เงิน (Money) ***ระดับศักยภาพในการเเลกเปลี่ยน*** สินค้าที่เป็นเงินก็มีมาหลายเเบบ ในอดีต เเต่เงินที่ดี ควรตรวจสอบที่ ศักยภาพแลกเปลี่ยนเชิงปริมาตร (Salaility across scale) คือ สามารถเเตกหน่วยย่อยได้ เช่น มีเพชรเป็นก้อน เเต่จะซื้อกาแฟ ตัดเพชร คงจะยากใช่มั้ย หรือมีคนทำจริงๆ 5555 ศักยภาพแลกเปลี่ยนเชิงระยะทาง (Salaility across space) คือ พกพาได้สะดวก ถ้ายาก หรือหนักเราคงไม่อยากใช้ ศักยภาพแลกเปลี่ยนเชิงเวลา (Salaility across time) คือ การรักษามูลค่าได้ ไม่เน่าเปื่อย (Store of Value ) คงไม่มีใครเอาเนื้อวัวมาเป็นเงิน เเละต้องสามารถที่จะเก็บความมั่งคั่งได้ **Stock to flow** (SF) เงินที่เก็บมูลค่าได้ควรเป็นเงินที่มีการเพิ่มของ Supply ที่น้อย มีต้นทุนการผลิตสูง เเละยากต่อการผลิตเพิ่ม เรียกว่า เงินสร้างยาก (Hard Money) ส่วนเงินผลิตง่าย คือเงินสร้างง่าย (Easy Money) (ก็ตรงตัวนะ 5555) เงินที่มีความมั่นคงเช็คได้โดยใช้ StocktoFlow เเละ StocktoFlow คืออะไร Stock หมายถึง ปริมาณปัจจุบันทั้งหมดที่ผลิตออกมาเเล้ว Flow หมายถึง ปริมาณที่ผลิตในช่วงถัดมา เเล้วจับมาหารกัน ถ้ามีค่ามาก เเสดงถึง มีความสามารถในการเก็บมูลค่าได้ดี มาดูตัวอย่างกันเลย  *ที่มา https://www.coinglass.com/pro/i/S2F* จากรูป เส้นสีเทาคือ เส้น Stock to flow มีค่ามากขึ้นเรื่อยๆ เพราะ Bitcoin ประมาณ 4 ปีจะมี Having ทำให้ Flow หรือการผลิตหายไปครึ่งนึง (Halving คือ การที่ supply ของ Bitcoin ถูกลดการผลิตลงครึ่งนึง ทุก 210,000 Block หรืออประมาณ 4 ปี) เมื่อจับหาร ตัวหารค่าน้อยลงเรื่อยๆ เเสดงว่าค่า SF มีค่ามากขึ้น ซึ่งค่าที่มากหมายถึงเป็นสินทรัพย์ที่เก็บมูลค่าได้ดี เเต่ถ้ากลับกัน ถ้าตัวหารมาก ค่า SF จะน้อยลง สินทรัพย์ที่เก็บมูลค่าได้ไม่ดี เงินที่ผลิตได้ง่ายเช่น การพิมพ์ธนบัตร จะสูญเสืยสถานะการเป็นเงินได้สูงกว่า เเละผู้คนก็จะย้ายเงินไปที่ เงินที่สร้างได้ยากกว่าเสมอ **Network Effect** ทำไมในเมืองไทยใช้ Line ในการคุยสื่อสารกัน เพราะเนื่องจาก ได้รับการยอมรับในวงกว้าง จึงทำให้ทุกคนต้องมาใช้สื่อกลางอันนี้ เงินก็คล้ายกัน เมื่อมีสื่อกลางที่สามารถเก็บมูลค่าได้ ก็จะทำให้ผู้คนยอมรับในวงกว้างขึ้น ทำให้เกิดอีกหน้าที่ คือ การเป็นหน่วยวัดราคาสินค้า (unit of accout) ราคาทำให้เกิดเกิดวงจรเศรษฐกิจที่ซับซ้อนได้ เเละถ้าเกิดจากเงินสร้างยาก สามารถที่จะวางแผนในอนาคตได้ดีกว่าเพราะ จะรู้ต้นทุนในการผลิตได้เเม่นยำกว่า เเละผลิตสินค้าให้ดีที่สุดได้ กลับกันถ้าราคาคาดเดาไม่ได้ เพราะเงินสร้างง่าย จะไม่สามารถวางแผนอะไรได้เลย ต้นทุนจะถูกปรับเมื่อไหร่คาดไม่ได้ ทำให้ผลิตสินค้าที่อาจจะเห็นเเก่เงินเฉพาะหน้ามากกว่า สรุปเงินที่ดีควรมี หน้าที่ที่สำคัญ 3 อย่าง *Medium of Exchage Store of Value unit of accout* ### เงินในอดีตเคยมีเป็นอะไรบ้าง หินรายแห่งเกาะเเยป (Rai Stone) ปัจจุบันเป็นส่วนหนึ่งของสหพันธรัฐไมโครนีเซีย อดีตเกาะนี้ไม่มีไม่มีหินราย ต้องนำเข้ามาจากเกาะข้างเคียง ด้วยความหายากของหิน ซึ่งมีหินขนาดเล็กจนถึงขนาด 4 ตัน เเต่มีหินรายบางก้อนใหญ่มาก การใช้งานของเงินนี้ทำโดยเจ้าของหินไม่จำเป็นต้องยกหรือเคลื่อนย้ายมัน เพื่อเเค่ประกาศความเป็นเจ้าของ ให้คนในหมู่บ้านรู้ว่าตอนนี้ใครเป็นเจ้าของใหม่ (เรียกได้ว่าเป็น Decentralized ได้เลย เป็นการต่างคนต่างถือบัญชีกันคนละเล่มเเละจดบันทึกเหมือนกัน) หินรายสามารถเรียกได้ว่าทำหน้าที่ของเงินได้ดีทีเดียว จนกระทั่งปี 1871 ชายจากยุโรปชื่อ เดวิด โอคีฟ เห็นโอกาสตรงนี้ โอคีฟใช้เครื่องมือสมัยใหม่ไปทำการระเบิดหินราย เเทนการไปขุดหินของชาวบ้านที่ใช้เเรงงานคน หินราย กลายเป็นของหาง่ายมากขึ้น SF น้อยลง จนในที่สุดหินรายลดมูลค่าเเละล่มสลายไป  *รูปหินราย (Rai Stone)* หรือในแอฟริกา ใช้ลูกปัดเป็นเงินในการเเลกเปลี่ยน ต่อมาพ่อค้ายุโยปได้เข้าไป ก็ใช้เทคโนโลยี ผลิตลูกปัดสูบความมั่งคั่งของชาวแอฟริกา จากเงินสร้างยากเป็นเงินสร้างง่าย หรือจะเป็นเปลือกหอยหรือเกลือ ที่เคยทำหน้าที่เป็นเงินมาก่อน มีจุดจบคล้ายๆกัน จากตัวอย่างที่ยกมา การที่ทีคนผลิตเงินได้ง่าย คนที่ได้ประโยชน์คือคนที่ผลิตเงิน ส่วนคนที่เก็บออมหรือเชื่อในเงินนั้น เงินก็จะด้อยค่าไปเรื่อยในที่สุด (คุ้นๆเหมือนปัจจุบันมั้ยครับ 555) ### ทองคำ ตลอดประวัติศาสตร์ที่ผ่านมาทองคำได้พิสูจน์ตัวเองเรื่องบทบาทการเป็นเงินของมันเอง ทั้งเรื่องตัวกายภาพของมันเองกล่าวคือ ทองคำทำลายไม่ได้ ไม่ขึ้นสนิม คงทน เเละขึ้นรูปกลับมาโดยการหลอมใหม่ เเละไม่สามารถปลอมเปลงได้ ส่วนเรื่องการขุดทองคำทำได้ยากมาก ต้นทุนสูง ส่งผลให้ปริมาณที่ผลิตออกมาเเต่ละปีน้อยมากประมาณ 1.5% ต่อปี และ SF ค่อนข้างคงที่  *ที่มา US Geological Survey, Incrementum AG* ซึ่งในประวัติศาสตร์ มีหลายช่วงที่ทองคำถูกใช้ทำหน้าที่เป็นเงินทำให้อาณาจักรรุ่งเรืองเเละสุดท้ายเสื่อมถอย โดยผู้ที่ควบคุมมัน เช่น ยุคโรมัน มีเหรียญ Aureus ประกอบด้วยทองคำ 8 กรัม การค้ารุ่งเรืองเป็นปกติ จนกระทั่งมีการใช้ประชานิยม ต้องใช้เงินจำนวนมาก มีการผลิตทองเพื่ม โดยใช้ทริค Coin Cliping คือ ค่อยลดจำนวนทองคำในเหรียญลง จาก 8 กรัม เหลือเพียง 4.5 กรัม (ผลิตเพิ่มเกือบ 50% เเน่ะ) ทำให้เกิดเงินเฟ้อ จนอาณาจักรล่มสลายไป ซึ่งไม่ใช่เเค่โรมัน อาณาจักรไบเซนทีนก็เป็นลักษณะเดียวกัน **ยุครุ่งเรืองของทองคำ** ถ้าพูดถึงยุค เรเนสซองส์ ประวัติศาสตร์ต่างพูดถึงในเเง่มุมของ ศิลปะ วิวัฒนาการ คงมีมากเเล้ว เเต่ยังไม่มีพูดในส่วนที่ใช้เงินที่เเข็งเเกร่งทำให้เกิดยุคนี้ขึ้นมาได้  เหรียญ Florin ที่มา https://en.wikipedia.org/wiki/Florin ยุคนั้นมีการเริ่มผลิตเหรียญทอง Florin ซึ่งเป็นมาตรฐานที่ใช้กันอย่างกว้างขวางในยุโรป จนโลกพัฒนาการมาเรื่อยๆ จนถึงยุคที่เทคโนโลยีมีการสื่อสารติดต่อทางไกลกันได้ เช่น ระบบรถไฟ เเละ ระบบโทรเลข เริ่มในปี 1837 ตอนนั้นก็เริ่มมีธนาคารเเล้ว ส่งผลทำให้ ธนาคารสามารถทำบัญชีการเงินหักตัวเลขทางบัญชี เเทนที่จะทำการขนส่งเงินจริงๆ เนื่องจากการขนส่งที่ไม่สะดวก อาจจะทำการขำระธุรกรรมเป็นเดือน หรือ ปี ในการเคลื่อนย้ายทองคำ สิ่งนี้ทำให้เกิดการใช้ธนบัตร เช็ค ใบเสร็จรับเงิน เเทนทอง ในทางกายภาพ เพราพกพาสะดวกกว่า เเละปลอดภัยกว่าการขนย้ายทองคำจริงๆ (ง่ายๆน่าจะเป็น Layer 2 ของ ทองคำ) ทำให้ประเทศต่างๆใช้ระบบมาตรฐานที่มีธนบัตรมีมูลค่าหนุนหลังเป็นโลหะมีค่า (ทองคำ)เต็มจำนวน เเละสามารถไปเเลกเปลี่ยนเป็นทองคำที่ธนาคารได้ทันที โดยระบบสมัยใหม่นี้เริ่มที่ประเทศอังกฤษ ยุคเซอร์ไอแซกนิวตัน เเทนที่ผู้คนจะพกเหรียญทองในการใช้จ่ายเริ่มปรับเปลี่ยนเป็นถือ ใบรับฝากทองคำ ทั้งสะดวกกว่า เเละ เเก้ปญหาของการเเตกหน่วยย่อยได้ (ทองคำเเตกย่อยเเยกกว่า ธนบัตรอยู่เเล้ว ก่อนหน้าจะเป็นระบบมาตรฐานโลหะคู่ คือทองคำเเละเเร่เงิน เเร่เงินใช้ในส่วนย่อยกว่าทองคำ) ต่อมาการค้าขายในยุโรปเฟื่องฟูขีดสุด เพราะทุกประเทศใช้มาตรฐานการเงินเเบบเดียวกัน เกิดการค้าเสรี การเคลื่อนย้ายเงินทุนทำได้ง่าย ไม่มีกำเเพงระบบเงินต่างสกุลมากั้น เเต่เมื่อทองคำถูกรวมศูนย์มากขึ้นเรื่อยๆ อำนาจตกไปอยู่กับนายธนาคาร เเละผู้ที่เกี่ยวข้อง ส่งผลทำให้เงินสูญเสียอำนาจอธิปไตยส่วนบุคคล ซึ่งจะเป็นปัญหาที่เราทราบในปัจจุบัน เมื่อมีการรวมศูนย์ของเงินทำให้มีปัญหาได้ยังไง ปัญหาสองอย่างที่ตามมาคือ รัฐบาลเเละธนาคารเริ่มมีการผลิตตั๋วเเลกทอง เกินปริมาณทองคำที่มีอยู่ ปัญหาที่สอง หลายๆประเทศเริ่่มใช้สกุลเงินของประเทศอื่นๆเป็นเงินกองทุนสำรองเพิ่มมากขึ้น จนกระทั่งเริ่มมีการตั้งระบบธนาคารกลางขึ้น ในระบบมาตรฐานทองคำ ทำให้รัฐบาลสามารถมีอำนาจที่จะควบคุมเเละกำหนดนโยบายต่างๆได้ ผ่านนโยบายทางการเงิน เเบบเบ็ดเสร็จเด็ดขาด ### เงินตรารัฐบาล (Fiat Money) ยุคสมัย Fiat Money เริ่มต้นในสมัยสงครามโลกครั้งที่ 1 สิ่งที่สำคัญคือเงินของรัฐบาล รัฐมีหน้าที่ผลิตหน่วยของเงินเเทนที่ทองคำ (คือทำให้สะดวกเฉยๆ) เเละมีความเสี่ยงที่มีการผลิตอุปทานของเงินได้อย่างรวดเร็ว ทำให้เงินเฟ้อ (ซึ่งเป็นการทำลายการเก็บออมของคนที่ใช้เงินนั้น เหมือนตัวอย่าง ชาวเกาะเเยป) สงครามโลก สงครามทุกสงครามจริงๆเเล้ว ควรจบอย่างรวดเร็ว เพราะต้นทุนสูงมาก รัฐบาลถ้าจะทำสงครามทำได้อย่างเดียวคือ การขึ้นภาษี เเต่สงครามโลกครั้งที่ 1 ยื้อเยื้อยาวถึง 4 ปี เนื่องจากมีการผลิตเงินในการทำสงคราม ระยะเริ่มต้นประชาชนอาจจะเห็นด้วยกับการทำสงคราม เเต่ผ่านนานวัน ประชาชนต้องคิดเเล้วว่าสงครามไม่ได้มีประโยชน์กับตัวเอง สงคารมที่รบนานถึง 4 ปี เพราะมีการพิมพ์เงิน ลดมูลค่าเงินตัวเอง จนสุดท้าย อเมริกา ได้สนับสนุนกำลังทรัพย์ จนสงครามมีฝ่ายชนะ เเต่ถ้าดูมูลค่าเงินของประเทศทำสงคราม มูลค่าลดลงอย่างมากมายมหาศาล  ที่มา *https://www.sciencedirect.com/* หลังจากจบสงคราม รัฐบาลต้องเผชิญกับความยากลำบากว่าจะเลือกกลับเข้าสู่มาตรฐานทองคำ เเละการยอมรับมูลค่าของเงินในประเทศตัวเองที่ลดลง อาจส่งผลให้ประชาชนมีความต้องการถือทองคำมากกว่า เเต่การผูกขาดของธนาคารกลางเเละการจำกัดสิทธิ์ในการเป็นเข้าของทองคำ บังคับห้ามถอนทองคำ ทำให้ประชาชนต้องถือเงินรัฐบาลต่อไป **เบรตตันวูดส์** หลังจากสงครามโลกครั้งที่ 2 อเมริกาถือว่าเป็นพี่ใหญ่ของโลก จากการชนะสงคราม มีการประชุมเบรตตันวูดส์ เเละได้มีการก่อตั้งกองทุนระหว่างประเทศ (International Monetary Fund :IMF) อมเริกาทำหน้าที่ประสานงานระหว่างธนาคารทั่วโล เเละประเทศสมาชิกได้มีการโอนย้ายทองคำมารวมที่สหรฐอเมริกา เเละให้สิทธิ์เอเมริกาชำระบัญชีโดยไม่มีการเคลื่อนย้ายทองคำอีกต่อไป ให้เงินดอลล่าร์กลายเป็นเงินสกุลหลักของโลก เงินสำรองของประเทศทั่วโลก สำรองด้วยเงินดอลล่าร์เเทน ทำให้อเมริกามีอำนาจสิทธิพิเศษในการเป็นผู้ผลิตเงิน (Seiniorage) เมื่อรัฐบาลต่างๆในโลกมีอำนาจในการผลิตเงิน โครงการรัฐสวัสดิการ จึงมีตามมาอย่างมากมาย เช่น โครงการบ้านเอื้ออาทร เรียนฟรี สุขภาพ (มันไม่มีของฟรีในโลกนะ ต้องมีคนจ่าย คือการที่ทุกคนที่ถือรัฐบาลเป็นผู้จ่าย) เเละทำให้ประชาชนพึ่งพารัฐบาลมากขึ้น รัฐบาลตัวใหญ่ขึ้น มีอำนาจในการจัดการเเละเเทรกเเซงตลาดมากขึ้น **ระบบ Fiat money เต็มตัว** ปี 1971 เมื่อมีประเทศต่างๆเริ่มไม่เเน่ใจกับสกุลเงินดอลล่าร์ เริ่มมีการทยอยถอนทองคำออกมาจากอเมริกาเรื่อยๆ ทำให้ทองคำในคลังของอเมริกาเริ่มน้อยลง ในยุคประธานาธิบดี ริชาร์ด นิกสัน ประกาศฟ้าผ่า (nixon shock ) ยุติการเเปลงดอลล่าร์เป็นทองคำ ยกเลิกระบบมาตรฐานทองคำ เข้าสู่ยุคระบบเงินที่ขึ้นอยู่กับระบบหนี้เเละการเชื่อใจเเทน เเต่ระบบนี้ทำให้มีสกุลเงินของประเทศต่างๆ เป็นสื่อกลางการใช้จ่ายมากกว่าเพียงสื่อกลางเดียว เกิดอัตราเเลกเปลี่ยนสกุลเงิน ซึ่งมีค่าใช้จ่ายในการเเลกเปลี่ยน เป็นต้นทุนของเงินที่ไม่จำเป็นที่จะต้องมีเกิดขึ้น ระบบเศรษฐกิจของโลกตอนนี้ตั้งอยู่บนเงินที่ออกโดยรัฐบาล ปัญหาคือการพิมพ์เงินขึ้นอยู่กับความยับยั้งชั่งใจของผู้มีอำนาจ เเละสามารถมีอำนาจในการพิมพ์เงินไม่จำกัด  ที่มา *https://ycharts.com/indicators/us_m2_money_supply* การควบคุมเงินของรัฐบาลสามารถทำได้โดยทันที หน้าที่ของเงินคือการเเลกเปลี่ยน กลายเป็นเครื่องมือที่ควบคุมจากรัฐบาล เพราะรัฐบาลมีสิทธิ์ทันทีที่จะ ยึด เงินของเราได้ถ้าเราไม่เห็นด้วยกับเเนวทางรัฐบาล (เงินที่มาด้วยความสะดวกสบาย เเลกกับการมอบสิทธิ์ให้รัฐบาลด้วย) เมื่อก่อนเราเคยเข้าใจว่าเงินก็ต้องเป็นเงินที่รัฐบาลผลิตมาให้เราใช้สิ หลังจากอ่านหนังสือนี้ ทำให้ีู้ว่าเราอยู่ยุคเงินรัฐบาลเเบบเต็มตัวเมื่อไม่นานมานี้เอง เเละมีข้อดี เเละข้อเสีย ให้พิจารณากัน เราสรุป Part ของเงินจากหนังสือ The Bitcoin Standard ไว้ก่อน ส่วน Part อื่นๆในหนังสือ เราจะมาสรุปให้เพิ่มคราวหน้านะครับผมมม @ 029eb0f9:d600b130
2024-11-17 12:43:33Bitcoin, the decentralized digital currency, has long been hailed as a beacon of freedom in the financial world. Since its inception in 2009, Bitcoin has been empowering individuals with unprecedented autonomy and flexibility, liberating them from the shackles of traditional financial systems. Financial Censorship Resistance Bitcoin's decentralized nature allows for peer-to-peer transactions without intermediaries, making it resistant to censorship. Users can send and receive bitcoins without fear of interference from governments, banks, or other third parties. This ensures that individuals have the freedom to make financial decisions without external control or manipulation. Borderless Transactions Bitcoin knows no borders. It enables seamless transactions across the globe, connecting people from diverse regions and economies. This global accessibility fosters international collaboration, trade, and innovation, promoting a more inclusive and interconnected world. Privacy and Anonymity Bitcoin transactions are pseudonymous, allowing users to maintain their financial privacy. This feature is particularly important for individuals living under oppressive regimes or those who value their financial secrecy. Financial Inclusion Bitcoin provides an opportunity for the unbanked and underbanked populations to participate in the global financial system. With a smartphone and internet connection, anyone can access and utilize Bitcoin, regardless of their geographical location or socio-economic status. Decentralized Governance Bitcoin's decentralized governance model ensures that decision-making power is distributed among users, rather than being controlled by a single entity. This promotes a community-driven approach, allowing users to contribute to the development and growth of the network. In conclusion, Bitcoin's freedom is multifaceted, offering: - Resistance to financial censorship - Borderless transactions - Privacy and anonymity - Financial inclusion - Decentralized governance As the world becomes increasingly digital, Bitcoin's freedom-centric approach is poised to empower individuals and communities, fostering a more equitable and connected global financial landscape.
@ 029eb0f9:d600b130
2024-11-17 12:43:33Bitcoin, the decentralized digital currency, has long been hailed as a beacon of freedom in the financial world. Since its inception in 2009, Bitcoin has been empowering individuals with unprecedented autonomy and flexibility, liberating them from the shackles of traditional financial systems. Financial Censorship Resistance Bitcoin's decentralized nature allows for peer-to-peer transactions without intermediaries, making it resistant to censorship. Users can send and receive bitcoins without fear of interference from governments, banks, or other third parties. This ensures that individuals have the freedom to make financial decisions without external control or manipulation. Borderless Transactions Bitcoin knows no borders. It enables seamless transactions across the globe, connecting people from diverse regions and economies. This global accessibility fosters international collaboration, trade, and innovation, promoting a more inclusive and interconnected world. Privacy and Anonymity Bitcoin transactions are pseudonymous, allowing users to maintain their financial privacy. This feature is particularly important for individuals living under oppressive regimes or those who value their financial secrecy. Financial Inclusion Bitcoin provides an opportunity for the unbanked and underbanked populations to participate in the global financial system. With a smartphone and internet connection, anyone can access and utilize Bitcoin, regardless of their geographical location or socio-economic status. Decentralized Governance Bitcoin's decentralized governance model ensures that decision-making power is distributed among users, rather than being controlled by a single entity. This promotes a community-driven approach, allowing users to contribute to the development and growth of the network. In conclusion, Bitcoin's freedom is multifaceted, offering: - Resistance to financial censorship - Borderless transactions - Privacy and anonymity - Financial inclusion - Decentralized governance As the world becomes increasingly digital, Bitcoin's freedom-centric approach is poised to empower individuals and communities, fostering a more equitable and connected global financial landscape. @ 98589a2e:bf49daa1
2024-11-17 11:08:27**В Санкт-Петербурге произошло несколько тенденций и изменений к 2040 году в сфере экономики и бизнеса.** ### ▎Новые профессии 1. Специалисты по устойчивому развитию: Экологи, инженеры и консультанты, работающие над проектами по устойчивому развитию и экосистемным услугам. 2. Кибербезопасность и IT: Эксперты по защите данных и разработчики программного обеспечения для защиты от киберугроз. 3. Биотехнологи: Специалисты, работающие в области генной инженерии, медицины и сельского хозяйства. 4. Управление умными городами: Профессионалы, занимающиеся управлением инфраструктурой и услугами с использованием IoT (Интернет вещей). 5. Специалисты по виртуальной реальности и дополненной реальности: Создатели контента для образования, развлечений и бизнеса. 6. Аналитики больших данных: Эксперты по анализу больших объемов данных для оптимизации бизнес-процессов и улучшения качества жизни.  ### ▎Финансовые источники города 1. Туризм: Санкт-Петербург остается культурной столицей, привлекающей туристов со всего мира благодаря своей богатой истории и архитектуре. 2. Технологический сектор: Развитие стартапов и IT-компаний стало основным источником дохода, особенно в области искусственного интеллекта и автоматизации. 3. Зеленая экономика: Инвестиции в возобновляемые источники энергии и устойчивые технологии принесли значительные прибыли. 4. Образование и наука: Университеты и исследовательские центры привлекают финансирование как из государственного, так и из частного секторов. 5. Экспорт высоких технологий: Разработка и экспорт инновационных технологий, включая программное обеспечение и биотехнологии.  ### ▎Бизнес в будущем 1. Гибридные модели работы: Удаленная работа и гибкие графики становятся нормой, что позволяет компаниям привлекать таланты из разных регионов. 2. Краудфандинг и краудинвестинг: Новые формы финансирования проектов становятся популярными, позволяя стартапам находить средства без традиционных банковских кредитов. 3. Цифровизация: Бизнес-процессы автоматизируются, что позволило снизить затраты и повысить эффективность. 4. Социальные предприятия: Бизнесы, ориентированные на социальные или экологические цели, стали все более распространенными. 5. Кросс-отраслевое сотрудничество: Сотрудничество между различными отраслями (например, технологии и искусство) стали важным аспектом для инноваций.  Санкт-Петербург стал примером города, который успешно адаптировался к изменениям в экономике, технологиях и обществе. Устойчивое развитие, инновации и разнообразие профессий - это ключевые факторы его успеха.
@ 98589a2e:bf49daa1
2024-11-17 11:08:27**В Санкт-Петербурге произошло несколько тенденций и изменений к 2040 году в сфере экономики и бизнеса.** ### ▎Новые профессии 1. Специалисты по устойчивому развитию: Экологи, инженеры и консультанты, работающие над проектами по устойчивому развитию и экосистемным услугам. 2. Кибербезопасность и IT: Эксперты по защите данных и разработчики программного обеспечения для защиты от киберугроз. 3. Биотехнологи: Специалисты, работающие в области генной инженерии, медицины и сельского хозяйства. 4. Управление умными городами: Профессионалы, занимающиеся управлением инфраструктурой и услугами с использованием IoT (Интернет вещей). 5. Специалисты по виртуальной реальности и дополненной реальности: Создатели контента для образования, развлечений и бизнеса. 6. Аналитики больших данных: Эксперты по анализу больших объемов данных для оптимизации бизнес-процессов и улучшения качества жизни.  ### ▎Финансовые источники города 1. Туризм: Санкт-Петербург остается культурной столицей, привлекающей туристов со всего мира благодаря своей богатой истории и архитектуре. 2. Технологический сектор: Развитие стартапов и IT-компаний стало основным источником дохода, особенно в области искусственного интеллекта и автоматизации. 3. Зеленая экономика: Инвестиции в возобновляемые источники энергии и устойчивые технологии принесли значительные прибыли. 4. Образование и наука: Университеты и исследовательские центры привлекают финансирование как из государственного, так и из частного секторов. 5. Экспорт высоких технологий: Разработка и экспорт инновационных технологий, включая программное обеспечение и биотехнологии.  ### ▎Бизнес в будущем 1. Гибридные модели работы: Удаленная работа и гибкие графики становятся нормой, что позволяет компаниям привлекать таланты из разных регионов. 2. Краудфандинг и краудинвестинг: Новые формы финансирования проектов становятся популярными, позволяя стартапам находить средства без традиционных банковских кредитов. 3. Цифровизация: Бизнес-процессы автоматизируются, что позволило снизить затраты и повысить эффективность. 4. Социальные предприятия: Бизнесы, ориентированные на социальные или экологические цели, стали все более распространенными. 5. Кросс-отраслевое сотрудничество: Сотрудничество между различными отраслями (например, технологии и искусство) стали важным аспектом для инноваций.  Санкт-Петербург стал примером города, который успешно адаптировался к изменениям в экономике, технологиях и обществе. Устойчивое развитие, инновации и разнообразие профессий - это ключевые факторы его успеха. @ fd208ee8:0fd927c1
2024-11-17 09:14:56You don't understand how insidious open-borders propaganda is, until you realize that _it's an attempt to remove all differentiating traits from humans_. They call this "strengthening individuality by removing nationality" (hello, newspeak), but what makes humans individual is their particular collection of traits, and nationality (and ethnicity, religion, etc. -- nationality is just the first domino they want to topple) is one of those.  Humans are not blank slates. Like DNA or physiognomy, our personalities are differing jumbles of cultural "letters". Each person selects consciously and subconsciously from amongst these letters, adding to or rejecting them, amplifying or suppressing them, twisting or combining them, building on top of them... and that's what makes you into You. Open borders is an attempt to reduce the number of cultural letters you can build your "You" out of. If you take away the word "German", I am not liberated. There is simply one less adjective, with which I can describe myself. You have merely eradicated information, crippled language, and reduced my choices. I can then no longer define myself according to "German things", but I can also no longer define myself in opposition to German things. ## Enter the Borg  We are easier to control and brainwash and persecute, if we are centralized and homogenized. As if the entire world were one, big prison and we were all forced to undergo the same education, wear the same clothes, follow the same rules, eat the same foods, enjoy the same entertainment, live the same lifestyle, share the same diseases and cures, enjoy the same lockdowns, join in the same cancel culture, fight the same wars. That is what globalization brings. That is the end game of Open Borders: * No more cultural evolution or revolution. * Genes, but no memes. * You can go everywhere, but everywhere is the same, so you just stay home. * You can meet people from all over, but they are all the same, so you just don't bother. * One mass of humanity, that can be easily molded and manipulated.
@ fd208ee8:0fd927c1
2024-11-17 09:14:56You don't understand how insidious open-borders propaganda is, until you realize that _it's an attempt to remove all differentiating traits from humans_. They call this "strengthening individuality by removing nationality" (hello, newspeak), but what makes humans individual is their particular collection of traits, and nationality (and ethnicity, religion, etc. -- nationality is just the first domino they want to topple) is one of those.  Humans are not blank slates. Like DNA or physiognomy, our personalities are differing jumbles of cultural "letters". Each person selects consciously and subconsciously from amongst these letters, adding to or rejecting them, amplifying or suppressing them, twisting or combining them, building on top of them... and that's what makes you into You. Open borders is an attempt to reduce the number of cultural letters you can build your "You" out of. If you take away the word "German", I am not liberated. There is simply one less adjective, with which I can describe myself. You have merely eradicated information, crippled language, and reduced my choices. I can then no longer define myself according to "German things", but I can also no longer define myself in opposition to German things. ## Enter the Borg  We are easier to control and brainwash and persecute, if we are centralized and homogenized. As if the entire world were one, big prison and we were all forced to undergo the same education, wear the same clothes, follow the same rules, eat the same foods, enjoy the same entertainment, live the same lifestyle, share the same diseases and cures, enjoy the same lockdowns, join in the same cancel culture, fight the same wars. That is what globalization brings. That is the end game of Open Borders: * No more cultural evolution or revolution. * Genes, but no memes. * You can go everywhere, but everywhere is the same, so you just stay home. * You can meet people from all over, but they are all the same, so you just don't bother. * One mass of humanity, that can be easily molded and manipulated. @ ac6f9572:8a6853dd
2024-11-17 09:14:36The Asian Bitcoin Technical Unconference is set!  8—10th February 2025 - Chang Mai, Thailand 🇹🇭 - - - We finally got (nearly) everything ready! ✅ Agenda? NO agenda! ✅ Venue is booked, ✅ Attendees confirmed, ✅ [Registration open](https://satsnfacts.btc.pub/#register) and... ✅ Merch now available! If you are around Asia this coming Febrary, come and **join us** in Chang Mai, Thailand 🇹🇭  Book your **seat** --> https://formstr.app/#/fill/b3b9bd115fe936848a5e03134fefff945287285d51b1dee4731fef6a1070c597 Submit an **idea** --> https://formstr.app/#/forms/cf02333ea3c0d0c21080df599373e289fa343a55e63a1abdc7f633d1594078ff Then... Buy your **ticket** --> https://satsnfacts.btc.pub/p/ticket/ And... Add some **merch** at check out --> https://satsnfacts.btc.pub/merch/ - - - If you like to support the event, and the participants joining, consider visit https://geyser.fund/project/satsnfacts - - - #SATSnFACTS #event #Biitcoin #Nostr #Lightning #ecash #health #creativity #unconference originally posted at https://stacker.news/items/771203
@ ac6f9572:8a6853dd
2024-11-17 09:14:36The Asian Bitcoin Technical Unconference is set!  8—10th February 2025 - Chang Mai, Thailand 🇹🇭 - - - We finally got (nearly) everything ready! ✅ Agenda? NO agenda! ✅ Venue is booked, ✅ Attendees confirmed, ✅ [Registration open](https://satsnfacts.btc.pub/#register) and... ✅ Merch now available! If you are around Asia this coming Febrary, come and **join us** in Chang Mai, Thailand 🇹🇭  Book your **seat** --> https://formstr.app/#/fill/b3b9bd115fe936848a5e03134fefff945287285d51b1dee4731fef6a1070c597 Submit an **idea** --> https://formstr.app/#/forms/cf02333ea3c0d0c21080df599373e289fa343a55e63a1abdc7f633d1594078ff Then... Buy your **ticket** --> https://satsnfacts.btc.pub/p/ticket/ And... Add some **merch** at check out --> https://satsnfacts.btc.pub/merch/ - - - If you like to support the event, and the participants joining, consider visit https://geyser.fund/project/satsnfacts - - - #SATSnFACTS #event #Biitcoin #Nostr #Lightning #ecash #health #creativity #unconference originally posted at https://stacker.news/items/771203 @ c11cf5f8:4928464d
2024-11-17 08:35:39Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/761231/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/771187
@ c11cf5f8:4928464d
2024-11-17 08:35:39Let's hear some of your latest Bitcoin purchases, feel free to include links to the shops or merchants you bought from too. If you missed our last thread, [here](https://stacker.news/items/761231/r/AG) are some of the items stackers recently spent their sats on. originally posted at https://stacker.news/items/771187 @ 841b017d:8bf0ee39
2024-11-17 07:51:29Good morning #Nostr...iches, I wish you a fantastic Sunday 🌎⚡️🫶🏻🕊️✨
@ 841b017d:8bf0ee39
2024-11-17 07:51:29Good morning #Nostr...iches, I wish you a fantastic Sunday 🌎⚡️🫶🏻🕊️✨ @ 6b0a60cf:b952e7d4
2024-11-17 07:02:11ビットコインのウォレットは取引形態によって2種類に分かれます。 <dl> <dt>オンチェーン(L1)</dt> <dd>取引がブロックチェーンに刻まれるタイプ。時間がかかるし手数料が高い。</dd> <dt>ライトニングネットワーク(L2)</dt> <dd>ブロックチェーンに刻む前の少額決済を目的としたレイヤー。高速で手数料が安い。</dd> </dl> NostrでZapを利用する場合はライトニングネットワーク(以下、LNと呼びます)のウォレットが使われますが、さらにその中でもZap対応/非対応で分かれることになります。 また、秘密鍵を誰が管理するかによっても2種類の呼び方に分かれます。 <dl> <dt>カストディアル</dt> <dd>秘密鍵をサービスの運営に預けるタイプ。</dd> <dt>ノンカストディアル/セルフカストディアル</dt> <dd>秘密鍵(シードフレーズ)を自分で持っておくタイプ。</dd> </dl> Nostrで人気がある[Wallet of Satoshi](https://www.walletofsatoshi.com/)(以下、WoSと呼びます)はLNのカストディアルウォレットです。 今回はLNのセルフカストディアルウォレットである[Phoenix](https://phoenix.acinq.co/)を使ってみて、その仕組みや注意点など、学んだことを記録したいと思います。 Phoenixでウォレットを作る場合、初回でシードフレーズ(12個の単語)が作られますので、大切に控えておきましょう。 ## WoSからPhoenixに送金してみる メイン画面左下にあるReciaveからQRCode表示画面へ遷移します。そこでcopyボタンを押して`Lightning invoice(text)`をコピーしましょう。   次に、WoSの画面からSendを選択し、クリップボードからの貼り付けを選択します。   金額を指定して送金します。  ## 送金した額が満額届いてないんだけど?  下の方に`Service Fees`とありますが、これはPhoenix運営(ACINQ)へのお布施ですね。結構高く見えますが初回だけです。 また`Miner Fees`という項目は、[mempool](https://mempool.space/)のfeeに連動して変わるようですが、これはチャネルを太くする(送受信できる金額の上限を上げる)ために使われる手数料になります。 ### 財布が重たくなると手数料が取られる? 有り体に言えばそういうことになります。以下のように10,000satsをもらう度にチャネル拡張のための手数料が引かれています。  上記の8,000satsを受け取っている時には手数料が発生していませんね。これはチャネル拡張が必要ないギリギリの金額を狙って送金したためです。送金前は8,859satsの余裕がありました。送金後は1,719satsに減っています。(余裕分がぴったり8,000sats減るわけではないようです。このへんの仕組みはよくわかりません。) (画面は左上⚙️マークの設定からPayment channelsから。)   ### 財布が軽くなると余裕が増える? 逆にPhoenixからWoSに5,000satsほど送金してみます。(手数料として24satsほど余計に抜かれました)   余裕(Inbound Liquidity)が5,883satsまで復活しています。受け取るばかりでなく、バランスよく送ることで財布を重たくしなければチャネル拡張せずに使い続けることができそうです。(太くしたチャネルは永遠に残るわけではなく、[1年まで](https://phoenix.acinq.co/faq#what-happens-after-a-year-of-reserving-liquidity)らしいです) ### 自動でチャネル拡張にsatsを使われたくない! 自動チャネル拡張を設定で無効化できます。左上⚙️マークの設定から`Channel management`から。   これでチャネル拡張が必要なほどの金額を送金しようとするとエラーになり失敗します。  ## まとめ セルフカストディアルウォレットならではの概念があり、謎の手数料が発生したりして怖いイメージがありましたが、どういう理由で手数料が発生するのかを知り、設定でのコントロールの仕方を習得することである程度怖いイメージを払拭することができました。 しかしカストディアルウォレット(特にWoS)の使いやすさを再認識することにもなりました。ただ自分で管理することの重要性も理解していますので、徐々に知識を深めていこうと思います。 ## 参考/謝辞 - [Phoenix wallet(フェニックスウォレット)の使い方!ビットコインのセルフカストディができるアプリを解説 - 知っとこ!ビットコイン図鑑](https://bitcoin-zukan.com/practical/phoenix-wallet/) - nostr:npub10zeurmg22wc89l8m3npw9cyu45cun0lvs6w3ep69cdpa25pna65s0994qz 様
@ 6b0a60cf:b952e7d4
2024-11-17 07:02:11ビットコインのウォレットは取引形態によって2種類に分かれます。 <dl> <dt>オンチェーン(L1)</dt> <dd>取引がブロックチェーンに刻まれるタイプ。時間がかかるし手数料が高い。</dd> <dt>ライトニングネットワーク(L2)</dt> <dd>ブロックチェーンに刻む前の少額決済を目的としたレイヤー。高速で手数料が安い。</dd> </dl> NostrでZapを利用する場合はライトニングネットワーク(以下、LNと呼びます)のウォレットが使われますが、さらにその中でもZap対応/非対応で分かれることになります。 また、秘密鍵を誰が管理するかによっても2種類の呼び方に分かれます。 <dl> <dt>カストディアル</dt> <dd>秘密鍵をサービスの運営に預けるタイプ。</dd> <dt>ノンカストディアル/セルフカストディアル</dt> <dd>秘密鍵(シードフレーズ)を自分で持っておくタイプ。</dd> </dl> Nostrで人気がある[Wallet of Satoshi](https://www.walletofsatoshi.com/)(以下、WoSと呼びます)はLNのカストディアルウォレットです。 今回はLNのセルフカストディアルウォレットである[Phoenix](https://phoenix.acinq.co/)を使ってみて、その仕組みや注意点など、学んだことを記録したいと思います。 Phoenixでウォレットを作る場合、初回でシードフレーズ(12個の単語)が作られますので、大切に控えておきましょう。 ## WoSからPhoenixに送金してみる メイン画面左下にあるReciaveからQRCode表示画面へ遷移します。そこでcopyボタンを押して`Lightning invoice(text)`をコピーしましょう。   次に、WoSの画面からSendを選択し、クリップボードからの貼り付けを選択します。   金額を指定して送金します。  ## 送金した額が満額届いてないんだけど?  下の方に`Service Fees`とありますが、これはPhoenix運営(ACINQ)へのお布施ですね。結構高く見えますが初回だけです。 また`Miner Fees`という項目は、[mempool](https://mempool.space/)のfeeに連動して変わるようですが、これはチャネルを太くする(送受信できる金額の上限を上げる)ために使われる手数料になります。 ### 財布が重たくなると手数料が取られる? 有り体に言えばそういうことになります。以下のように10,000satsをもらう度にチャネル拡張のための手数料が引かれています。  上記の8,000satsを受け取っている時には手数料が発生していませんね。これはチャネル拡張が必要ないギリギリの金額を狙って送金したためです。送金前は8,859satsの余裕がありました。送金後は1,719satsに減っています。(余裕分がぴったり8,000sats減るわけではないようです。このへんの仕組みはよくわかりません。) (画面は左上⚙️マークの設定からPayment channelsから。)   ### 財布が軽くなると余裕が増える? 逆にPhoenixからWoSに5,000satsほど送金してみます。(手数料として24satsほど余計に抜かれました)   余裕(Inbound Liquidity)が5,883satsまで復活しています。受け取るばかりでなく、バランスよく送ることで財布を重たくしなければチャネル拡張せずに使い続けることができそうです。(太くしたチャネルは永遠に残るわけではなく、[1年まで](https://phoenix.acinq.co/faq#what-happens-after-a-year-of-reserving-liquidity)らしいです) ### 自動でチャネル拡張にsatsを使われたくない! 自動チャネル拡張を設定で無効化できます。左上⚙️マークの設定から`Channel management`から。   これでチャネル拡張が必要なほどの金額を送金しようとするとエラーになり失敗します。  ## まとめ セルフカストディアルウォレットならではの概念があり、謎の手数料が発生したりして怖いイメージがありましたが、どういう理由で手数料が発生するのかを知り、設定でのコントロールの仕方を習得することである程度怖いイメージを払拭することができました。 しかしカストディアルウォレット(特にWoS)の使いやすさを再認識することにもなりました。ただ自分で管理することの重要性も理解していますので、徐々に知識を深めていこうと思います。 ## 参考/謝辞 - [Phoenix wallet(フェニックスウォレット)の使い方!ビットコインのセルフカストディができるアプリを解説 - 知っとこ!ビットコイン図鑑](https://bitcoin-zukan.com/practical/phoenix-wallet/) - nostr:npub10zeurmg22wc89l8m3npw9cyu45cun0lvs6w3ep69cdpa25pna65s0994qz 様 @ 97fc03df:8bf891df
2024-11-17 06:02:33**From Wealth Protection to Civilization Guardian, Bitcoin's Mechanical Consensus Provides the Ultimate Shield in the Artificial Intelligence Era** #### Gavin, BeeGee (Core Builders of Super Bitcoin & BEVM) #### November 15, 2024 -----------  **The Acceleration of Technology and Potential Threats: Hawking, Wiener, and Present Challenges** Humanity has entered the era of artificial intelligence, and with rapid technological advancements, we are facing unprecedented complexity and uncertainty. The swift progress of technology not only alters social structures but also introduces numerous potential threats, especially in the realm of artificial intelligence. Scientists like Stephen Hawking have long warned about the potential dangers of this trajectory. Hawking believed that the unbridled development of artificial intelligence could threaten human existence. He pointed out, "We may face various risks brought about by the rise of artificial intelligence in the near future." Similarly, Norbert Wiener, one of the founding fathers of cybernetics, cautioned about the harm of uncontrolled technology to human civilization, particularly during the implementation of automation and adaptive systems. In his book Cybernetics, Wiener mentioned, "Machines created by humans, if not properly controlled, may ultimately destroy our own civilization." In recent years, with the rapid development of AGI (Artificial General Intelligence) technology, the risk of technology spiraling out of control has become even more pronounced. Elon Musk has expressed deep concern over this, publicly stating that AGI could pose an existential threat to humanity. Consequently, he founded xAI, dedicated to developing safe and beneficial AGI for humankind. Additionally, Yuval Noah Harari, in his book The Nexus: A Brief History of Information Networks from the Stone Age to the AI Era, mentioned that artificial intelligence is no longer just a tool but possesses autonomous decision-making capabilities. This means AI may no longer heed human commands, thereby disrupting social order. These warnings clearly indicate that ensuring technological progress serves humanity—and preventing it from threatening human survival—has become a pressing and significant issue of our time. ----------- **The Limits of the Human Brain and the Collapse of Social Consensus** Turning our attention back to humanity, the explosive growth of information poses a severe challenge to the processing capacity of the human brain. The biological evolution of the human brain lags far behind the developmental speed of silicon-based life forms. As a species, humanity will face competition with an "artificial intelligence species." In the past, humans solved most complex problems through "social consensus." However, in the information age, traditional consensus mechanisms are evidently unable to cope with the increasing complexity. The exponential growth of information overwhelms our traditional ways of thinking; society is rapidly changing, yet our thinking and decision-making processes are increasingly lagging, leading to the gradual ineffectiveness of conventional consensus methods. James Rickards, in MoneyGPT: AI and the Threat to the Global Economy, proposes that cybernetics is a crucial tool to address this challenge. He believes that the accelerated reliance on technology for decision-making, especially in AI, will trigger split-second reactions, potentially leading to cascading collapses in financial systems and even society. He further points out that "cybernetics," derived from the Greek word "kybernētēs" (helmsman), refers to a way of continuously adjusting and optimizing system responses. It advocates guiding system operations through precise feedback mechanisms rather than taking overly drastic countermeasures. In the era of artificial intelligence, solely relying on traditional "social consensus" can no longer address these complex and rapidly evolving challenges. We urgently need a new, more effective mechanism to navigate the constantly shifting technological landscape and societal demands. ----------- **Mechanical Consensus: The Key to Addressing Complex Challenges** In this context, mechanical consensus emerges as an effective solution to current technological challenges, serving as a new form of self-organizing and decentralized consensus. Unlike traditional social consensus, which relies on human decision-making, mechanical consensus can self-regulate and reach agreements without human intervention through decentralized automated processes. As Wiener emphasized in his cybernetics, mechanical consensus optimizes systems via feedback mechanisms, ensuring stability and security even as information continues to proliferate. The Bitcoin network is one of the most successful examples of mechanical consensus. Bitcoin establishes a stable network without external intervention through miners' computational competition and economic incentives. In the Bitcoin network, miners participate in hash rate competitions to provide security and decentralized consensus, while Bitcoin's design ensures fairness and immutability throughout this process. This mechanism not only safeguards digital assets but also introduces a new governance model suited for the information age. The power of mechanical consensus lies in its ability to operate automatically according to predefined rules without centralized control, offering solutions to complex societal problems. It demonstrates how technology can transcend mere wealth protection, shifting towards broader safeguards for human life and civilization. ----------- **Bitcoin: From Crypto Asset to Civilization's Mechanical Guardian** Bitcoin is not just a cryptocurrency; it embodies the core principles of mechanical consensus. Satoshi Nakamoto's original intent in designing Bitcoin was to establish a self-adaptive, growth-oriented network that doesn't require trust in third parties—a concept realized through Bitcoin's consensus mechanism. At the heart of Bitcoin's consensus mechanism is an endless competition of computational power. Miners continually invest hash power to earn Bitcoin rewards, fueling the network's continuous growth and self-reinforcement. This self-reinforcing mechanism not only enhances the security and stability of the Bitcoin network but also bolsters its resilience against external attacks. Through this positive feedback loop, the Bitcoin network has expanded exponentially, with its market capitalization growing from zero in 2009 to over $1.8 trillion today, underscoring the success of mechanical consensus as manifested in "digital gold." However, the mechanical consensus represented by Bitcoin isn't limited to protecting digital assets; it offers a new solution for humanity to navigate the complexities of the information age. ----------- **Super Bitcoin: The Innovator Safeguarding Humanity's Future** Building on this foundation, Super Bitcoin emerges to further transcend the limitations of the original Bitcoin network. Through a five-layer architectural design, Super Bitcoin not only inherits the security of the Bitcoin network but also extends beyond Bitcoin's basic transaction functionality, bringing richer expansion capabilities to the network. Super Bitcoin integrates technologies such as the Proof-of-Work (PoW) consensus mechanism, the Lightning Network, and Taproot Consensus, forming a more efficient and flexible blockchain system. This new architecture positions Super Bitcoin not merely as a tool for protecting digital assets but as a platform capable of providing technological governance for human society. By leveraging decentralized and automated mechanical consensus, Super Bitcoin can promote technological advancement while mitigating risks, safeguarding human civilization from potential technological threats. It offers a secure, shared infrastructure for protocols and applications and continually expands its ecosystem to facilitate the achievement of broader human objectives. ----------- **Conclusion: Each Bitcoin Is a Guardian of Humanity's Future** Bitcoin (BTC) has a total fixed supply of 21 million units, while the global population exceeds 8.2 billion. Simple math shows that, on average, every 400 people share one BTC. From an asset perspective, this highlights Bitcoin's scarcity and value. However, from the standpoint of human life safety, each Bitcoin effectively safeguards 400 lives. The true value of cryptocurrency lies not merely in its representation of wealth but in the self-adaptive mechanical consensus that underpins it. Each of the 21 million Bitcoins carries the responsibility of protecting life. Through mechanical consensus, we have the opportunity to establish a more robust societal agreement in an era of information overload and rapid technological advancement. This can help humanity confront the intricate challenges posed by technology—especially those arising from artificial intelligence—and ensure the sustainable development of civilization and life.
@ 97fc03df:8bf891df
2024-11-17 06:02:33**From Wealth Protection to Civilization Guardian, Bitcoin's Mechanical Consensus Provides the Ultimate Shield in the Artificial Intelligence Era** #### Gavin, BeeGee (Core Builders of Super Bitcoin & BEVM) #### November 15, 2024 -----------  **The Acceleration of Technology and Potential Threats: Hawking, Wiener, and Present Challenges** Humanity has entered the era of artificial intelligence, and with rapid technological advancements, we are facing unprecedented complexity and uncertainty. The swift progress of technology not only alters social structures but also introduces numerous potential threats, especially in the realm of artificial intelligence. Scientists like Stephen Hawking have long warned about the potential dangers of this trajectory. Hawking believed that the unbridled development of artificial intelligence could threaten human existence. He pointed out, "We may face various risks brought about by the rise of artificial intelligence in the near future." Similarly, Norbert Wiener, one of the founding fathers of cybernetics, cautioned about the harm of uncontrolled technology to human civilization, particularly during the implementation of automation and adaptive systems. In his book Cybernetics, Wiener mentioned, "Machines created by humans, if not properly controlled, may ultimately destroy our own civilization." In recent years, with the rapid development of AGI (Artificial General Intelligence) technology, the risk of technology spiraling out of control has become even more pronounced. Elon Musk has expressed deep concern over this, publicly stating that AGI could pose an existential threat to humanity. Consequently, he founded xAI, dedicated to developing safe and beneficial AGI for humankind. Additionally, Yuval Noah Harari, in his book The Nexus: A Brief History of Information Networks from the Stone Age to the AI Era, mentioned that artificial intelligence is no longer just a tool but possesses autonomous decision-making capabilities. This means AI may no longer heed human commands, thereby disrupting social order. These warnings clearly indicate that ensuring technological progress serves humanity—and preventing it from threatening human survival—has become a pressing and significant issue of our time. ----------- **The Limits of the Human Brain and the Collapse of Social Consensus** Turning our attention back to humanity, the explosive growth of information poses a severe challenge to the processing capacity of the human brain. The biological evolution of the human brain lags far behind the developmental speed of silicon-based life forms. As a species, humanity will face competition with an "artificial intelligence species." In the past, humans solved most complex problems through "social consensus." However, in the information age, traditional consensus mechanisms are evidently unable to cope with the increasing complexity. The exponential growth of information overwhelms our traditional ways of thinking; society is rapidly changing, yet our thinking and decision-making processes are increasingly lagging, leading to the gradual ineffectiveness of conventional consensus methods. James Rickards, in MoneyGPT: AI and the Threat to the Global Economy, proposes that cybernetics is a crucial tool to address this challenge. He believes that the accelerated reliance on technology for decision-making, especially in AI, will trigger split-second reactions, potentially leading to cascading collapses in financial systems and even society. He further points out that "cybernetics," derived from the Greek word "kybernētēs" (helmsman), refers to a way of continuously adjusting and optimizing system responses. It advocates guiding system operations through precise feedback mechanisms rather than taking overly drastic countermeasures. In the era of artificial intelligence, solely relying on traditional "social consensus" can no longer address these complex and rapidly evolving challenges. We urgently need a new, more effective mechanism to navigate the constantly shifting technological landscape and societal demands. ----------- **Mechanical Consensus: The Key to Addressing Complex Challenges** In this context, mechanical consensus emerges as an effective solution to current technological challenges, serving as a new form of self-organizing and decentralized consensus. Unlike traditional social consensus, which relies on human decision-making, mechanical consensus can self-regulate and reach agreements without human intervention through decentralized automated processes. As Wiener emphasized in his cybernetics, mechanical consensus optimizes systems via feedback mechanisms, ensuring stability and security even as information continues to proliferate. The Bitcoin network is one of the most successful examples of mechanical consensus. Bitcoin establishes a stable network without external intervention through miners' computational competition and economic incentives. In the Bitcoin network, miners participate in hash rate competitions to provide security and decentralized consensus, while Bitcoin's design ensures fairness and immutability throughout this process. This mechanism not only safeguards digital assets but also introduces a new governance model suited for the information age. The power of mechanical consensus lies in its ability to operate automatically according to predefined rules without centralized control, offering solutions to complex societal problems. It demonstrates how technology can transcend mere wealth protection, shifting towards broader safeguards for human life and civilization. ----------- **Bitcoin: From Crypto Asset to Civilization's Mechanical Guardian** Bitcoin is not just a cryptocurrency; it embodies the core principles of mechanical consensus. Satoshi Nakamoto's original intent in designing Bitcoin was to establish a self-adaptive, growth-oriented network that doesn't require trust in third parties—a concept realized through Bitcoin's consensus mechanism. At the heart of Bitcoin's consensus mechanism is an endless competition of computational power. Miners continually invest hash power to earn Bitcoin rewards, fueling the network's continuous growth and self-reinforcement. This self-reinforcing mechanism not only enhances the security and stability of the Bitcoin network but also bolsters its resilience against external attacks. Through this positive feedback loop, the Bitcoin network has expanded exponentially, with its market capitalization growing from zero in 2009 to over $1.8 trillion today, underscoring the success of mechanical consensus as manifested in "digital gold." However, the mechanical consensus represented by Bitcoin isn't limited to protecting digital assets; it offers a new solution for humanity to navigate the complexities of the information age. ----------- **Super Bitcoin: The Innovator Safeguarding Humanity's Future** Building on this foundation, Super Bitcoin emerges to further transcend the limitations of the original Bitcoin network. Through a five-layer architectural design, Super Bitcoin not only inherits the security of the Bitcoin network but also extends beyond Bitcoin's basic transaction functionality, bringing richer expansion capabilities to the network. Super Bitcoin integrates technologies such as the Proof-of-Work (PoW) consensus mechanism, the Lightning Network, and Taproot Consensus, forming a more efficient and flexible blockchain system. This new architecture positions Super Bitcoin not merely as a tool for protecting digital assets but as a platform capable of providing technological governance for human society. By leveraging decentralized and automated mechanical consensus, Super Bitcoin can promote technological advancement while mitigating risks, safeguarding human civilization from potential technological threats. It offers a secure, shared infrastructure for protocols and applications and continually expands its ecosystem to facilitate the achievement of broader human objectives. ----------- **Conclusion: Each Bitcoin Is a Guardian of Humanity's Future** Bitcoin (BTC) has a total fixed supply of 21 million units, while the global population exceeds 8.2 billion. Simple math shows that, on average, every 400 people share one BTC. From an asset perspective, this highlights Bitcoin's scarcity and value. However, from the standpoint of human life safety, each Bitcoin effectively safeguards 400 lives. The true value of cryptocurrency lies not merely in its representation of wealth but in the self-adaptive mechanical consensus that underpins it. Each of the 21 million Bitcoins carries the responsibility of protecting life. Through mechanical consensus, we have the opportunity to establish a more robust societal agreement in an era of information overload and rapid technological advancement. This can help humanity confront the intricate challenges posed by technology—especially those arising from artificial intelligence—and ensure the sustainable development of civilization and life. @ 4ba8e86d:89d32de4
2024-10-29 12:30:05## Tutorial feito por Grom Mestre⚡ Poste original Abaixo. Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7 Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035 Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113 Boa tarde, camaradas do meu coeur! Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb. Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele. Dito isso, vamos prosseguir. TÓPICOS: Introdução Instalando e configurando o roteador e o navegador Conectando-se a serviços na I2P Configurações avançadas ## 1. Introdução ### 1.1 Definindo a DeepWeb. Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos. Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas. Vamos aos pontos individualmente: > São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração. > São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe... > São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio. https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg > Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador. A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação. https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança. As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar: • Lokinet • Zeronet • Freenet • I2P • Tor • Gnunet Porém, há alguns casos interessantes que não caem diretamente nessa regra . A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento. Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento. Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos. Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface. DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa. DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface. Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting). Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito. Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service. ## Instalando e configurando o roteador I2P Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela. O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela. Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas: • Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing ) • Modelo P2P • Todos os participantes da rede contribuem para ela • Fechado na rede - não é possível acessar a surface através da I2P • Otimizado para hidden services Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada. Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas. Referências: • https://geti2p.net/en/comparison/tor • https://geti2p.net/en/docs/how/garlic-routing • https://geti2p.net/en/about/intro • https://i2pd.readthedocs.io/en/latest/ ### 2. Instalando e configurando o roteador Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição. Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso. ### 2.1 Instalação do router Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação. O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ). Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P. Para usuários de Windows, segue abaixo os binários para instalação. • Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip ) • Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip ) • Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip ) A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'. Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070. https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg ### 2.2 Instalação e configuração do navegador Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado. Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas. ### 2.2.1 Escolhendo o navegador Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ ) ### 2.2.2 Criando um perfil e configurando o lançador Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile' https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg Coloquem um nome no seu perfil e cliquem em Finalizar https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador. Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'. Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho. Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf. https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg 2.2.3 Configurando o proxy Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora. Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings) https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg Configure o seu proxy como na figura abaixo. https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites. • http://identiguy.i2p • http://notbob.i2p • http://reg.i2p Se tudo ocorreu como conforme, a página será carregada. https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070) https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção. • noScript • JShelter Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações. Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem. https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado. Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP ## [TUTORIAL] Conectando-se ao XMPP pela I2P Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P. Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável. ### 3.1 Escolhendo o cliente XMPP Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada. Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ ) ### 3.2 Criando uma conta Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais. Para criar uma conta, siga os passos abaixo: Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk) https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela. https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'. https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente). Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel). https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo. https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções: • Tempo ocioso • Hora de Sistema Local • Sistema Operacional • Reprodução de Mídia https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg ### 3.3 Procurando por salas de bate-papo públicas Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?). https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg ### 3.4 Adicionando contatos Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'. https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir. https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :) https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg E com isso terminamos a terceira parte da série de tutoriais. ## [TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet. Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients BONUS: Conectando-se facilmente à I2P. https://youtube.com/watch?v=wGIh5tQcw68
@ 4ba8e86d:89d32de4
2024-10-29 12:30:05## Tutorial feito por Grom Mestre⚡ Poste original Abaixo. Part 1: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/229987/tutorial-entendendo-e-usando-a-rede-i2p-introdu%C3%A7 Part 2: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230035/tutorial-instalando-e-configurando-o-roteador-i2p?show=230035#q230035 Part 3: http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/230113/tutorial-conectando-se-ao-xmpp-pela-i2p?show=230113#q230113 Boa tarde, camaradas do meu coeur! Depois de muito tempo, e com o retorno da minha serotonina aos níveis basais, estou dando início a essa nova série de tutoriais. Espero que tirem muito proveito das informações passadas aqui para amplicarem o seu conhecimento da deepweb. Esta postagem trará antes algumas considerações iniciais que podem ser úteis para quem possui pouco ou nenhum contato prévio com outras tecnologias ou tenha um entendimento torto a respeito da deepweb. Aconselho a estes que deem um boa lida antes de partirem para os tópicos do tutorial, mas saibam que ele não é um pré requisito para ele. Dito isso, vamos prosseguir. TÓPICOS: Introdução Instalando e configurando o roteador e o navegador Conectando-se a serviços na I2P Configurações avançadas ## 1. Introdução ### 1.1 Definindo a DeepWeb. Muitos devem imaginar erroneamente que a deepweb se restrinja apenas à rede onion, mais precisamente aos seus hidden services, já que o Tor possui como uma das suas funções primárias proteger e burlar restrições governamentais e proteger o seus usuários através de métodos sofisticados de roteamento de pacotes e criptografia. Entretanto, ela é mais ampla do que se imagina dependendo da forma como a classificamos. Os ditos "profissionais" usam uma definição extremamente vaga e imprecisa do que seria a deepweb e a sua verdadeira abrangência. Para isso, criei uma definição um pouco melhor para ela: redes comunitárias, sobrepostas, anônimas e criptografadas. Vamos aos pontos individualmente: > São Comunitárias, pois os pontos de roteamento de pacotes na rede (relays ou routers) muitas vezes são mantidos de forma voluntária por usuários comuns. Não é necessário nenhuma infraestrutura sofisticada para ser um contribuinte na rede, basta ter um computador com acesso à internet e conhecimentos básicos para fazer a configuração. > São sobrepostas porque não estão acima ou abaixo da rede tradicional (diferente do que muitos imaginam). Os pacotes na DW trafegam entre os dados da surface e não em meios distintos (algo que não faz o menor sentido). Sabe aquele papo de camadas da DW ou aquela abobrinha da Mariana's Web? Então, tudo um monte de bosta derivado de Youtubers sensacionalistas iletrados em informática. Elitismo da minha parte? Quem sabe... > São anônimas porque não é simples determinar a origem e o destino dos pacotes entre nodes intermediários dado a natureza do roteamento. Em geral, aos menos para a rede onion, há pelo menos 3 relays entre você e o servidor, sendo que esse número duplica para hidden services (3 seus e 3 do serviço). A imagem abaixo ilustra bemocoteamento dos pacotes na onio. https://image.nostr.build/aea96f41d356157512f26b479ea8db5bce8693dd642f2bce0258d8e4b0dac053.jpg > Por fim, são criptografadas porque as conexões são fortemente protegidas por algoritmos sofisticados de criptografia. Além de não sabermos a origem dos dados, sequer podemos saber com facilidade o conteúdo dessas mensagens mesmo que os protocolos das camadas superiores (HTTP, HTTPS, FTP) sejam inseguros, dado que a criptografia da própria rede já as protege. Por isso é tão comum que sites da DW não usem HTTPS, pois as autoridades de certificados não os assinam para domínios da onion e certificados autoassinados vão disparar avisos no navegador. A imagem abaixo ilustra bem como é o roteamento onion usado pelo Tor. Perceba que o contéudo da mensagem está enrolado em 3 camadas de criptografia (como a de uma cebola), de modo que para revelar o contéudo original seria preciso quebrar, no pior dos casos, 3 camadas. Como mencionado antes, o método usado para isso é a criptografia assimétrica, muito similar ao PGP, porém com a sua própria implementação. https://image.nostr.build/7bfaaf29211c11b82049ef8425abb67738d085c41558e9339ec13cf49ea5b548.jpg Observação: Por mais que dentro da rede o encapsulamento proteja as mensagens internamente, entenda muito bem que isso não se aplica a sites da surface acessados pela onion. Ao desempacotar a última camada, a mensagem original é completamente exposta no exit node. Se ela não estiver protegida por uma camada adicional como TLS, seus pacotes estarão completamente expostos, algo que representa um sério risco de segurança. As redes que caem em ao menos três dessas definições (anonimato, sobreposição e criptografia) podem ser classificadas como deepwebs. Podemos citar: • Lokinet • Zeronet • Freenet • I2P • Tor • Gnunet Porém, há alguns casos interessantes que não caem diretamente nessa regra . A Yggdrasil ( https://yggdrasil-network.github.io/ ), uma rede de topologia mesh com foco em escalabilidade e eficiência de roteamento, possui três dessas características: comunitária, sobreposta e segura. Entretanto, os nodes não são anônimos e muitas vezes podem estar desprotegidos, já que se conectar à Yggdrasil é que equivalente a ligar o seu computador diretamente na rede sem a presença de um NAT/CGNAT, correndo o risco de expor portas de serviços da sua máquina caso elas não estejam protegidas por um firewall. A Yggdrasil na prática é exposta como um dispositivo de camada 3 (tipo um VPN), mas diferente de um, apenas endereços IPv6 dentro de uma faixa bem específica de IP são roteados por ela, o que permite que ela coexista com outros dispositivos sem haver conflitos de roteamento. Há quem argumente que a Yggdrasil é uma deepweb dado a sua sobreposição em relação à surface; outros podem argumentar que dado a falta de anonimato ela não se enquadraria nessa categoria. Independentemente disso é uma tecnologia muito interessante com ampla gama de aplicações, como encapsular tráfego de outras redes, como a I2P, e melhorar a eficiência de roteamento. Por fim, vamos desmitificar alguns mitos da DeepWeb muito difundidos. Não existem camadas da DW. Os pacotes da DW são sobrepostos e navegam juntos aos pacotes da surface. DeepWeb e DarkWeb não são coisas diferentes. São termos genéricos para a mesma coisa. DarkWeb não é o seu provedor de e-mail ou serviço de banco. Se eles não se enquadram nas categorias de um deepweb, então estão na surface. Você não é irrastreável na DW. Adversários motivados podem foder com você com facilidade (leia a respeito de ataques de Timing, correlação e fingerprinting). Mesmo que não seja possível ver o conteúdo de uma mensagem pela deepweb, é possível ao menos saber que você a acessou. ISPs podem ver esse tipo de tráfego como suspeito. Você não é um hacker só porque instalou o TorBrowser, mas pode ser considerado um se expor o IP de um hidden service. ## Instalando e configurando o roteador I2P Segue agora a seção 2 do tutorial do I2P. Mas antes apenas queria falar um pouco do projeto I2P. Apesar do foco do tutorial não ser para tratar da sua história, gostaria ao menos de fazer uma breve introdução sobre ela. O projeto I2P (Invisible Internet Protocol) é uma rede P2P descentalizada, anônima e segura para estabelecer a comunicação entre os usuários e serviços. Na I2P é possível usar serviços como mensageiros IRC, XMPP, web services, e-mail e até mesmo torrents. A I2P nasceu de um fork da Freenet no ano de 2003, porém possui diferenças drásticas em relação a ela. Há similaridades entre a I2P e o Tor, porém vale destacar algumas de suas vantagens. Sendo elas: • Garlic routing ( https://geti2p.net/en/docs/how/garlic-routing ) • Modelo P2P • Todos os participantes da rede contribuem para ela • Fechado na rede - não é possível acessar a surface através da I2P • Otimizado para hidden services Apesar disso, vale lembrar que o projeto é pequeno, desenvolvido por menos voluntários se comparado ao Tor e possui menos movimentação e financiamento para o seu desenvolvimento. Além disso, o Tor é um projeto muito mais maduro e bem documentado, algo que atrai mais usuários e desenvolvedores e torna a tarefa de encontrar e corrigir bugs mais fácil de ser realizada. Esses são pontos importantes que devemos levar em conta ao escolher a tecnologia para as nossas necessidades. Nem sempre há tecnologias ruins, as vezes apenas as empregamos as ferramentas erradas na resolução de certos problemas. Referências: • https://geti2p.net/en/comparison/tor • https://geti2p.net/en/docs/how/garlic-routing • https://geti2p.net/en/about/intro • https://i2pd.readthedocs.io/en/latest/ ### 2. Instalando e configurando o roteador Antes da criação do I2PBrowserBundle ( https://github.com/PurpleI2P/i2pdbrowser/releases/tag/1.3.3 ) , a única forma de se conectar à I2P era pela configuração manual de proxy no navegador. Muita gente ou não sabe ou tem MUUUUUITA preguiça de fazer isso e ficam resistentes de entrar na I2P dada essa restrição. Como eu quero ser um bom tutor eu farei do jeito mais "difícil", pois tanto eu desejo que vocês aprendam as nuances do processo como eu sei que vocês são inteligentes o suficiente para fazer isso. ### 2.1 Instalação do router Atualmente nós temos duas implementações do I2P: Uma em Java e outra em C++ (i2pd). Usaremos nesse tutorial a versão em C++ dado o seu baixo uso de recursos e facilidade de instalação. O I2Pd está disponível para Windows, Linux, MacOS e Android e possui binários pré-compilados nas releases ( https://github.com/PurpleI2P/i2pd/releases/tag/2.50.2 ) do projeto no Github. Usuários de Linux podem instalá-lo através do respectivo gerenciador de pacotes da sua distribuição, porém algumas distros não oferecem o pacote diretamente nos reposítórios oficiais, necessitando do uso de PPAs (Ubuntu), COPR (Fedora/RHEL) e afins. Vocês podem conferir as instruções oficiais para cada sistema nessa página ( https://i2pd.readthedocs.io/en/latest/user-guide/install/ ). Apesar desse tutorial ser voltado a usuários de desktop, o I2Pd também está disponível na loja do F-droid. Infelizmente poucos navegadores em Android permitem a configuração de proxies, porém na seção de Serviços na I2P eu tratarei brevemente de como se conectar a servidores de XMPP usando o ConversationI2P. Para usuários de Windows, segue abaixo os binários para instalação. • Versão 32bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win32_mingw.zip ) • Versão 64bits ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_win64_mingw.zip ) • Versão para Windows XP (pois é, kk) ( https://github.com/PurpleI2P/i2pd/releases/download/2.50.2/i2pd_2.50.2_winxp_mingw.zip ) A instalação é simples e direta. Após ela apenas abram o I2Pd para que o router inicie a operação de busca e conexão com os peers. Para usuários de Linux, vocês precisam ativar o serviços através do comando 'sudo systemctl start i2pd'. Se vocês desejam que o I2Pd inicie junto com o sistema usem o comando 'sudo systemctl enable --now i2pd'. Se tudo estiver funcionando corretamente, vocês serão capazes de abrir o webconsole do I2Pd no navegador através do endereço: 127.0.0.1:7070. https://image.nostr.build/ab205ae1071a2b705279e5ce2d6e912d8d11cc7d6dd0dc8a26b76724a27bd94b.jpg https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg ### 2.2 Instalação e configuração do navegador Apesar de qualquer navegador ser capaz de usar a I2P não é recomendado que usem qualquer um, especialmente o navegador que você usam no seu dia-a-dia. Recomendo que usem um navegador próprio para usar na I2P ou isolem suas atividades em um perfil separado. Em navegadores baseado no Firefox isso é relativamente simples, bastando adicionar a opção '--profile' e o caminho do perfil que vocês desejam usar. Nesse tutorial eu vou mostrar como criar um perfil novo no Librewolf e configurar no lançador para iniciar o perfil e abrir em uma janela anônima. Essas instruções são análogas para todos os sistemas, excetuando aquelas configurações mais exóticas. ### 2.2.1 Escolhendo o navegador Como citado, usarei o Librewolf como exemplo. Vocês podem baixar o instalador direto do site ou usar o gerenciador de pacotes do seu sistema no caso de Linux. Como é uma tarefa trivial eu não vou detalhar esse processo, pois todas as instruções estão em detalhes no site do navegador ( https://librewolf.net/installation/ ) ### 2.2.2 Criando um perfil e configurando o lançador Abram o navegador e digitem 'about:profiles' na barra de endereço. Criem um novo perfil clicando em 'Create New Profile' https://image.nostr.build/fa17e14600737ccfc92a415cec2fbfba226b950b2b97af7475927ae65abdbe11.jpg Coloquem um nome no seu perfil e cliquem em Finalizar https://image.nostr.build/62059e375000940f11b27ae77b9ec011f9baadbb5a84afc910d41841ce73e82d.jpg Perfis novos recém criados são iniciados por padrão. Se você deseja usar outro perfil por padrão deve mudar isso na seção 'about:profiles' do navegador. Agora vamos configurar o lançador do LibreWolf para iniciar o perfil do i2p e em uma janela anônima. Usarei o XFCE como referência para essa tarefa, mas saibam que o processo é análogo em sistemas como Windows ou DEs como KDE. Se quiserem também podem lançar via terminal através do comando 'librewolf --profile caminho_do_perfil --private-window'. Cliquem com o botão direito no ícone do Librewolf e abram as propriedades do atalho. Na guia lançador, no campo Comando, adicionem no final a opção '--private-window' e a opção '--profile caminho_do_perfil'. O caminho do perfil é aquele mostrado na seção 'about:profiles' do Librewolf. https://image.nostr.build/a7d6515d7825cb3bdcb681ecf71a97318dccba81eea7cc87fc5377ecc06065ee.jpg 2.2.3 Configurando o proxy Com o lançador configurado, abra o navegador nesse perfil. Vamos configurar o proxy para se conectar ao I2P agora. Abra as configurações digitando 'about:preferences' na barra de endereço. Na seção 'Geral' abra as configurações de rede (Network Settings) https://image.nostr.build/f37157bebf15ada616914f403e756cf9fcee4c9aaaa353196c9cc754ca4d7bc5.jpg Configure o seu proxy como na figura abaixo. https://image.nostr.build/41ebd05255a8129d21011518d400689308d9c0320408967003bf296771e0b96f.jpg Fecha as configurações. Se o seu proxy foi configurado corretamente tente abrir algum desses eepsites. • http://identiguy.i2p • http://notbob.i2p • http://reg.i2p Se tudo ocorreu como conforme, a página será carregada. https://image.nostr.build/ce29ae44743f06cfed591f082208c9612c59b3429ab46d90db48131b3bc3e99d.jpg OBSERVAÇÃO: A busca pelos peers é um pouco demorada, levando de 2 a 5 minutos para que um número mínimo necessário de peers sejam encontrados para estabelecer uma conexão estável. Você pode ver a lista de inbound e outbound tunnels na seção Tunnels do WebConsole (localhost:7070) https://image.nostr.build/285a0d765eaf5f33409f975cd720d0efa68ecc40a9da20bfd9cde0cd1f59a7b6.jpg IMPORTANTE: Apesar do Librewolf possuir defaults seguros, eu recomendo que vocês instalem as seguintes extensões para aumentar ainda mais a sua proteção. • noScript • JShelter Lembrem-se que vocês precisam desativar o proxy para acessar a clearnet. Depois disso reativem-no nas configurações. Outro detalhe: Se vocês tentarem digitar um endereço .i2p na barra de endereços do navegador sem especificar o protocolo (http), ao invés do Librewolf ir ao endereço ele vai realizar uma pesquisa. Para corrigir esse problema, vocês precisam adicionar a seguinte configuração do tipo boolean em 'about:config' como mostrado na imagem. https://image.nostr.build/4518ab817b131f7efe542b2d919b926099dce29a7b59bdd3c788caf53dbd071e.jpg Reiniciem o navegador e testem. Se tudo deu certo vocês não precisam especificar o protocolo ao digitar um endereço .i2p, bastando apenas digitar o endereço simplificado. Por fim, terminamos essa parte do tutorial. Na próximo parte trataremos de como podemos nos conectar a serviços hospedados na I2P como XMPP ## [TUTORIAL] Conectando-se ao XMPP pela I2P Essa é a terceira parte da série de tutoriais. Agora vamos tratar de algumas operações na rede, sendo uma delas conectando-se a um servidor de XMPP na I2P. Não se esqueça de ligar o router e manter ele ligado por alguns minutos antes de iniciar essas operações. O router demora um pouco para encontrar os peers e estabelecer uma conexão estável. ### 3.1 Escolhendo o cliente XMPP Existem diversos clientes XMPP capazes de se conectar usando um proxy. Um dos melhores é o Gajim, um cliente escrito em Python com diversas funcionalidades como criptografia OMEMO e PGP, workspaces separados, extensibilidade via plugins e uma interface bonita e organizada. Assim como ocorreu com o router, o Gajim está disponível por padrão na maioria das distros Linux. Use o seu gerenciador de pacotes para instala-lo. Em Windows você pode baixar o Gajim através desse link ( https://gajim.org/download/ ) ### 3.2 Criando uma conta Vamos primeiro criar uma conta no servidor. No nosso exemplo usarei o servidor oficial do projeto i2pd, o xmpp.ilita.i2p. Há diversos outros servidores XMPP no diretório de links notbob.i2p caso queiram explorar mais. Para criar uma conta, siga os passos abaixo: Abra o Gajim. Na barra de tarefas vá em Contas -> Adicionar Conta. Na nova janela que aparecer, clique em Adicionar Conta https://image.nostr.build/01413e7c6d00c238420e3b0c769dd8d7f7d6522754d2135d3e98a22944f79a27.jpg https://image.nostr.build/9f015861f33990871d96f03d5ec78036a65e3ad9f8ff6a38da18c5b27d31f6d5.jpg Na janela de adicionar contas, clique diretamente em Inscrever-se. Não precisa colocar as suas credencias como mostra a imagem (falha minha, ksksk) https://nostrcheck.me/media/c8411a22946e97467e0ee197ef7a0205ba05f2c67bde092041481ccc2cbbc66d/81938c8d278ce0562c2240341e203f3b70f51ee2db06ceb453f8a178df37fa84.webp Digite o nome do servidor no campo abaixo. Não esqueça de marcar a opção 'Configurações Avançadas' antes de clicar em Inscrever-se https://image.nostr.build/5ee4305a6a23e5c064446b0ce7a4cbc7e790c1ba237bd2495d0237b86a4df07f.jpg Vamos adicionar um novo proxy para essa conta. Para isso clique no botão 'Gerenciar proxies', ao lado do campo Proxy nas Configurações Avançadas https://image.nostr.build/daceb5436def55401d3974ce48d85771e5ebcec4e3f90eb1001df4609112ec12.jpg Adicione um novo proxy clicando no sinal de '+' abaixo da lista de proxies. Preencha os campos de acordo com a imagem abaixo e em seguida feche a janela. https://image.nostr.build/140b34c4e46e9295c073311d483d206201d9339a75f613fe4e829c14f3257bfe.jpg https://image.nostr.build/d365a63d81a14d763bffceb50b30eb53d81959623f8fe812175358a41b1fba53.jpg No campo de Proxy, selecione o proxy I2P. Preencha o restante dos campos de acordo com a imagem abaixo. Em seguida clique em 'Inscrever-se'. https://image.nostr.build/d06c11d9c6d19728bf5a58af2dd3e14d8ca0021456da09792a345ac0bfc90ad0.jpg Nesse momento uma mensagem pode aparecer pedindo para abrir uma exceção para o certificado TLS. Isso acontece porque trata-se de um certificado autoassinado que não foi validado por uma autoridade oficial. Apenas abra a exceção e prossiga (não há imagem para isso porque eu já abri essa exceção no meu cliente). Uma nova janela vai aparecer solicitando-lhe para inserir as suas credenciais. Tome cuidado aqui, pois não é para inserir o nome completo com o domínio, apenas o seu nome de usuário (ex: descartavel). https://image.nostr.build/dde2a6736bd00080fbeeb8076754e226971a412710b370d5559f7f4d5414f8b3.jpg Se tudo der certo, uma nova janela vai aparecer confirmando a sua inscrição. Coloque um nome e uma cor para a sua conta e clique em Conectar para concluir o processo. https://image.nostr.build/74934d3f1f3f4232eacee8e78e707936227f816c50ac6b52da5c81ec17557e69.jpg Para finalizar, nos detalhes da sua conta, modifique as suas configurações de privacidade para diminuir o fingerprint. Na seção de 'Privacidade', desligue as seguintes opções: • Tempo ocioso • Hora de Sistema Local • Sistema Operacional • Reprodução de Mídia https://image.nostr.build/d2ed5852a104c770b50c7b053d518d8af0b6289ced6b3ad4187492208c7ca649.jpg ### 3.3 Procurando por salas de bate-papo públicas Após criar a sua nova conta, vamos descobrir alguns serviços que o servidor oferece. Para isso, vá para Contas -> Descobrir serviços https://image.nostr.build/54928d1dd0e48365858b24c72097a9fabf677794e13f329fc0568211eefbe559.jpg Na seção 'Bate-papo em Grupo', selecione Chatrooms e clique em 'Navegar'. Ao fazer isso uma lista de chatroom públicos presentes no servidor vai aparecer. Fique a vontade para explorar, porém saiba que alguns servidores são moderados e não te permitem mandar mensagens sem sua conta ser aprovada pelo moderador (familiar?). https://image.nostr.build/1936bef51d58a1f6cfdf8bf8d84bfa64adc2a09b9c0fb1623b93a327f0b8cdd8.jpg https://image.nostr.build/89e8013b1cea1df0f80f6833bd6771c33101f404b0099b2d7330a5e57607baff.jpg ### 3.4 Adicionando contatos Para adicionar contatos à sua lista, clique no símbolo de '+' ao lado do campo de pesquisa e selecione 'Add Contact'. https://image.nostr.build/d3cadea27591355f674fba93765c3815282d112b2e80a592bb77a442c13dd4f4.jpg Coloque o endereço completo da conta que você deseja adicionar. Usarei a minha conta oficial nesse exemplo. Você tem a opção de anexar uma mensagem qualquer antes de enviar o convite. Clique em 'Adicionar Contato' para prosseguir. https://image.nostr.build/ff95b7aec2377c58d4253c5b7b3aabf141a92dd5f3e97f6e1f01ecb32a215d38.jpg https://image.nostr.build/6562e680e28c321ebbd009b5ade513f8a279aea33bc16aa9fb251f3507eb04af.jpg Se tudo ocorrer normalmente, o novo contato vai aparecer na sua lista. Dê dois-cliques na conta para abrir o chat. Não se esqueça de ativar a criptografia OMEMO antes de enviar qualquer mensagem. Agora você está pronto para conversar de forma segura :) https://image.nostr.build/ef7f783a311ad0f68a5408137f75dc2bc6c38f6e9656dc0d68d3267f5012f658.jpg E com isso terminamos a terceira parte da série de tutoriais. ## [TUTORIAL] Criando e conectando-se a um servidor XMPP na I2P e clearnet. Como configurar o seu próprio servidor XMPP. https://youtube.com/watch?v=Ot_EmQ8xdJwy Criando contas e conectando clientes Pidgin http://i2pd.readthedocs.io/en/latest/tutorials/xmpp/#creating-accounts-and-connecting-clients BONUS: Conectando-se facilmente à I2P. https://youtube.com/watch?v=wGIh5tQcw68 @ e1d968f7:5d90f764
2024-11-17 05:52:21When most people think of escorting, they imagine something out of a movie—glamorous, effortless, and always exciting. The reality? Well, it’s not quite as polished. Don’t get me wrong, there are moments of glamour, but there’s also a lot of hard work, emotional labour, and, at times, moments of doubt. In this post, I want to pull back the veil and show you the difference between the fantasy that some may think it is and the reality of this life. --- ### **The Fantasy: What People Expect** The fantasy surrounding escorting is something I’m sure we’ve all seen in movies, TV shows, and magazines. A beautiful woman in a stunning outfit, stepping into a luxurious hotel room or a sleek car, ready to seduce her client with a smile. There's a lot of emphasis on sex appeal, seduction, and effortless glamour. People assume we live a life of constant excitement, where every day is filled with luxurious dates and rich clients pampering us. And yes, there are elements of truth in that. I’ve been on some incredible dates, experienced lavish settings, and worn some gorgeous outfits. But the fantasy often overlooks the hard work that goes into it, the emotional and physical toll it can take, and the complexity of navigating human connection. --- ### **The Reality: Hard Work and Emotional Labour** Escort work isn’t just about showing up looking beautiful. It's a job, and like any job, it requires effort, skill, and preparation. The logistics alone can be overwhelming—arranging dates, coordinating schedules, planning outfits, dealing with payments, managing client expectations, and ensuring safety. And then, there’s the emotional side. Being an escort isn’t just about being physically available; it’s about creating an experience. I’m not just a body to be desired—I’m someone who listens, engages, and makes people feel comfortable, confident, and special. Some clients come with emotional baggage, some need more attention than others, and there are always those moments when the chemistry just isn’t there. That’s when you have to dig deep and deliver the service regardless, even if it’s a bit of a struggle on your part. --- ### **The Disconnect: Fantasy vs. Reality** The biggest disconnect I’ve noticed is that people often expect the escorting world to align exactly with the fantasy in their heads. They think it’s always glamorous and exciting, that the sex is always passionate, and that the money just flows in. But the reality is that a lot of the time, you’re dealing with real people—people who have their own insecurities, moods, and complexities. Sometimes, the job requires a lot more patience, empathy, and attention than most people realise. Clients may assume they know what to expect, but sometimes, things don’t go as planned. Sometimes the chemistry isn’t there. Sometimes the date is awkward, or you end up chatting about something deep rather than sharing a passionate moment. You might have a client who’s far more interested in talking about their day than anything physical. That’s not always what people expect when they book an escort, but that’s the reality of being there for someone. --- ### **The Glamour: When It All Comes Together** Even though there’s a lot of hard work behind the scenes, there are undeniably moments that do feel like the fantasy. When everything falls into place—when you’ve got a client who’s respectful, charming, and genuinely fun to be around—the experience can be incredible. There are those dates where the chemistry is undeniable, where both of us are on the same wavelength and the connection flows effortlessly. I’ll admit, there are times when I feel absolutely stunning, walking into a luxurious restaurant or slipping into a gorgeous hotel suite. That’s when the fantasy element becomes a reality, and it makes everything worth it. --- ### **The Takeaway: Embracing Both Worlds** At the end of the day, the fantasy and reality of escorting are intertwined. It’s a delicate dance of glamour and hard work, seduction and professionalism, connection and detachment. There are ups and downs, moments that feel like a dream and others that are grounded in reality. I’ve learned to embrace both sides of the job—the fantasy that keeps things exciting and the reality that keeps me grounded. It’s the balance between the two that makes escorting both challenging and rewarding. Tomorrow, I’ll delve into the more personal side of escorting—how I maintain my emotional well-being and balance after each booking. Until then, just remember, it’s not all glamorous and it’s not always easy, but it’s a life I’ve come to understand, appreciate, and, yes, even love in its own complex way. Rebecca x
@ e1d968f7:5d90f764
2024-11-17 05:52:21When most people think of escorting, they imagine something out of a movie—glamorous, effortless, and always exciting. The reality? Well, it’s not quite as polished. Don’t get me wrong, there are moments of glamour, but there’s also a lot of hard work, emotional labour, and, at times, moments of doubt. In this post, I want to pull back the veil and show you the difference between the fantasy that some may think it is and the reality of this life. --- ### **The Fantasy: What People Expect** The fantasy surrounding escorting is something I’m sure we’ve all seen in movies, TV shows, and magazines. A beautiful woman in a stunning outfit, stepping into a luxurious hotel room or a sleek car, ready to seduce her client with a smile. There's a lot of emphasis on sex appeal, seduction, and effortless glamour. People assume we live a life of constant excitement, where every day is filled with luxurious dates and rich clients pampering us. And yes, there are elements of truth in that. I’ve been on some incredible dates, experienced lavish settings, and worn some gorgeous outfits. But the fantasy often overlooks the hard work that goes into it, the emotional and physical toll it can take, and the complexity of navigating human connection. --- ### **The Reality: Hard Work and Emotional Labour** Escort work isn’t just about showing up looking beautiful. It's a job, and like any job, it requires effort, skill, and preparation. The logistics alone can be overwhelming—arranging dates, coordinating schedules, planning outfits, dealing with payments, managing client expectations, and ensuring safety. And then, there’s the emotional side. Being an escort isn’t just about being physically available; it’s about creating an experience. I’m not just a body to be desired—I’m someone who listens, engages, and makes people feel comfortable, confident, and special. Some clients come with emotional baggage, some need more attention than others, and there are always those moments when the chemistry just isn’t there. That’s when you have to dig deep and deliver the service regardless, even if it’s a bit of a struggle on your part. --- ### **The Disconnect: Fantasy vs. Reality** The biggest disconnect I’ve noticed is that people often expect the escorting world to align exactly with the fantasy in their heads. They think it’s always glamorous and exciting, that the sex is always passionate, and that the money just flows in. But the reality is that a lot of the time, you’re dealing with real people—people who have their own insecurities, moods, and complexities. Sometimes, the job requires a lot more patience, empathy, and attention than most people realise. Clients may assume they know what to expect, but sometimes, things don’t go as planned. Sometimes the chemistry isn’t there. Sometimes the date is awkward, or you end up chatting about something deep rather than sharing a passionate moment. You might have a client who’s far more interested in talking about their day than anything physical. That’s not always what people expect when they book an escort, but that’s the reality of being there for someone. --- ### **The Glamour: When It All Comes Together** Even though there’s a lot of hard work behind the scenes, there are undeniably moments that do feel like the fantasy. When everything falls into place—when you’ve got a client who’s respectful, charming, and genuinely fun to be around—the experience can be incredible. There are those dates where the chemistry is undeniable, where both of us are on the same wavelength and the connection flows effortlessly. I’ll admit, there are times when I feel absolutely stunning, walking into a luxurious restaurant or slipping into a gorgeous hotel suite. That’s when the fantasy element becomes a reality, and it makes everything worth it. --- ### **The Takeaway: Embracing Both Worlds** At the end of the day, the fantasy and reality of escorting are intertwined. It’s a delicate dance of glamour and hard work, seduction and professionalism, connection and detachment. There are ups and downs, moments that feel like a dream and others that are grounded in reality. I’ve learned to embrace both sides of the job—the fantasy that keeps things exciting and the reality that keeps me grounded. It’s the balance between the two that makes escorting both challenging and rewarding. Tomorrow, I’ll delve into the more personal side of escorting—how I maintain my emotional well-being and balance after each booking. Until then, just remember, it’s not all glamorous and it’s not always easy, but it’s a life I’ve come to understand, appreciate, and, yes, even love in its own complex way. Rebecca x @ 8d34bd24:414be32b
2024-10-27 22:30:18NOTE: *This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.* When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior. In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance. ## Seek the Welfare of the City Where I Have Sent You As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia. > Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1) What did God say to the Israelites about how they should live their life in Babylon? > “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare**.’ (Jeremiah 29:4-7) {emphasis mine} Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.” God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “*for in its welfare you will have welfare*.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price. We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands. We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves. ## Political Religion Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties. > No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13) Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God. When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally. > You shall have no other gods before Me. > > You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6) When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion. We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different. I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge: *I pledge allegiance to the Flag of the United States of America,\ and to the Republic for which it stands,\ one Nation under God,\ indivisible, with liberty and justice for all.* I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “*serve two masters*.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right. ## In the World, but Not of the World As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship[1](https://trustjesus.substack.com/p/should-christians-vote#footnote-1-150236181) and family are in heaven, not here on earth. We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ. > But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. **I have given them Your word; and the world has hated them, because they are not of the world**, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. **They are not of the world, even as I am not of the world**. Sanctify them in the truth; **Your word is truth**. (John 17:13-17) {emphasis mine} Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God. Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior. > **Do not love the world nor the things in the world**. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. **The world is passing away**, and also its lusts; but **the one who does the will of God lives forever**. (1 John 2:15-17) {emphasis mine} The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics. Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles: > Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13) There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “*as having been with Jesus*.” I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God. > Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, **so that they may be saved**. (1 Corinthians 10:32-33) {emphasis mine} Trust Jesus.\ \ your sister in Christ, Christy
@ 8d34bd24:414be32b
2024-10-27 22:30:18NOTE: *This article has some details that are specific to America, but the overall principles are applicable to all, and I believe it will be useful for all Christians.* When it comes to things like voting, Christians tend to err to one of two extremes and seem to find difficulty finding the right balance as defined by God. Some Christians refuse to vote or get involved with politics at all. They don’t want to dirty themselves with politics. They know that their true home is heaven, so they don’t seem to care much for the nations they live in. On the other hand, some Christians are so focused on politics fixing everything and creating heaven on earth that they can become idolatrous lifting up politicians as a kind of savior. In this article, I’m going to address both extremes, using the Bible, and hopefully help you find a Biblical balance. ## Seek the Welfare of the City Where I Have Sent You As Christians we are just passing through our time on earth. Our true, eternal home, our true citizenship, is in heaven. That doesn’t mean that we shouldn’t care what happens on earth. We shouldn’t be like the old saying, “some Christians are so heavenly minded that they aren’t any earthly good.” I think Christians should organize our time here on earth kind of like the Israelites were commanded to live during their 70 year exile in Babylon and Persia. > Now these are the words of the letter which Jeremiah the prophet sent from Jerusalem to the rest of the elders of the exile, the priests, the prophets and all the people whom Nebuchadnezzar had taken into exile from Jerusalem to Babylon. (Jeremiah 29:1) What did God say to the Israelites about how they should live their life in Babylon? > “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare**.’ (Jeremiah 29:4-7) {emphasis mine} Could we likewise say the same to Christians during their time on earth? “Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. Seek the welfare of the city, state, or nation where I have sent you to live for a short while, and pray to the Lord on its behalf; for in its welfare you will have welfare.” God expects us to live fruitful lives, to marry, to have many children (multiply), and to raise them up to do the same. He also wants us to seek the welfare of the city, state, and nation where God has put us. In a city, state, or nation with democratic elections, the best way to seek its welfare is to vote for honest candidates who support godly principles. We rightly understand that in our ungodly world there are no perfect candidates. It can even be hard to find mostly honest and mostly godly candidates, but we should seek to elect the best that is available. Why are we told to do this? We are told that “*for in its welfare you will have welfare*.” When we fail to vote, to teach our kids or support good schools, to live productive lives, and to generally live Godly lives, we WILL see the decline of our cities, states, and nations. We will pay the price. We are seeing exactly that decline because Christians have pulled out (and were pushed out) of the positions that influence the culture. We don’t have enough godly teachers, journalists, professors, advisors, economists, and politicians. We have given up the culture to those who oppose God, His people, and His commands. We are paying the price for withdrawing into the safety of our churches and leaving the world to the wolves. ## Political Religion Of course we also have an opposite extreme. We have some Christians that are too focused on politics and power. They spend all of their time and energy on political endeavors and very little, to none, on sharing the Gospel and being a godly example. Many act like they think a political candidate is going to save them from the culture, the media, the bureaucracy, or the government. They forget that there is only one Savior — the Lord Jesus Christ. They forget that God said things will get worse before they get better. They make idols out of politicians and religions out of political parties. > No servant can serve two masters; for either he will hate the one and love the other, or else he will be devoted to one and despise the other. You cannot serve God and wealth.” (Luke 16:13) Although this verse is specifically talking about being obsessed with wealth, it is applicable to anything that takes our focus, attention, and especially our worship away from God. When a person spends all of their time serving one candidate or party and little to no time serving God, they have chosen to serve another god and are guilty, even if inadvertently and unintentionally. > You shall have no other gods before Me. > > You shall not make for yourself an idol, or any likeness of what is in heaven above or on the earth beneath or in the water under the earth. You shall not worship them or serve them; for I, the Lord your God, am a jealous God, visiting the iniquity of the fathers on the children, on the third and the fourth generations of those who hate Me, but showing lovingkindness to thousands, to those who love Me and keep My commandments. (Exodus 20:3-6) When we look to a politician to save us from anything, we are making him/her a god before us. When we give our all to a political party, we are taking our heart away from God and giving it to an alternate religion. We may not think that we make idols in our modern world. It is true that we don’t usually carve them out of wood or mold them out of gold, but we have just as many idols as the Israelites did. They just look different. I hope you will seriously consider this next point because it may be very unpopular with many of my readers. There are lots of Christians that will throw as big, if not a bigger, fit at the desecration of the American flag than over the Bible. Nobody seems to fight to retain the pledge of allegiance more than a majority of Christians. I’d argue that the American flag has become a modern day idol and the “Pledge of Allegiance” has become a religious mantra repeated to the god of government. Look at the words of the pledge: *I pledge allegiance to the Flag of the United States of America,\ and to the Republic for which it stands,\ one Nation under God,\ indivisible, with liberty and justice for all.* I think the inclusion of the phrase “one Nation under God” makes Christians feel OK about this pledge originally invented by a socialist whose brother sold American flags. The important part, which is why I can’t say the pledge anymore, are the words, “I pledge allegiance to the Flag of the United States of America, and to the Republic for which it stands.” I really appreciate the principles America was founded upon, but as a Christian, I can only pledge allegiance to God. My allegiance isn’t to a flag (an idol) or the government (a god). I refuse to go through a religious ritual that includes particular stances, reciting special words, and showing undue respect. We cannot “*serve two masters*.” As Christians our master should be Christ alone. Anything that becomes more important than, or even equal to, the importance of God in our lives is idolatry. We need to get our priorities right. ## In the World, but Not of the World As we live our lives here on earth, we need to remember our God ordained purpose and our true allegiance to God. We need to remember our citizenship[1](https://trustjesus.substack.com/p/should-christians-vote#footnote-1-150236181) and family are in heaven, not here on earth. We want to have a positive influence on our culture, including working in influential positions and voting, but we should be most focused on personal evangelism and sharing the truth of the Bible. The best way to make a difference in our culture is to change hearts and minds through the Gospel of Jesus Christ. > But now I come to You; and these things I speak in the world so that they may have My joy made full in themselves. **I have given them Your word; and the world has hated them, because they are not of the world**, even as I am not of the world. I do not ask You to take them out of the world, but to keep them from the evil one. **They are not of the world, even as I am not of the world**. Sanctify them in the truth; **Your word is truth**. (John 17:13-17) {emphasis mine} Although we want to be a light in the world, we have been warned that doing so will make us not fit in. It will cause many non-Christians (and maybe a few Christians whose priorities are not right) to hate us. No matter the consequences, we need to stand on the truth of the Word of God. Too often, because we are living with those who are of this world, we start to look and act a lot like those of the world instead of looking and acting like our Savior. > **Do not love the world nor the things in the world**. If anyone loves the world, the love of the Father is not in him. For all that is in the world, the lust of the flesh and the lust of the eyes and the boastful pride of life, is not from the Father, but is from the world. **The world is passing away**, and also its lusts; but **the one who does the will of God lives forever**. (1 John 2:15-17) {emphasis mine} The fact that we should not love the things of the world or take on the character of things of the world is true in every part of our lives, but since we are talking here about politics, let us discuss the way many Christians talk politics. Many Christians talk about politics in the same manner as non-Christians — cursing, name calling, insulting, and doing whatever it takes to win, no matter whether it is moral or not. I know the “other side” cheats, lies, name-calls, etc., but we should not stoop to their level. Nobody ever won another to their point of view by cursing or name calling. There are ways to point our their errors, and even how horrific some of the things pushed are, without going so low. Jesus didn’t hold back from speaking the truth. He didn’t hesitate to point out error, but was never crude about it. We should be the same. We should shine a light in such a way that those around us see such a difference that they say something similar to what was said about the apostles: > Now as they observed the confidence of Peter and John and understood that they were uneducated and untrained men, they were amazed, and began to recognize them as having been with Jesus. (Acts 4:13) There should be something about our words, actions, and demeanor that amazes our opponents causing them to recognize us “*as having been with Jesus*.” I hope this post has been helpful, truthful, and not too offensive. In so many areas it is hard to find that perfect balance and to not allow ourselves to be pulled to either extreme to the detriment of our witness and our relationship to God. > Give no offense either to Jews or to Greeks or to the church of God; just as I also please all men in all things, not seeking my own profit but the profit of the many, **so that they may be saved**. (1 Corinthians 10:32-33) {emphasis mine} Trust Jesus.\ \ your sister in Christ, Christy @ 599f67f7:21fb3ea9
2024-10-26 11:54:10# Zer da Cashu? Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen. Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta: | **Cashu** | **Bitcoin (on-chain)** | |-----------------------|----------------------------| | Libururik gabe | Liburu banatua | | Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) | | Transakzio itsutuak | Transakzio publikoak | | Zentralizatua | Deszentralizatua | | Konfiantzazkoa | Konfiantzarik gabe | | Aldi baterako transakzioak | Betiko transakzioak | Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri. Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.  ## Cashu-ren erabilera kasu batzuk Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko. ## Historia Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen. ## Terminologia Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu. ### Mint Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko. Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu. ### Token Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera. Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko. ## Nola funtzionatzen duen, 5 urteko bati bezala azaldua  Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."  Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.  Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.  Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.   Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.   Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio. ### Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion? Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta. ### Zer gertatzen da itzulkinekin? Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du. ### Lightning sarearen papera konektatzeko elementu gisa Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.  ## Zer dator hurrengoa Cashu-rentzat? ### Programagarri den ecash Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira. ### Zorren froga eskema (Proof of Liabilities Scheme) Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu. ## Saiatu Cashu Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar.
@ 599f67f7:21fb3ea9
2024-10-26 11:54:10# Zer da Cashu? Cashu Bitcoinentzako Ecash protokolo irekia da, transakzio azkarrak eta doakoak eskaintzen dituena. Protokolo honen ezaugarri nabarmenetako bat pribatutasun ia perfektua eskaintzea da. Nostr nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg erabiltzaileak sortu zuen. Hona hemen Cashu eta on-chain Bitcoin alderatzen dituen taula, Bangkok 2023ko Bitcoin Konferentzian nostr:npub1cj6ndx5akfazux7f0vjl4fyx9k0ulf682p437fe03a9ndwqjm0tqj886t6-k aurkeztutako Nuts and Bolts hitzaldian oinarrituta: | **Cashu** | **Bitcoin (on-chain)** | |-----------------------|----------------------------| | Libururik gabe | Liburu banatua | | Titulartasun tokena | UTXO (Ustiaketa Ezberdinen Irteera) | | Transakzio itsutuak | Transakzio publikoak | | Zentralizatua | Deszentralizatua | | Konfiantzazkoa | Konfiantzarik gabe | | Aldi baterako transakzioak | Betiko transakzioak | Ikusten dugunez, Cashuk pribatutasuna hobetzeko konfiantza gabeko izaera eta deszentralizazioa sakrifikatzen ditu. Konpentsazio hauek zentzuzkoak dira zaintza-zerbitzuetan, erabiltzailea dagoeneko zerbitzu zentralizatu eta fidagarri bat erabiltzen ari baita. Zaintza tradizionaleko irtenbideek pribatutasun eskasa dute, zaintzaileak erabiltzailearen funtsak zenbat diren eta norekin ari den transakzioak egiten jakin dezakeelako. Horrek esan nahi du norbanakoak erraz helburu eta zentsura daitezkeela. Gainera, datu-erregistroek "honeypot" bihurtzeko arriskua dute, hau da, erasotzaileentzat erakargarri. Alderantziz, Cashu-ren mint-ek zaintzaile gisa jardun dezakete, baina erabiltzaileen nortasuna, duten funtsen kopurua edo norekin ari diren transakzioak egiten ezagutzeko aukerarik gabe. Mint-ek duten datu-erregistro bakarra gastatutako sekretuen zerrenda da, berriro erabili ezin direnak, baina erabiltzaileekin lotzeko modurik gabe. Horrela, Cashu-k pribatutasuna bermatzen du, zaintzaileak ez duelako inolako informaziorik erabiltzaileen jarduerei buruz, ohiko zaintza-soluzioekin gertatzen denaren kontrara.  ## Cashu-ren erabilera kasu batzuk Cashu-ren erabilera kasu batzuk honako hauek dira: bonuak, dagoeneko zentralizatuak eta zaintza-zerbitzuak dituztenak; baliabide bakoitzeko ordainketa (pay-per-resource) APIak, nostr bideratzaileak eta mixnet-ak bezalako zerbitzuetarako; sistema integratuak, kontu eta saldo eredu tradizionala ordezkatzen dutenak; eta truke/mixinge zerbitzuak, gordailuak eta ateratzeak deslotzeko, pribatutasuna hobetzeko. ## Historia Ecash David Chaum-ek 1982an asmatu zuen, sinadura itsuak erabiliz balio elektronikoaren transmisiorako protokolo gisa. Cashu Ecash-en inplementazio bat da, David Wagner-en 1996ko Chaum-en itsutze-aldaketan oinarrituta dagoena, eta nostr sortu zuen. ## Terminologia Cashu nola funtzionatzen duen ulertzen laguntzeko, lehenik eta behin funtsezko terminologia batzuk azalduko ditugu. ### Mint Cashu-ren mint-a erabiltzaileen funtsen zaintzailea da. Bere zeregina tokenak jaulkitzea eta erretzea da, baita bikoiztutako gastuak saihestea ere. Cashu-ren mint-a Lightning nodo baten gainean dago, beraz, Lightning ordainketak bidali eta jaso ditzake, beste mint batzuekin trukeak barne. Hala ere, Lightning nodoa lineaz kanpo badago ere, ecash tokenekin transakzioak egin daitezke. Lightning-ekin ez bezala, jasotzailea linean egon beharrik ez du tokenak jasotzeko. Mint-ak ez daki nor den erabiltzailea, zenbat funts dituzten edo norekin ari diren transakzioak egiten. Hala ere, mint-a erabiltzaileen funtsen zaintzailea denez, fidagarria den mint bat aukeratu behar duzu, eta eragilea nor den jakin. Erabil ezazu funts txikiekin edo tokenak berehala trukatu. ### Token Cashu token-a mint-ak sinatutako datu-puska bat da, eta erabiltzaileak token horiek bere zorroan gordetzen ditu. Ecash tokenak testu-kate hutsak direnez, edozein testu bidezko protokoloaren bidez bidal daitezke, adibidez, nostr, posta elektronikoa, SMS, etab. Cashu-k txanpon-sistema bat erabiltzen du, zenbateko finkatuak dituena. Analogia bat eginez, hau moneta fiduziarioen billeteen zenbatekoei dagokie. Adibidez, eurotan 5, 10, 20, 50, 100 euroko billeteak daude. Cashu-n, tokenak 2ren indarren arabera sailkatzen dira. Adibidez, 1, 2, 4, 8, 16, 32, 64, 128 satoshi, eta horrela aurrera. Zenbatekoak erabiltzea erabiltzaileen artean anonimotasuna areagotzeko egiten da, eta mint-ek transakzioak erabiltzaileen nortasunekin lotzea zailagoa bihurtzeko. ## Nola funtzionatzen duen, 5 urteko bati bezala azaldua  Erabiltzaile Alice-k Cashu token berriak sortu nahi ditu. Horregatik, Bob mint-aren arduradunarengana joaten da eta esaten dio: "Kaixo! Cashu token berriak sortu nahi ditut."  Bob-ek erantzuten dio: "Ados, ordaindu iezadazu eta bidali iezadazu sekretu itsu bat." Sekretu itsua esan nahi du Alice-k sekretua ezagutzen duela, baina Bob-ek ezin duela sekretu hori ikusi.  Alice-k sekretu bat sortzen du, eta ondoren itsutzen du, horrela Bob-ek ez dezan jakin zein den sekretu hori.  Alice-k Bob-i ordainketa egiten dio eta ordainketaren egiaztagiria eta sekretu itsua bidaltzen dizkio. Bob ordainketa jaso duela ziur dagoenean, Alice-ren sekretu itsua sinatzen du eta sinatutako sekretu itsua itzultzen dio. Bob-ek sinatu duelako, etorkizunean ziur egon daiteke tokena baliozkoa dela.   Alice-k Carol-i ordaindu nahi dio. Horretarako, sekretua eta sinatutako sekretu itsua desitsutzeko gakoa bidaltzen dizkio Carol-i.   Carol-ek bere tokena trukatu nahi du. Beraz, Bob-engana (mint-aren arduradunera) joaten da eta Alice-k eman dion sekretua eta desitsututako gakoa erakusten dizkio. ### Nola jakiten du mint-ak Carol-i zenbat satoshi eman behar dizkion? Lehenago aipatu genuen bezala, Cashu tokenak 2ren indarren araberako zenbatekoetan banatuta daude (1, 2, 4, 8, 16, 32...), paperezko diru billeteen antzera. Bob mint-ak zenbateko bakoitza sinatzeko gako pribatu berezi bat du. Adibidez, 1 satoshi zenbatekoaren tokenak sinatzeko gako pribatu bat du, 2 satoshi zenbatekoaren beste bat, 8 satoshi zenbatekoaren beste bat, eta abar. Horrela, Carol tokenak trukatzera datorrenean, Bob-ek badaki zein gako pribaturekin sinatu zuen token hori, eta horren arabera, tokenak zein zenbatekotakoak diren ezagutzen du. Horrela, Bob-ek Carol-i dagokion satoshi kopurua itzuli diezaioke, sinatutako tokenaren zenbatekoa kontuan hartuta. ### Zer gertatzen da itzulkinekin? Cashu-n ez dago itzulkinik diru fisikoan bezala. Horren ordez, mint-ari (Bob-i) eskatu behar diozu token zaharrak suntsitzeko eta berriak sortzeko, zenbateko berarekin. Adibide batekin azalduz: Demagun Alice-k bi token dituela, guztira 10 satoshi balio dutenak. Bata 8 satoshi da eta bestea 2 satoshi. Alice-k 9 satoshi bidali nahi dizkio Carol-i. Horretarako, mint-ari (Bob-i) eskatzen dio bere 2 satoshi tokena bi 1 satoshi token bihurtzeko. Horrela, Alice-k 9 satoshi bidal diezazkioke Carol-i: 8 satoshi token bat eta 1 satoshi token bat erabiliz. Gainera, beste 1 satoshi tokena berarentzat gordetzen du. ### Lightning sarearen papera konektatzeko elementu gisa Zer gertatzen da Alice-k David-i ordaindu nahi dionean, baina David-ek Bob-en mint-a ez du fidatzen, eta, aldiz, Erin ezagutzen du eta bere mint-a erabiltzen du? Alice-k bere tokenak Bob-en mint-ean trukatzen ditu, eta Bob-i eskatzen dio token horiek "urtzeko" edo Lightning satoshietara bihurtzeko. Ondoren, Bob-en mint-ak Lightning transakzio bat bidaltzen dio Erin-en mint-ari. Erin-en mint-ak transakzio hori jasotzen du, eta David-entzat token berriak sortzen ditu Lightning sarearen bidez Bob-en mint-etik jasotako satoshiekin. Horrela, Lightning sareak mint ezberdinak konektatzen ditu, erabiltzaileak (Alice eta David) mint ezberdinak fidatu arren, transakzioak segurtasunez egiteko.  ## Zer dator hurrengoa Cashu-rentzat? ### Programagarri den ecash Cashu-ri gastatzeko baldintzak gehitu ahal izango zaizkio, mint-ak baldintza horiek betearaziko dituelarik. Horrek ahalbidetu dezake kontratu adimendun sendoak sortzea, oinarrizko katean (Bitcoin blockchain) edo Lightning sarean sartu gabe. Horrela, ordainketa publikoak, lineaz kanpokoak eta maiztasun handikoak posible izango dira. ### Zorren froga eskema (Proof of Liabilities Scheme) Zorren Froga (PoL) Eskema Cashu-rentzat zaintzailea den mint-ak erabiltzaileak iruzurrez erabiltzea zailtzen du, epoka kontzeptua aurkeztuz. Eskema honetan, zaintzaile den mint-ak epoka bakoitzean gako pribatuak aldian-aldian biratzen ditu, eta azken epokan jaulkitako eta erretako tokenen zerrenda publikoak argitaratzen ditu. Hau Erreserben Froga (Proof of Reserves) eskemarekin uztartzen da, non erreserbak katean bertan multisig batean gordetzen diren. Horrela, mint-ak ezingo du bere erantzukizunak murriztu, erabiltzaileek iruzurra detektatzeko arriskua handitu gabe. Xehetasun gehiagorako, eskema honen azalpen osoa kontsultatu dezakezu. ## Saiatu Cashu Cashu probatzeko, [Nutstash] eta [eNuts] gidak erabil ditzakezu. Horretarako Lightning zorro bat eta telefono edo ordenagailu bat besterik ez duzu behar. @ b7274d28:c99628cb
2024-11-17 04:38:20There seems to be a bit of confusion going around about exactly what #AlbyHub is, and what it does, what use-cases it does and does not fit into. As someone who is using #Alby Hub on a daily basis and have been quite happy with it, I thought I might be able to shed some light on the matter from the perspective of a user. nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, please correct me if I get anything wrong in this article. Note: I am not in any way affiliated with Alby, except by being a satisfied user of their software, and have not been paid to write this article. I can understand the confusion surrounding Alby Hub, because it is not just one thing that works the same for all users of the product. There are various different ways you can have it set up, and while the end result is mostly the same functionality, the steps to get there are different for each version. There is the cloud (someone else's computer) version, the desktop version, the docker version, and the node (nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll or nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct) package version. In some of these versions, Alby Hub is acting as a standalone Lightning node, and in others it is merely a front-end that gives your existing node additional features, such as segregated wallets, but you must have an #LND instance already established that it is running alongside. ## Cloud This service is a standalone Lightning node running in the cloud and online 24/7. For that reason, it can be very attractive to users who may not be able to run their own node at home, or who do not have reliable power or internet services. It is still considered self-custodial, even though it is running on Alby's servers, because you hold your own keys. Since this version of Alby Hub is a standalone Lightning node, this means that all of your channel setup and liquidity is managed inside of your cloud-hosted Alby Hub. My assumption is that this Lightning node is reaching out to a #Bitcoin full node that Alby runs for all on-chain data and broadcasting channel-opens and closes. At the time of writing, the cost for this cloud-hosted node is 21,000 sats a month. You get some additional features by paying for this service that other versions of Alby Hub lack, though. You can have a custom Lightning address, instead of just an "UserName@getalby.com" address. You also get priority customer support with an in-app live chat, and access to the "Buzz" community that other users of Alby Hub do not get access to. There are other options for a cloud-hosted Alby Hub other than directly from Alby, as well. For instance, you can host your Alby Hub on nostr:npub1g26qnlumycdfs538kx4eyur7wpnh0tq5mcjx2nt7qhc9qxehuqpsk4y9fw or Render. These alternative hosting options may have a lower cost associated with them, but you will not have access to the additional features, such as a custom Lightning address or priority customer support. ## Desktop The desktop client is also a standalone node, but this time running on your own #Windows, #Mac, or #Linux desktop computer. You should only use this option on a computer you keep always online. This option is completely free, but you are responsible to keep your Alby Hub online, or else you will not be able to send and receive transactions on the go using a mobile wallet connected to your Alby Hub, such as #AlbyGo or nostr:npub1g26qnlumycdfs538kx4eyur7wpnh0tq5mcjx2nt7qhc9qxehuqpsk4y9fw. Moreover, your only option for a Lightning address is "UserName@getalby.com" and you don't receive priority customer support. As with Alby running in the cloud, since you are not running a full Bitcoin node, my assumption is that Alby Hub is reaching out to Alby's own full node for all on-chain data and for broadcasting channel-opens and closes. ## Docker You can also run Alby Hub on any local device or remote VPS that supports #Docker. This would also be a standalone node, so all the rules of running on your desktop apply. You should only use this option on a device that is online 24/7. ## Start9 & Umbrel Here is where we diverge from Alby Hub being its own standalone node. Instead, Alby Hub is installed on your #Start9 or #Umbrel, which must already be running an instance of LND as the Lightning node. LND, in turn, requires you to be running Bitcoin Core or other compatible Bitcoin implementation. In this case, Alby Hub is acting as an alternative front-end for your existing Lightning node, and giving it extra capabilities. It would be similar to #Thunderhub or Ride-the-Lightning #RTL. In my opinion, so long as you have reliable power and internet service, this is the best option available. Not only will you possess your own keys, but you will be running the software on your own device, dedicated to the task of hosting your Bitcoin software stack, and not your general computing needs. Moreover, Alby Hub will be reaching out to your own Bitcoin full node for all on-chain needs, including broadcasting channel-opens and closes. ## All Versions Now that you have one of the above versions of Alby Hub up and running, with channels open using Alby Hub as a standalone node, or as a front-end for your existing LND node on your Start9 or Umbrel, what can you do with it? What makes it any different than just using #Zeus to connect to your node via #LNDHub or #LightningTerminal? Plenty! At the basic level, the default wallet in Alby Hub will utilize your entire node's outbound liquidity as its balance. You can purchase Lightning channels from liquidity providers very easily, and purchase Bitcoin using a bank transfer or credit card directly within Alby Hub, so you have both inbound and outbound liquidity. For slightly more advanced users, you can also set up custom channels to any peer, so long as you have their node ID. You can then connect various services to have access to this main wallet, such as Nostr clients that support #NostrWalletConnect, or Alby's BuzzPay PoS terminal, or games like Paper Scissors HODL or Zappy Bird, and of course Alby's browser extension or Alby Go mobile wallet. Don't want a service to have unlimited access to your node's balance? You can set it a budget, and even set up an isolated balance for just that single application to have access to. If you connect your wallet with your Alby account, you will gain the benefit of having your Alby Lightning address connected to your Alby Hub wallet, so you can receive zaps directly to your self-custody node. There are a couple ways you can connect your Alby Hub wallet to a mobile wallet app. The first is using LNDHub with Zeus. I found the most success by doing this through my Alby account after connecting it to my Alby Hub wallet. It is my understanding that Zeus is also working on integrating Nostr Wallet Connect, so that will be an even easier option for using it as your mobile wallet. Note, though, this is NOT connecting to your self-custodial Zeus wallet using their node-on-a-phone option, if you have that set up. It is a remote connection to your Alby Hub node where Zeus is just a mobile interface. Your Zeus wallet's self-custodial balance will be entirely separate from your Alby Hub wallet balance, and you must select the wallet balance/node you want to use prior to conducting a transaction. Alby has also released Alby Go, which is a mobile wallet app with a very minimal interface that just works and uses Nostr Wallet Connect rather than LNDHub to connect to your node. Additionally, you can connect your wallet to several Podcasting 2.0 apps, such as nostr:npub1t8cmt7hjnyz0a99x5ppw9kpdsrtglst26aj3aw5s4r0rna3l3l5qk89gm4, #Curiocaster, #Castamatic, #LNBeats, and #PodcastGuru. Hat tip to nostr:npub177fz5zkm87jdmf0we2nz7mm7uc2e7l64uzqrv6rvdrsg8qkrg7yqx0aaq7 for reminding me of this functionality. For those who are fans of #Fountain for podcasts, since it has leaned heavily into #Nostr integration, nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2 has confirmed that nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5 will be receiving Nostr Wallet Connect support in an upcoming update, so you can use your Alby Hub wallet to boost, earn, and stream sats there. nostr:nevent1qvzqqqqqqypzpe8kjhc9hvzmyvf9tnxw84r3hrtece9xt0xvq9rx95nlpalfyyyjqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyghwumn8ghj7mn0wd68ytnhd9hx2tcprpmhxue69uhhyetvv9ujuen0w4h8gctfdchxvmf0qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg3waehxw309ahx7um5wghxcctwvshszrnhwden5te0dehhxtnvdakz7qghwaehxw309a5kucn00qhxummnw3ezuamfdejj7qgewaehxw309akk7mmwvfhkjtnwdaehgu339e3k7mf0qy28wumn8ghj7ctvvahjuat50phjummwv5hsqgy62xzfas5d0mjkmgwquscxykt9540cvtq9k9w9uyea2z7vru8aqv3mpqwc More interestingly, though, you can set up "Friends & Family" wallets that are separate from your main node balance and start with their own balance of 0 sats. Each of these wallet balances are tracked separately, though they use your node's liquidity for transacting. This is similar to setting up individual wallets within a tool like #LNBits or Lightning Terminal. However, I find that these wallets are far easier to set up and more versatile. Moreover, they can be connected to all of the same services previously mentioned via Nostr Wallet Connect, and they can each be connected with a separate Alby account so that each wallet has its own Lightning address, without having to own a domain and set up reverse proxies or any of the more technical aspects of setting up Lightning addresses for LNBits wallets. This, in my opinion, is the "killer feature" of Alby Hub. It enables anyone who runs any of the above versions to quickly and easily be an Uncle Jim for their family, who have no interest in learning how to set up self-custody wallets. The only thing you need to do is make sure your Lightning node always has enough outbound liquidity to cover their balances. If you fractionally reserve your own family members, you deserve what's coming to you. ## Conclusion So, what do you think? Is Alby Hub a good fit for your use case? If you don't really want to run a Lightning node and manage your own liquidity, it may not be a good fit, and you can check out some creat custodial options, such as nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch, nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq, or nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. For those of us who are willing to get our hands dirty for the sake of holding our own keys, then running a node in some sense is always going to be required, and that comes with the responsibility of managing liquidity. This is true for all of the good self-custody options available out there, such as nostr:npub148qm45zettnf6ekgkatnyfadunxwjpu8sy88mjdsgwc5f202d93qmejra7 or Zeus' Olympus node-on-a-phone option. Alby Hub, however, may just be the most feature-rich and user-friendly option that falls somewhere in the middle of running a full Bitcoin + Lightning node or running a node-on-a-phone option that often suffers from not being online 24/7 for receiving. At any rate, name another self-custodial Lightning option that you can connect to so many other applications using Nostr Wallet Connect. I'll wait.
@ b7274d28:c99628cb
2024-11-17 04:38:20There seems to be a bit of confusion going around about exactly what #AlbyHub is, and what it does, what use-cases it does and does not fit into. As someone who is using #Alby Hub on a daily basis and have been quite happy with it, I thought I might be able to shed some light on the matter from the perspective of a user. nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, please correct me if I get anything wrong in this article. Note: I am not in any way affiliated with Alby, except by being a satisfied user of their software, and have not been paid to write this article. I can understand the confusion surrounding Alby Hub, because it is not just one thing that works the same for all users of the product. There are various different ways you can have it set up, and while the end result is mostly the same functionality, the steps to get there are different for each version. There is the cloud (someone else's computer) version, the desktop version, the docker version, and the node (nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll or nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct) package version. In some of these versions, Alby Hub is acting as a standalone Lightning node, and in others it is merely a front-end that gives your existing node additional features, such as segregated wallets, but you must have an #LND instance already established that it is running alongside. ## Cloud This service is a standalone Lightning node running in the cloud and online 24/7. For that reason, it can be very attractive to users who may not be able to run their own node at home, or who do not have reliable power or internet services. It is still considered self-custodial, even though it is running on Alby's servers, because you hold your own keys. Since this version of Alby Hub is a standalone Lightning node, this means that all of your channel setup and liquidity is managed inside of your cloud-hosted Alby Hub. My assumption is that this Lightning node is reaching out to a #Bitcoin full node that Alby runs for all on-chain data and broadcasting channel-opens and closes. At the time of writing, the cost for this cloud-hosted node is 21,000 sats a month. You get some additional features by paying for this service that other versions of Alby Hub lack, though. You can have a custom Lightning address, instead of just an "UserName@getalby.com" address. You also get priority customer support with an in-app live chat, and access to the "Buzz" community that other users of Alby Hub do not get access to. There are other options for a cloud-hosted Alby Hub other than directly from Alby, as well. For instance, you can host your Alby Hub on nostr:npub1g26qnlumycdfs538kx4eyur7wpnh0tq5mcjx2nt7qhc9qxehuqpsk4y9fw or Render. These alternative hosting options may have a lower cost associated with them, but you will not have access to the additional features, such as a custom Lightning address or priority customer support. ## Desktop The desktop client is also a standalone node, but this time running on your own #Windows, #Mac, or #Linux desktop computer. You should only use this option on a computer you keep always online. This option is completely free, but you are responsible to keep your Alby Hub online, or else you will not be able to send and receive transactions on the go using a mobile wallet connected to your Alby Hub, such as #AlbyGo or nostr:npub1g26qnlumycdfs538kx4eyur7wpnh0tq5mcjx2nt7qhc9qxehuqpsk4y9fw. Moreover, your only option for a Lightning address is "UserName@getalby.com" and you don't receive priority customer support. As with Alby running in the cloud, since you are not running a full Bitcoin node, my assumption is that Alby Hub is reaching out to Alby's own full node for all on-chain data and for broadcasting channel-opens and closes. ## Docker You can also run Alby Hub on any local device or remote VPS that supports #Docker. This would also be a standalone node, so all the rules of running on your desktop apply. You should only use this option on a device that is online 24/7. ## Start9 & Umbrel Here is where we diverge from Alby Hub being its own standalone node. Instead, Alby Hub is installed on your #Start9 or #Umbrel, which must already be running an instance of LND as the Lightning node. LND, in turn, requires you to be running Bitcoin Core or other compatible Bitcoin implementation. In this case, Alby Hub is acting as an alternative front-end for your existing Lightning node, and giving it extra capabilities. It would be similar to #Thunderhub or Ride-the-Lightning #RTL. In my opinion, so long as you have reliable power and internet service, this is the best option available. Not only will you possess your own keys, but you will be running the software on your own device, dedicated to the task of hosting your Bitcoin software stack, and not your general computing needs. Moreover, Alby Hub will be reaching out to your own Bitcoin full node for all on-chain needs, including broadcasting channel-opens and closes. ## All Versions Now that you have one of the above versions of Alby Hub up and running, with channels open using Alby Hub as a standalone node, or as a front-end for your existing LND node on your Start9 or Umbrel, what can you do with it? What makes it any different than just using #Zeus to connect to your node via #LNDHub or #LightningTerminal? Plenty! At the basic level, the default wallet in Alby Hub will utilize your entire node's outbound liquidity as its balance. You can purchase Lightning channels from liquidity providers very easily, and purchase Bitcoin using a bank transfer or credit card directly within Alby Hub, so you have both inbound and outbound liquidity. For slightly more advanced users, you can also set up custom channels to any peer, so long as you have their node ID. You can then connect various services to have access to this main wallet, such as Nostr clients that support #NostrWalletConnect, or Alby's BuzzPay PoS terminal, or games like Paper Scissors HODL or Zappy Bird, and of course Alby's browser extension or Alby Go mobile wallet. Don't want a service to have unlimited access to your node's balance? You can set it a budget, and even set up an isolated balance for just that single application to have access to. If you connect your wallet with your Alby account, you will gain the benefit of having your Alby Lightning address connected to your Alby Hub wallet, so you can receive zaps directly to your self-custody node. There are a couple ways you can connect your Alby Hub wallet to a mobile wallet app. The first is using LNDHub with Zeus. I found the most success by doing this through my Alby account after connecting it to my Alby Hub wallet. It is my understanding that Zeus is also working on integrating Nostr Wallet Connect, so that will be an even easier option for using it as your mobile wallet. Note, though, this is NOT connecting to your self-custodial Zeus wallet using their node-on-a-phone option, if you have that set up. It is a remote connection to your Alby Hub node where Zeus is just a mobile interface. Your Zeus wallet's self-custodial balance will be entirely separate from your Alby Hub wallet balance, and you must select the wallet balance/node you want to use prior to conducting a transaction. Alby has also released Alby Go, which is a mobile wallet app with a very minimal interface that just works and uses Nostr Wallet Connect rather than LNDHub to connect to your node. Additionally, you can connect your wallet to several Podcasting 2.0 apps, such as nostr:npub1t8cmt7hjnyz0a99x5ppw9kpdsrtglst26aj3aw5s4r0rna3l3l5qk89gm4, #Curiocaster, #Castamatic, #LNBeats, and #PodcastGuru. Hat tip to nostr:npub177fz5zkm87jdmf0we2nz7mm7uc2e7l64uzqrv6rvdrsg8qkrg7yqx0aaq7 for reminding me of this functionality. For those who are fans of #Fountain for podcasts, since it has leaned heavily into #Nostr integration, nostr:npub1unmftuzmkpdjxyj4en8r63cm34uuvjn9hnxqz3nz6fls7l5jzzfqtvd0j2 has confirmed that nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5 will be receiving Nostr Wallet Connect support in an upcoming update, so you can use your Alby Hub wallet to boost, earn, and stream sats there. nostr:nevent1qvzqqqqqqypzpe8kjhc9hvzmyvf9tnxw84r3hrtece9xt0xvq9rx95nlpalfyyyjqythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyghwumn8ghj7mn0wd68ytnhd9hx2tcprpmhxue69uhhyetvv9ujuen0w4h8gctfdchxvmf0qythwumn8ghj7un9d3shjtnswf5k6ctv9ehx2ap0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg3waehxw309ahx7um5wghxcctwvshszrnhwden5te0dehhxtnvdakz7qghwaehxw309a5kucn00qhxummnw3ezuamfdejj7qgewaehxw309akk7mmwvfhkjtnwdaehgu339e3k7mf0qy28wumn8ghj7ctvvahjuat50phjummwv5hsqgy62xzfas5d0mjkmgwquscxykt9540cvtq9k9w9uyea2z7vru8aqv3mpqwc More interestingly, though, you can set up "Friends & Family" wallets that are separate from your main node balance and start with their own balance of 0 sats. Each of these wallet balances are tracked separately, though they use your node's liquidity for transacting. This is similar to setting up individual wallets within a tool like #LNBits or Lightning Terminal. However, I find that these wallets are far easier to set up and more versatile. Moreover, they can be connected to all of the same services previously mentioned via Nostr Wallet Connect, and they can each be connected with a separate Alby account so that each wallet has its own Lightning address, without having to own a domain and set up reverse proxies or any of the more technical aspects of setting up Lightning addresses for LNBits wallets. This, in my opinion, is the "killer feature" of Alby Hub. It enables anyone who runs any of the above versions to quickly and easily be an Uncle Jim for their family, who have no interest in learning how to set up self-custody wallets. The only thing you need to do is make sure your Lightning node always has enough outbound liquidity to cover their balances. If you fractionally reserve your own family members, you deserve what's coming to you. ## Conclusion So, what do you think? Is Alby Hub a good fit for your use case? If you don't really want to run a Lightning node and manage your own liquidity, it may not be a good fit, and you can check out some creat custodial options, such as nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch, nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq, or nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. For those of us who are willing to get our hands dirty for the sake of holding our own keys, then running a node in some sense is always going to be required, and that comes with the responsibility of managing liquidity. This is true for all of the good self-custody options available out there, such as nostr:npub148qm45zettnf6ekgkatnyfadunxwjpu8sy88mjdsgwc5f202d93qmejra7 or Zeus' Olympus node-on-a-phone option. Alby Hub, however, may just be the most feature-rich and user-friendly option that falls somewhere in the middle of running a full Bitcoin + Lightning node or running a node-on-a-phone option that often suffers from not being online 24/7 for receiving. At any rate, name another self-custodial Lightning option that you can connect to so many other applications using Nostr Wallet Connect. I'll wait. @ 599f67f7:21fb3ea9
2024-10-26 11:22:06# Zer da Cashu? Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu. ## eNuts eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du. ⚠️ **eNuts eta Cashu oraindik beta fasean daude**. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu. ## Probatu Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu. ### Instalatu Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako. ### Mint bat gehitzea Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu. 1. Joan Txoko Mint-era. Kopiatu mint URL-a. 2. eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a. 💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera. ### Tokenak sortzea Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun. 1. Erantzun **Bai**. 2. Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats. 3. Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu. Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu. ### Ecash-ekin transakzioak egitea Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari. 1. Ecash bidaltzeko, sakatu **Bidali > Ecash bidali**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu **Kopiatu eta partekatu**. 3. Aukeratu zenbatekoa. 4. Nahi izanez gero, gehitu ohar bat, eta sakatu **Jarraitu**. 5. Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, **coin selection** funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko. Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu. 6. Kopiatu token-a. Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu. 1. Ecash jasotzeko, sakatu **Jaso > Itsatsi eta berreskuratu Ecash**. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du. 💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu **Egiaztatu token-a gastatu den**. Token-a zain badago, **Itzuli token-a** sakatu dezakezu eta berriro zure zorroan izango duzu. ### Multimint trukeak Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean. Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia. 💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz. 1. Joan **Aukerak > Mint kudeaketa** atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan **Multimint trukeak** atalean. 2. Aukeratu trukatu nahi duzun mint-a. 3. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi** Lightning gastuen kalkulua egiteko. 4. Sakatu **Jarraitu**. 5. Egiaztatu xehetasunak, eta nahi izanez gero, **coin selection** funtzioa erabili. Ondoren, sakatu **Orain trukatu**. Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean. ### Ateratzea Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da: 1. Sakatu **Bidali > Lightning faktura ordaindu**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a. 3. LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu. 4. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi**. 5. Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu **Ateratzea**. Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du. ### Segurtasun kopiak Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean. eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du. - **Segurtasun-kopia bat sortzeko**, joan Aukerak > **Segurtasuna > Sortu babeskopia token**. Kopiatu token-a eta gorde toki seguru batean. Bestela, mint bakoitza banaka babestu dezakezu: - Horretarako, joan Aukerak > **Mint kudeaketa** atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu **Funtseak babestu**, kopiatu token-a eta gorde toki seguru batean. ### Berreskuratzea Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun. ### Nostr eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu: 1. Joan **Kontaktuak** atalera eta itsatsi zure Nostr gako publikoa. 2. eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero. Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du. ## Ondorioa Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez!
@ 599f67f7:21fb3ea9
2024-10-26 11:22:06# Zer da Cashu? Cashu Bitcoin-erako ecash protokolo ireki bat da, transakzio azkarrak eta komisio gabekoak eskaintzen dituena, pribatutasun ia perfektuarekin. Xehetasun gehiago nahi izanez gero, gure azalpena ikus dezakezu. ## eNuts eNuts Cashu-rako mugikorretarako zorro bikaina da, Android eta iOS (TestFlight) plataformetan eskuragarri dagoena. Mint anitzekin lan egitea ahalbidetzen du eta nostr bidez bidalketak egiteko aukera ere eskaintzen du. ⚠️ **eNuts eta Cashu oraindik beta fasean daude**. Funtsak galtzeko arriskua dago. Aplikazioa instalatzerakoan arriskuen inguruan irakurri. Galera ekonomikoei aurre egiteko gai zaren zenbateko txikiekin saiatu. ## Probatu Prozesu honetan zehar mint-ekin elkarreragin, ecash-a jaso eta bidali, segurtasun-kopiak egin, Lightning-era ateratzeak eta mint-en artean trukaketak egingo ditugu. Azkenik, nostr kontaktu funtzionalitatea probatuko dugu. ### Instalatu Sartu eNuts webgunera eta instalatu aplikazioa zure sistema eragilerako. ### Mint bat gehitzea Ecash-arekin elkarreragiteko, lehenik mint bat behar duzu. Mint honetan zure ecash token-ak sortzen eta itzultzen dira. Mint-a da zure Bitcoin-en zaindaria, baina ez daki nor zaren, norekin egiten duzun transakzioa, ezta zenbat diru duzun ere. Probetarako Txoko mint erabili dezakezu. 1. Joan Txoko Mint-era. Kopiatu mint URL-a. 2. eNuts-en, joan Aukerak > Mint kudeaketa eta sakatu + botoia. Itsatsi lehen urratsean kopiatu duzun mint URL-a. 💡 Mint gehigarriak ere gehitu ditzakezu. Mint publiko batzuk MintIndex-en aurki daitezke. Kontuan izan mint batzuek zenbateko jakin bat gordetzen dutela bideratze-gastuak ordaintzeko, eta, beraz, ezin dituzula zure sats guztiak atera. ### Tokenak sortzea Mint bat gehitu duzunean, eNuts-ek automatikoki galdetuko dizu mint horretatik Cashu token berriak sortu nahi dituzun. 1. Erantzun **Bai**. 2. Sortu faktura bat mintu nahi duzun zenbatekoarentzat. Zenbateko txiki batekin saiatu, adibidez, 100 sats. 3. Ordaindu faktura Lightning zorro batetik. Faktura ordaindutakoan, ecash token-ak izango dituzu. Prozesu honek aukera ematen dizu ecash token-ak sortzeko, eta horiek zure transakzioetarako erabiltzeko prest izango dituzu. ### Ecash-ekin transakzioak egitea Ecash-ekin transakzioak egitea, funtsean, datu multzoak bidaltzea eta jasotzea da. Funtzionalitate hauek zuk zeuk probatzeko, bidali eta jaso dezakezu zure buruari. 1. Ecash bidaltzeko, sakatu **Bidali > Ecash bidali**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidali nahi duzun mint-a. Ondoren, aukeratu **Kopiatu eta partekatu**. 3. Aukeratu zenbatekoa. 4. Nahi izanez gero, gehitu ohar bat, eta sakatu **Jarraitu**. 5. Berretsi ordainketa xehetasunak eta sortu token-a. Une honetan, **coin selection** funtzioa erabil dezakezu zein token erabili nahi dituzun hautatzeko. Ohartu token-ak 1 sat, 2 sats, 4 sats, 8 sats, 16 sats eta antzeko zenbatekotan sailkatuta daudela. Horiek 10 euroko, 20 euroko edo 50 euroko billeteak bezala irudika ditzakezu. 6. Kopiatu token-a. Une honetan, token-a beste norbaiti bidal diezaiokezu edo zure zorroan berreskuratu. Saiakera moduan, bigarren aukera hau egingo dugu. 1. Ecash jasotzeko, sakatu **Jaso > Itsatsi eta berreskuratu Ecash**. eNuts-ek automatikoki irakurriko du zure arbeletik eta token-a berreskuratuko du. 💡 Zure transakzioen historian ecash token-a zain dagoen egiaztatu dezakezu, eta hartzaileak ez badu berreskuratu, itzuli dezakezu. Horretarako, sakatu zure historiako irteerako transakzioan eta aukeratu **Egiaztatu token-a gastatu den**. Token-a zain badago, **Itzuli token-a** sakatu dezakezu eta berriro zure zorroan izango duzu. ### Multimint trukeak Mint desberdinen artean bidalketak eta jasotzeak posibleak diren galdetu baduzu, erantzuna bai da, neurri batean. Hala ere, Cashu token-ak zuzenean mint batetik bestera bidaltzea ez da zuzenean egiten; horren ordez, transakzioak Lightning-era bideratzen dira, mint bat Lightning nodo bat ere badelako. Cashu token-ak ez dira bateragarriak nodo desberdinen artean. Hau probatzeko, beste mint bat gehitu dezakezu oraindik egin ez baduzu, adibidez, cashme LNbits mint edo eNuts mint lehenetsia. 💡 Kontuan izan mint batzuek sats kopuru bat gordetzen dutela bideratze-gastuak ordaintzeko. Arazo hau konpontzeko, zure mint propioa sor dezakezu Bitcoin Txoko LNbits zorroarekin, Cashu luzapena aktibatuz. 1. Joan **Aukerak > Mint kudeaketa** atalera, eta aukeratu trukatu nahi duzun mint-a. Ondoren, joan **Multimint trukeak** atalean. 2. Aukeratu trukatu nahi duzun mint-a. 3. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi** Lightning gastuen kalkulua egiteko. 4. Sakatu **Jarraitu**. 5. Egiaztatu xehetasunak, eta nahi izanez gero, **coin selection** funtzioa erabili. Ondoren, sakatu **Orain trukatu**. Prozesu honetan, bidaltzen ari den mint-ak Lightning faktura bat ordaintzen du jasotzen ari den mint-aren bidez. Faktura osatu bezain laster, trukatuta dagoen token-a zure zorroaren saldoan agertu beharko litzateke jasotzen ari den mint-ean. ### Ateratzea Zure Cashu sats-ak berriro Lightning sats bihurtu nahi dituzunean, ateratzeko aukera duzu. Prozesua hauxe da: 1. Sakatu **Bidali > Lightning faktura ordaindu**. 2. Mint bat baino gehiago erabiltzen baduzu, aukeratu bidaliko duzun mint-a. 3. LN faktura edo LNURL atalean, sartu faktura bat, LNURL edo Lightning helbide bat; edo, besterik gabe, QR kode bat eskaneatu. 4. Aukeratu zenbatekoa eta sakatu **Kuotak aurreikusi**. 5. Egiaztatu xehetasunak, eta dena zuzen dagoela ikusi ondoren, sakatu **Ateratzea**. Prozesu hau amaitutakoan, mint-ak Cashu token-ak trukatzen ditu eta Lightning faktura ordaintzen du. ### Segurtasun kopiak Cashu token-ak babesteko prozesua, agian, ezberdina izango da Bitcoin eta Lightning zorroak babesteko ohiko prozesuekin alderatuta. Diru-funtsak datu blokeekin irudikatzen direnez, Cashu token-ak babesten dituzunean datu bloke horiek bakarrik babesten ari zara. Honek esan nahi du segurtasun-kopiak baliogabetzen direla transakzio berri bat egiten duzun bakoitzean. eNuts aplikazioak Cashu token bat sortzen du zure funts guztiekin, eta token horiek zein mint-ekoak diren jasotzen du. - **Segurtasun-kopia bat sortzeko**, joan Aukerak > **Segurtasuna > Sortu babeskopia token**. Kopiatu token-a eta gorde toki seguru batean. Bestela, mint bakoitza banaka babestu dezakezu: - Horretarako, joan Aukerak > **Mint kudeaketa** atalera eta aukeratu babestu nahi duzun mint-a. Ondoren, sakatu **Funtseak babestu**, kopiatu token-a eta gorde toki seguru batean. ### Berreskuratzea Berreskuratzeko, kopiatu babeskopia token-a eta ireki eNuts aplikazioa. Aplikazioak automatikoki irakurriko du zure arbelean dagoena eta galdetuko dizu token-a berreskuratu nahi duzun. ### Nostr eNuts aplikazioak Nostr integrazioa eskaintzen du, horrela zure kontaktu zerrendara ecash bidali ahal izateko. Funtzio hau erabiltzeko, honako pauso hauek jarraitu behar dituzu: 1. Joan **Kontaktuak** atalera eta itsatsi zure Nostr gako publikoa. 2. eNuts-ek zure kontaktu zerrenda eskuratuko du relays-etatik. Tamalez, bilaketa funtzioa oraindik ez dago eskuragarri, eta horrek kontaktu zuzena aurkitzea zaildu dezake, kontaktu asko izanez gero. Hartzaileak Nostr motako 4 mezu zuzena jasoko du, Cashu token-arekin. Hartzaileak mezu hau bere zorroan berreskuratu eta token-a erabili ahal izango du. ## Ondorioa Gida hau lagungarria iruditu zaizu? Saiatu Cashu token batzuk bidaltzen Nostr bidez! @ 1cb14ab3:95d52462
2024-11-17 00:57:41## Chef's notes I have been making this every Thanksgiving since I first tried it. One of my all time favorites. You can fry the shallots and refrigerate the night before to save time. Recipe is credit of The Pioneer Woman -- Go show some love below ⬇️ https://www.thepioneerwoman.com/food-cooking/recipes/a80624/thanksgiving-dinner-green-bean-casserole/ ## Details - ⏲️ Prep time: 35 min - 🍳 Cook time: 1 hr 30 min - 🍽️ Servings: 10 ## Ingredients - *FOR THE FRIED SHALLOTS* - 1/3 c. all-purpose flour - 1/2 tsp. cayenne - 1/2 tsp. garlic powder - 1/4 tsp. kosher salt - 1/4 tsp. black pepper - 4 large shallots, peeled and thinly sliced into rings - frying oil - *FOR THE GREEN BEANS AND GRAVY* - 2 1/2 lb. fresh green beans, trimmed and halved (use a little less if you like gravy to beans ratio) - 8 oz. bacon - 6 tbsp. unsalted butter, divided - 16 oz. sliced button mushrooms (for more mushroom flavor, use cremini variety) - 1/3 c. finely chopped shallots - 3 cloves (large) garlic, minced - 1/2 c. all-purpose flour - 1 c. low sodium chicken stock - 2 c. half-and-half - 2 tbsp. soy sauce - 1 tbsp. Worcestershire sauce - 2/3 c. grated parmesan cheese - 2 tsp. chopped fresh rosemary - 2 tsp. chopped fresh thyme - Kosher salt and freshly ground black pepper, to taste ## Directions 1. *FOR THE FRIED SHALLOTS* 2. In a medium bowl that has a lid, whisk together flour, cayenne, garlic powder, salt, and black pepper. Add sliced shallots. Place lid tightly on bowl and shake the bowl a few times to evenly coat shallots with flour mixture. 3. Pour canola oil into a medium saucepan to a 1-inch depth and place over medium-high heat. Heat to 325°F, using a deep-frying thermometer. Fry shallots in batches until golden brown and lightly crispy. Take care to not let them get too dark, as they will also bake for a bit in the oven on top of the casserole. This should take about 3–5 minutes per batch. Transfer to a paper towel lined baking sheet. Sprinkle lightly with kosher salt and set aside. 4. *FOR THE GREEN BEANS AND GRAVY* 5. Preheat oven to 375° F. 6. Bring a large pot of salted water to a boil and add green beans. Cook beans for 2–3 minutes, until bright green in color and tender crisp. Drain beans and pour into a large bowl of ice water to stop from cooking. Drain again and set aside. 7. In an extra large skillet with tall sides, over medium to medium-high heat, fry bacon until chewy-crisp. Transfer bacon from skillet to a paper towel lined plate to drain and cool. Once bacon has cooled, roughly chop and set aside. 8. Discard all but 2 tablespoons of the bacon fat from the skillet. Return skillet to stove top over medium heat. Add 2 tablespoons of the butter to the skillet. Once butter is melted, add the mushrooms and stir to incorporate. Cook, stirring regularly, until mushrooms are softened. Add chopped shallots and garlic, stirring to incorporate. Cook for another 2–3 minutes, until garlic is fragrant. 9. Now slide everything in the skillet to one side. Add remaining 4 tablespoons of butter to other side of skillet. When the butter is melted, sprinkle the flour over the butter, whisking all the while. A flat whisk works awesome here. Draw in as much liquid as you can, into the flour. The mixture will be very thick. Let it cook for one minute, until slightly browned and fragrant. Slowly whisk in chicken stock until flour mixture is smooth. Then whisk in the half and half. Now bring the entire contents of the skillet together, scraping the bottom of the skillet, and folding to incorporate. Turn heat up to medium-high and cook until thickened and bubbly, about 4–5 minutes, stirring periodically. 10. Remove skillet from heat. Stir in soy sauce and Worcestershire sauce. Then sprinkle Parmesan, rosemary, and thyme over the top and stir to combine. Now is the time to taste test and add more salt and pepper, if desired. I usually add about 1/2 teaspoon of salt and 1/4 teaspoon of black pepper at this point. Fold in blanched green beans. Transfer mixture to a baking dish and place in oven to bake for 30 minutes. Remove casserole from oven and arrange fried shallots and chopped bacon over the top, leaving green beans exposed around the perimeter of the dish. Place in oven and bake for another 5 to 10 minutes, or until edges of casserole are bubbling and the top is golden. Remove from oven and let rest for a few minutes before serving.
@ 1cb14ab3:95d52462
2024-11-17 00:57:41## Chef's notes I have been making this every Thanksgiving since I first tried it. One of my all time favorites. You can fry the shallots and refrigerate the night before to save time. Recipe is credit of The Pioneer Woman -- Go show some love below ⬇️ https://www.thepioneerwoman.com/food-cooking/recipes/a80624/thanksgiving-dinner-green-bean-casserole/ ## Details - ⏲️ Prep time: 35 min - 🍳 Cook time: 1 hr 30 min - 🍽️ Servings: 10 ## Ingredients - *FOR THE FRIED SHALLOTS* - 1/3 c. all-purpose flour - 1/2 tsp. cayenne - 1/2 tsp. garlic powder - 1/4 tsp. kosher salt - 1/4 tsp. black pepper - 4 large shallots, peeled and thinly sliced into rings - frying oil - *FOR THE GREEN BEANS AND GRAVY* - 2 1/2 lb. fresh green beans, trimmed and halved (use a little less if you like gravy to beans ratio) - 8 oz. bacon - 6 tbsp. unsalted butter, divided - 16 oz. sliced button mushrooms (for more mushroom flavor, use cremini variety) - 1/3 c. finely chopped shallots - 3 cloves (large) garlic, minced - 1/2 c. all-purpose flour - 1 c. low sodium chicken stock - 2 c. half-and-half - 2 tbsp. soy sauce - 1 tbsp. Worcestershire sauce - 2/3 c. grated parmesan cheese - 2 tsp. chopped fresh rosemary - 2 tsp. chopped fresh thyme - Kosher salt and freshly ground black pepper, to taste ## Directions 1. *FOR THE FRIED SHALLOTS* 2. In a medium bowl that has a lid, whisk together flour, cayenne, garlic powder, salt, and black pepper. Add sliced shallots. Place lid tightly on bowl and shake the bowl a few times to evenly coat shallots with flour mixture. 3. Pour canola oil into a medium saucepan to a 1-inch depth and place over medium-high heat. Heat to 325°F, using a deep-frying thermometer. Fry shallots in batches until golden brown and lightly crispy. Take care to not let them get too dark, as they will also bake for a bit in the oven on top of the casserole. This should take about 3–5 minutes per batch. Transfer to a paper towel lined baking sheet. Sprinkle lightly with kosher salt and set aside. 4. *FOR THE GREEN BEANS AND GRAVY* 5. Preheat oven to 375° F. 6. Bring a large pot of salted water to a boil and add green beans. Cook beans for 2–3 minutes, until bright green in color and tender crisp. Drain beans and pour into a large bowl of ice water to stop from cooking. Drain again and set aside. 7. In an extra large skillet with tall sides, over medium to medium-high heat, fry bacon until chewy-crisp. Transfer bacon from skillet to a paper towel lined plate to drain and cool. Once bacon has cooled, roughly chop and set aside. 8. Discard all but 2 tablespoons of the bacon fat from the skillet. Return skillet to stove top over medium heat. Add 2 tablespoons of the butter to the skillet. Once butter is melted, add the mushrooms and stir to incorporate. Cook, stirring regularly, until mushrooms are softened. Add chopped shallots and garlic, stirring to incorporate. Cook for another 2–3 minutes, until garlic is fragrant. 9. Now slide everything in the skillet to one side. Add remaining 4 tablespoons of butter to other side of skillet. When the butter is melted, sprinkle the flour over the butter, whisking all the while. A flat whisk works awesome here. Draw in as much liquid as you can, into the flour. The mixture will be very thick. Let it cook for one minute, until slightly browned and fragrant. Slowly whisk in chicken stock until flour mixture is smooth. Then whisk in the half and half. Now bring the entire contents of the skillet together, scraping the bottom of the skillet, and folding to incorporate. Turn heat up to medium-high and cook until thickened and bubbly, about 4–5 minutes, stirring periodically. 10. Remove skillet from heat. Stir in soy sauce and Worcestershire sauce. Then sprinkle Parmesan, rosemary, and thyme over the top and stir to combine. Now is the time to taste test and add more salt and pepper, if desired. I usually add about 1/2 teaspoon of salt and 1/4 teaspoon of black pepper at this point. Fold in blanched green beans. Transfer mixture to a baking dish and place in oven to bake for 30 minutes. Remove casserole from oven and arrange fried shallots and chopped bacon over the top, leaving green beans exposed around the perimeter of the dish. Place in oven and bake for another 5 to 10 minutes, or until edges of casserole are bubbling and the top is golden. Remove from oven and let rest for a few minutes before serving. @ 1cb14ab3:95d52462
2024-11-17 00:38:07## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 20 min - 🍽️ Servings: 4 ## Ingredients - 1 pound shrimp - 1 teaspoon granualted sugar - ½ cup all-purpose flour - ½ cup panko breadcrumbs - 1 teaspoon salt - ½ teaspoon black pepper - ¼ teaspoon garlic powder - ¼ teaspoon onion powder - ¼ teaspoon dried basil - 1 egg - 1 cup milk - 4 – 5 teaspoon chili garlic sauce - 1 teaspoon rice vinegar - ½ cup mayonnaise ## Directions 1. 1. Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. 2. 2. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. 3. 3. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. 4. 4. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. 5. 5. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side.
@ 1cb14ab3:95d52462
2024-11-17 00:38:07## Details - ⏲️ Prep time: 20 min - 🍳 Cook time: 20 min - 🍽️ Servings: 4 ## Ingredients - 1 pound shrimp - 1 teaspoon granualted sugar - ½ cup all-purpose flour - ½ cup panko breadcrumbs - 1 teaspoon salt - ½ teaspoon black pepper - ¼ teaspoon garlic powder - ¼ teaspoon onion powder - ¼ teaspoon dried basil - 1 egg - 1 cup milk - 4 – 5 teaspoon chili garlic sauce - 1 teaspoon rice vinegar - ½ cup mayonnaise ## Directions 1. 1. Make the sauce: Mix mayonnaise, chili garlic sauce, sugar, and rice vinegar in a bowl. Refrigerate. 2. 2. Prepare for frying: a) Combine beaten egg and milk in one bowl. b) Mix flour, panko, and seasonings in another bowl. 3. 3. Bread the shrimp: a) Coat each shrimp in flour mixture. b) Dip in egg mixture. c) Coat again in flour mixture. d) Arrange on a plate and refrigerate for 20 minutes. 4. 4. Fry the shrimp: a) Heat oil to 350F in a dutch oven. b) Fry shrimp for 2-3 minutes until golden. c) Drain on wire rack or paper towels. 5. 5. Serve: a) Coat fried shrimp with ¼ cup sauce. b) Serve with remaining sauce on the side. @ 6734e11d:c7e34e8f
2024-11-17 00:09:30Bereits 2023 entdeckte der Genomforscher Kevin McKernan, dass die mRNA-Impfstoffe von Pfizer/BioNTech DNA-Fragmente enthalten. Nun konnte er in einer Biopsie eines Darmkrebspatienten DNA-Sequenzen (SV40,Ori) des Pfizer-Impfstoffs nachweisen – und das ein Jahr nach der Impfung des Patienten. 👉McKernan (https://anandamide.substack.com/p/sv40-origin-of-replication-in-mammalian) Die hohe Menge an nachgewiesener Impfstoff-DNA lässt darauf schließen, dass sich der Impfstoff nach der Injektion im Körper des Patienten vermehrt haben könnte, so McKernan. Dies würde entweder auf eine Integration in das menschliche Genom oder auf eine unerwartete Replikationsfähigkeit der Impfstoff-DNA hinweisen. https://t.me/DrKayKlapproth https://t.me/initiative_demokratie
@ 6734e11d:c7e34e8f
2024-11-17 00:09:30Bereits 2023 entdeckte der Genomforscher Kevin McKernan, dass die mRNA-Impfstoffe von Pfizer/BioNTech DNA-Fragmente enthalten. Nun konnte er in einer Biopsie eines Darmkrebspatienten DNA-Sequenzen (SV40,Ori) des Pfizer-Impfstoffs nachweisen – und das ein Jahr nach der Impfung des Patienten. 👉McKernan (https://anandamide.substack.com/p/sv40-origin-of-replication-in-mammalian) Die hohe Menge an nachgewiesener Impfstoff-DNA lässt darauf schließen, dass sich der Impfstoff nach der Injektion im Körper des Patienten vermehrt haben könnte, so McKernan. Dies würde entweder auf eine Integration in das menschliche Genom oder auf eine unerwartete Replikationsfähigkeit der Impfstoff-DNA hinweisen. https://t.me/DrKayKlapproth https://t.me/initiative_demokratie @ e1d968f7:5d90f764
2024-11-16 21:47:35It’s funny how nerves can sneak up on you, no matter how prepared you think you are. My first booking wasn’t just about meeting a client—it was about stepping into an entirely new world. I’d rehearsed my outfit, practised my smile, and gone over every detail of what I’d say. But when the moment came, my heart was pounding like I’d just run a marathon. What if I wasn’t what they expected? What if I said something awkward? What if they were rude, or worse, unsafe? The questions spiralled through my mind as I stood outside the hotel room door. But then, I took a deep breath, straightened my shoulders, and knocked. --- ### **That First Meeting** When he opened the door, all the nerves came rushing back. He smiled warmly, offered me a glass of wine, and invited me to sit. I remember thinking, *This is it. I’m really doing this.* It felt surreal, like I was watching myself from the outside. We started talking—small talk at first, about the weather, travel, his work. To my surprise, the conversation flowed easily. Slowly but surely, my nerves began to fade. I realised he was just as human as I was, and I wasn’t alone in feeling a little nervous. --- ### **Breaking the Ice** The key to overcoming those first nerves was connection. He wasn’t just there for physical intimacy; he wanted someone to talk to, someone who made him feel seen and appreciated. That was my first lesson in escorting: people crave connection just as much as, if not more than, the physical side. As we talked, I found myself slipping into the role naturally. I laughed at his jokes, leaned in during the conversation, and mirrored his energy. It wasn’t an act—it was an exchange of energy, a mutual understanding that set both of us at ease. --- ### **The Moment I Found My Confidence** I’ll never forget the moment the nerves disappeared entirely. It wasn’t anything dramatic—just a moment when I saw him relax, his shoulders softening as he smiled. I realised then that I was in control of the situation. My presence had the power to create comfort, excitement, and connection. From that point on, I felt confident. I wasn’t just “playing a part”; I was being myself—an amplified version, perhaps, but still me. --- ### **Lessons From the First Nerves** Looking back, those first nerves were a good thing. They reminded me that this isn’t just a job—it’s stepping into someone’s personal world, even for a short time. It taught me to be present, to listen, and to adapt. Now, when I feel a flicker of nerves before a booking, I welcome it. It means I care about creating a memorable experience. It means I’m alive and still growing in this world. --- Tomorrow, I’ll share a little about the art of first impressions—how to read a client, set the tone, and make every encounter start on the right note. Until then, here’s to the power of stepping through the door, even when your heart is racing. Rebecca x
@ e1d968f7:5d90f764
2024-11-16 21:47:35It’s funny how nerves can sneak up on you, no matter how prepared you think you are. My first booking wasn’t just about meeting a client—it was about stepping into an entirely new world. I’d rehearsed my outfit, practised my smile, and gone over every detail of what I’d say. But when the moment came, my heart was pounding like I’d just run a marathon. What if I wasn’t what they expected? What if I said something awkward? What if they were rude, or worse, unsafe? The questions spiralled through my mind as I stood outside the hotel room door. But then, I took a deep breath, straightened my shoulders, and knocked. --- ### **That First Meeting** When he opened the door, all the nerves came rushing back. He smiled warmly, offered me a glass of wine, and invited me to sit. I remember thinking, *This is it. I’m really doing this.* It felt surreal, like I was watching myself from the outside. We started talking—small talk at first, about the weather, travel, his work. To my surprise, the conversation flowed easily. Slowly but surely, my nerves began to fade. I realised he was just as human as I was, and I wasn’t alone in feeling a little nervous. --- ### **Breaking the Ice** The key to overcoming those first nerves was connection. He wasn’t just there for physical intimacy; he wanted someone to talk to, someone who made him feel seen and appreciated. That was my first lesson in escorting: people crave connection just as much as, if not more than, the physical side. As we talked, I found myself slipping into the role naturally. I laughed at his jokes, leaned in during the conversation, and mirrored his energy. It wasn’t an act—it was an exchange of energy, a mutual understanding that set both of us at ease. --- ### **The Moment I Found My Confidence** I’ll never forget the moment the nerves disappeared entirely. It wasn’t anything dramatic—just a moment when I saw him relax, his shoulders softening as he smiled. I realised then that I was in control of the situation. My presence had the power to create comfort, excitement, and connection. From that point on, I felt confident. I wasn’t just “playing a part”; I was being myself—an amplified version, perhaps, but still me. --- ### **Lessons From the First Nerves** Looking back, those first nerves were a good thing. They reminded me that this isn’t just a job—it’s stepping into someone’s personal world, even for a short time. It taught me to be present, to listen, and to adapt. Now, when I feel a flicker of nerves before a booking, I welcome it. It means I care about creating a memorable experience. It means I’m alive and still growing in this world. --- Tomorrow, I’ll share a little about the art of first impressions—how to read a client, set the tone, and make every encounter start on the right note. Until then, here’s to the power of stepping through the door, even when your heart is racing. Rebecca x @ a79bb203:dde63268
2024-11-16 21:38:18I was quite happy with the result (about 3 hours of work) https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMYNb.jpg Bumblebees symbolize hard work, diligence, and productivity. originally posted at https://stacker.news/items/770779
@ a79bb203:dde63268
2024-11-16 21:38:18I was quite happy with the result (about 3 hours of work) https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FMYNb.jpg Bumblebees symbolize hard work, diligence, and productivity. originally posted at https://stacker.news/items/770779 @ 4fcac000:d2b37988
2024-11-16 20:25:00 1. Вертикальный борщ Это классическое русское блюдо будет адаптировано с использованием свежих овощей, выращенных на городских фермах. Борщ будет приготовлен с добавлением альтернативных белков, таких как бобовые или протеиновые добавки, что сделает его более питательным и полезным. 2. Пельмени с начинкой из насекомых В будущем пельмени могут стать не только вкусным, но и экологически чистым выбором. Начинка из насекомых, таких как сверчки или мучные черви, станет популярной благодаря своему высокому содержанию белка и низкому углеродному следу. 3. Суп из водорослей Этот суп будет приготовлен из местных водорослей, богатых витаминами и минералами. Он станет не только полезным, но и модным блюдом, отражающим устойчивый подход к питанию. 4. Чак-чак с суперфудами Традиционный татарский десерт чак-чак будет адаптирован с добавлением суперфудов, таких как семена чиа или киноа. Это сделает его более питательным и привлекательным для молодежи, стремящейся к здоровому образу жизни. 5. Гречневые блины с начинкой из фермерского творога Блины из гречневой муки, подаваемые с начинкой из свежего творога от местных фермеров и ягодами, станут популярным завтраком в кафе и ресторанах города. 6. Коктейли на основе кваса и трав Напитки на основе кваса с добавлением местных трав и ягод станут освежающим выбором для жителей Тюмени в жаркие дни. Эти коктейли будут не только вкусными, но и полезными. 7. Технологичные десерты Десерты, созданные с использованием 3D-печати, позволят создавать уникальные формы и текстуры. Например, шоколадные фигурки с начинкой из фруктового пюре или крема будут настоящим искусством на тарелке. Такие блюда не только удовлетворяют вкусовые предпочтения жителей, но и помогают сохранить окружающую среду.
@ 4fcac000:d2b37988
2024-11-16 20:25:00 1. Вертикальный борщ Это классическое русское блюдо будет адаптировано с использованием свежих овощей, выращенных на городских фермах. Борщ будет приготовлен с добавлением альтернативных белков, таких как бобовые или протеиновые добавки, что сделает его более питательным и полезным. 2. Пельмени с начинкой из насекомых В будущем пельмени могут стать не только вкусным, но и экологически чистым выбором. Начинка из насекомых, таких как сверчки или мучные черви, станет популярной благодаря своему высокому содержанию белка и низкому углеродному следу. 3. Суп из водорослей Этот суп будет приготовлен из местных водорослей, богатых витаминами и минералами. Он станет не только полезным, но и модным блюдом, отражающим устойчивый подход к питанию. 4. Чак-чак с суперфудами Традиционный татарский десерт чак-чак будет адаптирован с добавлением суперфудов, таких как семена чиа или киноа. Это сделает его более питательным и привлекательным для молодежи, стремящейся к здоровому образу жизни. 5. Гречневые блины с начинкой из фермерского творога Блины из гречневой муки, подаваемые с начинкой из свежего творога от местных фермеров и ягодами, станут популярным завтраком в кафе и ресторанах города. 6. Коктейли на основе кваса и трав Напитки на основе кваса с добавлением местных трав и ягод станут освежающим выбором для жителей Тюмени в жаркие дни. Эти коктейли будут не только вкусными, но и полезными. 7. Технологичные десерты Десерты, созданные с использованием 3D-печати, позволят создавать уникальные формы и текстуры. Например, шоколадные фигурки с начинкой из фруктового пюре или крема будут настоящим искусством на тарелке. Такие блюда не только удовлетворяют вкусовые предпочтения жителей, но и помогают сохранить окружающую среду. @ 5d4b6c8d:8a1c1ee3
2024-11-16 17:07:19We almost all survived! Sorry, @BlokchainB. You took what should have been a very safe Denver team and then neither their very good head coach nor the best player in the world showed up. **Ode to the fallen**: > In peace, may you leave this shore. In love, may you find the next. Safe passage on your travels, until our final journey to the ground. May we meet again. Let's all pour one out for Blok. ---------- # Winners' Recap The Pistons were really trying to get @supercyclone eliminated, but the Raptors were just too pathetic to hold onto the win. Despite putting up almost 50 points in the first quarter, Cleveland let the lowly Bulls back into the game. Ultimately, I doubt @realBitcoinDog was ever particularly concerned that the now 14-0 Cavs would put Chicago away. After seeming to have the game in hand, the Knicks somehow allowed cross-town rival Brooklyn back in the game. Thankfully for @gnilma's wallet, they made two big plays to close out the game. The Magic, sans young star Paolo, clobbered the supposedly contending 76ers. @Carresan really never had to sweat this one. In a game of which I watched not one second, the Hawks defeated the woeful Wizards and secured survival for the rest of us. # Other Notable Games The Jimmy-less Heat put a real whooping on the Pacers, who are looking miserable this season. OKC continues winning, despite having no centers in their rotation. I think 6'3" Lu Dort might be playing center. I caught a little bit of the Lakers, Warriors, and T-Wolves, all of whom looked good in their wins. # Prize Closing in on 50k! originally posted at https://stacker.news/items/770488
@ 5d4b6c8d:8a1c1ee3
2024-11-16 17:07:19We almost all survived! Sorry, @BlokchainB. You took what should have been a very safe Denver team and then neither their very good head coach nor the best player in the world showed up. **Ode to the fallen**: > In peace, may you leave this shore. In love, may you find the next. Safe passage on your travels, until our final journey to the ground. May we meet again. Let's all pour one out for Blok. ---------- # Winners' Recap The Pistons were really trying to get @supercyclone eliminated, but the Raptors were just too pathetic to hold onto the win. Despite putting up almost 50 points in the first quarter, Cleveland let the lowly Bulls back into the game. Ultimately, I doubt @realBitcoinDog was ever particularly concerned that the now 14-0 Cavs would put Chicago away. After seeming to have the game in hand, the Knicks somehow allowed cross-town rival Brooklyn back in the game. Thankfully for @gnilma's wallet, they made two big plays to close out the game. The Magic, sans young star Paolo, clobbered the supposedly contending 76ers. @Carresan really never had to sweat this one. In a game of which I watched not one second, the Hawks defeated the woeful Wizards and secured survival for the rest of us. # Other Notable Games The Jimmy-less Heat put a real whooping on the Pacers, who are looking miserable this season. OKC continues winning, despite having no centers in their rotation. I think 6'3" Lu Dort might be playing center. I caught a little bit of the Lakers, Warriors, and T-Wolves, all of whom looked good in their wins. # Prize Closing in on 50k! originally posted at https://stacker.news/items/770488 @ 4874b840:31b0b8c0
2024-11-16 14:57:37В Зеленоградске продолжается уход за бездомными кошками, а в сквере «Котофейня» поставлены новые домики с подогревом, кормушки и автоматы с кормом. Эти новые меры направлены на улучшение условий жизни уличных животных, которые в холодное время года становятся все более уязвимыми. Домики с подогревом обеспечат кошкам тепло и защиту от зимних морозов, что особенно важно для молодых и больных животных. Кормушки и автоматы с кормом лучше всего подходят жителям и туристам, чтобы легко кормить пушистых жителей сквера. Сотрудница одного из приютов Светлана Логунова, ответственная за уход за кошками в городе, отмечает, что такие инициативы крайне важны для создания комфортной среды для животных. > «Мы стараемся сделать так, чтобы наши кошки чувствовали себя в безопасности и могли получить заботу и уход» , — говорит она. Эти меры не только улучшают жизнь кошек, но и привлекают внимание туристов, которые приезжают в Зеленоградск, чтобы насладиться атмосферой «города кошек». Установка новых домиков и кормушек станет очередным шагом к созданию более заботливой и ответственной среды для бездомных животных. 
@ 4874b840:31b0b8c0
2024-11-16 14:57:37В Зеленоградске продолжается уход за бездомными кошками, а в сквере «Котофейня» поставлены новые домики с подогревом, кормушки и автоматы с кормом. Эти новые меры направлены на улучшение условий жизни уличных животных, которые в холодное время года становятся все более уязвимыми. Домики с подогревом обеспечат кошкам тепло и защиту от зимних морозов, что особенно важно для молодых и больных животных. Кормушки и автоматы с кормом лучше всего подходят жителям и туристам, чтобы легко кормить пушистых жителей сквера. Сотрудница одного из приютов Светлана Логунова, ответственная за уход за кошками в городе, отмечает, что такие инициативы крайне важны для создания комфортной среды для животных. > «Мы стараемся сделать так, чтобы наши кошки чувствовали себя в безопасности и могли получить заботу и уход» , — говорит она. Эти меры не только улучшают жизнь кошек, но и привлекают внимание туристов, которые приезжают в Зеленоградск, чтобы насладиться атмосферой «города кошек». Установка новых домиков и кормушек станет очередным шагом к созданию более заботливой и ответственной среды для бездомных животных.  @ 88dc84f5:c71164f7
2024-11-16 11:03:23The Rise of Bitcoin: Understanding the Revolutionary Cryptocurrency In the world of finance, few terms have generated as much buzz as Bitcoin. This decentralized digital currency has captured the imagination of investors, technologists, and economists alike. But what exactly is Bitcoin, and why has it become such a phenomenon? A Brief History Bitcoin's origins date back to 2008 when an individual or group of individuals, known only by the pseudonym Satoshi Nakamoto, published a whitepaper outlining the concept of a peer-to-peer electronic cash system. The first block of the Bitcoin blockchain, known as the Genesis Block, was mined in January 2009. How Bitcoin Works Bitcoin operates on a decentralized network, meaning no single entity controls it. Transactions are recorded on a public ledger called the blockchain, which ensures transparency and security. Here's a simplified breakdown of the process: 1. Mining: Powerful computers solve complex mathematical problems to validate transactions and create new Bitcoins. 2. Wallets: Users store their Bitcoins in digital wallets, protected by private keys. 3. Transactions: Bitcoins are transferred between wallets using unique addresses. Key Benefits So, what makes Bitcoin so appealing? 1. Decentralization: No government or institution controls Bitcoin. 2. Security: The blockchain ensures tamper-proof transactions. 3. Anonymity: Users can remain pseudonymous. 4. Limited Supply: Only 21 million Bitcoins will ever exist. 5. Accessibility: Anyone with an internet connection can participate. Challenges and Controversies Bitcoin's journey hasn't been without hurdles: 1. Volatility: Price fluctuations have been extreme. 2. Regulation: Governments struggle to classify and regulate Bitcoin. 3. Security Risks: Exchange hacks and wallet thefts have occurred. 4. Environmental Impact: Mining consumes significant energy. The Future of Bitcoin As Bitcoin continues to evolve, we can expect: 1. Mainstream Adoption: Increased acceptance by businesses and institutions. 2. Improved Infrastructure: Enhanced security and user-friendly interfaces. 3. Competition: Emergence of alternative cryptocurrencies (altcoins). Conclusion Bitcoin represents a fundamental shift in how we think about money and financial systems. While challenges persist, its potential to democratize access to financial services and provide an alternative store of value is undeniable. Whether you're a seasoned investor or curious newcomer, understanding Bitcoin is crucial for navigating the rapidly changing financial landscape.
@ 88dc84f5:c71164f7
2024-11-16 11:03:23The Rise of Bitcoin: Understanding the Revolutionary Cryptocurrency In the world of finance, few terms have generated as much buzz as Bitcoin. This decentralized digital currency has captured the imagination of investors, technologists, and economists alike. But what exactly is Bitcoin, and why has it become such a phenomenon? A Brief History Bitcoin's origins date back to 2008 when an individual or group of individuals, known only by the pseudonym Satoshi Nakamoto, published a whitepaper outlining the concept of a peer-to-peer electronic cash system. The first block of the Bitcoin blockchain, known as the Genesis Block, was mined in January 2009. How Bitcoin Works Bitcoin operates on a decentralized network, meaning no single entity controls it. Transactions are recorded on a public ledger called the blockchain, which ensures transparency and security. Here's a simplified breakdown of the process: 1. Mining: Powerful computers solve complex mathematical problems to validate transactions and create new Bitcoins. 2. Wallets: Users store their Bitcoins in digital wallets, protected by private keys. 3. Transactions: Bitcoins are transferred between wallets using unique addresses. Key Benefits So, what makes Bitcoin so appealing? 1. Decentralization: No government or institution controls Bitcoin. 2. Security: The blockchain ensures tamper-proof transactions. 3. Anonymity: Users can remain pseudonymous. 4. Limited Supply: Only 21 million Bitcoins will ever exist. 5. Accessibility: Anyone with an internet connection can participate. Challenges and Controversies Bitcoin's journey hasn't been without hurdles: 1. Volatility: Price fluctuations have been extreme. 2. Regulation: Governments struggle to classify and regulate Bitcoin. 3. Security Risks: Exchange hacks and wallet thefts have occurred. 4. Environmental Impact: Mining consumes significant energy. The Future of Bitcoin As Bitcoin continues to evolve, we can expect: 1. Mainstream Adoption: Increased acceptance by businesses and institutions. 2. Improved Infrastructure: Enhanced security and user-friendly interfaces. 3. Competition: Emergence of alternative cryptocurrencies (altcoins). Conclusion Bitcoin represents a fundamental shift in how we think about money and financial systems. While challenges persist, its potential to democratize access to financial services and provide an alternative store of value is undeniable. Whether you're a seasoned investor or curious newcomer, understanding Bitcoin is crucial for navigating the rapidly changing financial landscape. @ fff19d35:43344a0b
2024-11-16 09:16:00Bitcoin has touched a lot of life so far,Empowering the underprivileged kids, Educating them and giving them opportunities for better future amazing.@YakiHonne thank you for giving me this opportunity to always express my thoughts I love it here ❤️🥰
@ fff19d35:43344a0b
2024-11-16 09:16:00Bitcoin has touched a lot of life so far,Empowering the underprivileged kids, Educating them and giving them opportunities for better future amazing.@YakiHonne thank you for giving me this opportunity to always express my thoughts I love it here ❤️🥰 @ 7ab59492:cbdea708
2024-11-16 07:22:15Метро представляет собой современную транспортную систему с множеством инновационных решений, направленных на улучшение качества жизни горожан 🎨Архитектура и дизайн Современные станции: Станции метро спроектированы с учетом эстетики и функциональности. Появились стеклянные конструкции, естественного освещения и зеленые насаждения, которые создают комфортную атмосферу для пассажиров. - Интерактивные панели с информацией о времени прибытия поездов и навигацией по станциям. ⚡Энергоэффективность: Здания станций оснащены солнечными панелями и системами сбора дождевой воды для снижения потребления ресурсов 🌏Бесконтактные технологии: Пассажиры смогут использовать мобильные приложения для оплаты проезда и получения информации о расписании. Бесконтактные системы входа и выхода из метро сделали процесс более быстрым и удобным. 🌿Экологические инициативы Экологичный транспорт: Внедрение электрических поездов с нулевым ♥уровнем выбросов углерода ⚫Инфраструктура Сеть маршрутов: Метро интегрировано с другими видами общественного транспорта, такими как автобусы и трамваи, что обеспечивает удобные пересадки и улучшает доступность различных районов города. ♥Доступность для всех: Специальные лифты и пандусы на станциях метро 🍏Комфорт пассажиров: внутреннее оформление направлено на создание комфортной среды. Теперь предусмотрены зоны отдыха, а также Wi-Fi на станциях Метро в Благовещенске в 2040 году не просто средство передвижения, а важный элементом городской инфраструктуры, который доступен для всех!
@ 7ab59492:cbdea708
2024-11-16 07:22:15Метро представляет собой современную транспортную систему с множеством инновационных решений, направленных на улучшение качества жизни горожан 🎨Архитектура и дизайн Современные станции: Станции метро спроектированы с учетом эстетики и функциональности. Появились стеклянные конструкции, естественного освещения и зеленые насаждения, которые создают комфортную атмосферу для пассажиров. - Интерактивные панели с информацией о времени прибытия поездов и навигацией по станциям. ⚡Энергоэффективность: Здания станций оснащены солнечными панелями и системами сбора дождевой воды для снижения потребления ресурсов 🌏Бесконтактные технологии: Пассажиры смогут использовать мобильные приложения для оплаты проезда и получения информации о расписании. Бесконтактные системы входа и выхода из метро сделали процесс более быстрым и удобным. 🌿Экологические инициативы Экологичный транспорт: Внедрение электрических поездов с нулевым ♥уровнем выбросов углерода ⚫Инфраструктура Сеть маршрутов: Метро интегрировано с другими видами общественного транспорта, такими как автобусы и трамваи, что обеспечивает удобные пересадки и улучшает доступность различных районов города. ♥Доступность для всех: Специальные лифты и пандусы на станциях метро 🍏Комфорт пассажиров: внутреннее оформление направлено на создание комфортной среды. Теперь предусмотрены зоны отдыха, а также Wi-Fi на станциях Метро в Благовещенске в 2040 году не просто средство передвижения, а важный элементом городской инфраструктуры, который доступен для всех! @ a012dc82:6458a70d
2024-11-16 04:05:23**Table Of Content** - Bhutan's Renewable Energy Advantage - Leveraging Clean Energy for Crypto Mining - Economic Opportunities and Foreign Investment - Addressing Potential Challenges - Environmental Concerns and Sustainability - Conclusion - FAQ In recent years, Bitcoin and other cryptocurrencies have gained tremendous popularity and become a subject of interest for individuals and governments alike. While many countries have approached cryptocurrencies with caution or skepticism, the small Himalayan kingdom of Bhutan has taken a bold step by embracing crypto mining. Bhutan, known for its stunning landscapes and commitment to environmental sustainability, sees an opportunity to harness the power of crypto mining to drive economic growth. This article explores Bhutan's unique approach to Bitcoin mining and the potential benefits and challenges it presents. **Bhutan's Renewable Energy Advantage** Bhutan's decision to venture into crypto mining is strongly linked to its abundant renewable energy resources. The country is known for its hydropower potential, with a significant share of its energy needs met through hydroelectricity. Bhutan's commitment to clean energy aligns well with the energy-intensive nature of crypto mining. The country's surplus electricity production has caught the attention of crypto enthusiasts who seek environmentally friendly mining operations. **Leveraging Clean Energy for Crypto Mining** By capitalizing on its renewable energy advantage, Bhutan aims to attract crypto miners who are conscious of the environmental impact of their operations. With the vast amount of excess electricity available, Bhutan can offer competitive energy prices to attract mining operations that require a significant power supply. This unique proposition positions Bhutan as an attractive destination for sustainable crypto mining. **Economic Opportunities and Foreign Investment** Embracing crypto mining offers Bhutan the potential for significant economic growth and foreign investment. The revenue generated from mining operations can bolster the country's economy, create jobs, and contribute to infrastructure development. As the popularity of cryptocurrencies continues to rise, Bhutan can position itself as a crypto-friendly nation, attracting investment from both domestic and international players in the crypto industry. **Addressing Potential Challenges** While the decision to pursue crypto mining presents several advantages, Bhutan must also address potential challenges. The volatile nature of cryptocurrencies means that mining operations can be subject to market fluctuations. Bhutan will need to carefully manage the risks associated with crypto mining and develop strategies to mitigate potential financial uncertainties. Additionally, the country must ensure that mining activities do not put excessive strain on its power grid, leading to potential disruptions in the energy supply for other sectors. **Environmental Concerns and Sustainability** Given Bhutan's strong commitment to environmental conservation and sustainability, it is crucial to approach crypto mining with caution. The energy-intensive nature of mining can have adverse environmental impacts if not managed properly. Bhutan must establish strict regulations and standards to ensure that mining activities are conducted in an environmentally responsible manner. This may involve implementing energy-efficient mining technologies and monitoring the carbon footprint associated with crypto mining operations. **Conclusion** Bhutan's venture into crypto mining demonstrates its forward-thinking approach and willingness to embrace new technologies. By leveraging its renewable energy resources, the country aims to position itself as a sustainable destination for crypto mining, fostering economic growth and attracting foreign investment. However, Bhutan must strike a careful balance between reaping the benefits of crypto mining and addressing potential challenges, particularly in terms of market volatility, energy management, and environmental sustainability. With proper planning, regulation, and a commitment to sustainability, Bhutan's bet on crypto mining could prove to be a transformative step toward a prosperous future. **FAQ** **What is Bhutan's approach to crypto mining?** Bhutan has embraced crypto mining by leveraging its renewable energy resources, particularly its surplus hydroelectricity. The country aims to attract environmentally conscious miners by offering competitive energy prices and positioning itself as a sustainable destination for crypto mining. **Why is Bhutan interested in crypto mining?** Bhutan sees crypto mining as an opportunity for economic growth, job creation, and foreign investment. By capitalizing on the popularity of cryptocurrencies, the country can generate revenue and contribute to infrastructure development. **What are the potential challenges of crypto mining in Bhutan?** One challenge is the volatile nature of cryptocurrencies, which can subject mining operations to market fluctuations. Bhutan must also ensure that mining activities do not strain its power grid and cause disruptions in energy supply for other sectors. **How will Bhutan address environmental concerns?** Bhutan's commitment to environmental conservation and sustainability means it will establish strict regulations for crypto mining. The country aims to implement energy-efficient mining technologies and monitor the carbon footprint associated with mining operations to minimize environmental impact. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-11-16 04:05:23**Table Of Content** - Bhutan's Renewable Energy Advantage - Leveraging Clean Energy for Crypto Mining - Economic Opportunities and Foreign Investment - Addressing Potential Challenges - Environmental Concerns and Sustainability - Conclusion - FAQ In recent years, Bitcoin and other cryptocurrencies have gained tremendous popularity and become a subject of interest for individuals and governments alike. While many countries have approached cryptocurrencies with caution or skepticism, the small Himalayan kingdom of Bhutan has taken a bold step by embracing crypto mining. Bhutan, known for its stunning landscapes and commitment to environmental sustainability, sees an opportunity to harness the power of crypto mining to drive economic growth. This article explores Bhutan's unique approach to Bitcoin mining and the potential benefits and challenges it presents. **Bhutan's Renewable Energy Advantage** Bhutan's decision to venture into crypto mining is strongly linked to its abundant renewable energy resources. The country is known for its hydropower potential, with a significant share of its energy needs met through hydroelectricity. Bhutan's commitment to clean energy aligns well with the energy-intensive nature of crypto mining. The country's surplus electricity production has caught the attention of crypto enthusiasts who seek environmentally friendly mining operations. **Leveraging Clean Energy for Crypto Mining** By capitalizing on its renewable energy advantage, Bhutan aims to attract crypto miners who are conscious of the environmental impact of their operations. With the vast amount of excess electricity available, Bhutan can offer competitive energy prices to attract mining operations that require a significant power supply. This unique proposition positions Bhutan as an attractive destination for sustainable crypto mining. **Economic Opportunities and Foreign Investment** Embracing crypto mining offers Bhutan the potential for significant economic growth and foreign investment. The revenue generated from mining operations can bolster the country's economy, create jobs, and contribute to infrastructure development. As the popularity of cryptocurrencies continues to rise, Bhutan can position itself as a crypto-friendly nation, attracting investment from both domestic and international players in the crypto industry. **Addressing Potential Challenges** While the decision to pursue crypto mining presents several advantages, Bhutan must also address potential challenges. The volatile nature of cryptocurrencies means that mining operations can be subject to market fluctuations. Bhutan will need to carefully manage the risks associated with crypto mining and develop strategies to mitigate potential financial uncertainties. Additionally, the country must ensure that mining activities do not put excessive strain on its power grid, leading to potential disruptions in the energy supply for other sectors. **Environmental Concerns and Sustainability** Given Bhutan's strong commitment to environmental conservation and sustainability, it is crucial to approach crypto mining with caution. The energy-intensive nature of mining can have adverse environmental impacts if not managed properly. Bhutan must establish strict regulations and standards to ensure that mining activities are conducted in an environmentally responsible manner. This may involve implementing energy-efficient mining technologies and monitoring the carbon footprint associated with crypto mining operations. **Conclusion** Bhutan's venture into crypto mining demonstrates its forward-thinking approach and willingness to embrace new technologies. By leveraging its renewable energy resources, the country aims to position itself as a sustainable destination for crypto mining, fostering economic growth and attracting foreign investment. However, Bhutan must strike a careful balance between reaping the benefits of crypto mining and addressing potential challenges, particularly in terms of market volatility, energy management, and environmental sustainability. With proper planning, regulation, and a commitment to sustainability, Bhutan's bet on crypto mining could prove to be a transformative step toward a prosperous future. **FAQ** **What is Bhutan's approach to crypto mining?** Bhutan has embraced crypto mining by leveraging its renewable energy resources, particularly its surplus hydroelectricity. The country aims to attract environmentally conscious miners by offering competitive energy prices and positioning itself as a sustainable destination for crypto mining. **Why is Bhutan interested in crypto mining?** Bhutan sees crypto mining as an opportunity for economic growth, job creation, and foreign investment. By capitalizing on the popularity of cryptocurrencies, the country can generate revenue and contribute to infrastructure development. **What are the potential challenges of crypto mining in Bhutan?** One challenge is the volatile nature of cryptocurrencies, which can subject mining operations to market fluctuations. Bhutan must also ensure that mining activities do not strain its power grid and cause disruptions in energy supply for other sectors. **How will Bhutan address environmental concerns?** Bhutan's commitment to environmental conservation and sustainability means it will establish strict regulations for crypto mining. The country aims to implement energy-efficient mining technologies and monitor the carbon footprint associated with mining operations to minimize environmental impact. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 5d4b6c8d:8a1c1ee3
2024-11-16 00:24:01I've got Heat-Pacers on and I'm excited about some of the later games. Is anyone else tuning into the second night of the Emirates Cup? originally posted at https://stacker.news/items/769843
@ 5d4b6c8d:8a1c1ee3
2024-11-16 00:24:01I've got Heat-Pacers on and I'm excited about some of the later games. Is anyone else tuning into the second night of the Emirates Cup? originally posted at https://stacker.news/items/769843 @ 19f9afb8:ce50e4d3
2024-11-15 22:05:01## Chef's notes *Make sure you watch your roux closely. It can go from perfect to burnt in a moment. *Top with green onion tops. *Sprinkle a very small amount of file over top. *Andouille sausage is traditional but kielbasa is also a good substitute. ## Details - ⏲️ Prep time: 30 minutes for vegetable prep + ~1 hour for boiling chicken - 🍳 Cook time: ~2 hours - 🍽️ Servings: 8-10 ## Ingredients - 1 large onion - 1 large bell pepper - 2 medium stalks celery - 6-8 cloves garlic - ~3 lbs. bone-in, skin-on chicken; remove skin and set aside to render - ~1.5 lbs andouille sausage, browned - ~1/2 lb. tasso, optional - 2 green onions, chopped and separated - 2 cups okra, cut (frozen or fresh, not canned) - ~1 cup oil (rendered from chicken skins & sausage) - ~1 cup flour - 1-2 bay leaves ## Directions 1. Chop all vegetables and set aside. Render the fats from your chicken skins and sausages. 2. Combine your flour and rendered fats in a cast iron skillet and stir continually over medium –low heat until your roux is chocolate brown. Stir in about 1/4 tsp of flour at this stage and cook until it stops “fizzing”. (This is simply to add to the thickening power of the roux.) 3. While you are cooking your roux, boil your chicken until cooked through, remove from heat and broth, and set aside to cool for deboning . 4. Add your vegetables, roux, deboned chicken, sausage, hot sauce, Worcestershire, and spices/seasonings to your broth. Optional: sauté your vegetables, except okra, before adding to broth. (Only add the bottom portions of the green onion here, reserve the green tops for garnish.) 5. Cook until the okra is soft and no longer slimy, about 2 hours, at a low boil. (med-high heat) 6. Optional: reduce to a simmer about 10 minutes before finished and drop a few eggs to poach in the stew before serving. Do not stir. 7. Serve over rice.
@ 19f9afb8:ce50e4d3
2024-11-15 22:05:01## Chef's notes *Make sure you watch your roux closely. It can go from perfect to burnt in a moment. *Top with green onion tops. *Sprinkle a very small amount of file over top. *Andouille sausage is traditional but kielbasa is also a good substitute. ## Details - ⏲️ Prep time: 30 minutes for vegetable prep + ~1 hour for boiling chicken - 🍳 Cook time: ~2 hours - 🍽️ Servings: 8-10 ## Ingredients - 1 large onion - 1 large bell pepper - 2 medium stalks celery - 6-8 cloves garlic - ~3 lbs. bone-in, skin-on chicken; remove skin and set aside to render - ~1.5 lbs andouille sausage, browned - ~1/2 lb. tasso, optional - 2 green onions, chopped and separated - 2 cups okra, cut (frozen or fresh, not canned) - ~1 cup oil (rendered from chicken skins & sausage) - ~1 cup flour - 1-2 bay leaves ## Directions 1. Chop all vegetables and set aside. Render the fats from your chicken skins and sausages. 2. Combine your flour and rendered fats in a cast iron skillet and stir continually over medium –low heat until your roux is chocolate brown. Stir in about 1/4 tsp of flour at this stage and cook until it stops “fizzing”. (This is simply to add to the thickening power of the roux.) 3. While you are cooking your roux, boil your chicken until cooked through, remove from heat and broth, and set aside to cool for deboning . 4. Add your vegetables, roux, deboned chicken, sausage, hot sauce, Worcestershire, and spices/seasonings to your broth. Optional: sauté your vegetables, except okra, before adding to broth. (Only add the bottom portions of the green onion here, reserve the green tops for garnish.) 5. Cook until the okra is soft and no longer slimy, about 2 hours, at a low boil. (med-high heat) 6. Optional: reduce to a simmer about 10 minutes before finished and drop a few eggs to poach in the stew before serving. Do not stir. 7. Serve over rice. @ f33c8a96:5ec6f741
2024-11-15 21:45:12# Voltage Tipper ⚡ A Simple Lightning tipping app template built with NextJS and Voltage. [Voltage Tipper Video Walkthrough](https://www.youtube.com/watch?v=y2eFBtRLRUk) To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) **Run on Replit** [https://replit.com/@voltage-cloud/voltage-tipper](https://replit.com/@voltage-cloud/voltage-tipper) ## Table of Contents 1. [Deployment](#deployment) 2. [Environment Variables](#environment-variables) 3. [API](#api) 4. [Contributing](#contributing) 5. [License](#license) ## Deployment To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) ## Environment Variables - `NEXT_PUBLIC_HOST`: The host URL for your LND lightning node (not including port). - `NEXT_PUBLIC_INVOICE_MACAROON`: The invoice macaroon. - `NEXT_PUBLIC_READ_MACAROON`: The read-only macaroon. #### Host The host is your Node's 'API endpoint' you can copy it from your Voltage Dashboard, be sure to include 'https://'. Example: `https://plebdev.m.voltageapp.io` #### Macaroons The Invoice and Read macaroons are authentication tokens that allows you to interact with your LND node's REST API with permissions for reading data, and creating invoices. You can also grab a "Admin" macaroon for permissions to spend but that is not required here since we are only receiving through this webapp, so your funds are safu. **You can find your Macaroons in your Voltage Dashboard by visiting Manage Access -> Macaroon Bakery** ## API - `/api/lnurl` Returns lnurlPay response object defined in [LUD-06](https://github.com/lnurl/luds/blob/luds/06.md) - `/api/getlnurl` Returns bech32 encoded lnurlPay - `/.well-known/lnurlp/{NodeAlias}` This is your lightning address endpoint, returns lnurlPay response defined in [LUD-16](https://github.com/lnurl/luds/blob/luds/16.md) - `/api/callback?amount=21000` This is your callback endpoint that will return an invoice when `amount` query parameter is passed with millisat value ## Contributing Contributions are welcome! Please open an issue or submit a pull request. ## License This project is licensed under the MIT License. See the LICENSE file for details.
@ f33c8a96:5ec6f741
2024-11-15 21:45:12# Voltage Tipper ⚡ A Simple Lightning tipping app template built with NextJS and Voltage. [Voltage Tipper Video Walkthrough](https://www.youtube.com/watch?v=y2eFBtRLRUk) To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) **Run on Replit** [https://replit.com/@voltage-cloud/voltage-tipper](https://replit.com/@voltage-cloud/voltage-tipper) ## Table of Contents 1. [Deployment](#deployment) 2. [Environment Variables](#environment-variables) 3. [API](#api) 4. [Contributing](#contributing) 5. [License](#license) ## Deployment To deploy, click the button below, create a free Vercel account if you don't have one, fill in the required environment variables from your Voltage node, deploy, and everything should work! [](https://vercel.com/new/clone?repository-url=https%3A%2F%2Fgithub.com%2FAustinKelsay%2Fvoltage-tipper&env=NEXT_PUBLIC_HOST,NEXT_PUBLIC_INVOICE_MACAROON,NEXT_PUBLIC_READ_MACAROON&envDescription=The%20host%20url%20for%20your%20lnd%20lightning%20node%20(not%20including%20port)%2C%20the%20invoice%20macaroon%20and%20read%20only%20macaroon.&envLink=https%3A%2F%2Fdocs.voltage.cloud%2Flnd-node-api&project-name=voltage-tipper&repository-name=voltage-tipper) ## Environment Variables - `NEXT_PUBLIC_HOST`: The host URL for your LND lightning node (not including port). - `NEXT_PUBLIC_INVOICE_MACAROON`: The invoice macaroon. - `NEXT_PUBLIC_READ_MACAROON`: The read-only macaroon. #### Host The host is your Node's 'API endpoint' you can copy it from your Voltage Dashboard, be sure to include 'https://'. Example: `https://plebdev.m.voltageapp.io` #### Macaroons The Invoice and Read macaroons are authentication tokens that allows you to interact with your LND node's REST API with permissions for reading data, and creating invoices. You can also grab a "Admin" macaroon for permissions to spend but that is not required here since we are only receiving through this webapp, so your funds are safu. **You can find your Macaroons in your Voltage Dashboard by visiting Manage Access -> Macaroon Bakery** ## API - `/api/lnurl` Returns lnurlPay response object defined in [LUD-06](https://github.com/lnurl/luds/blob/luds/06.md) - `/api/getlnurl` Returns bech32 encoded lnurlPay - `/.well-known/lnurlp/{NodeAlias}` This is your lightning address endpoint, returns lnurlPay response defined in [LUD-16](https://github.com/lnurl/luds/blob/luds/16.md) - `/api/callback?amount=21000` This is your callback endpoint that will return an invoice when `amount` query parameter is passed with millisat value ## Contributing Contributions are welcome! Please open an issue or submit a pull request. ## License This project is licensed under the MIT License. See the LICENSE file for details. @ 1e286f5c:cc2c5009
2024-11-15 21:27:43### A Battle of Nutrients A question I often ask myself and to anyone that is willing to listen is: *****Why spend money on feeding plants a lone nutrient, when you can feed your plants and your soil a whole collection of nutrients (and more) that are water soluble?***** We can take a look into #Humic + #Fulvic #Acids, a list of nutrients that #microorganisms make available for plant uptake, or even applications of #AminoAcids. Each choice individually has vast array of benefits by themselves, for now we are going to take a look into Humic and Fulvic acids. ---- ## Average Chemical Formulas **Humic Acid** (*Darker Brown Color*): * C187 ( 187 #Carbon ) * H186 ( 186 #Hydrogen ) * O89 ( 89 #Oxygen ) * N9 ( 9 #Nitrogen ) * S1 ( 1 #Sulfur ) **Fulvic Acid** (*Yellow / Golden Color*) * C135 ( 135 Carbon ) * H182 ( 182 Hydrogen ) * O95 ( 95 Oxygen ) * N5 ( 5 Nitrogen ) * S2 ( 2 Sulfur ) --- ## A view into the scope.  Here you can see the difference in coloration between the darker brown and golden / yellow color. A sample taken from one of my #vermicompost bins. Bonus: A Hyaline Testate Amoeba in the process of cycling 2 fungal spores can be observed. (Hyaline = Biological substance with a glassy appearance) ---- These acids can be easily obtained through a #CompostTea brew or a #CompostExtract that you can create in your local #bioregion with supplies found all around you. If you are looking for the best bang for your buck, there's no better soil and nutrient architects than those found in nature. Compared to #fungi and #bacteria (we also can't simply cast aside the multiple trophic levels that break down #OrganicMatter), we are simply inefficient. However we can provide the environments and food sources to fight along side these #Organisms. As the Organisms break down the OM overtime, they are creating Humic and Fulvic Acids as well as other #Microaggregates, this is just one process that is transforming lifeless dirt into the dark brown, living #soil we associate as healthy soil. ---- Let's dive into some of the benefits these 2 acids bring to the table. ## Fulvic Acid: - Considered a powerful organic electrolyte. - Enhances cell division and elongation. - As a foliar spray, increases the plant's oxygen uptake capacity. - Increases chlorophyll production and increases the permeability of plant membranes, which lead to an improvement for the plant to uptake nutrients. - A unique capacity to dissolve minerals and trace elements. - Enhances photosynthesis. - Drought protection via improved moisture storage. - Dissolves silica and enhances the benefits of silica. - Increases stomata opening and transpiration. - Assists plant respiration and improves respiration of beneficial micro-organisms. - Influences multiple enzymatic processes. - Stimulates plants immune system. - ---- ## Humic Acid - Improves Soil Structure - Increases water holding capacity in soil. - Improves plant drought resistance. - Enhances uptake of Nitrogen by plants. - Stimulates plant enzymes and increases enzyme production. - Stimulates Growth and proliferation of beneficial microorganisms. - Enhances plant's natural resistance against diseases and pesticides. - Stimulates Root growth. - Increases the thickness of cell walls in fruit, leading to prolonged shelf life. - Increases germination and viability of seeds. - Helps increase physical appearance and nutritional value of crop yields. ---- These are far from a full list of benefits, but sheds light on some of the benefits that they bring to the table. As always, thank you for taking time and checking out the information i've provided. *Now Onward!* D. --- #Permies #Gardening #Microscopy #RegenerativeSoil #Regenerative
@ 1e286f5c:cc2c5009
2024-11-15 21:27:43### A Battle of Nutrients A question I often ask myself and to anyone that is willing to listen is: *****Why spend money on feeding plants a lone nutrient, when you can feed your plants and your soil a whole collection of nutrients (and more) that are water soluble?***** We can take a look into #Humic + #Fulvic #Acids, a list of nutrients that #microorganisms make available for plant uptake, or even applications of #AminoAcids. Each choice individually has vast array of benefits by themselves, for now we are going to take a look into Humic and Fulvic acids. ---- ## Average Chemical Formulas **Humic Acid** (*Darker Brown Color*): * C187 ( 187 #Carbon ) * H186 ( 186 #Hydrogen ) * O89 ( 89 #Oxygen ) * N9 ( 9 #Nitrogen ) * S1 ( 1 #Sulfur ) **Fulvic Acid** (*Yellow / Golden Color*) * C135 ( 135 Carbon ) * H182 ( 182 Hydrogen ) * O95 ( 95 Oxygen ) * N5 ( 5 Nitrogen ) * S2 ( 2 Sulfur ) --- ## A view into the scope.  Here you can see the difference in coloration between the darker brown and golden / yellow color. A sample taken from one of my #vermicompost bins. Bonus: A Hyaline Testate Amoeba in the process of cycling 2 fungal spores can be observed. (Hyaline = Biological substance with a glassy appearance) ---- These acids can be easily obtained through a #CompostTea brew or a #CompostExtract that you can create in your local #bioregion with supplies found all around you. If you are looking for the best bang for your buck, there's no better soil and nutrient architects than those found in nature. Compared to #fungi and #bacteria (we also can't simply cast aside the multiple trophic levels that break down #OrganicMatter), we are simply inefficient. However we can provide the environments and food sources to fight along side these #Organisms. As the Organisms break down the OM overtime, they are creating Humic and Fulvic Acids as well as other #Microaggregates, this is just one process that is transforming lifeless dirt into the dark brown, living #soil we associate as healthy soil. ---- Let's dive into some of the benefits these 2 acids bring to the table. ## Fulvic Acid: - Considered a powerful organic electrolyte. - Enhances cell division and elongation. - As a foliar spray, increases the plant's oxygen uptake capacity. - Increases chlorophyll production and increases the permeability of plant membranes, which lead to an improvement for the plant to uptake nutrients. - A unique capacity to dissolve minerals and trace elements. - Enhances photosynthesis. - Drought protection via improved moisture storage. - Dissolves silica and enhances the benefits of silica. - Increases stomata opening and transpiration. - Assists plant respiration and improves respiration of beneficial micro-organisms. - Influences multiple enzymatic processes. - Stimulates plants immune system. - ---- ## Humic Acid - Improves Soil Structure - Increases water holding capacity in soil. - Improves plant drought resistance. - Enhances uptake of Nitrogen by plants. - Stimulates plant enzymes and increases enzyme production. - Stimulates Growth and proliferation of beneficial microorganisms. - Enhances plant's natural resistance against diseases and pesticides. - Stimulates Root growth. - Increases the thickness of cell walls in fruit, leading to prolonged shelf life. - Increases germination and viability of seeds. - Helps increase physical appearance and nutritional value of crop yields. ---- These are far from a full list of benefits, but sheds light on some of the benefits that they bring to the table. As always, thank you for taking time and checking out the information i've provided. *Now Onward!* D. --- #Permies #Gardening #Microscopy #RegenerativeSoil #Regenerative @ 3ab7c210:d74e9dbf
2024-11-15 21:11:27Nostr and Bitcoin technology combined result in upgrading the entire concept of funding and raising money to drive innovation and improve the world. @Angor introduces a new P2P Funding Protocol and seeks to revolutionize how the capital is raised by stepping into this transformative space, leveraging the potential of Bitcoin and Nostr to advance adoption—not just of these technologies, but of every creative project that will emerge in the years to come. It's an opportunity to redefine funding entirely and how it is perceived. Funding can be done in more free way for both investors and project funders—free from risks and censorship. This marks a whole new era in how funding is done. @Angor, as a P2P funding protocol, aims to have a positive impact on individual lives, supporting project founders and investors by helping allocate their scarce resources safely. It’s also a shift in the structure of how capital is raised. The future of fundraising is evolving, with solutions already available. Angor embraces this idea and the opportunities that Nostr and Bitcoin offer, driving adoption of decentralized ideas further. Angor is here to lead this growing movement of decentralization and risk-free funding protocol.
@ 3ab7c210:d74e9dbf
2024-11-15 21:11:27Nostr and Bitcoin technology combined result in upgrading the entire concept of funding and raising money to drive innovation and improve the world. @Angor introduces a new P2P Funding Protocol and seeks to revolutionize how the capital is raised by stepping into this transformative space, leveraging the potential of Bitcoin and Nostr to advance adoption—not just of these technologies, but of every creative project that will emerge in the years to come. It's an opportunity to redefine funding entirely and how it is perceived. Funding can be done in more free way for both investors and project funders—free from risks and censorship. This marks a whole new era in how funding is done. @Angor, as a P2P funding protocol, aims to have a positive impact on individual lives, supporting project founders and investors by helping allocate their scarce resources safely. It’s also a shift in the structure of how capital is raised. The future of fundraising is evolving, with solutions already available. Angor embraces this idea and the opportunities that Nostr and Bitcoin offer, driving adoption of decentralized ideas further. Angor is here to lead this growing movement of decentralization and risk-free funding protocol. @ 5d4b6c8d:8a1c1ee3
2024-11-15 21:03:43This is a requested topic for a future podcast episode. I do have a giant spreadsheet with a bunch of stats and stuff in it to help figure this out, but I'm doing this off the top of my head. # My Top 10 1. Jordan: 6 titles, 6 Finals MVPs, 5 MVPs, 1 DPOY, and tops by my eye test 2. Lebron: 4 titles, 4 Finals MVPs, 4 MVPs, 20 All-NBAs, holds virtually all the career playoff stats 3. Kareem: 6 titles, 2 Finals MVPs, 6 MVPs, 15 All-NBAs, also the greatest HS and college player ever 4. Wilt: 2 titles, 1 Finals MVP, 4 MVPs, 10 All-NBAs, holds virtually all single game and single season records 5. Magic: 5 titles, 3 Finals MVPs, 3 MVPs, 10 All-NBAs, greatest passer of all time and played every position 6. Bird: 3 titles, 2 Finals MVPs, 3 MVPs, 10 All-NBAs, most well-rounded player ever 7. Russell: 11 titles, 5 MVPs, 11 All-NBAs, greatest winner in the history of professional sports 8. Duncan: 5 titles, 3 Finals MVPs, 2 MVPs, 15 All-NBAs, most underrated player in NBA history 9. Kobe: 5 titles, 2 Finals MVPs, 1 MVP, 15 All-NBAs, 12 All-Defense teams, more All-Star MVPs than anyone 10. Steph: 4 titles, 1 Finals MVP, 2 MVPs, 10 All-NBA, greatest shooter ever Honorable mentions: Shaq and Jokic Shaq and Steph are a toss-up to me. I came down on the side of positional balance. You could think of this as an All-time 1st and 2nd team, rather than purely a top 10. I expect Jokic to make it, but he's right in the middle of his prime and hasn't yet matched the career achievements of these guys. Let the arguments begin! originally posted at https://stacker.news/items/769603
@ 5d4b6c8d:8a1c1ee3
2024-11-15 21:03:43This is a requested topic for a future podcast episode. I do have a giant spreadsheet with a bunch of stats and stuff in it to help figure this out, but I'm doing this off the top of my head. # My Top 10 1. Jordan: 6 titles, 6 Finals MVPs, 5 MVPs, 1 DPOY, and tops by my eye test 2. Lebron: 4 titles, 4 Finals MVPs, 4 MVPs, 20 All-NBAs, holds virtually all the career playoff stats 3. Kareem: 6 titles, 2 Finals MVPs, 6 MVPs, 15 All-NBAs, also the greatest HS and college player ever 4. Wilt: 2 titles, 1 Finals MVP, 4 MVPs, 10 All-NBAs, holds virtually all single game and single season records 5. Magic: 5 titles, 3 Finals MVPs, 3 MVPs, 10 All-NBAs, greatest passer of all time and played every position 6. Bird: 3 titles, 2 Finals MVPs, 3 MVPs, 10 All-NBAs, most well-rounded player ever 7. Russell: 11 titles, 5 MVPs, 11 All-NBAs, greatest winner in the history of professional sports 8. Duncan: 5 titles, 3 Finals MVPs, 2 MVPs, 15 All-NBAs, most underrated player in NBA history 9. Kobe: 5 titles, 2 Finals MVPs, 1 MVP, 15 All-NBAs, 12 All-Defense teams, more All-Star MVPs than anyone 10. Steph: 4 titles, 1 Finals MVP, 2 MVPs, 10 All-NBA, greatest shooter ever Honorable mentions: Shaq and Jokic Shaq and Steph are a toss-up to me. I came down on the side of positional balance. You could think of this as an All-time 1st and 2nd team, rather than purely a top 10. I expect Jokic to make it, but he's right in the middle of his prime and hasn't yet matched the career achievements of these guys. Let the arguments begin! originally posted at https://stacker.news/items/769603 @ e1d968f7:5d90f764
2024-11-15 19:20:44Welcome to *Behind Closed Doors*, my daily dive into what it's really like to work as an escort. I'm Rebecca, and I’m excited to share this journey with you—an open, honest, and sometimes cheeky look behind the scenes of my world. This isn’t just about the physical side of escorting (though we’ll get to those stories); it’s about the whole experience: the clients, the emotions, the personal growth, and the challenges that come with it. Starting out, I had my share of nerves and doubts. This line of work has a lot of stereotypes attached, and everyone seems to have an opinion on it. But for me, becoming an escort has been a path to independence and empowerment. I get to choose who I spend my time with, set my own boundaries, and earn in a way that works for me. That level of freedom is priceless. Over the next posts, I'll be sharing the truths that many don’t see—moments that range from sexy to funny, uplifting to intense. Whether you're here out of curiosity, to challenge your own views, or just for a bit of escapism, I’m glad you’re joining me. Let’s break down some myths and get real about what it’s like to walk in my heels. So, cheers to new beginnings! Here’s to an adventure, to honesty, and to a little bit of mischief along the way. Rebecca x
@ e1d968f7:5d90f764
2024-11-15 19:20:44Welcome to *Behind Closed Doors*, my daily dive into what it's really like to work as an escort. I'm Rebecca, and I’m excited to share this journey with you—an open, honest, and sometimes cheeky look behind the scenes of my world. This isn’t just about the physical side of escorting (though we’ll get to those stories); it’s about the whole experience: the clients, the emotions, the personal growth, and the challenges that come with it. Starting out, I had my share of nerves and doubts. This line of work has a lot of stereotypes attached, and everyone seems to have an opinion on it. But for me, becoming an escort has been a path to independence and empowerment. I get to choose who I spend my time with, set my own boundaries, and earn in a way that works for me. That level of freedom is priceless. Over the next posts, I'll be sharing the truths that many don’t see—moments that range from sexy to funny, uplifting to intense. Whether you're here out of curiosity, to challenge your own views, or just for a bit of escapism, I’m glad you’re joining me. Let’s break down some myths and get real about what it’s like to walk in my heels. So, cheers to new beginnings! Here’s to an adventure, to honesty, and to a little bit of mischief along the way. Rebecca x @ e1d968f7:5d90f764
2024-11-15 19:15:56After yesterday’s introduction, let’s dive into one of the most common questions I get: *Why did you choose to become an escort?* It’s a question loaded with assumptions, and the answer is more complex than most people think. For me, it wasn’t a spur-of-the-moment decision. It was about control—over my time, my finances, and my life. Like many others, I’ve had traditional jobs, and while they were fine, they left me feeling boxed in. I craved something that allowed me to work on my own terms, to meet people, and to experience a kind of freedom that a 9-to-5 could never give me. But it wasn’t just about money or flexibility. I’ve always loved connecting with people on a deeper level, and this job lets me do that in ways I didn’t expect. There’s something fulfilling about creating moments of intimacy and understanding—whether it’s helping someone feel seen, offering companionship, or just giving them an escape from their daily lives. Of course, I had my hesitations. Would I feel safe? Would people judge me? Could I handle the emotional side of the work? I did my research, set boundaries, and slowly built the confidence to enter this world on my terms. Choosing this path wasn’t about desperation or lack of options—it was about taking charge of my life in a way that felt authentic to me. Escorting might not be for everyone, but for me, it’s been empowering, challenging, and deeply rewarding. Tomorrow, I’ll talk about one of the first steps I took to get started: creating my escort persona. Until then, thanks for coming along on this journey. Rebecca x
@ e1d968f7:5d90f764
2024-11-15 19:15:56After yesterday’s introduction, let’s dive into one of the most common questions I get: *Why did you choose to become an escort?* It’s a question loaded with assumptions, and the answer is more complex than most people think. For me, it wasn’t a spur-of-the-moment decision. It was about control—over my time, my finances, and my life. Like many others, I’ve had traditional jobs, and while they were fine, they left me feeling boxed in. I craved something that allowed me to work on my own terms, to meet people, and to experience a kind of freedom that a 9-to-5 could never give me. But it wasn’t just about money or flexibility. I’ve always loved connecting with people on a deeper level, and this job lets me do that in ways I didn’t expect. There’s something fulfilling about creating moments of intimacy and understanding—whether it’s helping someone feel seen, offering companionship, or just giving them an escape from their daily lives. Of course, I had my hesitations. Would I feel safe? Would people judge me? Could I handle the emotional side of the work? I did my research, set boundaries, and slowly built the confidence to enter this world on my terms. Choosing this path wasn’t about desperation or lack of options—it was about taking charge of my life in a way that felt authentic to me. Escorting might not be for everyone, but for me, it’s been empowering, challenging, and deeply rewarding. Tomorrow, I’ll talk about one of the first steps I took to get started: creating my escort persona. Until then, thanks for coming along on this journey. Rebecca x @ 2348ca50:32a055a8
2024-11-15 19:04:13[Electrical repair is often seen as a daunting task, one](https://seqelectricalandenergy.com.au/electrician-redbank-plains/) that can evoke a sense of dread in homeowners and business owners alike. The thought of dealing with electrical problems can be overwhelming, particularly when safety is a concern. Electrical systems are complex and, if not handled correctly, can lead to severe consequences, including fires, electrocution, and extensive property damage. In this article, we will explore the various aspects of electrical repair, the significance of addressing electrical issues promptly, and the factors that contribute to the perception of electrical repair as a big issue. Understanding the Complexity of Electrical Systems Electrical systems consist of intricate components that work together to power homes and businesses. These systems include wiring, circuit breakers, outlets, switches, and appliances. When an electrical issue arises, it often stems from a malfunction in one or more of these components. Common problems include faulty wiring, tripped circuit breakers, overloaded circuits, and malfunctioning outlets or switches. The complexity of electrical systems is one of the reasons why electrical repair is perceived as a significant issue. Unlike some home repairs, such as fixing a leaky faucet or patching a wall, electrical work requires specialized knowledge and skills. Improper repairs can lead to dangerous situations, which is why many people hesitate to tackle electrical issues on their own. Safety Concerns Safety is paramount when it comes to electrical work. The potential risks associated with electrical repairs include: Electrocution: Working with live wires poses a serious risk of electrocution. Even a minor shock can be harmful, while severe shocks can lead to fatal injuries. Electrical Fires: Faulty wiring or overloaded circuits can spark electrical fires, which can spread quickly and cause extensive damage to property and lives. Property Damage: Improper repairs can lead to further damage within the electrical system, resulting in costly repairs and potential loss of property. Due to these safety concerns, many individuals prefer to hire a licensed electrician to handle electrical repairs. Electricians are trained to follow safety protocols and ensure that all repairs meet local electrical codes. This professional expertise not only mitigates risks but also provides peace of mind to homeowners and business owners. The Cost Factor Another aspect that contributes to the perception of electrical repair as a significant issue is the cost. Electrical repairs can vary in price depending on the complexity of the problem, the materials needed, and the labor involved. While some minor repairs may be relatively inexpensive, more extensive issues can lead to substantial expenses. Homeowners may find themselves facing bills for: Service Calls: Many electricians charge a service fee for coming to inspect the problem. Parts and Materials: Replacement parts can vary in cost depending on the type and quality of the materials needed for the repair. Labor Costs: Electricians typically charge by the hour, and rates can vary based on experience and location. Code Compliance: In some cases, electrical repairs may require updates to comply with current codes, leading to additional expenses. This financial burden can make electrical repair seem like a significant issue, prompting homeowners to delay repairs, which can lead to even more costly problems in the future. Common Electrical Issues To better understand why electrical repair is often viewed as a big issue, let’s examine some common electrical problems that homeowners may encounter: Tripped Circuit Breakers: Frequent tripping of circuit breakers can indicate an overloaded circuit, a short circuit, or a ground fault. While resetting a breaker is simple, persistent issues may require professional attention. Flickering Lights: Flickering lights can result from loose wiring, a faulty light fixture, or an overloaded circuit. Addressing the underlying cause is crucial to prevent further electrical issues. Dead Outlets: Outlets that no longer work can be caused by faulty wiring, tripped breakers, or blown fuses. Identifying the cause is essential to restore power safely. Electrical Shocks: If a person experiences shocks when using an appliance or outlet, it indicates a serious problem that requires immediate attention. Burning Smells or Scorch Marks: Any burning smell or visible scorch marks around outlets or switches can signify overheating wiring, which poses a fire risk and necessitates immediate repair. DIY vs. Hiring a Professional When faced with electrical issues, homeowners often grapple with the decision of whether to attempt a DIY repair or hire a professional. While there are minor electrical tasks that can be safely performed by individuals with basic knowledge—such as replacing a light bulb or changing a fuse—most electrical repairs are best left to licensed electricians. Reasons to Hire a Professional: Expertise: Electricians have undergone extensive training and possess the skills necessary to diagnose and repair electrical issues safely and effectively. Safety Compliance: Professionals are familiar with local electrical codes and regulations, ensuring that repairs meet safety standards. Warranty and Insurance: Many licensed electricians offer warranties on their work, providing assurance that if something goes wrong, the repair will be covered. Additionally, they carry liability insurance to protect homeowners in case of accidents. Time and Convenience: Electrical repairs can be time-consuming, especially for those without experience. Hiring a professional saves time and reduces the risk of costly mistakes. The Importance of Timely Repairs Delaying electrical repairs can lead to escalating issues that may compromise safety and result in higher costs down the line. Here are some reasons why timely electrical repairs are essential: Preventing Further Damage: Addressing electrical problems promptly can prevent them from worsening, saving money on extensive repairs. Ensuring Safety: Timely repairs reduce the risk of electrical fires, shocks, and other safety hazards associated with malfunctioning electrical systems. Maintaining Property Value: Regular maintenance and prompt repairs help maintain the value of a property. Potential buyers may be deterred by known electrical issues, leading to decreased marketability. Improving Energy Efficiency: Faulty electrical systems can lead to increased energy consumption. Prompt repairs can improve energy efficiency, resulting in lower utility bills. Conclusion In conclusion, electrical repair is indeed a significant issue that requires careful consideration and prompt action. The complexity of electrical systems, coupled with safety concerns and potential costs, contributes to the perception that electrical problems are daunting. While some minor tasks can be handled by homeowners, most electrical repairs should be entrusted to licensed professionals to ensure safety and compliance with local codes. Timely repairs are crucial to prevent further damage, maintain safety, and preserve property value. By understanding the common electrical issues, weighing the pros and cons of DIY versus professional help, and recognizing the importance of addressing problems promptly, homeowners can navigate the complexities of electrical repair with confidence. Ultimately, addressing electrical issues proactively not only safeguards lives and property but also promotes a safe and efficient living environment.
@ 2348ca50:32a055a8
2024-11-15 19:04:13[Electrical repair is often seen as a daunting task, one](https://seqelectricalandenergy.com.au/electrician-redbank-plains/) that can evoke a sense of dread in homeowners and business owners alike. The thought of dealing with electrical problems can be overwhelming, particularly when safety is a concern. Electrical systems are complex and, if not handled correctly, can lead to severe consequences, including fires, electrocution, and extensive property damage. In this article, we will explore the various aspects of electrical repair, the significance of addressing electrical issues promptly, and the factors that contribute to the perception of electrical repair as a big issue. Understanding the Complexity of Electrical Systems Electrical systems consist of intricate components that work together to power homes and businesses. These systems include wiring, circuit breakers, outlets, switches, and appliances. When an electrical issue arises, it often stems from a malfunction in one or more of these components. Common problems include faulty wiring, tripped circuit breakers, overloaded circuits, and malfunctioning outlets or switches. The complexity of electrical systems is one of the reasons why electrical repair is perceived as a significant issue. Unlike some home repairs, such as fixing a leaky faucet or patching a wall, electrical work requires specialized knowledge and skills. Improper repairs can lead to dangerous situations, which is why many people hesitate to tackle electrical issues on their own. Safety Concerns Safety is paramount when it comes to electrical work. The potential risks associated with electrical repairs include: Electrocution: Working with live wires poses a serious risk of electrocution. Even a minor shock can be harmful, while severe shocks can lead to fatal injuries. Electrical Fires: Faulty wiring or overloaded circuits can spark electrical fires, which can spread quickly and cause extensive damage to property and lives. Property Damage: Improper repairs can lead to further damage within the electrical system, resulting in costly repairs and potential loss of property. Due to these safety concerns, many individuals prefer to hire a licensed electrician to handle electrical repairs. Electricians are trained to follow safety protocols and ensure that all repairs meet local electrical codes. This professional expertise not only mitigates risks but also provides peace of mind to homeowners and business owners. The Cost Factor Another aspect that contributes to the perception of electrical repair as a significant issue is the cost. Electrical repairs can vary in price depending on the complexity of the problem, the materials needed, and the labor involved. While some minor repairs may be relatively inexpensive, more extensive issues can lead to substantial expenses. Homeowners may find themselves facing bills for: Service Calls: Many electricians charge a service fee for coming to inspect the problem. Parts and Materials: Replacement parts can vary in cost depending on the type and quality of the materials needed for the repair. Labor Costs: Electricians typically charge by the hour, and rates can vary based on experience and location. Code Compliance: In some cases, electrical repairs may require updates to comply with current codes, leading to additional expenses. This financial burden can make electrical repair seem like a significant issue, prompting homeowners to delay repairs, which can lead to even more costly problems in the future. Common Electrical Issues To better understand why electrical repair is often viewed as a big issue, let’s examine some common electrical problems that homeowners may encounter: Tripped Circuit Breakers: Frequent tripping of circuit breakers can indicate an overloaded circuit, a short circuit, or a ground fault. While resetting a breaker is simple, persistent issues may require professional attention. Flickering Lights: Flickering lights can result from loose wiring, a faulty light fixture, or an overloaded circuit. Addressing the underlying cause is crucial to prevent further electrical issues. Dead Outlets: Outlets that no longer work can be caused by faulty wiring, tripped breakers, or blown fuses. Identifying the cause is essential to restore power safely. Electrical Shocks: If a person experiences shocks when using an appliance or outlet, it indicates a serious problem that requires immediate attention. Burning Smells or Scorch Marks: Any burning smell or visible scorch marks around outlets or switches can signify overheating wiring, which poses a fire risk and necessitates immediate repair. DIY vs. Hiring a Professional When faced with electrical issues, homeowners often grapple with the decision of whether to attempt a DIY repair or hire a professional. While there are minor electrical tasks that can be safely performed by individuals with basic knowledge—such as replacing a light bulb or changing a fuse—most electrical repairs are best left to licensed electricians. Reasons to Hire a Professional: Expertise: Electricians have undergone extensive training and possess the skills necessary to diagnose and repair electrical issues safely and effectively. Safety Compliance: Professionals are familiar with local electrical codes and regulations, ensuring that repairs meet safety standards. Warranty and Insurance: Many licensed electricians offer warranties on their work, providing assurance that if something goes wrong, the repair will be covered. Additionally, they carry liability insurance to protect homeowners in case of accidents. Time and Convenience: Electrical repairs can be time-consuming, especially for those without experience. Hiring a professional saves time and reduces the risk of costly mistakes. The Importance of Timely Repairs Delaying electrical repairs can lead to escalating issues that may compromise safety and result in higher costs down the line. Here are some reasons why timely electrical repairs are essential: Preventing Further Damage: Addressing electrical problems promptly can prevent them from worsening, saving money on extensive repairs. Ensuring Safety: Timely repairs reduce the risk of electrical fires, shocks, and other safety hazards associated with malfunctioning electrical systems. Maintaining Property Value: Regular maintenance and prompt repairs help maintain the value of a property. Potential buyers may be deterred by known electrical issues, leading to decreased marketability. Improving Energy Efficiency: Faulty electrical systems can lead to increased energy consumption. Prompt repairs can improve energy efficiency, resulting in lower utility bills. Conclusion In conclusion, electrical repair is indeed a significant issue that requires careful consideration and prompt action. The complexity of electrical systems, coupled with safety concerns and potential costs, contributes to the perception that electrical problems are daunting. While some minor tasks can be handled by homeowners, most electrical repairs should be entrusted to licensed professionals to ensure safety and compliance with local codes. Timely repairs are crucial to prevent further damage, maintain safety, and preserve property value. By understanding the common electrical issues, weighing the pros and cons of DIY versus professional help, and recognizing the importance of addressing problems promptly, homeowners can navigate the complexities of electrical repair with confidence. Ultimately, addressing electrical issues proactively not only safeguards lives and property but also promotes a safe and efficient living environment. @ f33c8a96:5ec6f741
2024-11-15 18:31:02# JavaScript Cheatsheet for Beginners ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Operators](#operators) 4. [Objects](#objects) 5. [Functions](#functions) 6. [Arrays](#arrays) 7. [Conditional Statements](#conditional-statements) 8. [Loops](#loops) 9. [Error Handling](#error-handling) 10. [ES6+ Features](#es6-features) 11. [DOM Manipulation](#dom-manipulation) 12. [Event Handling](#event-handling) 13. [Asynchronous JavaScript](#asynchronous-javascript) 14. [Modules](#modules) ## Variable Declaration In JavaScript, variables can be declared using `var`, `let`, or `const`. ```javascript var x = 5; // Function-scoped variable (avoid using in modern JavaScript) let y = 10; // Block-scoped variable const MAX_POINTS = 100; // Constant (cannot be reassigned) ``` - `var` is function-scoped and hoisted (avoid using in modern JavaScript). - `let` is block-scoped and can be reassigned. - `const` is block-scoped and cannot be reassigned (but object properties can be modified). ## Basic Data Types JavaScript has several basic data types. ```javascript let num = 42; // Number let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats) let str = "Hello, World!"; // String let bool = true; // Boolean let nullValue = null; // Null let undefinedValue; // Undefined let symbol = Symbol("unique"); // Symbol (ES6+) let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+) ``` - `Number`: Represents both integers and floating-point numbers. - `String`: Represents textual data. - `Boolean`: Represents `true` or `false`. - `Null`: Represents a deliberate non-value. - `Undefined`: Represents a variable that has been declared but not assigned a value. - `Symbol`: Represents a unique identifier. - `BigInt`: Represents integers larger than 2^53 - 1. ## Operators JavaScript includes various types of operators for different operations. ```javascript // Arithmetic Operators let sum = 5 + 3; // Addition: 8 let diff = 10 - 4; // Subtraction: 6 let product = 3 * 4; // Multiplication: 12 let quotient = 15 / 3;// Division: 5 let remainder = 17 % 5;// Modulus: 2 let power = 2 ** 3; // Exponentiation: 8 let increment = 5; increment++; // Increment: 6 let decrement = 5; decrement--; // Decrement: 4 // Assignment Operators let x = 10; // Basic assignment x += 5; // Addition assignment (x = x + 5) x -= 3; // Subtraction assignment x *= 2; // Multiplication assignment x /= 4; // Division assignment x %= 3; // Modulus assignment x **= 2; // Exponentiation assignment // Comparison Operators console.log(5 == "5"); // Equal to (with type coercion): true console.log(5 === "5"); // Strictly equal to: false console.log(7 != "7"); // Not equal to: false console.log(7 !== "7"); // Strictly not equal to: true console.log(10 > 5); // Greater than: true console.log(10 >= 10); // Greater than or equal to: true console.log(5 < 10); // Less than: true console.log(5 <= 5); // Less than or equal to: true // Logical Operators let a = true, b = false; console.log(a && b); // Logical AND: false console.log(a || b); // Logical OR: true console.log(!a); // Logical NOT: false // Nullish Coalescing Operator (ES2020) let nullValue = null; let defaultValue = nullValue ?? "default"; // "default" // Optional Chaining Operator (ES2020) let user = { address: { street: "123 Main St" } }; console.log(user?.address?.street); // "123 Main St" console.log(user?.contact?.email); // undefined // Bitwise Operators console.log(5 & 3); // Bitwise AND: 1 console.log(5 | 3); // Bitwise OR: 7 console.log(5 ^ 3); // Bitwise XOR: 6 console.log(~5); // Bitwise NOT: -6 console.log(5 << 1); // Left shift: 10 console.log(5 >> 1); // Right shift: 2 console.log(5 >>> 1); // Unsigned right shift: 2 // String Operators let str1 = "Hello"; let str2 = "World"; console.log(str1 + " " + str2); // Concatenation: "Hello World" let greeting = "Hello"; greeting += " World"; // Concatenation assignment // Type Operators console.log(typeof "Hello"); // "string" console.log(typeof 123); // "number" console.log(typeof true); // "boolean" console.log(obj instanceof Object); // Check if object is instance of a class ``` Key points about operators: - Arithmetic operators perform mathematical operations - Assignment operators combine operation with assignment - Comparison operators return boolean values - Logical operators work with boolean values and provide short-circuit evaluation - Nullish coalescing (??) provides a way to specify a default value - Optional chaining (?.) safely accesses nested object properties - Bitwise operators perform operations on binary representations - String operators handle string concatenation - Type operators help determine variable types ## Objects Objects are collections of key-value pairs. ```javascript let person = { name: "Alice", age: 30, sayHello: function() { console.log("Hello, my name is " + this.name); } }; // Accessing object properties console.log(person.name); // Alice console.log(person["age"]); // 30 // Calling object methods person.sayHello(); // Hello, my name is Alice // Adding a new property person.job = "Developer"; // Object destructuring (ES6+) let { name, age } = person; console.log(name, age); // Alice 30 ``` - Objects can contain properties and methods. - Properties can be accessed using dot notation or bracket notation. - New properties can be added dynamically. - Object destructuring allows you to extract multiple properties at once. ## Functions Functions are reusable blocks of code. ```javascript // Function declaration function greet(name) { return "Hello, " + name + "!"; } // Function expression const multiply = function(a, b) { return a * b; }; // Arrow function (ES6+) const add = (a, b) => a + b; // Default parameters (ES6+) function power(base, exponent = 2) { return Math.pow(base, exponent); } console.log(greet("Alice")); // Hello, Alice! console.log(multiply(3, 4)); // 12 console.log(add(5, 3)); // 8 console.log(power(3)); // 9 console.log(power(2, 3)); // 8 ``` - Functions can be declared using the `function` keyword or as arrow functions. - Arrow functions provide a more concise syntax and lexically bind `this`. - Default parameters allow you to specify default values for function arguments. ## Arrays Arrays are ordered lists of values. ```javascript let fruits = ["apple", "banana", "orange"]; // Accessing array elements console.log(fruits[0]); // apple // Array methods fruits.push("grape"); // Add to the end fruits.unshift("mango"); // Add to the beginning let lastFruit = fruits.pop(); // Remove from the end let firstFruit = fruits.shift(); // Remove from the beginning // Iterating over arrays fruits.forEach(fruit => console.log(fruit)); // Array transformation let upperFruits = fruits.map(fruit => fruit.toUpperCase()); // Filtering arrays let longFruits = fruits.filter(fruit => fruit.length > 5); // Reducing arrays let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0); // Spread operator (ES6+) let moreFruits = ["kiwi", "pear"]; let allFruits = [...fruits, ...moreFruits]; ``` - Arrays can contain elements of any type. - Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array. - Higher-order functions like `map`, `filter`, and `reduce` create new arrays. - The spread operator `...` can be used to combine arrays. ## Conditional Statements Conditional statements allow you to execute code based on certain conditions. ```javascript let age = 18; // if...else statement if (age >= 18) { console.log("You are an adult"); } else { console.log("You are a minor"); } // Ternary operator let status = age >= 18 ? "adult" : "minor"; // switch statement switch (age) { case 13: console.log("You're a teenager"); break; case 18: console.log("You're now an adult"); break; default: console.log("You're neither 13 nor 18"); } ``` - `if...else` statements allow you to execute different code blocks based on conditions. - The ternary operator provides a concise way to write simple if-else statements. - `switch` statements are useful when you have multiple conditions to check against a single value. ## Loops Loops allow you to repeat code multiple times. ```javascript // for loop for (let i = 0; i < 5; i++) { console.log(i); } // while loop let count = 0; while (count < 5) { console.log(count); count++; } // do...while loop let x = 0; do { console.log(x); x++; } while (x < 5); // for...of loop (ES6+) let numbers = [1, 2, 3, 4, 5]; for (let num of numbers) { console.log(num); } // for...in loop (for object properties) let person = { name: "Alice", age: 30 }; for (let key in person) { console.log(key + ": " + person[key]); } ``` - `for` loops are commonly used when you know how many times you want to iterate. - `while` loops continue as long as a condition is true. - `do...while` loops always execute at least once before checking the condition. - `for...of` loops are used to iterate over iterable objects like arrays. - `for...in` loops are used to iterate over object properties. ## Error Handling Error handling allows you to gracefully handle and recover from errors. ```javascript try { // Code that might throw an error throw new Error("Something went wrong"); } catch (error) { console.error("Caught an error:", error.message); } finally { console.log("This always runs"); } // Custom error class CustomError extends Error { constructor(message) { super(message); this.name = "CustomError"; } } try { throw new CustomError("A custom error occurred"); } catch (error) { if (error instanceof CustomError) { console.log("Caught a custom error:", error.message); } else { console.log("Caught a different error:", error.message); } } ``` - The `try` block contains code that might throw an error. - The `catch` block handles any errors thrown in the `try` block. - The `finally` block always executes, regardless of whether an error was thrown. - You can create custom error types by extending the `Error` class. ## ES6+ Features ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript. ```javascript // Template literals let name = "Alice"; console.log(`Hello, ${name}!`); // Destructuring let [a, b] = [1, 2]; let { x, y } = { x: 3, y: 4 }; // Default parameters function greet(name = "Guest") { console.log(`Hello, ${name}!`); } // Rest parameters function sum(...numbers) { return numbers.reduce((total, num) => total + num, 0); } // Spread operator let arr1 = [1, 2, 3]; let arr2 = [...arr1, 4, 5]; // Arrow functions const square = x => x * x; // Classes class Animal { constructor(name) { this.name = name; } speak() { console.log(`${this.name} makes a sound.`); } } // Promises const fetchData = () => { return new Promise((resolve, reject) => { // Asynchronous operation setTimeout(() => resolve("Data fetched"), 1000); }); }; // Async/Await async function getData() { try { const data = await fetchData(); console.log(data); } catch (error) { console.error(error); } } ``` - Template literals allow for easy string interpolation. - Destructuring makes it easy to extract values from arrays or properties from objects. - Default parameters provide fallback values for function arguments. - Rest parameters allow functions to accept an indefinite number of arguments as an array. - The spread operator can be used to expand arrays or objects. - Arrow functions provide a concise syntax for writing function expressions. - Classes provide a cleaner syntax for creating objects and implementing inheritance. - Promises and async/await simplify asynchronous programming. ## DOM Manipulation DOM manipulation allows you to interact with HTML elements on a web page. ```javascript // Selecting elements const element = document.getElementById("myElement"); const elements = document.getElementsByClassName("myClass"); const queryElement = document.querySelector(".myClass"); const queryElements = document.querySelectorAll(".myClass"); // Modifying elements element.textContent = "New text content"; element.innerHTML = "<strong>New HTML content</strong>"; element.style.color = "red"; element.classList.add("newClass"); element.classList.remove("oldClass"); // Creating and appending elements const newElement = document.createElement("div"); newElement.textContent = "New element"; document.body.appendChild(newElement); // Removing elements element.parentNode.removeChild(element); // or element.remove(); // Modern browsers ``` - The DOM (Document Object Model) represents the structure of an HTML document. - You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`. - Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`. - New elements can be created with `createElement` and added to the DOM with `appendChild`. - Elements can be removed using `removeChild` or the `remove` method. ## Event Handling Event handling allows you to respond to user interactions and other events. ```javascript const button = document.querySelector("#myButton"); // Adding event listeners button.addEventListener("click", function(event) { console.log("Button clicked!"); console.log("Event object:", event); }); // Removing event listeners function handleClick(event) { console.log("Button clicked!"); } button.addEventListener("click", handleClick); button.removeEventListener("click", handleClick); // Event delegation document.body.addEventListener("click", function(event) { if (event.target.matches("#myButton")) { console.log("Button clicked using event delegation!"); } }); // Preventing default behavior const link = document.querySelector("a"); link.addEventListener("click", function(event) { event.preventDefault(); console.log("Link click prevented"); }); ``` - Event listeners can be added to elements using the `addEventListener` method. - The event object contains information about the event that occurred. - Event listeners can be removed using `removeEventListener`. - Event delegation allows you to handle events for multiple elements with a single listener. - `preventDefault` can be used to stop the default action of an event. ## Asynchronous JavaScript Asynchronous JavaScript allows you to perform operations without blocking the main thread. ```javascript // Callbacks function fetchData(callback) { setTimeout(() => { callback("Data fetched"); }, 1000); } fetchData(data => console.log(data)); // Promises function fetchDataPromise() { return new Promise((resolve, reject) => { setTimeout(() => { resolve("Data fetched"); }, 1000); }); } fetchDataPromise() .then(data => console.log(data)) .catch(error => console.error(error)); // Async/Await async function fetchDataAsync() { try { const data = await fetchDataPromise(); console.log(data); } catch (error) { console.error(error); } } fetchDataAsync(); // Fetch API fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error:', error)); ``` - Callbacks are functions passed as arguments to be executed later. - Promises represent the eventual completion or failure of an asynchronous operation. - Async/await provides a more synchronous-looking way to write asynchronous code. - The Fetch API is a modern interface for making HTTP requests. ## Modules Modules allow you to organize your code into reusable pieces. ```javascript // math.js export function add(a, b) { return a + b; } export function multiply(a, b) { return a * b; } // main.js import { add, multiply } from './math.js'; console.log(add(5, 3)); // 8 console.log(multiply(4, 2)); // 8 // Default export // utils.js export default function sayHello(name) { console.log(`Hello, ${name}!`); } // main.js import sayHello from './utils.js'; sayHello("Alice"); // Hello, Alice! ``` - The `export` keyword is used to expose functions, objects, or primitives from a module. - The `import` keyword is used to bring functionality from other modules into the current module. - Default exports can be imported without curly braces and can be given any name when importing. This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs.
@ f33c8a96:5ec6f741
2024-11-15 18:31:02# JavaScript Cheatsheet for Beginners ## Table of Contents 1. [Variable Declaration](#variable-declaration) 2. [Basic Data Types](#basic-data-types) 3. [Operators](#operators) 4. [Objects](#objects) 5. [Functions](#functions) 6. [Arrays](#arrays) 7. [Conditional Statements](#conditional-statements) 8. [Loops](#loops) 9. [Error Handling](#error-handling) 10. [ES6+ Features](#es6-features) 11. [DOM Manipulation](#dom-manipulation) 12. [Event Handling](#event-handling) 13. [Asynchronous JavaScript](#asynchronous-javascript) 14. [Modules](#modules) ## Variable Declaration In JavaScript, variables can be declared using `var`, `let`, or `const`. ```javascript var x = 5; // Function-scoped variable (avoid using in modern JavaScript) let y = 10; // Block-scoped variable const MAX_POINTS = 100; // Constant (cannot be reassigned) ``` - `var` is function-scoped and hoisted (avoid using in modern JavaScript). - `let` is block-scoped and can be reassigned. - `const` is block-scoped and cannot be reassigned (but object properties can be modified). ## Basic Data Types JavaScript has several basic data types. ```javascript let num = 42; // Number let float = 3.14; // Number (JavaScript doesn't distinguish between integers and floats) let str = "Hello, World!"; // String let bool = true; // Boolean let nullValue = null; // Null let undefinedValue; // Undefined let symbol = Symbol("unique"); // Symbol (ES6+) let bigInt = 1234567890123456789012345678901234567890n; // BigInt (ES11+) ``` - `Number`: Represents both integers and floating-point numbers. - `String`: Represents textual data. - `Boolean`: Represents `true` or `false`. - `Null`: Represents a deliberate non-value. - `Undefined`: Represents a variable that has been declared but not assigned a value. - `Symbol`: Represents a unique identifier. - `BigInt`: Represents integers larger than 2^53 - 1. ## Operators JavaScript includes various types of operators for different operations. ```javascript // Arithmetic Operators let sum = 5 + 3; // Addition: 8 let diff = 10 - 4; // Subtraction: 6 let product = 3 * 4; // Multiplication: 12 let quotient = 15 / 3;// Division: 5 let remainder = 17 % 5;// Modulus: 2 let power = 2 ** 3; // Exponentiation: 8 let increment = 5; increment++; // Increment: 6 let decrement = 5; decrement--; // Decrement: 4 // Assignment Operators let x = 10; // Basic assignment x += 5; // Addition assignment (x = x + 5) x -= 3; // Subtraction assignment x *= 2; // Multiplication assignment x /= 4; // Division assignment x %= 3; // Modulus assignment x **= 2; // Exponentiation assignment // Comparison Operators console.log(5 == "5"); // Equal to (with type coercion): true console.log(5 === "5"); // Strictly equal to: false console.log(7 != "7"); // Not equal to: false console.log(7 !== "7"); // Strictly not equal to: true console.log(10 > 5); // Greater than: true console.log(10 >= 10); // Greater than or equal to: true console.log(5 < 10); // Less than: true console.log(5 <= 5); // Less than or equal to: true // Logical Operators let a = true, b = false; console.log(a && b); // Logical AND: false console.log(a || b); // Logical OR: true console.log(!a); // Logical NOT: false // Nullish Coalescing Operator (ES2020) let nullValue = null; let defaultValue = nullValue ?? "default"; // "default" // Optional Chaining Operator (ES2020) let user = { address: { street: "123 Main St" } }; console.log(user?.address?.street); // "123 Main St" console.log(user?.contact?.email); // undefined // Bitwise Operators console.log(5 & 3); // Bitwise AND: 1 console.log(5 | 3); // Bitwise OR: 7 console.log(5 ^ 3); // Bitwise XOR: 6 console.log(~5); // Bitwise NOT: -6 console.log(5 << 1); // Left shift: 10 console.log(5 >> 1); // Right shift: 2 console.log(5 >>> 1); // Unsigned right shift: 2 // String Operators let str1 = "Hello"; let str2 = "World"; console.log(str1 + " " + str2); // Concatenation: "Hello World" let greeting = "Hello"; greeting += " World"; // Concatenation assignment // Type Operators console.log(typeof "Hello"); // "string" console.log(typeof 123); // "number" console.log(typeof true); // "boolean" console.log(obj instanceof Object); // Check if object is instance of a class ``` Key points about operators: - Arithmetic operators perform mathematical operations - Assignment operators combine operation with assignment - Comparison operators return boolean values - Logical operators work with boolean values and provide short-circuit evaluation - Nullish coalescing (??) provides a way to specify a default value - Optional chaining (?.) safely accesses nested object properties - Bitwise operators perform operations on binary representations - String operators handle string concatenation - Type operators help determine variable types ## Objects Objects are collections of key-value pairs. ```javascript let person = { name: "Alice", age: 30, sayHello: function() { console.log("Hello, my name is " + this.name); } }; // Accessing object properties console.log(person.name); // Alice console.log(person["age"]); // 30 // Calling object methods person.sayHello(); // Hello, my name is Alice // Adding a new property person.job = "Developer"; // Object destructuring (ES6+) let { name, age } = person; console.log(name, age); // Alice 30 ``` - Objects can contain properties and methods. - Properties can be accessed using dot notation or bracket notation. - New properties can be added dynamically. - Object destructuring allows you to extract multiple properties at once. ## Functions Functions are reusable blocks of code. ```javascript // Function declaration function greet(name) { return "Hello, " + name + "!"; } // Function expression const multiply = function(a, b) { return a * b; }; // Arrow function (ES6+) const add = (a, b) => a + b; // Default parameters (ES6+) function power(base, exponent = 2) { return Math.pow(base, exponent); } console.log(greet("Alice")); // Hello, Alice! console.log(multiply(3, 4)); // 12 console.log(add(5, 3)); // 8 console.log(power(3)); // 9 console.log(power(2, 3)); // 8 ``` - Functions can be declared using the `function` keyword or as arrow functions. - Arrow functions provide a more concise syntax and lexically bind `this`. - Default parameters allow you to specify default values for function arguments. ## Arrays Arrays are ordered lists of values. ```javascript let fruits = ["apple", "banana", "orange"]; // Accessing array elements console.log(fruits[0]); // apple // Array methods fruits.push("grape"); // Add to the end fruits.unshift("mango"); // Add to the beginning let lastFruit = fruits.pop(); // Remove from the end let firstFruit = fruits.shift(); // Remove from the beginning // Iterating over arrays fruits.forEach(fruit => console.log(fruit)); // Array transformation let upperFruits = fruits.map(fruit => fruit.toUpperCase()); // Filtering arrays let longFruits = fruits.filter(fruit => fruit.length > 5); // Reducing arrays let totalLength = fruits.reduce((sum, fruit) => sum + fruit.length, 0); // Spread operator (ES6+) let moreFruits = ["kiwi", "pear"]; let allFruits = [...fruits, ...moreFruits]; ``` - Arrays can contain elements of any type. - Array methods like `push`, `pop`, `shift`, and `unshift` modify the original array. - Higher-order functions like `map`, `filter`, and `reduce` create new arrays. - The spread operator `...` can be used to combine arrays. ## Conditional Statements Conditional statements allow you to execute code based on certain conditions. ```javascript let age = 18; // if...else statement if (age >= 18) { console.log("You are an adult"); } else { console.log("You are a minor"); } // Ternary operator let status = age >= 18 ? "adult" : "minor"; // switch statement switch (age) { case 13: console.log("You're a teenager"); break; case 18: console.log("You're now an adult"); break; default: console.log("You're neither 13 nor 18"); } ``` - `if...else` statements allow you to execute different code blocks based on conditions. - The ternary operator provides a concise way to write simple if-else statements. - `switch` statements are useful when you have multiple conditions to check against a single value. ## Loops Loops allow you to repeat code multiple times. ```javascript // for loop for (let i = 0; i < 5; i++) { console.log(i); } // while loop let count = 0; while (count < 5) { console.log(count); count++; } // do...while loop let x = 0; do { console.log(x); x++; } while (x < 5); // for...of loop (ES6+) let numbers = [1, 2, 3, 4, 5]; for (let num of numbers) { console.log(num); } // for...in loop (for object properties) let person = { name: "Alice", age: 30 }; for (let key in person) { console.log(key + ": " + person[key]); } ``` - `for` loops are commonly used when you know how many times you want to iterate. - `while` loops continue as long as a condition is true. - `do...while` loops always execute at least once before checking the condition. - `for...of` loops are used to iterate over iterable objects like arrays. - `for...in` loops are used to iterate over object properties. ## Error Handling Error handling allows you to gracefully handle and recover from errors. ```javascript try { // Code that might throw an error throw new Error("Something went wrong"); } catch (error) { console.error("Caught an error:", error.message); } finally { console.log("This always runs"); } // Custom error class CustomError extends Error { constructor(message) { super(message); this.name = "CustomError"; } } try { throw new CustomError("A custom error occurred"); } catch (error) { if (error instanceof CustomError) { console.log("Caught a custom error:", error.message); } else { console.log("Caught a different error:", error.message); } } ``` - The `try` block contains code that might throw an error. - The `catch` block handles any errors thrown in the `try` block. - The `finally` block always executes, regardless of whether an error was thrown. - You can create custom error types by extending the `Error` class. ## ES6+ Features ES6 (ECMAScript 2015) and later versions introduced many new features to JavaScript. ```javascript // Template literals let name = "Alice"; console.log(`Hello, ${name}!`); // Destructuring let [a, b] = [1, 2]; let { x, y } = { x: 3, y: 4 }; // Default parameters function greet(name = "Guest") { console.log(`Hello, ${name}!`); } // Rest parameters function sum(...numbers) { return numbers.reduce((total, num) => total + num, 0); } // Spread operator let arr1 = [1, 2, 3]; let arr2 = [...arr1, 4, 5]; // Arrow functions const square = x => x * x; // Classes class Animal { constructor(name) { this.name = name; } speak() { console.log(`${this.name} makes a sound.`); } } // Promises const fetchData = () => { return new Promise((resolve, reject) => { // Asynchronous operation setTimeout(() => resolve("Data fetched"), 1000); }); }; // Async/Await async function getData() { try { const data = await fetchData(); console.log(data); } catch (error) { console.error(error); } } ``` - Template literals allow for easy string interpolation. - Destructuring makes it easy to extract values from arrays or properties from objects. - Default parameters provide fallback values for function arguments. - Rest parameters allow functions to accept an indefinite number of arguments as an array. - The spread operator can be used to expand arrays or objects. - Arrow functions provide a concise syntax for writing function expressions. - Classes provide a cleaner syntax for creating objects and implementing inheritance. - Promises and async/await simplify asynchronous programming. ## DOM Manipulation DOM manipulation allows you to interact with HTML elements on a web page. ```javascript // Selecting elements const element = document.getElementById("myElement"); const elements = document.getElementsByClassName("myClass"); const queryElement = document.querySelector(".myClass"); const queryElements = document.querySelectorAll(".myClass"); // Modifying elements element.textContent = "New text content"; element.innerHTML = "<strong>New HTML content</strong>"; element.style.color = "red"; element.classList.add("newClass"); element.classList.remove("oldClass"); // Creating and appending elements const newElement = document.createElement("div"); newElement.textContent = "New element"; document.body.appendChild(newElement); // Removing elements element.parentNode.removeChild(element); // or element.remove(); // Modern browsers ``` - The DOM (Document Object Model) represents the structure of an HTML document. - You can select elements using methods like `getElementById`, `getElementsByClassName`, `querySelector`, and `querySelectorAll`. - Elements can be modified by changing their properties like `textContent`, `innerHTML`, and `style`. - New elements can be created with `createElement` and added to the DOM with `appendChild`. - Elements can be removed using `removeChild` or the `remove` method. ## Event Handling Event handling allows you to respond to user interactions and other events. ```javascript const button = document.querySelector("#myButton"); // Adding event listeners button.addEventListener("click", function(event) { console.log("Button clicked!"); console.log("Event object:", event); }); // Removing event listeners function handleClick(event) { console.log("Button clicked!"); } button.addEventListener("click", handleClick); button.removeEventListener("click", handleClick); // Event delegation document.body.addEventListener("click", function(event) { if (event.target.matches("#myButton")) { console.log("Button clicked using event delegation!"); } }); // Preventing default behavior const link = document.querySelector("a"); link.addEventListener("click", function(event) { event.preventDefault(); console.log("Link click prevented"); }); ``` - Event listeners can be added to elements using the `addEventListener` method. - The event object contains information about the event that occurred. - Event listeners can be removed using `removeEventListener`. - Event delegation allows you to handle events for multiple elements with a single listener. - `preventDefault` can be used to stop the default action of an event. ## Asynchronous JavaScript Asynchronous JavaScript allows you to perform operations without blocking the main thread. ```javascript // Callbacks function fetchData(callback) { setTimeout(() => { callback("Data fetched"); }, 1000); } fetchData(data => console.log(data)); // Promises function fetchDataPromise() { return new Promise((resolve, reject) => { setTimeout(() => { resolve("Data fetched"); }, 1000); }); } fetchDataPromise() .then(data => console.log(data)) .catch(error => console.error(error)); // Async/Await async function fetchDataAsync() { try { const data = await fetchDataPromise(); console.log(data); } catch (error) { console.error(error); } } fetchDataAsync(); // Fetch API fetch('https://api.example.com/data') .then(response => response.json()) .then(data => console.log(data)) .catch(error => console.error('Error:', error)); ``` - Callbacks are functions passed as arguments to be executed later. - Promises represent the eventual completion or failure of an asynchronous operation. - Async/await provides a more synchronous-looking way to write asynchronous code. - The Fetch API is a modern interface for making HTTP requests. ## Modules Modules allow you to organize your code into reusable pieces. ```javascript // math.js export function add(a, b) { return a + b; } export function multiply(a, b) { return a * b; } // main.js import { add, multiply } from './math.js'; console.log(add(5, 3)); // 8 console.log(multiply(4, 2)); // 8 // Default export // utils.js export default function sayHello(name) { console.log(`Hello, ${name}!`); } // main.js import sayHello from './utils.js'; sayHello("Alice"); // Hello, Alice! ``` - The `export` keyword is used to expose functions, objects, or primitives from a module. - The `import` keyword is used to bring functionality from other modules into the current module. - Default exports can be imported without curly braces and can be given any name when importing. This cheatsheet covers many of the fundamental concepts in JavaScript. Each section provides code examples and explanations to help you understand and use these features effectively in your JavaScript programs. @ f33c8a96:5ec6f741
2024-11-15 18:25:12<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/kFUIfaCpXzA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:25:12<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/kFUIfaCpXzA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ f33c8a96:5ec6f741
2024-11-15 18:23:58<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/7dsR7um-DxA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:23:58<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/7dsR7um-DxA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ f33c8a96:5ec6f741
2024-11-15 18:21:00<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/QY6euaT_G_E?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:21:00<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/QY6euaT_G_E?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ f33c8a96:5ec6f741
2024-11-15 18:06:42<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/tGVxP4RgyI4?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:06:42<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/tGVxP4RgyI4?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 468f729d:5ab4fd5e
2024-11-15 17:52:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 468f729d:5ab4fd5e
2024-11-15 17:52:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 6bae33c8:607272e8
2024-11-15 17:41:15I went 4-1 again [last week](https://www.realmansports.com/p/circa-millions-bbf) to put myself at 8-2 for Q3 and 21-9 over the last six weeks. It’s too bad I did so poorly Weeks 1-4. **Browns +1 at Saints** — I don’t know why I’m taking Jameis Winston, but I figure the Saints are a good sell-high off their close win, and the Browns have more weapons in the passing game. **Ravens -3 at Steelers** — The Ravens are in a different class than the Steelers, and they’ll be up for this one. **Lions -14 vs Jaguars** — I usually don’t take double-digit favorites, but the Lions should grind Jacksonville into oblivion. **Titans +6 vs Vikings** — This one came to me in a vision of sorts. I asked my mind what should be my fifth pick, and it highlighted the Titans. (I did the same thing with the Bucs last week, but didn’t say anything about it because I hated the pick.) The Titans defense could give struggling Sam Darnold trouble too. **49ers -6.5 vs Seahawks** — Division games can go either way, but the Seahawks can’t pass protect to save their lives, and it feels like the 49ers are about to go on a run.
@ 6bae33c8:607272e8
2024-11-15 17:41:15I went 4-1 again [last week](https://www.realmansports.com/p/circa-millions-bbf) to put myself at 8-2 for Q3 and 21-9 over the last six weeks. It’s too bad I did so poorly Weeks 1-4. **Browns +1 at Saints** — I don’t know why I’m taking Jameis Winston, but I figure the Saints are a good sell-high off their close win, and the Browns have more weapons in the passing game. **Ravens -3 at Steelers** — The Ravens are in a different class than the Steelers, and they’ll be up for this one. **Lions -14 vs Jaguars** — I usually don’t take double-digit favorites, but the Lions should grind Jacksonville into oblivion. **Titans +6 vs Vikings** — This one came to me in a vision of sorts. I asked my mind what should be my fifth pick, and it highlighted the Titans. (I did the same thing with the Bucs last week, but didn’t say anything about it because I hated the pick.) The Titans defense could give struggling Sam Darnold trouble too. **49ers -6.5 vs Seahawks** — Division games can go either way, but the Seahawks can’t pass protect to save their lives, and it feels like the 49ers are about to go on a run. @ f15638f3:702ff079
2024-11-15 17:31:34I AM CARELITO
@ f15638f3:702ff079
2024-11-15 17:31:34I AM CARELITO @ 59f0660b:d5d24440
2024-11-15 17:27:53Bitcoin is often regarded as the only true decentralized digital currency offering freedom for several compelling reasons. Here are ten key points: 1. First-Mover Advantage Bitcoin was the first cryptocurrency, introduced in 2009 by Satoshi Nakamoto, and it set the standard for decentralization. It operates without any central authority or intermediary, serving as a trustless system【6】【8】. 2. Decentralized Network Bitcoin's network is maintained by a vast array of miners and nodes spread globally. This decentralization makes it nearly impossible for any single entity or group to control or manipulate the system【7】. 3. Immutable Blockchain Bitcoin's blockchain is immutable, meaning that once a transaction is confirmed, it cannot be altered. This ensures transparency and trust, key factors in maintaining decentralization【6】【9】. 4. Censorship Resistance Bitcoin transactions are peer-to-peer, bypassing banks and governments. This makes it difficult for any authority to censor transactions, providing freedom of use even in restrictive environments【9】【10】. 5. Open Source Code Bitcoin's code is open-source, allowing anyone to review, improve, or fork the project. This transparency ensures community trust and reduces reliance on centralized developers【6】【8】. 6. Proof-of-Work Consensus Bitcoin's proof-of-work (PoW) mechanism is considered one of the most secure and decentralized consensus models. It requires computational power to validate transactions, ensuring no entity can dominate easily【7】. 7. Fixed Supply Bitcoin has a hard cap of 21 million coins, enforced by its code. This scarcity makes it immune to inflationary policies or manipulation by centralized entities【8】. 8. Independence from Institutions Unlike many other cryptocurrencies tied to specific companies, protocols, or foundations, Bitcoin has no central organization controlling its development or marketing【6】【7】. 9. Resilient to Hard Forks Bitcoin’s governance model and community ethos have ensured it remains resilient despite several hard forks (e.g., Bitcoin Cash), which have not succeeded in supplanting Bitcoin’s dominance【9】【10】. 10. Global Acceptance and Network Effect Bitcoin has the largest adoption, recognition, and infrastructure compared to any other cryptocurrency. Its acceptance by individuals, merchants, and institutions reinforces its position as the leading decentralized digital currency【8】【10】. Other cryptocurrencies may claim decentralization but often have trade-offs like pre-mines, centralized foundations, or governance structures that reduce their degree of freedom compared to Bitcoin. Would you like to explore this further?
@ 59f0660b:d5d24440
2024-11-15 17:27:53Bitcoin is often regarded as the only true decentralized digital currency offering freedom for several compelling reasons. Here are ten key points: 1. First-Mover Advantage Bitcoin was the first cryptocurrency, introduced in 2009 by Satoshi Nakamoto, and it set the standard for decentralization. It operates without any central authority or intermediary, serving as a trustless system【6】【8】. 2. Decentralized Network Bitcoin's network is maintained by a vast array of miners and nodes spread globally. This decentralization makes it nearly impossible for any single entity or group to control or manipulate the system【7】. 3. Immutable Blockchain Bitcoin's blockchain is immutable, meaning that once a transaction is confirmed, it cannot be altered. This ensures transparency and trust, key factors in maintaining decentralization【6】【9】. 4. Censorship Resistance Bitcoin transactions are peer-to-peer, bypassing banks and governments. This makes it difficult for any authority to censor transactions, providing freedom of use even in restrictive environments【9】【10】. 5. Open Source Code Bitcoin's code is open-source, allowing anyone to review, improve, or fork the project. This transparency ensures community trust and reduces reliance on centralized developers【6】【8】. 6. Proof-of-Work Consensus Bitcoin's proof-of-work (PoW) mechanism is considered one of the most secure and decentralized consensus models. It requires computational power to validate transactions, ensuring no entity can dominate easily【7】. 7. Fixed Supply Bitcoin has a hard cap of 21 million coins, enforced by its code. This scarcity makes it immune to inflationary policies or manipulation by centralized entities【8】. 8. Independence from Institutions Unlike many other cryptocurrencies tied to specific companies, protocols, or foundations, Bitcoin has no central organization controlling its development or marketing【6】【7】. 9. Resilient to Hard Forks Bitcoin’s governance model and community ethos have ensured it remains resilient despite several hard forks (e.g., Bitcoin Cash), which have not succeeded in supplanting Bitcoin’s dominance【9】【10】. 10. Global Acceptance and Network Effect Bitcoin has the largest adoption, recognition, and infrastructure compared to any other cryptocurrency. Its acceptance by individuals, merchants, and institutions reinforces its position as the leading decentralized digital currency【8】【10】. Other cryptocurrencies may claim decentralization but often have trade-offs like pre-mines, centralized foundations, or governance structures that reduce their degree of freedom compared to Bitcoin. Would you like to explore this further? @ 59f0660b:d5d24440
2024-11-15 17:27:53Bitcoin is often regarded as the only true decentralized digital currency offering freedom for several compelling reasons. Here are ten key points: 1. First-Mover Advantage Bitcoin was the first cryptocurrency, introduced in 2009 by Satoshi Nakamoto, and it set the standard for decentralization. It operates without any central authority or intermediary, serving as a trustless system【6】【8】. 2. Decentralized Network Bitcoin's network is maintained by a vast array of miners and nodes spread globally. This decentralization makes it nearly impossible for any single entity or group to control or manipulate the system【7】. 3. Immutable Blockchain Bitcoin's blockchain is immutable, meaning that once a transaction is confirmed, it cannot be altered. This ensures transparency and trust, key factors in maintaining decentralization【6】【9】. 4. Censorship Resistance Bitcoin transactions are peer-to-peer, bypassing banks and governments. This makes it difficult for any authority to censor transactions, providing freedom of use even in restrictive environments【9】【10】. 5. Open Source Code Bitcoin's code is open-source, allowing anyone to review, improve, or fork the project. This transparency ensures community trust and reduces reliance on centralized developers【6】【8】. 6. Proof-of-Work Consensus Bitcoin's proof-of-work (PoW) mechanism is considered one of the most secure and decentralized consensus models. It requires computational power to validate transactions, ensuring no entity can dominate easily【7】. 7. Fixed Supply Bitcoin has a hard cap of 21 million coins, enforced by its code. This scarcity makes it immune to inflationary policies or manipulation by centralized entities【8】. 8. Independence from Institutions Unlike many other cryptocurrencies tied to specific companies, protocols, or foundations, Bitcoin has no central organization controlling its development or marketing【6】【7】. 9. Resilient to Hard Forks Bitcoin’s governance model and community ethos have ensured it remains resilient despite several hard forks (e.g., Bitcoin Cash), which have not succeeded in supplanting Bitcoin’s dominance【9】【10】. 10. Global Acceptance and Network Effect Bitcoin has the largest adoption, recognition, and infrastructure compared to any other cryptocurrency. Its acceptance by individuals, merchants, and institutions reinforces its position as the leading decentralized digital currency【8】【10】. Other cryptocurrencies may claim decentralization but often have trade-offs like pre-mines, centralized foundations, or governance structures that reduce their degree of freedom compared to Bitcoin. Would you like to explore this further?
@ 59f0660b:d5d24440
2024-11-15 17:27:53Bitcoin is often regarded as the only true decentralized digital currency offering freedom for several compelling reasons. Here are ten key points: 1. First-Mover Advantage Bitcoin was the first cryptocurrency, introduced in 2009 by Satoshi Nakamoto, and it set the standard for decentralization. It operates without any central authority or intermediary, serving as a trustless system【6】【8】. 2. Decentralized Network Bitcoin's network is maintained by a vast array of miners and nodes spread globally. This decentralization makes it nearly impossible for any single entity or group to control or manipulate the system【7】. 3. Immutable Blockchain Bitcoin's blockchain is immutable, meaning that once a transaction is confirmed, it cannot be altered. This ensures transparency and trust, key factors in maintaining decentralization【6】【9】. 4. Censorship Resistance Bitcoin transactions are peer-to-peer, bypassing banks and governments. This makes it difficult for any authority to censor transactions, providing freedom of use even in restrictive environments【9】【10】. 5. Open Source Code Bitcoin's code is open-source, allowing anyone to review, improve, or fork the project. This transparency ensures community trust and reduces reliance on centralized developers【6】【8】. 6. Proof-of-Work Consensus Bitcoin's proof-of-work (PoW) mechanism is considered one of the most secure and decentralized consensus models. It requires computational power to validate transactions, ensuring no entity can dominate easily【7】. 7. Fixed Supply Bitcoin has a hard cap of 21 million coins, enforced by its code. This scarcity makes it immune to inflationary policies or manipulation by centralized entities【8】. 8. Independence from Institutions Unlike many other cryptocurrencies tied to specific companies, protocols, or foundations, Bitcoin has no central organization controlling its development or marketing【6】【7】. 9. Resilient to Hard Forks Bitcoin’s governance model and community ethos have ensured it remains resilient despite several hard forks (e.g., Bitcoin Cash), which have not succeeded in supplanting Bitcoin’s dominance【9】【10】. 10. Global Acceptance and Network Effect Bitcoin has the largest adoption, recognition, and infrastructure compared to any other cryptocurrency. Its acceptance by individuals, merchants, and institutions reinforces its position as the leading decentralized digital currency【8】【10】. Other cryptocurrencies may claim decentralization but often have trade-offs like pre-mines, centralized foundations, or governance structures that reduce their degree of freedom compared to Bitcoin. Would you like to explore this further? @ 59f0660b:d5d24440
2024-11-15 17:17:30What is Yakihonne? Yakihonne is a decentralized social media platform built on the Nostr protocol and integrates Bitcoin as its financial layer. It provides a censorship-resistant environment for publishing and engaging with content like blogs, flash news, videos, and curated media. Yakihonne emphasizes freedom of speech, decentralized identity management, and seamless financial transactions via Bitcoin's Lightning Network【6】【7】【9】. --- Why Yakihonne? (6 Reasons) 1. Censorship Resistance: It ensures free speech by operating on a decentralized protocol, avoiding centralized control【7】【9】. 2. User Autonomy: Users retain full control over their data and identities using cryptographic keys【9】【10】. 3. Monetization with Bitcoin: Integrating the Lightning Network enables instant, borderless payments【6】【9】. 4. Interoperability: Supports cross-platform usage within the Nostr ecosystem, allowing users to move seamlessly across applications【6】. 5. Community-Driven Innovation: The platform evolves with input from its user base and developers【10】. 6. Privacy-Centric Design: Avoids the pitfalls of ad-based or surveillance-driven models seen in traditional social platforms【9】【10】. --- How Yakihonne Relates to Bitcoin and Nostr (5 Reasons) 1. Bitcoin Payments: Enables direct microtransactions via the Lightning Network, including features like tipping ("zaps") and monetizing content【7】【8】. 2. Decentralized Identity: Built on Nostr, Yakihonne uses cryptographic keypairs to ensure secure, private user authentication【6】【9】. 3. Aligned Philosophies: Both Nostr and Bitcoin prioritize decentralization and user sovereignty【6】. 4. Economic Incentives: By combining content creation with Bitcoin monetization, it aligns incentives for creators and participants【7】【9】. 5. Interoperable Ecosystem: Being Nostr-compatible, Yakihonne integrates smoothly into other decentralized applications that share similar values【6】【8】. --- The Future of Yakihonne (5 Predictions) 1. Increased Adoption: As demand for censorship-resistant platforms grows, Yakihonne is likely to attract more users【7】【8】. 2. Expansion of Features: Ongoing updates, like Yakihonne 2.0, suggest an emphasis on performance improvements and new tools for creators【9】. 3. Enhanced Financial Integration: The integration with Bitcoin and Lightning will grow, offering diverse monetization options【9】. 4. Broader Decentralized Ecosystem: Yakihonne's compatibility with Nostr positions it as a hub in the decentralized internet revolution【6】【7】. 5. Resilience to Censorship: As centralized platforms face increasing scrutiny, Yakihonne’s decentralized approach offers a viable alternative【9】【10】. Let me know if you'd like further details or links to explore these topics in-depth!
@ 59f0660b:d5d24440
2024-11-15 17:17:30What is Yakihonne? Yakihonne is a decentralized social media platform built on the Nostr protocol and integrates Bitcoin as its financial layer. It provides a censorship-resistant environment for publishing and engaging with content like blogs, flash news, videos, and curated media. Yakihonne emphasizes freedom of speech, decentralized identity management, and seamless financial transactions via Bitcoin's Lightning Network【6】【7】【9】. --- Why Yakihonne? (6 Reasons) 1. Censorship Resistance: It ensures free speech by operating on a decentralized protocol, avoiding centralized control【7】【9】. 2. User Autonomy: Users retain full control over their data and identities using cryptographic keys【9】【10】. 3. Monetization with Bitcoin: Integrating the Lightning Network enables instant, borderless payments【6】【9】. 4. Interoperability: Supports cross-platform usage within the Nostr ecosystem, allowing users to move seamlessly across applications【6】. 5. Community-Driven Innovation: The platform evolves with input from its user base and developers【10】. 6. Privacy-Centric Design: Avoids the pitfalls of ad-based or surveillance-driven models seen in traditional social platforms【9】【10】. --- How Yakihonne Relates to Bitcoin and Nostr (5 Reasons) 1. Bitcoin Payments: Enables direct microtransactions via the Lightning Network, including features like tipping ("zaps") and monetizing content【7】【8】. 2. Decentralized Identity: Built on Nostr, Yakihonne uses cryptographic keypairs to ensure secure, private user authentication【6】【9】. 3. Aligned Philosophies: Both Nostr and Bitcoin prioritize decentralization and user sovereignty【6】. 4. Economic Incentives: By combining content creation with Bitcoin monetization, it aligns incentives for creators and participants【7】【9】. 5. Interoperable Ecosystem: Being Nostr-compatible, Yakihonne integrates smoothly into other decentralized applications that share similar values【6】【8】. --- The Future of Yakihonne (5 Predictions) 1. Increased Adoption: As demand for censorship-resistant platforms grows, Yakihonne is likely to attract more users【7】【8】. 2. Expansion of Features: Ongoing updates, like Yakihonne 2.0, suggest an emphasis on performance improvements and new tools for creators【9】. 3. Enhanced Financial Integration: The integration with Bitcoin and Lightning will grow, offering diverse monetization options【9】. 4. Broader Decentralized Ecosystem: Yakihonne's compatibility with Nostr positions it as a hub in the decentralized internet revolution【6】【7】. 5. Resilience to Censorship: As centralized platforms face increasing scrutiny, Yakihonne’s decentralized approach offers a viable alternative【9】【10】. Let me know if you'd like further details or links to explore these topics in-depth! @ 84999652:2a24d806
2024-11-15 16:22:23### Gavin, BeeGee (Super Bitcoin和BEVM 核心建设者) 2024年11月15日 --- ### —— 从财产保护到文明守护,比特币的机械共识为人工智能时代提供终极护盾 **科技的加速与潜在威胁:霍金、维纳与当下挑战** 人类已经步入人工智能时代,随着技术的快速进步,我们正面对前所未有的复杂性和不确定性。科技的飞速发展不仅改变了社会结构,也带来了诸多潜在威胁,尤其是在人工智能领域。 霍金等科学家早已对这一进程的潜在危险发出警告。霍金认为,人工智能的无序发展有可能威胁到人类的生存,他指出:“我们可能在不久的将来面临人工智能崛起带来的种种风险。”同样,控制论奠基人之一的维纳也曾警告过科技失控对人类文明的危害,尤其是在自动化与自适应系统的推行过程中。维纳曾在《控制论》中提到,“人类创造的机器,若不加以控制,最终可能会摧毁我们自己的文明。” 近年来,随着AGI(通用人工智能)技术的飞速发展,科技失控的风险变得愈加突出。马斯克对此深感忧虑,并公开表示AGI有可能对人类构成生存威胁,因此他成立了xAI,致力于开发有益于人类的安全人工智能。此外,尤瓦尔·赫拉利在其《智人之上:从石器时代到AI时代的信息网络简史》中提到,人工智能已经不仅是工具,而是具备了自主决策的能力,这使得AI可能不再听从人类的指挥,进而对社会秩序构成冲击。 这些警告清楚地表明,如何确保科技进步服务于人类、避免其威胁人类生存,已成为当今亟待解决的重大问题。 **人类大脑的极限与社会共识的崩溃** 回到人类自身,信息的爆炸式增长对人类大脑的处理能力提出了严峻考验。人类大脑的生物进化远远落后于硅基生物的发展速度。人类作为一个种族,将面临着和“人工智能种族”的竞争。 在过去,人类通过“社会共识”解决了大多数复杂问题,然而在信息化时代,传统的共识机制显然已无法应对日益加剧的复杂性。信息量的指数级增长让我们的思维方式无法与之匹配,社会在快速变化的同时,我们的思维和决策却变得愈发滞后,导致传统的共识方式逐渐失效。 James Rickards 在《MoneyGPT: AI and the Threat to the Global Economy》中提出,控制论是应对这一挑战的重要工具。他认为,科技对决策的加速依赖,尤其是在AI领域,将引发秒级反应,可能导致金融系统甚至社会的连锁崩溃。他进一步指出,“控制论”是指一种不断调整和优化系统反应的思想方式,源自希腊语的“kybernētēs”(舵手),它倡导通过精准的反馈机制来引导系统运行,而不是采取过于激烈的应对措施。 在人工智能时代,单纯依靠传统的“社会共识”已经无法应对这些复杂、快速变化的挑战。我们亟需一种新的、更有效的机制,以应对不断变化的科技局势和社会需求。 **机械共识:应对复杂挑战的关键** 在这种背景下,机械共识作为一种新的自我组织、去中心化的共识形式,成为了应对当前科技挑战的有效方案。与传统的社会共识依赖于人为决策不同,机械共识通过去中心化的自动化博弈,能够在没有人为干预的情况下自我调节并达成一致。正如维纳在其控制论中所强调的,机械共识是一种通过反馈机制优化系统的方式,在信息不断增加的环境下,依然能够保证系统的稳定与安全。 比特币网络便是机械共识最成功的示例之一。比特币通过矿工的算力竞赛和经济激励机制,形成了一个无需外部干预的稳定网络。在比特币网络中,矿工们通过参与算力竞争,为网络提供安全性和去中心化的共识,而比特币的设计确保了这一过程的公平性与不可篡改性。其机制不仅保障了数字资产的安全性,也为信息时代带来了全新的治理模式。 机械共识所展现的力量,正是其能够在无中央控制的情况下,依据设定的规则自动运行,并为人类社会的复杂问题提供解决方案的能力。它让我们看到了技术能够如何超越单一的财富保护,转向对人类生命与文明更广泛的保障。 **比特币:从加密资产到文明守护者的机械共识** 比特币不仅仅是一种加密资产,它代表了机械共识的核心理念。中本聪设计比特币的初衷便是为了建立一个无需信任第三方的自适应增长型网络,而这一理念正是通过比特币的共识机制得以实现的。 比特币的共识机制背后,实际上是一场永无止境的算力竞赛。矿工们为获得比特币奖励,不断投入算力,推动网络的持续增长与自我强化。这种自我强化机制不仅增加了比特币网络的安全性和稳定性,同时也不断增强了其抵抗外部攻击的能力。通过这种正反馈机制,比特币的网络得以不断壮大,其市值从2009年的零增长到目前超过1.8万亿美元,证明了机械共识作为“数字货币”的成功。 然而,比特币所代表的机械共识不仅仅局限于保护数字资产,它为人类应对信息时代的复杂性提供了一个新的解决方案。 **Super Bitcoin:守护人类未来的革新者** 在此基础上,Super Bitcoin应运而生,进一步突破比特币网络的局限。 通过五层架构的设计,Super Bitcoin不仅继承了比特币网络的安全性,还突破了比特币单纯转账的功能,为比特币网络带来了更为丰富的扩展能力。Super Bitcoin在设计中集成了工作量证明(PoW)共识机制,闪电网络,Taproot Consensus等技术,形成了一个更高效、灵活的区块链体系。 这一新的架构使得Super Bitcoin不仅仅是一个数字资产的保护工具,它更像是一个能够为人类社会提供科技管控的平台。通过去中心化、自动化的机械共识,Super Bitcoin能够在控制风险的同时促进技术的发展,并保障人类文明免受潜在的科技威胁。它不仅为协议和应用提供了一个安全、共享的基础设施,更在不断扩展的生态系统中,提供了实现更多人类目标的可能。 **结语:每一枚比特币都是对人类未来的守护** 比特币(BTC)的总量恒定为2100万枚,而全球人口已超过82亿。简单计算,每400人平均共享一枚BTC。从资产角度看,这凸显了比特币的稀缺性和价值。然而,从人类生命安全的角度来看,每枚比特币实际上守护着400条生命。 加密货币的真正价值不仅在于其作为财富的象征,更在于其背后的自适应机械共识。2100万个比特币,每一枚都承载着守护生命的责任。通过机械共识,我们有机会在信息爆炸、科技进步的时代,建立一个更为坚固的社会共识,帮助人类应对复杂的科技尤其是人工智能带来的挑战,确保文明与生命的可持续发展。
@ 84999652:2a24d806
2024-11-15 16:22:23### Gavin, BeeGee (Super Bitcoin和BEVM 核心建设者) 2024年11月15日 --- ### —— 从财产保护到文明守护,比特币的机械共识为人工智能时代提供终极护盾 **科技的加速与潜在威胁:霍金、维纳与当下挑战** 人类已经步入人工智能时代,随着技术的快速进步,我们正面对前所未有的复杂性和不确定性。科技的飞速发展不仅改变了社会结构,也带来了诸多潜在威胁,尤其是在人工智能领域。 霍金等科学家早已对这一进程的潜在危险发出警告。霍金认为,人工智能的无序发展有可能威胁到人类的生存,他指出:“我们可能在不久的将来面临人工智能崛起带来的种种风险。”同样,控制论奠基人之一的维纳也曾警告过科技失控对人类文明的危害,尤其是在自动化与自适应系统的推行过程中。维纳曾在《控制论》中提到,“人类创造的机器,若不加以控制,最终可能会摧毁我们自己的文明。” 近年来,随着AGI(通用人工智能)技术的飞速发展,科技失控的风险变得愈加突出。马斯克对此深感忧虑,并公开表示AGI有可能对人类构成生存威胁,因此他成立了xAI,致力于开发有益于人类的安全人工智能。此外,尤瓦尔·赫拉利在其《智人之上:从石器时代到AI时代的信息网络简史》中提到,人工智能已经不仅是工具,而是具备了自主决策的能力,这使得AI可能不再听从人类的指挥,进而对社会秩序构成冲击。 这些警告清楚地表明,如何确保科技进步服务于人类、避免其威胁人类生存,已成为当今亟待解决的重大问题。 **人类大脑的极限与社会共识的崩溃** 回到人类自身,信息的爆炸式增长对人类大脑的处理能力提出了严峻考验。人类大脑的生物进化远远落后于硅基生物的发展速度。人类作为一个种族,将面临着和“人工智能种族”的竞争。 在过去,人类通过“社会共识”解决了大多数复杂问题,然而在信息化时代,传统的共识机制显然已无法应对日益加剧的复杂性。信息量的指数级增长让我们的思维方式无法与之匹配,社会在快速变化的同时,我们的思维和决策却变得愈发滞后,导致传统的共识方式逐渐失效。 James Rickards 在《MoneyGPT: AI and the Threat to the Global Economy》中提出,控制论是应对这一挑战的重要工具。他认为,科技对决策的加速依赖,尤其是在AI领域,将引发秒级反应,可能导致金融系统甚至社会的连锁崩溃。他进一步指出,“控制论”是指一种不断调整和优化系统反应的思想方式,源自希腊语的“kybernētēs”(舵手),它倡导通过精准的反馈机制来引导系统运行,而不是采取过于激烈的应对措施。 在人工智能时代,单纯依靠传统的“社会共识”已经无法应对这些复杂、快速变化的挑战。我们亟需一种新的、更有效的机制,以应对不断变化的科技局势和社会需求。 **机械共识:应对复杂挑战的关键** 在这种背景下,机械共识作为一种新的自我组织、去中心化的共识形式,成为了应对当前科技挑战的有效方案。与传统的社会共识依赖于人为决策不同,机械共识通过去中心化的自动化博弈,能够在没有人为干预的情况下自我调节并达成一致。正如维纳在其控制论中所强调的,机械共识是一种通过反馈机制优化系统的方式,在信息不断增加的环境下,依然能够保证系统的稳定与安全。 比特币网络便是机械共识最成功的示例之一。比特币通过矿工的算力竞赛和经济激励机制,形成了一个无需外部干预的稳定网络。在比特币网络中,矿工们通过参与算力竞争,为网络提供安全性和去中心化的共识,而比特币的设计确保了这一过程的公平性与不可篡改性。其机制不仅保障了数字资产的安全性,也为信息时代带来了全新的治理模式。 机械共识所展现的力量,正是其能够在无中央控制的情况下,依据设定的规则自动运行,并为人类社会的复杂问题提供解决方案的能力。它让我们看到了技术能够如何超越单一的财富保护,转向对人类生命与文明更广泛的保障。 **比特币:从加密资产到文明守护者的机械共识** 比特币不仅仅是一种加密资产,它代表了机械共识的核心理念。中本聪设计比特币的初衷便是为了建立一个无需信任第三方的自适应增长型网络,而这一理念正是通过比特币的共识机制得以实现的。 比特币的共识机制背后,实际上是一场永无止境的算力竞赛。矿工们为获得比特币奖励,不断投入算力,推动网络的持续增长与自我强化。这种自我强化机制不仅增加了比特币网络的安全性和稳定性,同时也不断增强了其抵抗外部攻击的能力。通过这种正反馈机制,比特币的网络得以不断壮大,其市值从2009年的零增长到目前超过1.8万亿美元,证明了机械共识作为“数字货币”的成功。 然而,比特币所代表的机械共识不仅仅局限于保护数字资产,它为人类应对信息时代的复杂性提供了一个新的解决方案。 **Super Bitcoin:守护人类未来的革新者** 在此基础上,Super Bitcoin应运而生,进一步突破比特币网络的局限。 通过五层架构的设计,Super Bitcoin不仅继承了比特币网络的安全性,还突破了比特币单纯转账的功能,为比特币网络带来了更为丰富的扩展能力。Super Bitcoin在设计中集成了工作量证明(PoW)共识机制,闪电网络,Taproot Consensus等技术,形成了一个更高效、灵活的区块链体系。 这一新的架构使得Super Bitcoin不仅仅是一个数字资产的保护工具,它更像是一个能够为人类社会提供科技管控的平台。通过去中心化、自动化的机械共识,Super Bitcoin能够在控制风险的同时促进技术的发展,并保障人类文明免受潜在的科技威胁。它不仅为协议和应用提供了一个安全、共享的基础设施,更在不断扩展的生态系统中,提供了实现更多人类目标的可能。 **结语:每一枚比特币都是对人类未来的守护** 比特币(BTC)的总量恒定为2100万枚,而全球人口已超过82亿。简单计算,每400人平均共享一枚BTC。从资产角度看,这凸显了比特币的稀缺性和价值。然而,从人类生命安全的角度来看,每枚比特币实际上守护着400条生命。 加密货币的真正价值不仅在于其作为财富的象征,更在于其背后的自适应机械共识。2100万个比特币,每一枚都承载着守护生命的责任。通过机械共识,我们有机会在信息爆炸、科技进步的时代,建立一个更为坚固的社会共识,帮助人类应对复杂的科技尤其是人工智能带来的挑战,确保文明与生命的可持续发展。 @ 5d4b6c8d:8a1c1ee3
2024-11-15 15:07:59Heading into episode 6, here's a rough outline of what we're planning on talking about. ~Stacker_Sports contest updates: UEFA, Cricket, NFL, NBA Bitcoiner Athletes: two sports celebrities were in the bitcoin news recently Hockey: a hot start for a surprising team NFL - our head-to-head fantasy matchup (if @grayruby still wants to talk about it after his team's reprehensible outing), - which contenders are on the outside looking in, - Why are the Bears so bad at picking OC's? Tyson vs Paul NBA - By popular demand, KAT Corner makes a return - Thoughts and expectations for the Emirates CUp - Can the best player win MVP on a garbage team? - Our early hits and misses of the season Degenerate Corner: bets we're excited about, platforms we're excited about, ongoing bets we have with each other. originally posted at https://stacker.news/items/769019
@ 5d4b6c8d:8a1c1ee3
2024-11-15 15:07:59Heading into episode 6, here's a rough outline of what we're planning on talking about. ~Stacker_Sports contest updates: UEFA, Cricket, NFL, NBA Bitcoiner Athletes: two sports celebrities were in the bitcoin news recently Hockey: a hot start for a surprising team NFL - our head-to-head fantasy matchup (if @grayruby still wants to talk about it after his team's reprehensible outing), - which contenders are on the outside looking in, - Why are the Bears so bad at picking OC's? Tyson vs Paul NBA - By popular demand, KAT Corner makes a return - Thoughts and expectations for the Emirates CUp - Can the best player win MVP on a garbage team? - Our early hits and misses of the season Degenerate Corner: bets we're excited about, platforms we're excited about, ongoing bets we have with each other. originally posted at https://stacker.news/items/769019 @ 2775fb0f:887f8193
2024-11-15 13:40:01
@ 2775fb0f:887f8193
2024-11-15 13:40:01 @ 6fff5148:a5dd5cdf
2024-11-15 12:17:03* #*🍞☕🍱MORNING TEA🍱☕🍞* _____________________________________ ```Forget about all the reasons why something may not work. You on____ly need to find one good reason why it will.``` _____________________________________ *_Victor IBiz_* 15.11.2024
@ 6fff5148:a5dd5cdf
2024-11-15 12:17:03* #*🍞☕🍱MORNING TEA🍱☕🍞* _____________________________________ ```Forget about all the reasons why something may not work. You on____ly need to find one good reason why it will.``` _____________________________________ *_Victor IBiz_* 15.11.2024 @ 44def29e:2052000d
2024-11-15 11:31:28Es un bosque de hayas situado en el municipio español de Cantalojas, Sierra de Ayllón, en el Sistema Central. Es uno de los hayedos más meridionales de Europa y destaca por su belleza y singularidad. Predominan las hayas, pero también hay robles, pinos, tejos, acebos y otras especies. Declarado Patrimonio de la Humanidad en 2017, junto con otros hayedos de Europa, como extensión de los Hayedos primarios de los Cárpatos. Track: https://elcorrelimos.com/hayedo-de-la-tejera-negra/ | | | | | --- | --- | --- | |  |  | | |  |  |  | |  |  |  |
@ 44def29e:2052000d
2024-11-15 11:31:28Es un bosque de hayas situado en el municipio español de Cantalojas, Sierra de Ayllón, en el Sistema Central. Es uno de los hayedos más meridionales de Europa y destaca por su belleza y singularidad. Predominan las hayas, pero también hay robles, pinos, tejos, acebos y otras especies. Declarado Patrimonio de la Humanidad en 2017, junto con otros hayedos de Europa, como extensión de los Hayedos primarios de los Cárpatos. Track: https://elcorrelimos.com/hayedo-de-la-tejera-negra/ | | | | | --- | --- | --- | |  |  | | |  |  |  | |  |  |  | @ 98589a2e:bf49daa1
2024-11-15 10:26:44**Эстетическая часть Санкт-Петербурга претерпела значительные изменения, отражая динамичное развитие города и его стремление к инновациям. С населением, достигшим 6,5 миллионов человек, культурные инициативы и мероприятия стали более разнообразными и доступными для всех жителей.**  ## Разнообразие культурных событий Санкт-Петербург продолжает оставаться центром культурной жизни России, предлагая жителям и туристам широкий спектр мероприятий: **Фестивали**: В городе проводятся многочисленные фестивали, такие как «Северное сияние», объединяющий музыку, искусство и литературу. Этот фестиваль стал площадкой для молодых талантов и известных артистов. **Театры и спектакли**: Петербургские театры активно развивают свои программы, предлагая как классические постановки, так и современные интерпретации. Фестиваль «Театр без границ» привлекает внимание к инклюзивным спектаклям с тифлокомментированием и сурдопереводом. **Выставки и арт-пространства**: В обновленном Апраксином дворе открылись новые галереи и коворкинги, где проводятся выставки современных художников и мастер-классы. Это пространство стало важным центром для творческих людей города.  ## Новые культурные объекты В Петербурге появились значимые культурные объекты: **Планетарий и океанариум**: Новый планетарий стал не только крупнейшим в стране, но и интерактивным центром изучения астрономии. Океанариум во Фрунзенском районе стал научно-познавательным центром, предлагающим уникальные выставки о морской биологии. **Культурные кластеры**: В рамках Генерального плана создано несколько культурных кластеров, в которых сосредоточены театры, художественные школы и образовательные центры. Это способствует обмену знаниями и культурному взаимодействию между различными направлениями искусства.  ## Устойчивое развитие культуры Культурная жизнь Петербурга также ориентирована на устойчивое развитие: **Зеленые насаждения**: новые парковые зоны и благоустроенные набережные стали местом проведения культурных мероприятий на свежем воздухе. Здесь организуются концерты, выставки и ярмарки. **Инклюзия в культуре**: культурные инициативы становятся более доступными для людей с ограниченными возможностями. Участие таких людей в культурной жизни города активно поддерживается с помощью специальных программ и мероприятий.  **Разнообразие мероприятий, новые культурные объекты и акцент на инклюзивности делают петербургскую культуру доступной и привлекательной для всех. Город продолжает развиваться, сохраняя свою уникальную атмосферу и традиции.** ### Как вам инициативы развития культурной жизни города?
@ 98589a2e:bf49daa1
2024-11-15 10:26:44**Эстетическая часть Санкт-Петербурга претерпела значительные изменения, отражая динамичное развитие города и его стремление к инновациям. С населением, достигшим 6,5 миллионов человек, культурные инициативы и мероприятия стали более разнообразными и доступными для всех жителей.**  ## Разнообразие культурных событий Санкт-Петербург продолжает оставаться центром культурной жизни России, предлагая жителям и туристам широкий спектр мероприятий: **Фестивали**: В городе проводятся многочисленные фестивали, такие как «Северное сияние», объединяющий музыку, искусство и литературу. Этот фестиваль стал площадкой для молодых талантов и известных артистов. **Театры и спектакли**: Петербургские театры активно развивают свои программы, предлагая как классические постановки, так и современные интерпретации. Фестиваль «Театр без границ» привлекает внимание к инклюзивным спектаклям с тифлокомментированием и сурдопереводом. **Выставки и арт-пространства**: В обновленном Апраксином дворе открылись новые галереи и коворкинги, где проводятся выставки современных художников и мастер-классы. Это пространство стало важным центром для творческих людей города.  ## Новые культурные объекты В Петербурге появились значимые культурные объекты: **Планетарий и океанариум**: Новый планетарий стал не только крупнейшим в стране, но и интерактивным центром изучения астрономии. Океанариум во Фрунзенском районе стал научно-познавательным центром, предлагающим уникальные выставки о морской биологии. **Культурные кластеры**: В рамках Генерального плана создано несколько культурных кластеров, в которых сосредоточены театры, художественные школы и образовательные центры. Это способствует обмену знаниями и культурному взаимодействию между различными направлениями искусства.  ## Устойчивое развитие культуры Культурная жизнь Петербурга также ориентирована на устойчивое развитие: **Зеленые насаждения**: новые парковые зоны и благоустроенные набережные стали местом проведения культурных мероприятий на свежем воздухе. Здесь организуются концерты, выставки и ярмарки. **Инклюзия в культуре**: культурные инициативы становятся более доступными для людей с ограниченными возможностями. Участие таких людей в культурной жизни города активно поддерживается с помощью специальных программ и мероприятий.  **Разнообразие мероприятий, новые культурные объекты и акцент на инклюзивности делают петербургскую культуру доступной и привлекательной для всех. Город продолжает развиваться, сохраняя свою уникальную атмосферу и традиции.** ### Как вам инициативы развития культурной жизни города? @ c2827524:5f45b2f7
2024-11-15 10:11:29<h2>Partigiani a Milano</h2> tra le tante opportunità che Milano mi ha regalato, c’è anche quella di aver conosciuto di persona un discreto numero di partigiani, quelli veri. Quando da bambina ho ascoltato le loro storie e capito le loro scelte, ero certa che – se fosse capitato a me – avrei certamente preso quella stessa decisione: <strong>stare dalla parte giusta</strong>. <h2>Il momento di decidere</h2> Prima del diploma ho deciso che volevo fare il <em>tecnico del suono</em>, che è effettivamente l’unico lavoro che sapevo fare fino al 2022. Vita meravigliosa: ho girato il mondo a spese delle varie produzioni che mi hanno ingaggiato. Poi, un giorno, ho deciso di soccorrere un grande amico in difficoltà, prendendo le sue parti e stravolgendo di fatto quella che fino al 2004 è stata una vita tranquilla e, fino a lì, noiosa. <strong>Noiosa per quello che sarebbe successo da quel momento in poi</strong>. Prendere le difese di una parte debole in un contenzioso feroce tra fratelli, ha di fatto sconvolto ogni paradigma conquistato fino a quel momento. Ho anche conosciuto una certa dose di cattiveria, visto le vere sembianze del male e scampato i suoi attacchi, ma questa è un’altra storia (di cui non posso scrivere perché vincolata a segreto professionale). <h2>Covidiozia</h2> Ogni evento o decisione, dal 2004 in poi, non è più stato lo stesso per me. Quello che di grosso ho notato sono state <strong>le enormi differenze tra me e ""“gli altri”""</strong>, cosa che all’inizio mi ha portato ad evidenziarle, esaltandole perfino. Poi è arrivato il compleanno del 2020, non festeggiato per colpa della covidiozia generale ormai dilagante. Quelle che erano delle piccole differenze da esaltare, tra ""“gli altri""” e me, si sono <strong>tradotte in speciazione: loro da una parte, io nella direzione esattamente opposta</strong>. Sono certa di essermi <strong>schierata dalla parte giusta</strong>; saranno i miei bias di conferma o di chi li appiccia, ma <strong>guardando indietro all'infanzia, a quando avevo promesso di decidere per il giusto, sono felice di aver mantenuto la promessa a quella bambina</strong>. <h2>Bitcoin</h2> Senza la covidiozia dilagante <strong>non avrei conosciuto Bitcoin</strong> Avrei continuato a condurre la mia insulsa vita come sempre, sebbene in un angolo diverso del mondo sempre nuovo e con un lavoro accattivante. Non avrei iniziato a studiare questa <strong>deliziosa tecnologia</strong>. Soprattutto, non avrei mai congiunto il mio cammino con tutti quelli che hanno avuto a loro modo una speciazione come la mia, staccando il proprio cammino da quello degli """altri""”. <h2>Anche se quella bambina non sapeva i dettagli, la ringrazio per avermi guidato su un sentiero che è – a tutti gli effetti – quello che più si avvicina alla realizzazione della mia felicità</h3>
@ c2827524:5f45b2f7
2024-11-15 10:11:29<h2>Partigiani a Milano</h2> tra le tante opportunità che Milano mi ha regalato, c’è anche quella di aver conosciuto di persona un discreto numero di partigiani, quelli veri. Quando da bambina ho ascoltato le loro storie e capito le loro scelte, ero certa che – se fosse capitato a me – avrei certamente preso quella stessa decisione: <strong>stare dalla parte giusta</strong>. <h2>Il momento di decidere</h2> Prima del diploma ho deciso che volevo fare il <em>tecnico del suono</em>, che è effettivamente l’unico lavoro che sapevo fare fino al 2022. Vita meravigliosa: ho girato il mondo a spese delle varie produzioni che mi hanno ingaggiato. Poi, un giorno, ho deciso di soccorrere un grande amico in difficoltà, prendendo le sue parti e stravolgendo di fatto quella che fino al 2004 è stata una vita tranquilla e, fino a lì, noiosa. <strong>Noiosa per quello che sarebbe successo da quel momento in poi</strong>. Prendere le difese di una parte debole in un contenzioso feroce tra fratelli, ha di fatto sconvolto ogni paradigma conquistato fino a quel momento. Ho anche conosciuto una certa dose di cattiveria, visto le vere sembianze del male e scampato i suoi attacchi, ma questa è un’altra storia (di cui non posso scrivere perché vincolata a segreto professionale). <h2>Covidiozia</h2> Ogni evento o decisione, dal 2004 in poi, non è più stato lo stesso per me. Quello che di grosso ho notato sono state <strong>le enormi differenze tra me e ""“gli altri”""</strong>, cosa che all’inizio mi ha portato ad evidenziarle, esaltandole perfino. Poi è arrivato il compleanno del 2020, non festeggiato per colpa della covidiozia generale ormai dilagante. Quelle che erano delle piccole differenze da esaltare, tra ""“gli altri""” e me, si sono <strong>tradotte in speciazione: loro da una parte, io nella direzione esattamente opposta</strong>. Sono certa di essermi <strong>schierata dalla parte giusta</strong>; saranno i miei bias di conferma o di chi li appiccia, ma <strong>guardando indietro all'infanzia, a quando avevo promesso di decidere per il giusto, sono felice di aver mantenuto la promessa a quella bambina</strong>. <h2>Bitcoin</h2> Senza la covidiozia dilagante <strong>non avrei conosciuto Bitcoin</strong> Avrei continuato a condurre la mia insulsa vita come sempre, sebbene in un angolo diverso del mondo sempre nuovo e con un lavoro accattivante. Non avrei iniziato a studiare questa <strong>deliziosa tecnologia</strong>. Soprattutto, non avrei mai congiunto il mio cammino con tutti quelli che hanno avuto a loro modo una speciazione come la mia, staccando il proprio cammino da quello degli """altri""”. <h2>Anche se quella bambina non sapeva i dettagli, la ringrazio per avermi guidato su un sentiero che è – a tutti gli effetti – quello che più si avvicina alla realizzazione della mia felicità</h3> @ 07907690:d4e015f6
2024-11-15 10:10:05PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP: ## Mengamankan Email (Enkripsi dan Dekripsi) - Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya. - Cara Kerja: - Pengirim mengenkripsi email menggunakan kunci publik penerima. - Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut. - Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup. ## Tanda Tangan Digital (Digital Signature) - Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah. - Cara Kerja: - Pengirim membuat tanda tangan digital menggunakan kunci privatnya. - Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim. - Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh. ## Melindungi File dan Dokumen - Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya. - Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya. - Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya. ## Mengamankan Backup Data - Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah. - Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman. - Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data. ## Perlindungan Identitas dan Anonimitas - Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online. - Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan. - Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka. ## Memverifikasi Integritas Perangkat Lunak - Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga. - Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan. - Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya. ## Komunikasi di Forum atau Jaringan Terdistribusi - Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim. - Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah. - Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka. --- ## Mengapa PGP Penting? - Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas. -Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan. - Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi. - Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital. --- ## Kelebihan PGP - Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi. - Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source. - Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data. ## Kekurangan PGP - Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam. - Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar. - Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan. --- PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.
@ 07907690:d4e015f6
2024-11-15 10:10:05PGP (Pretty Good Privacy) adalah protokol enkripsi yang digunakan untuk memastikan kerahasiaan, integritas, dan otentikasi data dalam komunikasi digital. Diciptakan oleh Phil Zimmermann pada tahun 1991, PGP menggunakan kombinasi teknik kriptografi asimetris (kunci publik dan kunci privat) serta simetris untuk melindungi informasi. Berikut adalah berbagai kegunaan PGP: ## Mengamankan Email (Enkripsi dan Dekripsi) - Kegunaan: Melindungi isi email agar hanya penerima yang memiliki kunci privat yang benar yang dapat membacanya. - Cara Kerja: - Pengirim mengenkripsi email menggunakan kunci publik penerima. - Hanya penerima yang memiliki kunci privat yang dapat mendekripsi dan membaca email tersebut. - Contoh: Jurnalis yang berkomunikasi dengan informan atau organisasi yang mengirim data sensitif dapat menggunakan PGP untuk melindungi komunikasi mereka dari penyusup. ## Tanda Tangan Digital (Digital Signature) - Kegunaan: Memastikan keaslian dan integritas pesan atau dokumen, memastikan bahwa pesan tidak diubah dan benar-benar berasal dari pengirim yang sah. - Cara Kerja: - Pengirim membuat tanda tangan digital menggunakan kunci privatnya. - Penerima dapat memverifikasi tanda tangan tersebut menggunakan kunci publik pengirim. - Contoh: Digunakan untuk memverifikasi keaslian dokumen hukum, email penting, atau perangkat lunak yang diunduh. ## Melindungi File dan Dokumen - Kegunaan: Mengenkripsi file sensitif agar hanya orang yang memiliki kunci dekripsi yang benar yang dapat membukanya. - Cara Kerja: File dienkripsi menggunakan kunci publik penerima, dan penerima menggunakan kunci privatnya untuk mendekripsinya. - Contoh: Perusahaan dapat menggunakan PGP untuk mengenkripsi laporan keuangan, data pelanggan, atau informasi penting lainnya sebelum membagikannya. ## Mengamankan Backup Data - Kegunaan: Mengenkripsi cadangan data penting untuk melindunginya dari akses yang tidak sah. - Cara Kerja: File backup dienkripsi dengan PGP sebelum disimpan, sehingga meskipun backup dicuri, data tetap aman. - Contoh: Organisasi menyimpan cadangan data klien di server eksternal yang dienkripsi dengan PGP untuk mencegah kebocoran data. ## Perlindungan Identitas dan Anonimitas - Kegunaan: Melindungi identitas pengirim dan penerima dalam komunikasi online. - Cara Kerja: Penggunaan enkripsi end-to-end menjamin bahwa hanya pihak yang berwenang yang dapat membaca pesan. - Contoh: Aktivis atau peneliti yang bekerja di negara dengan pengawasan ketat dapat menggunakan PGP untuk melindungi komunikasi mereka. ## Memverifikasi Integritas Perangkat Lunak - Kegunaan: Memastikan bahwa perangkat lunak atau paket yang diunduh berasal dari sumber yang terpercaya dan tidak dimodifikasi oleh pihak ketiga. - Cara Kerja: Pengembang menandatangani perangkat lunak menggunakan kunci privat mereka, dan pengguna dapat memverifikasi tanda tangan menggunakan kunci publik yang disediakan. - Contoh: Distribusi Linux atau aplikasi open-source sering kali menyertakan tanda tangan PGP untuk memverifikasi keasliannya. ## Komunikasi di Forum atau Jaringan Terdistribusi - Kegunaan: Memastikan privasi komunikasi di platform terdesentralisasi atau anonim. - Cara Kerja: Pesan dienkripsi sebelum dikirim dan hanya dapat didekripsi oleh penerima yang sah. - Contoh: Pengguna di forum yang membahas topik sensitif dapat menggunakan PGP untuk melindungi identitas mereka. --- ## Mengapa PGP Penting? - Keamanan yang Kuat: Kombinasi kriptografi asimetris dan simetris membuat PGP sangat sulit ditembus oleh peretas. -Privasi: Menjaga komunikasi Anda tetap aman dan pribadi dari penyadapan atau pengawasan. - Integritas: Memastikan bahwa pesan atau data yang dikirim tidak diubah selama transmisi. - Otentikasi: Membuktikan identitas pengirim melalui tanda tangan digital. --- ## Kelebihan PGP - Sangat Aman: Jika digunakan dengan benar, PGP menawarkan tingkat keamanan yang sangat tinggi. - Terbuka: Banyak digunakan di kalangan profesional dan komunitas open-source. - Fleksibel: Dapat digunakan untuk berbagai keperluan, mulai dari komunikasi email hingga penyimpanan data. ## Kekurangan PGP - Kompleks untuk Pemula: Relatif sulit digunakan oleh pengguna awam. - Pengelolaan Kunci yang Rumit: Memerlukan pengelolaan kunci publik/privat yang benar. - Tidak Ada Pemulihan Data: Jika kunci privat hilang, data yang dienkripsi tidak dapat dipulihkan. --- PGP adalah alat yang sangat berguna untuk memastikan keamanan dan privasi dalam komunikasi dan data. Dengan meningkatnya risiko kejahatan siber, penggunaan PGP menjadi semakin penting, terutama di sektor yang menangani data sensitif.